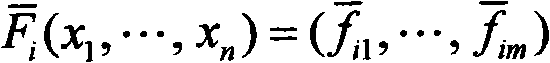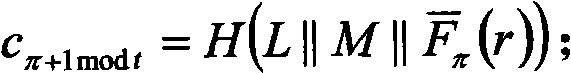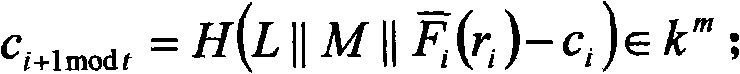Ring signature method for anonymizing information based on multivariate polynomial
A polynomial, ring signature technology, applied in the field of information security, can solve the problem of insecure ring signature system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0134] By applying the present invention and selecting different multi-variable public-key cryptographic systems, a new ring digital signature algorithm can be generated, which realizes the anonymity of the signer while realizing the authenticity and integrity of the electronic document. In the following embodiment, we use the unbalanced Oil-Vinegar signature system to construct an example of a ring signature that realizes the anonymity of the signer.
[0135] A ring signature scheme based on multi-variable public key cryptography Oil-Vinegar signature system:
[0136] Step 1. Generate System Parameters
[0137] 1) Set k=GF(q) to be a finite field characterized by p=2, where q=2 8 .
[0138] 2) Let o=30, v=64, m=30 be the number of equations in the multivariate equation system, and n=o+v=94 be the number of variables.
[0139] 3) Select H: {0, 1} * →k 30 A cryptographically secure collision-resistant one-way irreversible hash function.
[0140] Step 2. Key generation
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com