Identity authentication protocol method based on error correcting code
A technology of identity authentication and error-correcting codes, which is applied to user identity/authority verification, countermeasures against encryption mechanisms, and key distribution. small effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
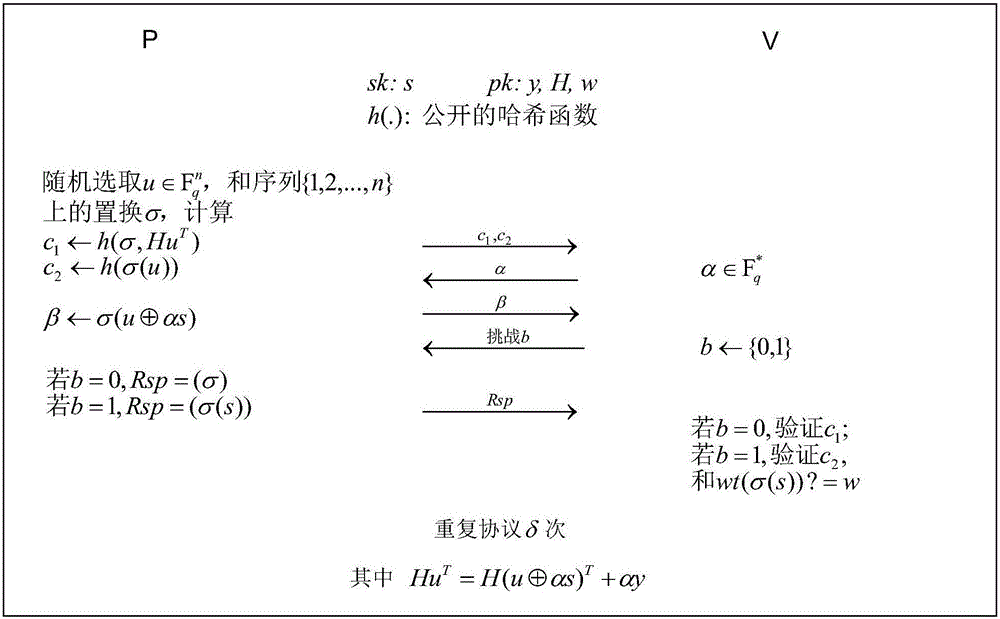
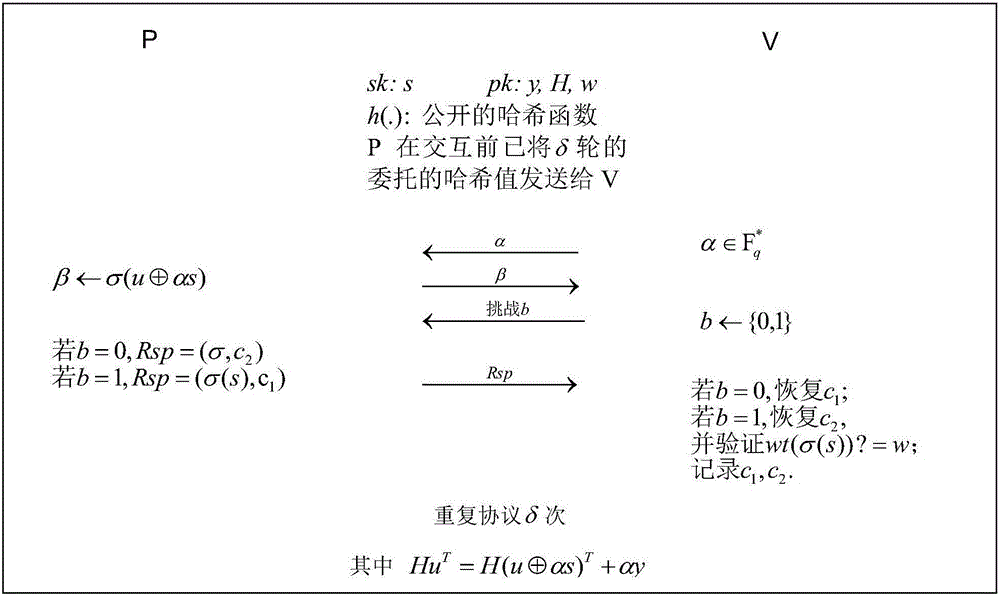
[0052] Embodiment 1. An identity authentication protocol method based on an error-correcting code
[0053] Specifically, the system parameters are set as follows: the code length of the quasi-dye error-correcting code C is n=128, the dimension k=64, the codimension r=64, the error-correcting capability of the code w=49, and the finite field F q Among them, q=256, indicating that the number of bits N=8 required by q. Generate a permutation function σ of seed length l σ =128, the output length l of the hash function h =160. In each round of the authentication protocol, the probability that the prover P cheats successfully is about 1 / 2, so the protocol goes through δ=16 rounds, and the probability that the prover P cheats successfully decreases to 2 -16 , can be ignored. Calculated by the following formula, the volume of the check matrix H of the quasi-dye correction code C is N×n=1024bits, the length of the ciphertext y is N×r=512bits, and the length of the key s is N×n=1024...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com