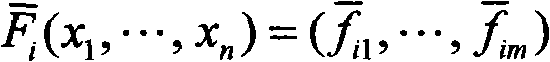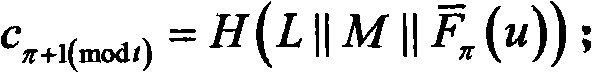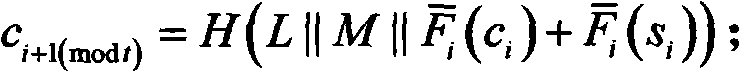Ring signature method for anonymizing information based on algebra
A ring signature and message technology, applied to the public key and key distribution of secure communication, can solve the problem of insecure ring signature system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0132] Anonymous ring signature scheme based on multi-variable public key cryptography oil-vinegar signature system:
[0133] Step 1. Generate System Parameters
[0134] 1) Set k=GF(q) to be a finite field characterized by p=2, where q=2 8 ;
[0135] 2) make o=30, v=64, m=30 is the number of equations in the multivariate equation system, and n=o+v=94 is the number of variables;
[0136] 3) Select H: {0, 1} * →k 30 A cryptographically secure collision-resistant one-way irreversible hash function. The system parameters are (k, q, p, l, m, n, H).
[0137] Step 2. Key generation
[0138] 1) Suppose there are t users in the ring, set U={u 0 , u 1 ,..,u t-1},
[0139] According to the multivariate public key cryptosystem, each user u i (0≤i≤t-1) randomly select F i is from k n to k m The reversible Oil-Vinegar polynomial map, Oil-Vinegar polynomial has the following form:
[0140] F i = Σ ...
Embodiment 2
[0173] Anonymous ring signature scheme based on multivariable public key cryptography Square+ signature system:
[0174] The square+ system is a multivariate polynomial system based on a singular characteristic field, which has relatively high security and can resist quantum computer attacks, and has high encryption and decryption efficiency. We combine the square+ system and propose a ring signature scheme based on the square+ system.
[0175] 1. The structure of Squaare+ system
[0176] Let k be a finite field of order q, where q≡3mod4. is the n+l expansion of k, where l makes n+l odd. F is the mapping from K to K, F(X)=X 2 , where X∈K.
[0177] Randomly choose an injective affine map L 1 :k n →k n+l ;d quadratic polynomials with n+l variables
[0178] g 1 ,..., g d ∈k[x 1 ,...,x n+l ]
[0179] and an invertible affine map L 2 :k n+l+d →k n+l+d . φ: K→k n+l , is an isomorphic map of vector spaces:
[0180]
[0181] Since φоFоφ -1 is a quadratic polyno...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com