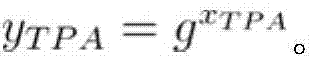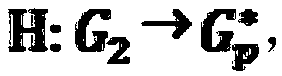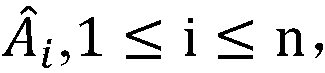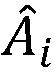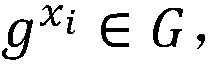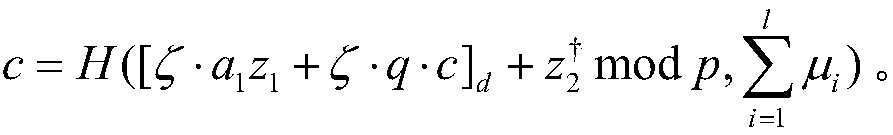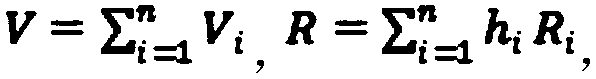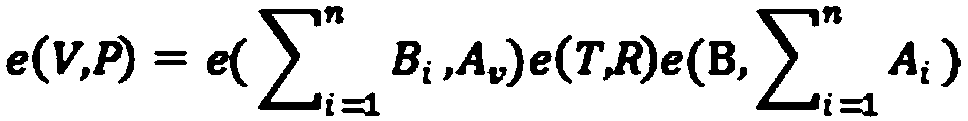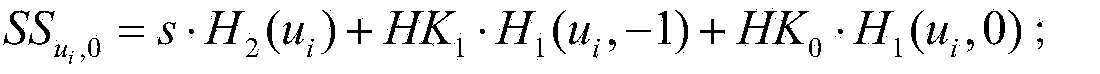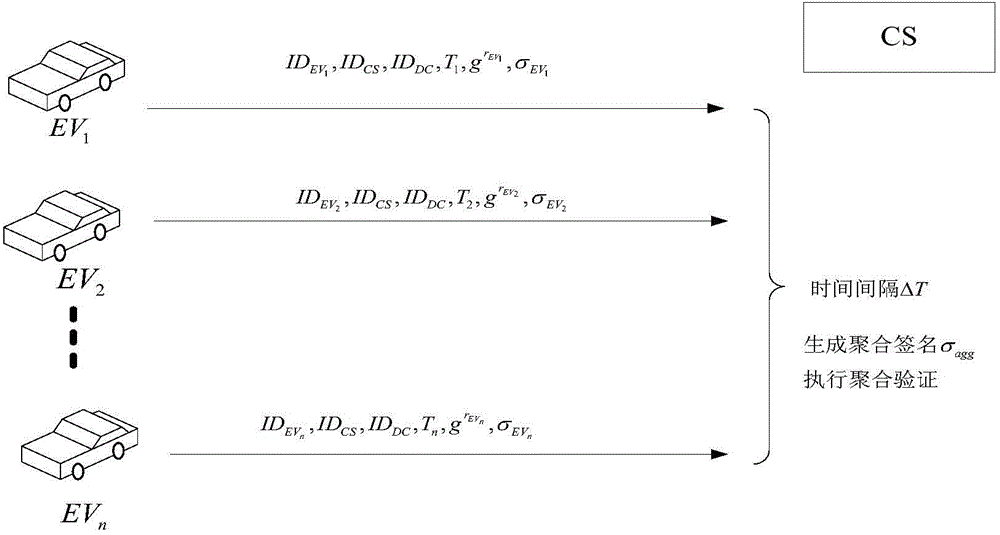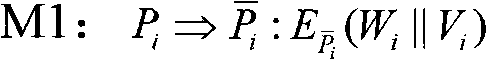Patents
Literature
63 results about "Aggregate signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
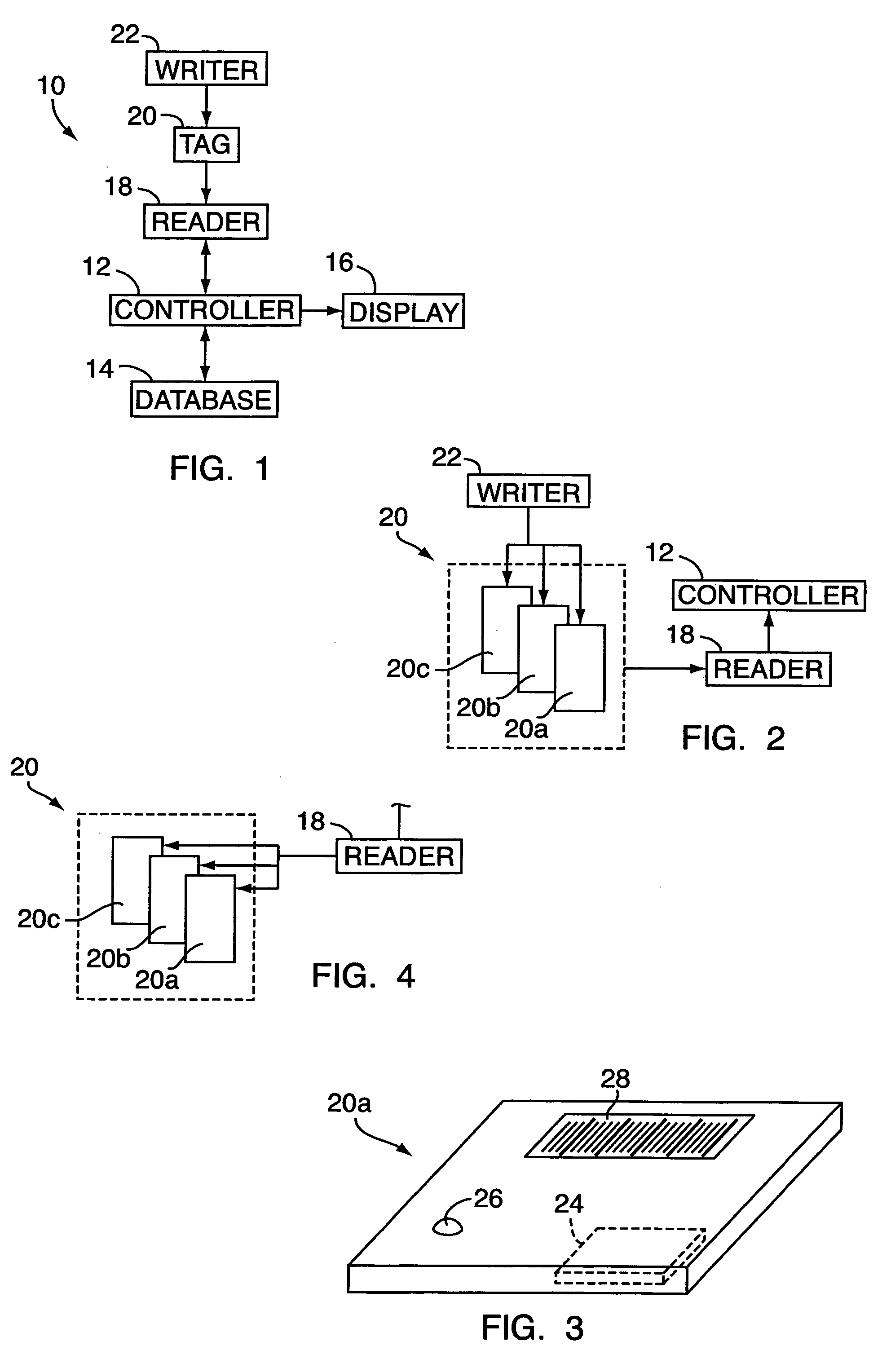
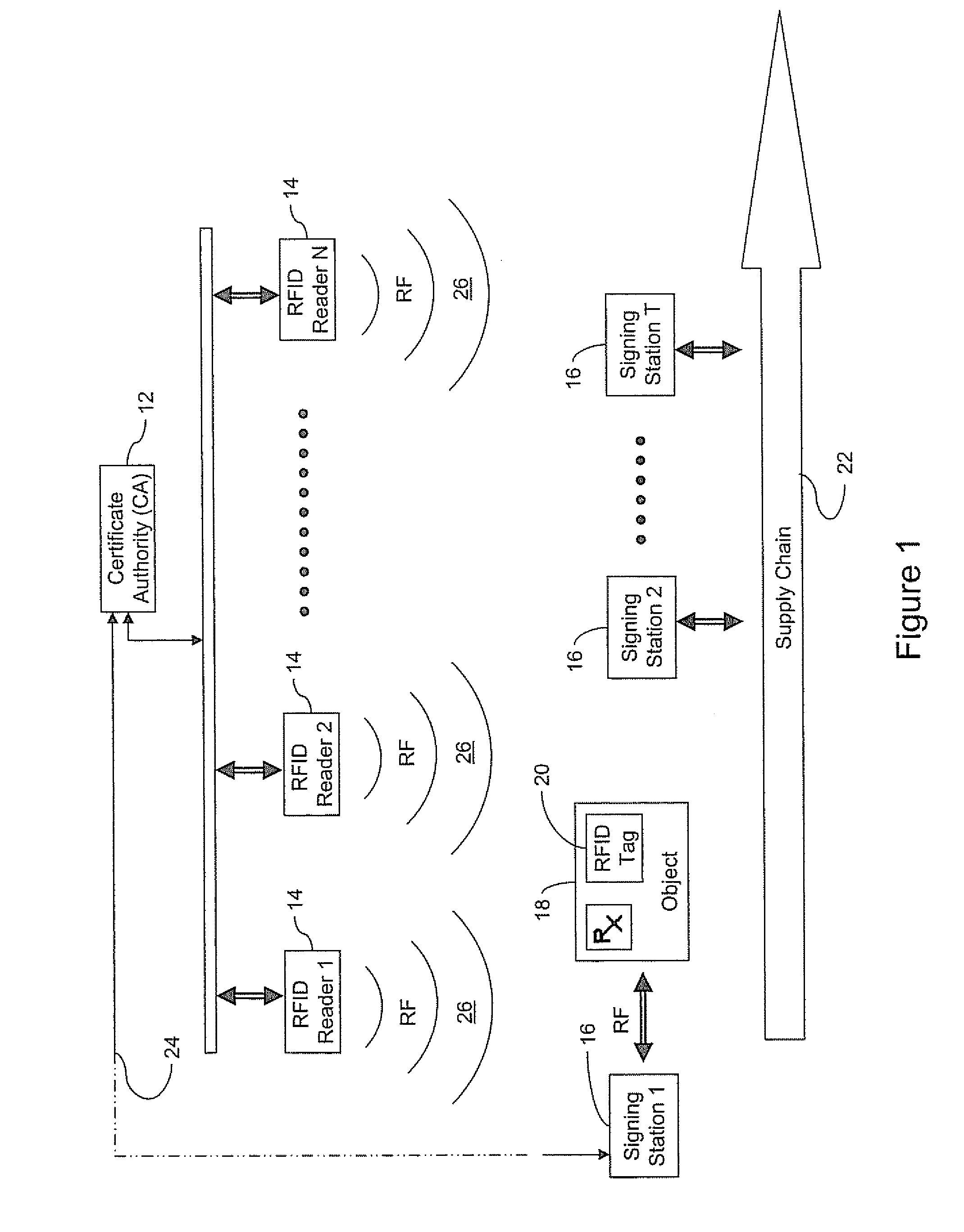
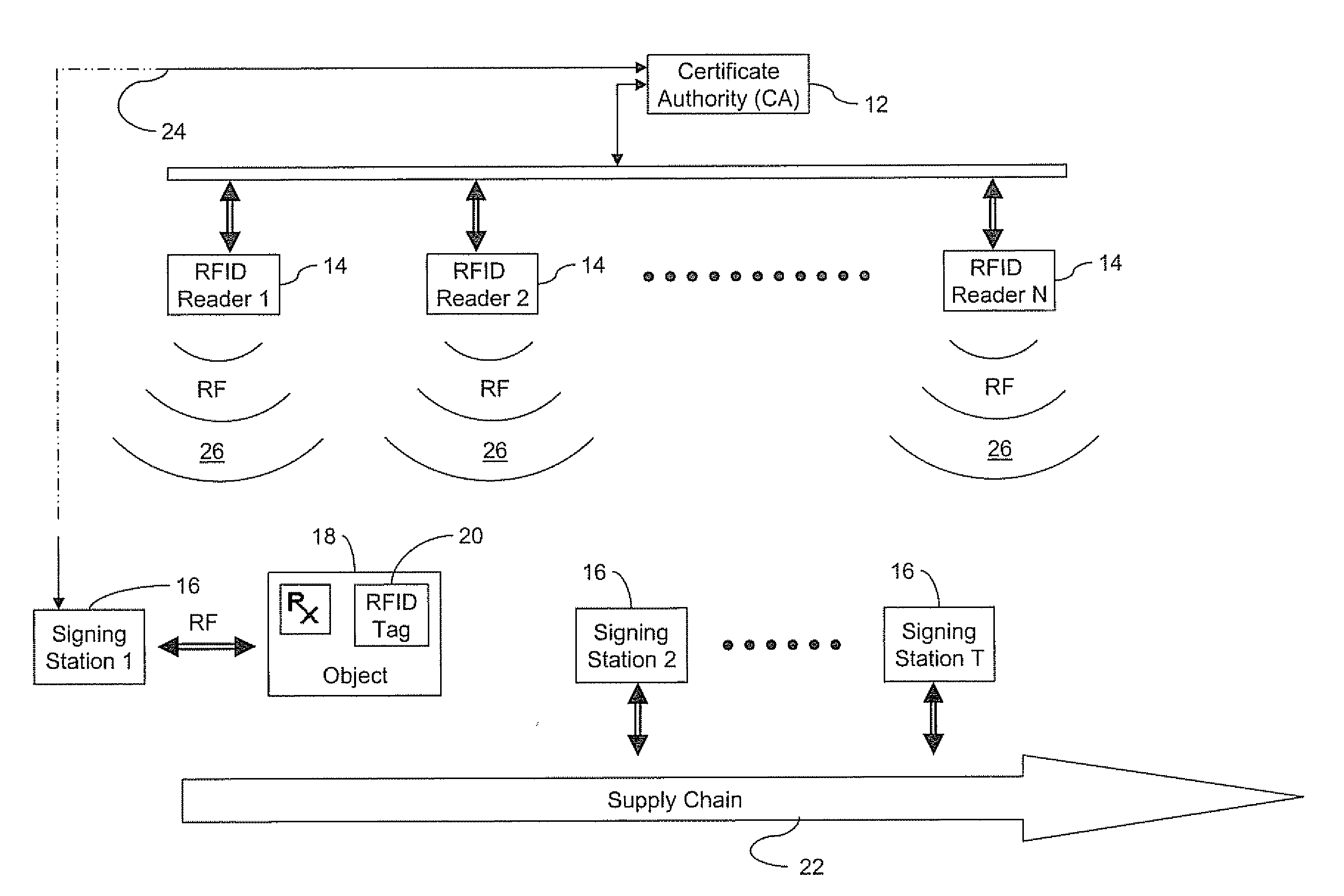
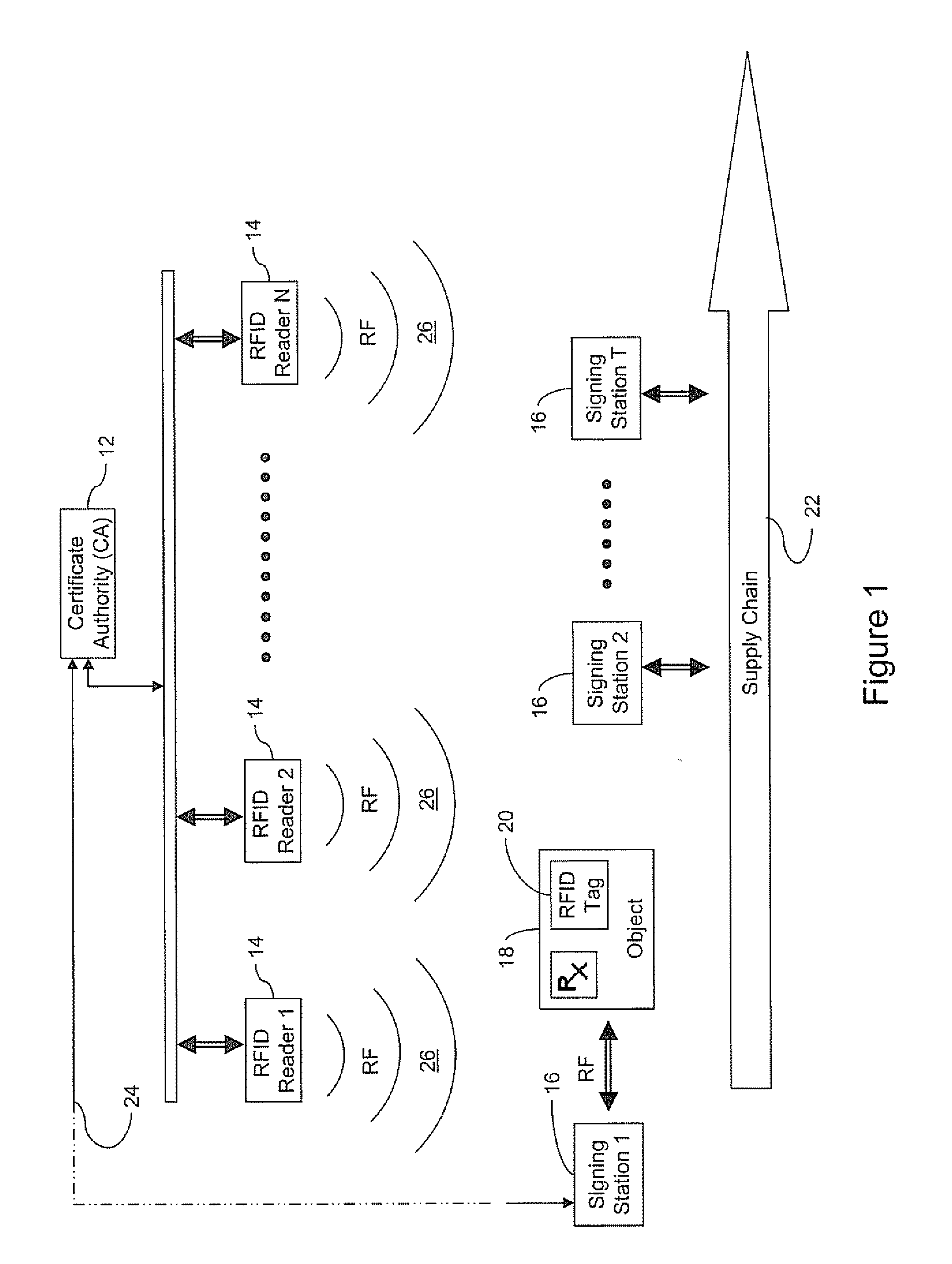
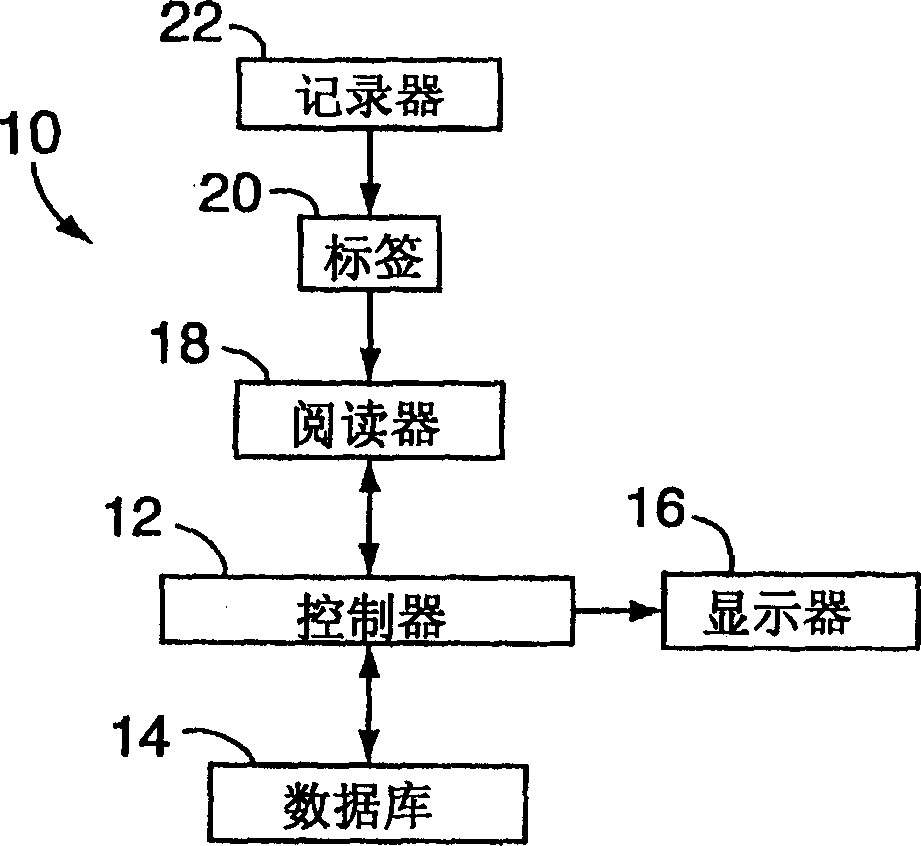
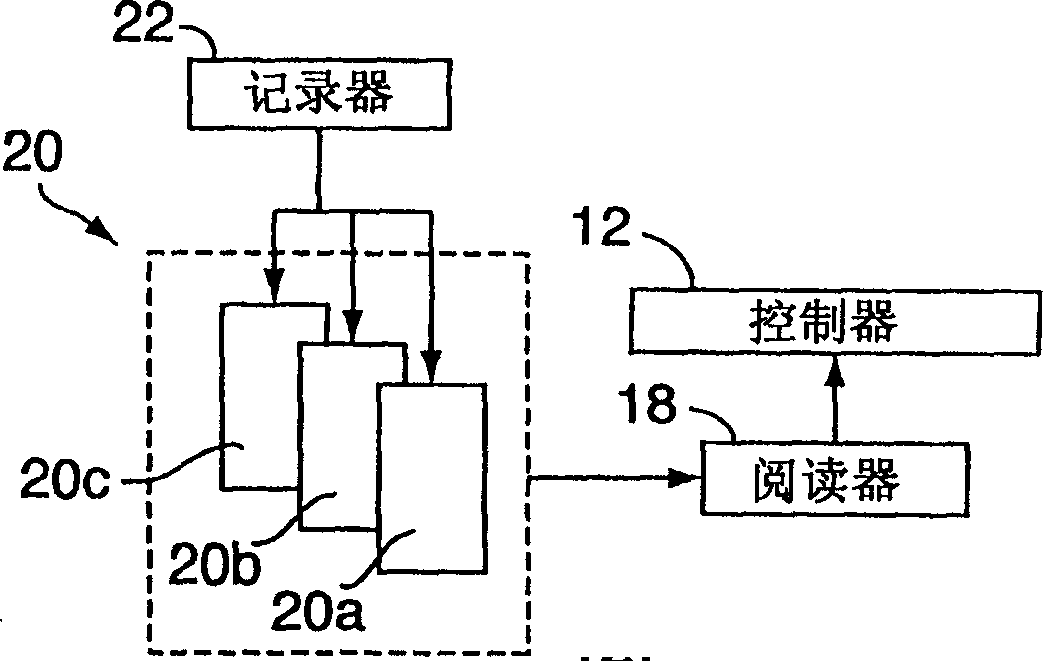
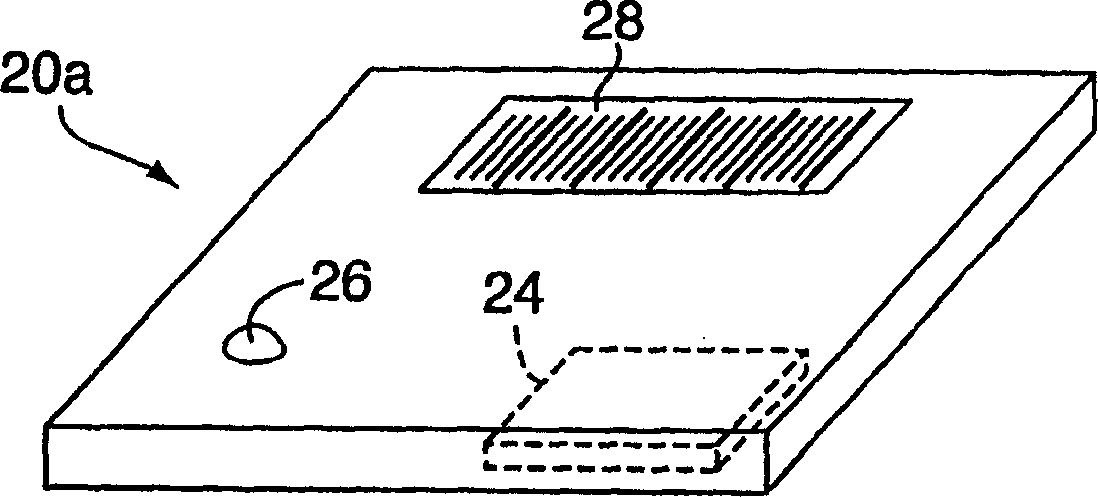
Electronic security system for monitoring and recording activity and data relating to cargo
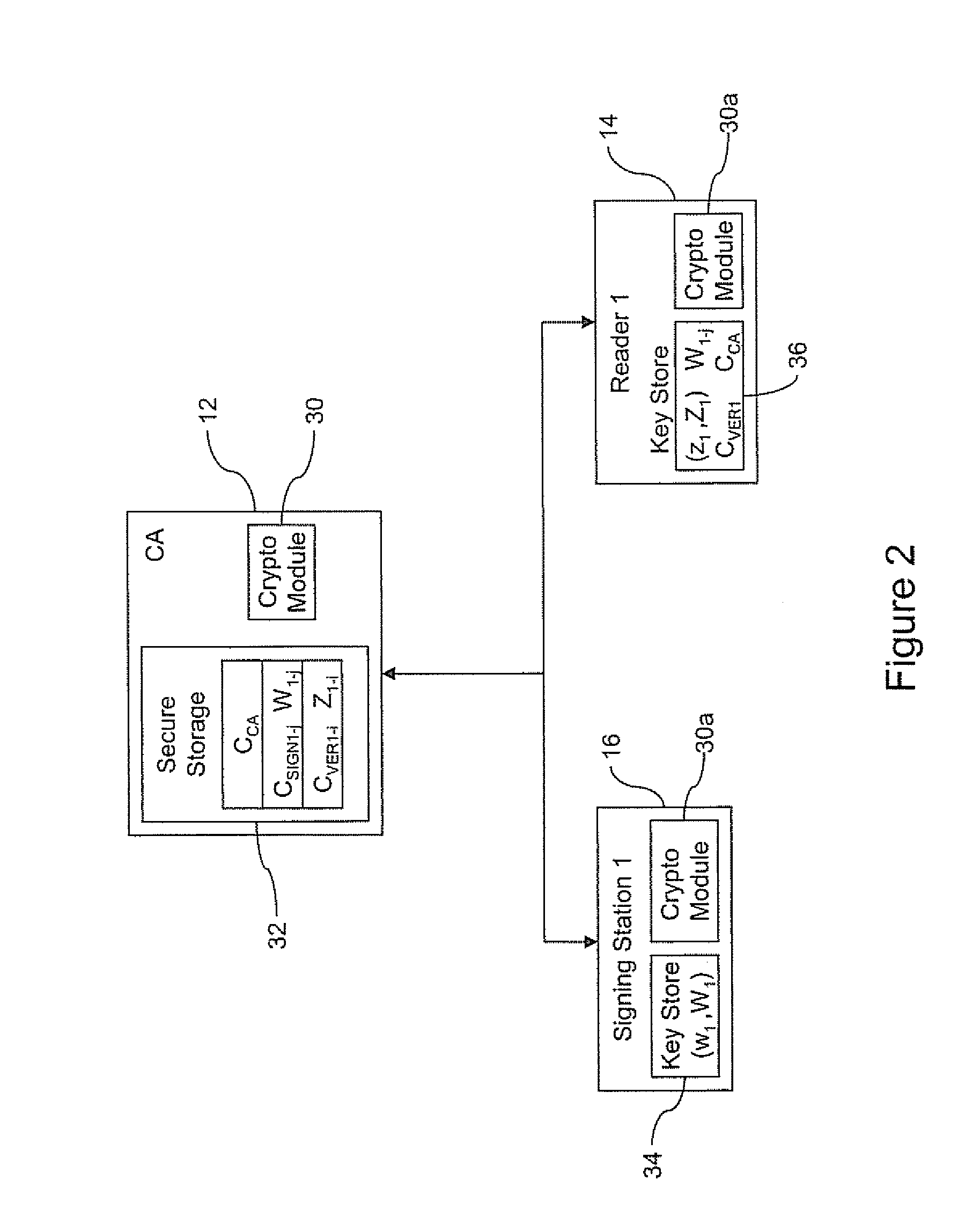
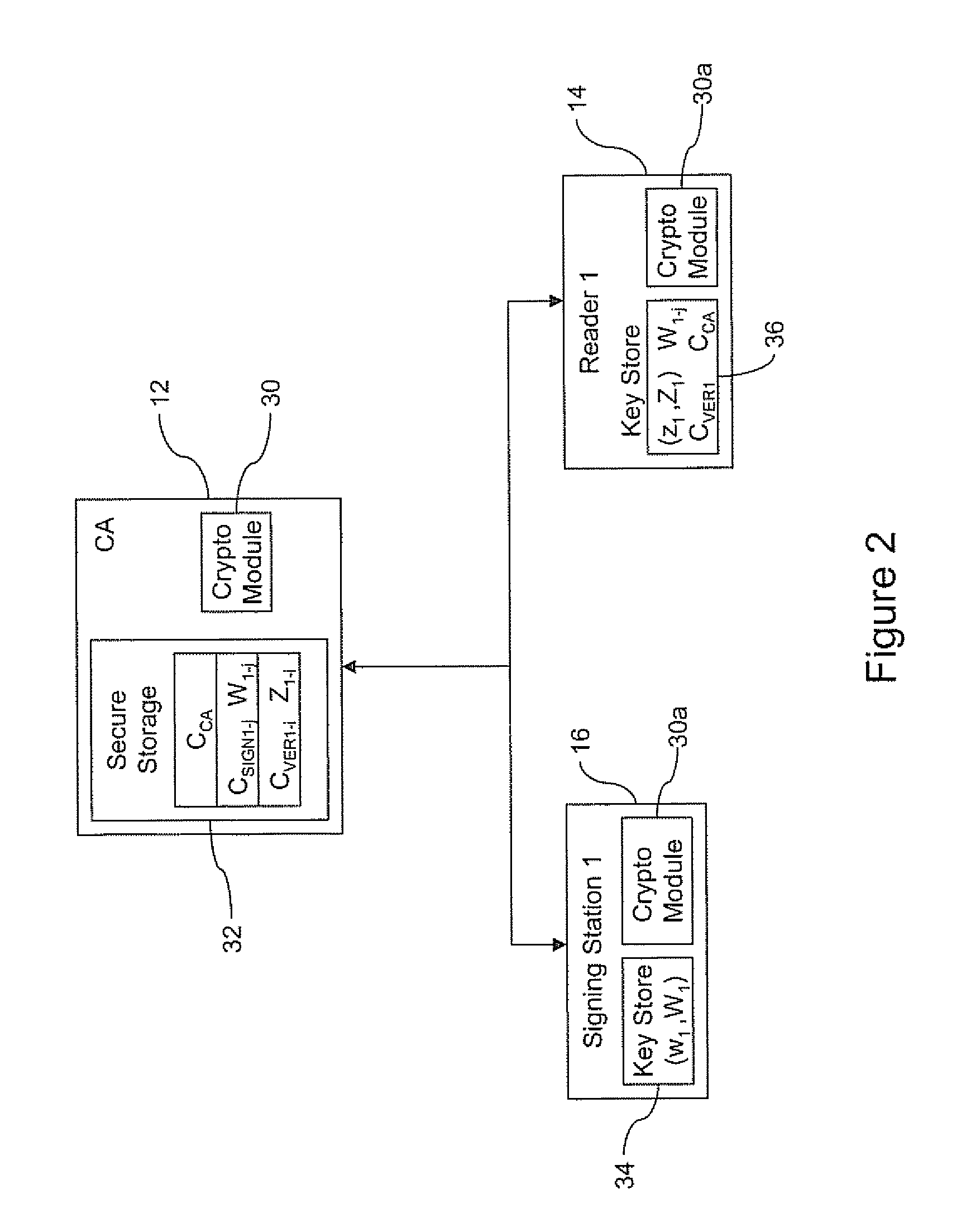
ActiveUS7012529B2Co-operative working arrangementsIndividual entry/exit registersData setData signal
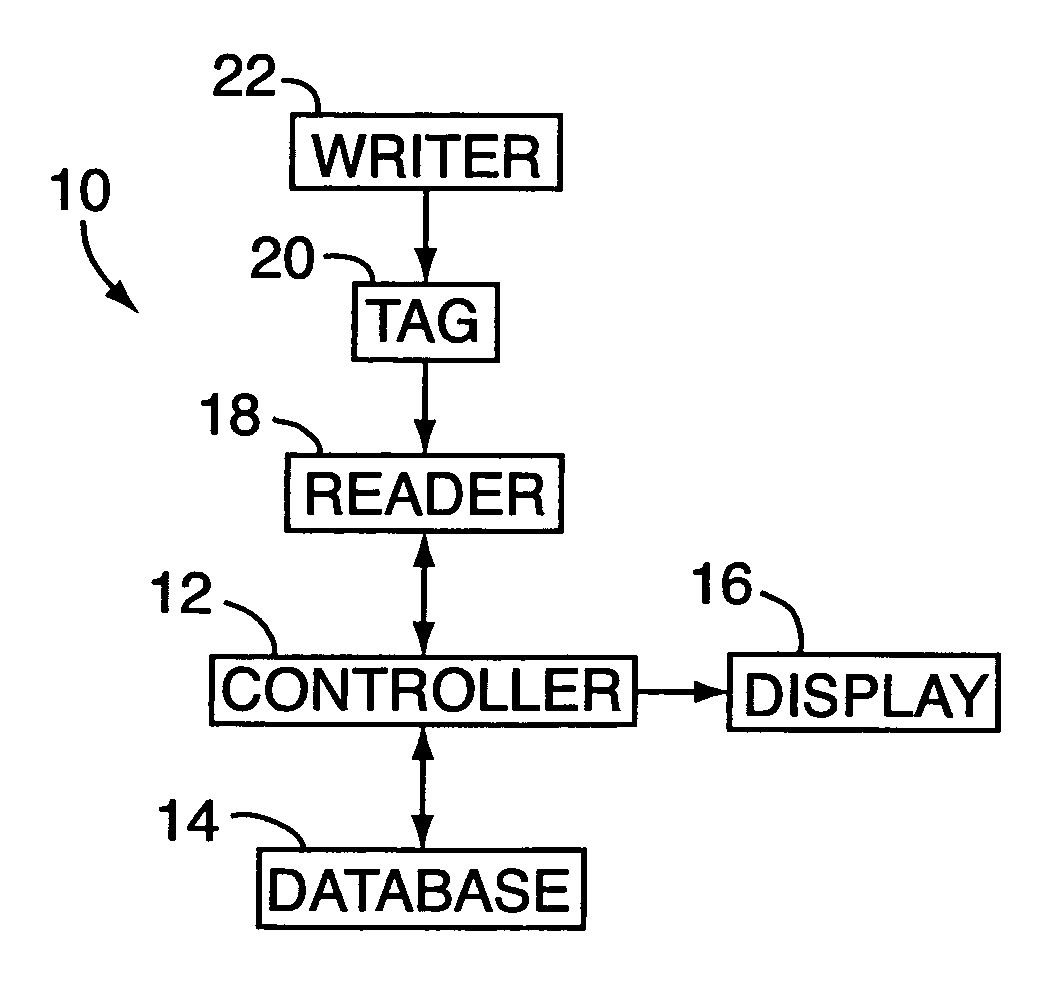
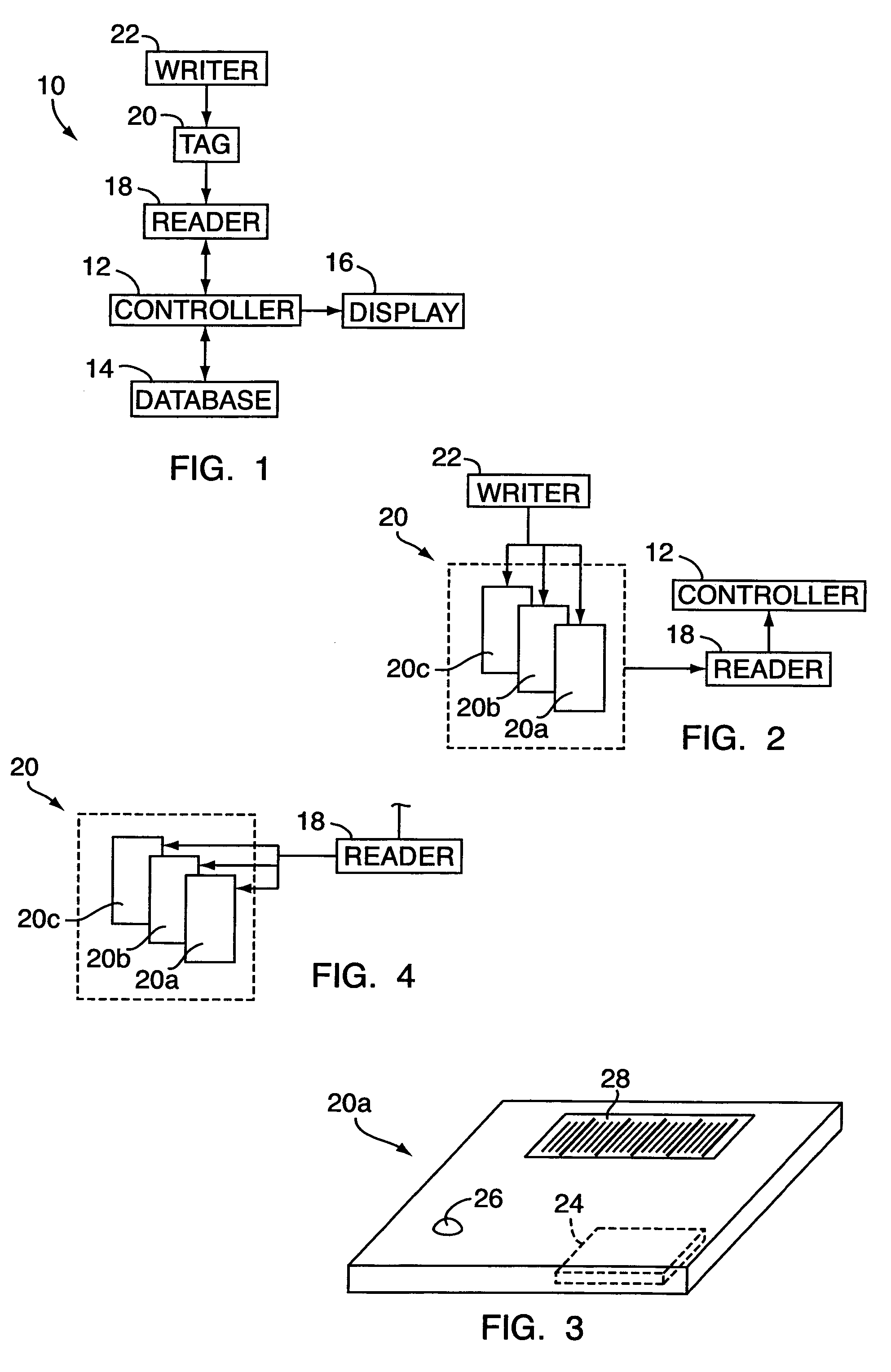
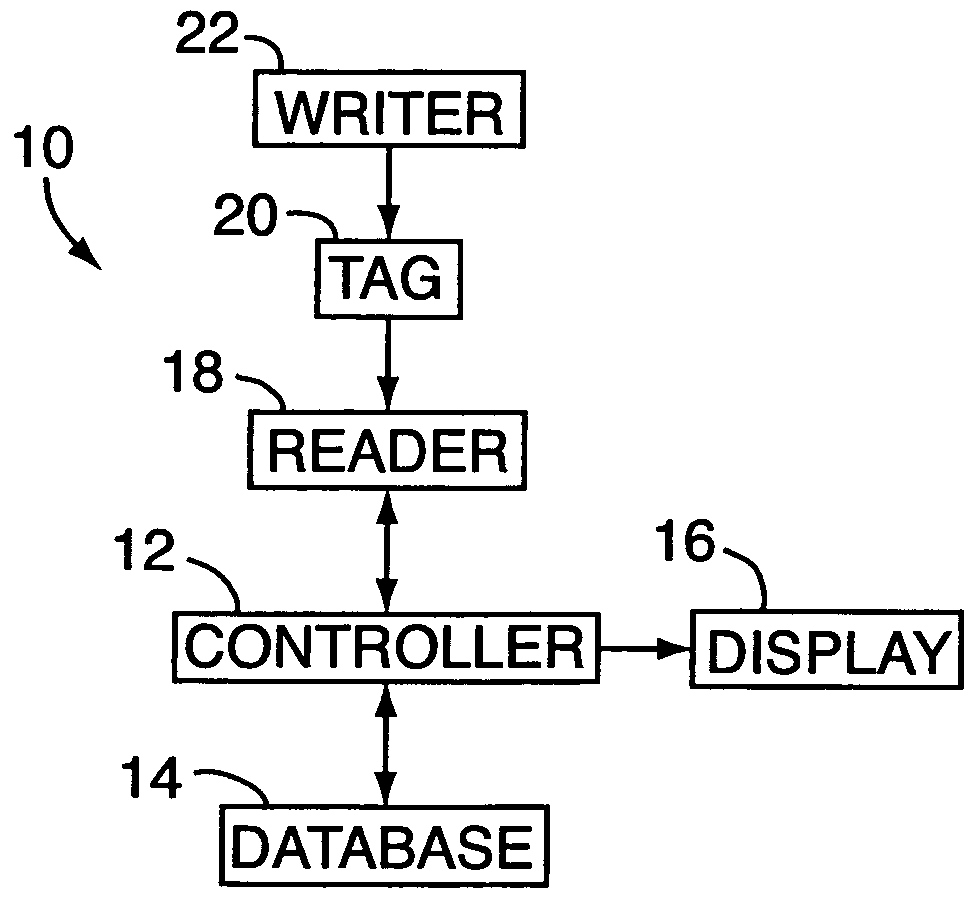
A tracking system for identifying contents of a container includes an electromagnetic identification apparatus that provides an electromagnetic signal indicative of a container content data set; a writer for use in encoding the container signal onto the apparatus; a controller for receiving the encoded signal and for storing the signal in a master database storage apparatus; and a reader configured outside the container for communicating with the electromagnetic identification apparatus and for receiving the encoded signal therefrom and corresponding to the container content data signal set. A system for tracking items in an assembly includes an apparatus for receiving electromagnetic identification tag signals; an apparatus for creating a first tier aggregate signature; an apparatus for storing the signature in a master database; and an apparatus for receiving modifying command signals for creating a second tier aggregate signature corresponding to a modified set of electromagnetic identification tags in an augmented assembly.
Owner:UNITED SECURITY APPL ID
Electronic security system for monitoring and recording activity and data relating to cargo
ActiveUS20050099292A1Co-operative working arrangementsIndividual entry/exit registersData setData signal
A tracking system for identifying contents of a container includes an electromagnetic identification apparatus that provides an electromagnetic signal indicative of a container content data set; a writer for use in encoding the container signal onto the apparatus; a controller for receiving the encoded signal and for storing the signal in a master database storage apparatus; and a reader configured outside the container for communicating with the electromagnetic identification apparatus and for receiving the encoded signal therefrom and corresponding to the container content data signal set. A system for tracking items in an assembly includes an apparatus for receiving electromagnetic identification tag signals; an apparatus for creating a first tier aggregate signature; an apparatus for storing the signature in a master database; and an apparatus for receiving modifying command signals for creating a second tier aggregate signature corresponding to a modified set of electromagnetic identification tags in an augmented assembly.
Owner:UNITED SECURITY APPL ID
Aggregate signature schemes
ActiveUS20080069347A1Electric signal transmission systemsMultiple keys/algorithms usageAggregate signatureManagement system
An authenticated RFID system is provided that uses elliptic curve cryptography (ECC) to reduce the signature size and read / write times when compared to traditional public key implementations such as RSA. Either ECDSA or ECPVS can be used to reduce the signature size and ECPVS can be used to hide a portion of the RFID tag that contains sensitive product identifying information. As a result, smaller tags can be used or multiple signatures can be written at different stages in a manufacturing or supply chain. A key management system is used to distribute the verification keys and aggregate signature schemes are also provided for adding multiple signatures to the RFID tags, for example in a supply chain.
Owner:MALIKIE INNOVATIONS LTD
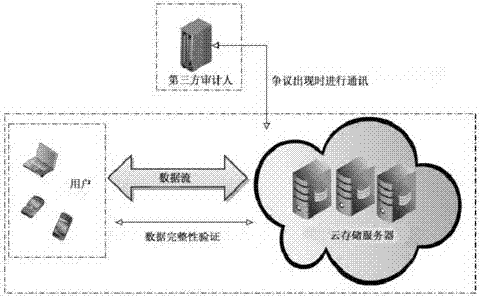
Remote data completeness verification method facing cloud storage
ActiveCN103699851AFlexible control over transparencyRealize protection controlDigital data protectionTransmissionThird partyData integrity
The invention provides a remote data completeness verification method facing cloud storage. According to the method, the aggregate signature and specified certifier signature technology is utilized, the verification function on the user data completeness by users and the third party auditors is realized, and meanwhile, the information of users for data completeness is enabled not to be leaked; the verification information transparency control is realized through the zero knowledge proving technology, and when the dispute exists between the users and a server, the third party auditors can generate the undeniable high-confidence-degree proving through the non-interactive zero knowledge proving technology. According to the method, under the condition that a cloud storage service provider is incredible, the accuracy of the cloud data completeness verification can also be ensured, and the method provided by the invention has the advantages that the realization is easy, the cost is low, the data protection performance is high, the third party audit is supported, the privacy protection mechanism is flexible, and the like.
Owner:HANGZHOU YUANTIAO TECH CO LTD
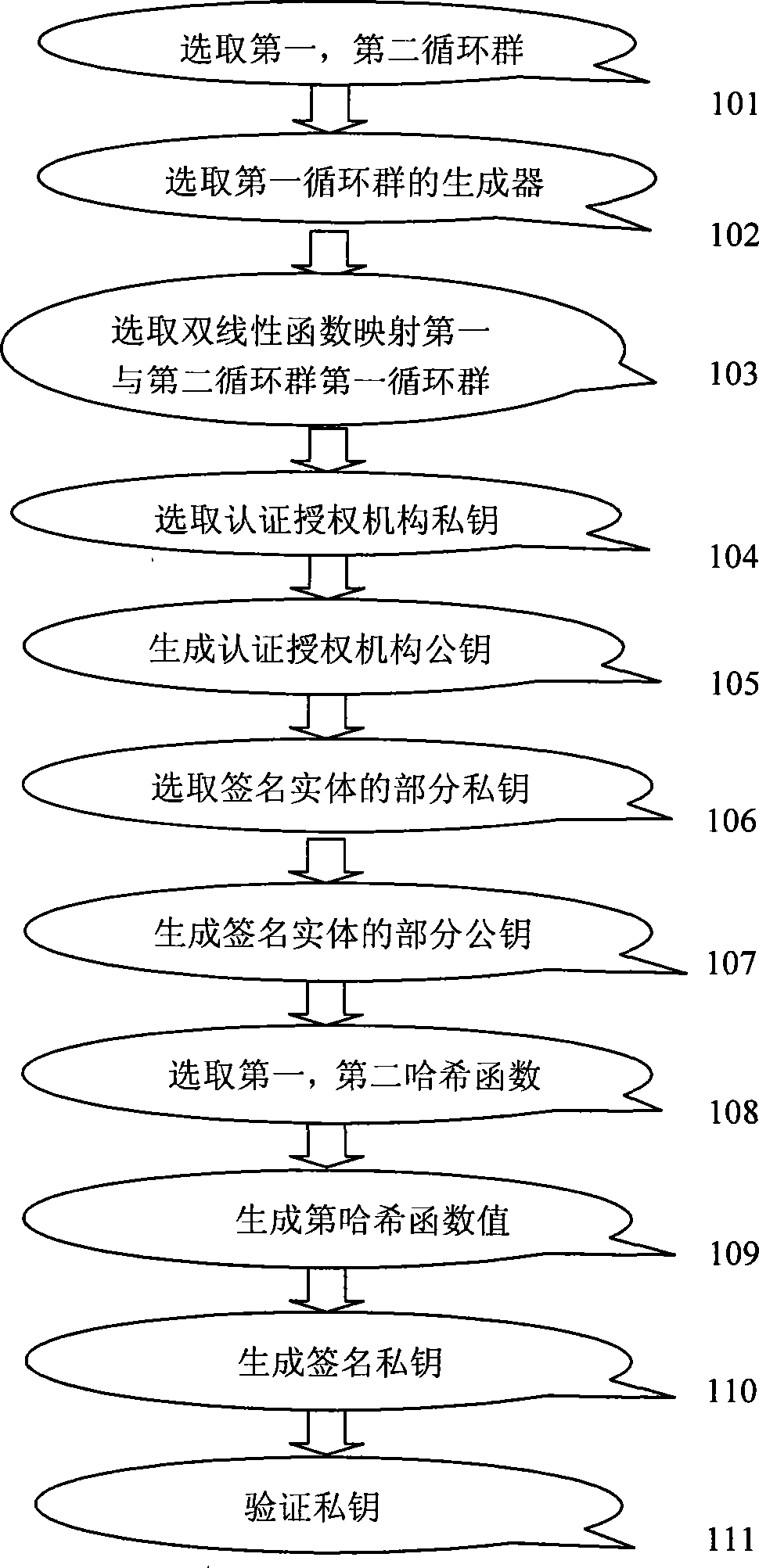
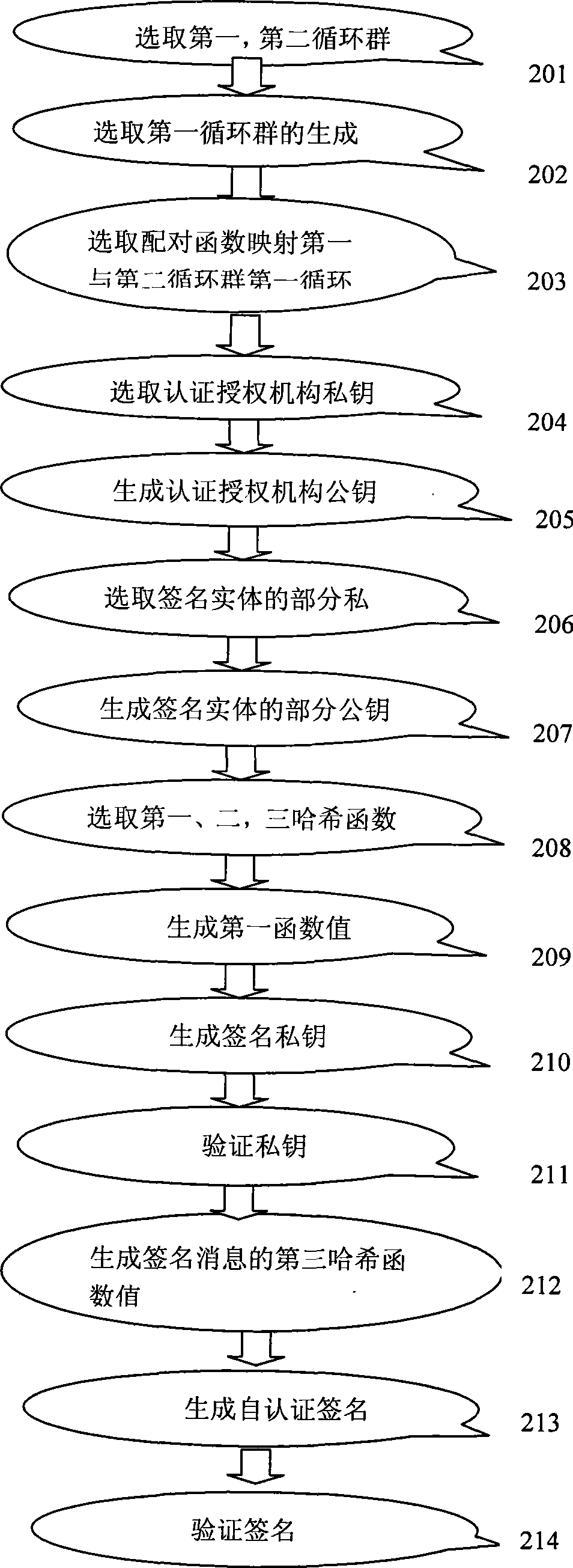
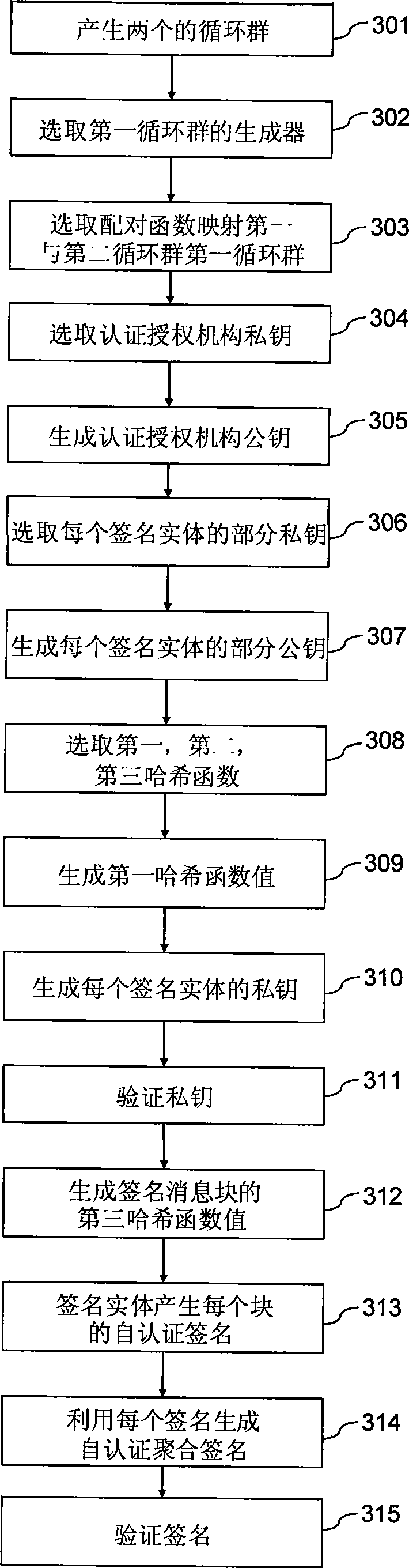
Elliptical curve-based method and elliptical curve-based device for self-authenticating signature
InactiveCN101547099AKey distribution for secure communicationUser identity/authority verificationAggregate signatureAuthentication
The invention discloses an elliptical curve-based method for self-authenticating signature, an extended signature method thereof, and a signature verification process. An authentication authorized organization generates part of signature private keys of a signature entity; and the signature entity uses part of self-selected private keys as well as received private keys from the authentication authorized organization to generate a signature private key. With an elliptical curve, the calculation efficiency is improved. And the invention provides an elliptical curve-based method for one-to-one self-authenticating signature, a method for self-authenticating aggregate signature and a method for generating a self-authenticating signature off line. The security of the methods is based on an SDH+CDH assumption put forward. The plurality of methods provided can meet the security requirement of signature protocols, improve signature efficiency to some extent and meet requirements of some special conditions.
Owner:张键红
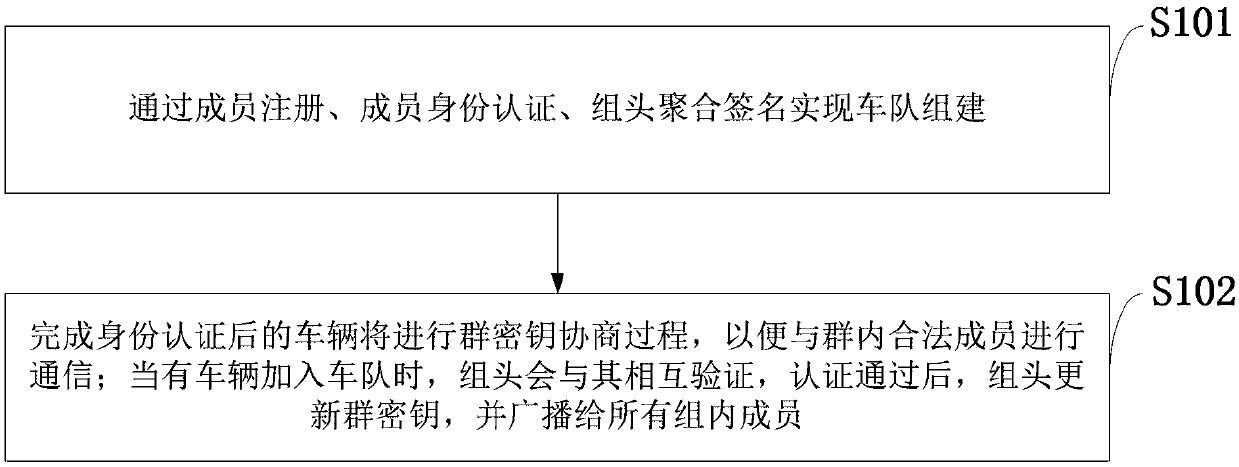
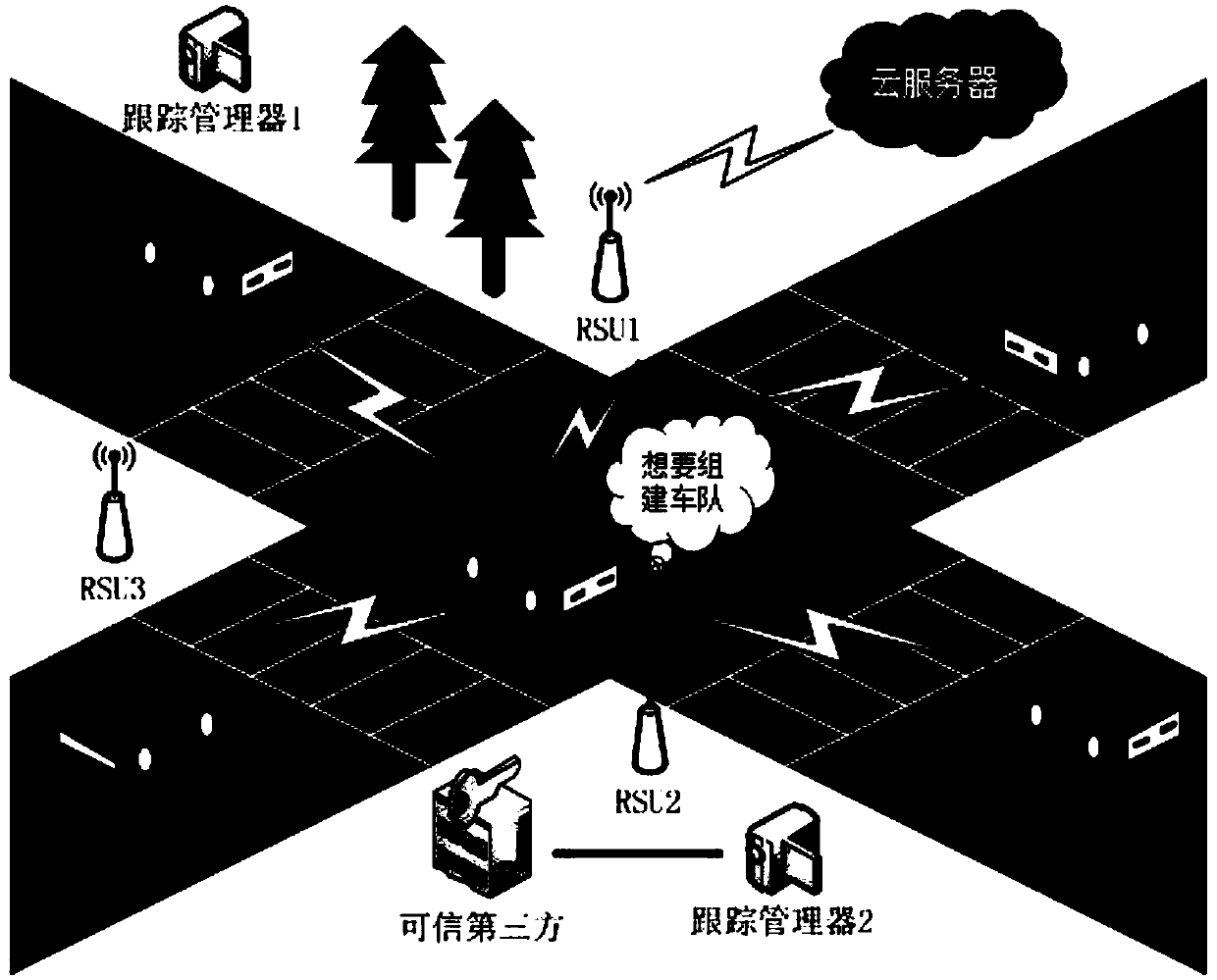
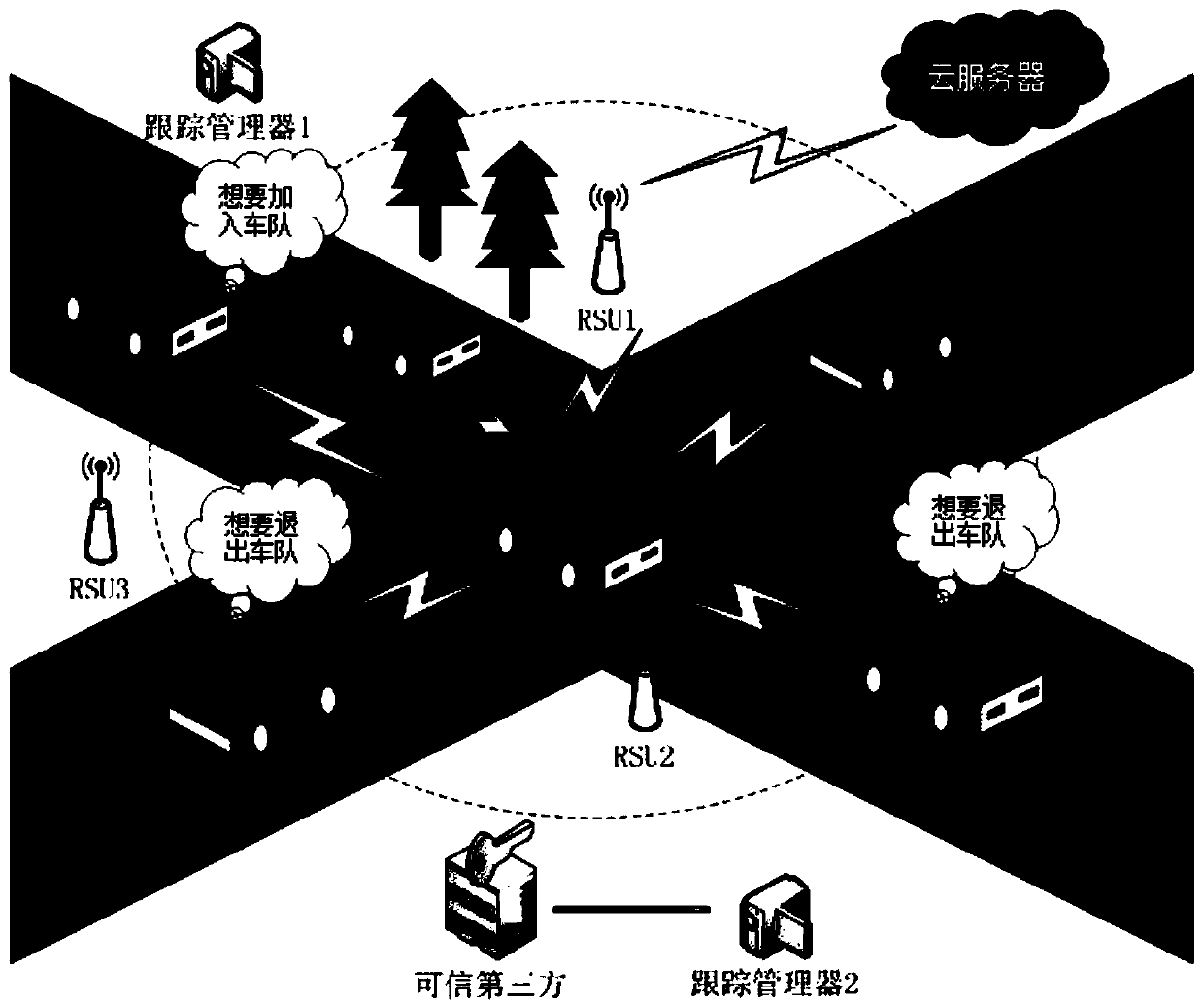
Motorcade establishment and management method and system based on block chain and PKI authentication mechanism
ActiveCN109687976ASolve authentication problemsTroubleshoot account management issuesKey distribution for secure communicationParticular environment based servicesSecure communicationThe Internet
The invention belongs to the technical field of safety communication between motorcades in Internet of Vehicles, and discloses a motorcade establishment and management method and system based on a block chain and a PKI authentication mechanism. The method is mainly divided into two parts of motorcade establishment and group key agreement and update; the motorcade establishment part comprises the following main processes of member registration, member identity authentication and group head aggregate signature; and the group key agreement and update part comprises the following main processes ofgroup key agreement and group key update for dynamic joining and exiting of a vehicle. According to the method and the system, the block chain is combined with the PKI authentication mechanism, a problem of identity authentication of the vehicle, a server and an RSU in the Internet of Vehicles is solved; the motorcade establishment is completed based on an elliptic curve, a bilinear pairing technology and an aggregate signature; and the group key agreement and update can be realized based on a DDH difficulty problem, the forward and backward safety is achieved, and the safety of member communication in the motorcade is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
Digital signatures including identity-based aggregate signatures
ActiveUS20050262353A1Good security proofUser identity/authority verificationSecret communicationDigital signatureKey generator
Methods and systems are provided that allow multiple identity-based digital signatures to be merged into a single identity-based “aggregate” digital signature. This identity-based aggregate signature has a shorter bit-length than the concatenation of the original unaggregated identity-based signatures. The identity-based aggregate signature can be verified by anyone who obtains the public keys of one or more Private Key Generators (PKGs), along with a description of which signer signed which message. The verifier does not need to obtain a different public key for each signer, since the signature scheme is “identity-based”; the number of PKGs may be fewer than the number of signers. Consequently, the total information needed to verify the identity-based aggregate signature—namely, a description of who signed what, the PKGs' public keys, and the identity-based aggregate signature itself—may be less than the information needed to verify separate digital signatures—namely, a description of who signed what, the public verification keys for all of the signers, and the concatenation of the signers' signatures. In some embodiments, the identity-based aggregate signature scheme has essentially the minimum-possible Kolmogorov complexity.
Owner:NTT DOCOMO INC
Method and device for generating signature, terminal and server
ActiveCN107968708AReduce the burden onReduce complexityKey distribution for secure communicationUser identity/authority verificationMultisignatureAggregate signature
The invention discloses a method and a device for generating a signature, a terminal and a server, and belongs to the technical field of information. According to the method, an aggregated signature is generated via sub-signatures of a plurality of signature parties, and an aggregated public key is generated based on public keys of the plurality of signature parties, so that the length of the acquired aggregated signature is less than that of a multi-signature acquired by splicing the plurality of sub-signatures, the length of the aggregated public key is less than that of a multi-public key acquired by splicing the plurality of public keys, and thus when the aggregated signature and the aggregated public key are transmitted via a network, the network transmission load is reduced, the storage space is saved when in storage, when the signature is verified, the aggregated public key and the aggregated signature are directly used for verifying a message to be signed, and the complexity ofsignature verification is greatly reduced.
Owner:TENPAY PAID TECH
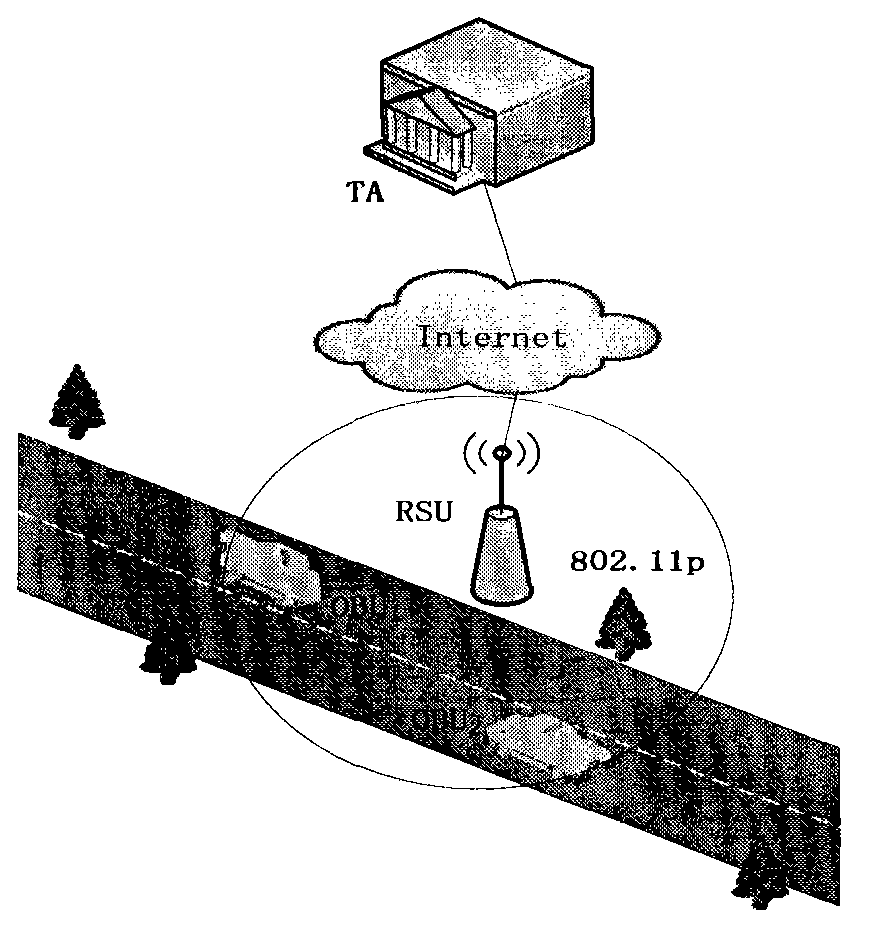
System and method for transmitting VANET (vehicle ad hoc network) safety information aggregate based on RSU (Remote Subscriber Unit)
InactiveCN103051726AProtect real identityAvoid monitoringTransmissionInformation transmissionAggregate signature
The invention discloses a method for transmitting a VANET (vehicle ad hoc network) safety information aggregate based on RSU (Remote Subscriber Unit). The RSU serves as a communication group leader, messages of legal vehicles in a governed region are subjected to information aggregating processing by an aggregate signature algorithm and are further transmitted to a monitoring center, the monitoring center verifies the correctness of signature information at one time through an inverse aggregate signature algorithm, and meanwhile when a false message is found, the real sender of the message can be accurately positioned by starting a tracing process under the assistance of an authentication center. The method has the advantages that double requirements on safety and efficiency of vehicle ad hoc network information transmission are effectively met, and limited transmission wideband is effectively saved on the premise of not affecting the safety by performing aggregating processing on vehicle safety information in the road side unit governed region in a vehicle ad hoc network.
Owner:杨涛
SYSTEM AND METHOD FOR PROVIDING SECURE COLLABORATIVE SOFTWARE AS A SERVICE (SaaS) ATTESTATION SERVICE FOR AUTHENTICATION IN CLOUD COMPUTING
ActiveUS20180034641A1Reduce computationReduce communication costsKey distribution for secure communicationMultiple keys/algorithms usageUser verificationThird party
An architecture and a method are disclosed for providing secure, scalable, and dynamic user configuration in the distributed network for the cloud computing to provide authentication and authorization for the plurality of the users to use the SaaS service. The system includes a hierarchical tree structure that configures the cloud-computing model by using the certificate less identity-based cryptography to establish the hierarchical relationship between the participating entities. The hierarchical model provides a hierarchical certificateless aggregate signature (HCL-AS) for authentication and non-repudiation for SaaS in cloud computing. The HCL-AS generates a collaborative aggregate signature at a parent level of each child node (users) without the loss of identity of the users in the resulting signature and sends an aggregated signature to the third-party software provider. The HCL-AS significantly reduces the computation and communication cost during the user verification and authentication.
Owner:INST FOR DEV & RES IN BANKING TECH IDRBT
System and method for generating keyless digital multi-signatures
ActiveUS20120324229A1Reduce riskRisk of timeUser identity/authority verificationPublic key infrastructure trust modelsHash functionTheoretical computer science
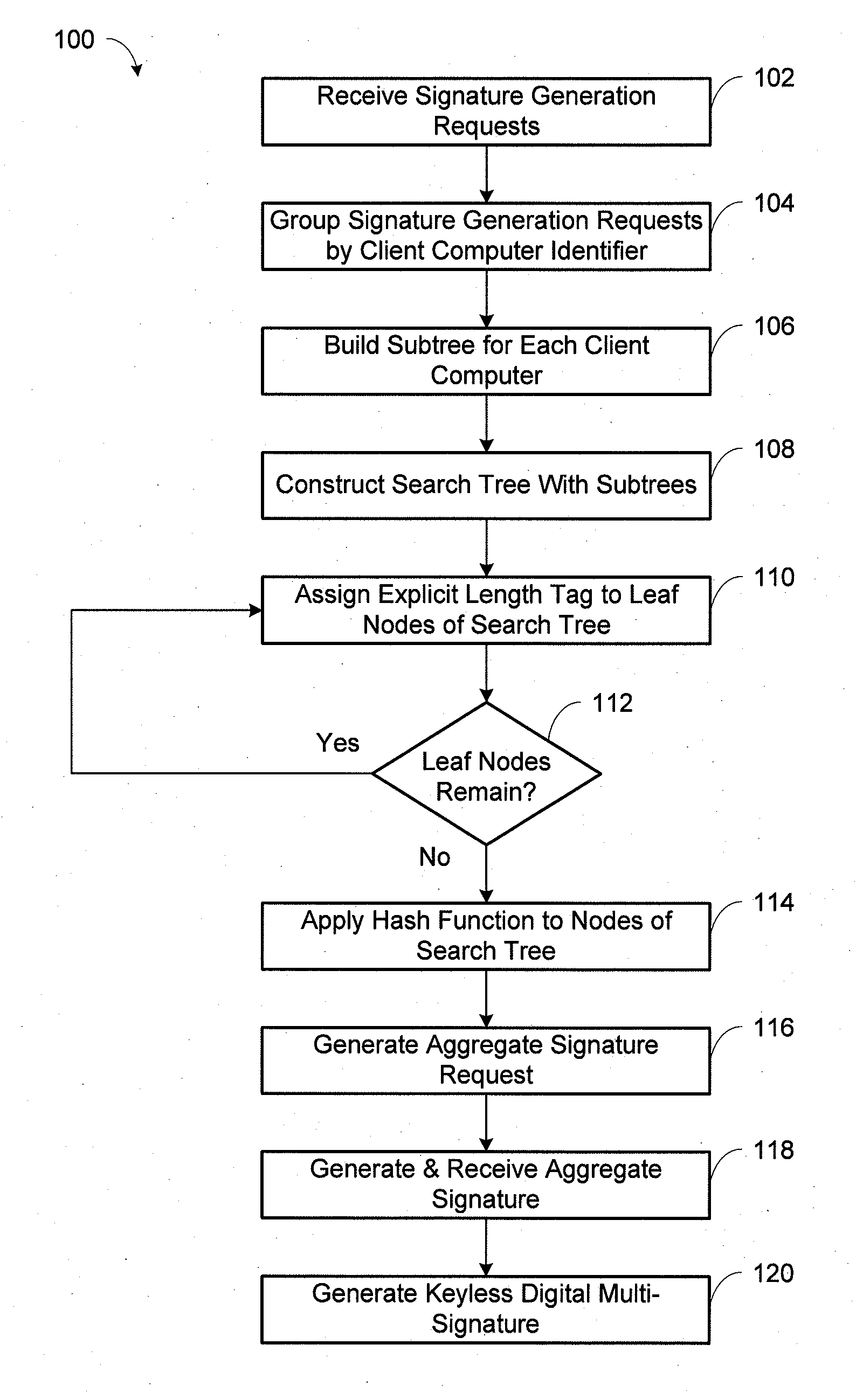
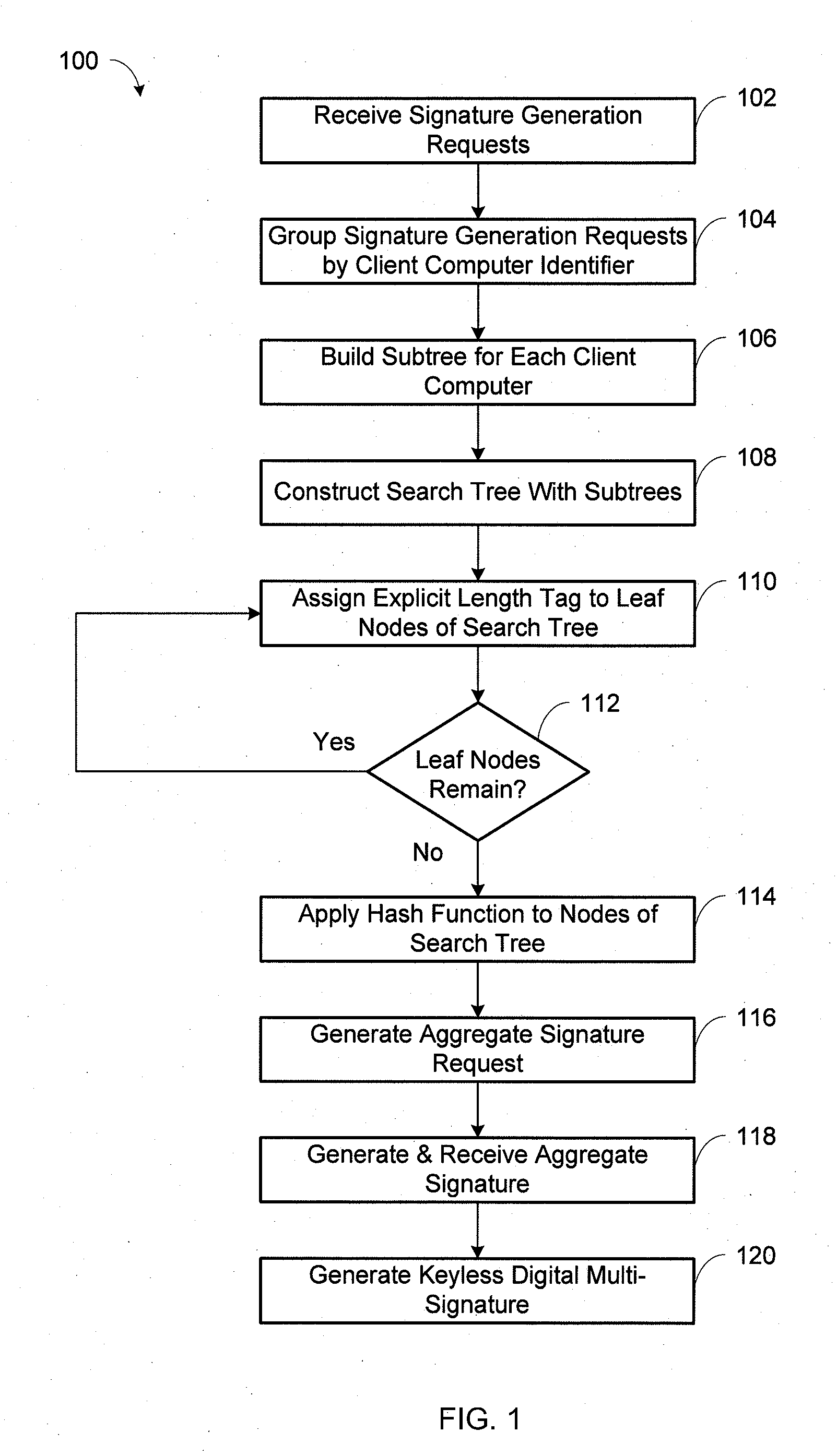
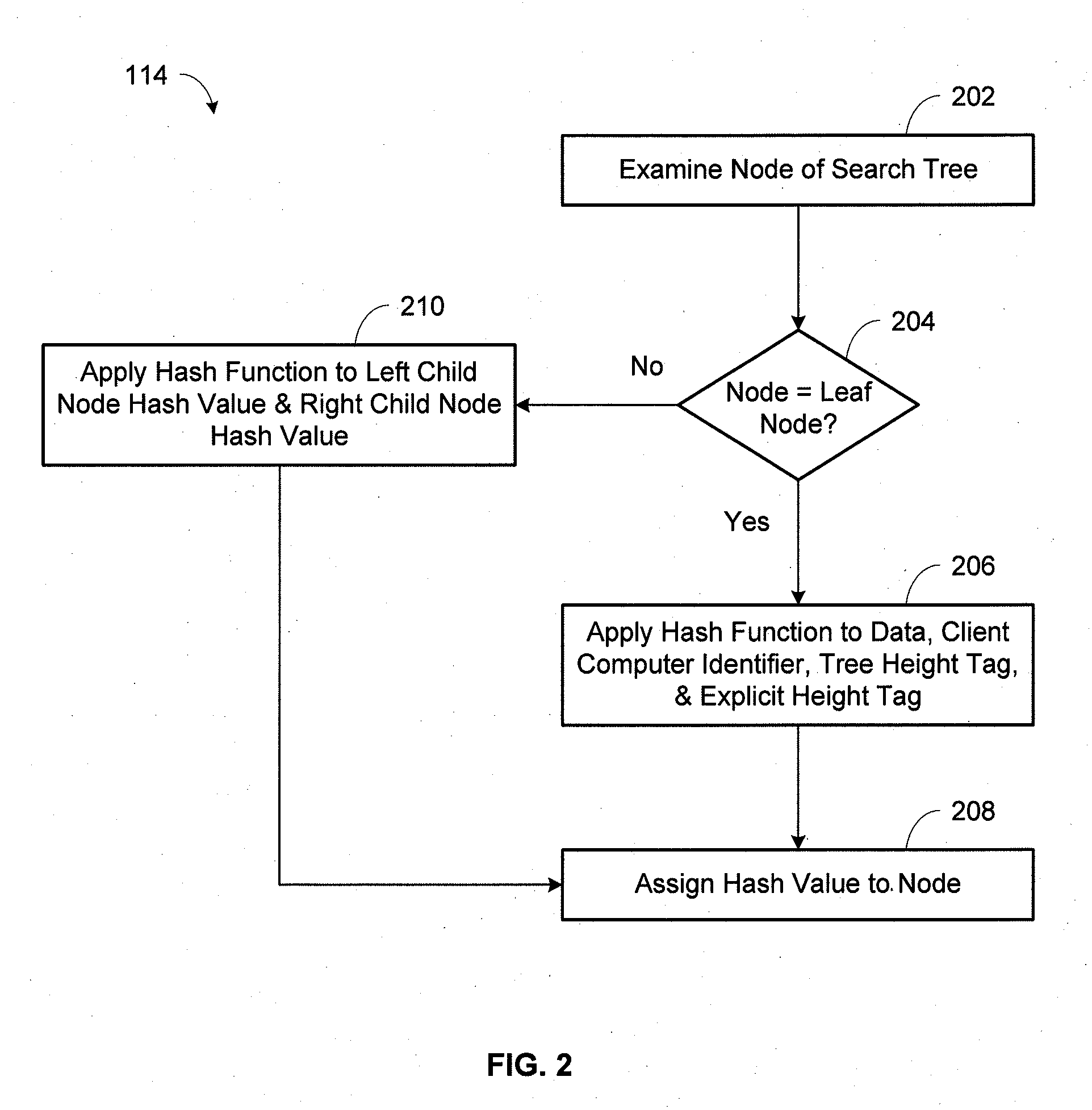
A method of generating a keyless digital multi-signature is provided. The method includes receiving multiple signature generation requests from one or more client computers, building subtrees based on the signature generation requests, and constructing a search tree including the subtrees. The method also includes assigning explicit length tags to leaf nodes of the search tree to balance the search tree and applying a hash function to each of the search tree nodes. The root hash value and the height of the search tree make up a generated aggregate signature request, followed by receiving an aggregate signature based on the aggregate signature request. The keyless digital multi-signature is generated based on the aggregate signature and contains an implicit length tag to verify that the number of signature generation requests is limited. The aggregate signature is generated if the height of the search tree does not exceed a predetermined height limitation.
Owner:GUARDTIME SA
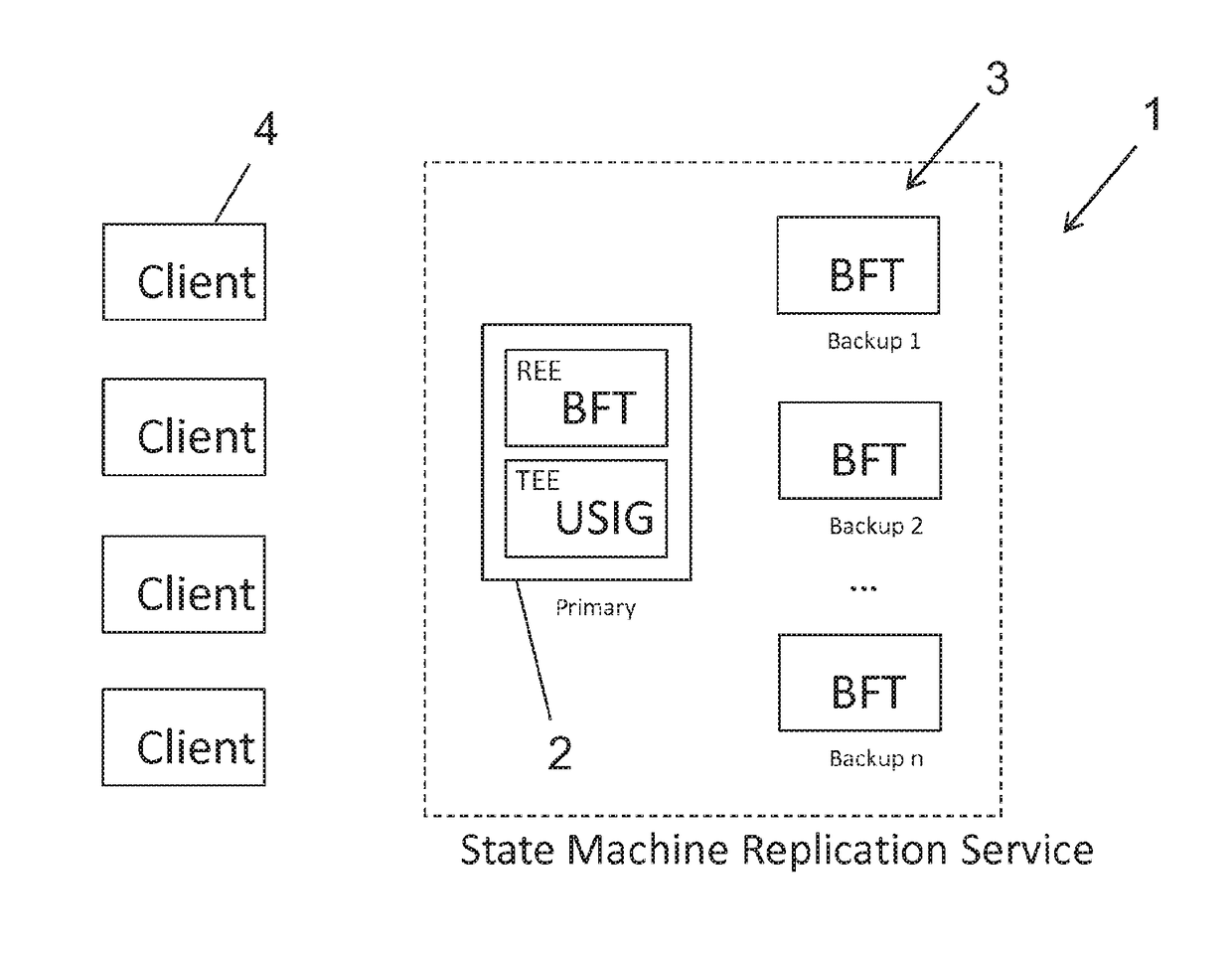
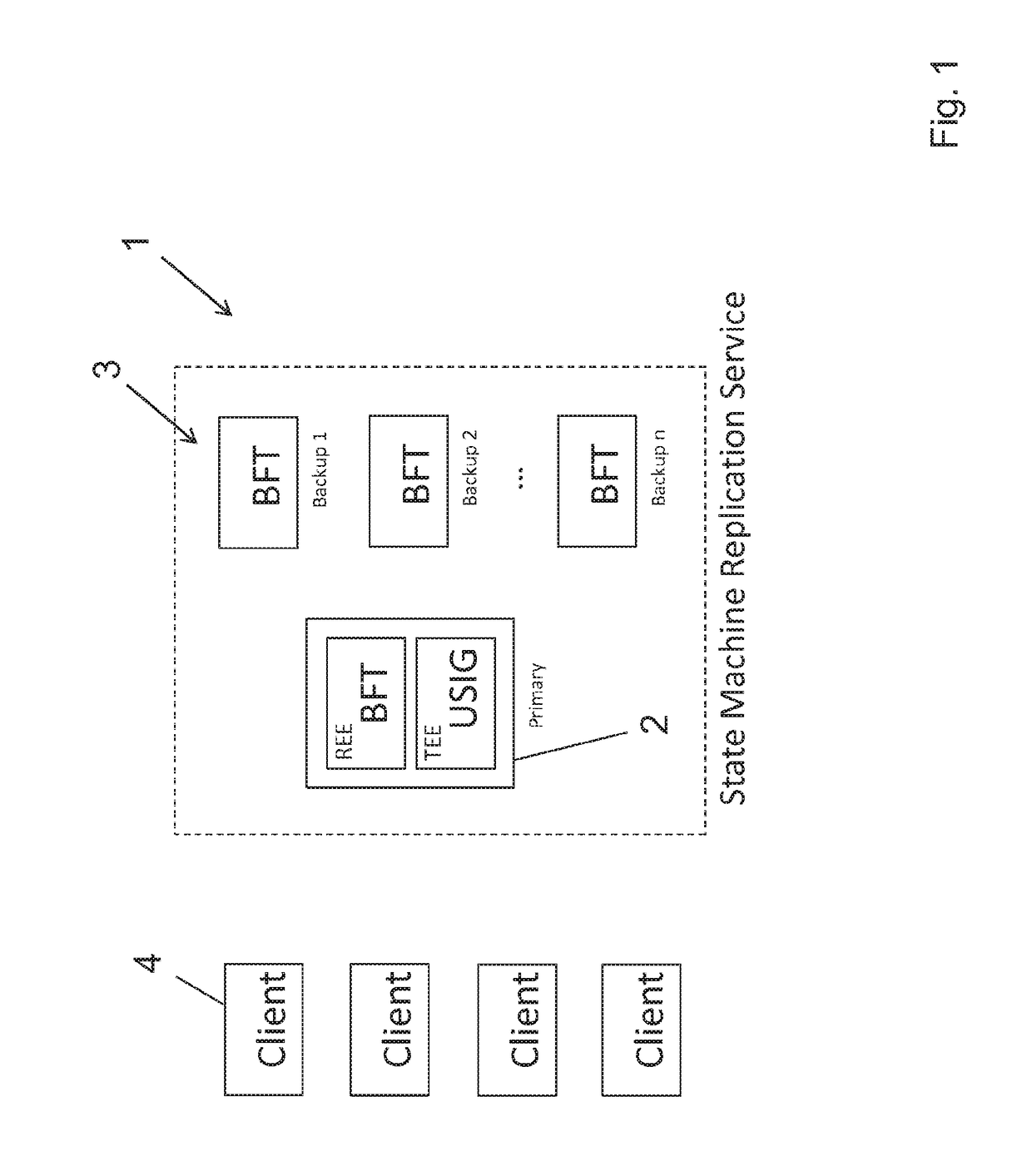
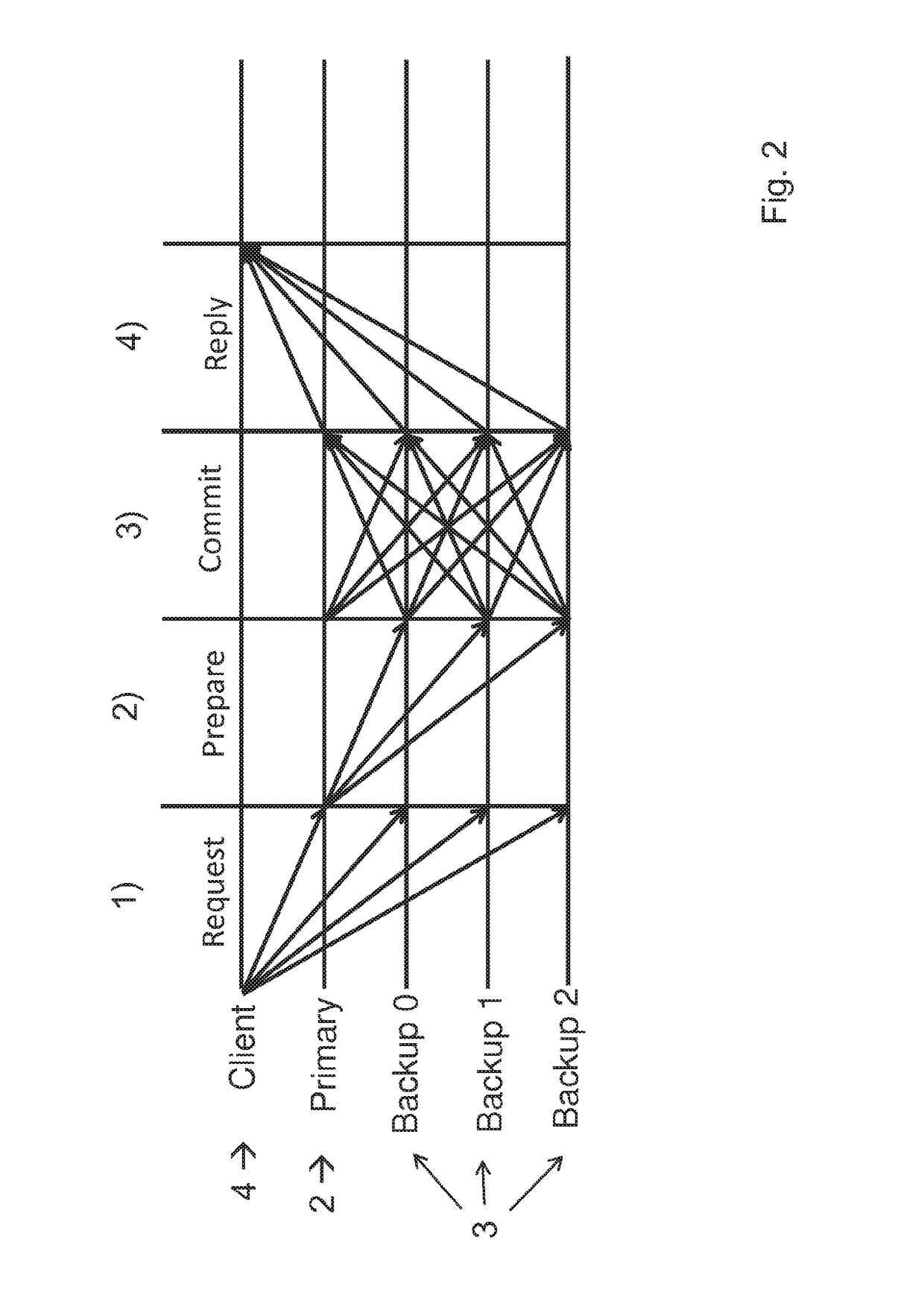
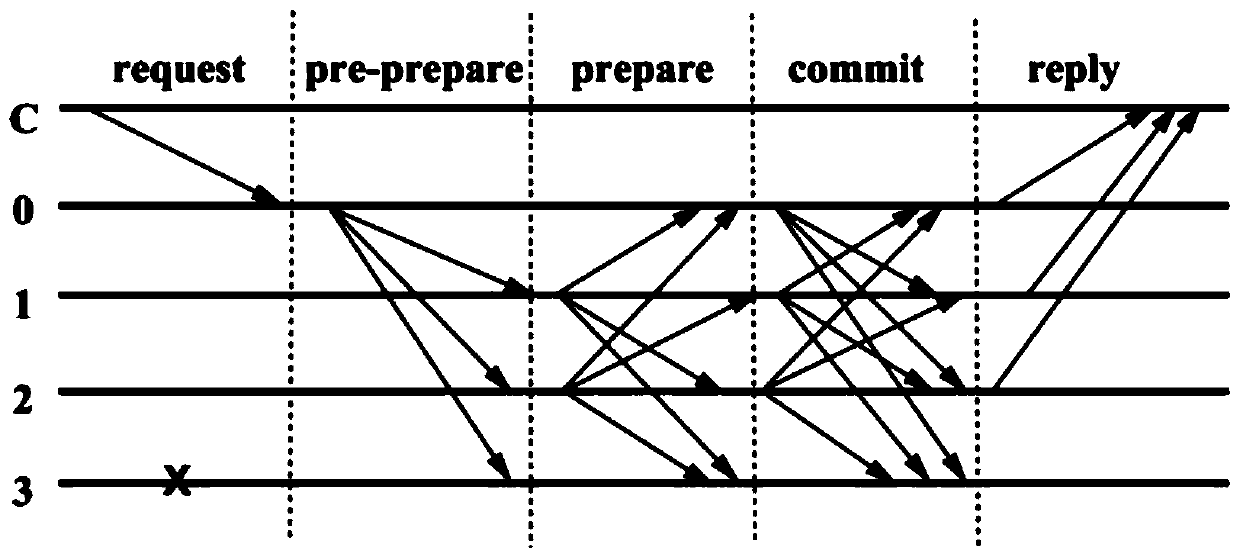
Method and system for byzantine fault-tolerance replicating of data on a plurality of servers
ActiveUS20180329783A1User identity/authority verificationError identificationByzantine fault toleranceUnique identifier
A method for byzantine fault-tolerant replication of data on a plurality of n servers includes performing, by a primary node (PN), a prepare procedure that includes computing a prepare message including a unique identifier and multicasting the prepare message to the REPN. The method further includes performing, by the PN, a commit procedure that includes receiving, from each of a portion of the REPN, a prepare message reply signature part and aggregating each of the prepare message reply signature parts to generate a prepare message reply aggregated signature, checking the validity of the prepare message reply aggregated signature, and upon determining that the prepare message reply aggregated signature is valid, computing a commit message including the prepare message reply aggregated signature and multicasting the commit message to the REPN. The method further includes transmitting, to the client, the commit message reply aggregated signature.
Owner:NEC CORP
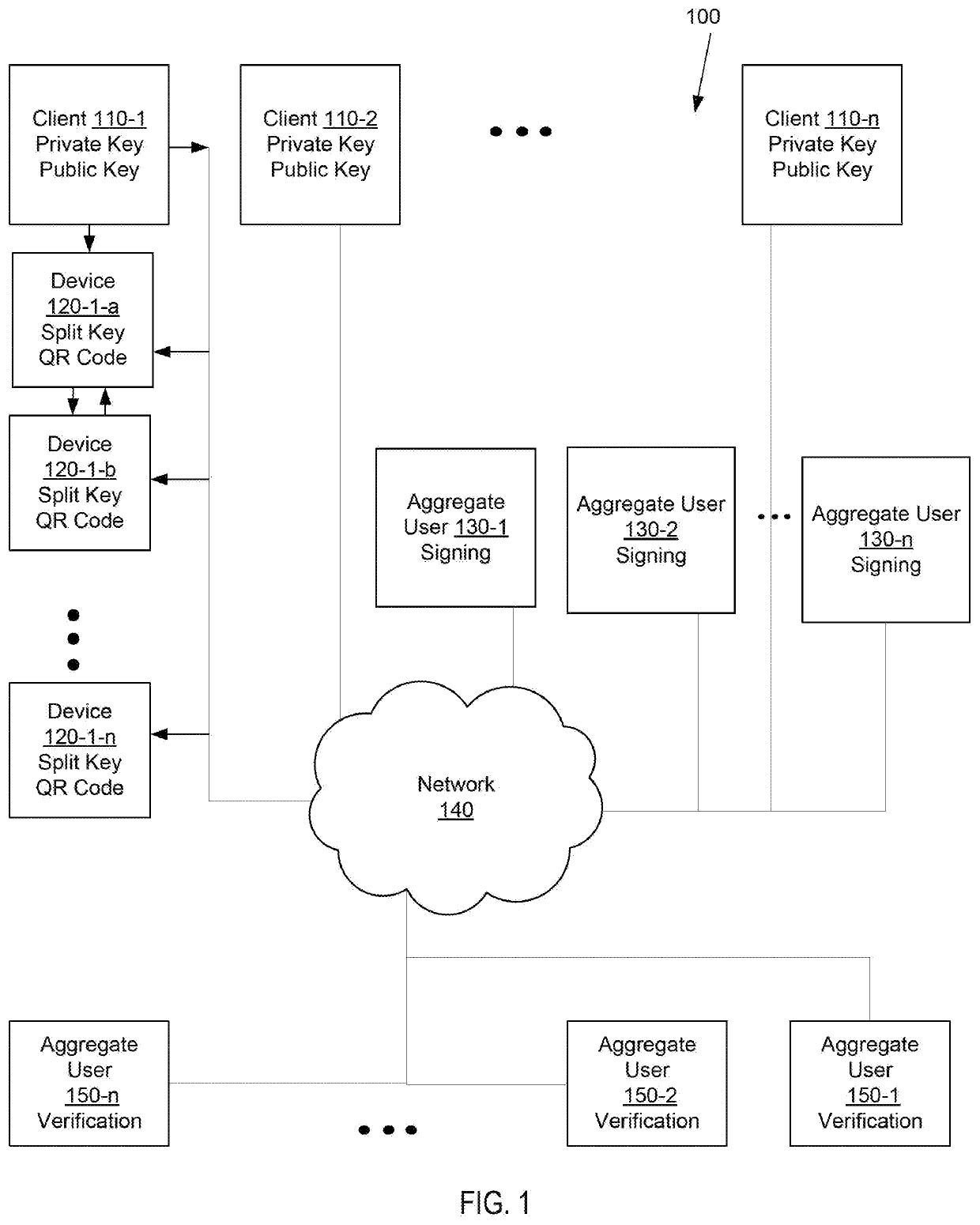
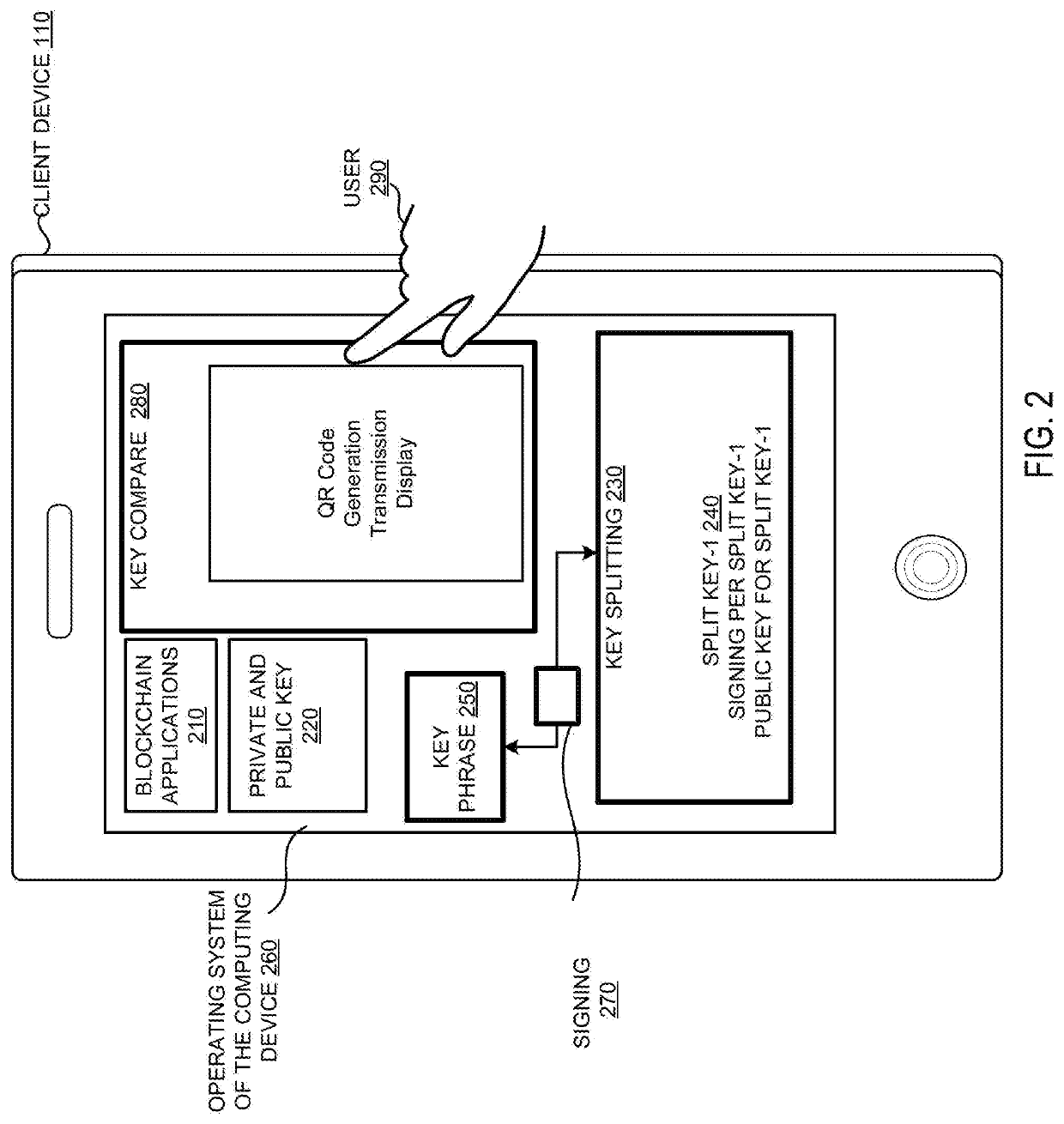
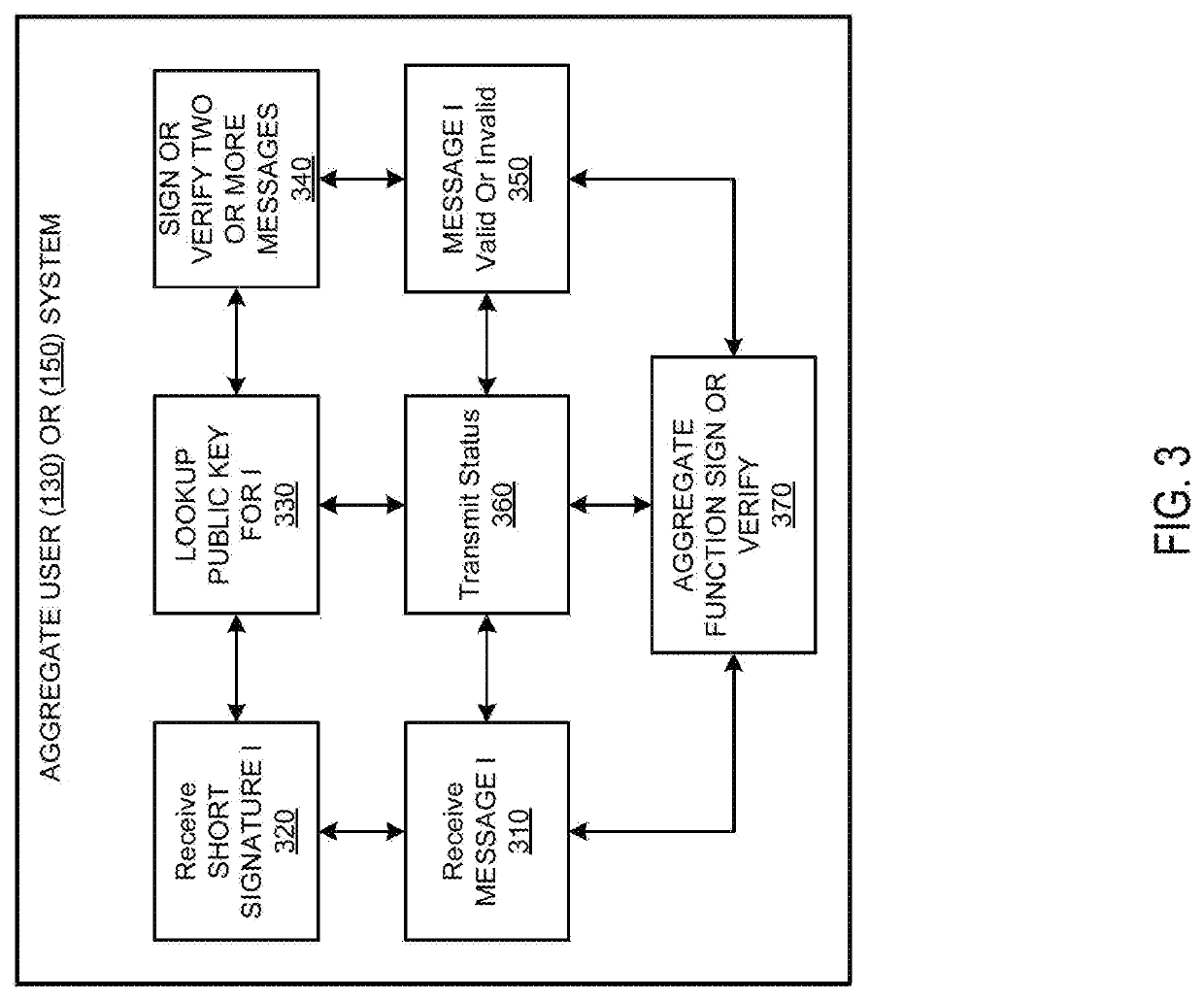
Systems and methods of aggregate signing of digital signatures on multiple messages simultaneously using key splitting
ActiveUS20200228349A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkInternet privacy
The systems and methods of aggregate signing of digital signatures on multiple messages simultaneously, comprising: receiving two or more digital messages wherein each message is signed using two or more digitally split keys from a private key and the two or more digital signatures of the message using the split key are combined to get a compressed short signature; receiving the compressed short signature for each message; receiving a public key associated with the private key for each message; aggregate signing the messages to output an aggregate signature. The aggregate signature can be further verified against any or all of the messages.
Owner:0CHAIN LLC
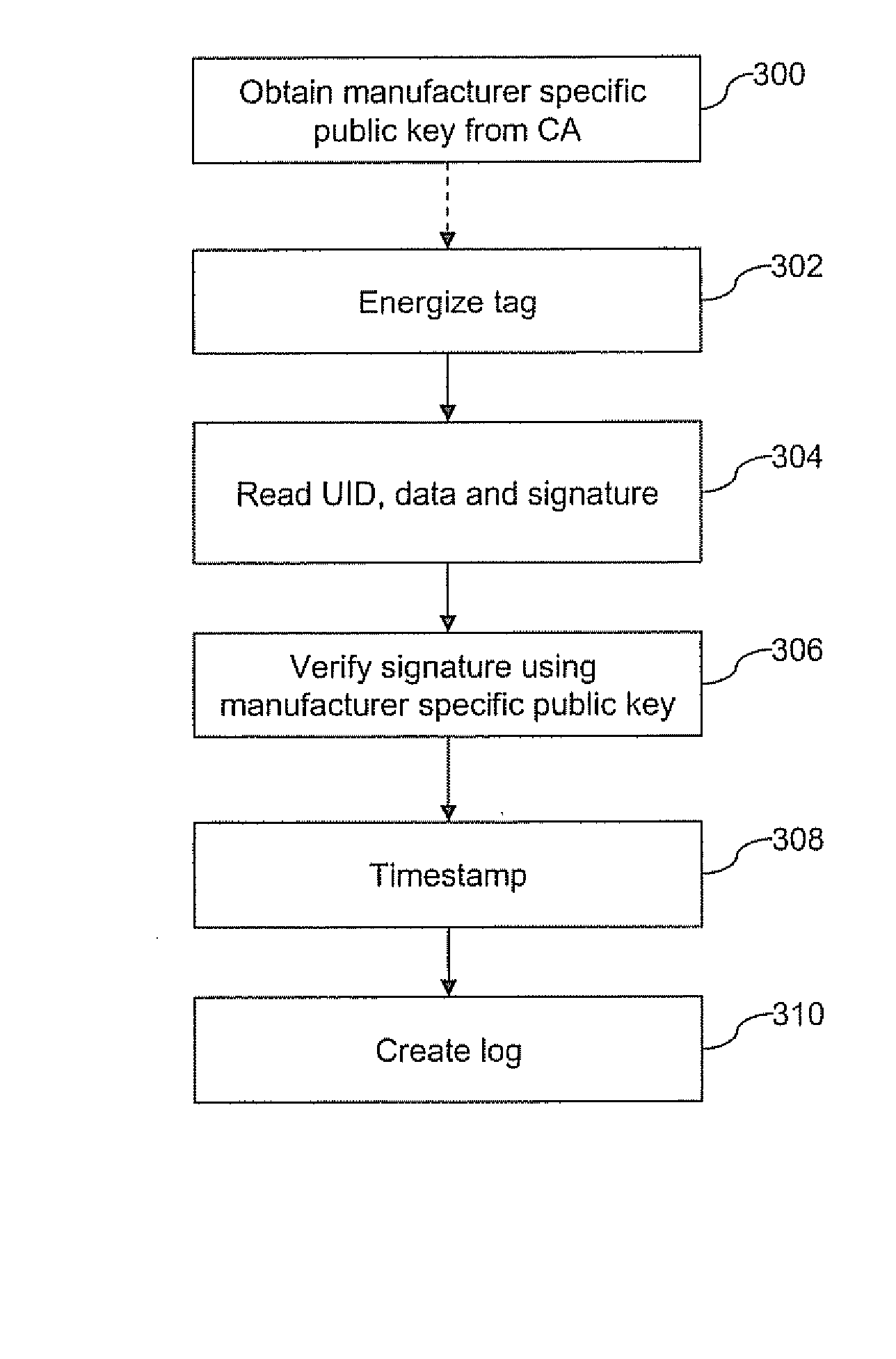
Authenticated radio frequency identification
ActiveUS20080150702A1Subscribers indirect connectionSecuring communicationAggregate signatureElliptic curve cryptography
An authenticated RFID system is provided that uses elliptic curve cryptography (ECC) to reduce the signature size and read / write times when compared to traditional public key implementations such as RSA. Either ECDSA or ECPVS can be used to reduce the signature size and ECPVS can be used to hide a portion of the RFID tag that contains sensitive product identifying information. As a result, smaller tags can be used or multiple signatures can be written at different stages in a manufacturing or supply chain. A key management system is used to distribute the verification keys and aggregate signature schemes are also provided for adding multiple signatures to the RFID tags, for example in a supply chain.
Owner:MALIKIE INNOVATIONS LTD
Encryption and signature schemes using message mappings to reduce the message size
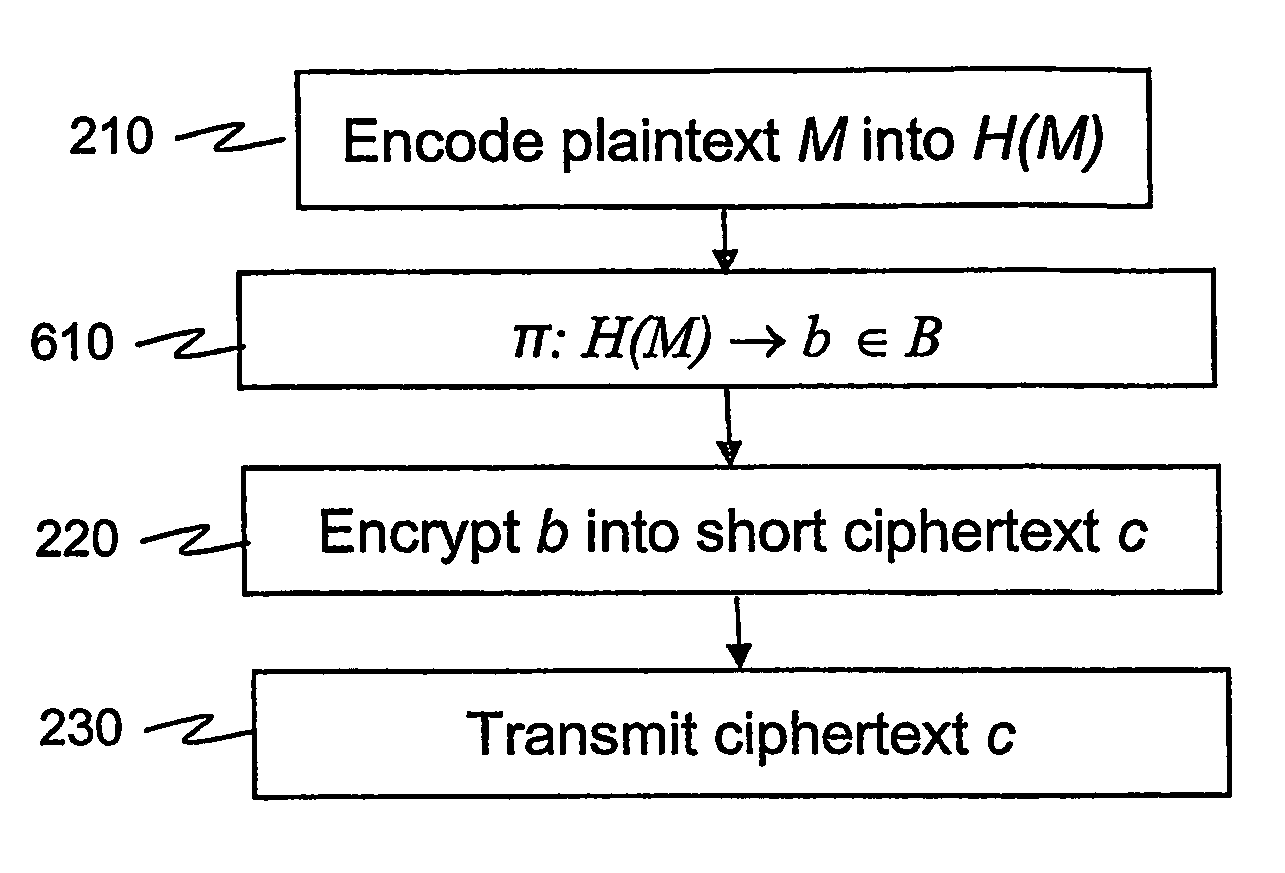
ActiveUS20060159259A1Computationally efficientBandwidth-reduced ring signaturePublic key for secure communicationUser identity/authority verificationComputer hardwareRing signature
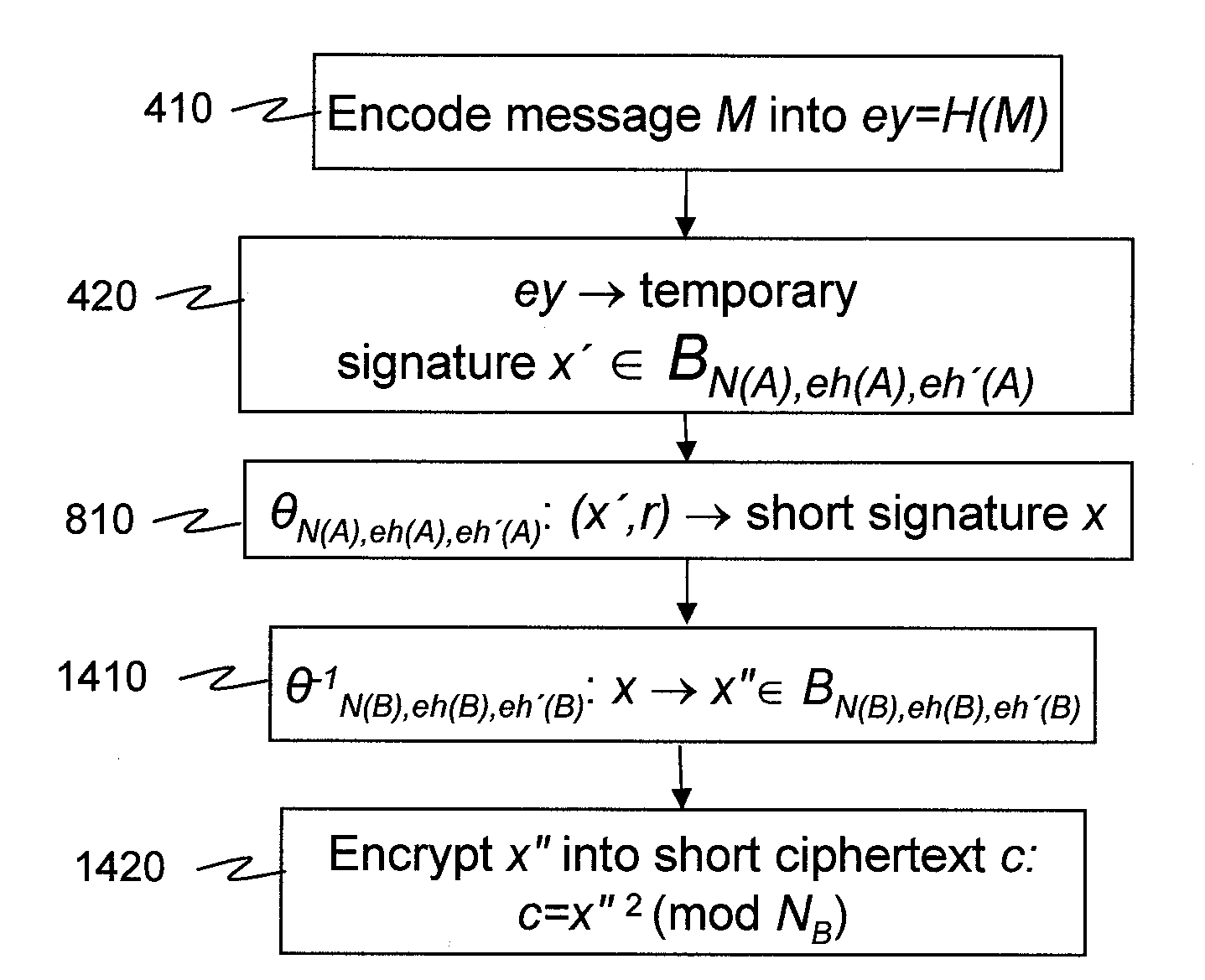
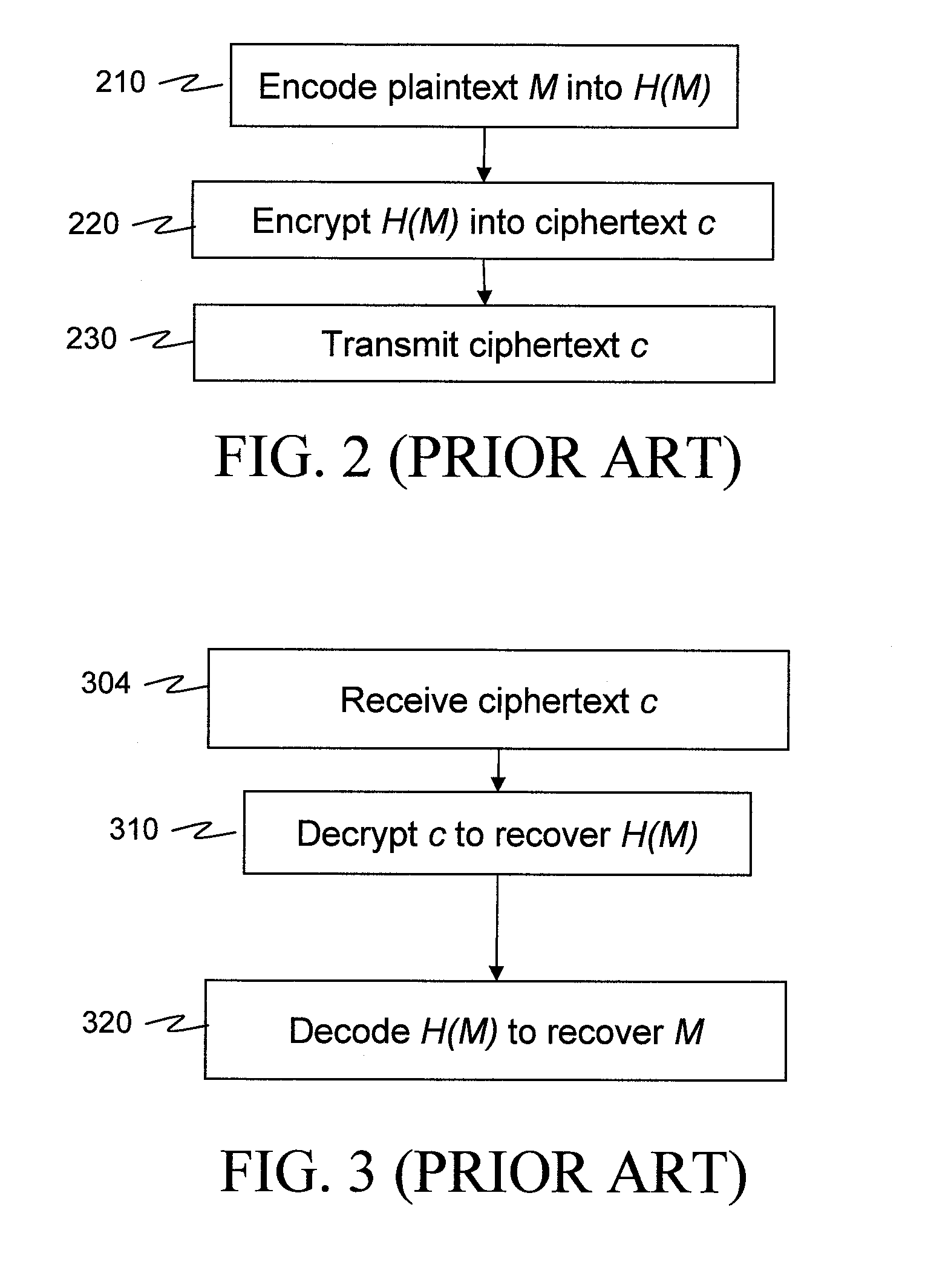
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h?] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
Consensus method of block chain data and related equipment
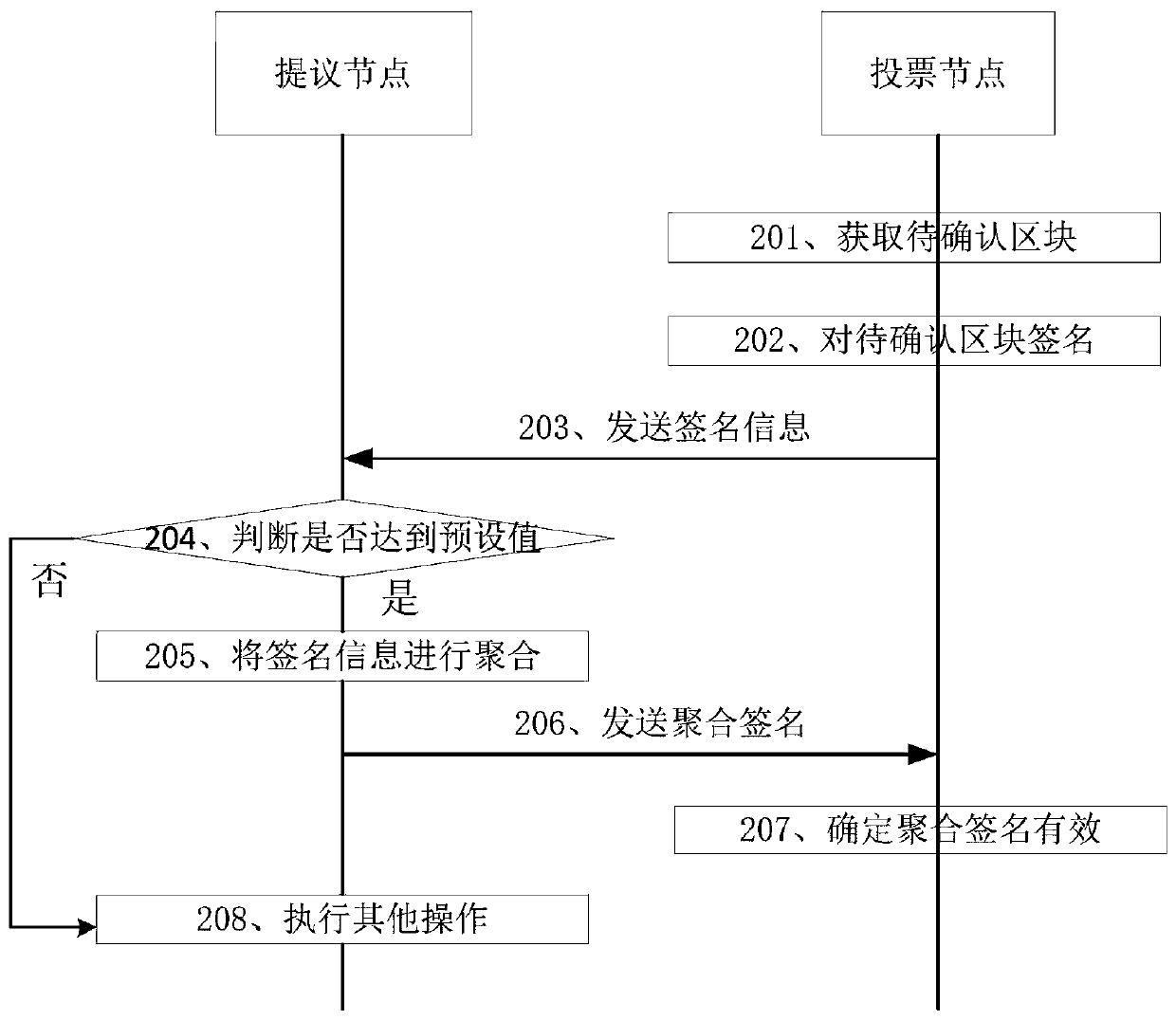
ActiveCN110300172AConsensus Process SimplifiedReduced risk of cloggingFinanceUser identity/authority verificationAggregate signatureBlockchain
The embodiment of the invention discloses a consensus method of block chain data, which comprises the following steps that: a proposal node receives signature information sent by a plurality of votingnodes respectively, and the signature information comprises signatures of blocks to be confirmed by the voting nodes by using a BLS signature algorithm; whether the number of the received signature information reaches a preset value or not is judged; if yes, the received plurality of pieces of signature information is utilized to aggregate and generate an aggregate signature by using a BLS signature algorithm; and the aggregation signature is sent to the voting node, so as to ensure that the to-be-confirmed block is valid when the voting node verifies the aggregation signature successfully. The embodiment of the invention further discloses a consensus system and device for the block chain data. Wherein an aggregation signature is generated by using a BLS signature algorithm in the consensus process of the block chain, signature votes from all the voting nodes can be aggregated, and the consensus process of the block chain is simplified, so that the risk of blockage in the network is reduced.
Owner:SHENZHEN THUNDER NETWORK TECH +1
A medical health monitoring network model information processing method and system based on signature aggregation
ActiveCN109584978AIntegrity guaranteedGuarantee authenticityDigital data protectionMedical equipmentThird partyInformation processing
The invention belongs to the technical field of information security, and discloses a medical health monitoring network model information processing method and system based on signature aggregation. The third party authority center provides a pair of public and private keys and a pseudo identity for the user sensor, and stores the real identity and the pseudo identity of the user in a key value pair form; The user sensor encrypts medical information through a public key of the medical server and signs the encrypted information by using a sensor private key; Enabling the aggregator to obtain aseries of information, and performing signature authentication and signature aggregation by the aggregator; The signature aggregation aims to save bandwidth and server storage space; And the medical server decrypts the data after performing the aggregate signature authentication, and provides the medical information of the patient to the medical care personnel. According to the invention, judgmentinformation of health care professionals is transmitted to a real patient through the third-party authority center and the aggregator; A plurality of signatures can be combined into a single aggregated signature through the aggregated signature, so that the bandwidth and the storage cost of the network are greatly reduced.
Owner:XIAN UNIV OF POSTS & TELECOMM
Multiple users-based outsourcing database audit method
InactiveCN106452748AImprove privacy protectionReduce the burden onKey distribution for secure communicationUser identity/authority verificationPlaintextData privacy protection
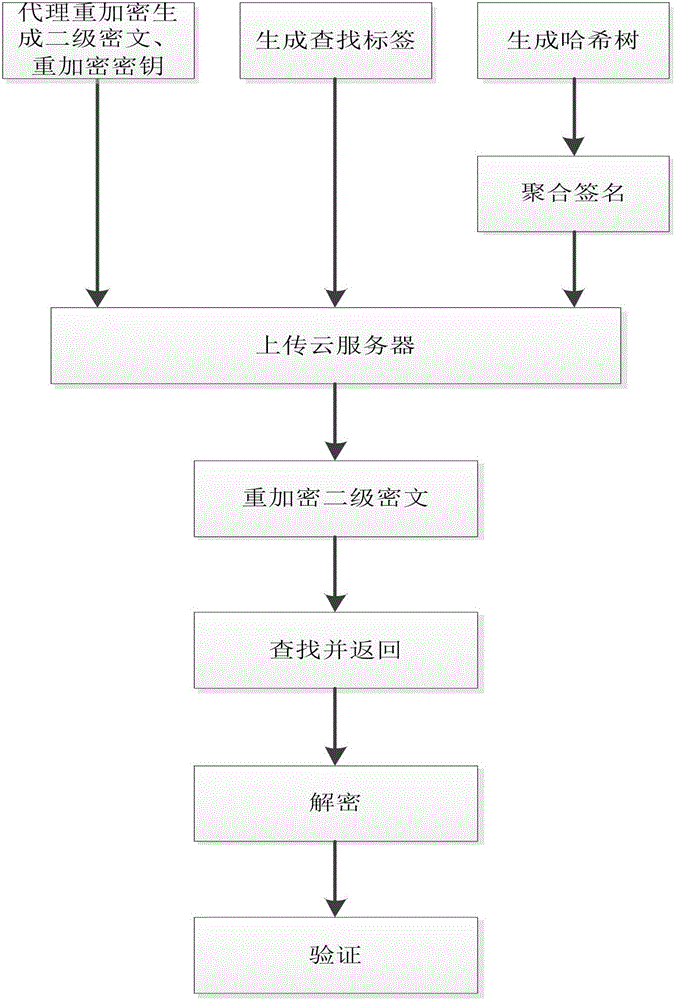
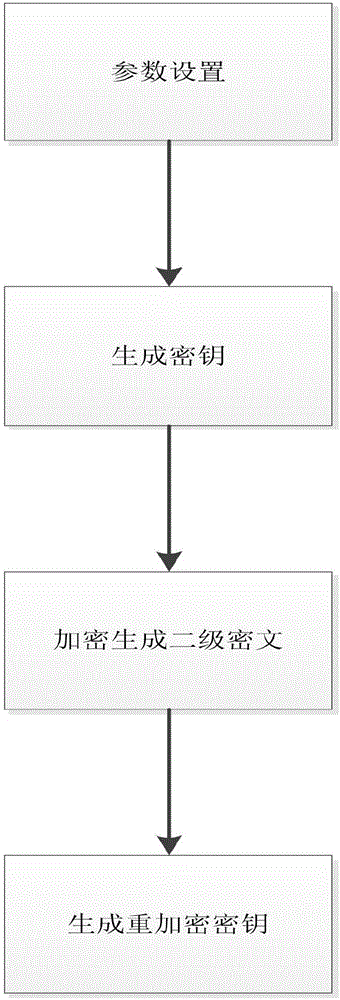
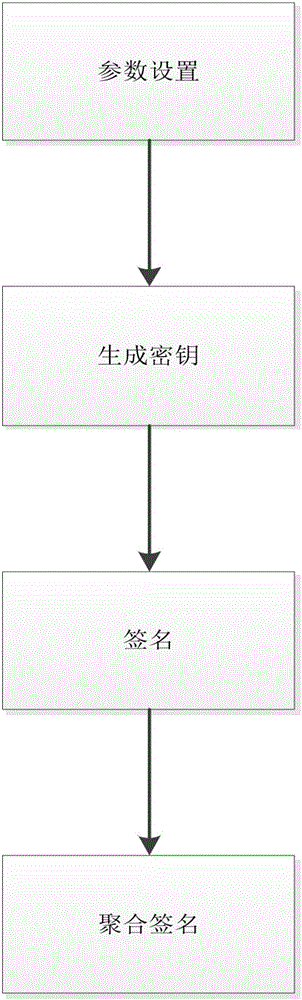
The present invention discloses a multiple users-based outsourcing database audit method, aiming to solve problems of low signature verification efficiency and complex decryption in the prior art. The method comprises a first step that a data owner encrypts data by using a proxy re-encryption method so as to form a second-level ciphertext, generates a re-encryption secret key by inquiring a public key of a user, generates a searching label by using an Evdokimov encryption manner, and generates hash tree root signature by using aggregate signature; and the signature, second-level ciphertext, re-encryption secret key and the searching label are transmitted to a cloud server; a second step that the cloud server encrypts the second-level ciphertext so as to generate a first-level ciphertext; a third step that a user sends a search request to the cloud server, and the cloud server searches and returns a corresponding first-level ciphertext; and a fourth step that the user decrypts the first-level ciphertext so as to form a plaintext, and performs aggregate verification on the plaintext. Through adoption of the method, the burden on the data owner is greatly reduced, interaction is reduced for one time, data privacy protection is improved, and the method can be applied to safe data outsourcing in a cloud calculation environment.
Owner:XIDIAN UNIV
Digital signatures including identity-based aggregate signatures
ActiveUS7664957B2User identity/authority verificationSecret communicationDigital signatureKey generator
Methods and systems are provided that allow multiple identity-based digital signatures to be merged into a single identity-based “aggregate” digital signature. This identity-based aggregate signature has a shorter bit-length than the concatenation of the original unaggregated identity-based signatures. The identity-based aggregate signature can be verified by anyone who obtains the public keys of one or more Private Key Generators (PKGs), along with a description of which signer signed which message. The verifier does not need to obtain a different public key for each signer, since the signature scheme is “identity-based”; the number of PKGs may be fewer than the number of signers. Consequently, the total information needed to verify the identity-based aggregate signature—namely, a description of who signed what, the PKGs' public keys, and the identity-based aggregate signature itself—may be less than the information needed to verify separate digital signatures—namely, a description of who signed what, the public verification keys for all of the signers, and the concatenation of the signers' signatures. In some embodiments, the identity-based aggregate signature scheme has essentially the minimum-possible Kolmogorov complexity.
Owner:NTT DOCOMO INC
Encryption and signature schemes using message mappings to reduce the message size
ActiveUS20100008496A1Computationally efficientBandwidth-reduced ring signatureKey distribution for secure communicationPublic key for secure communicationRing signatureCiphertext
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h″] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
Efficient aggregate digital signature method
ActiveCN108650097AResolve open issuesKey distribution for secure communicationUser identity/authority verificationAlgorithmDigital signature
The invention provides an efficient aggregate digital signature method, is a safe aggregate signature method that is the only one method based on the general finite group known so far, and solves thepublic problem that is unsolved in a long term in the field. The aggregate digital signature method is proved safely to introduce a new basic source language of non-malleable one-way function. The aggregate digital signature method greatly reduces the storage space and the authentication time of the signature, and is particularly suitable to be applied in the fields of blockchain and cryptocurrency.
Owner:SHANGHAI HUMIN BLOCKCHAIN TECH CO LTD
Lattice-based aggregate signature method and system
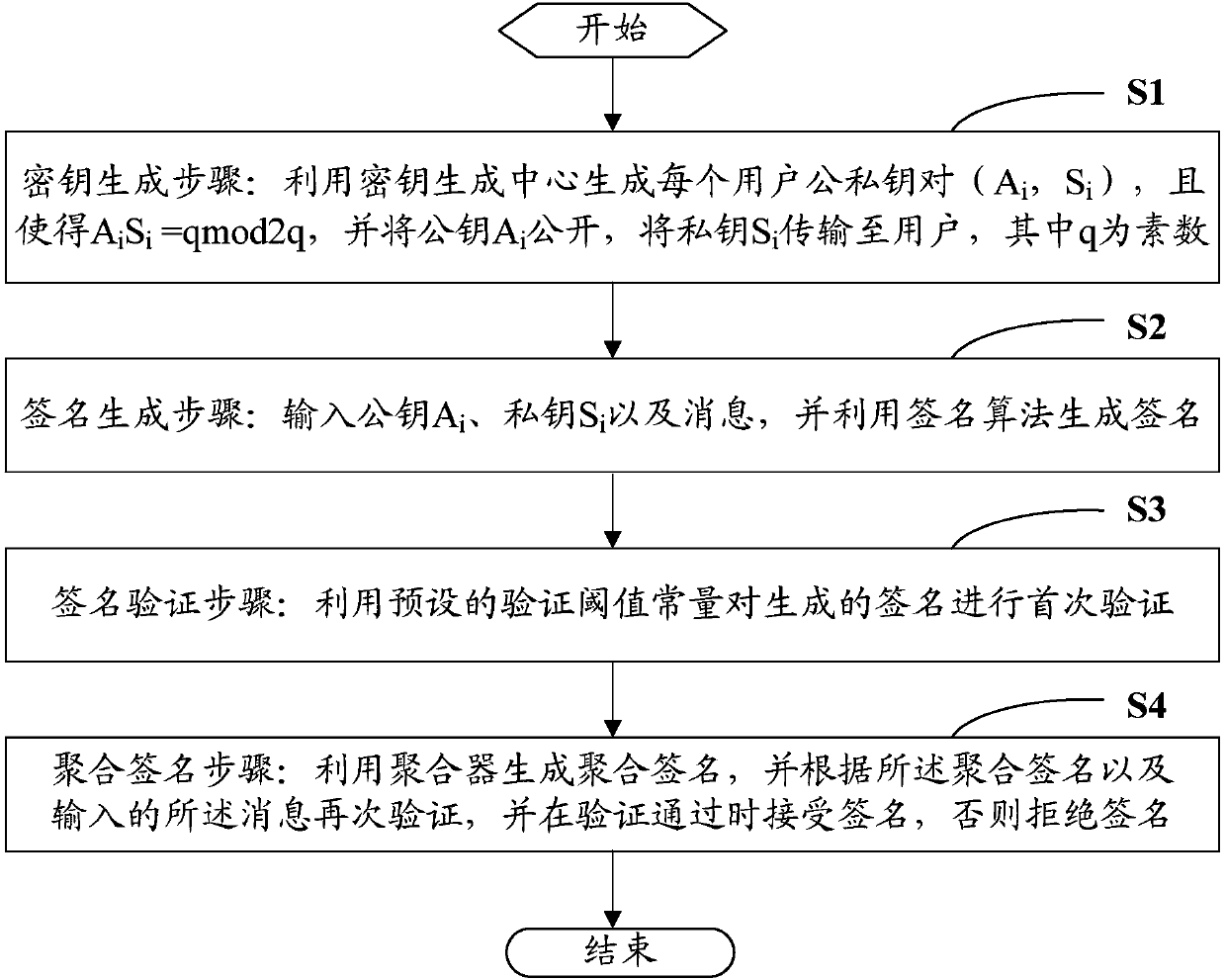
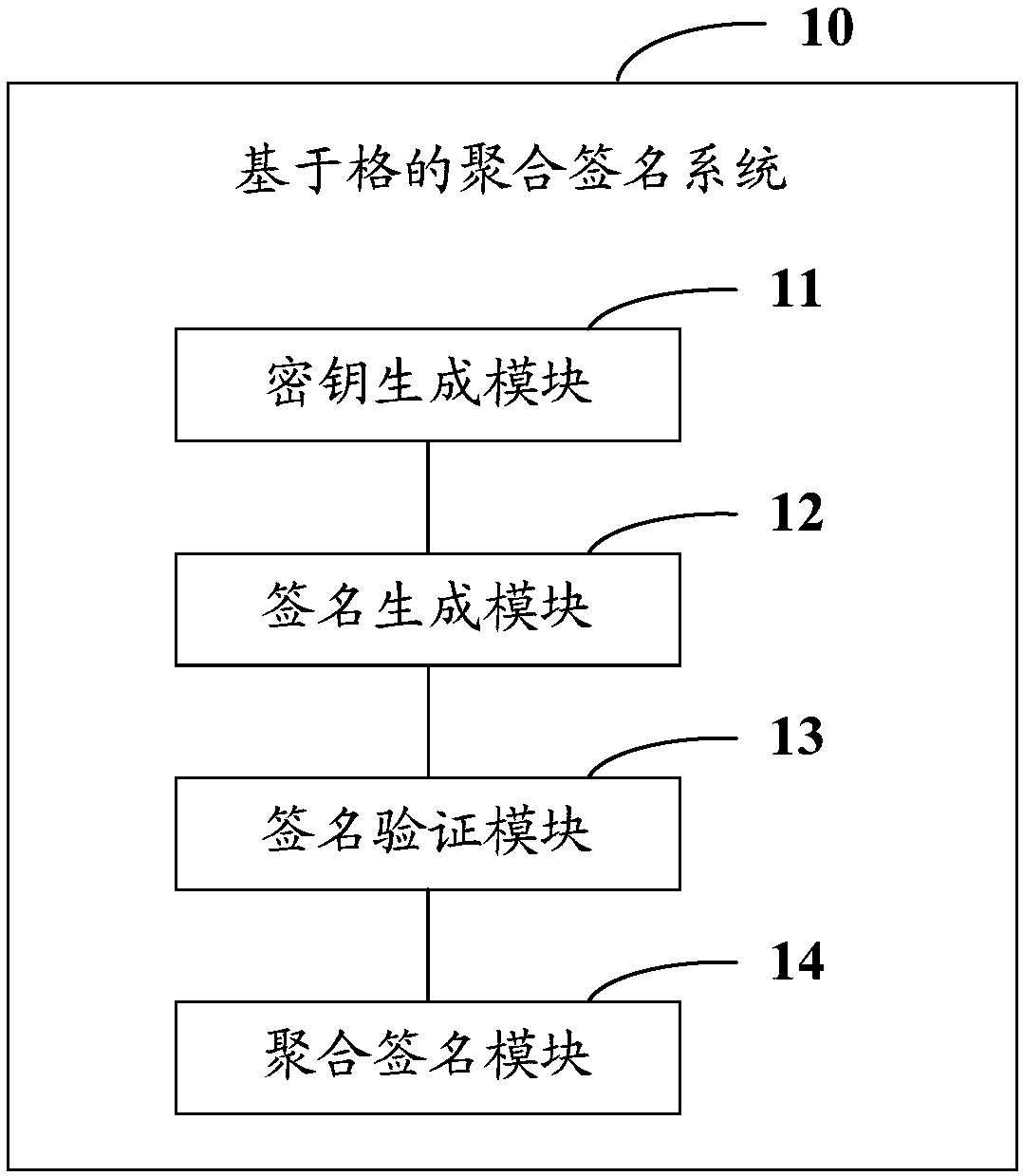
InactiveCN107592203AImprove verification efficiencyResist attackKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey generationAggregate signature
The invention provides a lattice-based aggregation signature method. The method comprises: a key generation step: generating each user public-private key pair (A, S) by using a key generating center, making AS equal to qmod2q, disclosing a public key A, and transmitting a private key S to a user, wherein q is a prime number; a signature generation step: inputting the public key A, the private key S and a message mui, and generating a signature by a signature algorithm; a signature verification step: performing first verification on a generated signature by using a preset verification threshold constant; and an aggregation signature step: generating an aggregation signature with an aggregator, performing secondary verification according to the aggregation signature and the input message mui, accepting the signature when the verification passes, otherwise rejecting the signature. The invention also provides a lattice-based aggregation signature system. Through thetechnical scheme provided by the invention, the verification efficiency of signatures can be increased.
Owner:深圳技术大学筹备办公室
Electronic security system for monitoring and recording activity and data relating to cargo
InactiveCN1809849ACo-operative working arrangementsElectric signalling detailsAggregate signatureData set
A tracking system for identifying contents of a container includes an electromagnetic identification apparatus that provides an electromagnetic signal indicative of a container content data set; a writer for use in encoding the container signal onto the apparatus; a controller for receiving the encoded signal and for storing the signal in a master database storage apparatus; and a reader configured outside the container for communicating with the electromagnetic identification apparatus and for receiving the encoded signal therefrom and corresponding to the container content data signal set. A system for tracking items in an assembly includes an apparatus for receiving electromagnetic identification tag signals; an apparatus for creating a first tier aggregate signature; an apparatus for storing the signature in a master database; and an apparatus for receiving modifying command signals for creating a second tier aggregate signature corresponding to a modified set of electromagnetic identification tags in an augmented assembly.
Owner:UNITED SECURITY APPL ID
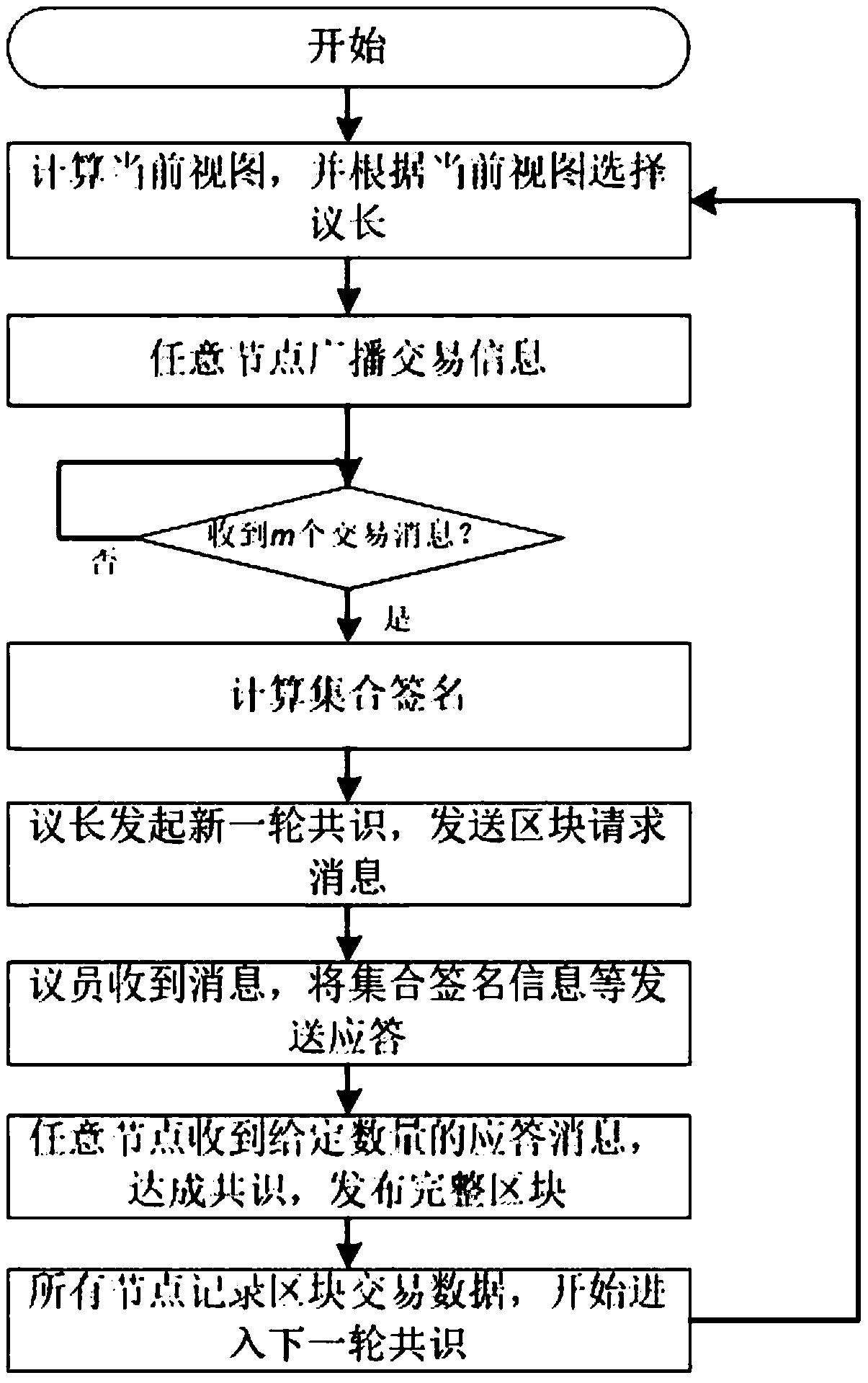
Game blockchain consensus method based on bilinear mapping algorithm and set signature algorithm
InactiveCN109194472AReduce consumptionImprove processing efficiencyKey distribution for secure communicationPublic key for secure communicationTransaction dataDigital Signature Algorithm
The present invention relates to a game blockchain consensus method based on a bilinear mapping algorithm and a set signature algorithm. The method comprises the steps of: broadcasting transaction data to a whole network through any node, and attaching signature of a sender to the transaction data; after a set node receives m messages without insertion, employing a set signature algorithm and a bilinear mapping algorithm to perform operation of the m messages to obtain a set signature, and sending the set signature in the round of consensus time; receiving set signature information with a given quantity by the any node in the network to reach a consensus and publish a whole block; and deleting the included transaction from the memory after any node receives the whole block, and starting the next round of consensus. The game blockchain consensus method based on the bilinear mapping algorithm and the set signature algorithm can aggregate the signatures of the m original messages into onesignature to reduce the confirmed consumption of the message transmission and allow the space complexity to be reduced to 1 / m of the original space complexity so as to improve the transaction processing efficiency and increase the network capacity.
Owner:广东微链科技有限公司
Identity-based aggregate signature method with parallel key-insulation
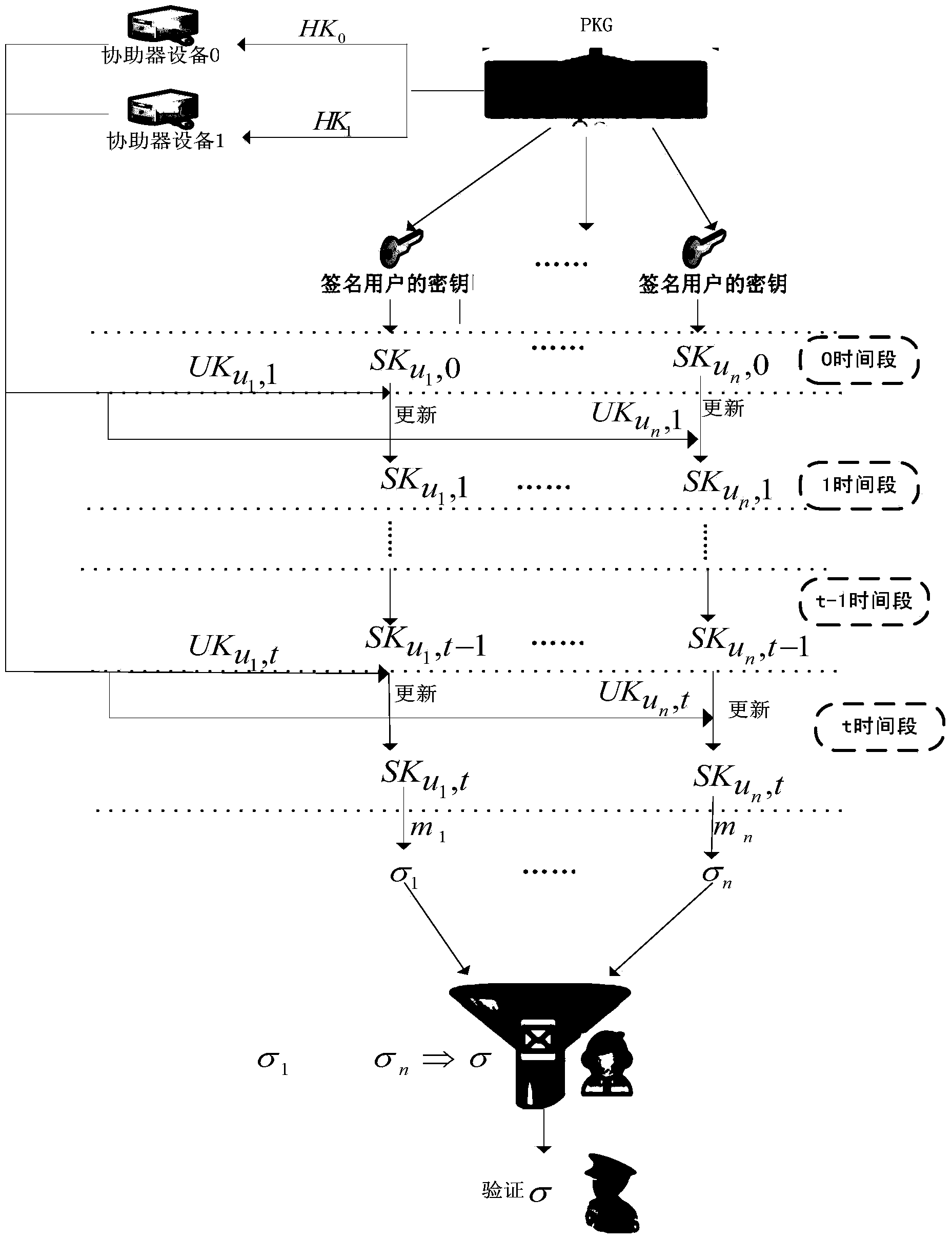
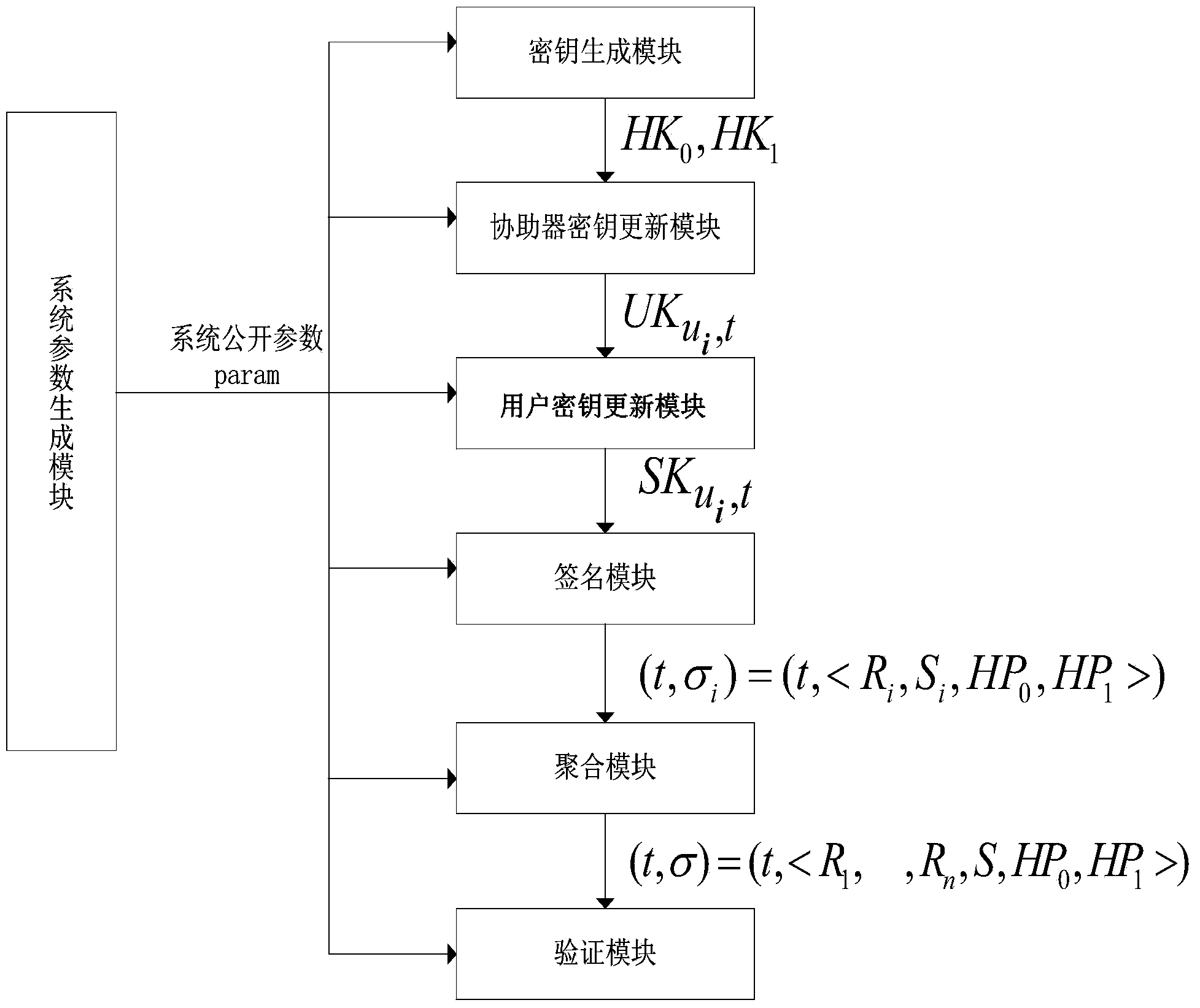
InactiveCN103414731AImprove securityImprove leakageUser identity/authority verificationAggregate signatureComputer security
The invention provides an identity-based aggregate signature method with parallel key-insulation. According to the identity-based aggregate signature method with parallel key-insulation, a set of n users who participate in the aggregate signature method is a set of n different messages, each user Pi (1<=i<=n) selects a message mi (1<=i<=n) which is different from others to conduct signature so that sigmai can be obtained, each generated signature sigmai is sent to an aggregation side, the aggregation side can conduct aggregation operation on the n relieved independent signatures, and a verification side verifies the aggregate signatures and determines whether the aggregate signatures come from the n designated users; at the same time, a key of each user is updated periodically, two assisting devices alternatively help the users to update the keys in each time period, and leakage of the keys of the users in one time period cannot influence the safety of a system in other time periods. The identity-based aggregate signature method with parallel key-insulation integrates the advantages of the parallel key-insulation mechanism and the advantages of an identity-based aggregate signature, the signature verification efficiency is improved, and the safety of the whole system is guaranteed.
Owner:QINGDAO UNIV
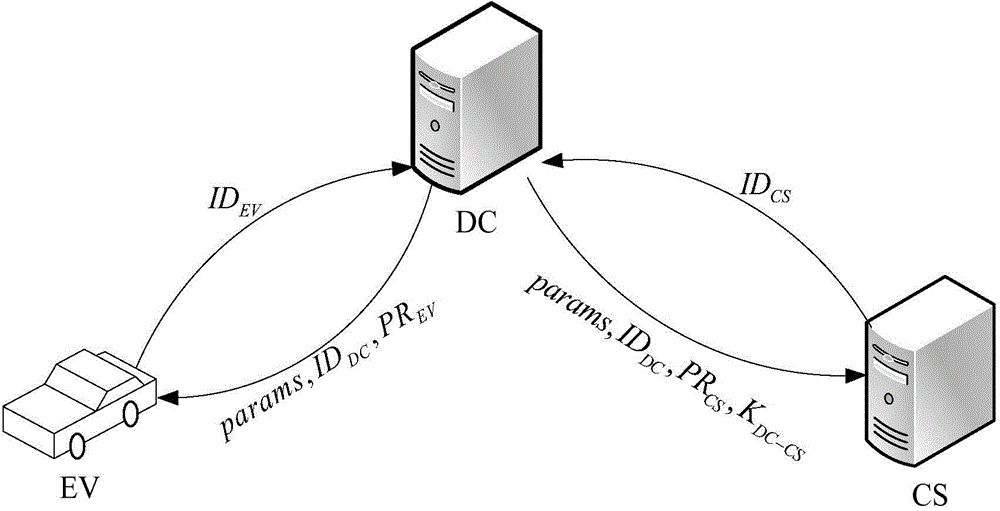
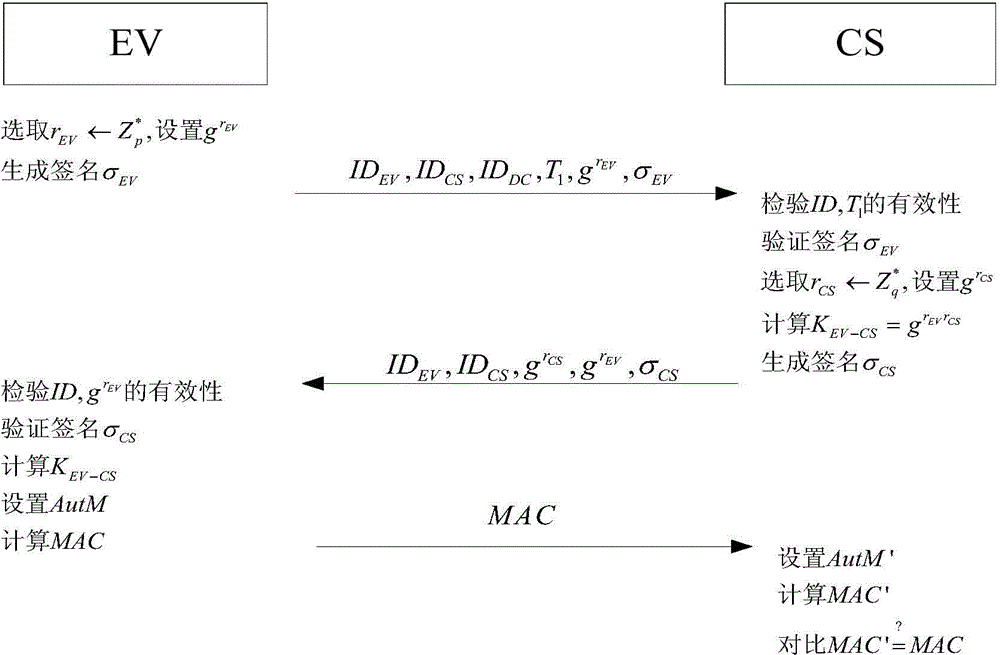
Access authentication method of electric automobile
The invention relates to an access authentication method of electric automobiles. The method comprises the following steps that: access authentication systems of the electric automobiles are established; access authentication between the electric automobiles and a charging station is carried out; and the charging station carries out batch signature authentication on the electric automobiles. According to the invention, identity aggregate signatures are introduced into identity validity inspection of the electric automobiles, and bidirectional authentication and session key negotiation are designed between the electric automobiles and the access authentication systems, so that the reasonable usage of the information resources in the station is ensured, and the safety of the whole network system is fundamentally ensured. The batch signature authentication mechanism enables the charging station to verify a plurality of electric automobile terminal signatures in the aggregate manner, the calculation load is lightened, and the performance is improved. The typical identity aggregate signature system is composed of five algorithms: system initialization, private key generation, signing, aggregation and aggregate verification, user identity information can be used to replace a public key thereof, the problem of high certificate cost is solved, and by compressing the plurality signatures into one, the high-efficiency verification is carried out.
Owner:STATE GRID CORP OF CHINA +2
Network device group authentication method in software-defined network
ActiveCN104780052ATimely detection of identity issuesReduce consumptionSpecial service provision for substationUser identity/authority verificationComputer moduleStructure of Management Information
The invention discloses a network device group authentication method in a software-defined network, in particular to a group authentication method based on the aggregate signature technology, and belongs to the field of communication. The method mainly involves an initialization module, a signature module, a verification module and seven steps. The network device group authentication method in the SDN is put forward under the SDN structure; by fully utilizing southing interfaces between the network devices and a controller and data links between the network devices, authentication of all network devices on a network device link can be completed by the controller through only one time authentication, and the controller bandwidth consumption of a traditional authentication method is reduced. In addition, the signature module for the SDN network devices involves the network device authentication step, and the identity problem of the previous network device can be found in time. The aggregate signature technology is adopted, and therefore the bandwidth consumption caused when signature data are transmitted between the network devices can be effectively lowered.
Owner:BEIHANG UNIV
Byzantine fault tolerance optimization method based on aggregate signature and storage medium
InactiveCN112532396AReduce trafficSolve the problem that is not suitable for large-scale node consensusUser identity/authority verificationByzantine fault toleranceComputer network
The invention relates to the technical field of block chains, and discloses a Byzantine fault tolerance optimization method based on aggregate signatures and a storage medium, and the method comprisesthe steps: S1, a Pre-Prepreme stage: a main node collects transactions in a transaction memory pool, packages the transactions into blocks, and broadcasts the blocks to all replica nodes for consensus; S2, a Prepare stage: after receiving the Prepare message sent by the main node, all the replica nodes send back a Prepare message to the main node; S3, a Commit stage: the main node verifies each Prepart information, verifies the signature of the replica node, aggregates the signatures passing the verification into a signature through a BLS signature, and broadcasts the aggregated signature andother necessary information to all other replica nodes for verification; and the copy node links the block to the chain tail of the block chain to finish synchronization after verifying that the copynode is correct according to the received Commit message. The problem that an existing Byzantine fault-tolerant protocol is not suitable for large-scale node consensus is solved.
Owner:GUANGDONG UNIV OF TECH
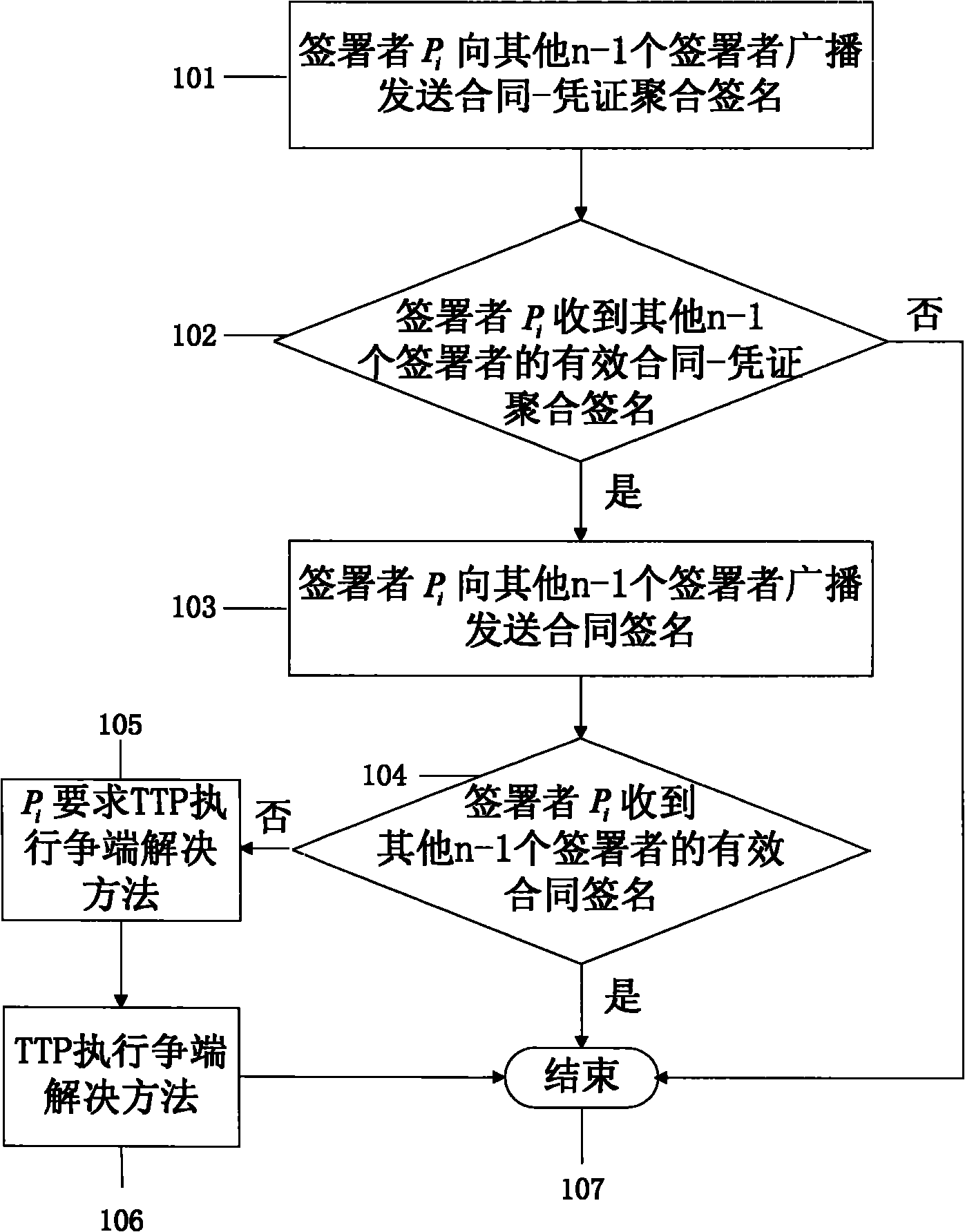
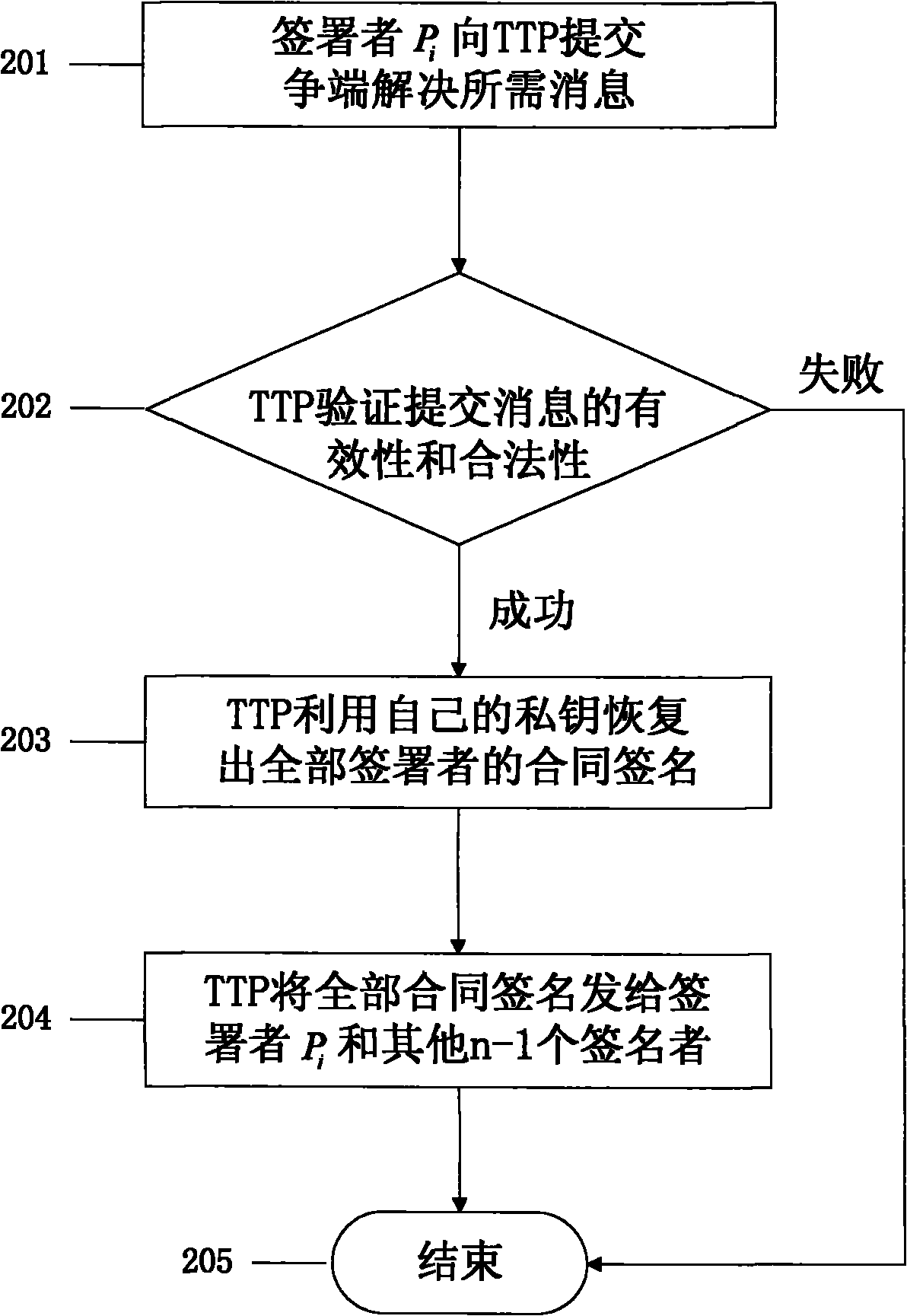
Multipartite contract signing method based on aggregated signature
The invention relates to a multipartite contract signing method based on aggregated signature, which is characterized in that signers participating in contract signing use aggregated signature and public key cryptosystem broadcasting methods to complete signing process, when any party refuses to admit the signing behavior, a third party can be involved to solve the disputes. The method needs support of an off-line trusted third party, and the trusted third party generates a certificate signature which can be used as an authorized signature for recovering the contract when disputes occur. In the method, a singer uses the certificate signature to generate a contract-certificate aggregated signature and sends the contract-certificate aggregated signature to other signers by broadcasting to complete commitment exchange; after reviving valid contract-certificate signatures of other signers, the signer sends the contract signature by broadcasting to complete the contract signature exchange; and when disputes occur in the exchange process, the signer request the trusted third party to execute a dispute resolution method. The method only needs tow rounds of unordered information exchange and has high execution efficiency and certifiable safety.
Owner:BEIJING UNIV OF POSTS & TELECOMM
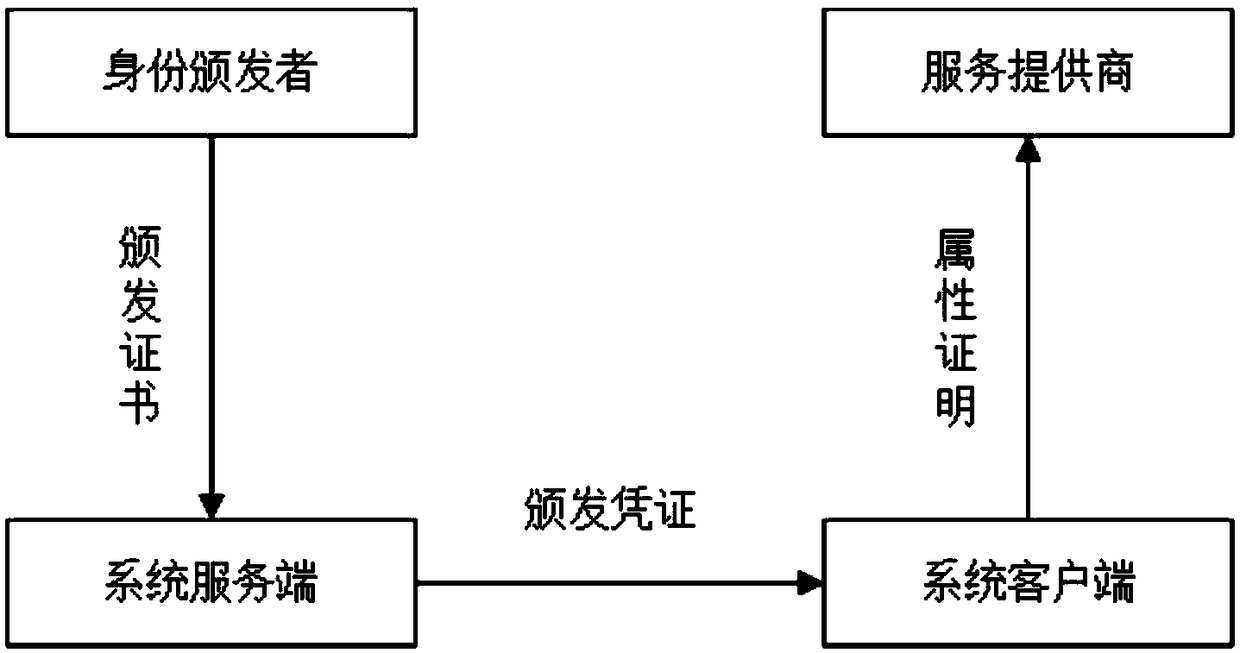
Identity attribute certification system and method for privacy protection
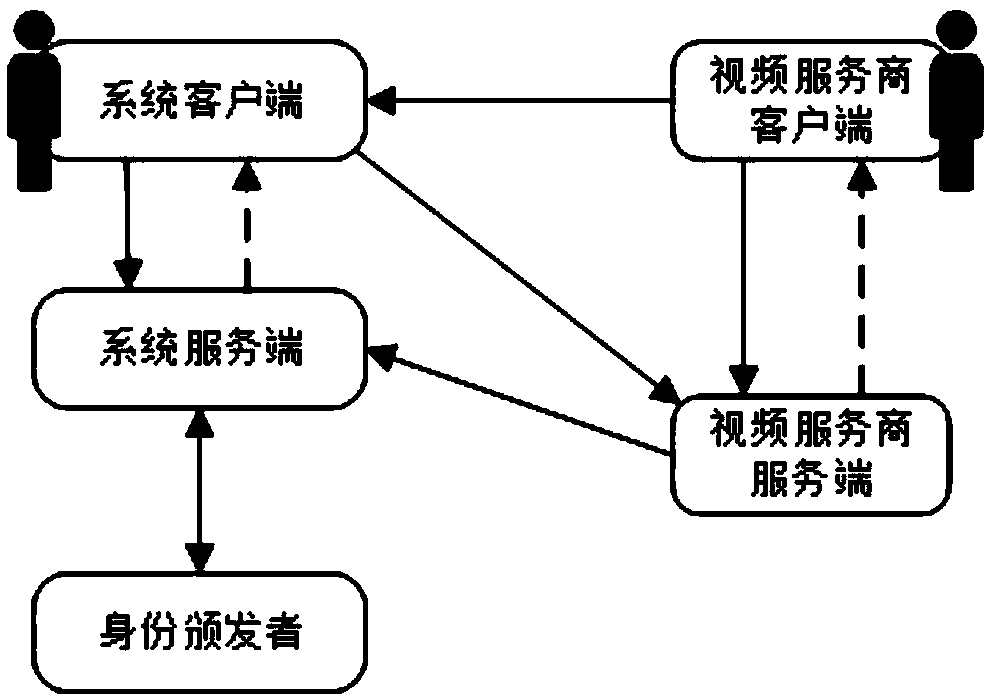
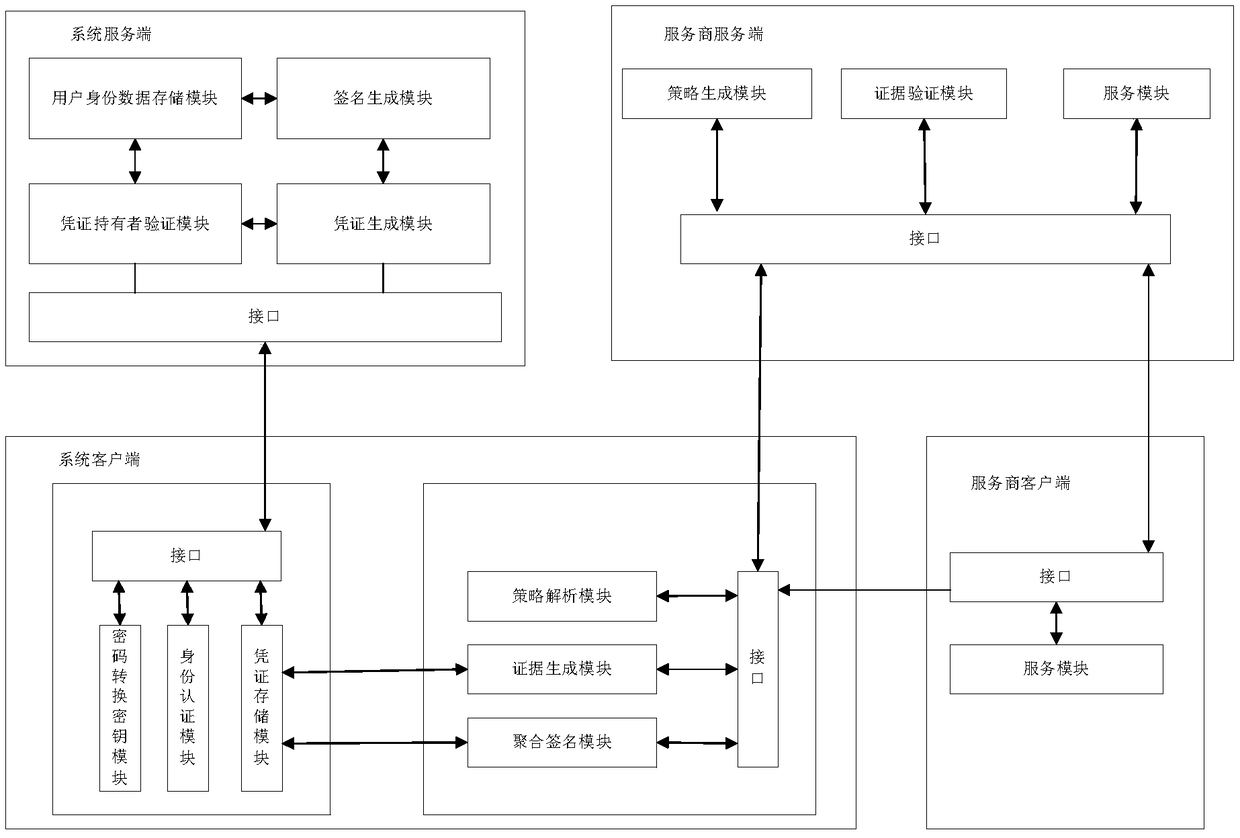
ActiveCN108769020AGuaranteed privacy protectionPrevent forgeryUser identity/authority verificationPrivacy protectionClient-side
The invention provides an identity attribute certification system and method for privacy protection. The system comprises a service-provider server, a service-provider client, a system server and a system client, wherein the service-provider server generates an access strategy of a service, sends the access strategy to the service-provider client, and performs verification on an evidence; the service-provider client sends a service request to the service-provider server, redirects the service request to the system client and forwards the access strategy to the system client; the system serverrequests a certificate of an attribute, re-signs the attribute in the certificate, generates a voucher of the attribute and issues the voucher to the system client; the system client retrieves an attribute label in the access strategy; if the voucher of the attribute is not stored in the system client, the system client applies to the system server for the voucher of the attribute; and the evidence for attribute certification is generated via an aggregate signature and is sent to the service-provider server. A service provider cannot obtain real attribute information of a user, so a privacy ofthe user is protected.
Owner:NORTHEASTERN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com