Identity-based aggregate signature method with parallel key-insulation
A technology of keys and identities, applied in the field of aggregated signatures, can solve problems such as assisting key threats to system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
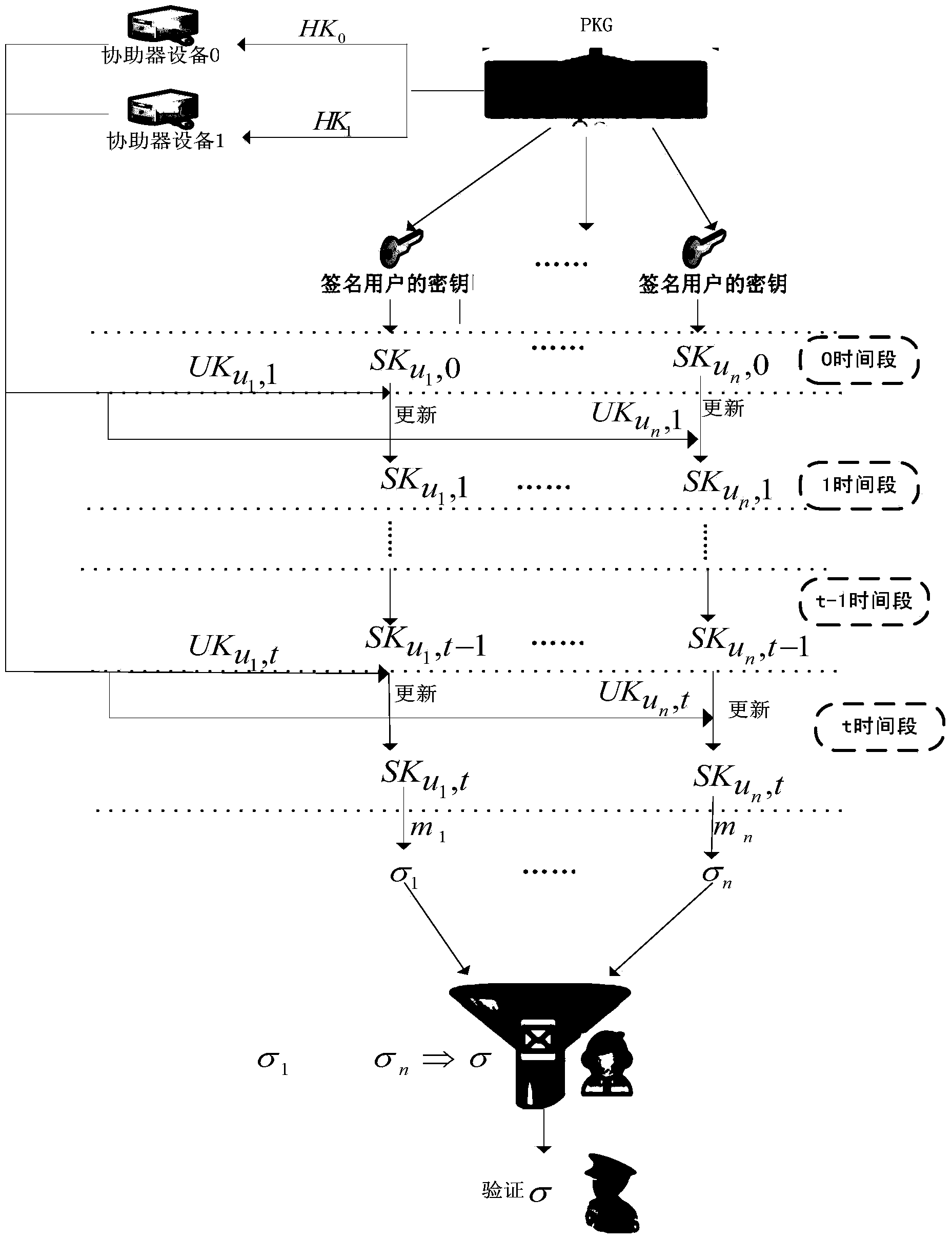
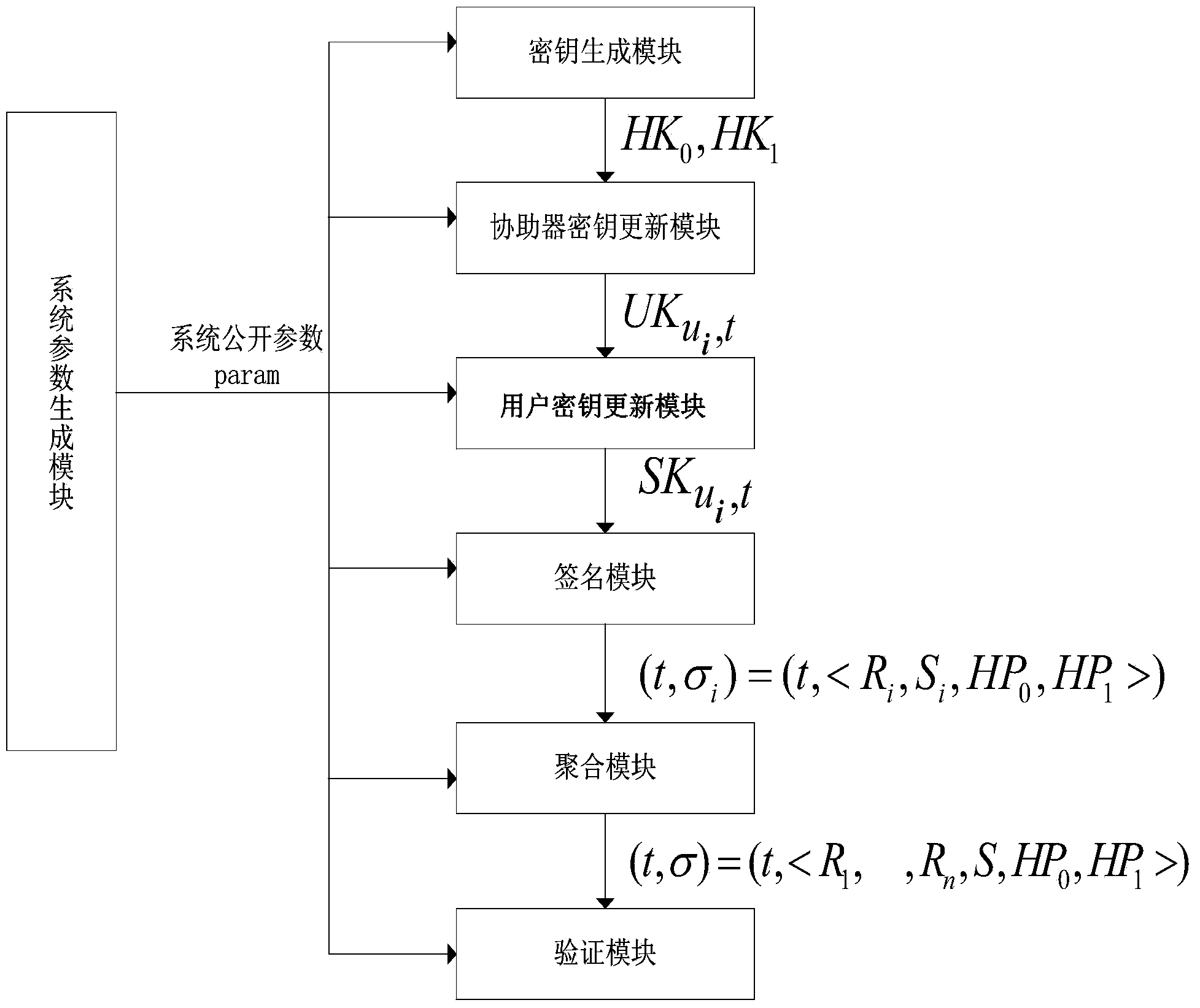
[0076] The invention provides an identity-based aggregation signature method with parallel key isolation, is the set of n users participating in the aggregated signature method, is a collection of n different messages, each user P i (1≤i≤n) choose different messages m i (1≤i≤n) to sign to get σ i , and put the generated signature σ i Sent to the aggregator, the aggregator can perform an aggregation operation on the received n independent signatures, and the verifier verifies the aggregate signature to make sure whether the generated aggregate signature comes from the specified n users.
[0077] The aggregated signature method further includes:
[0078] In the first step, the system parameter param generation step of the identity-based aggregate signature system with parallel key isolation;
[0079] The second step is the key generation step;
[0080] The third step is the key update step of the facilitator;
[0081] The fourth step is the user key update step;
[008...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com