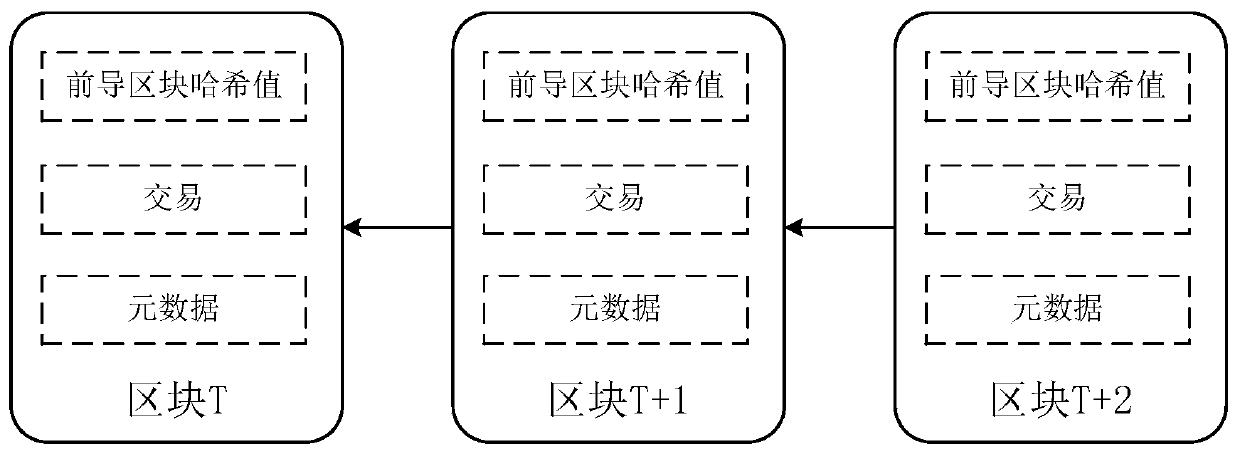
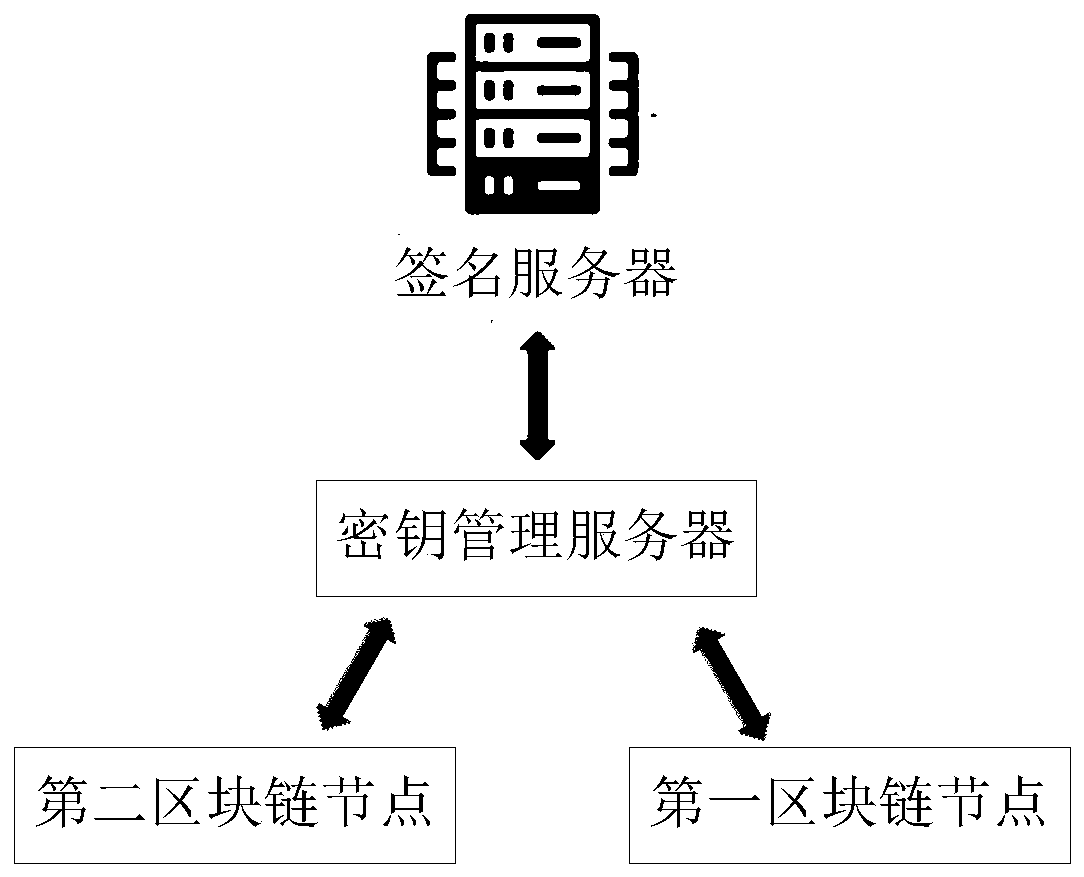
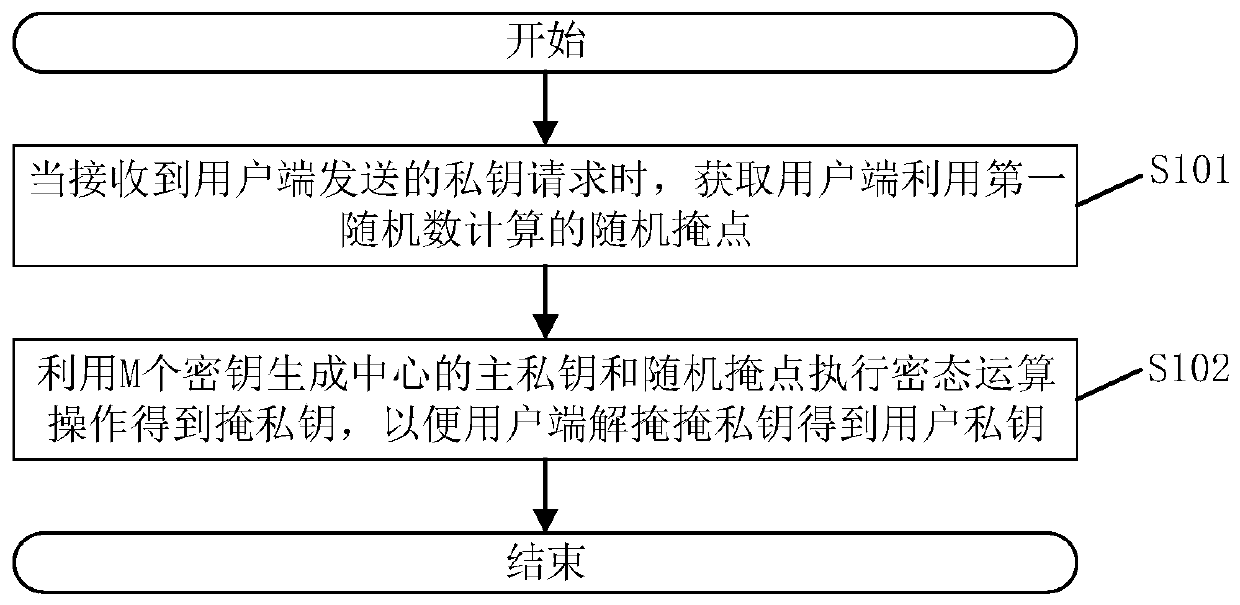
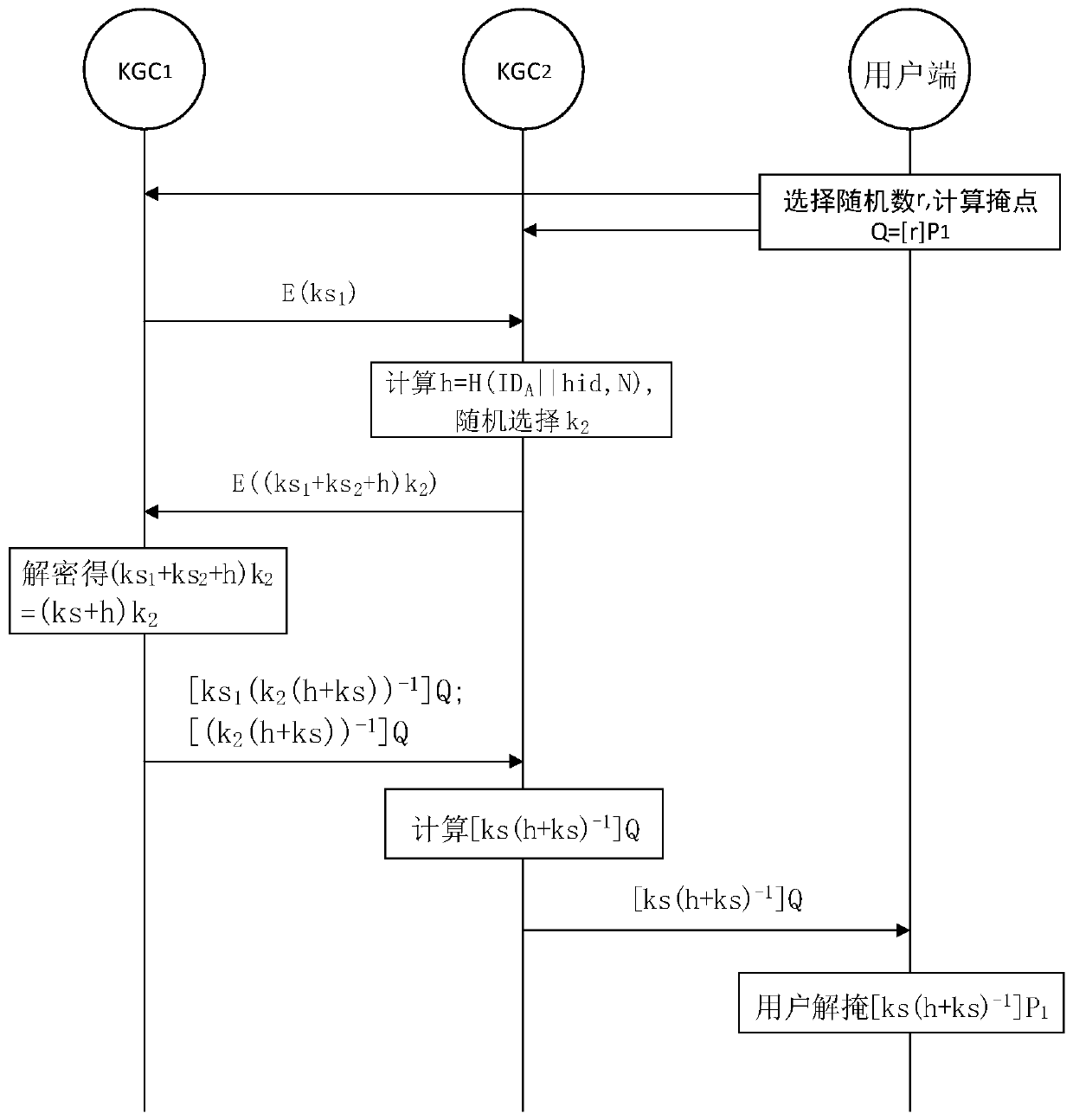
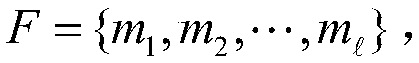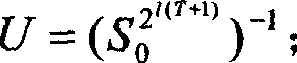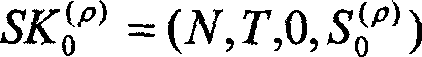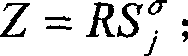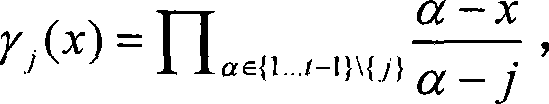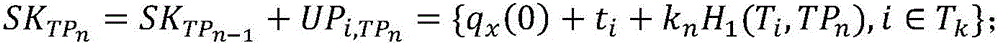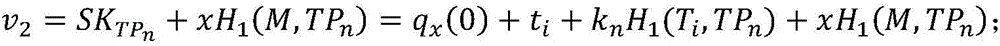Patents
Literature
277 results about "Key leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Key management method, device and system
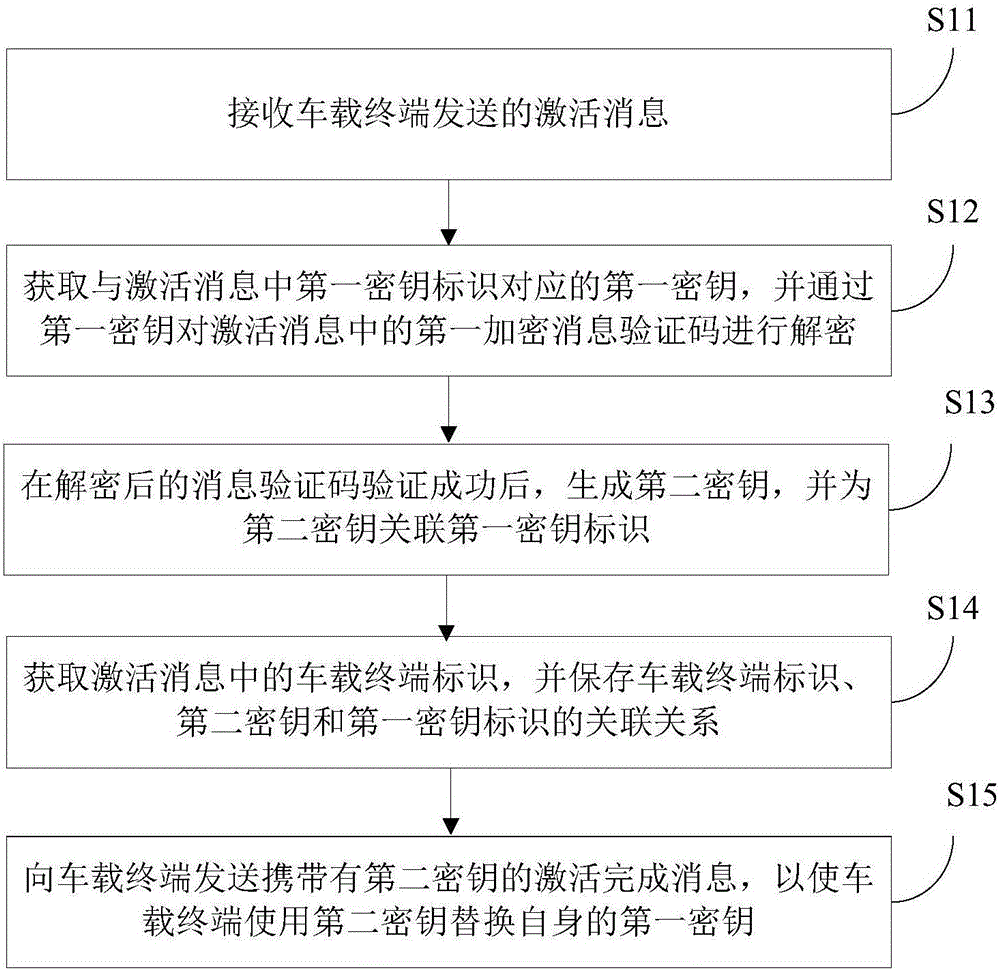
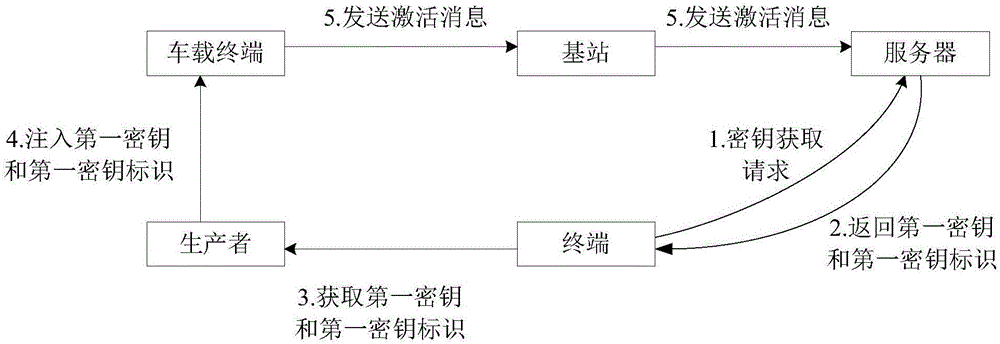
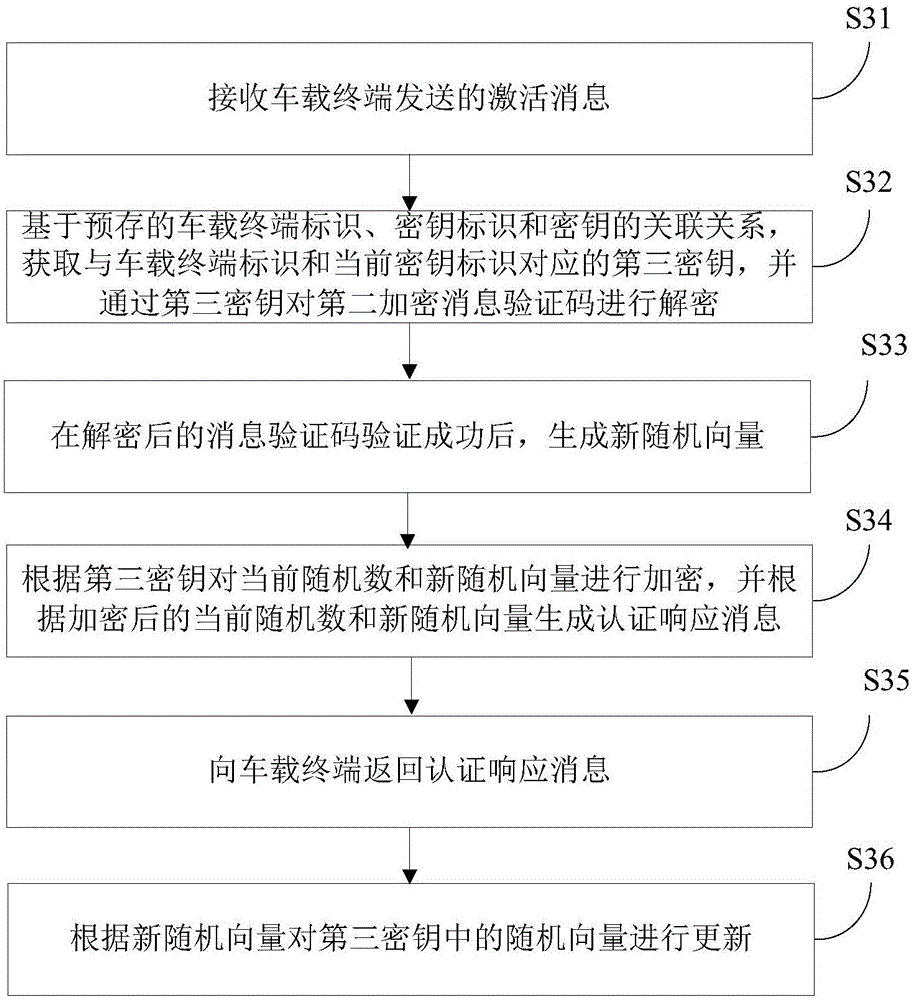
The present invention discloses a key management method, device and system. The method includes the following steps that: an activation message sent by a vehicle-mounted terminal is received; a first key corresponding to a first key identifier in the activation message is obtained, a first encrypted message authentication code in the activation message is decrypted through the first key; after the decrypted message authentication code is successfully verified, a second key is generated, and the second key is associated with the first key identifier; a vehicle-mounted terminal identifier in the activation message is obtained, and the association relations of the vehicle-mounted terminal identifier, the second key and the first key are saved; and an activation completion message carrying the second key is sent to the vehicle-mounted terminal. According to the method, key update is realized during a key activation process, a possibility of key leakage in a period from a time point when an initial key is generated to a time point when the initial key is injected into a vehicle-mounted terminal due to poor management can be eliminated, hazards caused by the leakage of the initial key can be decreased, and the security of the transmission of the Internet of Vehicles can be improved.
Owner:NEUSOFT CORP
Cloud storage data common auditing method possessing secret key leakage resistance characteristic
The invention belongs to the communication technology field and especially relates to a cloud storage data common auditing method possessing a secret key leakage resistance characteristic. The method mainly comprises the following steps of system initialization: blocking processing is performed on a data file so as to generate public and private key pairs of a cloud user and a cloud server; auditing identification generation: the cloud user sends the data file and a label, and a signature set of a data block to the cloud server; auditing challenge response: a third party auditor generates auditing challenge information and sends to the cloud server; the cloud server calculates combination information according to the auditing challenge information, gets signatures together and sends an auditing identification response information to the third party auditor; and the third party auditor verifies validity of the auditing identification response information. The method has advantages that a condition that digital signature forgery and auditing identification response information forgery caused by leakage of a user signature private key can be prevented; and a malicious cloud server is ensured not to generate the forged auditing identification response information to cheat a TPA and to pass through an auditing verification process.
Owner:SOUTHWEST PETROLEUM UNIV
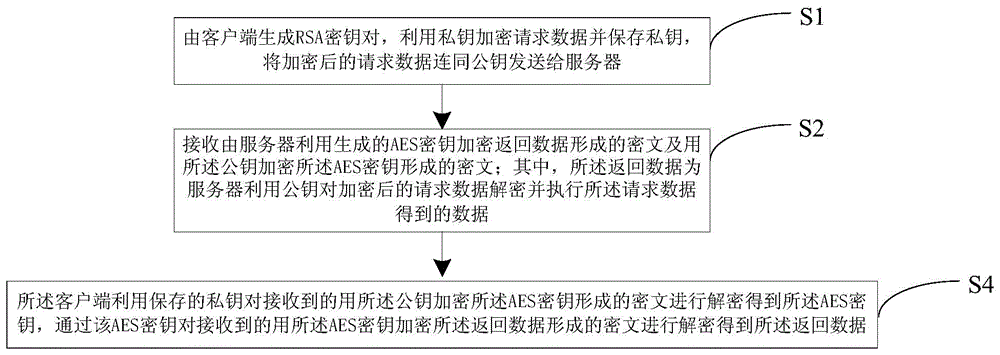
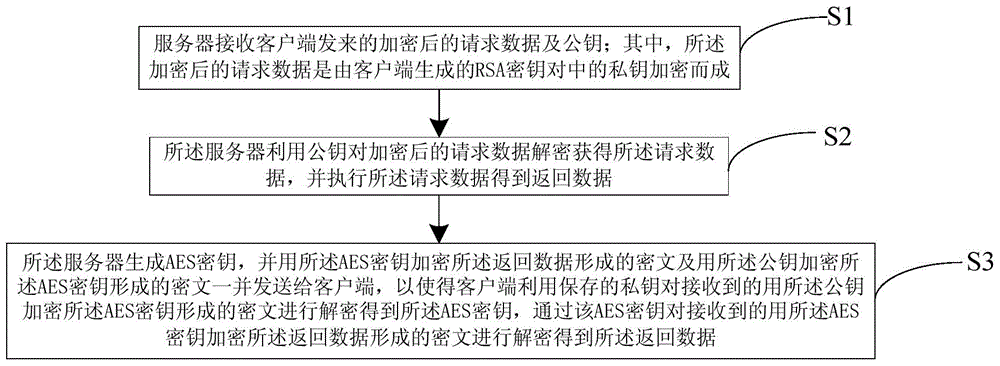
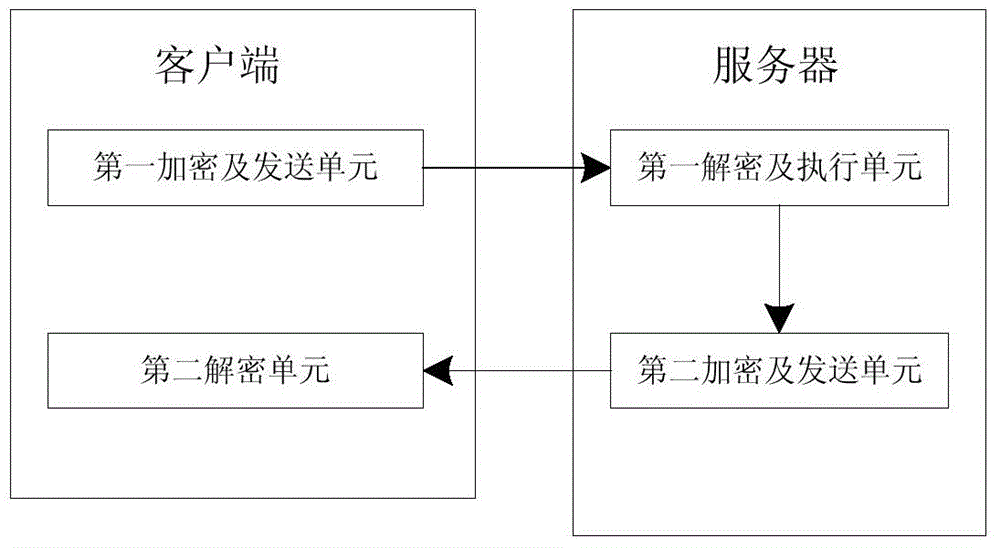
Hybrid encrypted network data security method and system
InactiveCN104821944APrevent leakageEncryption increaseTransmissionNetworked Transport of RTCM via Internet ProtocolCiphertext
The invention relates to a hybrid encrypted network data security method and system. The method comprises the steps that an RSA secret key pair is generated by a client terminal, request data are encrypted by utilizing a private key and the private key is stored, and the encrypted request data together with a public key are transmitted to a server; a cryptograph formed by the server via utilizing the generated AES secret key to encrypt returning data and a cryptograph formed via utilizing the public key to encrypt the AES secret key are received; the returning data are data obtained by the server via utilizing the public key to decrypt and perform the encrypted request data; and the client terminal utilizes the stored private key to decrypt the received cryptograph formed by encrypting the AES secret key via the public key so as to obtain the AES secret key, and the received cryptograph formed by encrypting the returning data via the AES secret key is decrypted by the AES secret key so that the returning data are obtained. A hybrid encryption mode of symmetric encryption and asymmetric encryption is adopted so that secret key leakage or decryption can be prevented, and network transmission data encryption can be increased. The client terminal controls the asymmetric secret key so that the number of requests can be reduced and efficiency can be enhanced.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Threshold digital signature method and system having forward security
InactiveCN101425902APublic key for secure communicationUser identity/authority verificationDigital signatureInformation security
The invention belongs to the technical field of information safety, which relates to a signature problem of numerical information, in particular to a numerical information method and a system thereof which can increase the difficulty of stealing a signature key for opponents and can lighten the influence of signature key leakage. The signature method adds a threshold mechanism and a sub-secret replacing mechanism through applying a Shamir secret sharing technology and a multiaspect security computing technology. The threshold mechanism enhances the security of the signature key, and can play the action of right dispersedness. The sub-secret replacing mechanism realizes the front safety of the signature key, namely even if obtaining the signature key of the current time bucket, the opponents also can not forge a legalized signature belonging to the previous time bucket through the key so that the validity of original signatures is protected, and the loss of key leakage is reduced. In addition, the signature method also comprises a member adding mechanism which enhances the security and the application range of the scheme.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
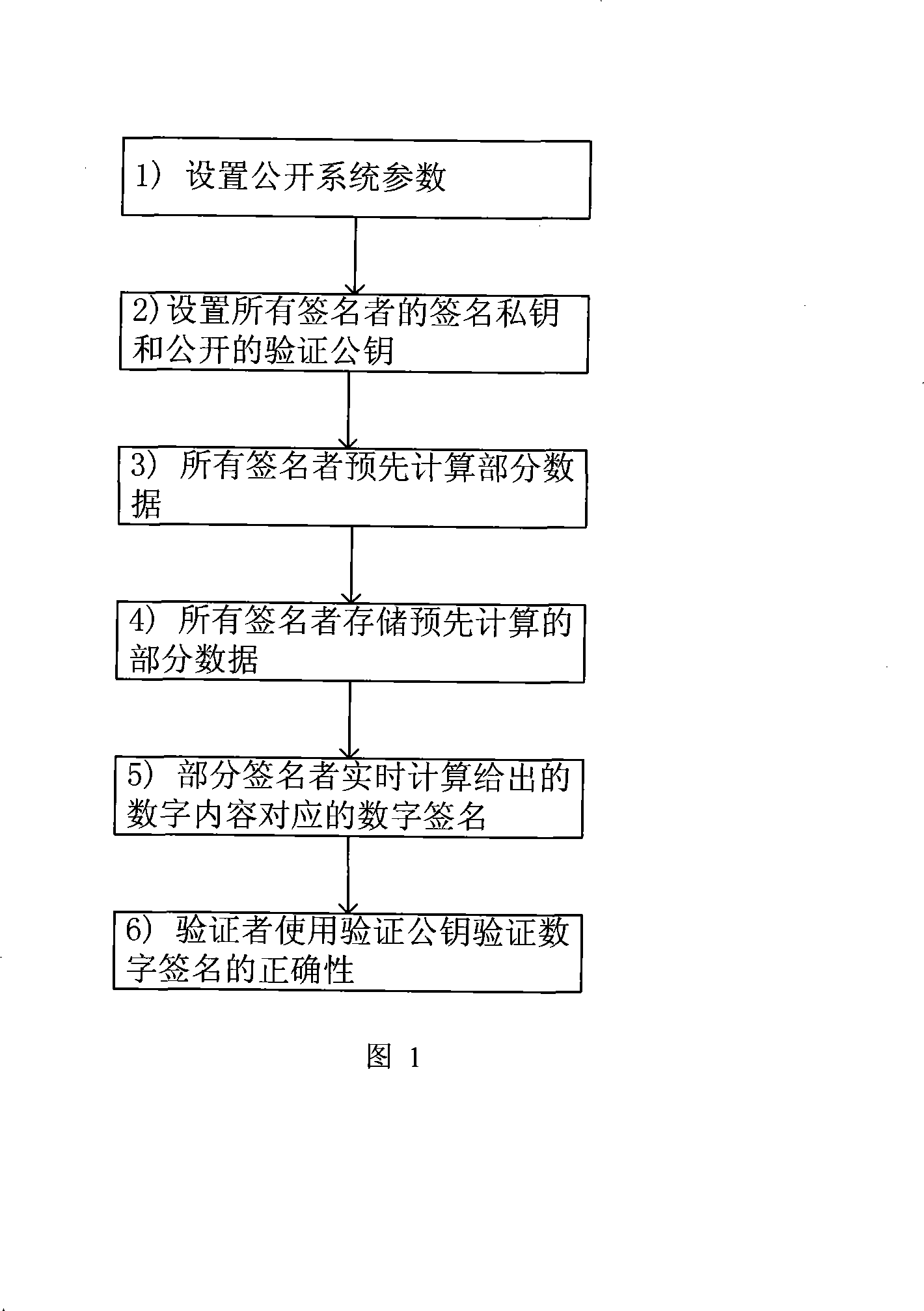
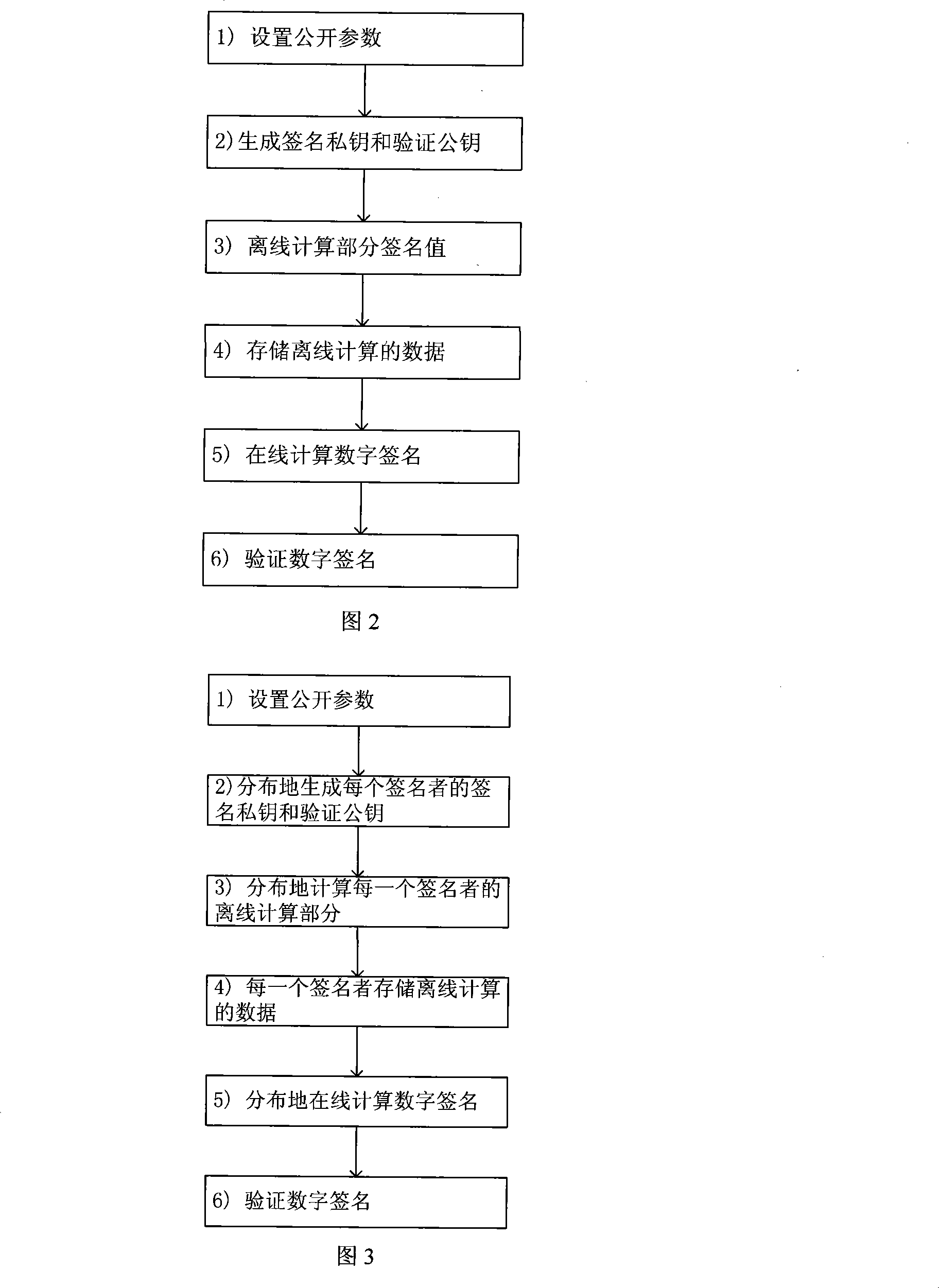
Realizing method of general-purpose digital signing scheme
ActiveCN101252431ASolve the problem of key disclosureReduce stepsUser identity/authority verificationGeneral purposeDigital signature
The invention relates to a method for realizing a universal digital signature scheme generating and verifying the digital content, comprising the following procedures: setting system parameters, generating a private key of the user signature and a public verifying key, and generating the digital signature in an off-line or on-line mode and verifying the digital signature. The invention creates a novel double-trapdoor chameleon function in a special way, so the limitation that the group inverse operation is needed when part of the data is calculated in advance in the background technique is solved, and the calculating amount is reduced; the limitation to the number of signers is removed; the problem of key leakage in the background technique of threshold digital signature scheme is solved; the calculating amount of the digital signature and verification is reduced; the signature length is shortened, and the memorizing requirement is reduced; therefore, the method has higher efficiency and better scalability.
Owner:GUANGZHOU XINRUI NETWORK TECH
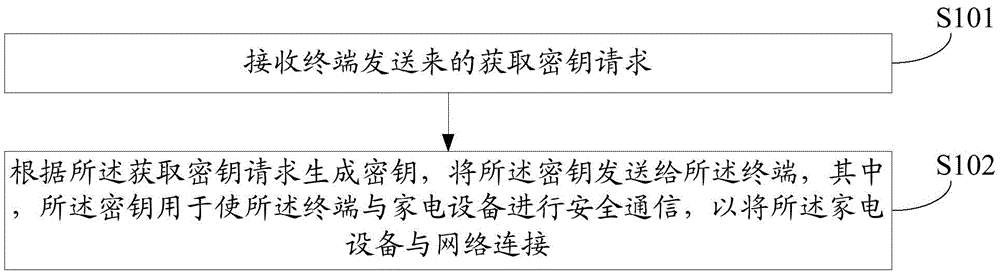
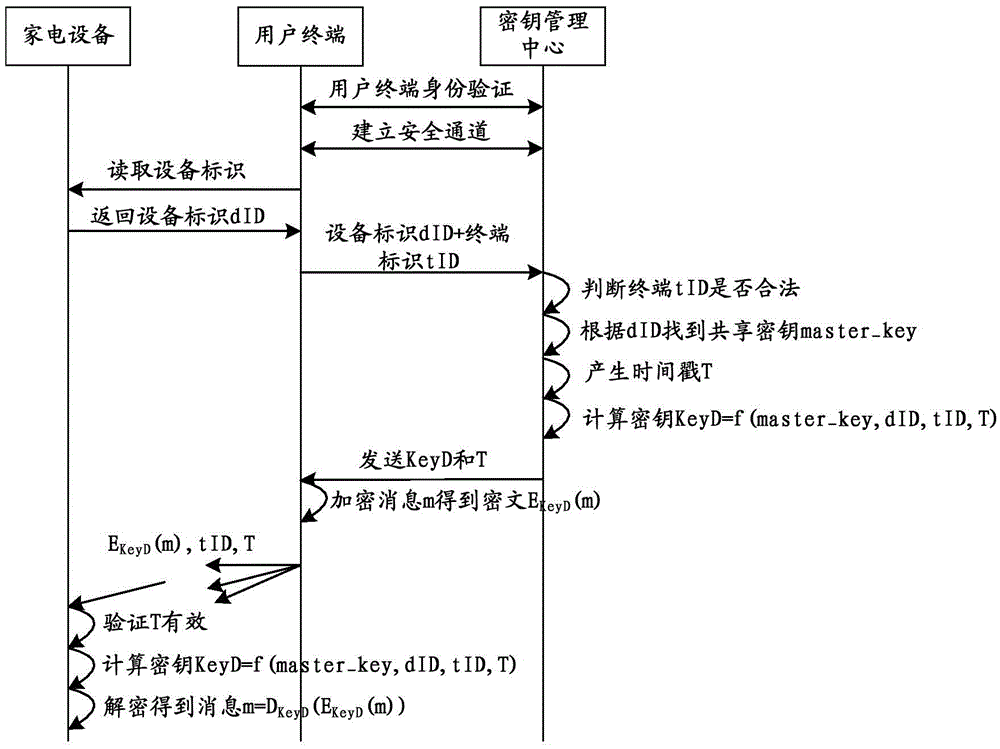
Key generation method, encrypted data analyzing method, devices and key managing center
ActiveCN105577680AReduce risk of leakageImprove securityKey distribution for secure communicationUser identity/authority verificationSecure communicationComputer terminal
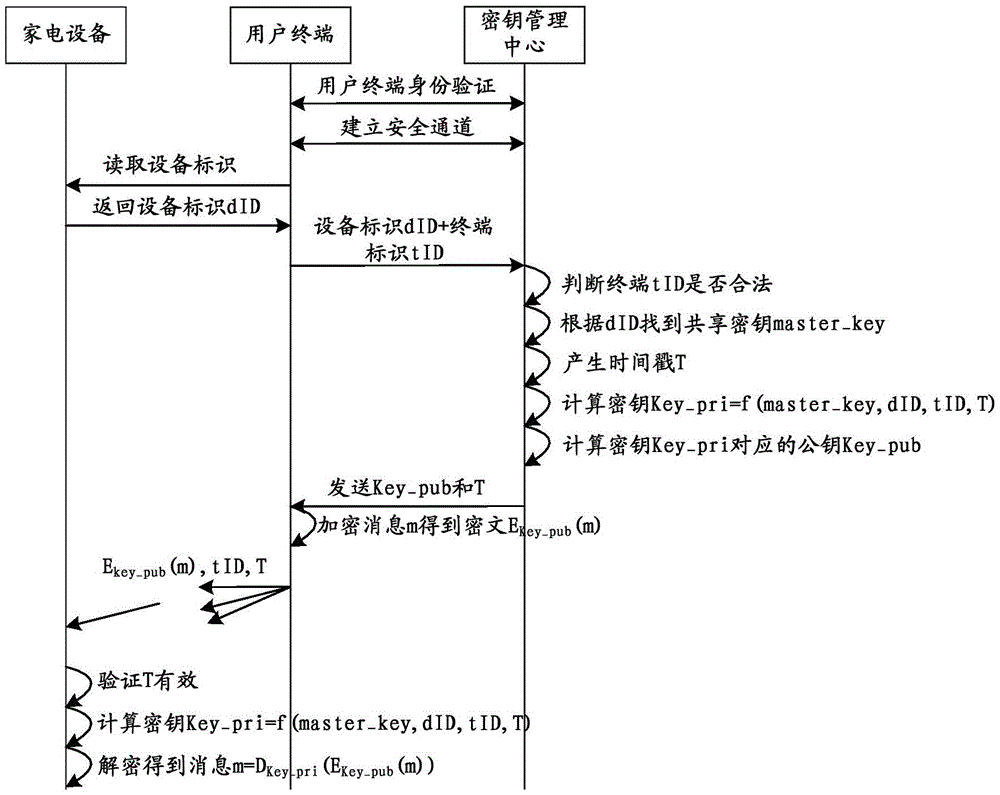
The invention discloses a key generation method, an encrypted data analyzing method, devices and a key managing center. According to the methods, the devices and the center of the invention, the key managing center receives a key obtaining request sent by a terminal; a key is generated according to the key obtaining request; the key is sent to the terminal; therefore, the terminal carries out secure communication with household appliances through the key; the household appliances are connected to a network; the key leakage risk is greatly reduced; and the problem in the prior art that the networking security of the configured household appliances is low is effectively solved.
Owner:QINGDAO HAIER INTELLIGENT HOME TECH CO LTD
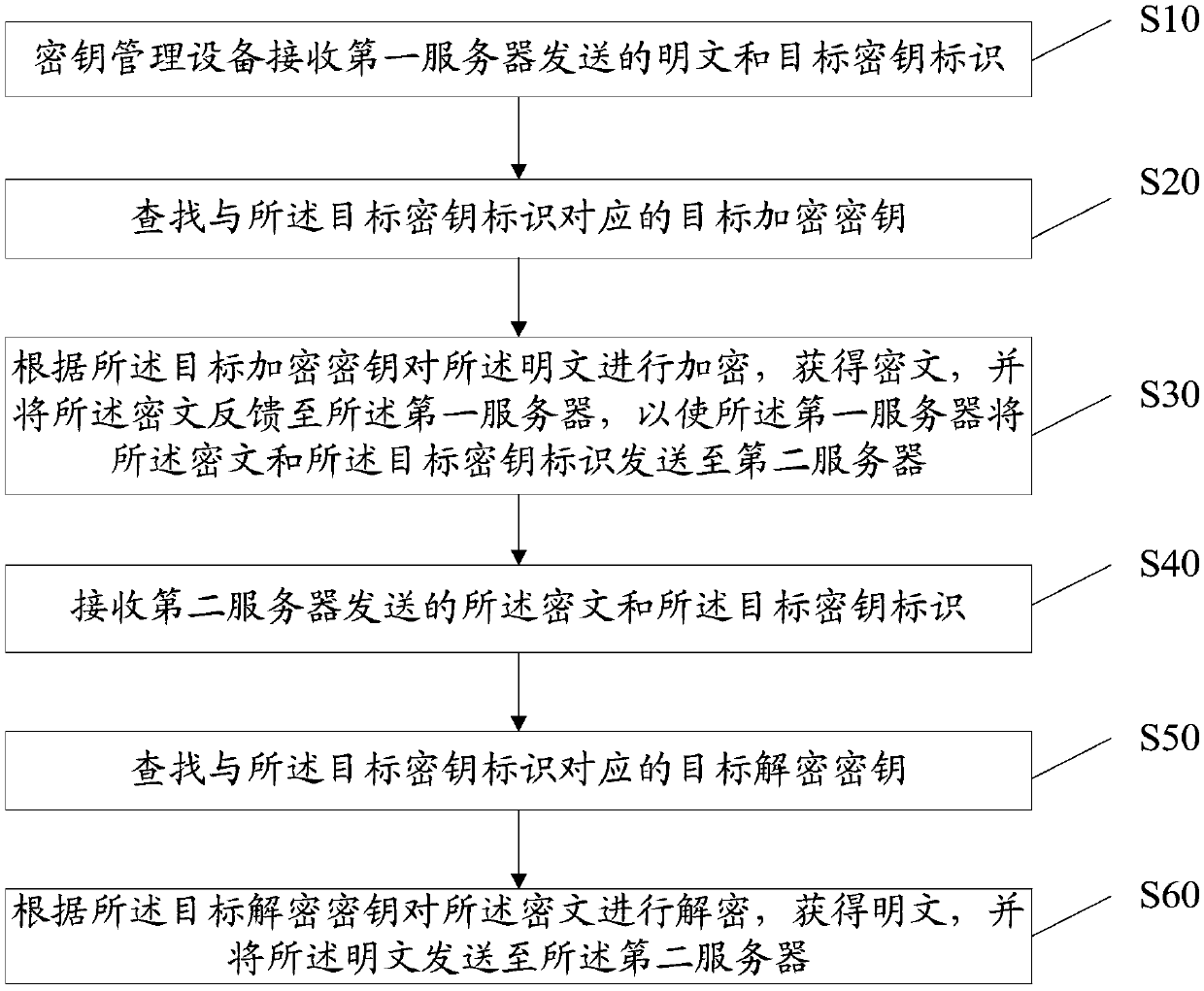
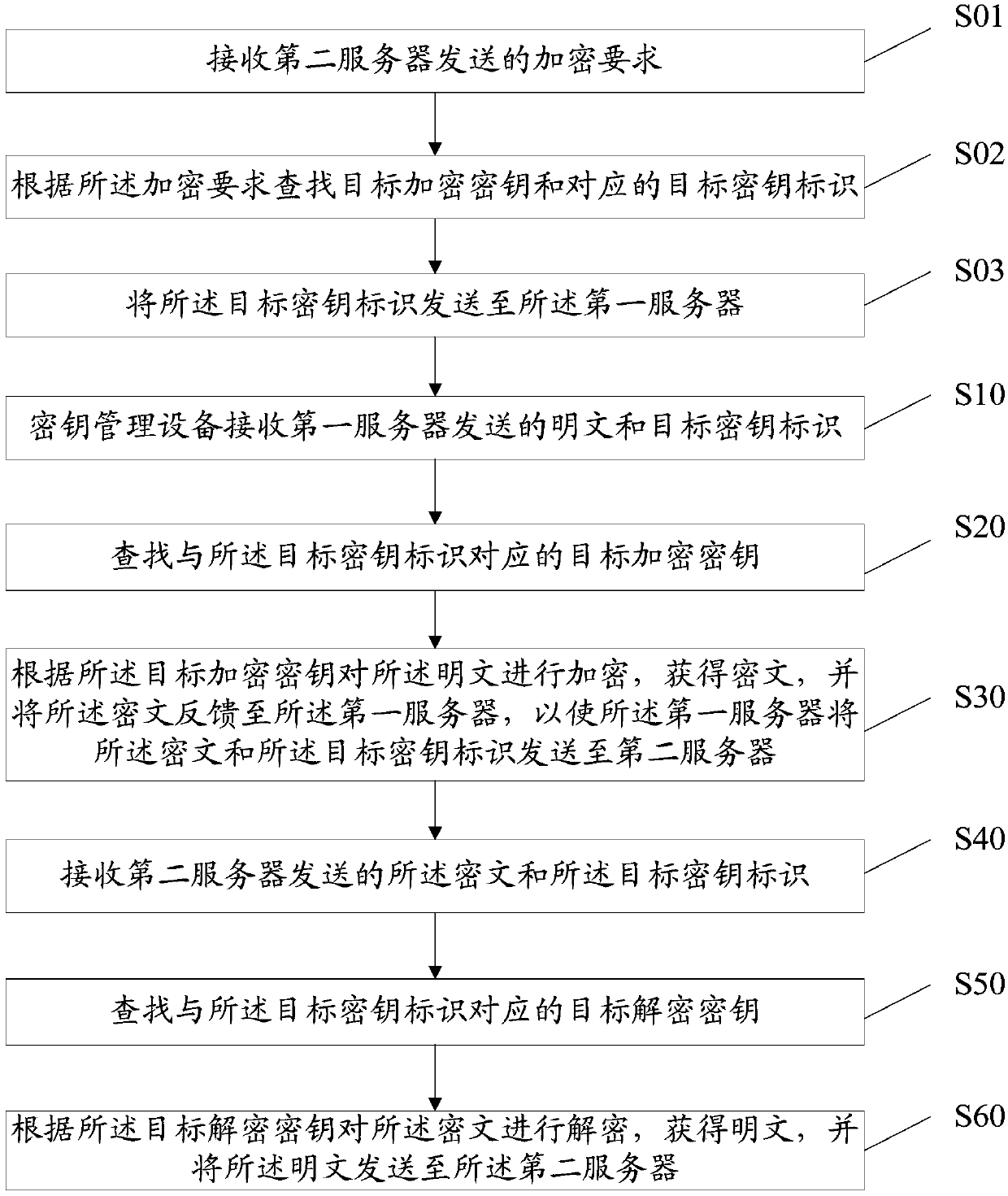
Key management method, equipment, storage medium and device
InactiveCN109728902AReduce risk of leakageReduce the Risk of MisappropriationKey distribution for secure communicationPlaintextCiphertext
The invention discloses a key management method, equipment, a storage medium and a device. The method comprises: enabling the key management equipment to receive a plaintext and a target key identifier sent by a first server; Searching a target encryption key corresponding to the target key identifier; encrypting the plaintext according to the target encryption key to obtain a ciphertext, and feeding the ciphertext back to the first server, so that the first server sends the ciphertext and the target key identifier to the second server; Receiving a ciphertext and a target key identifier sent by the second server; Searching a target decryption key corresponding to the target key identifier; And decrypting the ciphertext according to the target decryption key to obtain a plaintext, and sending the plaintext to a second server. The plaintext is encrypted and the ciphertext is decrypted through the key management device, the encryption and decryption security is improved, the first serverand the second server do not need to store the key, the risk of stealing in the key storage process is reduced, the key does not need to be transmitted, and the key leakage risk is reduced.
Owner:PING AN TECH (SHENZHEN) CO LTD
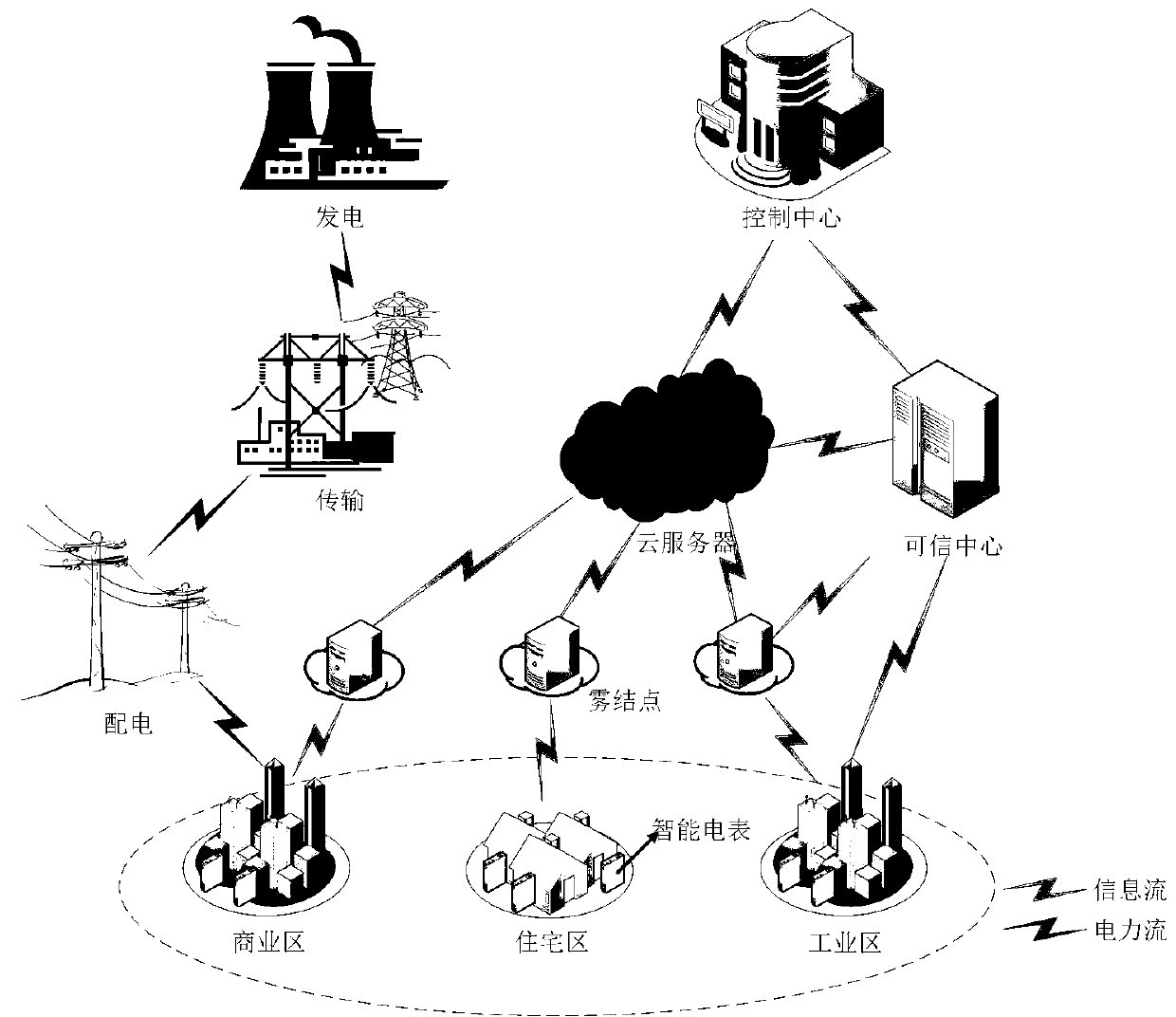
Statistical analysis method for secret key leakage resisting encrypted data aggregation in smart power grid
ActiveCN111294366AAchieve privacyAchieve protectionData processing applicationsMultiple keys/algorithms usageStatistical analysisCiphertext
The invention discloses a statistical analysis method for secret key leakage resisting encrypted data aggregation in a smart power grid. Each user area is responsible for one fog node; the fog node serves as a data aggregation gateway and a data repeater; user electric energy consumption data sent by an intelligent electric meter in a user area is aggregated for the first time by a fog node to obtain a fog-level aggregation ciphertext, the fog-level aggregation ciphertext is signed, and then the fog-level aggregation ciphertext and signature information are sent to a cloud server to be stored;the cloud server stores the aggregated ciphertext data and the signature information of different user areas in a database; data query, statistics and analysis services are provided for a control center of the intelligent power grid system; the cloud server can provide enough information for the control center on the premise of not destroying the privacy of any single user, so that the control center can calculate the sum, average value and variance of power consumption data of all users in a specified user area by utilizing the information.
Owner:SOUTHWEST PETROLEUM UNIV
Certificate-based forward security signature method and system thereof
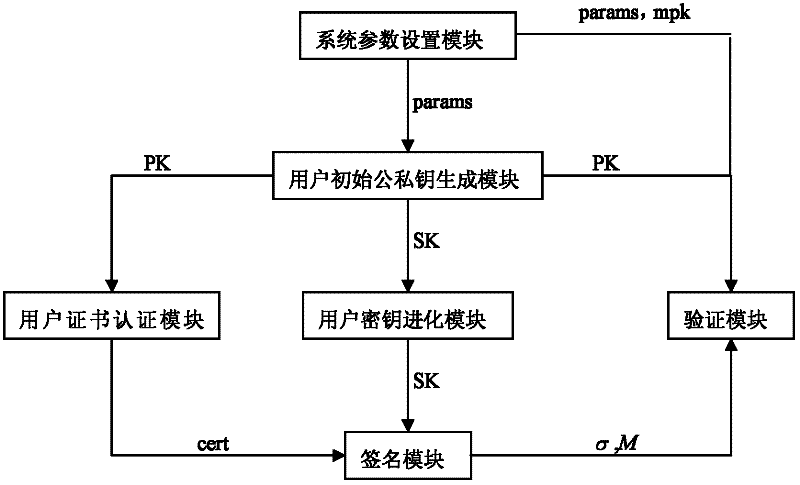
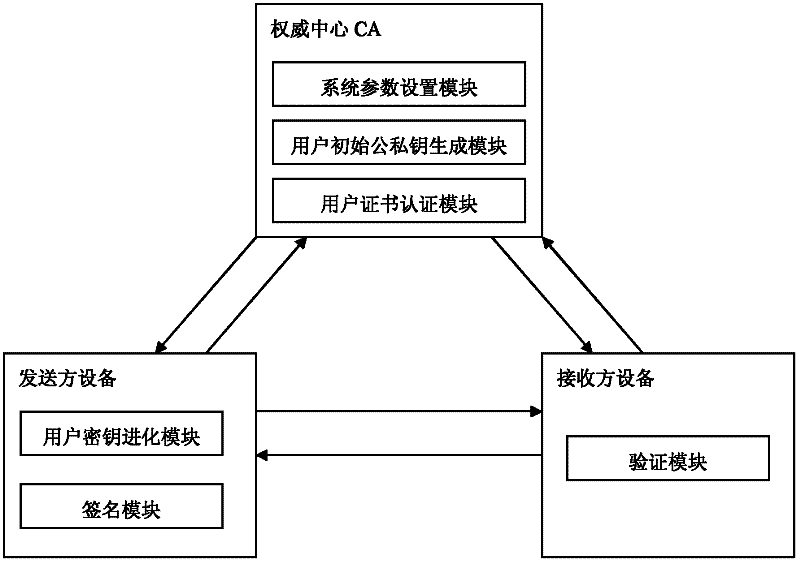
InactiveCN102420691APrevent leakageHigh utility valueKey distribution for secure communicationUser identity/authority verificationPasswordKey generation
The invention discloses a certificate-based forward security signature system. The system comprises: a system parameter setting module, a user initial public or private key generation module, a user certificate authentication module, a user secret key evolution module, a signature module and a verification module. The system parameter setting module generates a system main secret key and a public system parameter and sends to the other modules. The user initial public or private key generation module generates the public key and the initial private key of the each user. The user certificate authentication module issues the certificate to the valid user and sends to the signature module. The user secret key evolution module evolutes the private key of the user and sends to the signature module. The signature module generates the signature to any messages and sends to the verification module. The verification module verifies validity of the signature. By using the system, partial secret key leakage problems based on a certificate password system can be solved. A practical value is high. The invention also discloses a certificate-based forward security signature method.
Owner:HOHAI UNIV
Security authentication method for wireless network
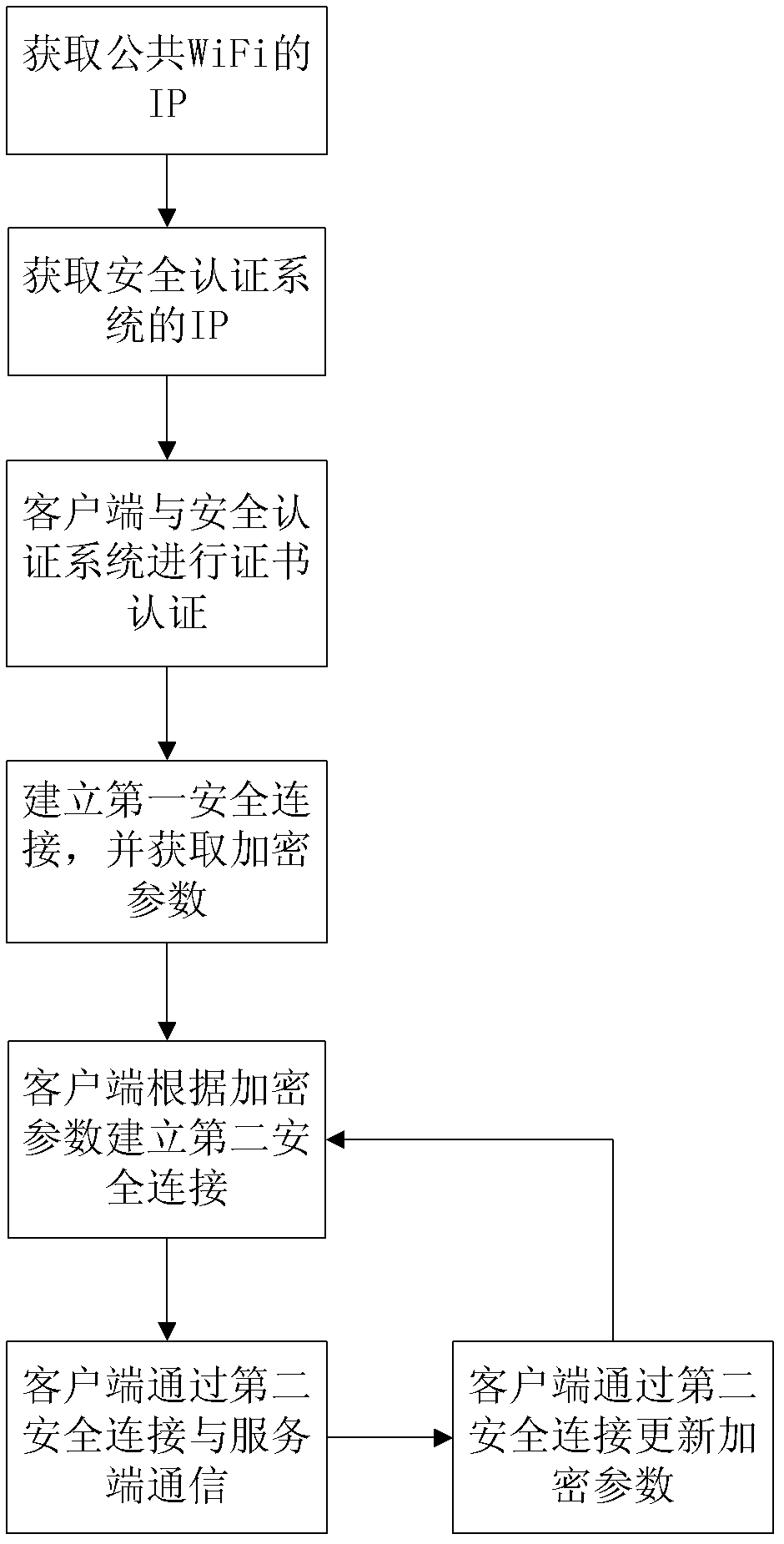
ActiveCN102547695AImplement Live BindingAvoid the possibility of leakageConnection managementSecurity arrangementBrute forceIp address
The invention relates to a security authentication method for a wireless network. A wireless fidelity (WiFi) server and a client are involved, and the security authentication method comprises the following steps that: a, an authentication service program is deployed in the client, and the client is connected to a public open system of the WiFi server to acquire a corresponding internet protocol (IP) address; b, according to the IP address, the client acquires and accesses an IP address of a security authentication system of the WiFi server; c, the WiFi server authenticates a client certificate; d, the client which passes the authentication establishes first security connection with the WiFi server and acquires encryption parameters; e, the client establishes a second security connection with the security authentication system of the WiFi server according to the encryption parameters; and f, the client and the WiFi server communicate and are updated through the second security connection. By the security authentication method, the client and the WiFi server can be connected easily and quickly by using a complex key and a complex encryption way; and meanwhile, the security during connecting can be guaranteed by using a method of updating the key regularly to ensure that brute force-based cracking and possibility of key leakage are avoided.
Owner:成都飞鱼星科技股份有限公司
IBAKA (Identity Based Authentication and Key Agreement) method
InactiveCN102624528AAnti-disclosure and masquerade attackResists man-in-the-middle attacksKey distribution for secure communicationPublic key for secure communicationProtocol for Carrying Authentication for Network AccessImpersonation attack
The invention discloses an IBAKA (Identity Based Authentication and Key Agreement) method. The method comprises the following steps that: a user at a sending terminal generates first authentication data for authenticating the identity of the user at the sending terminal and sends the first authentication data to a user at a receiving terminal; the user at the receiving terminal carries out legality authentication on the identity of the user at the sending terminal according to the received first authentication data; if authenticating that the identity of the user at the sending terminal is legal, the user at the receiving terminal generates second authentication data which does not contain key information of the user at the sending terminal, sends the second authentication data to the user at the sending terminal and generates a conversation key of the receiving terminal; the user at the sending terminal carries out legality authentication on the identity of the user at the receiving terminal according to the received second authentication data; and if the identity of the user at the receiving terminal is authenticated to be legal by a sensing terminal, the user at the sending terminal generates a conversation key of the sending terminal. The method disclosed by the invention can be used for solving the problem that a risk of denial of service attack, key leakage impersonation attack or temporal key leakage attack exists in an IBAKA protocol.
Owner:NO 61 INST OF GENERAL STAFF
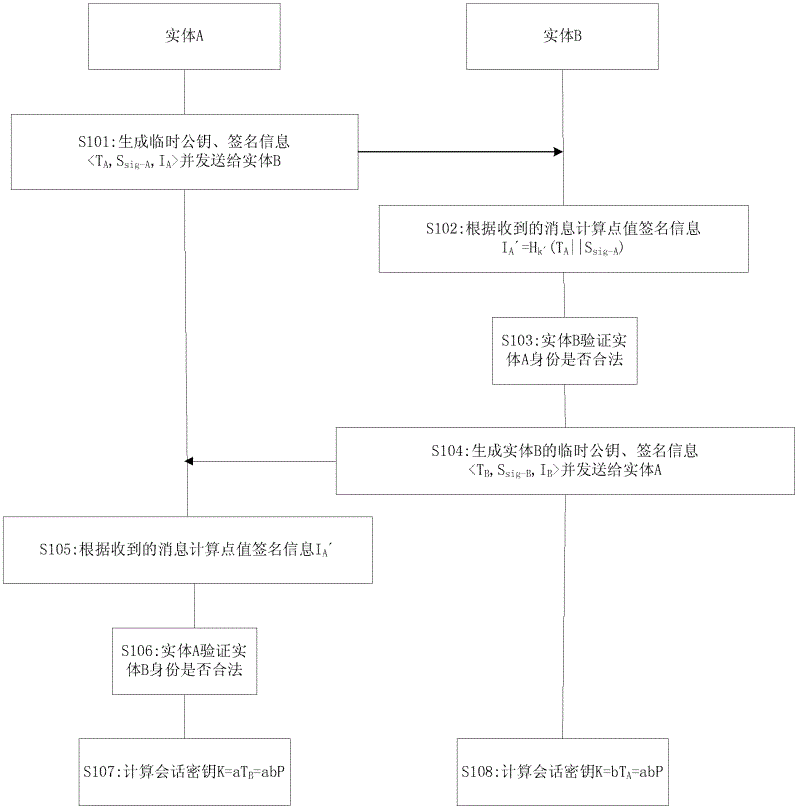
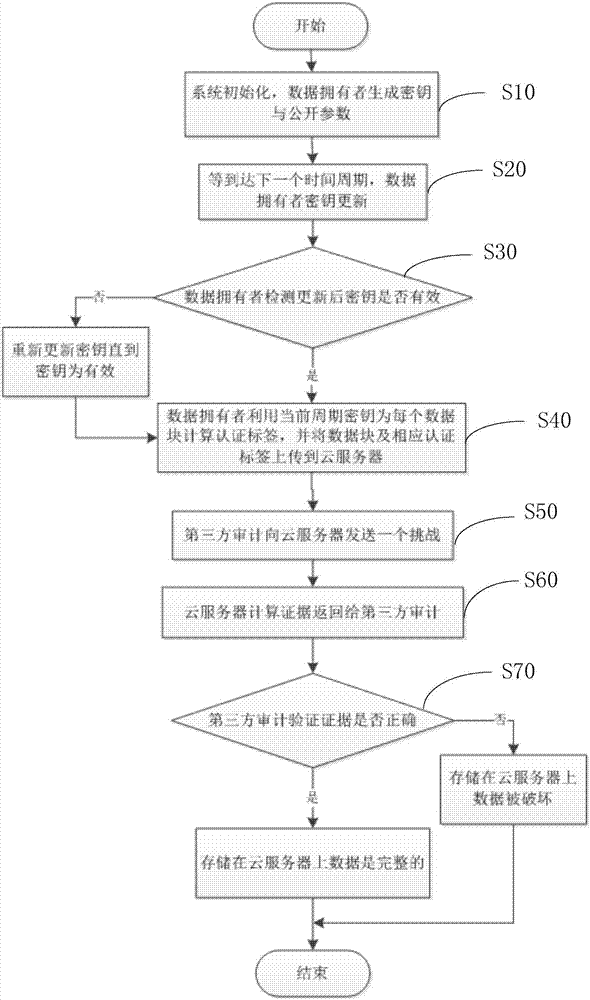
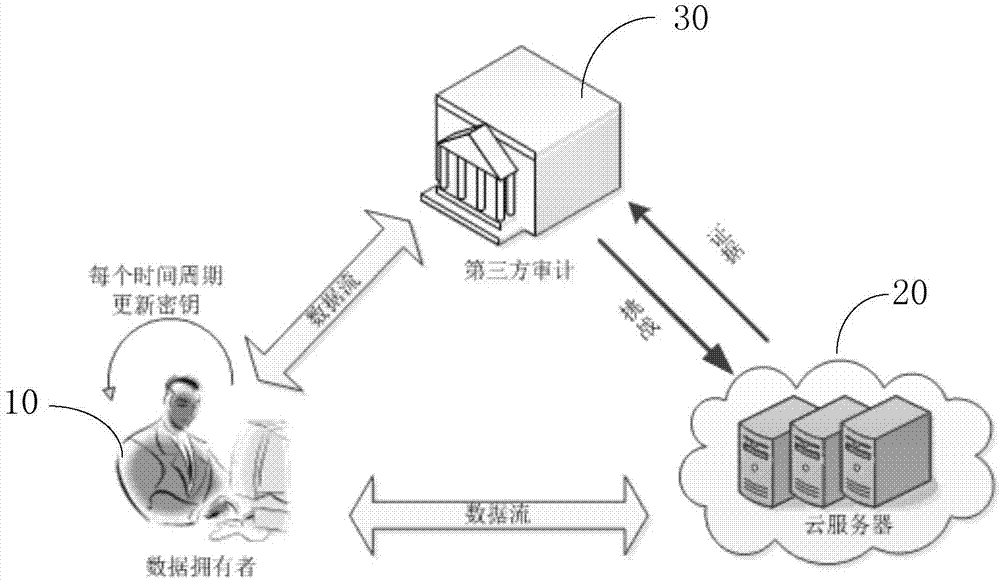
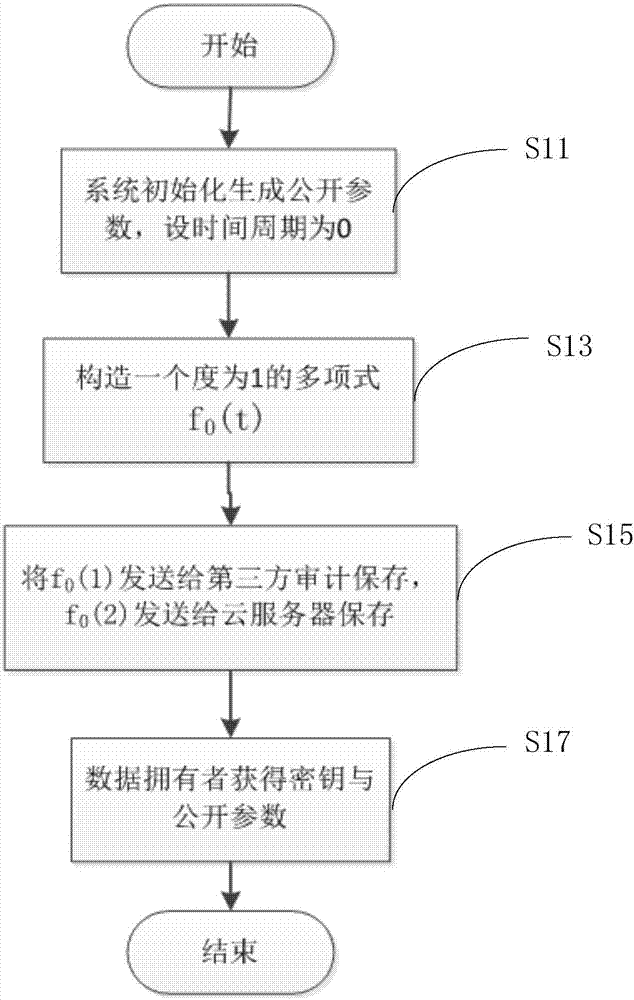
Key-updating-compatible bidirectional secure cloud storage data integrity detection method
ActiveCN107426165AHarm reductionSupport securityKey distribution for secure communicationThird partyData integrity
The present invention discloses a key-updating-compatible bidirectional secure cloud storage data integrity detection method. The method includes the following steps: initializing a system to generate parameters; obtaining by a data owner a key and a public parameter; updating the key of the data owner; checking by the data owner the validity of the updated key; using by the data owner the key of the current time period to calculate the authentication label for each data block and uploading the data blocks and the corresponding authentication labels to the cloud server; sending by a third-party audit (TPA ) a challenge to the cloud server; calculating by the cloud server the evidence to be returned to the third-party for auditing; and verifying the correctness of the evidence by the third-party audit. The invention reduces the security problem caused by the key leakage of the data owner through the key updating, divides the data owner key into two parts and saves them in different ways to realize the forward security and the backward security of the key leakage, and uses a random mask technology to protect the privacy of data.
Owner:ANHUI UNIVERSITY
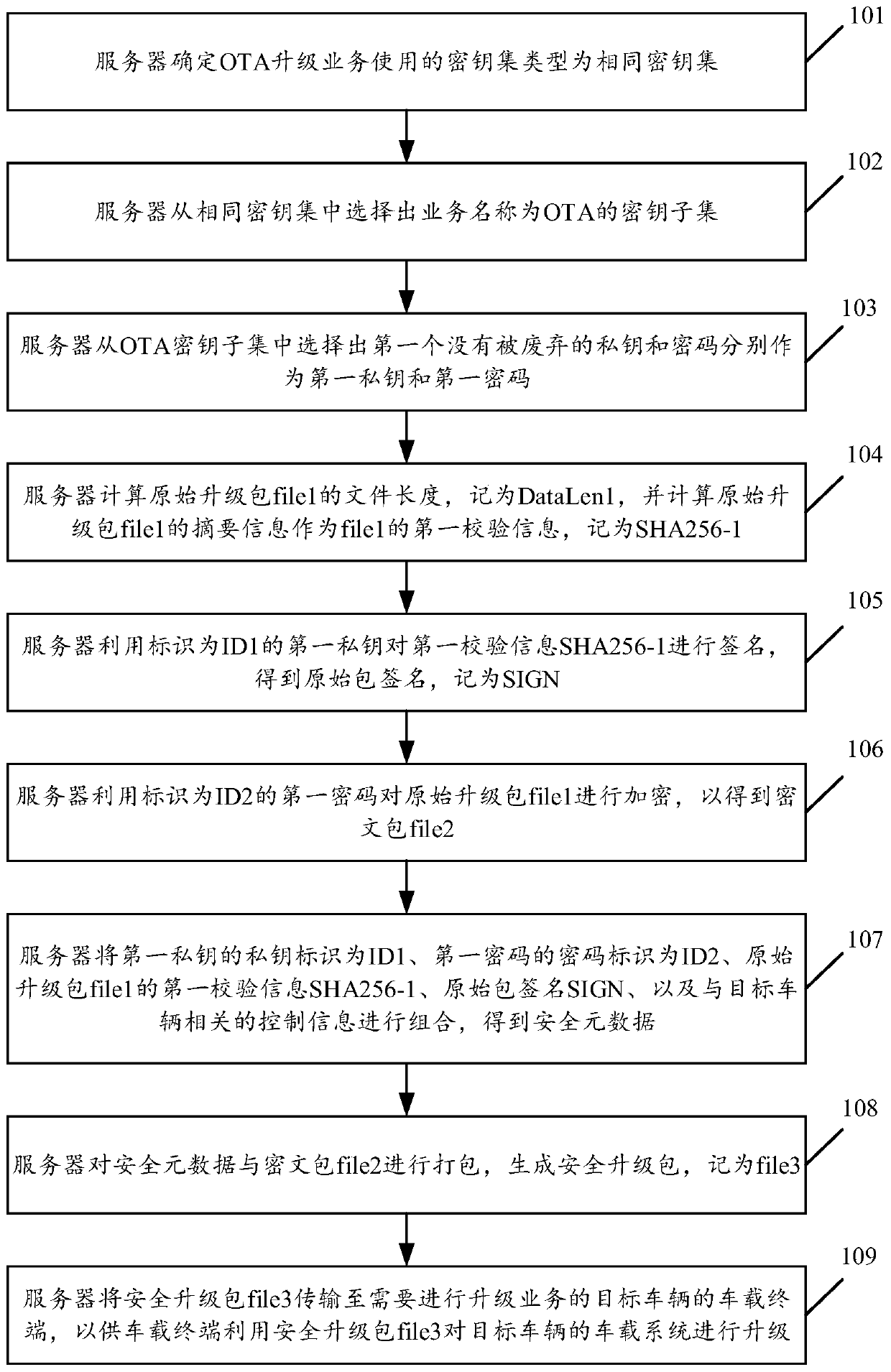
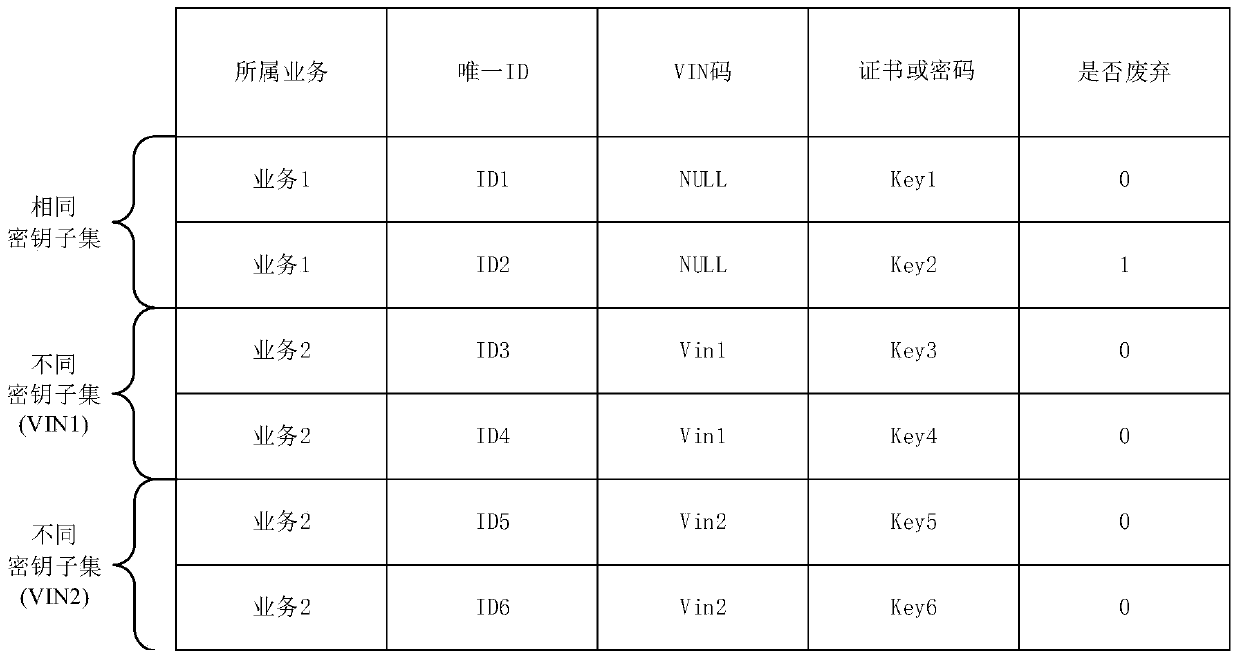
Upgrading method and upgrading system for vehicle-mounted system of automobile, server and vehicle-mounted terminal
ActiveCN110225063AHarm reductionRealize security permission separation designEncryption apparatus with shift registers/memoriesUser identity/authority verificationPasswordComputer terminal
The invention discloses an upgrading method and system of an automobile vehicle-mounted system, a server and a vehicle-mounted terminal. The method comprises the steps that the server determines a keyset type corresponding to the service type of an upgrading service at this time; a first private key and a first password are selected from the key set belonging to the key set type; the first private key and the first password are utilized to sign and encrypt the original upgrade package so as to obtain a security upgrade package, and the identification information of the used certificate and password are added into the security upgrade package; the security upgrade package is transmitted to a vehicle-mounted terminal of the target vehicle; the vehicle-mounted terminal restores the identification information of the used certificate and password from the security upgrade package; therefore, a first public key corresponding to the first private key and a second password corresponding to the first password are obtained and utilized to carry out signature verification and decryption on the security upgrade package. The vehicle-mounted system is upgraded by using the restored original upgrade package, so that the key separation of the service level is realized, the key can be replaced at any time, and the possibility and the harm degree of key leakage are reduced.
Owner:GUANGZHOU XIAOPENG MOTORS TECH CO LTD
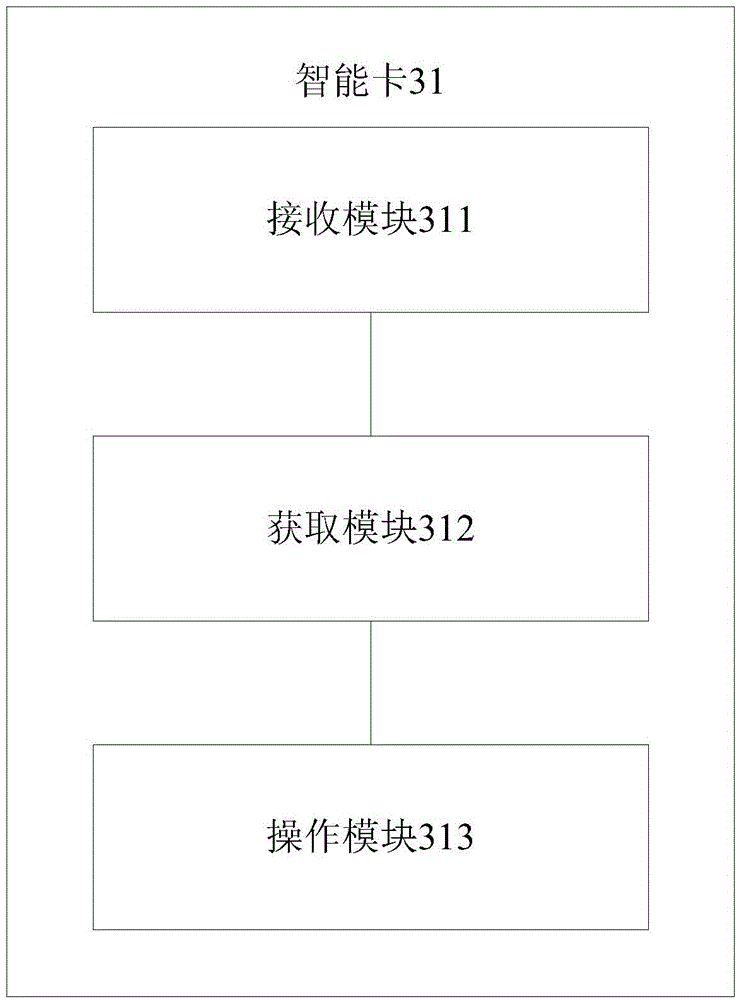
Smart card based secret key application method and application apparatus
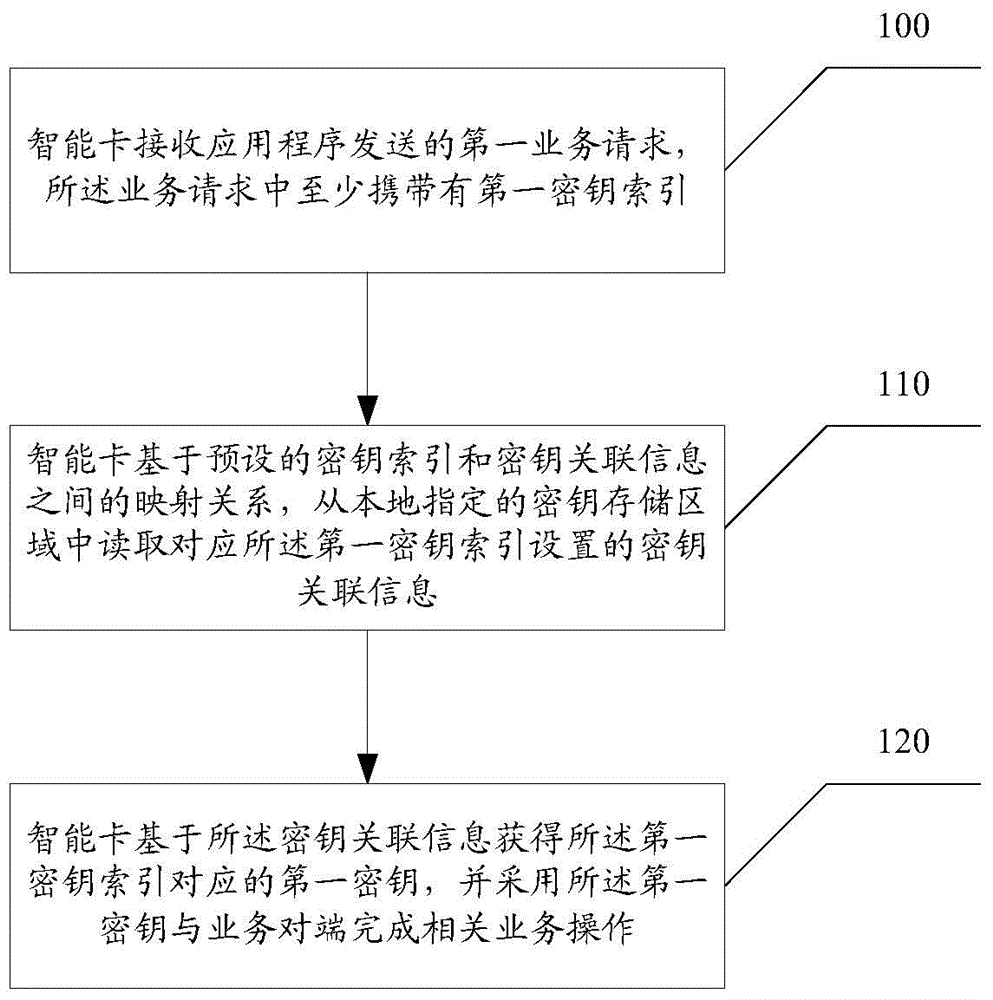
ActiveCN105678192AAvoid the risk of interactionAvoid the risk of leaking keysDigital data protectionInternal/peripheral component protectionSmart cardKey storage
The invention discloses a smart card based secret key application method and an application apparatus for reducing potential safety hazards of secret key leakage. The method comprises: after the smart card receives a first business request sent by an application program, based on a mapping relation between a first secret key index and secret key associated information carried by the first business request, the smart card reads the secret key associated information arranged corresponding to the first secret key index from a secret key storage region designated locally, and obtains a first secret key corresponding to the first secret key index based on the secret key associated information, and employs the first secret key and business to end to complete relevant operation. In this way, when the smart card is processing the first business request, the first secret key is obtained from the secret key storage region designated locally by the mapping relation between the firs secret key index and the secret key associated information, rather than obtained directly from the application program, which prevents safety hazards of secret key leakage caused by attacks to the application programs by hackers or Trojan virus.
Owner:SUMAVISION TECH CO LTD
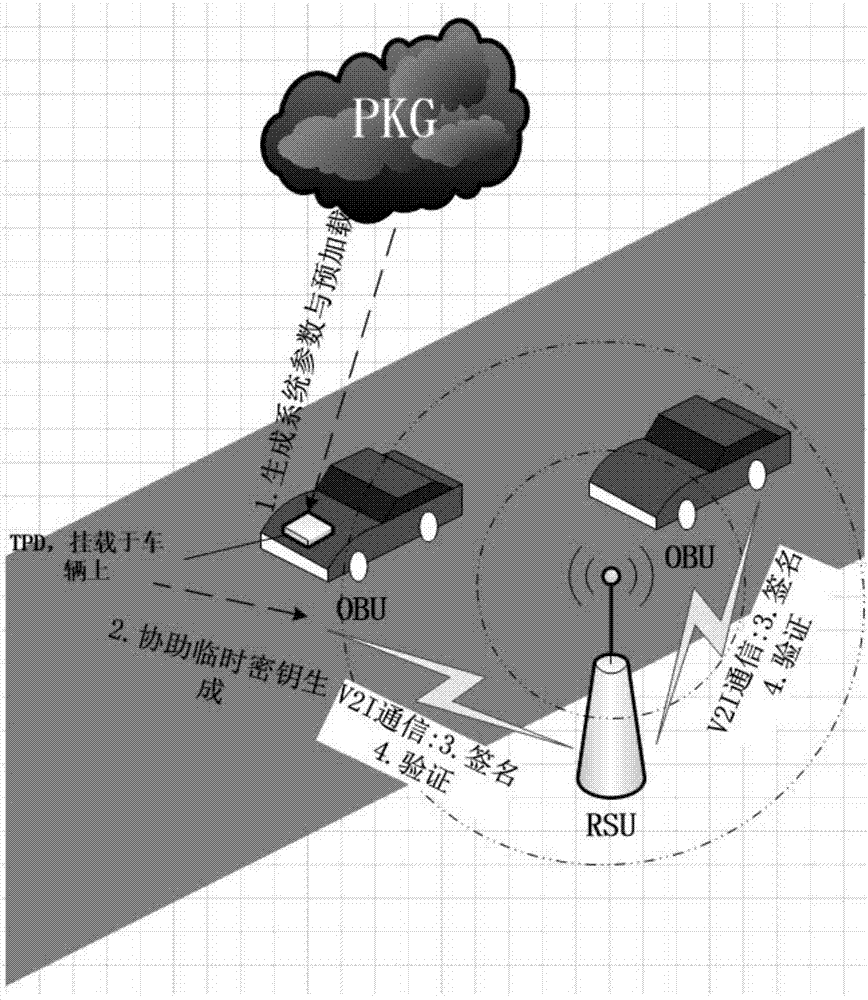
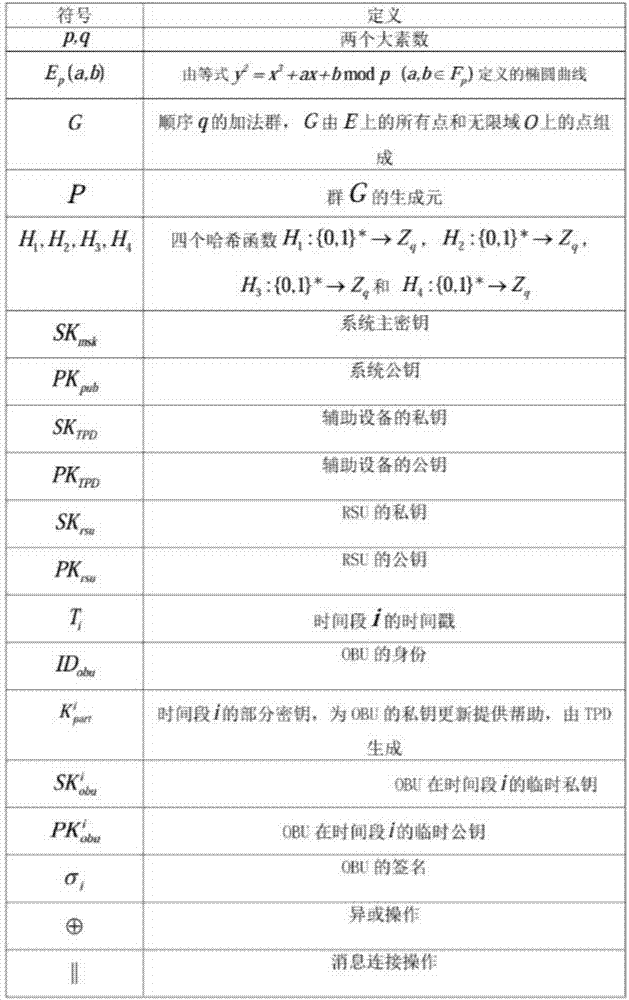
Key-insulated safe car networking V2I authentication system and method
ActiveCN107979840ANo security impactShorten the timeParticular environment based servicesVehicle infrastructure communicationInformation processingCost calculation
The invention provides a key-insulated safe car networking V2I authentication system and method and relates to the field of car networking. Although many car networking oriented safety authenticationschemes exist at present, the schemes are all basically based on an assumption that 'keys are safely saved', and most of the schemes are constructed by using bilinearity. However, a car networking environment has excellent openness, an intelligent terminal and other information processing equipment board on vehicles are generally inadequate in safety protection, and resources are constrained. Therefore, key leakage risk and cost calculation problems need to be considered while designing the authentication scheme. The invention provides an effective safety authentication method for solving theproblems, and the safety authentication method is applicable to authentication during communication between vehicles and infrastructure in a car networking state. By using a key-insulated method, thekey safety of the whole system is not reduced even if temporary keys leak, and the method has anonymity and forward and backward safety. Moreover, according to the method, lightweight elliptic curve operation is adopted, so that the authentication process is effective.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
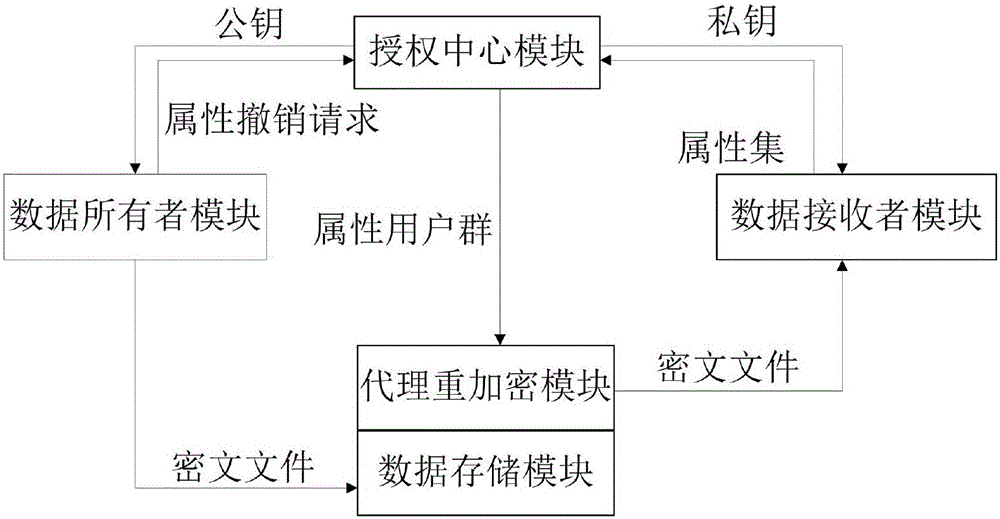
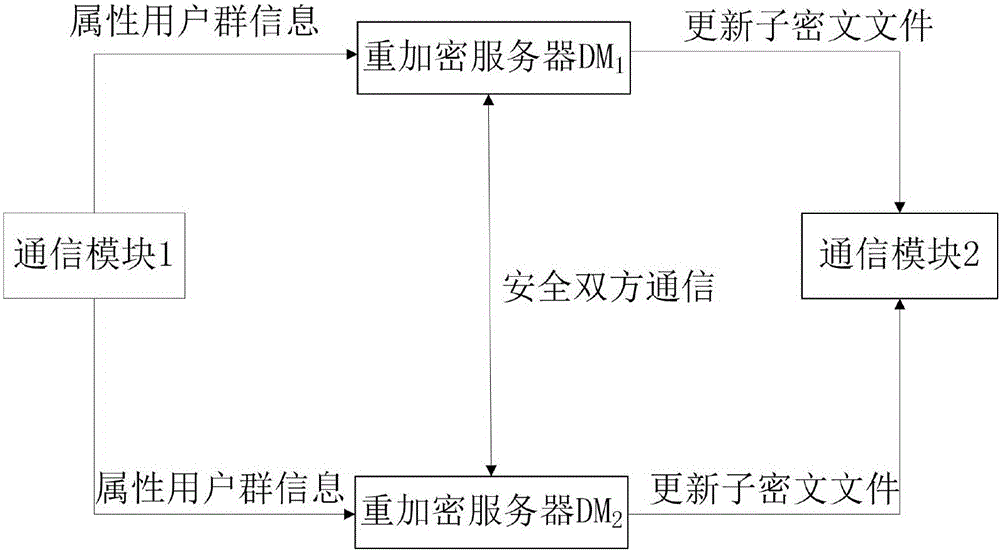
Encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes
ActiveCN106059768ALeak resistanceOvercoming property revocation flawsKey distribution for secure communicationPublic key for secure communicationCiphertextDisk encryption
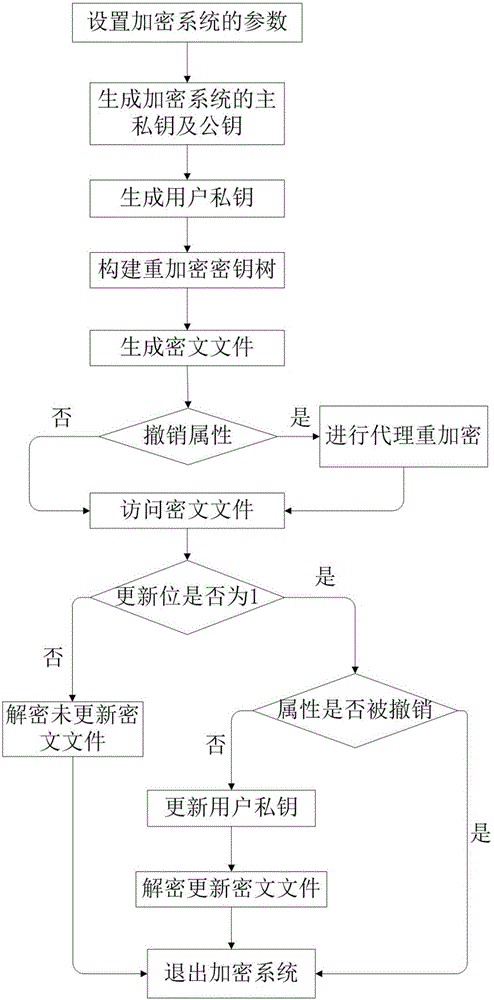
The present invention provides an encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes. The method comprises: 1, setting the parameters of an encryption system; 2, generating the main private key and the public key of the encryption system; 3, generating a user private key; 4, building a re-encryption key tree; 5, generating a cryptograph file; 6, cancelling attributes; 7, performing re-encryption agency; 8, accessing the cryptograph file; 9, determining whether the update position of the cryptograph file is 1 or not; 10, decrypting an un-updating cryptograph file; 11, updating the private key; 12, decrypting the update cryptograph file; and 13, quitting the encryption system. Through adoption of a dual-agency re-encryption server model, the encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes can resist the leakage of the re-encryption key. When the attributes are cancelled, an attribute user group is employed to construct the re-encryption key tree so as to effectively, timely and accurately cancel the indirect attributes. When the encryption is performed, the secret is dispersed to resist the conspiracy attack.
Owner:XIDIAN UNIV
Data transmission method and device based on key authentication
ActiveCN109302369AReduce the probability of leakageEnsure safetyUser identity/authority verificationUnique identifierKey authentication
The invention discloses a data transmission method and device based on key authentication. The method comprises the following steps: sending digital certificate information to a client by a server, and sending summary information of the digital certificate information and a combined unique identifier value including a handshake information context information identifier and a digital certificate information identifier to a key server; determining a private key corresponding to the digital certificate information by the key server according to the summary information, signing the combined unique identifier value by using the private key, sending a signature value to the server, and sending the signature value to the client by the server; and after the client verifies that the signature value is valid by using a public key corresponding to the digital certificate information, carrying out data interaction by the client and the server. According to the data transmission method provided bythe invention, the problem of the server that the private key must be deployed at the front end and the client executes TLS 1.3 handshaking is solved, and the private key and a certificate are deployed on different equipment, so that the server cannot read private key contents, thus the probability of private key leakage is reduced, and the safety of the private key is guaranteed.
Owner:GUIZHOU BAISHANCLOUD TECH CO LTD
Group key management method supporting user identity authentication
ActiveCN106301788ARelieve pressureReduce the possibility of leaksKey distribution for secure communicationPublic key for secure communicationPaired DataUser authentication
The invention discloses a group key management method supporting user identity authentication. The method comprises steps that comprises steps that an information sender, an information receiver and a trusted third party participating in identity verification and key management are included; the trusted third party is responsible for establishing an integral key system and managing the identity information of users; the information sender is used for acquiring an identity voucher disclosed by the data receiver from the trusted third party, carrying out encryption in combination with the private key pair data, utilizing the private information to realize data signature and then sending the data after signature to a whole multicast system, and the information receiver is used for carrying out decryption and source verification through utilizing a public key and the private key data. Compared with a traditional key scheme, key management pressure and key leakage possibility are greatly reduced.
Owner:WUHAN UNIV
Signature processing method, related device and equipment
ActiveCN110545190AReduce workloadAvoid hidden dangersKey distribution for secure communicationUser identity/authority verificationWorkloadServer-side
The invention discloses a signature processing method, which comprises the steps of obtaining first to-be-processed data of a first blockchain node, the first to-be-processed data comprising first target data; sending first target data in the first to-be-processed data to a signature server, so as to enable the signature server to perform signature processing on the first target data by adopting the private key to obtain signature information; receiving signature information sent by the signature server; and sending the signature information to the second blockchain node, so as to enable the second blockchain node to update the blockchain account book according to the signature information. The invention further discloses a signature processing device and equipment. The whole signature processing process is carried out in the signature server, and the private key is stored at the signature server side, so that the hidden danger of private key leakage caused by the fact that the blockchain node is broken through can be prevented, the signature processing work is stripped from the blockchain node, and the workload of the blockchain node is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
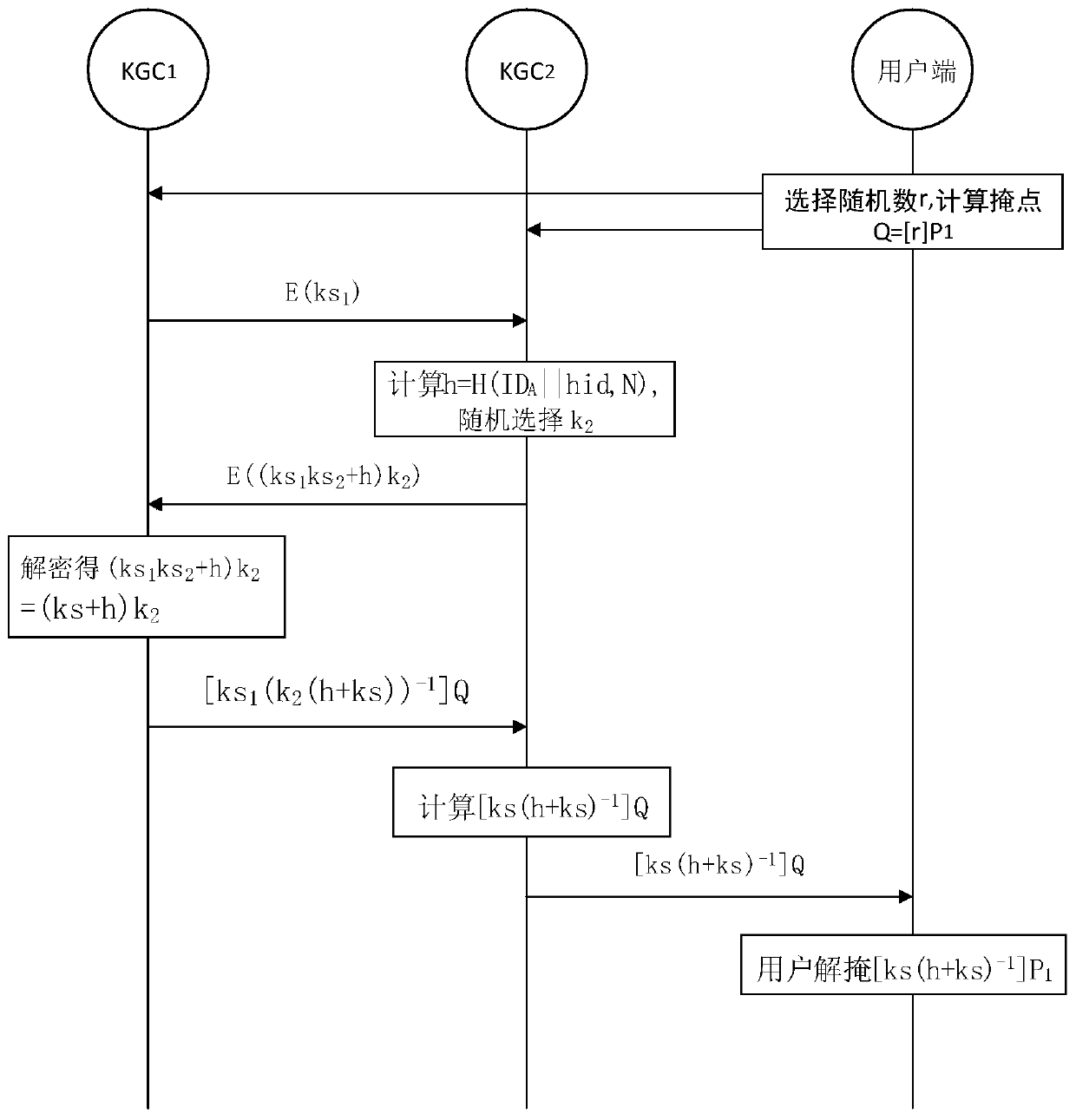
User private key generation method and system, readable storage medium and electronic equipment
ActiveCN110166239ALeakage will not result inPrevent leakageKey distribution for secure communicationCommunication with homomorphic encryptionKey generationSystem safety
The invention relates to a user private key generation method, a user private key generation system, a computer readable storage medium and electronic equipment. The user private key generation methodcomprises the steps that when a private key request sent by a user side is received, a random mask point calculated by the user side through a first random number is acquired; and the main private keys of the M key generation centers and the random mask point are utilized to execute a secret state operation so as to obtain a mask private key, thereby enabling the user side to demask the mask private key so as to obtain the user private key. According to the method, user private key leakage can be avoided, and the system security is improved.
Owner:成都卫士通信息产业股份有限公司
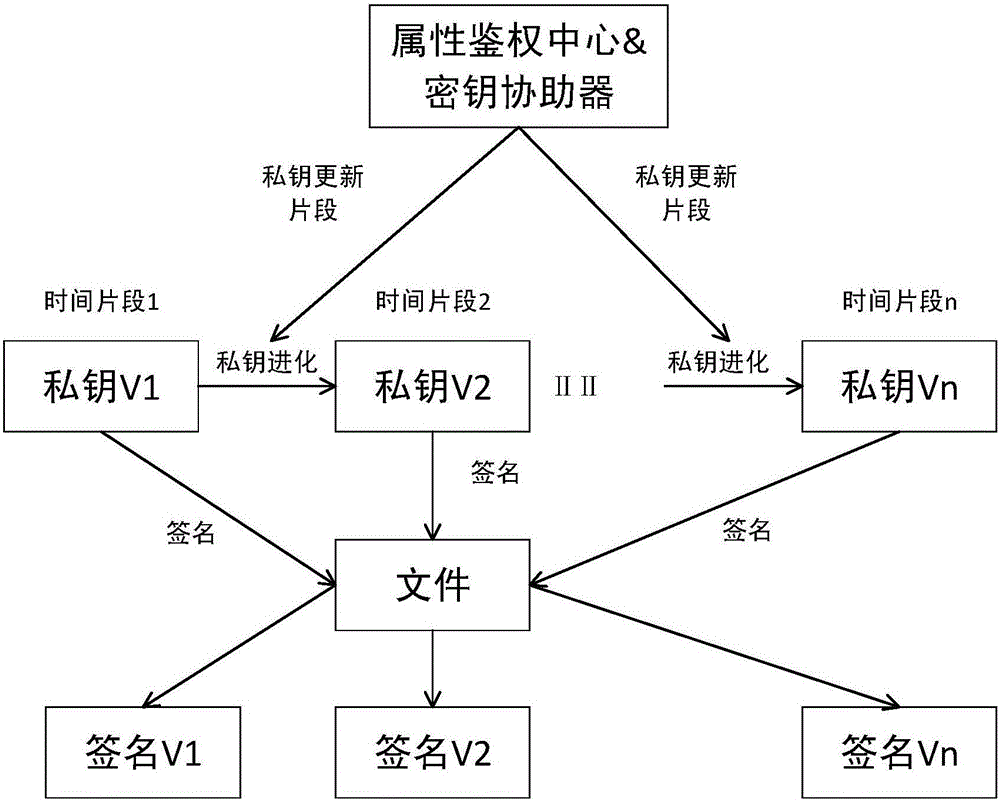
Key isolation signing method based on attribute
ActiveCN106027240APublic authenticationFront and rear safety assuranceKey distribution for secure communicationPublic key for secure communicationSystem timeBilinear pairing
The invention discloses a key isolation signing method based on attribute, which aims at problems of lack of protective measures for key leakage and increase of computation overhead of a terminal caused by bilinear pairing operation in the prior art. A whole signing system is divided into several independent time slices, when the system enters into a new time slice, a key helper generates a private key updating slice, and a user updates a private key. For a certain file, the user signs with the private key corresponding to the current time slice, and verification result of a signature is also corresponding to a certain time slice of the system. If the private key of the user is leaked within a certain time slice, the system also can keep forward security and backward security in other time slices, and thus, harm of private key leakage is minimized. In a process of signing, any operation of bilinear pairing is not required, and computation overhead of a user terminal is reduced. When system time slices evolve, system public parameters are not required to be updated again, and communication overhead caused by synchronization of the public parameters is reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
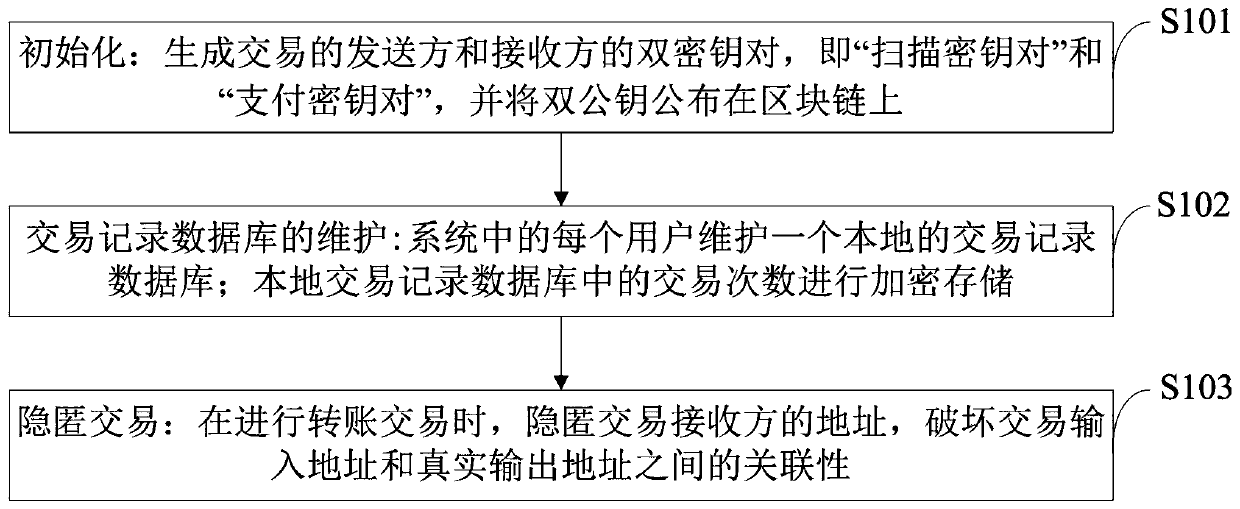
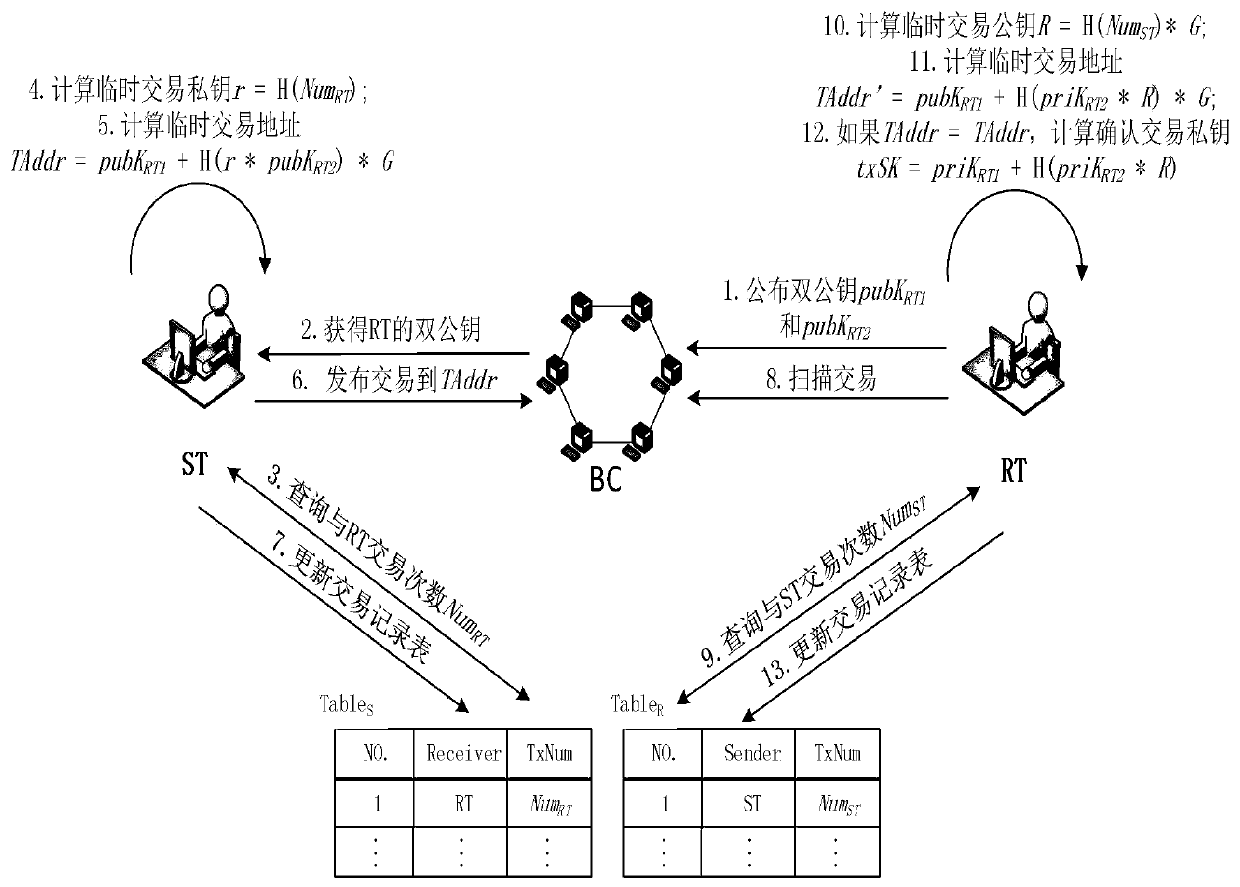
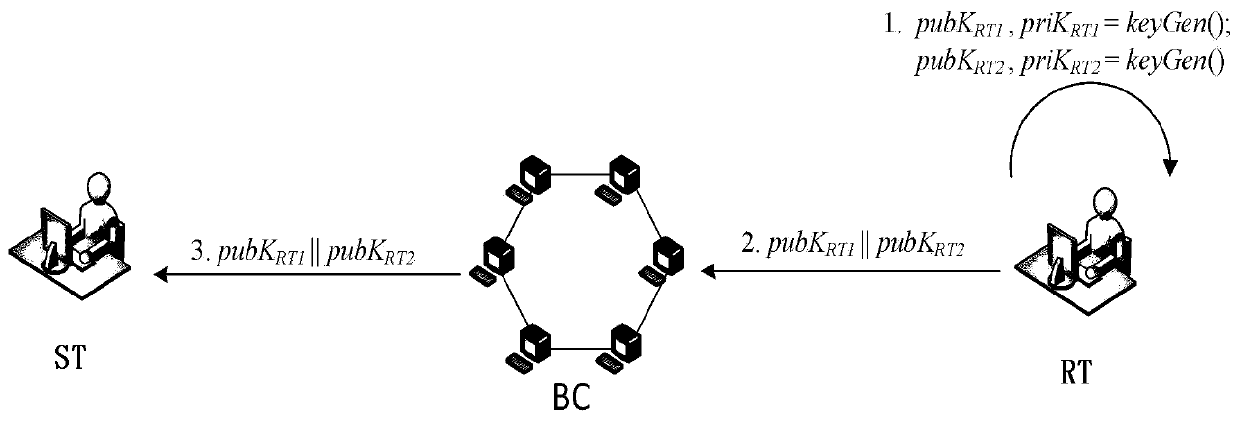
Method for implementing blockchain dual-key hidden address protocol without temporary key leakage
ActiveCN110675265ASolve privacy and security issuesFinanceDigital data protectionInformation processingEngineering
The invention belongs to the technical field of blockchain privacy information processing, and discloses a method for implementing a blockchain dual-key hidden address protocol without temporary key leakage, which comprises the following steps of initializing, generating a dual-key pair of a sender and a receiver of a transaction, and publishing the dual public keys on a blockchain; maintaining atransaction record database, enabling each user in the system to maintain a local transaction record database, and encrypting and storing the transaction times in the local transaction record databases; and hiding the transaction, hiding the address of the transaction receiver when the transfer transaction is carried out. According to the invention, the correct operation of the transaction can beensured under the condition that the transaction temporary key is not leaked, and the privacy security problem caused by the leakage of the transaction temporary key in a double-key hidden address protocol which is widely used at present is effectively solved; in addition, an enemy or an attacker cannot construct a transaction temporary output address same as that of the sender, and cannot calculate a transaction confirmation private key corresponding to the transaction temporary output address.
Owner:SICHUAN NORMAL UNIVERSITY
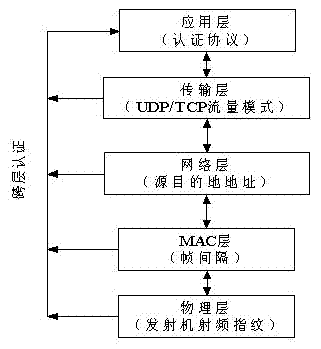
Radio-frequency-fingerprint-based challenge-response authentication protocol method
InactiveCN102904724AAchieve high-strength authenticationAddressing leak detection exposure issuesUser identity/authority verificationSecurity arrangementRadio frequency signalPhysical layer
The invention relates to a radio-frequency-fingerprint-based challenge-response authentication protocol method. A challenger communicates with a responder through a wireless medium, and the method comprises the following two stages, namely an initial stage and an operational stage, wherein the initial stage comprises the following steps that: the responder acquires a radio frequency signal of the challenger through the wireless medium and detects a challenger radio frequency fingerprint (RFF) in the signal, and the acquired challenger RFF is stored in a memory; and the operational stage comprises the following steps that: after receiving the radio frequency signal of the challenger and detecting the RFF in the signal, the responder reads the stored challenger RFF in the memory, and compares the RFF which is detected currently with the stored RFF, if the RFF which is detected currently is matched with the stored RFF, a protocol continues operating, and if the RFF which is detected currently is not matched with the stored RFF, the protocol stops operating. By the method, high-strength identity authentication of physical layer information of both communication parties is realized, majority of attacks such as pretending, replay, monitoring and denial of service which are cloned by a communication party can be resisted, and the method is favorable for avoiding the phenomena of secret key leakage and public detection.
Owner:NANTONG UNIVERSITY
Mobile terminal intelligent card based data transmission method and mobile terminal
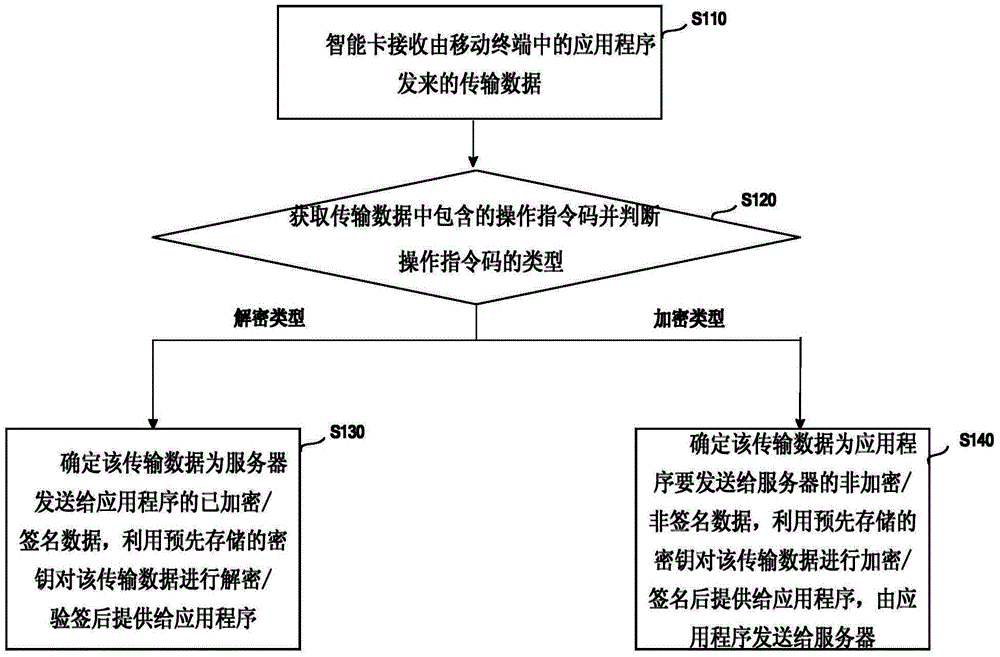
InactiveCN104184892APrevent leakageImprove securityDigital data authenticationSubstation equipmentOperating instructionApplication programming interface
The invention discloses a mobile terminal intelligent card based data transmission method and a mobile terminal so as to solve a problem of secret key leakage existing in the prior art. The method comprises the steps that an intelligent card receives data transmitted by an application program in the mobile terminal; operating instruction codes contained in the transmitted data are acquired, and corresponding operations are carried out according to the types of the operating instruction codes. When the operating instruction codes comprise a decryption / signature verification type of instruction code, decryption / signature verification is carried out on the transmitted data by using a pre-stored secret key, and then the transmitted data is provided for the application program; or when the operating instruction codes comprise an encryption / signing type of instruction code, encryption / signing is carried out on the transmitted data by using the pre-stored secret key, and then the transmitted data is provided for the application program. The intelligent card and the application program are communicated through at least one of the following interfaces: an application program interface used for storing / reading short messages, an application program interface used for writing / reading an address list, an application program interface used for accessing to a GP card, an application program interface used for writing or reading an SIM card short message center and an application program interface used for reading STK menu data.
Owner:GUILIN WEIWANG INTERNET INFORMATION TECH CO LTD
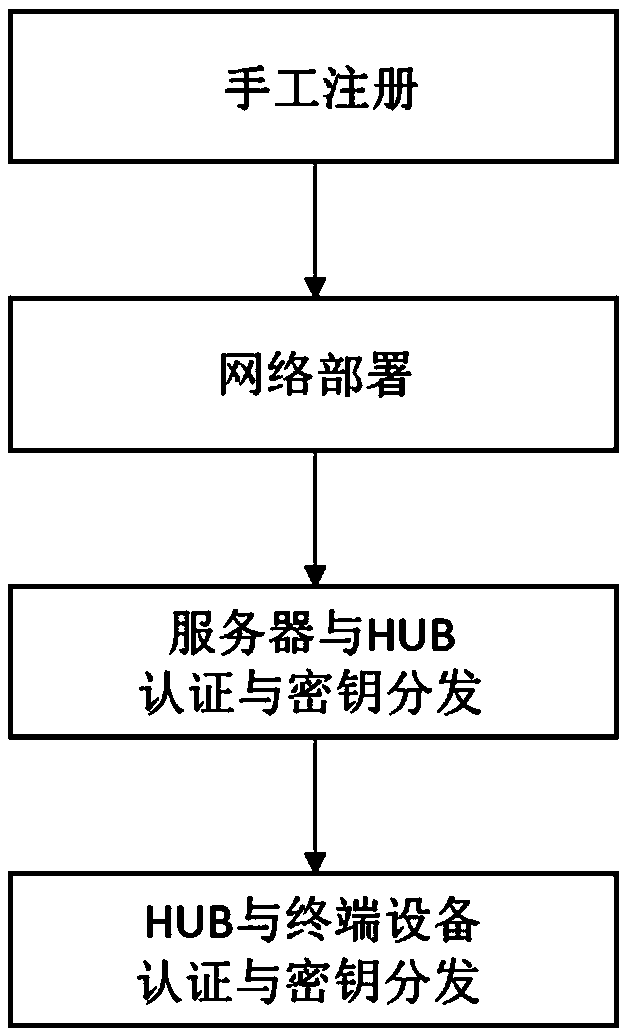
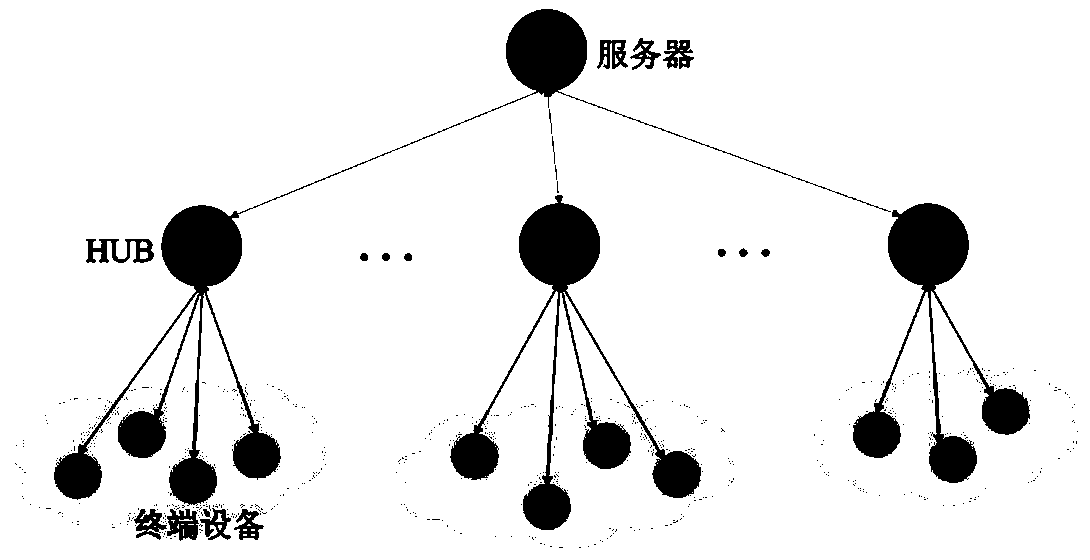
A device authentication and key distribution system and method based on a physical unclonable function
The invention discloses an equipment authentication and key distribution system and method based on a physical unclonable function. The system comprises a server, an HUB and terminal equipment, The method comprises the steps that before network deployment, manually registering all HUBs and terminal equipment on a server; Deploying network equipment according to the three-layer tree topology structure; carrying out identity authentication and key distribution between the devices, including authentication and key distribution between the server and the HUB and authentication and key distributionbetween the HUB and the terminal device. Based on the PUF, bidirectional authentication and key distribution among the server, the HUB and the terminal equipment can be realized. Different from a traditional secret key pre-storage mode and a public key mode, the method has the advantages that the PUF serves as an authentication factor and a secret key generator, secret key leakage can be prevented, the calculation amount can be reduced, and the method can be widely applied to low-energy-consumption Internet of Things equipment with limited resources.
Owner:南京浩天科技有限公司
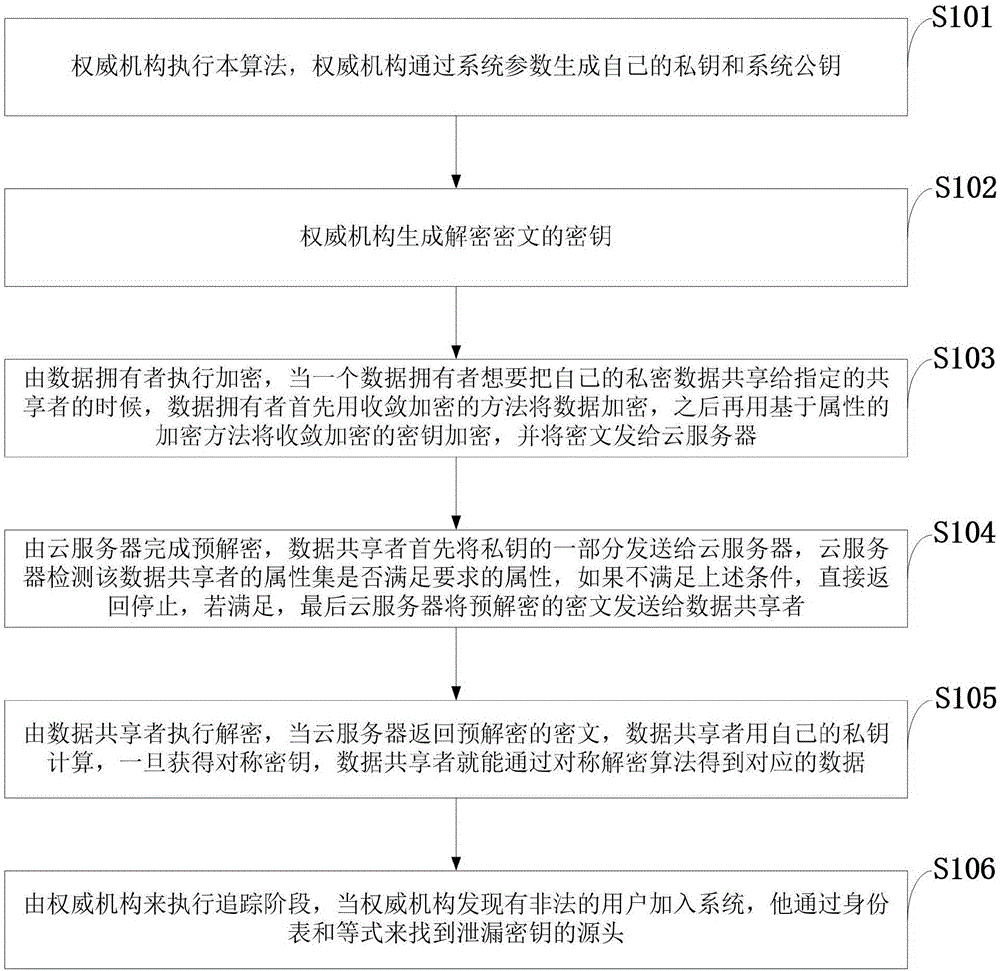
High-efficiency traceable data sharing method based on mobile cloud environment
ActiveCN106506474AImprove securitySmall amount of calculationUser identity/authority verificationAttribute-based encryptionCiphertext
The invention discloses a high-efficiency traceable data sharing method based on a mobile cloud environment, and the method comprises the steps: employing the technology of convergence encryption and traitor tracing; enabling a data owner to carry out encryption, wherein the data owner firstly encrypts the data through a convergence encryption method when the data owner wants to share his own private data to a specified sharer, secondly encrypts a secret key through employing an encryption method based on attributes after convergence encryption, and transmits a ciphertext to a cloud server; enabling an authority mechanism to execute tracing, and finding the source of secret key leakage through an identity table and equality when the authority mechanism finds an illegal user visiting a system. The method employs the convergence encryption, and the encryption of the secret key is only related with the data, thereby improving the safety of data in the system. In addition, in order to prevent a legal user from leaking a secret key for his own benefits, the method adds one traitor tracing algorithm to trace the source of the secret key leakage. An experiment indicates that the method is high in efficiency, and is practical.
Owner:XIDIAN UNIV
A bidirectional authentication method for a server and a terminal
InactiveCN103634266ANo leakage issuesEfficiently findPublic key for secure communicationUser identity/authority verificationEncryption decryptionServer-side
The invention discloses a bidirectional authentication method for a server and a terminal. Two pairs of secret keys which are preset in a server side and a terminal and a negotiated encryption-decryption algorithm are used, and accordingly a bidirectional authentication mode is realized via a fixed process. The two pairs of secret keys are one pair of public keys and one pair of private keys. The one pair of public keys and the one pair of private keys are used and respectively stored at the server and the terminal side, and encryption and decryption processing is carried out through the negotiated algorithm. The beneficial effects of the present invention are that: through the secret keys stored in advance and the negotiated encryption-decryption algorithm, identification of clients is carried out employing asymmetric encryption in order to find client information highly efficiently at the server side; bidirectional authentication is carried out through symmetrical encryption and decryption inside the server and terminal in order to realize network plaintext transmission of authentication information without causing secret key leakage problems and to achieve the effect that correct bidirectional authentication can not be carried out even if either one of the public keys or the private keys is broken through.
Owner:SHANGHAI LINGPAN INFORMATION TECH
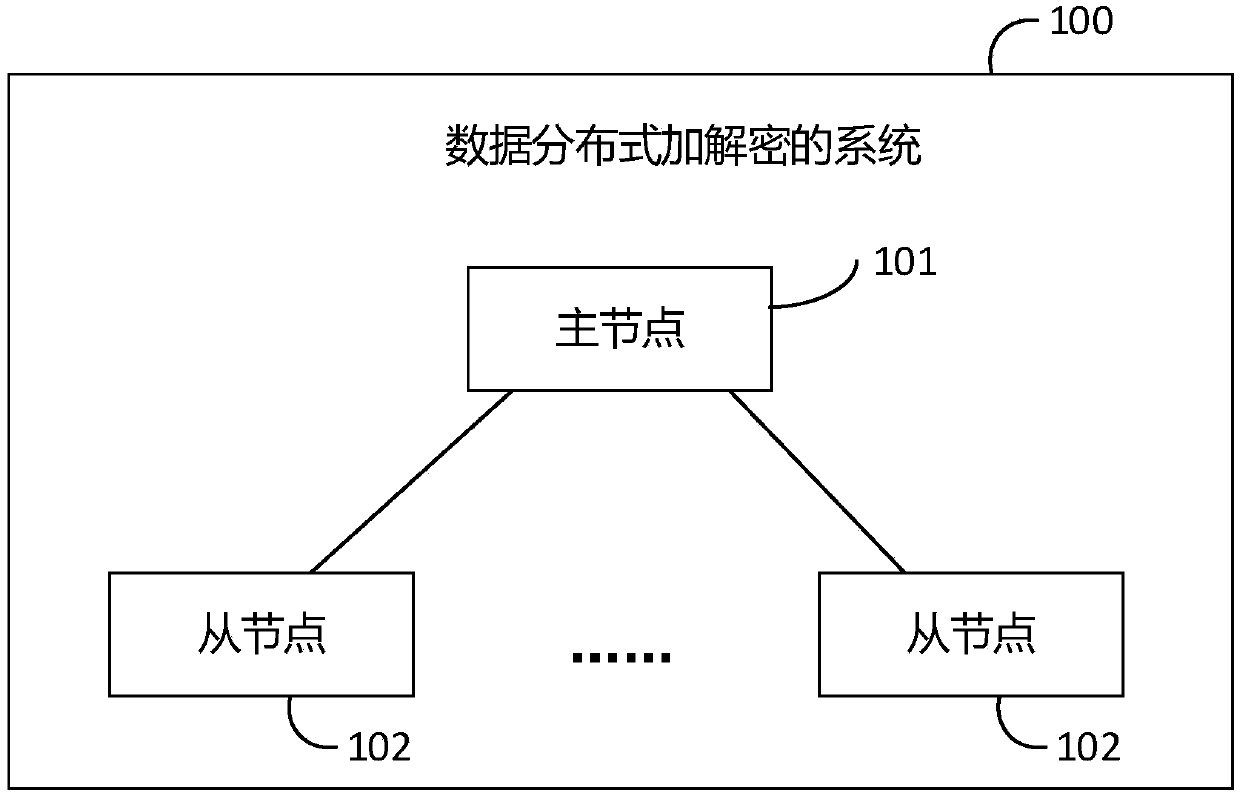
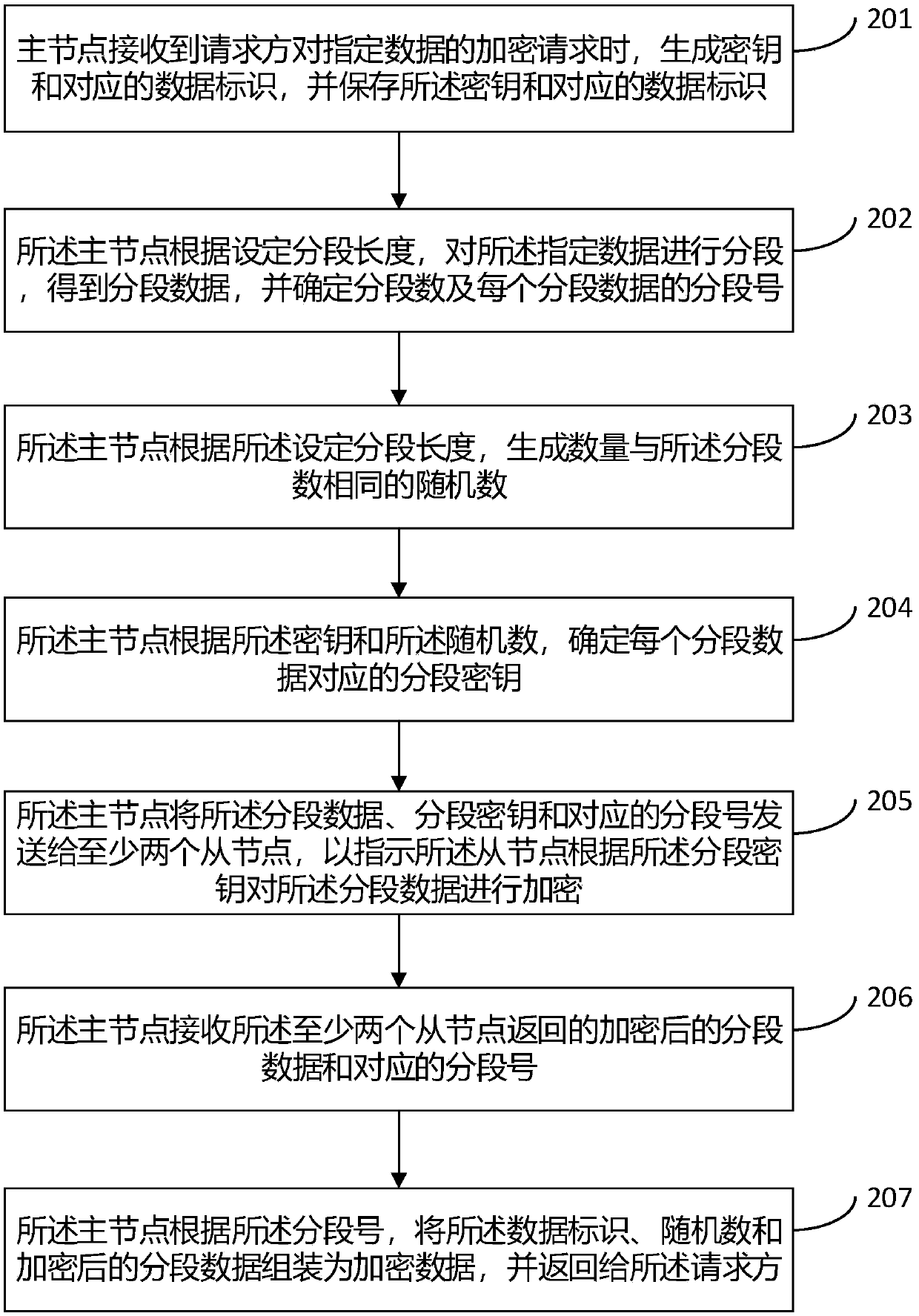
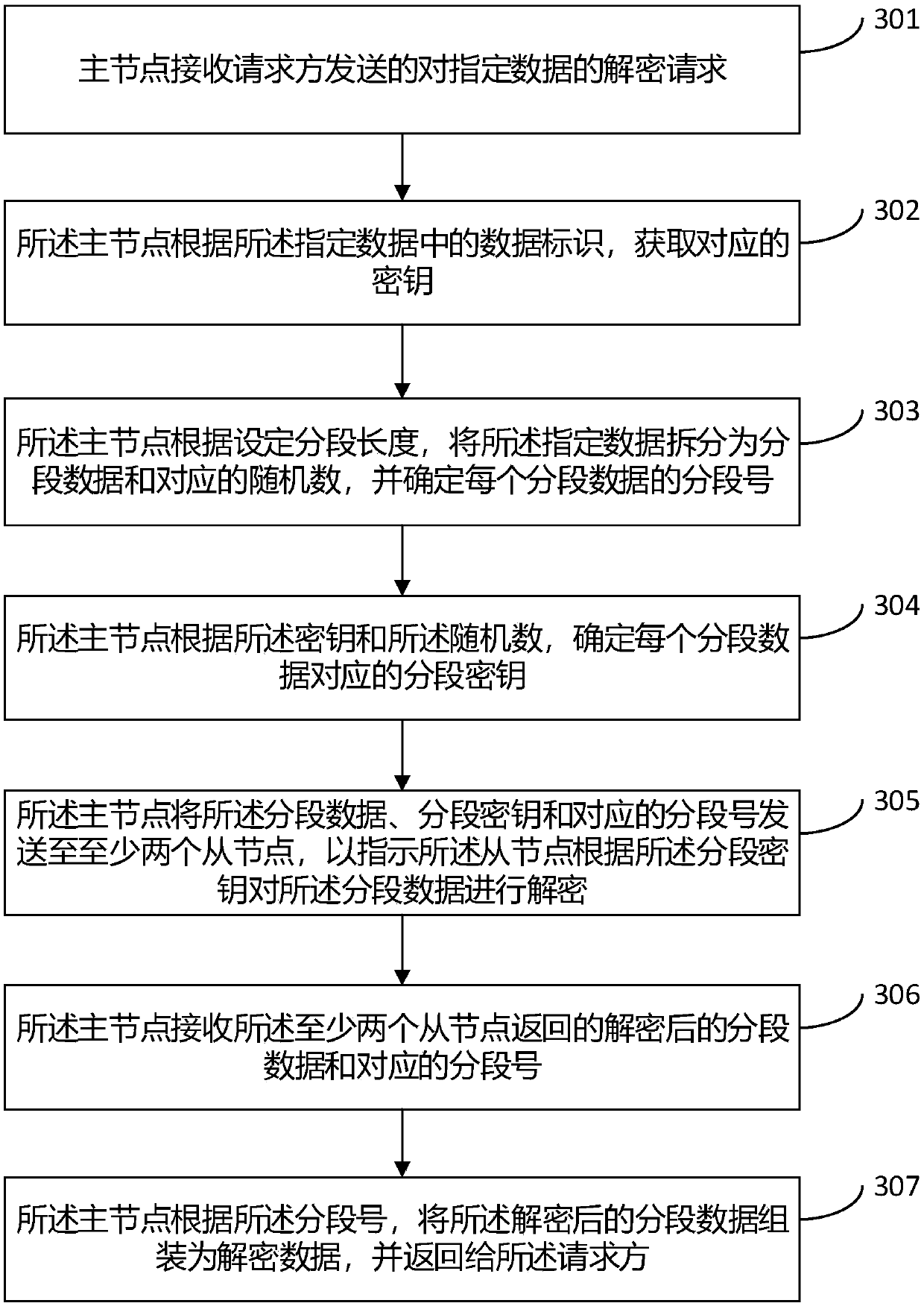
System, method and device for data distributed encryption and decryption, electronic device and medium
ActiveCN109635573AImprove securityReduce risk of leakageDigital data protectionComputer hardwareEncryption
The invention provides a system, a method and a device for data distributed encryption and decryption, an electronic device and a medium. The system comprises: a master node, used for receiving an encryption and decryption request of specified data sent by a requester, dividing the specified data into segmented data according to a set segmented length, determining a segmented secret key of each segmented data, and sending the segmented data, the segmented secret keys and the segmented numbers to at least two slave nodes, and the segmented secret keys corresponding to the segmented data are different; and at least two slave nodes, used for encrypting and decrypting the segmented data according to the segmented key, and sending the encrypted and decrypted segmented data and the segmented number to the master node. The main node is also used for assembling the encrypted and decrypted segmented data into encrypted and decrypted data according to the segment number and returning the encrypted and decrypted data to the requester. According to the invention, the master node uniformly receives the encryption and decryption request and distributes the segmented data to the slave node for encryption and decryption, and the keys of the segmented data are different, so that the risk of key leakage is reduced, and the security of the data is improved.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
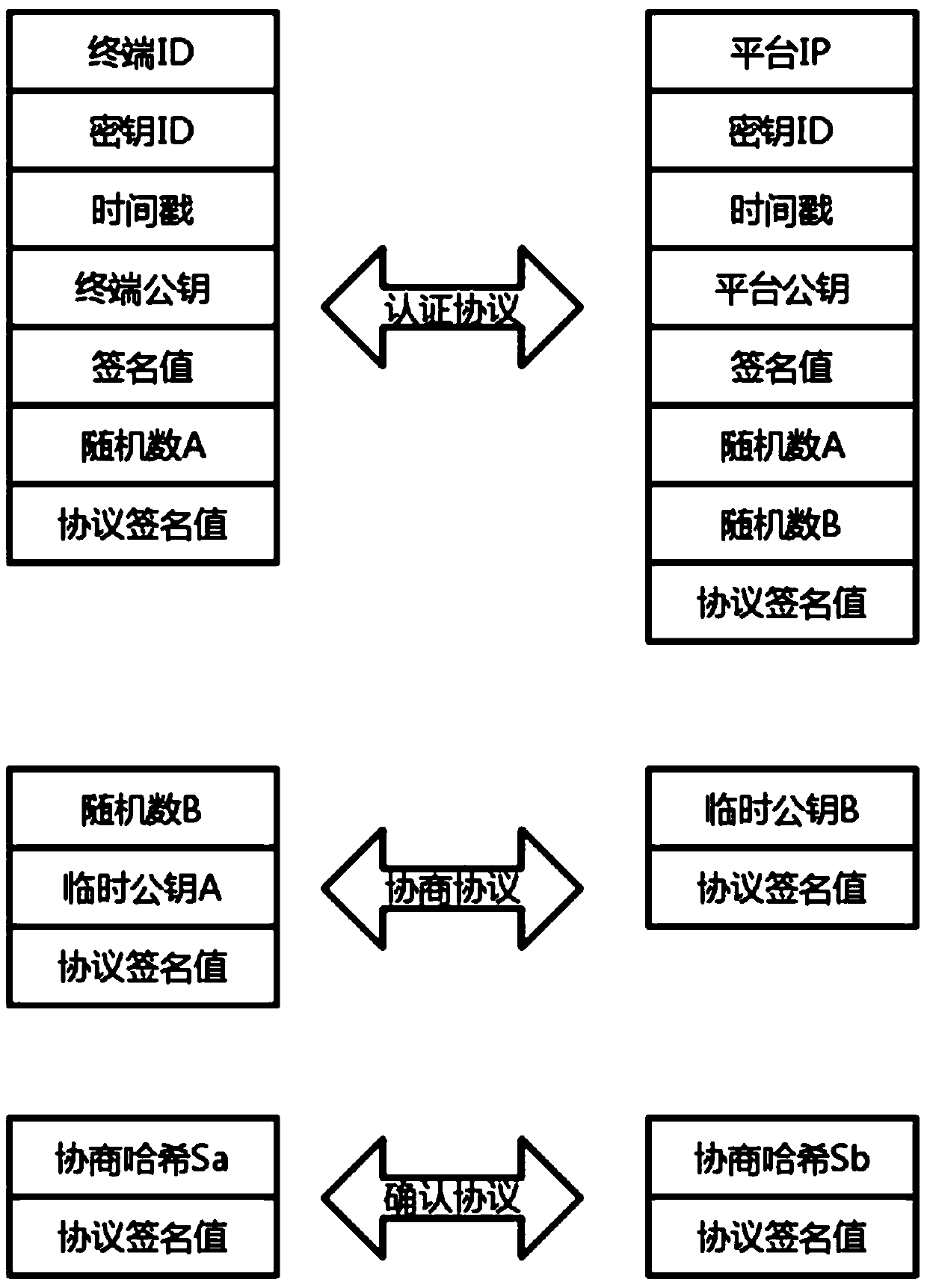
Bidirectional authentication method and system for vehicle-mounted terminal and central platform
ActiveCN111314274AReduce risk of leakageEnhanced couplingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesIn vehicleKey leakage
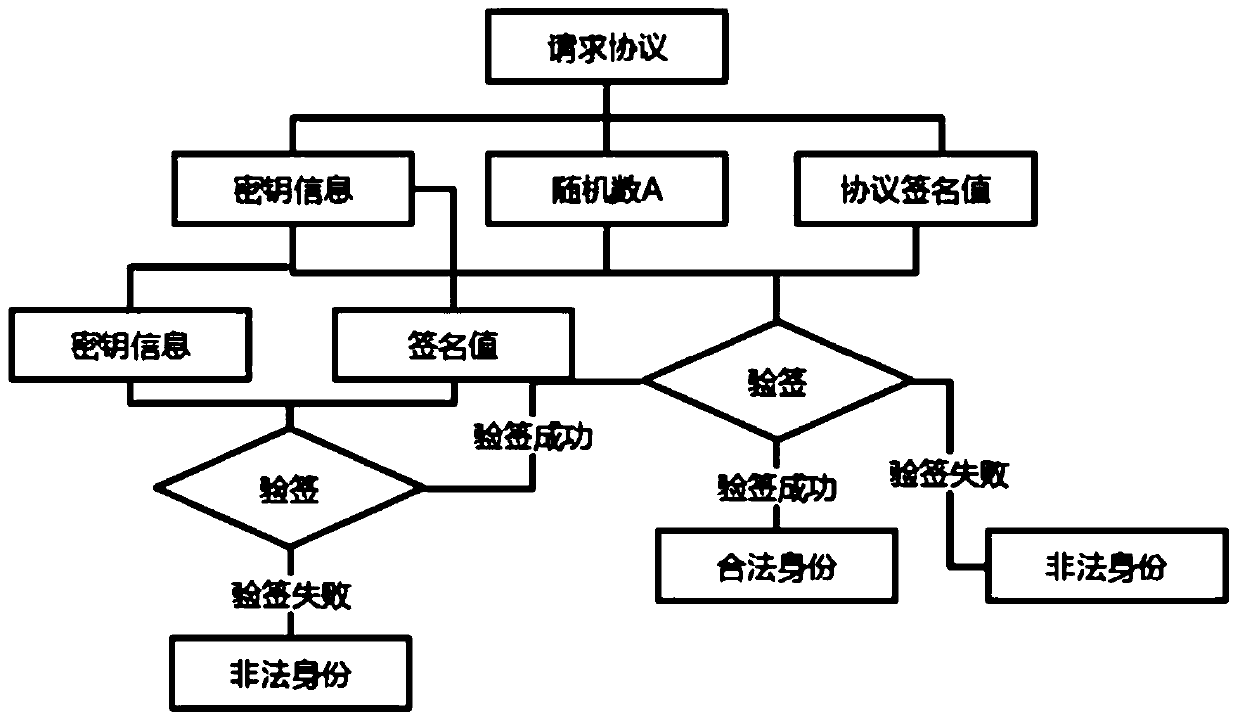
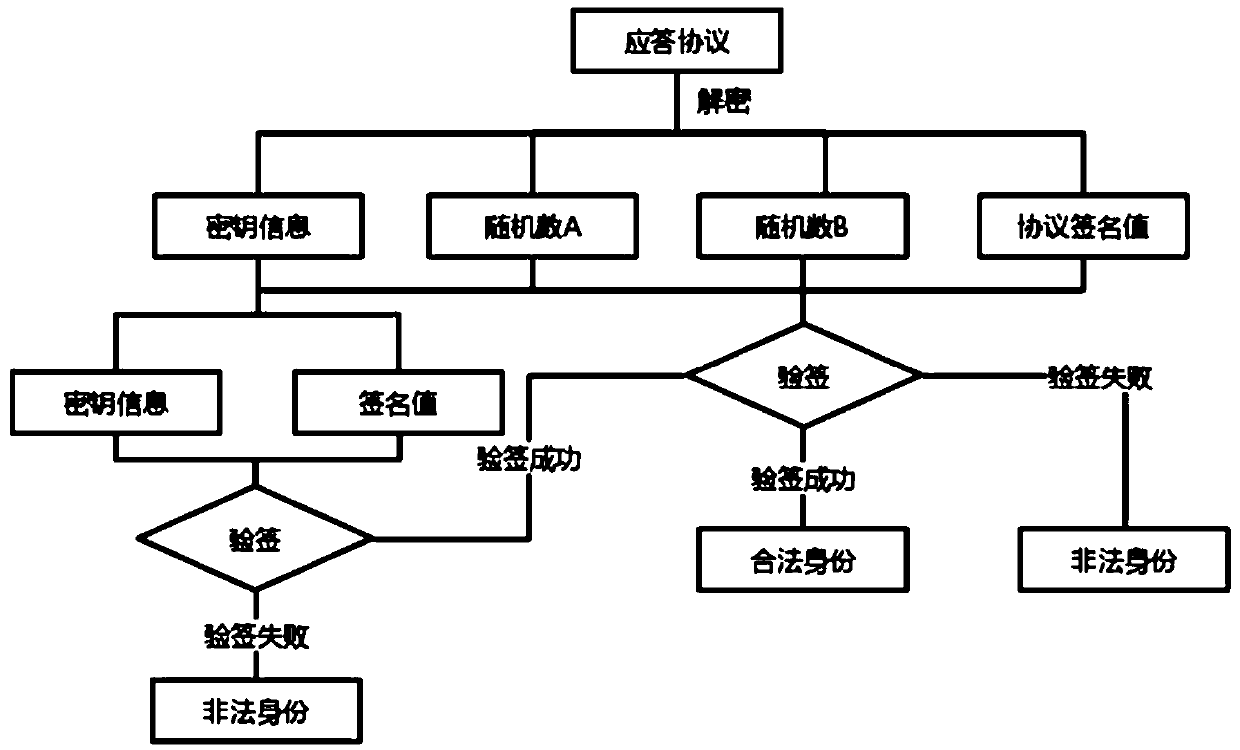
The invention relates to a bidirectional authentication method and system for a vehicle-mounted terminal and a central platform, and the method comprises the steps: distributing corresponding unique secret key information to the vehicle-mounted terminal and the central platform, signing a signature value signed by a private key through the secret key information, and issuing a secret key information signature public key to the vehicle-mounted terminal and the central platform for mutual authentication; the vehicle-mounted terminal and the central platform perform mutual authentication througha secret key information signature public key, and judge whether the secret key information is legal or not according to a terminal / platform ID, a secret key ID and a timestamp in the secret key information; according to a temporary public key and a random number generated by the vehicle-mounted terminal and the central platform in the interaction process of the vehicle-mounted terminal and the central platform, a session key is negotiated by combining a public / private key of the vehicle-mounted terminal and the central platform, and encryption communication is performed through the negotiatedsession key. According to the invention, the coupling problem of the central platform and the key management system is improved, the terminal key leakage risk is reduced, and the two-party authentication efficiency is improved.
Owner:XIAMEN YAXON NETWORKS CO LTD
Data processing method and system
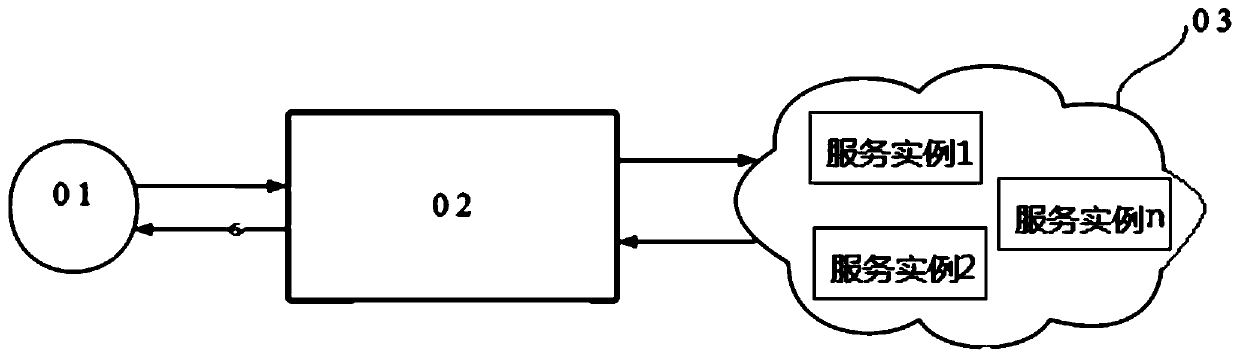
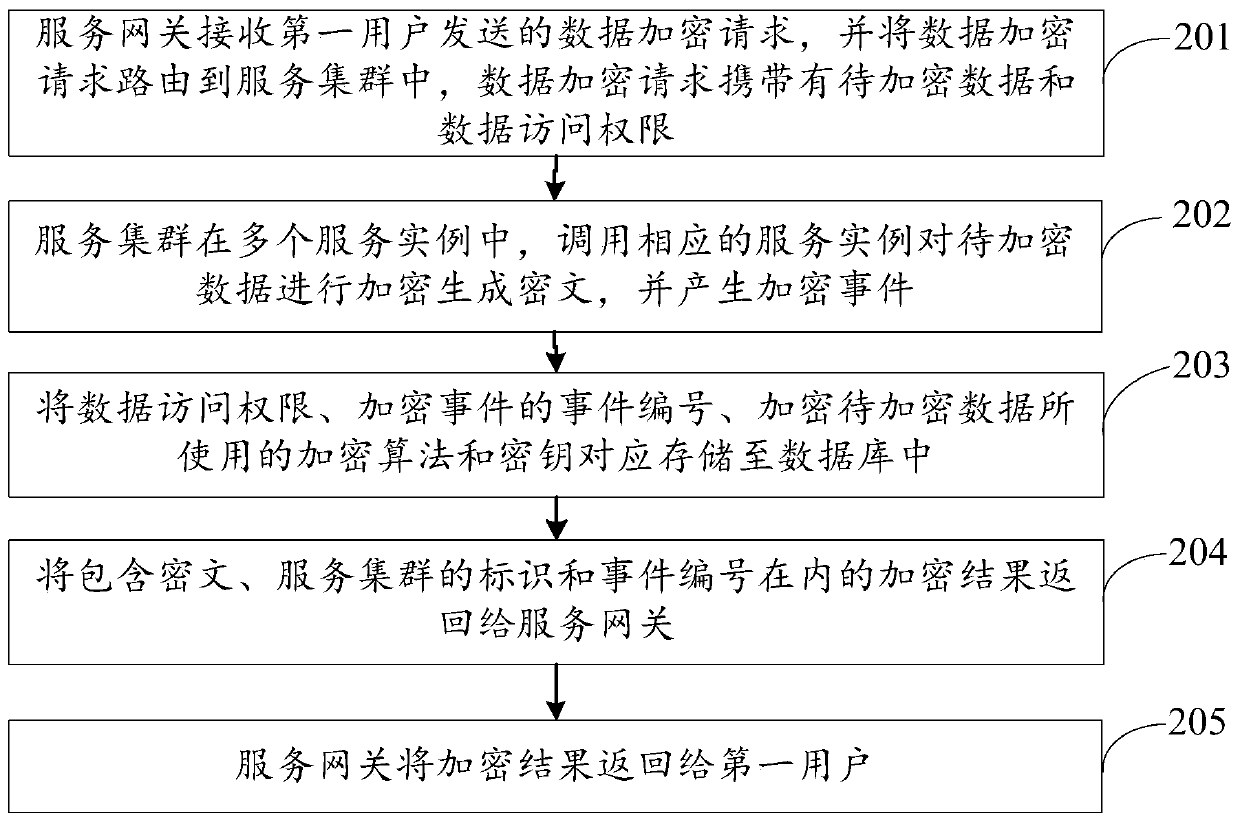
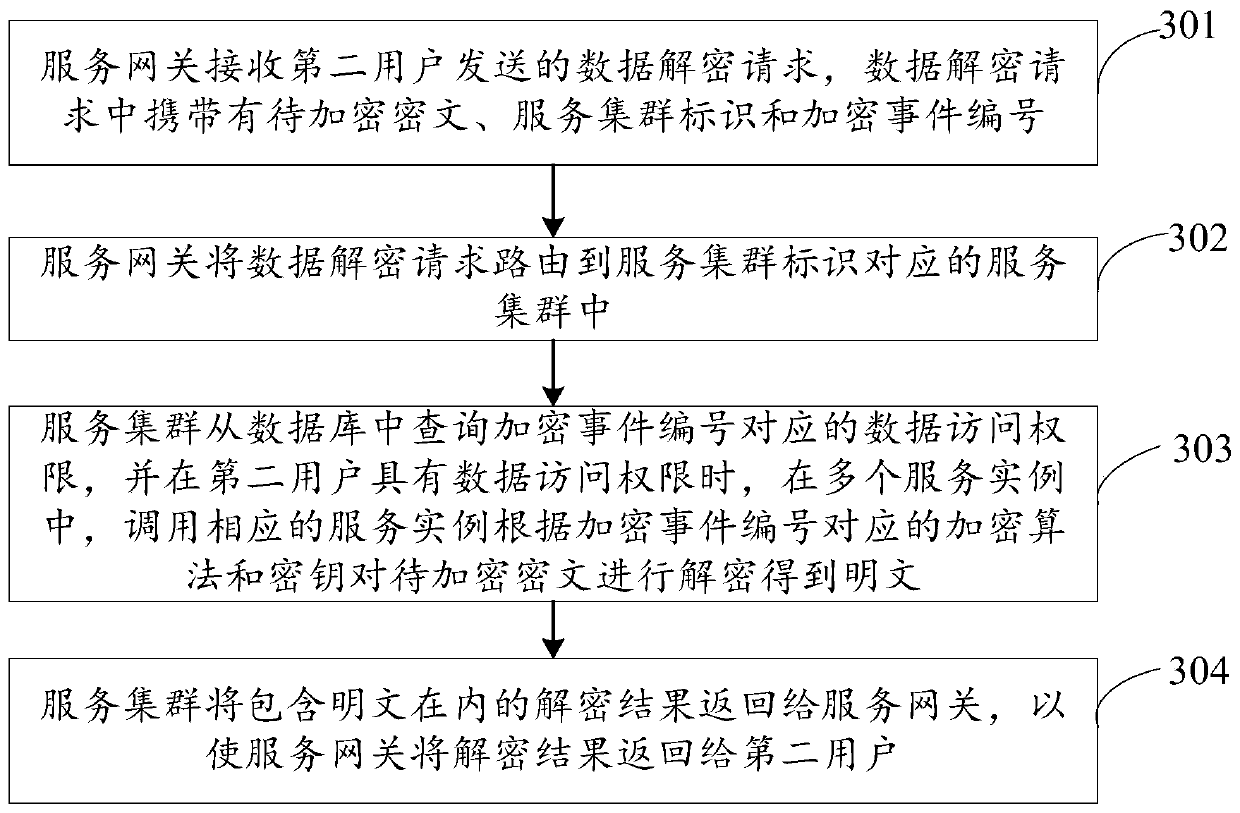
ActiveCN110061983AImprove securityReduce the risk of compromised keysTransmissionCiphertextData access
The invention discloses a data processing method and system, and belongs to the technical field of data security, and the method comprises the steps that a service gateway receives a data encryption request sent by a first user, and routes the data encryption request to a service cluster, and the data encryption request carries to-be-encrypted data and a data access authority; the service clustercalls a corresponding service instance to encrypt the to-be-encrypted data in the plurality of service instances to generate a ciphertext, and generates an encryption event; the data access authority,the event number of the encryption event, the encryption algorithm used for encrypting the to-be-encrypted data and the secret key are correspondingly stored into a database; an encryption result including the ciphertext, the identifier of the service cluster and the event number are returned to the service gateway; and the service gateway returns the encryption result to the first user. According to the embodiment of the invention, the risk of secret key leakage of a data producer and a data user can be reduced, so that the data security is higher; and a guarantee is provided for landing ofa data access permission minimization principle.
Owner:深圳市云网万店科技有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com