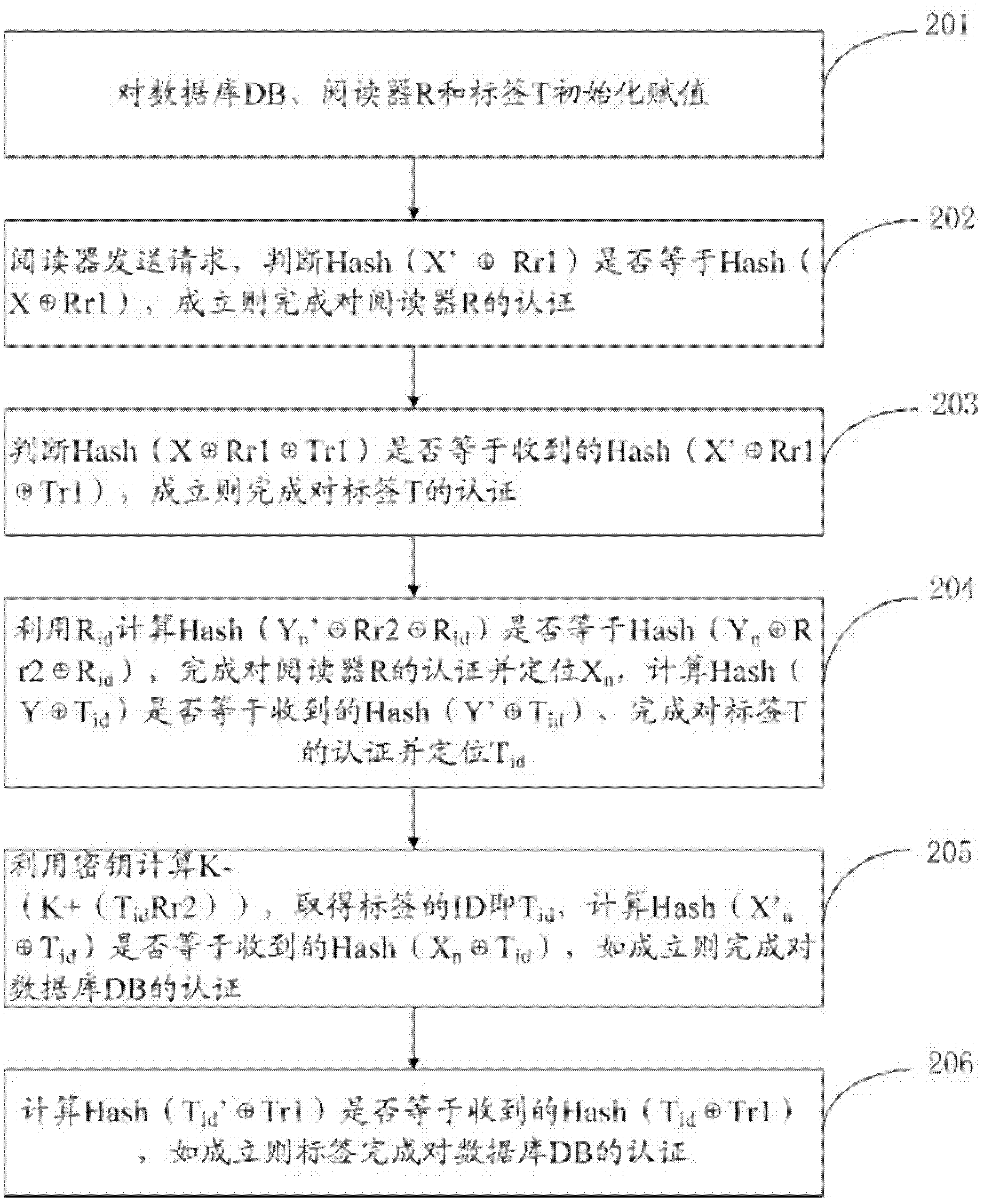Patents
Literature
76results about How to "Achieve privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
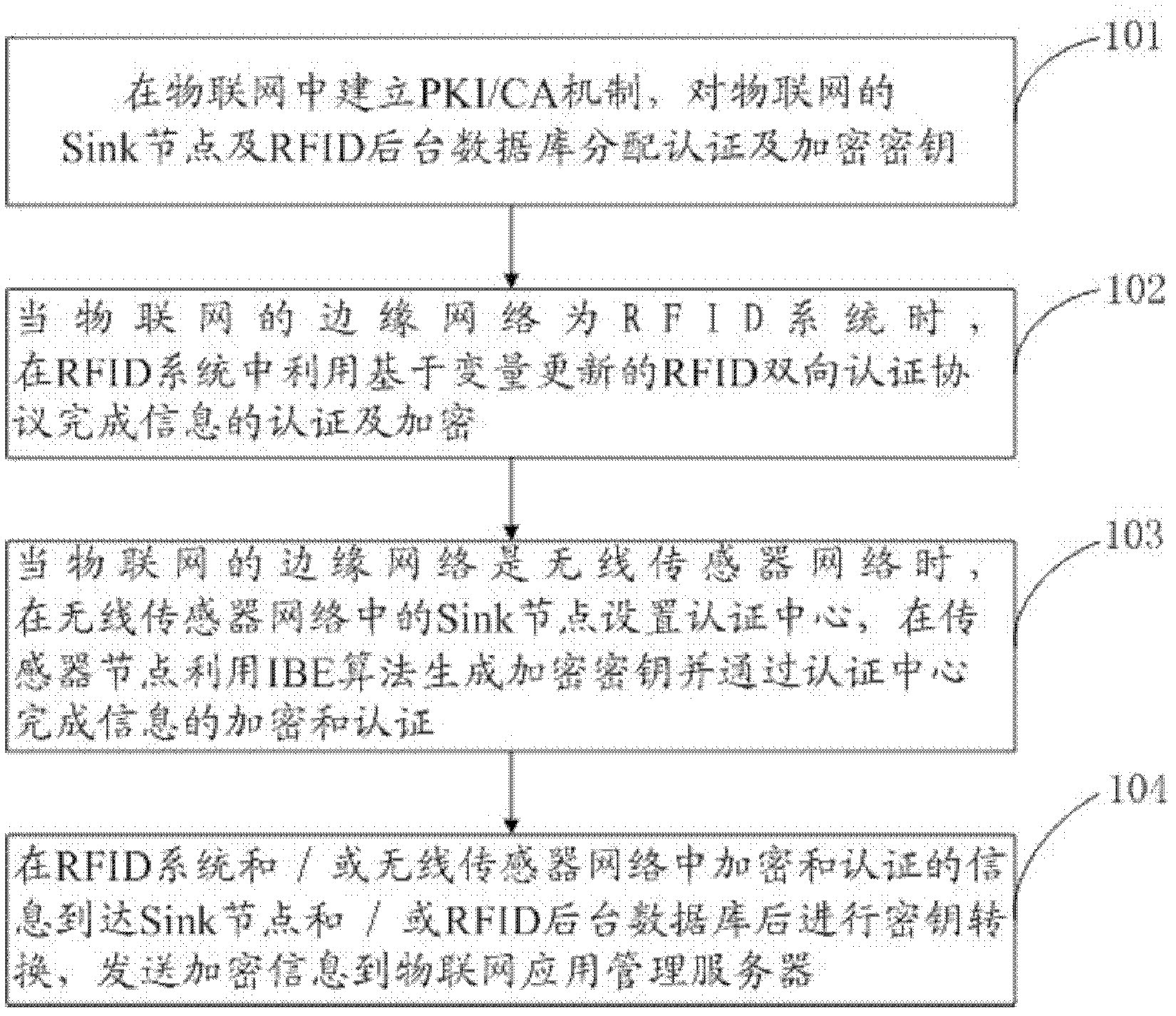
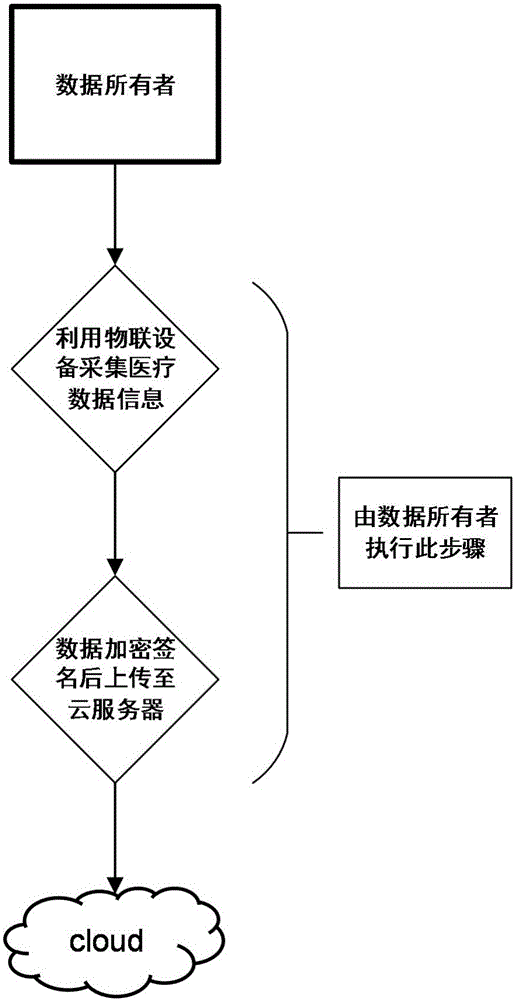
Method and system for internet of things information transmission
ActiveCN103166919AImprove securityGuaranteed privacyUser identity/authority verificationInformation transmissionThe Internet
The invention discloses a method and a system for internet of things information transmission. Firstly, a public key infrastructure / certificate authority (PKI / CA) mechanism is established in the internet of things and an authentication key and an encryption key are distributed to an aggregation node of the internet of things; transmitted information is encrypted and authorized in an edge network of the internet of things; and key conversion is conducted after the encrypted and authorized information reaches the aggregation node of the internet of things and the information encrypted again is sent to an application management server of the internet of things. According to the method and the system for the internet of things information transmission, the internet of things can effectively resist interior attack, information safety transmission level is improved and complexity of encryption and safety authentication calculation in the edge network of the internet of things is reduced.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
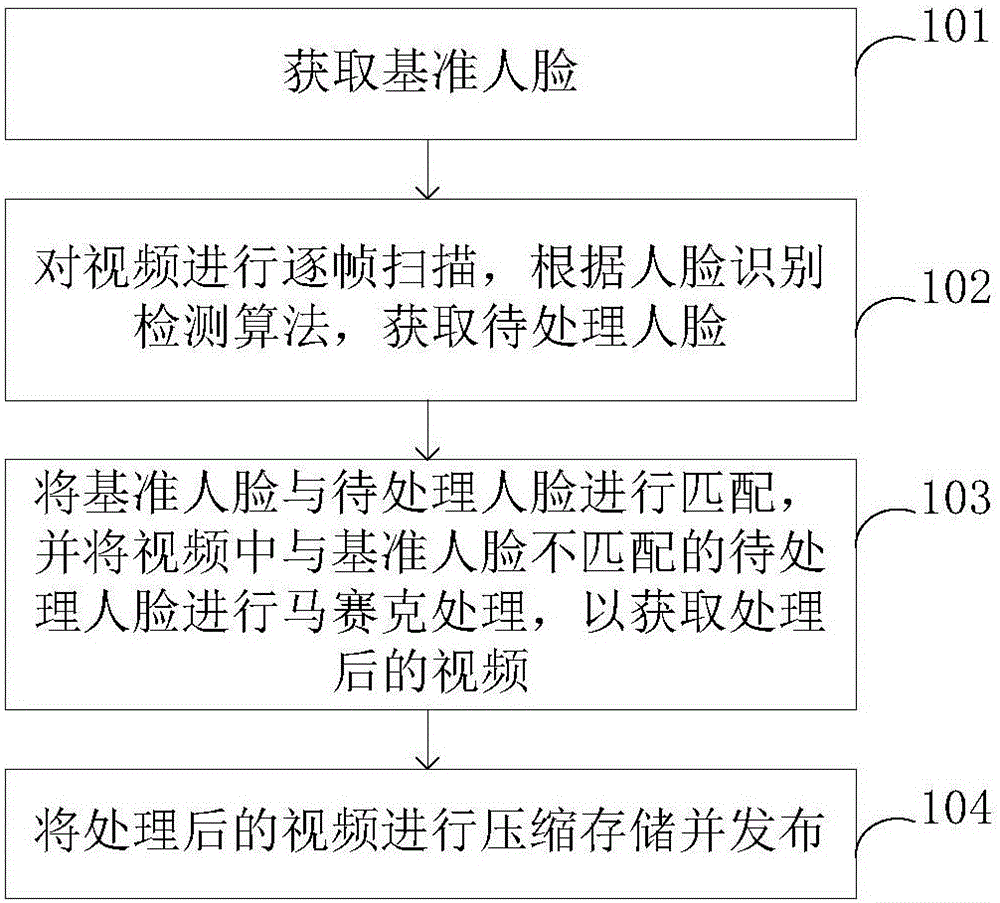
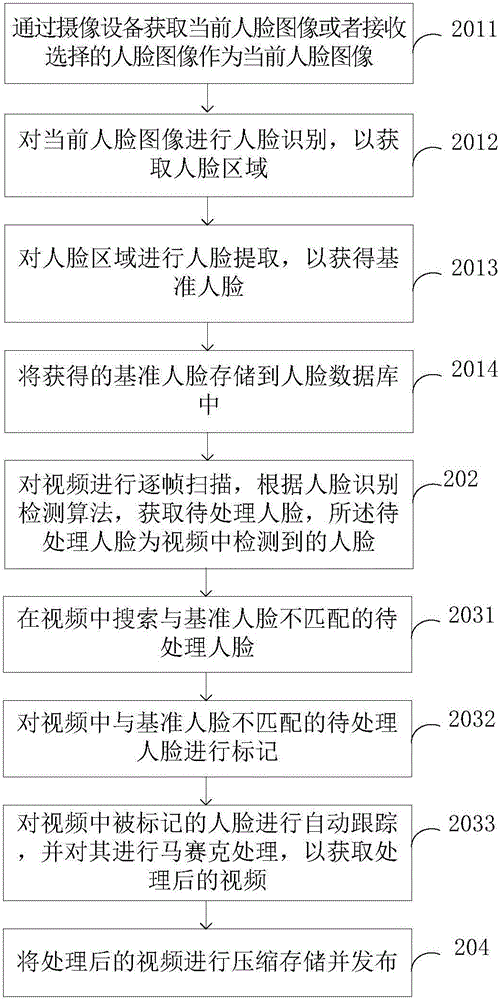
Privacy protecting method and privacy protecting device
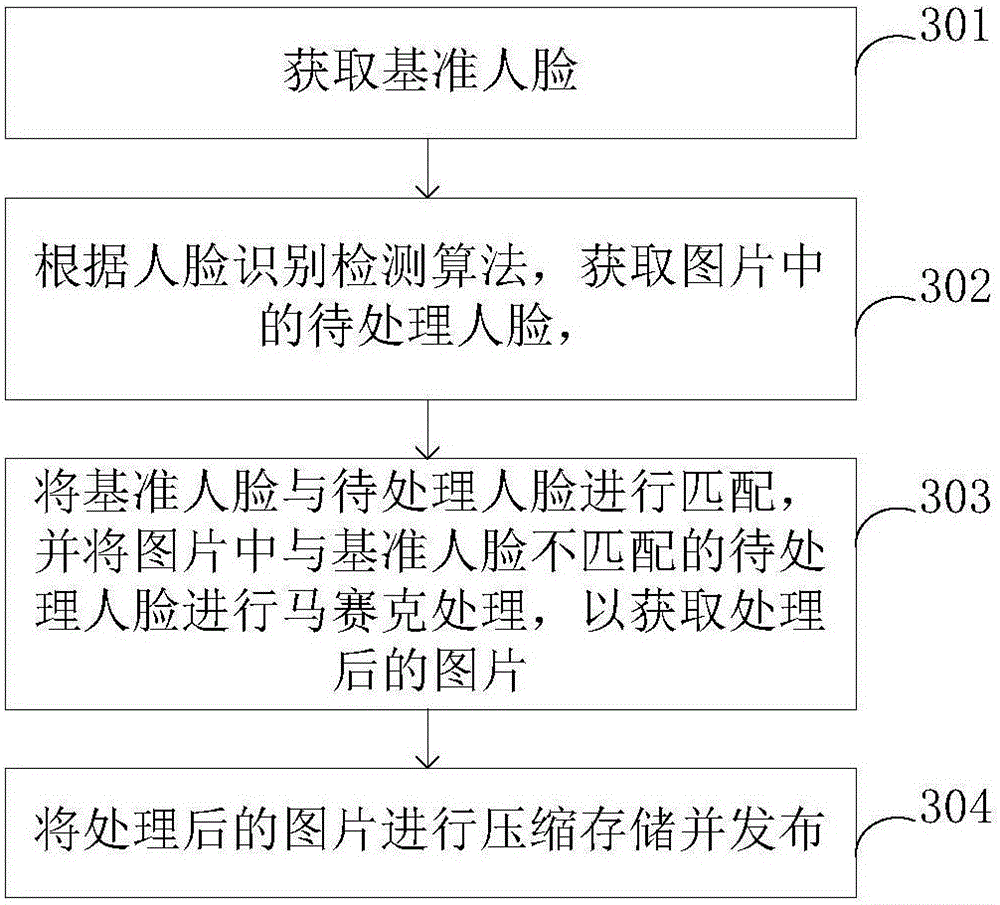
InactiveCN105957001APrivacy protectionAchieve privacyGeometric image transformationCharacter and pattern recognitionPublic placePrivacy protection
The invention provides a privacy protecting method and a privacy protecting device, wherein the privacy protecting method comprises the steps of acquiring a reference face, performing frame-to-frame scanning on a video, and acquiring a to-be-processed face according to a face identification detecting algorithm; performing matching between the reference face and the to-be-processed face, and performing mosaic processing on the to-be-processed face which does not match the reference face in the video; performing compression storage of the processed video and publishing the processed video. According to the privacy protecting method and the privacy protecting device with the video processing manner, mosaic processing can be performed on the faces of non-focused personnel in the video, thereby protecting privacy of the non-focused personnel. The privacy protecting method and the privacy protecting device can be utilized for realizing privacy protection at places where face identification is utilized, such as schools, hospitals and public places.
Owner:成都致学教育科技有限公司
Methods of protecting against spam electronic mail
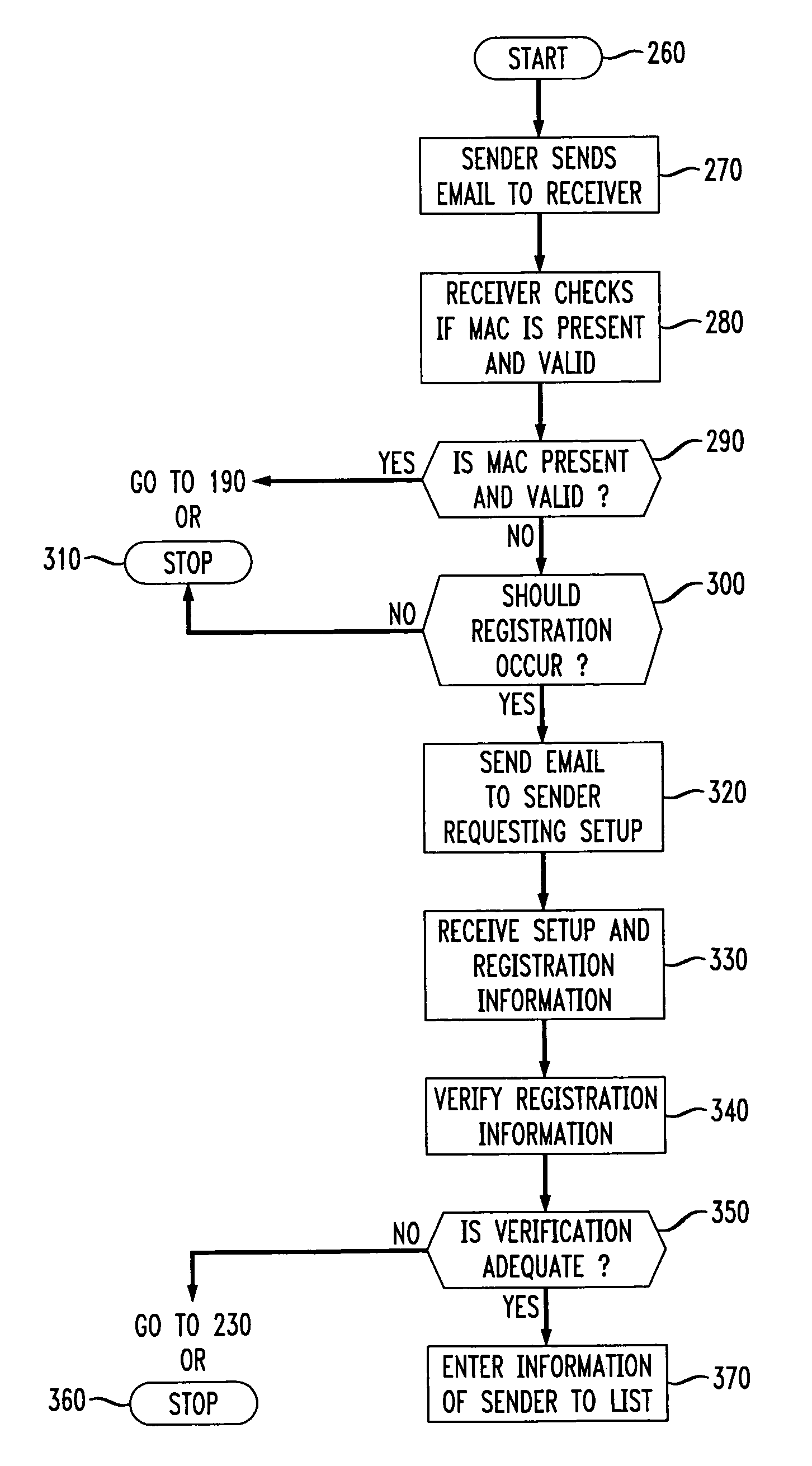
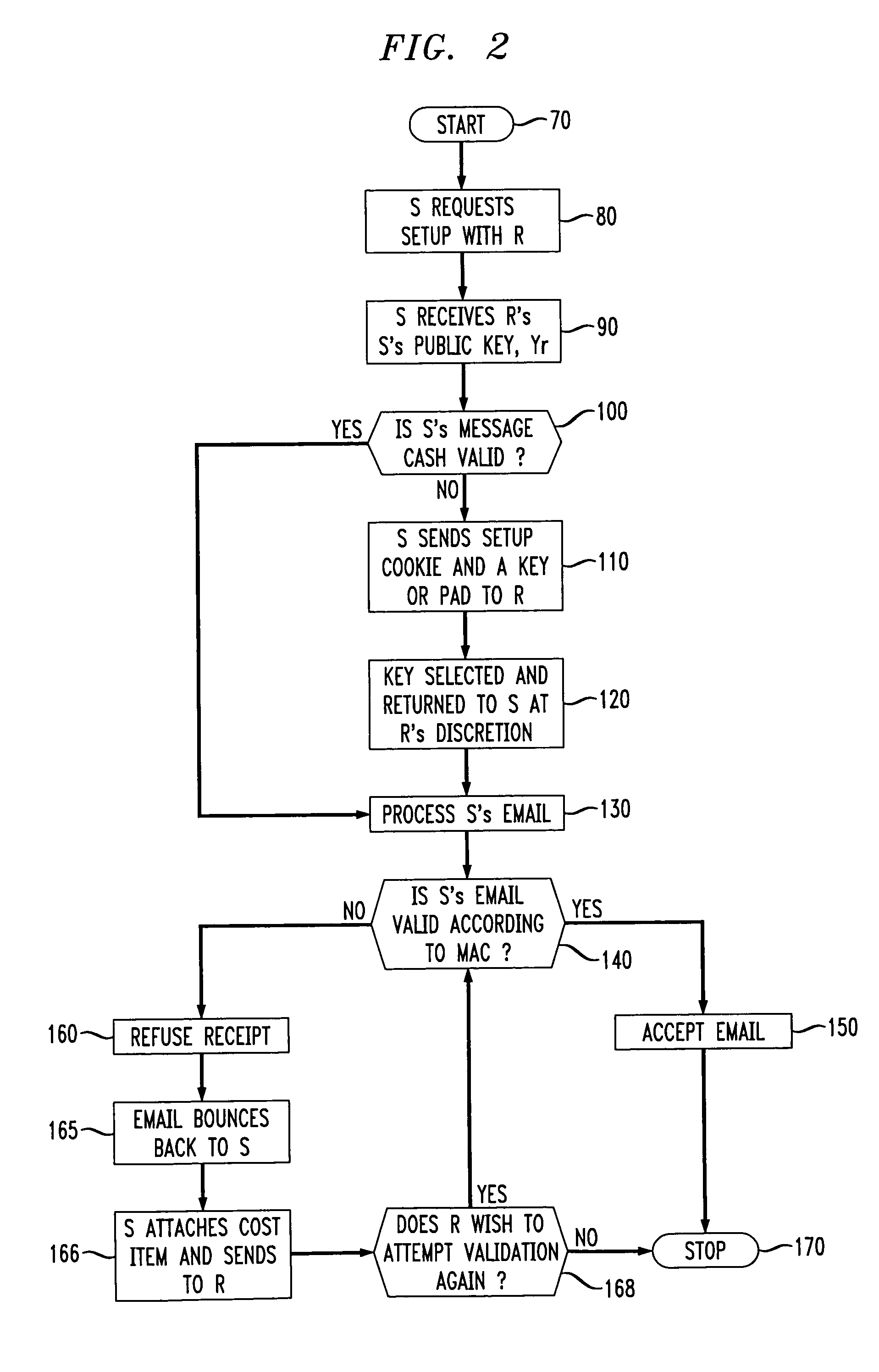
InactiveUS7644274B1Efficient and computationally non-intensiveSave resourcesUser identity/authority verificationInternet privacyElectronic mail
Methods of preventing spam email in an email system include determining whether a sender of email to a receiver of email has paid a required setup price or cost to become a registered sender of email to the receiver. If it is determined that the sender has not paid the required setup cost, then the receiver can reject the sender's email to thereby eliminate the receipt of unwanted spam messages. In order to qualify as a registered sender, the sender undergoes a qualification scheme wherein it pays the required cost, which may be for example monetary or computationally related, and is assigned an encrypted key by the receiver which allows the sender to send to the receiver email authenticated using the unique key associated with the sender and receiver. The receiver has the option of accepting or rejecting email from a sender in this fashion and can change the required setup cost or requirement at any time to ensure that the sender does not try to corrupt the email system once registered.
Owner:RPX CORP +1
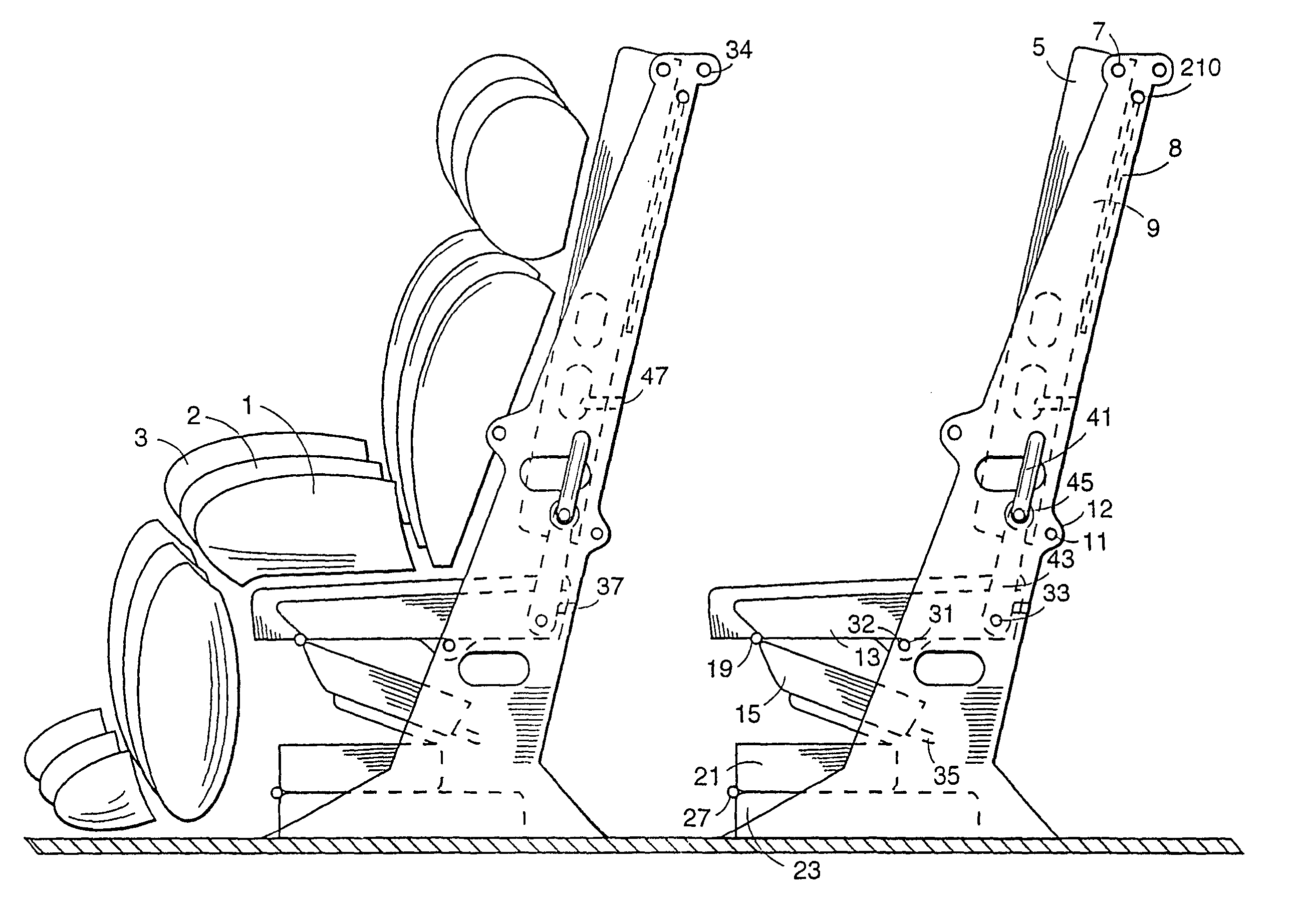
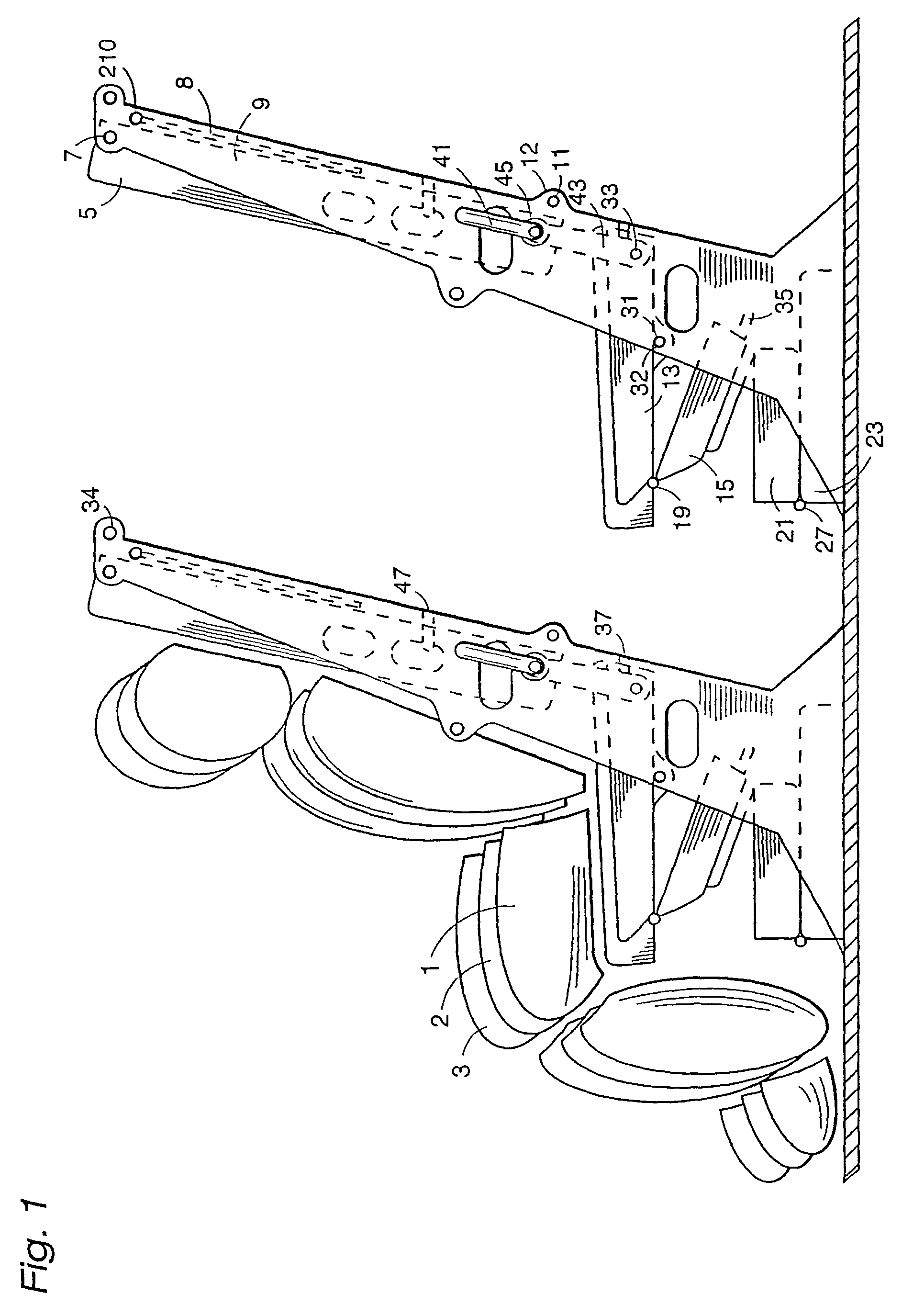
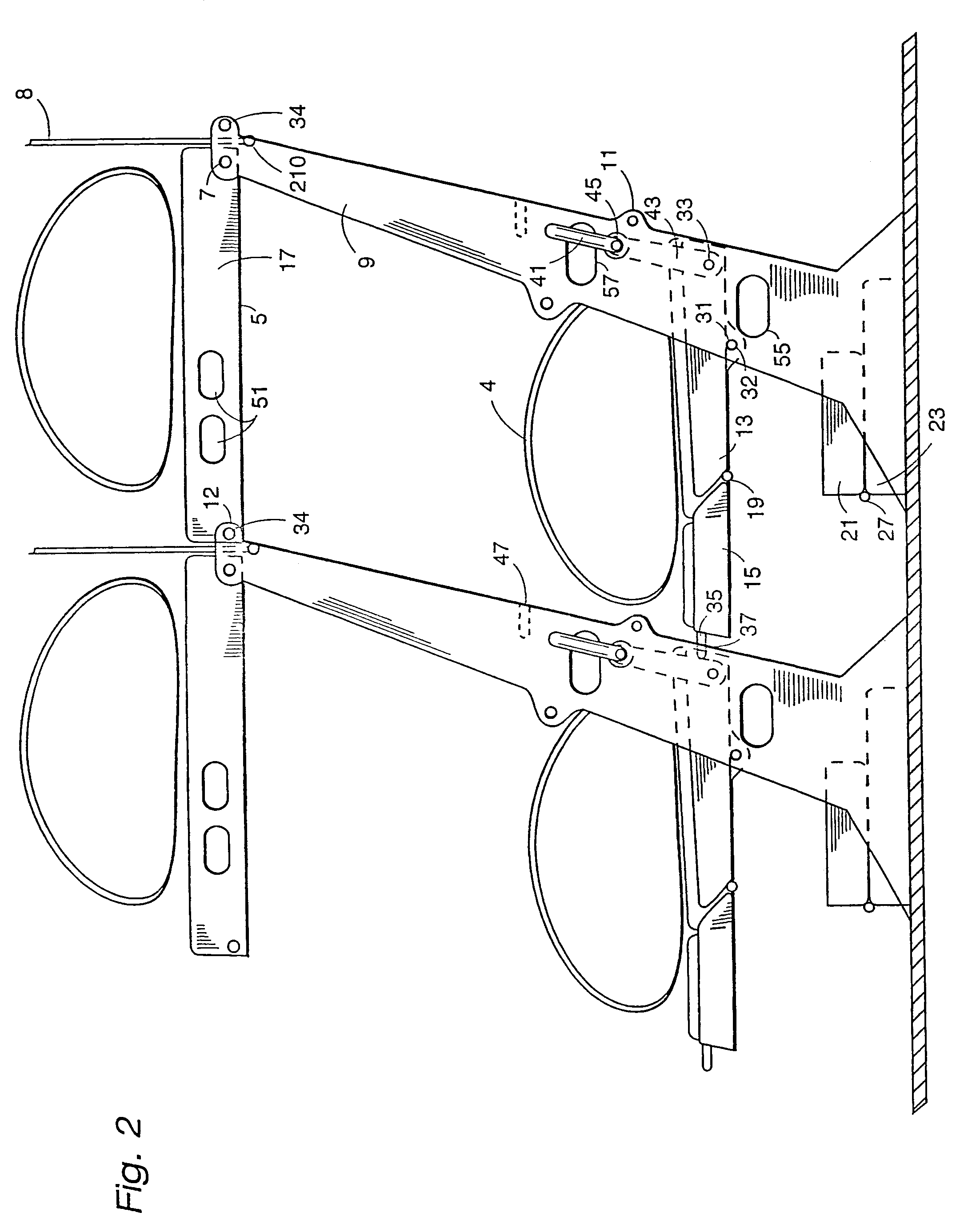
Seats that convert to sleeper bunks
InactiveUS7070149B2Widen meansReduce seat loadSupports/holding devicesVehicle seatsEngineeringMechanical engineering
Passenger accommodations are easily and rapidly convertible from conventional seats to bunk beds and back. A support structure (9) supports a seat pad (13) and a seat pad extension (15) and also rotatably supports a seat back (5). The seat pad extension (15) and seat back (5) are partially supported by the support structure (9) of a row of seats ahead of the convertible seats when the convertible seats are converted to bunk beds. A third bunk bed (21,23) may be unfolded under the lower bunk bed formed by the seat pad (13, 15).
Owner:AIR NEW ZEALAND
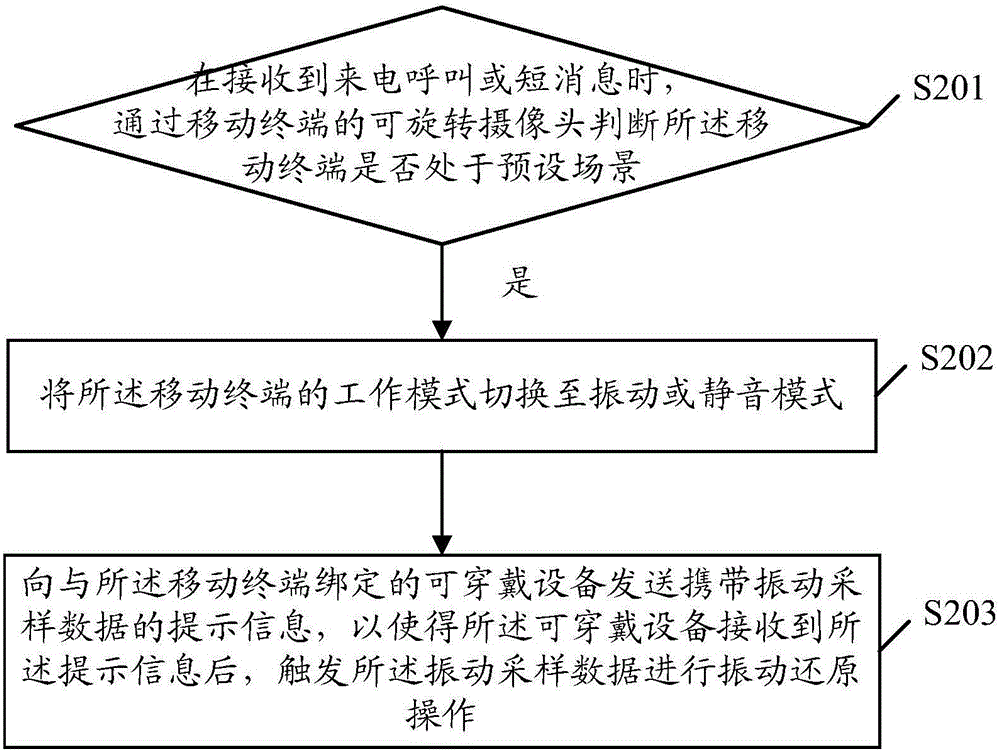
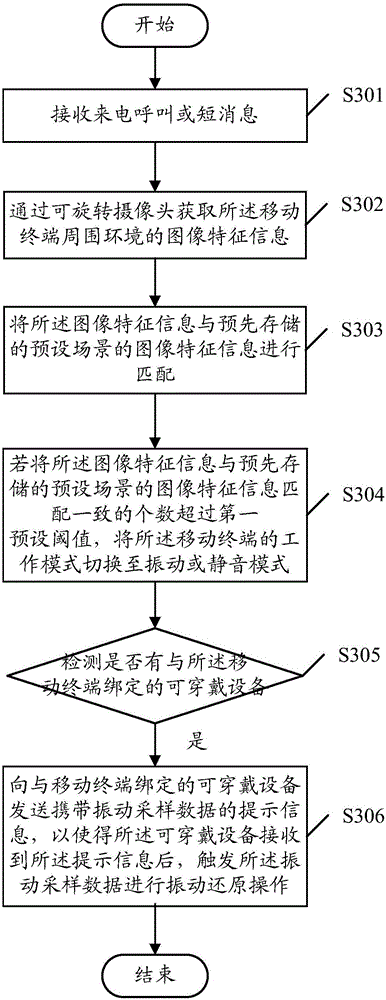
Information prompting method and mobile terminal
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
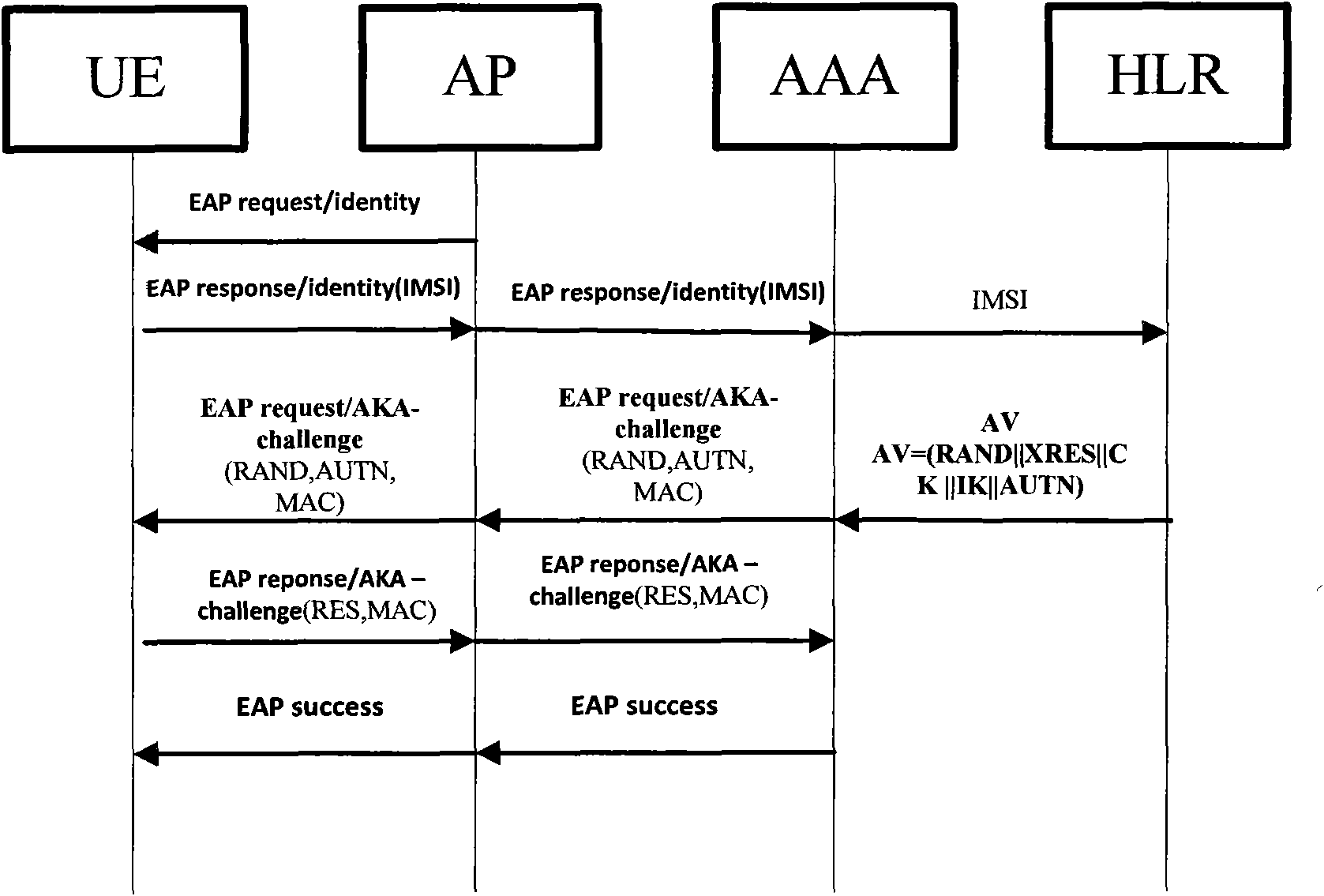
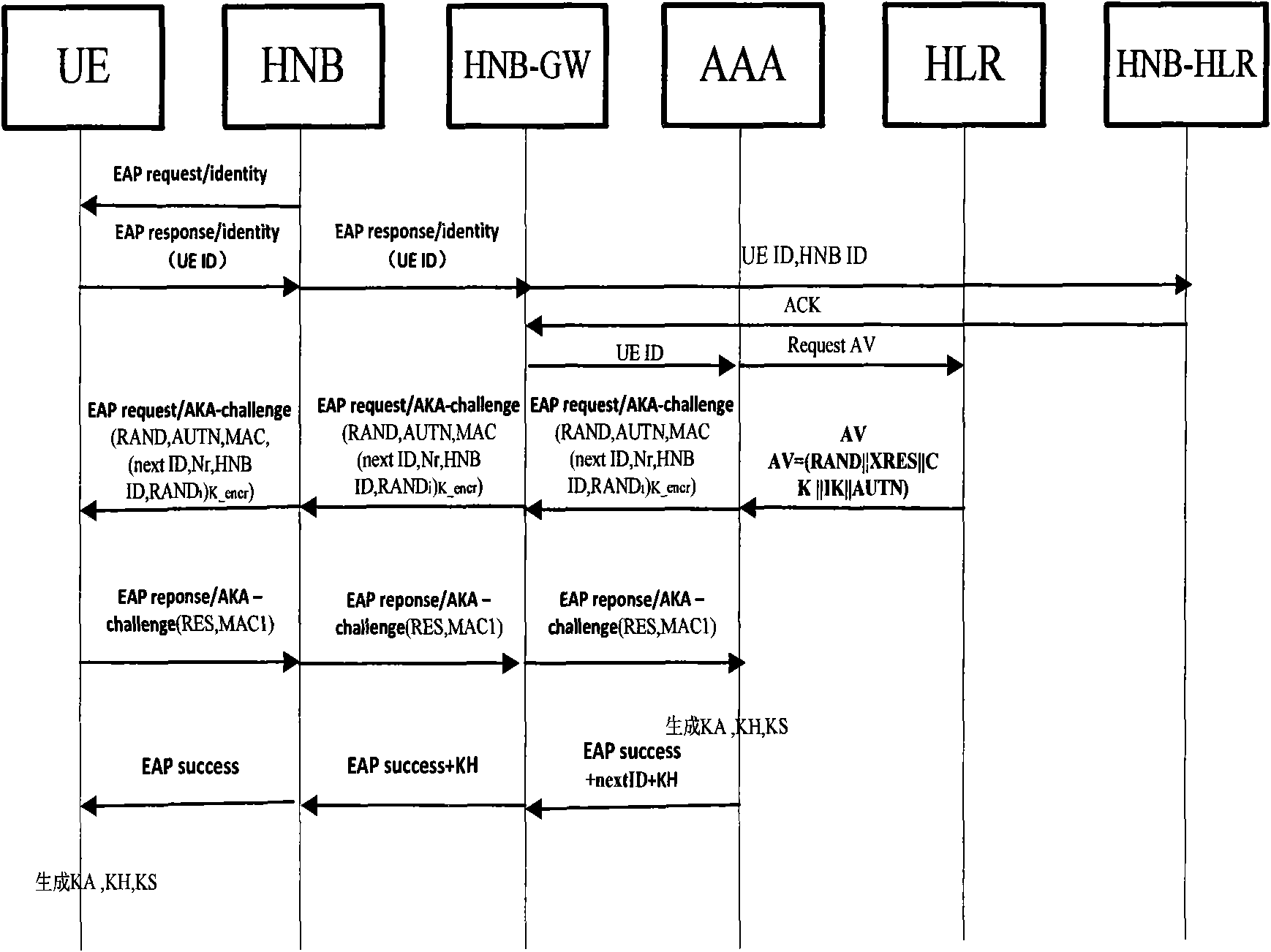
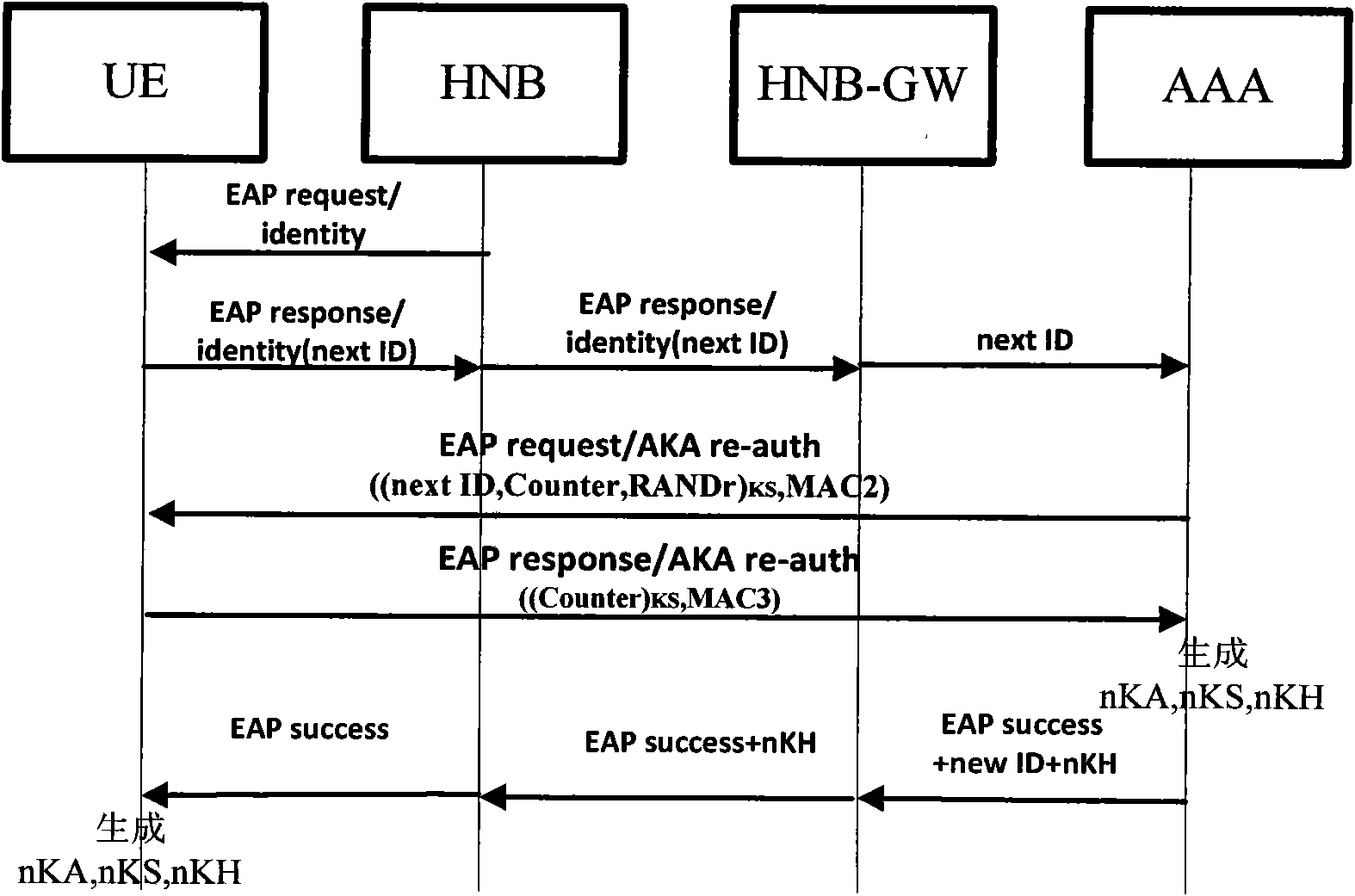
Method of access authentication and recertification in home NodeB system of user terminal
InactiveCN101854629ARealization of privacyAchieve privacySecurity arrangementDigest access authenticationAuthentication server
The invention discloses methods of access authentication and recertification of a user terminal in a home NodeB system, mainly overcoming the defect that the existing standard does not provide an authentication method of the user terminal for accessing a core network through the home NodeB. The access authentication process comprises the following steps: firstly, simultaneously sending the identification of a user and the identification of the home NodeB to HNBHLR to inquire, judging according to whether the identification of the user exists in the CSG list of the home NodeB; and secondly, adopting the modified EAP-AKA protocol to perform authentication between the user terminal and a authentication server. The recertification process comprises the following steps: firstly, judging according to whether the identification of the user is as the same as the identification stored in the home NodeB network, and secondly, using a hierarchy secret key to modify the existing EAP-AKA recertification method to realize the mutual authentication between the user terminal and the authentication server. The methods of the invention has the advantages of simple processes, high efficiency, reliable performance, good safety and the like, thus being applicable to the access authentication and recertification of the user terminal in the home NodeB system.
Owner:XIDIAN UNIV
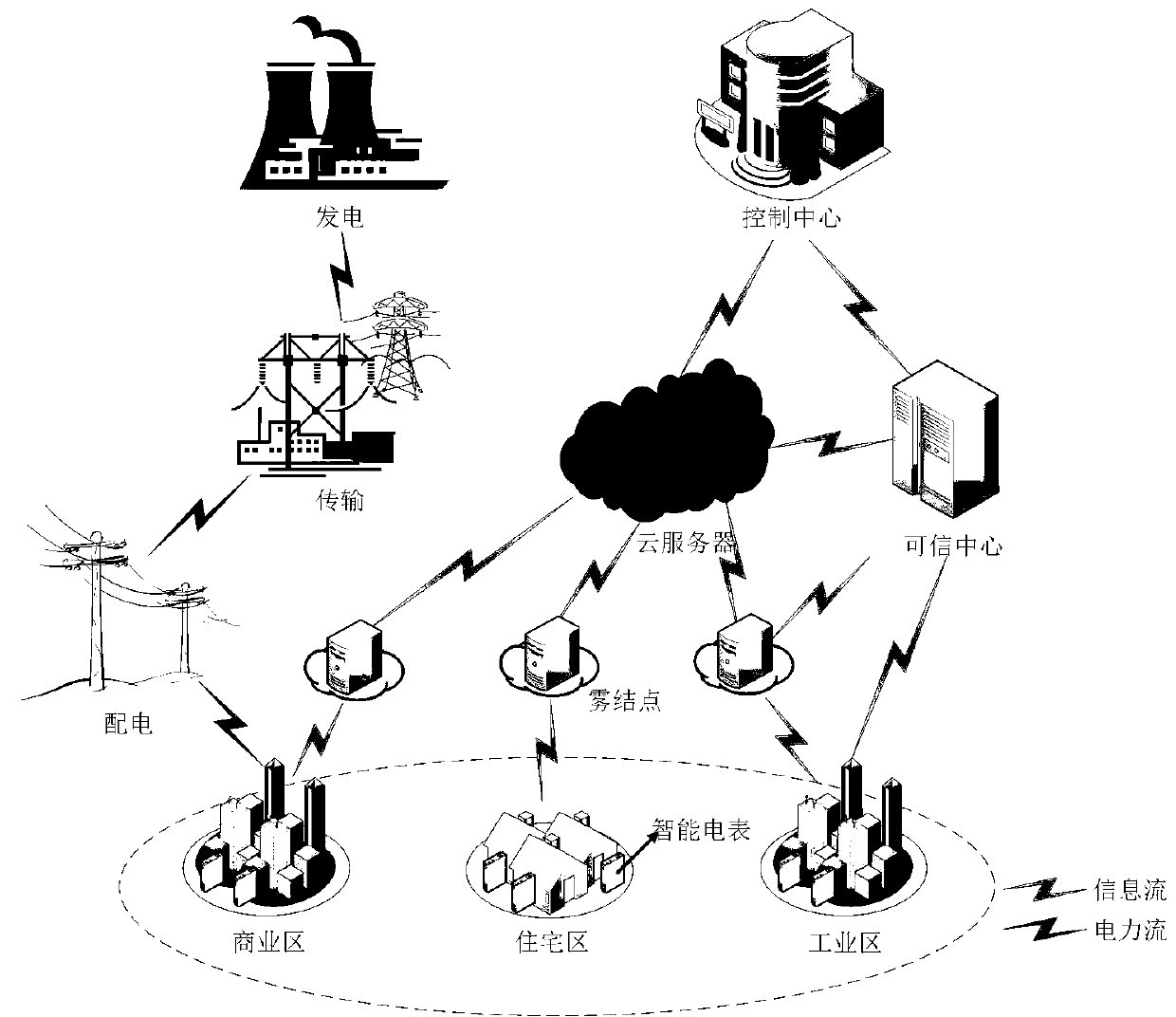
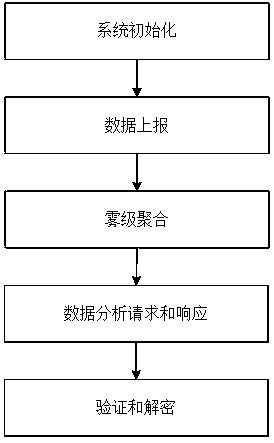
Statistical analysis method for secret key leakage resisting encrypted data aggregation in smart power grid
ActiveCN111294366AAchieve privacyAchieve protectionData processing applicationsMultiple keys/algorithms usageStatistical analysisCiphertext
The invention discloses a statistical analysis method for secret key leakage resisting encrypted data aggregation in a smart power grid. Each user area is responsible for one fog node; the fog node serves as a data aggregation gateway and a data repeater; user electric energy consumption data sent by an intelligent electric meter in a user area is aggregated for the first time by a fog node to obtain a fog-level aggregation ciphertext, the fog-level aggregation ciphertext is signed, and then the fog-level aggregation ciphertext and signature information are sent to a cloud server to be stored;the cloud server stores the aggregated ciphertext data and the signature information of different user areas in a database; data query, statistics and analysis services are provided for a control center of the intelligent power grid system; the cloud server can provide enough information for the control center on the premise of not destroying the privacy of any single user, so that the control center can calculate the sum, average value and variance of power consumption data of all users in a specified user area by utilizing the information.
Owner:SOUTHWEST PETROLEUM UNIV
Dynamic host configuration protocol (DHCP) message forwarding method for transparent interconnection of lots of links (TRILL) network and routing bridge
ActiveCN102307144AAchieve privacyReduce the chance of being attackedNetworks interconnectionDistribution treeMedia access control
The invention discloses a dynamic host configuration protocol (DHCP) message forwarding method for a transparent interconnection of lots of links (TRILL) network and a routing bridge. The method comprises the following steps that: the routing bridge (RB) setting a DHCP message trusted port transmits a used unique virtual multicast group address in the TRILL network to the other RBs in the TRILL network, and each RB performs virtual multicast group pruning for a multicast distribution tree; when receiving a request message, the RB setting the trusted port modifies a destination media access control (MAC) address of the message into a broadcast address and forwards the message; and when receiving the request message, the RB not setting the trusted port modifies the destination MAC address of the message into a virtual multicast group address and forwards the message along the multicast distribution tree. Based on the same inventive concept, the invention also discloses the RB. By the method and the RB, DHCP message forwarding privacy can be achieved, and chances of attacking the network can be reduced.
Owner:NEW H3C TECH CO LTD
Smart city system
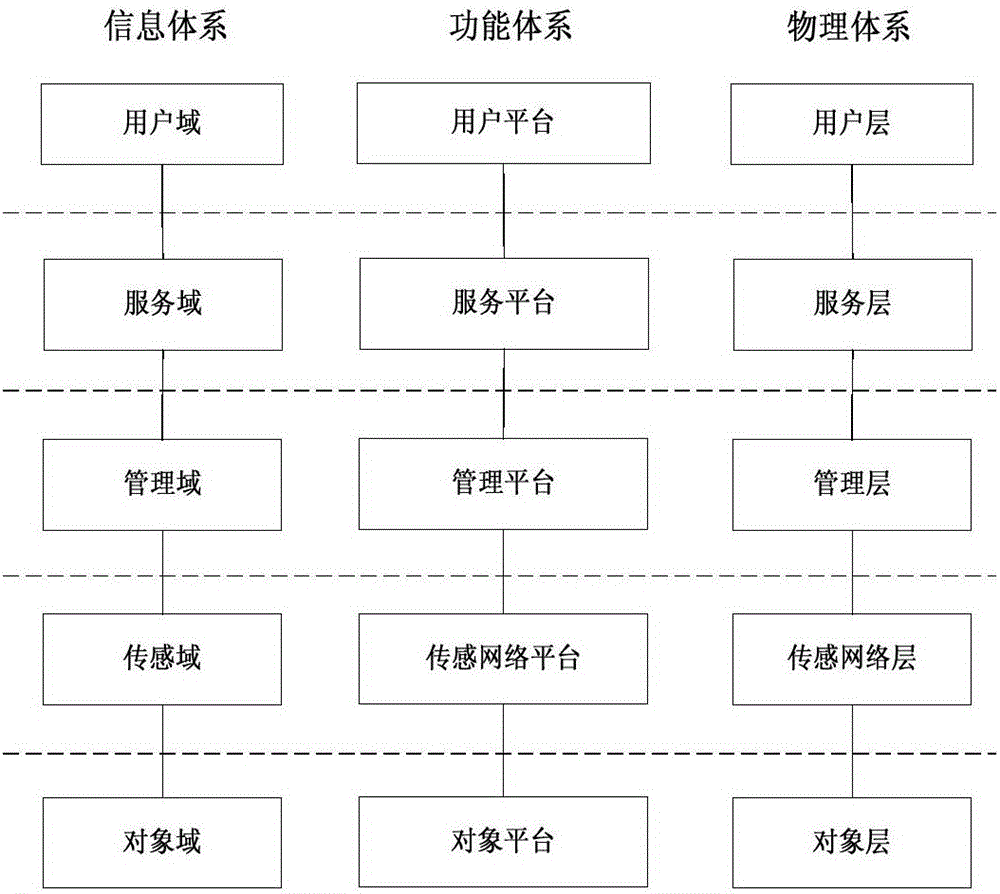
InactiveCN106302683AImplement management functionsClear functionData processing applicationsHome automation networksSmart cityPhysical system
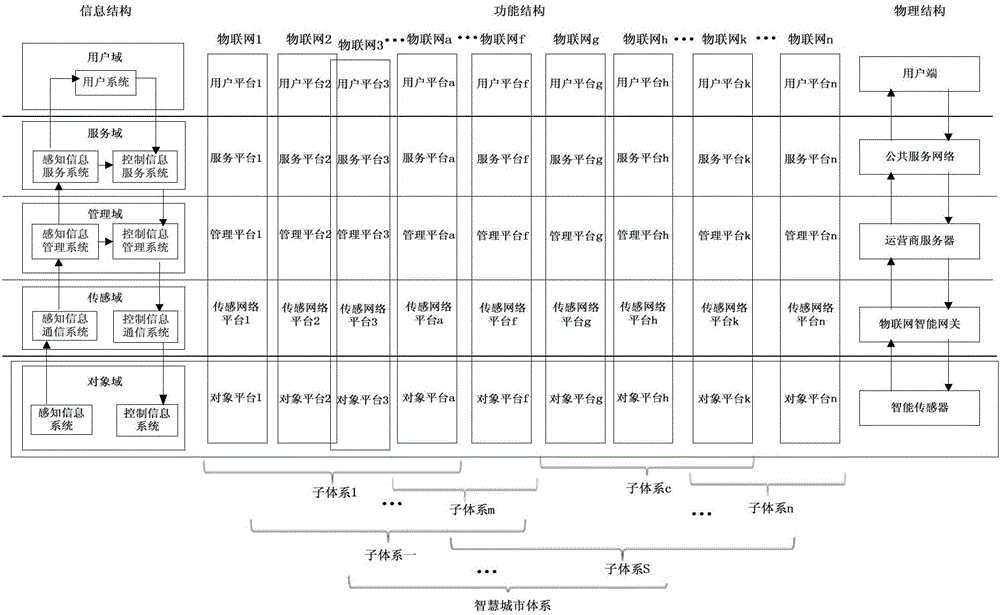
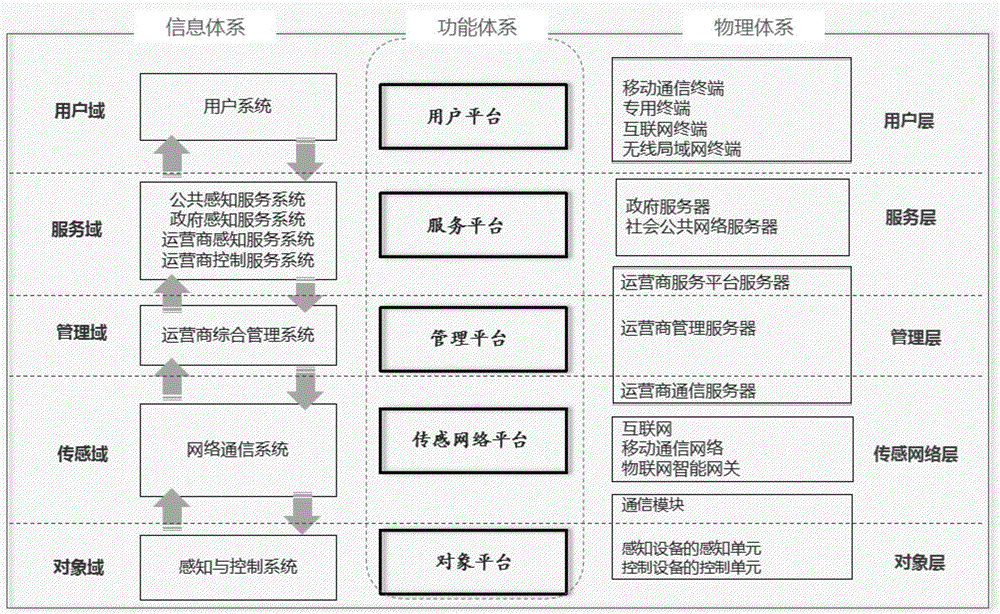
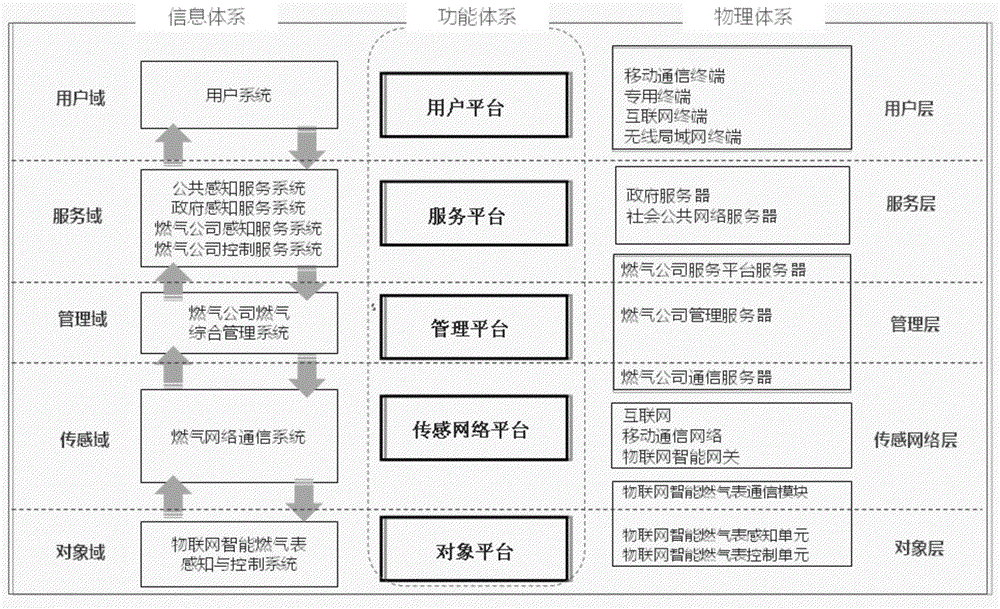
The invention discloses a smart city system, which comprises a function system, a physical system and an information system, wherein the function system is a form of functional performance, the information system is a way of function realization, and the physical system is a carrier for providing a physical support for function realization; the function system is of a five-platform structure; the physical system is of a five-layer structure; and the information system is of a five-domain structure. Detailed division is carried out on the smart city system, and the smart city system accurately describes which functions a smart city realizes and how to realize the functions from three dimensions of the function system, the physical system and the information system. Through setting the technical features, the smart city system with the clear system, the explicit functions, the hardware matching and the clear information transfer can be constructed, the basic model guarantee is provide for final realization of the smart city, and the application range is wide.
Owner:CHENGDU QINCHUAN IOT TECH CO LTD
Intelligent medical service method based on undistinguishable confusion
ActiveCN105978854AFlexible Control AllocationAssignment Convenience ControlKey distribution for secure communicationData processing applicationsCiphertextData access
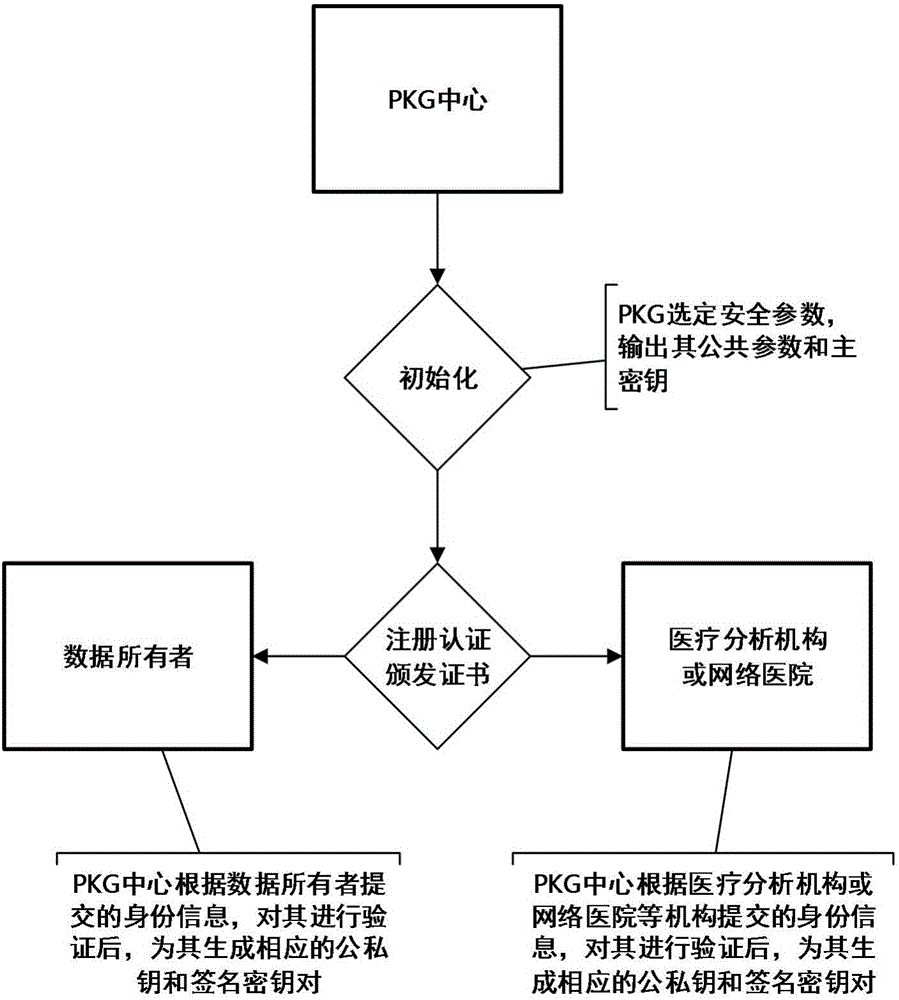
The invention discloses an intelligent medical service method based on undistinguishable confusion, which is characterized in that a data owner independently decides allocation for the medical data access authority through carrying out security symmetric encryption on medical information uploaded to a cloud server; a medical data analysis mechanism carries out confusion on a medical data analysis program by using an undistinguishable confusion technology, the confused program is deployed to the cloud server, and security analysis is carried out on the medical data by using a confusion program so as to acquire a correct medical analysis result; and the access authority of other related mechanisms for a ciphertext can be controlled conveniently without changing the ciphertext structure by using a key sharing scheme. According to the invention, the privacy of data is realized, interaction of keys is reduced, and storage and management of a great number of keys are avoided; the integrity and the effectiveness of data can be verified; and the access type of medical data is decided by the user, the overall structure of an algorithm is not change at the same time, and the expansibility of the scheme is enhanced.
Owner:XIDIAN UNIV
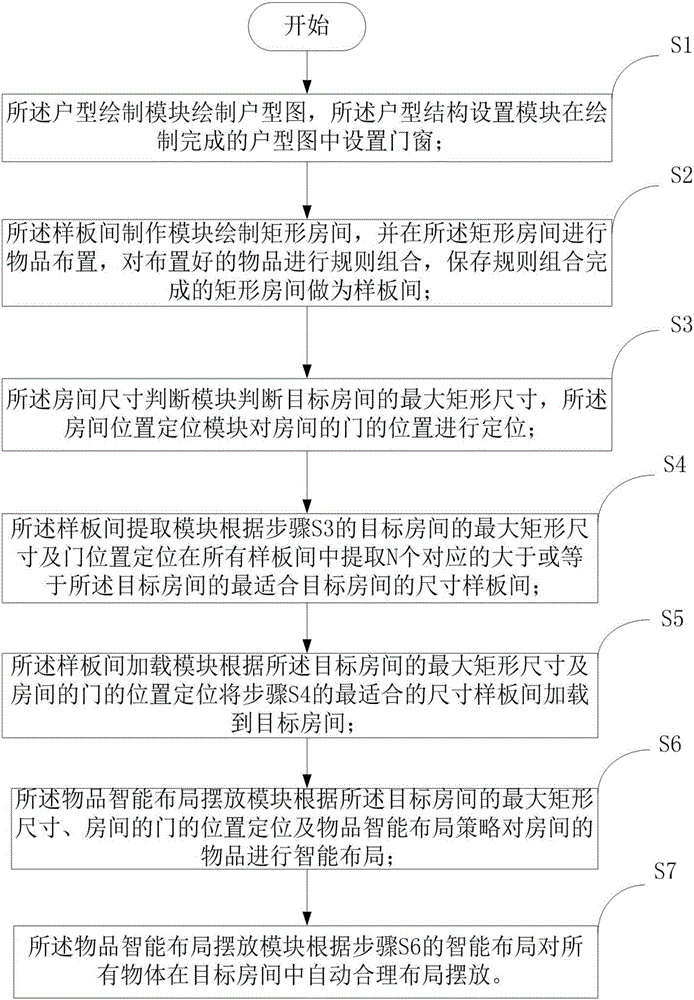
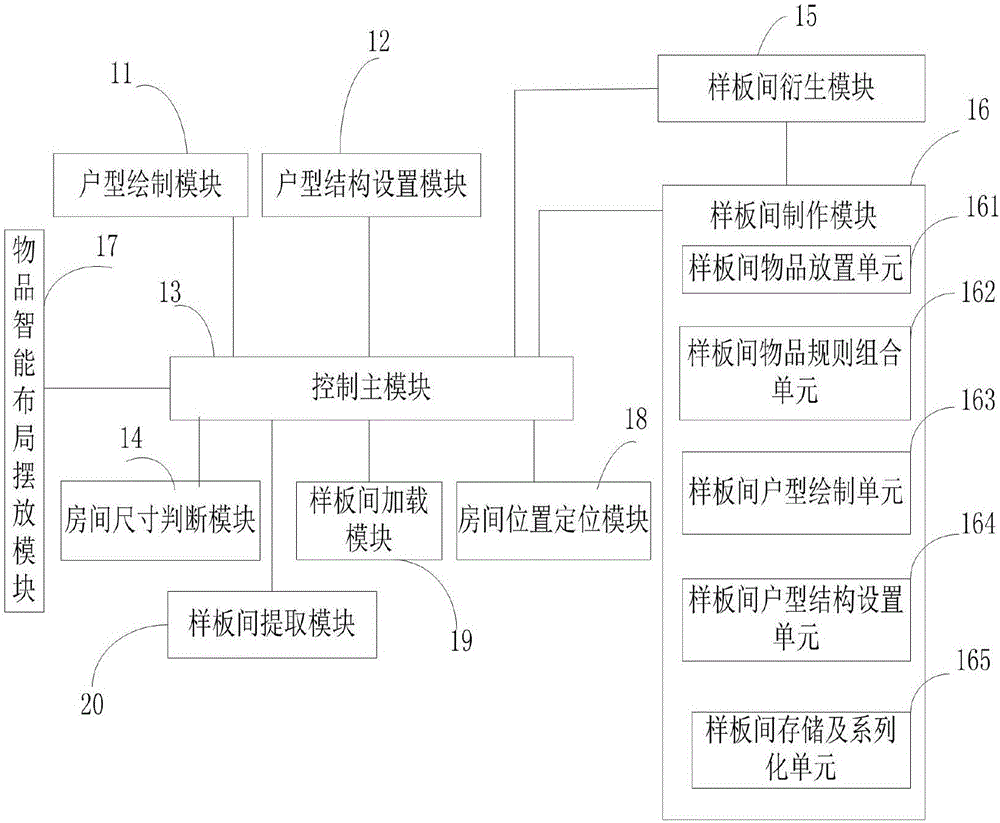
Structure and article intelligent layout method and system for designing home furnishings and house types
InactiveCN106815440AFlexible reuseReduce labor costsGeometric CADDesign optimisation/simulationSize determinationManufacturing engineering
The invention provides a structure and article intelligent layout method for designing home furnishings and house types. The method includes the following steps that a house-type drawing module draws a house-type image, and a house-type structure setting module sets doors and windows in the house-type image which is drawn completely; a prototype-room manufacturing module draws a rectangular room, lays out the articles in the rectangular room, and conducts regular combination on the articles which are laid out, and the rectangular room ofwhich the articles are regularly combinedis stored and serves as a prototype room; a room-size determination and calculation module determines the largest rectangular size of a target room, anda room-location positioning module conducts positioning on the locations of the doors and windows of the target room.The structure and article intelligent layout method for designing the home furnishings and the house types can conduct layout intelligently, the labor cost is reduced, the efficiency of spatial layout is improved, the quality of design schemes is controllable, and high-quality design schemes can be flexiblyreused regarding different home furnishings and house types. The invention further providesa structure and article intelligent layout system for designing the home furnishings and the house types.
Owner:SHENZHEN BINCENT TECH
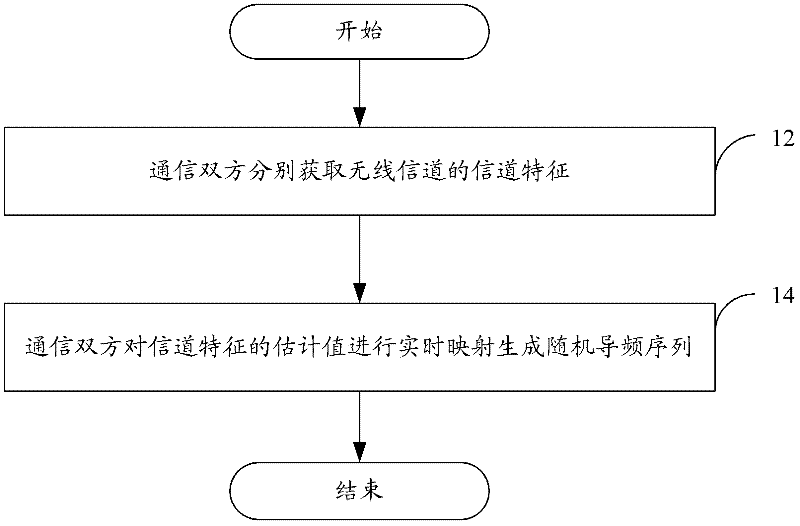
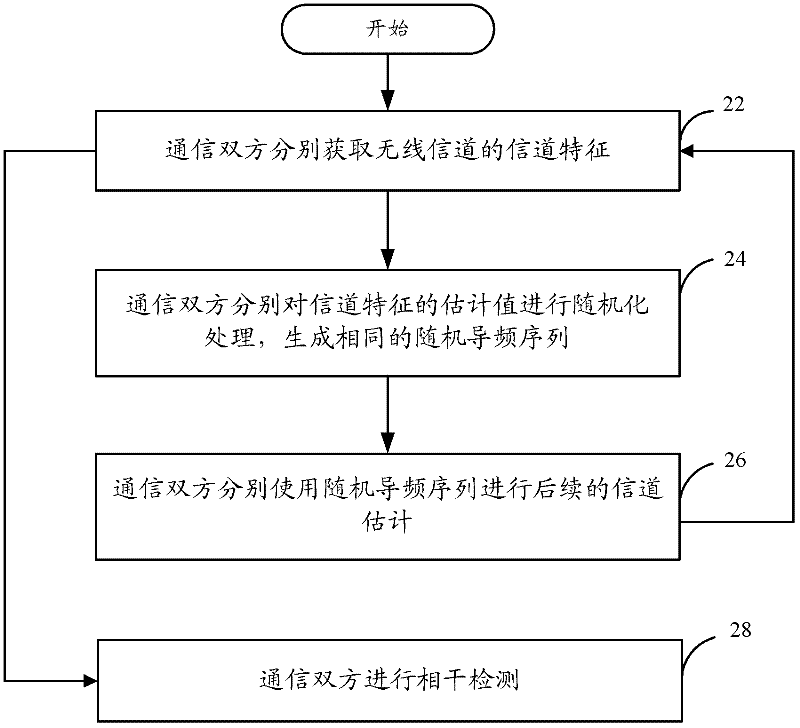
Pilot frequency sequence generation method and system
ActiveCN102238116AAchieve randomnessAchieve privacyBaseband system detailsMulti-frequency code systemsCommunications securityGeneration process
The invention discloses a pilot frequency sequence generation method and system, wherein the method comprises the following steps that: both parties in communication respectively obtain the channel characteristic of a wireless channel; and the both parties in communication map an estimation value of the channel characteristic in real time to generate a random pilot frequency sequence. With the method and the system provided by the invention, both legal parties in communication can obtain consistent channel characteristics based on the reciprocity of uplink and downlink channels, and further generate the private and random pilot frequency sequence based on characters of physical layer information of a wireless communication system, wherein the generation process is free from transmitting related information in the wireless channel, so that communication security is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
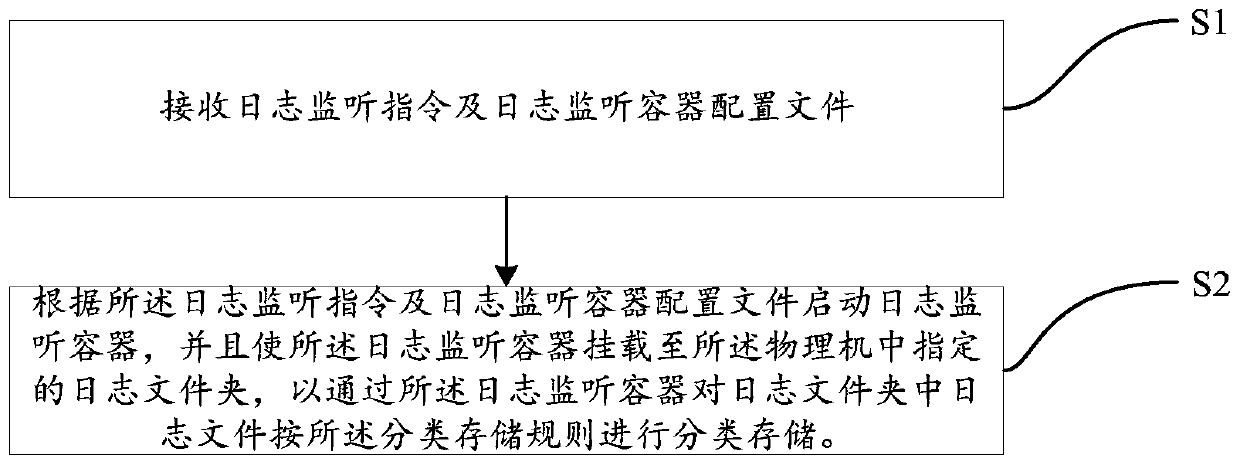
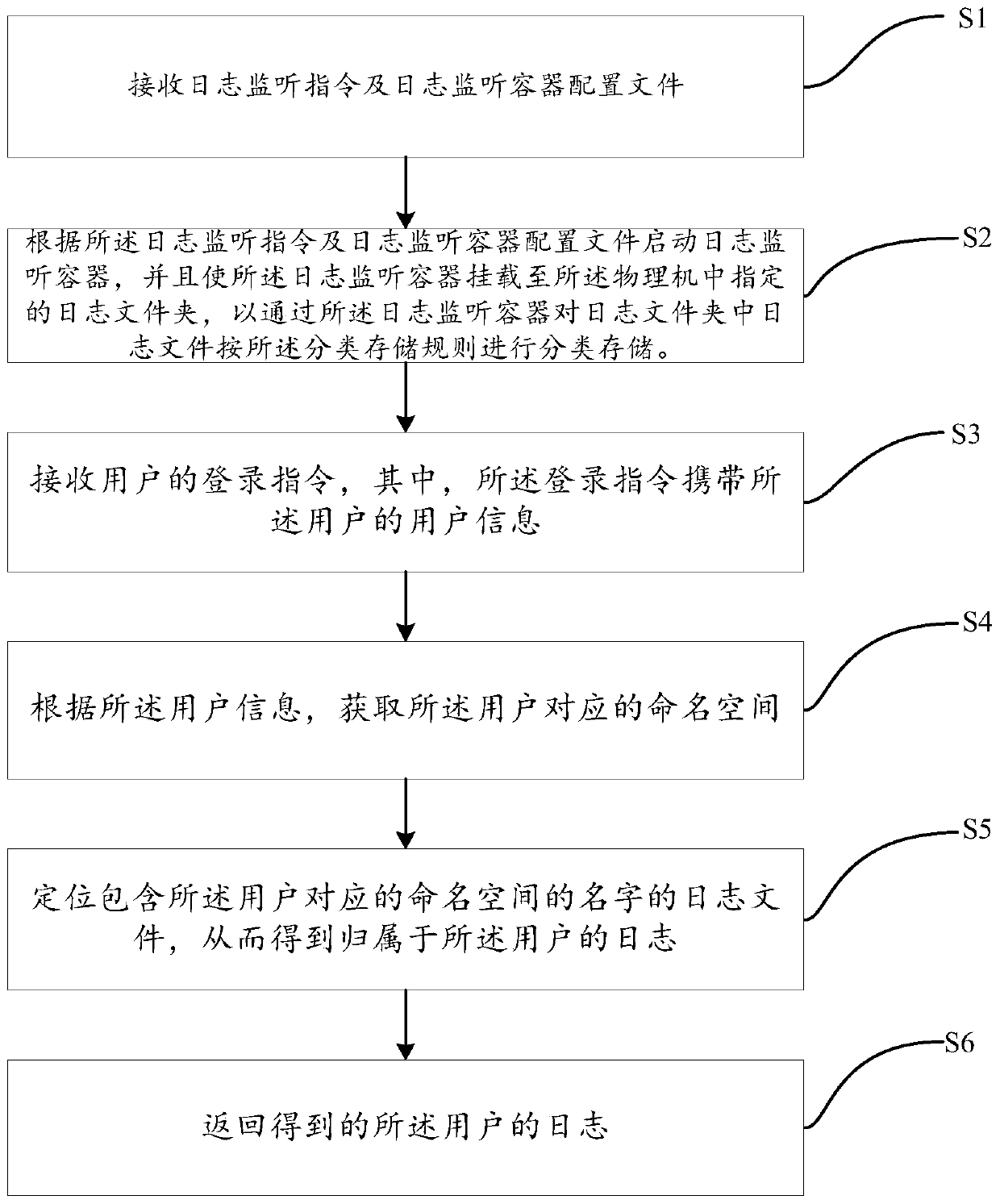
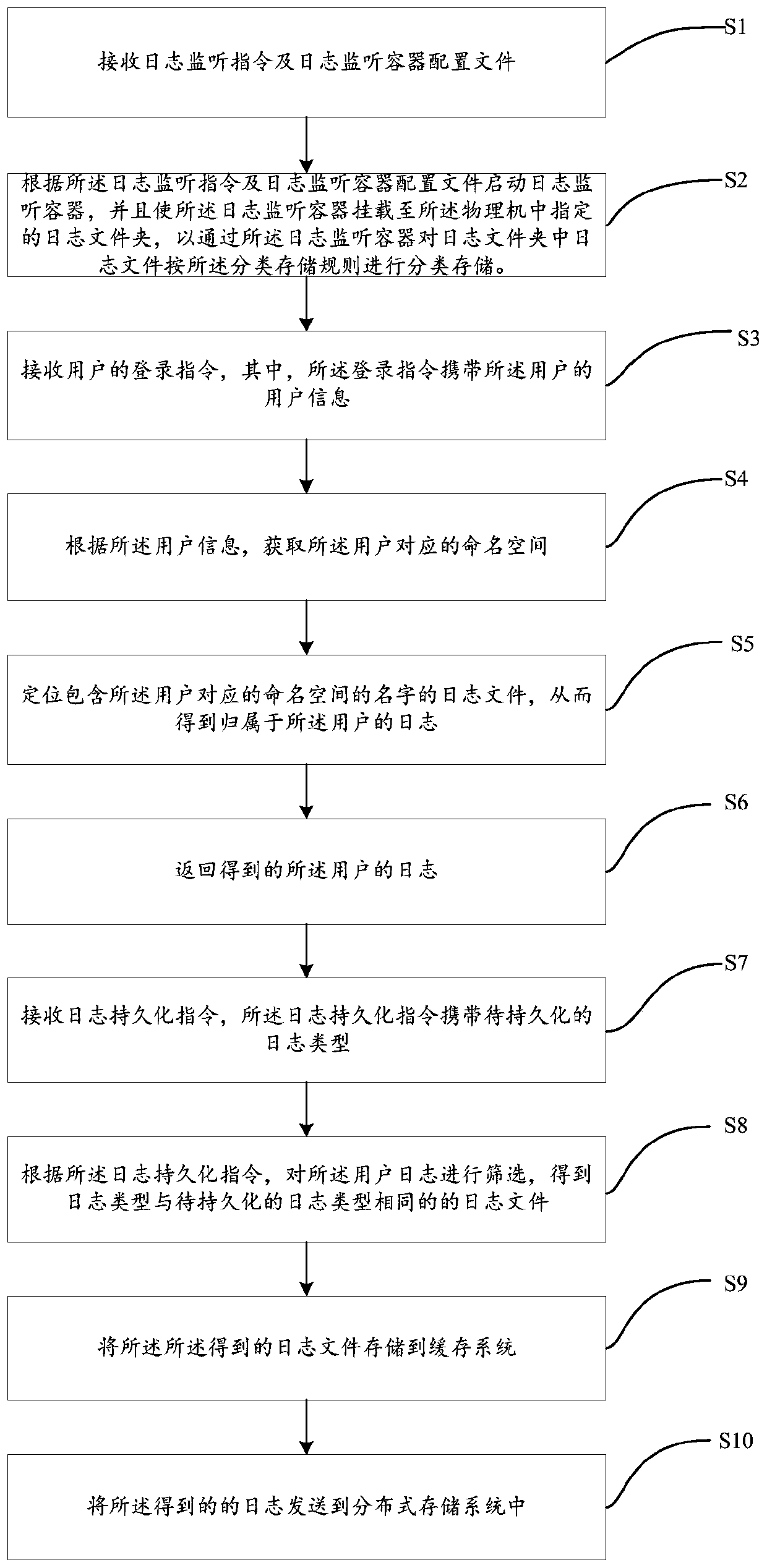
Automatic log processing method and device and computing equipment
The invention relates to the technical field of cloud services, and particularly discloses an automatic log processing method and device and computing equipment, and the method comprises the steps: receiving a log monitoring instruction and a log monitoring container configuration file, the log monitoring container configuration file carrying a classified storage rule; And starting a log monitoring container according to the log monitoring instruction and the log monitoring container configuration file, and enabling the log monitoring container to be mounted to a log folder specified in the physical machine so as to perform classified storage on the log files in the log folder according to the classified storage rule through the log monitoring container. Therefore, by utilizing the schemeprovided by the invention, the logs can be stored in a classified manner.
Owner:CLOUDMINDS SHANGHAI ROBOTICS CO LTD
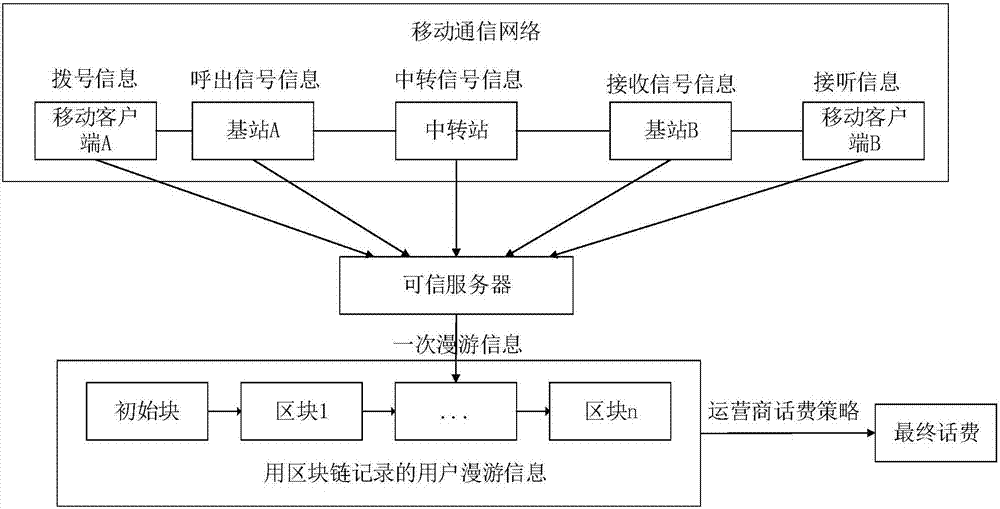
Block chain-based roaming telephone expenses recording and settlement method
InactiveCN107027111AAvoid inaccuracyImprove service qualityAccounting/billing servicesTransmissionBlockchainTelephone exchange
The present invention relates to the roaming telephone expenses recording and settlement method field of a block chain, in particular discloses a block chain-based roaming telephone expenses recording and settlement method which aims to solve the problem of the conventional roaming telephone expenses recording and settlement method that the operators and the user information are asymmetric, so that the information is not open and transparent, such as the telephone expenses, etc., and accordingly, the service quality of the operators declines. The technical scheme of the application comprises establishing a dialing information partition block chain based on a block chain technology, calling out the information partition block chain, transferring the information partition block chain, receiving the information partition block chain, and answering the information partition block chain; and then joining the partition block chain into a roaming telephone expenses full block chain, thereby realizing the whole open and transparent roaming telephone expenses recording and settlement, and improving the service quality of the operators.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
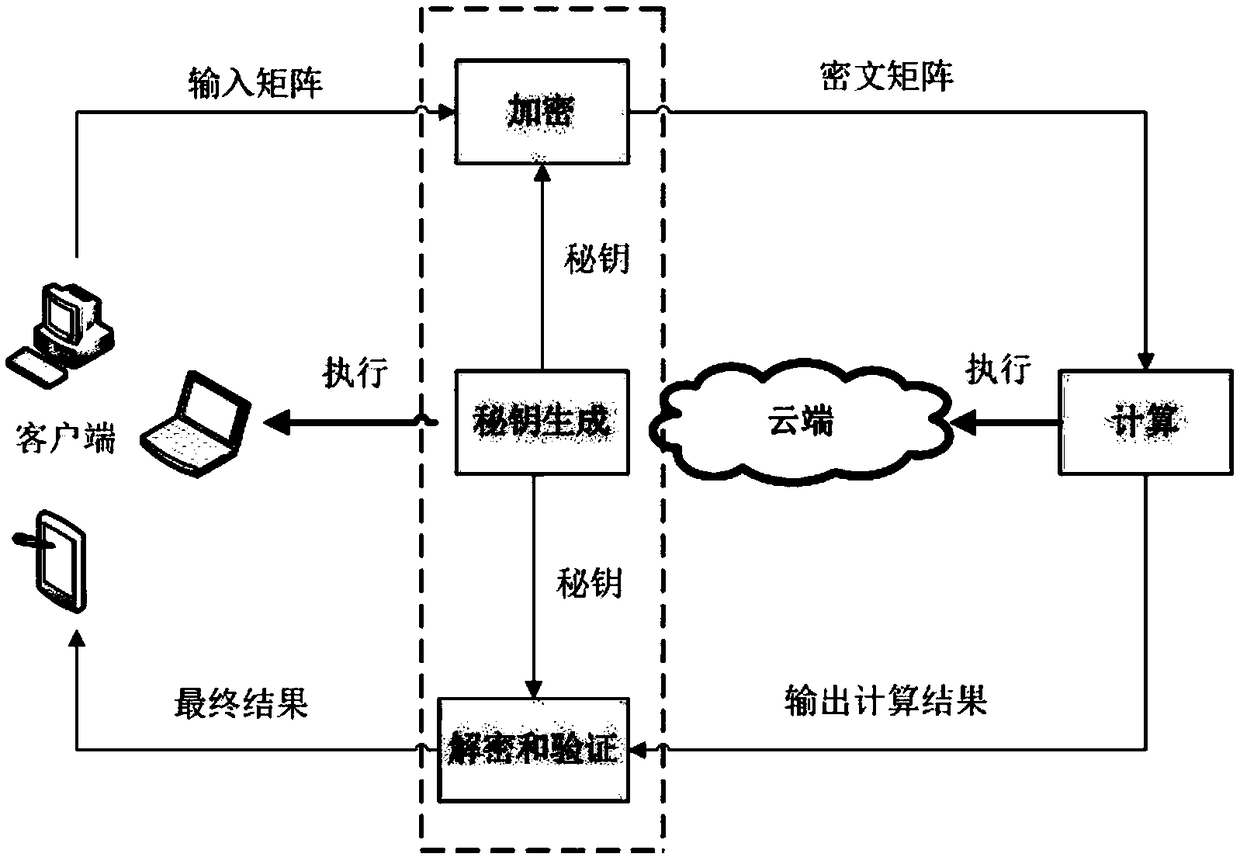
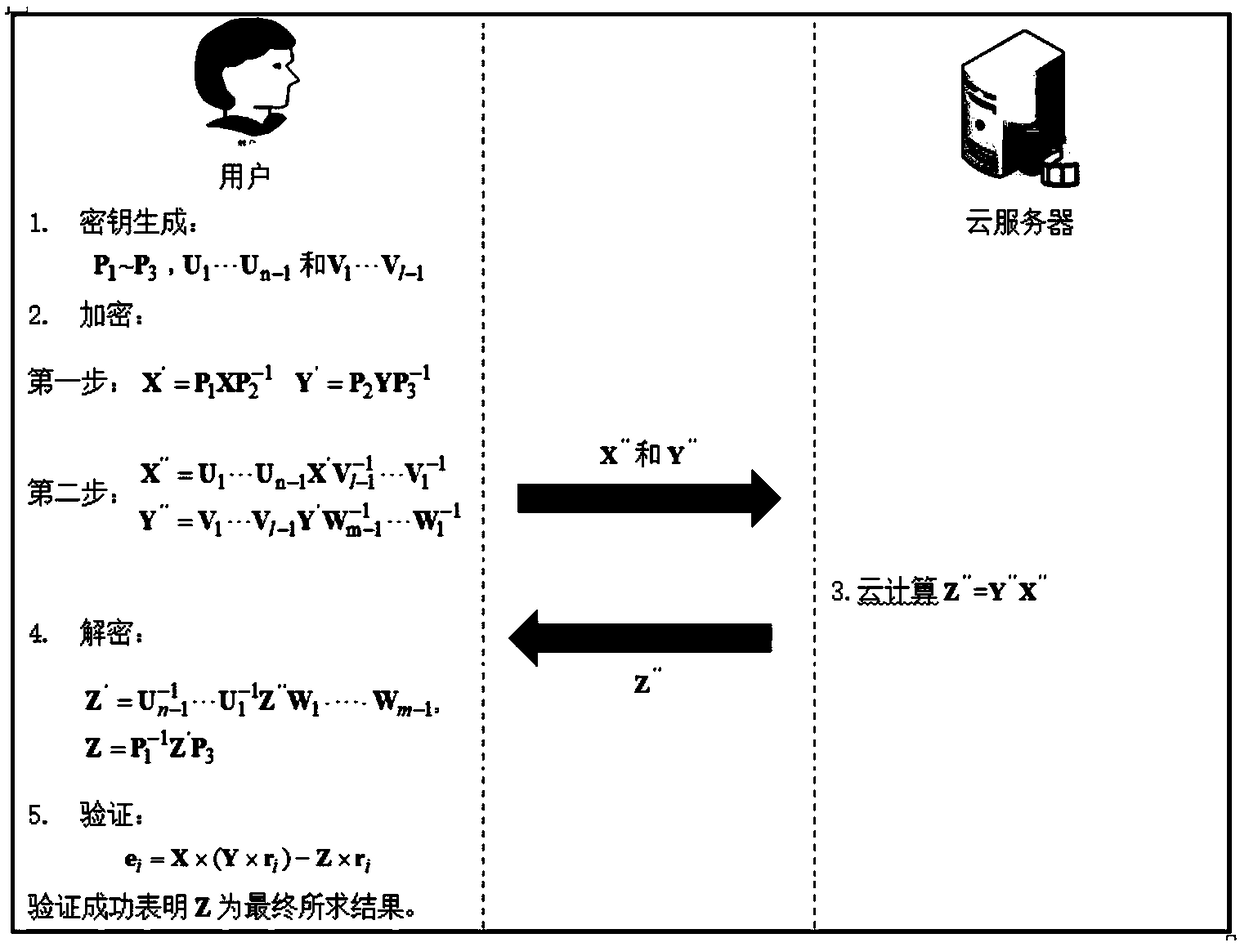
Secure outsourcing algorithm for large-scale matrix operation
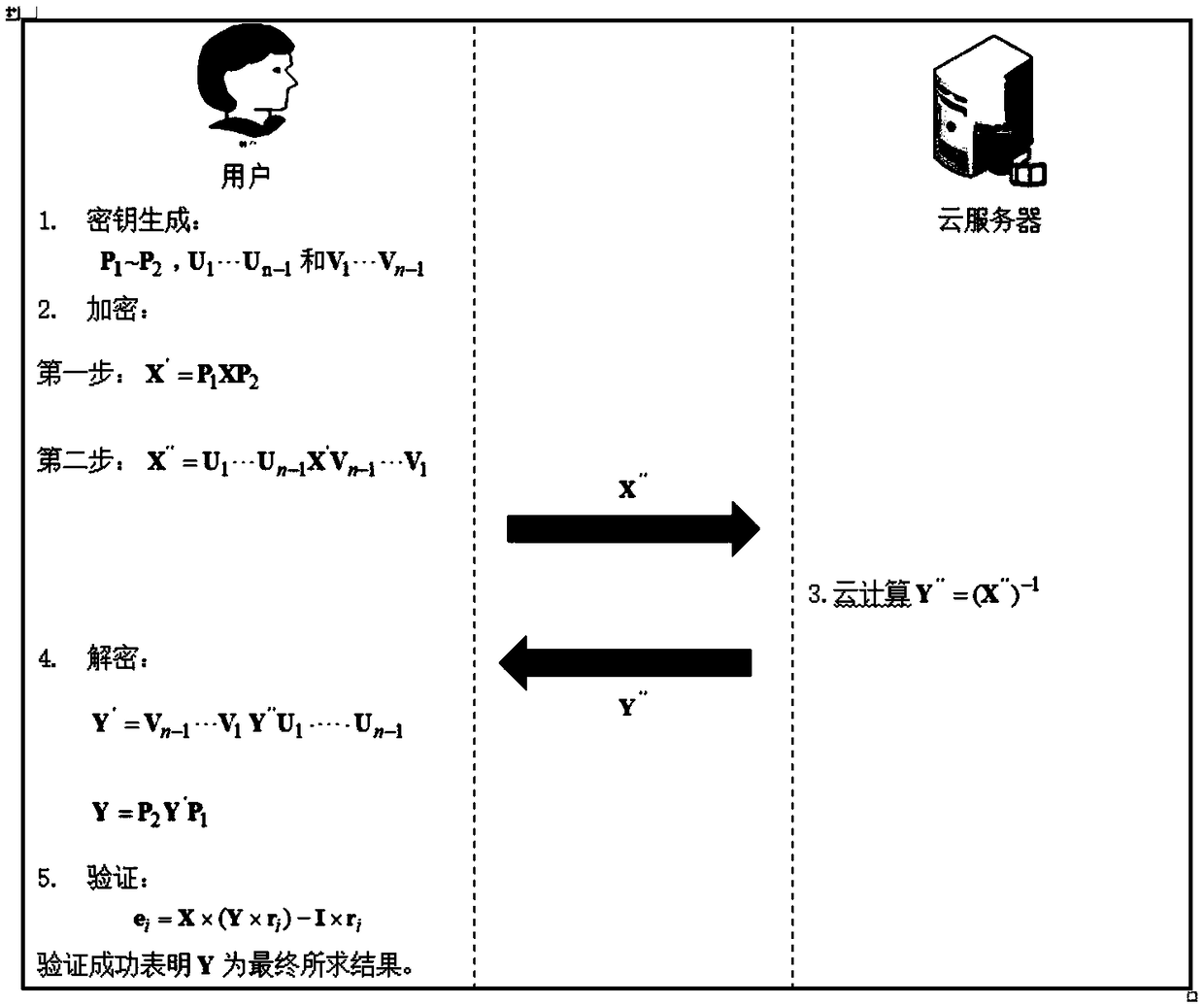
ActiveCN109460536AAchieve privacyAchieving verifiabilityTransmissionManufacturing computing systemsMatrix multiplicationComputer science
The invention provides a secure outsourcing algorithm for large-scale matrix operation, which adopts a continuous sparse 11-module matrix transformation encryption technology with a simple structure.On the one hand, multiple sparse transformations can encrypt dense matrices continuously, thus protecting the statistical information of specific elements of the original matrices; On the other hand,the combinability of matrix multiplication and the simplicity of sparse matrix structure ensure the high efficiency of matrix encryption and decryption. In addition, the technology has good universality, suitable for outsourcing MM, MIC, MDC and other matrix operations, giving good consideration to the privacy of input and output, high efficiency verifiability and efficiency.
Owner:QINGDAO UNIV
System and method for security management of Internet archives based on attributes
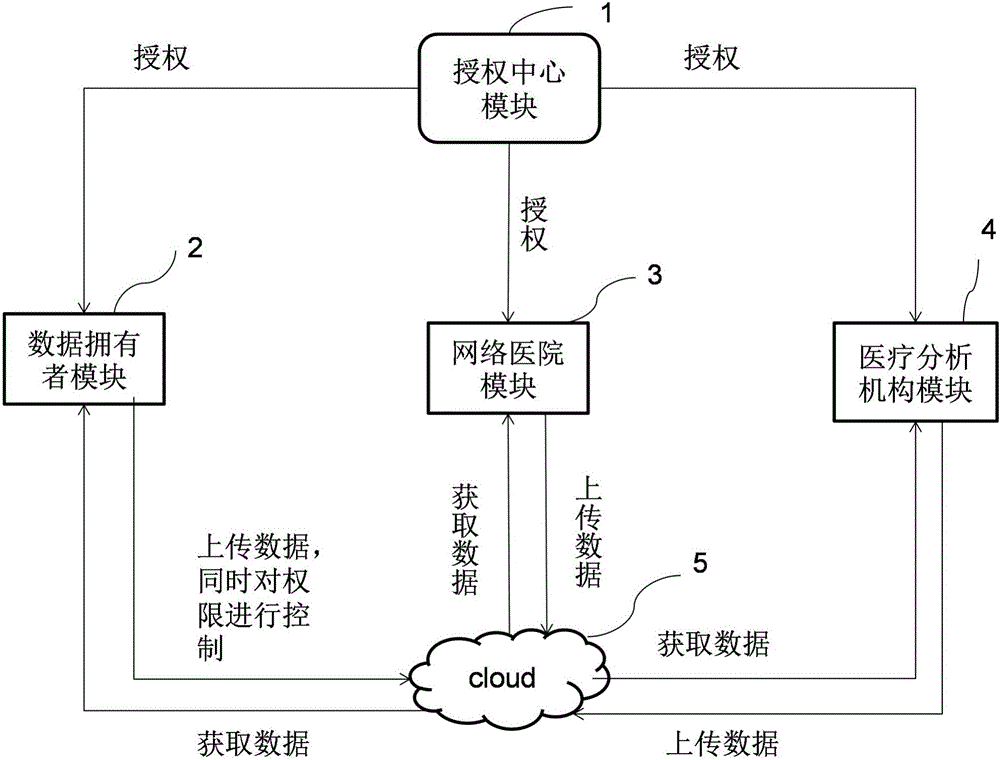
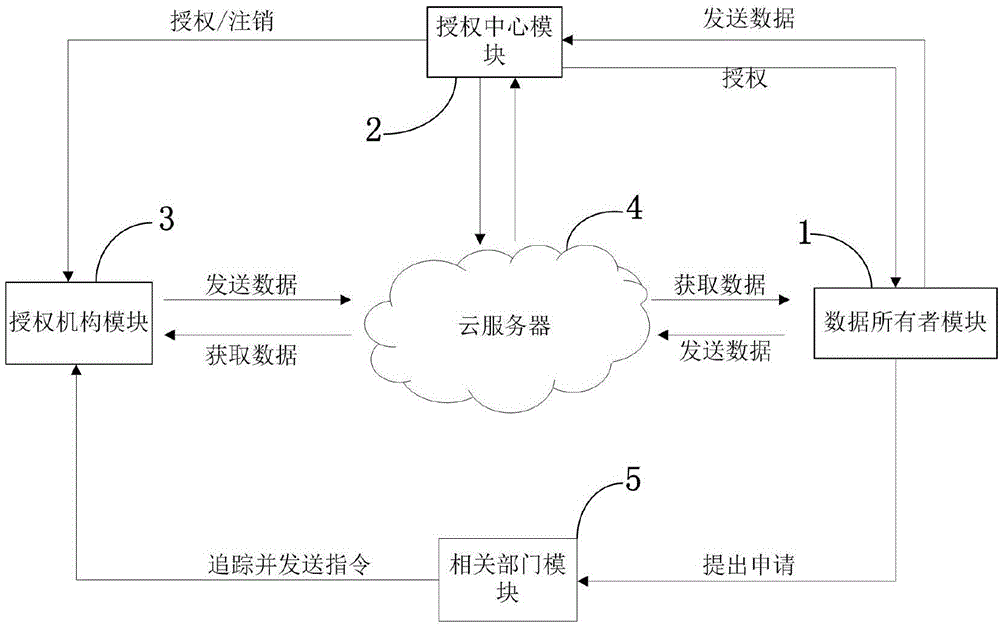
ActiveCN104618366AAchieve privacyReduce interactionTransmissionSafety management systemsThe Internet
The invention discloses a system and a method for security management of Internet archives based on attributes; the system comprises a data owner module, an authorization center module, an authorization mechanism module, a Cloud server and a relevant department module. In the method, an information encryption technology based on the attributes is combined, a chain type storage technology is utilized and the security share of personnel archives in the Cloud server is realized with respect to the features of the personnel archives; and a uniform and secure management system for the Internet archives is formed by defining a system model and constructing a plurality of protocols. The data privacy is realized, the interaction of secret keys is reduced and the storage and management of a plurality of secret keys are avoided; the access of the authorization mechanism to the data is limited by setting double barriers; in addition, the system and the method for security management of the Internet archives based on the attributes eliminates the disadvantage that a new method or new software needs to be developed when some kind of information was increased in the past.
Owner:XIDIAN UNIV
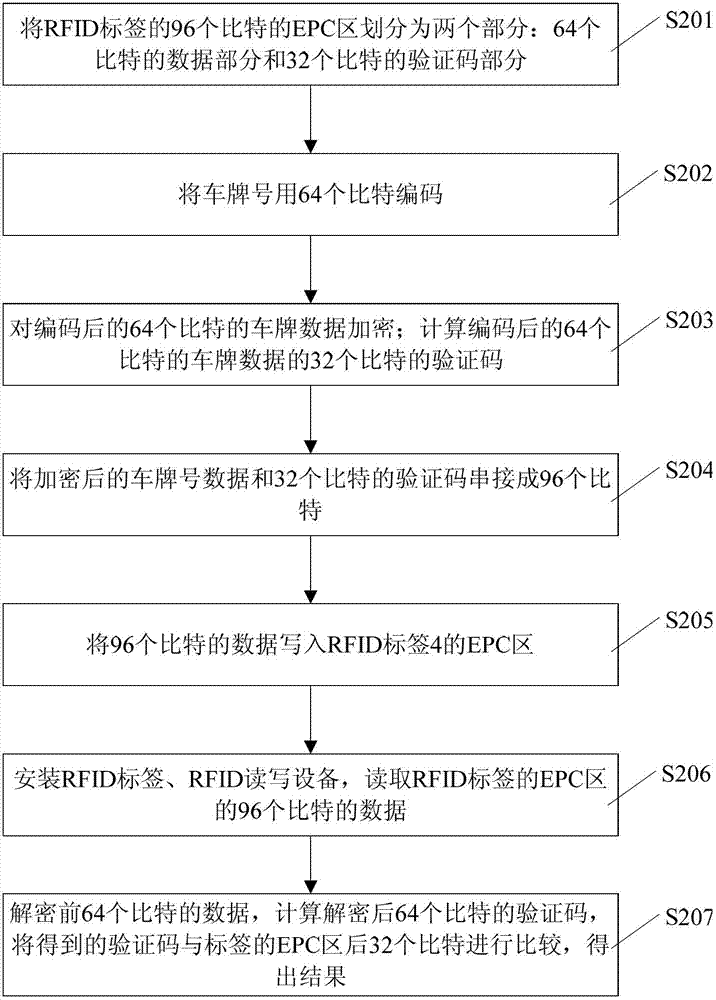
Radio frequency tag data coding method and radio frequency tag data coding system for vehicle identification
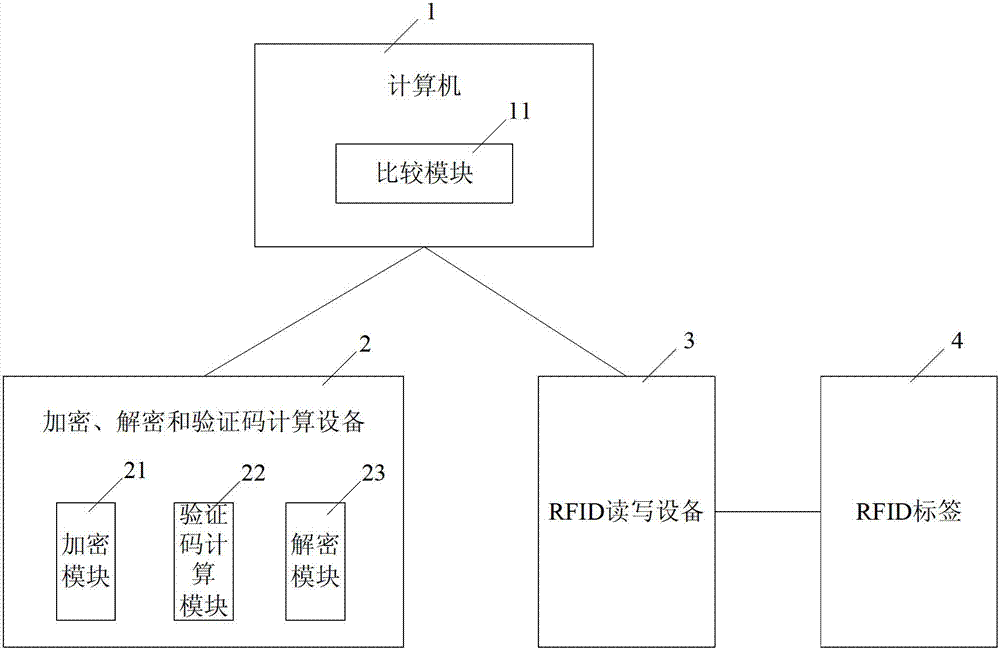
ActiveCN103714357AAchieve privacyAchieve tamper resistanceCo-operative working arrangementsComputer hardwareRadio frequency
The invention discloses a radio frequency tag data coding system and a radio frequency tag data coding method for vehicle identification. The system comprises a computer, an encryption / decryption and verification code calculation device, an RFID reading-writing device and an RFID tag. The computer divides an EPC region of the RFID tag into a data part and a verification code part and codes a license plate number; the encryption / decryption and verification code calculation device encrypts the coded license plate number data and calculates the verification code of the license plate number data; the computer concatenates the license plate number data and the verification code; the RFID reading-writing device writes the concatenation data into the EPC region; the encryption / decryption and verification code calculation device carries out decryption to obtain decryption data and calculates the verification code; and the computer compares the decrypted verification code with the verification code part of the EPC region and judges whether data in the EPC region is tampered. The defect that data encryption and verification code calculation cannot be carried out due to the fact that the license plate number is stored in the EPC region of the RFID tag in the prior art is overcome.
Owner:BEIJING INST OF COMP TECH & APPL
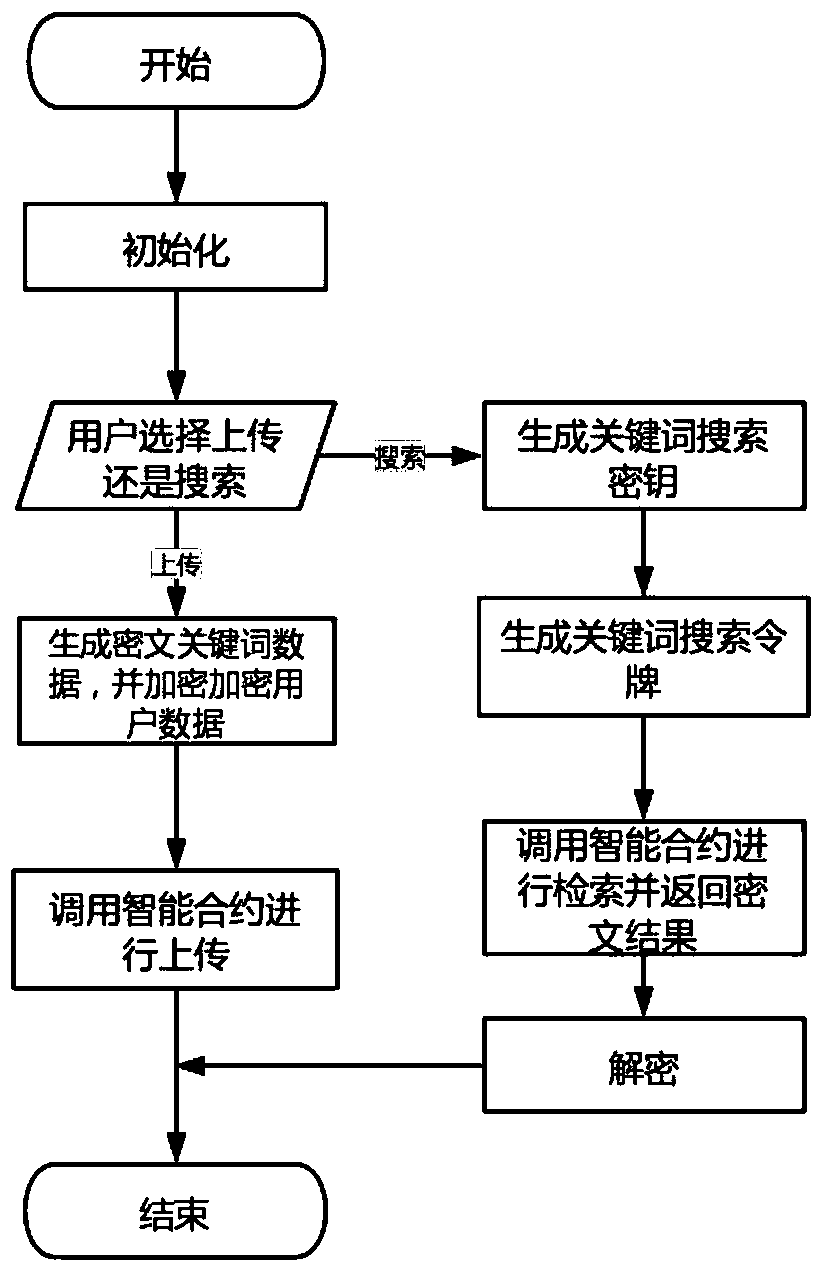
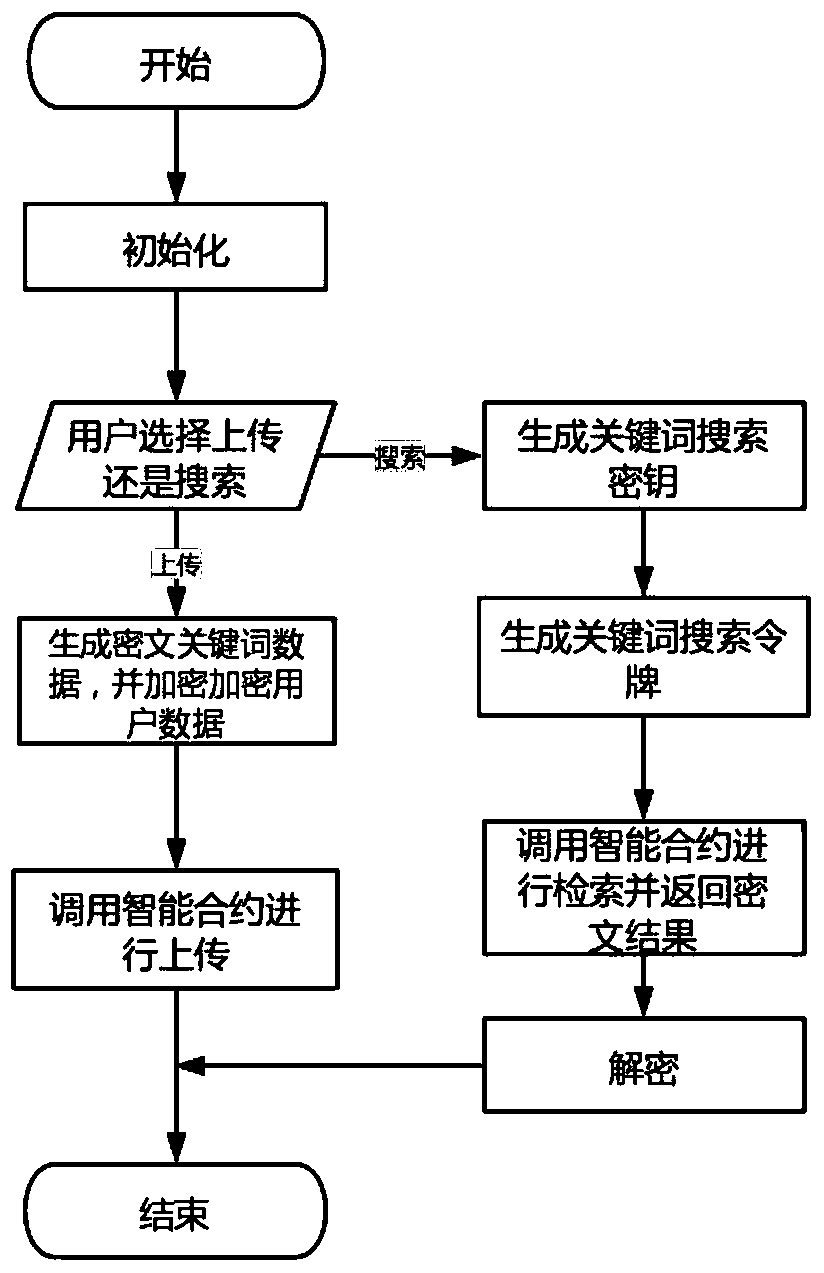
Ciphertext retrieval method based on block chain
PendingCN111143471AAchieve privacyFull chain search implementationDatabase distribution/replicationDigital data protectionBlockchainData needs
The invention discloses a ciphertext retrieval method based on a block chain. The ciphertext retrieval method comprises the following steps: initializing to generate a public parameter and a master key; generating a keyword search key according to the attribute set of a user; generating ciphertext keyword data according to an access control strategy and data keywords provided by a data owner, encyprting user data through symmetric encryption, and uploading the ciphertext keyword data and the ciphertext data to the block chain by calling an intelligent contract; generating a corresponding keyword search token according to the keyword provided by the data demander and the keyword search key; transmitting eacj keyword search token to an intelligent contract, wherein the intelligent contract matches the keyword data of each ciphertext number on the chain with the keyword search token; and decrypting the obtained ciphertext. On the basis of block chain ciphertext retrieval, attribute-basedciphertext retrieval is improved, user data is uploaded in a ciphertext form, and the permission of a user to the data is determined through user attributes.
Owner:BEIJING UNIV OF TECH
Group-building method and device, transaction method and system
InactiveCN109377364AAvoid technical disadvantages that cannot ensure the concealment of transactionsAchieve privacySpecial service provision for substationFinanceBlockchainGroup method
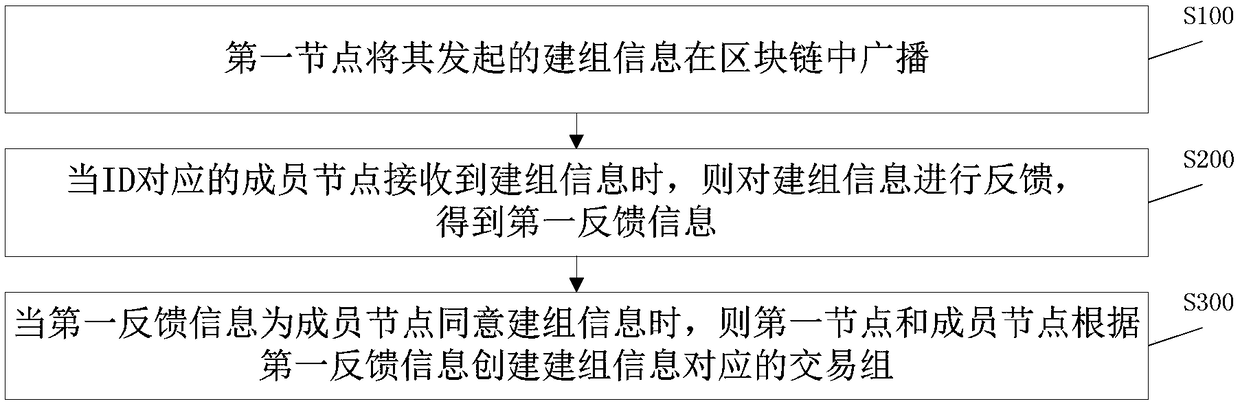
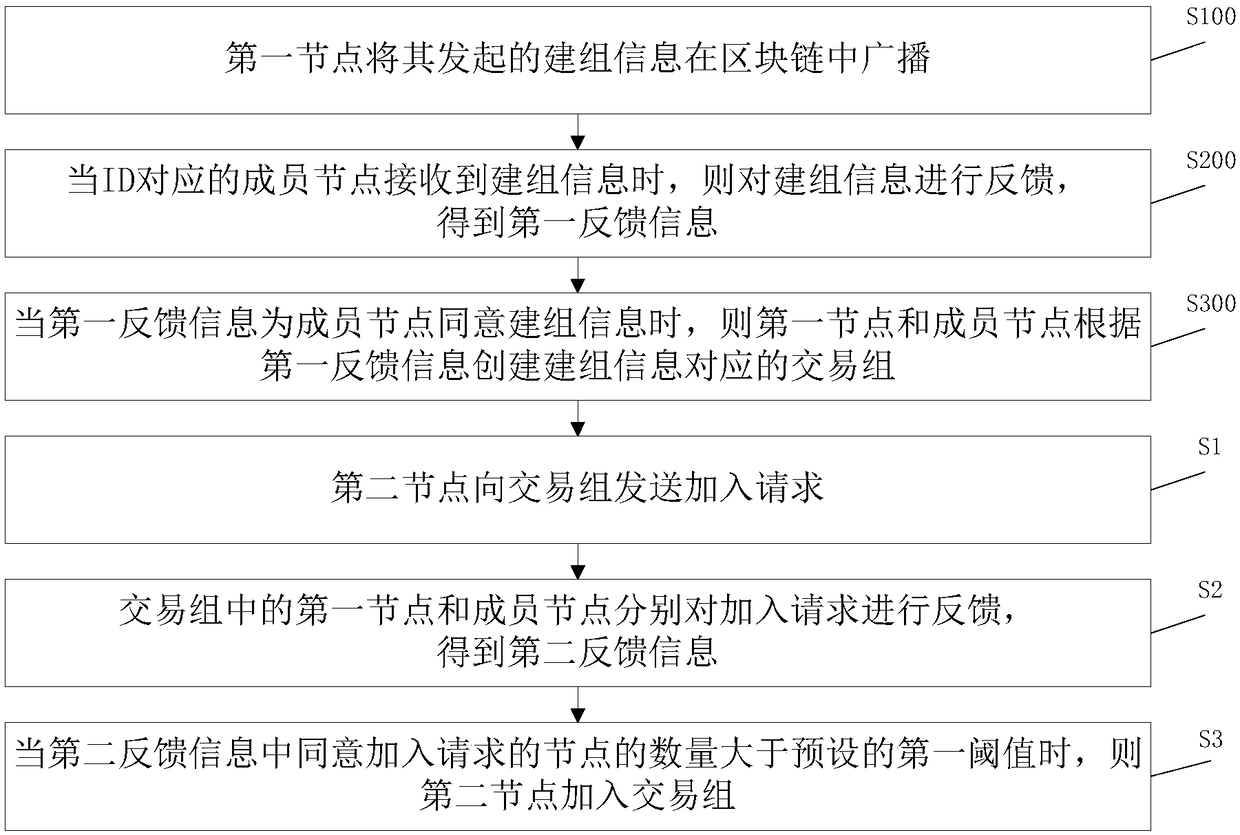
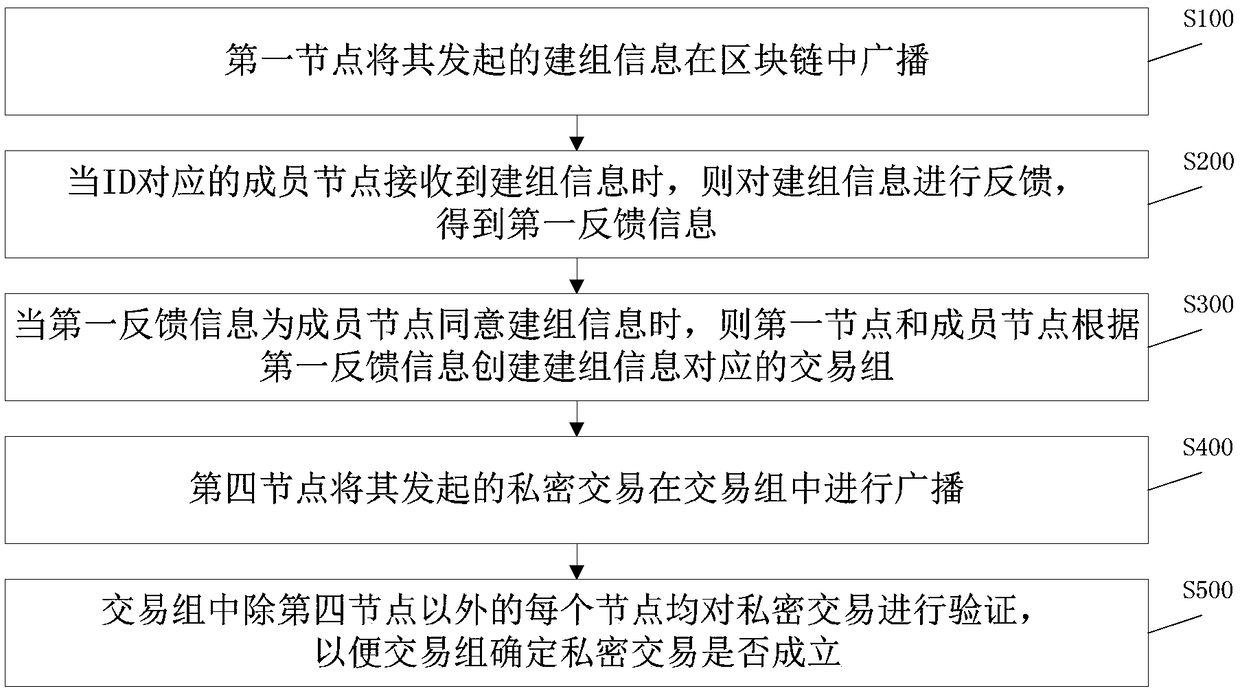
Embodiments of the present invention relate to a grouping method and apparatus, a transaction method and a system. The group building method comprises the following steps: a first node broadcasts thegroup building information initiated by the first node in a block chain, and the group building information comprises an ID corresponding to a member node; When the member node corresponding to the IDreceives the group building information, the group building information is fed back to obtain the first feedback information; When the first feedback information is the member node agrees to set up the group information, the first node and the member node create a transaction group corresponding to the set up information according to the first feedback information. According to the technical proposal provided by the present embodiment, the invention avoids the technical drawbacks in the prior art that when all transactions in the block chain are carried out in the whole block chain, the concealment of the transactions cannot be ensured, and realizes the technical effect that internal transactions can occur between some nodes, and the internal transactions are not informed by the externalnodes, thereby realizing the privacy of the transactions occurring in the internal nodes.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Ultraviolet-proof and blue-ray-proof coating liquid, glass and manufacturing method of glass
ActiveCN112646398AEasy constructionExtended service lifeRadiation-absorbing paintsOptical elementsPtru catalystUltraviolet lights
The invention relates to the technical field of surface coating coating, in particular to a functional coating coated on the surface of glass, and particularly provides an ultraviolet-proof blue-light-proof coating liquid, glass and a manufacturing method of the glass. The ultraviolet-proof and blue-ray-proof coating liquid comprises silica sol and a chelating agent, wherein the silica sol comprises silicate, a first solvent, a first coupling agent, a first catalyst and deionized water; and the chelating agent comprises an ultraviolet light absorber, a blue light absorber, a second solvent, a second catalyst and a second coupling agent. The coating liquid can reduce the ultraviolet transmittance and the blue light transmittance, can meet the requirements for ultraviolet insulation and blue light prevention at the same time, has excellent aging resistance, abrasion resistance and the like, can prolong the normal service life of a base material, is extremely low in VOC emission, and has the advantages of being environmentally friendly, good in construction performance and the like. The ultraviolet-proof and blue-light-proof coating can further meet regulations of laws and regulations of glass for automobiles.
Owner:FUYAO GLASS IND GROUP CO LTD
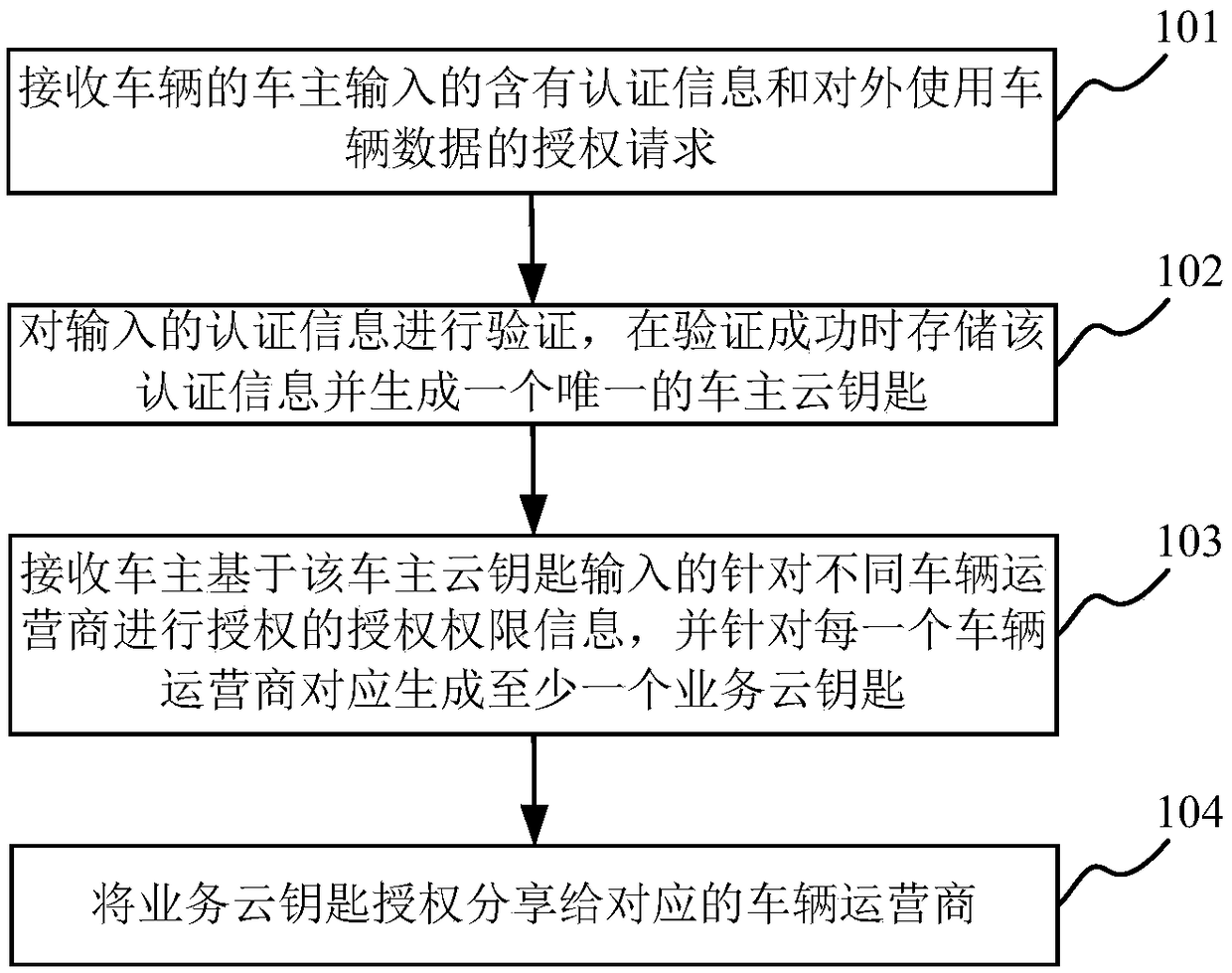
Method and system for generating and authorizing virtual cloud key
ActiveCN109361715AUniqueness guaranteedAchieve control and privacyKey distribution for secure communicationAuthorizationControllability
The invention discloses a method and system for generating and authorizing a virtual cloud key. The method comprises the following steps: receiving an authorization request input by a vehicle owner including authentication information and externally used vehicle data, wherein the authentication information comprises a vehicle owner name, a mobile phone number, and an engine number of the vehicle;verifying the authentication information, storing the authentication information and generating a unique vehicle owner cloud key when the verification is successful, wherein the vehicle owner cloud key comprises the authentication information and the vehicle data; receiving authorization permission information for authorization of different vehicle operators input by the vehicle owner based on thevehicle owner cloud key, and correspondingly generating at least one business cloud key for each vehicle operator, wherein the business cloud key comprises an authorized vehicle operator name, an authorized vehicle service permission, and an authorization validity period; and sharing the business cloud key authorization with the corresponding vehicle operator. The method and system for generatingand authorizing a virtual cloud key realize the unique identification of the vehicle use right, ensure the controllability of the vehicle, realize controllability and privacy of the open data of thevehicle factory under the authorization state, and finally achieve the separation of the vehicle property right and the use right.
Owner:钛马信息网络技术有限公司
Combustion gas alarm IoT (Internet of Things) system for industrial and commercial purposes
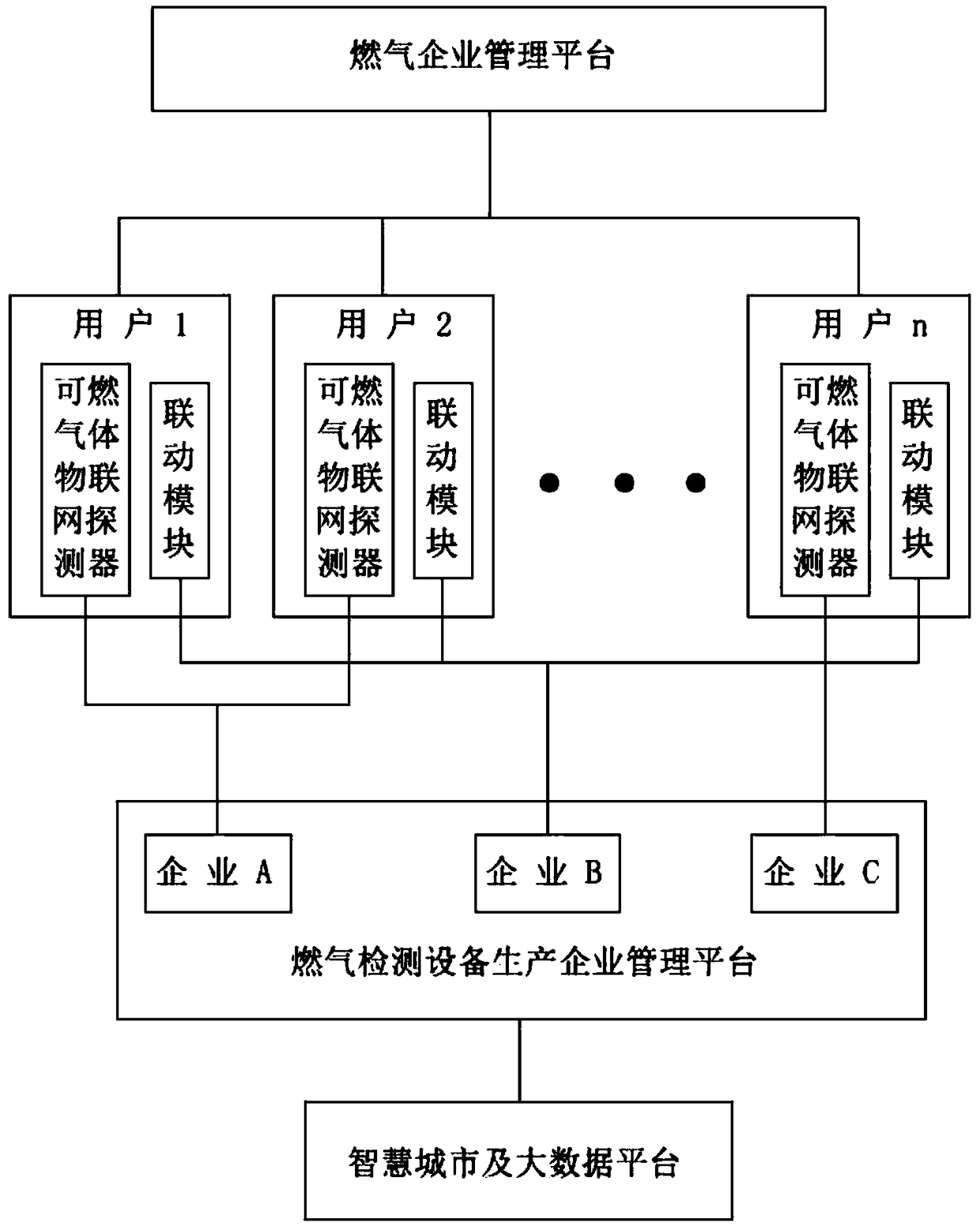
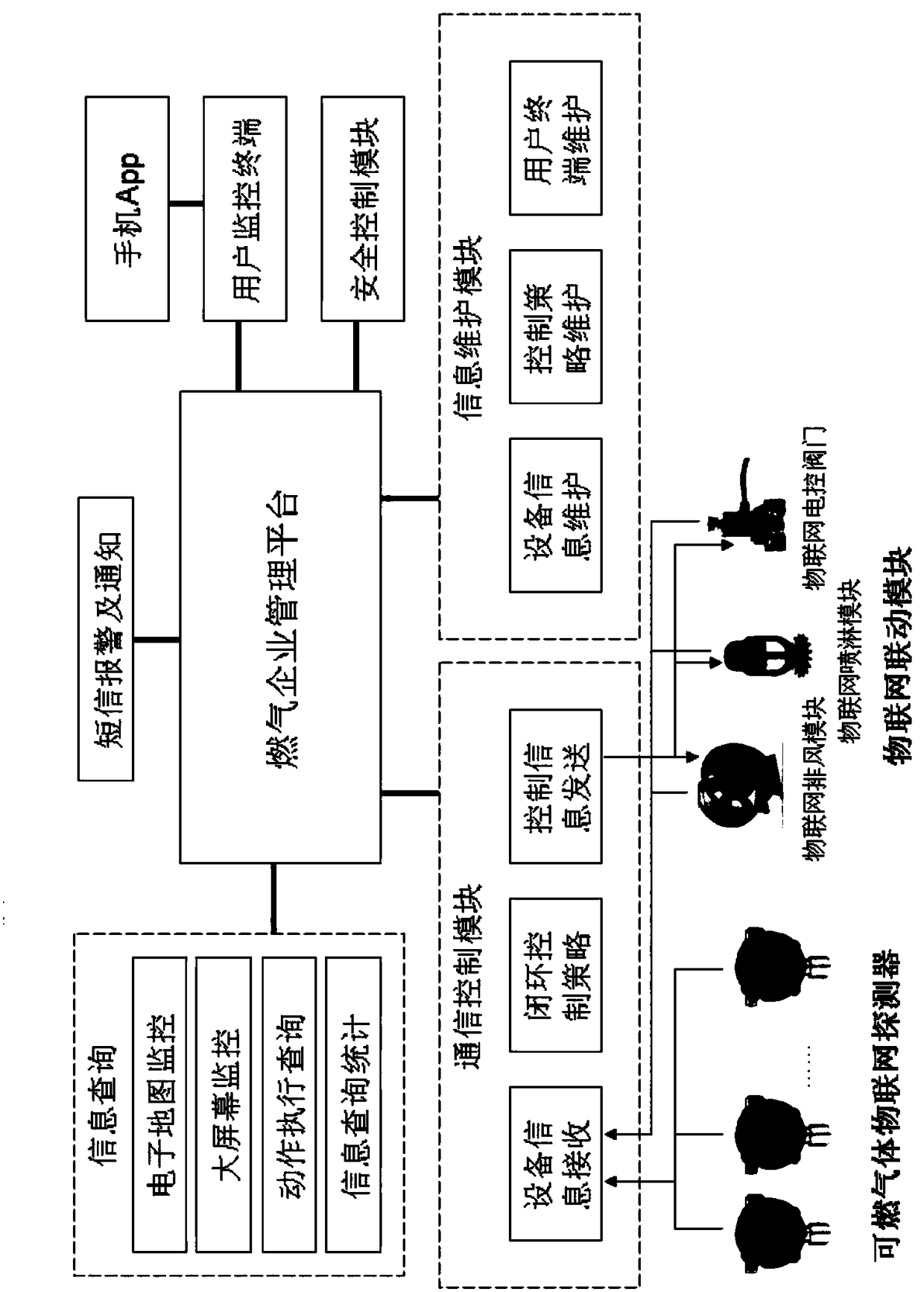
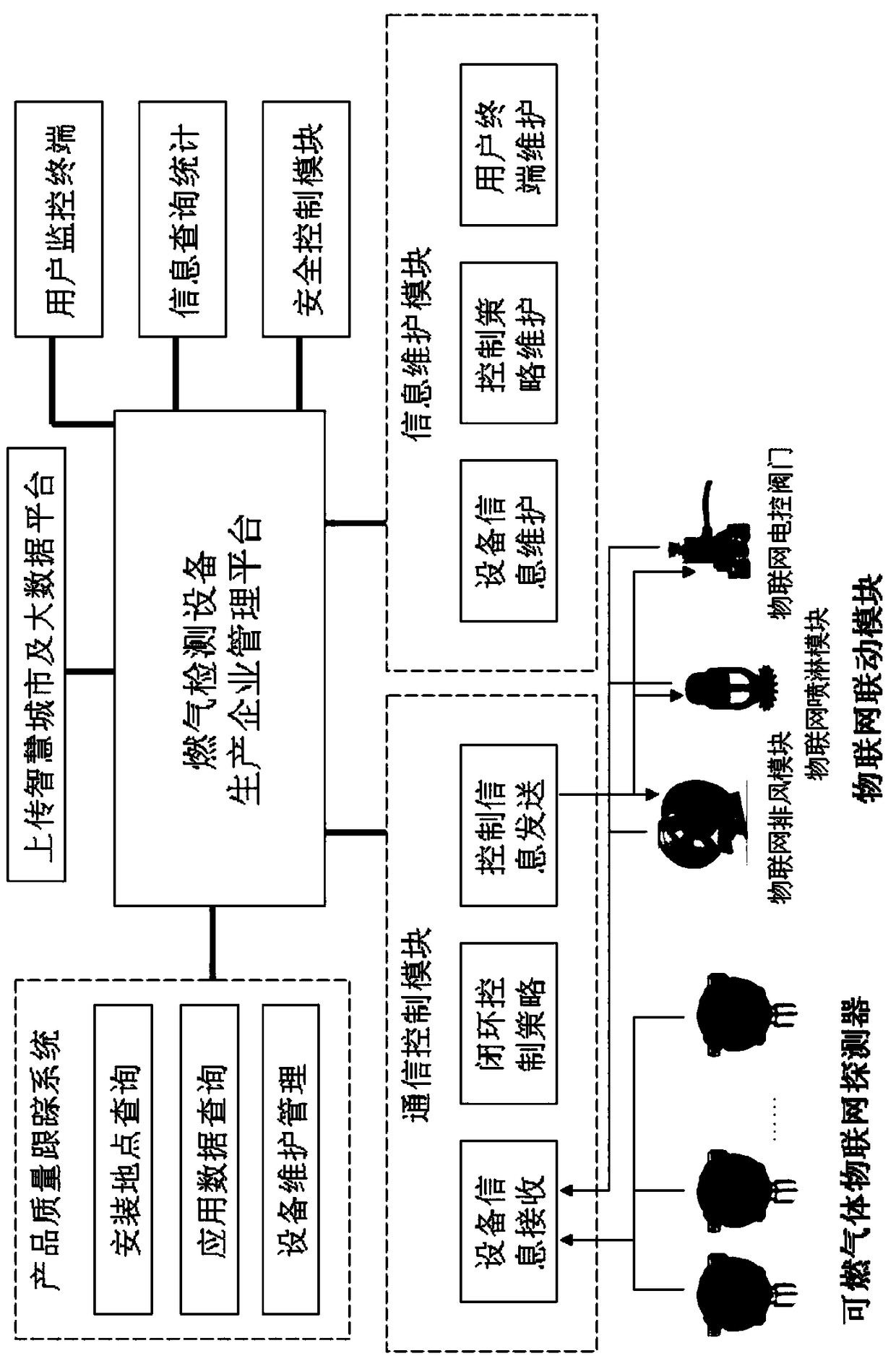
InactiveCN108961691ARealize gas monitoring and alarmGuaranteed uptimeAlarmsComputer moduleCombustible gas
The invention provides a combustion gas alarm IoT system for industrial and commercial purposes. The system comprises a user, a user management platform and an equipment management platform; the userprovides an installation environment for a combustible gas IoT detector and a linkage module; the user management platform monitors the user by, obtaining alarm information of the combustible gas IoTdetector and controlling motion of the linkage module of the user; the equipment management platform monitors the combustible gas IoT detector and linkage module, and obtains equipment state information of the combustible gas IoT detector and the linkage module. The concept of IoT is introduced, and the brand new networking manner is used to change application form of a present system and product.Information is integrated in the wireless networking mannerwhich realizes product quality tracking and comprehensive management of users.
Owner:吴天文
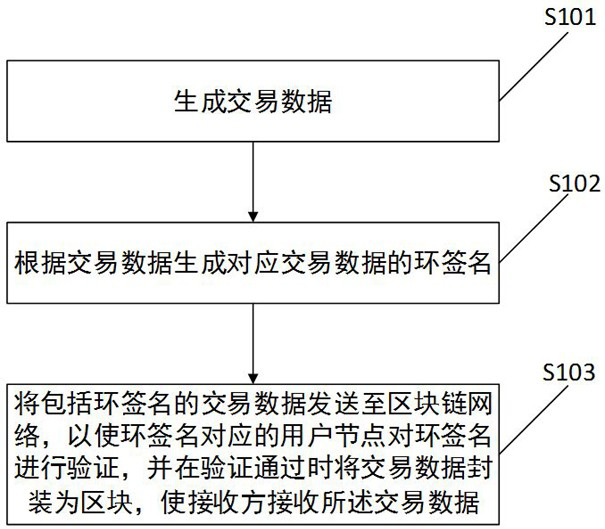
Block chain-oriented privacy transaction method and related device
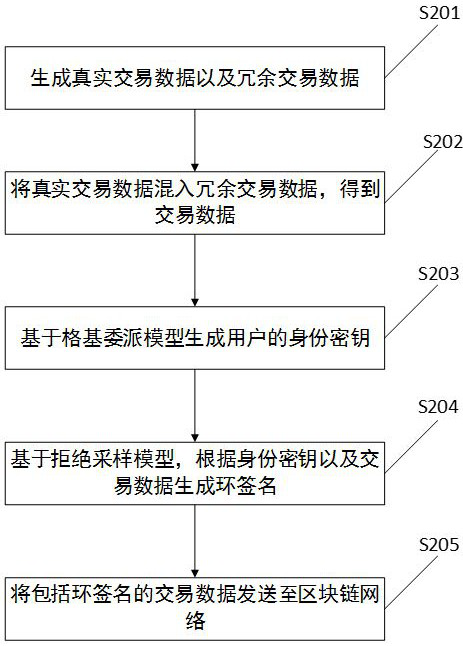
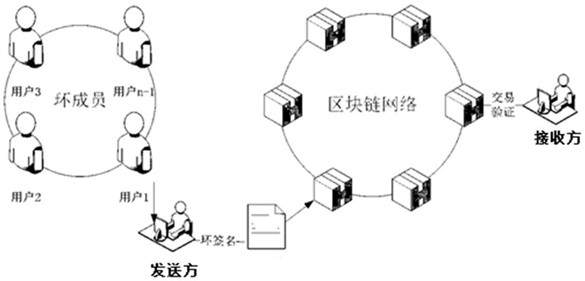
The invention discloses a blockchain-oriented private transaction method and a related device. The method comprises the steps of generating transaction data; generating a ring signature corresponding to the transaction data according to the transaction data; and sending transaction data including the ring signature to a block chain network, so that a user node corresponding to the ring signature verifies the ring signature, and when the verification is passed, packaging the transaction data into a block, so that a receiver receives the transaction data. By adding the ring signature to the transaction data and sending the transaction data including the ring signature to the block chain network based on the ring signature after verification of other users is passed, privacy of the users can be realized through anonymity of the ring signature, and user information is protected from being leaked.
Owner:STATE GRID E COMMERCE CO LTD +2
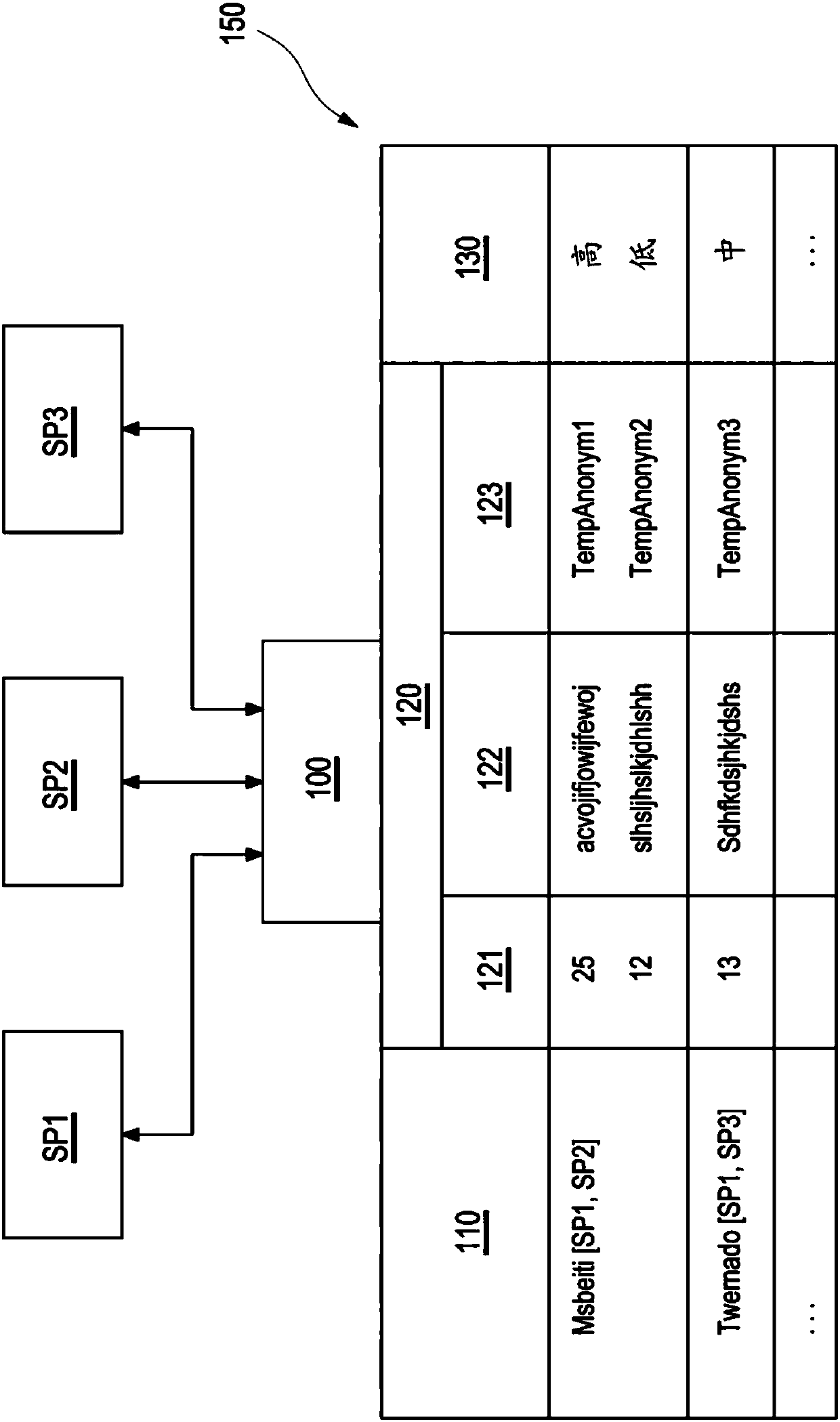
System And Method For Providing User With Access To Different Services Of Service Providers
ActiveCN107846394AAchieve privacyDigital data authenticationSecurity arrangementIt service providersInternet privacy
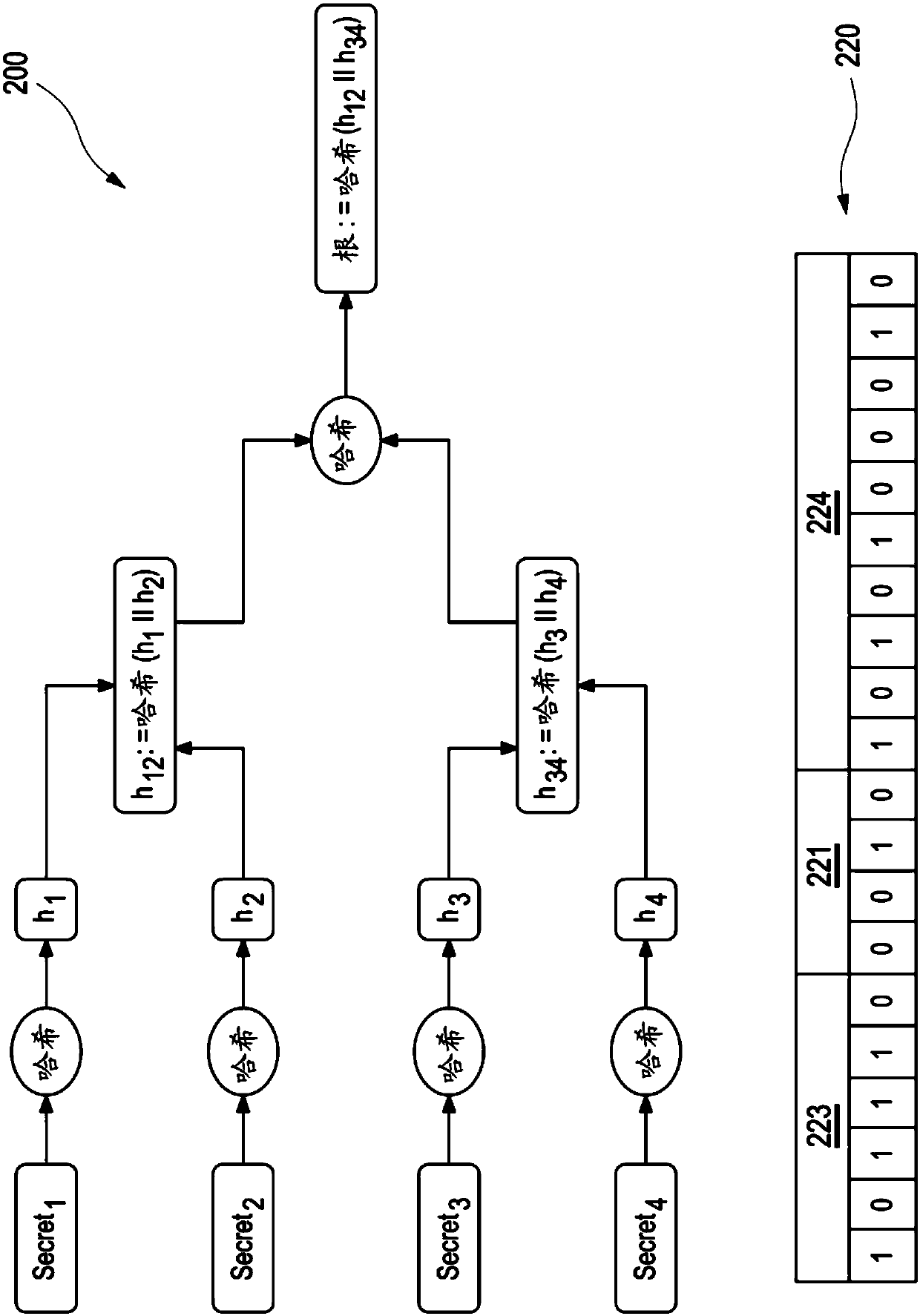
The present invention refers to a system and a method for providing a user with an access to different services of service providers. The system comprises at least a D-ID middleware (620) and a D-ID-agent (610), wherein, whenever the user intends to access one desired service of the different services, the user selects one pseudonym and the D-ID agent (610) reveals a secret of a pseudonym-specificnumber of secrets and a corresponding authentication path as derived from a pseudonym-specific Merkle-tree (650) to the service provider, the service provider forwards the pseudonym to the D-ID middleware (620) in order to receive a corresponding root value and trust level, and computes based on the secret and the authentication path a root value and verifies if it is matching with the root valueit has received from the D-ID middleware (620) for the pseudonym, thus verifying that the user is the owner of the pseudonym and if yes, allowing to the user access to the desired service in the casethat the trust level of the selected pseudonym corresponds to that one required by the at least one service provider. The invention further refers to a respective method.
Owner:DEUTSCHE TELEKOM AG
Internet of things system
InactiveCN106302686AAchieve effectivenessAchieve securityData processing applicationsNetwork topologiesStructure of Management InformationThe Internet
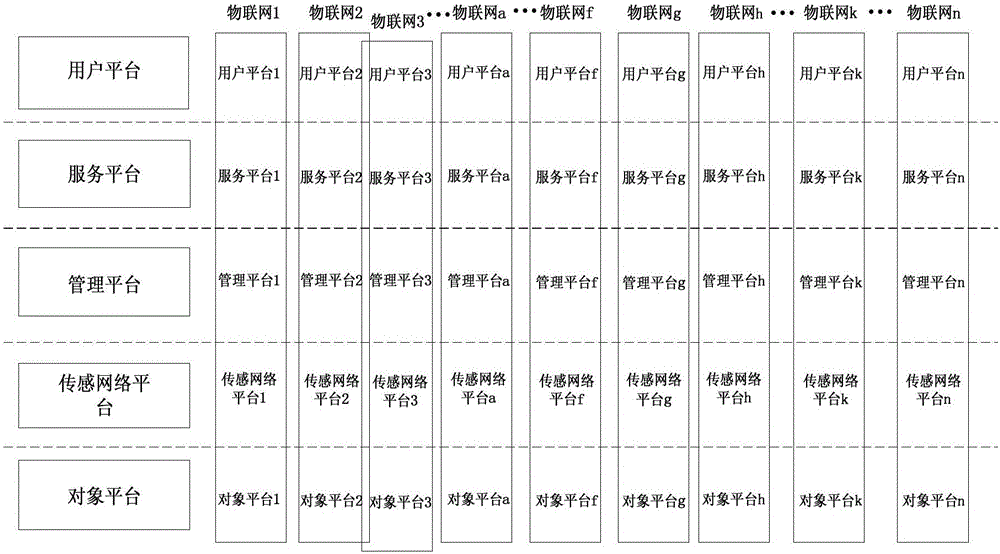
The invention discloses an Internet of things system. The Internet of things system comprises a functional system, a physical system and an information system, wherein the functional system is a functional expression form; the information system is a functional implementation way; the physical system is a carrier for providing physical support for functional implementation; the functional system consists of five platforms, namely, an object platform, a sensing network platform, a management platform, a service platform and a user platform; and the physical system and the information system also consist of five parts. The Internet of things system is described in detail and divided into the three dimensions of the functional system, the physical system and the information system, and accurate description of which functions need to be implemented by Internet of things and how to implement the functions is made. Through setting of the technical characteristics, the Internet of things system characterized by clear system, definite functions, matched hardware and clear information running can be constructed, and the application range of the Internet of things system is wide.
Owner:CHENGDU QINCHUAN IOT TECH CO LTD
Box extractable locker and management system and operation method of locker management system
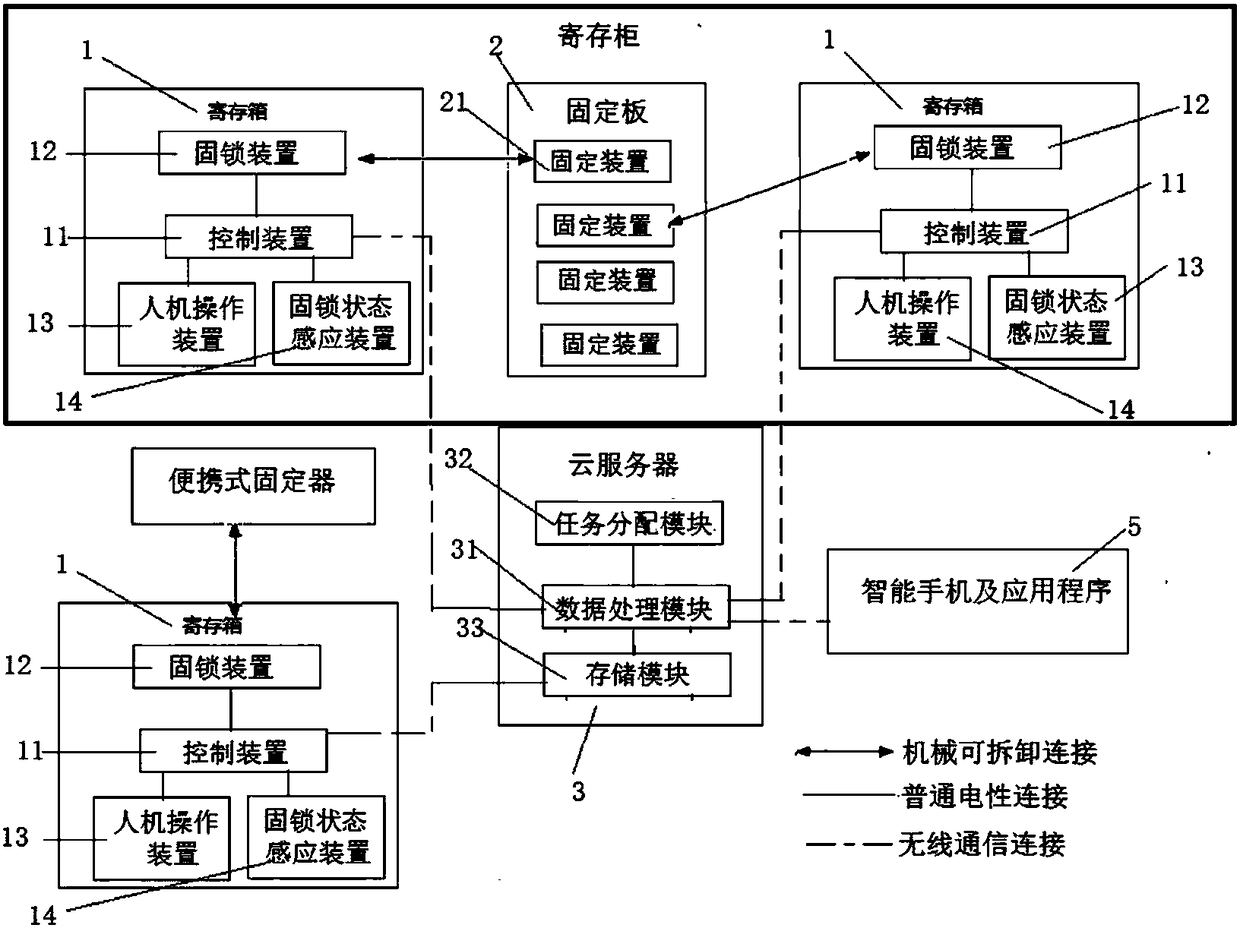
PendingCN108091070AAchieve securityAchieve privacyApparatus for meter-controlled dispensingIndividual entry/exit registersLogistics managementControl system
Provided is amanagement control system of a box extractable locker. The management control system includes a plurality of lockers andcloud serverswhich are installed in multiple places; the lockersareprovided with a plurality of deposit boxes andfixing boards; the deposit boxesare provided withcontrol devices, locking-in devices, man-machine operation devices andlocking-in state sensing devices,and the locking-in devices and the man-machine operation devices are electrically connected with the control device; the locking-in devices are detachably connected with the fixing boards; the controldevicesare provided withwireless communication modules, box body storage modules and processor modules, the wireless communication modulesare connected with the cloud server data, and the wireless communication modules and the box body storage modulesare connected with the processor modules; according to the management control system, the lockersare constituted by the independent deposit boxes,the cloud serversareused for separately and independently managing and controlling the lockers, move of the entire deposit boxes is achieved while logistics distribution is conducted, even though logistics staffsdo not need to be authorized to openboxes, goods can be delivered tospecified addresses, and the security and privacy oftransportation are achieved.
Owner:SUZHOU AORU PLASTIC
Secondary plating-prior-to-etching metal frame subtraction imbedded chip normal-installation bump structure and process method
ActiveCN103646939AAchieve privacyChieve protectiveSemiconductor/solid-state device detailsSolid-state devicesPlastic packagingOxidation resistant
The invention relates to a secondary plating-prior-to-etching metal frame subtraction imbedded chip normal-installation bump structure and a process method. The structure comprises a metal substrate fame (1). The metal substrate fame (1) is internally provided with base islands (2) and pins (3). The back surface of each base island (2) is flush with the step surface of each pin (3). The step surface of each pin (3) is provided with a metal layer (4). The back surface of each base island (2) is normally equipped with a chip (6). The surface of the chip (6) is connected with the surface of the metal layer (4) through a metal line (7). The metal substrate fame (1) is internally filled with plastic packaging material (8). The front surface of the plastic packaging material (8) is flush with the step surface of the pin (3). The back surface of the plastic packaging material (8) is flush with the back surface of the metal substrate fame (1). The front surface of the base island (2), the front surface and the back surface of each pin (3) as well as the front surface and the back surface of the metal substrate fame (1) are provided with an anti-oxidation layer (9). The back surface of each pin (3) is provided with a metal ball (10). The beneficial effect of the structure and method is that: the problem that the function and the application performance of a conventional metal lead frame are limited since an object cannot be imbedded in the metal lead frame is solved.
Owner:JCET GROUP CO LTD
One-time eroding-before-plating metal frame subtraction embedded chip inversely-arranged salient point structure and technological method
ActiveCN103681580AAchieve privacyChieve protectiveSemiconductor/solid-state device detailsSolid-state devicesPlastic packagingEngineering
The invention relates to a one-time eroding-before-plating metal frame subtraction embedded chip inversely-arranged salient point structure and a technological method. The one-time eroding-before-plating metal frame subtraction embedded chip inverse arranged salient structure is characterized in that a metal substrate frame is included, a paddle and pins are arranged in the metal substrate frame, chips are arranged on the back face of the paddle and the step surfaces of the pins through bottom filled glue, plastic packaging materials wrap the area of the periphery of the paddle, the area between the paddle and the pins, the area between the pins, the areas on the upper portion of the paddle, the areas on the upper portions of the pins, the area on the lower portion of the paddle, and the area on the lower portions of the pins and the chips, the plastic packaging materials are aligned with the upper surface and the lower surface of the metal substrate frame, anti oxidation layers are plated on or organic solderability preservative (OSP) wraps the front face of the paddle, the front faces and the back faces of the pins and the surface of the metal substrate frame, and metal balls are arranged on the back faces of the pins. The one-time eroding-before-plating metal frame subtraction embedded chip inversely-arranged salient point structure has the advantages of being capable of solving the problem that the function and the application performance of a metal wire frame are restricted due to the fact that objects cannot be buried in the plate thickness of the traditional metal wire frame.
Owner:JCET GROUP CO LTD
Fault-tolerant safe lightweight data aggregation method in smart grid environment
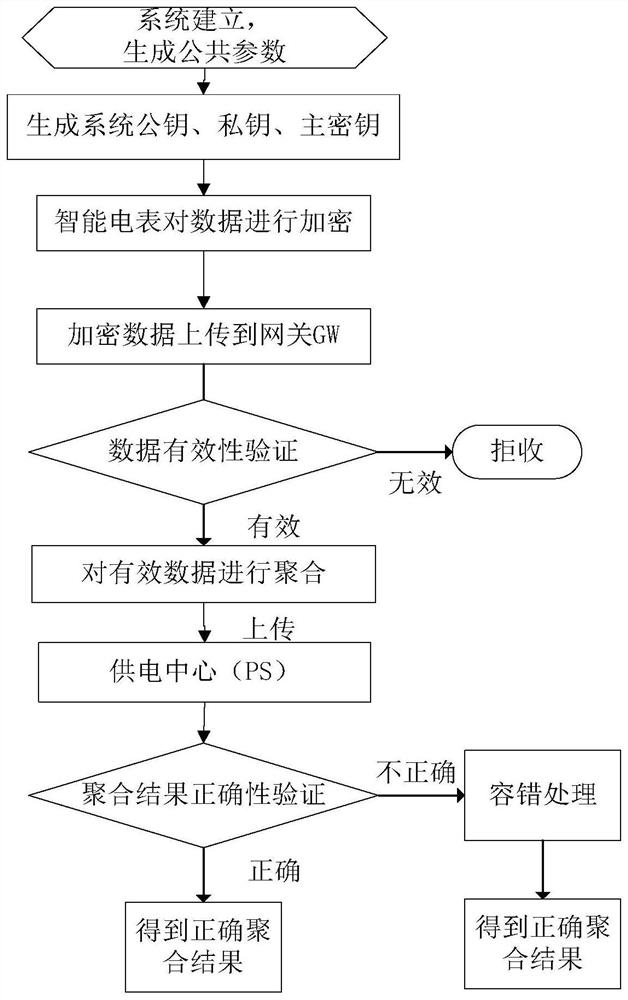
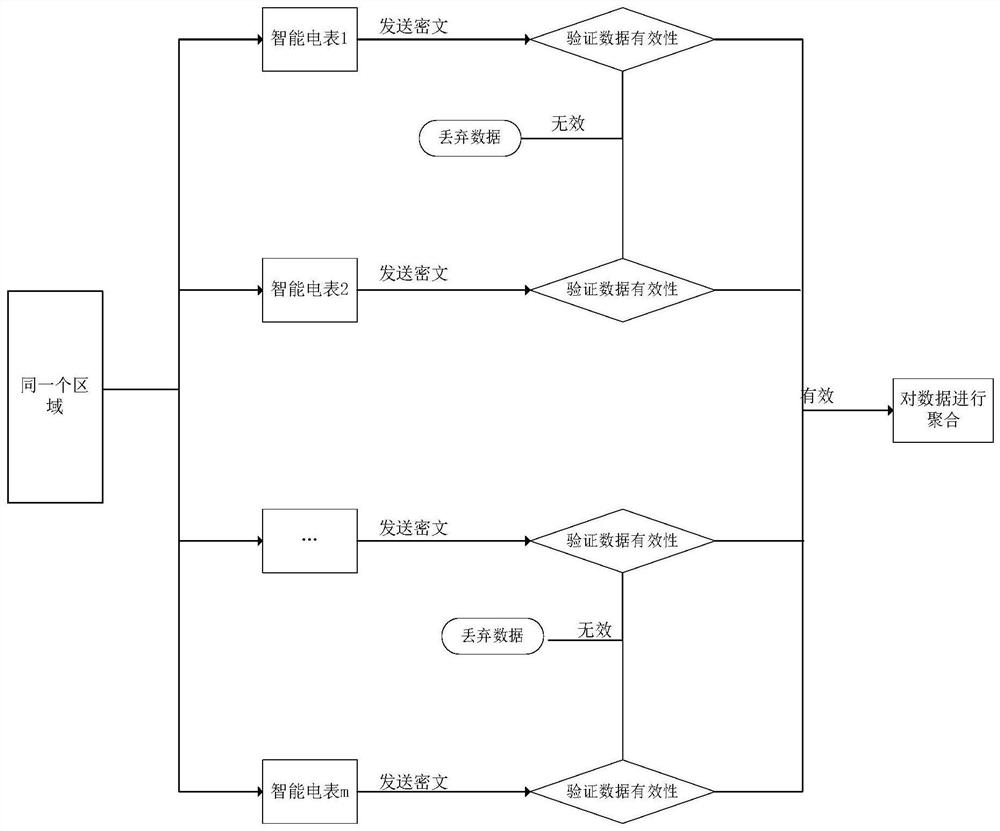
InactiveCN113382016AGuaranteed validityRealize data aggregationUser identity/authority verificationData aggregatorPrivacy protection
The invention discloses a fault-tolerant safe lightweight data aggregation method in an intelligent power grid environment, and relates to the technical field of data aggregation in the intelligent power grid environment. The use of an intelligent electric meter causes a serious privacy problem to fine-grained measurement of household energy consumption. Meanwhile, due to various reasons in the actual situation, the intelligent electric meter cannot upload the electric quantity data to the aggregator, the power supply center cannot know which users cannot upload the data in time, and the obtained aggregation result is wrong. According to the method, lightweight data aggregation is realized on the basis of completing privacy protection and fault tolerance. In addition, the data aggregation method provided by the invention reduces the number of times of communication interaction between entities in the authentication process, thereby improving the efficiency of data aggregation and reducing the response time. Through performance analysis, the calculation overhead is ensured to be lightweight under the condition of ensuring that an aggregation result is correct. Security analysis and security proof show that the proposed method is secure.
Owner:JINAN UNIVERSITY
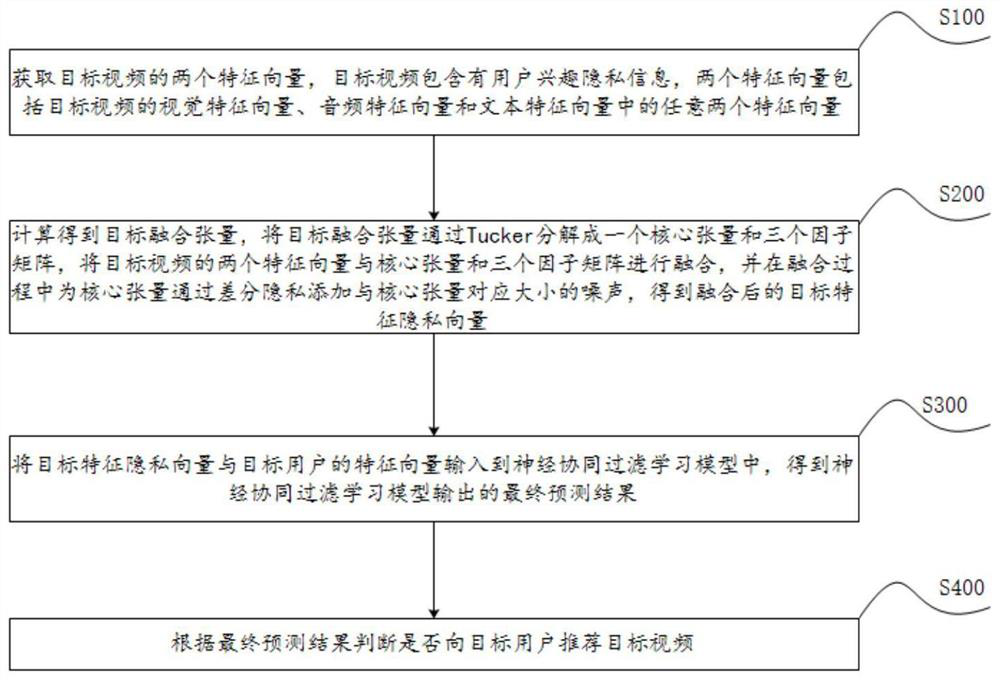
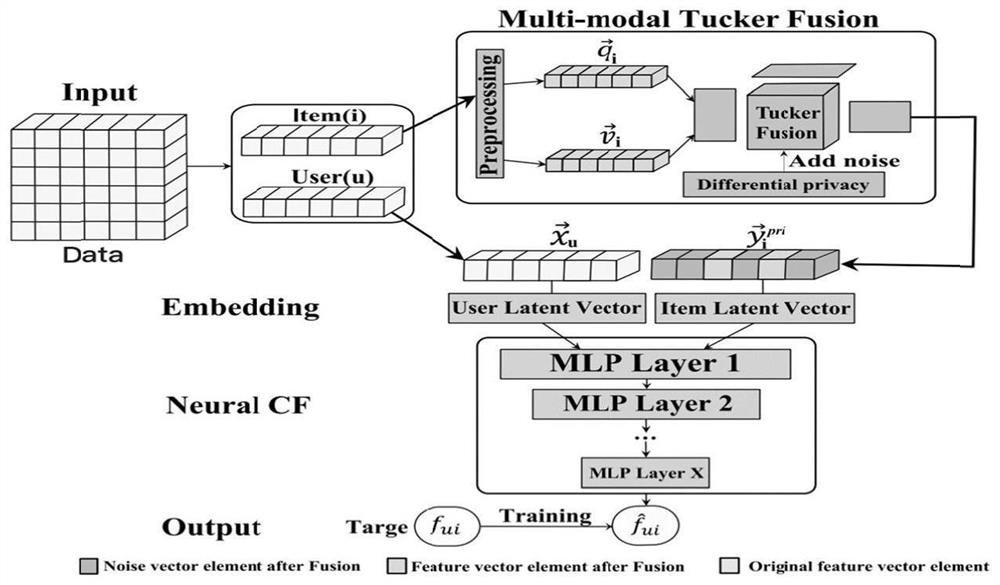
Short video recommendation method, system and equipment
PendingCN114117203APrediction is accurateImprove privacy protectionDigital data information retrievalCharacter and pattern recognitionNoise (video)Feature vector
The invention discloses a short video recommendation method, system and device, and the method comprises the steps: obtaining two feature vectors of a target video, decomposing a target fusion tensor into a core tensor and three factor matrixes through Tucker, and fusing the two feature vectors of the target video with the core tensor and the three factor matrixes by using Tucker fusion, adding noise for the core tensor through differential privacy in the fusion process to obtain a fused target feature privacy vector, and then calculating a final prediction result through neural collaborative filtering. Whether to recommend the target video to the target user is judged through the final prediction result, and privacy protection, feature fusion and a recommendation system are realized on the whole.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com