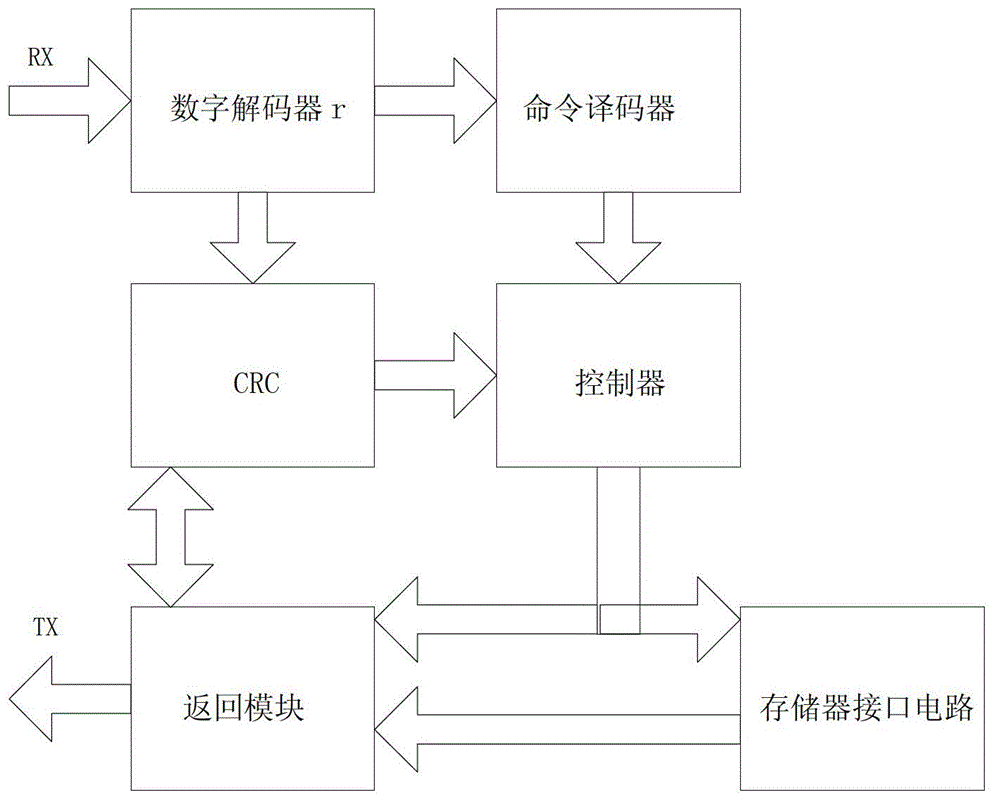
Patents
Literature
86results about How to "Achieve tamper resistance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
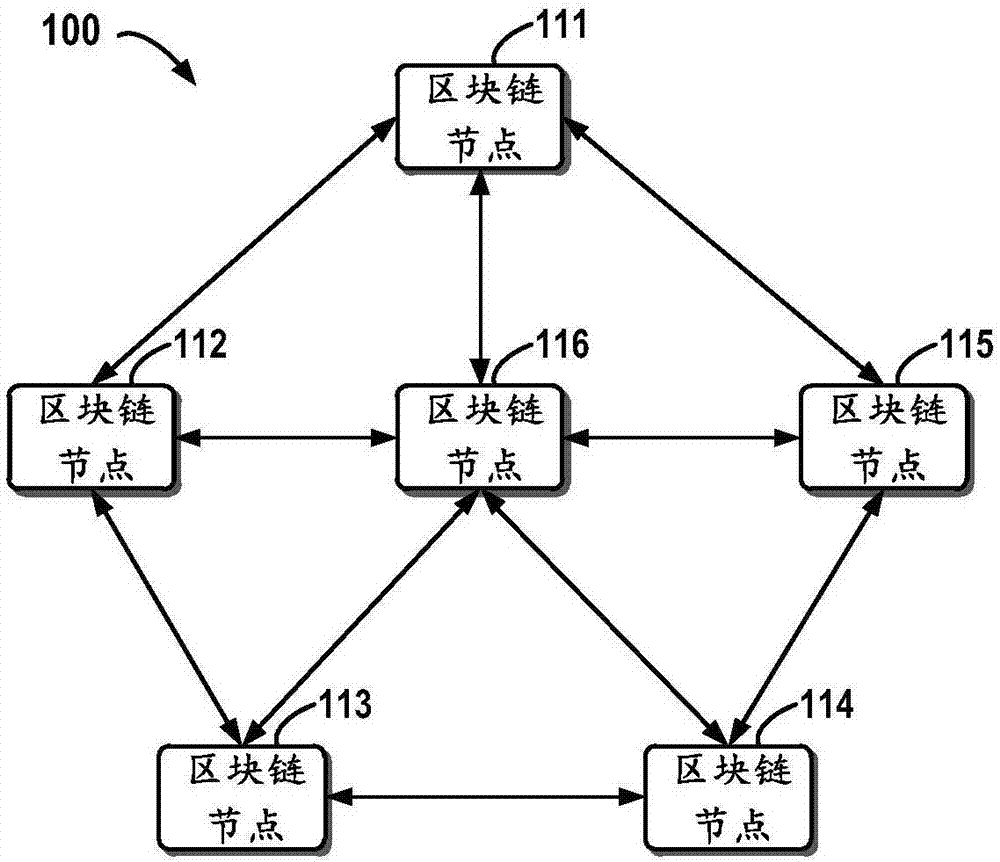
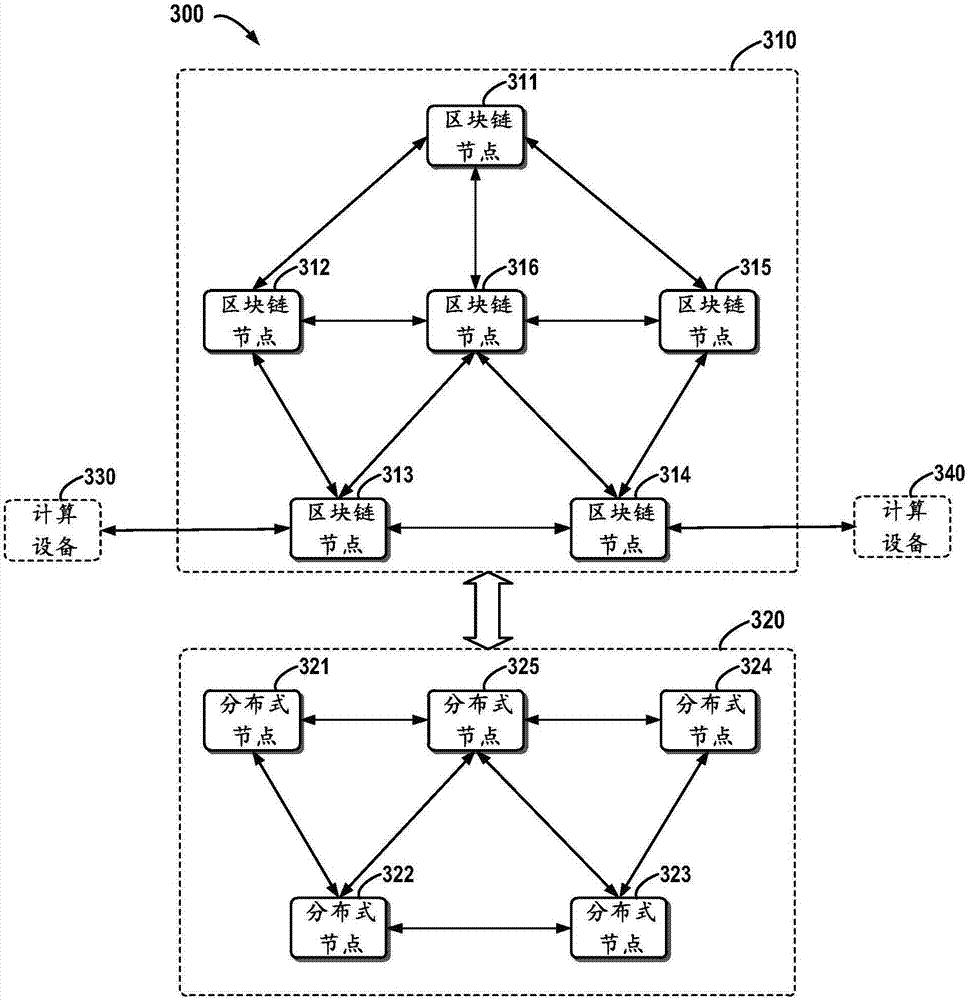
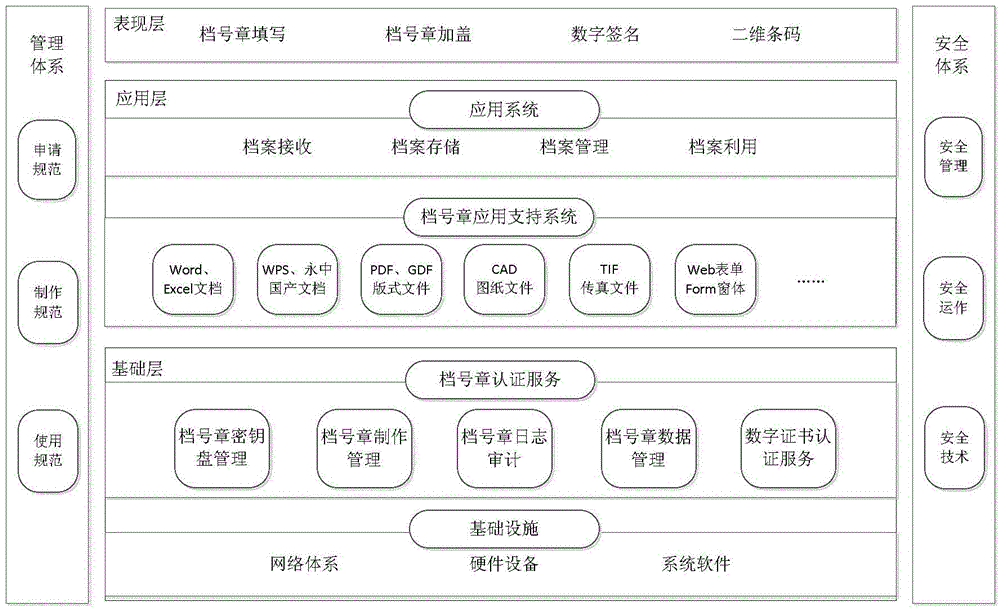
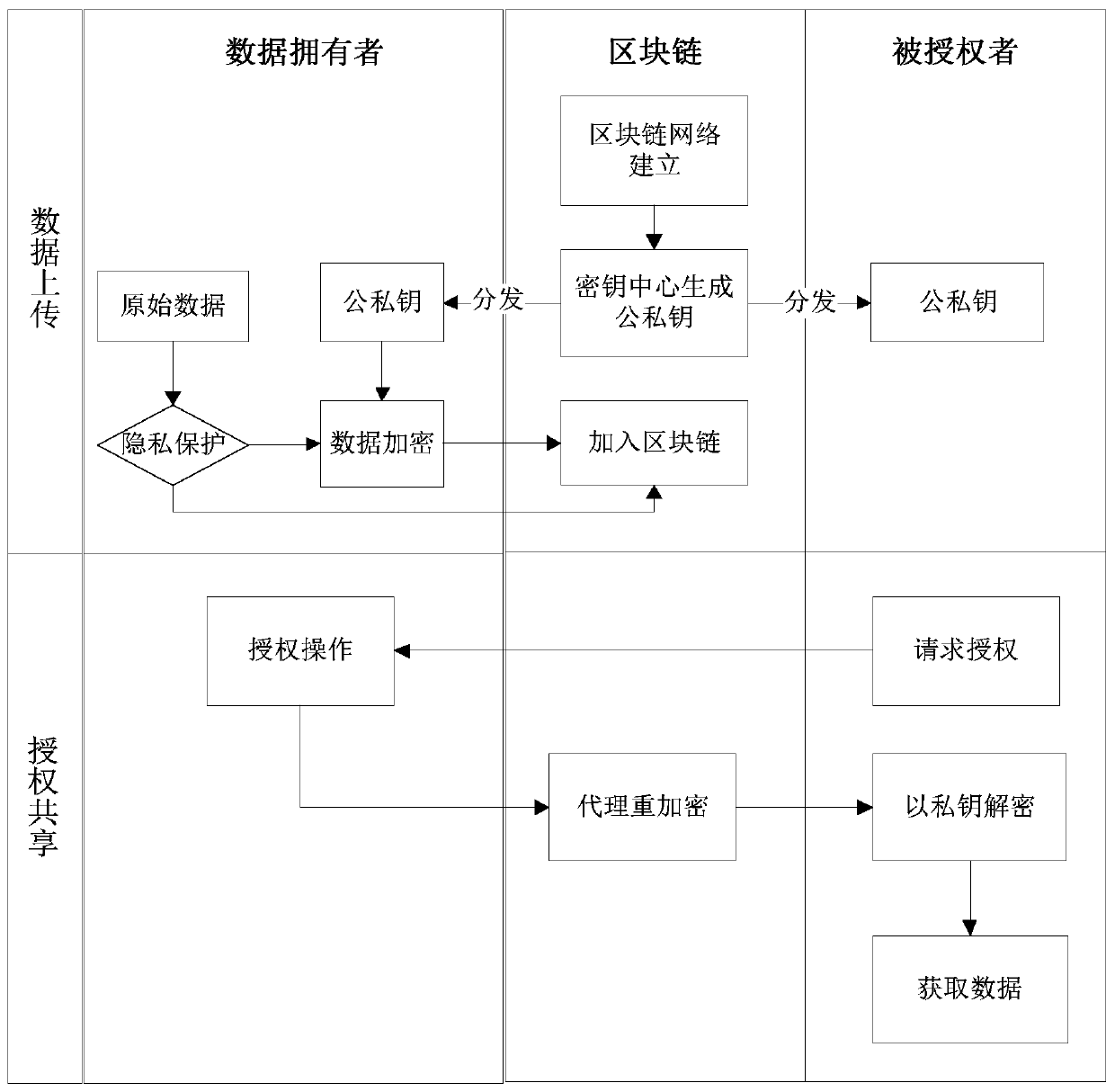
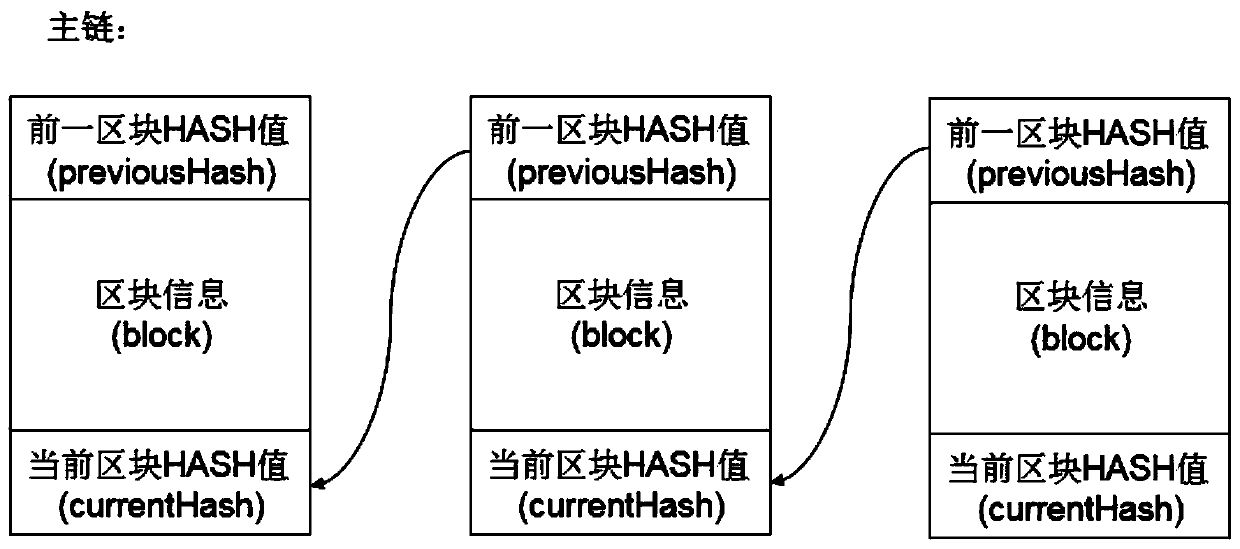
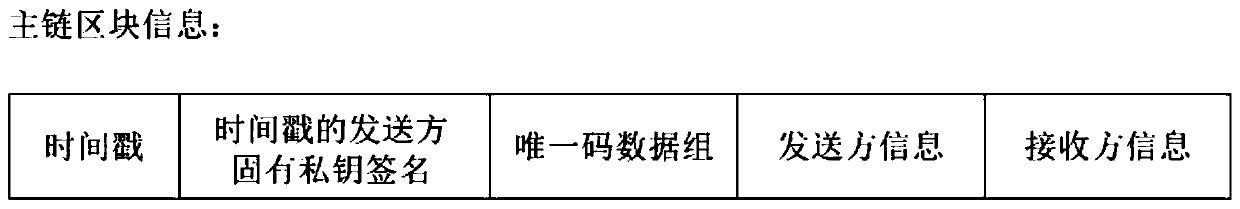
Block chain-based distributed storage
InactiveCN107273410ASolve the problem of limited node capacityAchieve tamper resistanceFile access structuresSpecial data processing applicationsTamper resistanceDistributed File System
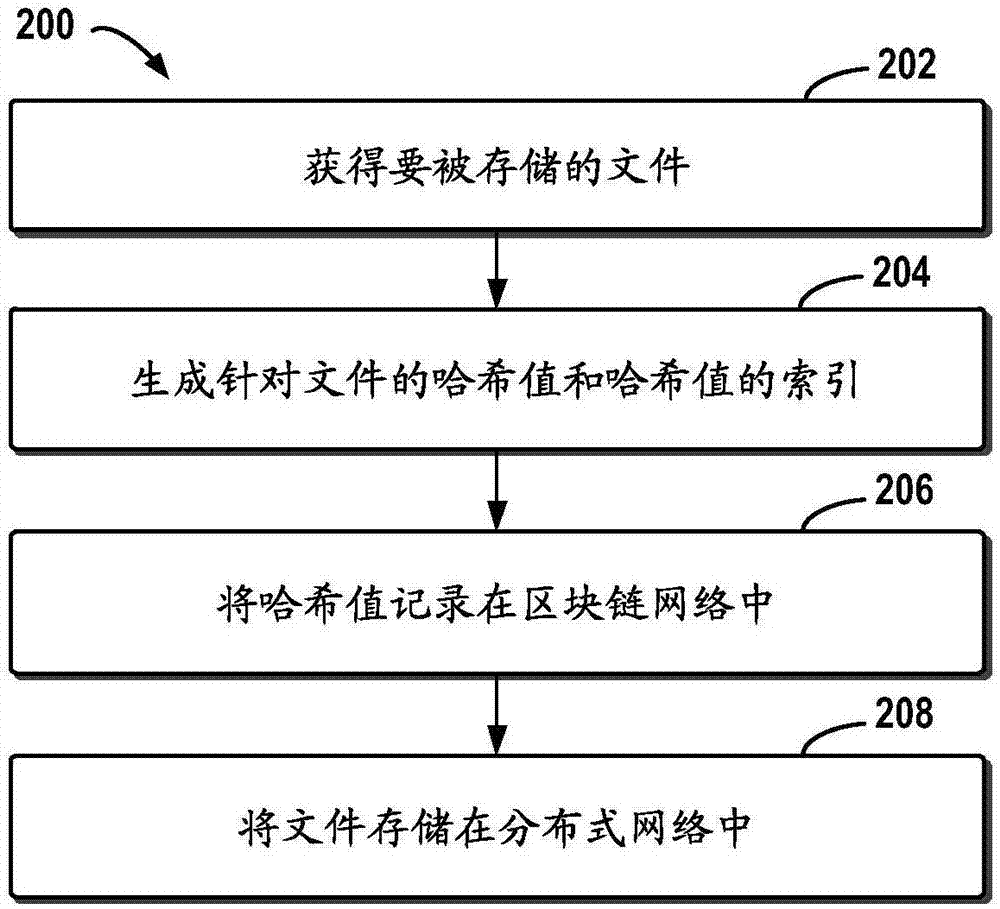
The embodiment of the disclosure relates to block chain-based distributed storage, and discloses a block chain-based distributed storage method. The method includes: obtaining a file which needs to be stored, and generating a hash value and an index of the hash value for the file. The method also includes: recording the hash value in a block chain network, and storing the file in a distributed network, wherein the file is located on the basis of the hash value in the distributed network. Therefore, according to the embodiment of the disclosure, tampering proofing and the distributed storage of the file can be realized through combining a block chain and a distributed file system, thus the problem of the limited capacity of block chain nodes is solved, and the authenticity and the availability of the stored file are effectively guaranteed.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
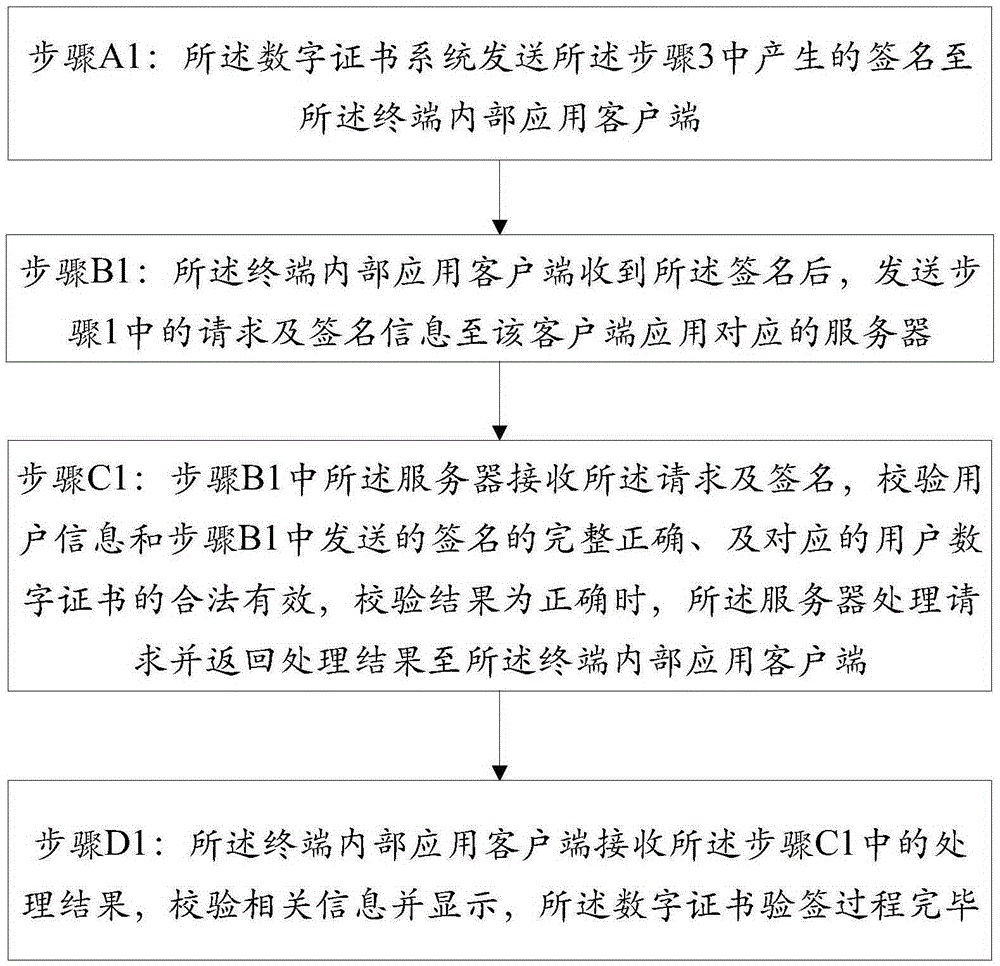
Method and system for identity verification of digital certificate based on TEE (Trusted Execution Environment)
ActiveCN105429760AEnsure true willEnsure that the identity verification process can reflect the true willUser identity/authority verificationPasswordPersonal identity verification
The invention discloses a method for identity verification of a digital certificate based on a TEE (Trusted Execution Environment). The method comprises pre-configuration of a digital certificate system through a terminal, a digital certificate signature process and a digital certificate signature verification process. The method is characterized in that the terminal is provided with the TEE; the digital certificate signature process is carried out on the terminal and is used for utilizing a private key of the digital certificate to sign for a user request; the digital certificate signature verification process is used for authenticating identity of a requested user, and the authentication method comprises verification of validity and effectiveness of the digital certificate and integrity and correctness of the signature, wherein the digital certificate signature process is carried out under the TEE; the sensitive information, such as a user key, identity information, biological characteristic information and password information, is stored through a secure storage module, so that the problems that the signature process is carried out in REE and the sensitive information of the user is stored under the REE environment to cause privacy disclosure and stolen hidden danger of property in the prior art are avoided.
Owner:神州融安数字科技(北京)有限公司
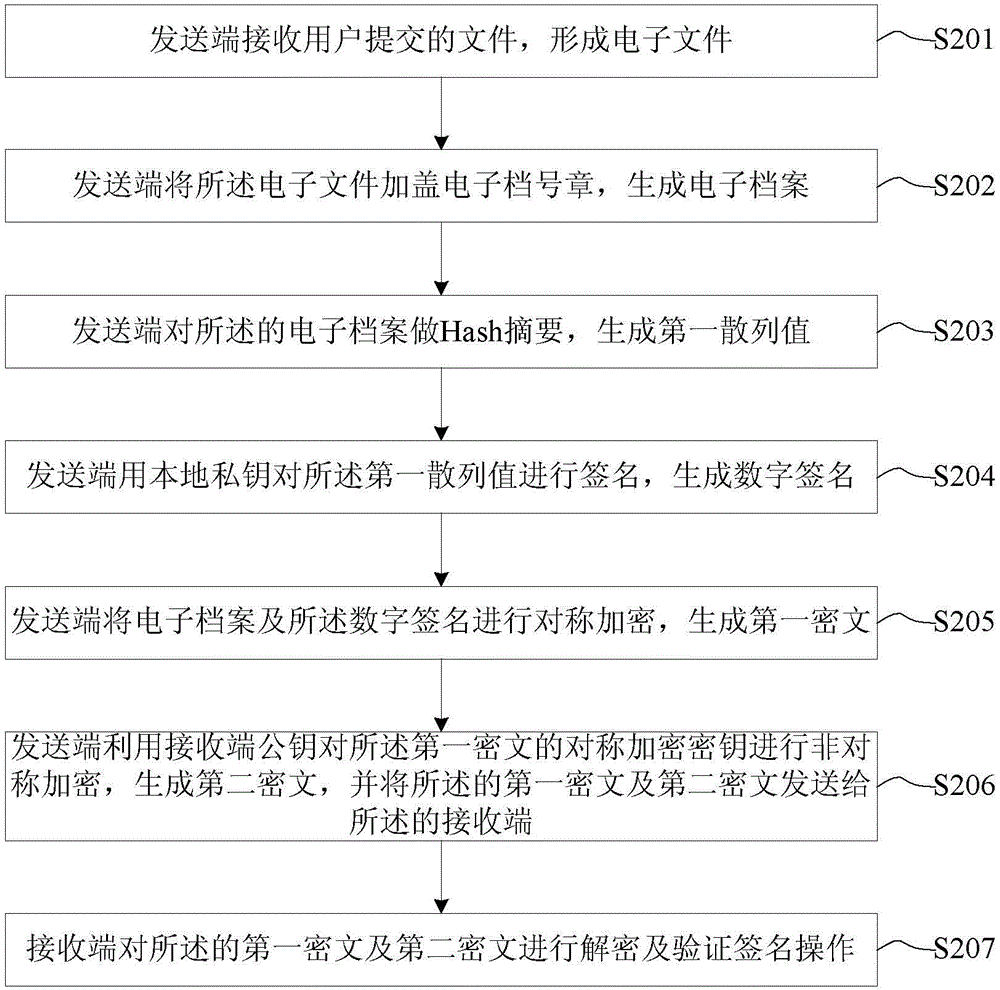
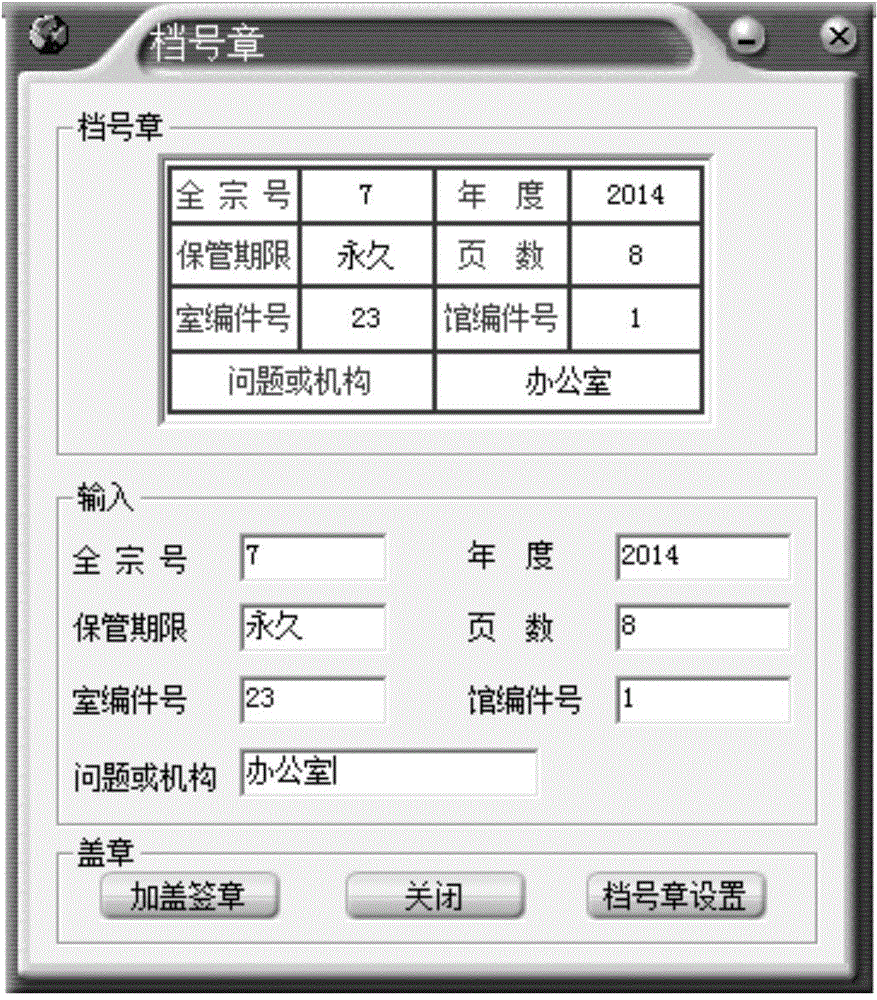
Electronic record validation method and device
ActiveCN104320257AAnti-counterfeitingAchieve tamper resistanceUser identity/authority verificationDigital signatureCiphertext
The invention provides an electronic record validation method and device. The electronic record validation method comprises the steps that a sending end receives files submitted by users and forms electronic files; the sending end seals electronic file number seals on the electronic files to generate electronic records; the sending end makes Hash abstracts for the electronic records to generate first hash values; the sending end uses local private keys to perform hash value signature so as to generate digital signatures; the sending end conducts symmetrical encryption on the electronic records and the digital signatures to generate first ciphertexts; the sending end utilizes a public key of a receiving end to perform asymmetrical encryption on symmetrical encryption keys of the first ciphertexts so as to generate second ciphertexts and sends the first ciphertexts and the second ciphertexts to the receiving end; the receiving end conducts decryption and signature operation verification on the first ciphertexts and the second ciphertexts. The electronic record validation method and device can prevent the electronic records from being counterfeited, tampered and disavowed.
Owner:李名选 +4
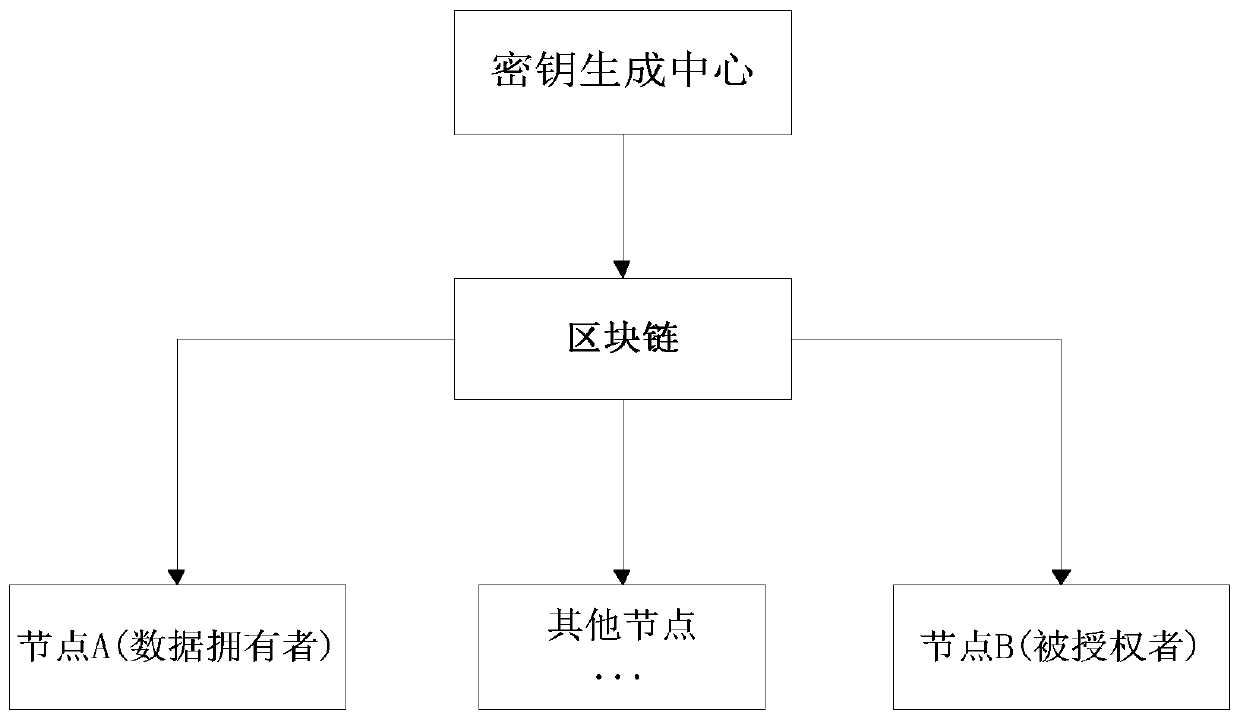
Blockchain data access authority control method based on proxy re-encryption
ActiveCN111191288AImplement authorized accessReduce the certification processDigital data protectionCiphertextInternet privacy
The invention discloses a blockchain data access authority control method based on proxy re-encryption, and aims at the authorization sharing access type. The method comprises the steps: encrypting plaintext information through employing a symmetric secret key to generate a content ciphertext, and encrypting the symmetric secret key through employing an own public key to generate a secret key ciphertext; uploading the content ciphertext and the key ciphertext to a block chain; obtaining a public key of the authorized node on the block chain according to an access authorization application initiated by the authorization node, and generating an authorization key according to the own private key and the public key of the authorized node; uploading the authorization key to the block chain, wherein the authorization key is used for the block chain to perform proxy re-encryption calculation in combination with the key ciphertext to generate a proxy re-encryption key; and the proxy re-encryption key is used for the authorized node to analyze by using the own private key to obtain a symmetric key, and the symmetric key is used for the authorized node to decrypt the content ciphertext to obtain the plaintext information. According to the method, the data of different security levels is classified so that fine-grained permission access control of the data level is realized on the block chain.
Owner:CETHIK GRP
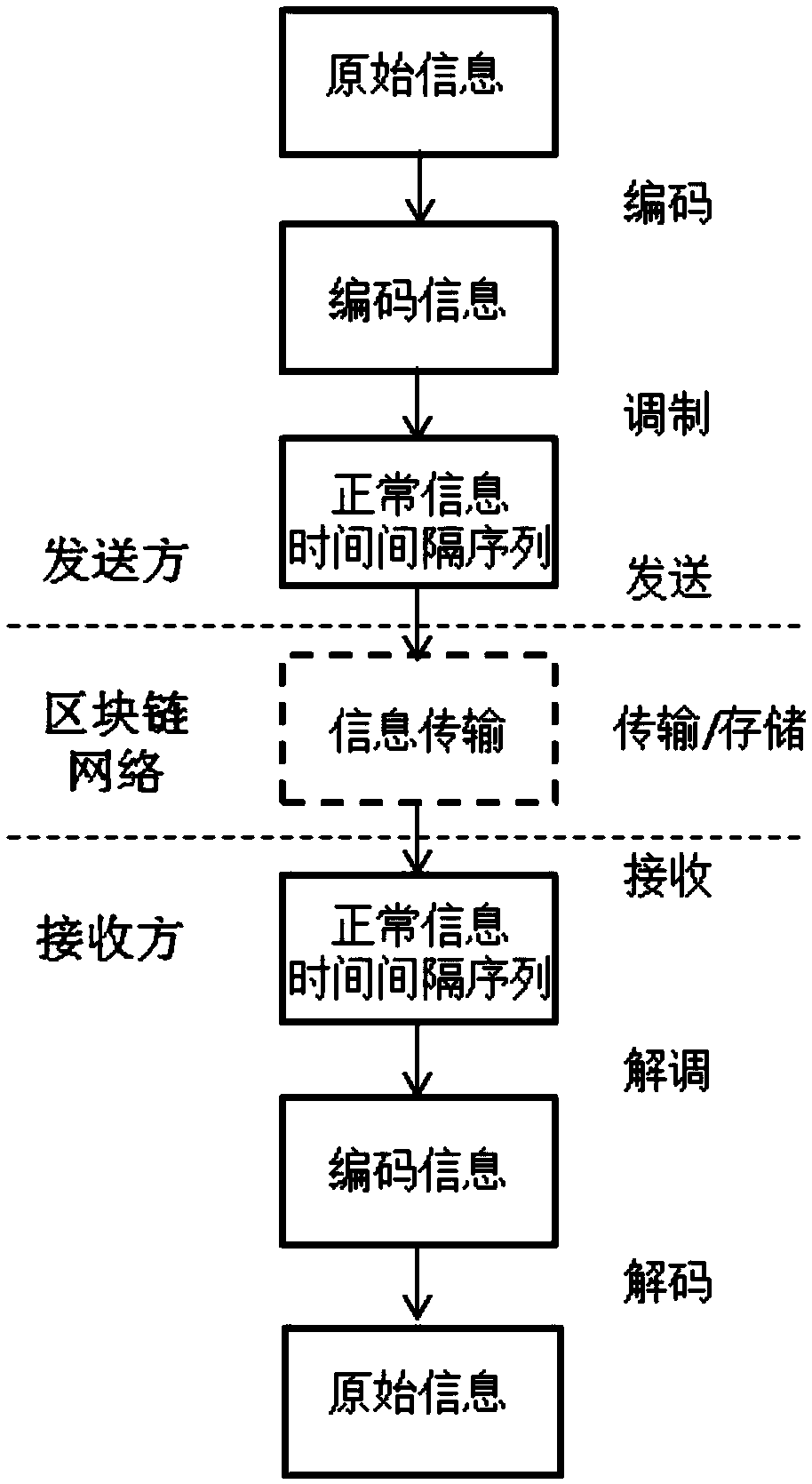
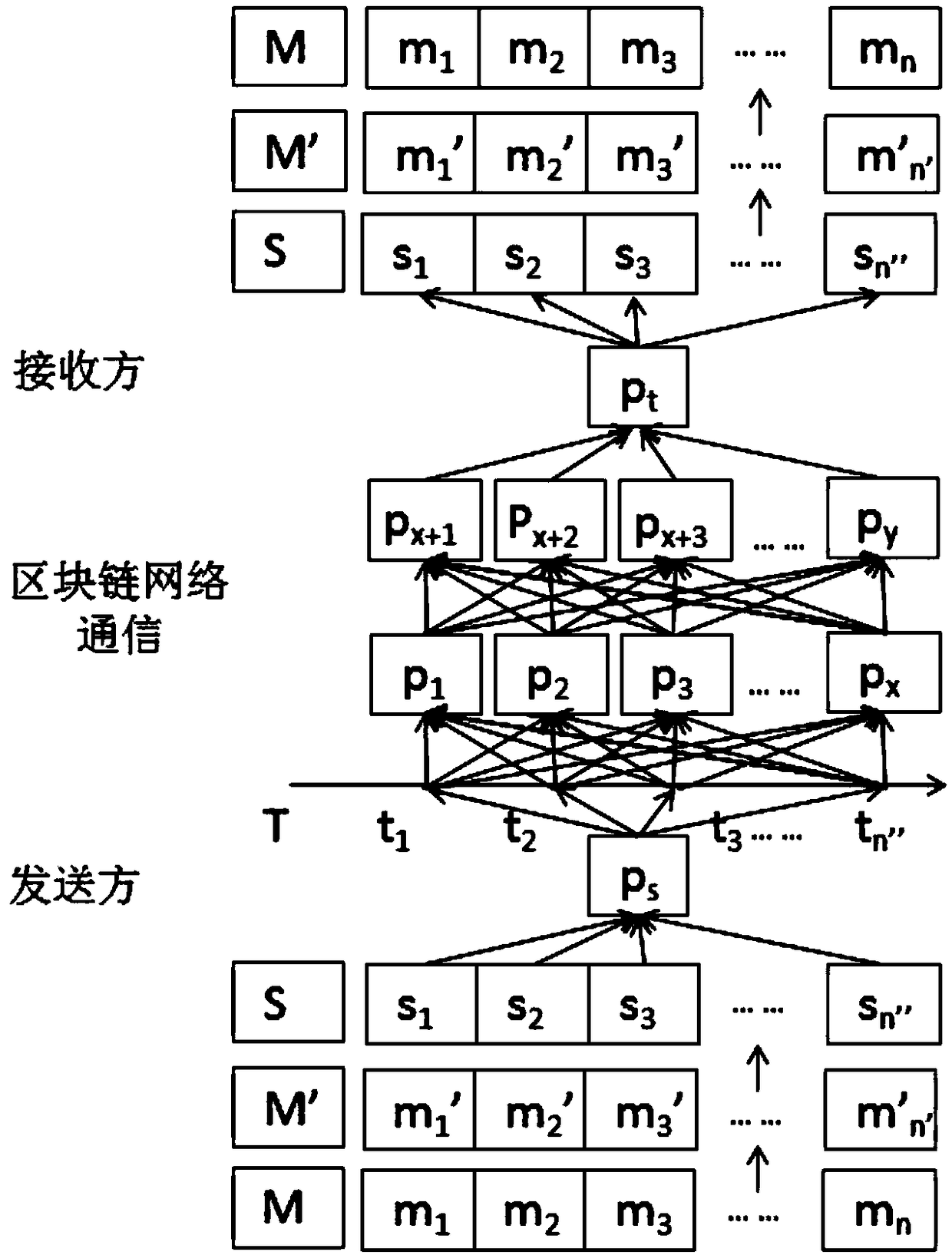
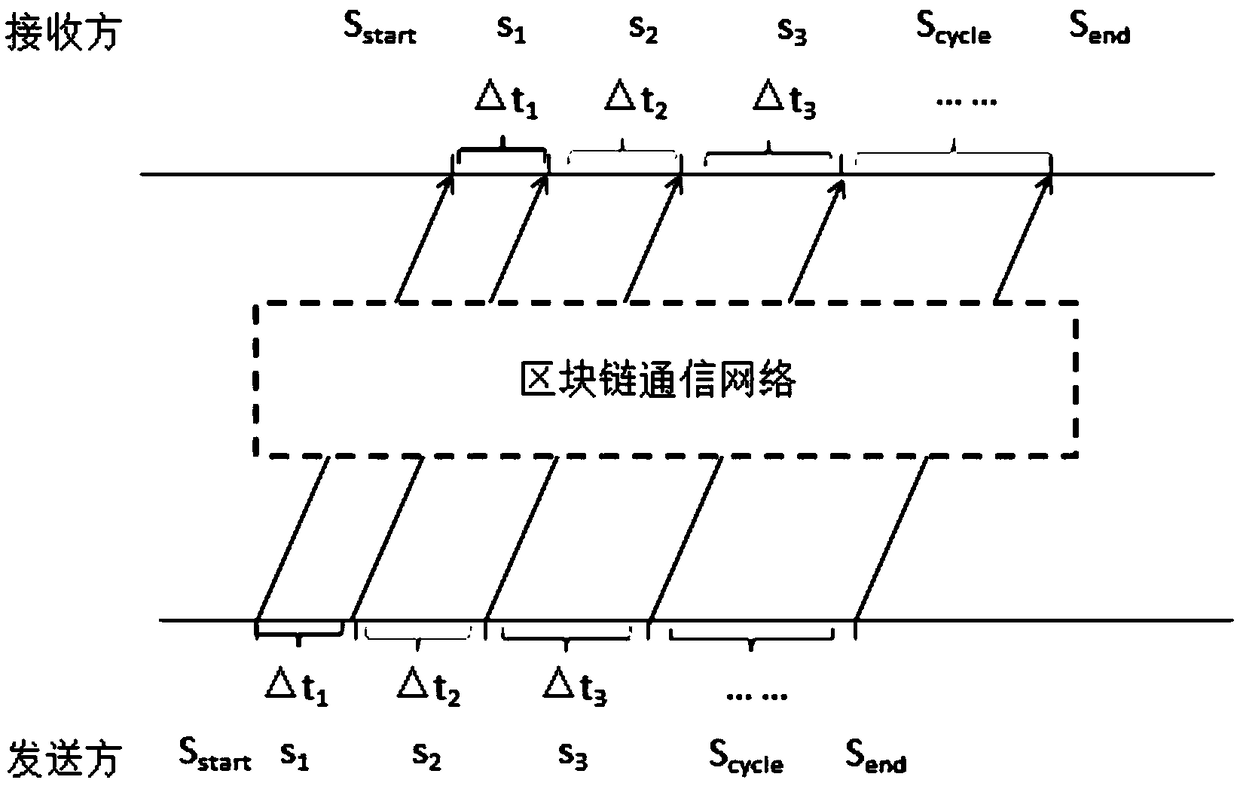
A concealed communication method in a block chain network environment
ActiveCN109040115AOvercome disadvantagesImprove anti-interference abilityUser identity/authority verificationChain networkBlockchain
The invention relates to a concealed communication method in a block chain network environment. The original concealed information is encoded by using a predetermined source encoding or channel encoding mechanism. The encoded information is modulated with the time interval of the information by a predetermined modulation method in advance to generate a time interval sequence of normal informationtransmission to be sent to a block chain network, and each information of the time interval sequence of the normal information transmission is timestamped by a block chain mechanism. By using the P2Pnetwork transmission mechanism and the distributed chain storage mechanism under the block chain network environment, the time interval sequence of the normal information is transmitted and stored with high reliability. By observing the block chain network, the receiver of the concealed information obtains the time interval sequence of the normal information transmission sent by the sender, and the acquired information in a manner of information time interval is demodulated to obtain demodulated information; the demodulated information is decoded.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
Power terminal data security management method based on block chain
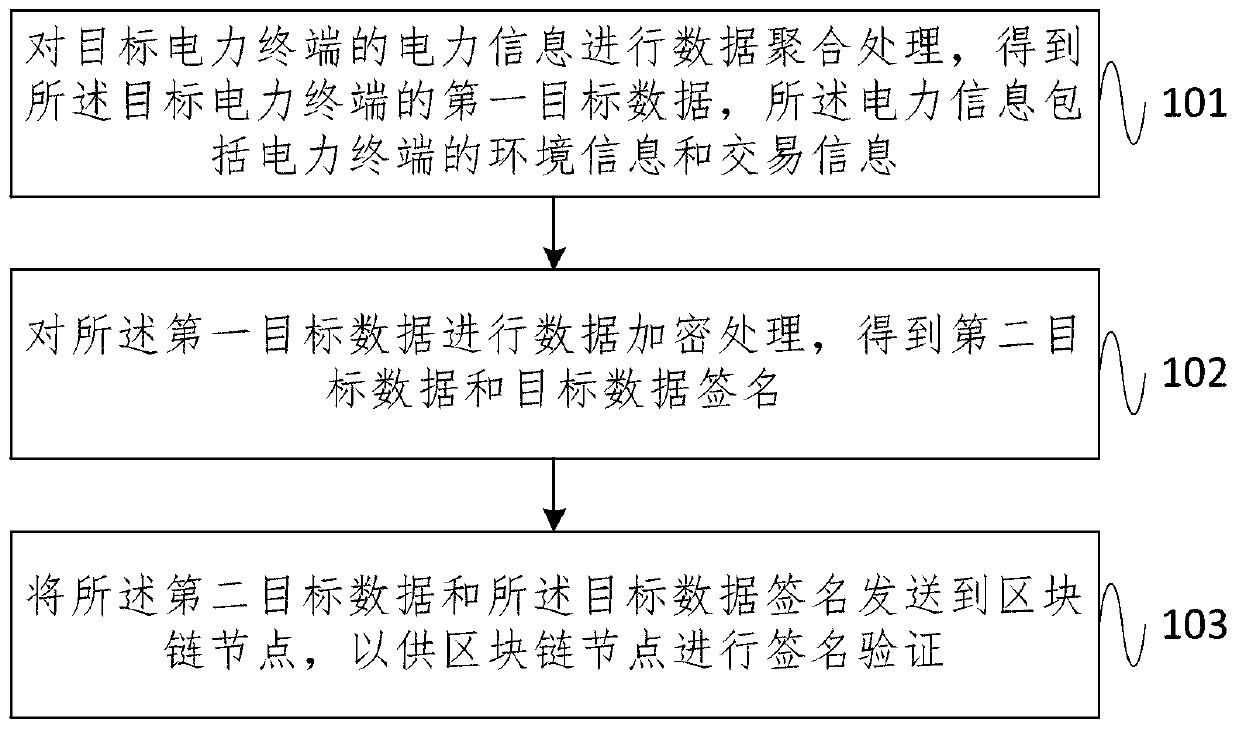
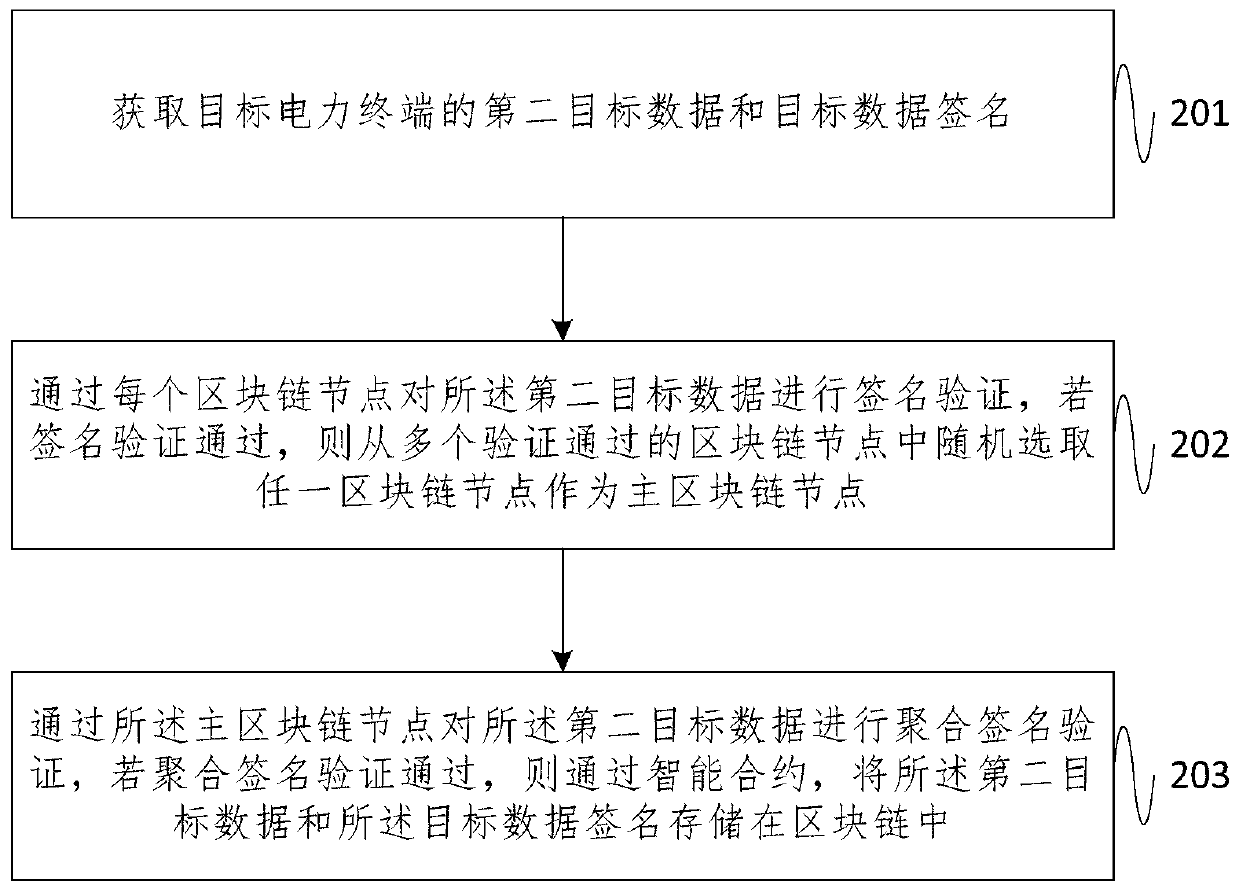
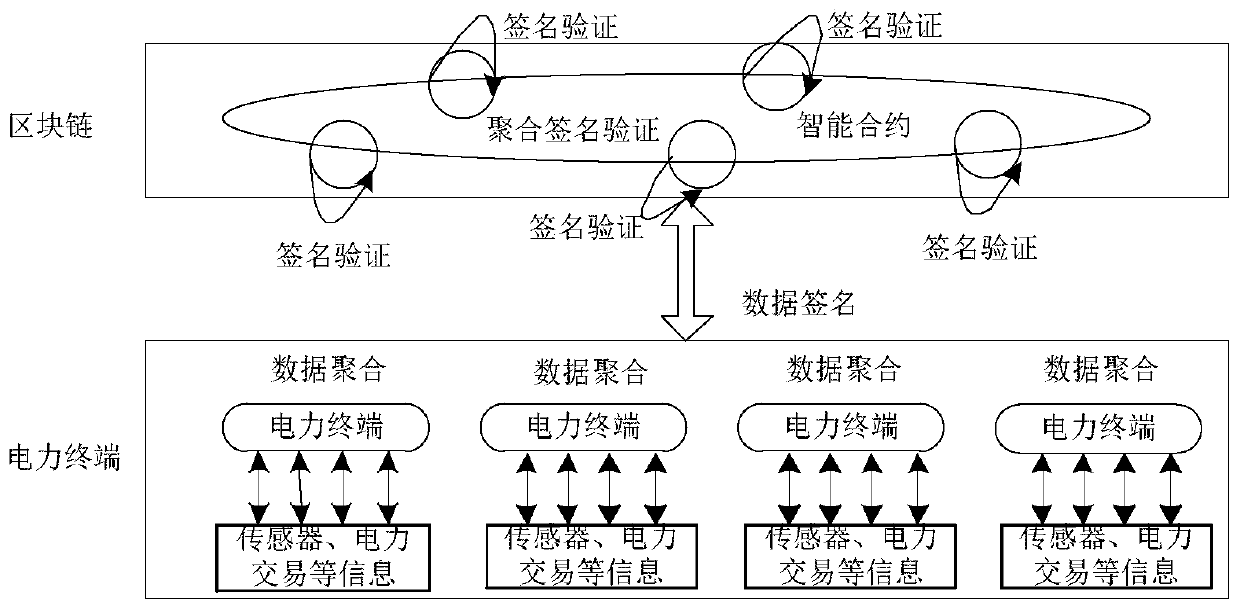
PendingCN111209334AImprove integrityImprove confidentialityData processing applicationsUser identity/authority verificationConfidentialityData aggregator
The embodiment of the invention provides a power terminal data security management method based on a block chain, and the method comprises the steps: carrying out the data aggregation processing of the power information of a target power terminal, and obtaining the first target data of the target power terminal, wherein the power information comprises the environment information and transaction information of the power terminal; performing data encryption processing on the first target data to obtain second target data and a target data signature; and sending the second target data and the target data signature to a blockchain node, so as to enable the blockchain node to perform signature verification. According to the embodiment of the invention, the integrity and confidentiality of the electric power data collected and generated by the electric power terminal are improved, so that the electric power data is not artificially modified in the application and storage process, and the consistency and tamper resistance of the electric power data in the application and storage process are realized.
Owner:国网河北省电力有限公司雄安新区供电公司 +1
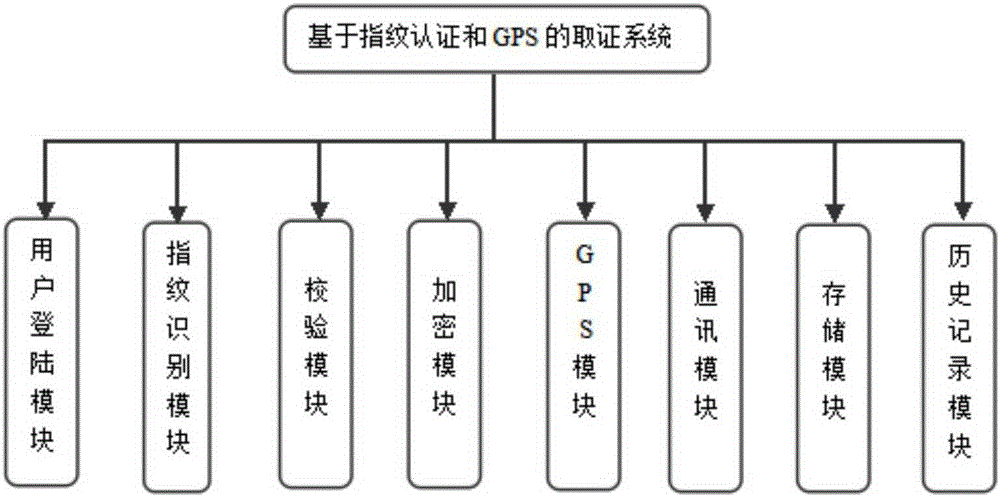
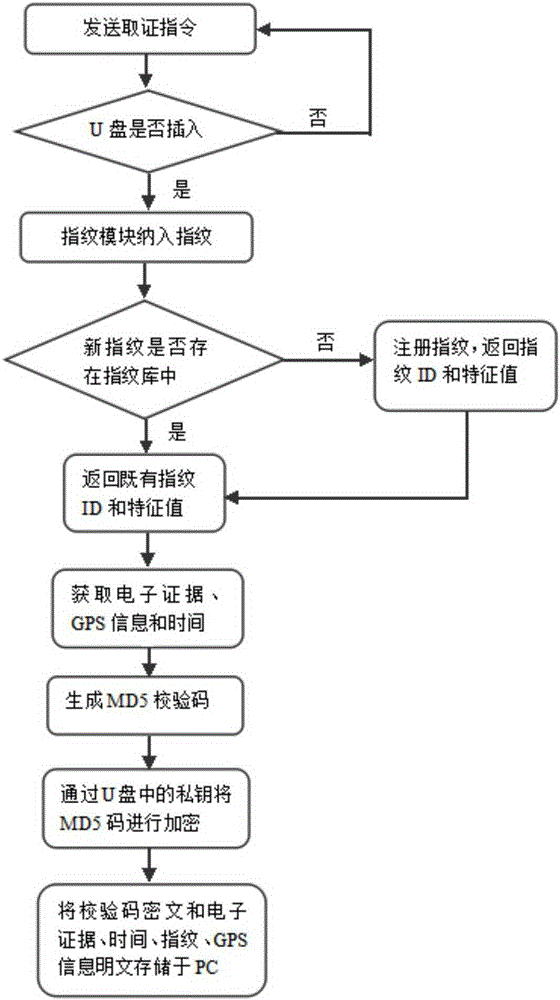
Evidence collecting system and method based on fingerprint authentication and GPS
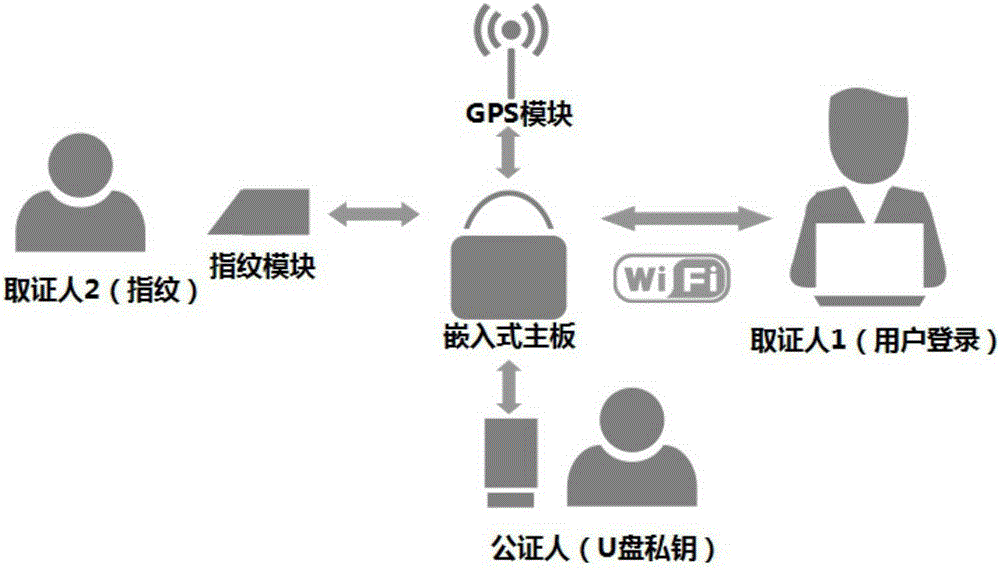
ActiveCN105260640ANotary guaranteeIntegrity guaranteedDigital data authenticationEvidence collectionElectronic data
The invention discloses an evidence collecting system and method based on fingerprint authentication and a GPS. According to the method, an evidence collecting operator combines Hash results generated by electronic evidences with generation time, operator information, recorded fingerprints and GPS positioning information to be taken as evidences, and electronic data for evidence collection is subjected to secondary fixing through an encryption algorithm, so as to realize unchangeable verification. The functions of electronic data secondary change prevention, original edition electronic data verification, batch electronic data similarity matching and the like can be realized.
Owner:NANJING UNIV OF POSTS & TELECOMM
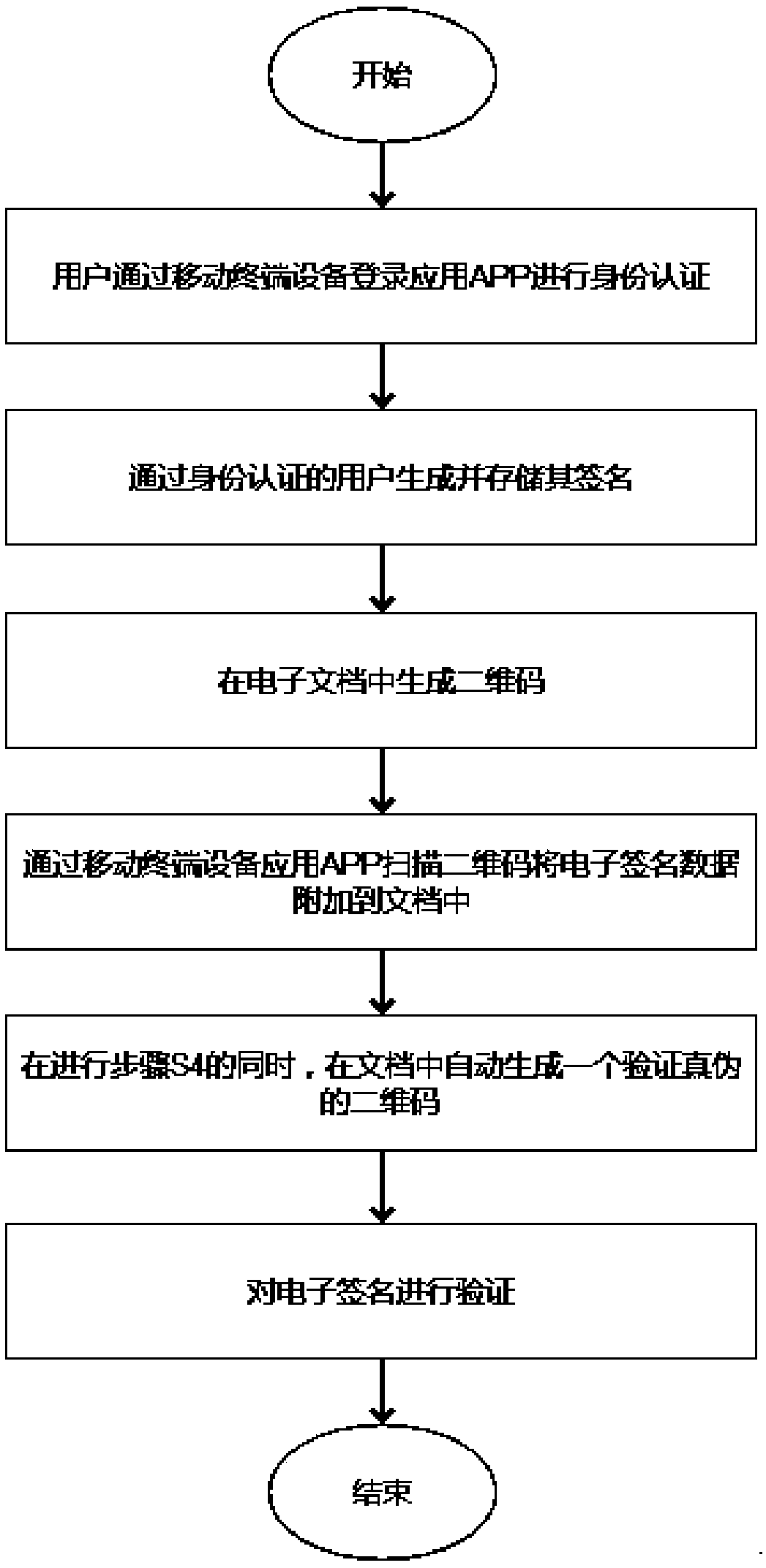
An electronic signature method
ActiveCN109190347AAchieve tamper resistanceSolve security and convenience issuesDigital data protectionDigital data authenticationElectronic documentDigital document
The invention discloses an electronic signature method. The method comprises the steps of performing authentication via a client by a user; generating and storing an electronic signature of an authenticated user by the client; generating a two-dimensional code to be signed by the server in an electronic document to be signed; scanning the two-dimensional code to be signed generated in the step 3 by the client, appending the electronic signature data generated in the step 2 to the electronic document to be signed, and simultaneously generating a verification two-dimensional code for verifying authenticity in the electronic document to be signed; scanning scans the verification two-dimensional code generated in step 4 by the client to verify the authenticity of the electronic signature. Theelectronic signature method realizes the anti-tampering and traceability of signature by digital certificate, biometric identification and two-dimensional code verification, so it solves the securityand convenience problems in the process of user remote signature.
Owner:江苏诺安科技有限公司
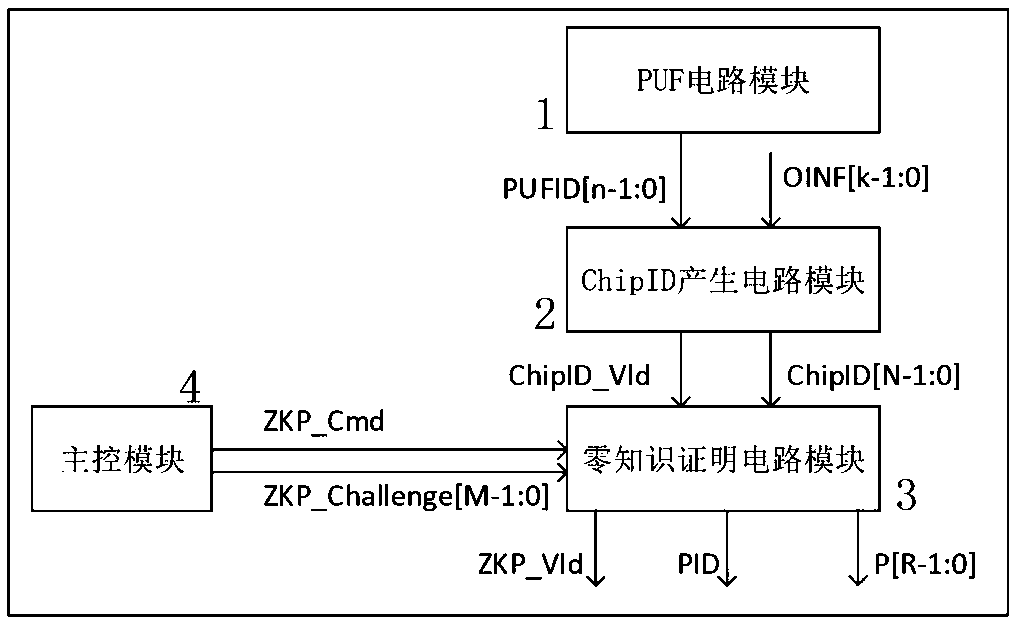
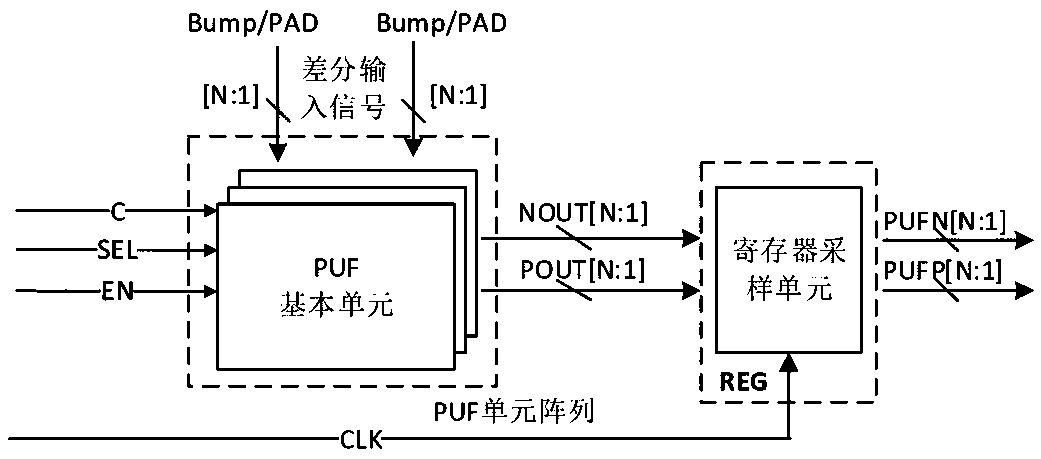
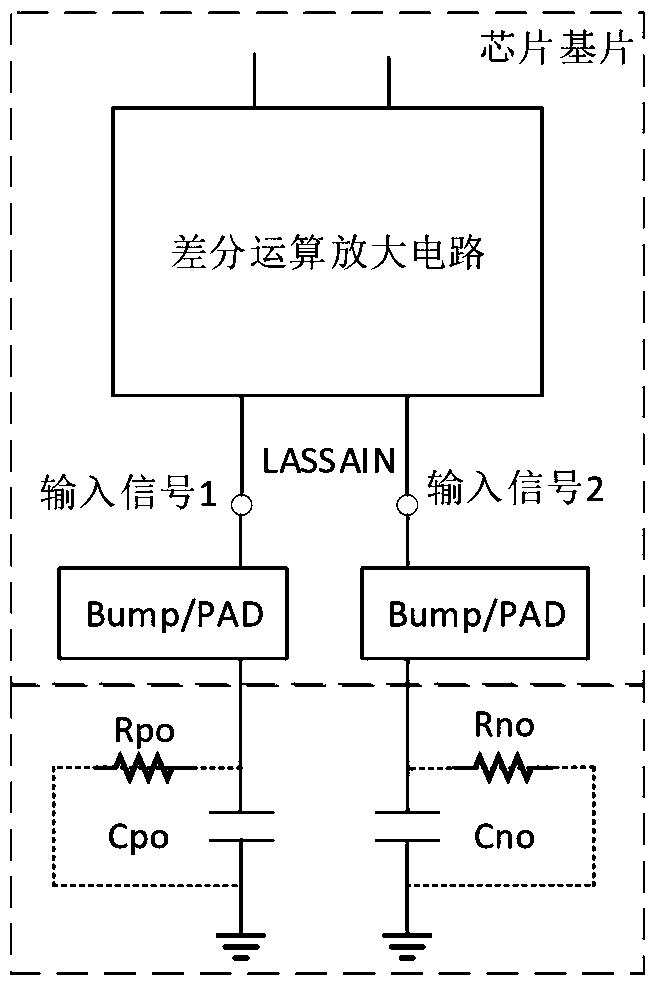
Security chip based on PUF and zero knowledge proof, application method, system and medium
ActiveCN110324151AImplement identity authenticationAchieve tamper resistanceUser identity/authority verificationDigital signatureZero-knowledge proof
The invention discloses a security chip based on PUF and zero knowledge proof, an application method, a system and a medium. The security chip based on PUF and zero knowledge proof comprises a PUF circuit module, a ChipID generation circuit module, a zero knowledge proof circuit module and a main control module. The zero knowledge proof circuit module comprises a first execution circuit used for generating a publicable zero knowledge identification number PID and a second execution circuit used for generating a proof code P. An identity authentication application method comprises the step of realizing the identity authentication method based on the lightweight security chip based on the security chip. The identity authentication method does not need a complex interactive protocol. The request end and the server end only need to execute zero knowledge proof calculation. Compared with a digital signature and authentication method based on a public key cryptographic algorithm, the identity authentication method is simpler and has the advantages of good universality, high security, low authentication overhead, simple authentication process and the like.
Owner:北京智涵芯宇科技有限公司
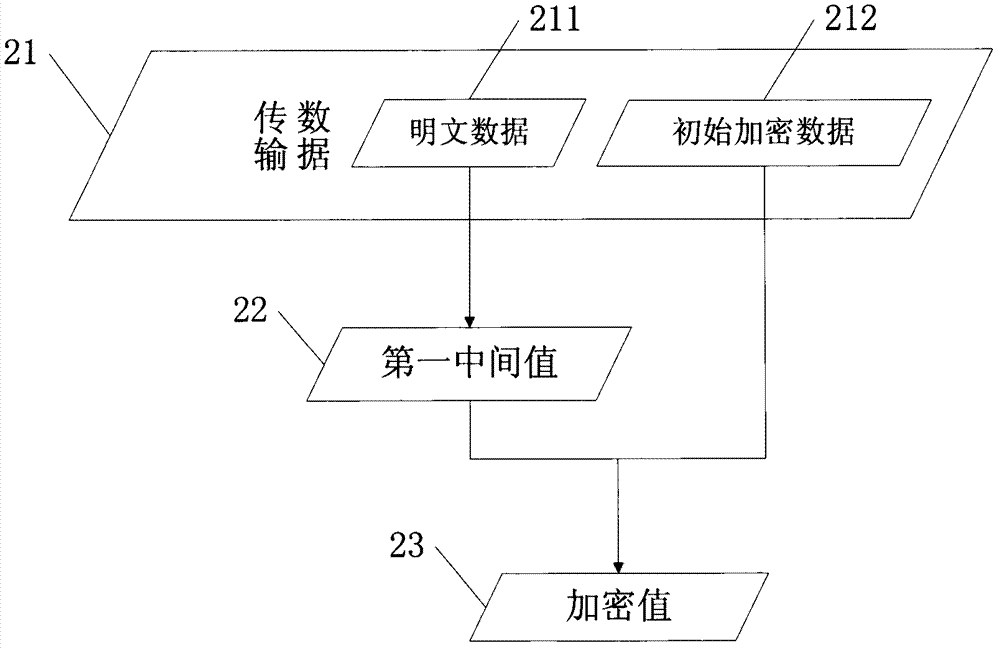
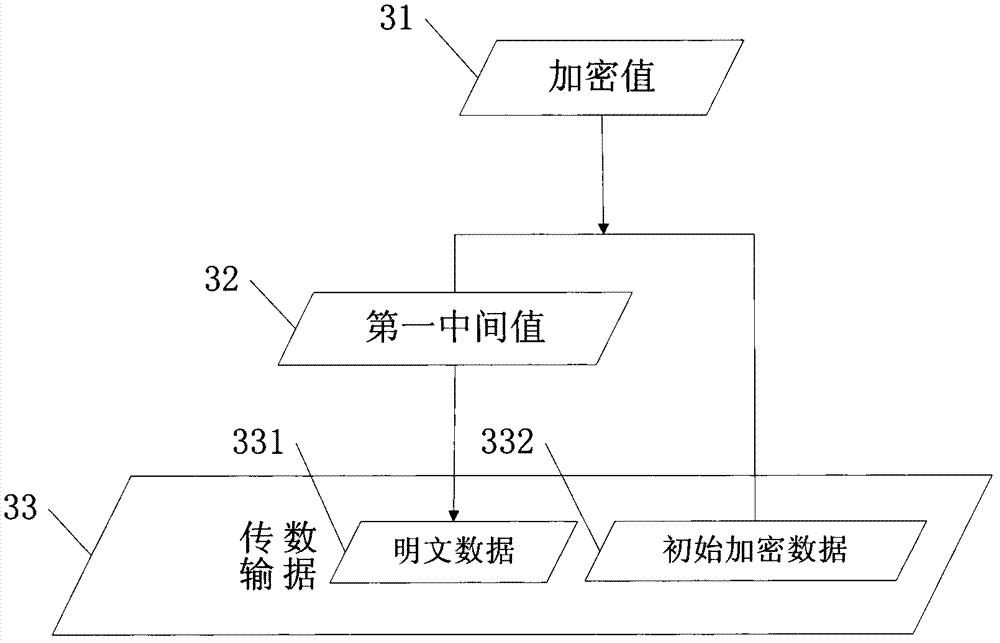
Encryption control method and device capable of achieving tamper-proofing and repudiation-proofing by means of public key infrastructure (PKI)
InactiveCN103117851AAchieving non-repudiationAchieve tamper resistancePublic key for secure communicationDigital data protectionPlaintextTamper resistance
The invention provides an encryption control method and a device capable of achieving tamper-proofing and repudiation-proofing by means of public key infrastructure (PKI). The encryption control method and the device capable of achieving tamper-proofing and repudiation-proofing by means of the PKI are used for enabling data being transmitted to be encrypted by a sending end, wherein the data being transmitted includes initial encryption data and clear data. The encryption control method capable of achieving tamper-proofing and repudiation-proofing by means of the PKI comprises the following steps: (1) conducting a first encryption algorithm on the clear data, and enabling an algorithm result to be a first median; (2) conducting a second encryption algorithm on the initial encryption data and the first median, and enabling an algorithm result to be an encrypted value, and the encrypted value is sent to a corresponding receiving end by the sending end. The invention further provides an encryption control device capable of achieving tamper-proofing and repudiation-proofing by means of the PKI and a corresponding financial transaction processing system. According to the encryption control method and the device capable of achieving tamper-proofing and repudiation-proofing by means of the PKI, encryption processing is conducted on clear data and encryption data (initial encryption data) in a message to achieve encryption for a transaction message. Therefore, encryption scheme which is simple and easy to carry out can be utilized to achieve the purpose of tamper-proofing and repudiation-proofing for transaction data.
Owner:银视通信息科技有限公司
Crop seed safety traceability system based on block chain technology
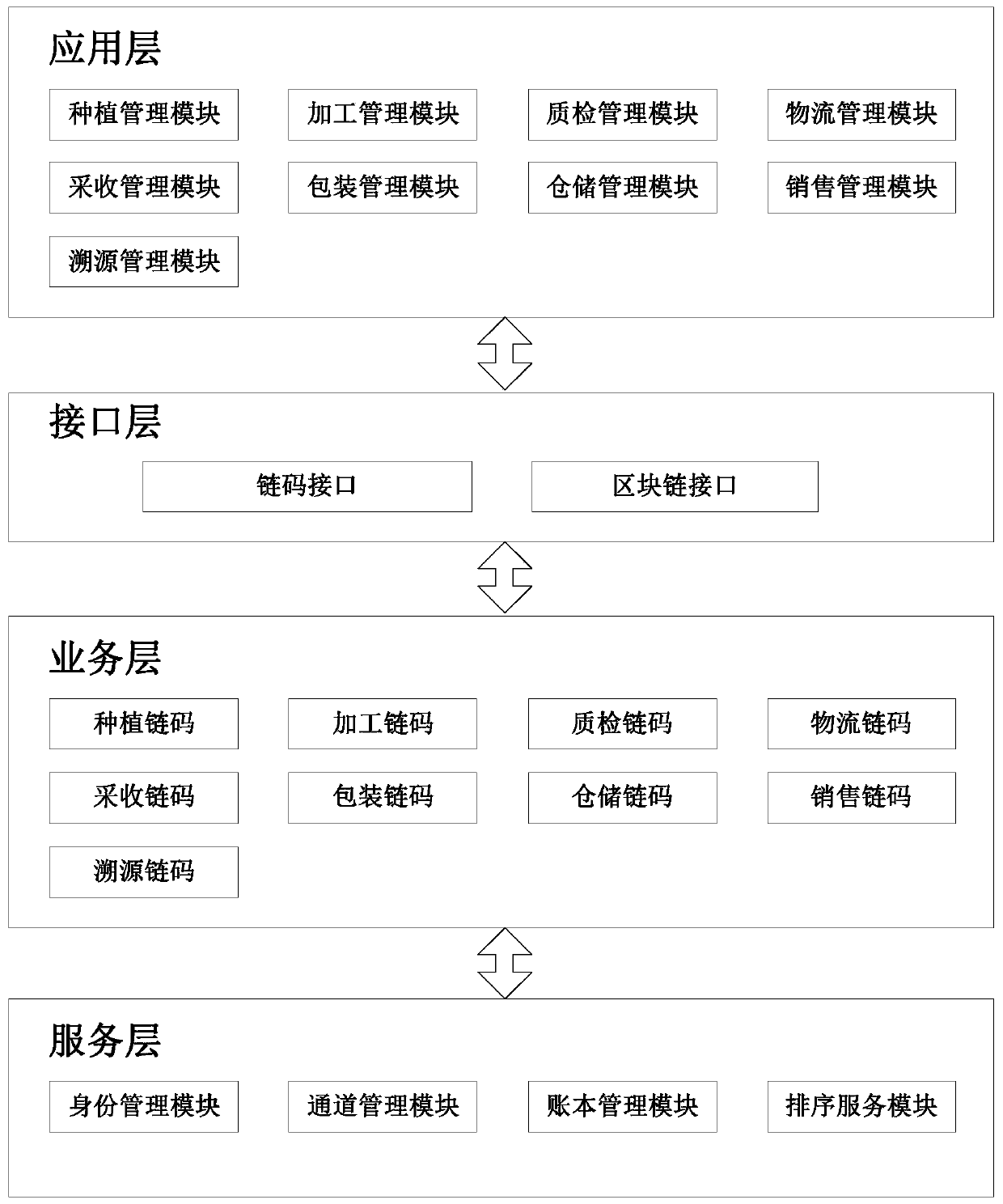
PendingCN110135860AImprove product qualityEnhance brand imageFinanceInterprogram communicationSystems managementHuman–computer interaction
The invention provides a crop seed safety traceability system based on a block chain technology. The crop seed safety traceability system comprises a service layer, a business layer, an interface layer and an application layer, wherein the service layer provides network and data processing service for the business layer; the service layer provides a service logic function of the system; the interface layer provides an intermediate message service for the service layer and the application layer; the application layer provides man-machine interaction service and performs information interactionwith the business layer; the service layer comprises a block chain network, and the block chain is returned to the application layer through the block chain network. The invention provides a crop seedsafety traceability system based on a block chain technology. The security, integrity and authenticity of data recorded on the chain are ensured through the block chain network, the functions of tamper-proofing, information sharing, traceability system management strengthening and the like are achieved, and the market competitiveness of crop seeds and the enterprise brand image are improved whilethe quality of crop seed products is improved.
Owner:SUN YAT SEN UNIV
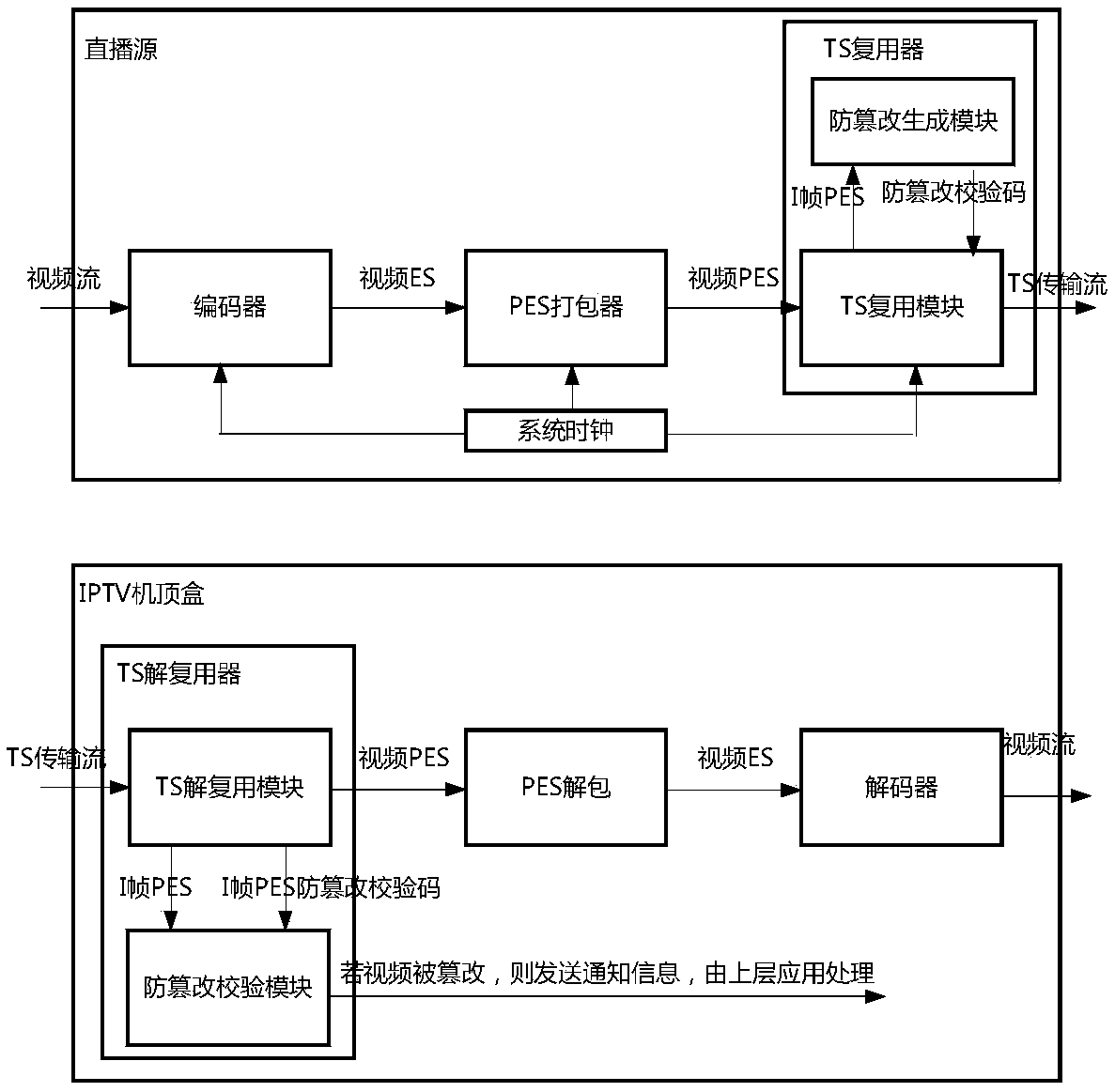
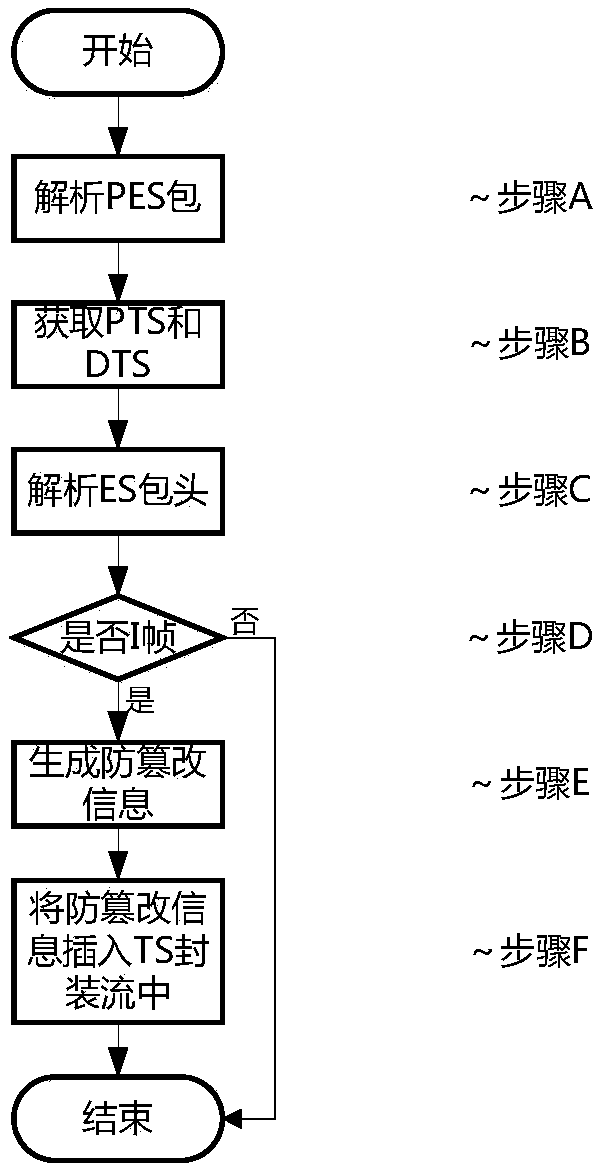
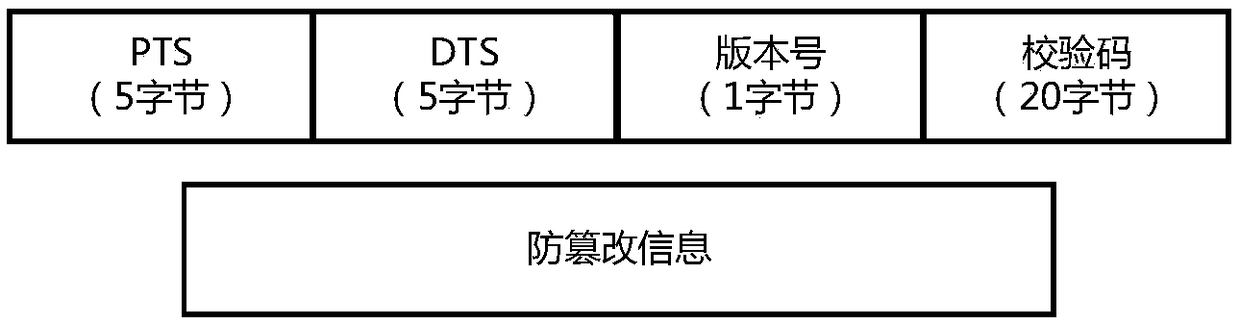
Anti-tampering method of IPTV multicast contents
The invention discloses an anti-tampering method of IPTV multicast contents. On a live broadcast source end, a TS multiplexer is modified, and an anti-tampering generation module is added; when a TS multiplexing module detects that the PES is carried as an I frame, the anti-tampering generation module is called to transmit the PES and to package the obtained anti-tampering information in a TS transmission stream; and on a terminal side, a TS demultiplexer is modified, and an anti-tampering verification module is added; and a TS demultiplexing module detects the PES of the I frame and the corresponding anti-tampering in real time and calls the anti-tampering verification module to complete anti-tampering verification. By adoption of the anti-tampering method disclosed by the invention, theanti-tampering security of the IPTV multicast content is improved, no dependence is made on the hardware, and the transformation of the existing system is small.
Owner:天翼智慧家庭科技有限公司
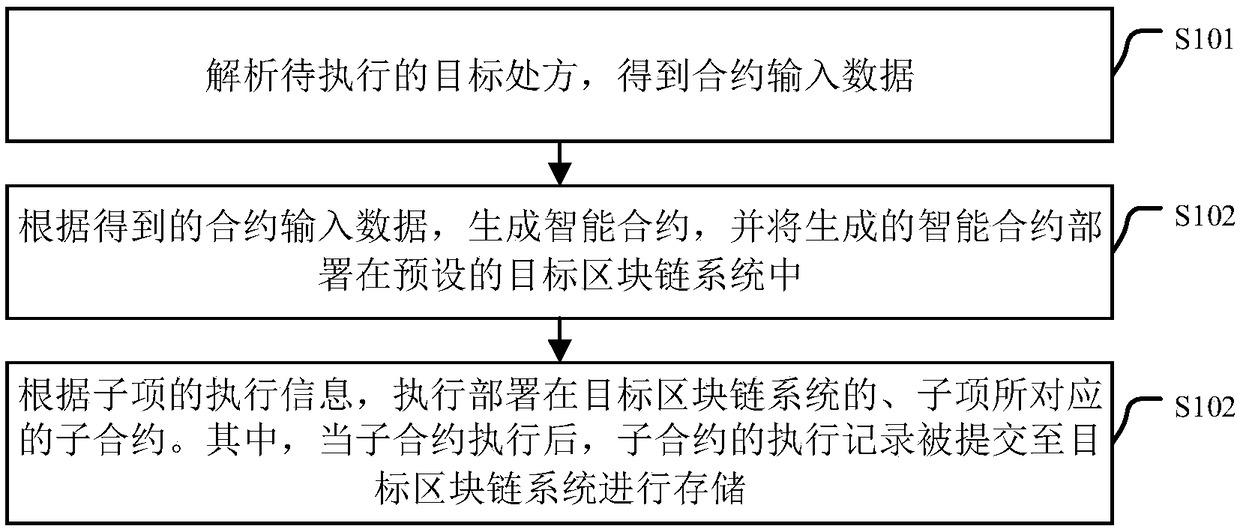
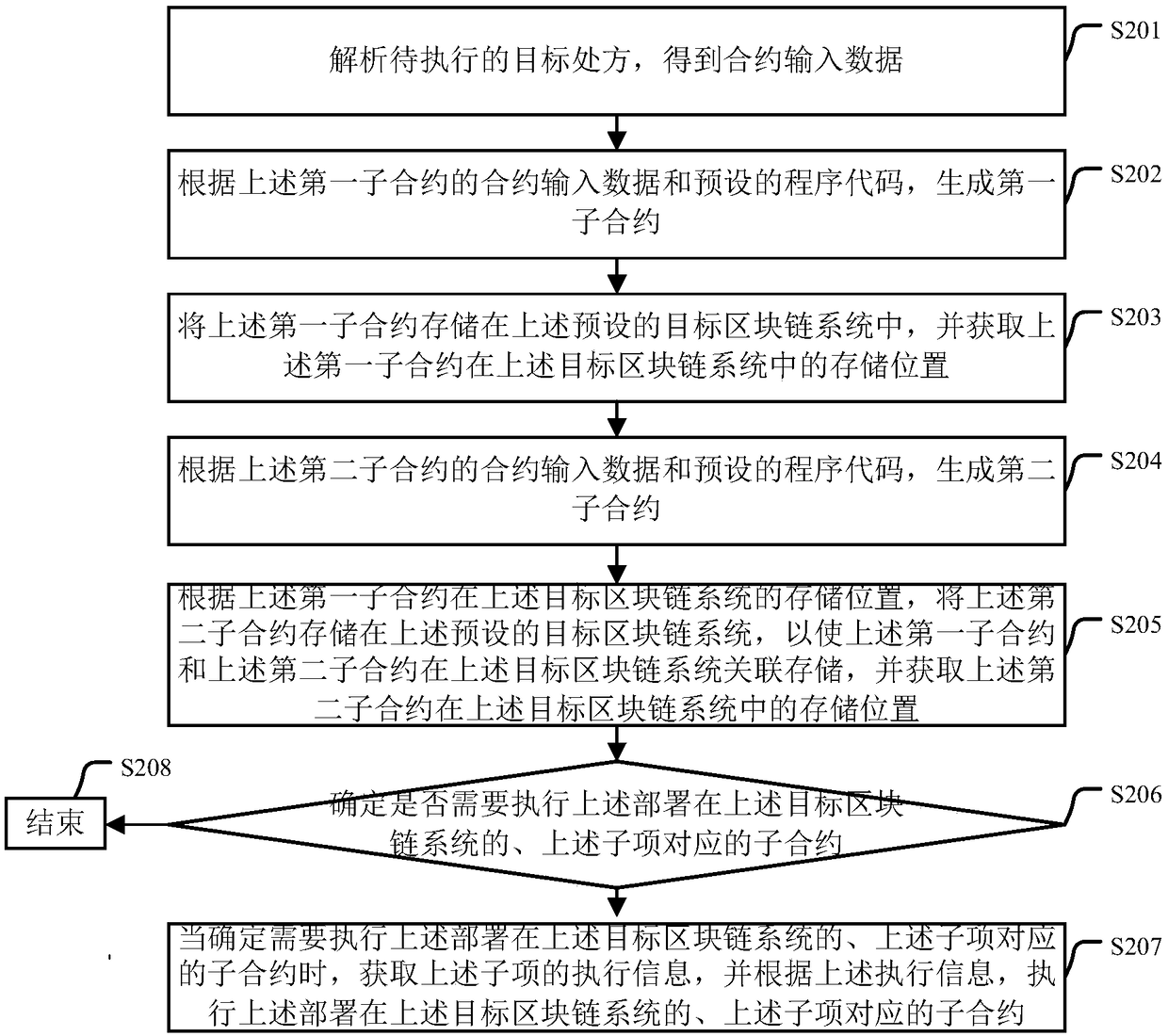
Prescription execution method and device, equipment and storage medium
ActiveCN108665953AExecute precise controlImprove securityDrug and medicationsOffice automationMedical prescriptionSmart contract
The embodiment of the invention provides a prescription execution method and device, equipment and a storage medium. The method comprises the steps that a to-be-executed target prescription is parsed,contract input data is obtained, wherein the target prescription comprises at least one sub item; according to the obtained contract input data, an intelligent contract is generated, the generated intelligent contract is deployed in a preset target block chain system, wherein the intelligent contract comprises at least one sub contract, and one sub item corresponds to one sub contract; accordingto execution information of the sub item, the sub contract which corresponds to the sub item and is deployed in the target block chain system is executed; after the sub contract is executed, the execution record of the sub contract is submitted to the target block chain system for storing, and when the sub contract is executed abnormally, abnormal event reminding is conducted. By adopting the provided method, the safety of prescription execution can be improved.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD +1
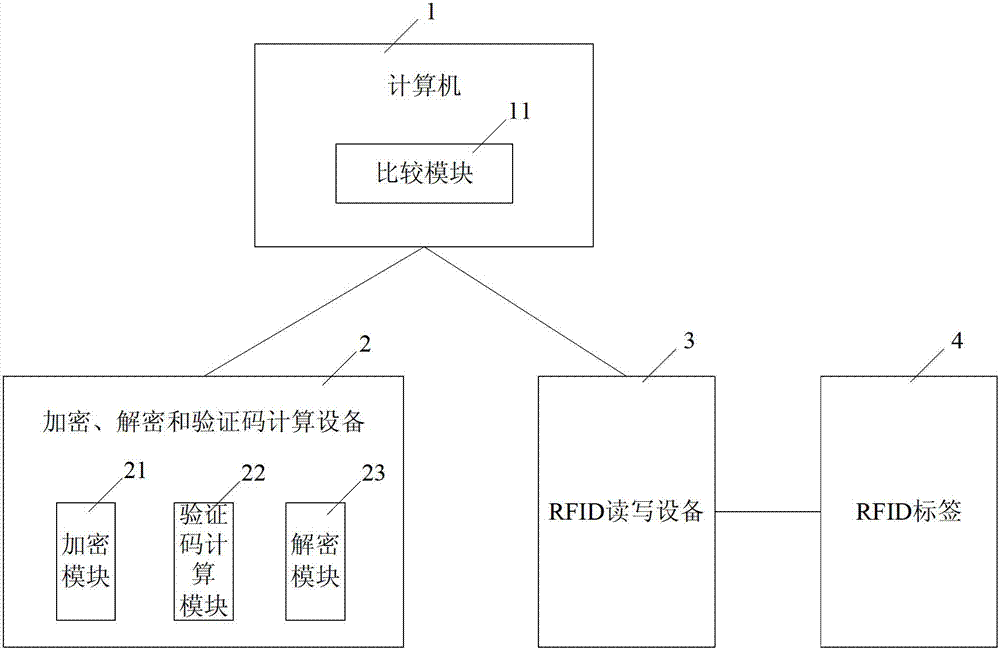
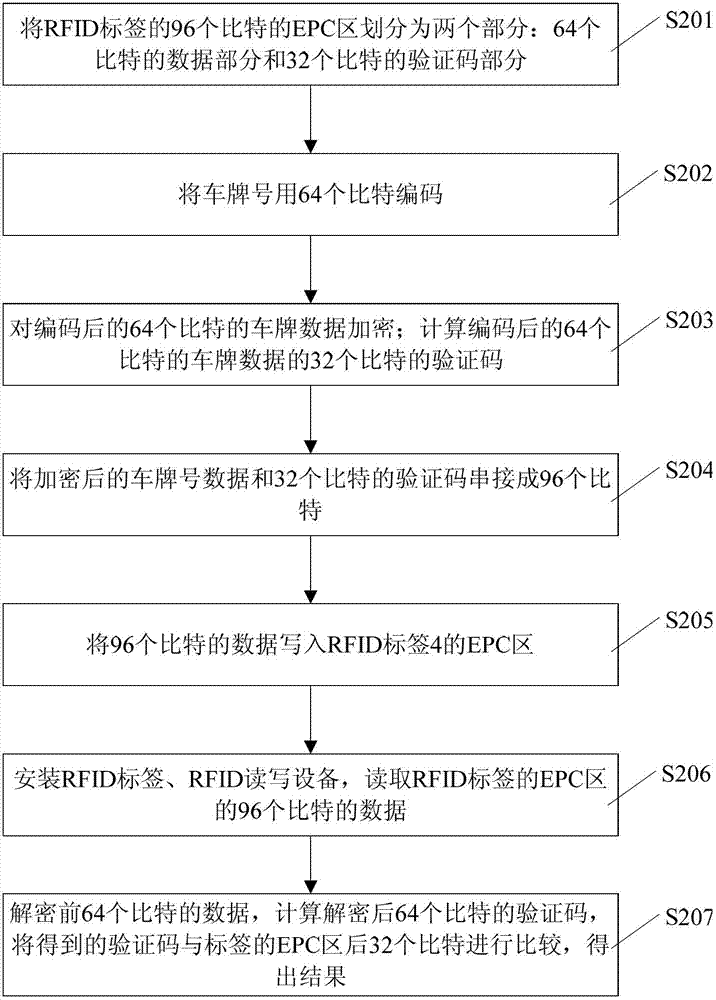
Radio frequency tag data coding method and radio frequency tag data coding system for vehicle identification
ActiveCN103714357AAchieve privacyAchieve tamper resistanceCo-operative working arrangementsComputer hardwareRadio frequency
The invention discloses a radio frequency tag data coding system and a radio frequency tag data coding method for vehicle identification. The system comprises a computer, an encryption / decryption and verification code calculation device, an RFID reading-writing device and an RFID tag. The computer divides an EPC region of the RFID tag into a data part and a verification code part and codes a license plate number; the encryption / decryption and verification code calculation device encrypts the coded license plate number data and calculates the verification code of the license plate number data; the computer concatenates the license plate number data and the verification code; the RFID reading-writing device writes the concatenation data into the EPC region; the encryption / decryption and verification code calculation device carries out decryption to obtain decryption data and calculates the verification code; and the computer compares the decrypted verification code with the verification code part of the EPC region and judges whether data in the EPC region is tampered. The defect that data encryption and verification code calculation cannot be carried out due to the fact that the license plate number is stored in the EPC region of the RFID tag in the prior art is overcome.
Owner:BEIJING INST OF COMP TECH & APPL
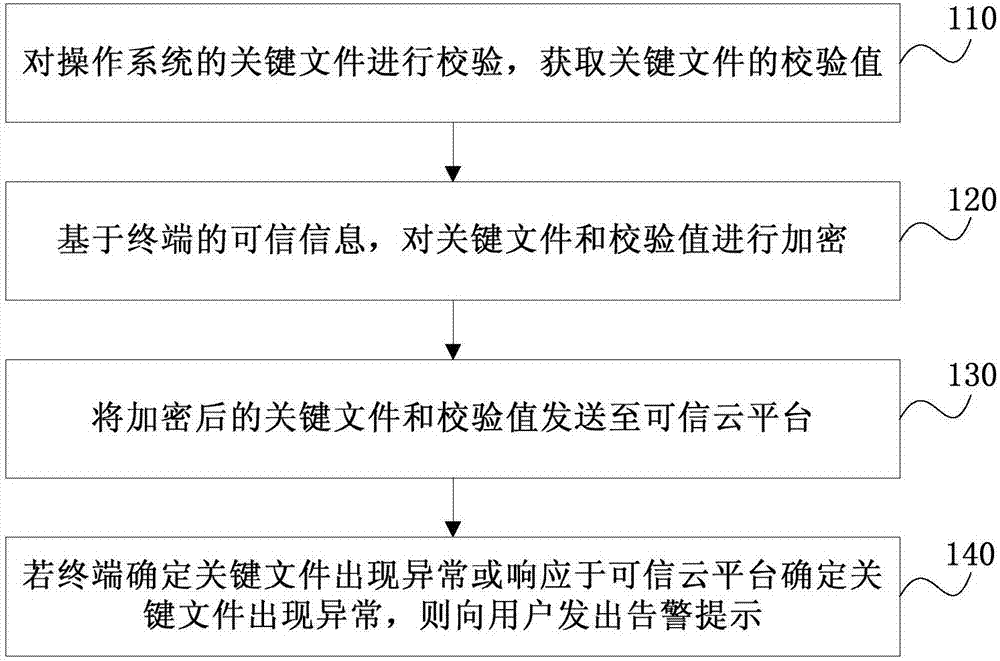
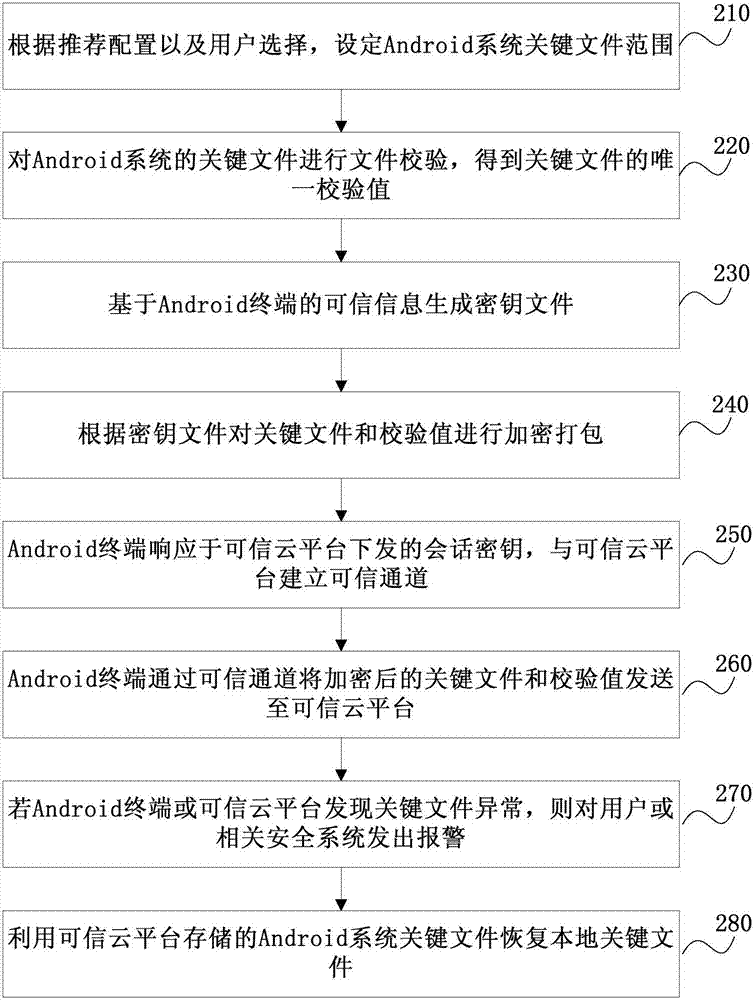
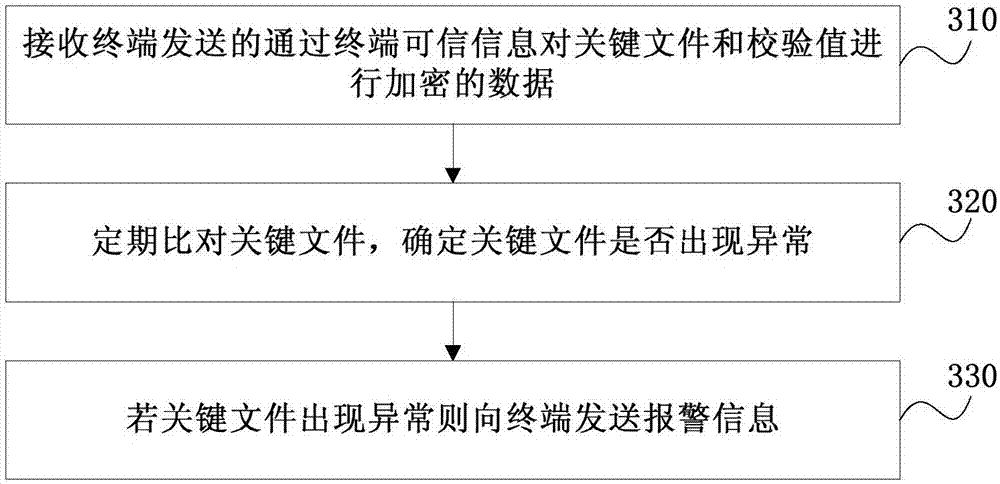
File tamper-proofing method and system, terminal and trusted cloud platform
ActiveCN107995148AEnsure safetyAchieve tamper resistanceDigital data protectionTransmissionTamper resistanceDocument security
The invention discloses a file tamper-proofing method and system, a terminal and a trusted cloud platform, and relates to the field of mobile terminal security. The method comprises the following steps: checking key files of an operating system to obtain check values of the key files; encrypting the key files and the check values based on trusted information of the terminal; transmitting the encrypted key files and check values to the trusted cloud platform; and if the terminal determines the exception of the key files or the exception of the key files in response to the trusted cloud platform, giving an alarm prompt to a user to realize tamper proofing of the key files. Through adoption of the file tamper-proofing method and system, trusted information of an operator on the terminal and the trusted cloud platform of the operator are fully utilized to ensure the file security of a terminal user from the underlying layer.
Owner:CHINA TELECOM CORP LTD
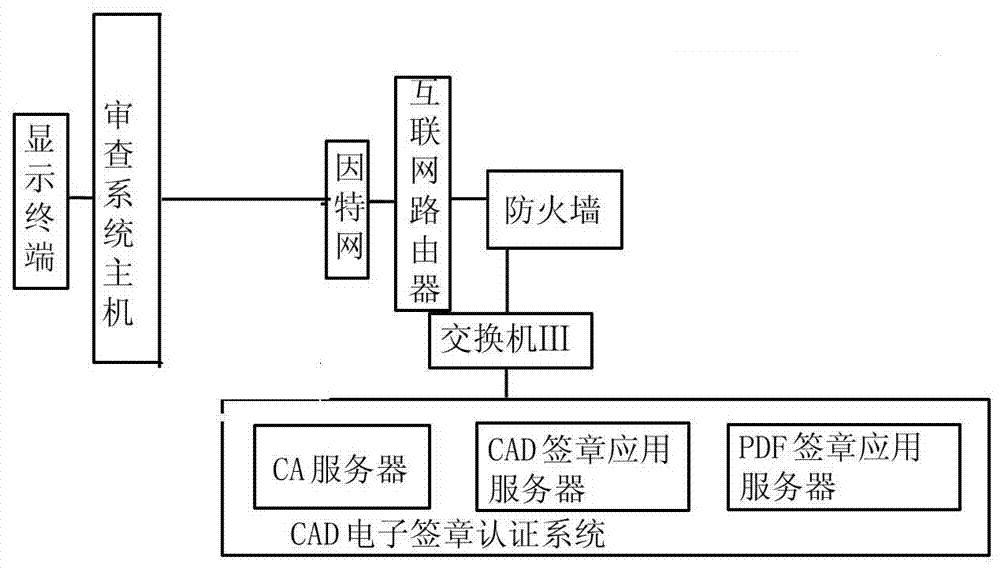
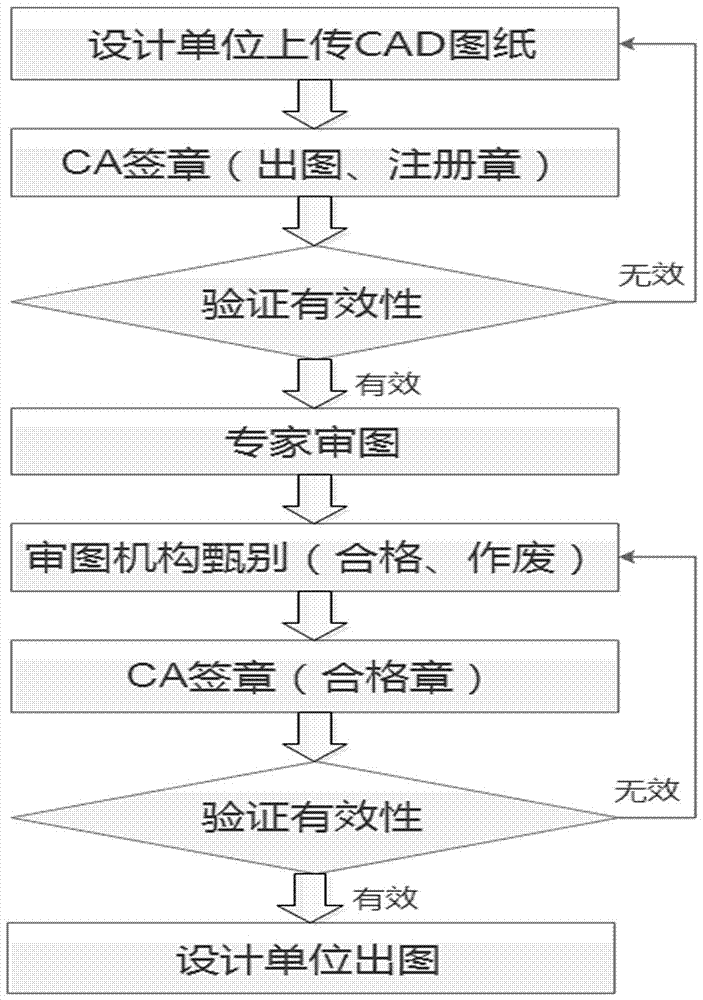
CAD signature certification system used for construction drawing examination and CAD signature certification method used for construction drawing examination
ActiveCN107347007AIntegrity guaranteedEnsure safetyKey distribution for secure communicationUser identity/authority verificationApplication serverPassword
The invention discloses a CAD signature certification system used for construction drawing examination. An examination system host is connected with the input end of a CA signature server through the Internet, an Internet router and a firewall. The output end of the CA signature server is connected with the CAD signature application server and a PDF signature application server. The invention further discloses a CAD signature certification method used for construction drawing examination. The method comprises the steps of 1 logging in the CAD signature certification system through a login password; 2 waiting for a CA certificate authority to issue a CA certificate; 3 ensuring that a CAD drawing is marked with a signature identifier; 4 confirming each professional CAD drawing; 5 calling the key and signature of the CA signature server to carry out electronic signature on the drawing; 6 verifying the CA signed CAD drawing through drawing experts; 7 carrying out CA qualified signature again according to screening; and 8 downloading the drawing by a design organization. The validity of the CA qualified signature is verified through a signature plug-in.
Owner:泰州市抗震办公室 +1
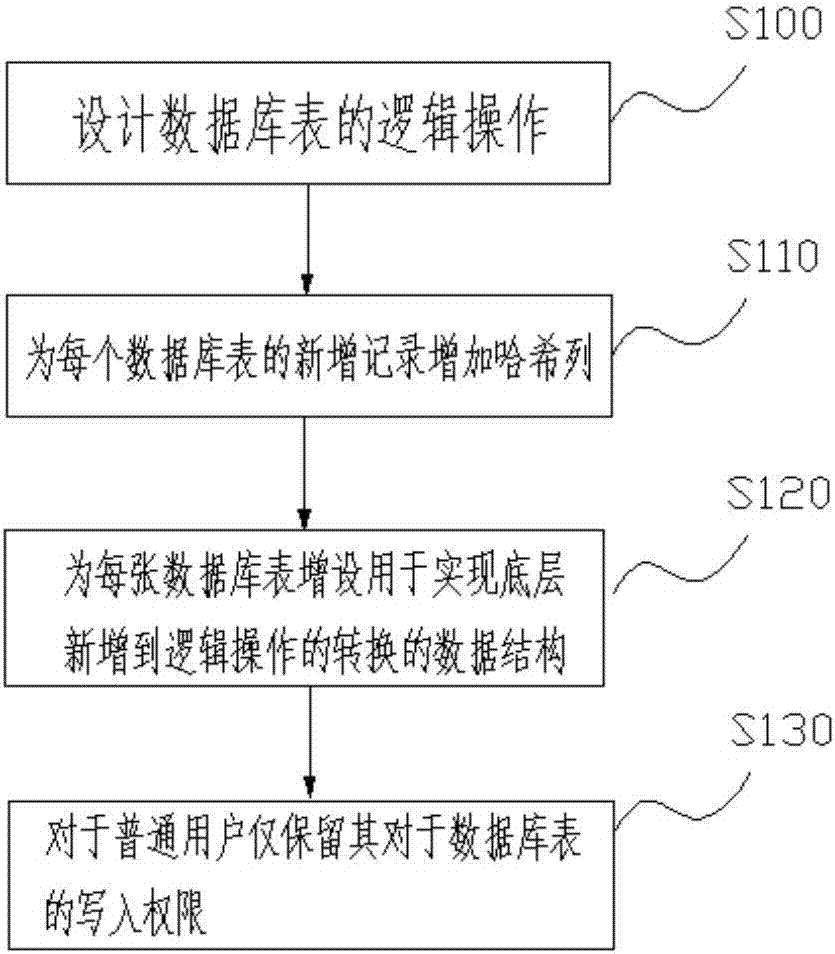
Database tamper-proofing method and system applied to data security products
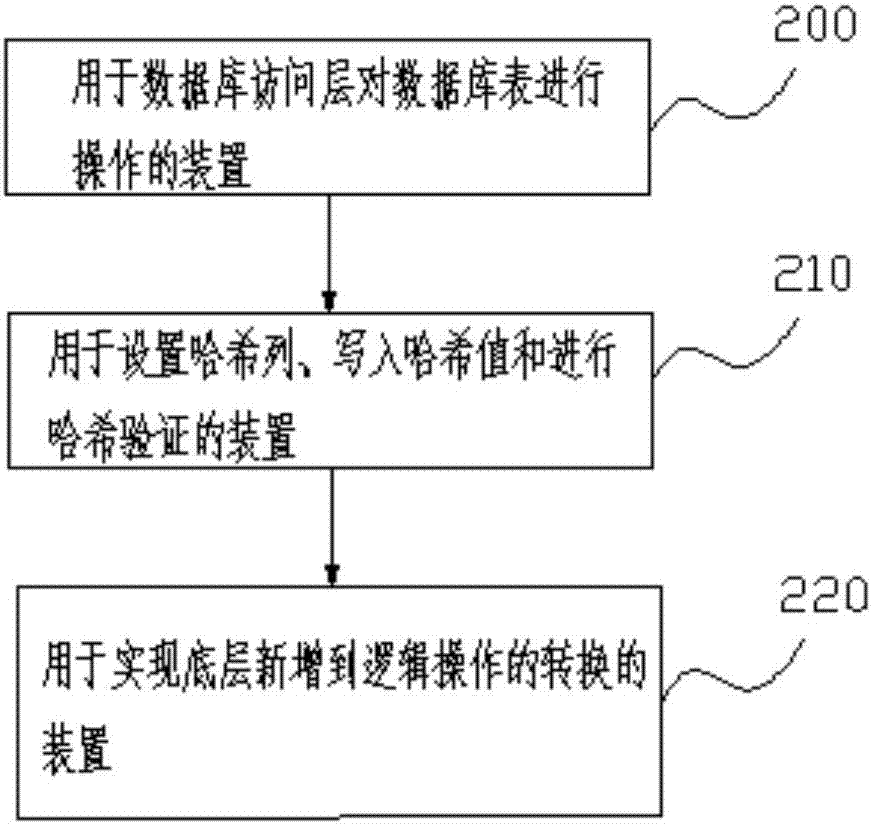
InactiveCN107193910AReserved operationAchieve tamper resistanceDigital data protectionSpecial data processing applicationsTamper resistanceComputer science
A database tamper-proofing method applied to data security products is provided. The method comprises: designing a logic operation for a database table. The logic operation comprises logical addition, logical deletion, and logical modification. The logic addition is newly adding a valid data record; the logical deletion is newly adding a deletion record for representing that object data has been deleted; and the logical modification firstly executes logic deletion for recording that the object data has been deleted, and executes logic addition for recording modified object data and identifications of the object data. According to the technical scheme of the present invention, since only write permissions to the database table of ordinary users are retained, and each database table contains a data structure for implementing conversion from the bottom addition to the logic operation, so that only-addition operations are used to stimulate the addition, deletion and modification operations on the bottom of the datable table; and the hash value is recorded in the only-addition operation process to be taken as fingerprint verification to ensure the authenticity of the audit history, so that not only all operations of the database access layer are retained, but also tamperresistance in the whole process of the history of all the database objects is realized.
Owner:四川盛世天成信息技术有限公司
Intelligent education system and method based on virtual reality and big data
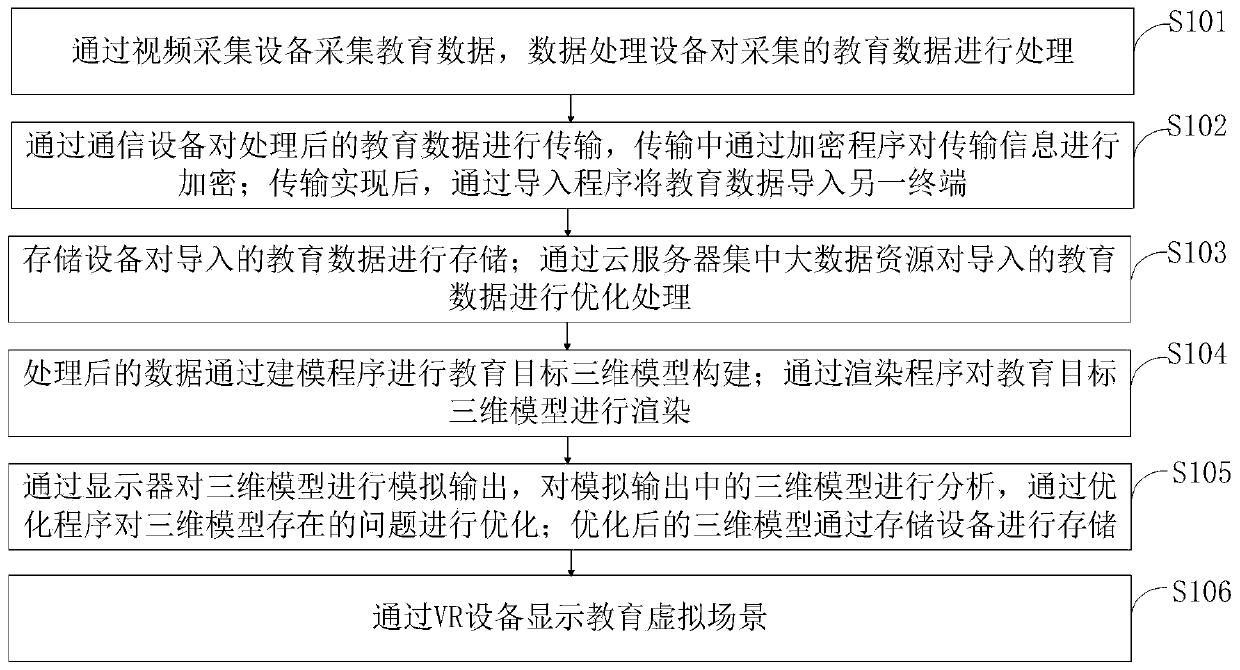
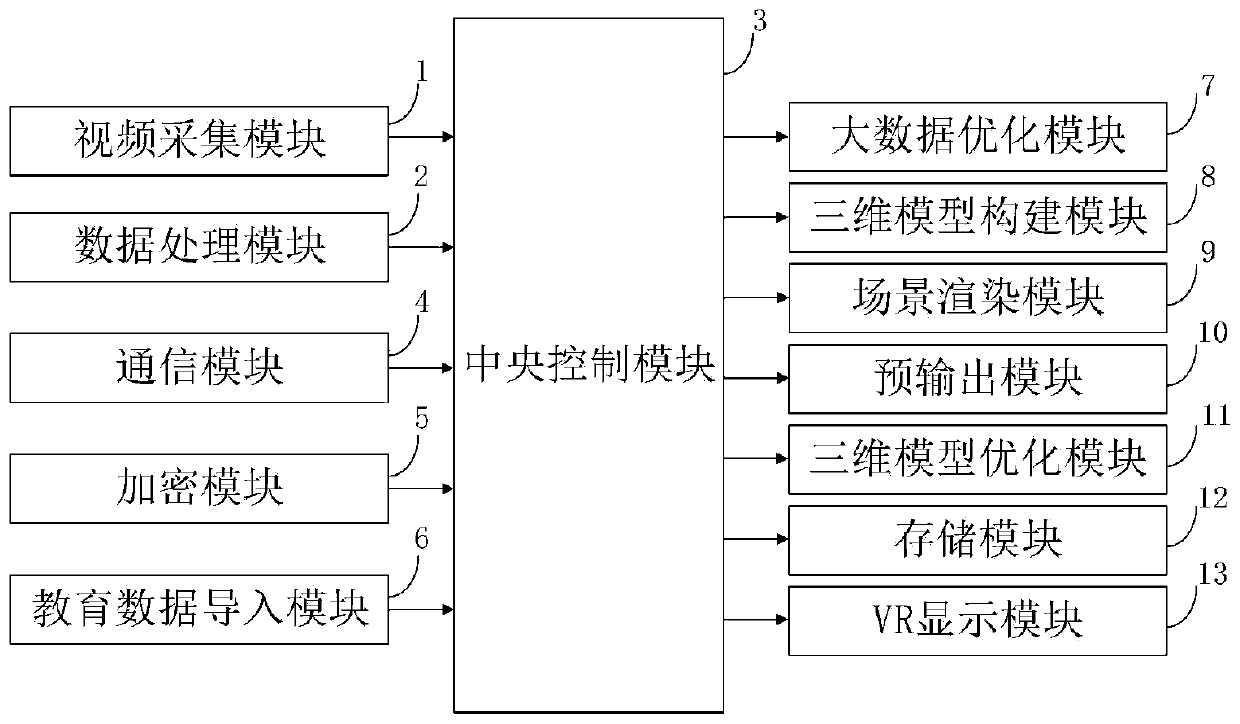
PendingCN111274482AProcessing speedImprove reliabilityInput/output for user-computer interactionData processing applicationsAcquisition apparatusSoftware engineering
The invention belongs to the technical field of wisdom education, and discloses a wisdom education system and method based on virtual reality and big data, and the method comprises the steps: collecting education data through video collection equipment, and enabling data processing equipment to process the collected education data; transmitting the education data through the communication device,and encrypting the transmission information through the encryption program; big data resources are concentrated through the cloud server to optimize the education data; constructing an education target three-dimensional model through a modeling program; rendering the education target three-dimensional model through a rendering program; carrying out simulation output on the three-dimensional modelthrough a display, and optimizing problems existing in the three-dimensional model through an optimization program; and displaying the education virtual scene through VR equipment. According to the invention, the accuracy of resource collection can be improved through the big data optimization module; and the storage module effectively realizes tamper-proofing of the education information and improves the reliability of the education information.
Owner:DALIAN JIAOTONG UNIVERSITY
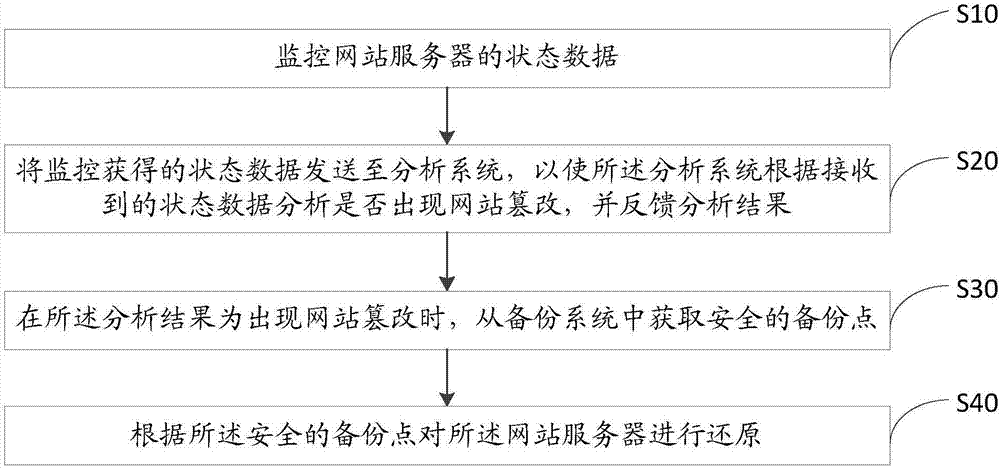
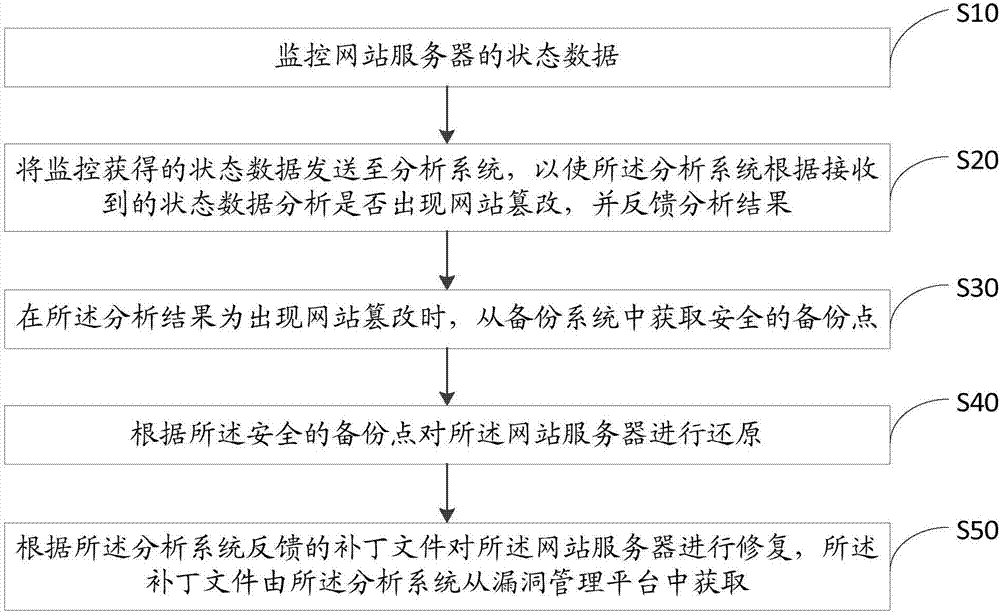
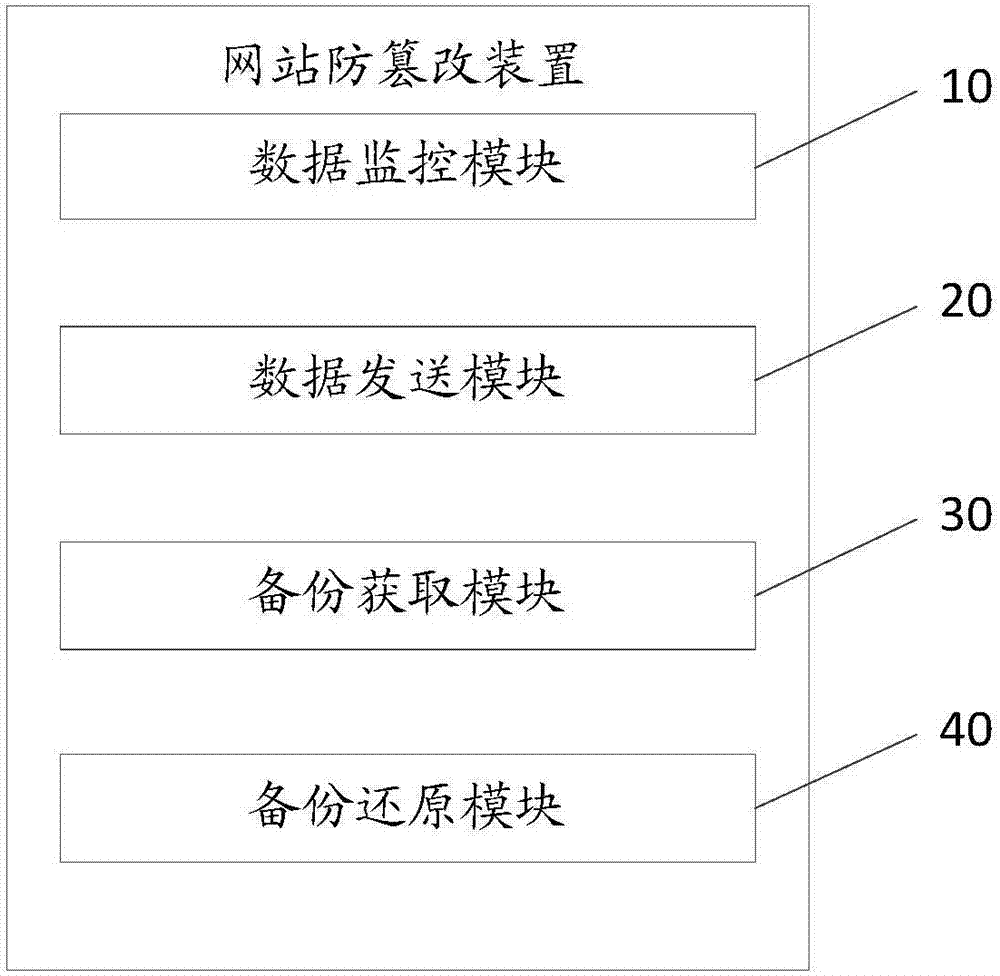
Website tamper-proofing method and apparatus
The invention discloses a website tamper-proofing method. The method comprises steps of monitoring status data of a web server; transmitting the status data obtained by the monitoring to an analysis system, enabling the analysis system to analyze whether the website is tampered based on the received status data and feeding back the analysis result; obtaining a secure backup point from a backup system when the analysis result indicates that the website is tampered; and restoring the web server according to the secure backup point. The invention also discloses a website tamper-proofing apparatus. When the website is detected as tampered, the web server is restored according to the secure backup point, so that the website tampering resistance is effectively achieved.
Owner:深圳市科力锐科技有限公司
Food label unique code publishing and circulation traceability method based on block chain main and auxiliary chain technology
PendingCN110335051ASmall amount of calculationLighten the burden on hardwareCommerceBlockchainTimestamp
The invention discloses a food label unique code publishing and circulation traceability method based on a block chain main and auxiliary chain technology. The commodity label unique code informationblock chain technology based on public and private key pairing verification is adopted. Main chain and auxiliary chain information counterfeiting prevention, tampering prevention and replay preventionare achieved, food label unique code network propagation and independent chaining and rapid tracing of single piece of food information can be achieved, and a user comprises a third-party mechanism,manufacturers at all levels, a dealer and a consumer which are connected with the Internet. Server databases of the third-party mechanism, manufacturers and dealers at all levels store food label information block chain account books in server databases, new legal verification data issued by other parties is received in real time, local account books are updated in time, new data blocks are hookedaccording to food transfer conditions, and new block chain data are issued; and a consumer obtains the latest timestamp block chain from a plurality of enterprise servers during code scanning, and calculates and obtains the food traceability information chain by comparing the latest timestamp block chain.
Owner:烟台市同翔网络科技有限责任公司
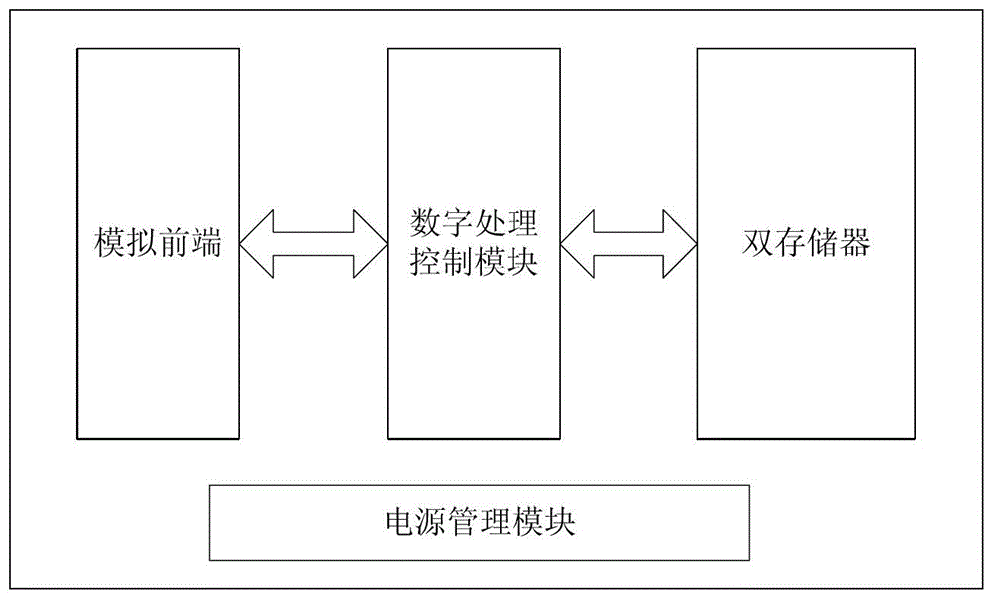
Electronic vehicle license plate with double-memory chip
InactiveCN103915116AMeet the needs of flexible applicationsLow costRead-only memoriesVehicle componentsMemory chipComputer module
The invention discloses an electronic vehicle license plate with a double-memory chip, and relates to electronic technology. The electronic vehicle license plate comprises a simulation front-end module, a memory module and a digit processing control module connected with the simulation front-end module and the memory module; and the memory module comprises a permanent memory cell and an erasable memory cell, and the permanent memory cell is used for storing vehicle registration information. The electronic vehicle license plate overcomes the disadvantages that conventional electronic vehicle license plate is bad in safety and short in storage time.
Owner:CHENGDU KILOWAY ELECTRONICS CO LTD +1
Commodity authenticity detecting method and system based on two-dimension code
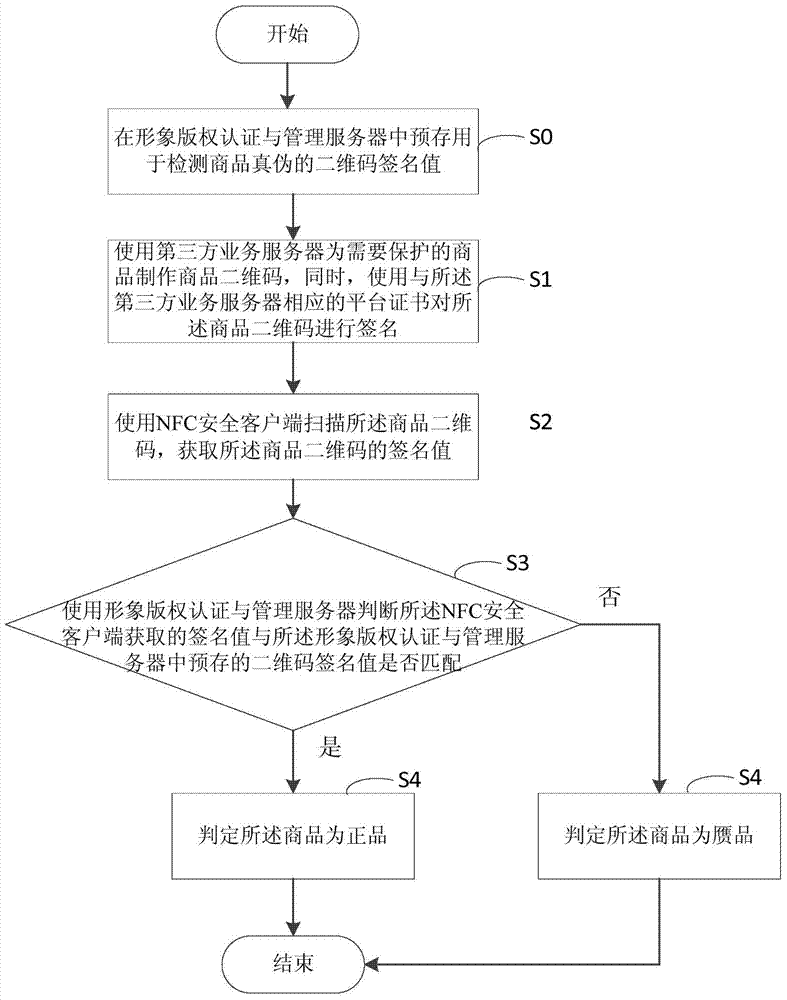
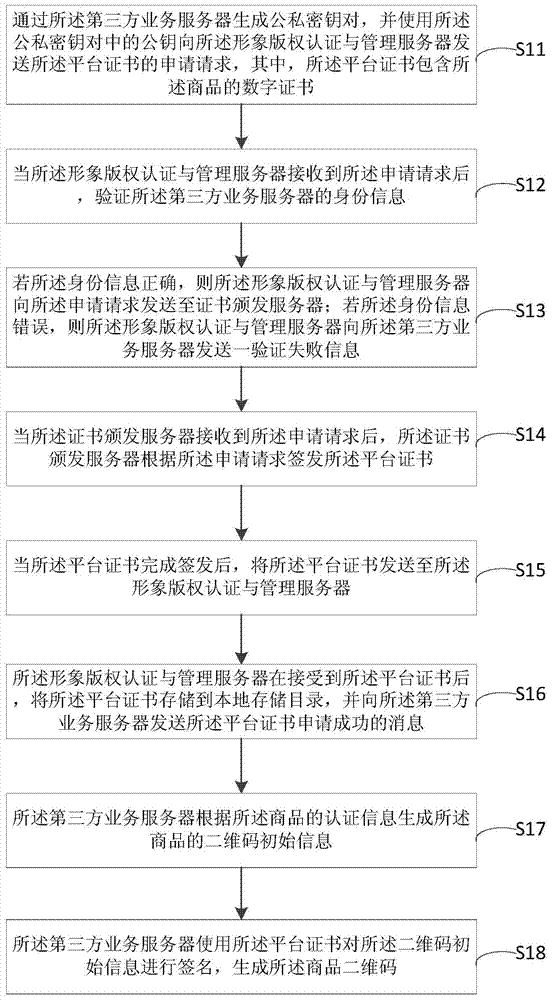
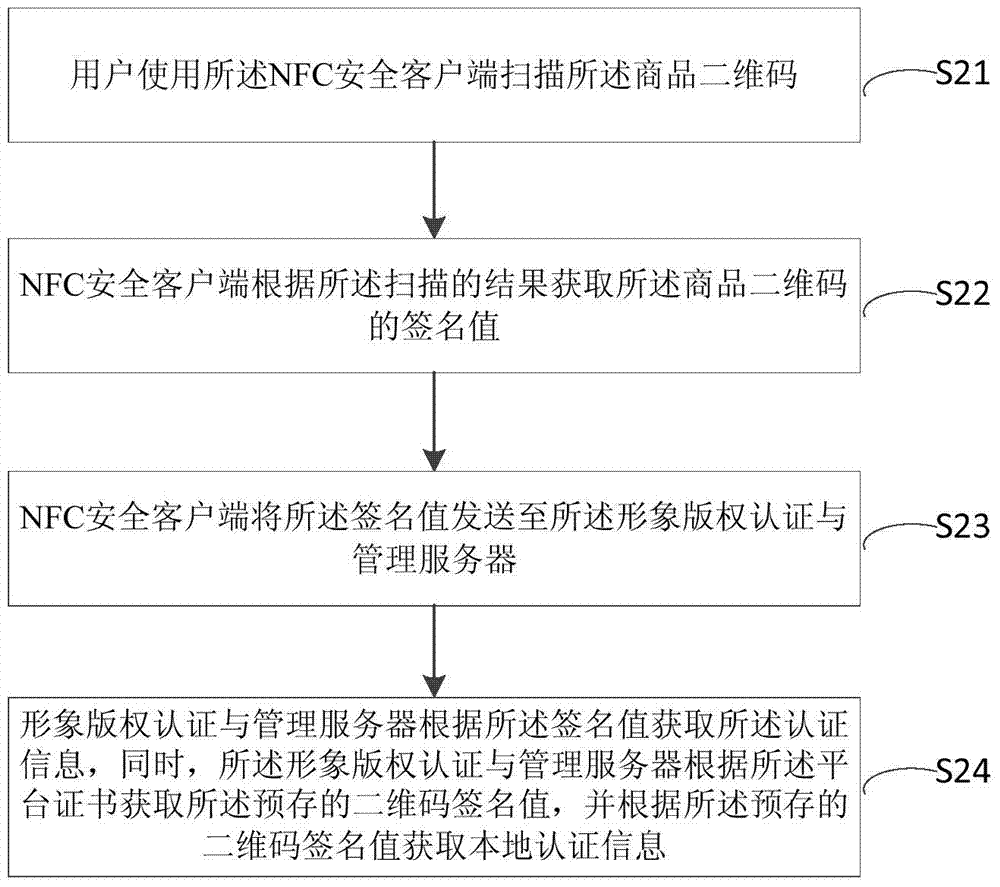
ActiveCN104732400AProtection of legal rightsAchieve protectionDigital data authenticationCommerceThird partyData source
The invention discloses a commodity authenticity detecting method and system based a two-dimension code. The method comprises the steps that a third party service server is used for manufacturing the commodity two-dimension code for a commodity, and meanwhile the commodity two-dimension code is signed through a platform certificate corresponding to the third party service server; an NFC safety client side is used for scanning the commodity two-dimension code, and a signature value of the commodity two-dimension code is obtained; whether the signature value obtained by the NFC safety client side is matched with the two-dimension code signature value prestored in an image copyright authentication and management server or not is judged through the image copyright authentication and management server; if the signature value obtained by the NFC safety client side is matched with the two-dimension code signature value prestored in the image copyright authentication and management server, it is judged that the commodity is an authentic product. The legal right of commodity manufacturers is protected from a data source, data credibility and safety of data through the secret key technology, the NFC technology and the two-dimension code technology.
Owner:卓望数码技术(深圳)有限公司
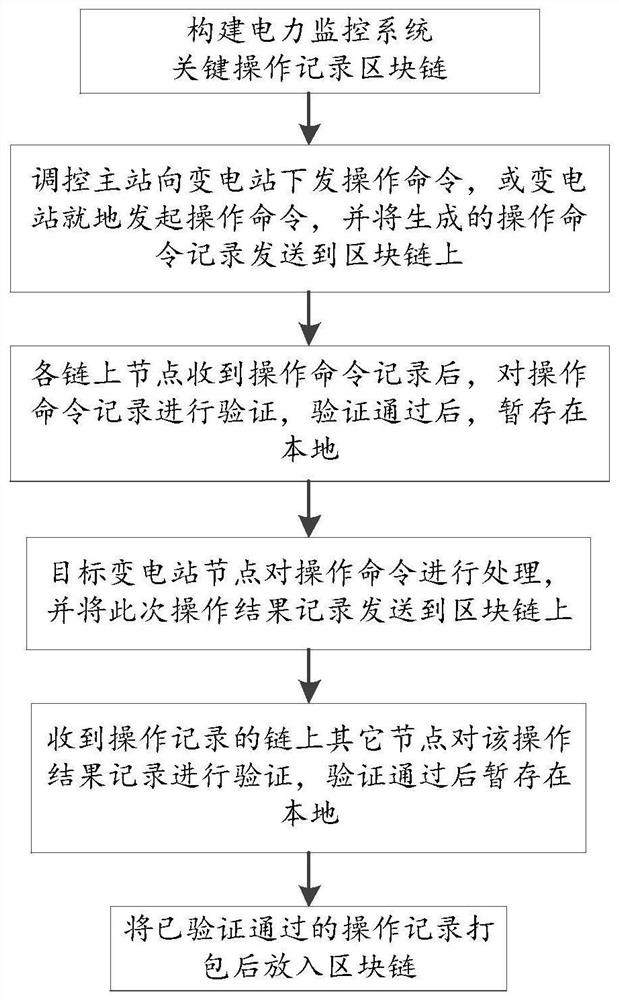
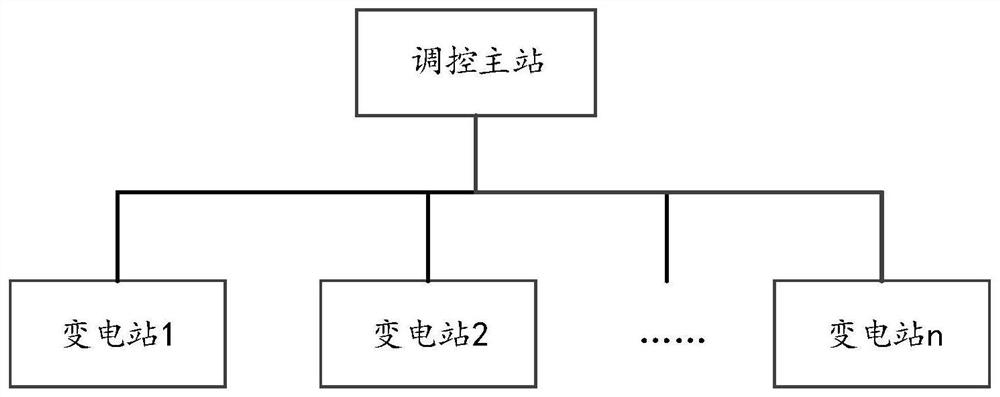
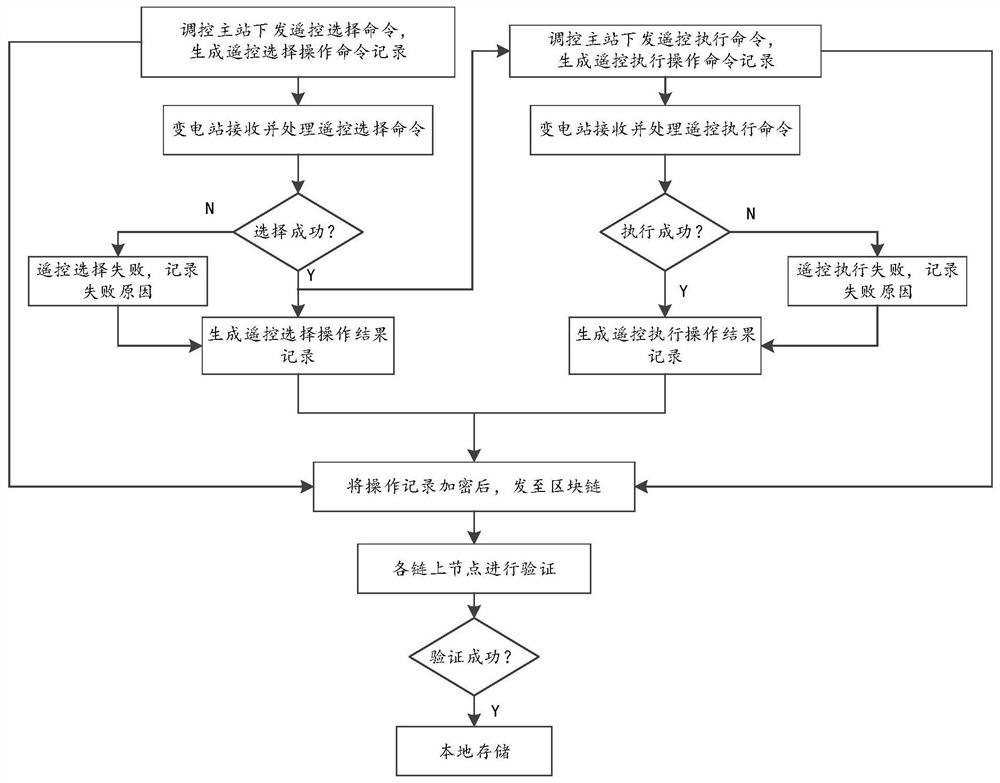
Operation record processing method in power monitoring based on block chain
ActiveCN111769639AReliable transmissionComplete dataCircuit arrangementsDigital data protectionSystem informationReliable transmission
The invention provides an operation record processing method in power monitoring based on a block chain. The method comprises the following steps: combining the block chain technology, constructing ablock chain for a regulation and control main station and an accessed transformer substation; generating an operation command record and an operation result record for the key operation of the power system; adding the operation records into the block chain. The method achieve the characteristics of reliable transmission, complete data, primary anti-repudiation and the like. Public transparency, tamper resistance and traceability of all the operation records are achieved, the safety problem of key operation record information of the power monitoring system is solved, and a powerful support is provided for information safety of the power monitoring system.
Owner:INTEGRATED ELECTRONICS SYST LAB
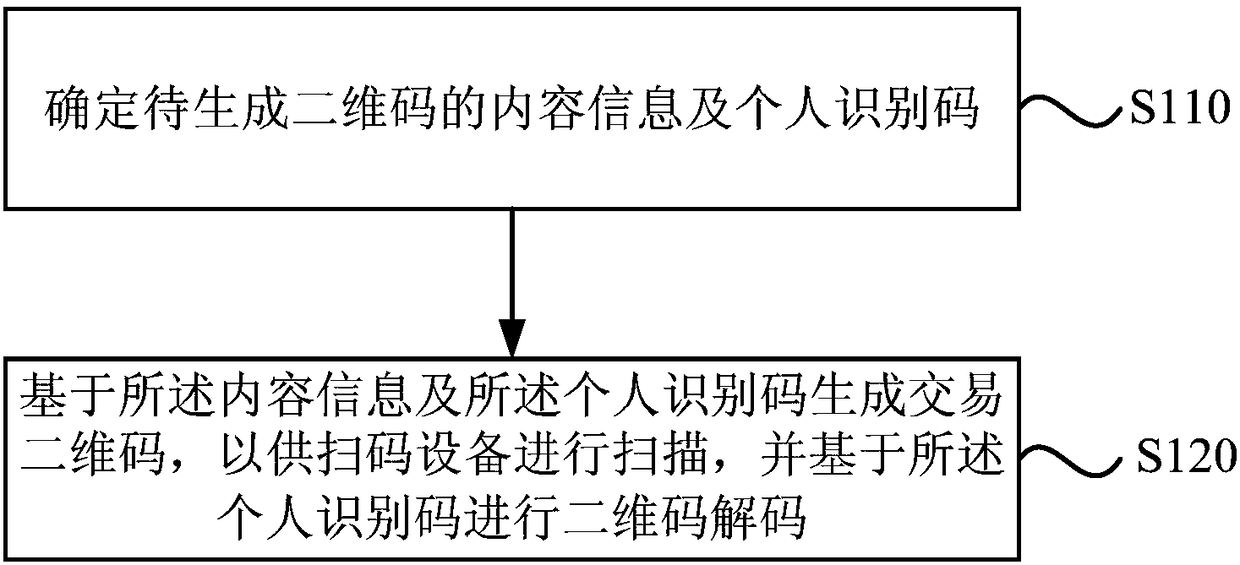
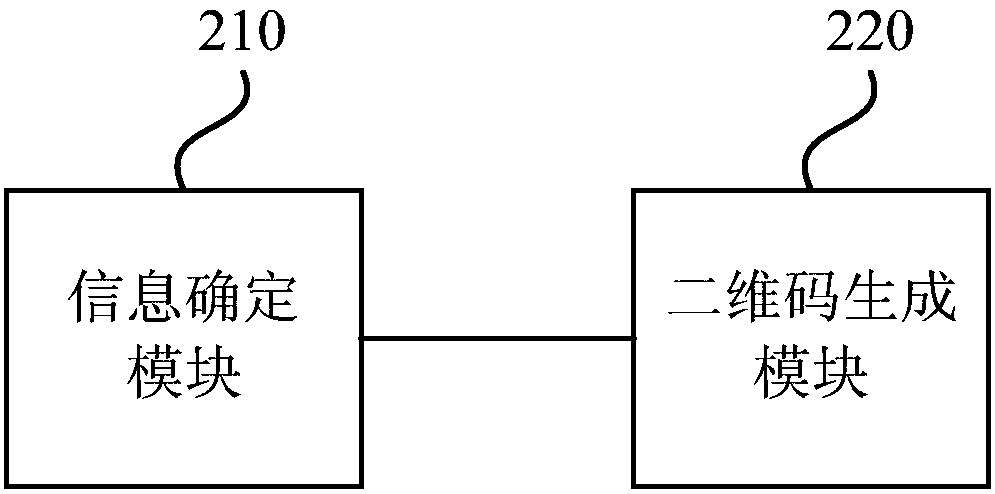
Two-dimensional code generation method, two-dimensional code decoding method, devices, transaction system and storage medium
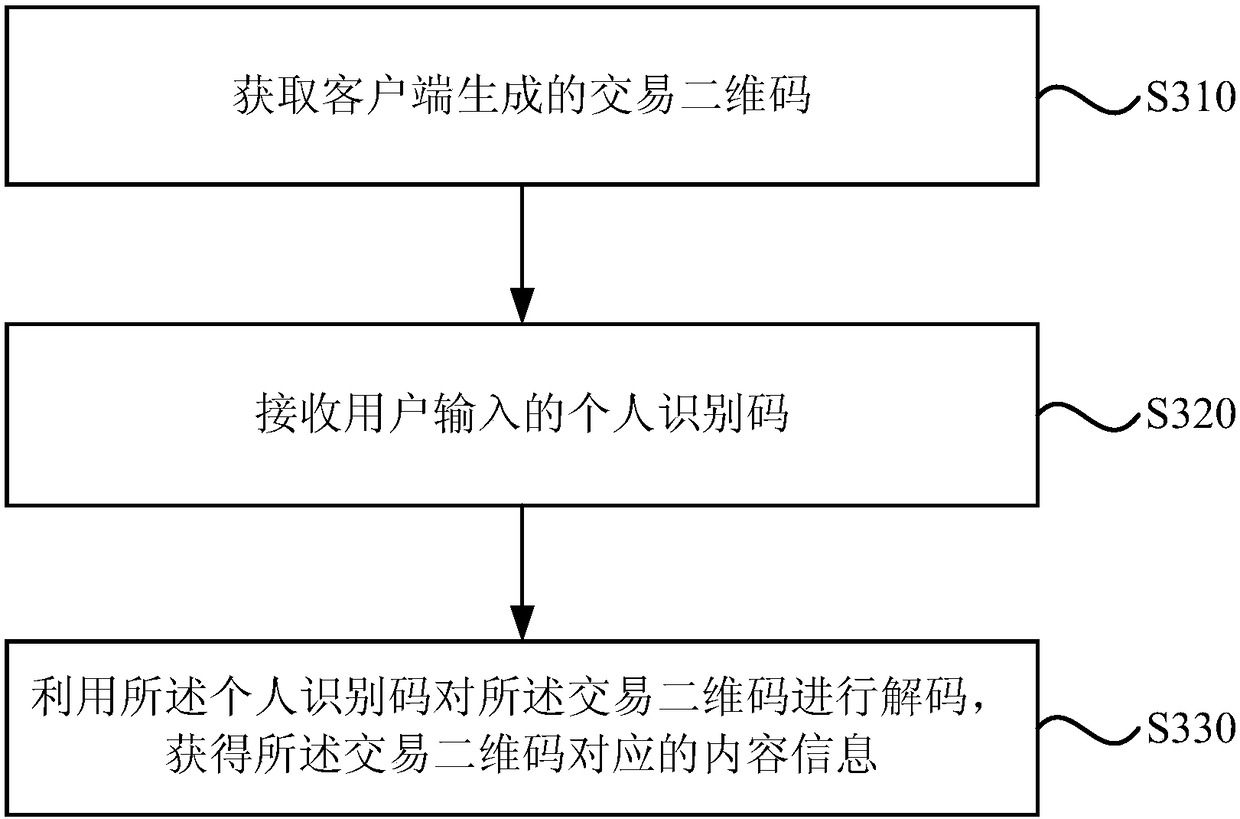
InactiveCN108268921ASafety of tradementSolve the problem of being easily exploited by illegal copyingPayment protocolsRecord carriers used with machinesComputer hardwarePersonal identification number
The embodiment of the invention discloses a two-dimensional code generation method, a two-dimensional code decoding method, a two-dimensional code generation device, a two-dimensional code decoding device, a transaction system and a storage medium. The two-dimensional code generation method includes the following steps that: the content information of a two-dimensional code to be generated and a personal identification code are determined; and a transaction two-dimensional code is generated on the basis of the content information and the personal identification code, so that a transaction device can perform code two-dimensional code decoding on the basis of the personal identification code. With the above technical schemes of the invention adopted, a manual link is added into a two-dimensional code transaction process, and therefore, the anti-counterfeiting, anti-copying and anti-tampering of the two-dimensional code can be realized, the problem that a two-dimensional code is easily copied and utilized illegally in a two-dimensional code-based transaction process can be solved, the illegal use of a generated two-dimensional code is effectively avoided, and two-dimensional code-based transactions can be safer.
Owner:SHANGHAI PEOPLENET SECURITY TECH
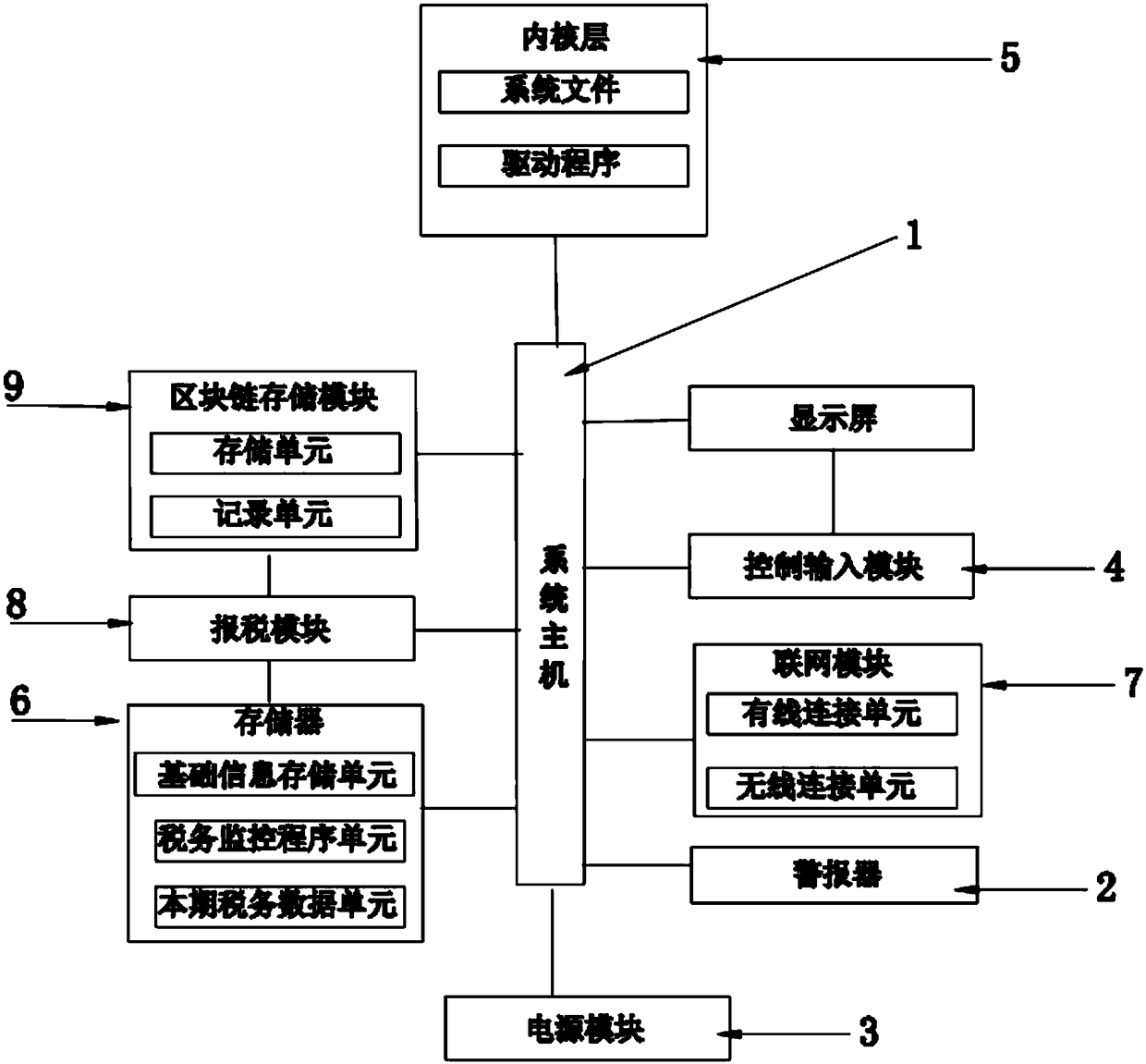
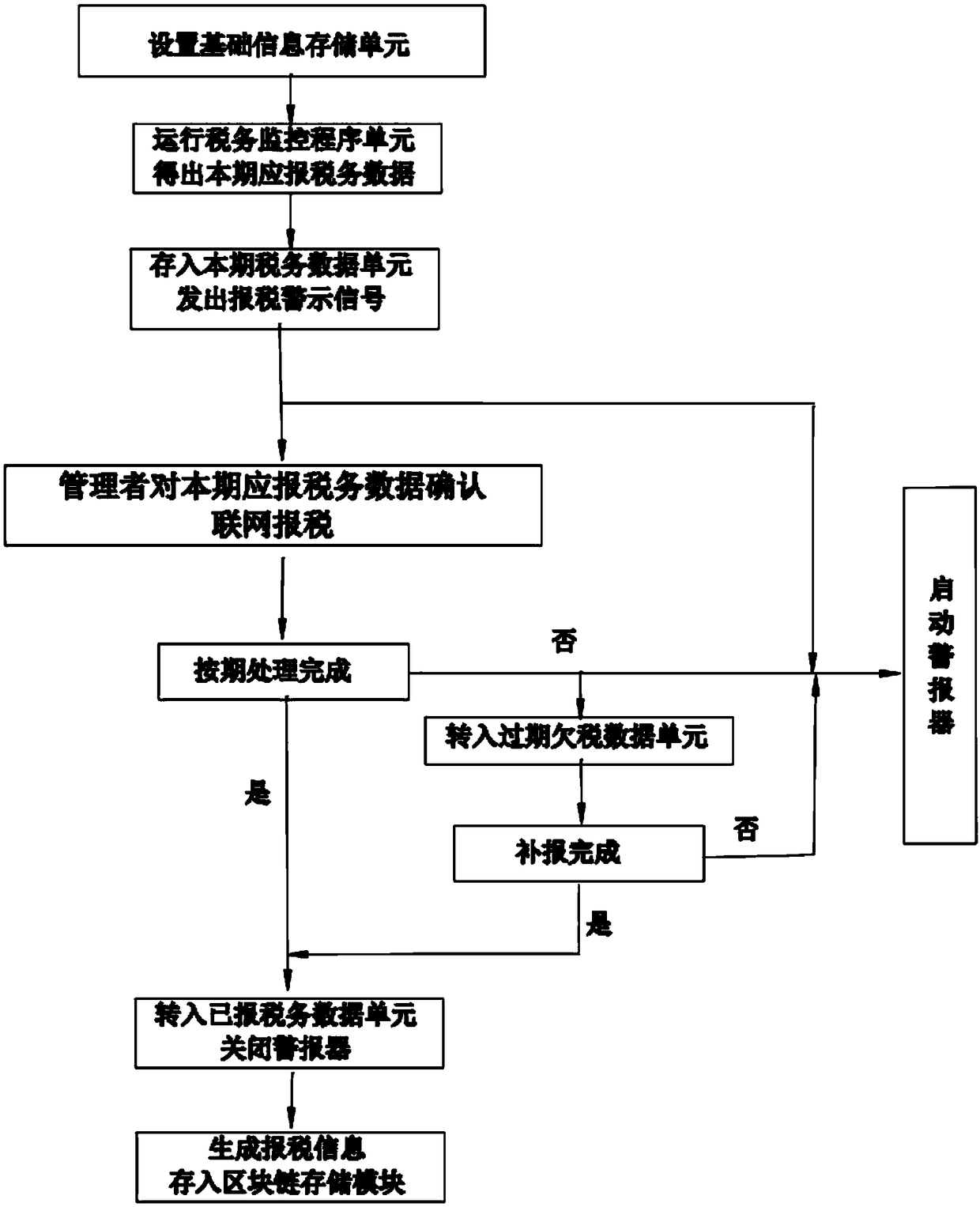
A tax monitor system and monitoring method
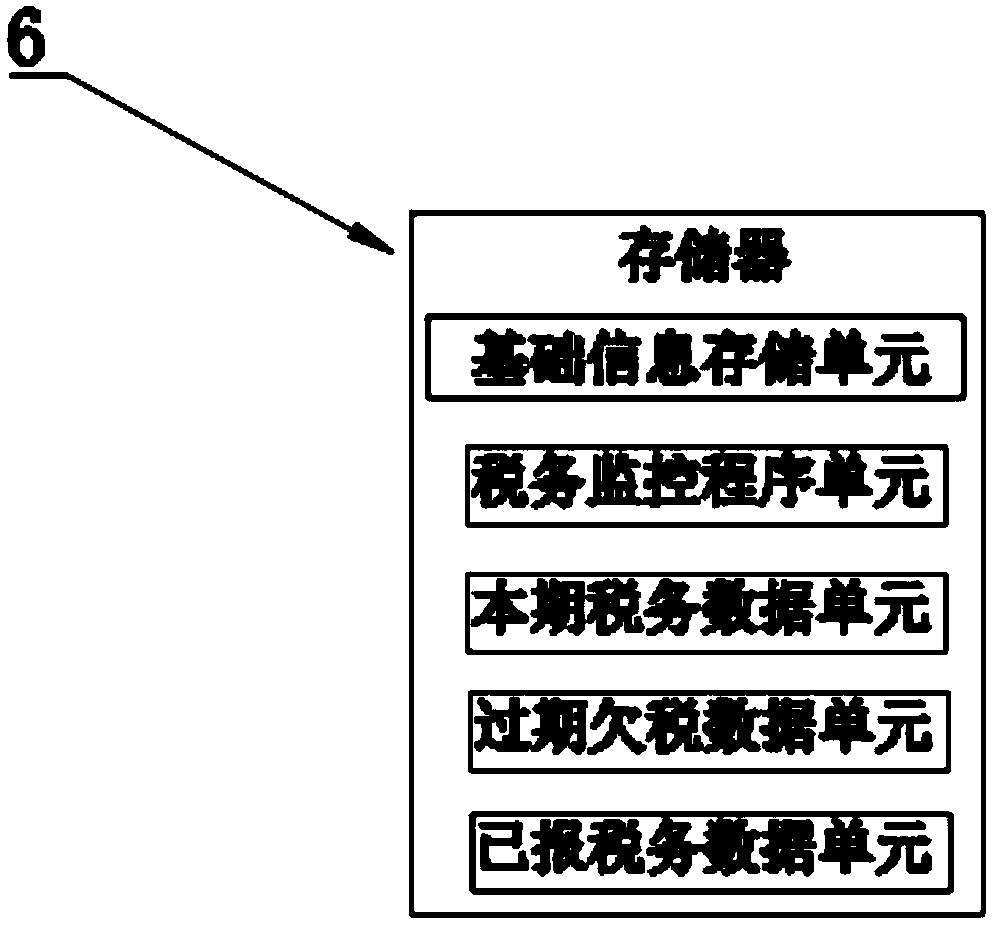
The invention discloses a tax monitoring system and a monitoring method. The system includes a system host, an alarm, a power module, a control input module, a kernel layer, a networking module, a taxdeclaration module and a block chain storage module, the memory includes a basic information storage unit, a tax Data Unit and a Tax Monitoring Procedure Unit for the current period, the system hostruns the tax monitor, reads the basic information from the basic information storage unit to perform calculations, obtains the tax data of the current period and stores them in the tax data unit of the current period and activating the alarm to send out the tax declaration warning signal, the manager operation control input module confirms or modifies the tax data to be reported in the current period. After confirmation, the system mainframe controls the operation of the tax declaration module, starts the tax declaration operation, and stores the tax declaration information in the block chainstorage module after the tax declaration is completed. The tax monitoring system or the tax monitoring method of the invention is simple in operation and high in efficiency, can reduce or reduce the behavior of the enterprise violating the tax law, and can reduce the economic loss and the bad influence caused by the tax problems of the enterprise.
Owner:东莞市恒邦企业服务有限公司
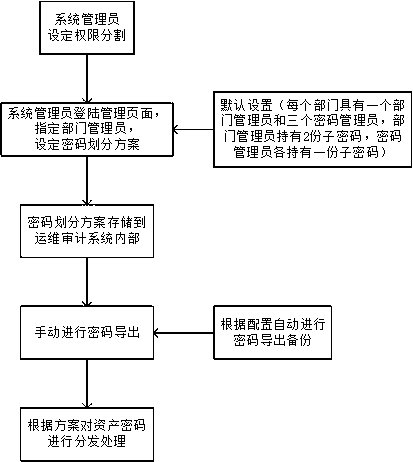
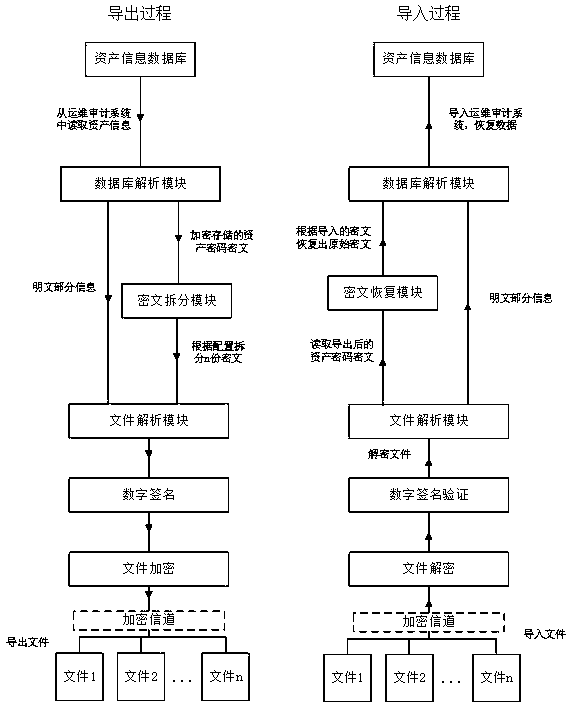
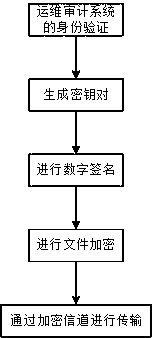
Asset password exporting method used for operation and maintenance audit system
ActiveCN109302400ARealize security protectionFix security issuesUser identity/authority verificationTamper resistancePlaintext
The invention discloses an asset password exporting method used for an operation and maintenance audit system. A password sharing module matches a divided sub ciphertext with information of a plaintext part and transmits into a file parsing module as one record, and the file parsing module encapsulates data and outputs n different password export files; hash values of generated file additional user names are taken, and a key pair generated for each user is digitally signed; according to preset authority segmentation, the file is distributed for each user, and the file of each user is reversibly encrypted by using a login password of the user; and the file is transmitted to a host of the corresponding user by using an encrypted channel. The method disclosed by the invention realizes safetyprotection on the export files. The method disclosed by the invention performs distribution management on the export files and realizes the authority segmentation of asset information export. By virtue of a digital signature mechanism, source traceability and tamper-proofing are realized. Safety during backup of asset information is guaranteed, and an attacker possibly existing in an intranet is effectively resisted.
Owner:CHENGDU DBAPP SECURITY
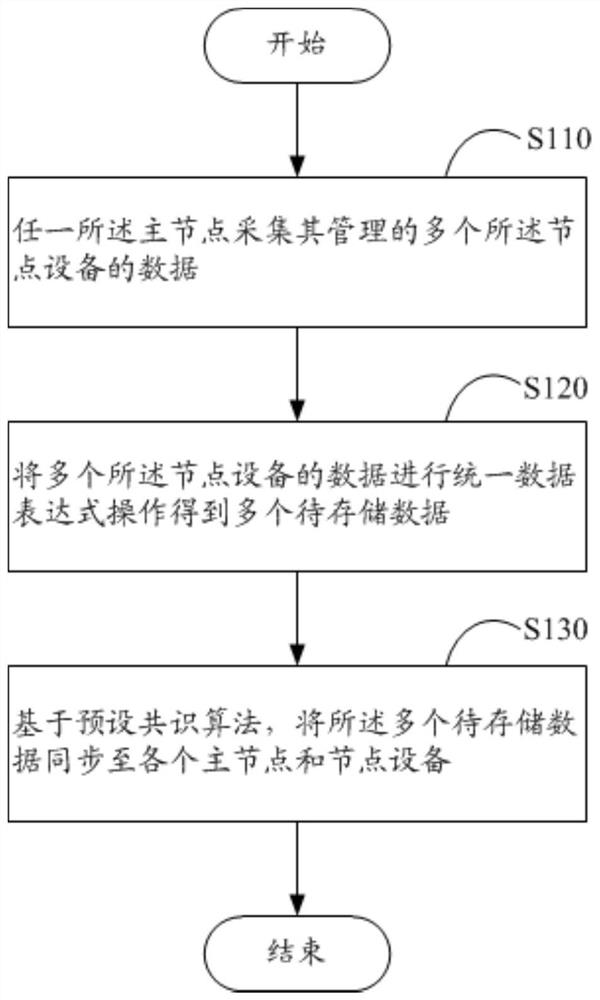
Internet-of-Things data storage method based on blockchain and Internet-of-Things system
PendingCN112003925AAchieve sharingAchieve synchronizationSecuring communicationData synchronizationTamper resistance
The invention discloses an Interne-of-Things data storage method based on a blockchain and an Interne-of-Things system. The Internet of Things at least comprises two main nodes in communication connection with each other, and each main node manages a plurality of sets of node equipment in communication connection with the main nodes. The Interne-of-Things data storage method based on the blockchain comprises the steps of: collecting data, by means of an arbitrary main node, of the plurality of sets of node equipment managed by the main node; performing unified data expression operation on thedata of the plurality of sets of node equipment to obtain a plurality of pieces of to-be-stored data; and based on a preset consensus algorithm, synchronizing the plurality of pieces of to-be-stored data to each main node and node equipment. According to the Internet-of-Things data storage method based on the blockchain and the Internet-of-Things system of the invention, the blockchain is adoptedto realize sharing and synchronization of the Interne-of-Things equipment data. Due to the fact that the blockchain has tamper resistance, the Interne-of-Things data written into the blockchain cannotbe maliciously forged or modified, and distributed storage, tamper resistance or loss of the Interne-of-Things data are achieved.
Owner:上海和数软件有限公司
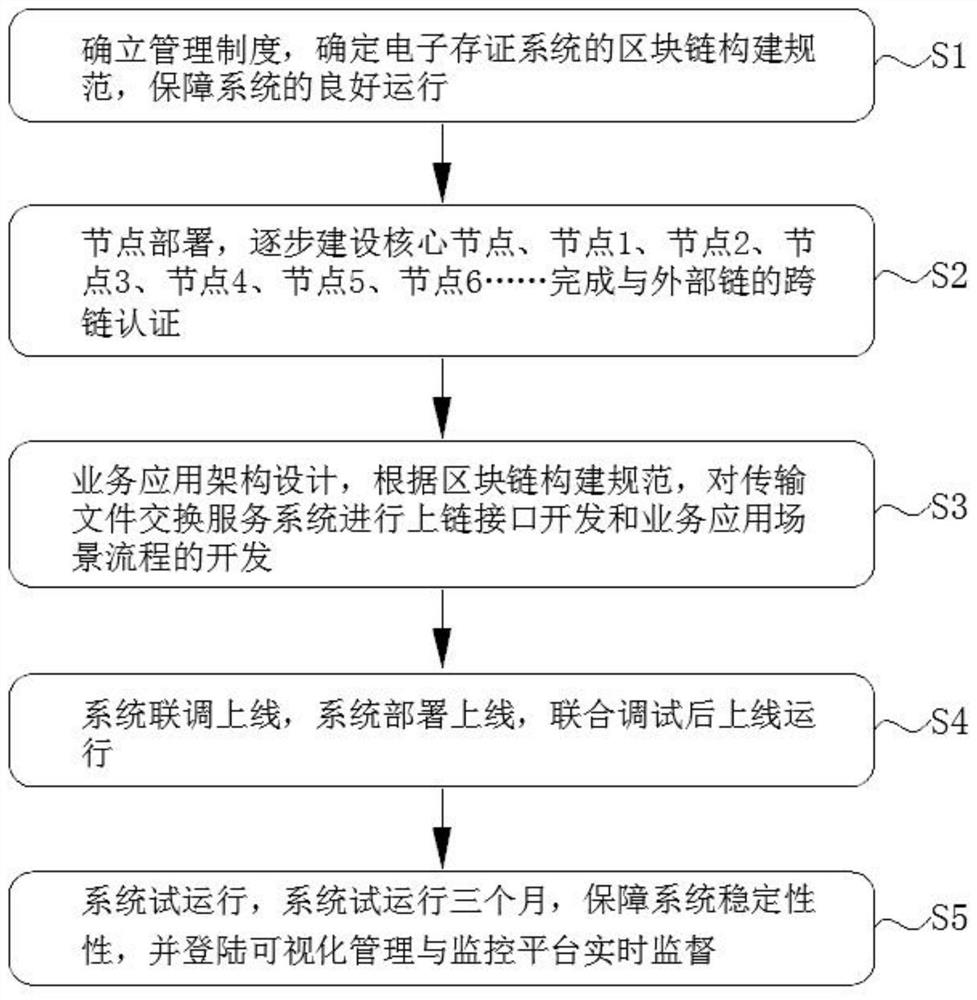
Electronic evidence storage system and operation method
InactiveCN113393240AAchieve tamper resistanceAchieving non-repudiationDatabase distribution/replicationDigital data protectionResource poolData exchange
The invention relates to the technical field of information management, and discloses an electronic evidence storage system and an operation method of the electronic evidence storage system. The system comprises a block chain, a transmission file exchange service system used for data exchange, and a visual management and monitoring platform used for carrying out data exchange supervision and management on the transmission file exchange service system, all departments establish a shared data resource pool, resources in the pool are subjected to evidence storage supervision through the block chain, safety and credibility are guaranteed, all resource pool data are maintained and utilized jointly based on the block chain, so that data security sharing among all units of the cross-department is realized, authenticity and credibility of case materials in the cross-department circulation process are ensured by utilizing the block chain technology, tampering prevention, repudiation prevention and abuse right prevention of the case materials are realized, and meanwhile, a case handling department can be promoted to carry out work according to laws, and law enforcement is standardized.
Owner:海南海锐众创科技有限公司
Cross-system electronic document secure exchange and sharing method
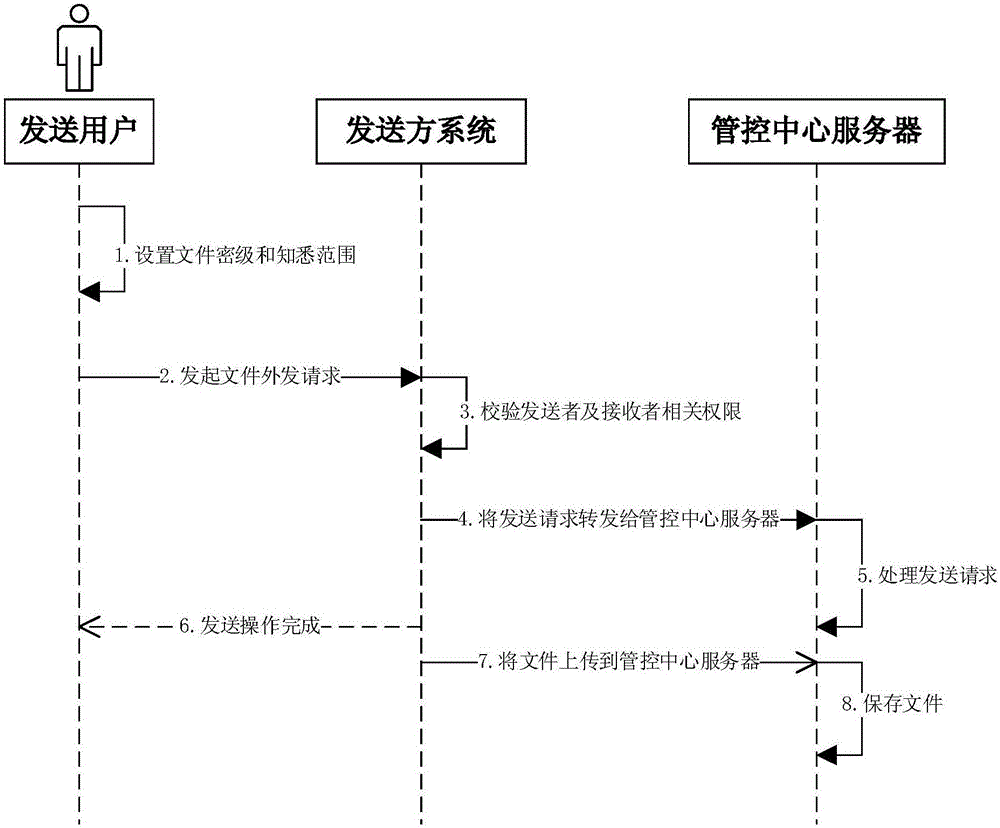
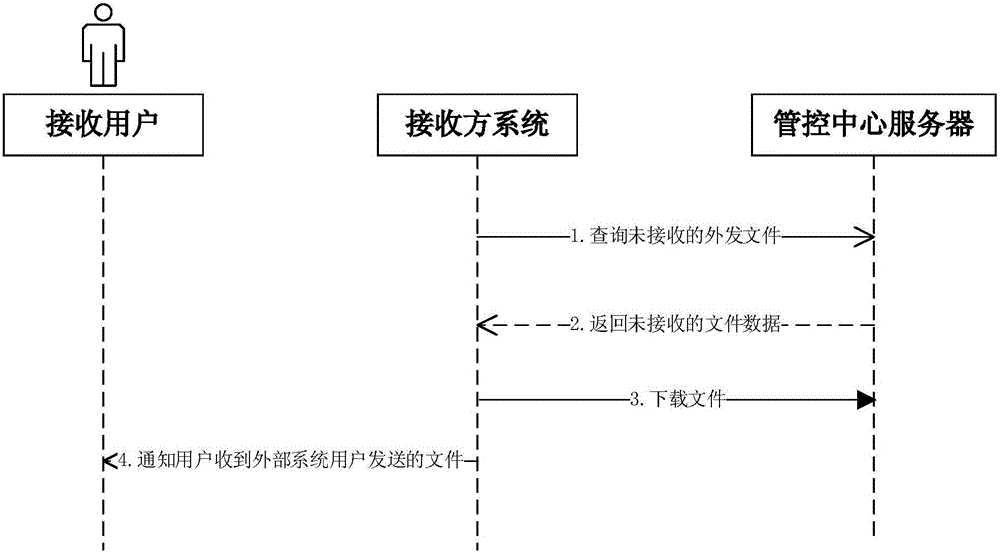
InactiveCN106778302AAchieve inseparability and tamper-proofPrevent high density and low flowDigital data protectionTransmissionClient-sideSystem service
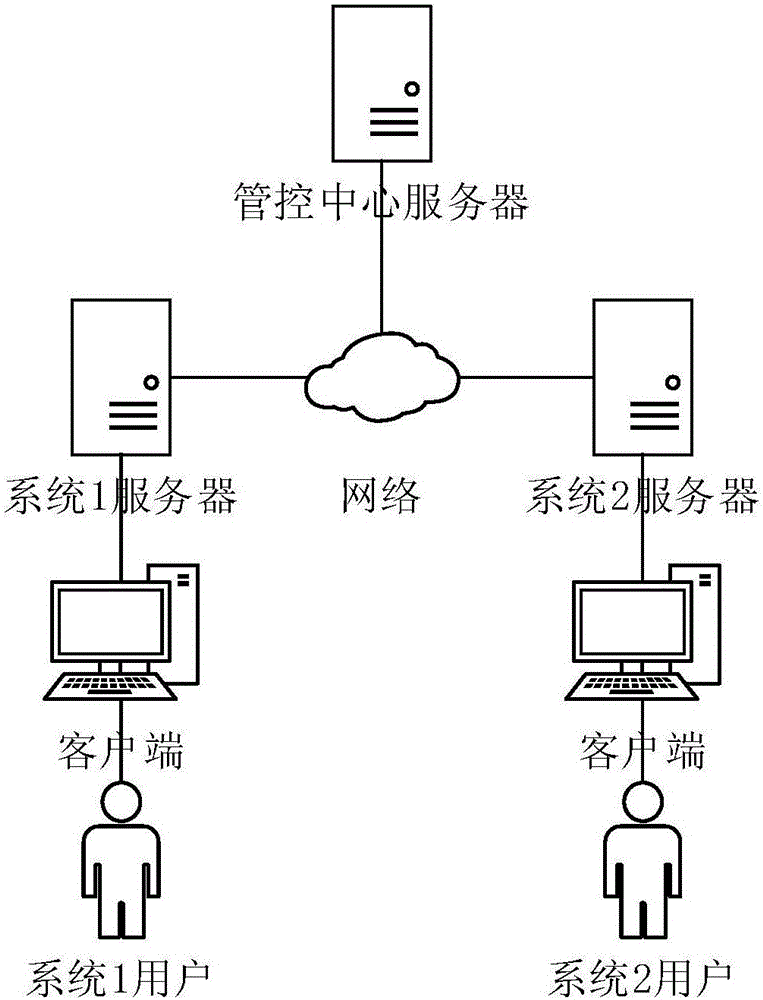
The invention discloses a cross-system electronic document secure exchange and sharing method, and belongs to the technical field of information security and computer software. The method includes the steps that firstly, a sender system user puts forwards a sending request for sending an electronic document to other systems at a client to a local system server side; secondly, after a sender system server completes security detection, the request is transmitted to a management and control center server, and the electronic document is uploaded to the management and control center server; thirdly, the management and control center server receives the request and saves the electronic document; fourthly, a receiver system server issues a request to the management and control center server to inquire the electronic document sent to a receiver system user by a sender system; fifthly, a receiver system downloads the electronic documents from a management and control center and informs the receiver system user. The method can be used for cross-system electronic document exchange and sharing.
Owner:AVICIT CO LTD
Food label unique code publishing and circulation tracing method based on blockchain main and auxiliary chain technology
InactiveCN111401927AAnti-counterfeitingAchieve tamper resistanceDatabase distribution/replicationDigital data protectionTimestampThe Internet
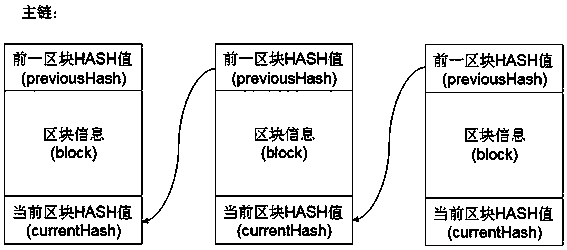
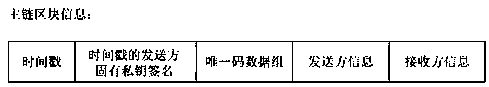
The invention discloses a food label unique code publishing and circulation tracing method based on a blockchain main and auxiliary chain technology. The method comprises the steps: employing the commodity label unique code information blockchain technology based on public and private key pairing verification; enabling a front-stage production enterprise and a rear-stage production enterprise or asales enterprise for producing a certain piece of food in a circulation chain to link unique code information blocks of food labels into a secondary chain through a private key and public key pairedverification method, and adding the auxiliary chain and the timestamp into the main chain as block information, so the counterfeiting prevention, tampering prevention and replay prevention of the mainchain and the auxiliary chain information are realized, and network propagation of the unique code of the food label and independent chaining and rapid tracing of single food information can be realized, wherein users comprise a third-party mechanism, manufacturers at all levels, dealers and consumers which are connected with the Internet respectively; the server databases of the third-party mechanism, manufacturers and dealers at all levels are used for storing food label information blockchain account books, receiving new legal verification data issued by other parties in real time, updating local account books in time, hooking new data blocks according to food transfer conditions, and issuing new blockchain data; and enabling a consumer to obtain the latest timestamp blockchain from aplurality of enterprise servers during code scanning, and performing calculation to obtain the food traceability information chain by comparing the latest timestamp blockchain.
Owner:綦昱钧
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com