Security chip based on PUF and zero knowledge proof, application method, system and medium
A zero-knowledge proof and security chip technology, which is applied in the field of security chips based on PUF (Physically Unreproducible Function) and zero-knowledge proof, can solve the problem of not meeting the security certification requirements of the Internet of Things environment, the long time required for certification, and the increased Big security risks and other issues, to achieve the effect of simple and efficient authentication process, fast authentication speed, and simple interface
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
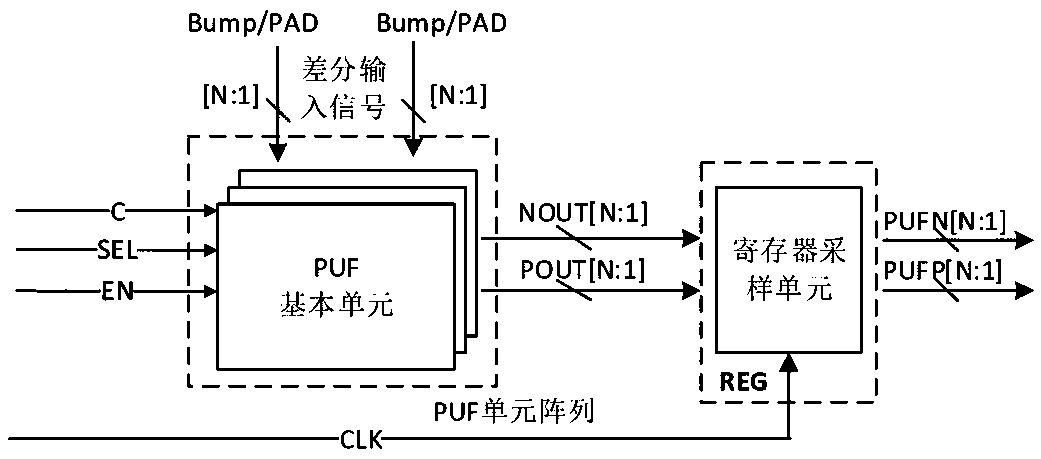
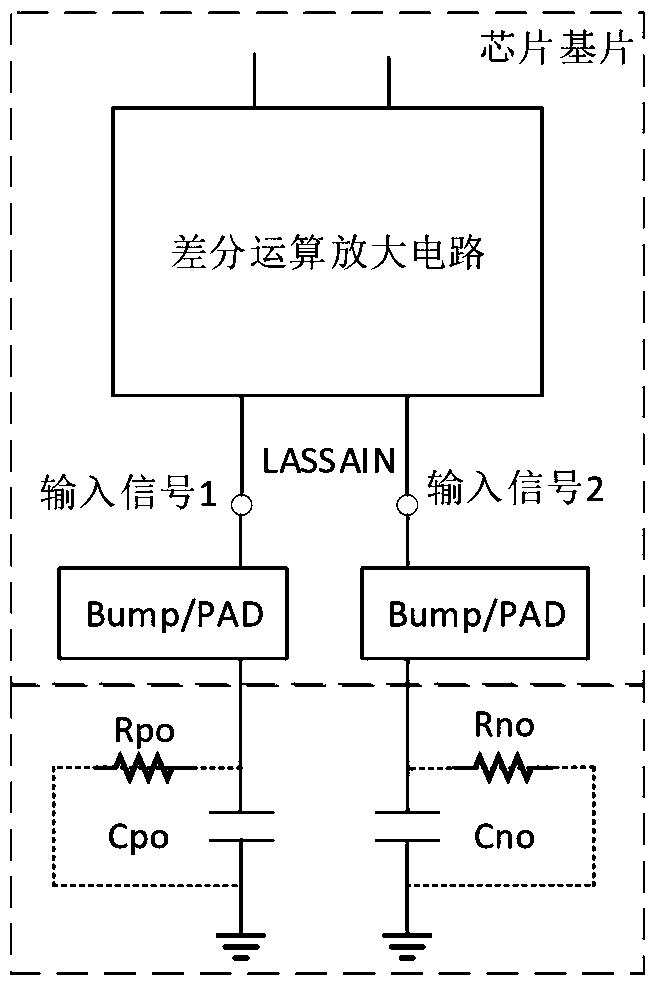
Image
Examples
Embodiment approach
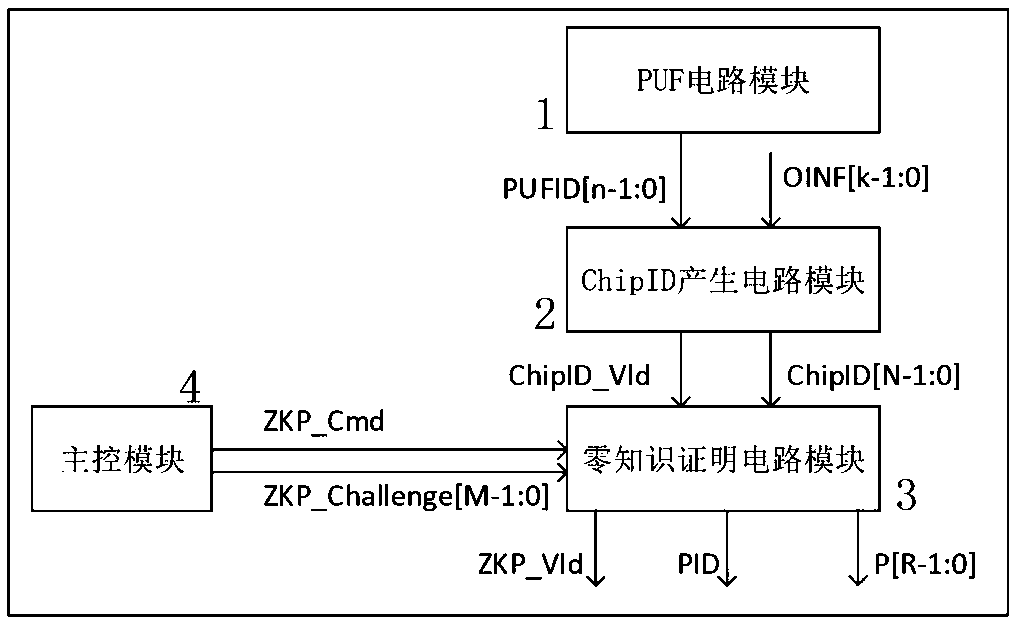
[0078] In this embodiment, the function expression of the first execution circuit to generate a publicly available zero-knowledge identification number PID according to the ChipID is shown in formula (1):
[0079] PID = ModMult(ChipID, ChipID, Z) (1)
[0080]Among them, PID represents a publicly available zero-knowledge identification number, ChipID is a unique chip ID, Z is a specified large integer, and ModMult(ChipID, ChipID, Z) represents the result of multiplying ChipID and ChipID to take the modulus of the large integer Z. The function expression of the ID number generated by the GEN_PID command for zero-knowledge identification is shown in formula (1): the first execution circuit squares the value of ChiID and takes the modulus of the large number Z, where Z is a large integer. In order to achieve sufficient security, The number of bits of Z needs to reach 1024 bits; PID is a publicly available zero-knowledge identification number. Due to the difficulty of factoring lar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com