Patents
Literature
52results about How to "Avoid the authentication process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Authentication method, system, authentication server and terminal equipment
ActiveCN101867929AImprove securityAvoid the authentication processSecurity arrangementWeb authenticationRequest for information
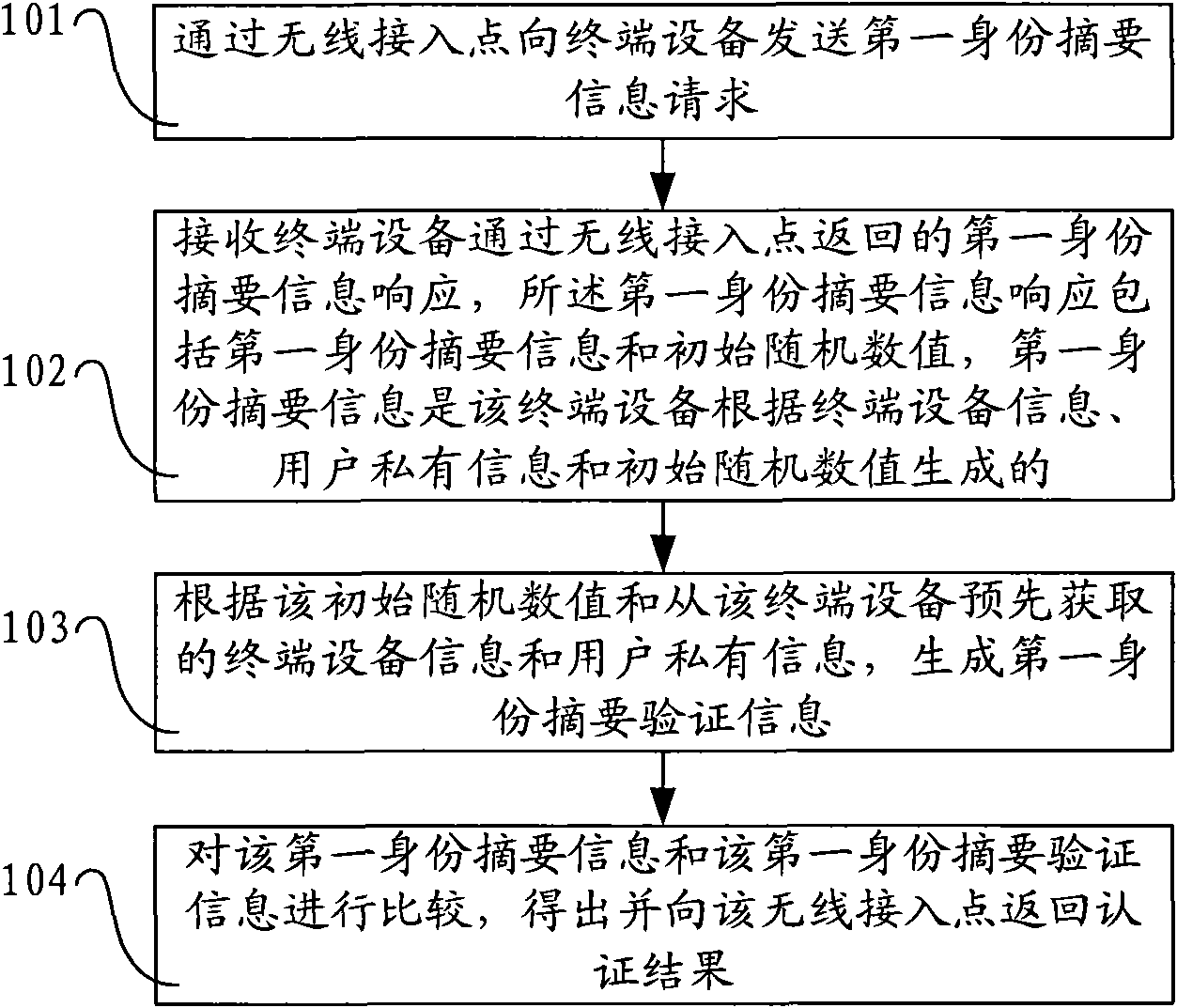
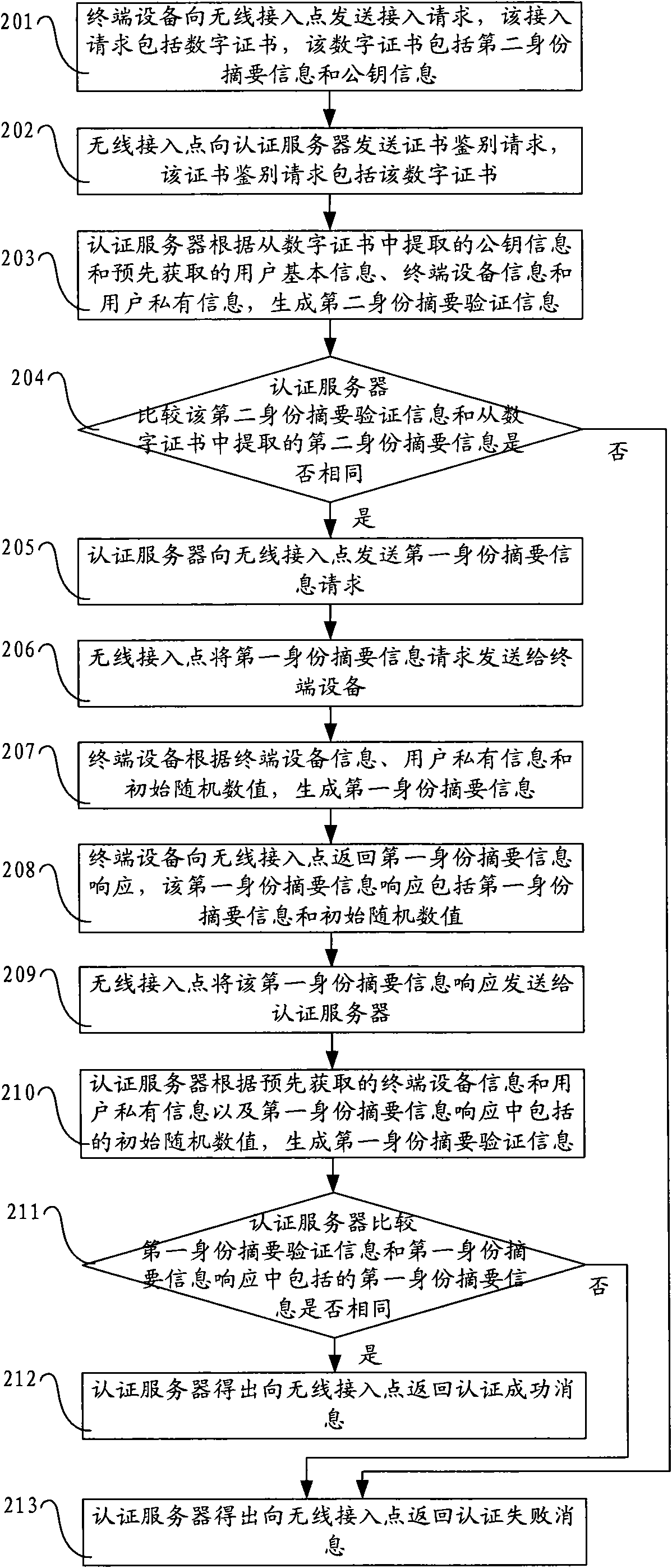
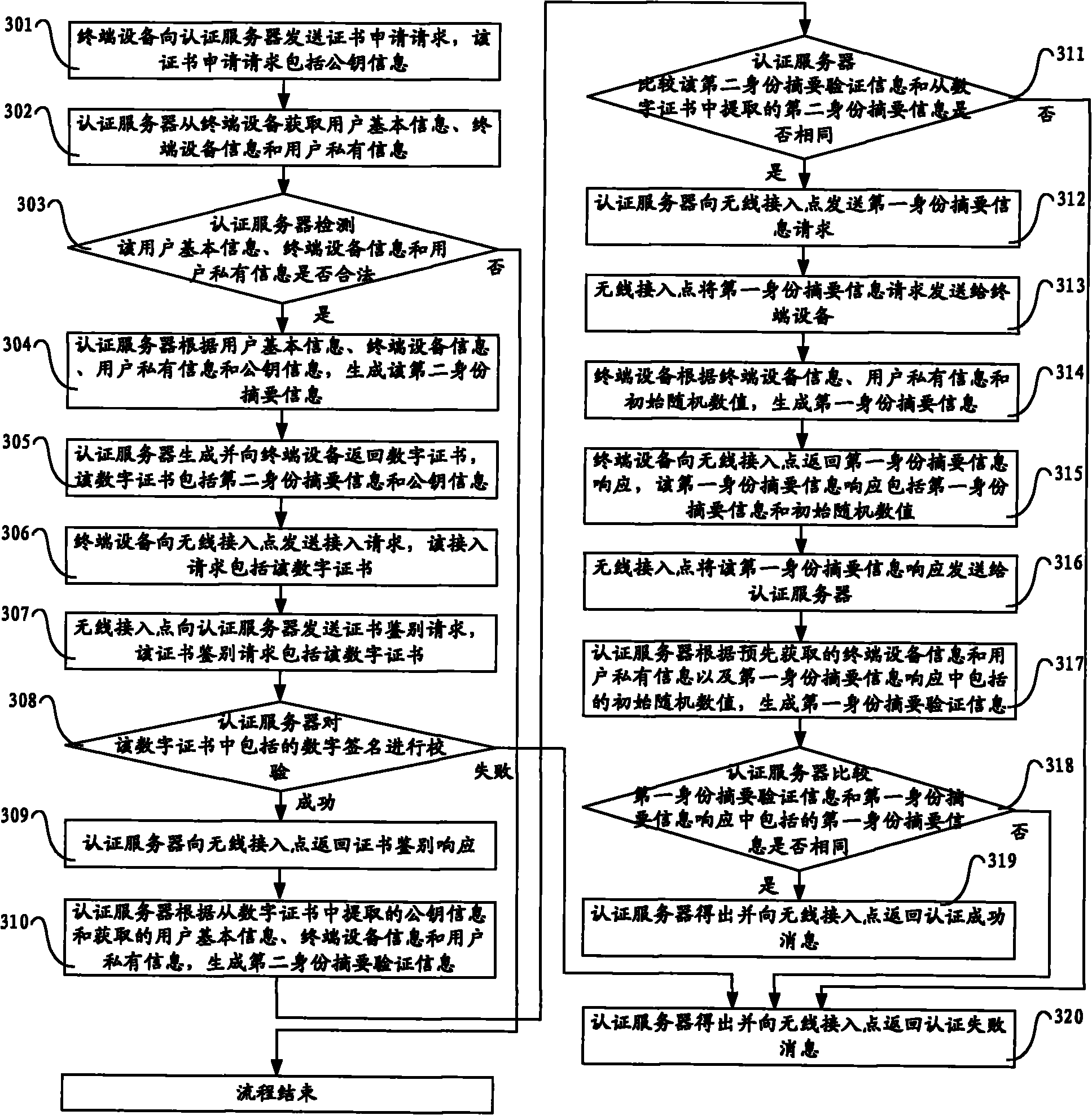
The invention discloses an authentication method, a system, an authentication server and terminal equipment. The method comprises the following steps: sending a first identity abstract information request to the terminal equipment through a wireless access point; receiving the first identity abstract information response returned by the terminal equipment through the wireless access point, wherein the first identity abstract information response comprises first identity abstract information and initial random values, and the first identity abstract information is generated by the terminal equipment according to the terminal equipment information, user private information and the initial random values; generating first identity abstract verification information according to the initial random values, the terminal equipment information obtained in advance from the terminal equipment and the user private information; and comparing the first identity abstract information and the first identity abstract verification information to obtain authentication results, and returning the authentication results to the wireless access point. The technical scheme of the embodiment of the inventionimproves the safety of the network authentication.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Identity authentication method based on face and authentication apparatus thereof
ActiveCN102375970AAvoid the authentication processImprove authentication capabilitiesCharacter and pattern recognitionFace detectionStatistical analysis
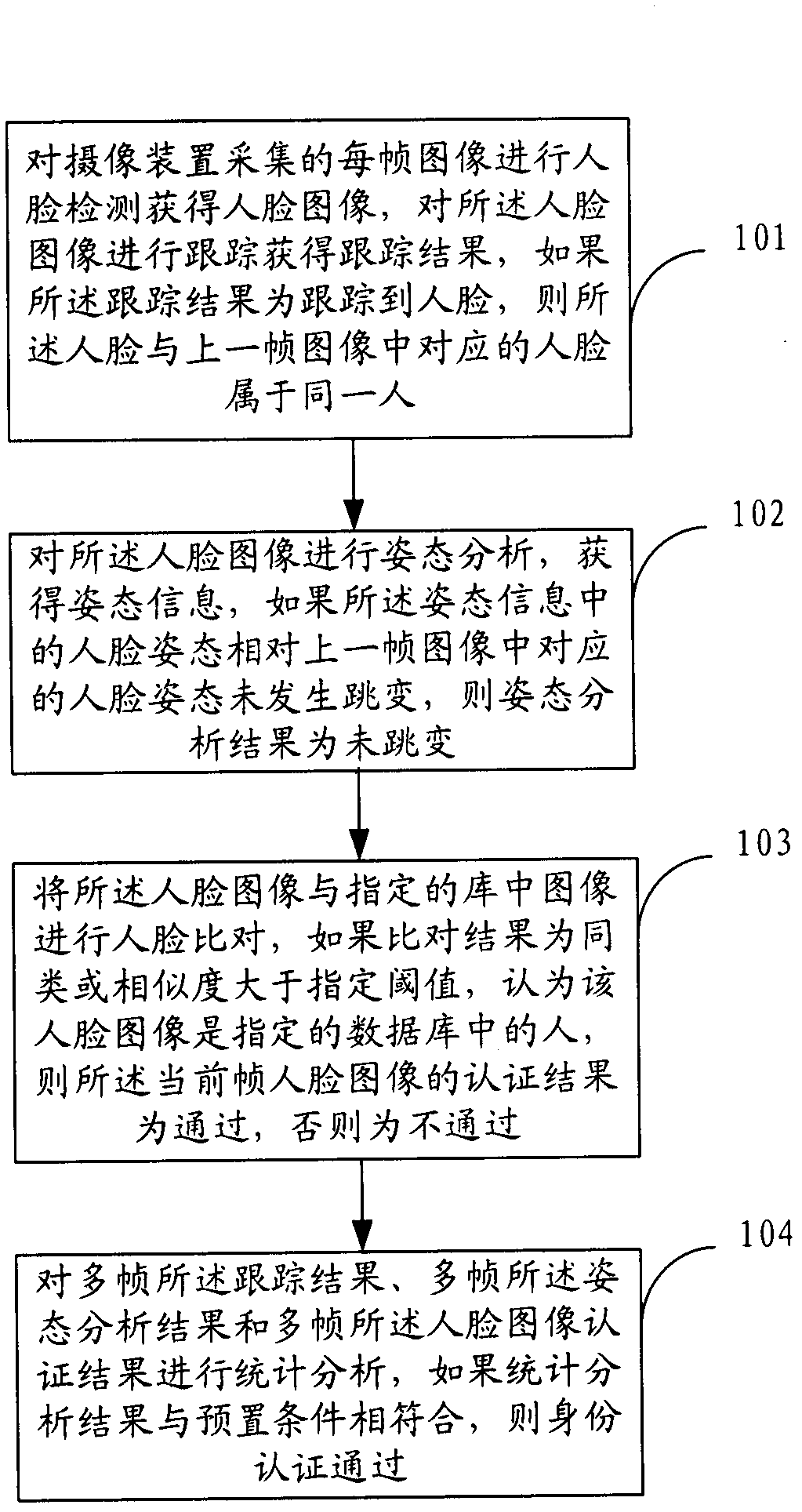
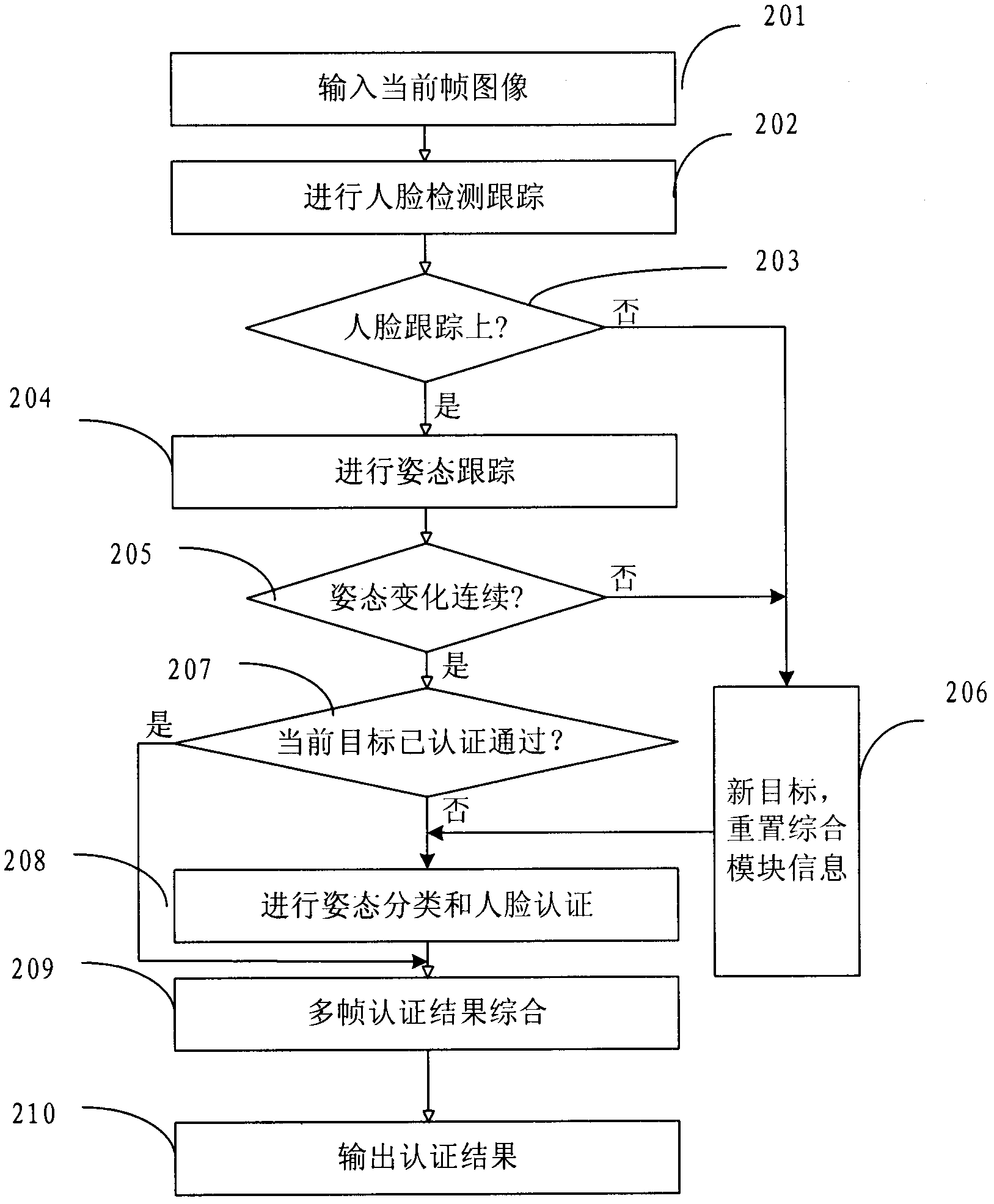
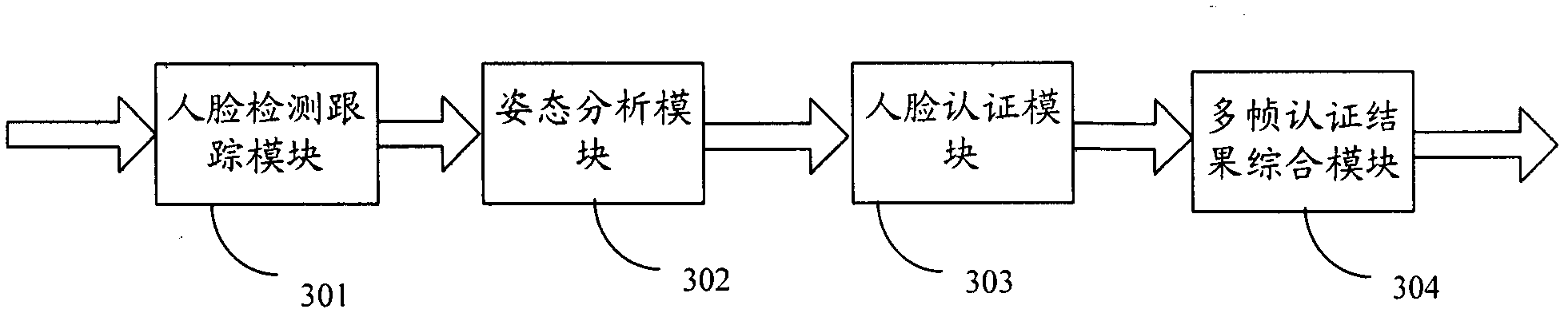
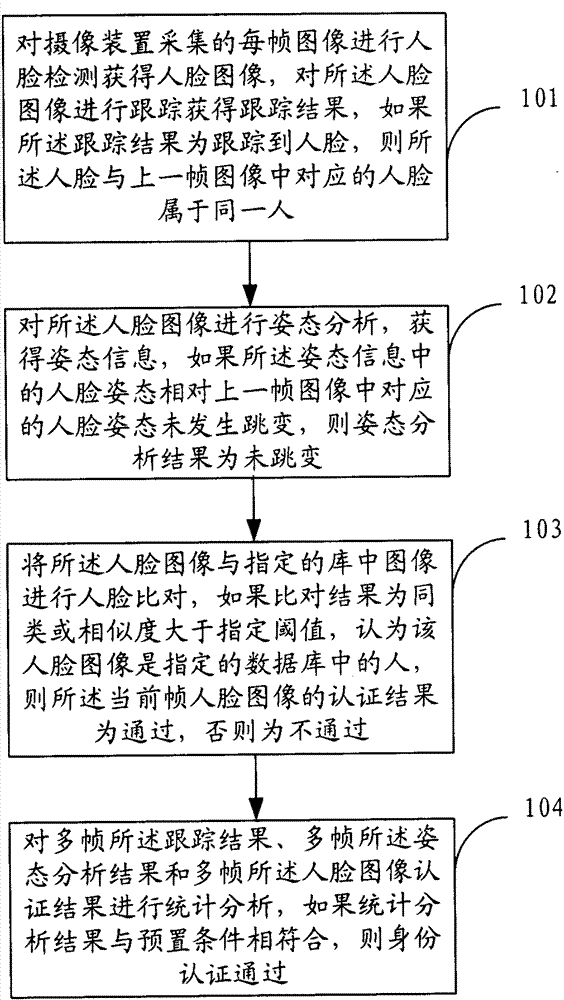
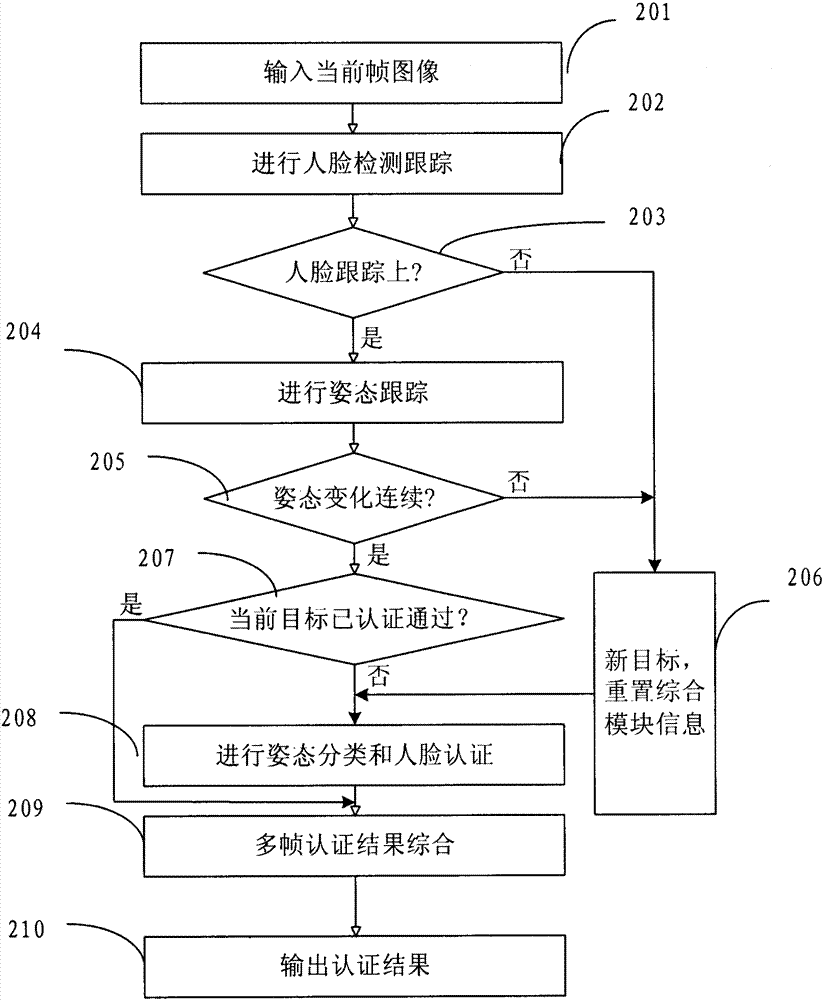
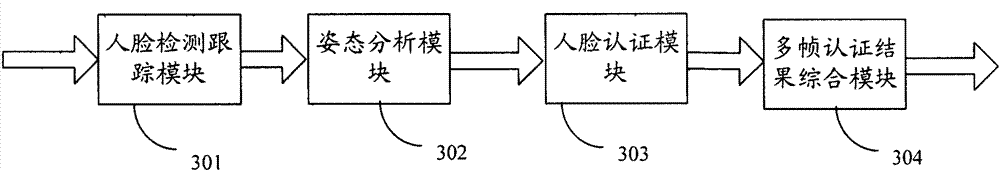
The invention provides an identity authentication method based on a face and an authentication apparatus thereof. The method comprises the following steps: carrying out face detection on each frame of image acquired by a camera device to obtain a face image, and tracking the face image to obtain a tracking result; carrying out an attitude analysis, wherein if a face attitude in obtained attitude information is not jumped relative to a face attitude corresponding to a prior frame of image, an attitude analysis result is not jumped; carrying out face comparison; carrying out statistics analysis on a plurality of frames of tracking results, a plurality of frames of attitude analysis results and a plurality of frames of face image authentication results, wherein if a statistics analysis result is in accordance with a preset condition, identity authentication is passed. According to the method and the apparatus thereof in the invention, a two-dimensional flat picture is utilized to distinguish a photograph from a human, in the prior art utilizing three-dimensional information and carrying out photograph identification cause that a system identification speed is substantially decreased and an application requirement can not satisfied, and the above technical problem is solved in the invention.
Owner:GUANGDONG VIMICRO
System and method for preventing fraud of certification information, and recording medium storing program for preventing fraud of certification information
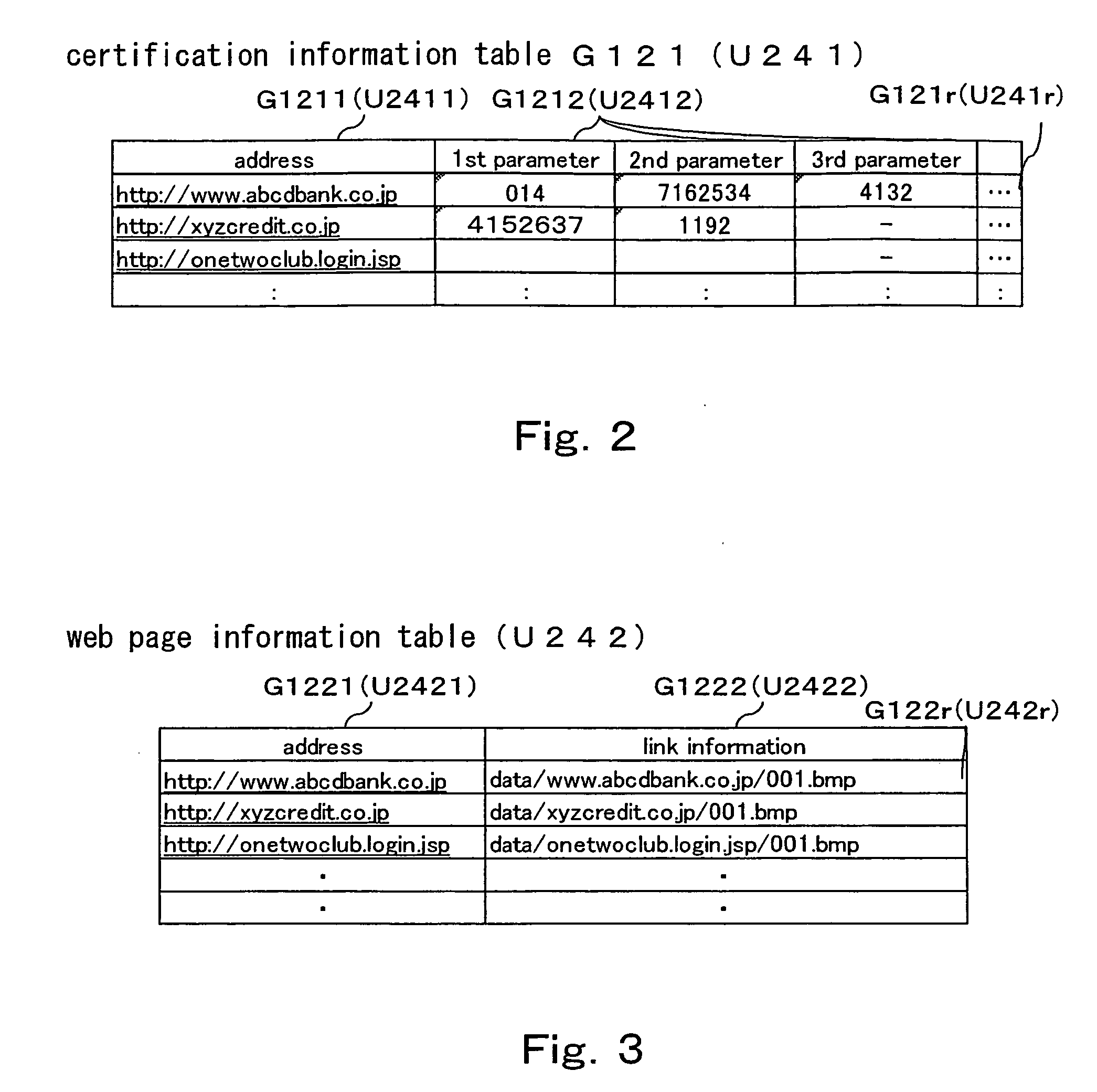
InactiveUS20060179315A1Prevent fraudAvoid the authentication processMemory loss protectionUser identity/authority verificationWeb siteWeb storage
A system for preventing fraud of certification information performs a processing step of processing web page data, a first comparing step of comparing the web page data processed in the processing step with web page data stored in a web page storage unit in association with URL of the data, a second comparing step of comparing URLs of the web page data similar to each other when the first comparing step determines that the web page data are similar to each other, and an address attention message adding step of adding an address attention message to the web page data processed in the processing step when the second comparing step determines that the URLs differ. Therefore, a user who is to access a web site can determine whether or not this web site is authentic, and certification information fraud can be prevented beforehand.
Owner:FUJITSU LTD
Certificate-free remote anonymous authentication method based on third party in cloud application
ActiveCN104052608AAchieve anonymityImprove securityUser identity/authority verificationData switching networksNetwork managementService provider
The invention discloses a certificate-free remote anonymous authentication method based on a third party in a cloud application, and the method mainly solves the problem that remote bidirectional authentication in the prior art is poor in safety. The method is achieved through the steps that (1) a network manager M initializes a system; (2) the network manager M conducts identity register on a user U, and issues a system account to the user U; (3) the network manager conducts identity register on a service provider S, and sends part of the identity information of the legitimate user U to the service provider S; (4) the user U sends a service request to the service provider S in an anonymous mode through the system account; (5) the service provider S and the user U conduct bidirectional authentication. According to the method, the requirement for a certificate is omitted, the defects of secret key trusteeship are omitted as well, safety in anonymous bidirectional authentication is improved, and the method can be used for identity authentication when a remote user in a wireless body area network conducts service request.
Owner:XIAN XIDIAN BLOCKCHAIN TECH CO LTD
Cookie information processing method and device in browser
ActiveCN103841188AEasy loginImprove experienceTransmissionSpecial data processing applicationsInformation processingOperational system
The embodiment of the invention discloses a Cookie information processing method and device in a browser. The method includes the following steps that when a website is logged in with an account for the first time, Cookie information after the first successful log-in is obtained; an inner kernel edition of the current browser is inquired; when the inner kernel edition is the first edition, execution of a program sequence at the first offset in an application program network module of an operation system where the browser exists is intercepted, and a correlation relation between the account and the website is obtained; a corresponding relation between the correlation relation and the Cookie information is set up; the Cookie information and the corresponding relation are stored on designated positions respectively. Even if the same website is logged in by multiple accounts, the Cookie information can be used for carrying out automatic log-in. Log-in operation of a user with multiple accounts can be easier and more convenient and user experience is promoted.
Owner:BEIJING QIHOO TECH CO LTD
Method and cloud system for registering cluster control server and node control server
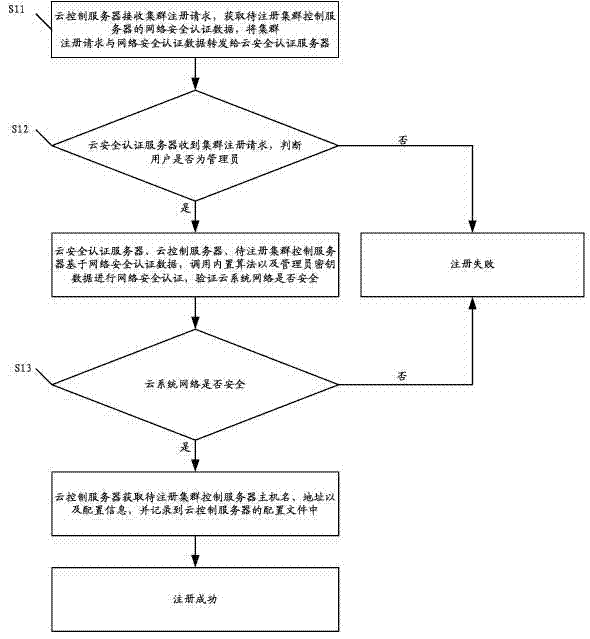
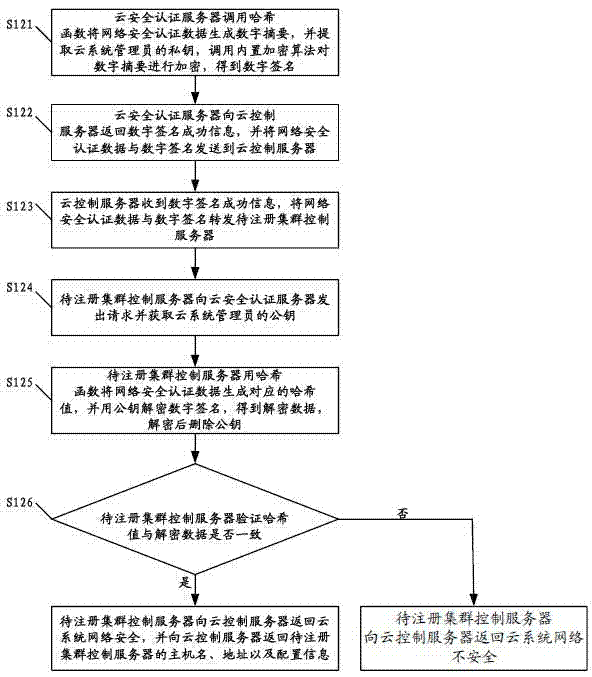
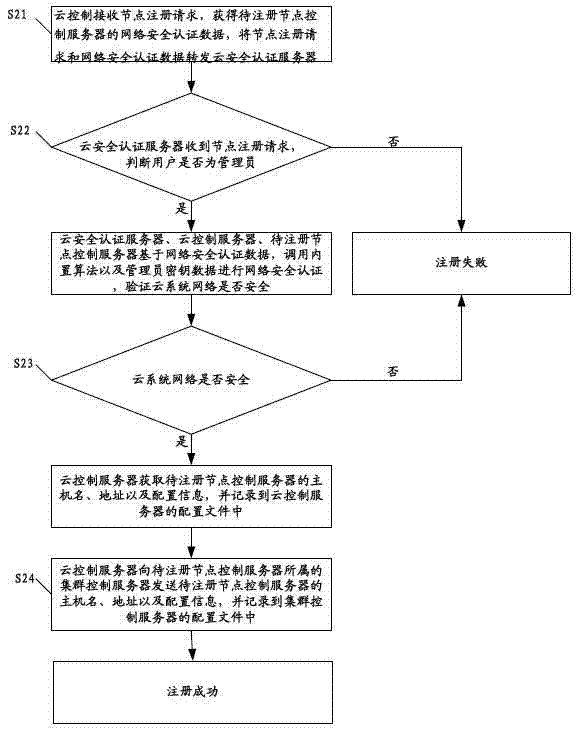
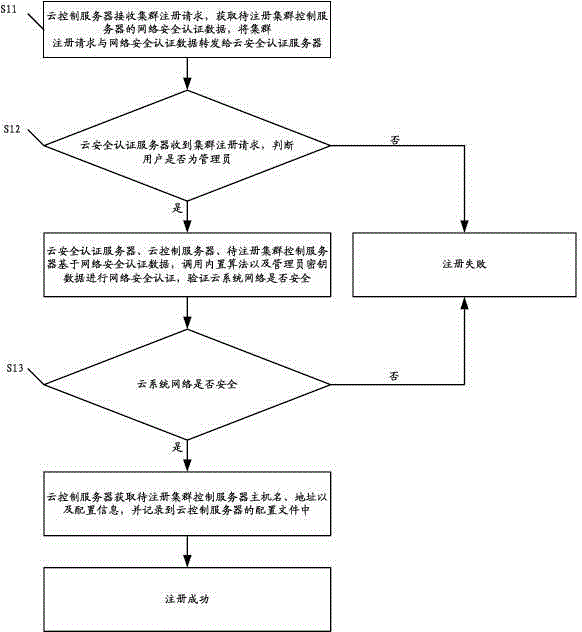
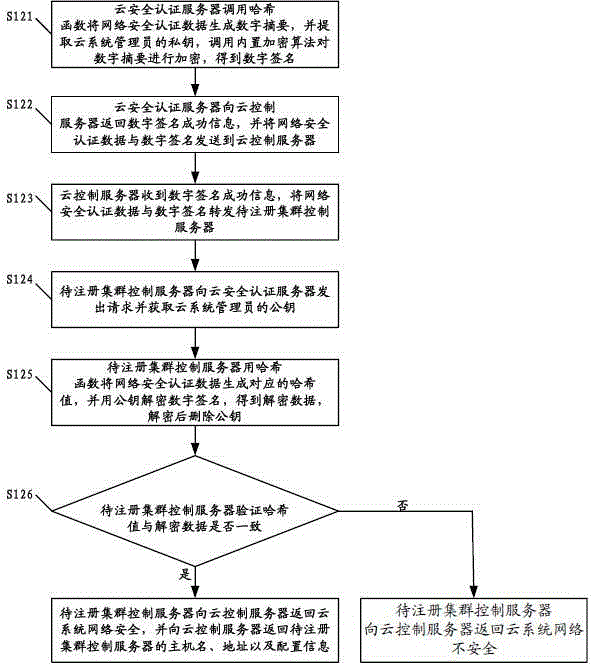
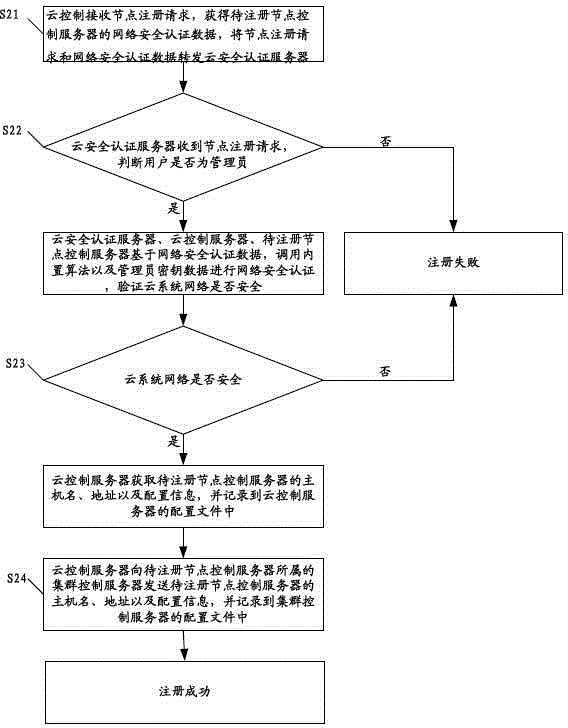
ActiveCN102833256AAvoid the authentication processThe authentication server prevents theTransmissionAuthentication serverSecurity authentication
The invention discloses a method for registering a cluster control server. The method comprises the following steps that a cloud control server receives a cluster registration request, obtains network security authentication data and forwards the cluster registration request and the network security authentication data to a cloud security authentication server; the cloud security authentication server determines whether a user is an administrator, if yes, the cloud security authentication server, the cloud control server and a cluster control server to be registered carry out network security authentication, and whether the cloud system network is safe is verified; if the cloud system network is safe, the cloud control server obtains the host name, the address and the configuration information of the cluster control server to be registered, the host name, the address and the configuration information are recorded into configuration files, and finally the registration is successful; and if else, the registration is failed. The invention also discloses a method and a cloud system for registering a node control server. The embodiment of the invention can increased the security of the registration process for registering the cluster control server and the node control server.
Owner:GCI SCI & TECH
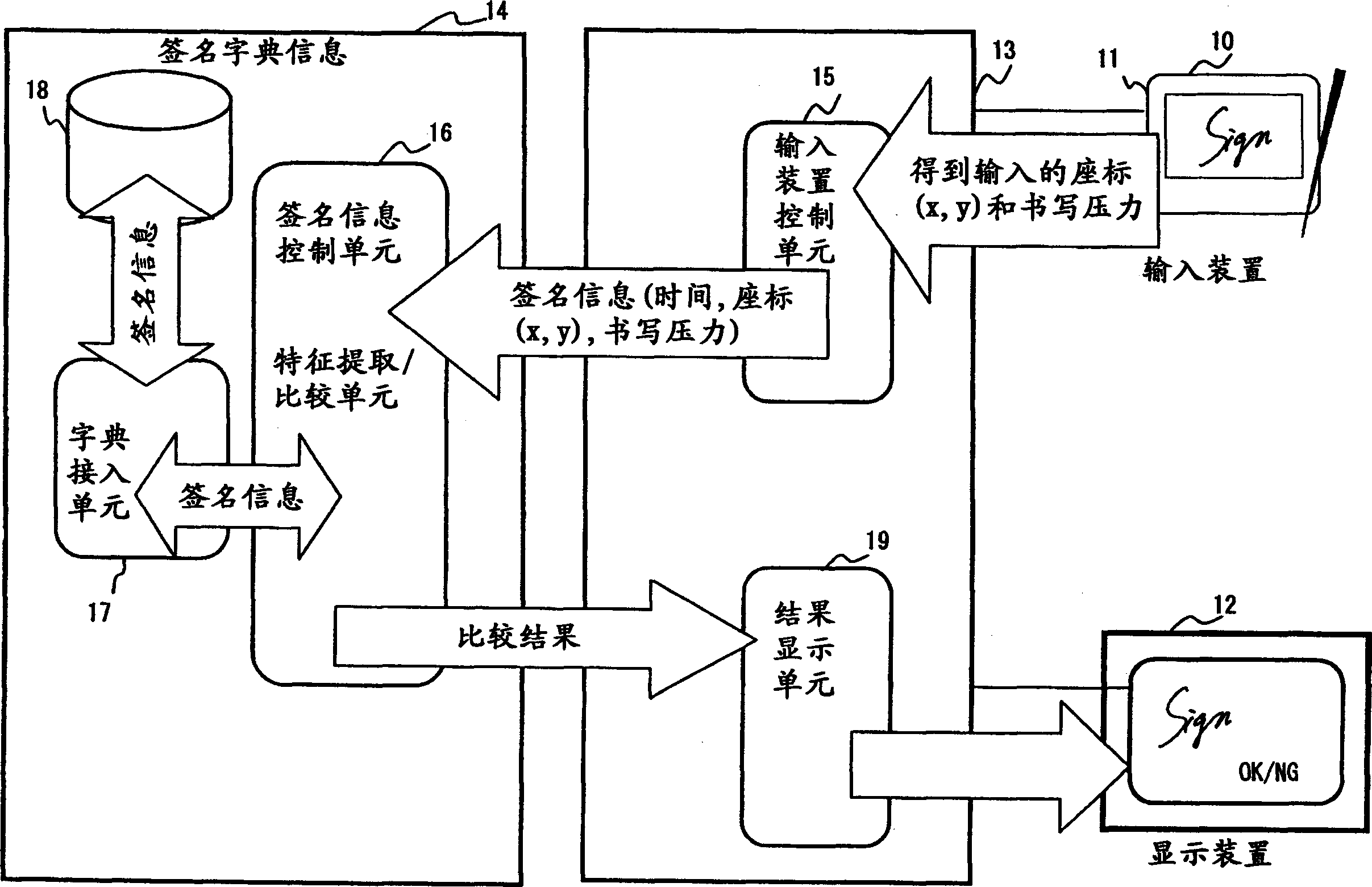
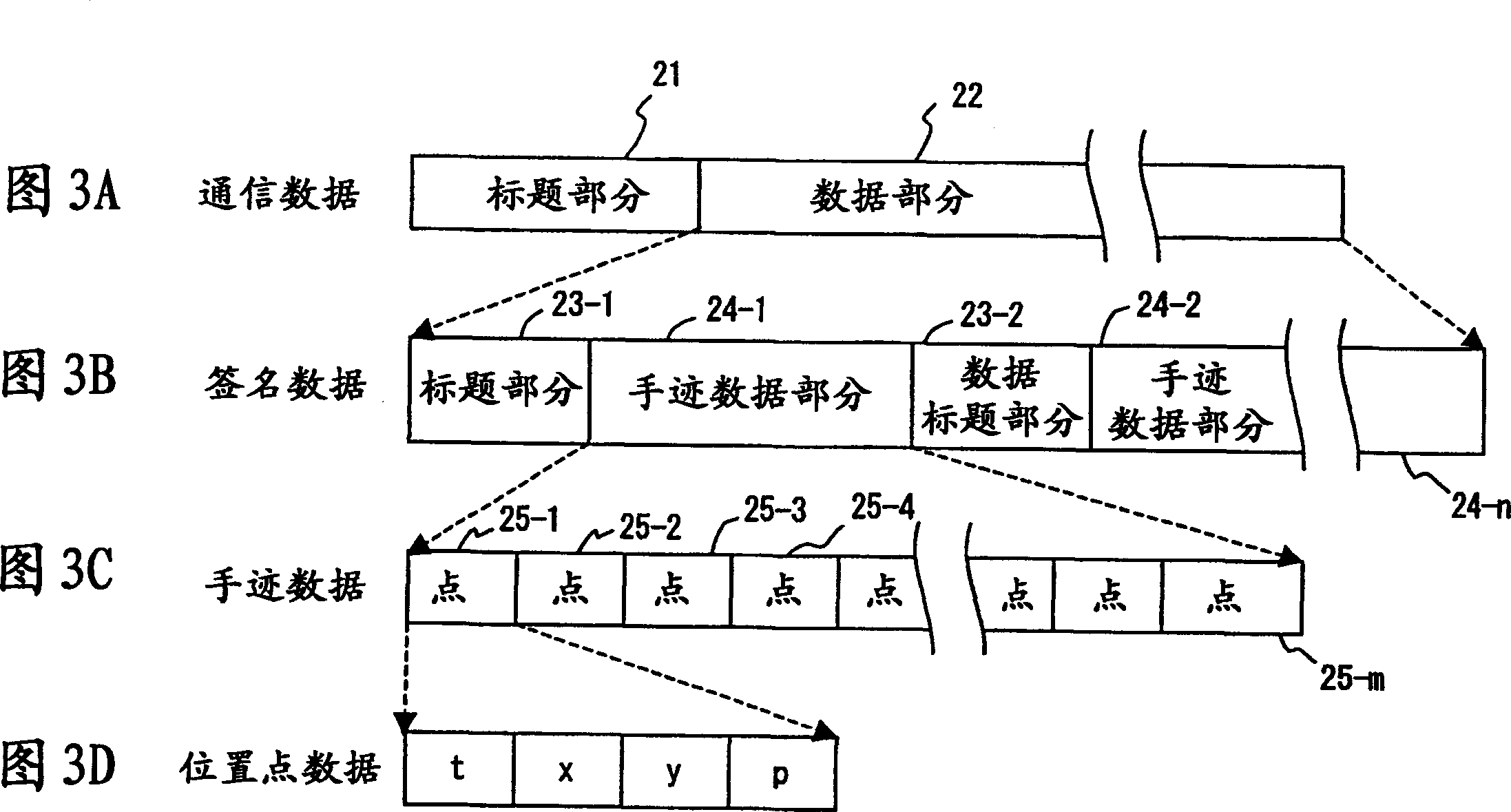
Hand-wirte signature recognition program, method and device
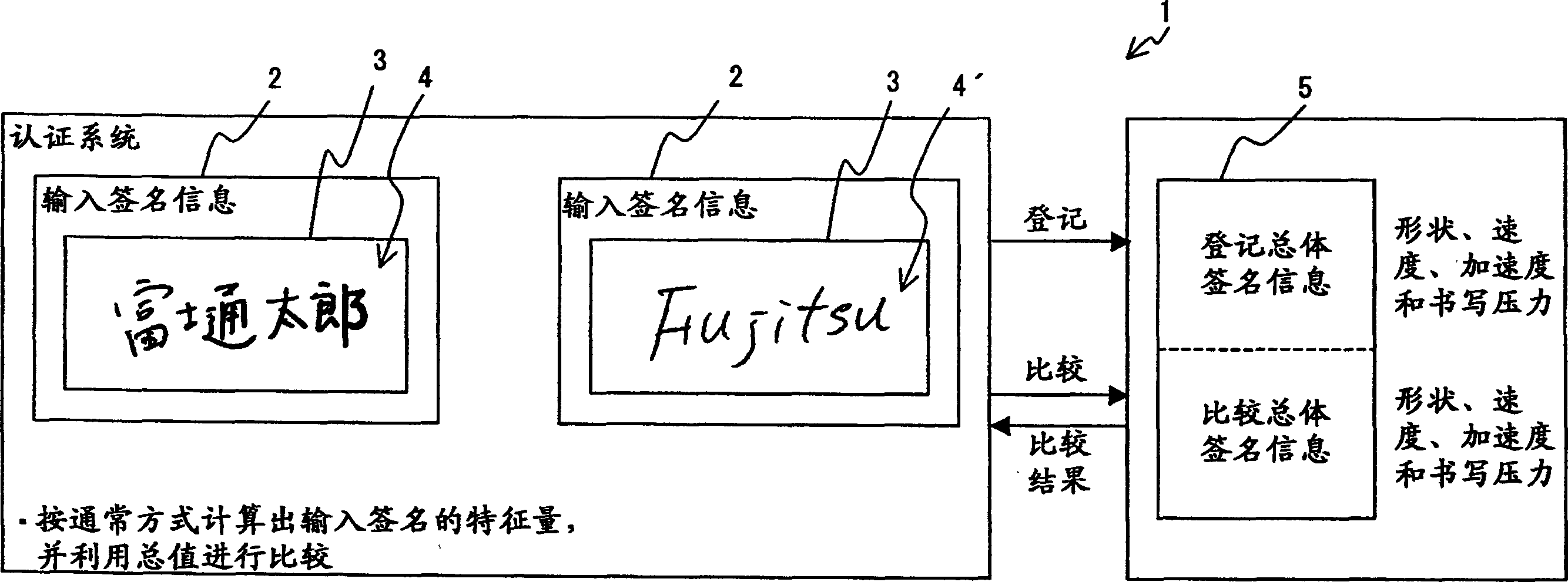
InactiveCN1445723AAvoid the authentication processAvoid false rejectionsImage analysisSpecial data processing applicationsHandwritingPattern recognition
The invention provides a handwritten signature authentication program, method and device. When registering a signature, input a Japanese signature such as "Fujitsu" ("Fujitsu") or an English signature such as "Fujitsu" n times through the input device of the input device of a signature authentication system, and calculate handwriting shape, writing speed, and writing acceleration and elements of writing pressure. Set the combination of nC2 for each element of the input data n times, get the inverse of each similarity, calculate the average value of the similarity of each element, determine the weight of each similarity according to the average value, and calculate the four elements and define it as the total similarity of the registered signatures. During the authentication process, the signature data to be compared is input / output m times. The total similarity of the signatures to be compared can be obtained in the same way.
Owner:FUJITSU LTD
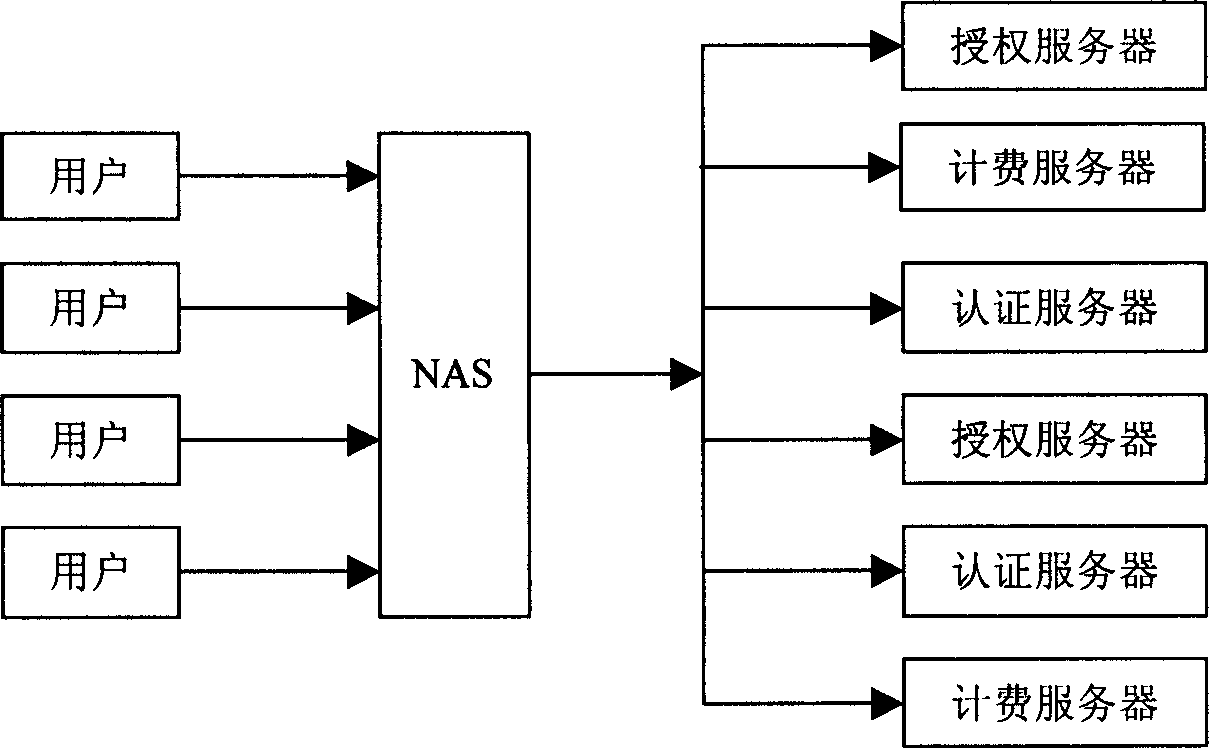
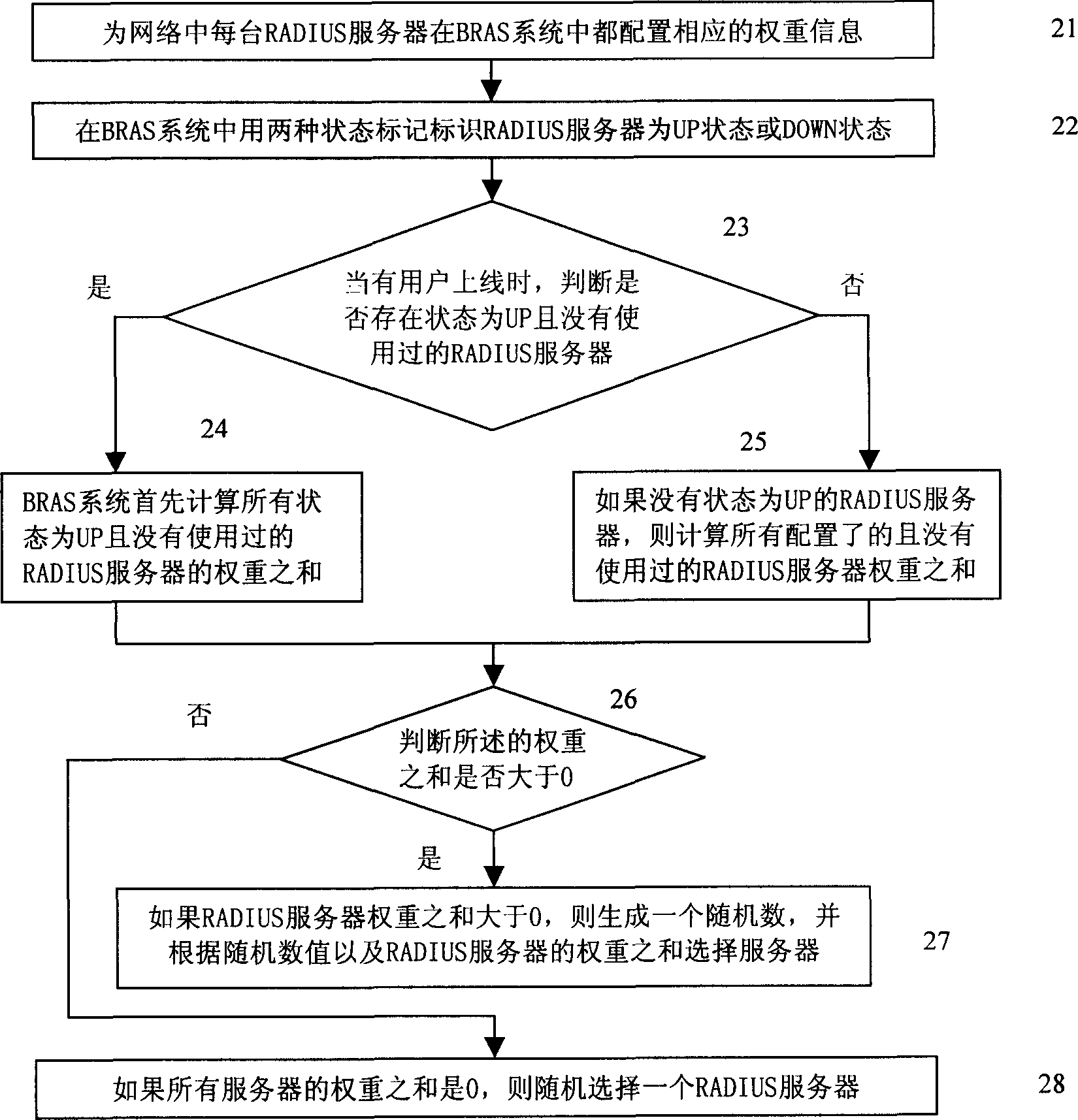
User access method and apparatus based on multiple users
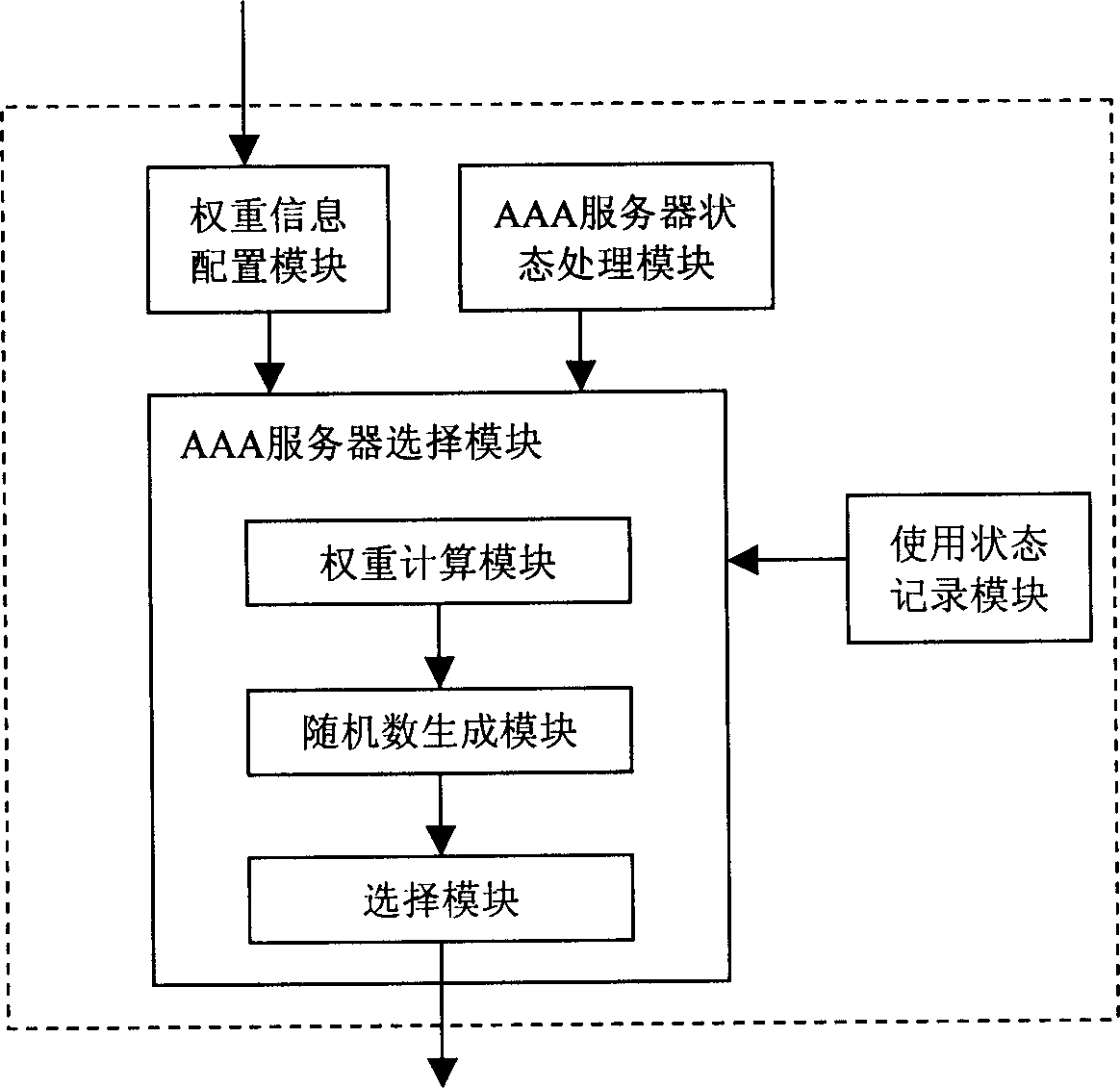
ActiveCN1863120AIncrease the likelihood of successfully connecting to the networkLoad balancingMetering/charging/biilling arrangementsUser identity/authority verificationAccess methodAuthorization
The invention relates to a multiserver-based user access method and device, mainly comprising: first, configuring weight information of several AAA (Authentication, Authorization and Accounting) servers in network; then, as a user accesses to the network, selecting an AAA server according to the weight information to process authentication, authorization and accounting messages in the user access course. Therefore, it can effectively prevent overweight burden of a single AAA server in master-backup mode and simultaneously effectively reduces probability of network jam. In a word, it can avoid failure in authorization or accounting operation in the network access course.
Owner:HUAWEI TECH CO LTD
Wireless access point safe authentication method and system
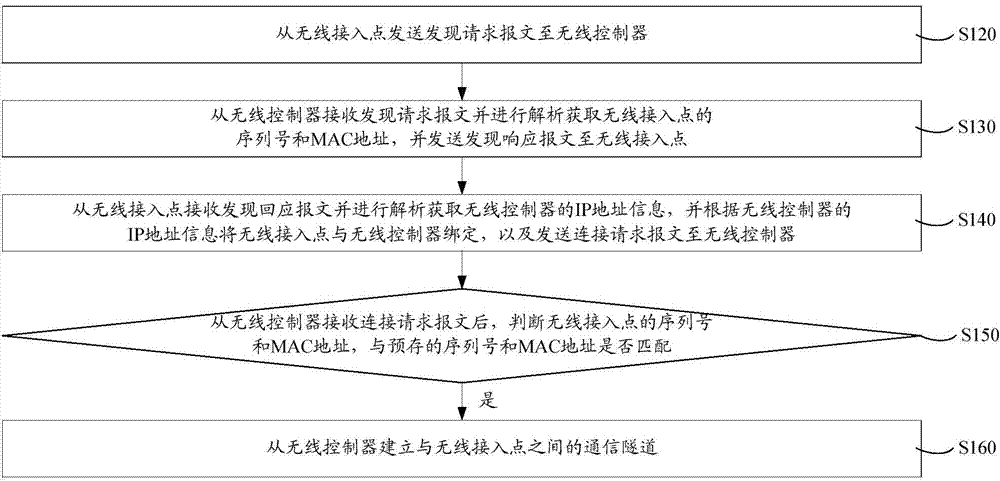
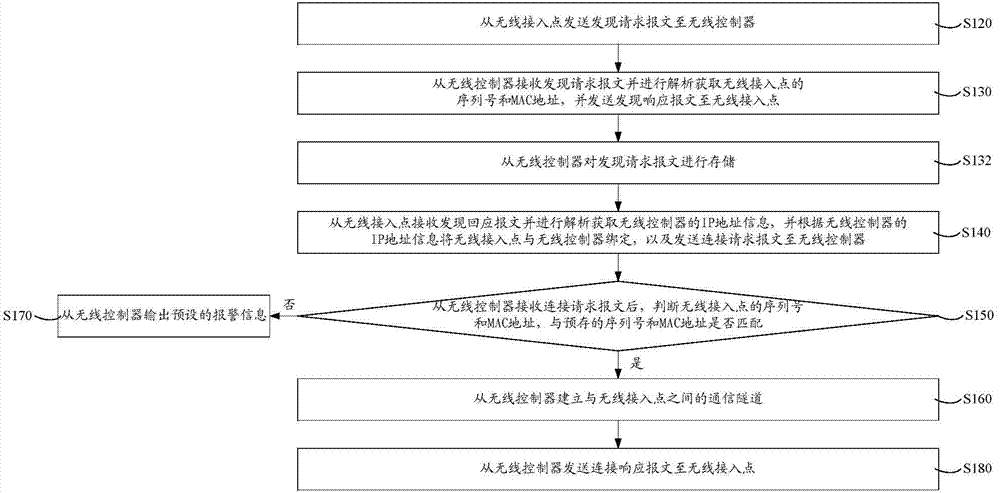
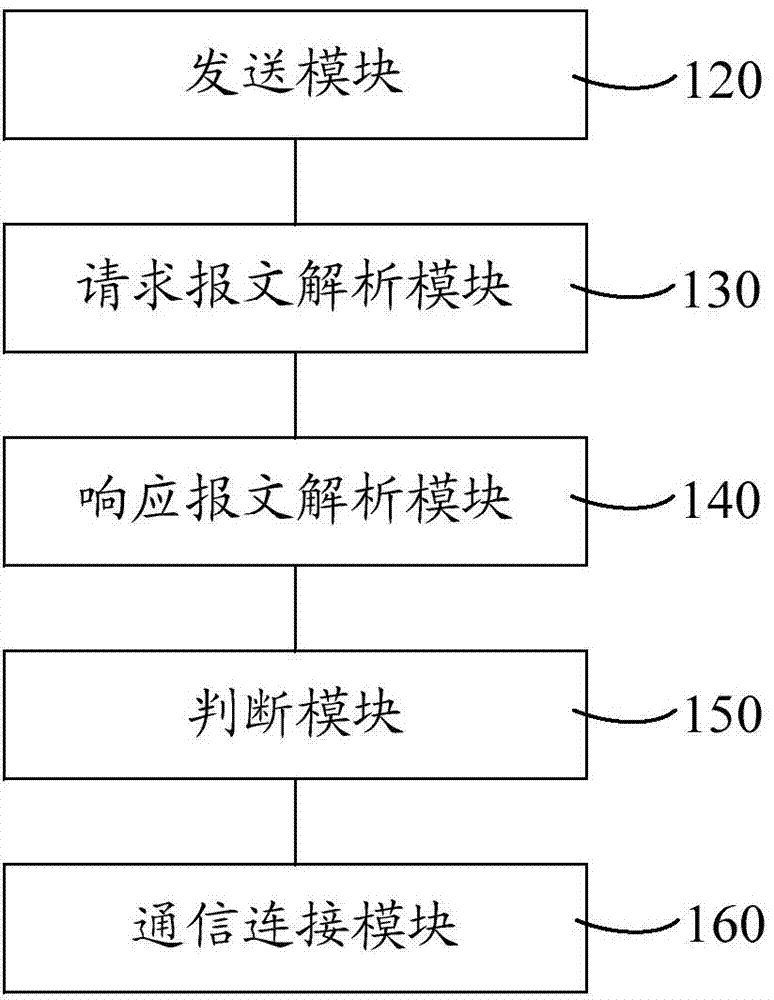
ActiveCN104125568AAvoid the authentication processImprove authentication accuracyConnection managementSecurity arrangementTelecommunicationsWireless control
Disclosed is a wireless access point safe authentication method and system. The method comprises transmitting a discovery request message from a wireless access point to a wireless controller; receiving the discovery request message from the wireless controller, analyzing the discovery request message to obtain the serial number and the MAC (media access control) address of the wireless access point, and transmitting a discovery responding message to the wireless access point; receiving the discovery responding message from the wireless access point and analyzing the discovery responding message to obtain the IP (Internet protocol) address information of the wireless controller, binding the IP address information with the wireless controller, and transmitting a connection request message to the wireless controller; after receiving the connection request message from the wireless controller, determining whether the serial number and the MAC address of the wireless access point are matched with a prestored serial number and a prestored MAC address; if so, establishing a communication channel between the wireless controller and the wireless access point. By taking that whether the serial number and the MAC address of the wireless access point are matched as the access basis, the wireless access point safe authentication method and system prevents unallowed wireless access points from access to the wireless controller, thereby improving the authentication accuracy.
Owner:湖南恒茂信息技术有限公司
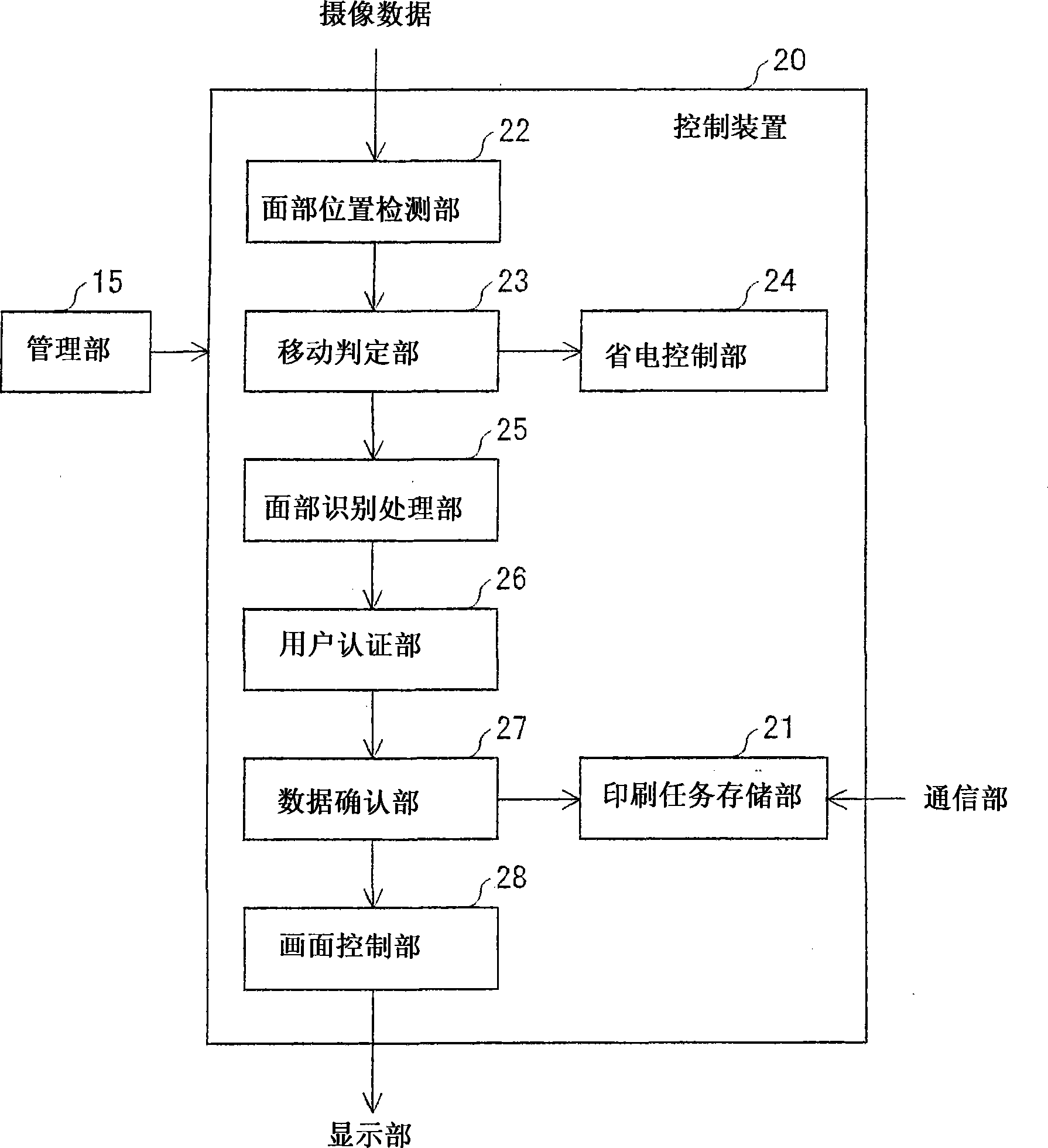
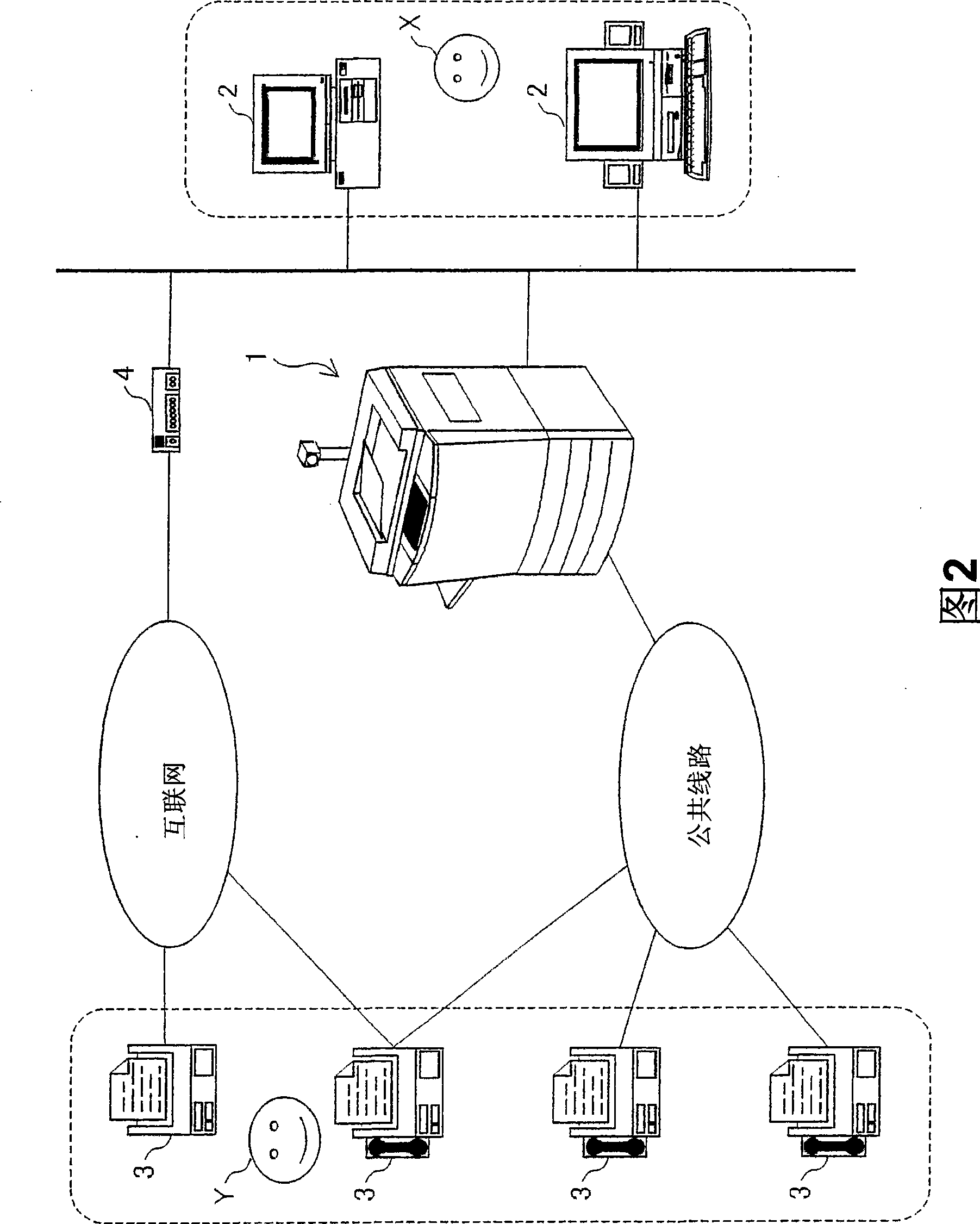
Control device, image forming apparatus, method of controlling image forming apparatus, and recording medium
ActiveCN101459751AAvoid the authentication processEasy to operateCharacter and pattern recognitionPictoral communicationPattern recognitionLocation detection
A control device of the present invention includes: a face position detecting section for detecting a position of a user's face in an image captured by a capturing device; a face recognition processing section for checking a partial image against reference face images, the partial image being at the position detected in the captured image, and extracting a reference face image that matches the face in the partial image; a user authentication section for specifying a user name that corresponds to the extracted reference face image; and a data checking section for (i) checking whether or not a multifunction printer receives print data added with the specified user name, and (ii) if it is confirmed that the multifunction printer receives the print data, operating an image forming section of the multifunction printer to form an image based on the print data. This realizes a control device which (i) authenticates a user in an easy way in which impersonation can be prevented without inconvenient operation, and (ii) prevents another user from accidentally viewing a printed matter.
Owner:SHARP KK
Energy-efficient identity authentication method in multi-level clustering wireless sensor network
ActiveCN102612035AKeep your identity safeAvoid the authentication processEnergy efficient ICTNetwork topologiesMobile wireless sensor networkWireless mesh network
The invention provides an energy-efficient identity authentication method in a multi-level clustering wireless sensor network, which belongs to the technical field of computer networks. According to the method disclosed by the invention, a symmetric encryption algorithm is taken as the basis, a base station is used for transferring identity information, and all the nodes only need to be subjected to double-way identity authentication with cluster head nodes according to the characteristics of the multi-level clustering wireless sensor network, so that the unnecessary authentication process is avoided. According to the energy-efficient identity authentication method disclosed by the invention, the energy-efficient whole-network necessary identity authentication can be realized in the multi-level clustering wireless sensor network, and identity safety of the nodes of the whole network can be ensured at minimum energy cost.
Owner:福建汇智数字通达科技有限公司
Method of providing a signing key for digitally signing verifying or encrypting data and mobile terminal
InactiveCN1700699AImprove adaptabilityEasy to useKey distribution for secure communicationSecure communicationPayment transaction
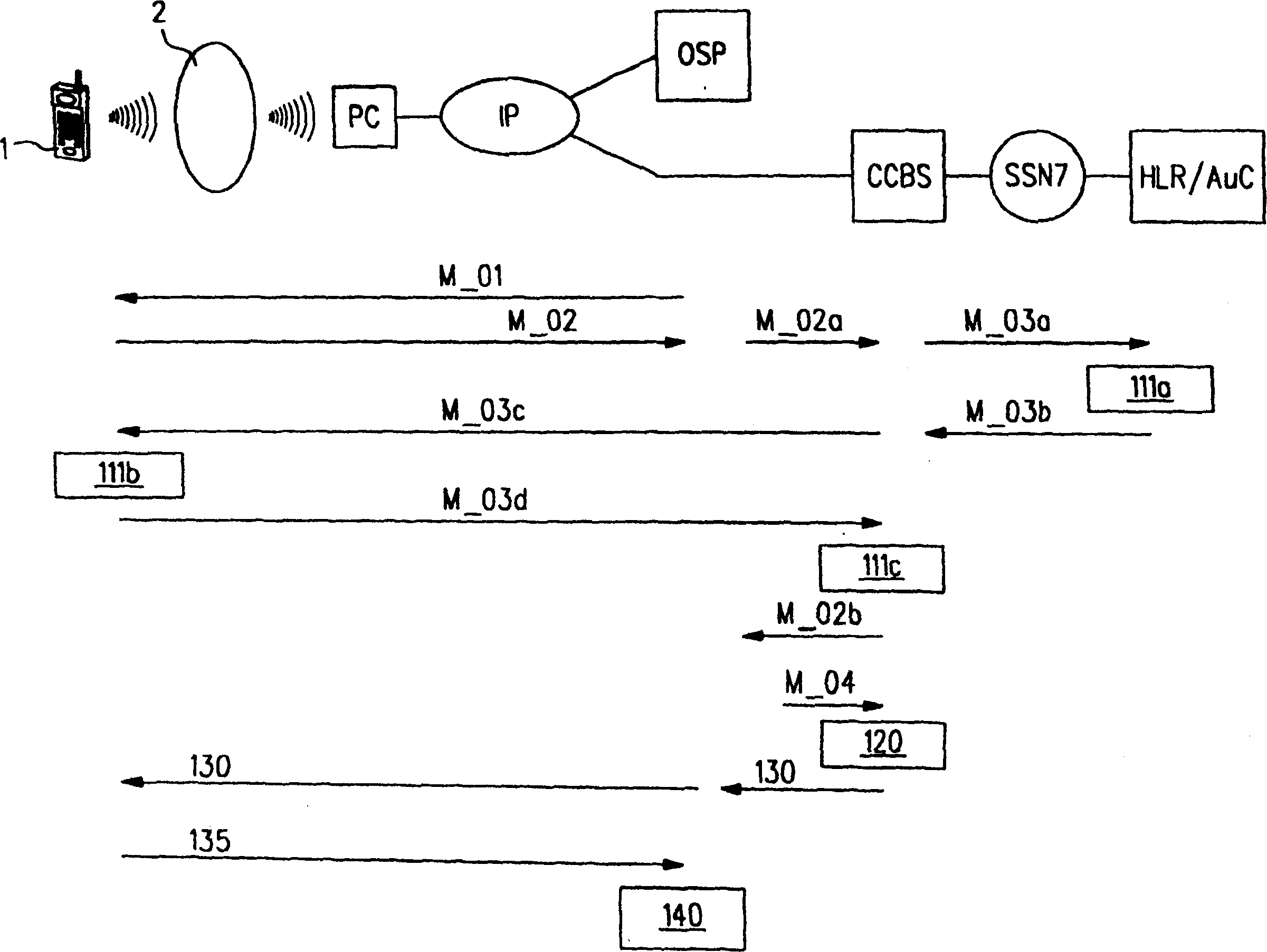
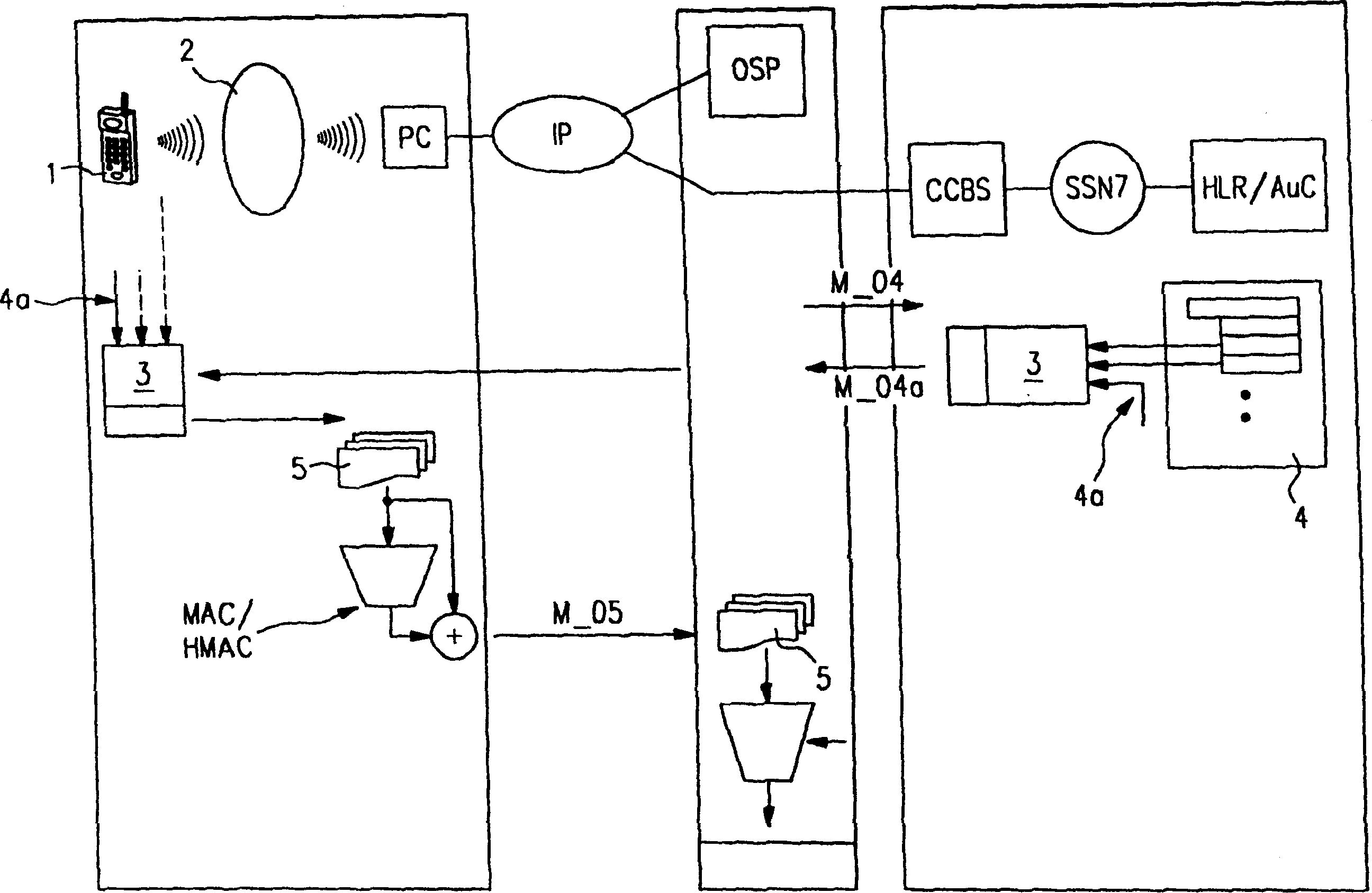
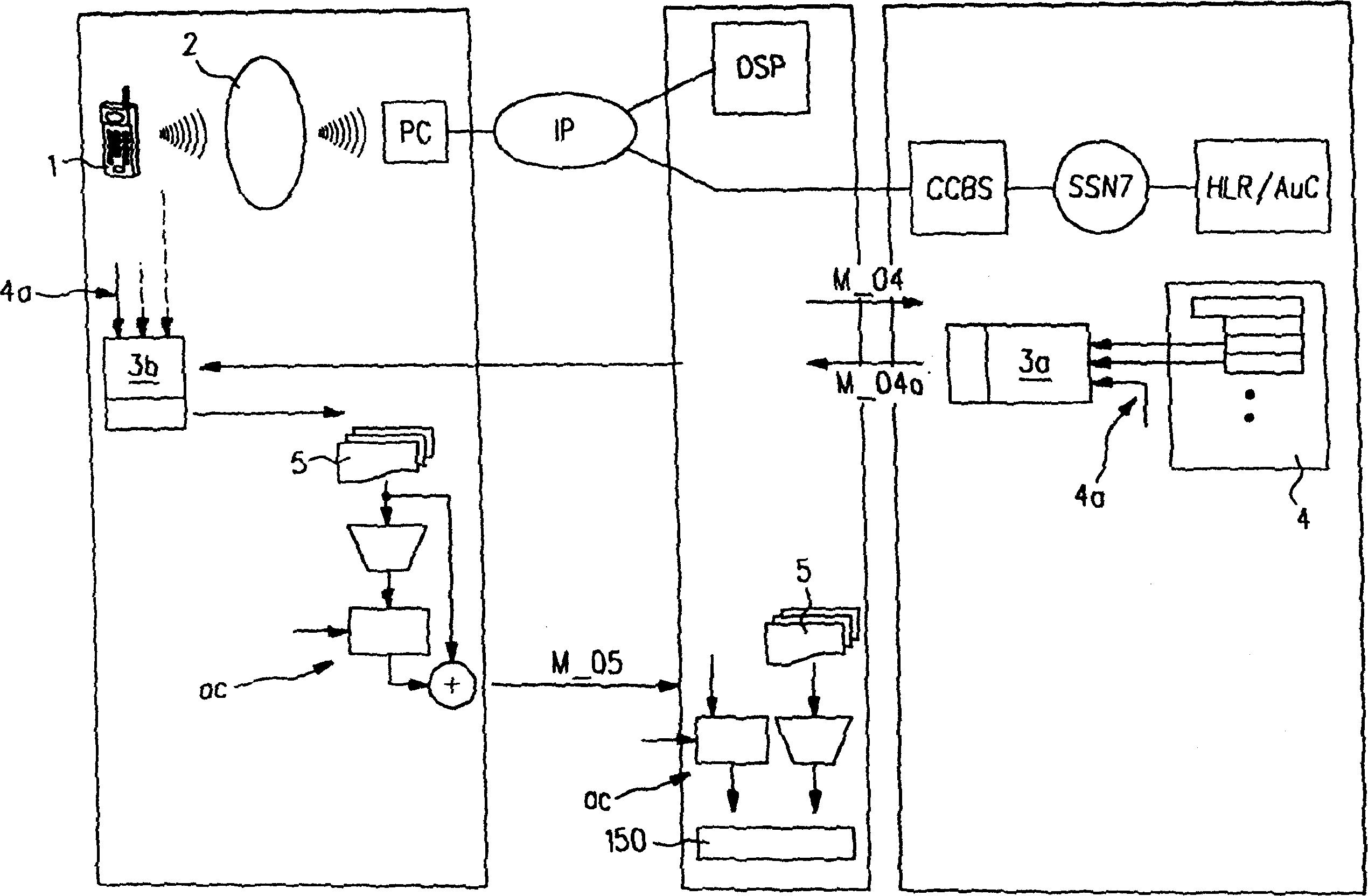
The present invention relates to a method of providing a key, in particular for digitally signing, verifying or encrypting data to be exchanged between a first party and a second party, comprising steps of transmitting (100) an identification code, which is uniquely identifying said first party, from said first party to a gateway (CCBS), verifying (110) said identification code by said gateway (CCBS) by using (111) an authentication server (AUC), and creating (120) a signing key. Said method is characterized by providing (130) said signing key to said first party and / or to said second party. A transmission of said signing key via a secure communications channel, in particular via a GSM-based communications infrastructure, improves the security of payment transactions. The present invention further relates to a mobile terminal (1) and a gateway (CCBS).
Owner:ALCATEL LUCENT SAS
Processing method for platform identity recognition and authority authentication
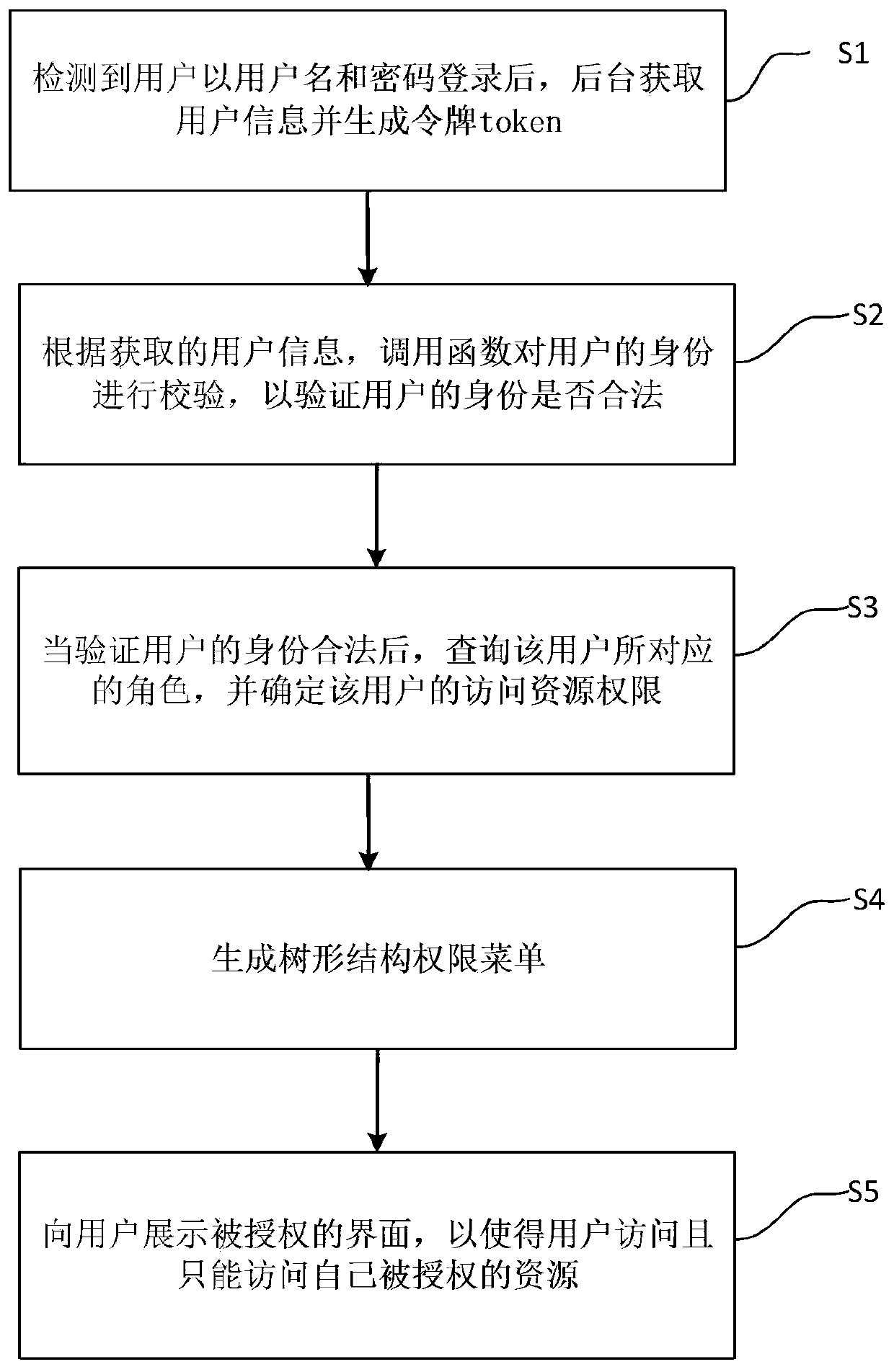
InactiveCN110688643AResolve authenticationSolve the problem of rights managementDigital data authenticationIdentity recognitionPassword
The invention provides a platform identity recognition and authority authentication processing method, which comprises the following steps: after detecting that a user logs in with a user name and a password, a background acquiring user information and generating a token; according to the obtained user information, calling a function to verify the identity of the user so as to verify whether the identity of the user is legal or not; when the identity of the user is verified to be legal, inquiring the role corresponding to the user, and determining the access resource permission of the user; generating a tree structure permission menu; and displaying the authorized interface to the user, so that the user can access and only can access own authorized resources. According to the invention, the problems of platform user identity authentication and authority management are solved, multi-terminal login is avoided, identity counterfeiting and illegal resource access are prevented, user information is protected, and the practicability is high.
Owner:BEIJING GEO POLYMERIZATION TECH
Control method and device for terminal communication, and management server
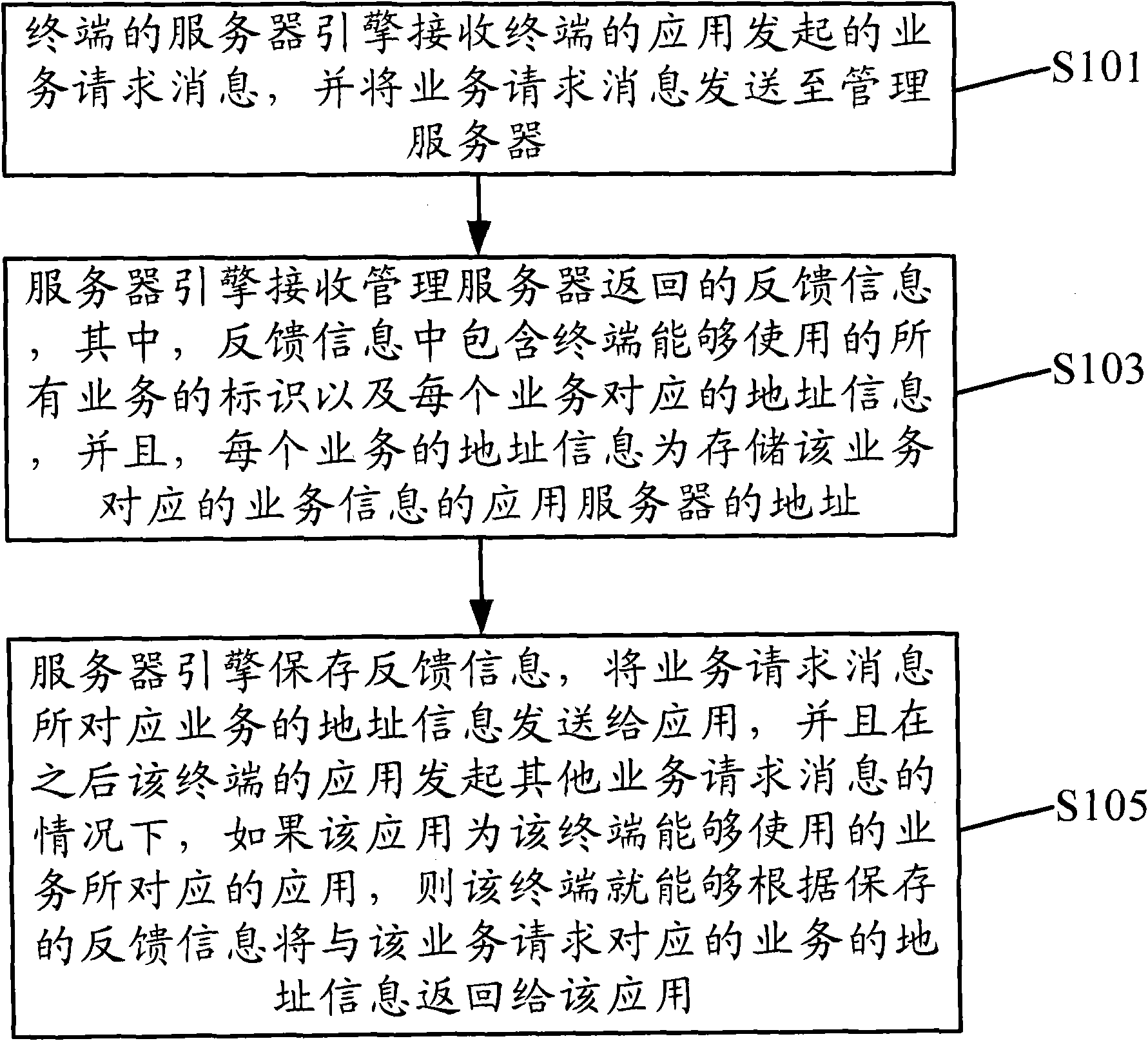
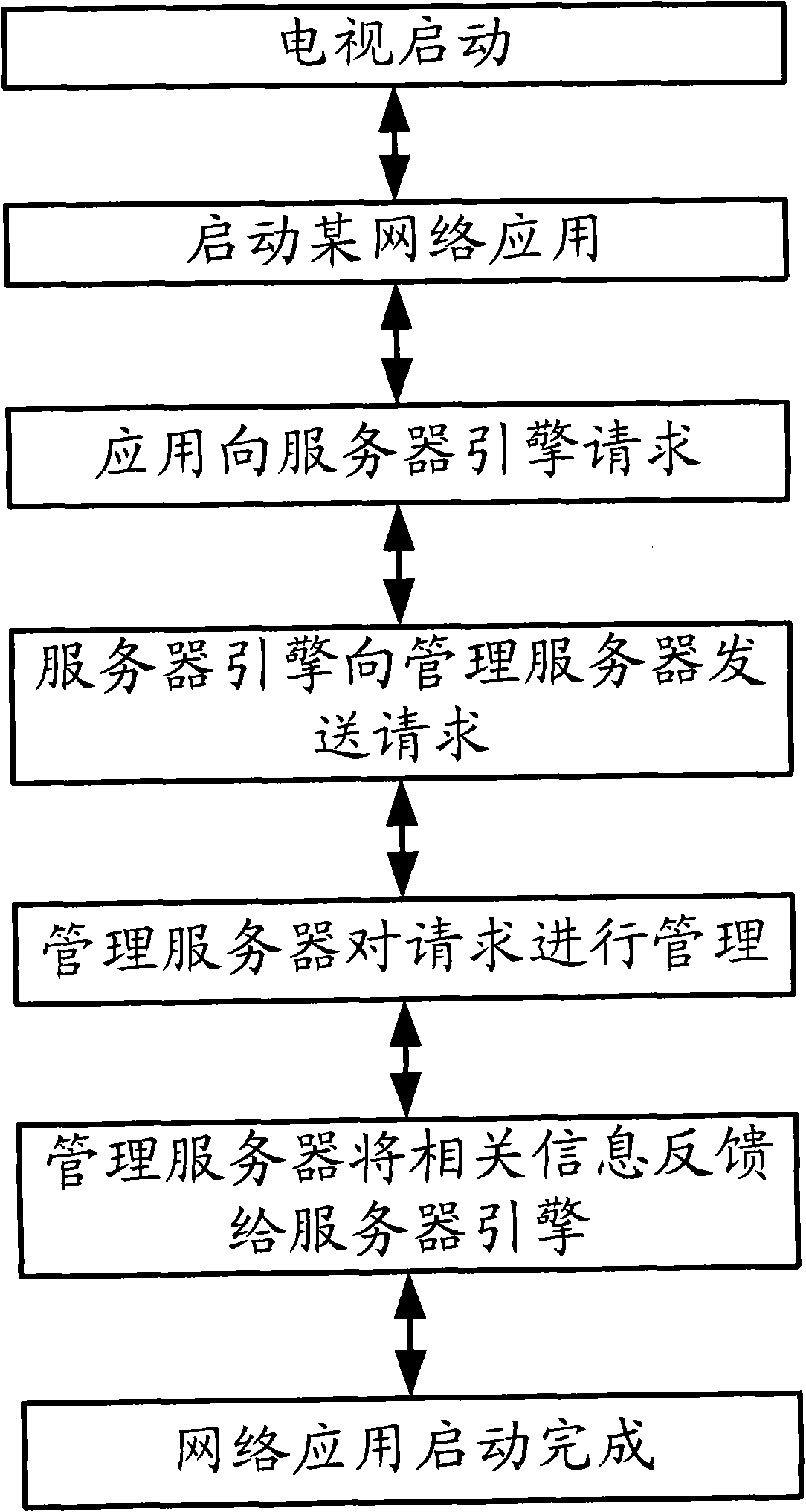
The invention discloses a control method and a device for terminal communication, and a management server. The method comprises: a server engine of a terminal receives a business request message that originates from an application of the terminal, and sends the business request message to the management server; and the server engine receives feedback information returned by the management server. The feedback information comprises identifiers of all businesses that the terminal can use and address information corresponding to each business, and in addition, the address information of each address is the address of an application server that stores the business information corresponding to the business. The server engine stores the feedback information, sends the address information of the business corresponding to the business request message to the application, and when the application of the terminal initiates another business request message later, the server engine returns the address information of the business corresponding to the other business request to the application according to the stored feedback information.
Owner:HAIER GRP CORP +4
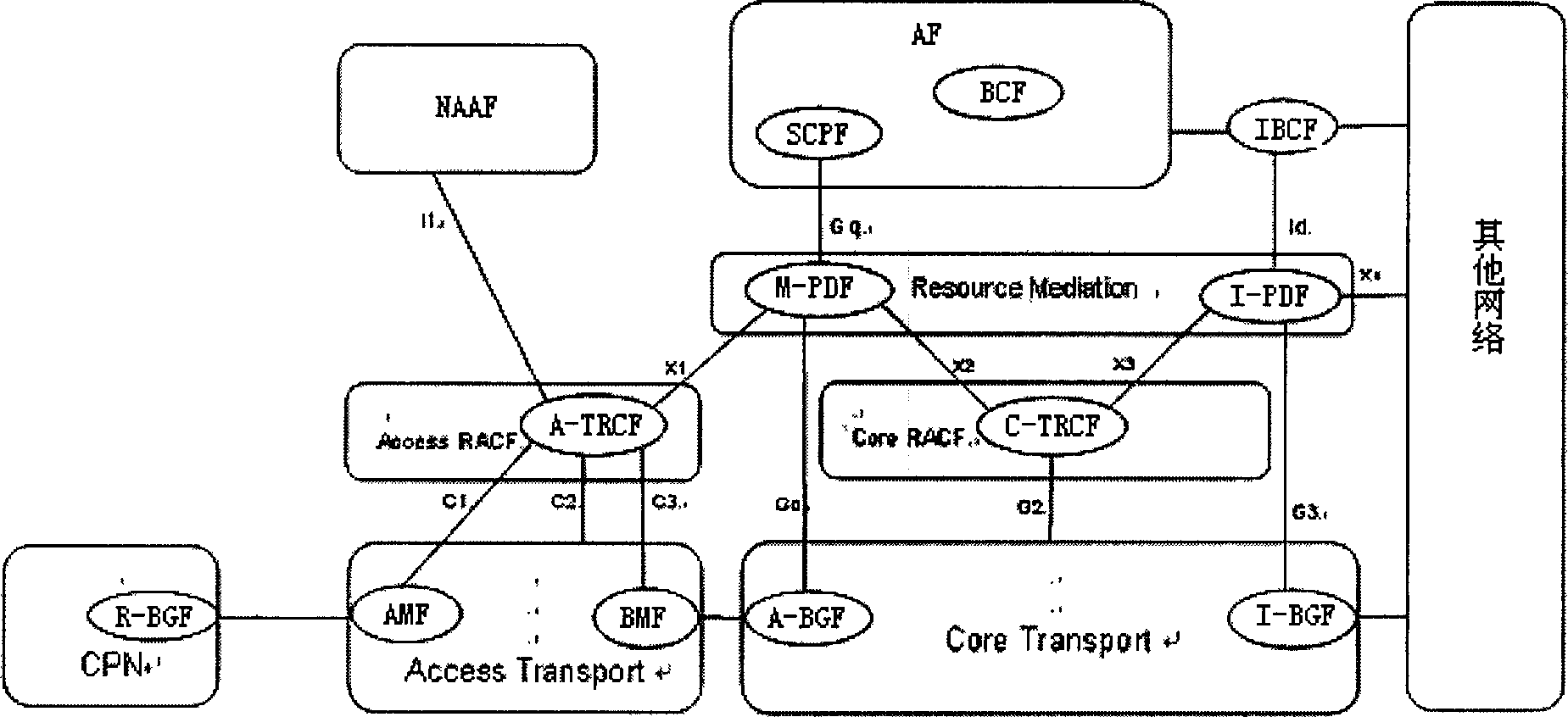
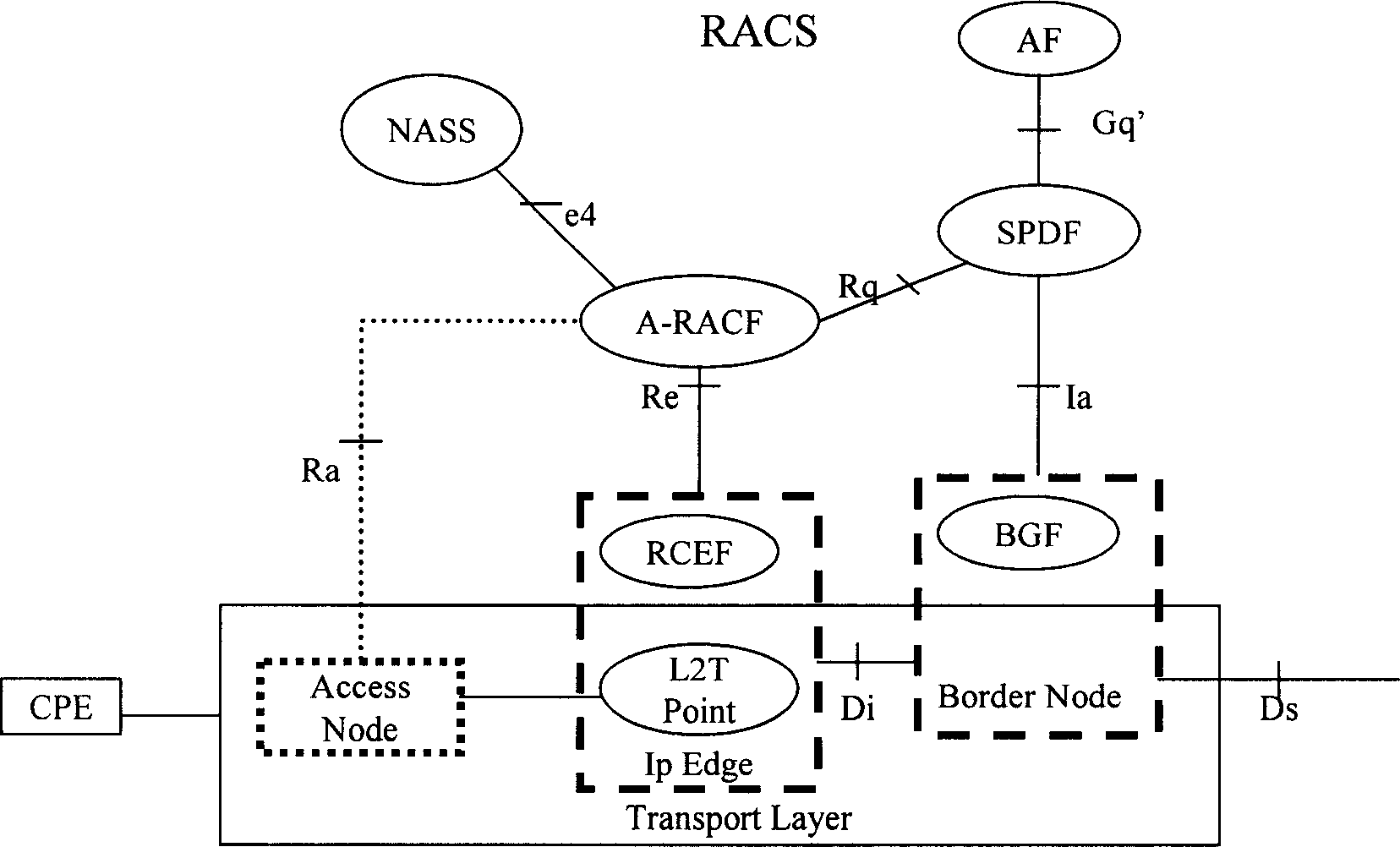
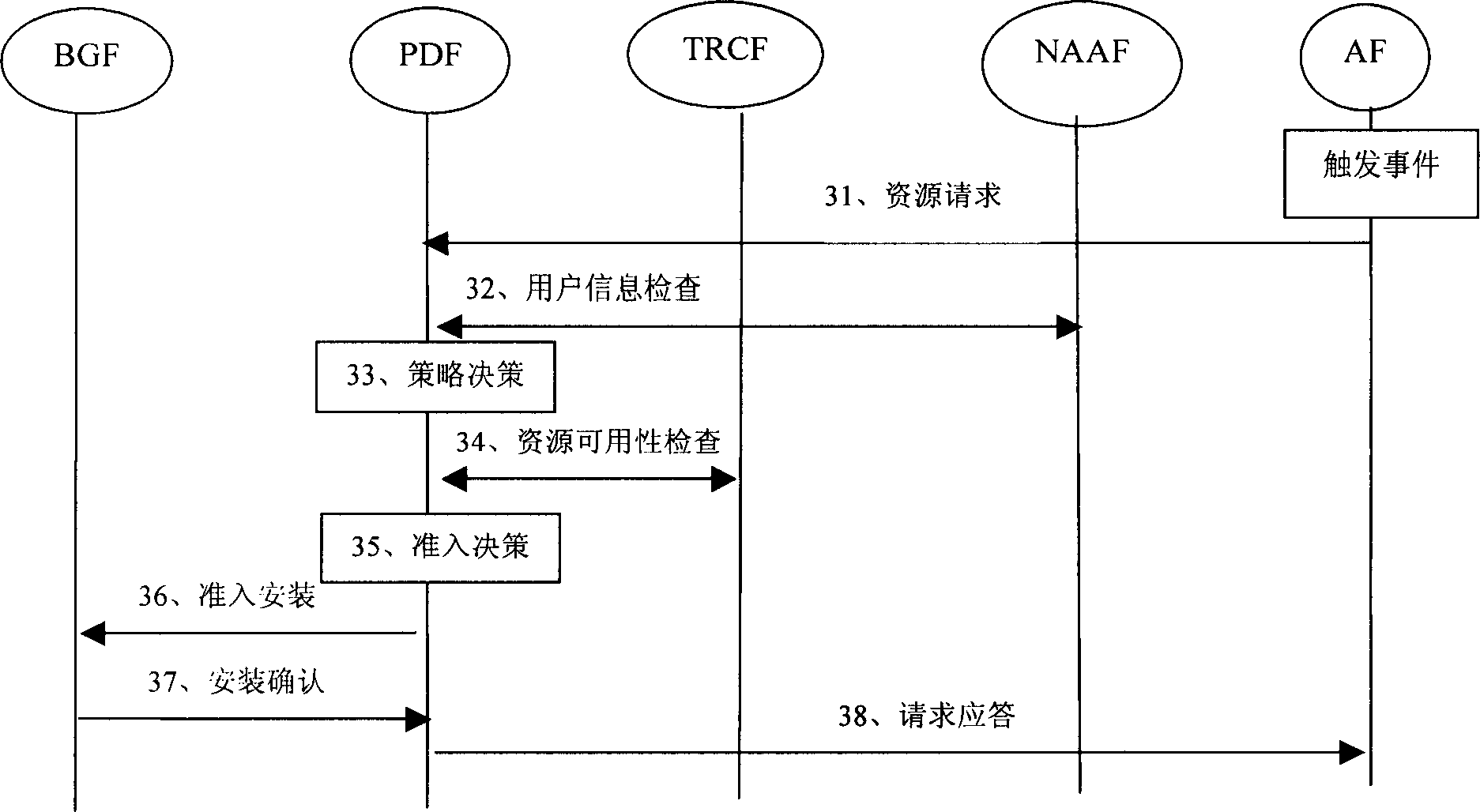
Method and device for implementing proxy demand mode resource preservation in next generation network
ActiveCN101159740AAvoid the authentication processSimplify the resource authorization processData switching networksPolicy decisionQuality of service
The invention relates to a method and a device for achieving resource reservation of agent solicitation mode in the network of the next generation. A resource arbitration strategy decision function entity receives a resource request message sent by an application function entity, detects whether to conform to a user configuration file and a network operation strategy rule, detects whether the related transmission network has an available resource satisfying the requirement, and make admittance decision of the resource request according to the detection result. Correspondingly, the invention also provides a device for achieving resource reservation of agent solicitation mode in the network of the next generation. The invention not only can support various terminals with different service quality negotiation abilities but also can negotiate the service quality requirement parameter of a streaming media, or determines the service quality requirement parameter by the application function entity according to the type of the streaming media and the service operation strategy.
Owner:HUAWEI TECH CO LTD
Method for implementing resource preretention of agency requir mode in next network
InactiveCN1832449ADetermination of Service Quality Requirement ParametersAvoid the authentication processNetwork traffic/resource managementStore-and-forward switching systemsQuality of serviceOperational strategy
This invention relates to a resource preservation method of an agent request mode in the next generation network including: an applied function entity sends a resource request with necessary resource request parameter information of a user to an arbitration strategy decision function entity, which makes out an admittance decision, if the admittance is passed, it sends an admittance installation instruction to BGF to set and store the parameter information on it, the BGF entity controls the transfer of user flows entering into the network to guarantee the service quality grade needed by users.
Owner:HUAWEI TECH CO LTD
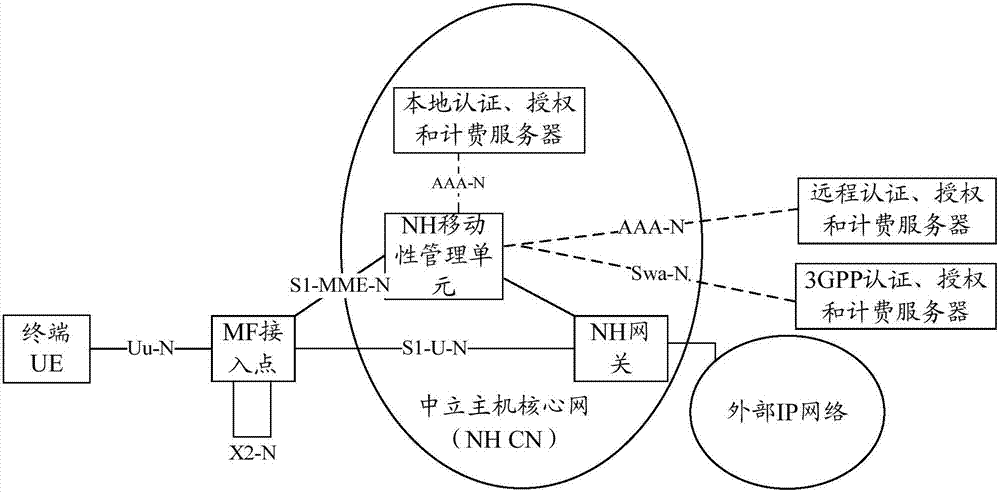
Method and device for accessing network by terminal, and terminal thereof
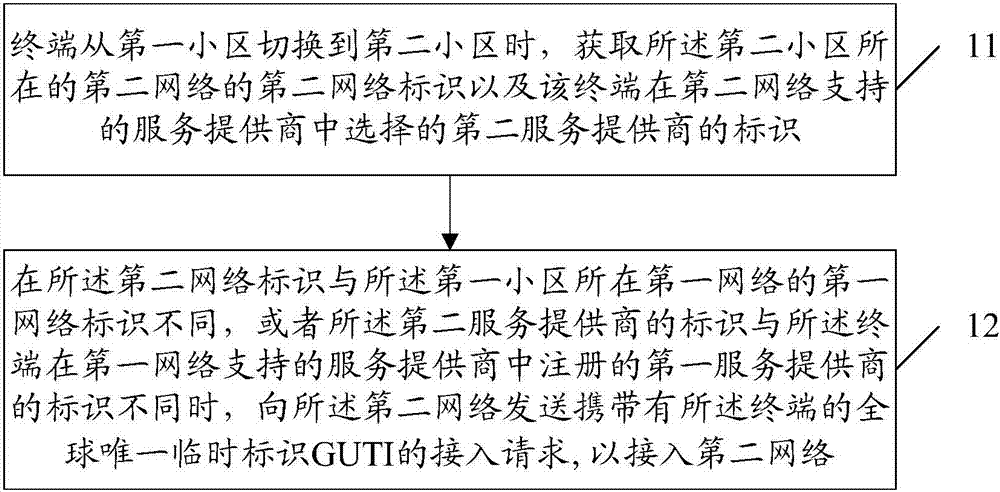
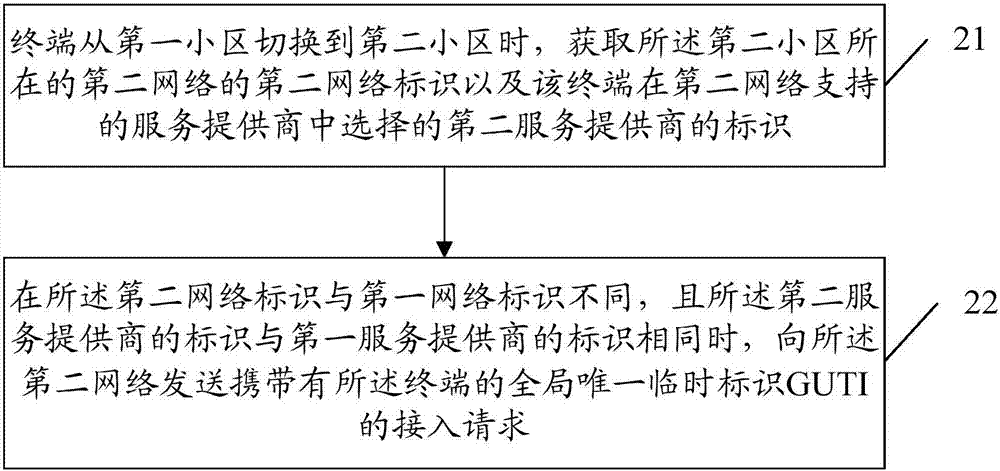
ActiveCN107205251AImprove performanceAvoid the authentication processAssess restrictionConnection managementAccess networkService provision
The invention provides a method and a device for accessing a network by a terminal, and a terminal thereof. The method comprises the steps of when the terminal switches from a first cell to a second cell, acquiring a second network identification of a second network in which the second cell exists and the identification of a second service provider that is selected from the service providers that are supported by the second network; and when the second network identification is different from the first network identification of a first network in which the first cell exists, or the identification of the second service provider is different from the identification of a first service provider which is registered in the service provider that is supported by the first network, transmitting an accessing request which carries a global unique temporary identification (GUTI) of the terminal to the second network for accessing the second network, so that the network side can acquire context information of the terminal in the network according to the GUTI, thereby preventing terminal verification, bearing establishing / releasing, reducing network signaling load and improving network performance.
Owner:BAICELLS TECH CO LTD
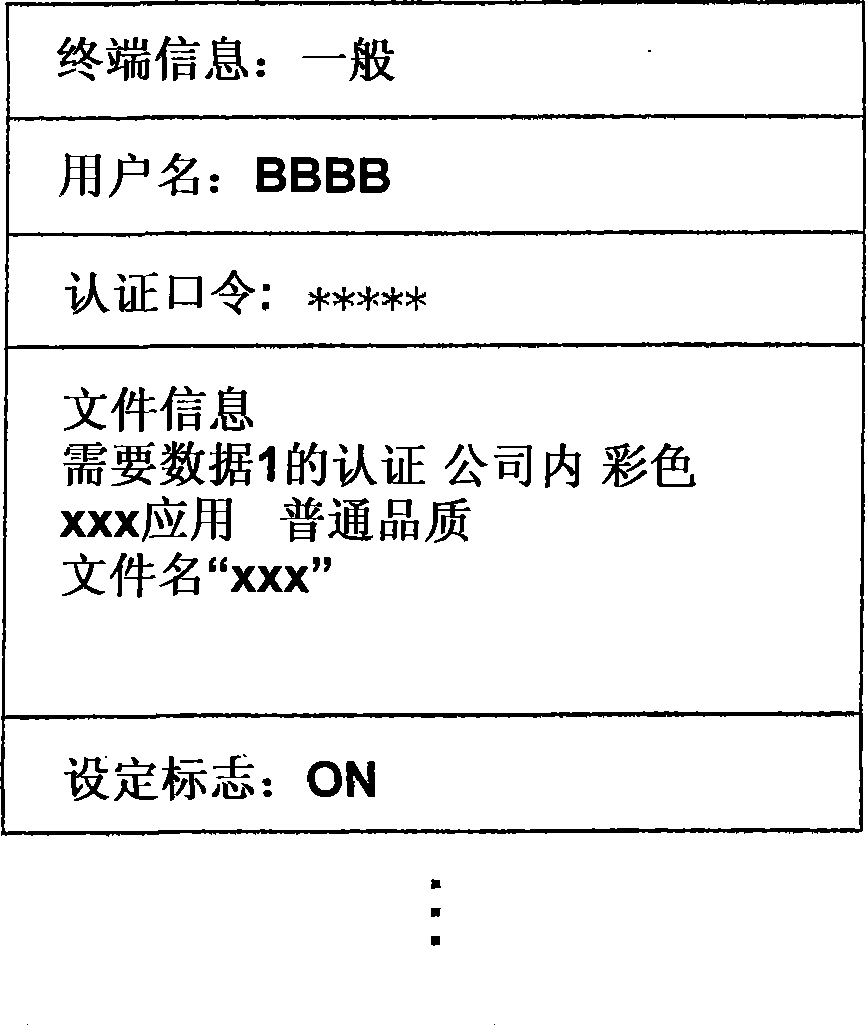
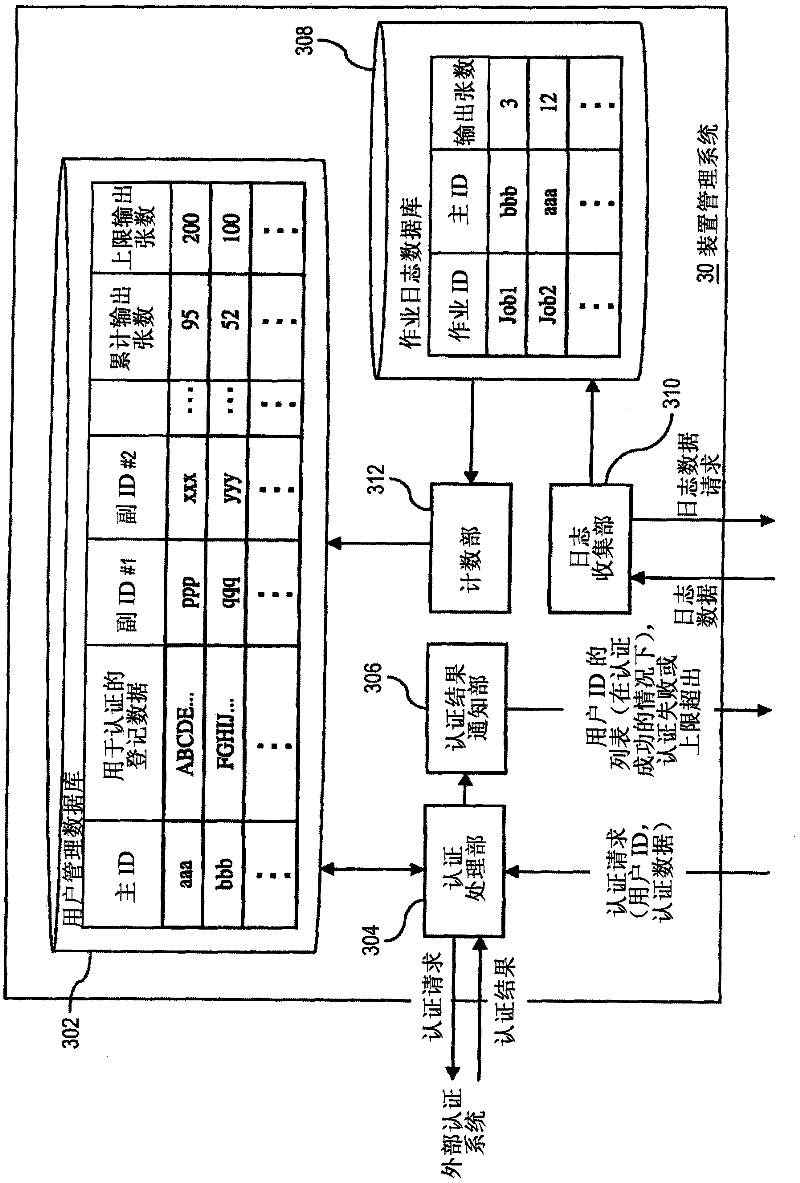
Printing authentication system, printing device, device management apparatus and related method
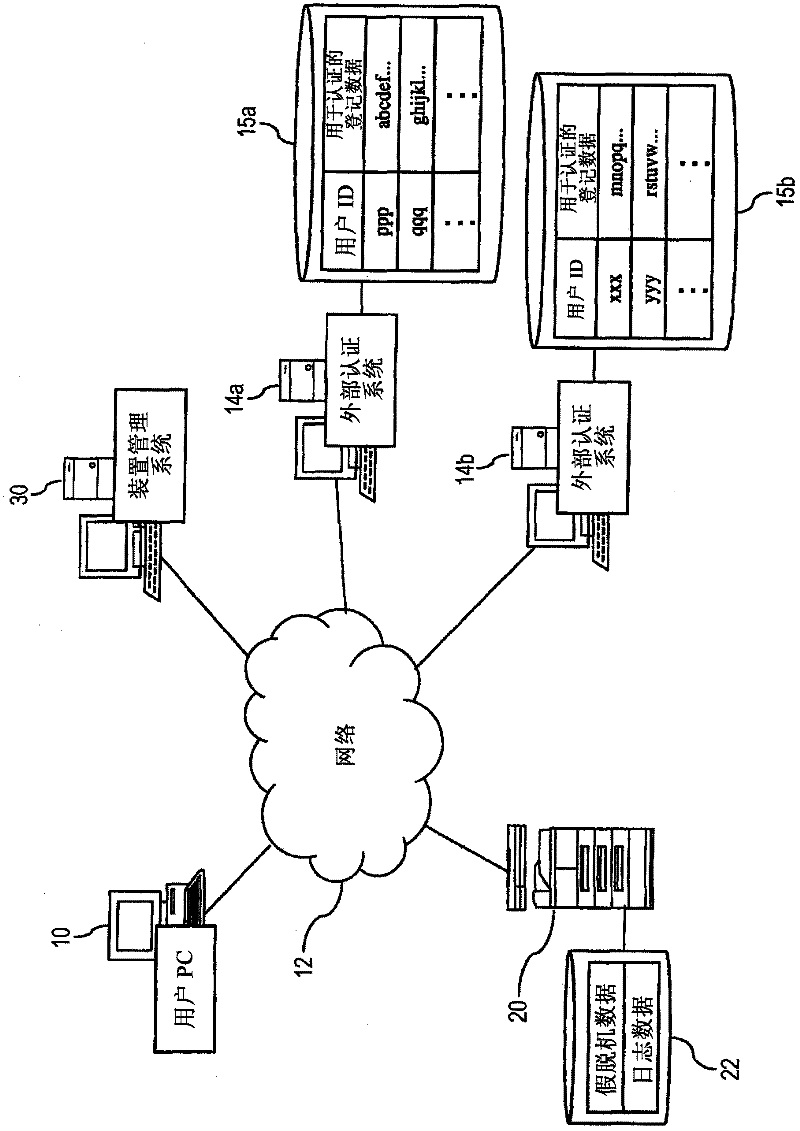
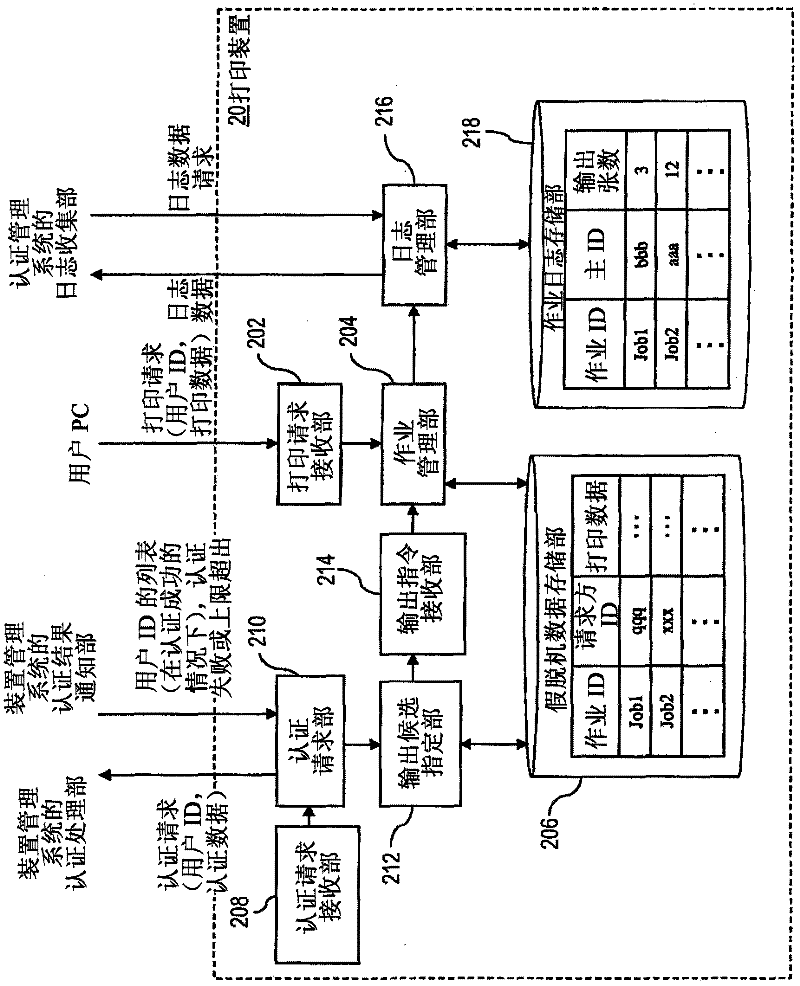
ActiveCN102456112AAvoid the authentication processComputer security arrangementsDigital output to print unitsAuthentication systemDatabase
A printing authentication system includes an identification information storage unit, a providing unit and a specifying unit. The identification information storage unit stores, as an identification information set, plural pieces of user identification information given to a same user. If authentication is valid with regard to an authentication request accompanying specific user identification information, the providing unit reads out a specific user identification information set including the specific user identification information from the identification information storage unit and provides the specific user identification information set. If user identification information, associated with print data, of a requester who requests printing of the print data matches any one of the user identification information constituting the specific identification information set, the specifying unit specifies the print data as a printing target.
Owner:FUJIFILM BUSINESS INNOVATION CORP
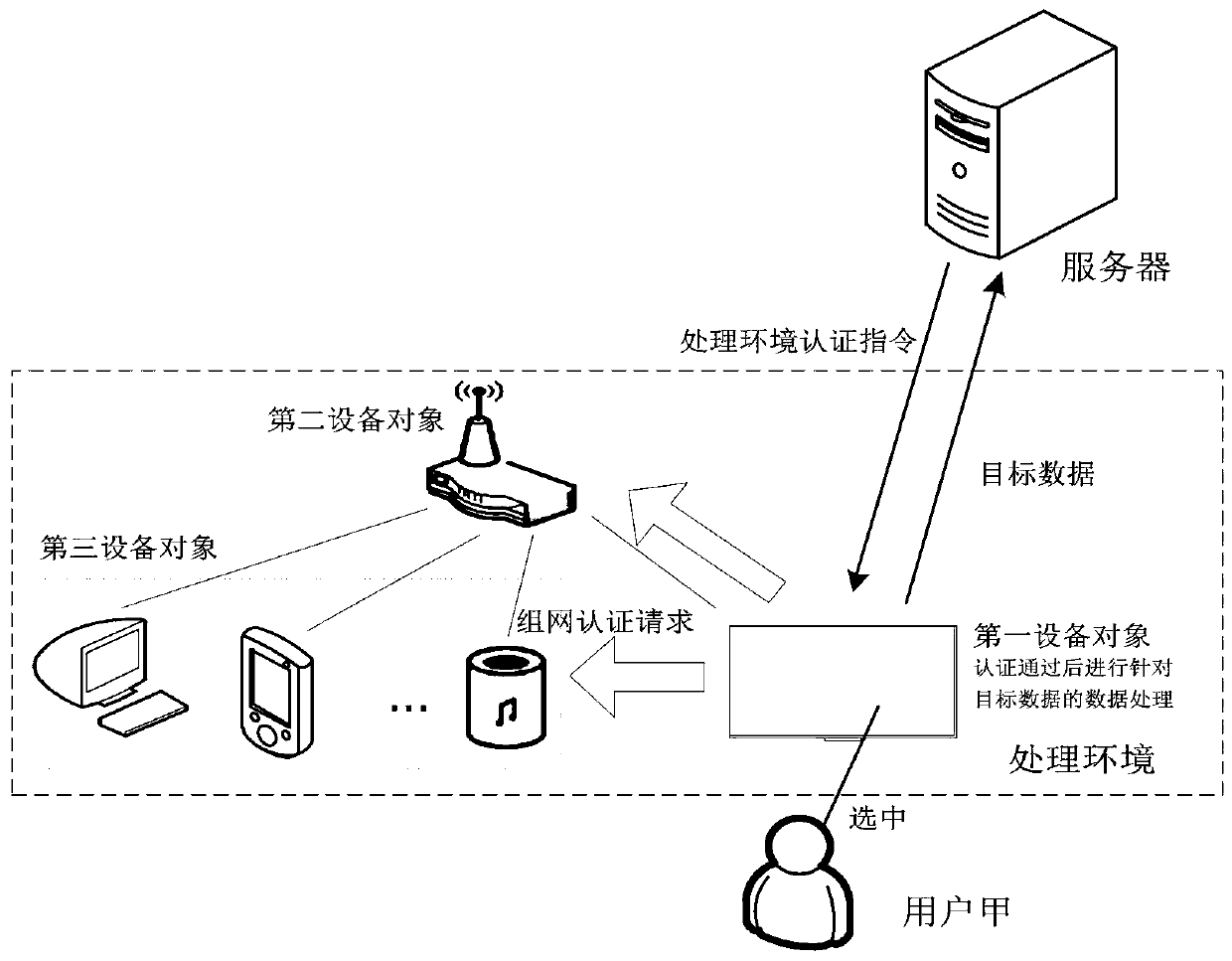
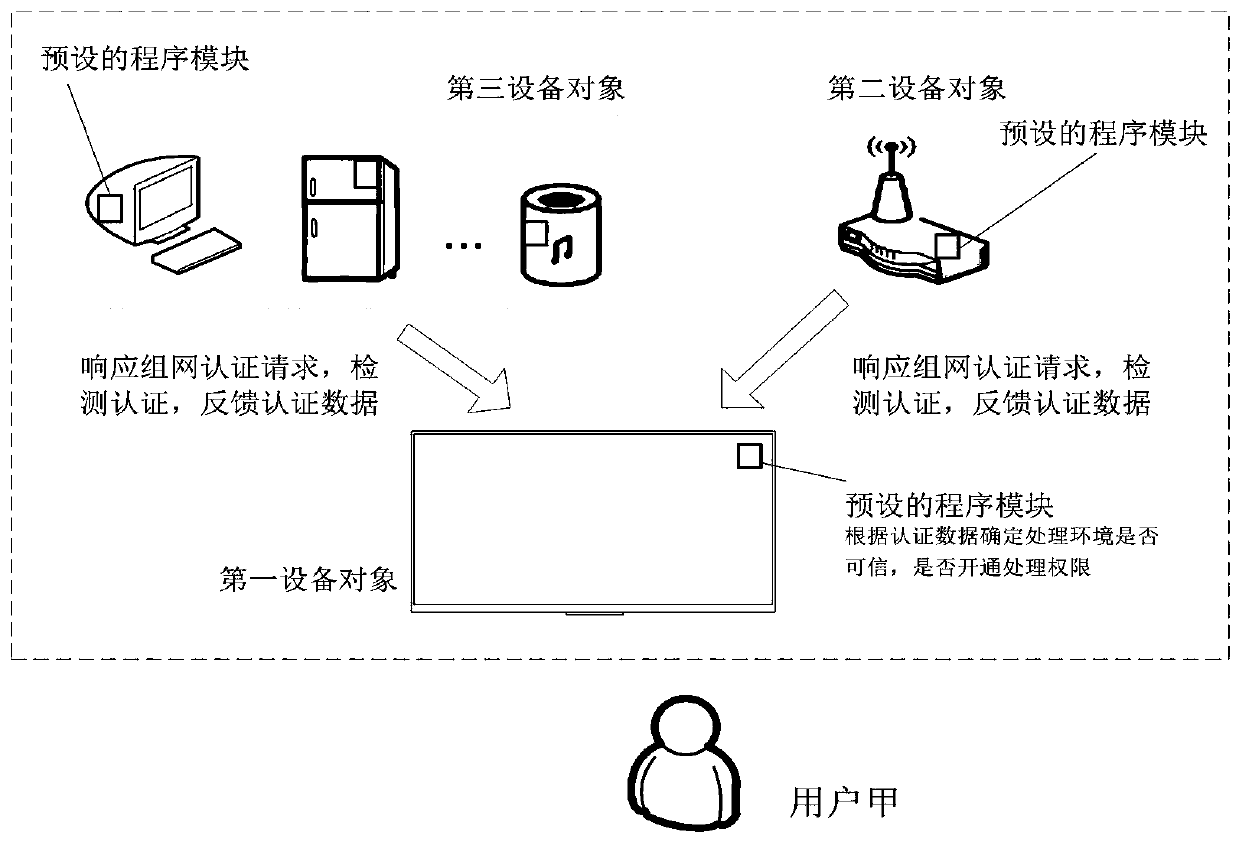
Data processing method and device and processing permission obtaining method and device
ActiveCN110290109ABalance safety and convenienceAvoid the authentication processUser identity/authority verificationUser needsData processing
The invention provides a data processing method and device and a processing permission obtaining method and device. The data processing method is applied to a first equipment object, and comprises the following steps: receiving and obtaining and sending target data to a server according to a data processing request; receiving and responding to an authentication instruction of a processing environment fed back by the server, initiating a networking authentication request in the processing environment to obtain authentication data of a second equipment object and authentication data of a third equipment object in the processing environment, and determining an authentication result according to the authentication data of the second equipment object and the authentication data of the third equipment object; and under the condition that the authentication result is that the authentication is passed, obtaining a processing permission to perform data processing on the target data. Therefore, credibility authentication can be carried out through other equipment objects in the same processing environment according to user requirements, data processing can be efficiently, safely and conveniently completed through the first equipment object, the processing efficiency is improved, and the user experience is improved.
Owner:蚂蚁蓉信(成都)网络科技有限公司
Authentication method, device and equipment and computer readable storage medium
ActiveCN111654861AAvoid the authentication processSave signaling resourcesSecurity arrangementHigh level techniquesAuthenticationComputer engineering
The invention discloses an authentication method, device and equipment, and a computer readable storage medium, relates to the technical field of communication, and aims to solve the problem of signaling resource waste caused by a complex authentication process in the prior art. The method comprises the steps of obtaining an authentication result of a terminal from an AUSF under the condition thata first authentication request sent by an AMF is received. The embodiments of the present invention can save signaling resources.
Owner:CHINA MOBILE COMM LTD RES INST +1
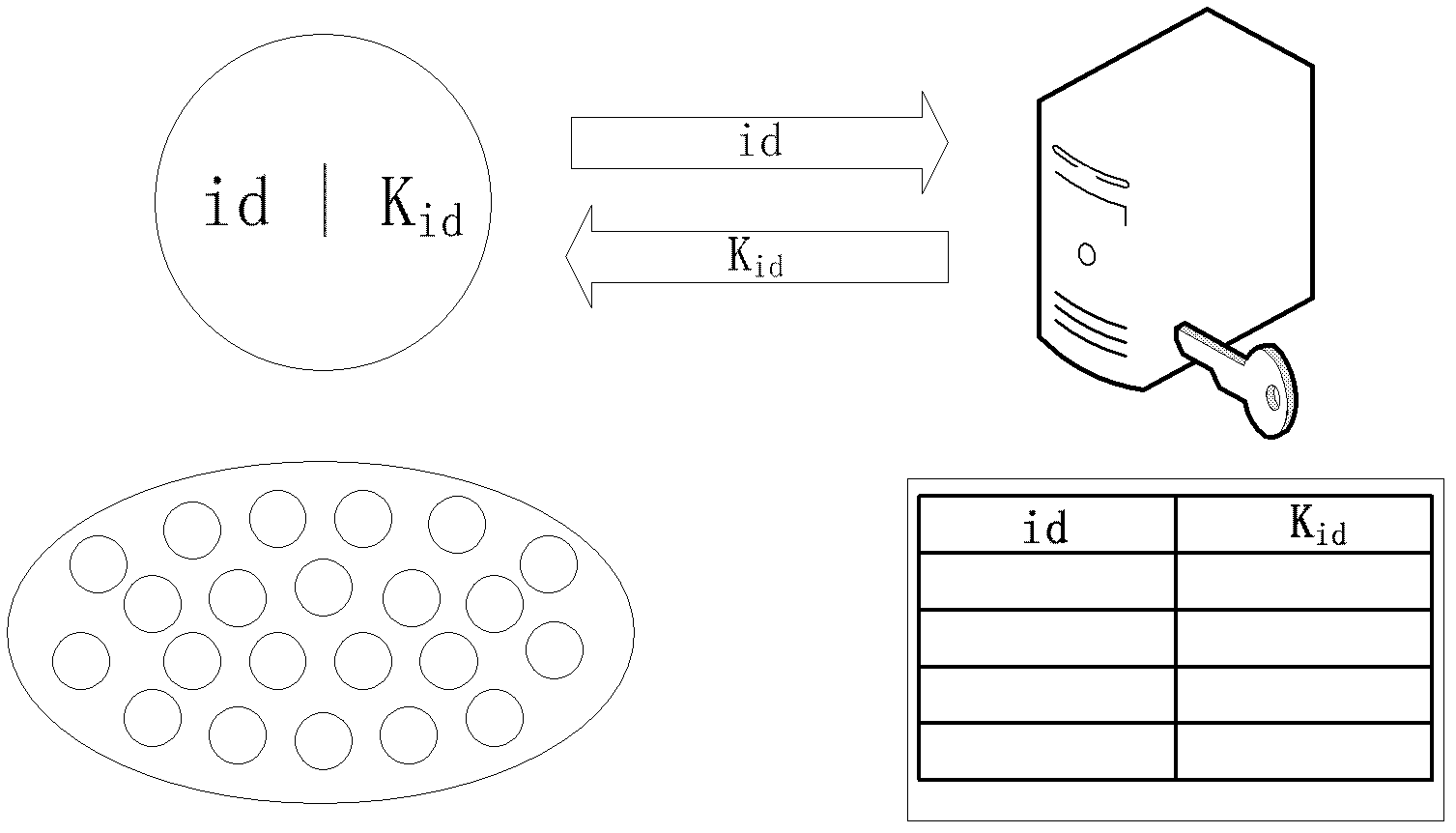
One-way data conversion apparatus and device authentication system
InactiveCN1525685AImprove securityIncrease the total number of groupsUser identity/authority verificationCoding/ciphering apparatusAuthentication systemComparator
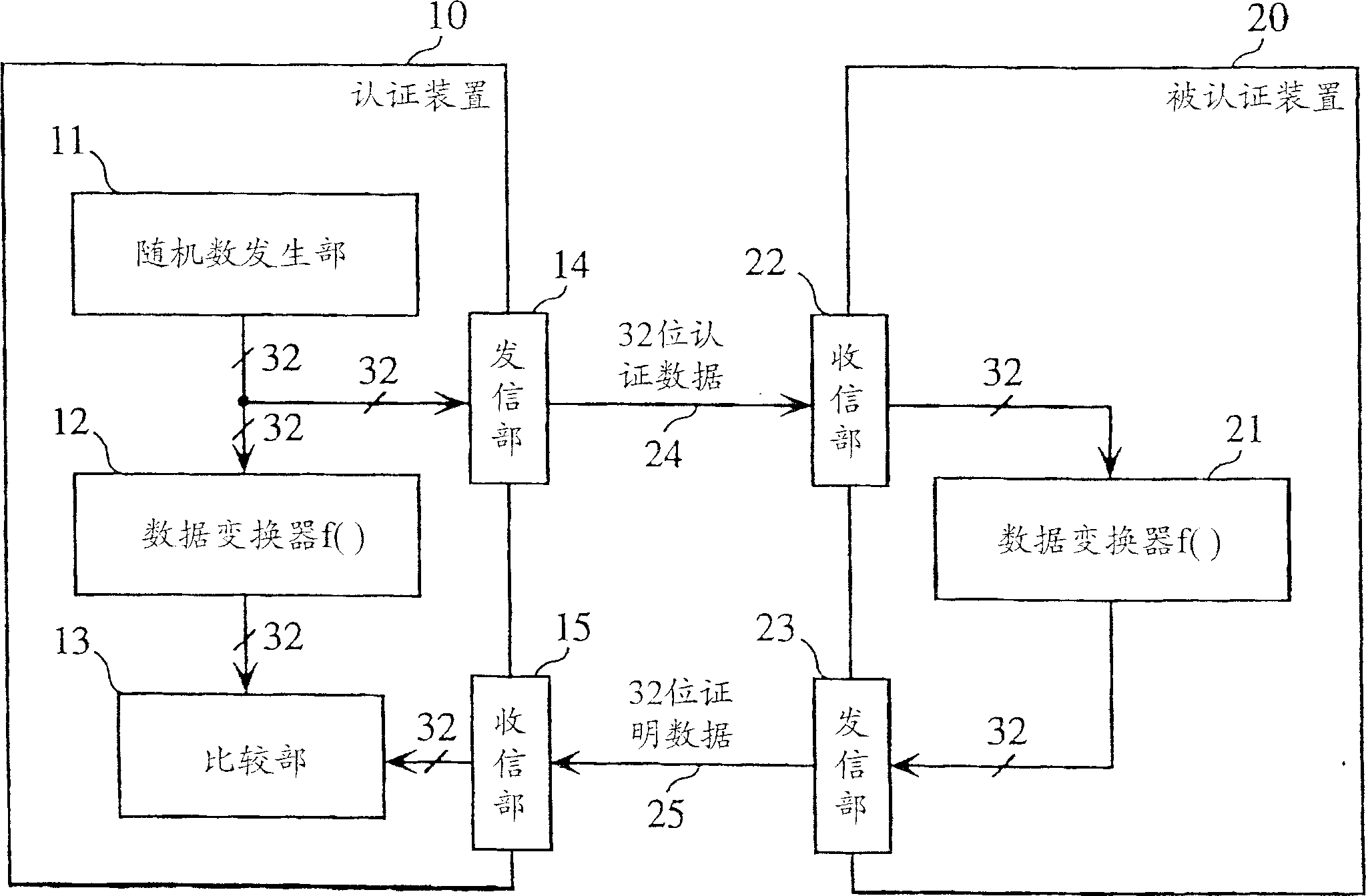
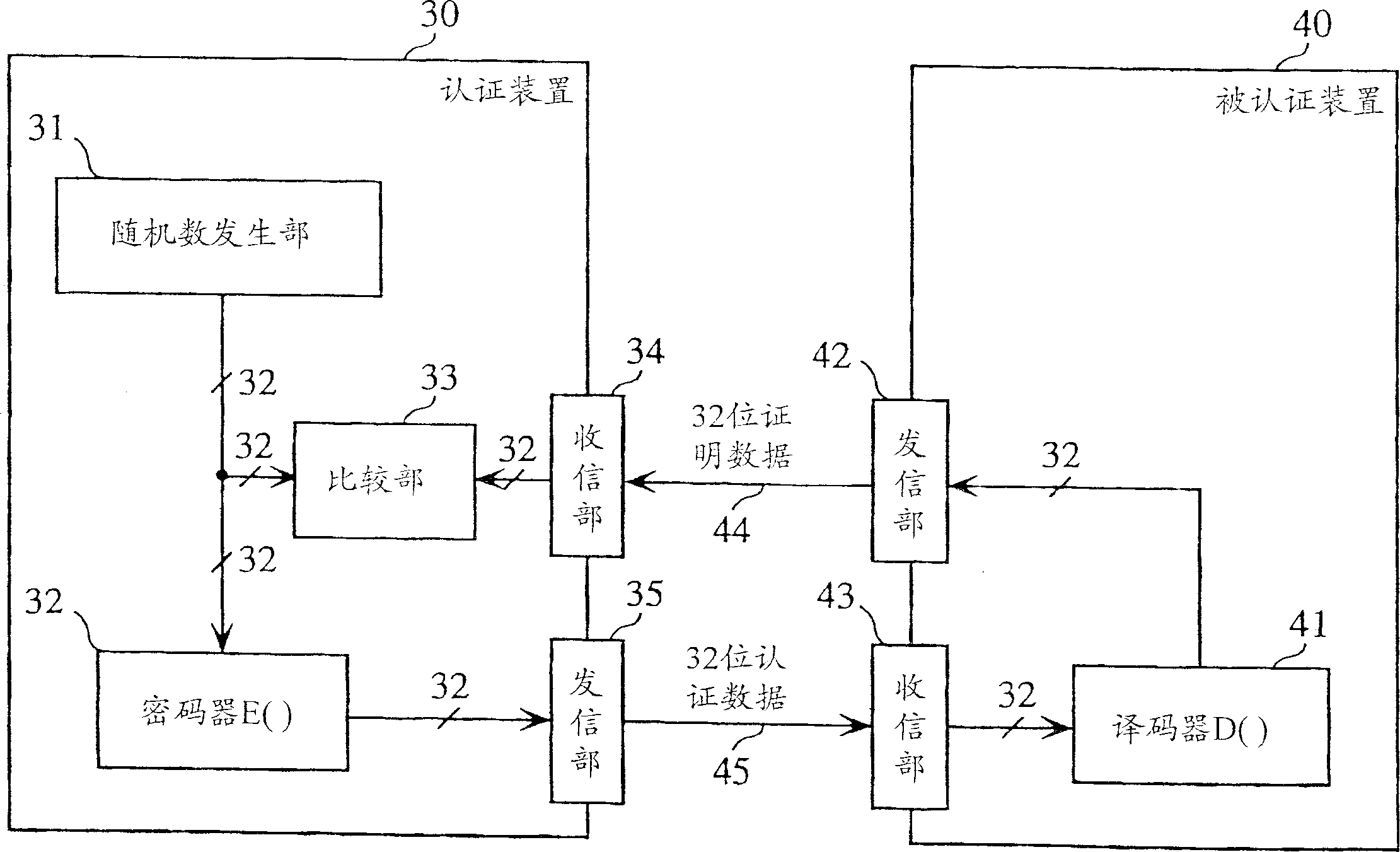
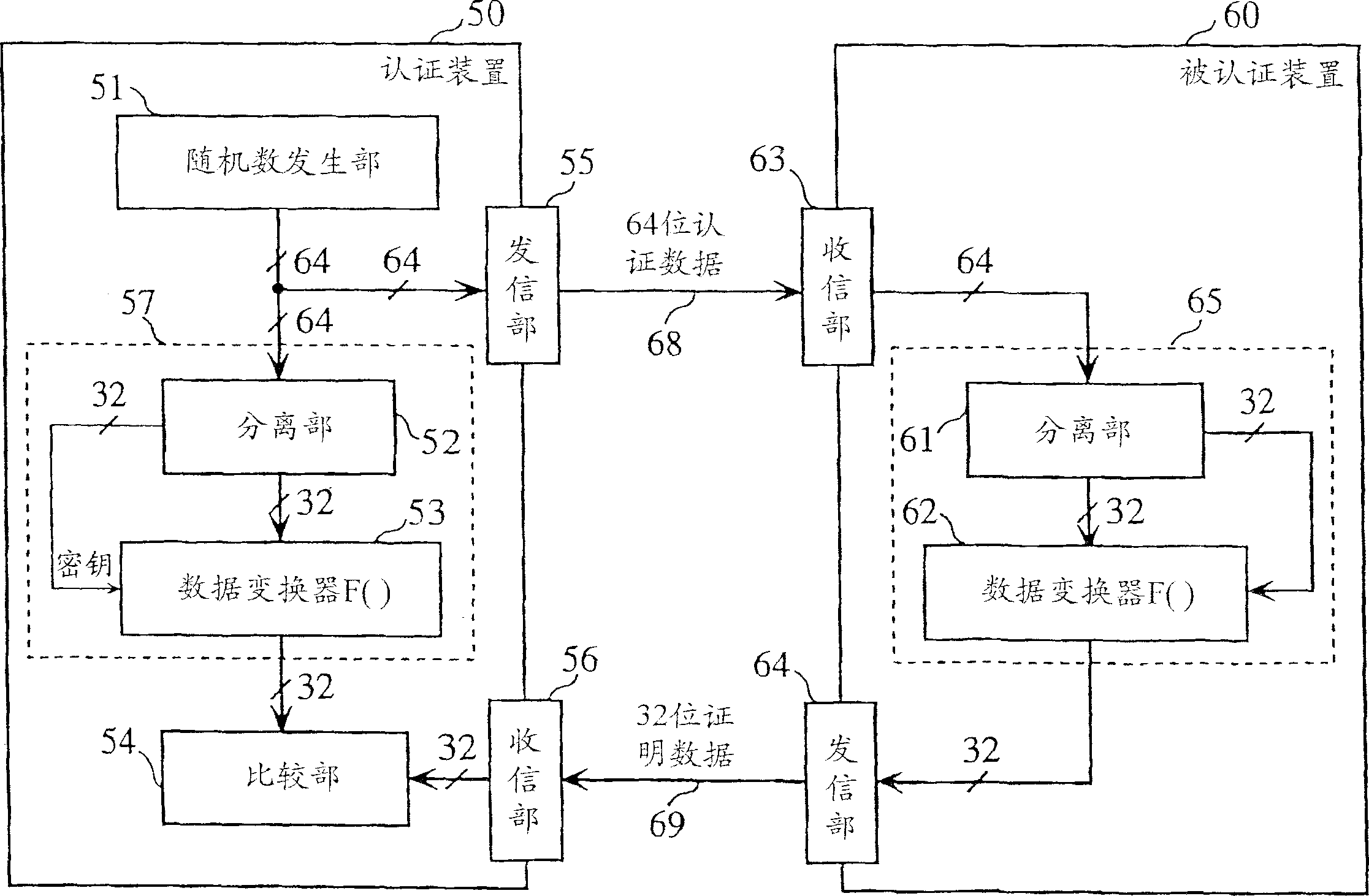
The verifier apparatus 50 includes a random number generation unit 51 that generates a 2n-bit random number, a separator unit 52 that separates the random number into two sets of n-bit data, a data conversion module 53 that converts one set of separated data using the other set of separated data as a key, and a comparator unit 54 that judges whether the converted result matches claimant data sent back from the claimant apparatus 60. The claimant apparatus 60 includes a separator unit 61 and a data conversion module 62 that have the same functions as the separator unit 52 and the data conversion module 53 in the verifier apparatus 50. The claimant apparatus 60 generates n-bit claimant data from the 2n-bit random number generated by the verifier apparatus 50, and sends the generated claimant data to the verifier apparatus 50.
Owner:PANASONIC CORP +1
A face-based identity authentication method and authentication device
ActiveCN102375970BAvoid the authentication processImprove authentication capabilitiesCharacter and pattern recognitionFace detectionPattern recognition
The invention provides an identity authentication method based on a face and an authentication apparatus thereof. The method comprises the following steps: carrying out face detection on each frame of image acquired by a camera device to obtain a face image, and tracking the face image to obtain a tracking result; carrying out an attitude analysis, wherein if a face attitude in obtained attitude information is not jumped relative to a face attitude corresponding to a prior frame of image, an attitude analysis result is not jumped; carrying out face comparison; carrying out statistics analysis on a plurality of frames of tracking results, a plurality of frames of attitude analysis results and a plurality of frames of face image authentication results, wherein if a statistics analysis result is in accordance with a preset condition, identity authentication is passed. According to the method and the apparatus thereof in the invention, a two-dimensional flat picture is utilized to distinguish a photograph from a human, in the prior art utilizing three-dimensional information and carrying out photograph identification cause that a system identification speed is substantially decreased and an application requirement can not satisfied, and the above technical problem is solved in the invention.
Owner:GUANGDONG VIMICRO
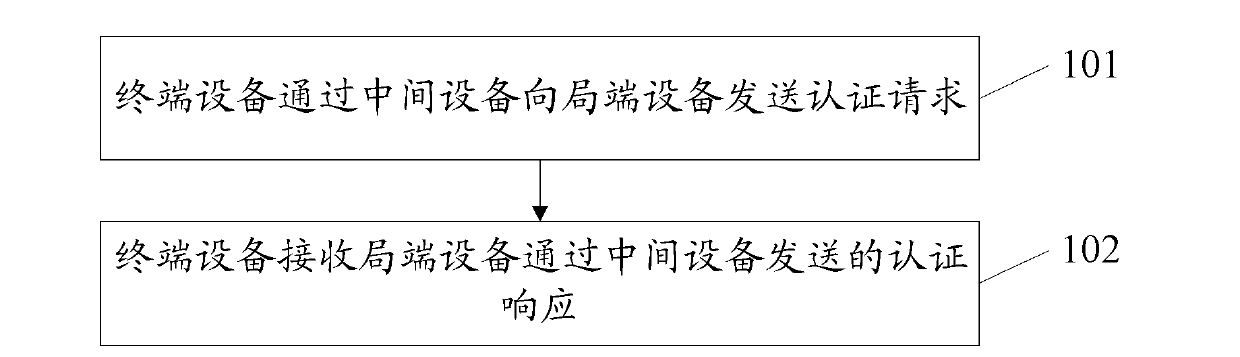
Authentication method, apparatus and system
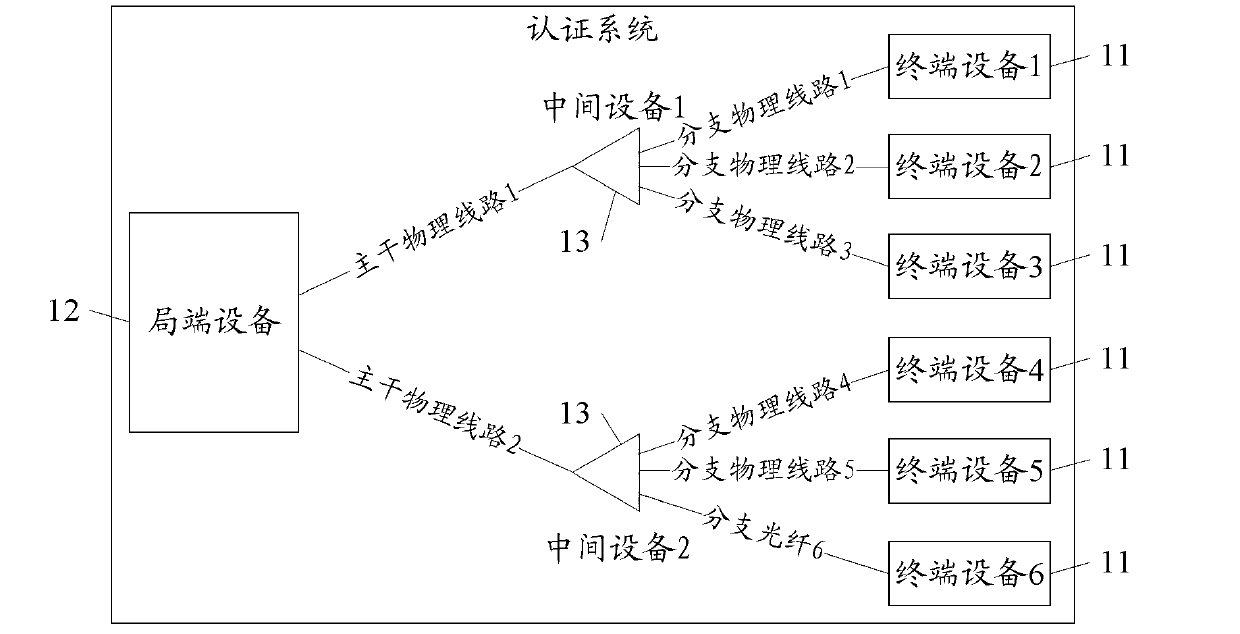
ActiveCN103222249AAvoid the authentication processReduce the burden onMultiplex system selection arrangementsTransmissionTerminal equipmentComputer science
An embodiment of the invention provides an authentication method, an apparatus and a system. The invention relates to the field of communication technology. The invention solves the problem that when the terminal is replaced, the physical identification information after replacing changes accordingly, the authentication apparatus carries out authentication of the terminal after replacing, and the process is very tedious, which increases the burden of the system and reduces the performance of the system. The concrete steps comprises: the terminal equipment sends an authentication request from intermediate equipment to central office terminal equipment; the terminal equipment receives the authentication response sent by the central office terminal equipment by the intermediate equipment, and the authentication response is carried out by the central office terminal equipment for the terminal equipment according to the authentication request and is returned after authentication. The invention can be applied to the authentication process of the terminal.
Owner:HUAWEI TECH CO LTD
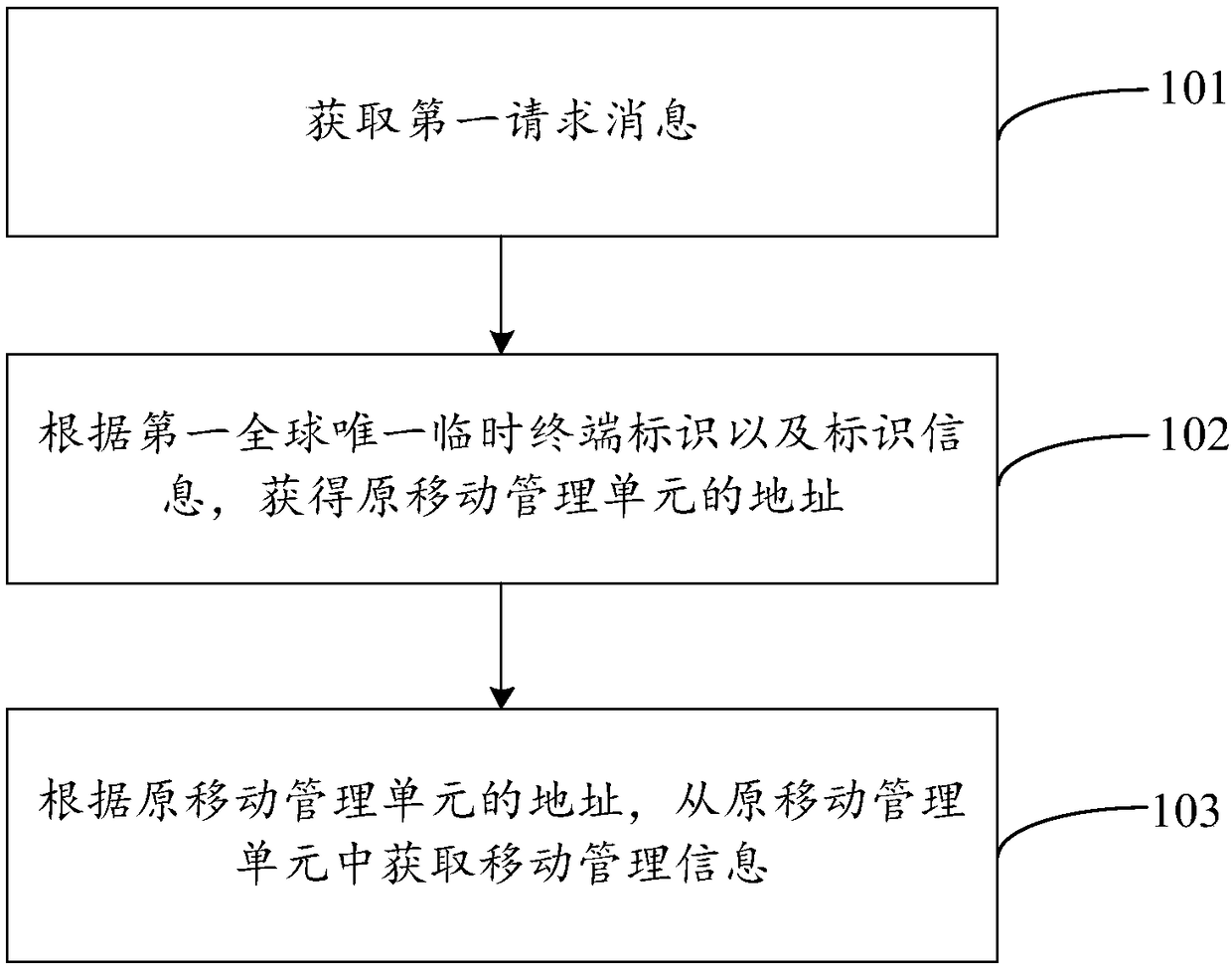
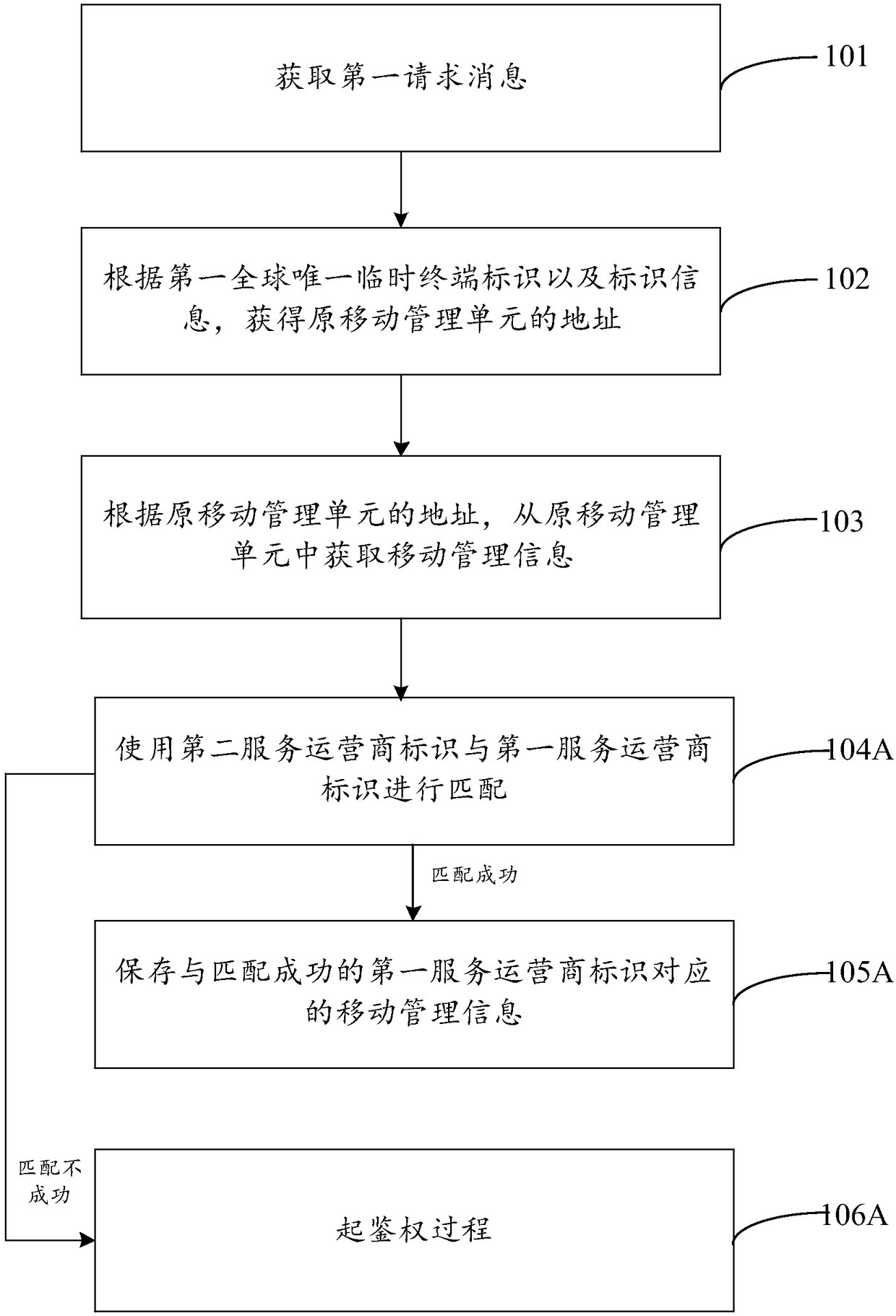
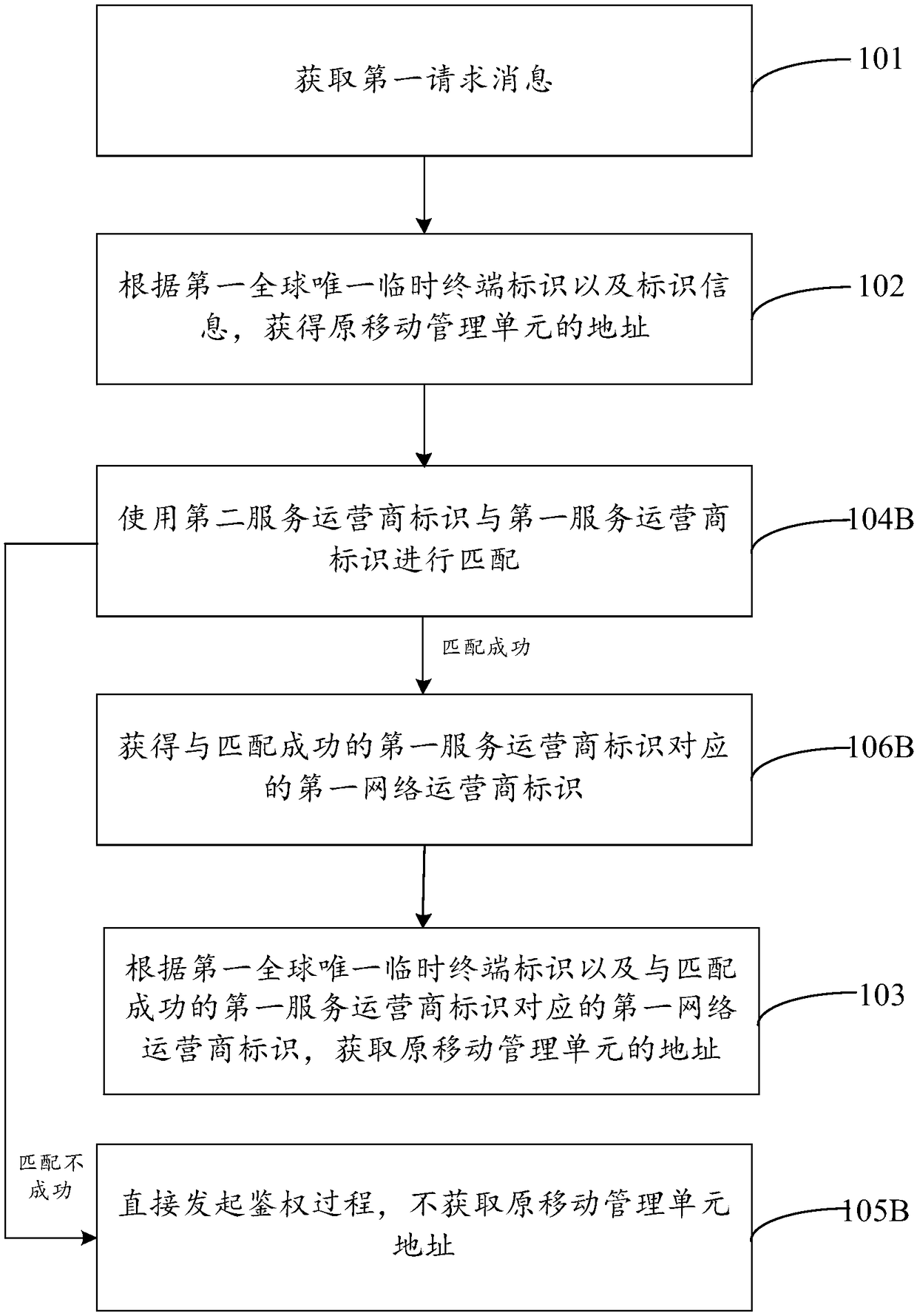
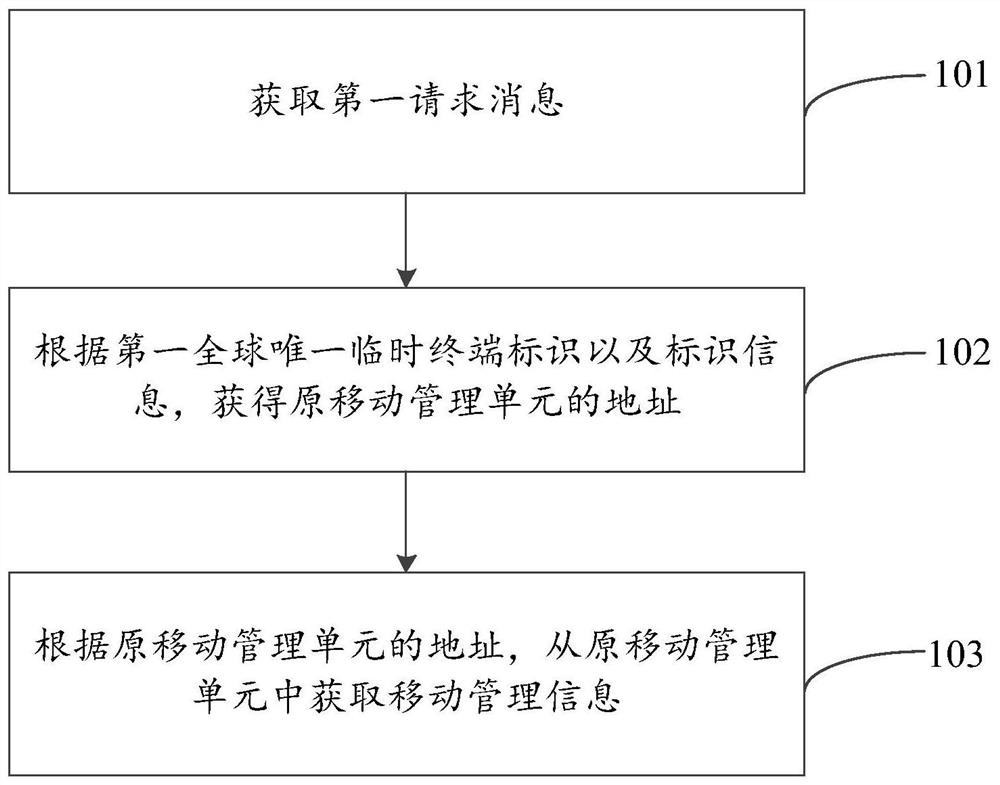
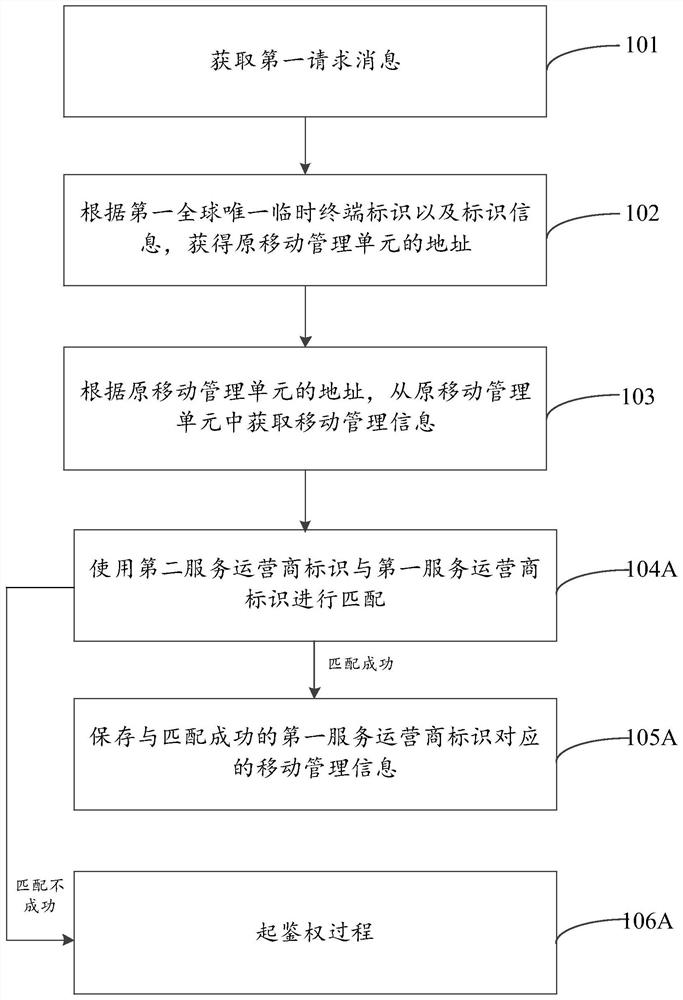
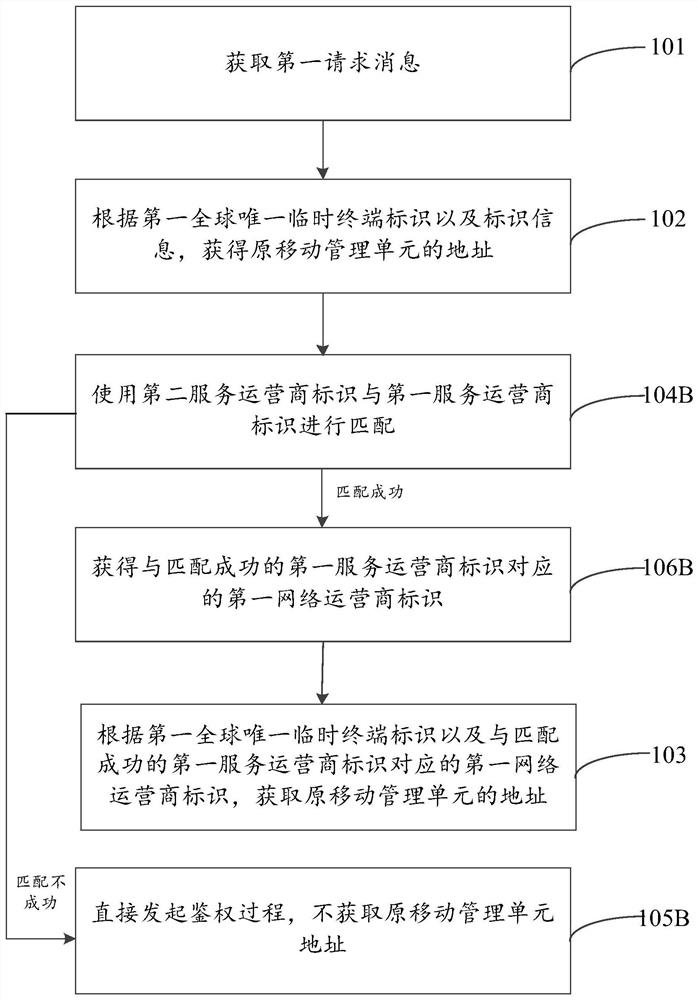
Method and device for acquiring mobile management information, and computer readable storage medium
ActiveCN108271230AReduce overheadReduce the burden onSecurity arrangementNetwork performanceManagement unit
Embodiments of the invention provide a method and a device for acquiring mobile management information, and a computer readable storage medium, relating to the field of communication technologies. Inone aspect, the method provided by the embodiments of the invention is configured to acquire a first request message that carries at least one first global unique temporary terminal identifier and atleast one piece of identifier information including a first network operator identifier, then obtain the address of an original mobile management unit according to the first global unique temporary terminal identifier and the identifier information, and further acquire the mobile management information from the original mobile management unit according to the address of the original mobile management unit. Therefore, the technical solution provided by the embodiments of the invention is capable of reducing the network burden and the network overhead to a certain extent, thereby improving the network performance.
Owner:BAICELLS TECH CO LTD
Radio resource control method and device, electronic equipment and storage medium
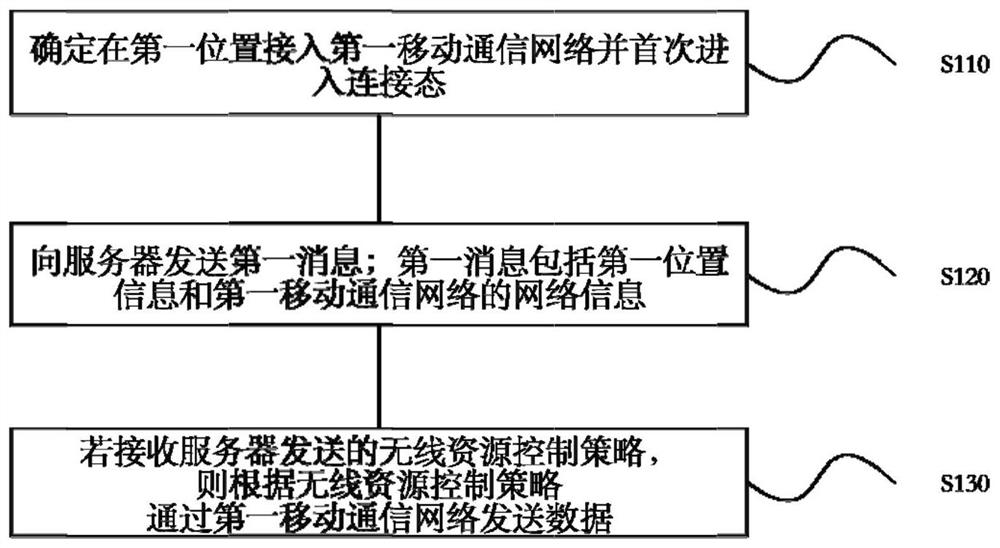
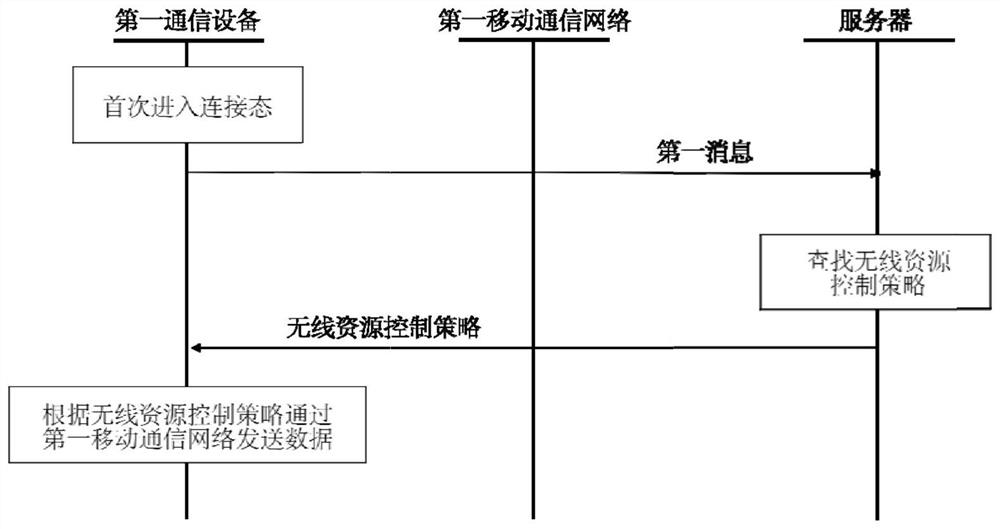
ActiveCN112449440AReduce the possibilityImprove experienceConnection managementMobile communication networkCommunication device
The invention is applicable to the technical field of wireless communication, and provides a wireless resource control method, which comprises the following steps: determining access to a first mobilecommunication network at a first position and entering a connection state for the first time; sending a first message to a server, wherein the first message comprises first position information and network information of a first mobile communication network, the first message is used for instructing the server to search for a wireless resource control strategy corresponding to the first positioninformation and the network information of the first mobile communication network; and if the wireless resource control strategy sent by the server is received, sending data through the first mobile communication network according to the wireless resource control strategy. Therefore, the possibility of RRC release is reduced, the authentication process of frequently initiating a service request isfurther avoided, the first communication device can provide a continuous data communication server under the condition of reasonable power consumption, and the user experience is improved.
Owner:SHENZHEN UCLOUDLINK NETWORK TECH CO LTD
Method for registering cluster control server, node control server and cloud system
ActiveCN102833256BAvoid the authentication processThe authentication server prevents theTransmissionAuthentication serverSecurity authentication
The invention discloses a method for registering a cluster control server. The method comprises the following steps that a cloud control server receives a cluster registration request, obtains network security authentication data and forwards the cluster registration request and the network security authentication data to a cloud security authentication server; the cloud security authentication server determines whether a user is an administrator, if yes, the cloud security authentication server, the cloud control server and a cluster control server to be registered carry out network security authentication, and whether the cloud system network is safe is verified; if the cloud system network is safe, the cloud control server obtains the host name, the address and the configuration information of the cluster control server to be registered, the host name, the address and the configuration information are recorded into configuration files, and finally the registration is successful; and if else, the registration is failed. The invention also discloses a method and a cloud system for registering a node control server. The embodiment of the invention can increased the security of the registration process for registering the cluster control server and the node control server.
Owner:GCI SCI & TECH
Operation method of electric energy meter based on multi-working mode
ActiveCN108120948BEnsure on-site operationEnsure site operation safetyElectrical measurementsMode controlControl engineering
Owner:NINGBO SANXING MEDICAL & ELECTRIC CO LTD
frame support
ActiveCN106660763BReduce switching operationsReduce vibrationVehicle fittings for liftingMixer accessoriesInsertion stentEngineering
Owner:FRIEDRICH WILH SCHWING GMBH
User authentication method for application program and mobile terminal equipment
ActiveCN104751046BSave resourcesAvoid the authentication processDigital data authenticationTerminal equipmentUser authentication
Owner:CHINA MOBILE COMM GRP CO LTD
A method and device for acquiring mobility management information, and a computer-readable storage medium
ActiveCN108271230BReduce overheadReduce the burden onSecurity arrangementCyber operationsNetwork overhead
Embodiments of the present invention provide a method and device for acquiring mobility management information, and a computer-readable storage medium, and relate to the technical field of communications. On the one hand, the method provided by the embodiment of the present invention obtains the first request message, the first request message carries at least one first globally unique temporary terminal identifier and at least one identification information including the first network operator identifier; thus Obtain the address of the original mobility management unit according to the first globally unique temporary terminal identifier and the identifier information; furthermore, acquire mobility management information from the original mobility management unit according to the address of the original mobility management unit. Therefore, the technical solutions provided by the embodiments of the present invention can reduce network load and network overhead to a certain extent, thereby improving network performance.
Owner:BAICELLS TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com