Certificate-free remote anonymous authentication method based on third party in cloud application
An anonymous authentication, certificate-free technology, applied in the field of information security, can solve the problems of high computational complexity, inability to resist public key replacement attacks, not considering the limited storage space of users, etc., to achieve high security, achieve anonymity, and improve security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
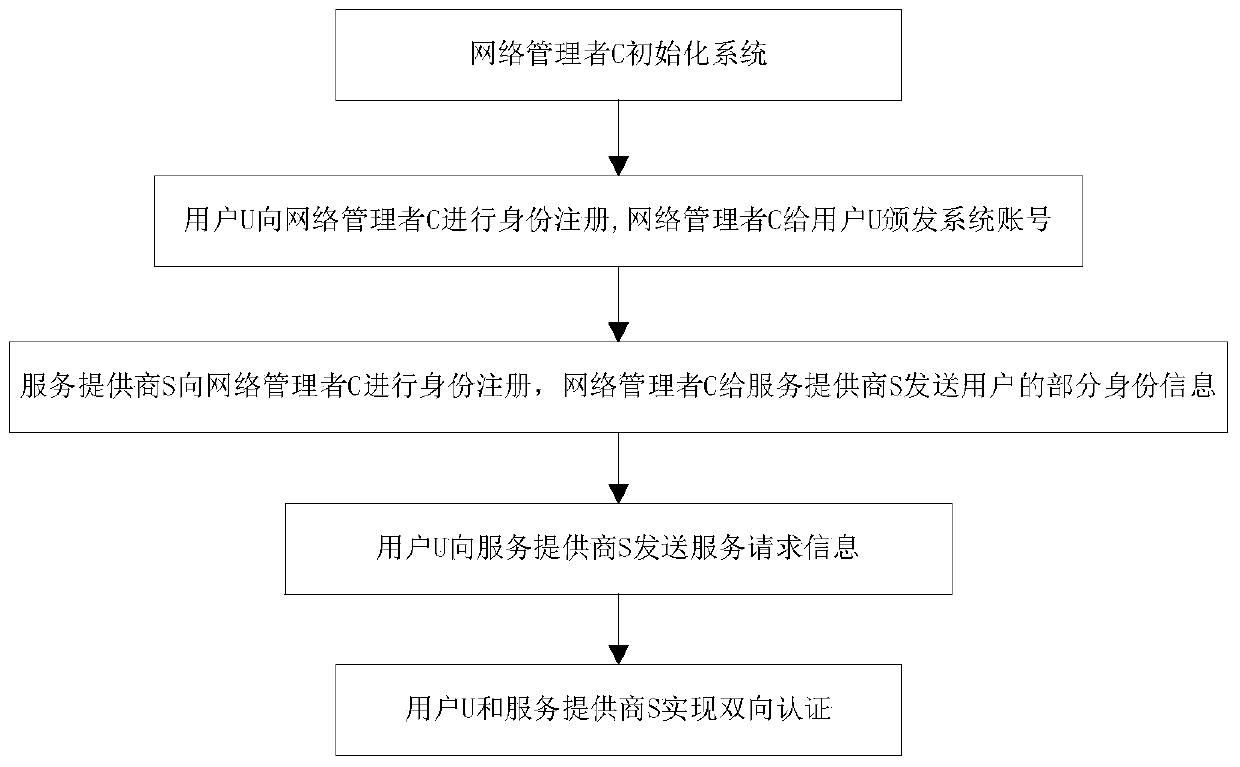
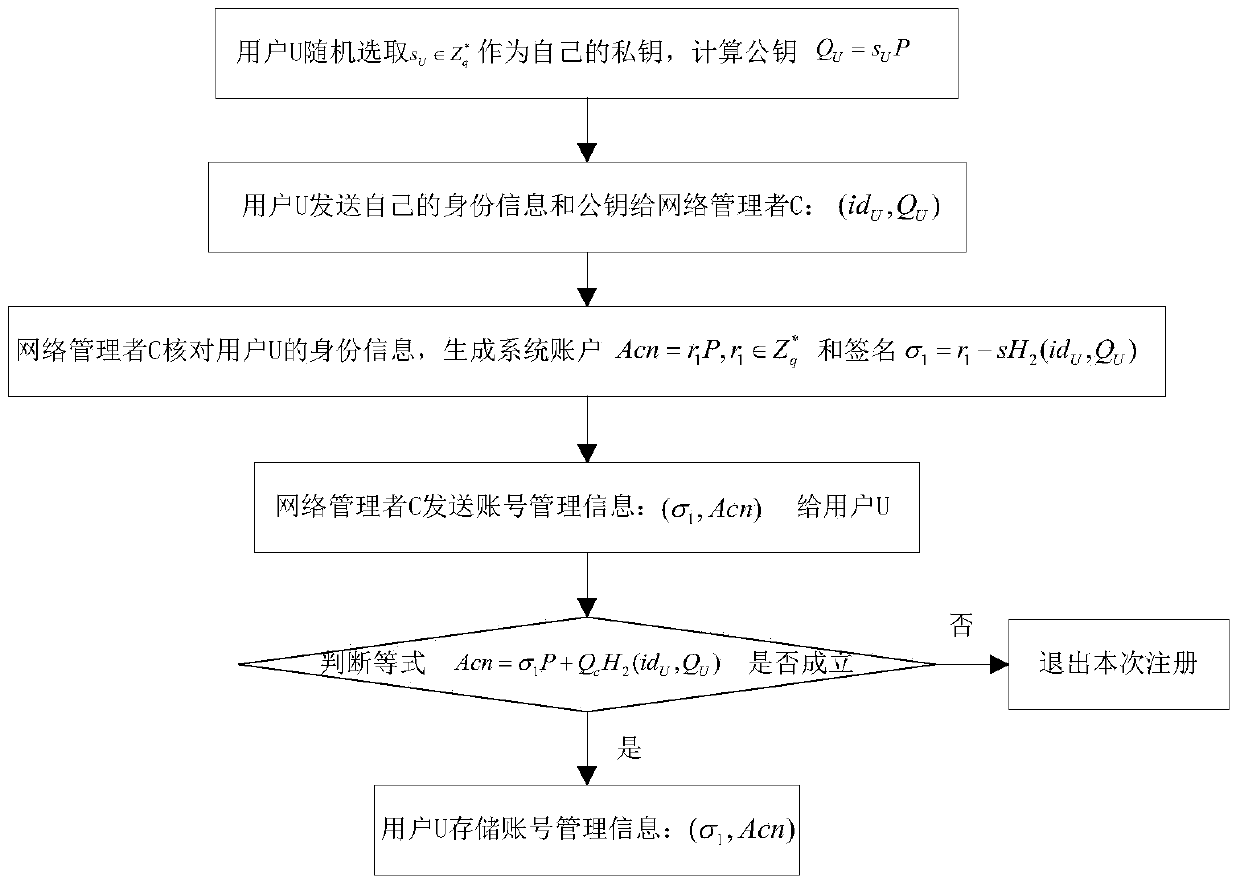
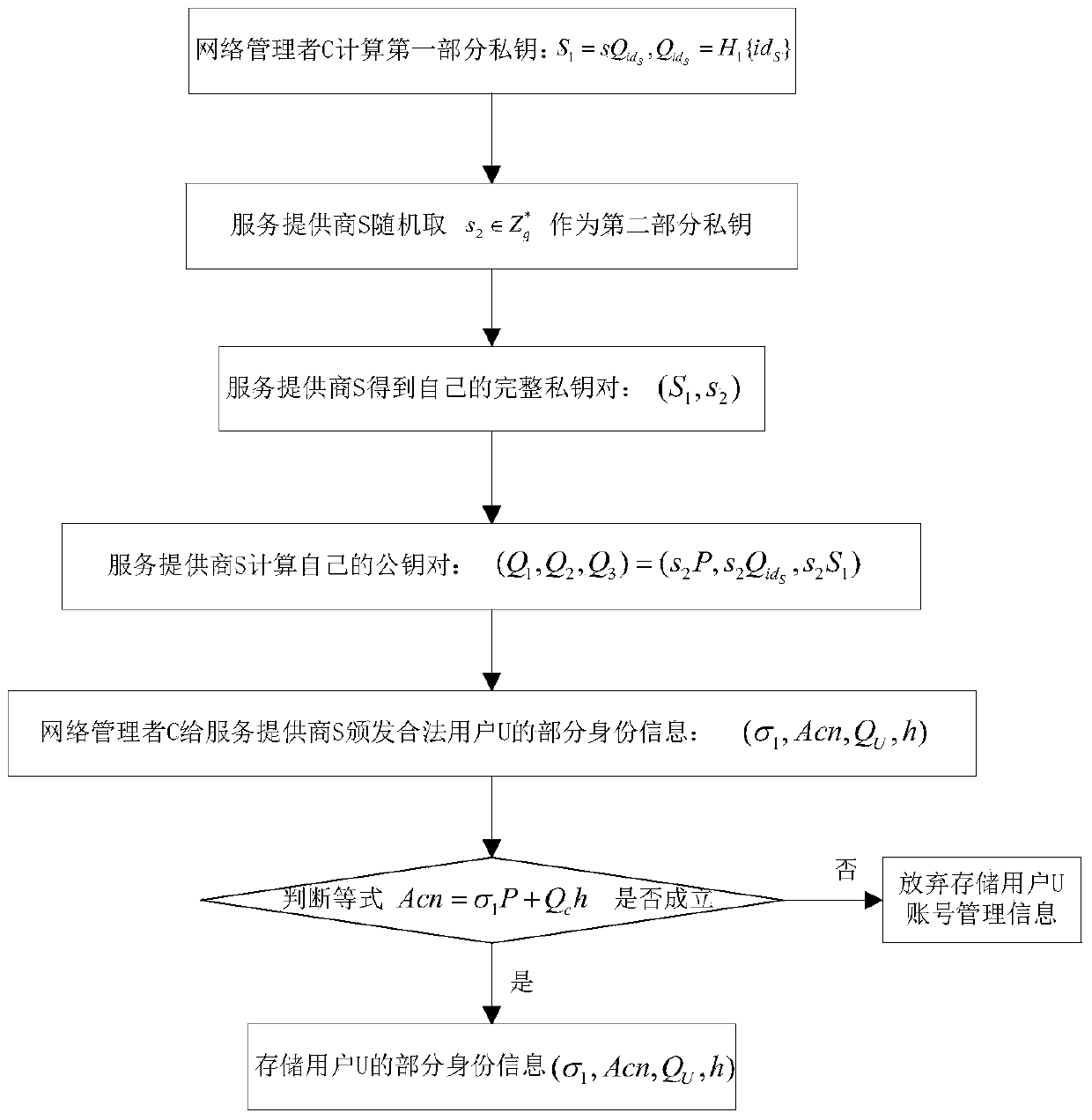
[0028] refer to figure 1 , the implementation steps of the present invention are as follows:
[0029] Step 1, network manager M initializes the system:
[0030] (1a) The network manager M determines the size of the safety factor l and the prime number q according to the safety requirements, and uses the elliptic curve to select the appropriate cyclic addition group G 1 and the cyclic multiplicative group G 2 Construct a bilinear pairing map e(G 1 ,G 2 ) → G 2 ;
[0031] (1b) The network manager M chooses two collision-free hash functions H 1 :{0,1} * →G 1 with Among them, H 1 It is to map 0 / 1 sequences of different lengths to the cyclic addition group G 1 An element-wise hash function on H 2 It is the 0 / 1 of different lengths and the cyclic addition group G 1 The elements in are mapped to the integer multiplicative group of modq The hash function of an element on ;
[0032] (1c) The integer multiplication group of the network manager M from modq randomly sel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com