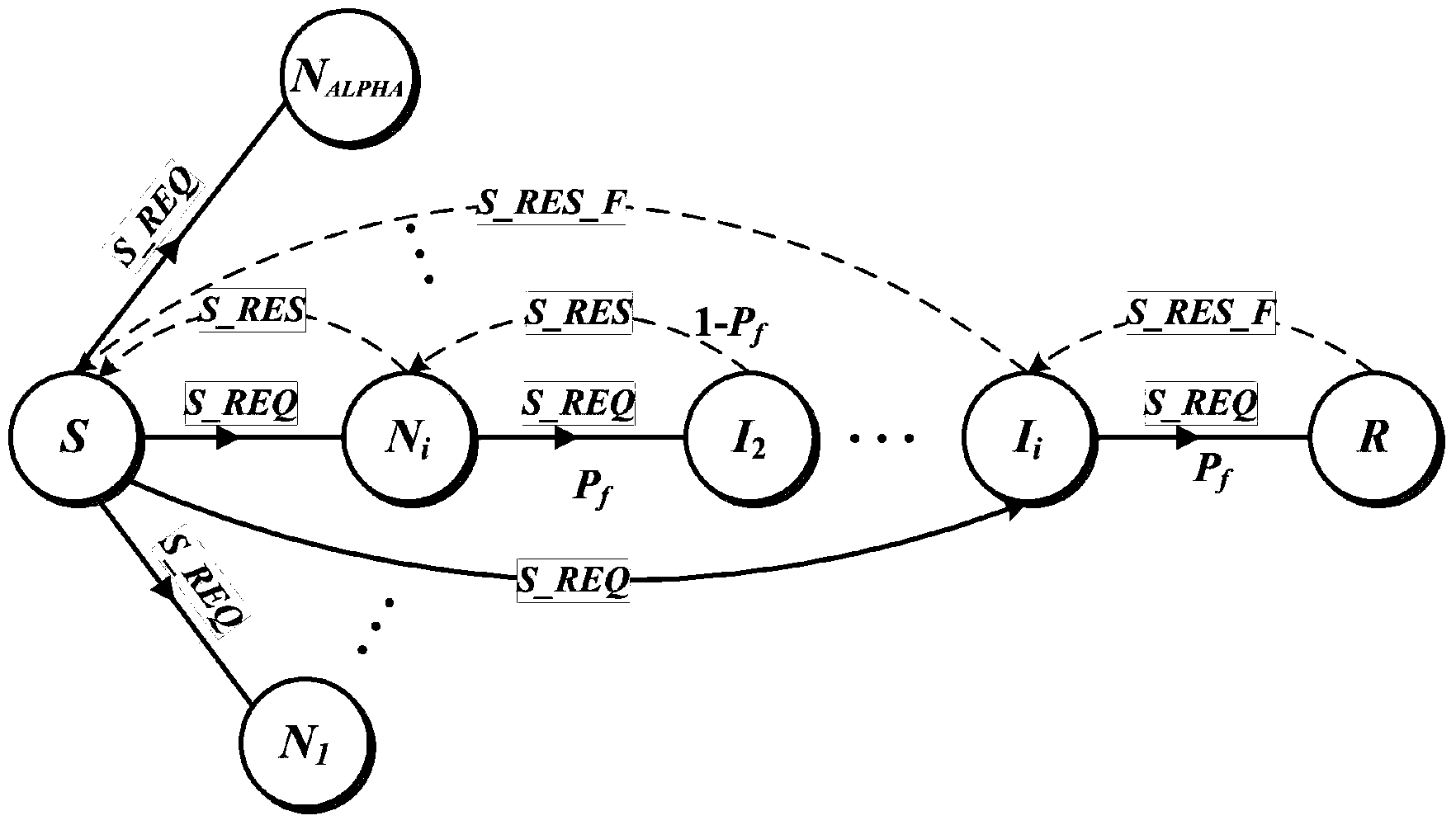
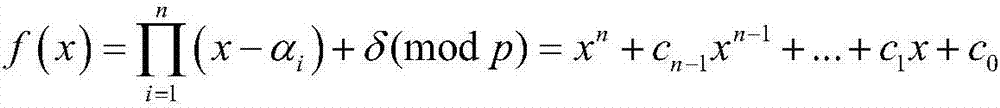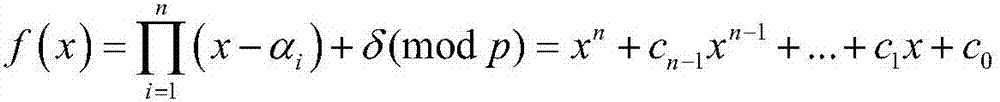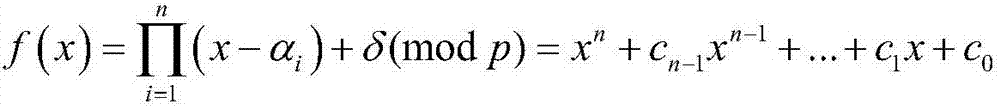Patents
Literature
238results about How to "Enhanced anonymity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
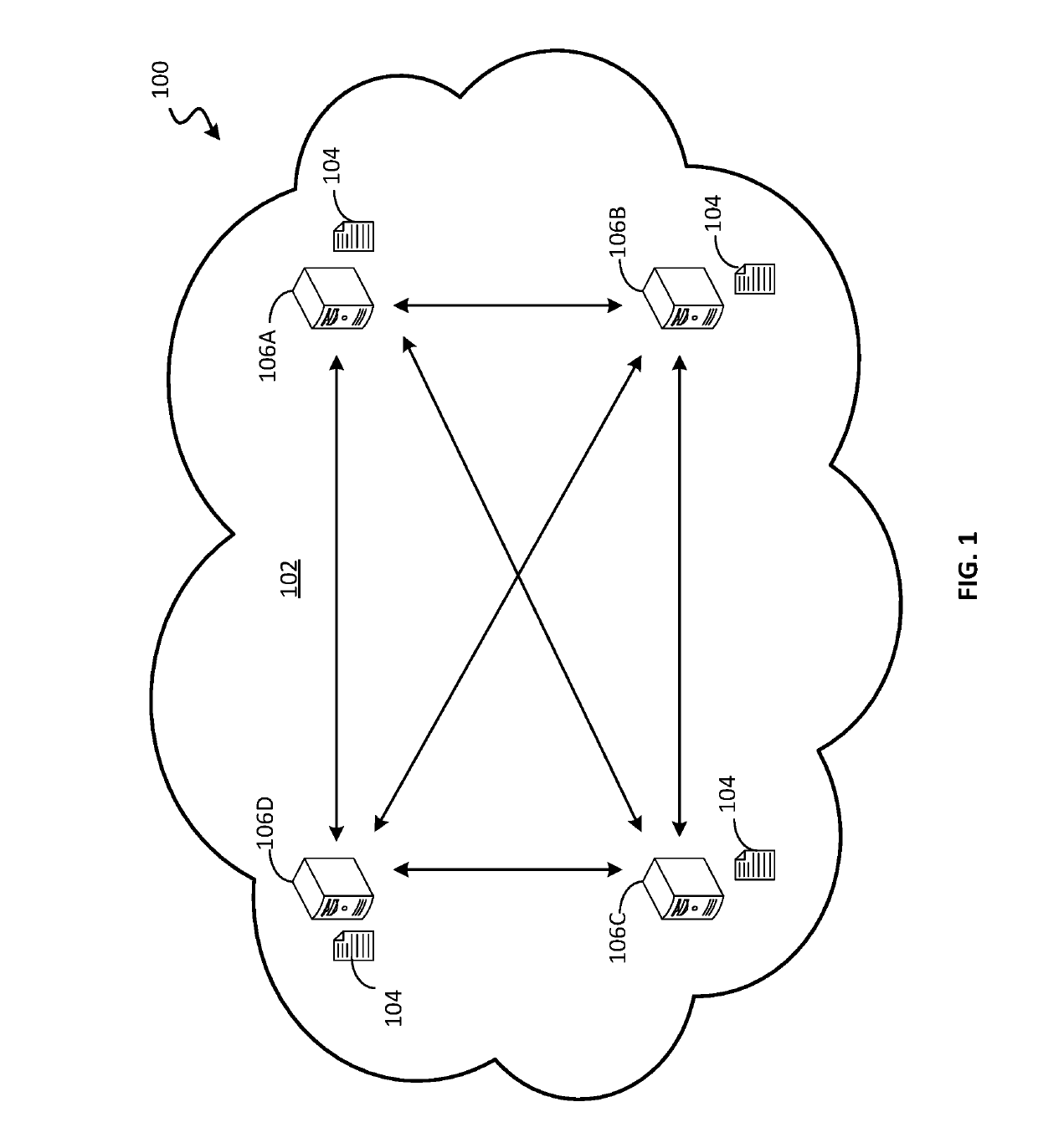
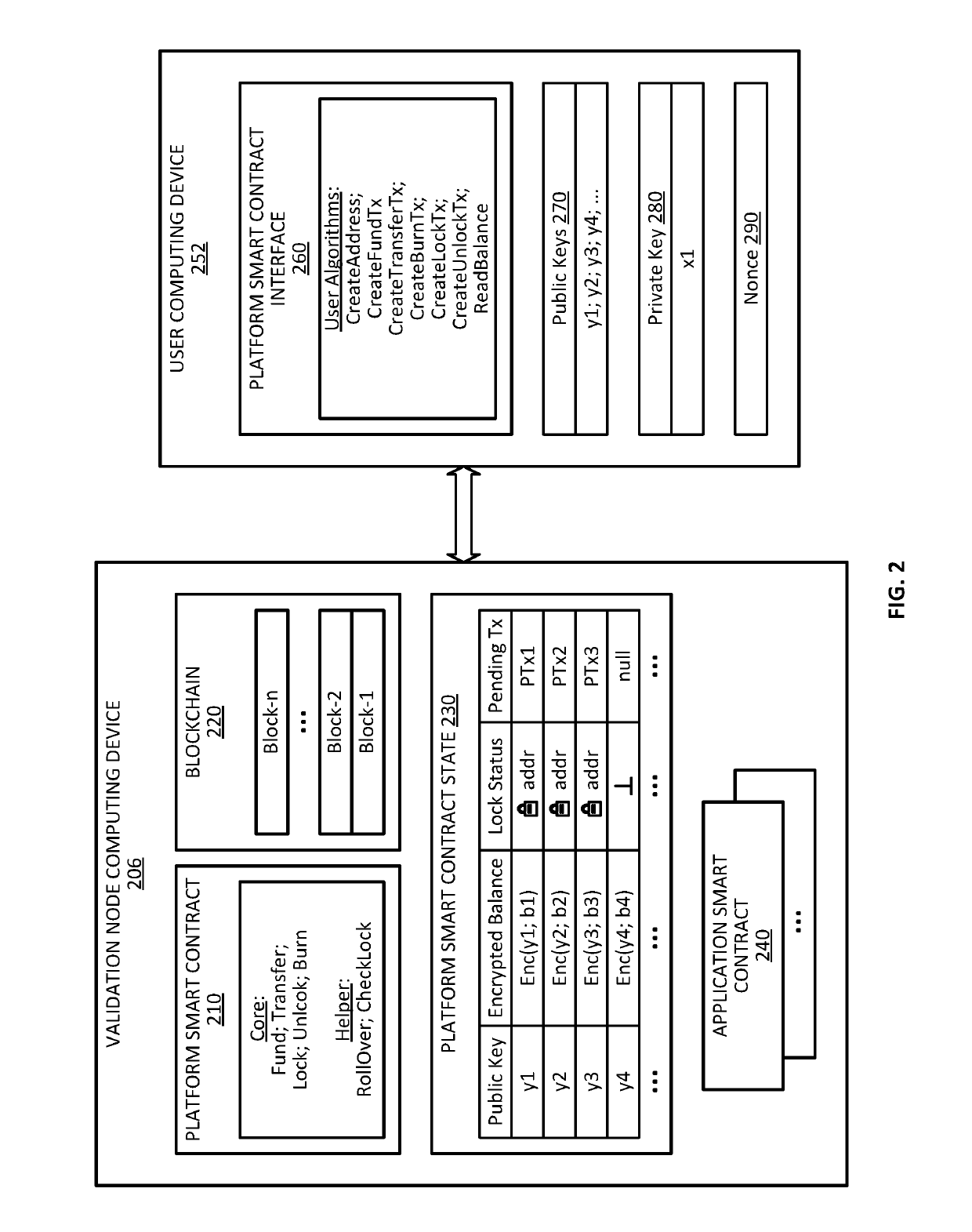
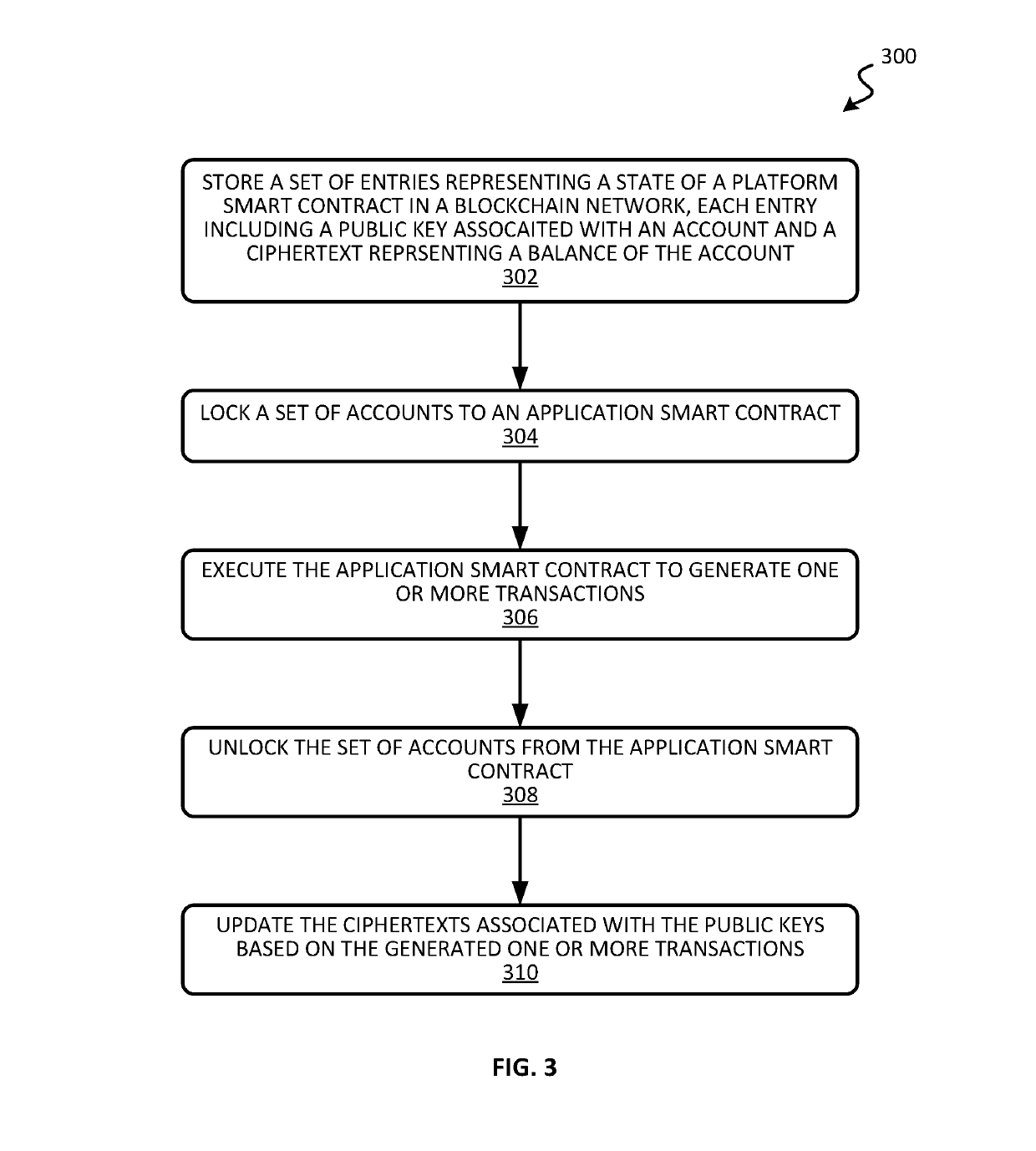
Blockchain system for confidential and anonymous smart contracts
ActiveUS20190164153A1Improve confidentialityEnhanced anonymityEncryption apparatus with shift registers/memoriesCryptography processingInternet privacyPrivacy preserving
Blockchain-based, smart contract platforms have great promise to remove trust and add transparency to distributed applications. However, this benefit often comes at the cost of greatly reduced privacy. Techniques for implementing a privacy-preserving smart contract is described. The system can keep accounts private while not losing functionality and with only a limited performance overhead. This is achieved by building a confidential and anonymous token on top of a cryptocurrency. Multiple complex applications can also be built using the smart contract system.
Owner:VISA INT SERVICE ASSOC +1
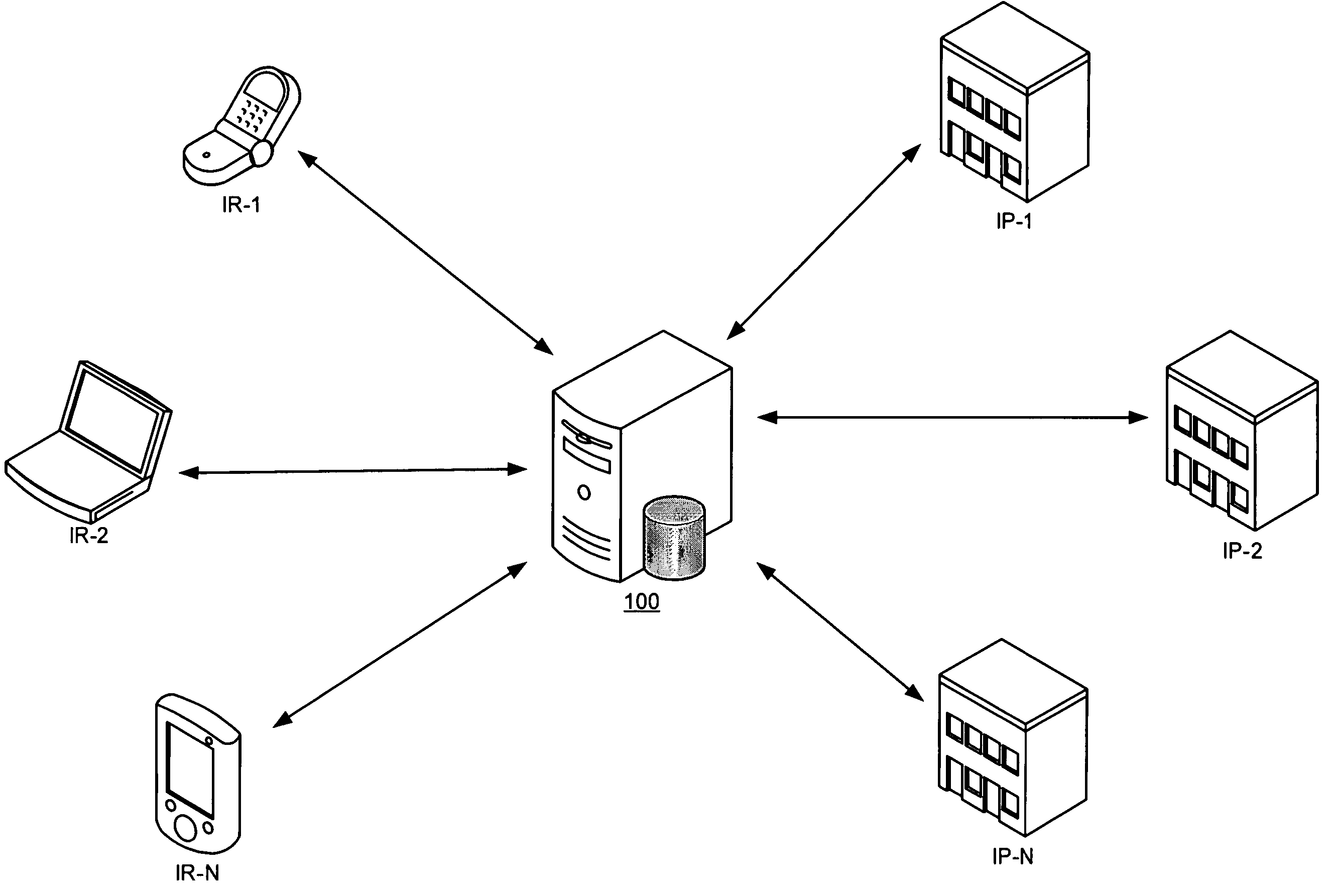
Public relations communication methods and systems
InactiveUS20060059129A1Easily search for informationEasy to getWeb data indexingData switching networksEmail addressSpamming
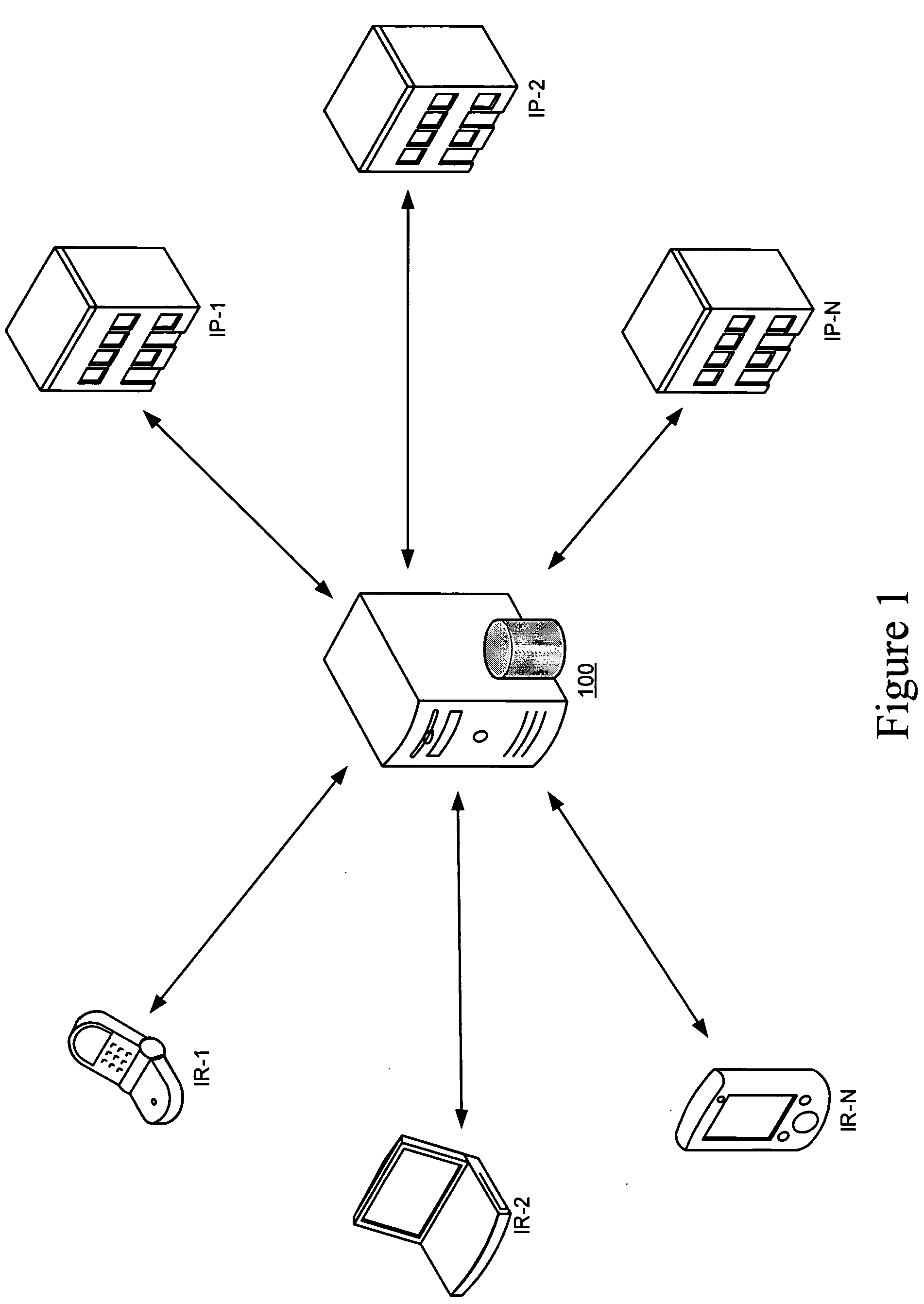
An arrangement for distributing information from Information Providers (IP) to Information Recipients (IR) that utilizes the email system and the Internet to communicate with popular hardware devices—computers, PDAs, cellular phones, etc. IRs receive information anonymously and only the information desired. IPs do not need to “spam” the world in the hope of getting their information into the right hands because it is organized in a manner that allows IRs to receive exactly what they are looking for. Information is provided by an IP to an IR in response to a request from an IR. A PR server organizes and stores information uploaded by IPs, retrieves information requested by an IR and sends an automated response to the IR. A web domain is associated with the PR server provides a common email addressing scheme for communicating between the PR server and the IRs.
Owner:AZUMA HIDEYUKI
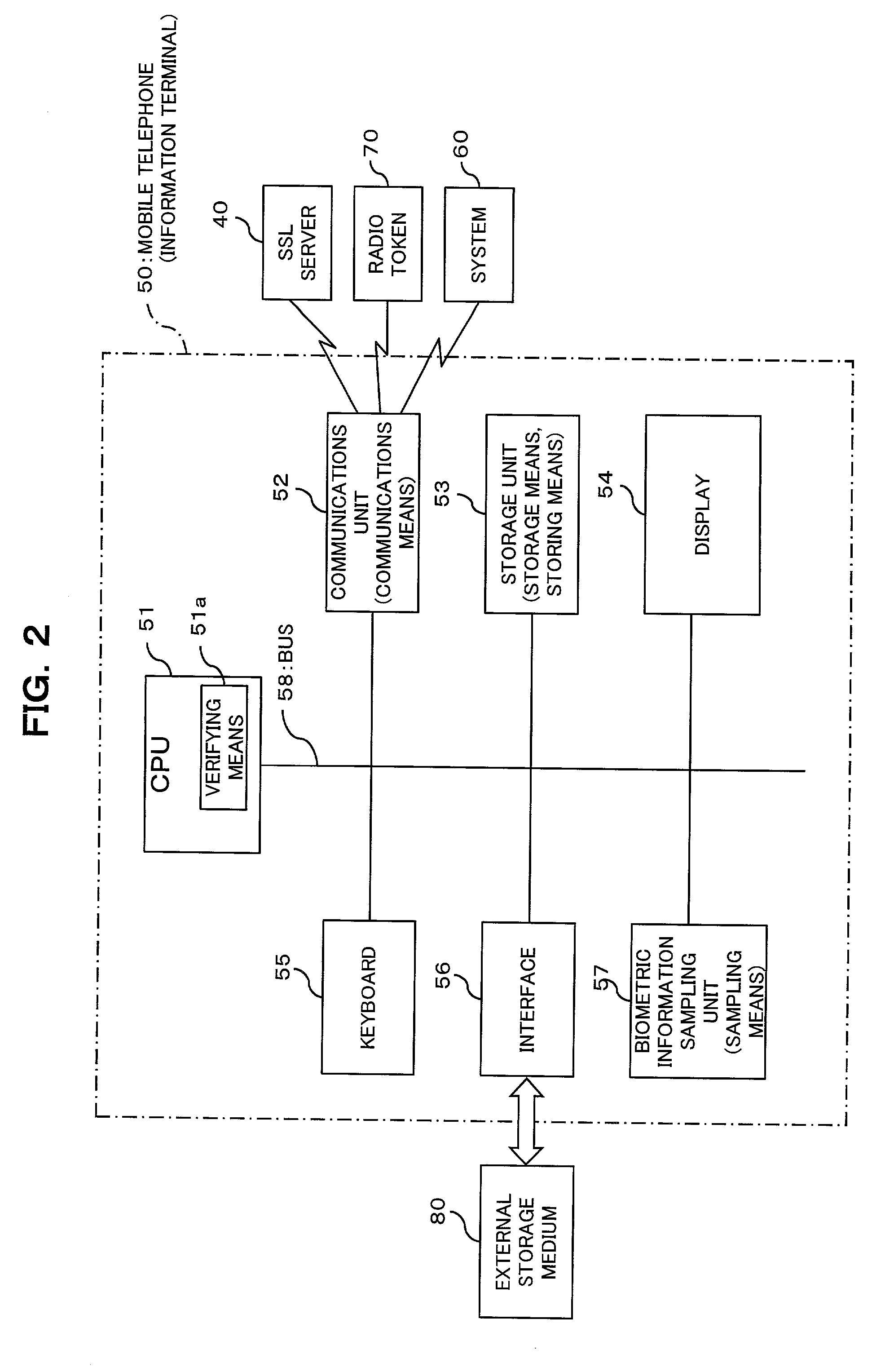
Confidential information management system and information terminal for use in the system
InactiveUS20030004881A1Simplify user operationsAvoid problemsUser identity/authority verificationUnauthorized memory use protectionUser verificationInternet privacy
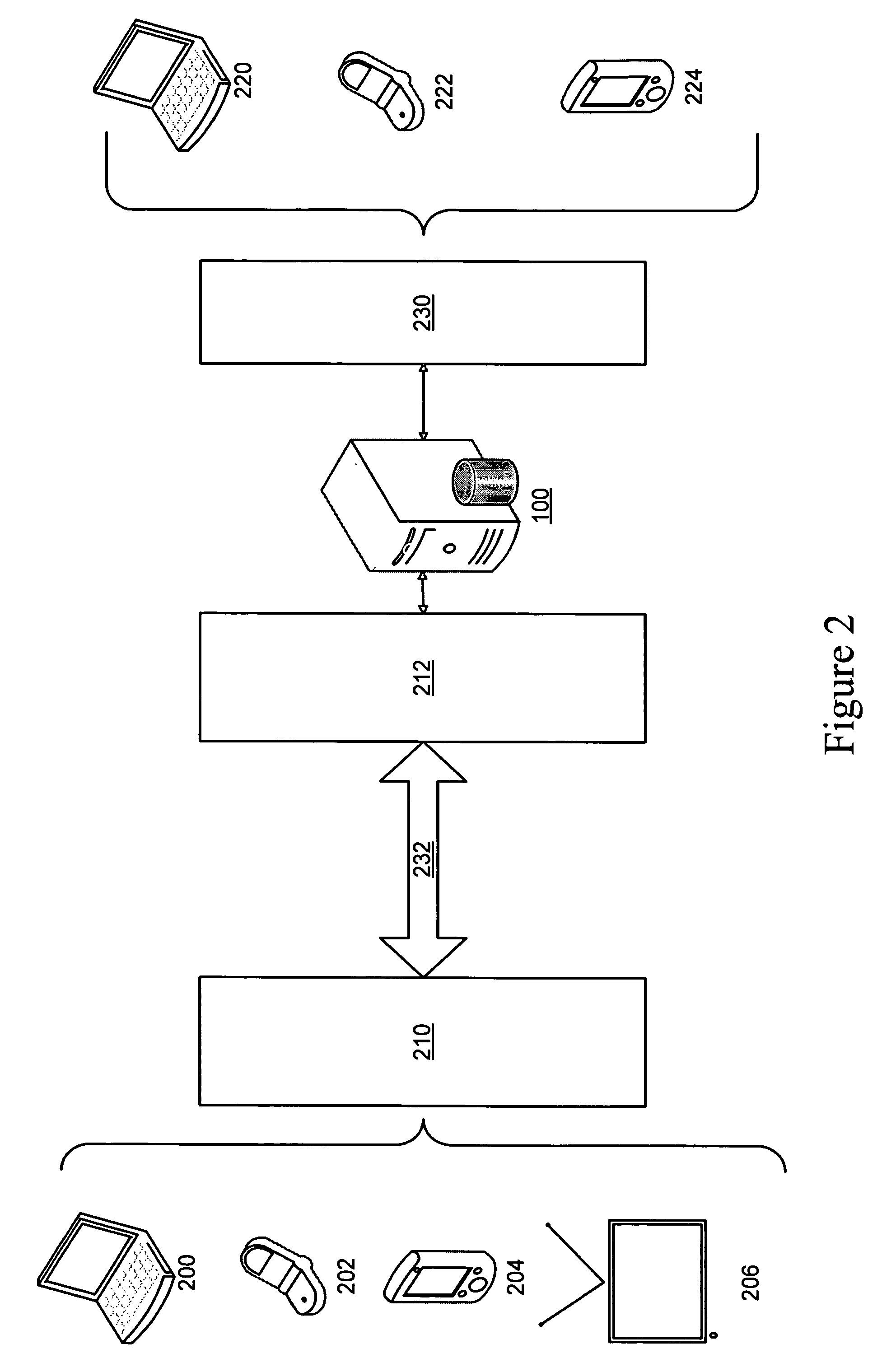
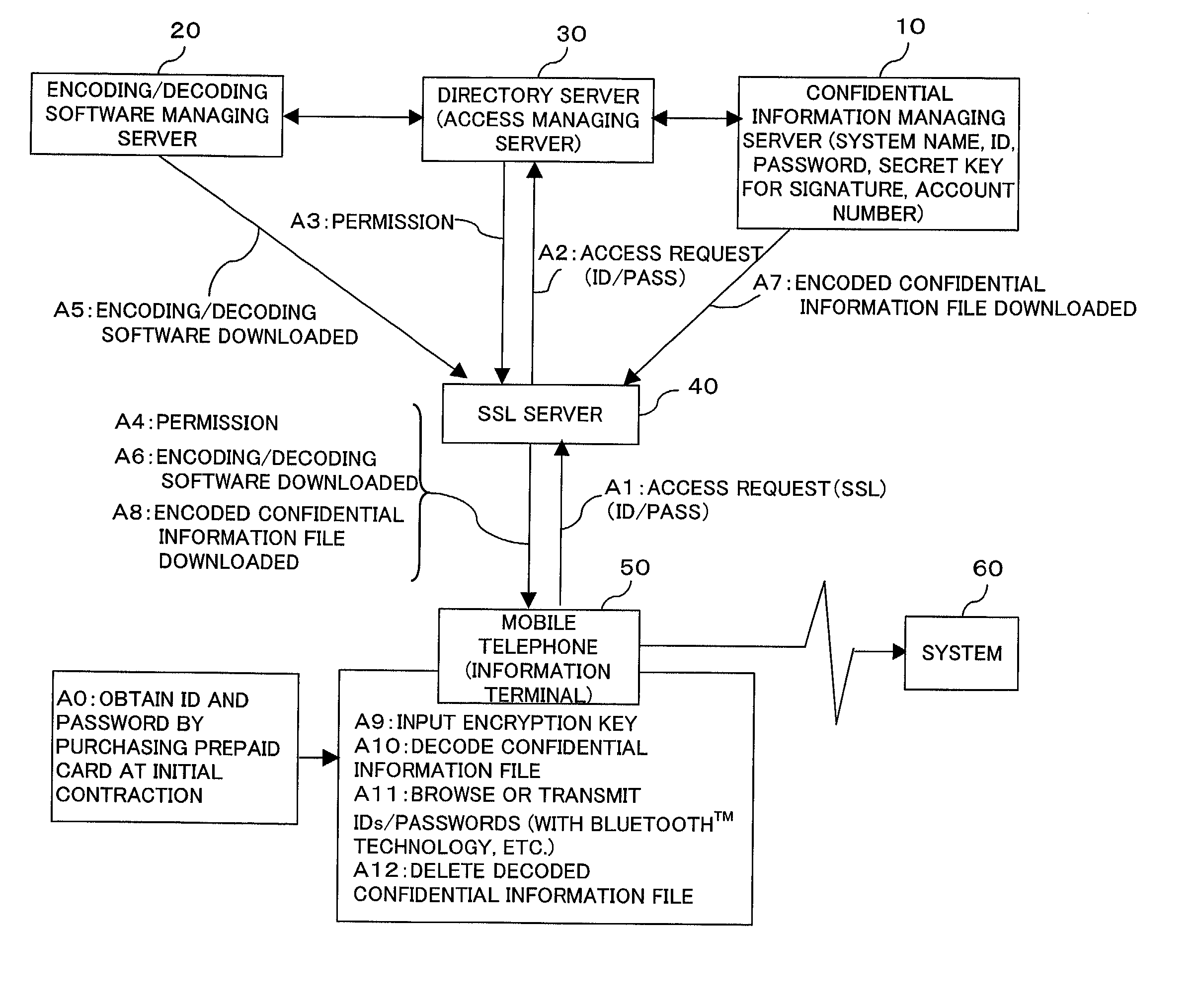
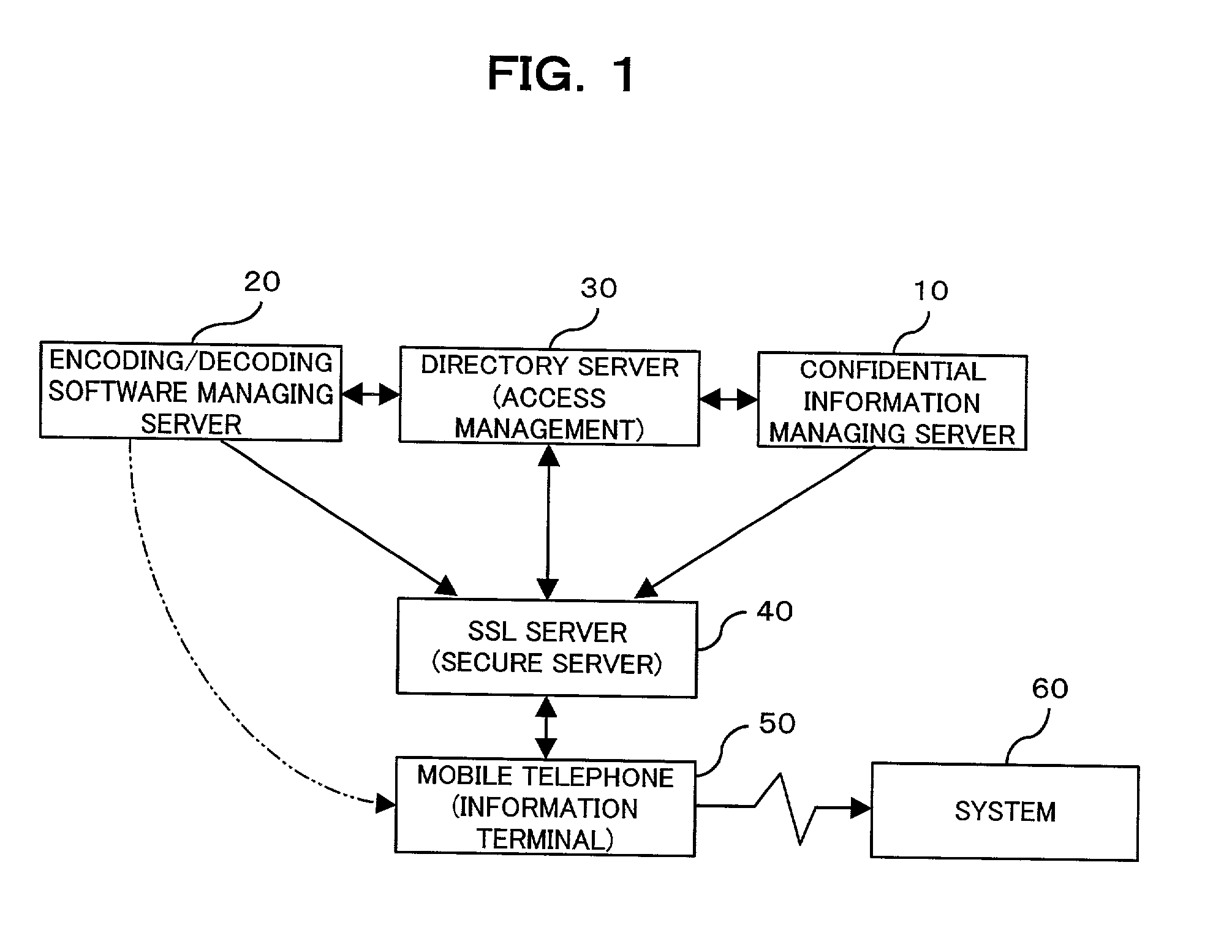
The present invention provides a confidential information management system which allows users to securely obtain confidential information files containing various confidential information, which files are securely stored in the present system, anywhere and anytime, using a minimum of confidential information. A confidential information file and encoding / decoding software are downloaded to an information terminal from a confidential information managing server and an encoding / decoding software managing server, respectively, so that the confidential information file is decoded on the information terminal by using the encoding / decoding software. The present system is applicable to various (computer) systems which store and manage confidential information (ID numbers, passwords, encryption keys, digital certificates, etc.) for use in user verification.
Owner:FUJITSU LTD
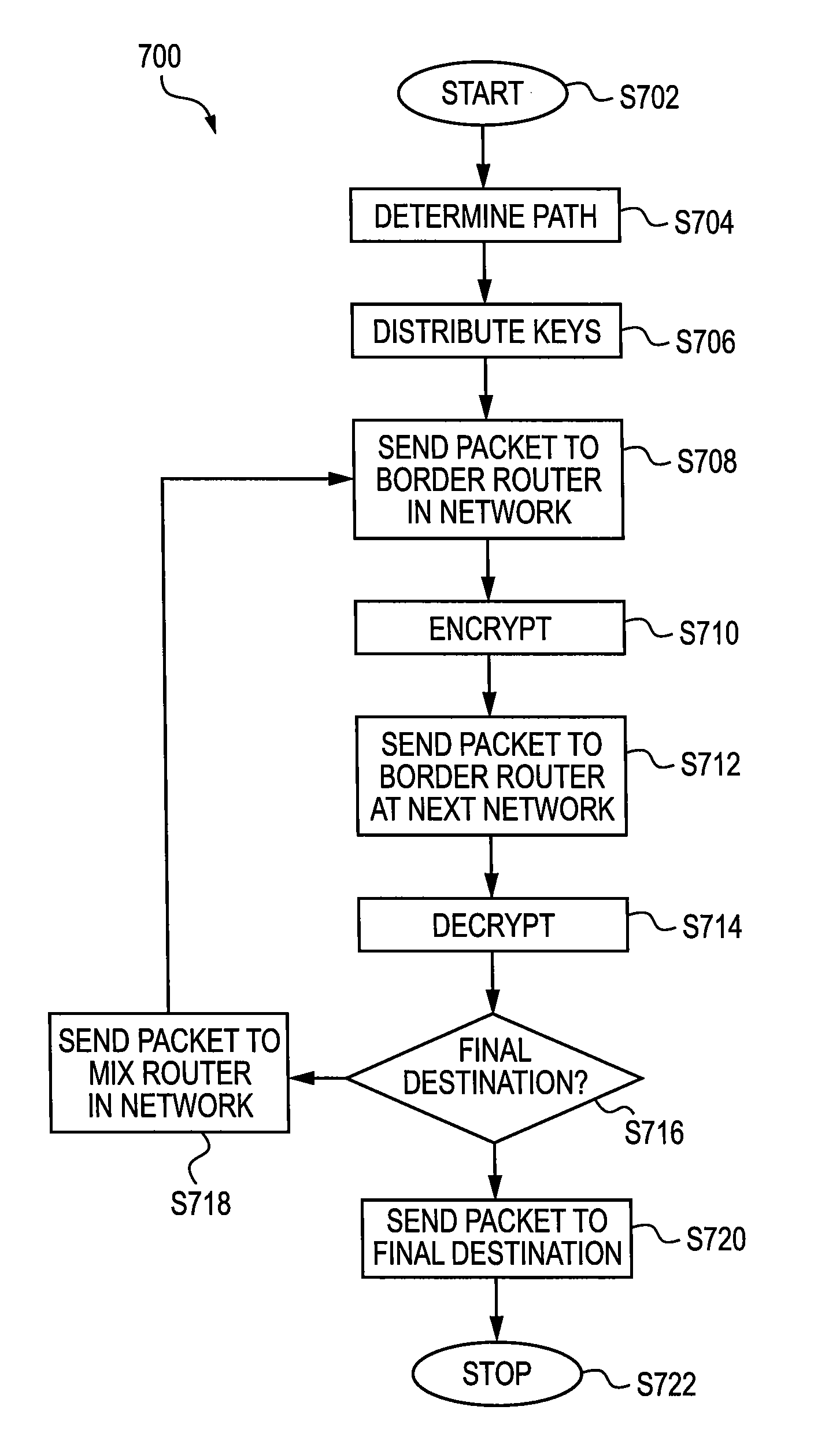
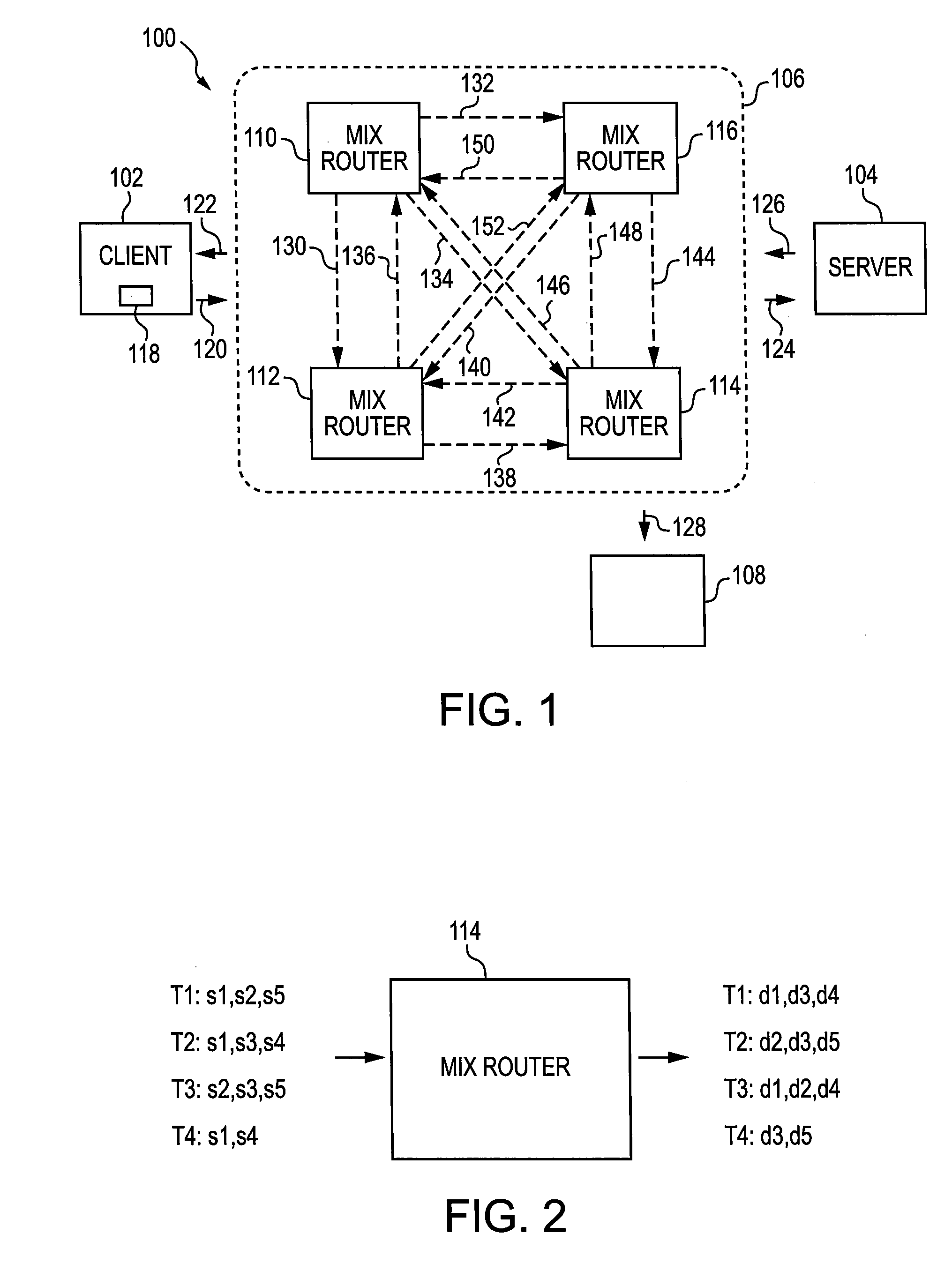
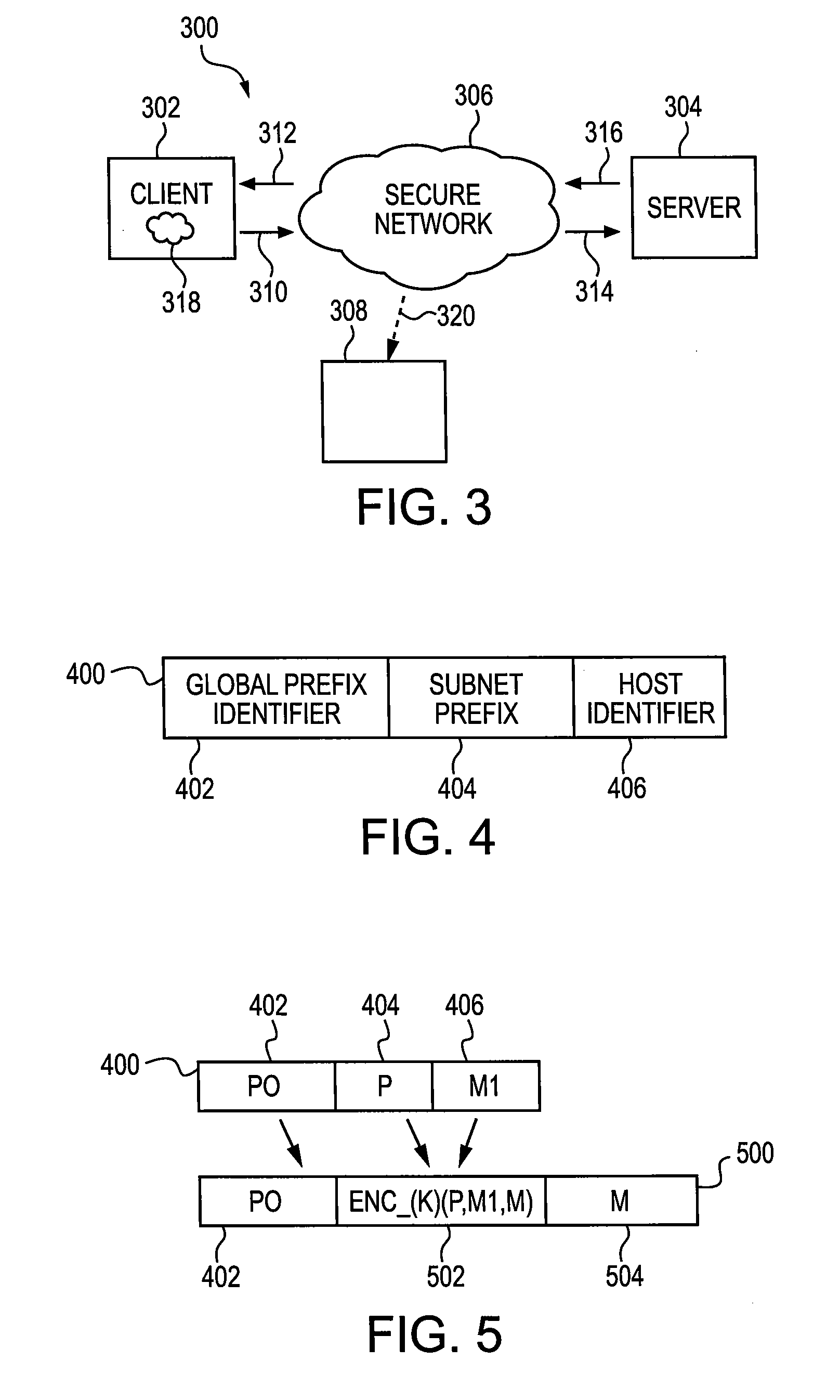
System and Method of Encrypting Network Address for Anonymity and Preventing Data Exfiltration
ActiveUS20090228708A1Avoid data breachesEnsure normal communicationDigital data processing detailsUser identity/authority verificationNetwork packetNetwork addressing
A method is provided for sending a data packet from a client through a network and to a server. The data packet is a data structure having an originating address portion and destination address portion. The network includes a first mix router and a second mix router. The client has a client address, whereas the first mix router has a first mix router address, the second mix router has a second mix router address and the server has a server address. The method includes encrypting the originating address portion of the data packet and encrypting the destination portion of the data packet, transmitting the encrypted data packet, decrypting the originating address portion of the encrypted data packet and the destination portion of the encrypted data packet, providing a first data packet and providing a second data packet. Specifically, the encrypting the originating address portion of the data packet is based on the client address and the encrypting the destination portion of the data packet is based on one of the first mix router address and the second mix router address. The encrypting generates an encrypted data packet. The encrypted data packet is transmitted to the one of the first mix router and the second mix router, wherein it is decrypted to generate a decrypted data packet. The first data packet is based on the decrypted data packet and is provided to the other of the first mix router and the second mix router. The second data packet is provided to the server.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
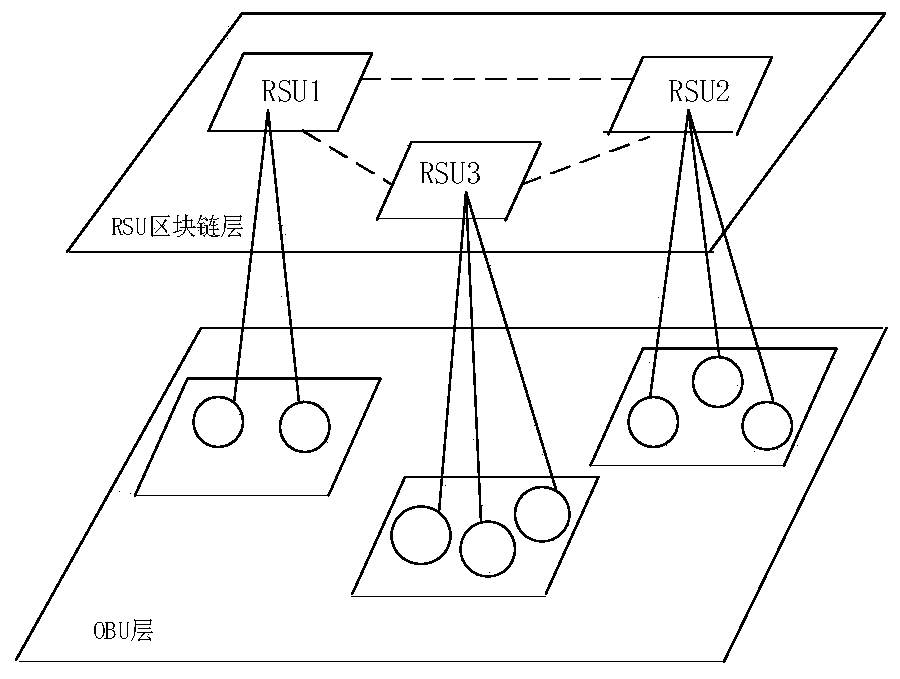
Supervisory blockchain system and method
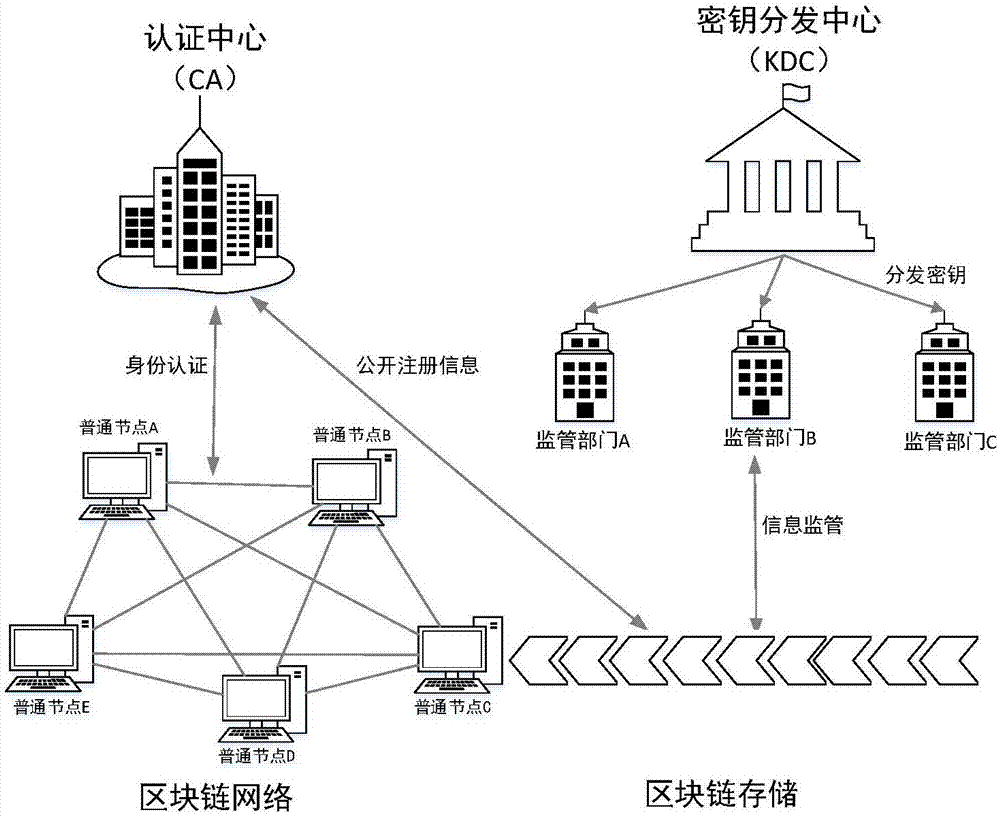
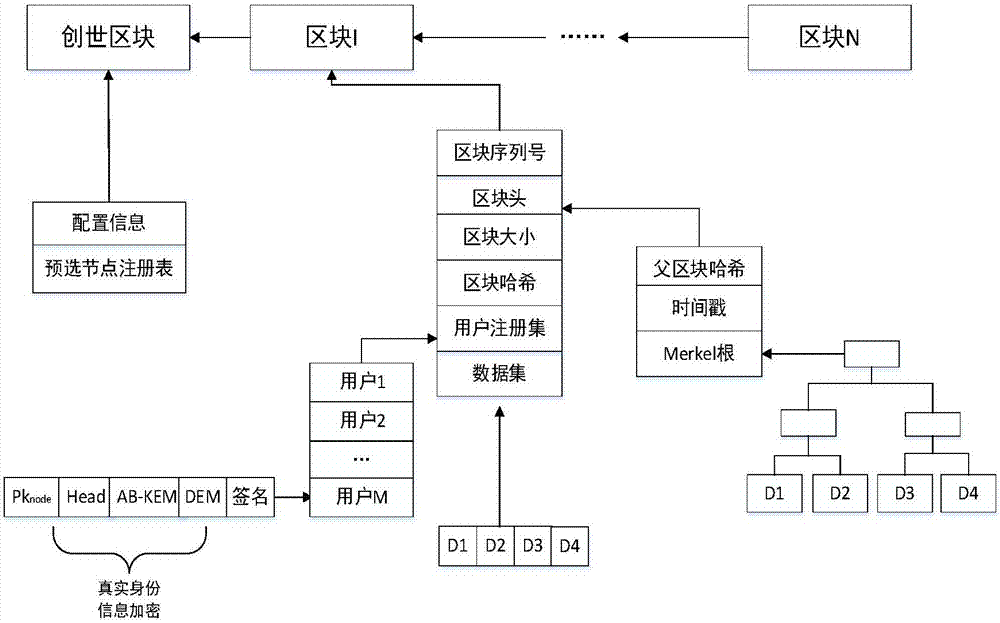
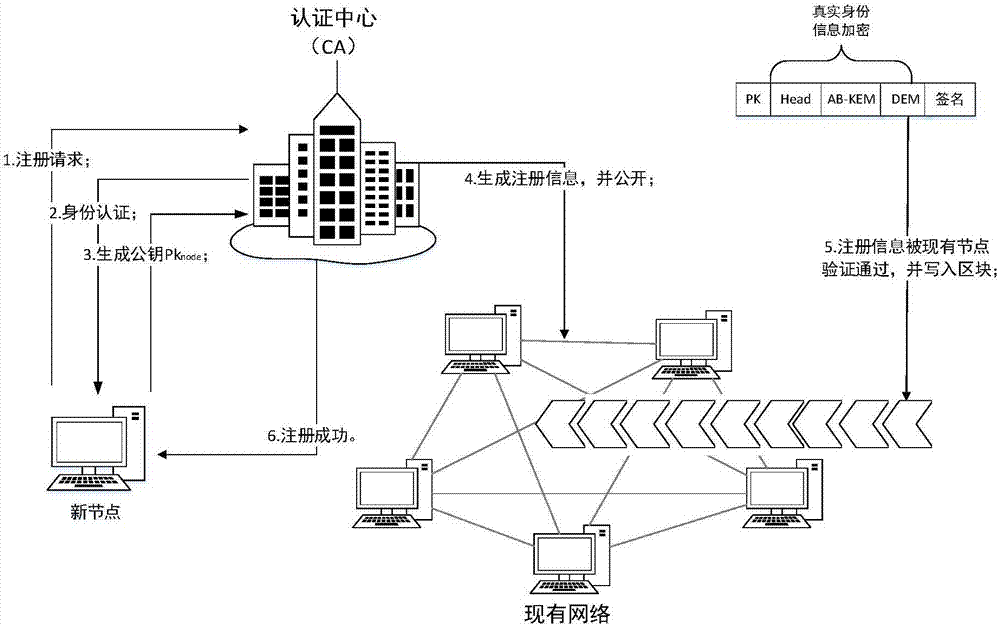
ActiveCN107483198AProtect anonymityAddresses the disadvantages of unsupervised featuresKey distribution for secure communicationUser identity/authority verificationBlockchainKey distribution center
The invention relates to a supervisory blockchain system and method. The system comprises a certificate authority (CA), a key distribution center (KDC), a supervision department and a common node, wherein the CA performs identity authentication for the common node to generate registration information about the node, and the registration information is opened to a blockchain network and waits to be written into a blockchain to complete the registration of the node; the KDC prepares supervision rules, defines a complete attribute set of the supervision department, and distributes keys to the supervision department according to specific attributes of the supervision department; the supervision department acquires the keys from the KDC, monitors network transactions of the blockchain, and adopts the own keys to decrypt the node registration information in the blockchain and acquire the real identity of the node when an abnormal account occurs; and the common node interacts with the CA, performs identity authentication, and joins the blockchain to operate after completing the registration. According to the system and method disclosed by the invention, a supervisory blockchain is constructed by using ABE, signatures and other cryptography techniques, different supervision departments are allowed to supervise data of the blockchain system according to different functions, and thus the occurrence of illegal acts and the like can be prevented.
Owner:INST OF INFORMATION ENG CAS
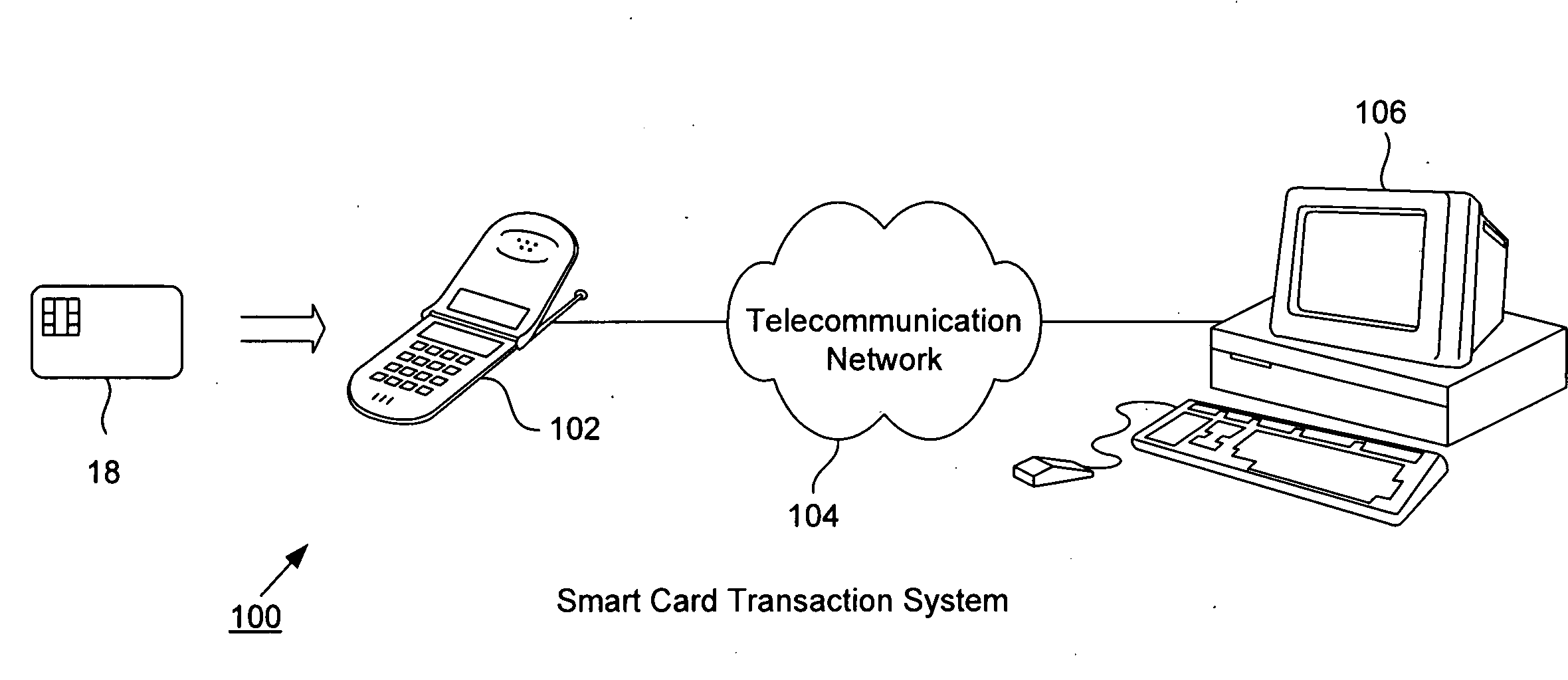
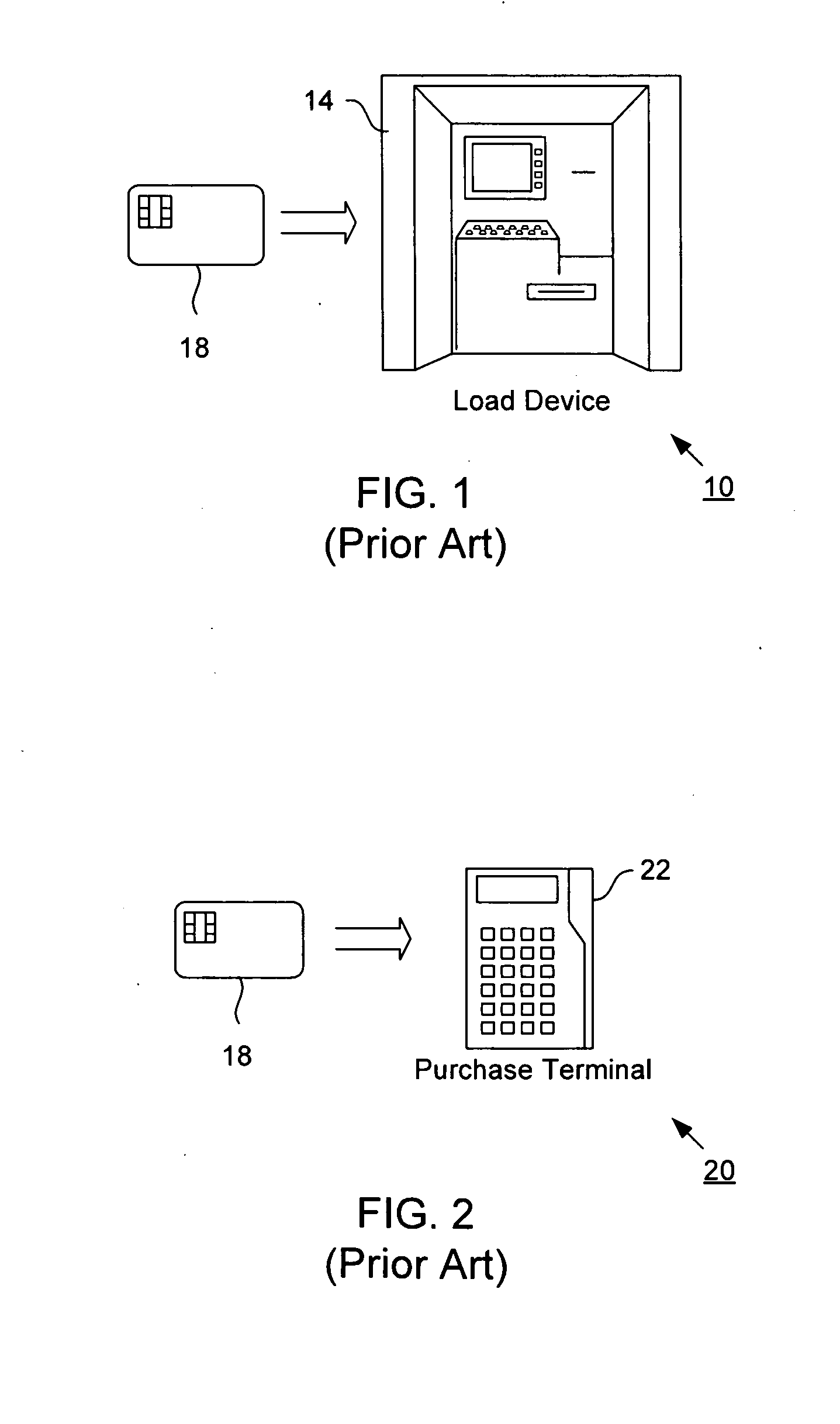
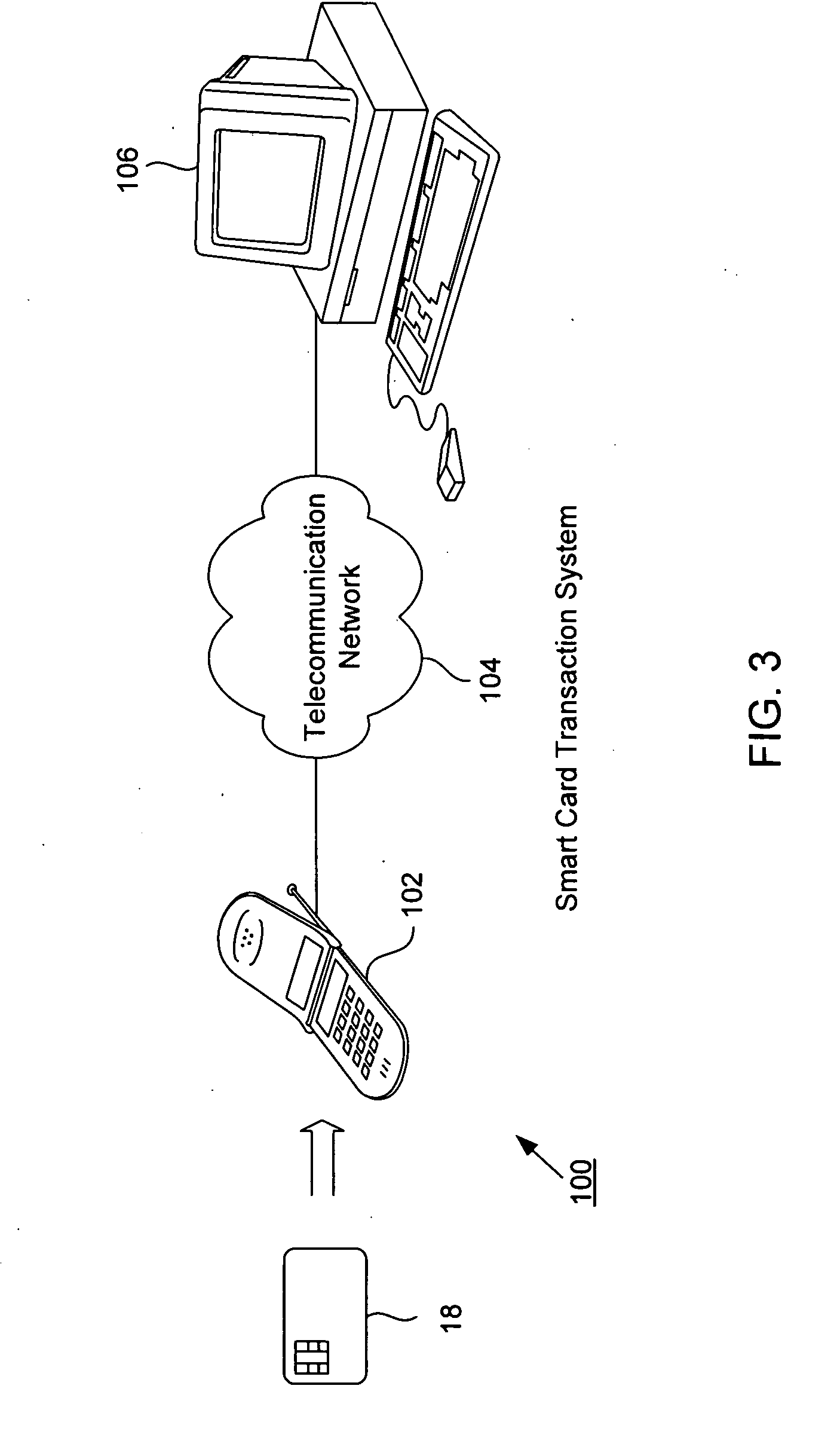
Smart card load and purchase transactions using wireless telecommunications network
InactiveUS20090030843A1Enhanced anonymityPrivacy protectionFinanceMultiple keys/algorithms usagePaymentMerchant services
A smart card transaction allows a consumer to load value onto a smart card and to make purchases using a smart card with a mobile telephone handset over the telecommunications network. For loading, the system includes: a mobile telephone handset including a card reader; a gateway computer; a funds issuer computer; and an authentication computer. The mobile telephone handset receives a request from a user to load a value onto the smart card. The handset generates a funds request message which includes the value and sends the funds request message to a funds issuer computer. The funds issuer computer debits an account associated with the user. Next, the handset generates a load request message with a cryptographic signature and sends the load request message to an authentication computer which authenticates the smart card. The handset receives a response message which includes a cryptographic signature and an approval to load. Finally, the handset validates the second cryptographic signature and loads the value onto the smart card. For payment, the system includes a merchant server and a payment server. First, the handset sends an order request message to the merchant server computer, and in return receives a purchase instruction message. The handset processes the purchase instruction message locally, and then sends a draw request message to a payment server computer. The payment server computer sends a debit message which includes a cryptographic signature and an approval to debit the smart card. Finally, the handset validates the cryptographic signature and debits the smart card.
Owner:VISA INT SERVICE ASSOC
TLS tunneling
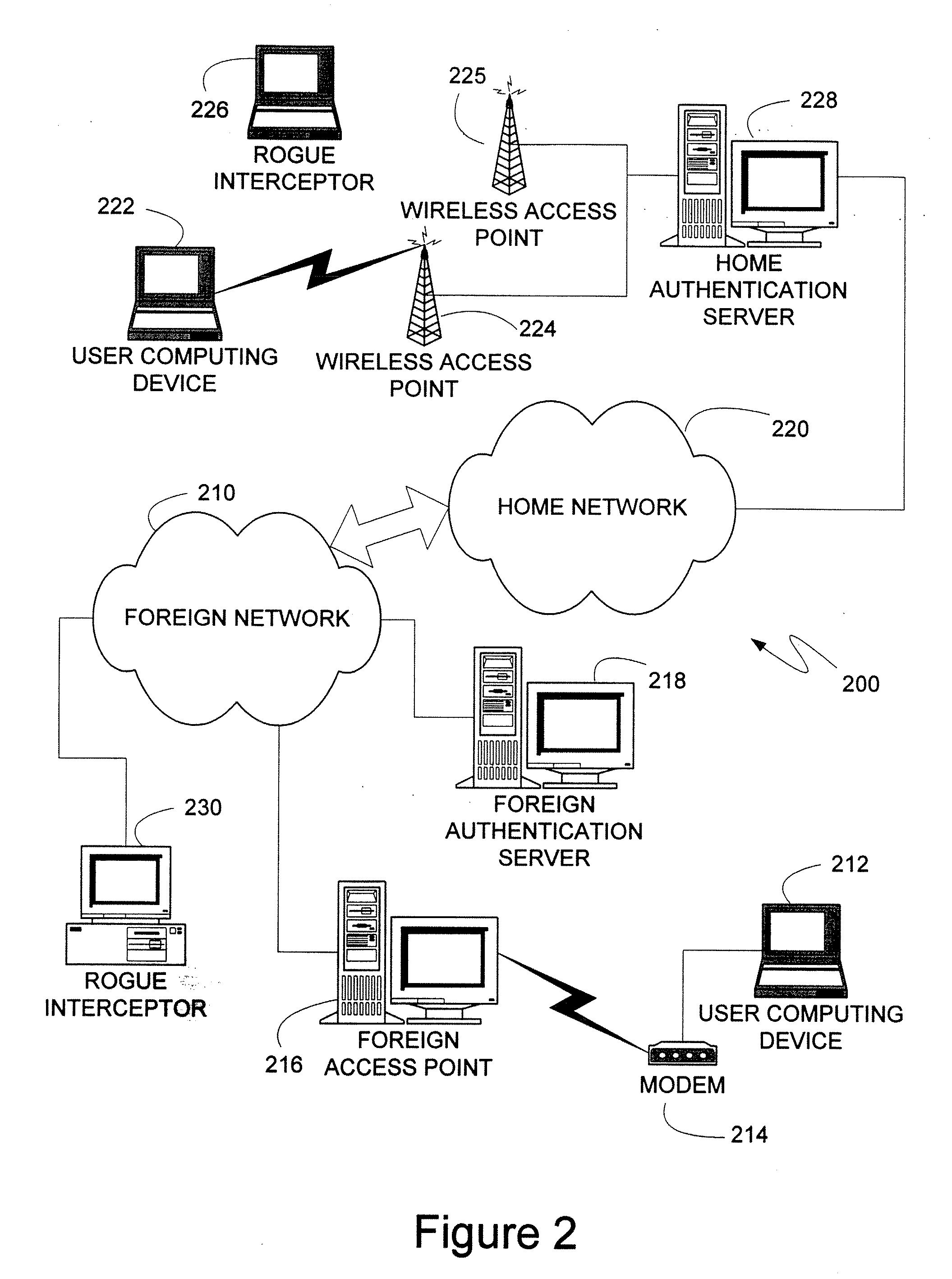
InactiveUS7529933B2Reduce interceptionProtect normal transmissionUser identity/authority verificationSecret communicationSecure communicationWireless mesh network
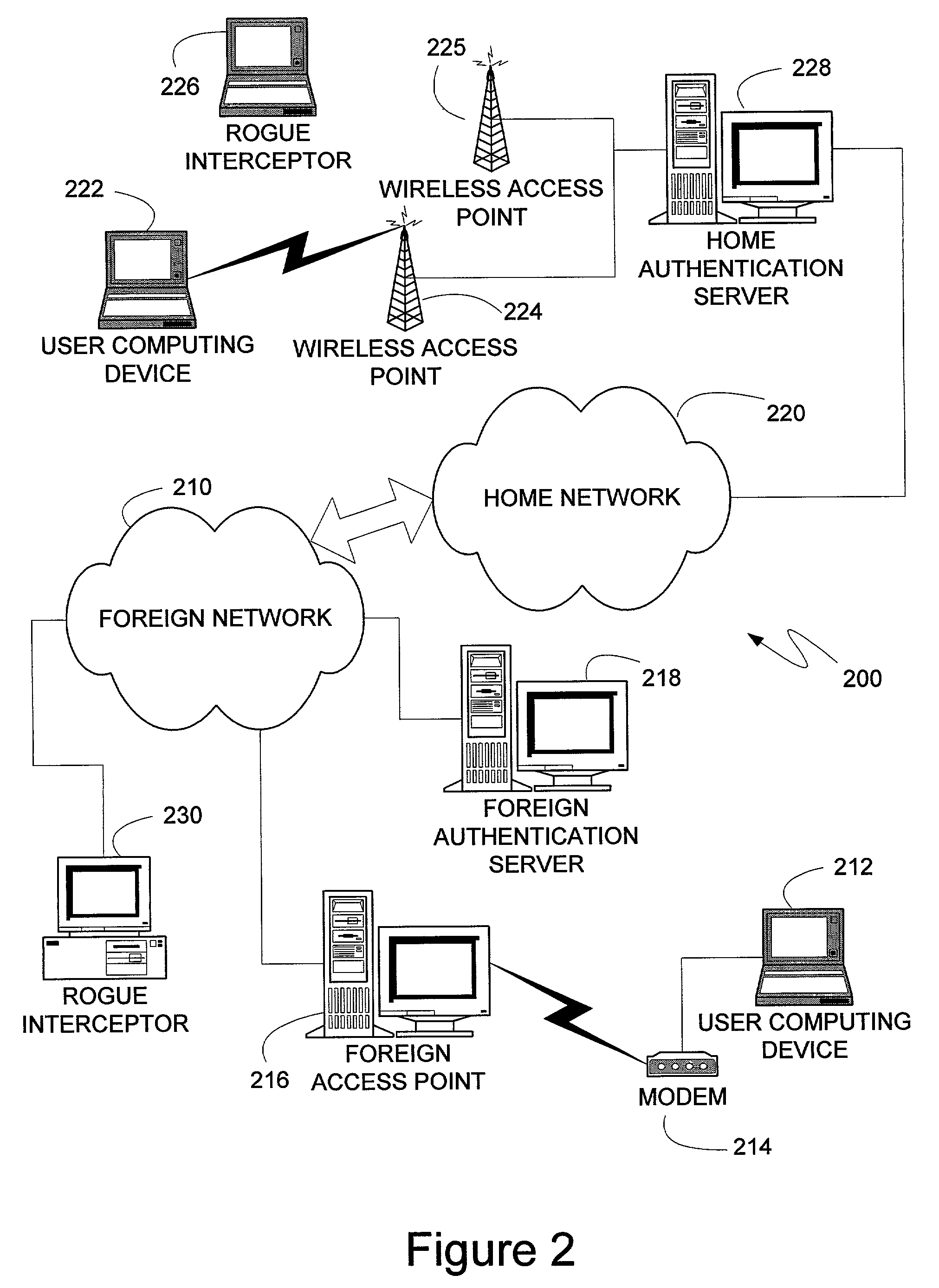
An authentication protocol can be used to establish a secure method of communication between two devices on a network. Once established, the secure communication can be used to authenticate a client through various authentication methods, providing security in environments where intermediate devices cannot be trusted, such as wireless networks, or foreign network access points. Additionally, the caching of session keys and other relevant information can enable the two securely communicating endpoints to quickly resume their communication despite interruptions, such as when one endpoint changes the access point through which it is connected to the network. Also, the secure communication between the two devices can enable users to roam off of their home network, providing a mechanism by which access through foreign networks can be granted, while allowing the foreign network to monitor and control the use of its bandwidth.
Owner:MICROSOFT TECH LICENSING LLC
Certified Abstracted and Anonymous User Profiles For Restricted Network Site Access and Statistical Social Surveys
InactiveUS20110145570A1Enhanced anonymityEstablish dependabilitySecuring communicationChat roomInternet privacy
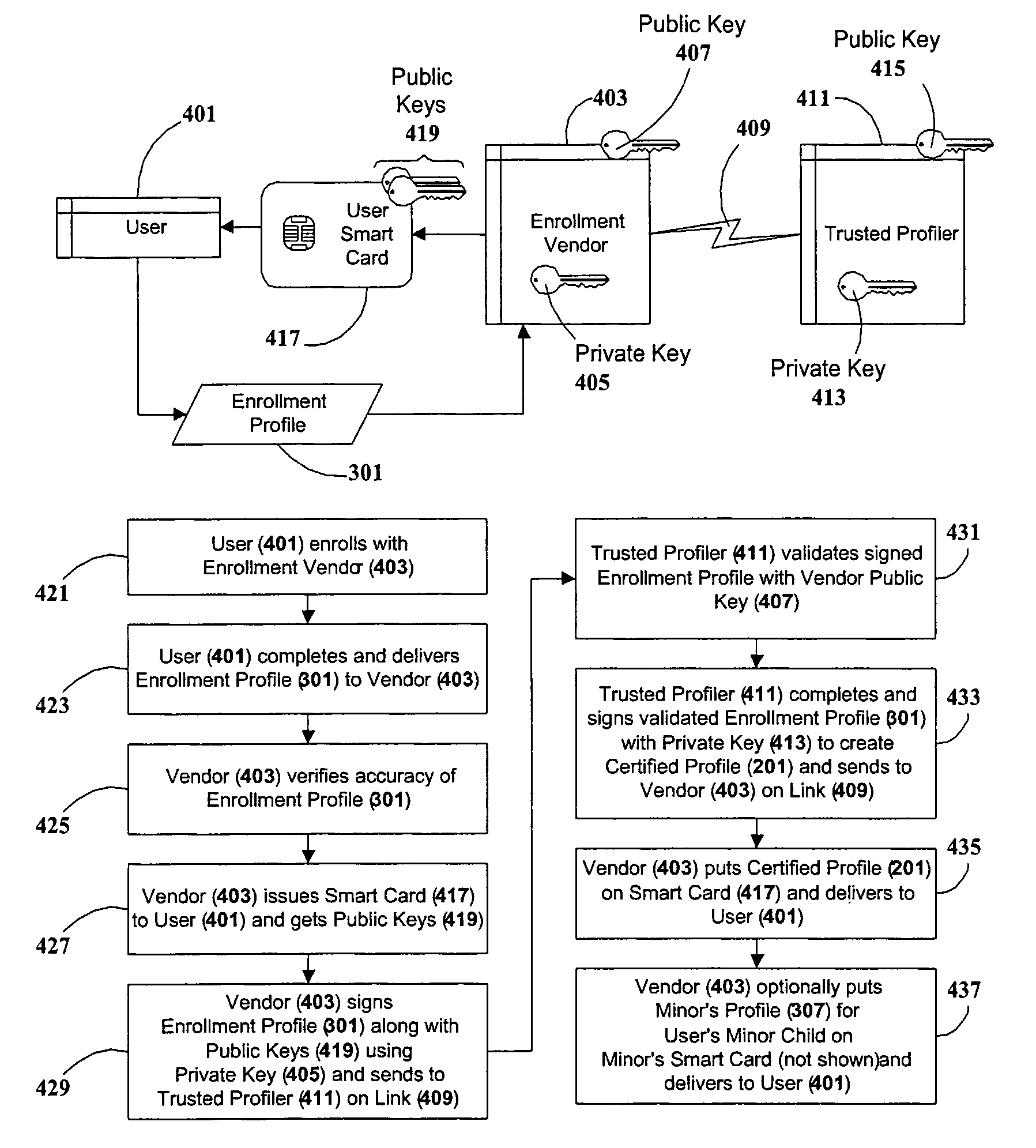
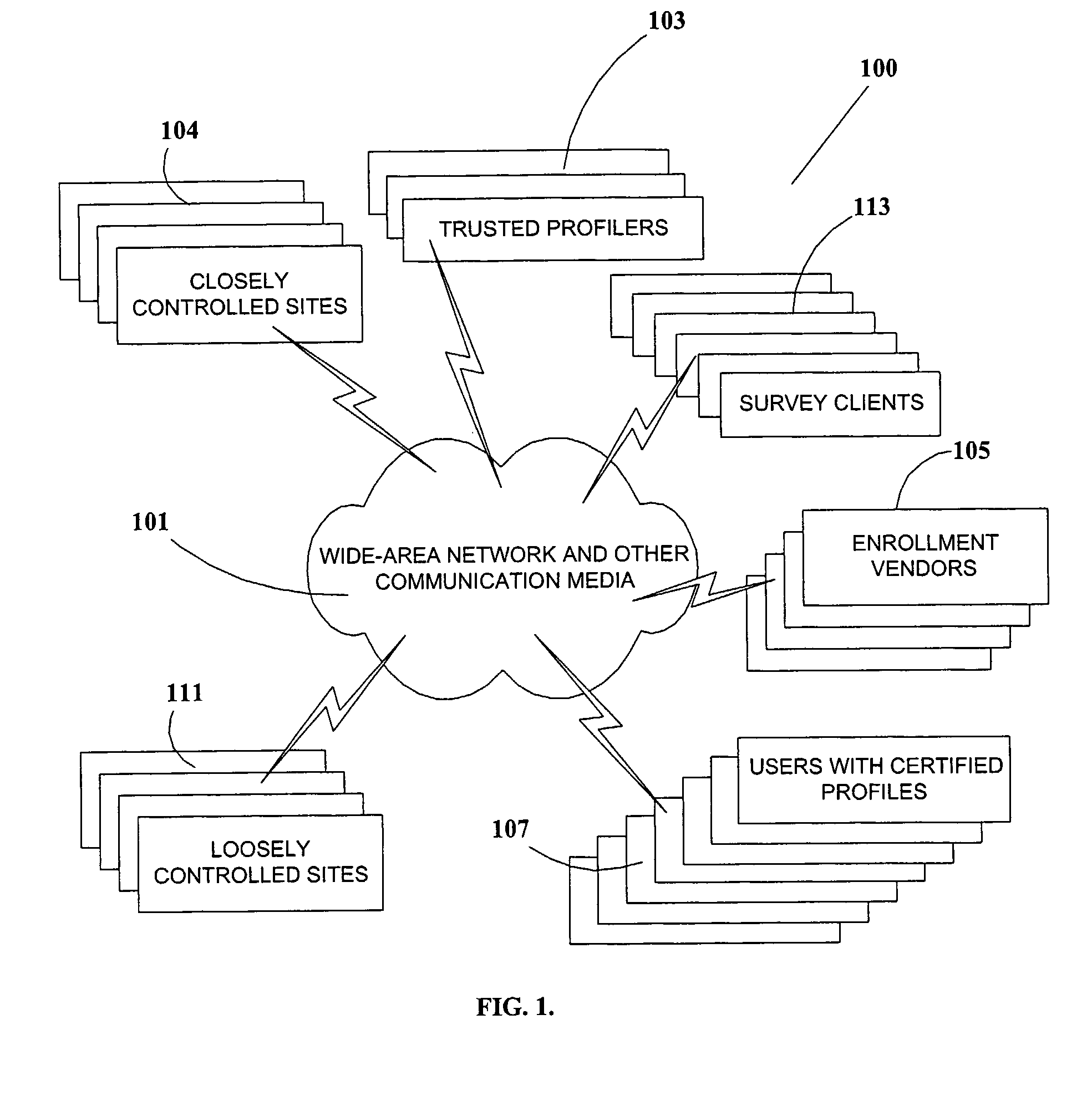
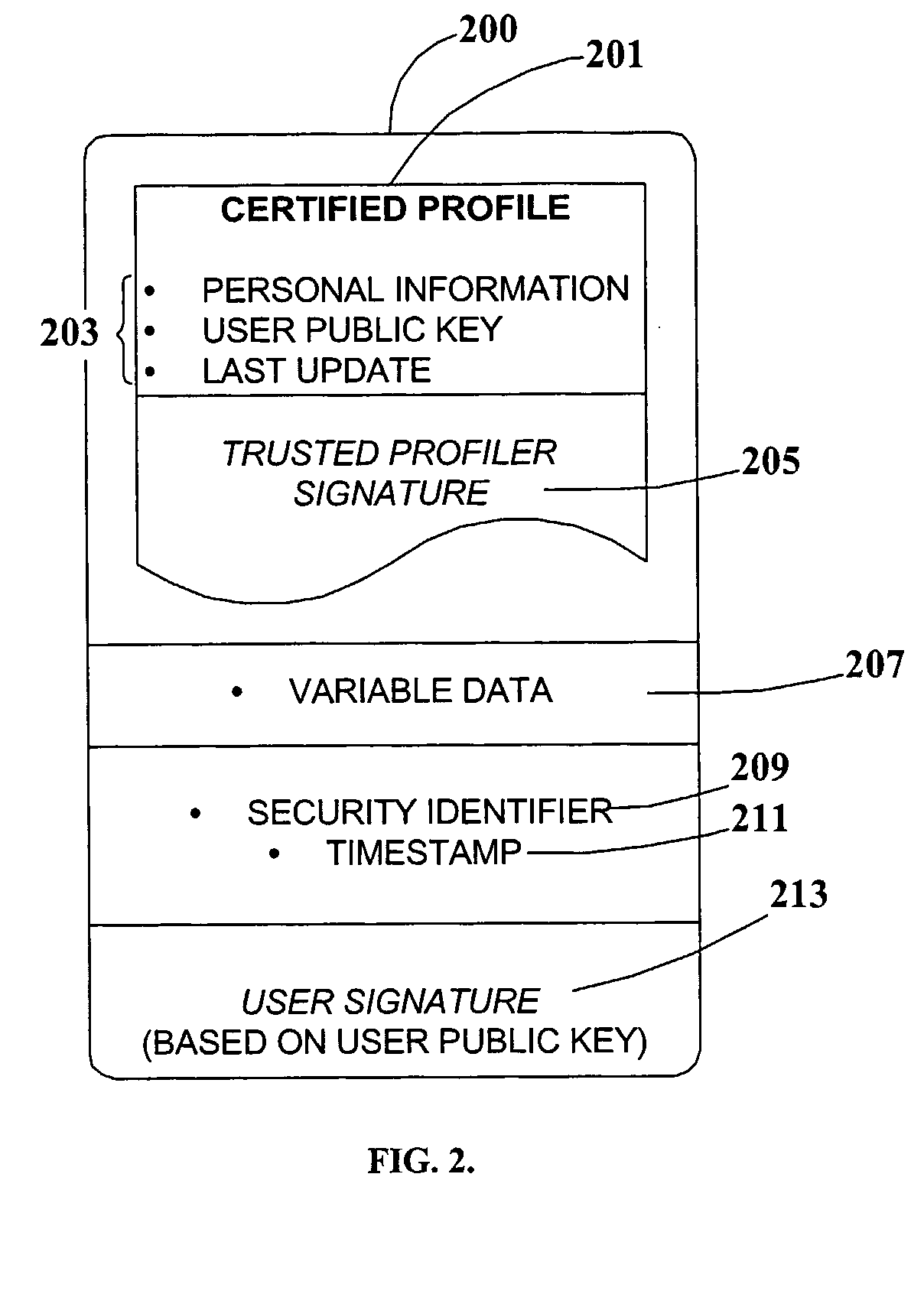
An arrangement, system, and methods for creating and distributing authenticated personal information for users of network services and participants in social surveys, and in chat rooms and other forums. A trusted organization verifies that personal information presented by a user is correct, and authenticates the information in an encapsulated form as “certified profiles” within a smart card or other secure portable hardware device issued to the user Certified profiles are authenticated by digital signatures of the trusted organization and the profile users. Personal information in certified profiles can be in raw and / or in statistically-processed and abstracted form, and can be tailored by the user for specific needs to include whatever personal information is required, and to exclude all other personal information. By the use of unique aliases, it is possible for users to anonymously access restricted network sites and participate in surveys, while still satisfying recipients that supplied personal information is accurate, and for surveys that the user has not responded to the same survey more than once. Users enroll for certified profiles via trusted enrollment vendors who market the service to the public and also make hardware and software available to users for managing, maintaining, and distributing the certified profiles.
Owner:FORTRESS GB
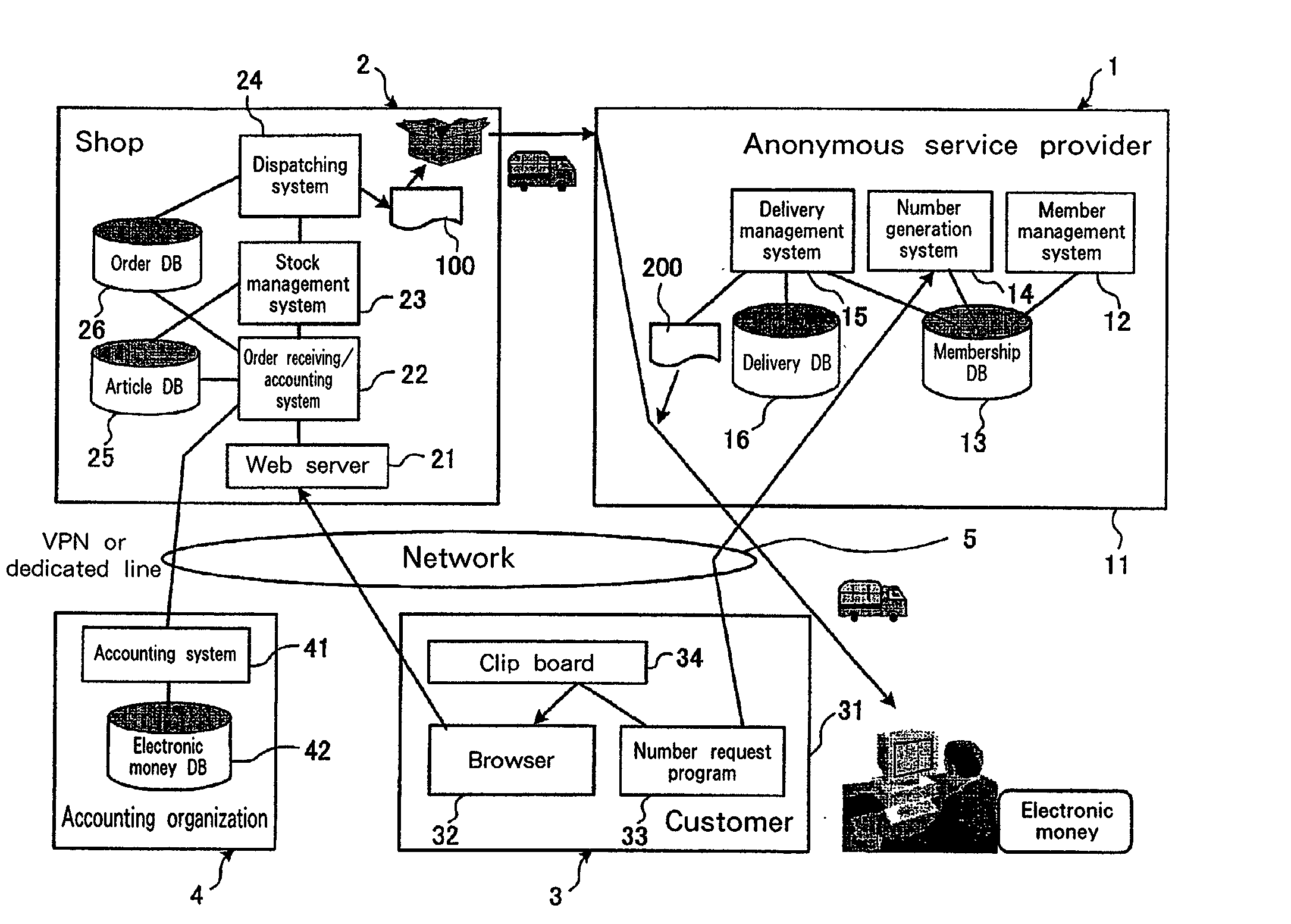
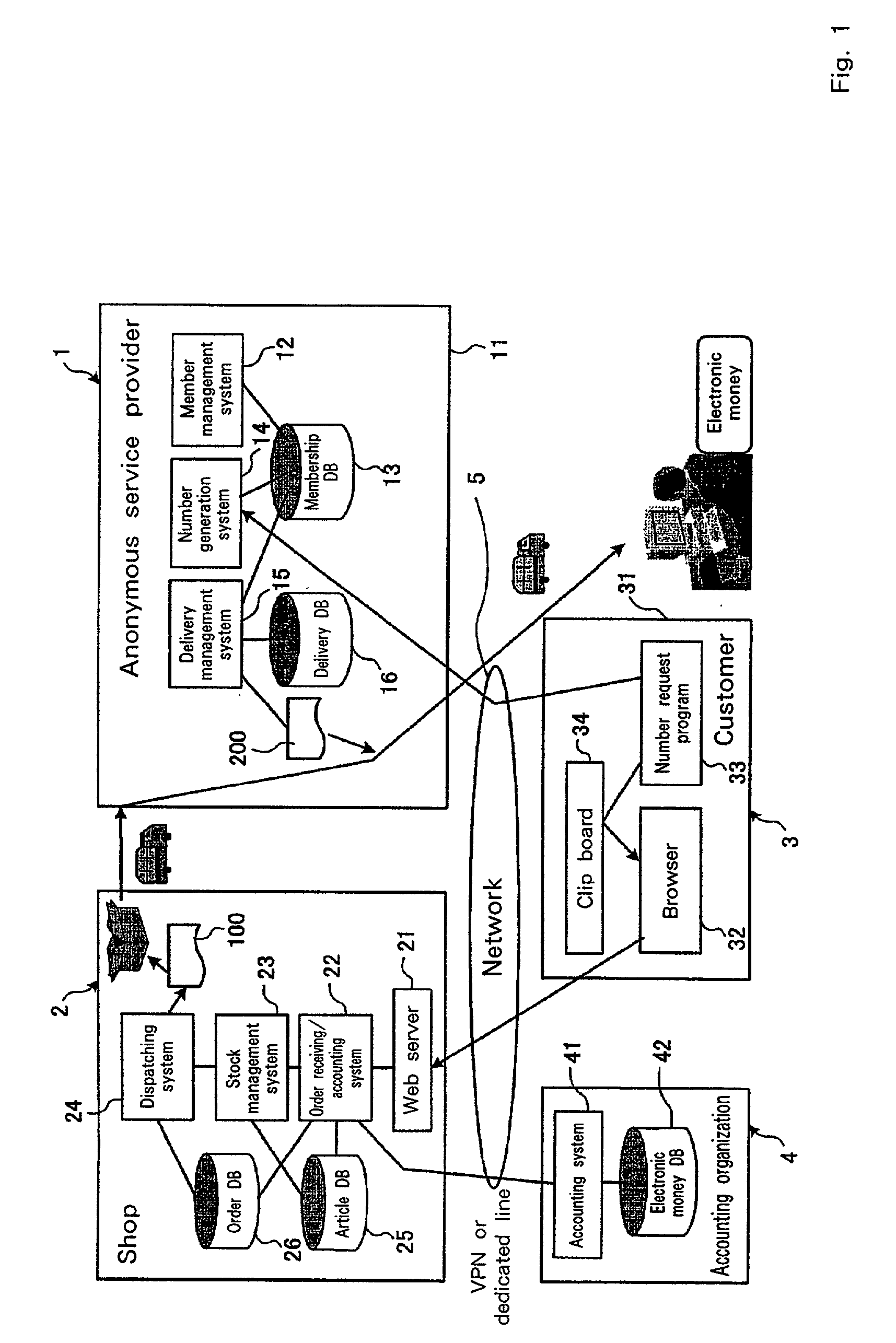
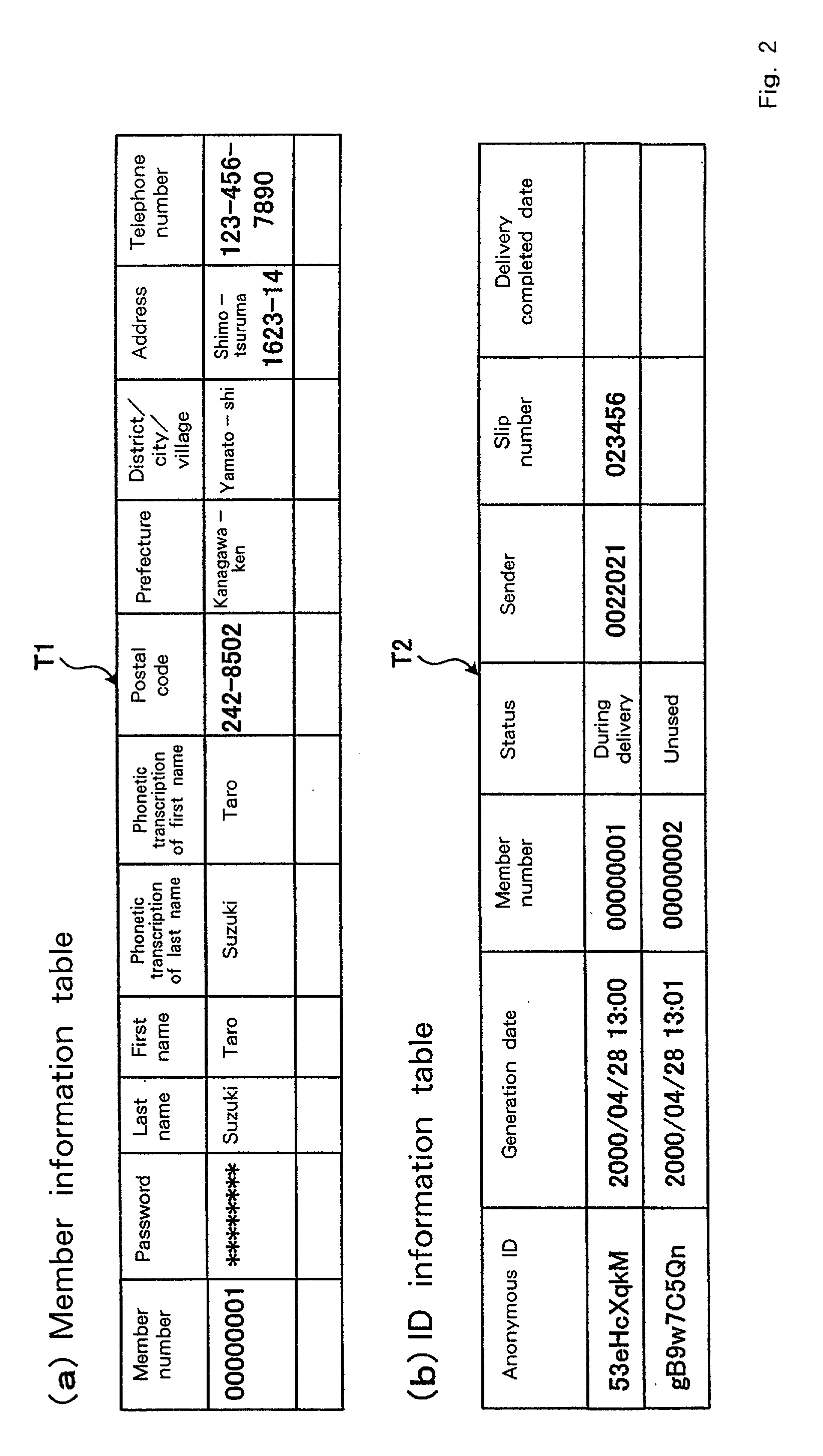
Goods delivery method, online shopping method, online shopping system, server, and vender server
InactiveUS20020022967A1Enhanced anonymityBuying/selling/leasing transactionsLogisticsAnonymityWorld Wide Web
[Object]It is one object of the present invention to provide a goods delivery method for improving the anonymity of a customer, and an online shopping method, an online shopping system, a server, and a shop server therefor. [Constitution]A customer 3 orders an article from a shop 2 by using an anonymous ID. The shop 2 attaches, to the article, a slip 100 on which not personal information for the customer 3 is printed, and dispatches the article to an anonymous service provider 1. Thereafter, the anonymous service provider 1 replaces the slip 100 with a slip 200 on which the name and address of the customer 3 is printed, and delivers the article to the customer 3.
Owner:IBM CORP
Tls tunneling
ActiveUS20070157027A1Reduce interceptionProtect normal transmissionUser identity/authority verificationMultiple digital computer combinationsSecure communicationRelevant information
An authentication protocol can be used to establish a secure method of communication between two devices on a network. Once established, the secure communication can be used to authenticate a client through various authentication methods, providing security in environments where intermediate devices cannot be trusted, such as wireless networks, or foreign network access points. Additionally, the caching of session keys and other relevant information can enable the two securely communicating endpoints to quickly resume their communication despite interruptions, such as when one endpoint changes the access point through which it is connected to the network. Also, the secure communication between the two devices can enable users to roam off of their home network, providing a mechanism by which access through foreign networks can be granted, while allowing the foreign network to monitor and control the use of its bandwidth.
Owner:MICROSOFT TECH LICENSING LLC
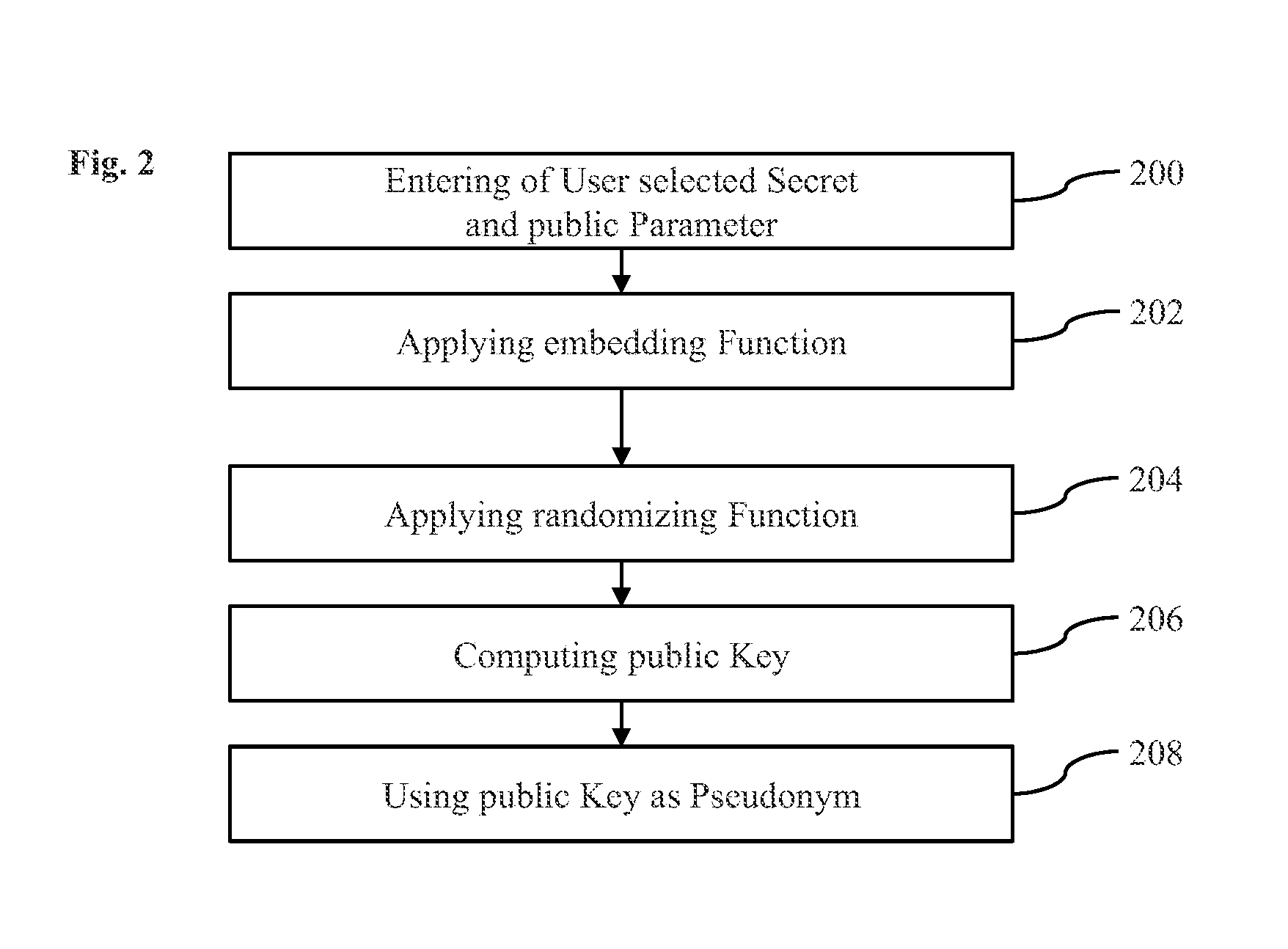
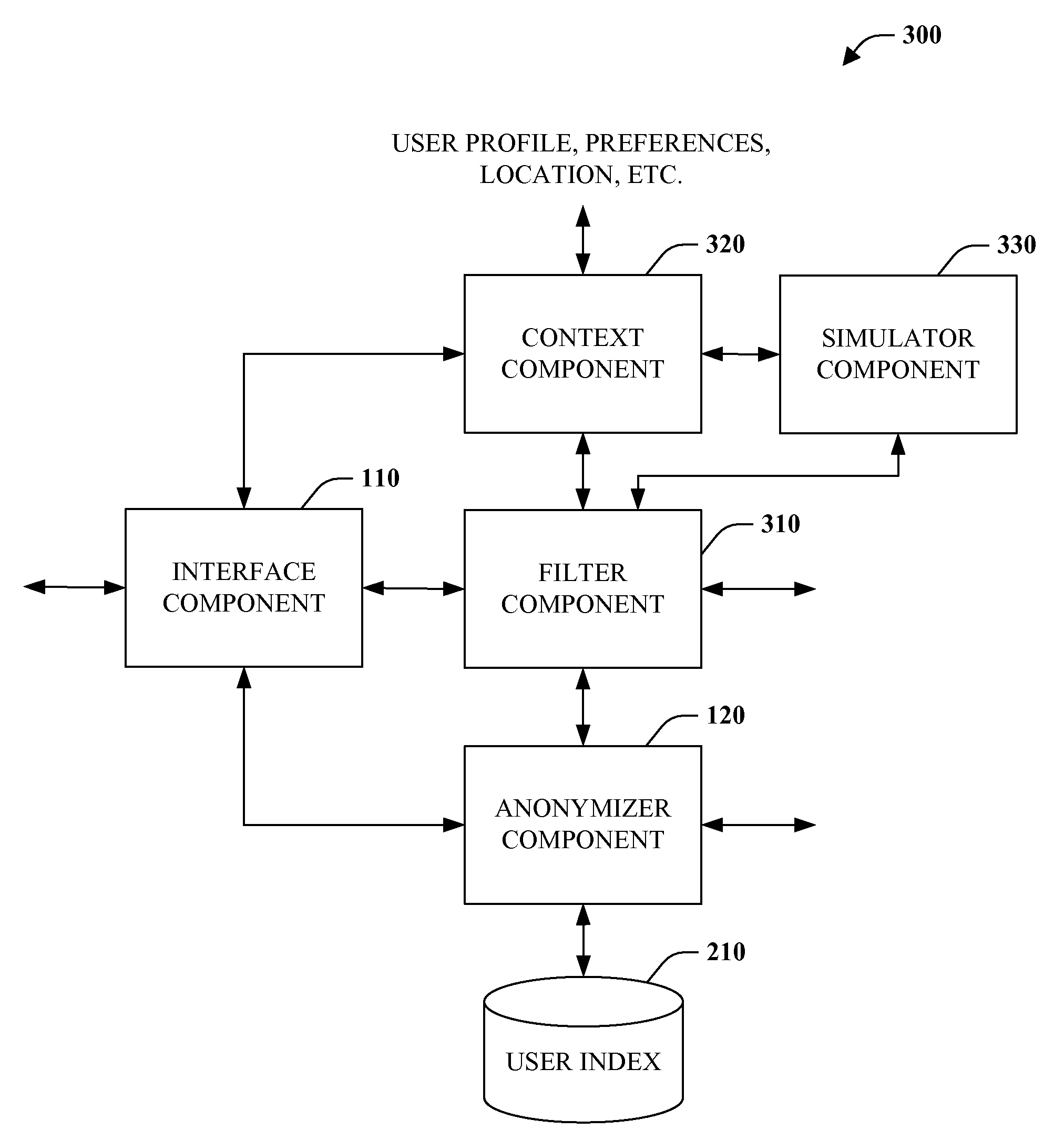
Computer implemented method for performing cloud computing on data being stored pseudonymously in a database
ActiveUS20110179286A1Enhanced anonymityEfficient implementationPublic key for secure communicationUnauthorized memory use protectionComputer scienceCloud computing
The invention relates to a computer implemented method for performing cloud computing on data of a first user employing cloud components, the cloud components comprising a first database and a data processing component, wherein an asymmetric cryptographic key pair is associated with the first user, said asymmetric cryptographic key pair comprising a public key and a private key, the data being stored pseudonymously non-encrypted in the first database with the data being assigned to an identifier, wherein the identifier comprises the public key, the method comprising retrieving the data from the first database by the data processing component, wherein retrieving the data from the first database comprises receiving the identifier and retrieving the data assigned to the identifier from the first database, wherein the method further comprises processing the retrieved data by the data processing component and providing a result of the analysis.
Owner:SPALKA ADRIAN +1
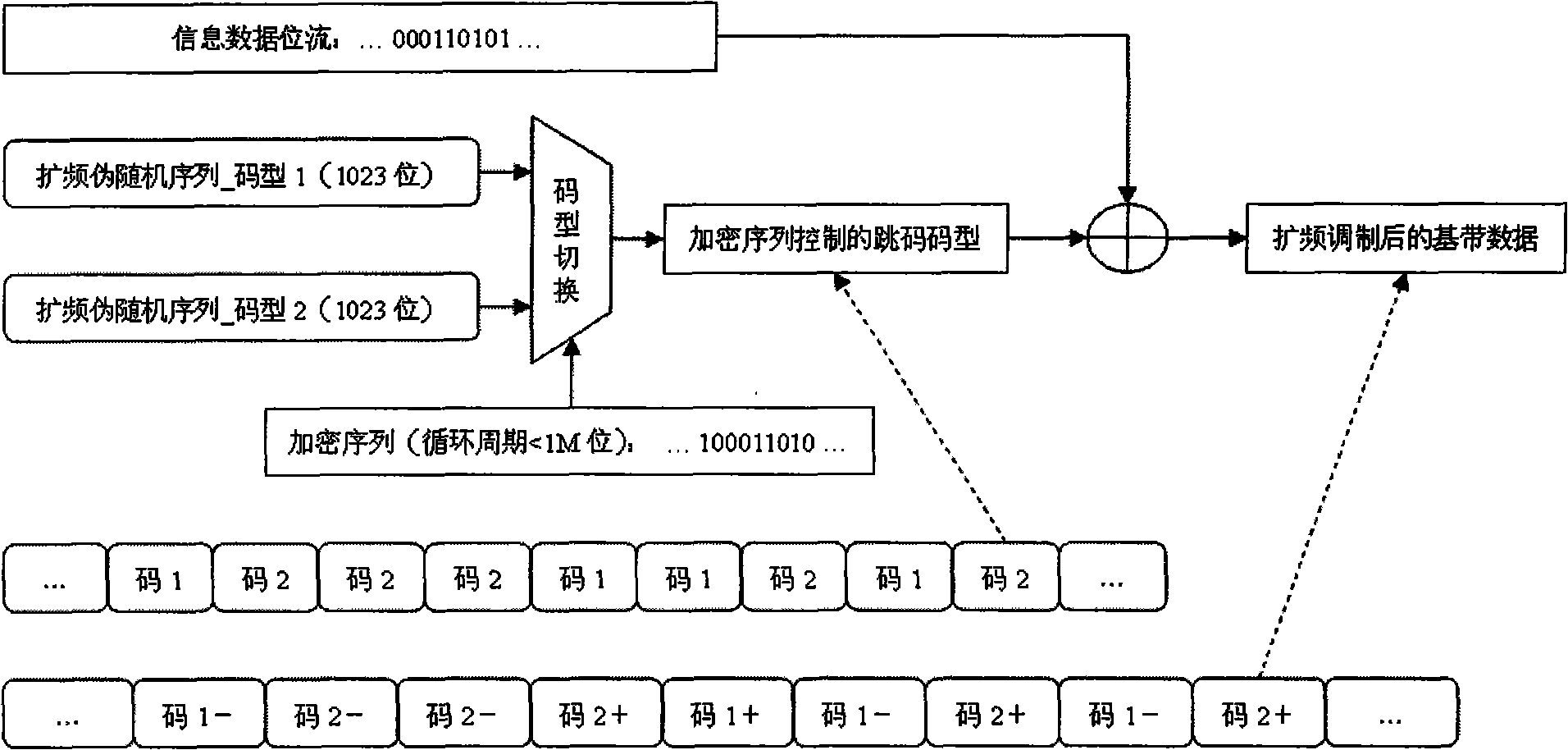
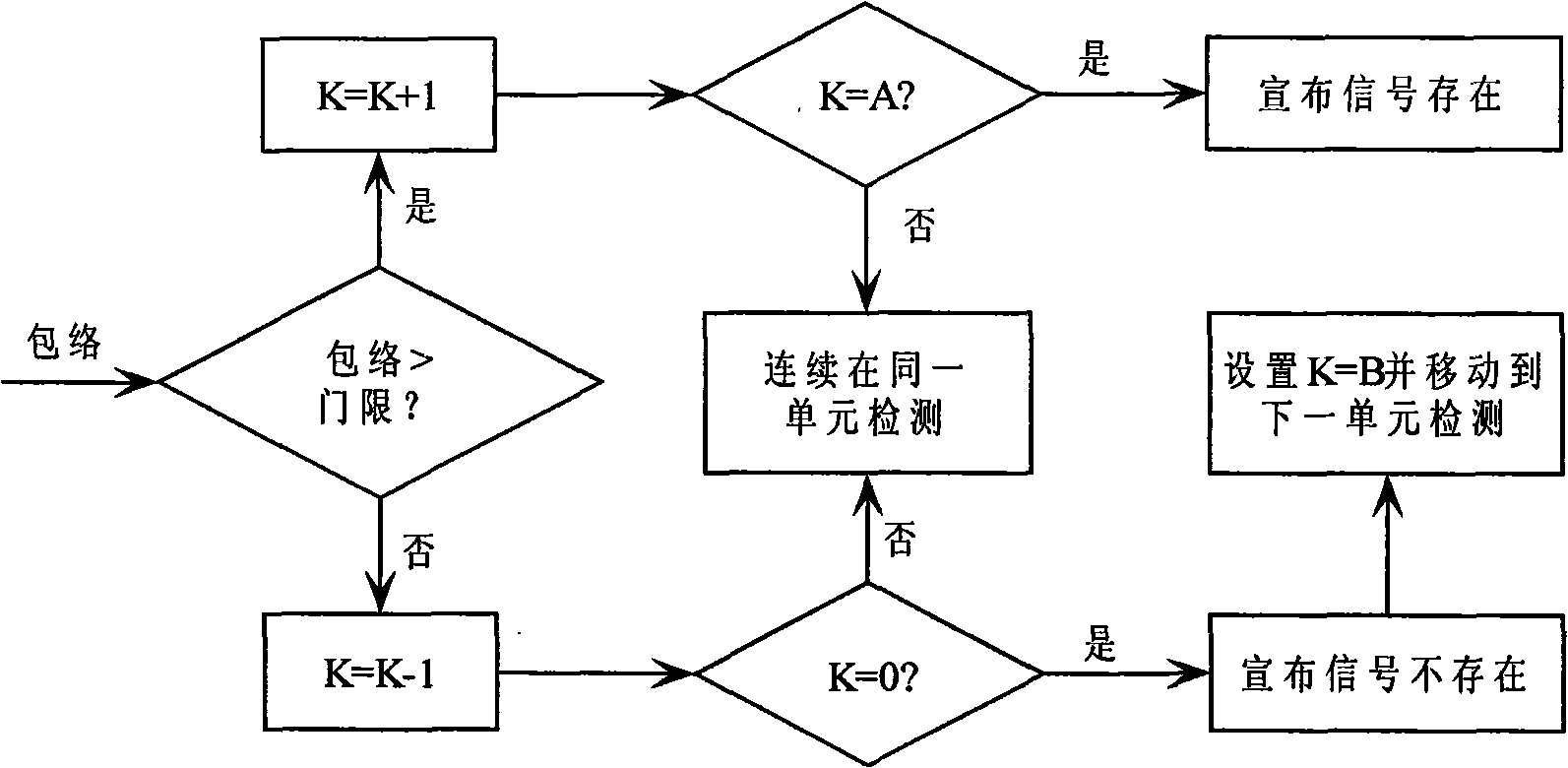
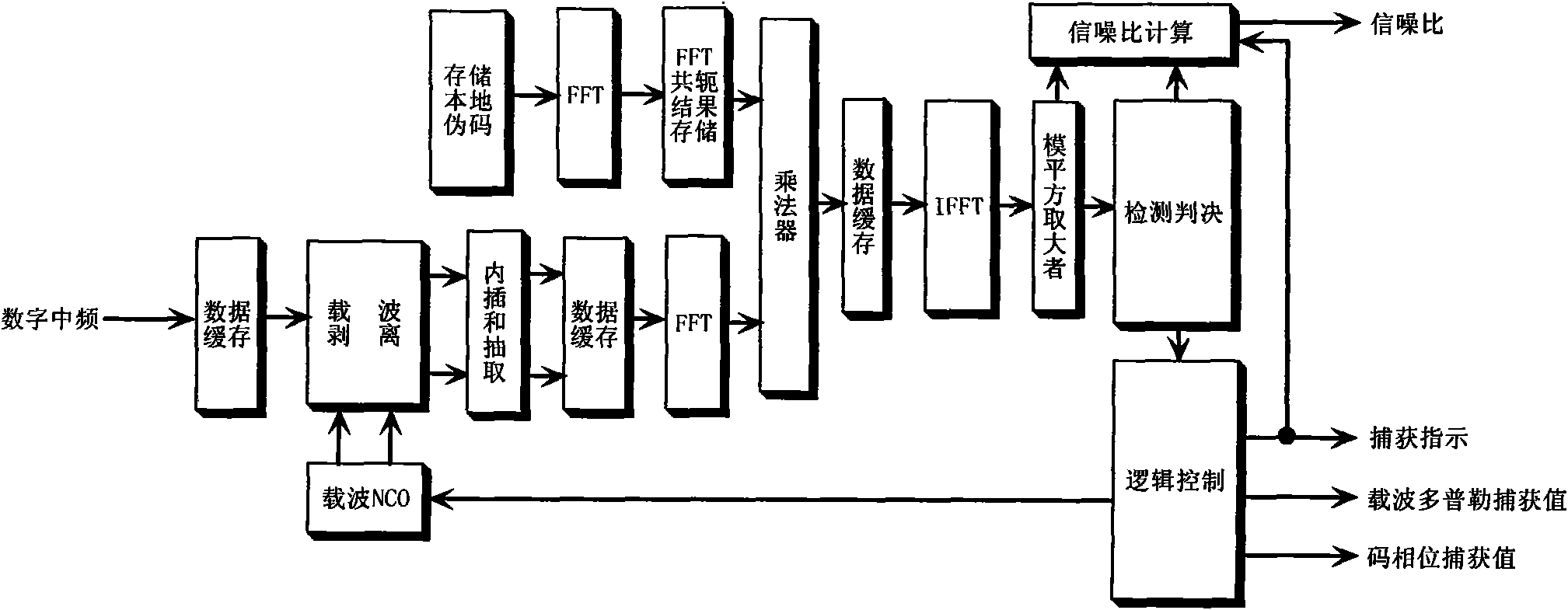
Generation and capture system of encrypted frame hopping spread spectrum signal of air fleet link
InactiveCN101777933AEnhanced anonymityImprove anti-interference abilityTransmissionDigital signal processingCarrier signal
The invention relates to a generation and capture system of an encrypted frame hopping spread spectrum signal of an air fleet link, belonging to the technical field of aeronautical data link and radio navigation. The invention discloses a system framework of an encrypted frame hopping spread spectrum signal generation and capture method which can be implemented on a digital signal processor (DSP)and a FPGA (field programmable gate array) of a circuit board, and provides a baseband signal generation algorithm of an encrypted frame hopping spread spectrum system to replace a traditional long periodic sequence spread spectrum code and a compound pseudo code by absorbing the advantages of the easy capture of the compound pseudo code and the difficult breaking of the long periodic sequence spread spectrum code; and meanwhile, the invention provides two advanced and high-performance encrypted frame hopping spread spectrum signal capture algorithms, i.e. a frequency domain parallel capture method of the encrypted frame hopping spread spectrum signal of based on a FFT (fast fourier transform algorithm) and a direct capture method of the encrypted frame hopping spread spectrum signal based on a matching filter and the FFT. The invention solves the problem of difficult capture of the traditional long periodic sequence spread spectrum code. The method can be widely applied to satellite navigation receivers, range measurement systems and communication systems based on a quiescent carrier modulation direct sequence spread spectrum system.
Owner:NAT SPACE SCI CENT CAS
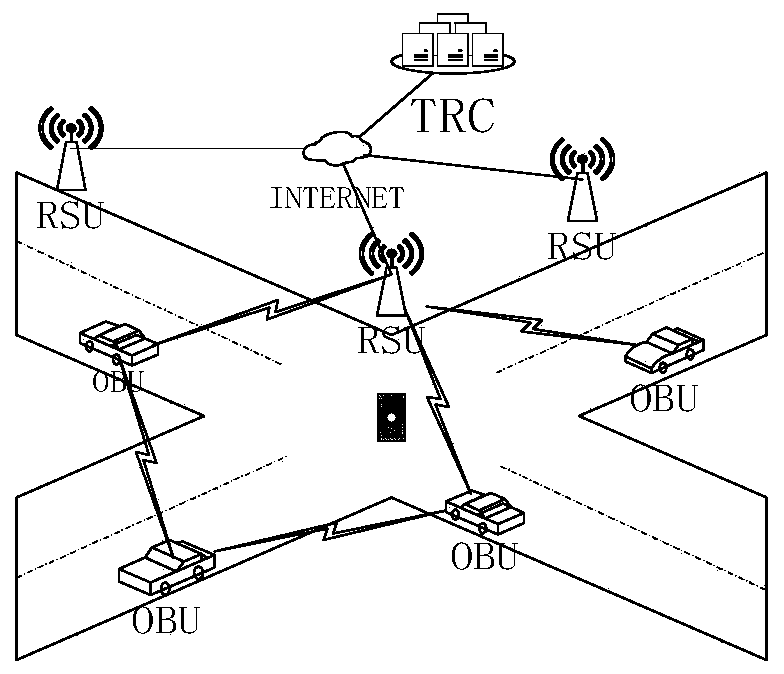
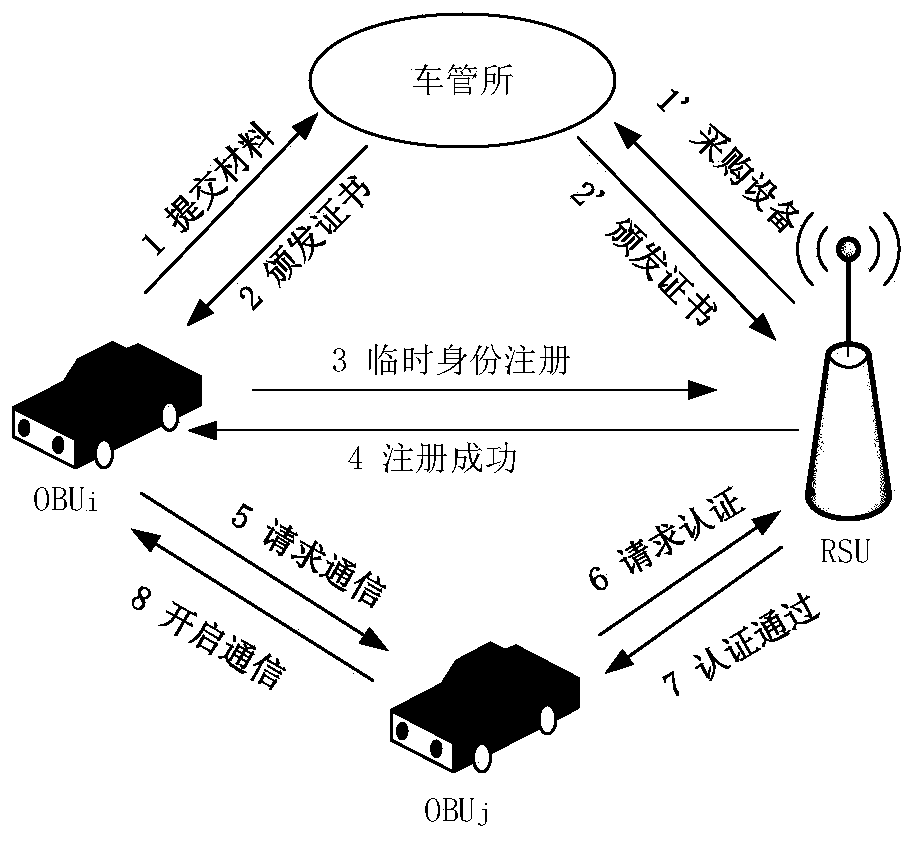
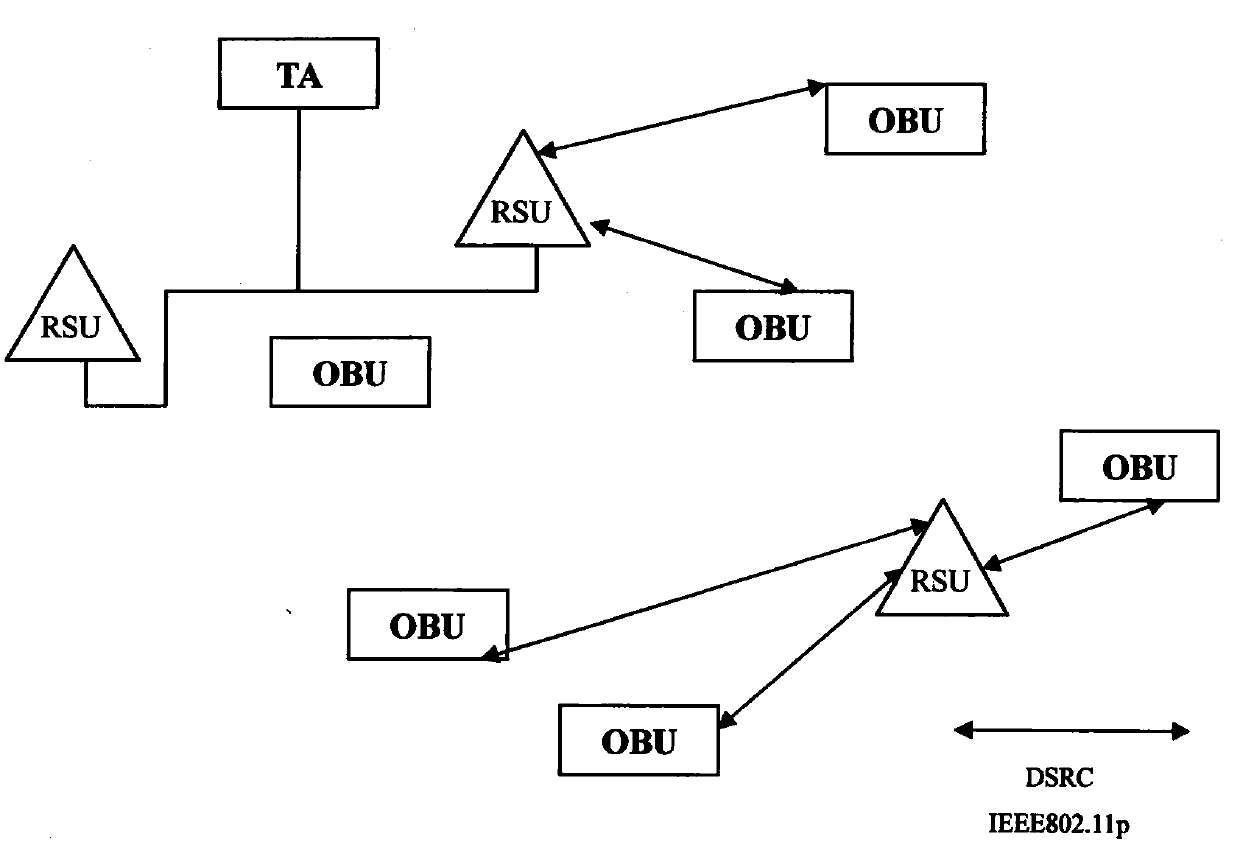
Efficient anonymous identity authentication method in Internet of Vehicles environment
ActiveCN111372248AImprove authentication efficiencyEnhanced anonymityPublic key for secure communicationParticular environment based servicesInternet privacyAttack
The invention provides an efficient anonymous identity authentication method in an Internet of Vehicles environment, and belongs to the technical field of Internet of Vehicles security. According to the technical scheme, the method comprises the following steps of vehicle offline registration, online registration and rapid identity authentication. The method has the beneficial effects that a temporary identity certificate Token mechanism is set, so that the authentication efficiency is improved while the vehicle anonymous two-way communication is realized; a block chain distributed account book mode is utilized, so that data traceability and tamper resistance are guaranteed, and the problems of relatively low identity authentication efficiency, easiness in attack and the like caused by traditional PKI authentication centralization of the Internet of Vehicles are solved; the combination of the blockchain PBFT consensus mechanism and the smart contract greatly reduces the authenticationtime delay of the traditional method.
Owner:NANTONG UNIVERSITY
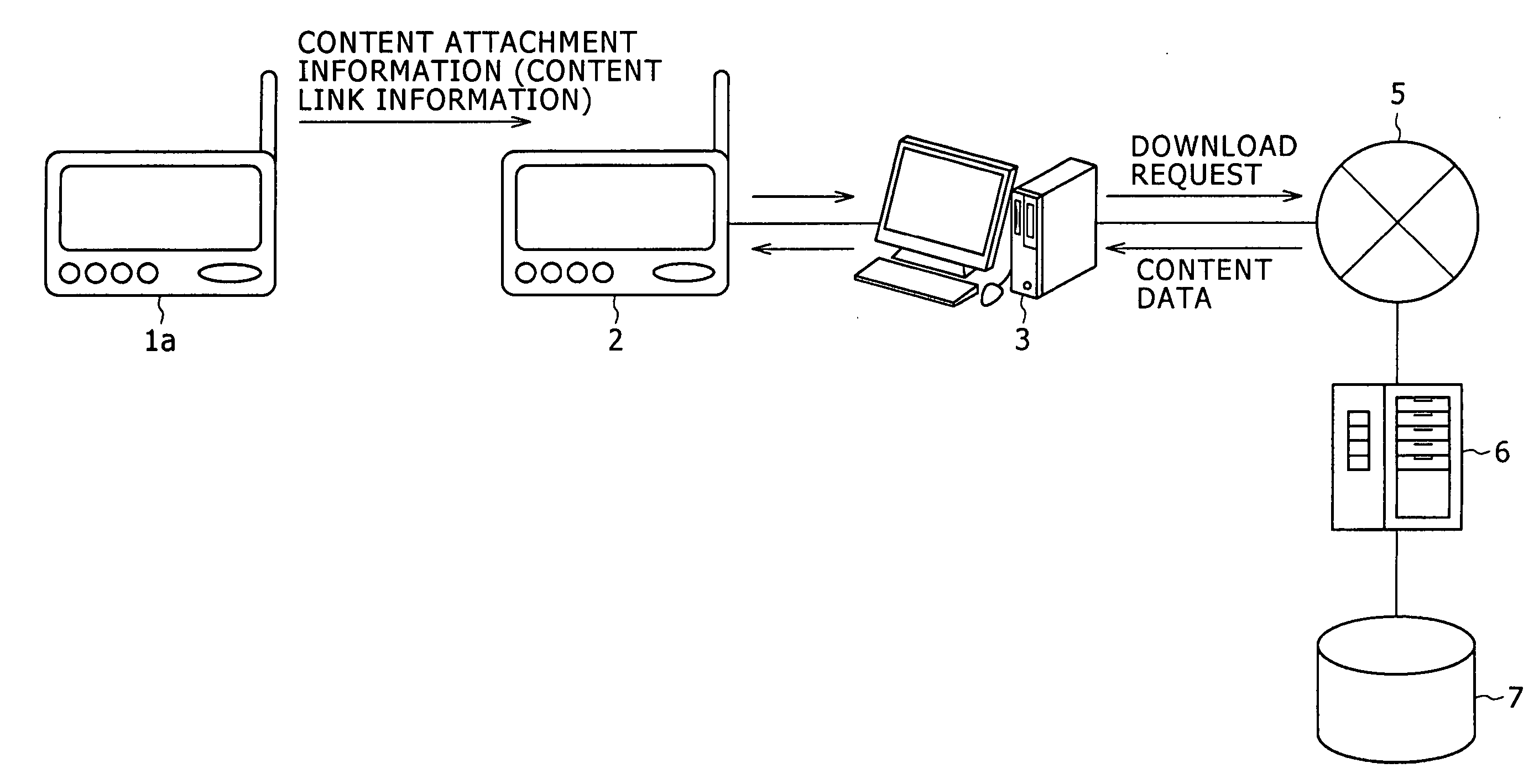
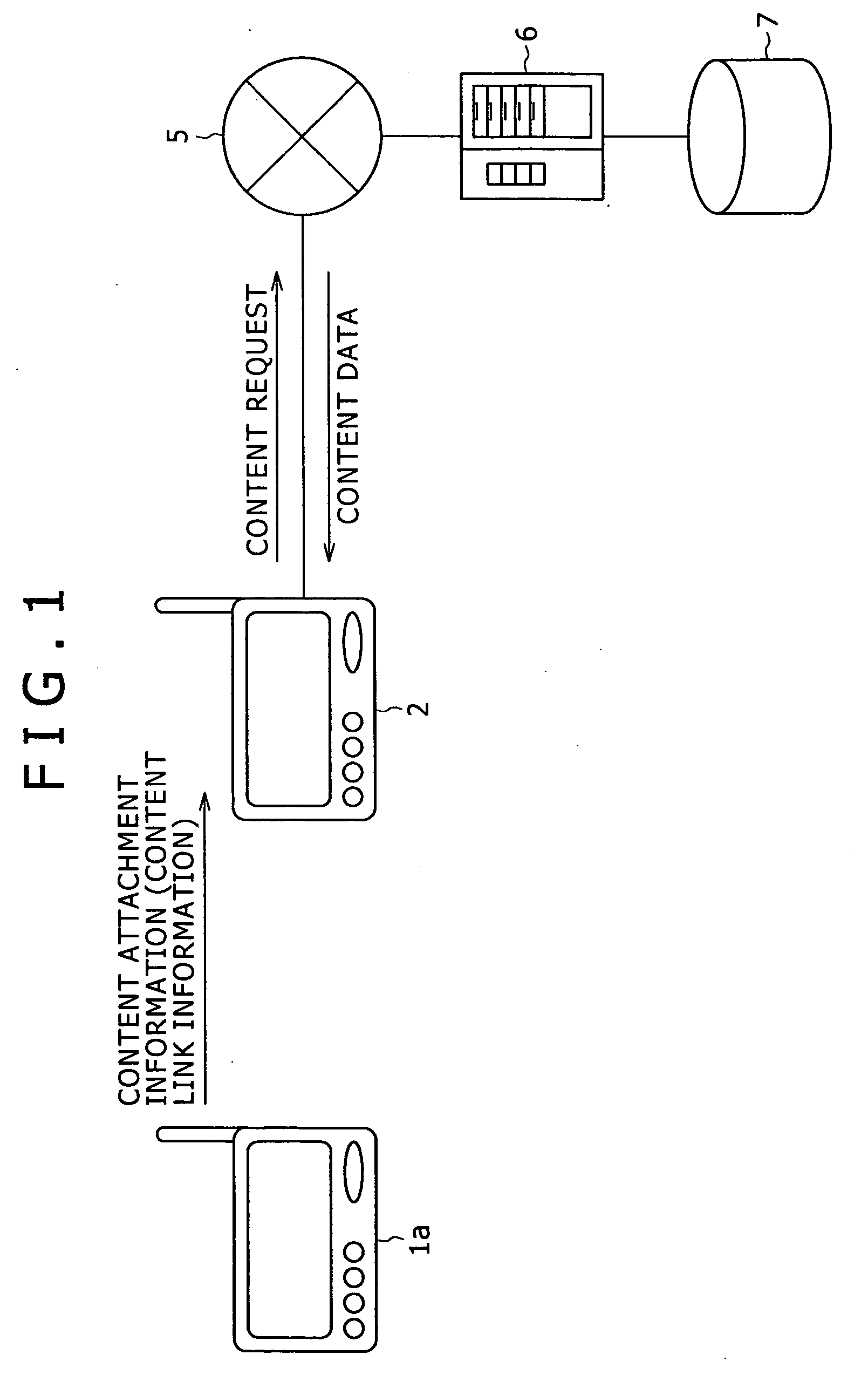
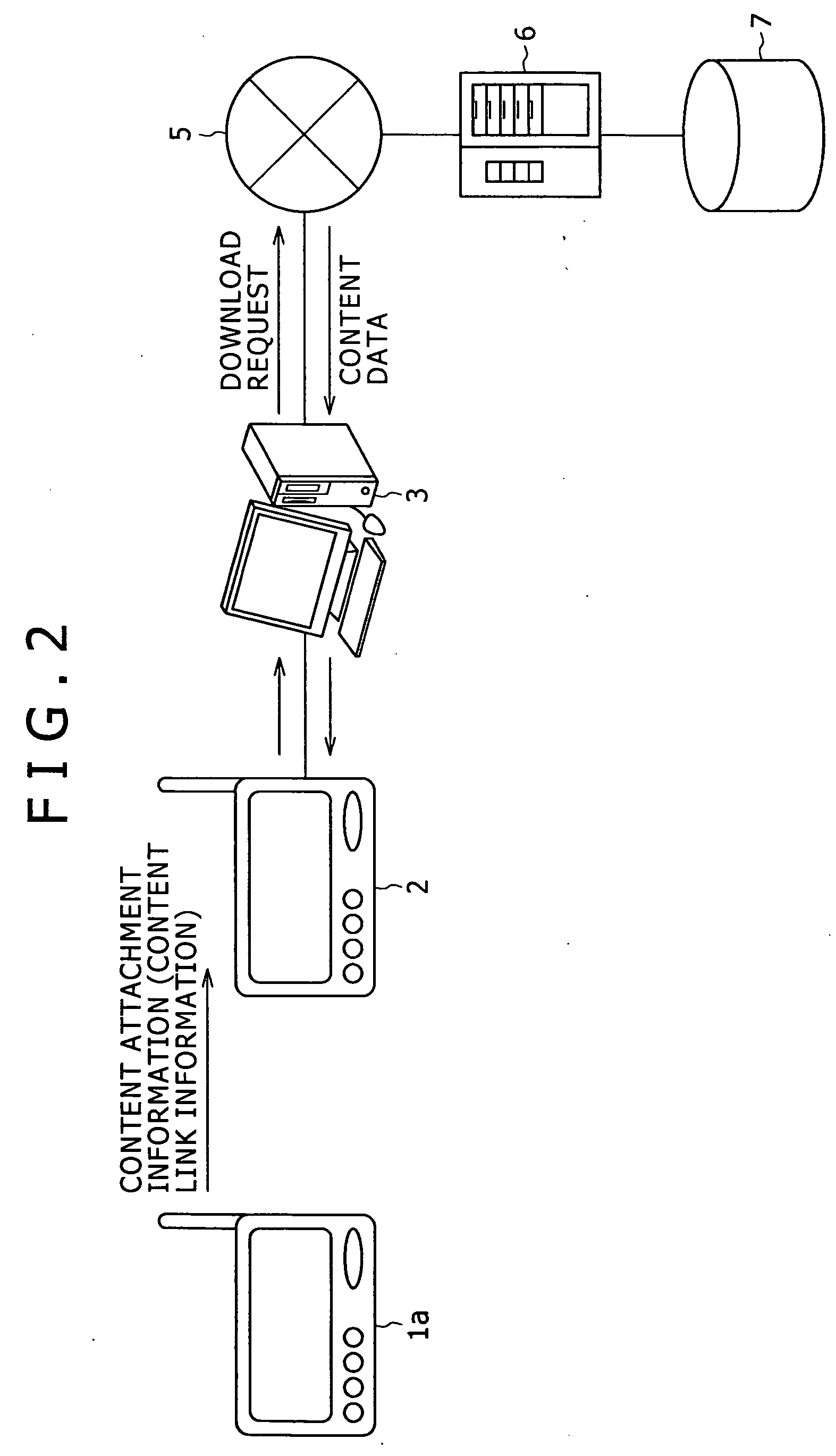
Communication device and method thereof
InactiveUS20070043739A1Easy to receiveSlow acquisitionMetadata audio data retrievalNetwork topologiesData contentWorld Wide Web
A communication method is disclosed which includes: first step of sending content attachment information including content link information from a sending device to a receiving device; and second step of connecting either the receiving device or a host device connected therewith to a server on a network in accordance with the content link information so as to receive and download content body data, content preview data, or content-related information from the server.
Owner:SONY CORP
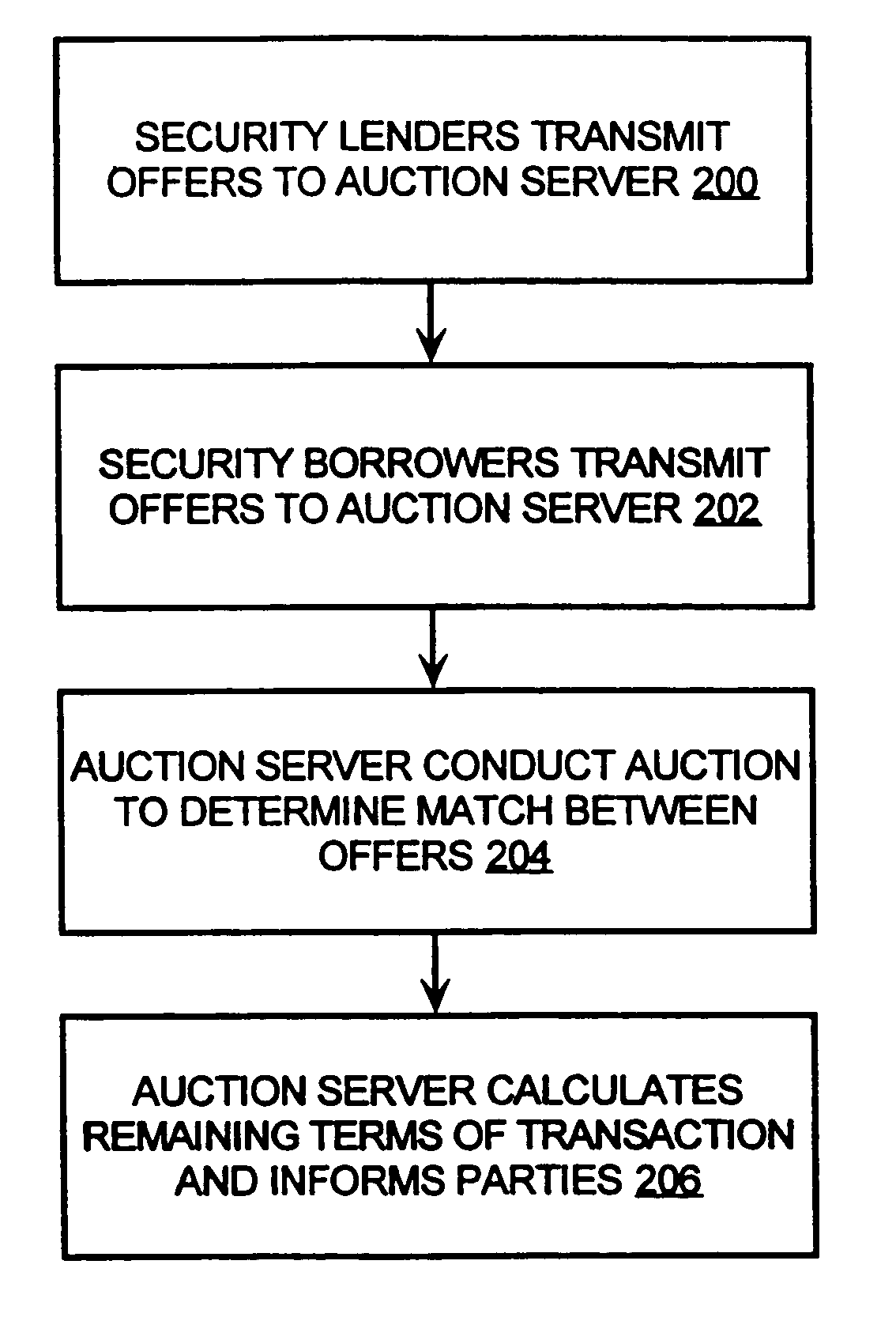
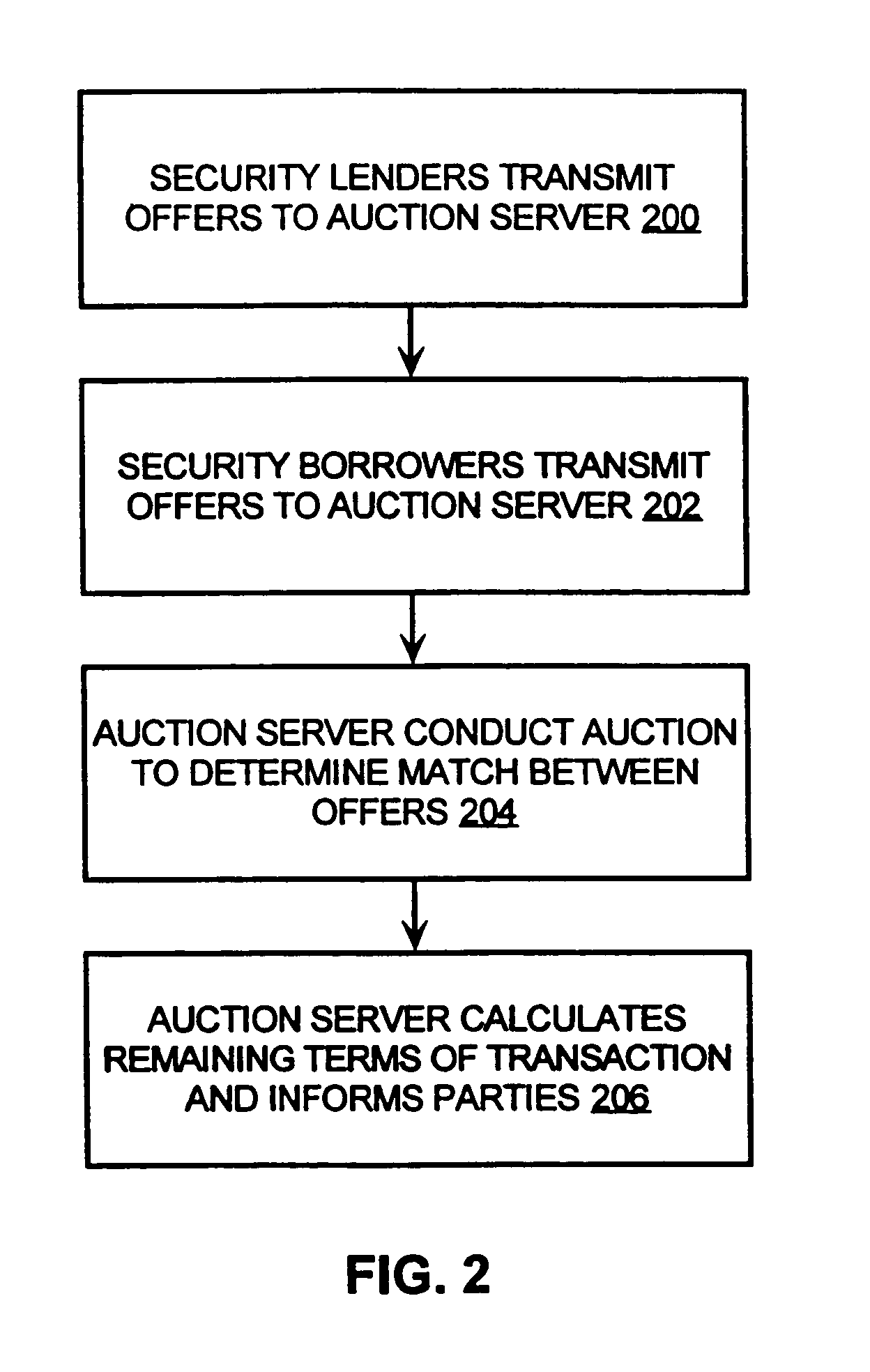
Computer borrow and loan securities auction system
ActiveUS7349881B1High transparencyLow costFinanceComputer security arrangementsLeased lineLarge size
An auction system is disclosed which allows users to participate using their own, or the exchanges, or a brokers, computers, suitably connected to the auction system. This connection may use the internet or a private leased line or an alternative network. The invention involves a method and system for providing auction mechanisms, including a wide variety of types of auctions as described below, and a central counterparty for assuming credit risk between borrowers and lenders, if the borrowers and lenders chose not to transact with each other. This method and auction system provides a means for borrowers and lenders of securities to meet more efficiently, to trade at a better price, to trade in larger size, to trade more rapidly, and, in some cases eliminate the role of the broker as an intermediary between borrower and lender. This mechanism facilitates not only a borrowing and subsequent short sale of securities but also the financing of securities.
Owner:LOCKWOOD DAVID
Method for anonymous identification of the profiles of subscribers in a communication system and corresponding module
InactiveUS20050076124A1The process is convenient and fastEnhanced anonymityAssess restrictionSpecial service for subscribersTelecommunications linkCommunications system
Methods and apparatus for anonymous identification of the profiles of subscribers in a communication system, wherein subscribers define and store subscriber-specific profiles via a respective input unit in a respective communication terminal and / or in a respective module respectively coupled to a respective communication terminal. Each respective module communication terminal is used to collect the profiles of other subscribers of the communication system on the basis of a wireless, locally defined network technology which are compared to the profiles defined and stored in the respective communication terminal whereupon they are discarded according to a subscriber-specific correlation threshold or communicated to the respective subscriber. A communication link is set up by an intermediate coupled provider of the communication system between subscribers when the respective subscriber activation occurs. A module is also disclosed that can be integrated in a mobile communication terminal or on a mobile communication terminal via an interface. The module includes a memory unit for storing profiles, a collector unit functioning on the basis of a wireless, locally defined network technology for collecting (scanning) profiles of subscribers, a correlation unit for comparing profiles, and a signaling / synchronizing unit.
Owner:SIEMENS AG
Vehicle-mounted network message authentication protocol
InactiveCN106713326AKey security hasReduce dependenceUser identity/authority verificationCommunication unitProtocol for Carrying Authentication for Network Access
The invention provides a vehicle-mounted network message authentication protocol. A vehicle-mounted ad-hoc network comprises a trusted authentication center, a vehicle-mounted unit and roadside units, the message authentication protocol uses a threshold proxy re-signature algorithm to protect vehicle privacy information, the signature of a message by a vehicle-mounted communication unit is converted into the signature of the same message by an authentication center, thereby reducing the risk that the signature tracks the vehicle-mounted unit and realizing the anonymity of communication messages. Re-signature keys are dispersed to a plurality of roadside communication units in a threshold mode for management, thereby reducing the decoding success rate of the re-signature keys and preventing the roadside communication units from abusing the proxy signature right. The authentication center traces a real vehicle releasing a false message to solve the problem of calling back illegal vehicles. The protocol has relatively high security and a relatively low storage cost, has unforgeability, robustness, message authentication, replay attack resistance and traceability, and can greatly improve the privacy of network member information.
Owner:SHANGHAI DIANJI UNIV
Anonymous and secure network-based interaction
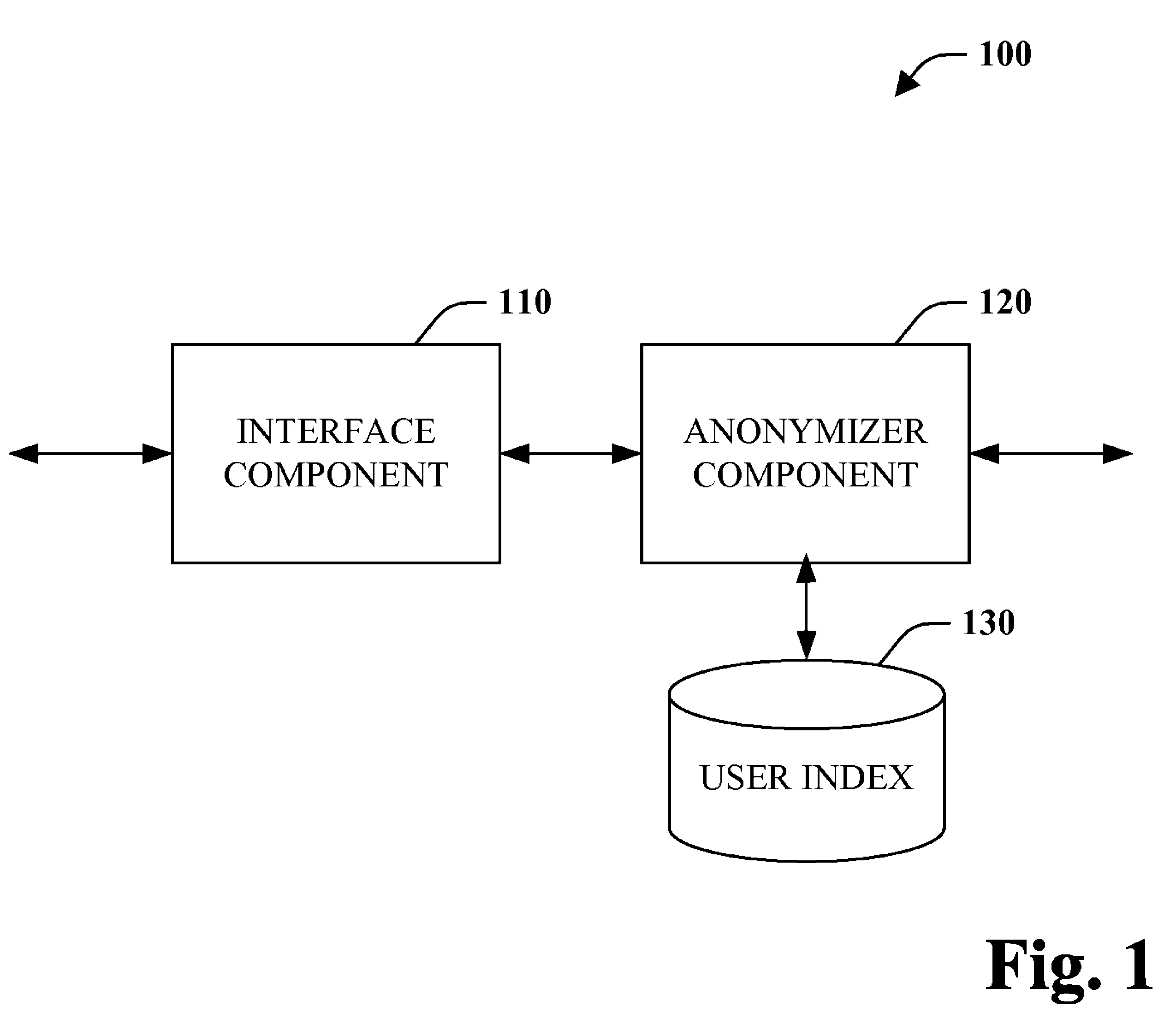
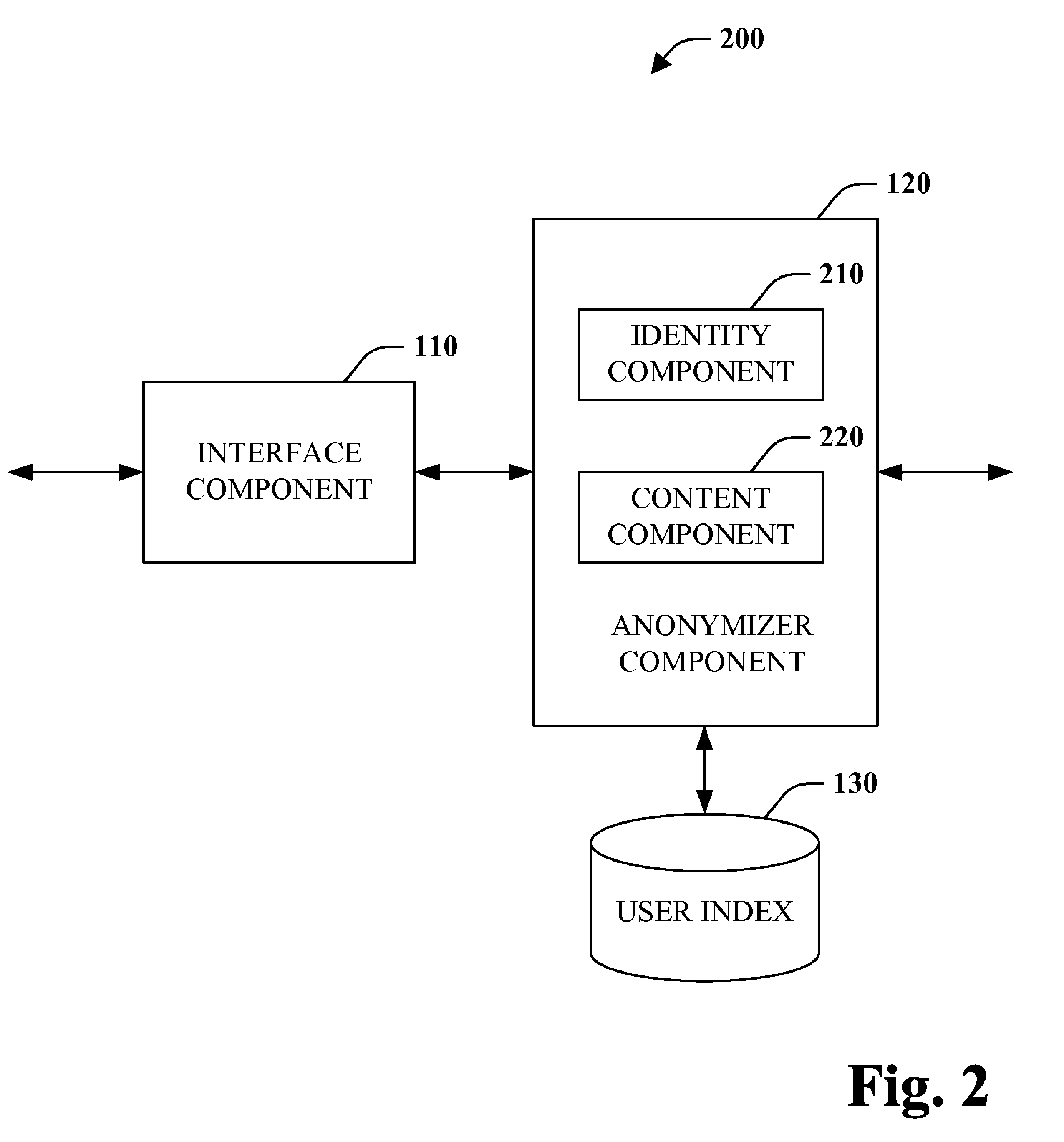
ActiveUS7984169B2To offer comfortEnhanced anonymityMultiple digital computer combinationsInternal/peripheral component protectionThird partyInternet privacy
The subject disclosure pertains to anonymous network interaction. More specifically, mechanisms are provided to ensure anonymity with respect network interaction such that third parties are unable to determine the source and / or intent of communications. Accordingly, entities can anonymize all outgoing and / or incoming data packets so as to mitigate outside entities from learning about information being sought and / or provided. For example, a user or corporation can employ an anonymizer with respect to web searching so that outside entities are not able to determine what information is attempted to be accessed and by whom.
Owner:MICROSOFT TECH LICENSING LLC
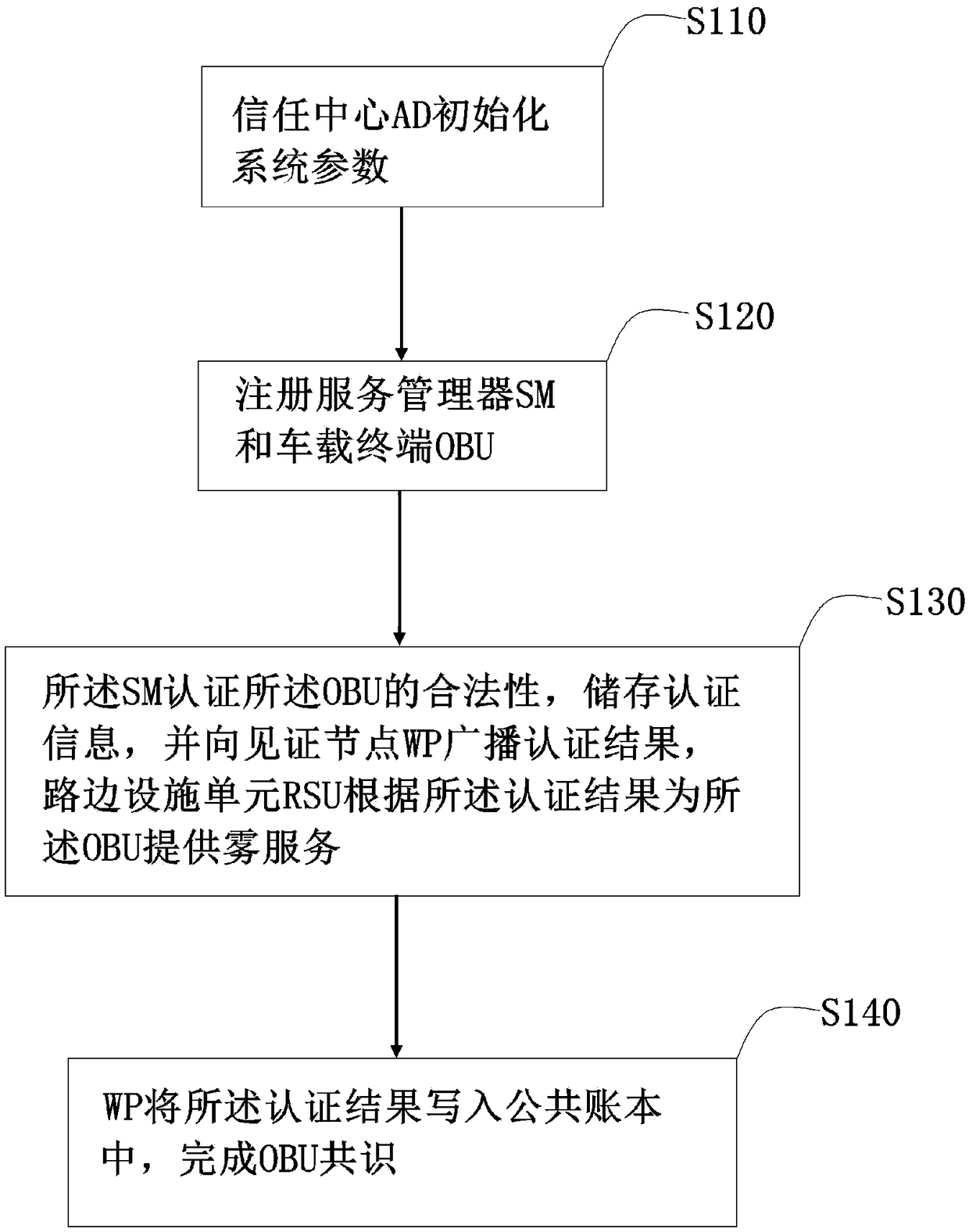
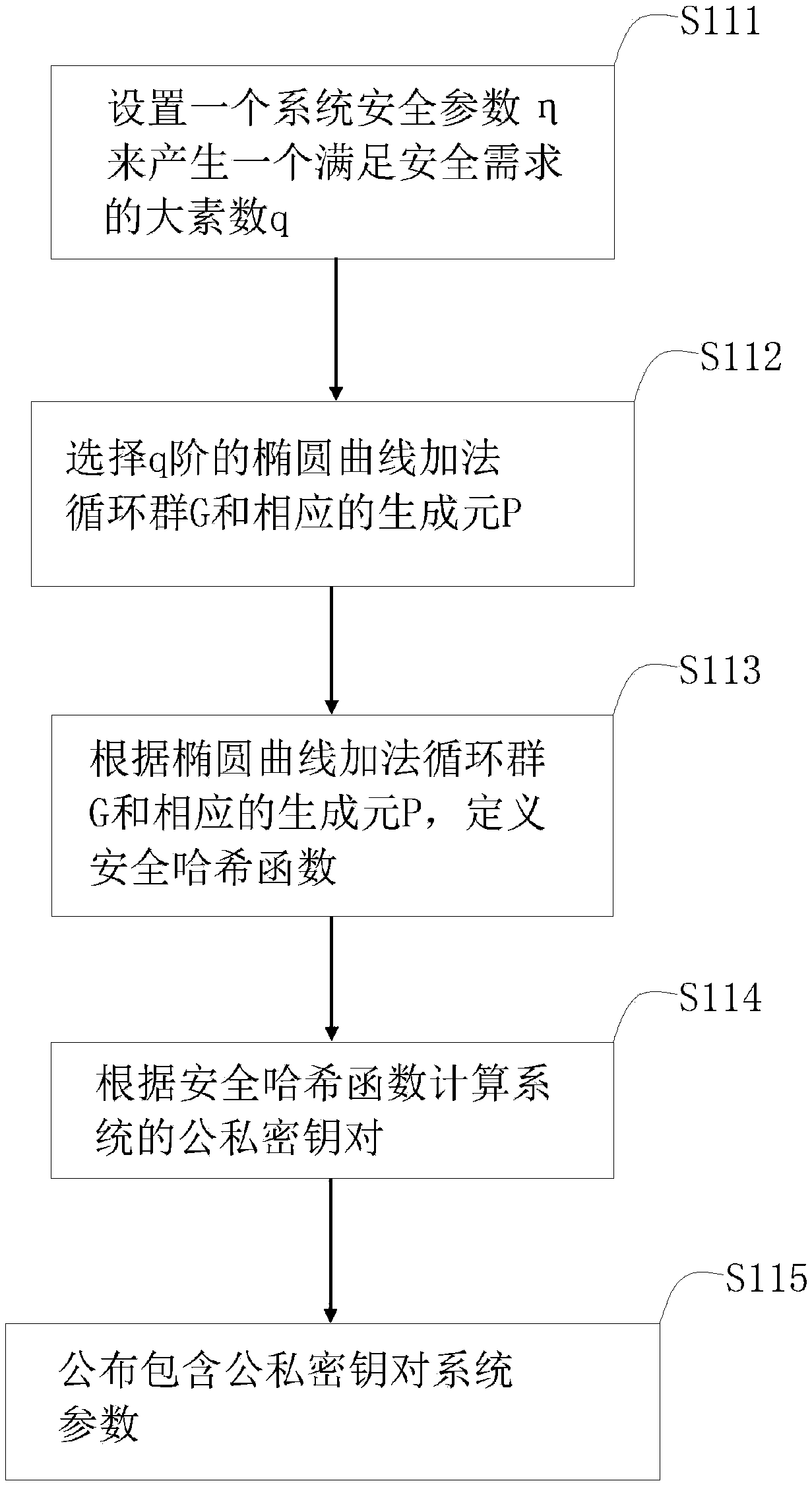
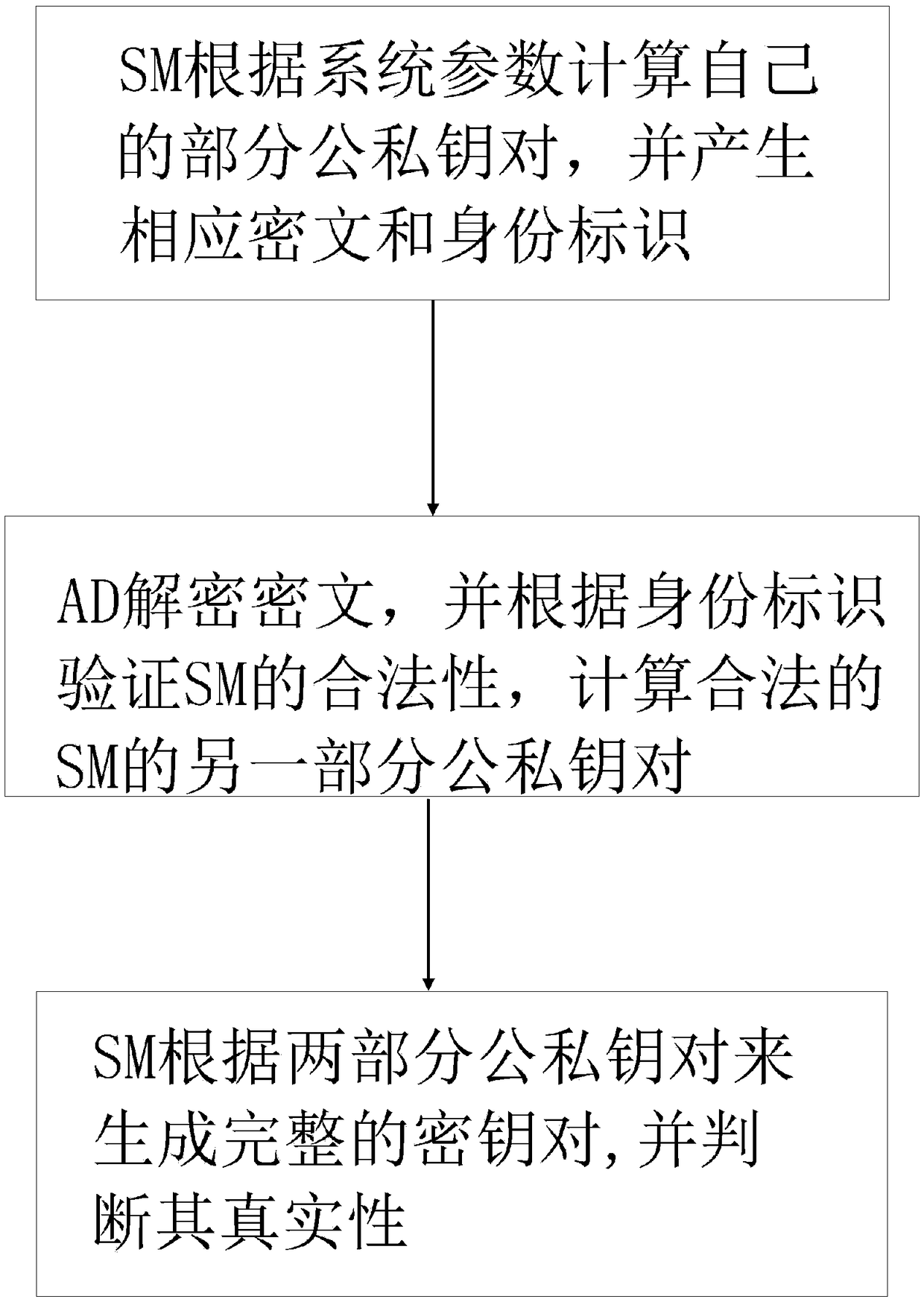
Vehicle fog data light-weight anonymous access authentication method based on blockchain assistance
InactiveCN109194610AProtect private informationEnhanced anonymityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPublic accountOn board
The present invention provides a vehicle fog data light-weight anonymous access authentication method based on blockchain assistance, and relates to the technical field of network communication safetyof urban traffic operation management. The method comprises the steps of: arranging one witness node (WP) in a management range of each service manager (SM), initializing system parameters through antrusted center AD, and registering the SM and a OBU (On Board Unit); allowing the SM to authenticate the validity of the OBU, storing the authentication information, broadcasting an authentication result to the WP, and providing fog service to the OBU according to the authentication result by a roadside facility unit RSU; and writing the authentication result into a public account by the WP to complete OBU consensus. The vehicle fog data light-weight anonymous access authentication method based on blockchain assistance can protect the user privacy information while ensuring the identity authenticity of a vehicle user accessing the fog service so as to achieve the vehicle anonymous authentication and allow users to select the time and the frequency of replacement of the pseudonym by themselves; the non-interactive autonomous cross-domain authentication is achieved, and the communication delay is effectively reduced; and moreover, the authentication information management is simplified,and the risk that a single database is tampered is effectively avoided.
Owner:BEIJING JIAOTONG UNIV
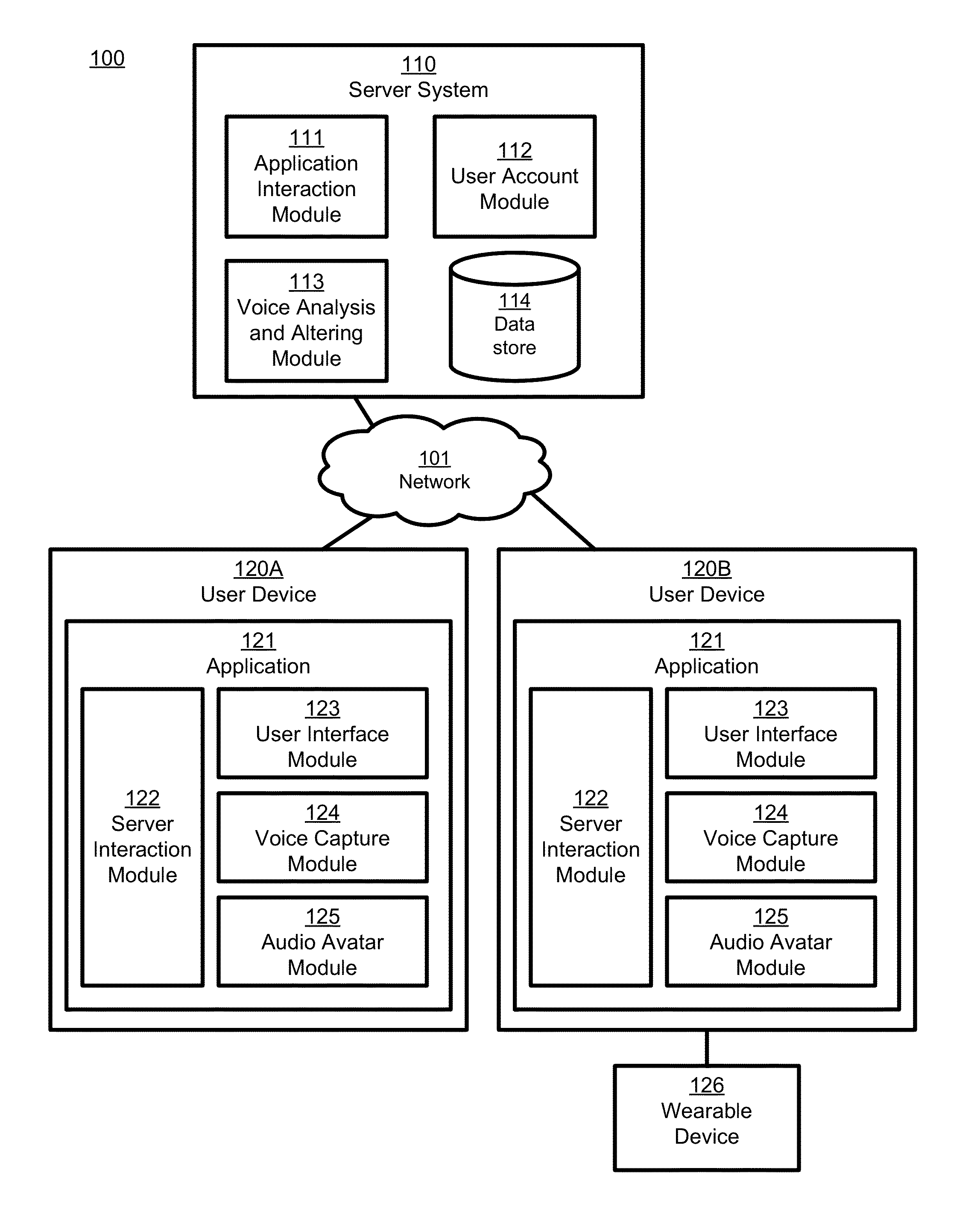
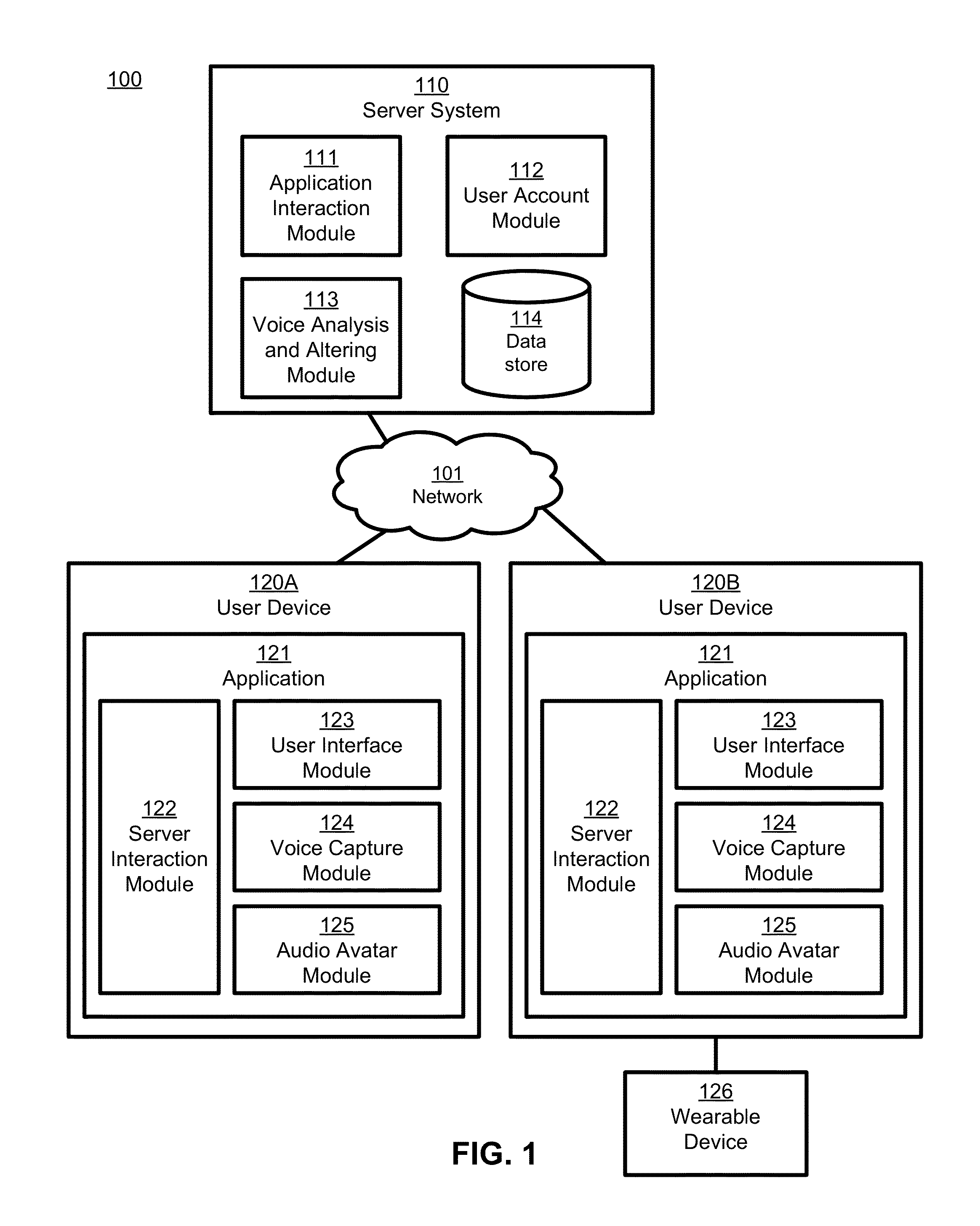
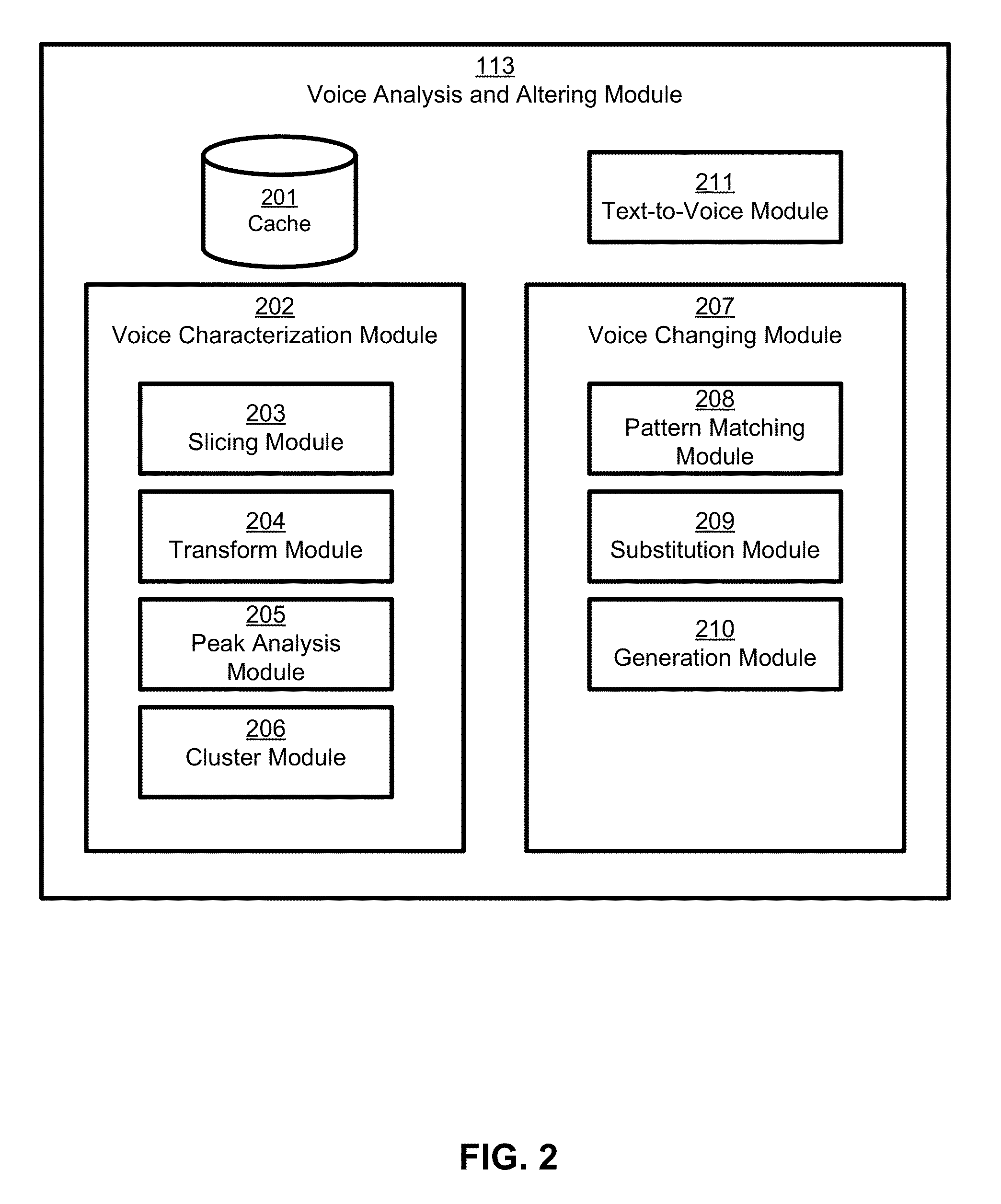
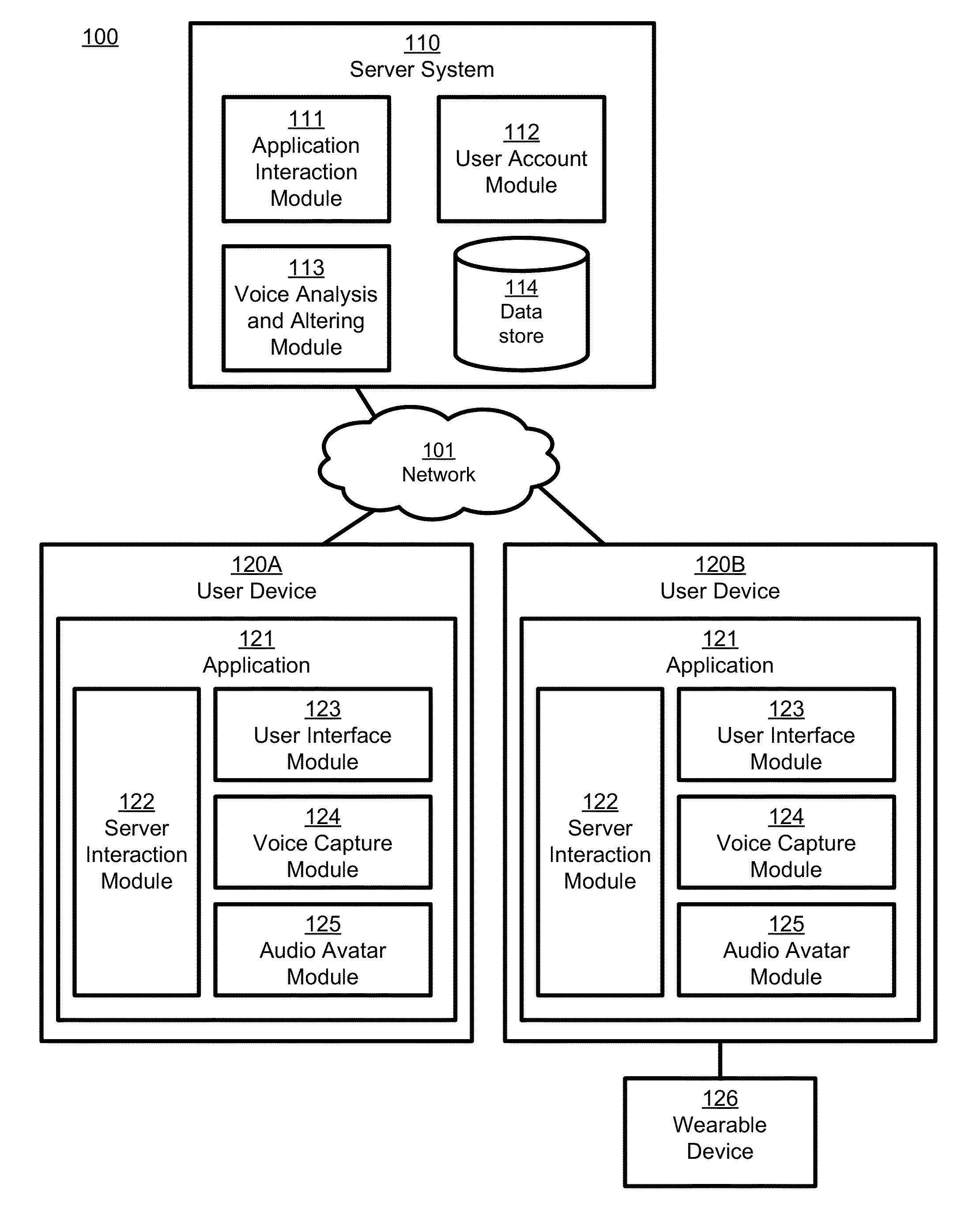
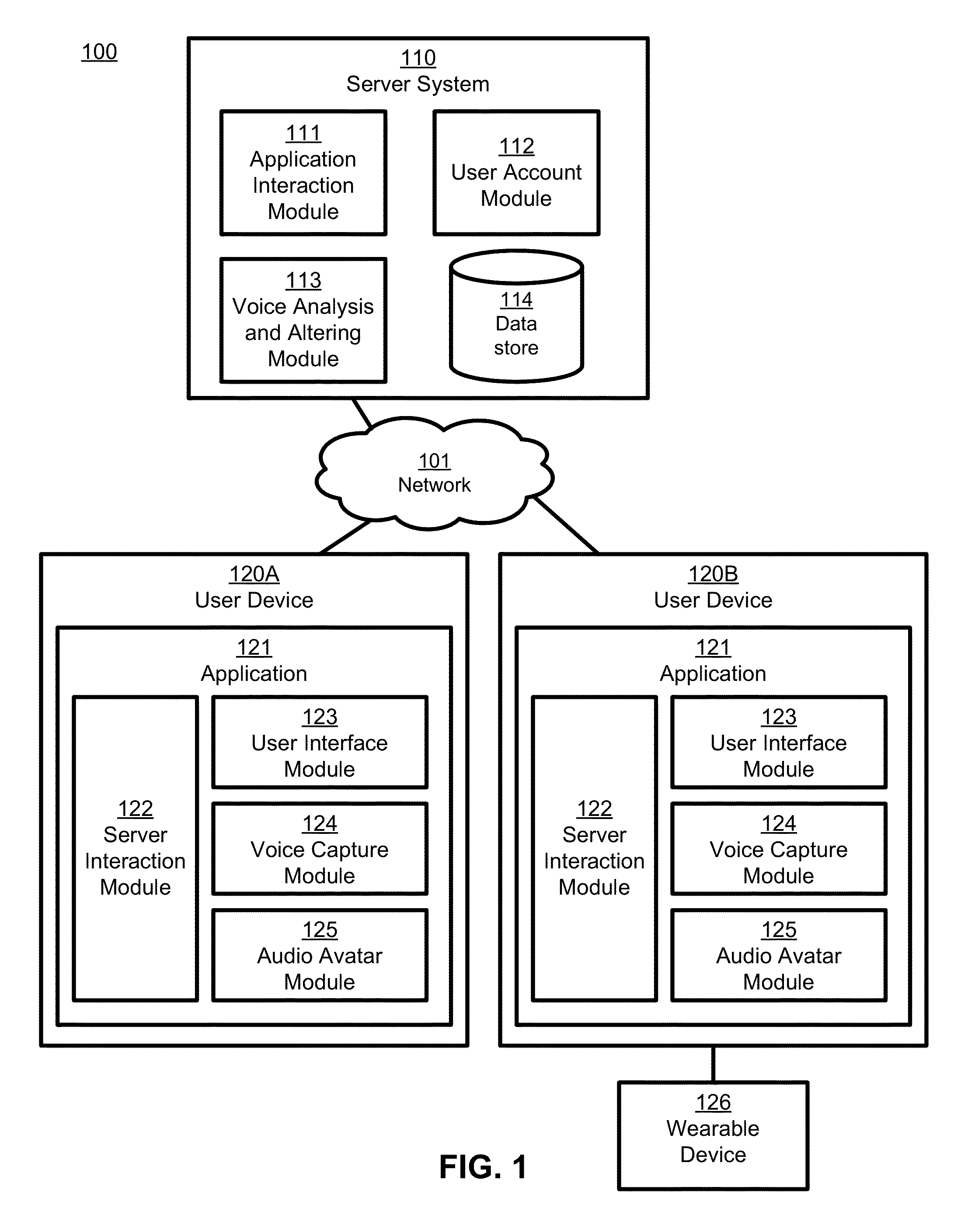
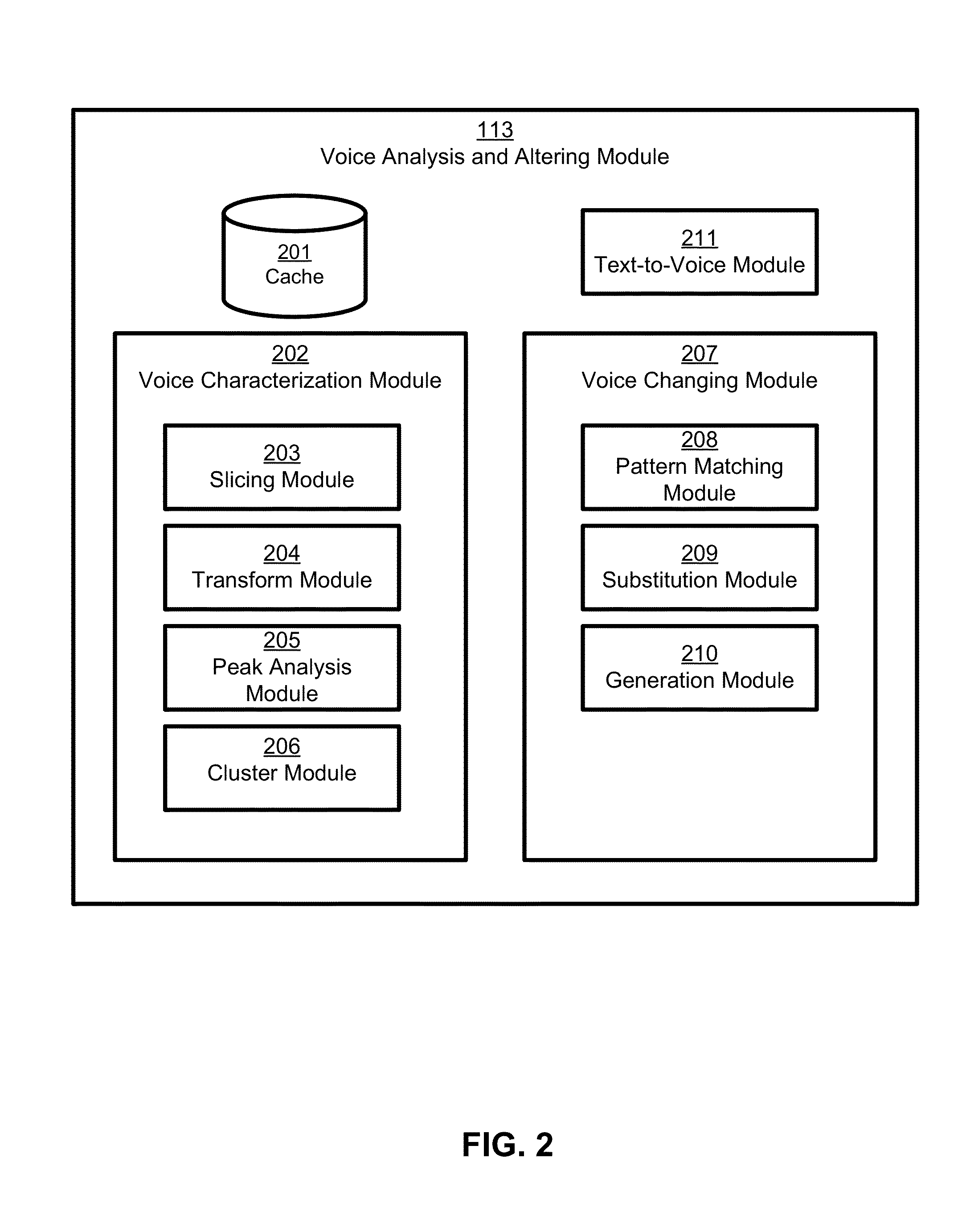
Creation and application of audio avatars from human voices
ActiveUS9324318B1Good express their authentic selfEnhancing user experience/engagementSpeech synthesisSpeech soundSocial web
A subject voice is characterized and altered to mimic a target voice while maintaining the verbal message of the subject voice. Thus, the words and message are the same as in the original voice, but the voice that conveys the words and message in the altered voice is different. Audio signals corresponding to the altered voice are output, for example to an application for playback to a user, or to another application or device for subsequent playback by the user or someone else. In one embodiment, the altered voice is posted to a social network. In other embodiments, the altered voice is used by other software applications or consumer electronics applications, such as GPS guidance systems, ebook readers, voice-based intelligent personal assistants, chat applications, and / or others that use voice as an input or output.
Owner:OBEN INC
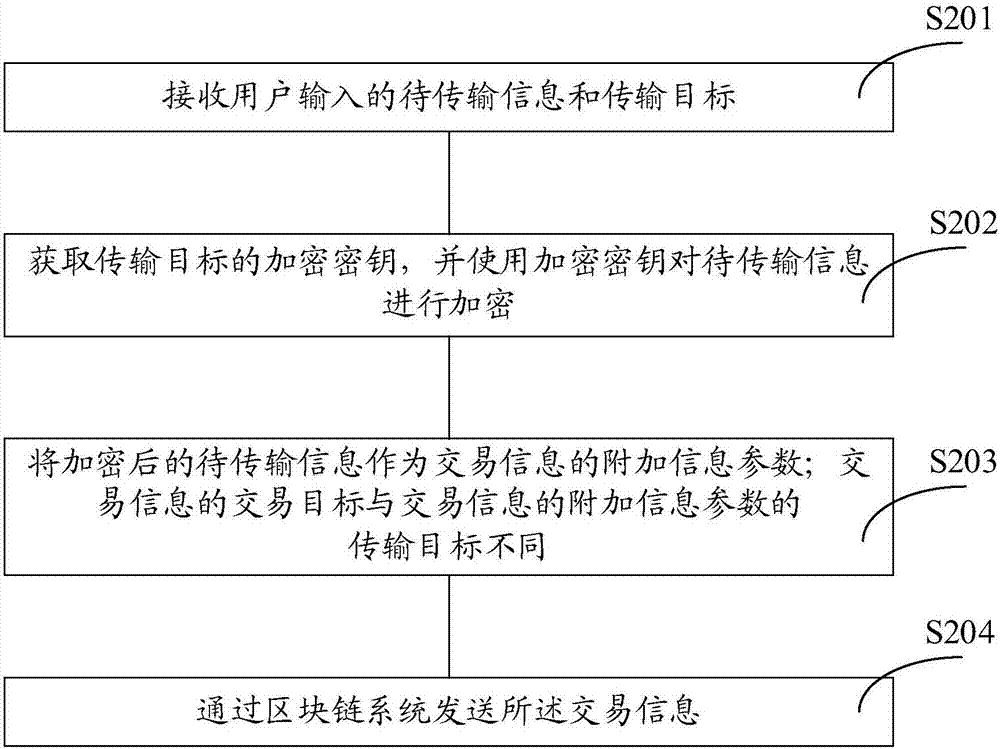
Information transmitting method, processing method and device
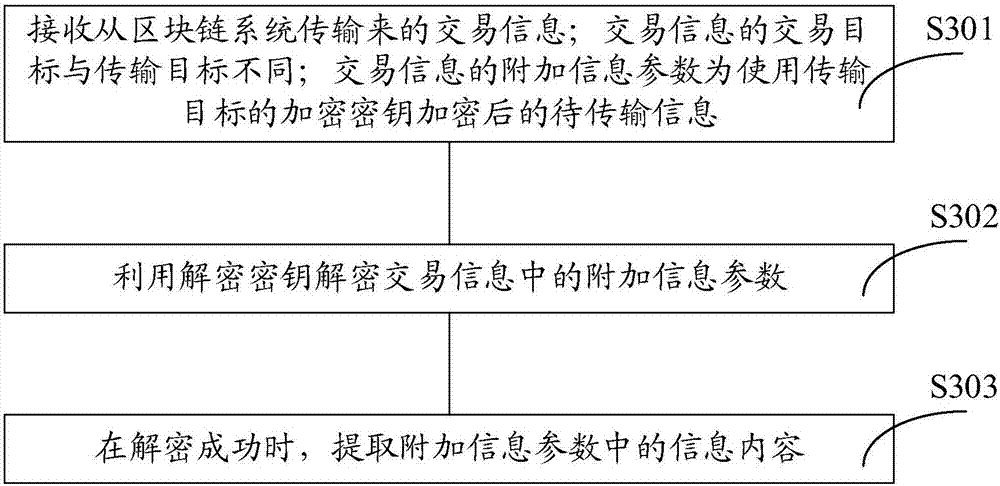
ActiveCN107248994AReceived successfullyEnhanced anonymityKey distribution for secure communicationUser identity/authority verificationUser inputChain system
The invention discloses an information transmitting method, a processing method and a device, so as to improve communication anonymity. The information transmitting method comprises steps: a transmitter receives to-be-transmitted information and a transmission target inputted by a user; the encryption key of the transmission target is acquired, and the encryption key is used for encrypting the to-be-transmitted information; the to-be-transmitted information after encryption is used as an additional information parameter for transaction information, wherein the transaction target of the transaction information is different from the transmission target; and the transaction information is transmitted through a block chain system. A receiver receives the transaction information transmitted from the block chain system; a decryption key is used for decrypting the additional information parameter in the transaction information; and after successful decryption, the information content in the additional information parameter is extracted. Thus, an attacker can not acquire the real identity of a user of the transmission target. Thus, when the technical scheme disclosed by the invention is adopted, the anonymity of anonymous communication can be enhanced.
Owner:UNION MOBILE PAY
PUF-based three-factor anonymous user authentication protocol method in Internet of Things
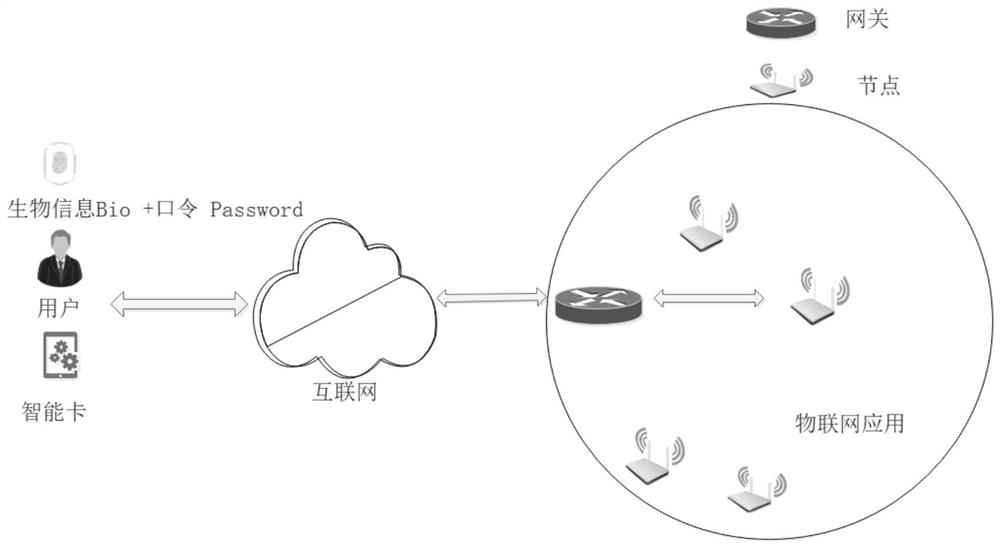
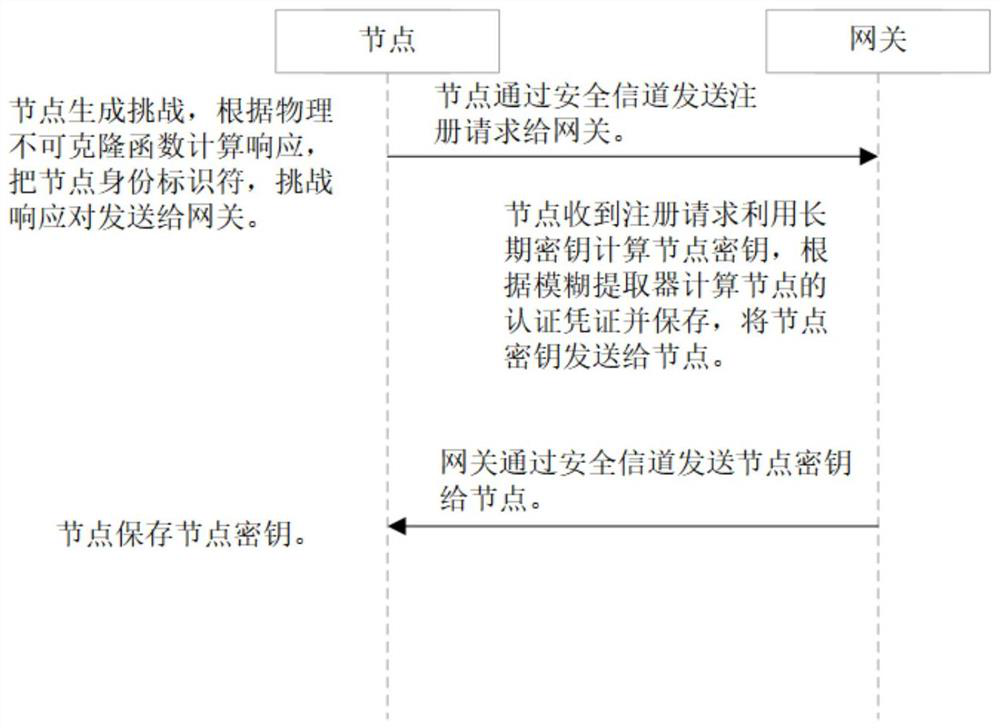
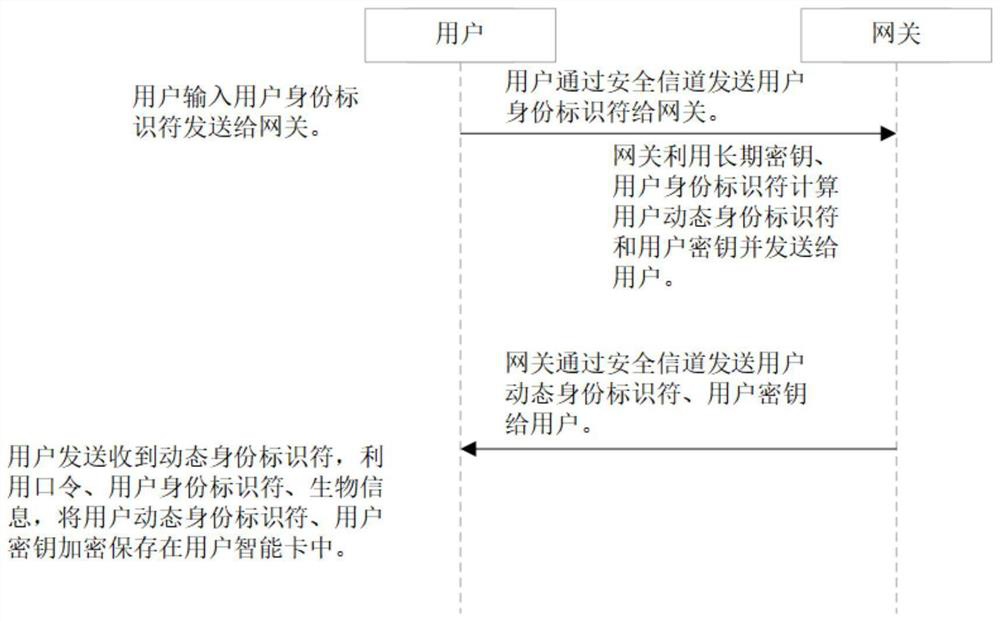
ActiveCN111818039ASave memorySave computing powerKey distribution for secure communicationSecurity arrangementAttackThe Internet
The invention discloses a PUF (Physical Unclonable Function)-based three-factor anonymous user authentication protocol method in the Internet of Things, which solves the security problems such as physical clone attacks and the like, and is implemented by the following steps that: a gateway generates a long-term key for registration and key negotiation of nodes and users; the node sends a PUF-basedchallenge and response to the gateway, and the gateway generates an authentication certificate and sends a node key to the node to complete registration; the user sends the identity identifier to thegateway, the gateway generates a user dynamic identity identifier and a user key and sends the user dynamic identity identifier and the user key to the user, and the user encrypts and stores the userdynamic identity identifier and the user key in the smart card to complete registration; and the user, the gateway and the node perform mutual authentication and key agreement to form a PUF-based three-factor anonymous user authentication protocol method in the Internet of Things. Based on three-factor authentication, smart card loss, password guessing attack and the like can be resisted; the method achieves the anonymity of the user and the node, is small in calculation amount, is high in efficiency, is suitable for IOT nodes with limited resources, and is used for IOT safety communication.
Owner:XIDIAN UNIV
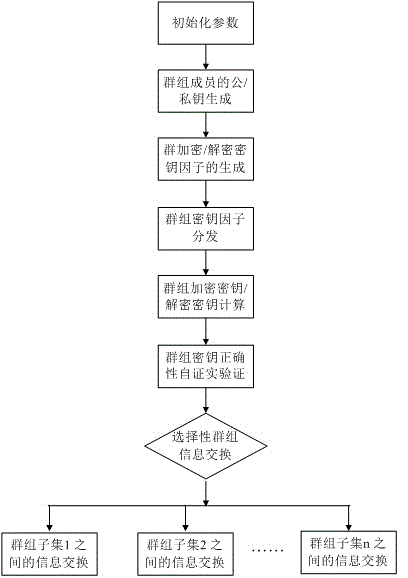
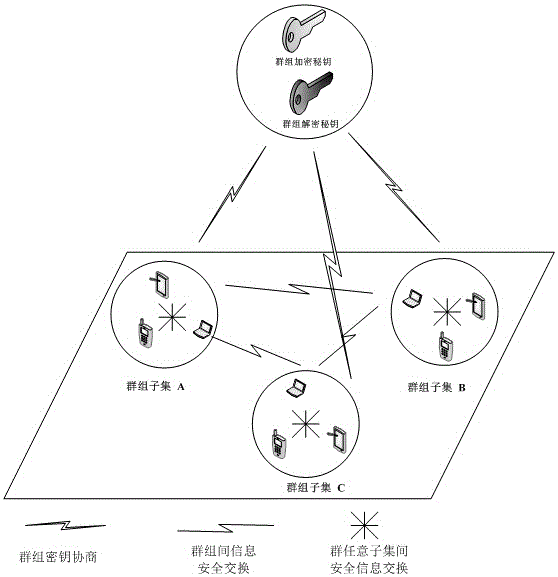
Flexible asymmetric group key negotiation method
ActiveCN106027241AConducive to the protection of personal privacy informationProtect personal privacy informationKey distribution for secure communicationNon symmetricProtocol for Carrying Authentication for Network Access
The invention discloses a flexible asymmetric group key negotiation method. The method comprises the steps of carrying out parameter initialization by members participating in group key negotiation, thereby generating public / private key pairs; blinding group contribution key shares through the public / private key pairs, and broadcasting group key shares; after the rest members receive corresponding broadcasting key shares, carrying out combination calculation, thereby obtaining group keys; and verifying whether calculated group keys are correct or not by the group members, encrypting communication information through the group keys if the calculated group keys are correct, and exchanging group security information. According to the method, members in or out of a group can select any one subset object in the group for secret information exchange; an object not selected by an information sender cannot decrypt the shared information; the group members can negotiate an encryption key and a decryption key which are consistent; the group members can verify the correctness of the keys; anonymity of the members participating in group key negotiation can be realized; and the personal private information of the group members can be protected.
Owner:河南招源科技有限公司
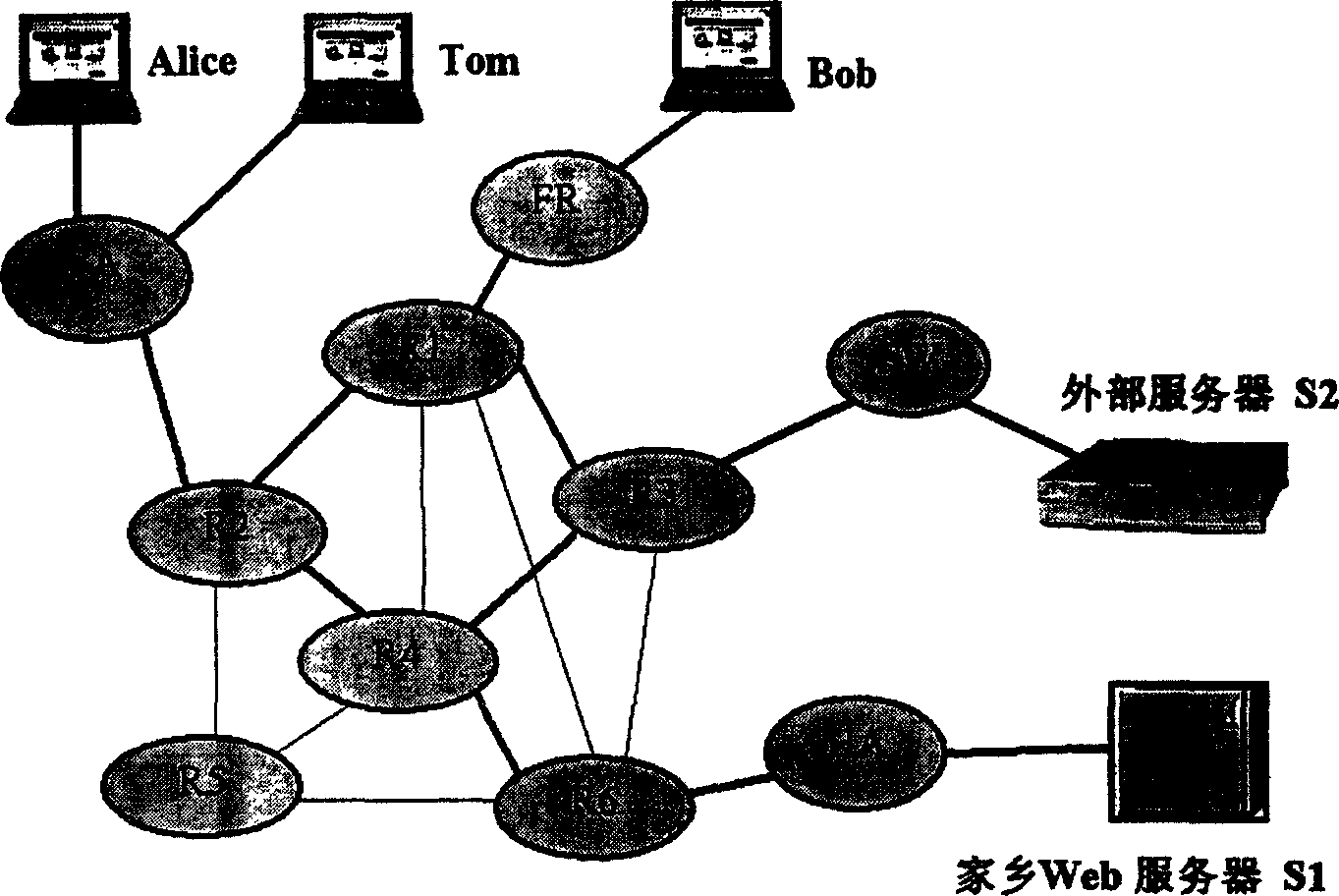
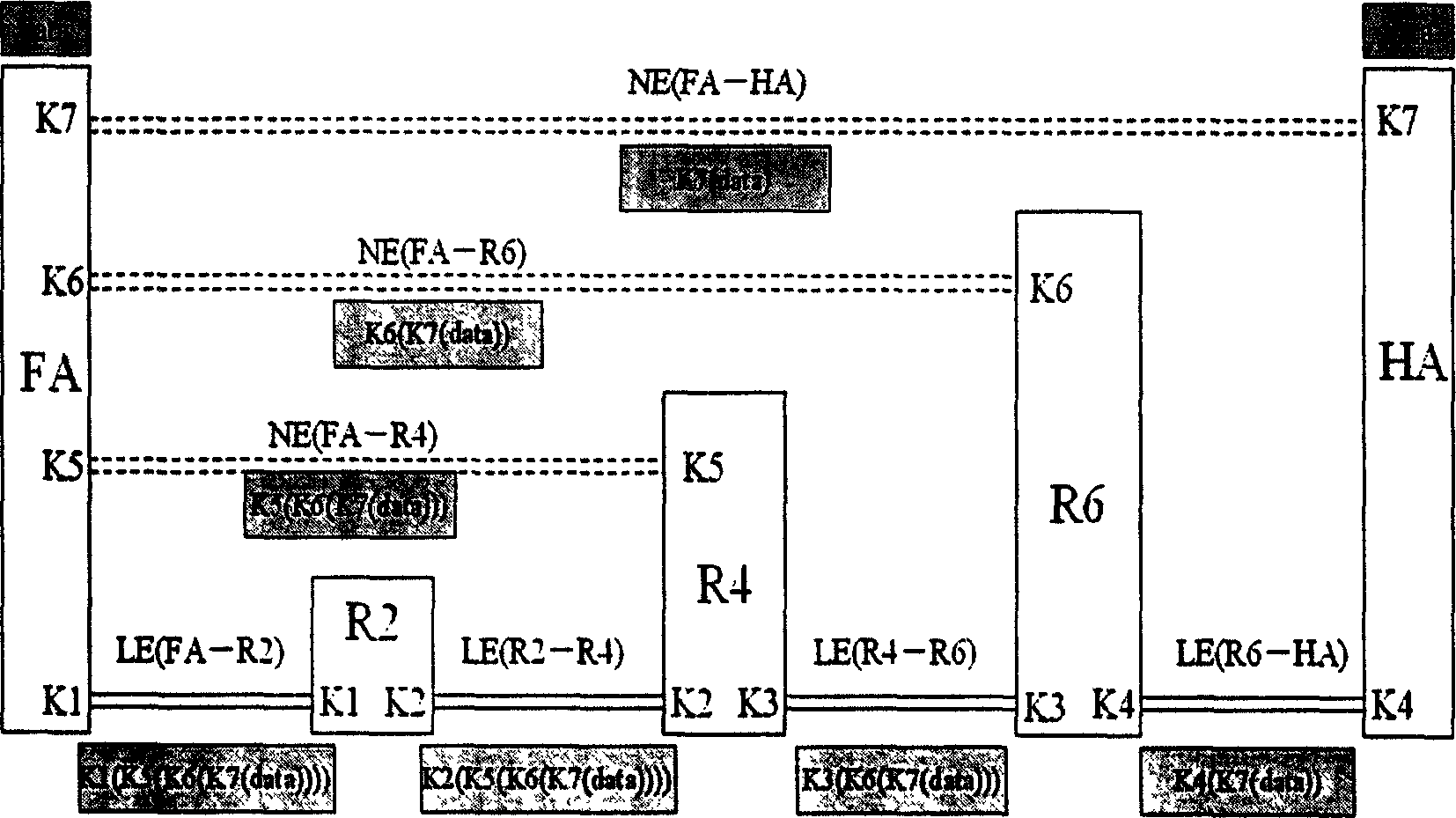
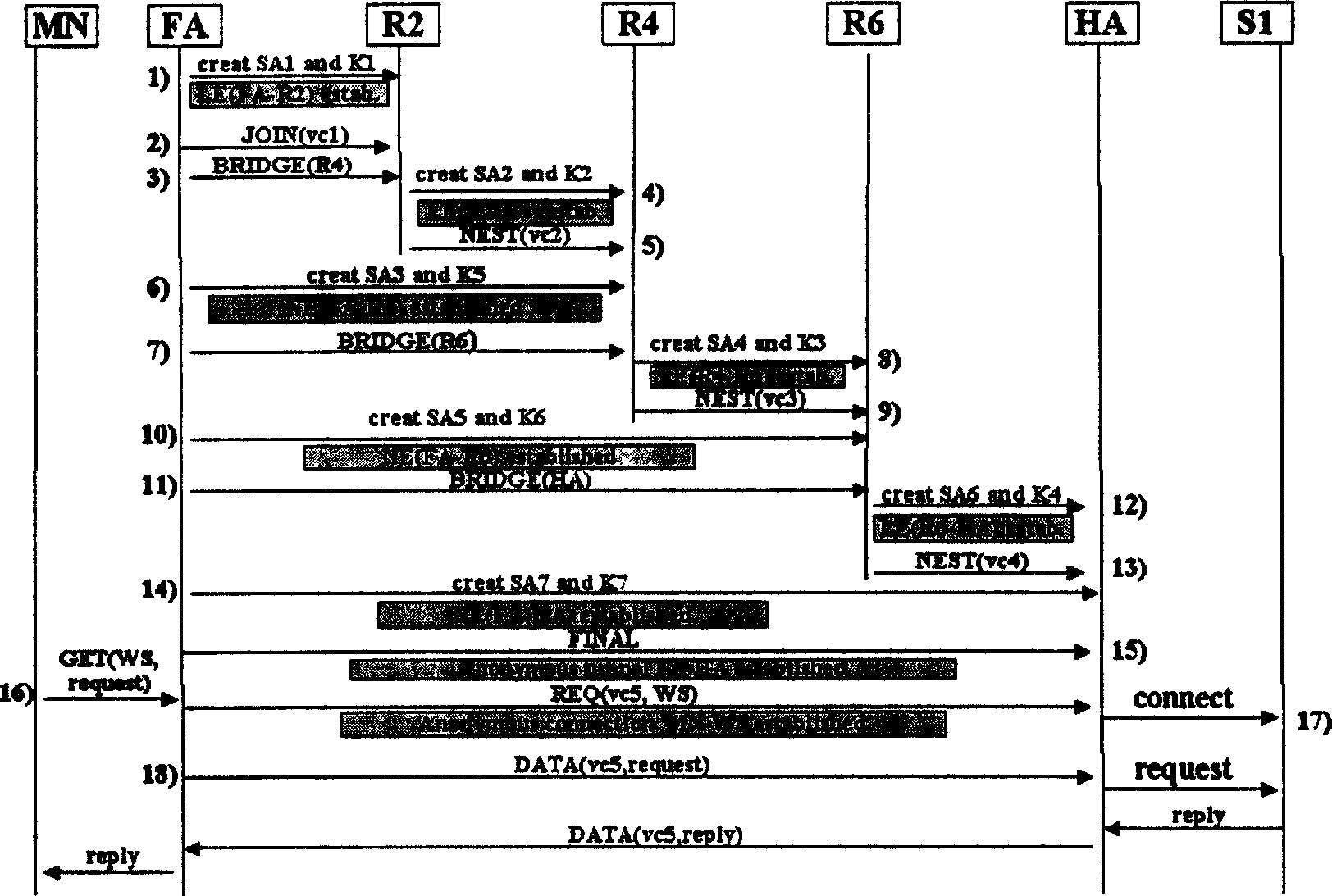
Anonymous connection method of broadband radio IP network
InactiveCN1564508ASave memoryWeak computing powerData switching networksSecuring communicationEncapsulated dataForeign agent
When mobile user logs on network to access host server, foreign agent FA and host agent HA are as network intermediate agent. Anonymity encapsulation method includes following step: selecting anonymous route in network layer, building anonymous connection, carrying out data encapsulation, as well as combination of polygenous network nested anonymous encapsulation and link encryption at intermediate router. Following measures are taken I the invention: encapsulating data packet transmitted, sharing anonymous channel, anonymous connection of distributed type route and anonymous encapsulation etc. The invention optimizes system capability of resisting interior attack to router and exterior attack to physical chain. Advantages are: favorable anonymity, transparency, expansibility and robustness.
Owner:XIDIAN UNIV
Creation and application of audio avatars from human voices
ActiveUS20160104474A1Enhance experience/engagementAdd anonymitySpeech synthesisGuidance systemRemote assistance
A subject voice is characterized and altered to mimic a target voice while maintaining the verbal message of the subject voice. Thus, the words and message are the same as in the original voice, but the voice that conveys the words and message in the altered voice is different. Audio signals corresponding to the altered voice are output, for example to an application for playback to a user, or to another application or device for subsequent playback by the user or someone else. In one embodiment, the altered voice is posted to a social network. In other embodiments, the altered voice is used by other software applications or consumer electronics applications, such as GPS guidance systems, ebook readers, voice-based intelligent personal assistants, chat applications, and / or others that use voice as an input or output.
Owner:OBEN INC
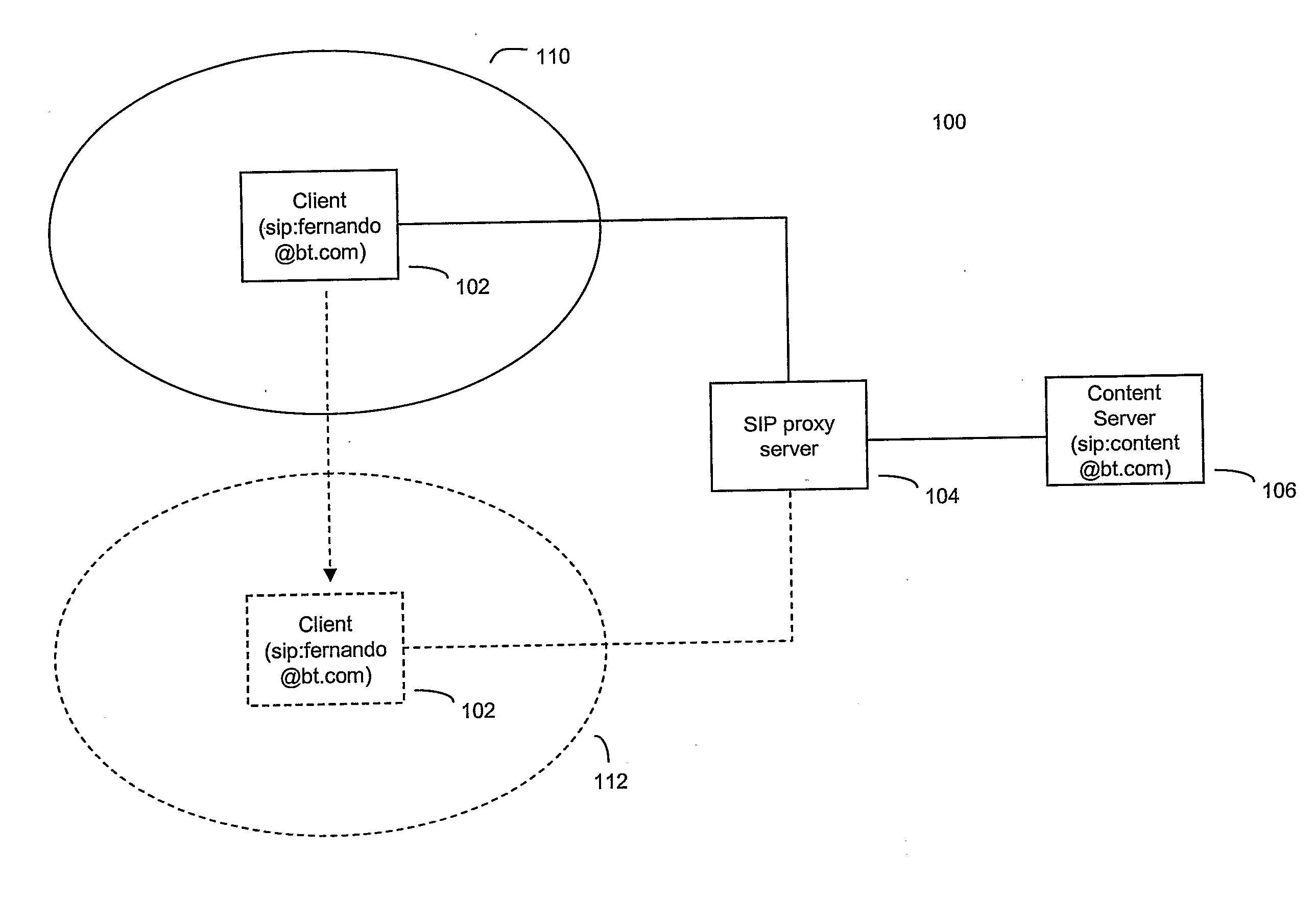
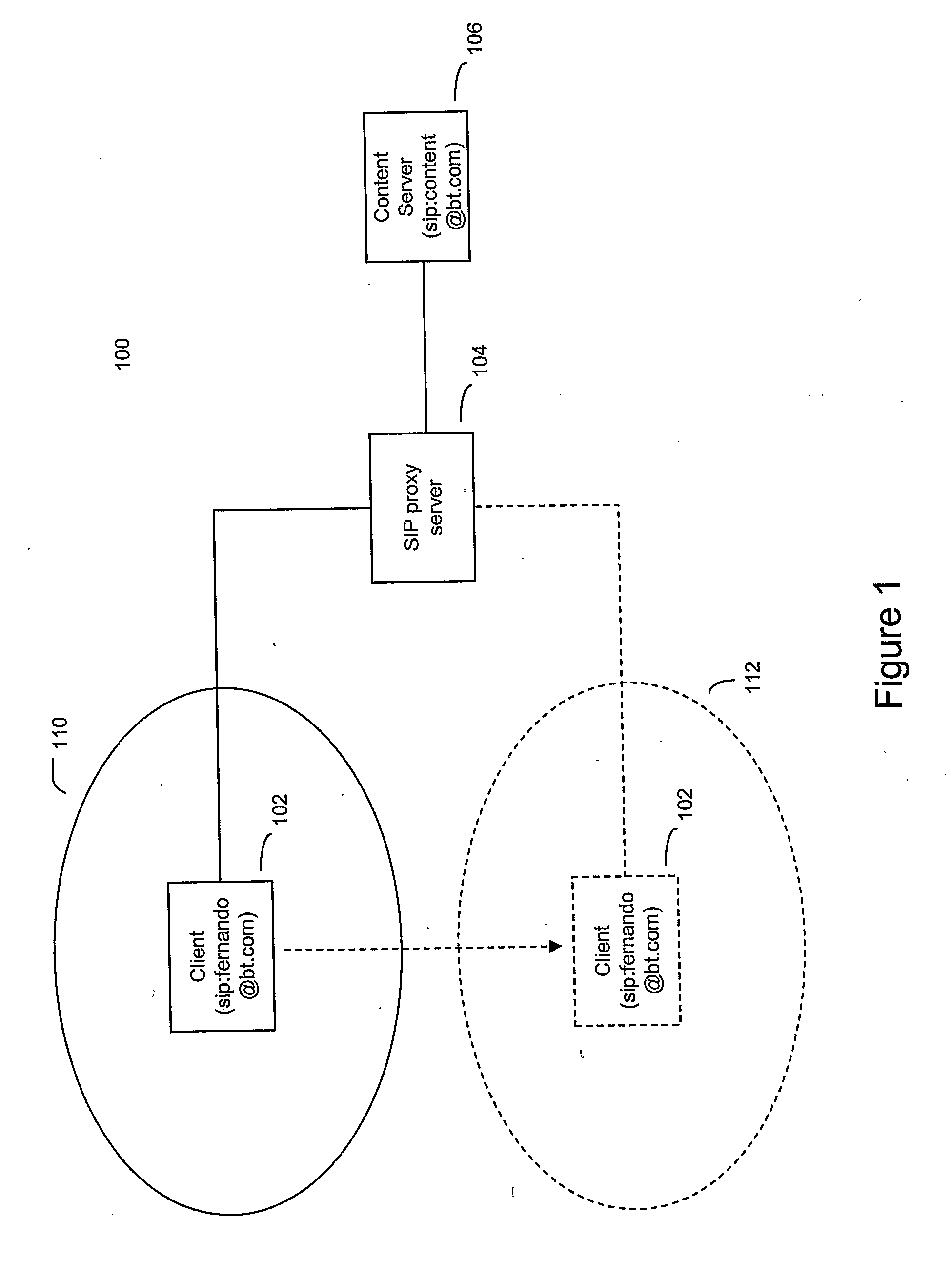
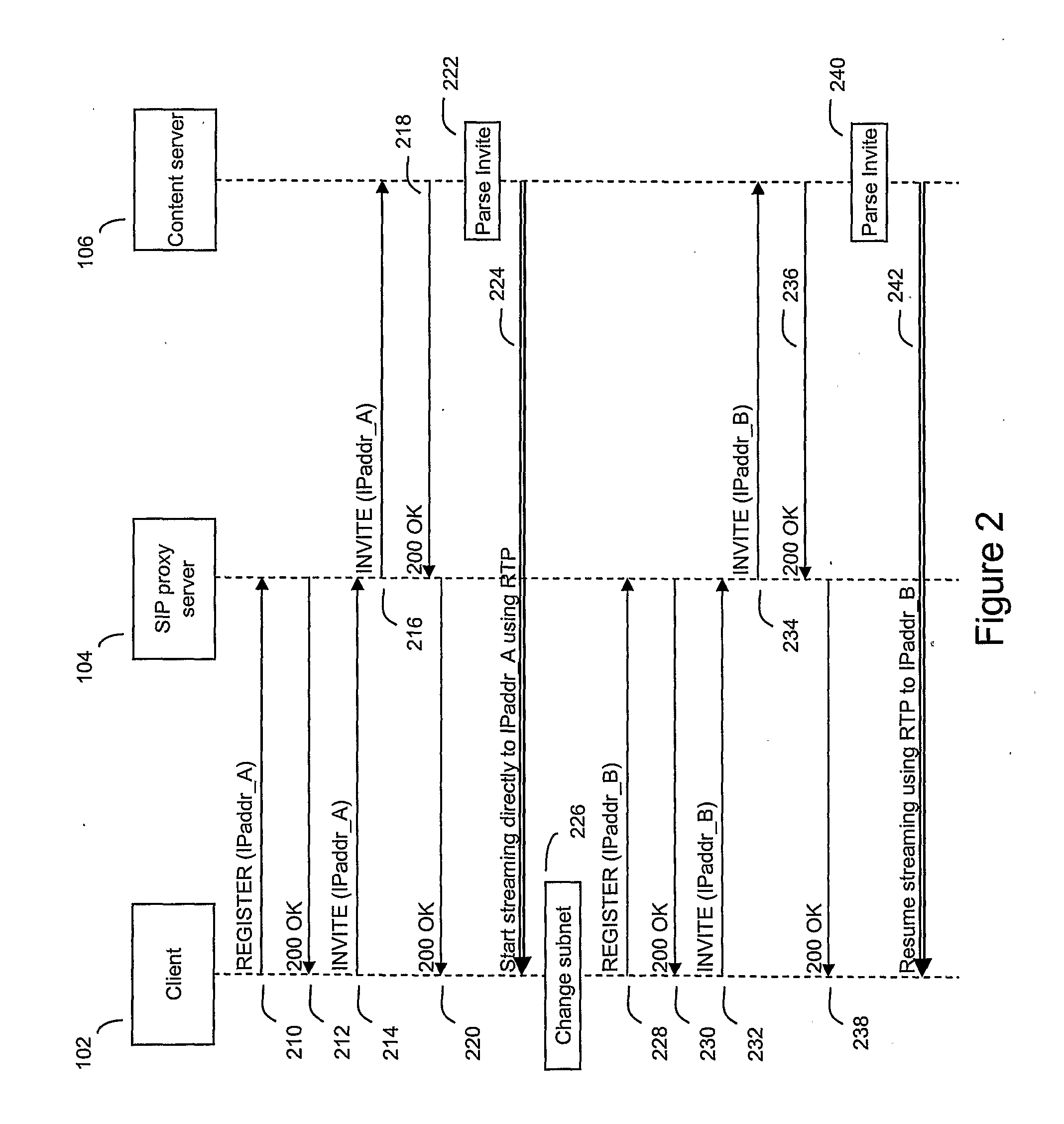
Fast handover using sip
ActiveUS20090177785A1Overcome delayNegates needMultiple digital computer combinationsWireless network protocolsSession Initiation ProtocolData stream
A method of handling a data stream during a handover in a communications network comprising a first user agent having a fixed address, a proxy server and a second user agent, said method comprising the steps of: mapping at the proxy server the fixed address with a dynamic network address allocated to the first user agent; sending a request by the first user agent to the second user agent for a data stream; generating by the second user agent in response to the request a plurality of messages each comprising part of the data stream requested and the fixed address of the first user agent, wherein the message is a session initiation protocol message, and sending the messages to the proxy server; receiving the messages at the proxy server and determining the mapped dynamic network address corresponding to the fixed address in the message, and forwarding the messages to the determined dynamic network address; and when the first user agent is allocated a new dynamic network address, replacing by the proxy server the mapped dynamic network address with the new dynamic network address and forwarding the received messages to the new dynamic network address.
Owner:BRITISH TELECOMM PLC
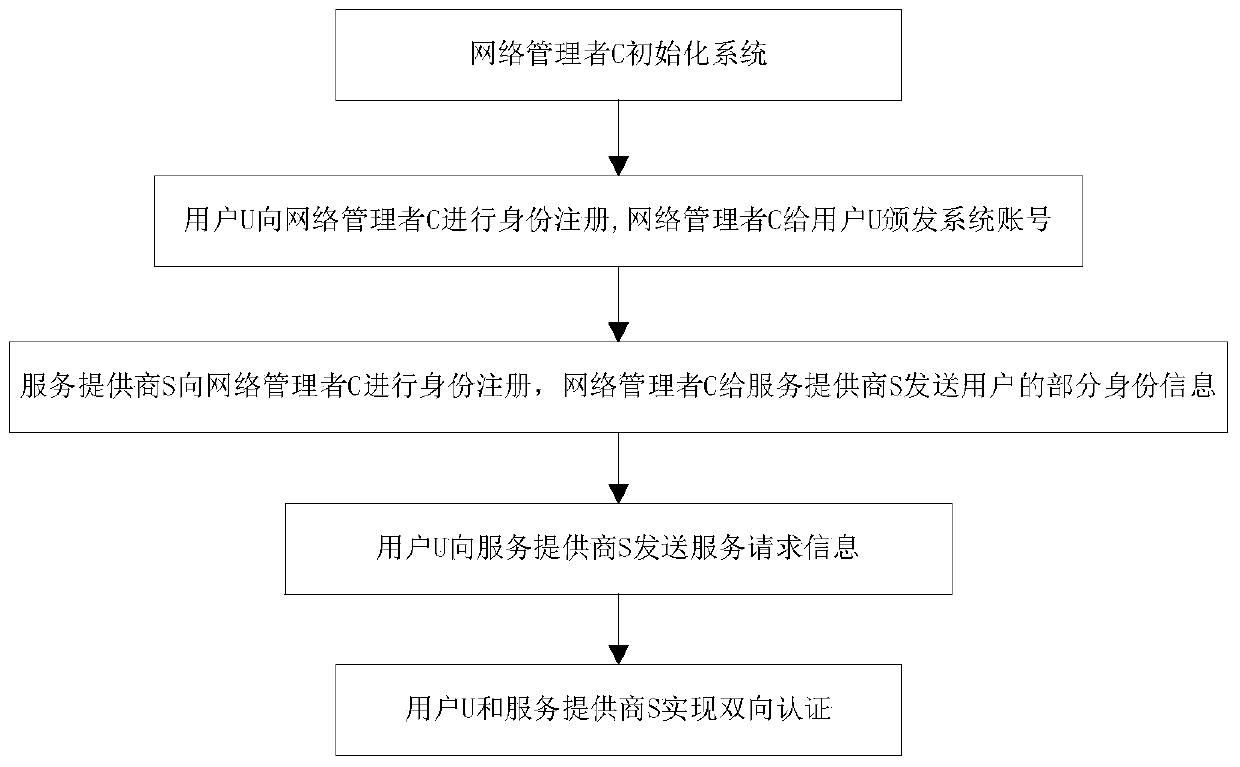
Certificate-free remote anonymous authentication method based on third party in cloud application
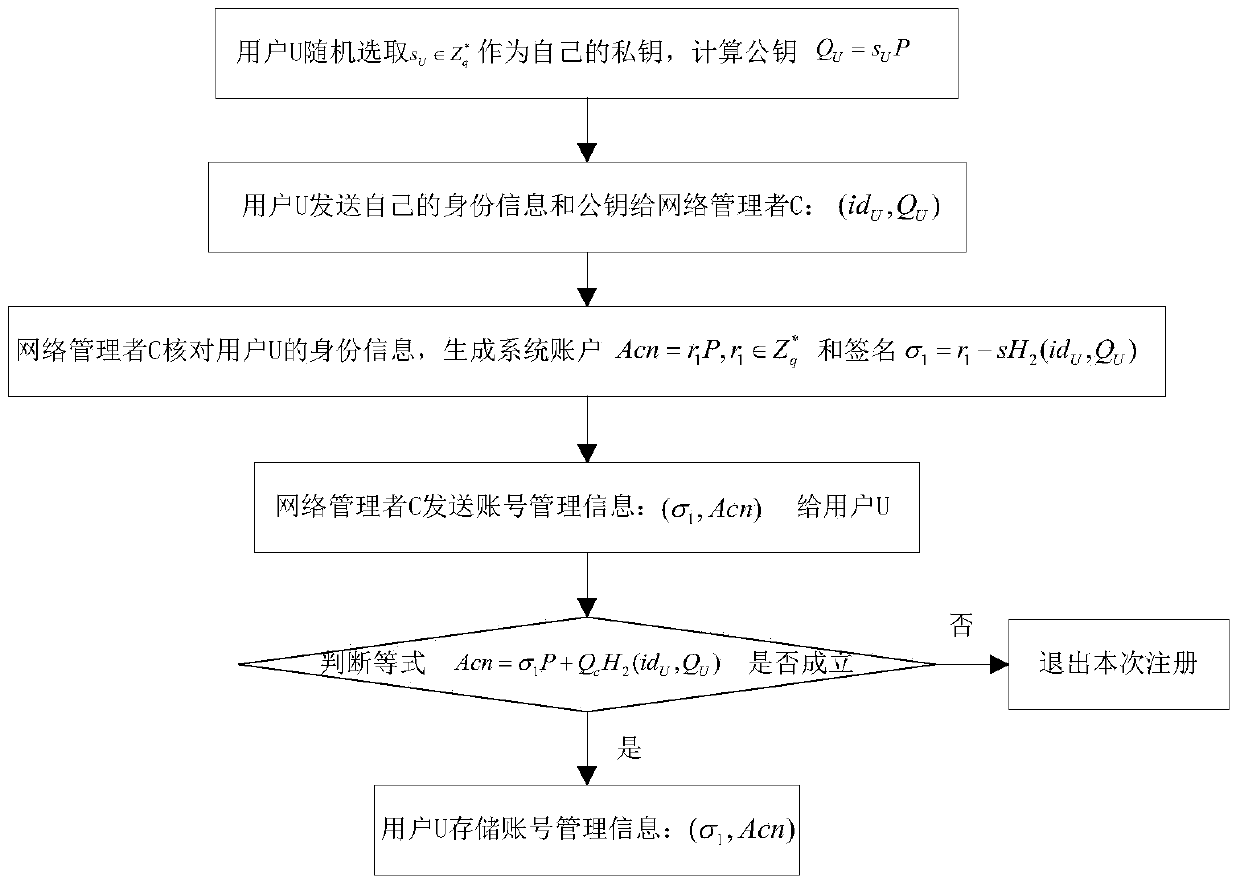
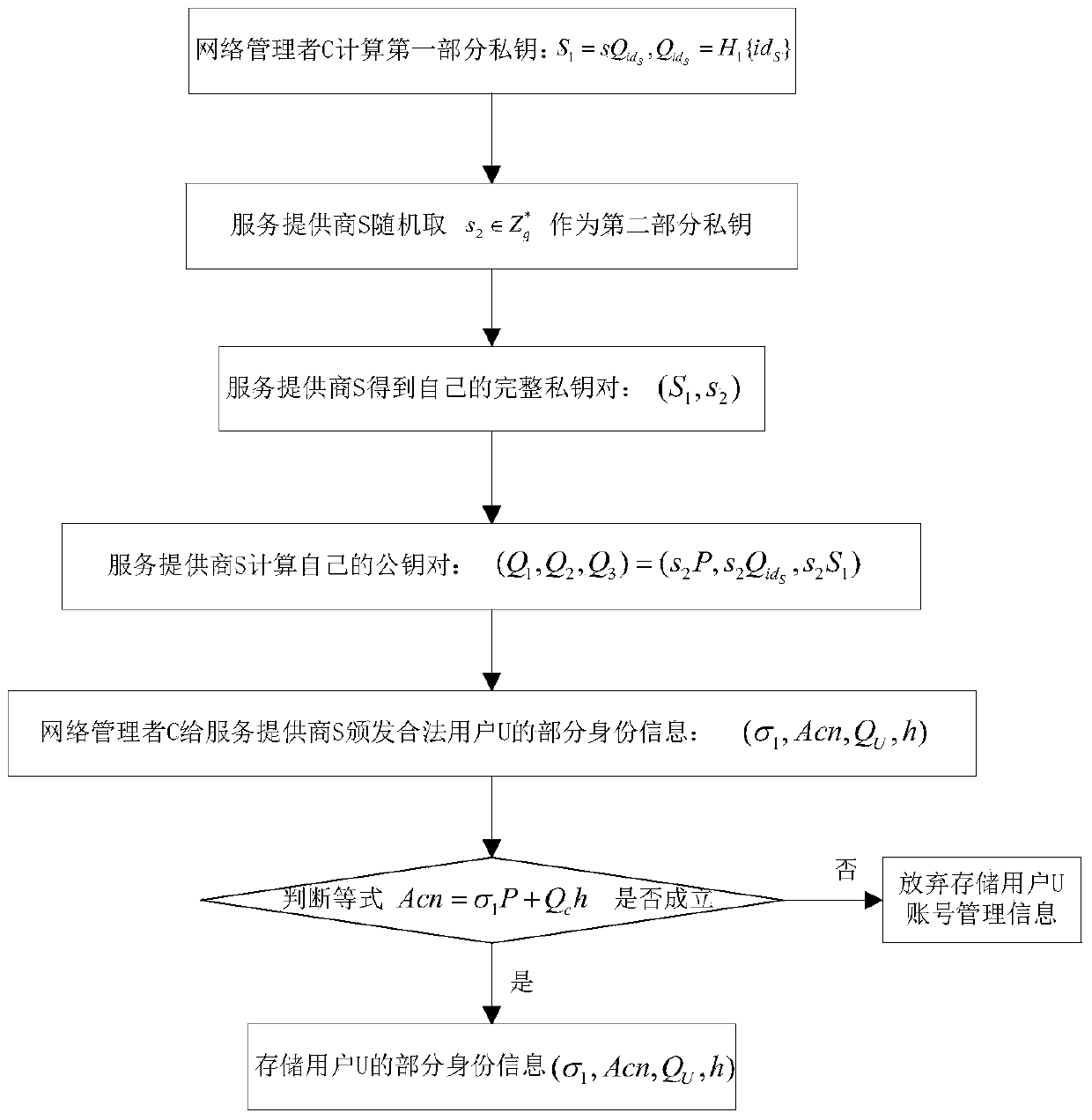
ActiveCN104052608AAchieve anonymityImprove securityUser identity/authority verificationData switching networksNetwork managementService provider
The invention discloses a certificate-free remote anonymous authentication method based on a third party in a cloud application, and the method mainly solves the problem that remote bidirectional authentication in the prior art is poor in safety. The method is achieved through the steps that (1) a network manager M initializes a system; (2) the network manager M conducts identity register on a user U, and issues a system account to the user U; (3) the network manager conducts identity register on a service provider S, and sends part of the identity information of the legitimate user U to the service provider S; (4) the user U sends a service request to the service provider S in an anonymous mode through the system account; (5) the service provider S and the user U conduct bidirectional authentication. According to the method, the requirement for a certificate is omitted, the defects of secret key trusteeship are omitted as well, safety in anonymous bidirectional authentication is improved, and the method can be used for identity authentication when a remote user in a wireless body area network conducts service request.
Owner:XIAN XIDIAN BLOCKCHAIN TECH CO LTD
Distributed hash table network-based anonymous communication method
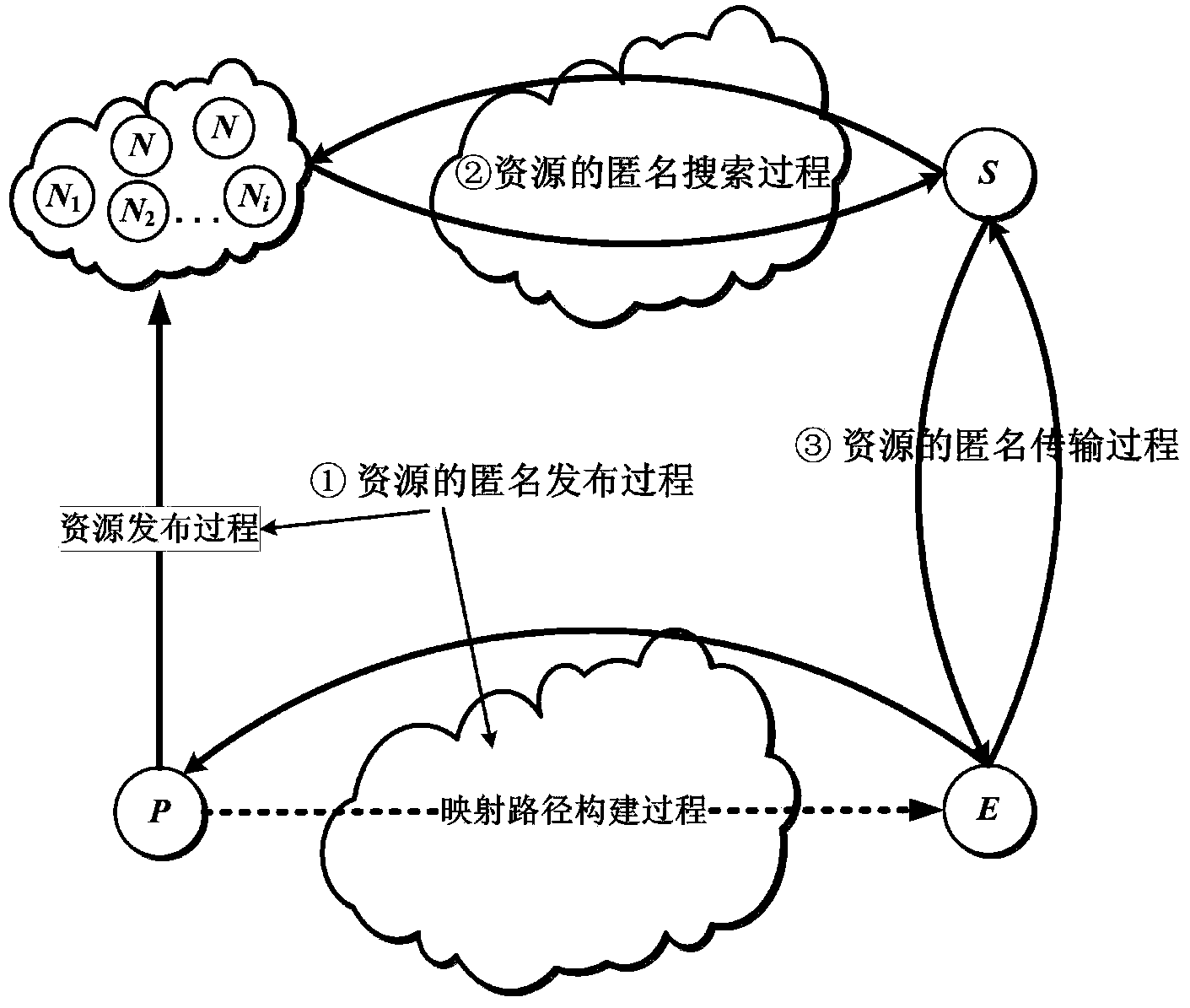
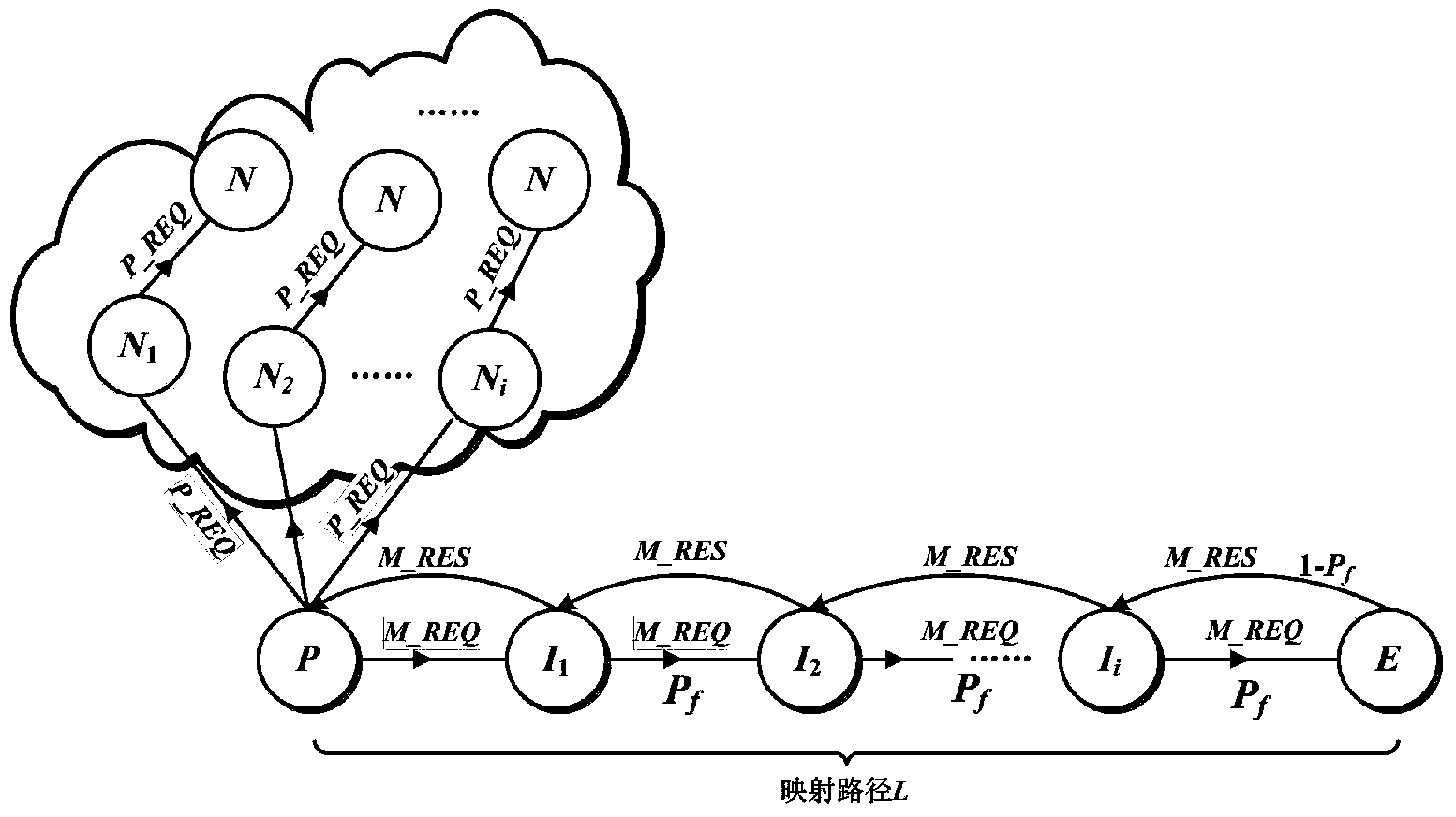
ActiveCN104168265AAchieve the purpose of normal operationRealization of anonymous communicationTransmissionSecure transmissionUser privacy
The invention relates to a distributed hash table (DHT) network-based anonymous communication method. With regard to three kinds of basic operations, including the resource publishing operation, the resource searching operation, and the resource transmission operation, of the traditional DHT network, a certain anonymous mechanism and security mechanism are introduced, thereby solving an anonymous communication problem in the DHT network. An anonymous mapping path is constructed at the resource publishing stage and a mapping node is determined, so that an anonymous base is provided for the resource publishing operation; a probabilistic forwarding strategy is used at the resource searching stage, so that the resource searching operation has the anonymous property; and at the resource loading and transmission stage, the mapping node is used as a relay node to carry out data transmission and combination with the session key encryption data is used, thereby guaranteeing the anonymous transmission and secure transmission of data. On the basis of combination of the three parts, sender anonymity, receiver anonymity, and communication relation anonymity are realized, thereby achieving objectives of user privacy protection and secure and stable operation of the whole DHT network.
Owner:NANJING UNIV OF POSTS & TELECOMM
Elliptic curve-based efficient and anonymous certificateless multi-receiver signcryption method
ActiveCN106936593AReduce multiplicationImprove computing efficiencyPublic key for secure communicationUser identity/authority verificationCiphertextSigncryption
The invention discloses an elliptic curve-based efficient and anonymous certificateless multi-receiver signcryption method. The method is used for solving the technical problem in the prior art that an existing certificateless multi-receiver signcryption method is low in operation efficiency. According to the technical scheme of the invention, firstly, a user public key and a partial private key, generated by a private key generation center PKG, are sent to a user. Secondly, after the user receives the user public key and the partial private key, the user calculates its own private key. Meanwhile, the user verifies whether the received user public key and the received partial private key are valid or not. If valid, the operation is continued. Otherwise, the operation is stopped. Thirdly, the signcryption algorithm is adopted to design an elliptic curve and the ciphertext information does not include the identity information of a sender and a recipient. Finally, the ciphertext information is broadcasted. Only authorized recipients can fairly decrypt and verify the ciphertext information. According to the technical scheme of the invention, the signcryption process is designed to conduct based on the elliptic curve. Therefore, the multiplication operation on the elliptic curve is reduced, and the calculation efficiency is improved.
Owner:XIDIAN UNIV
Method for protecting privacy of identity information based on sensitive information measurement
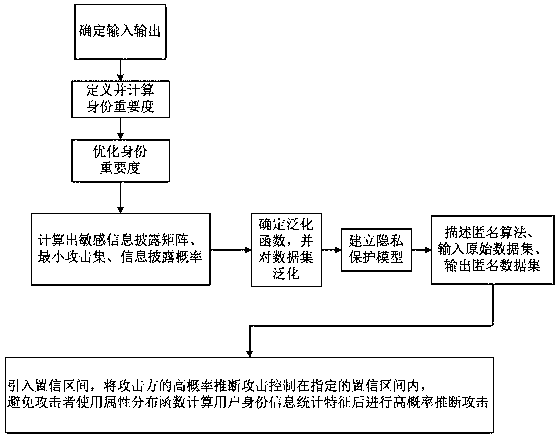
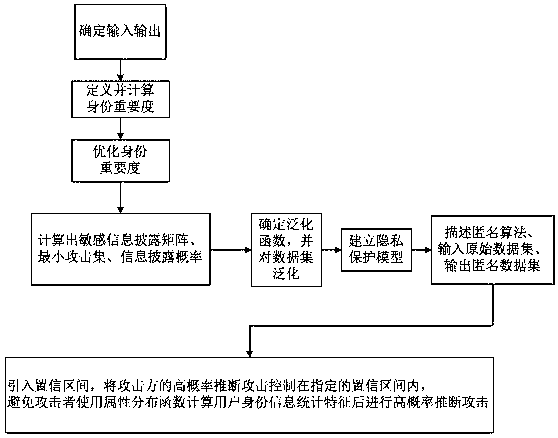
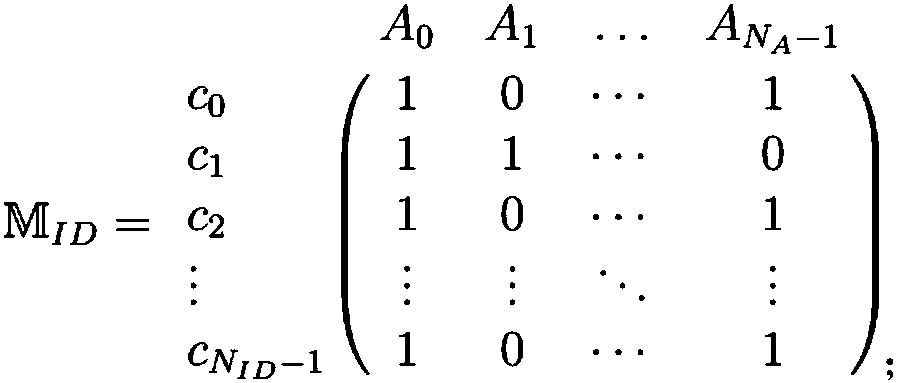
ActiveCN106940777AEffective protectionImprove protectionDigital data protectionData setInference attack
The invention discloses a method for protecting privacy of identity information based on sensitive information measurement. The method comprises the comprises the following steps of S1, determining input and output; S2, defining and calculating identity importance degree; S3, optimizing the identity importance; S4, calculating a sensitive information disclosing matrix, a minimum attack set and an information disclosing probability; S5, determining a generalizing function, and generalizing a dataset; S6, establishing a background knowledge attack-avoidance privacy protection model; S7, describing a (gamma, eta)-Risk anonymity algorithm, inputting an original dataset D, and outputting an anonymity dataset D'; S8, introducing a confidence interval, controlling the high-probability inference attack of an attacking party within the specified confidence interval, so as to avoid a user using an attribute distribution function to calculate the identity information of the user, calculate features, and perform high-probability inference attack. The method has the advantages that the problem of difficulty in effectively treating the privacy information attack based on background knowledge attack in the existing privacy protection method is solved, and the key identity and identity sensitive information are more comprehensively and effectively protected.
Owner:湖南宸瀚科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com