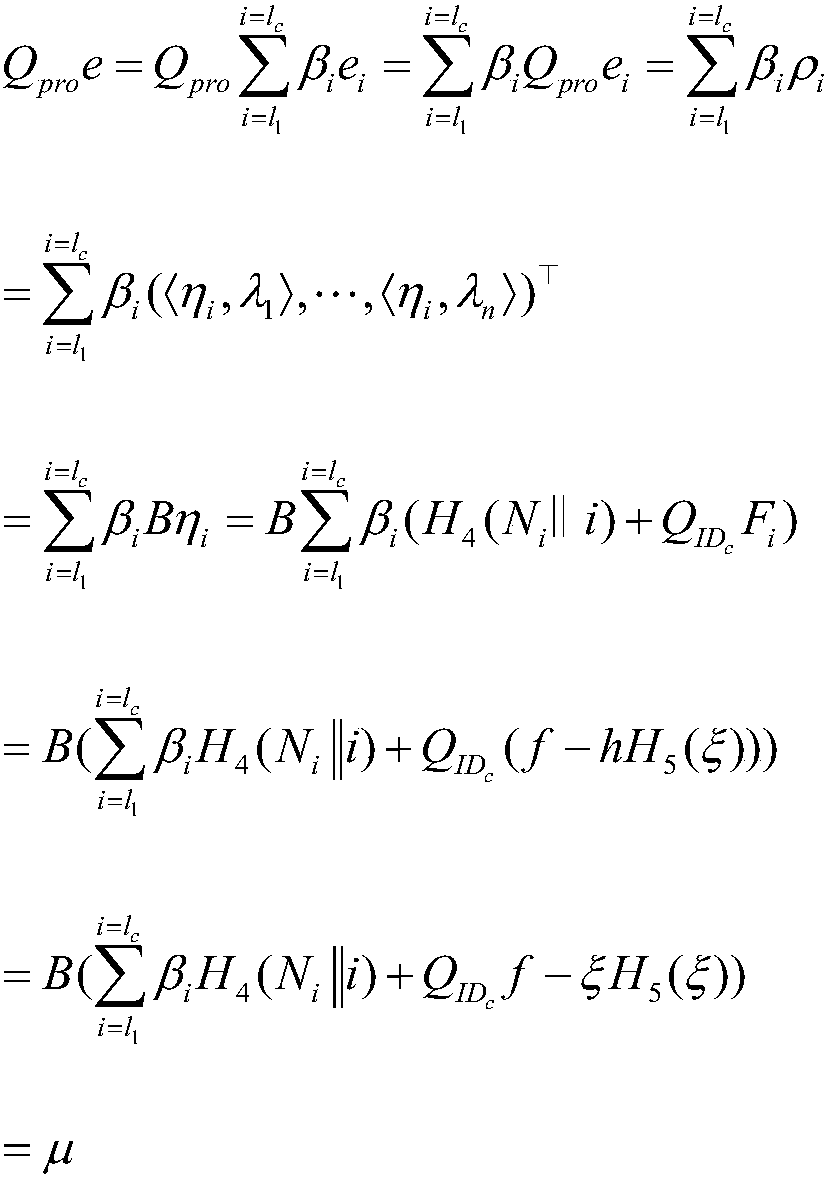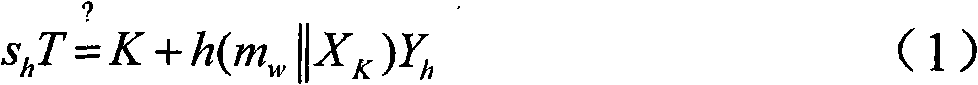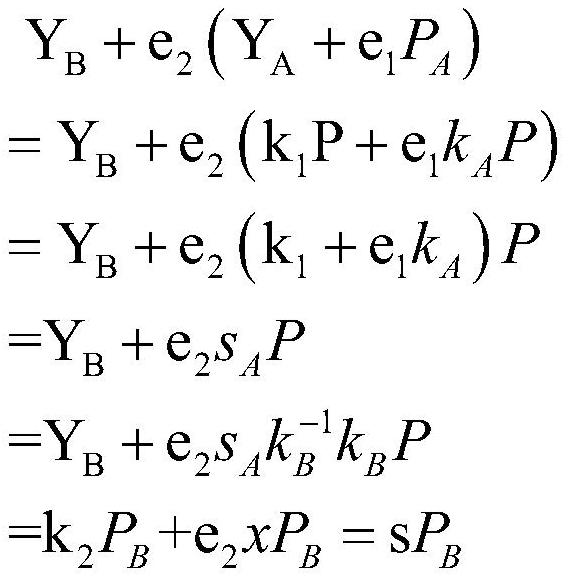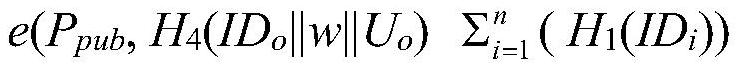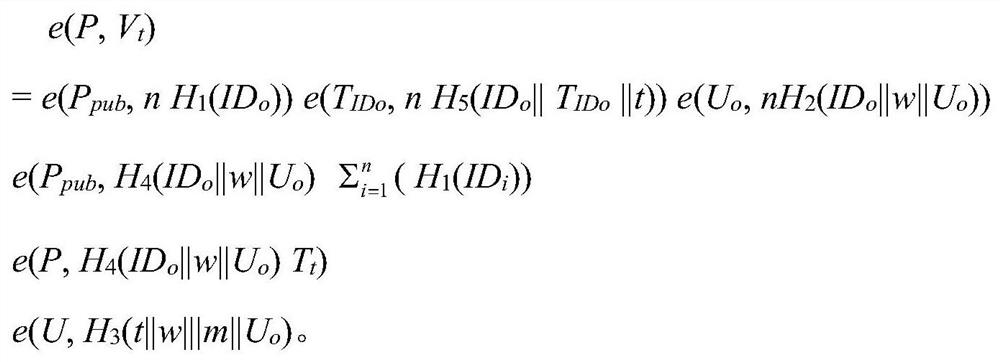Patents
Literature
72 results about "Proxy signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
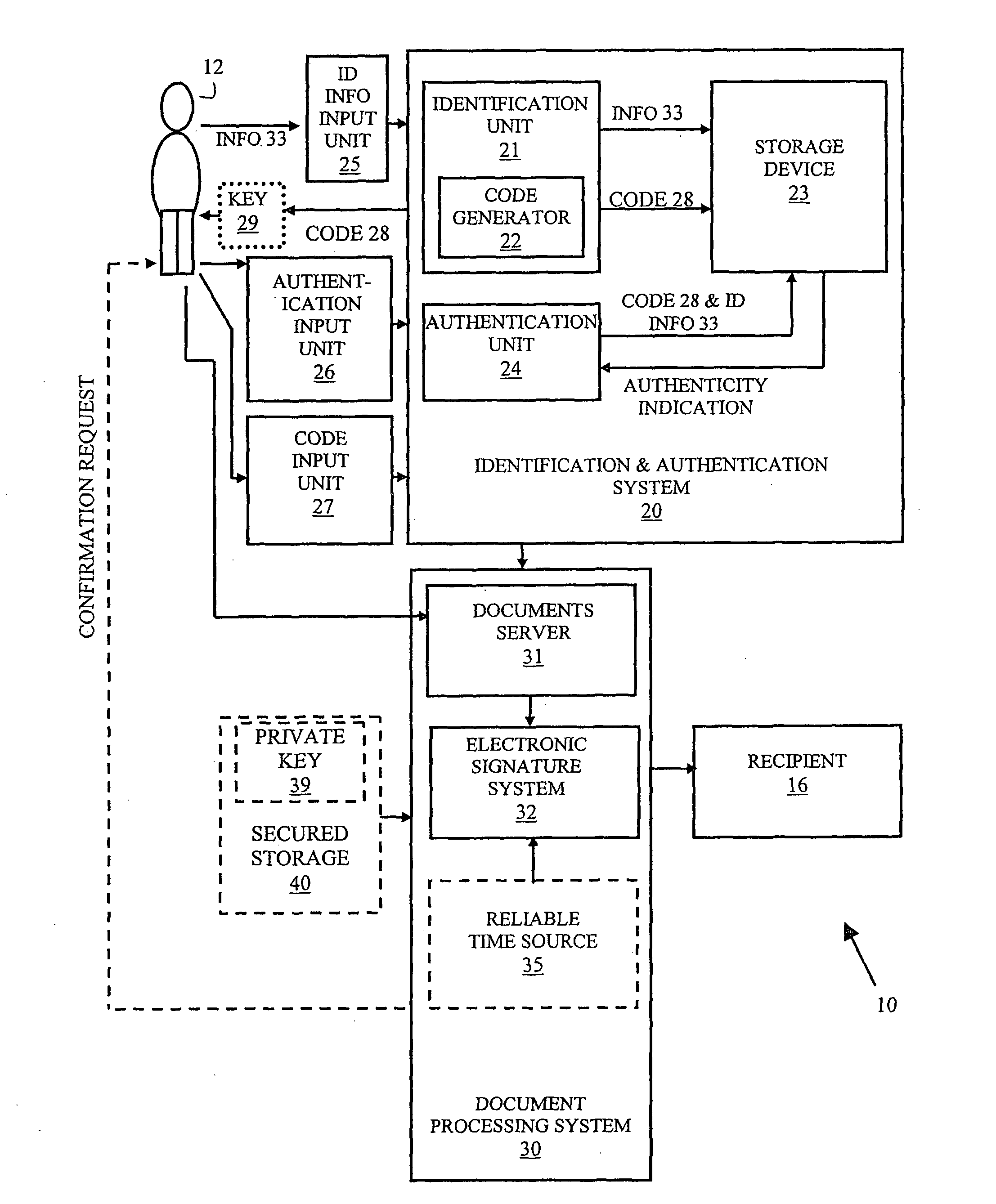
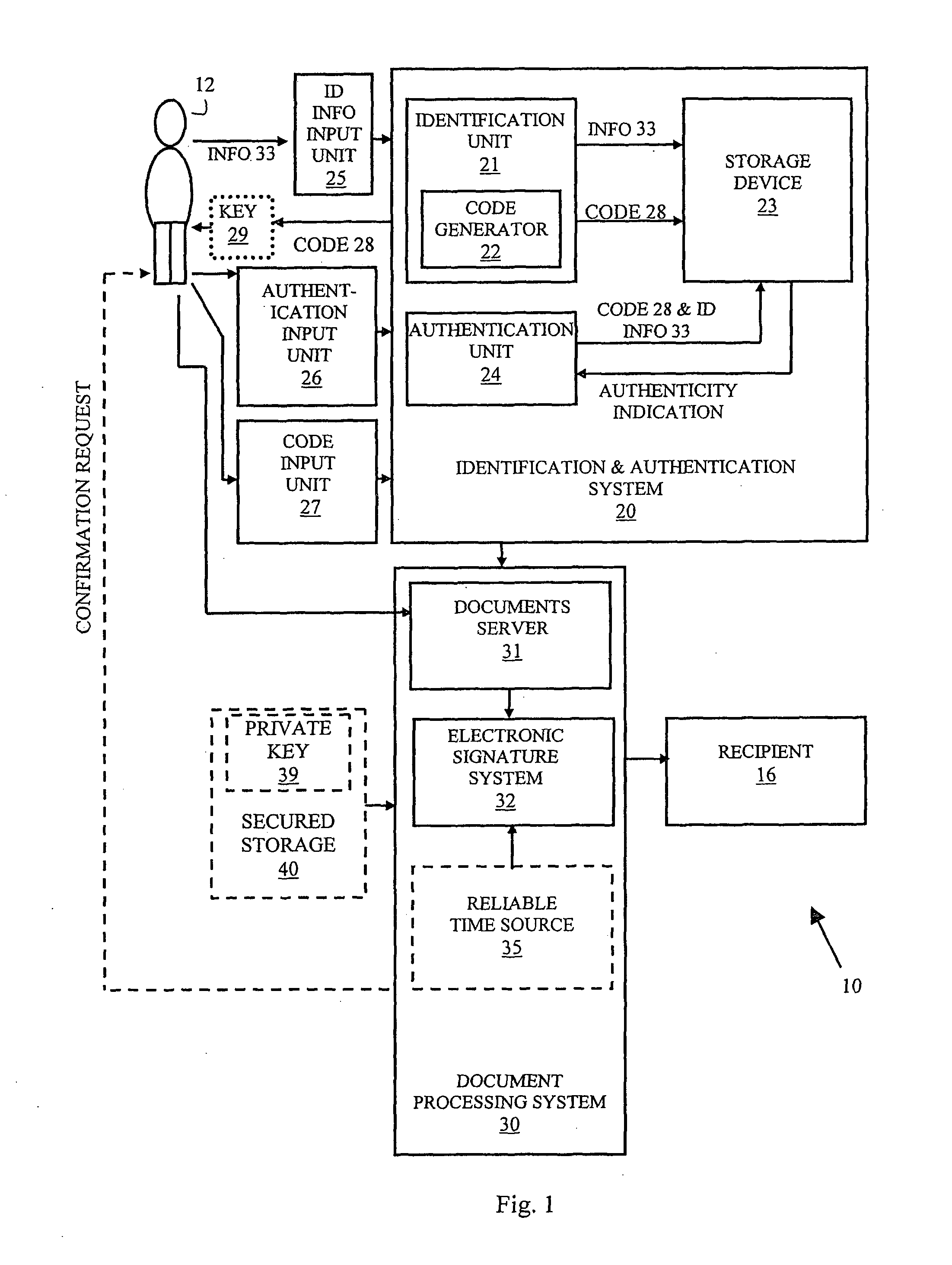
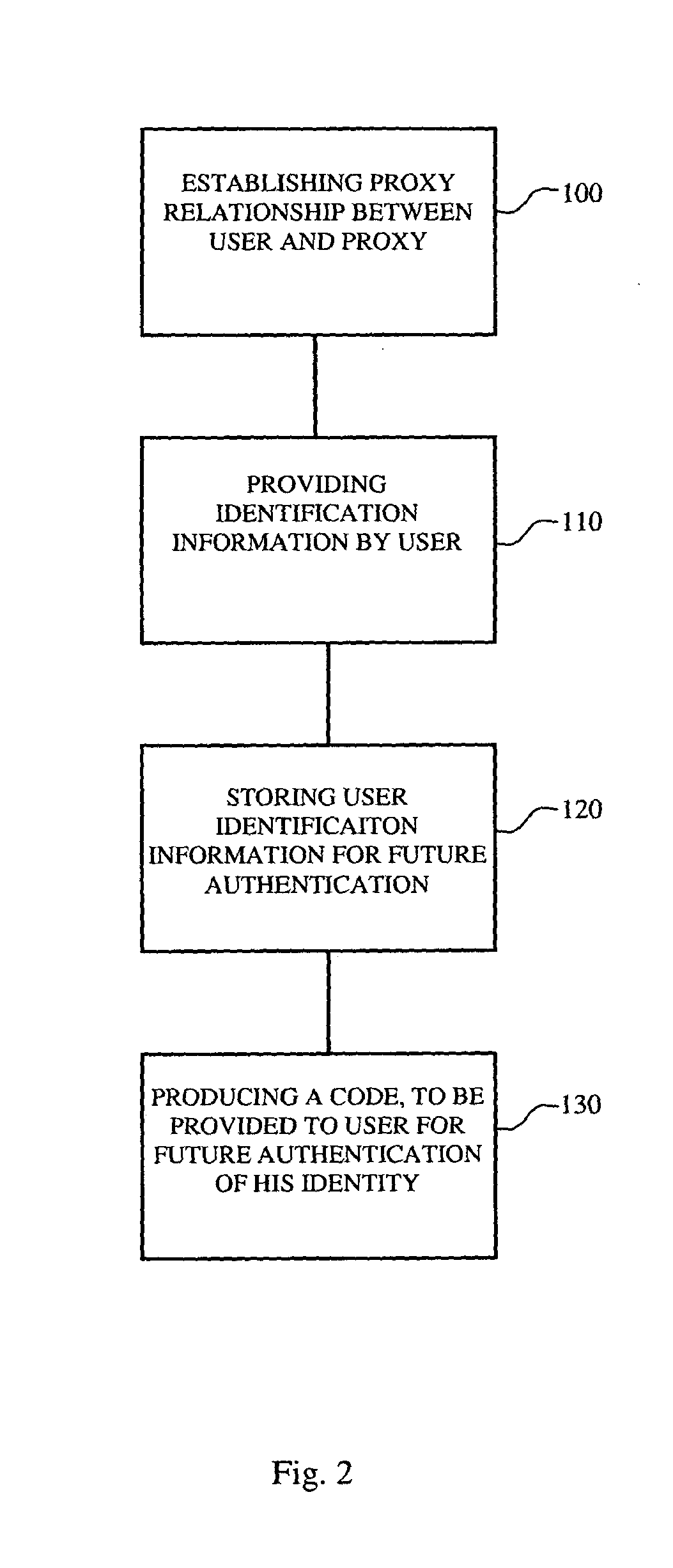
System and method for electronic signature via proxy
A system and method are disclosed for providing proxy signature to user documents comprised of an identification and authentication system, input means to enable providing identification information by the user to the identification and authentication system, authentication input means to enable providing authentication information by the user to the system, an electronic signature system, and a documents server for receiving documents from the user for electronic signature The system may comprise a storage device, an identification sub-system adapted to receive identification information from said user via said information input means and store the identification information in the storage device, an authentication sub-system adapted to authenticate the identity of the user based on information stored in said storage device and information provided by the user during authentication process via said authentication information input means The electronic signature system is adapted to apply a signature to documents provided by the user.
Owner:FELDBAU MICHAEL
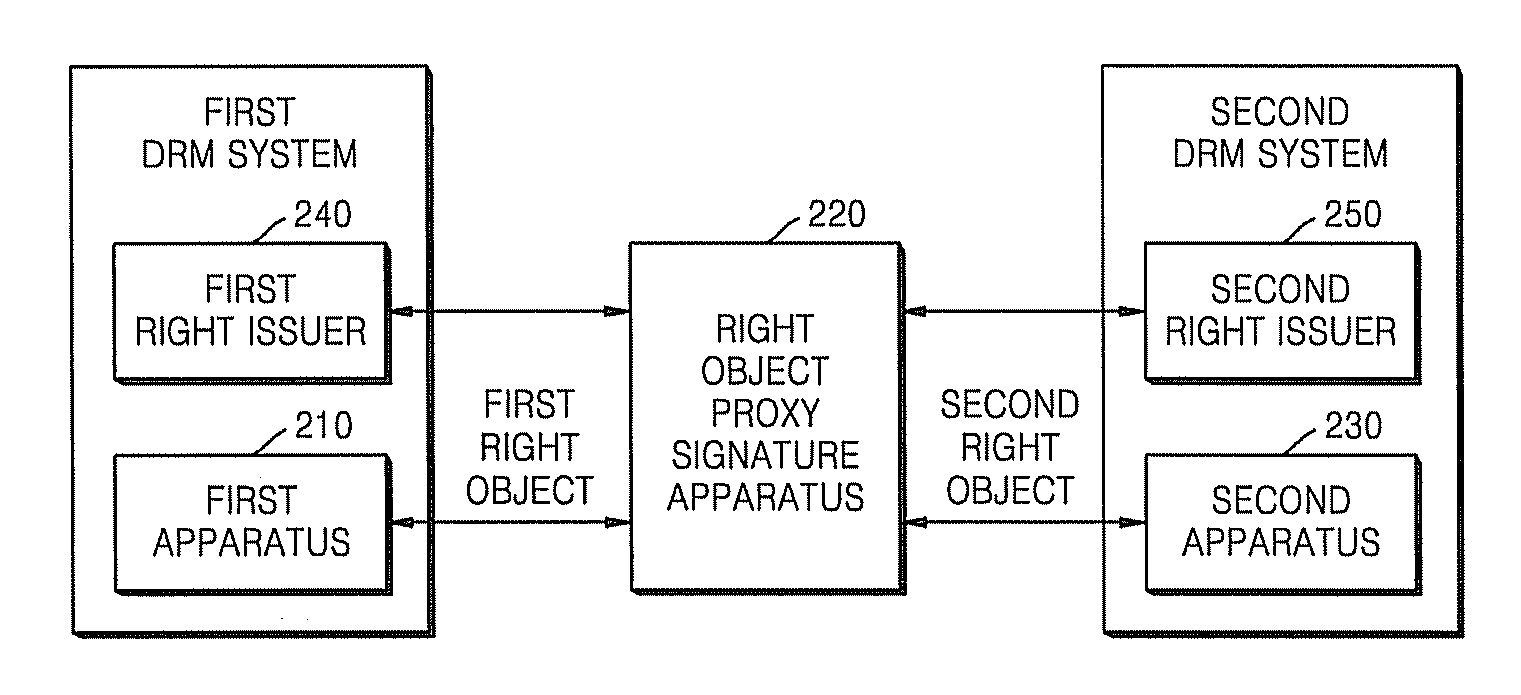
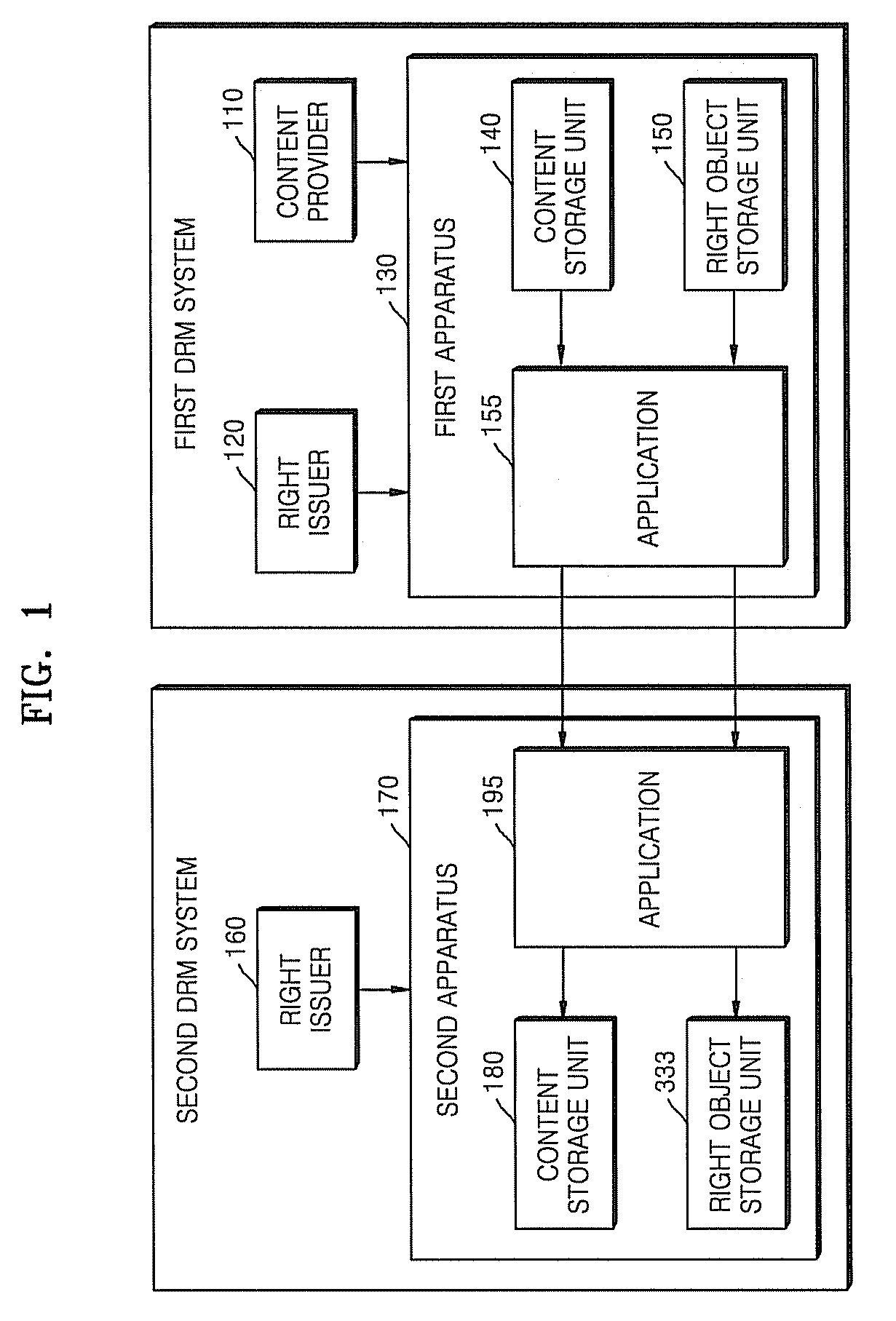
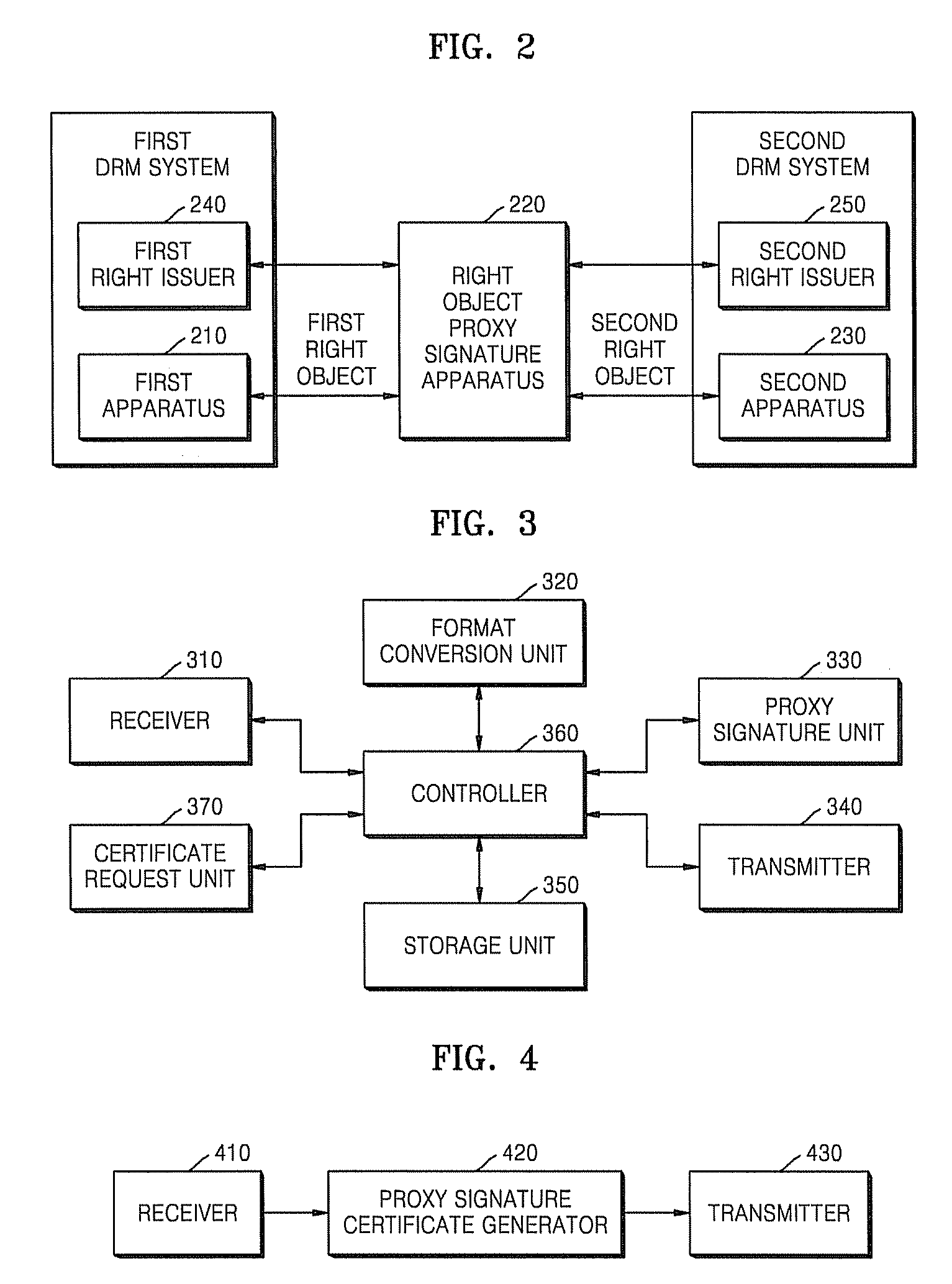
Method and apparatus for generating proxy-signature on right object and issuing proxy signature certificate
InactiveUS20080126801A1Public key infrastructure trust modelsSpecial data processing applicationsProxy signatureComputer security
A method and apparatus for generating a proxy signature on a right object, and a method and apparatus for issuing a proxy signature certificate. The right object proxy signature method includes receiving a proxy signature certificate in which authority for right object conversion is specified, from a right issuer; receiving a right object from a first apparatus; signing the right object; and transmitting the signed right object and the proxy signature certificate to a second apparatus. Accordingly, by allowing a right object to be signed by a third right object proxy signature apparatus, not by a right issuer, users can freely share their own content between a variety of apparatuses, and the right issuer can reduce the load associated with the conversion and signature of right objects.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for agent signature
InactiveCN101051901ASatisfy non-repudiationUser identity/authority verificationCommerceSurrogate keyOperability
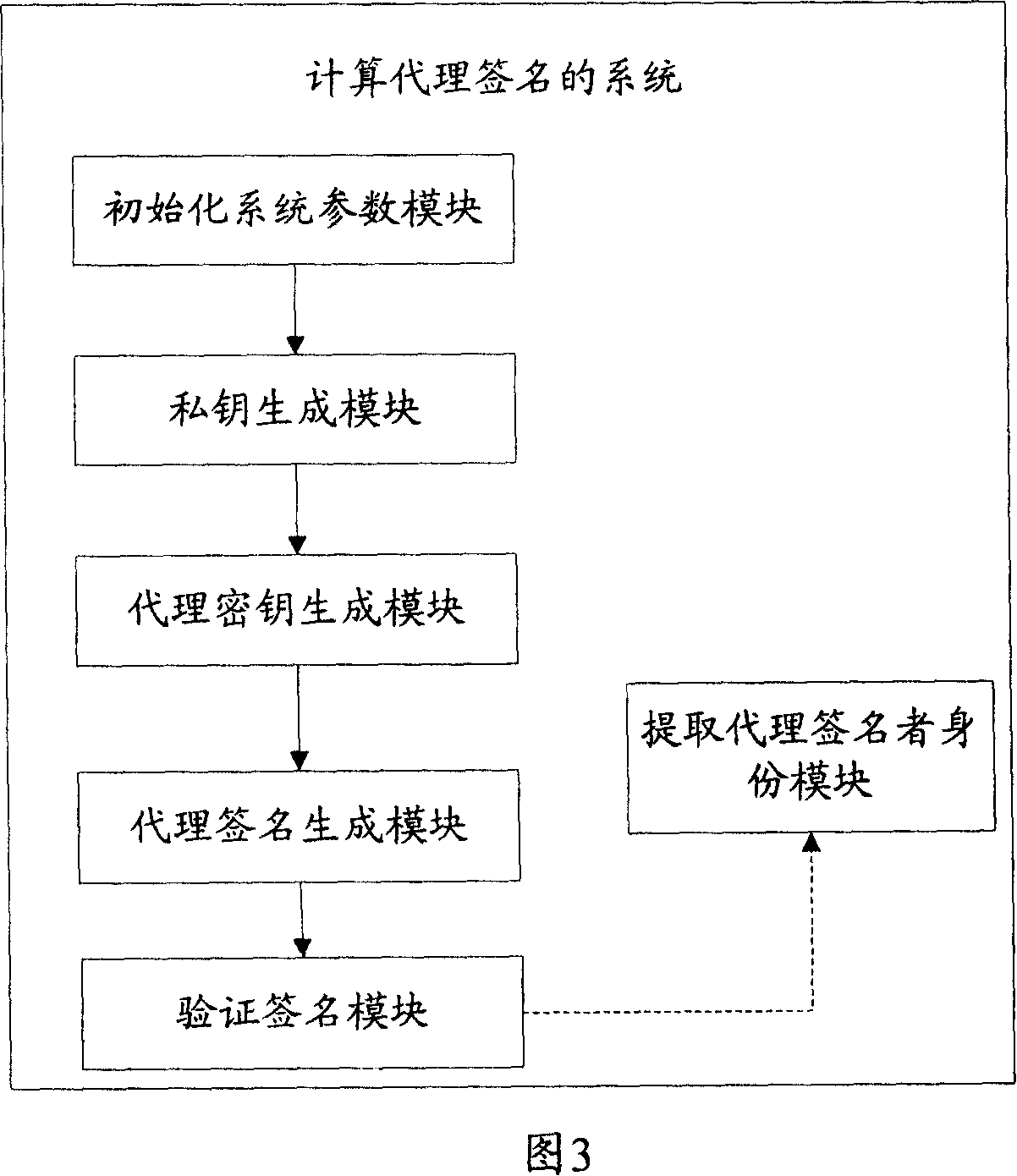
The invention solves issues that disadvantages of poor operability and difficulty for implementing undeniable characteristic of server exist in current technique. The disclosed method for proxy signature includes steps: initializing system parameters; based on system parameters to generate private key of proxy signer; original signer generates proxy key of proxy signer; proxy signer generates proxy signature for message; validating proxy signature. The invention also discloses a system of proxy signature. The system includes module for initializing system parameters, private key generation module, proxy key generation module, proxy signature generation module, module for validating signature, and module for picking up Id of proxy signer. The invention satisfies undeniable characteristic of server, protects proxy signer, and the security is based on RSA.
Owner:SHANGHAI JIAO TONG UNIV +1
Vehicle-mounted network message authentication protocol
InactiveCN106713326AKey security hasReduce dependenceUser identity/authority verificationCommunication unitProtocol for Carrying Authentication for Network Access
The invention provides a vehicle-mounted network message authentication protocol. A vehicle-mounted ad-hoc network comprises a trusted authentication center, a vehicle-mounted unit and roadside units, the message authentication protocol uses a threshold proxy re-signature algorithm to protect vehicle privacy information, the signature of a message by a vehicle-mounted communication unit is converted into the signature of the same message by an authentication center, thereby reducing the risk that the signature tracks the vehicle-mounted unit and realizing the anonymity of communication messages. Re-signature keys are dispersed to a plurality of roadside communication units in a threshold mode for management, thereby reducing the decoding success rate of the re-signature keys and preventing the roadside communication units from abusing the proxy signature right. The authentication center traces a real vehicle releasing a false message to solve the problem of calling back illegal vehicles. The protocol has relatively high security and a relatively low storage cost, has unforgeability, robustness, message authentication, replay attack resistance and traceability, and can greatly improve the privacy of network member information.
Owner:SHANGHAI DIANJI UNIV
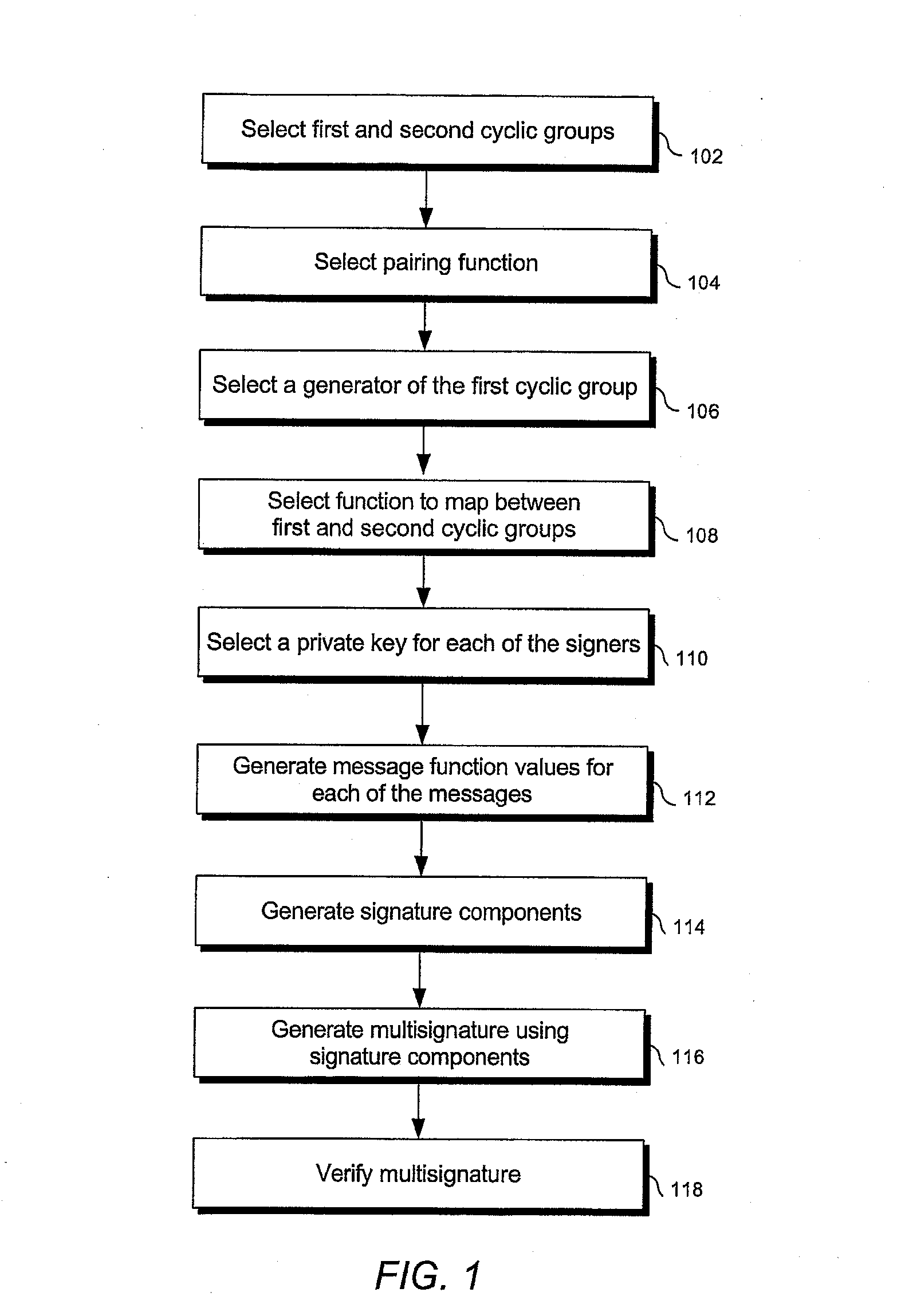
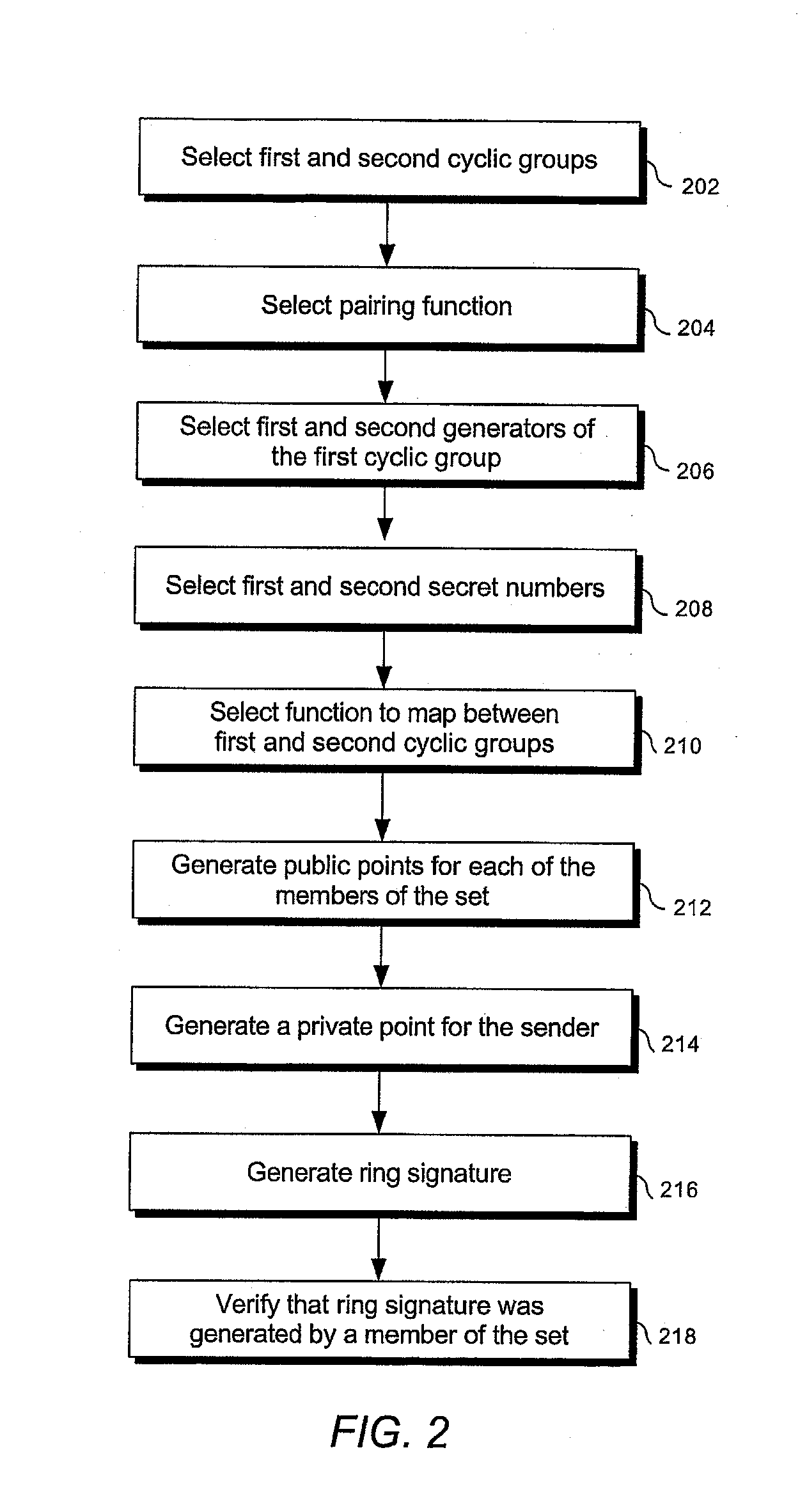
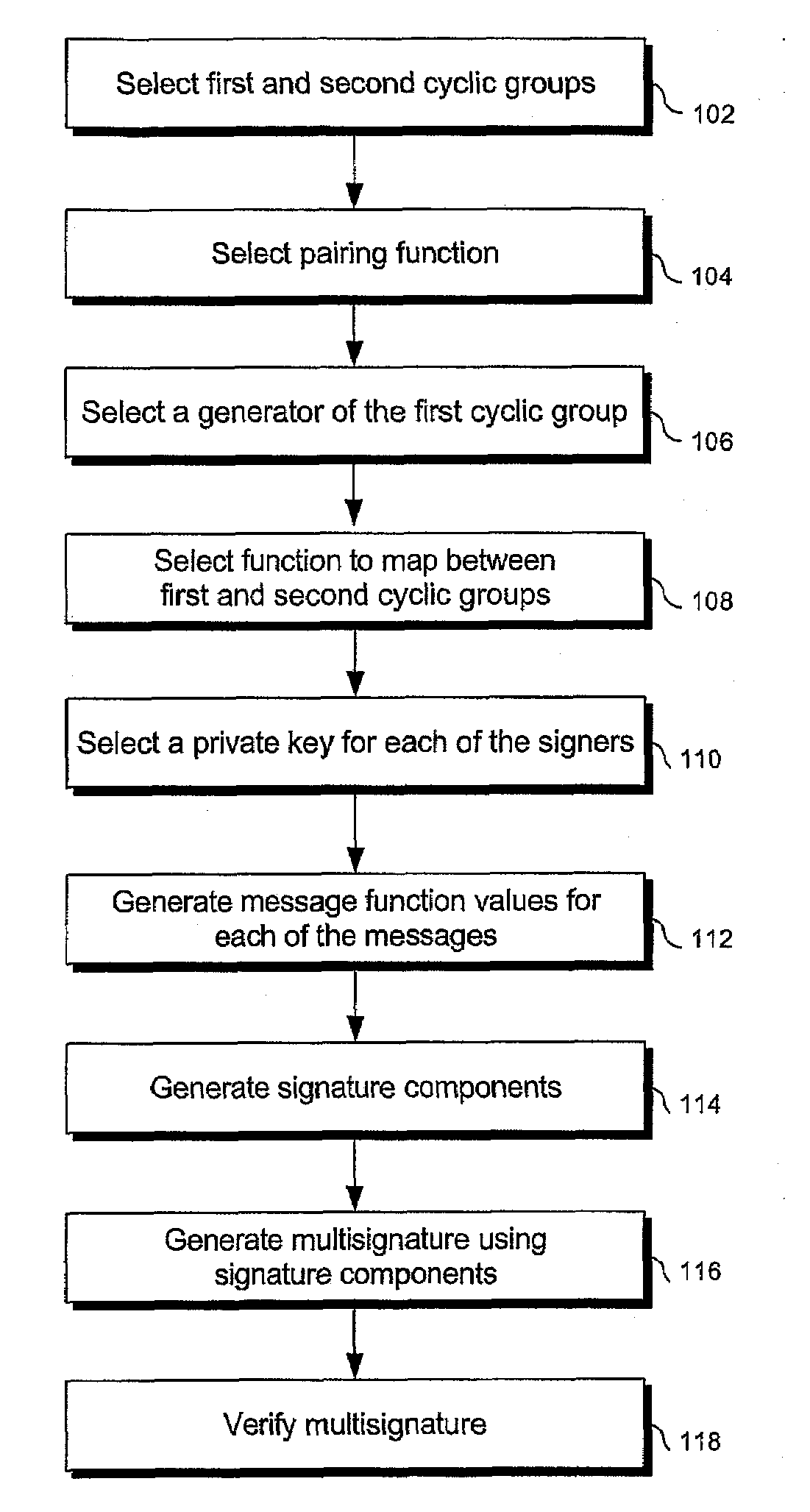
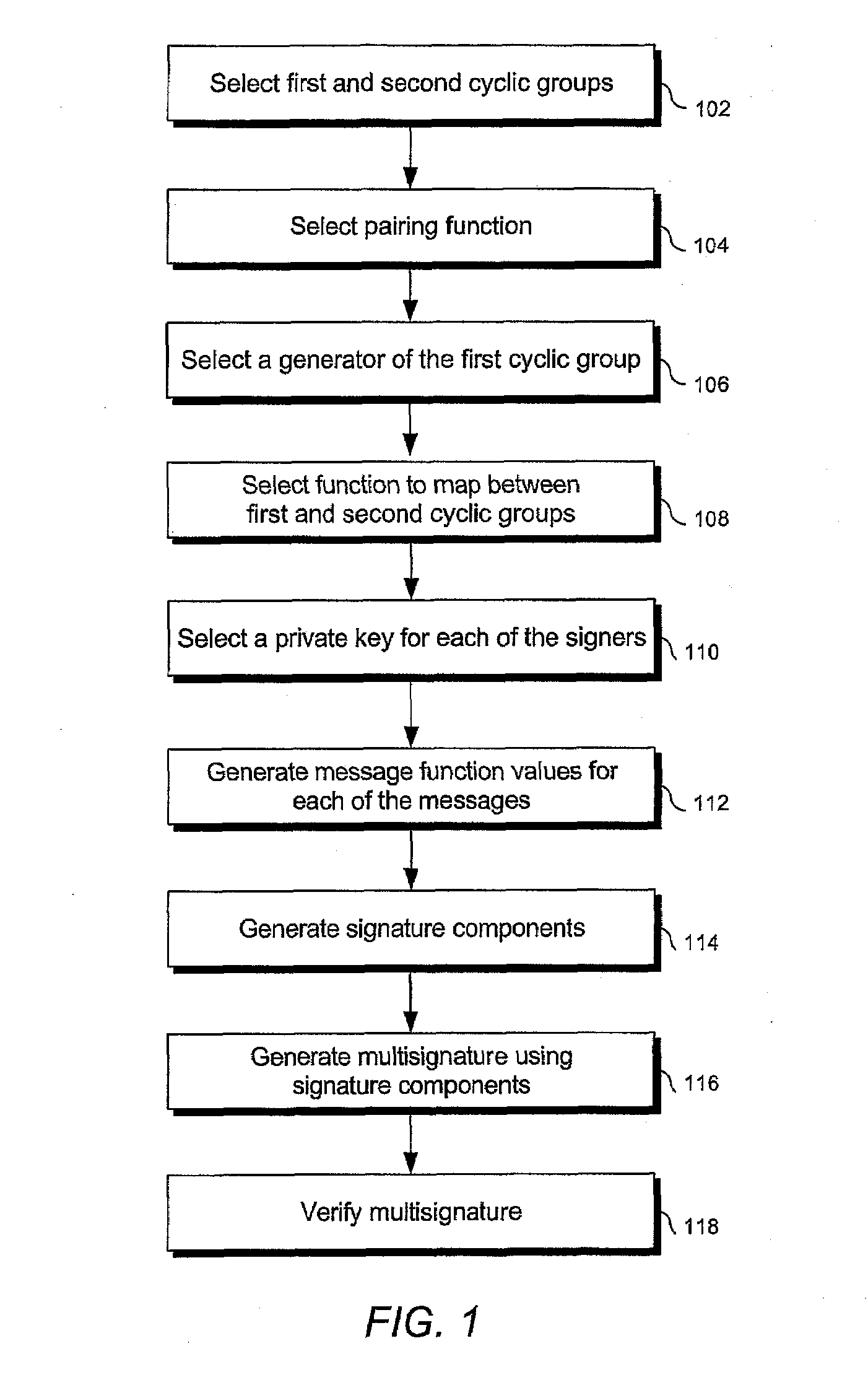
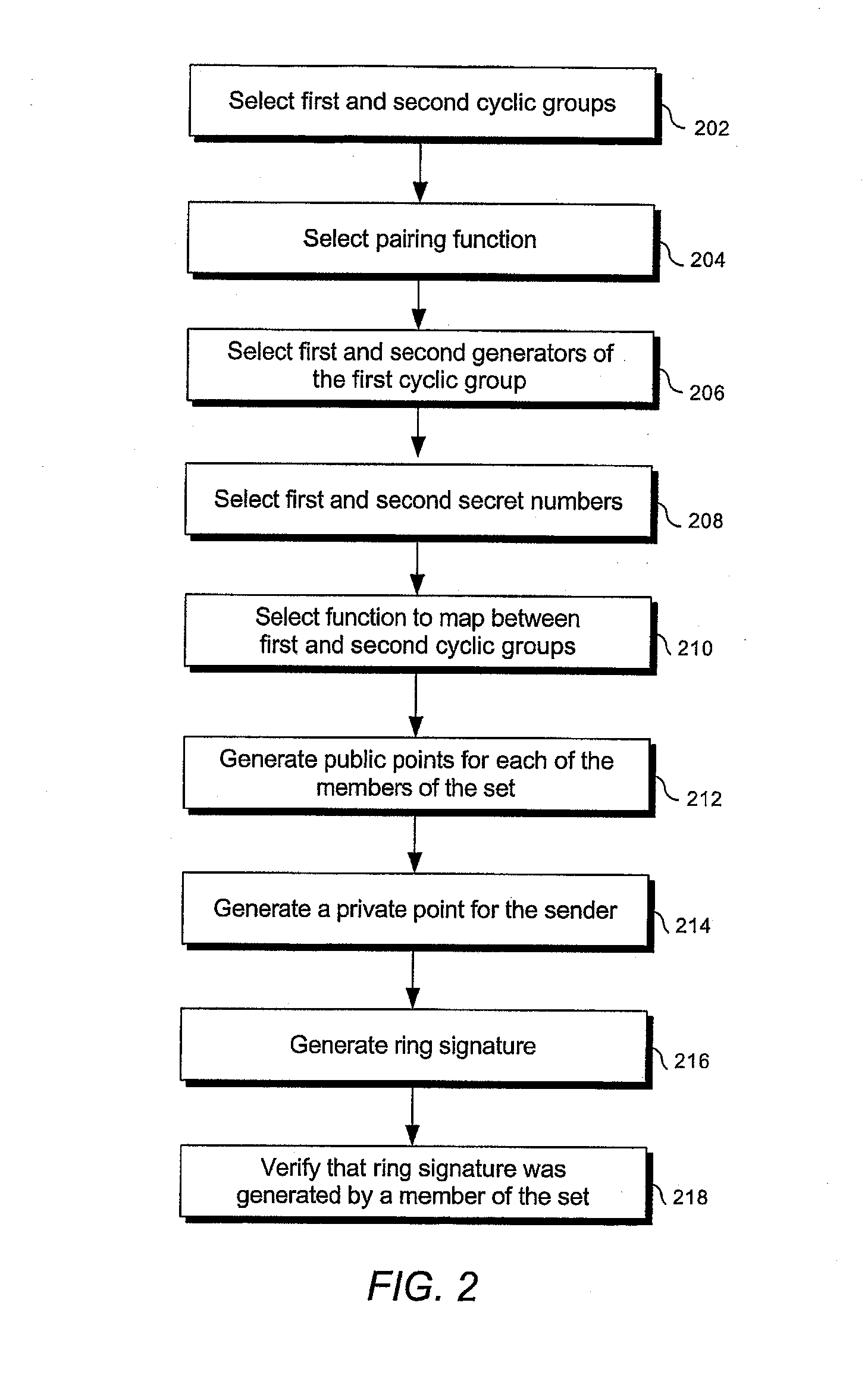
Signature schemes using bilinear mappings
InactiveUS20080178005A1User identity/authority verificationCoding/ciphering apparatusRing signatureMultisignature
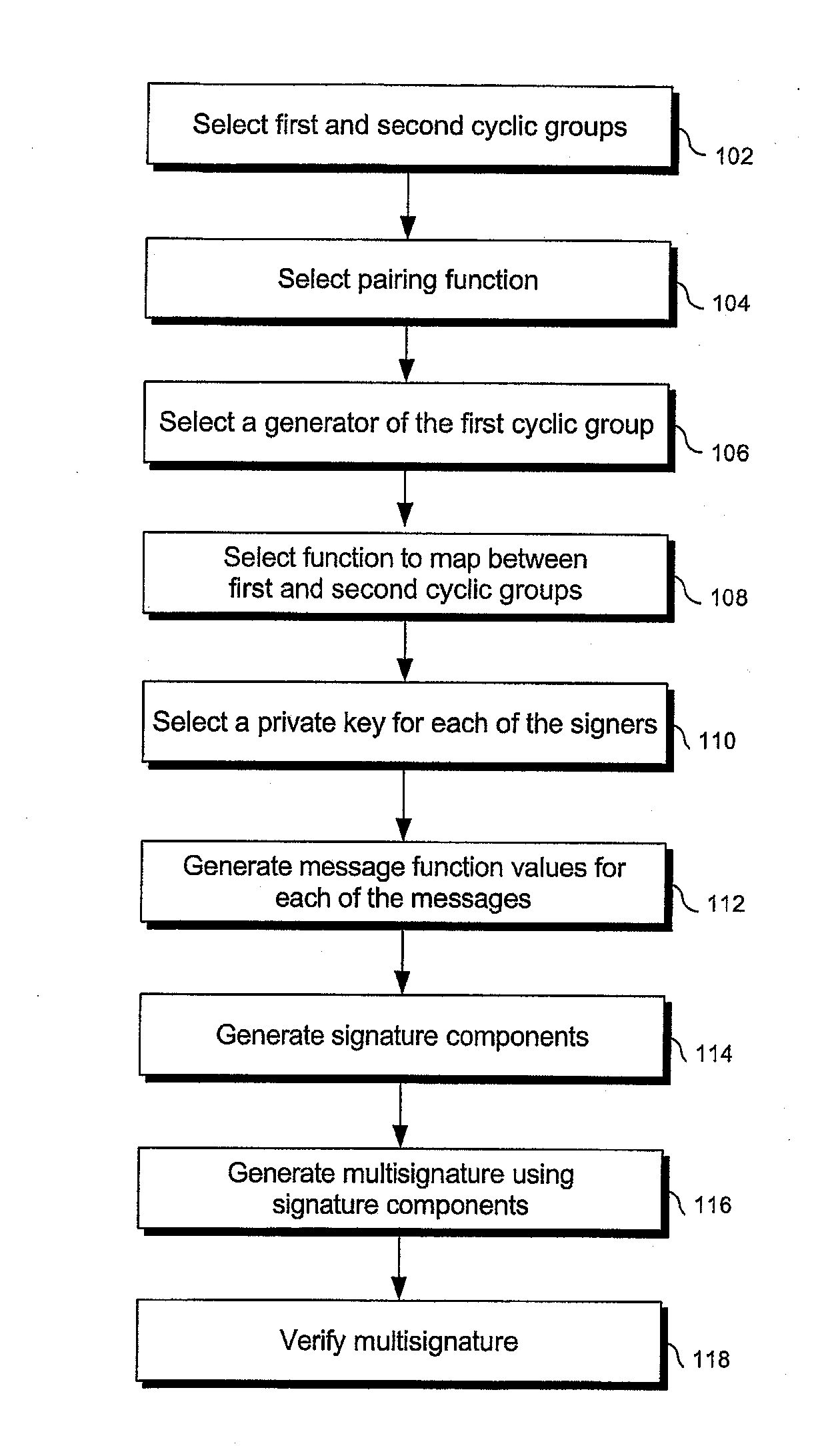
Methods and systems are provided for generating and verifying signatures of digital messages communicated between signers and verifiers. Using bilinear mappings, such as Weil or Tate pairings, these methods and systems enable generation and verification of efficient multisignatures, identity-based ring signatures, hierarchical proxy signatures, and hierarchical online / offline signatures.
Owner:NTT DOCOMO INC
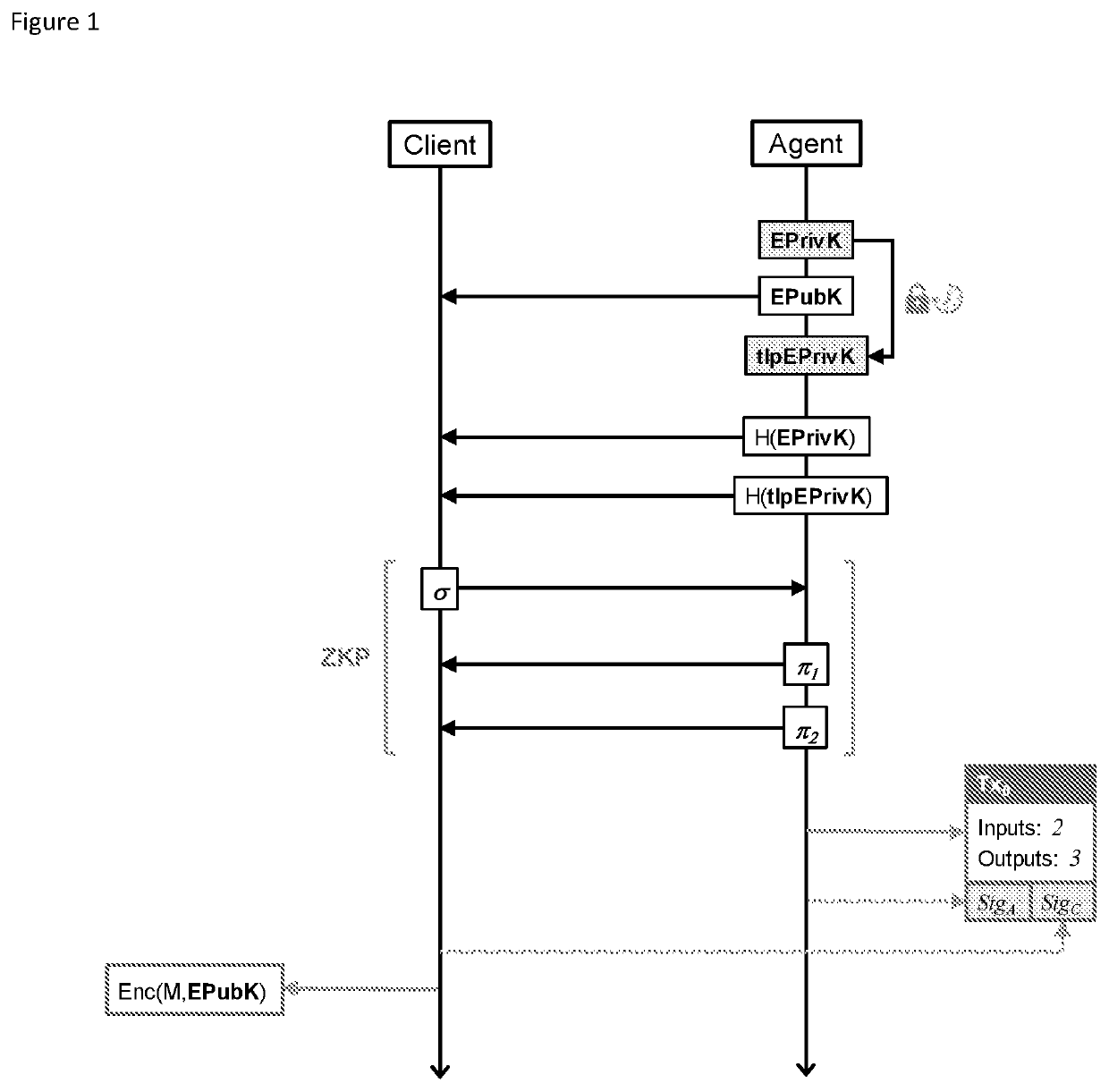
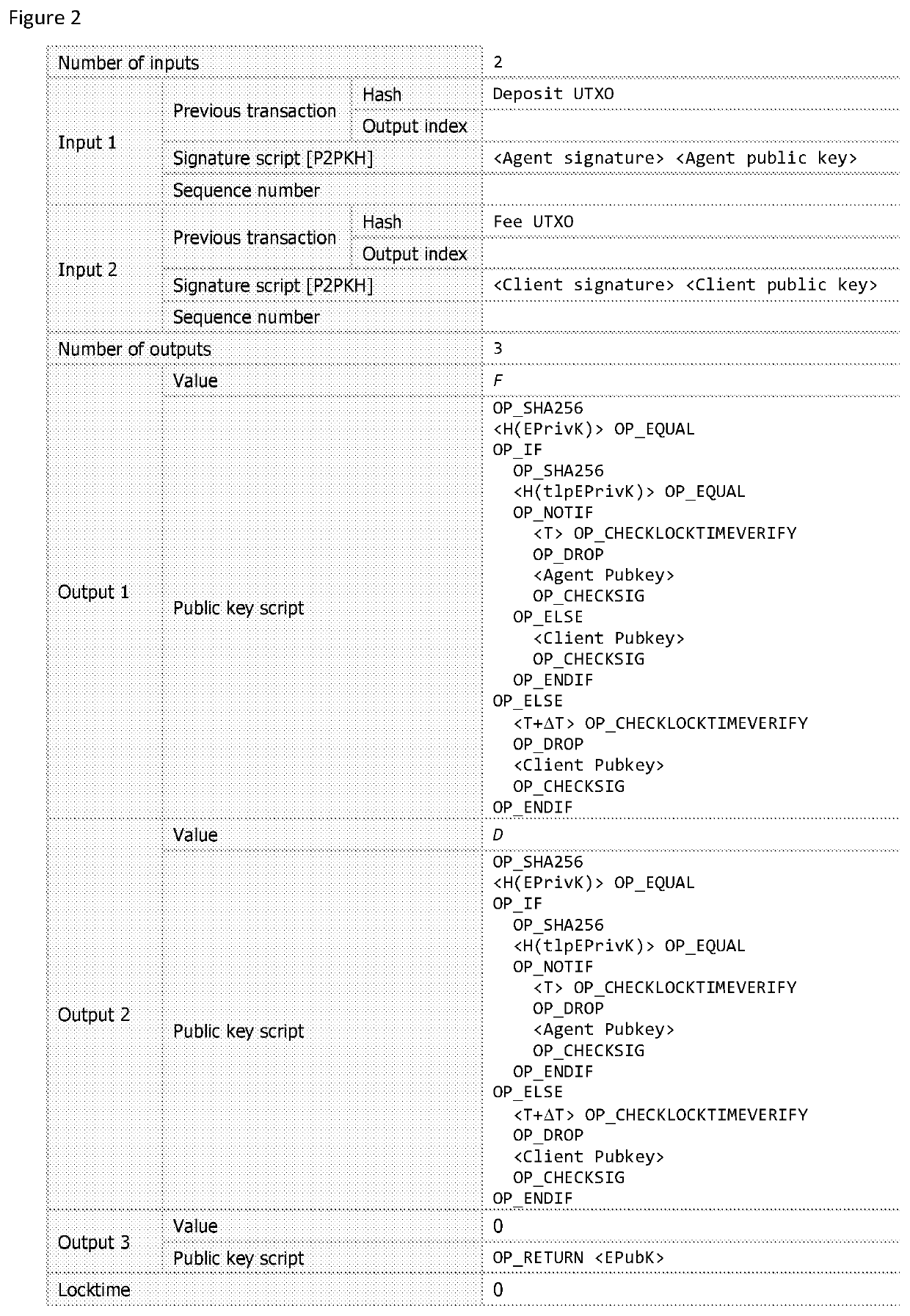
Computer-implemented system and method for time release encryption over a blockchain network
ActiveUS20200136815A1Security breachDifficult to useKey distribution for secure communicationPublic key for secure communicationInternet privacyEngineering
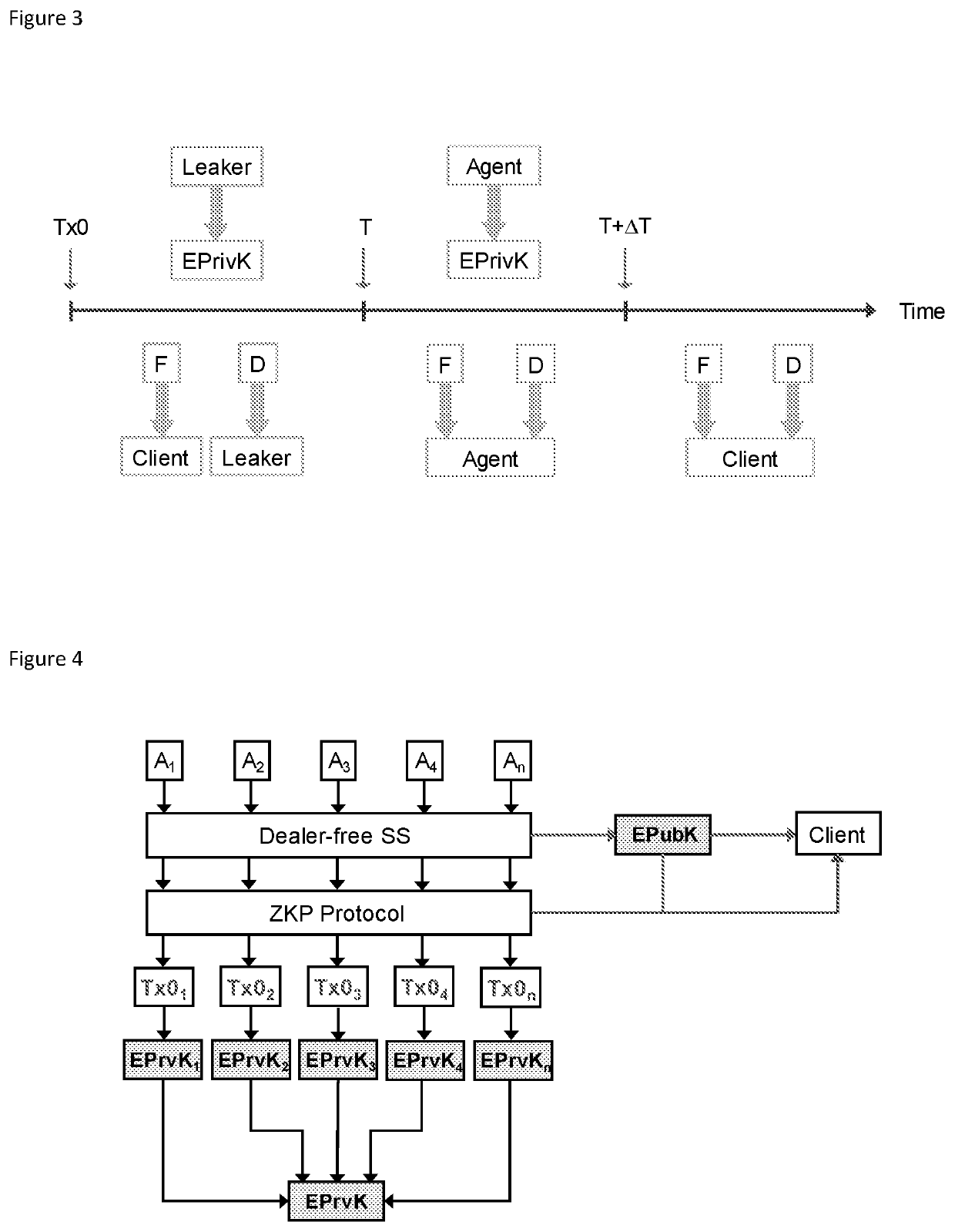
A computer-implemented method is described for generating a encryption public key on a blockchain network and enabling access to a corresponding encryption private key after a specified time period. The method comprising constructing a digital time-lock contract between an agent and a client on the blockchain network, the agent having an agent address on the blockchain network and an associated agent signature, and the client having a client address on the blockchain network and an associated client signature. The digital time-lock contract specifies that the agent holds the encryption private key corresponding to the encryption public key on the blockchain network and then releases the encryption private key to the blockchain network within a specified time window. The agent provides a first cryptographic asset for holding and then releasing the encryption private key to the blockchain network within the specified time window, the first cryptographic asset being transferrable to the agent address on the blockchain network when the encryption private key is released to the blockchain network within the specified time window. The client provides a second cryptographic asset to the agent for holding and then releasing the encryption private key to the blockchain network within the specified time window, the second cryptographic asset being transferrable to the agent address on the blockchain network when the encryption private key is released to the blockchain network within the specified time window. If the encryption private key is released prior to the time window opening then the second cryptographic asset is transferrable to the client address on the blockchain network. If the encryption private key is not released prior to the time window closing then the second cryptographic asset is transferrable to the client address on the blockchain network. The digital time-lock contract can be broadcast to the blockchain network for mining onto the blockchain.
Owner:NCHAIN LICENSING AG
Lattice-based cloud storage data safety auditing method supporting data proxy uploading
InactiveCN107124272AAvoid complex managementResist attackKey distribution for secure communicationUser identity/authority verificationCommunications securityOriginal data
The invention belongs to the technical field of information safety, and in particular relates to a lattice-based cloud storage data safety auditing method supporting data proxy uploading. The auditing method provided by the invention helps a data owner authorize a proxy signature generating data to a proxy signer and upload the proxy signature to a cloud server, and also helps a credible auditor to audit completeness of the cloud storage data. The auditing method provided by the invention achieves construction of a random mask code based on an original image sampling algorithm on the lattice, so that the credible auditor can be effectively prevented from recovering original data block information of an original signer from a data file. The credible auditor only needs to compute a linear combination with limited a computation amount instead of computing bilinear pairings with higher cost and modular exponentiation during a cloud storage data completeness verification process, so that the auditing method is very beneficial to the credible auditor in the aspect of computing efficiency. Meanwhile the method provided by the invention can effectively resist attacks of a quantum computer, and thus have very important application value in cloud computing environment of post-quantum communication security.
Owner:SOUTHWEST PETROLEUM UNIV
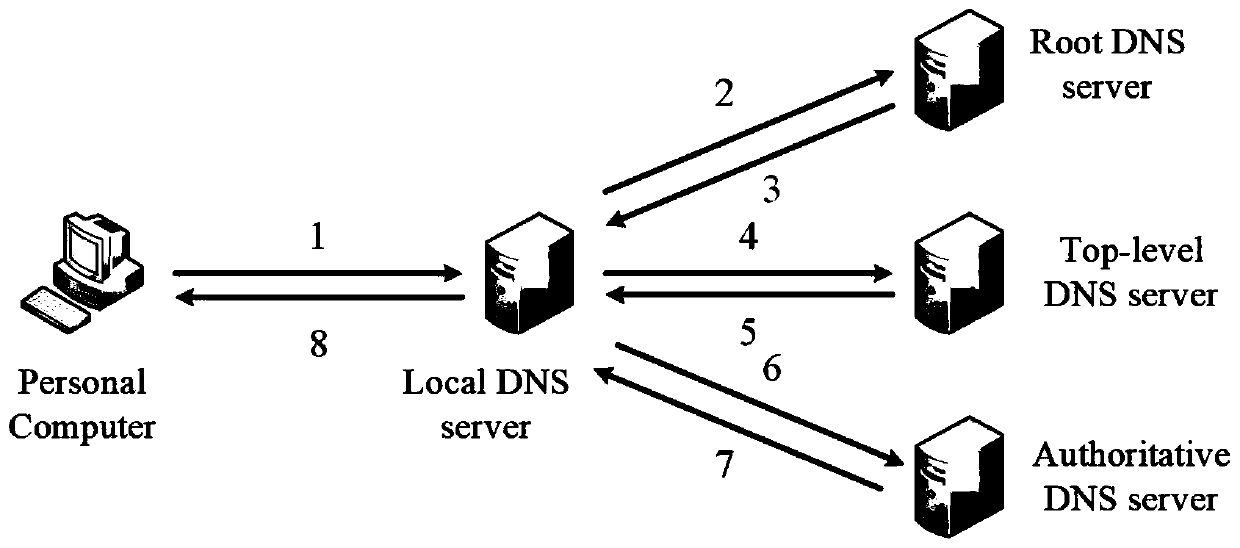
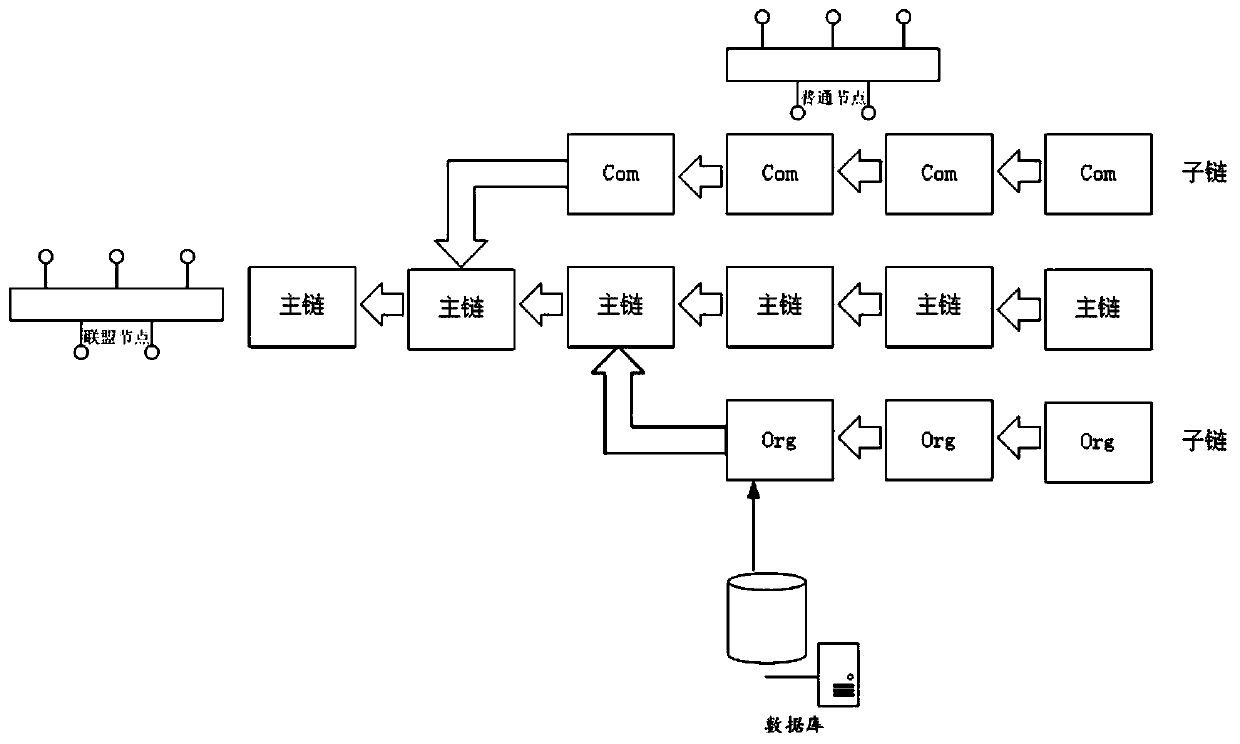
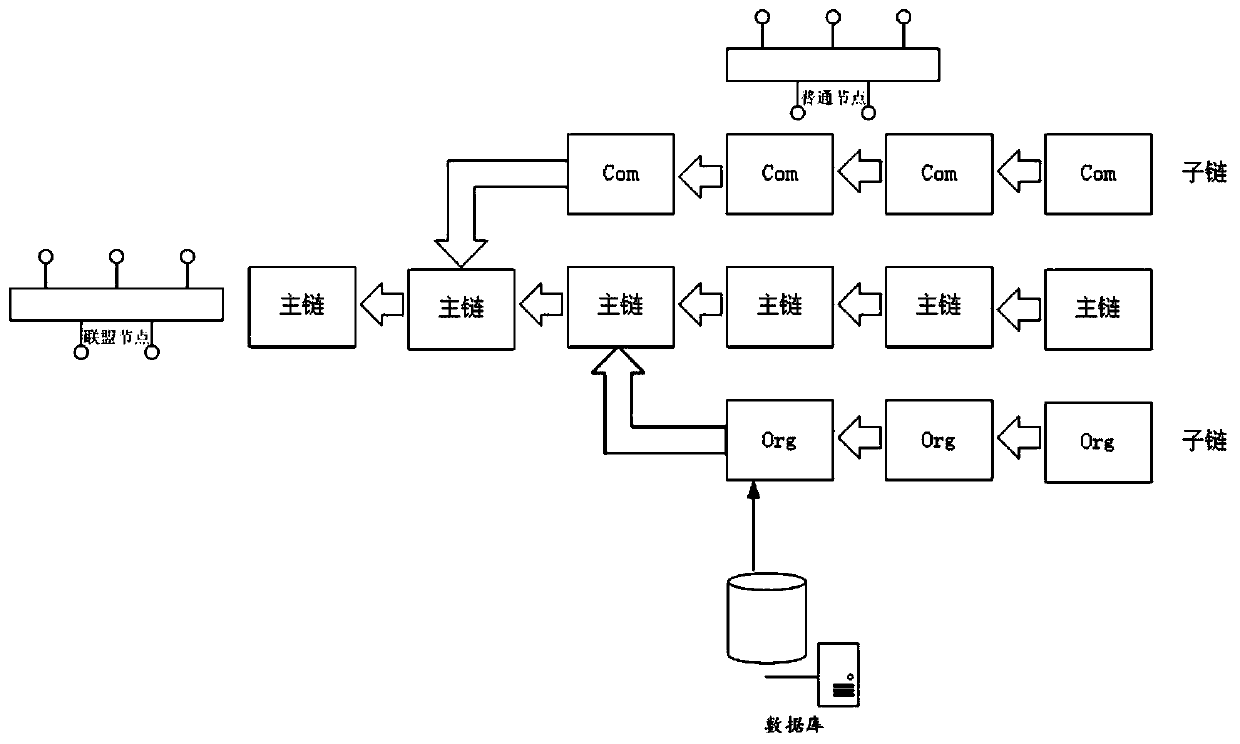
DNS system based on block chain technology
ActiveCN110012126AImprove securityImprove scalabilityUser identity/authority verificationExtensibilityAnonymity
According to the DNS system based on the block chain technology, a main chain is adopted to record a small amount of important information and is mainly responsible for storing requests on a top-leveldomain and Hash values of sub-chains; wherein the plurality of sub-chains are respectively connected with the main chain, can be expanded, migrated and properly discarded, and are mainly responsiblefor storing all operation requests under a specific TLD, different sub-chains store records under different TLDs, and all the sub-chains and the main chain maintain the same block height; the nodes are distributed on the main chain and the sub-chains and allow only the main chain and part of the sub-chains to be stored; anonymity of voting process alliance nodes is ensured by utilizing a linkablering signature technology; the node processes the operation on the sub-chain which is not stored by using the proxy signature, the throughput of the system is improved by using the fragmentation technology, the technical problems of poor security, limited performance, poor expansibility and low throughput in the prior art are solved, and the technical effects of higher security, higher expandability, higher throughput and better anonymity are achieved.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
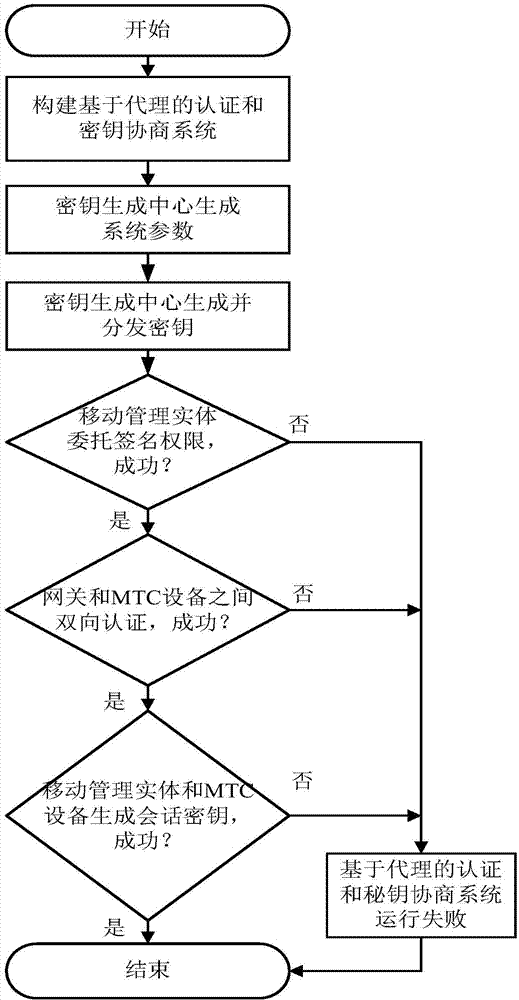
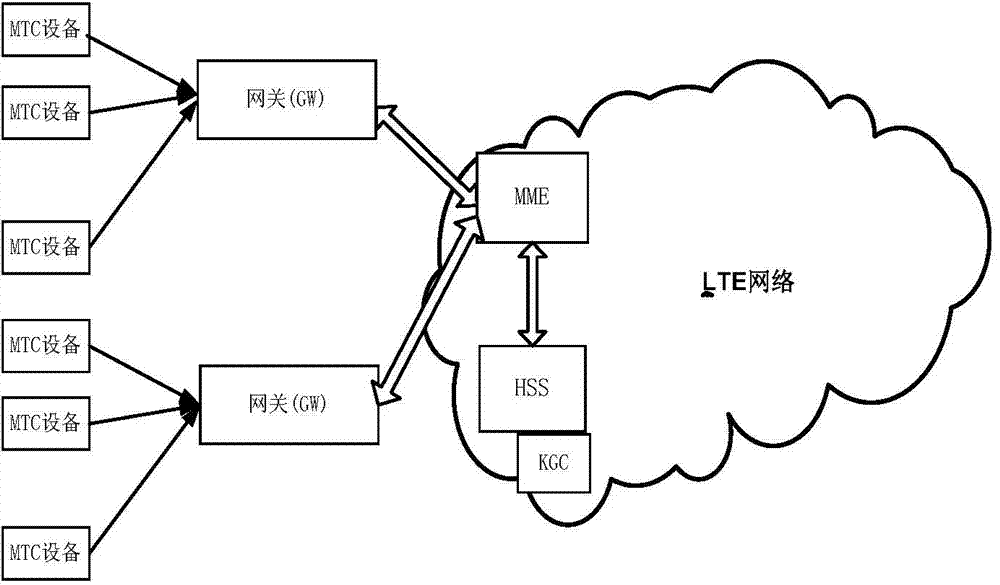
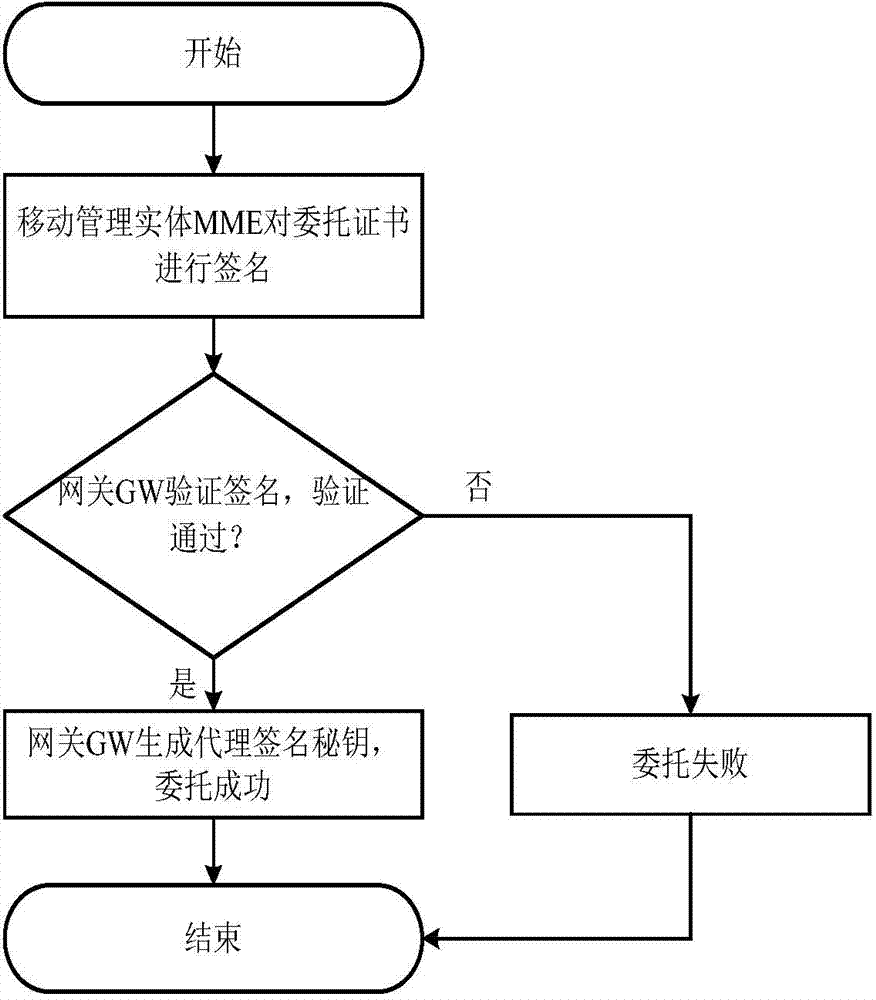
Machine-type communication authentication and key agreement method based on proxy
ActiveCN103596167AAvoid signaling congestionReduce loadSecurity arrangementMobility managementComputer science
The invention discloses a machine-type communication authentication and key agreement method based on proxy, and mainly aims to solve the signaling jamming problem in the prior art. The method includes the steps that an authentication and key agreement system based on the proxy is established; a key generation center generates system parameters and calculates and distributes keys corresponding to identity information of mobility management entities, identity information of gateways and identity information of machine-type communication equipment; the mobility management entities entrust the gateways with signature permission; bidirectional authentication is conducted between the entrusted gateways and the machine-type communication equipment; the machine-type communication equipment and the mobility management entities generate session keys. The degree of signaling jamming caused when a large amount of machine-type communication equipment simultaneously has access to networks is reduced through proxy signatures by utilizing the gateways to achieve authentication and key agreement of the machine-type communication equipment in the LTE networks, and the method can be widely applied to the LTE networks in future.
Owner:XIDIAN UNIV
Signature schemes using bilinear mappings
ActiveUS20080133926A1User identity/authority verificationCoding/ciphering apparatusRing signatureMultisignature
Methods and systems are provided for generating and verifying signatures of digital messages communicated between signers and verifiers. Using bilinear mappings, such as Weil or Tate pairings, these methods and systems enable generation and verification of efficient multisignatures, identity-based ring signatures, hierarchical proxy signatures, and hierarchical online / offline signatures.
Owner:NTT DOCOMO INC
Control method, program and system for link access
InactiveUS20130138962A1Public key for secure communicationUser identity/authority verificationEncryptionProxy signature
A plurality of users is assumed in which user A is the owner of content providing the source of a link, user B is the owner of the content providing the destination of the link, and user C is a viewer. Each user has a private key and a public key, and the public keys are shared by the users. User B selects user C in advance as a viewer. User B creates data including a value in which an encryption key with a proxy signature generated on the basis of the public key of user C and its own private key is encrypted using the public key of user A, and distributes the data to user A, which is the owner of the content providing the source of the link. User A decrypts the received data including the value using its own private key. This makes a function available based on encryption with the proxy signature. User A converts the link information using this function, signs the information using its own private key, and sends it to user C. User C verifies the signature by checking the received information using the public key of user A and the public key of user B, extracts the link information generated by user A using the function, decrypts it using its own private key, and obtains the link information.
Owner:IBM CORP
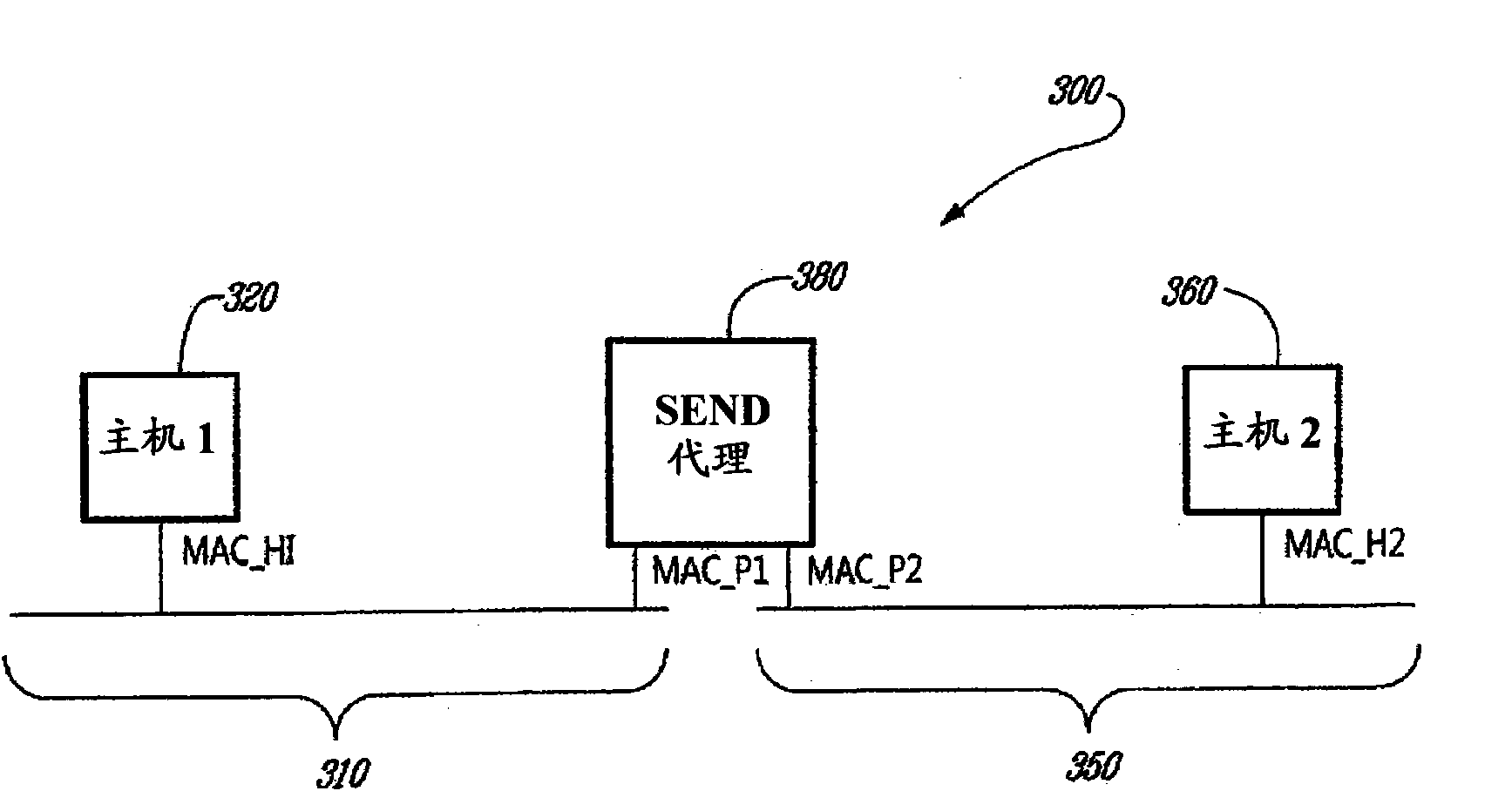
Secure neighbor discovery between hosts connected through a proxy
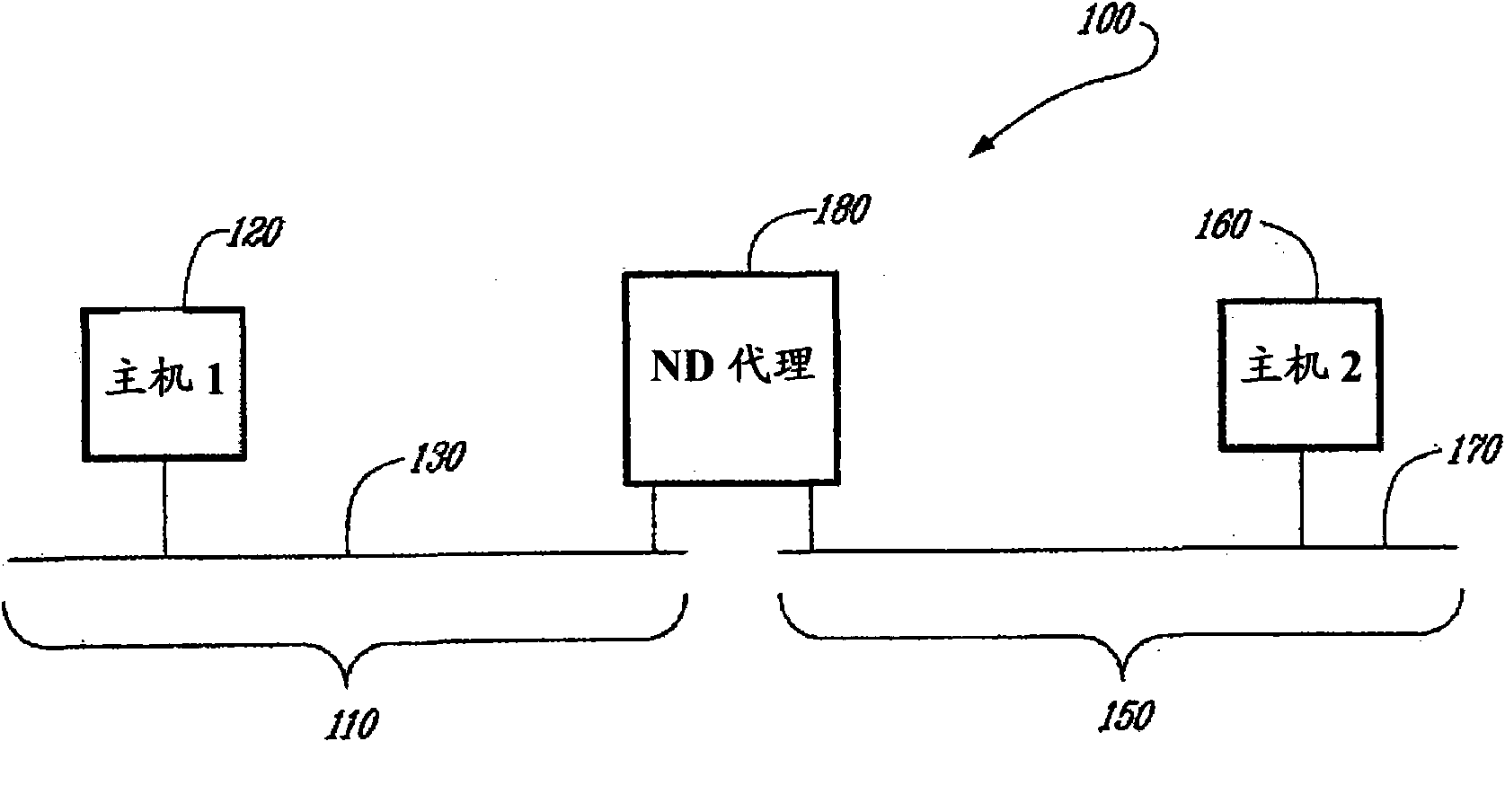
InactiveCN101843075AAllow legalityDigital data protectionWireless network protocolsSecure Neighbor DiscoveryComputer network
A method, a proxy and a host are provided for securing neighbor discovery (ND) signaling between hosts when the hosts are connected through the proxy. A first host sends an original ND message comprising a first signature based on an address of the first host. The proxy removes the address of the first host and substitutes its own address in a modified ND message. The proxy then places a copy of the address of the first host in a new field and builds a proxy signature based on the own address of the proxy and on the new field. The new field and the proxy signature are added to the modified ND message. A second host receives the modified ND message from the proxy and verifies the proxy signature. The second host reconstructs the original ND message content and then verifies the first signature.
Owner:TELEFON AB LM ERICSSON (PUBL)
Proxy signature method and system based on lattice
InactiveCN103986576ASmall sizeReduce computational complexityUser identity/authority verificationComputation complexityRound complexity
The invention provides a proxy signature method and system based on a lattice. The proxy signature method includes the steps of secret key generation, proxy signature secret key generation, proxy verification, proxy signature, verification and the like. The proxy signature method and system based on the lattice have the advantages that the proxy signature method based on a small integer problem on the lattice is disclosed, and the size of a proxy signature private key is reduced by reducing the dimension of the proxy signature private key. Besides, matrix multiplication is mainly used in the aspect of calculation. Compared with the methods of discrete logarithm and big integer problem factorization, modular exponentiation and match operation are not used, and accordingly computation complexity is lower.
Owner:SHENZHEN UNIV
Distributed signature method and system based on identity
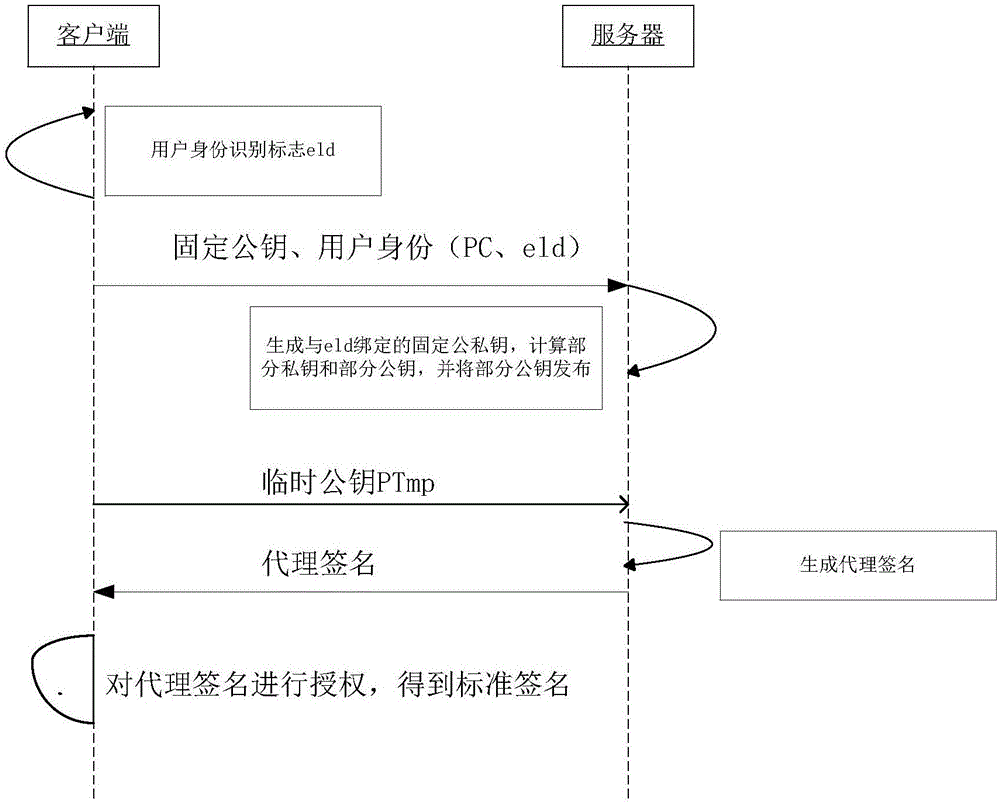
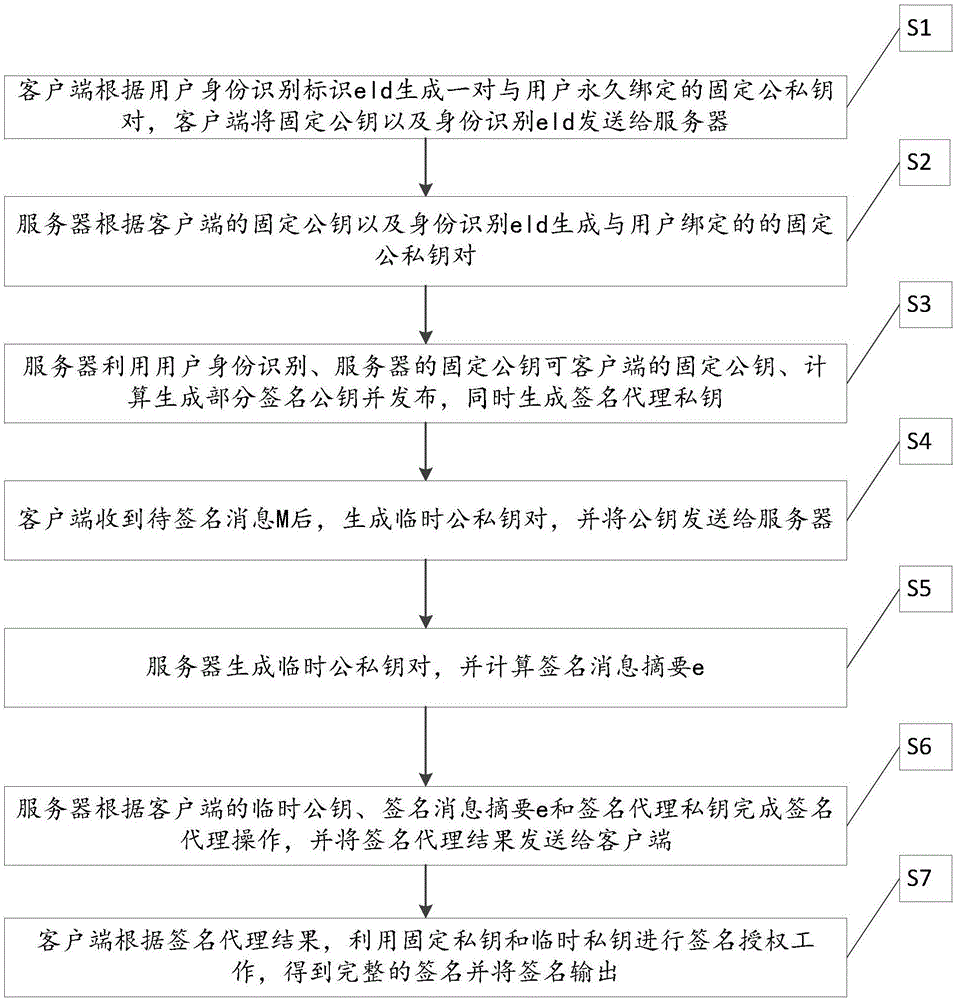
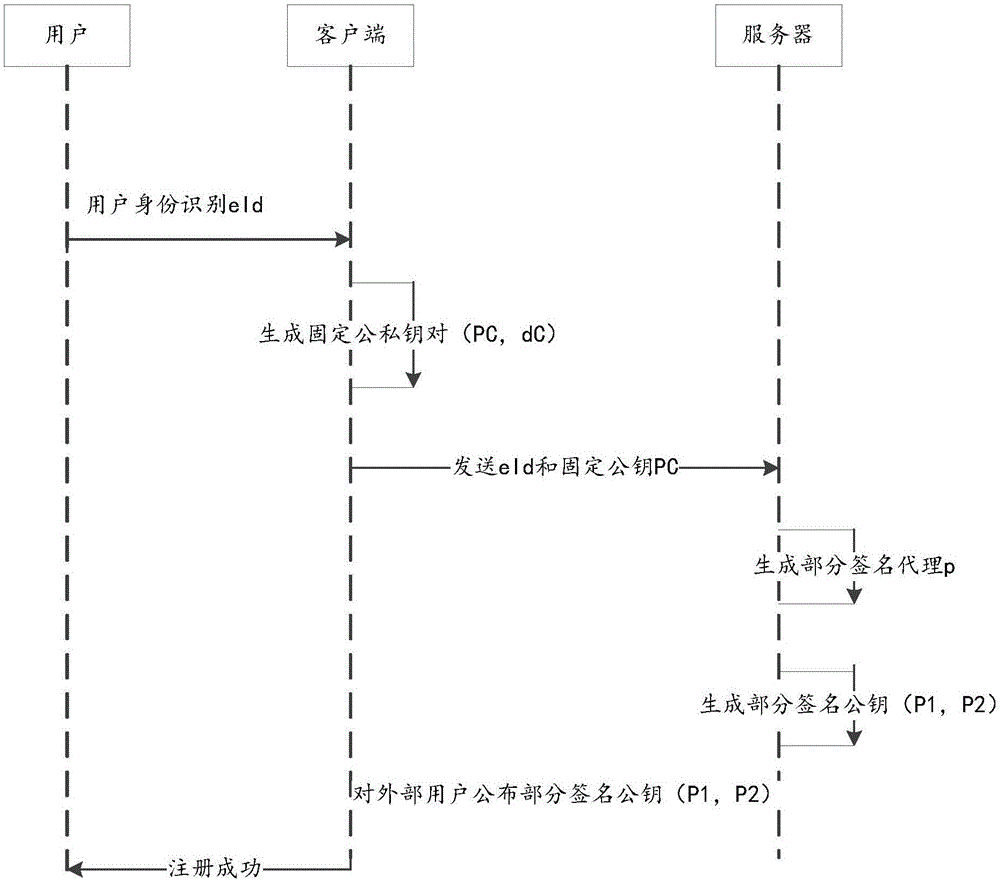
ActiveCN106851635AOvercome the shortcoming of unreliable heart PKGEnsure safetyPublic key for secure communicationUser identity/authority verificationClient-sideKey generation
The invention relates to a distributed signature method and system based on identity. The distributed signature method comprises a user registration phase and a distributed signature phase, the user registration phase comprises: a client maintains two pairs of public and private keys at first, one pair is fixed public and private keys, and the other pair is temporary public and private keys; a server also maintains two pairs of fixed public and private keys, one pair is fixed public and private keys, and the other pair is temporary public and private keys generated after signature activity is initiated; the client sends user identity and the fixed public keys to the server, the server calculates a part of private keys and a part of corresponding public keys by using its own fixed public and private keys, and opens a part of public keys; and the distributed signature phase comprises: the server accomplishes signature preprocessing work and sends proxy signature to the client, and the client performs signature authorization work at last to obtain a signature message. By adoption of the distributed signature method and system provided by the invention, the defect that key generation center PKG cannot be trusted is overcome, and meanwhile, if the security of the client cannot be guaranteed, the private keys are not leaked.
Owner:BEIJING SANSEC TECH DEV
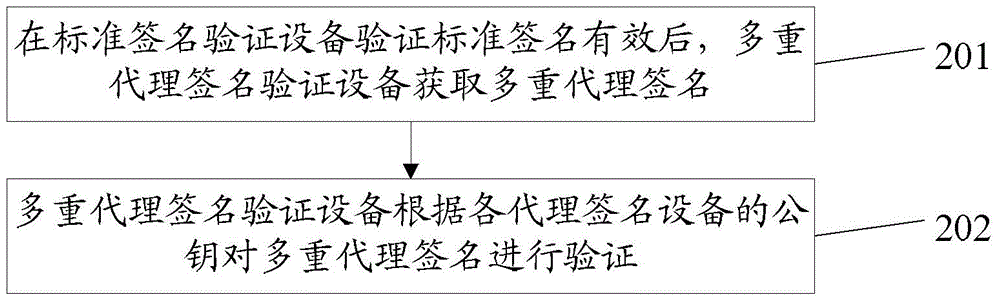
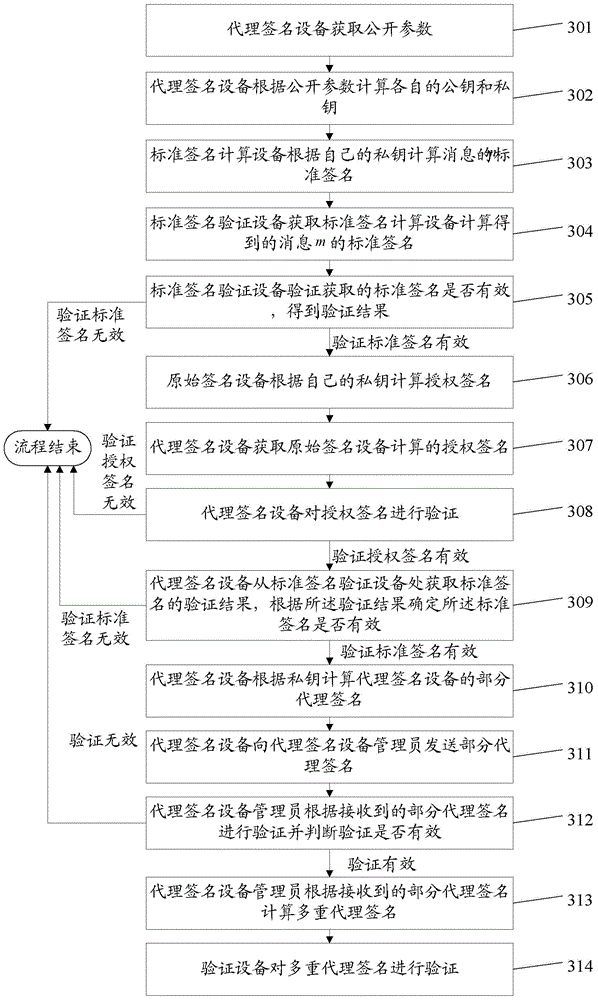
Method and device for certificateless multi-proxy signature
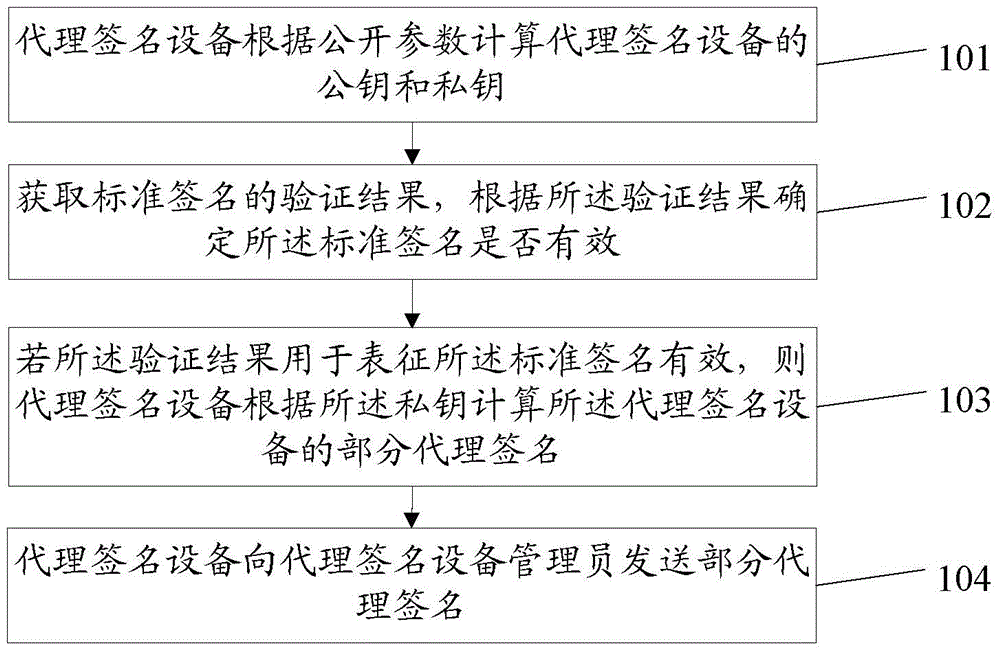
ActiveCN104468476ASmall amount of calculationReduce computing timeUser identity/authority verificationBilinear pairingMulti proxy
The invention discloses a method and device for certificateless multi-proxy signature, relates to the technical field of communication, and solves a problem of heavy computation load of certificateless multi-proxy signature conducted by bilinear pairings. The method of the invention specifically includes: computing, by a proxy signature apparatus, a public key and a secret key of the proxy signature apparatus in accordance with public parameters, the public key being corresponding to the secret key; obtaining a verification result of a standard signature, and determining whether the standard signature is valid in accordance with the verification result; if the verification result represents the standard signature is valid, computing, in accordance with the secret key, partial proxy signature of the proxy signature apparatus; and transmitting the partial proxy signature to a proxy signature apparatus manager, so that, after the proxy signature apparatus manager computes a multi-proxy signature in accordance with the partial proxy signature, a multi-proxy signature verifying apparatus verifies the multi-proxy signature. The method and the device can be applicable for certificateless multi-proxy signature.
Owner:HUAWEI DEVICE CO LTD
Control method, program and system for link access
InactiveUS20130138965A1Public key for secure communicationUser identity/authority verificationEncryptionProxy signature
A plurality of users is assumed in which user A is the owner of content providing the source of a link, user B is the owner of the content providing the destination of the link, and user C is a viewer. Each user has a private key and a public key, and the public keys are shared by the users. User B selects user C in advance as a viewer. User B creates data including a value in which an encryption key with a proxy signature generated on the basis of the public key of user C and its own private key is encrypted using the public key of user A, and distributes the data to user A, which is the owner of the content providing the source of the link. User A decrypts the received data including the value using its own private key. This makes a function available based on encryption with the proxy signature. User A converts the link information using this function, signs the information using its own private key, and sends it to user C. User C verifies the signature by checking the received information using the public key of user A and the public key of user B, extracts the link information generated by user A using the function, decrypts it using its own private key, and obtains the link information.
Owner:IBM CORP
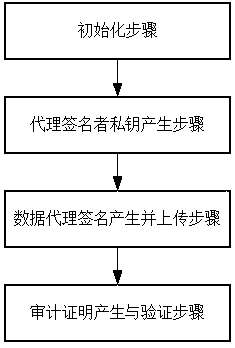
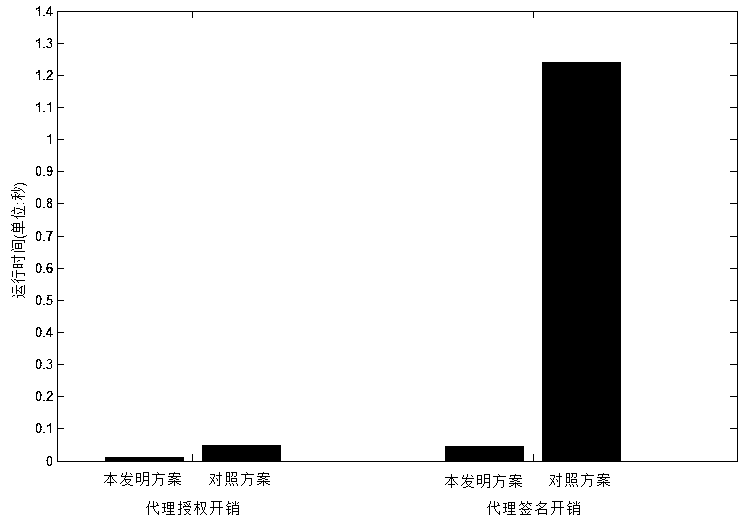
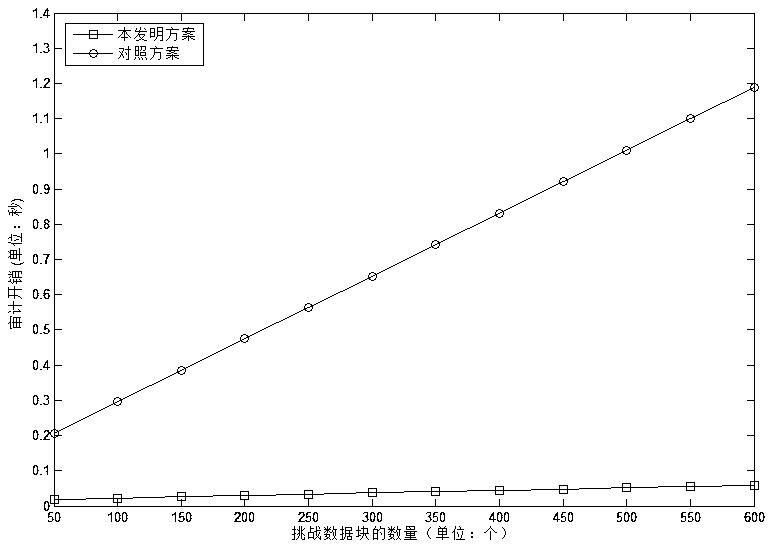
Identity-based cloud storage efficient auditing method capable of acting and uploading data
ActiveCN108712259AFacilitates integrity auditsGuaranteed confidentialityUser identity/authority verificationConfidentialityPassword
The invention discloses an identity-based cloud storage efficient auditing method capable of acting and uploading data, comprising: an initialization step, a proxy signer private key generating step,a data proxy signature generating and uploading step, and an auditing certificate generating and verifying step. The auditing method provided by the invention helps the data owner to authorize the proxy signer to generate the proxy signature of the data and upload the same to the cloud server, and helps the trusted auditor to perform integrity auditing on the cloud storage data. By compressing thedata file into a homomorphic message authentication code, using the elliptic curve signature algorithm to digitally sign the message authentication code of the data block, encrypting the data file with a lightweight stream password, and finally storing the signature set and the ciphertext in the cloud server, thus not only ensuring the confidentiality of data files, but effectively solving the problem of integrity verification of the remote cloud storage data.
Owner:SOUTHWEST PETROLEUM UNIV
Apparatus and method for domain management using proxy signature
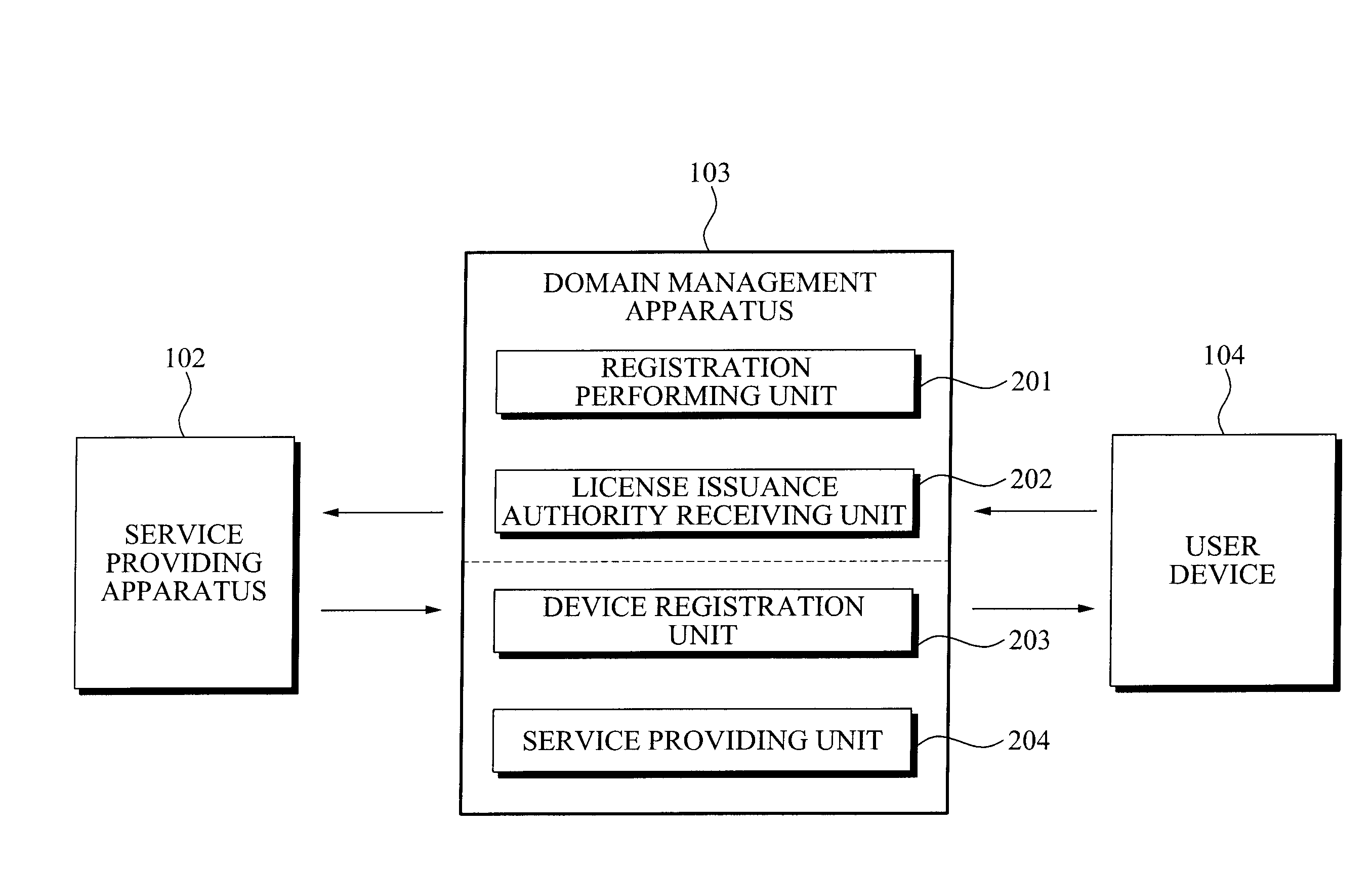
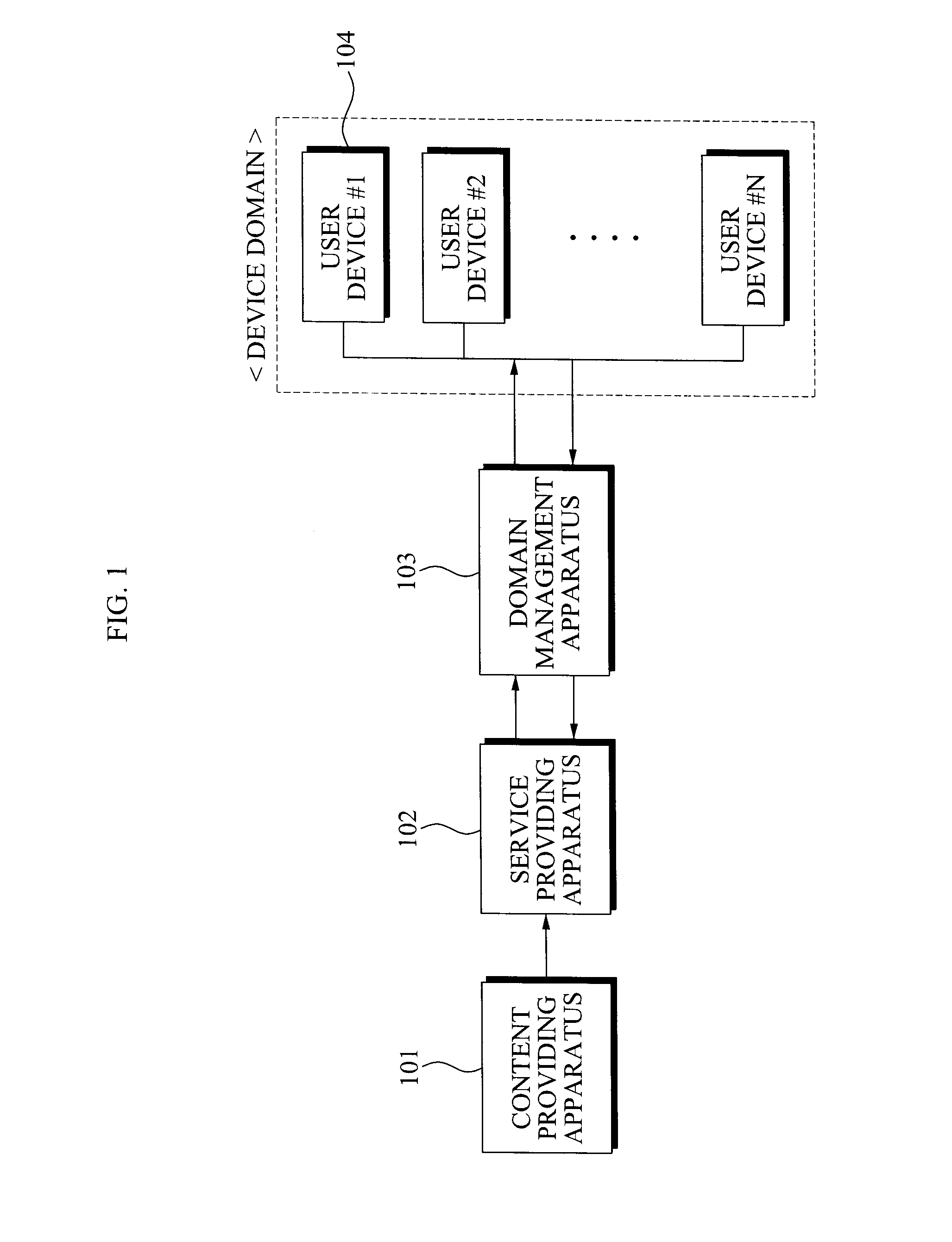
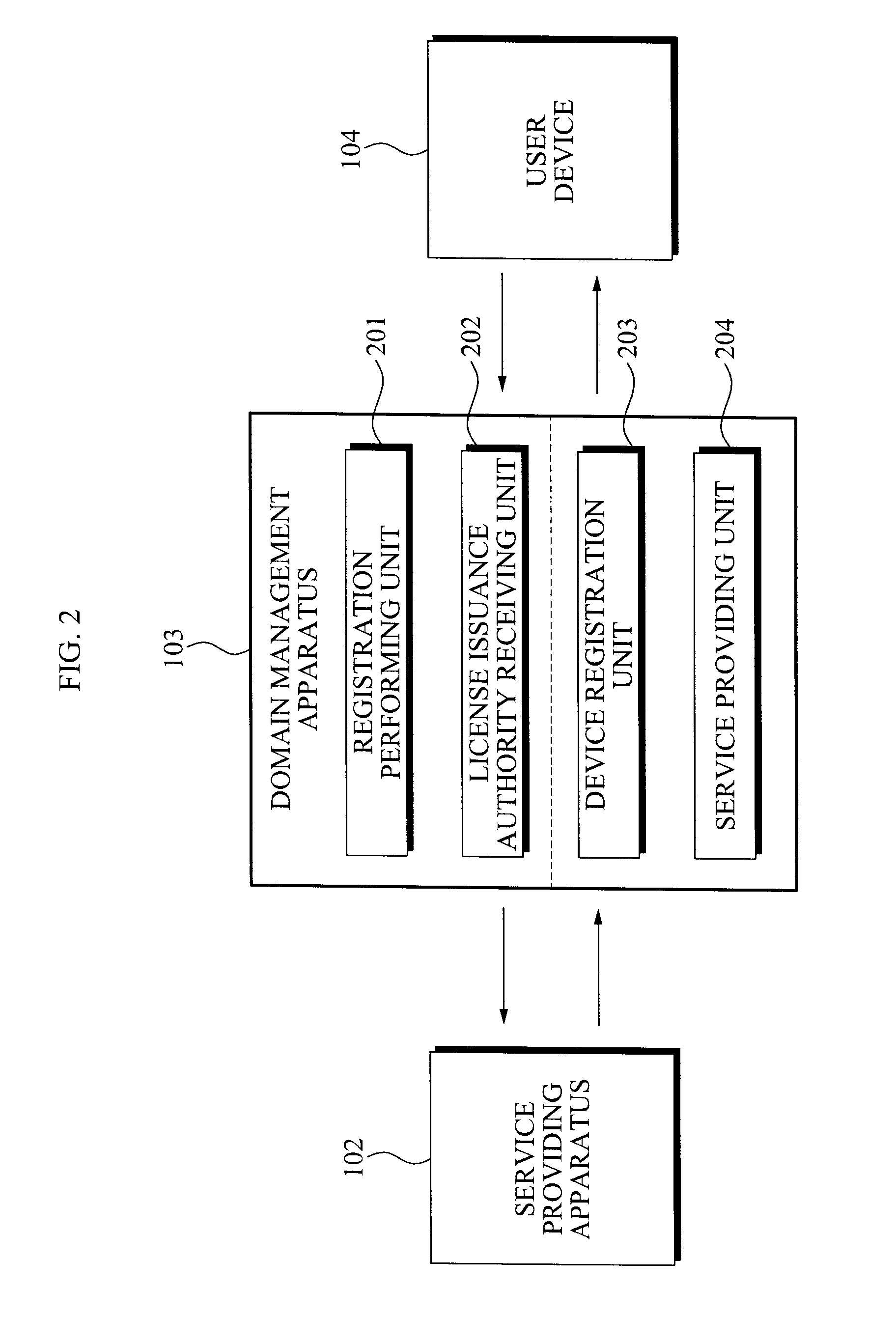
InactiveUS20090150982A1OptimizationEfficient managementDigital data processing detailsUser identity/authority verificationUser deviceService provision
A domain management apparatus and method using a proxy signature is provided. A domain management apparatus which manages a device domain being a set of at least one user device, the apparatus including: a registration performing unit for performing a registration procedure for registering the domain management apparatus in a service providing apparatus; a license issuance authority receiving unit for receiving a license issuance authority for content use from the service providing apparatus; and a service providing unit for providing the at least one user device with a content service and a license generated by the license issuance authority.
Owner:SAMSUNG ELECTRONICS CO LTD
Key exchange authentication method with no need of hometown network participation when in roaming
InactiveCN101674576AReduce loadProtect against Denial of Service DoS attacksPublic key for secure communicationUser identity/authority verificationKey exchangeThird party
The invention discloses a key exchange authentication method with no need of hometown network participation when in roaming, belonging to the field of wireless communication. The key exchange authentication method comprises the steps of initializing, registering, authenticating and establishing a session key. When in the initializing, firstly a public key and a private key are selected by a hometown network authentication server and a foreign network authentication server; and then the public key therein is issued by a third-party authentication server. When in registering, a mobile node submits identity information to the hometown network authentication server privately; and the hometown network authentication server uses the private key for calculation and delivers a secrete value abouta proxy signature to the mobile node privately. When in the authenticating and establishing the session key, the mobile node sends an authentication request report to the network authentication server; the network authentication server decrypts the request report and authenticates the identity of the mobile node; if the mobile node is legal, the session key is calculated and confirmation information is replied to the mobile node; the mobile node decrypts and determines the confirmation information; and the network authentication server is credible and obtains the session key.
Owner:ZHEJIANG UNIV
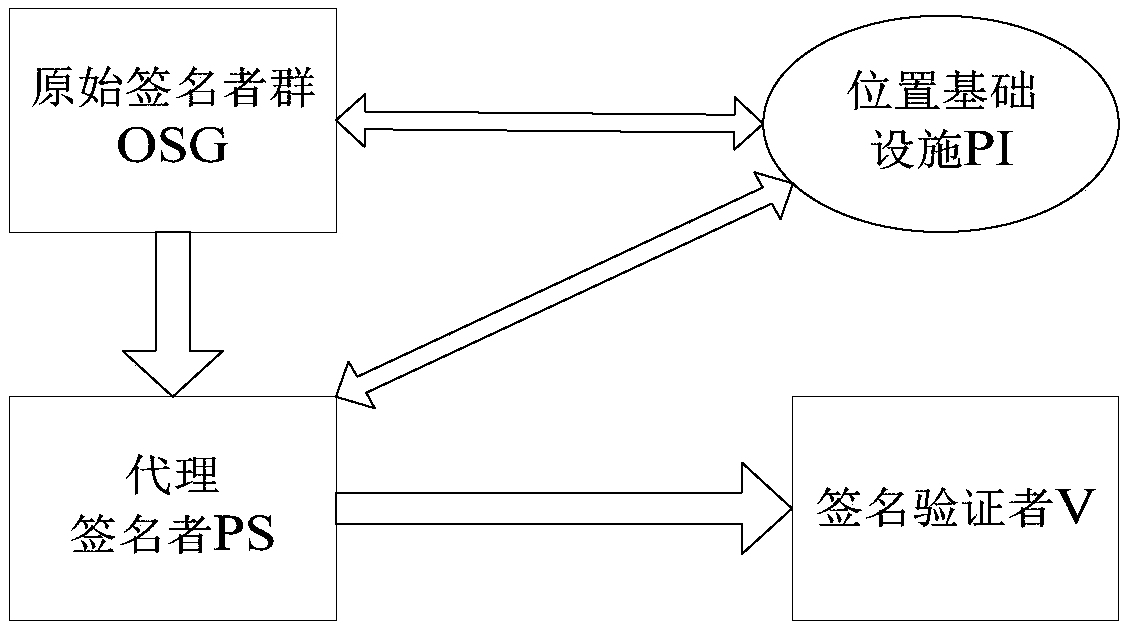
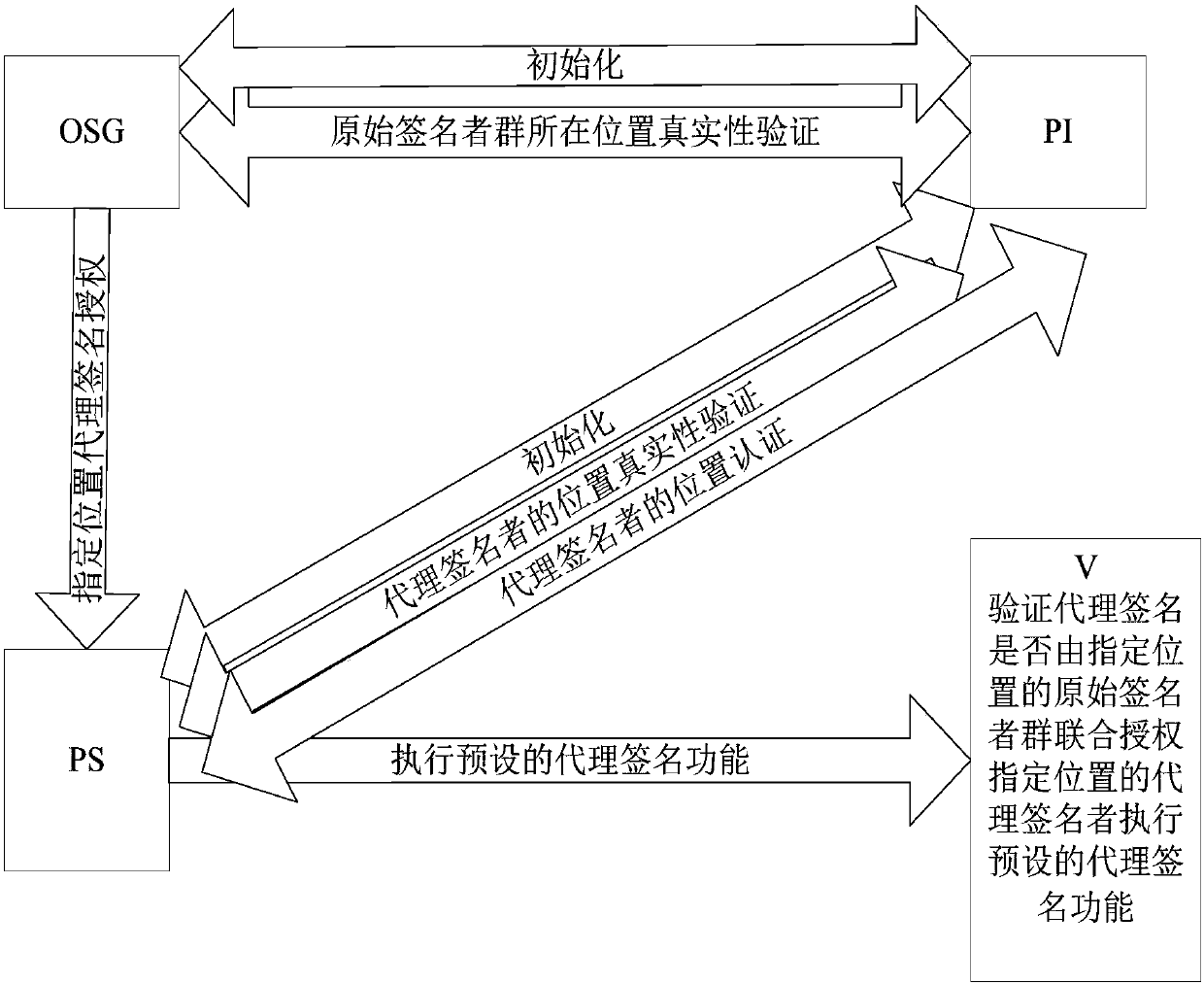
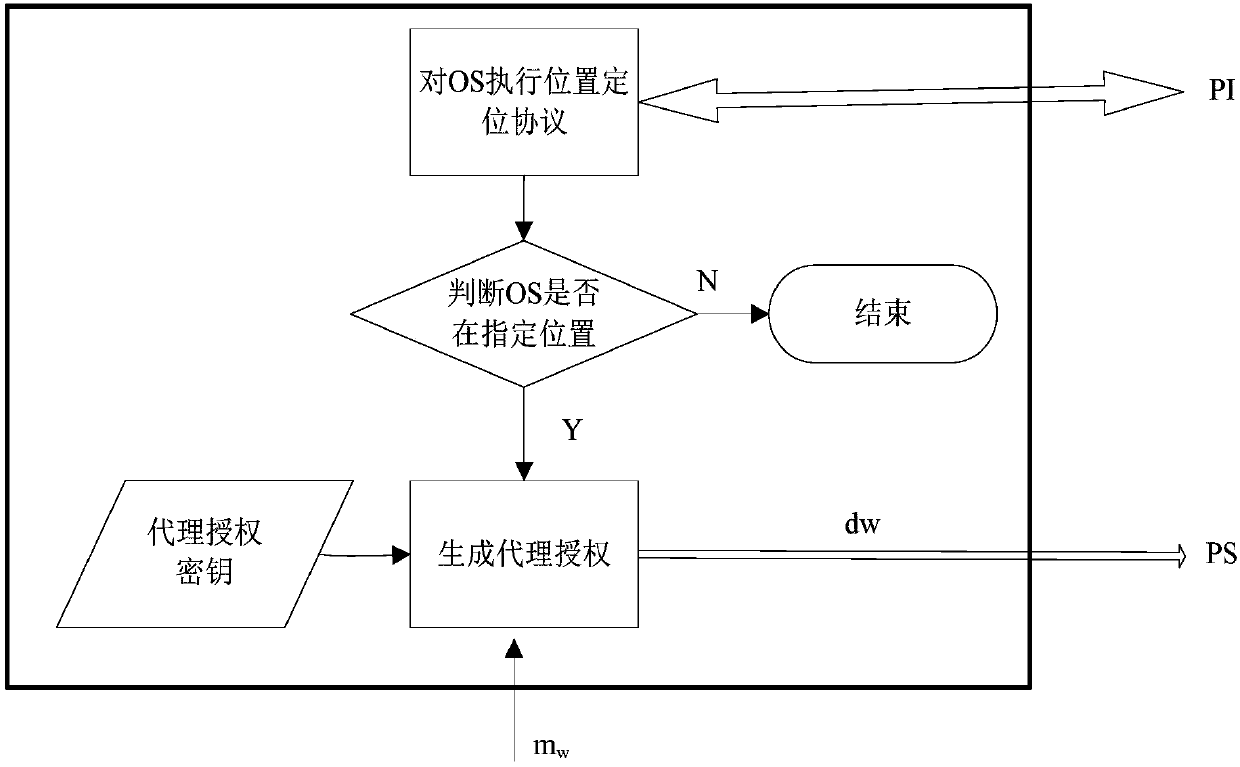
Proxy multi-signature method and system based on position
ActiveCN107846281AGuaranteed reliabilityEnsure safetyUser identity/authority verificationAuthorizationComputer science
The invention provides a proxy multi-signature method and system based on position. The proxy multi-signature method based on the position comprises the following steps: the initialization of a proxysigner PS, a original signer group OSG and a position infrastructure PI is performed; the authenticity verification of the position where the original signer group OSG is located is completed under the participation of the PI, the authenticity verification of the position of the proxy signer PS is verified through the PI, and the designated position proxy signature authorization of the proxy signer PS is completed by the original signer group OSG; the proxy signer PS completes its own position authentication function under the support of the PI and then performs the proxy signature function for specific information; and a proxy signature verifier V completes the verification that the proxy signature of the preset information is performed by the original signer group of the designated position combined with the proxy signer of the designated position. The proxy multi-signature method based on the position provided by the invention has high safety and wide application range, and realizesthe transfer of the authentication power of identity and position.
Owner:SHANGHAI INST OF TECH
Method and apparatus for generating proxy-signature on right object and issuing proxy signature certificate
InactiveCN101192261AComputer security arrangementsPublic key infrastructure trust modelsProxy signatureComputer security
A method and apparatus for generating a proxy signature on a right object, and a method and apparatus for issuing a proxy signature certificate. The right object proxy signature method includes receiving a proxy signature certificate in which authority for right object conversion is specified, from a right issuer; receiving a right object from a first apparatus; signing the right object; and transmitting the signed right object and the proxy signature certificate to a second apparatus. Accordingly, by allowing a right object to be signed by a third right object proxy signature apparatus, not by a right issuer, users can freely share their own content between a variety of apparatuses, and the right issuer can reduce the load associated with the conversion and signature of right objects.
Owner:SAMSUNG ELECTRONICS CO LTD
Motorcade-oriented safe mobility management method based on aggregation certification
ActiveCN108390909AReduce overheadReduce switching delayKey distribution for secure communicationParticular environment based servicesThe InternetMobility management
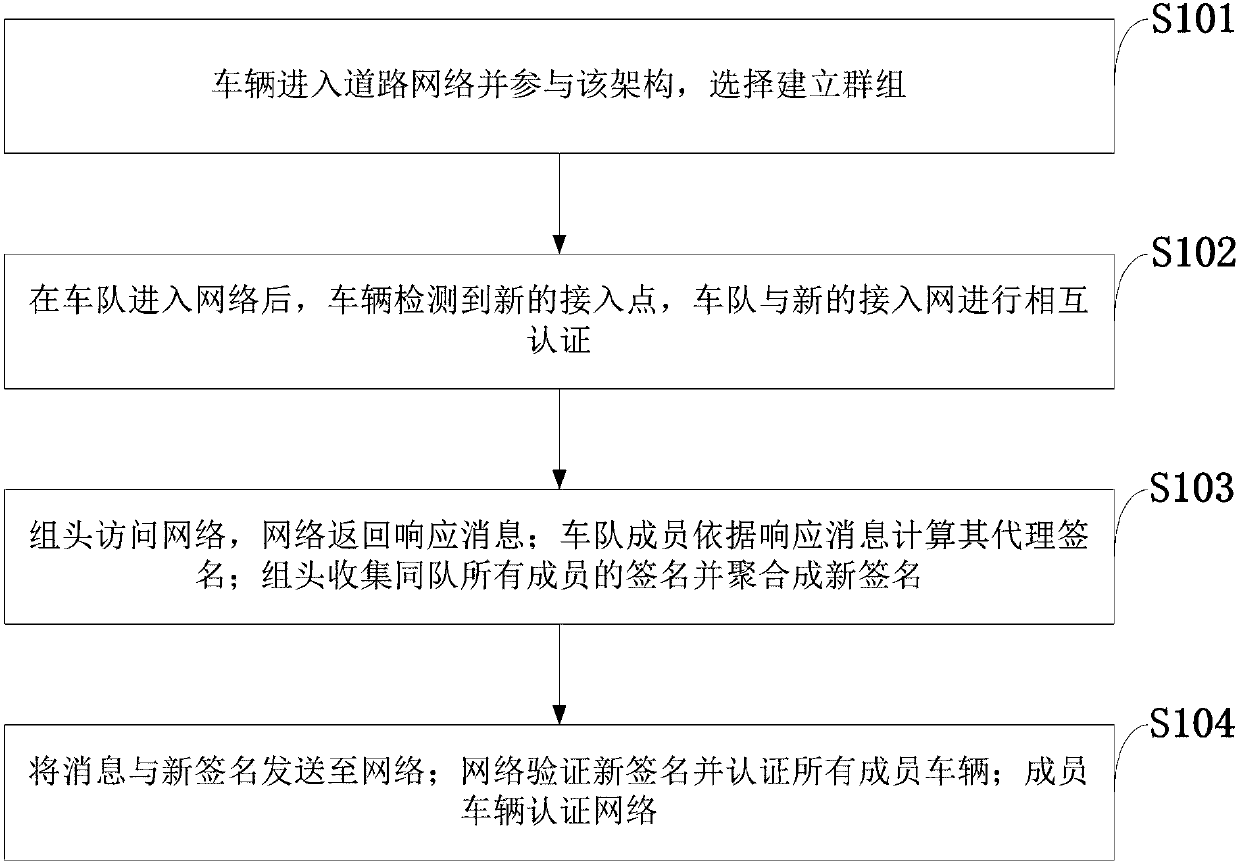
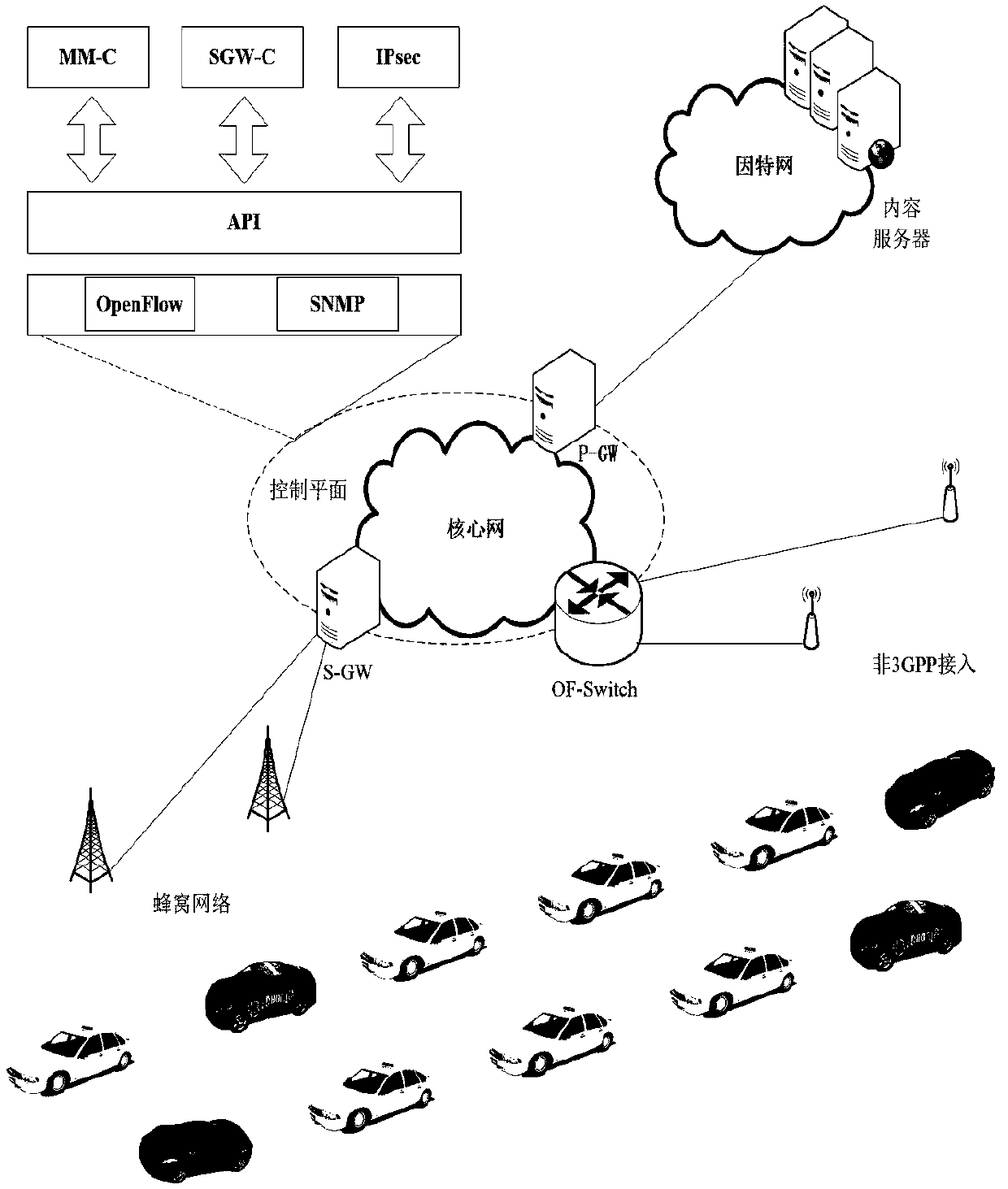
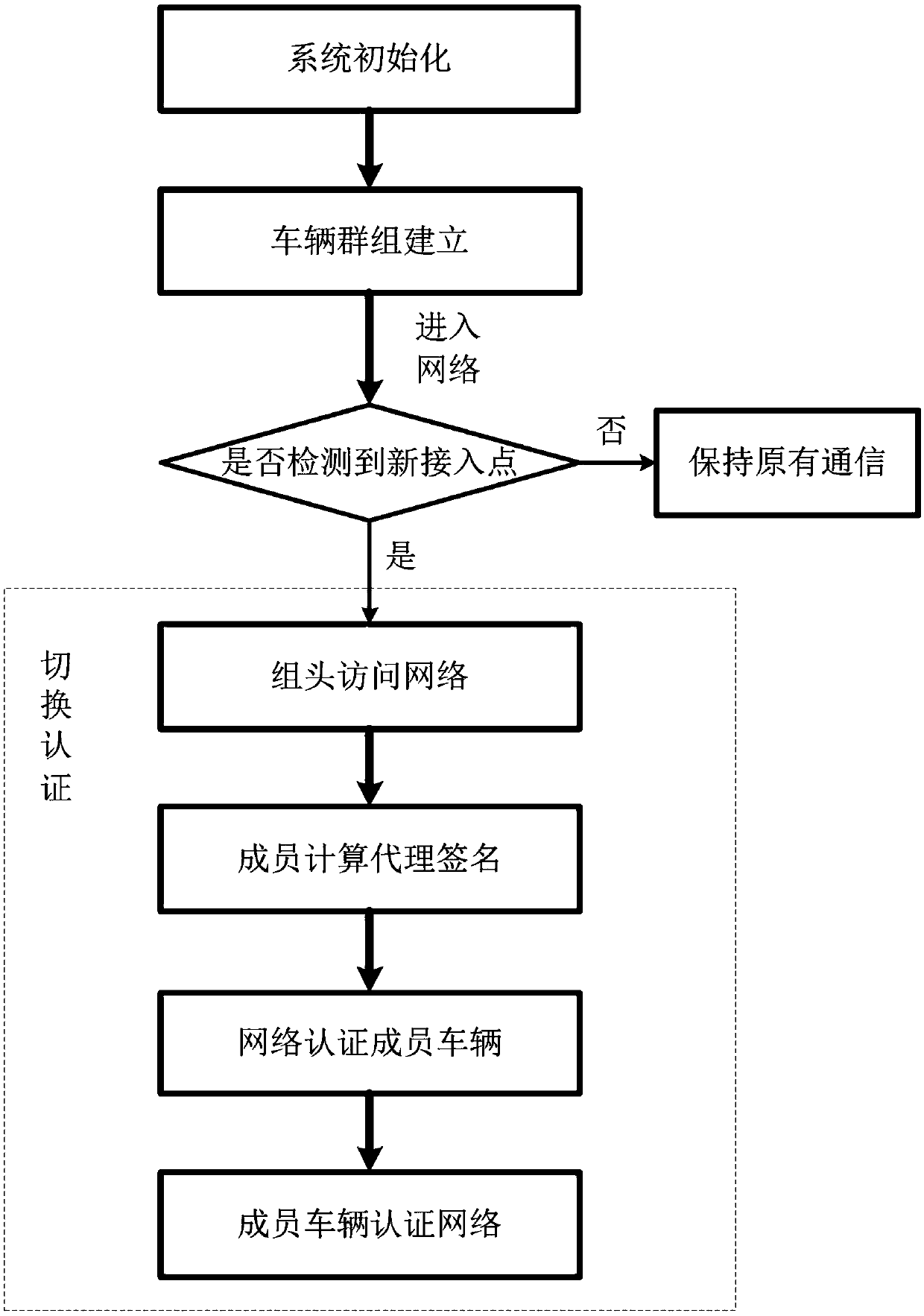
The invention belongs to the technical field of Internet of Vehicles, and discloses a motorcade-oriented safe mobility management method based on aggregation certification. An Internet of Vehicle-cellular network architecture which defines the network based on software is used, a vehicle enters into a road network and takes participate in the architecture, and then chooses to build a group; when amotorcade enters into the network, a new access point is detected by the vehicle, and the motorcade and a new access network perform mutual authentication; a group head accesses to the network, and the network returns back a response message; a motorcade member calculates a proxy signature thereof according to the response message; the group head collects signatures of all members in the same motorcade and aggregates into a new signature; then, the message and the new signature are sent to the network; the network verifies the new signature and authenticates all the member vehicles; and the member vehicles authentication the network. In combination with MIPv6-based mobility management, the method provided by the invention can realize safe and efficient motorcade-oriented mobility management, reduce authentication signaling overhead and switching delay and simultaneously guarantee data security of vehicle users.
Owner:XIAN UNIV OF POSTS & TELECOMM
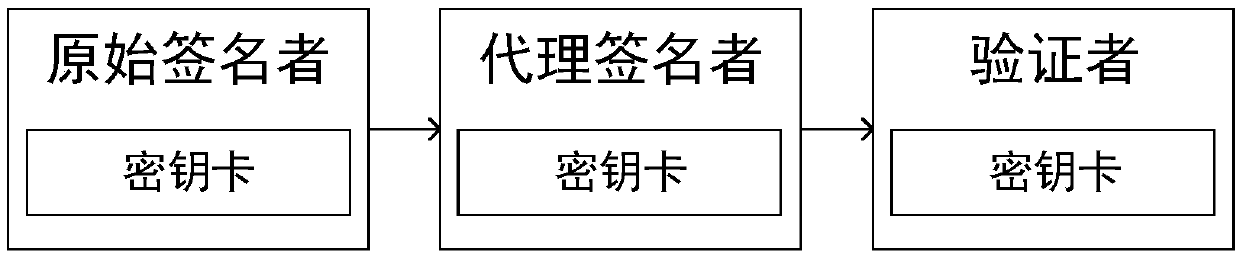
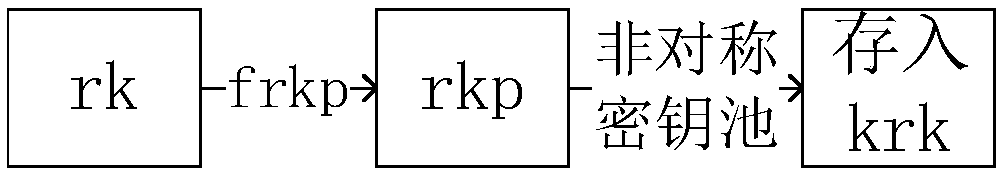
Anti-quantum computing proxy digital signature method and signature system based on asymmetric key pool, and computer equipment
ActiveCN109560926AAvoid crackingReduce the possibilityKey distribution for secure communicationPublic key for secure communicationSurrogate keyQuantum computer
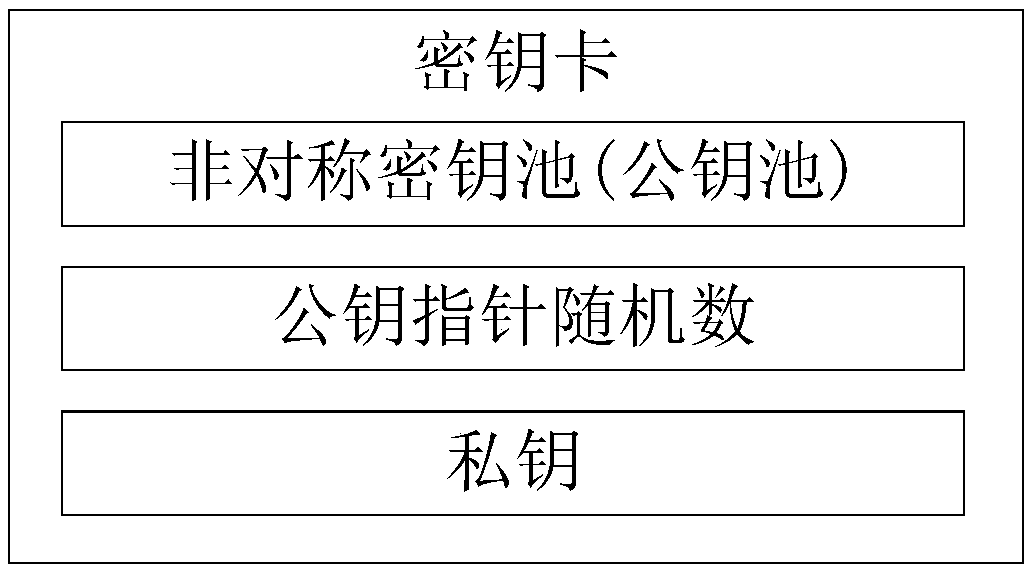
The invention relates to an anti-quantum computing proxy digital signature method and an anti-quantum computing proxy digital signature system based on an asymmetric key pool, and computer equipment.The anti-quantum computing proxy digital method comprises the steps that: an original signature party uses a signature private key of the original signature party to generate a proxy key, and transmits an original text to be signed, the proxy key and a public key pointer random number corresponding to a signature public key of the original signature party to a proxy signature party; the proxy signature party obtains the signature public key of the original signature party from a secret key card of the proxy signature party according to the public key pointer random number, and utilizing the signature public key to verify the proxy key; performing signature operation on the original text by utilizing the proxy key to generate a file signature by the proxy signature party after the verification passes, and transmitting the original text, the file signature and the public key pointer random number to a verification party; and the verification party obtains a signature public key of the original signature party from a secret key card of the verification party according to the public key pointer random number, and verifies file the signature by utilizing the signature public key.
Owner:RUBAN QUANTUM TECH CO LTD
High non-camouflage realization method of revocable proxy signature
InactiveCN103825882AAvoid Forged SignaturesAchieving strong unmasqueradabilityTransmissionGeneration processHash function
The invention discloses a high non-camouflage realization method of a revocable proxy signature, for solving the problem of poor security of a conventional method capable of revoking a proxy signature. The technical scheme comprises an original singer authorization process, an authorization verification process, a proxy signature generation process, a signature validity verification process and a proxy revoking process. According to the invention, by use of the same method, the authorization of an original signer to a proxy singer is generated, and a proxy signature is generated through introducing an anti-bump Hash function, so that an attacker is prevented from signature forgery in case that the attacker does not have the secret key of a user, thus the high-camouflage of a revocable proxy signature is realized, and it is proved that the proxy signature improves the security of the revocable proxy signature in a standard model.
Owner:XIDIAN UNIV
Quantum agent blind signature method and system based on cluster state
ActiveCN110166253AVerifiableGreat Entanglement PersistenceKey distribution for secure communicationUser identity/authority verificationCluster stateCrowds
The invention discloses a quantum agent blind signature method and system based on a cluster state. The cluster state is used as a carrier of a quantum blind signature. The GHZ state is only used forkey distribution. The method comprises five communication parties, respectively a message owner Alice holding to-be-signed information, an initial signing party Bob which cannot sign normally, an agent signing party Bob1, an agent signing party Bob2 and a trusted receiver Charlie. Bob can authorize a proxy signature crowd group, and during the Bob vacancy period, an agent signature person represents the Bob to execute signature. Only when two agent signers Bob1 and Bob2 cooperate with each other, can the Bob be represented to generate a signature, the Charlie is an authorized and credible receiver, and the Charlie receives an Alice file and verifies whether the signature on the file is completed by the cooperation of the two agent signers. According to the quantum agent blind signature method based on the cluster state provided by the invention, on the basis of keeping the GHZ state and the W state of the cluster state, greater entanglement continuity is achieved, and the safety is higher.
Owner:NORTHWEST UNIV(CN)
Proxy digital signature method based on elliptic curve
PendingCN113849861ASuitable for agency authorizationVerification procedure is simpleDigital data protectionDigital data authenticationKey generationAuthorization
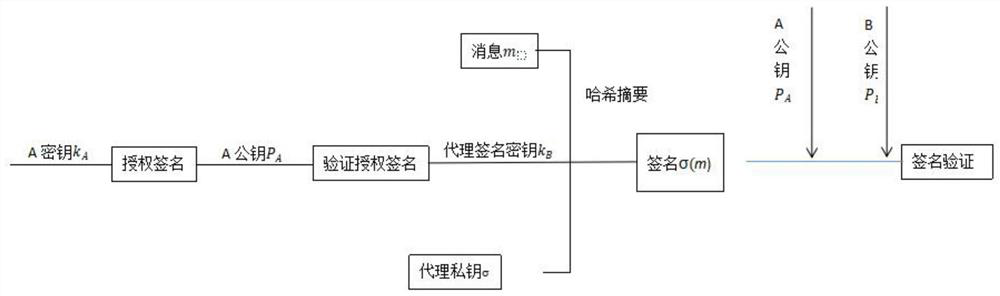
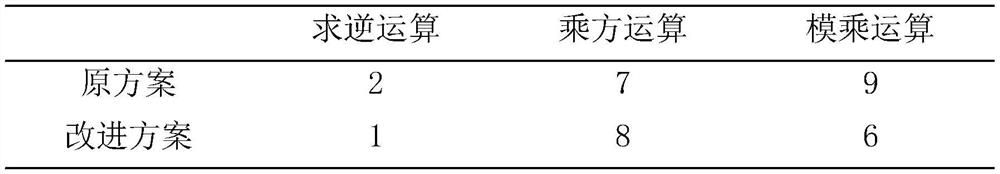
The invention discloses a proxy digital signature method based on an elliptic curve. The method specifically comprises the following steps: S1, an initialization process; S2, a delegation process; S3, a proxy key generation process; and S4, a verification process of the proxy secret key. In the proxy signature scheme of the invention, the proxy signature contains a private key kB of the B, any other person cannot pretend to be the B because of not knowing the private key kB, and the B cannot repudiate the signature; and an authorization parameter sA is equivalent to e1kA+k1(modn) comprises a private key kA of an original signer, and only B authorized by A can generate an effective proxy signature. The method is suitable for temporary and short-term agent authorization; the method is suitable for the condition that different persons are verified each time; the verification program is simple; and in the method, other people cannot pretend, and different roles in the scheme cannot pretend to each other.
Owner:JIANGSU OCEAN UNIV
Sensitive data anonymous access method based on knowledge signatures
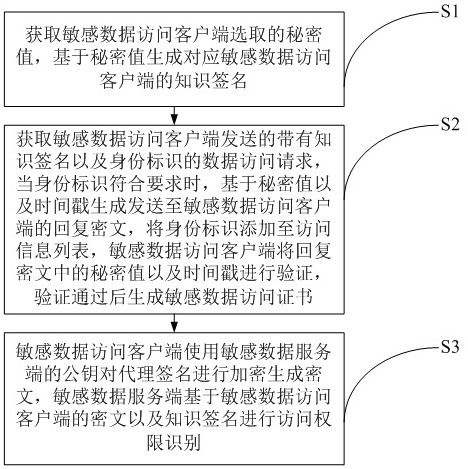
The invention provides a sensitive data anonymous access method based on knowledge signatures. The method comprises the steps of: generating the knowledge signatures corresponding to sensitive data access clients based on secret values; and acquiring a data access request with a knowledge signature and an identity identifier sent by a sensitive data access client, generating a reply ciphertext sent to the sensitive data access client based on the secret value and the timestamp, and adding the identity identifier to an access information list, wherein the sensitive data access client encrypts the proxy signature by using a public key of the sensitive data server to generate a ciphertext, and the sensitive data server identifies the access authority based on the ciphertext of the sensitive data access client and the knowledge signature. The sensitive data access client and the sensitive data server can complete identity verification and authorization processes without intervention of a management platform, are flexible and efficient, and are suitable for cross-domain multi-party sensitive data access scenes. In the authorization process, the sensitive data access client can perform anonymous access, and the privacy of the sensitive data access client is also protected.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +1
Identity-based multi-proxy signature method and device for protecting private key
ActiveCN113346992ADoes not increase the risk of leakageAvoid revocation of identity issuesKey distribution for secure communicationUser identity/authority verificationPhysical securityInternet privacy
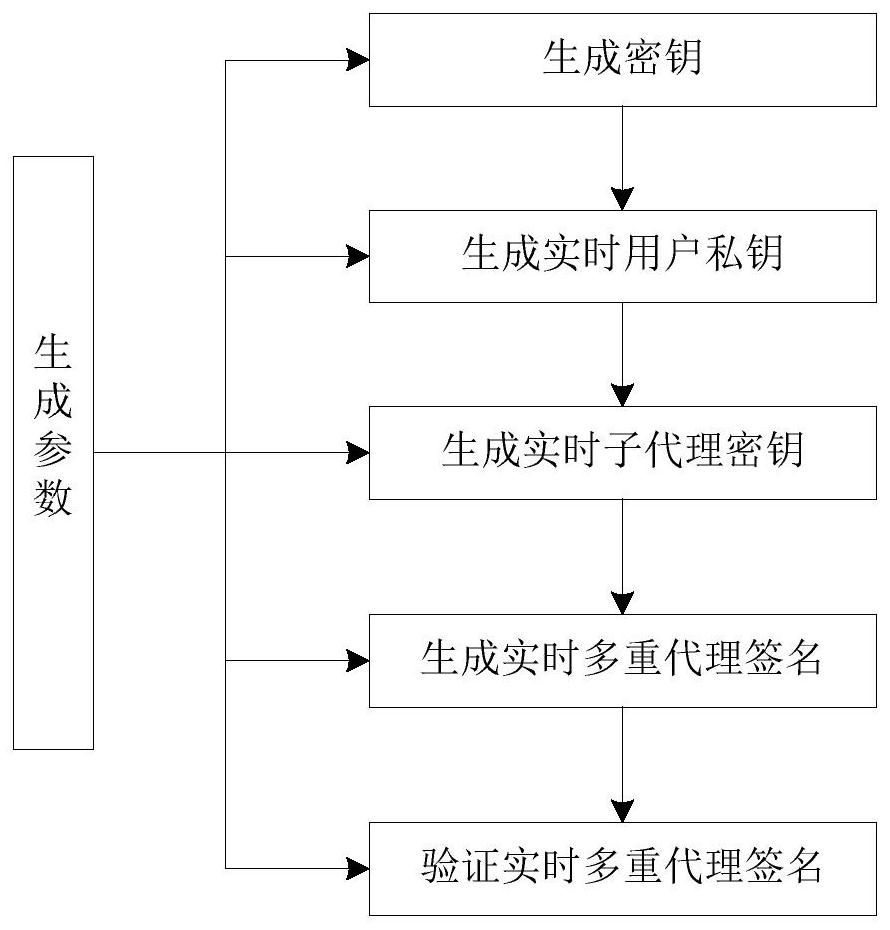
The invention discloses an identity-based multi-proxy signature method and device for protecting a private key. The method comprises the following steps: (1) constructing an identity-based multi-proxy signature system and establishing system parameters; (2) generating a real-time user private key and an assistant secret key; (3) generating real-time sub-proxy keys of n proxy signers; (4) combining the n proxy signers to generate a real-time multi-proxy signature; and (5) after receiving the real-time multi-proxy signature, the message verifier verifying the real-time multi-proxy signature by using the identity of the original signer and the identities of the n proxy signers. According to the invention, an independent and physically safe credible assistor is arranged for each original signer and proxy signer, and the assistor helps the original signer and proxy signer to generate the initial private key of the cryptosystem when the original signer and proxy signer utilize the secret values selected by the original signer and proxy signer, so that the identity revocation problem is avoided, and the key leakage prevention function is realized.
Owner:HUAIYIN INSTITUTE OF TECHNOLOGY
Block chain hosting transaction method and system for multi-party collaborative privacy protection
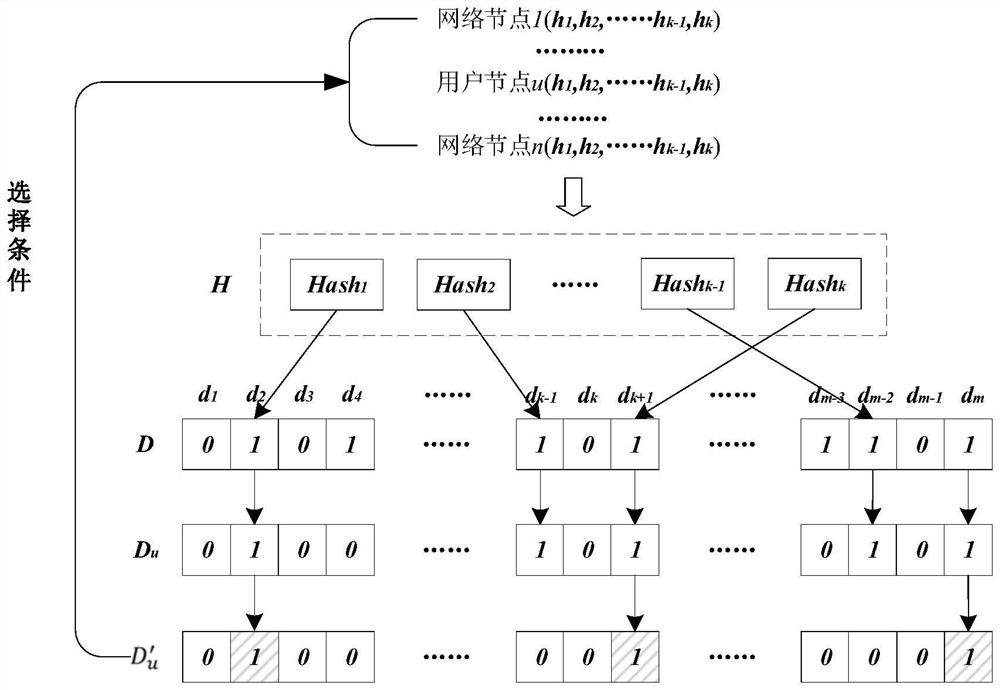
PendingCN114565386AEnhanced anonymityAvoid exposureDigital data protectionPayment protocolsDigital currencyComputer network
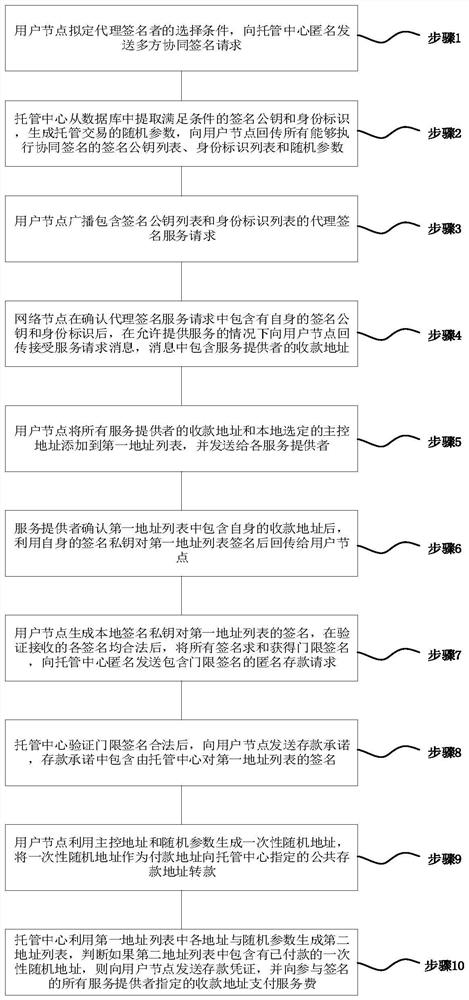
The invention relates to a block chain trusteeship transaction method and system for multi-party collaborative privacy protection, and the method comprises the steps: initiating a deposit request to a trusteeship center through a user node, and enabling the trusteeship center to distribute a signature public key and identity information of a legally registered proxy signature service provider for the user node; then providing self-signature components for the user node by a service provider through negotiation, and aggregating the signature components which contain the self-signature of the user and are not less than a threshold number so as to obtain a threshold signature with a collaborative protection characteristic, so that the independent signature of the user node is completely hidden in the threshold signature; a personal signature of a user node is prevented from being directly exposed to a hosting center under the condition that a signature validity verification function is ensured, so that a digital currency input address and a signer identity cannot be associated; in addition, the trusteeship center isolates the user deposit transaction from the payment service fee transaction, and the deposit address of the user node is transparent to the service provider, so that the user anonymization is completely realized.
Owner:潘林浪
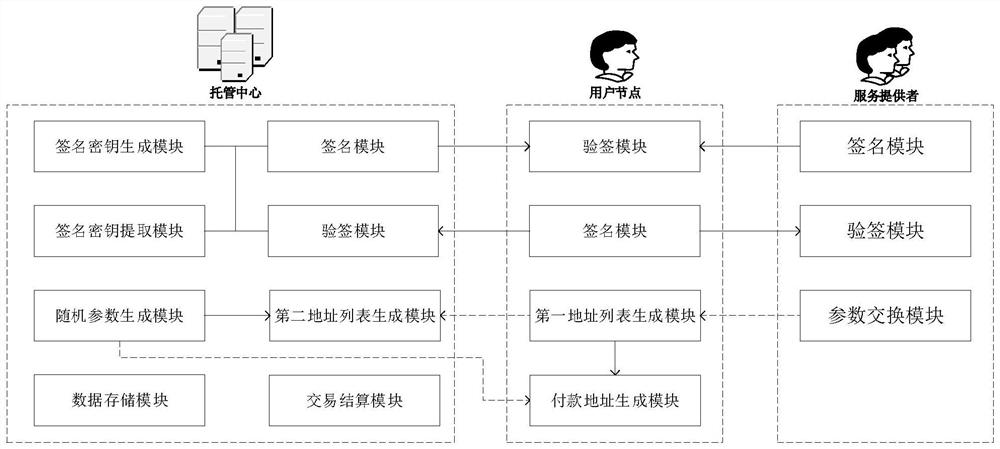
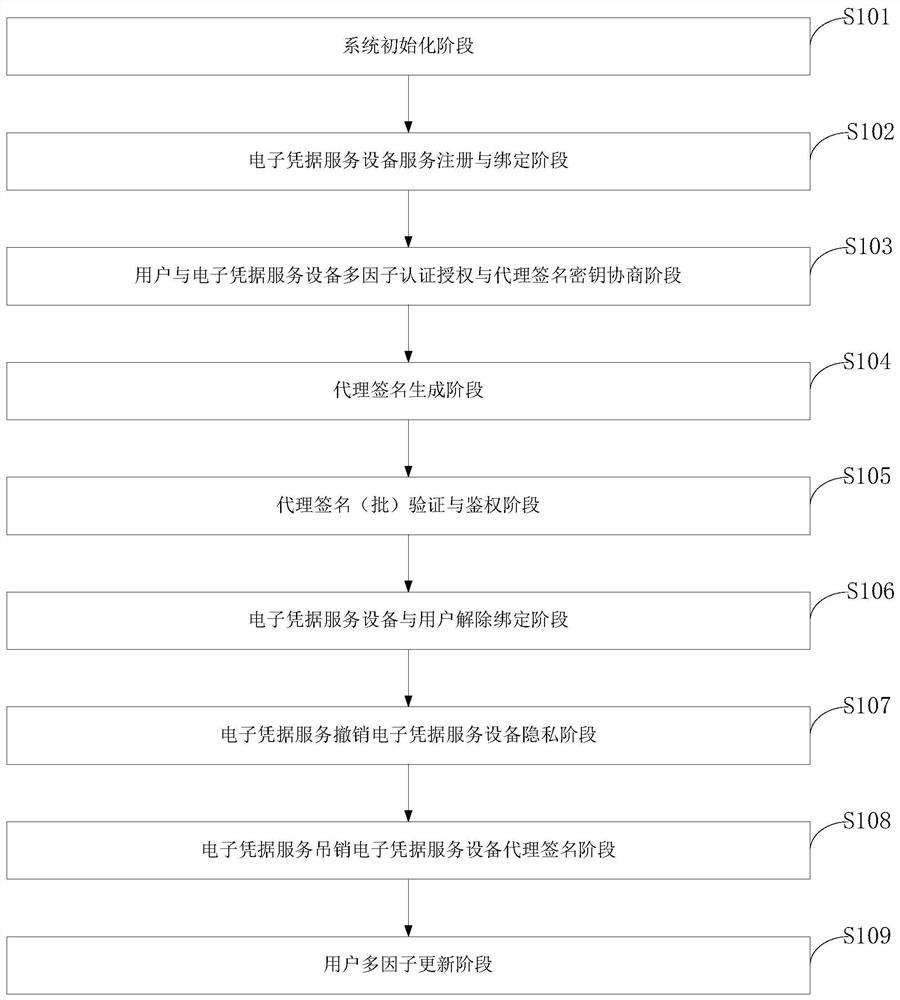
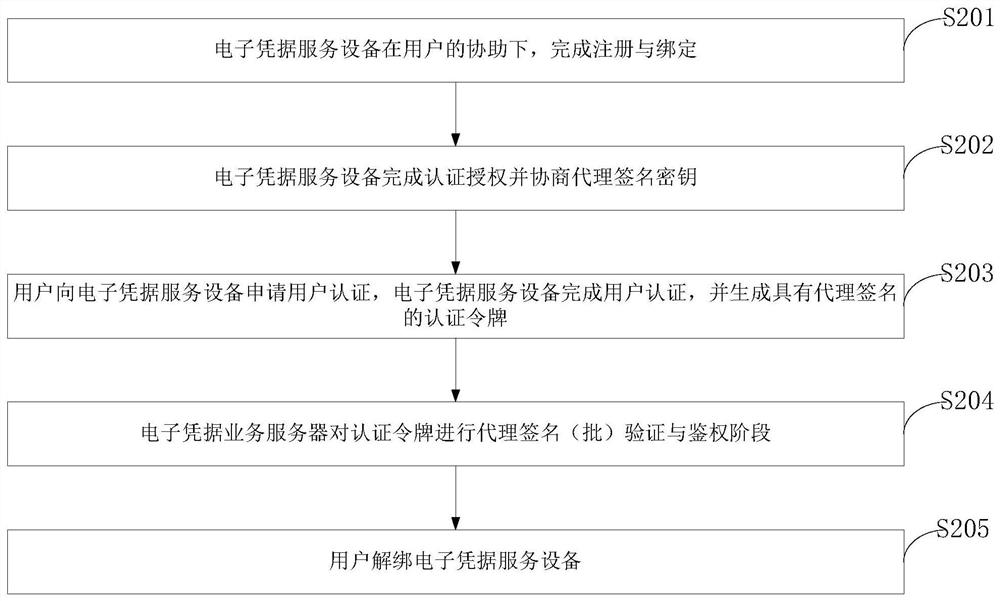
Security authentication and authorization control method, control system and program storage medium
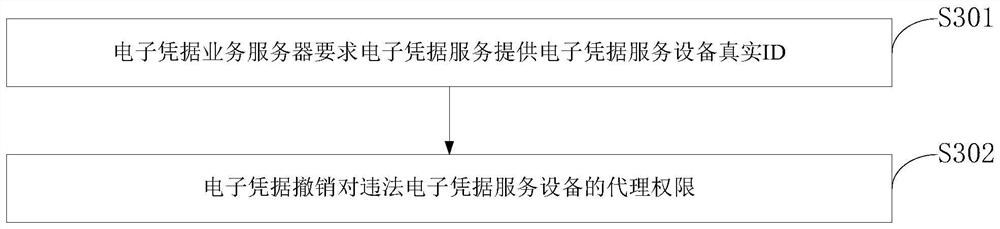
ActiveCN112968779ADistinguishable withAvoid abuseUser identity/authority verificationData packInternet privacy
The invention belongs to the technical field of communication network security, and discloses a security authentication and authorization control method, a control system and a program storage medium. After a user completes registration and binding with an electronic credential service device, an electronic credential authentication service submits user authentication information to the electronic credential service device, and generates a user service authentication code. Immediately, the electronic credential service equipment completes agreement of the proxy signature right and the signature key with the electronic credential authentication service equipment. After the user completes authentication interaction with the electronic credential service equipment, the user obtains the token with the proxy signature, and then authentication access to other services of the electronic credential can be achieved by adding the token into the data packet. The electronic credential may perform signature verification or batch verification on the token according to other services. For the agency signer with violation, privacy revocation can be realized and the abuse behavior can be graded, so that the abuse behavior of the agency signer can be further corrected.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com