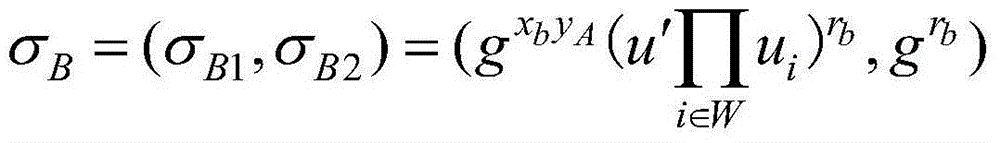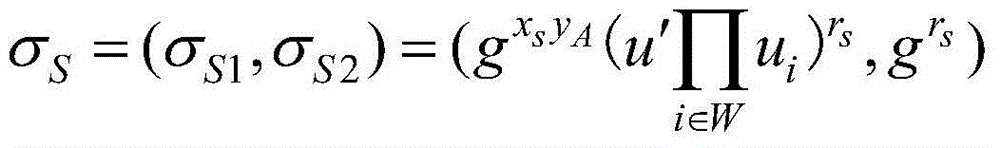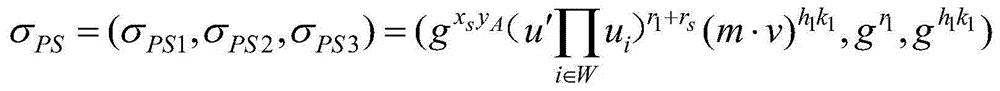High non-camouflage realization method of revocable proxy signature
A proxy signature and implementation method technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of non-masquerading and poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The specific steps of the method for realizing the strong unforgeability of the revocable proxy signature of the present invention are as follows:
[0040] Glossary:
[0041] SEM: Security Mediator, Security Mediator;
[0042] KGC: Key Generation Center, Key Generation Center, is responsible for generating the public keys of original signer A and proxy signer B;
[0043] A: original signer;
[0044] B: proxy signer;
[0045] C: signature verifier;
[0046] sk A : private key of original signer A, including sk Ax and sk Ay two parts;
[0047] sk B : private key of proxy signer B, including sk Bx and sk By two parts;
[0048] pk A : The public key of the original signer A, including pk Ax and pk Ay two parts;
[0049] pk B : public key of proxy signer B, including pk Bx and pk By two parts;
[0050] π: system public parameters;
[0051] l: system security parameters selected by the key generation center KGC;
[0052] p: a large prime number selected b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com