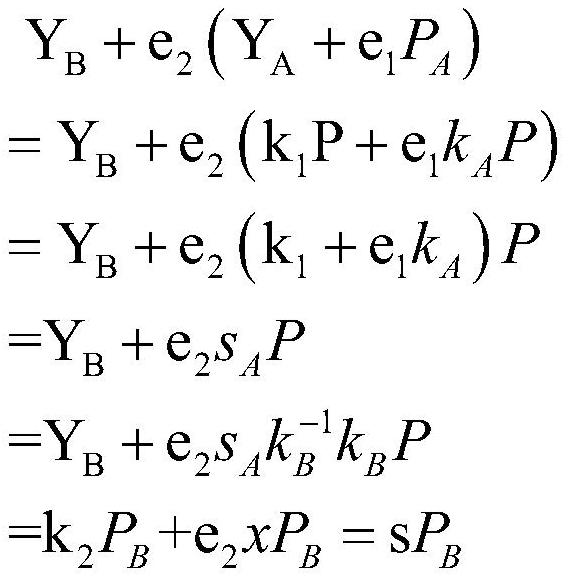Proxy digital signature method based on elliptic curve
An elliptic curve and digital signature technology, applied in digital data authentication, digital data protection, electronic digital data processing, etc., can solve the non-repudiation of abolishing the signature power of the proxy signer B, failing to obtain the original signer, and not meeting the signature requirements Sex and other issues, to achieve the effect of simple verification procedures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
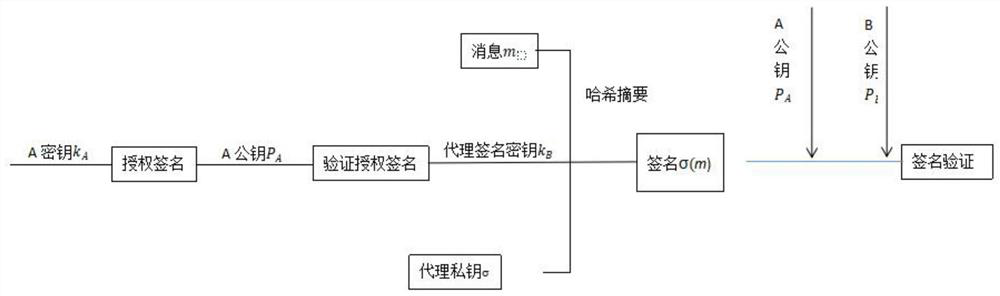
[0049] Example: see figure 1 , the present invention provides a technical solution: a proxy digital signature method based on elliptic curve, the specific method steps are as follows:
[0050] S1: initialization process; A represents the original signer; B represents the proxy signer; C represents the proxy signature verifier;
[0051] S11: Let E be built on a finite field F q An elliptic curve on P ∈ E and the order of point P is n;
[0052] S12: A randomly selects a positive integer k A , 0A A =k A P;
[0053] S13: B randomly selects a positive integer k B , 0B B =k B P;
[0054] S14: Public coefficient parameters {E, n, P, P A , P B};
[0055] S2: Entrustment process; A pairs entrusted information m A Do the following:
[0056] S21: A randomly selects k 1 , 01 A =k 1 P=(x A ,y A );
[0057] S22: Calculate r A ≡x A mod n, e 1 =h(m A ,r A ), s A ≡ e 1 k A +k 1 (mod n);
[0058] S23: Will (m A ,Y A ,s A ) to B, (Y A ,s A ) is to A to m A The s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com