Security setting and verifying method based on VR (Virtual Reality) equipment and terminal
A security verification and equipment technology, applied in the field of communications, can solve problems such as poor user experience and inability to perform verification, and achieve the effect of simple verification procedures, providing user experience, and a strong sense of context
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Embodiments of the present invention provide a VR device-based security setting and verification method and a terminal, which are used to improve user experience.
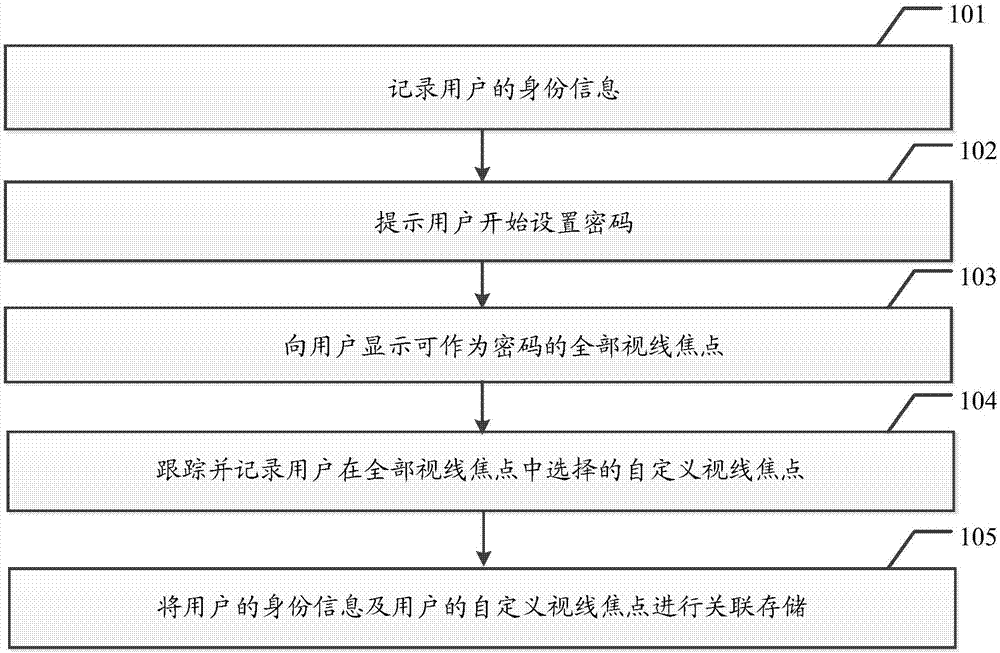
[0023] see figure 1 , an embodiment of the VR device-based security setting method in the embodiment of the present invention includes:
[0024] 101. Record the user's identity information;
[0025] When a user uses a VR device as a security tool, in order to ensure the accuracy and privacy of user information, the VR device binds and stores the user's identity information and password to facilitate the later verification of the user's identity by the VR device. Before the user sets a password, the user's identity information will be recorded.
[0026] 102. Prompt the user to start setting a password;
[0027] After the user enters his identity information in the VR device, the VR device prompts the user to start setting a password, and the user then enters his own password according to the prompt of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com