Blockchain evidence storage method and system based on witness side and shared symmetric key
A technology of symmetric key and symmetric encryption algorithm, applied in transmission system, digital transmission system, key distribution, can solve the problem of insufficient guarantee of the security, reliability and objectivity of certificate storage, lack of independent third-party witnesses, etc. problem, to ensure the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
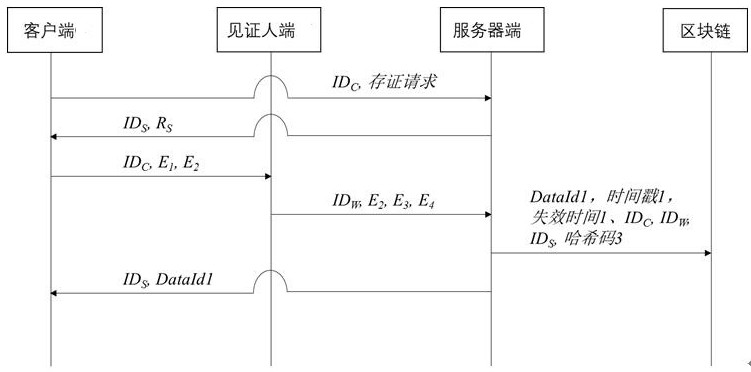
[0061] Blockchain storage method based on witness terminal and shared symmetric key
[0062] Including the client, the witness, and the server, where the server and the client share the first master key MK CS , the server and the witness share the second master key as MK SW , the witness end shares the third master key with the client MK CW .
[0063] The client, witness and server send data to each other through an encrypted channel, which can be SSL, TLS or HTTPS.
[0064] Such as figure 1 shown, including the following steps:
[0065] Step 1: the client encrypts the data Edata to be authenticated to form the first encrypted data and the second encrypted data, and the client sends the first encrypted data and the second encrypted data to the witness end; the first encrypted data It can be decrypted by the witness, and the second encrypted data can be decrypted by the server.
[0066] Step 1 specifically includes the following steps:
[0067] Step 1.1: The client s...
Embodiment 2
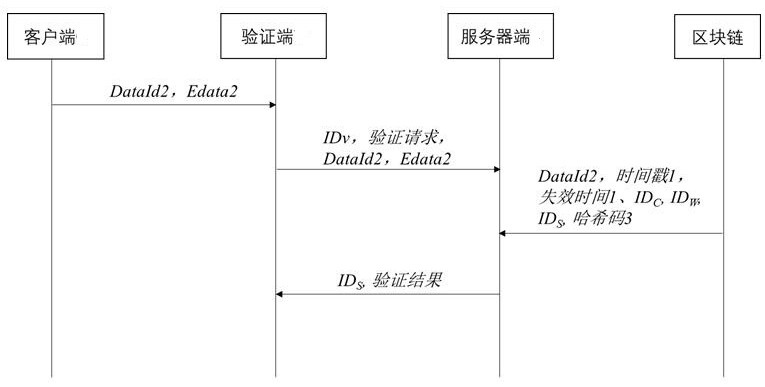
[0106] A blockchain certificate storage system based on witness terminal and shared symmetric key
[0107] include:
[0108] The client, the client encrypts the data to be authenticated Edata to form the first encrypted data and the second encrypted data, and the client sends the first encrypted data and the second encrypted data to the witness end; the first The encrypted data can be decrypted by the witness, and the second encrypted data can be decrypted by the server;
[0109] At the witness end, the witness end decrypts the first encrypted data to obtain the data Edata to be authenticated, and encrypts the data Edata to be authenticated to form the third encrypted data and the fourth encrypted data, and the witness end encrypts the second encrypted data The data, the third encrypted data, and the fourth encrypted data are sent to the server;
[0110] On the server side, the server side performs data verification according to the second encrypted data, the third encrypted...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com