Patents
Literature
3260 results about "Data verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data verification is a process in which different types of data are checked for accuracy and inconsistencies after data migration is done. It helps to determine whether data was accurately translated when data is transferred from one source to another, is complete, and supports processes in the new system. During verification, there may be a need for a parallel run of both systems to identify areas of disparity and forestall erroneous data loss.
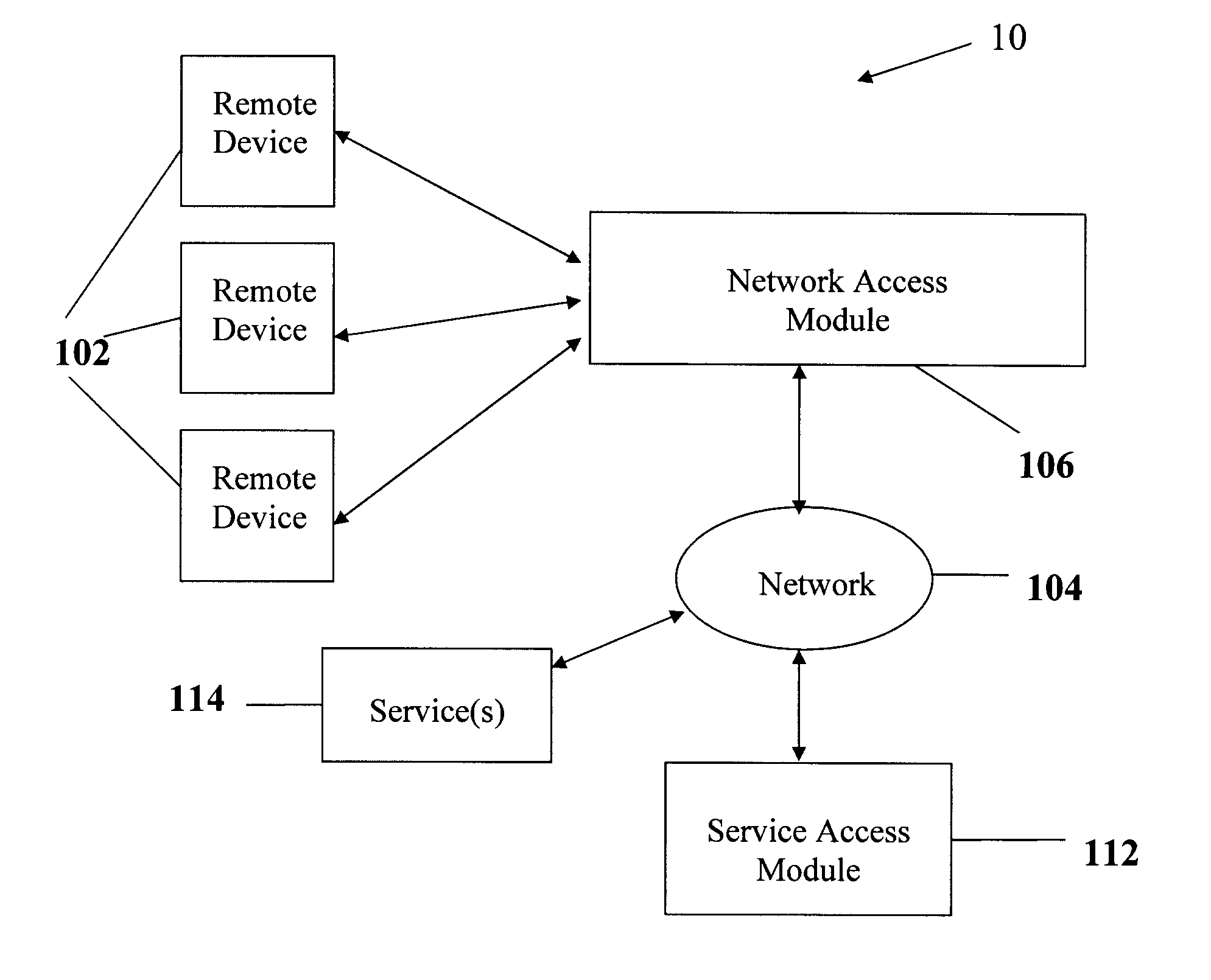
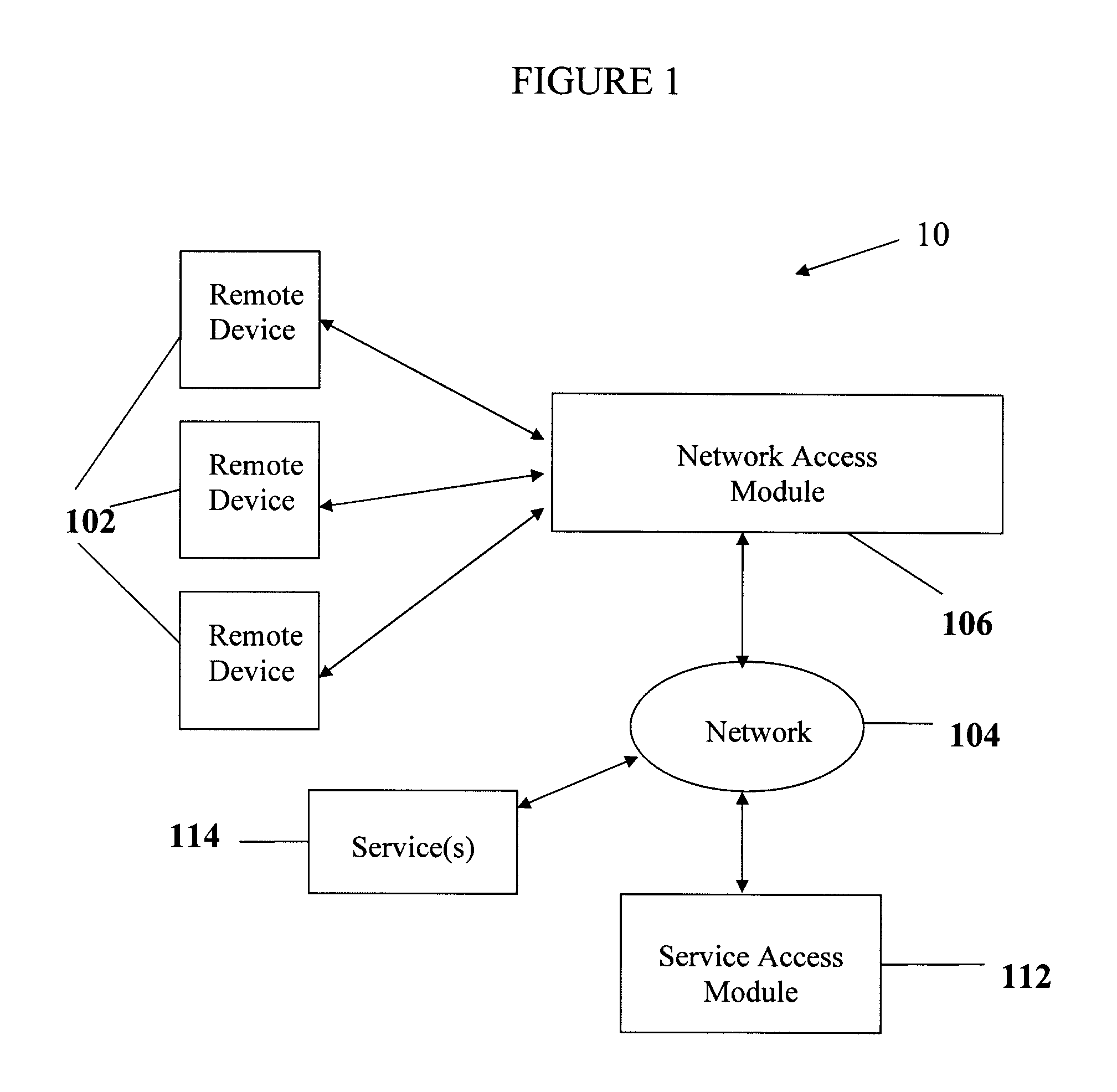
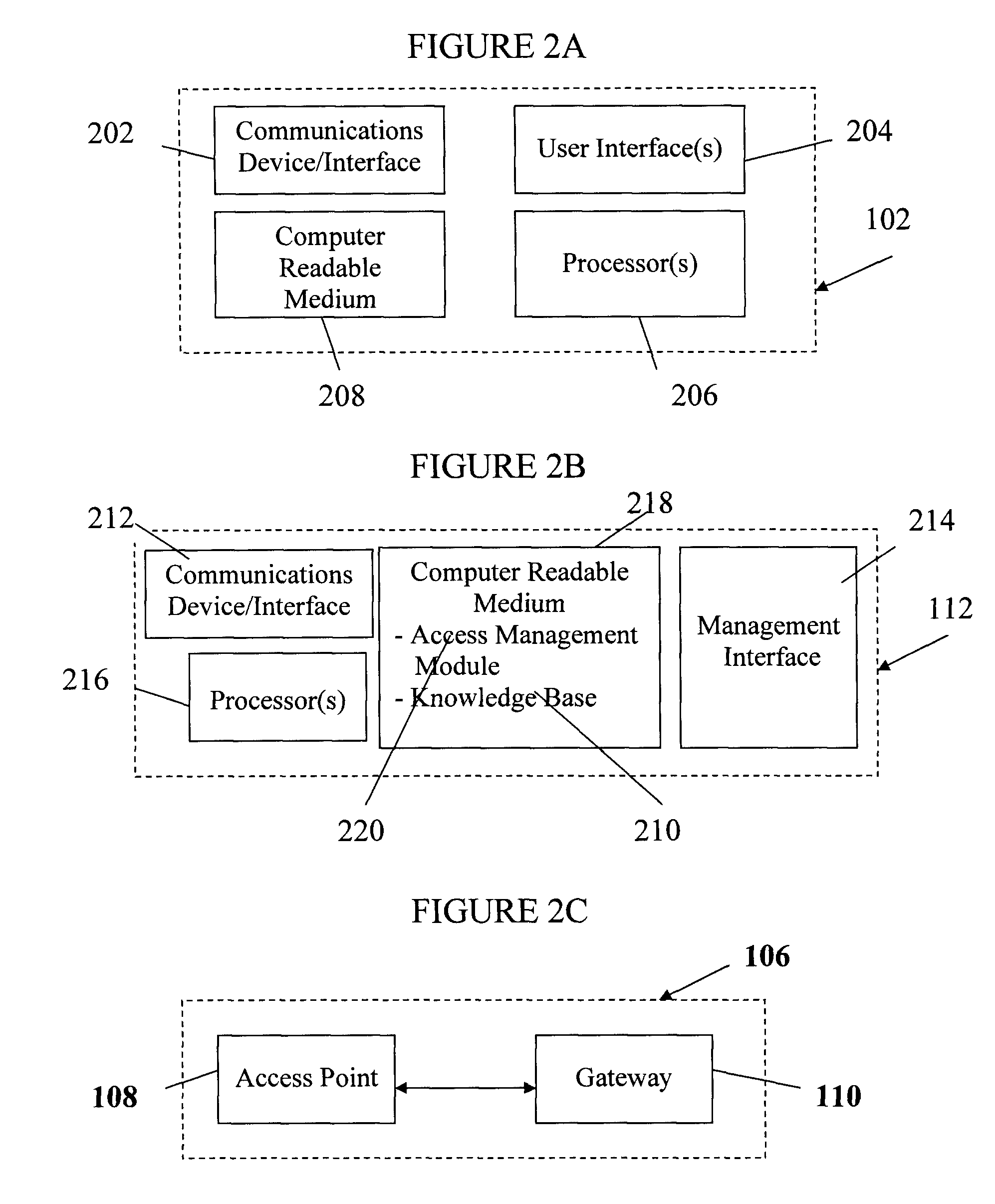
Remote service access system and method
InactiveUS20100107225A1Limited accessDigital data processing detailsMultiple digital computer combinationsData validationComputer network
A wireless service access system and method are disclosed. One aspect of the disclosed system provides a remote device wireless access to one or more services over a communication network, the system comprising a network access module adapted for communicating wirelessly with the remote device and for receiving therefrom identifying data; and a service access module, communicatively linked to the network access module, for authenticating the remote device based on the identifying data and authorizing access to the one or more services thereto via the network access module.
Owner:DATAVALET TECH
System and method for integrating and validating genotypic, phenotypic and medical information into a database according to a standardized ontology
InactiveUS20070178501A1Safest and most effective treatmentGood decisionData processing applicationsMicrobiological testing/measurementData validationMedical record
The system described herein enables clinicians and researchers to use aggregated genetic and phenotypic data from clinical trials and medical records to make the safest, most effective treatment decisions for each patient. This involves (i) the creation of a standardized ontology for genetic, phenotypic, clinical, pharmacokinetic, pharmacodynamic and other data sets, (ii) the creation of a translation engine to integrate heterogeneous data sets into a database using the standardized ontology, and (iii) the development of statistical methods to perform data validation and outcome prediction with the integrated data. The system is designed to interface with patient electronic medical records (EMRs) in hospitals and laboratories to extract a particular patient's relevant data. The system may also be used in the context of generating phenotypic predictions and enhanced medical laboratory reports for treating clinicians. The system may also be used in the context of leveraging the huge amount of data created in medical and pharmaceutical clinical trials. The ontology and validation rules are designed to be flexible so as to accommodate a disparate set of clients. The system is also designed to be flexible so that it can change to accommodate scientific progress and remain optimally configured.
Owner:NATERA
Systems and methods for client-based web crawling
InactiveUS20050071766A1The process is fast and accurateReducing server-client communication trafficData processing applicationsWeb data indexingData validationSource Data Verification
The present invention provides systems and methods for obtaining information from a networked system utilizing a distributed web crawler. The distributed nature of clients of a server is leveraged to provide fast and accurate web crawling data. Information gathered by a server's web crawler is compared to data retrieved by clients of the server to update the crawler's data. In one instance of the present invention, data comparison is achieved by utilizing information disseminated via a search engine results page. In another instance of the present invention, data validation is accomplished by client dictionaries, emanating from a server, that summarize web crawler data. The present invention also facilitates data analysis by providing a means to resist spoofing of a web crawler to increase data accuracy.
Owner:MICROSOFT TECH LICENSING LLC
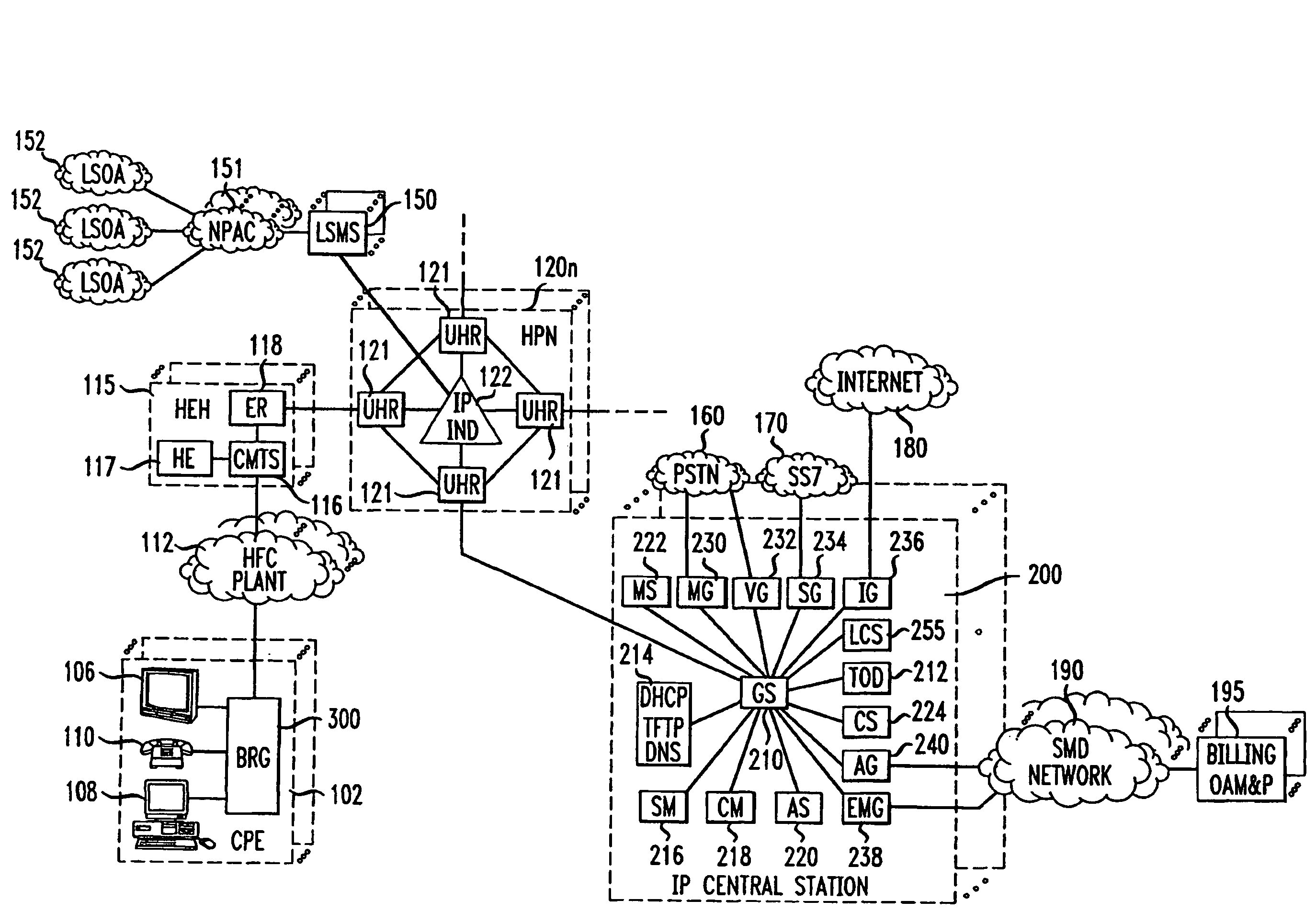
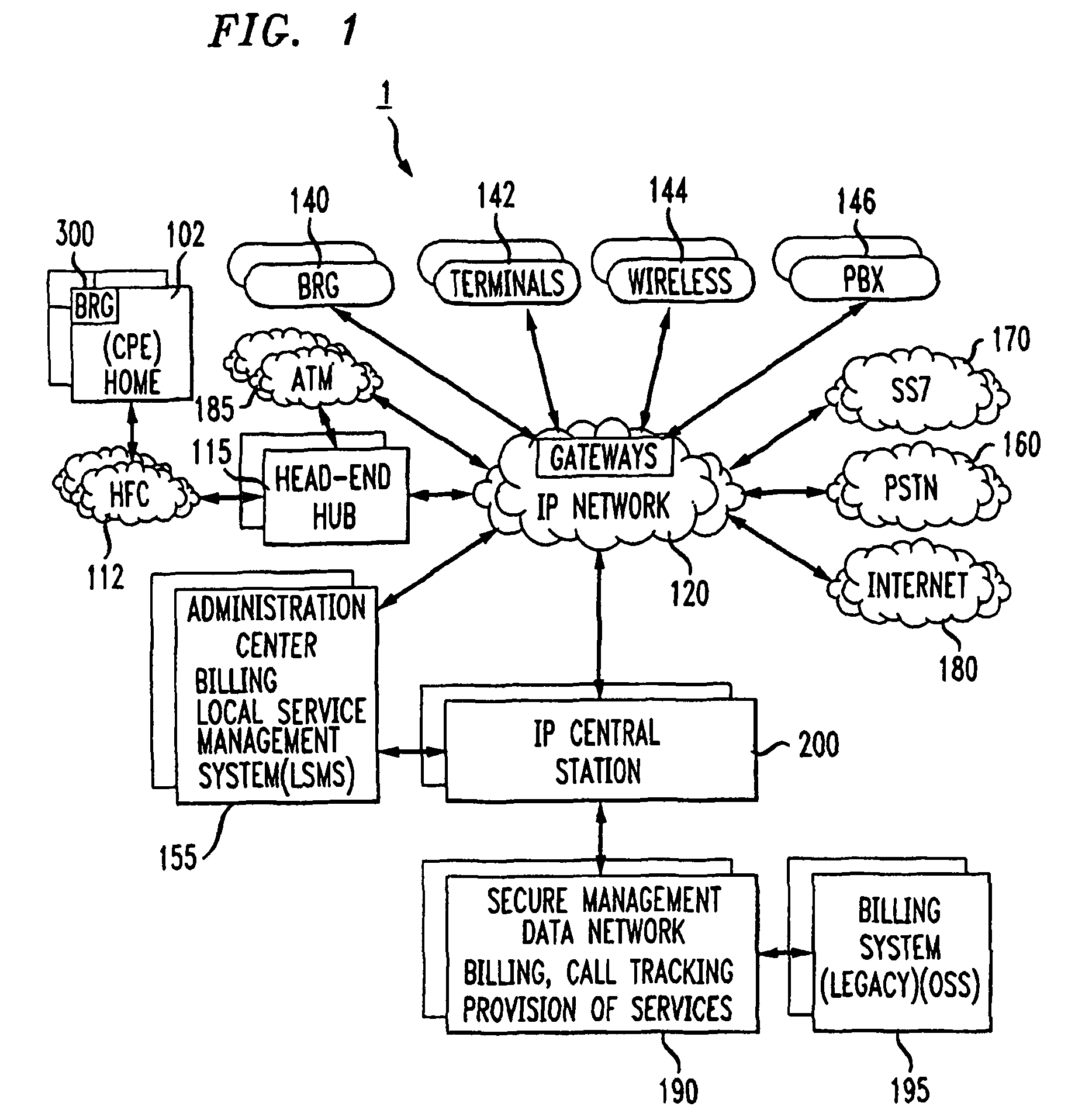
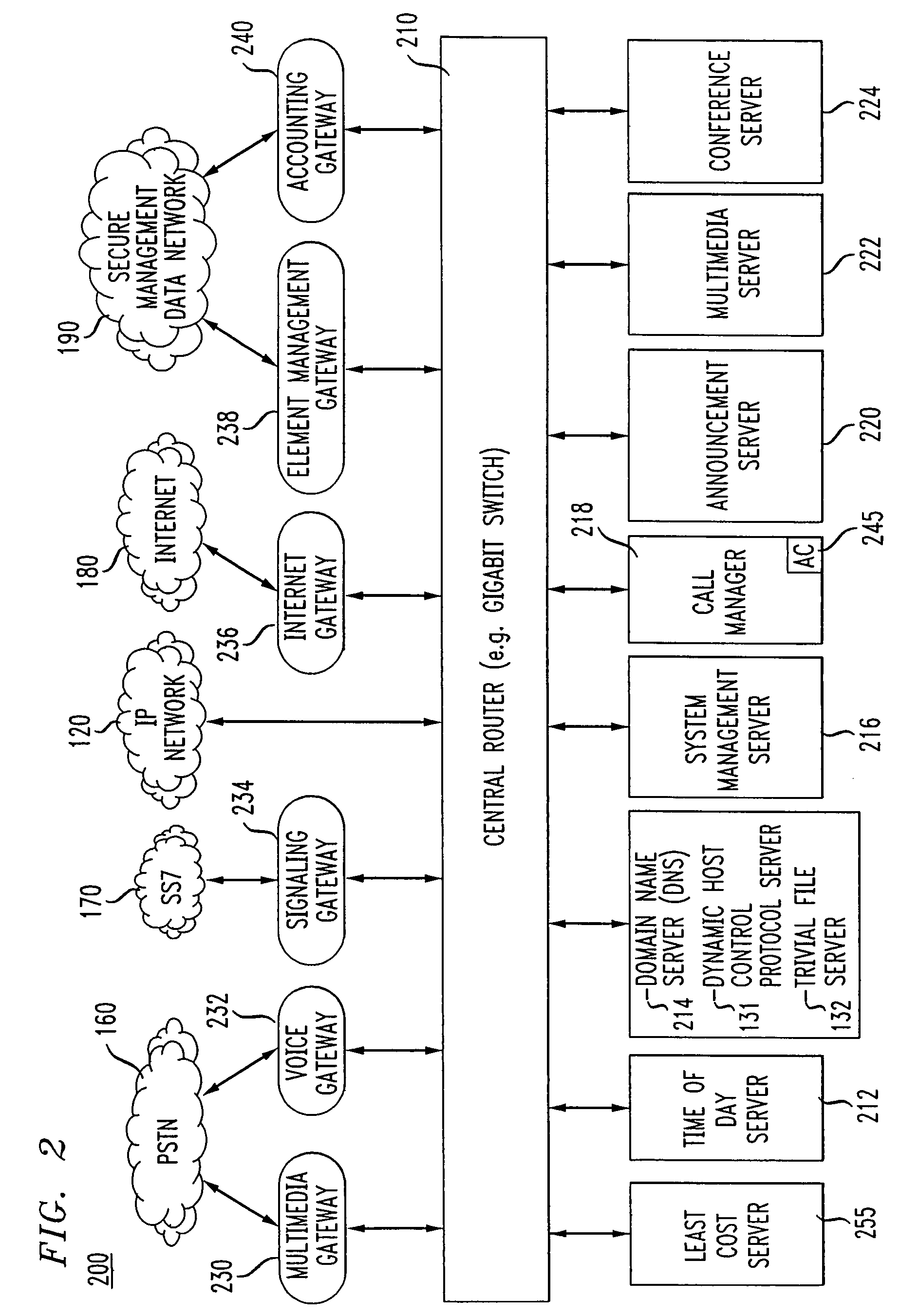
Method for billing IP broadband subscribers
InactiveUS7760711B1Metering/charging/biilling arrangementsTelephonic communicationQuality of serviceLeast cost
A method of billing a variable bit rate communication between a first terminal and a distant terminal to a broadband subscriber permits changing billing parameters during a call in real time in response to user inputs including user requested changes in quality of service, changes in data rate and changes in preferred service provider. A variable bit rate communication to be billed has a variable quality of service related to the degree of utilization of a plurality of different networks. The billing method comprises the steps of i.) receiving user identification data at a first terminal and data representing a required bit rate and a default quality of service selected by the user, ii.) verifying the user identification data to be associated with the broadband service subscriber, iii.) determining least cost alternative network resources available for achieving the communication at the user selected default quality of service and the required bit rate, iv.) determining cost data associated with the network resources, v.) outputting to the user a least cost for the communication according to their selected default quality of service and alternative least cost network resources, vi.) coupling the first terminal and the distant terminal via the least cost determined network resources at the default quality of service and the required bit rate responsive to user authorization and vii.) billing for the communication at the default quality of service and according to the required bit rate after the termination of the communication.
Owner:AT&T INTPROP II L P
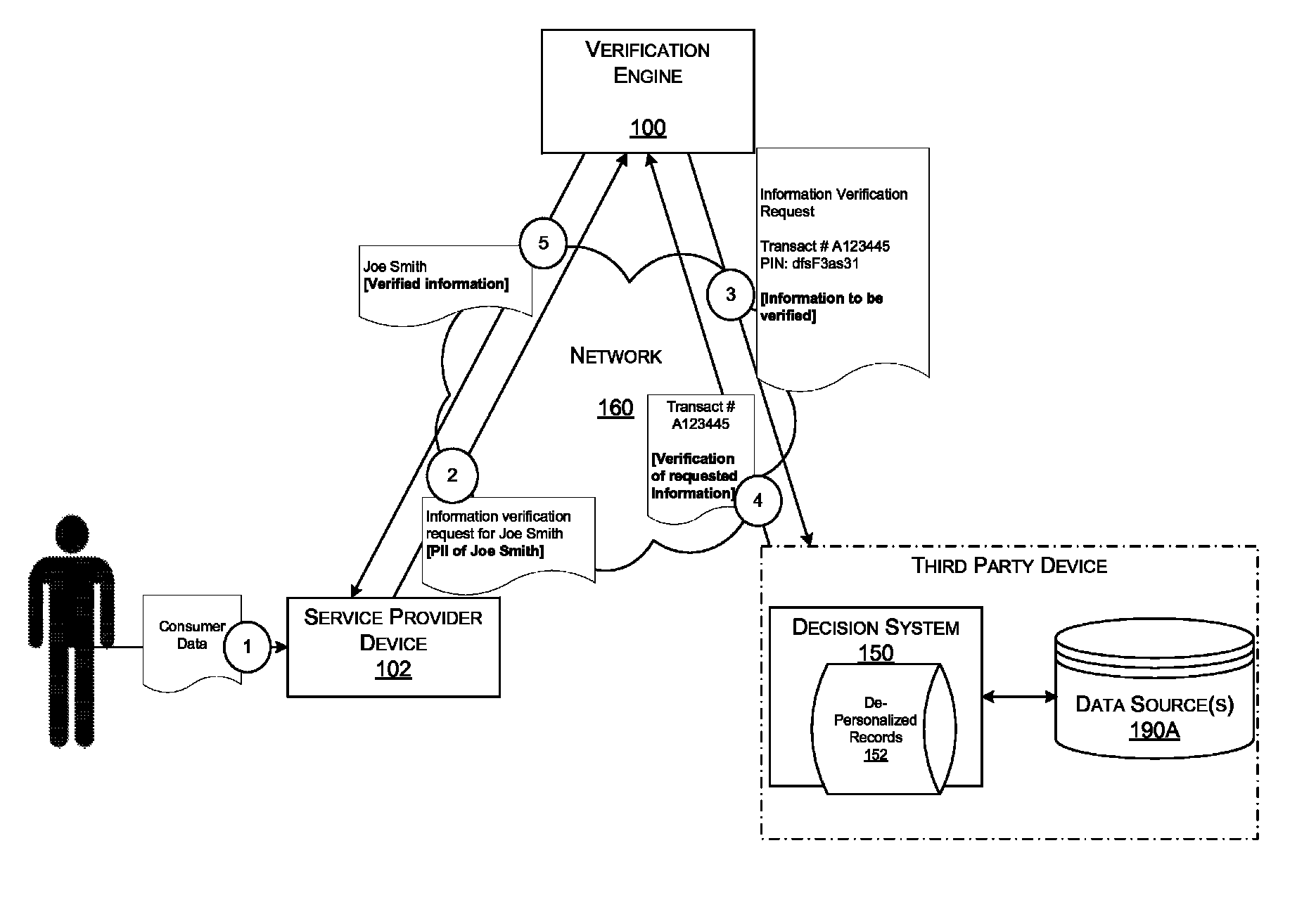
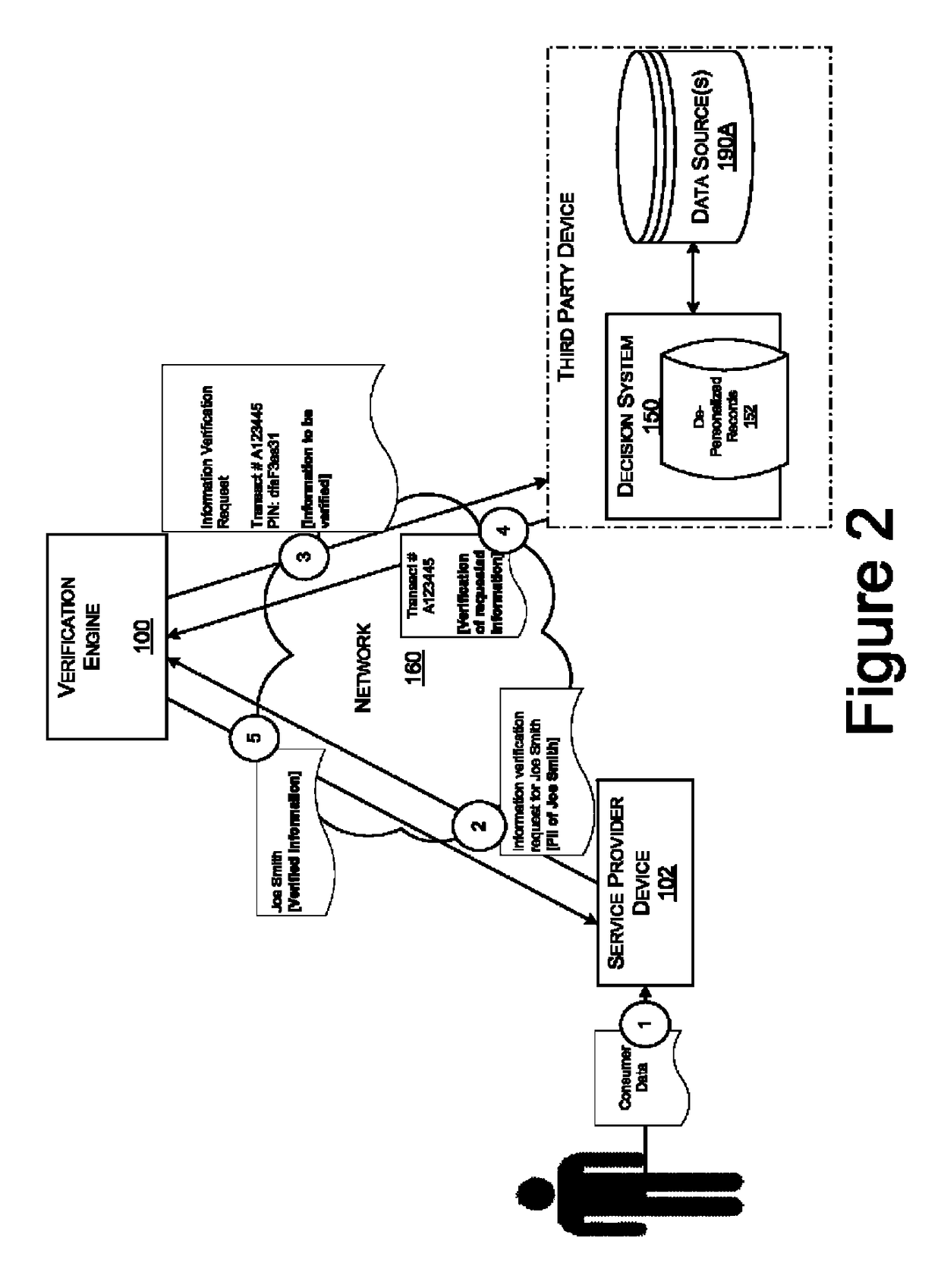
Data verification using access device
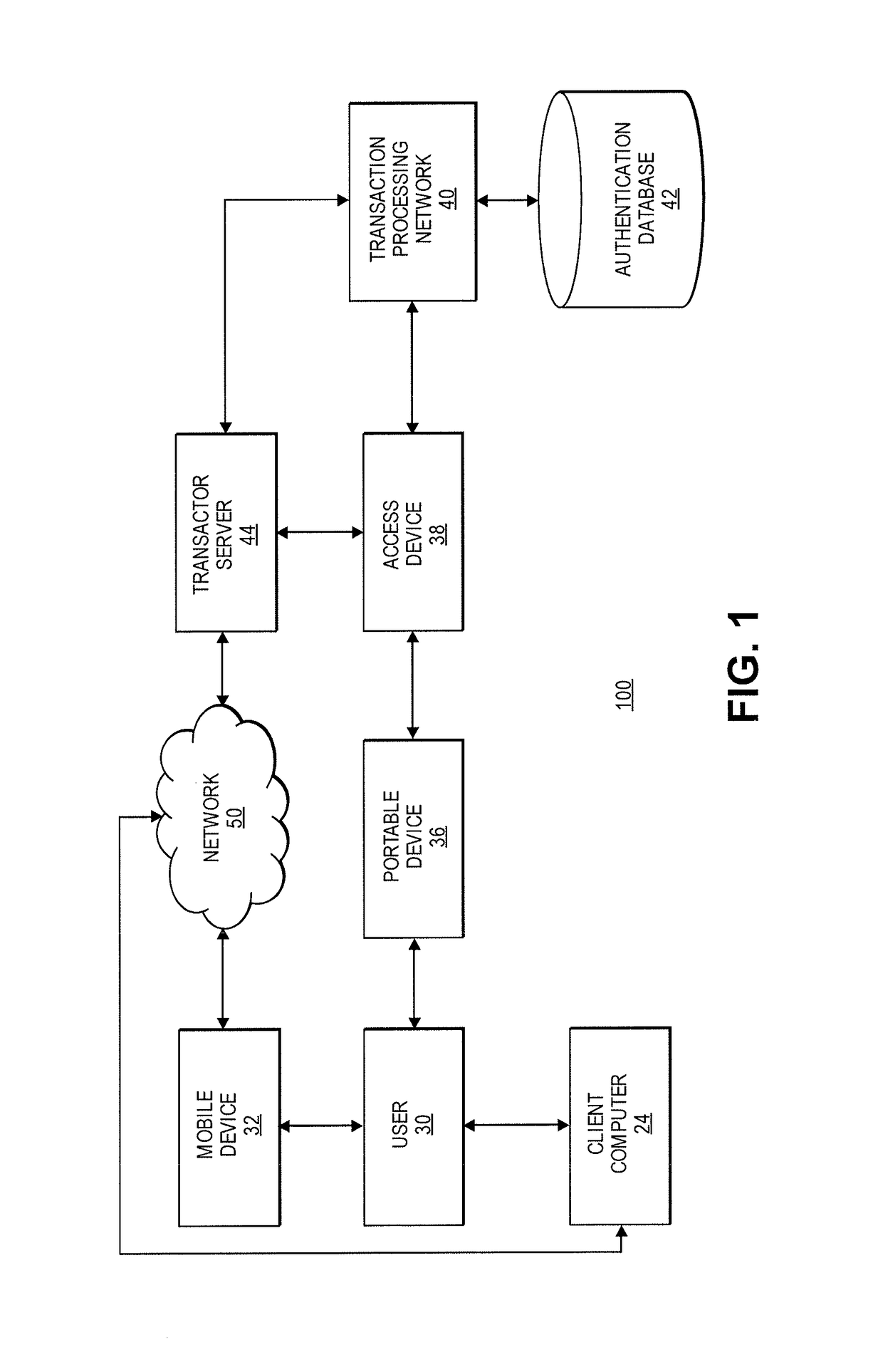
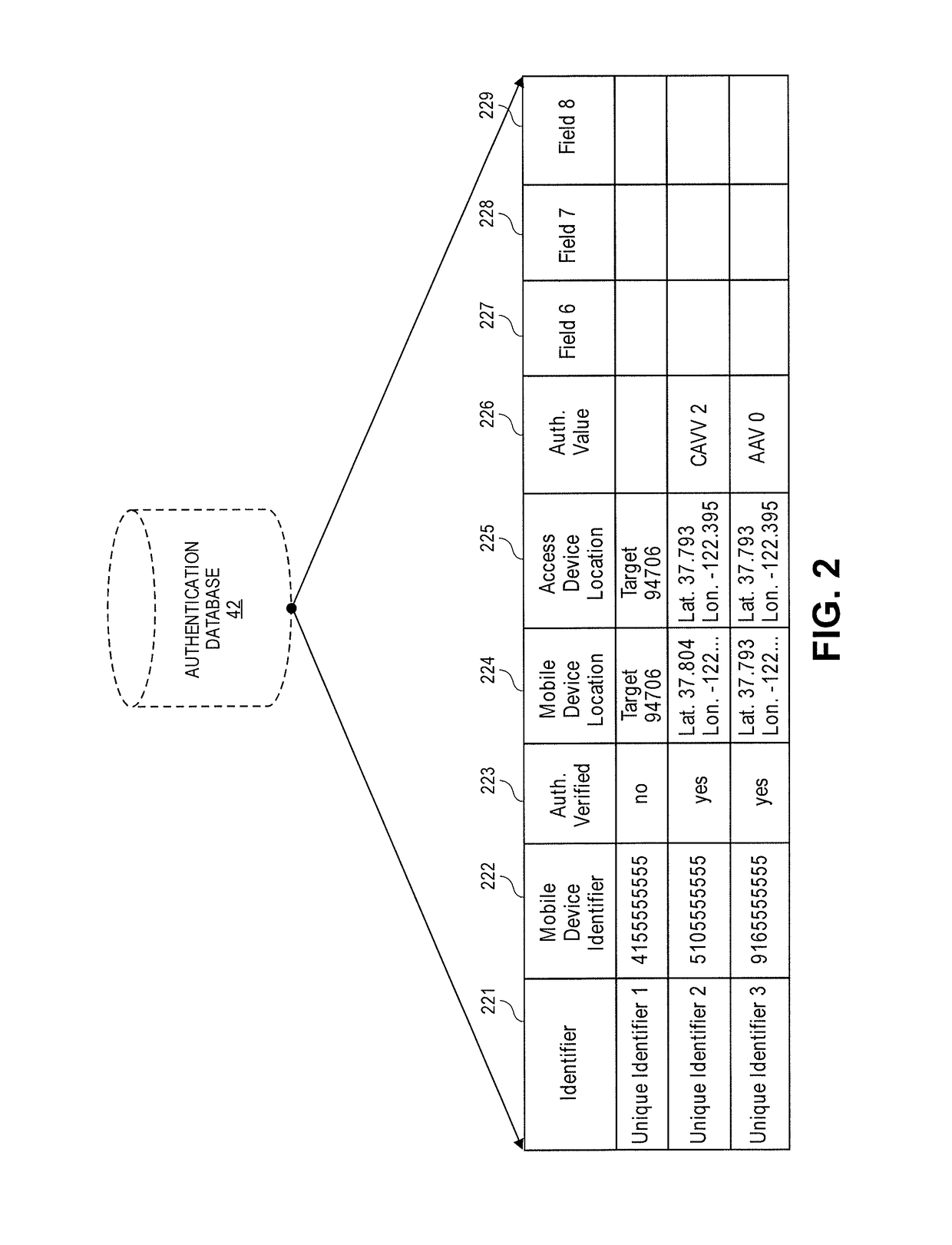
ActiveUS9680942B2Reduce transactionDigital data processing detailsLocation information based serviceTransaction dataMobile device
An embodiment of the invention is directed to a method comprising receiving, at a server computer, information for a portable device that includes a mobile device identifier and storing, by the server computer, the information for the portable device that includes the mobile device identifier in a database associated with the server computer. The method further comprising receiving, by the server computer, transaction data from an access device for a transaction conducted at the access device, determining, by the server computer, from the transaction data that the transaction is associated with the portable device, determining, by the server computer, a location of the access device, determining, by the server computer, a location of a mobile device associated with the mobile device identifier, determining, by the server computer, that the location of the mobile device matches the location of the access device, and marking, by the server computer, the stored information for the portable device as authentication verified.
Owner:VISA INT SERVICE ASSOC
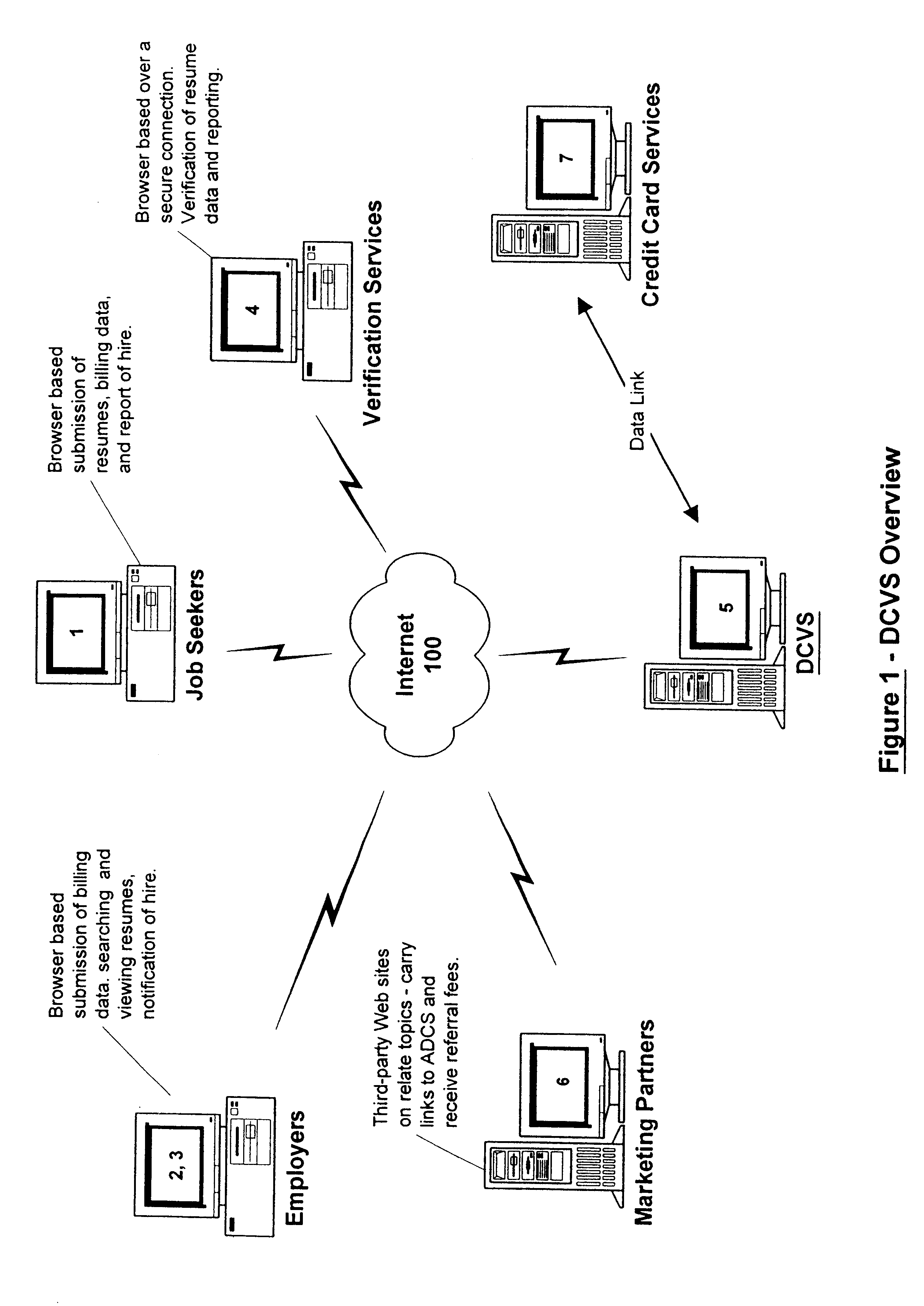
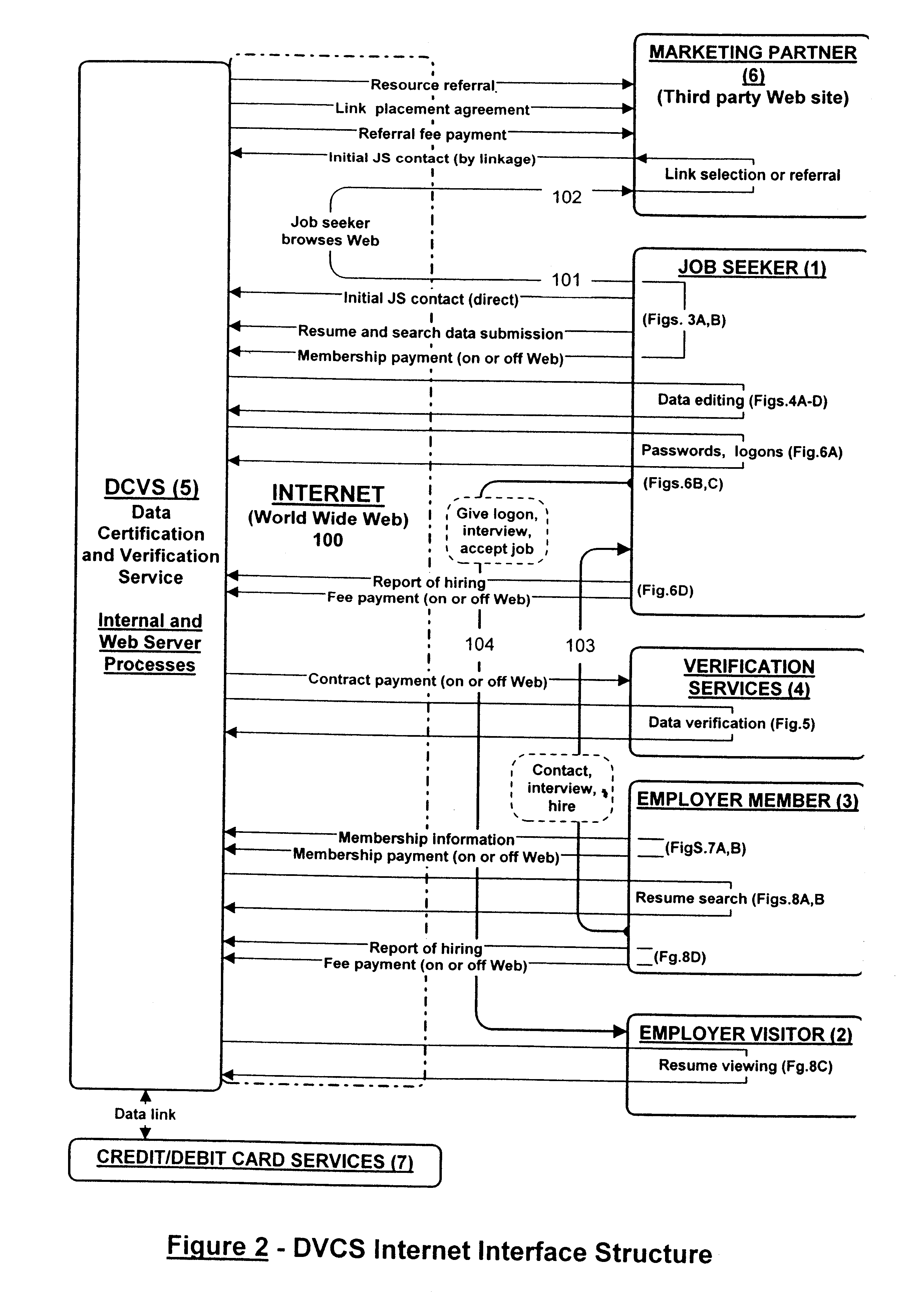
Data certification and verification system having a multiple-user-controlled data interface
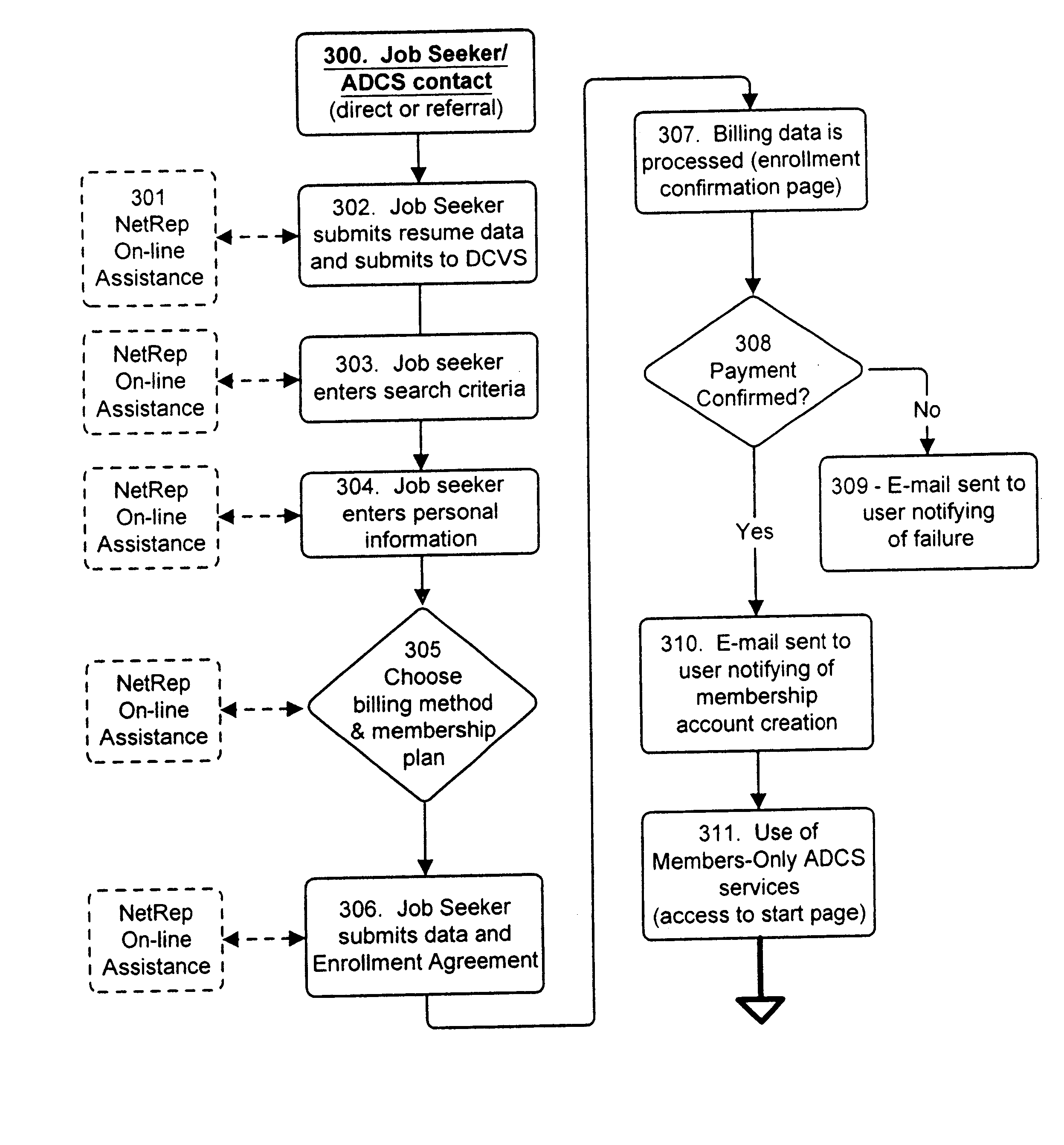
InactiveUS6658400B2Preserve valueFast and cost-effective operationComputer security arrangementsOffice automationData validationSource Data Verification
A method and apparatus is described for multiple-party data attribute management system and interface structure which permits different categories of users to contribute and control different types of source data, while adding informational value to data contributed by other users. The system provides a secure repository for verified and authenticated data, and provides a system of controlled access to the repository. The preferred embodiment of the invention comprises a data verification and certification system which in a principal embodiment is useful to create a data bank to match job seekers with potential employers based on verified resume data and employer specified search criteria. The interface structure The system of the invention preferably includes computer databases and interactive Internet based server systems.
Owner:VERIFIED HIRING
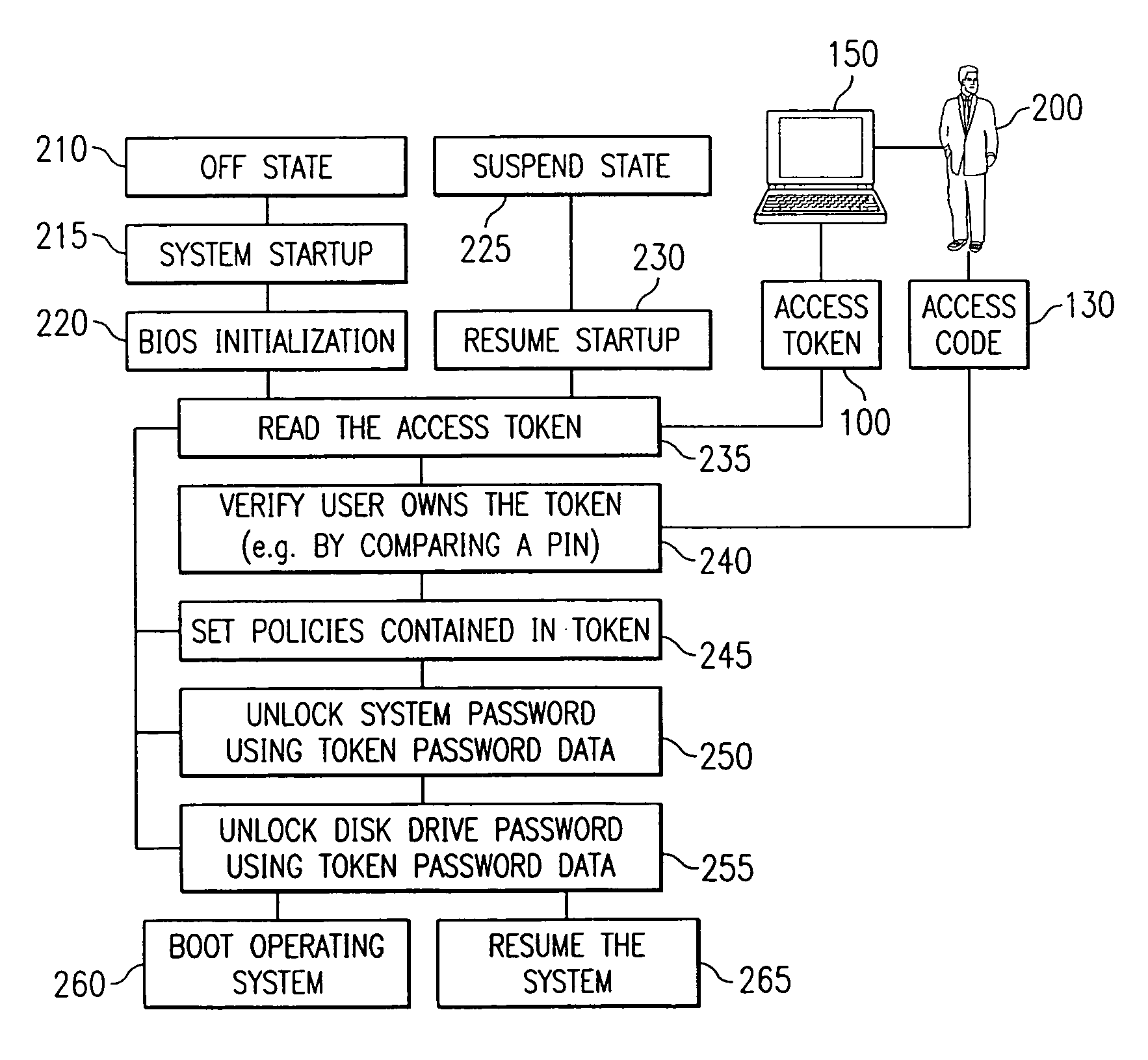
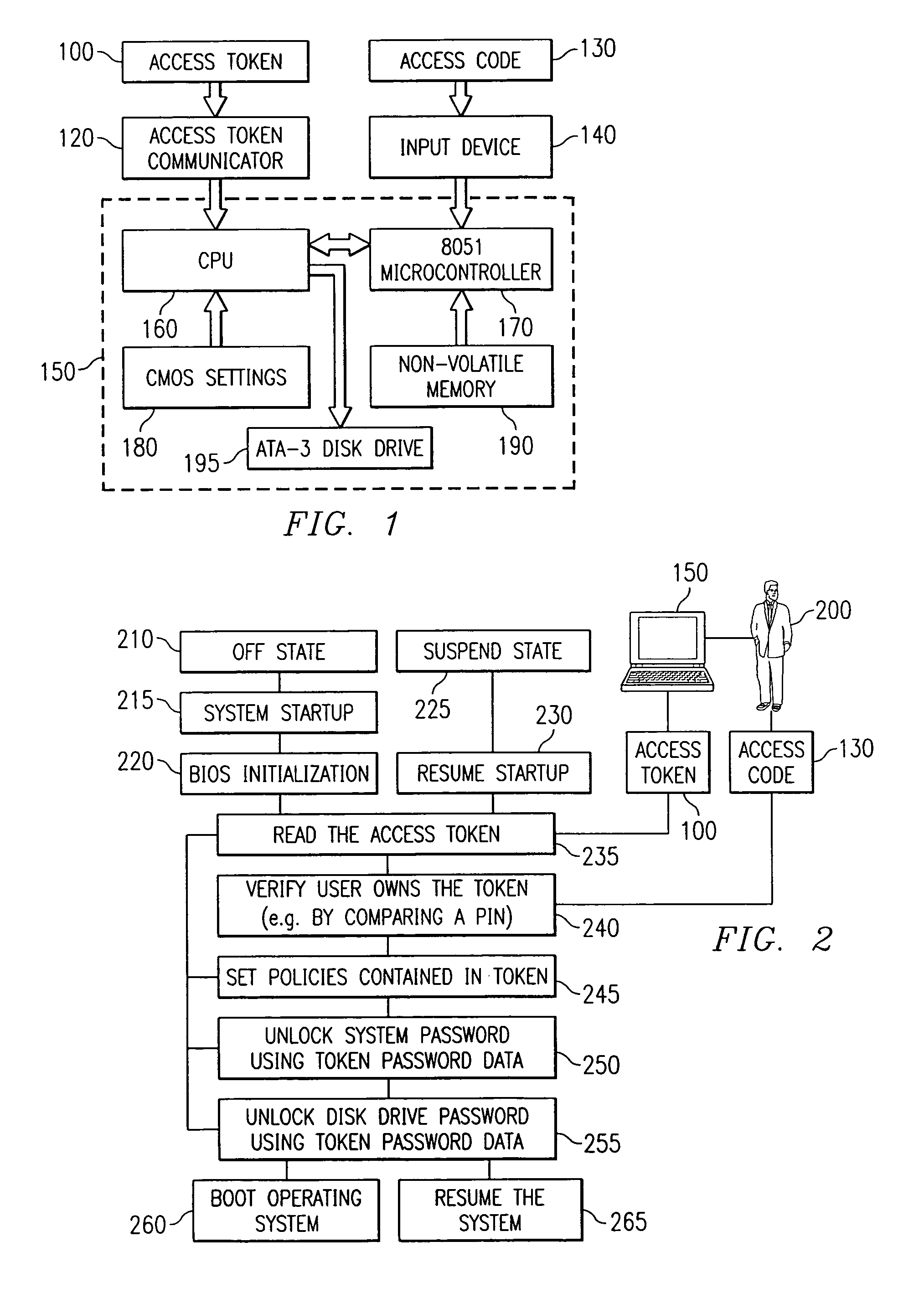
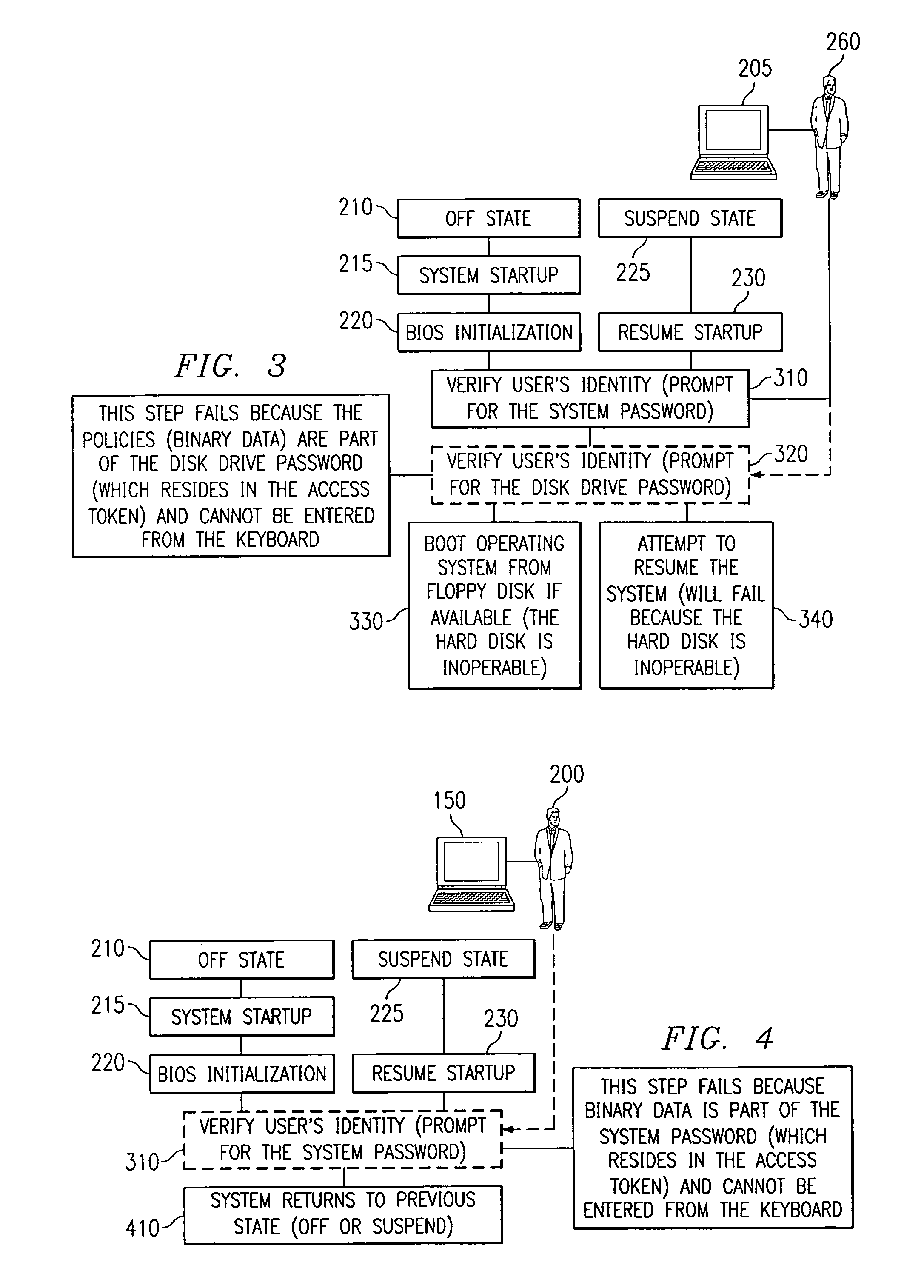
Portable computer system with hierarchical and token-based security policies
InactiveUS7111321B1Reduce the possibilityError detection/correctionVolume/mass flow measurementSource Data VerificationComputerized system
A computer system including a processor, an access token communicator capable of being coupled to the processor and adapted to read an access token, an input device coupled to the processor that is able to receive verification data that confirms authorized access of the access token, and software executable on the processor that includes instructions to control access to the processor and including code to access the access token and the verification data, code to verify the validity of the access token using the verification data, code to set security policies in the processor, and code to control access to resources in the processor based on the security policies. In addition, a method for reading an access token, verifying the validity of the access token, setting security policies in a computer system, and unlocking a computer system and a nonvolatile storage device attached to the computer system.
Owner:DELL PROD LP
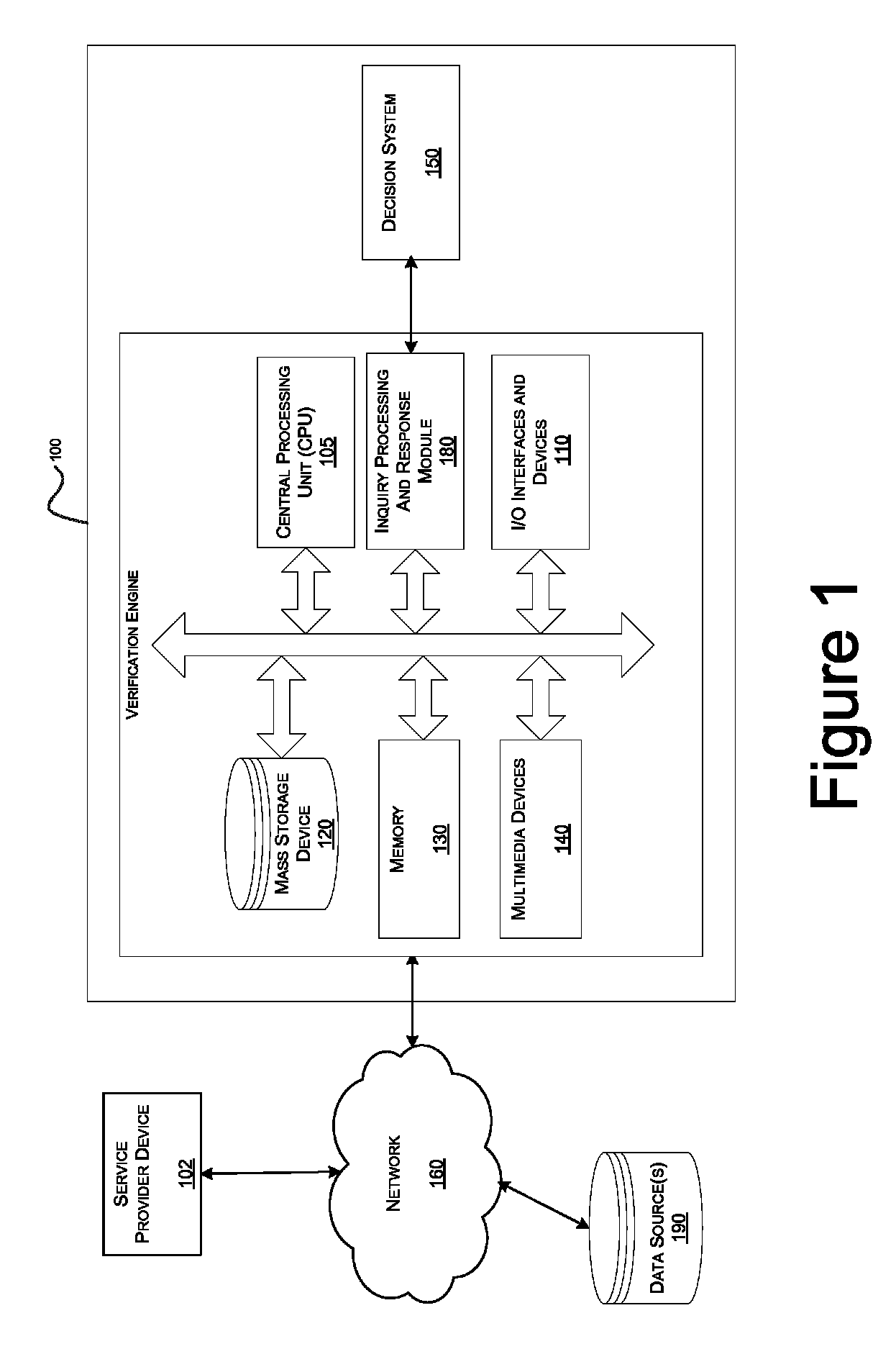
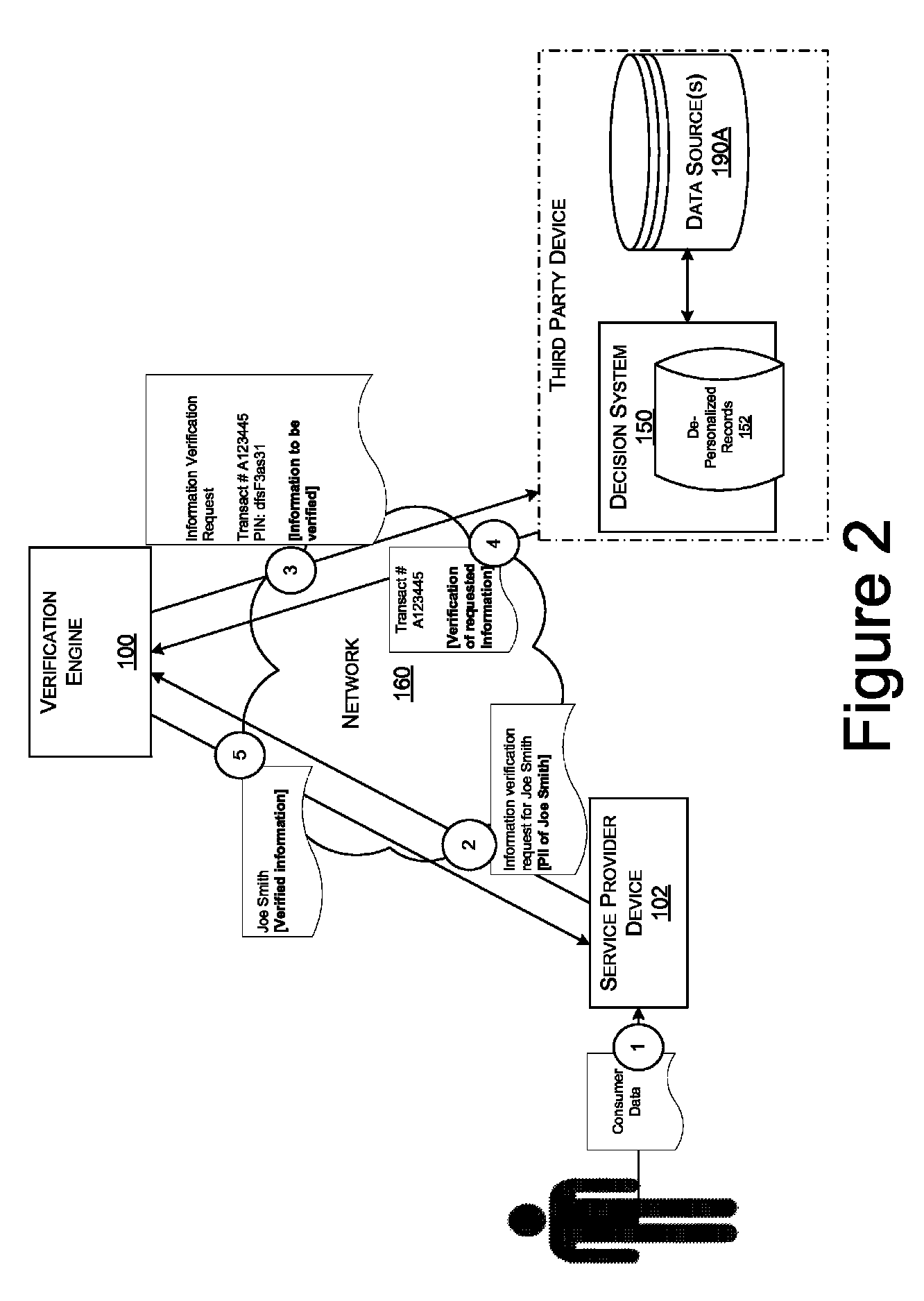
Systems and methods for data verification
Systems and methods for verifying data including income and employment, assets, healthcare claims, clinical data, and other types of data subject to various regulatory and / or privacy restrictions.
Owner:EXPERIAN INFORMATION SOLUTIONS
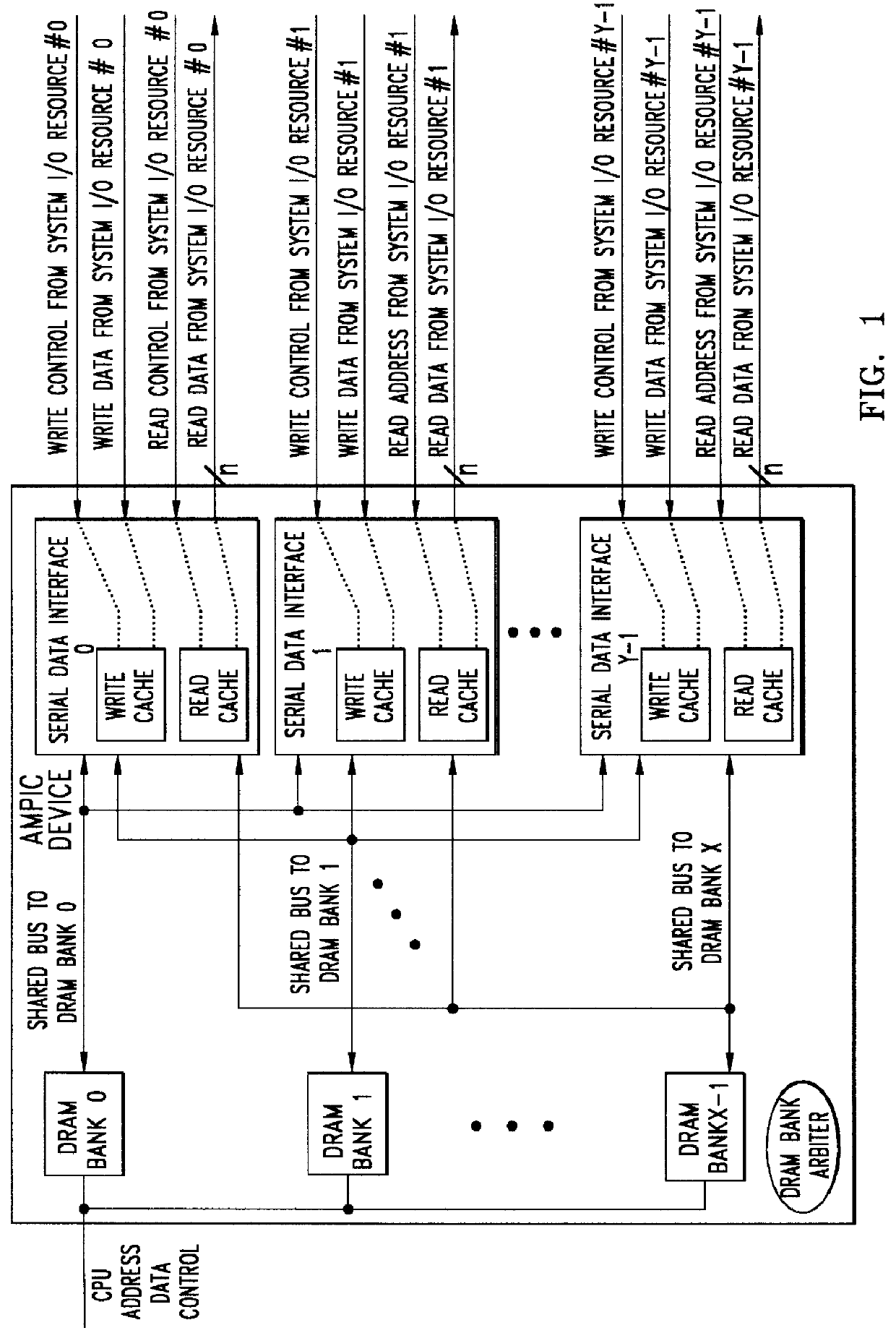
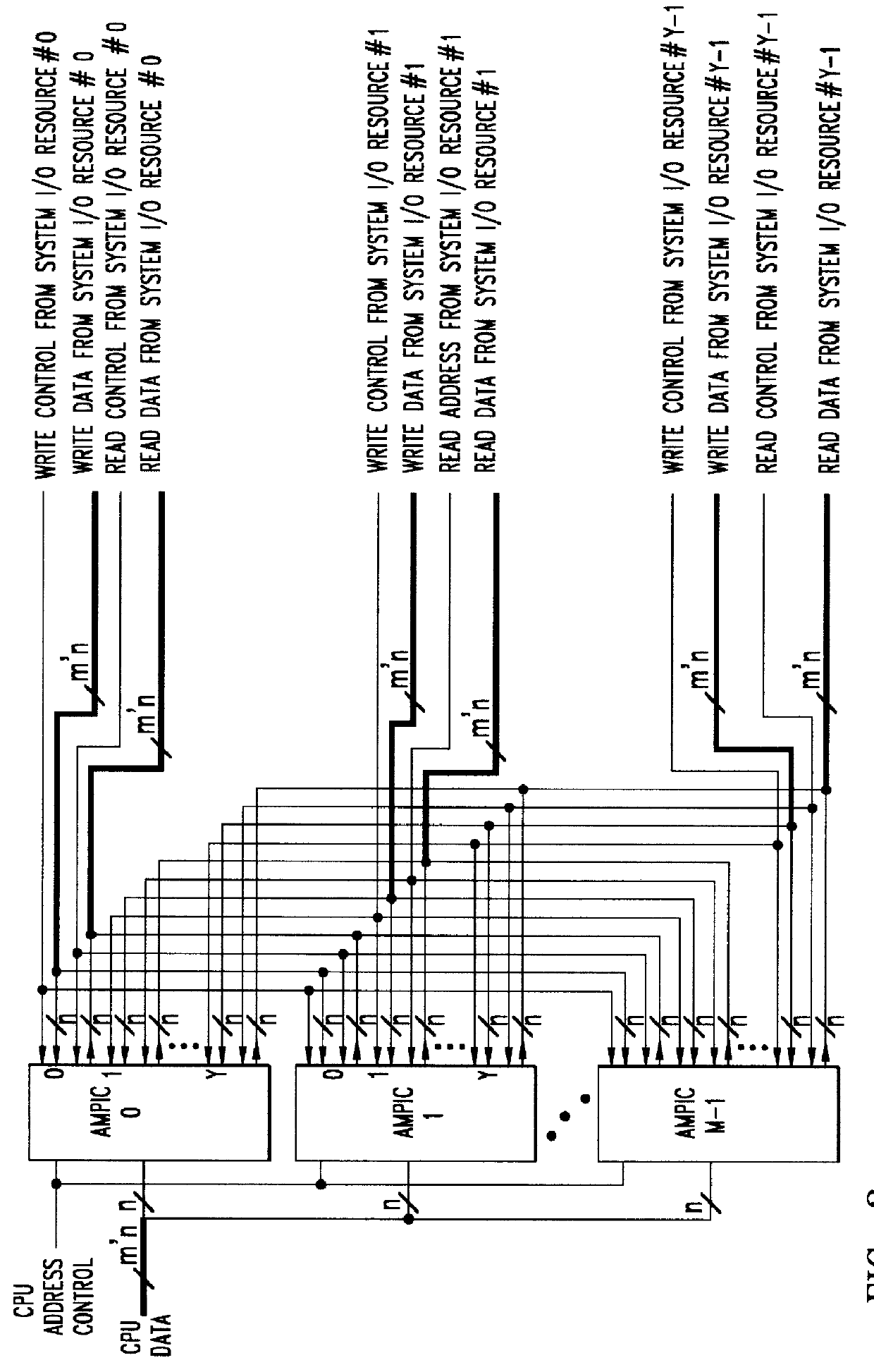
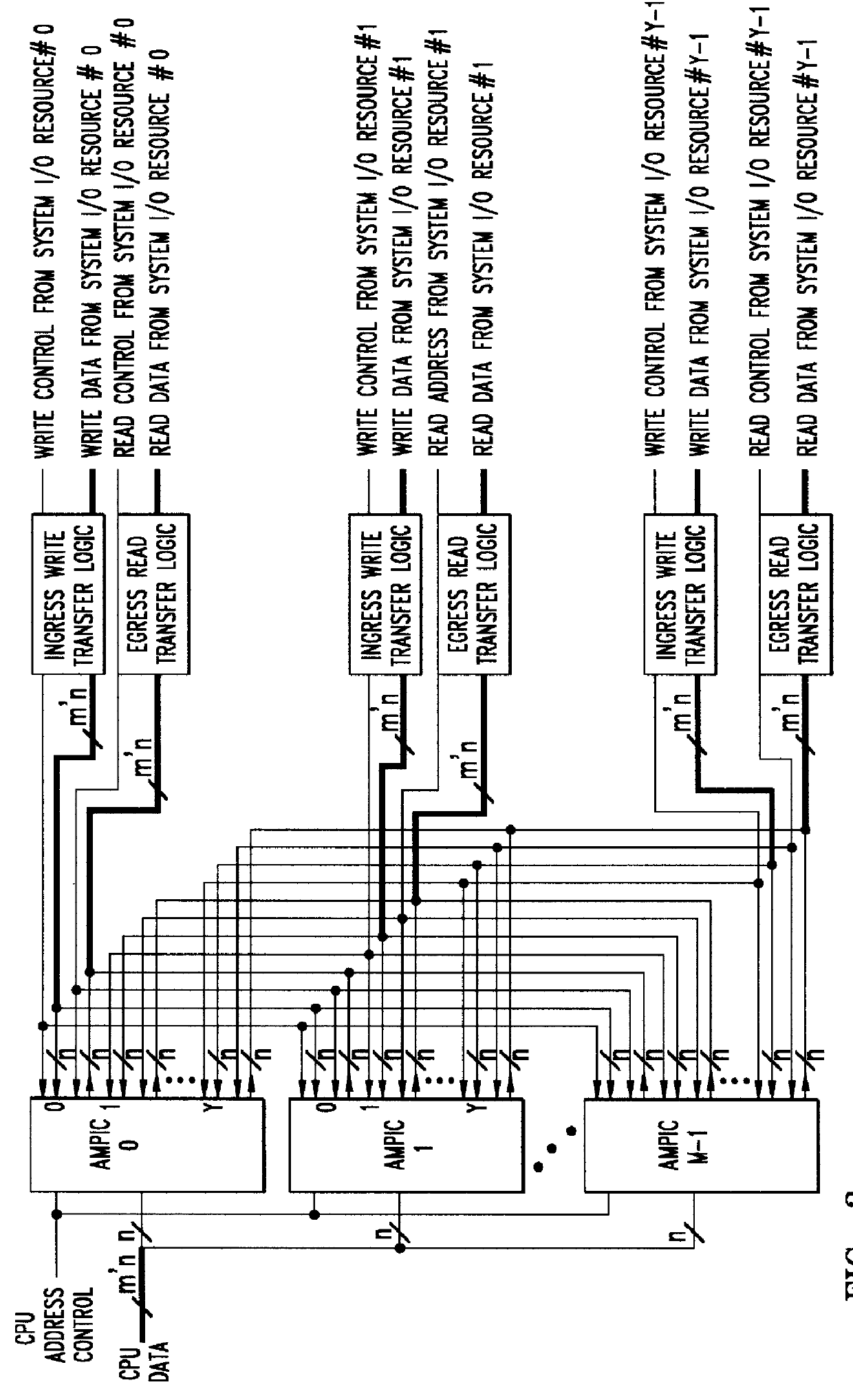
Method of and apparatus for validating data read out of a multi port internally cached dynamic random access memory (AMPIC DRAM)
InactiveUS6085290AEliminates race conditionMemory architecture accessing/allocationMemory adressing/allocation/relocationData validationStatic random-access memory
An apparatus for and method of enhancing the performance of a multi-port internal cached DRAM (AMPIC DRAM) by providing an internal method of data validation within the AMPIC memories themselves to guarantee that only valid requested data is returned from them, or properly marked invalid data. A modified technique for identifying bad data that has been read out of AMPIC memory devices in the system.
Owner:NEXABIT NETWORKS +1
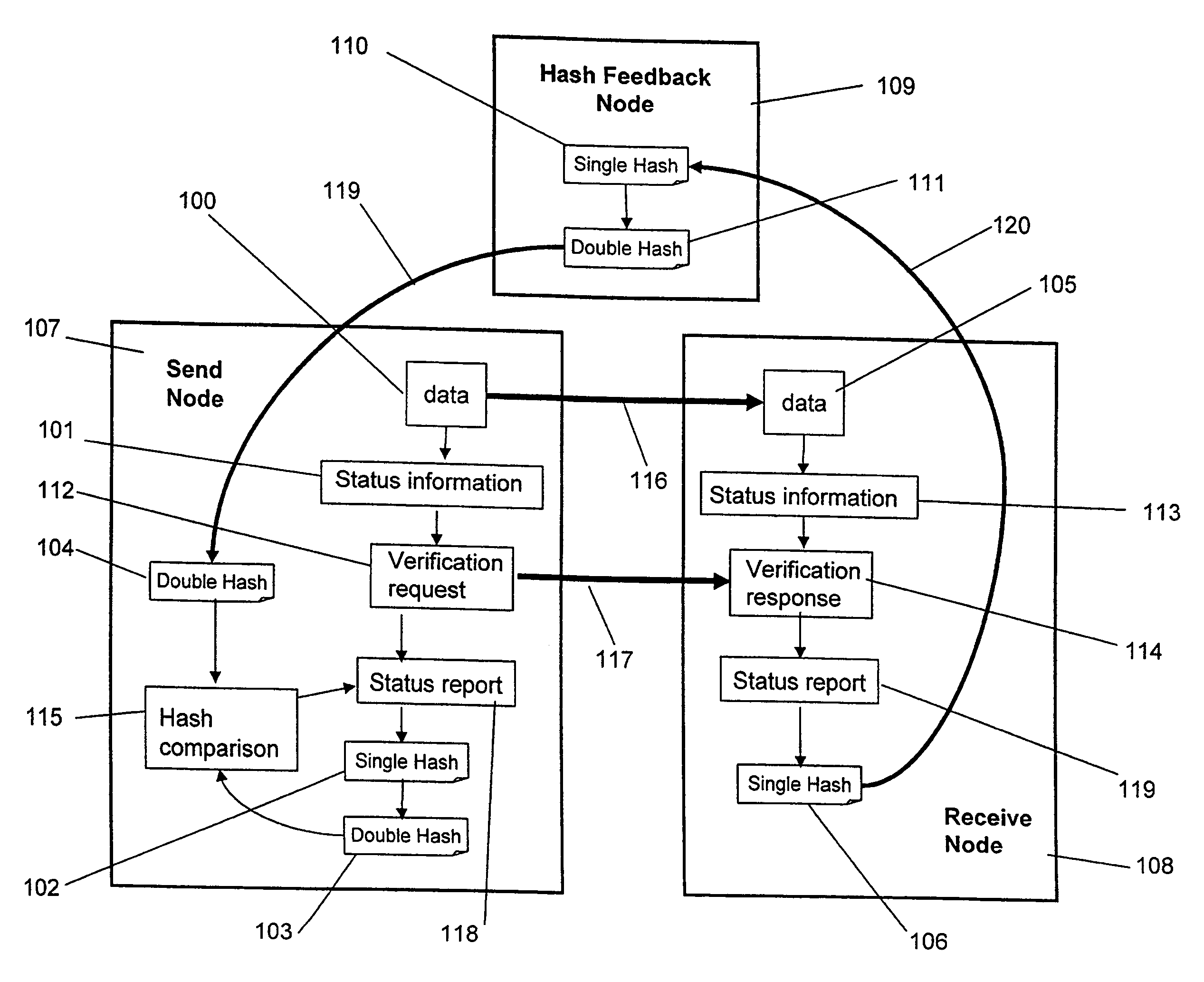
One-way data transfer system with built-in data verification mechanism
Embodiments of the present invention are directed to a one-way data transfer system with built-in data verification mechanism, comprising three nodes (Send Node, Receive Node, and Feedback Node) wherein (1) the three nodes are interconnected with each other by a one-way data link, and (2) the Feedback Node is designed solely for processing and relaying data verification information from the Receive Node to the Send Node. In these embodiments, the Send Node is capable of verifying the status of data it transferred to the Receive Node over a one-way data link without sacrificing the unidirectionality of data flow in the system and thereby compromising the level of security provided by use of one-way data links.
Owner:OWL CYBER DEFENSE SOLUTIONS LLC
Integrated monitoring system information platform for transformer substation
InactiveCN103441571AEasy accessImprove data utilizationCircuit arrangementsInformation technology support systemSource Data VerificationTransformer
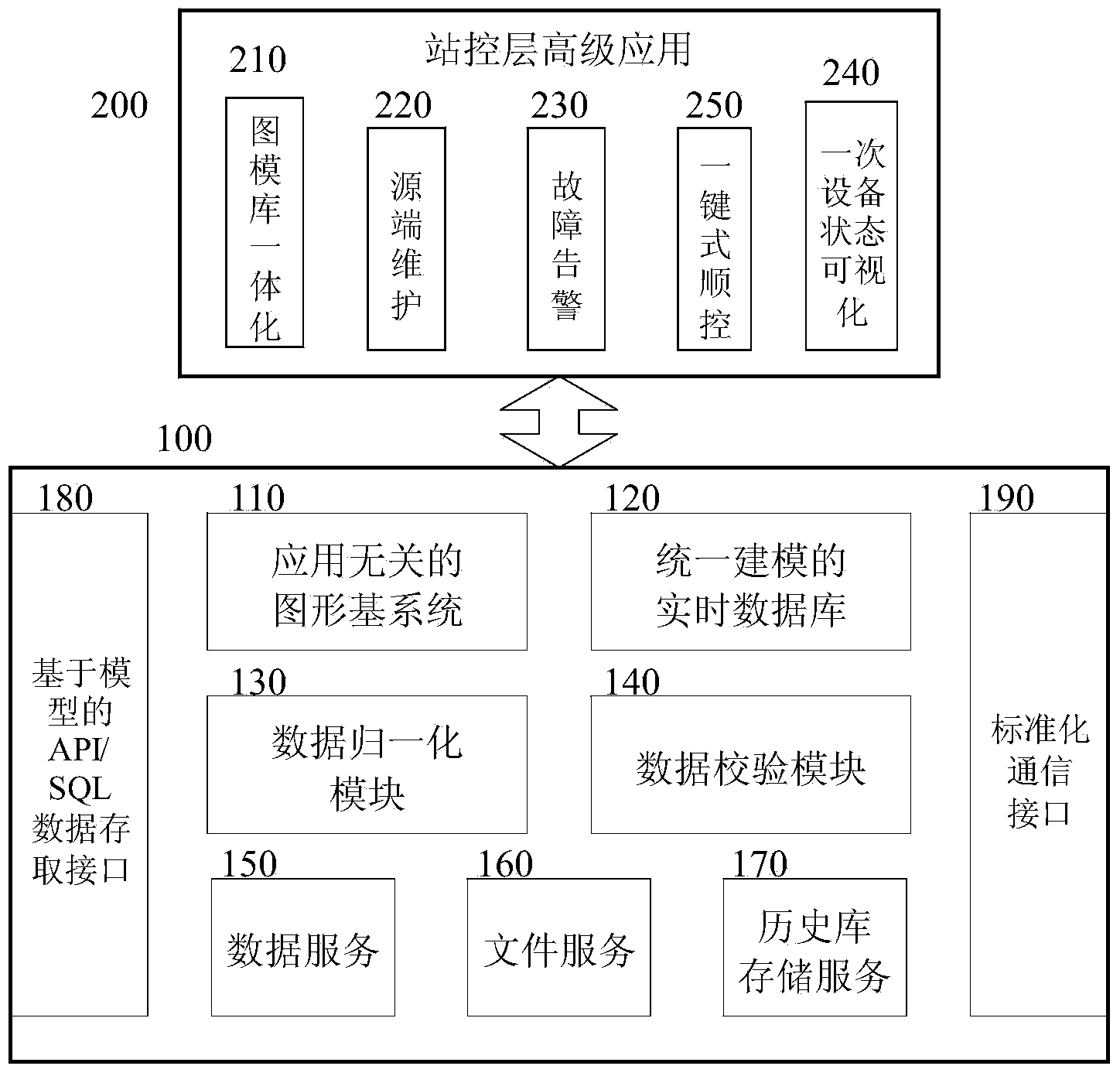
The invention relates to a circuit device used for providing distant indication for conditions of a distribution network and carrying out distant control on a switching device in the distribution network, in particular to an integrated monitoring system information platform for a transformer substation. The integrated monitoring system information platform comprises an integrated information platform body and a station level advanced application module. The integrated information platform body comprises an application-independent graphic base system, a real-time database based on the unified modeling technology, a data normalization module, a data verification module, a data service module, a file service module and a historical library storage service module. The station level advanced application module comprises a graphic, model and library integrated module, a source side maintenance module, a primary equipment status visualization module and a one-button sequential control module. According to the integrated monitoring system information platform, by arranging and integrating functions of various subsystems and carrying out data structure reconstitution on the unified platform, the use ratio and interactivity of data are improved, the reliability, integration and maintainability of the system are improved, and new functional subsystems can have access to the transformer substation conveniently.
Owner:STATE GRID CORP OF CHINA +3
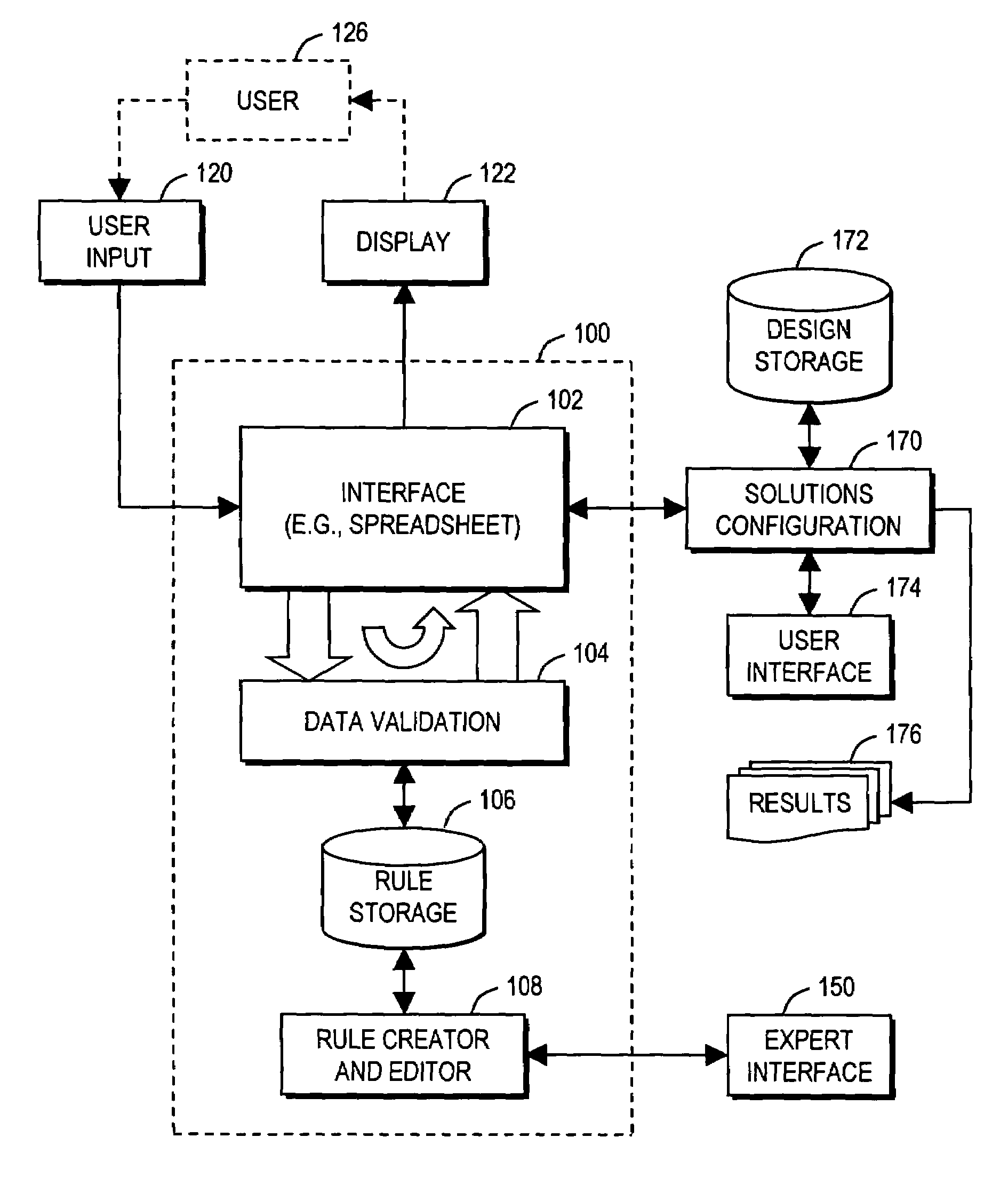
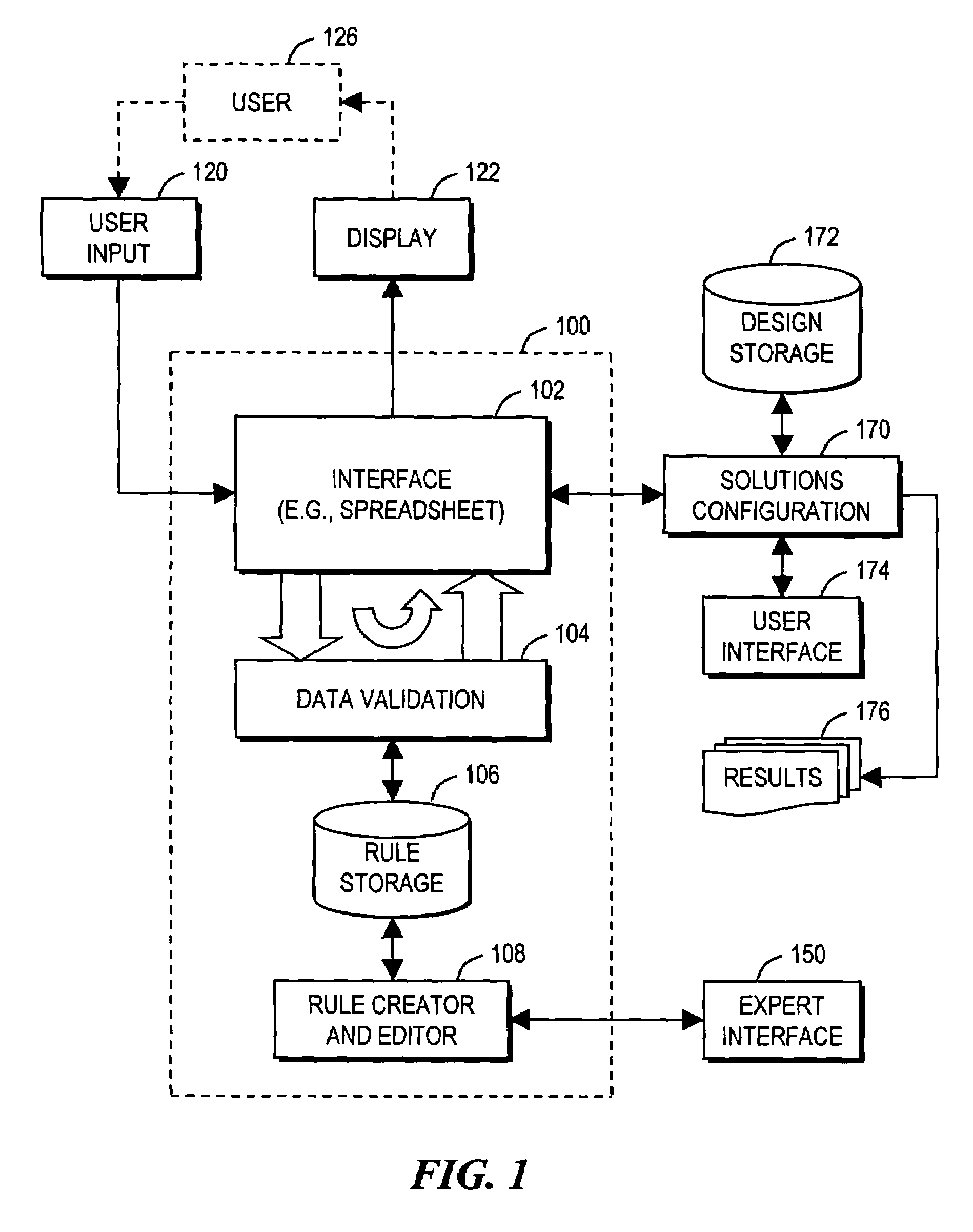
Arrangement for guiding user design of comprehensive product solution using on-the-fly data validation
A computer-implemented method guides a user in designing a product defined by data. The method involves examining (420) items of the data to detect whether each item conforms to rules (106) or violates the rules; performing (431 . . . ) at least one action in response to a detection of a rule violation; displaying (450) the data to the user in a manner emphasizing at least one particular data item that caused the rule violation; receiving (460) any new data input from the user; and repeating the examining, action performing, and displaying steps using the new data. The displaying step may involve displaying data defining a current state of the product in a tabular (spreadsheet) format, including displaying data detected to have caused the rule violation in a first manner that is visibly distinct from displaying other data that is not detected to have caused the rule violation.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
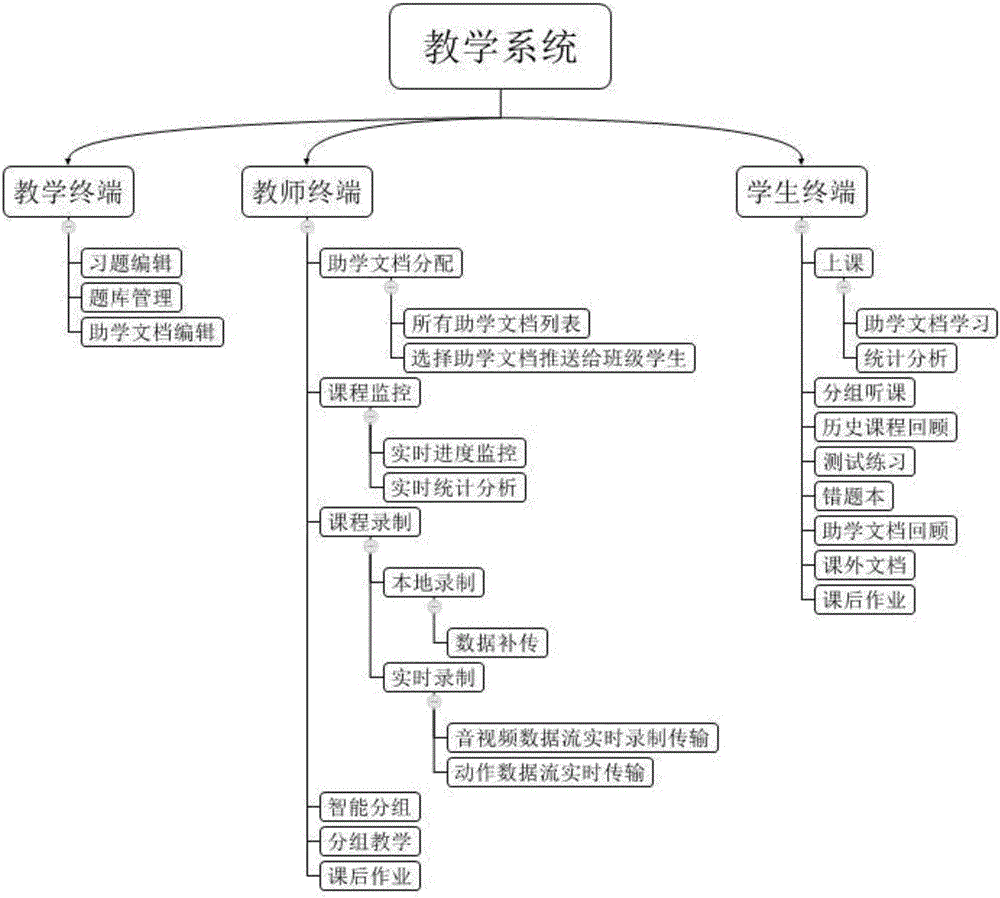
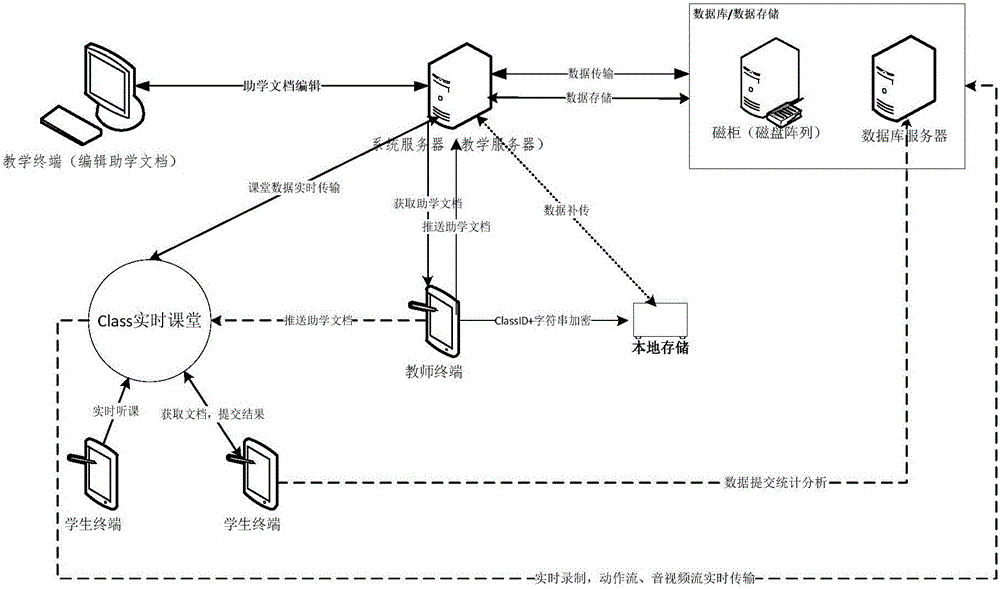
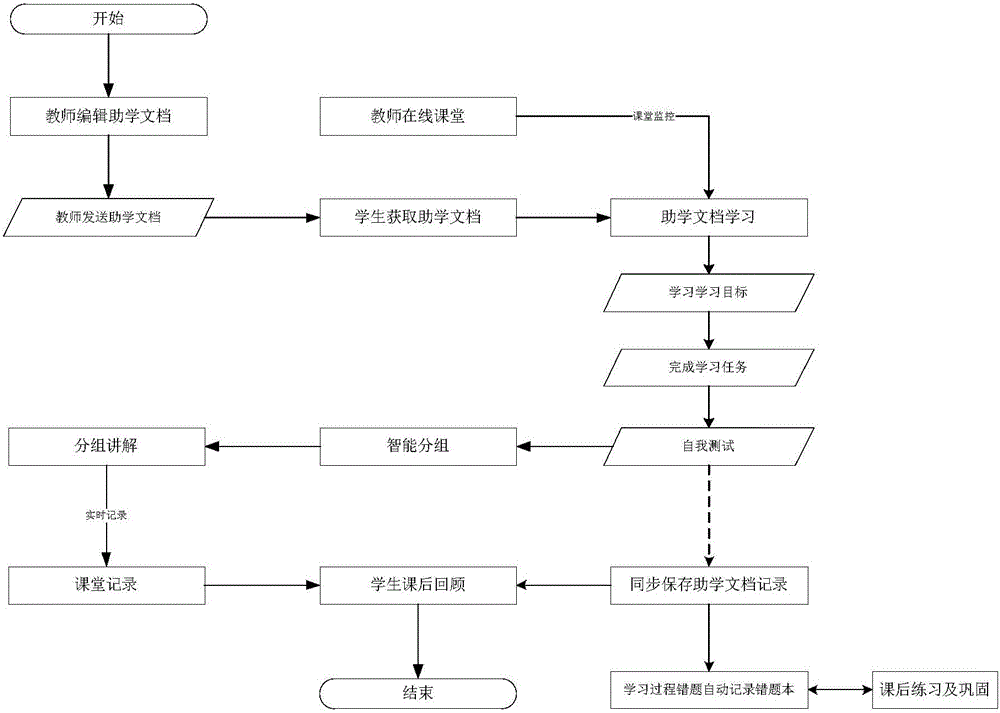
Internet teaching method and system
ActiveCN105869091AImprove learning efficiencyImprove learning effectData processing applicationsElectrical appliancesTimestampSource Data Verification
The invention provides an Internet teaching method and system for developing teaching activities through the Internet including a wireless communication network, and particularly discloses a method and system capable of recording the Internet teaching process in real time and accurately and efficiently storing the Internet teaching process in a cloud side. The method includes the step of evaluating educational document learning results by students to learn and distinguish learning situations of students of different levels, thereby achieving targeted differential teaching, tutoring, homework doing, exercising and the like and easily improving the learning efficiency and learning effect, especially continuously improving the students at different learning progresses. Furthermore, by means of a data return gateway, a data verification mechanism, a timestamp verification mechanism, an audio and video flow verification mechanism, a data complementary transmitting mechanism, a local fragmentation encrypting, storing and uploading mechanism and other means, recorded data is stored in the cloud side efficiently and accurately.
Owner:鹰硕(韶关)信息产业集团有限公司
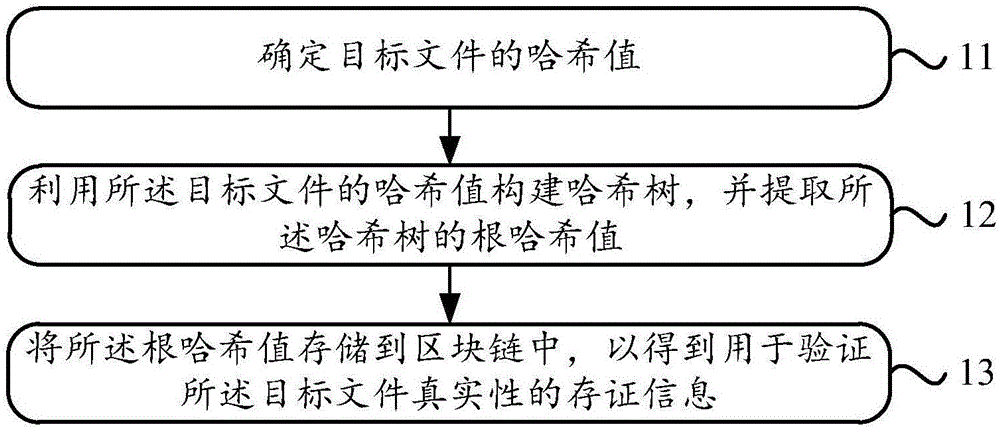
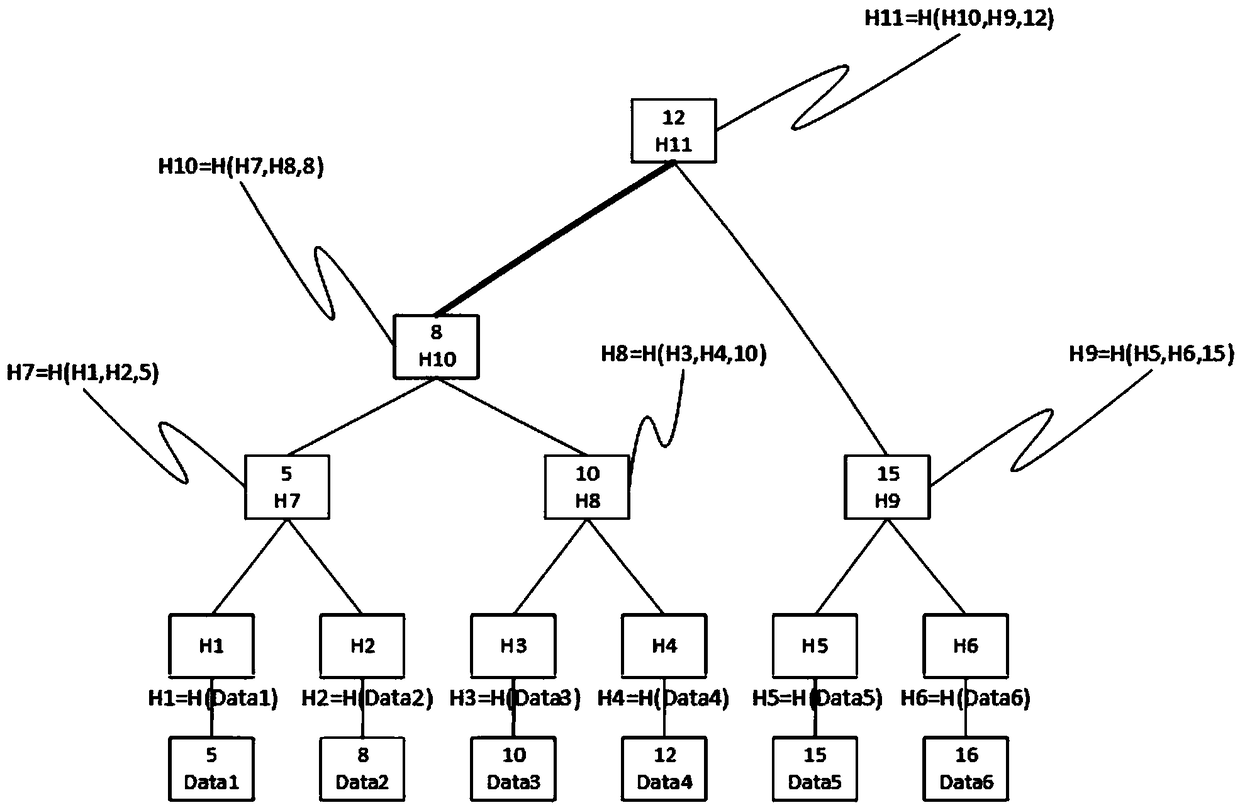
Data storage method, data verification method and device
ActiveCN106815530AAuthenticity checkDigital data protectionComputer hardwareSource Data Verification
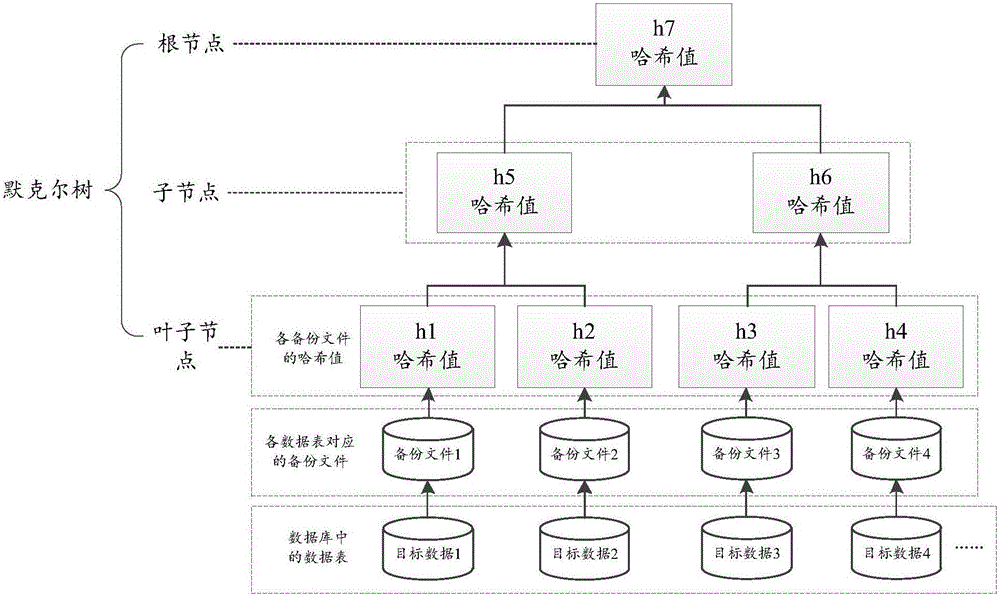
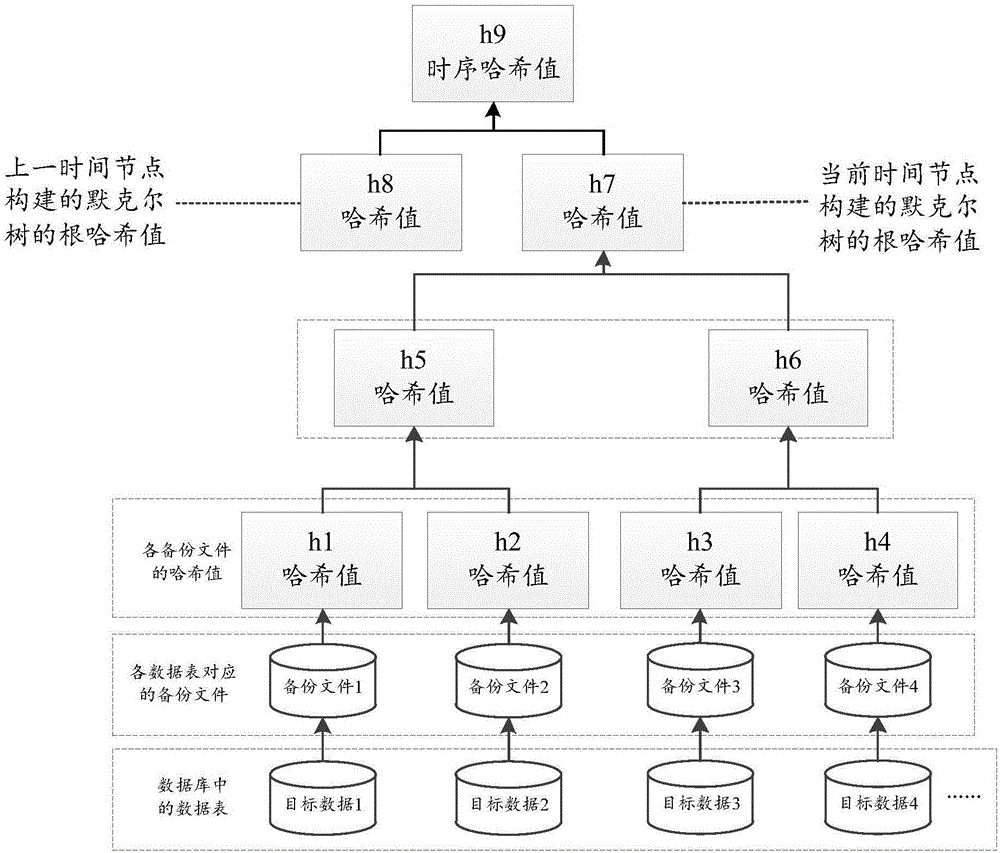
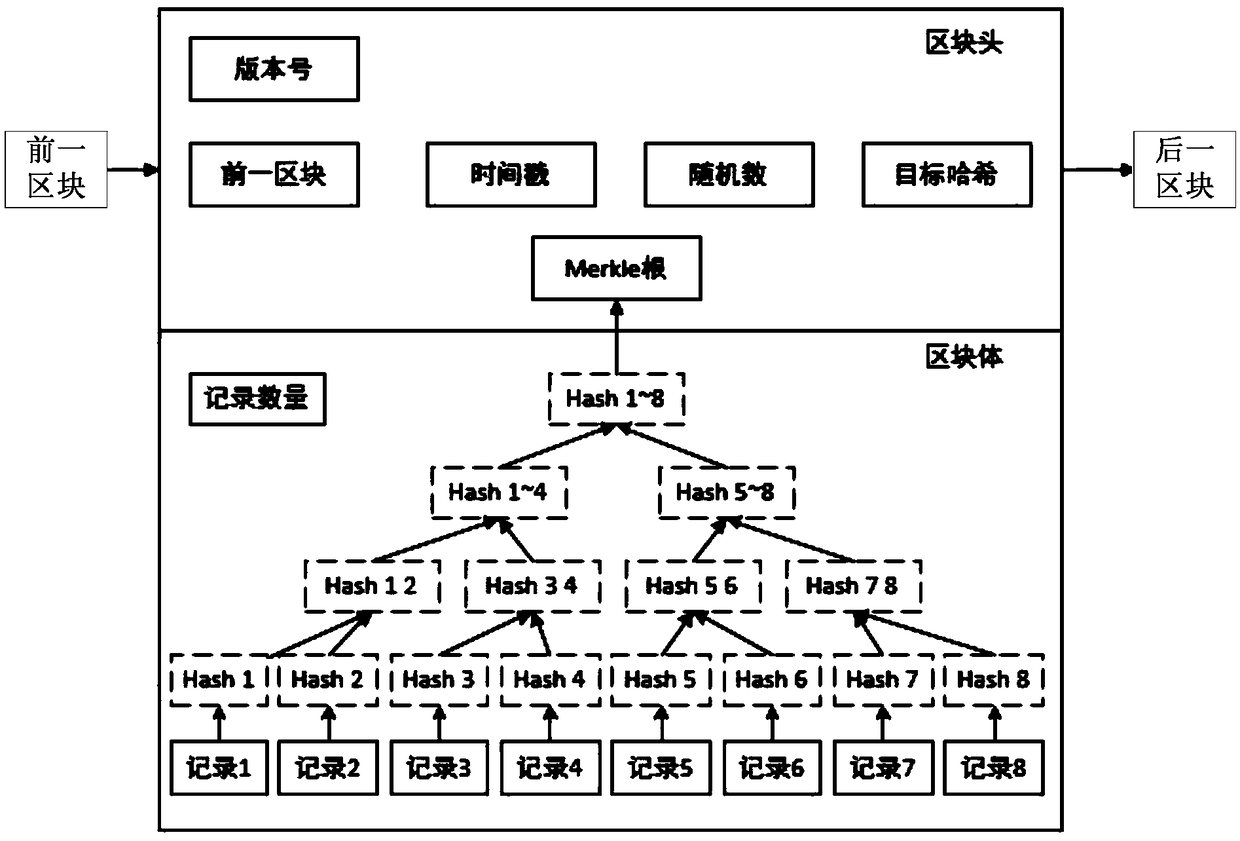
The invention discloses a data storage method. The data storage method is used for solving the problem that the truth of the data cannot be guaranteed in the prior art. The method comprises the following steps: confirming a Hash value of a target file; utilizing the Hash value of the target file to construct a Hash tree and extracting a root Hash value of the Hash tree; storing the root Hash value in a block chain, thereby acquiring storage information of the truth of the target file, wherein the storage information includes a sign of a block of the Hash value of the target file, a storage time stamp of the target file and the Hash value of the target file. The invention also discloses a data storage device, a data verification method and a data verification device.
Owner:北京爱接力科技发展有限公司
An indexing method for a keyword key on a block chain database
ActiveCN109165224AAchieve queryabilityImprove securityDigital data protectionPayment protocolsSource Data VerificationOriginal data
The invention provides an indexing method for a keyword key on a block chain database, which relates to the technical field of block chain data query. Firstly, the common node generates transaction records according to the original data with keyword input by the user; the storage node packages the transaction into a block; the block data is written into the disk file; transaction data is queried according to the key value, and a query result is output; normal users verify the trustworthiness of the results. The invention indexes directly according to the data keyword to realize the data inquiry. The transaction structure in the traditional block chain is extended to store the schema structure similar to the traditional database, which improves the applicability. Data authority is managed according to digital signature technology to improve data security. Whether the index is tampered with or not is judged through MerkleRBTree self-perceiving, and whether the transaction is tampered with or not is judging according to the transaction hash, so as to ensure that the data is not tampered with. At the same time, the data verification function of the lightweight node is realized, so thatthe query end can effectively detect the data credibility.
Owner:NORTHEASTERN UNIV
Method and apparatus and program storage device including an integrated well planning workflow control system with process dependencies
Owner:SCHLUMBERGER TECH CORP
Data verification method based on block chains and data verification system thereof
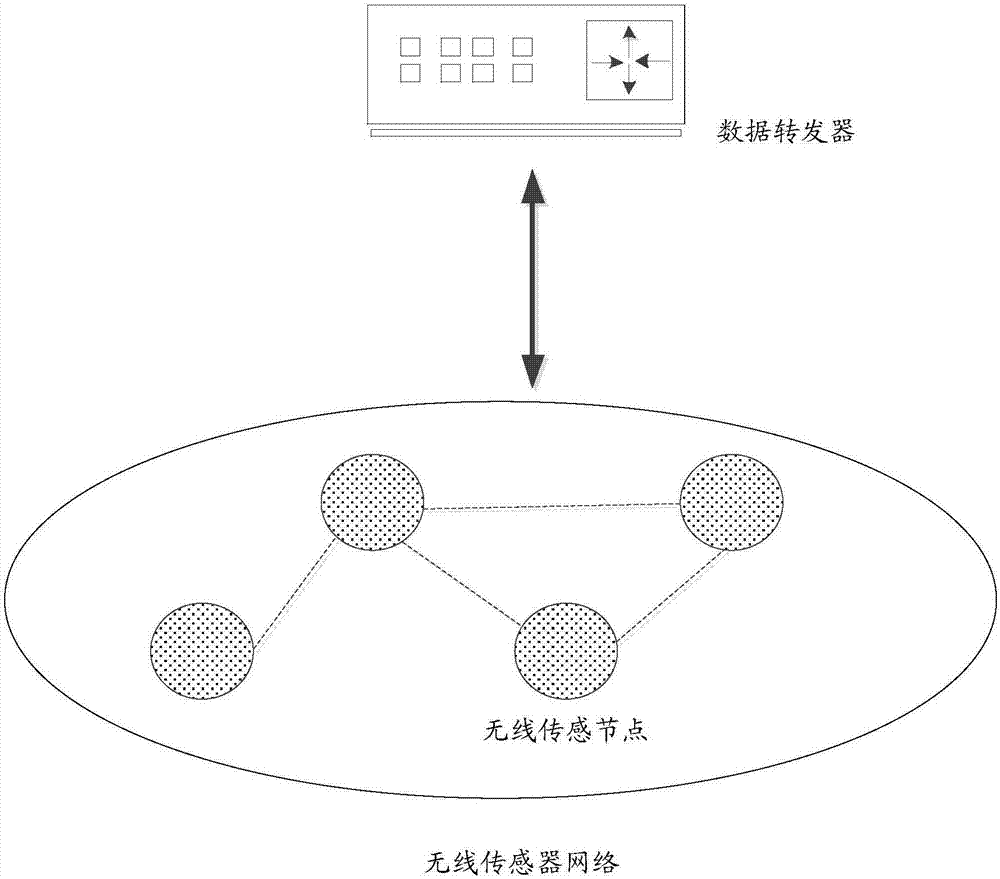
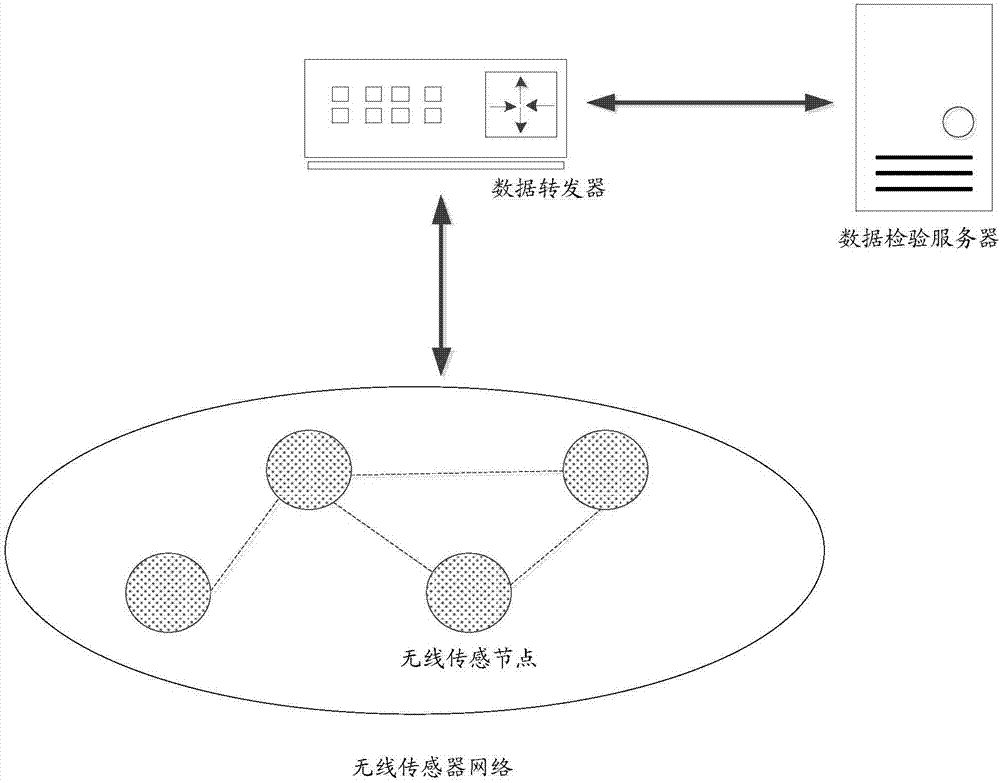
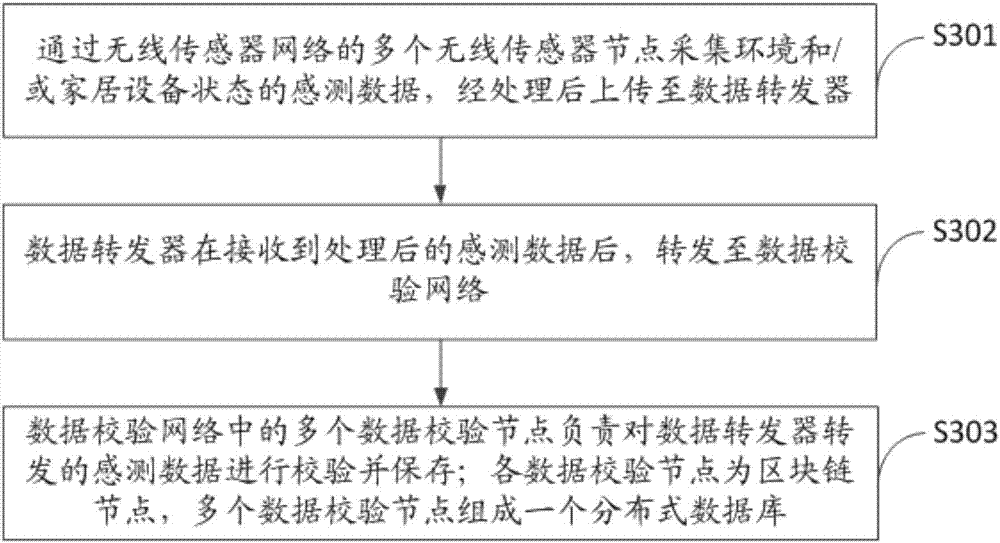
ActiveCN107249009AOvercome efficiencyOvercome speedWireless commuication servicesTransmissionSource Data VerificationData verification
The invention discloses a data verification method based on block chains and a data verification system thereof. The data verification method comprises the steps that the sensing data of the environment and / or household equipment state are acquired through multiple wireless sensor nodes of a wireless sensor network and processed and then uploaded to a data repeater; the data repeater receives the processed sensing data and then forwards the sensing data to a data verification network; multiple data verification nodes in the data verification network are responsible for verifying and saving the sensing data; and all the data verification nodes are block chain nodes, and multiple data verification nodes form a distributed database. The data verification task is completed by using the data verification nodes, and the verification work is distributed to the verification nodes from the data repeater so that the problems of being low in verification efficiency, low in speed, high in transmission delay and vulnerable because of the excessively centralized verification task can be overcome, and the nodes are excited to actively authenticate the data and rapidly complete the verification task so that the whole verification system is not influenced by single node failure of any node.
Owner:GUANGDONG UNIV OF TECH
Device system and method for secure data communication based on sound waves
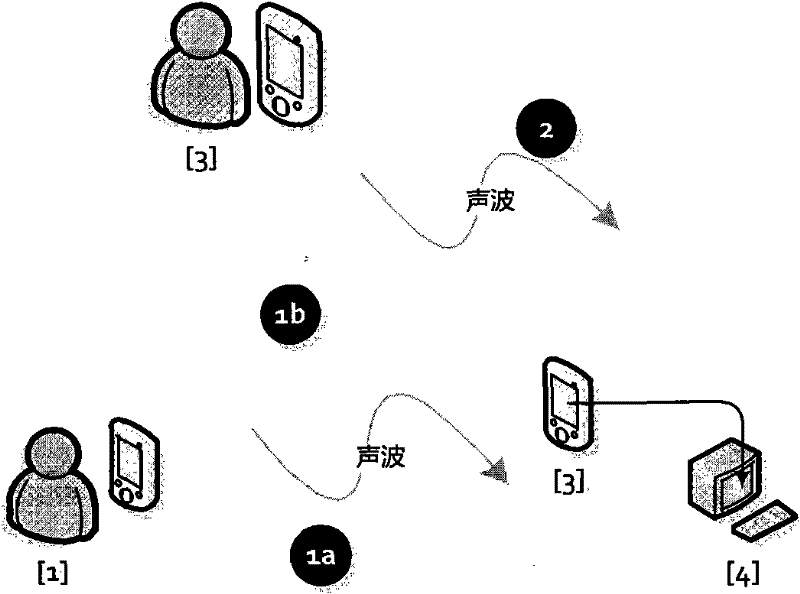
InactiveCN102299747AQuick collectionLow costNear-field transmissionSonic/ultrasonic/infrasonic transmissionComputer hardwareData integrity
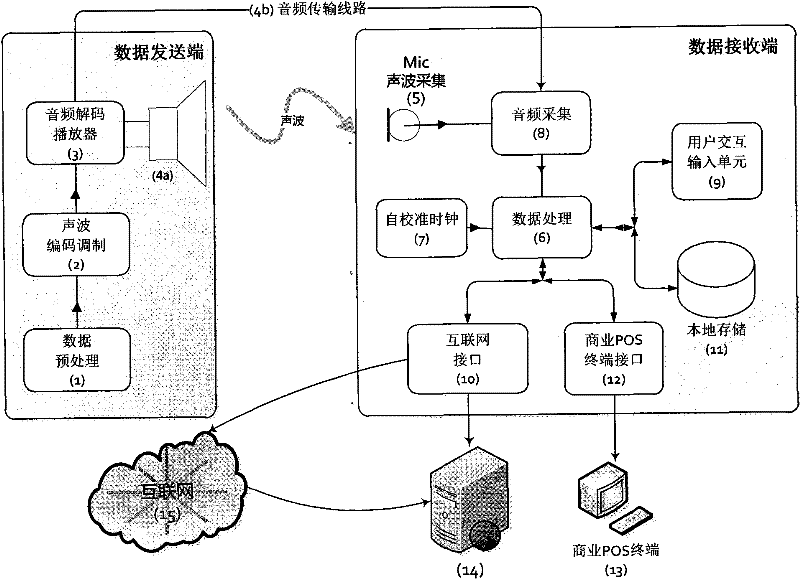
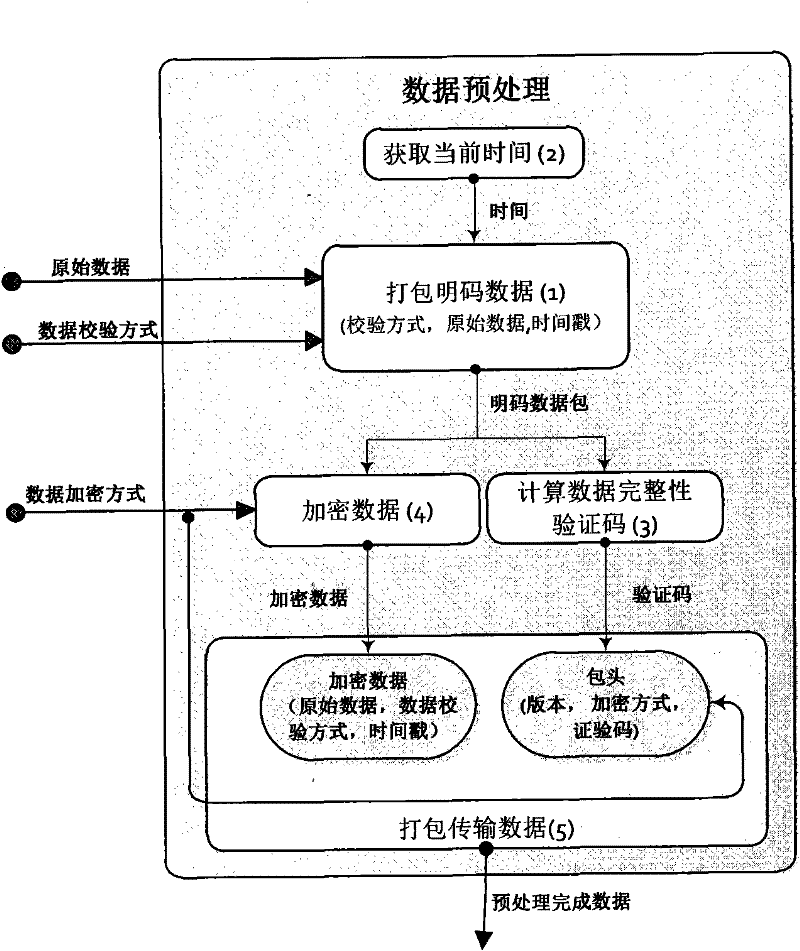
The present invention discloses an apparatus, a system and a method for short-range sound wave communication. The system realizes non-contact secure transmission by using the sound wave as the data transmission medium, and also can realize a reliable and secure data link directly through an audio connection. The invention systematically constructs multiple end-to-end transmission verification mechanisms for the process of data transmission: transmission data integrity verification, valid time verification, password verification, service data verification and data encryption; and according to the security level of the data, the sending end specifies the requirements for encryption and data verification in the transmission data so as to notify the reception end which verifications should be performed to the data packets, how to perform the verifications, etc. By using the same verification processing manner, operations can be performed to the data (e.g. the payment and settlement function of an account). With lower cost, the present invention can realize the reliable communication of a small data volume using sound wave, and has certain security.
Owner:SHANGHAI CLOUDWAY INFORMATION TECH +1
NAND Flash-based data recording method and recording controller
InactiveCN102169462AReduce usageImprove acceleration performanceInput/output to record carriersMemory adressing/allocation/relocationStatic random-access memoryControl signal
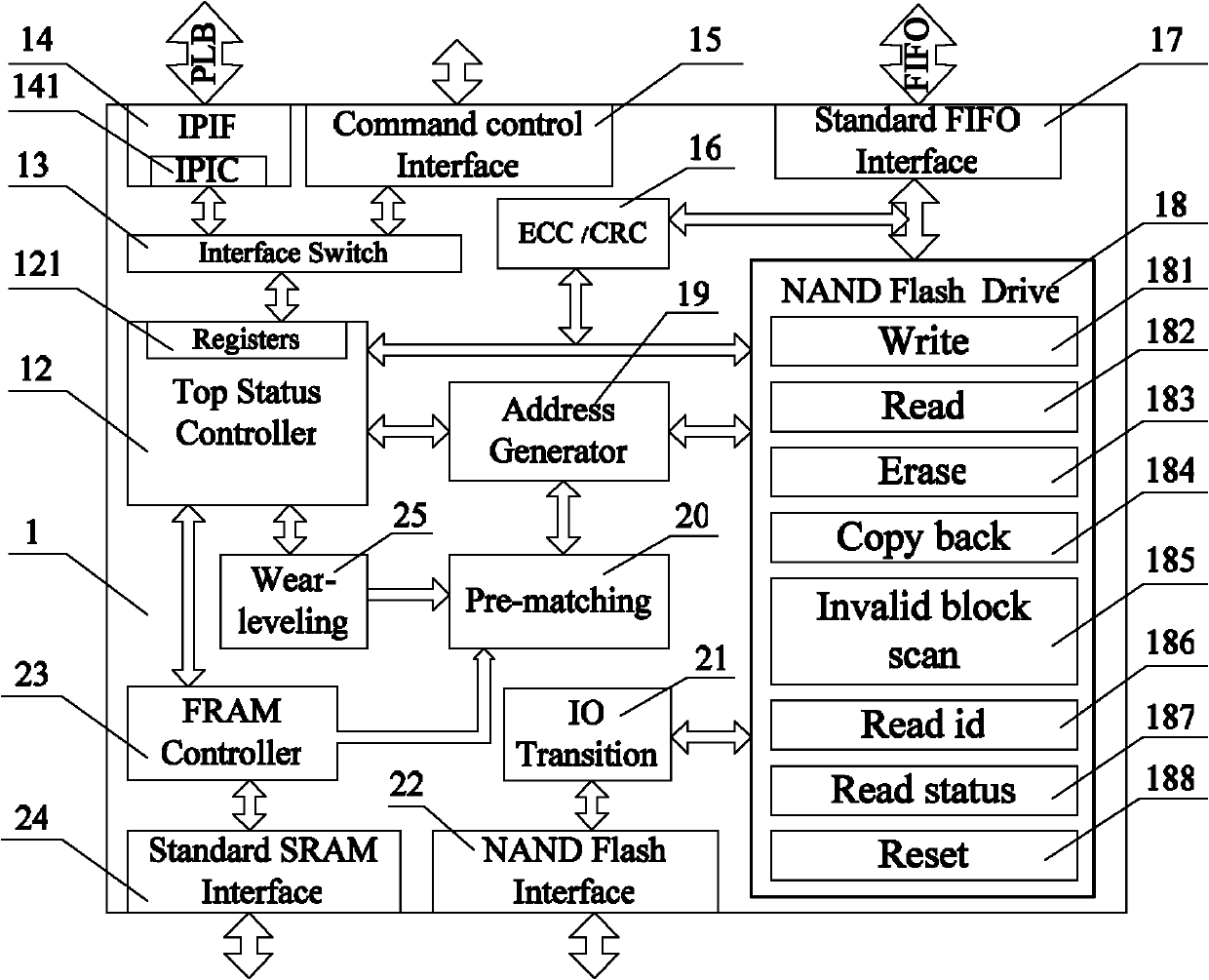
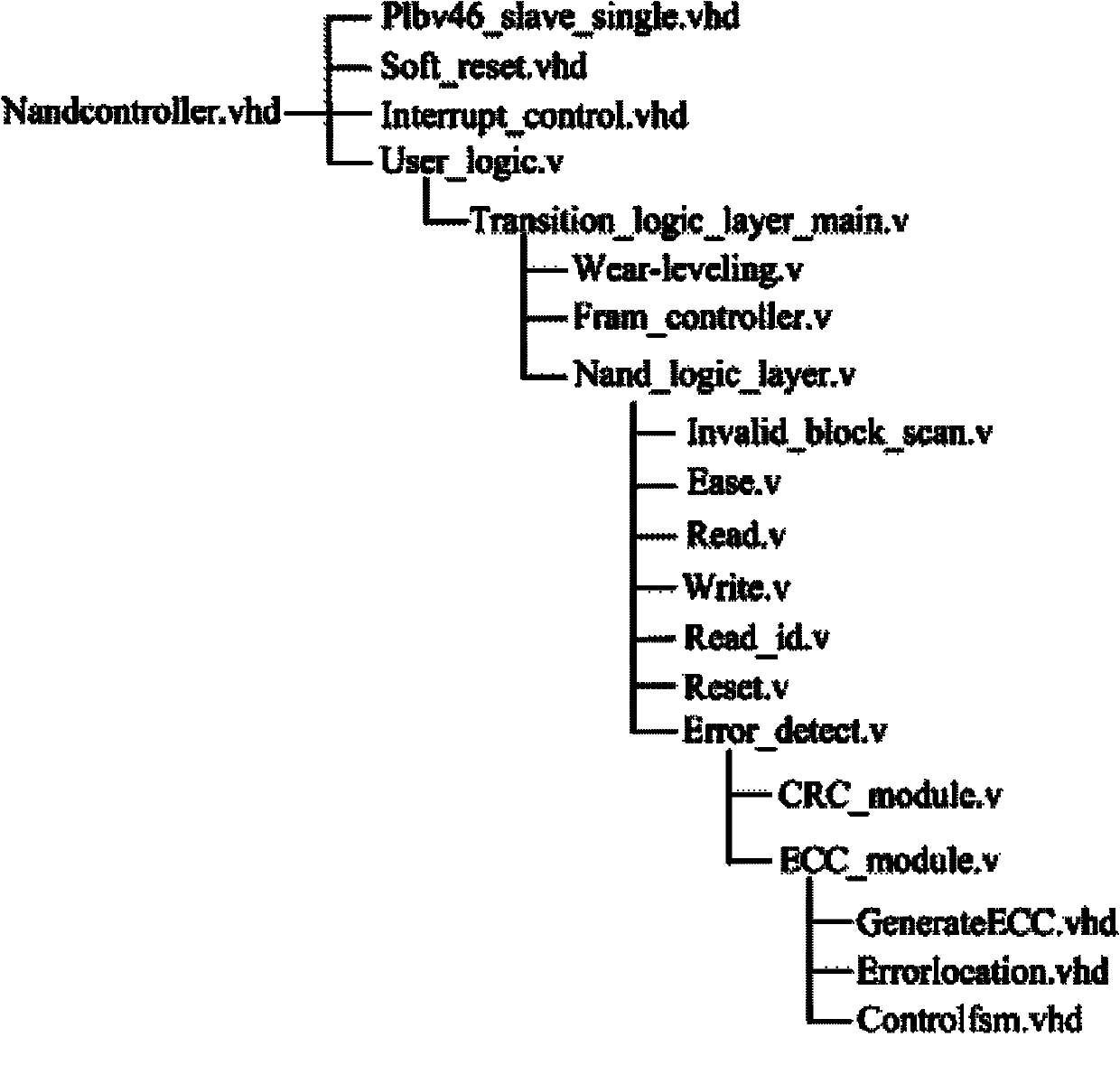
The invention discloses an NAND Flash-based data recording method and an NAND Flash-based data recording controller. The method comprises the following methods: a hardware bad block management method comprising the following steps of: when a sudden bad block appears, jumping to a next matched valid block without time delay to continuously record, and finally writing the data lag of a page before the bad block appears back to the jumped valid block; a hardware balance method comprising the following step of: starting the erasing-writing operation in succession to the last erasing-writing address so that the erasing-writing times of each block of the NAND Flash is approximately equal; and an input output (IO) expansion method comprising the following steps of: converting data bit width and switching control signals so that a single NAND Flash driver can control multiple chips and multiple groups of NAND Flashes. The controller comprises a ferroelectric random access memory (FRAM) controller, a top state controller, a loss equalizer, an interface switching module, a pre-matching module, an address generating module, a register set, a data verification module, a standard first in first out (FIFO) interface, a standard static random access memory (SRAM) interface, a command control interface and the NAND Flash driver. The whole controller can be mounted on a processor local bus (PLB) of an embedded processor, and data conversion between a control signal and a state signal can be performed through the command control interface and an external module.
Owner:INST OF OPTICS & ELECTRONICS - CHINESE ACAD OF SCI
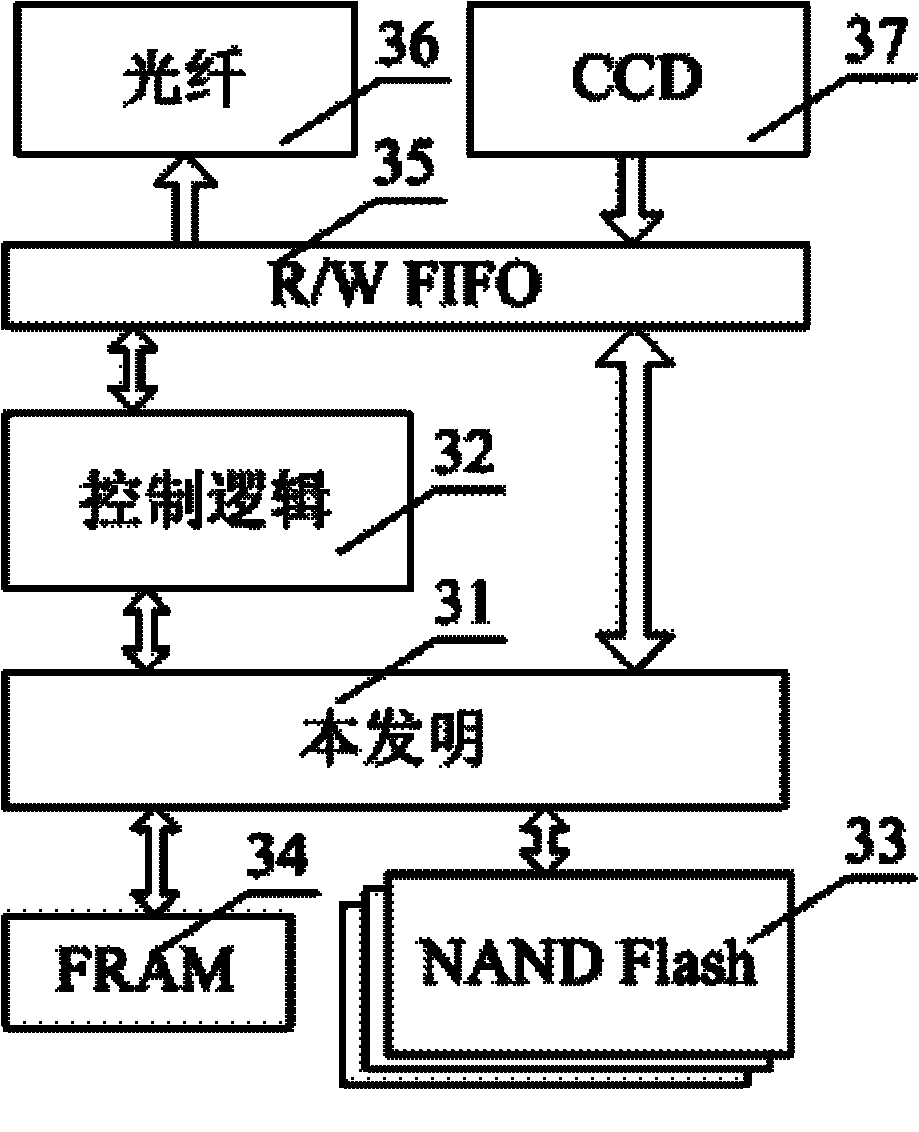
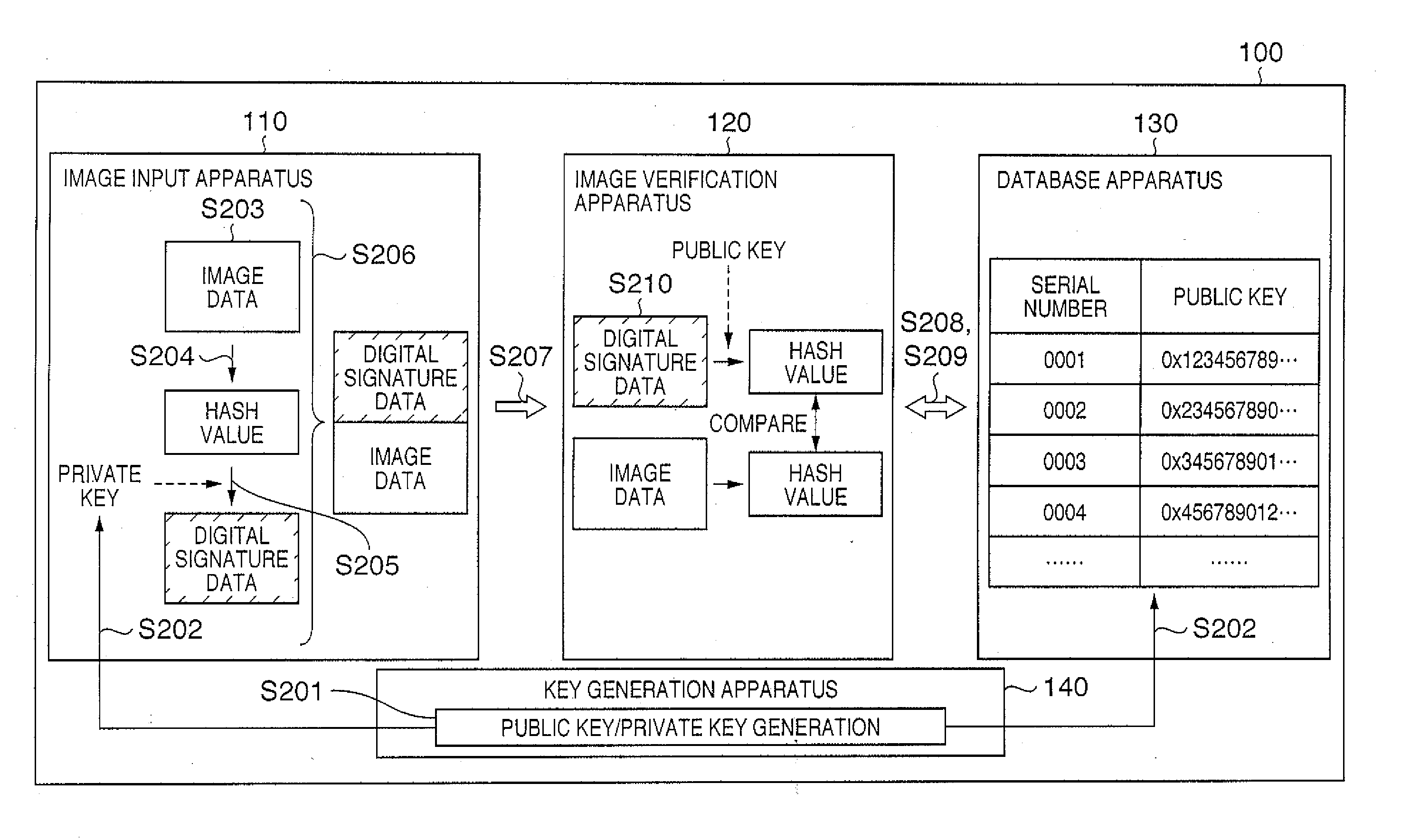
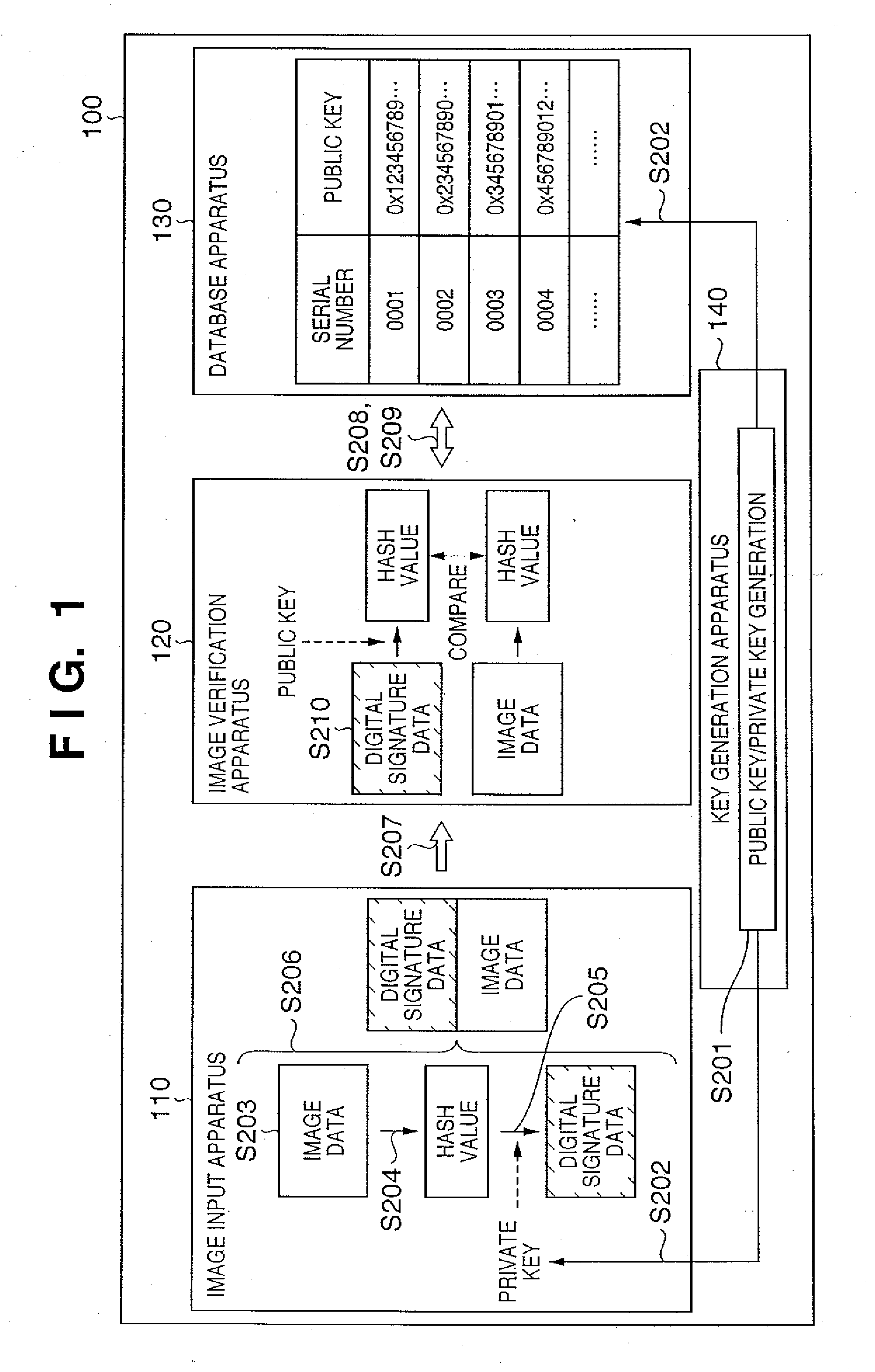
Image data verification
InactiveUS20060248348A1Key distribution for secure communicationUser identity/authority verificationSource Data VerificationVerification system
An image verification system includes an image input apparatus, image verification apparatus, and database apparatus. The image input apparatus generates verification information for image data by using a private key and adds the verification information and predetermined information unique to the image input apparatus to the image data. The image verification apparatus verifies that the image data has been altered or not by using the verification information and a public key corresponding to the private key. The database apparatus stores the public key in association with the predetermined information in the a storage unit and provides the public key to the image verification apparatus.
Owner:CANON KK
Internet protocol compatible access authentication system
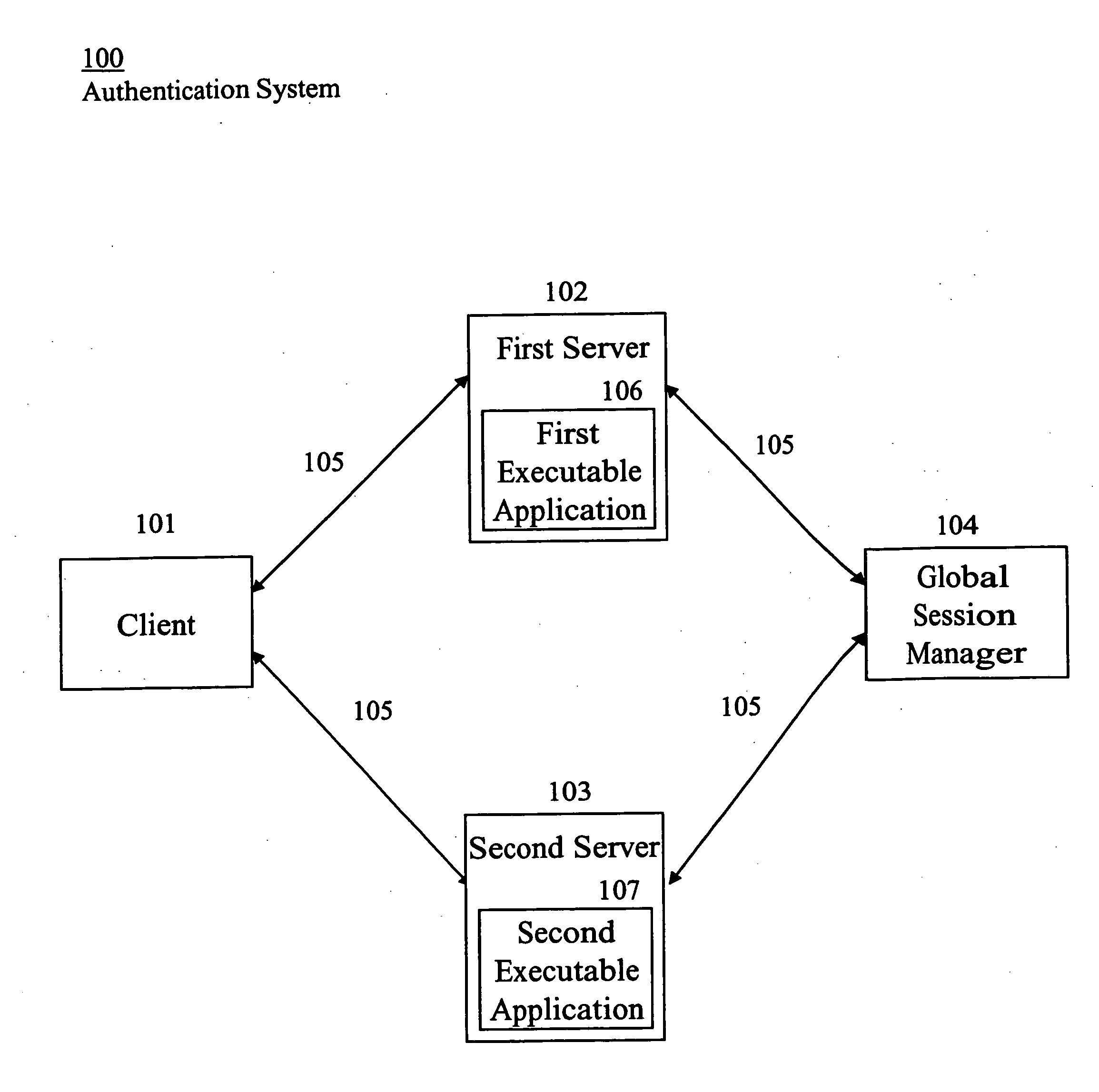
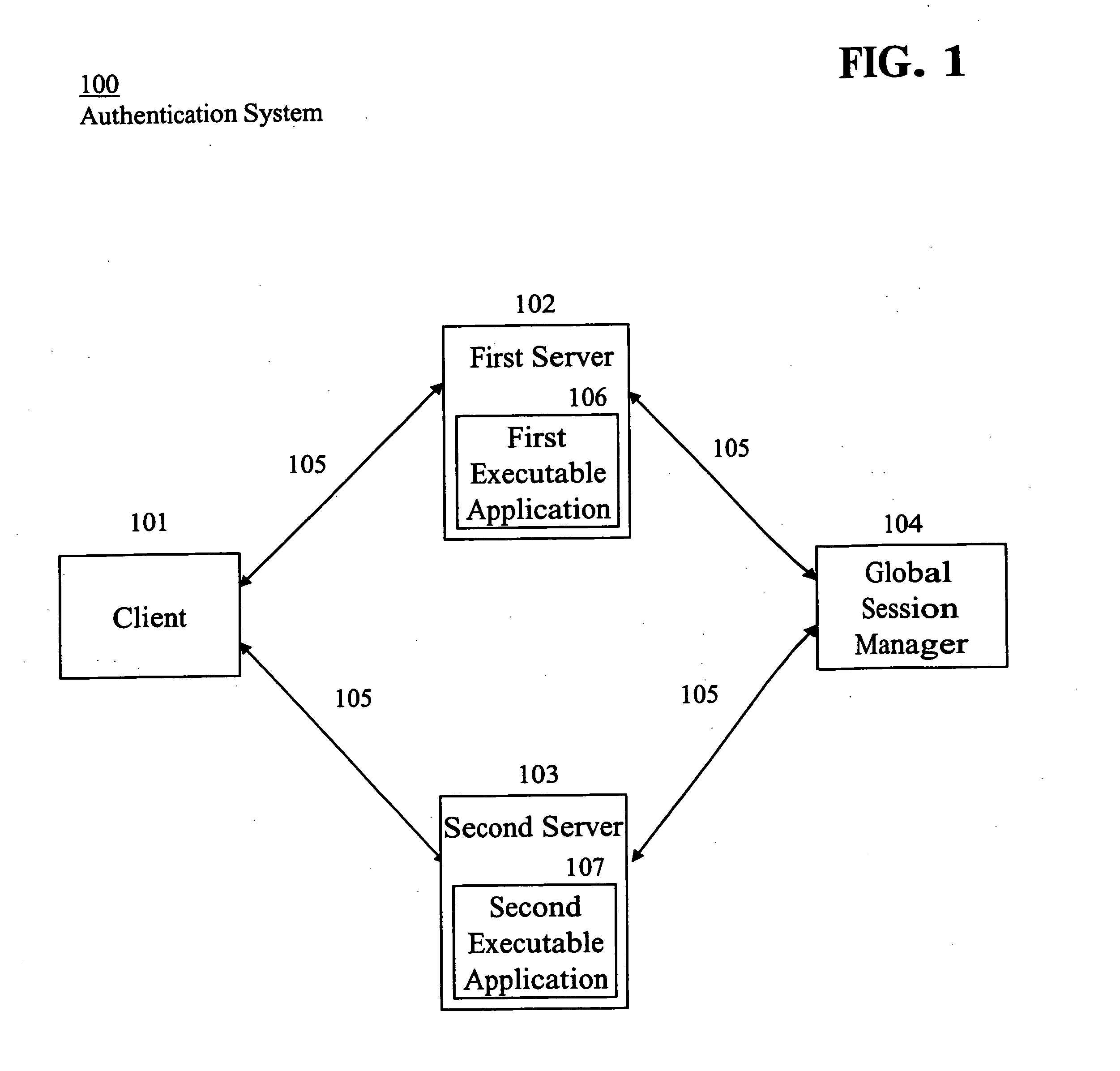
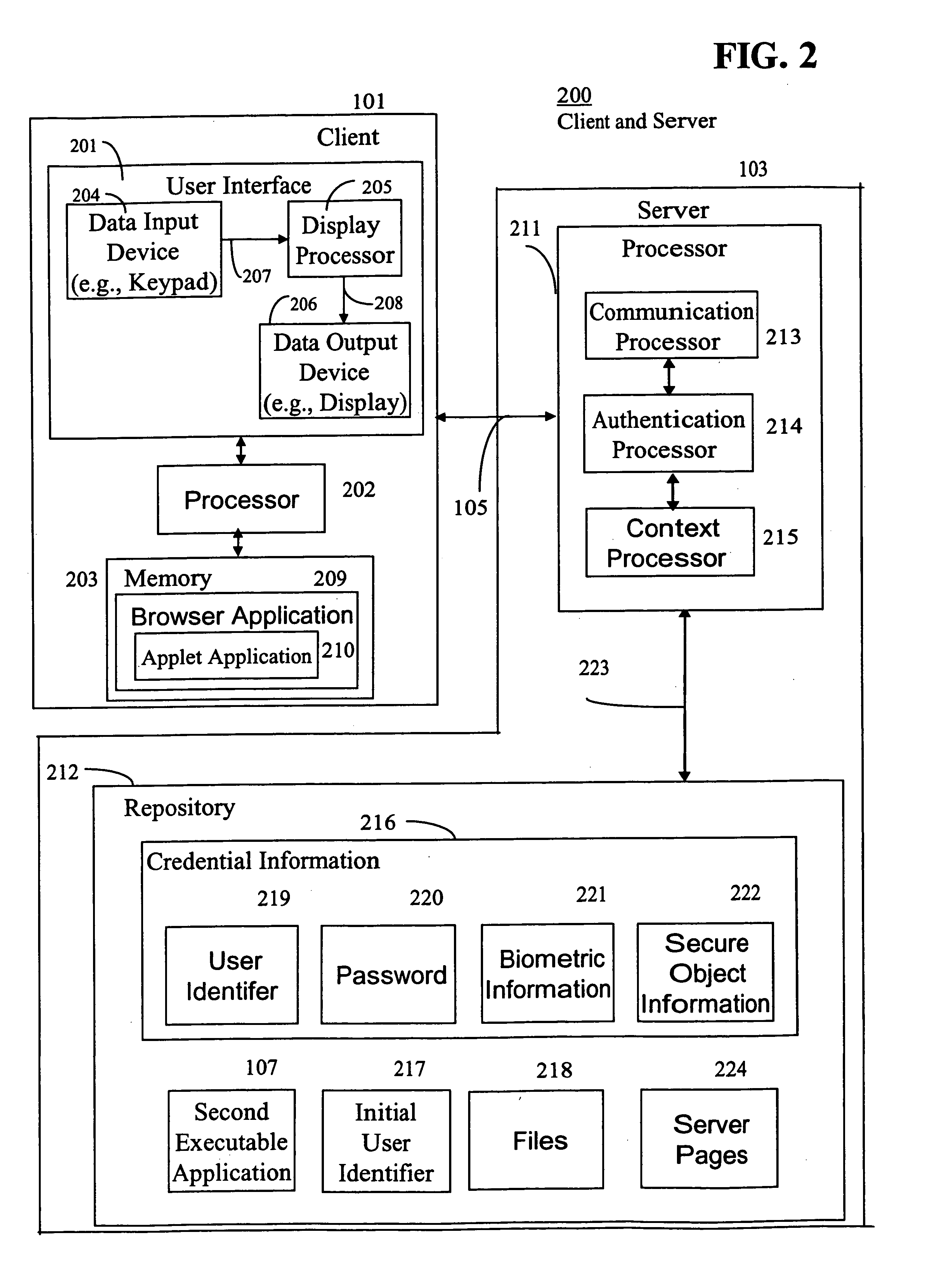
InactiveUS20050144482A1Digital data processing detailsMultiple digital computer combinationsData validationPassword
An Internet compatible system, for use in authenticating user access to information, includes a repository and an authentication processor. The repository associates an initial user identifier with a particular executable application and with credential information. The credential information includes a first user identifier and a corresponding first password, which enable user access to the particular executable application. The authentication processor receives data representing the initial user identifier. The authentication processor detects a browser application initiated request for credential information in response to a user command to the browser application to access a particular executable application. The authentication processor validates whether credential information derived from the repository, using the received initial user identifier, authorizes a user to access the particular executable application in response to a detected browser application initiated request. The authentication processor provides validated authorized credential information derived from the repository to the browser application to enable a user to access the particular executable application in response to successful validation.
Owner:SIEMENS MEDICAL SOLUTIONS HEALTH SERVICES CORPORAT
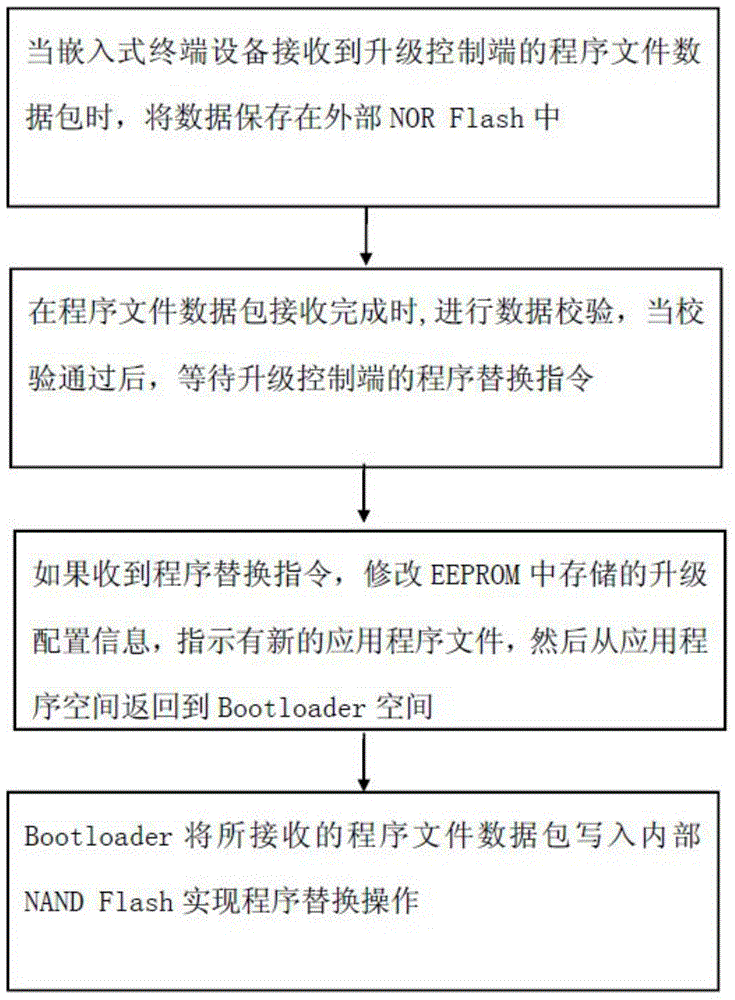
Embedded device program updating method and system
The invention provides an embedded device program updating method and system. The method comprises the steps that a device receives a program file data packet and saves the program file data packet in an external NOR Flash; data verification is conducted on the data packet, and upgrading configuration information stored in an EEPROM is modified when a program replacing instruction is received and then fed back to a Bootloader space from an application program space; a Bootloader writes the received program file data packet into an internal NAND Flash to achieve program replacement. According to the embedded device program updating method and system, a reliable upgrading method is provided, a solution to an accidental power failure of the device during upgrading is provided, upgrading can be continued after power is retrieved, and upgrading and backup recovery are supported at the same time.
Owner:CHENGDU WANWEI TUXIN INFORMATION TECH
Document scanner, system and method
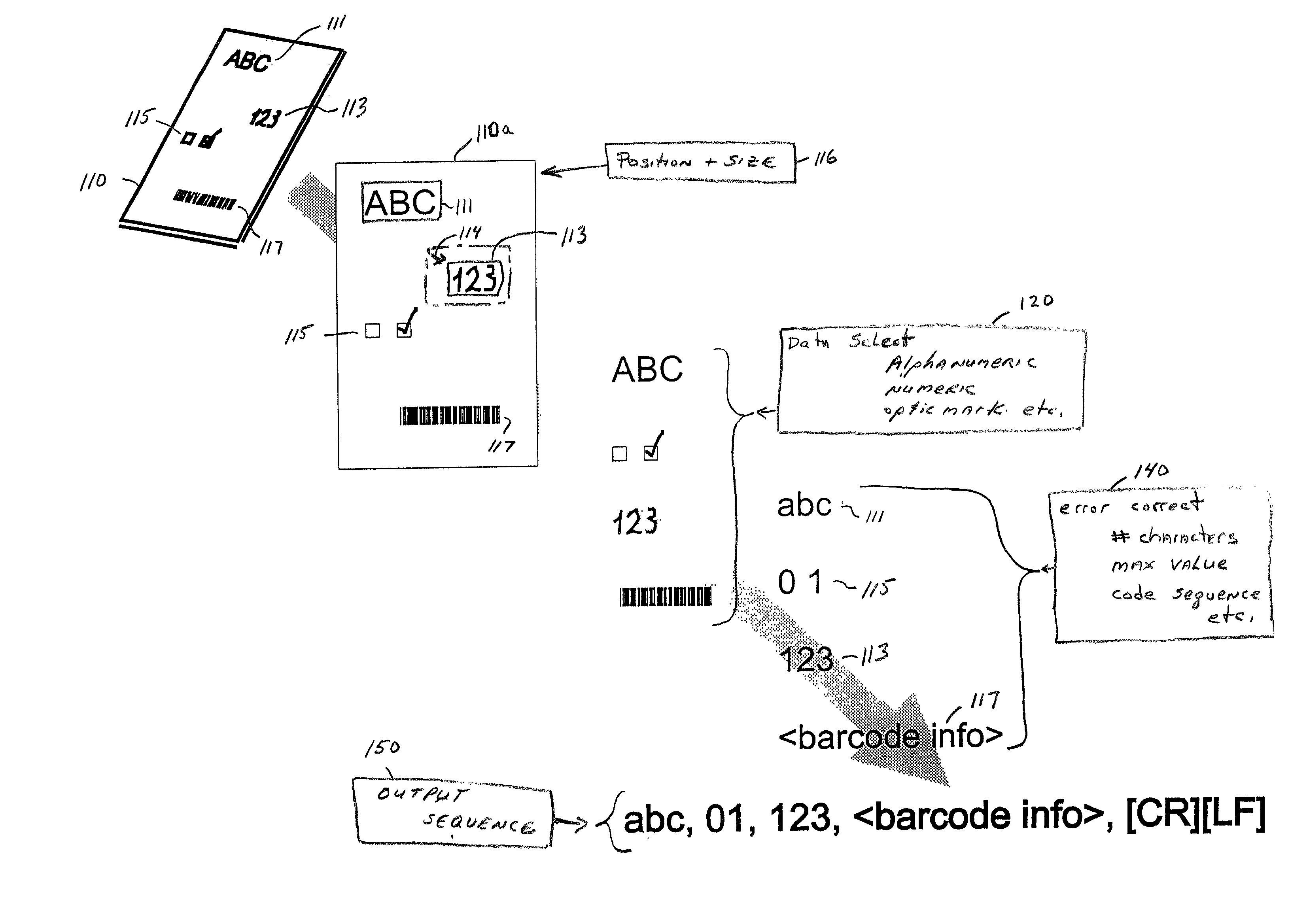
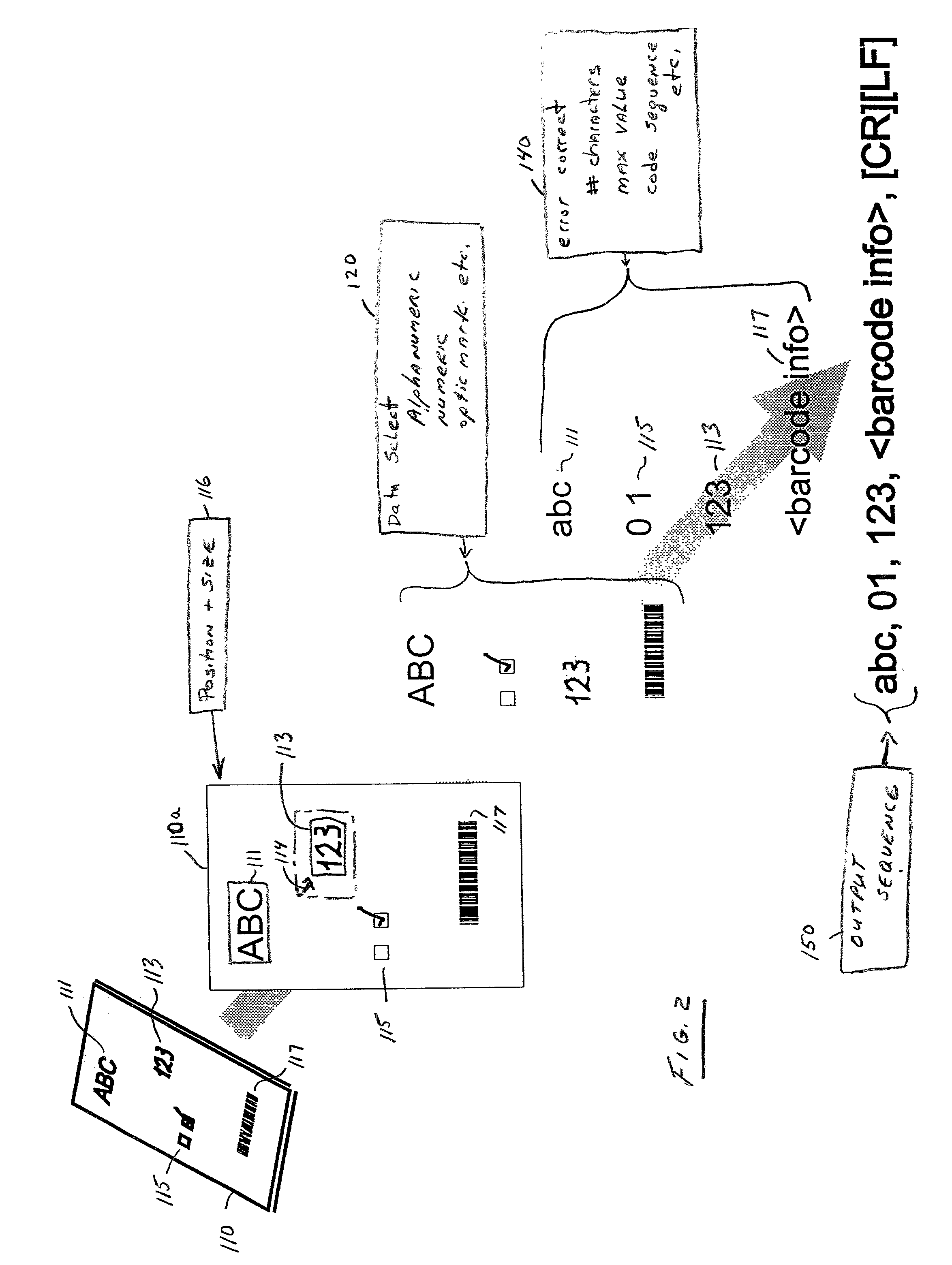
The document scanner, system and method operates in conjunction with a document imprinted with data and a plurality of form documents adapted to have data imprinted thereon. The documents have at least one and typically many data image fields. Ultimately, the document scanner, system and method outputs a delimited string of decoded characters to another computer system via a common computer communications port. The method includes either scanning a form document to obtain positional information of the data field or fields or inputting a topological description of the field. Typically, the operator identifies descriptors for each data field which include data field size information, data type information, the presence or absence of data validation parameters, the presence or absence of data error reporting and data correction routines or parameters, and data output destination information. The data output destination information locates the decoded data in a certain sequence or location in the delimited string of decoded characters output to the coupled computer system. The document scanner, system and method scans the document imprinted with data and captures an image thereof. The scanned input document image is compared with the stored forms, and particularly the stored data field descriptors utilizing positional, data field size and data type information. The system selects one of the stored forms, extracts the data from each data field, decodes or calculates the data, and validates the data (in the presence of data validation parameters) and stores the decoded / calculated data. A data error reporting and data correction system, activated in the presence of the data error reporting and correction descriptor, enables correction of errors.
Owner:MULTISCAN
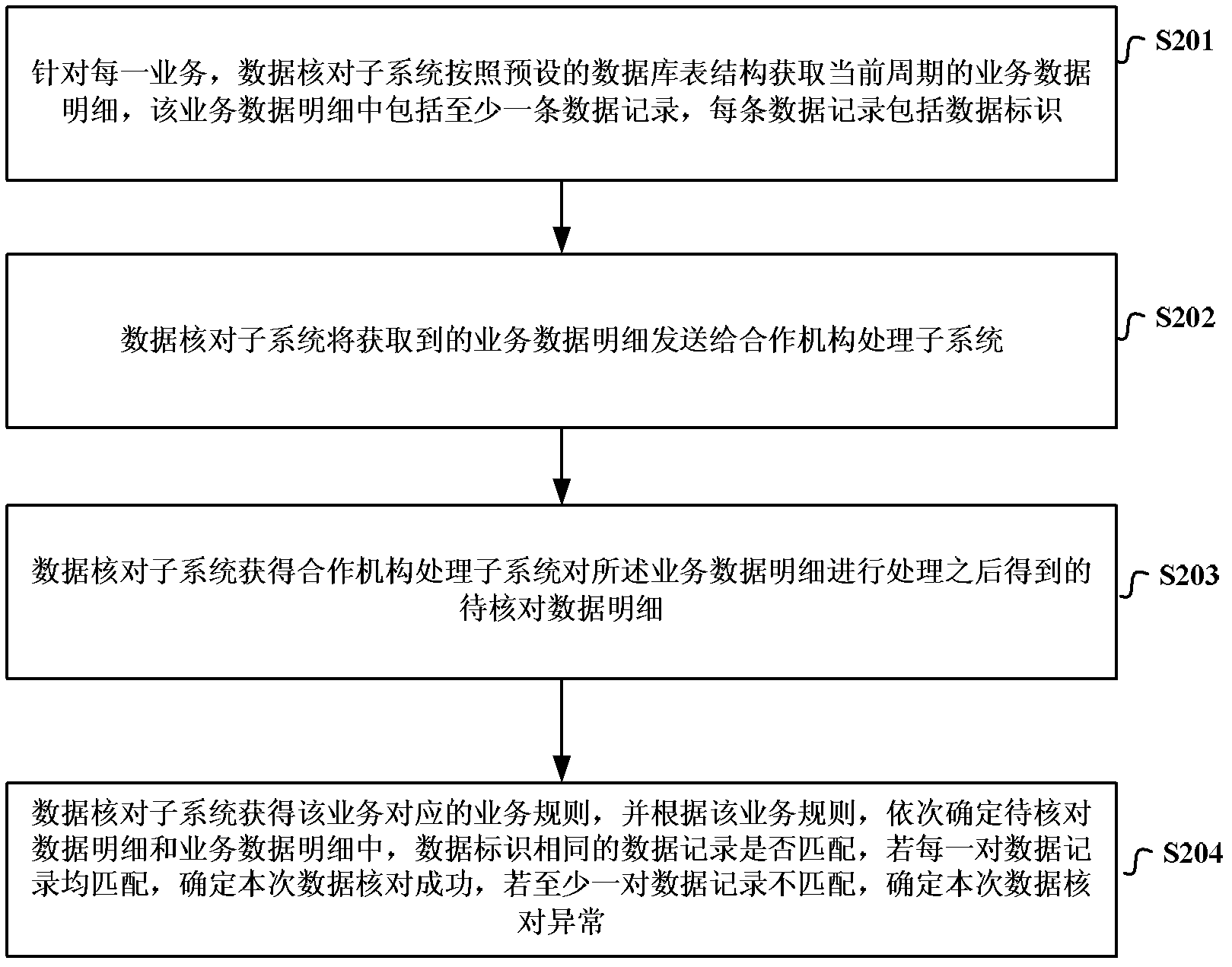
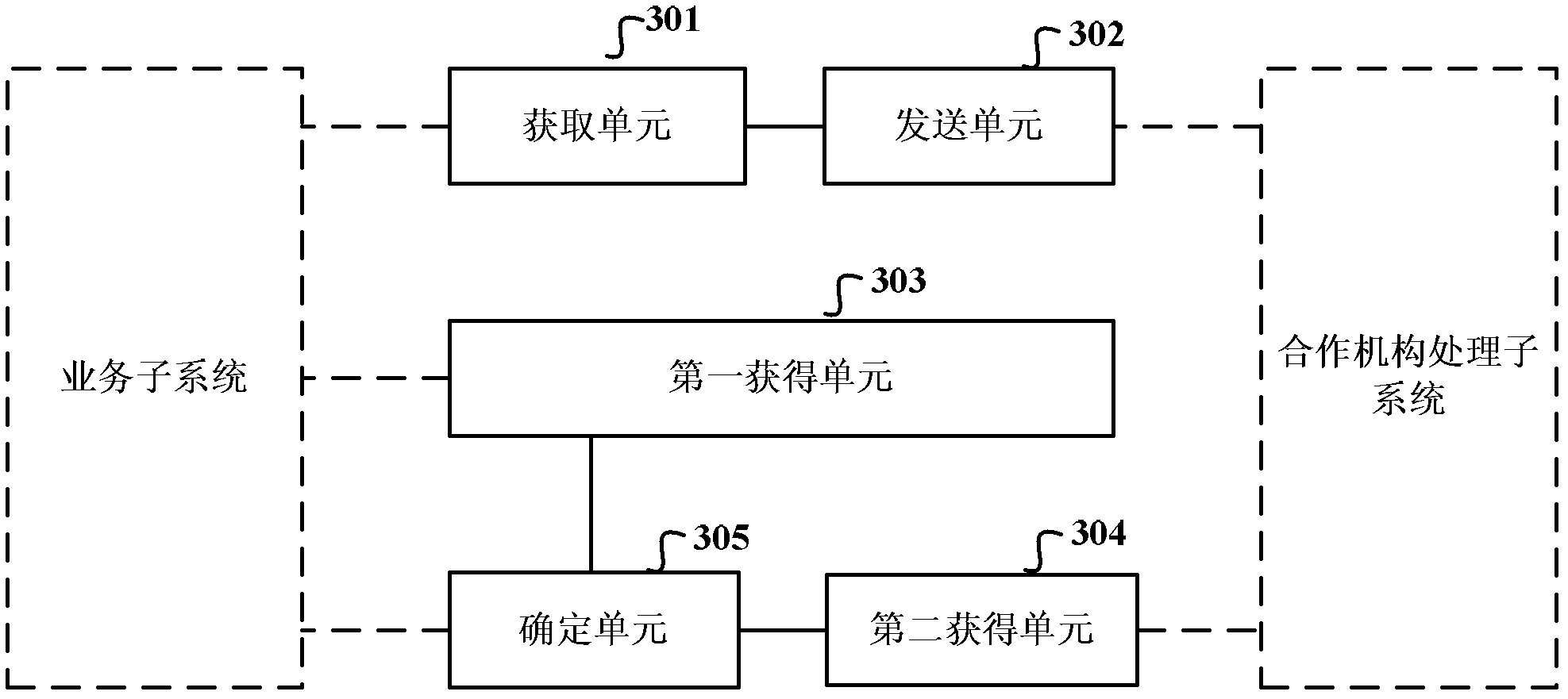
System, method and device of verification of data
InactiveCN103136276ASimplify processing logicSave processing resourcesSpecial data processing applicationsSource Data VerificationBusiness data
The invention discloses a system, a method and a device of verification of data so as to simplify the processing logic of the verification of the data and save the processing resources of equipment aiming at business data of different types. The system of the verification of the data comprises a service sub-system, a data verification sub-system and a cooperating mechanism processing sub-system. The service sub-system is used for configurating the service rule of each service, and storing the service data details of the service according to a preset period. The data verification sub-system is used for acquiring the service data details and sending the service data details to the cooperating mechanism processing sub-system when a current period is finished, receiving data details to be verified sent by the cooperating mechanism processing sub-system, and sequentially matching each data record according to the pre-allocated service rules. If each pair of data records is matched, the verification of the data is confirmed to be successful, and if at least one pair of data records is not matched, the verification is confirmed to be abnormal. The cooperating mechanism processing sub-system is used for processing each data record after receiving the service data details, obtaining the data details to be verified, and sending the data details to be verified to the data verification sub-system.
Owner:ALIBABA GRP HLDG LTD
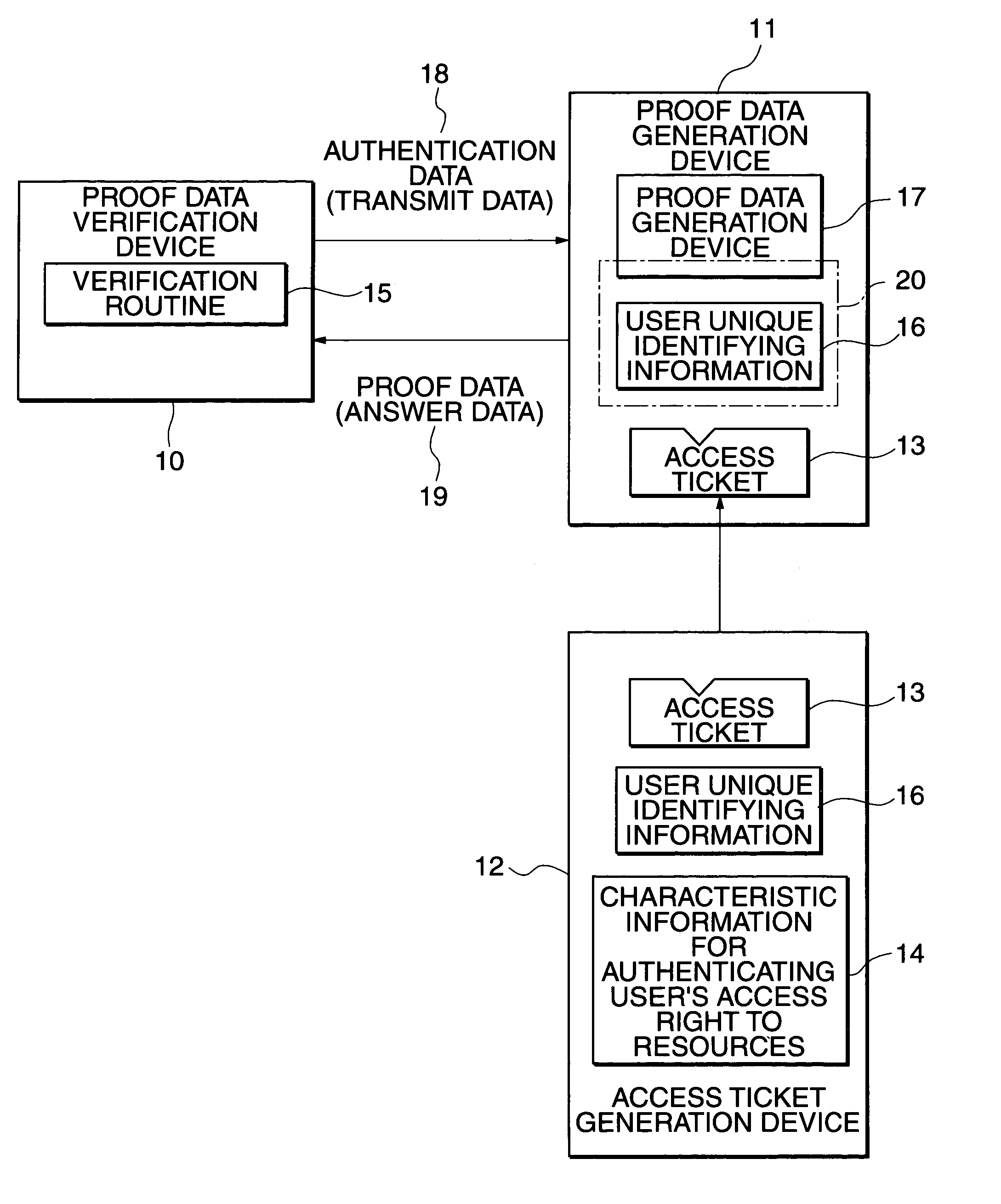
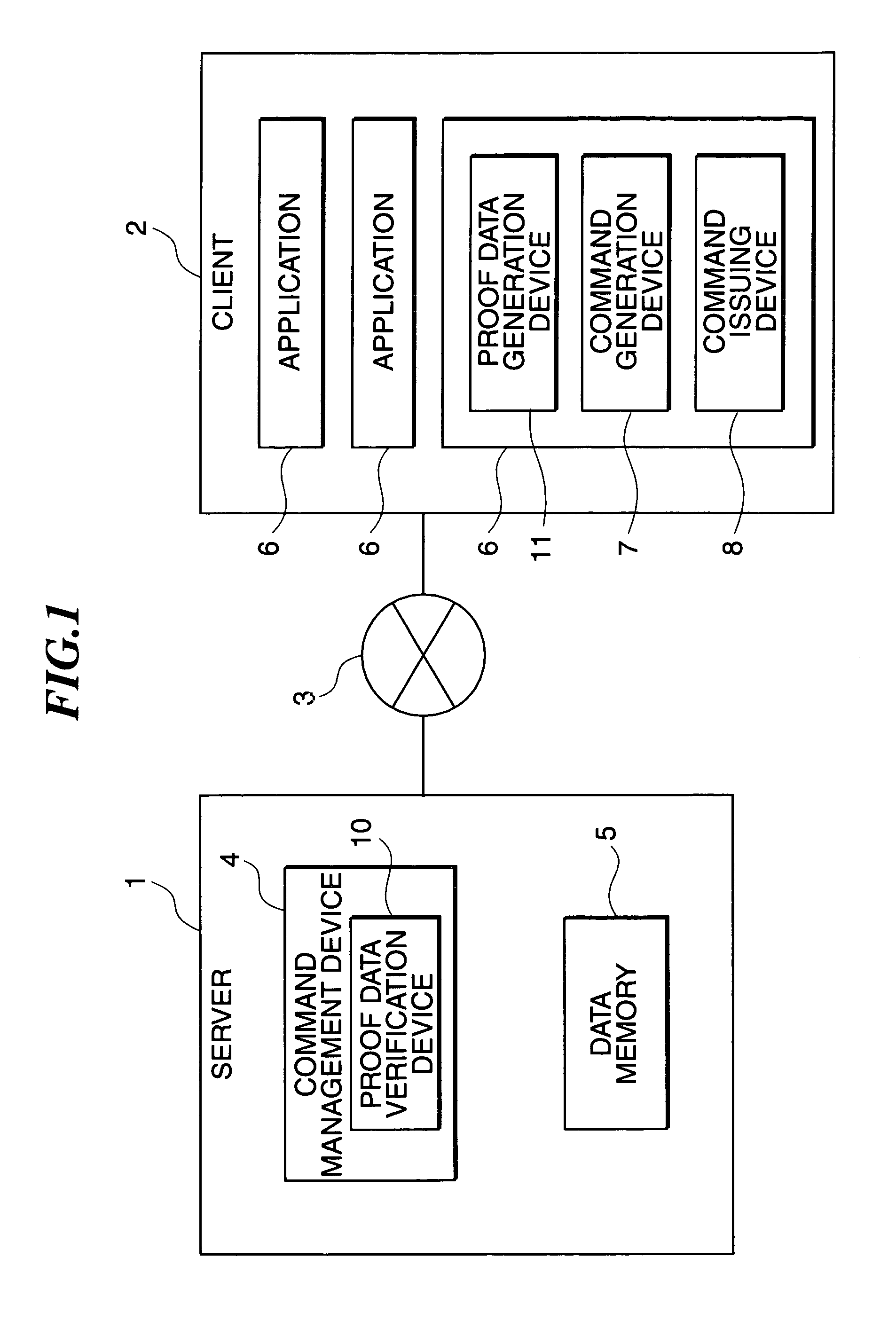
Data storage device provided with function for user's access right
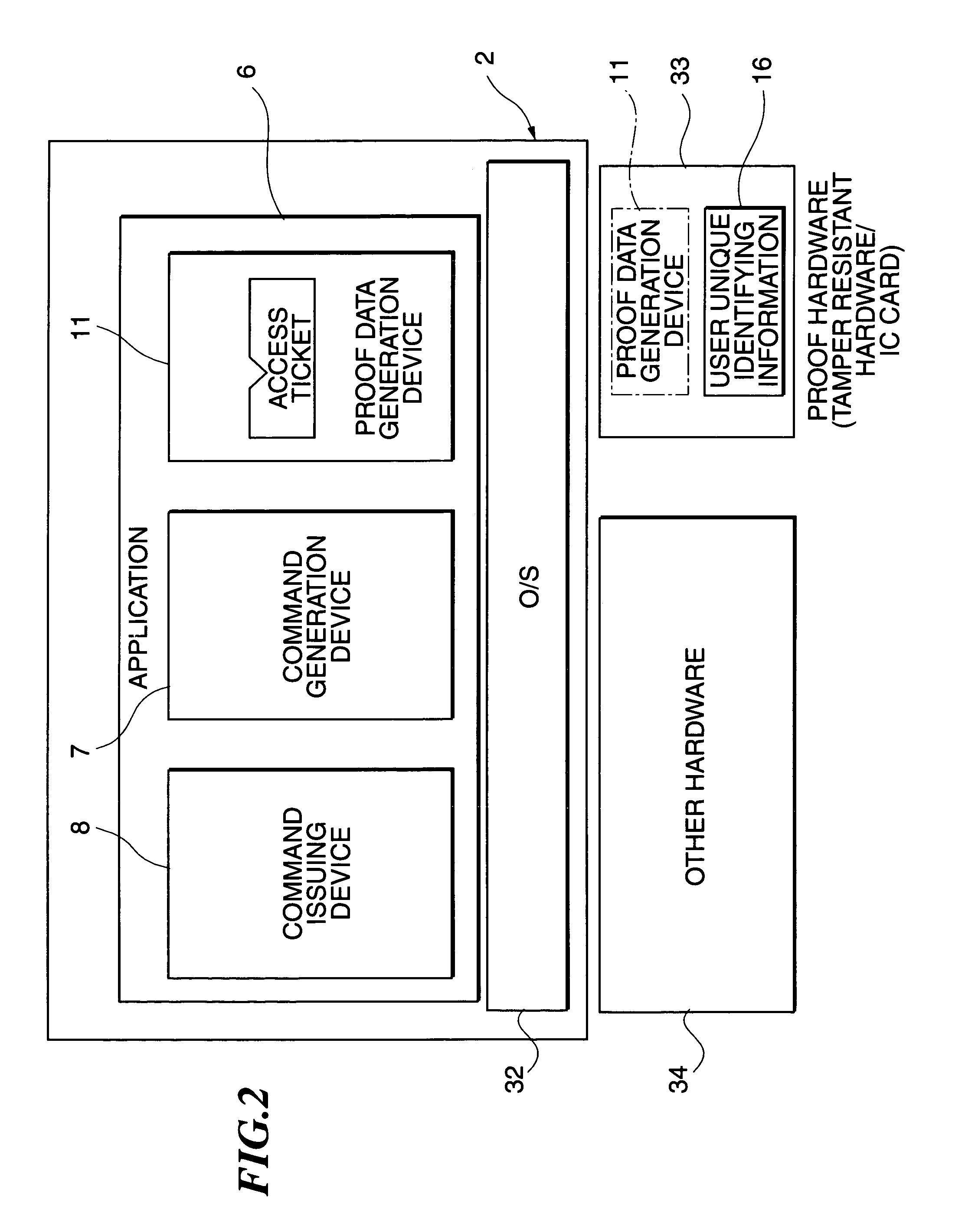
InactiveUS7155745B1Protection technologyImprove abilitiesProgram control using stored programsDigital data processing detailsHard disc driveSource Data Verification
An application of a client includes a proof data generation device, a command generation device, and a command issuing device. A command and proof data are sent to a server from the application of the client, and a command management device of the server receives them. A proof data verification device verifies the access right of a user to the application on the basis of the proof data, and enables a data storage device to be accessed in accordance with the command, if the verification is successful. The data storage device, used instead of a commonly used hard disk drive, includes a phase change type optical memory or a phase separation type optical memory to execute write once recording. Thus, the access to the data storage device is flexibly controlled.
Owner:FUJIFILM BUSINESS INNOVATION CORP
System and method for tax filing, data processing, data verification and reconciliation
A system and method for processing transaction and use tax data, verifying tax calculations / determinations, reconciling calculation / determination errors, and filing and / or paying taxes owed to the appropriate jurisdictions is provided.
Owner:STP GRP LLC
Systems and methods for data verification
Systems and methods for verifying data including income and employment, assets, healthcare claims, clinical data, and other types of data subject to various regulatory and / or privacy restrictions.
Owner:EXPERIAN INFORMATION SOLUTIONS
Method for precisely marking arriving time of initial wave of fault generated traveling waves for electricity transmission line
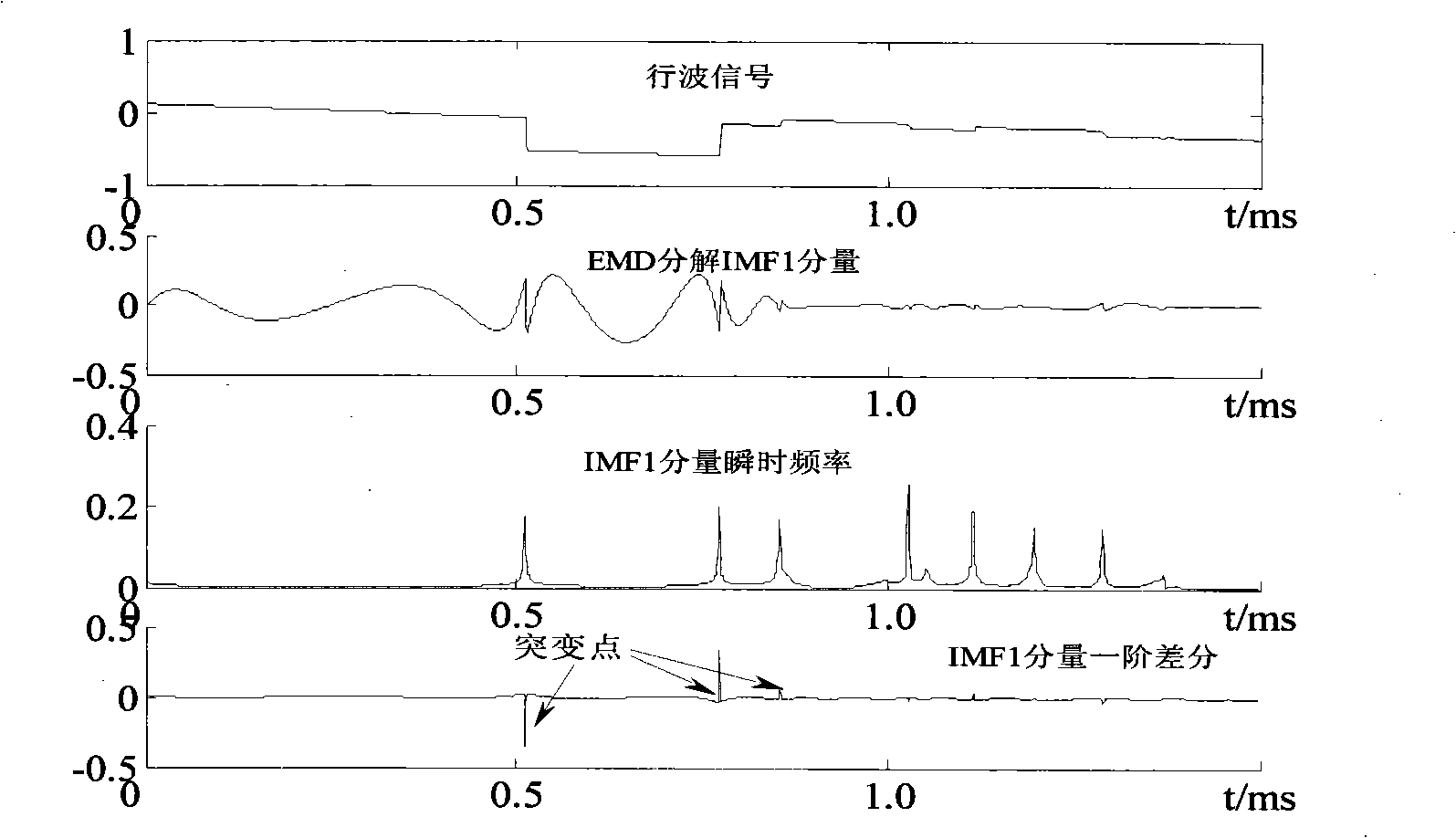
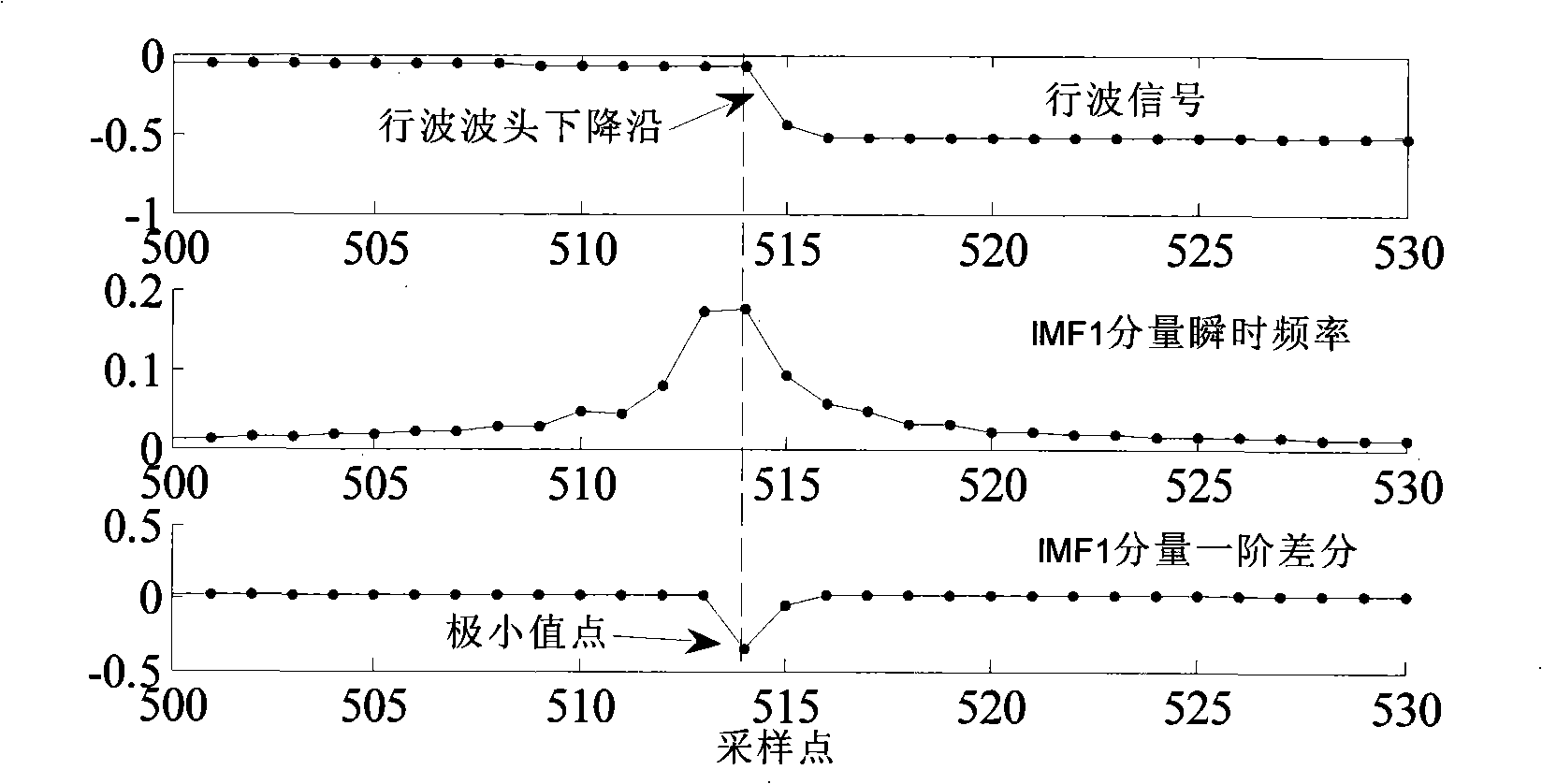
ActiveCN101291055ACalculation speedNo lossEmergency protective circuit arrangementsFault locationDecompositionOriginal data
The invention relates to a method for precisely calibrating the arrival moment of initial wave head of traveling wave in transmission line faults by utilizing Hilbert-Huang transformation (HHT). The method comprises the following steps that: HHT transformation is carried out to faulty traveling wave data; EMD decomposition is carried out first, and IMF1 component intensively embodies the high frequency information of raw data and completely self-adapts to the time scale of the raw data; the IMF1 component is taken as an investigation object; an order difference curve of the IMF1 component is evaluated, and Hilbert transformation is carried out to the order difference curve so as to obtain an instantaneous frequency curve of the IMF1 component; the advantages of two curves are combined to seek an extreme point, and the extreme point is compared with the raw data to obtain the precise calibration for the arrival moment of the head of a traveling wave, and error is controlled to be less than one sampling point. In a strong-noise environment, IMF2 or IMF3 is selected, and the precise calibration for the arrival moment of the head of the traveling wave can be achieved as well according to the method. All the other mathematical methods cannot achieve the precision of the method of the invention. Principle analysis, simulation data and engineering data verification show that the method is precise to calibrate the arrival moment of the initial wave head of the traveling wave in transmission line faults.
Owner:KUNMING UNIV OF SCI & TECH
Method and system for managing a healthcare network
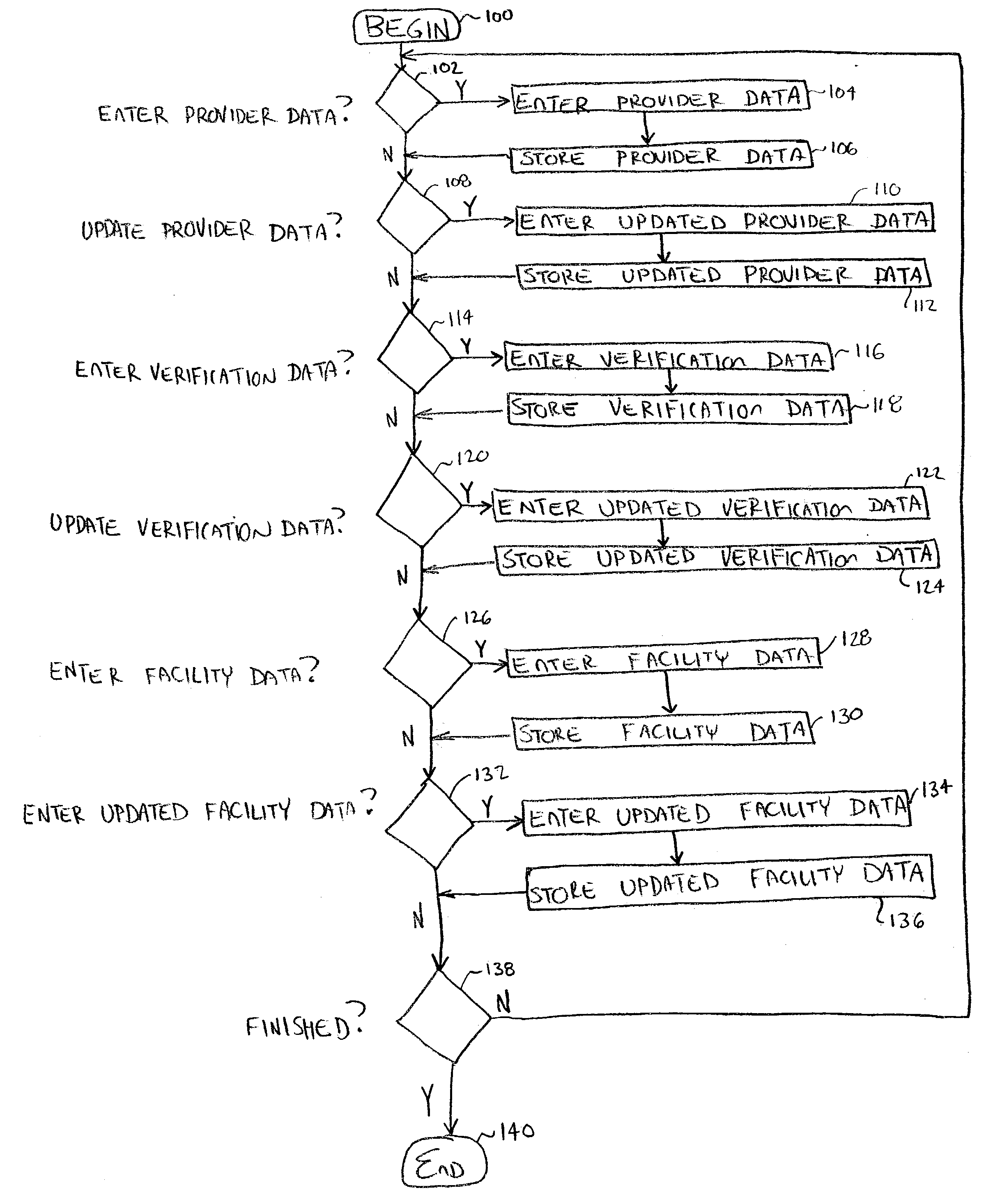
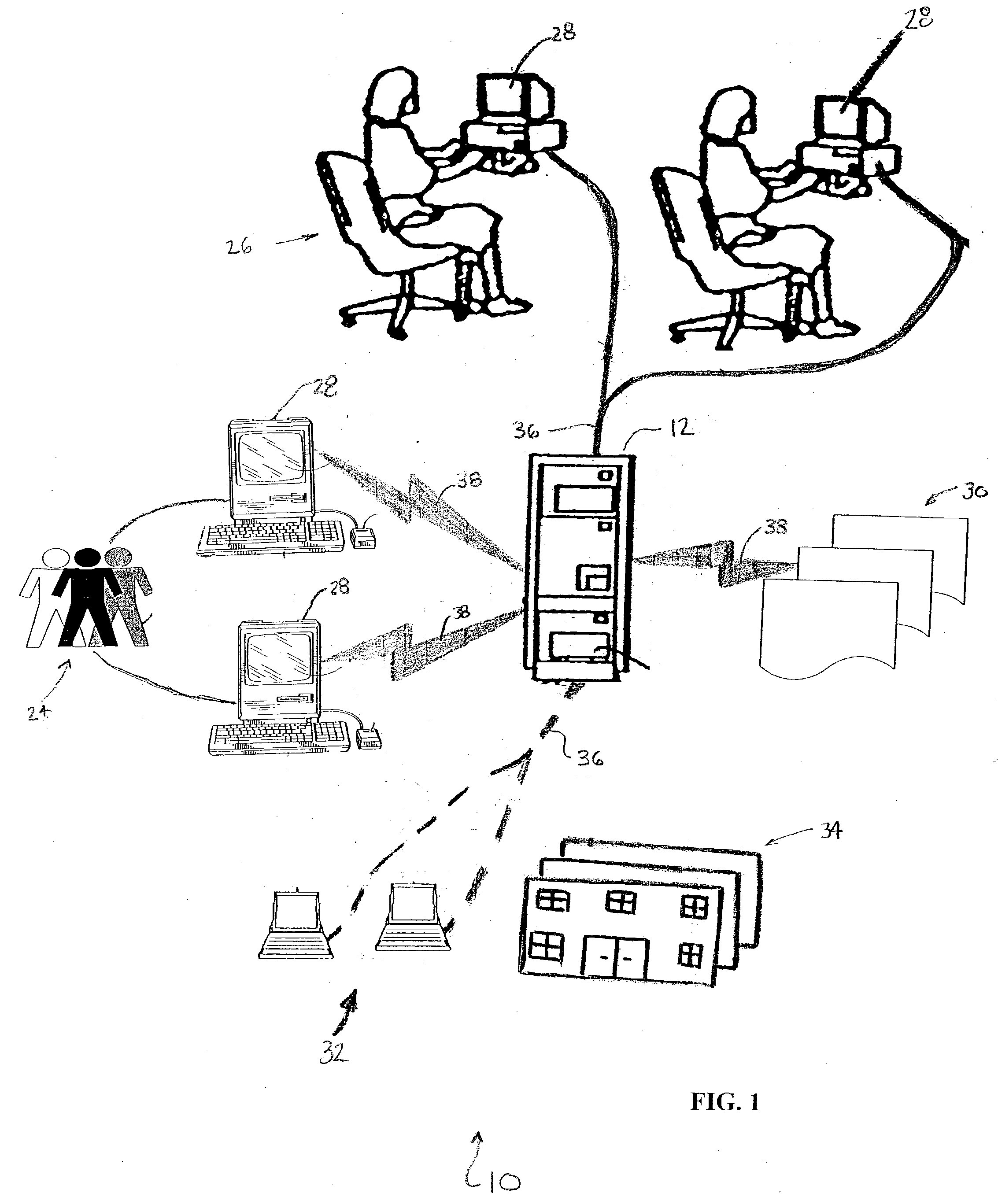
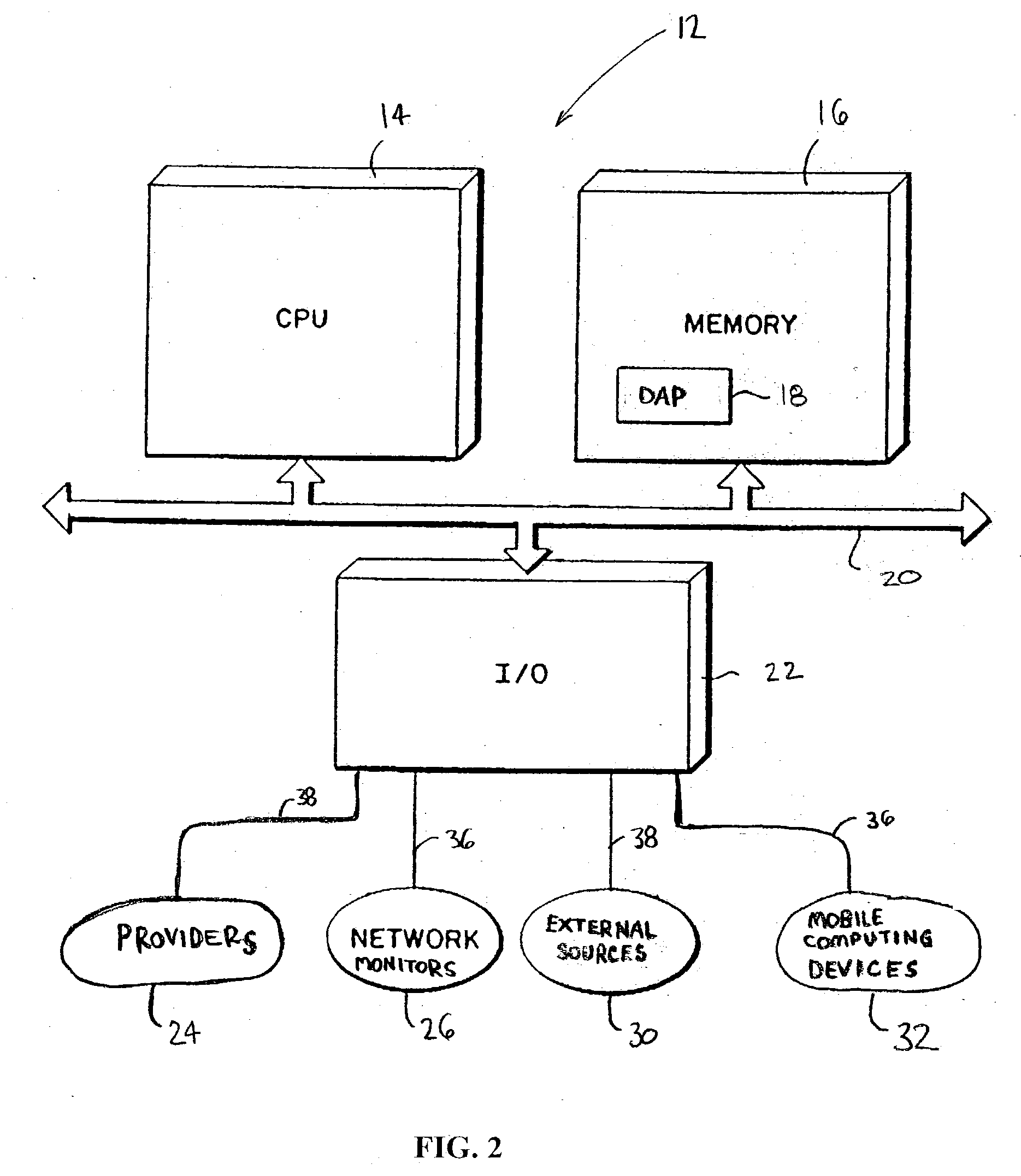
InactiveUS20030236682A1Quickly and efficiently identifyTelemedicinePatient personal data managementRelational databaseElectronic form
A method for managing a healthcare network comprising providing a relational database for provider data, verification data, facility data, updated provided data, updated verification data, and updated facility data. Automated notification is provided when it is time to up-date the provider data, verification data, facility data, and whether it has been done. Providers, network monitors, and facilities are so notified. The data is provided through a telecommunication, internet; or other electronic session, and compared relative to one or more objective standards. The objective standards are provided via one or more electronic forms stored within the database. These electronic forms also facilitate data capture by healthcare providers and healthcare facilities, and can be pre-populated with information from the database. Mobile computer devices capture information at the facilities, which is then downloaded into the database. The method can be implemented as a computer-readable storage medium or as computer executable code stored thereon.
Owner:INDEPENDENT PHYSICIANS NETWORK
Data verification system for a near field communications enabled display
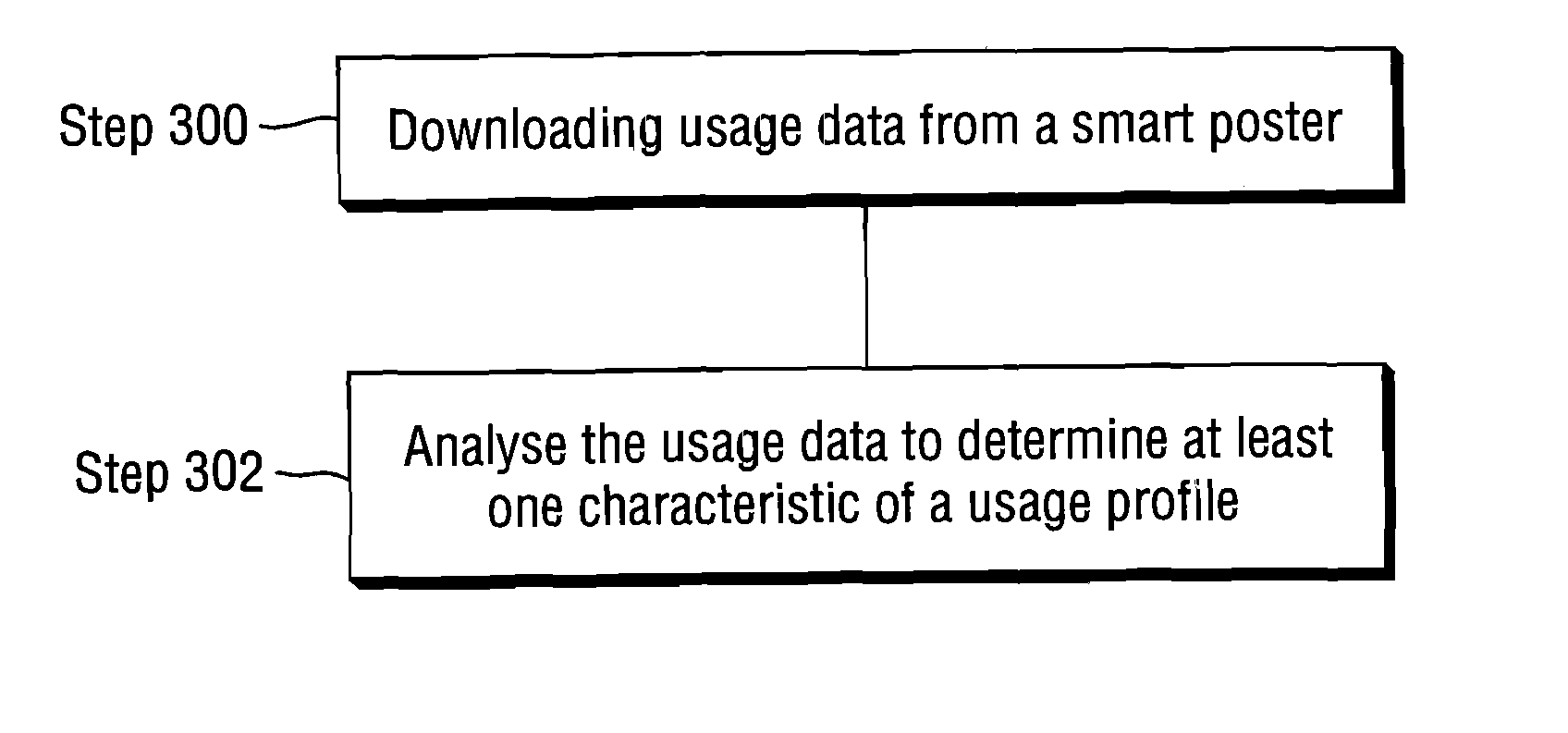
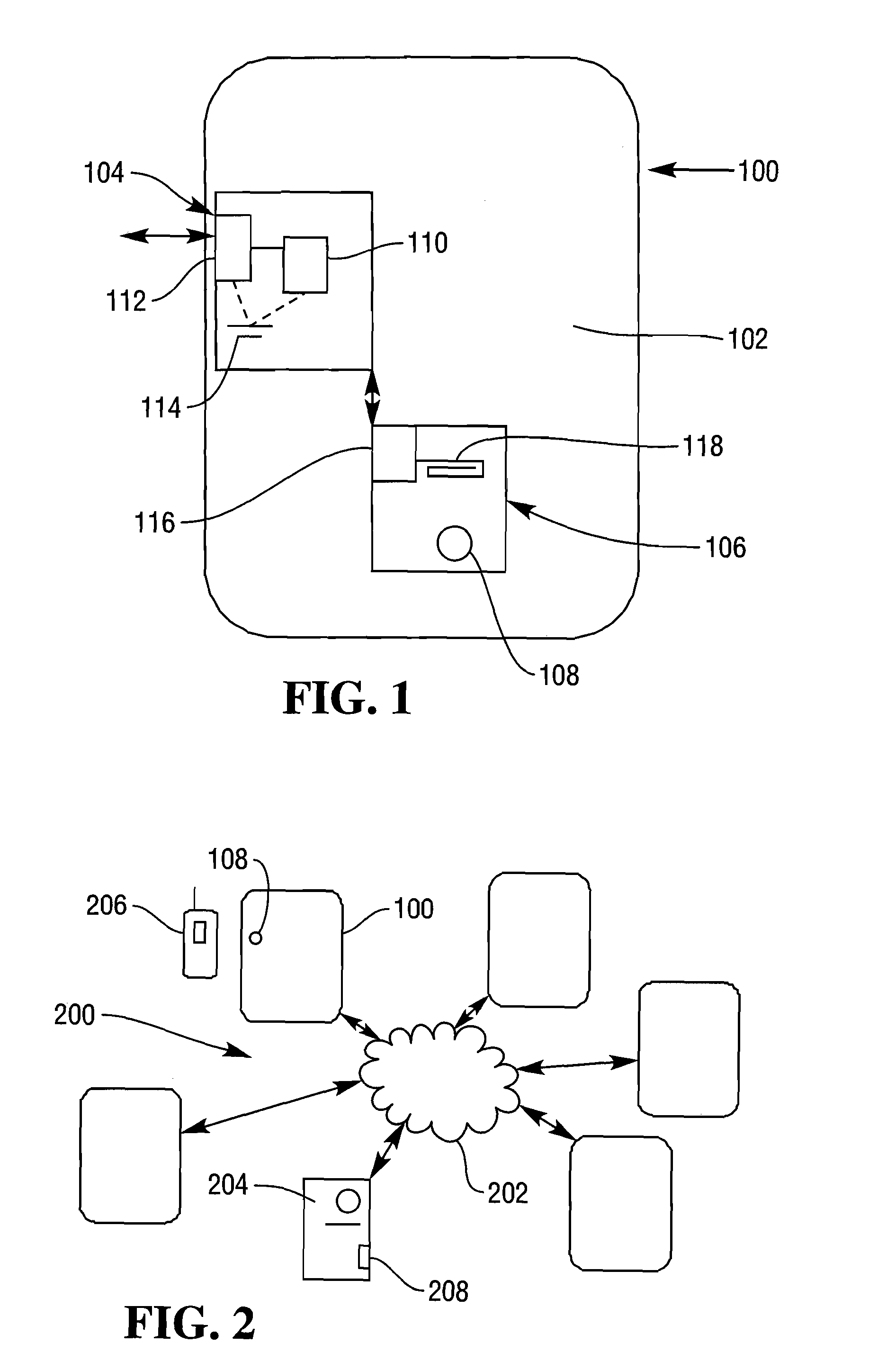
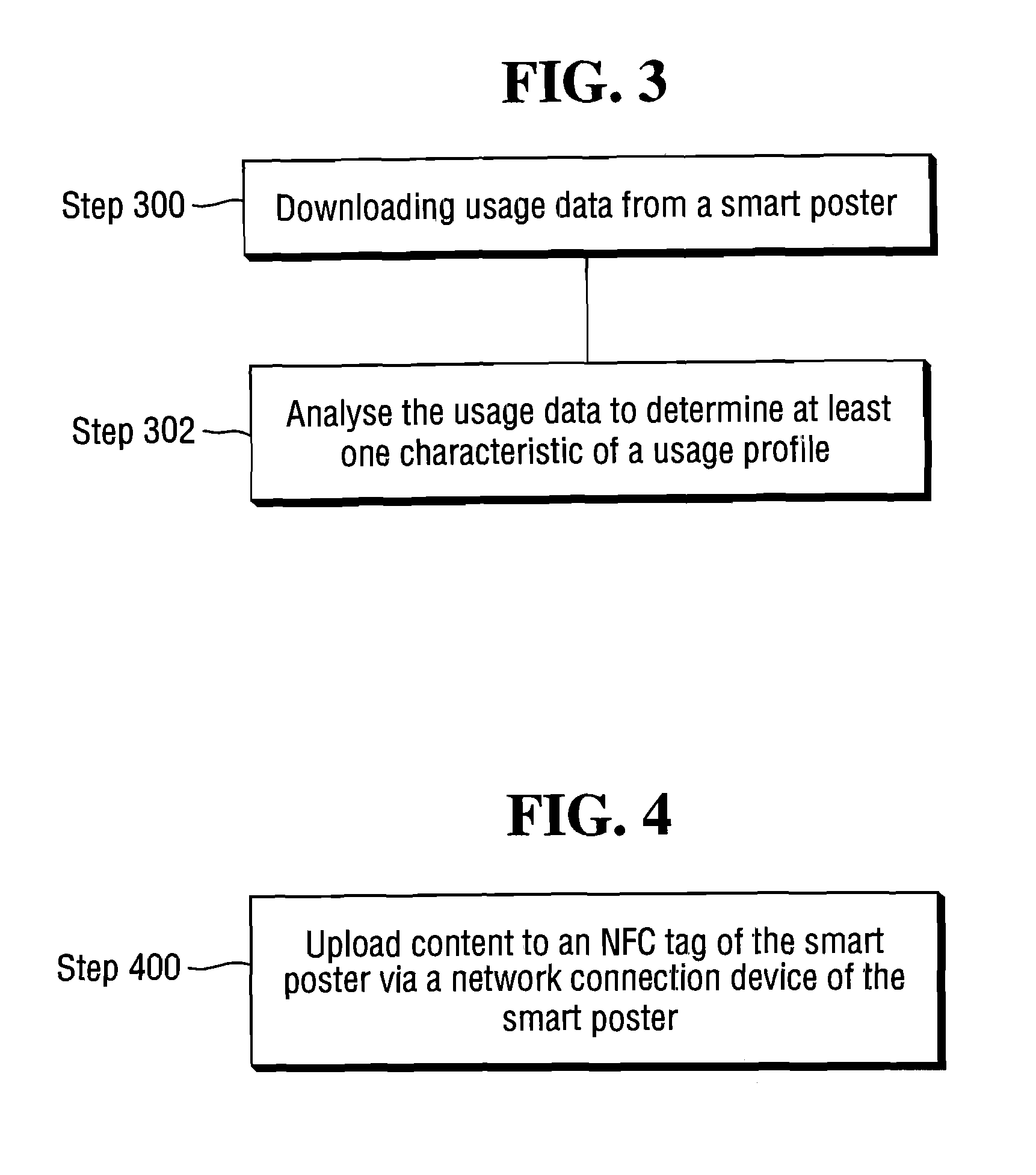
ActiveUS8126505B2Maximizing numberGood curative effectNear-field transmissionSpecial service for subscribersComputer hardwareSource Data Verification
An NFC enabled telecommunications communication device is mounted behind the touch point of a smart poster. The content data downloadable from the smart poster is managed remotely, monitored and usage data of the smart poster analyzed at a server via the telecommunications device.
Owner:NCR CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com