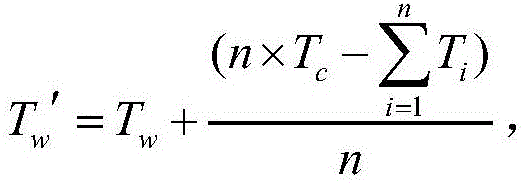Patents
Literature
217 results about "Valid time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
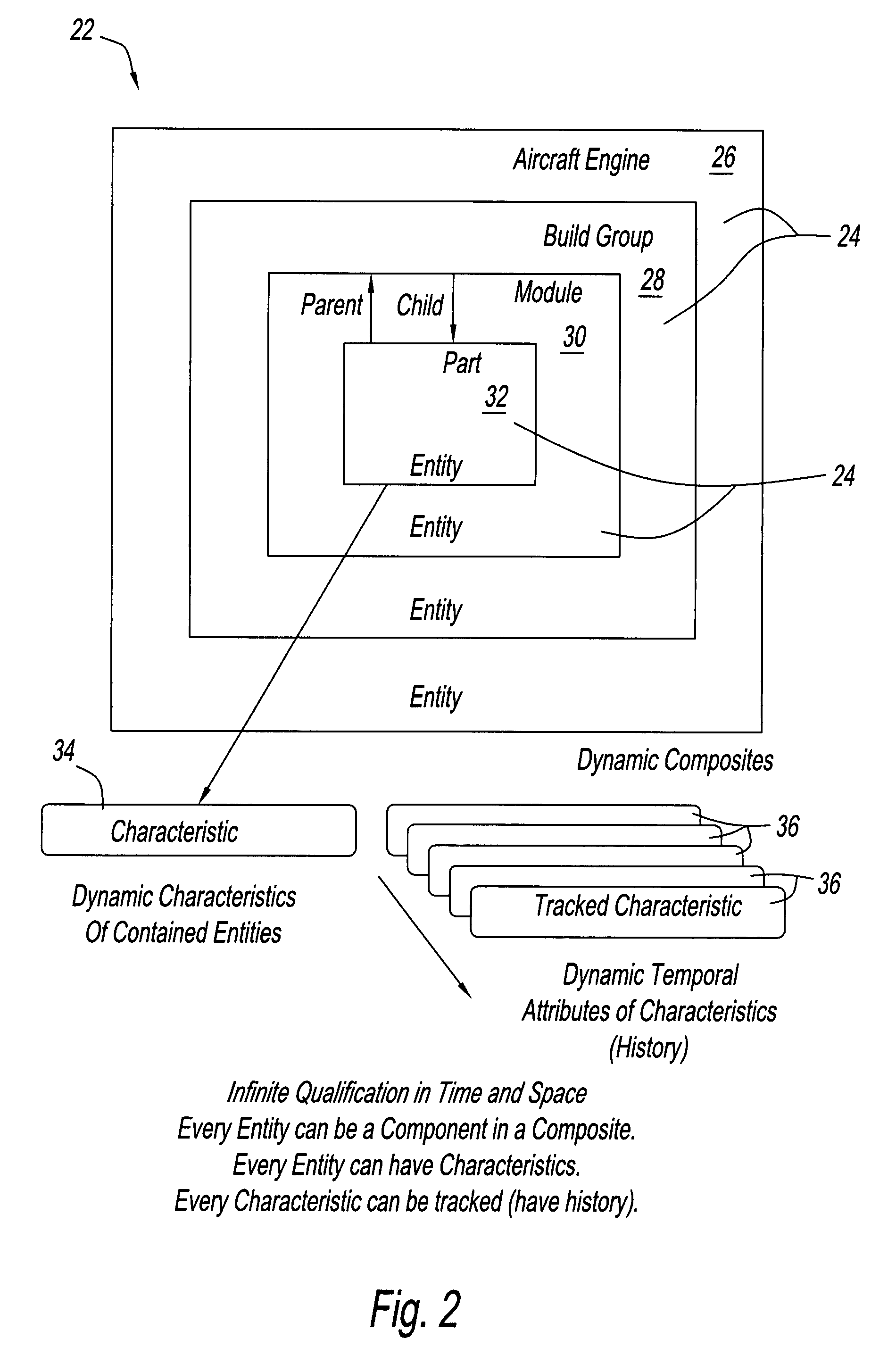
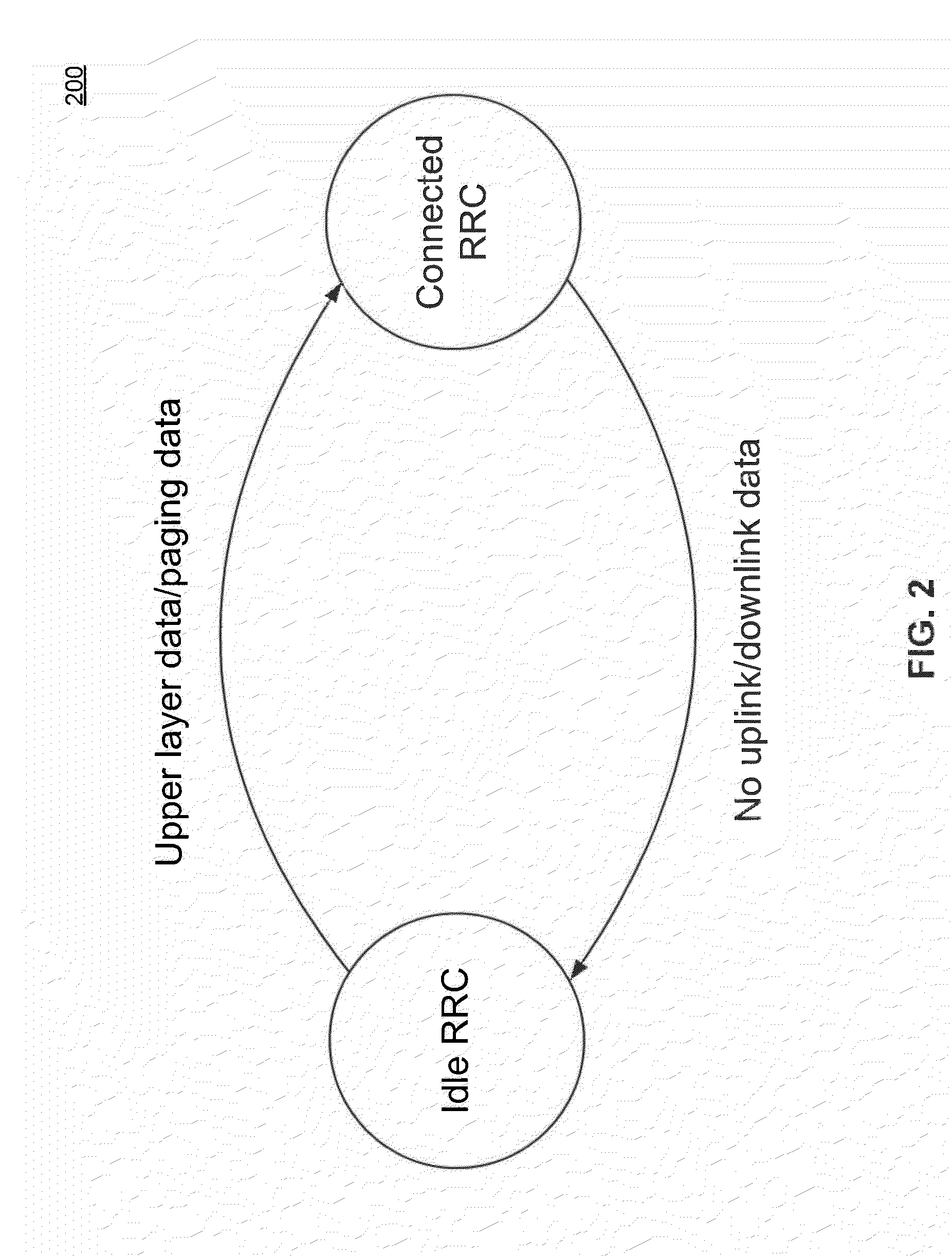
In temporal databases, valid time (VT) is the time period during which a database fact is valid in the modeled reality. As of December 2011, ISO/IEC 9075, Database Language SQL:2011 Part 2: SQL/Foundation included clauses in table definitions to define "application-time period tables" (that is, valid-time tables). Valid time was coined by Richard T. Snodgrass and his doctoral student.
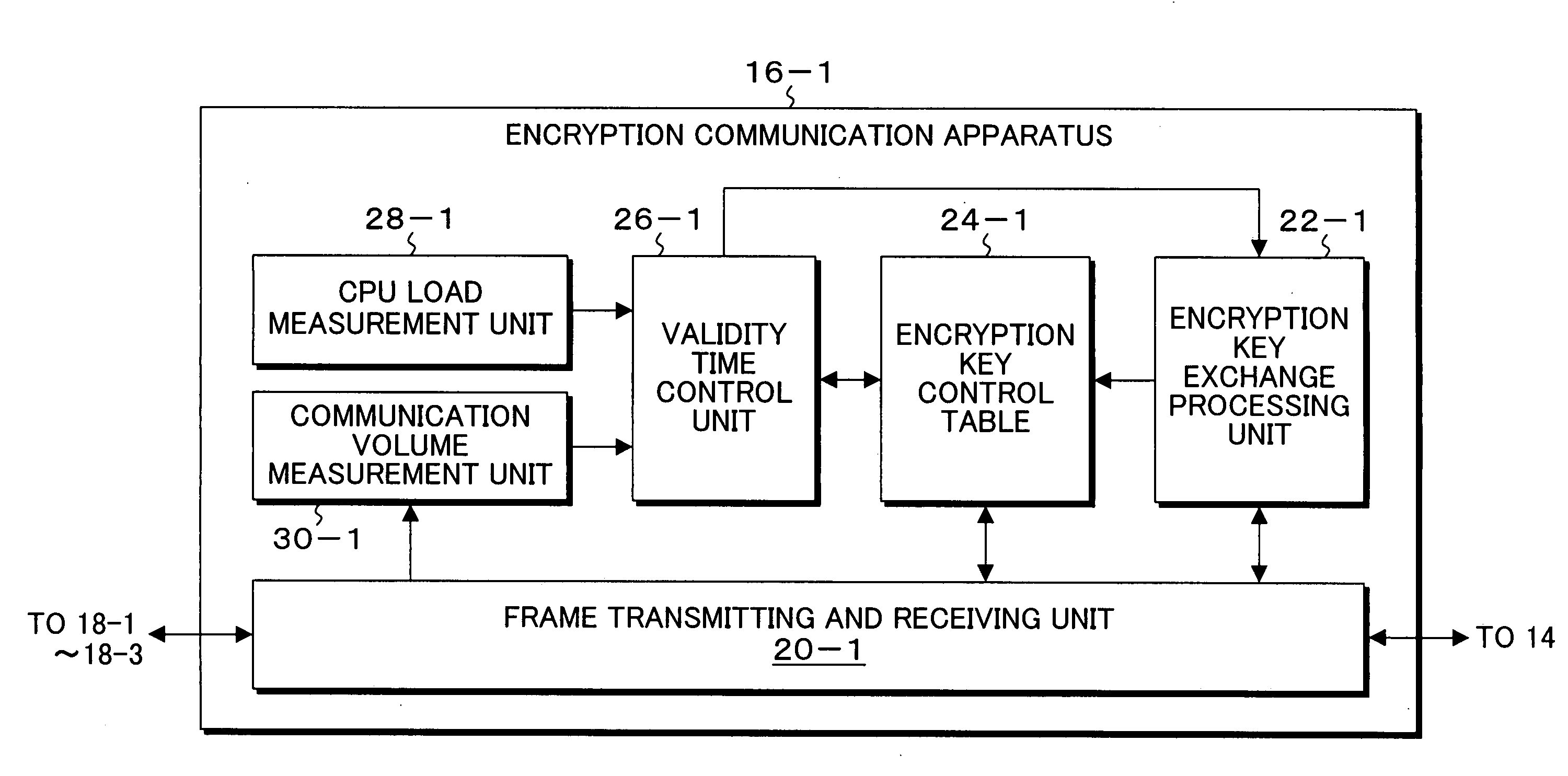
Encryption communication system, apparatus, method, and program
InactiveUS20080098226A1Avoid it happening againUser identity/authority verificationComputer hardwareCommunications system
A plurality of encryption communication apparatuses to which terminal apparatuses are connected are connected via a network, data received from the terminal apparatus which is a transmission source is encrypted by the encryption communication apparatus and transmitted to the other encryption communication apparatus, and data received from the other encryption communication apparatus is decrypted and transmitted to the terminal apparatus which is a transmission destination. Upon initiation of first communication with the other encryption communication apparatuses, the encryption communication apparatus generates and exchange encryption keys according to an encryption key exchange protocol, records them in the encryption key control table and, and sets validity time so as to control that. The encryption key is subjected to encryption key update when validity time is close; however, even during validity time period, when the state that CPU load is low is determined, the encryption key of the encryption communication apparatus which is a counterpart having a small communication volume is searched, and the encryption key is updated.
Owner:FUJITSU LTD
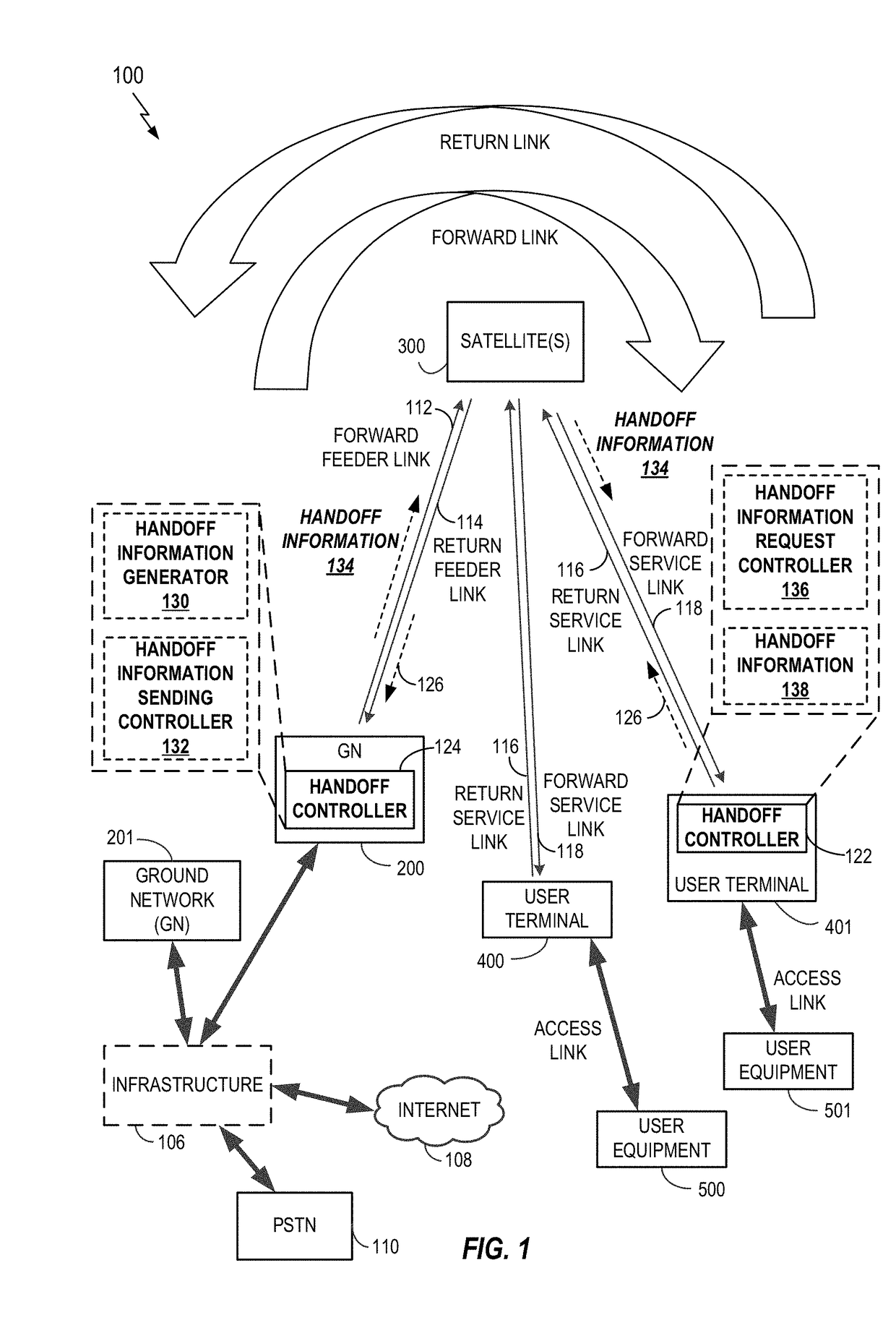
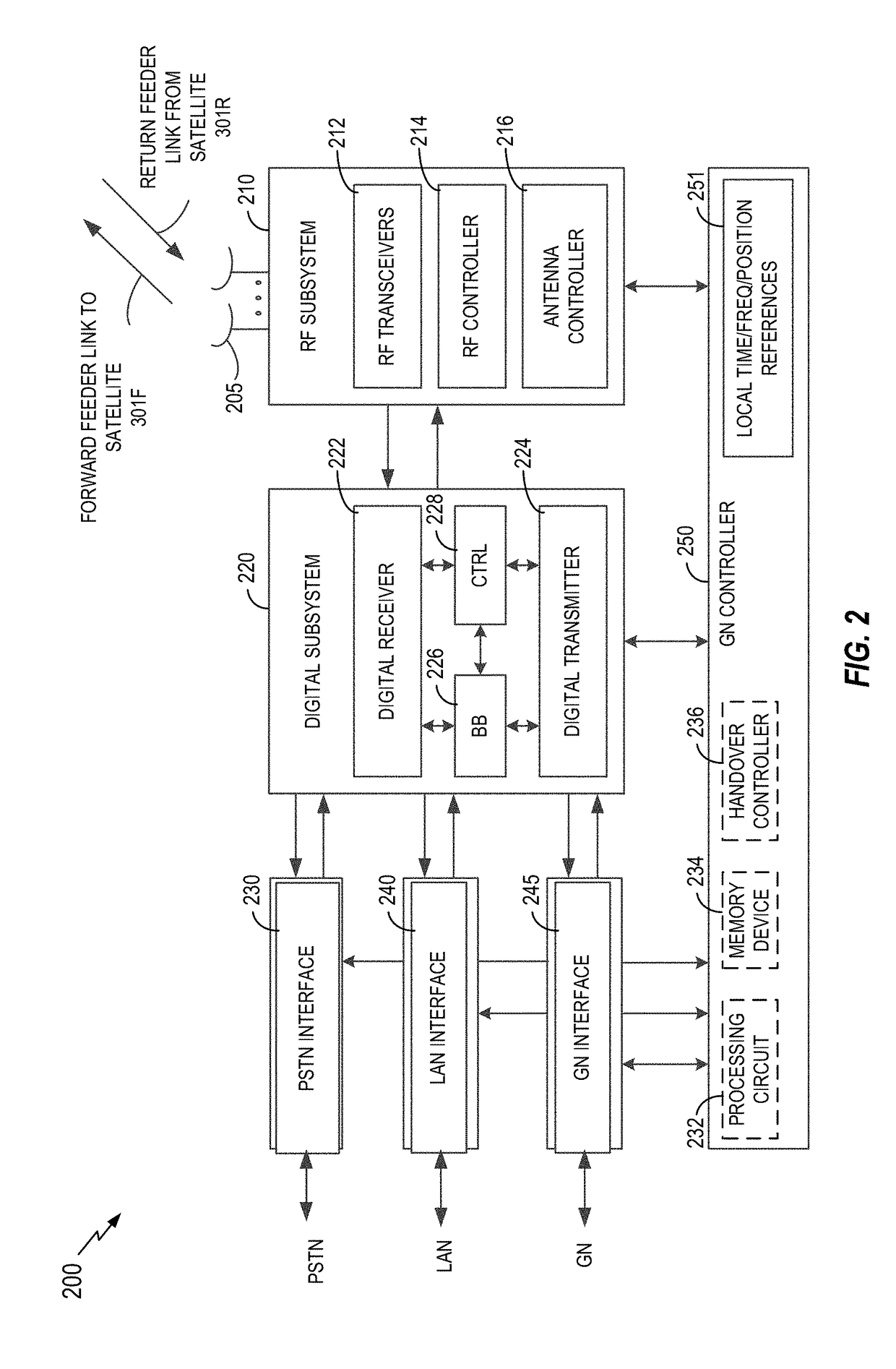
Handoff for satellite communication
Various aspects of the disclosure relate to handoff (e.g., idle mode handoff or other types of handoff) for a user terminal. In some aspects, a user terminal (UT) may request idle mode handoff information from a ground network (GN). Idle mode handoff information may include, for example, start times for a set of satellites, whereby each particular start time indicates when the UT may handoff to the corresponding satellite. The UT may send the request for idle mode handoff information to the GN when the UT has a defined number of valid entries (e.g., one unexpired entry) remaining in an idle mode handoff table. In some aspects, the idle UT may send the request for idle mode handoff information to the GN based on a time associated with a particular entry in an idle mode handoff table or based on a time of validity of an idle mode handoff table.
Owner:QUALCOMM INC
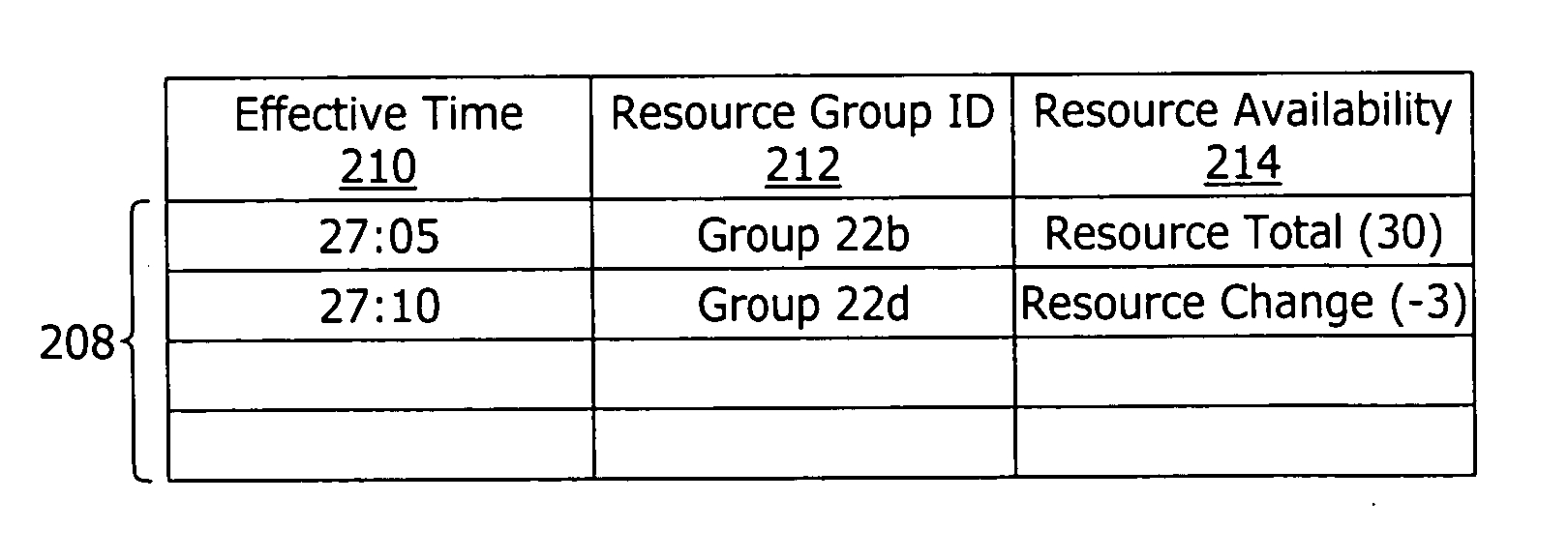
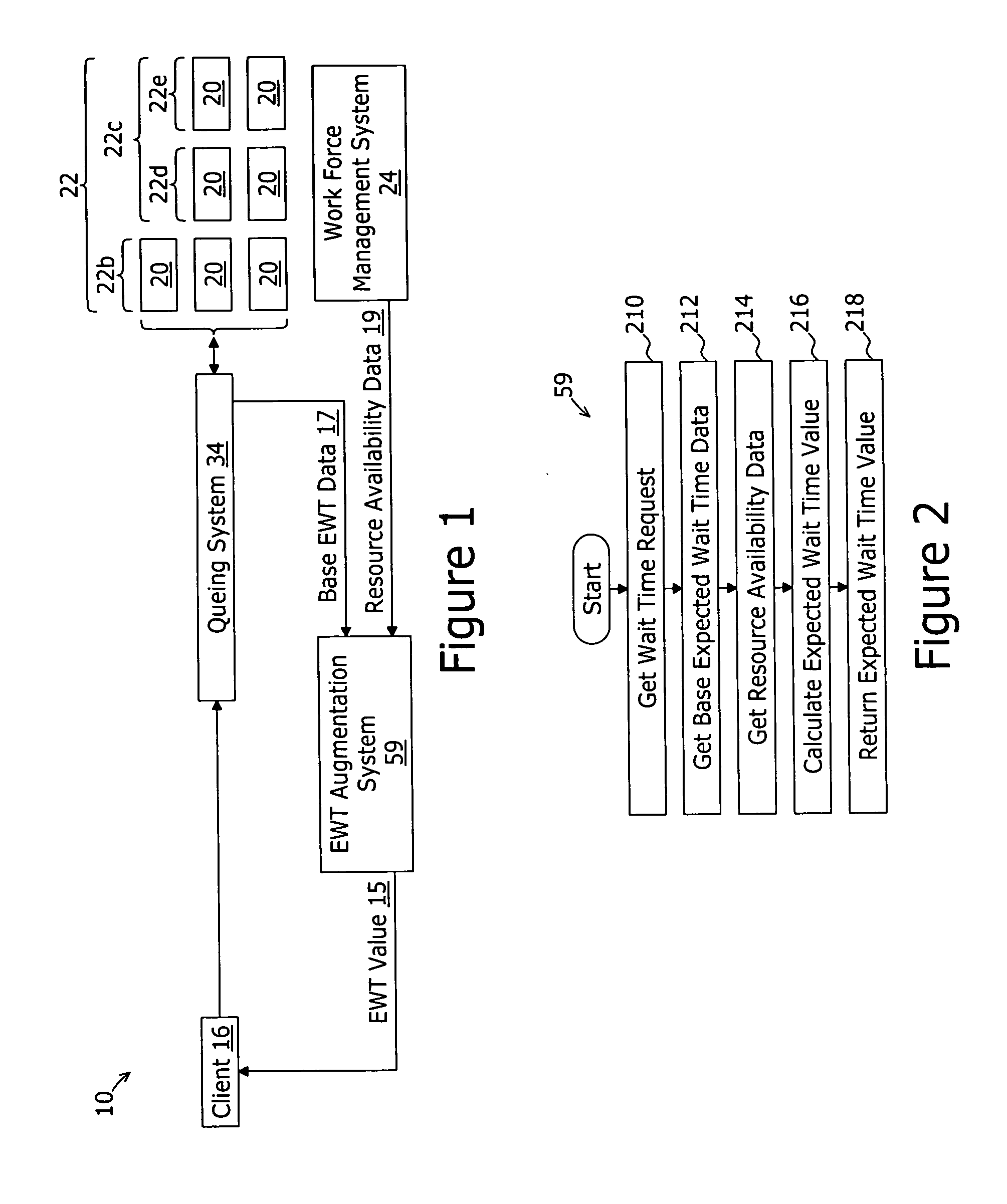
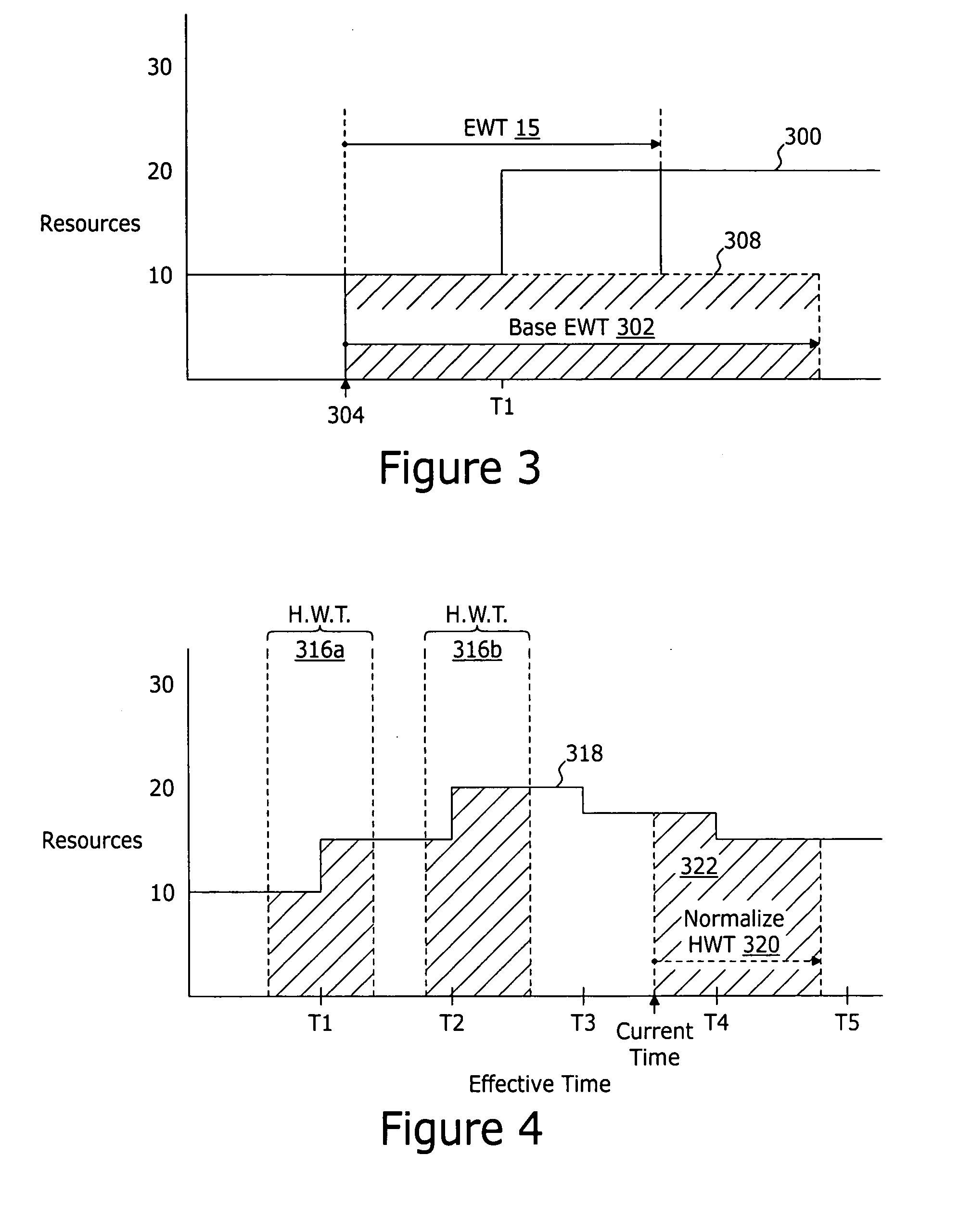
Expected wait time augmentation system and method
An expected wait time augmentation system generates an expected wait value representing a time duration expected to elapse before a subject client is connected to a resource for servicing. The expected wait time augmentation system comprises an interface to a work force management system for obtaining resource availability data and a wait time augmentation model for calculating an expected wait time value as a function of base expected wait time data and the resource availably data. The estimated wait time value is provided to the subject client. The resource availability data includes, but is not limited to, for a period of time: i) availability of resources; and ii) a scheduled change in the availability of resources. The scheduled change in the availability of resources may comprise a combination of data representing an effective time and a quantity of resources scheduled to be available at the effective time.
Owner:VIRTUAL HOLD TECH
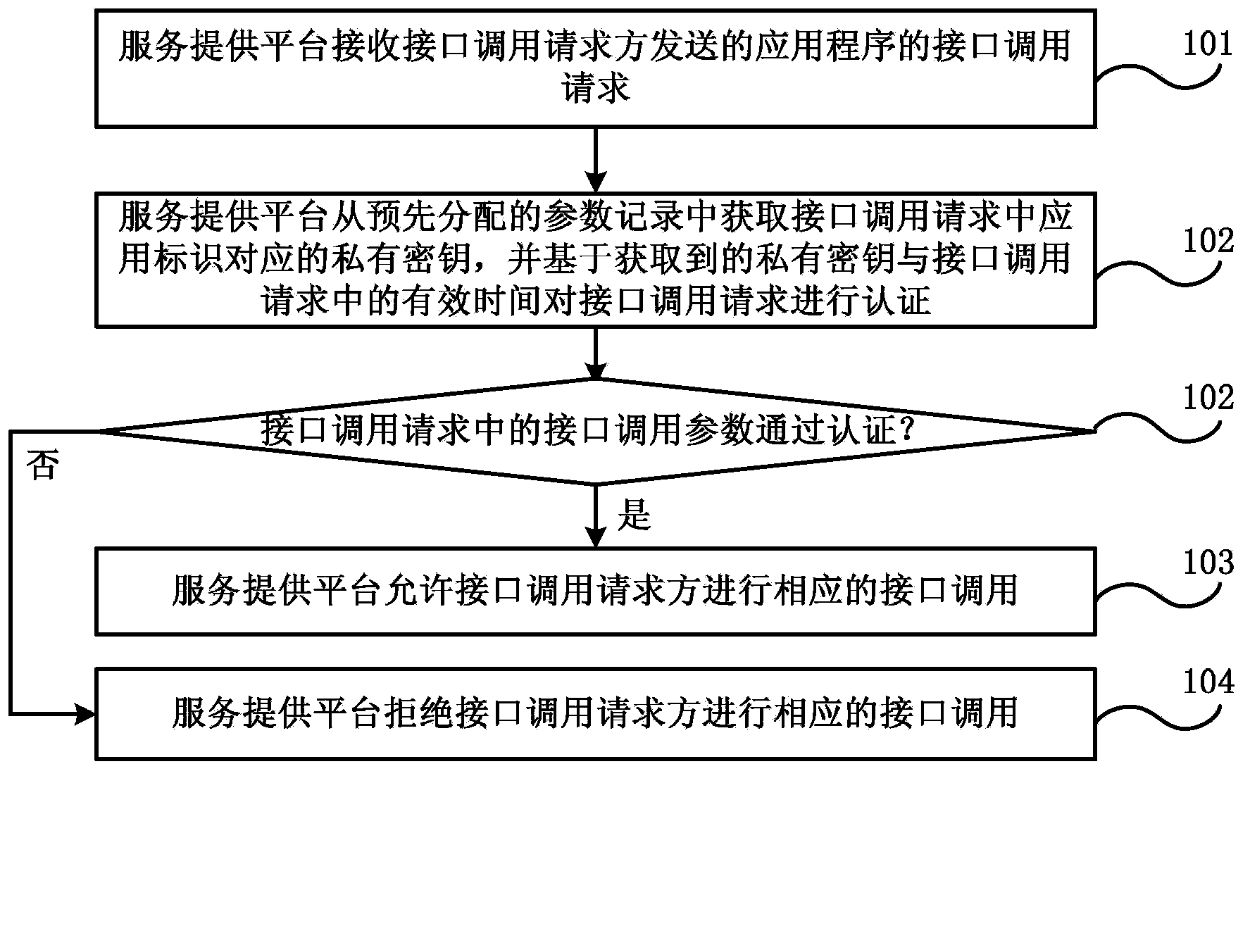
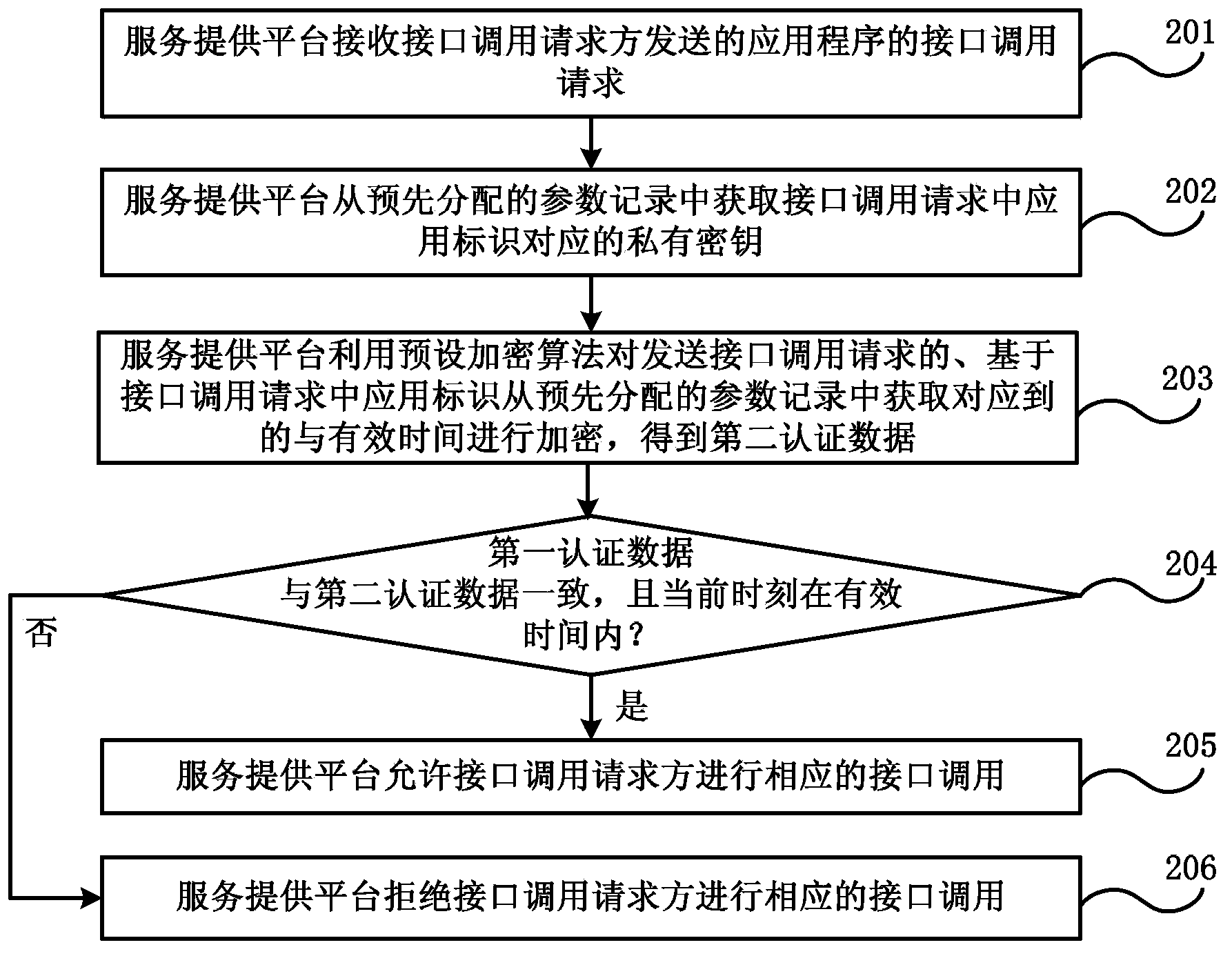
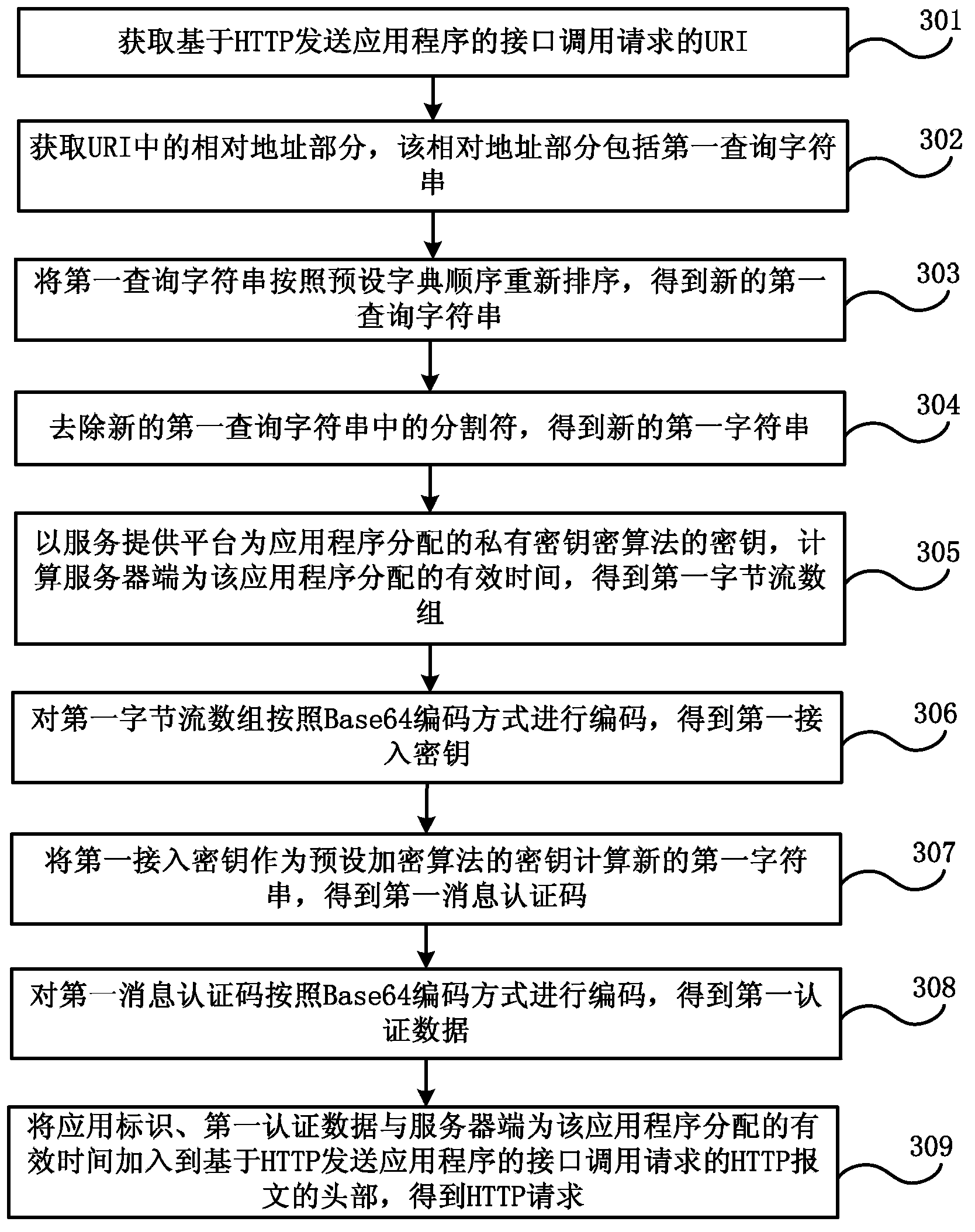
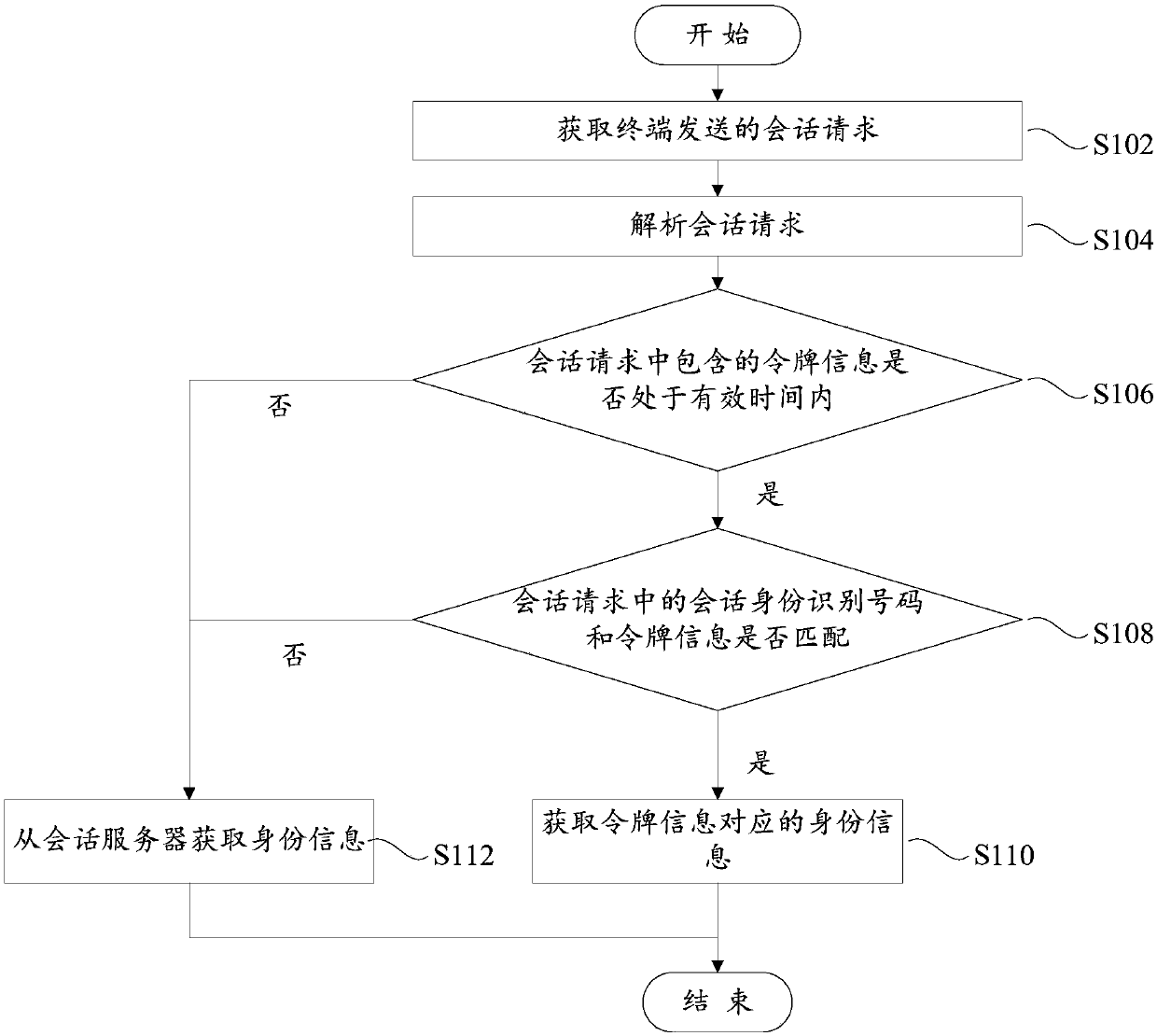
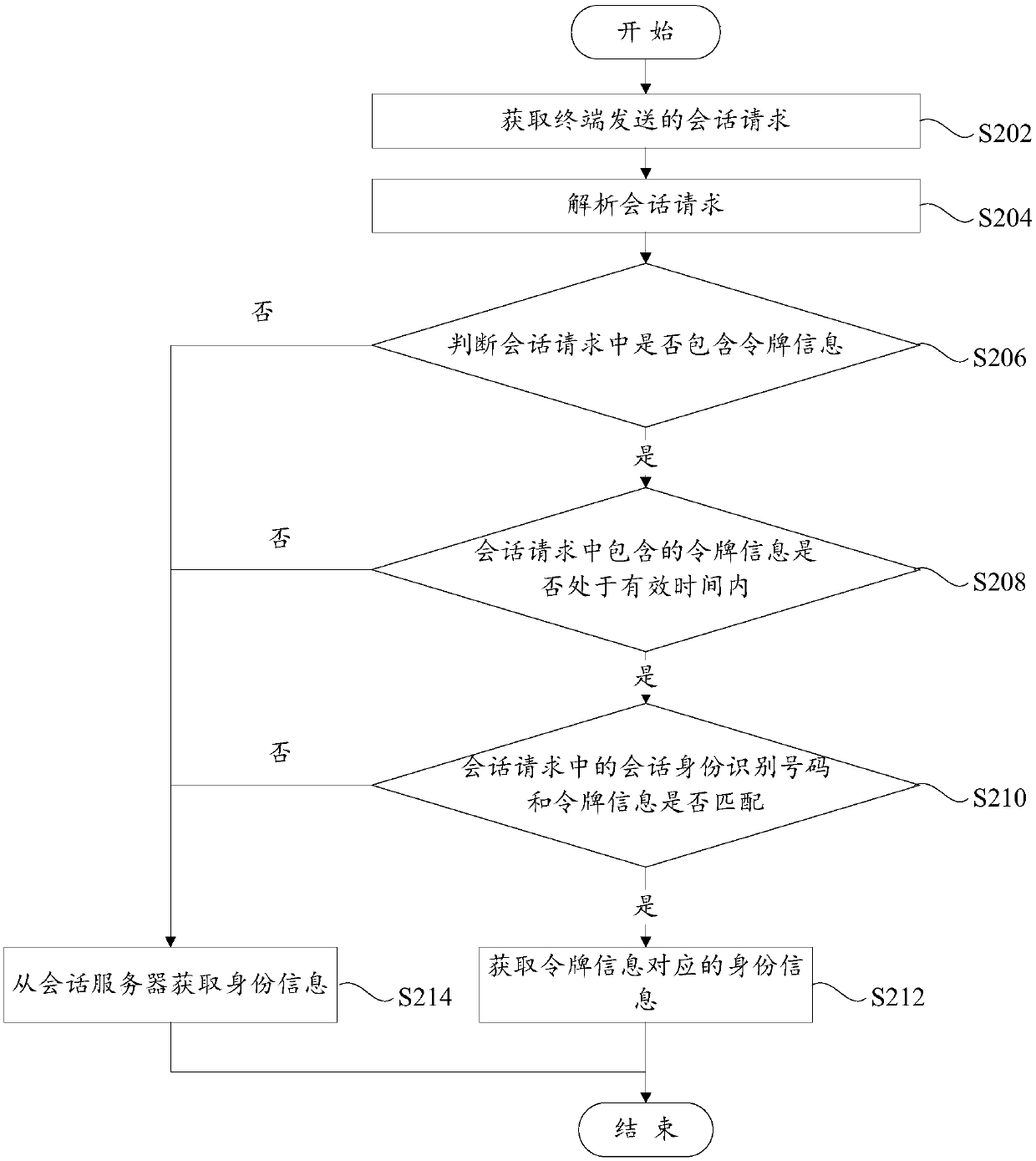
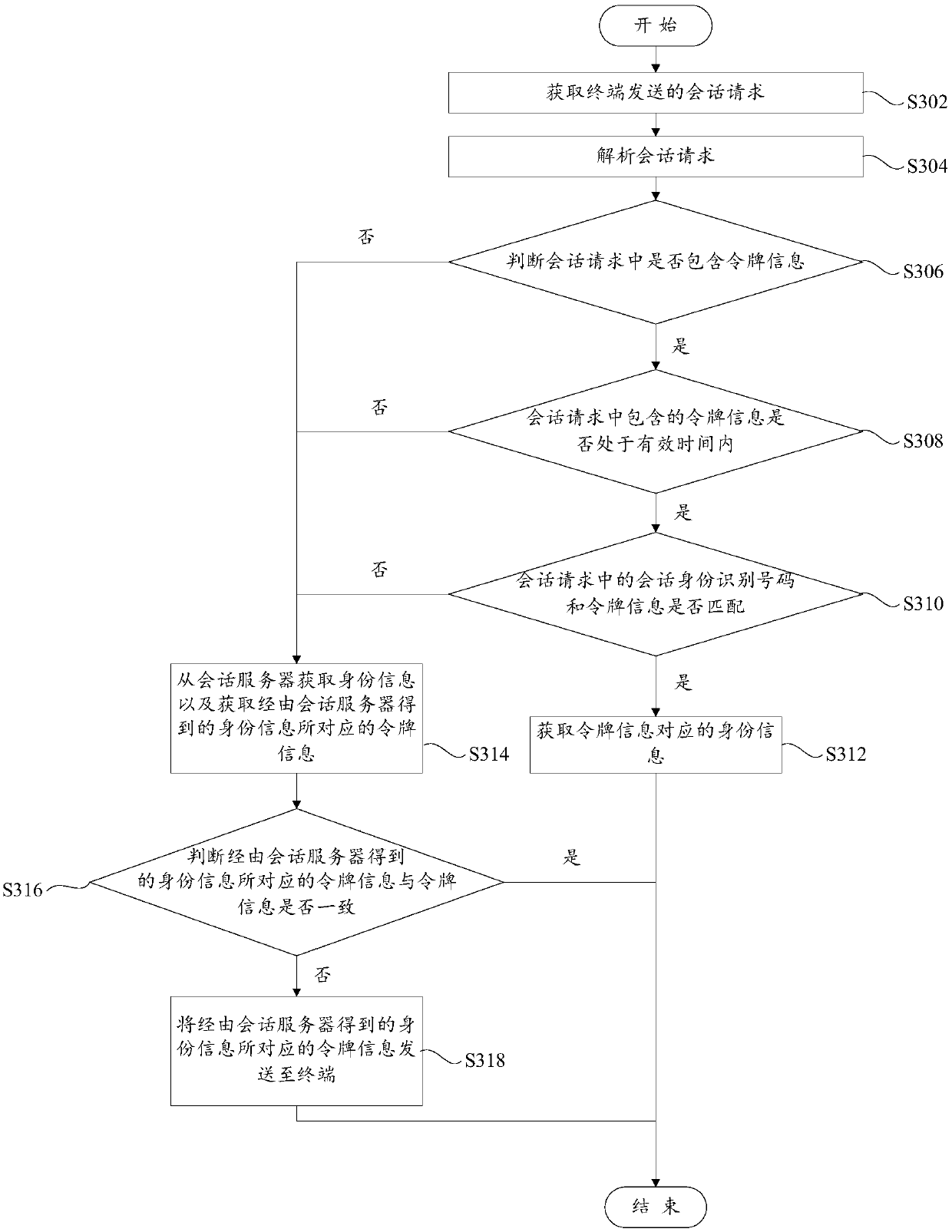
Authentication method for invoking open interface and system
The embodiment of the invention discloses an authentication method for invoking an open interface and a system for executing the method. The method comprises the following steps: a service provision platform receives an interface invoking request of an application program transmitted by a server side or a client side, wherein the interface invoking parameters comprise application identification, a private secret key and valid time allocated by the server side for the interface invoking; the private secret key is allocated by the service provision platform when the server side is registered in the service provision platform; the client side logs in the server side, acquires authentication and acquires the interface invoking parameters from the server side; the service provision platform acquires the private secret key corresponding to the application identification from the pre-assigned parameter records, and authenticates the interface invoking request based on the acquired private secret key; if the authentication is successful, the corresponding interface invoking is permitted; or, the interface invoking request party is refused to invoke the corresponding interface. The authentication method can ensure the interface invoking security, the interface invoking process is simple, and the interface invoking efficiency is high.
Owner:CHINA TELECOM CORP LTD
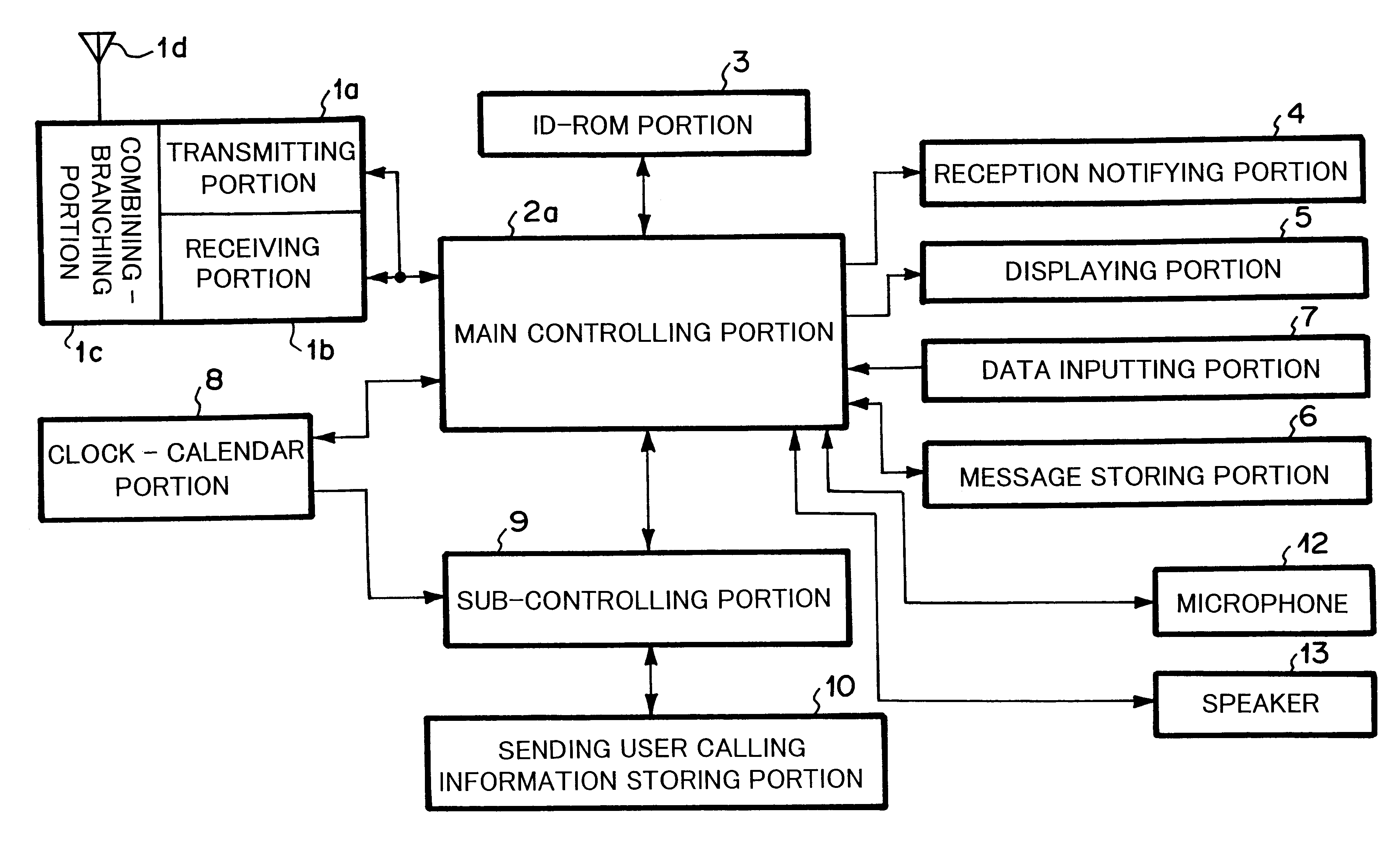
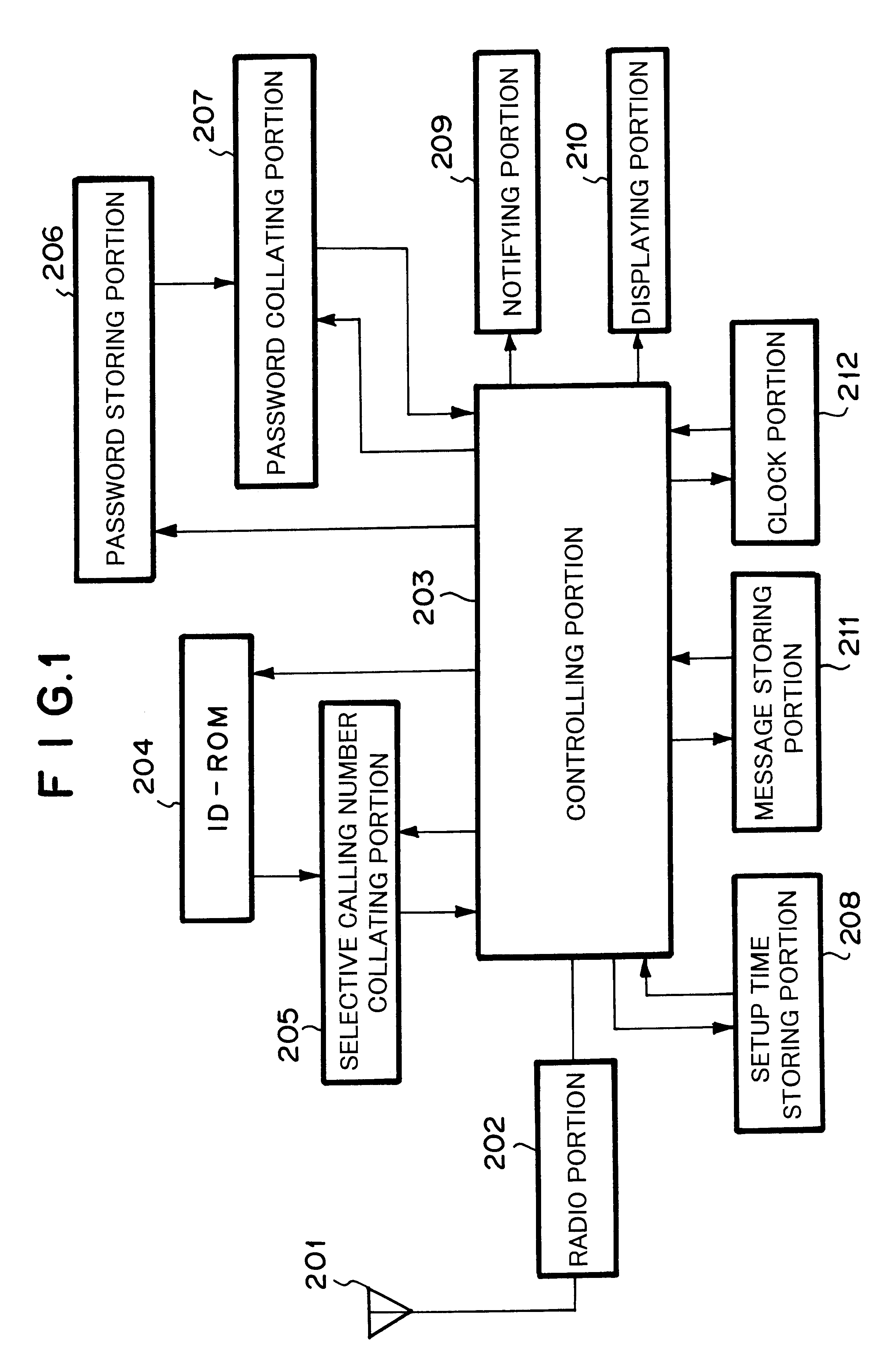
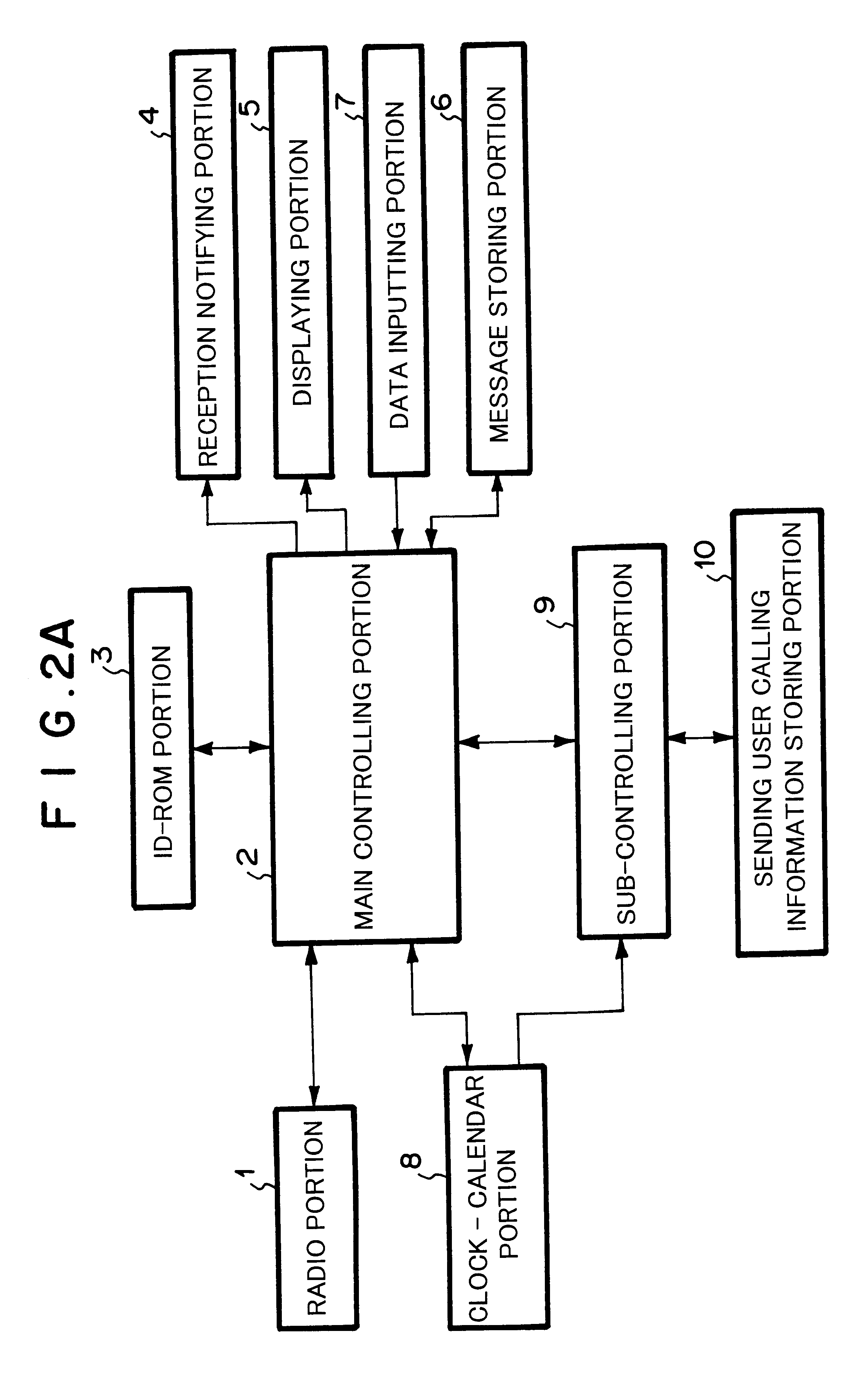
Radio selective calling receiver and portable telephone apparatus for efficiently managing received call
InactiveUS6411827B1Cordless telephonesFrequency-division multiplex detailsTemporal informationSelective calling
A radio selective calling receiver comprising a receiving for receiving the radio calling signal containing sending user information that allows the receiving user to identify the sending user and assign a priority level to the sending user, a plurality of types of notifying for notifying the receiving user of the received radio calling signal in different manners, a time counting for setting up and counting the current time and date, an information storing for setting up and storing notification state information and time information through information inputting and information displaying for the receiving user, the notification state information representing a receiving operation and a notifying operation of the radio calling signal, the time information representing a valid date range and a valid time range of the receiving operation and the notifying operation, and a controlling for searching, collating, searching, comparing and controlling the notifying operations corresponding to the searched notification state information.
Owner:NEC CORP
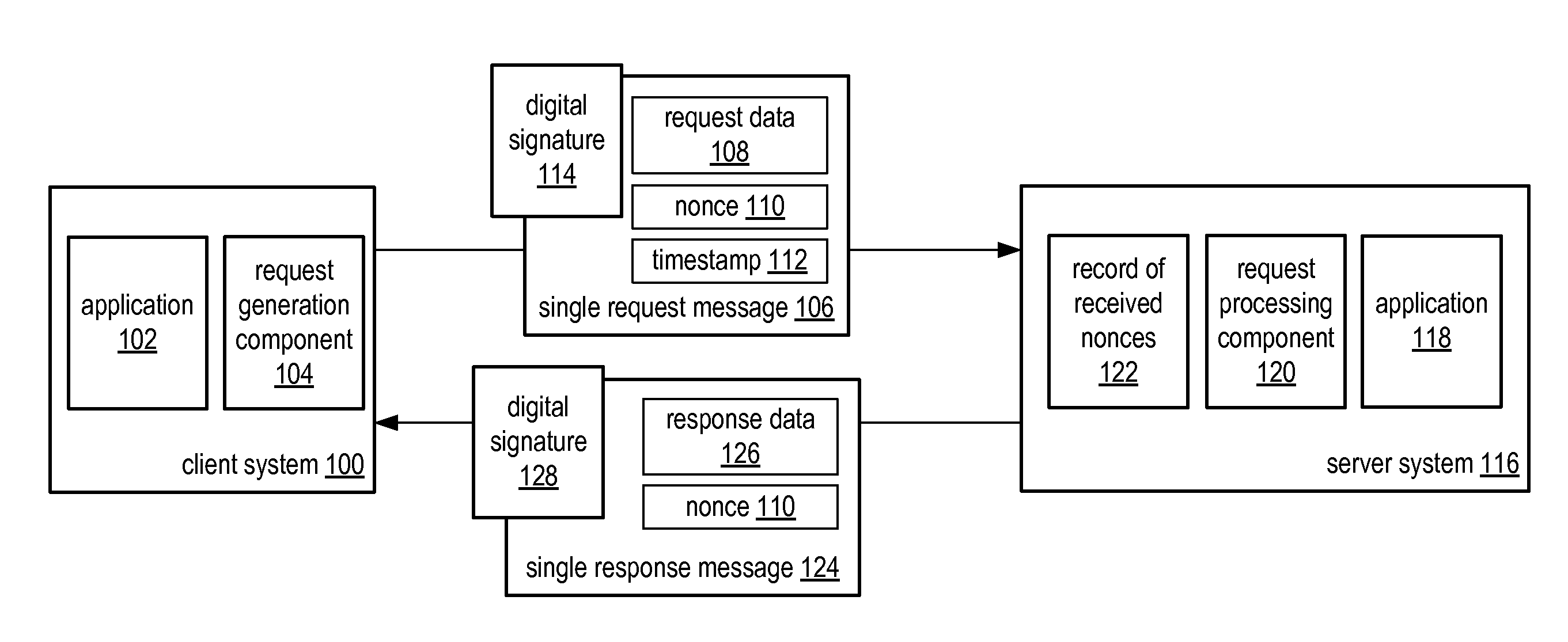
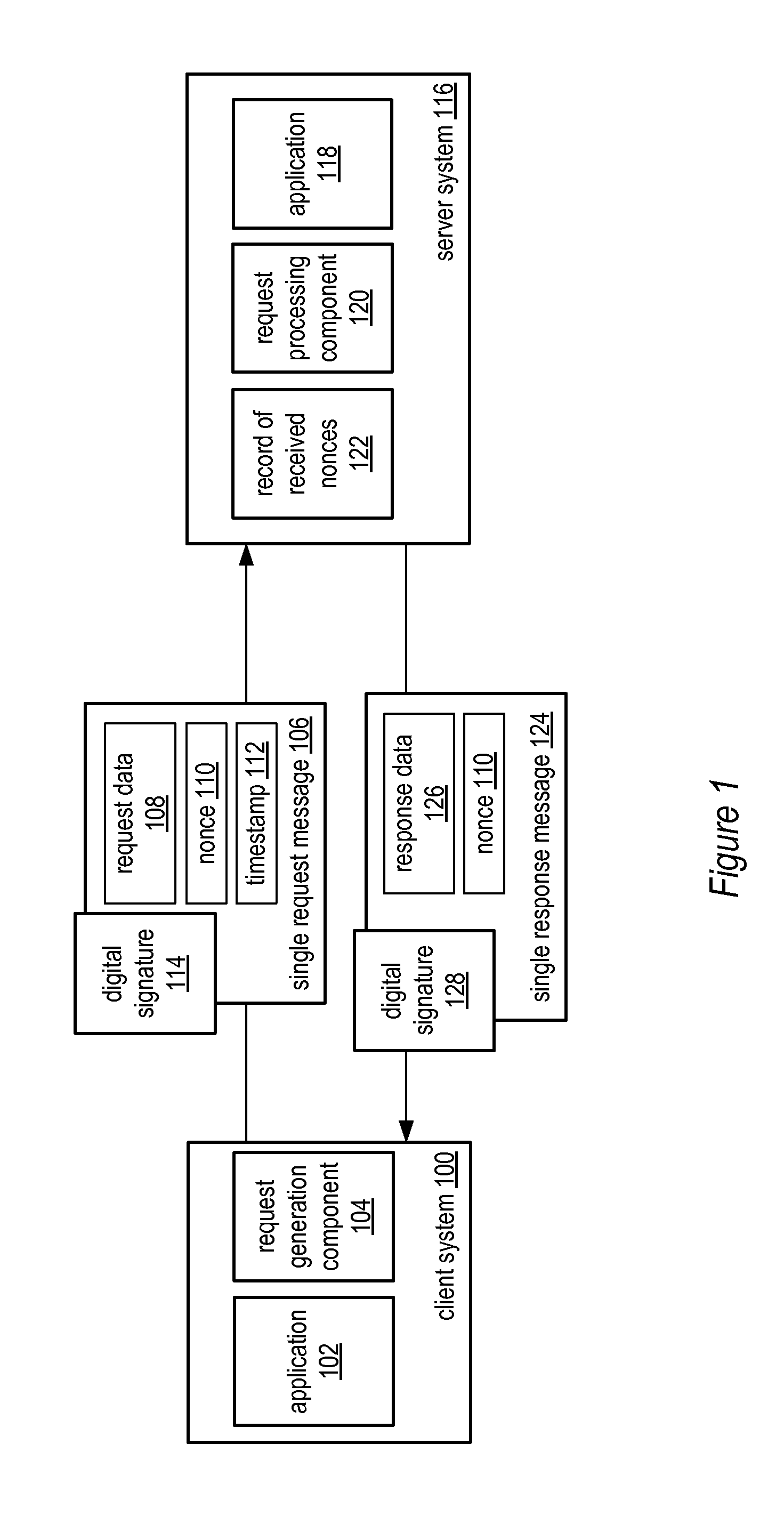
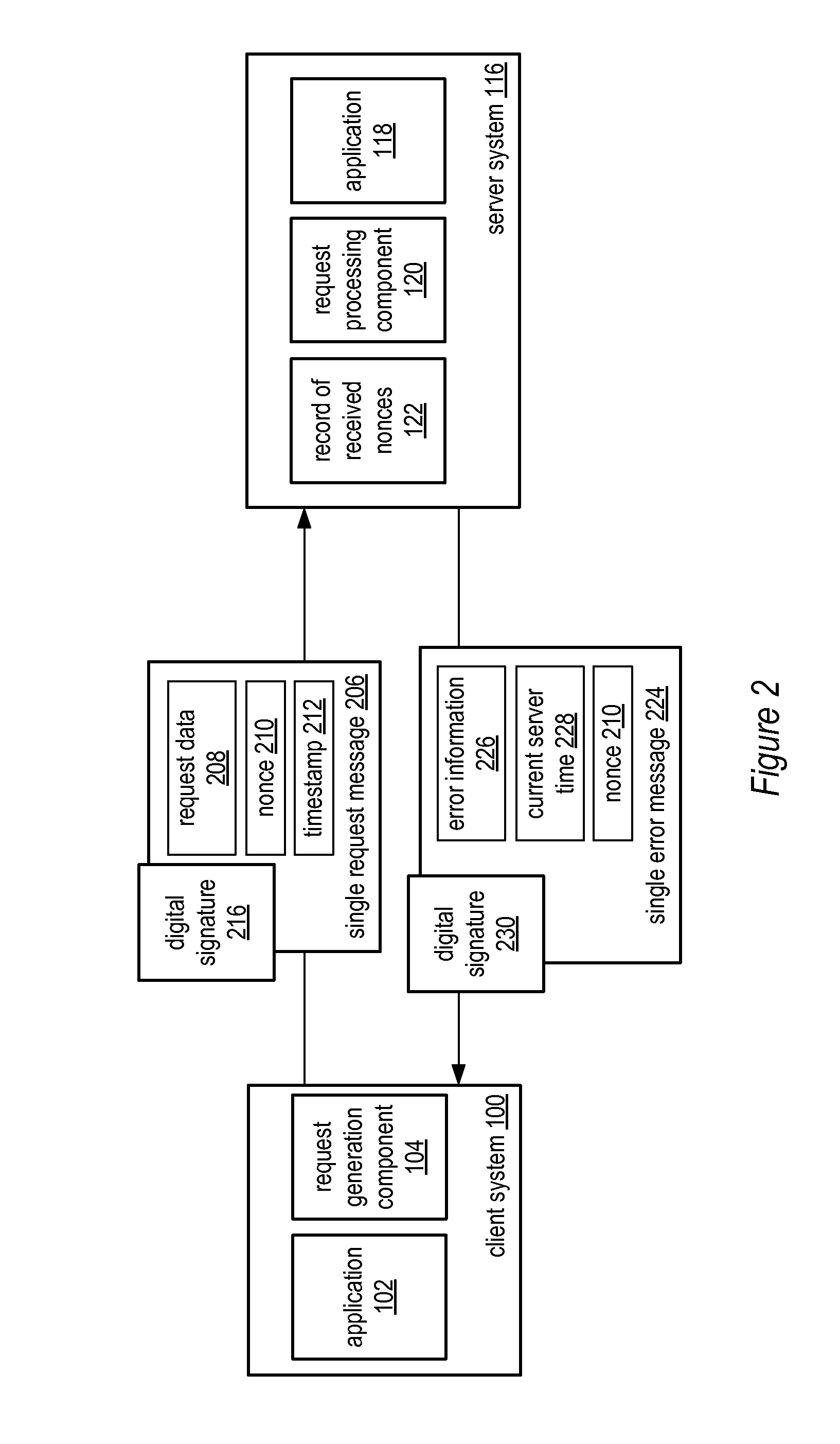
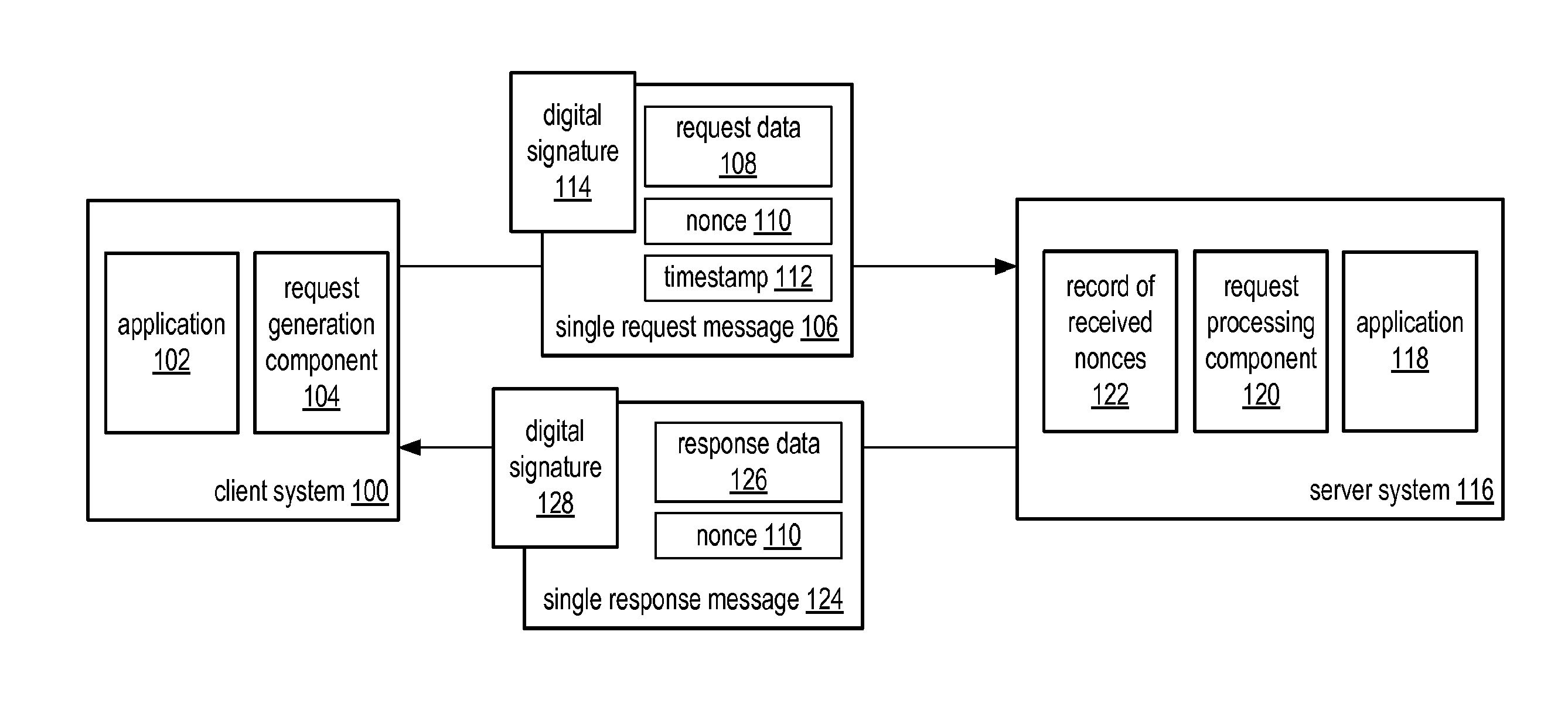
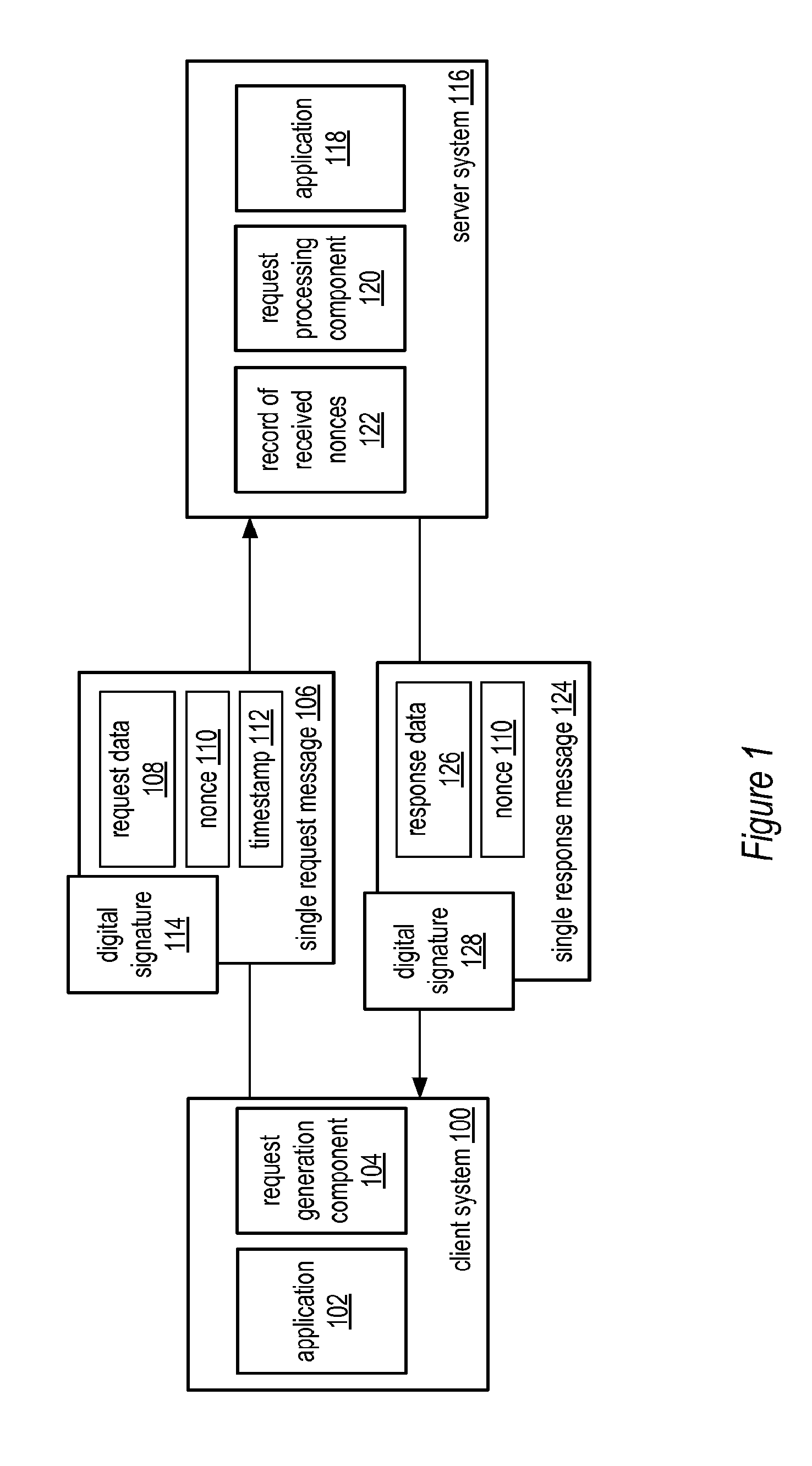
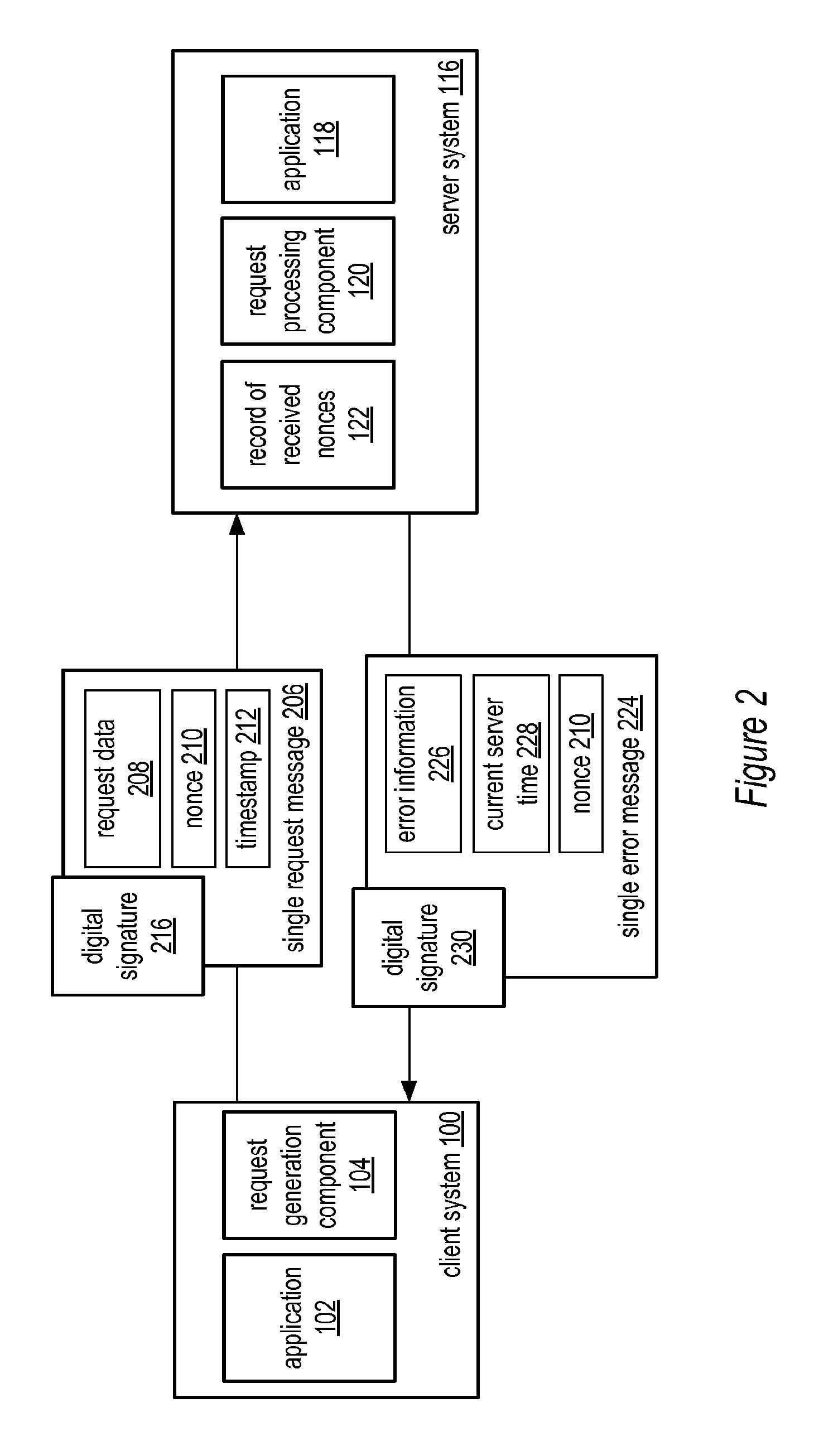
System and method for a single request—single response protocol with mutual replay attack protection
Various embodiments of a system and method for a single request—single response protocol with mutual replay attack protection are described. Embodiments may include a system that receives multiple single request messages, each of which may include a respective nonce, timestamp, and digital signature. The system may create a record of previously received nonces that, at any given time, may include multiple message nonces received within a valid period of time prior to that given time. To validate a given single request message the system may verify the digital signature of the that message, determine that the timestamp of that message indicates a time within the valid period of time prior to the current time, and determine the nonce of the that message is not present within the record of previously received nonces. The system may send a single response message that includes the same nonce as the validated message.
Owner:ADOBE SYST INC
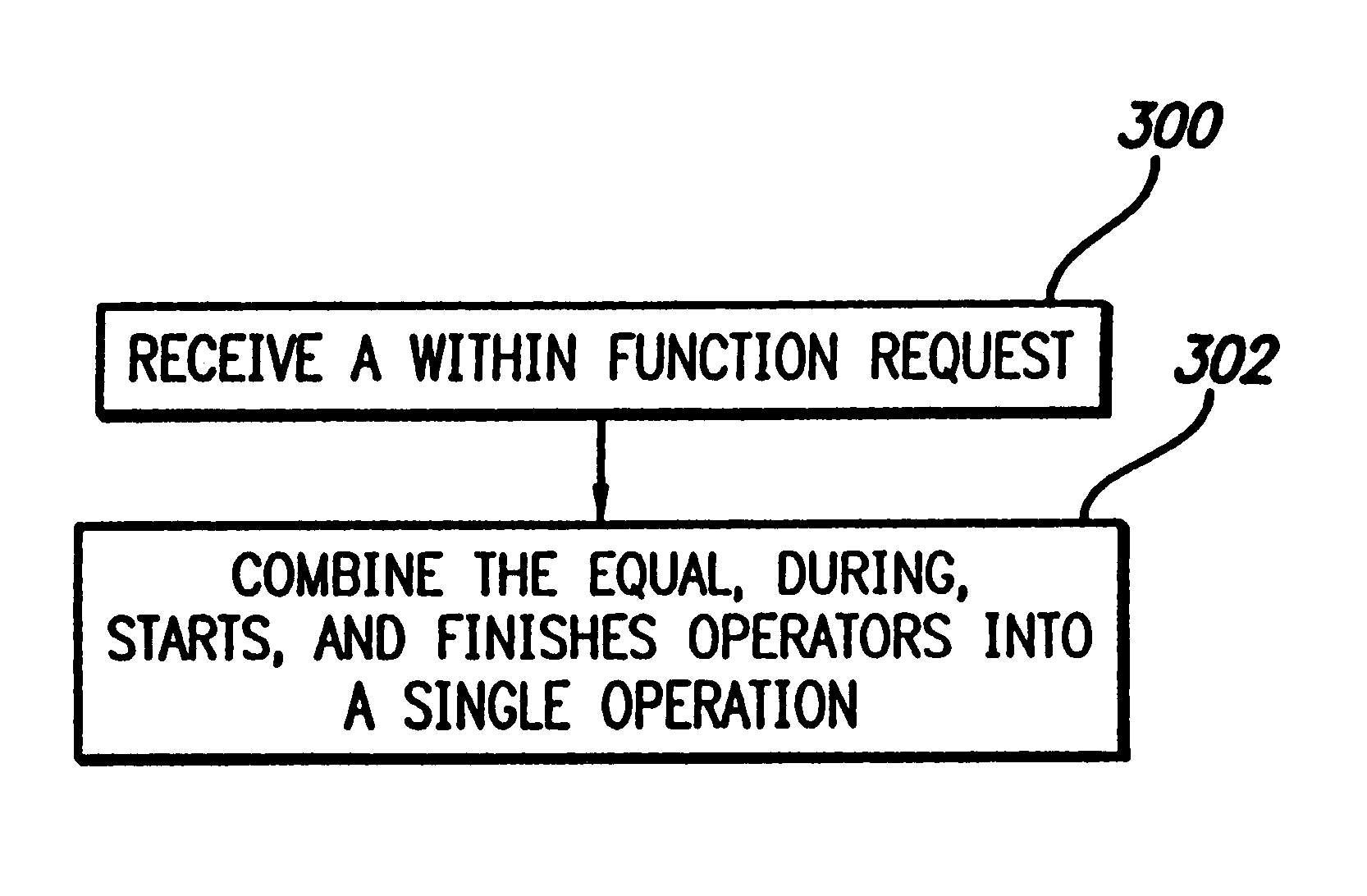
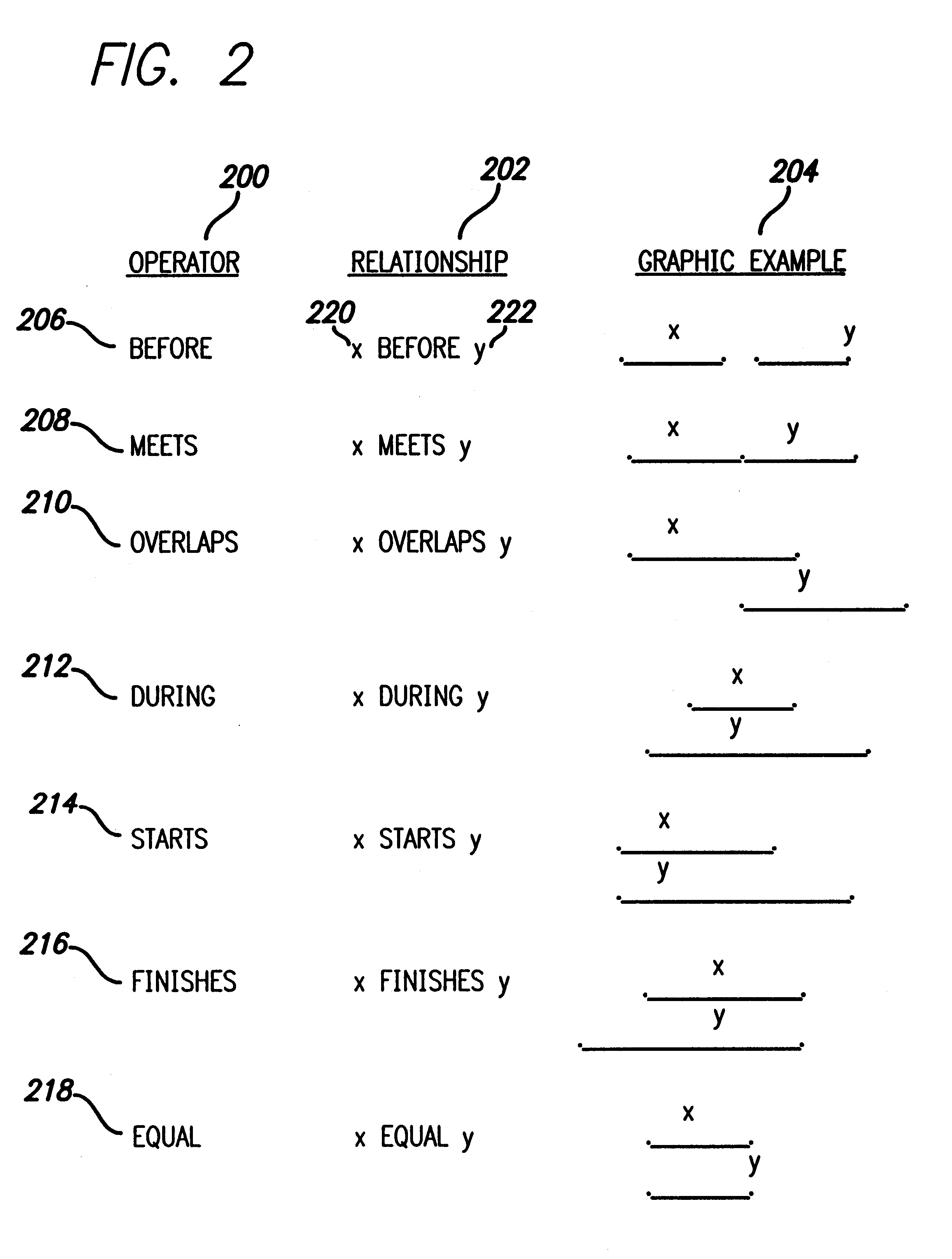
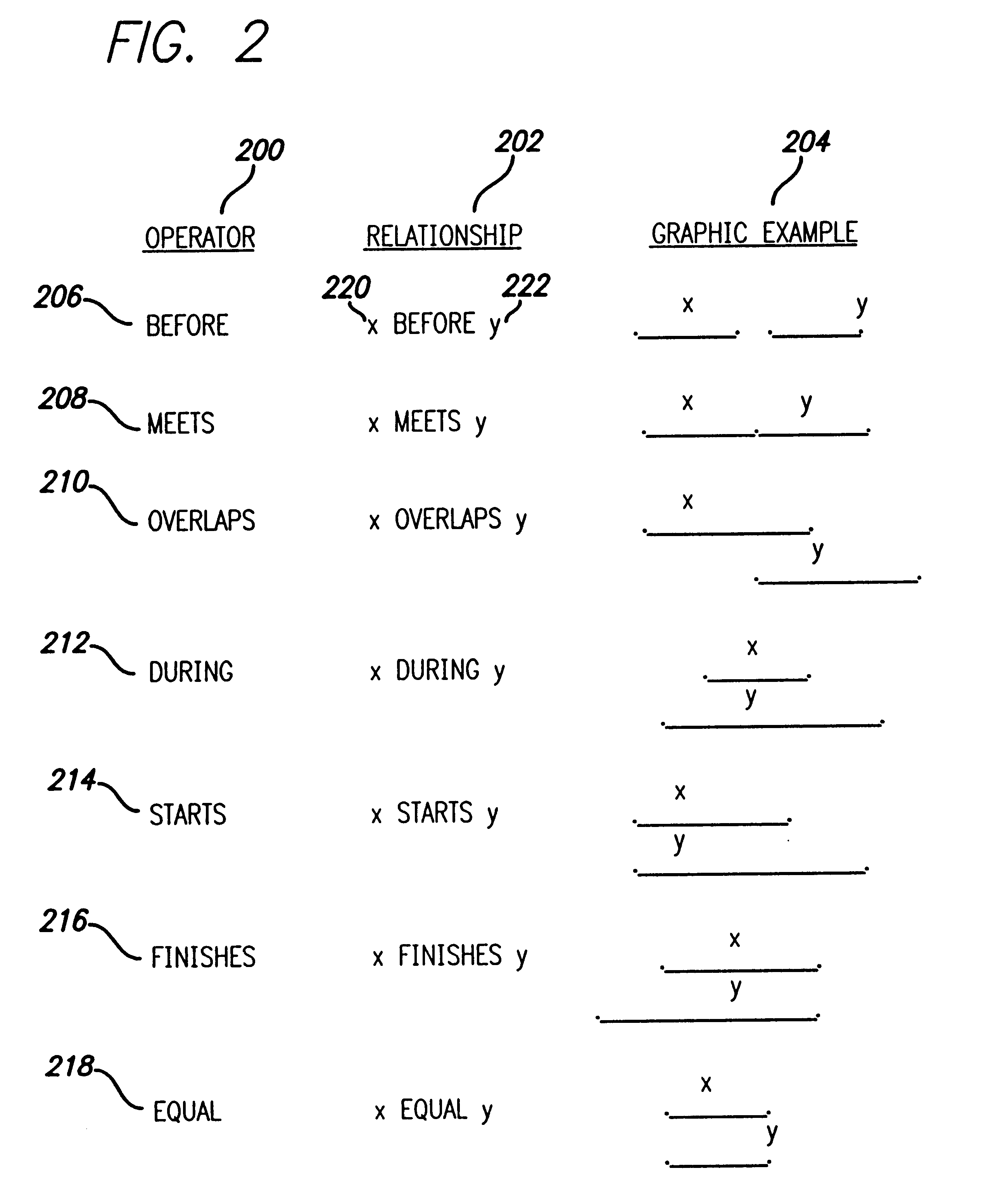
Technique for detecting a subsuming temporal relationship of valid time data in a relational database management system
InactiveUS6647382B1Data processing applicationsRelational databasesRelational database management systemTime data
A method, apparatus, and article of manufacture for detecting subsuming temporal relationships in a relational database. In accordance with the present invention, an invocation of a within operation that specifies a first event and a second event is received. In response to the invocation, a combination of temporal relationships between the first event and the second event is evaluated to determine (1) whether the second event starts at the same time as the first event or whether the second event starts before the first event and (2) whether the second event ends at the same time as the first event or whether the second event ends after the first event.
Owner:GOOGLE LLC
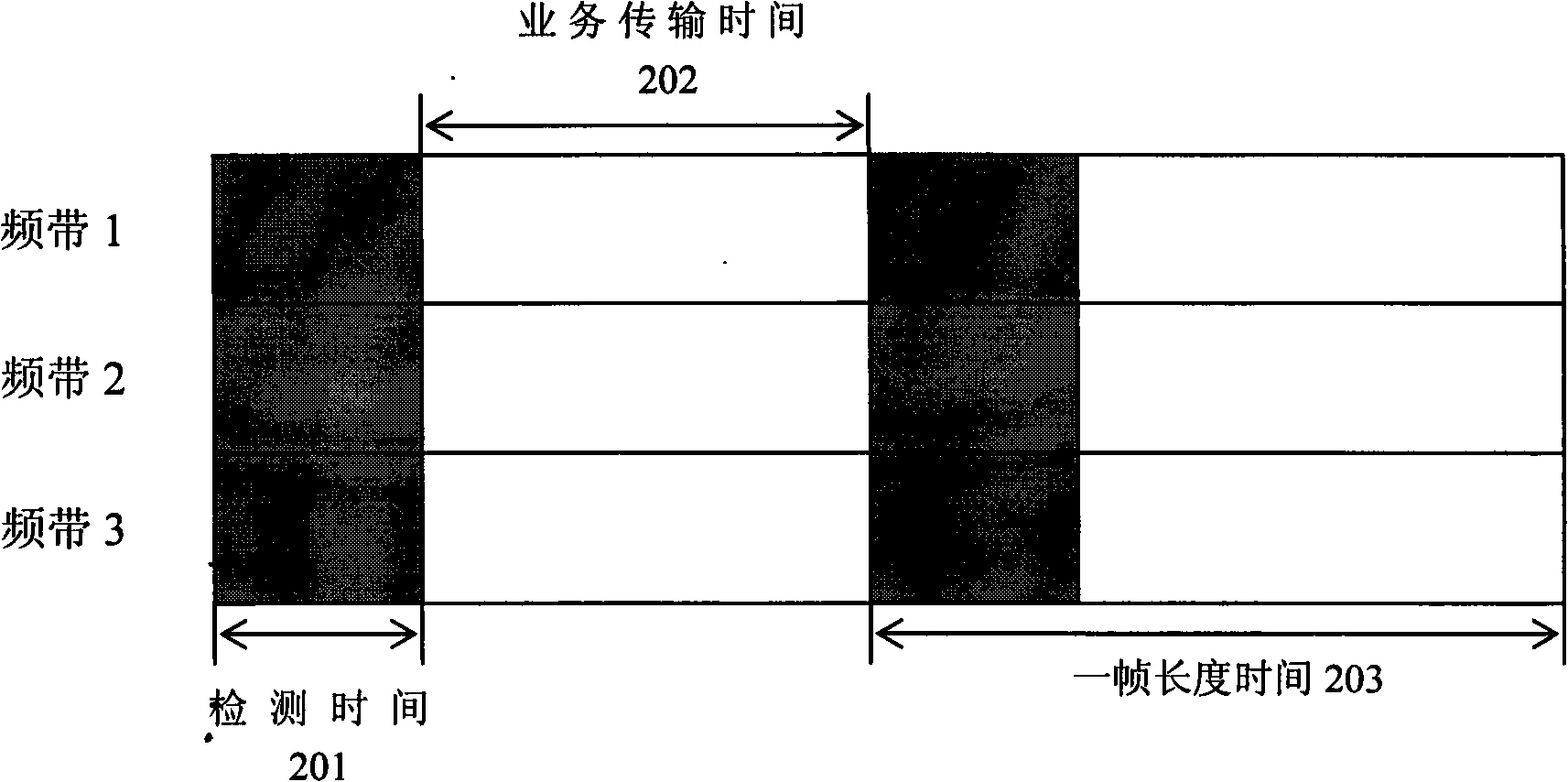
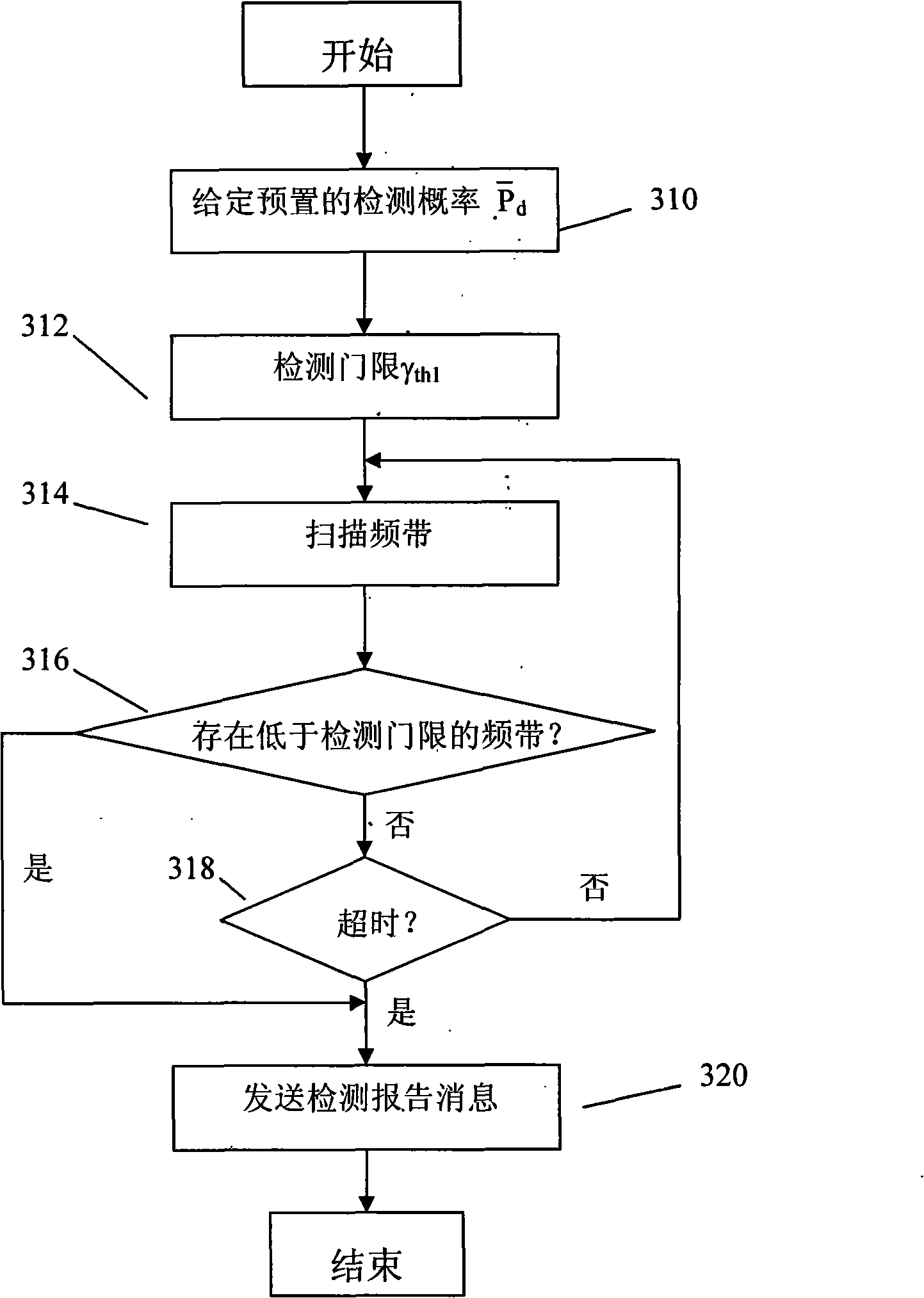
Band dynamic selecting and time scheduling method in heterogeneous network
InactiveCN101527915AReduce mutual interferenceNetwork traffic/resource managementNetwork planningQuality of serviceFrequency spectrum
The invention provides a band dynamic selecting and time scheduling method in a heterogeneous network, relating to a method and equipment for dynamically selecting usable frequency resources in a plurality of main system bands in a heterogeneous network system based on the cognitive technology, in particular to a method and equipment used for opportunity spectrum access, frequency resource efficient utilization, and combination of heterogeneous network resource amalgamation and user business service quality (QoS) assurance. The invention has the band dynamic selecting method as follows: firstly, aiming to different main system characteristics, an average main system user detection threshold of each main system of a base station CBS accessory is defined and cognized, and the threshold is an average value of the prior detection threshold in a wireless network transmission environment; secondly, according to the average main system user detection threshold and the throughput needs of a secondary system user, scanning efficient time of CBS to each main system is defined; thirdly, the CBS selects the optimal main system band from a usable band list according to a request of a user, the wireless transmission characteristics and a channel state of a band channel are the basis for selecting the optimal band, and interruption of the equipment CPE transmission throughput is preset according to the user.
Owner:NANJING UNIV OF POSTS & TELECOMM
Vehicular Ad hoc network routing method based on autonomously acquired road information
InactiveCN103281742ADensity gainIncrease the probability of successful deliveryTransmissionWireless communicationTime delaysVehicle driving
The invention discloses a vehicular Ad hoc network routing method based on autonomously acquired road information. The method is characterized in that when a packet forwarding direction and a vehicle driving direction are different, on the basis of the valid time of links and the distance from a predicted position of a vehicle to a target intersection, forwarding priority values of nodes are calculated, and therefore the valid time of packet transmission lines is long, and the stability of the links is improved during a routing process, and moreover, a node forwarding packet near a destination node is selected by combining the directions, and therefore the transmission time of the packet and the condition that the packet is transmitted repeatedly on the same road segment are reduced, and the time delay of packet transmission is greatly reduced. According to the method disclosed by the invention, road density information can be acquired more accurately, and moreover, routing nodes which are more efficient are selected by utilizing real-time road information more effectively. As a piecewise autonomous road density estimation method and a packet forwarding scheme of integrating a direction parameter and a position parameter are adopted by the method, the goal that the vehicle autonomously acquires the real-time road density information is achieved.
Owner:NANJING UNIV OF POSTS & TELECOMM +1
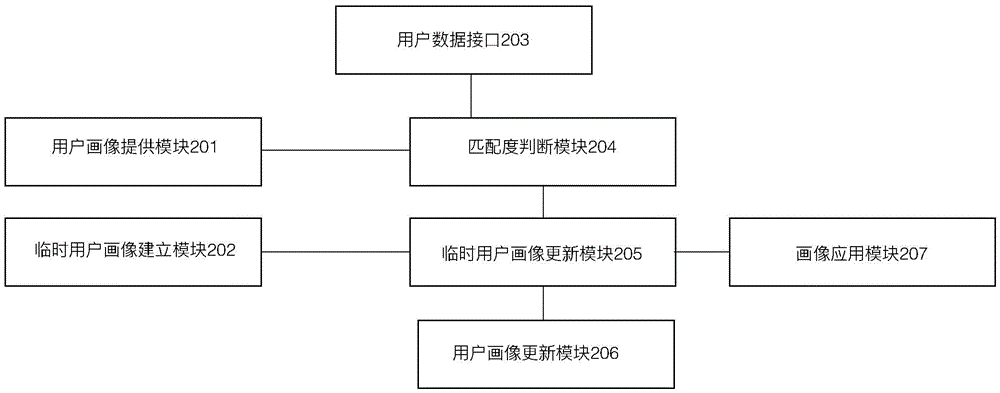
Big data-based user portrayal establishing method and user portrayal management system
ActiveCN105574159AAchieve maintenanceImplement selective inheritanceSpecial data processing applicationsManagement systemBig data
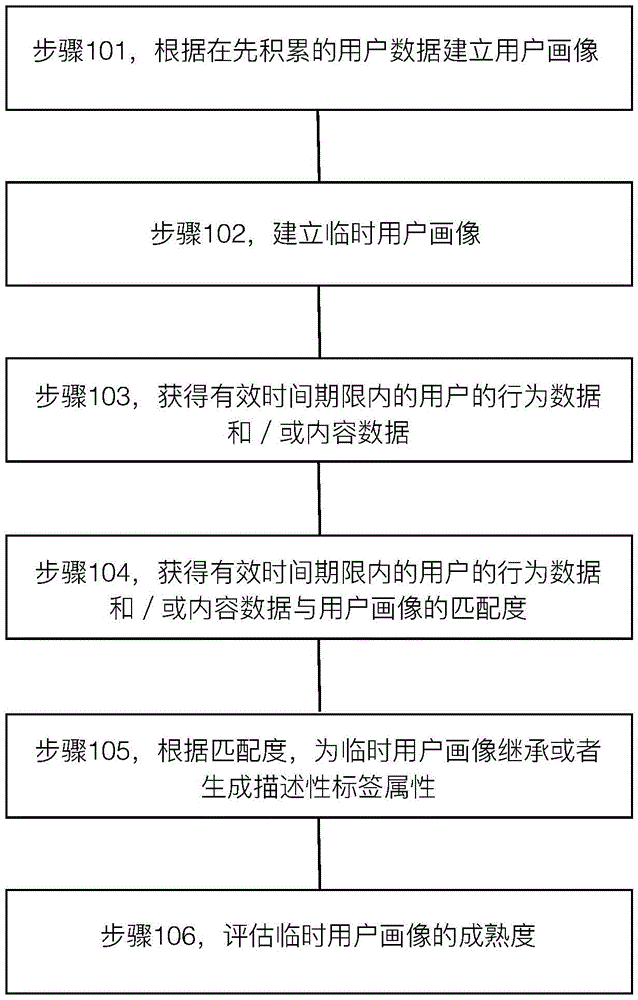
The invention discloses a big data-based user portrayal establishing method and a user portrayal management system. The method comprises the following steps: establishing a temporary user portrayal by utilizing the user behaviors and / or contents in a valid time period; enabling the temporary portrayal to inherit a descriptive label attribute matched with the user behaviors and / or contents in the valid time period from a user portrayal; and when the user behaviors and / or contents in the valid time period are not matched with the descriptive label attribute of the user portrayal, newly establishing a descriptive label attribute in the temporary user portrayal. According to the method and system disclosed in the invention, the user portrayal can be effectively maintained according to the data of the user behaviors and / or contents, and especially when the user behaviors and / or contents have step shift, the influences of the cumulative data which has advantage on the distribution statistical law and does not accord with the current contents and behaviors of the user can be rapidly obsoleted.
Owner:STRAIT INNOVATION INTERNET CO LTD
System and Method for a Single Request - Single Response Protocol with Mutual Replay Attack Protection
Owner:ADOBE SYST INC
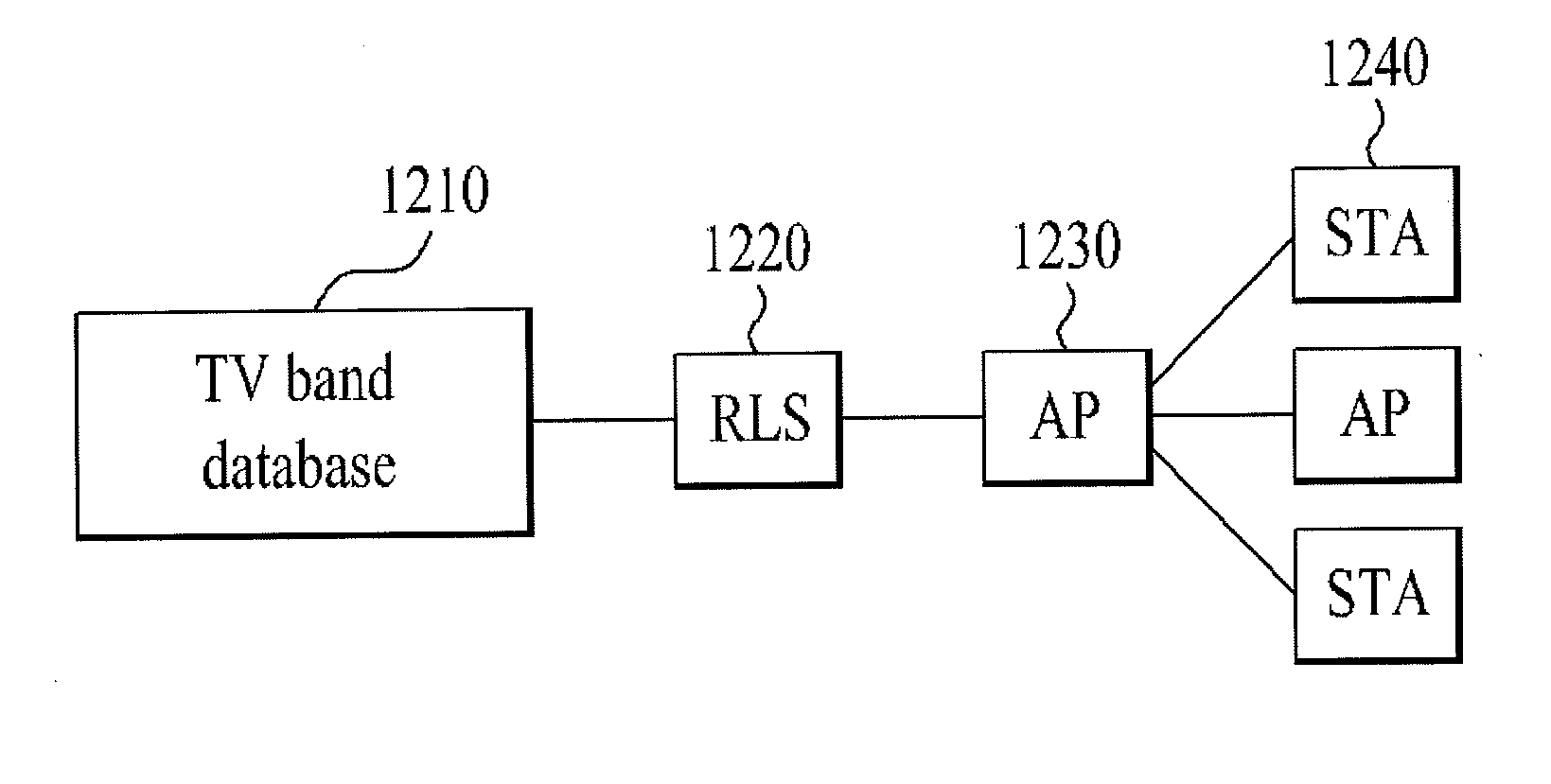
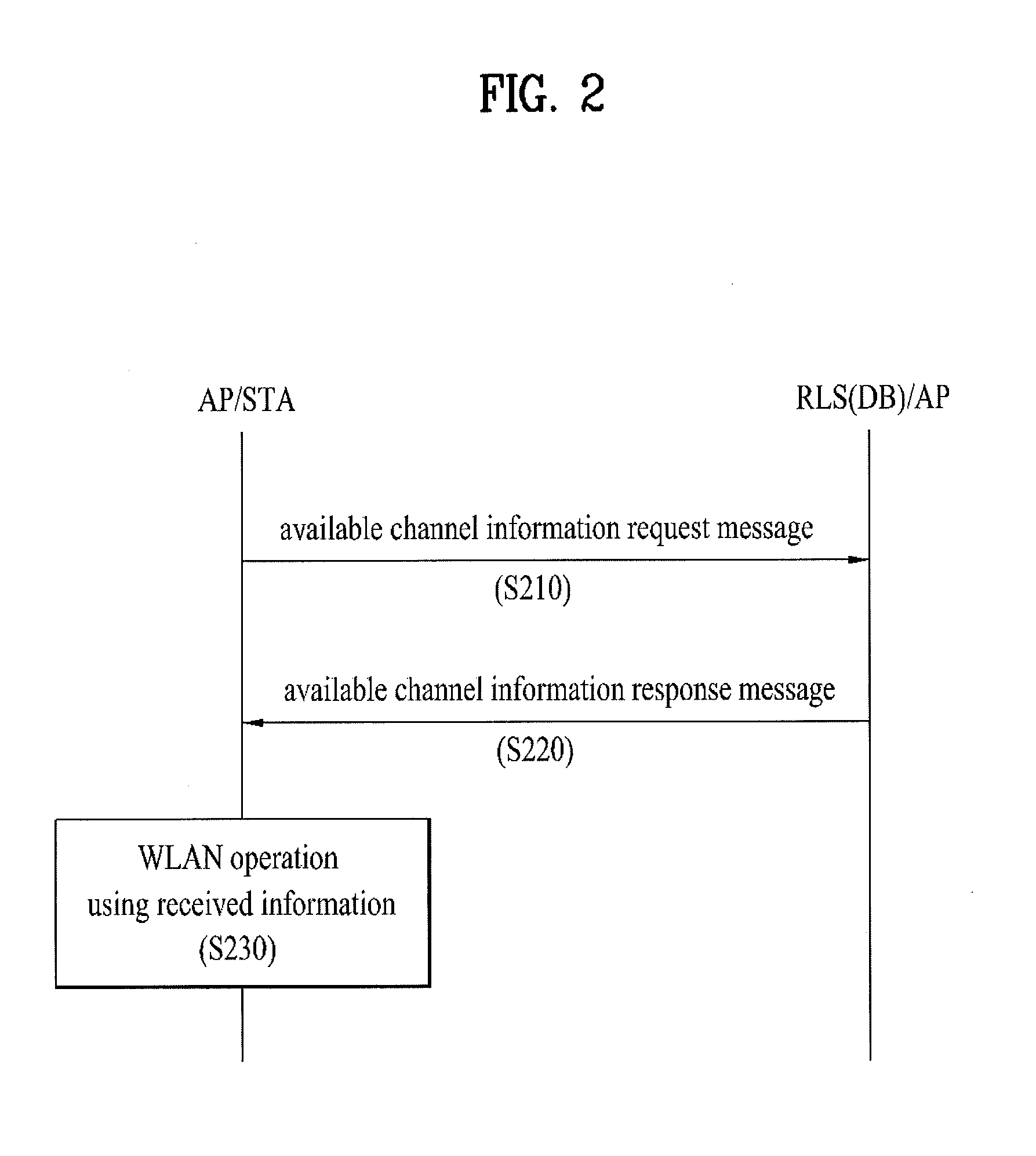
Station Operation Method and Apparatus in TV Whitespace
ActiveUS20120218956A1Efficient collectionPower managementResource management arrangementsTelecommunicationsTv whitespace
The present invention relates to a station (hereinafter, ‘STA’) operation method and apparatus in a TV whitespace. In a TVWS band, when an STA operating as an unlicensed device with permission to operate in an available channel not used by a licensed device needs to operate in the TVWS band by acquiring information on the available channel, the STA transmits an available channel information request message to a device having database information; receives, from the device having database information, an ACK message for the available channel information that includes (a) identification information on an available channel, (b) information on the maximum allowable power level in the available channel, and (c) information on valid time of the available channel; and transmits / receives a signal using the information of (a), (b) and (c), i.e., using the maximum allowable power level within the valid time in the available channel.
Owner:LG ELECTRONICS INC
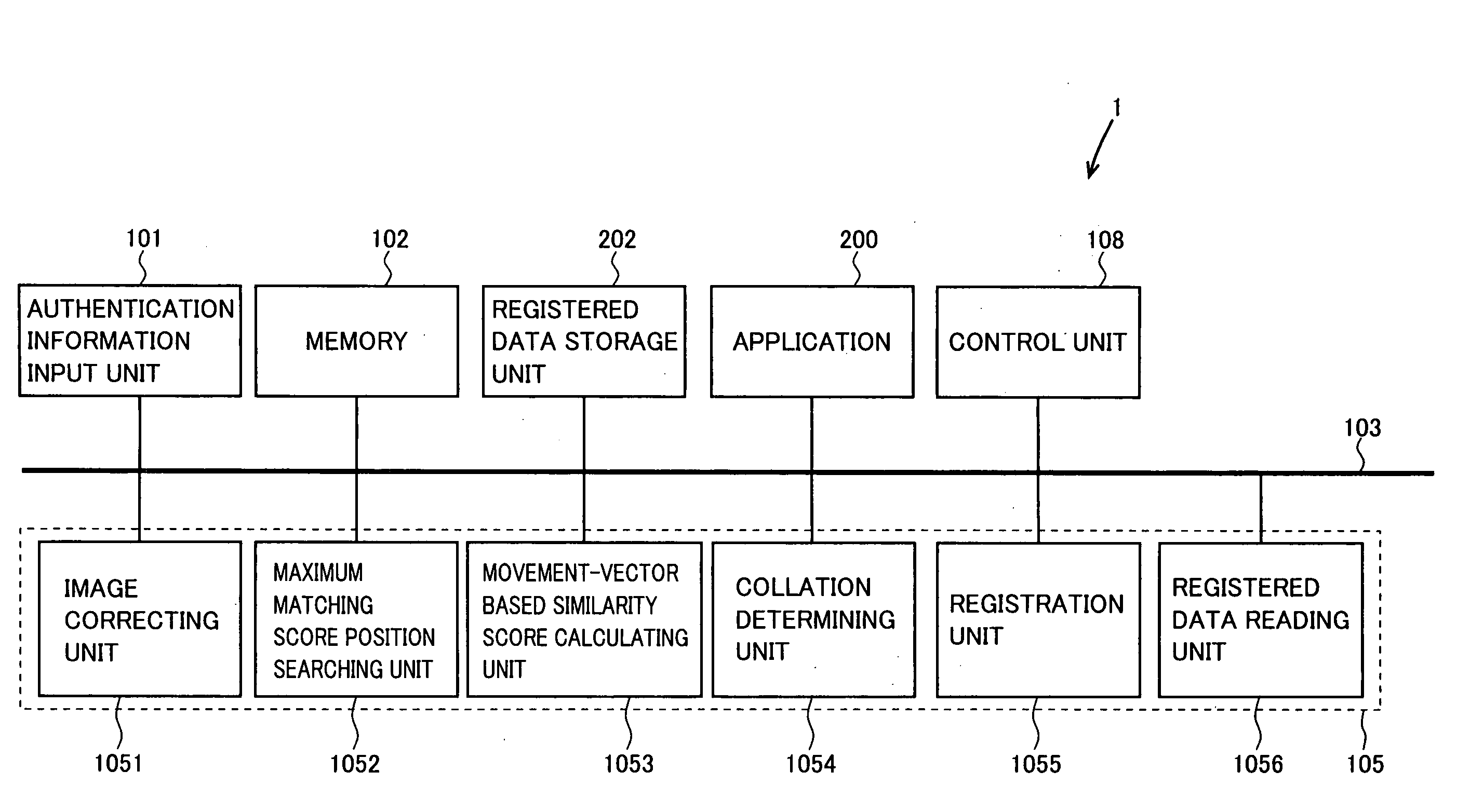
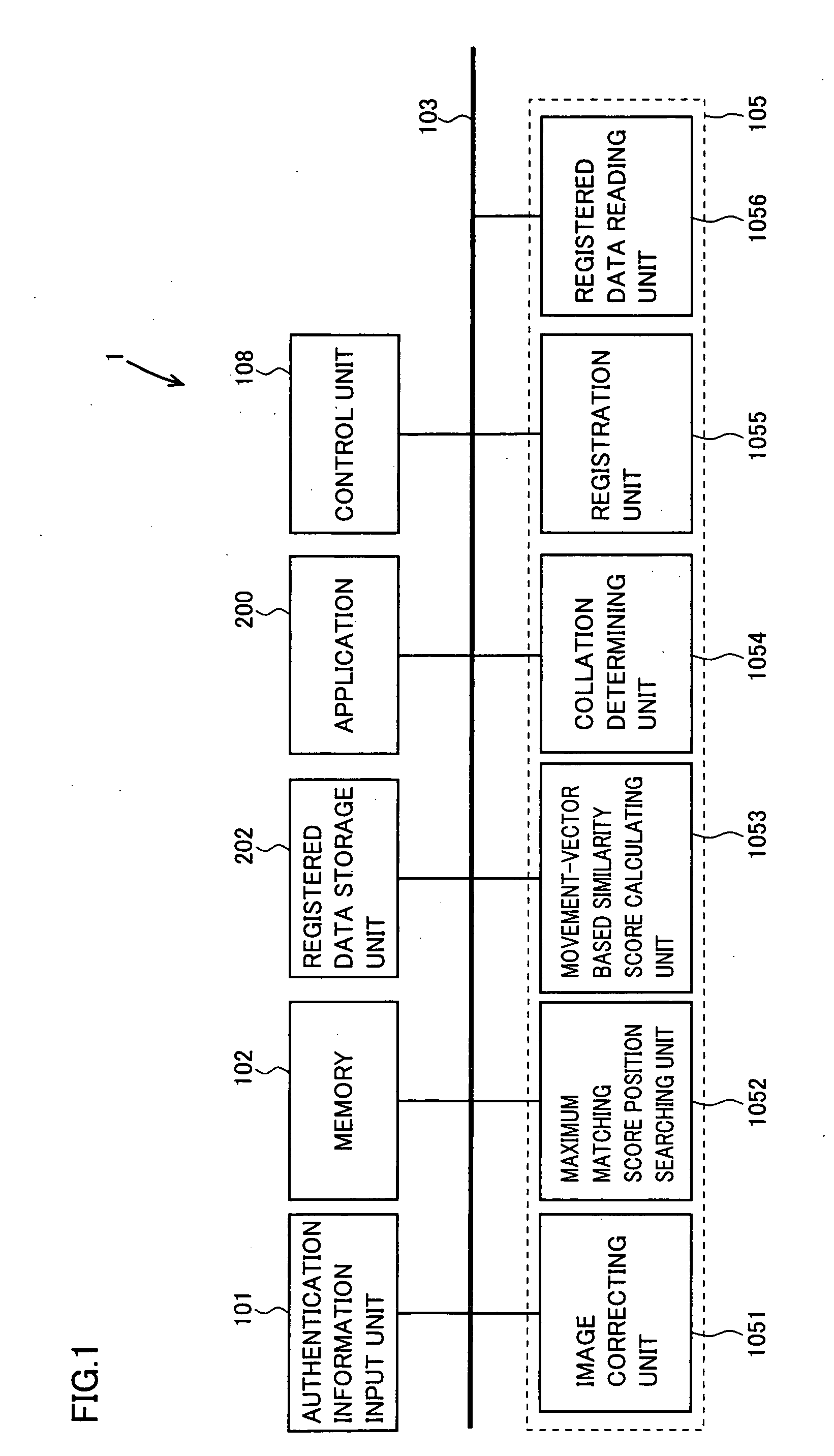
Information processing apparatus preventing unauthorized use
InactiveUS20070192591A1Raise security concernsUnauthorized useDigital data authenticationIndividual entry/exit registersComputer hardwareInformation processing
A degree of security set for an application and a valid time corresponding to the degree of security are stored in a memory. When an authentication unit performs user authentication using a fingerprint image input through an authentication information input unit and authorizes use of the application by the user, a control unit monitors lapse of the valid time corresponding to the application. When the valid time expires, the control unit request the user to input authentication information, and authentication is repeated at the authentication unit.
Owner:SHARP KK
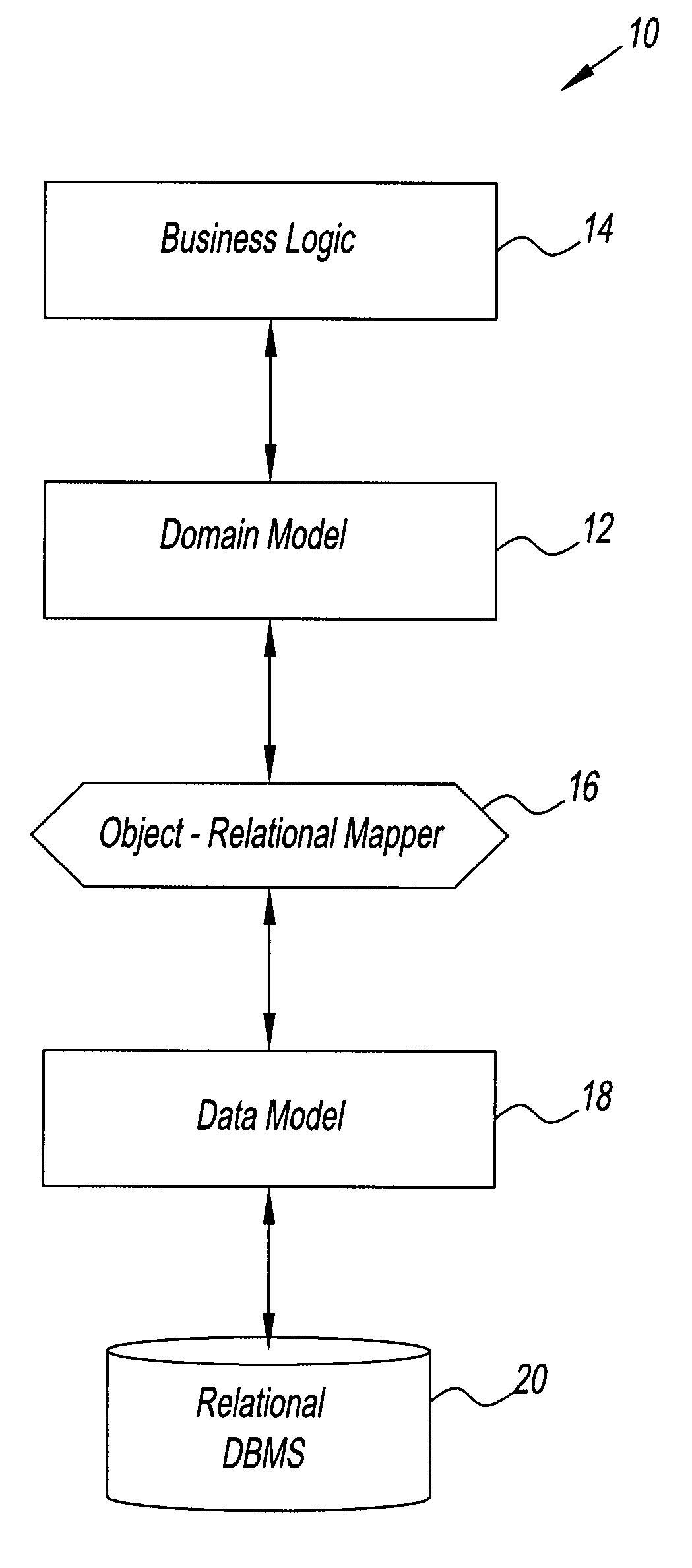
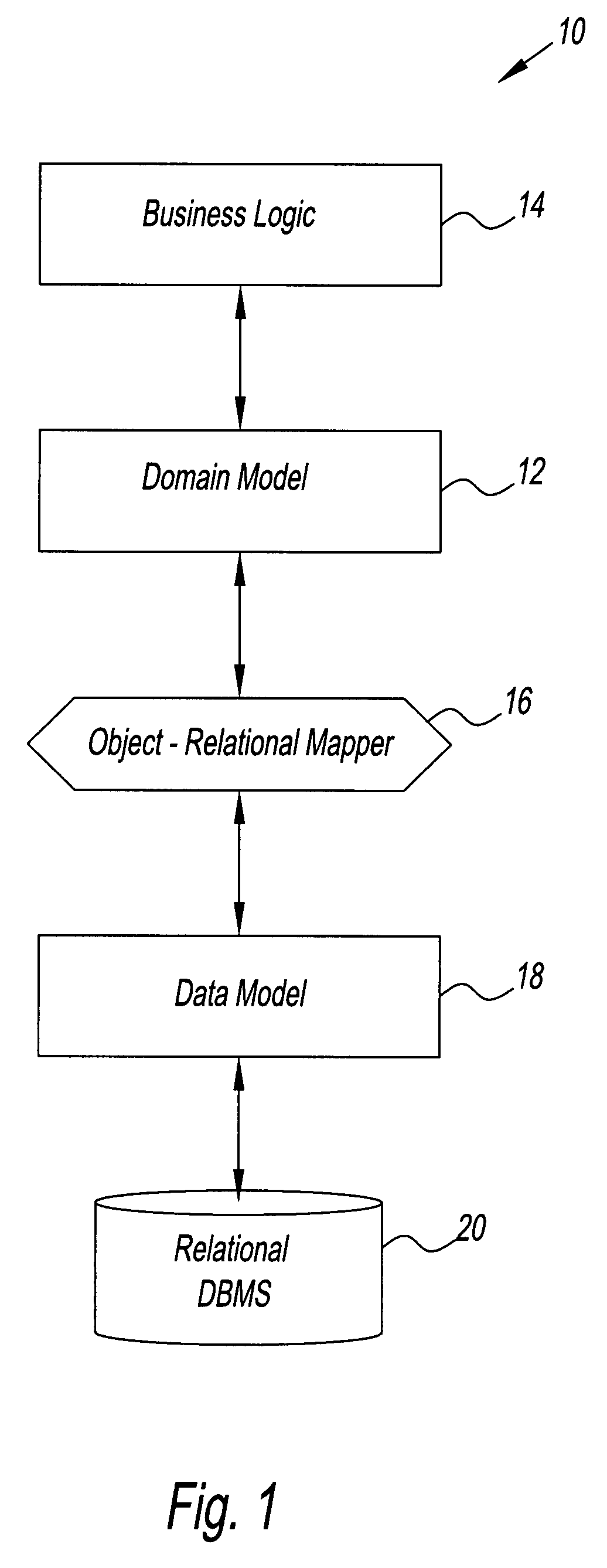
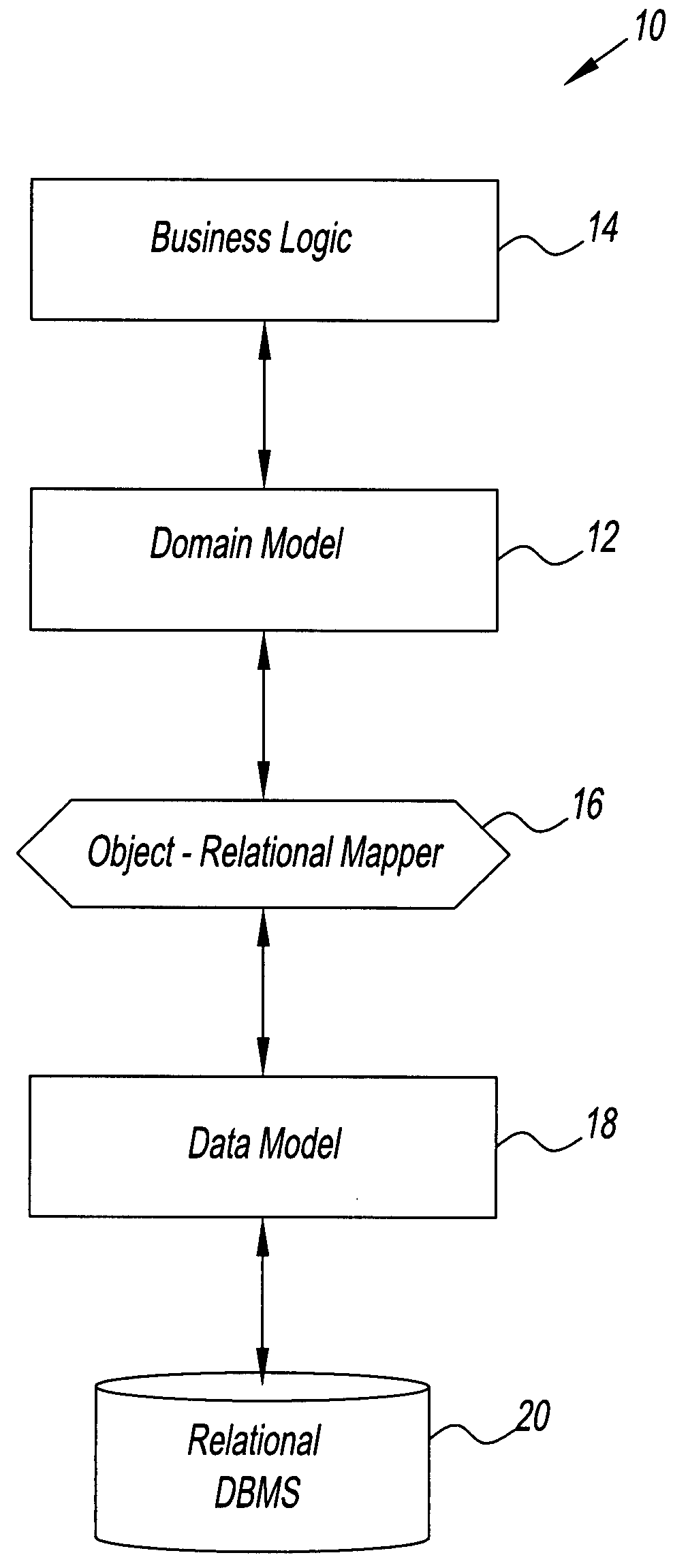
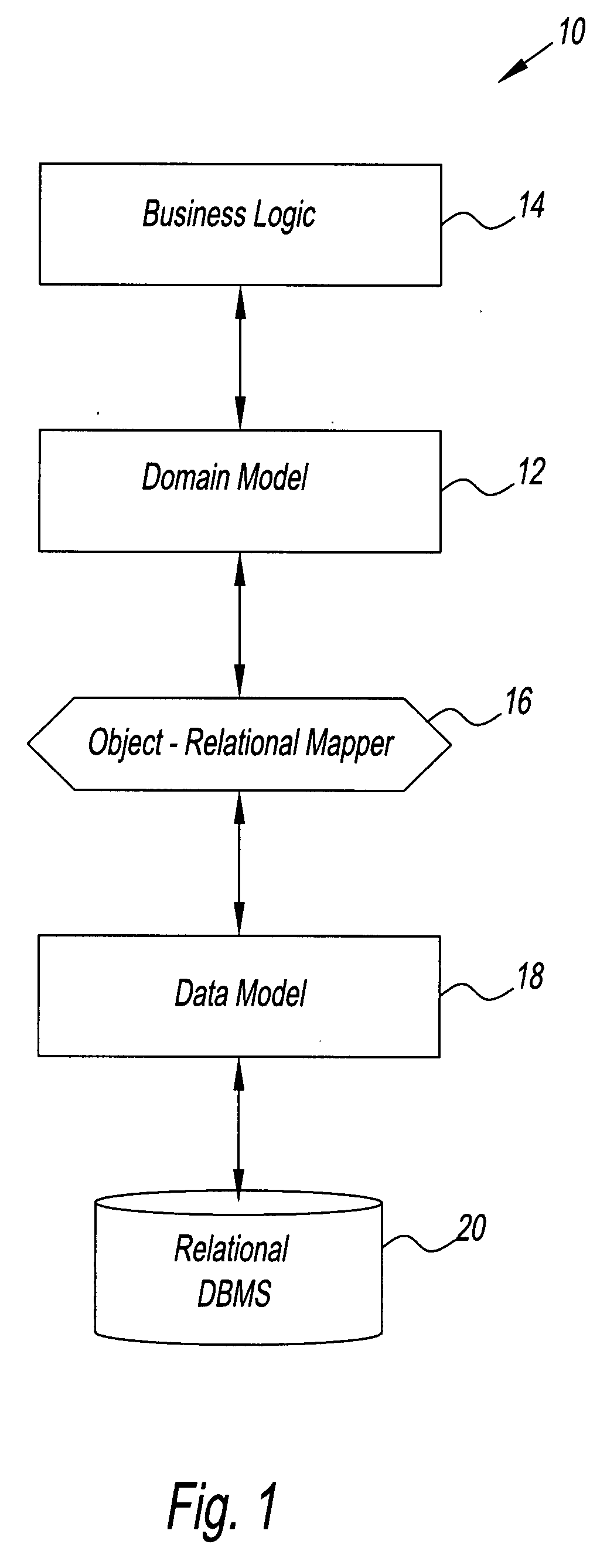
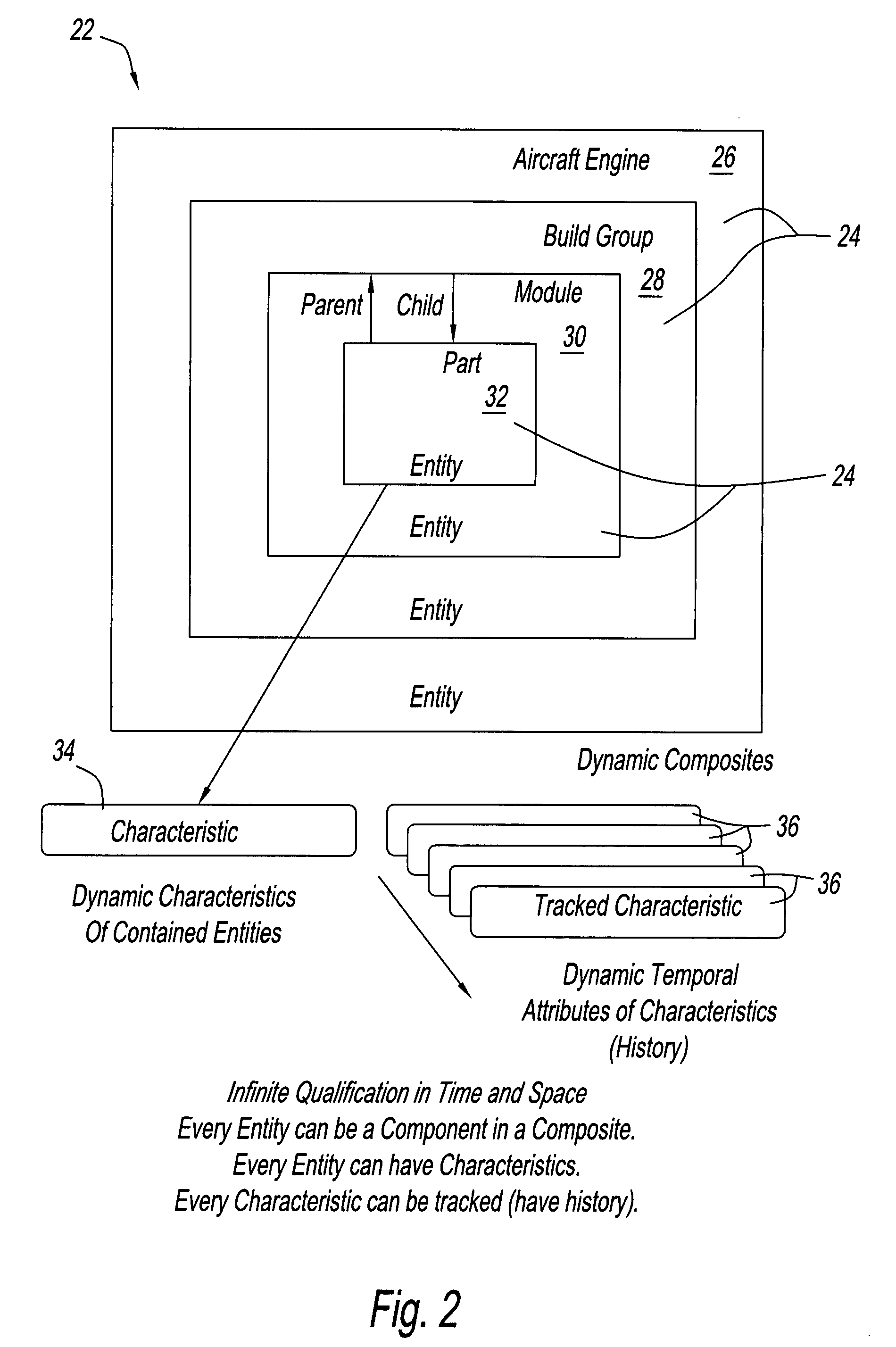
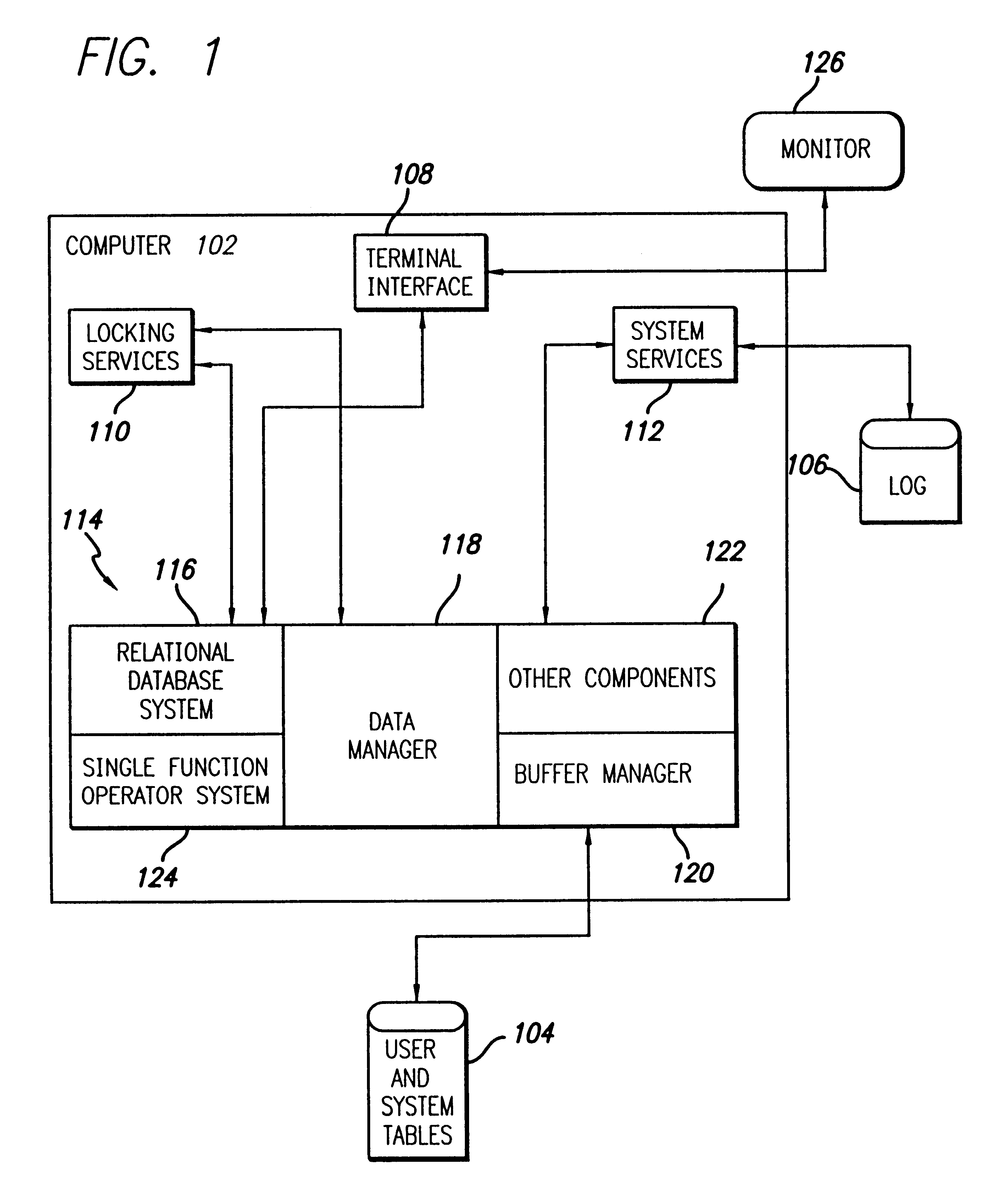
System and method for creating an object model
InactiveUS7734659B2Digital data processing detailsRelational databasesTemporal informationDomain model
A method for creating a dynamic domain model of an object. The method includes storing and organizing temporal information about the object in a bitemporal database that includes both a valid time and a transaction time for the information. The information is inserted into a plurality of tables in the database and a key is assigned to each of the plurality of tables. A composite representing the object is formed to represent a state of the object at the current time or at any previous time by dynamically linking the information by key, based on a business logic and a request made by a user.
Owner:RAYTHEON TECH CORP
Device binding method and system based on Internet of Things and washing machine
ActiveCN107800687AImprove accuracyImprove securityData switching networksFailure rateWireless router
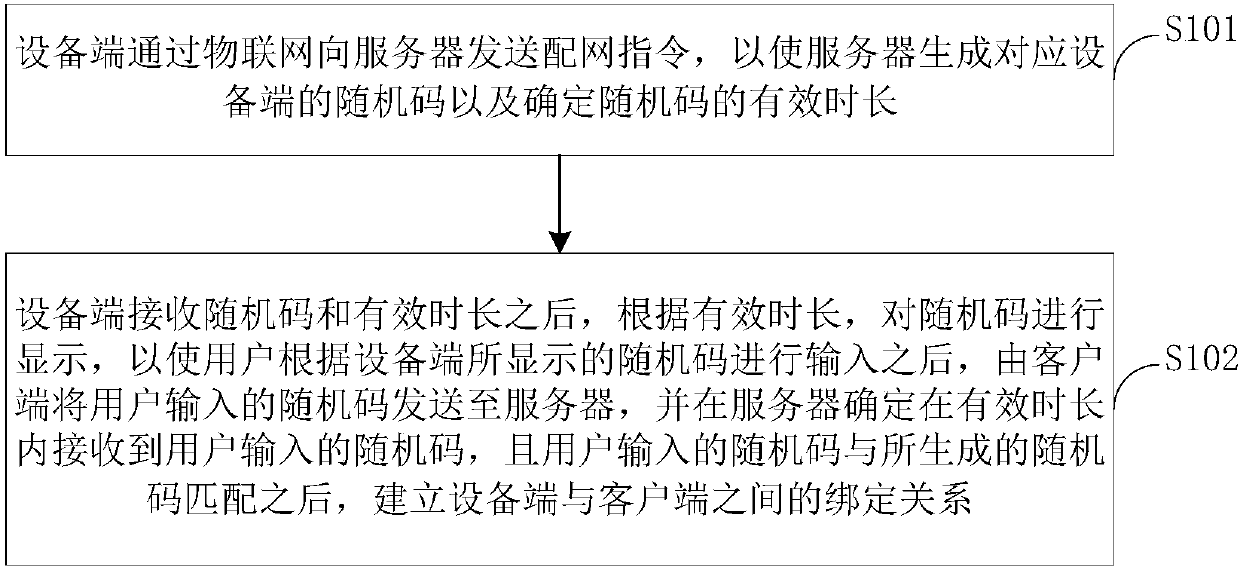
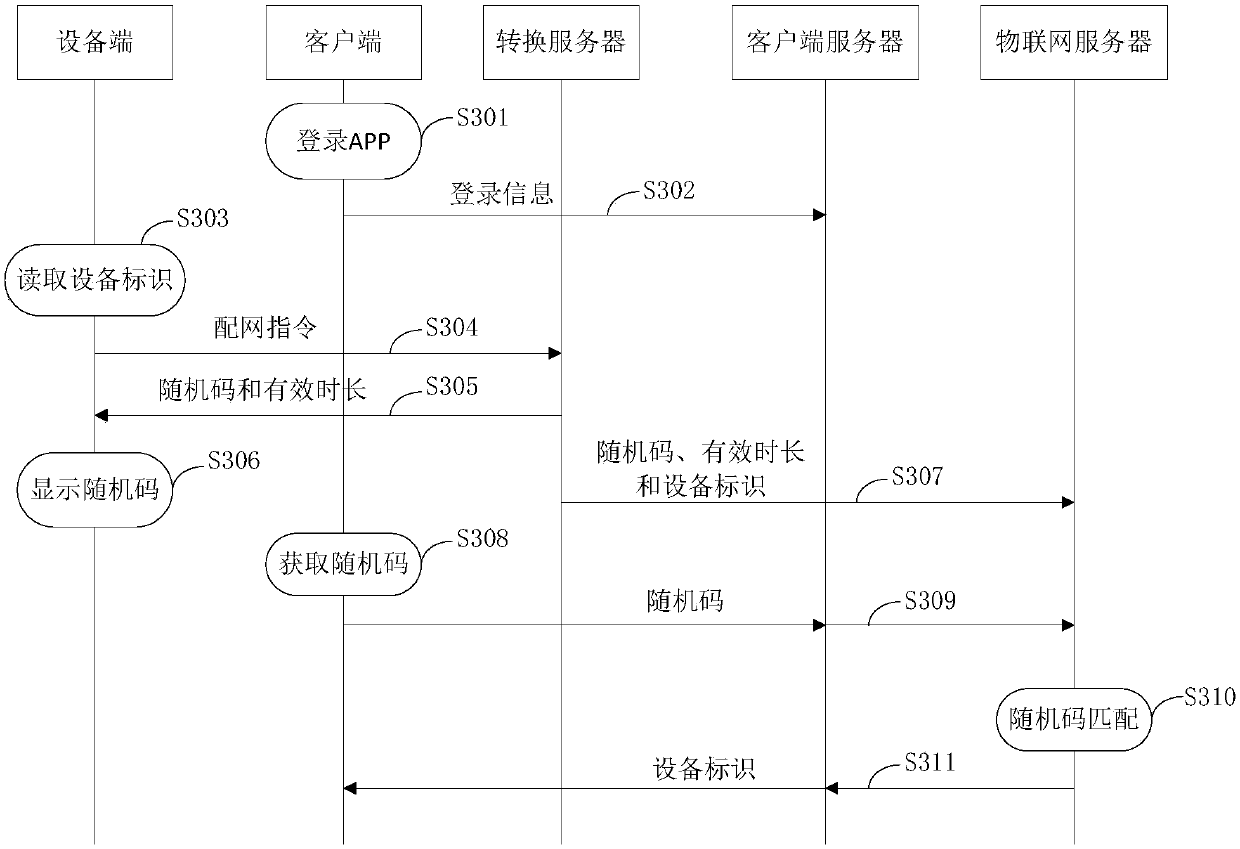
The invention provides a device binding method and system based on the Internet of Things and a washing machine. The method comprises the steps that a device sends a network distribution instruction to a server through the Internet of Things to enable the server to generate a random code corresponding to the device and a valid time; and the device displays the random code according to the valid time, a client sends a random code input by a user to the server, and after the server determines that the server receives the random code input by the user in the valid time, and the random code inputby the user is matched with the generated random code, a binding relation between the device and the client is established. According to the device binding method, the device completes binding betweenthe device and the client through the Internet of Things, and compared with the prior art that binding between the device and the client is achieved through a WIFI module, multiple steps such as thedevice needs to establish connection with a wireless router are avoided, and the technical problems that in the prior art, the binding steps are complex, the failure rate is high, a long time is consumed, and the user experience is poor are solved.
Owner:WUXI LITTLE SWAN ELECTRIC CO LTD
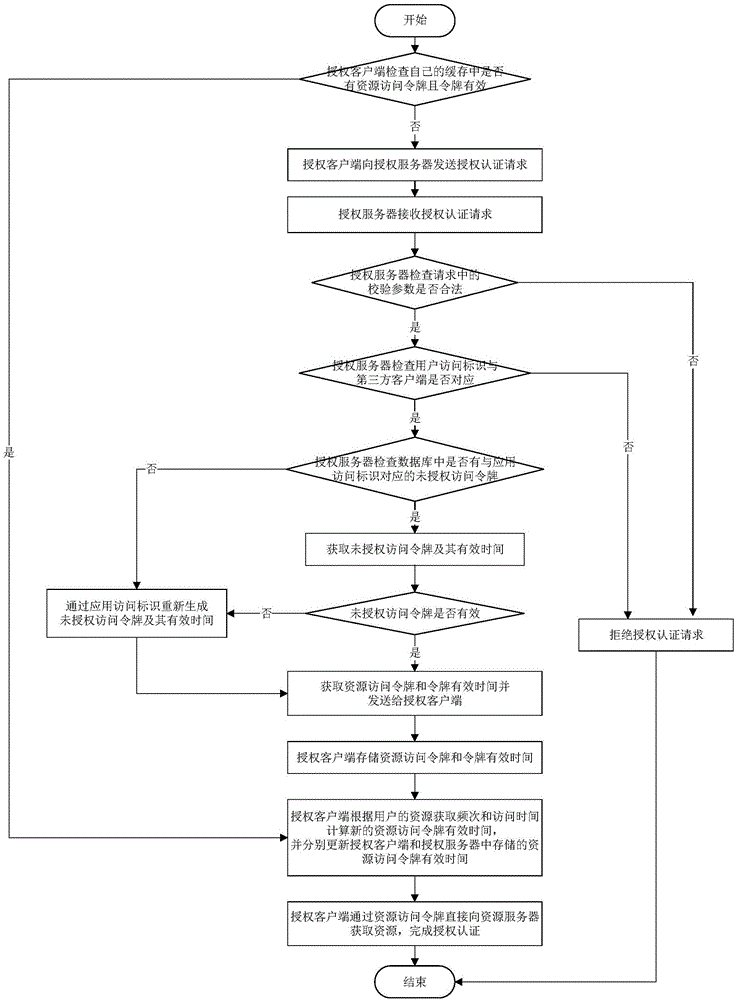
Open platform authorization and authentication system and method based on OAuth protocol
ActiveCN106534175AConvenient authorization and authentication operationsAvoid Repeated Authorization and AuthenticationTransmissionAcquisition timeOpen platform
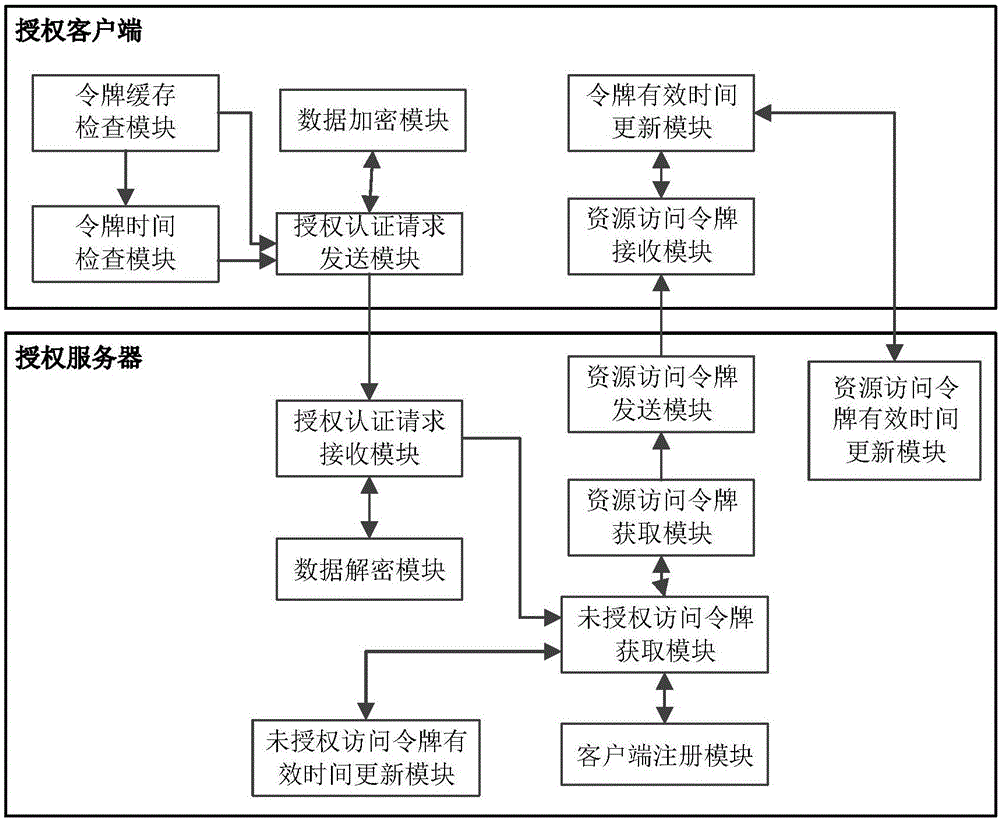
The invention discloses an open platform authorization and authentication system and method based on an OAuth protocol, and mainly aims to solve the problem of misuse of a resource access token since the valid time of the resource access token is not optimized or limited reasonably in the prior art. The system comprises an authorization client and an authorization server, wherein the authorization client is used for transmitting an authorization and authentication request, receiving the resource access token and the valid time of the token through function modules inside the authorization client, and resetting the valid time of the token according to acquisition times and time of user resources; and the authorization server is used for receiving and checking the authorization and authentication request, acquiring an unauthorized access token and the valid of the token through function modules inside the authorization server, generating a resource access token and the valid time of the token, and transmitting the resource access token and the valid time of the token to the authorization client. Through adoption of the open platform authorization and authentication system and method, an authorization and authentication process is simplified, and the resource security is improved. The open platform authorization and authentication system and method can be applied to an authentication and authorization process during acquisition of open platform resources.
Owner:XIDIAN UNIV
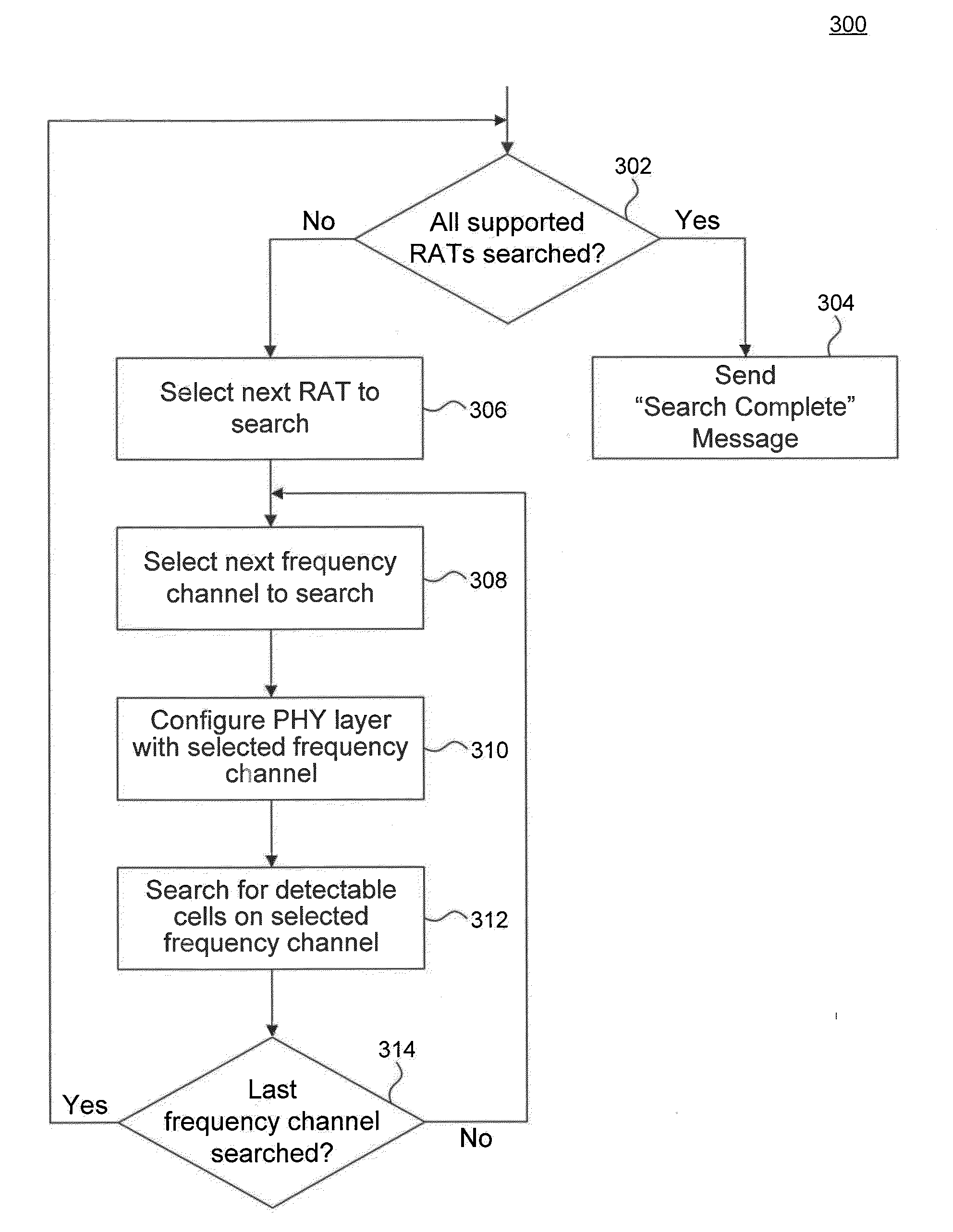
Enhanced Higher Priority Public Land Mobile Network (HPPLMN) Search
ActiveUS20140155061A1Assess restrictionWireless commuication servicesPublic land mobile networkAccess frequency
Embodiments provide an enhanced approach for Higher Priority Public Land Mobile Network (HPPLMN) search. In one embodiment, information acquired during a search (for each detected cell per frequency channel) is saved in a database and persisted in the database based on a validity time. An idle mode-to-connected mode transition by the UE, rather than aborting the search, only suspends the search for it to be resumed at a later time upon a connected mode-to-idle mode transition by the UE. Saved search data that is valid at the time of the transition is maintained and the frequency channel(s) associated with it is not re-searched in the current search. In an embodiment, the search is resumed based on weights that are associated with frequency channels, where a weight indicates a priority for visiting the frequency channel.
Owner:BELL NORTHERN RES LLC
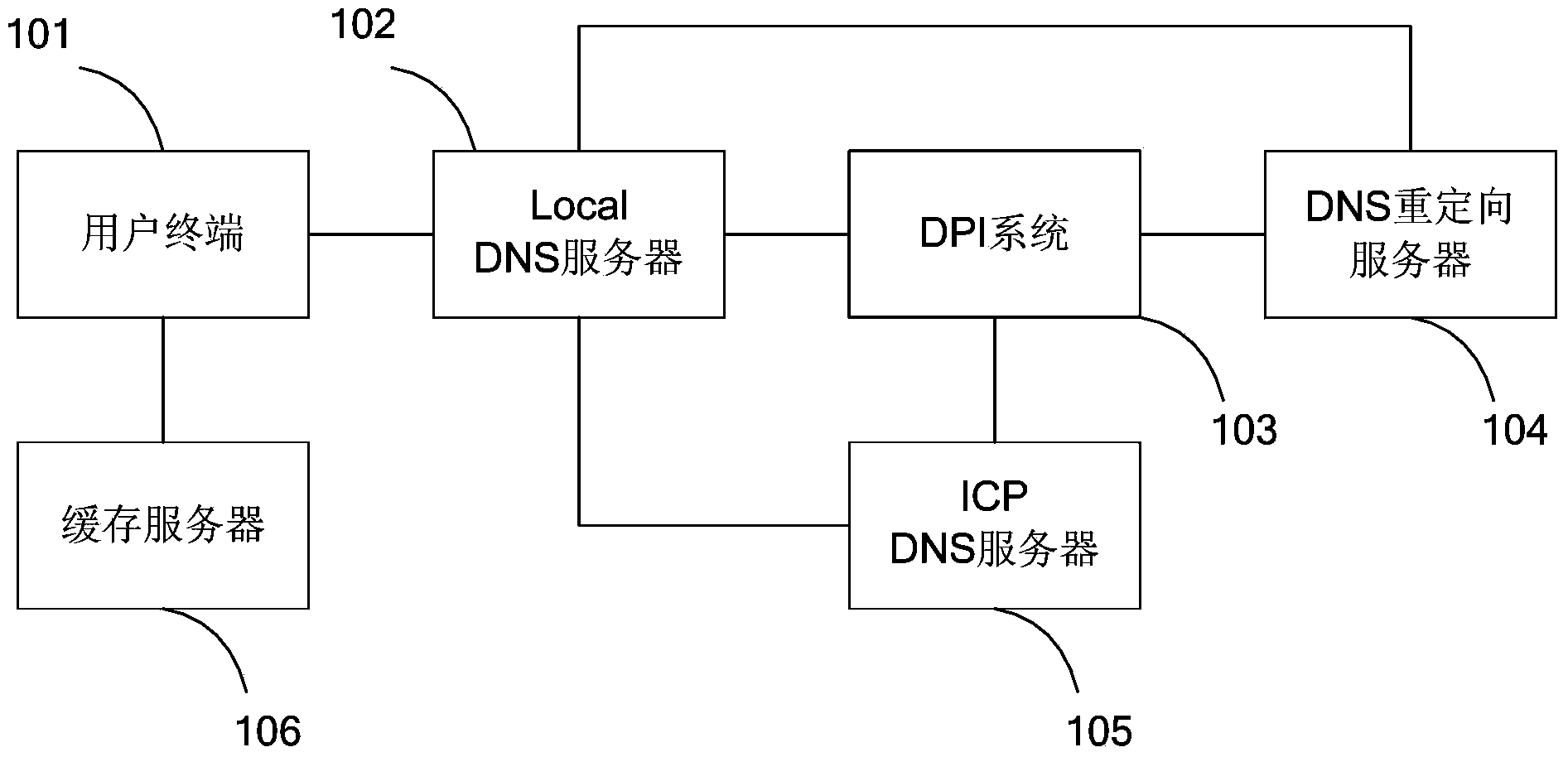
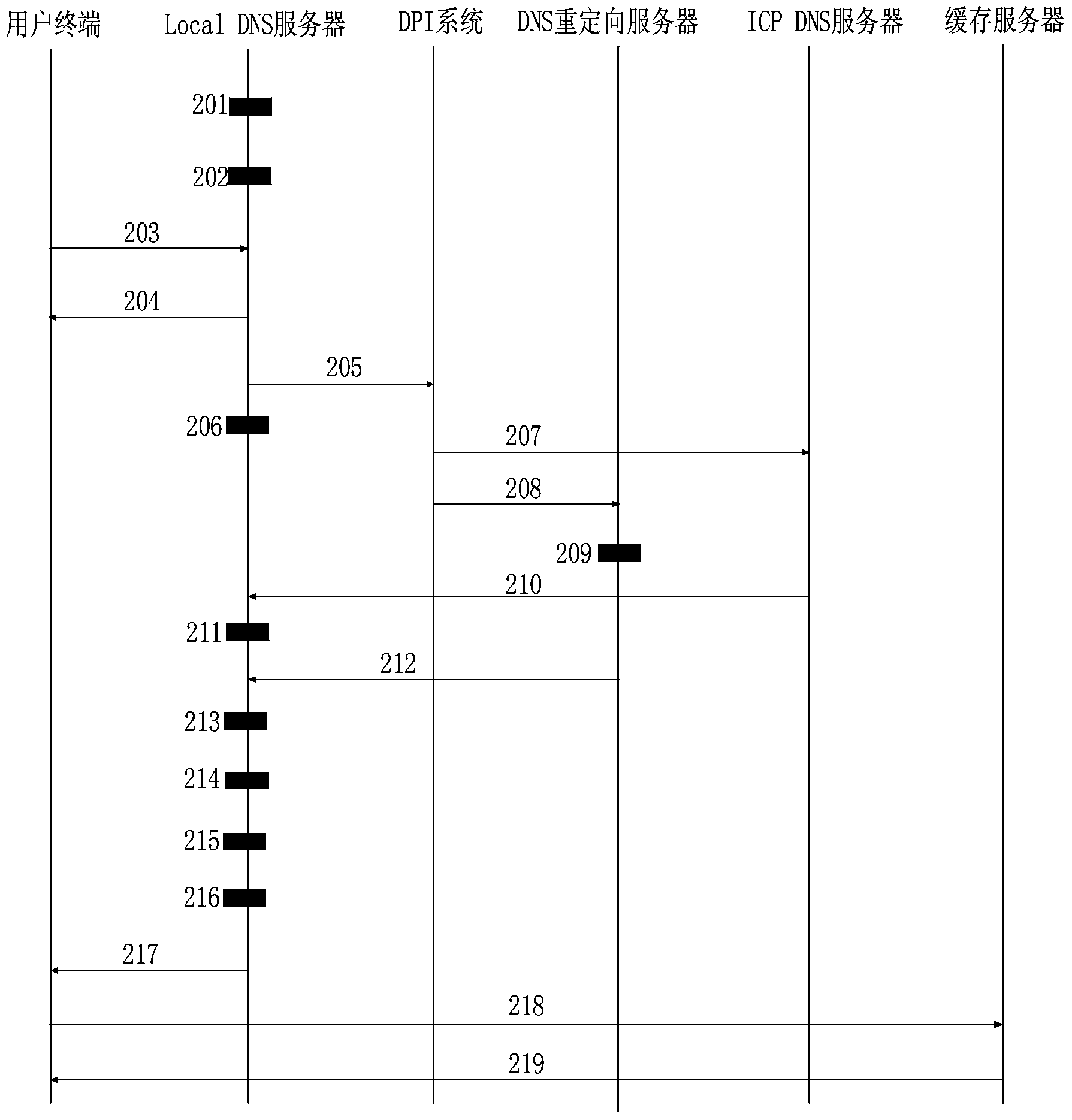
Method and system of implementing HTTP (Hyper Text Transport Protocol) cache
The invention discloses a method and a system of implementing an HTTP (Hyper Text Transport Protocol) cache. The system comprises a user terminal, a Local DNS (Domain Name Server), a DPI (Data Processing Installation) system, a DNS redirect server, an ICP (Internet Content Provider) DNS server and a cache server, wherein through starting using and monitoring a timer, if only a DNS resolution result fed back by the DNS redirect server is guaranteed to be received in a valid time bucket of T2-T1, a user can be guaranteed to use the cache, thereby avoiding the problems that the existing DNS hijack scheme replies the DNS resolution result more early in the ICP DNS server than in the DNS redirect server, and then the cache is unable to serve the user of a home network, and through TTL (Time To Live) advanced iterative query and cache refresh mechanisms, effective duration of the resolution result of the cache in the Local DNS server is implemented, the problem that the user needs to wait DNS query in a DNS query process to generate time delay is avoided, user perception is greatly improved and system efficiency is improved.
Owner:CHINA MOBILE GRP BEIJING
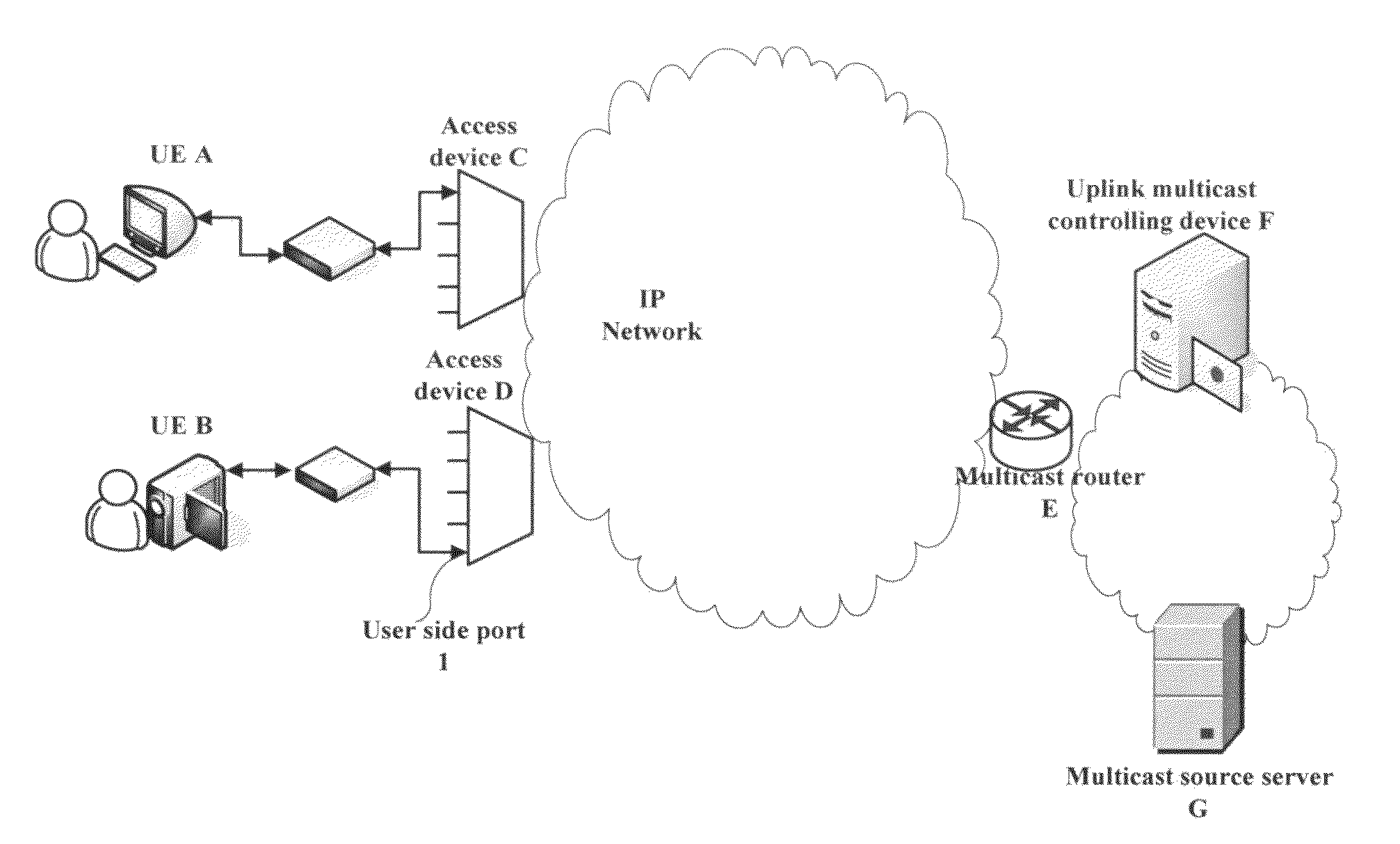
Method and apparatus for controlling uplink multicast service
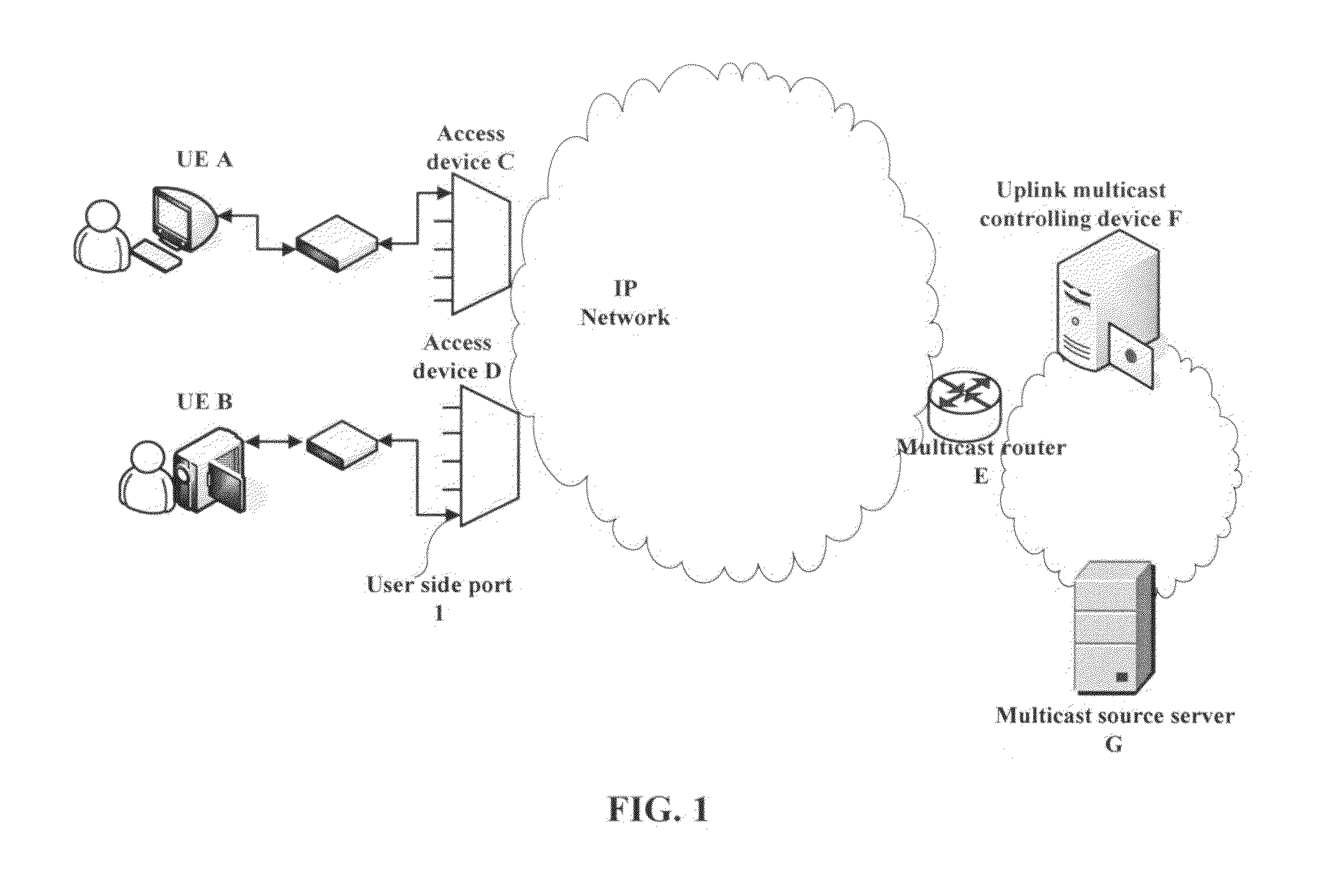
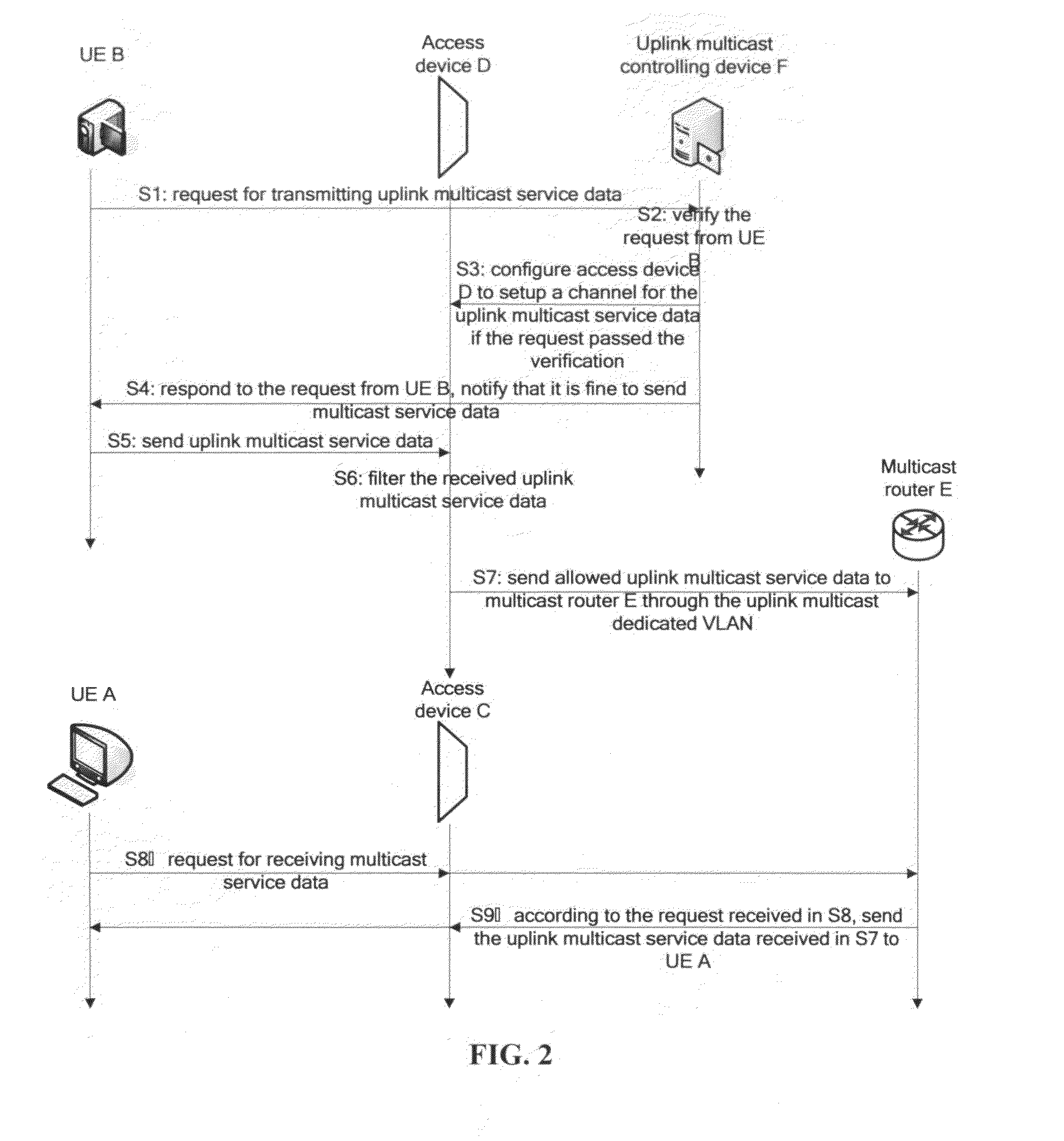
ActiveUS20100195651A1Effectively managed and controlledBroadcast transmission systemsData switching by path configurationData streamControl communications
The present invention provides a method and apparatus for controlling the transmission of uplink multicast service data in communication network. According to the invention, a user equipment sends request to a multicast controlling device for the permission of providing uplink multicast data stream; once the uplink multicast controlling device has verified and accepted the request, it will assign multicast address, bandwidth, valid time for it and update the uplink multicast forwarding table at the access device to establish an uplink multicast dedicated VLAN. After that, the access device will forward multicast data from the UE according to the uplink multicast forwarding table configured by the uplink multicast controlling device, to be specific, allowed multicast packets to be forwarded into the uplink multicast dedicated VLAN, and get to the multicast router via the uplink multicast dedicated VLAN. Finally, the multicast router will take the responsibility of multicast distributing of the uplink multicast service data. Based on the present invention, the access of uplink multicast and the data transmission can be well controlled, the multicast routers provide multicast service to the network in a centralized manner. Also, this is compatible with the existing multicast and unicast services.
Owner:ALCATEL-LUCENT USA INC
License valid time check method and apparatus
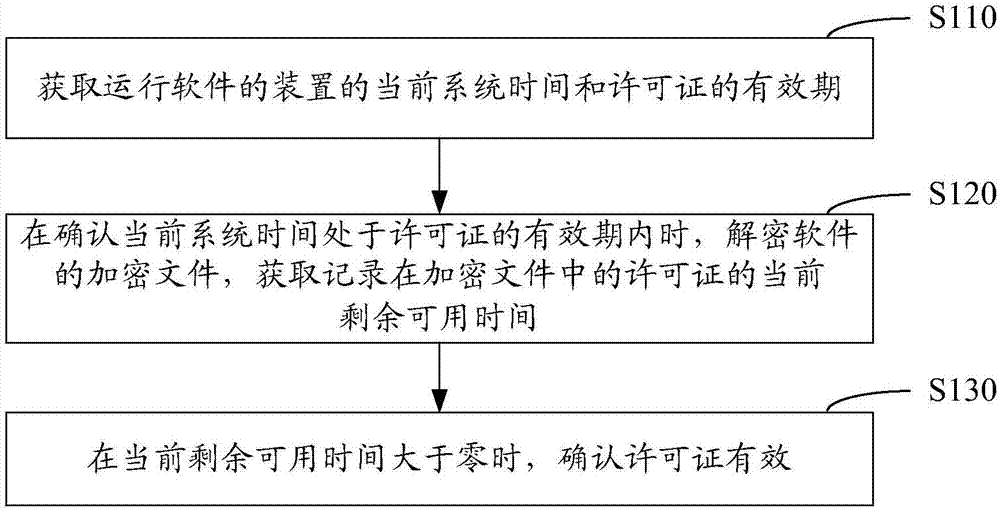
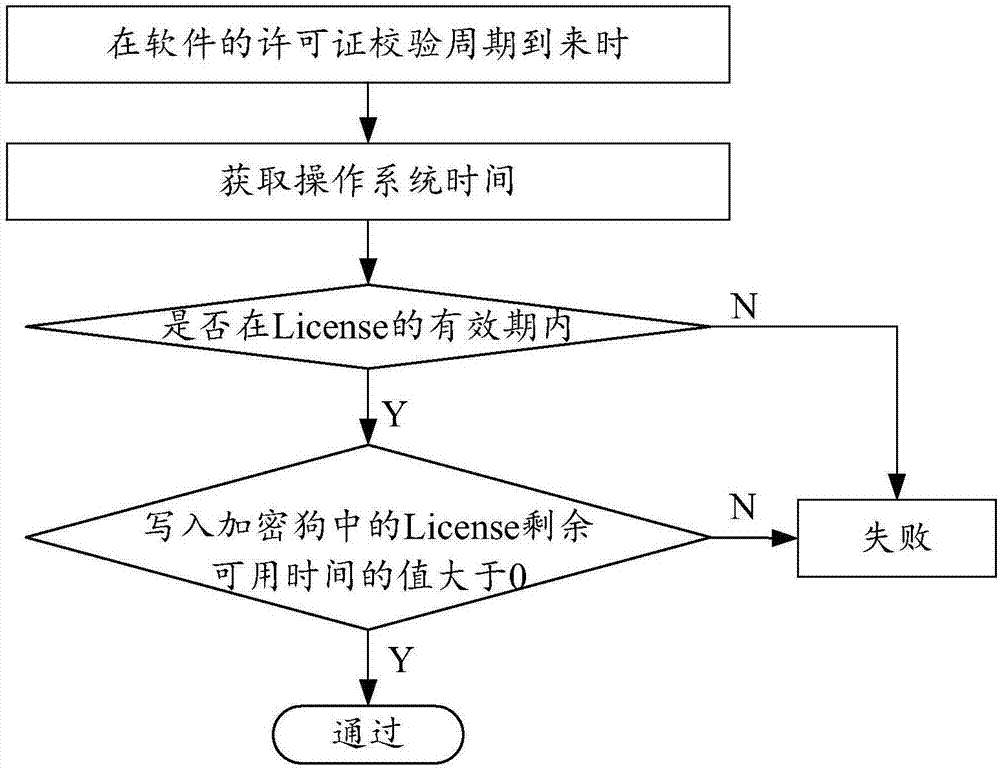
ActiveCN107341368APrevent artificial crackingImprove accuracyDigital data protectionProgram/content distribution protectionSystem timeLicense
The invention relates to a license valid time check method and apparatus. The license valid time check method comprises the following steps of obtaining current system time of an apparatus running software, and a validity period of a license; when it is confirmed that the current system time is in the validity period of the license, decrypting an encrypted file of the software to obtain current residual available time recorded in the encrypted file; and when the current residual available time is greater than 0, confirming that the license is valid. The accuracy of judging the valid time of the license is enhanced through a regular multiple mechanism; accurate judgment of system time check can be ensured; and the problem that the expired license still can continue to be used when the system time is manually modified can be solved.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD
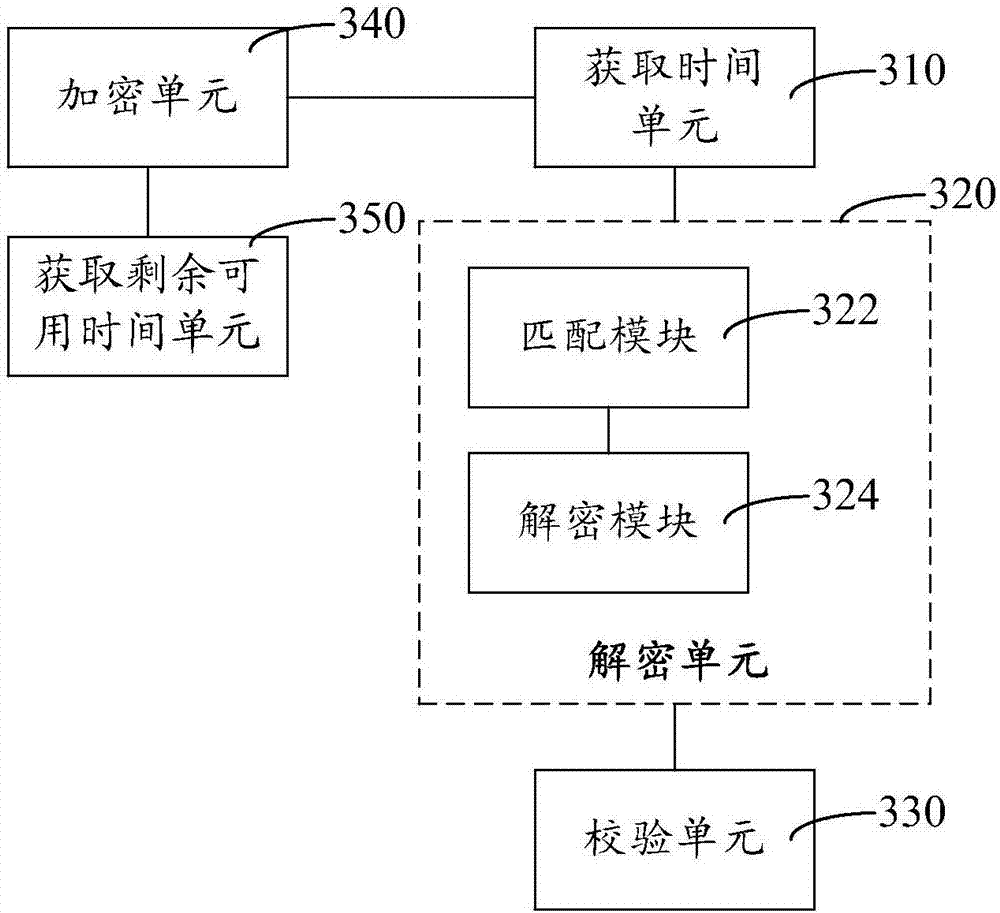
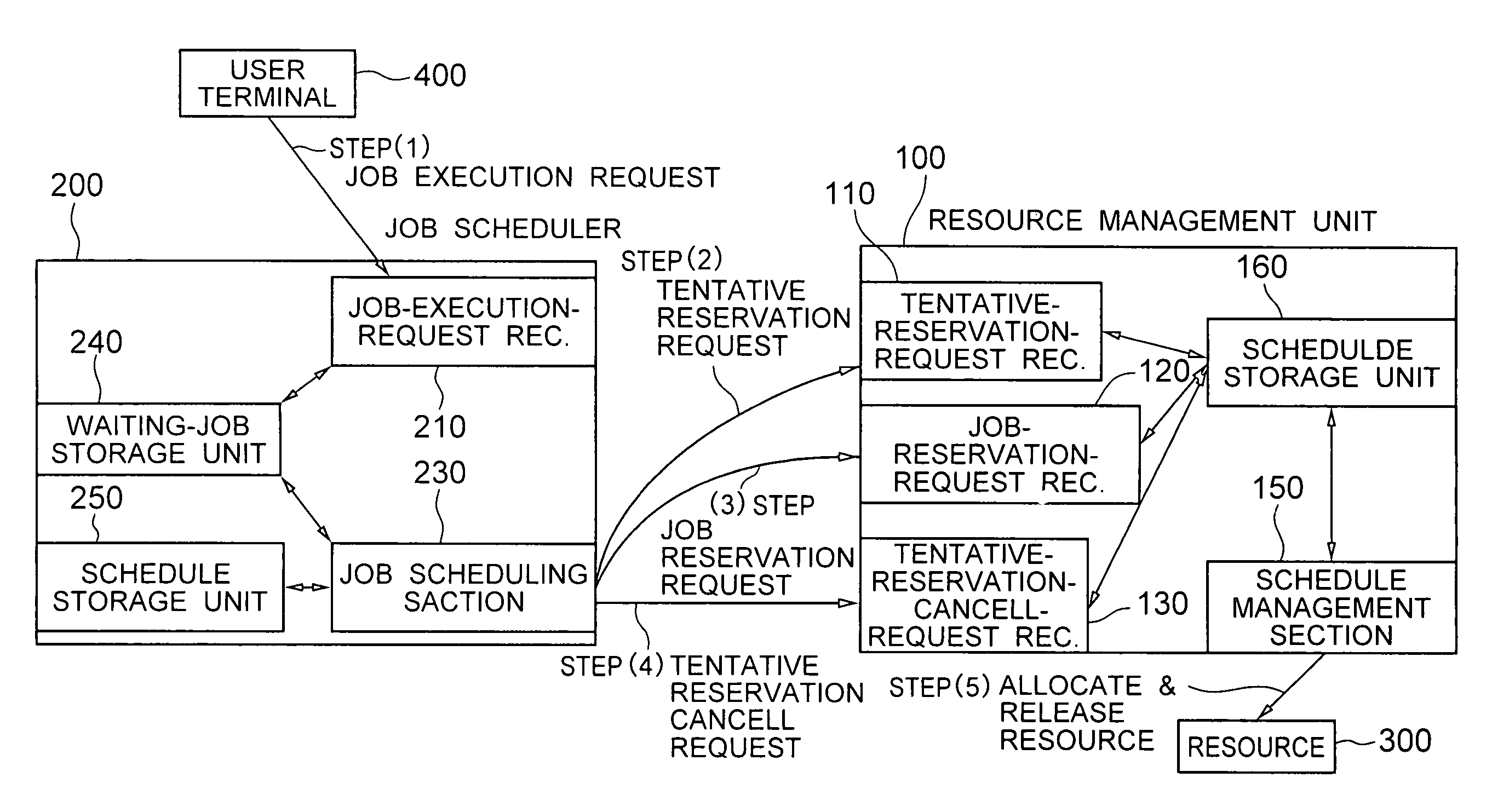
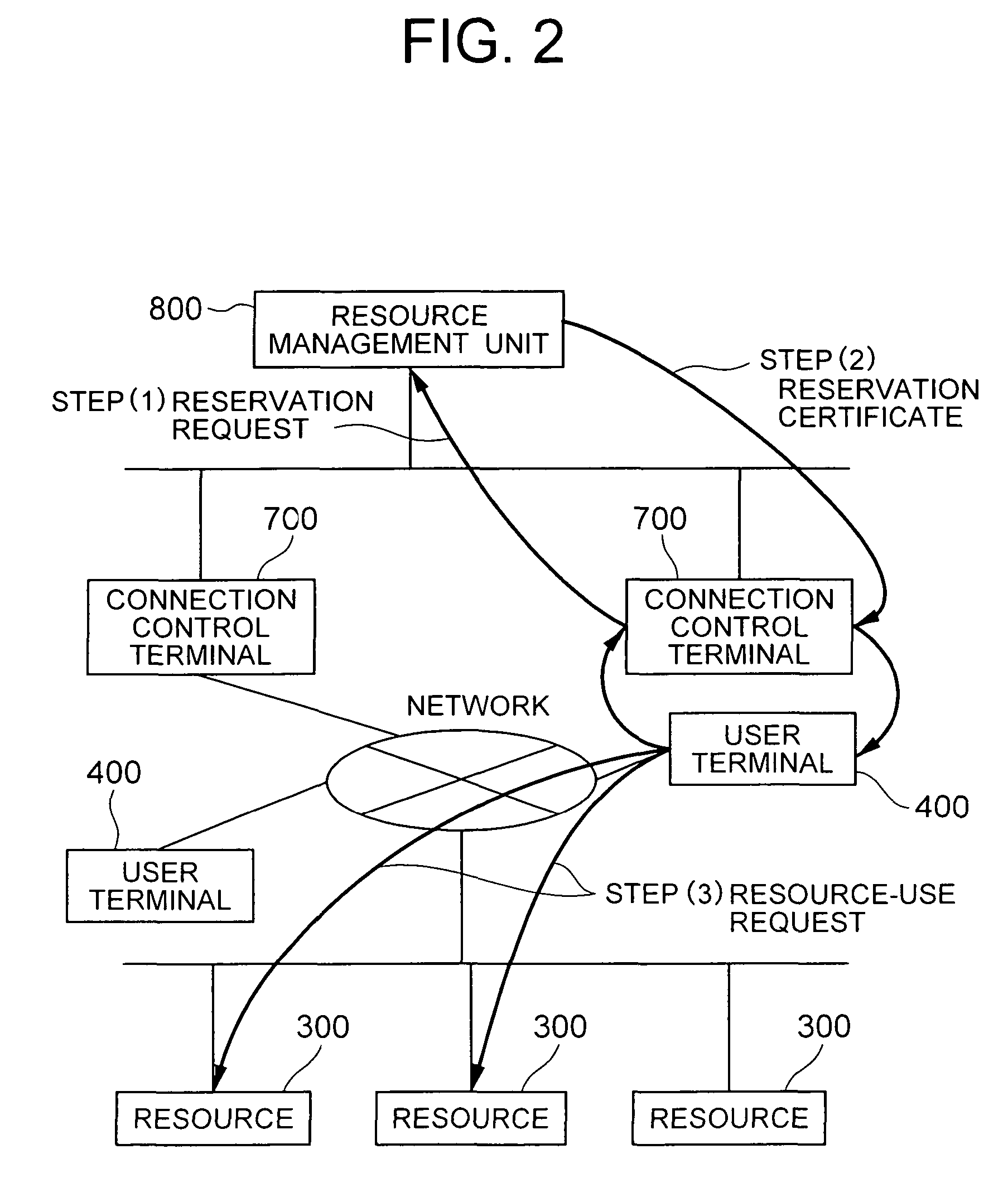
System for confirming and cancelling tentative resource reservation within the valid time indicates period during which the tentative reservation request is valid
ActiveUS8166484B2Improve usabilityResource allocationDigital computer detailsResource managementJob scheduler
For a resource reservation in a distributed resource system, a tentative reservation request and a job reservation request are issued from a job scheduler to a resource management unit. The tentative reservation is valid for a short time period, and cannot coexist with another tentative reservation or the job reservation. In order to actually use resources, a job reservation must be issued after registration of the tentative reservation. If a tentative reservation request is received for a resource to which another tentative reservation request is already accepted, the tentative reservation request is stored in a wait queue, which is successful if the another tentative reservation is cancelled or failed due to the expiration of the validity time period.
Owner:NEC CORP
System and method for creating an object model
InactiveUS20080301181A1Digital data processing detailsRelational databasesTemporal informationDomain model
A method for creating a dynamic domain model of an object. The method includes storing and organizing temporal information about the object in a bitemporal database that includes both a valid time and a transaction time for the information. The information is inserted into a plurality of tables in the database and a key is assigned to each of the plurality of tables. A composite representing the object is formed to represent a state of the object at the current time or at any previous time by dynamically linking the information by key, based on a business logic and a request made by a user.
Owner:RAYTHEON TECH CORP
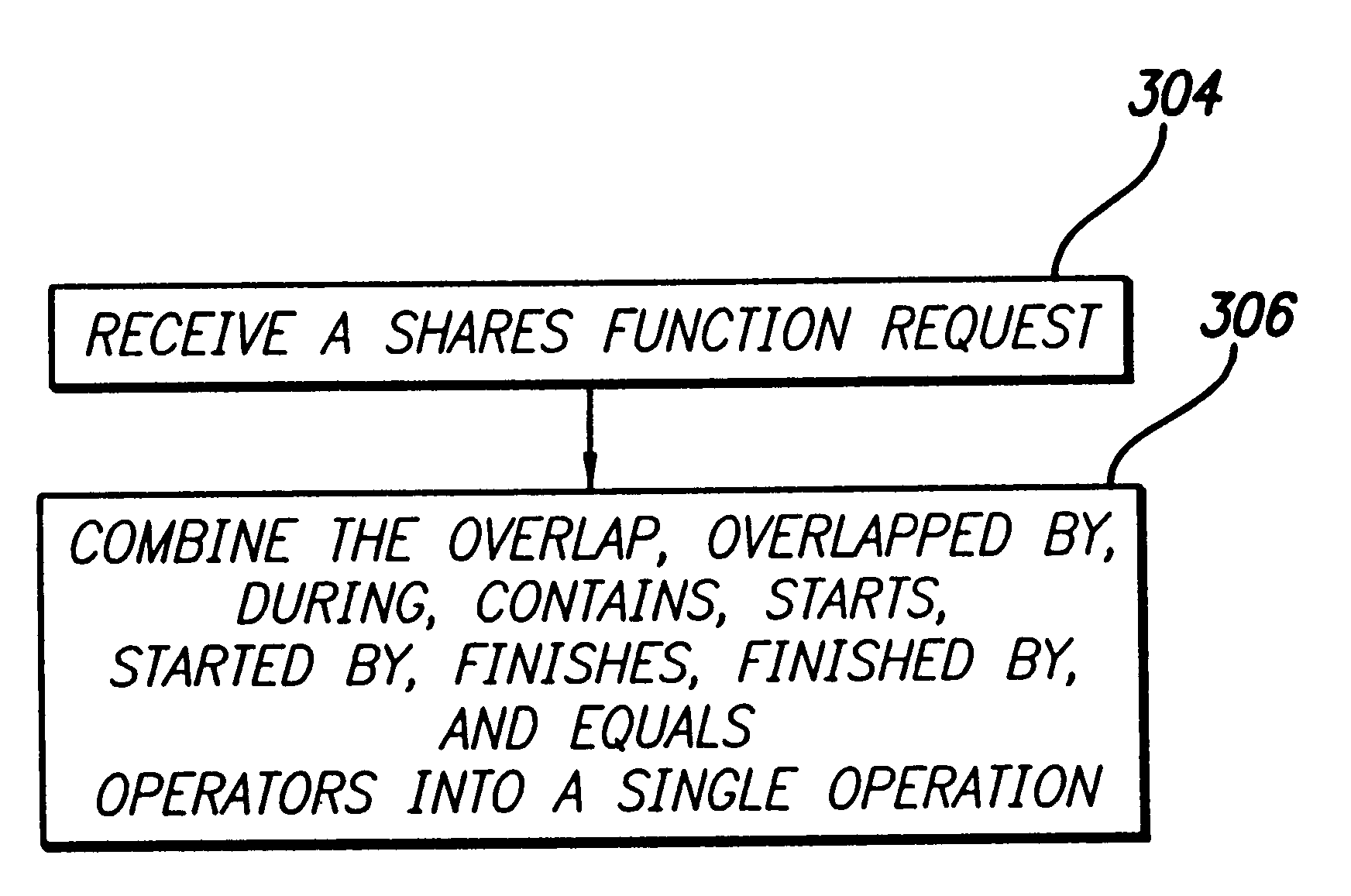
Technique for detecting a shared temporal relationship of valid time data in a relational database management system
InactiveUS6691097B1Data processing applicationsRelational databasesRelational database management systemTime data
A method, apparatus, and article of manufacture for detecting shared temporal relationships in a relational database. In accordance with the present invention, an invocation of a shares operation that specifies a first event and a second event is received. In response to the invocation, a combination of temporal relationships between the first event and the second event are evaluated to determine whether (1) the second event ends after the first event starts and the first event ends after the second event starts or (2) the first and second events start and end at the same time.
Owner:SAP AG
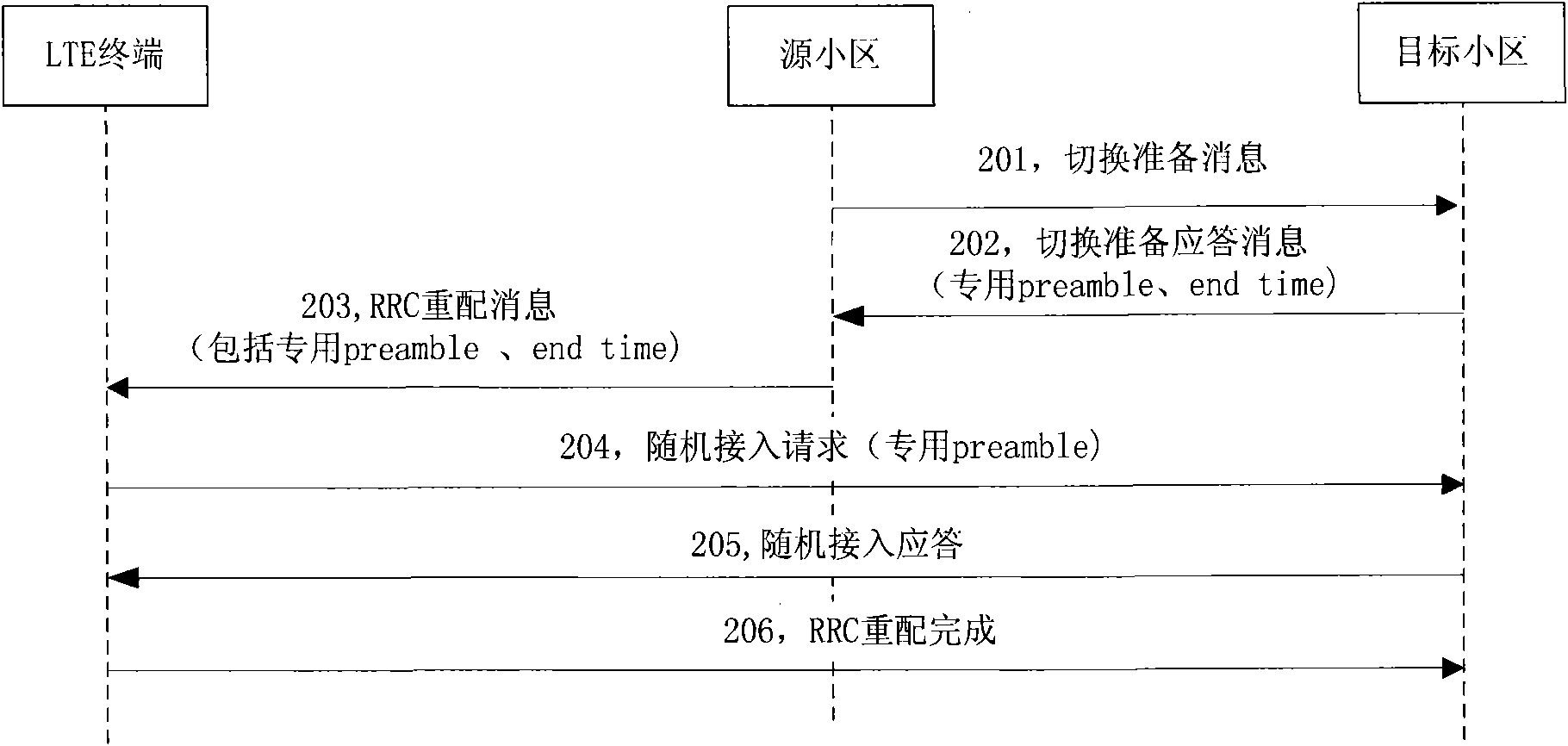
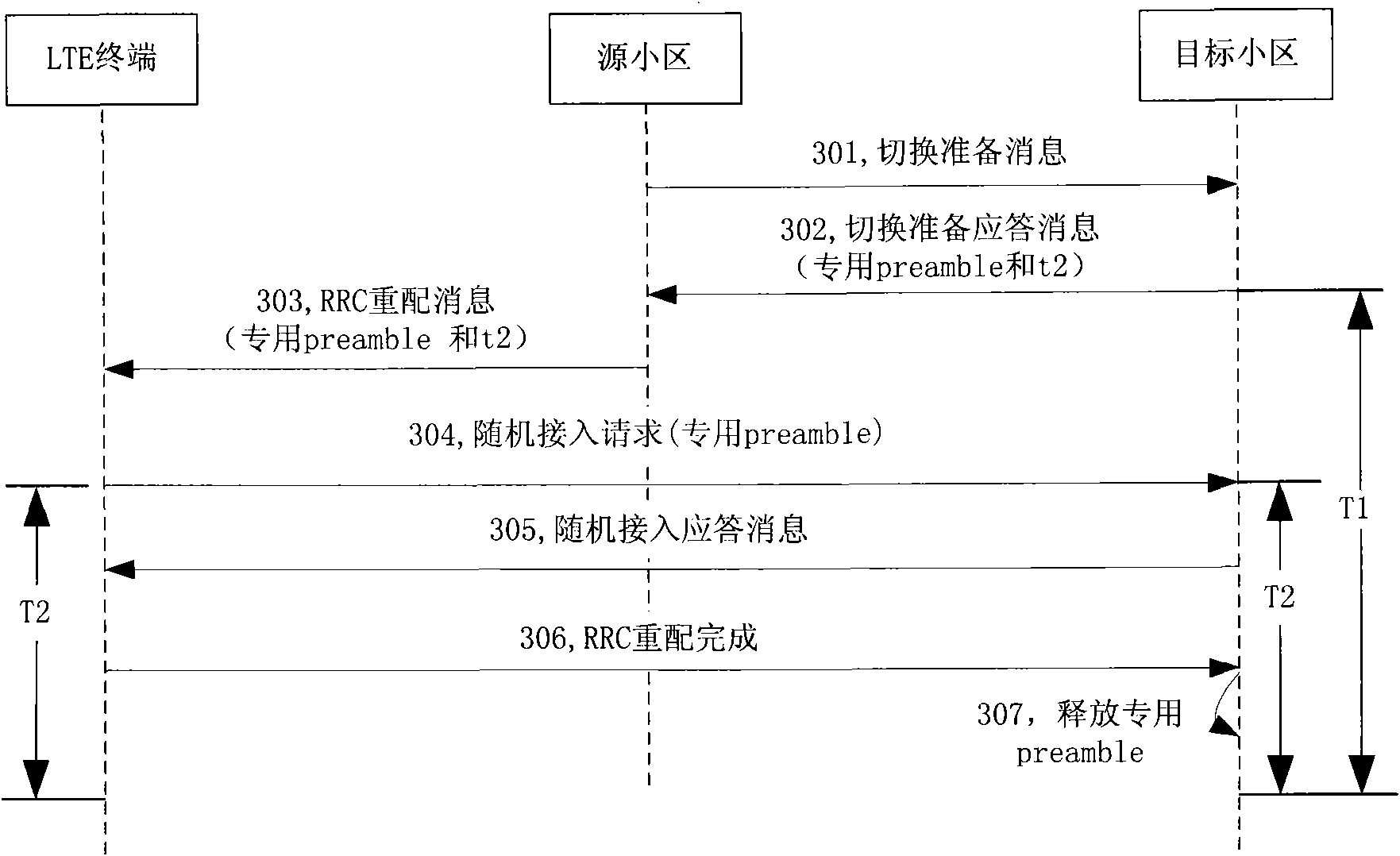
Method for improving service efficiency of special leader sequence and terminal switching method
InactiveCN101572920ATime synchronizationImprove efficiencyConnection managementService efficiencyReal-time computing
The invention discloses a method for improving the service efficiency of a special leader sequence, comprising the following steps: when a terminal switches from a source cell to a target cell, the target cell sets the special leader sequence and a valid time length using the special leader sequence; the terminal uses the special leader sequence during the period of the valid time length to launch random access in the target cell; and the valid time length is calculated when the terminal firstly launches the random access leader message in the target cell. The method ensures that the time for the terminal to stop using the leader sequence is synchronous with the time for the target cell to release the leader sequence used by the terminal, thereby improving the service efficiency of the leader sequence and the terminal switch success ratio.
Owner:ZTE CORP
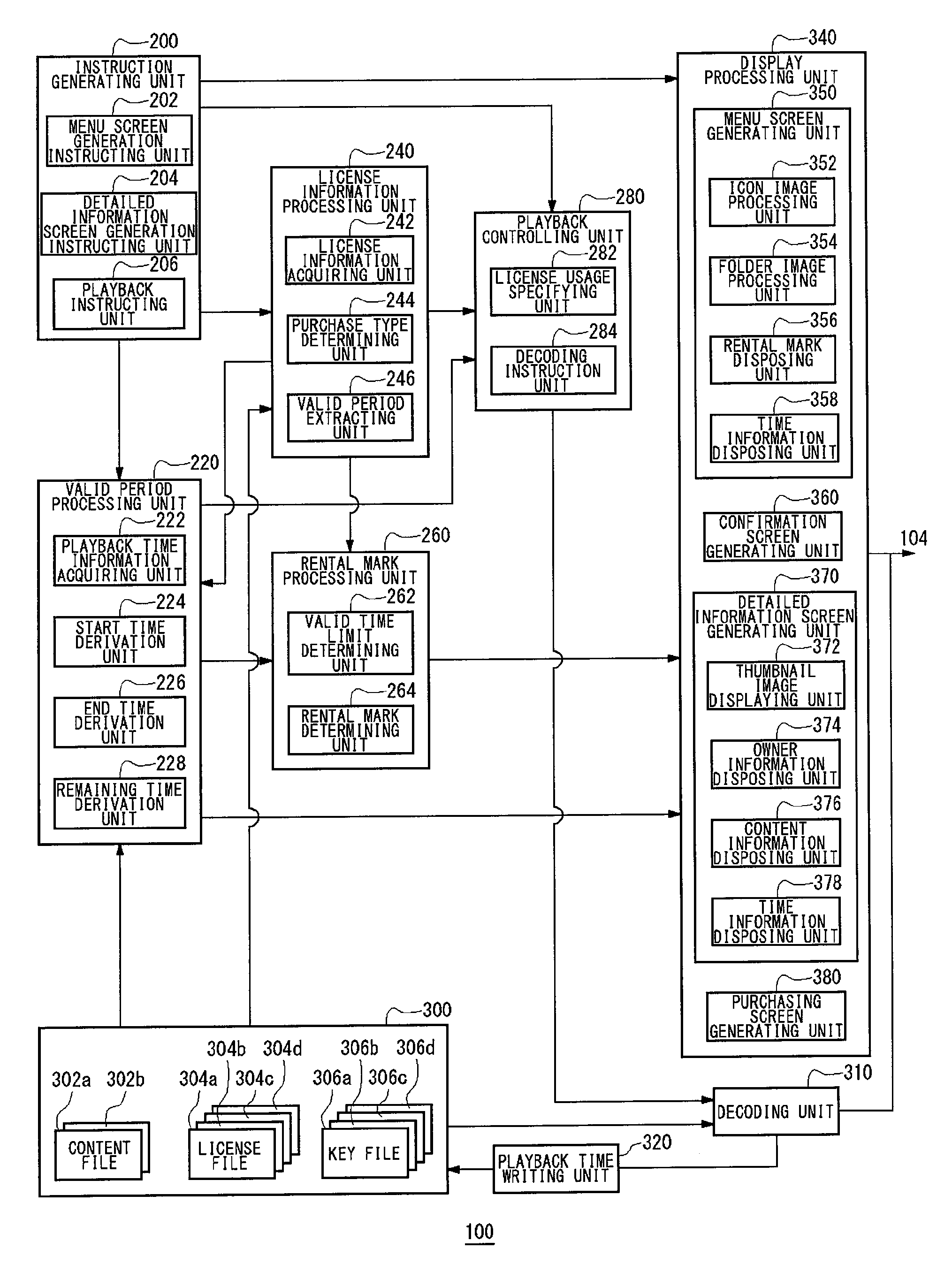
Information processing device
ActiveUS20110131115A1Improve user friendlinessTwo-way working systemsBuying/selling/leasing transactionsInformation processingImaging processing
A purchase type determining unit 244 determines whether content is rental content, which has a valid time limit for enjoying, from purchasing type information included in the license information. An icon image processing unit 352 disposes an icon image of the content in a menu screen. In case the content is determined to be rental content by the purchase type determining unit 244, a rental mark disposing unit 356 disposes a rental mark indicating that associated content is rental content near the icon image of the content or disposes the rental mark so as to overlap with the icon image of the content.
Owner:SONY COMPUTER ENTERTAINMENT INC
Session access method and server
InactiveCN109587251AEnsure safetyImprove securityUser identity/authority verificationAccess methodValid time
Owner:YONYOU NETWORK TECH
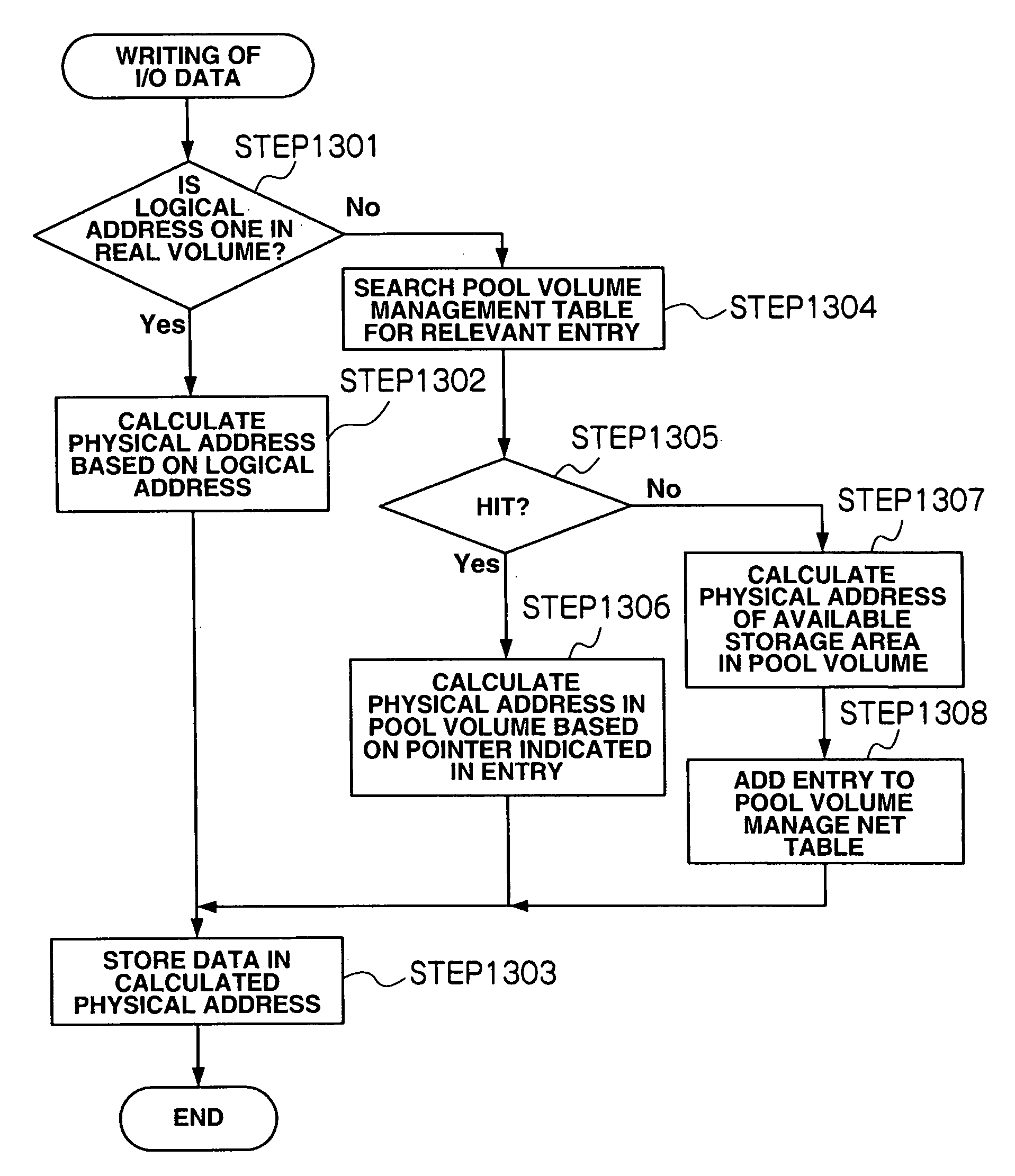
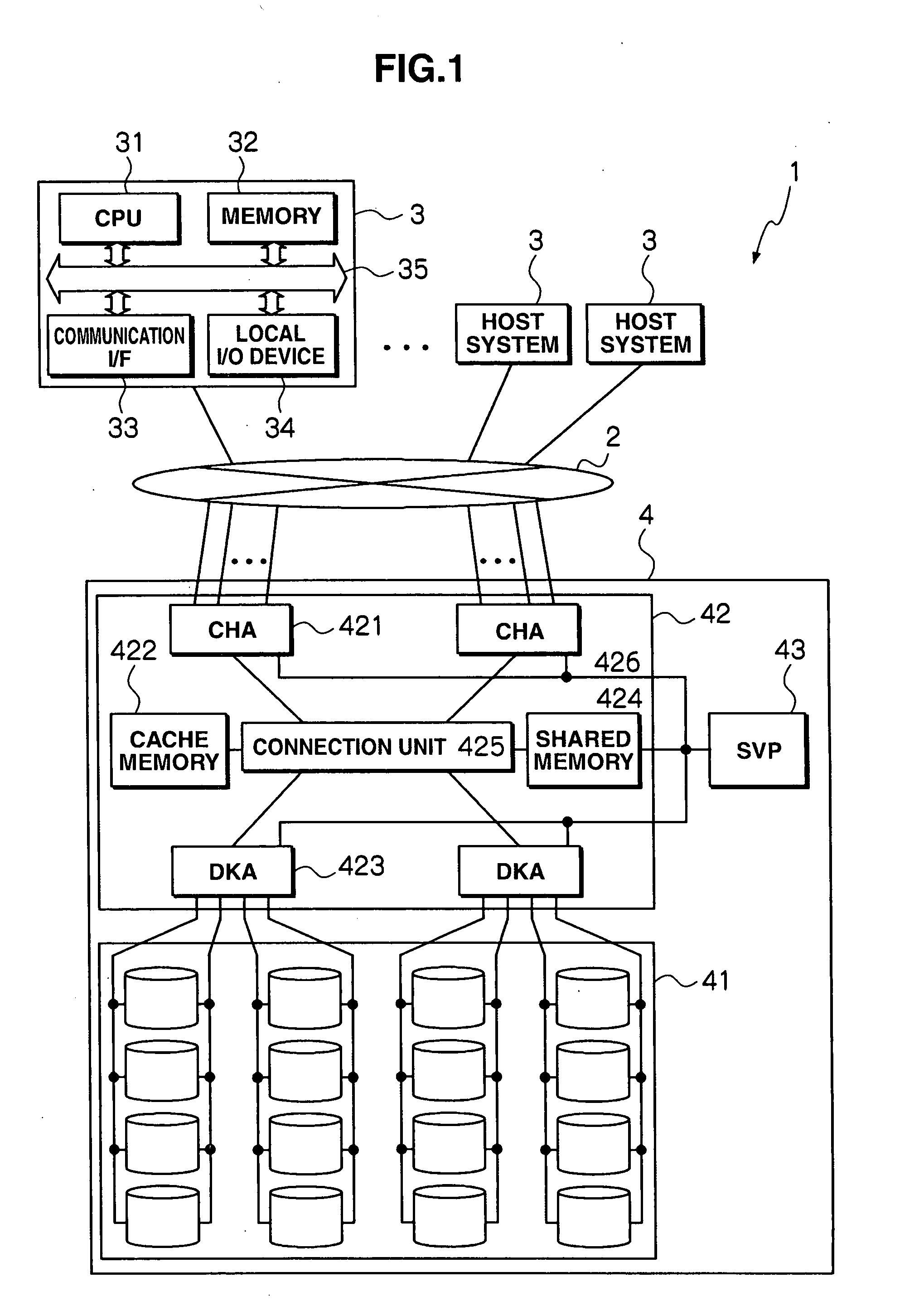
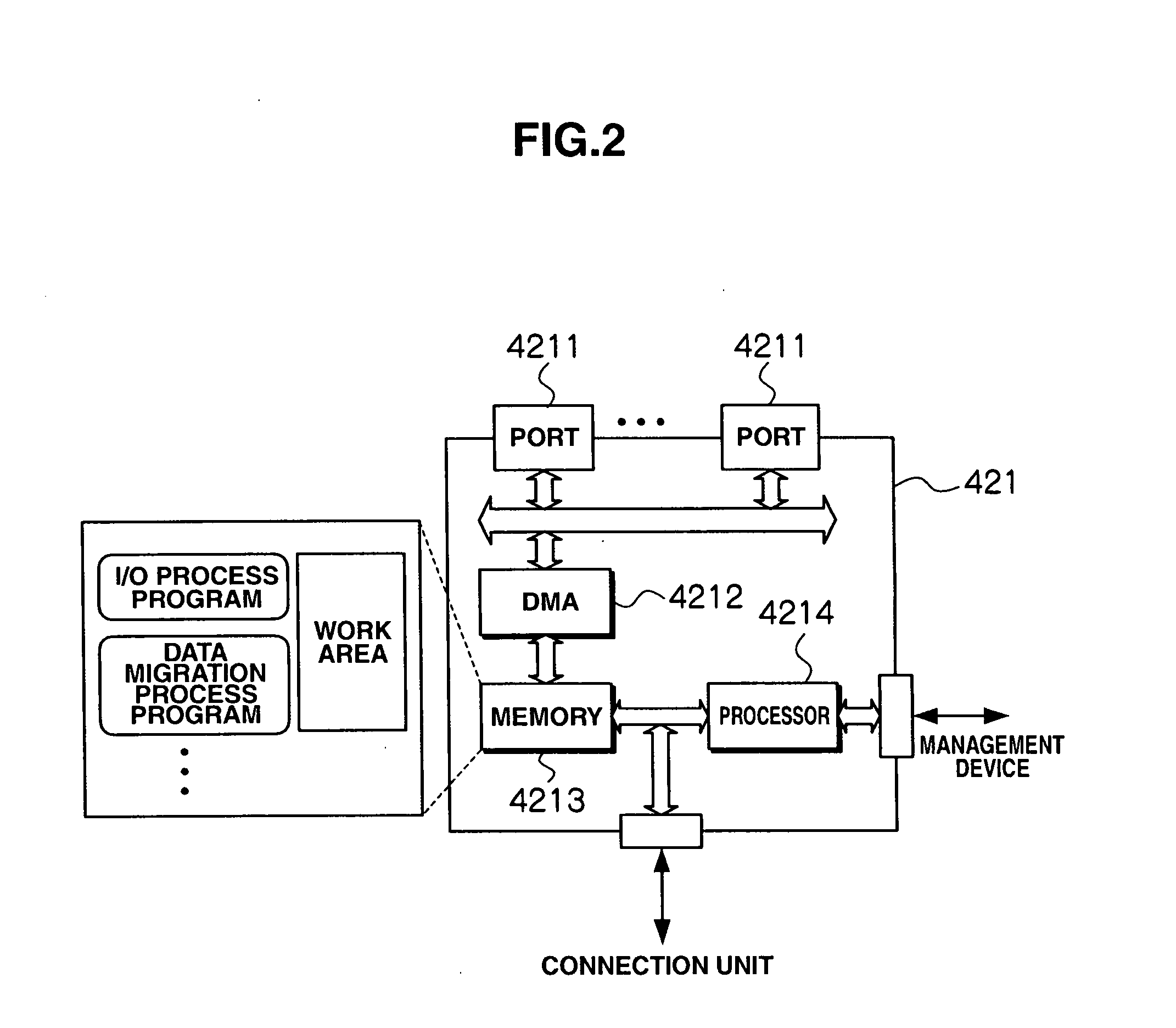
Storage apparatus and data management method using the same
InactiveUS20080147960A1Improve performancePrevent degradationMemory systemsInput/output processes for data processingData managementData migration
The expansion of a mapping table with additional mapping information involved in the access to virtual volumes is prevented and so a search in the mapping information within a valid time period is ensured, thereby preventing degradation of system performance. A storage apparatus, which defines virtual volumes to which storage areas are dynamically allocated, has a data migration function to migrate data between the virtual volumes and real volumes. With the data migration function, the mapping information for the migrated data is deleted from the mapping table, and accordingly, the size of the mapping table can be limited.
Owner:GOOGLE LLC
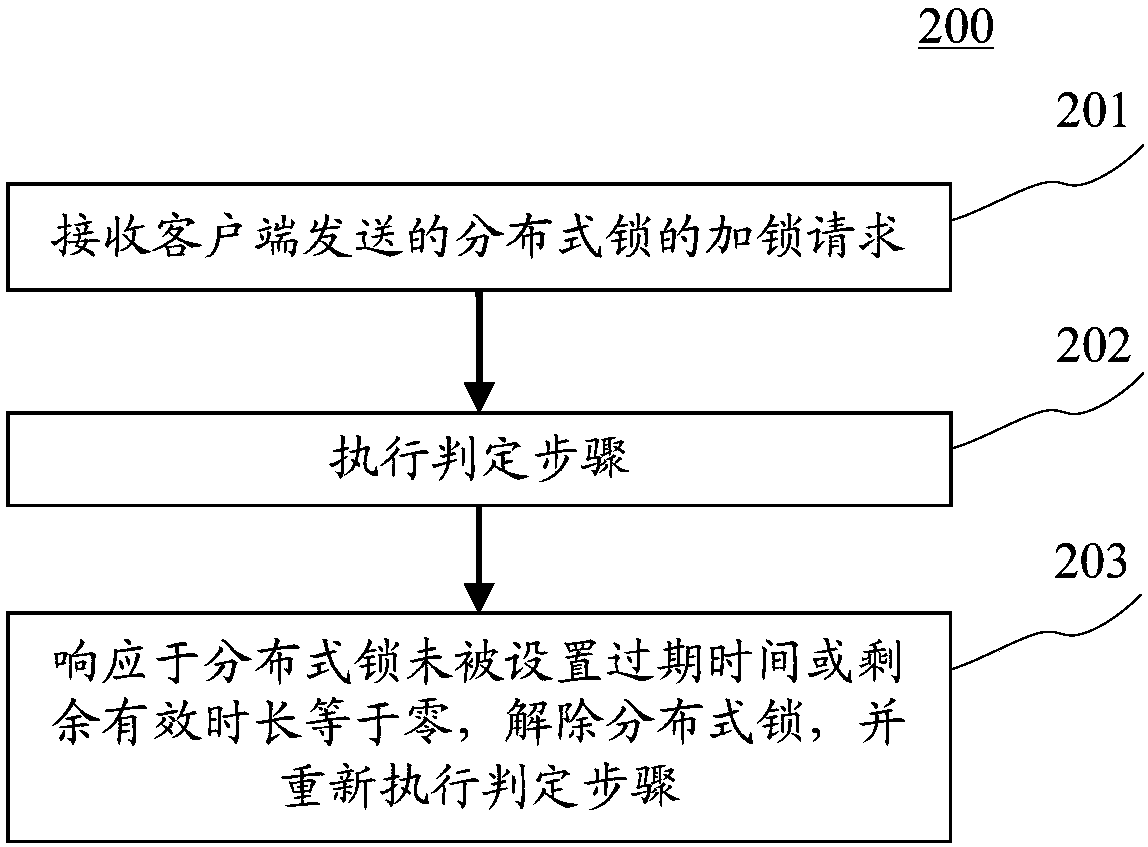
Control method and device of distributed-type lock
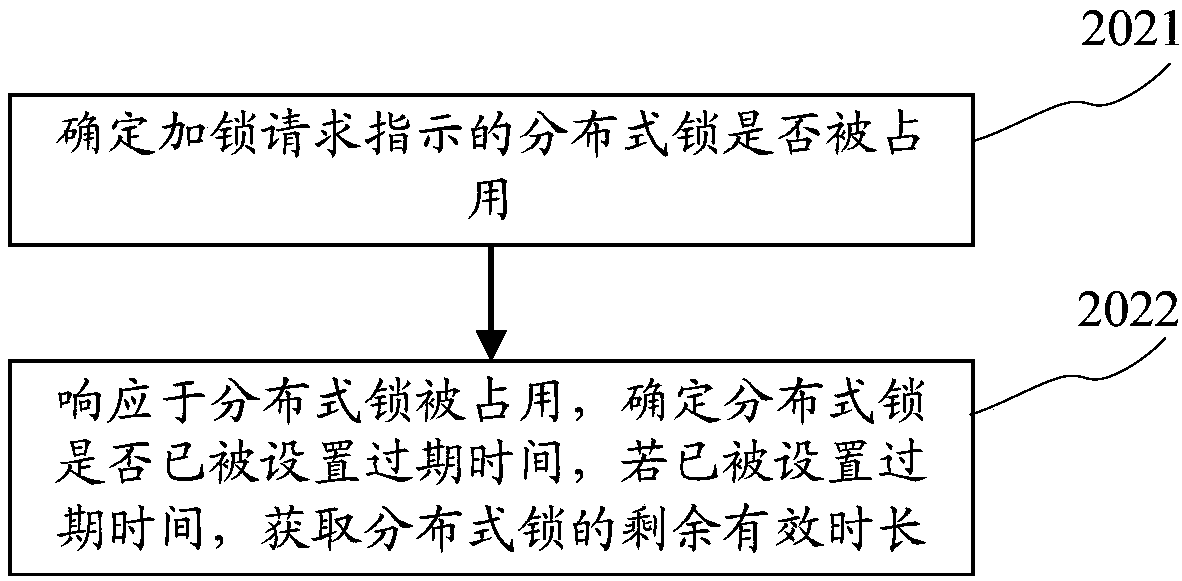
InactiveCN107818018AEffective controlEasy to controlProgram synchronisationTransmissionExpiration TimeClient-side
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
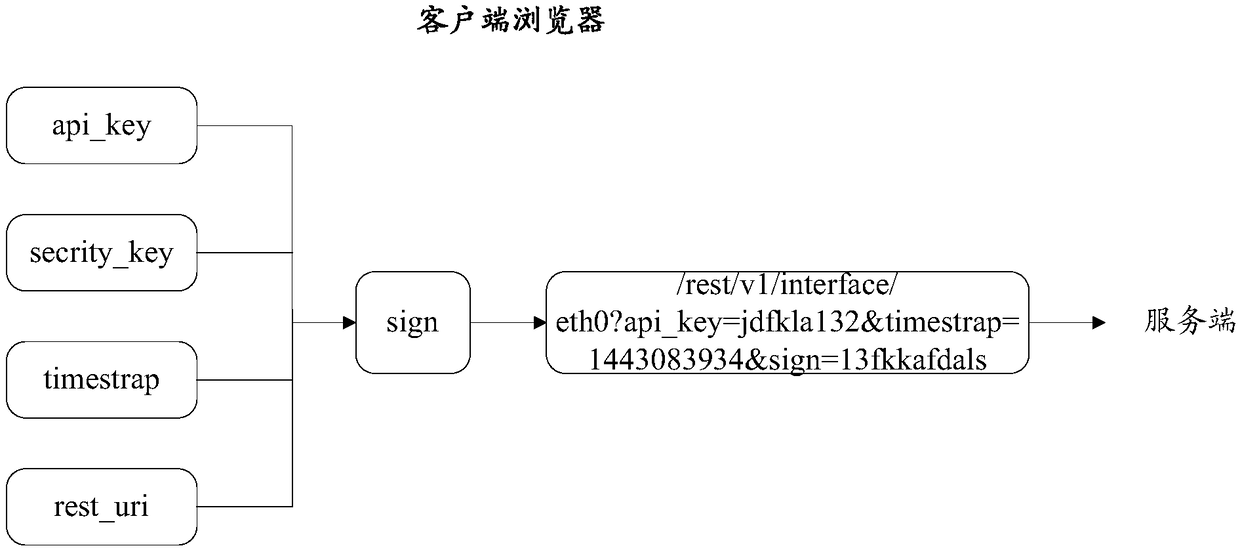
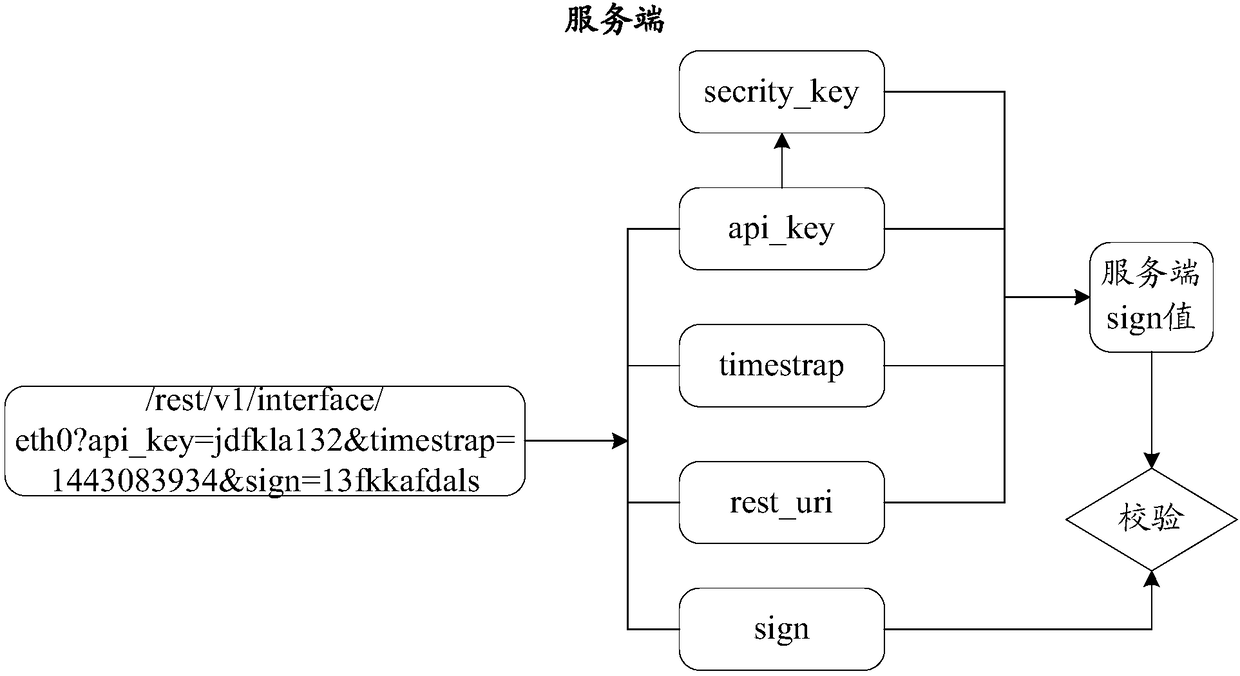
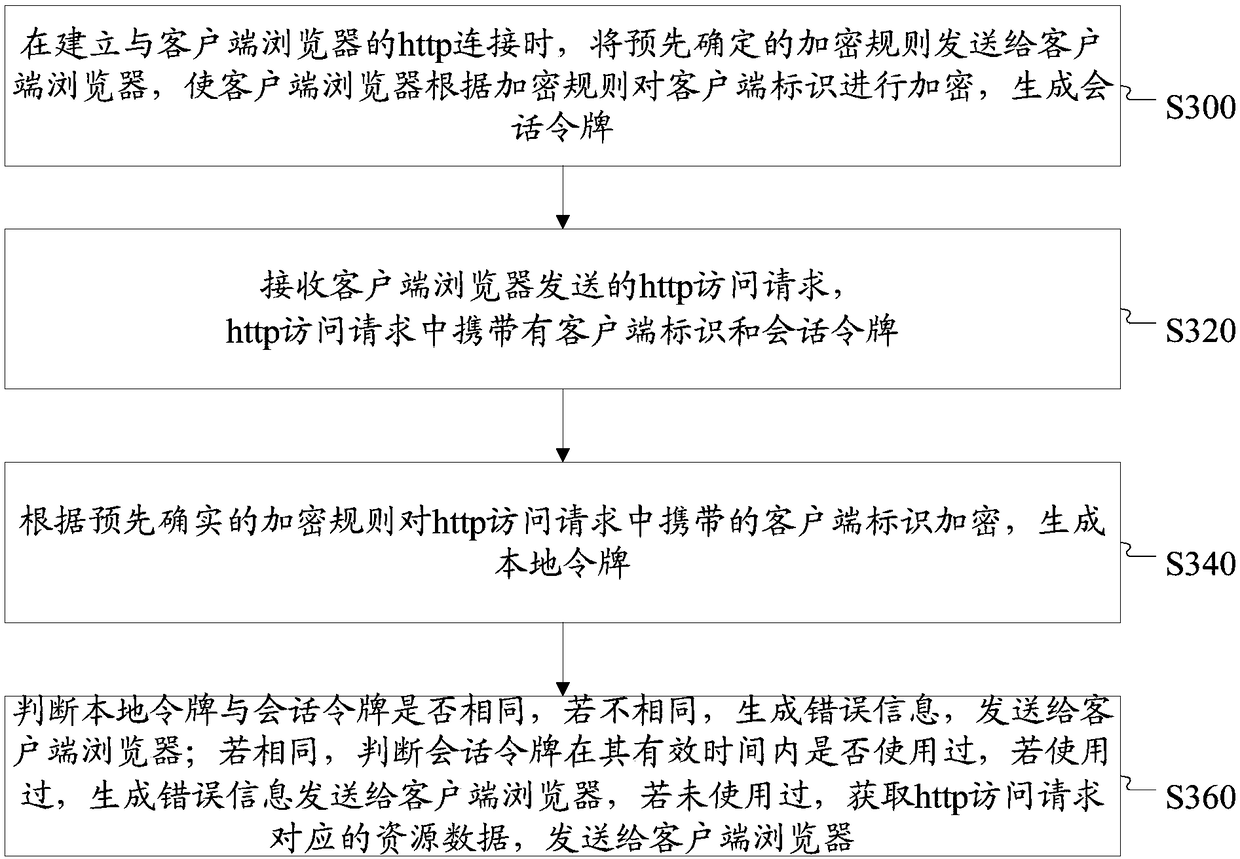
Http (hypertext transfer protocol) access method, http server and http system
ActiveCN108259437AAvoid reuseEnsure safetyKey distribution for secure communicationUser identity/authority verificationAccess methodClient-side
The invention discloses an http (hypertext transfer protocol) access method, an http server and an http system. The method comprises the steps of sending a predetermined encryption rule to a client browser when http connection with the client browser is established; receiving an http access request which is sent by the client browser and carries a client identity and a session token; encrypting the client identity carried in the http access request according to the predetermined encryption rule and generating a local token; and sending resource data corresponding to the http access request tothe client browser when the local token is the same as the session token and the session token is not used in valid time. According to the method, the server and the system, the session token is generated through utilization of the specific encryption rule and whether the received session token is used in the valid time or not is judged, so the session token is prevented from being reused in the valid time, the two-level security protection of the http access in a client browser / server mode is realized, and the data security is ensured.
Owner:ULTRAPOWER SOFTWARE
Network data security system and protecting method thereof
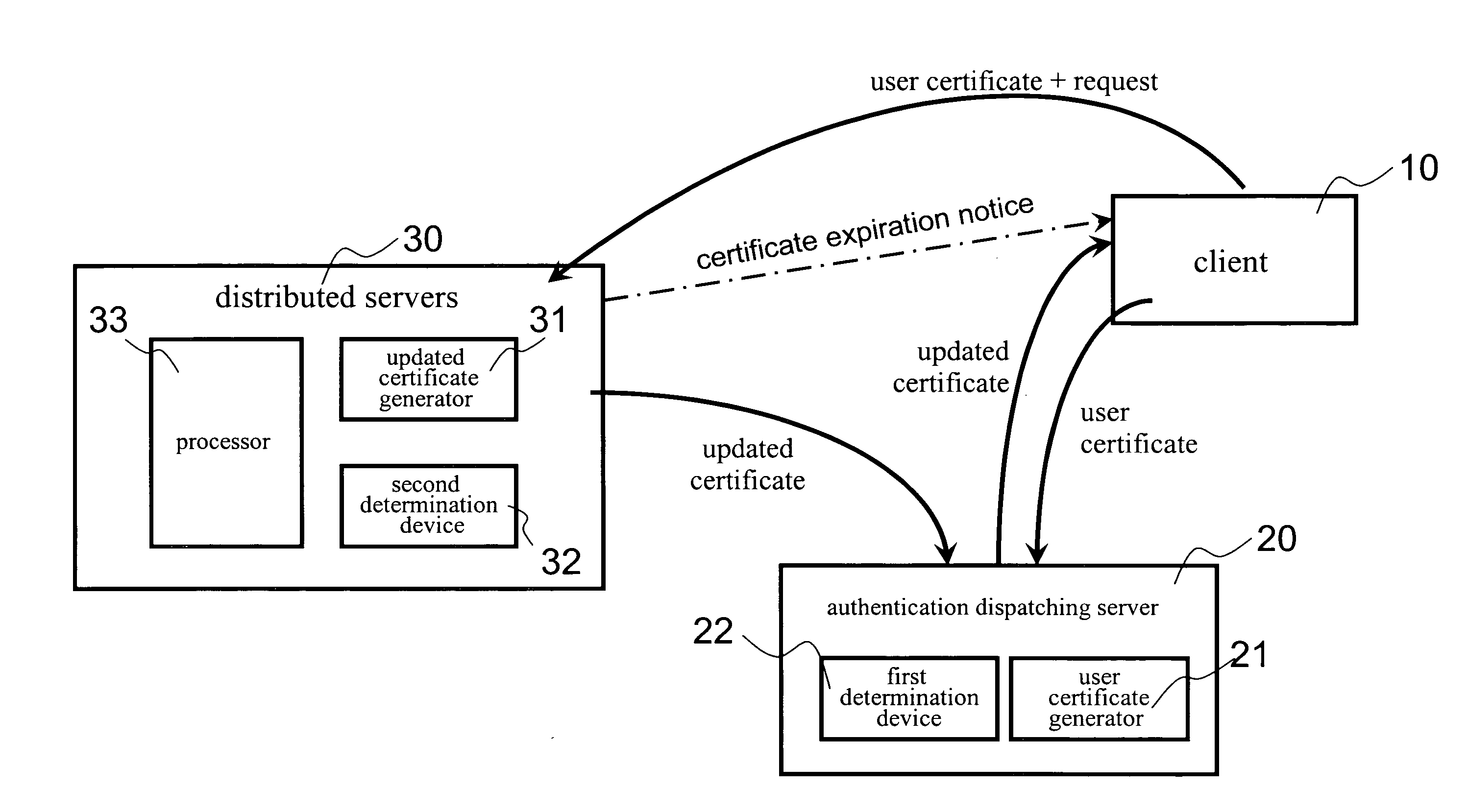
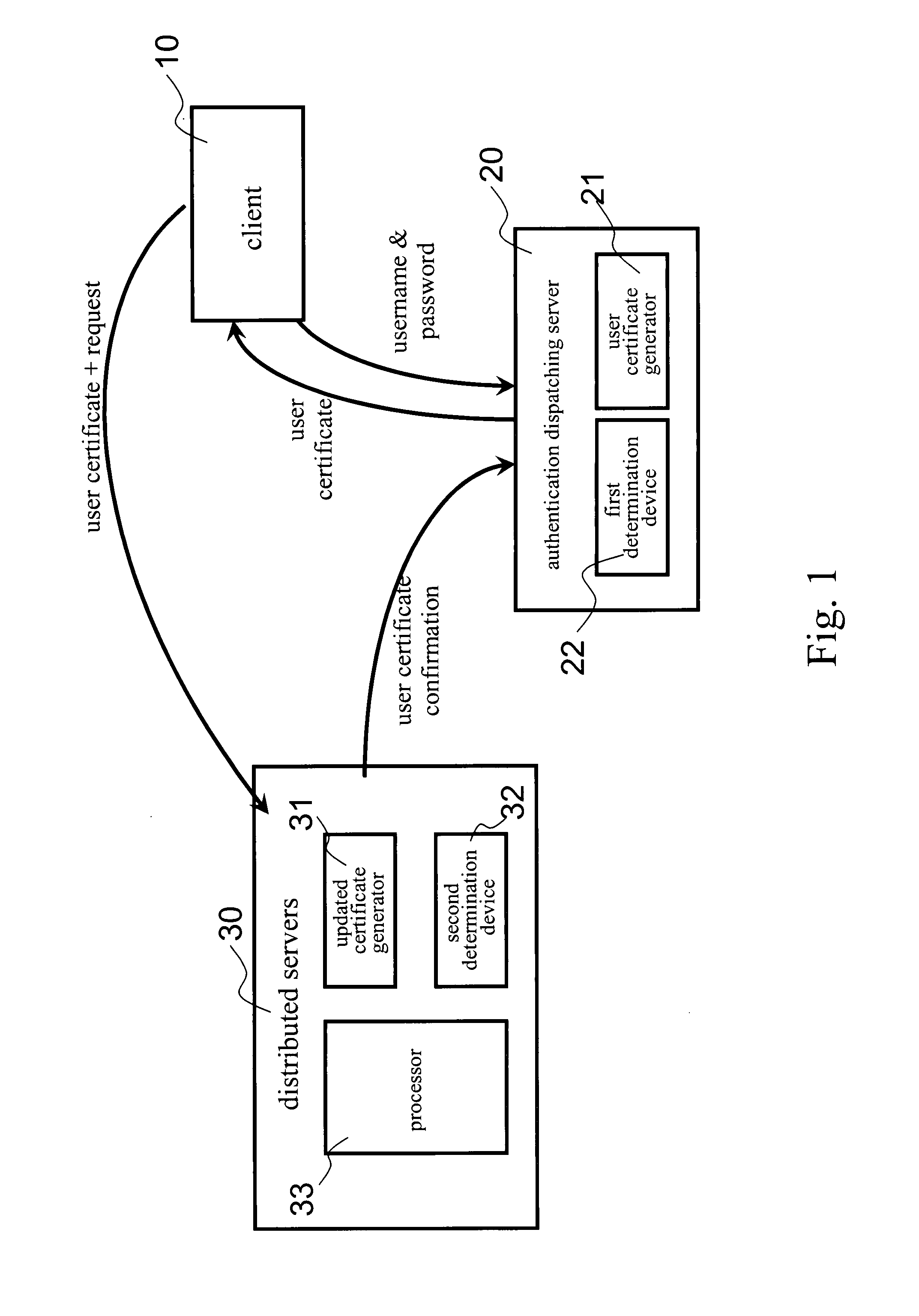
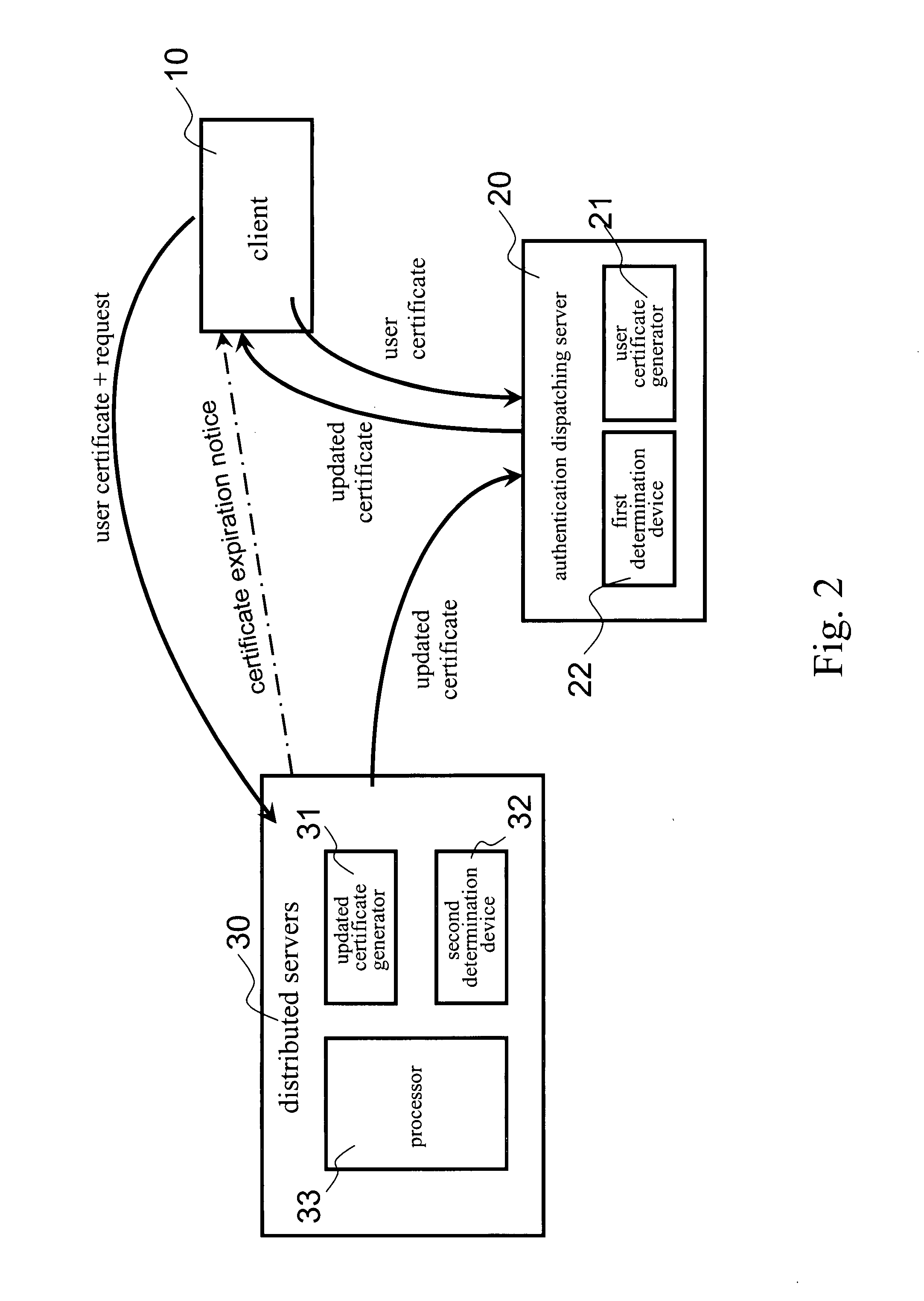
InactiveUS20080222412A1Network securityEnsure safetySecuring communicationDistributed serversClient-side
The invention presents a network data security system and a protecting method applied in network data transmission. Meanwhile the network data security system includes a client, an authentication dispatching server and a number of distributed servers. The authentication dispatching server includes a first determination device and a user certificate generator; and each distributed server includes a second determination device, a second user certificate generator and a processor. The method for protecting data of the present invention introduces the authentication dispatching server providing the client with a user certificate in a valid period of time and further introduces an updated certificate mechanism for preventing the user certificate from being stolen and further preventing network data from being let out.
Owner:KINGHOOD TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com