Patents
Literature
548 results about "Transaction time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In temporal databases, transaction time (TT) is the time during which a fact stored in the database is considered to be true. As of December 2011, ISO/IEC 9075, Database Language SQL:2011 Part 2: SQL/Foundation included clauses in table definitions to define "system-versioned tables" (that is, transaction-time tables).
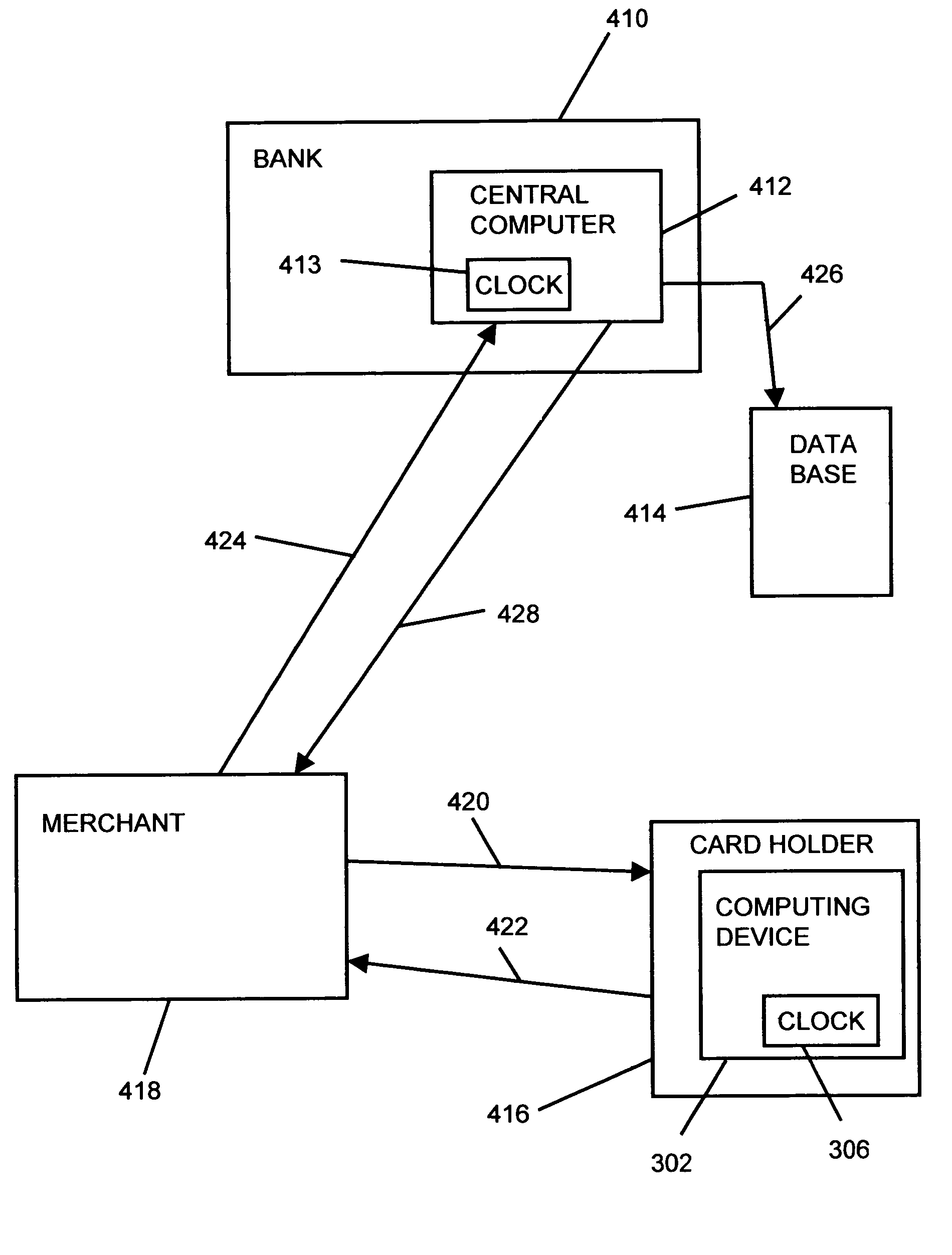
System, method and program product for account transaction validation
ActiveUS7347361B2Low costEasy to manufactureFinanceCredit schemesTransaction dataFinancial transaction
Owner:LOVETT ROBERT
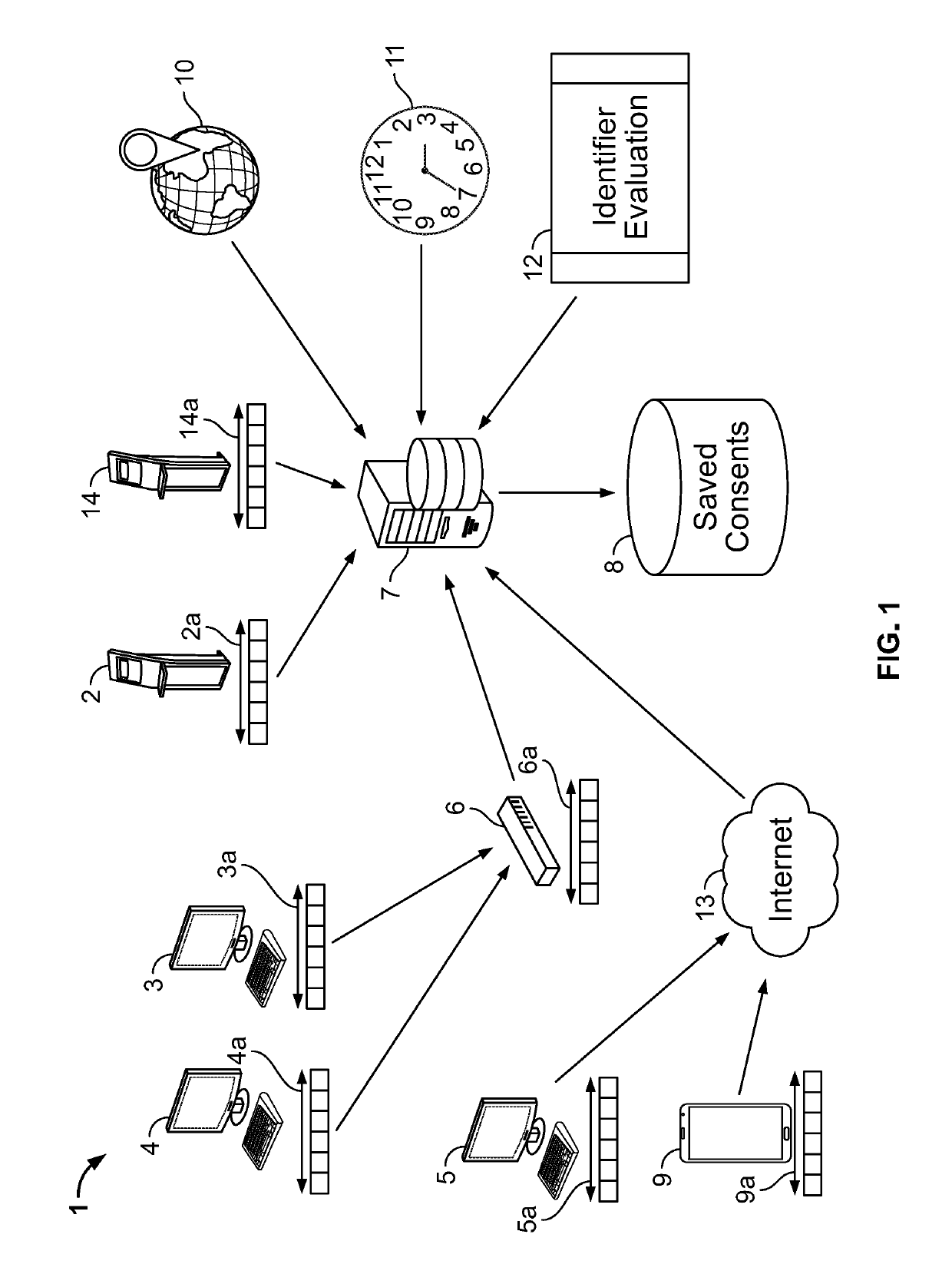
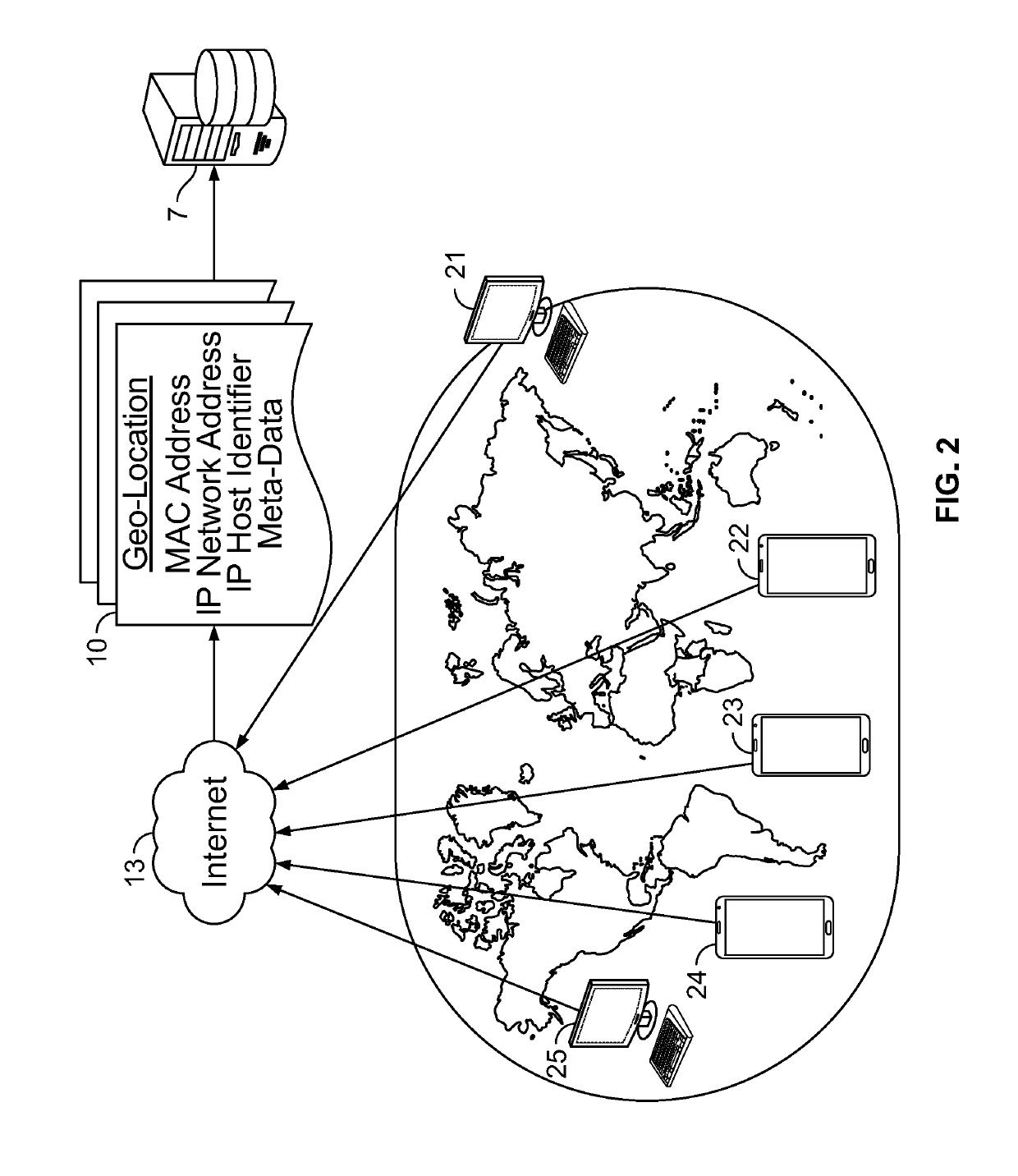
Dynamic digital consent
ActiveUS10417401B2Improve performanceDigital data protectionDigital data authenticationIp addressGeolocation
Method and apparatus for a system to harden digital consents. The system uses an evaluation of geographic locations, transaction times, and device identities to control the upload of consent data. Evaluations occur using numerous techniques including MAC address evaluation, IP address evaluation, meta-data evaluation, and physical location of restricted equipment such as ATMs and kiosks. Reliability of consent data entered into the system may be enhanced by strictly evaluating geographic locations, transaction times, and / or device identities.
Owner:BANK OF AMERICA CORP
System, method and program product for account transaction validation
A system, method and program product for account transaction validation which may be downloaded or otherwise installed on a networked computing device such as a cell phone or other networked computing device. The networked computing device provides an encrypted validation code to a merchant for each transaction. The validation code is uniquely computed for each transaction and may be based on transaction time and / or other transaction data. The code algorithm is unique for each cardholder. Only the bank transaction center has knowledge of the particular algorithm for each cardholder. When transaction details such as transaction dollar amount are included in the generation of the code, the code may be used to validate the reported transaction dollar amount. An algorithm is disclosed for generating a unique code based on time and / or transaction dollar amount.
Owner:LOVETT ROBERT
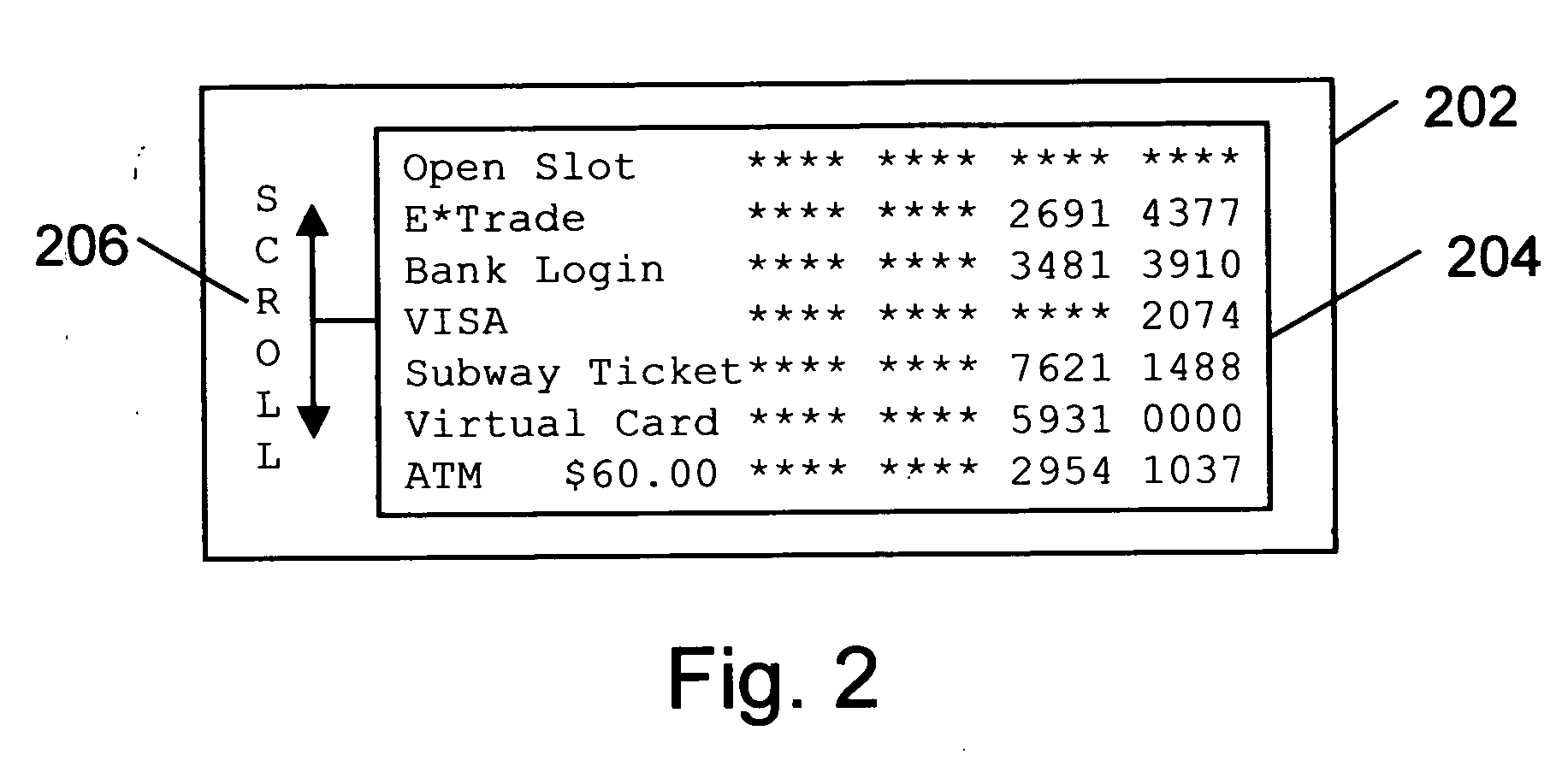
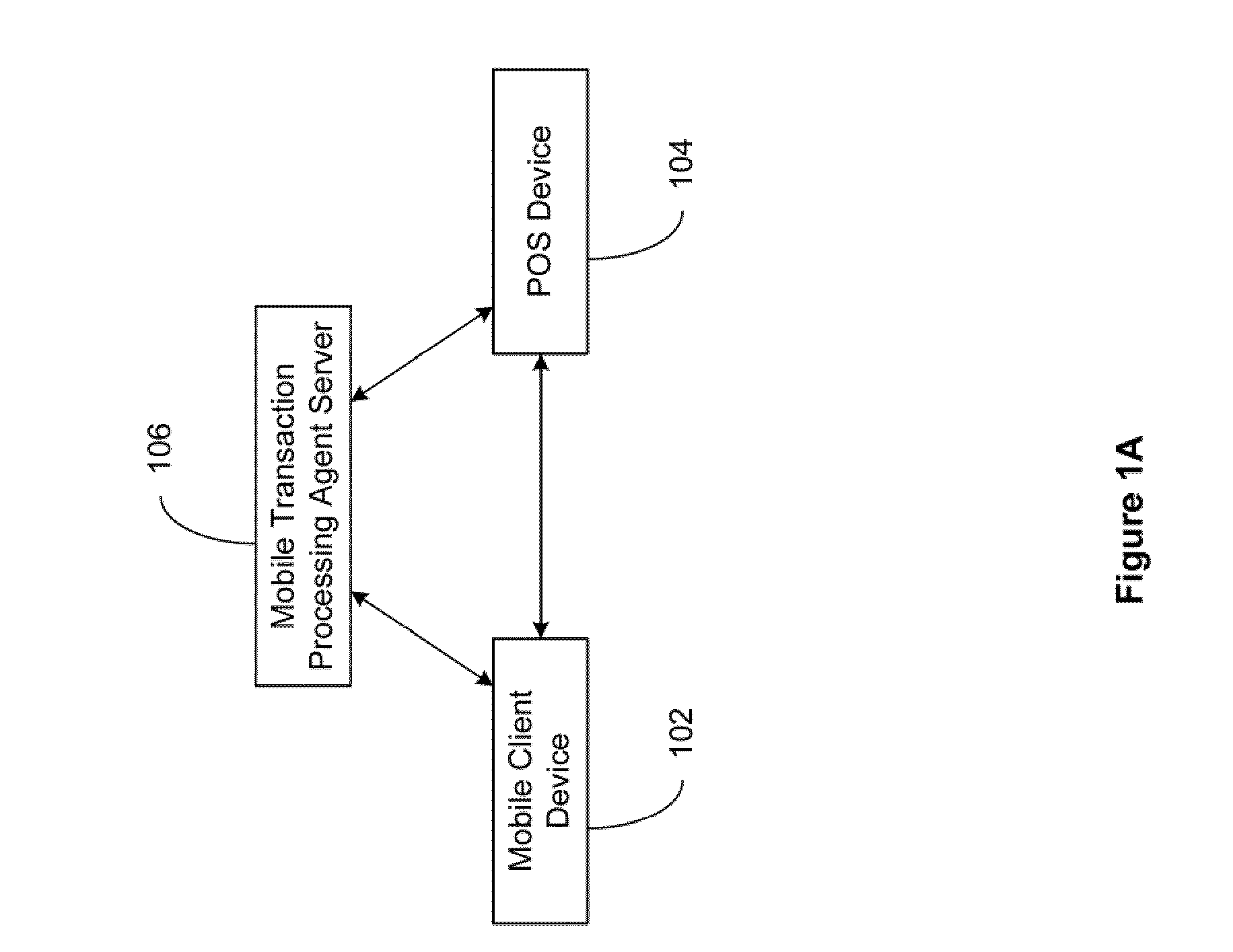
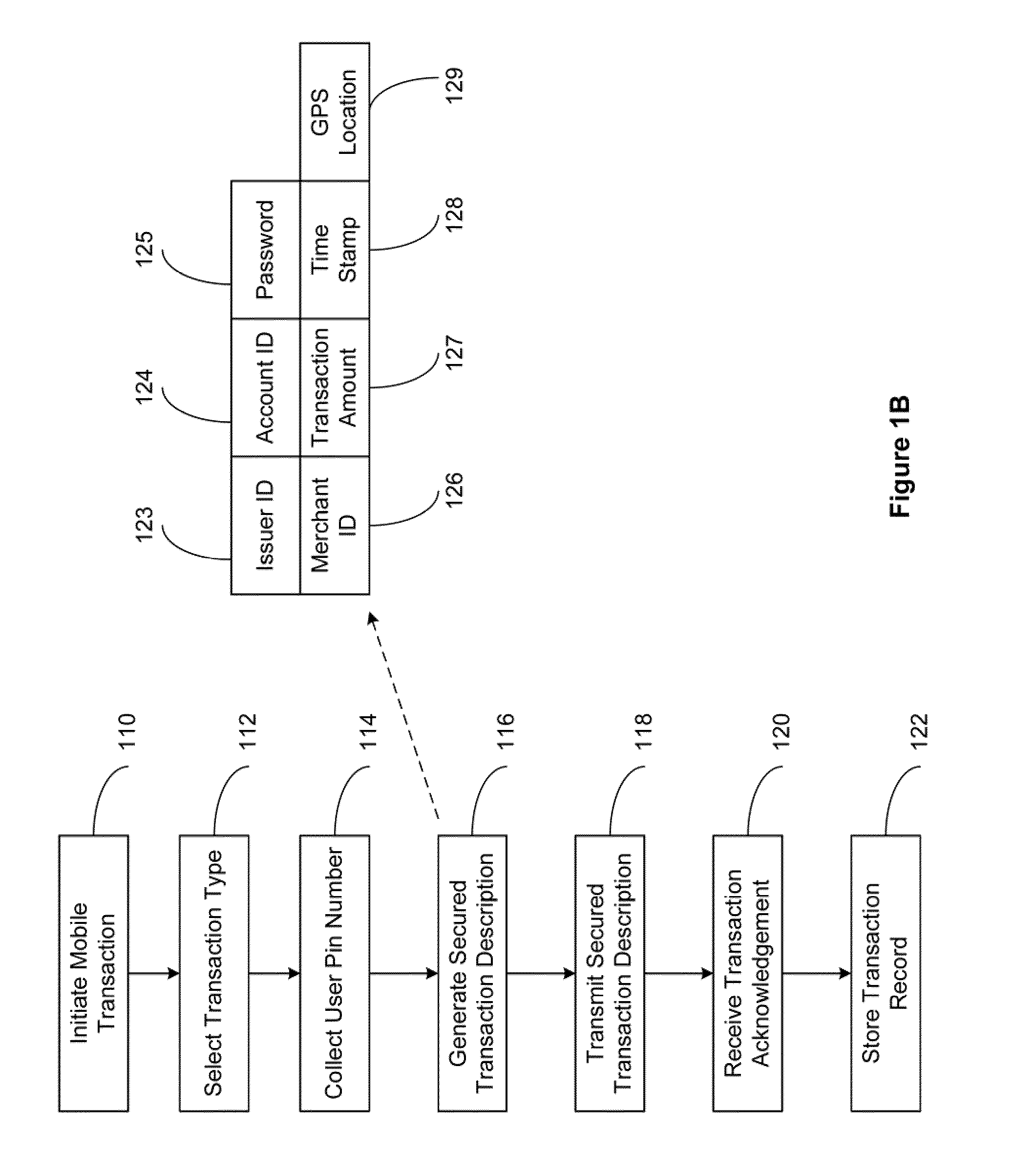
Secured Mobile Transaction Device
InactiveUS20110191161A1Improve securityFinanceBuying/selling/leasing transactionsPasswordMobile transaction
The present invention relates to a secured transaction system. In one embodiment, a mobile client device includes a user interface configured to enable a user to select a transaction type and collect a user pin number, a processor configured to generate a secured transaction description using the transaction type and the user pin number, wherein the secured transaction description includes issuer ID, account ID, merchant ID, password, transaction amount, and transaction time stamp, and the processor is further configured to transmit the secured transaction description to a mobile processing agent for processing, and receive a transaction record from the mobile transaction processing agent, and a memory configured to store the transaction record in the mobile client device.
Owner:DAI XIA
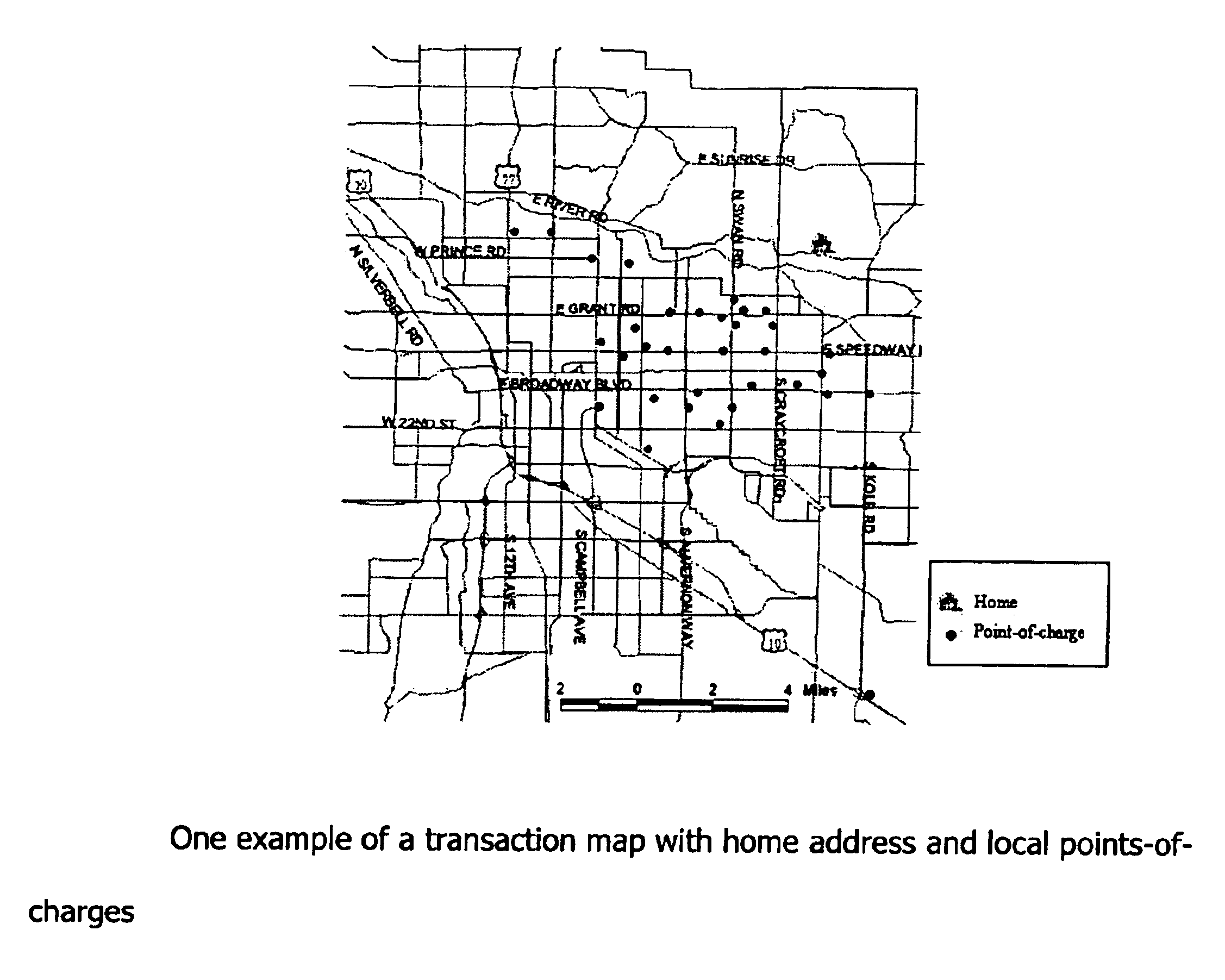
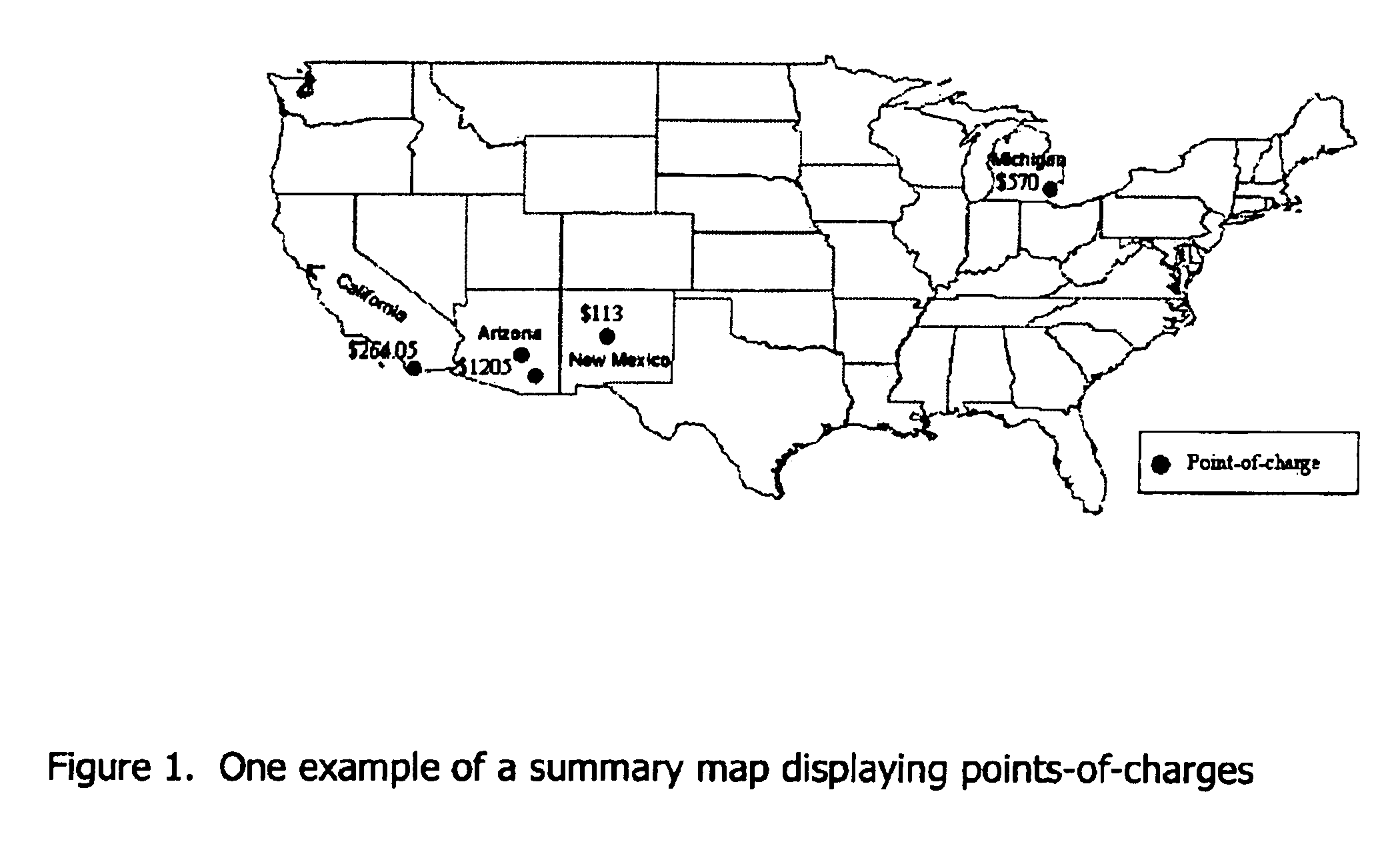
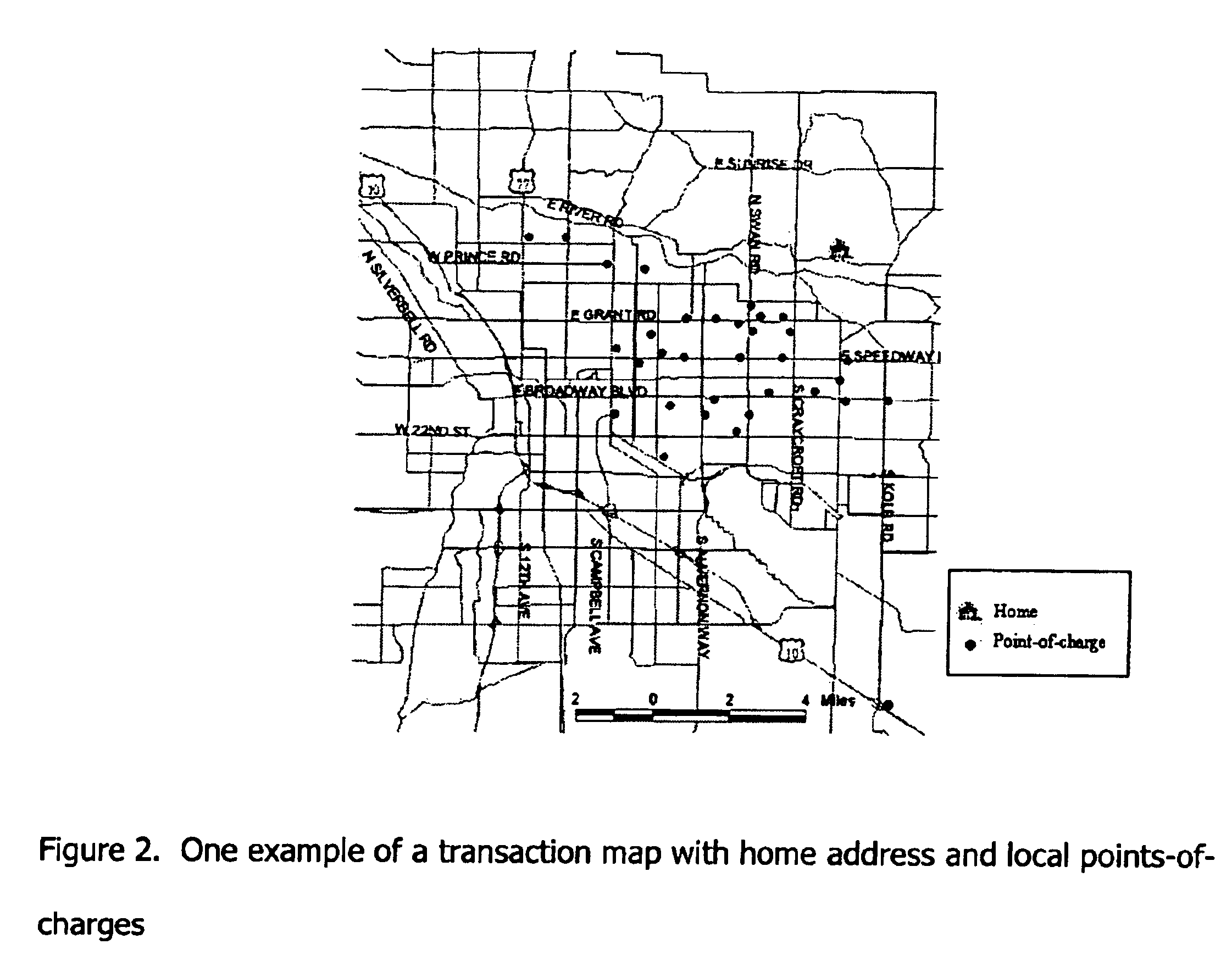
Transaction maps embedded within or provided with charge-card billing statements
InactiveUS6883708B1Improving marketing potentialDifficult to comprehendBilling/invoicingPayment circuitsFinancial transactionRule system
A method and system is described herein to summarize and present charge-card transactions through one or more maps linked to charge-card billing statements. In addition to a conventional tabular transaction list, the invented system provides charge-card transaction maps, which display the physical location of points-of-charges geo-referenced to a map. Transactions are listed individually and / or are summarized by the number of transactions, the timing of transactions, the amount of transactions, the transactions categories, local-area and none-local-area transactions, sensitive transactions, geographic unit, or any combination thereof. The method and system integrates database and geographic information system technology with a rule system.
Owner:FIEDLER RENO +1
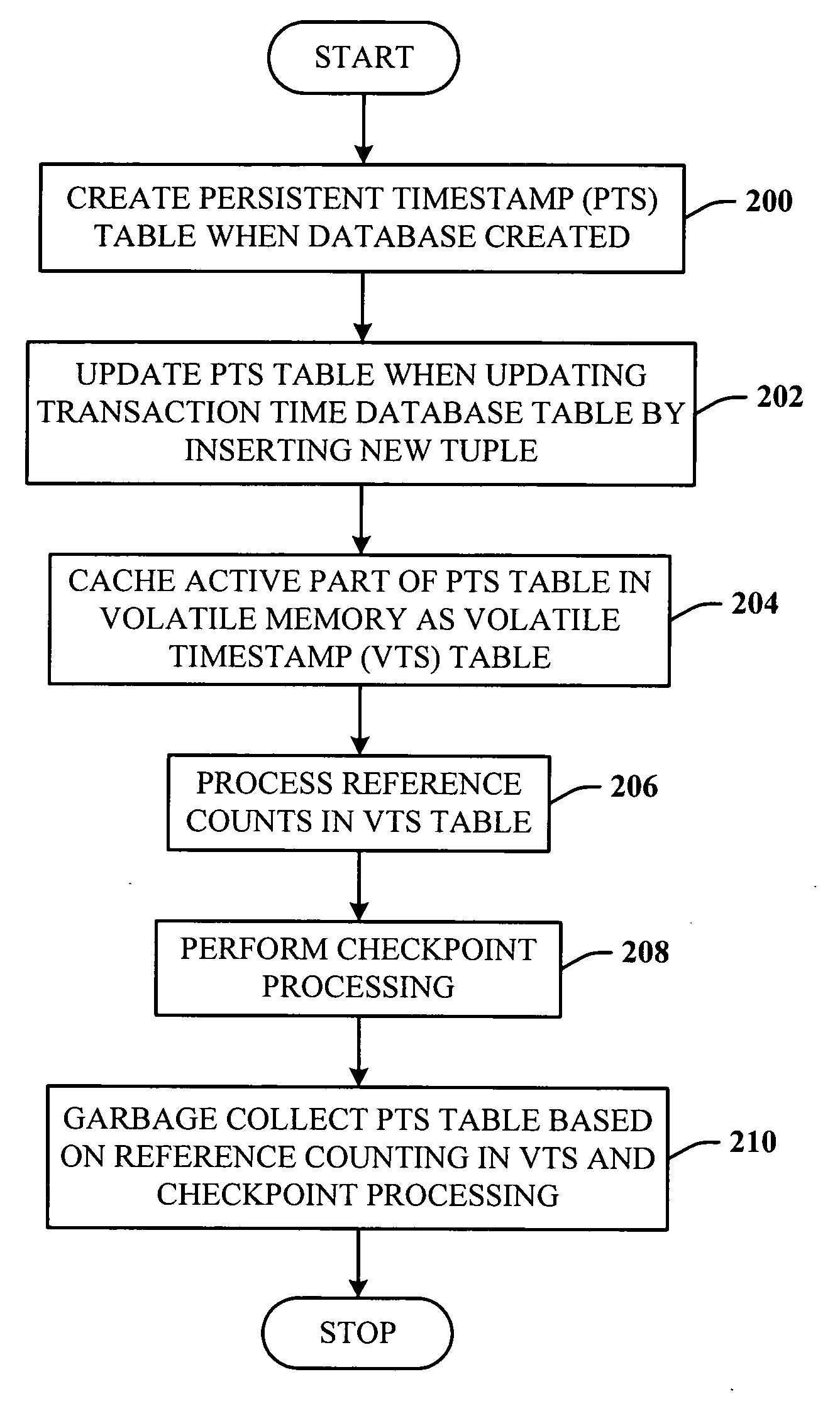
Lazy timestamping in transaction time database
InactiveUS20060167960A1Minimize accessEfficient record timestamping processData processing applicationsDigital data information retrievalTemporal databaseTimestamp
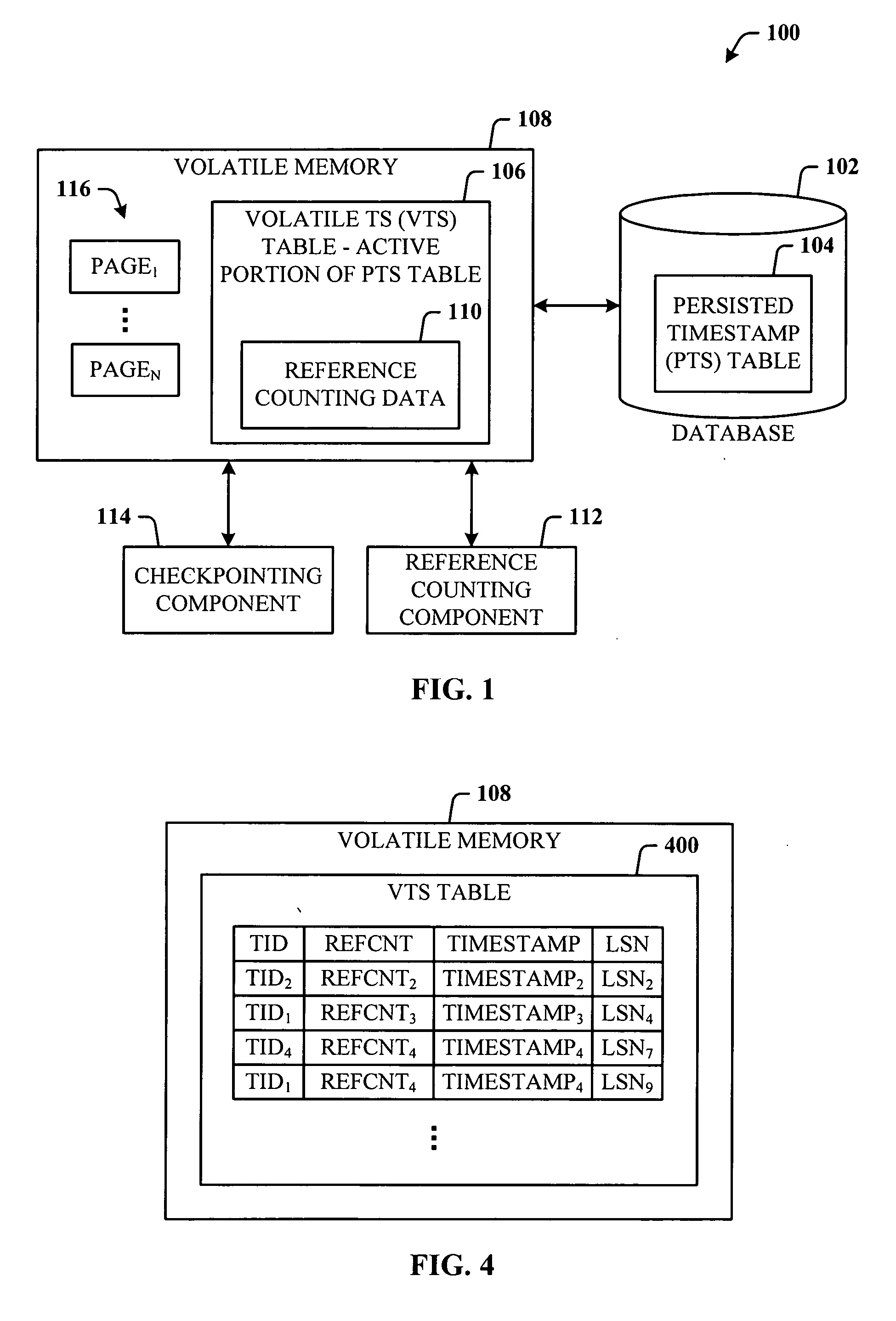
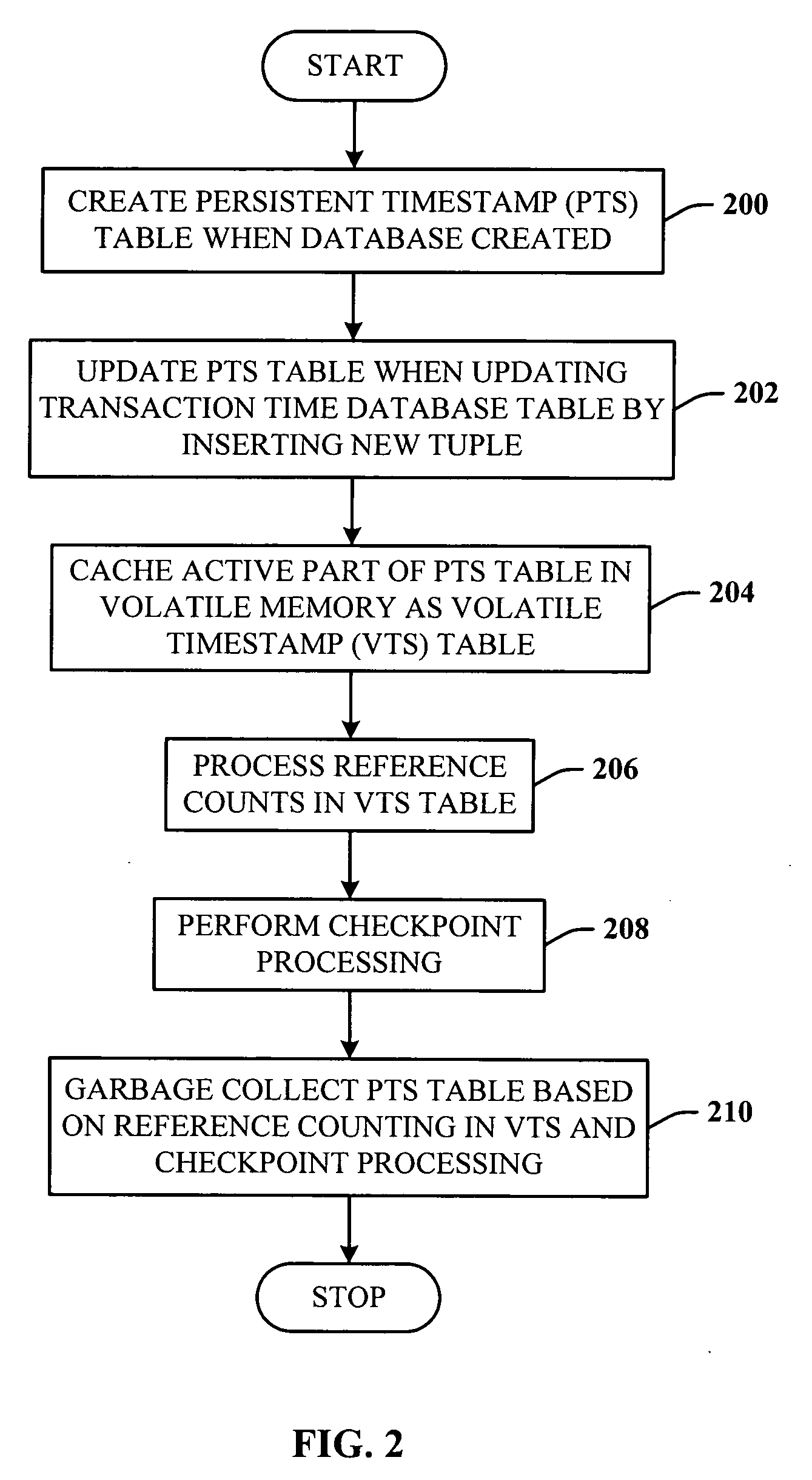
Lazy timestamping in a transaction time database is performed using volatile reference counting and checkpointing. Volatile reference counting is employed to provide a low cost way of garbage collecting persistent timestamp information about a transaction by identifying exactly when all record versions of a transaction are timestamped and the versions are persistent. A volatile timestamp (VTS) table is created in a volatile memory, and stores timestamp, reference count, transaction ID, and LSN information. Active portions of a persisted timestamp (PTS) table are stored in the VTS table to provide faster and more efficient timestamp processing via accesses to the VTS table information. The reference count information is stored only in the VTS table for faster access. When the reference count information decrements to zero, it is known that all record versions that were updates for a transaction were timestamped. A checkpointing component facilitates checkpoint processing for verifying that timestamped records have been written to the persistent database and that garbage collection of the PTS table can be performed for transaction entries with zero reference counts.
Owner:MICROSOFT TECH LICENSING LLC
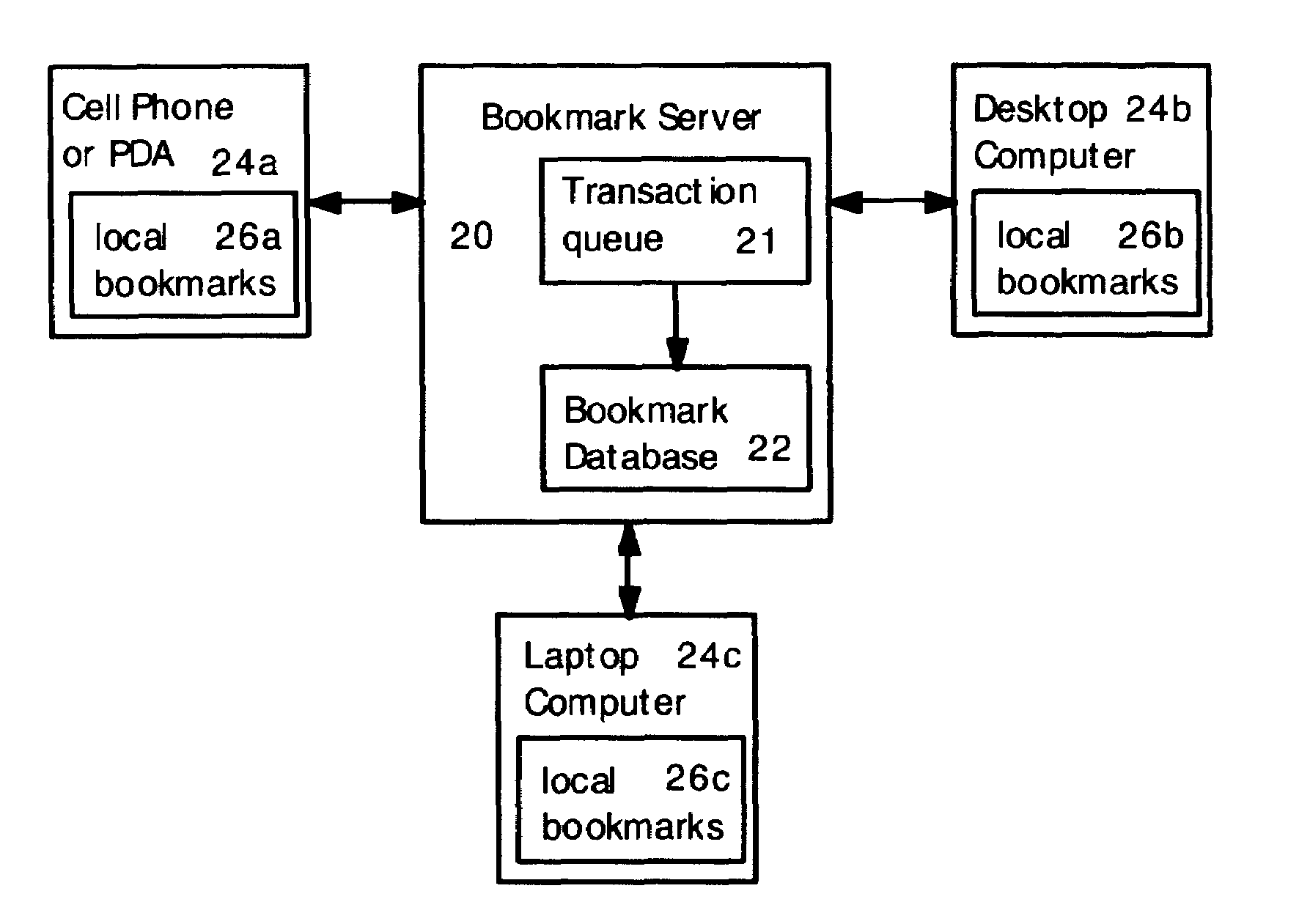
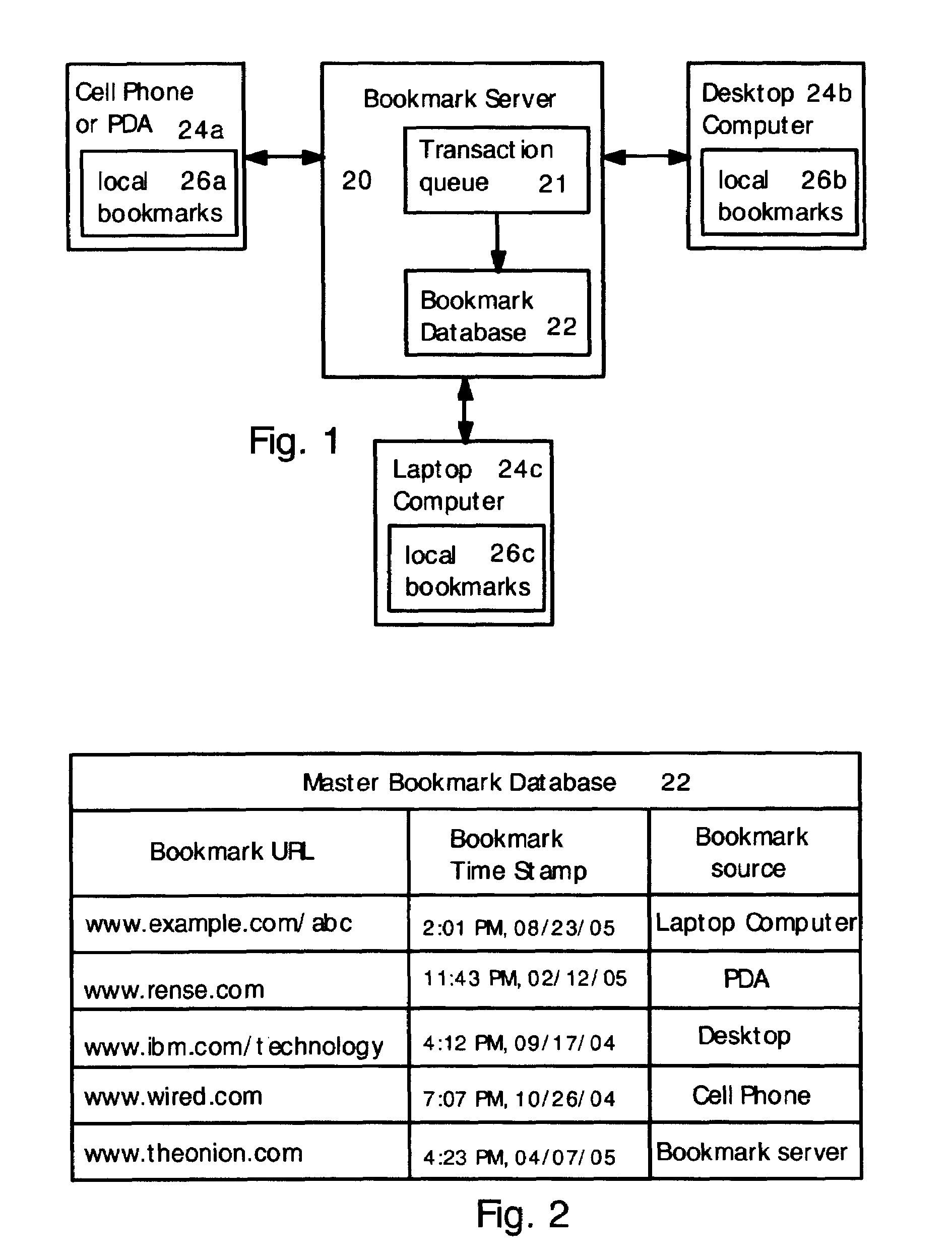
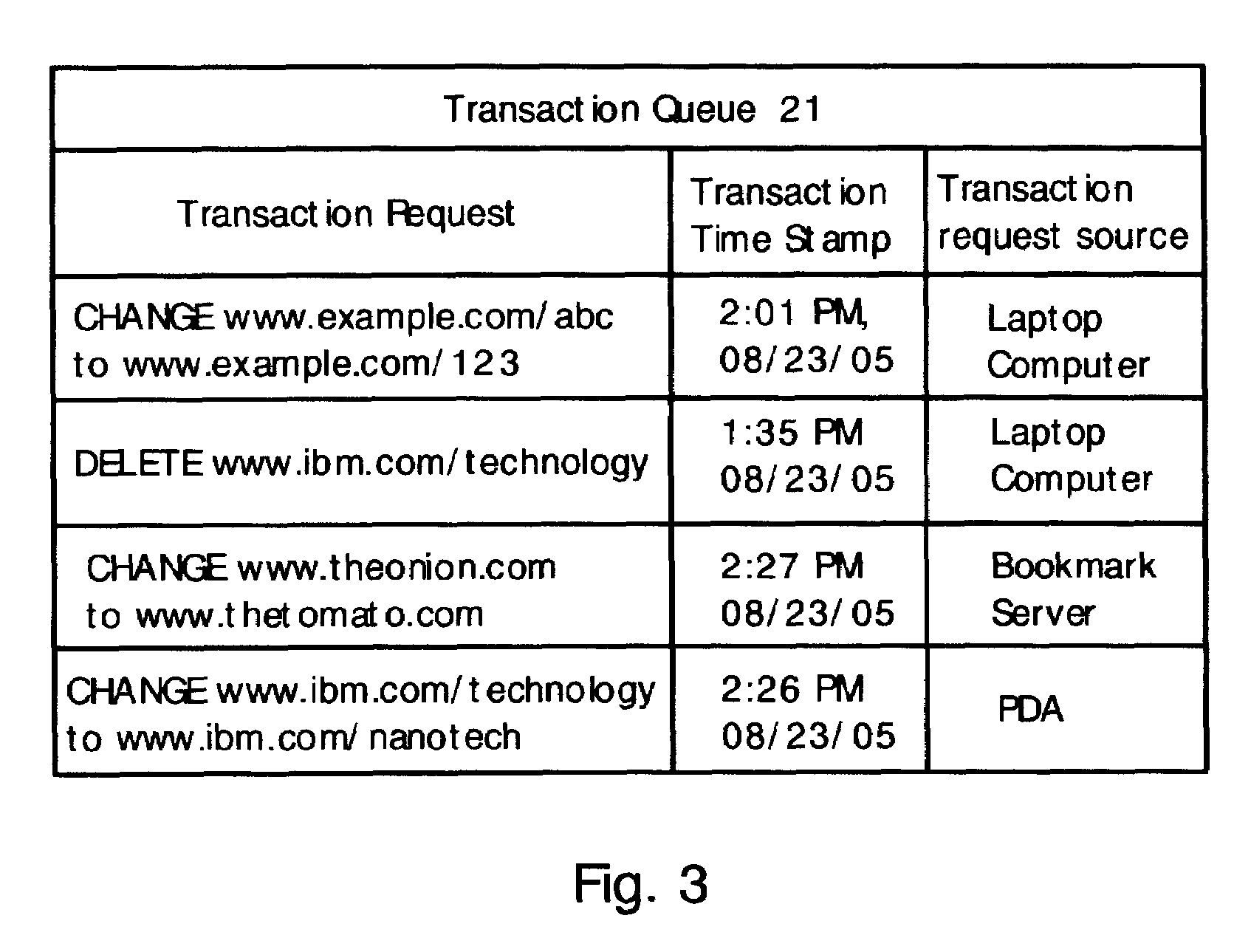
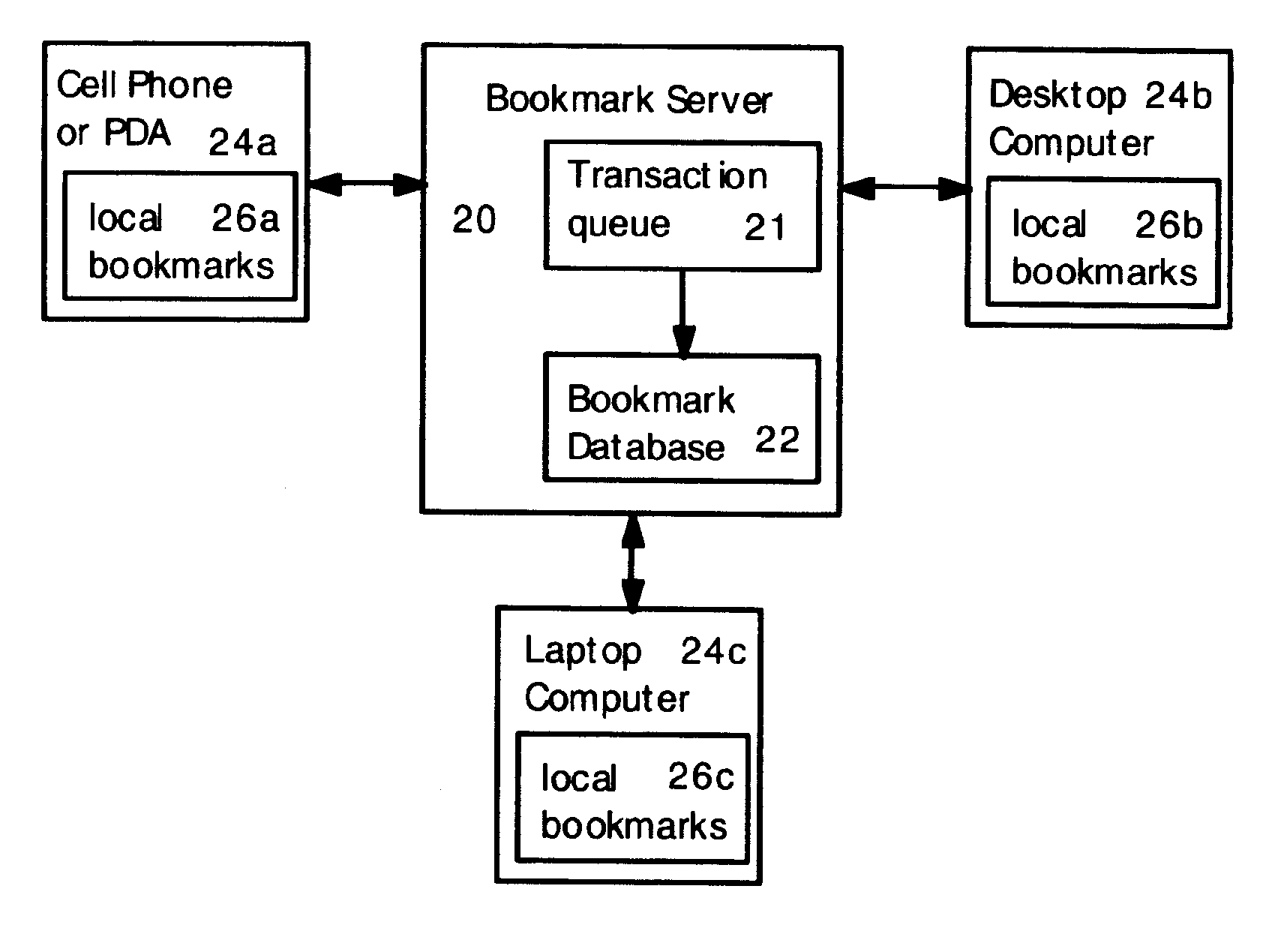
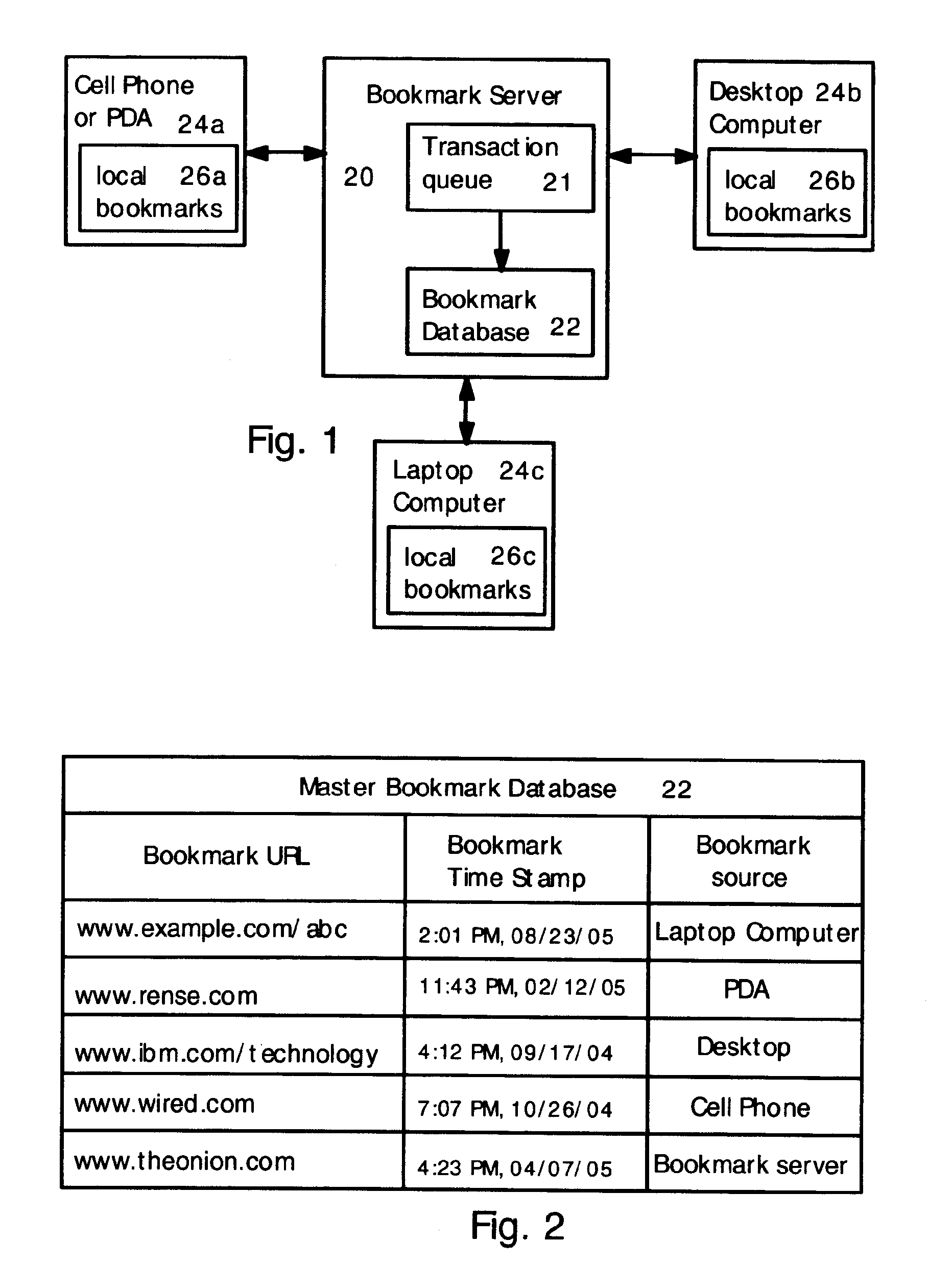
Method for synchronizing and updating bookmarks on multiple computer devices
ActiveUS7711707B2Digital data information retrievalDigital data processing detailsComputer scienceDatabase
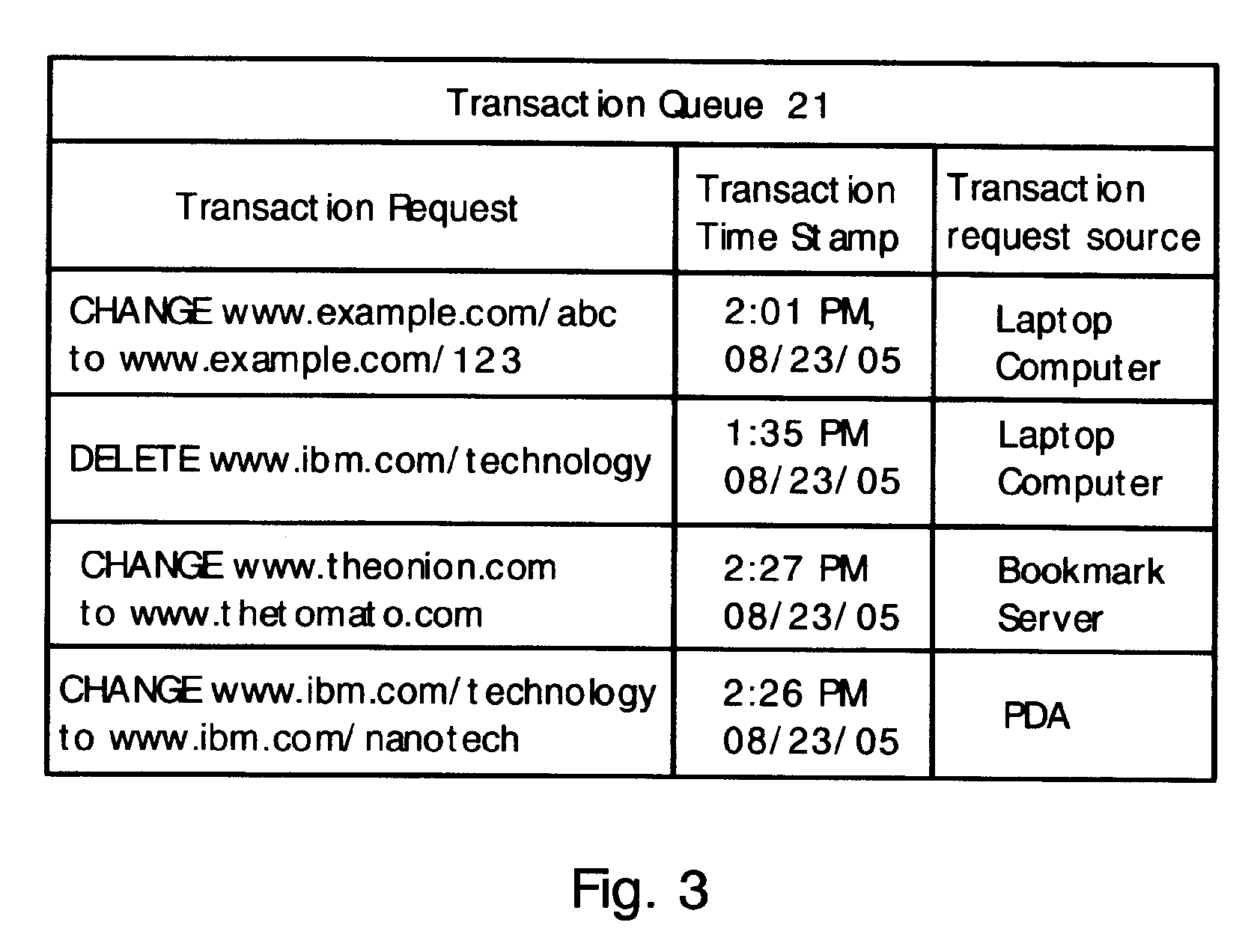
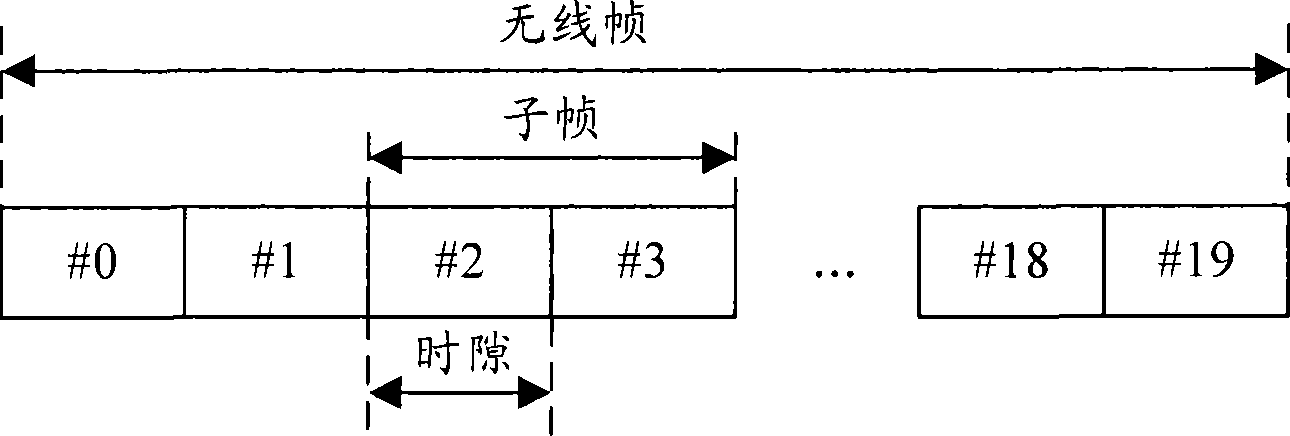
Multiple computer devices are networked, and one device is designated as a bookmark server. The bookmark server stores and maintains a master bookmark database that is available to all the networked devices. Each bookmark in the bookmark database includes a bookmark time stamp. If a bookmark is added, deleted or changed at any device, then a transaction request is sent to the bookmark server. The transaction request includes a transaction time stamp indicating the time that the transaction request was created. The bookmark server analyzes the transaction requests according to the time stamps. If multiple transaction requests are received for a single bookmark, then only the most recent transaction request is honored and other transaction requests related to the bookmark are ignored. Also, a transaction request is ignored if the transaction time stamp is older than the corresponding bookmark time stamp.
Owner:TWITTER INC
Transaction time tracking and reporting system
InactiveUS20050021529A1Special service for subscribersSpecial data processing applicationsThe InternetContact center
A method and apparatus are provided for compiling performance reports in a contact center serving a plurality of clients through the Internet using a plurality of agents. The method includes the steps of opening a transaction file for saving information about Internet exchanges between an agent of the plurality of agents and a client of the plurality of clients and measuring indicia of activity for the Internet exchanges between the agent and client. The method further includes the steps of adding the measured indicia of activity to the transaction file and compiling a report based upon the transaction file.
Owner:WILMINGTON TRUST NAT ASSOC AS ADMINISTATIVE AGENT +1
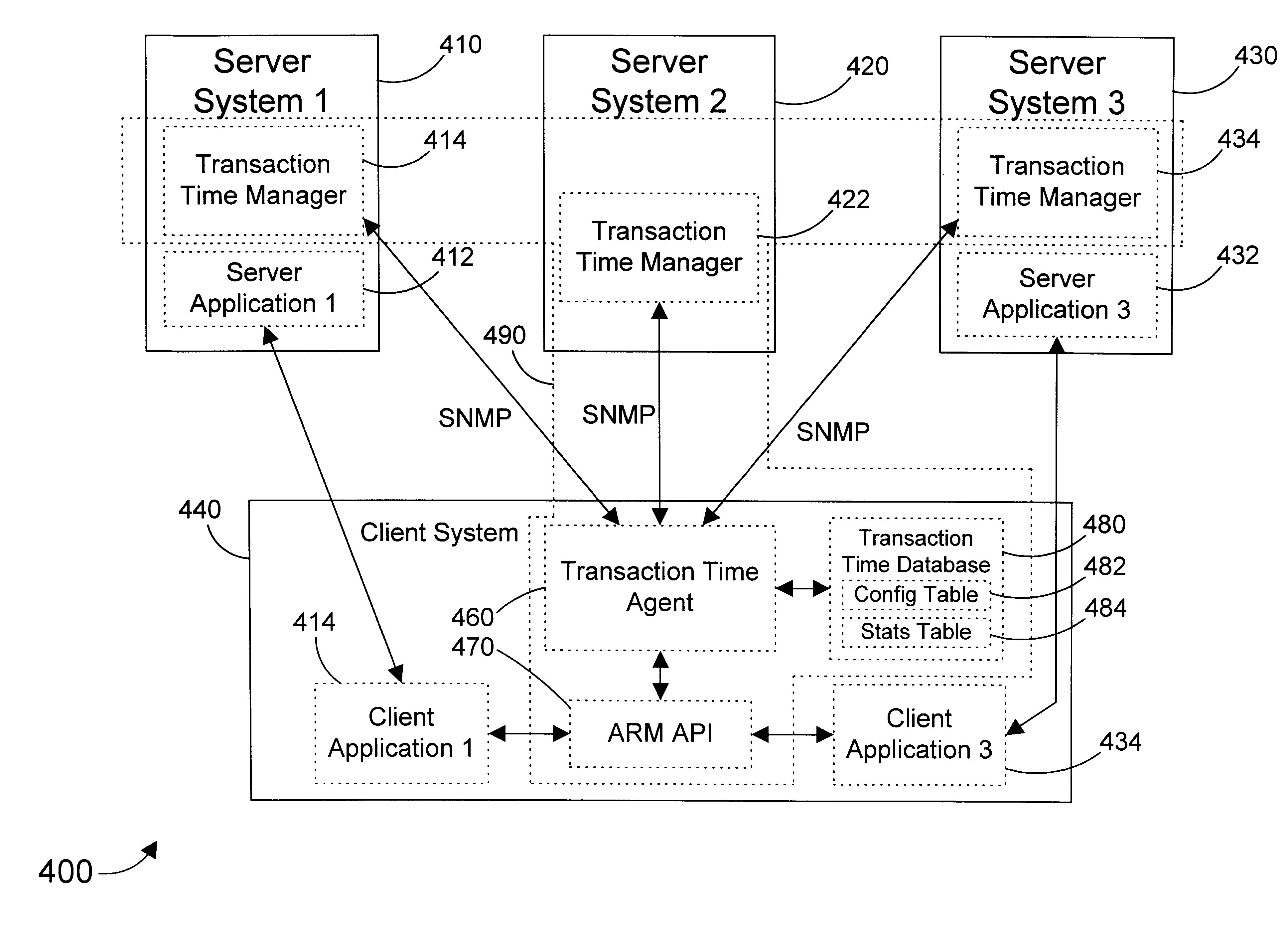
Apparatus and method for measuring transaction time in a computer system
InactiveUS6178449B1Simple protocolEfficient communicationHardware monitoringMultiple digital computer combinationsTime dataClient machine
A transaction time measurement mechanism has a transaction time manager running on a server computer system, a transaction time agent running on a client computer system that is coupled to the server computer system via a network, and a simple protocol for allowing them to directly and efficiently communicate. The transaction time agent is configured according to configuration data stored in a configuration table in a transaction time database, and stores transaction time data in a statistics table according to this configuration. The data in the statistics table is indexed to allow retrieving only the transaction time data of interest. The simple communication protocol supports multiple transaction time managers in a network computing environment that may all communicate with a single client.
Owner:IBM CORP
Time-Of-Transaction Foreign Currency Conversion
InactiveUS20100145744A1Improve conversion rateComplete banking machinesFinanceCredit cardIssuing bank
Owner:PLANET PAYMENT
Rapid transaction alliance chain construction method compatible with multiple asset types
ActiveCN107038639AWidely compatibleReduce time to achieveFinanceElectronic credentialsFinancial transactionWorkload
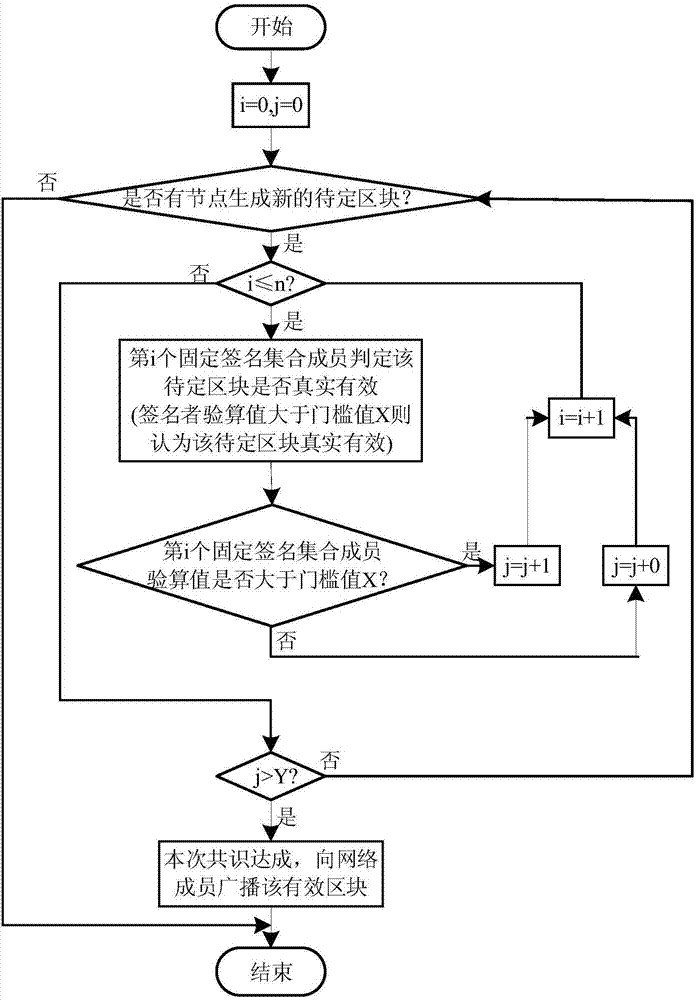
The invention discloses a rapid transaction alliance chain construction method compatible with multiple asset types. The alliance chain technology is introduced to realize transaction intercommunication of multiple types of digit assets, based on that system safety is guaranteed, a fixed multi-party signature consensus mechanism is introduced to replace workload to prove the dynamic multi-party signature mechanism, and the transaction time is substantially shortened. The method is advantaged in that through breaking transaction barriers among the different asset types, wide compatibility of the transaction system with the various asset types is realized, moreover, a fixed signature set scheme is employed, the consensus achievement time of each node in the system can be substantially reduced, transaction is rapidly achieved, asset transfer efficiency is substantially improved, superior robustness for a Byzantine failure problem is realized, and cracking is difficult.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Data existence authentication system, authentication method and verification method
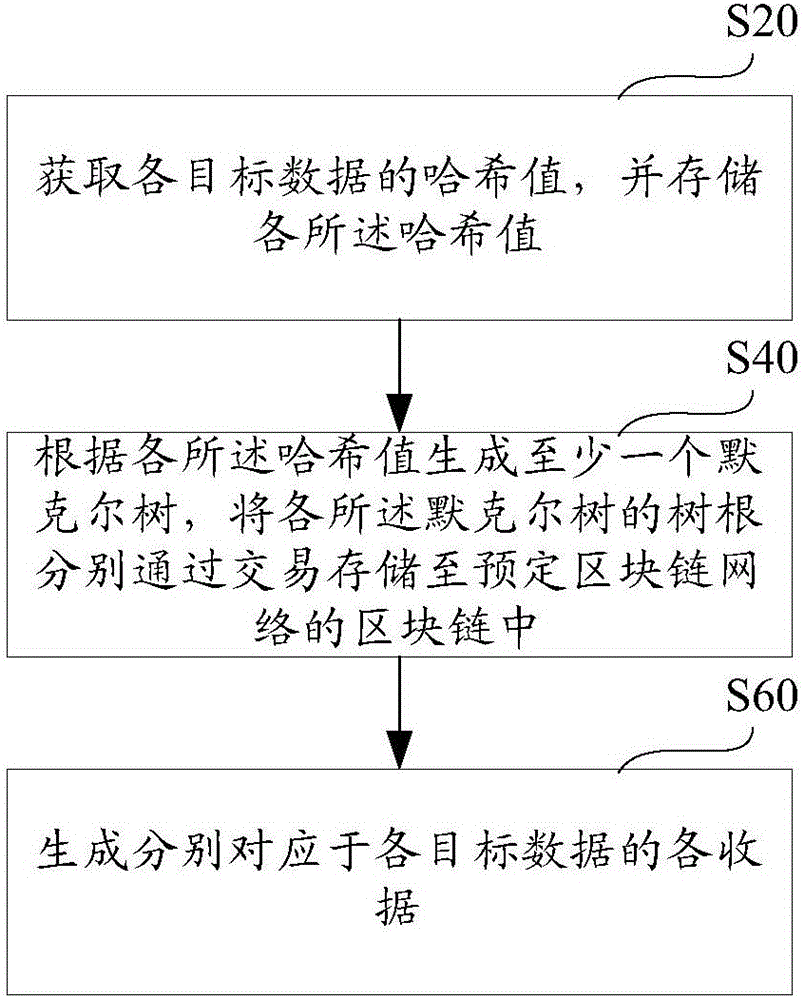
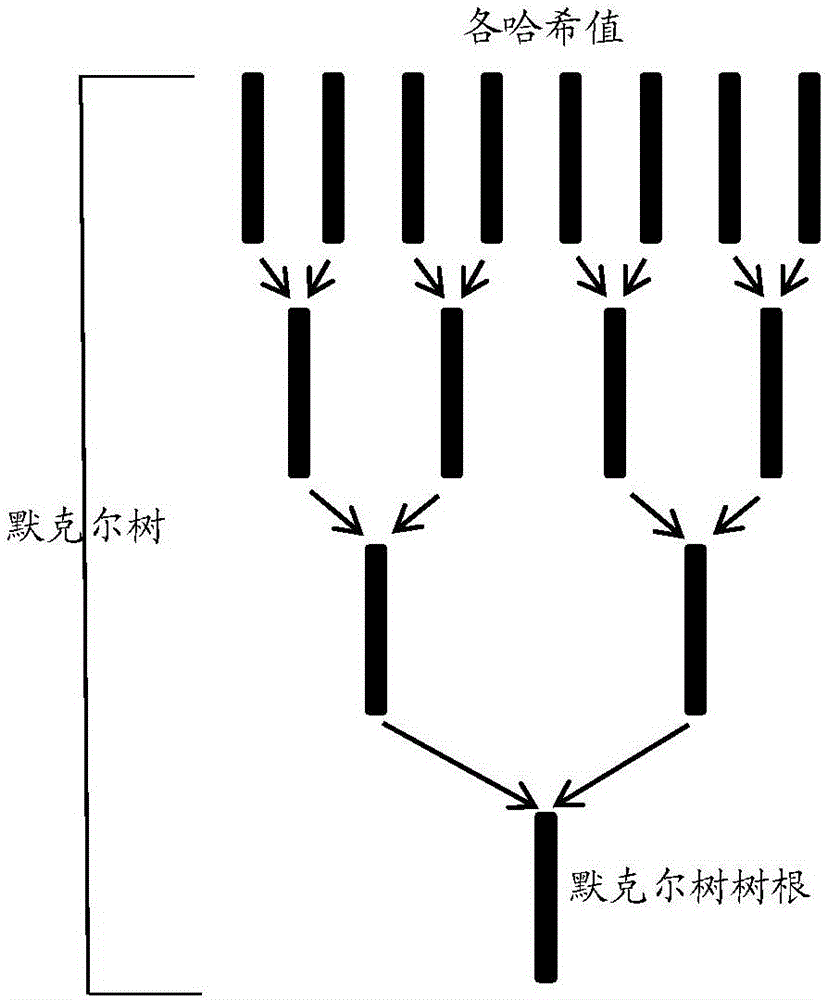
ActiveCN106407795AReduce certification costsSimple pathDigital data authenticationTree rootValidation methods
The invention provides a data existence authentication system, a data existence authentication method and a data existence verification method. The authentication method comprises the steps of obtaining hash values of target data, and storing the hash values; generating at least one Merkel tree according to the hash values, and storing tree roots of the Merkel tree in block chains of a predetermined block chain network through trading; and generating receipts corresponding to the target data respectively, wherein the receipts comprise corresponding target hash values, corresponding tree roots and paths of the Merkel tree, and trading data storage paths, and the paths comprise the hash values sequentially paired with the target hash values to finally generate the tree roots. According to the data existence authentication system, the data existence authentication method and the data existence verification method, the authentication of the existence of the target data in the trading time can be realized through the trading without depending on an authentication mechanism by utilizing characteristics of the Merkel tree and a characteristic that data in the block chains cannot be rewritten, the trading only needs to store the tree roots in the block chains, and the authentication of batch data can be finished by one-time trading, so that the authentication cost is greatly reduced.
Owner:BEIJING ZHONGXIANG BIT TECH
Method of one time authentication response to a session-specific challenge indicating a random subset of password or PIN character positions
InactiveUS20060136317A1Highly elevated and enhanced securityEfficient deploymentComplete banking machinesFinancePasswordRecognition algorithm
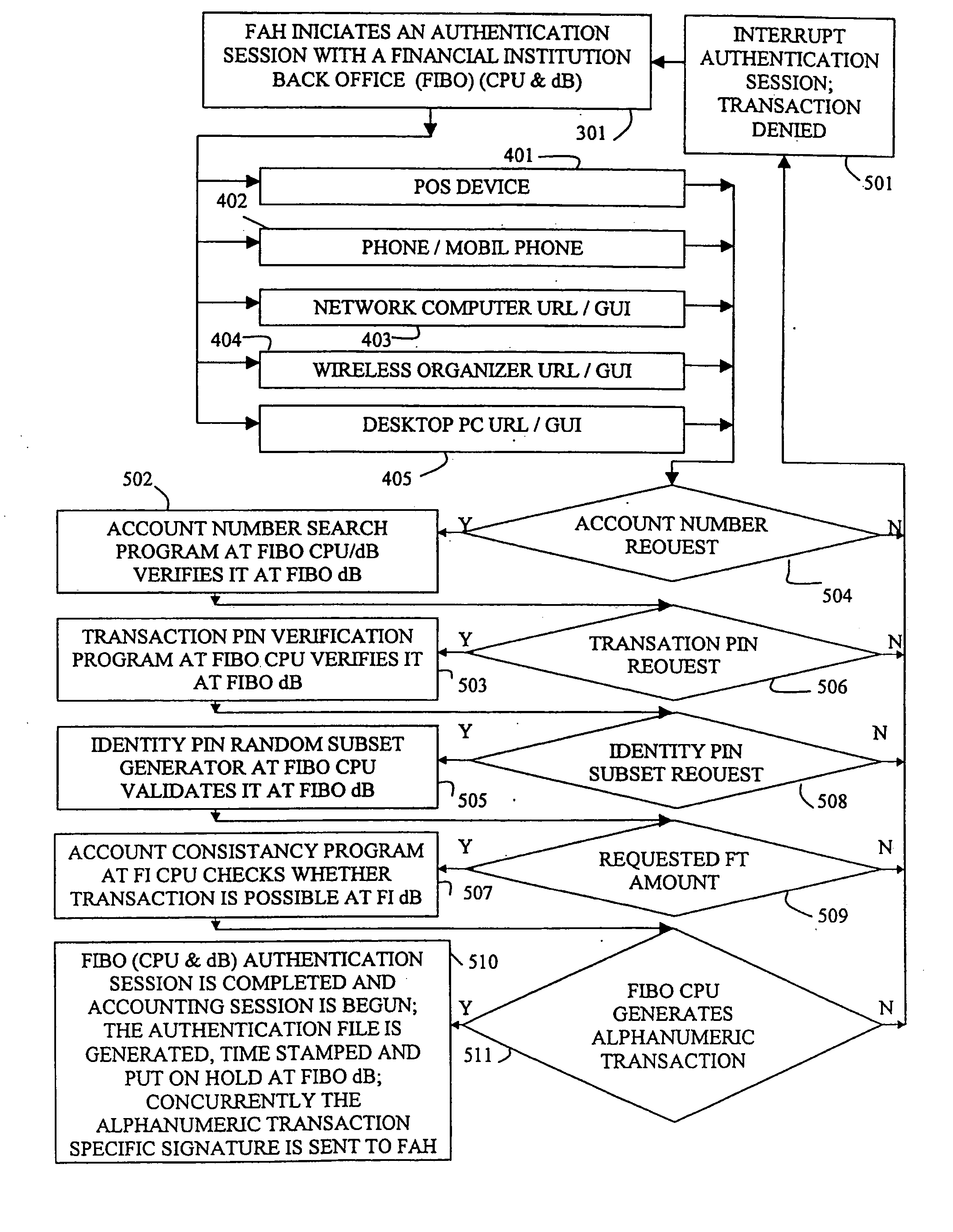
Financial institution back office computerized transaction-processing system with embedded privacy and security layer (EPSL) enables strong transaction authentication prior to a merchant or vendor contact, based on a user account number, transaction conditions like anticipated transaction time and money, user two-factor authentication with a static transaction PIN and a transaction session-specific random partial password or PIN recognition algorithm. User enters the user name and then, challenged by server with a random session-specific subset of a password or PIN character's consecutive position numbers, enters based on cognitive association a one time authentication response. The authentication session is interactive, transaction session-specific, and followed by either a transaction denial or an alphanumeric transaction signature generated by EPSL for this specific transaction. Then, the user submits her request to a transaction counterpart along with the transaction signature. The merchant or vendor requests an authorization session with EPSL.
Owner:AUTHERNATIVE INC
Method for synchronizing and updating bookmarks on multiple computer devices
ActiveUS20070136305A1Digital data information retrievalDigital data processing detailsComputer deviceTransaction time
Multiple computer devices are networked, and one device is designated as a bookmark server. The bookmark server stores and maintains a master bookmark database that is available to all the networked devices. Each bookmark in the bookmark database includes a bookmark time stamp. If a bookmark is added, deleted or changed at any device, then a transaction request is sent to the bookmark server. The transaction request includes a transaction time stamp indicating the time that the transaction request was created. The bookmark server analyzes the transaction requests according to the time stamps. If multiple transaction requests are received for a single bookmark, then only the most recent transaction request is honored and other transaction requests related to the bookmark are ignored. Also, a transaction request is ignored if the transaction time stamp is older than the corresponding bookmark time stamp.
Owner:TWITTER INC
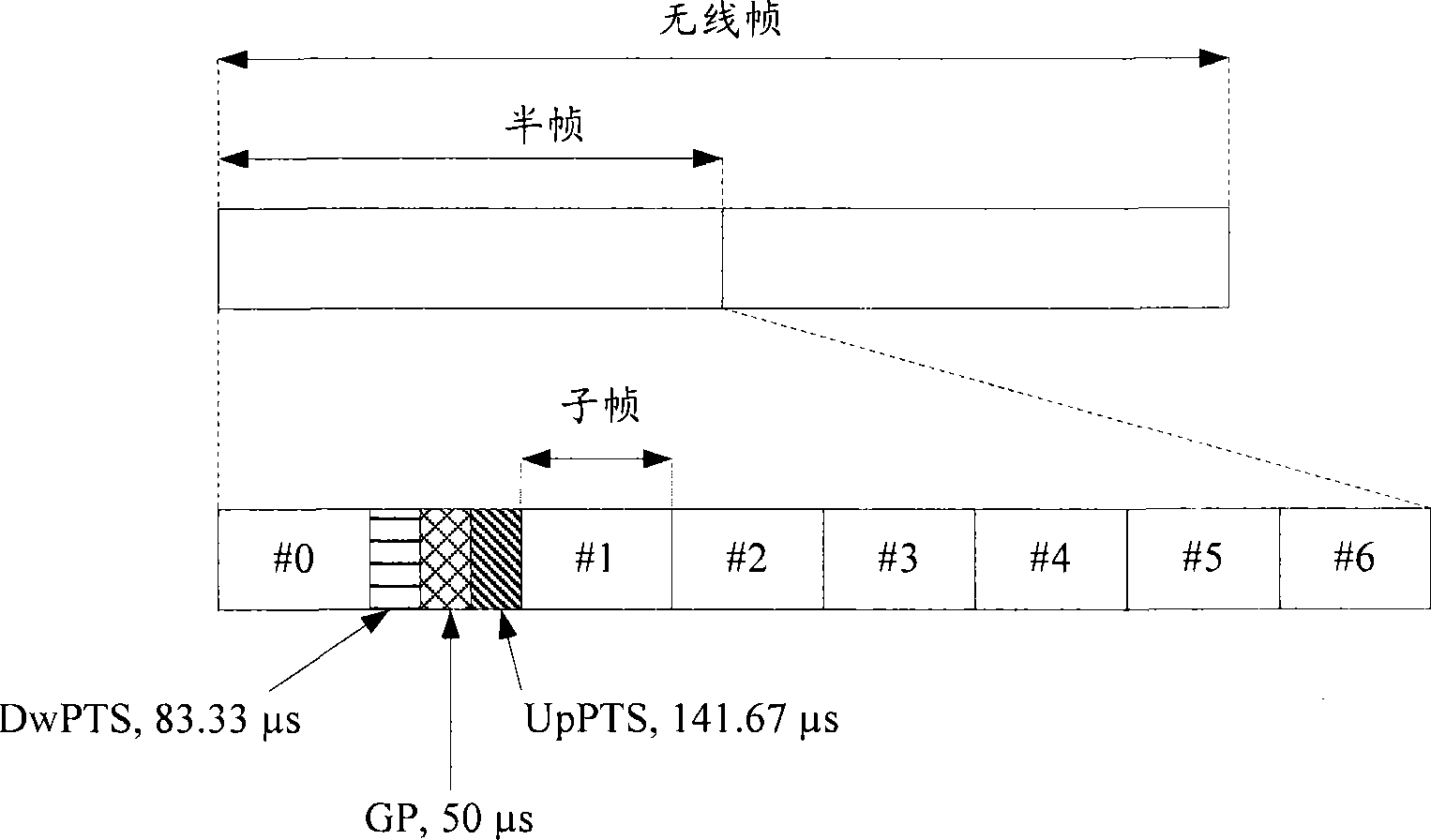
Transmission method and apparatus for time division duplexing system
InactiveCN101425845AFlexible supportFlexible configurationRadio transmission for post communicationGuard intervalTime-division multiplexing
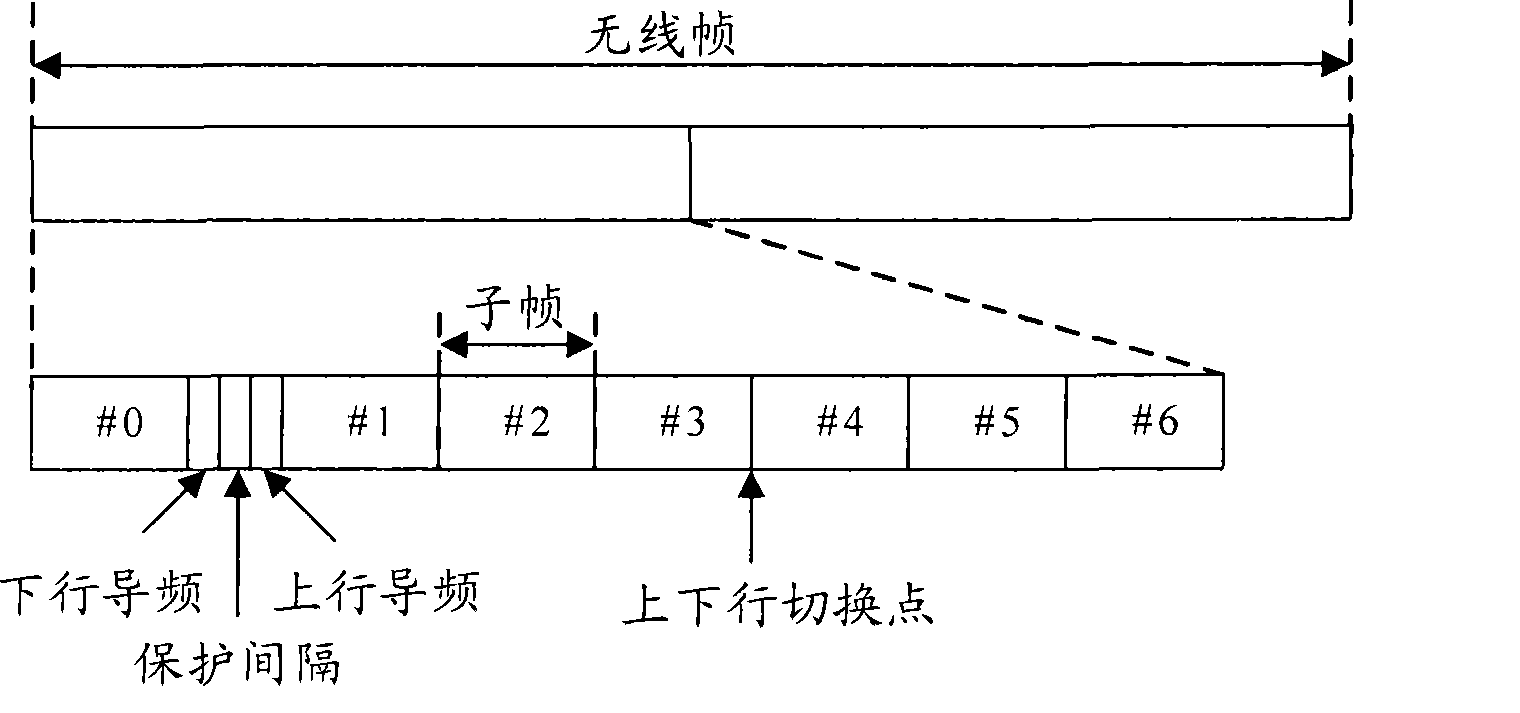
The invention discloses a transmission method of a time division duplex system, which comprises the following steps: a radio frame structure used for transaction transmission and configured on a network side comprises two 5ms half frames, each of which is composed of eight 0.5ms transaction time slot zones and one 1ms special time slot zone, and two continuous transaction time slots are one subframe of which the length is 1ms; the special time slot zone comprises three special time slots, i.e. a downlink pilot frequency time slot, a protection interval and an uplink pilot frequency time slot; the lengths of the downlink pilot frequency time slot, the protection interval and the uplink pilot time slot in the special time slot zones are confirmed according to the requirements of a coverage range so as to confirm the radio frame structure used for the transaction transmission; and the network side and the terminal carry out the transaction transmission by using the radio frame. The invention reconfigures the frame structure to flexibly configure the downlink pilot frequency time slot, the protection time interval or the uplink pilot frequency time slot in the special time slot zones according to the requirements of the coverage so as to flexibly support different coverage ranges.
Owner:CHINA ACAD OF TELECOMM TECH
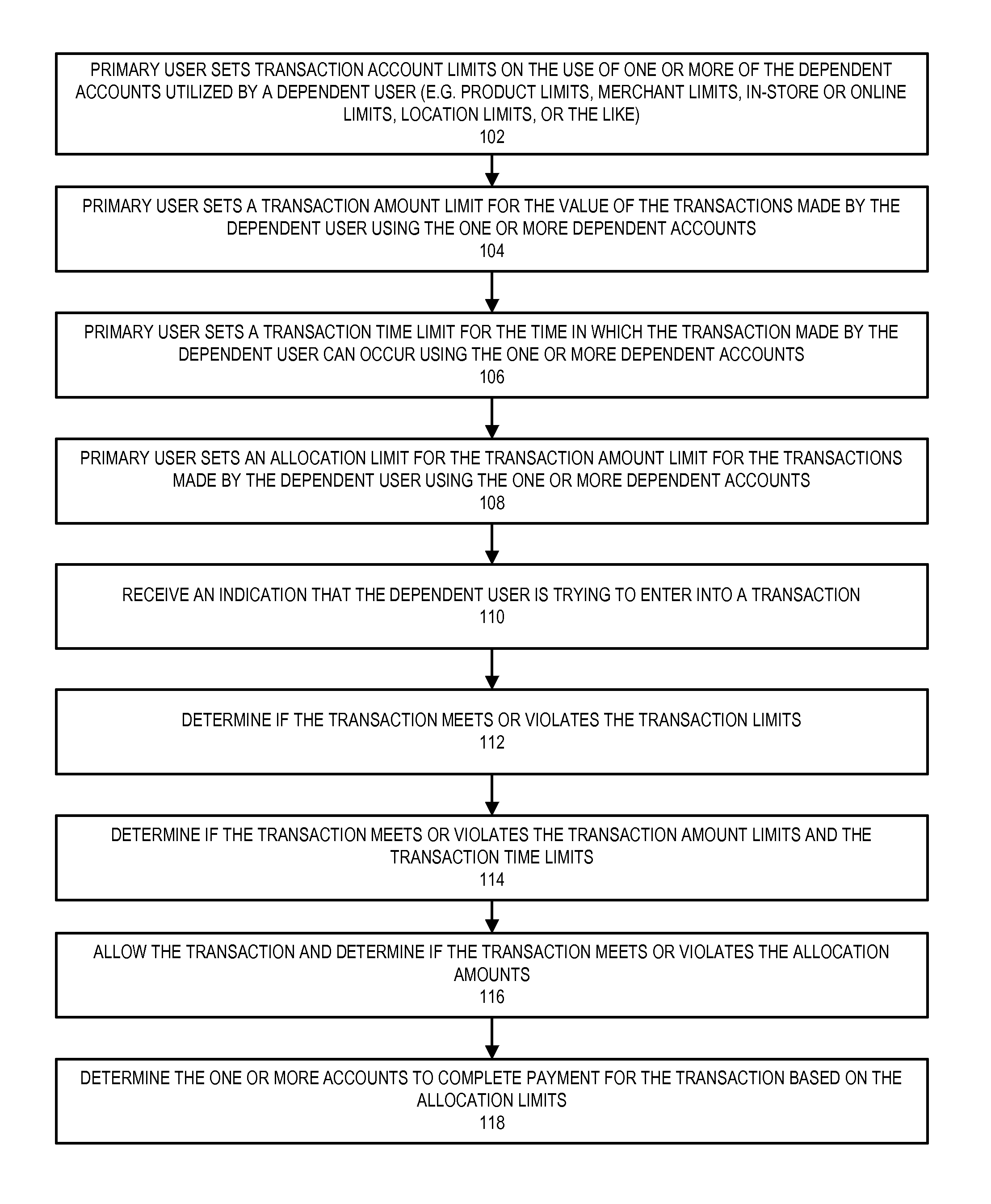
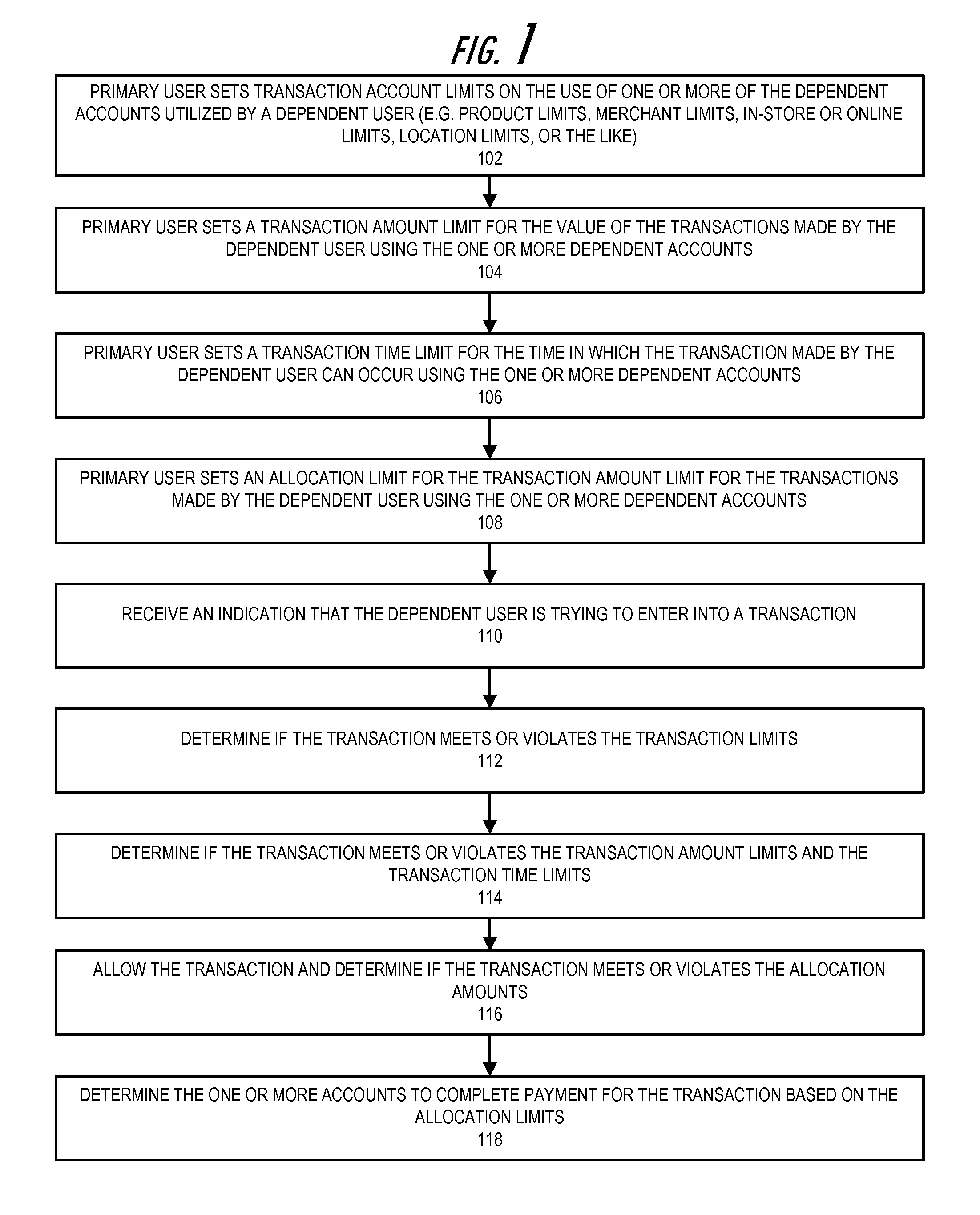
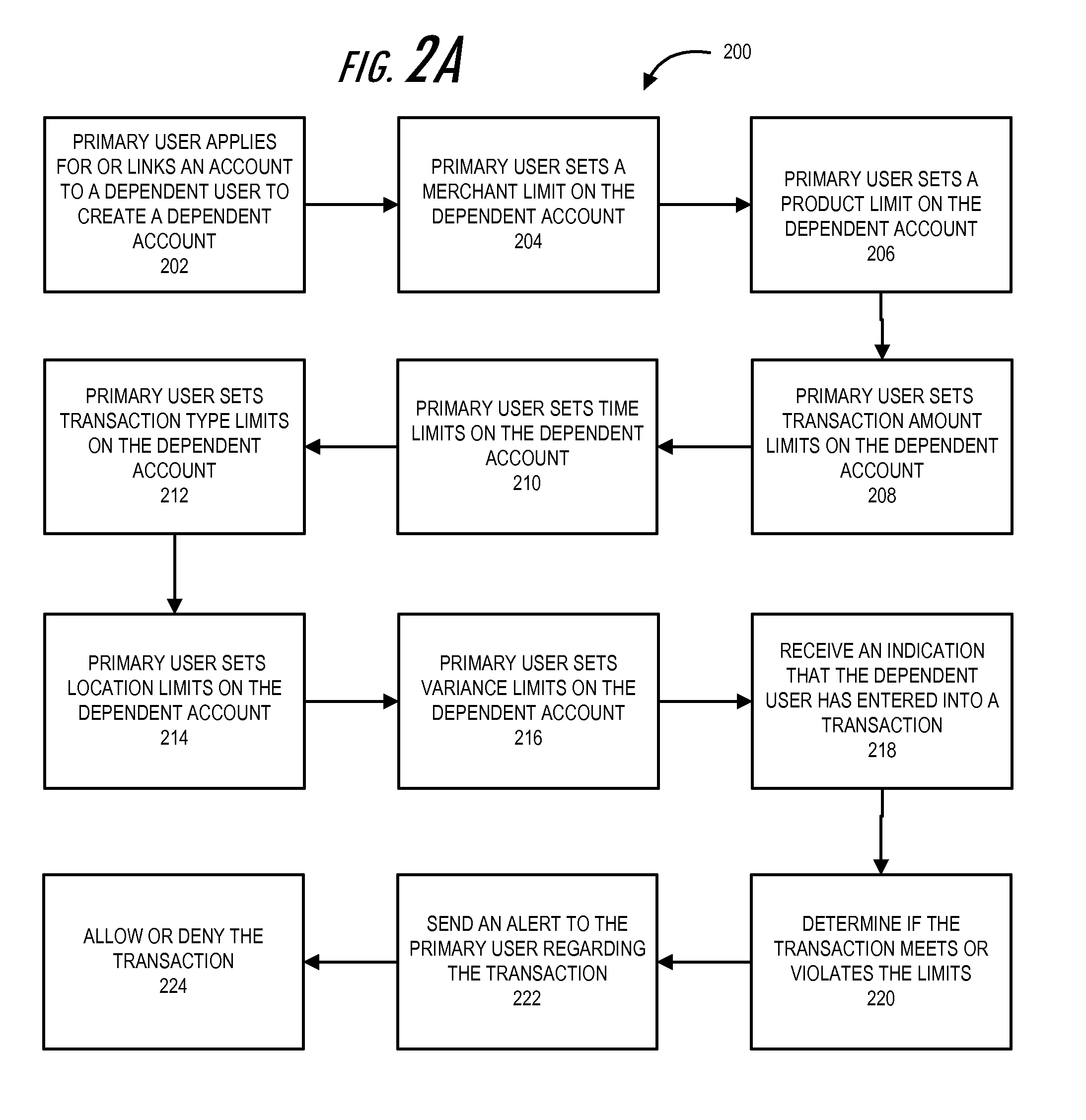
Purchase limits with primary account holder control
Embodiments of the prevent invention allow a primary user to create a dependent account in order to control and monitor the transactions made by a dependent user that is authorized to use the dependent account. The primary user can limit the transactions that the dependent user can make at a store or for products. The primary user can set transaction amount limits and transaction time limits on the transactions the dependent user can make at the blocked / approved stores or on the blocked / approved products. The primary user can set other limits, such as transaction type limits (e.g., in store purchase vs online purchase, or the like), location limits (e.g., radius location, zip code, state, region, or the like), or variance limits (e.g., particular transactions may be a percentage or dollar amount over the limits).
Owner:BANK OF AMERICA CORP
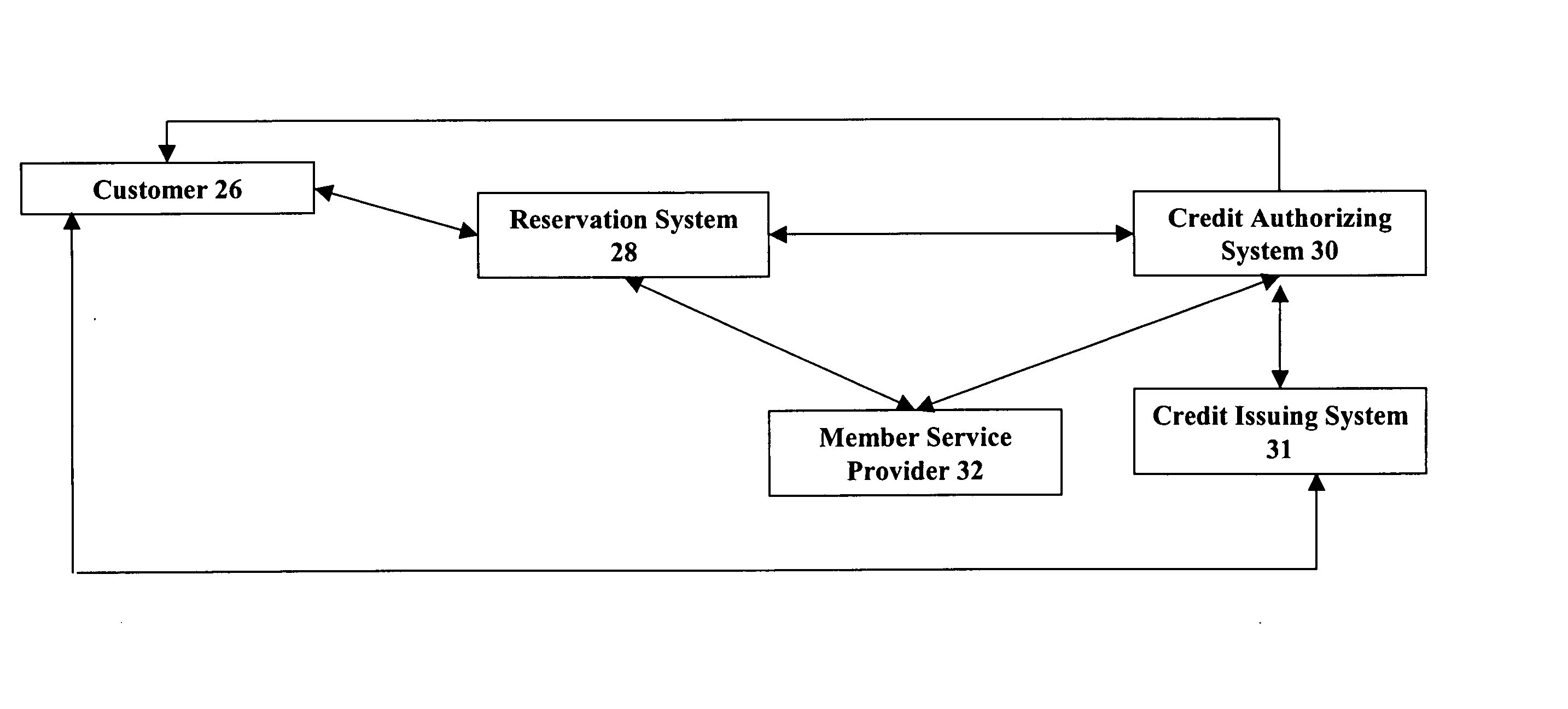
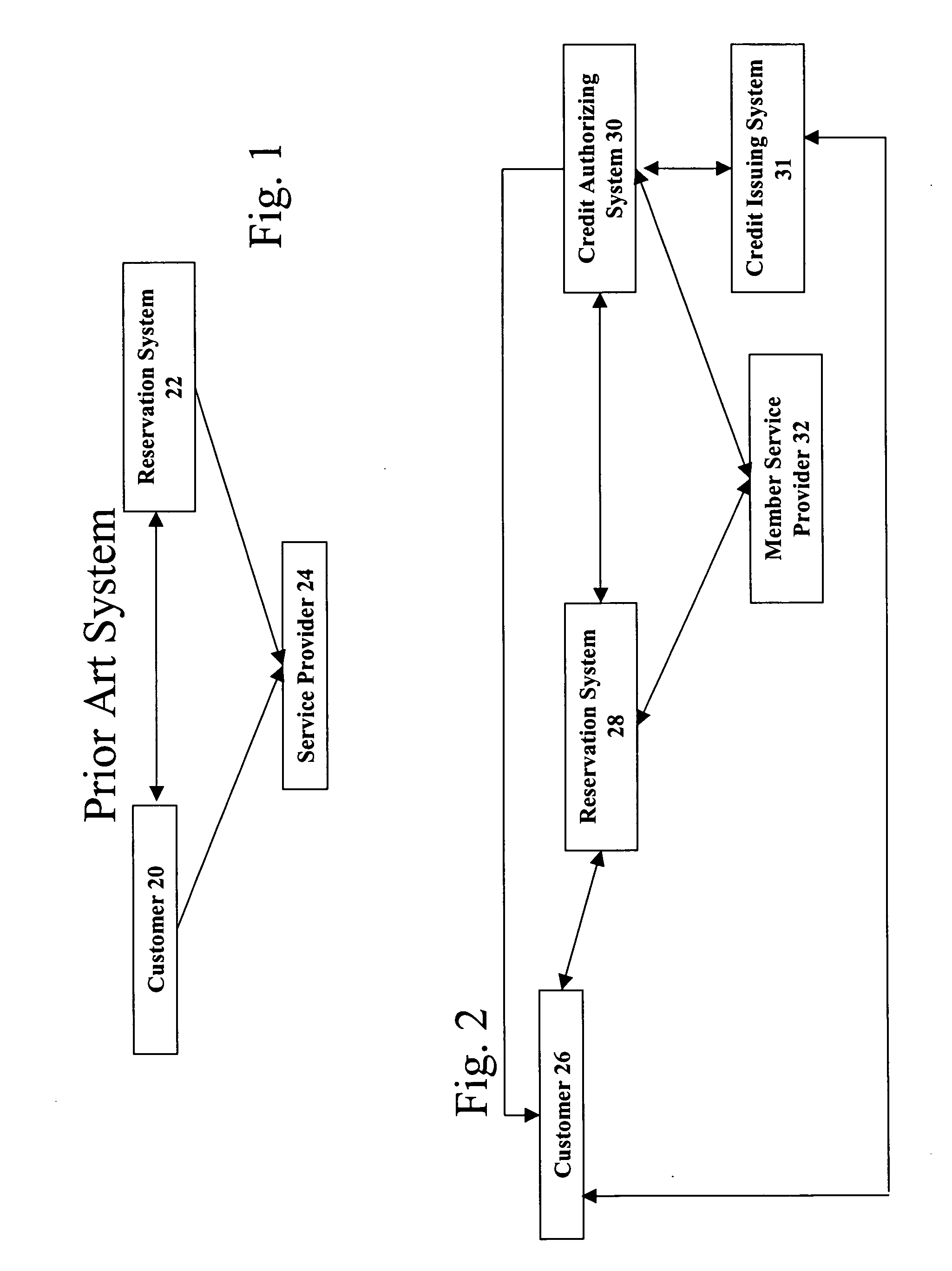
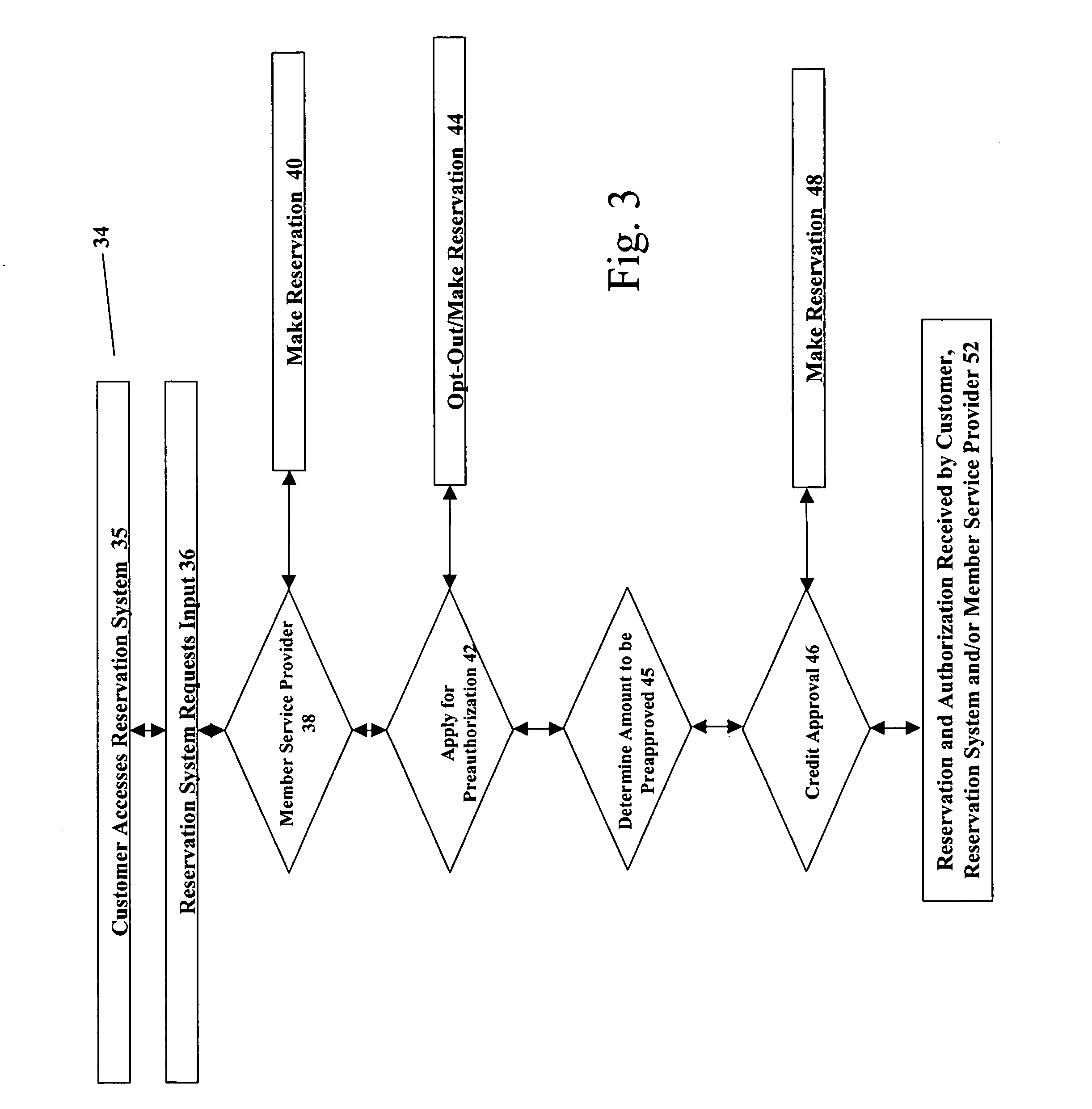
Reservation-based preauthorization payment system
A method and system for allowing the setting of reservations and the pre-authorization of credit to purchase a desired service for which a reservation is made. A customer accesses a reservation system that is integrated with a credit authorization system. The customer may make a reservation and substantially simultaneously become pre-authorized to pay for services to be provided at the reservation by one of any number of credit providers. Pre-authorized credit and reservation information is then supplied to the service provider in advance of services being provided, expediting the overall transaction time and allowing for a secure and cardless transaction procedure. The reservation and preauthorization information are typically stored upon the reservation system and then passed to the point-of-sale systems, but other types of input / output storage devices could be used to perform this function.
Owner:CARDFREE
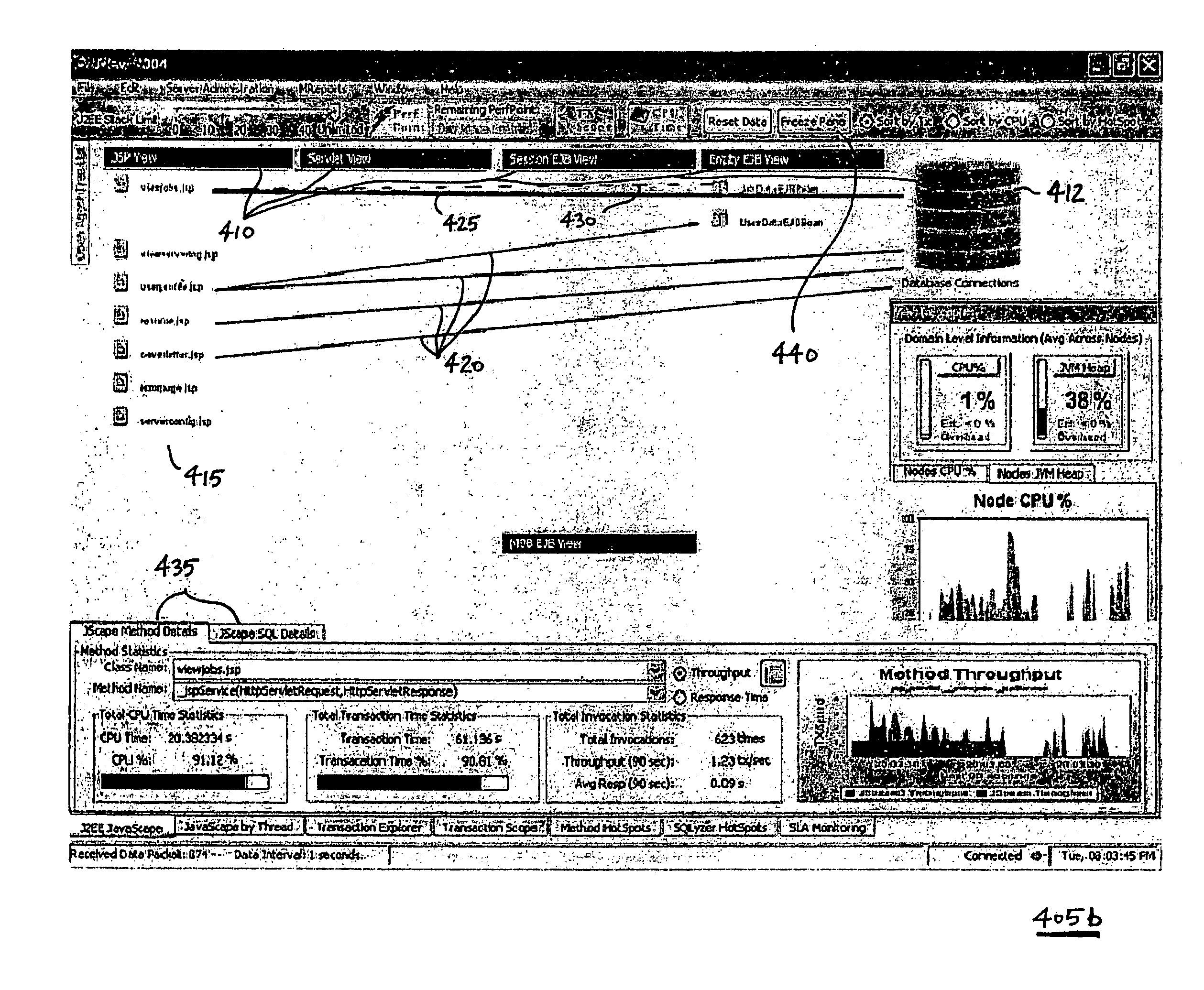
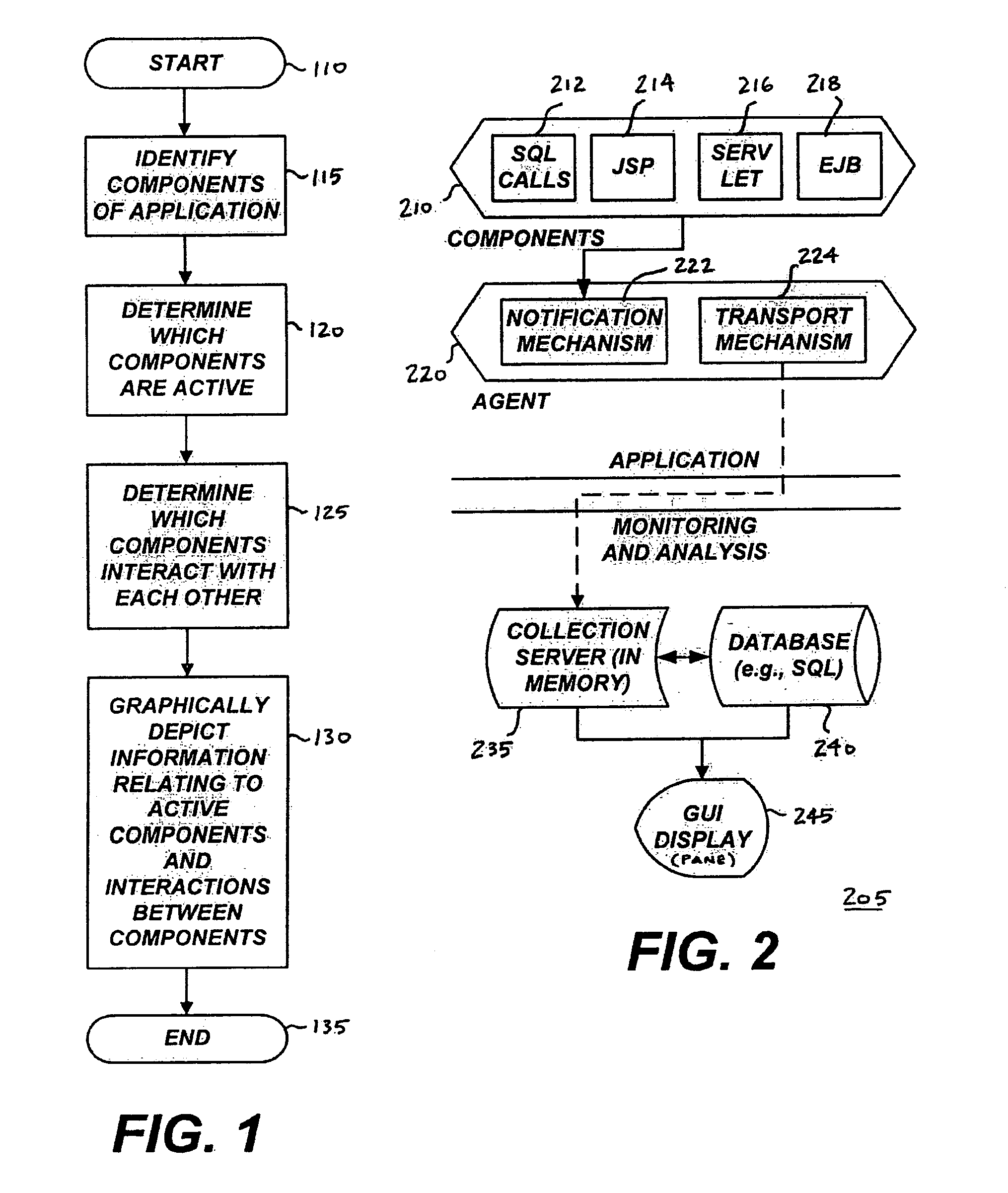
Visual landscape for multi-tiered application environment component interactions
ActiveUS7382371B1Application and quickly and efficientlyData quickly and efficientlyDrawing from basic elementsError detection/correctionApplication serverAnalysis tools
A system and a method to provide a visual landscape of a server-centric application framework (SCAF) with multiple tiers, multiple components, component interactions, and performance monitoring and analysis. The system and method includes a multi-tiered visual display of component interactions, tuning, monitoring, and analyzing of custom-developed application server components, and alert system for production grade performance monitoring. The system is comprised of a native agent, which interfaces with the an appropriate SCAF machine running the SCAF application server. The agent gathers and sends data transactionally to an enterprise data collector that persists the data and authenticates users / permissions to view the data. The displayed data may include component links, interactions, response times, transaction time degradations, general object performance metrics, and hardware / process performance data. Further, a data-mining system allows access to reporting and analysis tools that aid in delivering optimization recommendations to administrator and developers.
Owner:DYNATRACE
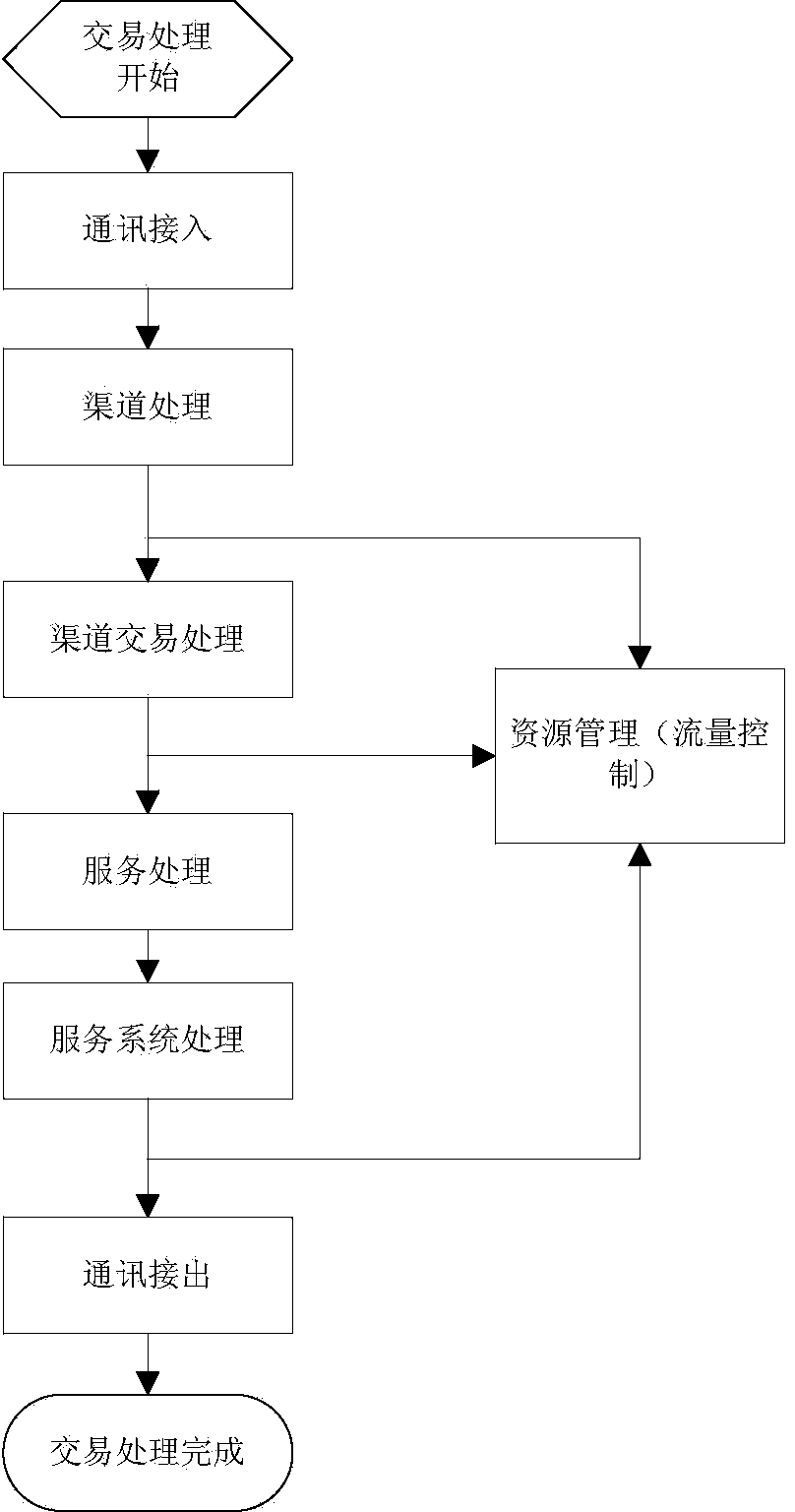
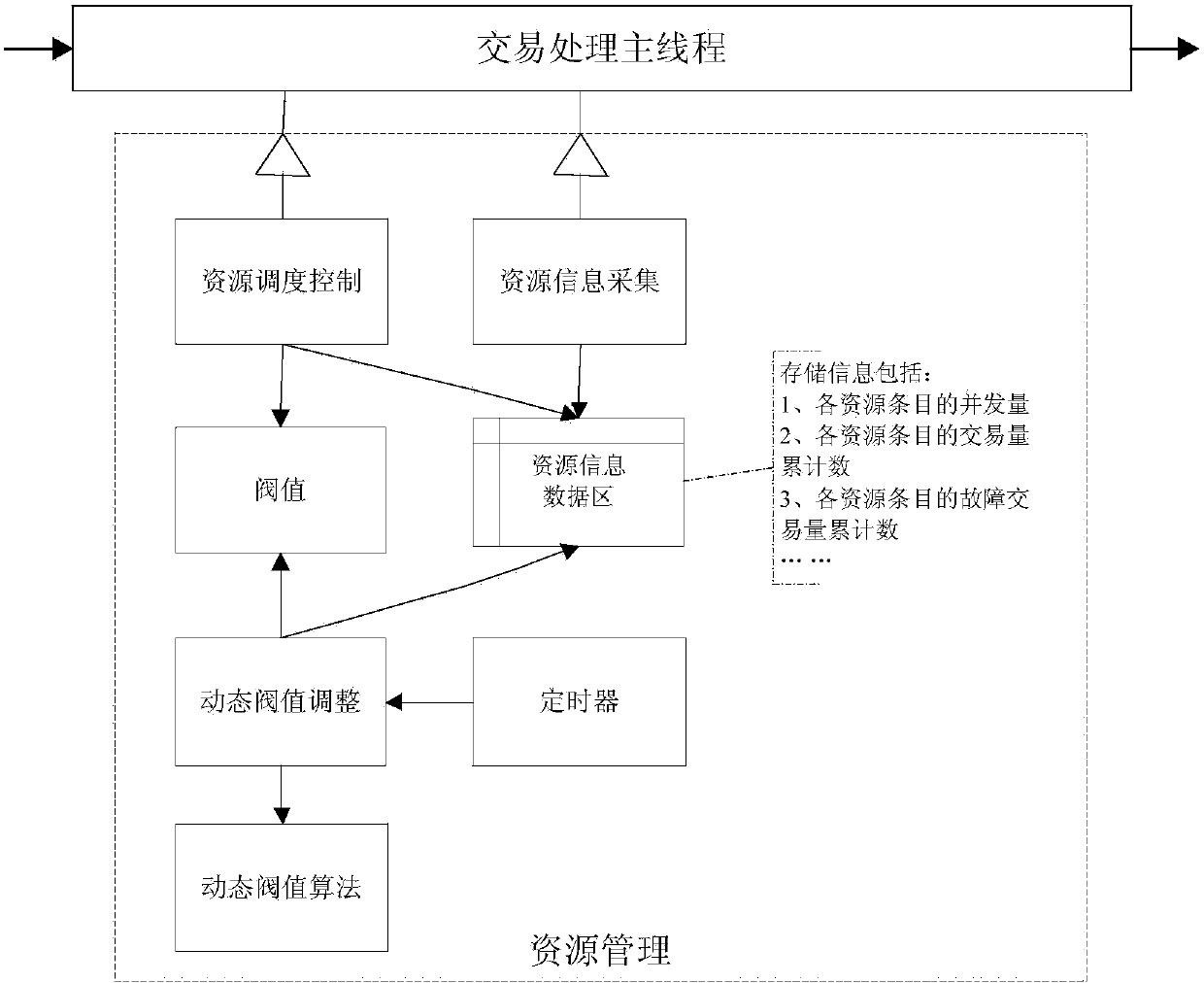
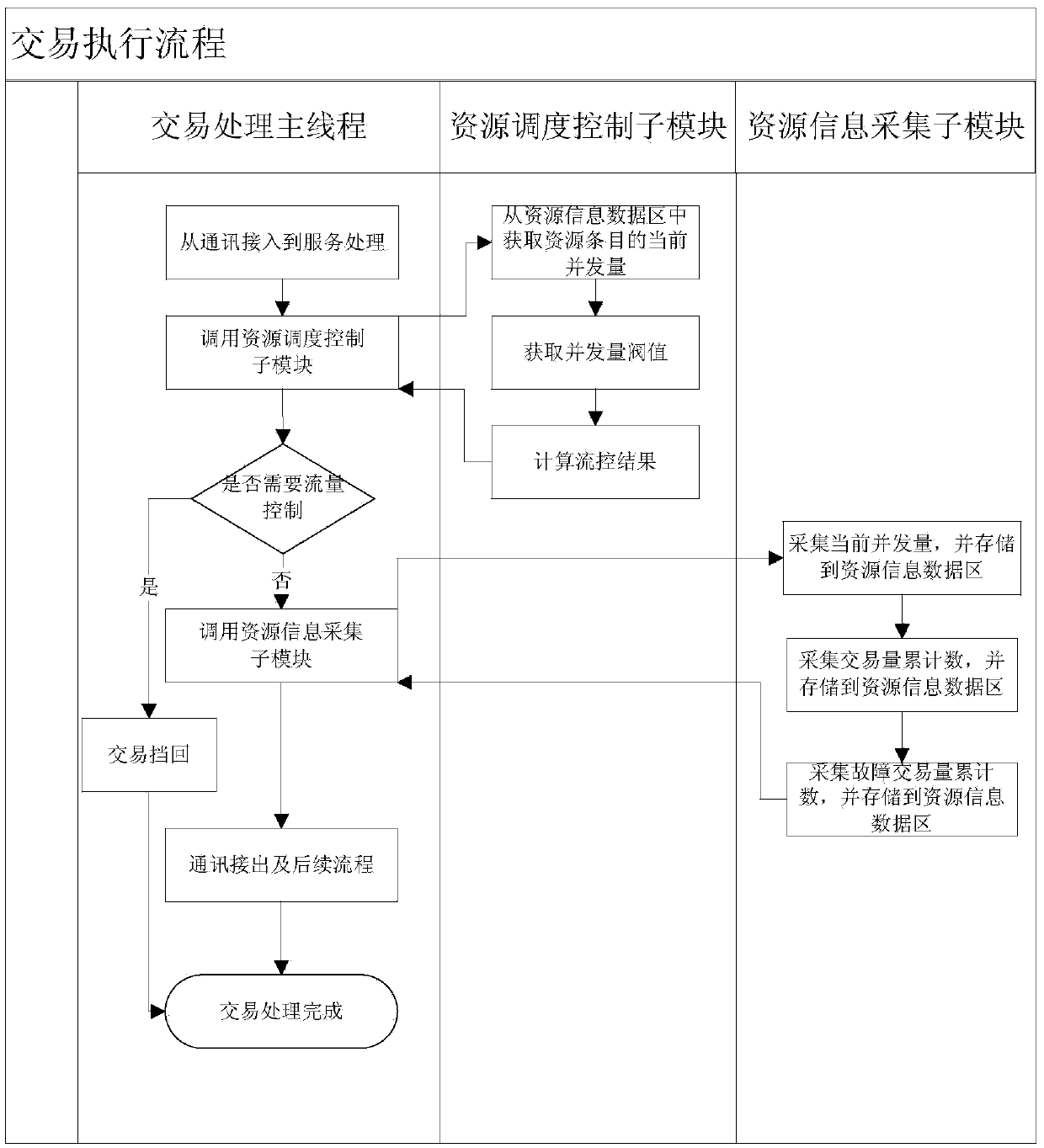
Flow control method and device for computer system
InactiveCN104090823AImprove real-time performanceImprove effectivenessResource allocationTraffic capacityComputerized system
The invention provides a flow control method for a computer system. The flow control method comprises the following steps: calling a resource management module for dynamically adjusting transaction concurrency quantity threshold value at one or more nodes of each processing link of transactions in the computer system, wherein the resource management module is used for dynamic adjustment according to the fault rate of the transactions, the fault rate of the transactions refers to a ratio of accumulation value of faulted transactions of a target resource to total accumulation value of transactions of the resource within a sampling time cycle, and the faulted transactions are transactions with transaction response time exceeding transaction time standards. In addition, the invention further provides a corresponding flow control device. By implementing the method and the device, the transaction concurrency quantity can be multi-dimensionally acquired and controlled and is dynamically adjusted according to the transaction fault rate, and the transaction channel blockage of the system is effectively relieved.
Owner:CHINA CONSTRUCTION BANK
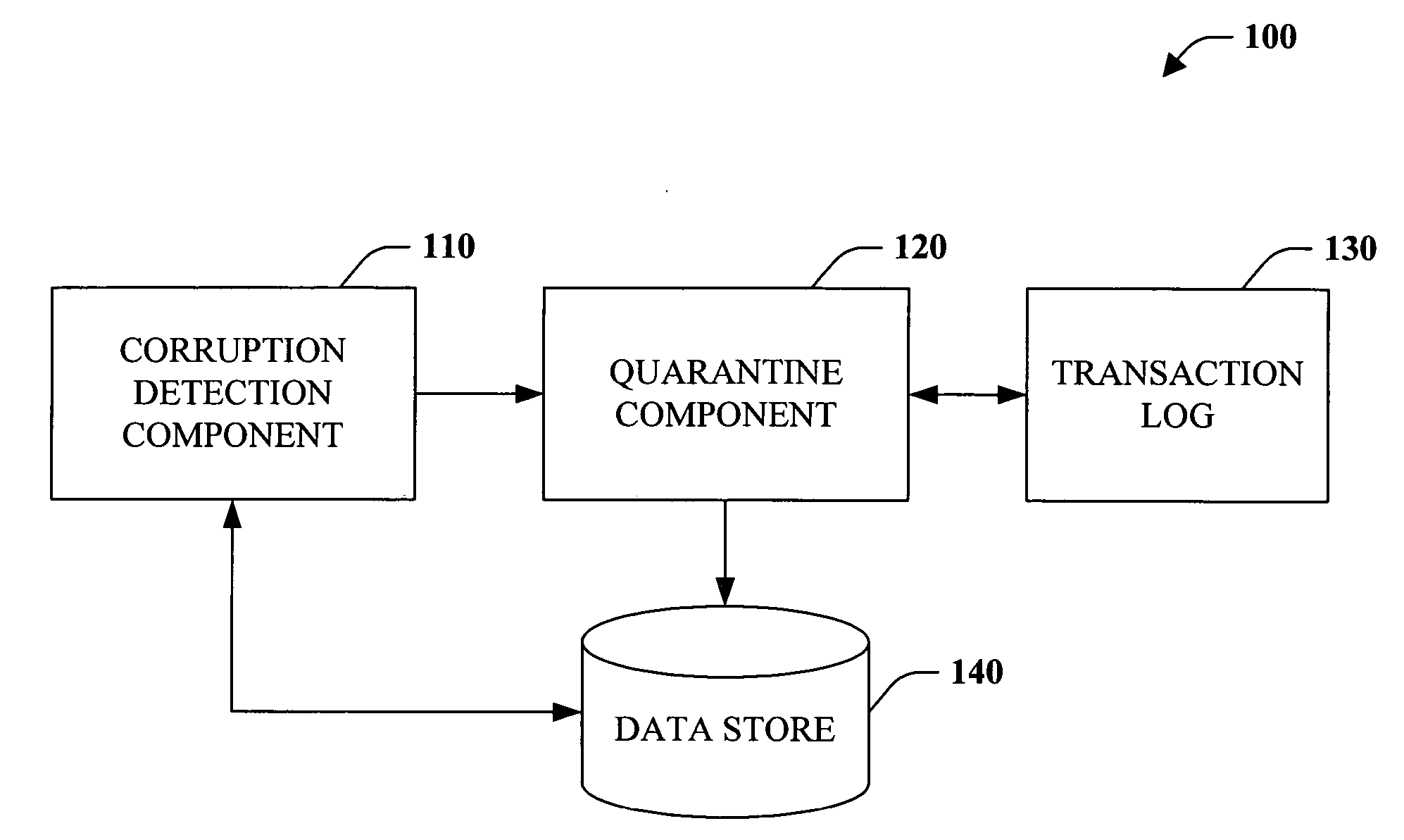
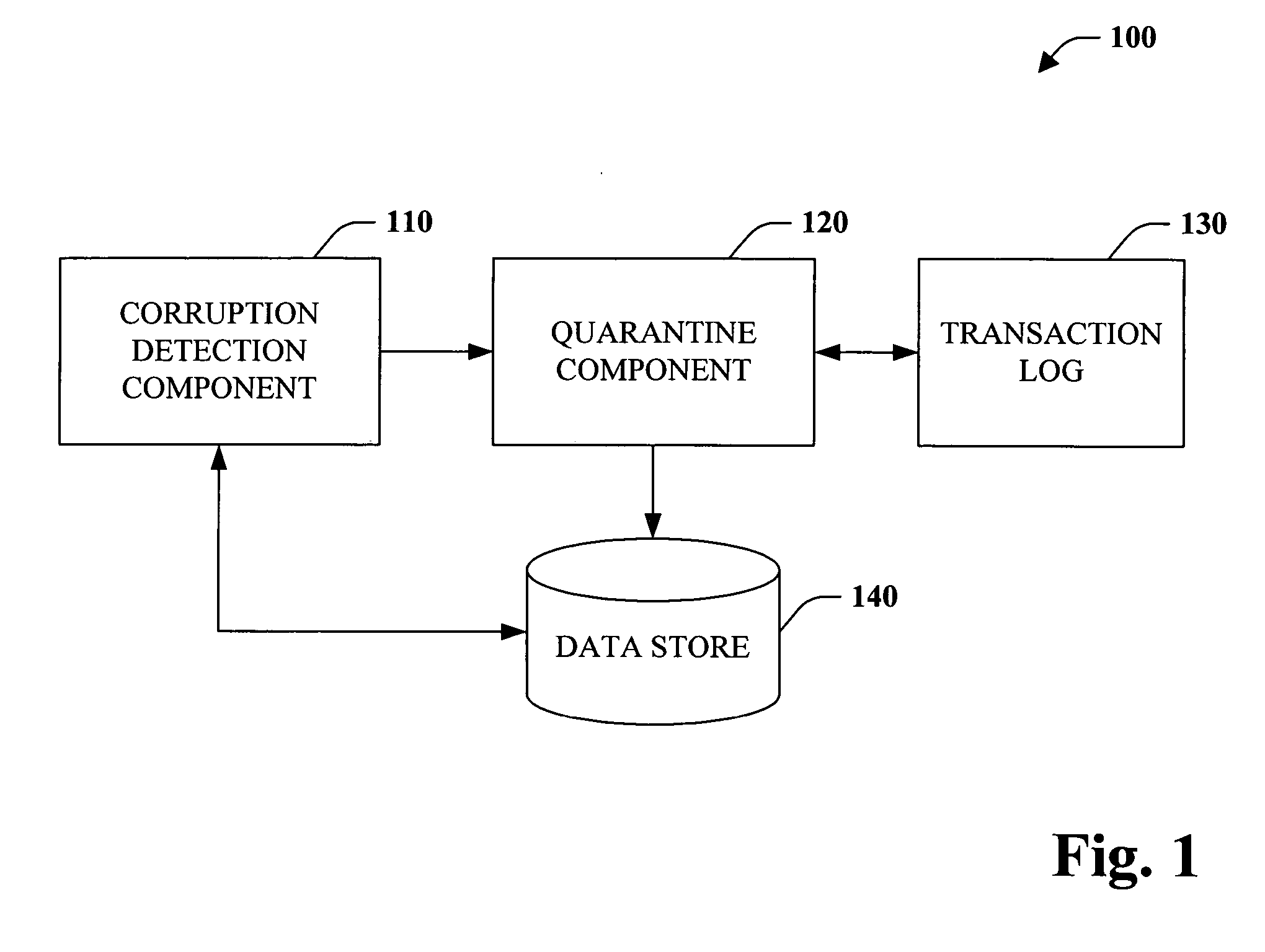
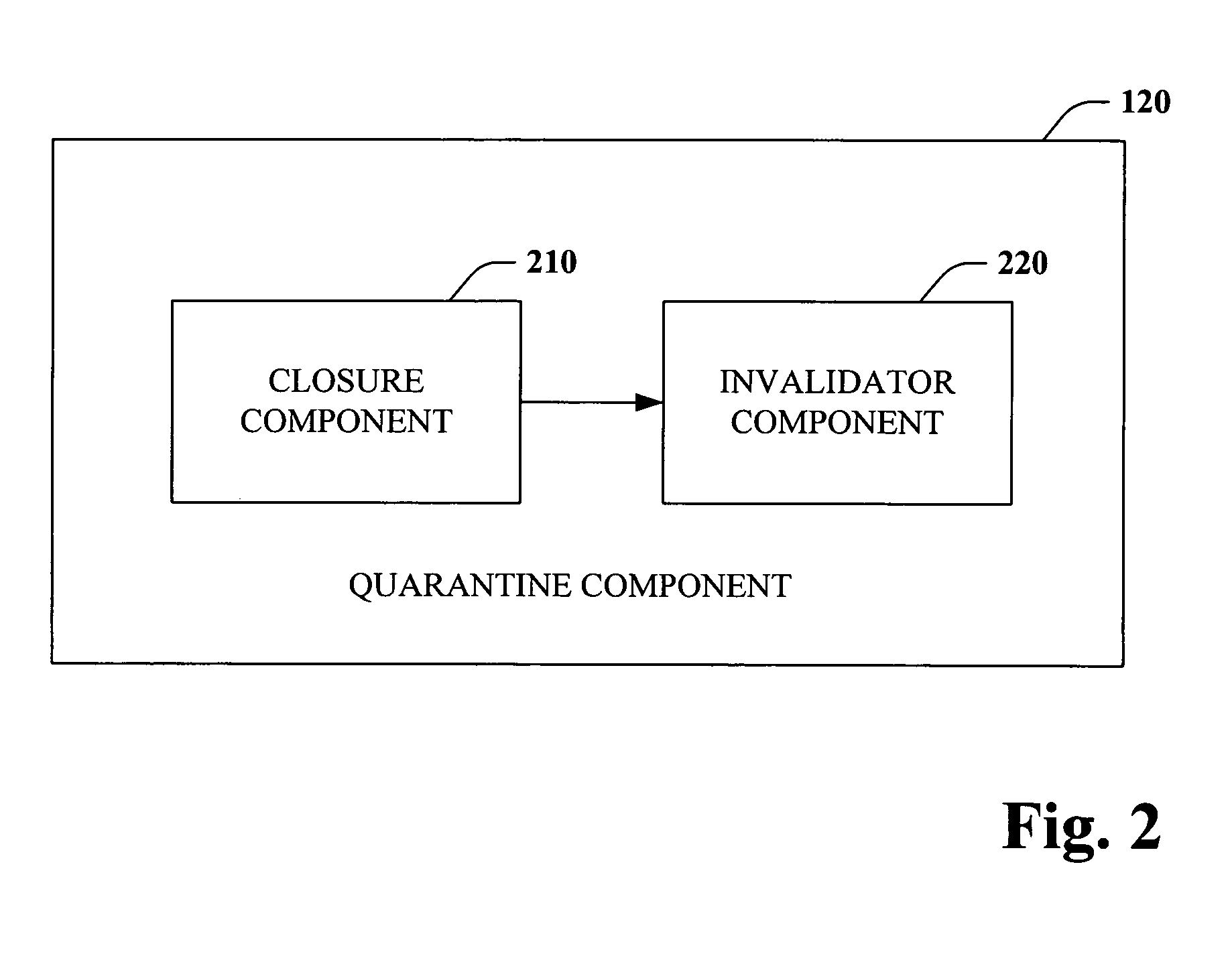
Database corruption recovery systems and methods
ActiveUS20060259518A1Improve abilitiesEliminate needDigital data processing detailsData acquisition and loggingTemporal databaseData needs
The subject invention pertains to data store corruption recovery. More specifically, the invention concerns systems and methods for identifying corrupt data in a manner that prevents de-committing or removal of valid or consistent transactions from a database. This can be accomplished at least in part by logging the identities of data items that a transaction reads. Furthermore, the subject invention provides for employment of a multi-version (or transaction-time) database to reduce significantly reduce any down time or database unavailability caused by a corrupt transaction and associated corrupt data items. Accordingly, no backups need to be installed and only updates by the original corrupt transaction and transactions that read corrupt data need to be de-committed or removed.
Owner:MICROSOFT TECH LICENSING LLC
Mechanism and method for specified temporal deployment of rules within a rule server
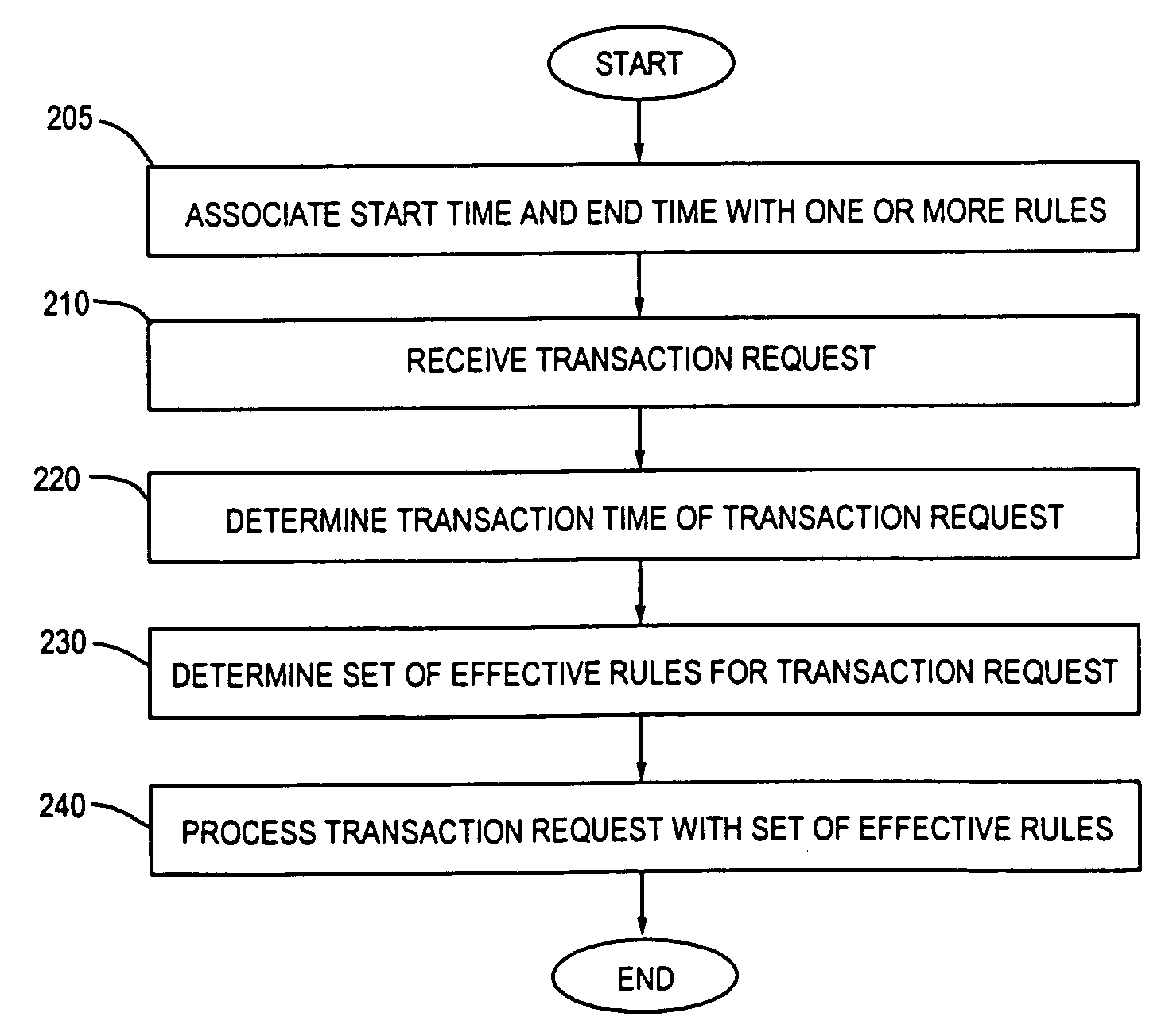
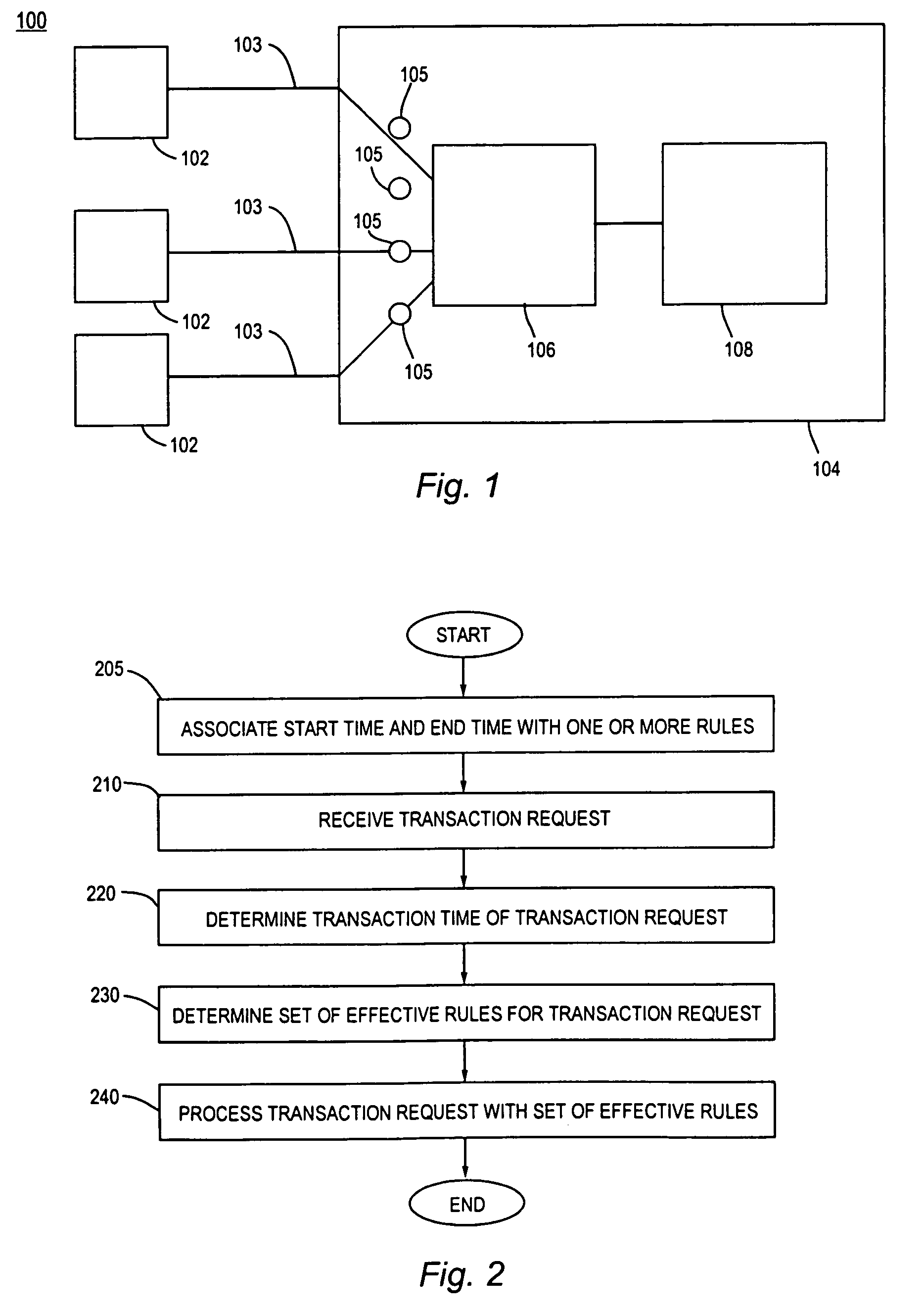
InactiveUS6944604B1Difficult to determineDigital data processing detailsKnowledge representationStart timeImproved method
An improved method and mechanism for specified temporal deployment of rules within a rules server. A rules server applies a set of rules, stored within a rulebase, to a given set of input values or parameters. Each rule is associated with a start time and an end time. Upon receiving a transaction request, a transaction time is determined for the transaction request. Subsequently, a set of effective rules within the ruleset are identified by the rules server, wherein each effective rule has a start time before the transaction time, and an end time that is after the transaction time. The rule server applies only the set of effective rules to the transaction.
Owner:FAIR ISAAC & CO INC
Systems and methods for convenient and secure mobile transactions
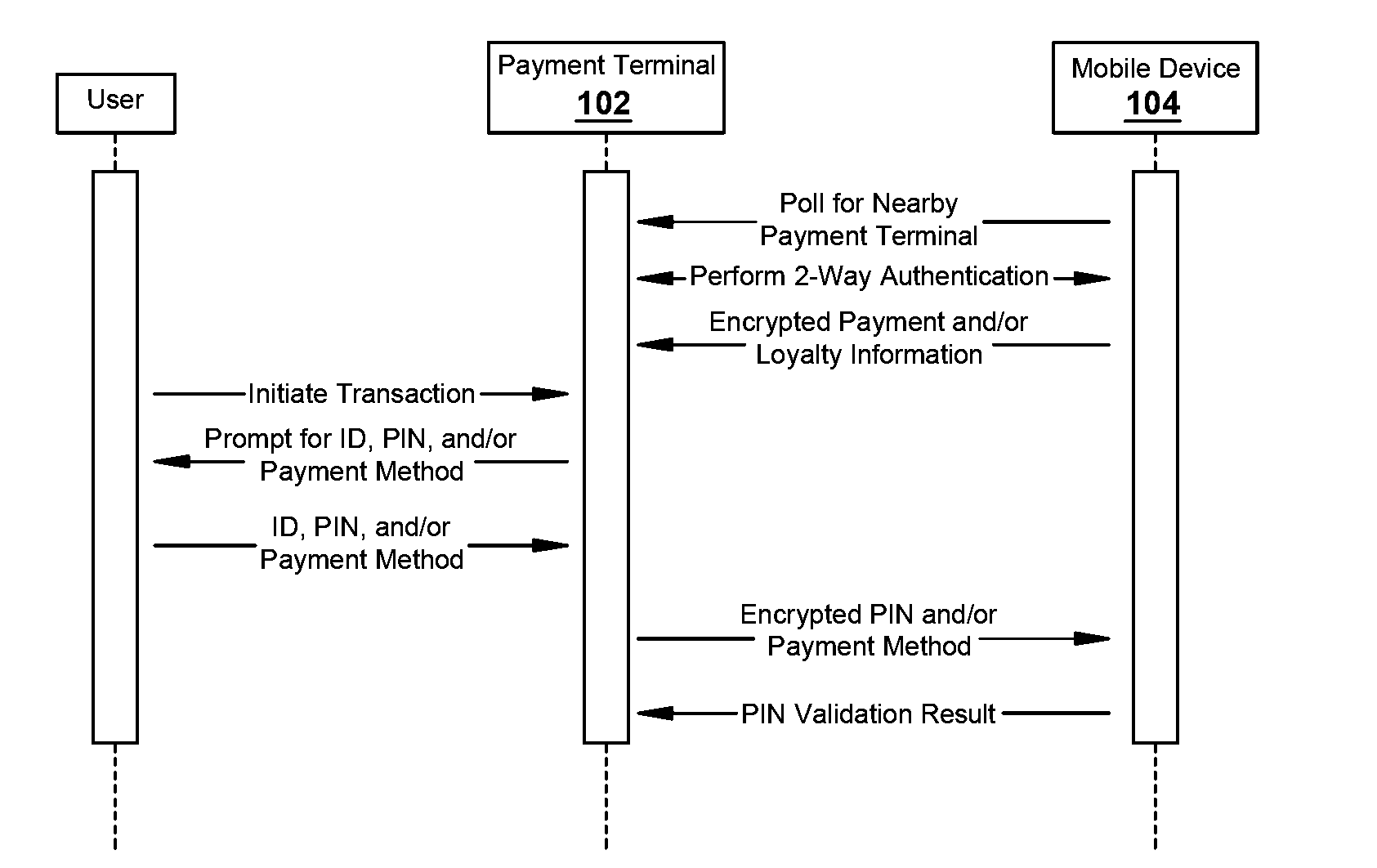
ActiveUS20150143116A1Easy to completeShorten transaction timeCryptography processingUser identity/authority verificationComputer terminalMobile transaction
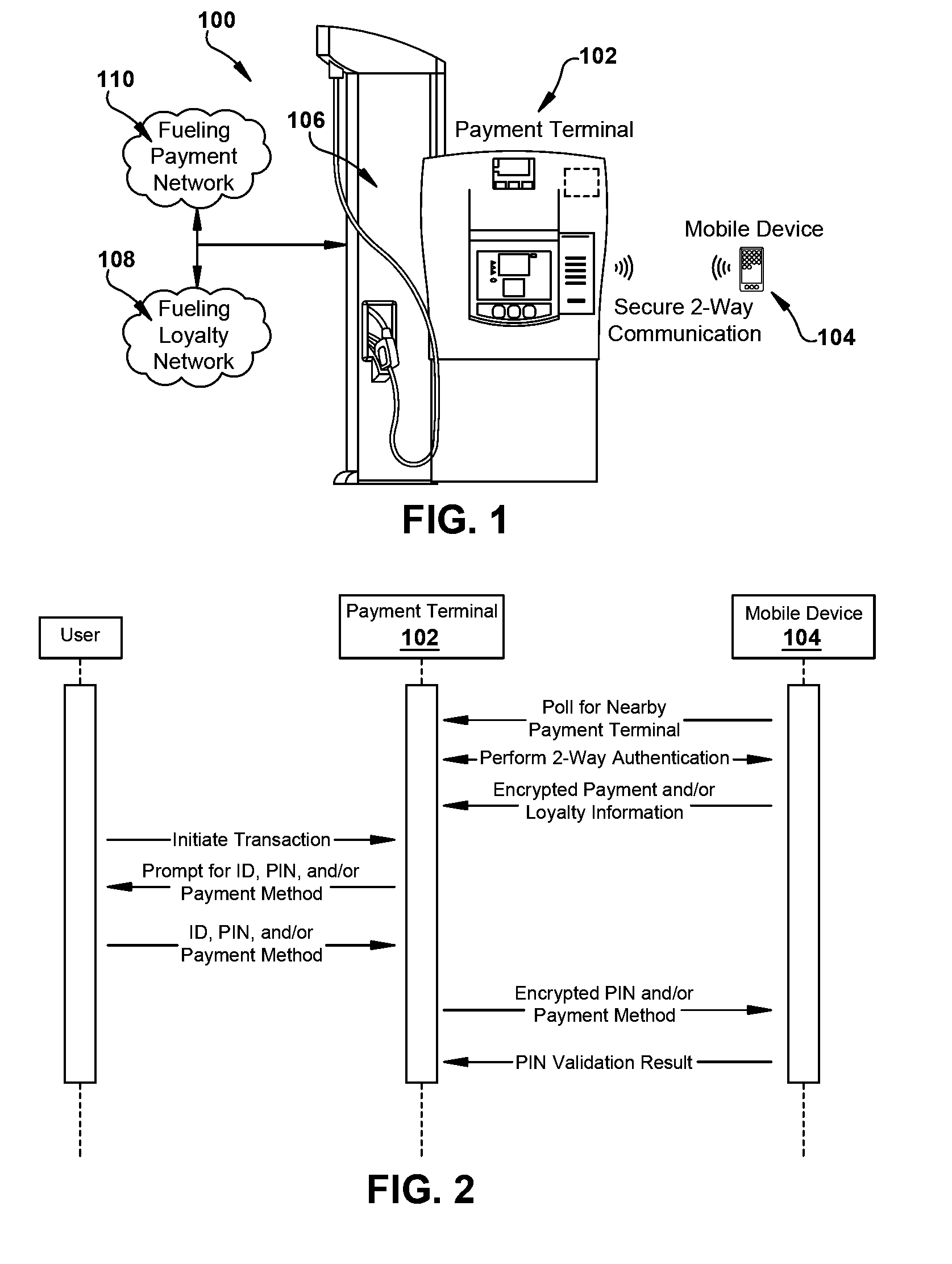
Systems and methods for conducting convenient and secure mobile transactions between a payment terminal and a mobile device, e.g., in a fueling environment, are disclosed herein. In some embodiments, the payment terminal and the mobile device conduct a mutual authentication process that, if successful, produces a session key which can be used to encrypt sensitive data to be exchanged between the payment terminal and the mobile device. Payment and loyalty information can be securely communicated from the mobile device to the payment terminal using the session key. This can be done automatically, without waiting for the user to initiate a transaction, to shorten the overall transaction time. The transaction can also be completed without any user interaction with the mobile device, increasing the user's convenience since the mobile device can be left in the user's pocket, purse, vehicle, etc.
Owner:WAYNE FUELING SYST
Method and apparatus for Blockchain billing
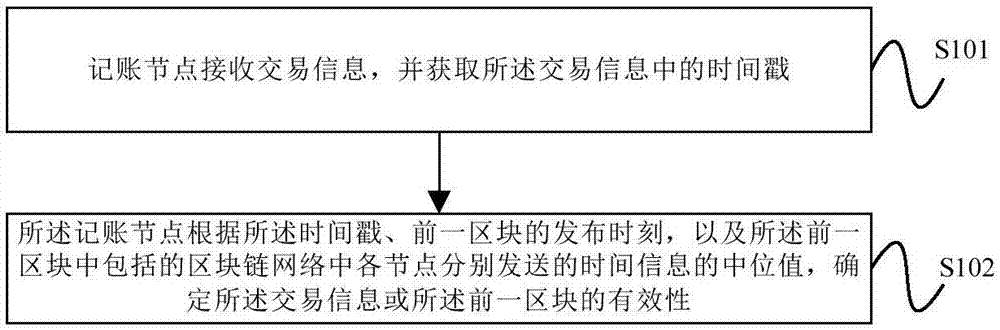
The embodiments of the present invention provide a method and an apparatus for Blockchain billing. The method includes: a billing node receives the transaction information and obtains a timestamp in the transaction information; and the billing node determines the validity of the transaction information or the previous block according to the timestamp, the issuing moment of the previous block, and the median value of the time information sent respectively by the various nodes in a Blockchain network contained in the previous block. According to the invention, based on the timestamp of the received transaction information, the issuing moment of the previous block and the median value of the time information sent respectively by the various nodes in a Blockchain network contained in the previous block, the validity of the transaction information or the previous block can be determined, which avoids the chaos or loss of account books caused by the chaos of time and avoids the deliberate concealment of transactions from hacker nodes. Therefore, transaction security using Blockchain can be ensured.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
System and method for transaction learning
ActiveUS20160125317A1Digital computer detailsKnowledge representationPersonalizationTransaction data
A system and method a method for providing for providing personalized transaction learning and tagging. The method may include tagging transactions associated with one or more financial accounts belonging to an account holder, whether the account holder be the primary, secondary, or a related account holder, such as a spouse, parent, guardian, and the like. The method may include linking all accounts belong to and / or associated with an account holder and receiving transaction data from each linked account, including, for example, transaction date, transaction time, transaction amount, merchant name, merchant location, merchant identifier, account number used in transaction, SKU-level transaction information, and / or other purchase identifiers (e.g., merchant-provided product / service name, account holder-provided product / service name, and the like). Once the system receives the transaction data, the system may query the account holder for input regarding the transaction data. The input may include tagging the transaction as belonging to a particular spending category and / or affirming or denying that the transaction belongs to a particular category. The system may receive and create categories based on account holder data, demographic data, credit data, and account holder profile data.
Owner:CAPITAL ONE SERVICES
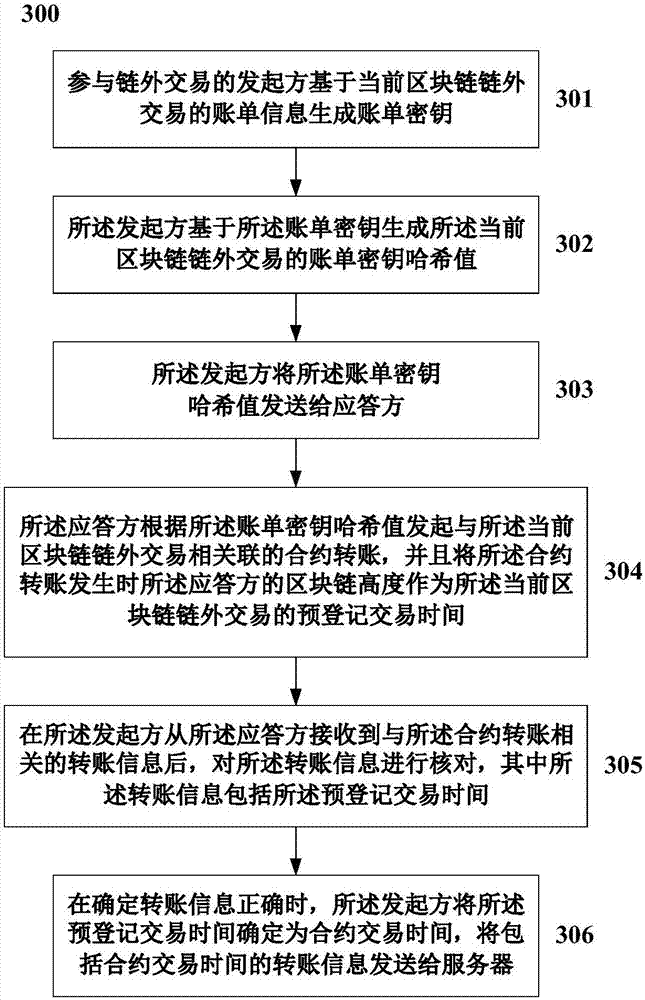
Method and apparatus for determining transaction time of block chain off-chain transaction
The invention relates to a method for determining a transaction time of a block chain off-chain transaction. The method comprises the steps in which, an initiator participating in an off-chain transaction generates a bill secret key based on bill information of the current block chain off-chain transaction; the initiator generates a bill secret key hash value of the current block chain off-chain transaction based on the bill secret key; the initiator sends the bill secret key hash value to a responder; the responder initiates a contract transfer associated with the current block chain off-chain transaction according to the bill secret key hash value, and the block chain height of the responder when the contract transfer occurs is taken as the pre-registered transaction time of the current block chain off-chain transaction; when receiving the transfer information related to the contract transfer from the responder, the initiator verifies the transfer information; and when determining that the transfer information is correct, the initiator determines the pre-registered transaction time as the contract transaction time and sends the transfer information including the contract transaction time to a server.
Owner:陈佺
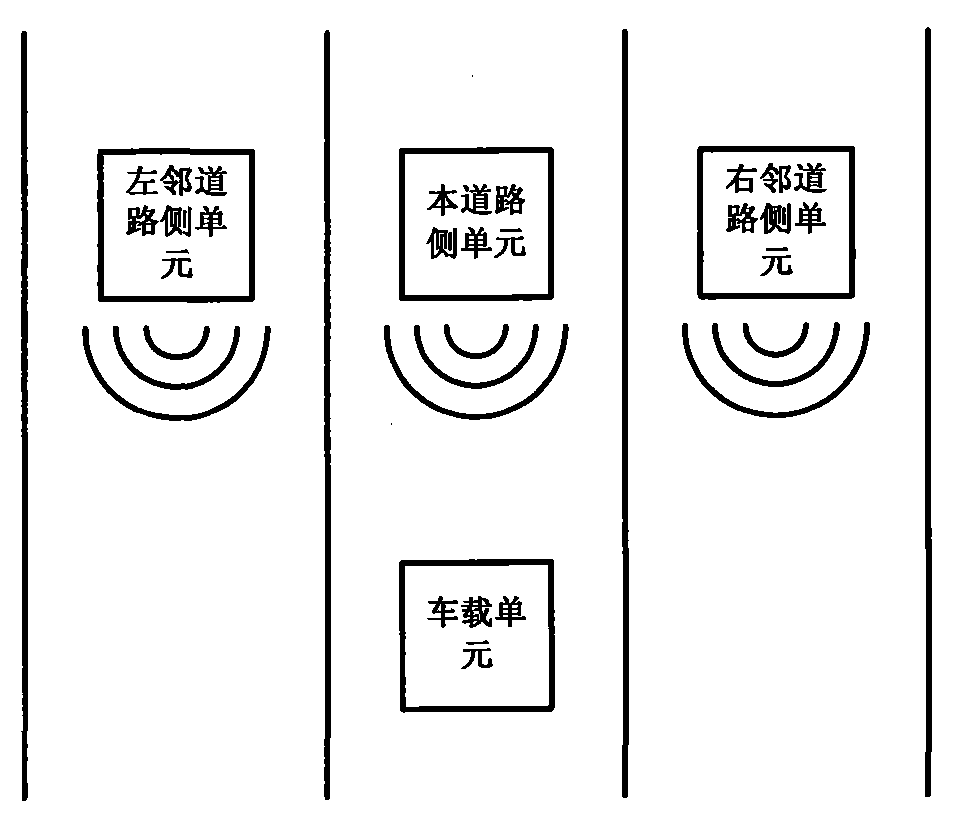
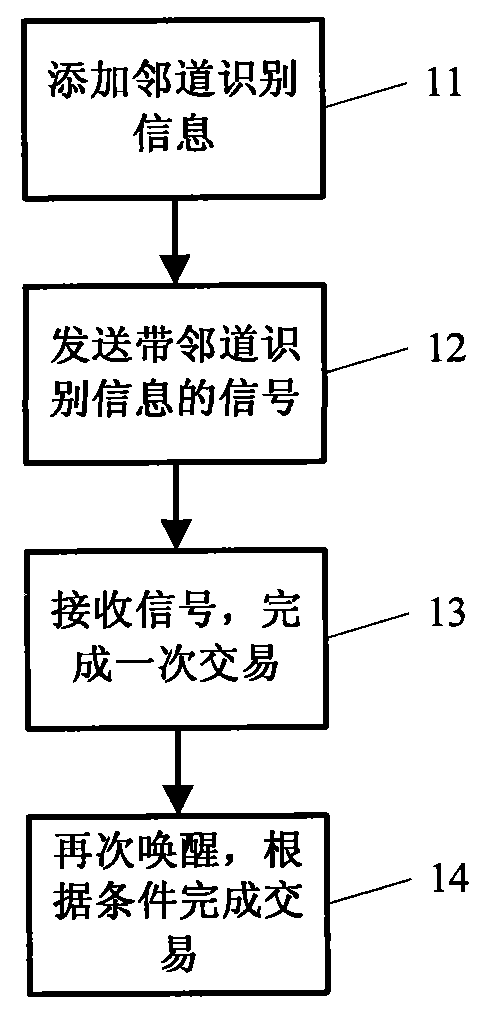
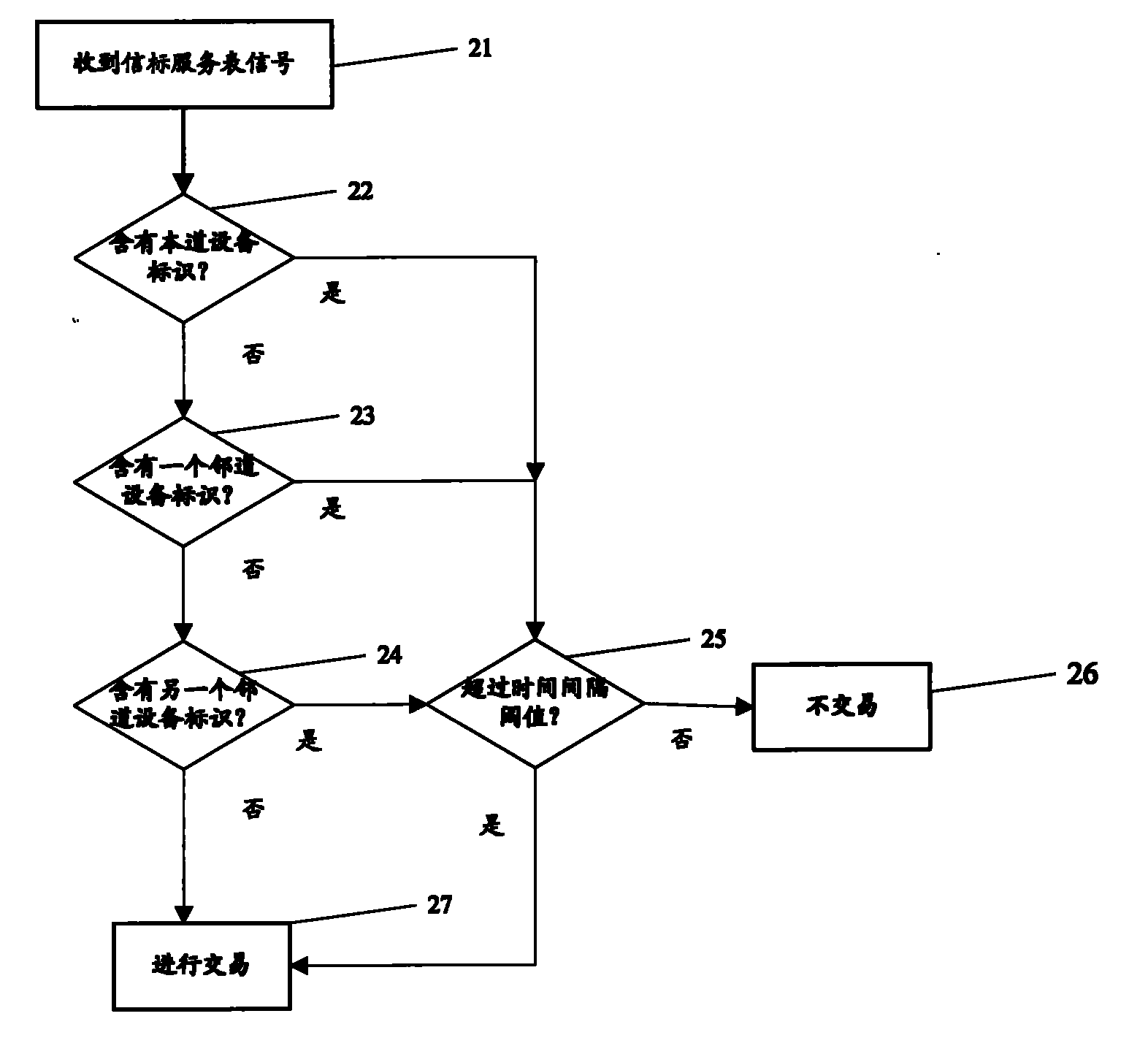
Method for sending ETC service signal, method for receiving ETC service signal, road side unit and vehicle-mounted unit
ActiveCN102096951AReduce misjudgmentLow costTicket-issuing apparatusTransmissionEngineeringElectronic toll collection
The invention discloses a method for sending an electronic toll collection (ETC) service signal, a method for receiving the ETC service signal, a road side unit and a vehicle-mounted unit. Identification information of an adjacent road side unit is added into the road side unit, the vehicle-mounted unit acquires the identifier of the adjacent road side unit when receiving a beacon service table (BST) signal so as to determine which ones are the adjacent side units, and the original transaction time interval for only judging the road is modified to be the transaction time interval for judging both the road and the adjacent road during judgment of the transaction interval; therefore, the problem of repeat transaction caused by the influence of the adjacent road is solved.
Owner:NANJING ZHONGXING SOFTWARE
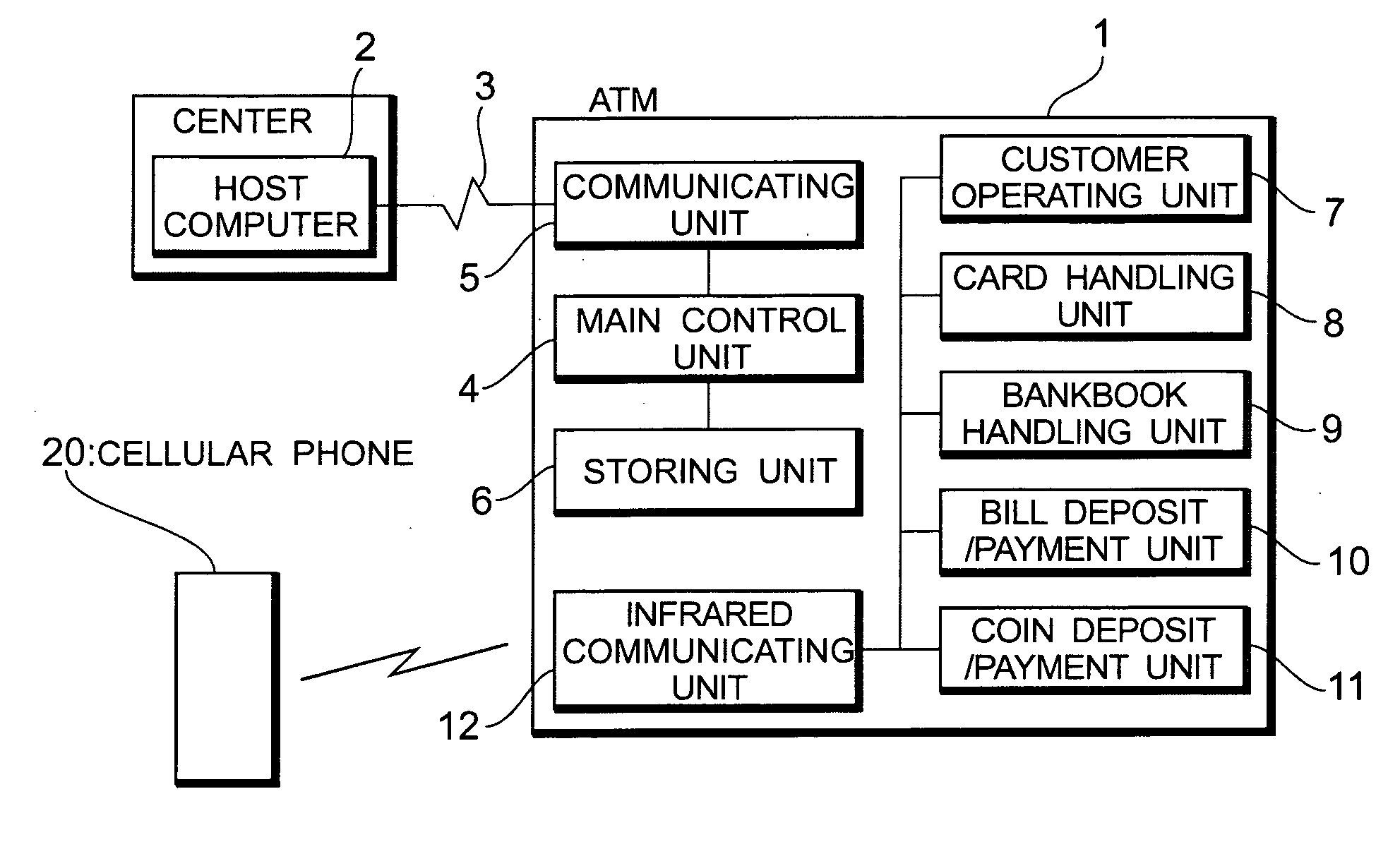
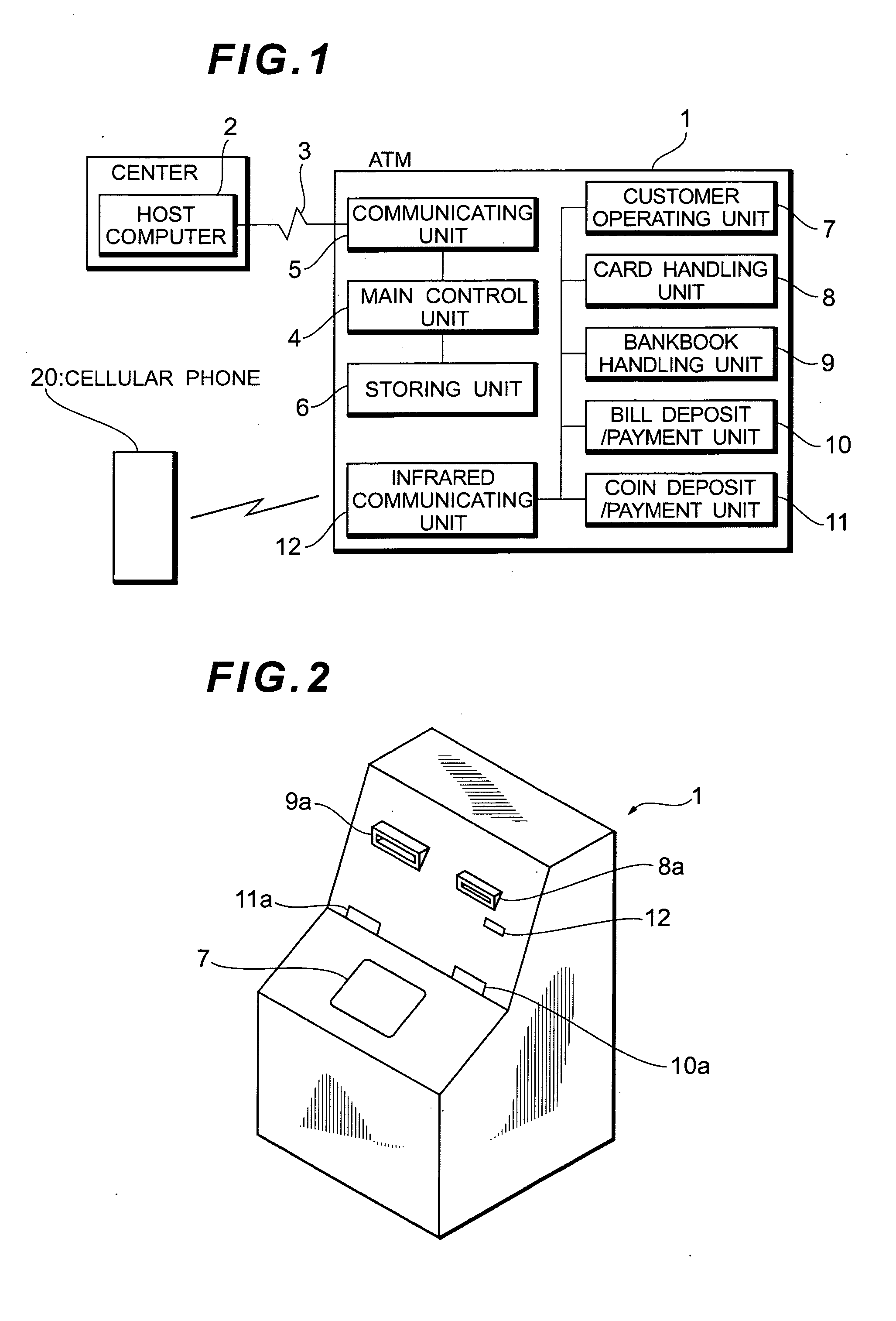
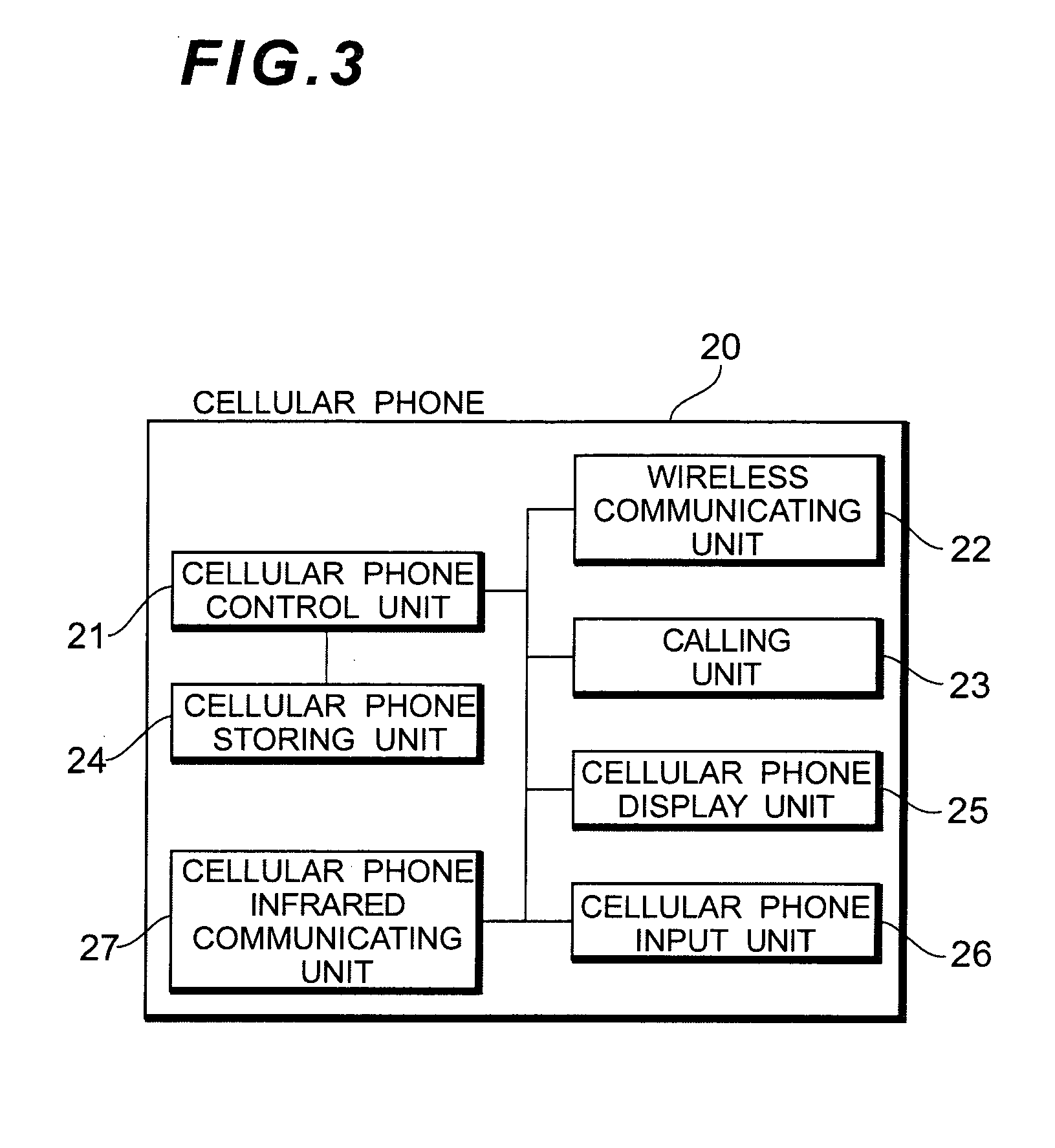
Automatic transaction system
InactiveUS20050262017A1Shorten transaction timeEasy to operateComplete banking machinesFinanceTransaction dataCellular telephone
An automatic transaction system has a cellular phone of a customer and an automatic teller machine (ATM) which can directly communicate with the cellular phone by infrared communication. When the customer performs a transaction by the ATM, transaction information such as transfer information registered in the cellular phone is directly inputted to the ATM and the ATM executes a transaction process by the transaction information which was directly received. When transaction data which is used in the transaction by the ATM is inputted once, transaction time in the ATM can be shortened by the simple operation.
Owner:OKI ELECTRIC IND CO LTD
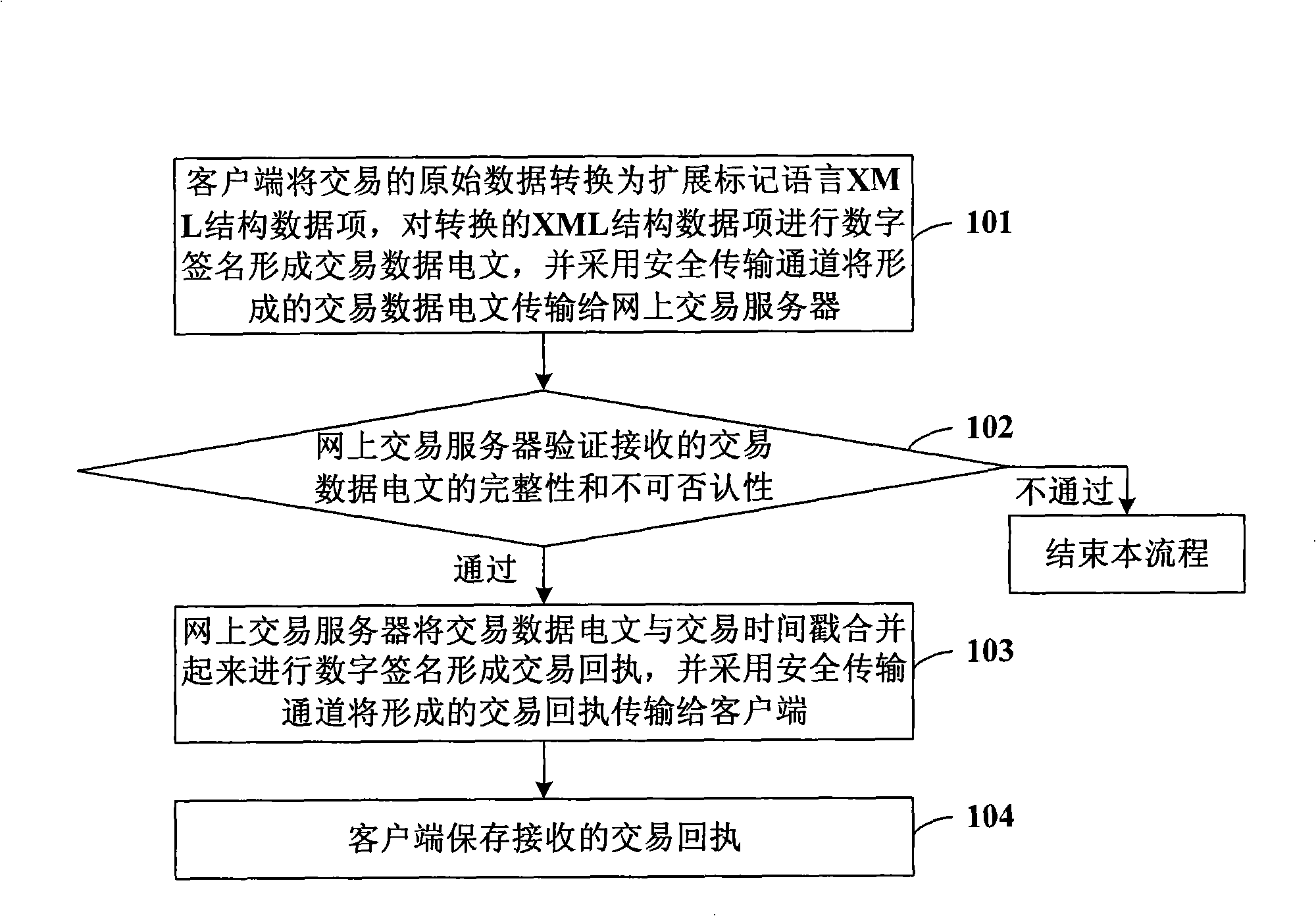
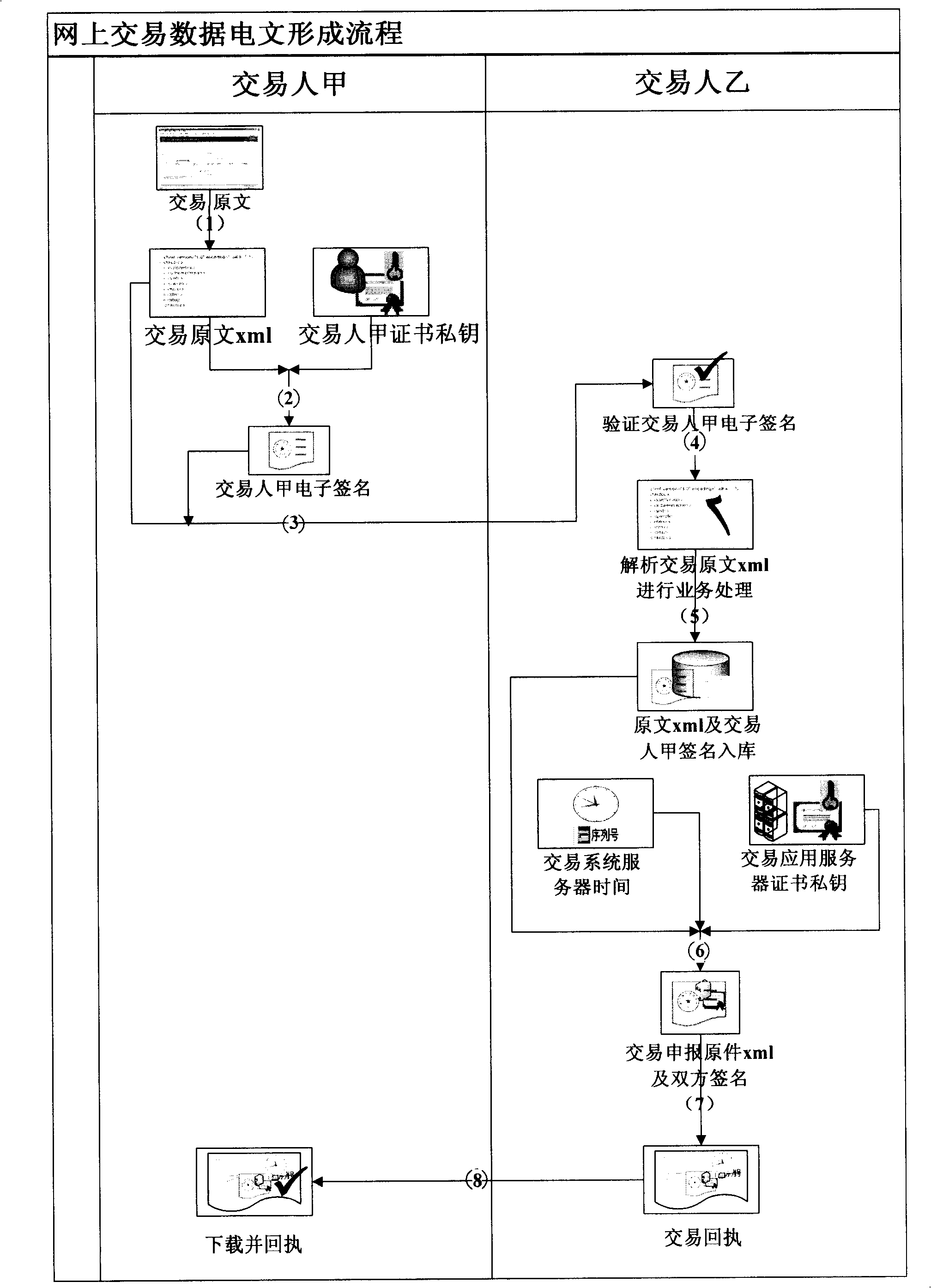
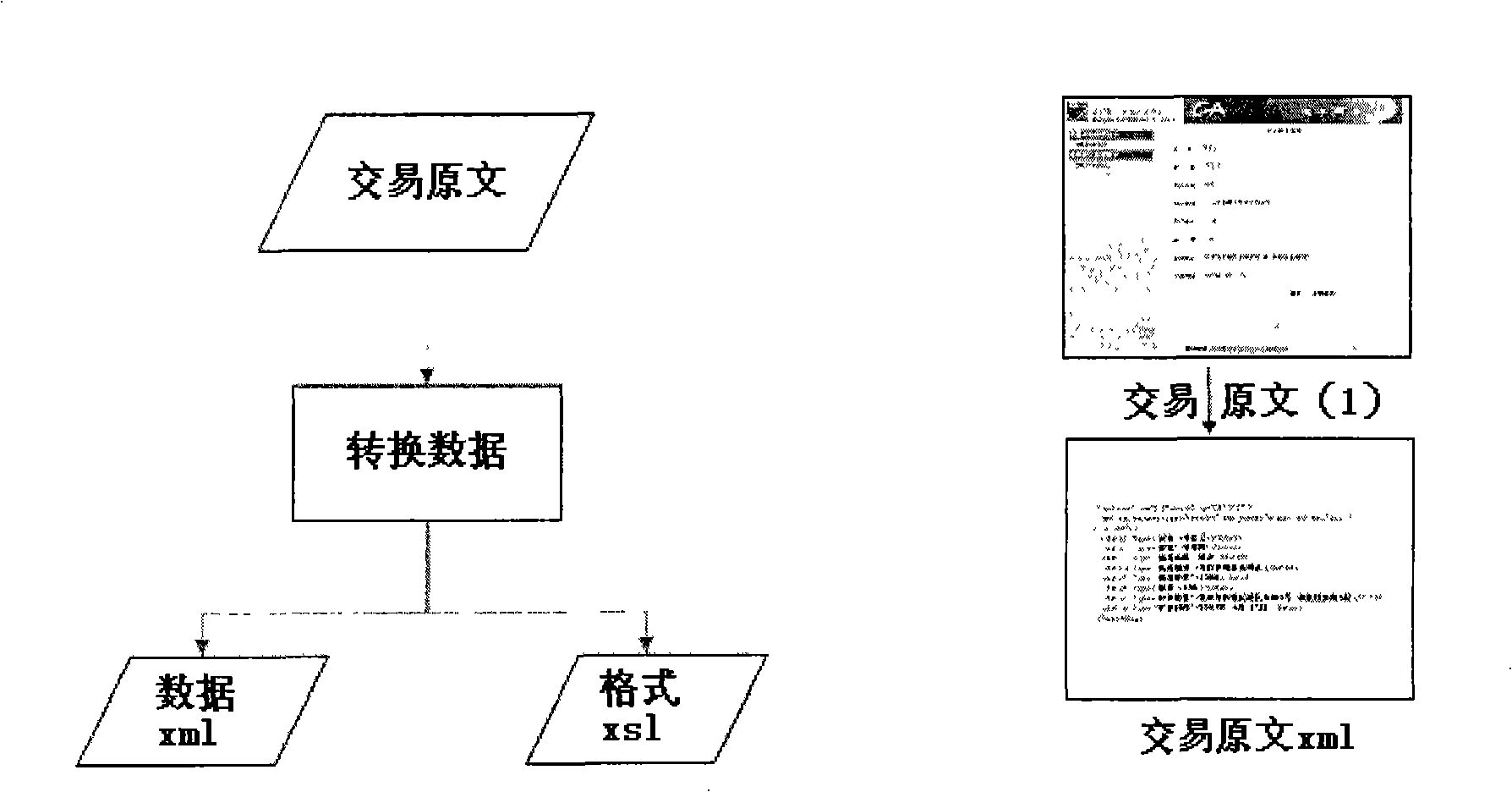
Method for implementing network transaction data text
InactiveCN101295387AOvercome efficiencyOvercoming demandsUser identity/authority verificationCommerceTransaction serviceOriginal data
The invention discloses a method for realizing an on-line transaction data message, comprising the steps that: A. a client converts the transacted original data into a XML structural data item, the converted XML structural data item is carried out the digital signature to form the transaction data message, a safety transmission channel is adopted to transmit the formed transaction data message to an on-line transaction server; B. the on-line transaction server verifies the completeness and the non-repudiation of the received transaction data message, if the verification is passed, the transaction data message is saved; C. the on-line transaction server merges the transaction data message and a transaction time stamp to carry out the digital signature to form a transaction receipt, and the safety transmission channel is adopted to transmit the formed transaction receipt to the client; and D. the client saves the received transaction receipt. The usage of the invention can overcome the shortcoming that the existing on-line transaction data message is not in line with the requirements of the electronic signature law in the aspects of having written effectiveness, original document effectiveness, file saving requirements and evidence effectiveness.
Owner:BEIJING CERTIFICATE AUTHORITY
Method of one time authentication response to a session-specific challenge indicating a random subset of password or PIN character positions
InactiveUS7681228B2Efficient deploymentDigital data processing detailsUser identity/authority verificationPasswordRecognition algorithm
Financial institution back office computerized transaction-processing system with embedded privacy and security layer (EPSL) enables strong transaction authentication prior to a merchant or vendor contact, based on a user account number, transaction conditions like anticipated transaction time and money, user two-factor authentication with a static transaction PIN and a transaction session-specific random partial password or PIN recognition algorithm. User enters the user name and then, challenged by server with a random session-specific subset of a password or PIN character's consecutive position numbers, enters based on cognitive association a one time authentication response. The authentication session is interactive, transaction session-specific, and followed by either a transaction denial or an alphanumeric transaction signature generated by EPSL for this specific transaction. Then, the user submits her request to a transaction counterpart along with the transaction signature. The merchant or vendor requests an authorization session with EPSL.
Owner:AUTHERNATIVE INC
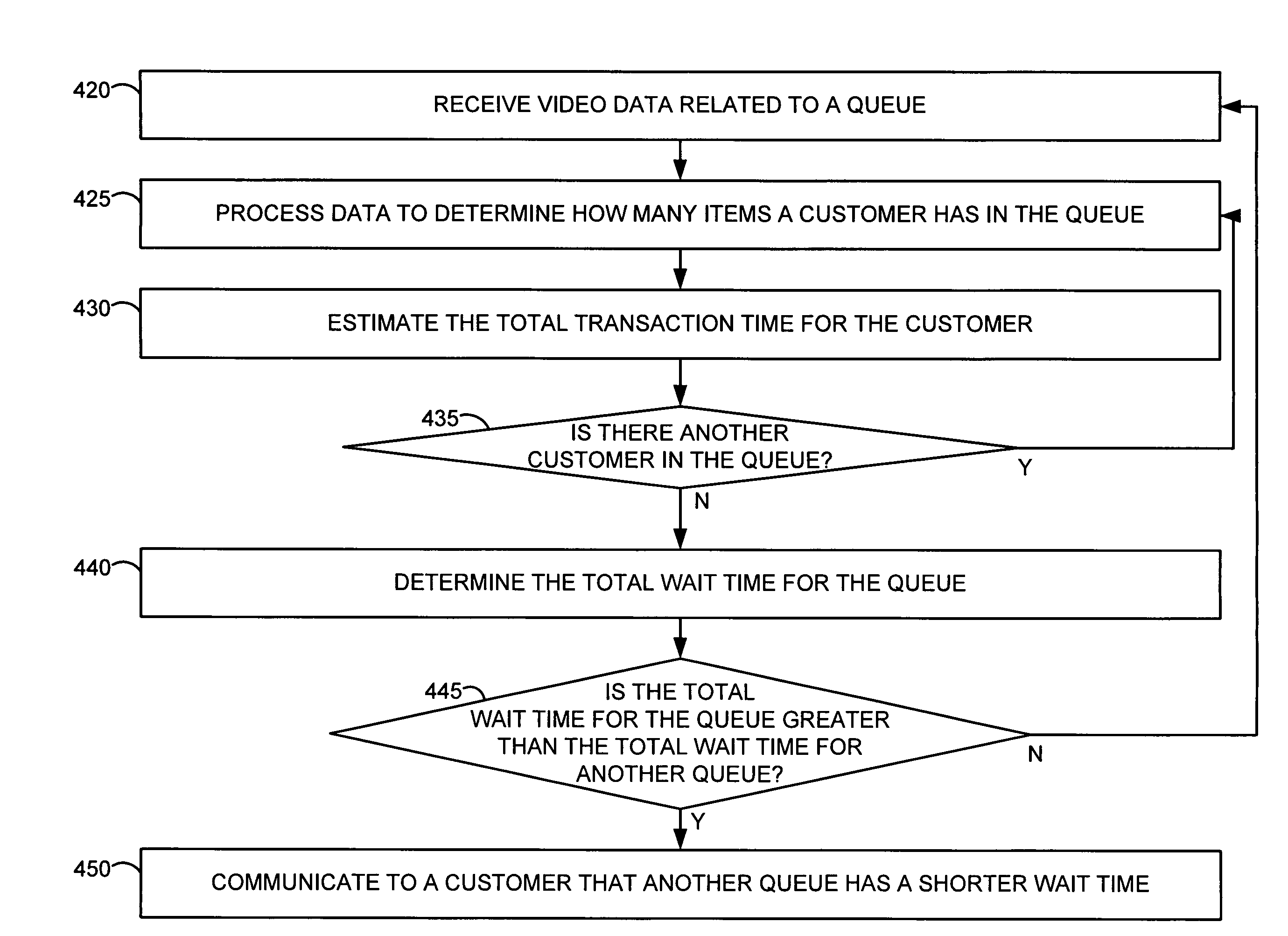
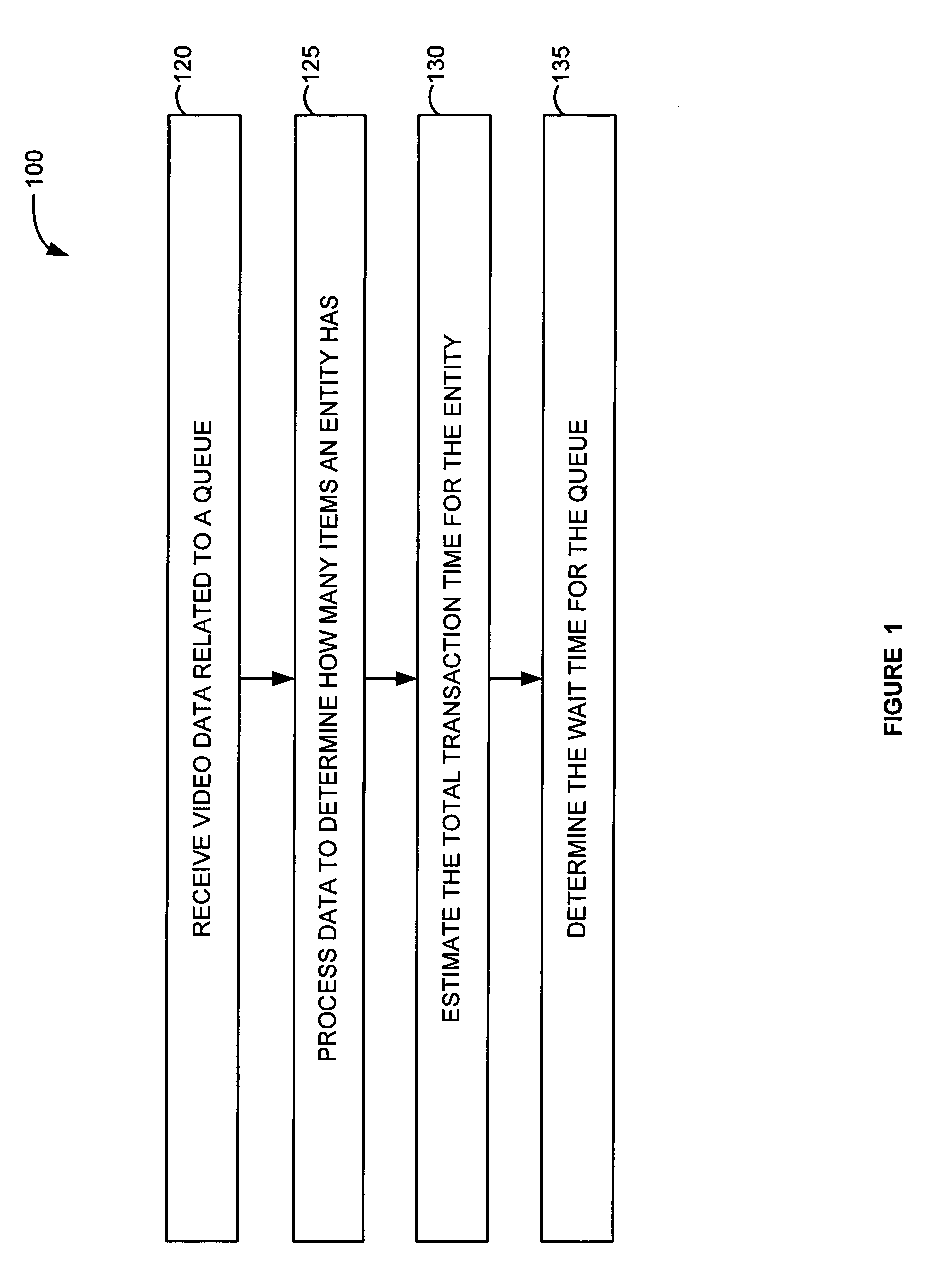
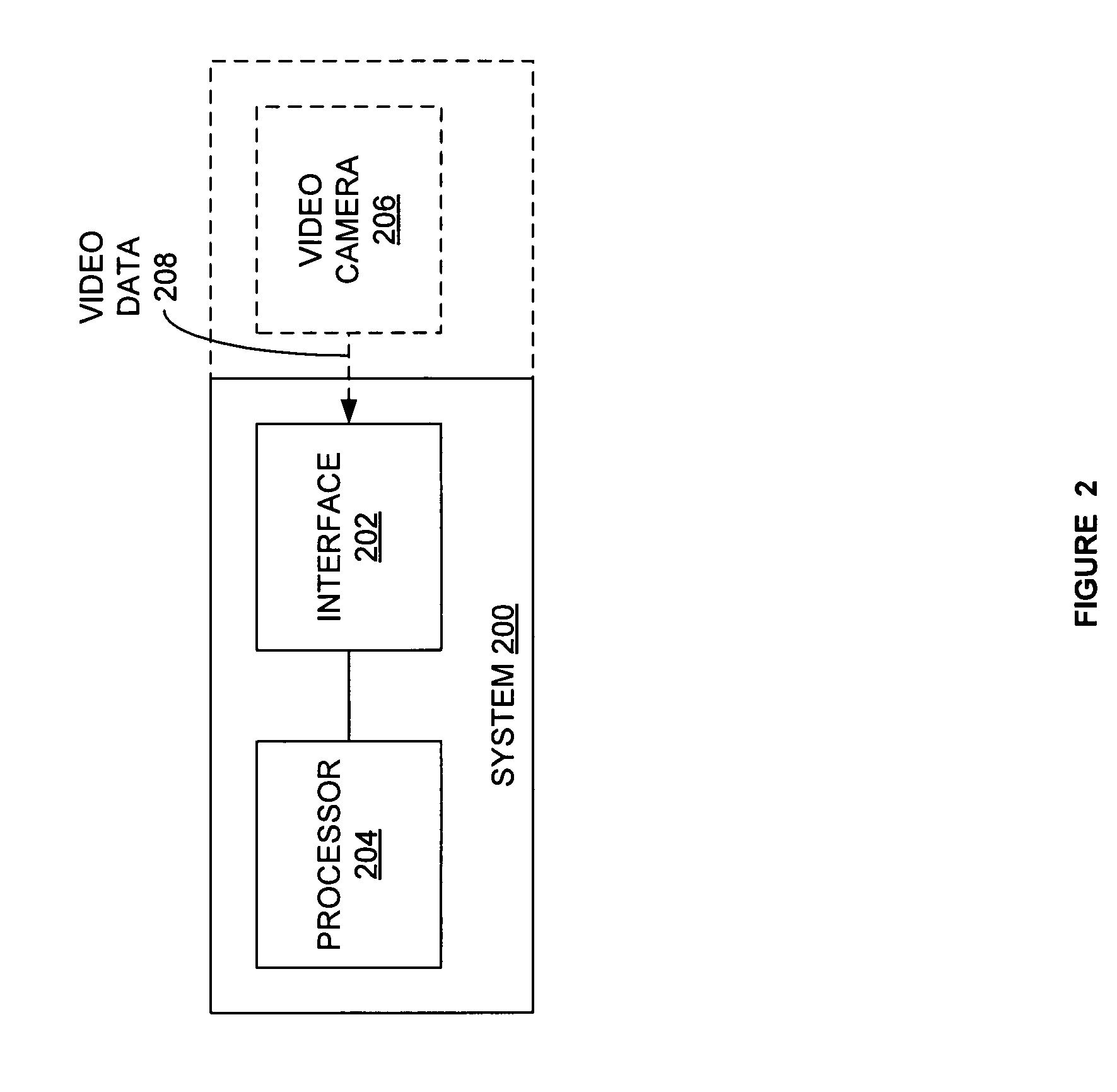
Systems and methods for transaction queue analysis
A method and system for determining a wait time for a transaction queue is disclosed. In the method, video data related to a first transaction queue is received. The video data is processed to determine a number of items presented by a first entity for a transaction in the first transaction queue. A total transaction time is estimated for the first entity based on the number of items presented by the first entity and a transaction time for each of the number of items. A wait time for the first transaction queue is determined based on the estimated total transaction time for the first entity. If the wait time for the first transaction queue is greater than a first threshold, then the availability of a second transaction queue is indicated to a second entity.
Owner:VERINT SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com