Patents
Literature
32results about How to "Reduce certification costs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
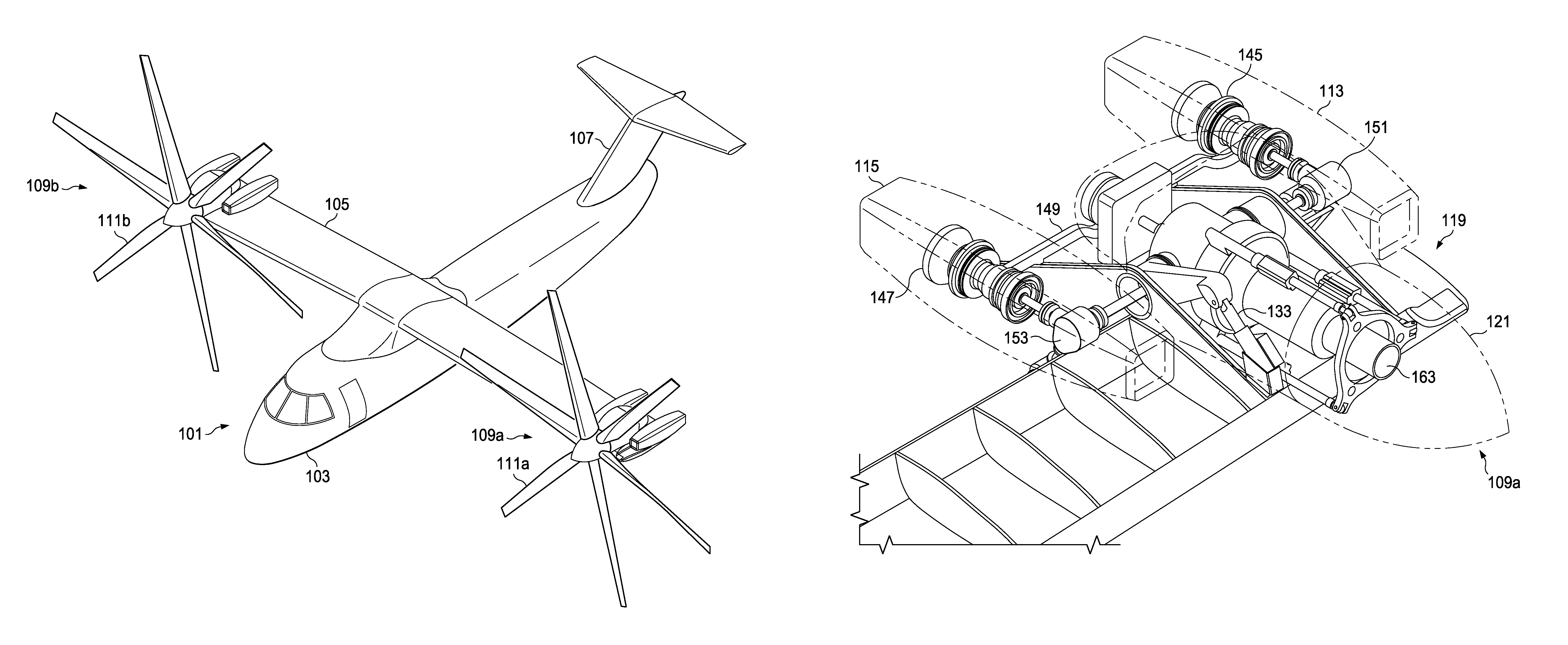
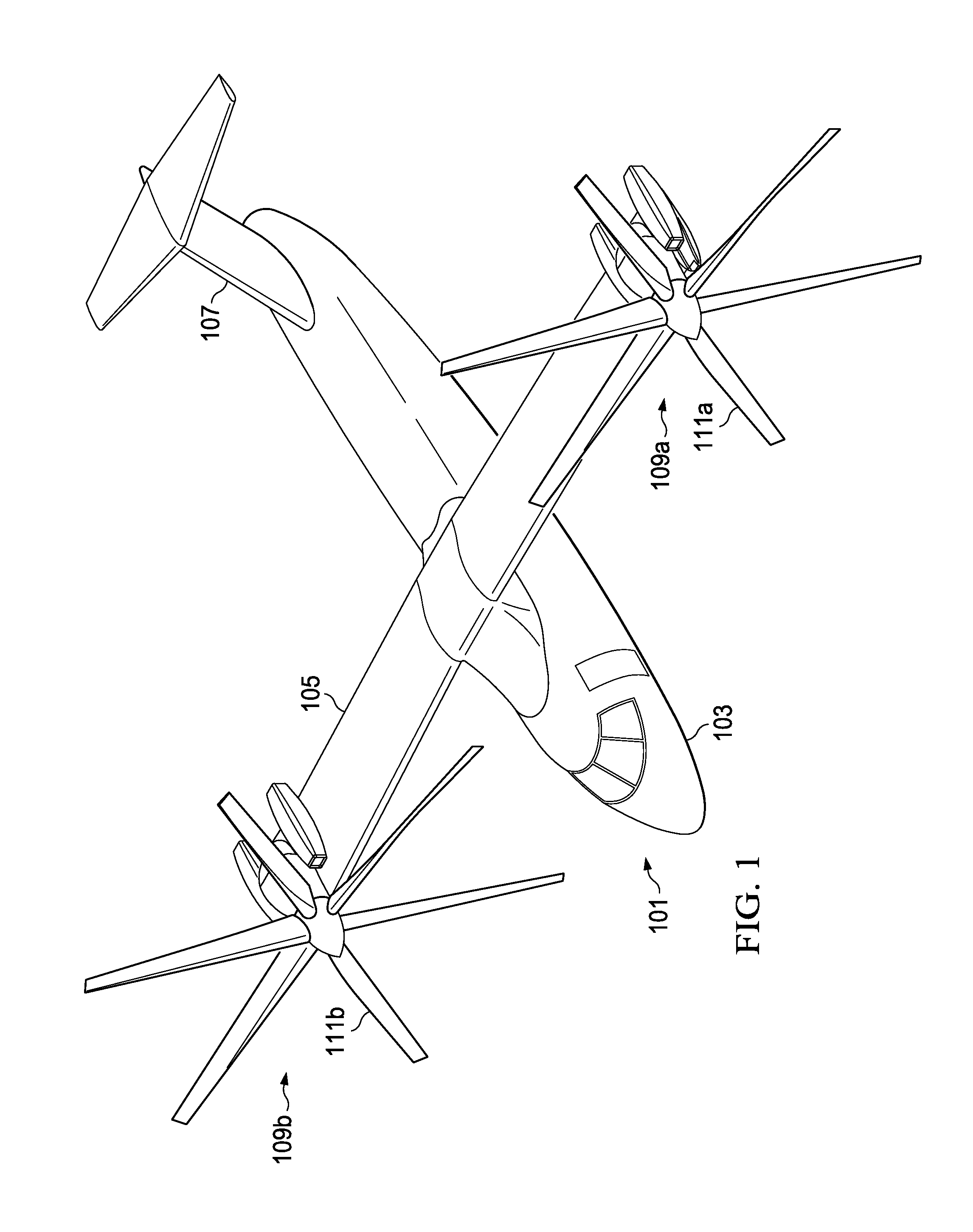
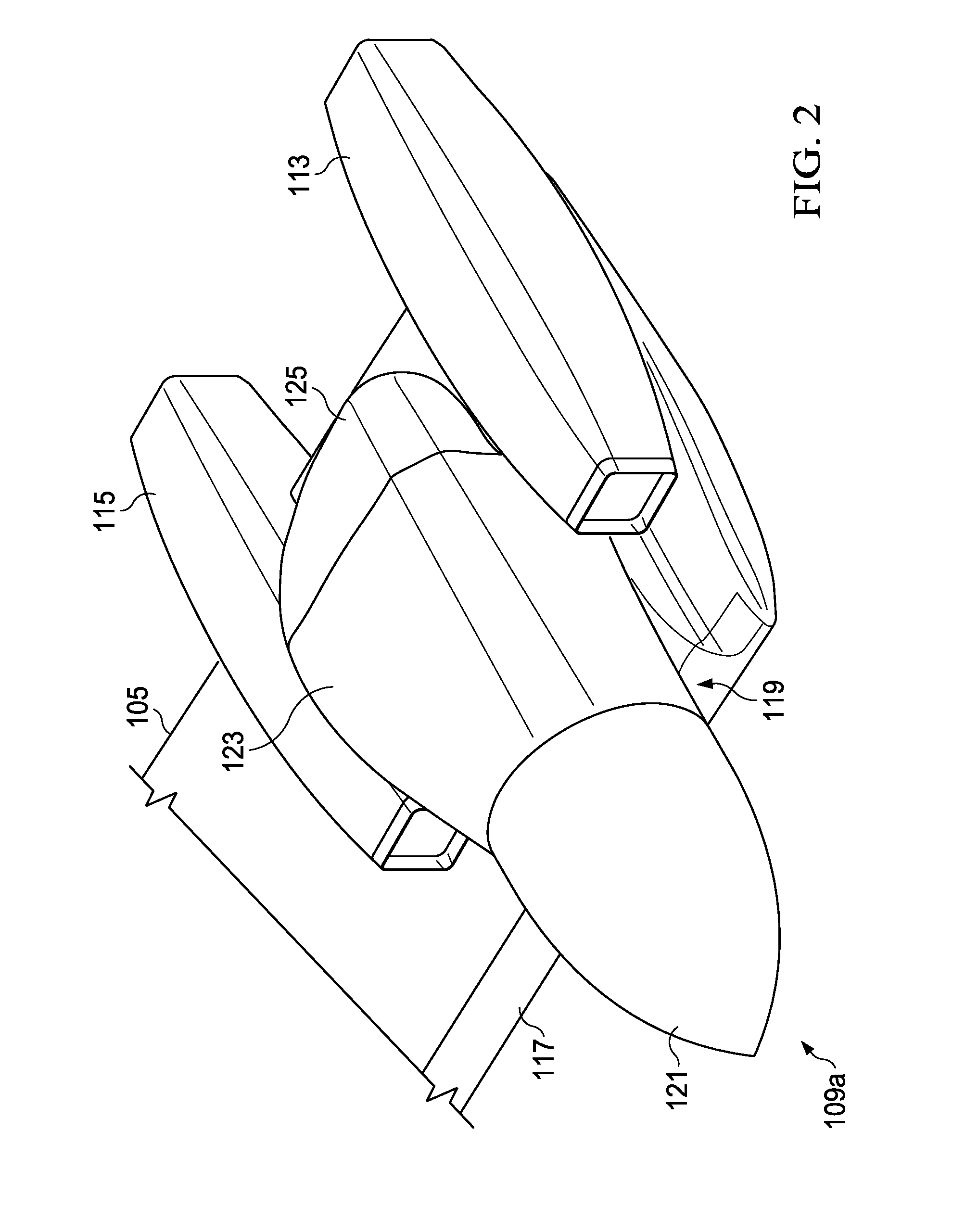
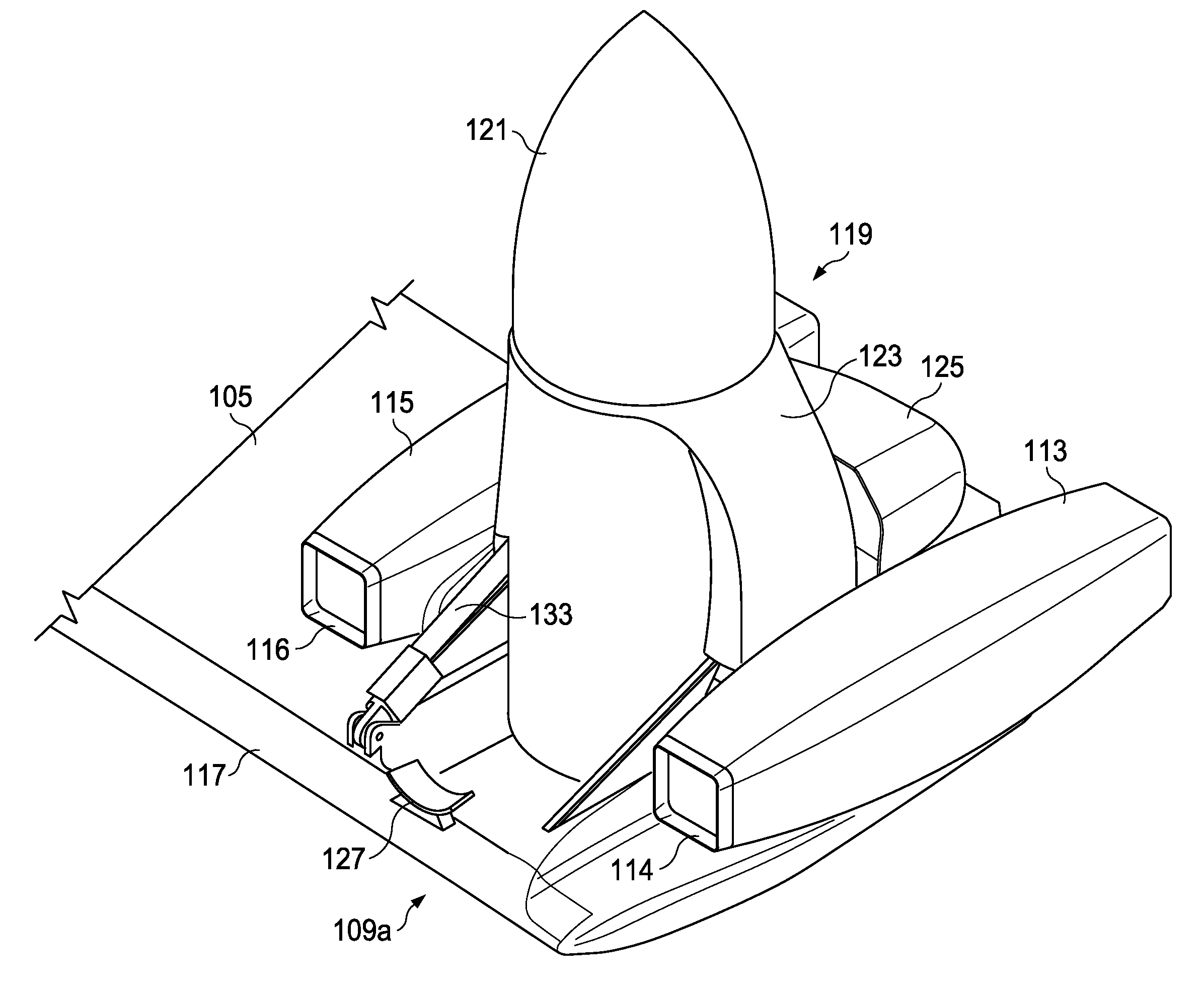
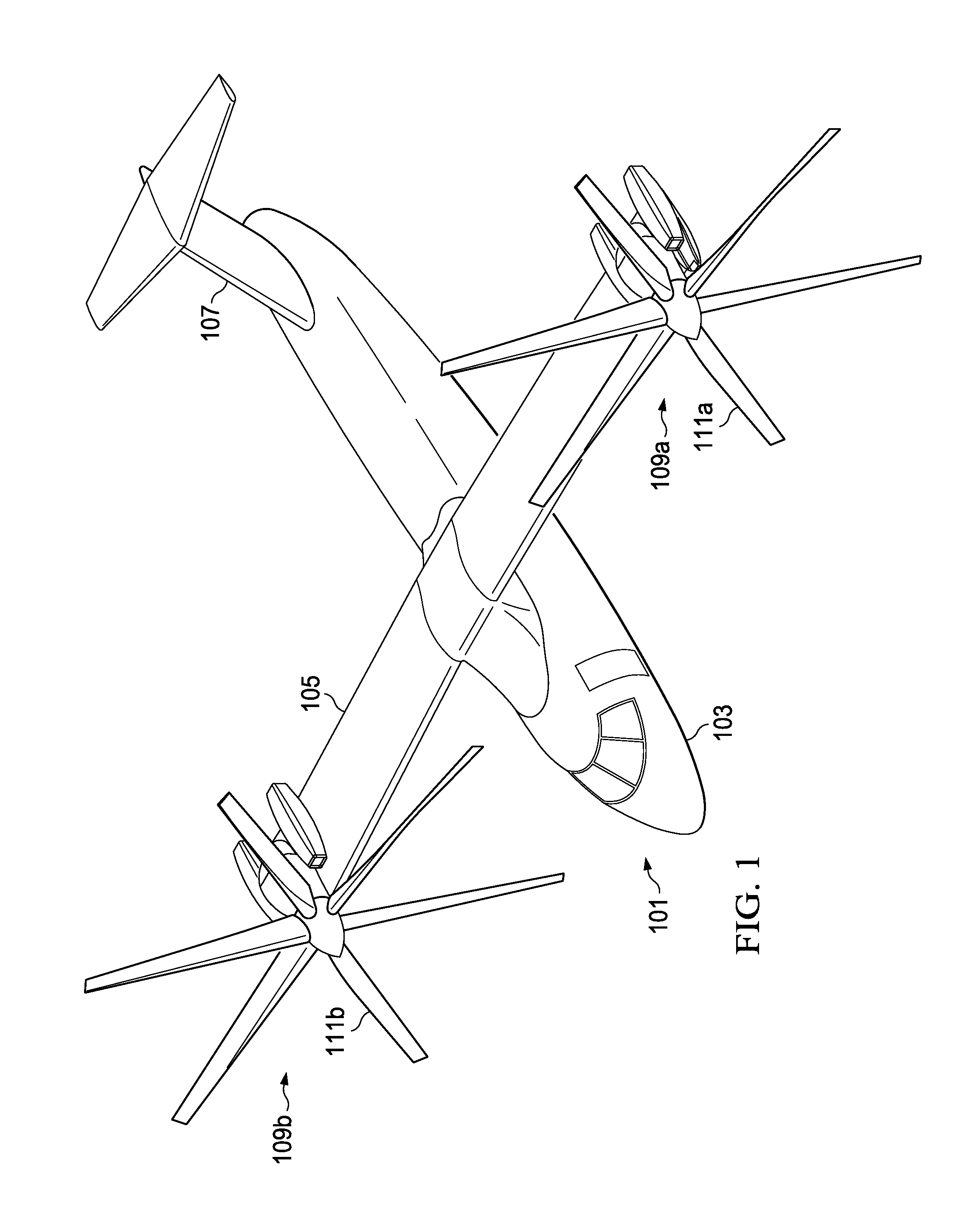
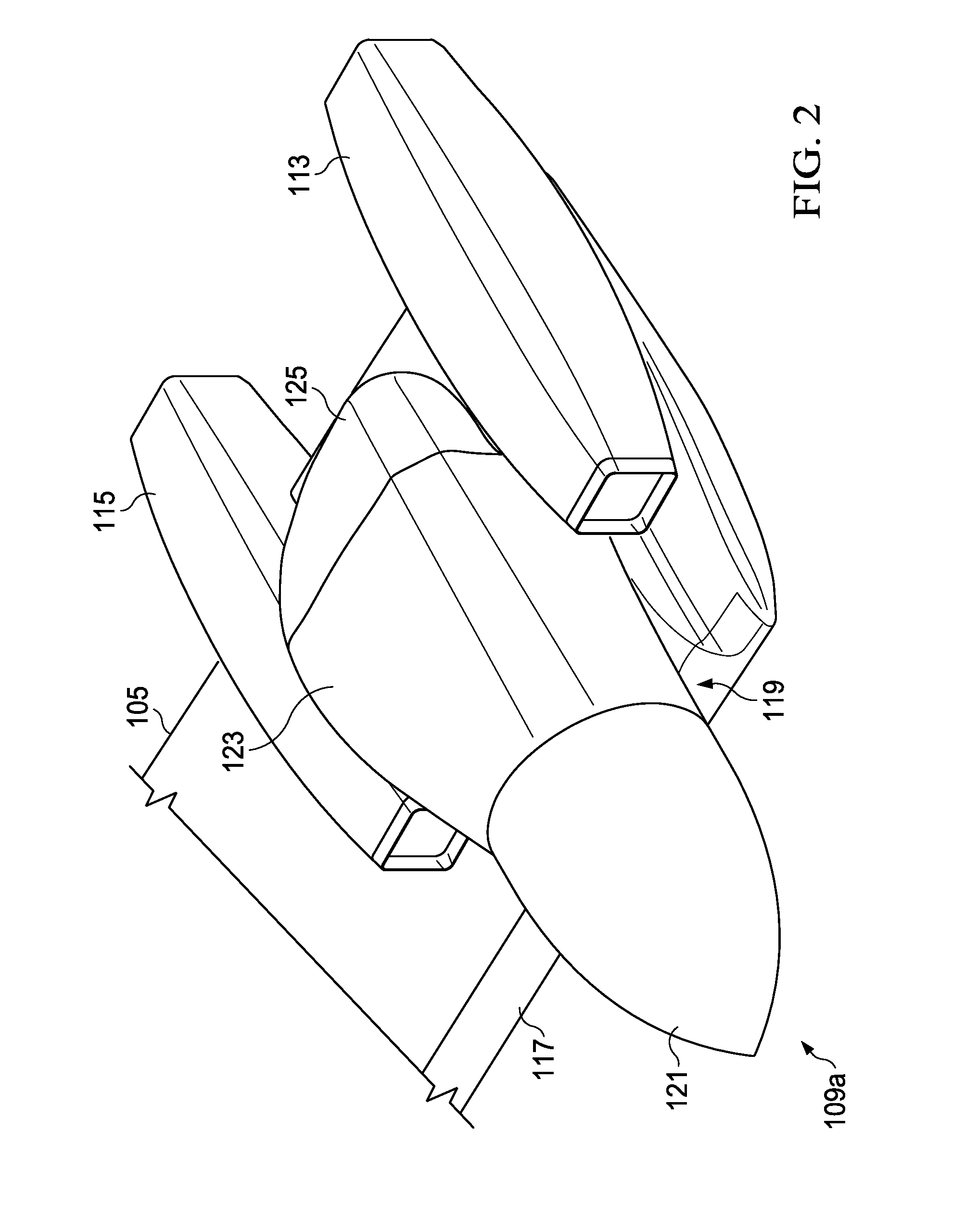
Tilt rotor aircraft with fixed engine arrangement
ActiveUS8602347B2Reduce certification costsIncrease choiceAircraft power plant componentsDepending on number of power plantsEngineeringRotary wing
The system of the present application includes an engine and pylon arrangement for a tilt rotor aircraft in which the engine is fixed in relation to a wing portion of the aircraft, while the pylon is rotatable. The pylon supports a rotor hub having a plurality of rotor blades. Rotation of the pylon allows the aircraft to selectively fly in a helicopter mode and an airplane mode, as well as any combination thereof.
Owner:TEXTRON INNOVATIONS
Tilt Rotor Aircraft with Fixed Engine Arrangement
ActiveUS20120199699A1Reduce certification costsIncrease choiceAircraft power plant componentsDepending on number of power plantsAirplane modeAirplane
The system of the present application includes an engine and pylon arrangement for a tilt rotor aircraft in which the engine is fixed in relation to a wing portion of the aircraft, while the pylon is rotatable. The pylon supports a rotor hub having a plurality of rotor blades. Rotation of the pylon allows the aircraft to selectively fly in a helicopter mode and an airplane mode, as well as any combination thereof.
Owner:TEXTRON INNOVATIONS
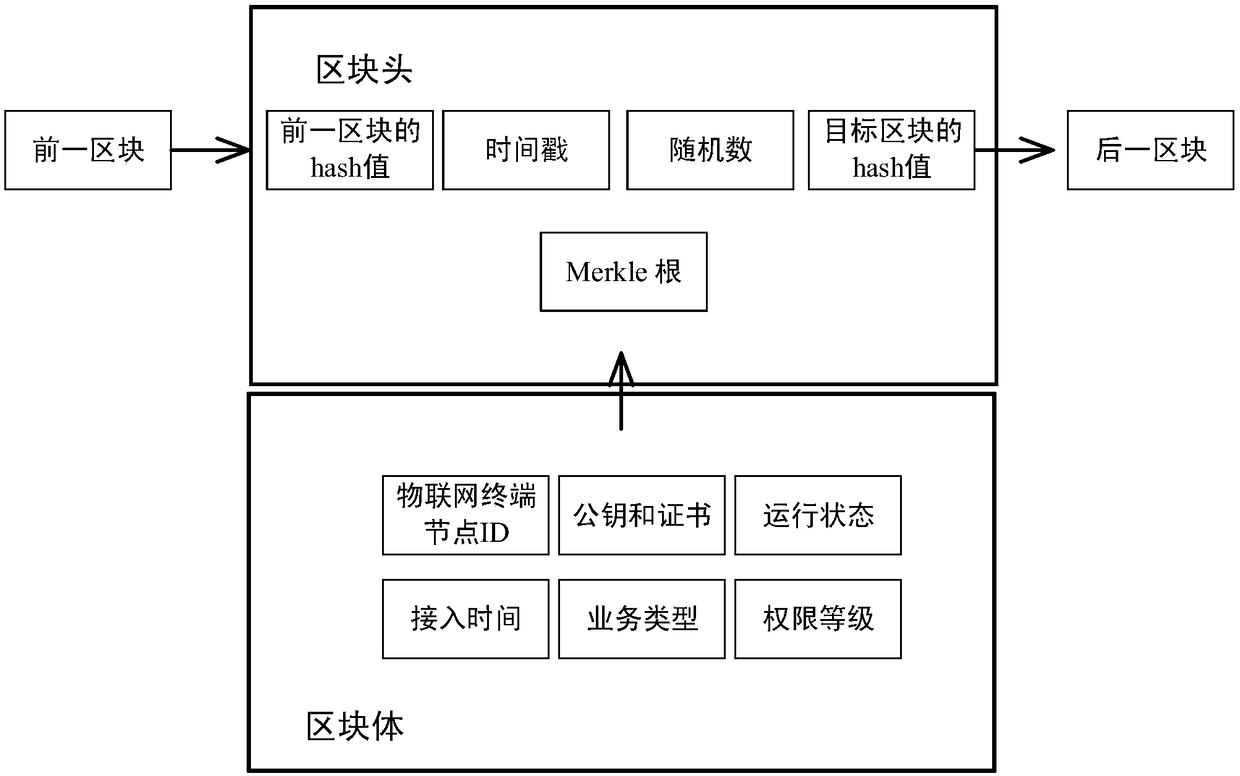
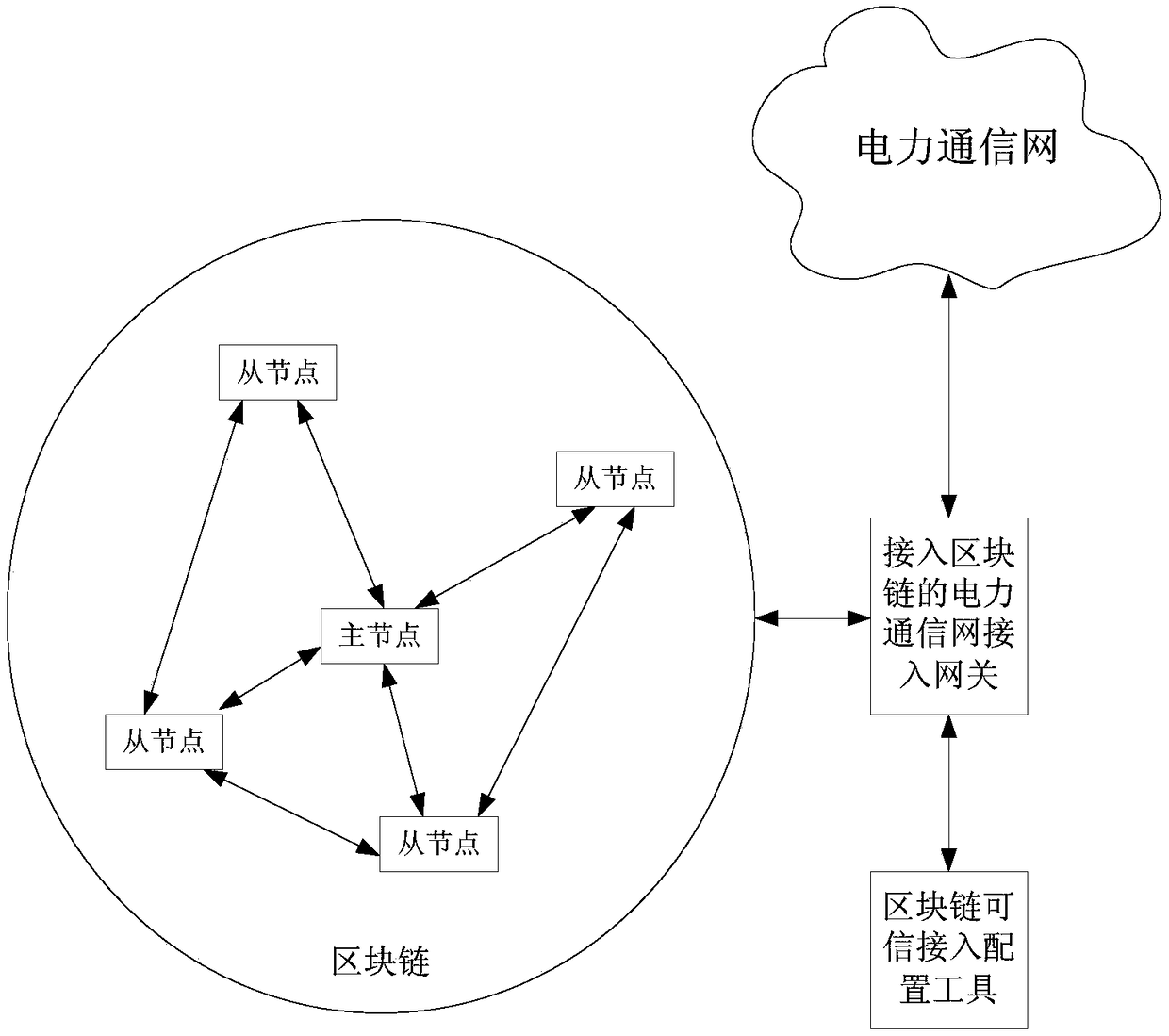
Block chain-based method for accessing power Internet of Things terminal
InactiveCN109495516AReduce communication pressureReduce computing pressureKey distribution for secure communicationUser identity/authority verificationAccess methodCiphertext
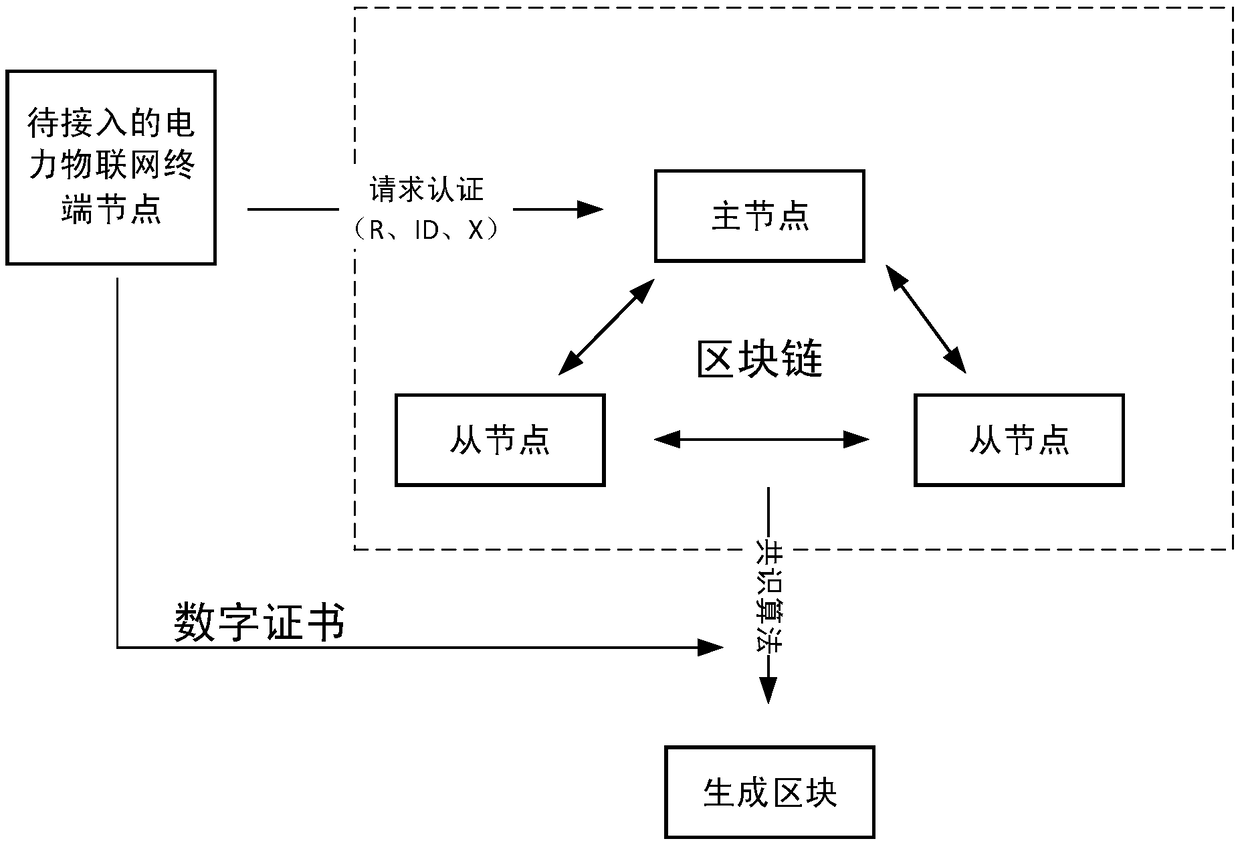
The invention provides a Block chain-based method for accessing a power Internet of Things terminal, comprising the steps of: connecting a to-be-accessed power Internet of Things terminal to a masternode, and initiating an authentication request; the master node responding to the authentication request, and randomly selecting nodes that meet the condition of a threshold number from the block chain to form an authentication group; encrypting a public key G and an identity ID of the to-be-accessed power Internet of Things terminal by using a private key to obtain a digital signature ciphertextX, and sending the identity ID, a terminal public value R and the digital signature ciphertext X to the master node; the master node encapsulating and sending the authentication request information toa member node of the authentication group; the authentication group running PBFT consensus algorithm, and obtaining an authentication result by performing distributed authentication through two-two exchanging of the authentication information between the nodes of the authentication group; generating a new block in the block chain, and returning confirmation information to the to-be-accessed powerInternet of Things terminal; and the power Internet of Things terminal returning encrypted confirmation information to an access gateway. The block chain-based power Internet of Things terminal access method can improve the security and efficiency of authentication.
Owner:JIANGSU ELECTRIC POWER CO
System and method for strong authentication of internet of things equipment and related devices
ActiveCN105827573AImprove work efficiencyReduce certification costsTransmissionInternet of ThingsStrong authentication
The invention provides a system and a method for strong authentication of internet of things equipment and related devices. An authorization code is generated by adopting a mode of combining a mobile phone APP client and a simple numeric keyboard and using the internet of things to which internet of things equipment is connected so as to carry out access authentication on the internet of things equipment. On the basis of effectively ensuring the authentication security by using the dynamically generated authorization code, strong authentication of the internet of things equipment can be realized by only inputting the authorization code once into an authentication module installed on the internet of things equipment, the number of operating times of strong authentication of the internet of things equipment is reduced to one, thereby greatly improving the working efficiency. Meanwhile, a recognition sub-module is not required to be additionally increased, and the authentication cost can be effectively reduced.
Owner:CHINA MOBILE GROUP SHANDONG
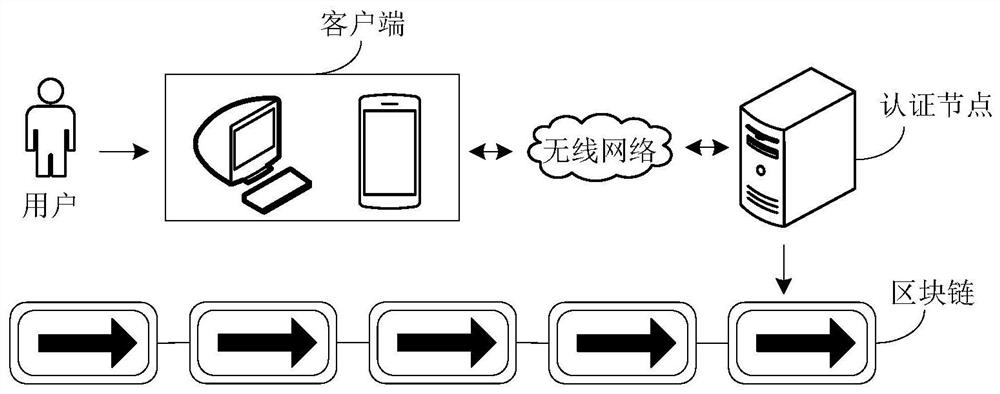
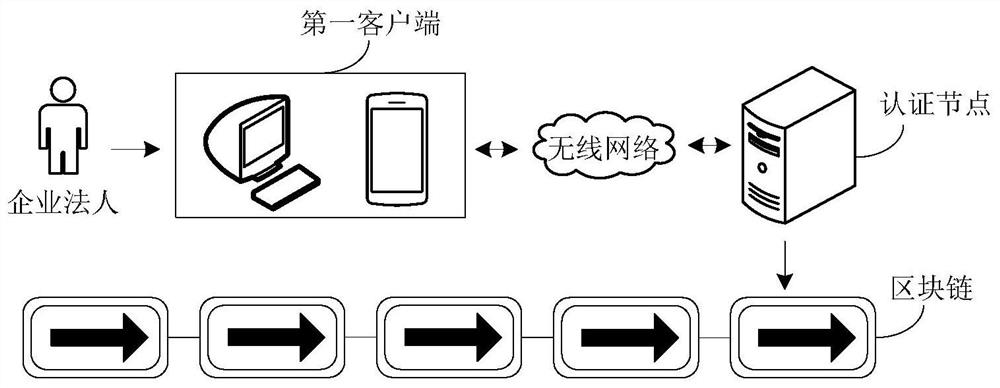
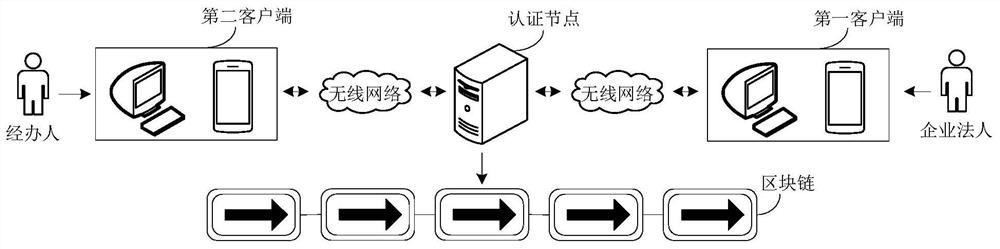
Enterprise authentication and authentication tracing method, device and equipment based on block chain
ActiveCN110336797AThe certification process is transparentGuaranteed to be tamper-proofSecuring communicationTamper resistanceClient-side
One or more embodiments of the present specification provide an enterprise authentication and authentication tracing method, device and equipment based on block chain, the authentication method comprises: receiving an enterprise authentication request sent by a client, the enterprise authentication request comprising to-be-authenticated enterprise information, legal person identity information andauxiliary authentication information; authenticating the identity of the enterprise according to the enterprise information, and authenticating the identity of the enterprise legal person according to the legal person identity information and the auxiliary authentication information; and if the identity authentication of the enterprise is passed and the identity authentication of the enterprise legal person is passed, generating an enterprise authentication record, and writing the enterprise authentication record into the block chain. According to the embodiment of the invention, based on thetrusted execution environment of the block chain, the authentication process of the enterprise is transparent and visible in multiple directions, the credibility and notarization of the authentication process of the enterprise are realized, the authentication result is linked, and the tamper resistance and judicial effectiveness of the authentication result and the traceability of the authentication process of the enterprise are ensured.
Owner:ADVANCED NEW TECH CO LTD
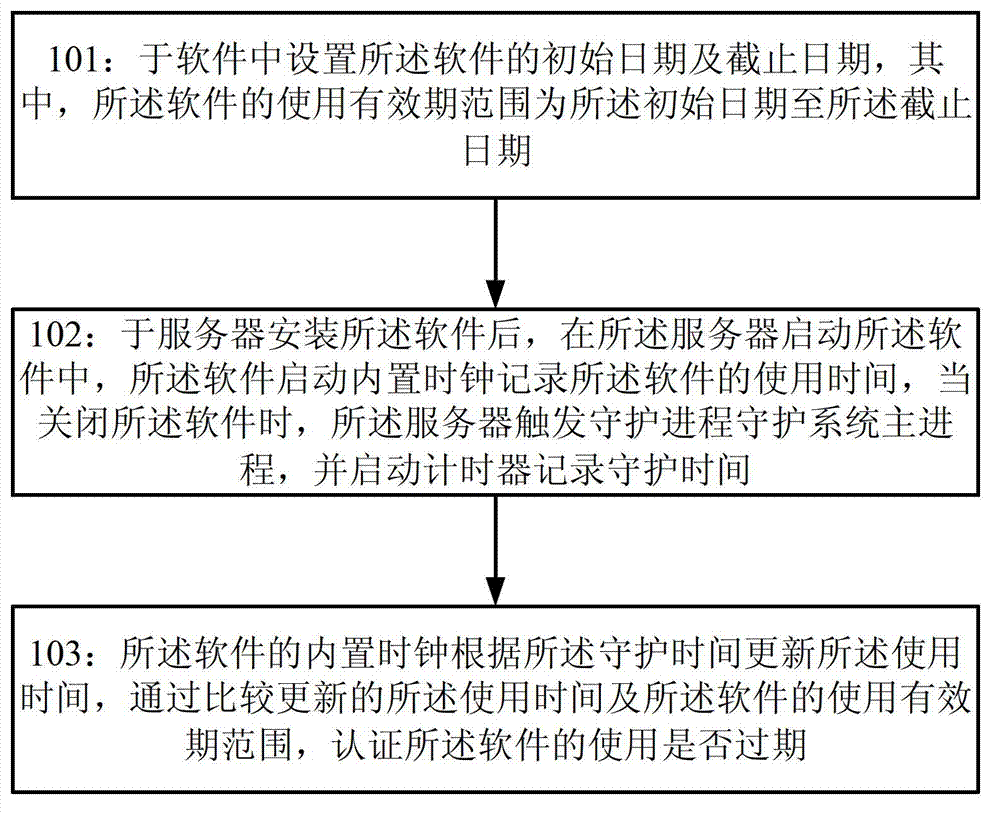
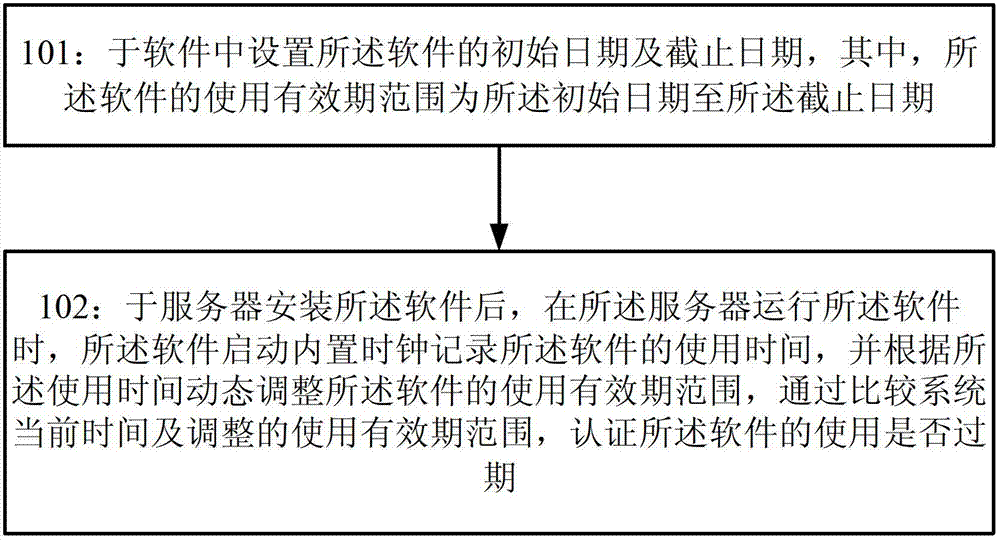
Control method and system for period of validity of software
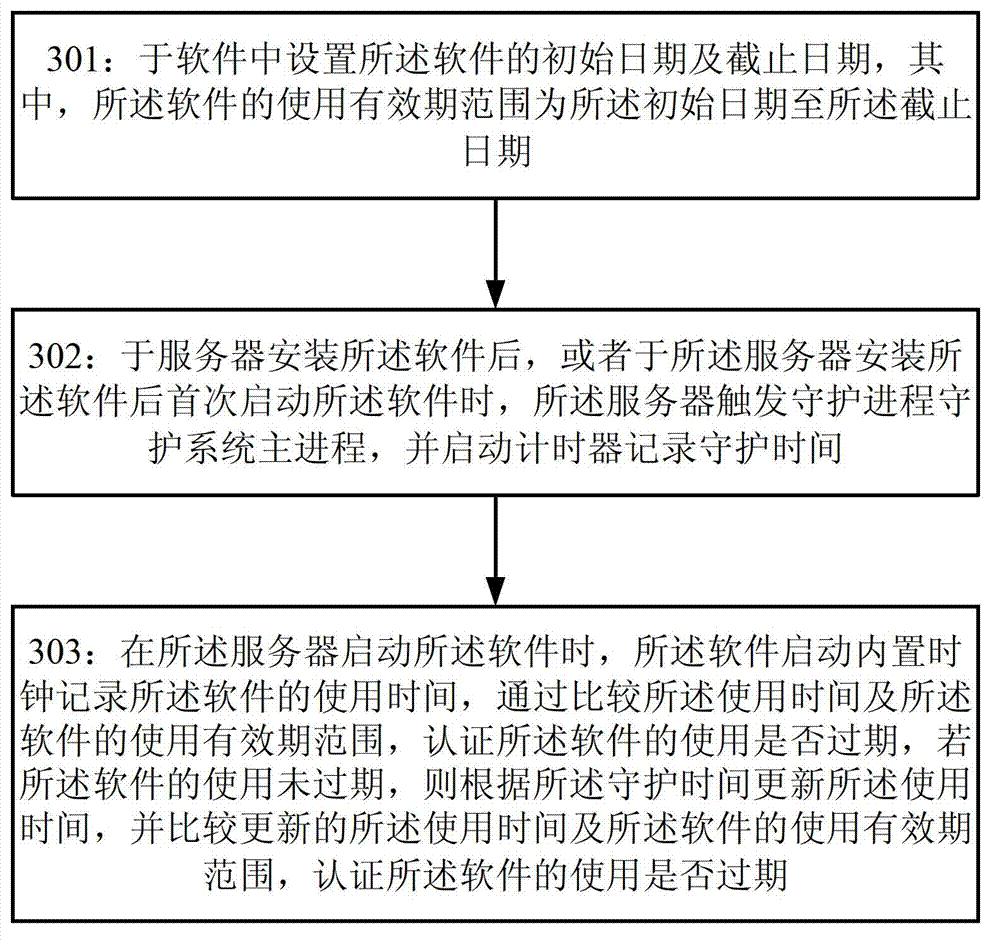
InactiveCN102779258AGuaranteed accuracyImprove reliabilityComputer security arrangementsSoftware engineeringTimer
The invention provides a control method and system for a period of validity of software. The method comprises the following steps of: setting an initial date and an expiration date of the software in the software, wherein the period of validity of the software ranges from the initial date to the expiration date; after installing the software in a server and when the server starts the software, starting a built-in clock by the software to record the service life of the software, triggering a guard process to guard a system main process when the software is closed, and starting a timer to record the guard time; updating the service time according to the guard time by the built-in clock of the software, and comparing the updated service time with the period of validity of the software to confirm whether the usage of the software expires.
Owner:SUZHOU CODYY NETWORK SCI & TECH
Cloud security authentication method and authentication device
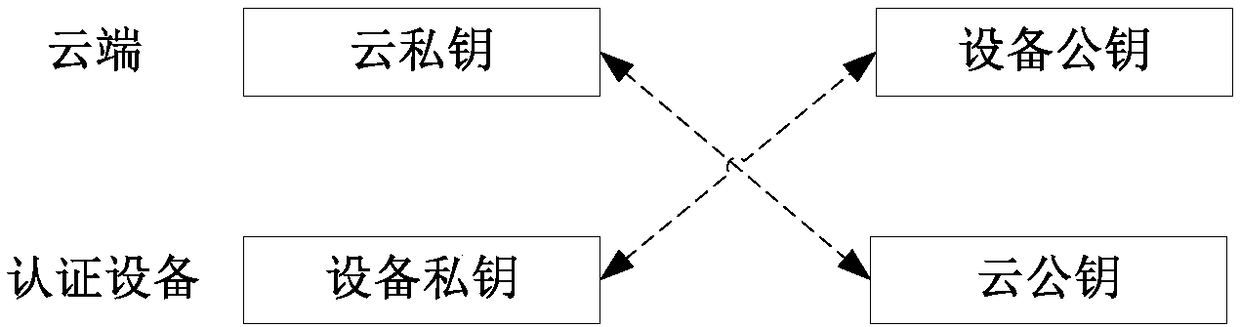
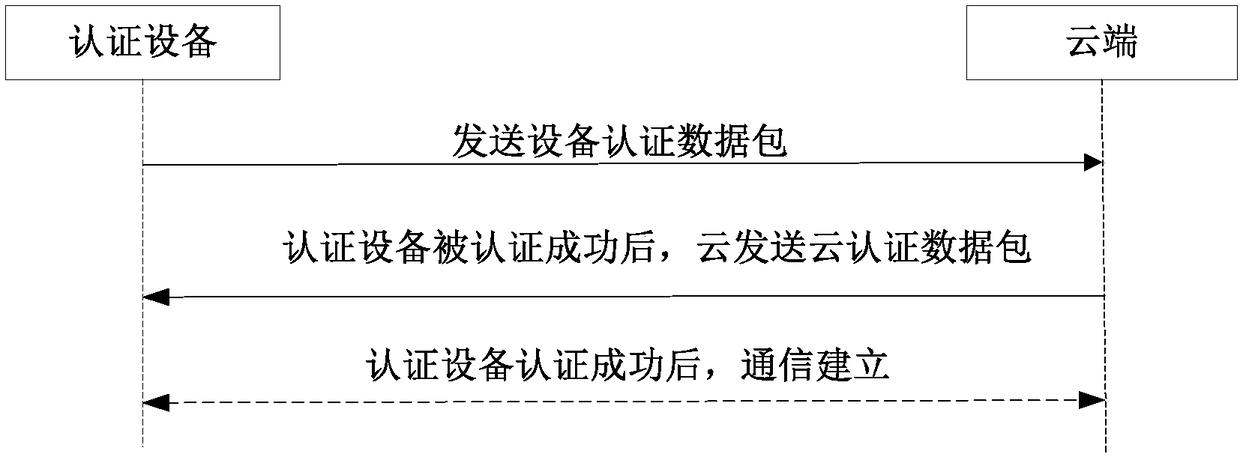
InactiveCN108134783ANo cost increaseImprove securityKey distribution for secure communicationUser identity/authority verificationNetwork packetSecurity authentication
The invention provides a cloud security authentication method, comprising a cloud authentication step that an authentication device carries out signature through utilization of a device private key stored in the authentication device, thereby obtaining a device authentication data packet, the authentication device sends the device authentication data packet to the cloud, and a cloud receives the device authentication data packet and then carries out signature authentication on the device authentication data packet through utilization of a device public key stored in the cloud; and an authentication device authentication step that a cloud device carries out signature through unitization of a cloud private key stored in the cloud, thereby obtaining a cloud authentication data packet, the cloud sends the cloud authentication data packet to the authentication device, and the authentication device receives the cloud authentication data packet and then carries out signature authentication through utilization of a cloud public key stored in the authentication device. The invention also relates to the cloud security authentication device. According to the method and the device, the deviceauthentication security is improved, moreover, the authentication cost is low, and the hardware cost does not need to be increased.
Owner:HANGZHOU BROADLINK ELECTRONICS TECH
A cloud security fast distribution network method and distribution network system
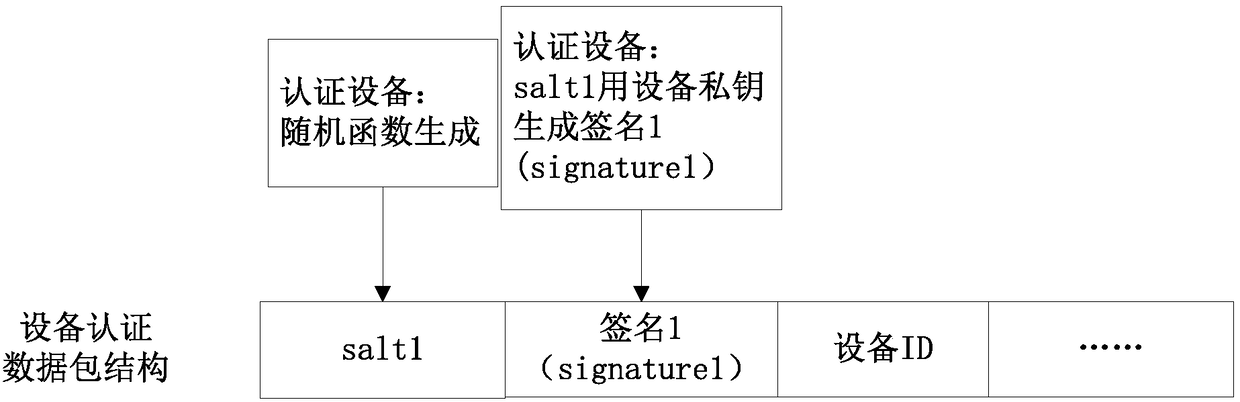
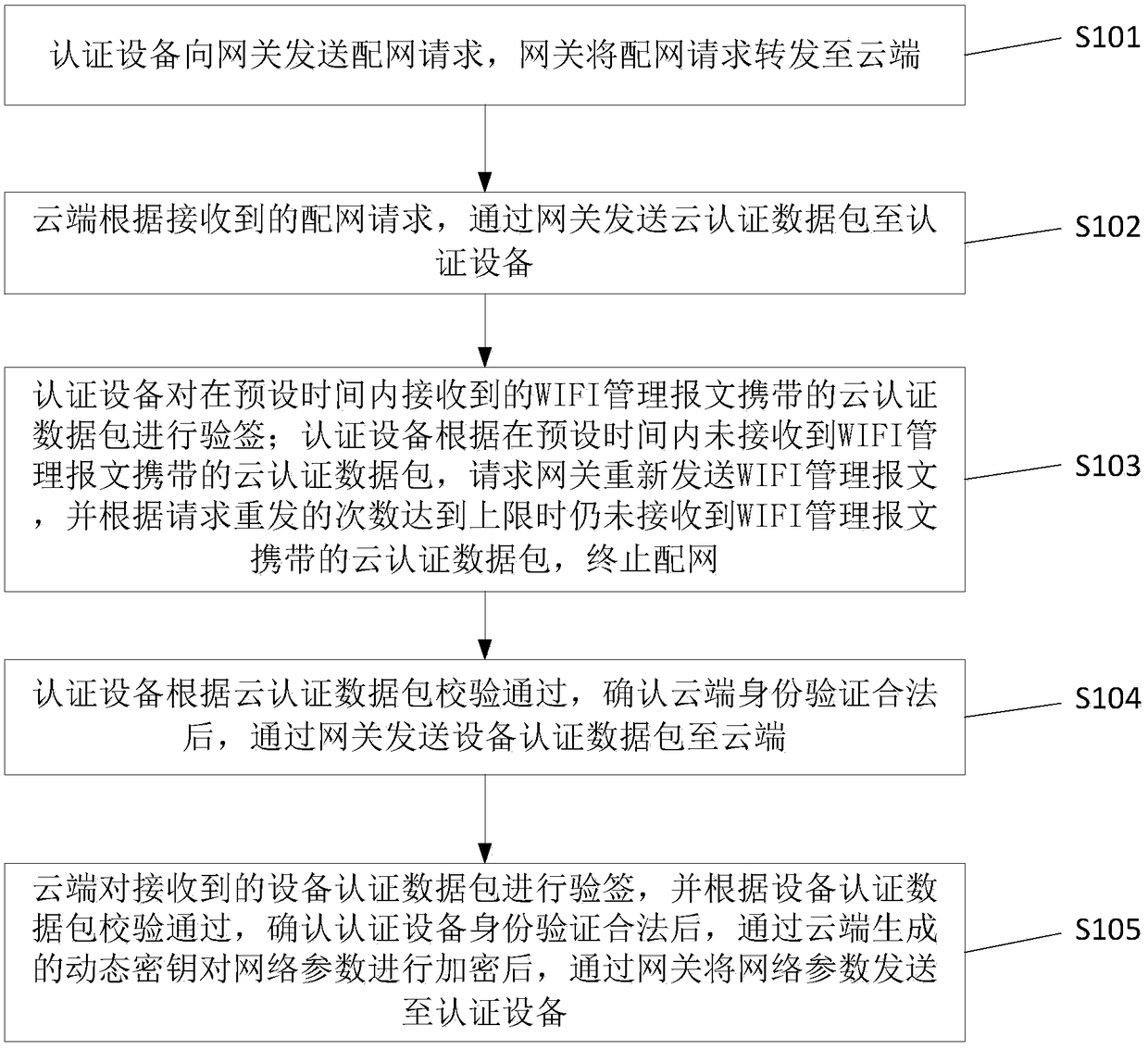
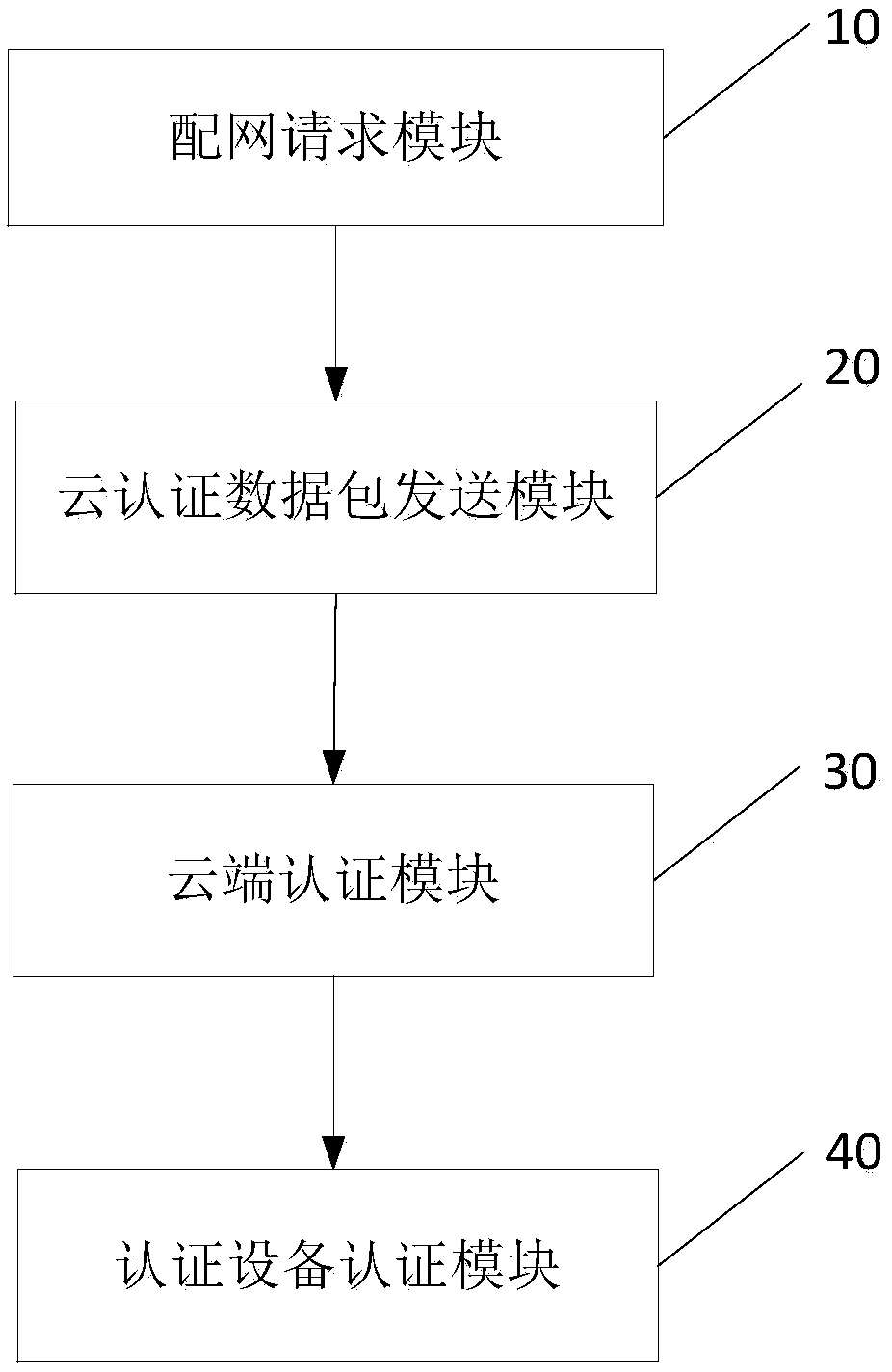
InactiveCN109005537AStrong signalImprove securityUser identity/authority verificationSecurity arrangementNetwork packetKey authentication
The invention discloses a cloud safe and fast distribution network method and a distribution network system. The method comprises the following steps: an authentication device sends a distribution network request to a gateway, and the gateway forwards the distribution network request to a cloud end; the cloud end sends the cloud authentication data packet to the authentication device through the gateway according to the received distribution network request; the authentication device checks and signs the received cloud authentication data packets, verifies that the cloud authentication is legal according to the cloud authentication data packets, and sends the device authentication data packets to the cloud through the gateway after verifying that the cloud authentication is legal; the cloud end checks and signs the received equipment authentication data packets, and sends the network parameters to the authentication device through the gateway after verifying that the authentication device is legal according to the equipment authentication data packets; device authentication packets and cloud authentication packets are carried by WIFI management messages. The invention realizes two-way identity authentication, dynamic key authentication and extreme speed distribution network, greatly improves safety and convenience, and improves user experience.
Owner:HANGZHOU BROADLINK ELECTRONICS TECH
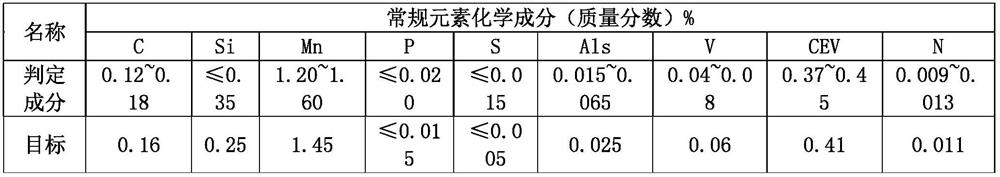
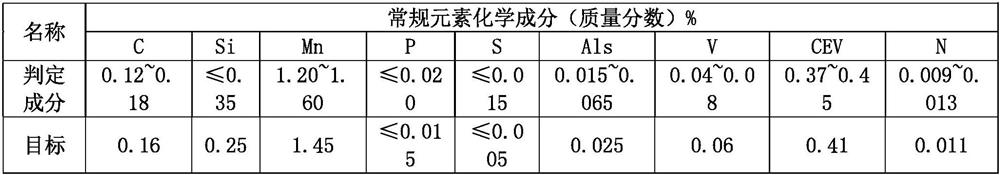
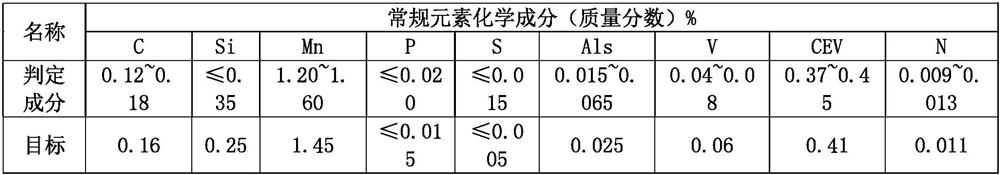
RH nitrogen-blowing alloying process capable of accurately controlling nitrogen content of nitrogen-containing steel grade
ActiveCN112899440AImprove hit rateReduce manufacturing costManufacturing convertersProcess efficiency improvementVacuum pumpingNitrogen gas
The invention discloses an RH nitrogen-blowing alloying process capable of accurately controlling the nitrogen content of a nitrogen-containing steel grade. The RH nitrogen-blowing alloying process capable of accurately controlling the nitrogen content of the nitrogen-containing steel grade comprises the following steps: desulfurized molten iron and scrap steel are smelted in a converter, oxygen is blown from the top, and nitrogen is blown from the bottom; LF refining and RH vacuum refining are sequentially carried out on molten steel, a mechanical pump vacuum system is adopted for RH, specifically, argon / nitrogen switching is carried out on RH circulation gas, the nitrogen flow is 90-150 Nm<3> / h, the nitrogen pressure is 1.0-1.8 Mpa, RH vacuum air-pumping is carried out, the pressure is reduced to 273 Pa or below from atmospheric pressure, and RH air-pumping lasts for 5-10 min; temperature measurement and sampling are carried out, and the chemical components and the nitrogen component content of the molten steel are analyzed; the component content of the molten steel is adjusted according to the sampling analysis result, the RH vacuum degree is adjusted to 4-15 kpa, nitrogen is rapidly increased in the molten steel, and the average nitrogen increasing amount is 3.0-3.50 ppm / min; and after the molten steel meets the technical requirements of the steel grade, the RH is finished, re-pressing is carried out, a steel ladle is opened for blowing argon from the bottom, and calcium treatment in a metal calcium feeding line is carried out. According to the invention, the nitrogen content fluctuation of the molten steel can be accurately controlled to be + / -5ppm, the technical requirements of the steel grade are met, the quality of the steel grade is ensured, and the production cost is reduced.
Owner:CHONGQING IRON & STEEL CO LTD
Software authentication method and system
InactiveCN102779247AEfficient authenticationImprove experienceComputer security arrangementsTime limitAuthentication
The invention provides a software authentication method and system. The method comprises the following steps of: setting an initial date and a deadline date of software in the software, wherein a utilization validity period range of the software ranges from the initial date to the deadline date; after the software is mounted on a server, recording utilization time of the software by starting an internally-arranged clock through the software when the software is operated by the server; dynamically adjusting the utilization validity period range of the software according to the utilization time; and comparing the current time of the system with the adjusted utilization validity period range to authenticate whether the utilization of the software exceeds the time limit or not.
Owner:SUZHOU CODYY NETWORK SCI & TECH
Distributed power transaction credible identity management method and system, and computer equipment
PendingCN113761497AWide applicabilitySolve the problem of security bottleneckFinanceDatabase distribution/replicationPrivacy protectionFinancial transaction
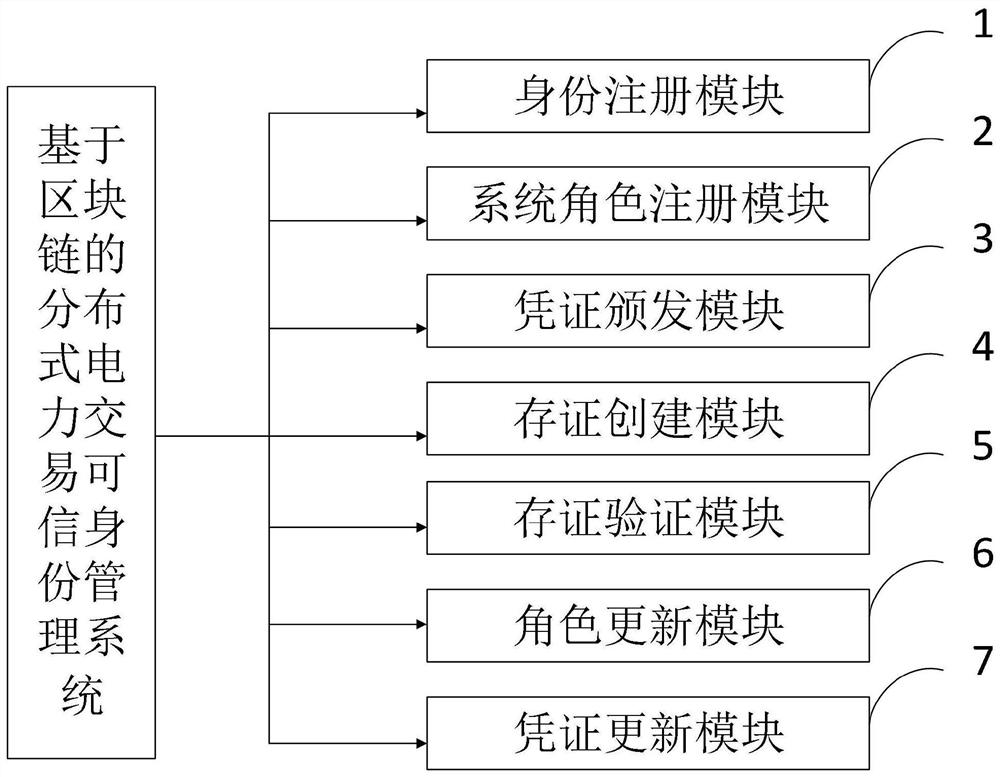
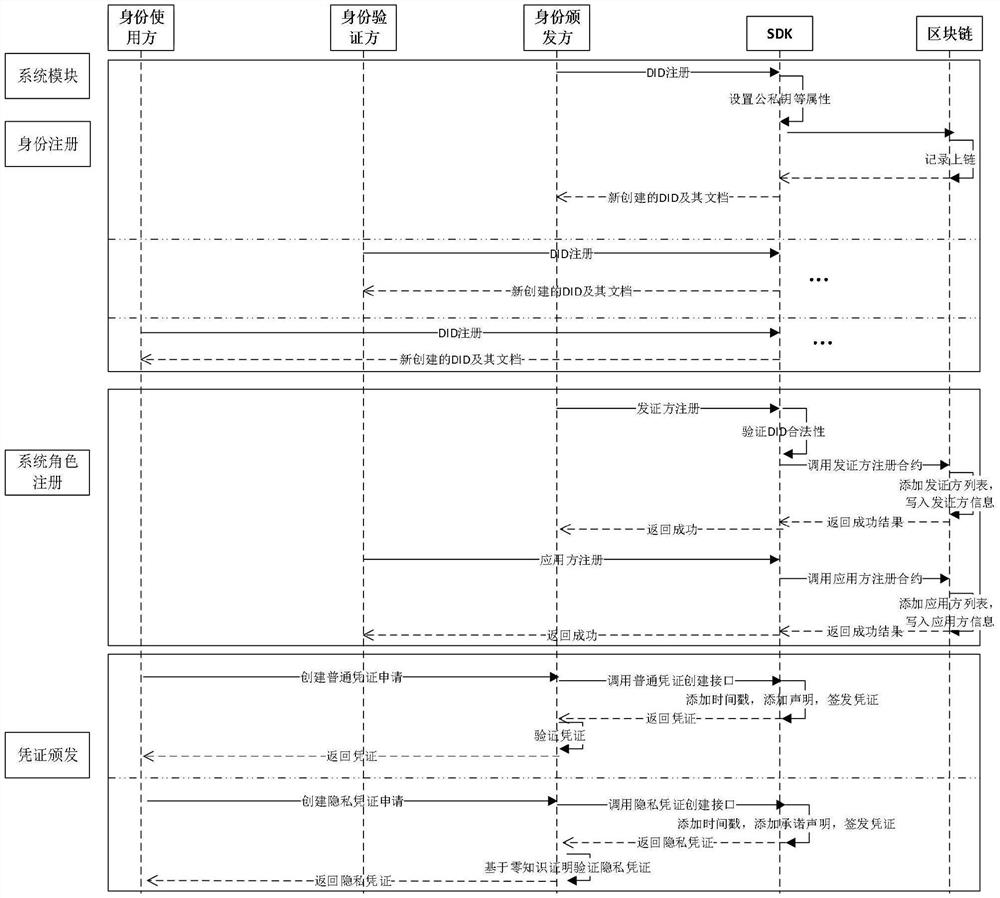
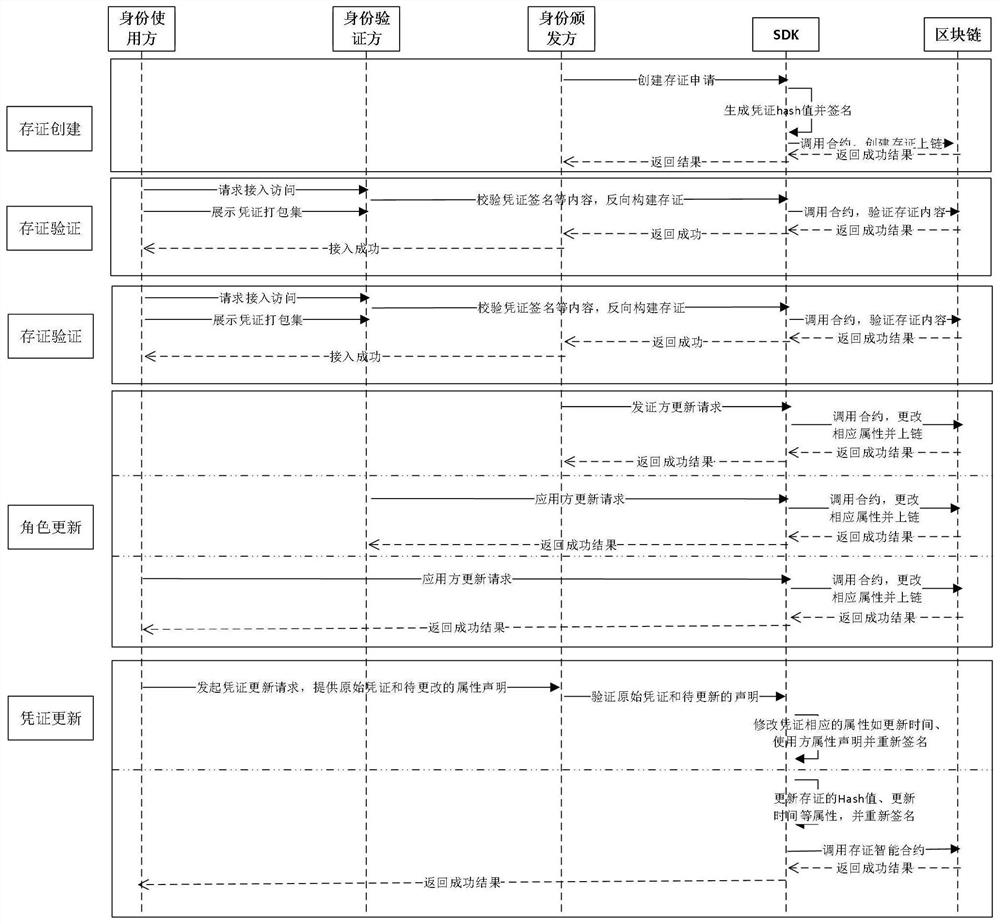
The invention belongs to the technical field of information security, and discloses a distributed power transaction credible identity management method and system, and computer equipment. The distributed power transaction credible identity management system comprises an identity registration module, a system role registration module, a voucher issuing module, a storage certificate creation module, a storage certificate verification module, a role updating module and a voucher updating module. Based on the blockchain, distributed identity identification, verifiable declaration, zero-knowledge proof and other technologies, autonomous control of entity (human, machine and object) identities in a distributed scene is achieved, identity security authentication, authorization and data exchange in a privacy protection state are achieved, and a brand-new, safe and efficient distributed authentication system is provided. Meanwhile, the system provides the capabilities of autonomous identity management, agile access, privacy authentication and the like of the distributed heterogeneous entity, the authentication mode is convenient, and the authentication cost is low.
Owner:INFORMATION COMM COMPANY STATE GRID SHANDONG ELECTRIC POWER +2
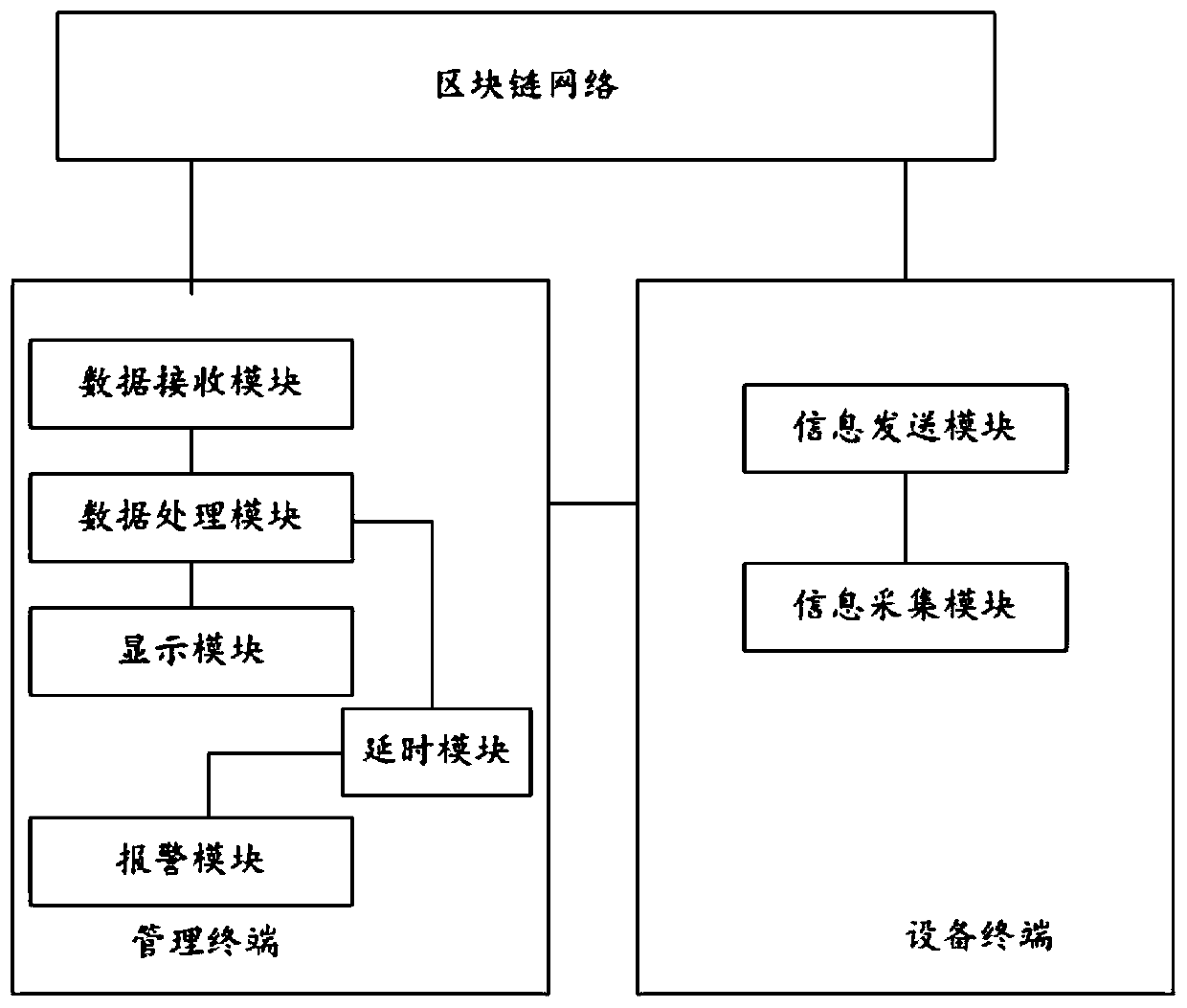
Ubiquitous power Internet of Things intelligent management system
InactiveCN110620820AReduce computing pressureReduce certification costsData switching networksPower gridThe Internet
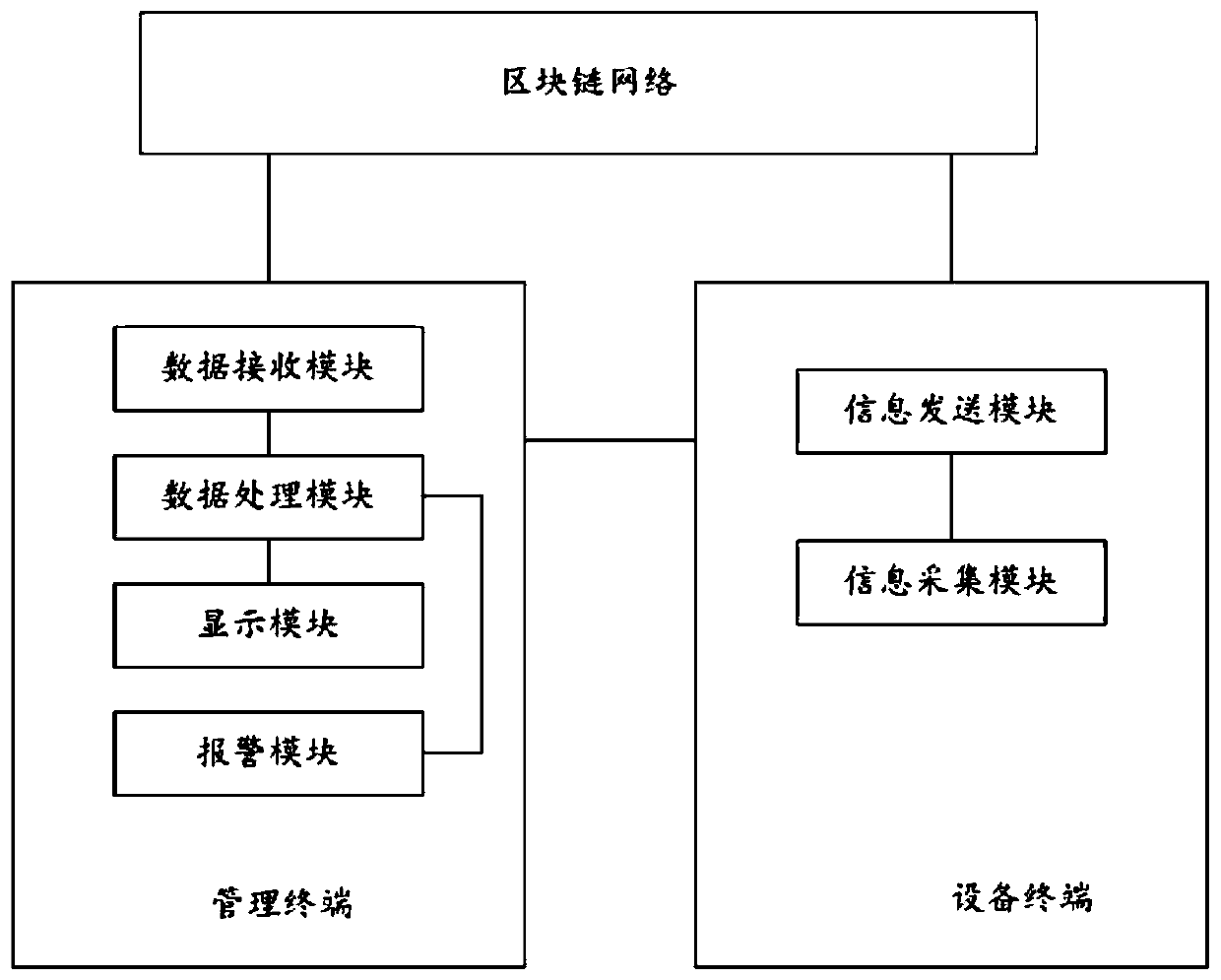
The invention provides a ubiquitous power internet of things intelligent management system. The ubiquitous power internet of things intelligent management system comprises an equipment terminal and amanagement terminal, the equipment terminal is provided with an information acquisition module and an information sending module; the information acquisition module is used for acquiring Internet of Things data of the equipment terminal; and the information sending module is used for sending the Internet of Things data to each node in the blockchain network to judge the legality of the Internet ofThings data, and if the Internet of Things data is legal, writing the Internet of Things data into the management terminal and the blockchain respectively. Internet of Things data is sent to each node in a block chain network to carry out legality judgment of the Internet of Things data; and if the Internet of Things data is legal, writing the Internet of Things data into a management terminal and a block chain to prevent data loss or change, thereby preventing the normal life of people from being influenced by power grid data management breakdown if the terminal fails in a traditional structured center mode, and ensuring the normal operation of a power grid.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
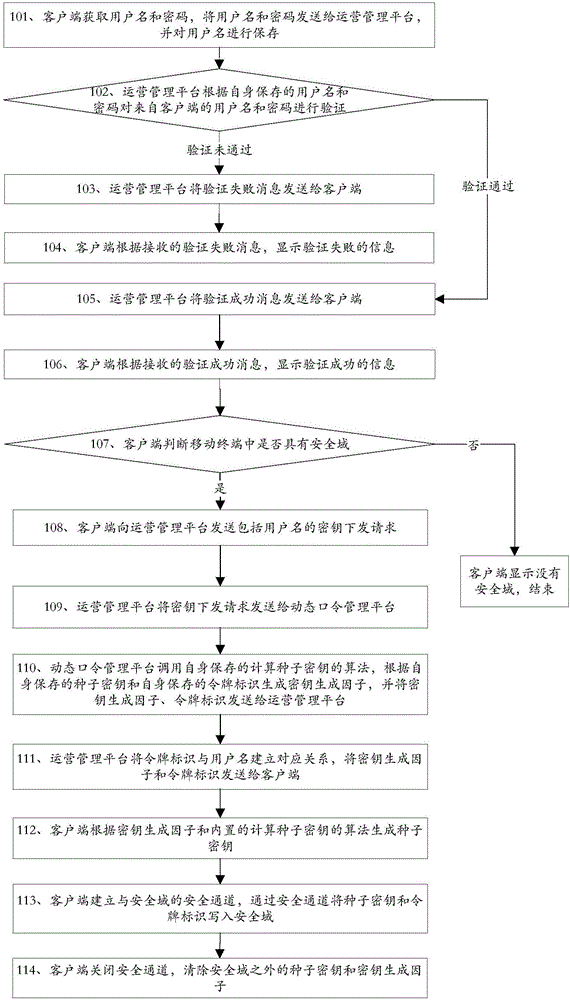
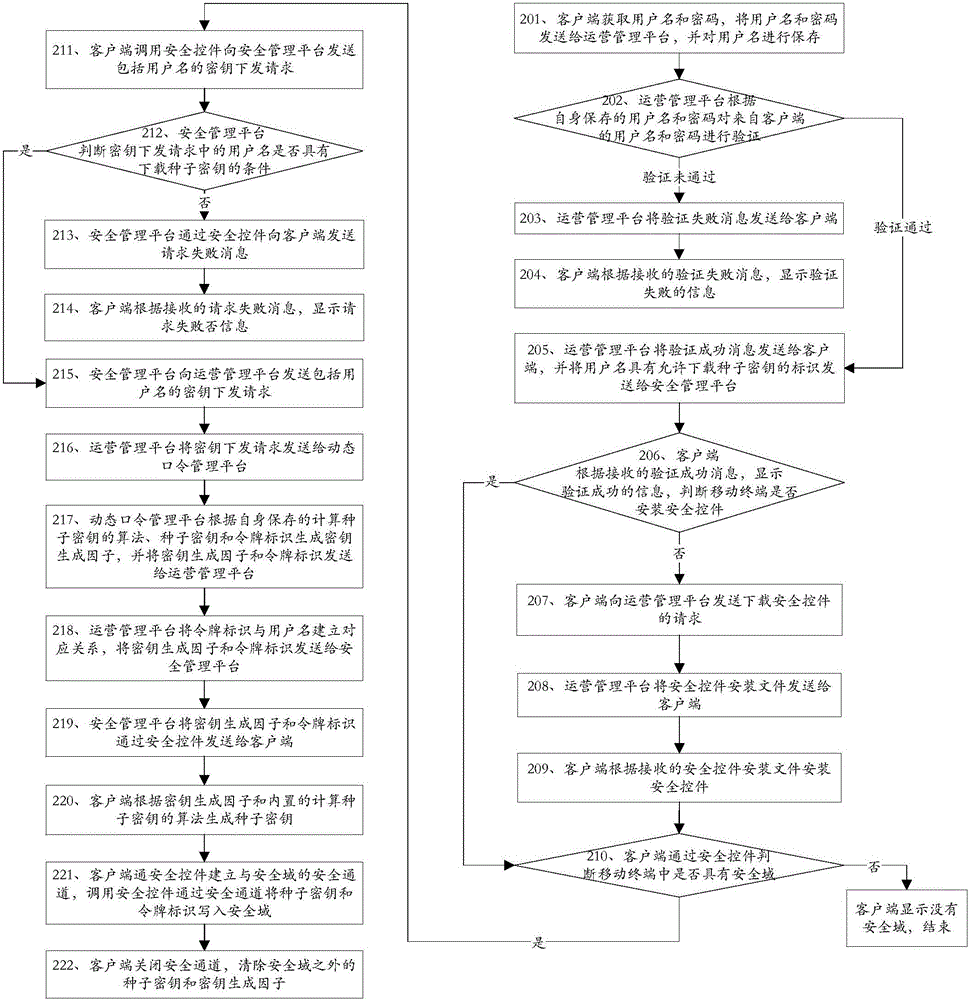
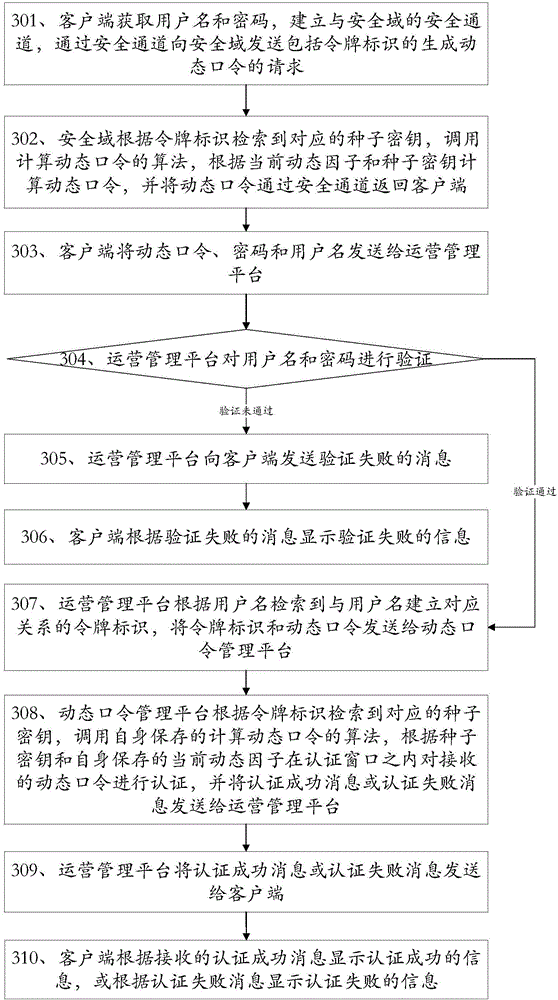
Methods and devices for key distribution, dynamic password generation and authentication
ActiveCN106060069AAvoid interceptionPrevent leakageKey distribution for secure communicationPasswordSecurity domain
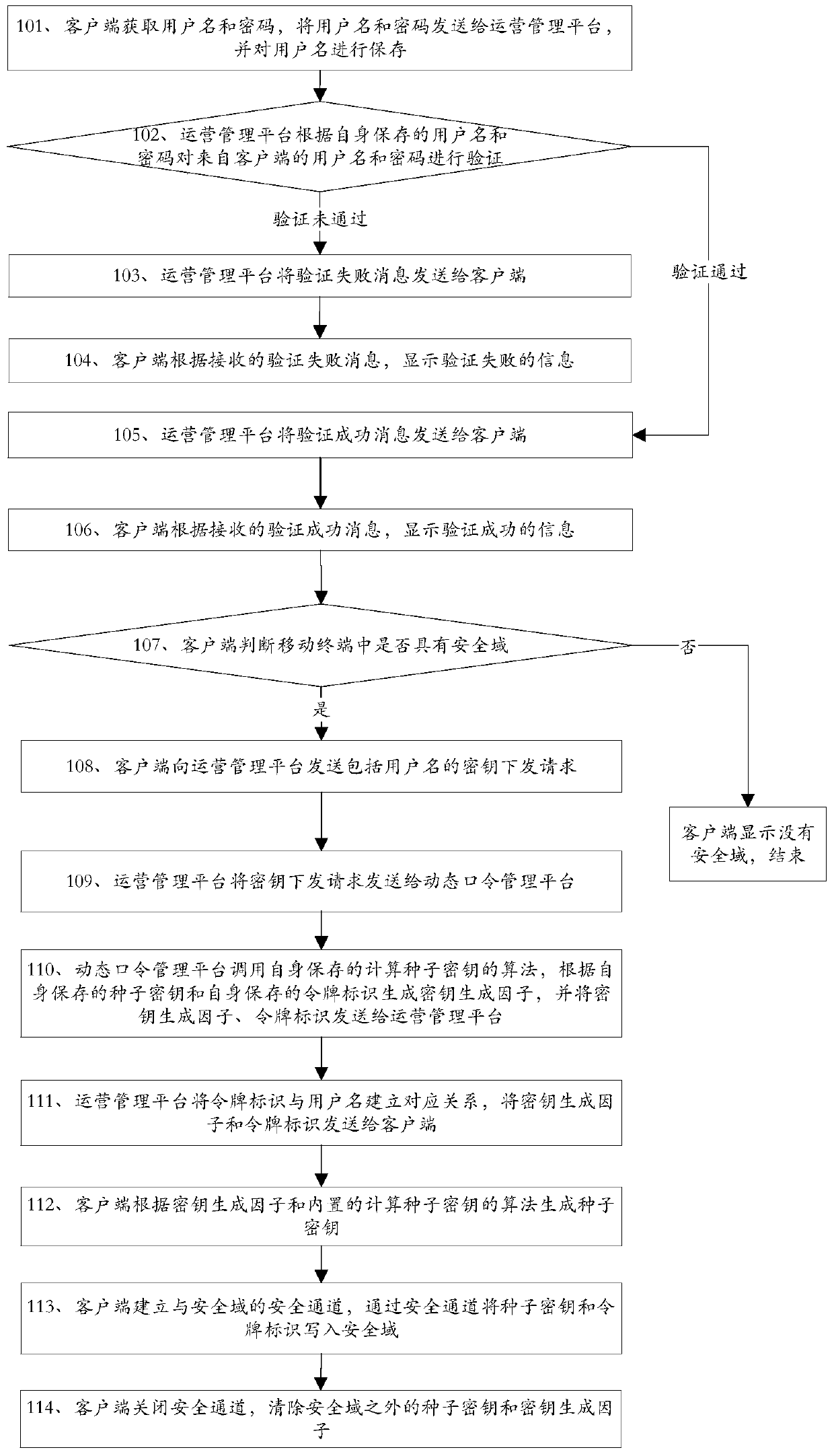
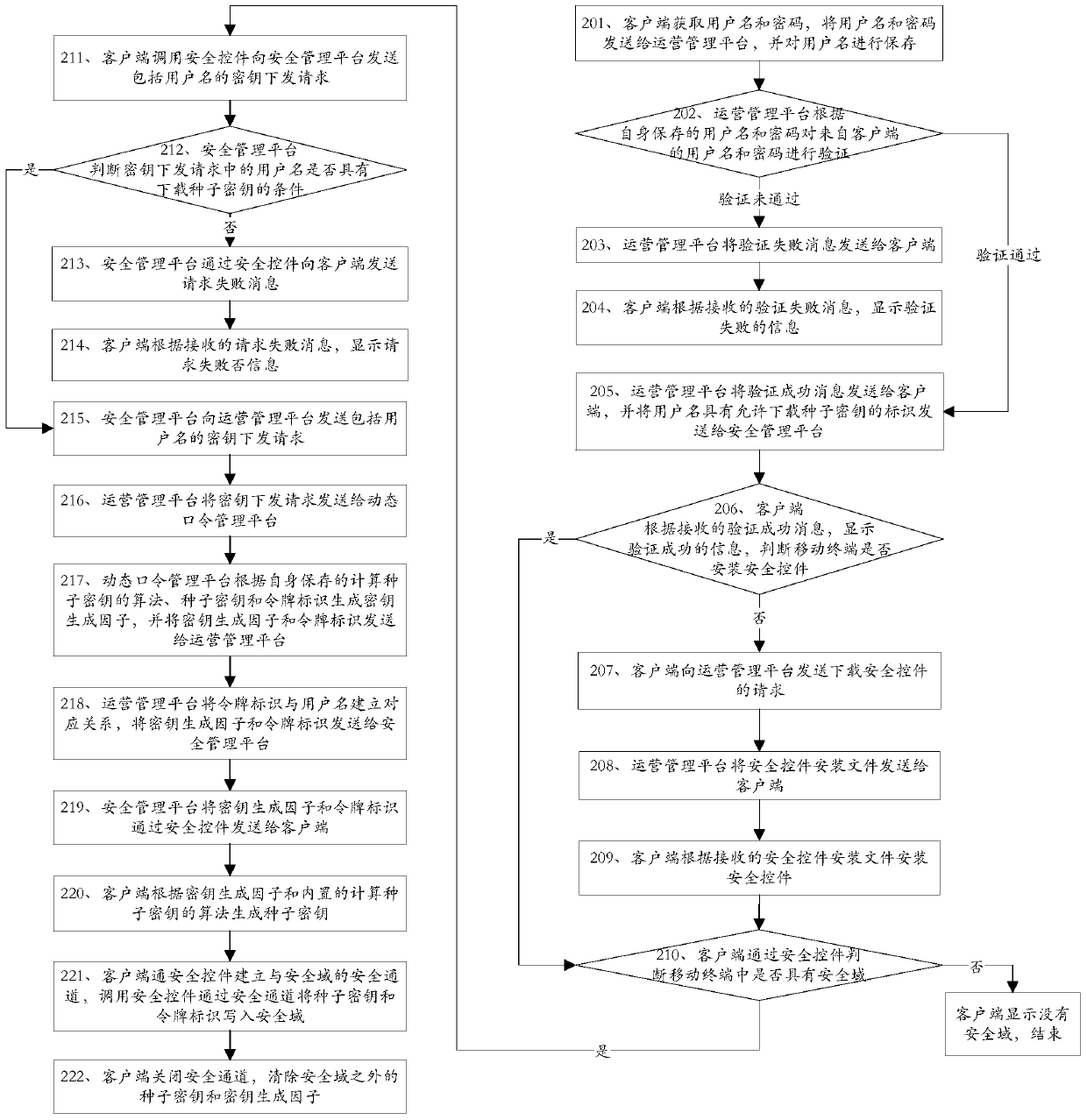
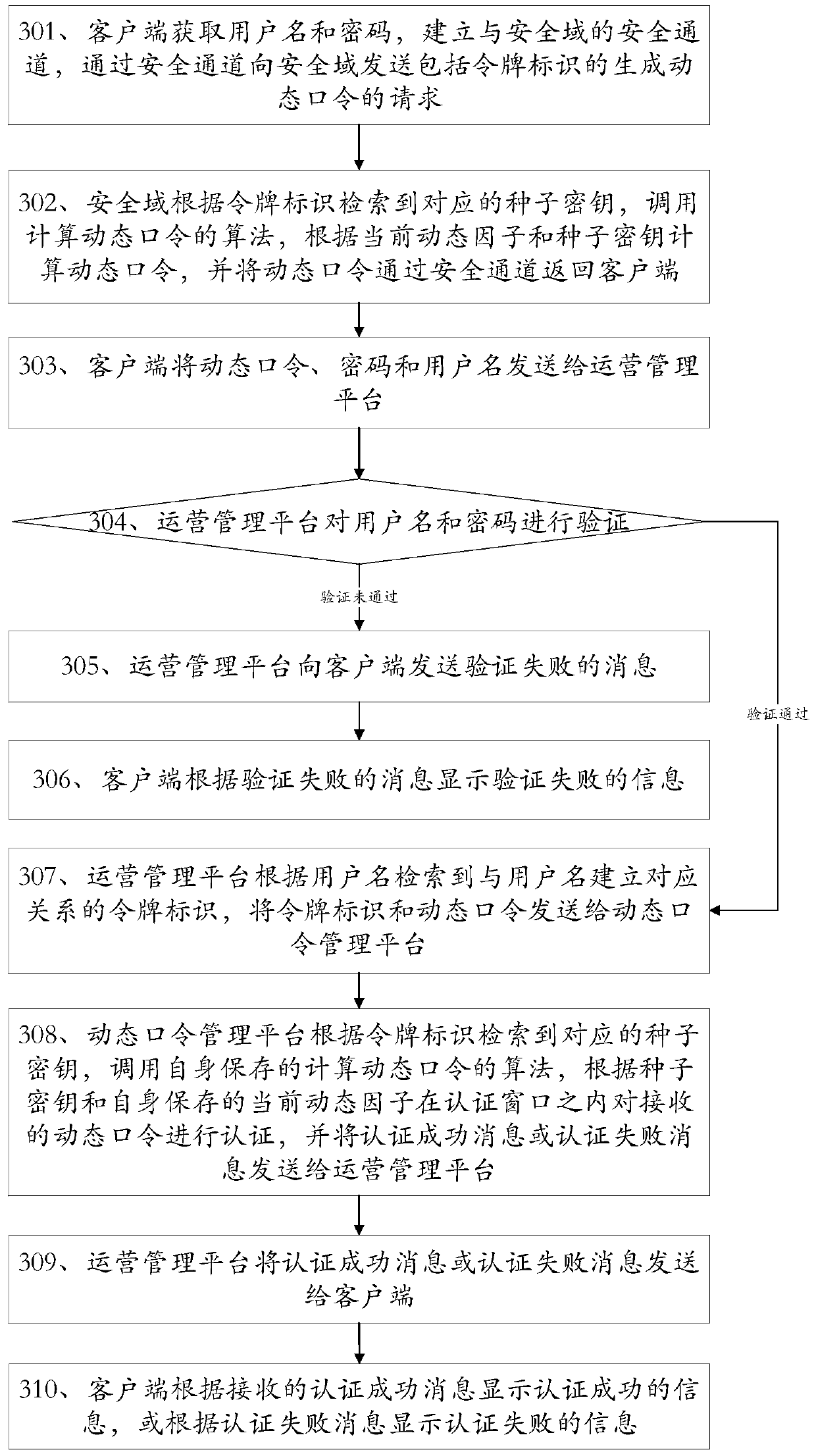
The invention discloses methods and devices for key distribution, dynamic password generation and authentication, and belongs to the field of information security. The key distribution method comprises that a client sends a key distribution request including a user name to an operation management platform; the client receives a key generation factor and a token identifier from the operation management platform; the client calls a built-in algorithm for calculating a seed key, generates the seed key according to the key generation factor and the token identifier, and saves the token identifier; and the client establishes a security channel with a security domain, and writes the seed key and the token identifier into the security domain via the security channel. According to the methods and the devices, the client downloads the key generation factor from a server platform, and calculates the seed key by using the key generation factor, so that divulgence of the seed key is avoided in the key distribution process; a dynamic token is not needed when a dynamic password is calculated, so that the authentication cost is reduced; and the methods and the devices are convenient to operate, unlikely to go wrong and good in security.
Owner:FEITIAN TECHNOLOGIES
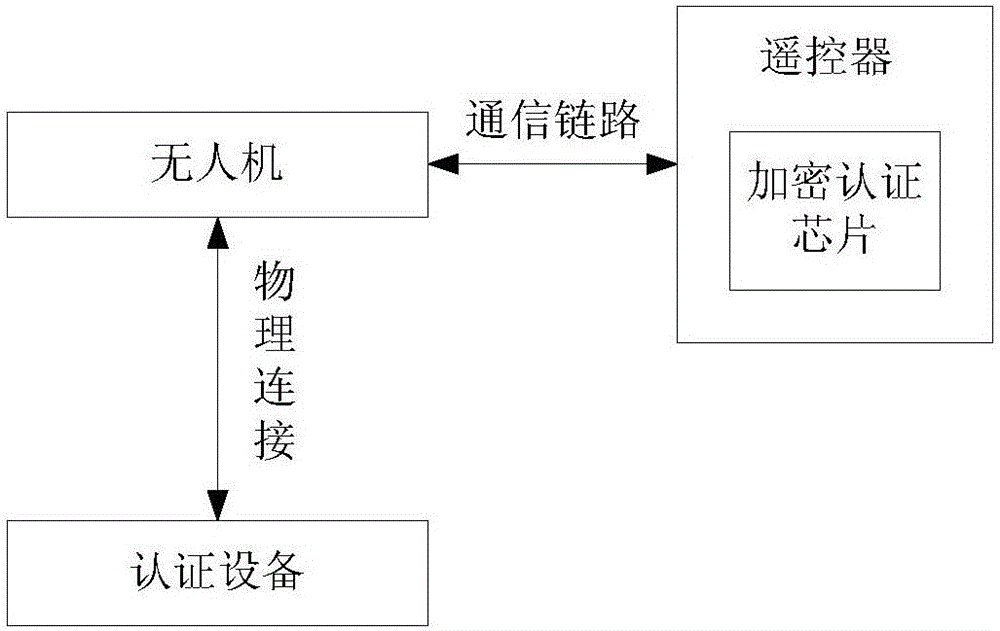
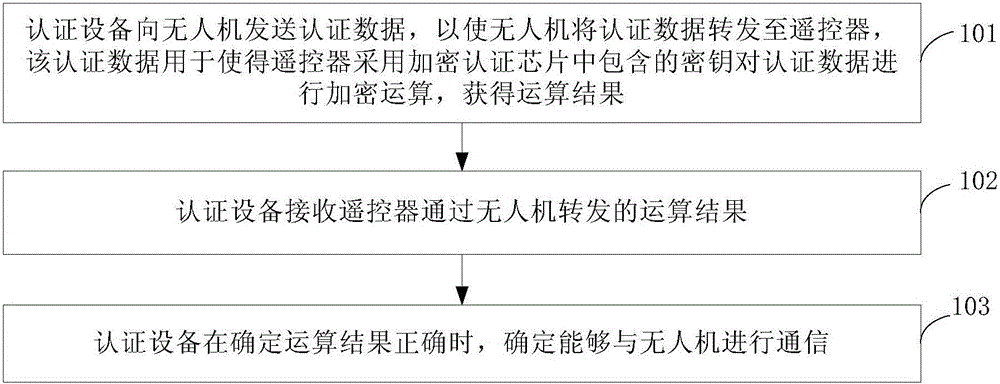
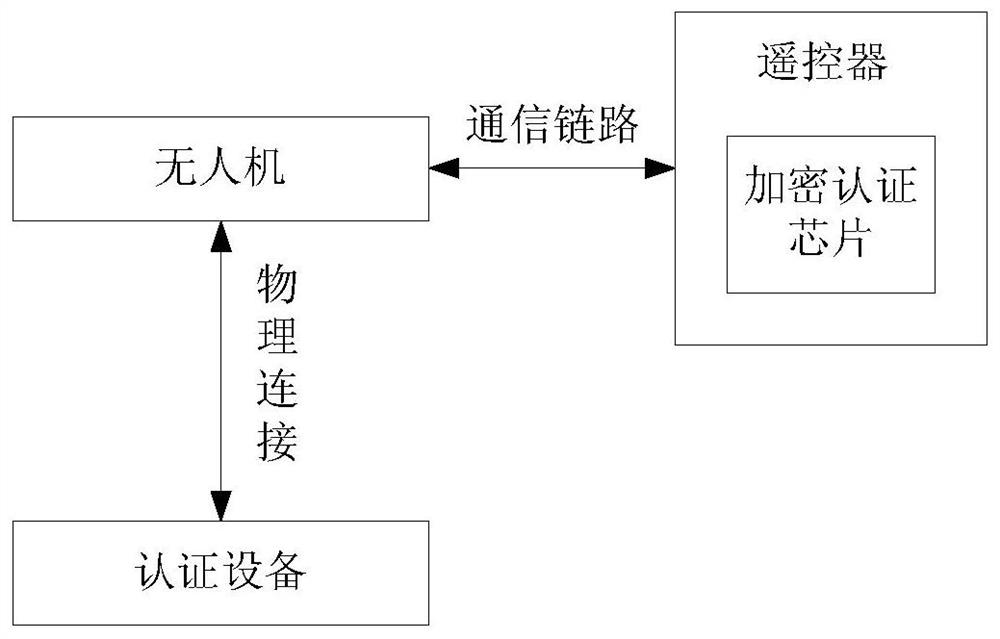
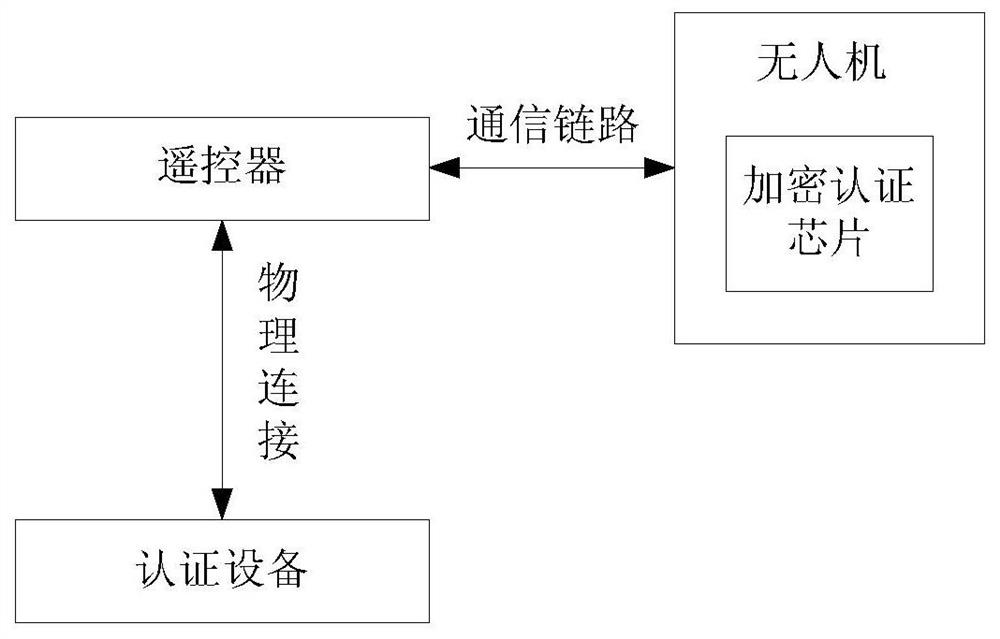
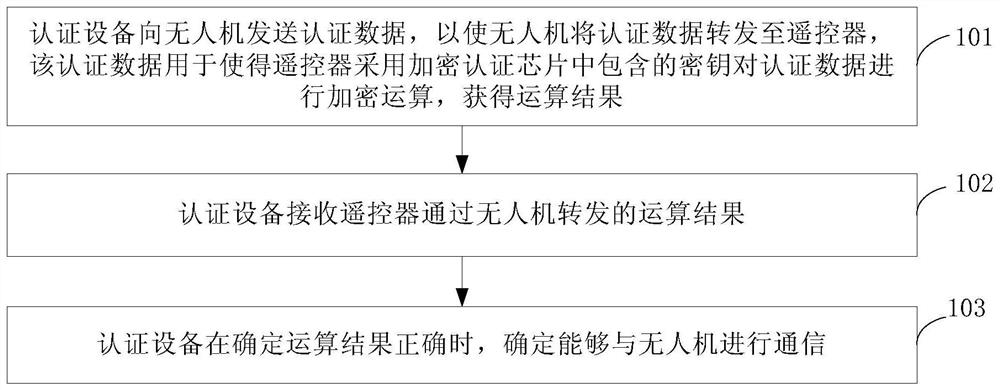
Facility authentication method, device, authenticated facility, unmanned plane and remote controller
ActiveCN106797387AAchieve authenticationReduce certification costsKey distribution for secure communicationTransmission systemsEncryptionComputer science
The invention provides a facility authentication method, a device, an authenticated facility, an unmanned plane and a remote controller. The method comprises the following steps: sending authentication data to an unmanned plane by an authenticated facility so that the unmanned plane can send the authentication data to a remote controller, using the secret key contained in an encryption authenticated chip to carry out encryption calculation on the authentication data by the remote controller to obtain the calculation results, wherein the encryption authenticated chip is implanted in the remote controller; receiving the calculation results from the remote controller by the authenticated facility through the unmanned plane; and carrying out communication with the unmanned plane, when the authenticated facility judges that the calculation result is correct. Through the remote authentication mode, the authentication of unmanned plane and remote controller is realized by implanting an encryption authenticated chip in the remote controller, the authentication cost is saved, and the authentication efficiency is improved.
Owner:SZ DJI TECH CO LTD
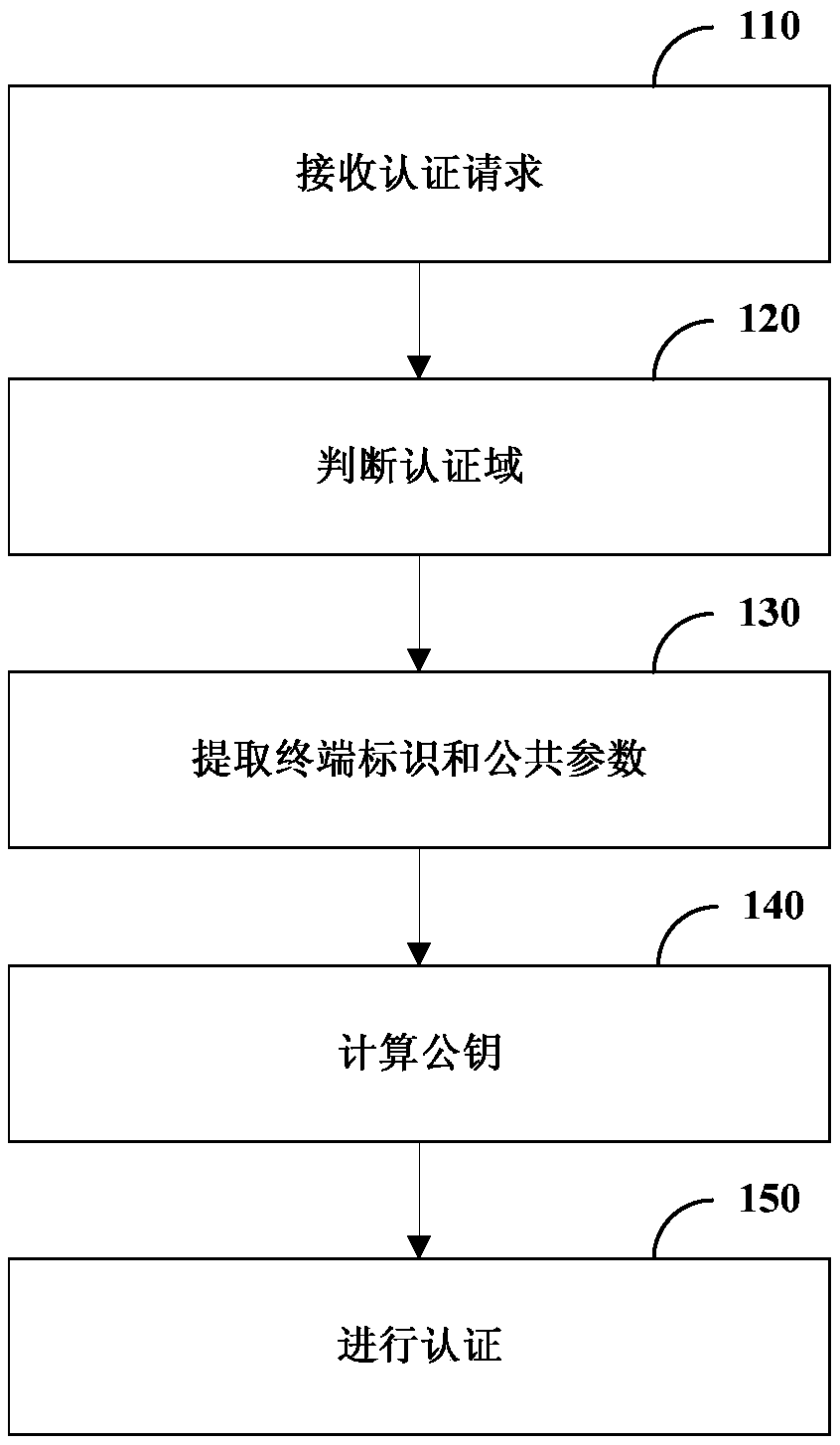
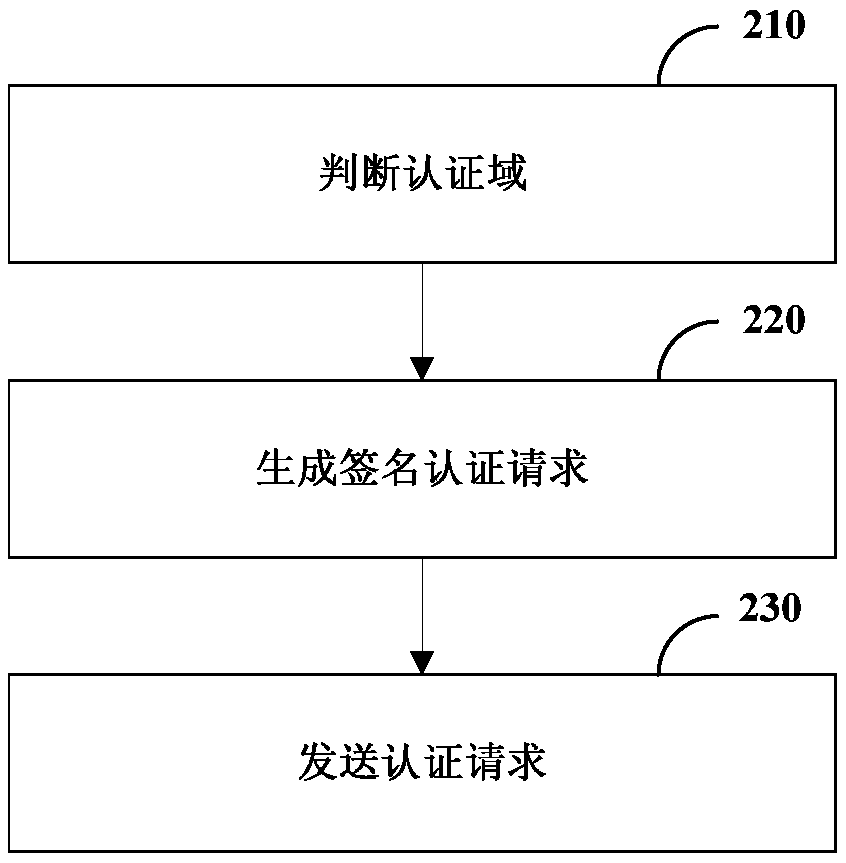
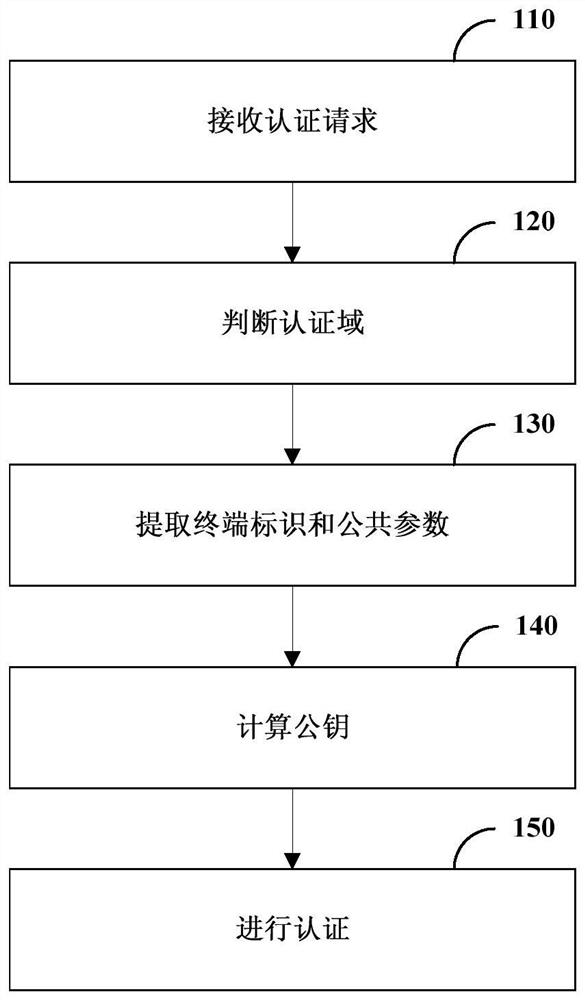
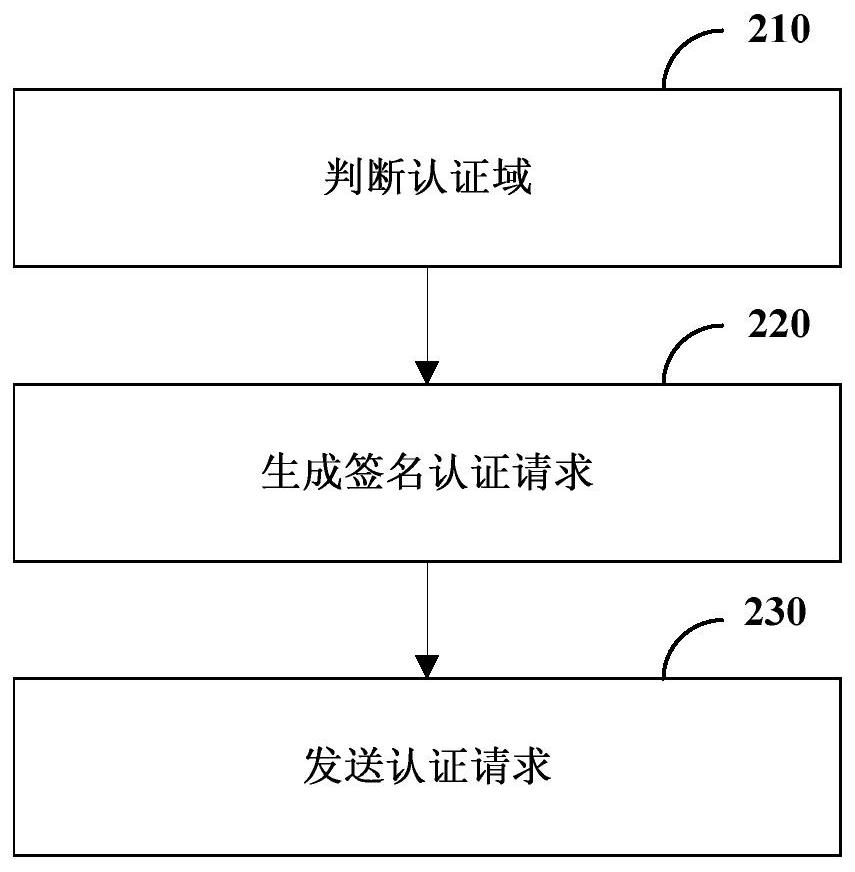
Authentication method and device, terminal and computer readable storage medium
ActiveCN111106931AImplement peer-to-peer authenticationImprove authentication efficiencyKey distribution for secure communicationEngineeringAuthentication
The invention relates to an authentication method and device, a terminal and a computer readable storage medium, and relates to the technical field of mobile communication. The method comprises the steps that a first terminal receives an authentication request sent by a second terminal; the first terminal judges whether the first terminal and the second terminal are in the same authentication domain; under the condition of being in different authentication domains, the first terminal extracts an identifier of the second terminal in the authentication request and a public parameter of the authentication domain where the second terminal is located; the first terminal calculates a public key according to the identifier of the second terminal and the public parameter; and the first terminal authenticates the second terminal by using the public key. According to the technical scheme, the authentication efficiency can be improved, and the authentication cost is reduced.
Owner:CHINA TELECOM CORP LTD
Radio device with two radio units and a method for the transmission of information
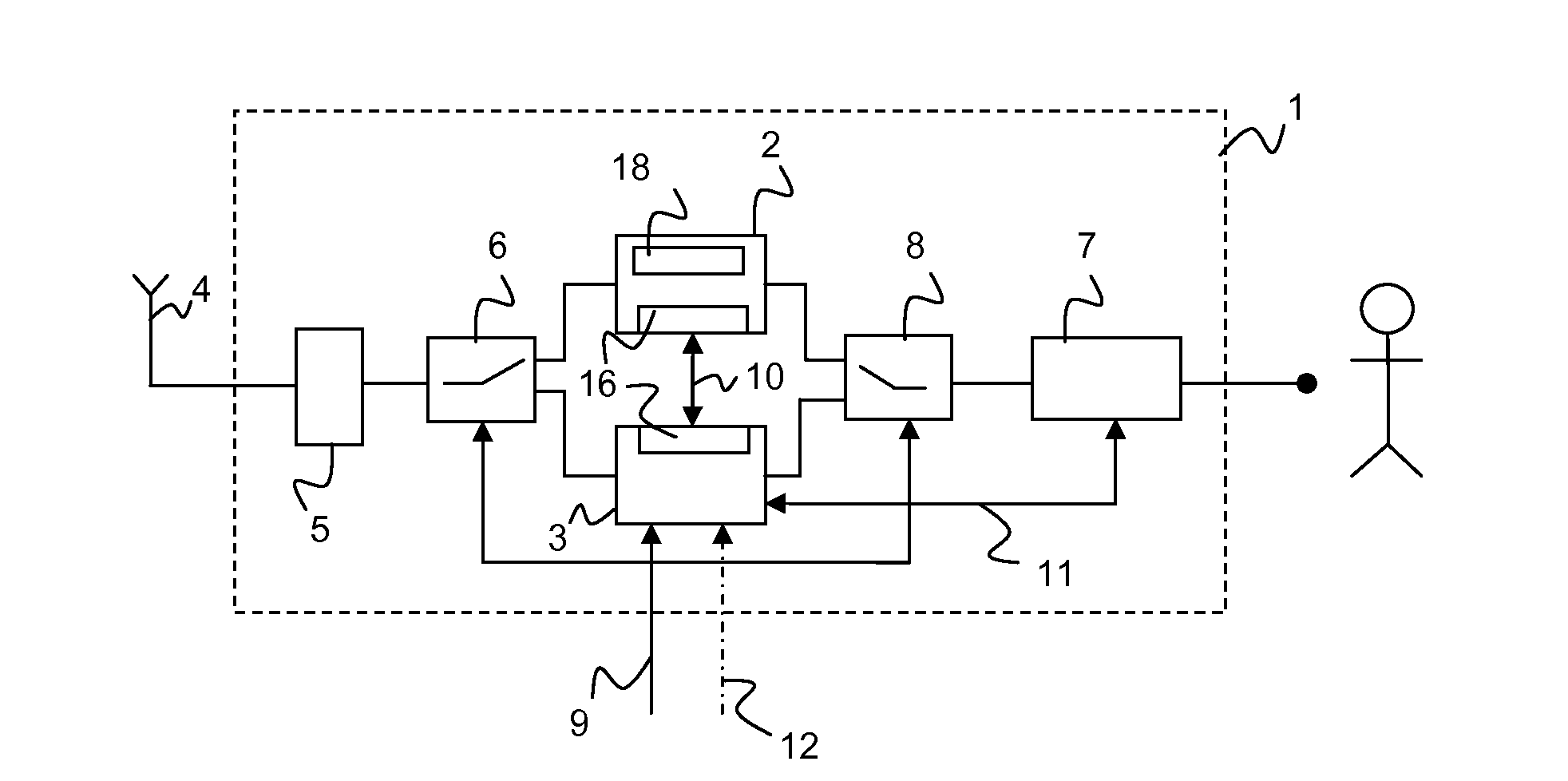
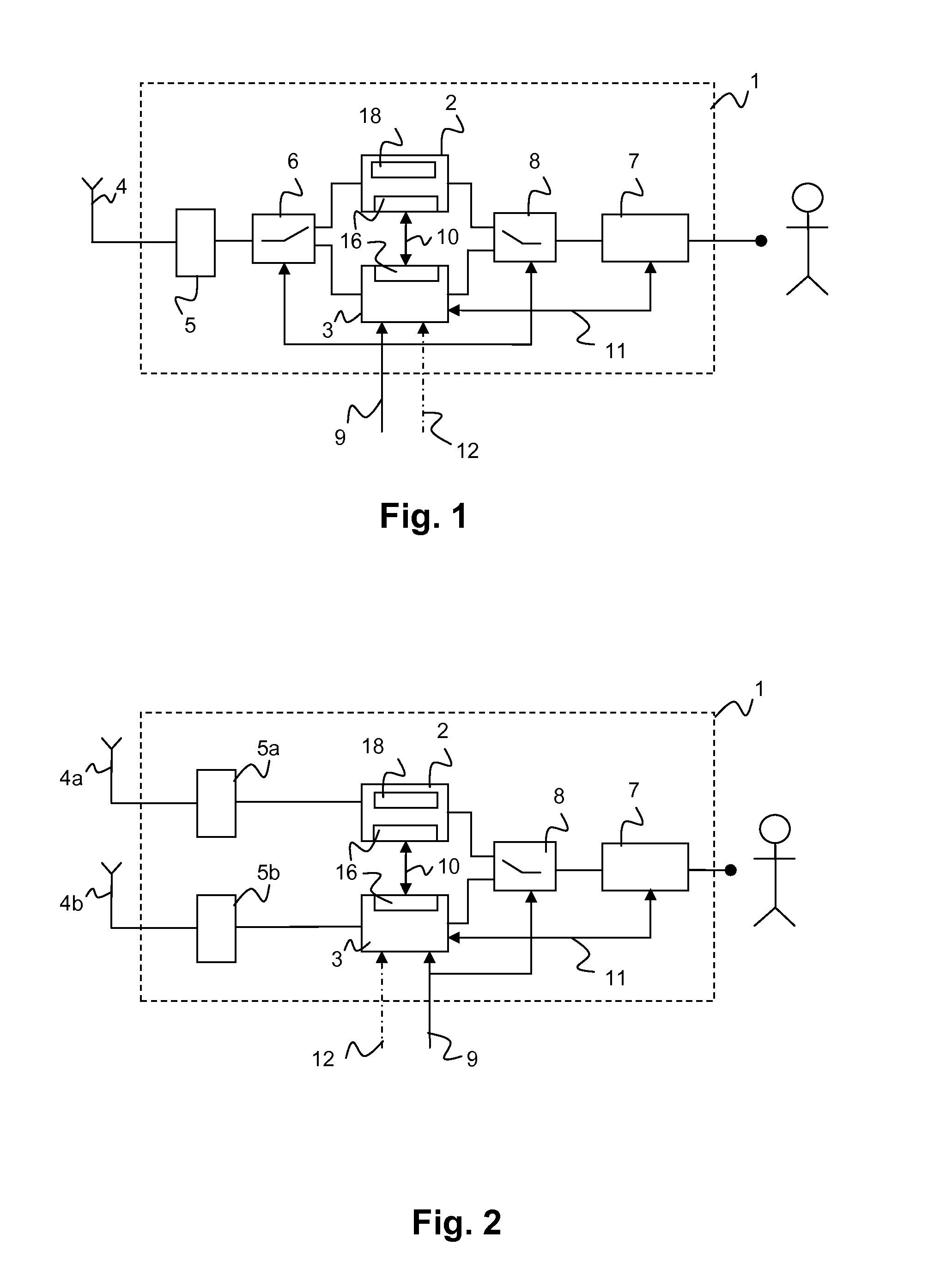
ActiveUS20150350903A1Reduce development costsSimple and efficient reconfiguration/expansionAssess restrictionUser identity/authority verificationRadio equipmentComputer science
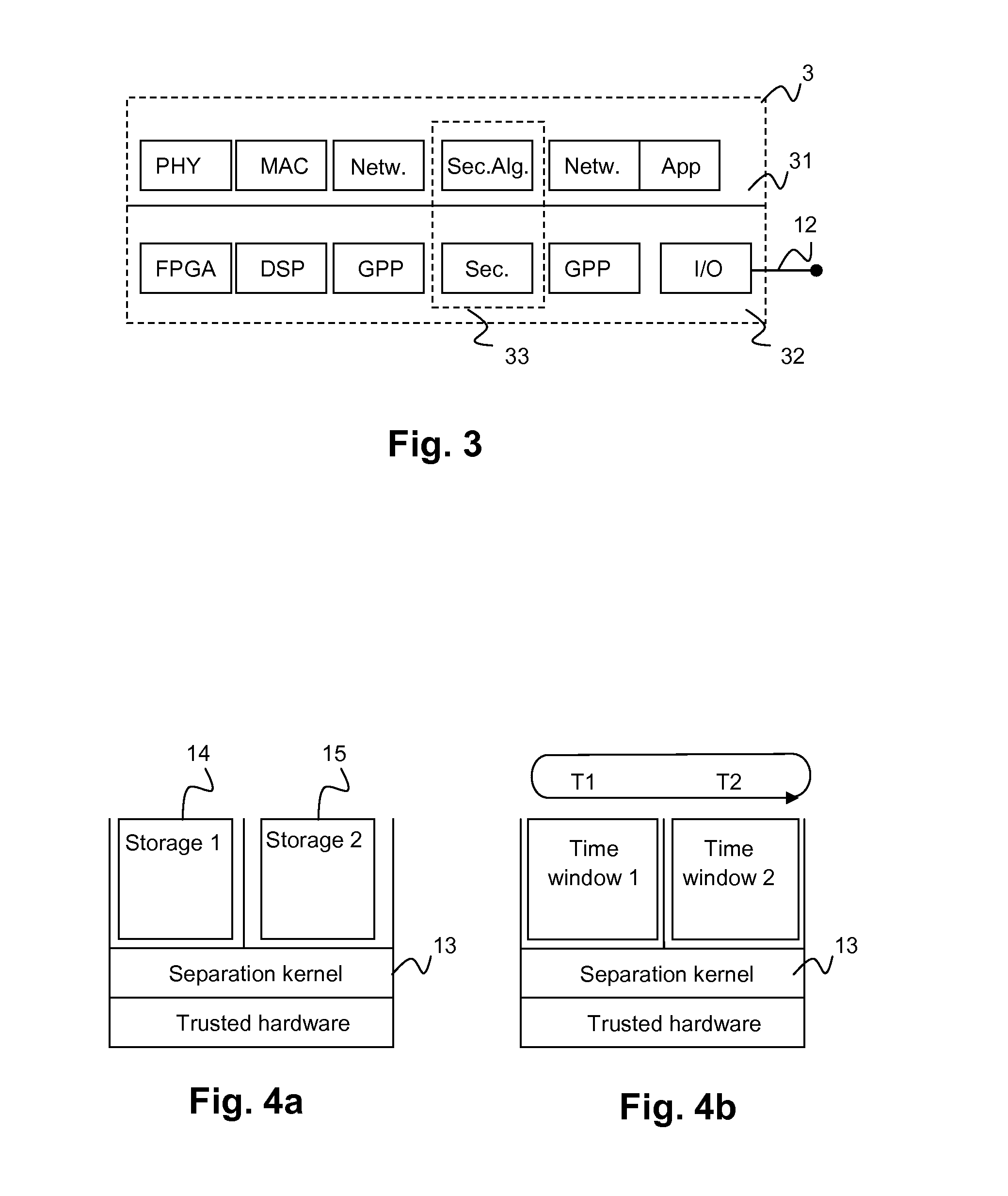
A radio device is provided with a first radio unit and a second radio unit, wherein the first radio unit provides a certified functionality which is certified by an authorized certification authority. The second radio unit provides a certified functionality, wherein the functionality of the second radio unit is different from the functionality of the first radio unit, and the functionality of the second radio unit is similarly certified by an authorized certification authority. Furthermore, a method is provided for the transmission of information via the radio device.
Owner:ROHDE & SCHWARZ GMBH & CO KG
A method and device for key distribution, dynamic password generation and authentication
ActiveCN106060069BAvoid interceptionPrevent leakageKey distribution for secure communicationPasswordSecurity domain
The invention discloses methods and devices for key distribution, dynamic password generation and authentication, and belongs to the field of information security. The key distribution method comprises that a client sends a key distribution request including a user name to an operation management platform; the client receives a key generation factor and a token identifier from the operation management platform; the client calls a built-in algorithm for calculating a seed key, generates the seed key according to the key generation factor and the token identifier, and saves the token identifier; and the client establishes a security channel with a security domain, and writes the seed key and the token identifier into the security domain via the security channel. According to the methods and the devices, the client downloads the key generation factor from a server platform, and calculates the seed key by using the key generation factor, so that divulgence of the seed key is avoided in the key distribution process; a dynamic token is not needed when a dynamic password is calculated, so that the authentication cost is reduced; and the methods and the devices are convenient to operate, unlikely to go wrong and good in security.
Owner:FEITIAN TECHNOLOGIES
Blockchain-based enterprise certification, certification traceability method, device and equipment
ActiveCN110336797BThe certification process is transparentGuaranteed to be tamper-proofSecuring communicationInternet privacyBusiness enterprise
One or more embodiments of this specification provide a blockchain-based enterprise authentication, authentication traceability method, device, and equipment, wherein the authentication method includes: receiving an enterprise authentication request sent by a client, wherein the enterprise authentication request includes The enterprise information, legal person identity information and auxiliary authentication information; the identity of the enterprise is authenticated according to the enterprise information, and the identity of the enterprise legal person is authenticated according to the legal person identity information and auxiliary authentication information; if the identity authentication of the enterprise passes and the identity of the enterprise legal person If the authentication is passed, an enterprise authentication record is generated, and the enterprise authentication record is written into the blockchain. Through this embodiment, based on the trusted execution environment of the blockchain, not only the enterprise's authentication process is transparent and visible to multiple parties, but also the enterprise's authentication process is credible and notarizable, and the authentication result is uploaded to the chain to ensure that the authentication result cannot be tampered with. and judicial effectiveness, as well as the traceability of the enterprise certification process.
Owner:ADVANCED NEW TECH CO LTD
Method and device for information authentication
ActiveCN109150857BLow costReduce certification costsUser identity/authority verificationTerminal equipmentAuthentication server
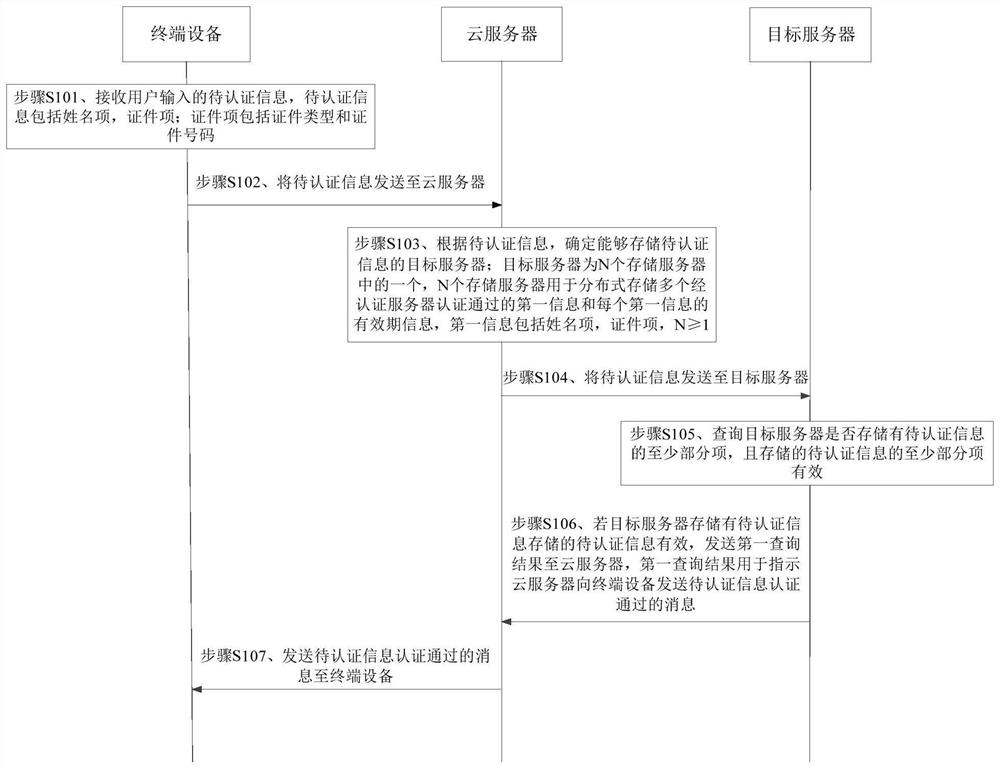
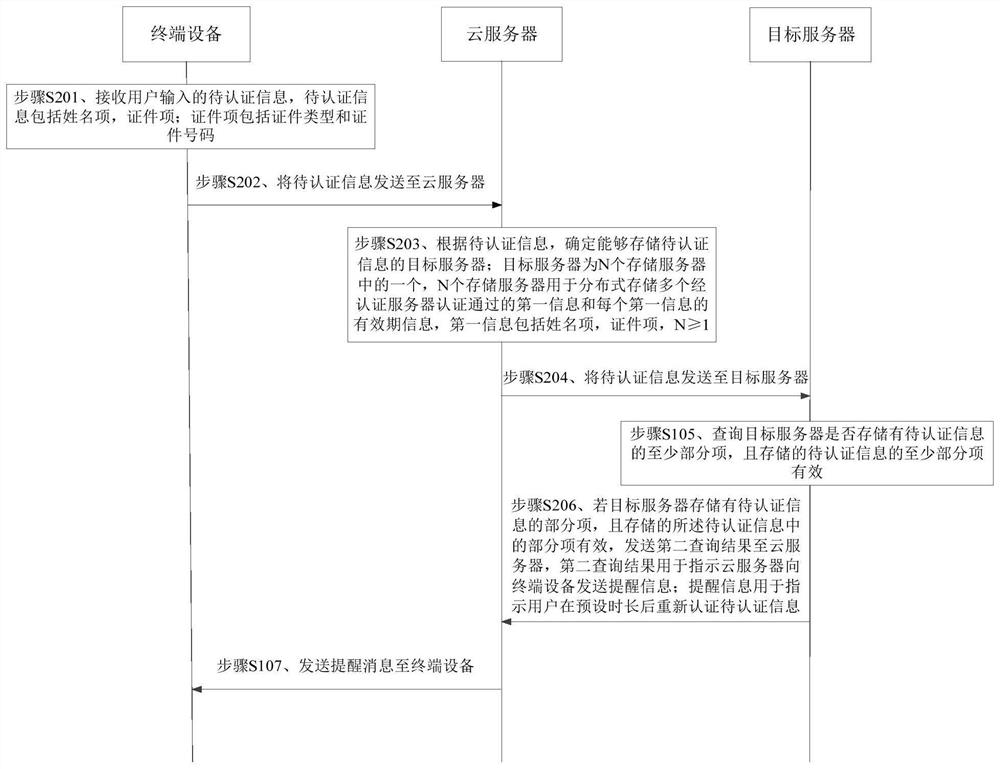
The present application provides a method and device for information authentication. The method includes: according to the information to be authenticated from the terminal device, determine a target server capable of storing the information to be authenticated, and send the information to be authenticated to the target server; there are N target servers One of the storage servers, N storage servers are used for distributed storage of a plurality of first information authenticated by the authentication server and the validity period information of each first information; receiving the query result sent by the target server; if the query result indicates that the target server If the information to be authenticated is stored in and the stored information to be authenticated is valid, a message that the information to be authenticated is passed is sent to the terminal device. The method and device of the present application effectively reduce the authentication cost.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Train control and management system and train system
ActiveCN113682347AReduce the workload of certificationReduce certification costsSignalling indicators on vehicleControl engineeringNetwork control
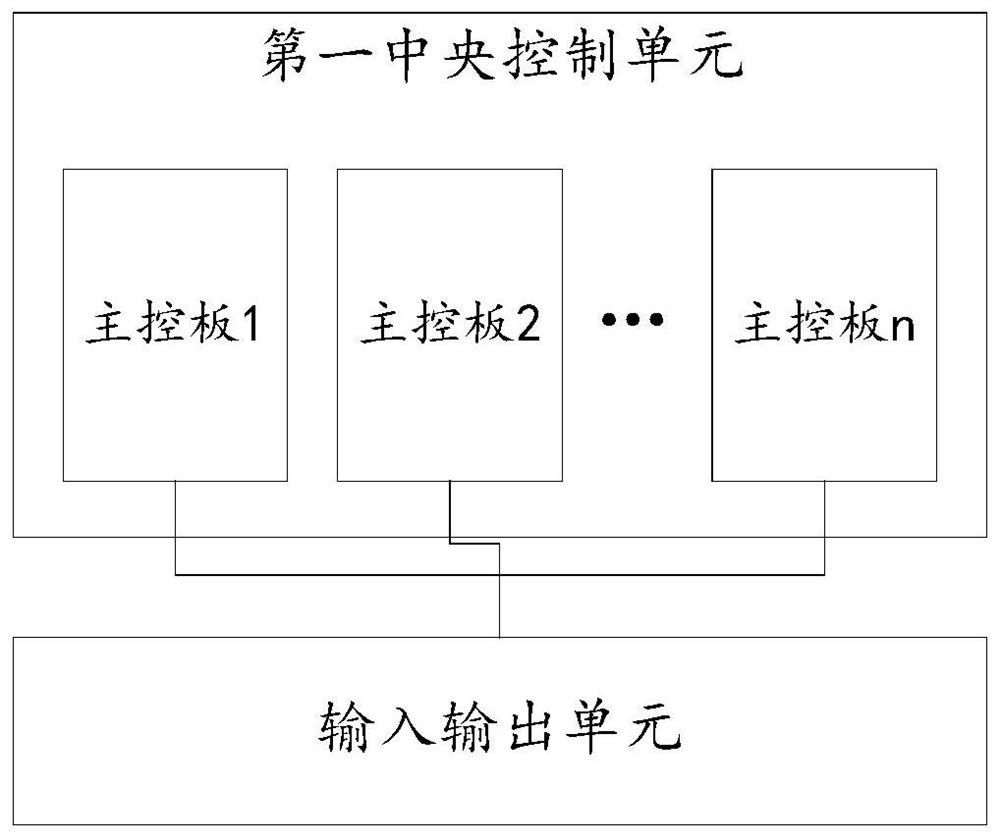
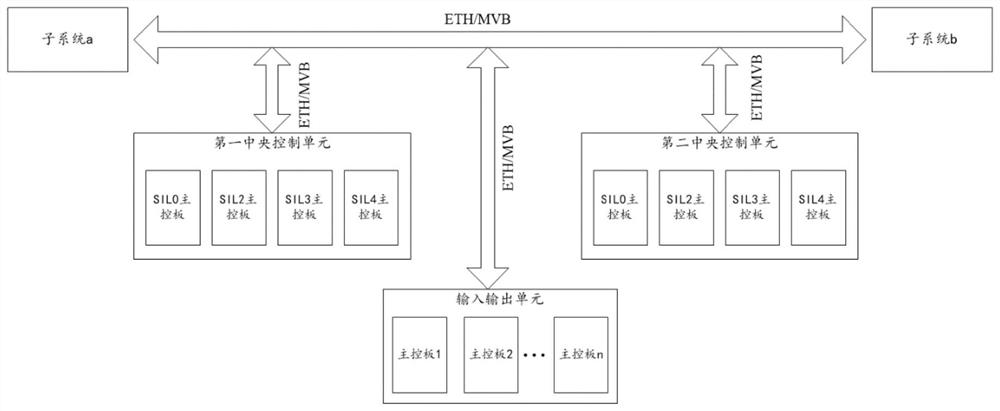
The invention provides a train control and management system and a train system, and relates to the technical field of network control of urban rail transit trains, the train control and management system comprises a first central control unit and an input and output unit; the first central control unit comprises a plurality of main control boards, the different main control boards are mutually independent, and functional modules running on the different main control boards have different safety levels; and the input and output unit is respectively connected with each main control board. According to the technical scheme provided by the invention, the authentication workload can be greatly reduced, so that the authentication cost is reduced.
Owner:ZHUZHOU CSR TIMES ELECTRIC CO LTD
Data existence authentication system, authentication method and verification method
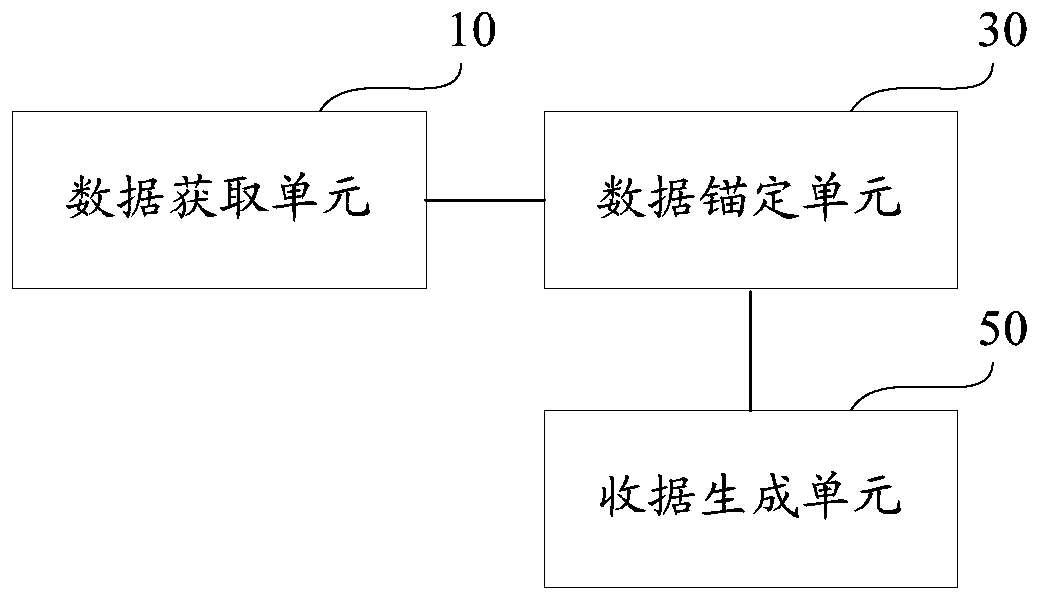
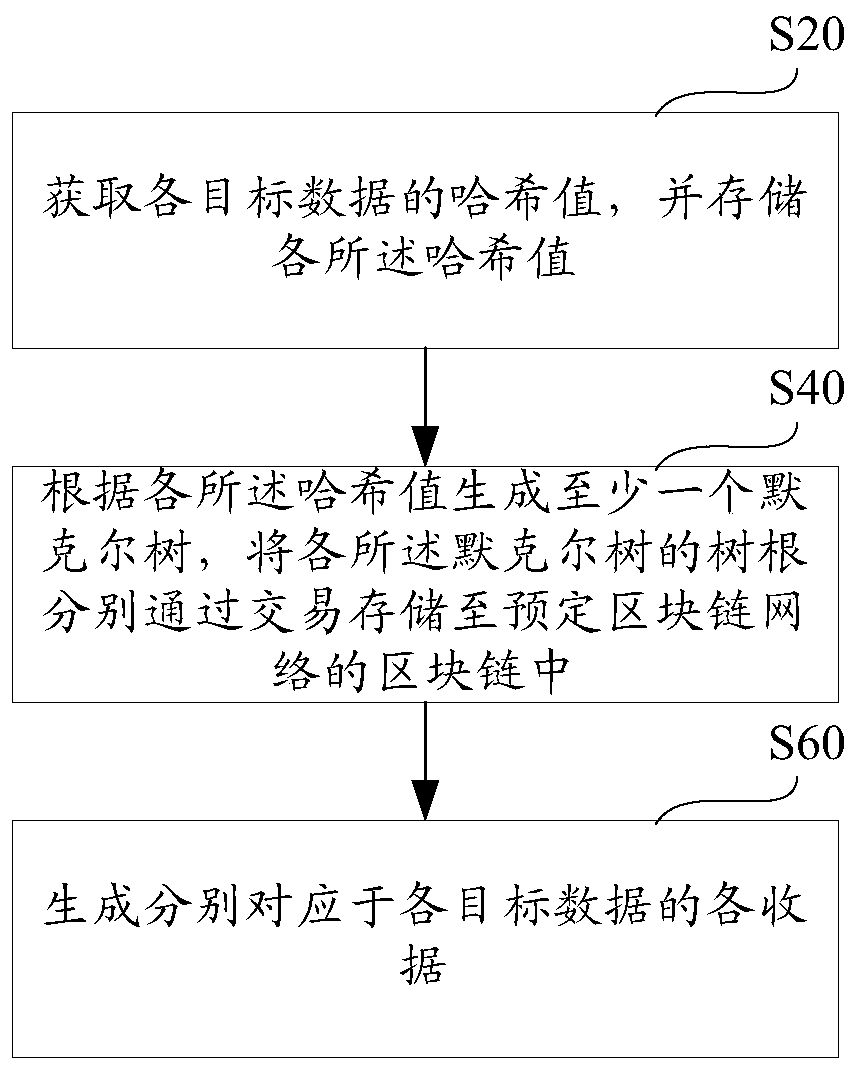
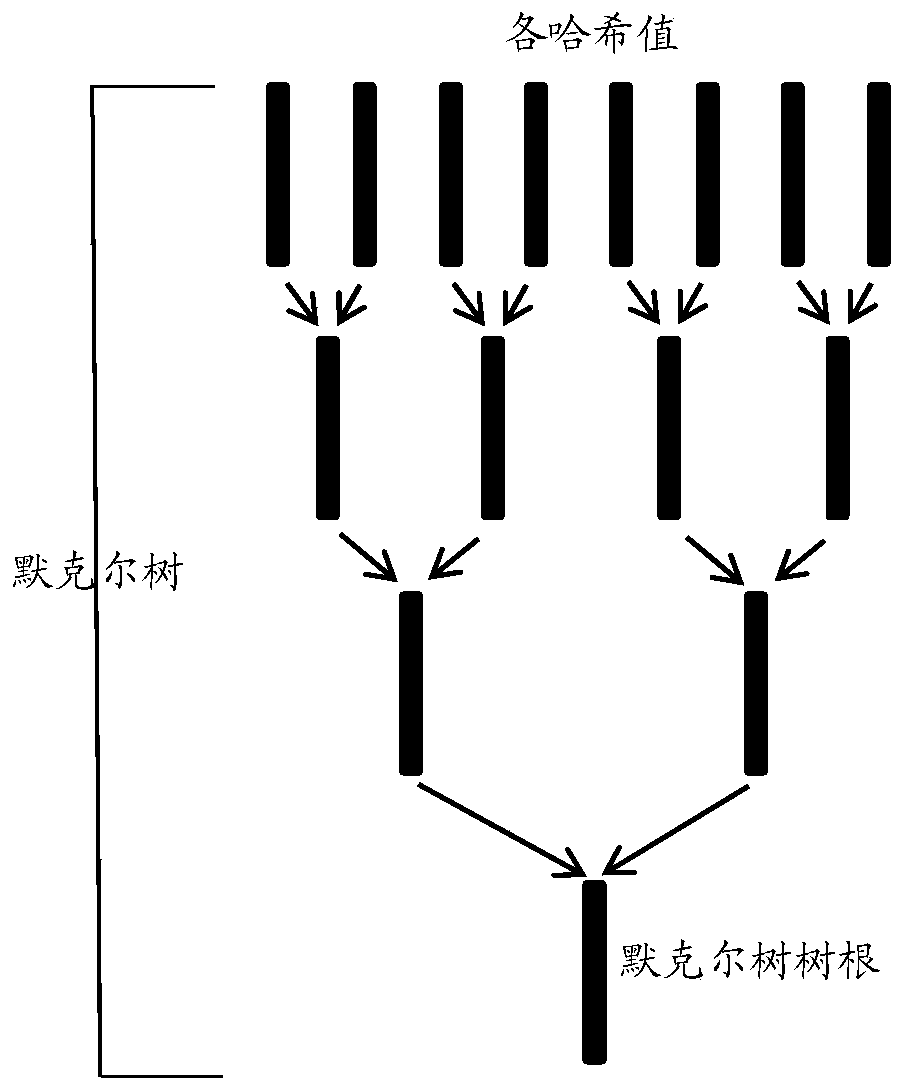
ActiveCN106407795BReduce certification costsSimple pathDigital data authenticationTree rootValidation methods
The invention provides a data existence authentication system, a data existence authentication method and a data existence verification method. The authentication method comprises the steps of obtaining hash values of target data, and storing the hash values; generating at least one Merkel tree according to the hash values, and storing tree roots of the Merkel tree in block chains of a predetermined block chain network through trading; and generating receipts corresponding to the target data respectively, wherein the receipts comprise corresponding target hash values, corresponding tree roots and paths of the Merkel tree, and trading data storage paths, and the paths comprise the hash values sequentially paired with the target hash values to finally generate the tree roots. According to the data existence authentication system, the data existence authentication method and the data existence verification method, the authentication of the existence of the target data in the trading time can be realized through the trading without depending on an authentication mechanism by utilizing characteristics of the Merkel tree and a characteristic that data in the block chains cannot be rewritten, the trading only needs to store the tree roots in the block chains, and the authentication of batch data can be finished by one-time trading, so that the authentication cost is greatly reduced.
Owner:BEIJING ZHONGXIANG BIT TECH
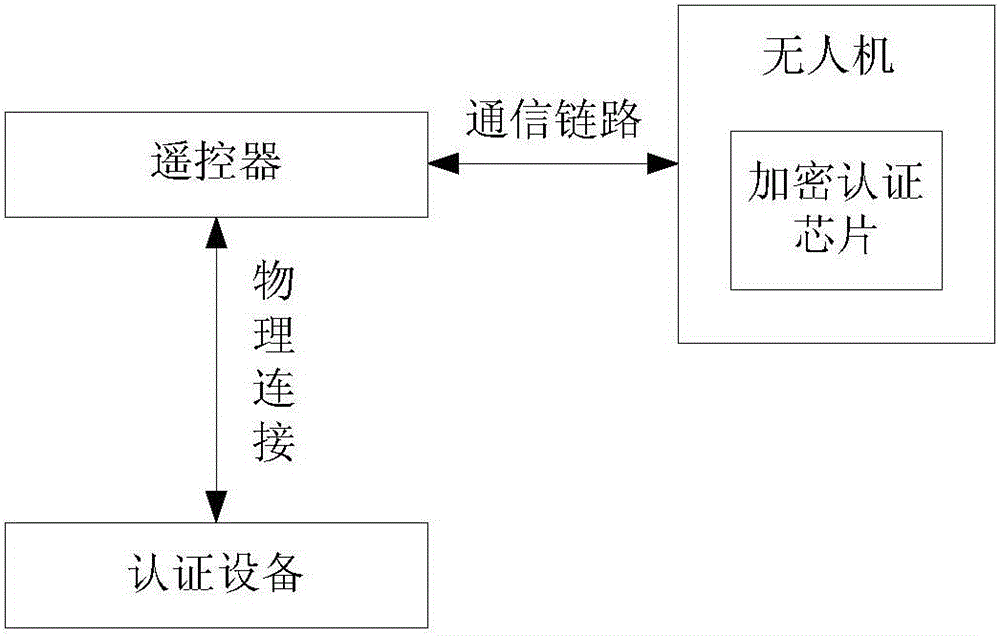
Device authentication method, device, authentication device, drone, and remote controller
ActiveCN106797387BAchieve authenticationReduce certification costsKey distribution for secure communicationTransmission systemsComputer hardwareRemote control
The present invention provides a method and device for device authentication, an authentication device, an unmanned aerial vehicle and a remote controller. The method comprises: the authentication device sends authentication data to the unmanned aerial vehicle so that the unmanned aerial vehicle forwards the authentication data to the remote controller, the authentication data being used for enabling the remote controller to encrypt the authentication data using a key contained in an encryption authentication chip to obtain an operation result, wherein the remote controller is embedded with the encryption authentication chip; the authentication device receives the operation result forwarded by the remote controller via the unmanned aerial vehicle; and the authentication device determines that it is possible to communicate with the unmanned aerial vehicle when determining that the operation result is correct. Through the remote authentication mode, the authentication device can realize authentication of the unmanned aerial vehicle and the remote controller only by using the encryption authentication chip embedded in the remote controller, thus saving the cost of authentication, and improving the efficiency of authentication processing.
Owner:SZ DJI TECH CO LTD
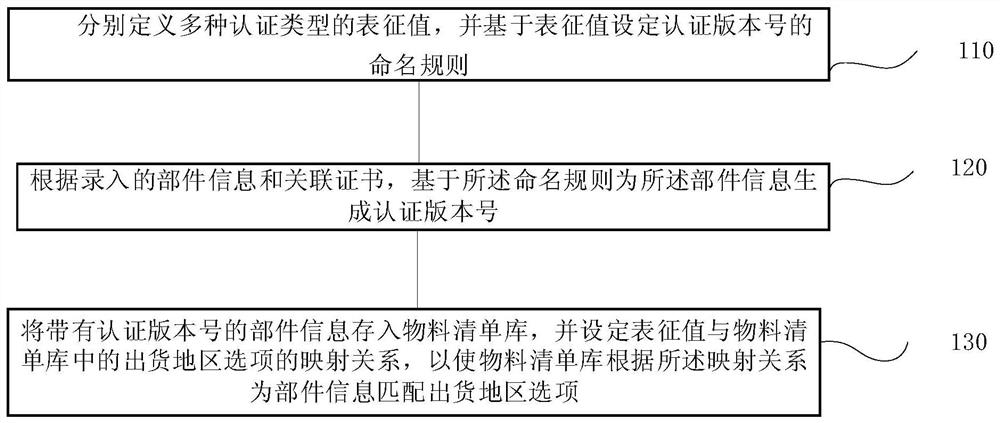
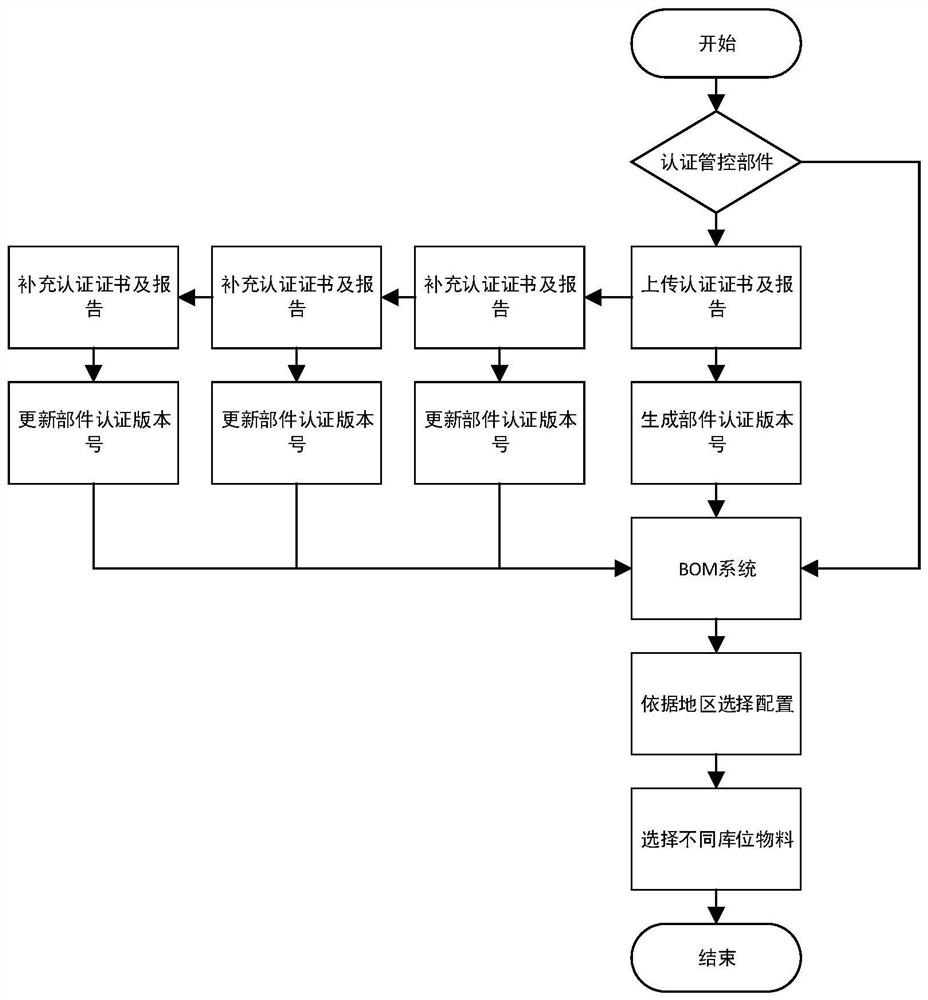
Server component authentication control method and system, terminal and storage medium
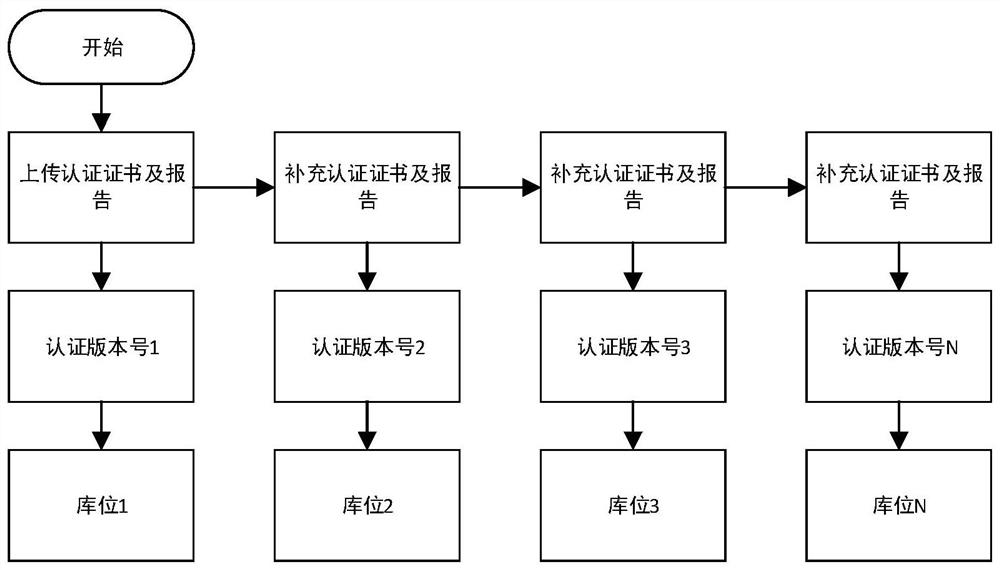
The invention provides a server component authentication management and control method and system, a terminal and a storage medium, and the method comprises the steps: respectively defining representation values of a plurality of authentication types, and setting a naming rule of an authentication version number based on the representation values; generating an authentication version number for the component information based on the naming rule according to the input component information and the associated certificate; and storing the component information with the authentication version number into a bill of material library, and setting a mapping relationship between the characterization value and shipping area options in the bill of material library, so that the bill of material library matches the shipping area options for the component information according to the mapping relationship. According to the method and the system, parts which are not authenticated or of which the authentication types do not accord with order shipment areas cannot be selected during product production, and the compliance and the consistency of the server are ensured.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
An identity authentication system and authentication method based on cross-network transmission and ctid network certificate authentication
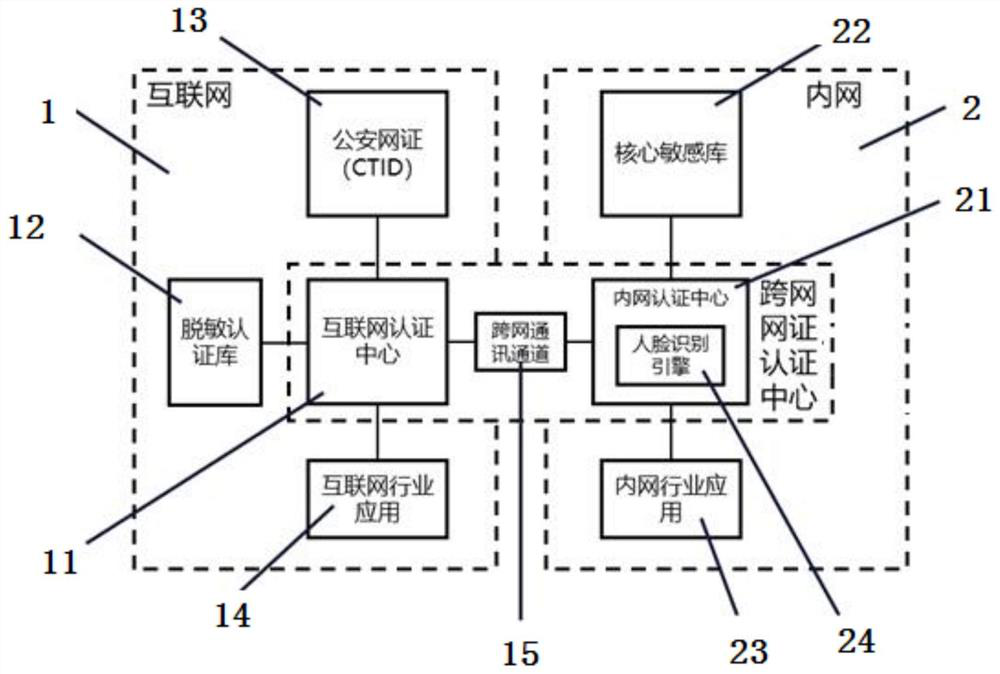
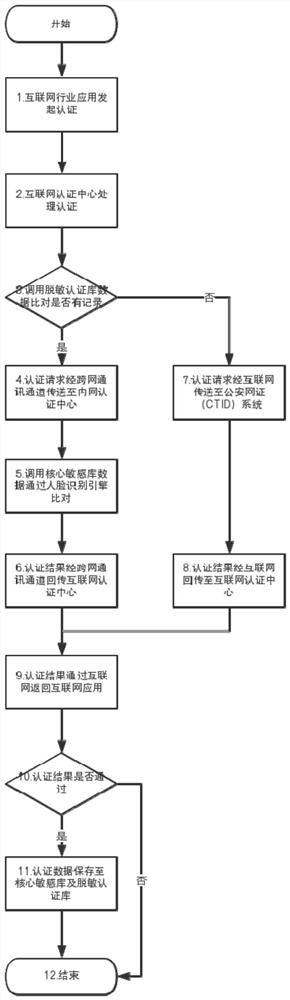
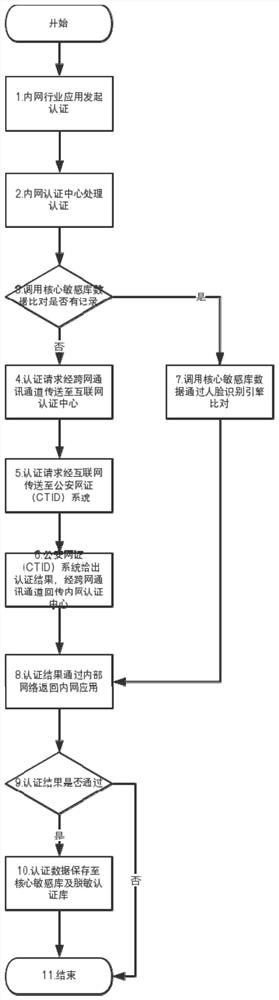
ActiveCN110557366BEnsure safetyReduce certification costsSecuring communicationInternet privacyEngineering
Owner:ANHUI JIYUAN SOFTWARE CO LTD +1
System, method and related device for strong authentication of Internet of things equipment
ActiveCN105827573BReduction in the number of strong authentication operationsGuaranteed authentication securityTransmissionThe InternetStrong authentication
The present invention provides a system, method and related device for strong authentication of Internet of Things equipment. Using the combination of the mobile APP client and the simplest number keyboard, using the Internet of Things connected to the Internet of Things devices, an authorization code is generated for access authentication of the Internet of Things devices. On the basis of using the dynamically generated authorization code to effectively ensure the security of authentication, it is only necessary to enter the authorization code once on the authentication module installed on the Internet of Things device to realize the strong authentication of the Internet of Things device, and the strong authentication operation of the Internet of Things device The number of times is reduced to 1, which greatly improves the work efficiency. At the same time, there is no need to add additional identification sub-modules, which can effectively reduce the certification cost.
Owner:CHINA MOBILE GROUP SHANDONG
Authentication method, equipment and system
ActiveCN102333081BSolve the connection bottleneck problemFacilitated releaseTransmissionMultiplexingConnection number
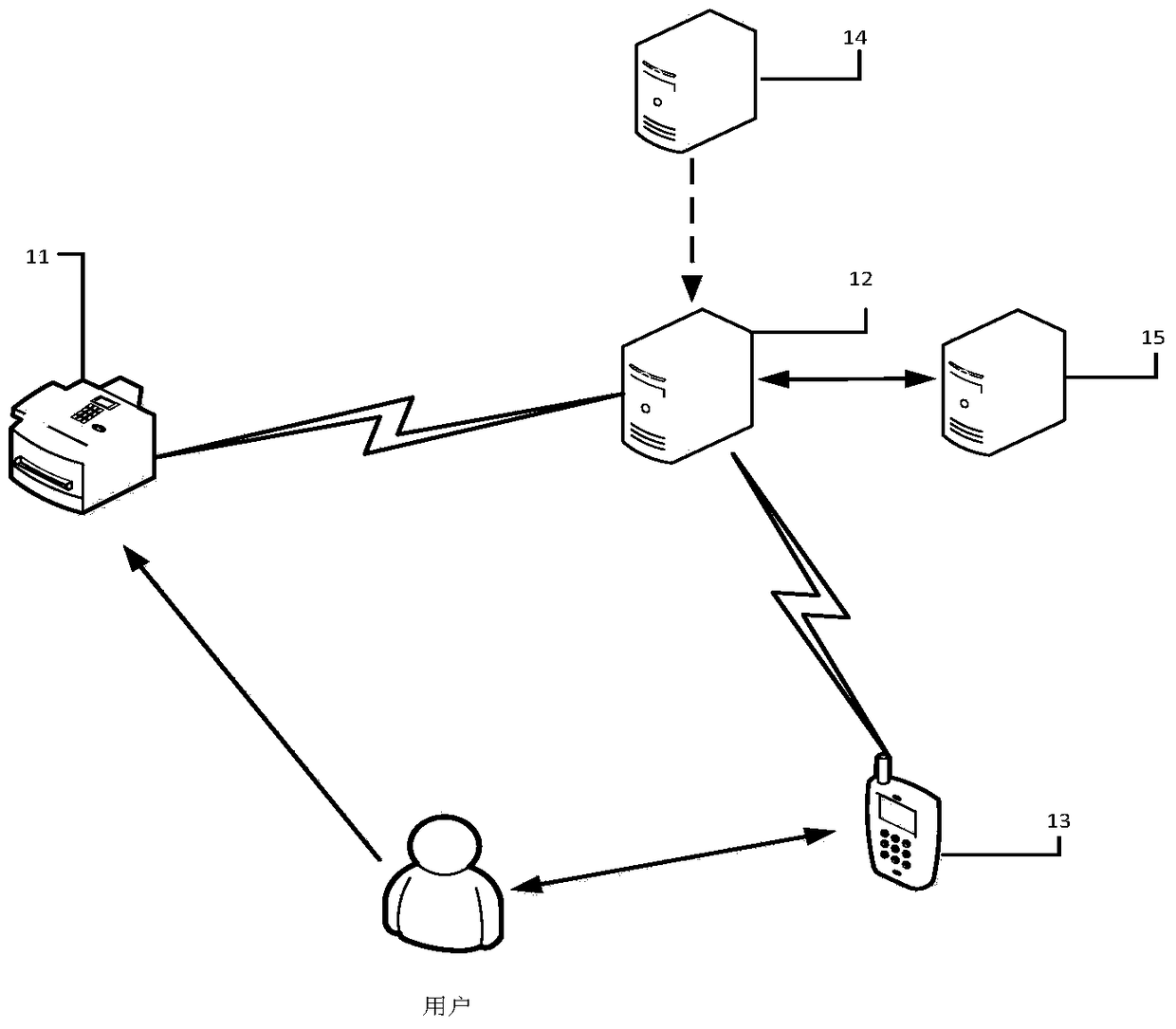
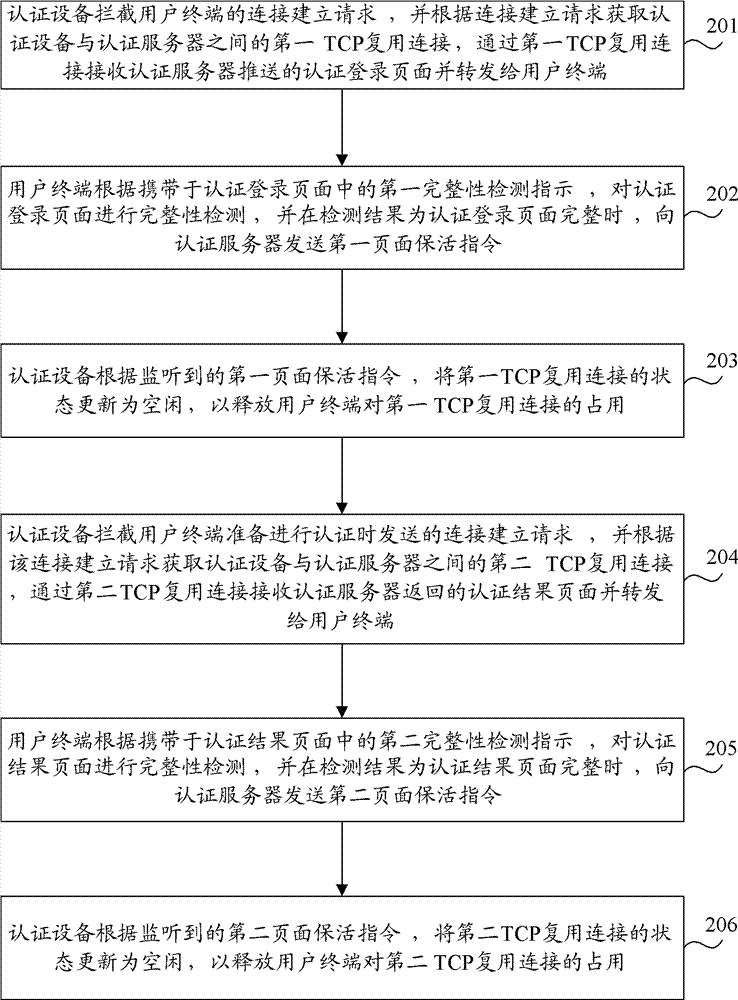
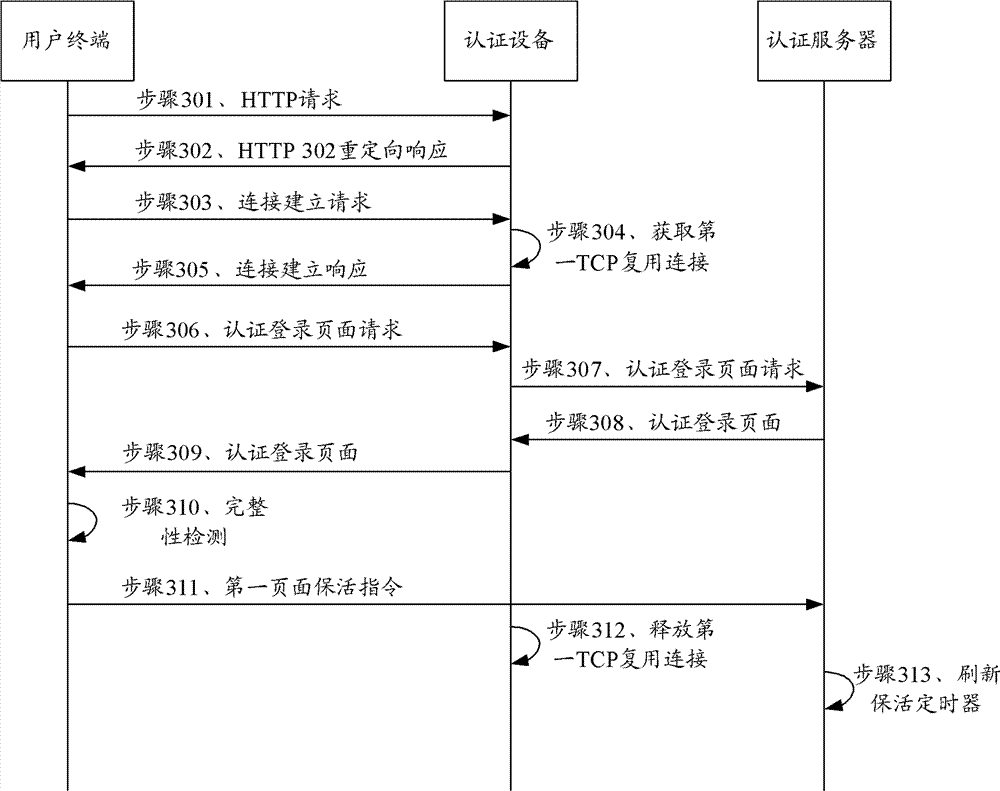
The invention provides an authentication method, equipment and system. The method comprises the following steps: the authentication equipment intercepts an authentication connection establishing request of a user terminal and acquires a target TCP (Transmission Control Principle) multiplexing connection according to the authentication connection establishing request; the authentication equipment transmits the intercepted authentication request information of the user terminal to an authentication server through the target TCP multiplexing connection, receives an authentication response page returned by the authentication server through the target TCP multiplexing connection and forwards the authentication response page to the user terminal; the user terminal carries out integrity detection on the authentication response page according to an integrity detection instruction in the authentication response interface and transmits a page keep-alive instruction to the authentication server when a detection result indicates the authentication response page is integral; and the authentication equipment releases the occupancy of the user terminal to the target TCP multiplexing connection according to the monitored page keep-alive instruction. According to the technical scheme disclosed by the invention, the problem of connection number bottleneck faced by the authentication server in the prior art is solved, and the network operation cost and the authentication cost are reduced.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Source housing
InactiveCN102446568AImprove versatilityReduce certification costsPortable shielded containersEngineeringRadiation
The invention relates to a source housing comprising: an outer housing, wherein the outer housing comprises an outer housing body and an outer housing sealing cover; an inner housing arranged in the outer housing, wherein the inner housing comprises an inner housing body and an inner housing sealing cover; and a radiation source adapter arranged inside the inner housing, wherein the outer surface of the radiation source adapter is matched with the inner surface of the inner housing body and the radiation source adapter can be detached from the inner housing body; the radiation source adapter is provided with a through hole for receiving a radiation source; and one end of the through hole of the radiation source adapter is connected to the bottom of the inner housing body, while the other end thereof is connected to the inner housing sealing cover. The source housing of the invention is suitable for sealing various radiation sources and also capable of shielding rays in non-radiation directions to a certain extent; therefore, an external shielding material is saved.
Owner:SHANGHAI SONGS LAB TECH DEV +1
Authentication method, apparatus, terminal, and computer-readable storage medium
ActiveCN111106931BImplement peer-to-peer authenticationImprove authentication efficiencyKey distribution for secure communicationEngineeringAuthentication
The present disclosure relates to an authentication method, device, terminal and computer-readable storage medium, and relates to the technical field of mobile communication. The method includes: the first terminal receives an authentication request sent by the second terminal; the first terminal determines whether it is in the same authentication domain as the second terminal; in the case of being in a different authentication domain, the first terminal extracts the second terminal in the authentication request The identifier of the second terminal and the public parameter of the authentication domain where the second terminal is located; the first terminal calculates the public key according to the identifier of the second terminal and the public parameter; the first terminal uses the public key to authenticate the second terminal. The technical solution of the present disclosure can improve the authentication efficiency and reduce the authentication cost.
Owner:CHINA TELECOM CORP LTD
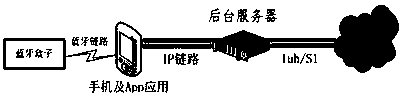
A security authentication system and corresponding method utilizing operator network
InactiveCN104796891BImprove stabilityImprove securitySecurity arrangementSecurity authenticationAuthentication system
The present invention provides a safety authentication system utilizing an operator's network, including a SIM card interface device, a mobile terminal, and a background server for accessing the operator's core network; the SIM card interface device is provided with an SE chip and a SIM card slot, The SIM card is arranged in the SIM card slot, and the SIM card interface device is used to forward the authentication information of the SIM card to the background server through the mobile terminal; the mobile terminal is used to read the SIM card in the interface device information, register to the core network of the operator through the background server, and communicate with the background server through the IP communication network; the background server establishes a standard Iuh or S1 connection for the mobile terminal, and transmits signaling; utilizes the authentication information of the received SIM card Perform security authentication on mobile terminals. The invention does not require human participation and roaming charges are not required for overseas authentication, the authentication cost is low, the process is simple, and the stability and security are high.
Owner:BEIJING TRAVELRELY SOFTWARE TECH CO LTD
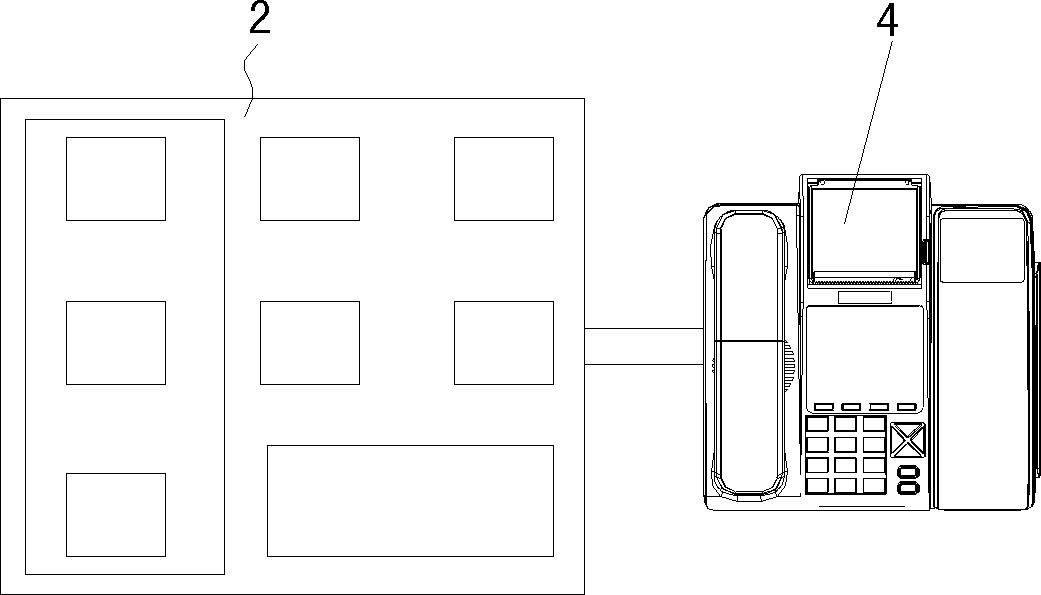
Payment terminal capable of realization of splittable combination of secure payment and mobile payment and payment method thereof
The invention discloses a payment terminal capable of realization of splittable combination of secure payment and mobile payment and a payment method thereof. The payment terminal comprises two modules: a secure payment module and a mobile payment module, wherein the two modules are encapsulated respectively and independently and then are connected. More specifically, the secure payment module comprises a keyboard, a display screen, a magnetic card reader, an IC card read-write device, and a printed circuit board; and the mobile payment module consists of a keyboard, a main display screen, a non-contact IC card read-write device, a wireless communication module, a printing module, a telephone module and a printed circuit board. Moreover, the secure payment module and the mobile payment module are provided with identification communication modules; the secure payment module can be connected to an existing mobile payment terminal; and the mobile payment module can be connected to a financial POS machine. According to the invention, security certification is only required by the secure payment module; not only can the secure payment module and the mobile payment module be used in combination in an on-line mode, but also the secure payment module can be used separately in combination with an existing mobile payment terminal in an on-line mode and the mobile payment module can be used separately in combination with an existing financial POS machine in an on-line mode.
Owner:FUJIAN NEWLAND PAYMENT TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com