Distributed power transaction credible identity management method and system, and computer equipment
A distributed power and identity management technology, applied in the field of information security, can solve problems such as low security, difficulty, interconnection and interoperability, and achieve the effect of protecting identity privacy, strengthening broad applicability, and simplifying the application process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
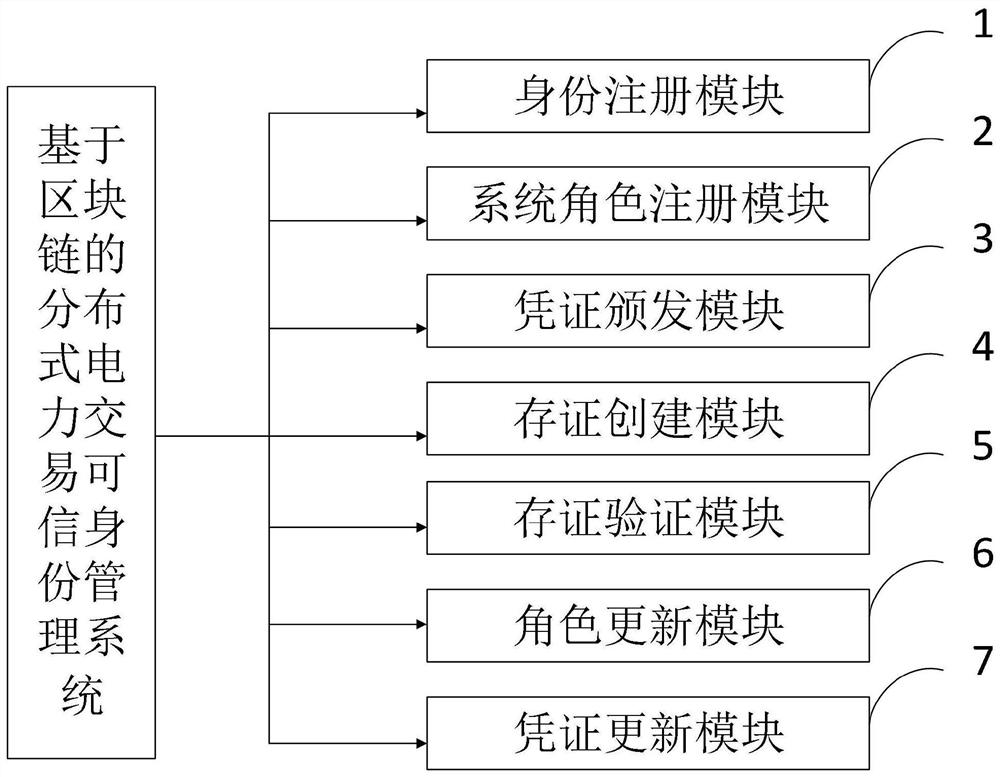
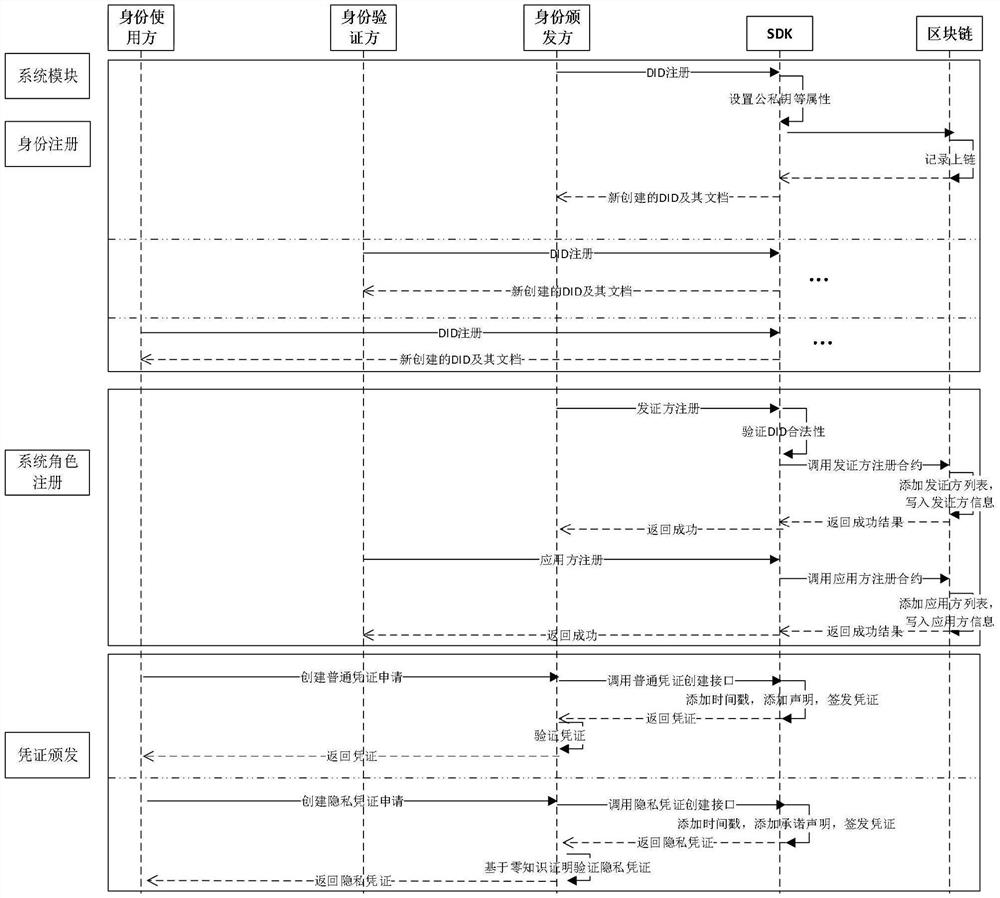
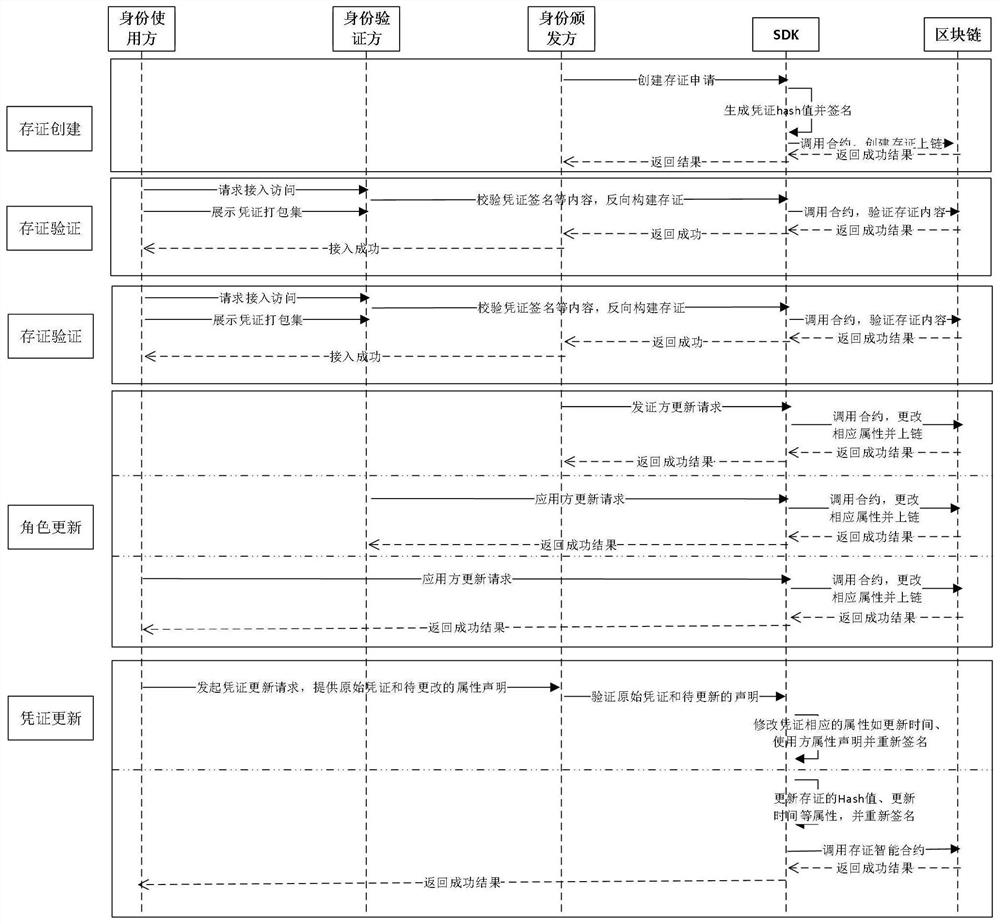
[0112] Aiming at the decentralization and ubiquitous interconnection requirements of the smart grid and the energy Internet, the present invention realizes the realization of entities (human, machine, etc.) , Thing) identity autonomous control, realize identity security authentication, authorization and data exchange under the state of privacy protection, and provide a new, safe and efficient distributed authentication system. At the same time, the system provides capabilities such as autonomous identity management, agile access, and privacy authentication of distributed heterogeneous entities, and the authentication method is convenient and the authentication cost is low.
[0113] The present invention provides a blockchain-based trusted authentication system for distributed power transactions. The ecological roles of the system include an identity issuer, an identity user, and an identity verifier.
[0114] Among them, the identity issuer refers to those entities that are we...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com