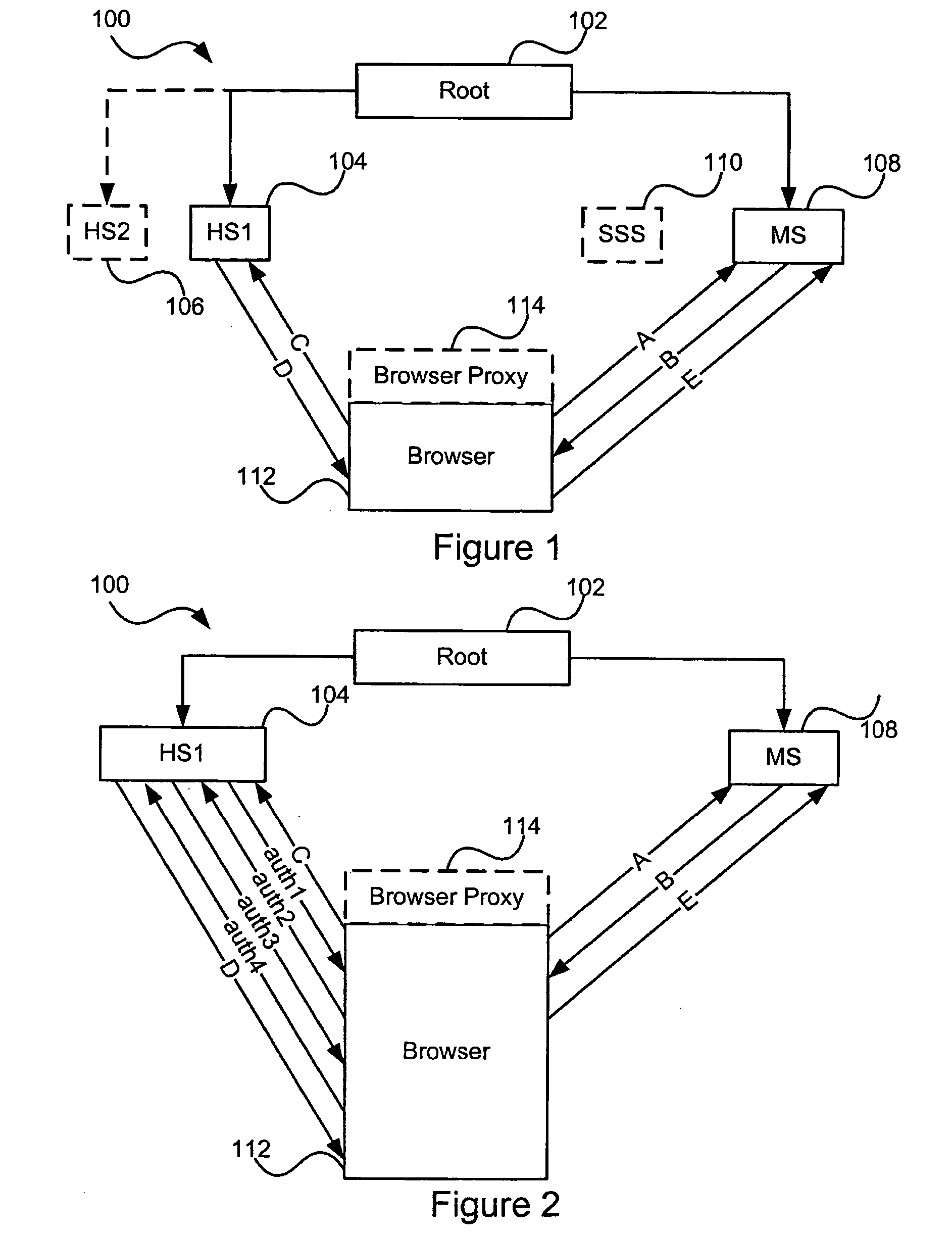
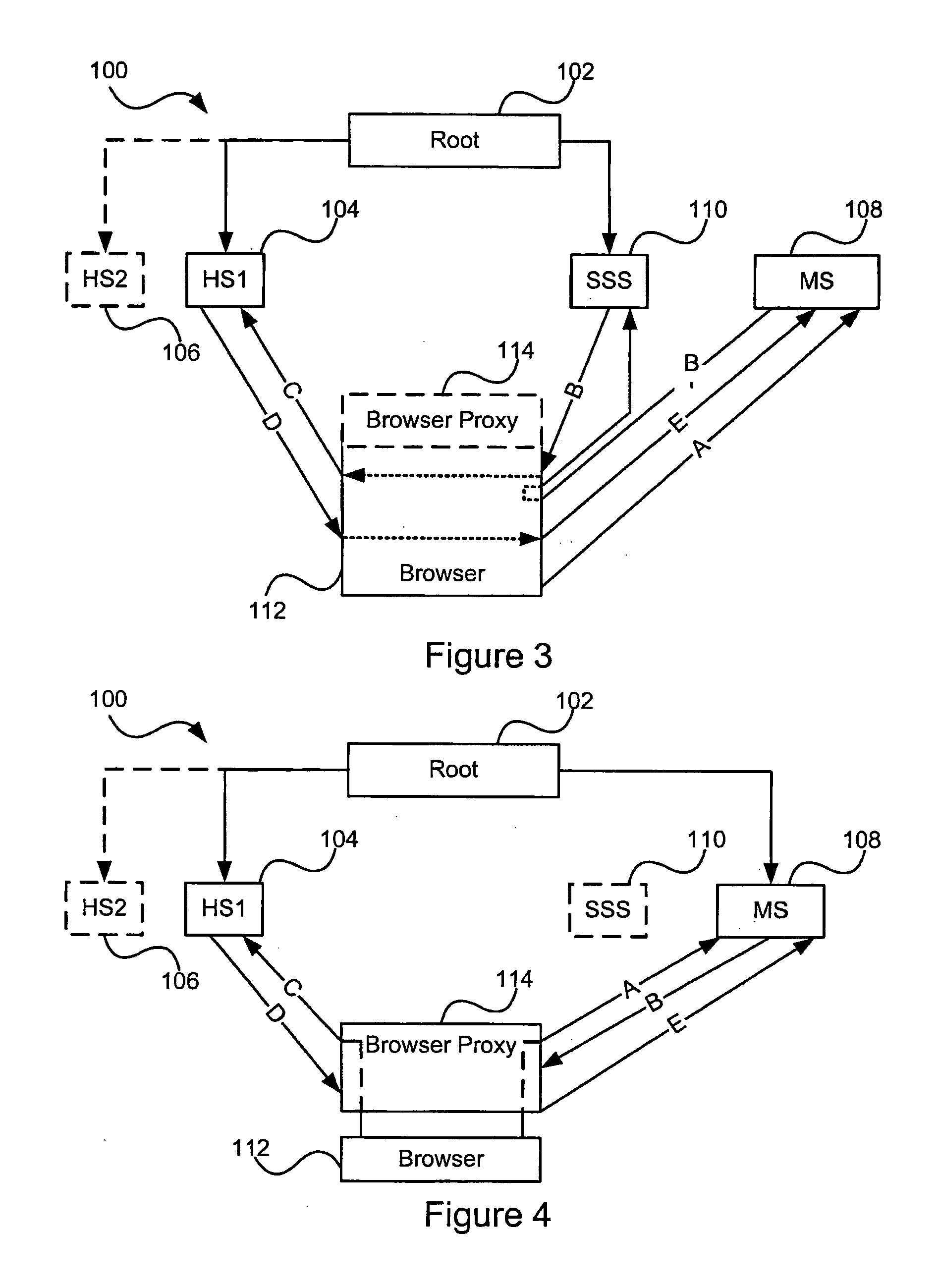
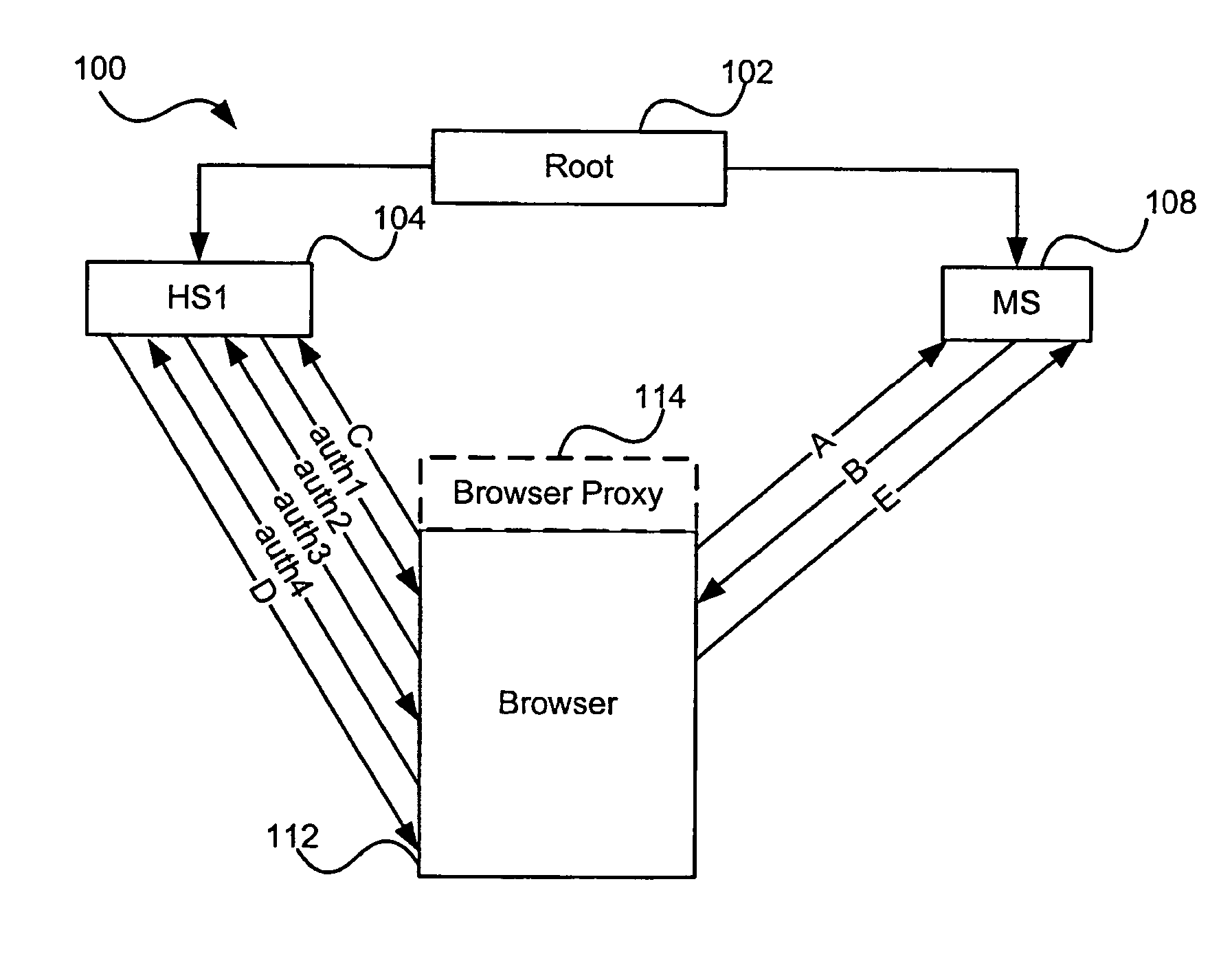
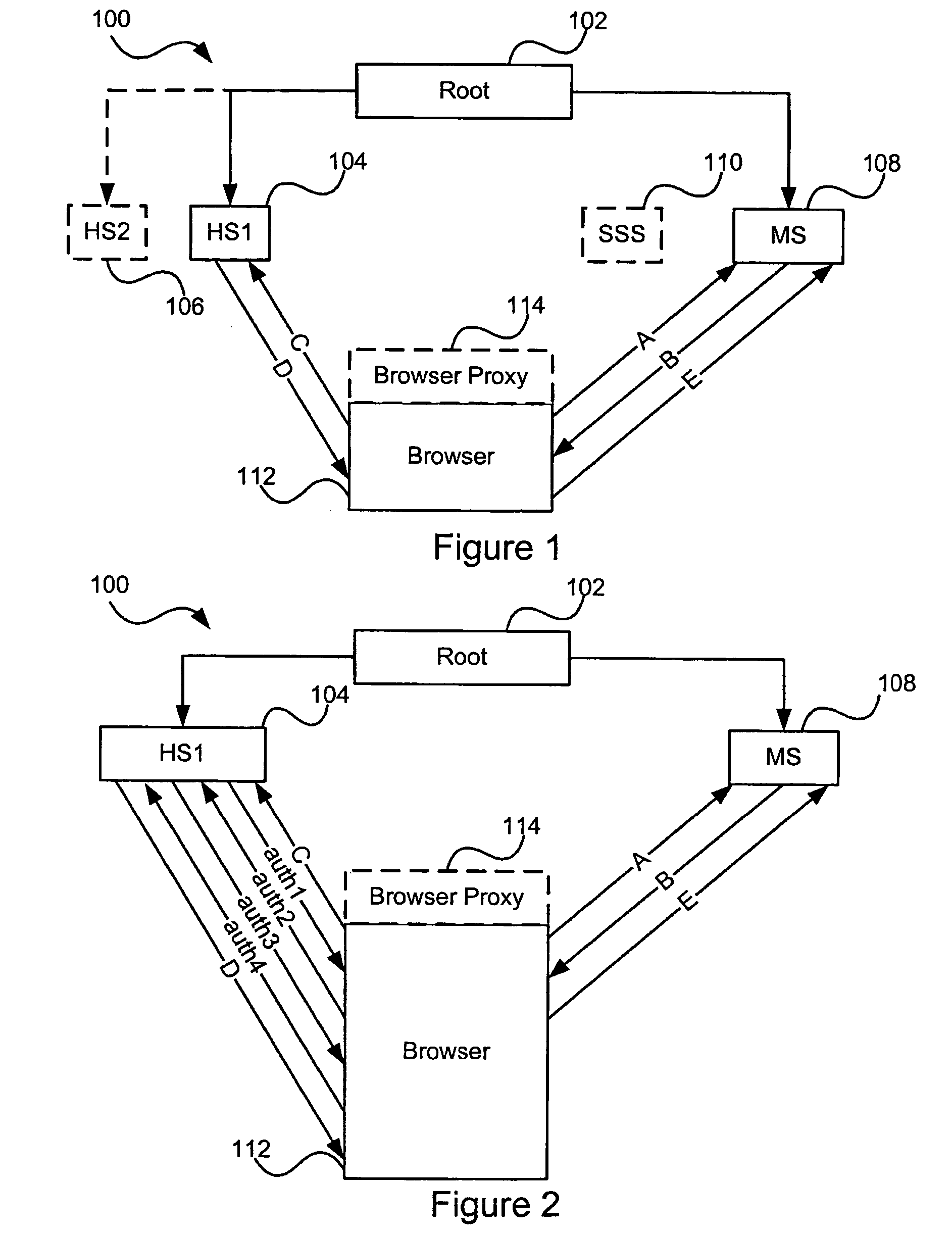
Patents
Literature
233 results about "Identity management system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
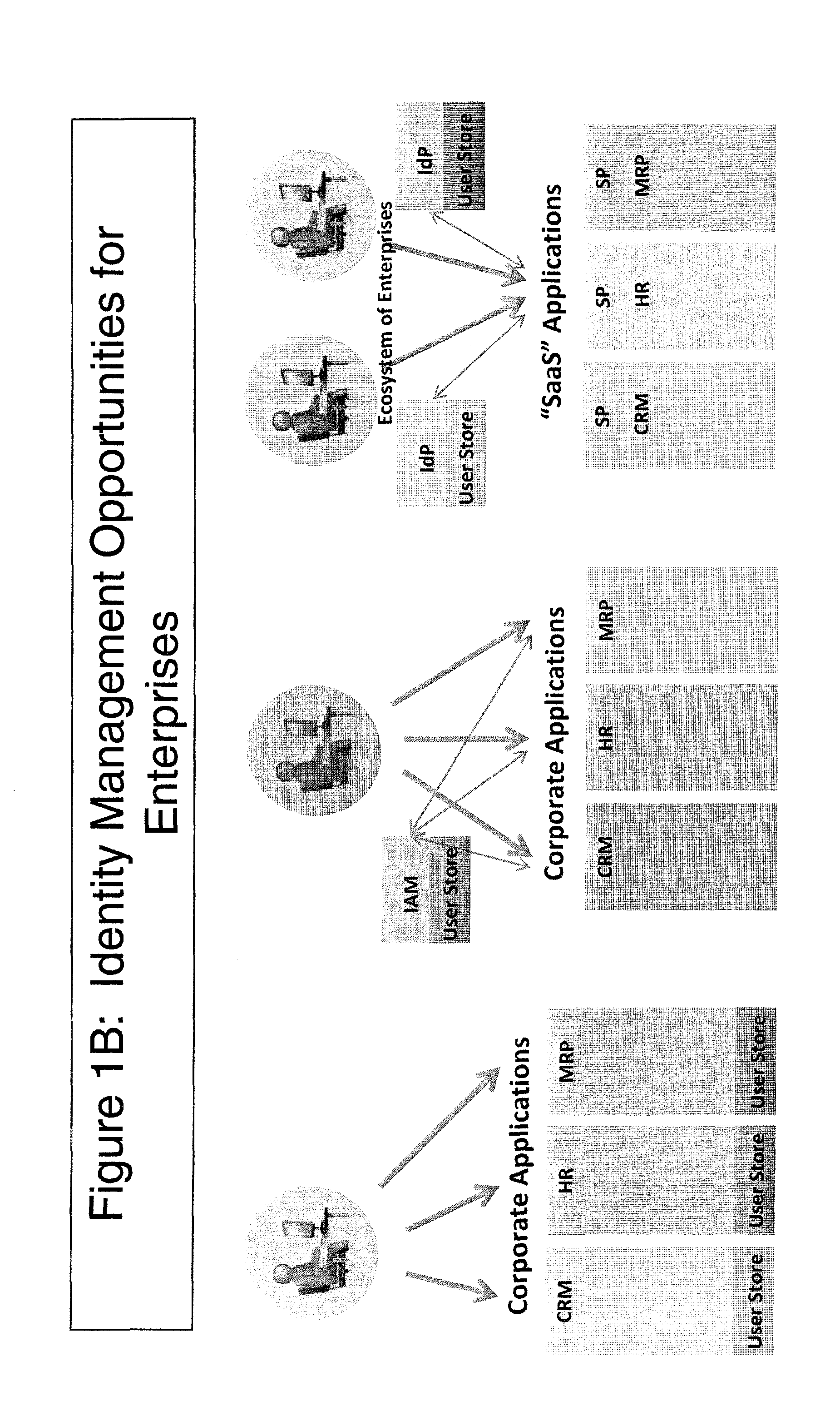
An identity management system refers to an information system, or to a set of technologies that can be used for enterprise or cross-network identity management...
Blockchain identity management system based on public identities ledger
ActiveUS9635000B1Effectively prevents unauthorized sharingMultiple keys/algorithms usagePublic key for secure communicationSystems managementIdentity management system
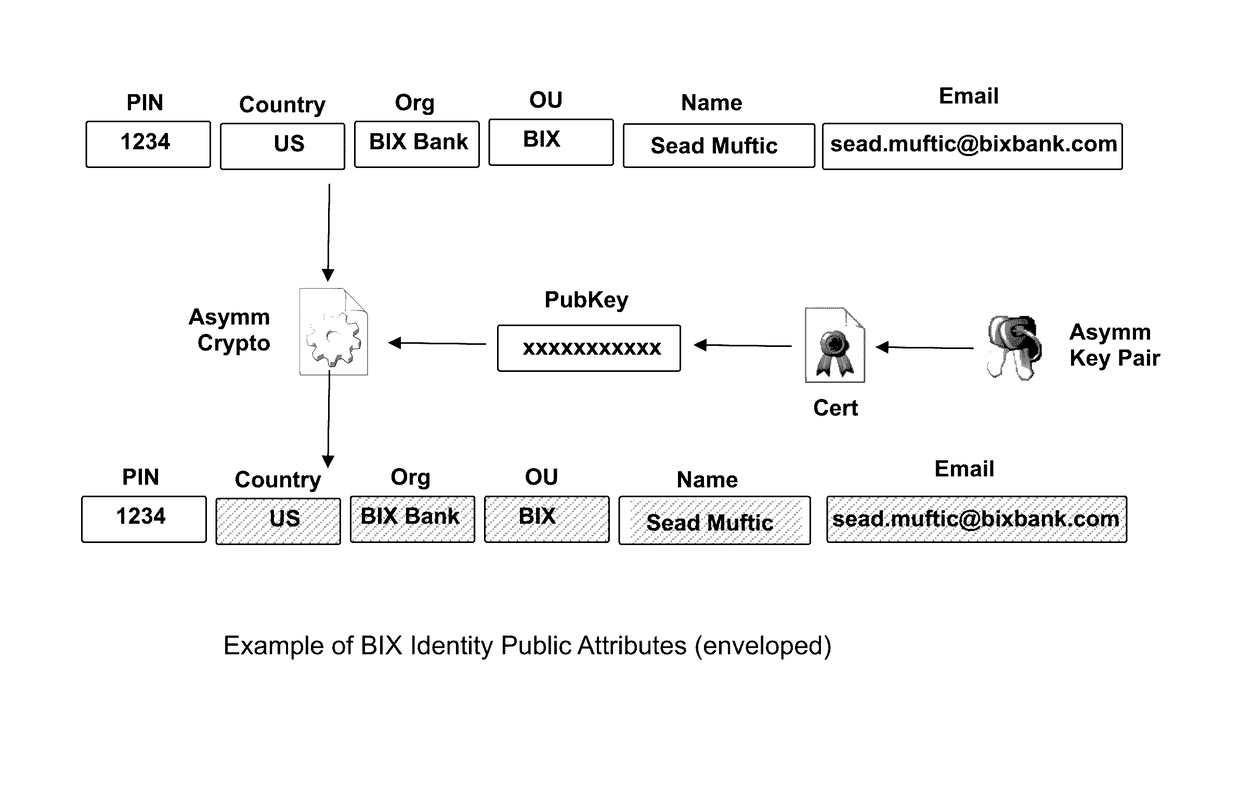
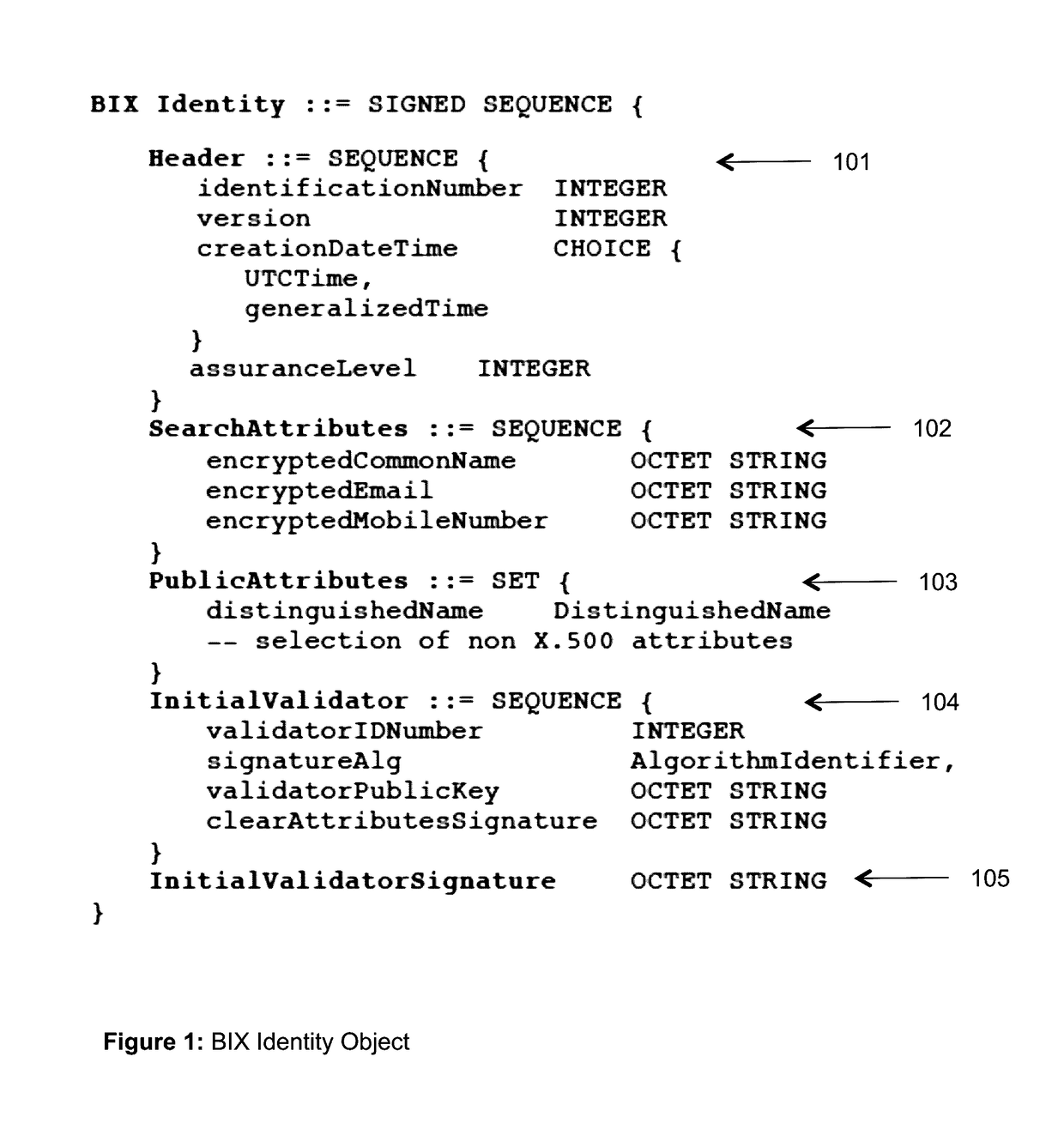
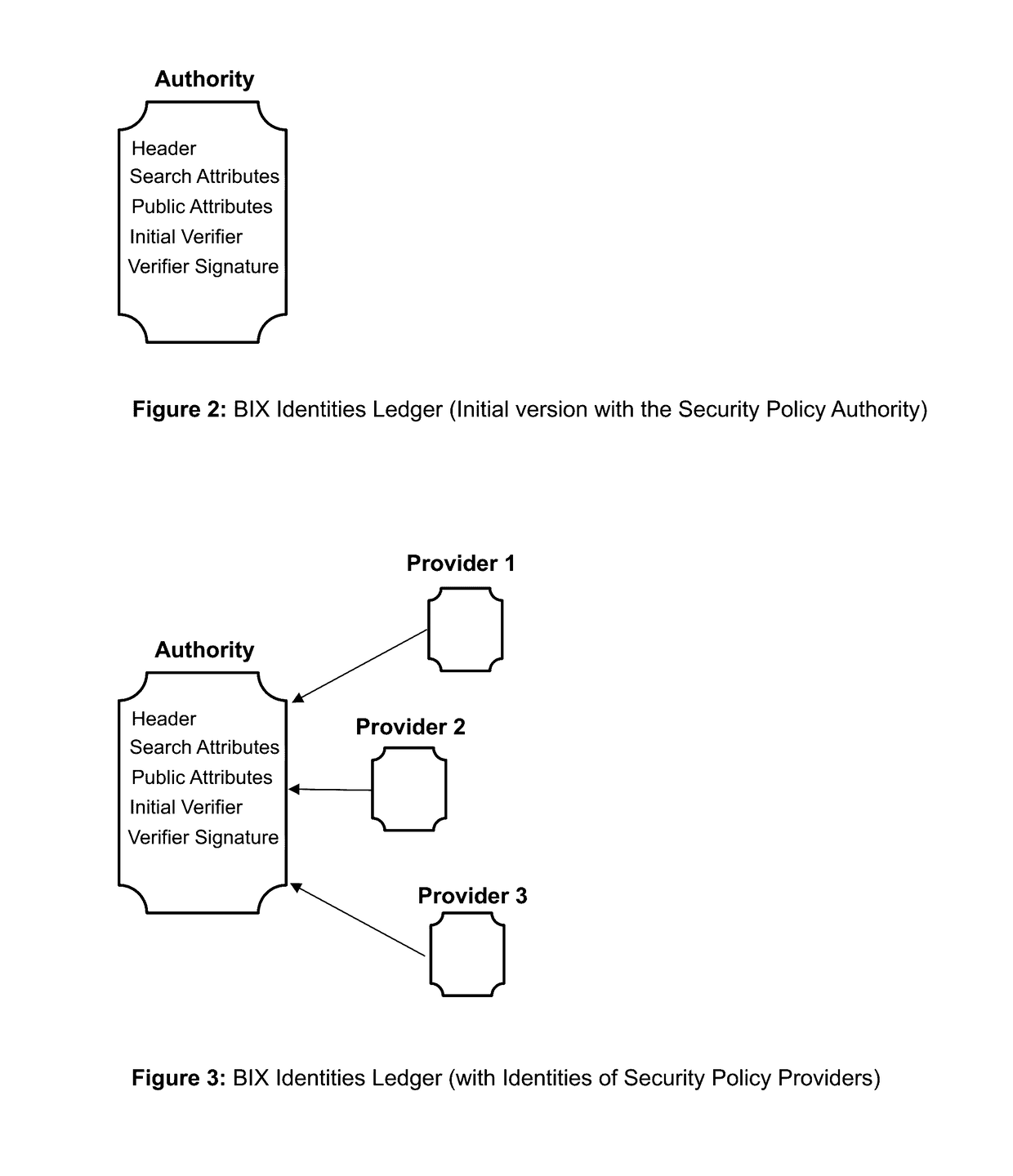
The invention describes an identity management system (IDMS) based on the concept of peer-to-peer protocols and the public identities ledger. The system manages digital identities, which are digital objects that contain attributes used for the identification of persons and other entities in an IT system and for making identity claims. The identity objects are encoded and cryptographically encapsulated. Identity management protocols include the creation of identities, the validation of their binding to real-world entities, and their secure and reliable storage, protection, distribution, verification, updates, and use. The identities are included in a specially constructed global, distributed, append-only public identities ledger. They are forward- and backward-linked using the mechanism of digital signatures. The linking of objects and their chaining in the ledger is based on and reflect their mutual validation relationships. The identities of individual members are organized in the form of linked structures called the personal identities chains. Identities of groups of users that validated identities of other users in a group are organized in community identities chains. The ledger and its chains support accurate and reliable validation of identities by other members of the system and by application services providers without the assistance of third parties. The ledger designed in this invention may be either permissioned or unpermissioned. Permissioned ledgers have special entities, called BIX Security Policy Providers, which validate the binding of digital identities to real-world entities based on the rules of a given security policy. In unpermissioned ledgers, community members mutually validate their identities. The identity management system provides security, privacy, and anonymity for digital identities and satisfies the requirements for decentralized, anonymous identities management systems.
Owner:MUFTIC SEAD
Dispensing digital objects to an electronic wallet
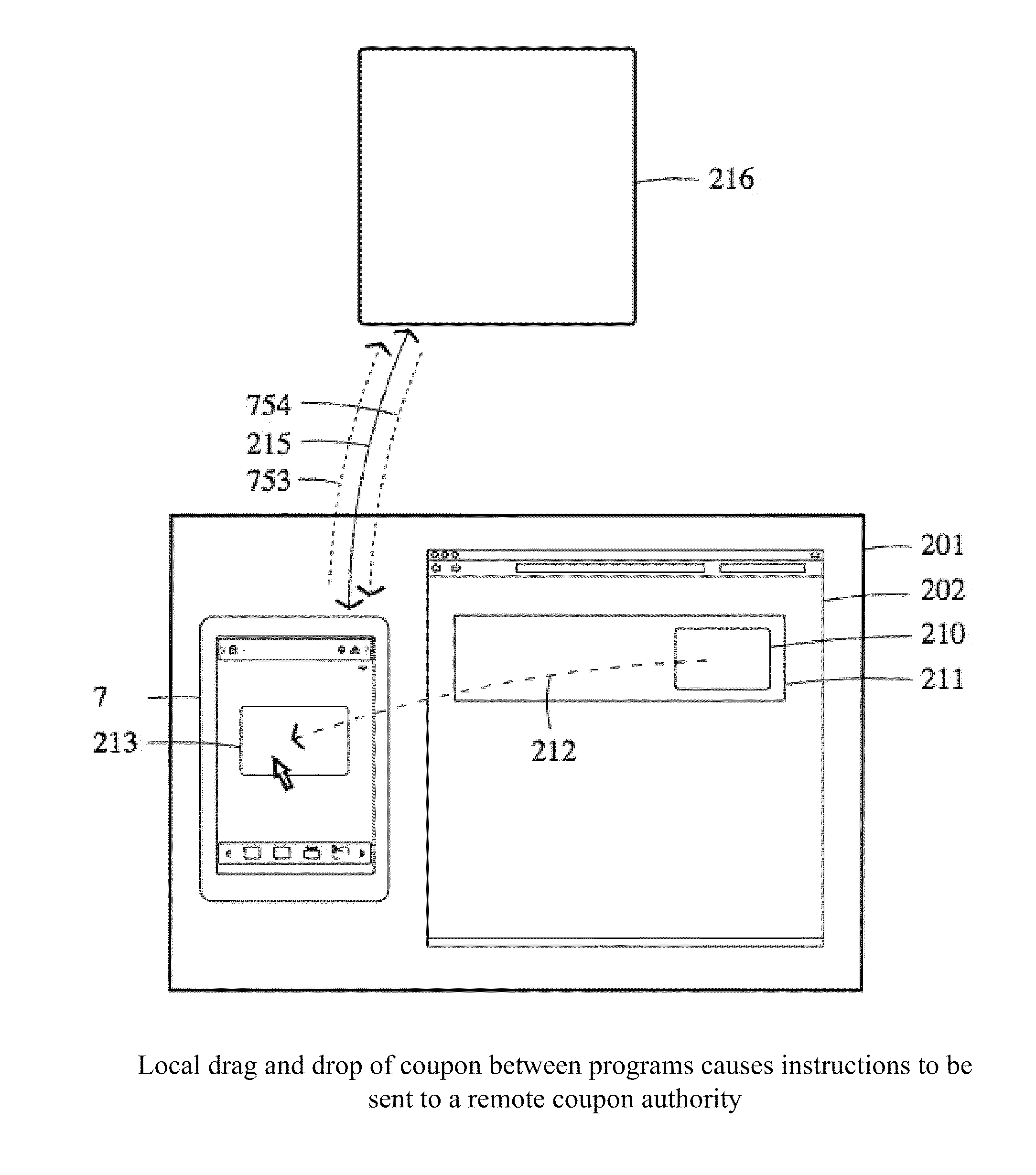
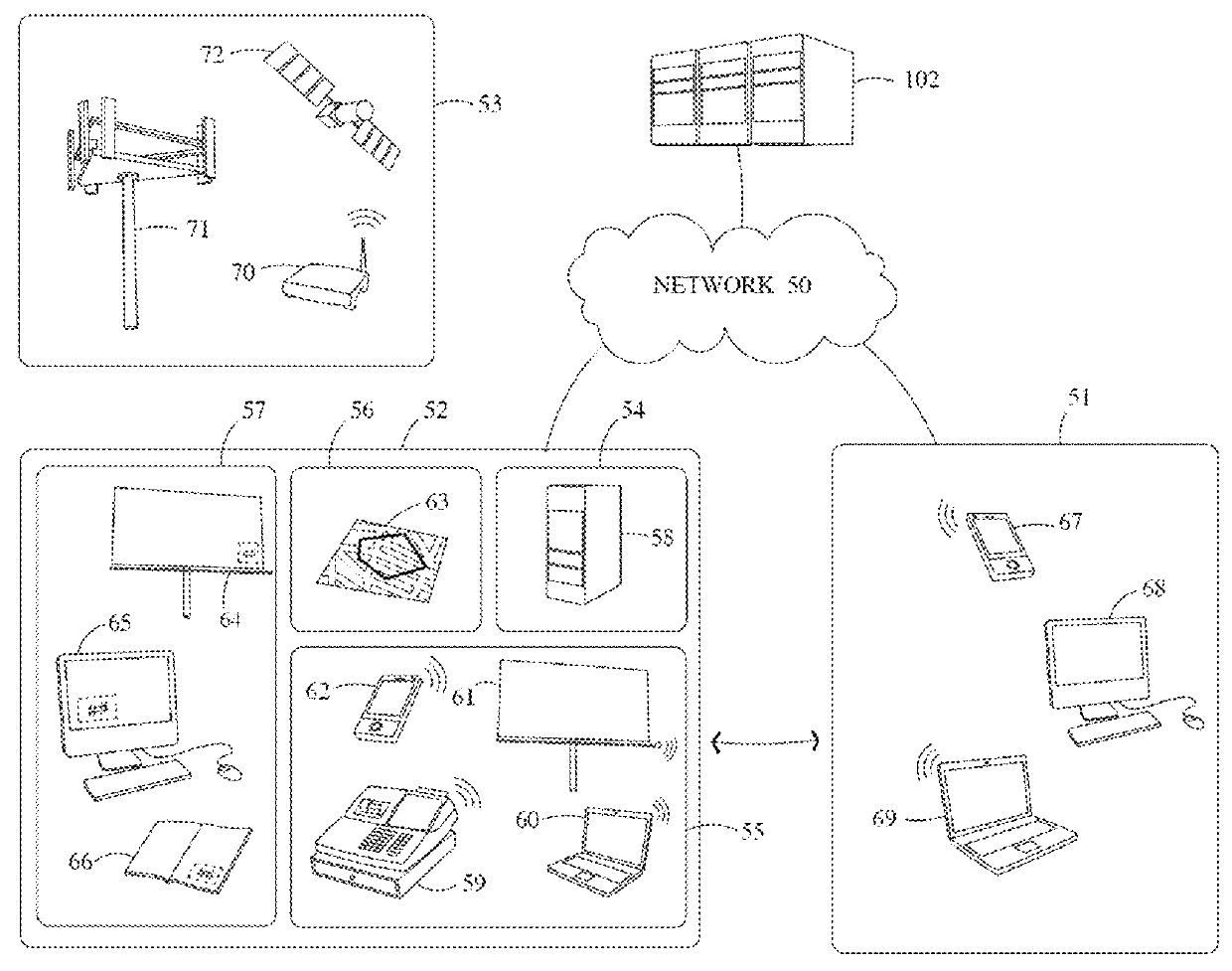
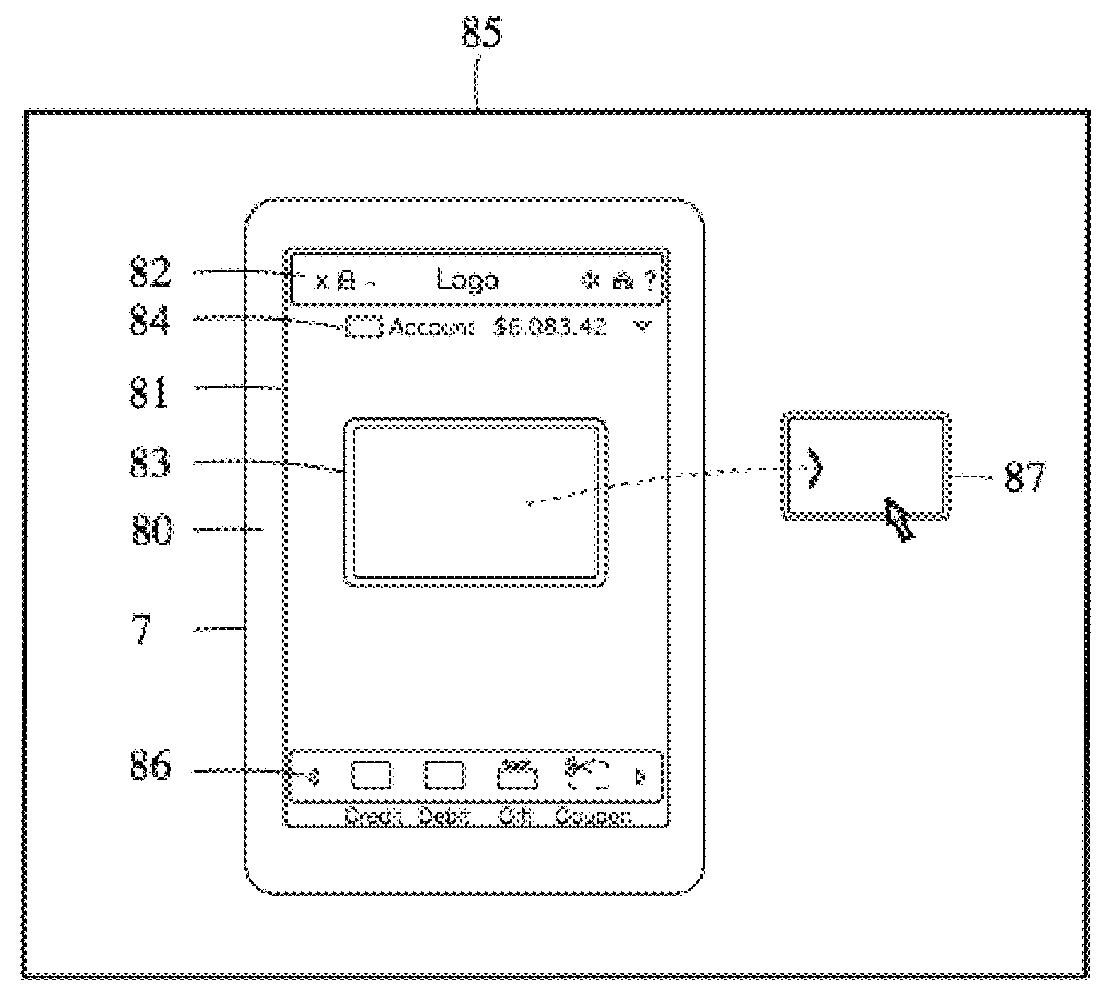
A configuration system and method is disclosed that includes a unified and integrated configuration that is composed of a payment system, an advertising system, and an identity management system such that the unified system has all of the benefits of the individual systems as well as several additional synergistic benefits. Also described are specific configurations including the system's access point architecture, visual wallet simulator user interface, security architecture, coupon handling as well as the system's structure and means for delivering them as targeted advertising, business card handling, membership card handling for the purposes of login management, receipt handling, and the editors and grammars provided for customizing the different types of objects in the system as well as the creation of new custom objects with custom behaviors. The configurations are operable on-line as well as through physical presence transactions.
Owner:GOOGLE LLC
Localized access
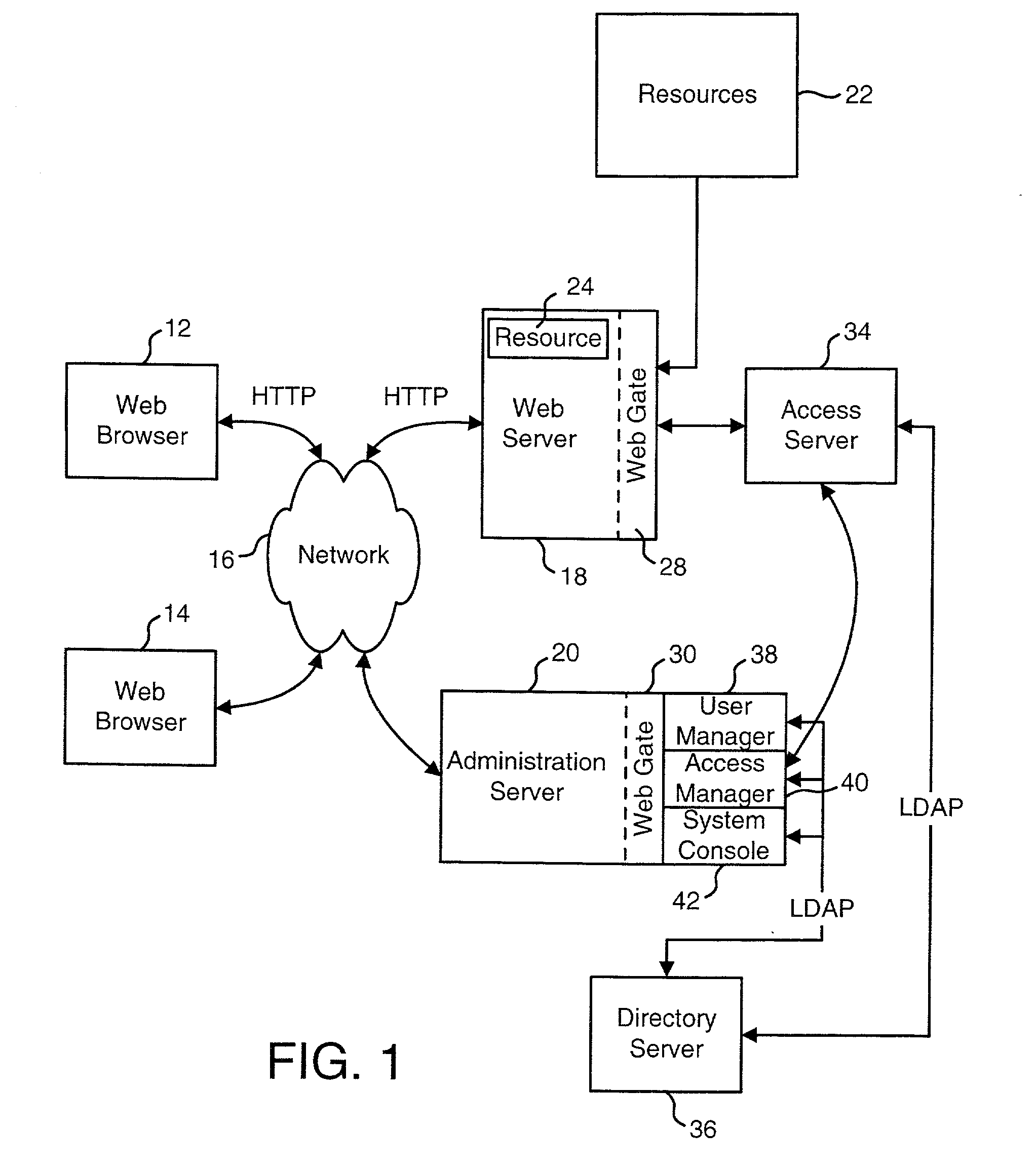
InactiveUS7080077B2Data processing applicationsDigital data processing detailsIdentity management systemDatabase
An identity management system manages identity profiles that store information about various entities. A localized access feature for an identity management system allows for a set of identity profiles to be grouped together in order to define a locale. Users outside the locale can be restricted from accessing identity profiles inside the locale. Alternatively, users outside the locale can be restricted from accessing certain attributes of identity profiles inside the locale.
Owner:ORACLE INT CORP
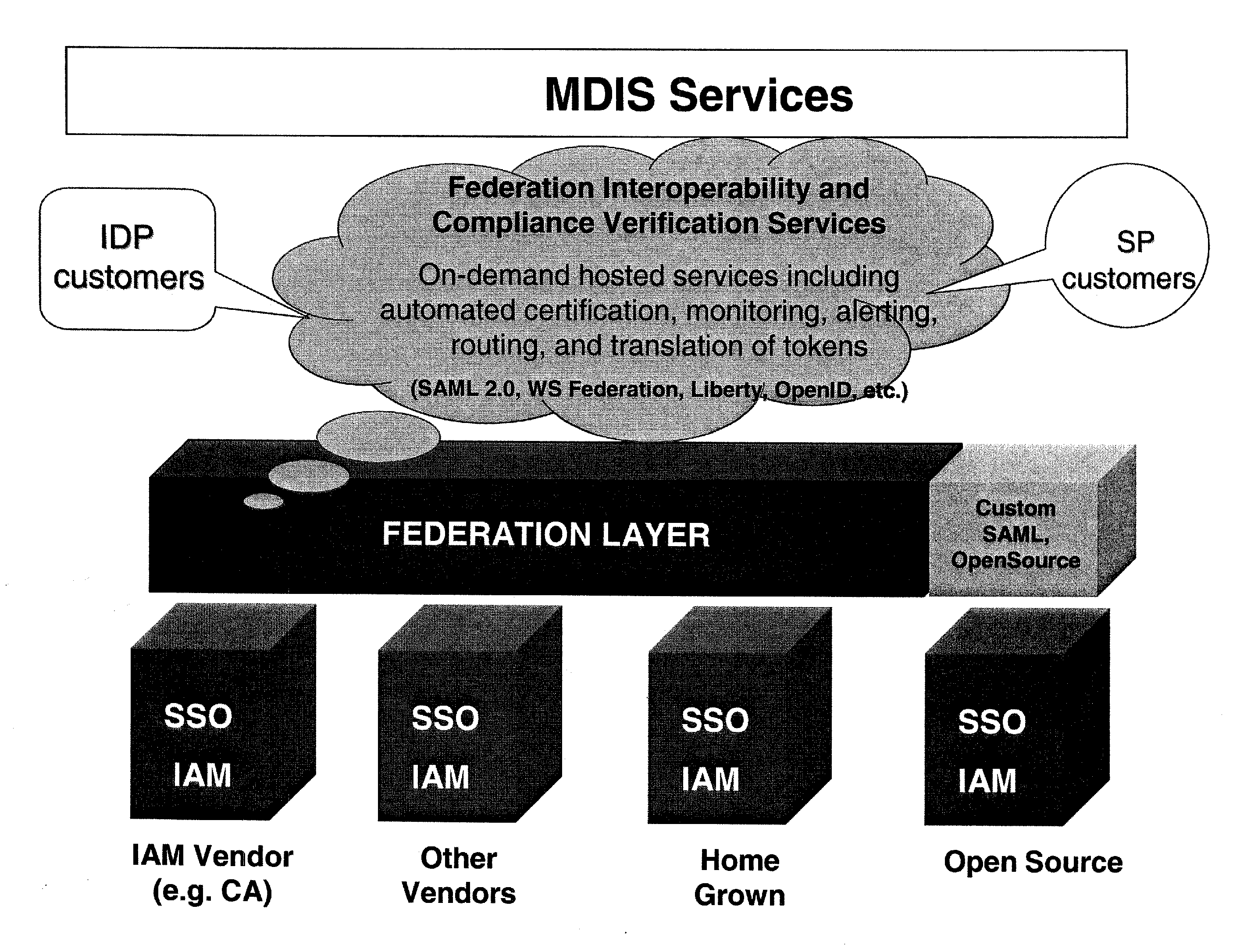
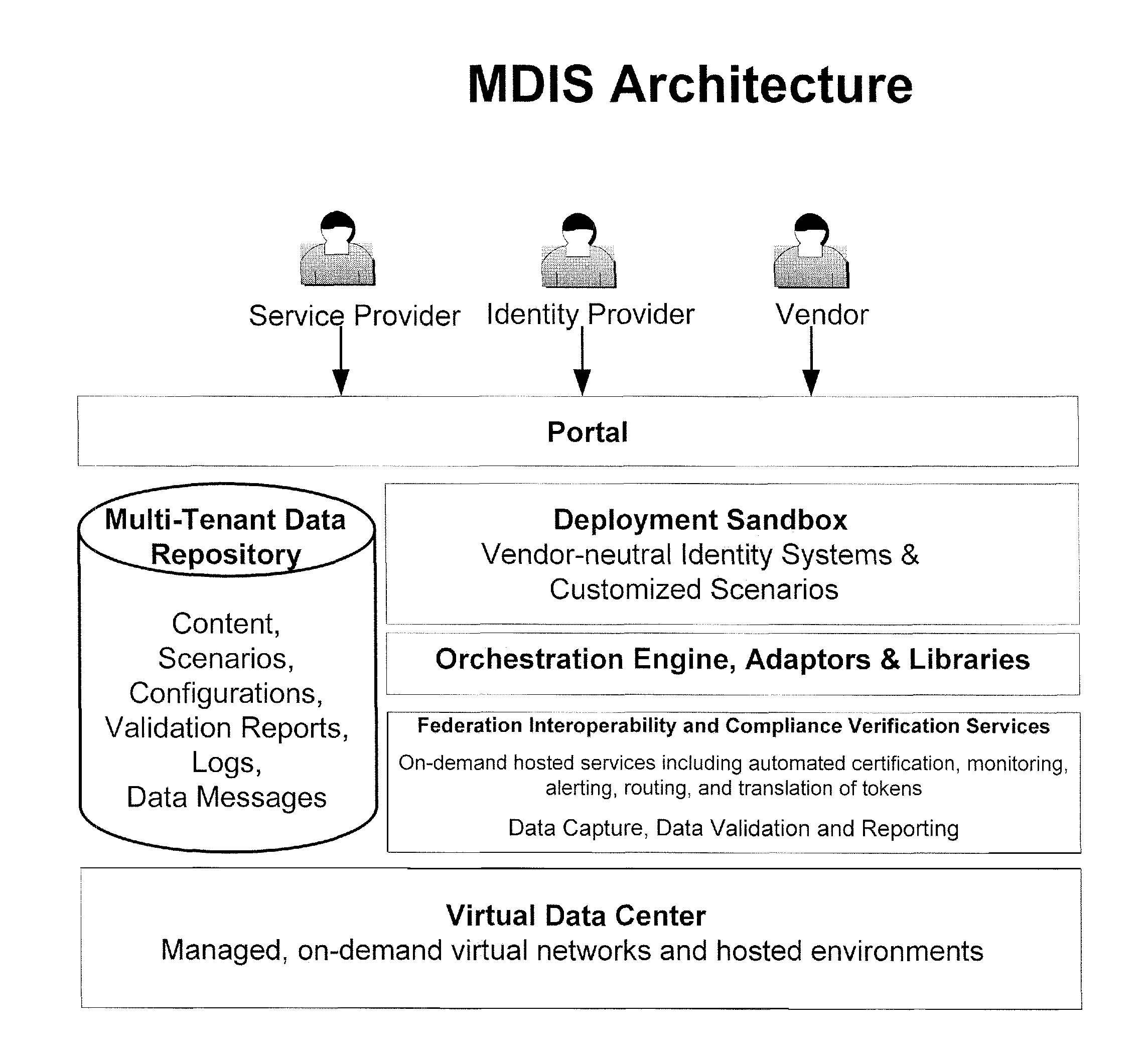
Method and Apparatus for Multi-Domain Identity Interoperability and certification
ActiveUS20090089625A1Memory loss protectionDigital data processing detailsInternet privacyFederated identity
A method and apparatus to provide identity management deployment interoperability and compliance verification. In one embodiment, the system also provides on-demand services including automated certification, monitoring, alerting, routing, and translation of tokens for federated identity related interactions between multi-domain identity management systems is provided.
Owner:FUGEN SOLUTIONS
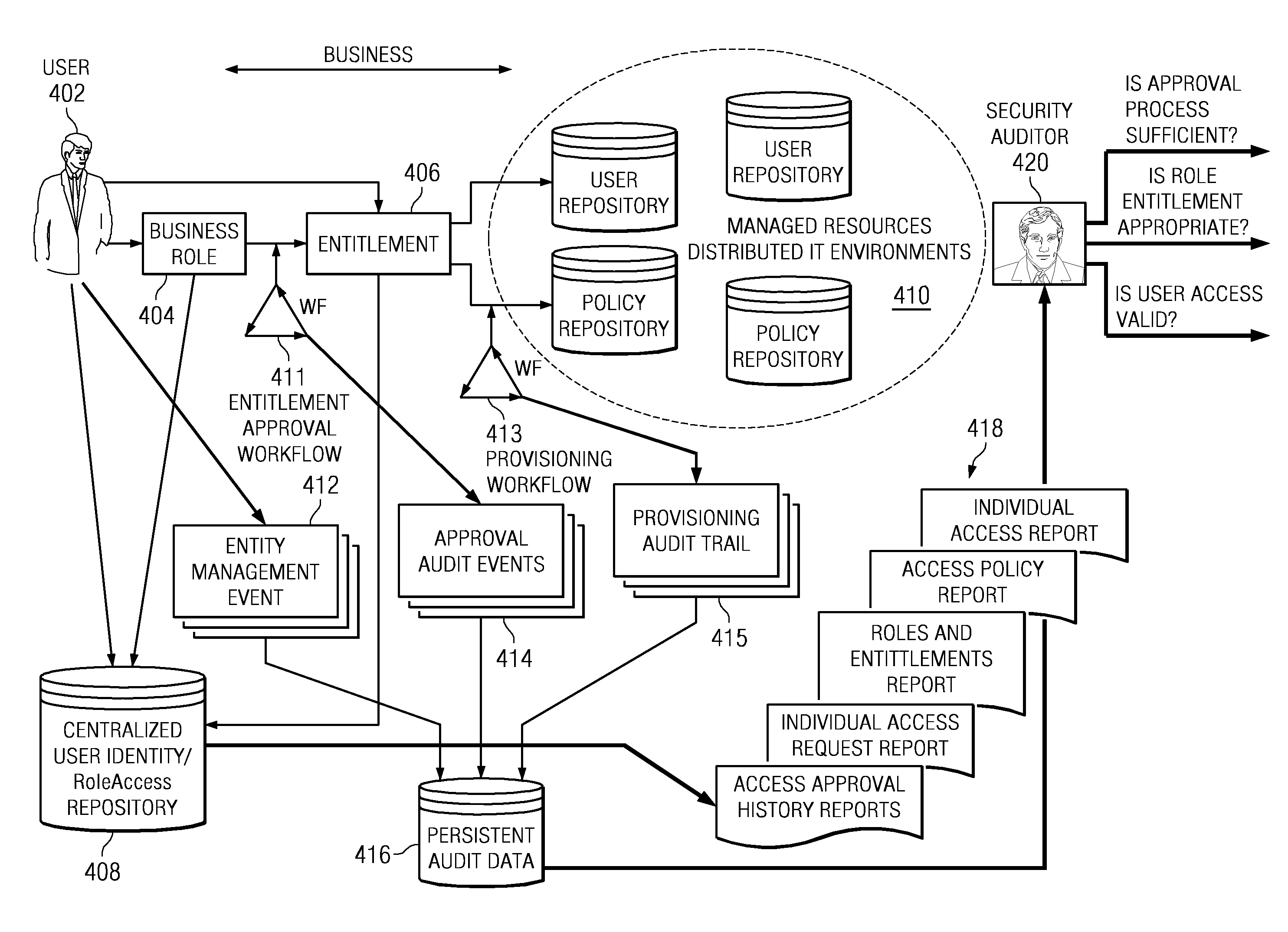
Managing user access entitlements to information technology resources
ActiveUS20090150981A1Digital data processing detailsUser identity/authority verificationData processing systemInterface layer
A computer implemented method, data processing system, and computer program product for logical management and provisioning of business applications within the framework of an identity management system. The illustrative embodiments providing an interface layer to map respective attributes, permissions, and resource accounts in a data repository needed to represent access to business applications via a managed service in the identity management system. The illustrative embodiments define user entitlements on a user account associated with the managed service. The illustrative embodiments provision user access to the business applications via the managed service in the identity management system upon user request.
Owner:SERVICENOW INC
Localized access
InactiveUS20020091745A1Limited accessData processing applicationsDigital data processing detailsIdentity management systemDatabase
An identity management system manages identity profiles that store information about various entities. A localized access feature for an identity management system allows for a set of identity profiles to be grouped together in order to define a locale. Users outside the locale can be restricted from accessing identity profiles inside the locale. Alternatively, users outside the locale can be restricted from accessing certain attributes of identity profiles inside the locale.
Owner:ORACLE INT CORP
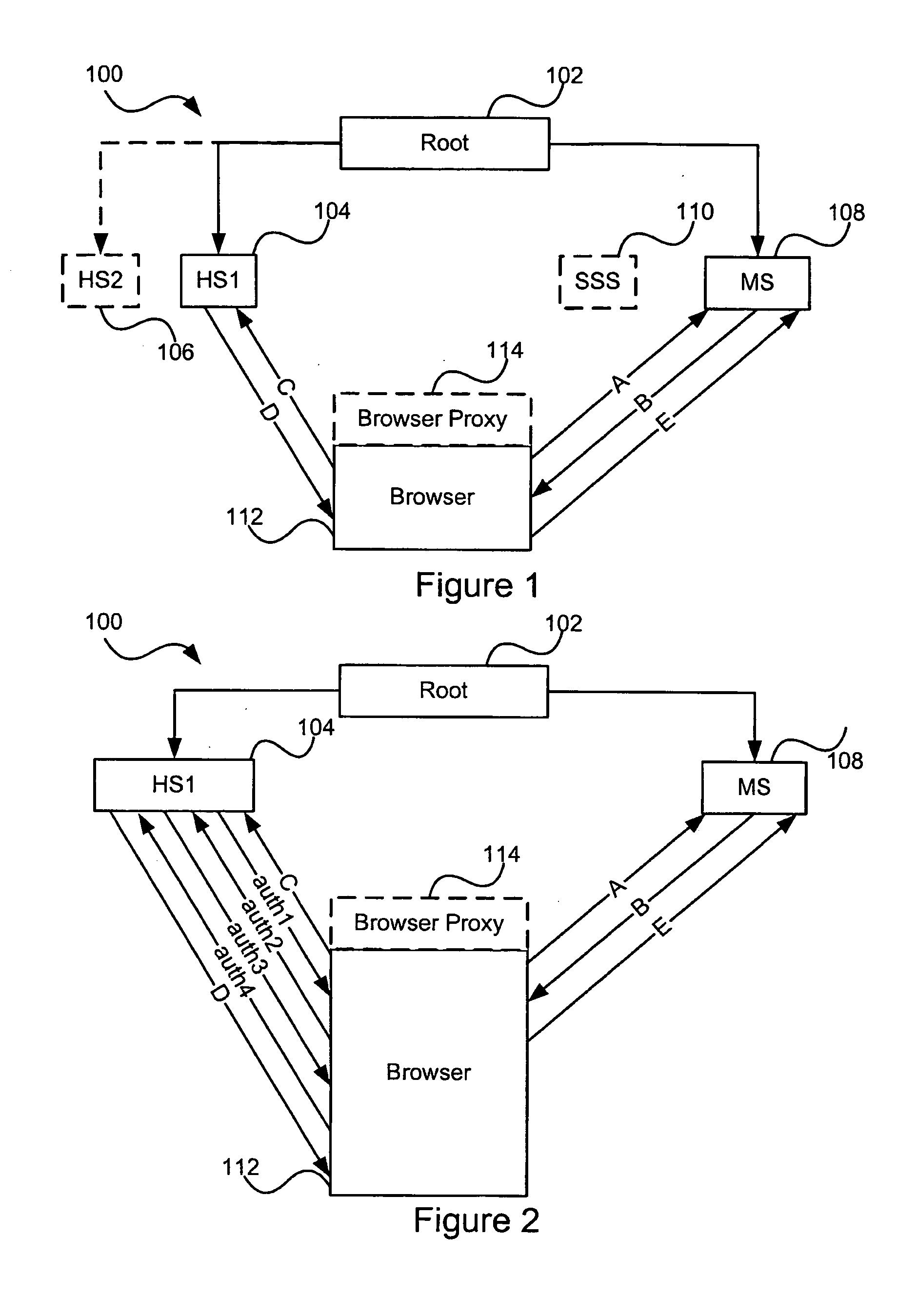
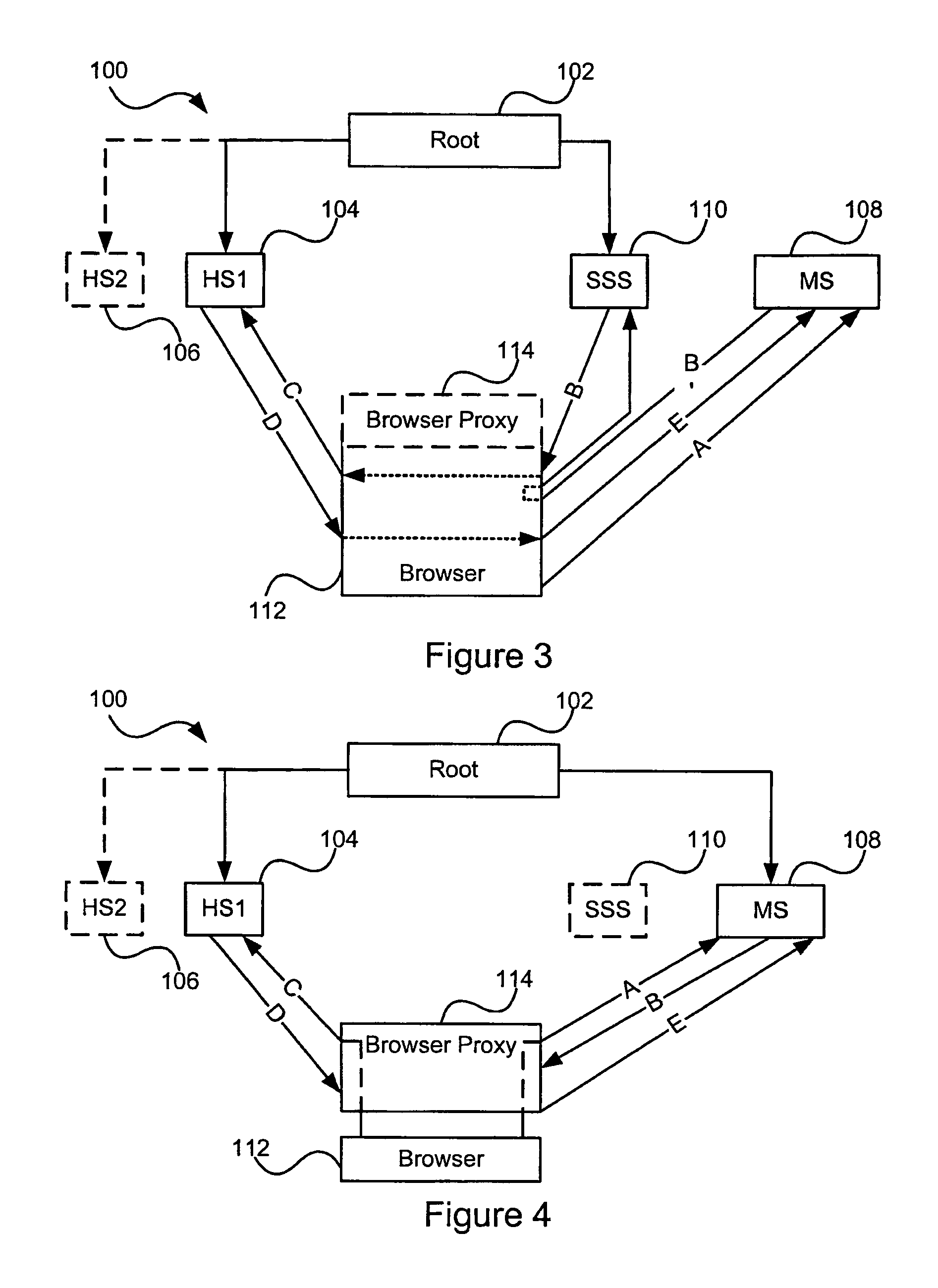
Distributed hierarchical identity management system authentication mechanisms
ActiveUS20050283614A1Data taking preventionUser identity/authority verificationThird partyInternet privacy
A set of methods, and systems, for use in an identity management system are disclosed herein. A modular user identity information datastore using hardware accelerated encryption for user data security operates in a network for receiving requests for, and issuing responses containing user information including third party accredited assertions.
Owner:CALLAHAN CELLULAR L L C
System and method for the reversible leasing of anonymous user data in exchange for personalized content including targeted advertisements
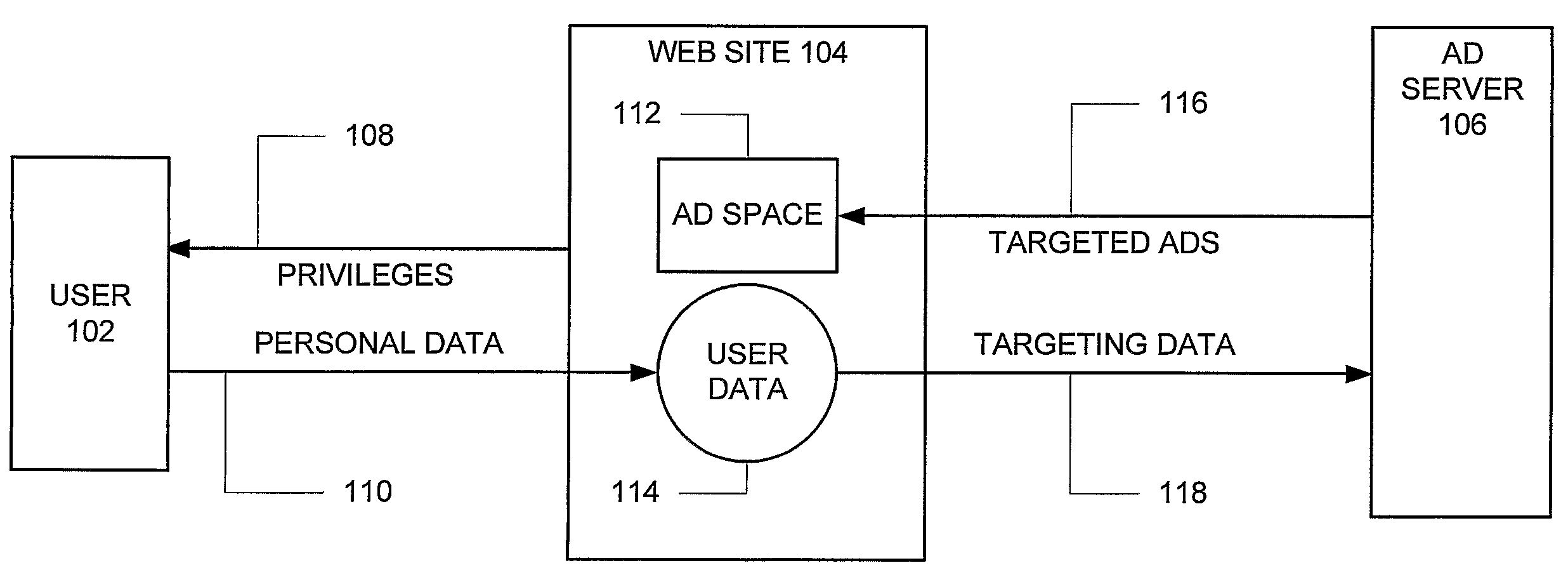
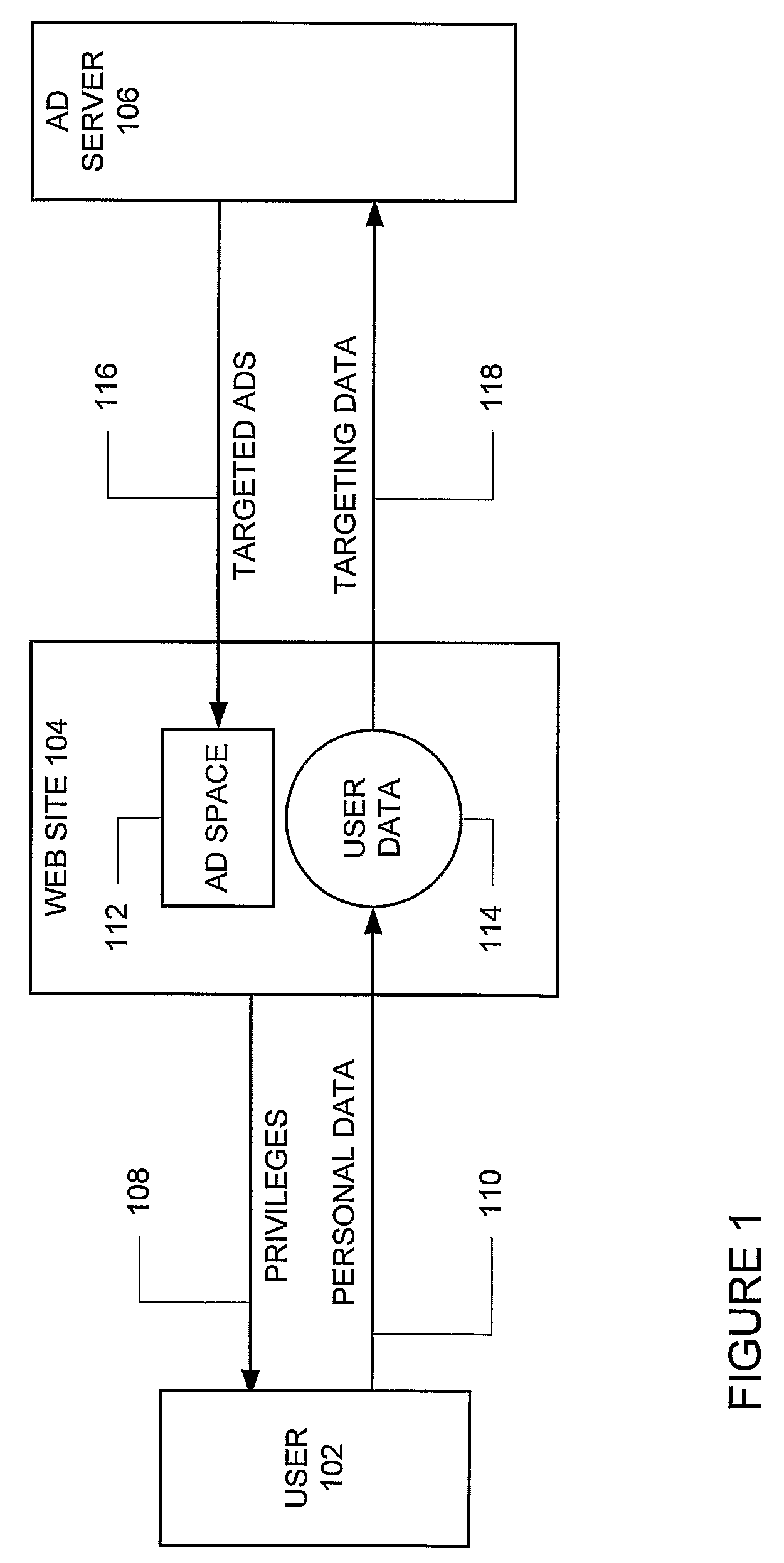
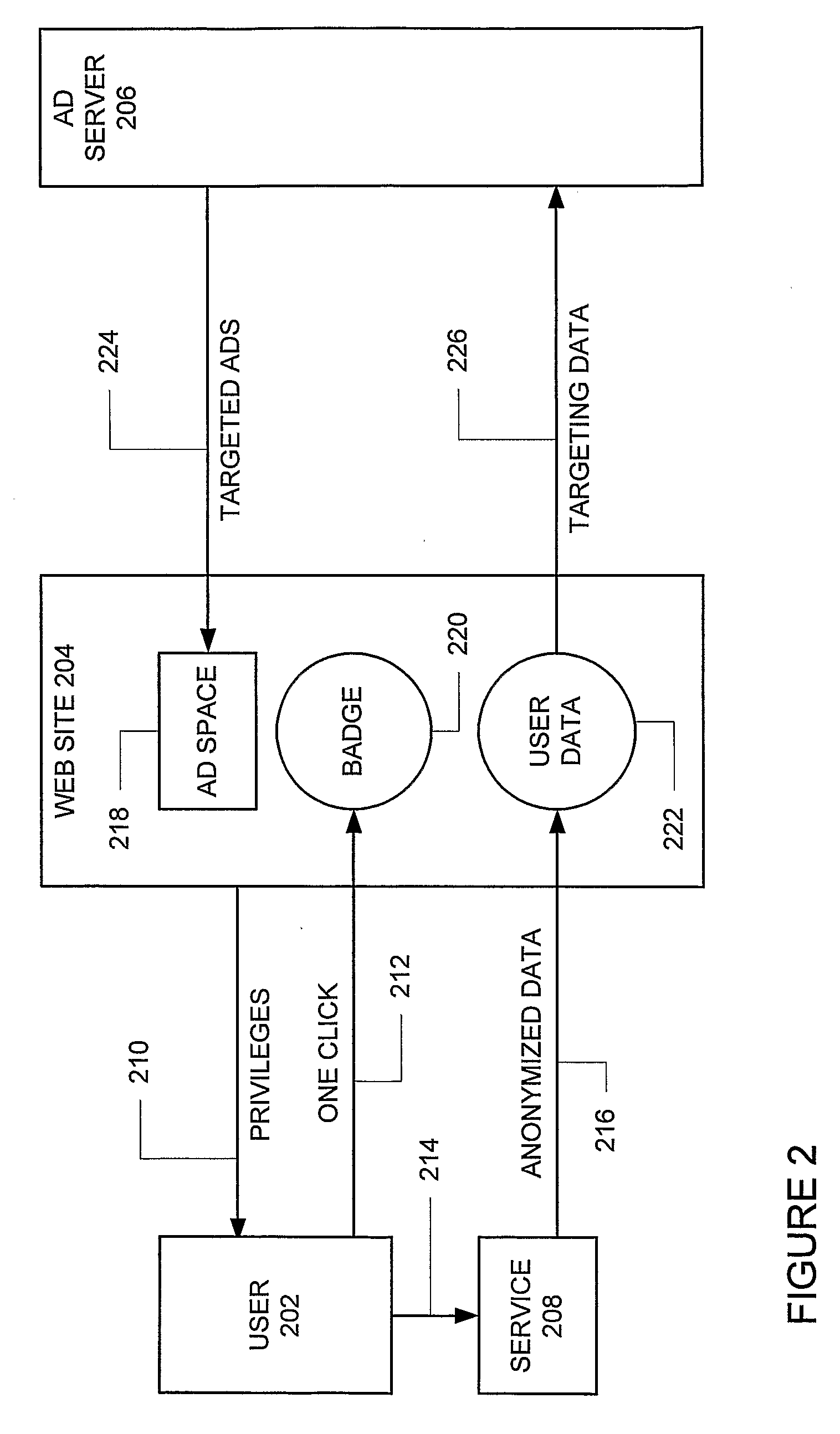
A system and method for the reversible leasing of anonymous user data in exchange for personalized content including targeted advertisements includes: (a) helping users gather and manage data representing their interests (404); (b) distilling this data to a condensed and anonymous form (434); (c) making it easy to review, edit, and add to this data; (d) providing a simple way for sites to ask for this data (414); (e) enabling users to grant reversible access to a site with one click (432); (f) providing sites with multiple ways to access and use this data once the user has granted access (424) and (g) motivating the user to keep their data accurate and up-to-date (403). In this manner, Internet users can lease data to web sites in a way that is convenient, secure, and under user control, respecting the user desire for transparency and privacy, and avoiding the complexity and trust issues experienced by both users and web sites when utilizing identity management systems.
Owner:PREFPASS
Identity management system and method
ActiveUS7571473B1Digital data processing detailsUnauthorized memory use protectionApplication softwareIdentity management system
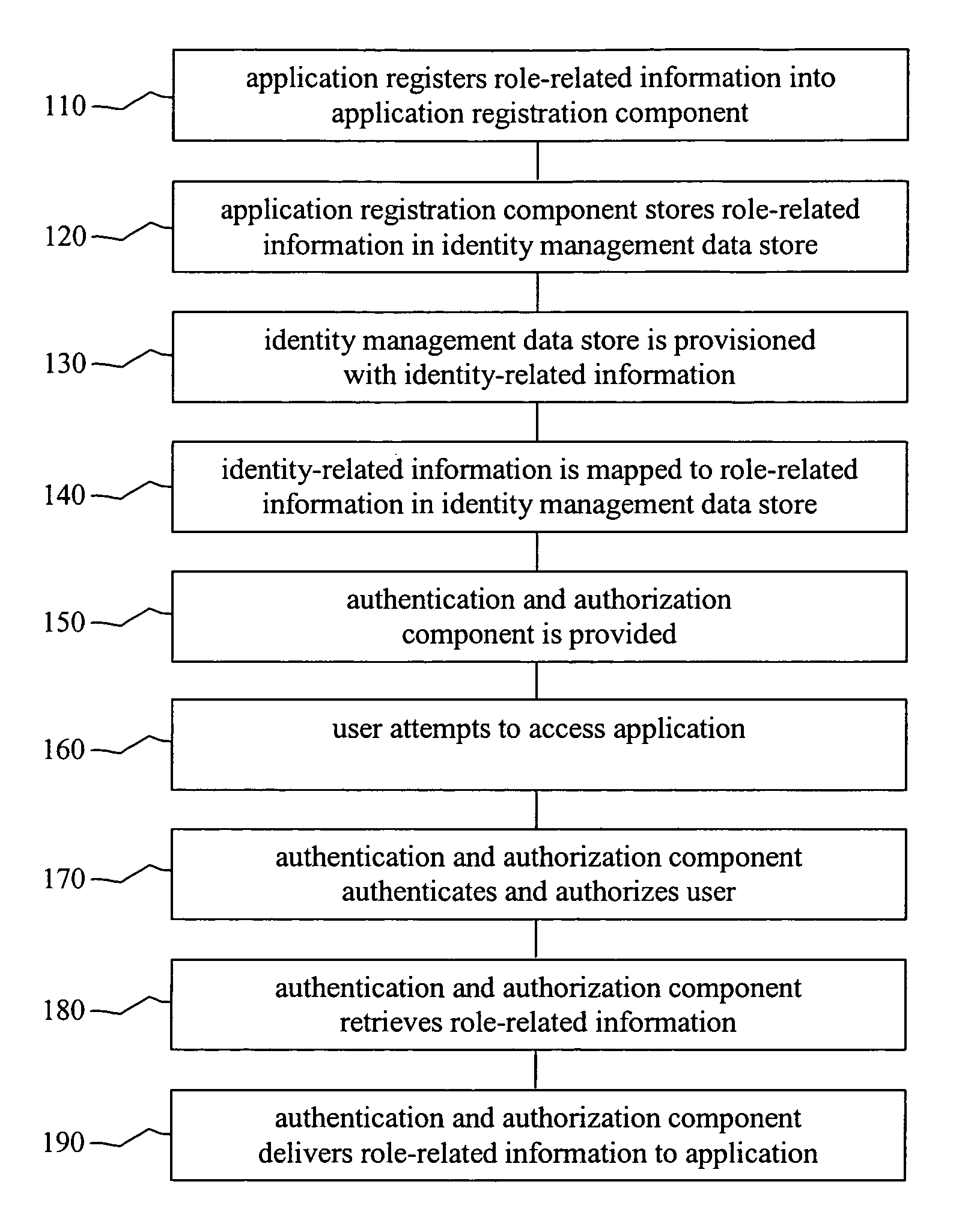
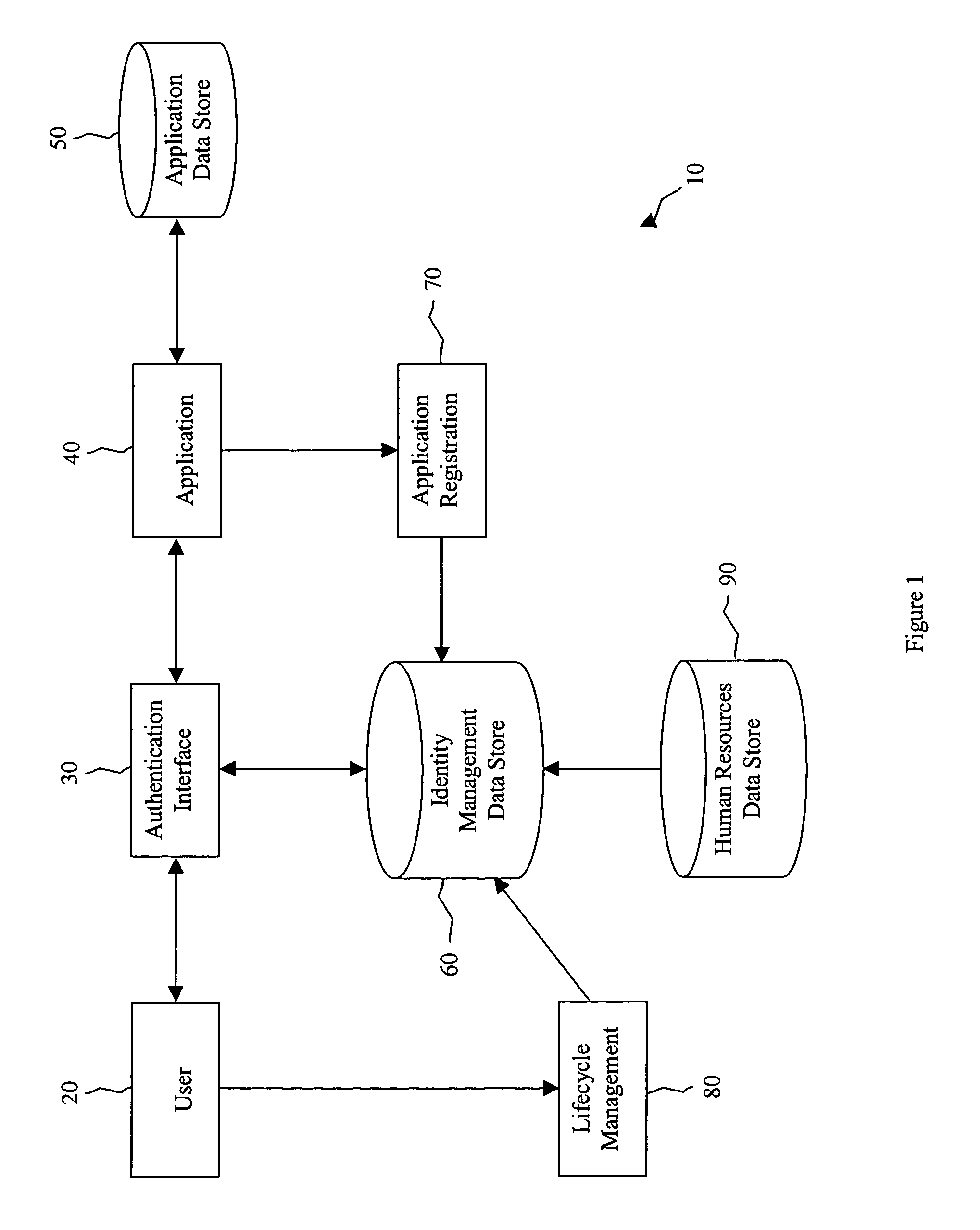
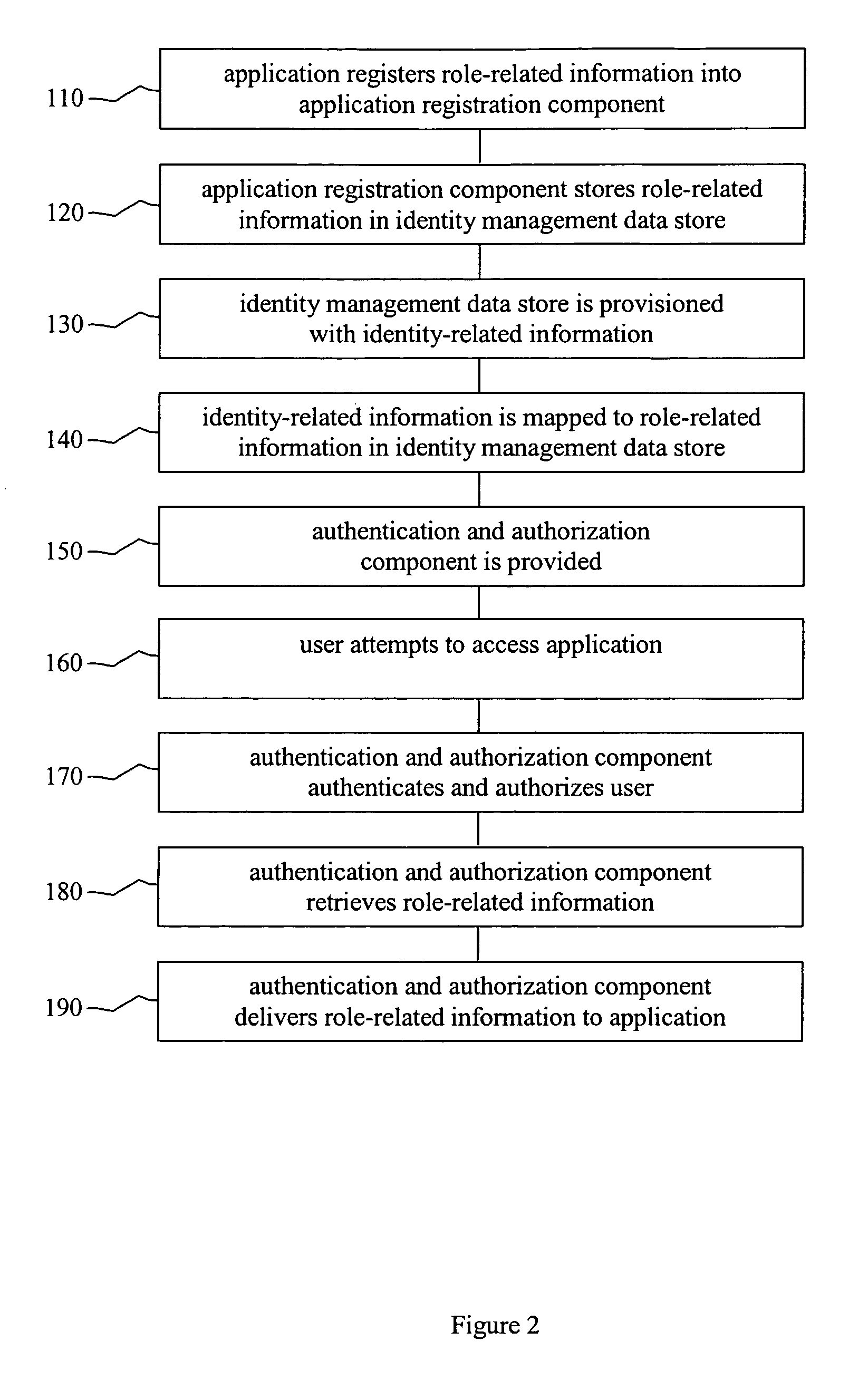
A system is for identity management is provided. The system includes an identity management data store, a human resources input, an application registration component, and a security component. The identity management data store stores identity-related information for a user of an application. The identity-related information is mapped within the identity management data store to role information for the user of the application. The human resources input provisions the identity management data store with the identity-related information. The application registration component facilitates the application to provision the identity management data store with the role information for the user of the application. The security component authenticates the user and authorizes the user for access to the application based on the identity-related information. The security component retrieves the role information mapped to the identity-related information and delivers the role information to the application.
Owner:T MOBILE INNOVATIONS LLC
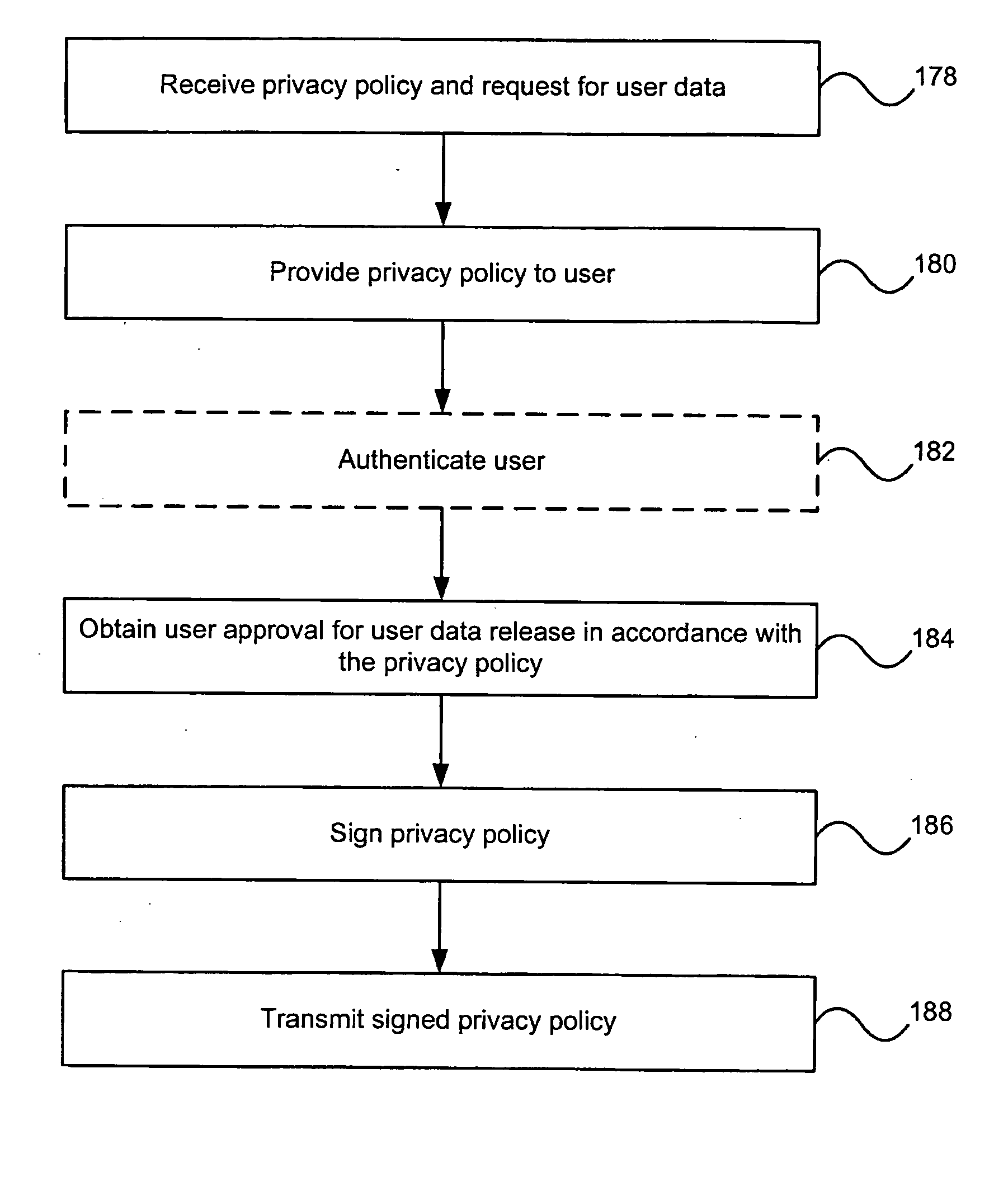
Auditable privacy policies in a distributed hierarchical identity management system
ActiveUS20050283443A1User identity/authority verificationPayment architectureThird partyInternet privacy
A set of methods, and systems, for enabling the audit tracking of user agreement with policies, such as privacy policies in an authenticated fashion is disclosed herein. The method and system make use of third party signatures of privacy policies to show user approval of the policy as it pertains to released data.
Owner:CALLAHAN CELLULAR L L C
Auditable privacy policies in a distributed hierarchical identity management system
Owner:CALLAHAN CELLULAR L L C
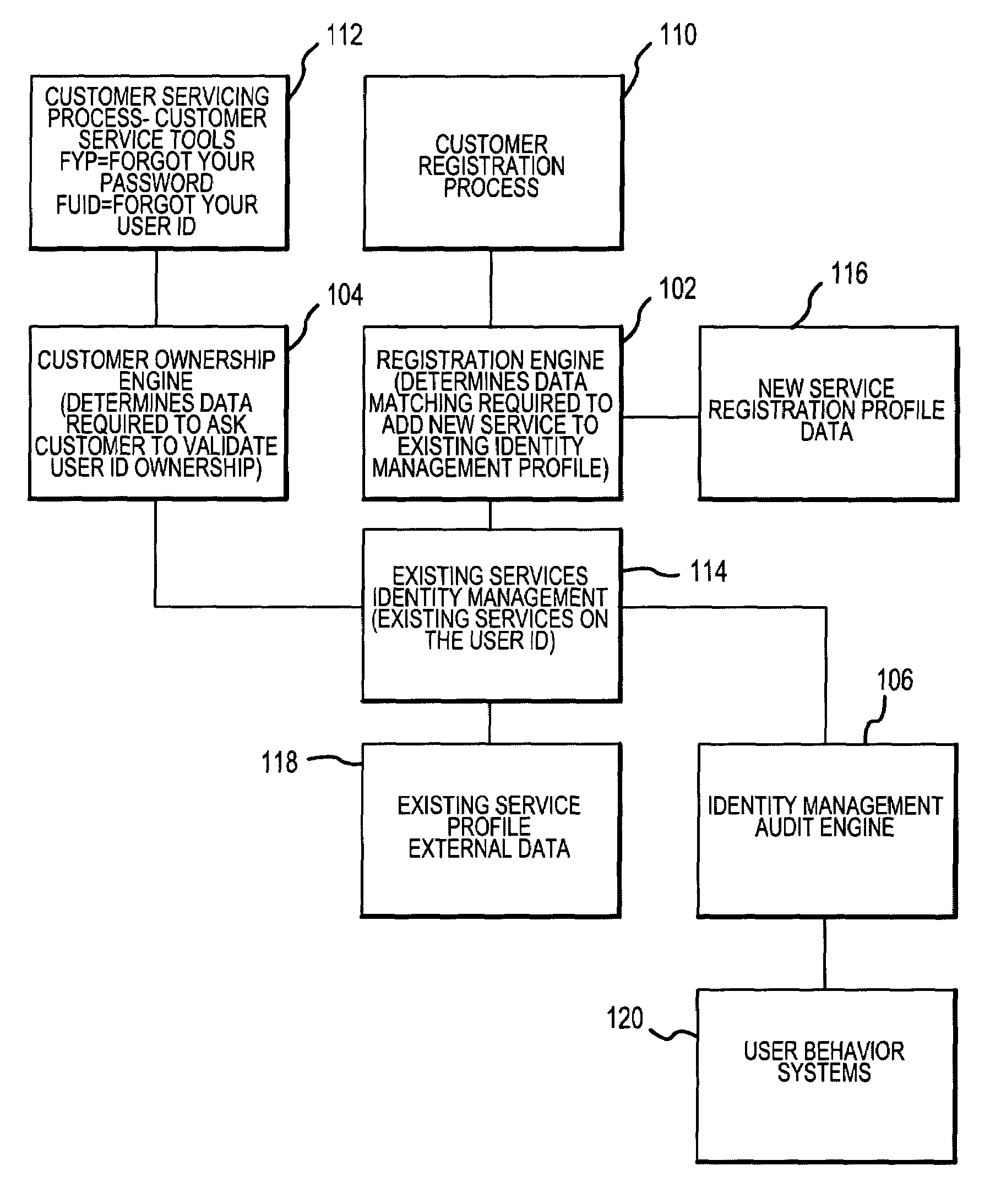
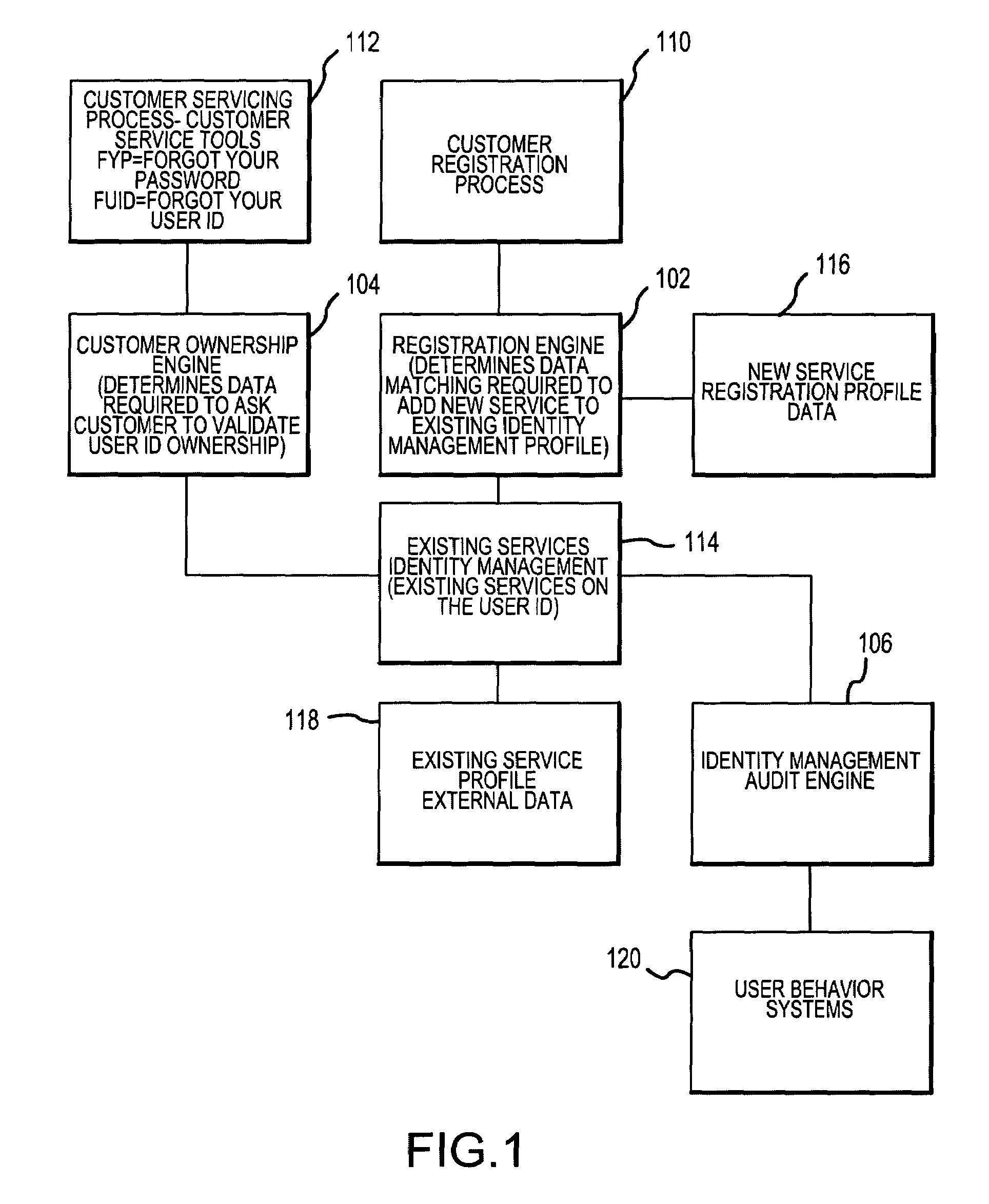
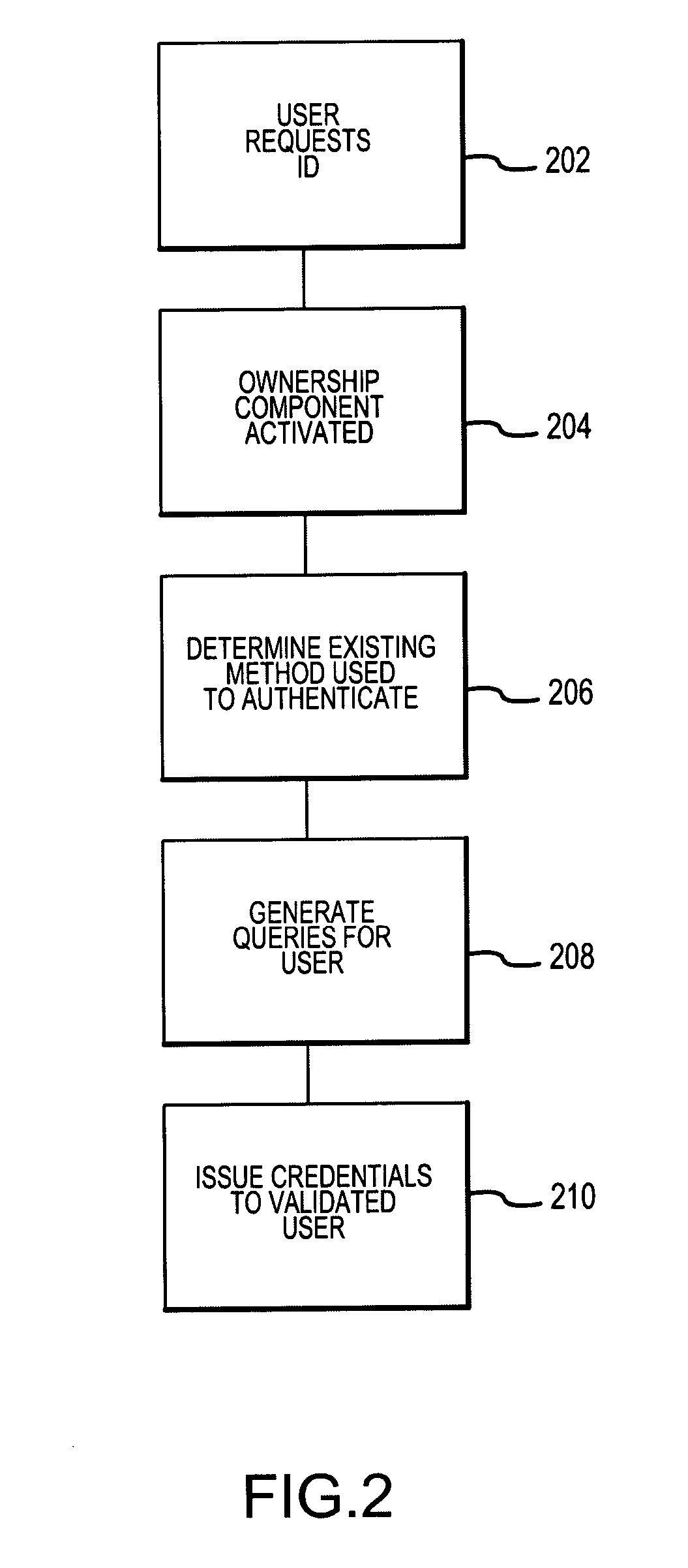
Method and system for implementing and managing an enterprise identity management for distributed security
InactiveUS7143095B2FinanceMultiple digital computer combinationsPrivileged identity managementComputerized system
An Enterprise Identity Management system includes a registration component, an ownership component, and an audit component. The registration component is configured to associate a user ID with specific accounts that are accessible via a computer system. The ownership component is configured to verify the ownership of the accounts. The audit component is configured to perform periodic checks to ensure the validity of the association between the user ID and the ownership of the accounts.
Owner:LIBERTY PEAK VENTURES LLC
Method for managing shared accounts in an identity management system
ActiveUS20110277016A1Digital data processing detailsUser identity/authority verificationComputer networkIdentity management system
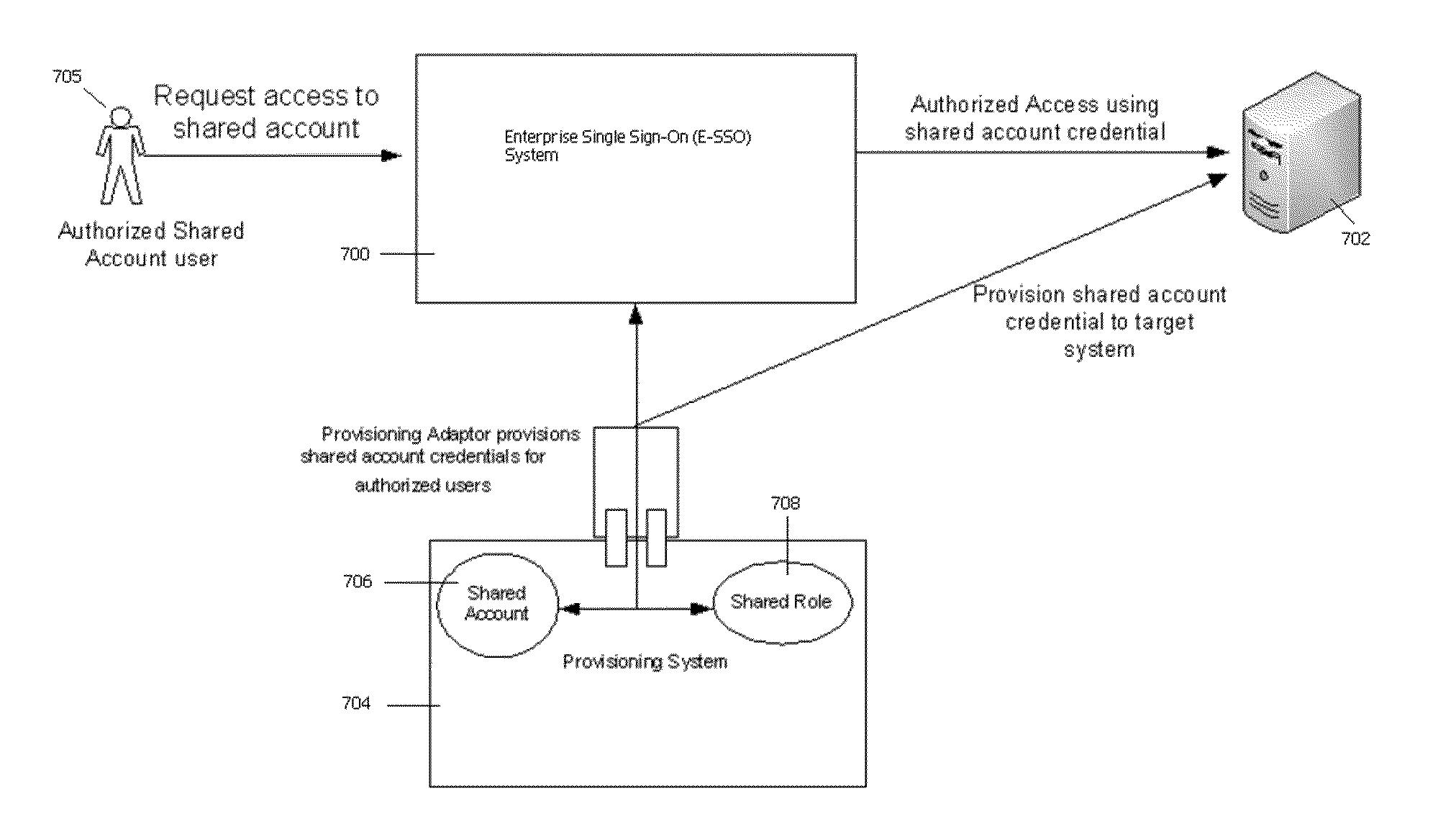
This disclosure describes a method of and system for provisioning of shared account credentials to provide authorized access to shared or delegated accounts. Preferably, an enterprise single sign-on (E-SSO) system is used to manage the shared account or control delegation of account access, and preferably the shared or delegated account credential is not exposed to the end user. The described technique enables temporary delegation of account privileges to a member of a shared role. Using the described approach, an information technology (IT) account may be shared so that a user who needs to perform a shared duty can do so in the context of a shared role and without having control over the account itself. The approach facilitates delegating the use of a single account to one of a member of the shared role.
Owner:IBM CORP
Method for Replacing Traditional Payment and Identity Management Systems and Components to Provide Additional Security and a System Implementing Said Method
InactiveUS20140108241A1Improve securityReduce in quantityFinanceComputer security arrangementsComputer hardwarePayment
An electronic wallet system that protects payment accounts, identification and other personal information found within a typical wallet with a secure electronic vault (first) device that can be part of a physical wallet, insert to a wallet, or in other embodiments, wearable / portable devices. A unique biometrically enabled multi-factor authentication process ensures only owners of the information can copy the information to the device or retrieve it thereafter. Authenticated users may then select payment, identification, medical or virtually any private information via touch display or voice command on the vault or on another (second) device that operates in conjunction with the vault. The second device comprises, for example, a programmable card with dynamic magnetic stripe, cell phone, or other wearable technology, that initiates and processes a payment and / or transfer of private information.
Owner:GARMIN INT
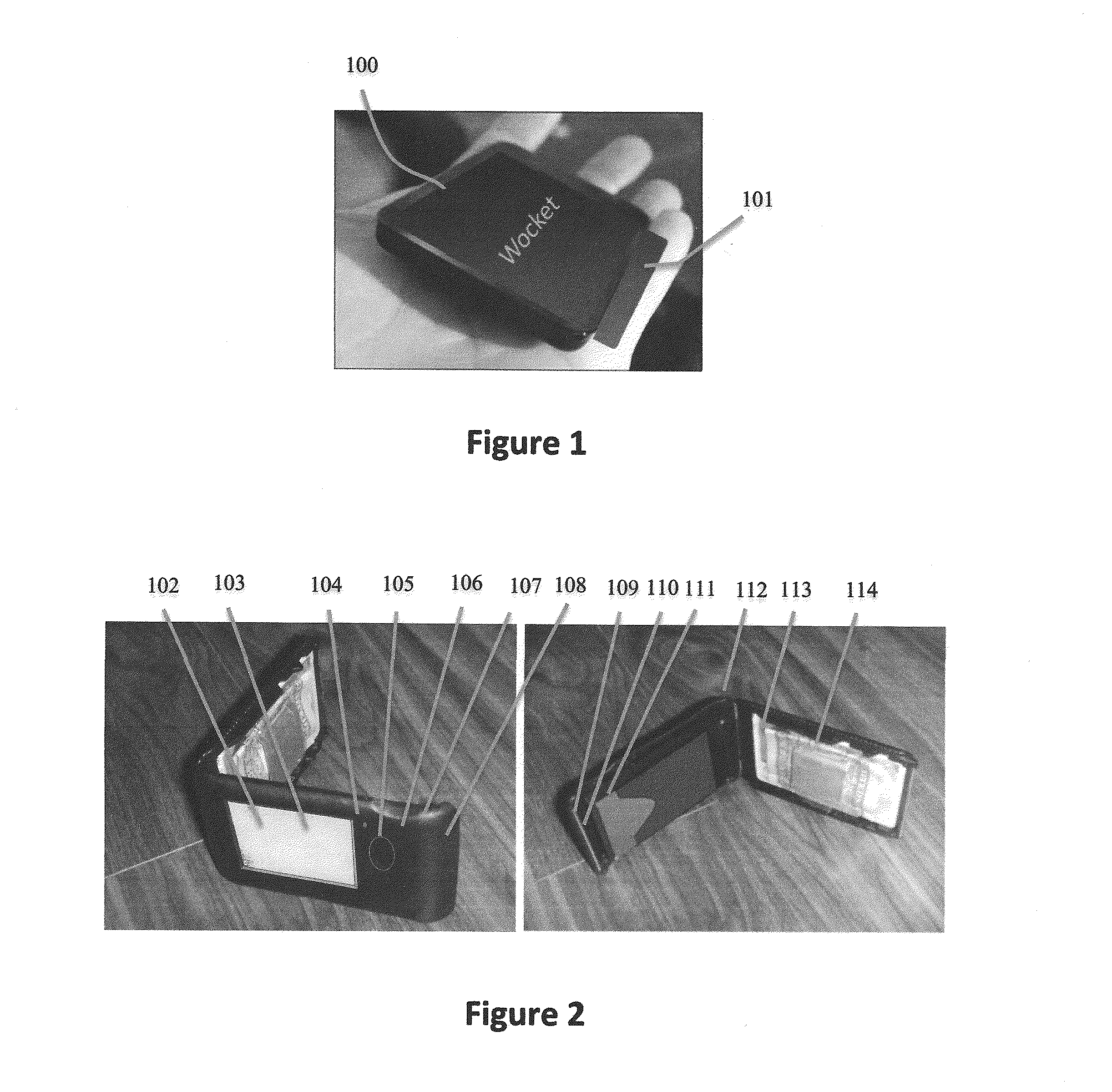
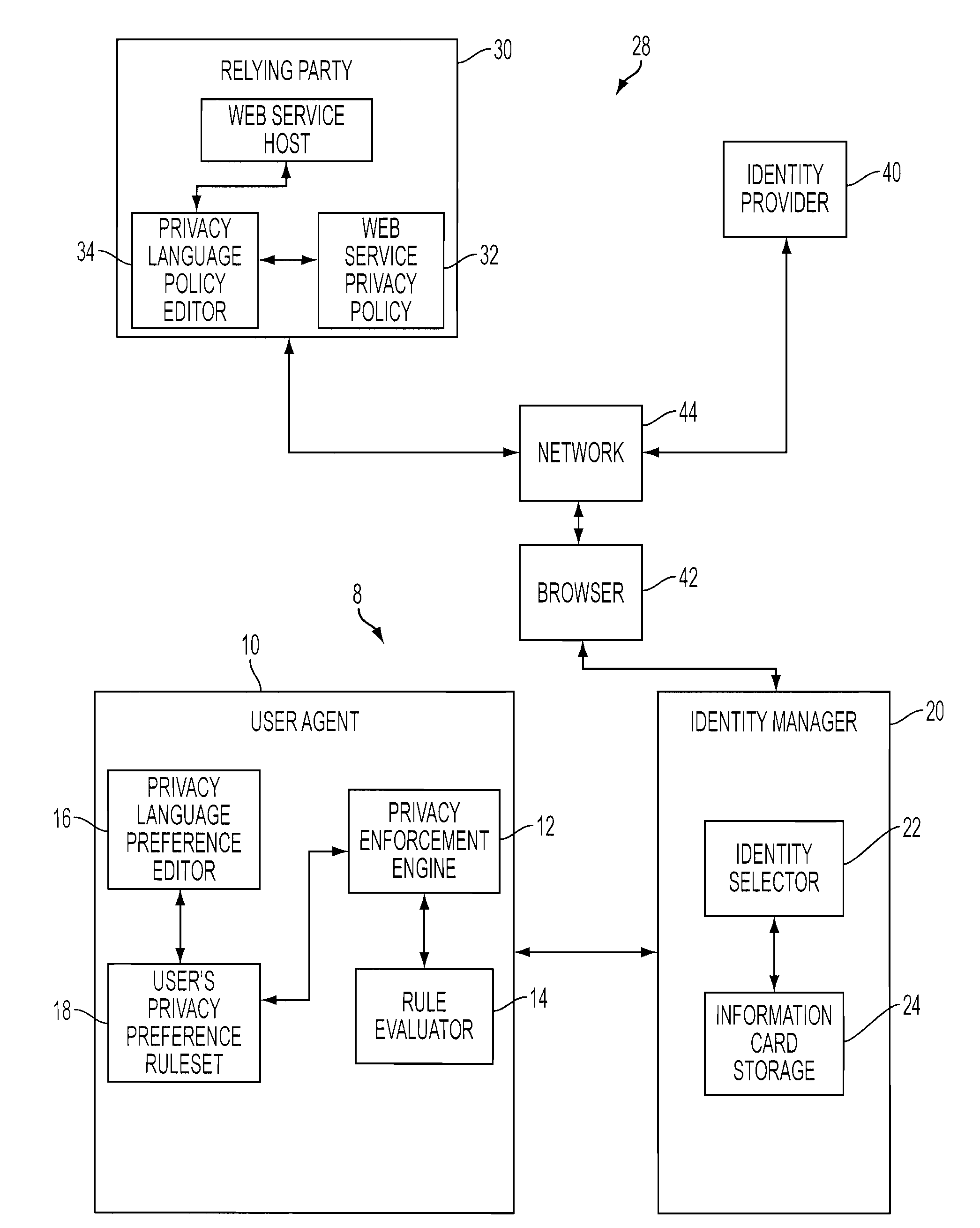
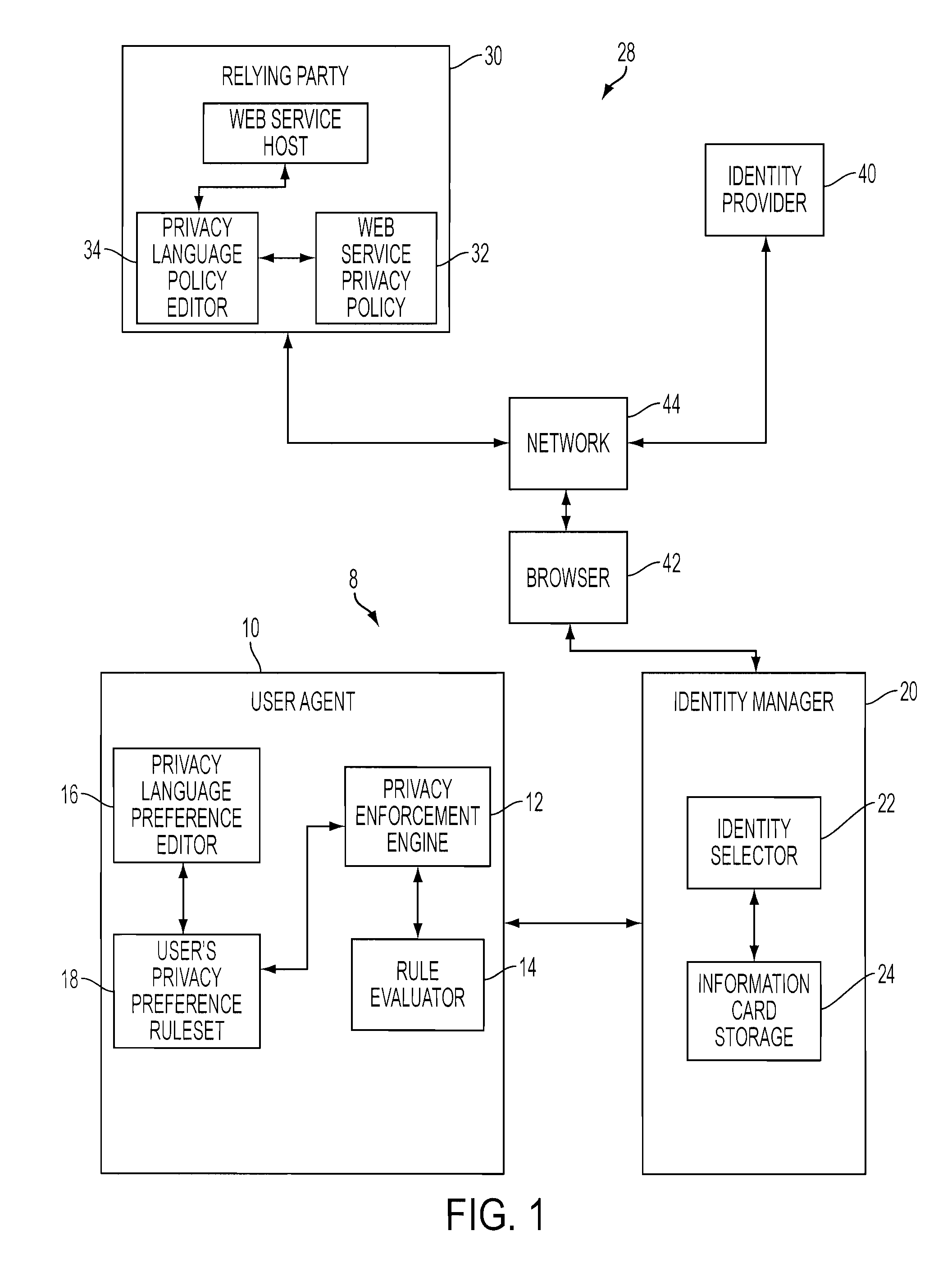
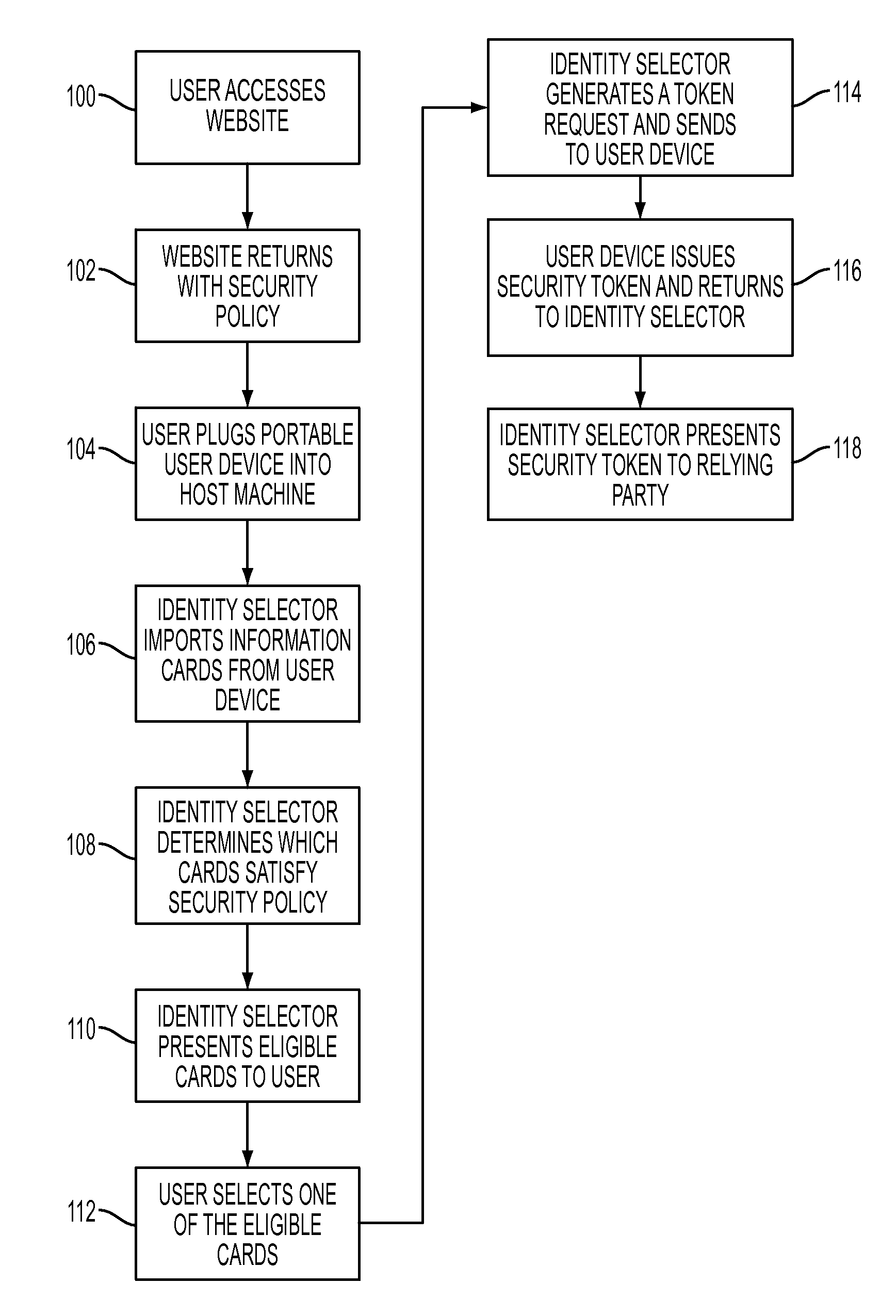
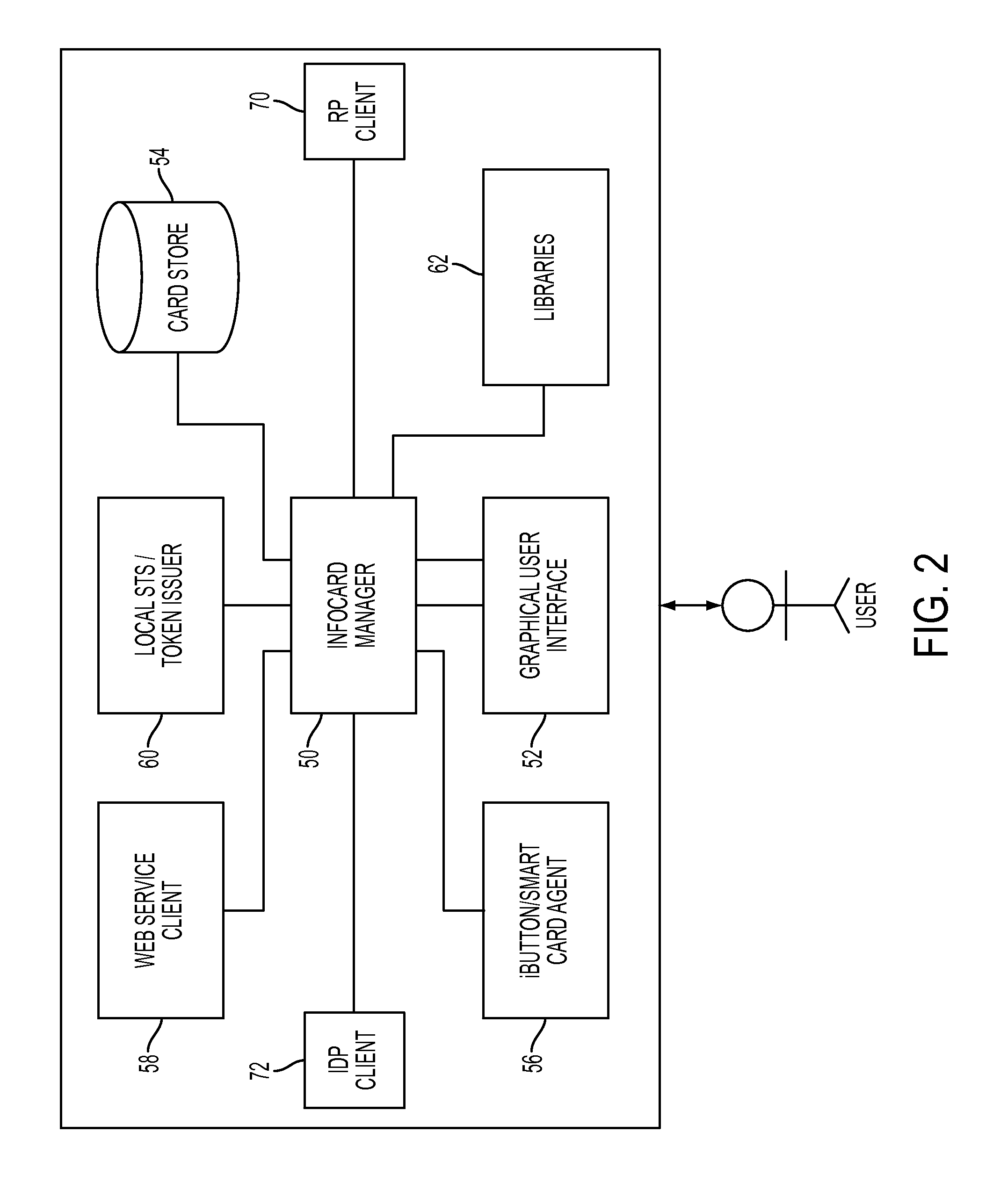
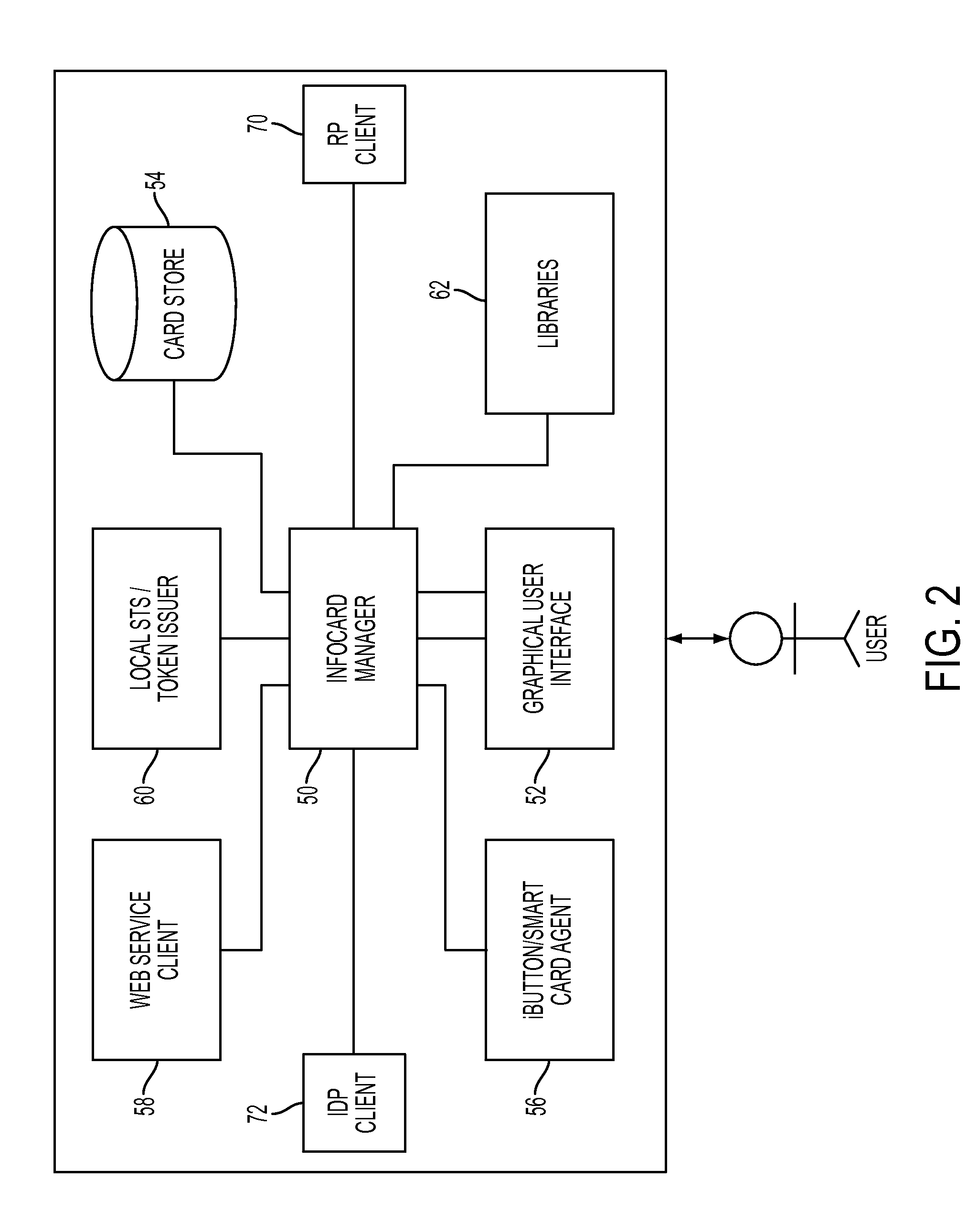
User agent to exercise privacy control management in a user-centric identity management system
A client-side user agent operates in conjunction with an identity selector to institute and exercise privacy control management over user identities managed by the identity selector. The user agent includes the combination of a privacy enforcement engine, a storage of rulesets expressing user privacy preferences, and a preference editor. The editor enables the user to direct the composition of privacy preferences relative to user identities. The preferences can be applied to individual cards and to categorized groups of attributes. The engine evaluates the proper rulesets against the privacy policy of a service provider. The privacy preferences used by the engine are determined on the basis of specifications in a security policy indicating the attribute requirements for claims that purport to satisfy the security policy.
Owner:IBM CORP
Distributed hierarchical identity management system authentication mechanisms
ActiveUS7454623B2Data taking preventionUser identity/authority verificationThird partyInternet privacy
A set of methods, and systems, for use in an identity management system are disclosed herein. A modular user identity information datastore using hardware accelerated encryption for user data security operates in a network for receiving requests for, and issuing responses containing user information including third party accredited assertions.
Owner:CALLAHAN CELLULAR L L C
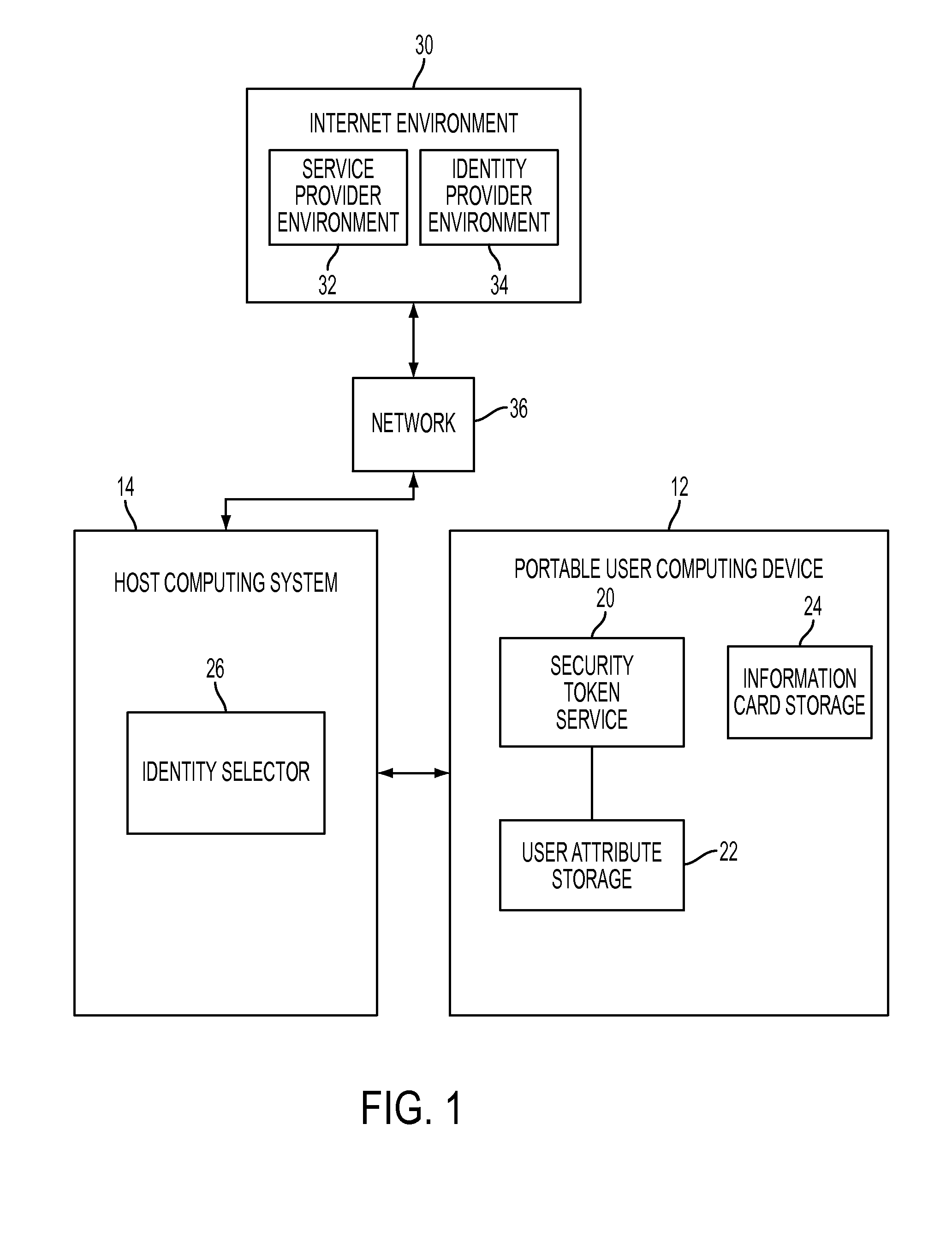
System integrating an identity selector and user-portable device and method of use in a user-centric identity management system
ActiveUS8402526B2Digital data processing detailsMultiple digital computer combinationsInformation CardUser device
Owner:PHILIPS NORTH AMERICA LLC
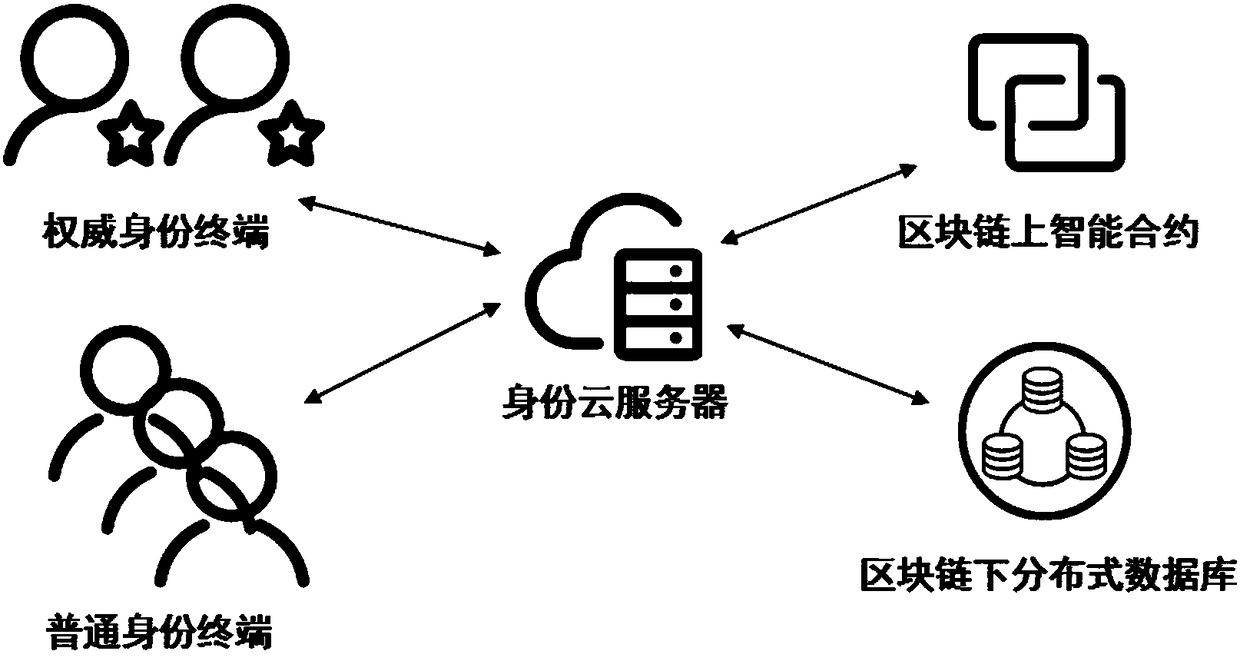
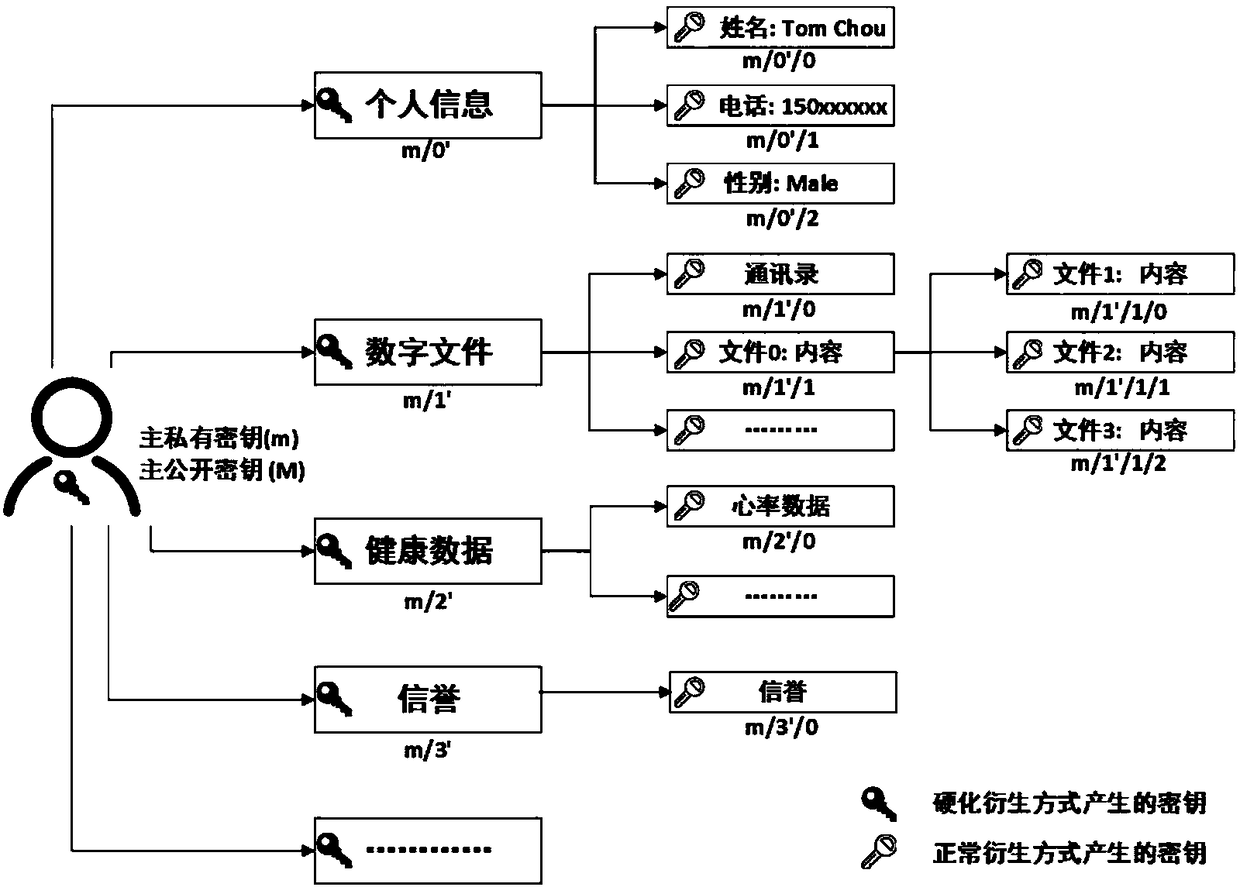
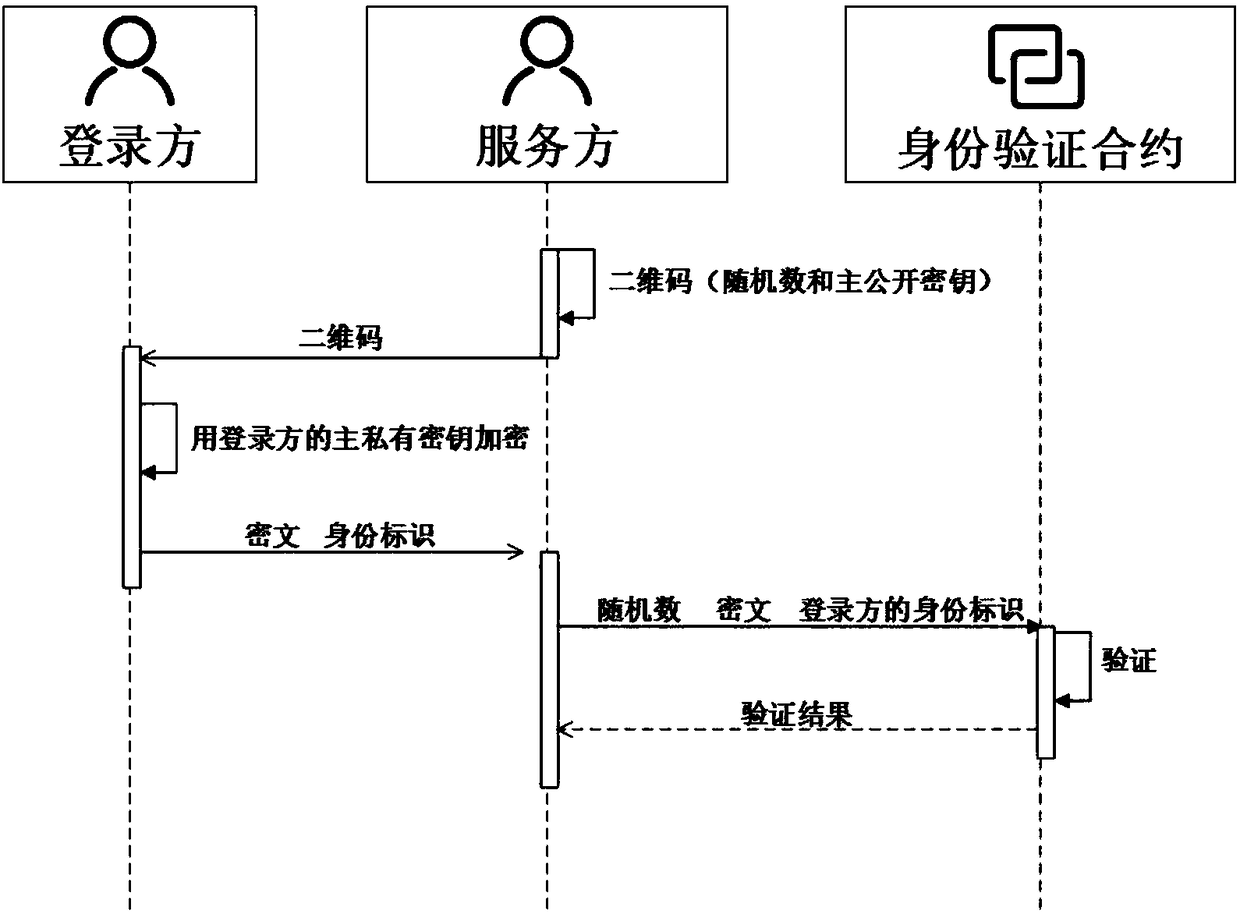
Self-certified digital identity management system and method based on smart contract
ActiveCN108234515AImplement passwordless loginMaster self-managementUser identity/authority verificationDigital identitySelf certified
The invention discloses a self-certified digital identity management system and method based on a smart contract. An identity terminal sends a public key and associated digital information to a cloudserver via the Internet, and accomplishes registration and login of digital identity, and the authorization, operation and verification of digital information depending on the smart contract on a block chain and a distributed database under the block chain. A unique identity of the whole network can be provided, passwordless login is achieved by scanning a two-dimensional code, the login mode of the traditional username and password is broken through, and a user entirety can securely and effectively manage the digital identity and the associated digital information, on-demand authorization, operation and verification of information are achieved, thus realizing a decentralized, self-certified digital identity management system.
Owner:安徽中科晶格技术有限公司
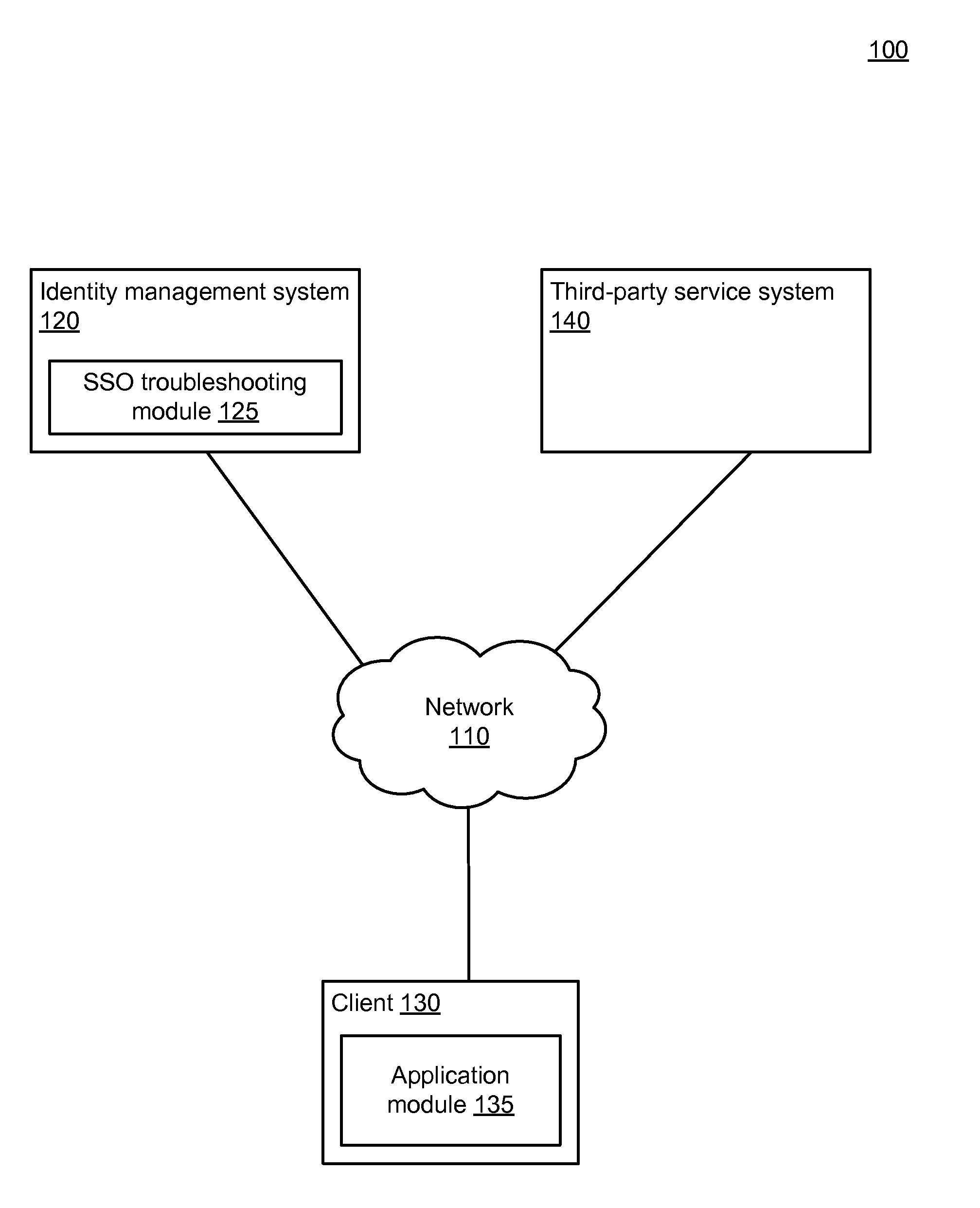
Detection And Repair Of Broken Single Sign-On Integration
ActiveUS20160080360A1Digital data processing detailsMultiple digital computer combinationsThird partyPassword
An identity management system provides single sign-on (SSO) services to clients, logging the clients into a variety of third-party services for which the clients have accounts. An SSO integration is stored for each of the third-party services, the SSO integration including information that allows the identity management system to automate the login for the corresponding third-party service, such as locations of the login pages, and / or identities of username and password fields. The identity management system uses different techniques in different embodiments to detect that a given SSO integration is broken (i.e., no longer permits login for its corresponding third-party service) and / or to repair the SSO integration.
Owner:OKTA
Redundant multifactor authentication in an identity management system
InactiveUS20100132019A1Digital data processing detailsUser identity/authority verificationIdentity providerDependability
A redundant multifactor identity authentication system provides users with a secure mechanism for providing identity information through the use of redundant independent identity providers in concert with each other so that resources are accessed only through a combination of providers. By eliminating reliance on a single provider, security is increased as is reliability. Similarly, redundant credentials can be provided to relying parties to ensure that the relying party receives proof of a credential without requiring a specific credential.
Owner:BLAME CANADA HLDG
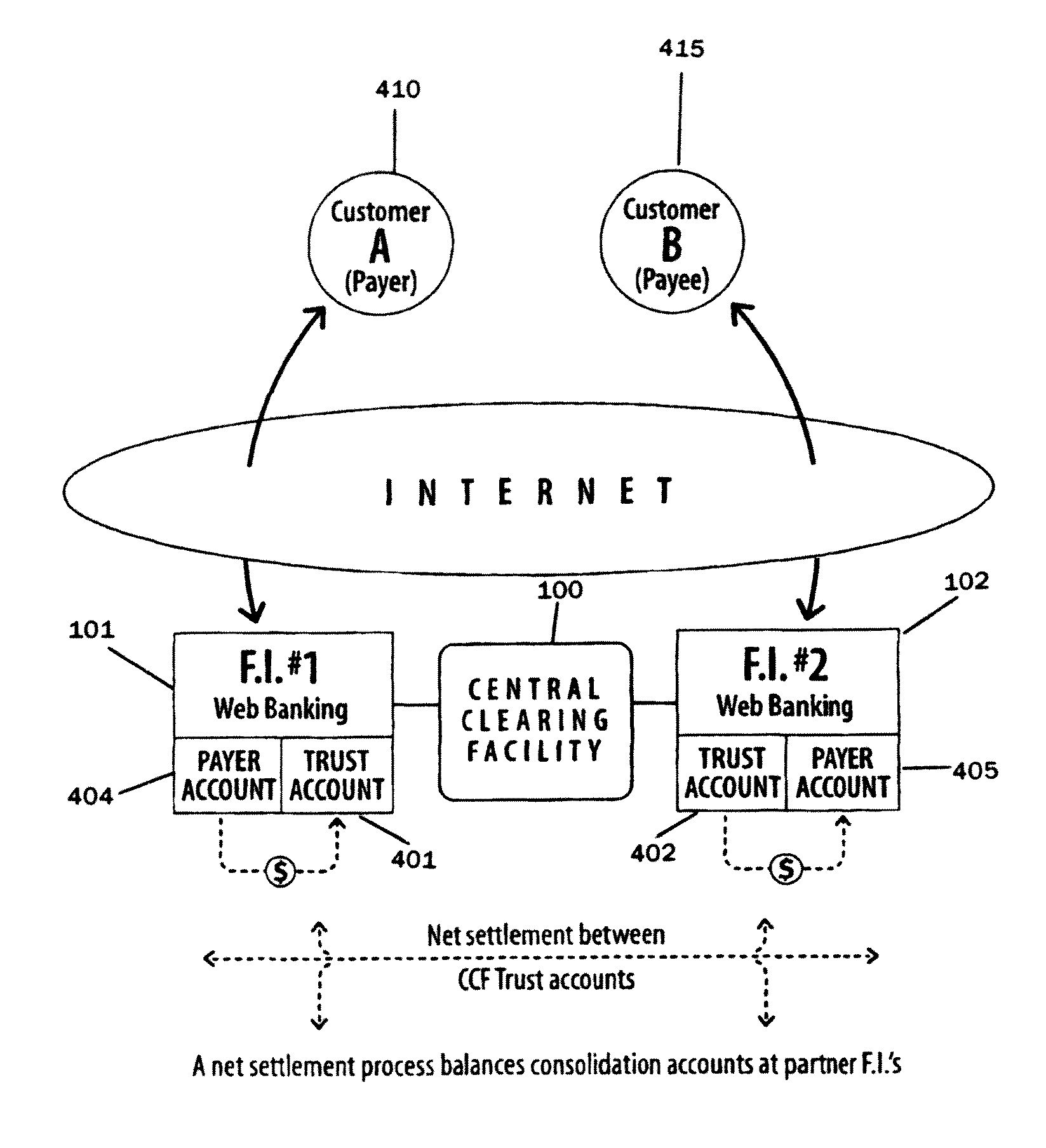
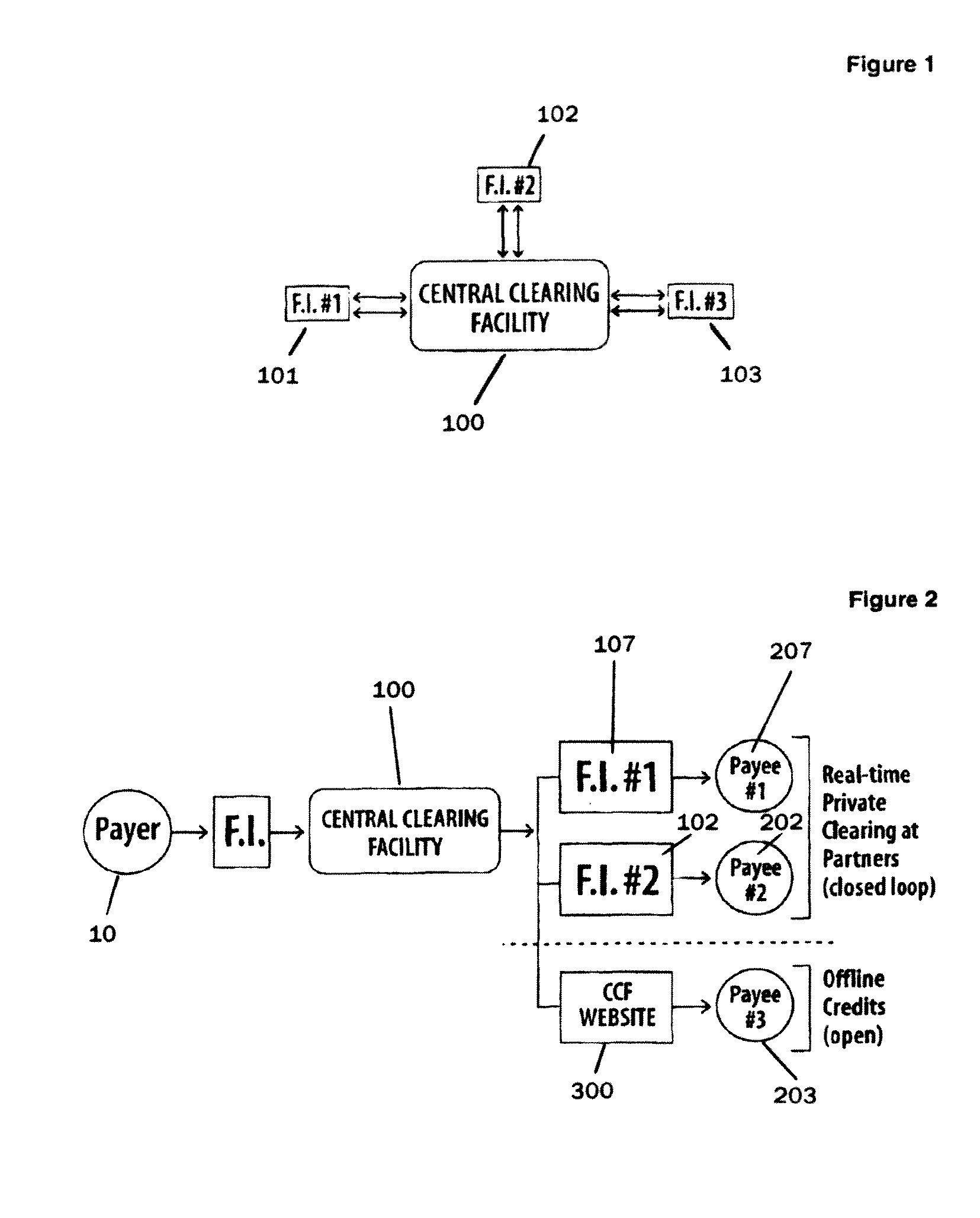
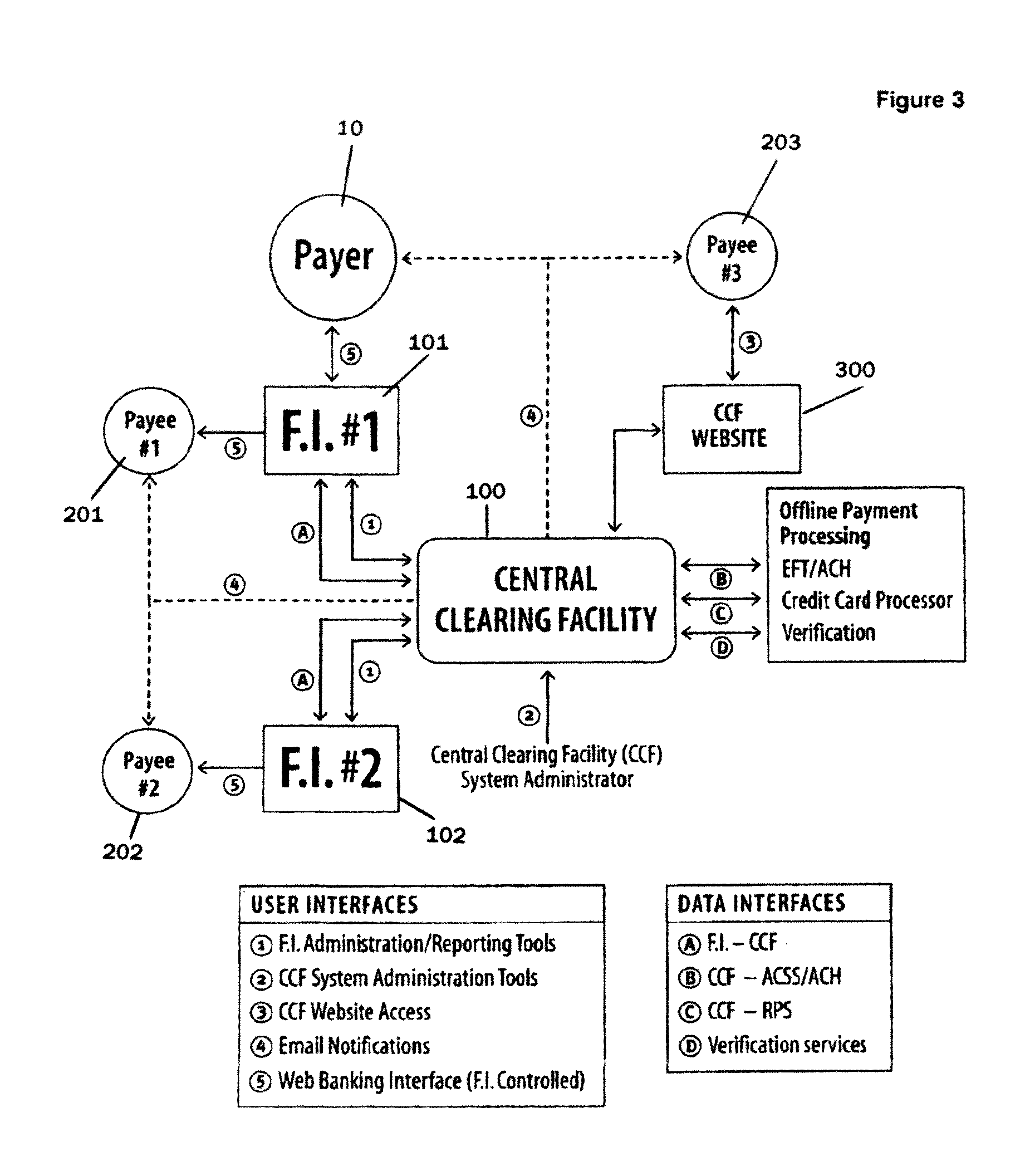
Online payment transfer and identity management system and method
ActiveUS7844546B2Facilitates online bankingFacilitating cross-sellingFinanceDigital data authenticationApplication serverIdentity management system
A payment transfer method for transferring funds from a payer to payee is provided, including designating a payee and specifying a payment amount and an account; debiting the funds from the account and crediting a first trust account; and identifying the payee by verifying responses received in response to one or more challenge-response questions defined by the payer. If the one or more responses are verified, a second trust account may be debited and a payee account credited with the payment amount. The first and second trust accounts may then be reconciled. There is also provided a payment transfer facility for transferring funds., comprising an application server for storing payment data relating to a transfer of funds and a notification server for providing a notification of the transfer of funds.
Owner:INTERAC CORP
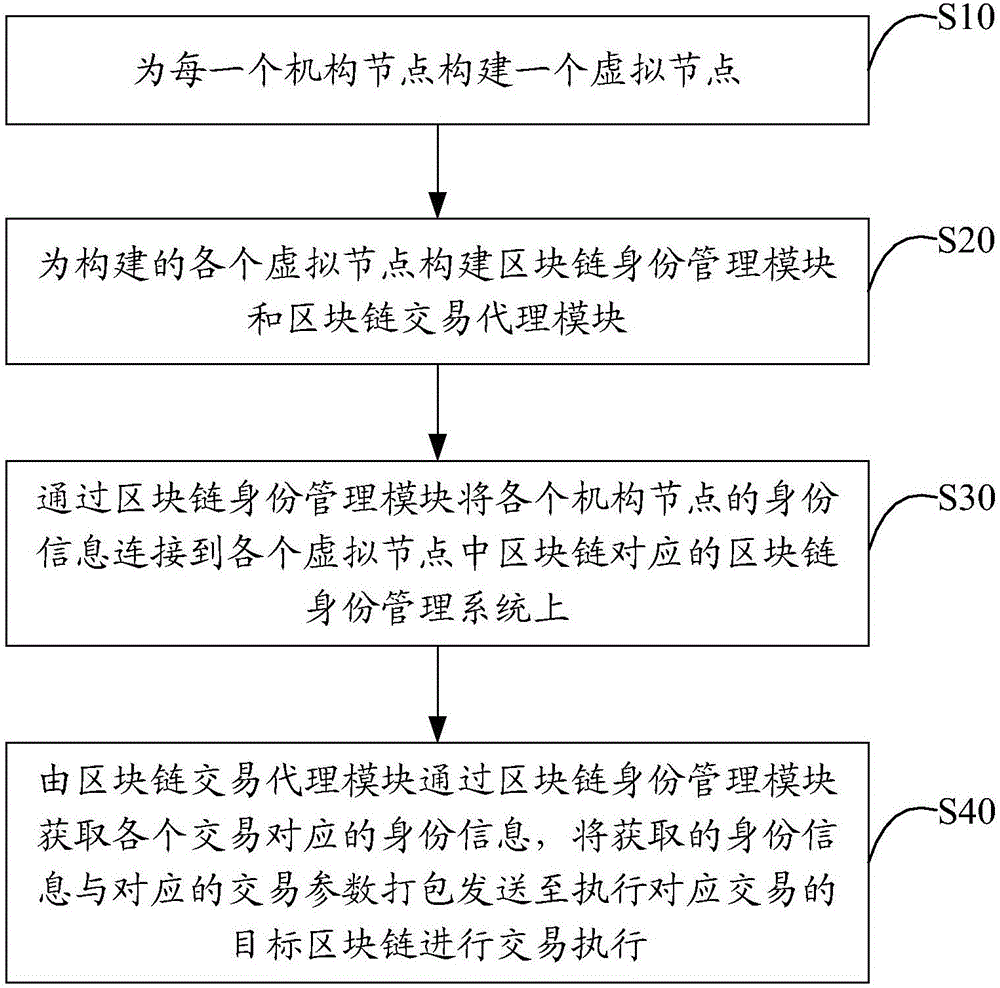
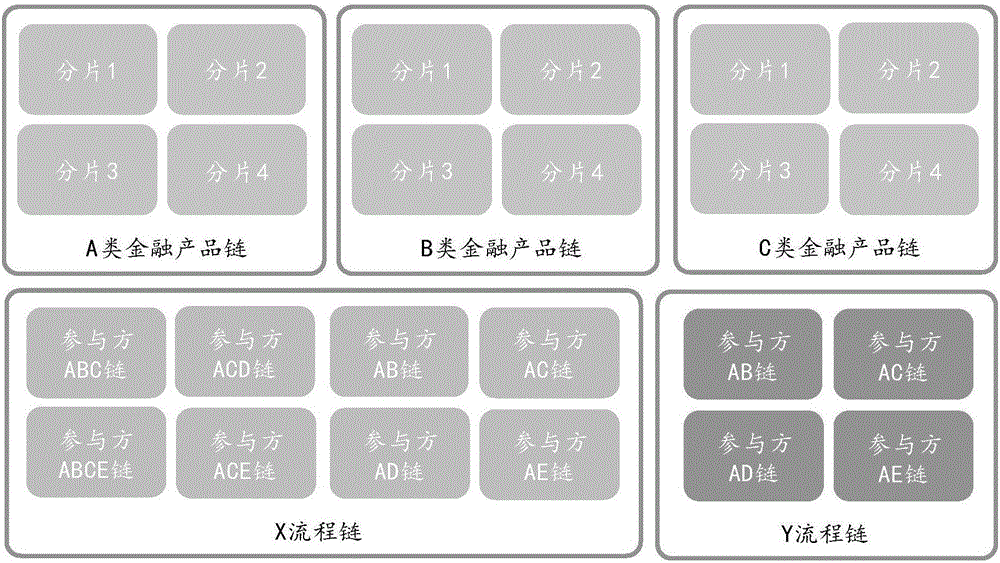
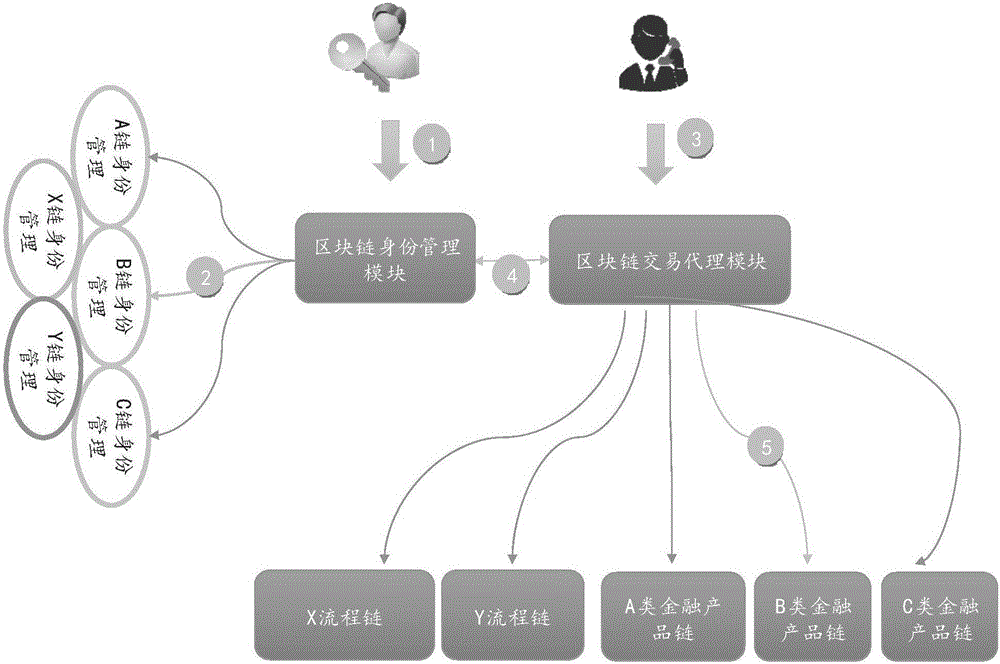
Multi-chain management method and system based on block chain
ActiveCN106530083AEffective automation managementFinanceCryptography processingFinancial transactionIdentity management system
The invention discloses a multi-chain management method and system based on a block chain. The method comprises the following steps: constructing a virtual node for each mechanism node, wherein the virtual nodes comprise node groups generated based on the block chain which is participated in by each mechanism node for processing different matters and / or flows; constructing a block chain identity management module and a block chain transaction agent module for each constructed virtual node; through the block chain identity management modules, connecting identity information of each mechanism node to a block chain identity management system corresponding to the block chain in each virtual node; and the block chain transaction agent module obtaining the identity information corresponding to each transaction through the block chain identity management module, packaging the obtained identity information and corresponding transaction parameters to generate packaging information, and sending the packaging information to a target block chain executing the corresponding transaction for transaction execution. According to the invention, effective automatic management of multiple block chain nodes is realized.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
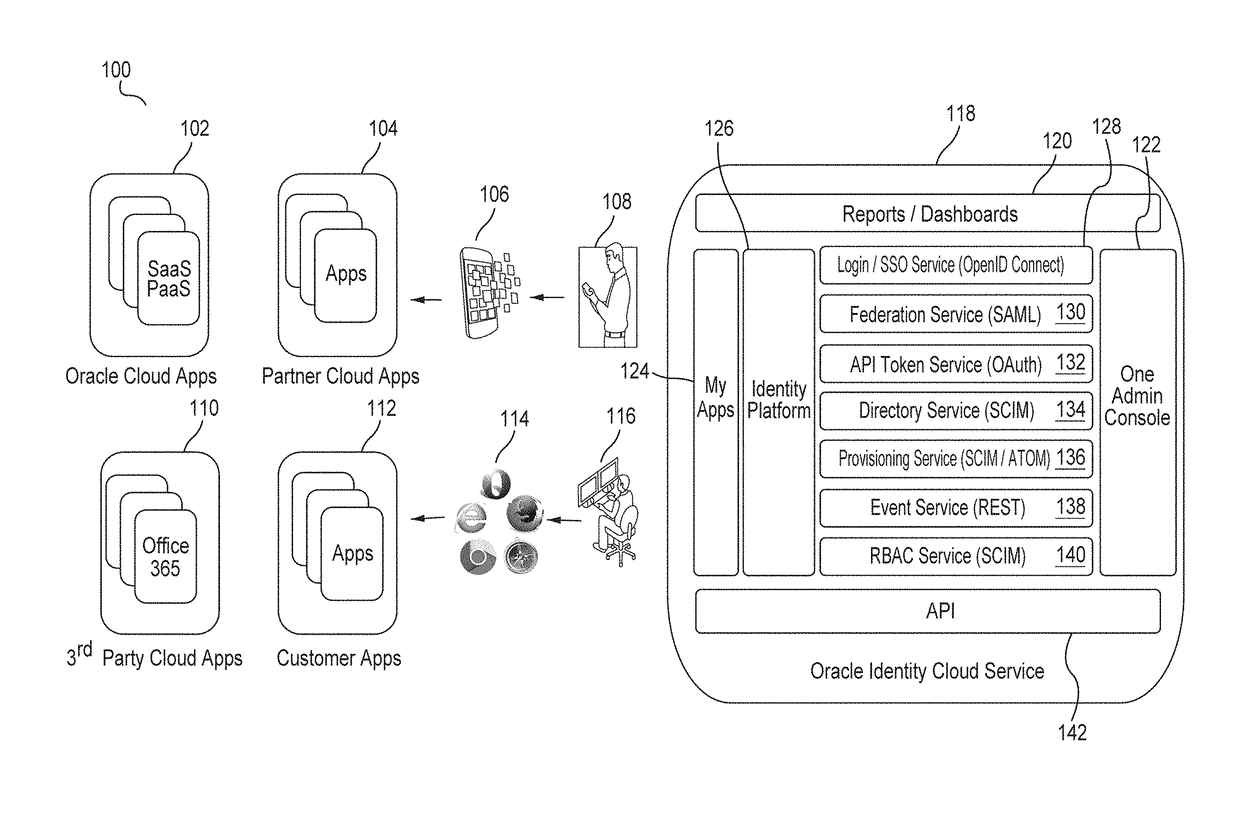
Identity cloud service authorization model with dynamic roles and scopes
ActiveUS20170329957A1Digital data authenticationProgram/content distribution protectionApplication softwareAccess token
A system for authorizing access to a resource associated with a tenancy in an identity management system that includes a plurality of tenancies receives an access token request for an access token that corresponds to the resource, the request including user information and application information, the user information including roles of a user and the application information including roles of the application. The system evaluates the access token request by computing dynamic roles and corresponding dynamic scopes for the access token including a second intersection between the dynamic roles of the user and the dynamic roles of the application. The system then provides the access token that includes the computed static scopes, where the scopes are based at least on the roles of the user and the roles of the application, and further including the computed dynamic roles and corresponding dynamic scopes.
Owner:ORACLE INT CORP
Managing user access entitlements to information technology resources
ActiveUS8132231B2Digital data processing detailsMultiple digital computer combinationsData processing systemInterface layer
A computer implemented method, data processing system, and computer program product for logical management and provisioning of business applications within the framework of an identity management system. The illustrative embodiments providing an interface layer to map respective attributes, permissions, and resource accounts in a data repository needed to represent access to business applications via a managed service in the identity management system. The illustrative embodiments define user entitlements on a user account associated with the managed service. The illustrative embodiments provision user access to the business applications via the managed service in the identity management system upon user request.
Owner:SERVICENOW INC
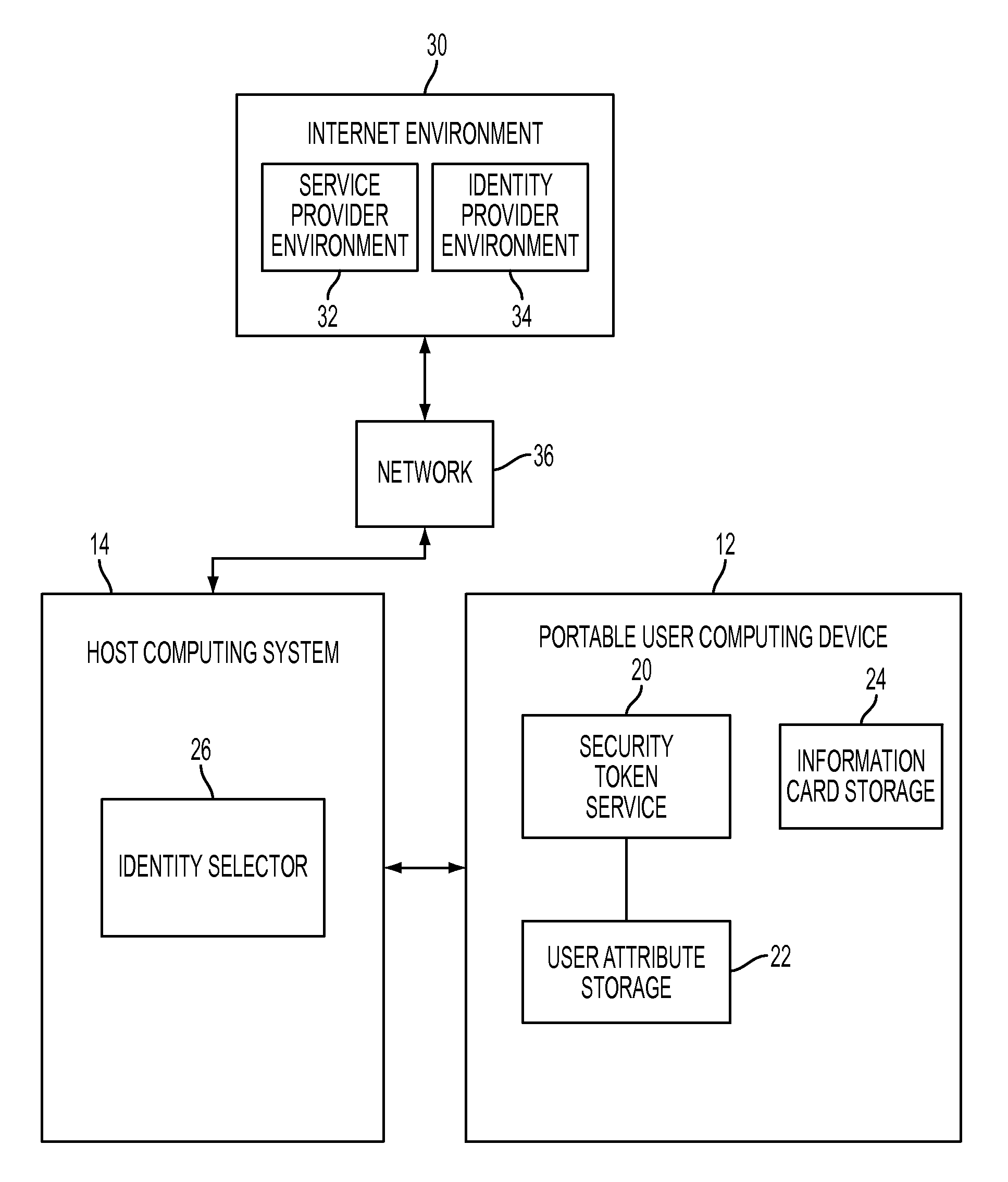
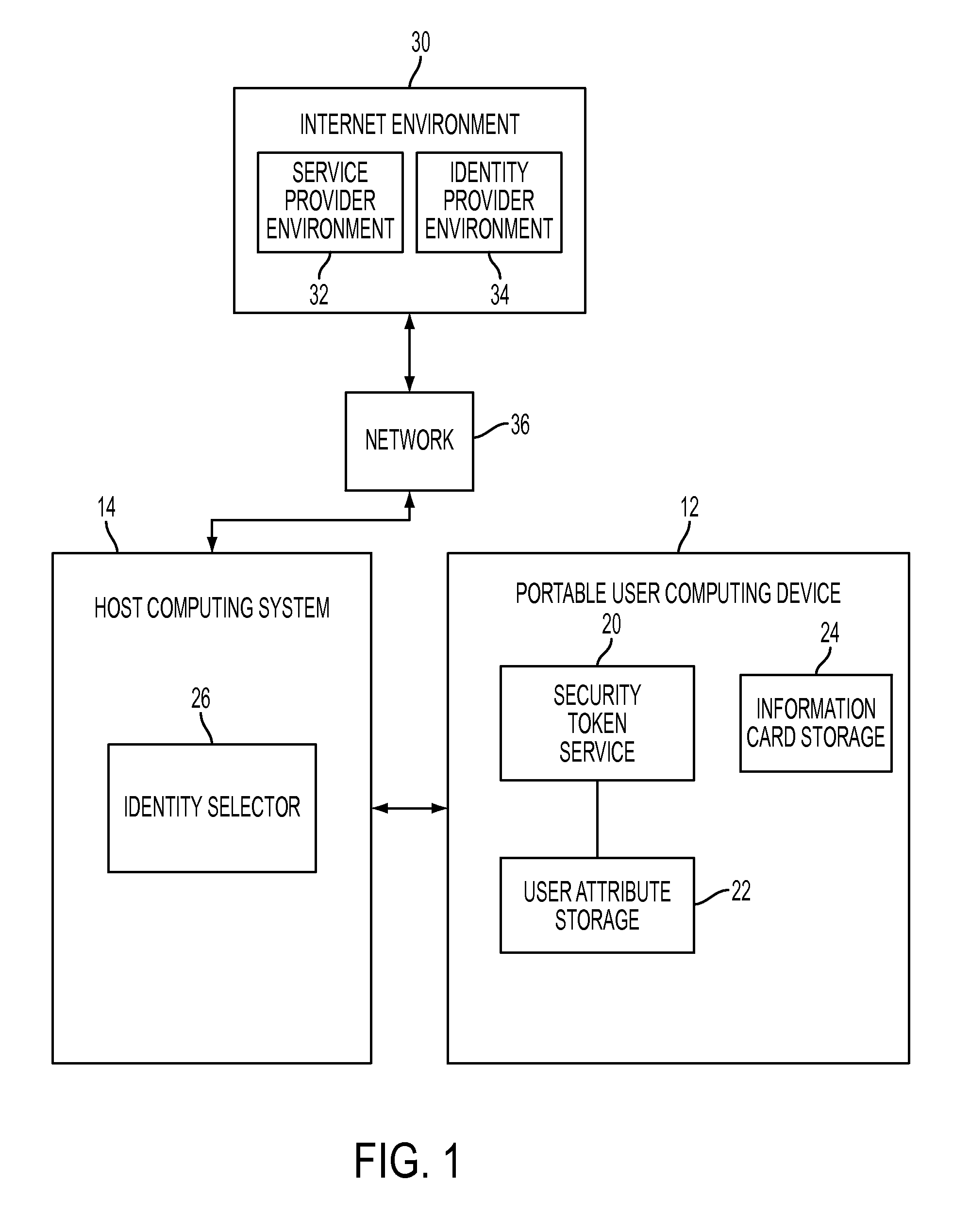
User-portable device and method of use in a user-centric identity management system
ActiveUS20090300747A1Digital data processing detailsMultiple digital computer combinationsInformation CardUser device
A user-portable computing device configured as a smart card enables a user to carry identification information and to generate security tokens for use in authenticating the user to a service provider. The device includes memory for storing user identities as information cards that are exported to a host computer, presented to a user in visual form, and then selected for use in the authentication process. A security token service installed on the device issues a security token in response to a token request sent from the host computer that references the selected user identity. The security token service uses user attribute information stored on the user device to compose the claim assertions needed to issue the security token. The token is returned to the host computer and used to facilitate the authentication process.
Owner:IBM CORP
Virtual Identity System and Method for Web Services
InactiveUS20100049790A1Improve experienceAdvertisementsNatural language data processingThird partyWeb application
A comprehensive identity management system for users of multiple Web applications. The system supports multiple standards spanning both inbound and outbound single sign-on and integration with an application directory for coupling discovery of third-party applications with single sign-on.
Owner:INFINITY IP BANK INT SUZHOU COMPANY
Method and apparatus for multi-domain identity interoperability and compliance verification
ActiveUS8434129B2Memory loss protectionDigital data processing detailsInternet privacyFederated identity
Owner:FUGEN SOLUTIONS
Dispensing digital objects to an electronic wallet
A configuration system and method is disclosed that includes a unified and integrated configuration that is composed of a payment system, an advertising system, and an identity management system such that the unified system has all of the benefits of the individual systems as well as several additional synergistic benefits. Also described are specific configurations including the system's access point architecture, visual wallet simulator user interface, security architecture, coupon handling as well as the system's structure and means for delivering them as targeted advertising, business card handling, membership card handling for the purposes of login management, receipt handling, and the editors and grammars provided for customizing the different types of objects in the system as well as the creation of new custom objects with custom behaviors. The configurations are operable on-line as well as through physical presence transactions.
Owner:GOOGLE LLC
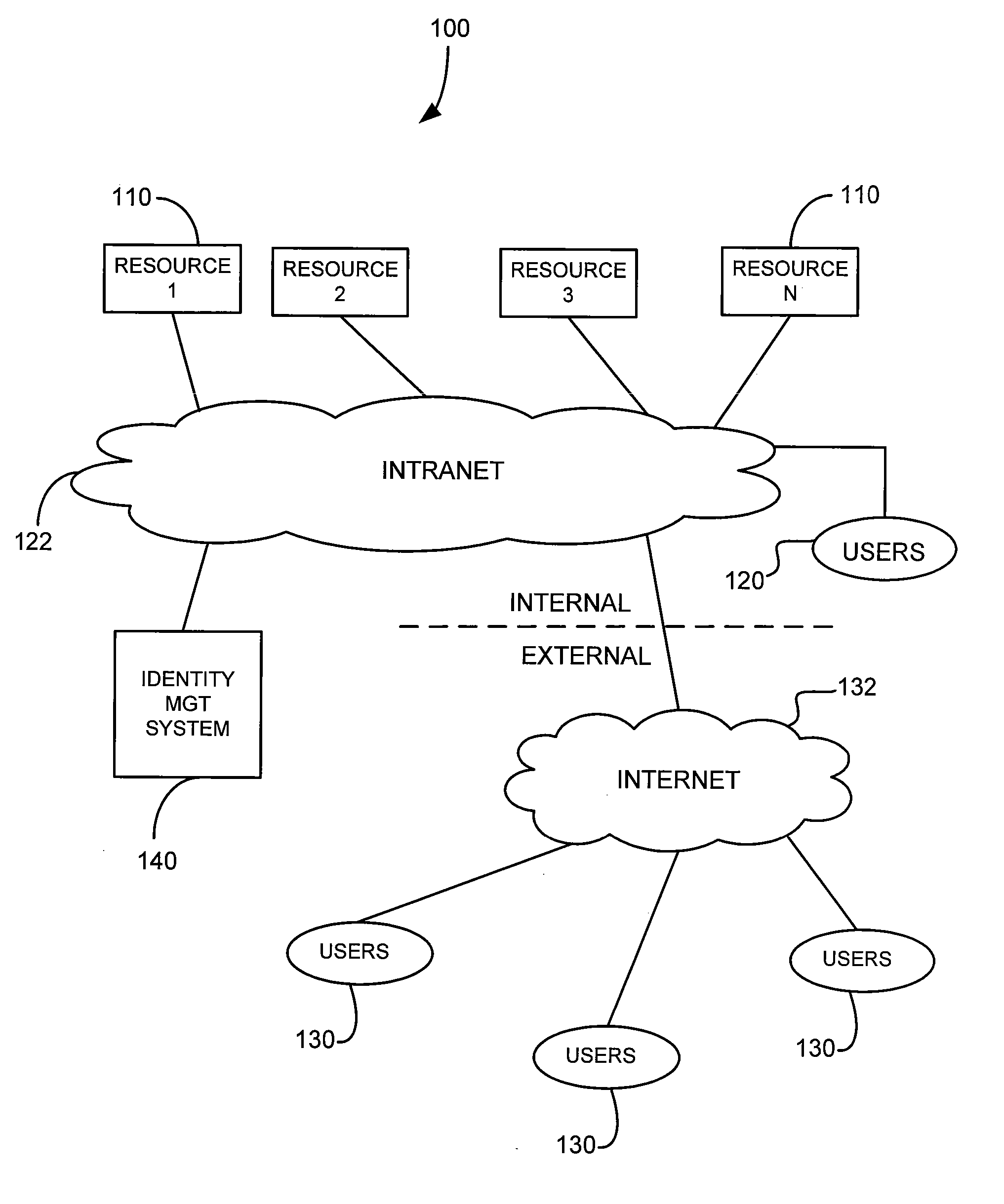
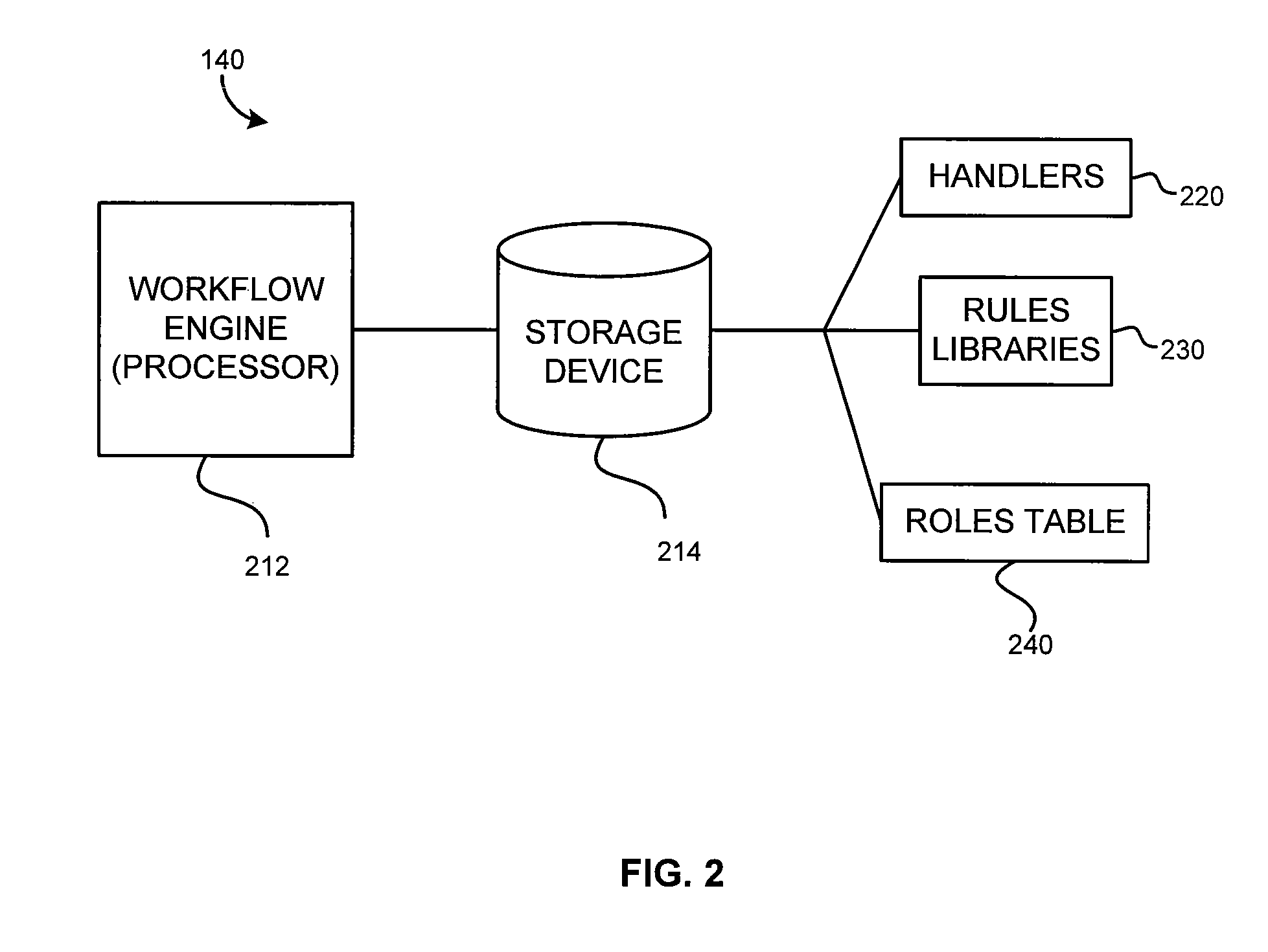
Identity management system for managing access to resources
InactiveUS20070073699A1Efficient designEasy maintenanceComputer security arrangementsSpecial data processing applicationsIdentity management systemEnterprise networking
An enterprise network has a plurality of applications or resources and an identity management (IDM) system for provisioning of users at those resources. The IDM system uses handlers and rules libraries for provisioning. The handlers organize provisioning tasks that are common to all the resources. The rules libraries have a library for each resource, within each library a rule set for each handler, and within each rule set a rule subset for each provisioning transaction type. Any number of different transactions types are permitted, such create a new employee account, terminate an account, disable an account, and create a new contractor account.
Owner:AEGIS BUSINESS GROUP
Identity authentication method and system, and computer readable storage medium
InactiveCN107547514AUser identity/authority verificationDigital data authenticationSystems designIdentity management system
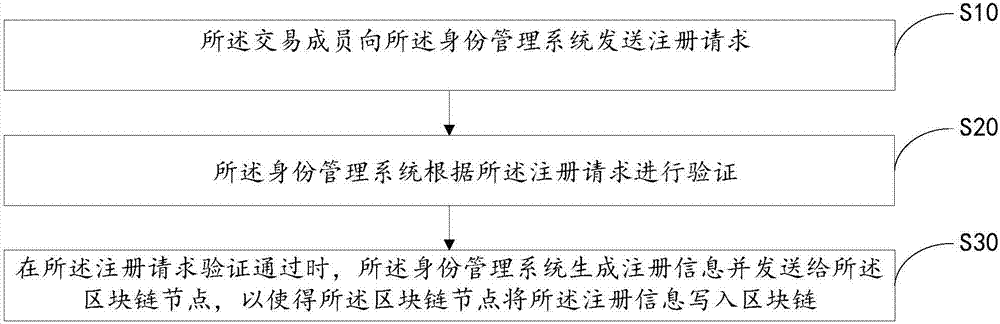
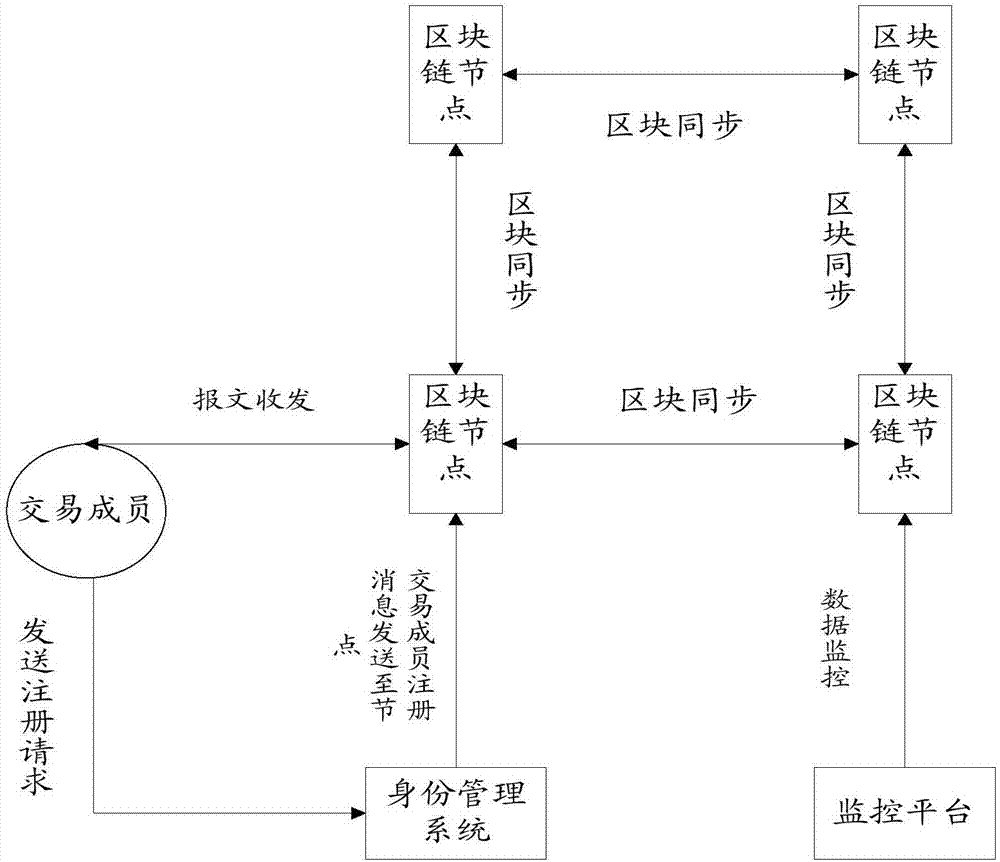
The invention discloses an identity authentication method. The method comprises the following steps: transmitting a registration request to an identity management system by a transaction member; verifying by the identity management system according to the registration request; and when the registration request passes the verification, generating registration information and sending the registration information to a block chain node by the identity management system, so as to enable the block chain node to write the registration information into a block chain. The invention further discloses anidentity authentication system and a computer readable storage medium. The invention can simplify the design of the identity authentication system and an identity authentication process.
Owner:CHINA MERCHANTS BANK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com