Patents
Literature
45 results about "Self certified" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Self-Certification (New York City Department of Buildings) Jump to navigation Jump to search. Self-Certification, officially known as Professional Certification, is a process by which licensed professionals may bypass a full review of a building project by the New York City Department of Buildings.
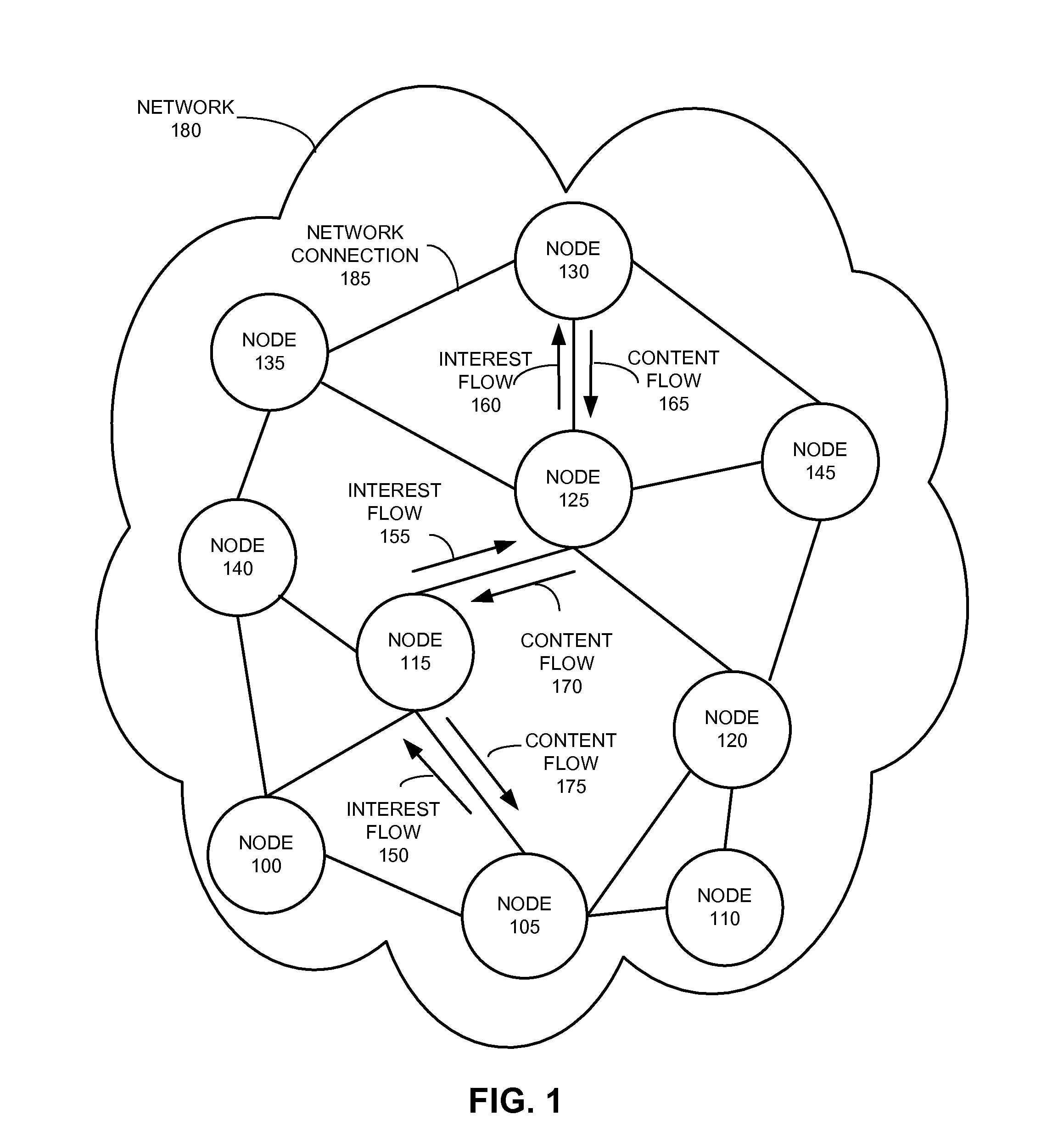
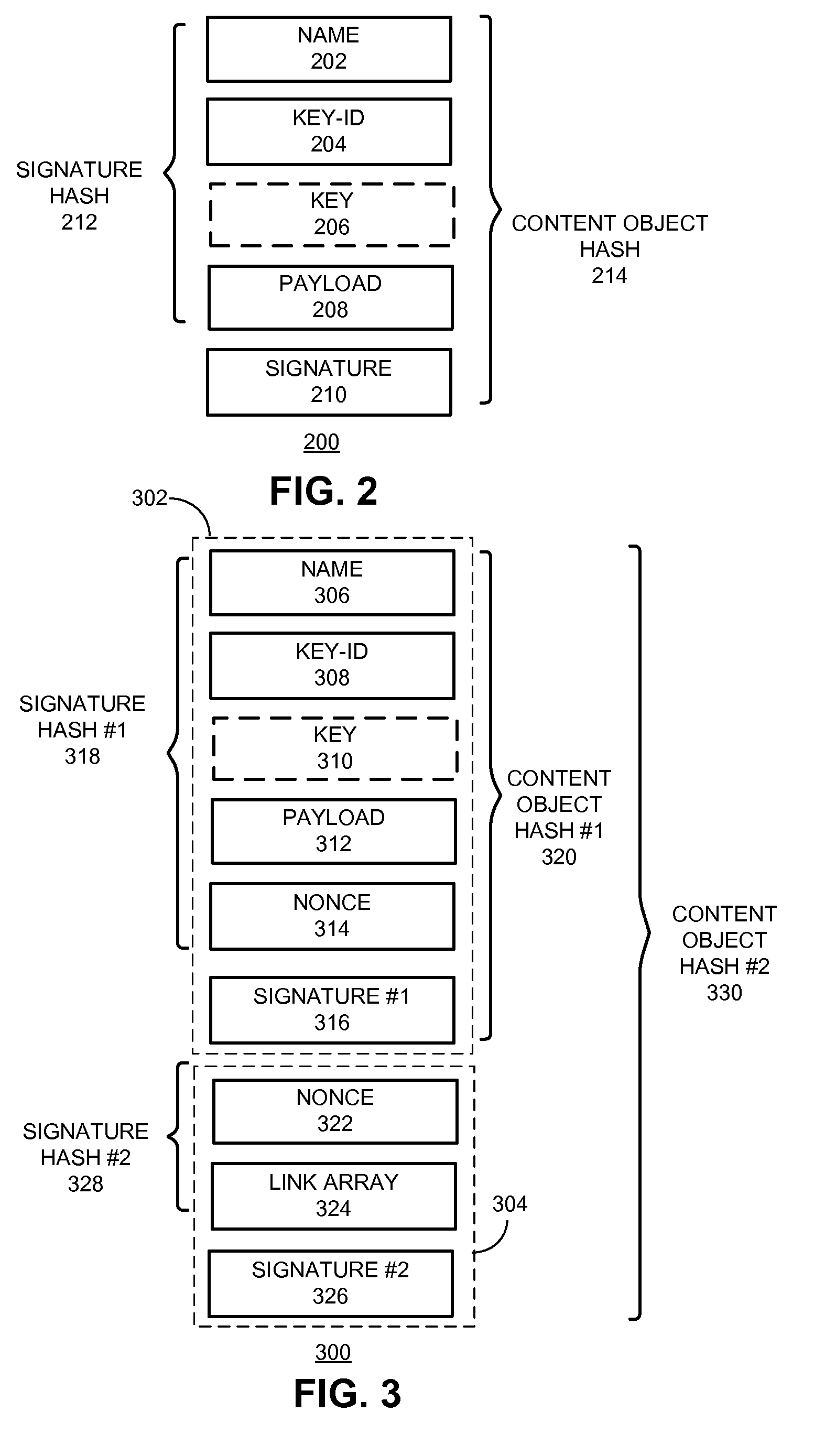
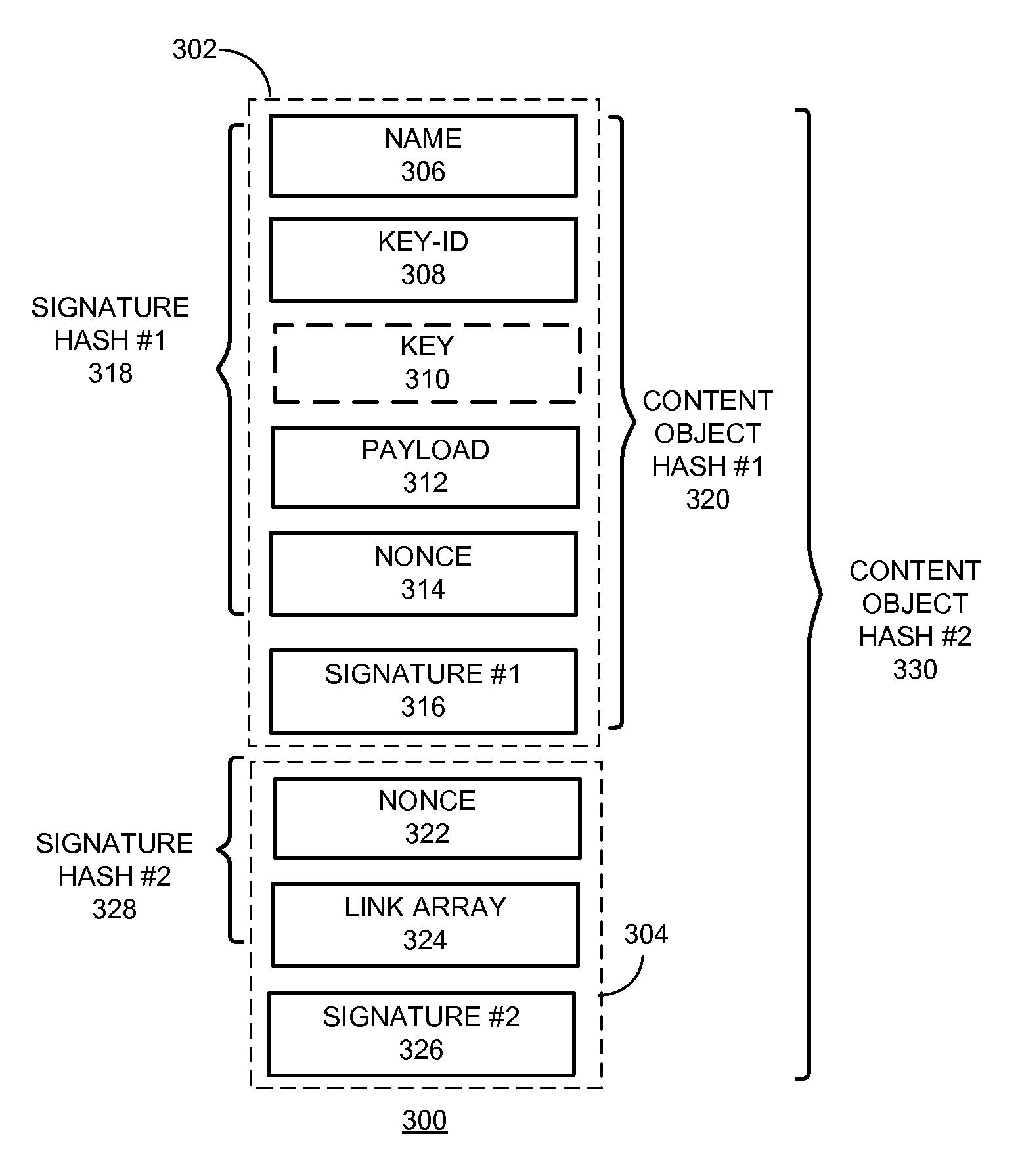
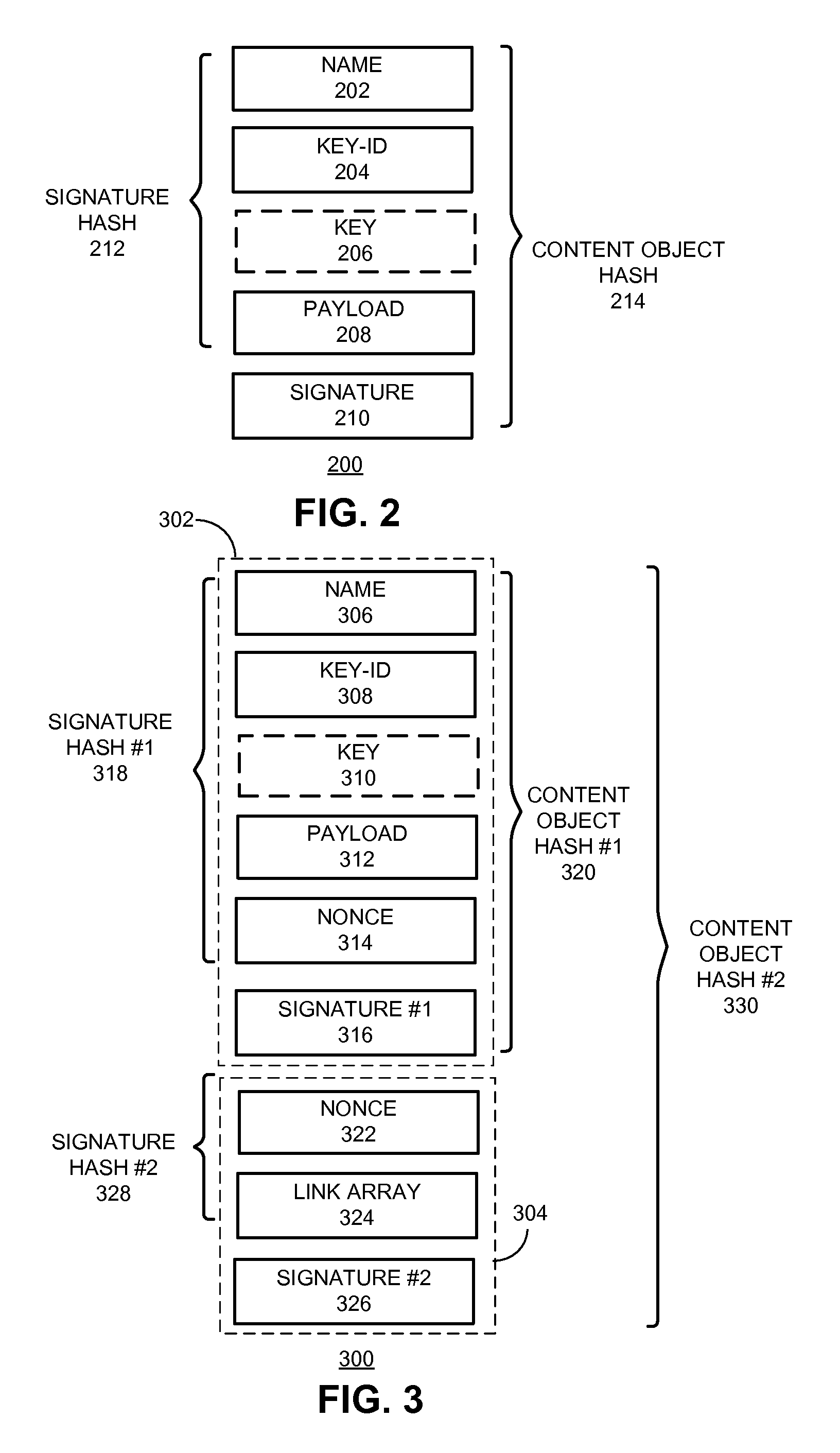
System for distributing nameless objects using self-certifying names
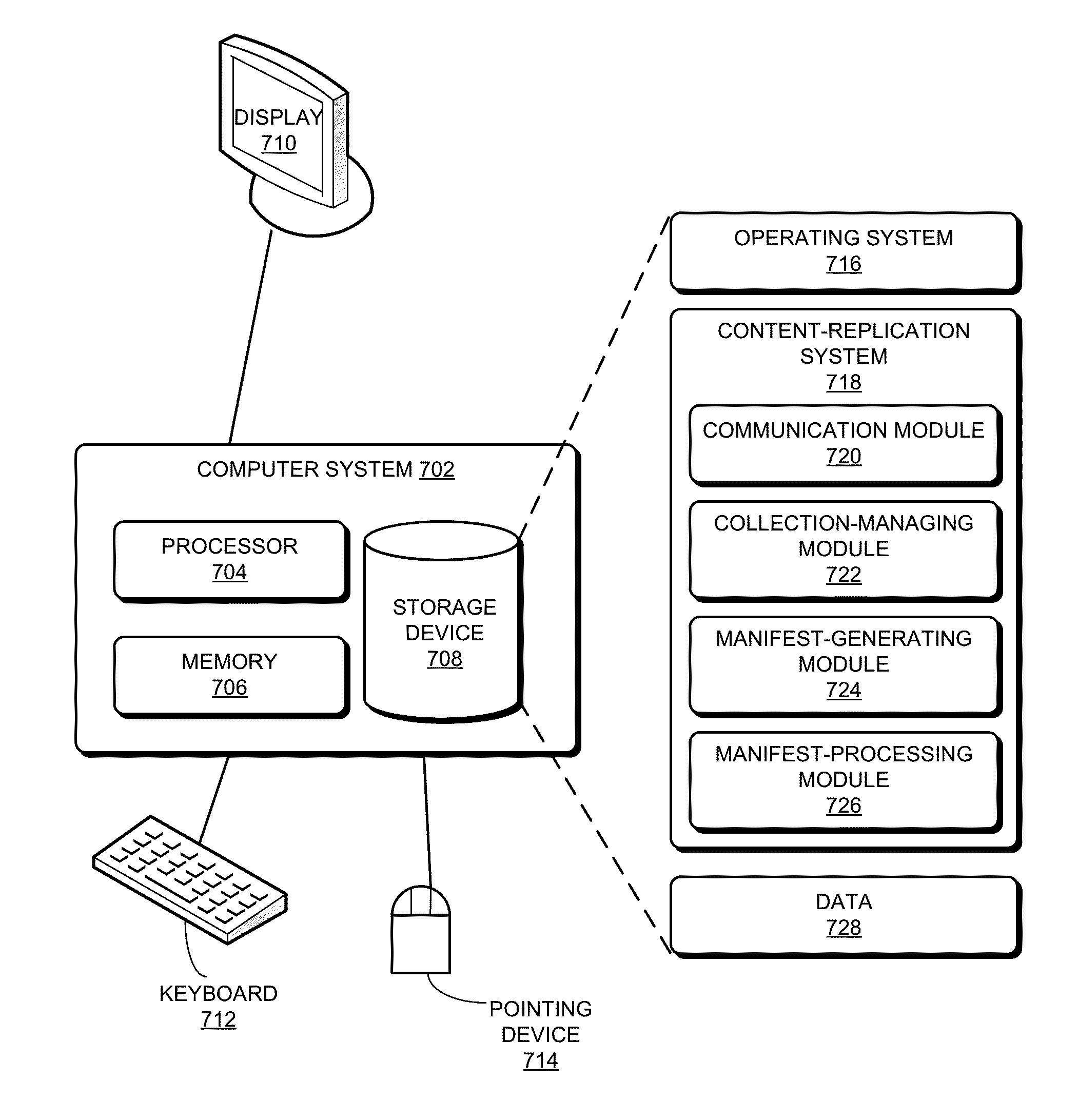
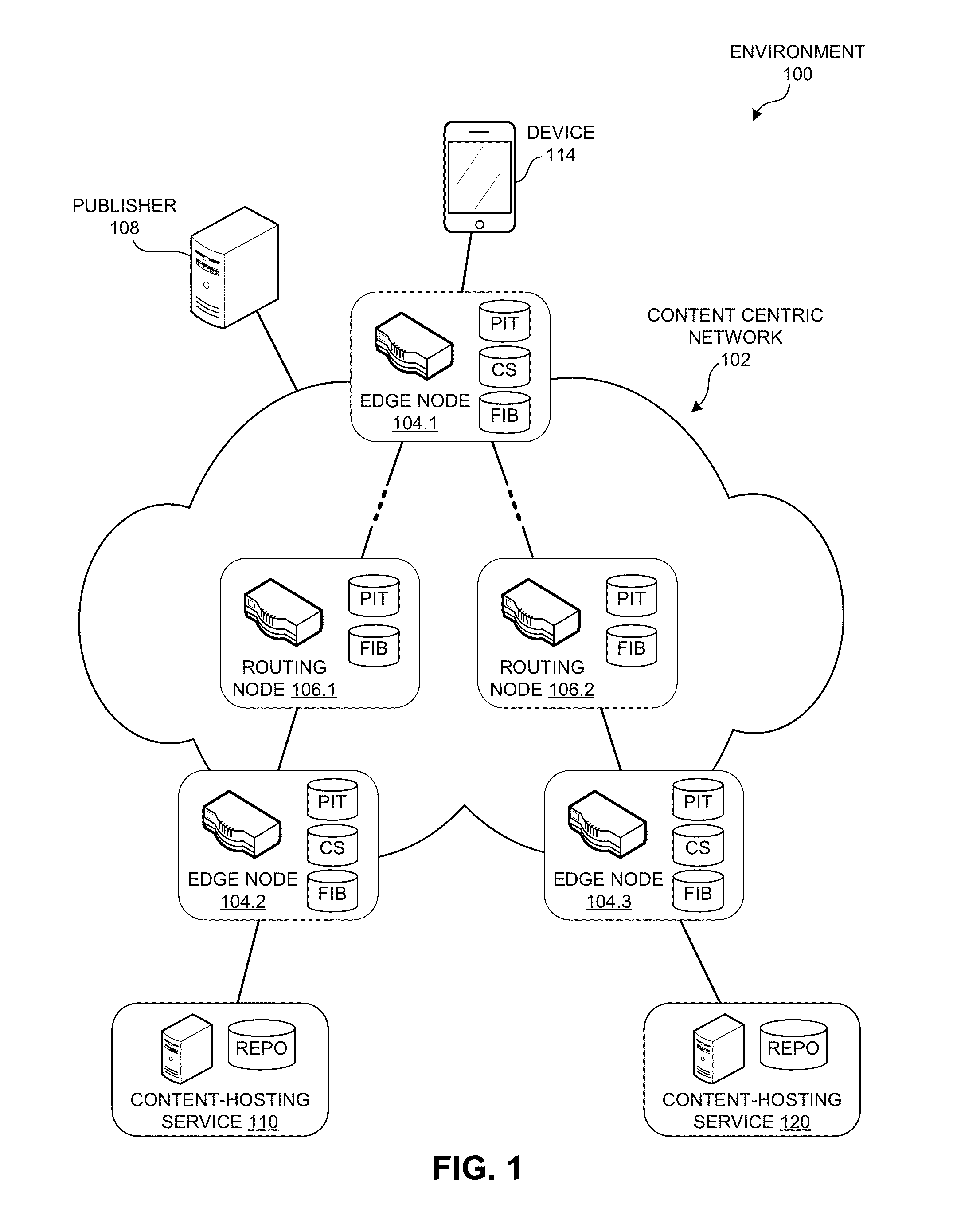
ActiveUS20160019275A1Digital data processing detailsDatabase distribution/replicationSelf certifiedContent centric
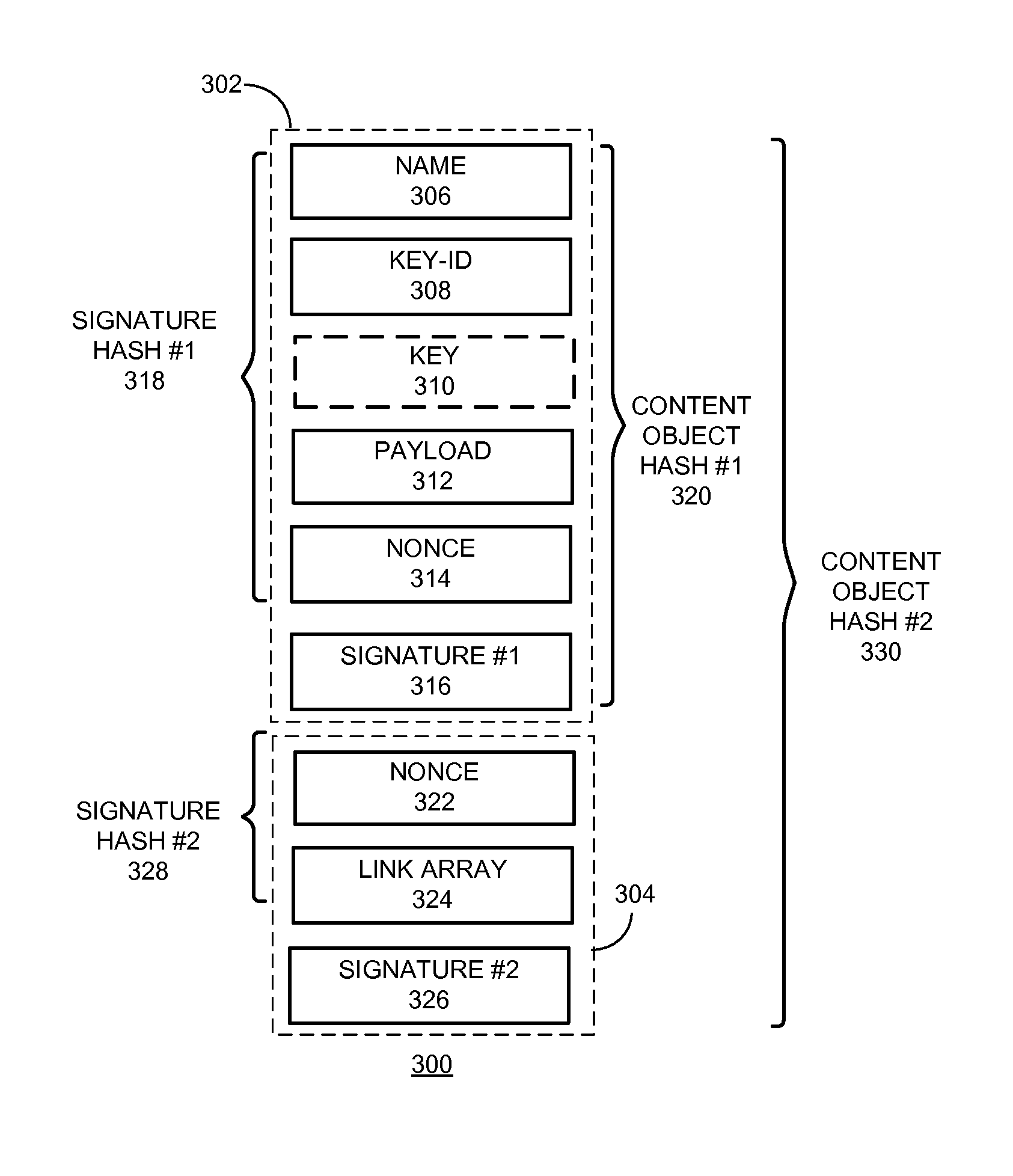
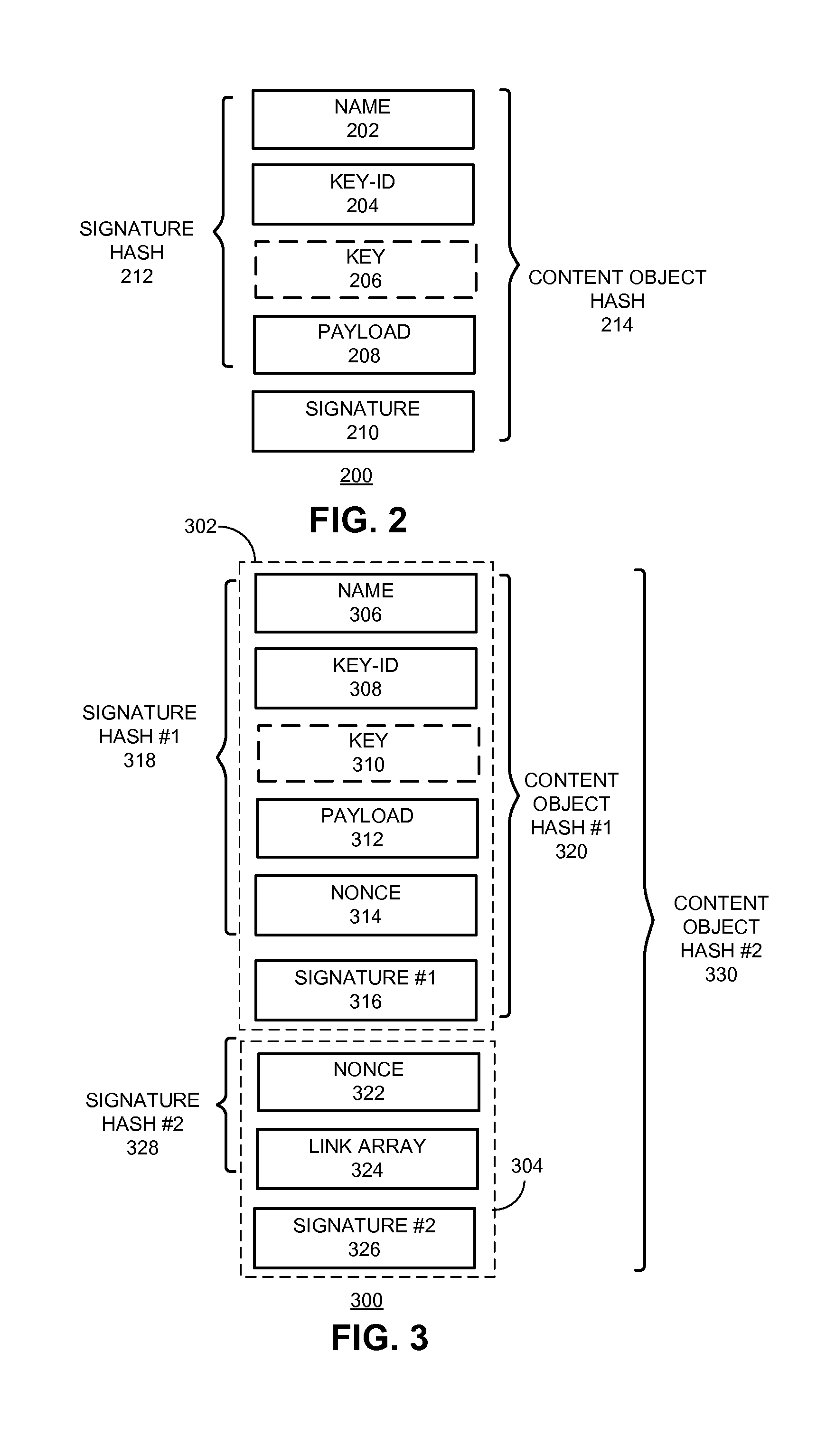
A content replication system can cache nameless Content Object across multiple replica servers in a Content Centric Network (CCN). During operation, a CCN client can obtain a nameless Content Object from one or more content-hosting services by disseminating an Interest for a data collection, and receives a Content Object that includes a manifest for the data collection. The manifest can include Content Object hash (COH) values for a set of other Content Objects of the data collection. The client then determines a name prefix for a content-hosting service that hosts the data collection, and generates another Interest for a Content Object of the data collection. This Interest's name includes the name prefix for the content-hosting service, and also includes a COH value for the respective Content Object. The client disseminates the new Interest over CCN to obtain the respective Content Object of the data collection.
Owner:CISCO TECH INC
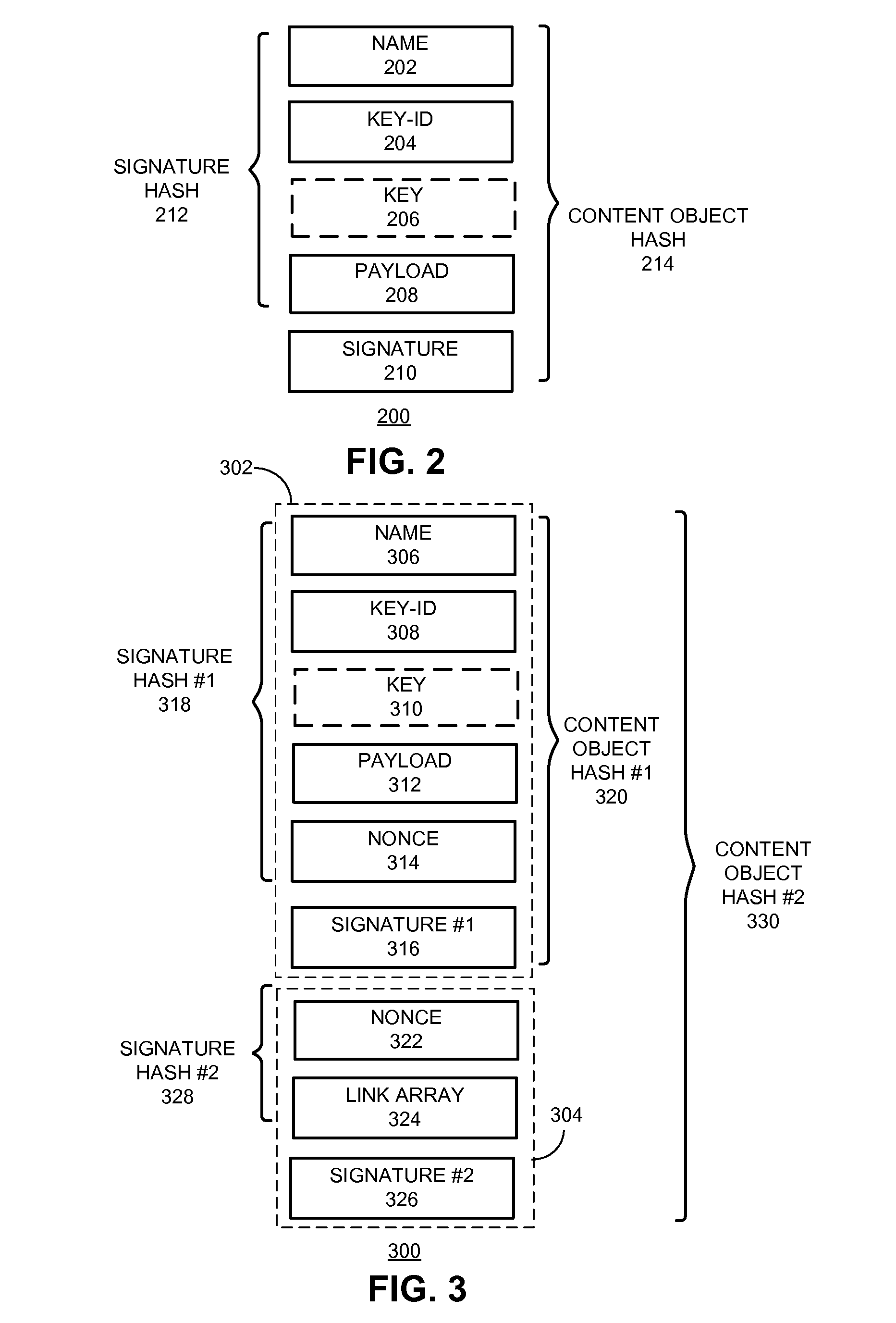
System and method for circular link resolution with computable hash-based names in content-centric networks
ActiveUS20150349961A1For easy referenceUser identity/authority verificationUnauthorized memory use protectionSelf certifiedContent centric
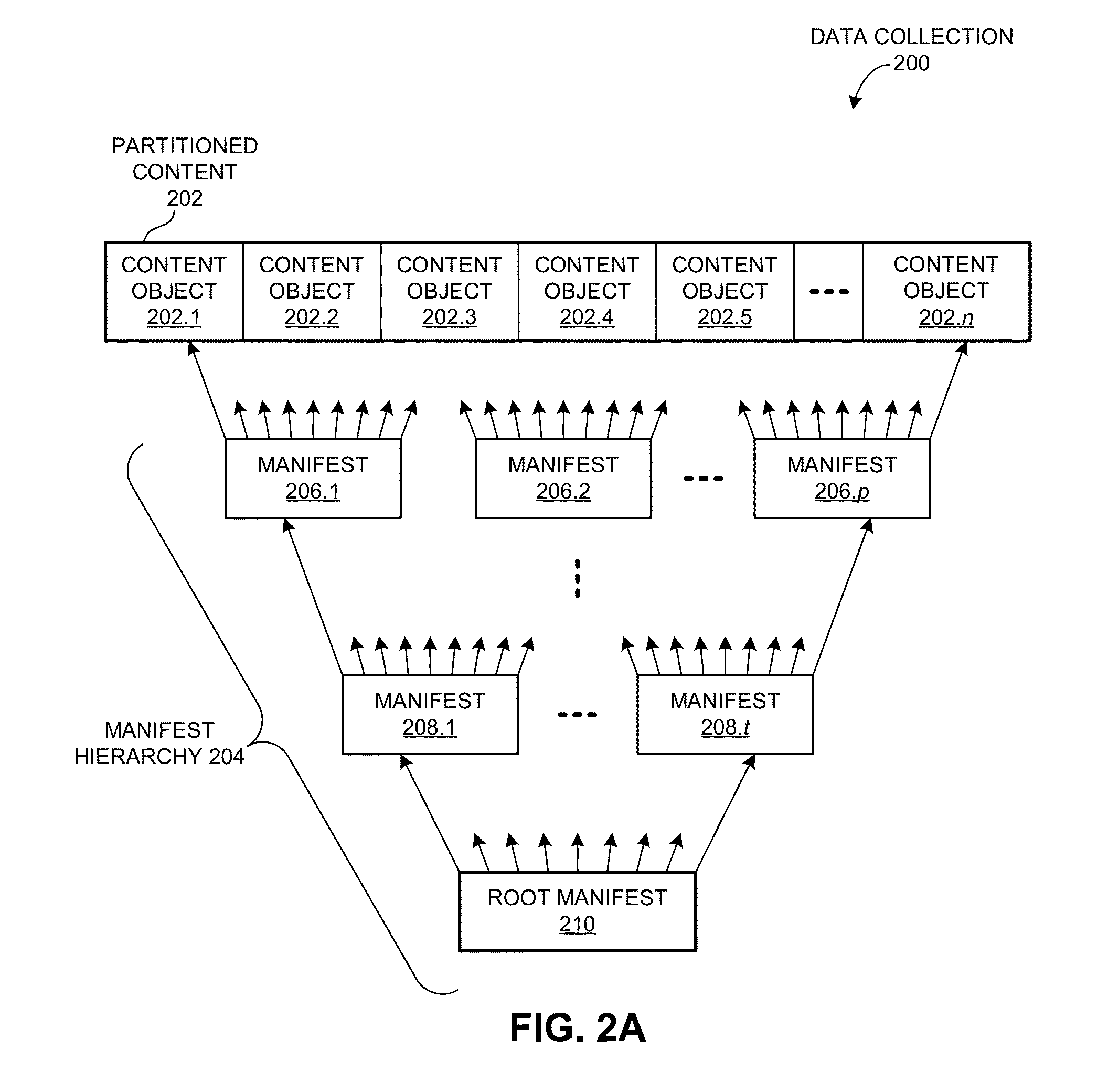
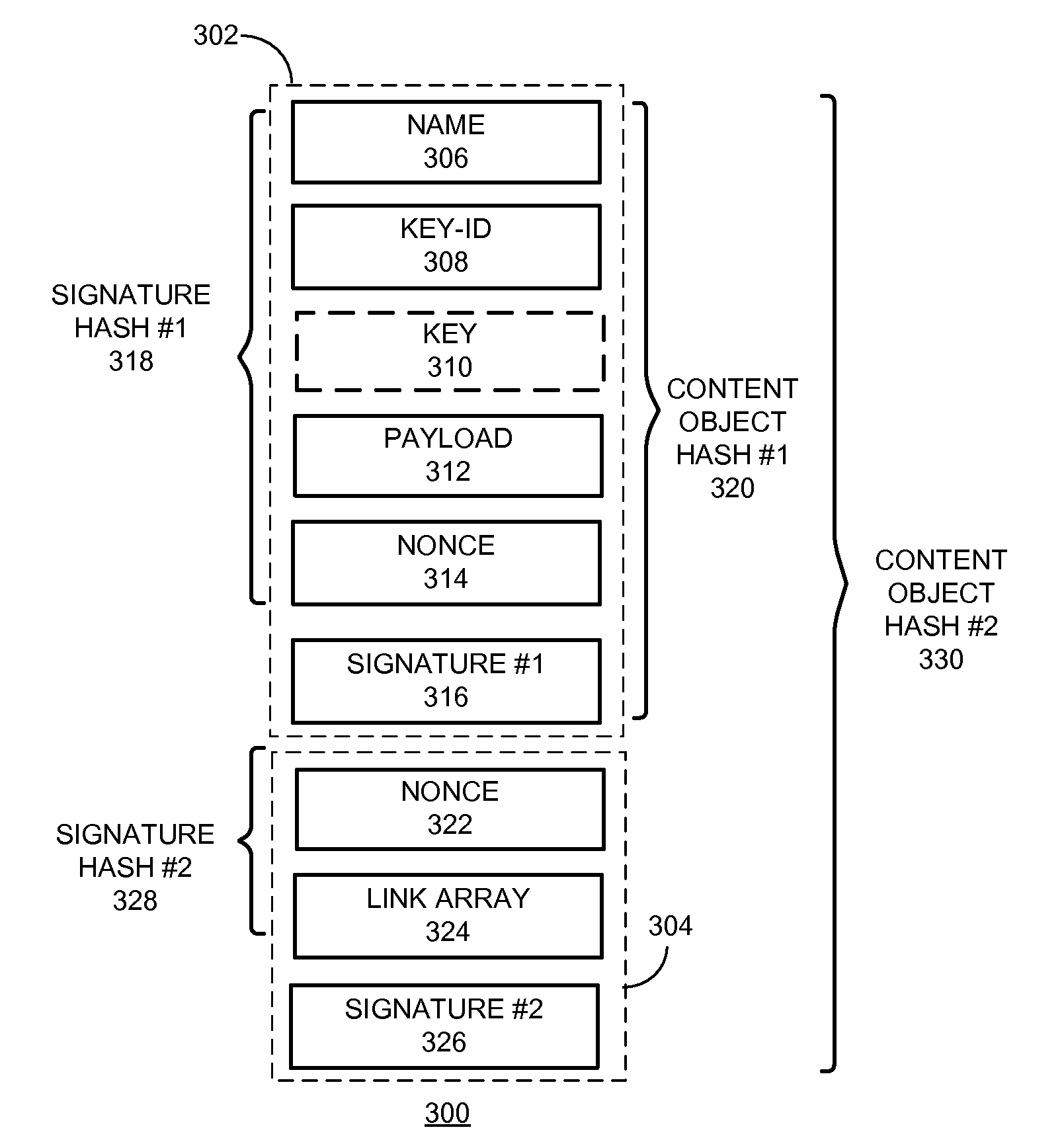
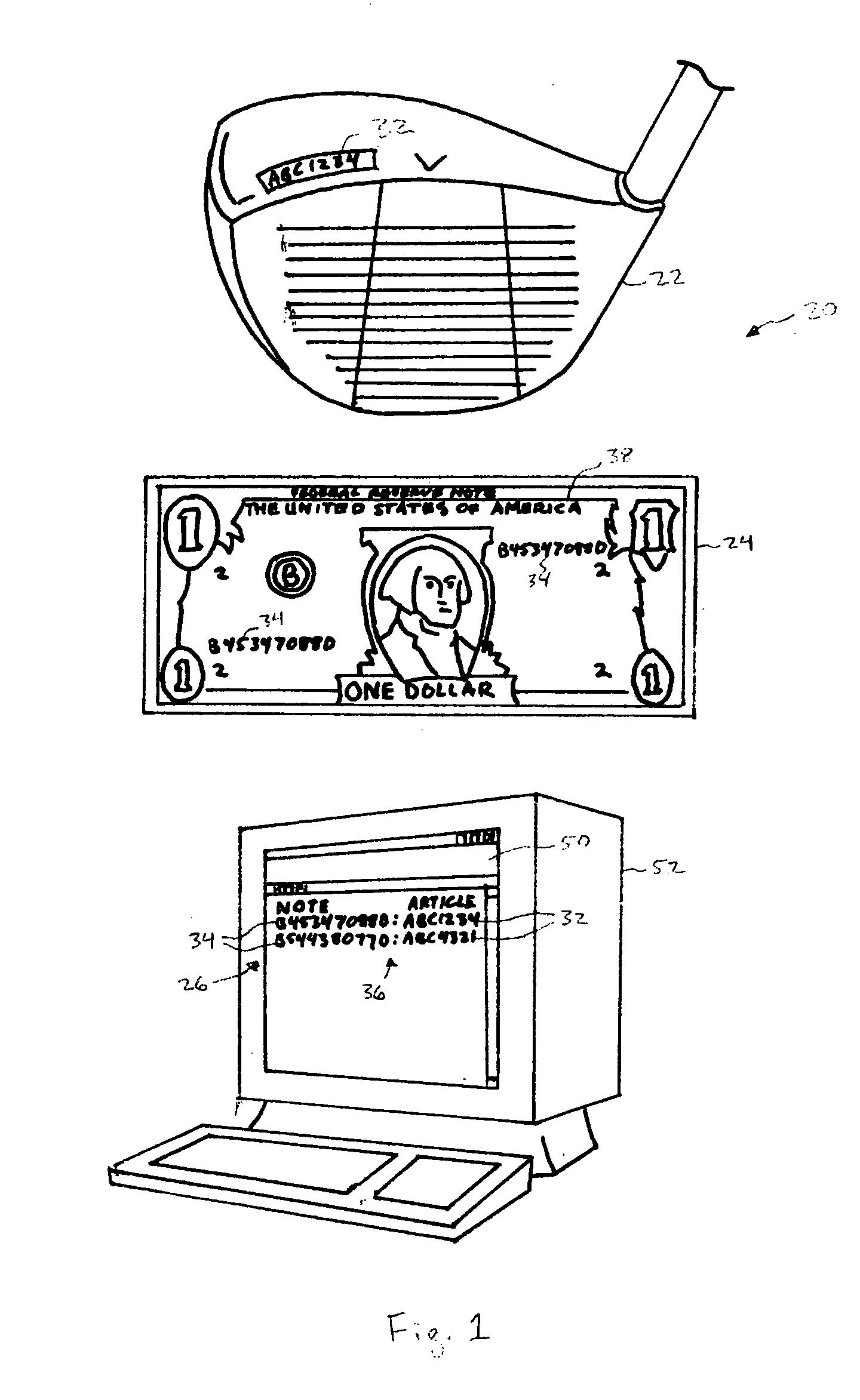
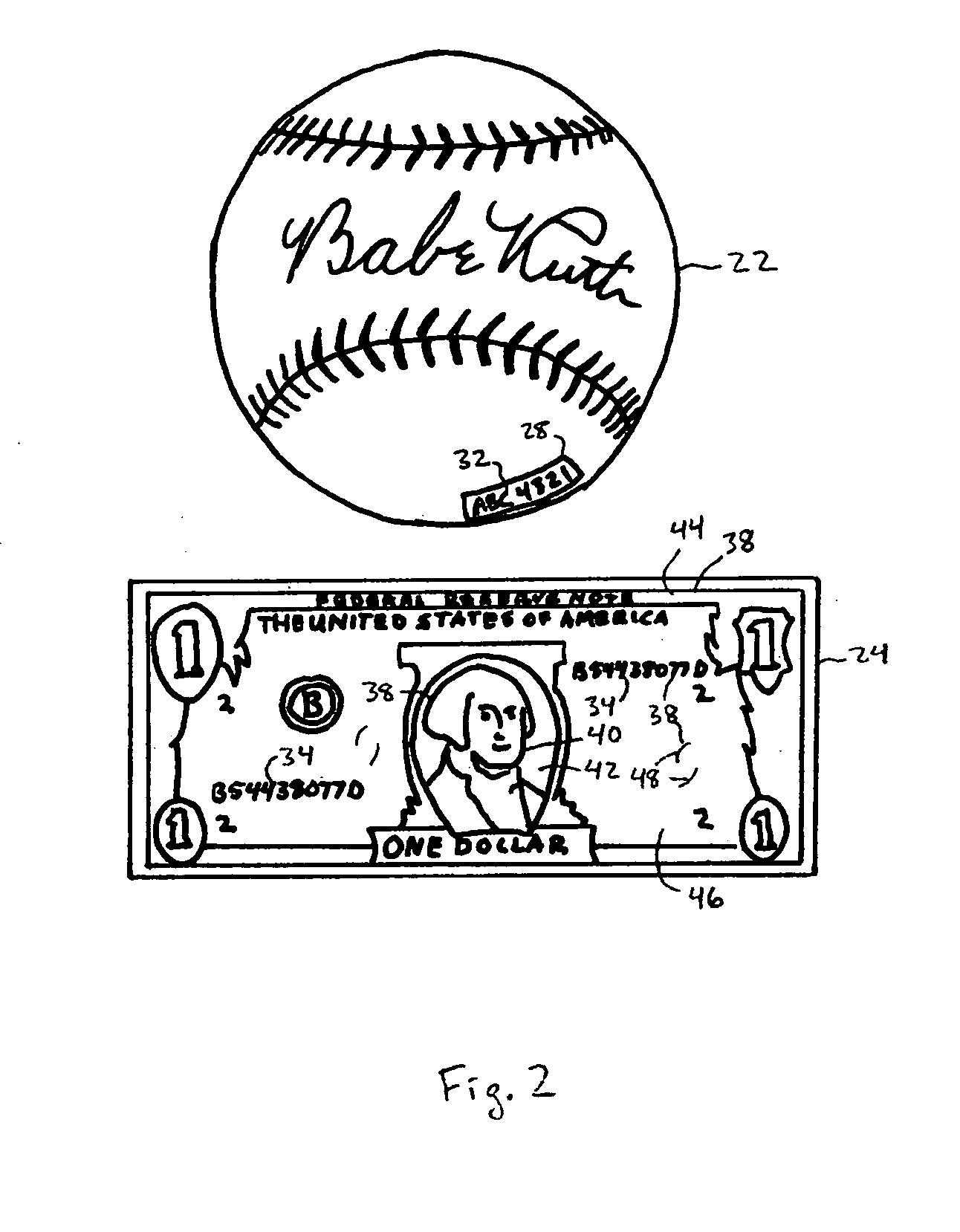
One embodiment of the present invention provides a system for constructing a linked object. During operation, the system constructs a first portion of the linked object. The first portion includes at least one or more data items and a computable identifier calculated based on the one or more data items, and the first portion is referenced by a self-certified name associated with the linked object. The system constructs a second portion of the linked object. The second portion includes at least the computable identifier and an external link that references a second linked object using a self-certified name associated with the second linked object.
Owner:CISCO TECH INC
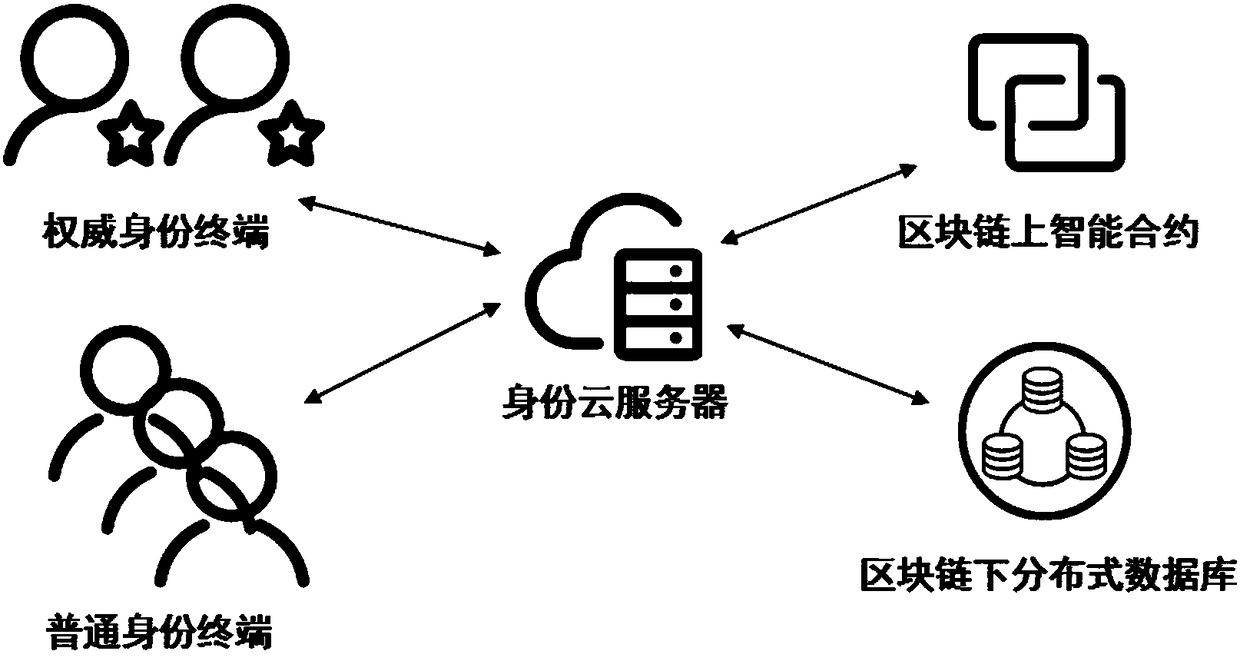
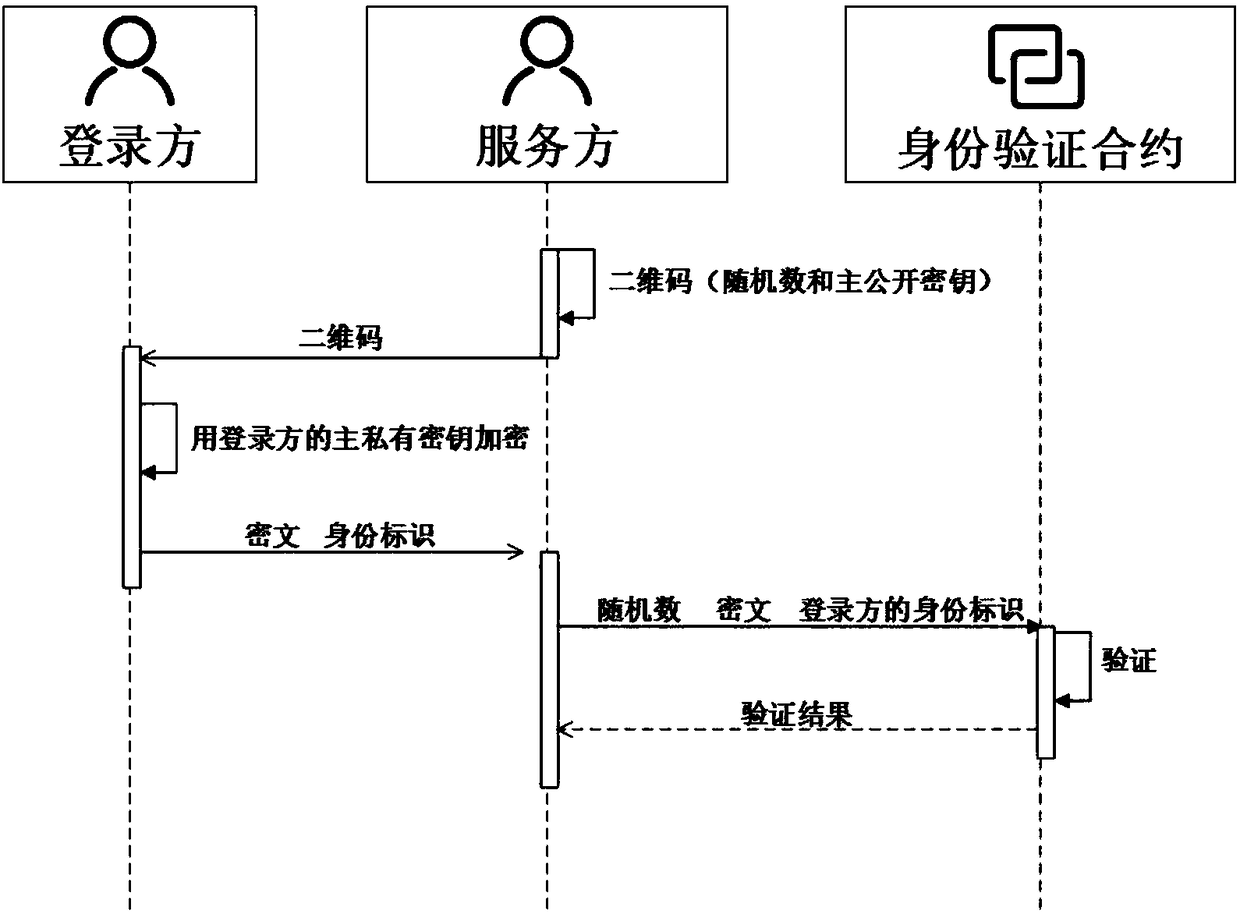
Self-certified digital identity management system and method based on smart contract
ActiveCN108234515AImplement passwordless loginMaster self-managementUser identity/authority verificationDigital identitySelf certified
The invention discloses a self-certified digital identity management system and method based on a smart contract. An identity terminal sends a public key and associated digital information to a cloudserver via the Internet, and accomplishes registration and login of digital identity, and the authorization, operation and verification of digital information depending on the smart contract on a block chain and a distributed database under the block chain. A unique identity of the whole network can be provided, passwordless login is achieved by scanning a two-dimensional code, the login mode of the traditional username and password is broken through, and a user entirety can securely and effectively manage the digital identity and the associated digital information, on-demand authorization, operation and verification of information are achieved, thus realizing a decentralized, self-certified digital identity management system.
Owner:安徽中科晶格技术有限公司
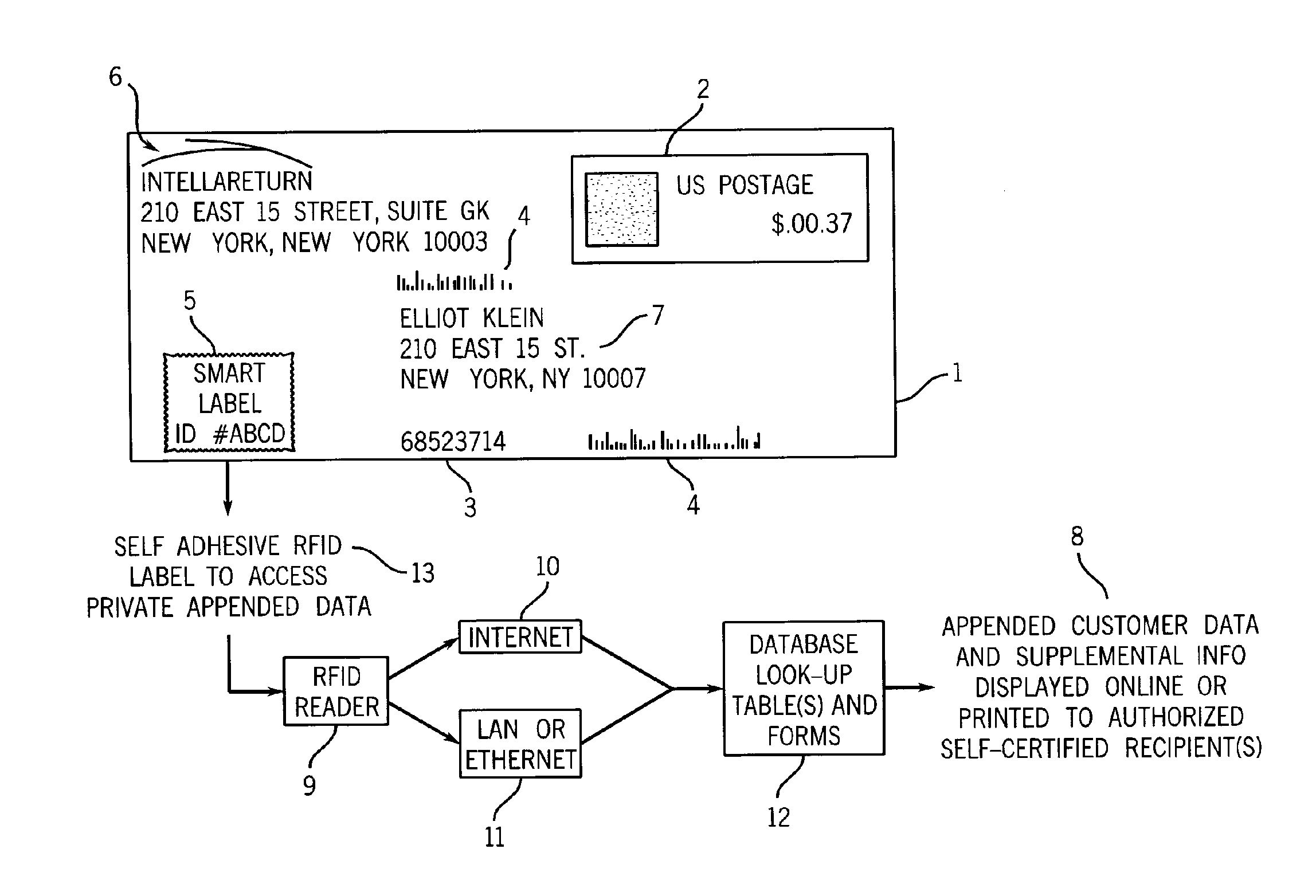
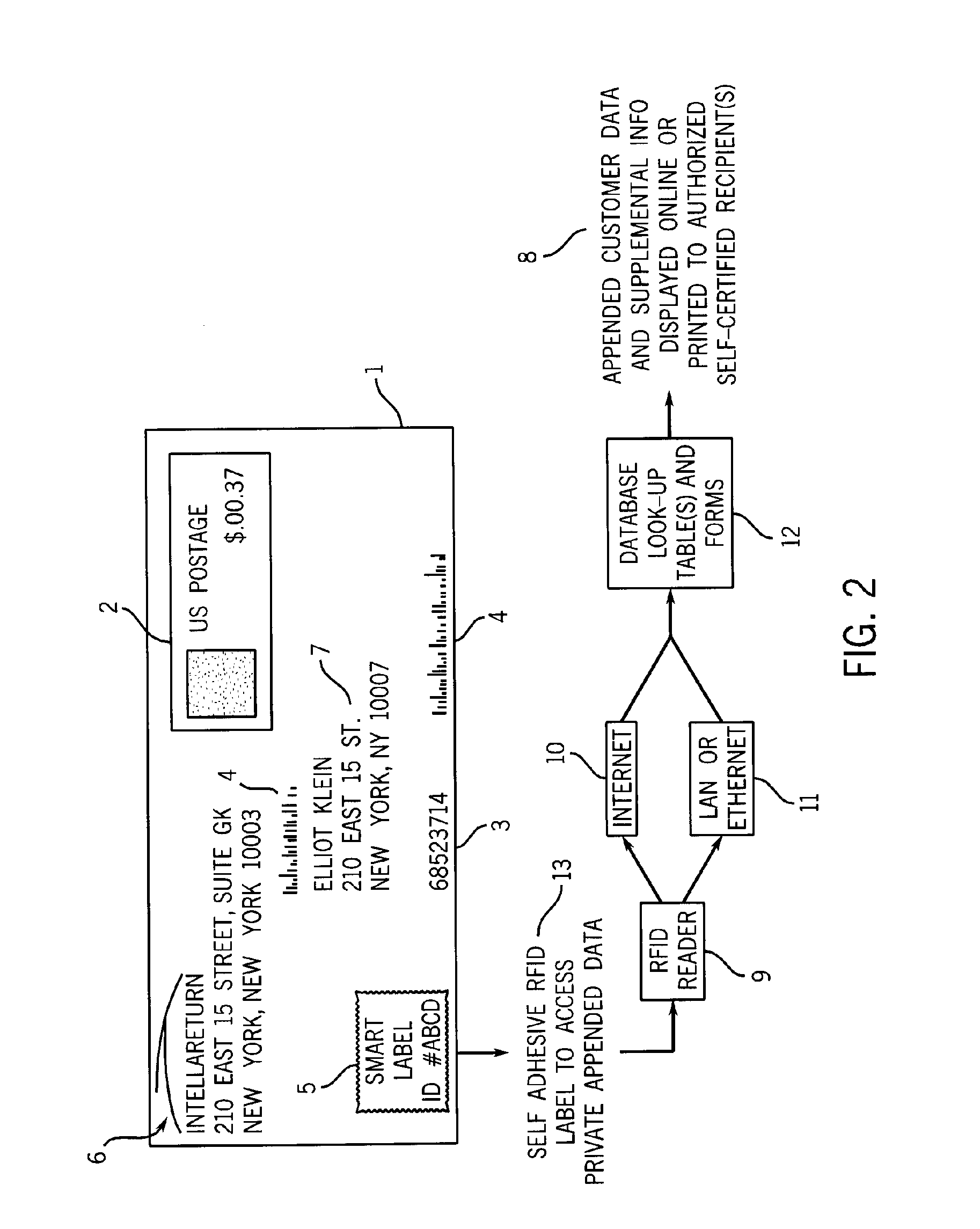
Data append method for sent postal mail
InactiveUS20060010086A1Expand the role of U.SFranking apparatusProgram controlDigital identitySelf certified
Method to manage an electronic interface by radio-frequency identification (“RIFD”) transponder to retrieve supplemental data for U.S. Postal Service sent mailings under non-negotiable privacy and digital identity registration policy standards, pursuant to data registration templates and self-certification standards.
Owner:KLEIN ELLIOT S
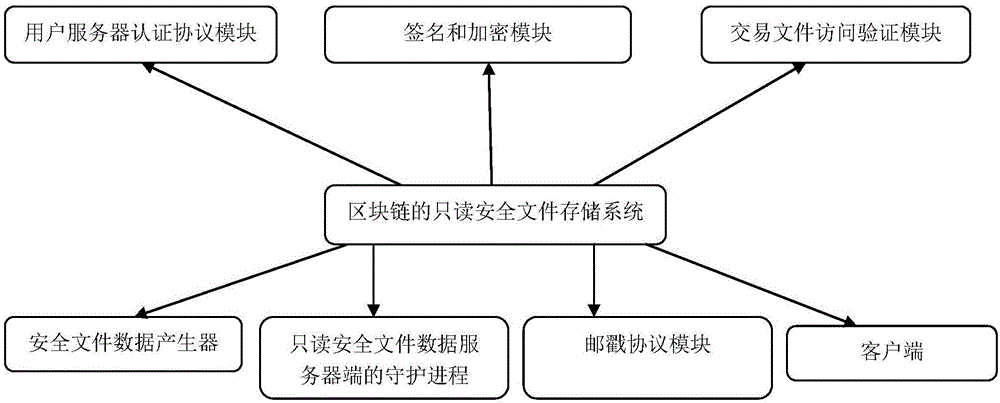
Read-only security file storage system for block chain and method thereof
InactiveCN106295401AFaster and more complete recoveryExtended storage timeInput/output to record carriersDigital data protectionData integrityCiphertext
The invention provides a read-only security file storage system for a block chain. The system comprises: (1) a user server authentication protocol module used for executing a mutual authentication protocol between a user and a server via a self-certified path name; (2) a signature and encryption module used for correctly encrypting a transaction file; (3) a transaction file access verification module used for verifying the trustworthiness of the user; (4) a security file data generator; (5) a daemon of a read-only security file data server; and (6) a client, wherein a traditional path is converted into data and digital signature is carried out in a client environment, then the data is distributed to an arbitrary number of running servers, and the daemon receives the request of the client and returns the data; and (7) a postmark protocol module used for detecting the integrity of transaction data. By adoption of the storage system and the method provided by the invention, the storage time of a large file system is shortened, and a creator can complete cryptographic operation, data creation and decryption according to ciphertext in an environment without a network.
Owner:SHENZHEN FANXI ELECTRONICS CO LTD
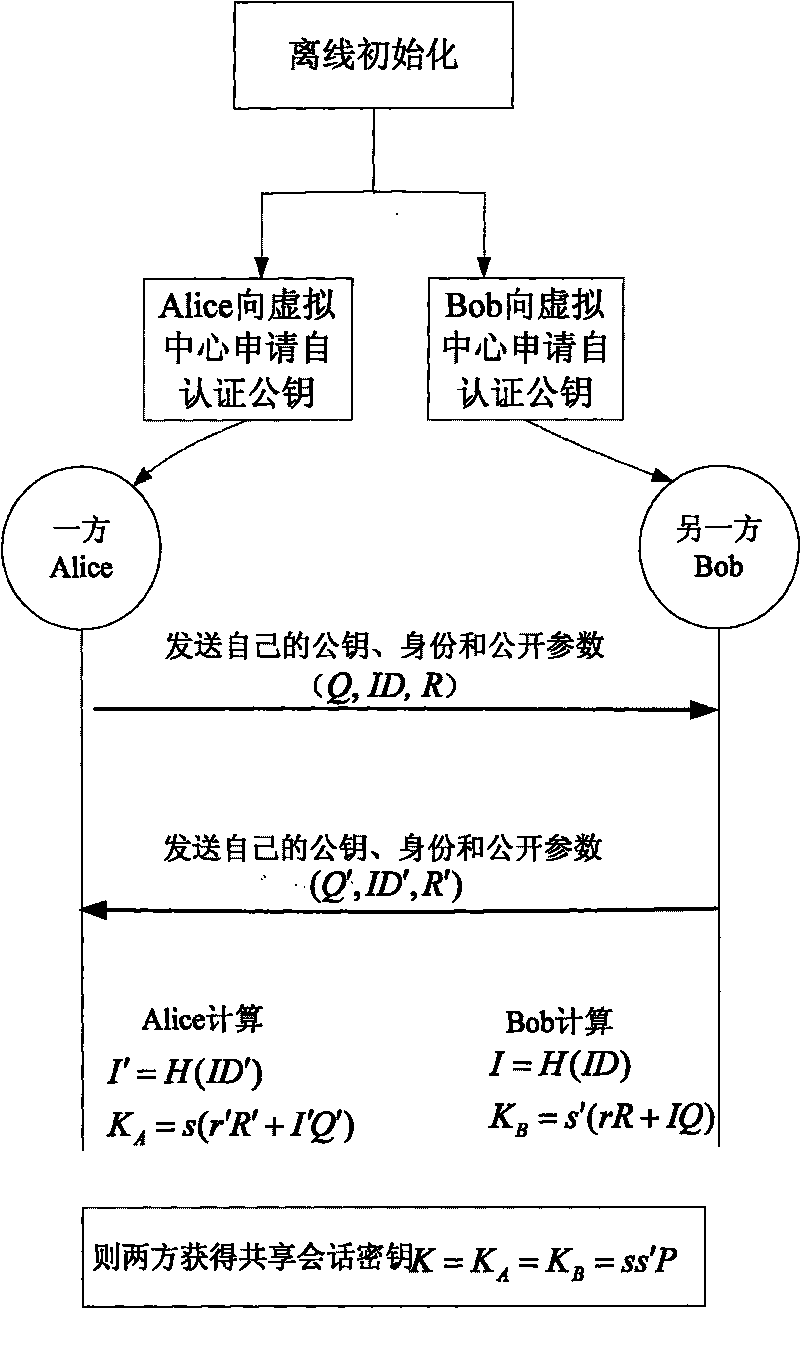
Two-party key agreement method based on self-certified public key
InactiveCN101702804AReduce storageReduce communicationPublic key for secure communicationNetwork topologiesStatus changedSession key
The invention discloses a two-party key agreement method based on a self-certified public key, mainly solving the complicated certificate management problem in the traditional PKI technology to realize the self-certified two-party key share and reduce the network resource expenses. The method comprises the following steps of: allocating shared keys to n virtual central nodes by utilizing a threshold cryptology; selecting an individual secret random number by one party of a session, calculating public parameters, sending the individual identity and the public parameters to a virtual center to apply an individual self-certified public key; selecting an individual secret random number by the other one party of the session, calculating public parameters, sending the individual identity and the public parameters to the virtual center to apply an individual self-certified public key; after mutually exchanging the self-certified public key, the identity and the public parameters by two parties of the session, respectively calculating the shared session key. In the invention, a light code ECC is used as a theoretical basis without the certificate management, the key escrow and the safe signal path, so that the man-in-the-middle attack can be resisted, and the invention is suitable for the mobile self-organization network safety communication with the limited resources.
Owner:XIDIAN UNIV
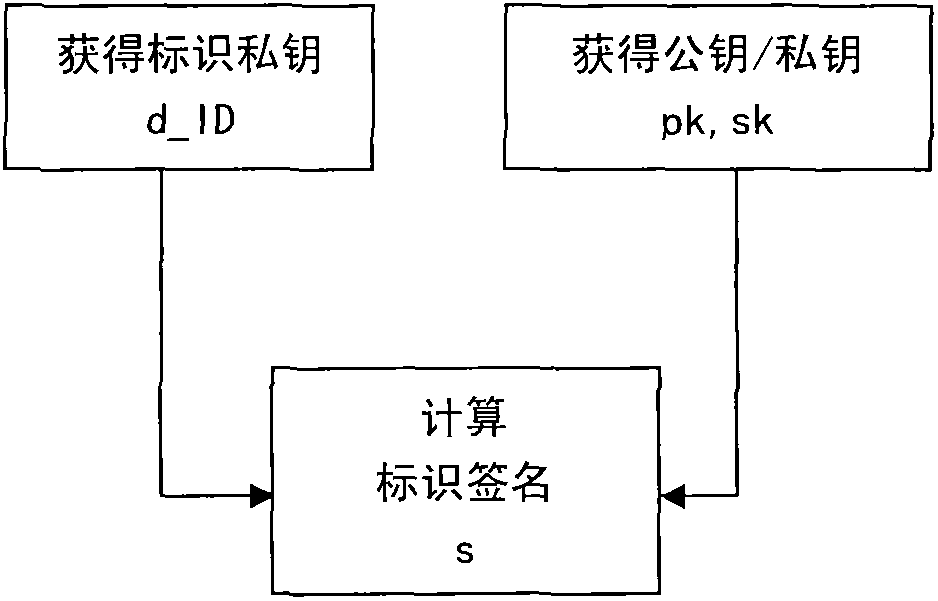
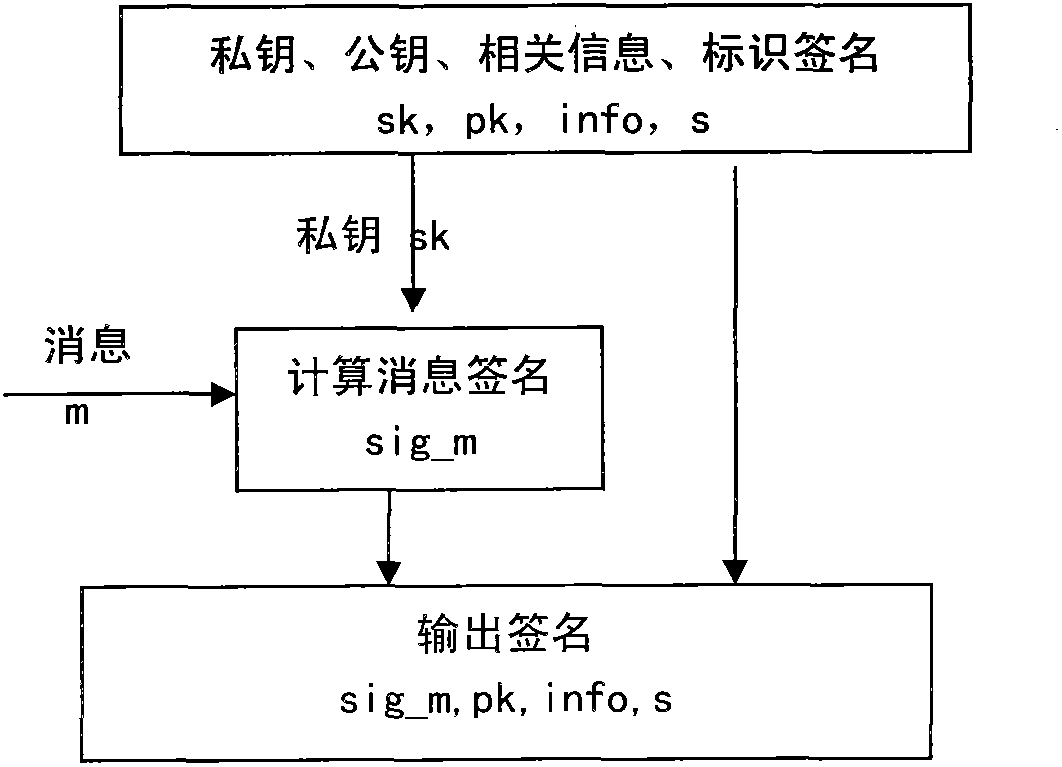
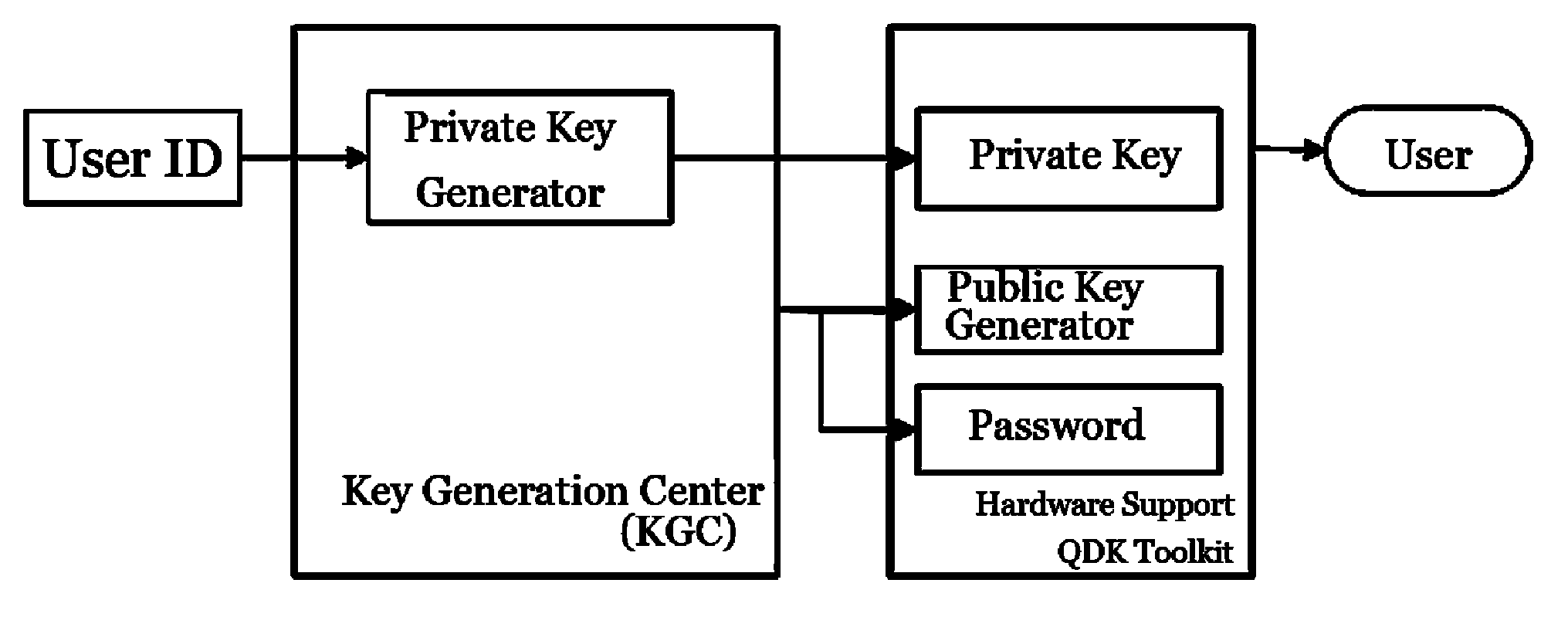
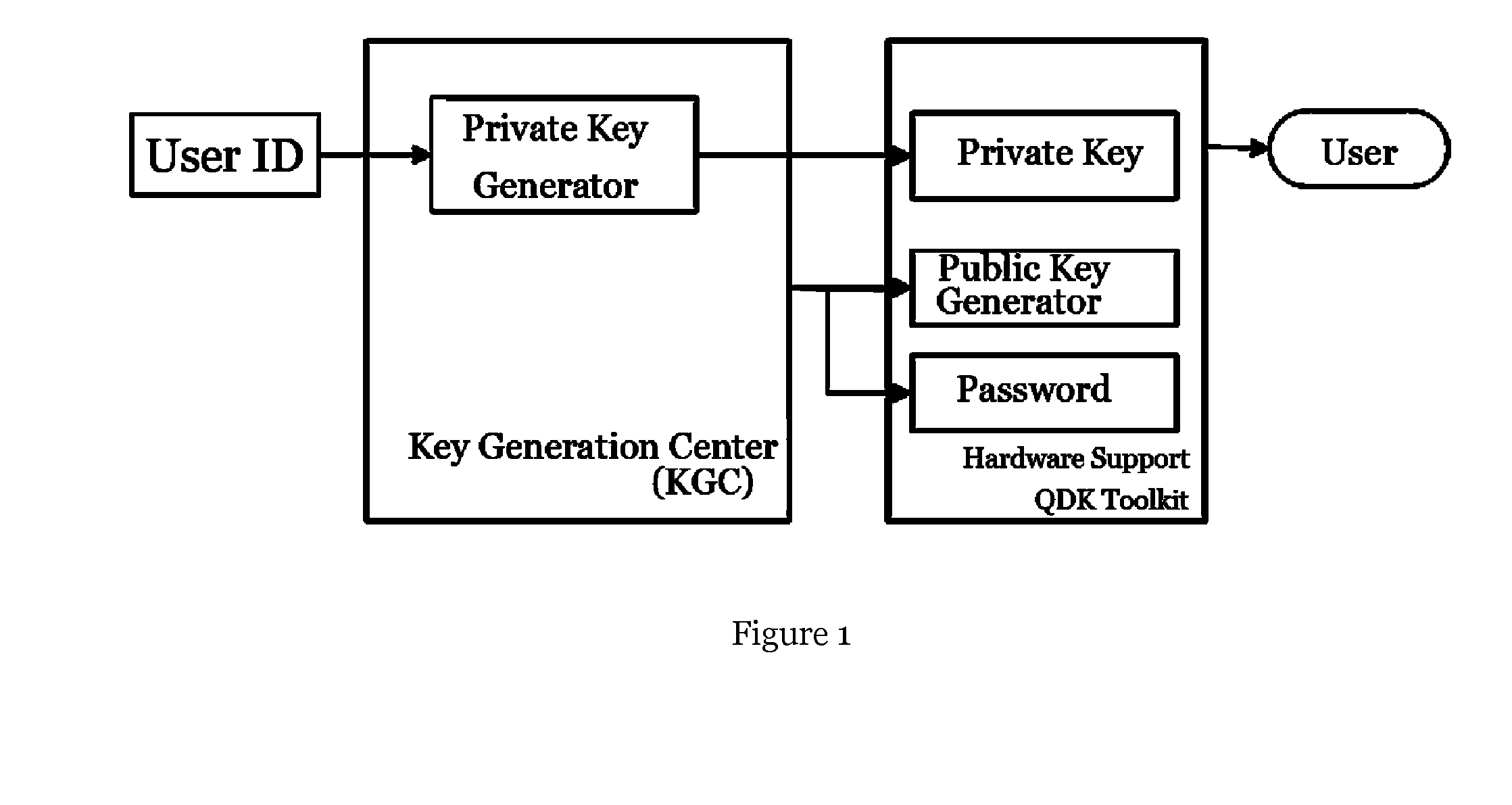
System and method for computing private keys for self certified identity based signature schemes
ActiveUS20190372763A1Key distribution for secure communicationUser identity/authority verificationSelf certifiedStatus changed
Owner:HUAWEI INT
Method for combining identity-based cryptography and conventional public key cryptography
InactiveCN102215111ATroubleshoot hosting issuesPublic key for secure communicationUser identity/authority verificationSelf certifiedPublic key cryptosystem
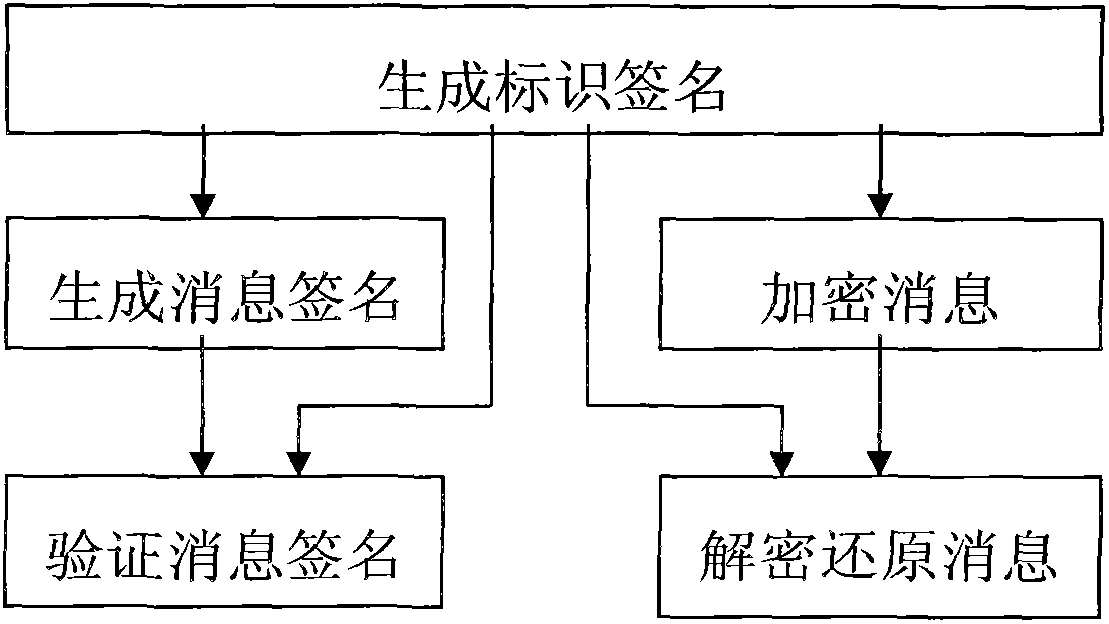
The invention discloses a method for combining an identity-based cryptography and a conventional public key cryptography. Potential hazards in the private key hosting of the identity-based cryptography can be solved. Compared with other similar methods such as certificate-based encryption (CBE), a certificateless public key cryptography (CL-PKC) or a self-certified public key cryptography (SC-PKC), the method has the advantage of avoiding the limitations of the public key cryptography. The method provided by the invention comprises a signature method and an encryption method. The signature method comprises the following three steps of: 1, generating an identity signature; 2, generating a message signature; and 3, verifying the message signature. The encryption method comprises the following three steps of: 1, generating the identity signature; 2, encrypting a message; and 3, decrypting and recovering the message.
Owner:BEIJING ZTE DIGITAL TECH
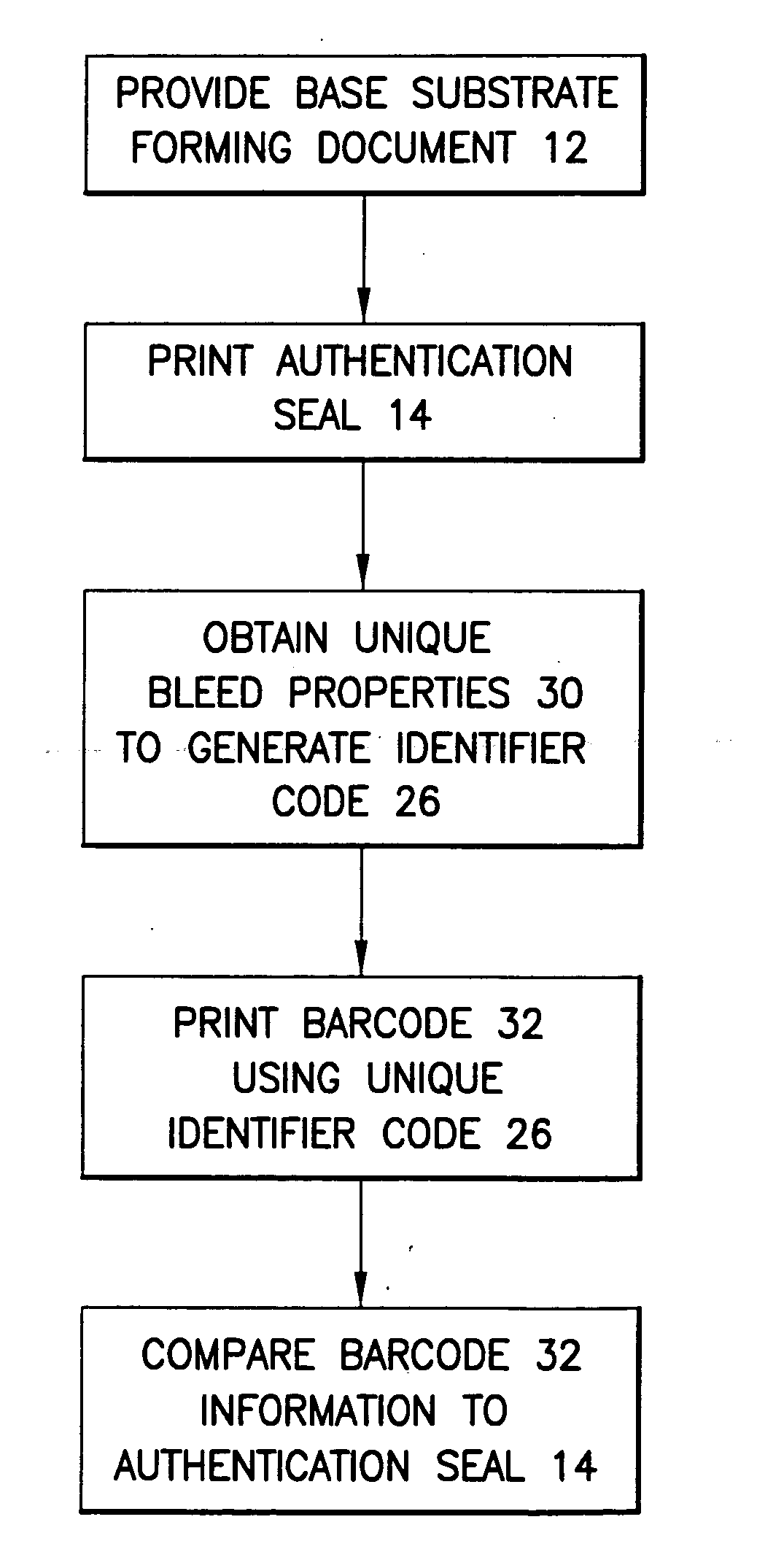
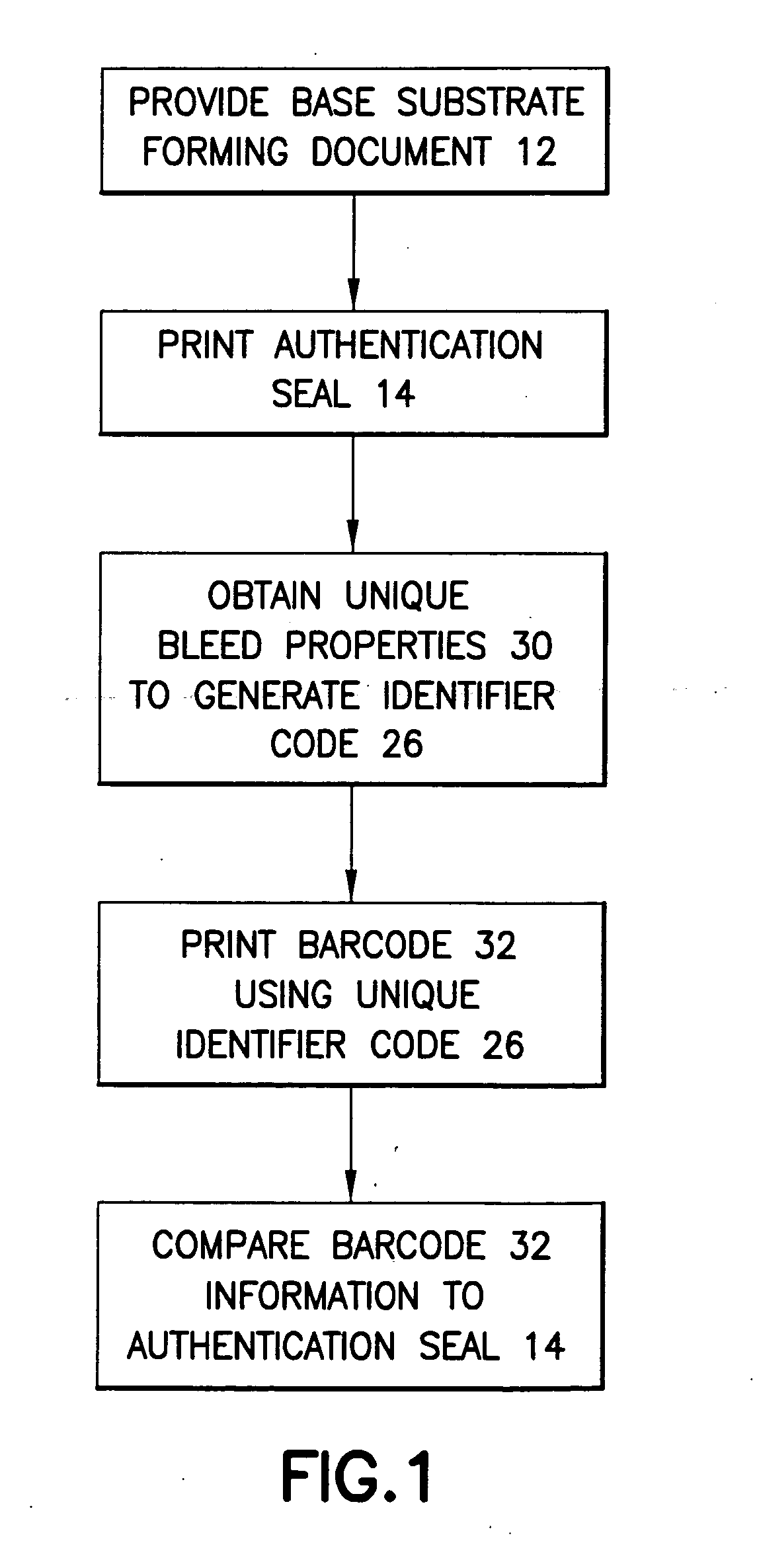
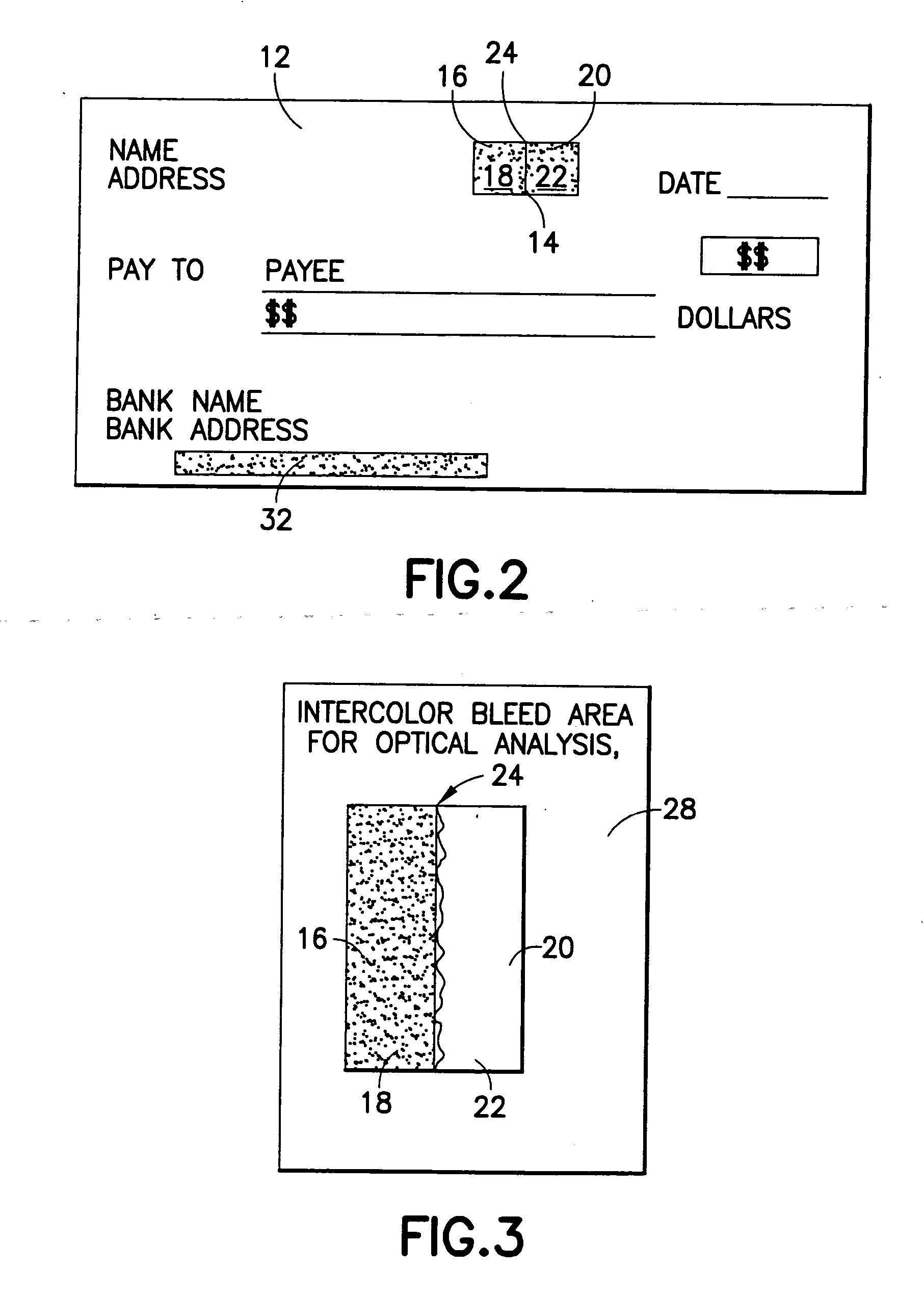
Method for creating self-authenticating documents
InactiveUS20060282672A1User identity/authority verificationCharacter and pattern recognitionSelf certifiedSubstrate Interaction
In accordance with an embodiment of the invention, a method for creating a self-authenticating document is disclosed. The method comprises: providing a base substrate forming the document; printing an authentication seal on the document, the authentication seal comprising a printed portion comprising an ink creating a bleed area on the document where the ink and the substrate interact; and obtaining unique bleed properties of the bleed area. The bleed properties are obtained by scanning the bleed area upon termination of bleeding or drying to provide a description of the ink and substrate interaction to generate an identifier code representing the unique bleed properties. The method further comprises generating a signature of the identifier code, encoding the identifier code in an information carrier, and associating the information carrier with the document or storing the signed identifier code in a remote verification seal code that is not printed on the document. The authentication seal is capable of being scanned and compared to the information carrier or to the remote verification seal code, wherein the verification seal code is not located on the document and comprises the same code information as the identifier code.
Owner:PITNEY BOWES INC
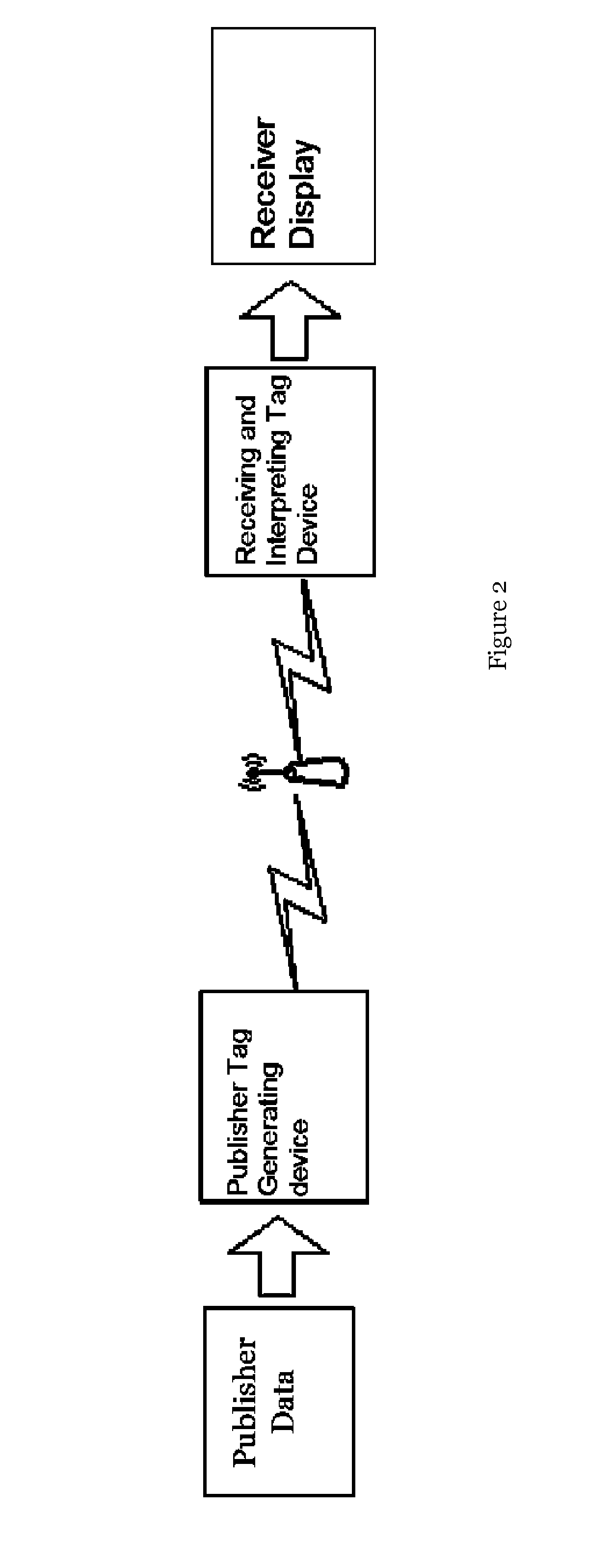
Self-authenticated tag generation method and interpretation method used in the self-authenticated key system
InactiveUS20150058633A1Rich relevant informationNot easily be tamperedUser identity/authority verificationThird partySelf certified
The present invention relates to a self-authenticated tag generation method and interpretation method used in the self-authenticated key system, which comprises the following steps: inputting data by the publisher; generating tag via a self-authenticated tag device by the publisher; transmitting generated tag to the receiver; interpreting tag via the self-authenticated tag device by the receiver; and displaying data. The present invention is easy and safe, the generated self-authenticated tag can be transmitted by various carriers, can distinguish the object and upload abundant information without easily tampered. Moreover, the acquisition of the public key is not achieved by the third party, which decreases wasting the network resources, and avoids the unsecure factors brought by the third party.
Owner:QUASI STELLAR ALPHA
Routing method, routing device, packet forwarding method and packet forwarding system
ActiveCN102546419ASmall scaleImprove packet forwarding efficiencyData switching networksSelf certifiedBorder Gateway Protocol
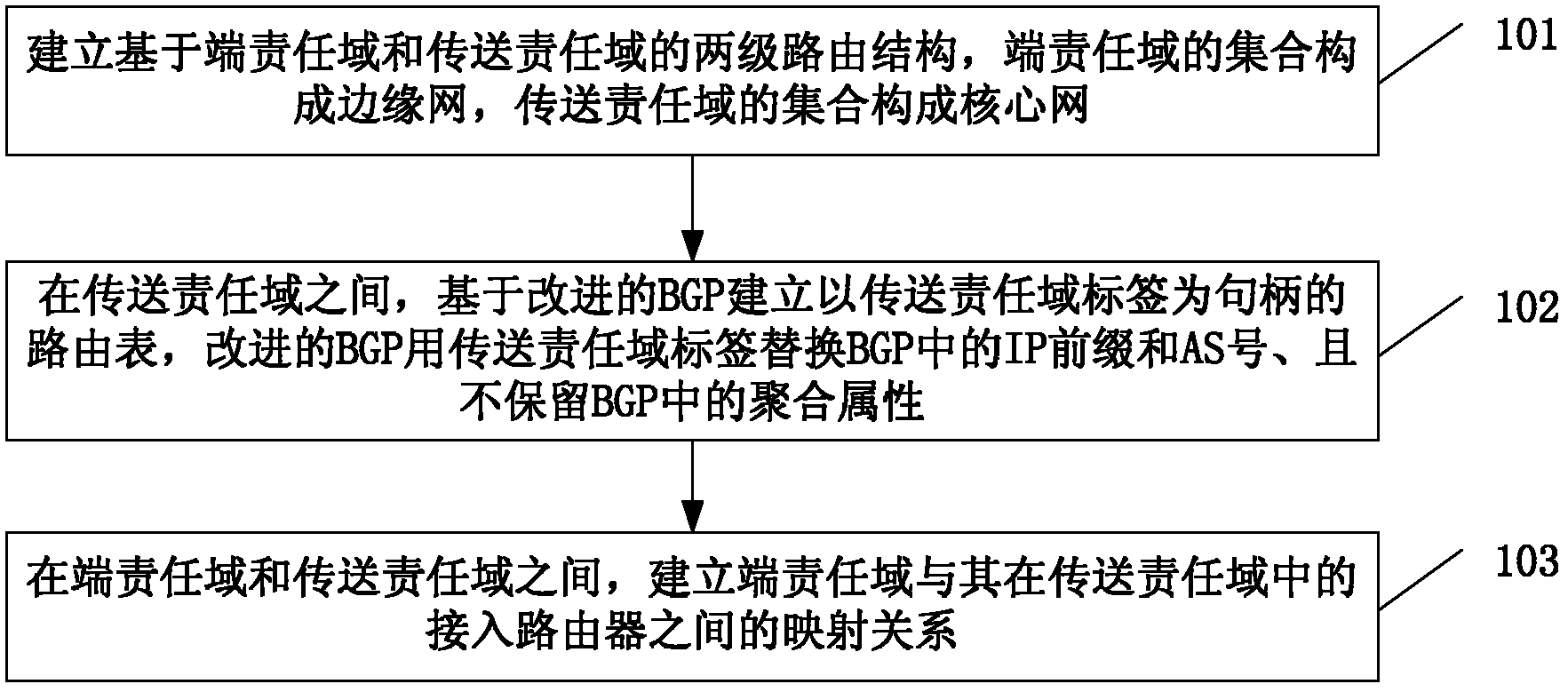
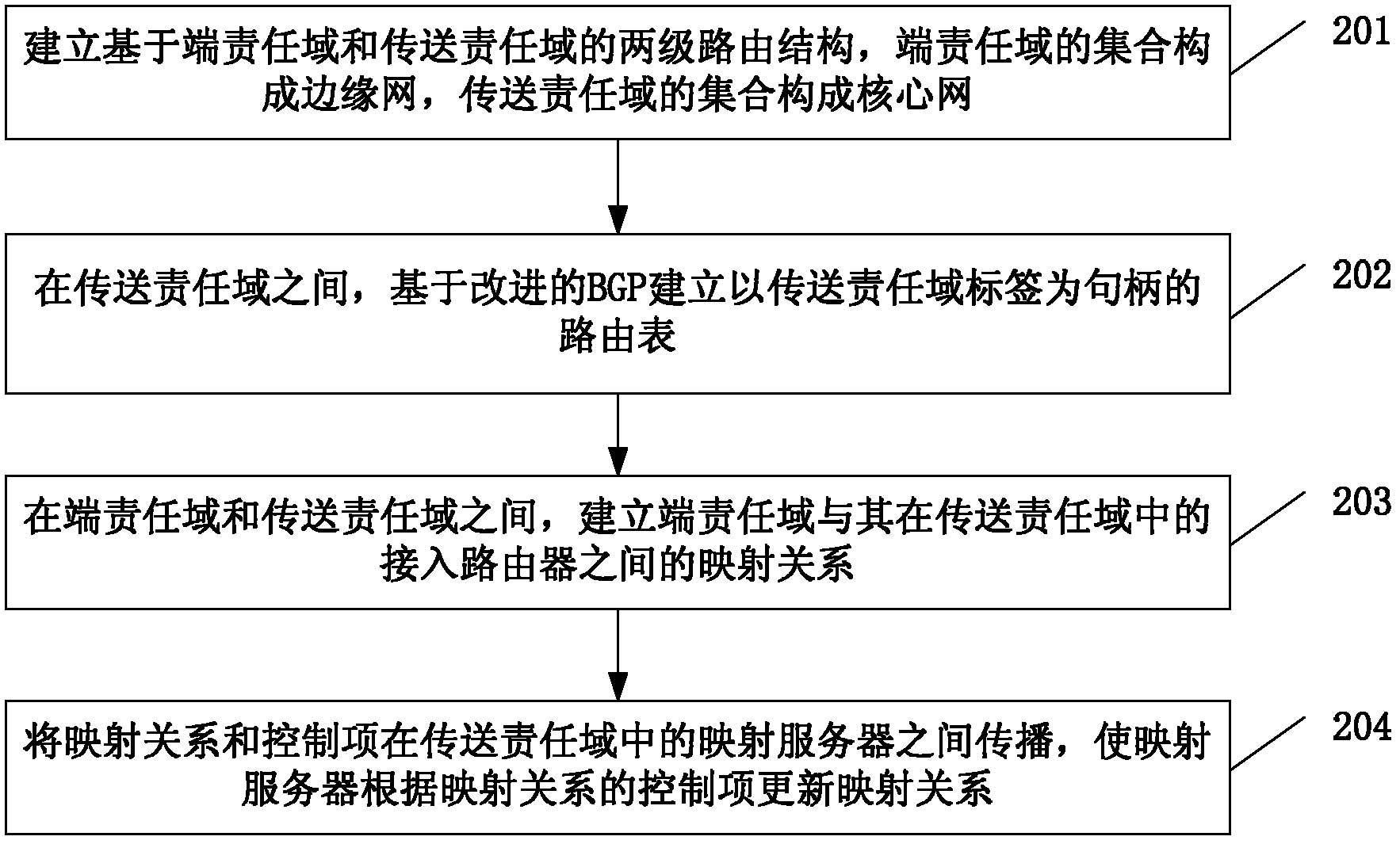
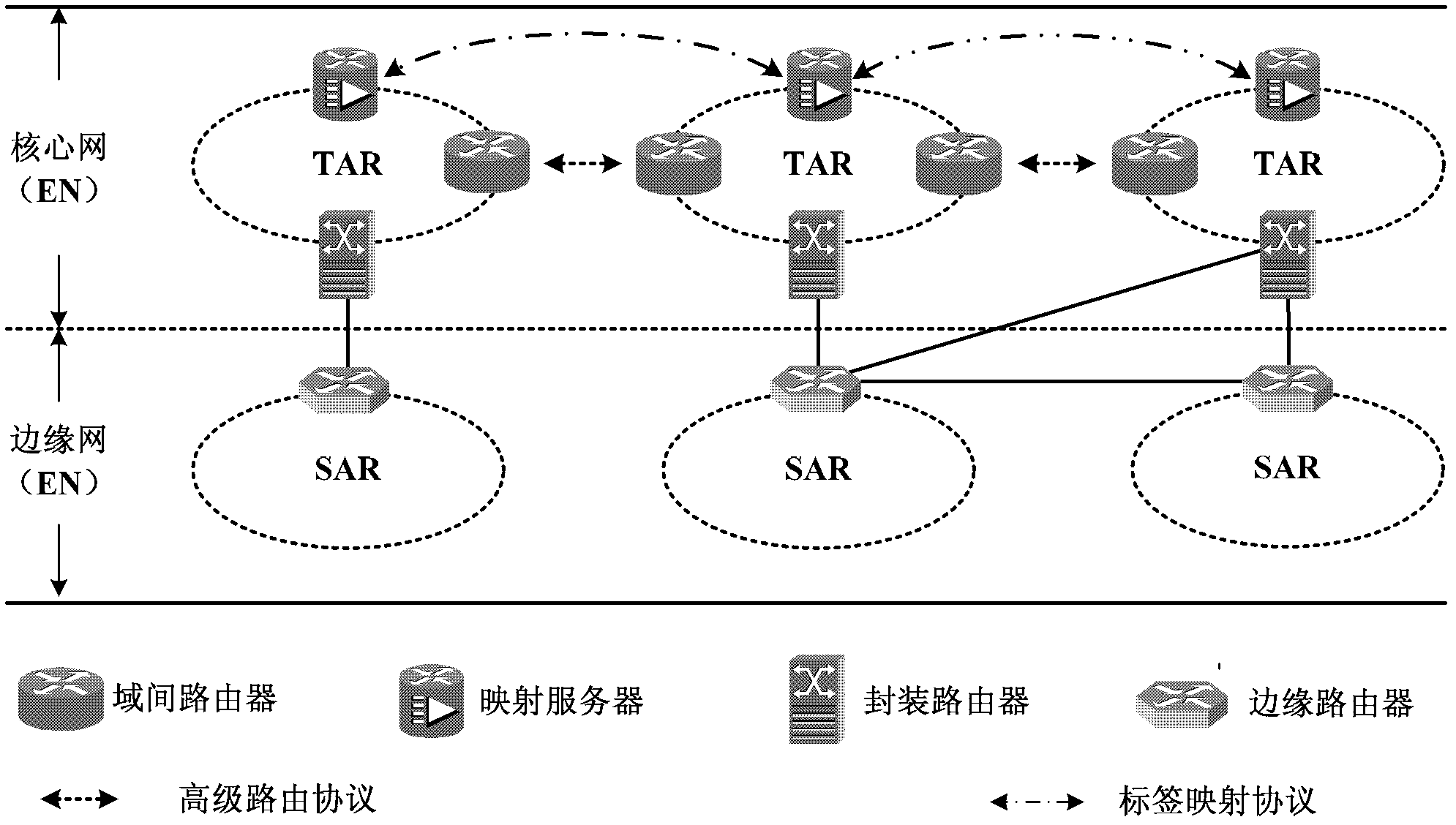
The invention provides a routing method, a routing device, a packet forwarding method and a packet forwarding system and relates to the technical field of routing. The routing method comprises the following steps of: establishing a two-stage routing structure on the basis of end responsibility domains and transmission responsibility domains, wherein an edge network is formed by integration of the end responsibility domains and a core network is formed by integration of the transmission responsibility domains; among the transmission responsibility domains, establishing a routing table which takes transmission responsibility domain labels as handles on the basis of an improved BGP (Border Gateway Protocol), replacing an IP (Internet Protocol) prefix and an AS (Autonomous System) number in the BGP with the transmission responsibility domain labels for the improved BGP and not reserving the aggregate attribute in the BGP; and between the end responsibility domains and the transmission responsibility domains, establishing a mapping relation between the end responsibility domains and access routers of the end responsibility domains in the transmission responsibility domains. In the invention, the scheme is adopted to greatly reduce the scale of the routing table and provide the excellent routing expandability when supporting the domain labels with the self-certifying characteristics. Moreover, in the packet forwarding process, due to the small scale of the routing table, the packet forwarding efficiency is greatly improved.
Owner:北京地平线轨道技术有限公司
Authentication system and method
An exemplary embodiment providing one or more improvements includes an authentication system which allows an article to be authenticated using an article serial number connected with the article and a self-authenticating document having a serial number that is associated with the article serial number. Access to a database containing the association is provided and the article is authenticated by self authenticating the document and accessing the database to determine the association.
Owner:MASSOUD GEORGE
System and method for circular link resolution with hash-based names in content-centric networks
ActiveUS20150341175A1For easy referenceUser identity/authority verificationProgramming languageSelf certified
One embodiment of the present invention provides a system for constructing a linked object. During operation, the system constructs a first portion of the linked object. The first portion includes at least a nonce, and the first portion is referenced by a self-certified name associated with the linked object. The system constructs a second portion of the linked object. The second portion includes at least the nonce and one or more external links, and a respective external link references a second linked object using a self-certified name associated with the second linked object.
Owner:CISCO TECH INC
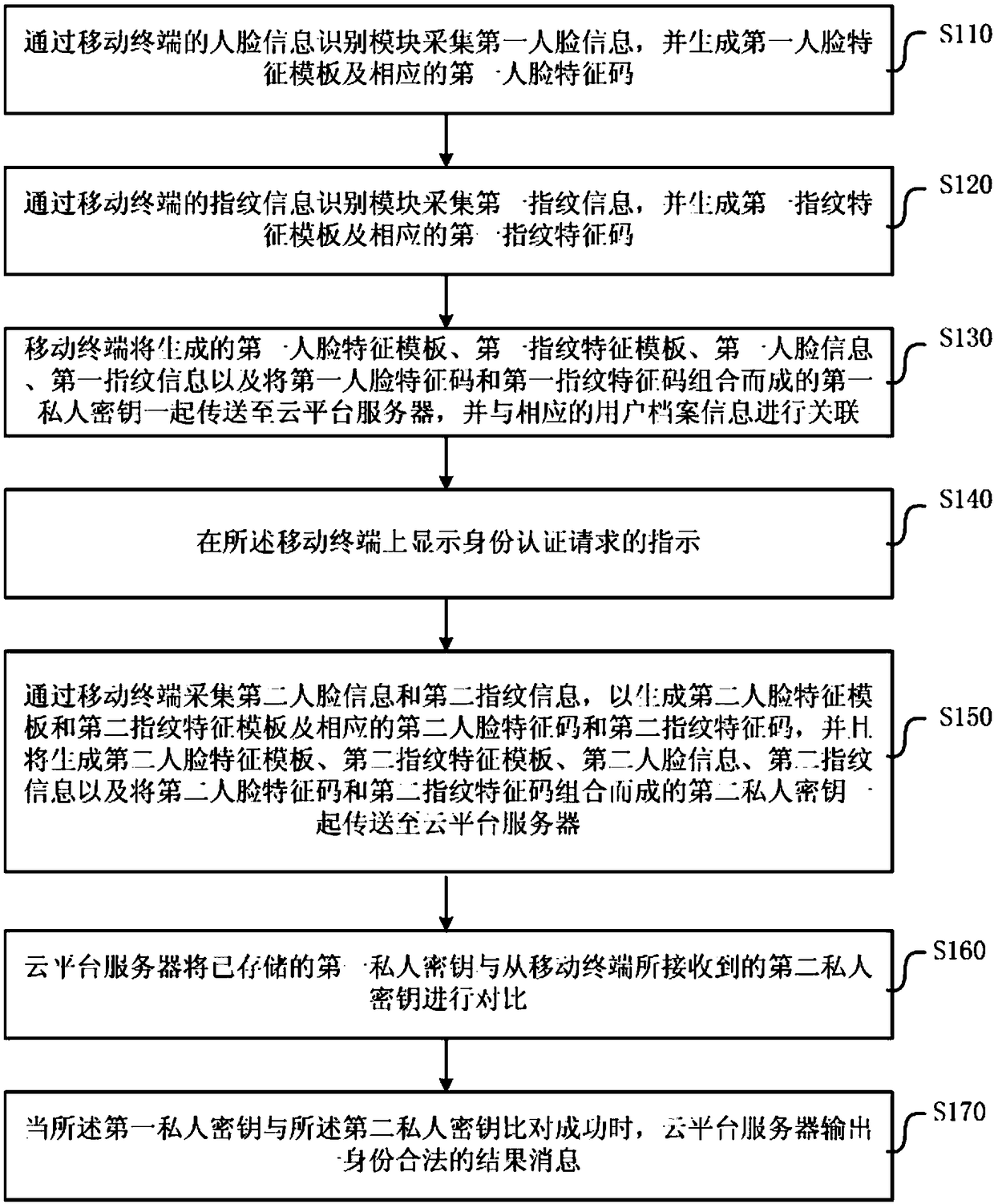
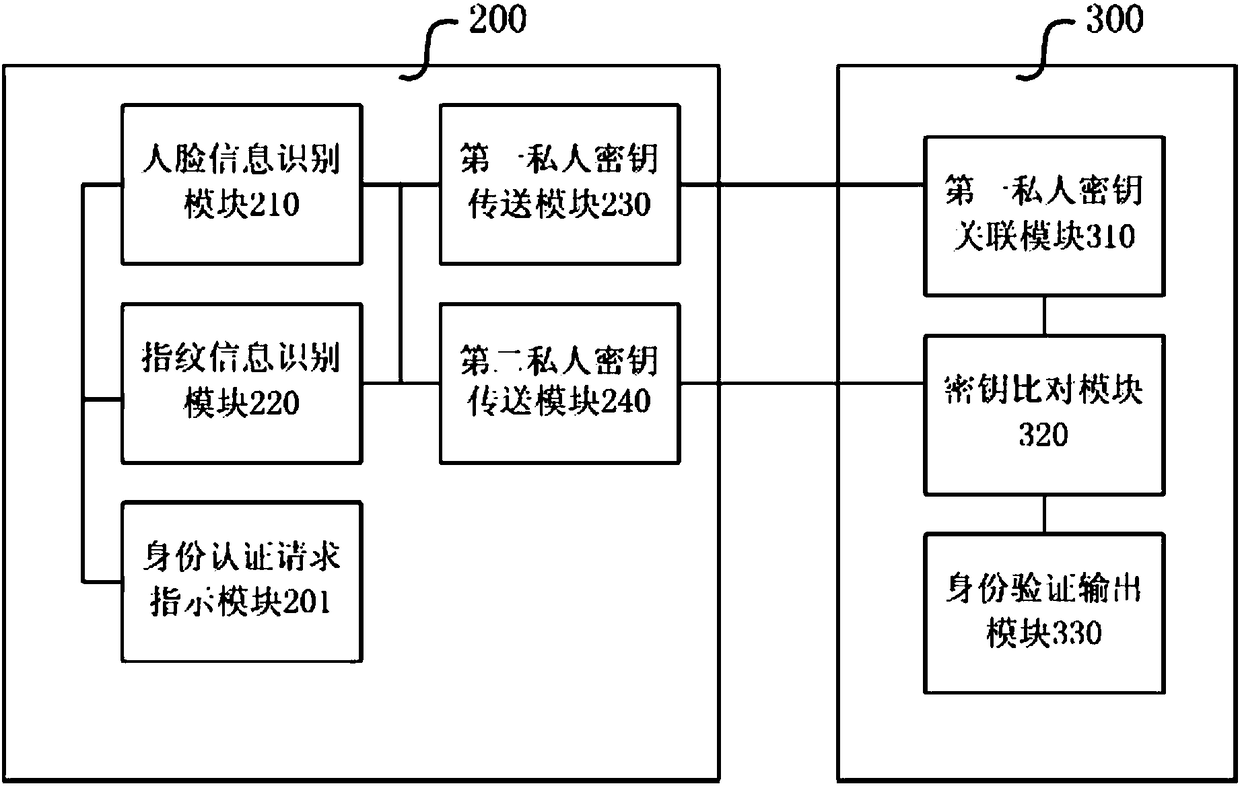
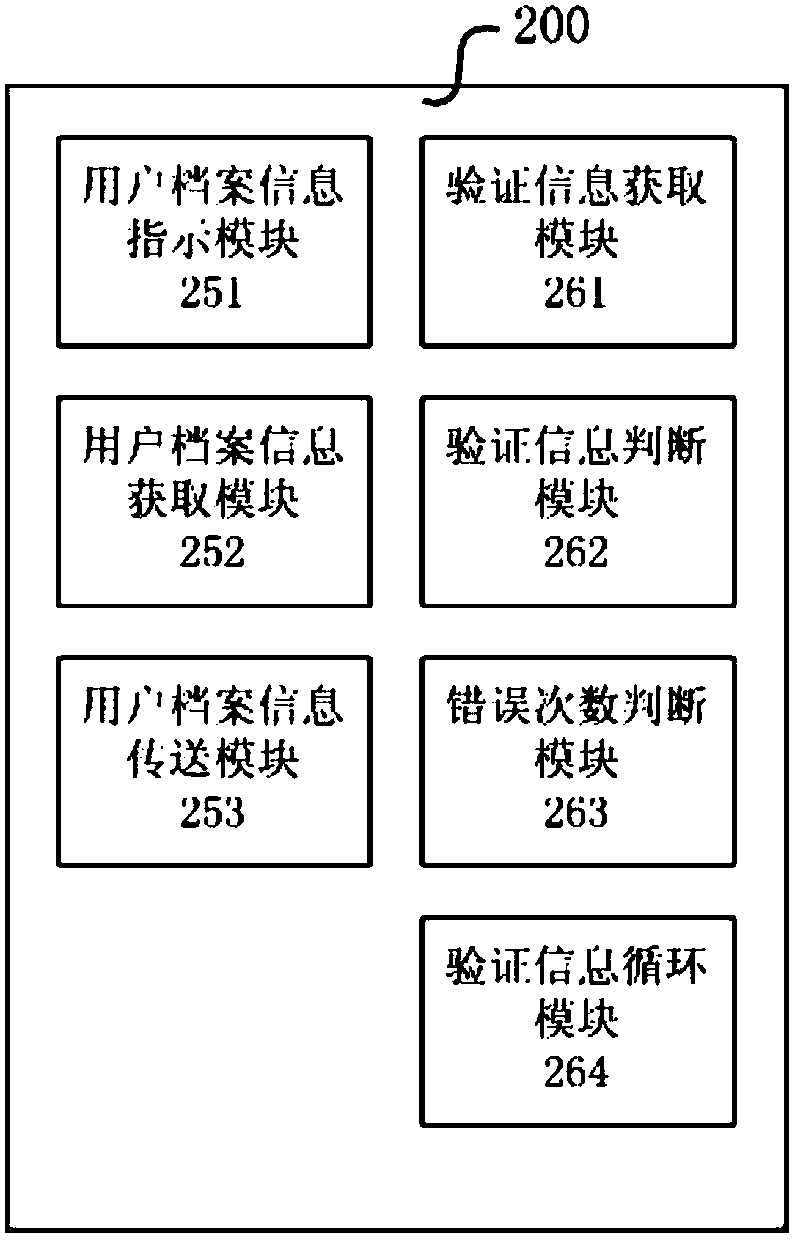
Face recognition identity self-certifying method and system
InactiveCN108121902AFast authenticationAuthentication is convenientDigital data authenticationTransmissionPattern recognitionSelf certified
The invention discloses a face recognition identity self-certifying method. The face recognition identity self-certifying method comprises the following steps: (a) acquiring first face information bya mobile terminal, and generating a first face feature template and a first face feature code; (b) acquiring first fingerprint information by the mobile terminal, and generating a first fingerprint feature template and a first fingerprint feature code; (c) transmitting the template, the information and a first private key to a cloud platform server by the mobile terminal, and associating the template, the information and the first private key with user archival information; (d) displaying an instruction of an identity authentication request on the mobile terminal; (e) acquiring second face information and second fingerprint information by the mobile terminal to generate a second face feature temperature, a second fingerprint feature template, a second face feature code and a second fingerprint feature code, and transmitting the templates, the information and a second private key to the cloud platform server; (f) comparing the first private key to the second private key by the cloud platform server; and (g) when comparison is successful, outputting an identity legal message.
Owner:上海亦源智能科技有限公司
System and method for circular link resolution with computable hash-based names in content-centric networks
ActiveUS9276751B2For easy referenceDigital data processing detailsUser identity/authority verificationSelf certifiedContent centric
One embodiment of the present invention provides a system for constructing a linked object. During operation, the system constructs a first portion of the linked object. The first portion includes at least one or more data items and a computable identifier calculated based on the one or more data items, and the first portion is referenced by a self-certified name associated with the linked object. The system constructs a second portion of the linked object. The second portion includes at least the computable identifier and an external link that references a second linked object using a self-certified name associated with the second linked object.
Owner:CISCO TECH INC
Systems and methods for verification of a verifiable device
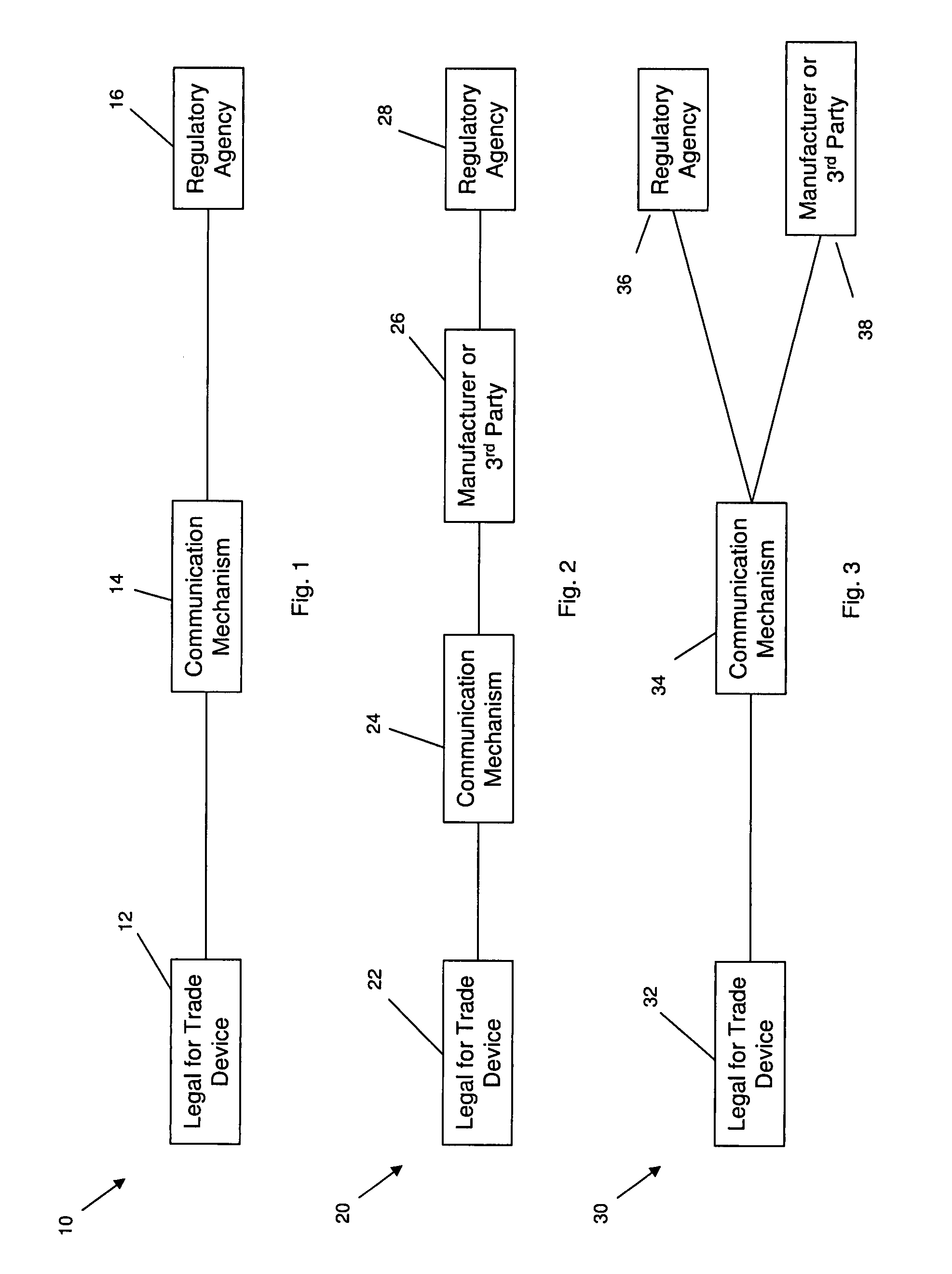
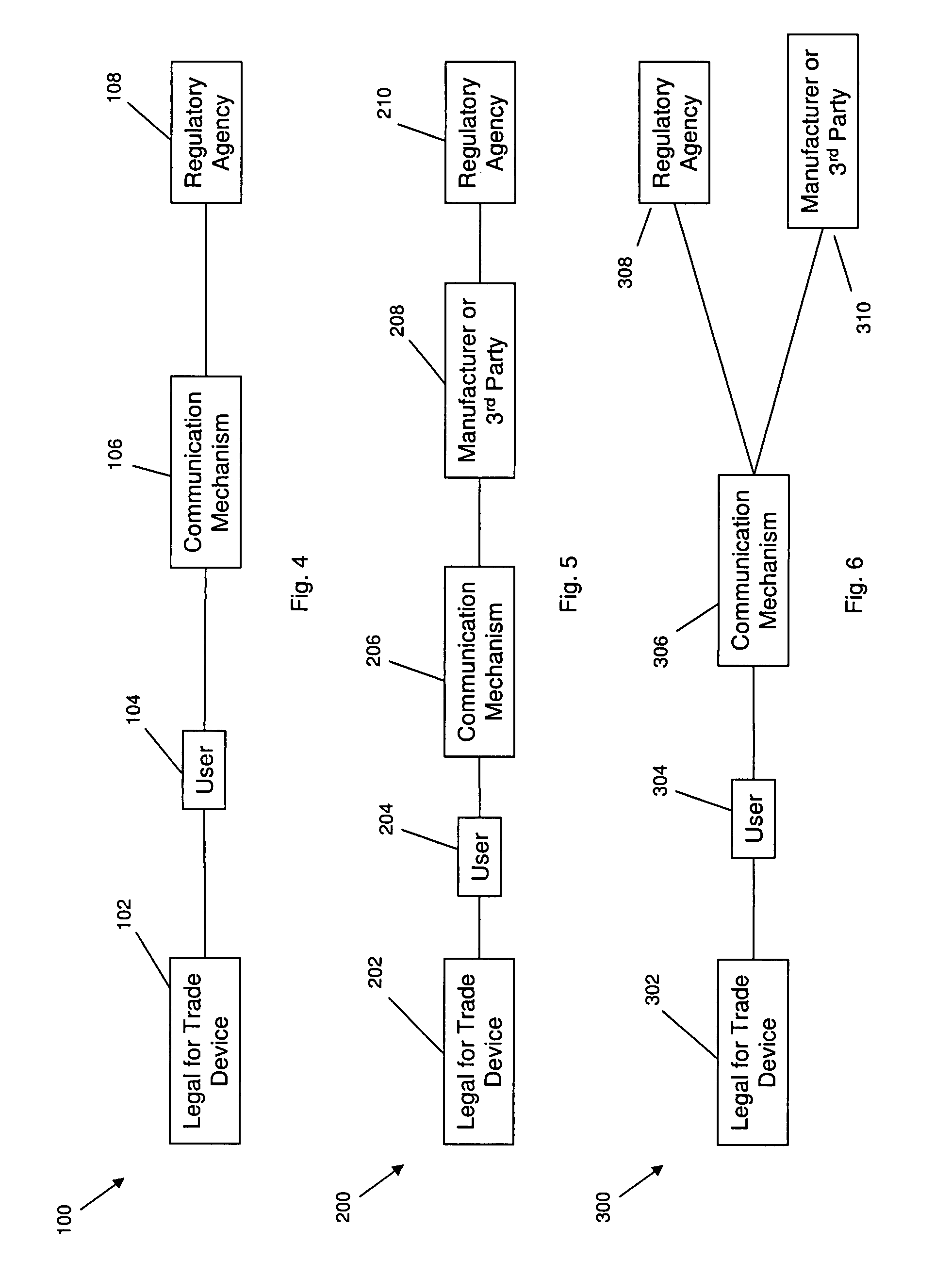
InactiveUS20080103716A1Testing/calibration apparatusMeasurement arrangements for variableSelf certifiedRegulatory agency
Systems and methods for effectuating verification and certification of verifiable devices. Preferably, but not necessarily, such certification occurs or is communicated remotely. A verifiable device may be directly or indirectly connected to an appropriate regulatory agency through a communication mechanism. One or more tests may be performed on the verifiable device to verify that the device is functioning properly. The test results are directly or indirectly transmitted to the regulatory agency. If the tests were passed then the verifiable device may be approved for use. When self-certification or remote certification is provided for, the need for in-person verification and certification procedures by agency personnel may be eliminated.
Owner:METTLER TOLEDO INC
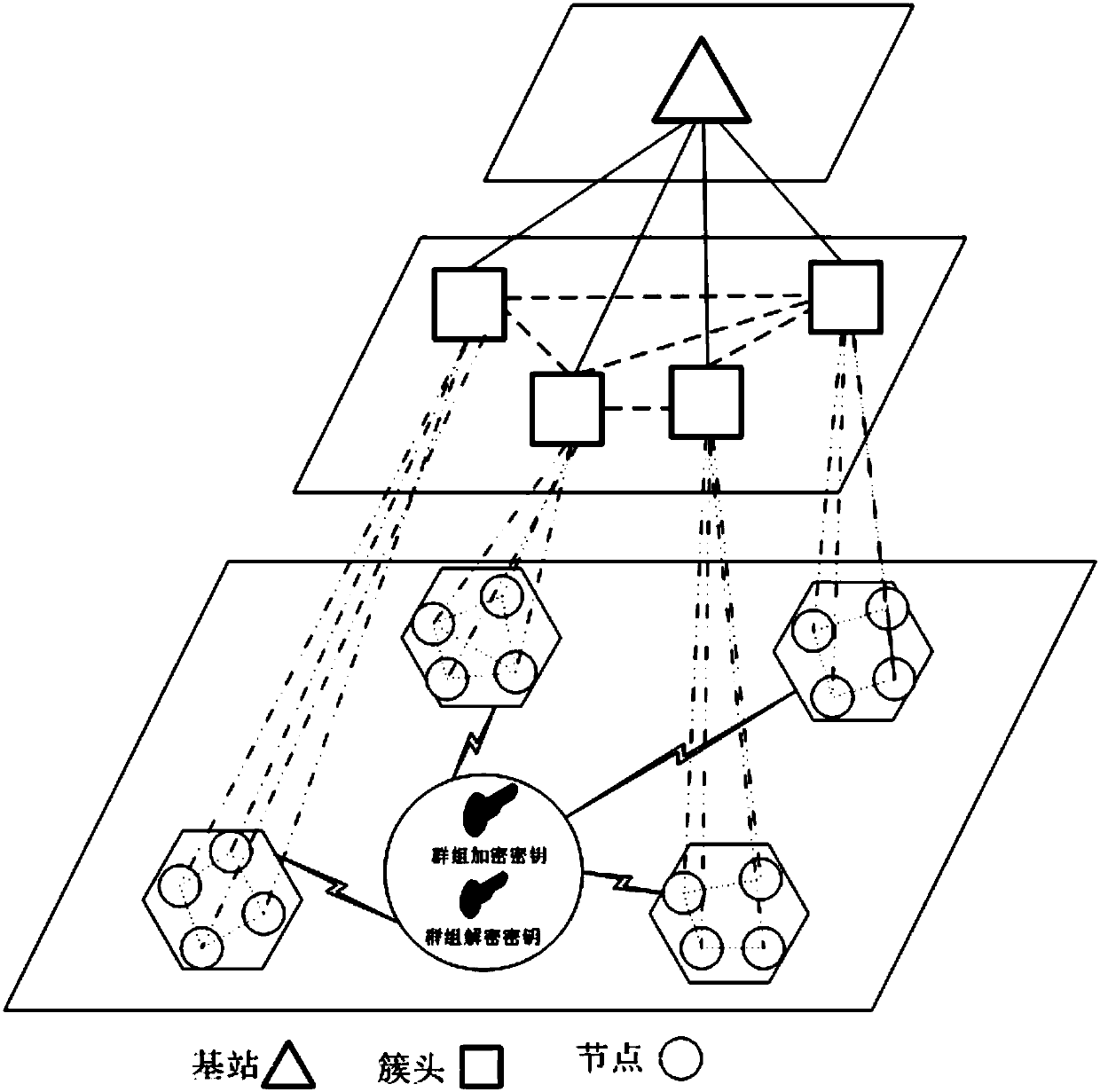
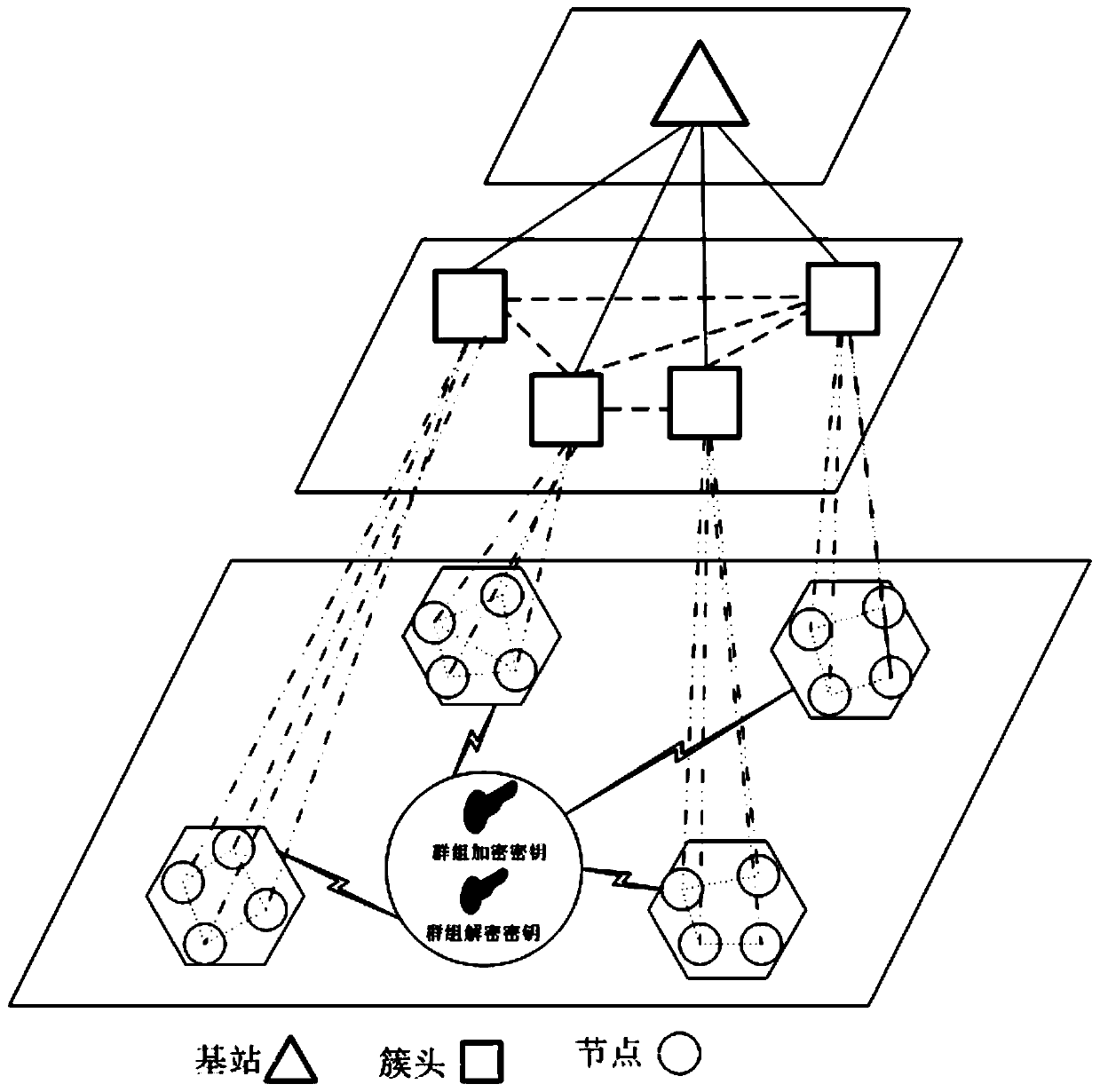
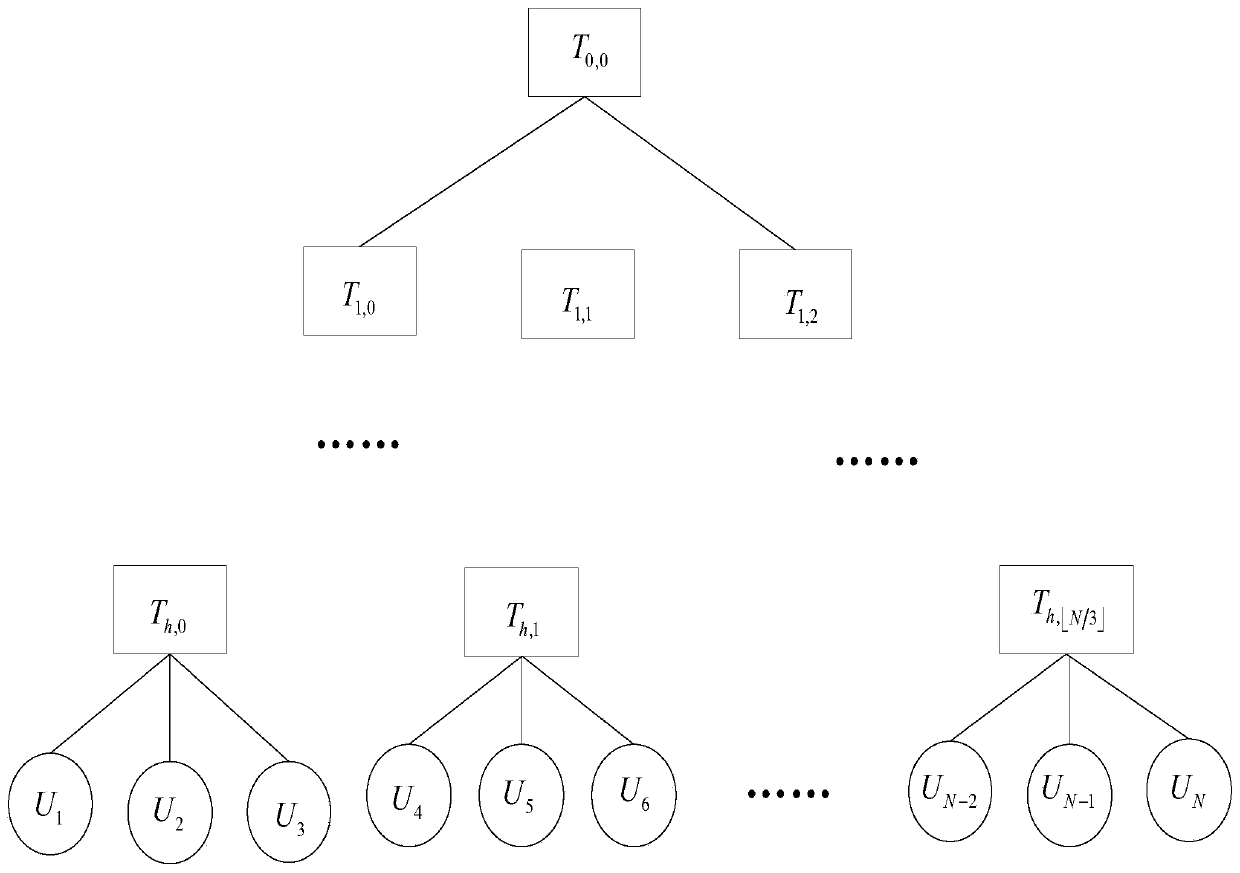
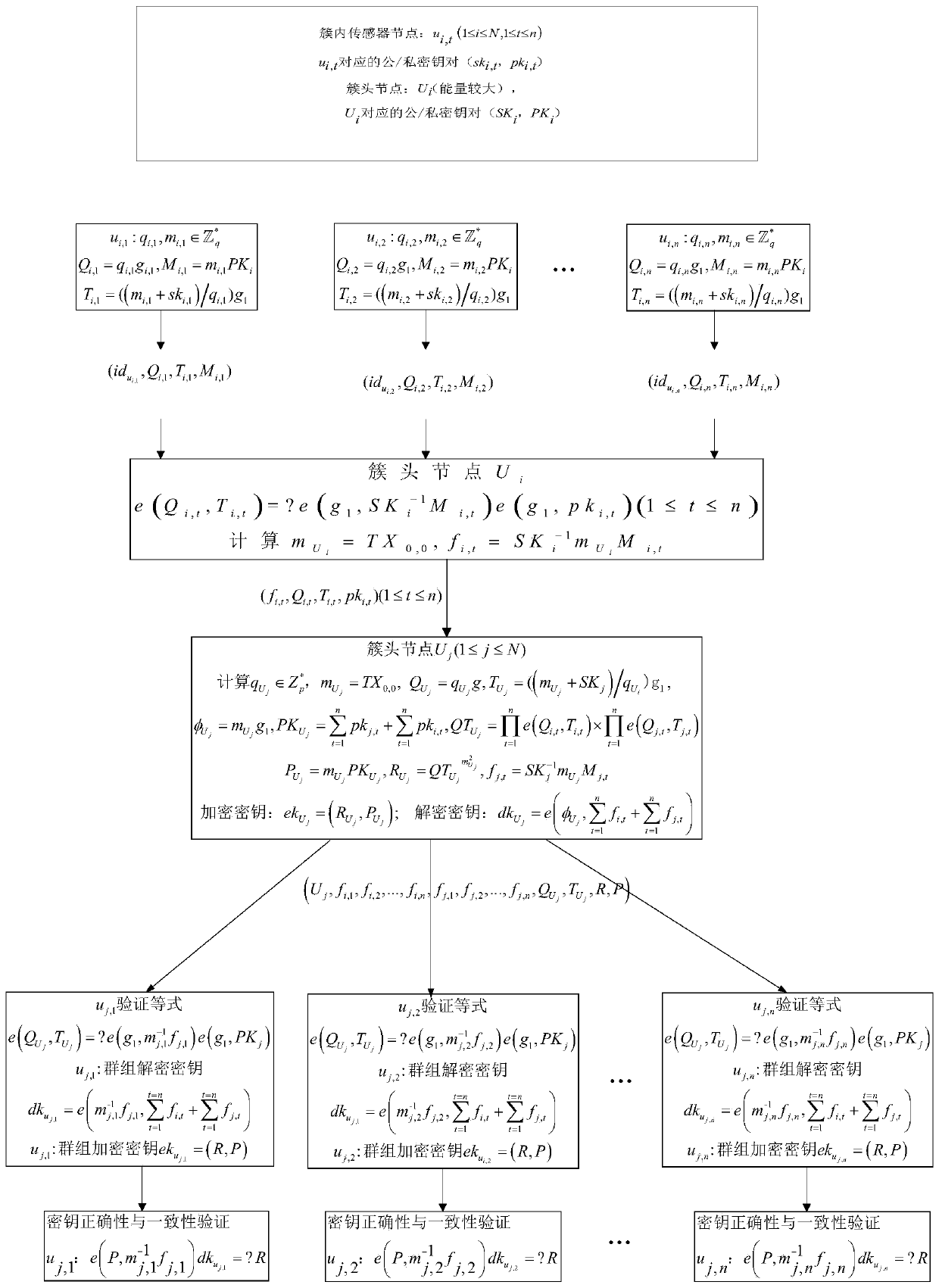
Cross-cluster asymmetric group key negotiation method in wireless sensor network
ActiveCN107204845ARealize secret information exchangeReduce communication consumptionKey distribution for secure communicationNetwork topologiesMobile wireless sensor networkLine sensor
The invention provides a cross-cluster asymmetric group key negotiation method in a wireless sensor network. The method comprises steps as follows: an allied and shared key between clusters is established, cluster heads are taken as bridging nodes, and sensor nodes of different nodes have the same group key factor information; an asymmetric computation algorithm is designed in the group key negotiation process, more computation and communication traffic of the sensor nodes are migrated to the cluster head nodes with larger energy, and the lightweight property of computation and communication overhead of the sensor nodes is ensured; self-certification property of keys is realized, additional communication rounds are not required, the sensor nodes can self-certify the correctness in computing the group keys, and the correctness and the safety of the group key negotiation are guaranteed. Group key negotiation of the sensor nodes distributed in different clusters in the wireless sensor network is realized, a safe communication channel is established, the scale of cooperative computation and information sharing of sensor node groups is further expanded, energy consumption of the sensor nodes is reduced, and the service life of the sensor nodes is prolonged.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
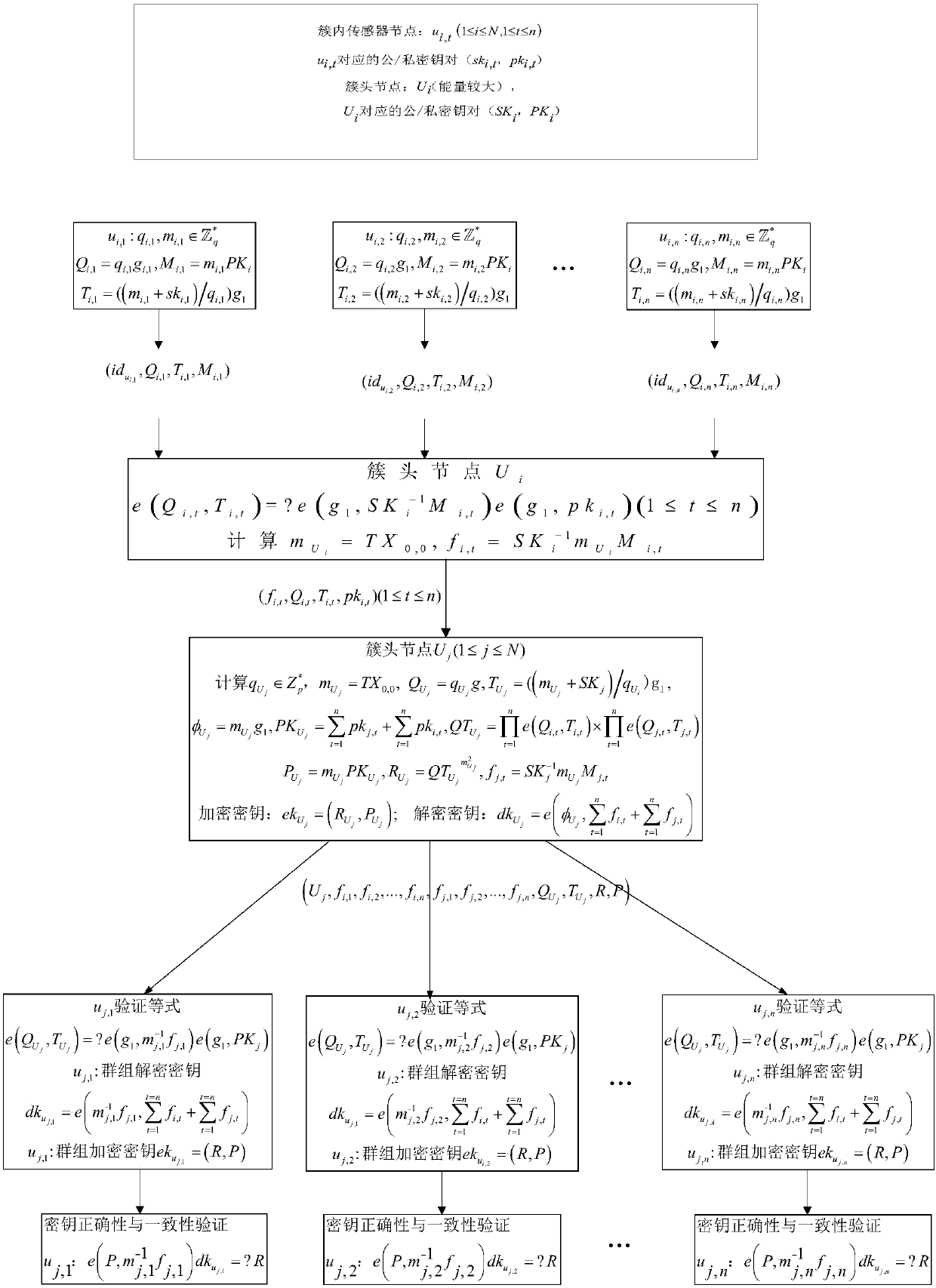
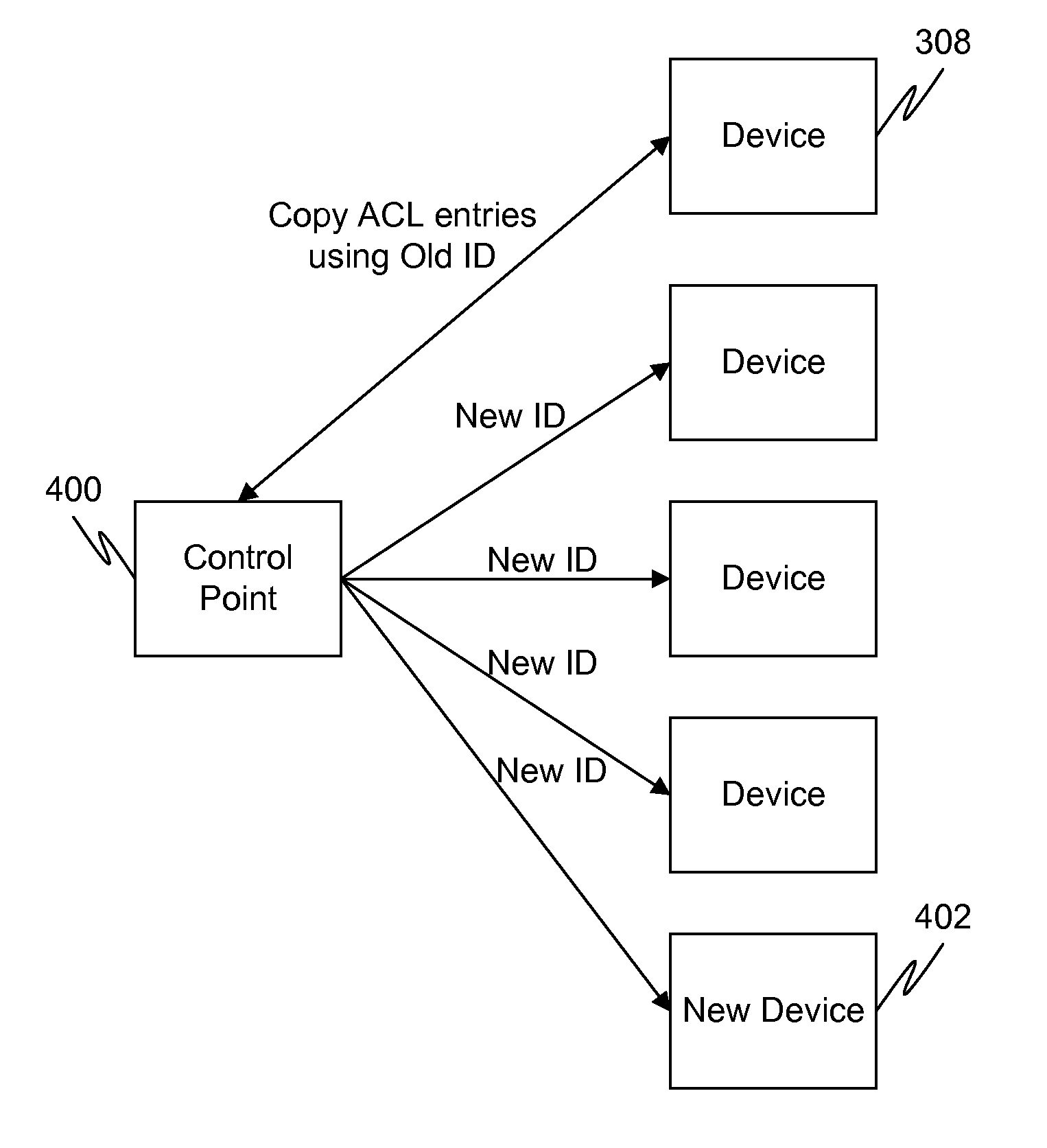
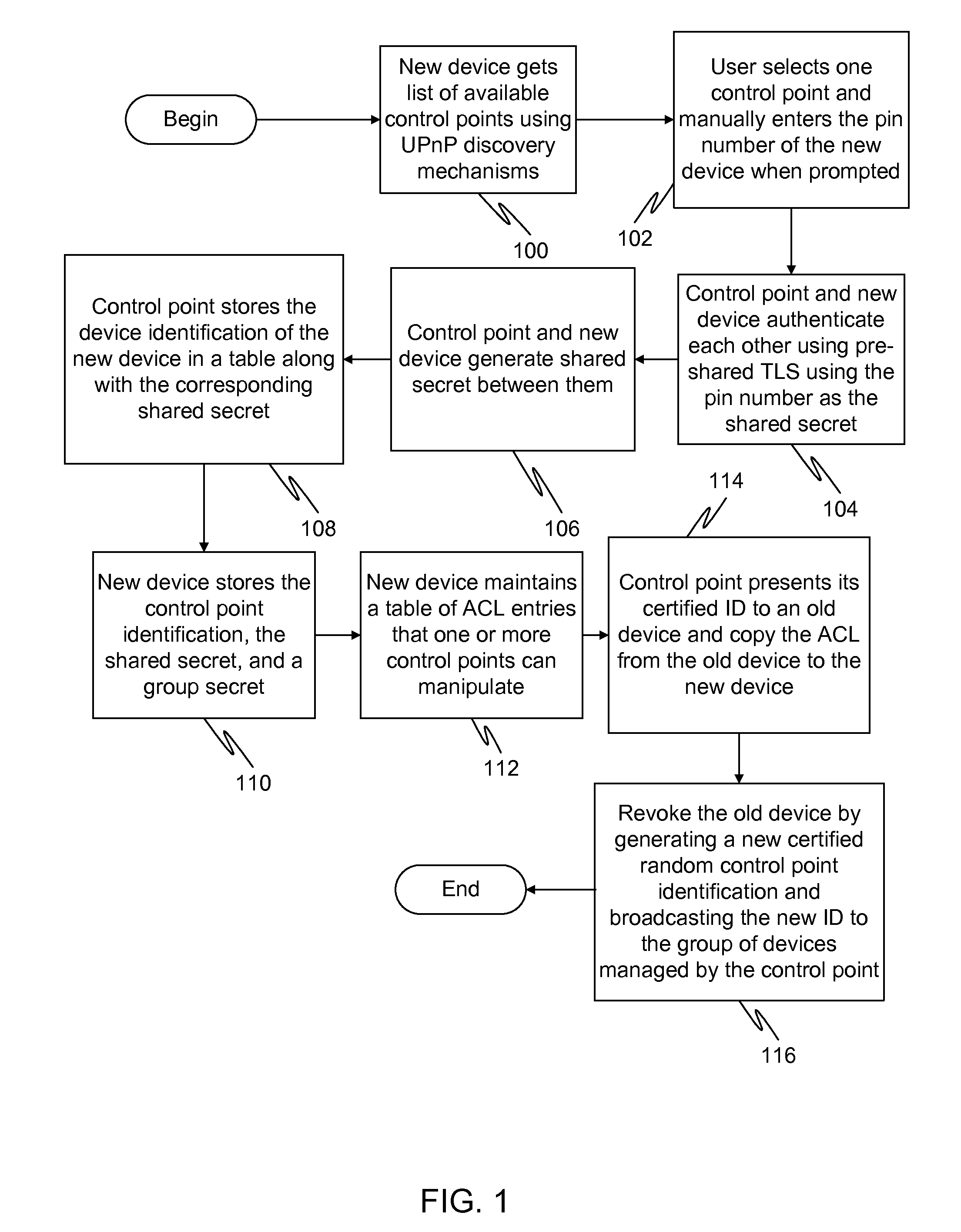
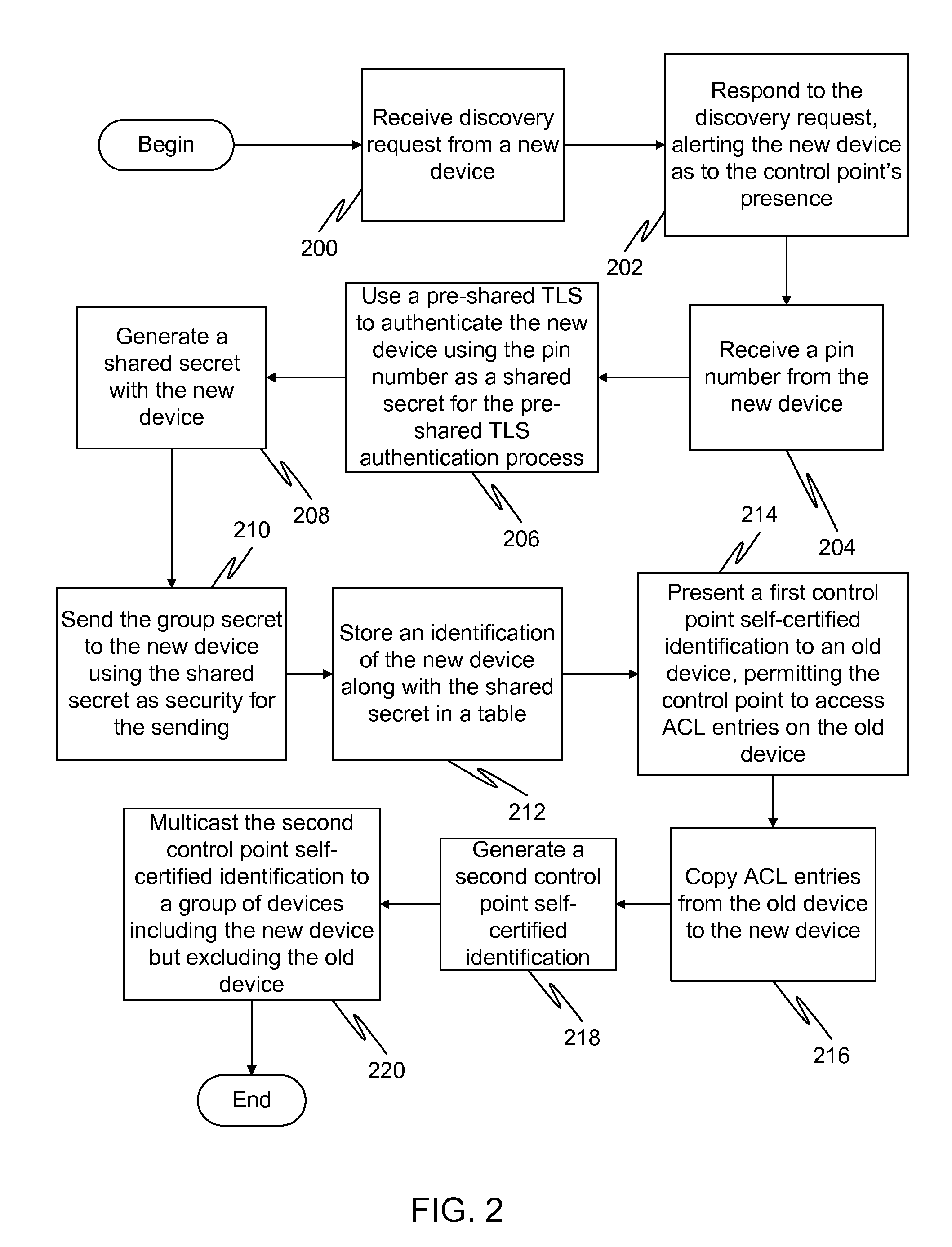
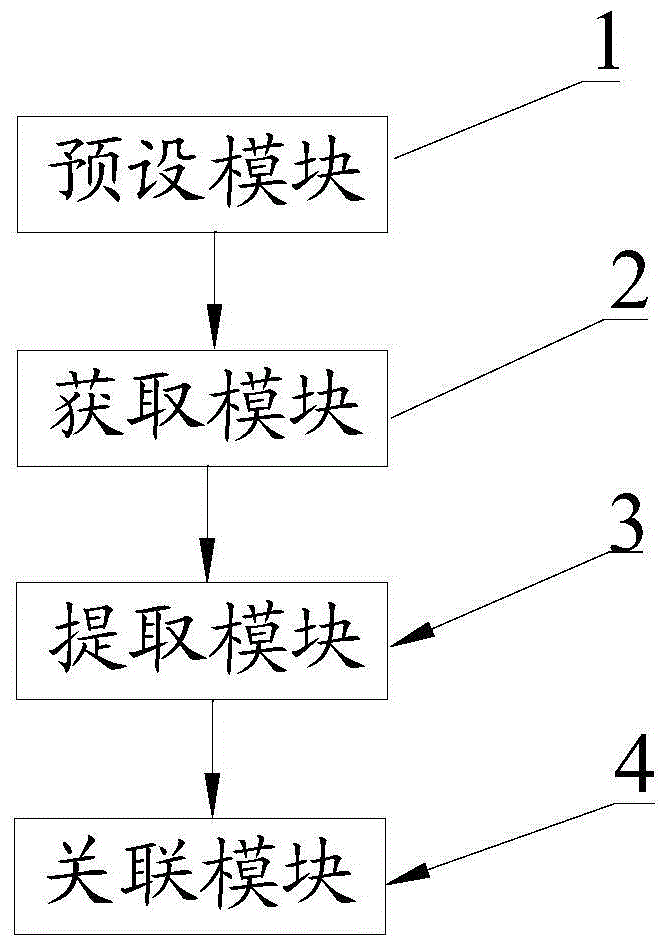
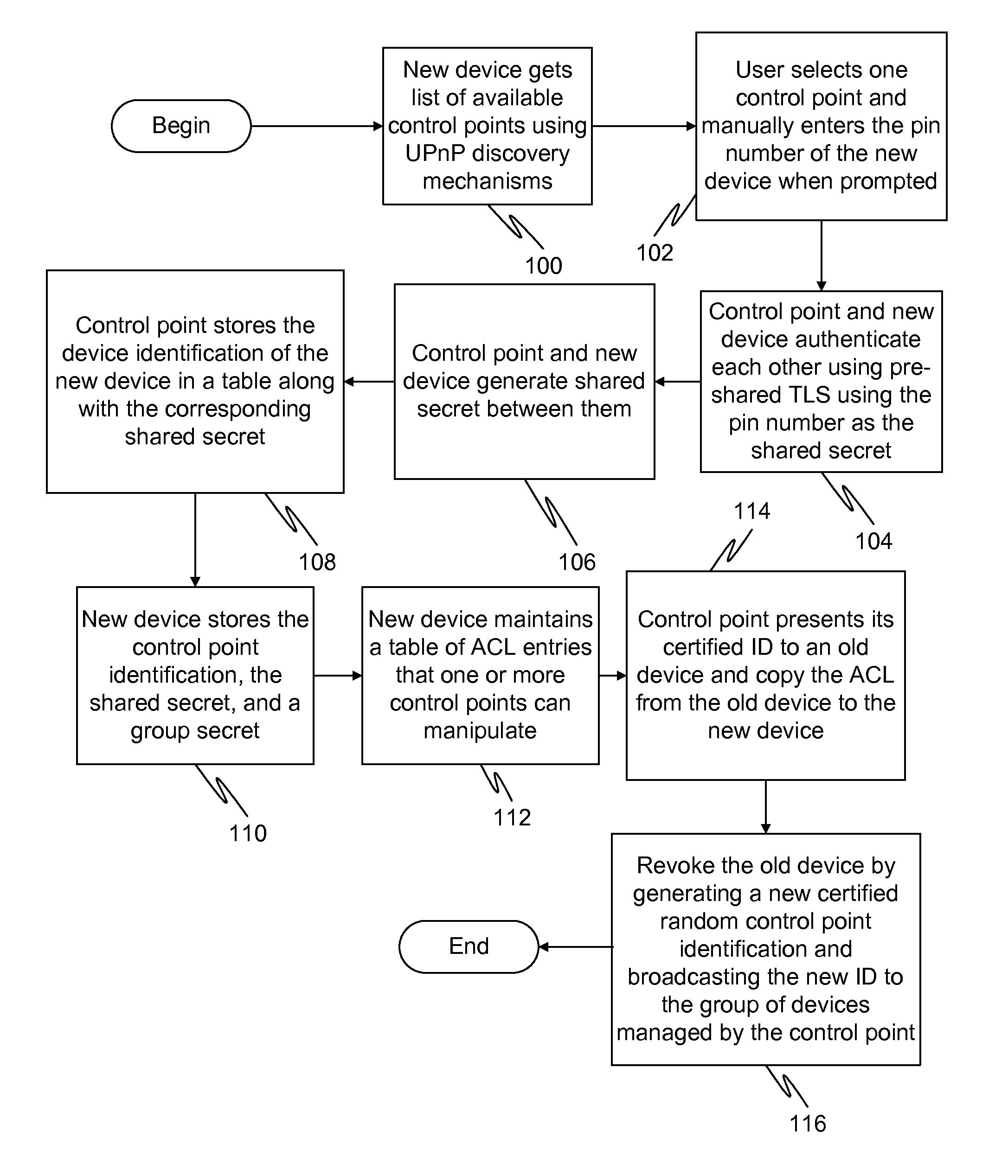
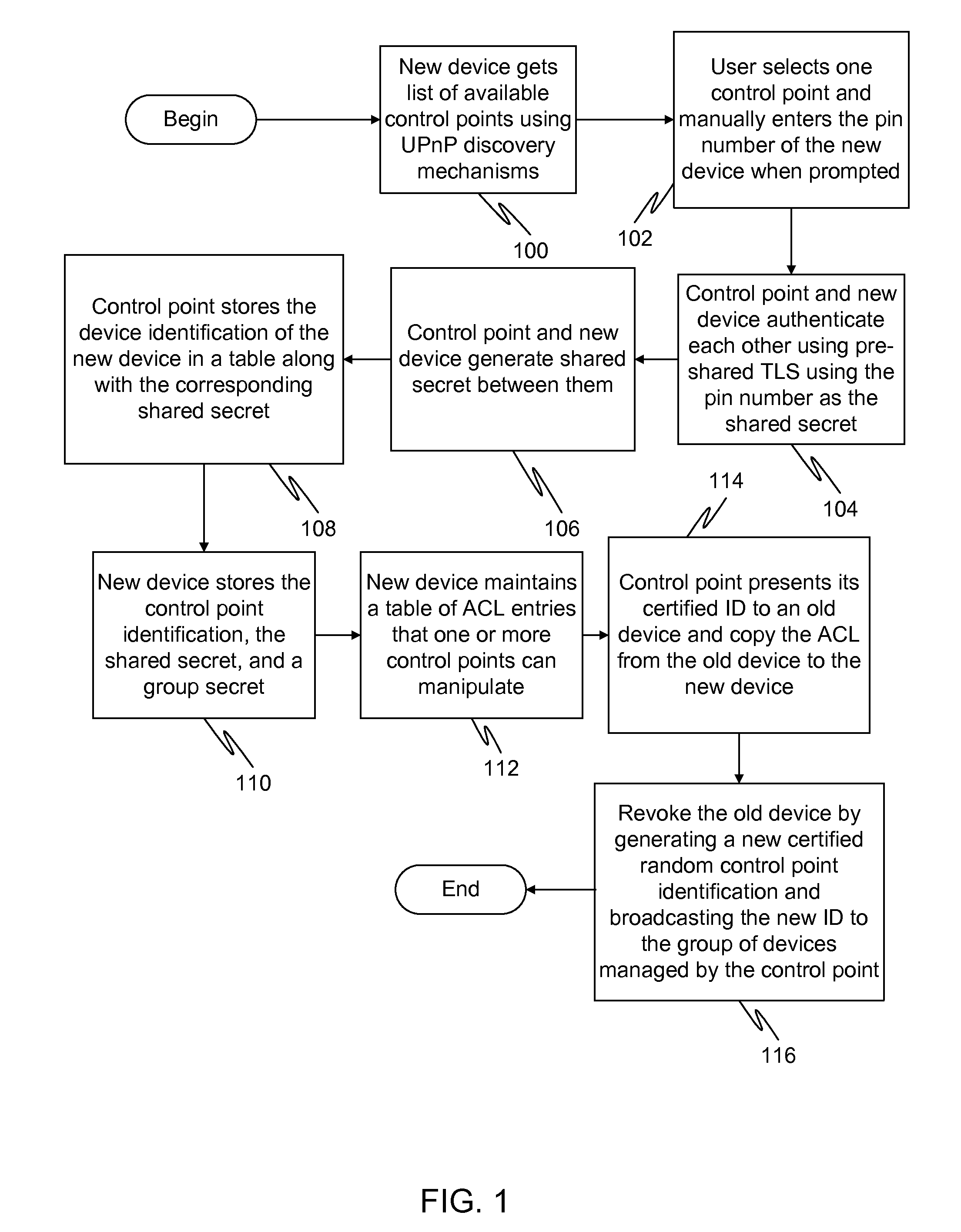
Generation of self-certified identity for efficient access control list management
InactiveUS20100251348A1Digital data processing detailsUser identity/authority verificationSelf certifiedOperating system
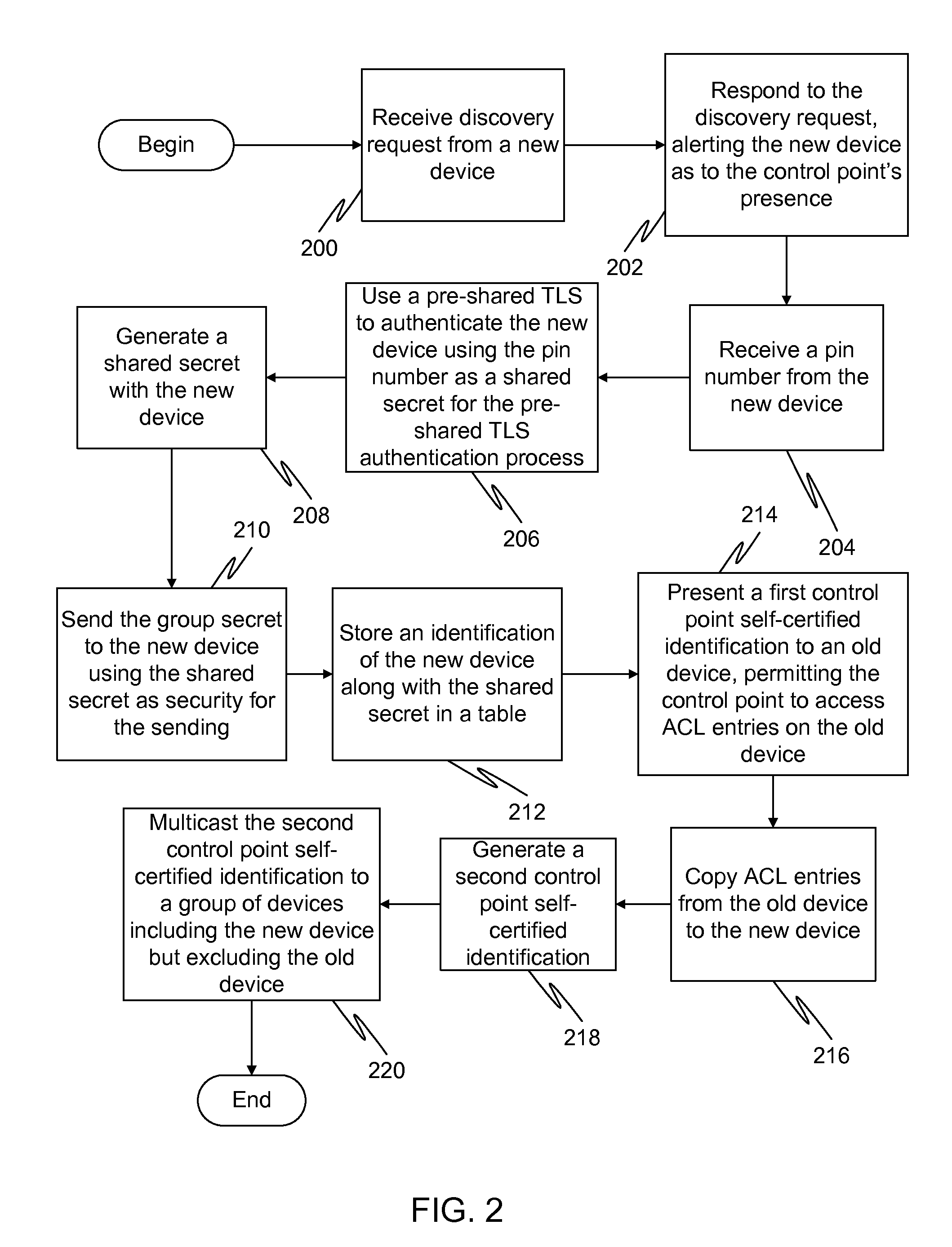
In a first embodiment of the present invention, a method for registering a new device to a control point in a home network is provided, the method comprising: generating a first self-certified identification at the control point, the generation using a pseudo-random generated number and using an identification of the control point; and sending a secure message to the new device containing the first self-certified identification.
Owner:SAMSUNG ELECTRONICS CO LTD
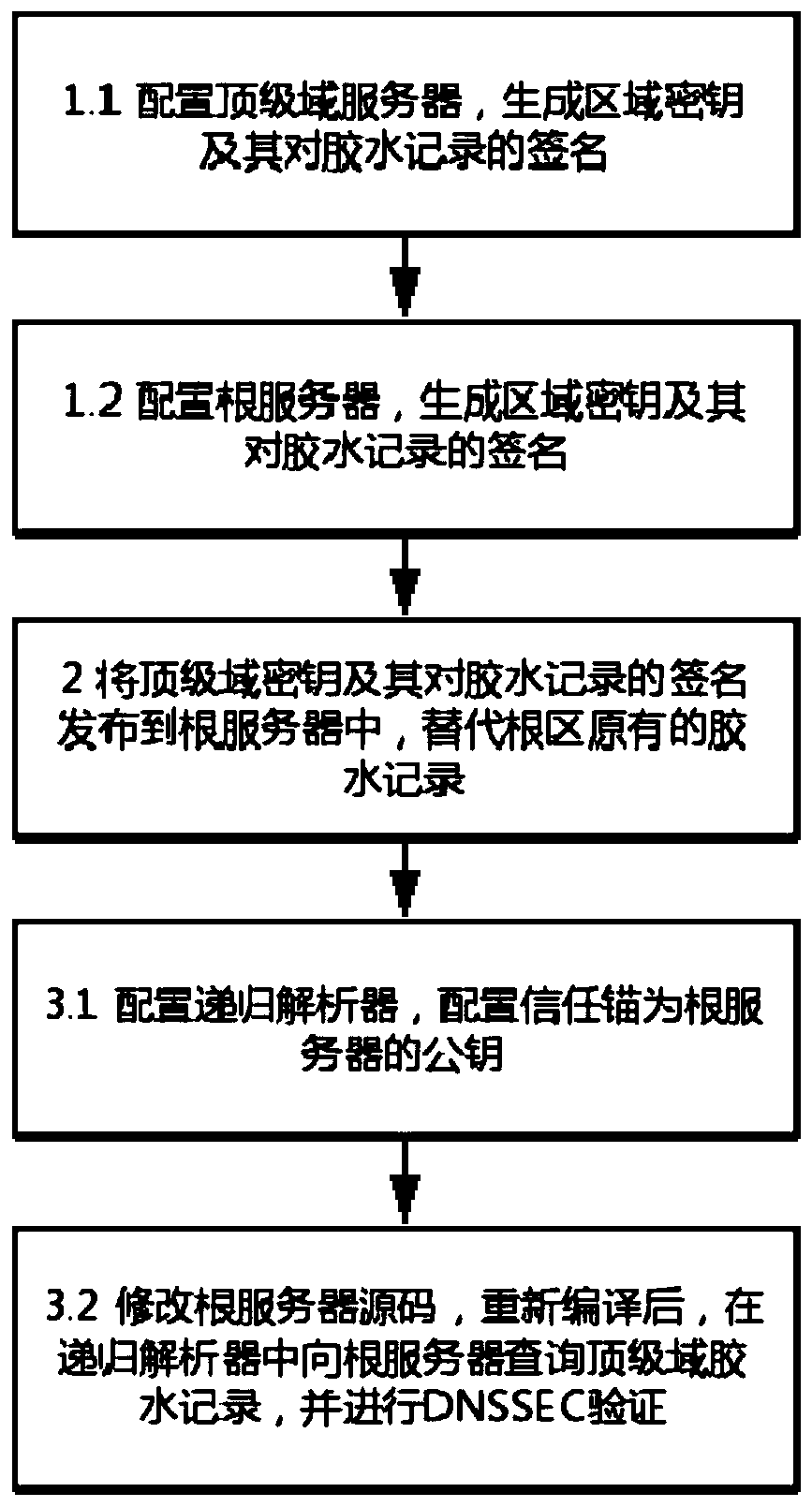
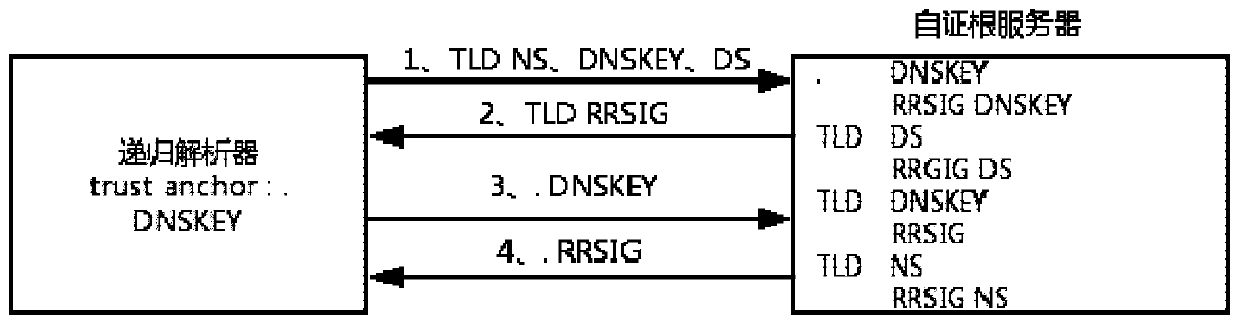
Self-certified root implementation method based on open source DNS software
ActiveCN110071810AImprove securitySelf-Certifying Root ImplementationKey distribution for secure communicationUser identity/authority verificationSelf certifiedOpen source
The invention discloses a self-certified root implementation method based on open source DNS software, and relates to the technical field of DNS security improvement. The invention aims to solve the problem that the root area glue record is tampered due to the fact that a signature mechanism for the root area glue record is not provided in an existing DNSSEC scheme. The method comprises the following steps: generating a regional key and a signature of the regional key to a glue record in a root server and a top-level domain server; and releasing the top-level domain key and the glue record signature thereof to a root server to replace the original glue record of the root region, and querying the top-level domain glue record from the root server on a recursive analyzer and carrying out DNSSEC verification. According to the self-certified root scheme, potential safety hazards that glue records in a DNSSEC scheme may be tampered are improved, and the safety of the glue records in the rootregion is improved by adding signatures of the glue records in the root region. By modifying the source code of the open source DNS software, a trust chain of glue recording from the root domain to the top domain is established in the root region, and self-certification of the root is achieved.
Owner:HARBIN INST OF TECH
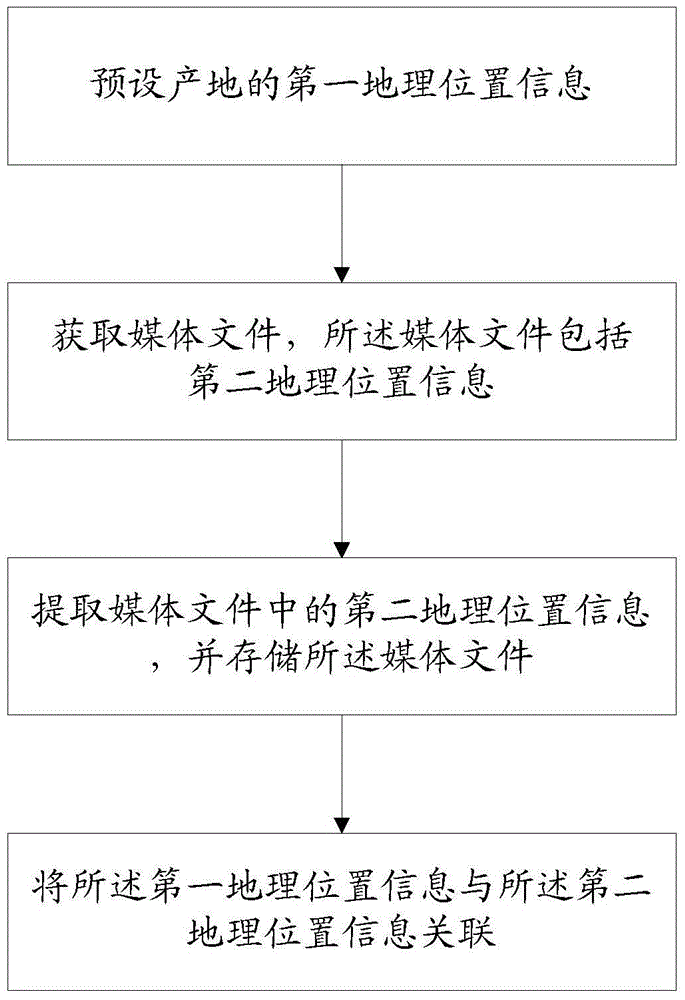
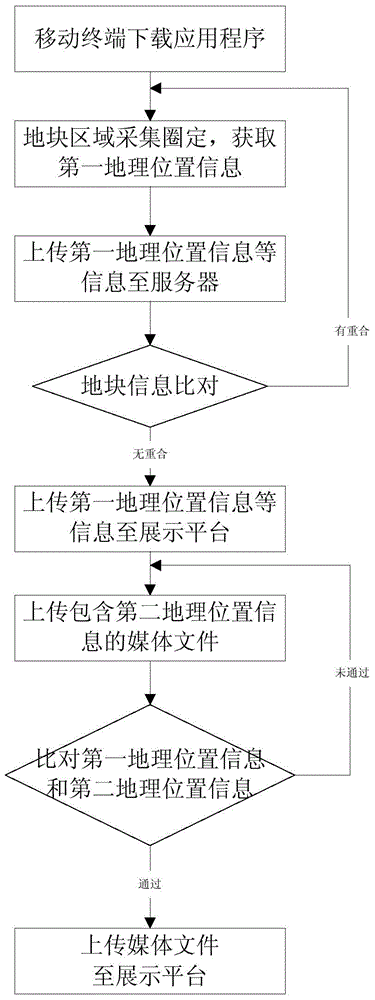
Place of origin self-certifying method and system
InactiveCN104933151AClear sourceImplement self-authenticationSpecial data processing applicationsSelf certifiedComputer science
The invention discloses a place of origin self-certifying method and system. The method comprises the steps of presetting first geographical position information of the place of origin; acquiring a media file, wherein the media file comprises second geographical position information; extracting the second geographical position information in the media file, and storing the media file; and associating the first geographical position information with the second geographical position information. Through coordinate setting of the media file like photos or videos and so on, consumers can clearly know the origin of the media file, and producer self-certification is realized. The media file is uploaded in real time, so that the method is convenient and fast, the consumers can know the whole production process of products, and the product credibility is improved.
Owner:刘建峰 +1
Generation of self-certified identity for efficient access control list management
InactiveUS8600058B2Digital data processing detailsUser identity/authority verificationSelf certifiedOperating system
In a first embodiment of the present invention, a method for registering a new device to a control point in a home network is provided, the method comprising: generating a first self-certified identification at the control point, the generation using a pseudo-random generated number and using an identification of the control point; and sending a secure message to the new device containing the first self-certified identification.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for circular link resolution with hash-based names in content-centric networks
ActiveUS9455835B2For easy referenceUser identity/authority verificationProgramming languageSelf certified
One embodiment of the present invention provides a system for constructing a linked object. During operation, the system constructs a first portion of the linked object. The first portion includes at least a nonce, and the first portion is referenced by a self-certified name associated with the linked object. The system constructs a second portion of the linked object. The second portion includes at least the nonce and one or more external links, and a respective external link references a second linked object using a self-certified name associated with the second linked object.
Owner:CISCO TECH INC
Dual-recognition recognition device based on entrance guard card and face recognition
ActiveCN111554021AImprove privacyImprove securityCharacter and pattern recognitionIndividual entry/exit registersSelf certifiedInternet privacy
The invention discloses a dual-affirmation recognition device based on an entrance guard card and face recognition. The invention belongs to the technical field of access control, the identity authentication authority main bodies can be innovatively interchanged; the resident performs mastering and identity authentication by himself / herself; face recognition is integrated on an existing access control card. When identity authentication is carried out, the access control card carries out information collection and information comparison. Therefore, the self-authentication of the resident is completed; personal information interaction between residents and the access control system is avoided; only after the authentication is passed, the access control card sends an authentication passing signal to the access control system; the privacy and the safety of personal information of residents can be greatly improved; certain guarantee is provided for residents in the information era of data explosion. Meanwhile, humanistic care is fully shown, identity authentication rights are given to the residents, contradiction between property management and the residents can be effectively avoided,the harmony degree of a community is increased, great convenience can be provided for life, and high popularization value is achieved.
Owner:江西拓世智能科技股份有限公司
System and method for computing private keys for self certified identity based signature schemes
ActiveCN110268676AKey distribution for secure communicationUser identity/authority verificationSelf certifiedInternet privacy
This document describes a system and method for generating private keys for devices participating in a self-certified identity based encryption scheme whereby the private key is used by the devices to establish a common session key for encoding digital communications between devices.
Owner:HUAWEI INT
Keycard and keycard-lock
InactiveUS20120125999A1Improve securityImprove correspondenceBuilding locksAnti-theft devicesSelf certifiedRadioactive agent
To acquire a keycard, the creation of whose clone is impossible, and a keycard-lock that is locked / unlocked by the keycard.Key information constituted by randomly disposed metal granules, fiber pieces, a hologram chip, fluorescent substance granules, radioactive substance granules, or iridescent material, which is obtained by chance, is provided to a card. By inserting the keycard into the keycard-lock, and storing data based on the key information of the keycard in the keycard-lock, the keycard is registered in the keycard-lock. The data is encrypted by using a crypt key stored in the keycard-lock. By comparing the data of keycard inserted into the keycard-lock and the data obtained by decrypting the encrypted data registered in the keycard-lock, the keycard-lock is locked / unlocked. In addition, data based on the information of the keycard is encrypted and stored in a self-certifying keycard information chip installed in the keycard.
Owner:INT FRONTIER TECH LAB
Generation and authentication method of self-certified public key of mobile self-organized network
InactiveCN101702805AReduce storageReduce communicationPublic key for secure communicationUser identity/authority verificationLimited resourcesSelf certified
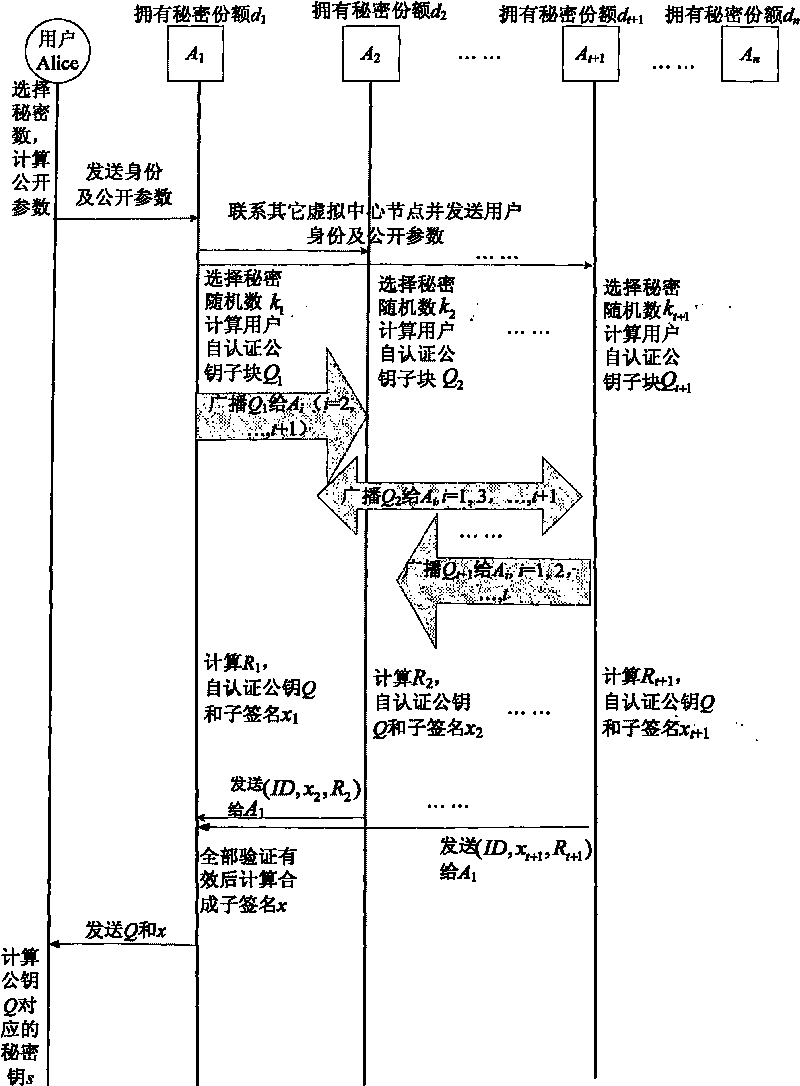
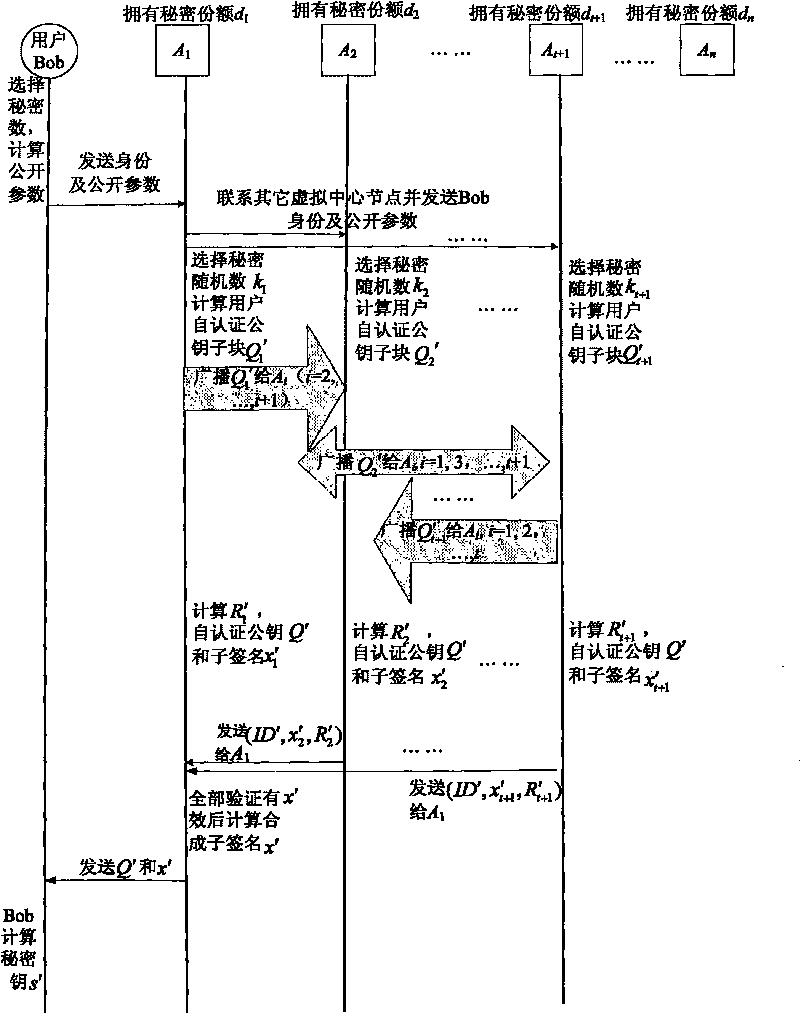
The invention discloses a management method of self-certified public key of a mobile self-organized network on the basis of ECC, comprising the following steps: a shared key is distributed to n virtual central nodes by threshold cryptology; a user chooses a secret random number to calculate a public parameter, and identity and the public parameter are sent to a nearby virtual central node A1; A1 contacts with other virtual central nodes and sends the user information to the nodes; each publisher Ai chooses a random secret integer and calculates as well as broadcasts a self-certified public key subblock Qi to other publishers according to the secret integers and parameters published by the user; each publisher Ai calculates a self-certified public key Q, a sub-signature xi and an intermediate quantity Ri and sends (r, I, xi and Ri) to a synthesizer; the synthesizer calculates and synthesizes a signature x after all sub-signatures are qualified after authentication and sends Q and x to the user; the user calculates a secret key s according to the x; and the authenticity of the self-certified public key of the user is verified. The invention has no certificate management, no key escrow and no secure channel, so that the invention is suitable for the safe communication of the mobile self-organization network with limited resource.
Owner:XIDIAN UNIV
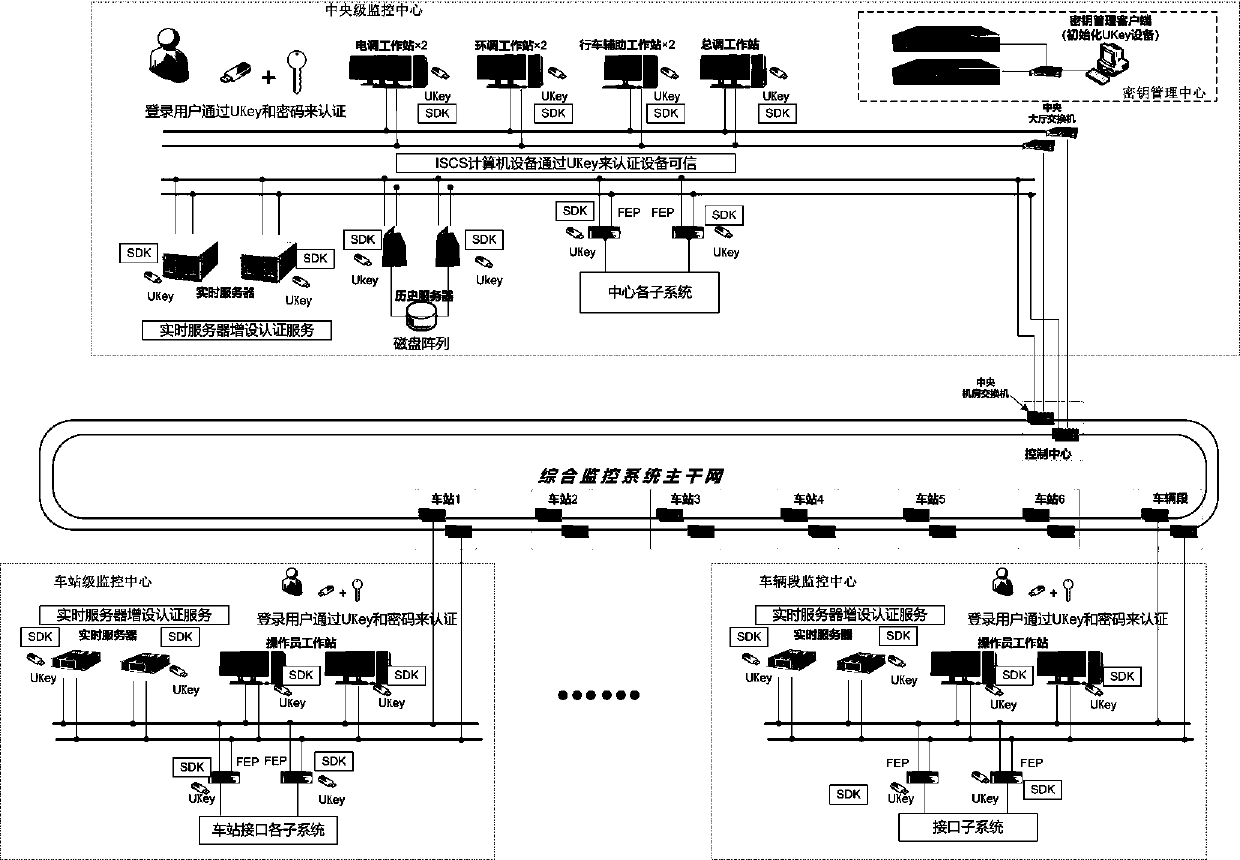
Subway comprehensive monitoring system based on SM3 and SM4 communication encryption
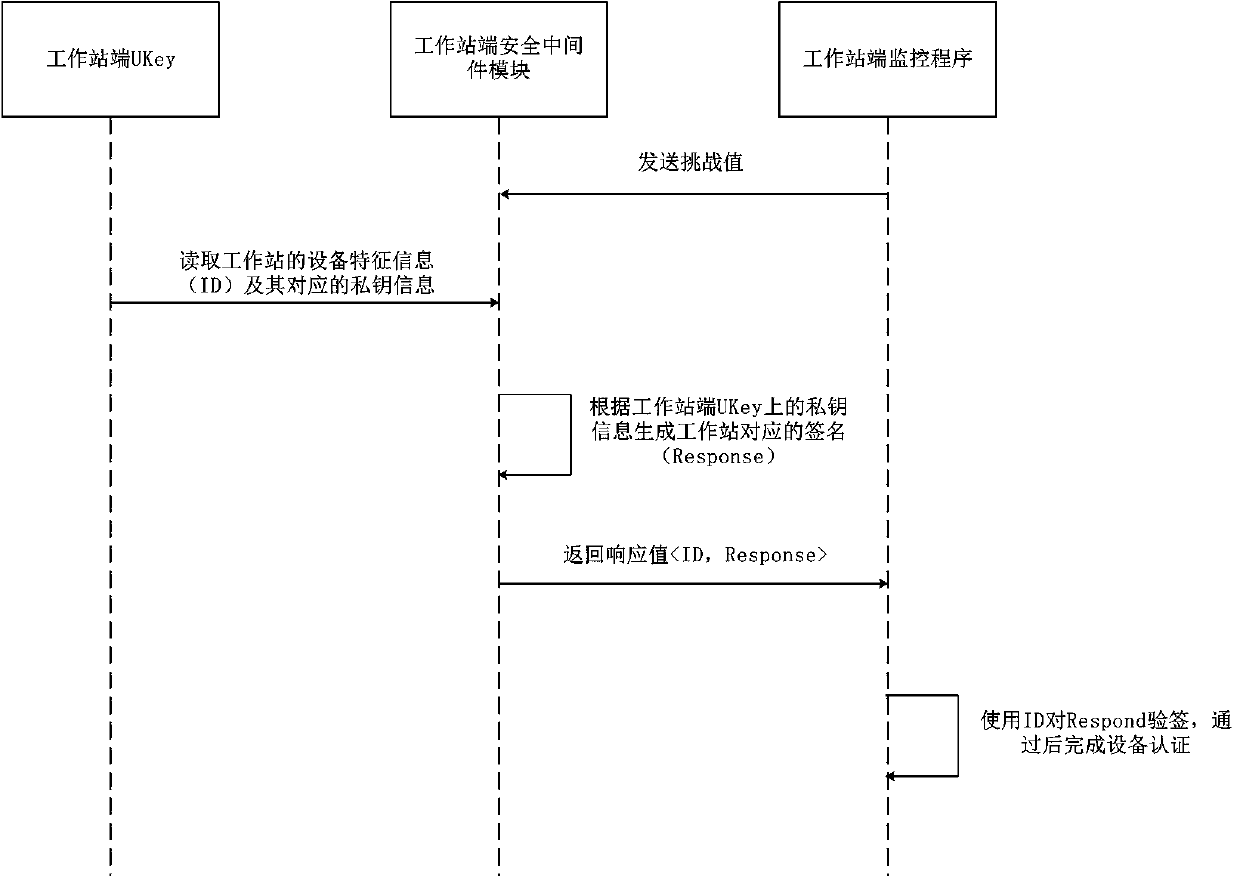
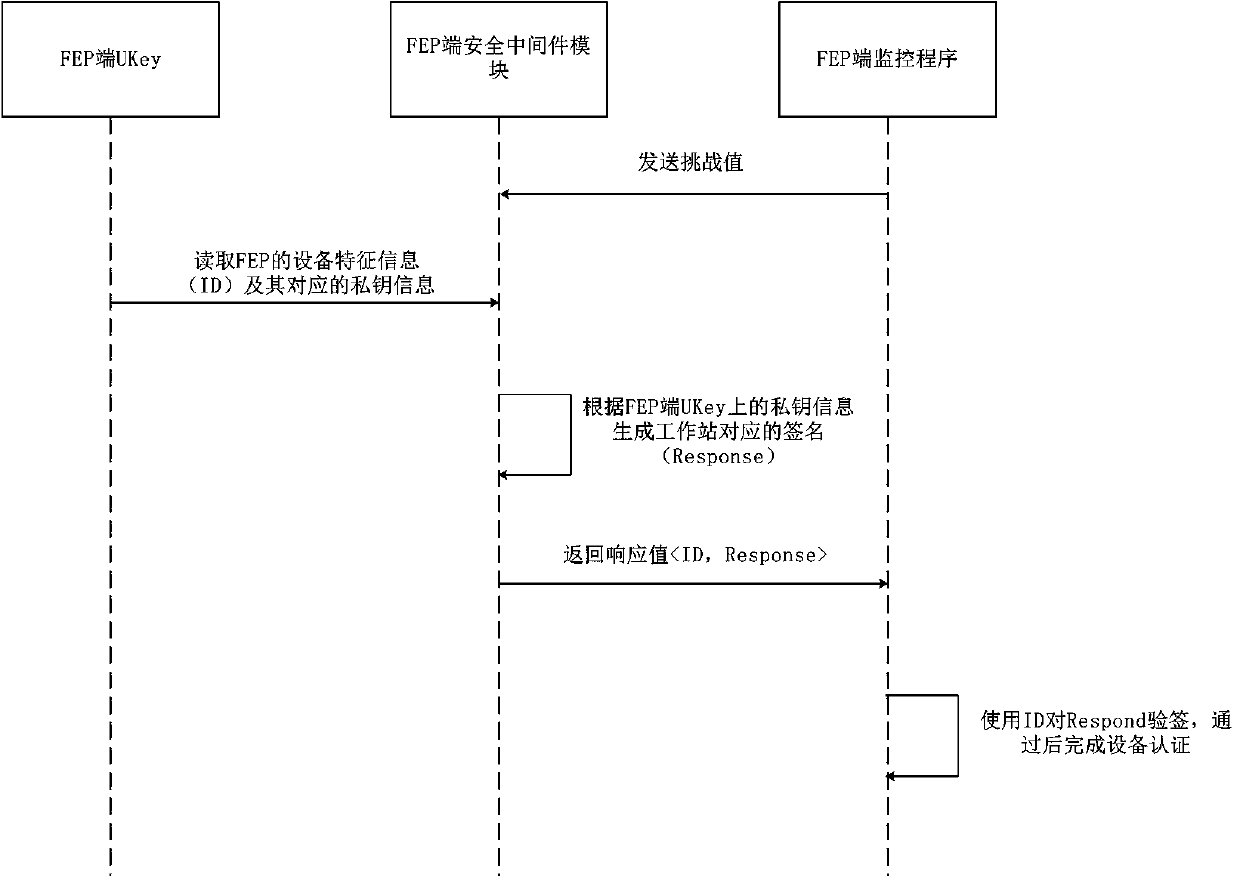
ActiveCN110838910AImprove securityPrevent trespassKey distribution for secure communicationWorkstationEmbedded system
The invention relates to a subway comprehensive monitoring system based on SM3 and SM4 communication encryption, and belongs to the technical field of subway monitoring. The system comprises a key management center and a plurality of monitoring centers. The monitoring centers are connected through an integrated monitoring system backbone network. Each monitoring center comprises a workstation, anFEP and a server which are connected through a network bus. The workstation, the FEP and the server are respectively provided with a workstation end UKey, an FEP end UKey and a server end UKey; and the workstation, the FEP and the server are all provided with security middleware modules. When the monitoring program needs to be started each time; self-authentication of equipment is carried out through a workstation, FEP, a UKey corresponding to a server and a security middleware module, meanwhile, a server side needs to be authenticated by a user for an operator, a corresponding monitoring program can be started only after the authentication is passed, and then key agreement and data encryption communication are carried out. According to the invention, illegal invasion can be effectively avoided, and the safety of the subway integrated monitoring system is improved.
Owner:郑州地铁集团有限公司 +1
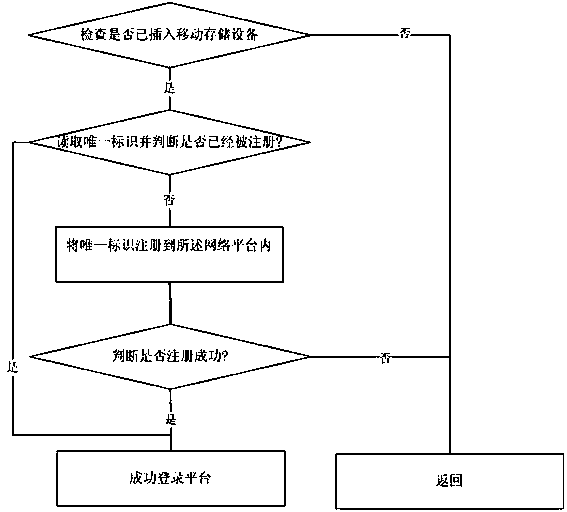
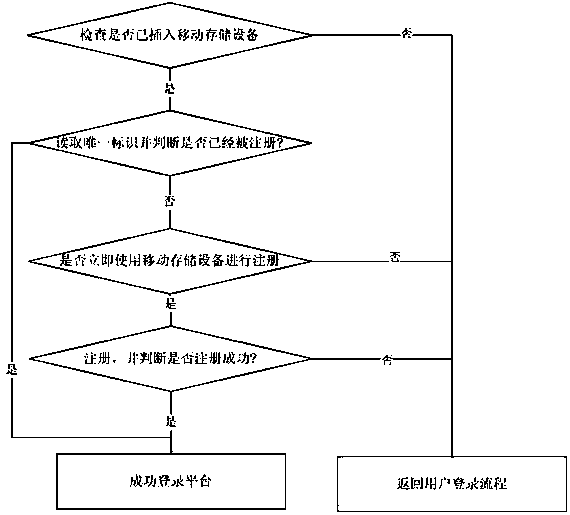
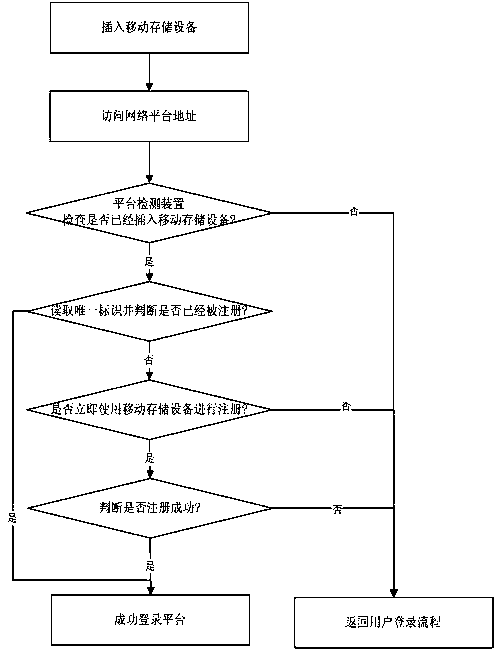
A network platform and method for self-certifying mobile storage devices
InactiveCN104518871BSimple self-authenticationConvenient self-certificationUser identity/authority verificationSelf certifiedUnique identifier
The invention provides a network platform and a method for performing self-service authentication on mobile storage equipment. The method comprises the following steps: checking whether the mobile storage equipment is inserted into a local computer or not through a detection step; reading a unique identifier of the equipment; if the unique identifier is not registered, guiding registration of the unique identifier, and logging on; and if the unique identifier is registered, logging on. According to the method, network access authentication is directly performed on the mobile storage equipment through a reading way without any pre-configuration. Specific to first log-on, log-on can be performed after registration. Specific to non-first log-on, direct log-on is performed. Plug and play is realized; pre-configuration of internal information does not need to be performed on the mobile storage equipment; binding is not required; and the technical problem that pre-configuration and binding are required in the prior art is effectively solved. The method for performing self-service authentication on the mobile storage equipment is simple, convenient and rapid.
Owner:NEW FOUNDER HLDG DEV LLC +1
Cross-cluster asymmetric group key agreement method in wireless sensor networks
ActiveCN107204845BRealize secret information exchangeReduce communication consumptionKey distribution for secure communicationNetwork topologiesLine sensorMobile wireless sensor network
The invention provides a cross-cluster asymmetric group key negotiation method in a wireless sensor network. The method comprises steps as follows: an allied and shared key between clusters is established, cluster heads are taken as bridging nodes, and sensor nodes of different nodes have the same group key factor information; an asymmetric computation algorithm is designed in the group key negotiation process, more computation and communication traffic of the sensor nodes are migrated to the cluster head nodes with larger energy, and the lightweight property of computation and communication overhead of the sensor nodes is ensured; self-certification property of keys is realized, additional communication rounds are not required, the sensor nodes can self-certify the correctness in computing the group keys, and the correctness and the safety of the group key negotiation are guaranteed. Group key negotiation of the sensor nodes distributed in different clusters in the wireless sensor network is realized, a safe communication channel is established, the scale of cooperative computation and information sharing of sensor node groups is further expanded, energy consumption of the sensor nodes is reduced, and the service life of the sensor nodes is prolonged.
Owner:河南招源科技有限公司
Method and device for storing roses on block chains
PendingCN110569306AImprove experienceUser identity/authority verificationDatabase distribution/replicationSelf certifiedPurchasing
The invention discloses a method and device for storing roses on block chains, and the method comprises the steps that a block chain node receives a rose data chaining request sent by a merchant terminal, the rose data chaining request comprises a rose name, the number of roses and a rose number, and the rose number comprises a rose color and a rose variety; after the merchant signature in the rose data chaining request passes the verification, the merchant signature is stored in a block chain; a rose flower purchase data uploading request sent by the merchant terminal is received, wherein therose flower purchase data uploading request comprises rose flower purchase time, purchaser identity information and purchased rose flower numbers; and after the merchant signature in the rose purchase data chaining request is verified successfully, the merchant signature is stored in the blockchain. The purchase information and the information of roses can be stored in the block chains; therefore, the rose flower purchasing experience of the user can be improved, and a merchant can self-certify the credit.
Owner:BEIJING AIMORECE TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com