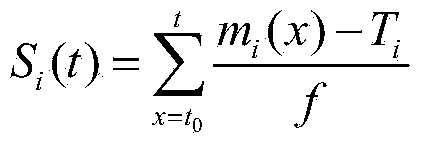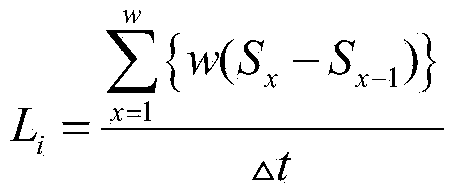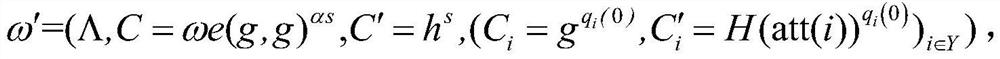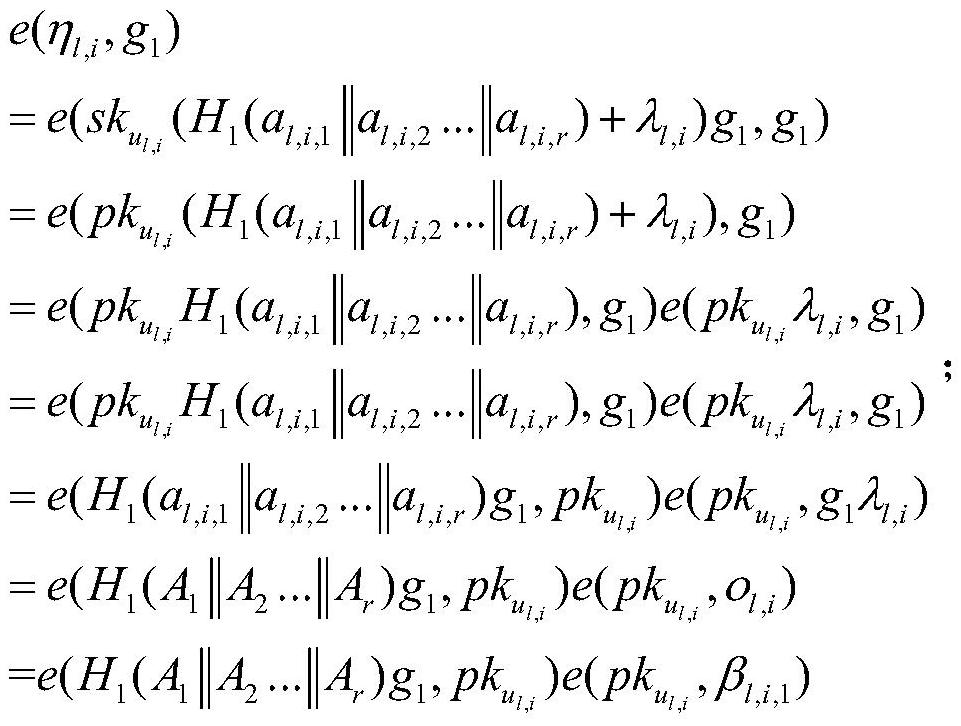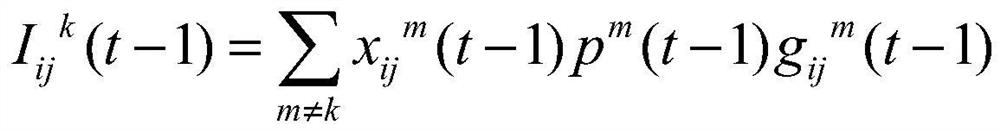Patents
Literature
44results about How to "Reduce communication consumption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
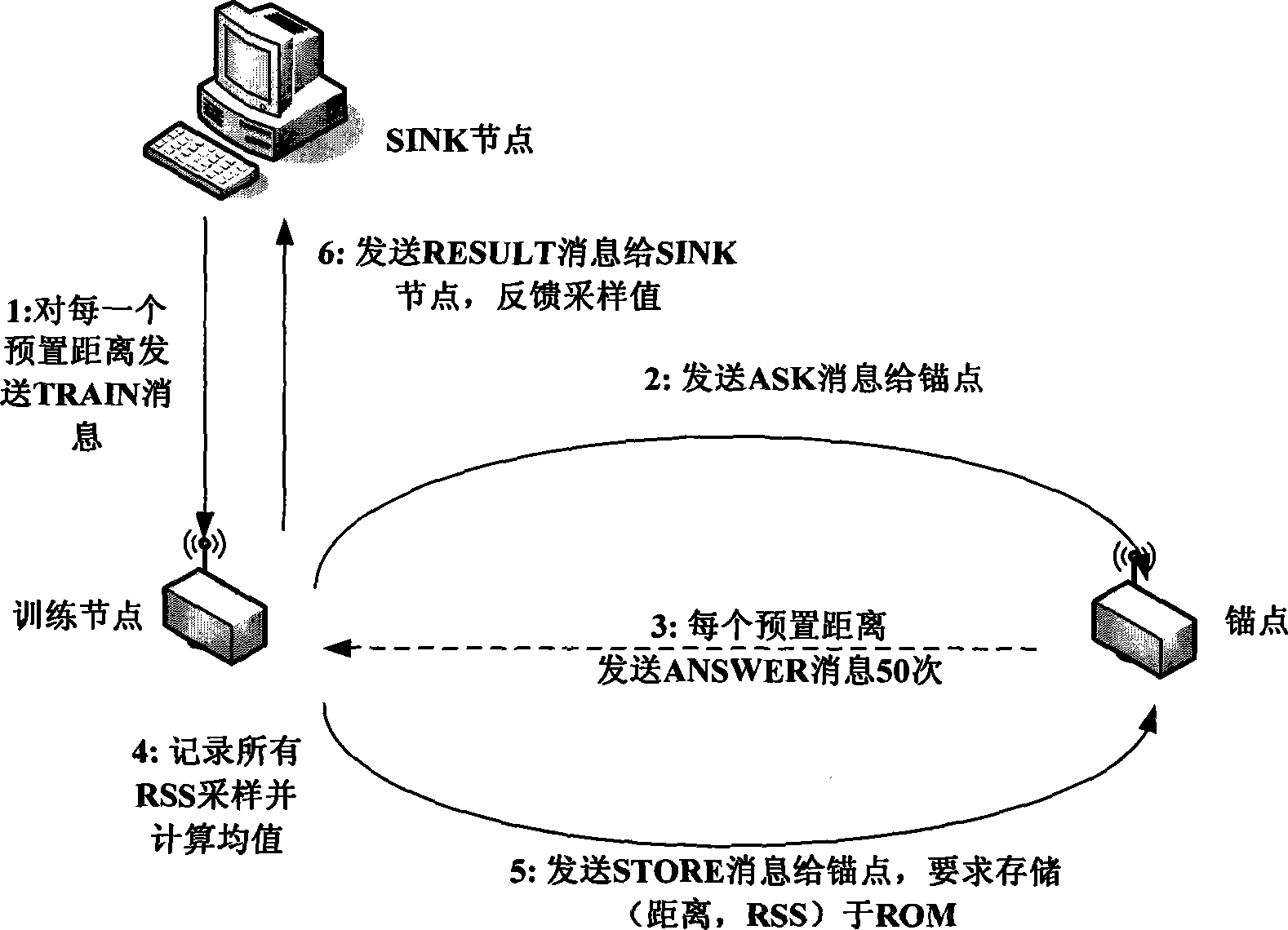
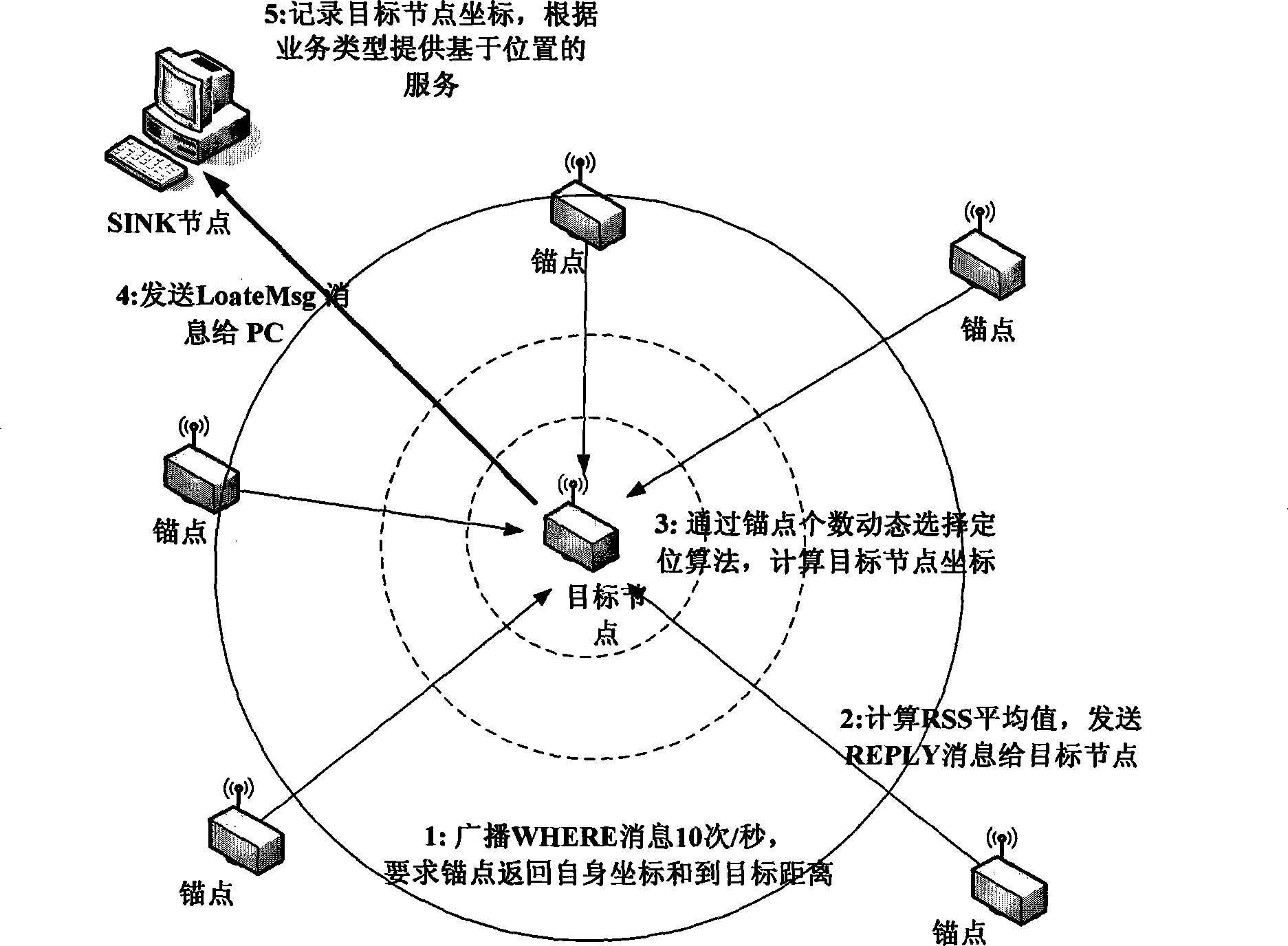
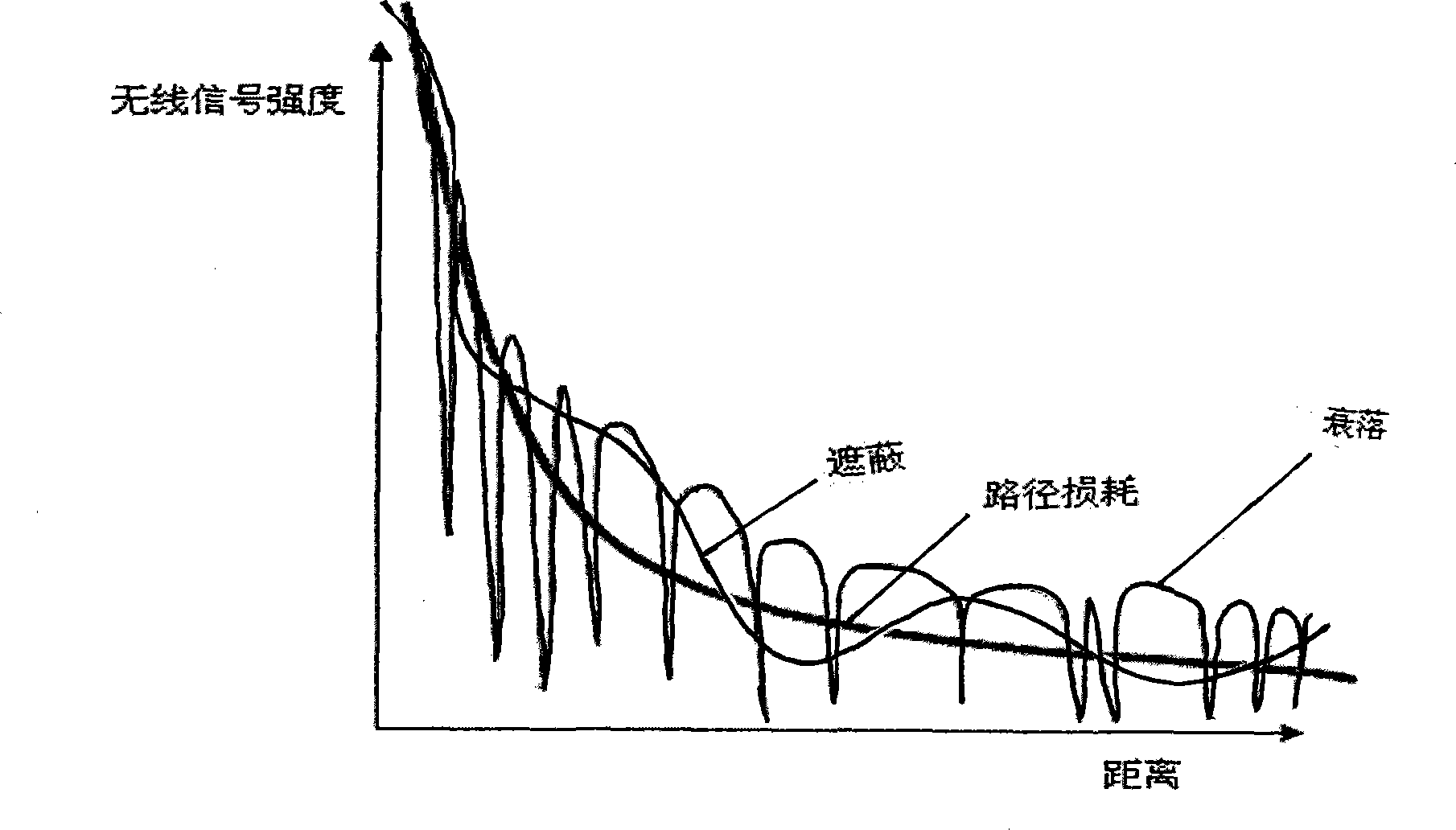
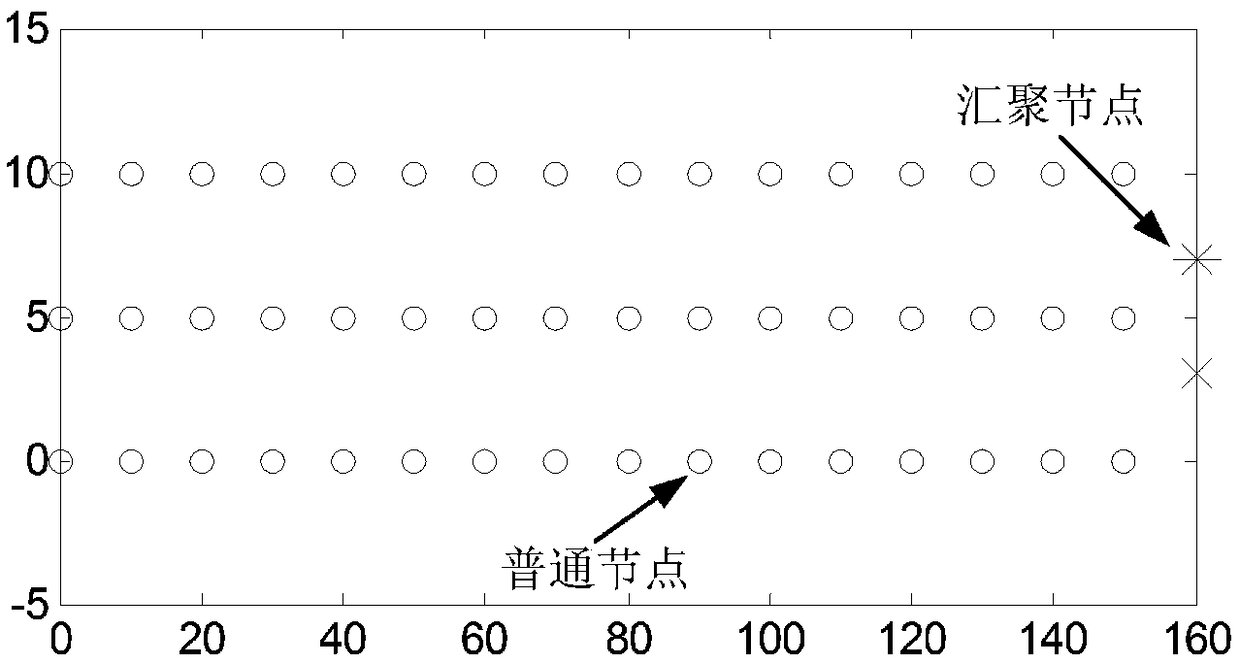
Node indoor locating method based on wireless signal strength in wireless sensor network
InactiveCN101247650AReduce communication consumptionSmall amount of calculationPosition fixationRadio/inductive link selection arrangementsWireless mesh networkAnchor point
The present invention belongs to node self-localization field in large-scale wireless sensor network, and discloses a node indoor localization method based on wireless signal intensity, which main includes: getting relationship curve of signal intensity and distance, and putting forward concept of effective wireless signal intensity (Effective RSS, ERSS); obtaining coordinates of target node by selecting localization arithmetic (ERSS filter + maximum likelihood estimation, triangle localization, approximate location estimation) according with anchor point amount through distance between anchor point and target by training RSS curve; providing alerting service by using physics coordinate, providing navigation service according with route arithmetic and address chain by using sign coordinate (for example in hall). Precisely localization of indoor target can be realized in condition of low-cost, simple initial configuration, and a plurality of services based on location can also be provided.
Owner:JIAXING WIRELESS SENSOR NETWORKS CENT CAS
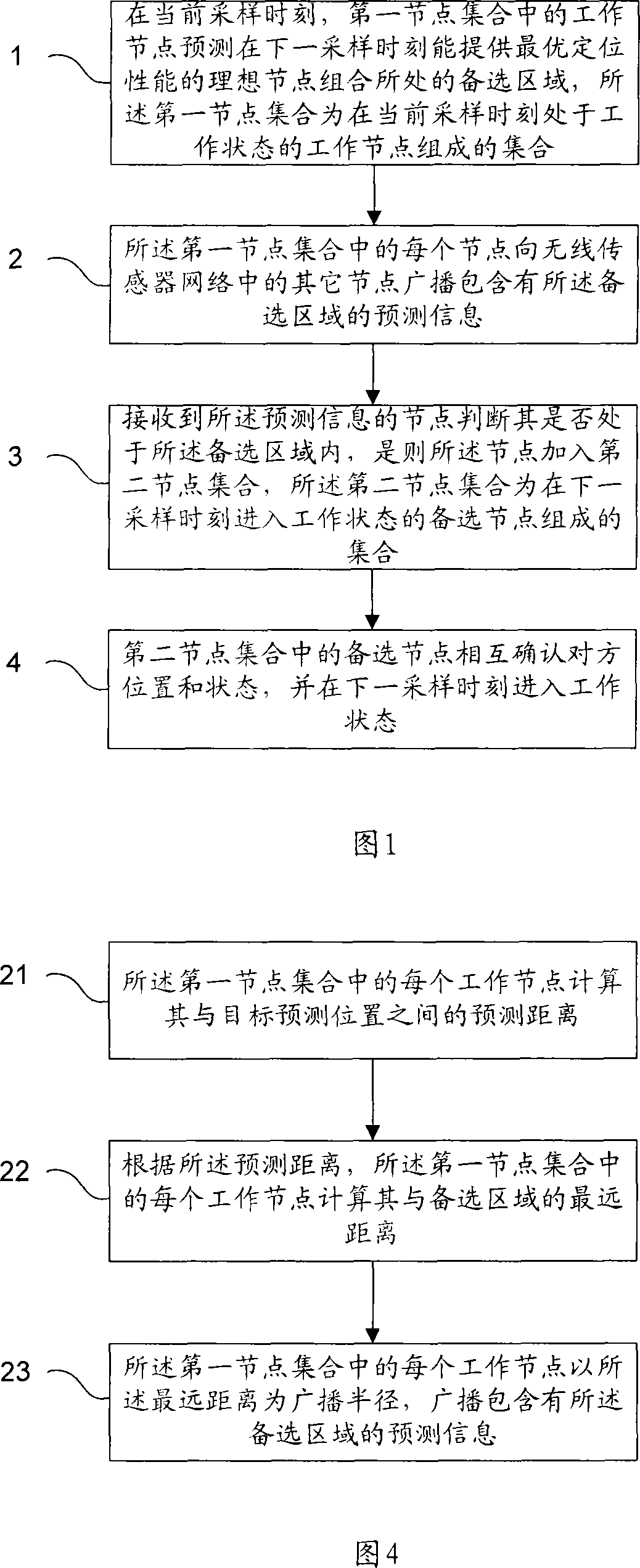
Wireless sensor network local type node managing method
InactiveCN101252495ABalance storage capacityReduce storage capacityData switching by path configurationRadio/inductive link selection arrangementsLocal typeAlternative methods
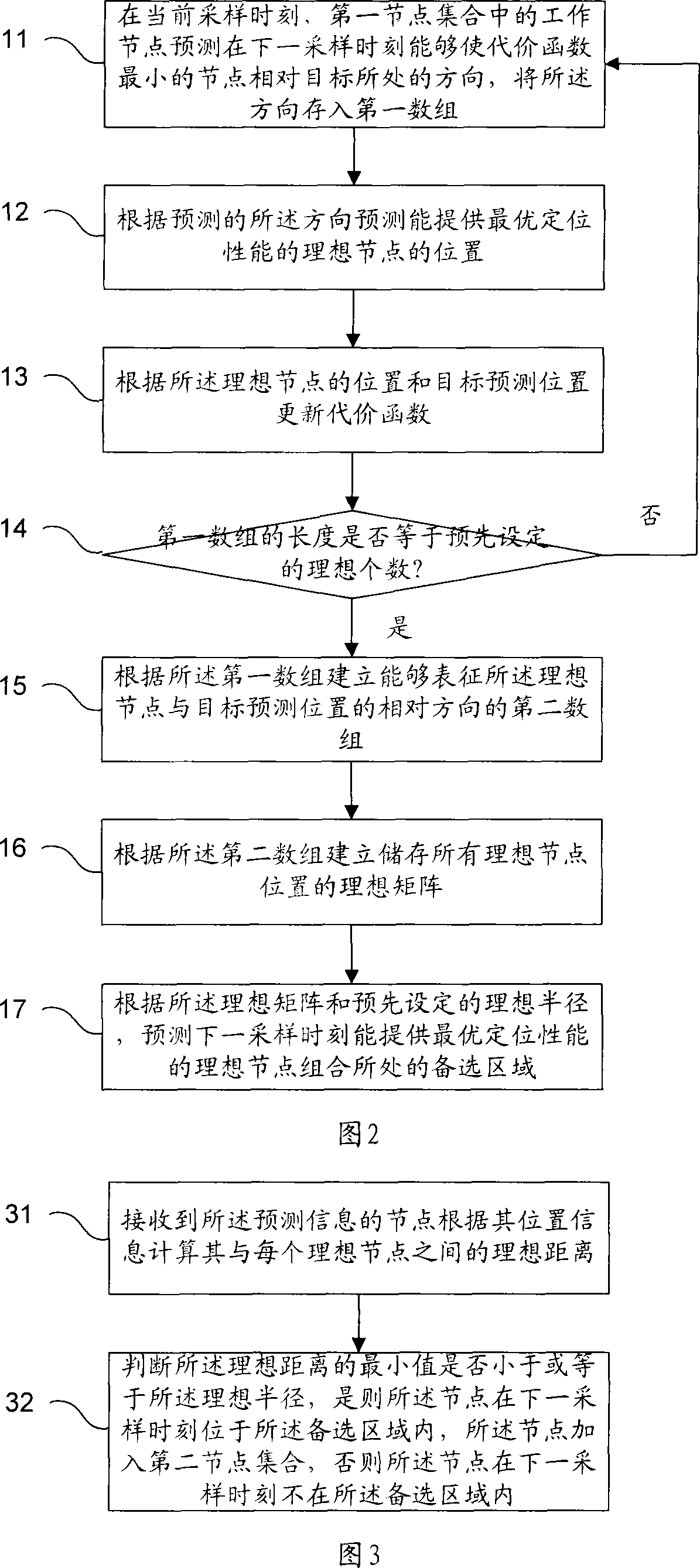
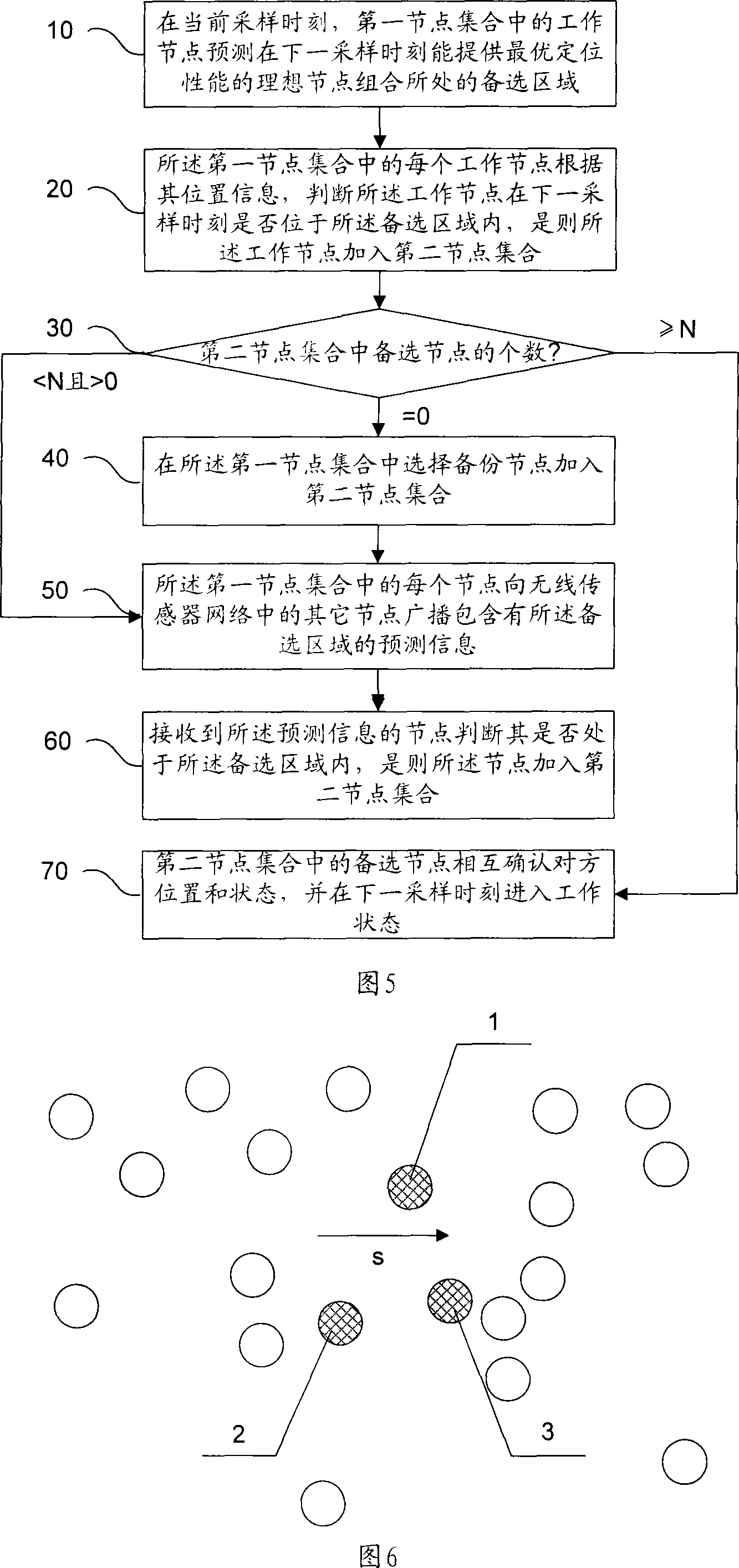
The invention relates to a local type node management method of the wireless sensor network, which comprises the steps that at the current sampling time, a working node in a first node collection can predict that the alternative area where the ideal node combination with the optimum positioning performance at the time of the next sampling is positioned can be provided; each node in the first node collection can broadcast the forecasting information including the alternative area to other nodes in the wireless sensor network; the node which receives the forecasting information judged whether is positioned within the alternative area, and if the node is positioned within the alternative area, the node is added to a second node collection; the alternative nodes in the second node collection can mutually confirm the location and the condition of the other node, and the alternative nodes can come into the working condition at the next sampling time. The invention can effectively avoid the disadvantages that the computing load of the traditional overall type node management method is large, the storage demand is large, the complexity of the system is large, the structure is complex, the expansibility is not strong etc., the invention can rapidly obtain the node combination which can position the object with very high precision, the working complexity of the system can be reduced, and the network service life can be prolonged.
Owner:BEIHANG UNIV
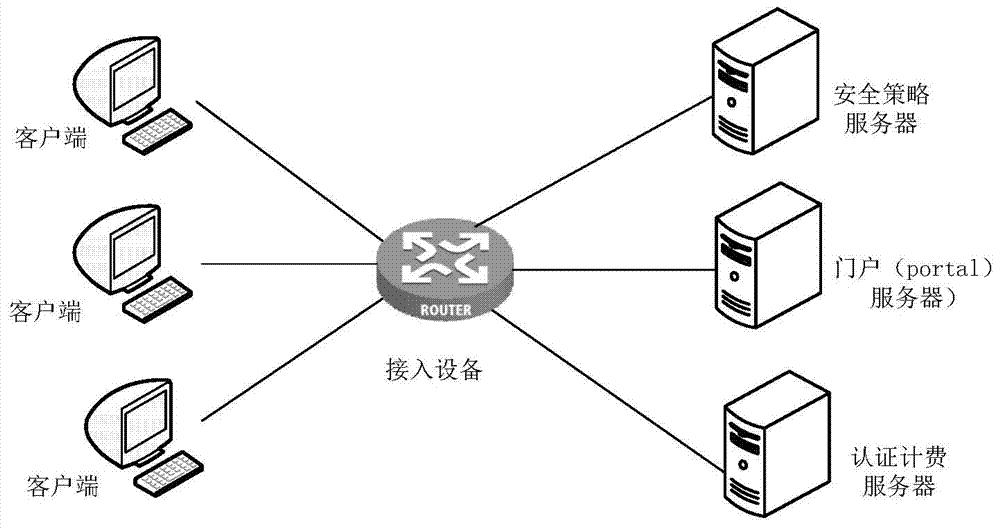
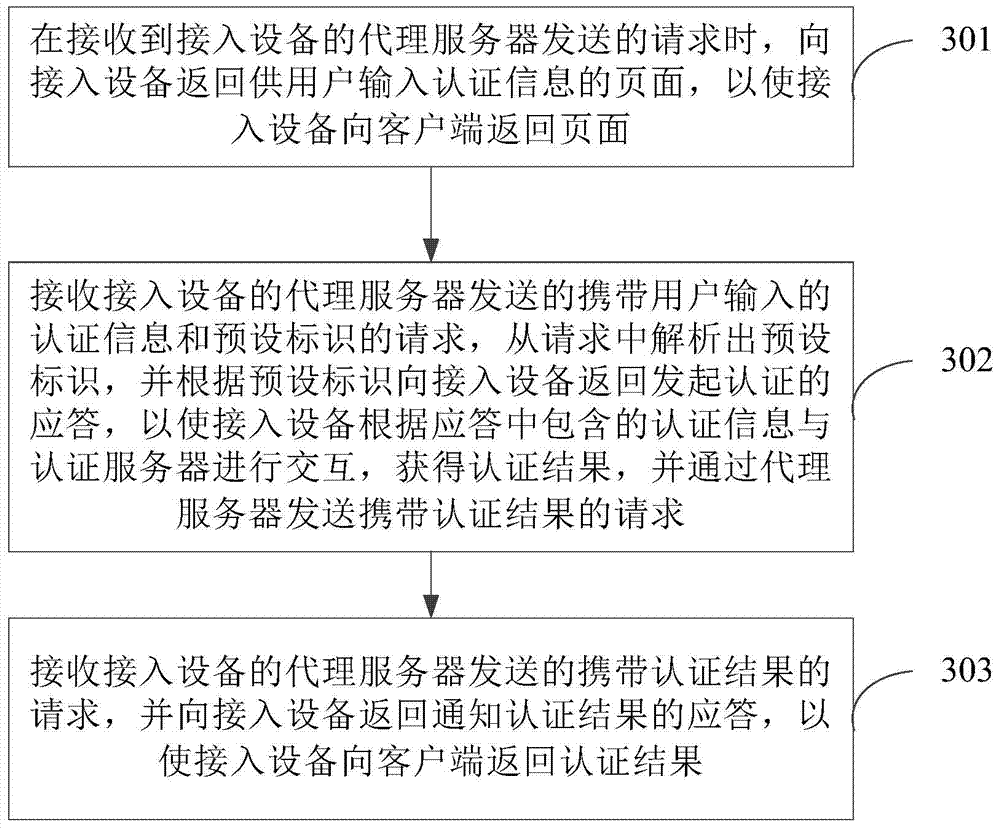
Method and apparatus for realizing portal authentication
ActiveCN104852919AReduce communication consumptionReduce performance consumptionTransmissionClient-sideFixed time
The application provides a method and apparatus for realizing portal authentication. The method comprises: receiving a request sent by a client, carrying out interaction with a portal server by a proxy server, returning a page for authentication information inputting by a user to the client; receiving the authentication information inputted by the user and sending a request carrying the authentication information and a preset identifier to the portal server by the proxy server to enable the portal server to return response information containing the authentication information for launching authentication according to the preset identifier; and carrying out interaction with an authentication server according to the response to obtain an authentication result, sending a request containing the authentication result to the portal server by the proxy server, and receiving a response, for authentication result notification, returned by the portal server, thereby returning the authentication result to the client. According to the embodiment of the invention, UDP messages can be sent at fixed time without any access equipment, thereby effectively reducing communication consumption in a network.
Owner:NEW H3C TECH CO LTD
Method for monitoring state of cloud data center
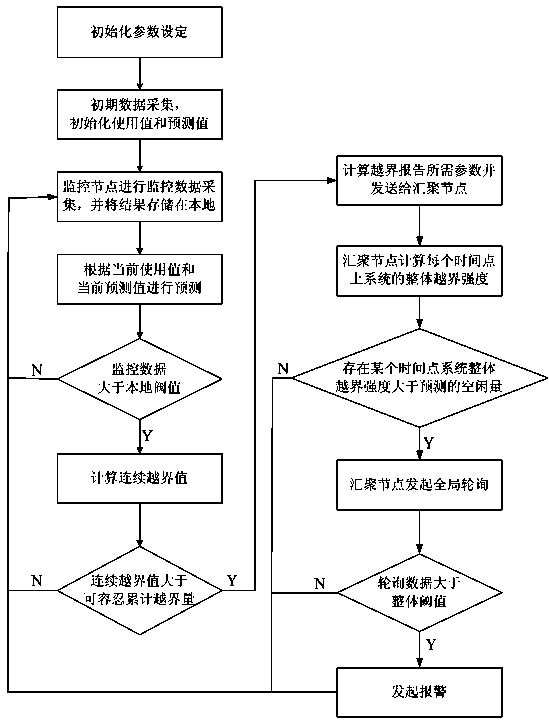
ActiveCN103825779AEffective filteringReduce resource consumptionData switching networksSoftware simulation/interpretation/emulationResource consumptionBorder crossing
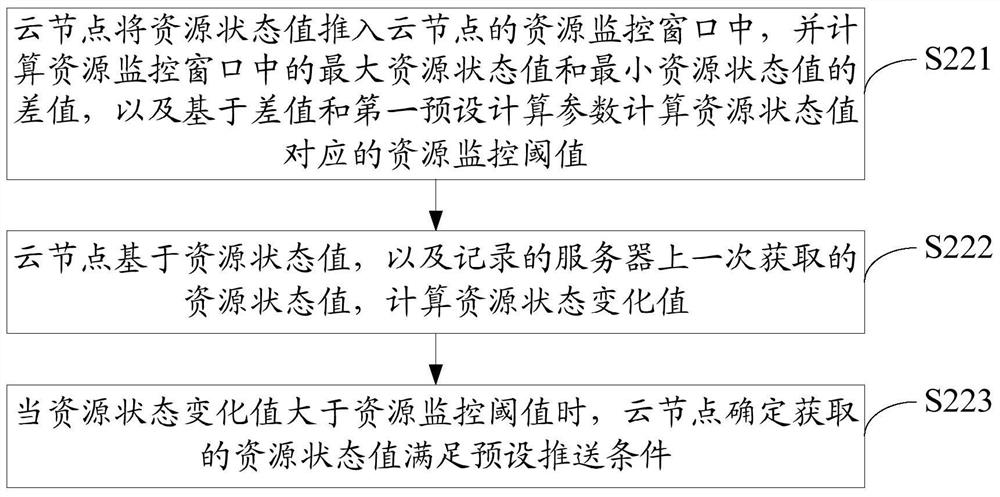
The invention discloses a method for monitoring the state of a cloud data center, and belongs to the technical field of cloud computing. The method comprises the steps that first, the whole threshold values of monitoring objects and the local threshold values of monitoring nodes are preset according to different monitoring objects, and then the tolerable accumulative border crossing amount is set for the monitoring nodes; when state border crossing happens to the monitoring nodes locally, the monitoring nodes accumulate the local border crossing values until the accumulative value reaches the tolerable accumulative border crossing amount, relevant data such as weighted average border crossing strength of local continuous border crossing are sent to an aggregation node; the aggregation node is used for predicating the whole state of a system on the basis of history polling to obtain a system idle value; if the received weighted average border crossing strength exceeds the predicated idle value, global polling is conducted, the system using vale in the future is predicated according to the global polling, and whether an alarm is triggered or nor is determined. According to the method for monitoring the state of the cloud data center, the communication consumption needed by state monitoring can be well lowered, and therefore the resource consumption of the cloud data center is lowered on the whole.
Owner:北京华麒通信科技有限公司
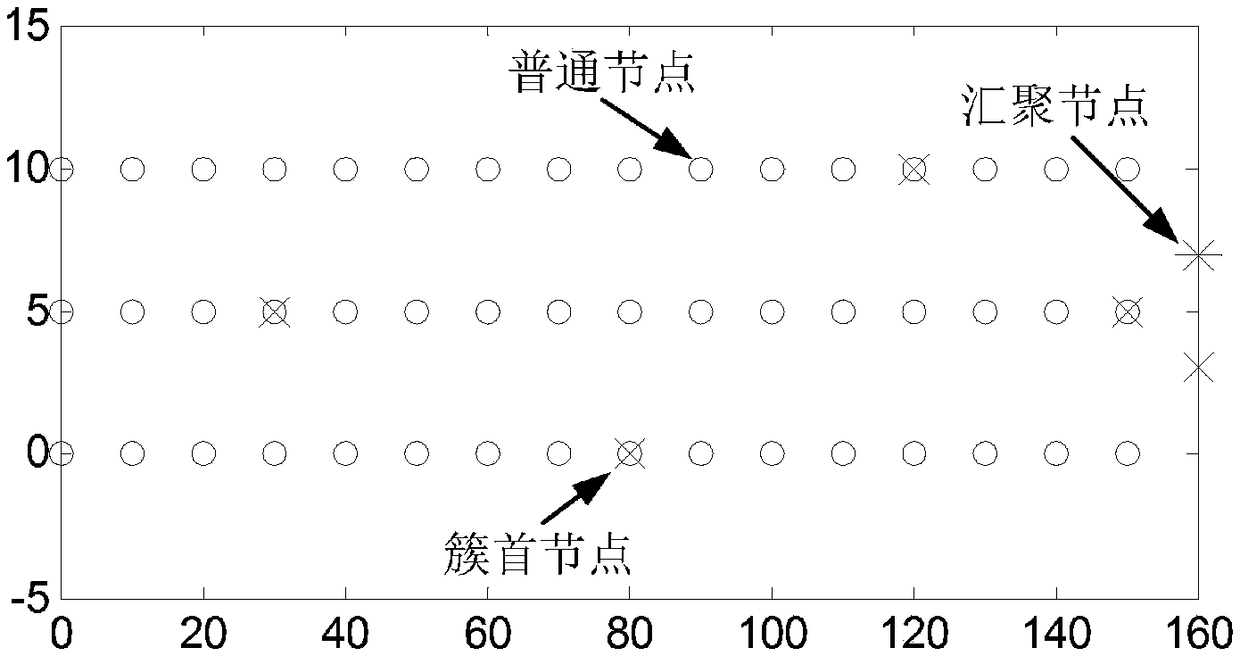
WSNs clustering routing method under long and narrow topology
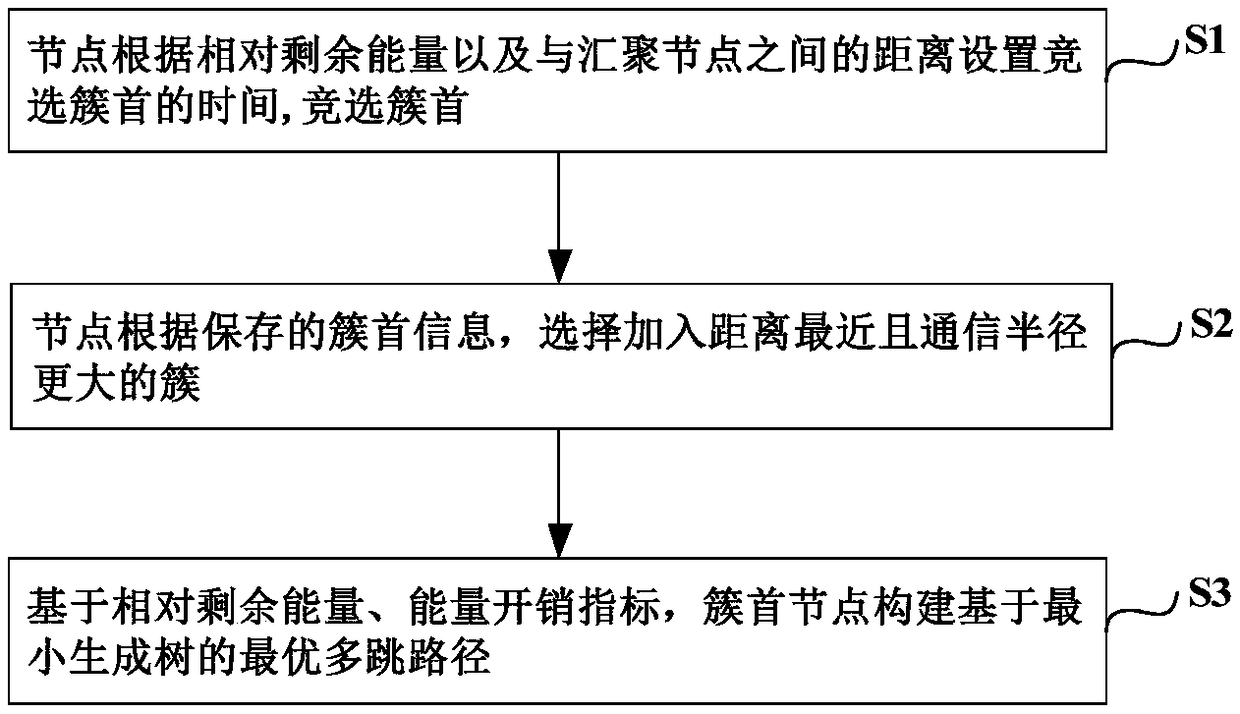
ActiveCN108777877AImproved Local Election MethodReduce control overheadNetwork topologiesHigh level techniquesRest energyShortest distance
The invention discloses a WSNs clustering routing method under long and narrow topology. The method comprises the following steps that at a cluster head campaigning stage, the cluster head campaigningtime is set for each node according to the relative rest energy and the distance between the gathering nodes; when the time is shorter, the campaigning succeeding possibility is higher; at the cluster forming stage, the nodes select to add the cluster with the shortest distance and the greater communication radius according to the stored cluster head information; at a multi-hop path building stage, on the basis of the relative rest energy and energy expenditure index, the cluster head node builds the optimum multi-hop path based on the minimum spanning tree. The WSNs clustering routing methodunder the long and narrow topology can realize more effective data transmission at each routing stage; the network transmission efficiency and the node load balance can be improved, so that the energy consumption of each node can be balanced; the network life period can be prolonged.
Owner:SUZHOU UNIV OF SCI & TECH
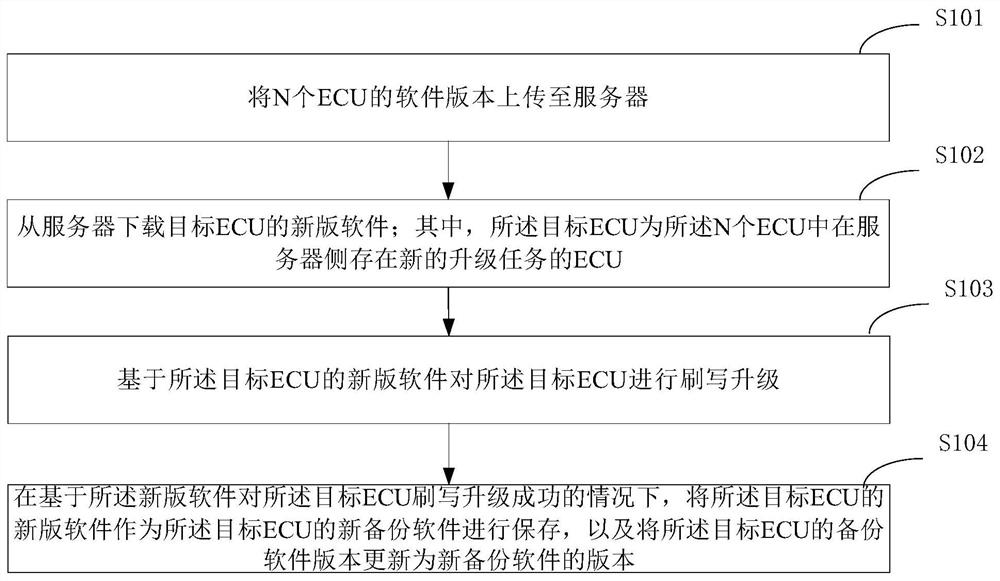
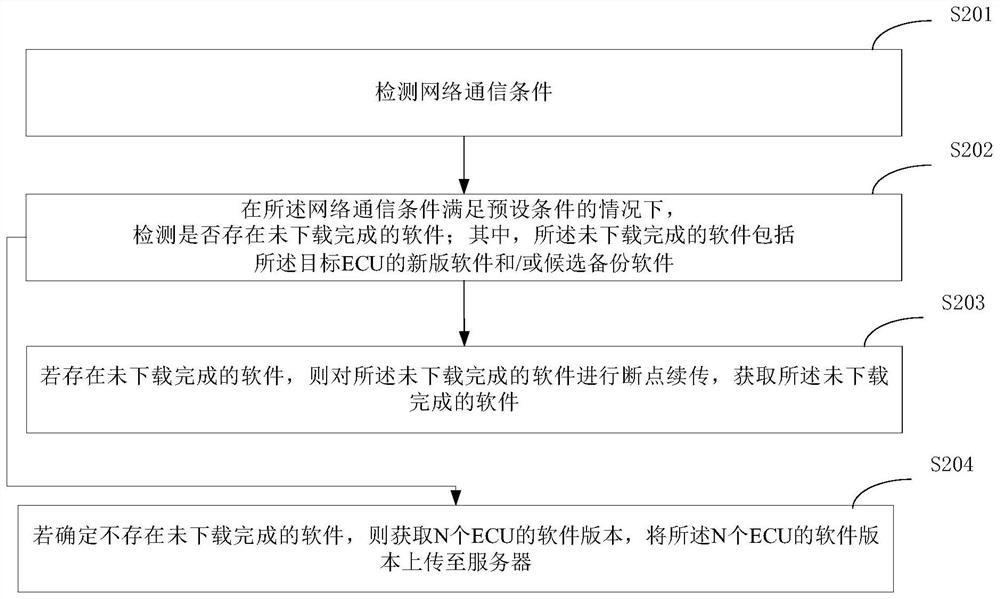
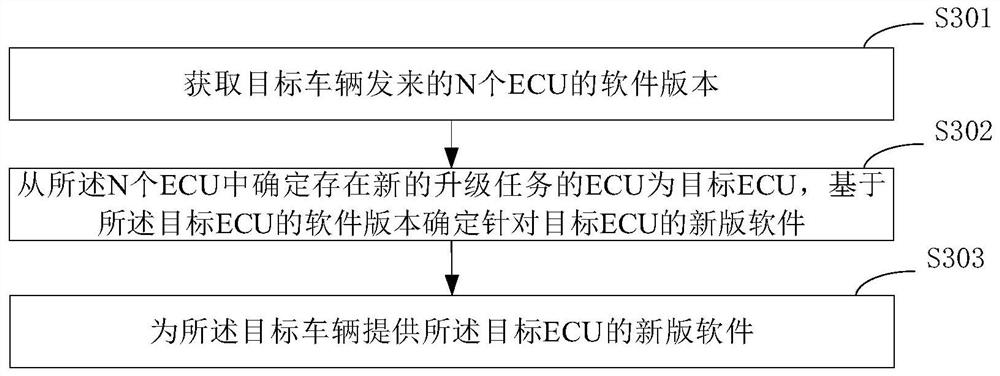
Software version updating method, server, vehicle and computer storage medium
PendingCN112099845AImprove processing efficiencyReduce communication consumptionVersion controlElectric/fluid circuitSoftware engineeringServer-side
The invention discloses a software version updating method, a server, a vehicle and a computer storage medium. According to a specific implementation scheme, the method comprises the following steps:uploading software versions of N ECUs to a server, wherein N is an integer greater than or equal to 1; downloading new edition software of a target ECU from the server, wherein the target ECU is an ECU with a new upgrading task on a server side in the N ECUs; flashing and upgrading the target ECU based on the new version software of the target ECU; and under the condition that the target ECU is successfully flashed and upgraded on the basis of the new version of software, storing the new version of software of the target ECU as new backup software of the target ECU, and updating the version ofthe backup software of the target ECU into the version of the new backup software.
Owner:HUMAN HORIZONS (SHANGHAI) CLOUD COMPUTING TECH CO LTD
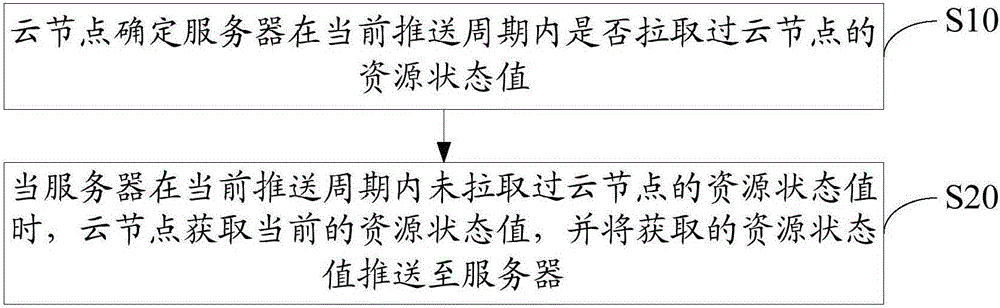
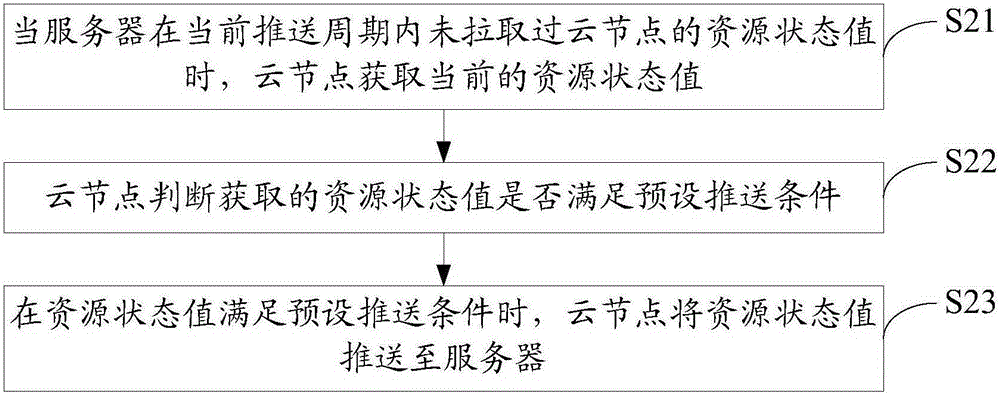
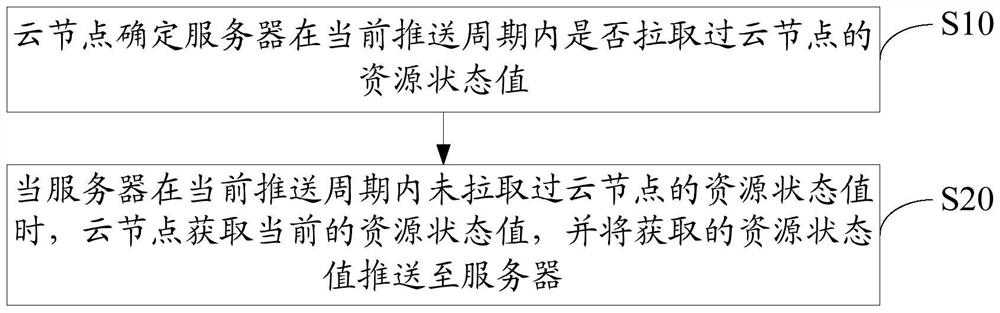
Resource monitoring method, device and system
ActiveCN106487601AReduce network transmissionReduce communication consumptionData switching networksData centerMonitoring system
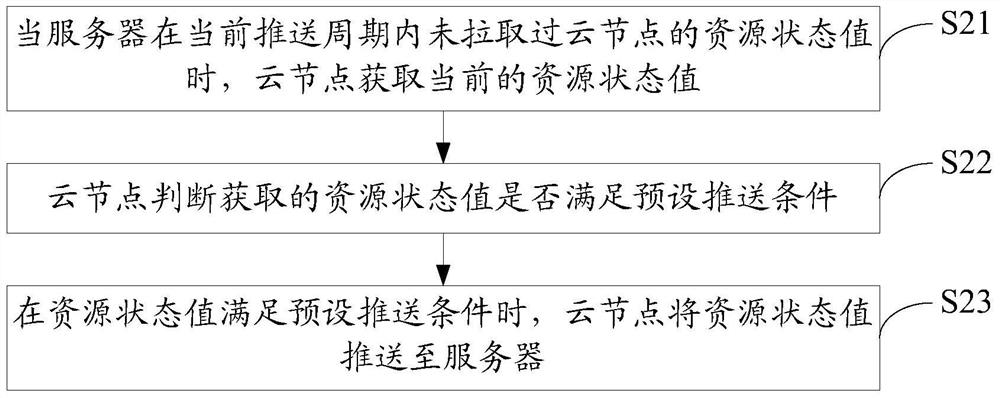
The invention discloses a resource monitoring method, device and system. The resource monitoring method comprises the steps that a cloud node determines whether a resource state value of the cloud node is pulled in a current push cycle or not; and when a server does not pull the resource state value of the cloud node in the current push cycle, the cloud node obtains a current resource state value and pushes the obtained resource state value to the server. The invention also discloses a resource monitoring device. The invention also discloses a resource monitoring system. According to the method, the device and the system, the communication consumption for resource monitoring of a cloud computing data center can be reduced.
Owner:ZTE CORP
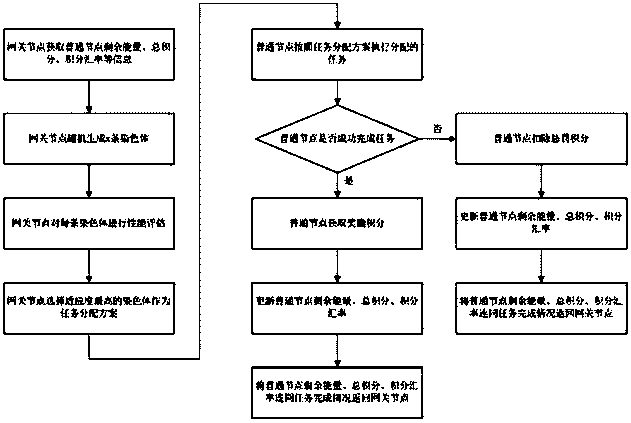
Wireless sensor network and node task distribution method thereof
ActiveCN104540171AImproved Space Exploration CapabilitiesExtend the life cycleNetwork traffic/resource managementNetwork topologiesTask completionWireless mesh network
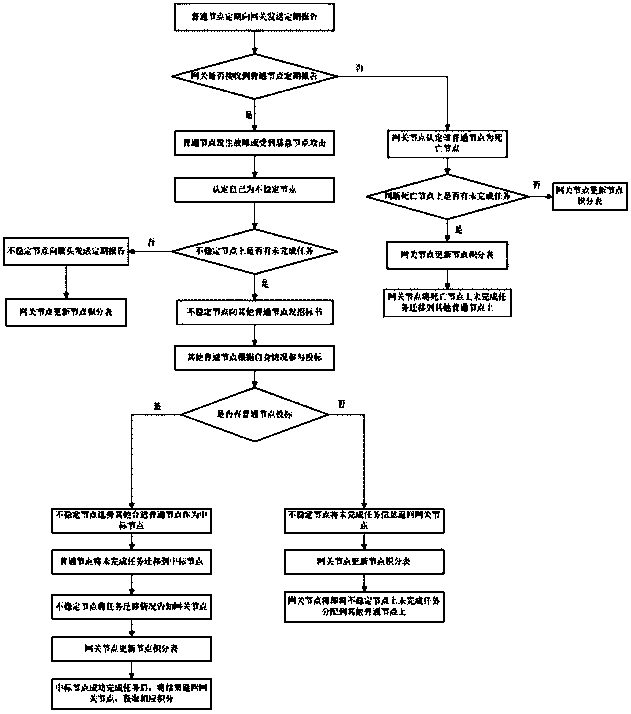
The invention relates to a wireless sensor network and a node task distribution method thereof. The wireless sensor network comprises a gateway node and multiple common nodes. The wireless sensor network is characterized in that the gateway node and the multiple common nodes are formed through linkage in a wireless multi-hop mode, the gateway node is provided with power supply, and the common nodes are provided with no power supply, are randomly arranged and are moved no longer once the common nodes are arranged well. The gateway node in the wireless sensor network allocates interdependent subtasks based on a genetic algorithm, an integral incentive mechanism is introduced to an allocation algorithm, grading is conducted on the common nodes according to node integrals, accordingly loads of all nodes are balanced, and the life cycle of a network is prolonged. Under the situation that the nodes are unstable, uncompleted tasks on unstable points can be migrated to other appropriate nodes, task completion within time limit is ensured, and task allocation efficiency and completion quality are improved.
Owner:常州初欣文化科技有限公司
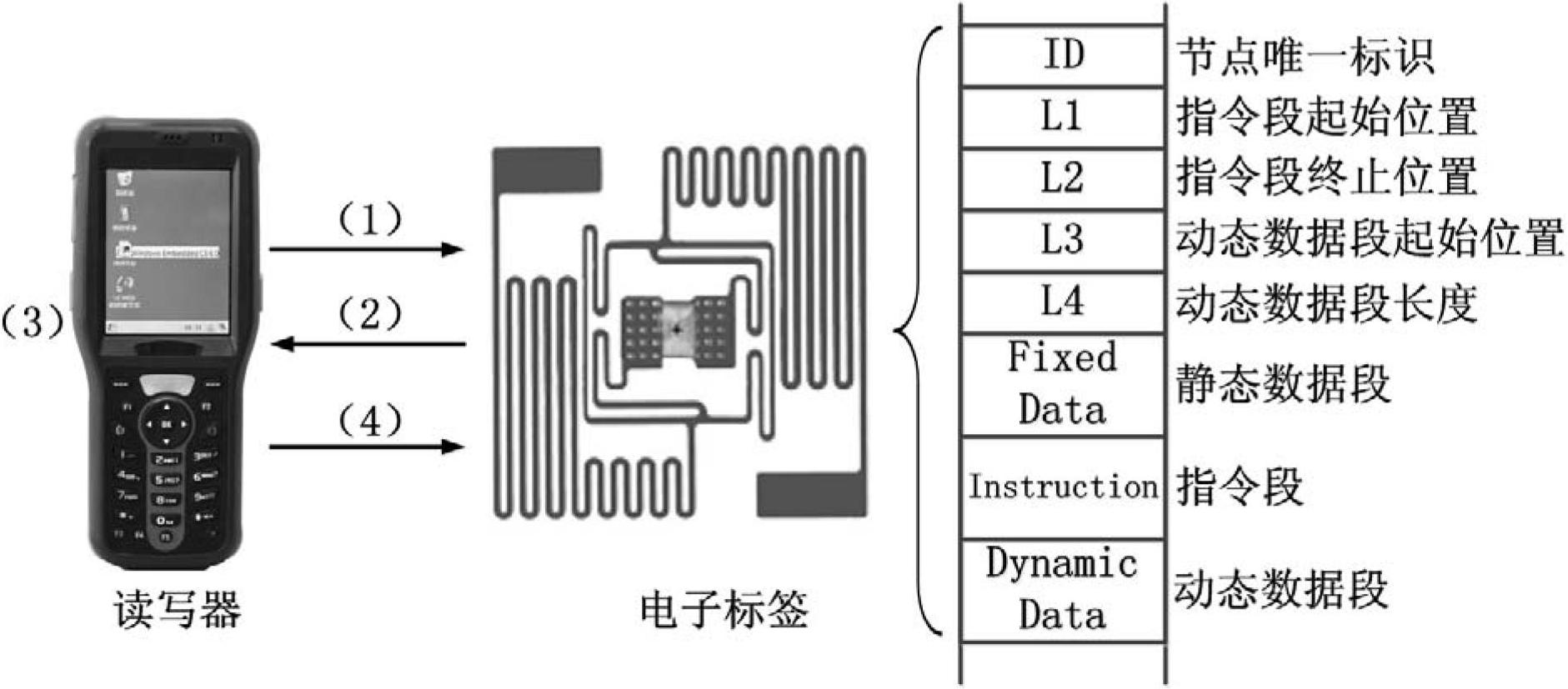
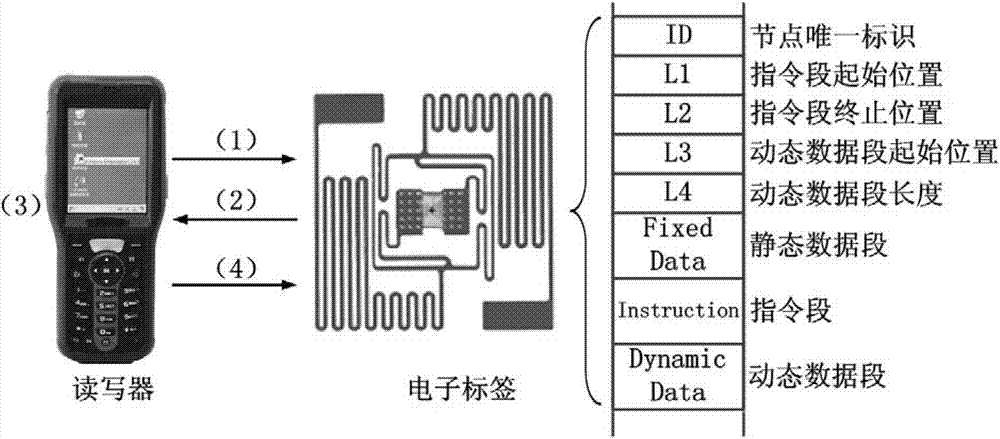
Intelligent electronic label information system and information interaction method thereof
ActiveCN102682317AReduce manufacturing costImprove management efficiencyCo-operative working arrangementsData privacy protectionData information
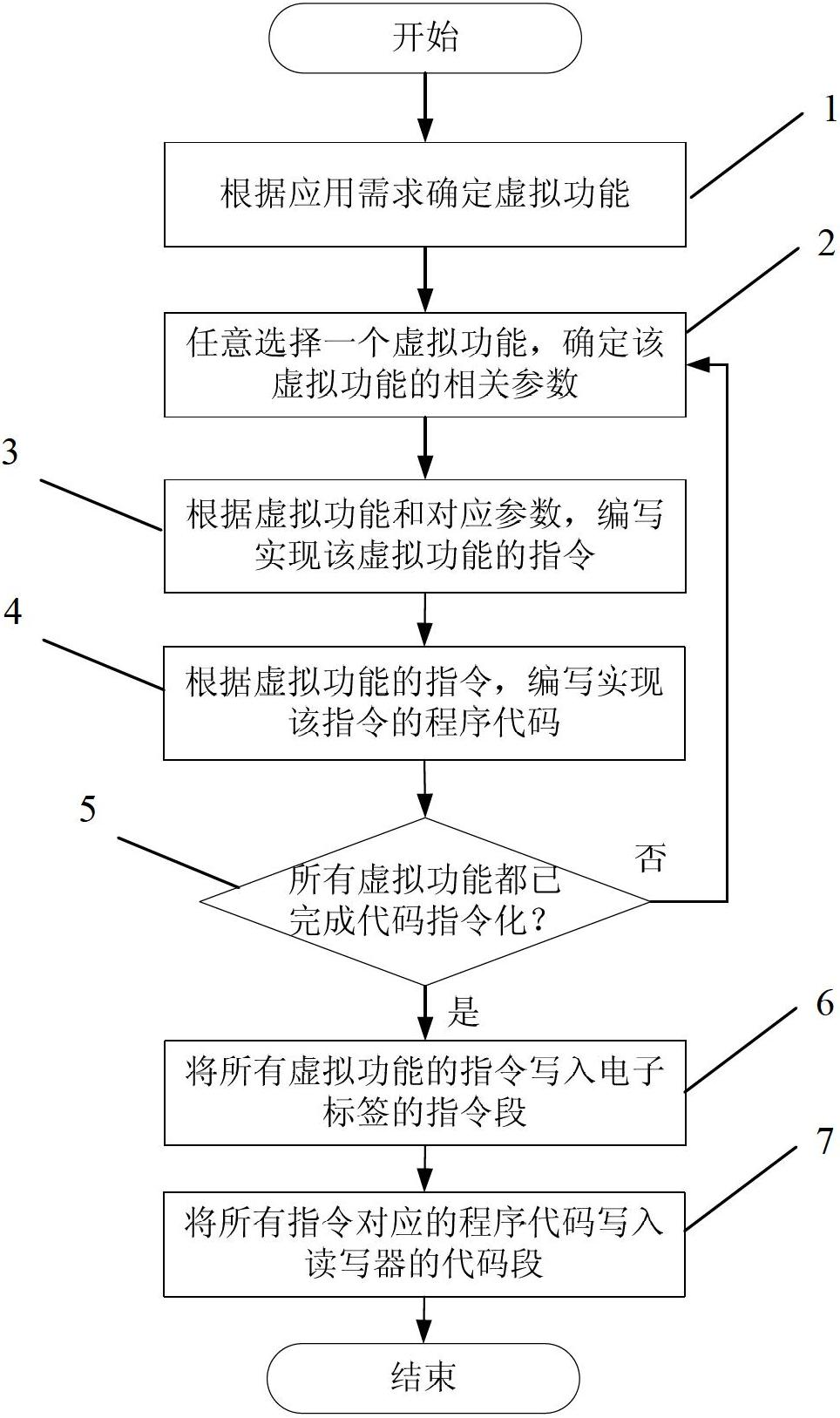
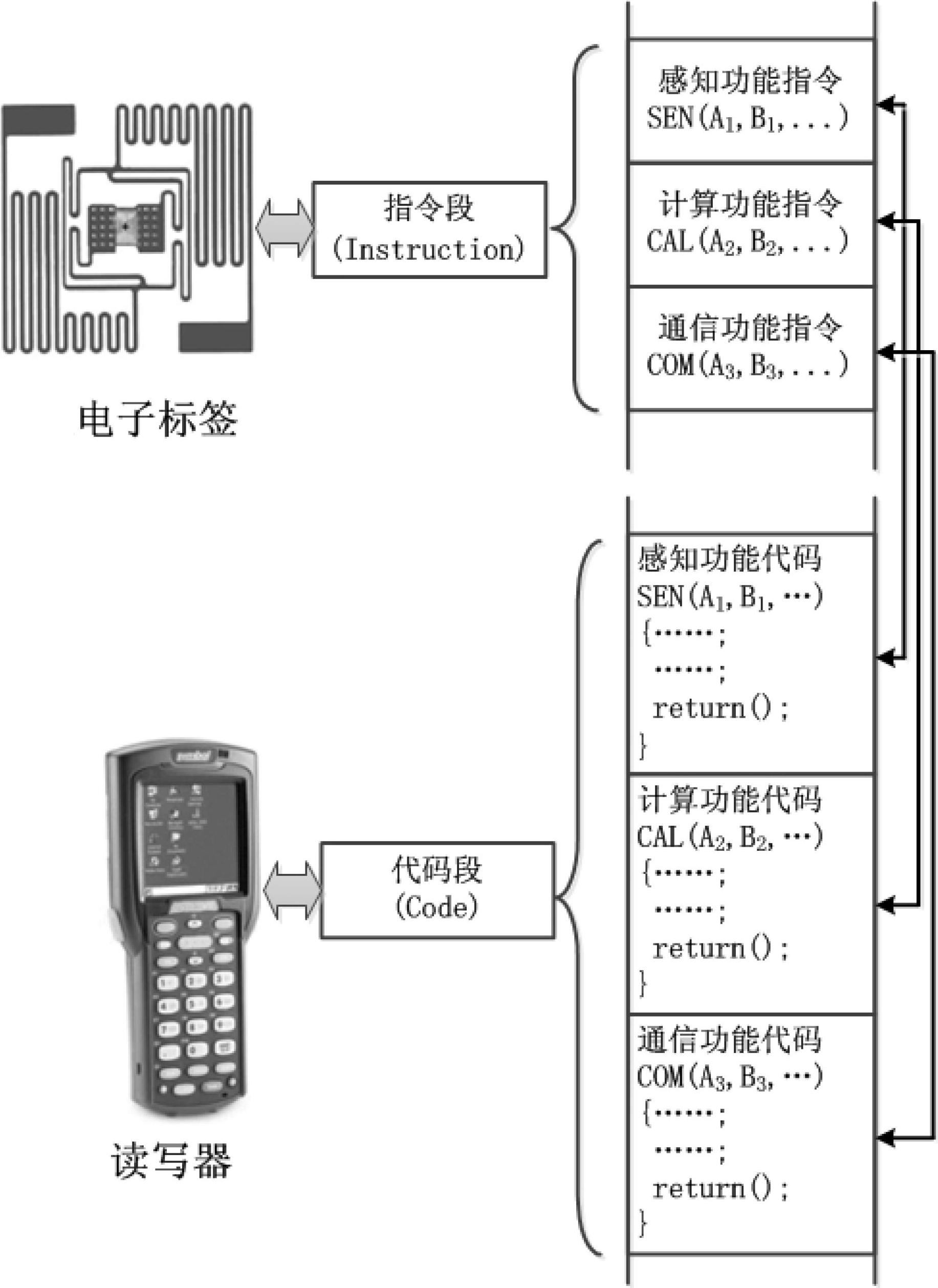
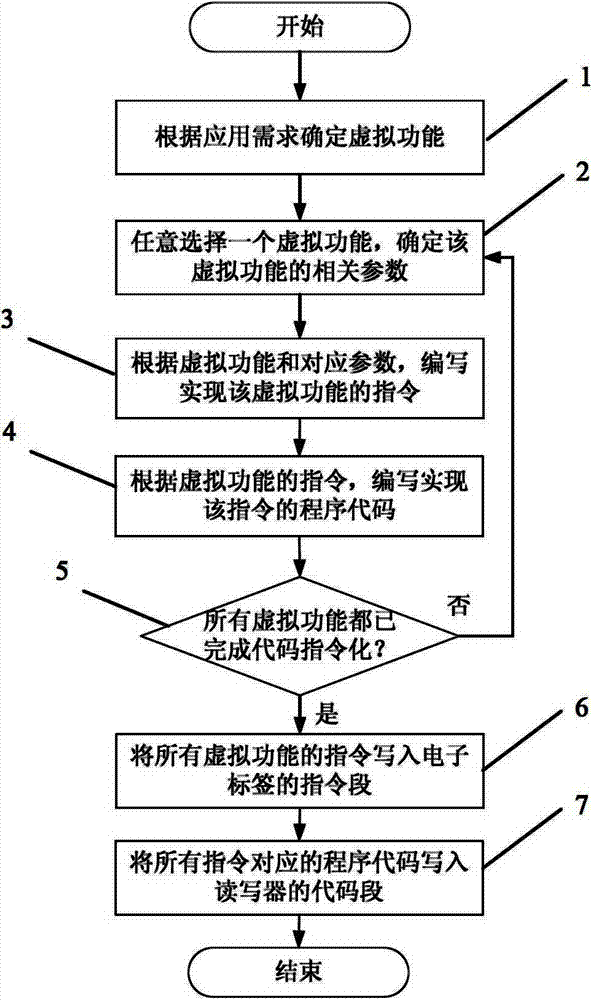
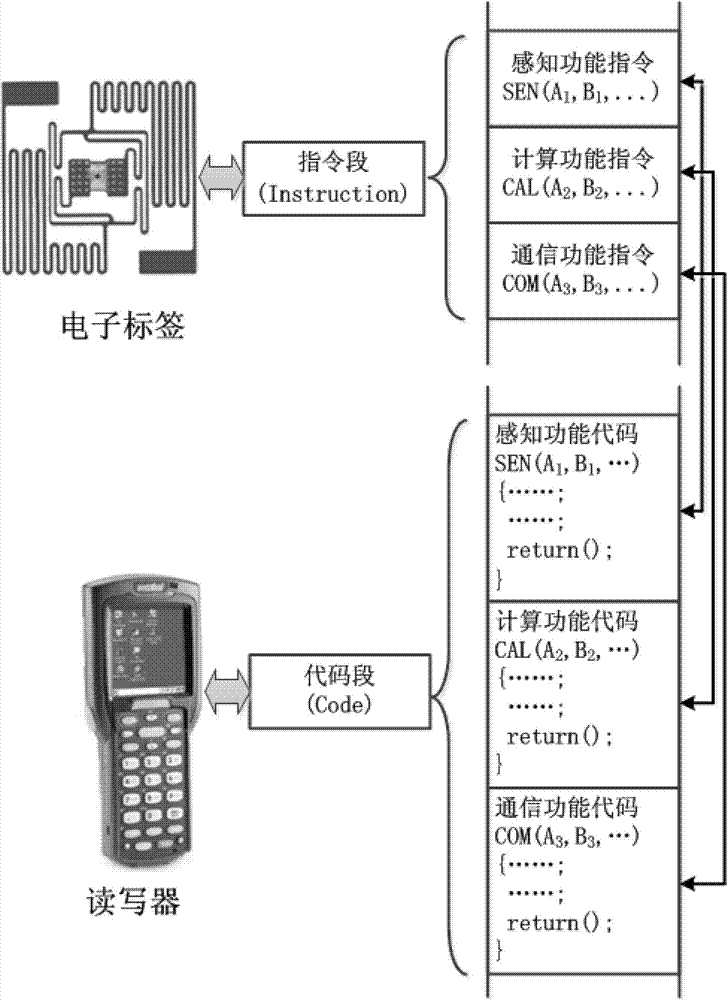
The invention provides an intelligent electronic label information system, which comprises an electronic label and a reader-writer, wherein the electronic label stores an instruction which can be read by the reader-writer; and the reader-writer stores a procedure code corresponding to the instruction and is used for reading the instruction stored by the electronic label and executing the corresponding procedure code. By the intelligent electronic label information system, the equipment manufacturing cost of the electronic label system can be greatly reduced, and the management and running efficiency can be improved; and the implementation range of the electronic label system can be deeply expanded. Furthermore, the storage space of the electronic label is effectively saved, and the transmission consumption and the communication consumption during partial interaction can be reduced. Moreover, a phenomenon that all types of data information are concentratively transmitted to a uniform background server is avoided, the bandwidth consumption and the communication cost of large-scale data transmission in multiple types of application are reduced, the probability that important data information leaks is reduced, and data privacy protection is facilitated.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
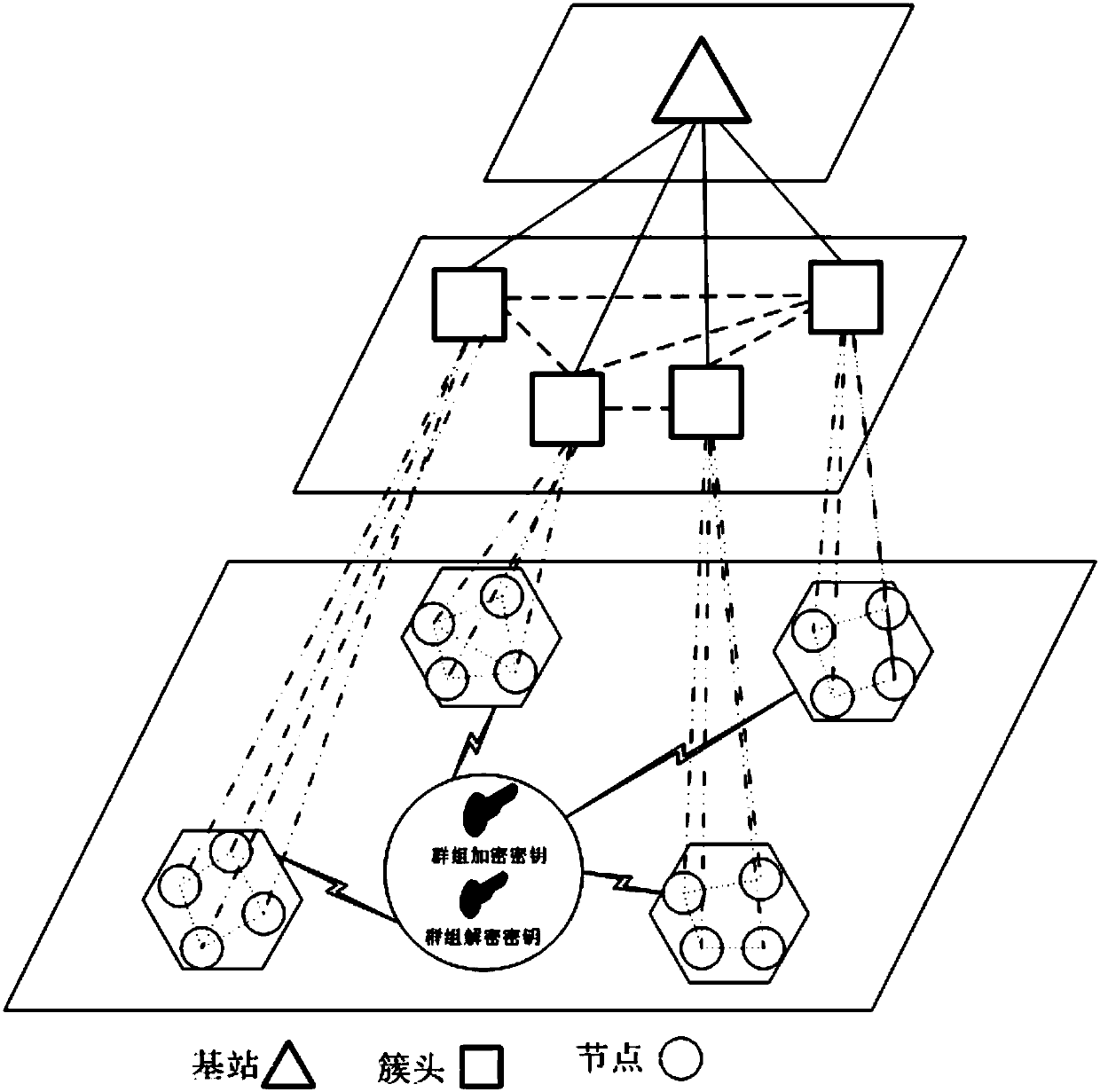
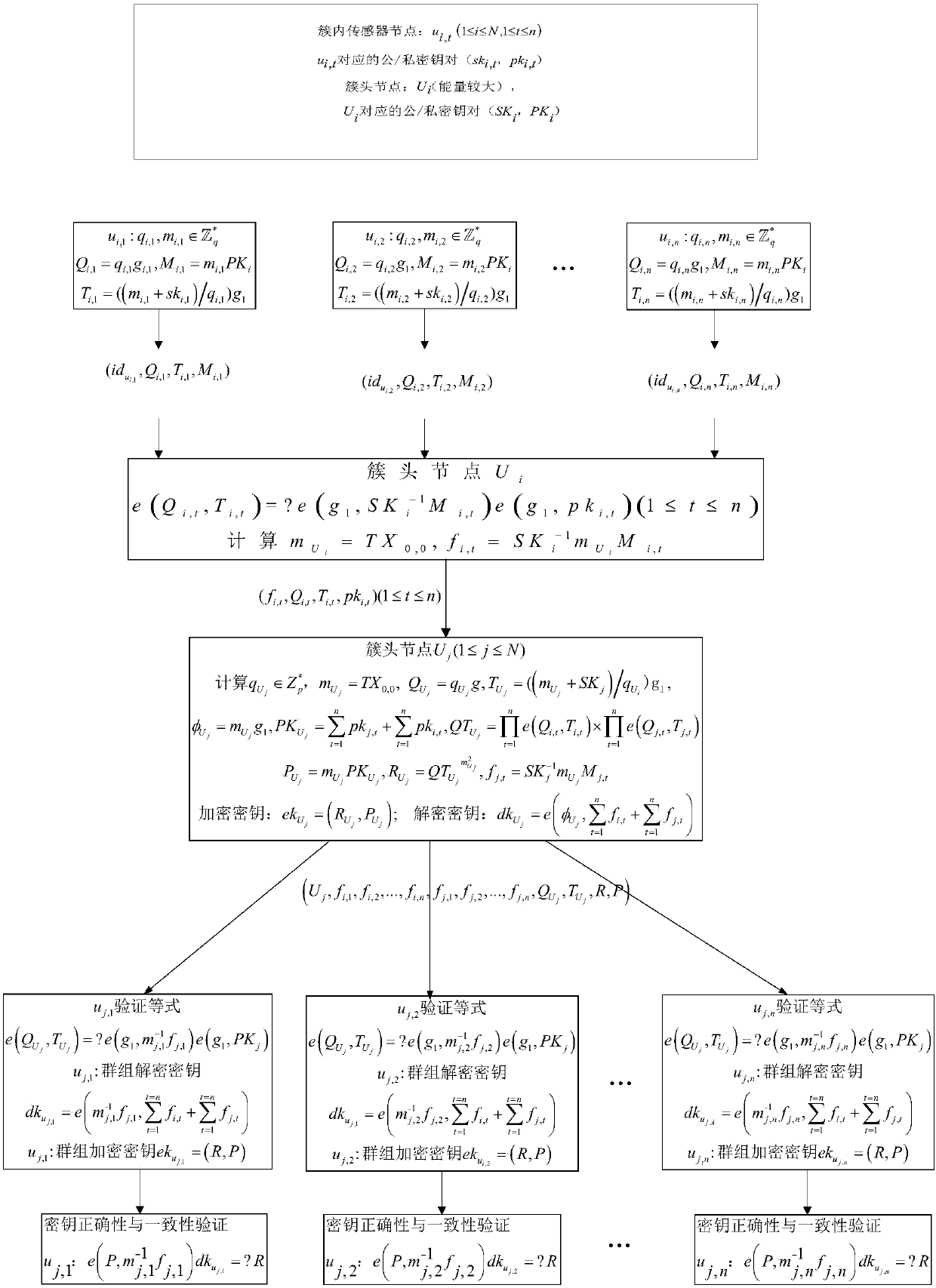
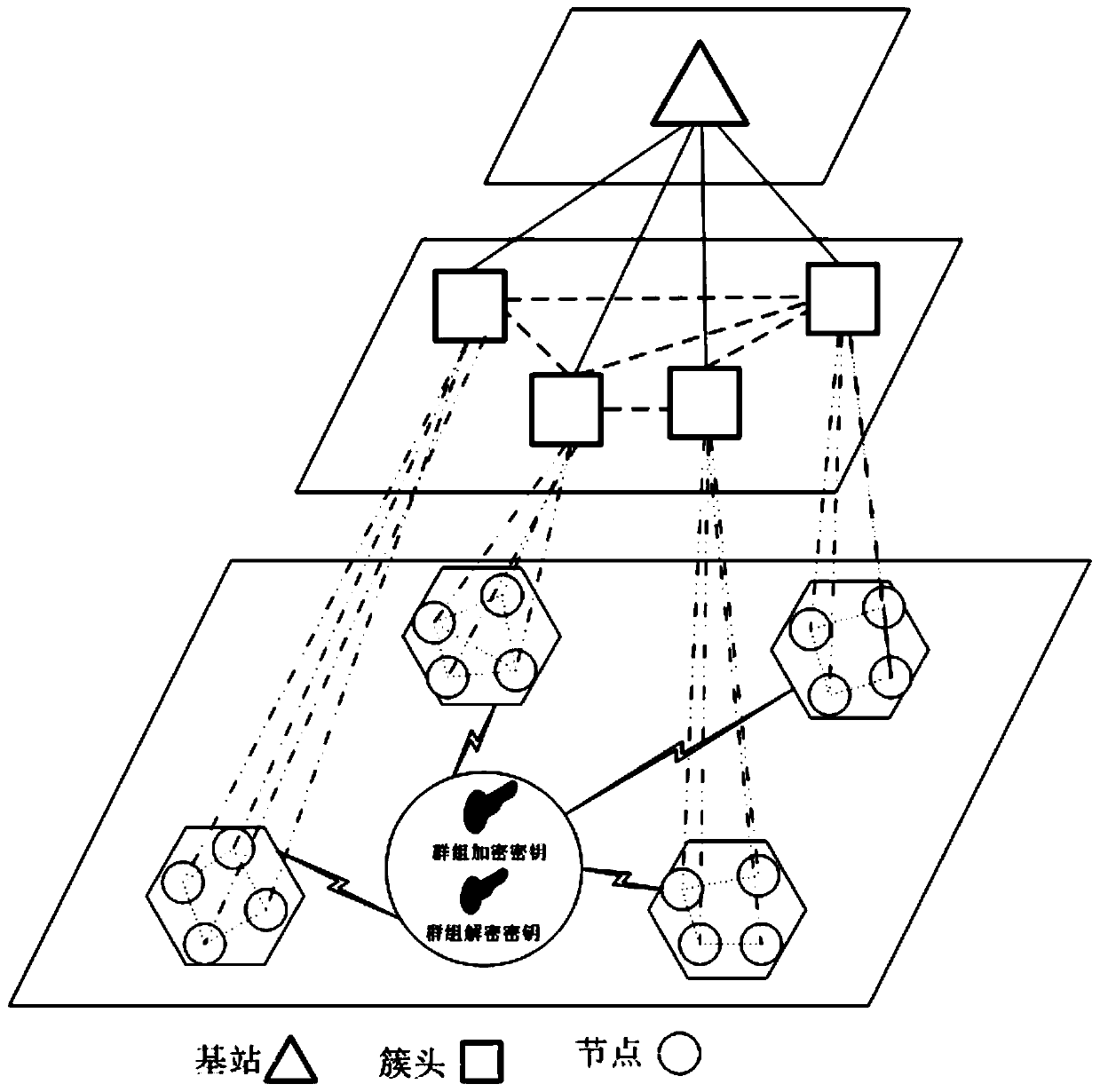
Cross-cluster asymmetric group key negotiation method in wireless sensor network
ActiveCN107204845ARealize secret information exchangeReduce communication consumptionKey distribution for secure communicationNetwork topologiesMobile wireless sensor networkLine sensor
The invention provides a cross-cluster asymmetric group key negotiation method in a wireless sensor network. The method comprises steps as follows: an allied and shared key between clusters is established, cluster heads are taken as bridging nodes, and sensor nodes of different nodes have the same group key factor information; an asymmetric computation algorithm is designed in the group key negotiation process, more computation and communication traffic of the sensor nodes are migrated to the cluster head nodes with larger energy, and the lightweight property of computation and communication overhead of the sensor nodes is ensured; self-certification property of keys is realized, additional communication rounds are not required, the sensor nodes can self-certify the correctness in computing the group keys, and the correctness and the safety of the group key negotiation are guaranteed. Group key negotiation of the sensor nodes distributed in different clusters in the wireless sensor network is realized, a safe communication channel is established, the scale of cooperative computation and information sharing of sensor node groups is further expanded, energy consumption of the sensor nodes is reduced, and the service life of the sensor nodes is prolonged.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
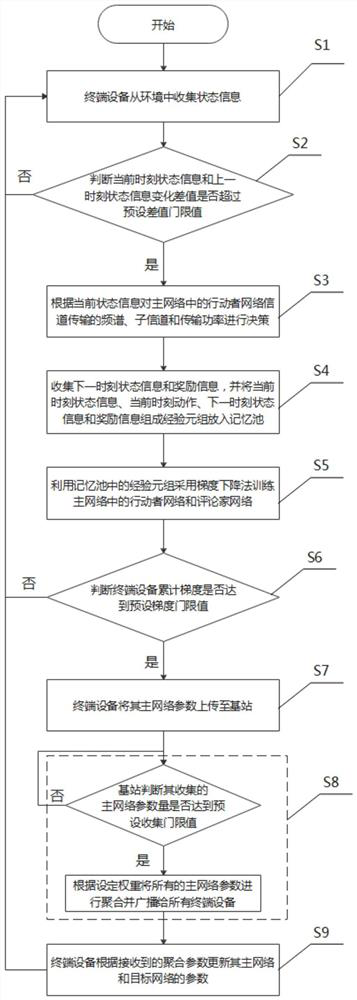
Frequency spectrum resource management and distribution method based on federated learning
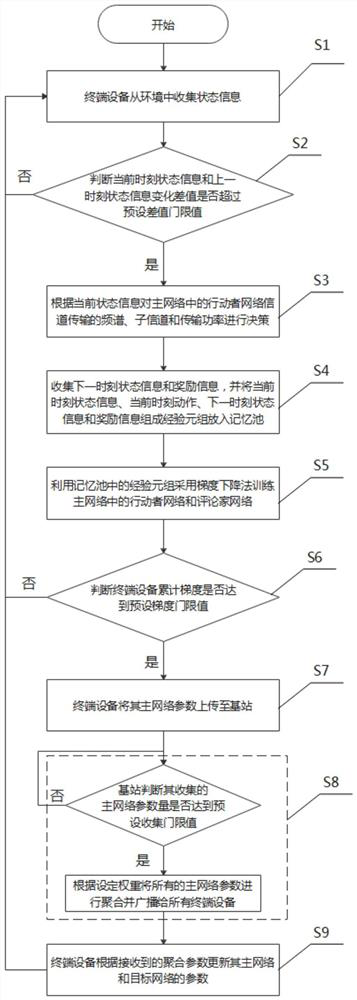
ActiveCN113038616AImprove Spectrum Utilization EfficiencyFast convergenceData switching networksHigh level techniquesFrequency spectrumTerminal equipment
The invention discloses a frequency spectrum resource management and allocation method based on federated learning. The method comprises the steps: enabling the terminal equipment to collect the state information from an environment; if the information change exceeds a threshold value, making a decision of a frequency spectrum, a sub-channel and transmission power of channel transmission; enabling the terminal equipment to collect the state information and reward information at the next moment after the decision, and adopting a gradient descent method to train an actor network and a reviewer network in the main network; when the accumulated gradient of the terminal equipment reaches a preset gradient threshold value, uploading the main network parameters of the terminal equipment to the base station; after the quantity of the main network parameters collected by the base station reaches a threshold value, aggregating the main network parameters according to a preset weight and broadcasting to all the terminal equipment; and enabling the terminal equipment to update the parameters of the main network and the target network after receiving the aggregation parameters. In order to solve the problems of low spectrum utilization rate, easy leakage of user privacy and the like in the prior art, the invention adopts an asynchronous federated learning mode, and has the advantage of low communication consumption while solving the problems.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
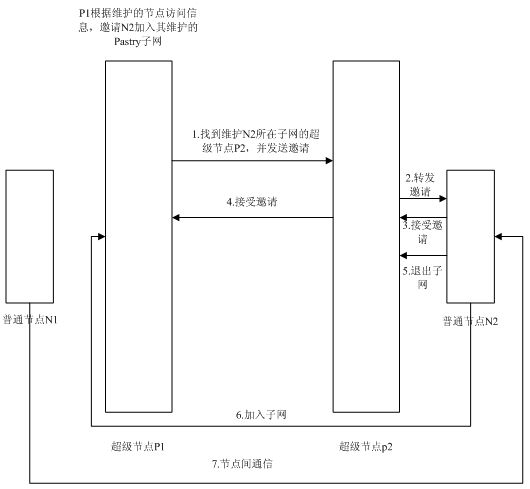
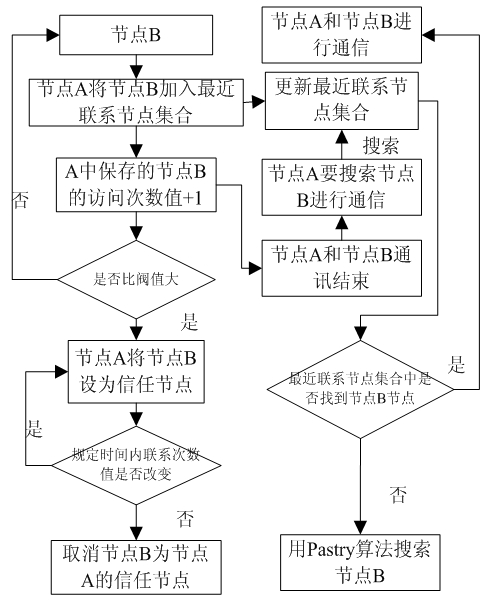
Hybrid Pastry network for voice over Internet protocol (VoIP) service
InactiveCN102104518AAvoid troubleNo wasteInterconnection arrangementsLoop networksTimestampGroup method
The invention discloses a hybrid Pastry network for a voice over Internet protocol (VoIP) service, which belongs to the technical field of networks. Nodes in the hybrid Pastry network provided by the invention are divided into super nodes and ordinary nodes, wherein the super nodes form a main Pastry network; each super node manages a Pastry sub-network consisting of the ordinary nodes, and keepsand maintains all the information of the nodes in the Pastry sub-networks managed by the super nodes; and when the nodes in the Pastry sub-networks are required to communicate with the other nodes, the other nodes are first searched in the Pastry sub-networks where the nodes are, and if the Pastry sub-networks where the nodes are do not comprise the other nodes, the other nodes are searched in the other sub-networks by the main Pastry network. The hybrid Pastry network also utilizes a dynamic contact frequency grouping method and a recently-contacting node set-trust mechanism method to further improve the searching efficiency of communication among the nodes in the network, and simultaneously introduces a timestamp mechanism to more timely update a node state table and improve the real-time of Internet calls.
Owner:NANJING UNIV OF POSTS & TELECOMM
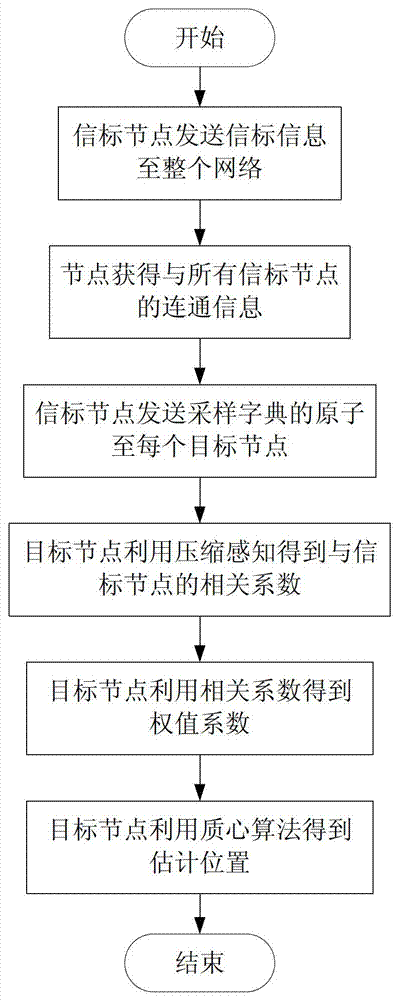
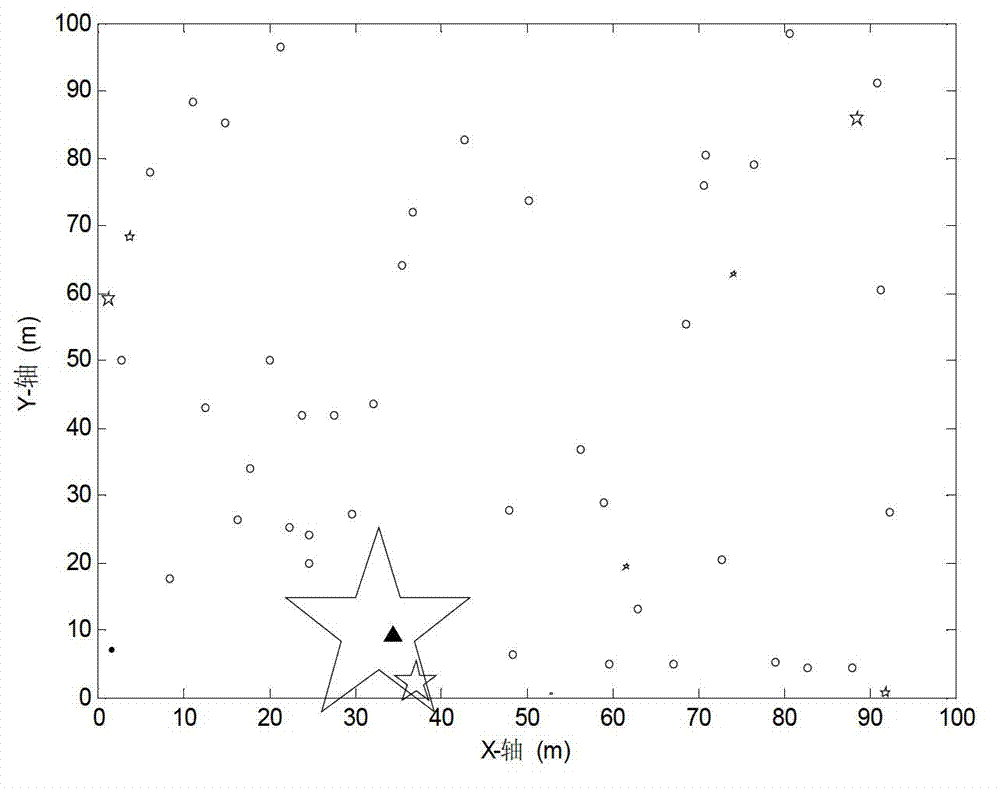
Wireless sensor network node positioning method based on compressed sensing theory
InactiveCN103200669AStrong energy efficiencyStrong reliabilityWireless communicationCorrelation coefficientWeight coefficient
The invention provides a wireless sensor network node positioning method based on a compressed sensing theory. Firstly, special information sent by beacon nodes is used for obtaining communication information of all nodes to the beacon nodes; and then a sampling matrix is obtained through the communication information obtained by the utilization of the beacon nodes, compressed communication information is obtained through target nodes, and correlation coefficients of the target nodes and all beacon nodes are obtained through a compressed sensing algorithm. Lastly, a weight coefficient of each beacon node to the target nodes is obtained by using the correlation coefficients, and an estimate position of each target node is obtained by the utilization of a centroiding algorithm. According to the wireless sensor network node positioning method based on the compressed sensing theory, the compressed sensing theory is introduced, and the correlation of the target nodes and the beacon nodes on geographic positions is fully dug. Due to the fact that the wireless sensor network node positioning method based on the compressed sensing theory fulfills four conditions, the wireless sensor network node positioning method based on the compressed sensing theory is reliable, effective, general in application, and suitable for node self-positioning of large scale networks.
Owner:HARBIN ENG UNIV
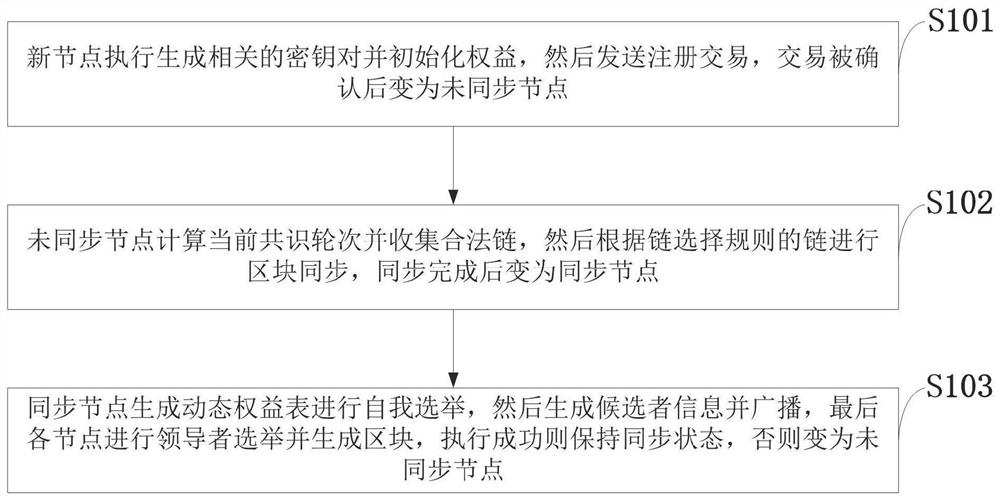
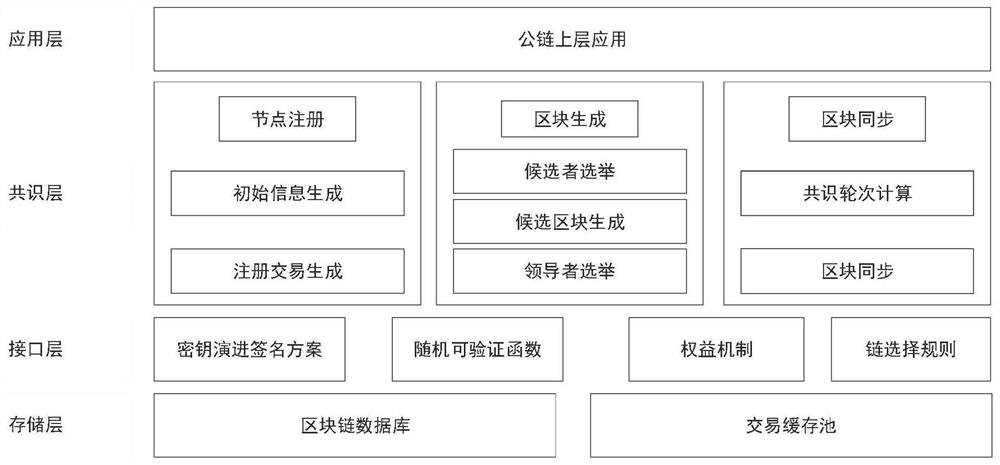
Extensible and secure consensus method and system, storage medium and intelligent terminal
ActiveCN113452747AOvercome efficiencyOvercome securitySecuring communicationComputer networkEngineering
The invention belongs to the technical field of a distributed system consensus mechanism and a block chain public chain, and discloses an extensible and secure consensus method and system, a storage medium and an intelligent terminal, comprising three protocols of node registration, block generation and block synchronization; according to a node registration protocol, a new node generates initial information and initialized right information, generates a node registration transaction by using public information and right information, and then sends the node registration transaction to a consensus network for node registration to become a network node; according to a block generation protocol, a consensus node generates a node right share table and a random number to perform candidate election, then a candidate generates compressed candidate blocks and broadcasts the compressed candidate blocks, and other nodes verify candidate block information and then select the candidate blocks meeting conditions as leaders to generate blocks; according to the block synchronization protocol, an unsynchronized node calculates a current consensus round and verifies the legality of a received chain, and a chain is selected for synchronization by using a chain selection rule. The security attribute of the scheme is improved, and the expandability of the scheme is effectively improved.
Owner:XIDIAN UNIV +1
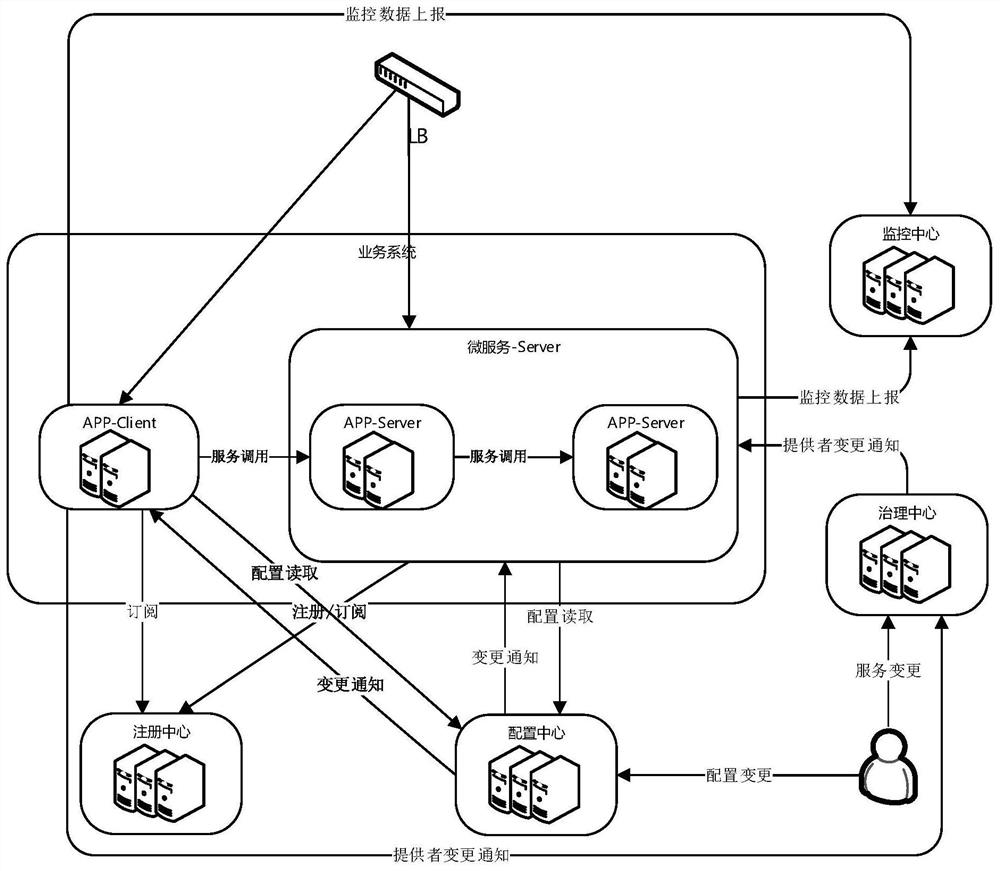
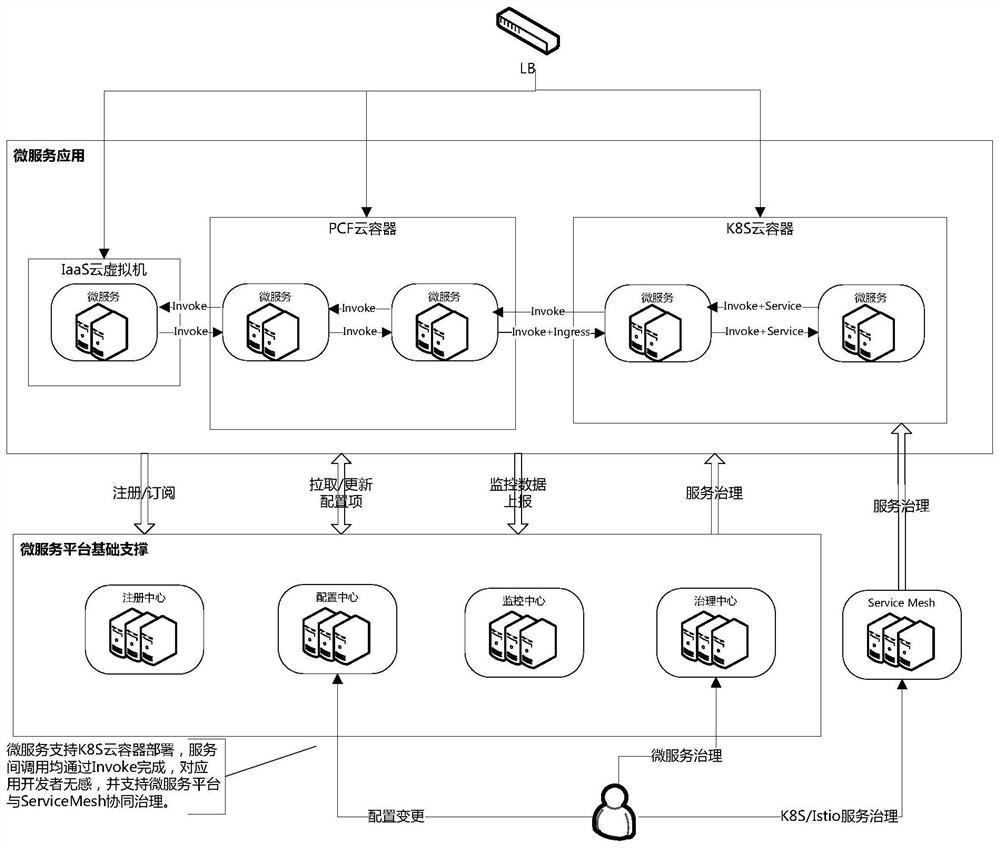
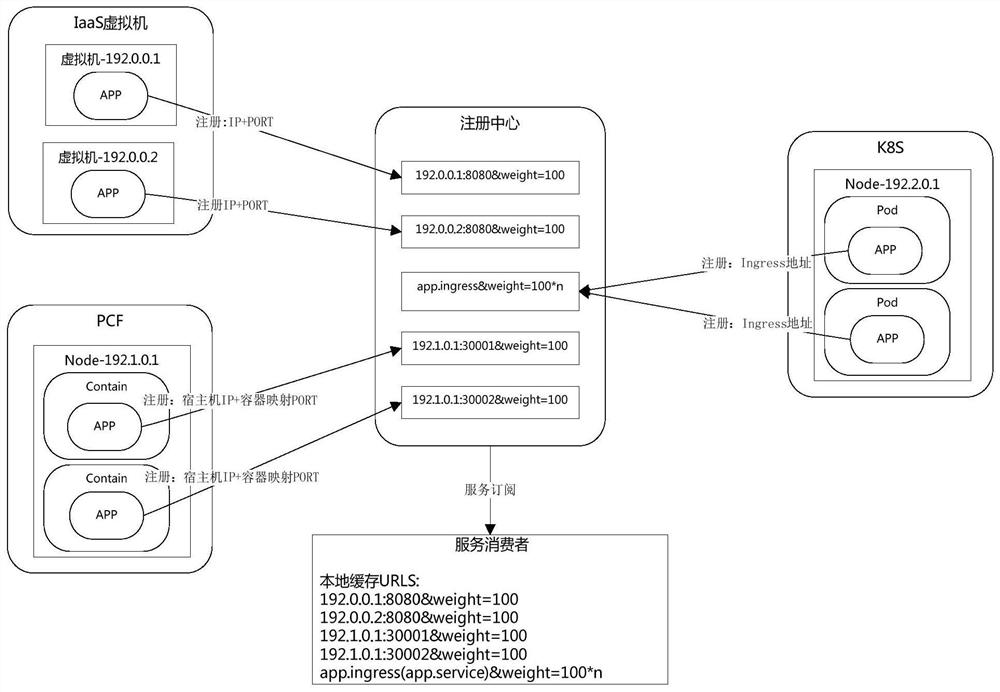
Heterogeneous cloud-oriented cloud native micro-service platform
PendingCN113596110AReduce communication consumptionReduce transaction timeResource allocationTransmissionService providerInformation monitoring
The invention relates to a heterogeneous cloud-oriented cloud native micro-service platform, which comprises a micro-service application subsystem, a micro-service application deployed based on a Kubernetes cloud management platform, a Cloud Foundry cloud management platform and an IaaS cloud virtual machine, and a cloud native micro-service adaptation operation of the heterogeneous cloud constructed by combining a micro-service platform basic support subsystem and a ServiceMesh technology, the micro-service platform basic support subsystem interacts with the micro-service application subsystem, receives registration and subscription requests of the micro-service application subsystem, and provides information configuration, information monitoring and service management channels for a management user side; the management user side manages and maintains the micro-service application deployed by the Kubernetes cloud management platform through ServiceMesh, so as to realize the function management of the micro-service basic component; and a service calling party subscribes the total service list information from the registration center, and selects a service provider to send a request according to a load balancing algorithm. Compared with the prior art, the method has the advantages of realizing unified micro-service management of the heterogeneous cloud management platform and the like.
Owner:交通银行股份有限公司太平洋信用卡中心
Location privacy protection anonymous query method based on SF-blind filtering protocol
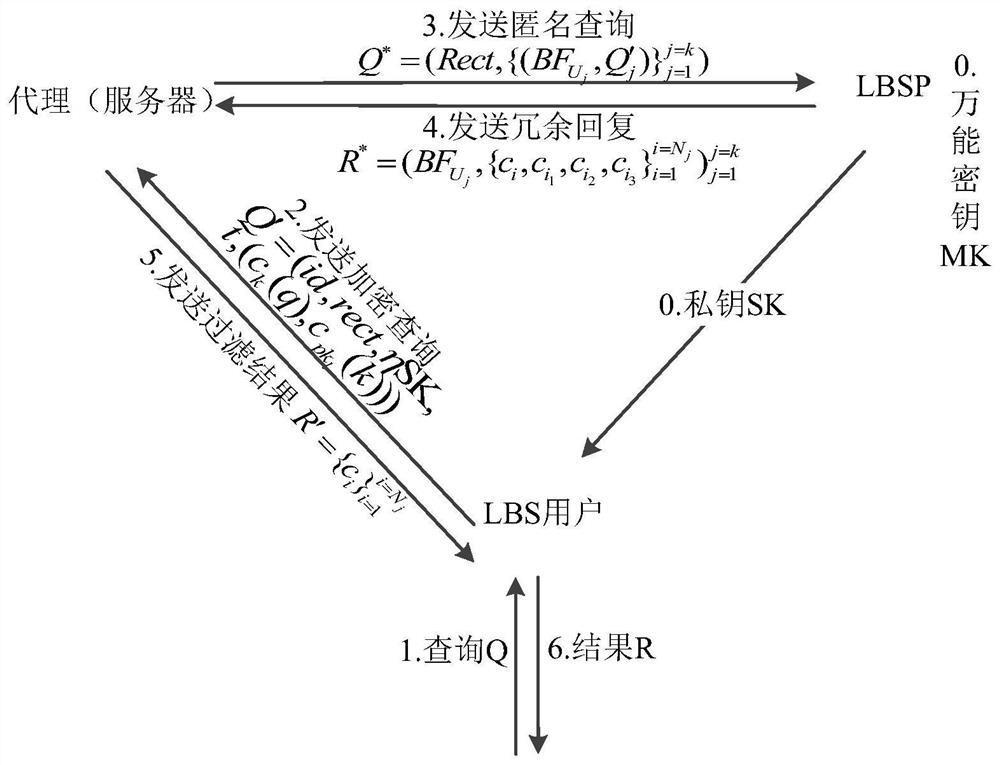
InactiveCN113468440AFind and verify fastEnsure safetyDigital data information retrievalDigital data protectionPrivacy protectionData file
The invention discloses a location privacy protection anonymous query method based on an SF-blind filtering protocol. The method comprises the following steps: during LBS query, generating a data file tag through methods such as a Bloom filter and the like, and hiding sensitive information including identity and position of an LBS user for an LBSP; and hiding, by the LBSP, the returned result from the agent through a blind filtering method based on the SF, wherein each POI of the LBS user is stored in the LBSP; when the POI is returned as one of the results of a certain query, encryption is carried out through a session key, the LBSP calculates parameters related to the position of the POI at the same time to serve as input of blind filtering, and in a blind filtering protocol, SF is generated and a public key of the LBSP is used for encrypting and adding into response of the LBSP; thereby, only the private key of the LBS user whose attribute satisfies the access tree can decrypt and obtain the SF, and the accurate demand of the legal user for the location service is matched.
Owner:SHAANXI UNIV OF SCI & TECH
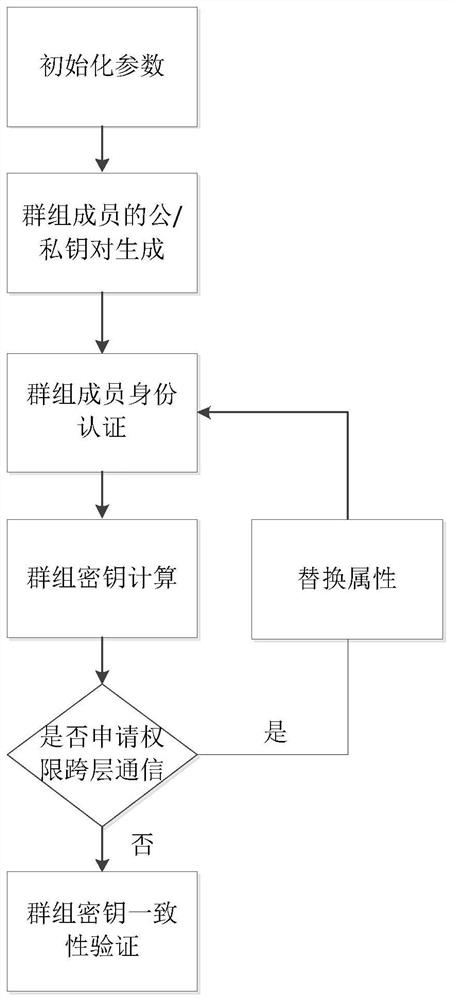
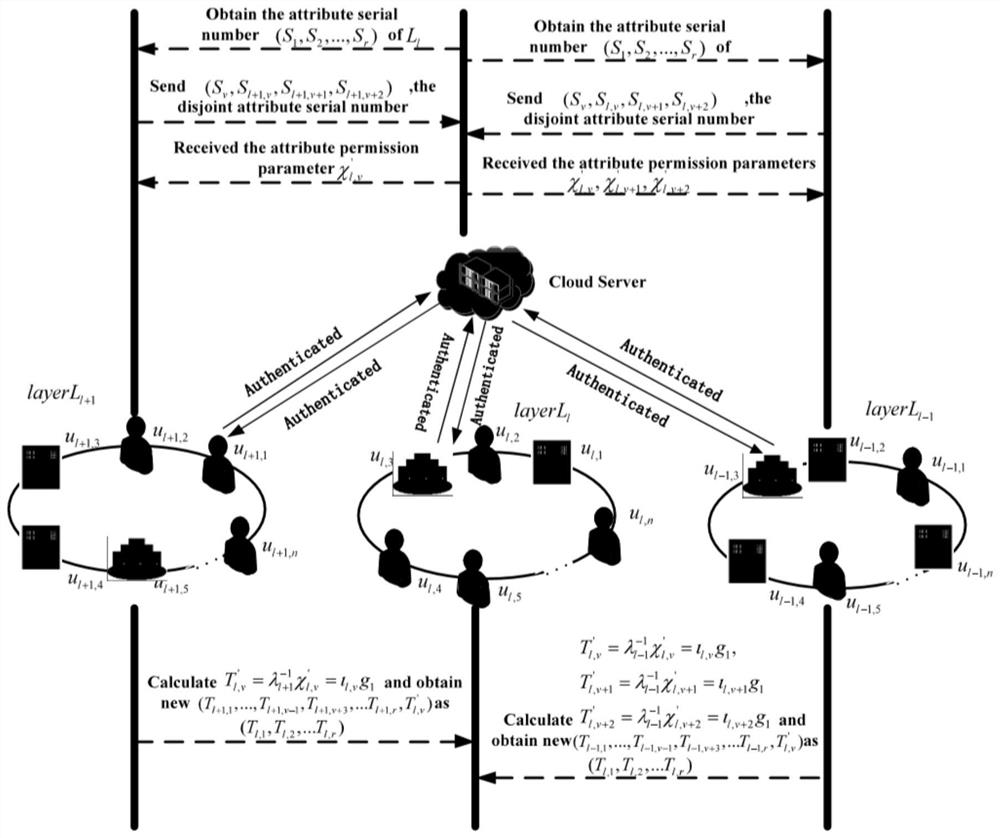
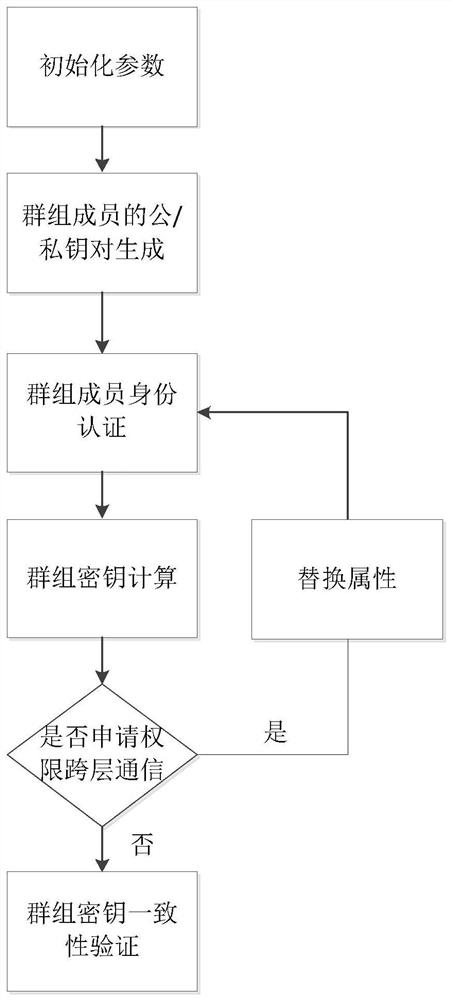
Hierarchical dynamic group key negotiation method based on privacy protection
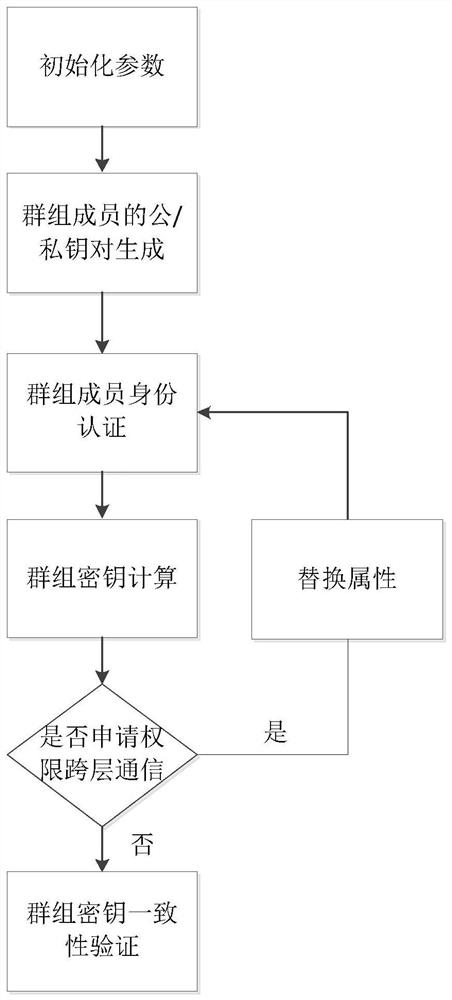
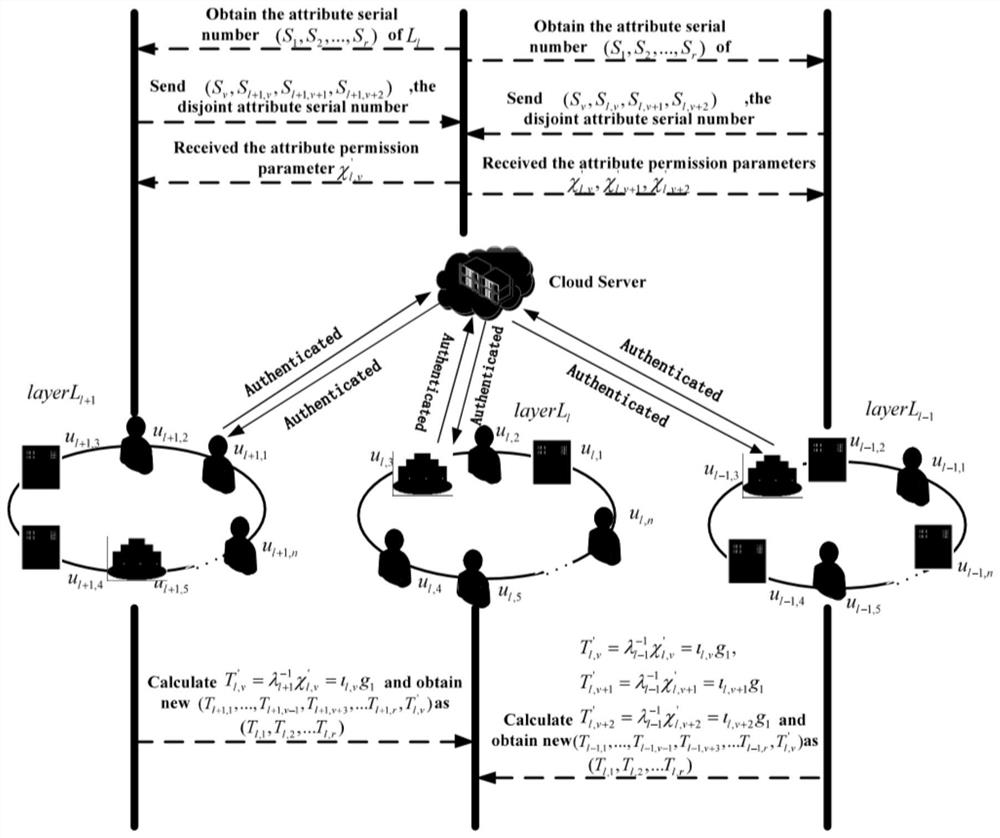
ActiveCN113346993AGuaranteed reliabilityCommunication securityKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessPrivacy protection
The invention provides a hierarchical dynamic group key negotiation method based on privacy protection, which comprises the following steps of: initializing protocol parameters in a group key agreement network domain, generating public / private key pairs of an authentication center and terminal members, performing identity authentication of hidden attributes by the terminal members, and after the authentication is successful, carrying out group key agreement on the terminal members. The terminal member calculates an encryption key and a decryption key according to the attribute weight of the terminal member, verifies the consistency of the keys, and can also apply for attribute change from the authentication center to participate in group key negotiation of a high layer or a low layer. According to the method, the identity authentication technology with hidden attributes is adopted, leakage of personal privacy information can be avoided during identity authentication. Meanwhile, the threshold permission is set according to the attribute weights, group communication is participated in with different confidentialities, the reliability of data communication is improved, and a double-authentication mechanism of identity authentication and attribute weight matching is adopted, so that the reliability of data communication is improved. The safety of the system is improved to a great extent, and the group key negotiation is more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Bullet screen data processing method and device, storage medium and electronic equipment
PendingCN113573134AEasy to handleReduce communication consumptionSelective content distributionComputer hardwareArray data structure
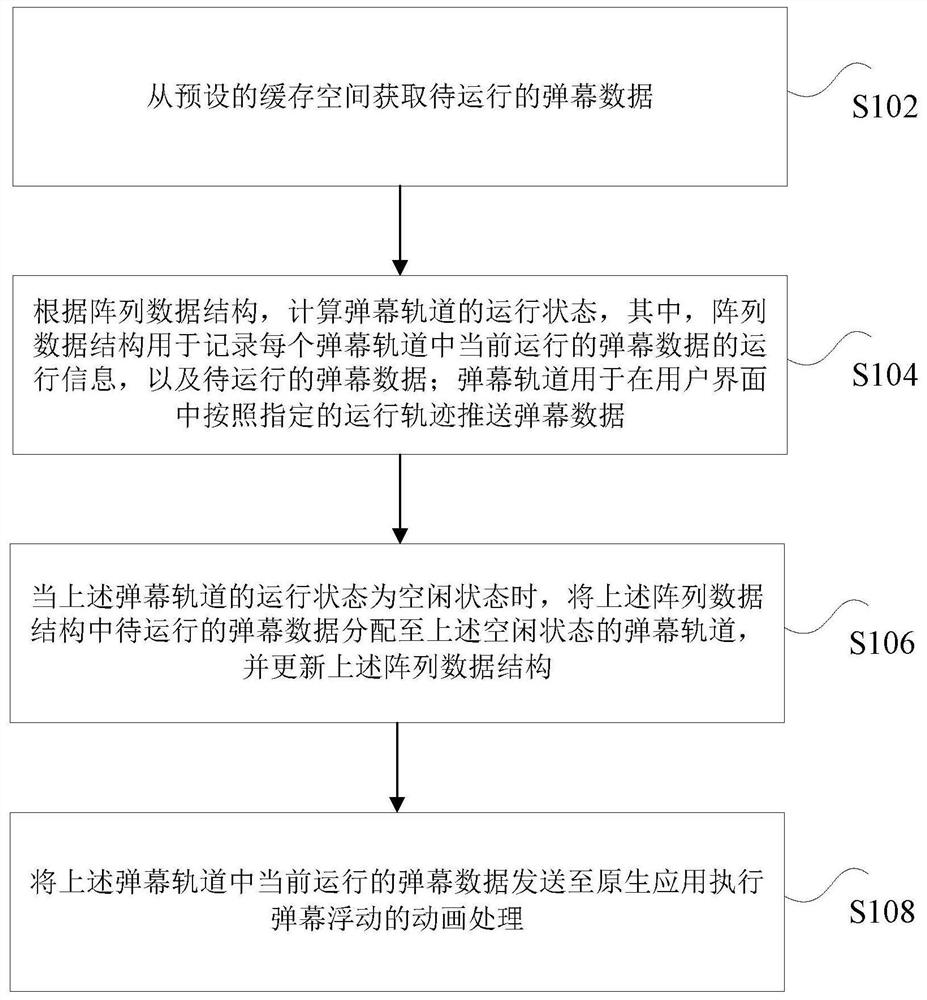
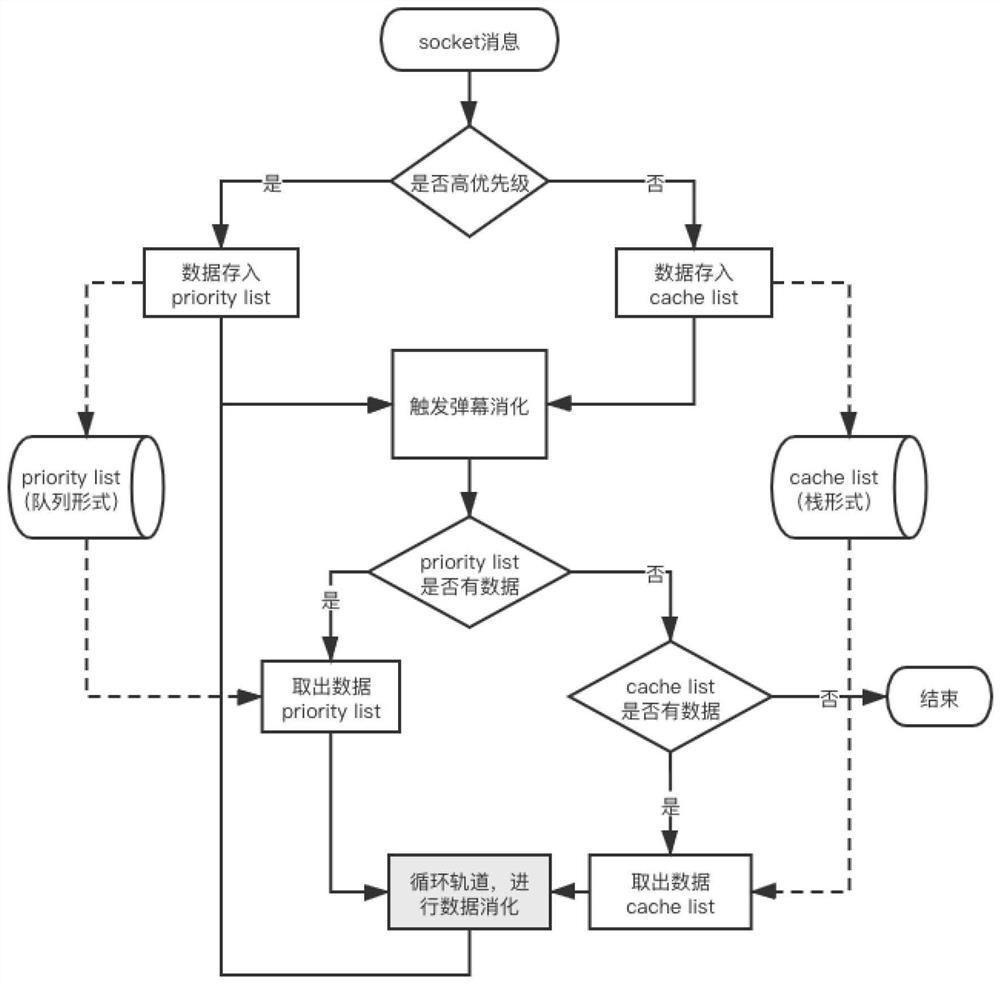
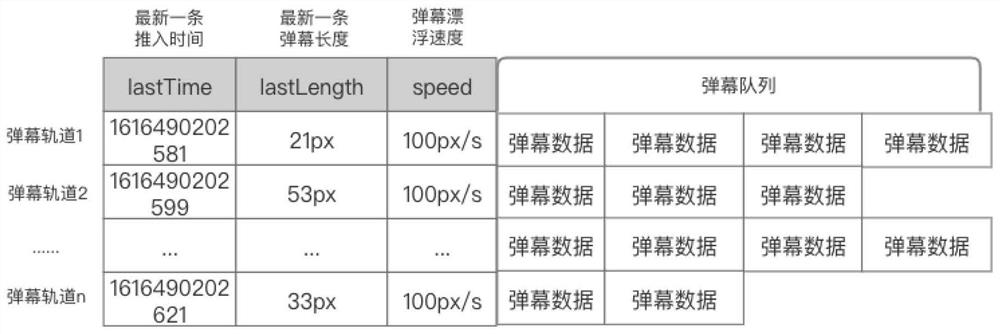
The invention relates to a bullet screen data processing method and device, a storage medium and electronic equipment. The method comprises the following steps: acquiring bullet screen data to be operated from a preset cache space; according to an array data structure, calculating the running state of the bullet screen track, wherein the array data structure is used for recording running information of bullet screen data running currently in each bullet screen track and bullet screen data to be run, and the bullet screen track is used for pushing bullet screen data in the user interface according to a specified moving track; when the operation state of the bullet screen track is an idle state, allocating bullet screen data to be operated in the array data structure to the bullet screen track in the idle state, and updating the array data structure; and sending the bullet screen data currently running in the bullet screen track to the native application to execute animation processing of bullet screen floating. According to the method and the device, the technical problem of relatively high communication consumption between the JS process and the native application caused by relatively low bullet screen data processing performance in the prior art is solved.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Construction method, topology analysis method and device of power grid subgraph based on area division
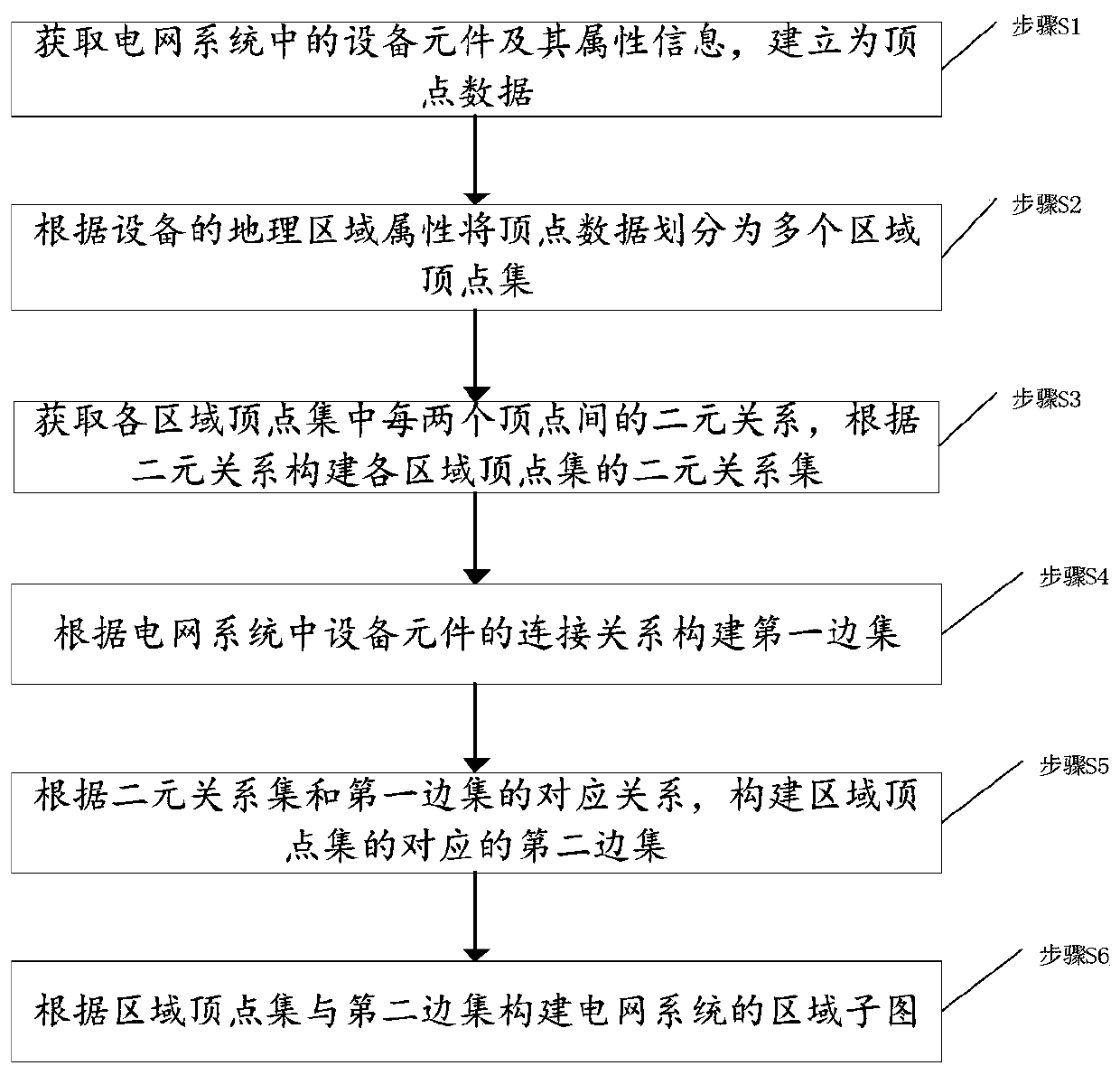
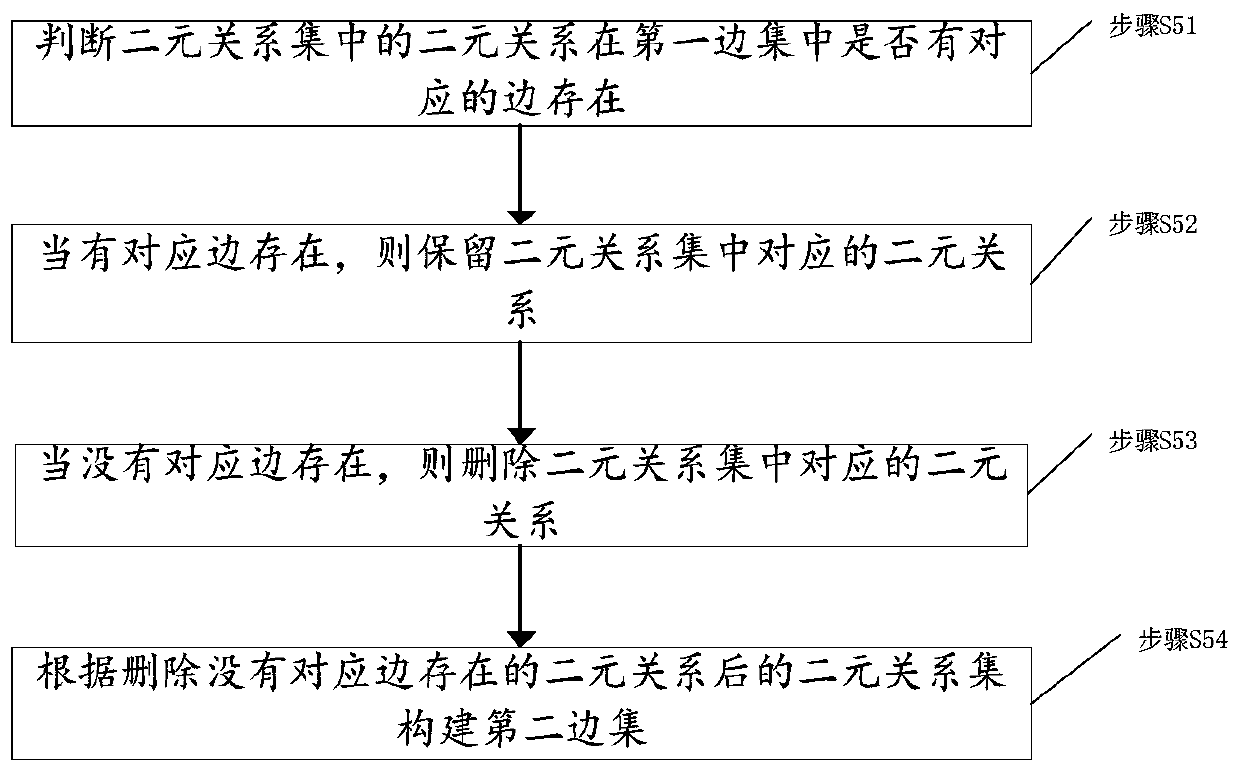
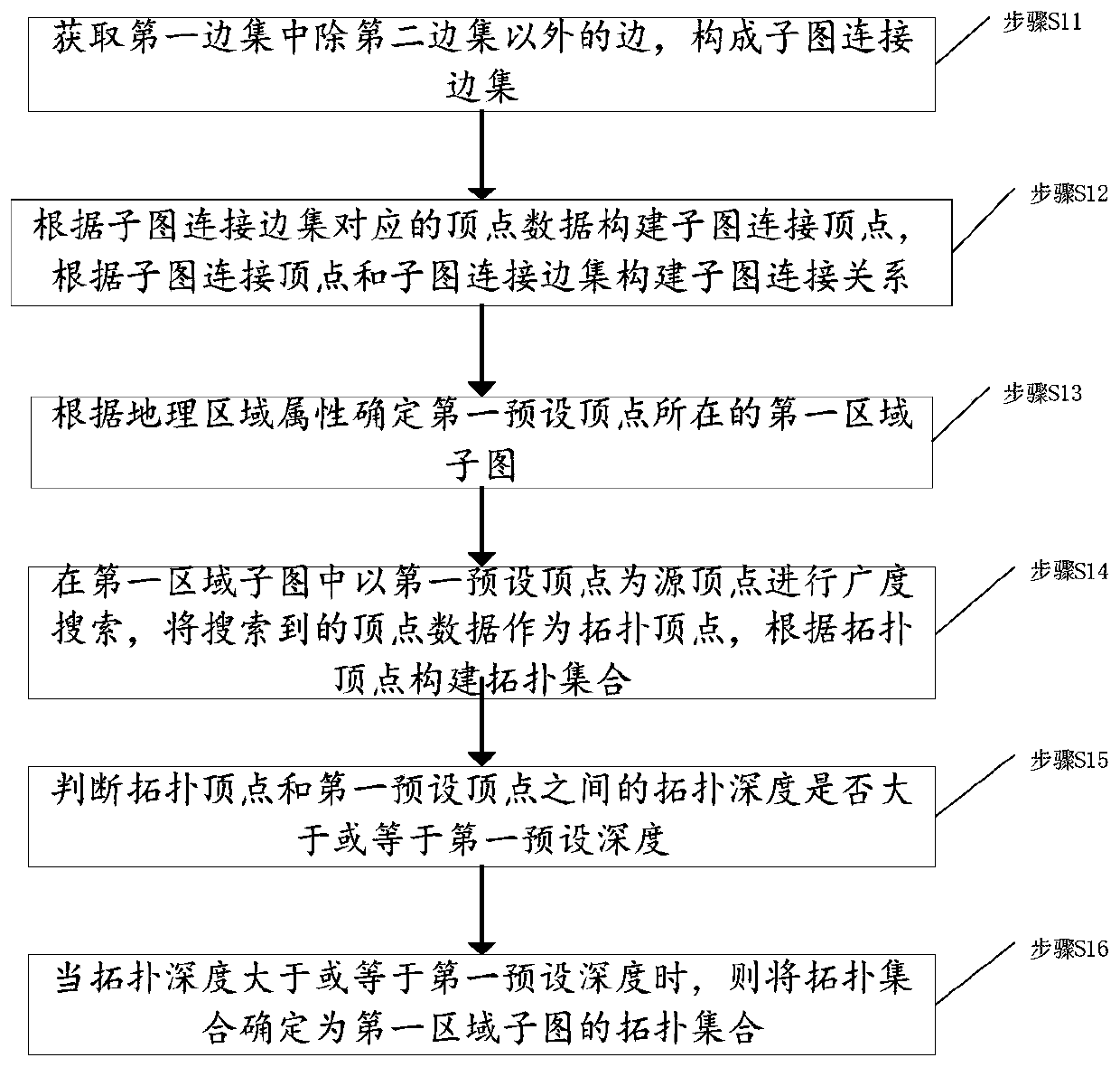
ActiveCN109412149BNot lostReduce communication consumptionAc network circuit arrangementsGeographic regionsAlgorithm
The invention discloses a power grid sub-graph construction method based on region division, a topology analysis method, a power grid sub-graph construction device based on region division, and a topology analysis device. The power grid sub-graph construction method comprises the following steps: acquiring equipment components and attribute information thereof in a power grid system for establishment as vertex data; dividing the vertex data into a plurality of region vertex sets according to a geographic region attribute of the equipment; acquiring a binary relationship between each two vertices in each region vertex set, and constructing a binary relationship set of each region vertex set according to the binary relationship; constructing a first edge set according to the connection relationship of the equipment components in the power grid system; constructing a second edge set corresponding to the region vertex sets according to the correspondence between the binary relationship setand the first edge set; and constructing a region sub-graph of the power grid system according to the region vertex sets and the second edge set. By implementing the invention to effectively divide the power grid data, the divided sub-graphs are relatively balanced in scale, thereby realizing distributed storage and parallel processing of the power grid data, and improving the efficiency of topology analysis.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
An intelligent electronic label information system and its information interaction method
ActiveCN102682317BReduce manufacturing costImprove management efficiencyCo-operative working arrangementsData privacy protectionSoftware engineering
The invention provides an intelligent electronic label information system, which comprises an electronic label and a reader-writer, wherein the electronic label stores an instruction which can be read by the reader-writer; and the reader-writer stores a procedure code corresponding to the instruction and is used for reading the instruction stored by the electronic label and executing the corresponding procedure code. By the intelligent electronic label information system, the equipment manufacturing cost of the electronic label system can be greatly reduced, and the management and running efficiency can be improved; and the implementation range of the electronic label system can be deeply expanded. Furthermore, the storage space of the electronic label is effectively saved, and the transmission consumption and the communication consumption during partial interaction can be reduced. Moreover, a phenomenon that all types of data information are concentratively transmitted to a uniform background server is avoided, the bandwidth consumption and the communication cost of large-scale data transmission in multiple types of application are reduced, the probability that important data information leaks is reduced, and data privacy protection is facilitated.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Cross-cluster asymmetric group key agreement method in wireless sensor networks
ActiveCN107204845BRealize secret information exchangeReduce communication consumptionKey distribution for secure communicationNetwork topologiesLine sensorMobile wireless sensor network
The invention provides a cross-cluster asymmetric group key negotiation method in a wireless sensor network. The method comprises steps as follows: an allied and shared key between clusters is established, cluster heads are taken as bridging nodes, and sensor nodes of different nodes have the same group key factor information; an asymmetric computation algorithm is designed in the group key negotiation process, more computation and communication traffic of the sensor nodes are migrated to the cluster head nodes with larger energy, and the lightweight property of computation and communication overhead of the sensor nodes is ensured; self-certification property of keys is realized, additional communication rounds are not required, the sensor nodes can self-certify the correctness in computing the group keys, and the correctness and the safety of the group key negotiation are guaranteed. Group key negotiation of the sensor nodes distributed in different clusters in the wireless sensor network is realized, a safe communication channel is established, the scale of cooperative computation and information sharing of sensor node groups is further expanded, energy consumption of the sensor nodes is reduced, and the service life of the sensor nodes is prolonged.
Owner:河南招源科技有限公司
Dynamic cluster radius-based non-uniform clustering method for wireless sensor network
PendingCN113490253AReduce the number of membersReduce communication consumptionPower managementNetwork topologiesDynamic clusteringEngineering
The invention discloses a dynamic cluster radius-based non-uniform clustering method for a wireless sensor network. The wireless sensor network comprises a base station and a plurality of sensor nodes, wherein the base station is fixedly located in a network center and can collect data of the whole network sensor through a multi-hop routing transmission method, and the data comprises the collected data and electric quantity information of the base station. The sensor nodes are randomly deployed on the wireless sensor network to monitor the surrounding environment, and data are transmitted among the sensor nodes through routing, so that different nodes have different energy consumption rates. According to the method, the defects in the prior art are overcome, and the cluster radius can be automatically changed along with the operation of the network, namely, the cluster radius of the cluster head with more residual energy is increased, more loads are actively borne, and tasks are shared for other cluster heads; the cluster radius of the cluster head with small residual energy is reduced, and some loads are reduced to save energy, so that the purpose of better uniformizing the energy consumption of the network is achieved.
Owner:NANJING UNIV OF POSTS & TELECOMM
A Method of Spectrum Resource Management and Allocation Based on Federated Learning
ActiveCN113038616BImprove Spectrum Utilization EfficiencyFast convergenceTransmissionHigh level techniquesFrequency spectrumTerminal equipment
The invention discloses a method for managing and allocating frequency spectrum resources based on federated learning. The method includes that the terminal device collects state information from the environment; if the information change exceeds a threshold value, making a decision on the frequency spectrum, sub-channel and transmission power of the channel transmission; the terminal device collects the state information and reward information at the next moment after the decision, And use the gradient descent method to train the actor network and critic network in the main network; when the cumulative gradient of the terminal device reaches the preset gradient threshold, the main network parameters are uploaded to the base station; the main network parameters collected by the base station reach the threshold After the value is set, the main network parameters are aggregated and broadcast to all terminal devices according to the preset weight; the terminal devices update the parameters of their main network and target network after receiving the aggregated parameters. In order to solve the problems of low spectrum utilization rate and easy disclosure of user privacy in the prior art, the present invention adopts an asynchronous federated learning method, and has the advantage of low communication consumption while solving the above problems.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
A Privacy-Preserving Hierarchical Dynamic Group Key Agreement Method
ActiveCN113346993BImprove securityEnsure safetyKey distribution for secure communicationUser identity/authority verificationConfidentialityPrivacy protection
The invention proposes a layered dynamic group key negotiation method based on privacy protection. The steps are: initializing the protocol parameters in the group key negotiation network domain, generating public / private key pairs of the authentication center and terminal members, Terminal members perform identity authentication of hidden attributes. After successful authentication, terminal members calculate encryption keys and decryption keys according to their own attribute weights to verify the consistency of the keys. Terminal members can also apply to the authentication center to change attributes to participate in High-level or low-level group key negotiation. The invention adopts the identity authentication technology of hidden attributes, which can avoid the leakage of personal privacy information while performing identity authentication, and set threshold authority according to the attribute weight value, participate in group communication with different confidentiality, and improve the reliability of data communication. The dual authentication mechanism of identity authentication and attribute weight matching greatly improves the security of the system and makes group key negotiation more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Boundary Node Identification Method for Distributed Wireless Sensor Networks
InactiveCN105050099BReduce complexityReduce computational complexityNetwork topologiesNetwork planningMobile wireless sensor networkRound complexity
Owner:ZHONGBEI UNIV
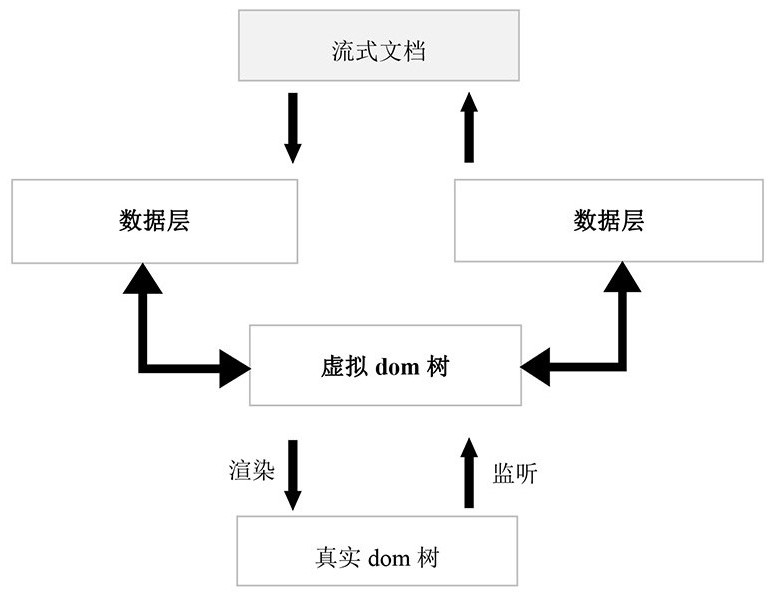
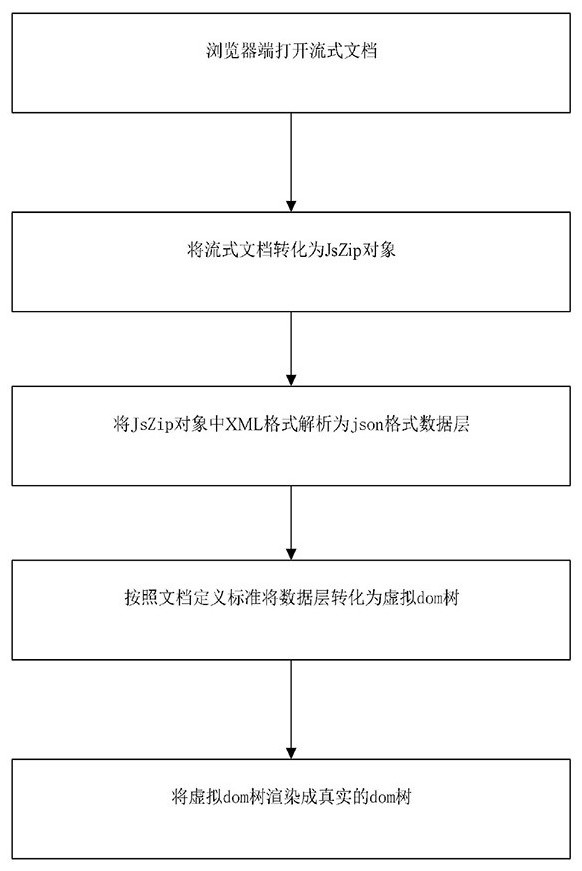
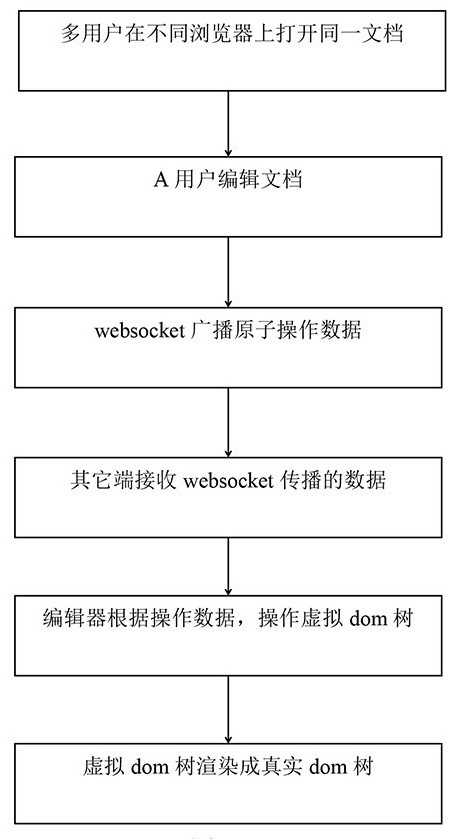
Streaming document online editing method
ActiveCN113723064AReduce communication consumptionHigh speedText processingTransmissionWebSocketEngineering
The invention relates to the technical field of data processing, in particular to a streaming document online editing method. The method comprises an online editing mode and a collaborative editing mode, the online editing mode comprises the steps of opening a streaming document through a browser end, and particularly, directly performing format conversion on the streaming document through JavaScript; monitoring cursor changes and events, operating the virtual dom tree, changing a data layer, and rendering a real dom tree; the collaborative editing mode specifically comprises the steps of opening the same document at a plurality of different browser ends, and connecting the websocket service at the same time; monitoring atomization operations of all users by an editor to generate corresponding atomization operation data; and receiving by the and broadcasting to all online editing browser ends. The communication consumption between the front end and the rear end is effectively reduced, and the influence of the network environment is avoided.
Owner:冠群信息技术(南京)有限公司
Resource monitoring method, device and system
ActiveCN106487601BReduce network transmissionReduce communication consumptionData switching networksMonitoring systemEngineering
Owner:ZTE CORP
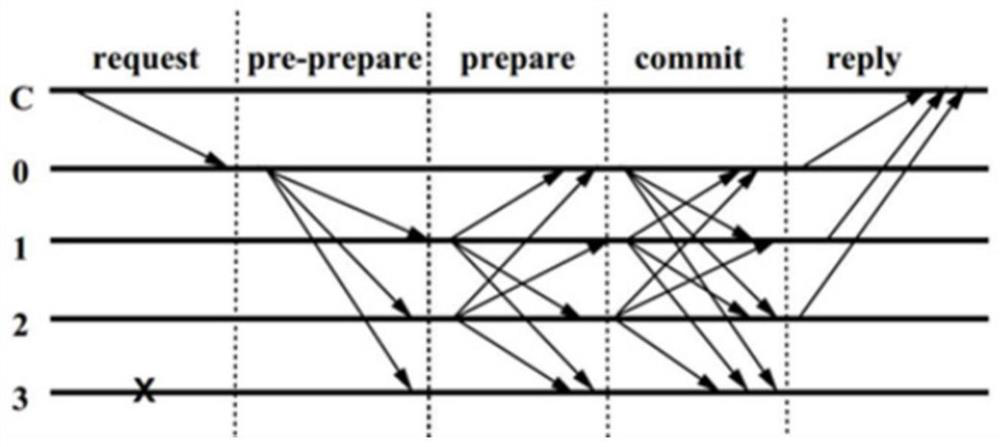
Improved PBFT consensus method and device, intelligent terminal and storage medium
ActiveCN112866399ASave time and costReduce communication consumptionTransmissionComputer networkEngineering
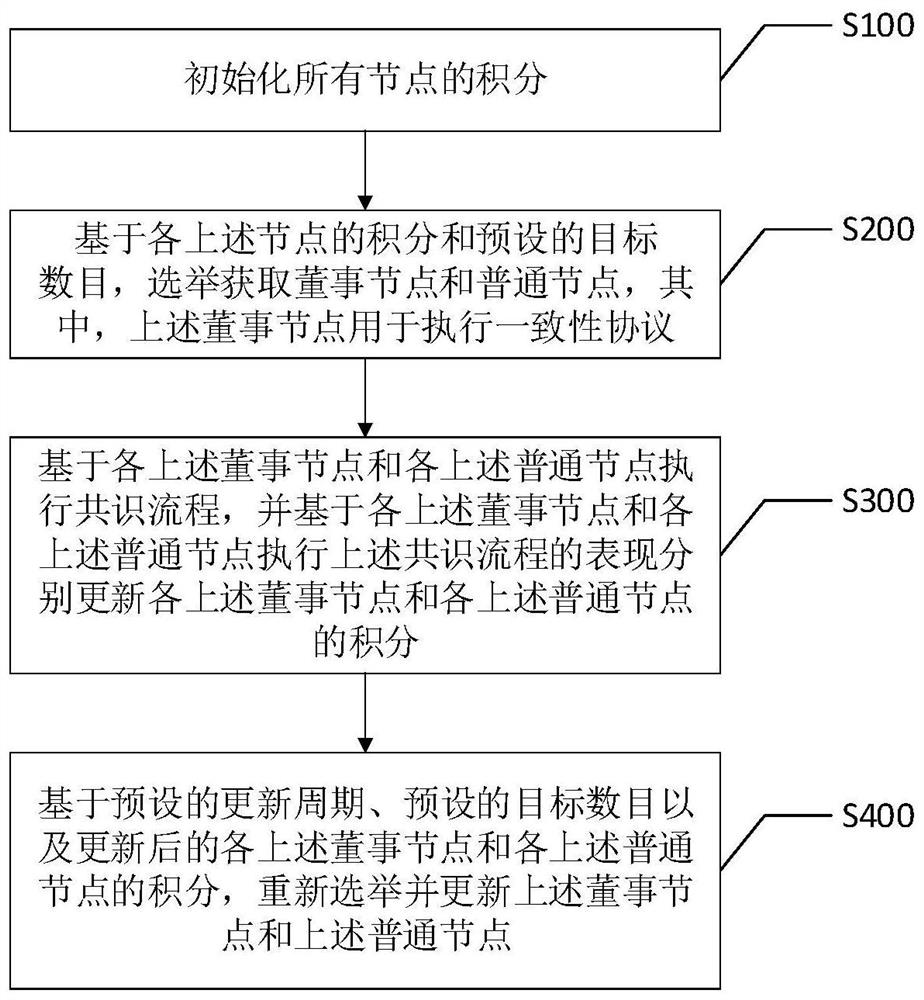
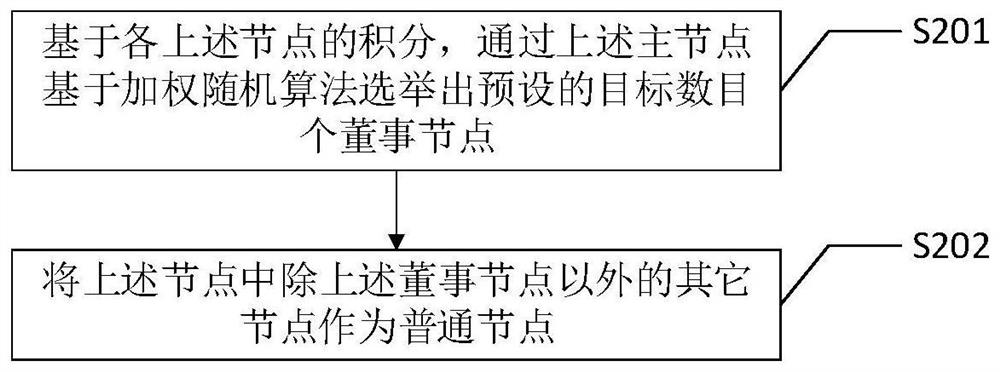
The invention discloses an improved PBFT consensus method and device, an intelligent terminal and a storage medium, and the improved PBFT consensus method comprises the steps: initializing the integrals of all nodes; based on the integral of each node and a preset target number, selecting and obtaining board nodes and common nodes, wherein the board nodes are used for executing a consistency protocol; executing a consensus process based on the board nodes and the common nodes, and updating the integral of the board nodes and the common nodes based on the performance of executing the consensus process by the board nodes and the common nodes; and re-electing and updating the board nodes and the common nodes based on a preset updating period, a preset target number and the updated integrals of the board nodes and the common nodes. According to the improved PBFT consensus method provided by the scheme of the invention, the communication consumption is reduced, and the time cost of the block chain is reduced.
Owner:SHENZHEN UNIV
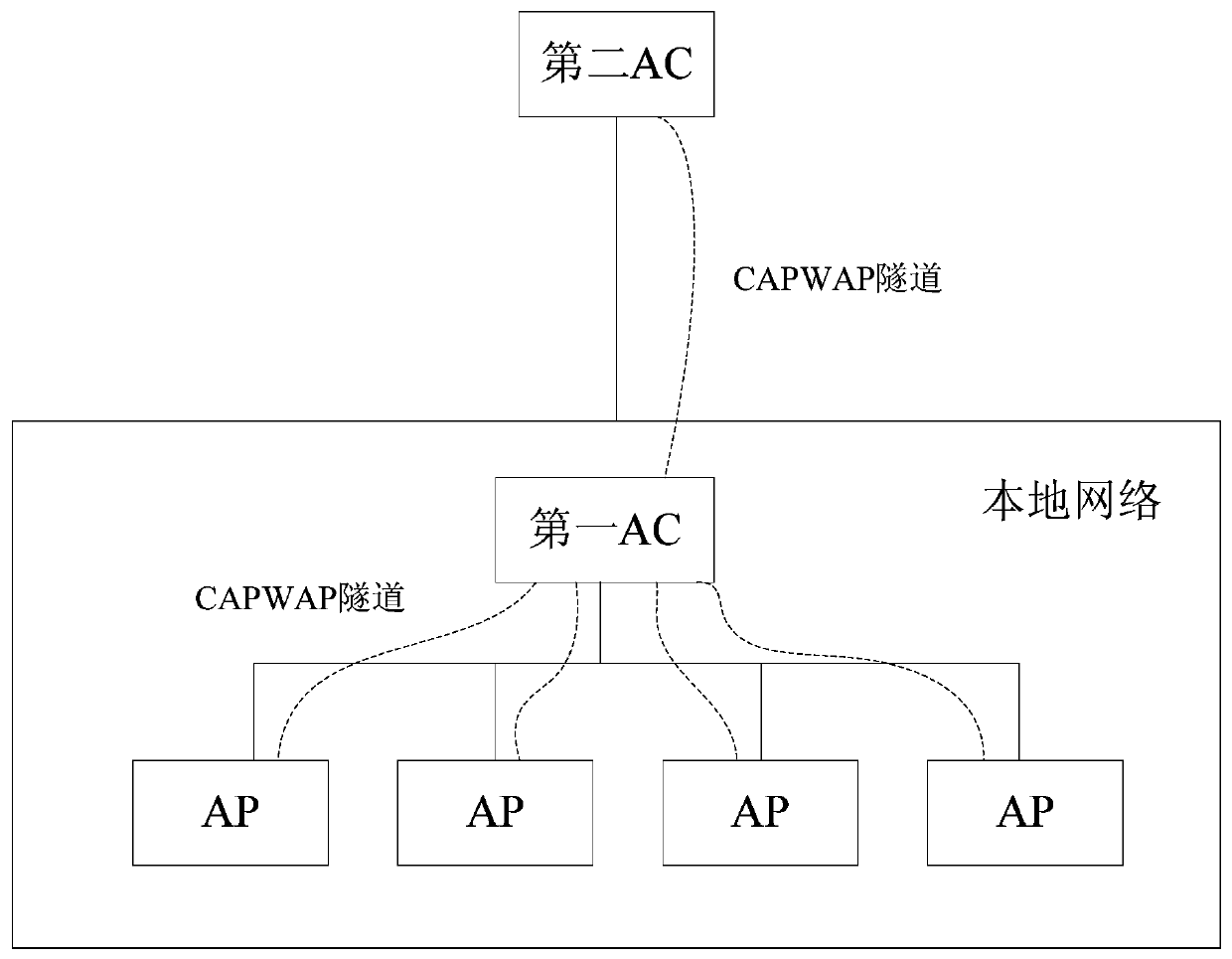
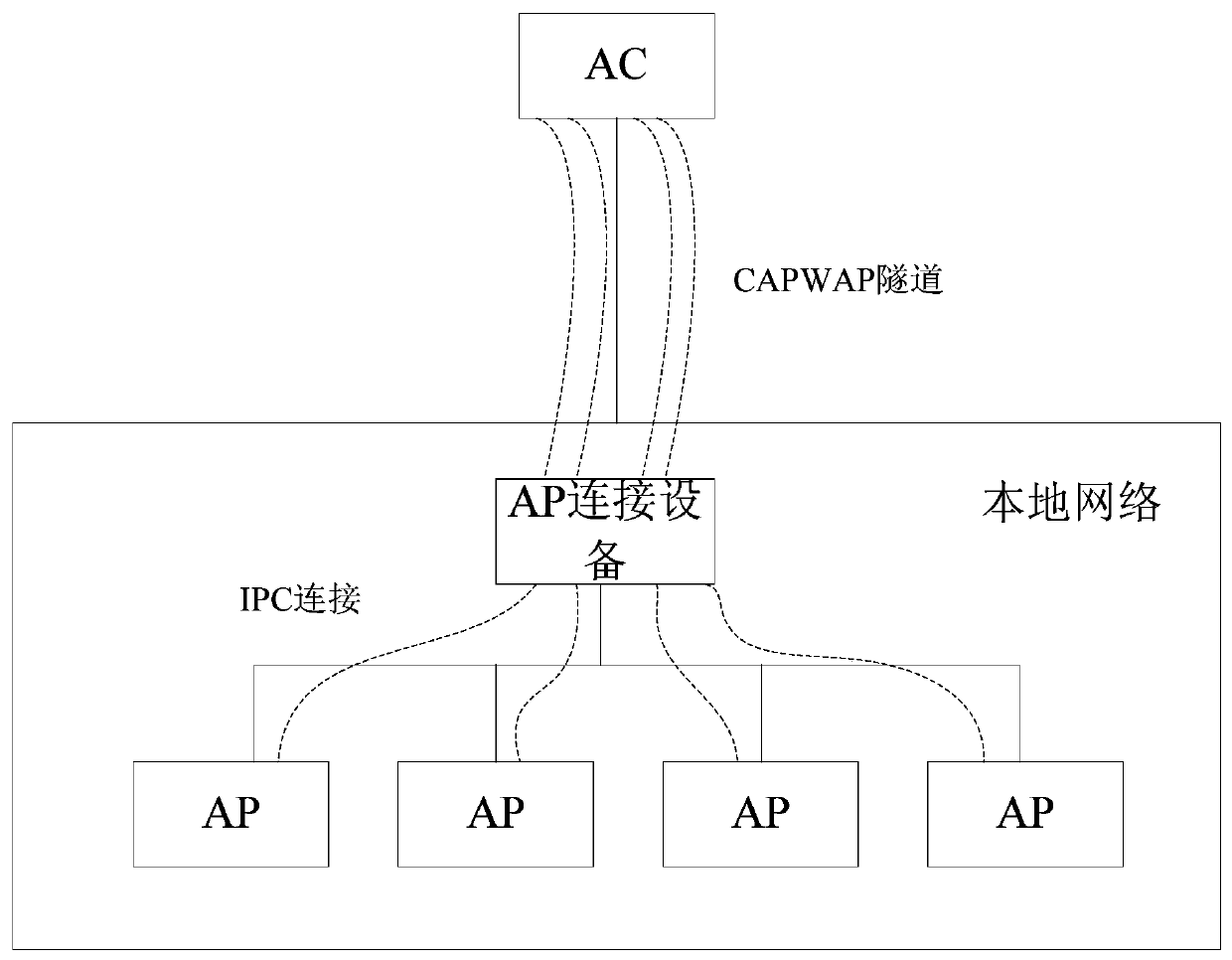
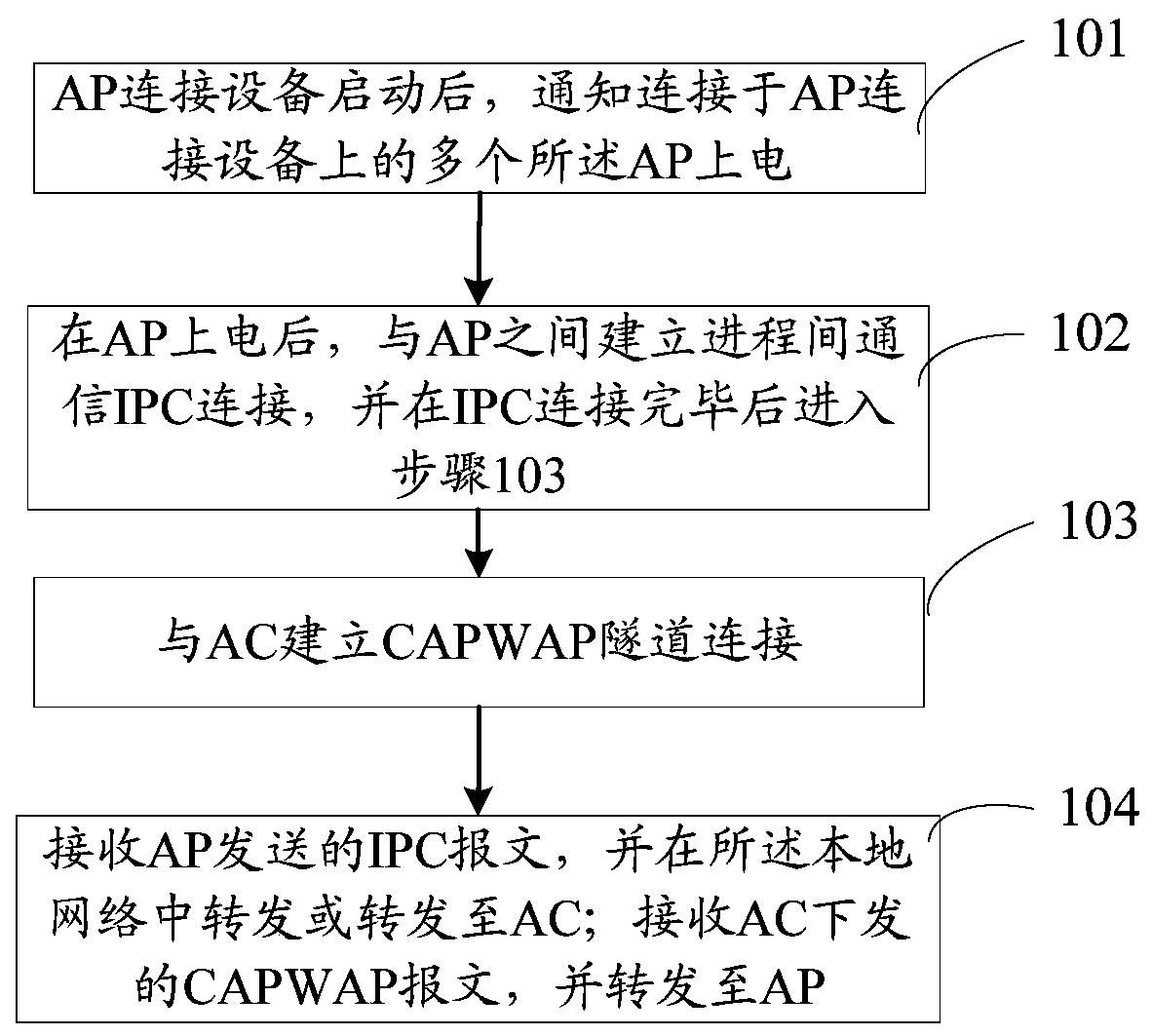
Method and device for managing wireless access point ap
ActiveCN105848168BReduce communication consumptionEasy to handlePower managementNetwork topologiesTelecommunicationsInter-process communication
Owner:NEW H3C TECH CO LTD
A Fault Detection Method for Multiple AGV Fixed Range Cruise System with Low Communication and Computational Consumption
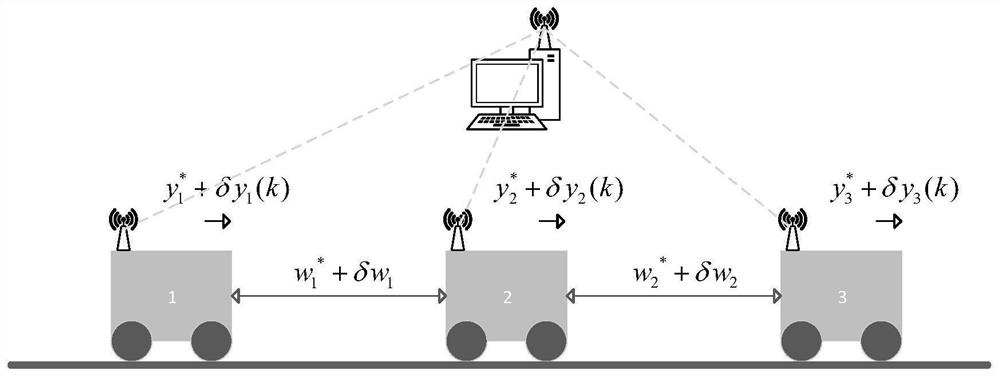
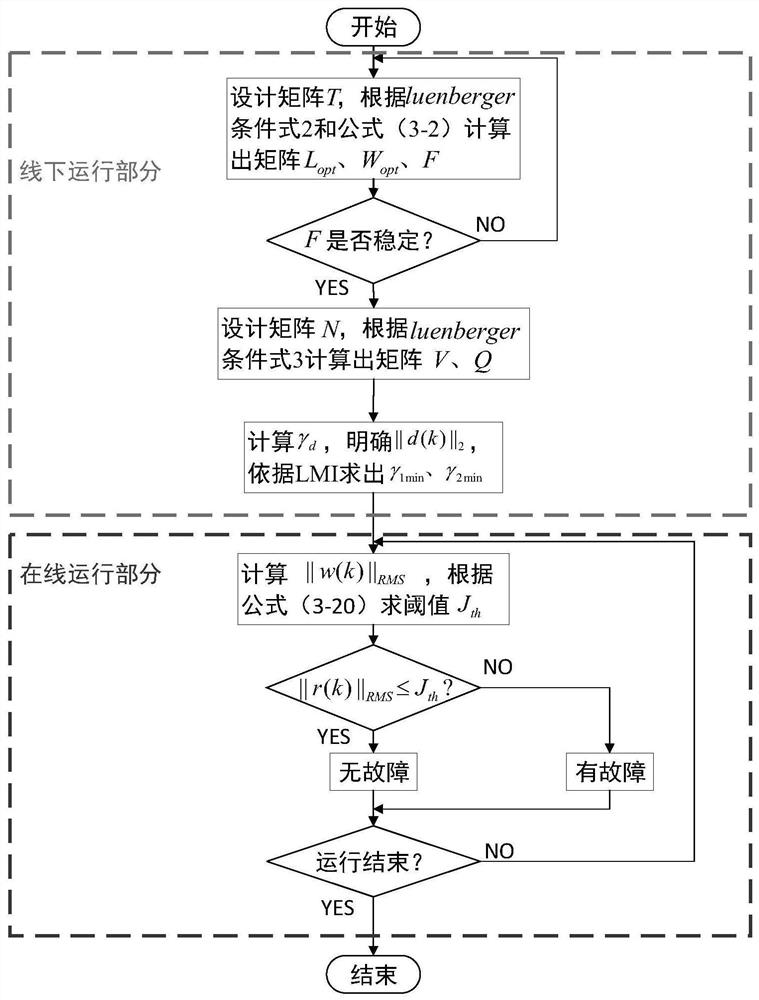
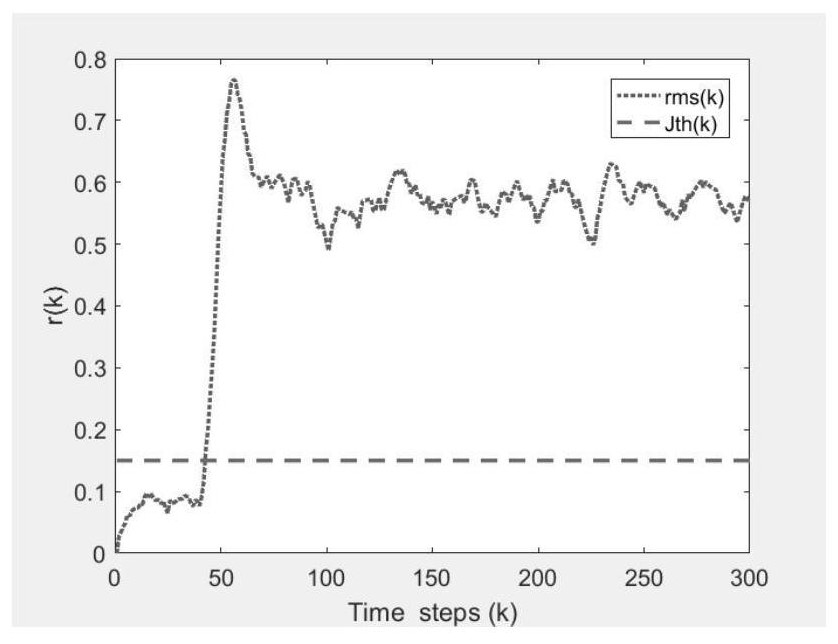
ActiveCN113848876BAvoid occupyingReduce communication consumptionPosition/course control in two dimensionsVehiclesState spaceActuator fault
The invention provides a multi-AGV fixed-distance cruise system fault detection method with low communication and calculation consumption, and belongs to the technical field of fault detection. The technical solution is: firstly construct a discrete time invariant state space model of multi-AGV fixed-range cruise system including AGV actuator failure; secondly, set up an event trigger mechanism for information communication; then construct an error system including event-triggered transmission error influence and H ∞ / H ∞ type of performance indicators. The beneficial effects of the present invention are: the present invention can reduce the communication consumption of the multi-AGV fixed-range cruise system under the framework of the event trigger mechanism, reduce the calculation consumption of the online fault diagnosis process, and realize the optimal fault of the multi-AGV fixed-range cruise system detection.
Owner:NANTONG UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com