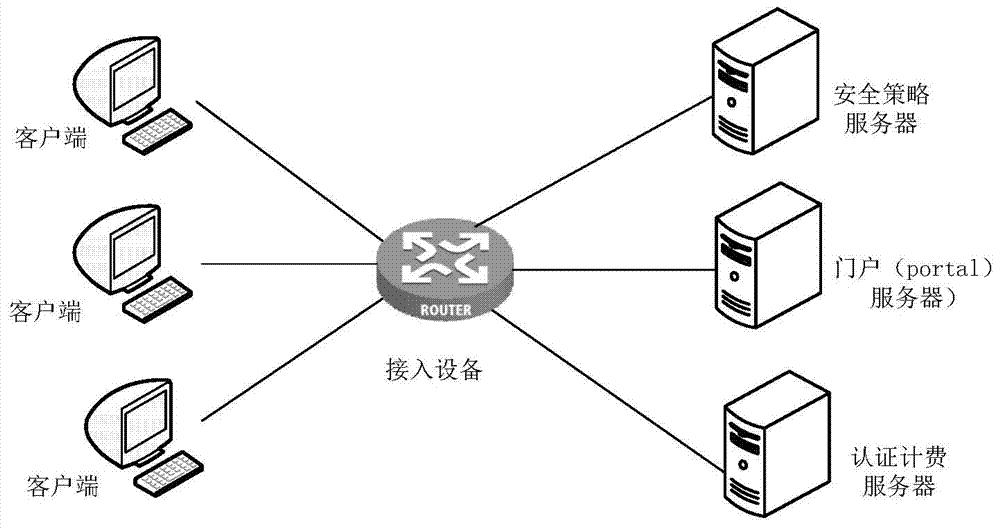
Patents
Literature
385results about How to "Reduce performance consumption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
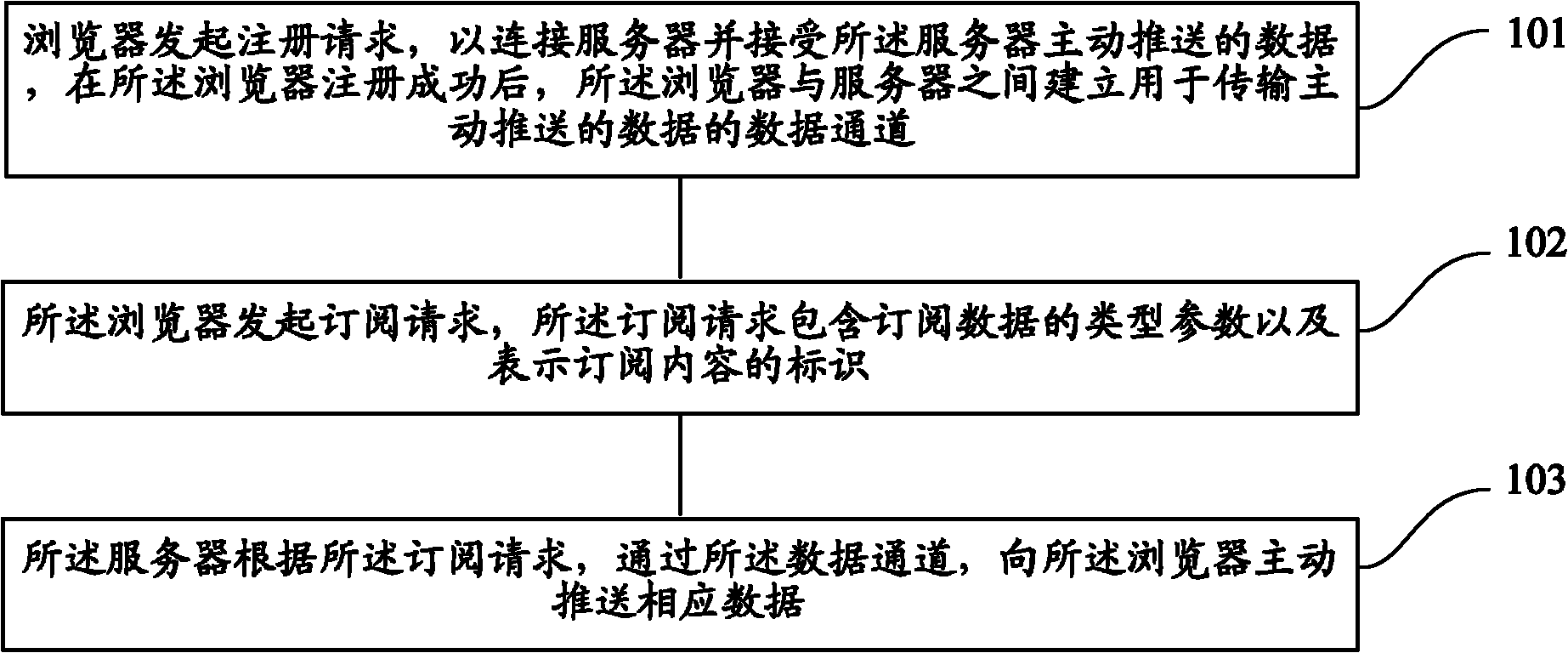
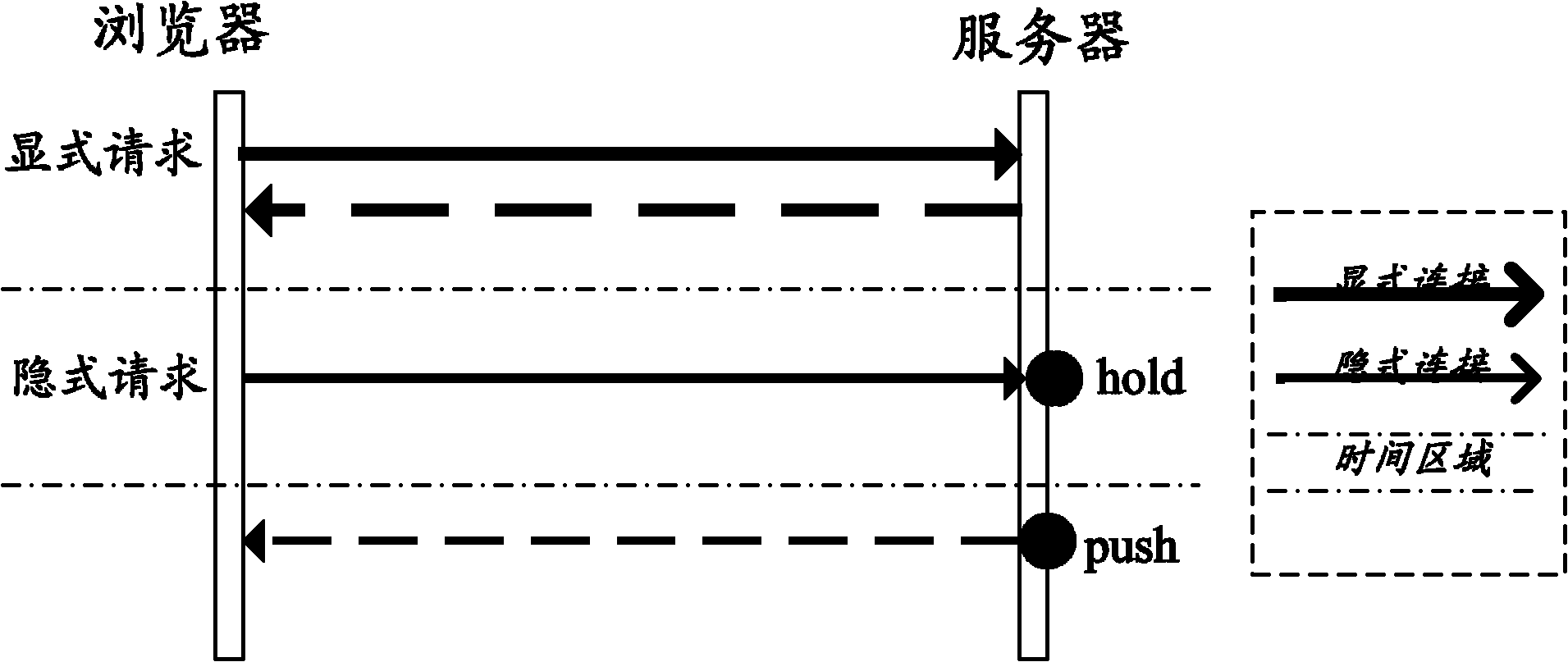
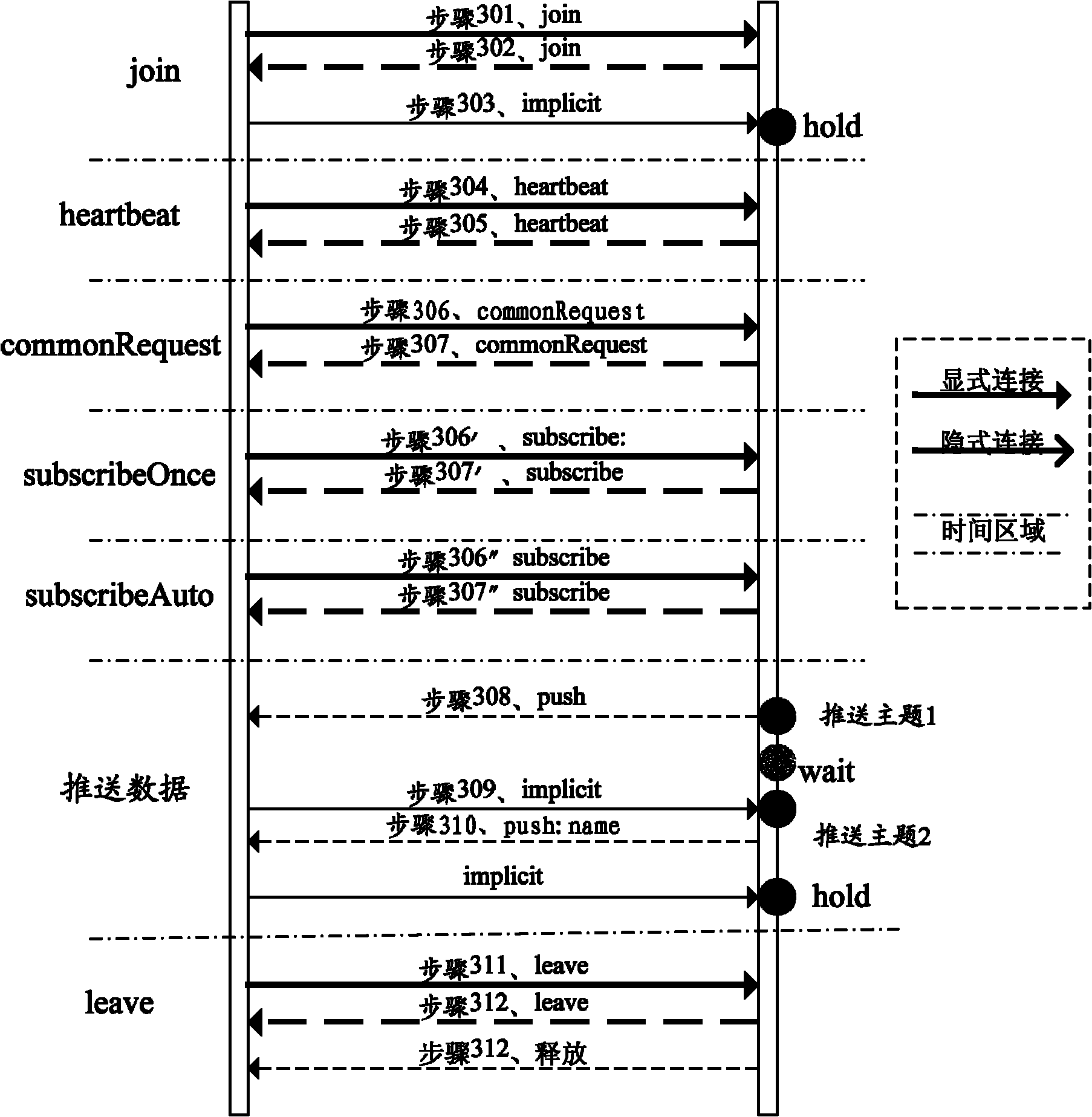
Method and system for pushing data actively by server
InactiveCN102035893AReduce occupancyReduce performance consumptionTransmissionSpecial data processing applicationsReal-time dataD channel
The invention discloses a method and a system for pushing data actively by a server. The method comprises the following steps that: a browser initiates a registering request to be connected the server and receive the data pushed by the server actively, and after the browser is registered successfully, a data channel for transmitting the data pushed actively is established between the browser and the server; the browser initiates a subscription request, wherein the subscription request contains type parameters of subscription data and identifiers for expressing subscription contents; and the server pushes the corresponding data to the browser actively by the data channel according to the subscription request. By the method and the system, the requirement of real-time data pushing of the browser can be met, the concurrency of an application system can be improved, and the performance consumption of the server can be reduced.
Owner:AGRICULTURAL BANK OF CHINA
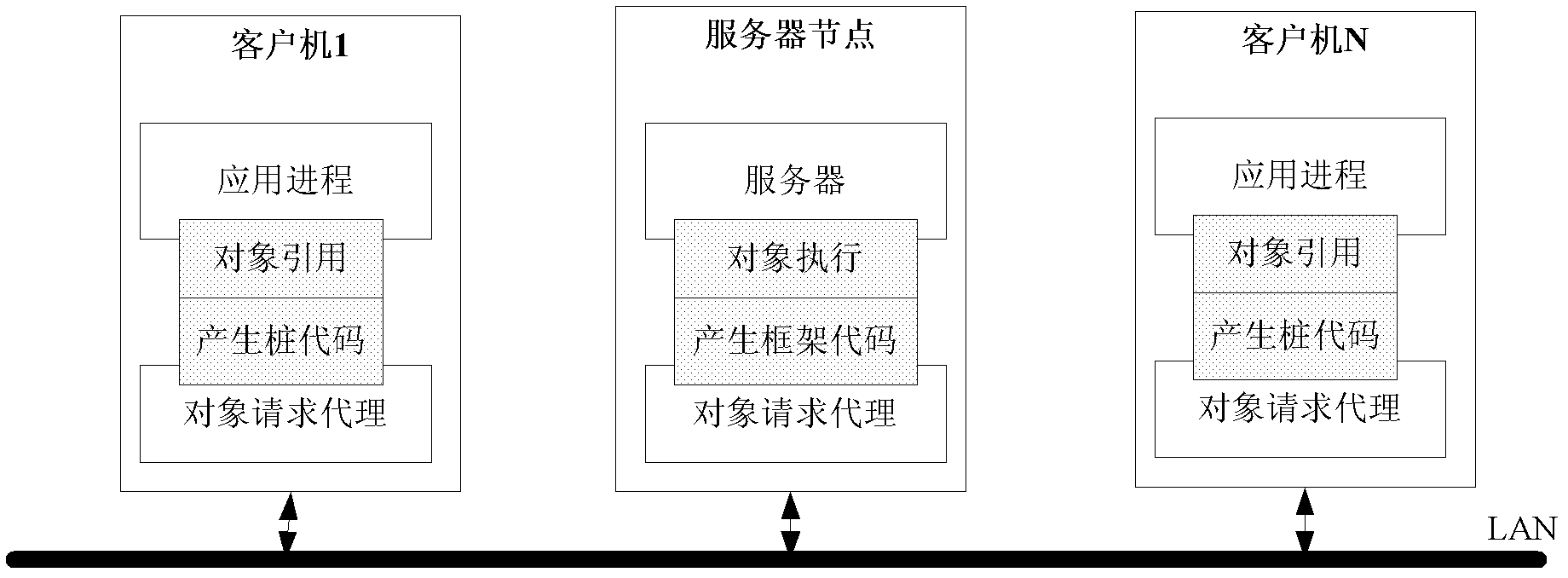
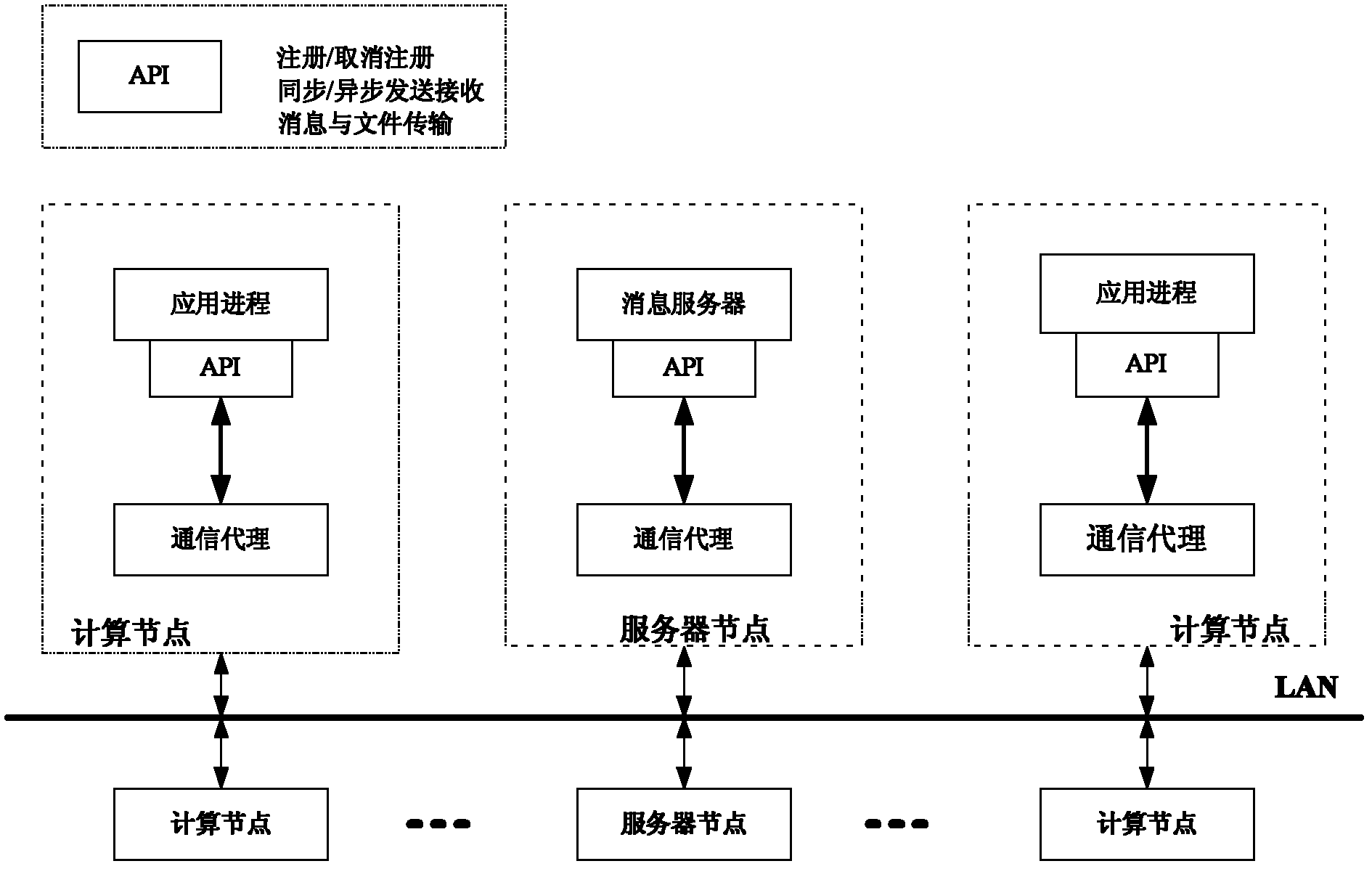
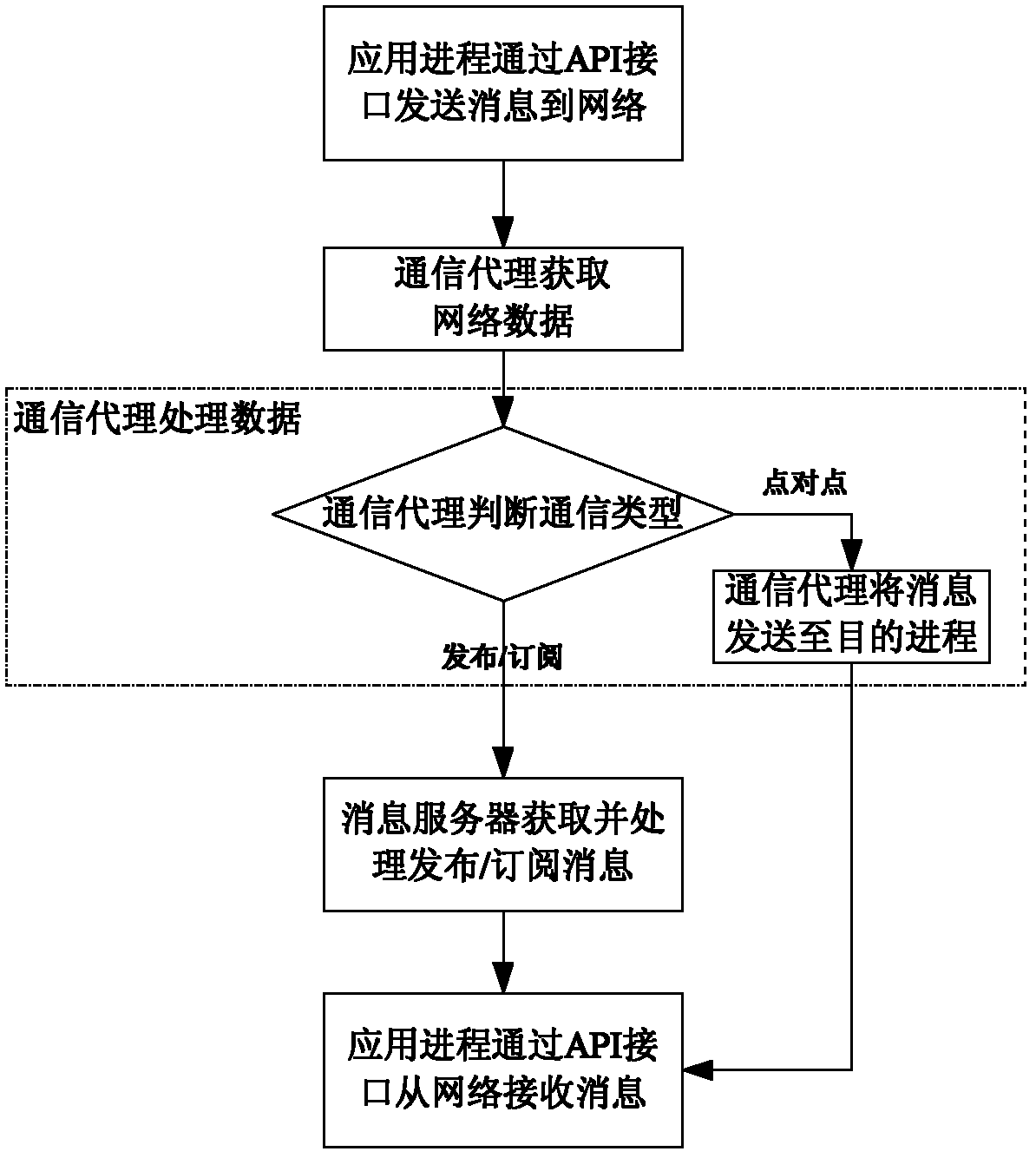
A communication platform and communication method adapted to private cloud environment
ActiveCN102291467AReduce overheadReduce development difficultyTransmissionCluster systemsDistributed computing
The invention relates to a communication platform and method suitable for a private cloud environment. The communication platform at least comprise two computing nodes and a server node, wherein the computing nodes and the server node are connected with each other through a network to form a distributed cluster system; each computing node represents a host in a system; the host comprises a plurality of application processes; a communication agent is mounted on each node; all application processes in the nodes are connected with a local communication agent through a standard API (Application Program Interface) provided by a communication platform, so that point-to-point communication among application processes is realized; and a message server application process is mounted on the server node, so that one-to-many communication among the application processes is realized. The invention has the beneficial effect that: the defects that the conventional private cloud system communication mode is only provided with one synchronous communication mode, a communication object is only limited to a single node and the conventional client / server mode is adopted in a communication domain are overcome.
Owner:四川易诚智讯科技有限公司
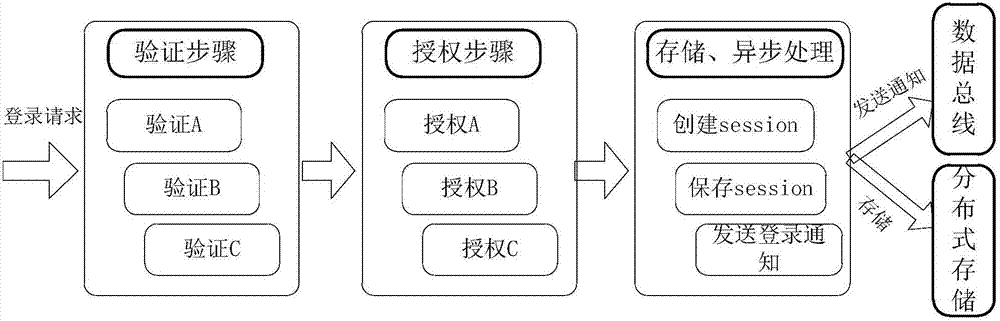
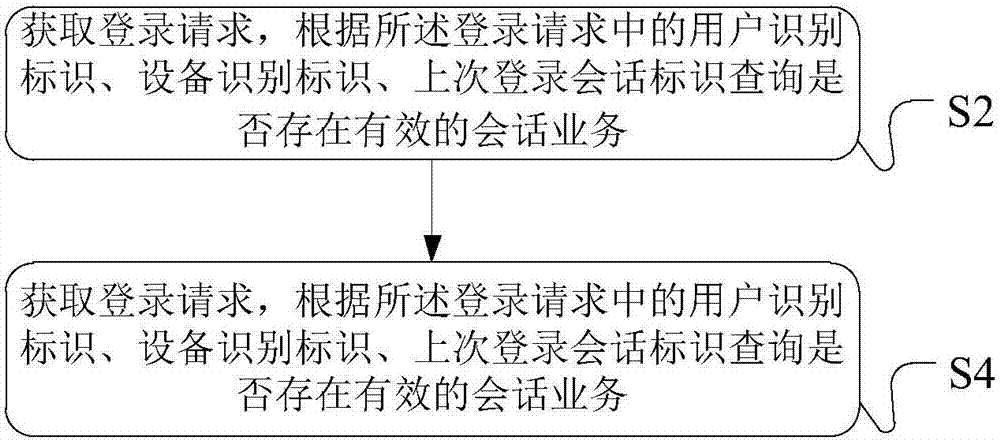
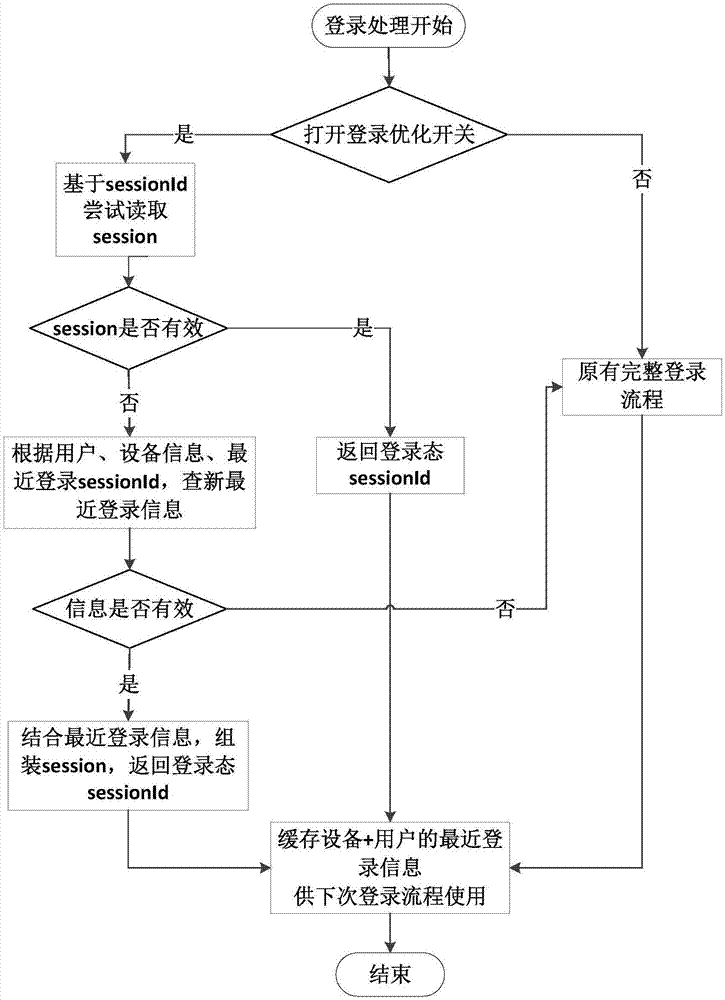
Login processing method, service processing method, apparatuses, and server
The embodiment of the invention discloses a login processing method, a service processing method, apparatuses, and a server. The login processing method may comprise the steps of obtaining a login request of a client, and querying whether a valid session service exists in server cached data according to a user recognition Id, a device recognition Id and a last-time login session Id; if the valid session service exists, directly taking a session Id that is no invalid at a last time as well as a session Id of the valid session service as a session Id for a session service of the login request, thereby implementing the reuse of an existing session; or otherwise, reestablishing a session Id according to latest login information.
Owner:ADVANCED NEW TECH CO LTD
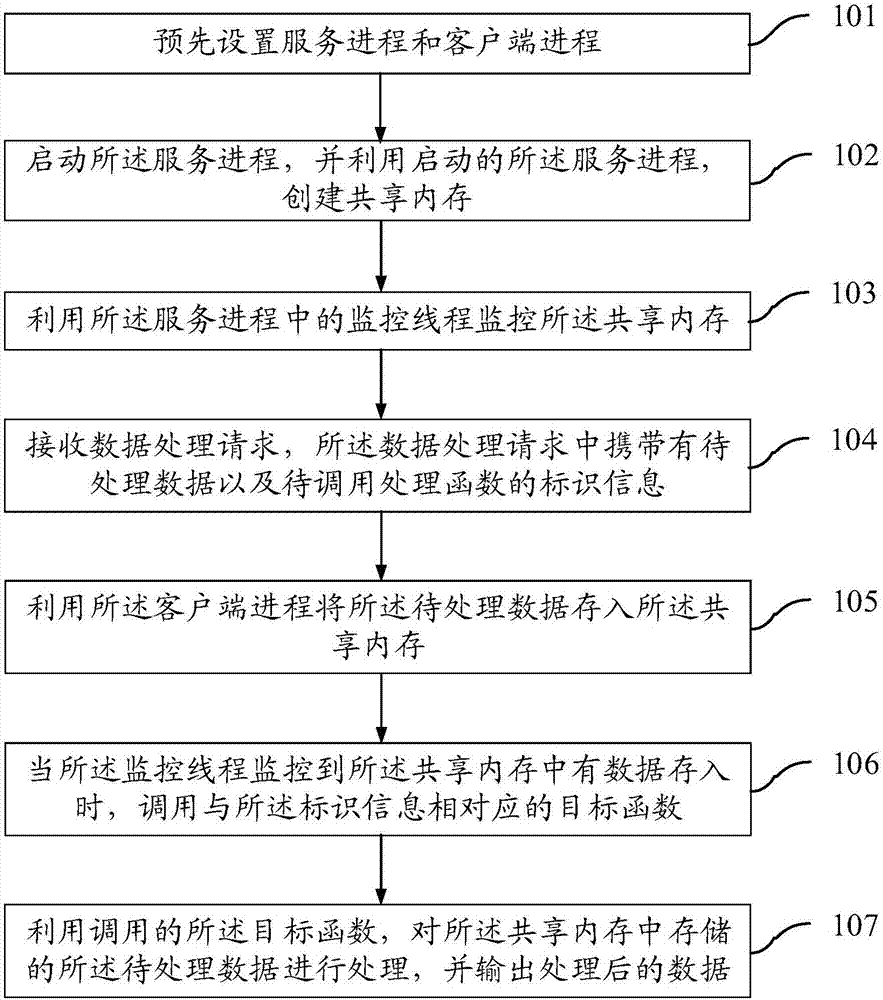
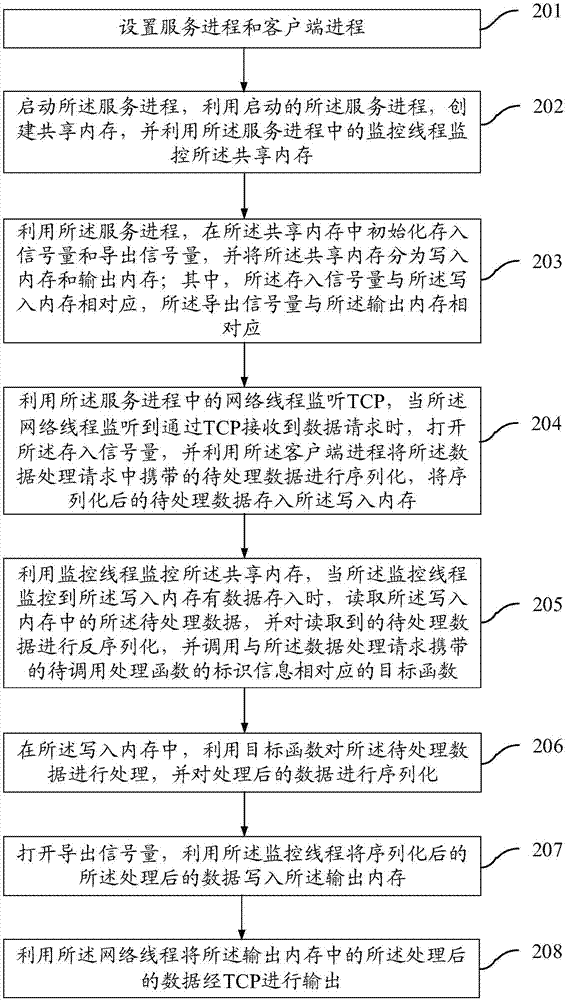
Interprocess function invocation method and device based on shared memory
InactiveCN107491355ASimple methodReduce performance consumptionResource allocationInterprogram communicationData processingService process
The invention provides an interprocess function invocation method and device based on a shared memory. The method includes the steps of setting a service process and a client process in advance; starting the service process, and using the started service process to establish the shared memory; using a monitoring thread in the service process to monitor the shared memory; receiving a data processing request, wherein the data processing request carries to-be-processed data and the identification information of a to-be-invoked processing function; using the client process to store the to-be-processed data into the shared memory; when the monitoring thread monitors that the data is stored in the shared memory, invoking the target function corresponding to the identification information; processing the to-be-processed data stored in the shared memory by using the invoked target function, and outputting the processed data. According to the scheme, the performance consumption of a system can be reduced, and the method and device are especially suitable for embedded equipment with limited performances.
Owner:SHANDONG INSPUR COMML SYST CO LTD
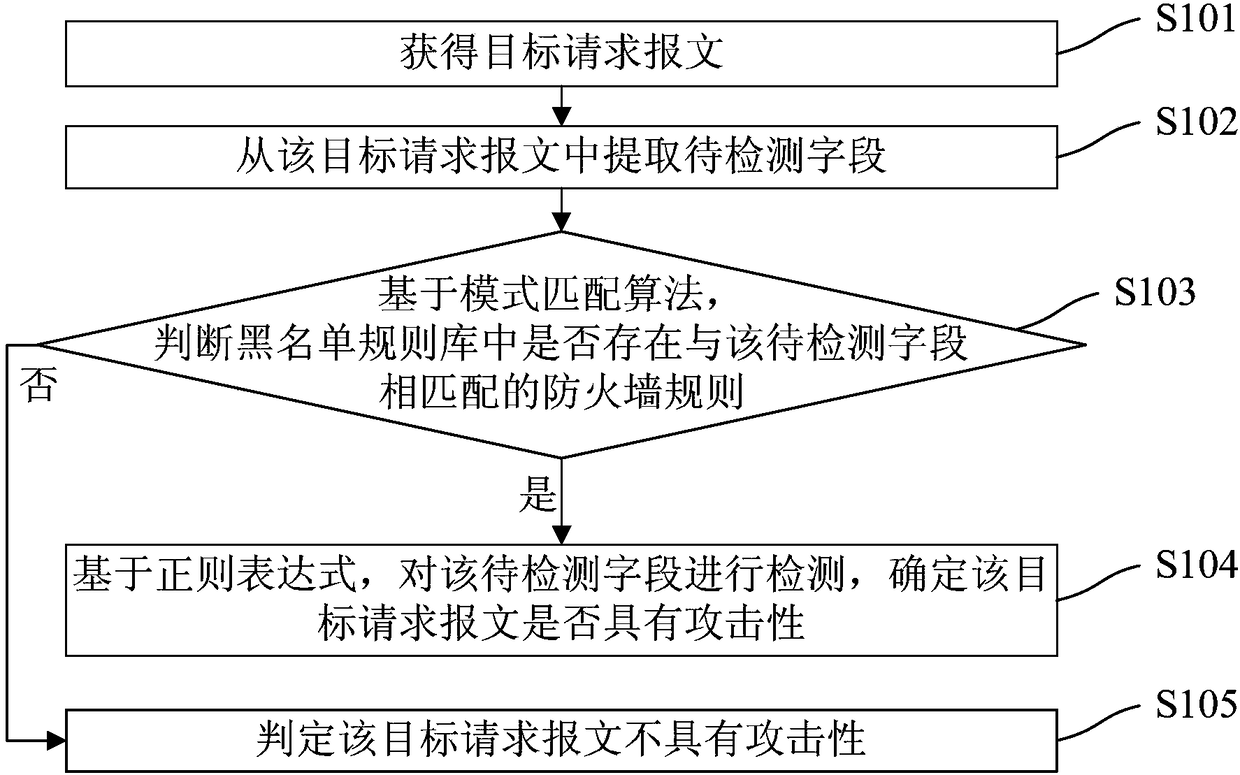
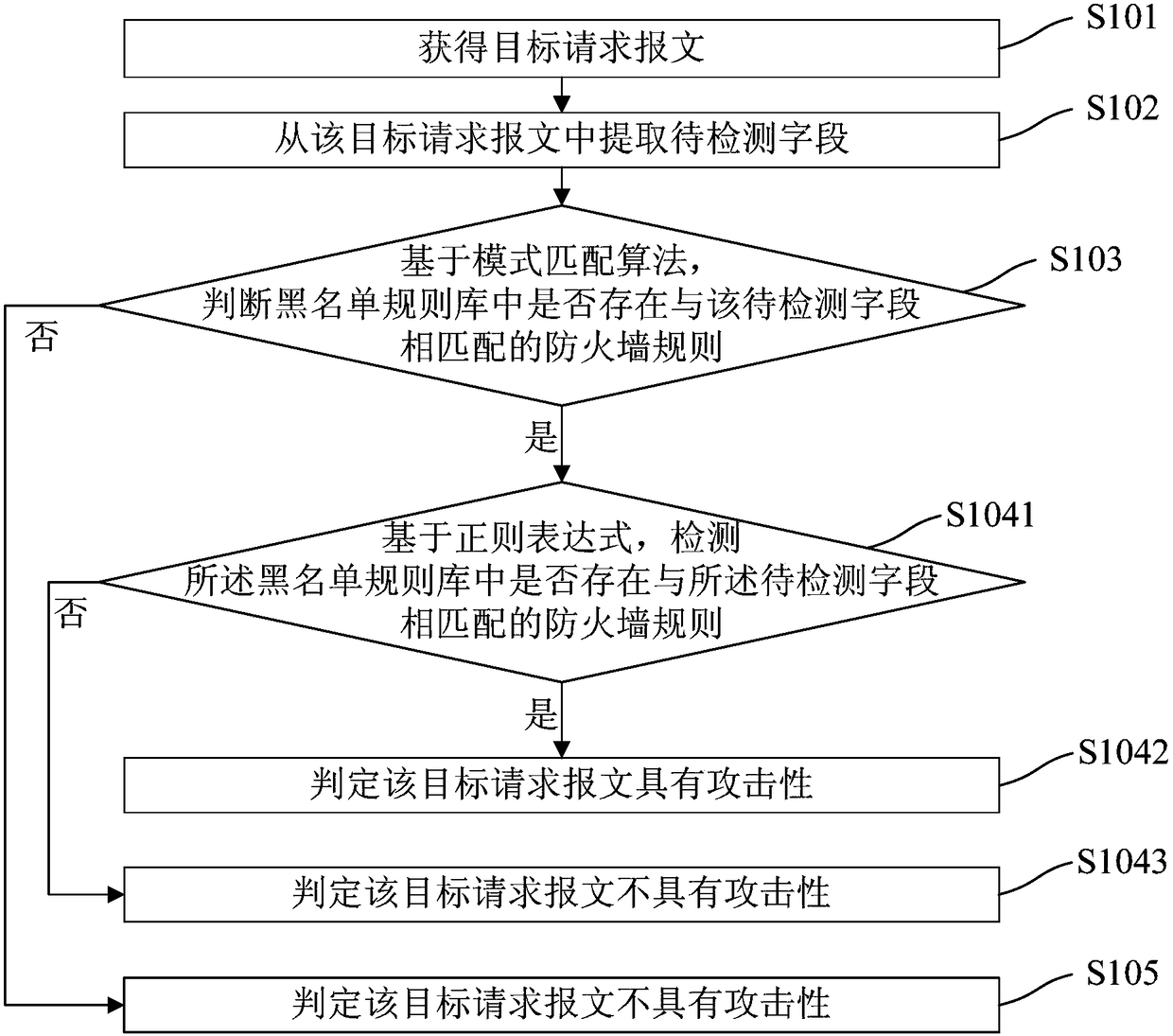
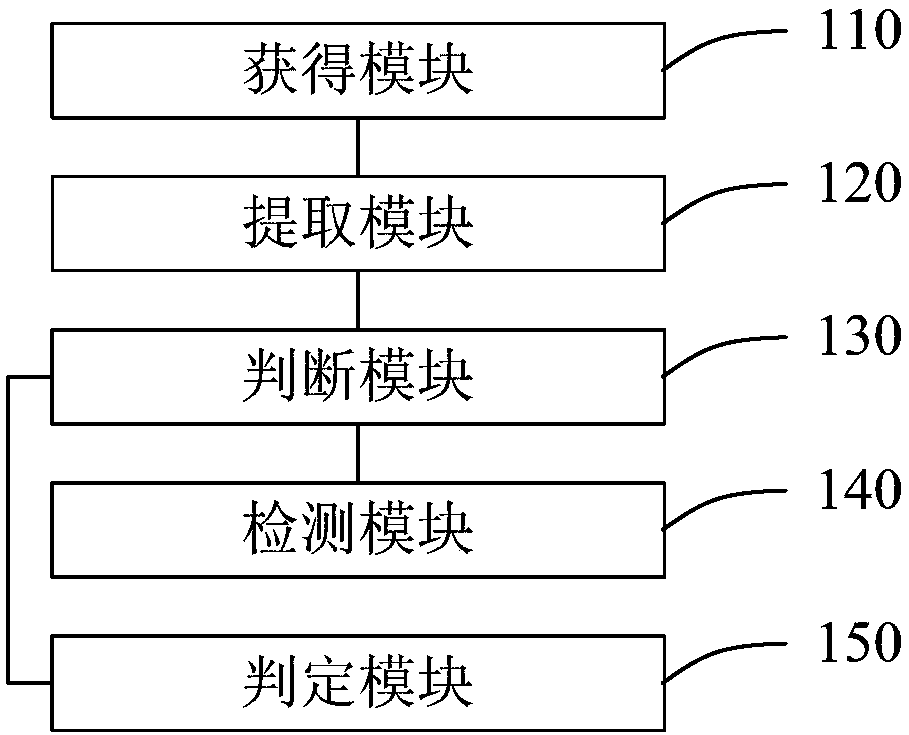
Attack detection method and device
InactiveCN108111466AReduce CPU usageImprove work efficiencyTransmissionOccupancy ratePattern matching
The embodiments of the invention disclose an attack detection method and device; the method comprises the following steps: firstly, acquiring a target request message; extracting a to-be-detected field from the target request message; then, judging whether a firewall rule matched with the to-be-detected field exists in a blacklist rule base based on a pattern matching algorithm; if yes, detectingthe to-be-detected field based on a regular expression and determining whether the target request message is offensive or not; if not, directly judging that the target request message is not offensive. According to the scheme provided by the invention, for a normal legal request message, when attack detection is carried out, the CPU occupancy rate and the system performance consumption of a firewall system can be greatly reduced; moreover, most of the messages received by the firewall system are legal, so according to the embodiments of the invention, the working efficiency of the firewall system can be greatly improved.
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD +1
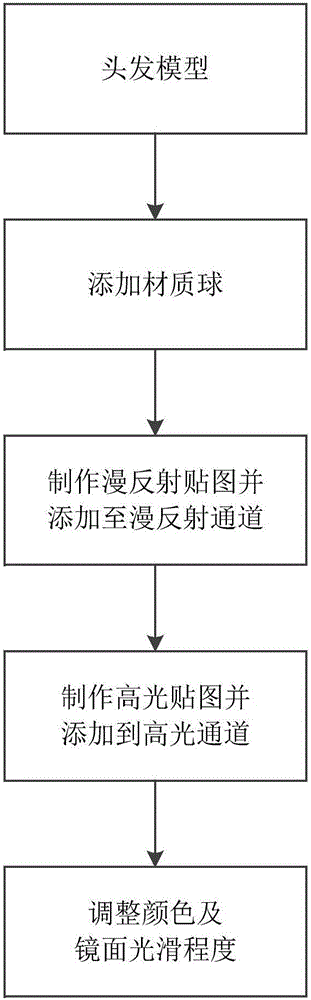
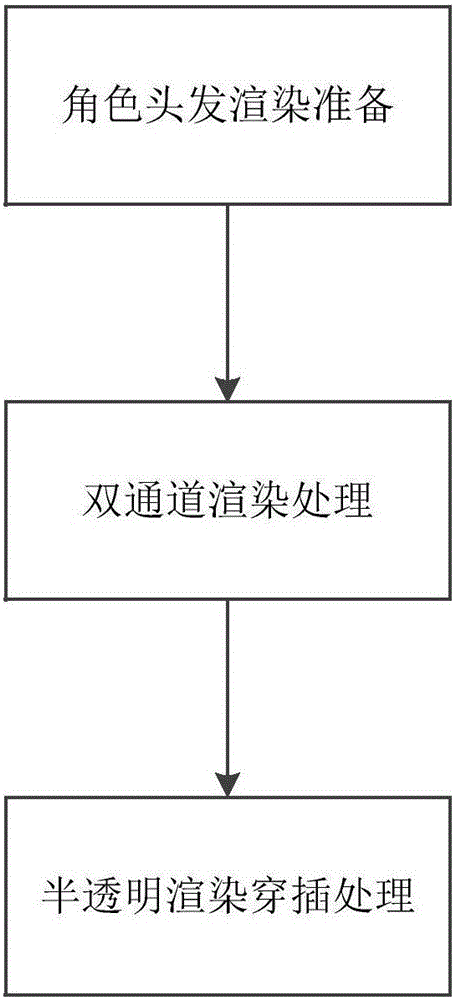
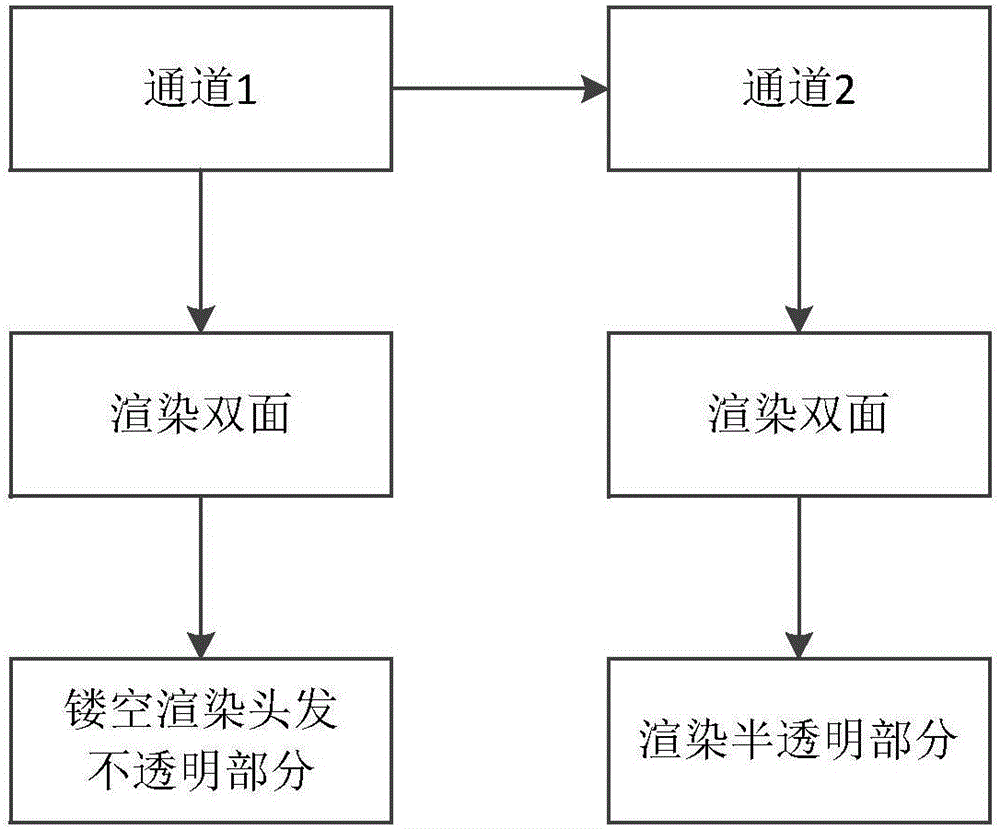
Hair processing method and system for game role
ActiveCN106815883ALayeredReduce performance consumptionAnimationVideo gamesComputer visionLight source
The invention provides a hair processing method and system for a game role. The method comprises: a simulated light source is established, an own color of a hair model and light and dark information are drawn at a diffuse map, and a high-light map of the hair model is superposed with the simulated light source; a transparent part and a non-transparent part of the obtained hair model are rendered by using dual channels; and interspersed processing including mesh segmentation execution is carried out on the rendered hair model and dynamic rendering of the hair model is carried out. The hair processing method and system have the following beneficial effects: the hair expression effect becomes vivid with good layering effect; performance consumption caused by a real light source can be reduced and a specific light source effect can be processed, so that the high light expression becomes vivid in detail; because of semi-transparent mixing, high-efficiency processing of rendering and interspersed processing is realized; and the interspersed problem caused by semi-transparent mixing can be solved and real-time triangular sorting can be avoided, and a hair rendering interspersing problem can be solved efficiently.
Owner:ZHUHAI KINGSOFT ONLINE GAME TECH CO LTD +1
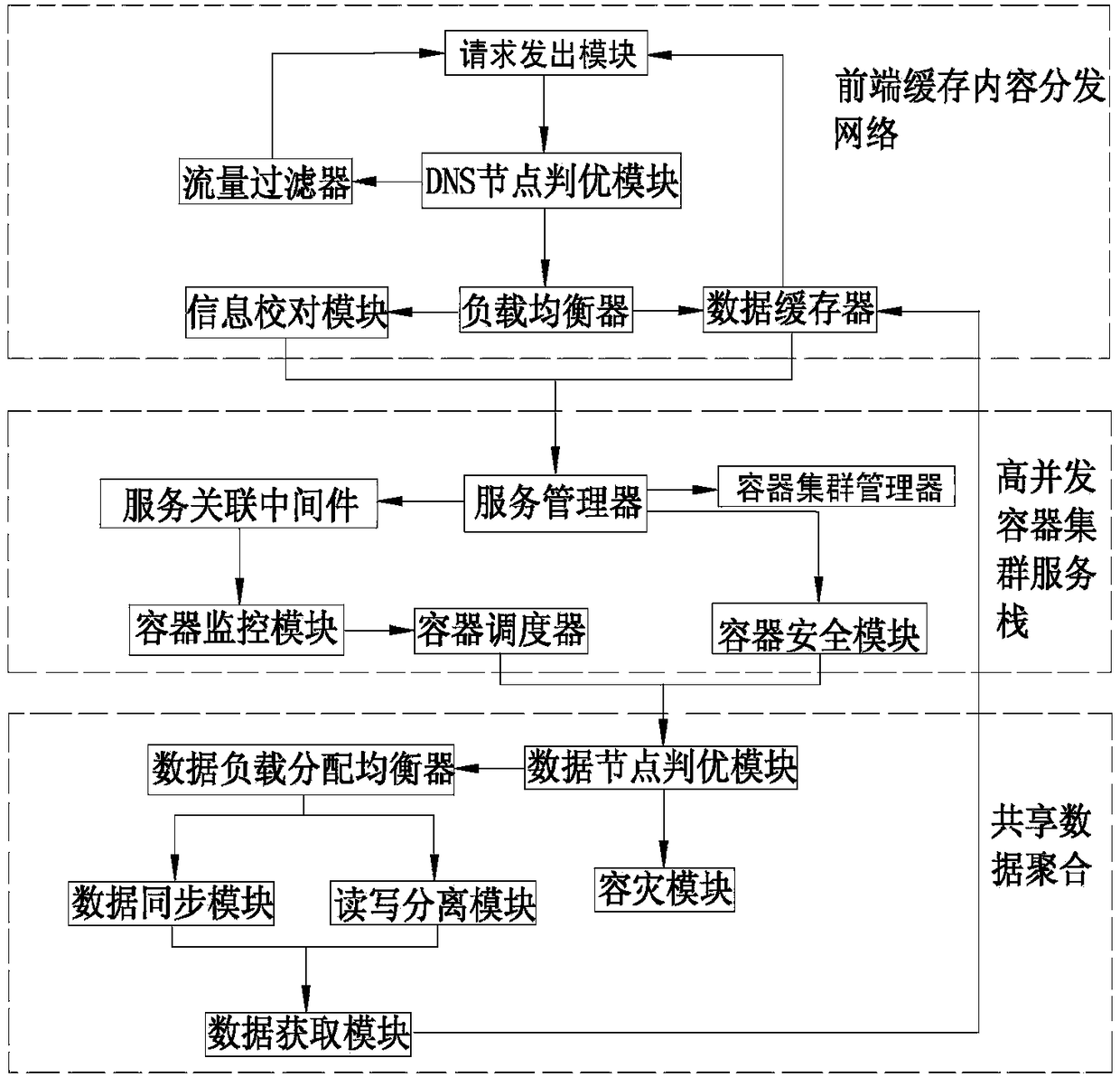
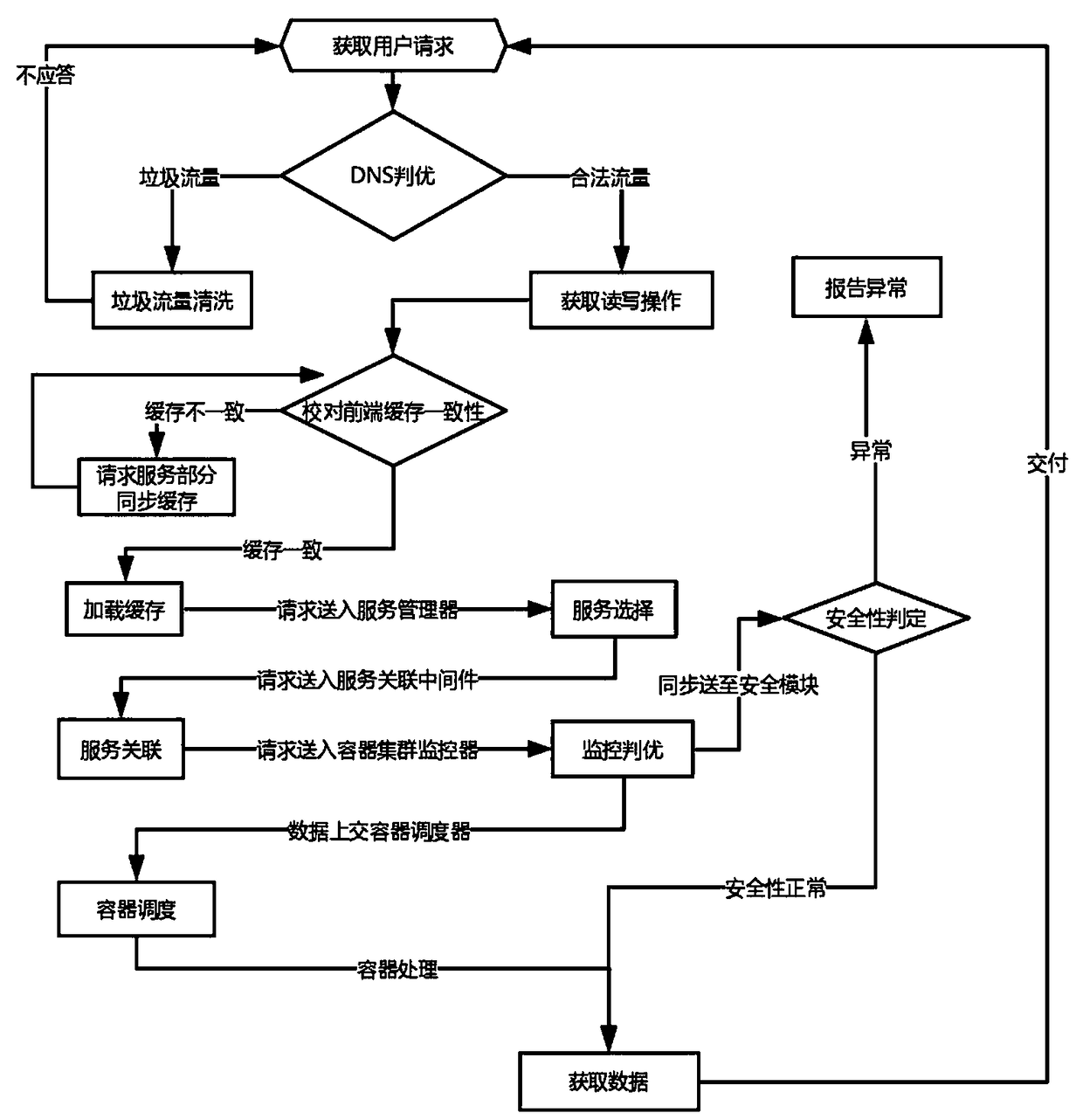
Distributed WEB micro service container cluster architecture system and implementation method thereof
ActiveCN108737548AHigh speedOvercome the disadvantage of unresponsive or even paralyzedTransmissionData synchronizationContent distribution
The invention discloses a distributed WEB micro service container cluster architecture system and an implementation method thereof. The system comprises a front-end cache content distribution network,a high concurrent container cluster service stack and a shared data aggregation, wherein the front-end cache content distribution network contains a load balancer, a data buffer, an information proofreading module, a traffic filter, and a DNS node arbitration module; the high concurrent container cluster service stack contains a container monitoring module, a container scheduler, a container cluster management module, a service association middleware, a service manager, and a container security module; and the shared data aggregation contains a data load distribution equalizer, a data synchronization module, a reading and writing separation module, and a disaster recovery module. The method comprises the steps of: obtaining a user request, performing DNS arbitration, cleaning garbage traffic, acquiring reading and writing operations, proofreading consistency of module verification information, loading caching, selecting a service, associating the service, monitoring arbitration, scheduling the container, determining security, and acquiring data. The invention is applicable to system architectures in large distributed services.
Owner:NANJING UNIV OF POSTS & TELECOMM
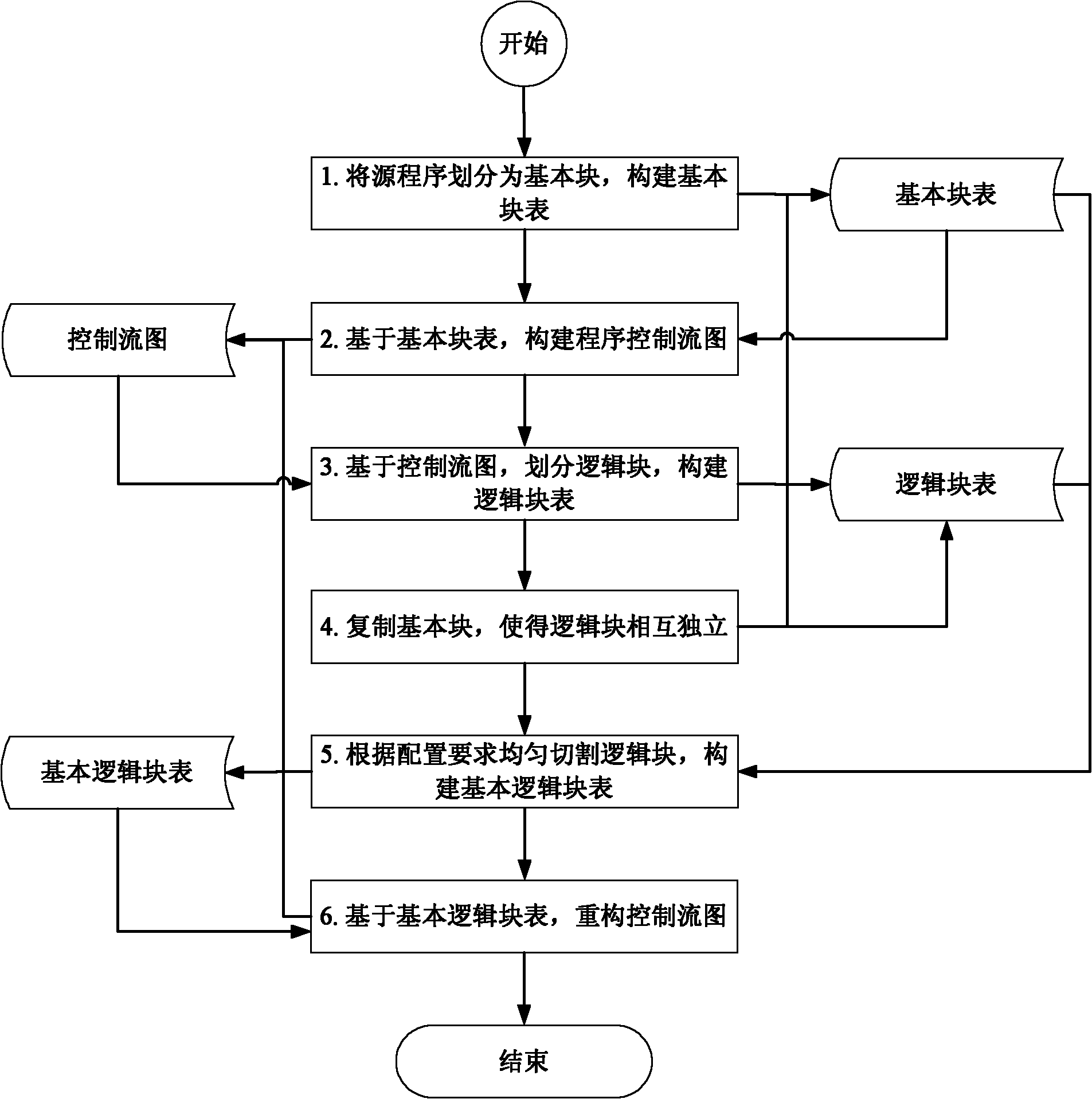
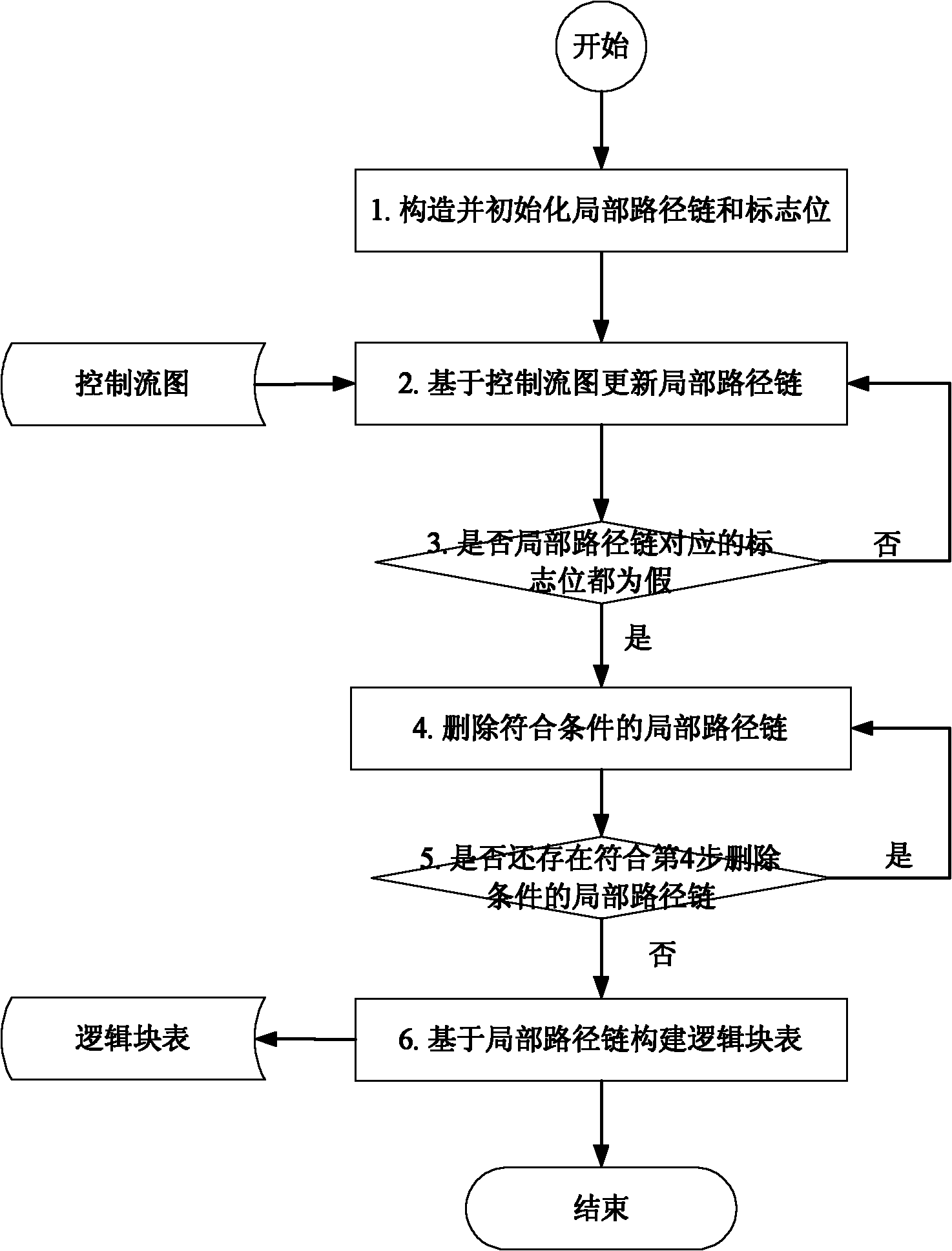
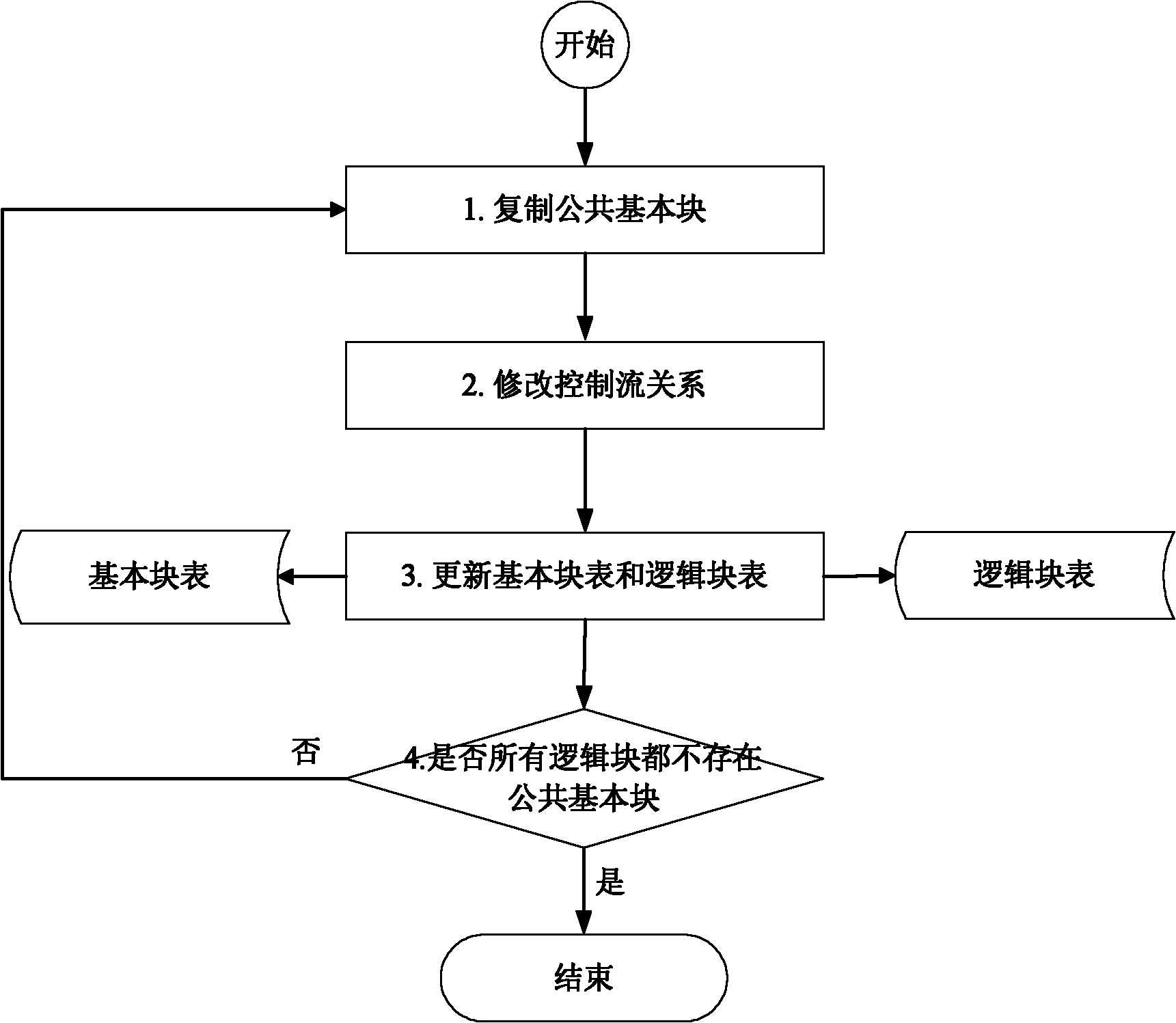
Control flow error detection optimizing method based on reconstructed control flow graph
InactiveCN101944064AImprove error detection rateImprove efficiencySoftware testing/debuggingControl flowTheoretical computer science
The invention discloses a control flow error detection optimizing method based on a reconstructed control flow graph, which aims at providing a novel control flow error detection optimizing method based on a reconstructed control flow graph and solving the problems of low error detection efficiency and the like. The technical scheme thereof is characterized by dividing a source program into basic blocks, constructing a basic block table, and constructing a program control flow graph based on the basic block table; then dividing into logical blocks on the basis of the control flow graph, constructing a logical block table, and copying the basic blocks so as to enable the logical blocks to be mutually independent; evenly cutting the logical blocks according to the configuration requirements, and constructing a basic logical block table; and finally reconstructing the program control flow graph based on the basic logical block table. On the basis of the reconstructed control flow graph, the existing control flow error detection algorithm can be realized; and by adopting the method of the invention, the dividing of the basic blocks can be flexibly configured, so that the existing control flow error detection algorithm can be directly applied on the basis of the reconstructed control flow graph, and the efficiency of the error detection algorithm is effectively improved.
Owner:NAT UNIV OF DEFENSE TECH
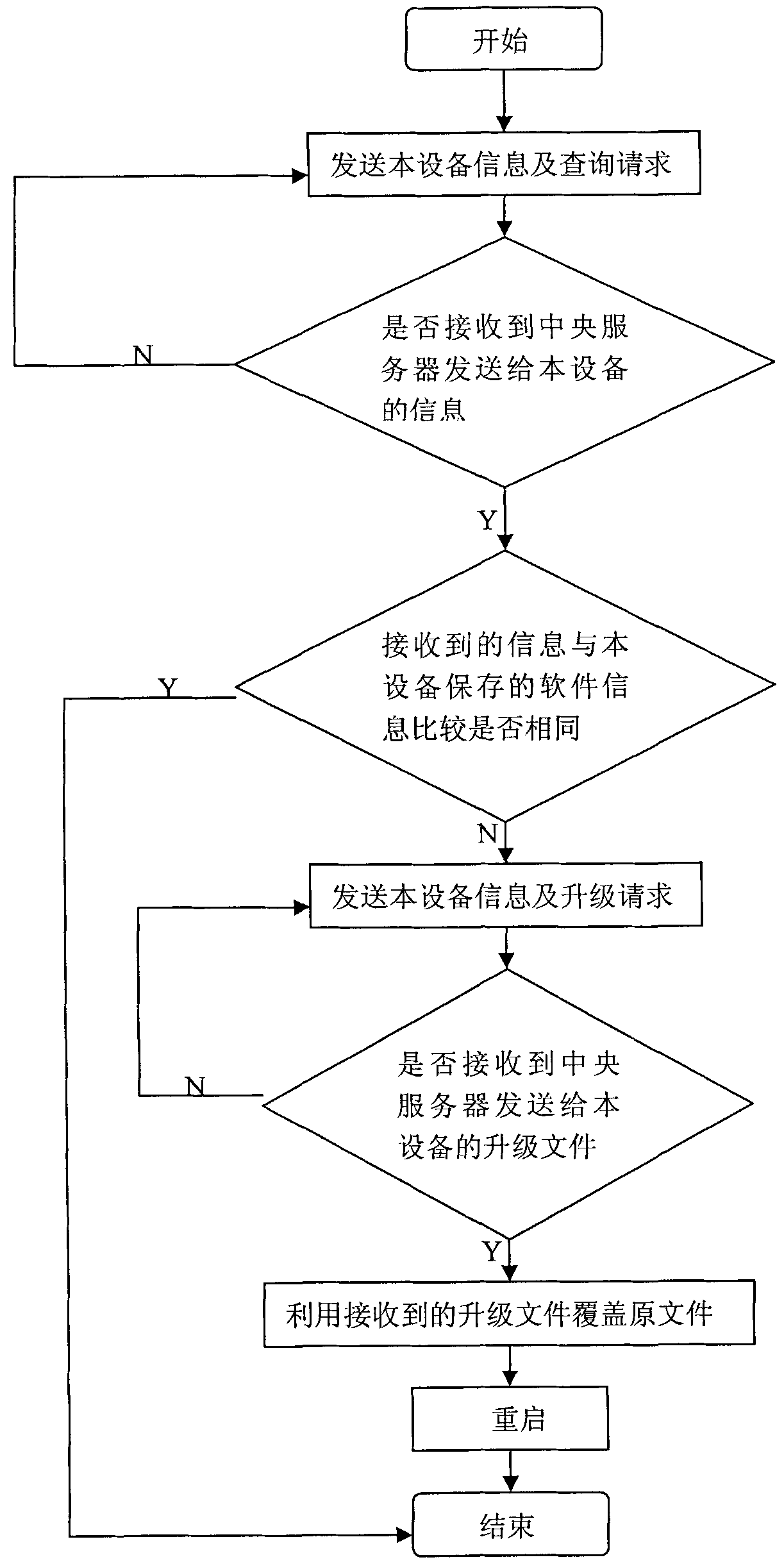
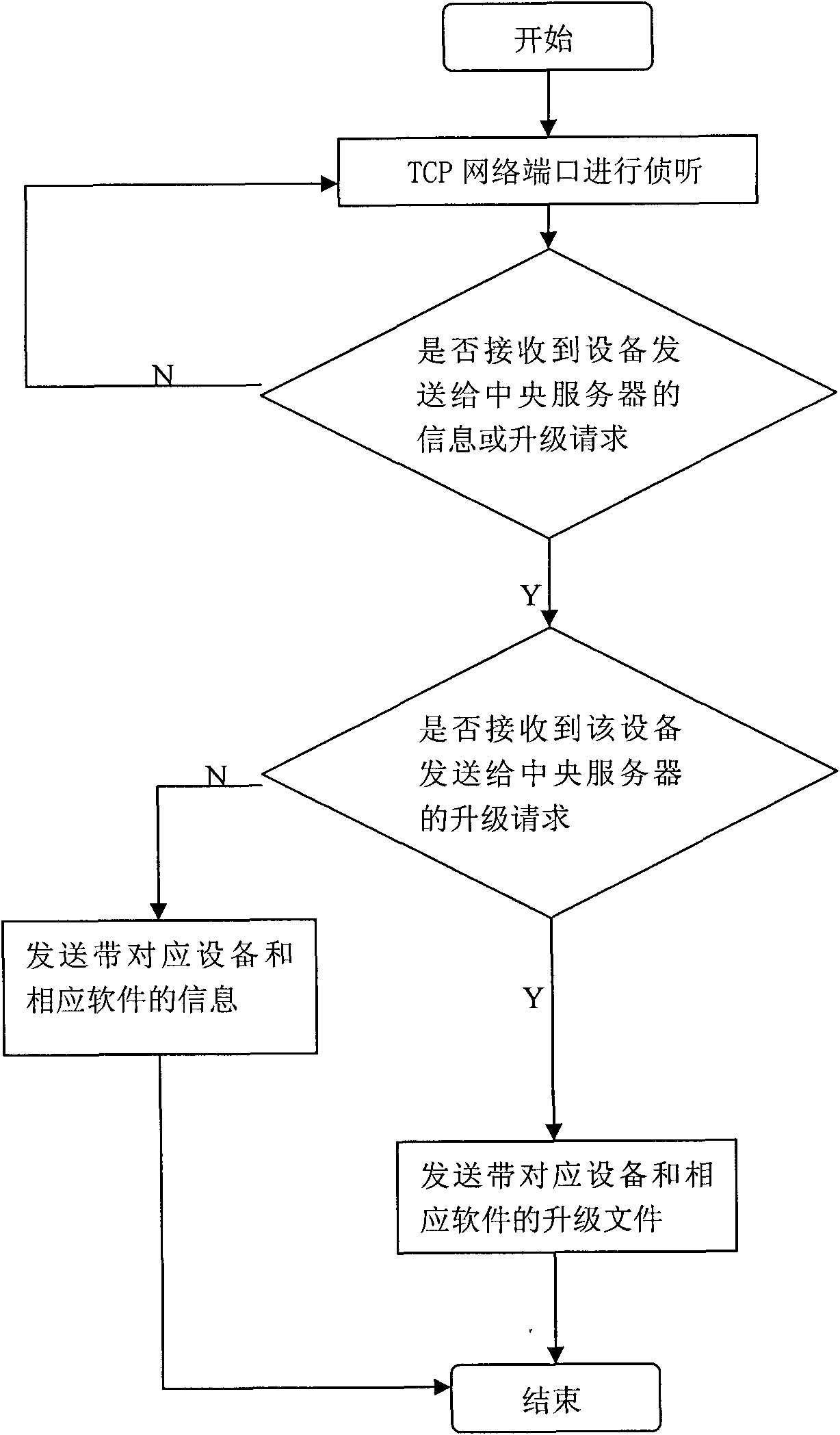
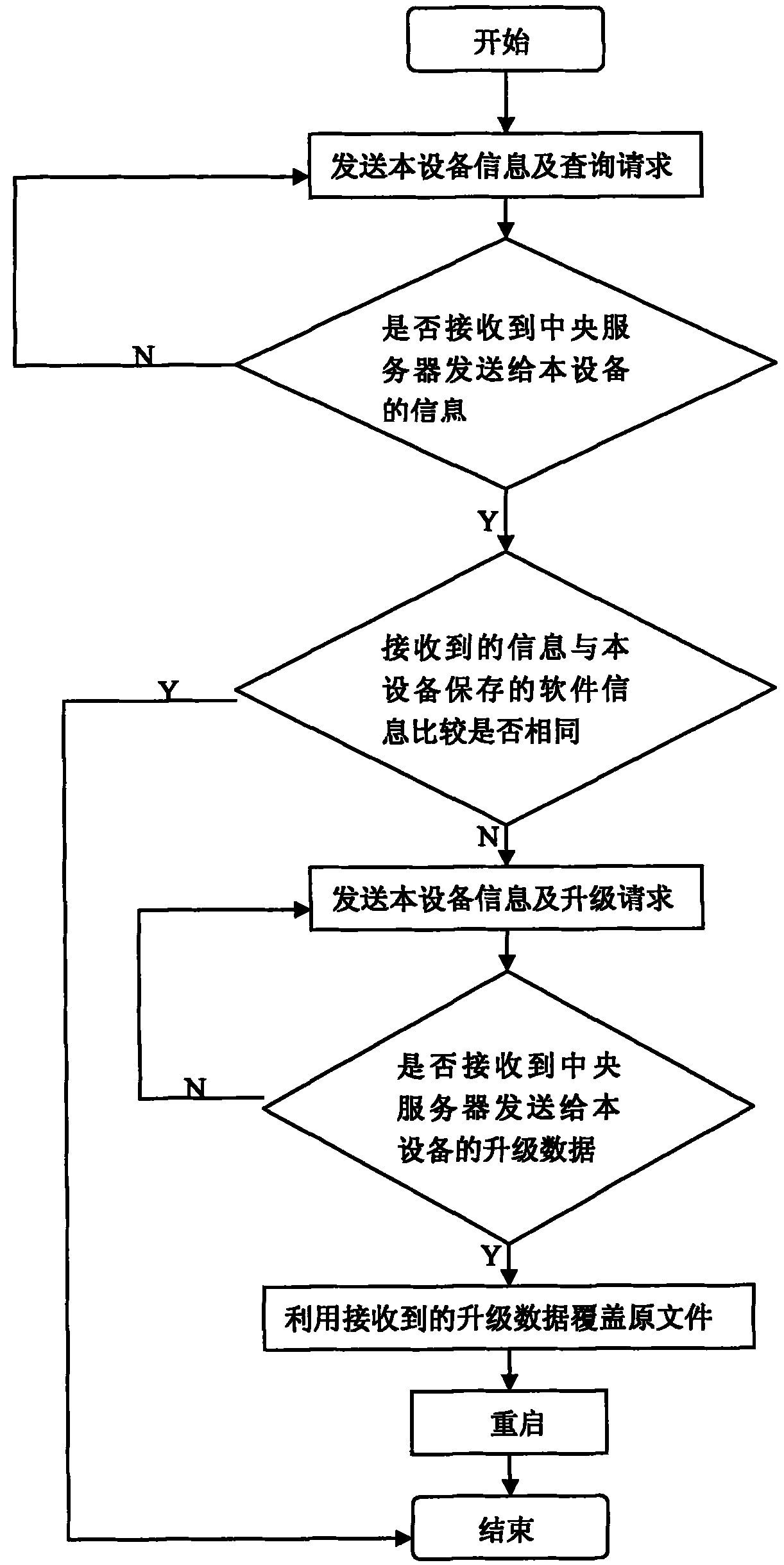
Remote automatic upgrading method for digital monitoring equipment
InactiveCN101841536AEasy to deployEasy maintenanceData switching networksComputer hardwareMonitor equipment
The invention discloses a remote automatic upgrading method for digital monitoring equipment. The method comprises the following two parts: the digital monitoring equipment upgrades a client program, and the central server upgrades a service program. The method comprises the following specific steps: after the monitoring equipment is started, transmitting an inquiry request to a central management server at regular intervals; when the port of the central server monitors that the monitoring equipment requires the inquiry request, upgrading the service program and transmitting the information of the corresponding software to the monitoring equipment; after the monitoring equipment receives the information, comparing the information with the locally stored information; and when the comparison result indicates that upgrading is allowable, requiring the central server to download a corresponding file, covering the file and rebooting the system. The invention has the advantages of simple layout and maintenance, high efficiency and flexibility, can use the mode of regular detection by using the digital monitoring equipment, and does not need too complicated manual intervention.
Owner:SHENZHEN INFINOVA
Image rendering method, image rendering device and storage medium
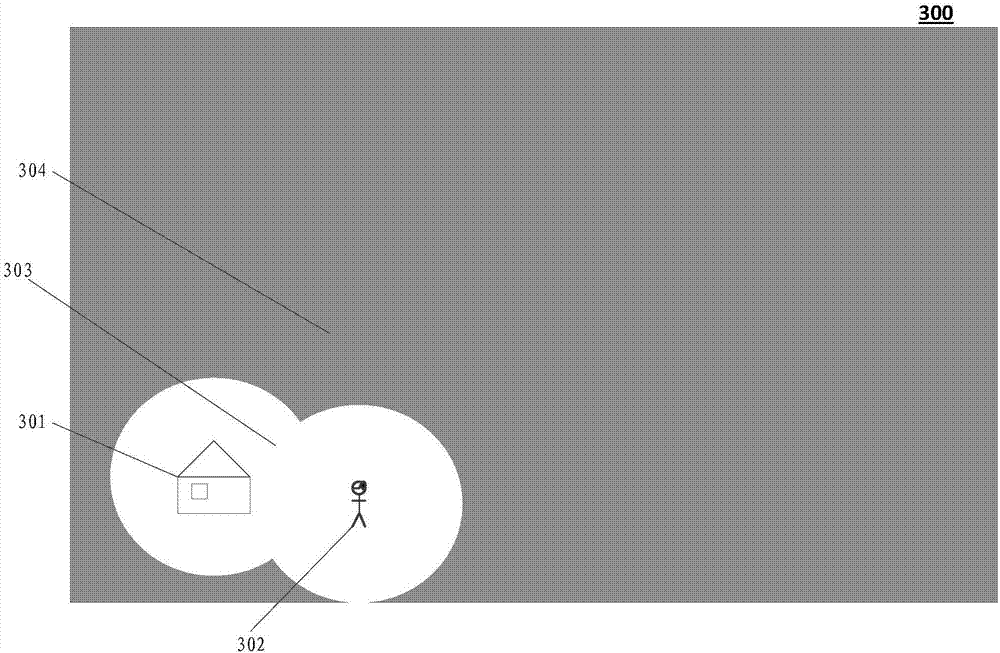
ActiveCN107958480AReduce performance consumptionTexturing/coloring3D-image renderingComputer graphics (images)Virtual space
The present application discloses an image rendering method. The method includes the following steps that: when it is detected that the state of a virtual object in a virtual space changes, the location data of the virtual object related to an image frame to be rendered currently, in the virtual space, are acquired, and a target texture state in target texture state data which is corresponding toat least one target texture coordinate is updated according to the location data of the virtual object; as for the image frame to be rendered currently and an image which is behind the image frame andappears before the state of the virtual object changes next time, an image formed by superposing target textures in the image frame to be rendered currently and the image which is behind the image frame and appears before the state of the virtual object changes next time is determined according to the target texture state data; and the image formed by superposing the target textures in the imageframes is rendered. The present invention also provides a corresponding device and a storage medium.
Owner:TENCENT TECH SHANGHAI
Database migration method and system
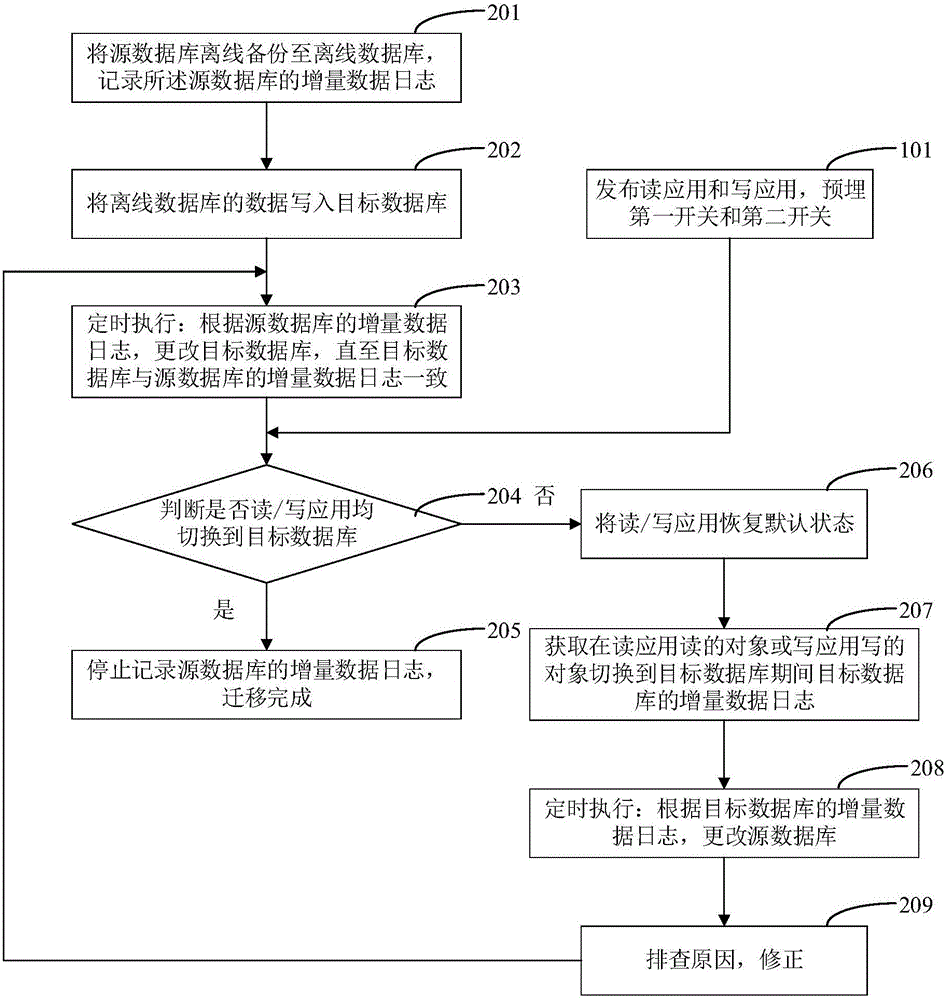
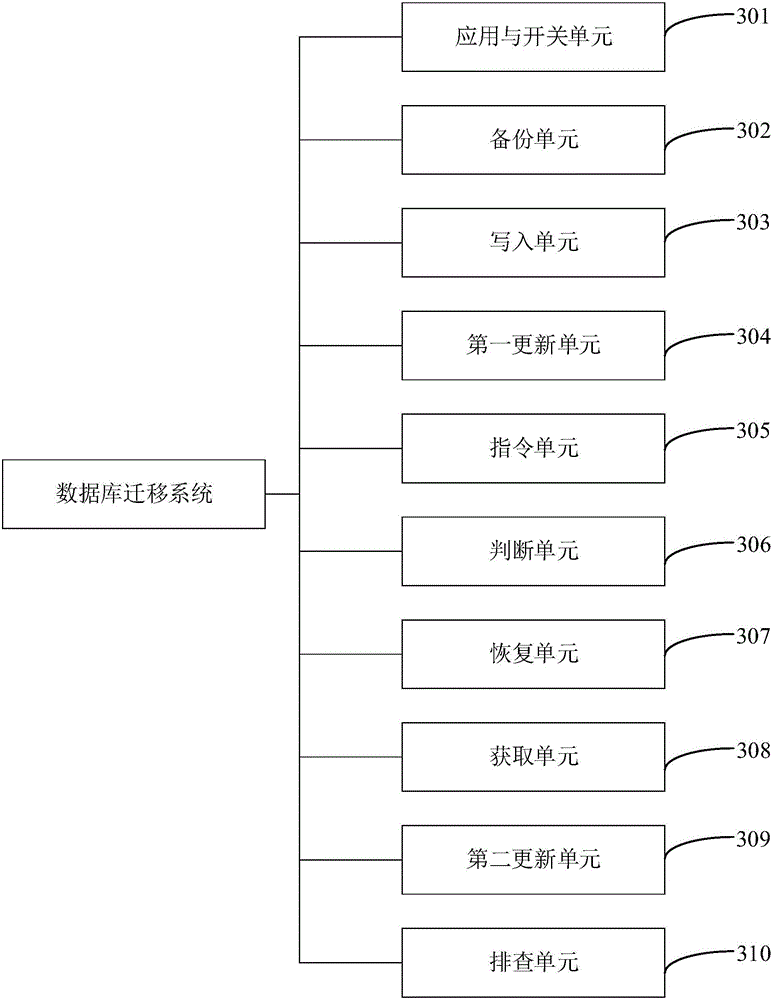
ActiveCN105868343AReduce performance consumptionMake Migration SeamlessSpecial data processing applicationsDatabase applicationTarget database
The invention discloses a database migration method and system. The method comprises the steps that a reading application and a writing application are released, and a first switch and a second switch are embedded; a source database is backed-up to an off-line database in an off-line mode; data of the off-line database is written into a target database; the target database is changed according to incremental data logs of the source database; whether the reading / writing application is switched to the target database is judged; if yes, recording of incremental data logs of the source database is stopped, and migration is completed; if not, the reading / writing application is recovered to be in a default stat; incremental data logs of the target database are obtained; according to the incremental data logs of the target database, the source database is changed; reasons are checked, and correction is carried out. The defects that performance consumption is large and application is intercepted when database migration is achieved in the prior art are overcome, and big data and big concurrent data seamless migration is achieved on the premise of not affecting database application and user using.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
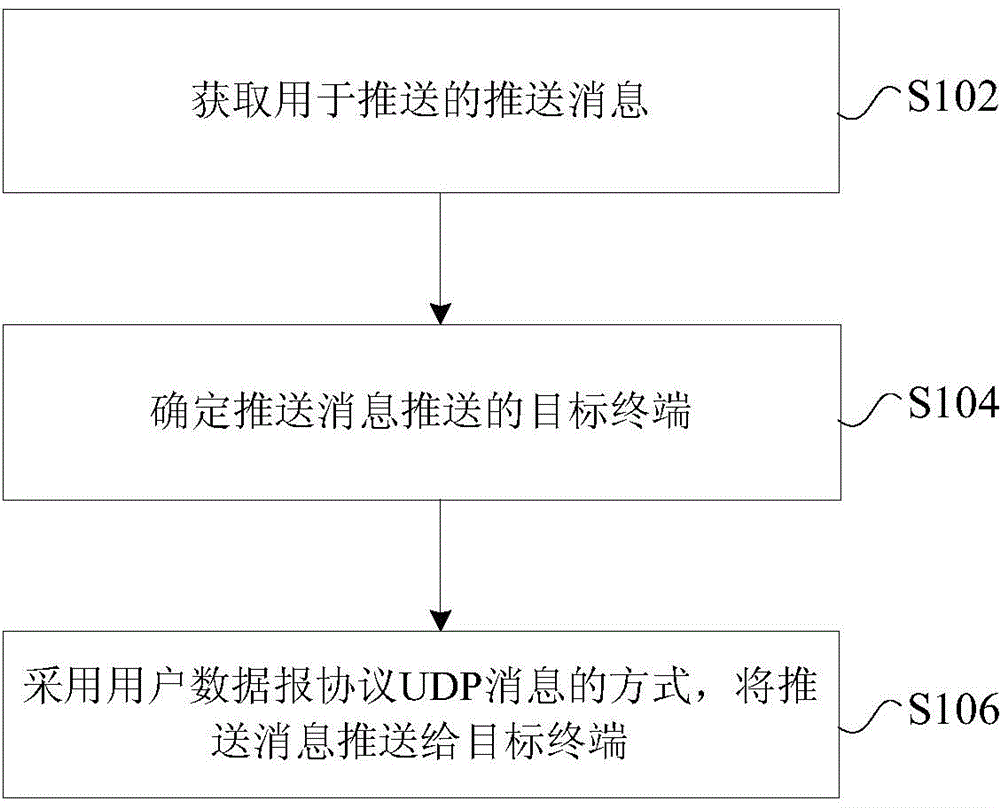
Message pushing processing method, message pushing processing device, pushing server and application server
InactiveCN105323205AReduce performance consumptionImprove push efficiencyMessaging/mailboxes/announcementsTransmissionApplication serverComputer terminal
The invention provides a message pushing processing method, a message pushing processing device, a pushing server and an application server. The method comprises the following steps: acquiring a push message to be pushed; determining a target terminal to which the push message is pushed; and pushing the push message to the target terminal in the form of user datagram protocol UDP message. According to the invention, the problem in the related technologies that the performance consumption is high and the pushing efficiency is low for a server to push a message to a terminal based on an HTTP protocol, the performance consumption of the system is reduced, and the pushing efficiency is improved.
Owner:ZTE CORP
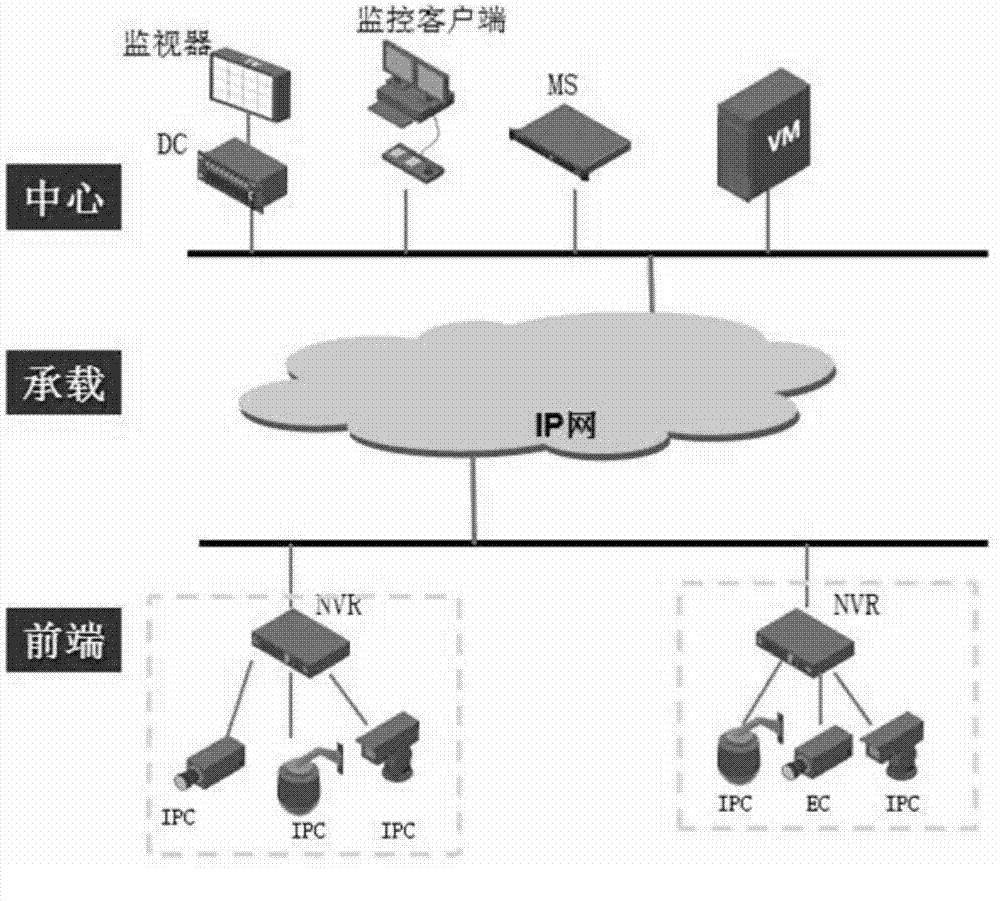
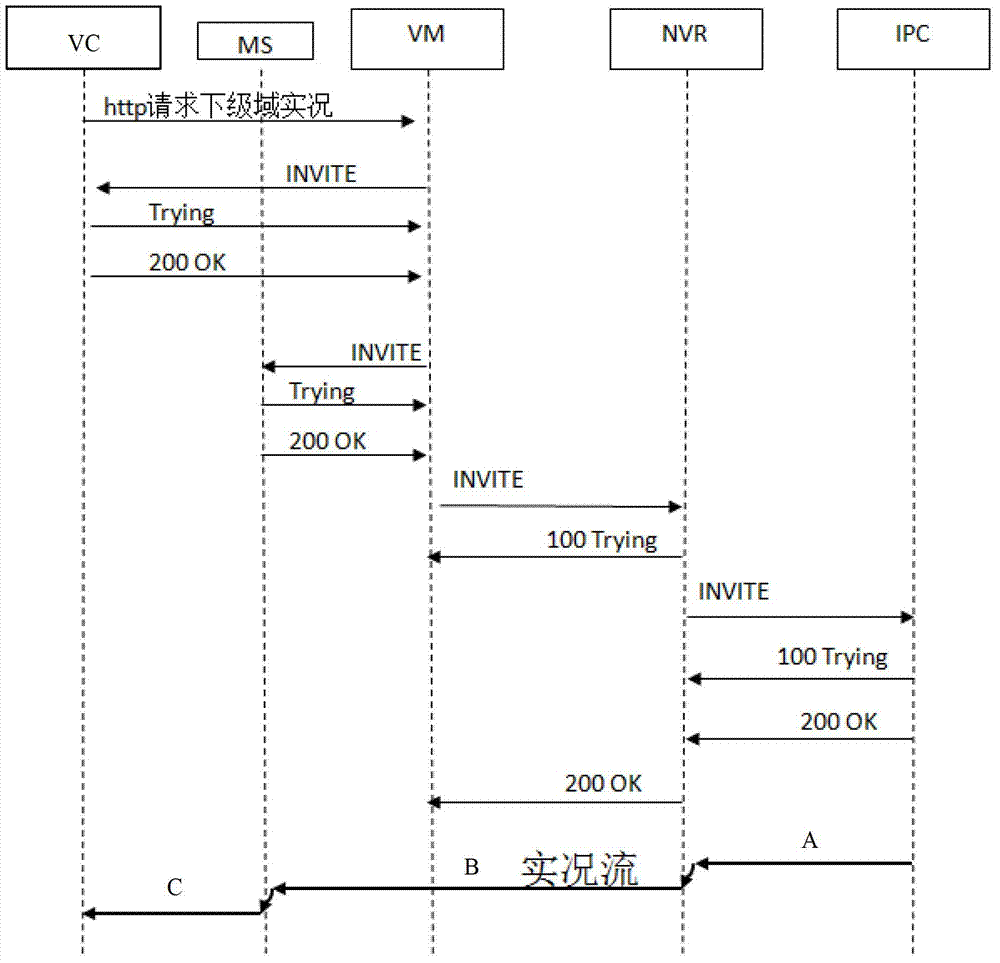
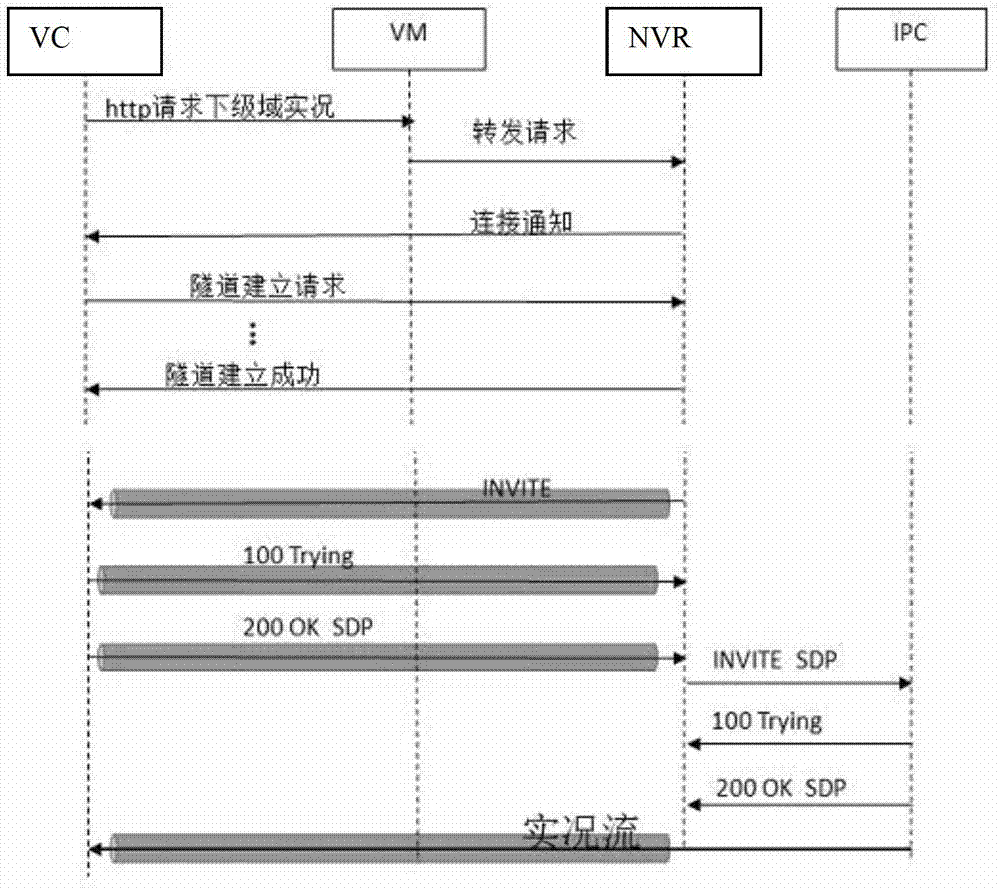
Method for processing monitor service and network video recorder (NVR)
ActiveCN102811174ARelieve pressureEasy accessClosed circuit television systemsNetworks interconnectionVirtual memoryTelecommunications
The invention provides a method for processing a monitor service, wherein the method comprises the steps of receiving a monitor service request which is transmitted by a virtual memory (VM) in a central domain by a network video recorder (NVR), and informing a monitor service request terminal to establish a channel with the NVR; allocating an address to the terminal from a private network address pool, and establishing route information which points to the terminal; sending a signaling of processing the monitor service to the terminal by the NVR through the channel, and sending the signaling of processing the monitor service to a coding terminal under the management of the NVR; receiving a monitor service data packet which is sent by the coding terminal by the NVR, transferring the monitor service data packet to a channel interface which is connected with the monitor service request terminal depending on a route which points to the monitor service request terminal to send the data packet to the terminal through the channel. Owing to the establishment of the channel, the treatment for sending the private network data packet to the outer network by the NVRis just transferred depending on a channel route which is established in the local part, thereby reducing the performance consumption, and simplifying the maintenance and management of the outer network central domain equipment on the private network equipment under the NVR.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
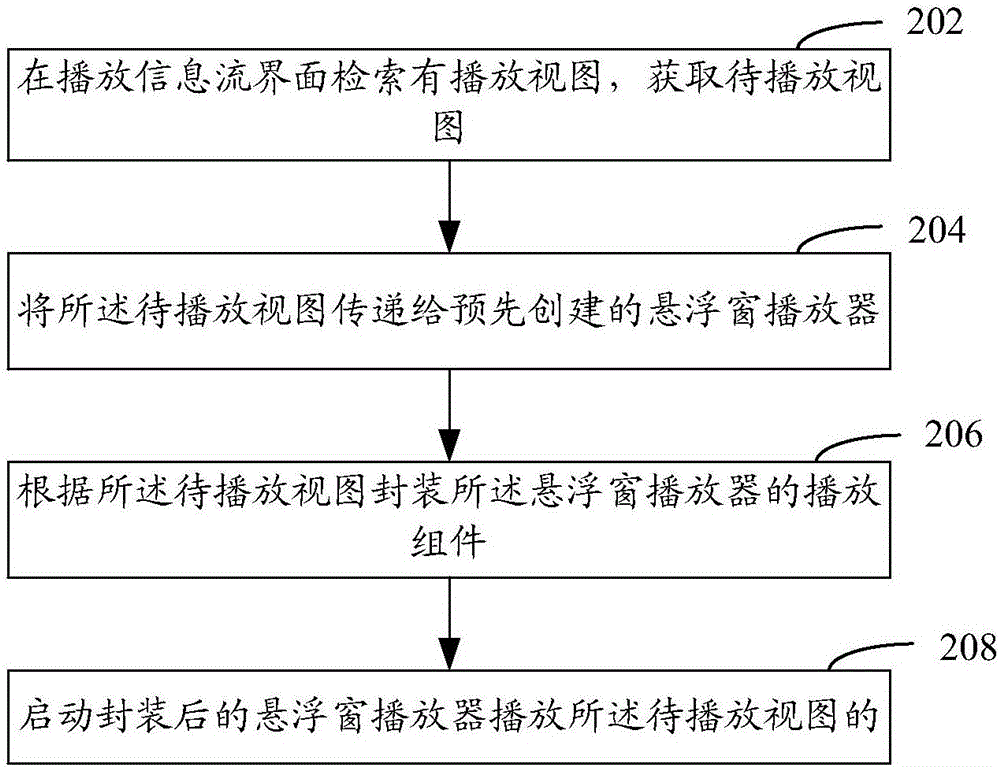
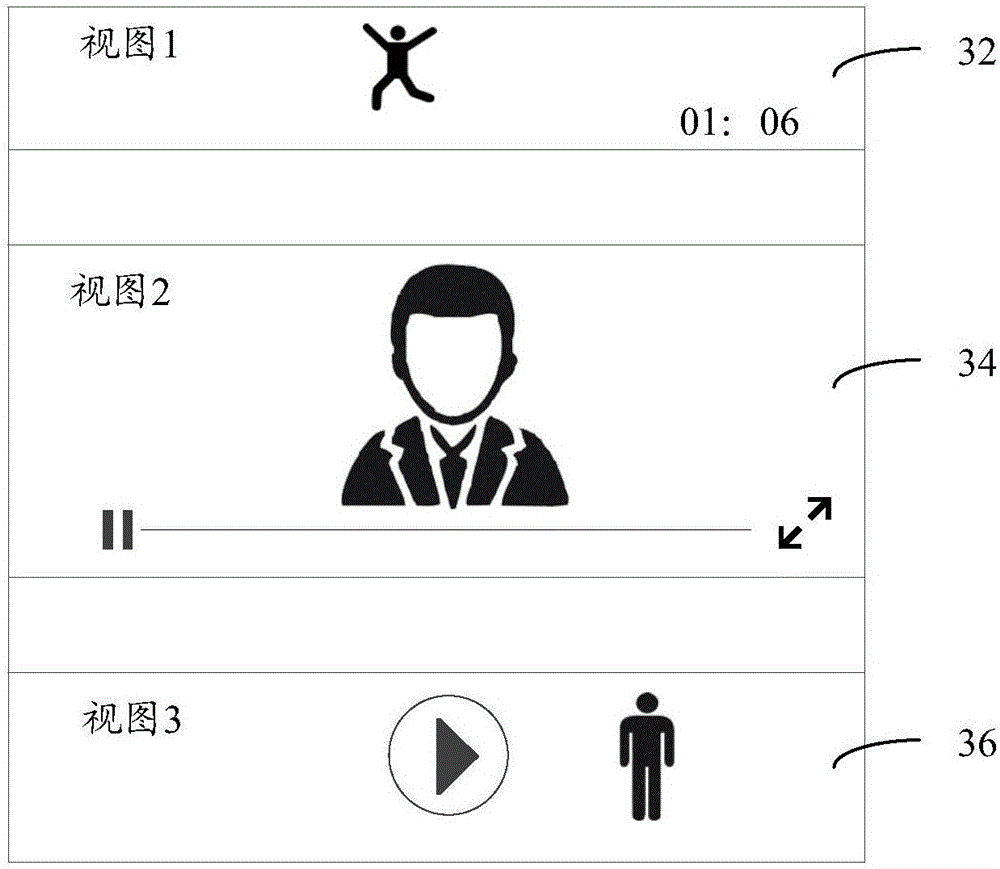
Video playing method and device
InactiveCN106792089AReduce performance consumptionSelective content distributionComputer graphics (images)
The invention relates to a video playing method and device. The method comprises the following steps: retrieving that playing views exist on a play information flow interface, and obtaining a view to be played; sending the view to be played to a pre-created suspension window player; encapsulating the play components of the suspension window player according to the view to be played; and starting the encapsulated suspension window player to play the view to be played. According to the video playing method and device disclosed by the invention, through the steps of retrieving that the playing views exist on the play information flow interface, obtaining the view to be played, sending the view to be played to the suspension window player, and playing the view to be played through the suspension window player, different playing views do not need to be plugged in different players, and thus the performance consumption of the system can be reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Game data processing method and device and storage medium
ActiveCN113423018AAvoid inaccuraciesSynchronization reliabilitySpeech analysisVideo gamesData streamTimestamp
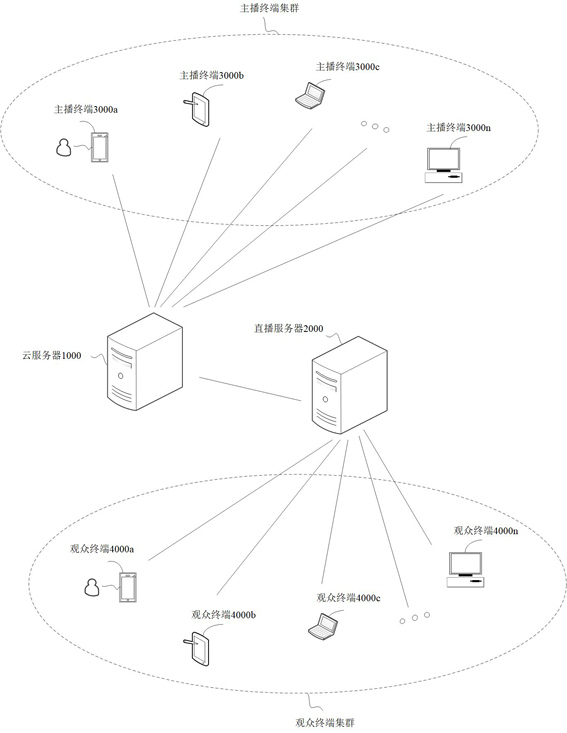
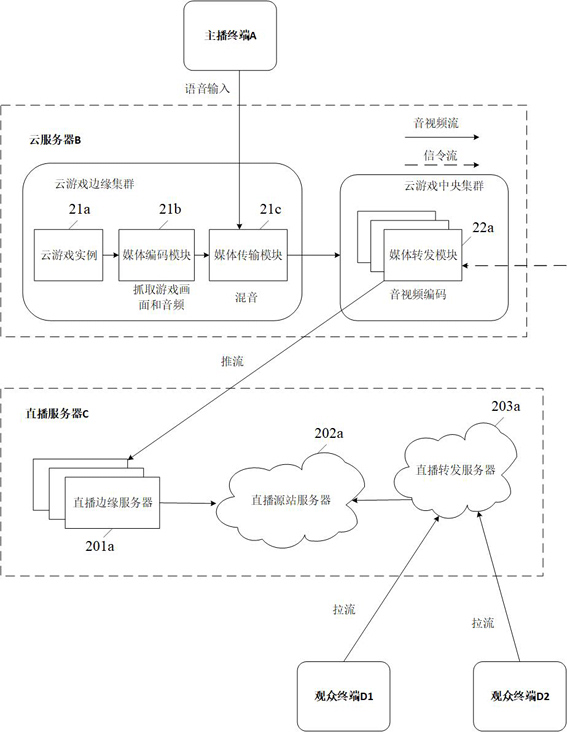
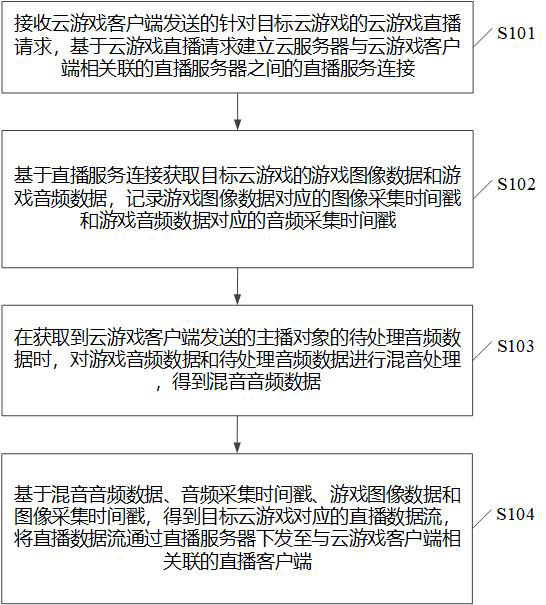
The embodiment of the invention discloses a game data processing method and device and a storage medium. The method comprises the steps of receiving a cloud game live broadcast request sent by a cloud game client, and building a live broadcast service connection based on the cloud game live broadcast request; acquiring game image data and game audio data of the target cloud game based on the live broadcast service connection, wherein an image acquisition timestamp corresponding to the game image data and an audio acquisition timestamp corresponding to the game audio data are timestamps under the same reference system; when to-be-processed audio data of an anchor object sent by the cloud game client is obtained, performing audio mixing processing on the game audio data and the to-be-processed audio data to obtain mixed audio data; and obtaining a live broadcast data stream based on the mixed audio data, the audio acquisition timestamp, the game image data and the image acquisition timestamp, and issuing the live broadcast data stream to a live broadcast client associated with the cloud game client through a live broadcast server. According to the invention, the reliability of audio and video synchronization can be realized.
Owner:TENCENT TECH (SHENZHEN) CO LTD
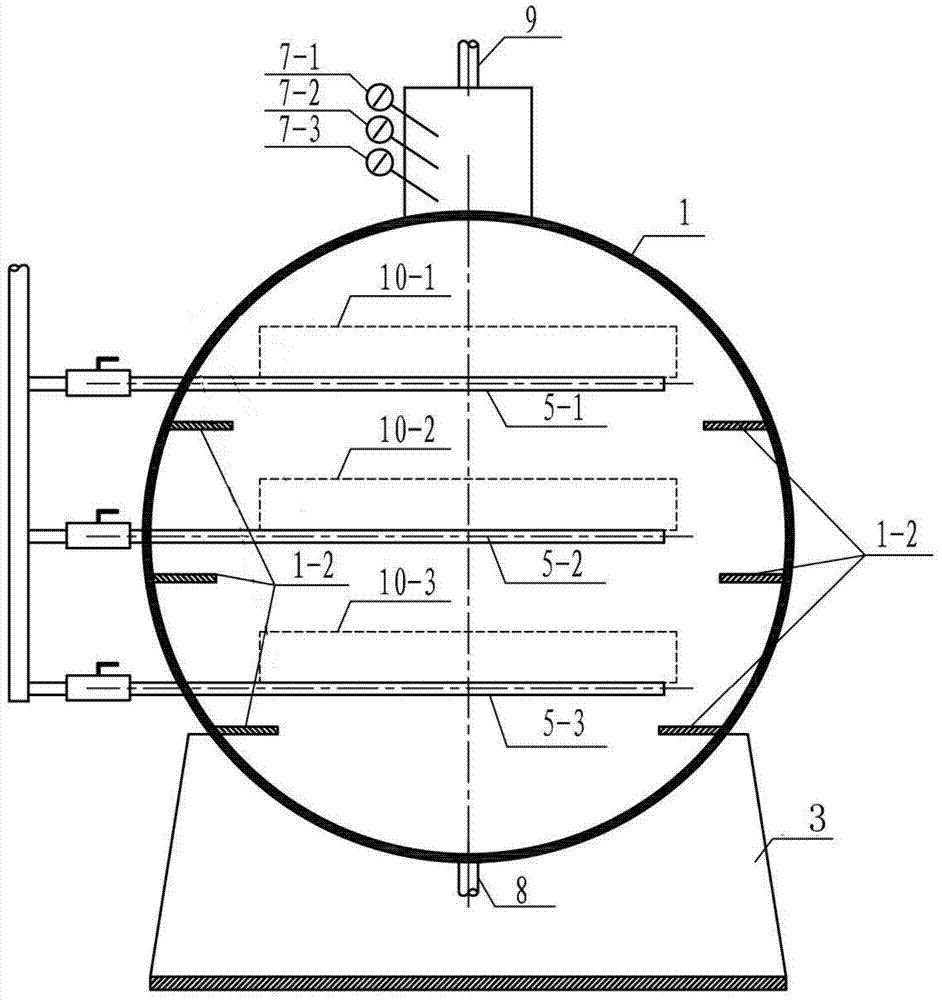
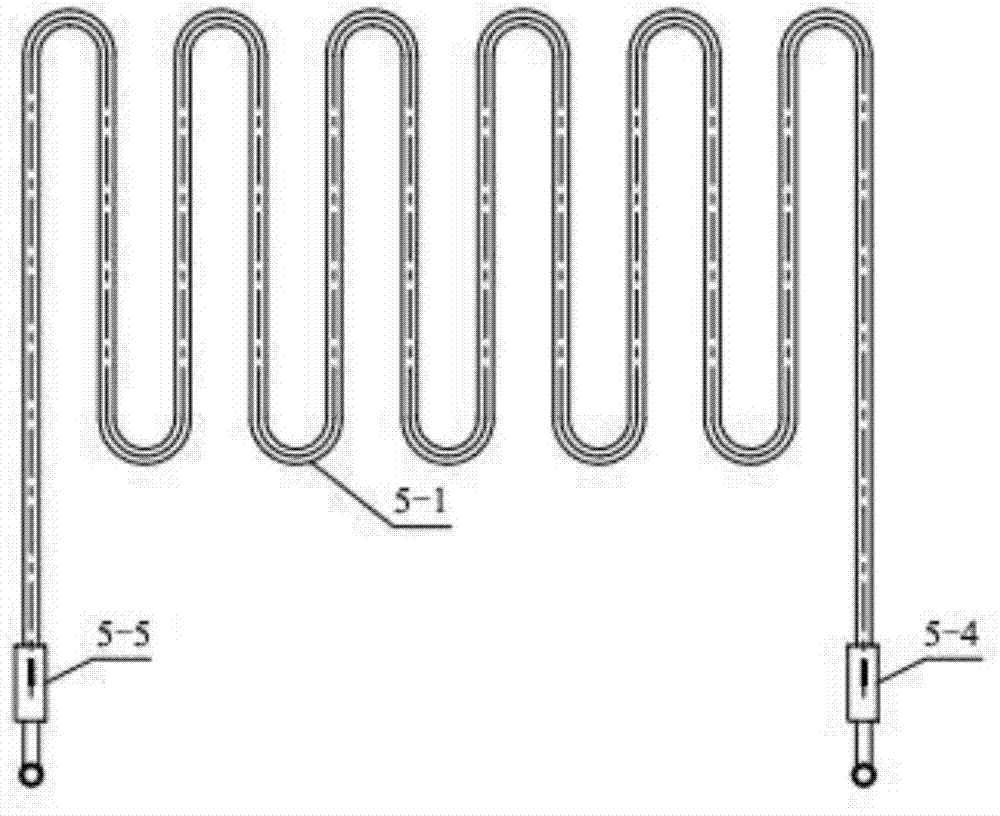
Solid state fermentation reactor and application thereof
InactiveCN104845877AThoroughly sterilizedStable fermentationBioreactor/fermenter combinationsBiological substance pretreatmentsAutomatic controlSteel jacket
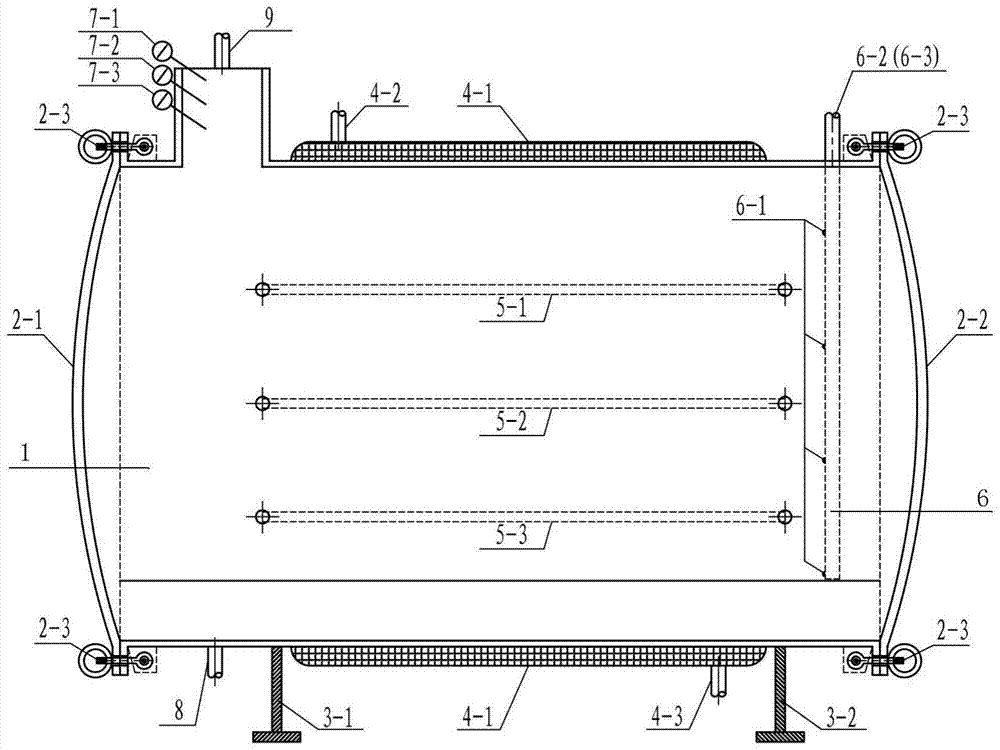
The invention discloses a solid state fermentation reactor and an application thereof. The reactor comprises a horizontal cylindrical stainless steel fermentation tank body, a stainless steel jacket is welded on the outer wall of the above tank, and the tank is also provided with a gas outlet, probes, a steam inlet, a steam outlet, a material outlet, movable top covers and a two-fluid spray device; and coil pipes and trays are arranged in the inner cavity of the tank body. The invention also discloses an application of the reactor in cultivation of aerobic, anaerobic and facultative anaerobic microbes. The reactor has the advantages of simple structure, convenience and practicality, can solve the problems of difficult material disinfection, easy bacterial contamination, large labor intensity and low working efficiency of traditional solid state fermentation, realizes automatic control of the solid state fermentation process, and facilitates industrial application of the solid state fermentation.
Owner:NANJING UNIV OF TECH
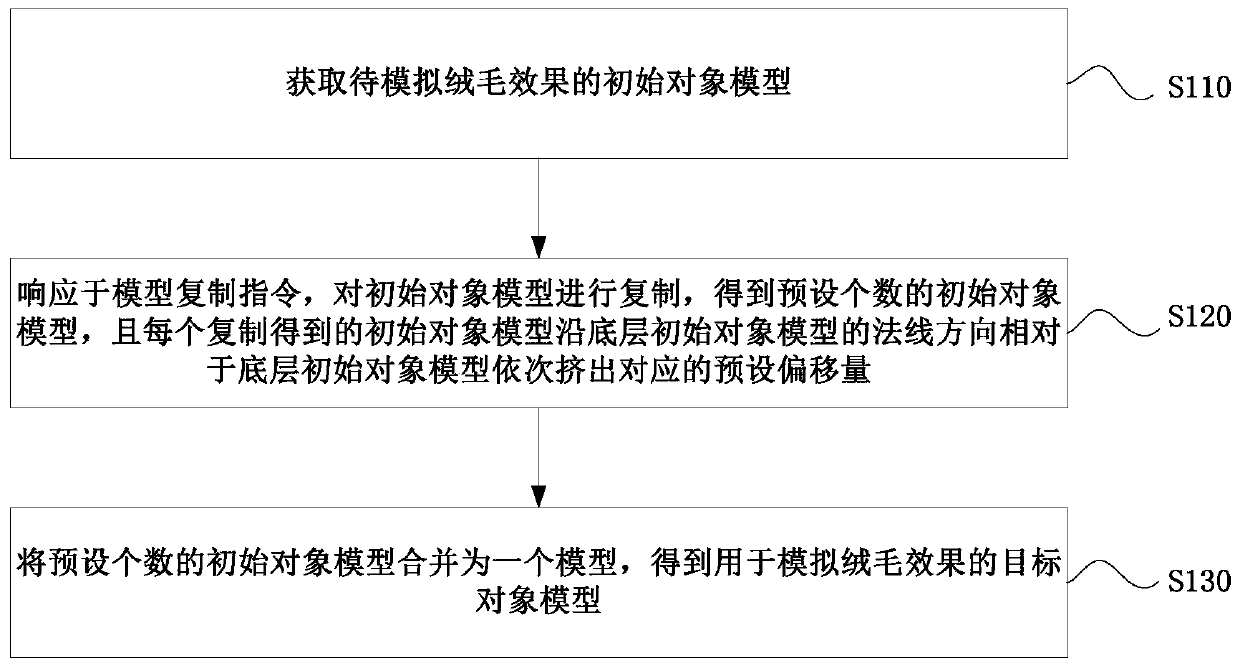
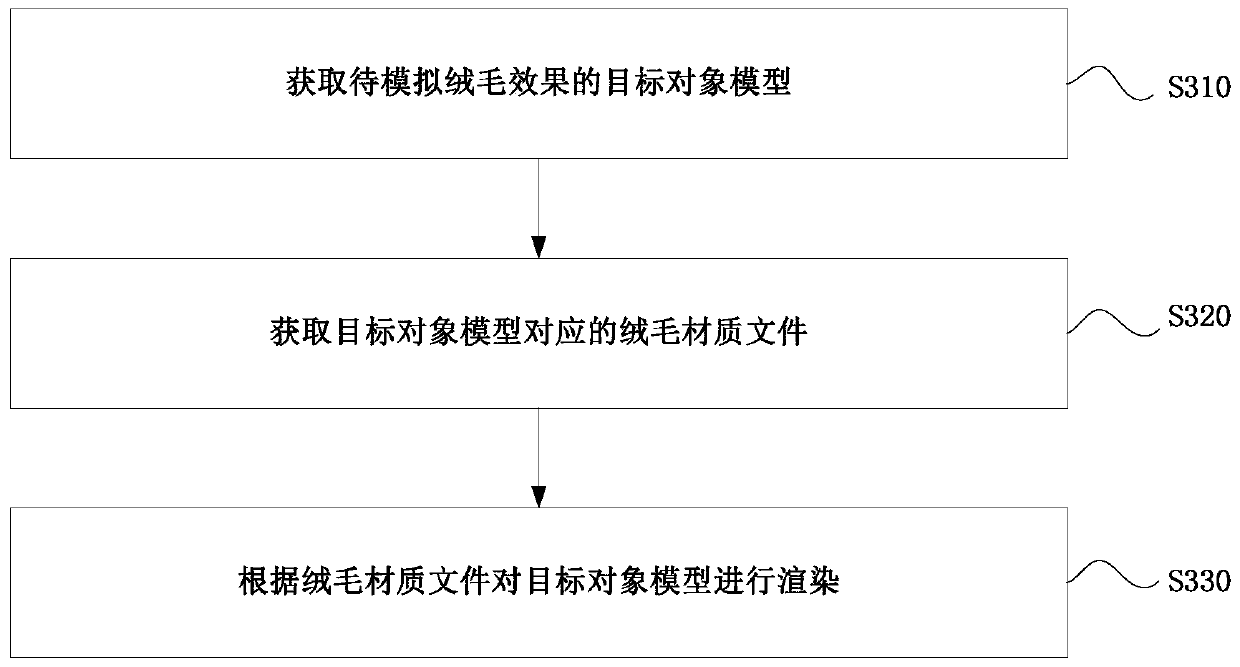
Implementation method and device of fluff effect and terminal
PendingCN111462313AAlleviate high performance consumptionReduce limitations3D modellingManufacturing computing systemsComputer hardwareComputational science
The invention provides a fluff effect implementation method and device and a terminal, and relates to the technical field of computer graphics images.The method comprises the steps that initial objectmodels of a to-be-simulated fluff effect are obtained and copied in response to a model copying instruction, and a preset number of initial object models are obtained; each copied initial object model extrudes corresponding preset offsets in sequence relative to the bottom-layer initial object model along the normal direction of the bottom-layer initial object model; and combining the preset number of initial object models into one model to obtain a target object model for simulating a fluff effect. According to the method, the target object model for simulating the fluff effect can be directly obtained; according to the method, fluff with a multi-layer effect can be simulated without multi-channel rendering, and the problems of high performance consumption and high limitation of a methodfor simulating the fluff effect by rendering in the prior art are solved, so that the technical effects of reducing the rendering times, reducing the performance consumption and meeting the configuration requirements are achieved.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
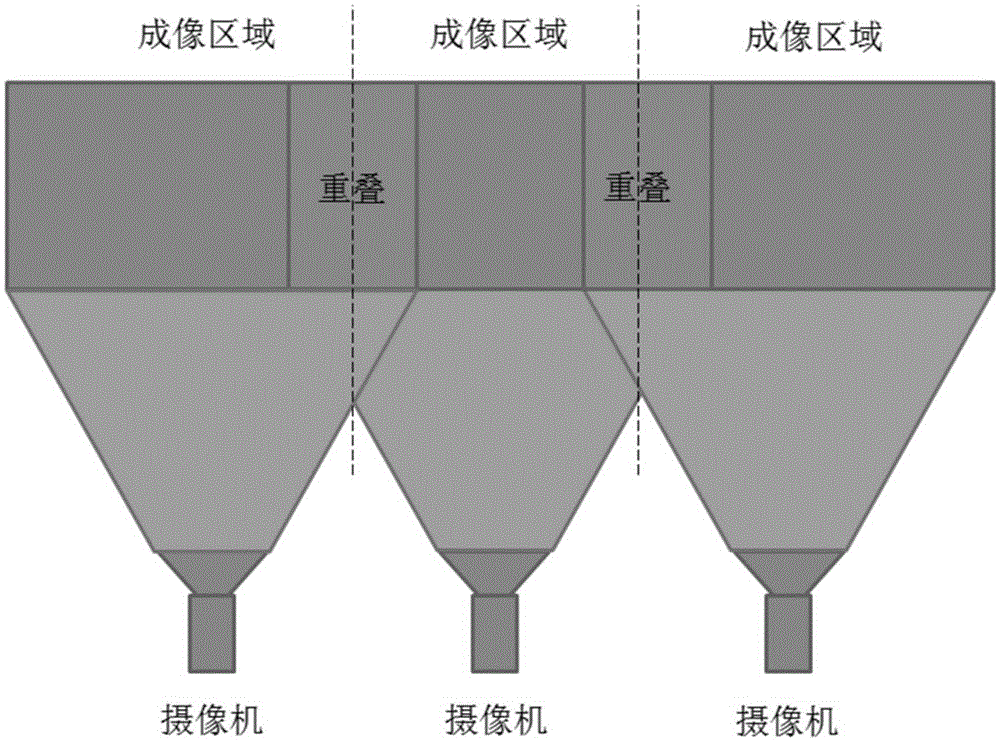
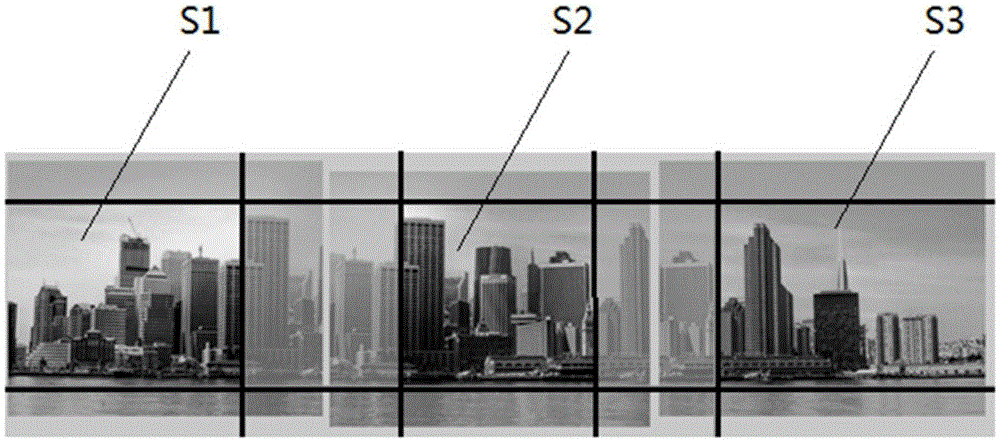
Multi-image splicing method and device
InactiveCN105306837AReduce performance consumptionIncrease the number of camerasTelevision system detailsColor television detailsImage resolutionVideo camera
The invention discloses a multi-image splicing method, comprising the steps that: a decoding terminal obtains region information of regions needing to be spliced in images shot by cameras to be spliced and a splicing position relation of the cameras to be spliced, and sends the obtained region information of the regions needing to be spliced to corresponding cameras; the cameras to be spliced encode the images according to the region information of the regions needing to be spliced and output images to be spliced; and the decoding terminal simultaneously display the images to be spliced output by the cameras to be spliced according to the splicing position relation to form a complete image. The invention further correspondingly discloses a multi-image splicing device. By adopting the method and the device disclosed by the invention, the images to be spliced of multiple cameras can be played at corresponding positions after being decoded to achieve an image splicing effect without subsequent image processing of the decoding terminal, thereby reducing the performance consumption of the decoding terminal, not limiting the number and resolution of the cameras to be spliced anymore, and meanwhile, enriching the image splicing usage and application scene.
Owner:ZHEJIANG UNIVIEW TECH
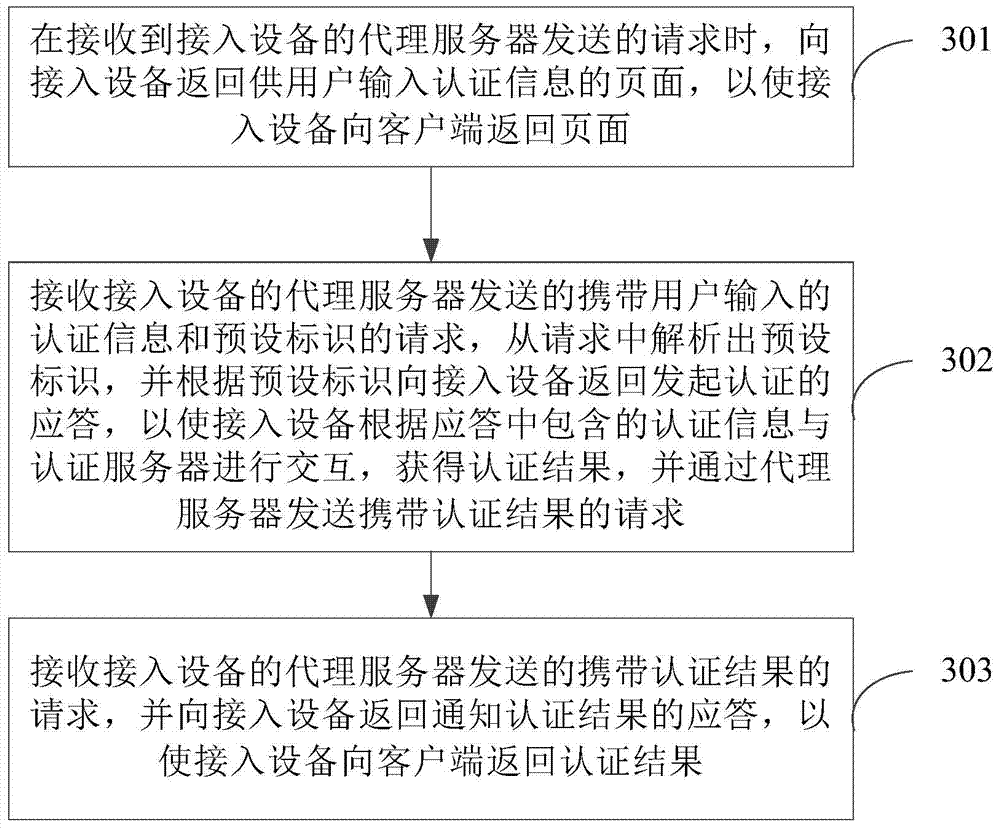
Method and apparatus for realizing portal authentication
ActiveCN104852919AReduce communication consumptionReduce performance consumptionTransmissionClient-sideFixed time
The application provides a method and apparatus for realizing portal authentication. The method comprises: receiving a request sent by a client, carrying out interaction with a portal server by a proxy server, returning a page for authentication information inputting by a user to the client; receiving the authentication information inputted by the user and sending a request carrying the authentication information and a preset identifier to the portal server by the proxy server to enable the portal server to return response information containing the authentication information for launching authentication according to the preset identifier; and carrying out interaction with an authentication server according to the response to obtain an authentication result, sending a request containing the authentication result to the portal server by the proxy server, and receiving a response, for authentication result notification, returned by the portal server, thereby returning the authentication result to the client. According to the embodiment of the invention, UDP messages can be sent at fixed time without any access equipment, thereby effectively reducing communication consumption in a network.
Owner:NEW H3C TECH CO LTD
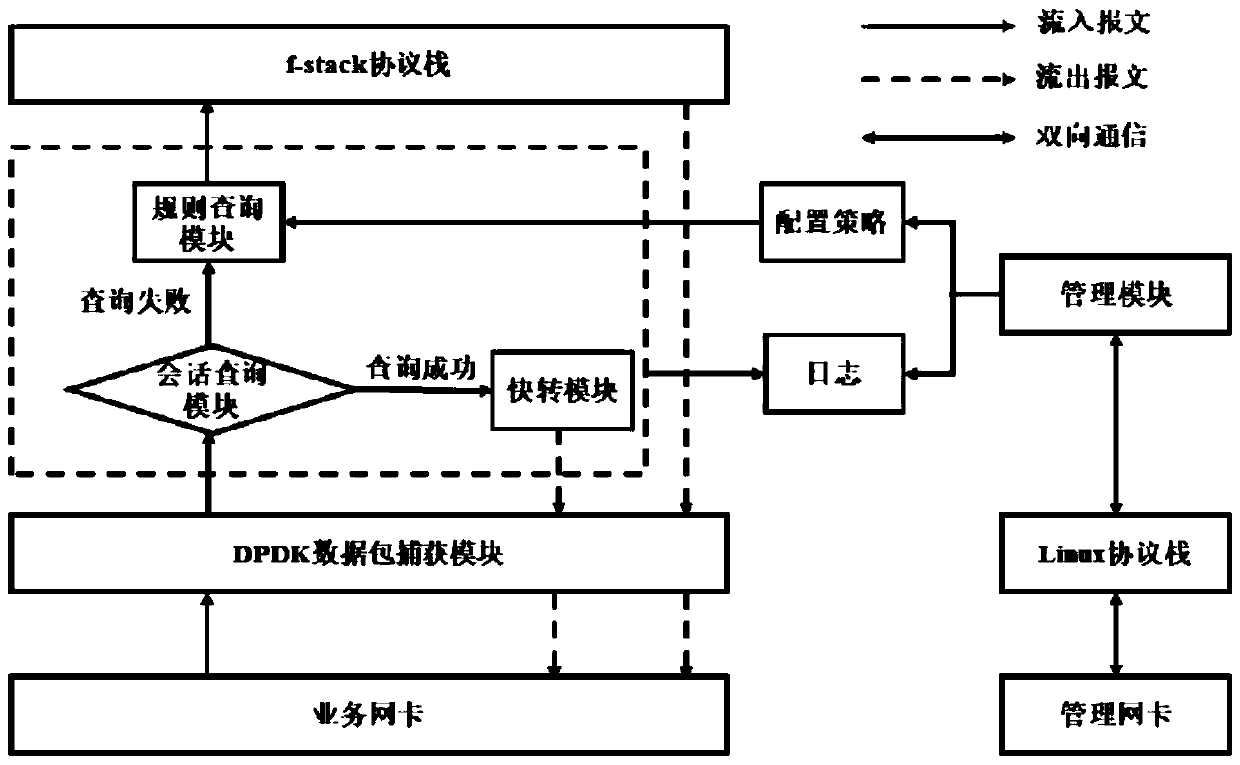
Firewall based on DPDK virtualization management system and implementation method thereof
The invention provides a firewall based on a DPDK virtualization management system and an implementation method thereof. According to the invention, interruption is intercepted by using a DPDK pollingtechnology; according to the working principle that the UIO technology bypasses the kernel protocol stack and the message received by the network card is mapped to the user mode protocol stack f-stack through the UIO technology, the performance consumption during data packet capture is greatly reduced, and the data packet processing performance of the firewall is improved. A quick forwarding pathis added before a data packet enters an f-stack protocol stack; according to the method, session check is carried out on the data packet captured by the DPDK, and the flow of which the session is established is directly forwarded from the recorded port, so that the performance loss of the data packet in the process of passing through the protocol stack is reduced, the packet forwarding rate is improved, and the data processing performance of the firewall of the virtualization management system is further improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Data safety storage method in cloud environment
ActiveCN106534176AEnhance and avoid data transferEnhancing and Avoiding Data SecurityEncryption apparatus with shift registers/memoriesExclusive orEncryption
The invention discloses a data encryption method in a cloud environment. A sending end encrypts a dynamic token generated in advanced according to an encryption algorithm, an encryption result is used as a secret key, data is subjected to AES symmetric encryption according to the secret key to form an encrypted data part, the dynamic token is subjected to Exclusive OR, replacement, substitution and shifting and is spliced with the encrypted data part, a check code is calculated according to the data obtained after splicing, and the encrypted data part is transmitted after being spliced; and a receiving end with the same dynamic token and secret key with a receiving end carries out unpacking on data to obtain a check code to be verified and an encrypted data part after receiving the data, the encrypted data part is subjected to calculation to obtain a check code, the check code is compared with the check code to be verified, if the check code is the same with the check code to be verified, the data is correct data and the encrypted data part is stored and subjected to other processing, and on the contrary, the data is incorrect data, the data is regarded as tampered data and the data is abandoned. The data encryption method in the cloud environment, which is disclosed by the invention, can prevent leakage and prevent tampering, and is low in performance consumption.
Owner:西安交大捷普网络科技有限公司
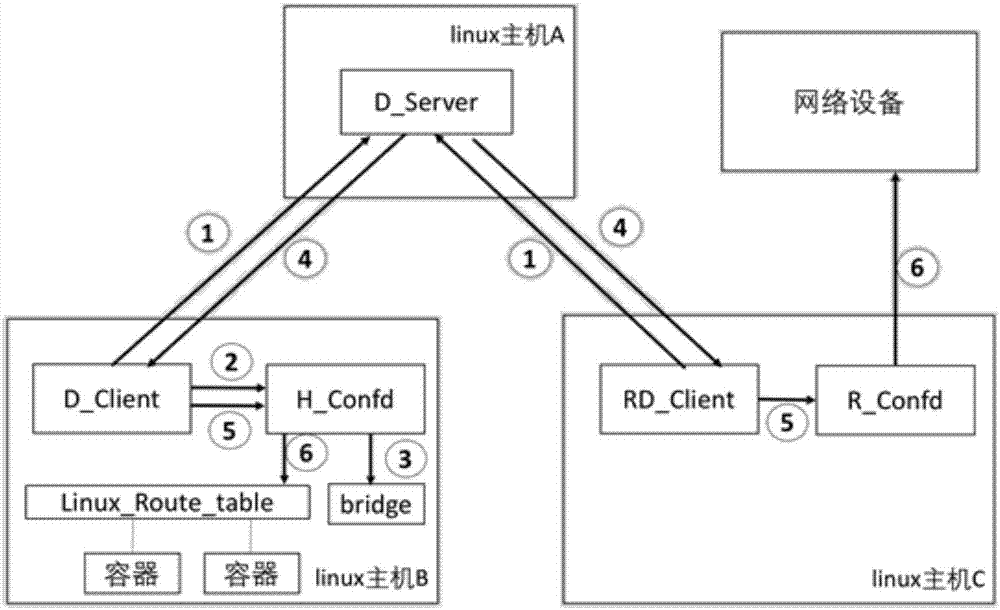
Cross-host mutual access system based on docker containers and control method thereof
The invention discloses a cross-host mutual access system based on docker containers and a control method thereof. The system comprises a host and a plurality of node hosts. The host and the node hosts are connected through a network. A database is arranged on the host. The host detects a connection operation state of each node host periodically, issues updating messages and allocates IP address or network segments. Each node host receives a route configured with an IP address segment employed by other node container. A next hop address of the route is an interface IP address of the node host. Each node host carries out route configuration on a network device connected with the node host, so the whole cross-host mutual access system forms pure static route configuration and each node route can be directly checked and modified. The docker containers in the system can carry out mutual access with a traditional physical network, also can carry out cross-host mutual access, are safe and reliable and are easy to maintain. The package of a server for data packages is greatly reduced. The performance consumption resulting from the package is reduced.
Owner:SHANGHAI SNC NET INFORMATION TECH CO LTD
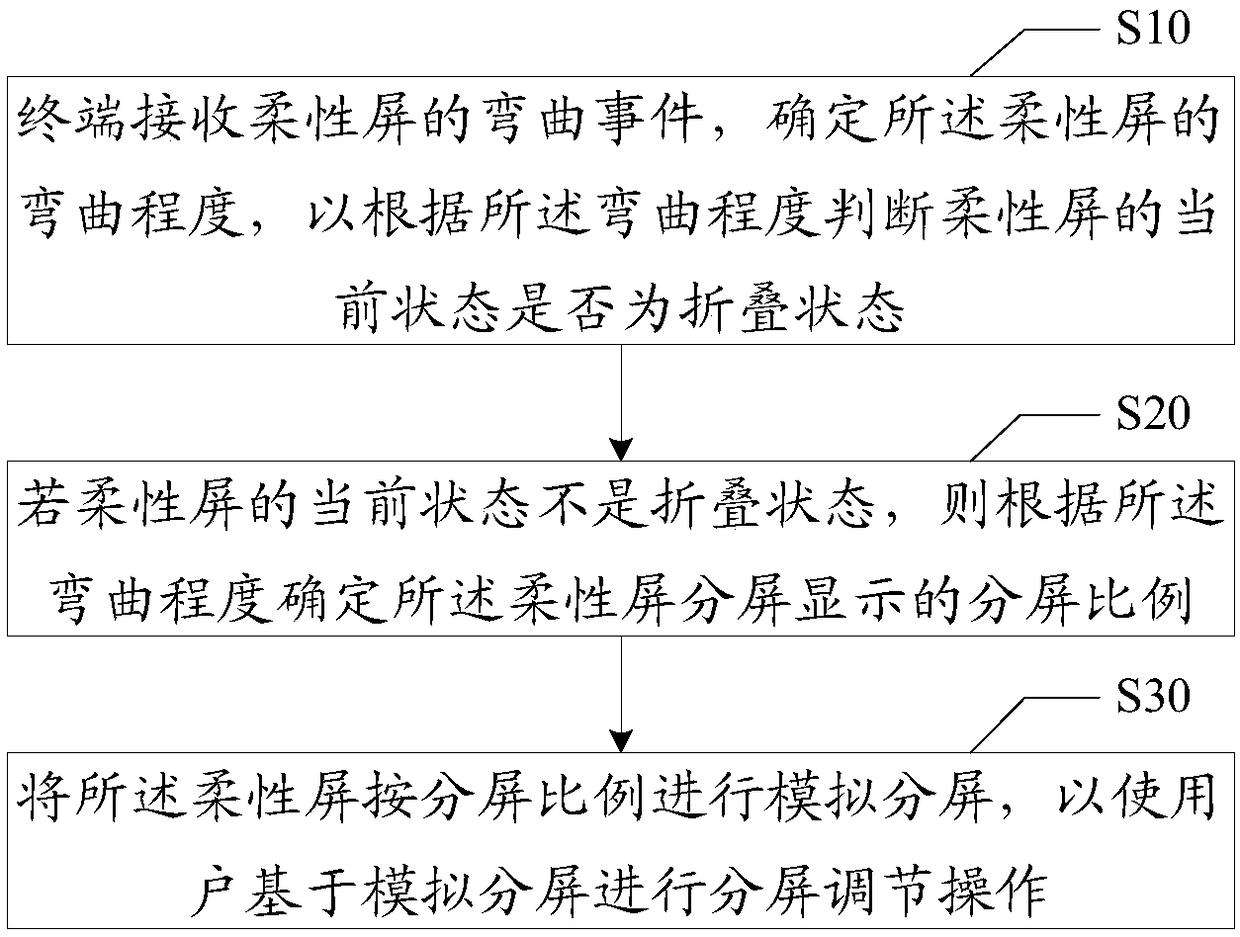
Screen splitting method based on flexible screen, terminal and computer storage medium
ActiveCN108196804AImprove visual experienceReduce performance consumptionDigital output to display deviceSimulation basedComputer engineering
The invention discloses a screen splitting method based on a flexible screen. The method comprises the steps that a terminal receives a bending event of the flexible screen, the bending degree of theflexible screen is determined, and whether the current state of the flexible screen is a folding state is judged according to the bending degree; if the current state of the flexible screen is not thefolding state, a screen splitting ratio of screen-split display of the flexible screen is determined according to the bending degree; and simulated screen splitting is performed on the flexible screen according to the screen splitting ratio, so that a user performs screen-split adjustment operation based on simulated screen splitting. The invention furthermore discloses the terminal and a computer storage medium. According to the method, the bending degree of the flexible screen is determined according to the bending angle of the flexible screen of the terminal by the user, and intelligent screen splitting is performed on the flexible screen of the terminal according to the bending degree and the size of the flexible screen of the terminal, so that a terminal display picture better adaptsto screen splitting, and the visual experience of the user is improved.
Owner:NUBIA TECHNOLOGY CO LTD
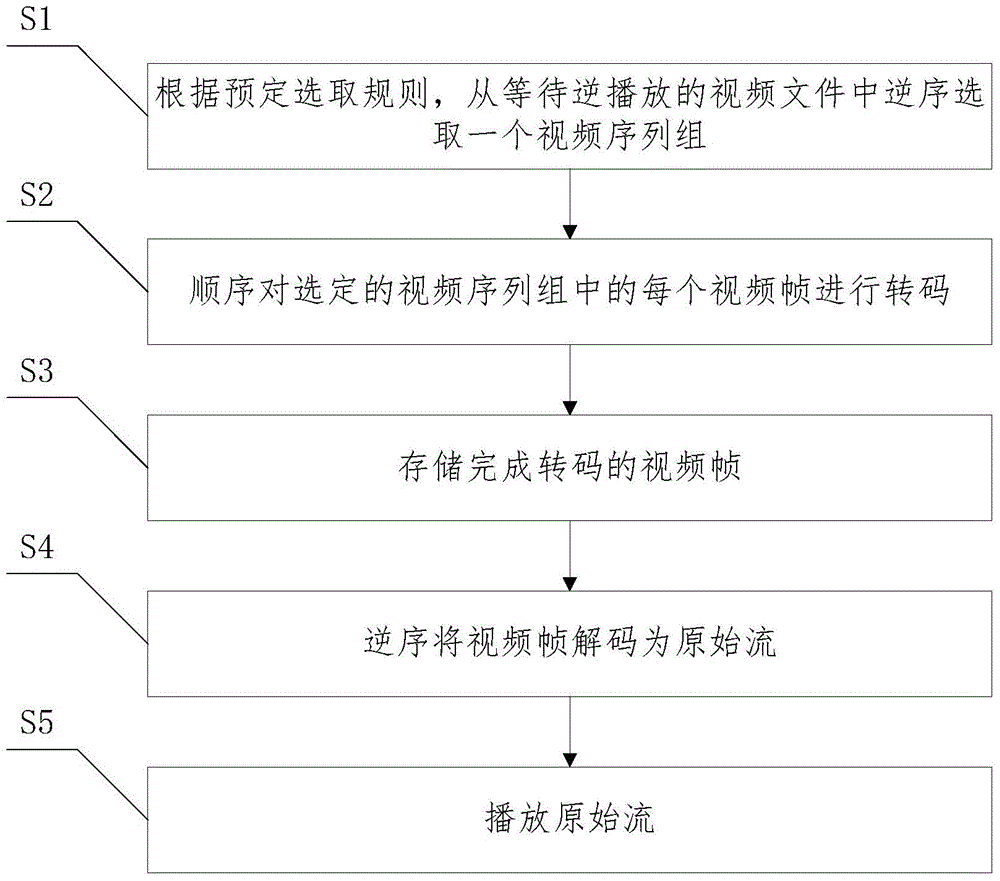
Reverse playing method and system of video files
ActiveCN106303379ASave storage spaceReduce performance consumptionClosed circuit television systemsDigital video signal modificationReverse orderComputer graphics (images)
The invention provides a reverse playing method and system of video files. According to the method and system, a video sequence group is selected form video files to be played in a reverse order according to a preset selection rule, each video frame in the selected video sequence group is transcoded in sequence, the video frames which accomplish transcoding are stored, the video frames are decoded as original stream in a reverse order, the original stream is played, and reverse playing of the video files is realized. According to the method and system, the video sequence group with the format of I frames is obtained through transcoding of the video sequence group and is stored in a memory, I frames are taken out from the memory in a reverse order through the decoder, reverse playing of the video files is realized, the storage space of the memory is saved, the performance consumption of the decoder is reduced, and the function of the player is expanded.
Owner:HANGZHOU HIKVISION DIGITAL TECH
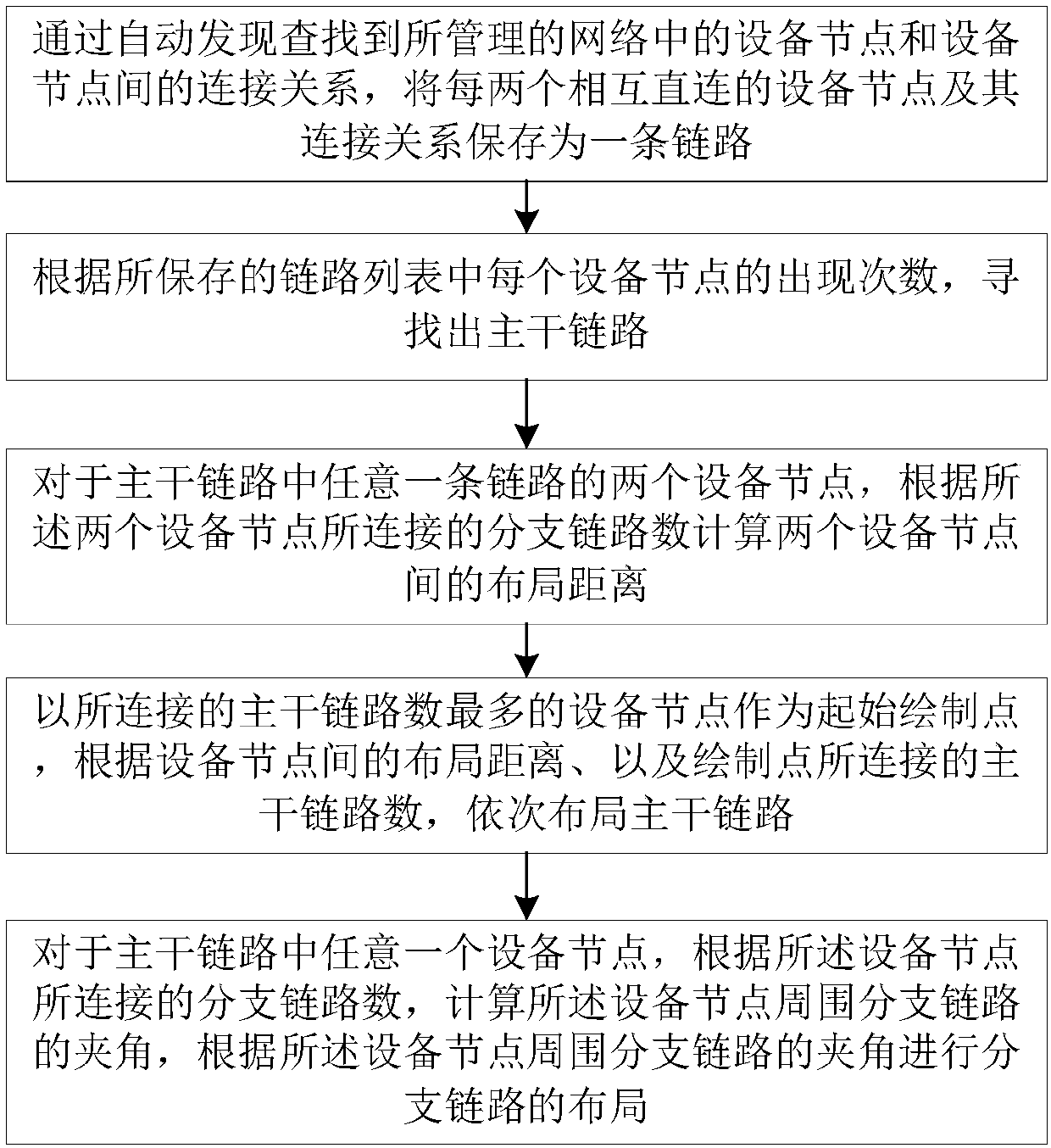
Network topology layout method and apparatus
ActiveCN107749803ADrawn preciselyAvoid paralysisClosed circuit television systemsData switching networksNetwork topologyLinked list
The invention discloses a network topology layout method and apparatus. The method comprises the following steps: storing each two interconnected device nodes and a connecting relation thereof as a link, finding a main link according to the occurrence time of each device node in a stored link list, and for the two device nodes of any link in the main link, calculating a layout distance between thetwo device nodes according to the number of branch links connected with the two device nodes; then using the device node having the largest number of connected main links as a starting drawing node,and laying the main links in sequence according to the layout distance between the device nodes and the number of the main links connected with the drawing node; and finally, calculating the includedangles of the branch links on the surrounding of the device nodes according to the number of the branch links connected with the device nodes, and laying the branch links according to the included angles of the branch links on the surrounding of the device nodes. By adoption of the method and apparatus disclosed by the invention, the network topology structure can be accurately drawn, and the network topology structure is clearly displayed.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
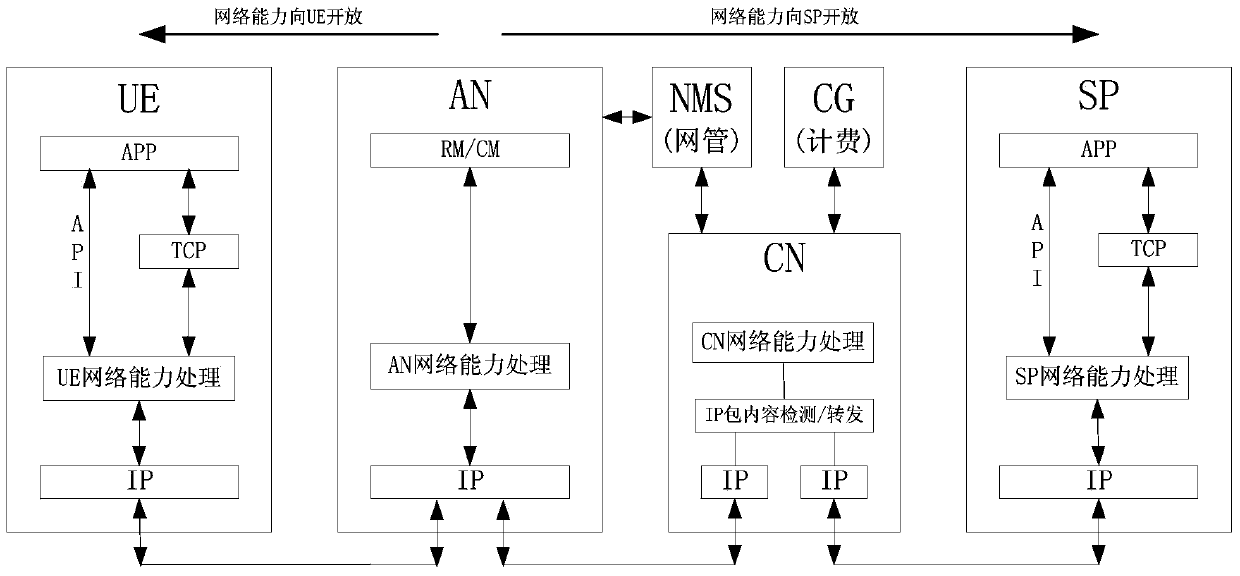
Business channel-based network capacity opening method and device thereof
InactiveCN103702352AReduce performance consumptionSynchronization of business requestsWireless communicationData packComputer science
The invention provides a business channel-based network capacity opening method and a device thereof. A related function of opening network capacity information is added under the condition of not increasing hardware investment of an operator on the existing network element. Meanwhile, the accounting function based on data packet content detection is widely deployed as to a core network (CN), so that the related function of opening the network capacity is increased, and consumption on the performance of the original hardware is tiny. The network capacity information travels on the original business channel in the aspect of time delay, so that the network capacity information is basically synchronous with the business request of a user, and the time delay is at the millisecond level.
Owner:郭凯文
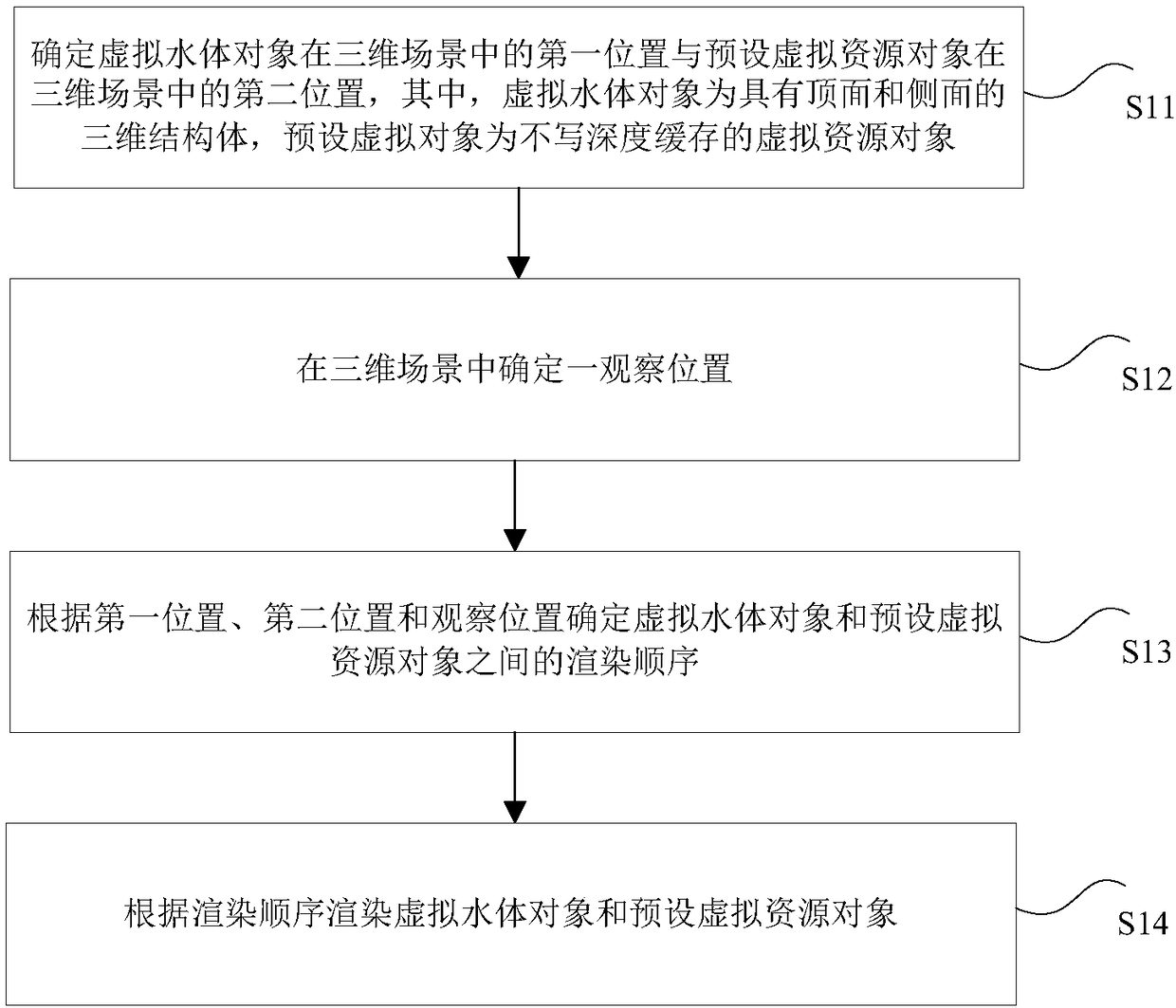
Rendering method for virtual resource object in three-dimensional scene
InactiveCN108230436AFix rendering effectsSolve efficiency problemsVideo games3D-image renderingComputer graphics (images)Virtual water
The invention discloses a rendering method and device for a virtual resource object in a three-dimensional scene, a storage medium, a processor and a terminal. The method is applied to electronic equipment comprising a display unit and a camera-shooting unit. The virtual resource object comprises a virtual water body object and a preset virtual resource object. The method comprises the steps thatan image of a real scene is captured through the camera-shooting unit of the electronic equipment, and a three-dimensional scene is constructed with the image of the real scene being a background; a first position of the virtual water body object in the three-dimensional scene and a second position of the preset virtual resource object in the three-dimensional scene are determined, wherein the virtual water body object is a three-dimensional structural body with a top face and side faces, and the preset virtual object is a virtual resource object not writing a depth cache; an observation position is determined in the three-dimensional scene according to the image, captured by the camera-shooting unit of the electronic equipment, of the real scene; the rendering order of the virtual water body object and the preset virtual resource object is determined according to the first position, the second position and the observation position; and the virtual water body object and the preset virtual resource object are rendered according to the rendering order. Through the rendering method and device, the storage medium, the processor and the terminal, the technical problems that the water body rendering effect and efficiency cannot be both considered, and interaction cannot be realized are solved.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
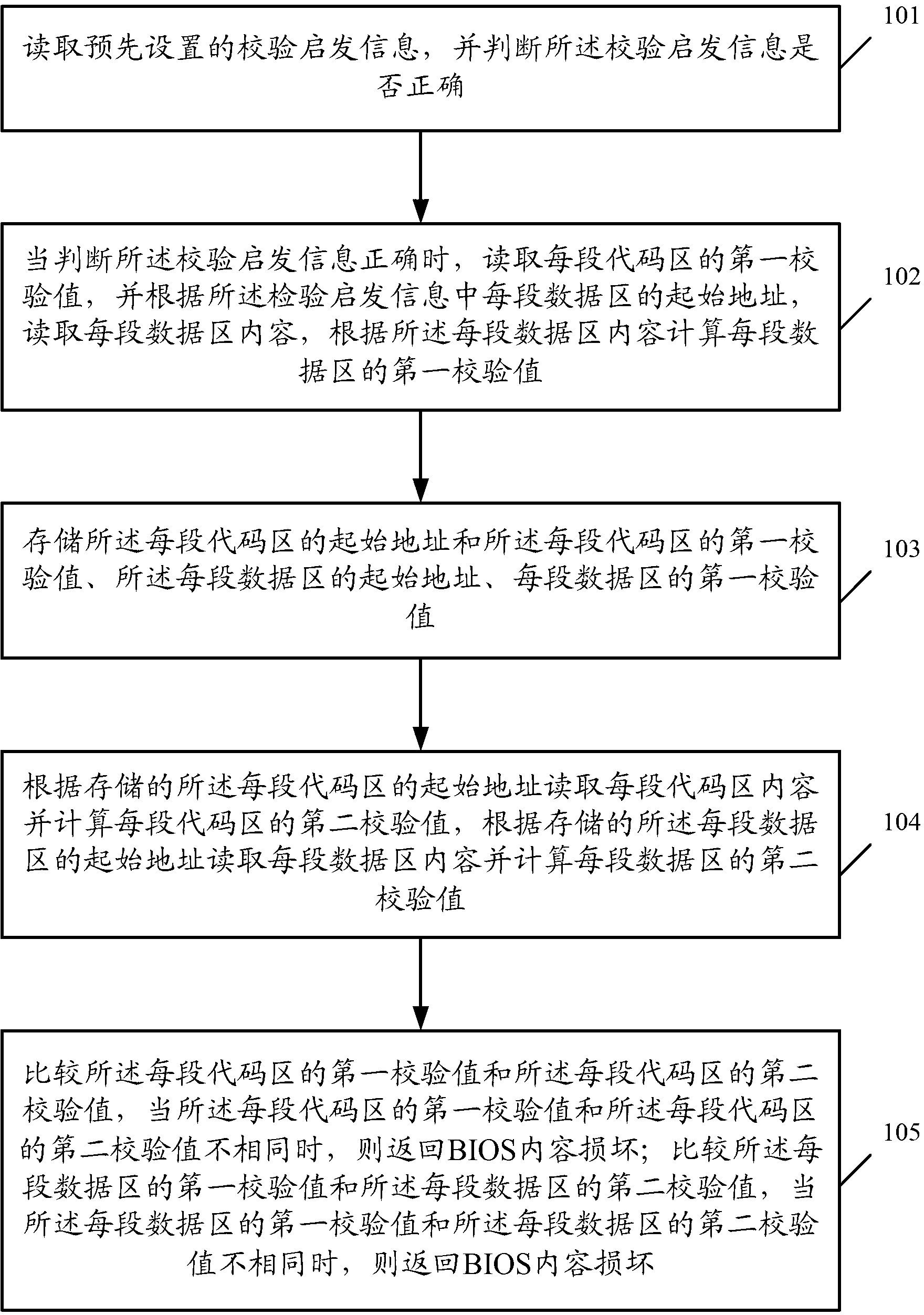
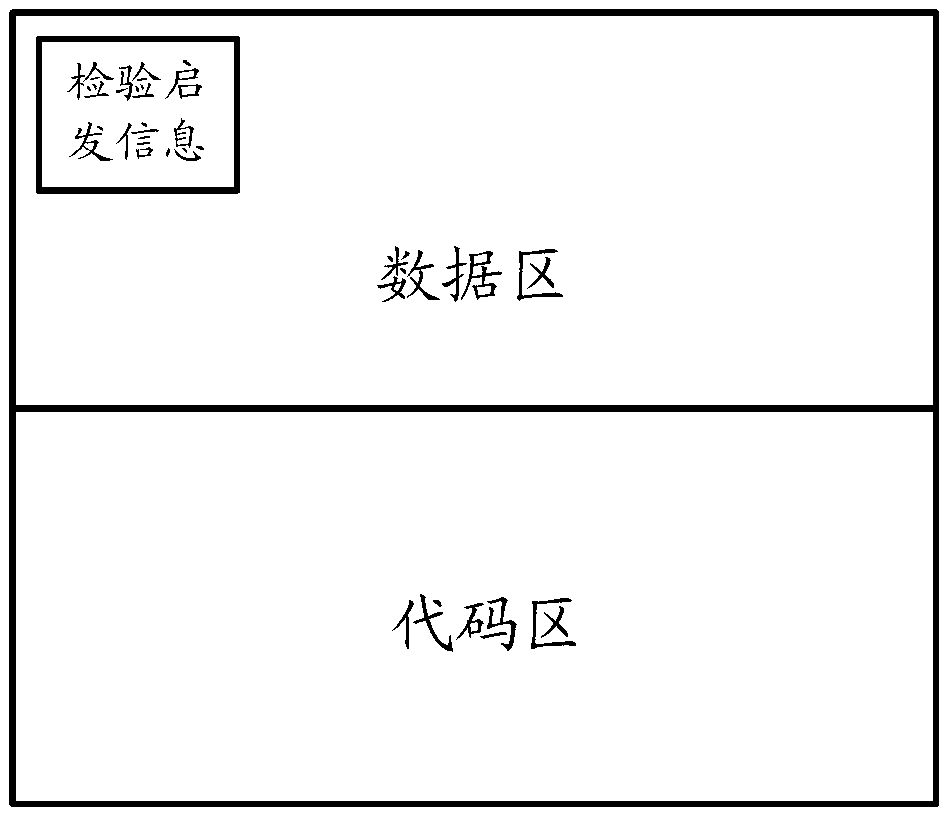
Method and equipment for checking basic input output system (BIOS)
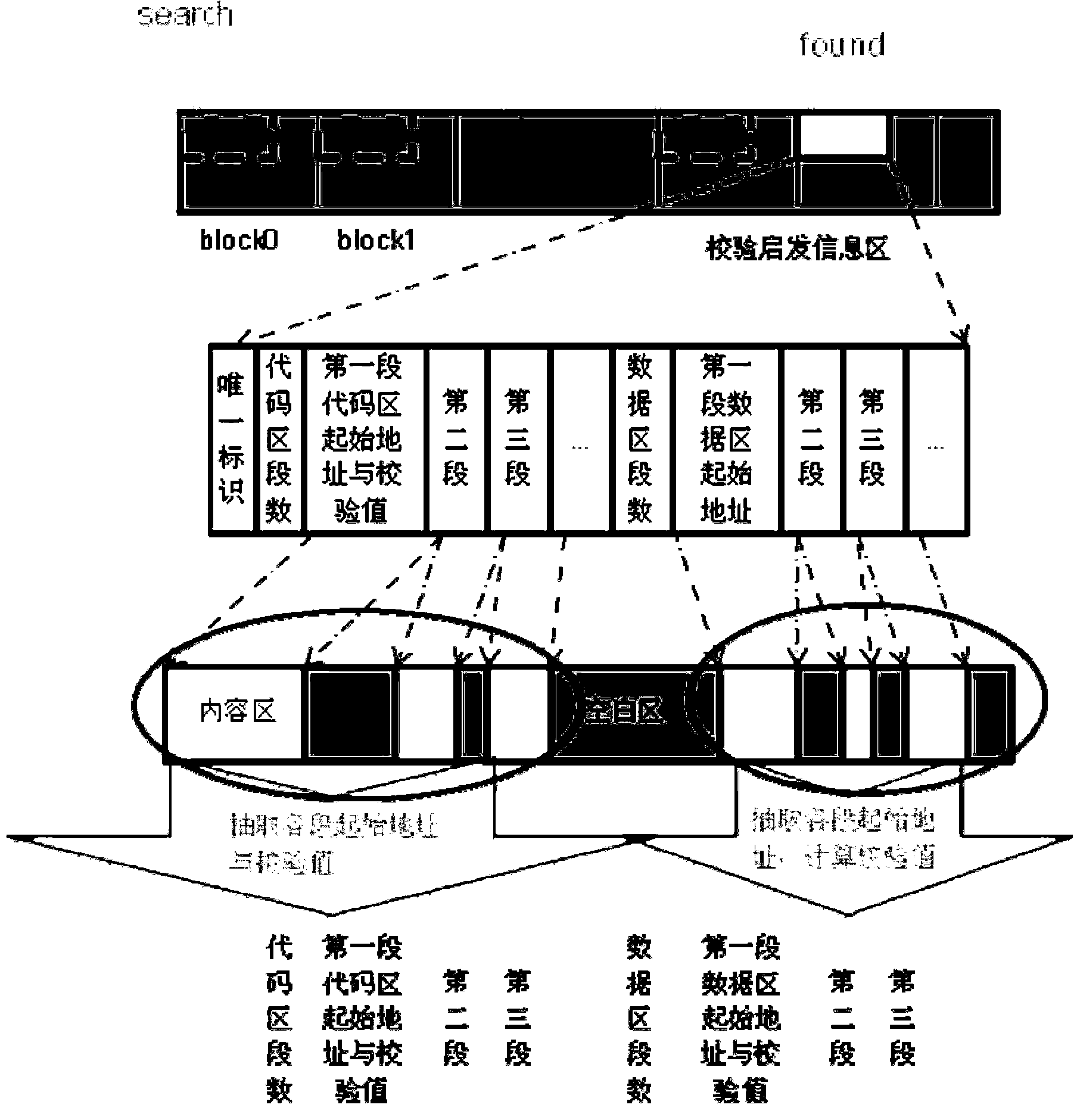
ActiveCN103226505ARealize full coverage detectionImprove efficiencyDetecting faulty computer hardwareBIOSComputer science
The embodiment of the invention provides a method and equipment for checking a BIOS (basic input output system). The method comprises the steps as follows: reading preset check heuristic information; storing a start address and a first check value of each code region and a start address and a first check value of each data region; comparing the first check value with a second check value of each code region and the first check value with a second check value of each data region; and when the first check value is not equal to the second check value, returning information that the BIOS content is damaged. According to the method, the data regions and the code regions in the BIOS content can be fully detected, the general flexible BIOS detection algorithm can be realized, and the method can automatically adapt to the BIOS specification upgrading and is suitable for both the traditional BIOS and a BIOS with an EFI (Extensible Firmware Interface); and the blank region in the BIOS content can be skipped in the checking process, so that the efficient online BIOS content detection algorithm is realized and the performance consumption is reduced to the hilt.
Owner:XFUSION DIGITAL TECH CO LTD
FEDAV (fault-tolerant event detection algorithm based on voting)
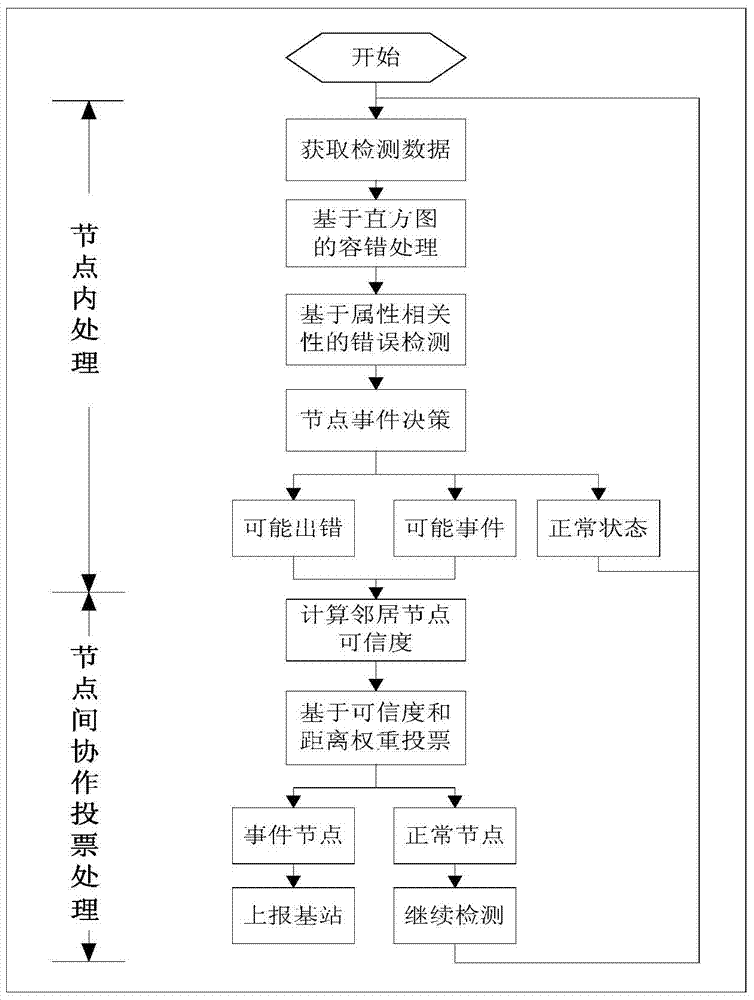
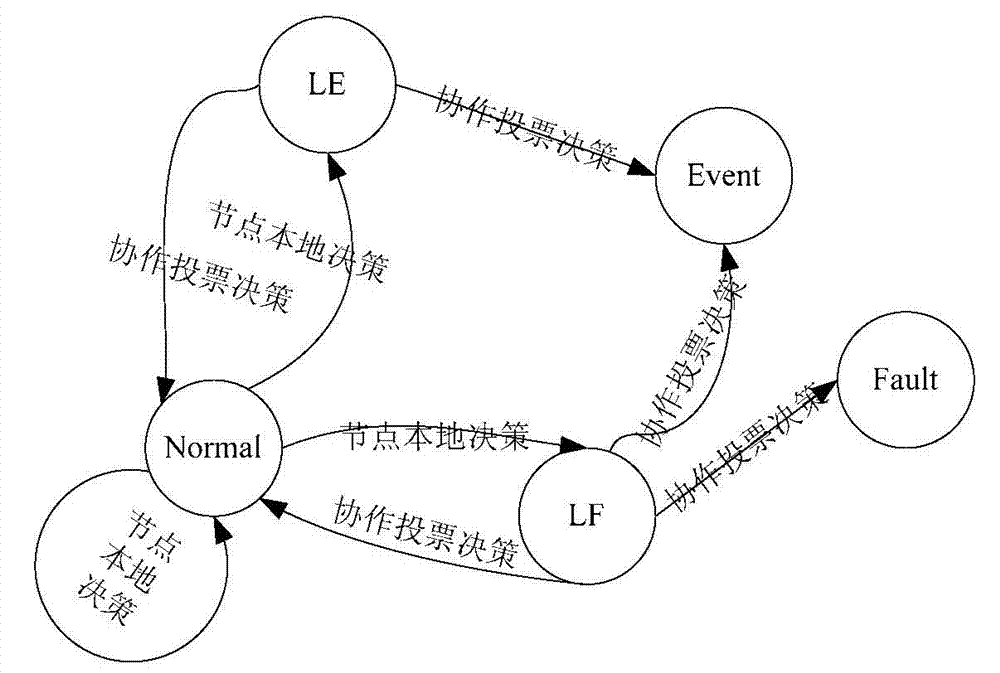
InactiveCN103533571AEasy to detectReduce performance consumptionWireless communicationFalse alarmComputer science
The invention discloses an FEDAV which comprises the following steps which are executed sequentially: (1), detection data of each node is acquired; (2), the detection data is subjected to fault-tolerant processing on the basis of a histogram; (3), the detection data is subjected to local error detection on the basis of attribute correlation to distinguish LF nodes and primary Normal nodes; (4), the primary Normal nodes are subjected to local event decision to distinguish LE nodes and Normal nodes; (5), credibility of neighbor nodes of the LF nodes and the LE nodes are computed; and (6), voting is performed based on the credibility and distance weighting, so that the nodes are judged to be either Event nodes or Normal nodes. The FEDAV has a higher event detection rate, a higher error correction rate, a lower event false alarm rate, a lower mistaken introduction rate as well as lower capacity consumption.
Owner:SOUTHEAST UNIV
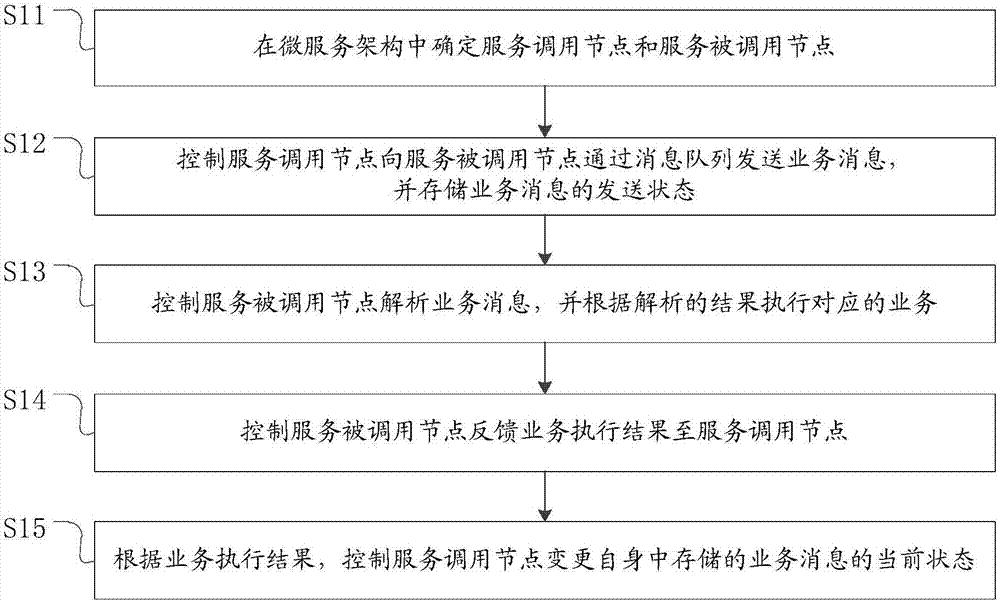
Distributed transaction processing method based on micro service architecture
ActiveCN106909467AEnsure consistencyReduce the number of communicationsInterprogram communicationMessage queueNetwork communication
The invention discloses a distributed transaction processing method based on a micro service architecture. The method comprises the following steps: determining a service call node and a service called node in a micro service architecture; controlling the service call node to send a service message to the service called node through a message queue, and storing the sending status of the service message; controlling the service called node to resolve the service message and executing the corresponding service according to the resolution result; controlling the service called node to feed the service execution result back to the service call node; and controlling the service call node to change the current status of the service message stored therein according to the service execution result. The service call node changes the status of own service message according to the feedback information of the service called node, and a message queue mechanism is used for saving the message status without relying on the specific development language and platform, so that the data consistency of distributed transaction is ensured, the number of network communication times between the two nodes is reduced, the communication time is short, and the system performance consumption is low.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com