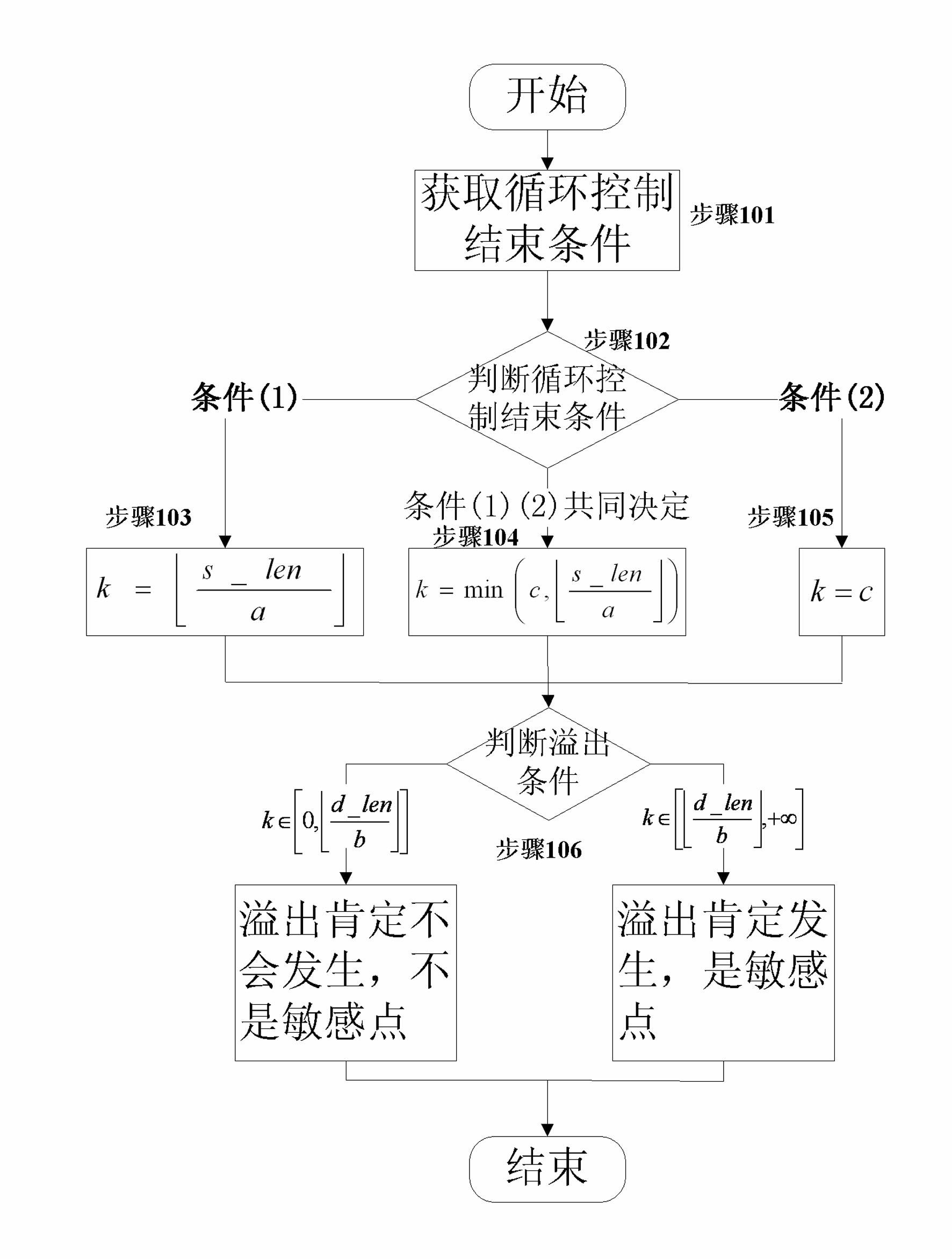
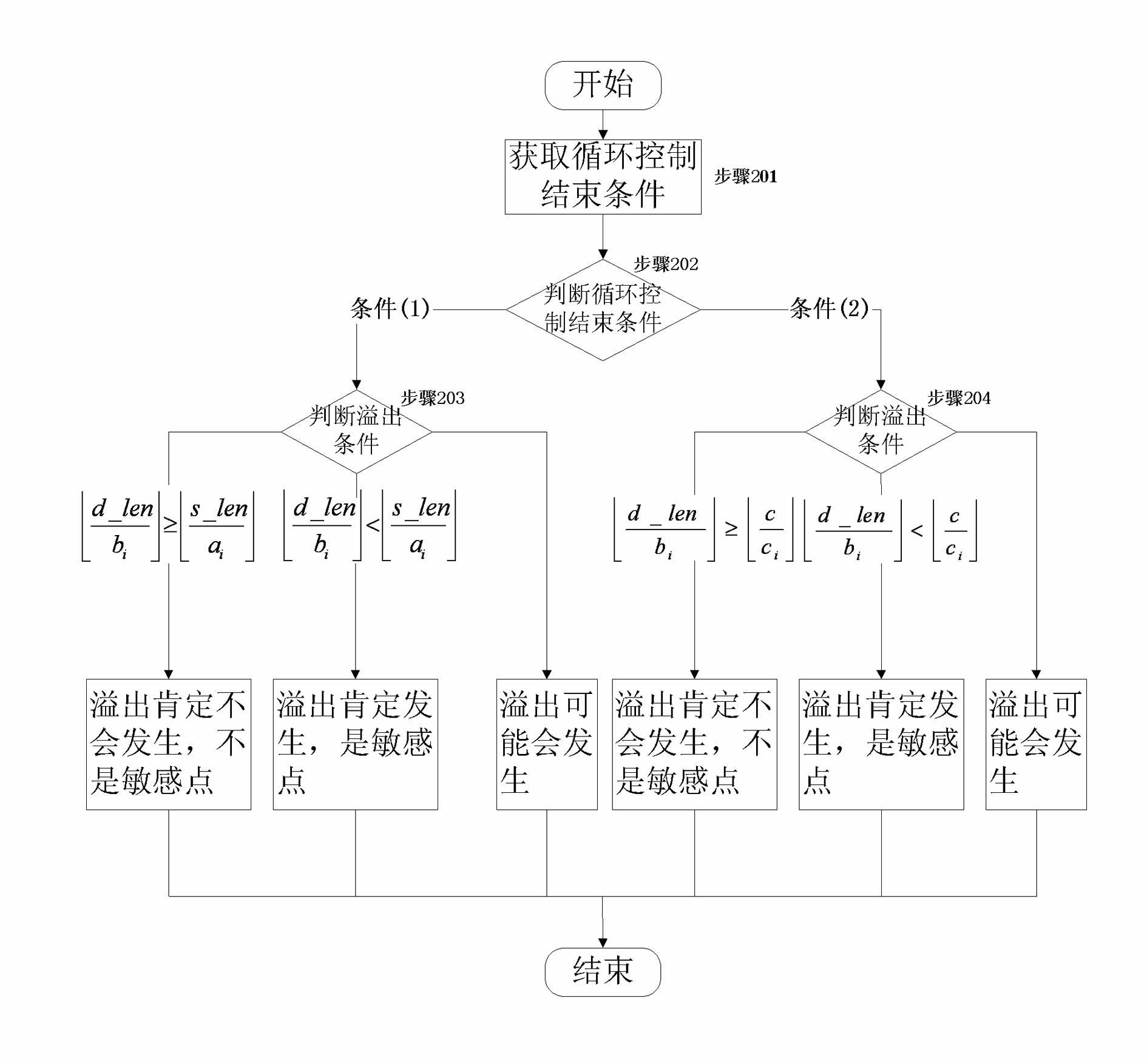
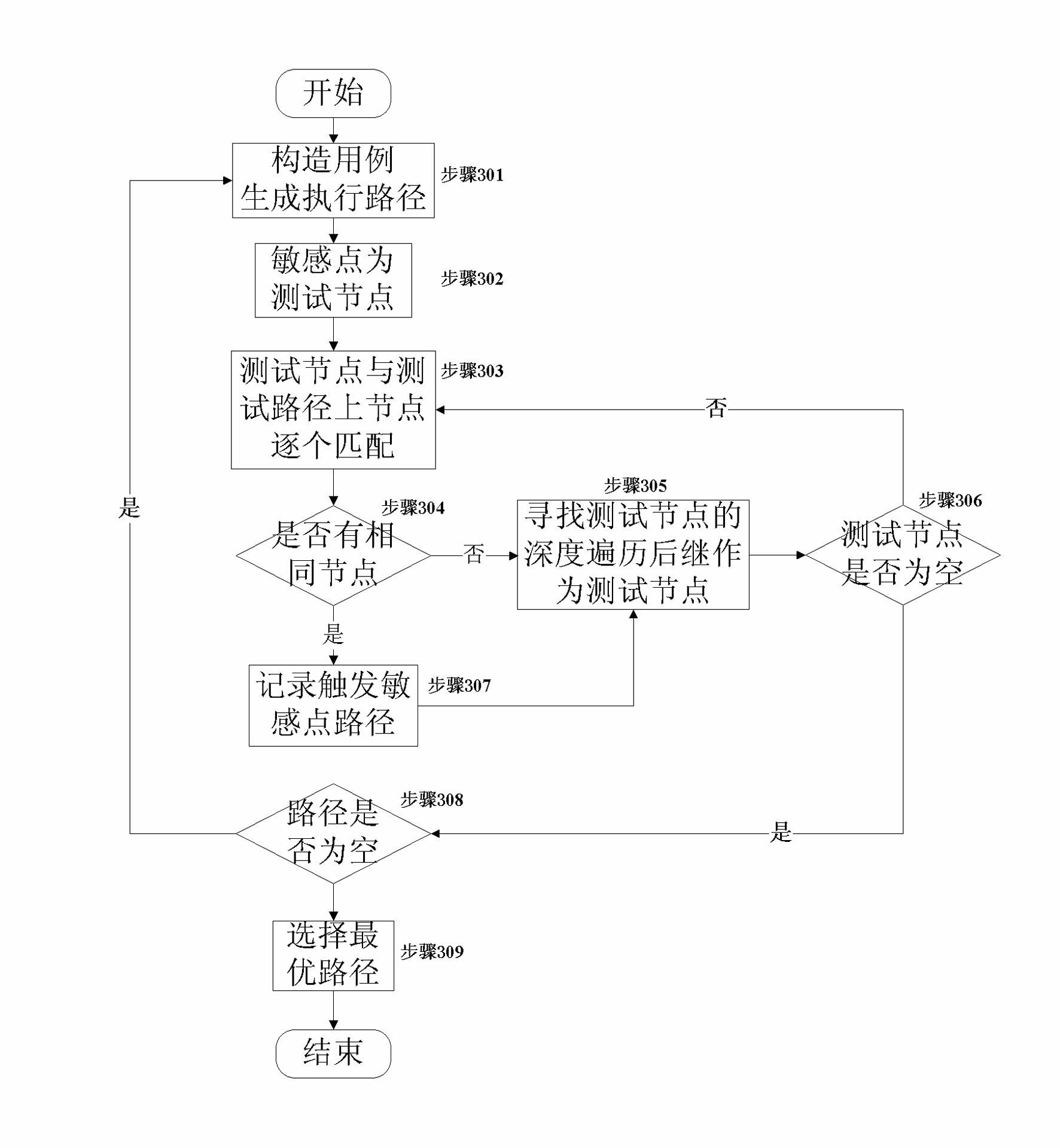
Patents
Literature
482 results about "Control flow graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
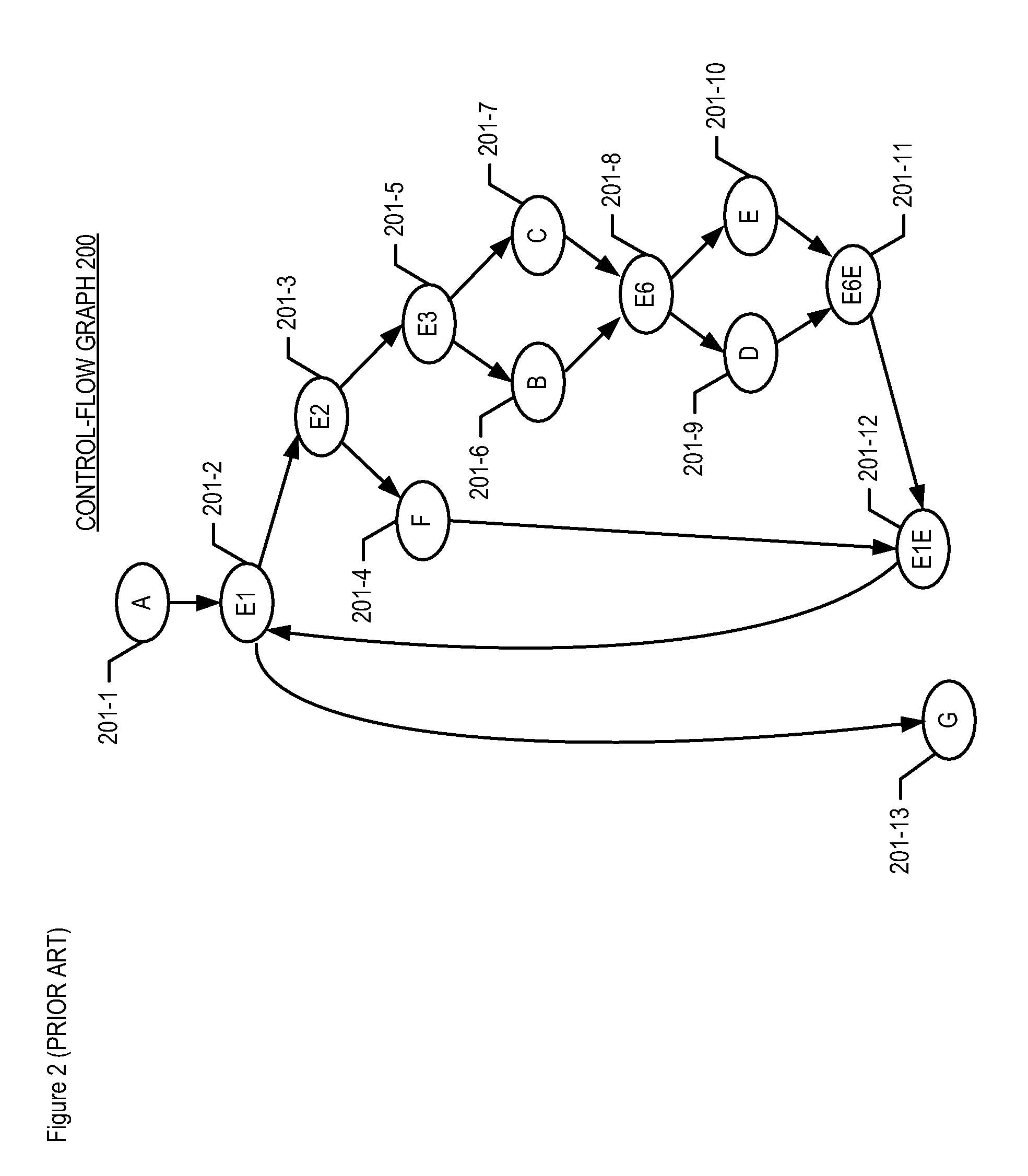
In computer science, a control-flow graph (CFG) is a representation, using graph notation, of all paths that might be traversed through a program during its execution. The control-flow graph is due to Frances E. Allen, who notes that Reese T. Prosser used boolean connectivity matrices for flow analysis before.
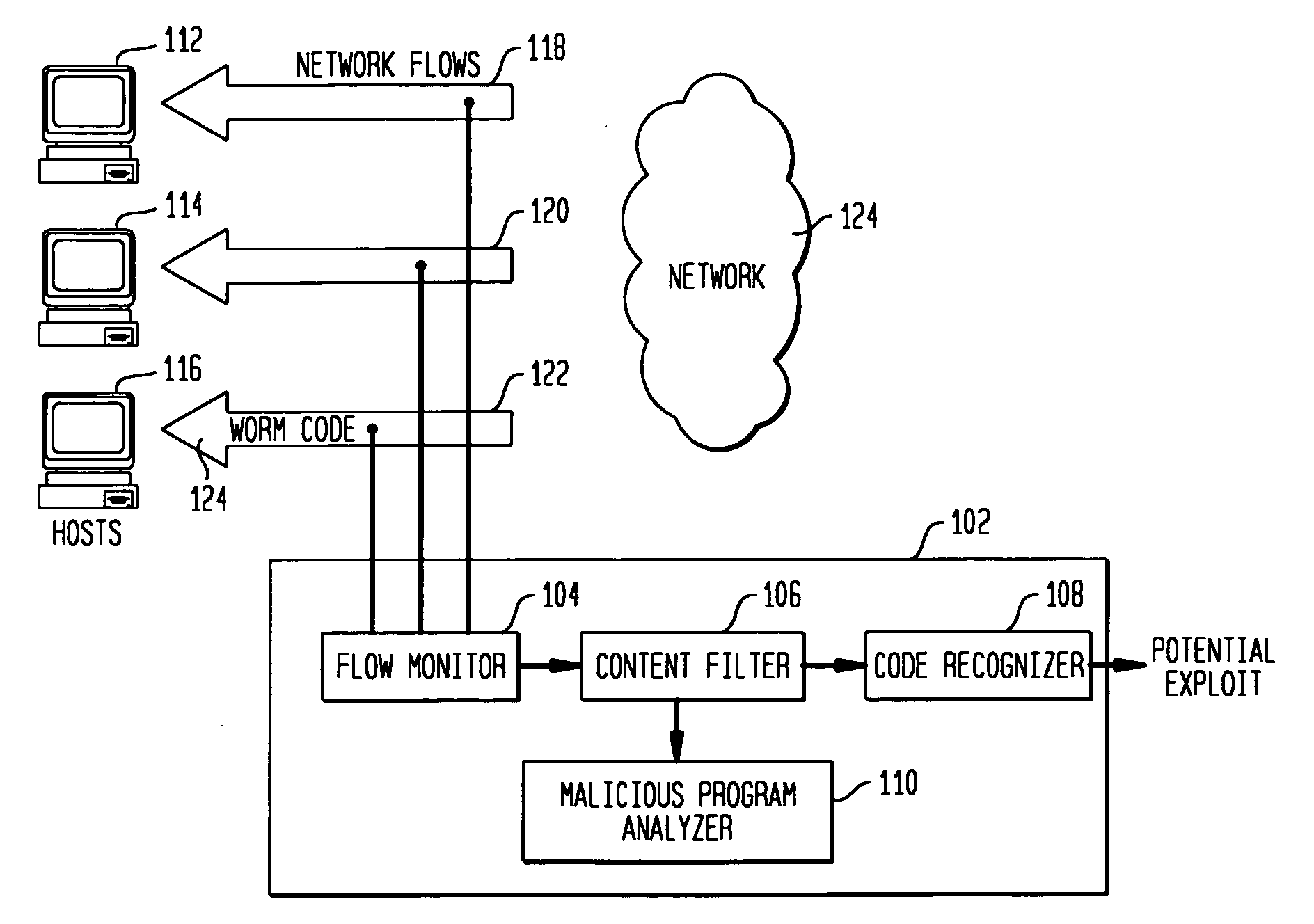
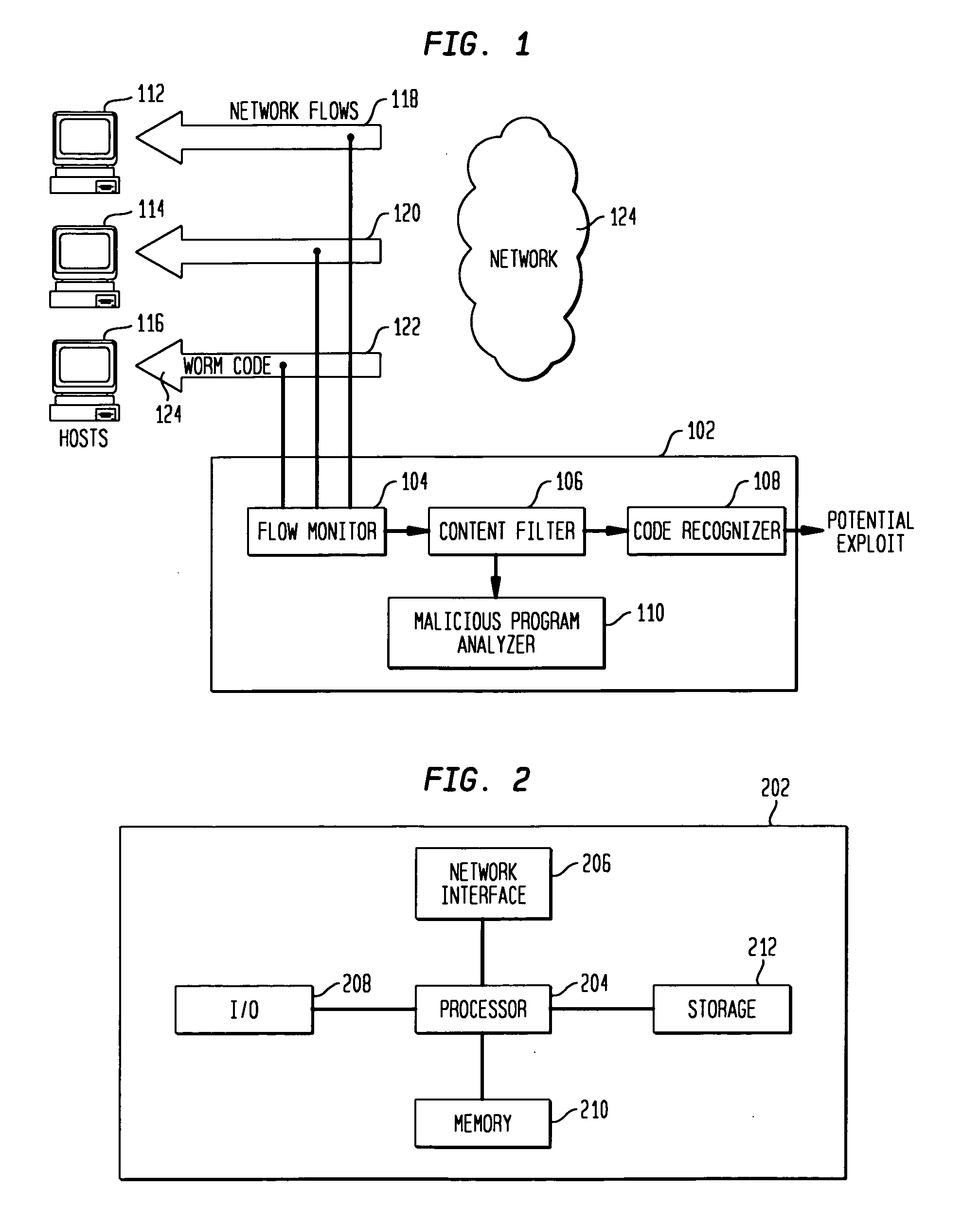
Detecting exploit code in network flows
InactiveUS20090328185A1Memory loss protectionUnauthorized memory use protectionData streamNetwork packet
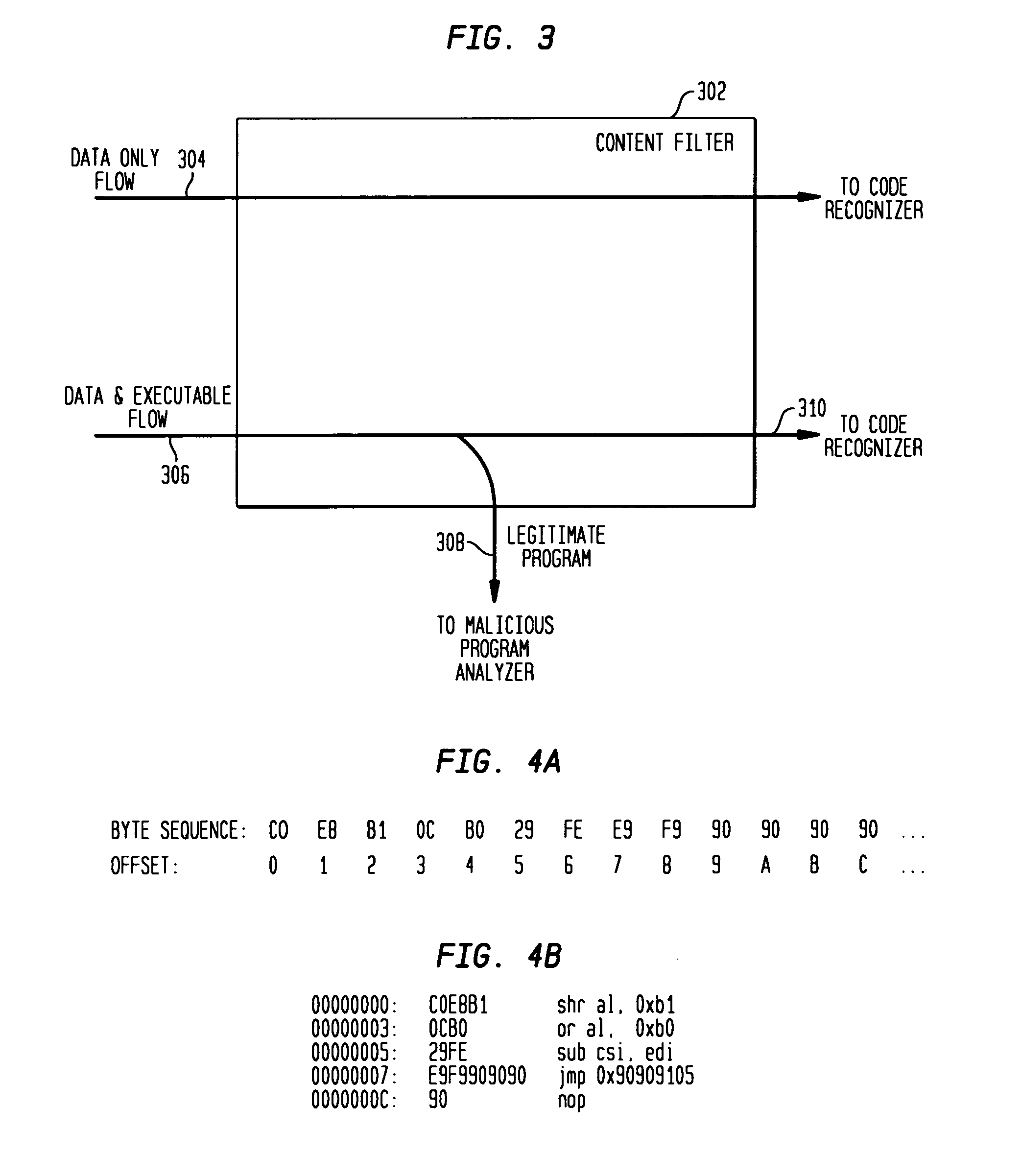
Disclosed is a method and apparatus for detecting exploit code in network flows. Network data packets are intercepted by a flow monitor which generates data flows from the intercepted data packets. A content filter filters out legitimate programs from the data flows, and the unfiltered portions are provided to a code recognizer which detects executable code. Any embedded executable code in the unfiltered data flow portions is identified as a suspected exploit in the network flow. The executable code recognizer recognizes executable code by performing convergent binary disassembly on the unfiltered portions of the data flows. The executable code recognizer then constructs a control flow graph and performs control flow analysis, data flow analysis, and constraint enforcement in order to detect executable code. In addition to identifying detected executable code as a potential exploit, the detected executable code may then be used in order to generate a signature of the potential exploit, for use by other systems in detecting the exploit.
Owner:TELCORDIA TECHNOLOGIES INC
Reconfigurable processing
ActiveUS20070198971A1Reduce signal delayReduce areaEnergy efficient ICTSoftware engineeringPathPingComputer architecture
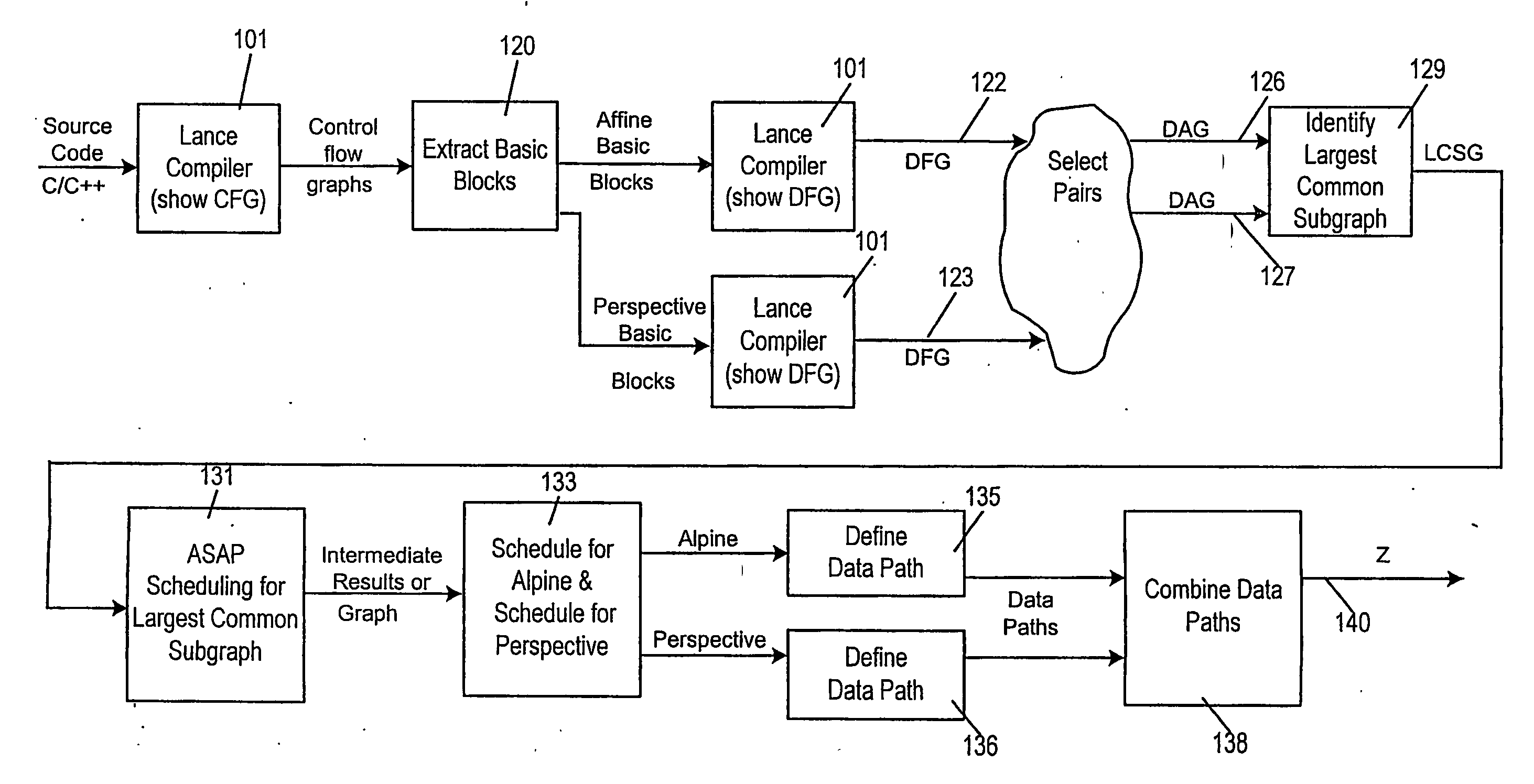
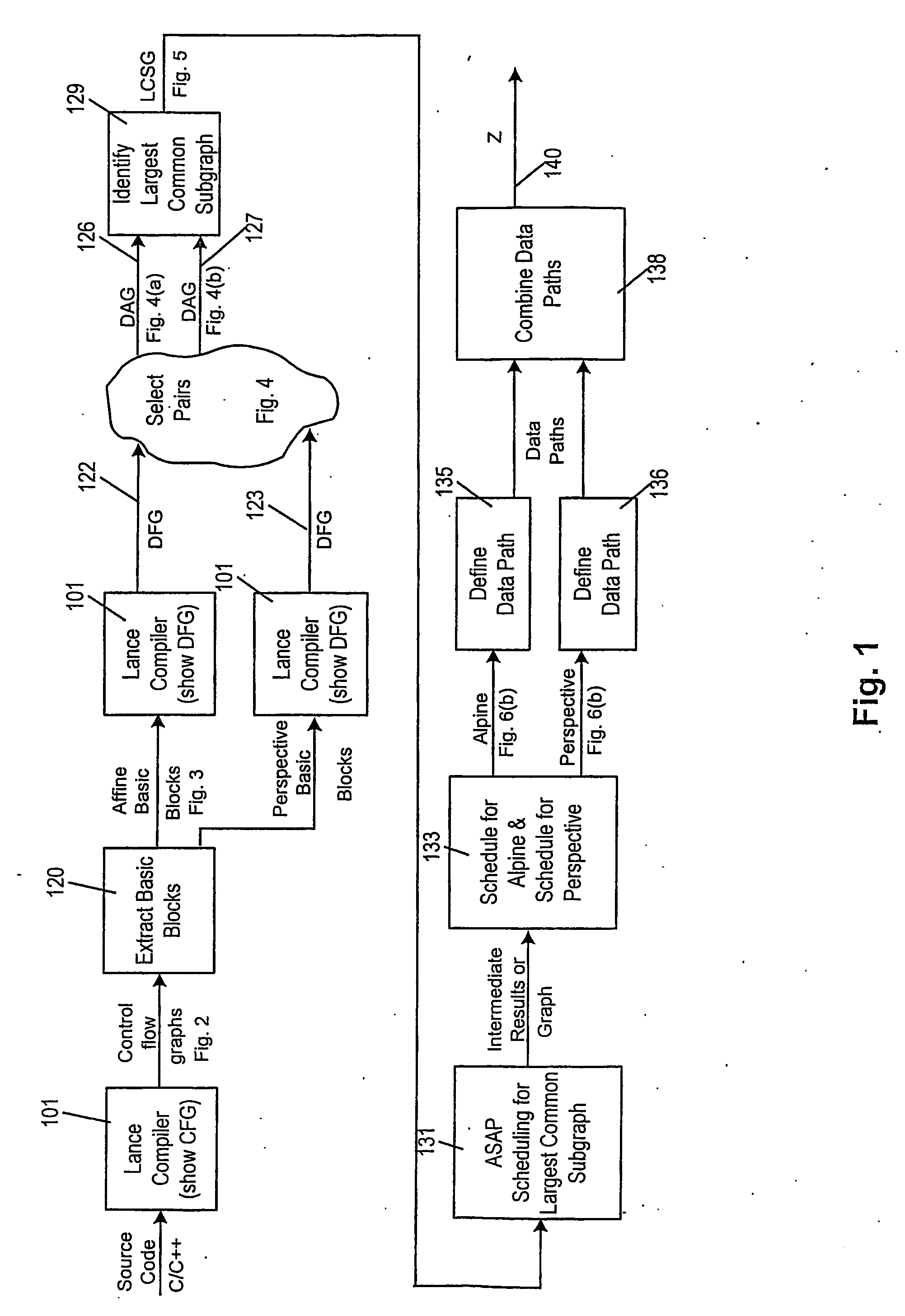
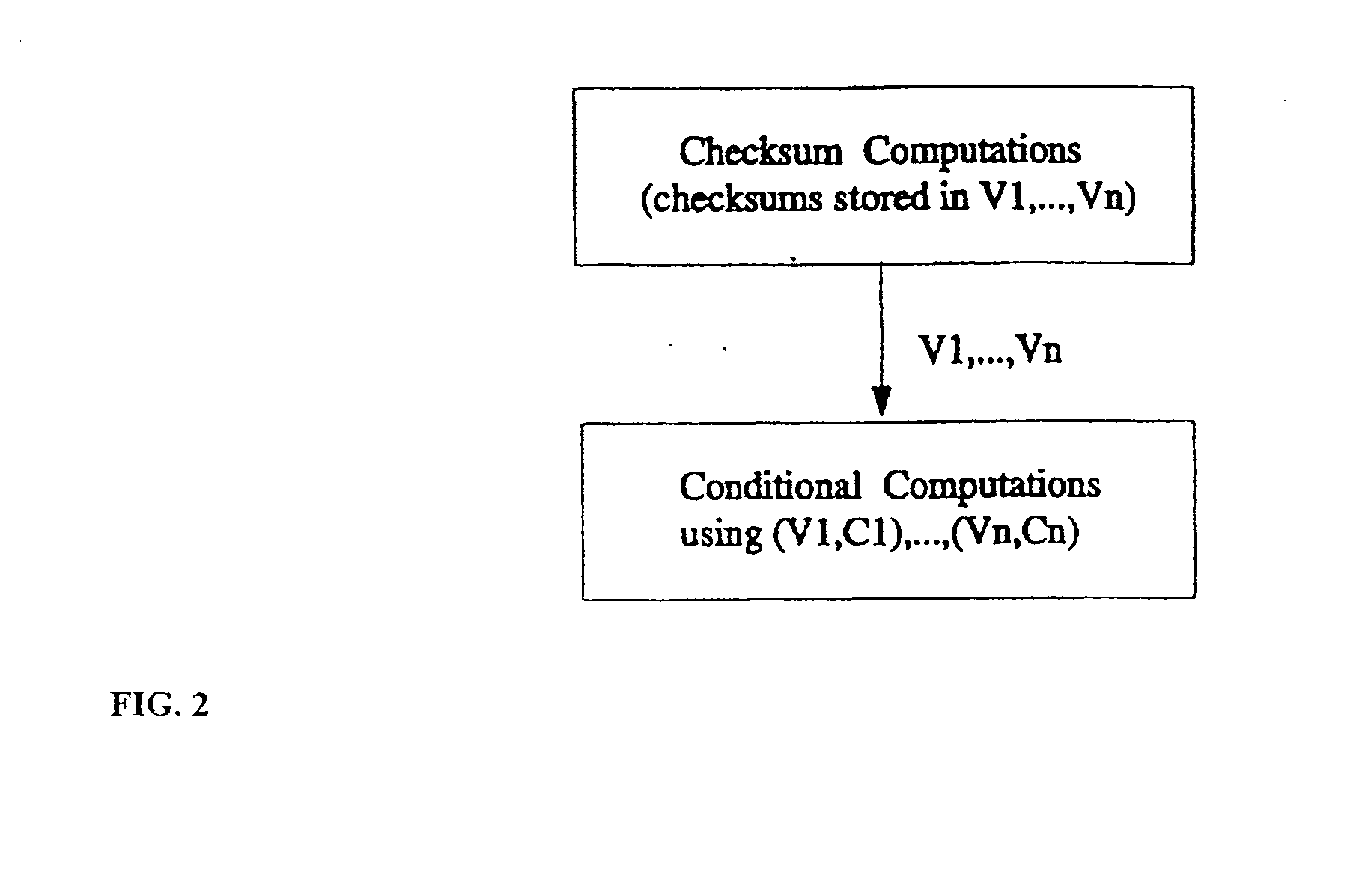
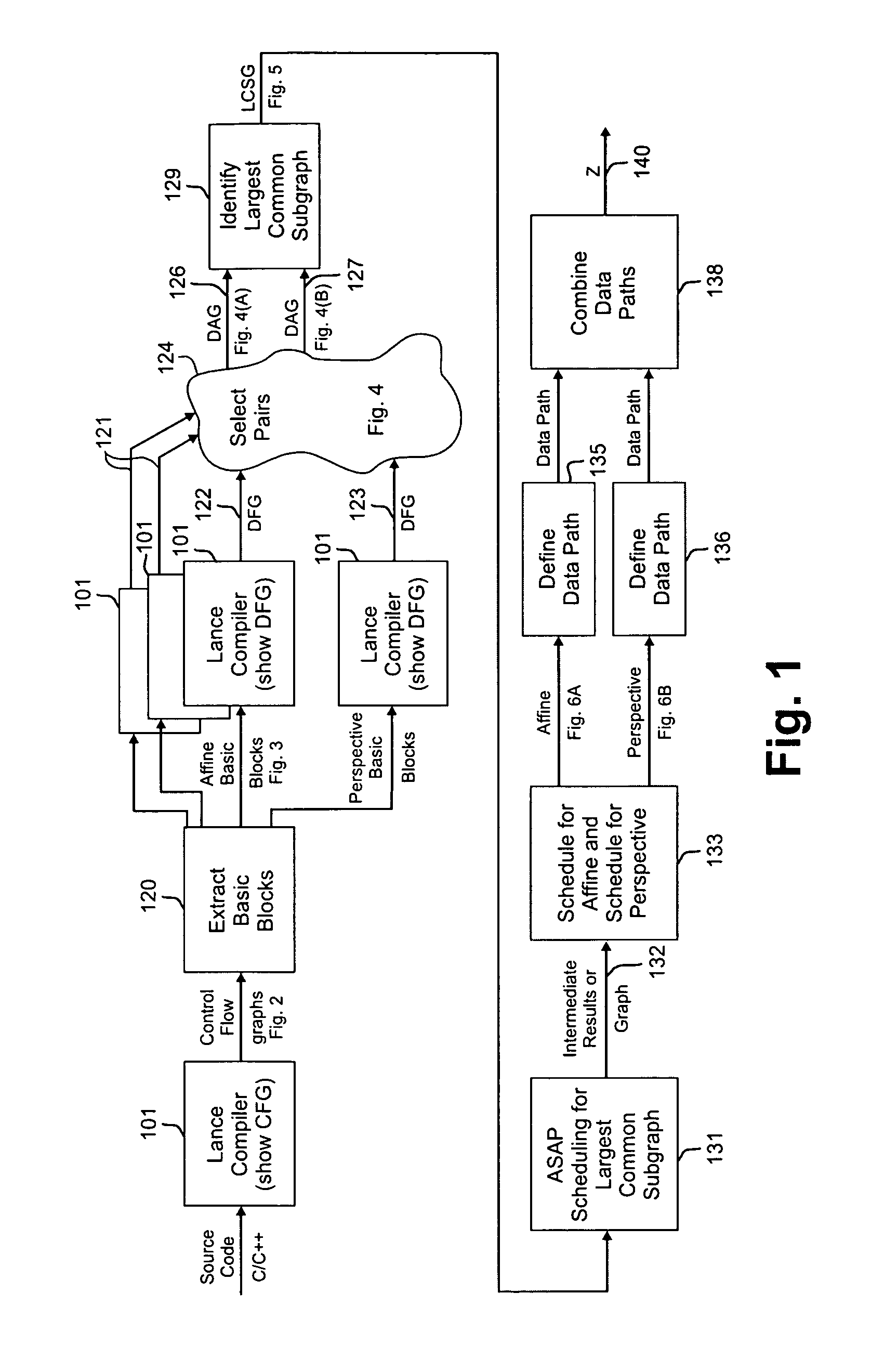
A method of producing a reconfigurable circuit device for running a computer program of moderate complexity such as multimedia processing. Code for the application is compiled into Control Flow Graphs representing distinct parts of the application to be run. From those Control Flow Graphs are extracted basic blocks. The basic blocks are converted to Data Flow Graphs by a compiler utility. From two or more Data Flow Graphs, a largest common subgraph is determined. The largest common subgraph is ASAP scheduled and substituted back into the Data Flow Graphs which also have been scheduled. The separate Data Flow Graphs containing the scheduled largest common subgraph are converted to data paths that are then combined to form code for operating the application. The largest common subgraph is effected in hardware that is shared among the parts of the application from which the Data Flow Graphs were developed. Scheduling of the overall code is effected for sequencing, providing fastest run times and the code is implemented in hardware by partitioning and placement of processing elements on a chip and design of the connective fabric for the design elements.
Owner:ARIZONA STATE UNIVERSITY
Method and system for tamperproofing software
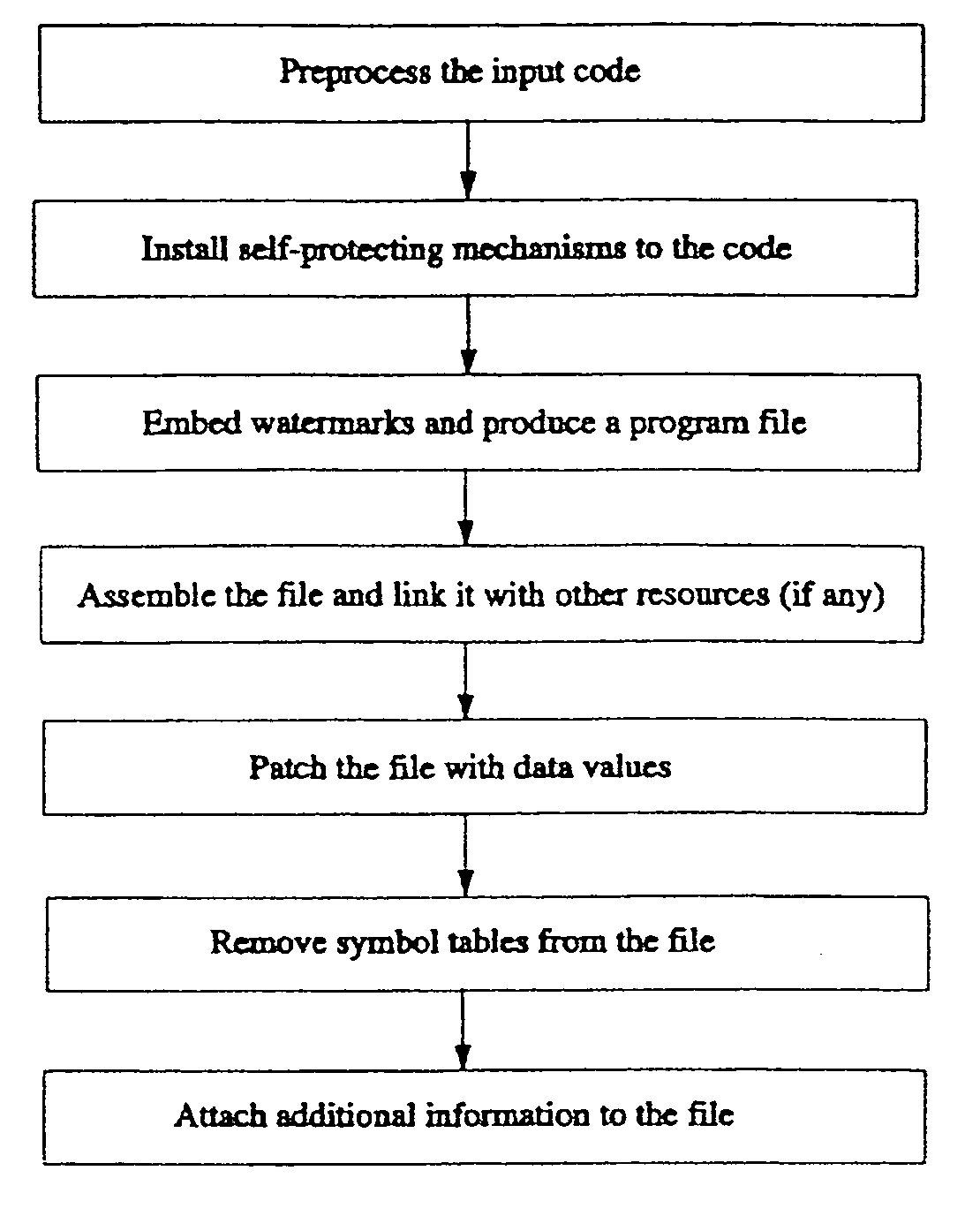
InactiveUS20060031686A1User identity/authority verificationUnauthorized memory use protectionCoding blockObfuscation
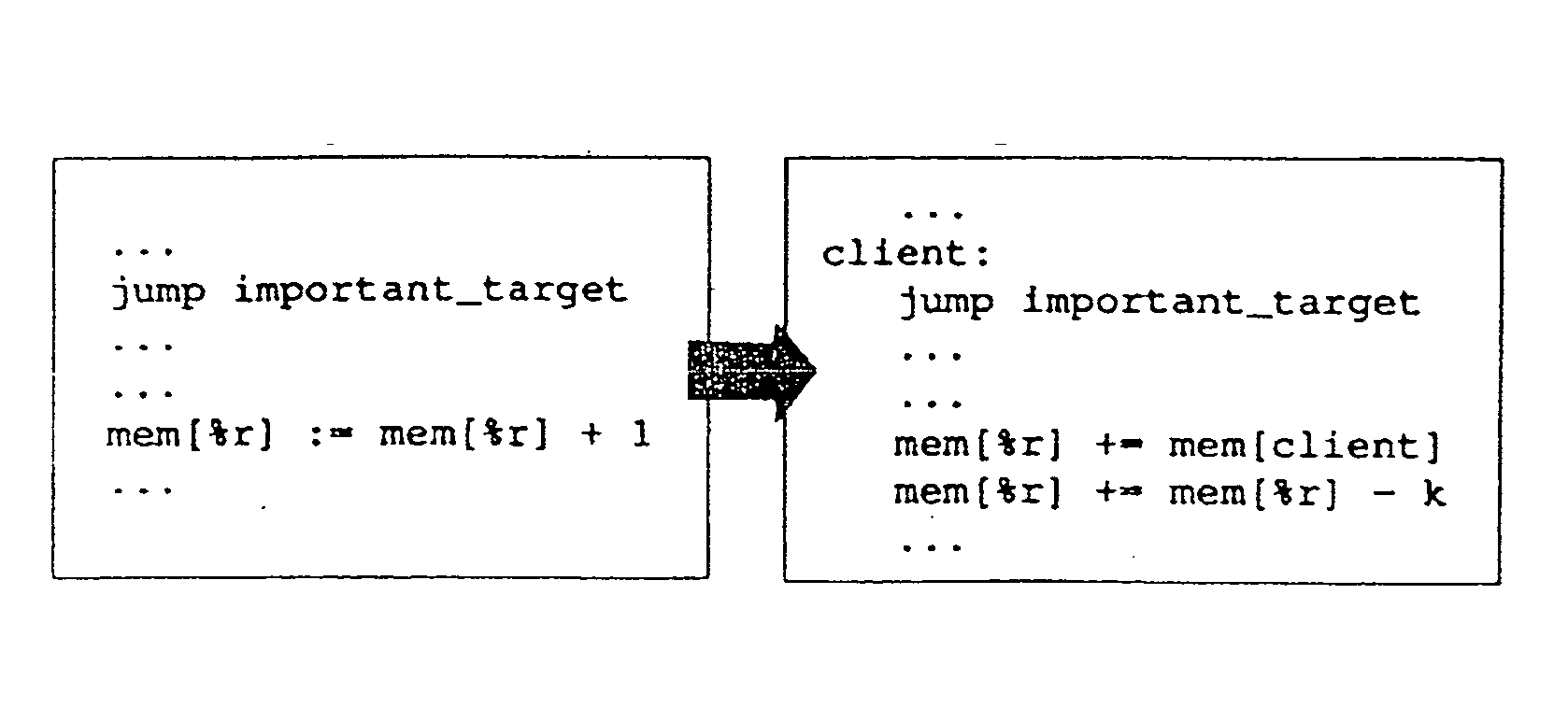
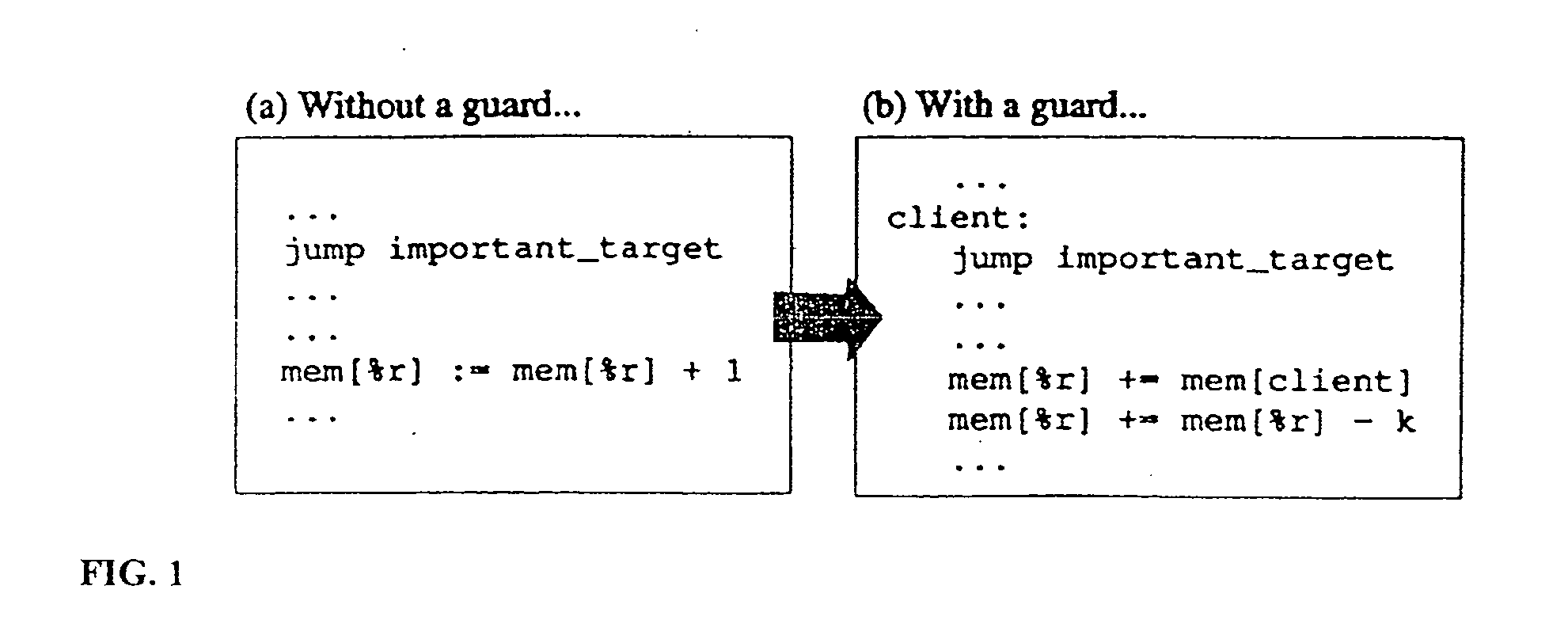
Method of protecting host application code comprising a plurality of code blocks. The method includes steps of preprocessing the host application code; obfuscating the host application code; installing guards in the host application code to protect client blocks; randomly rearranging the code blocks of the host application code; linking the rearranged host application code with other resources to produce a binary executable image; and patching the binary executable image with data values to be used by the guard. The method can be used to install a plurality of guards to form a distributed network of guards that cooperatively protect the host application code and the other guards in the network. The installation of the guards can be performed automatically using a guard formation graph; and guard formation graph customization parameters. The obfuscation step can include control flow graph merging, cloning, and data-aliasing.
Owner:PURDUE RES FOUND INC
Reconfigurable processing
ActiveUS8281297B2Reduce the amount requiredQuick switchEnergy efficient ICTSoftware engineeringControl flowProcessing element
A method of producing a reconfigurable circuit device for running a computer program of moderate complexity such as multimedia processing. Code for the application is compiled into Control Flow Graphs representing distinct parts of the application to be run. From those Control Flow Graphs are extracted basic blocks. The basic blocks are converted to Data Flow Graphs by a compiler utility. From two or more Data Flow Graphs, a largest common subgraph is determined. The largest common subgraph is ASAP scheduled and substituted back into the Data Flow Graphs which also have been scheduled. The separate Data Flow Graphs containing the scheduled largest common subgraph are converted to data paths that are then combined to form code for operating the application. The largest common subgraph is effected in hardware that is shared among the parts of the application from which the Data Flow Graphs were developed. Scheduling of the overall code is effected for sequencing, providing fastest run times and the code is implemented in hardware by partitioning and placement of processing elements on a chip and design of the connective fabric for the design elements.
Owner:ARIZONA STATE UNIVERSITY
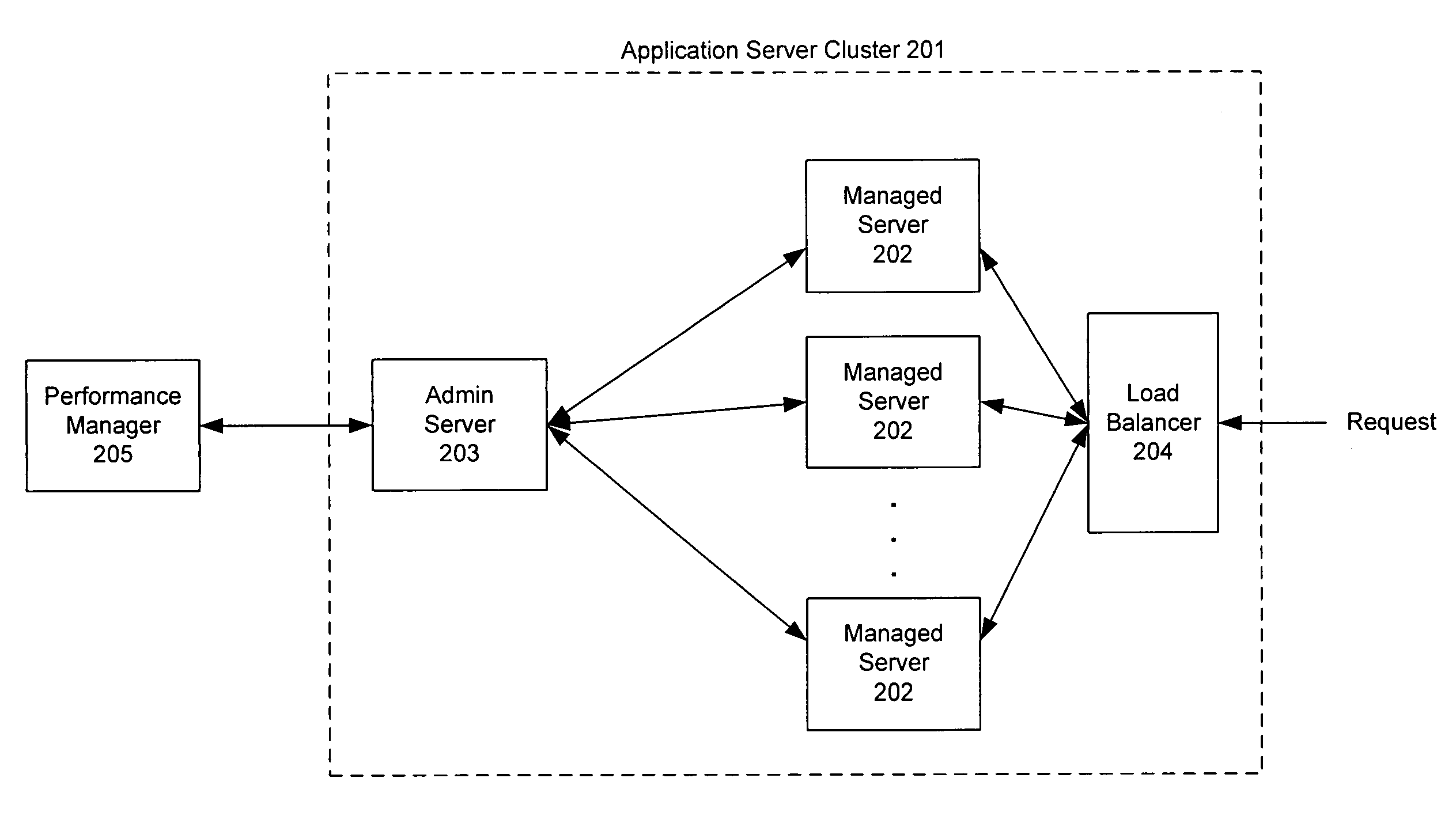
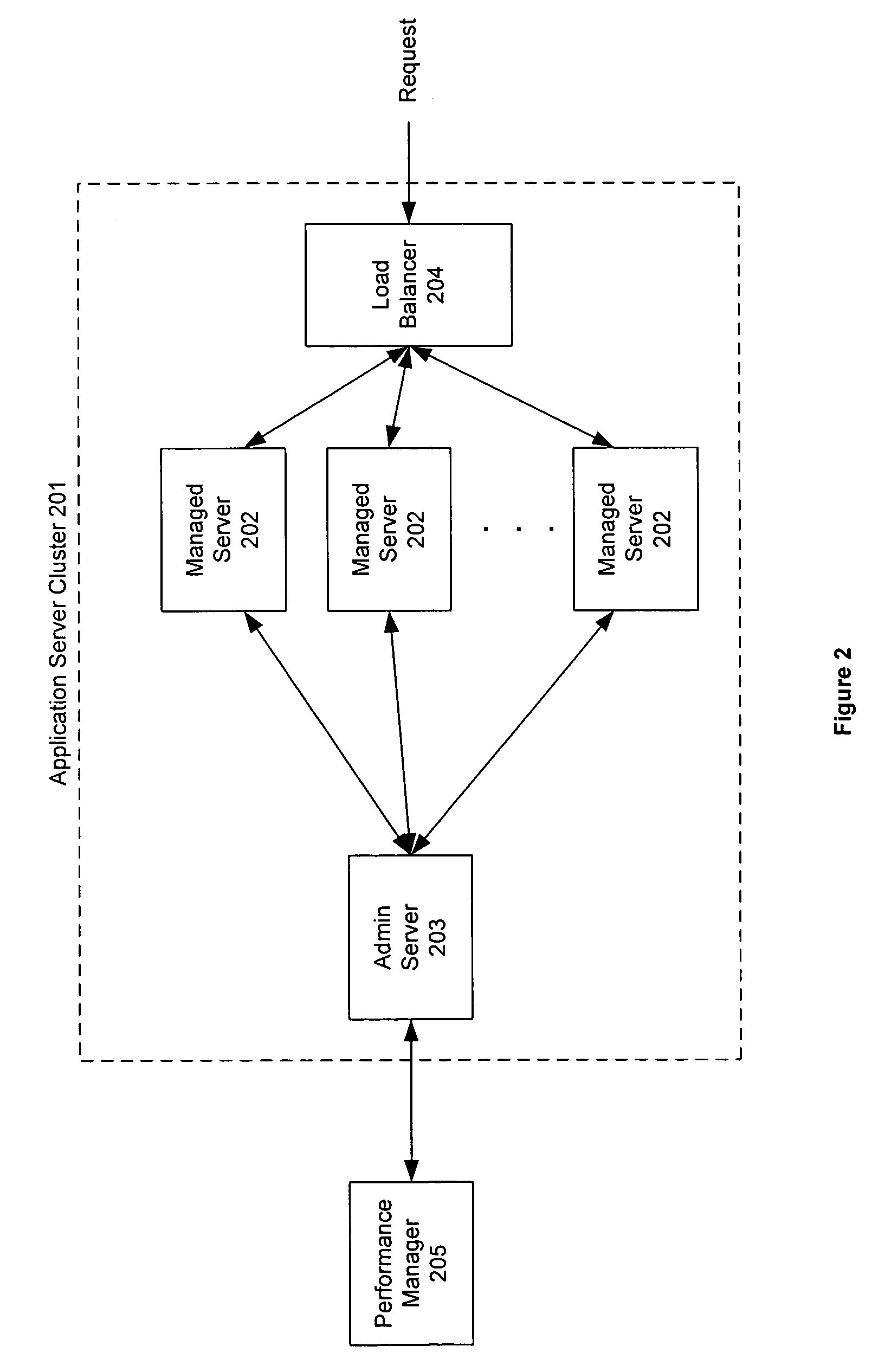
Monitoring and performance management of component-based applications
ActiveUS7627671B1Error detection/correctionDigital computer detailsManagement toolApplication software
Invention manages underlying application objects that support implemented business functions. A performance manager accesses and interprets application metadata and execution environment metadata, using a hierarchical entity to model complex relationships between application abstractions, components and resources. The performance manager encodes common behavioral and architecture information in models resulting from analysis of component architecture standards, vendor application servers, development tools and administration tools. The performance manager conducts inter-component dependency and control flow analysis, for example by generating control flow graphs from application metadata and performing byte code analysis without access to application source code. The performance manager collects metrics from standardized and vendor-specific sources, instruments interpreters (such as the Java Virtual Machine), and collects and utilizes resource metrics, code performance metrics, configuration parameters, and transaction, failure and lifecycle events.
Owner:ORACLE INT CORP
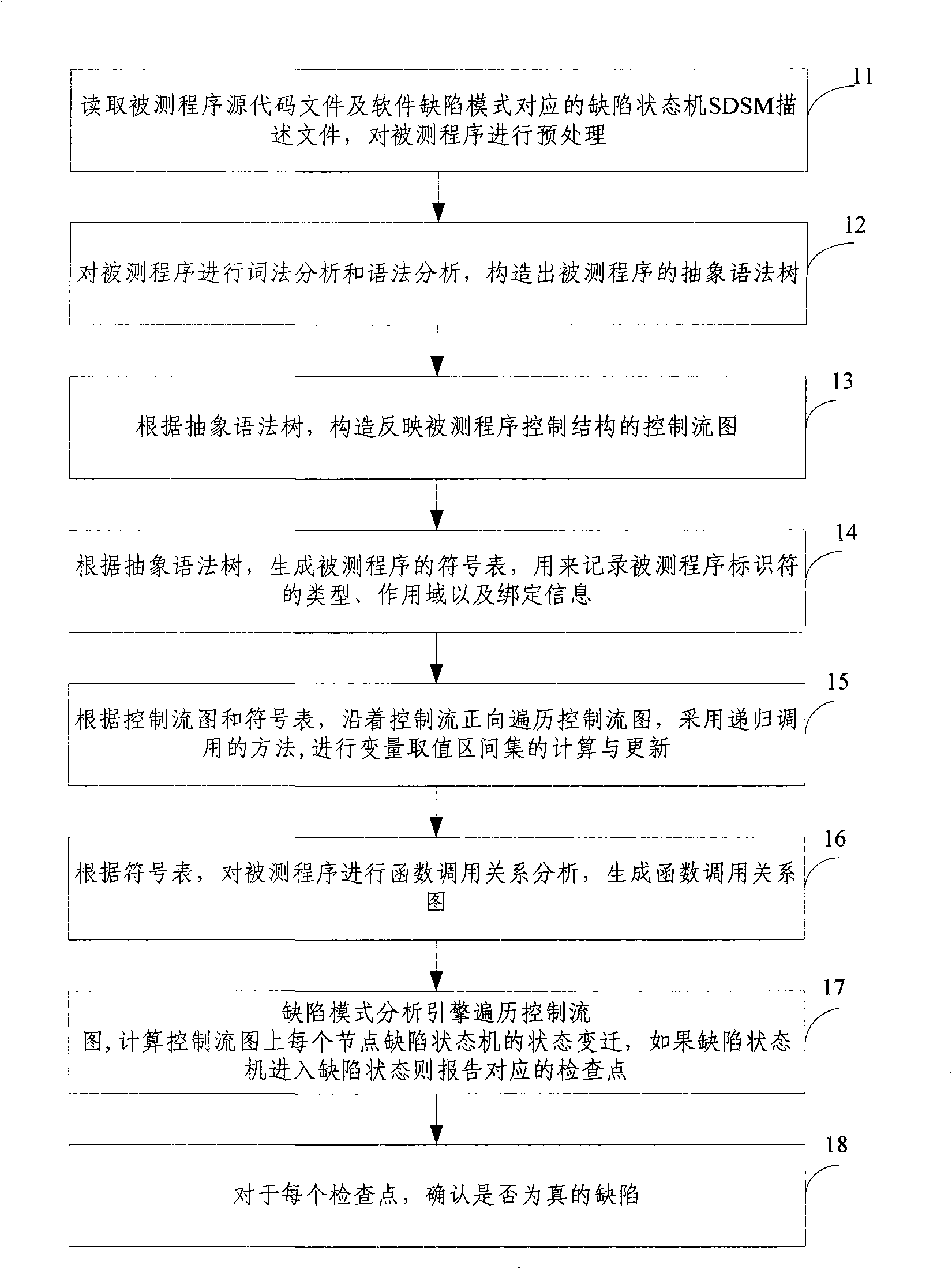
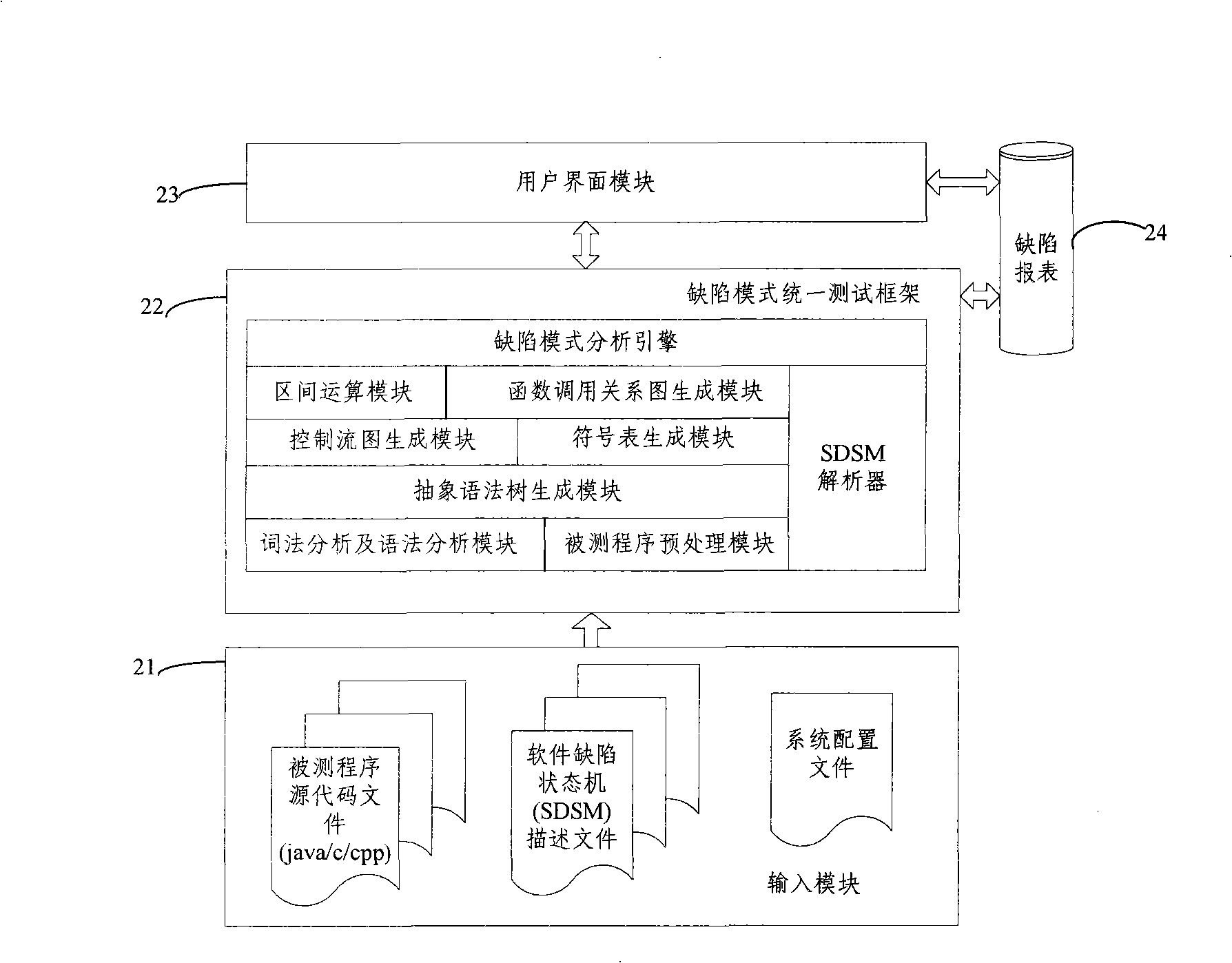
Test method and system based on software defect mode
InactiveCN101286132AReduce false positivesImprove test accuracySoftware testing/debuggingControl flowPresent method
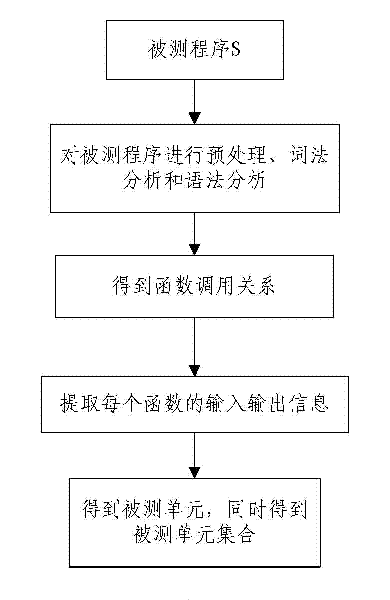
The invention discloses a testing method based on software defect mode, comprising the steps of: reading source code files of programs to be tested and SDSM description file of a defect state machine, carrying out pre-processing of the programs to be tested, analyzing the SDSM description file; carrying out lexical analysis and grammar analysis of the programs to be tested and constructing abstract syntax tree; generating a control flow graph and a symbol table according to the abstract syntax tree and carrying out the calculating and updating of variable value interval sets according to the control flow graph and the symbol table; carrying out function invoking relation analysis of the programs to be tested and generating a function invoking relation graph; searching the control flow graph by taking the function as unit according to the function invoking relation graph, calculating the state migration of each node defect state machine on the control flow graph, and reporting corresponding checking point when the defect state machine enters the defect state. The invention also discloses a testing system based on software defect mode, which comprises an input module, a defect mode uniformity testing frame and a user interface module and completes the uniform test on the programs to be tested.
Owner:BEIJING UNIV OF POSTS & TELECOMM
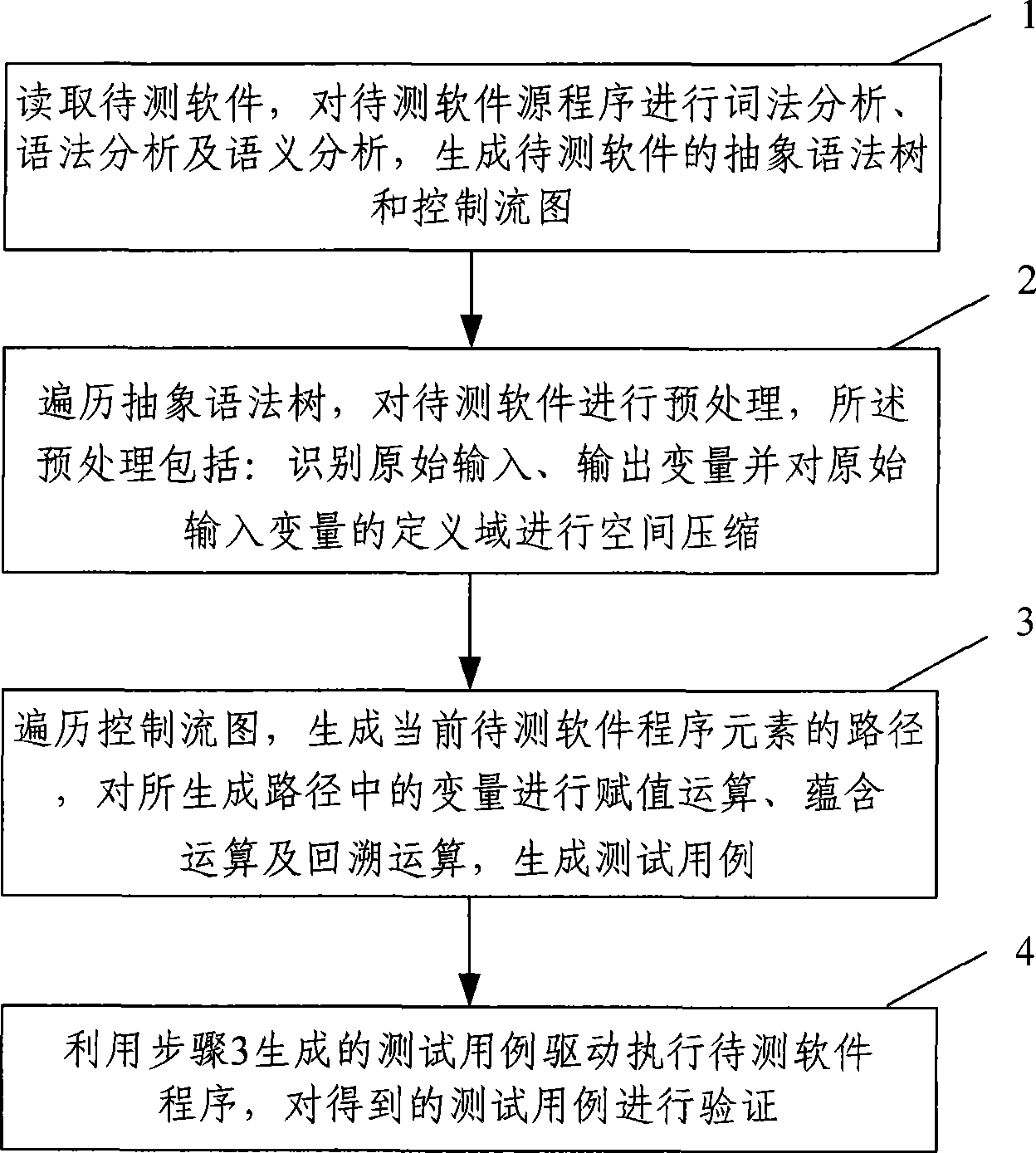
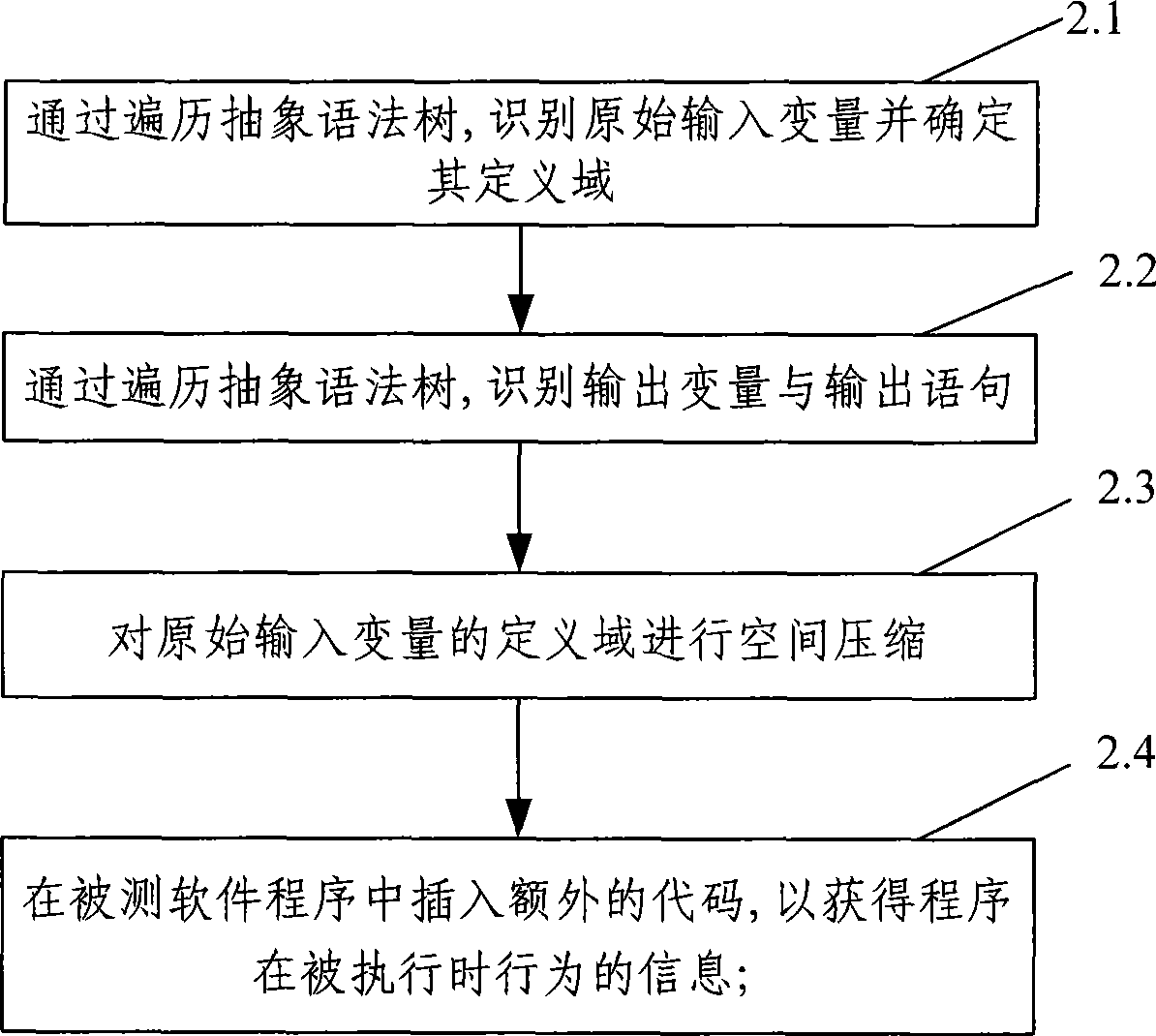
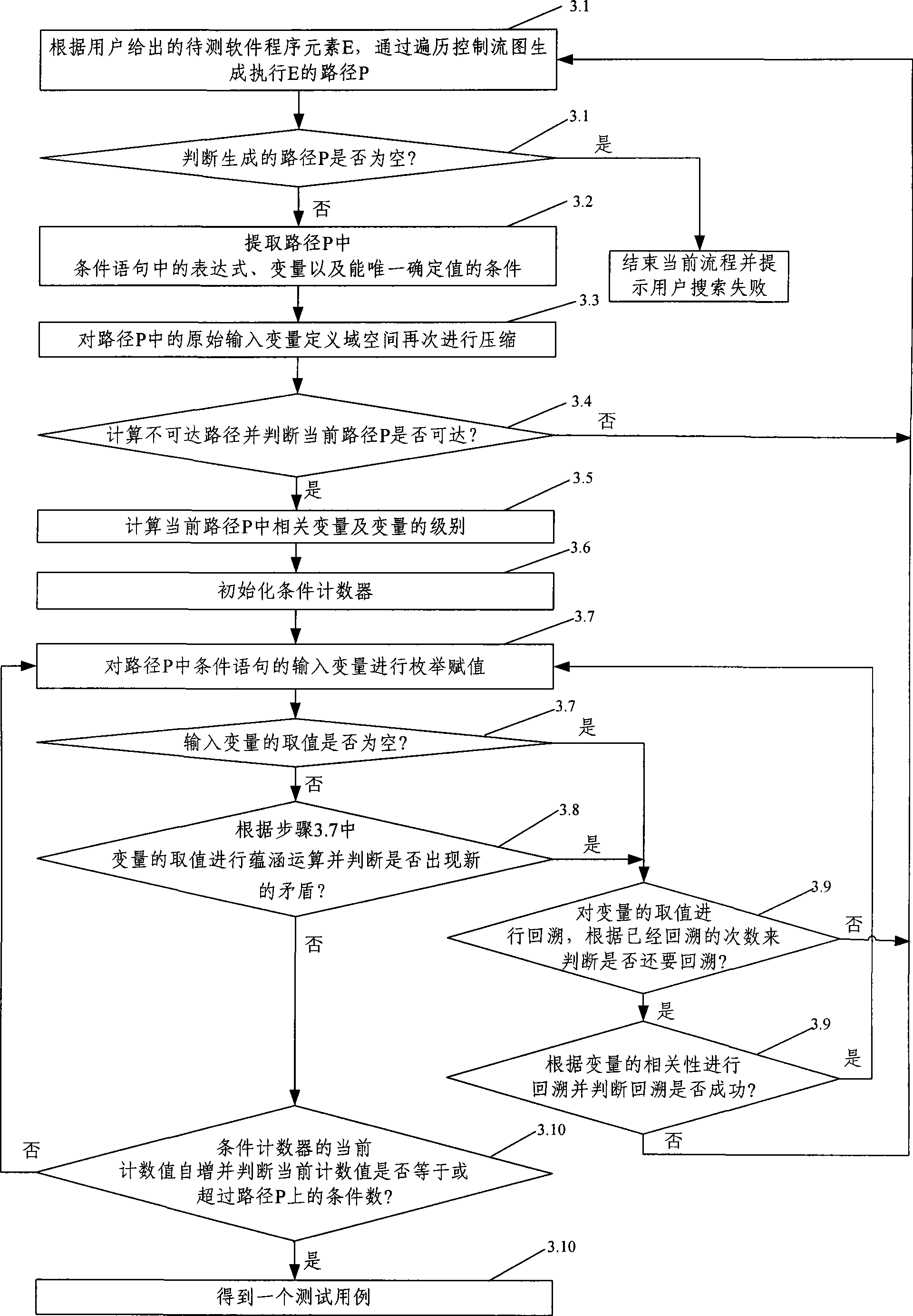
Software test case automatic generating method and system
InactiveCN101436128AImprove efficiencyHigh degree of automationSoftware testing/debuggingSpecific program execution arrangementsControl flowLexical analysis
The invention provides a method for automatically generating software test cases. The method comprises the following steps of: A. reading to-be-tested software, carrying out lexical analysis, syntax analysis and semantic analysis on a source program of the to-be-tested software and generating an abstract syntax tree and a control flow graph of the to-be-tested software; B. preprocessing the source program of the to-be-tested software by traversing the generated abstract syntax tree, identifying initial input-output variables and compressing the space of a definition domain of the initial input variables; and C. generating a path of program elements of the current to-be-tested software by traversing the control flow graph, carrying out assignment operation, implication operation and backtracking operation on the variables in the path, and generating the test cases. The invention also provides a system for automatically generating software test cases. The method and the system for automatically generating the software test cases can accurately and automatically generate the test cases according to the given program elements of the to-be-tested software and verify the generated test cases, thereby improving the accuracy, efficiency and automation degree of the test cases.
Owner:BEIJING UNIV OF POSTS & TELECOMM
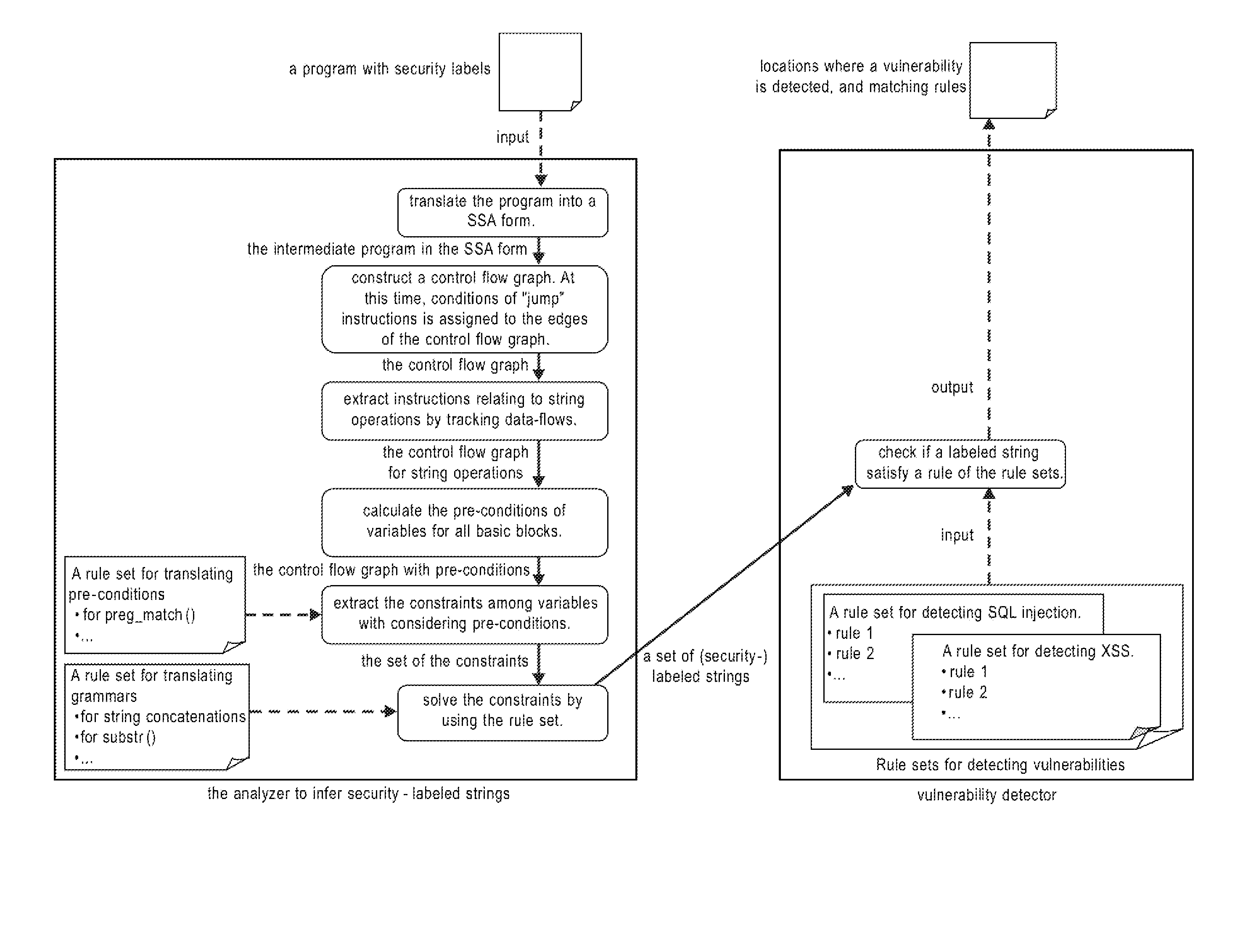
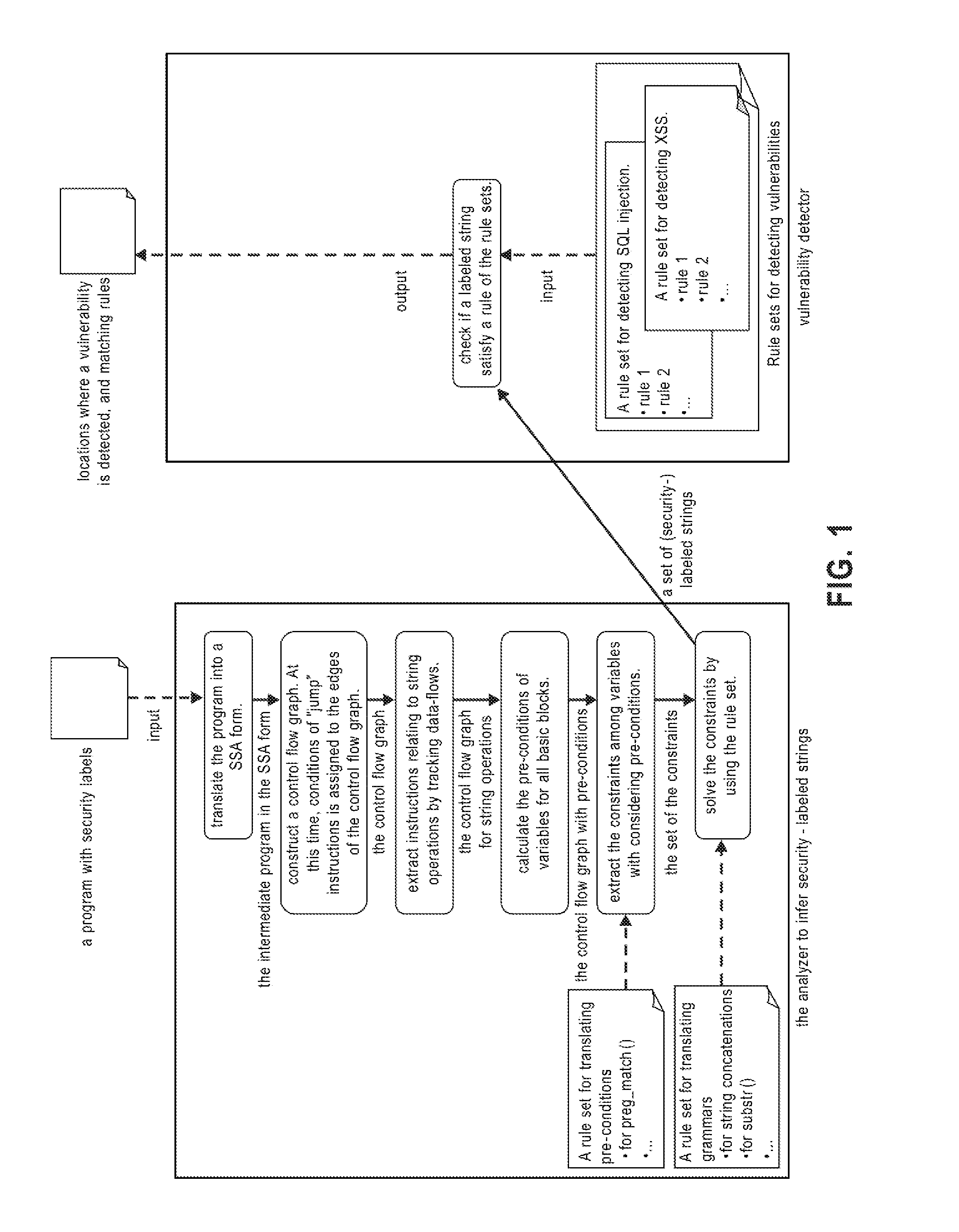
Systems, methods and computer program products for string analysis with security labels for vulnerability detection
InactiveUS7530107B1Suppress false detectionDetailed analysisMemory loss protectionError detection/correctionLocation detectionPre-condition
Systems, methods and computer program products for string analysis with security labels for vulnerability detection. Exemplary embodiments include a method in a computer system configured to analyze security-labeled strings and to detect vulnerability, the method including receiving a program with security labels, translating the program into a static single assignment form, constructing a control flow graph having basic blocks as nodes, extracting instructions relating to string functions and object variables, calculating pre-conditions of variables for the basic blocks, extracting constraints among the variables subject to a rule set for translating pre-conditions, solving the constraints and obtaining a set of strings that he object variables form as a context-free grammar to obtain a set of security-labeled strings, checking if the set of security-labeled strings satisfies a rule of the rule set for translating pre-conditions and identifying locations in the program where a vulnerability is detected.
Owner:IBM CORP
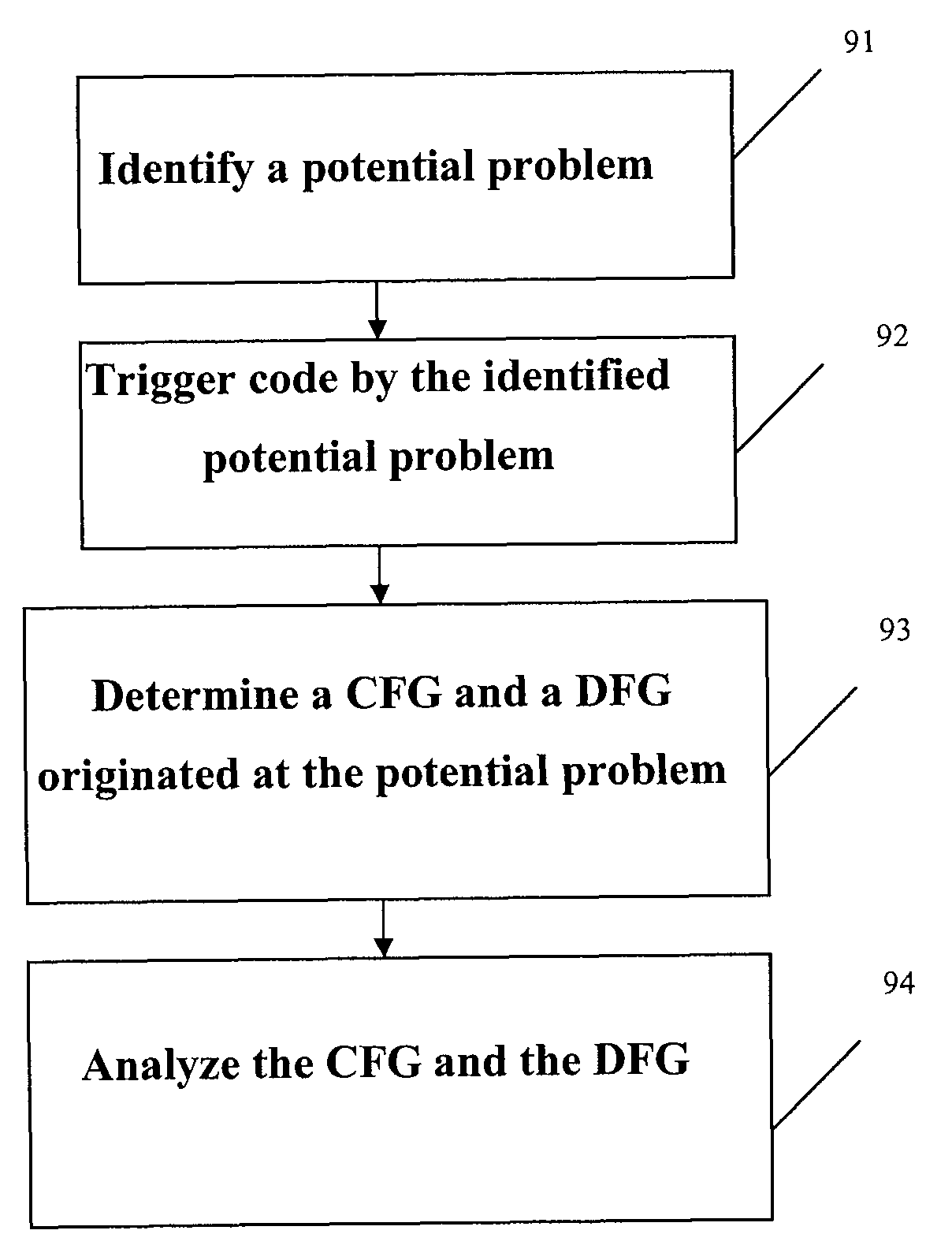
System and method for detecting defects in a computer program using data and control flow analysis
ActiveUS7900193B1Keep trackError detection/correctionSpecific program execution arrangementsTheoretical computer scienceControl flow analysis
A system and method for identifying errors in a computer software include: identifying a potential problem in the computer software; triggering a portion of the computer software by the identified potential problem; determining a control flow graph and a data flow graph for the triggered portion of the computer software originating at the identified potential problem; and analyzing the control flow graph and the data flow graph to verify that the identified potential problem is an actual error. The potential problem may be identified using test tools such as a static analysis tool or a unit test tool.
Owner:PARASOFT
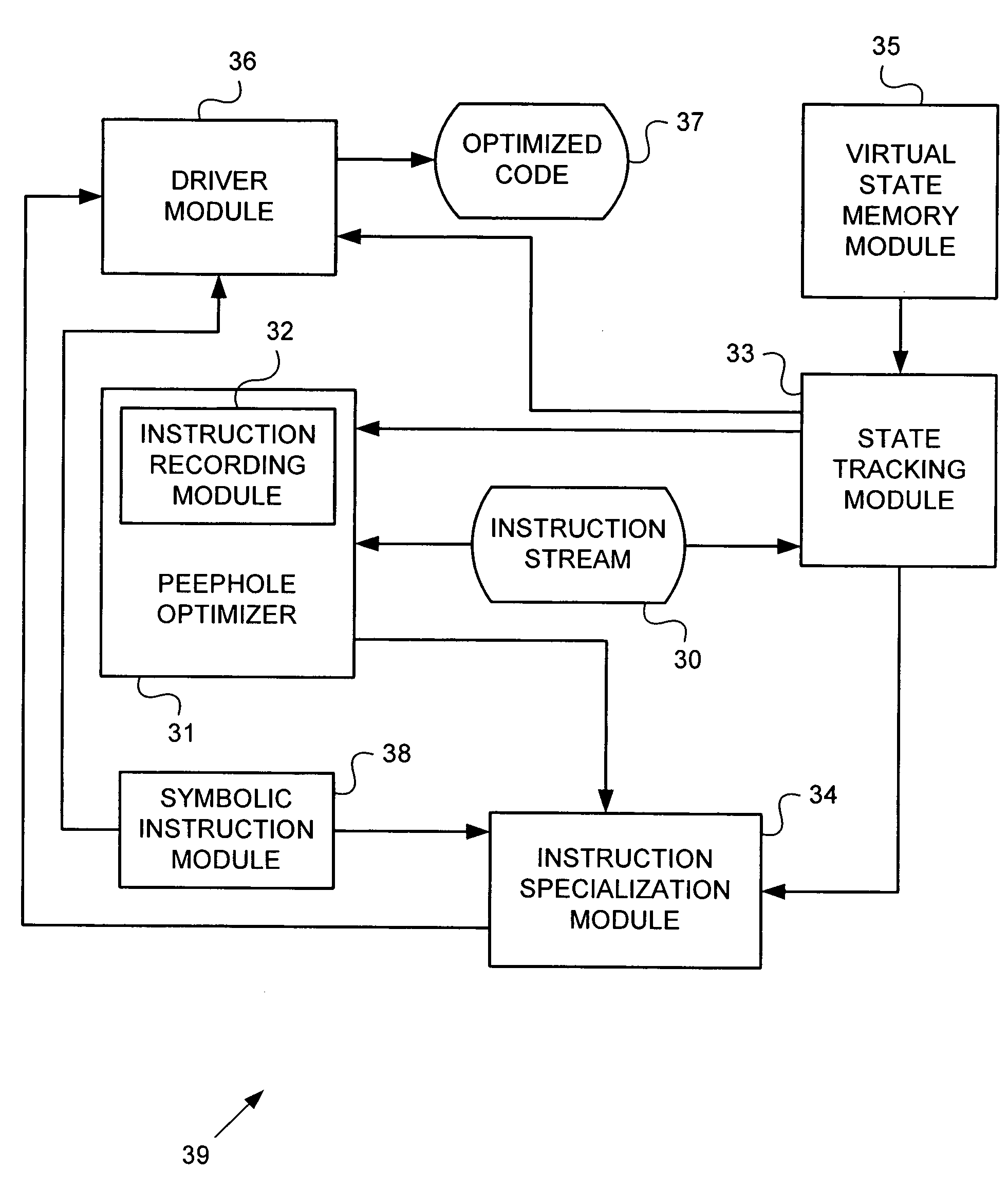
Countering polymorphic malicious computer code through code optimization
InactiveUS7624449B1Memory loss protectionError detection/correctionCopy propagationParallel computing
Methods, apparati, and computer-readable media for determining whether computer code (30) contains malicious code. In a method embodiment, the computer code (30) is optimized (40) to produce optimized code; and the optimized code is subject to a malicious code detection protocol. In an embodiment, the optimizing (40) comprises at least one of constant folding (53), copy propagation (54), non-obvious dead code elimination (62,63), code motion (49), peephole optimization (52), abstract interpretation (59,68), instruction specialization (55), and control flow graph reduction (44).
Owner:NORTONLIFELOCK INC
API use action discovering and malice deciding method after confusion of multi-tier synergism
InactiveCN101359352ASolve the problem that it is difficult to find the behavior of API function callsEasy to understandPlatform integrity maintainanceProgram controlSequence databaseConfusion
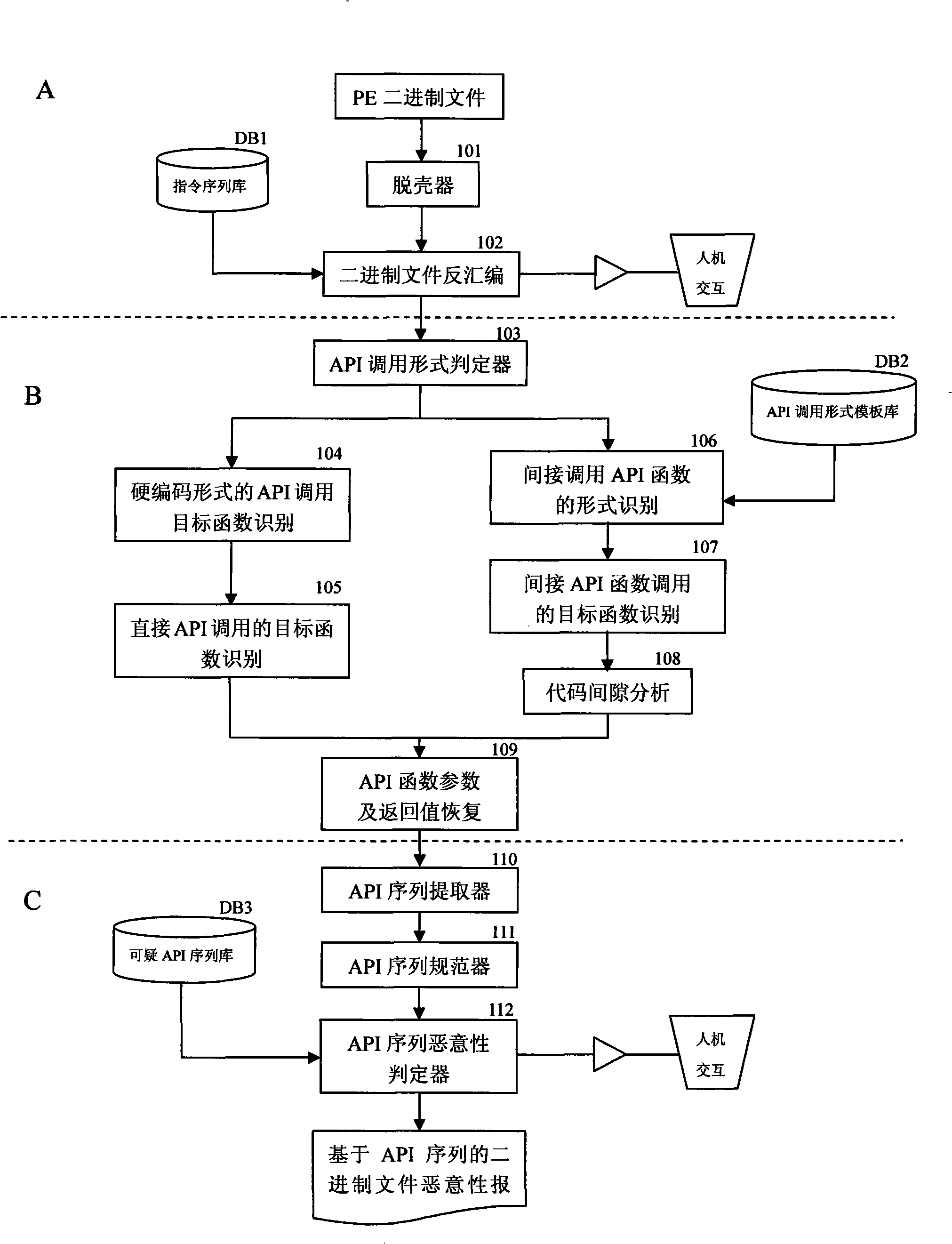
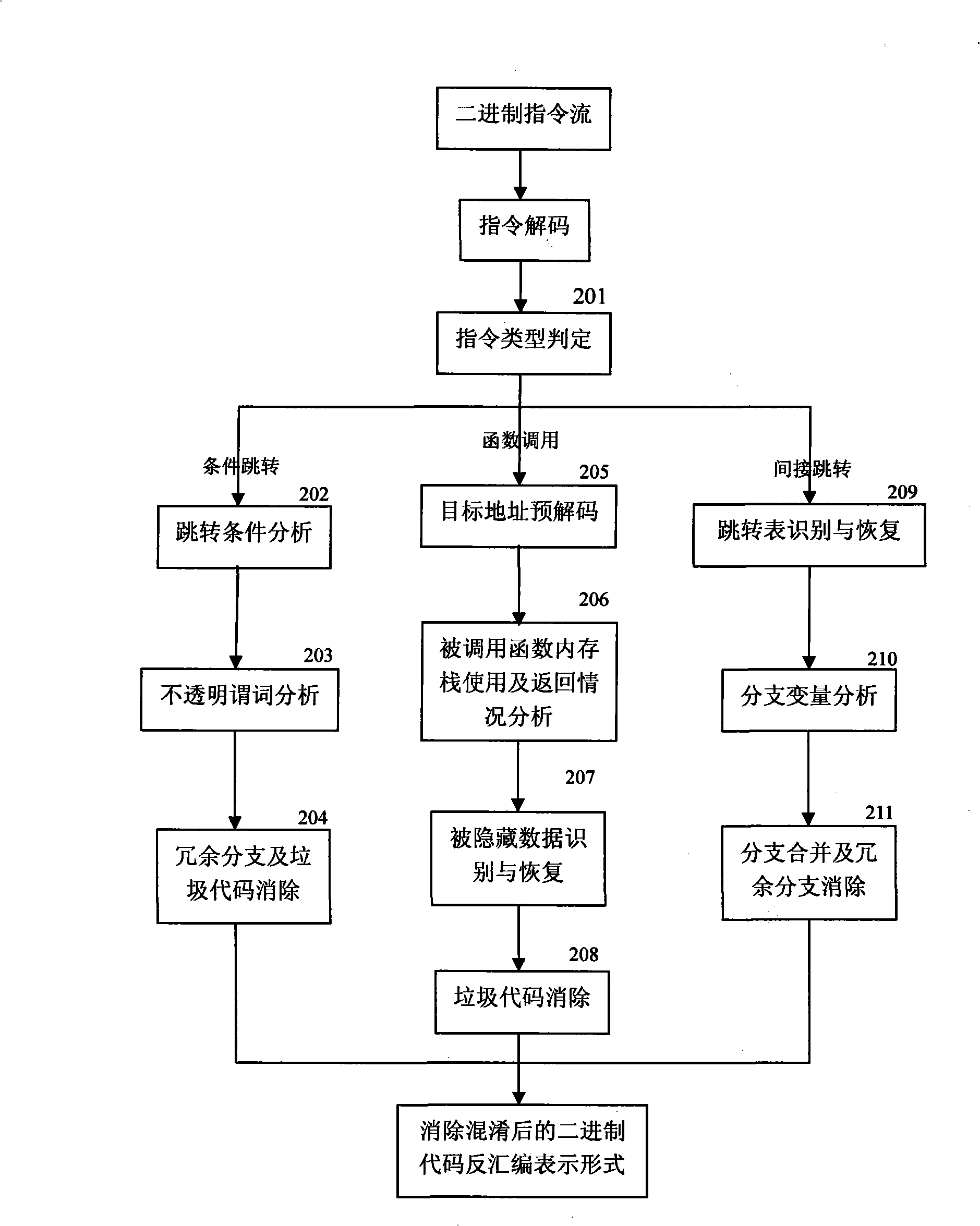
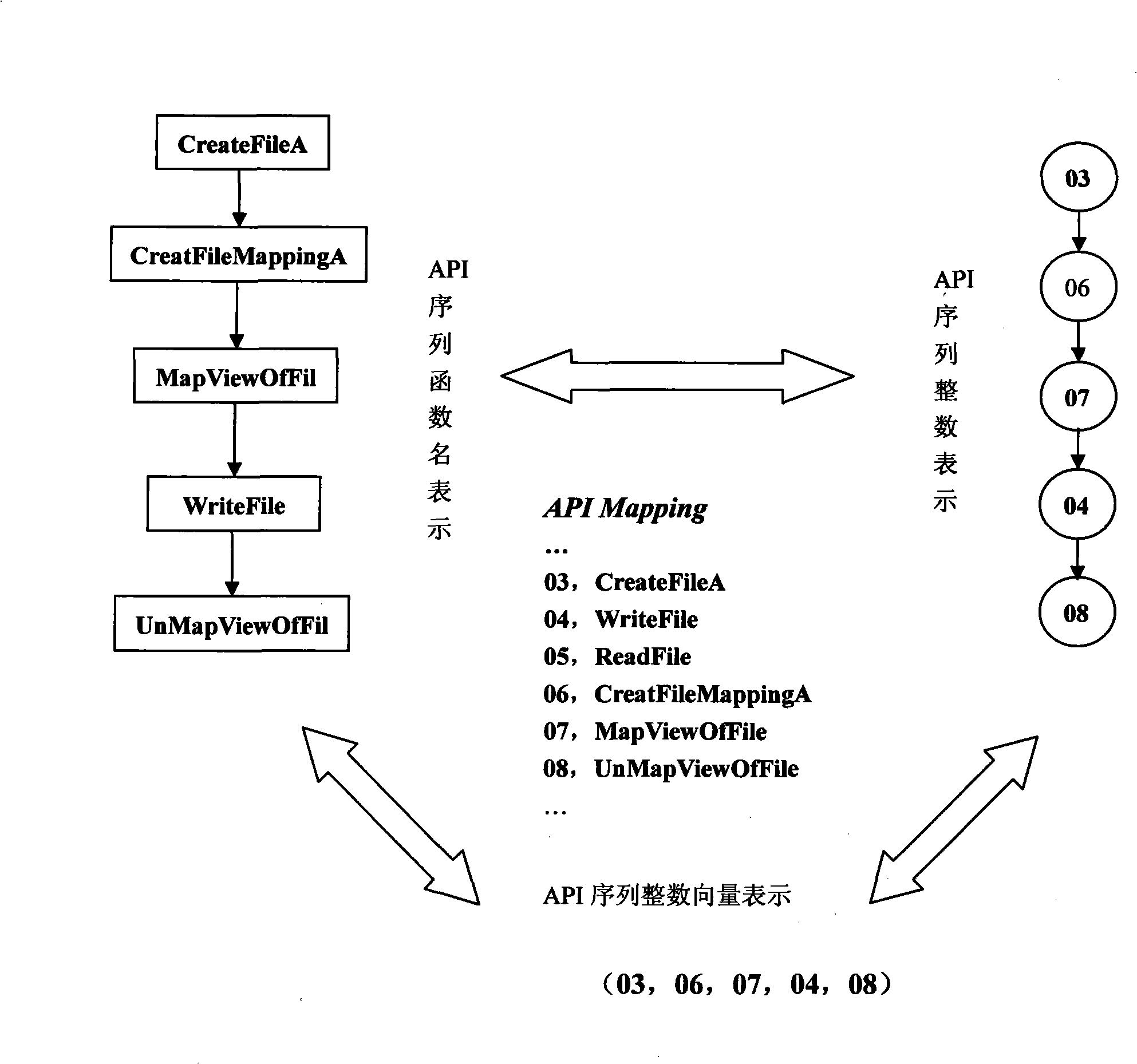
The invention relates to a stratification synergic detection and judgment method for detecting the confused API call behavior and judging the maliciousness of the call behavior; the detection and judgment method includes three steps: firstly, the binary code for being analyzed is disassembled to establish the control flow graph (CFG) of the program; the known unconventional instruction or data sequence provided with the API function call capability and stored in the database DB1 is adopted to recognize the unconventional call behavior of the API function; secondly, the generation operation of the API sequence called by the target program is finished; the API function is recognized and recovered in the aspects of direct call and indirect call; finally, the extraction of the API sequence and the maliciousness judgment operation are finished; the extraction of the sequence is finished and based on the control flow graph (CFG) of the program; then the obtained sequence is normalized according to the format stored in the suspected API sequence database; the invention provides a stratification synergic detection and judgment method for detecting the confused API call behavior and judging the maliciousness of the call behavior, which has the advantages of wide recognition range, accurate recognition and high efficiency.
Owner:THE PLA INFORMATION ENG UNIV
Method for determining software test process sufficiency based on coverage rate quantitative indicators
InactiveCN102419728AImprove efficiencyImprove accuracySoftware testing/debuggingAlgorithmLexical analysis
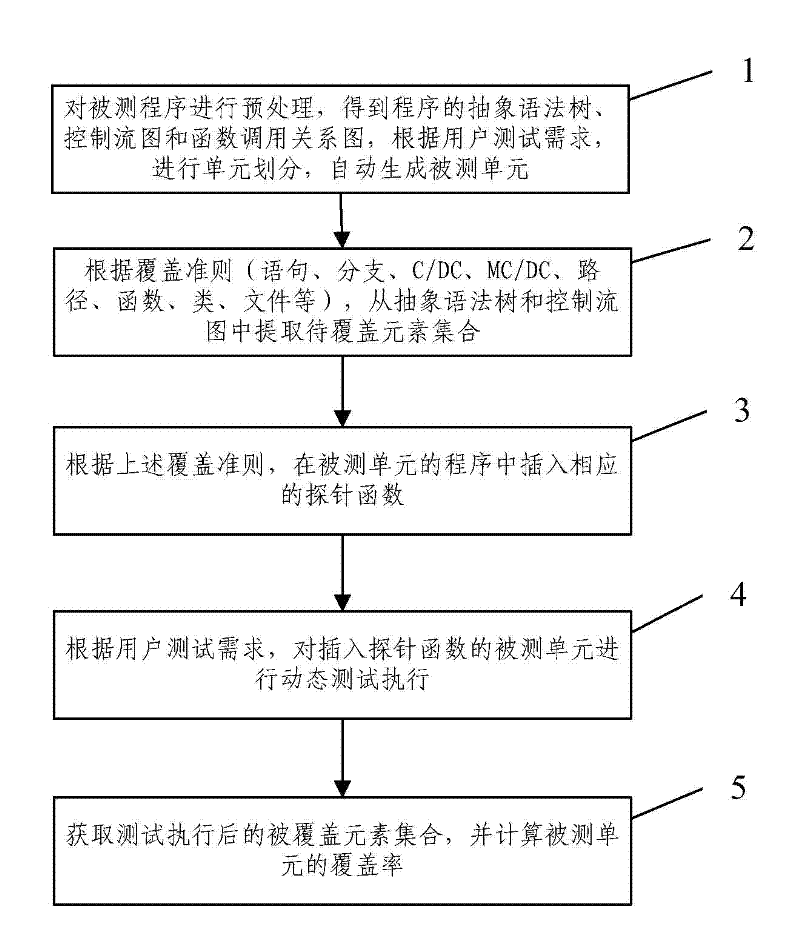
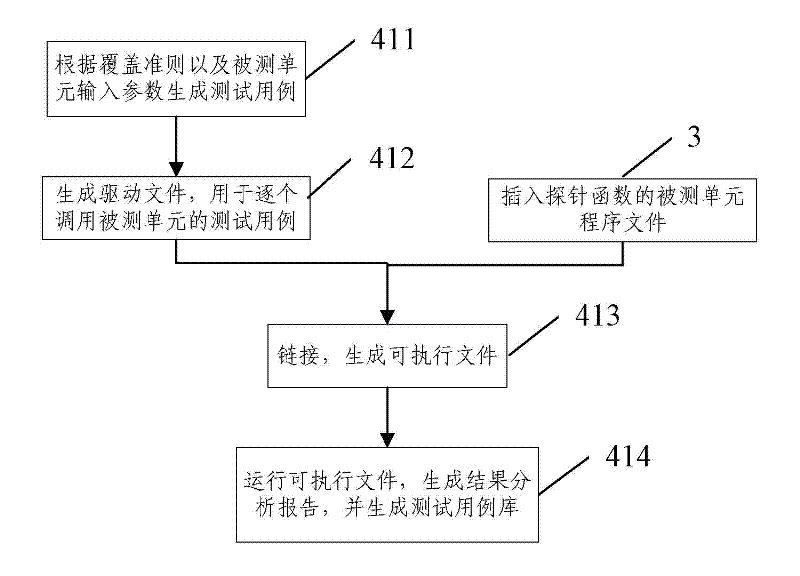
The invention provides a method for determining software test process sufficiency based on coverage rate quantitative indicators. The method comprises the following steps of: A, performing precompilation, lexical analysis and syntax analysis on a tested program to acquire the calling relationship diagram of the abstract syntax tree, the control flow graph and the function of the program, and automatically generating a tested unit according to the test requirement of a user; B, extracting a corresponding element set to be covered in the tested unit from the abstract syntax tree and the control flow graph according to a coverage criterion; C, inserting a corresponding probe function into the program of the tested unit according to the coverage criterion; D, dynamically testing the tested unit into which the probe function is inserted by selecting a system automatic executing mode or a user manual executing mode according to the test requirement of the user; and E, acquiring the covered element set of the tested unit according to the returned information of dynamic test execution, and calculating the coverage rate of the tested unit. By the method, the efficiency and the accuracy of a software evaluation test can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
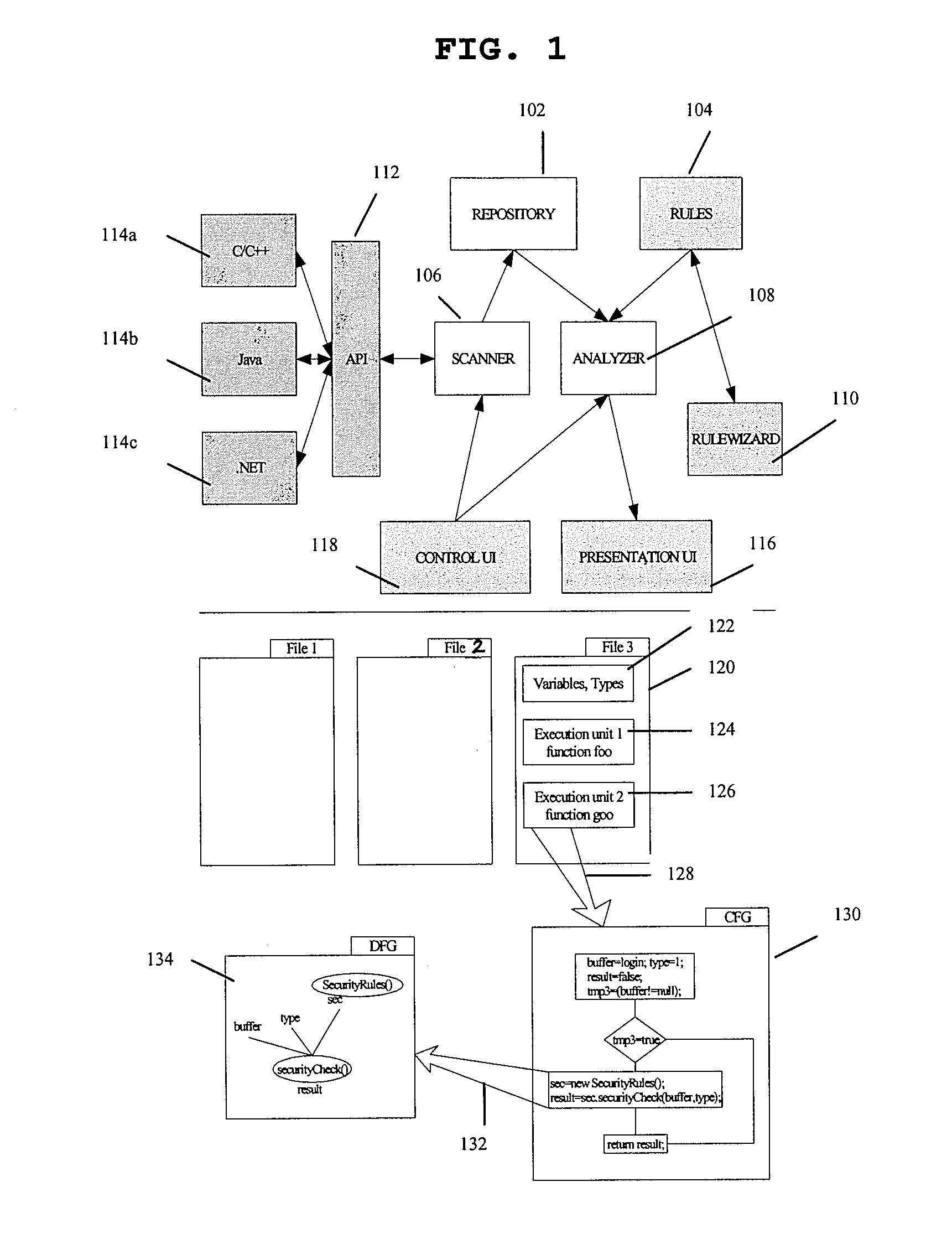
Constructing control flows graphs of binary executable programs at post-link time
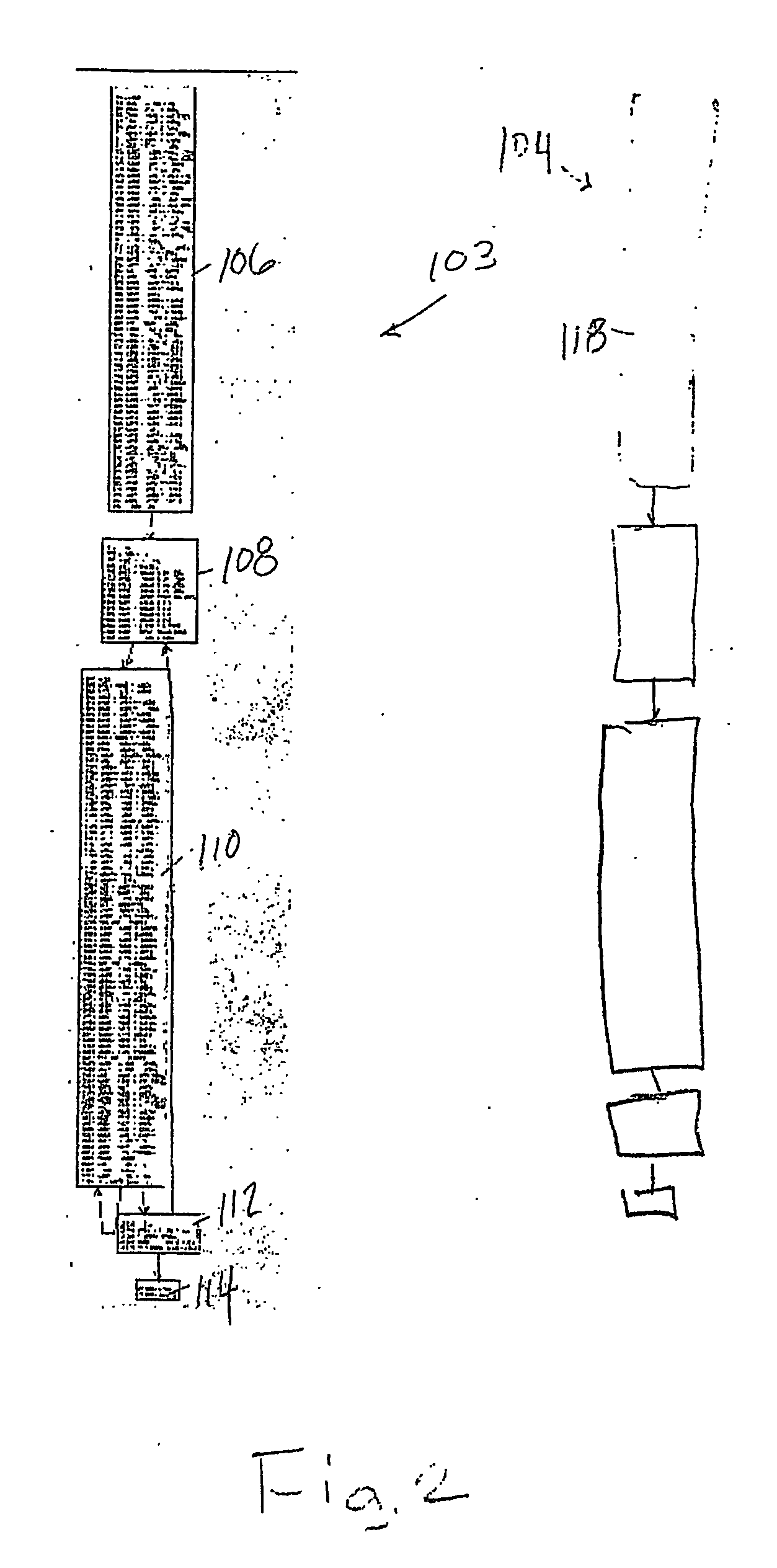
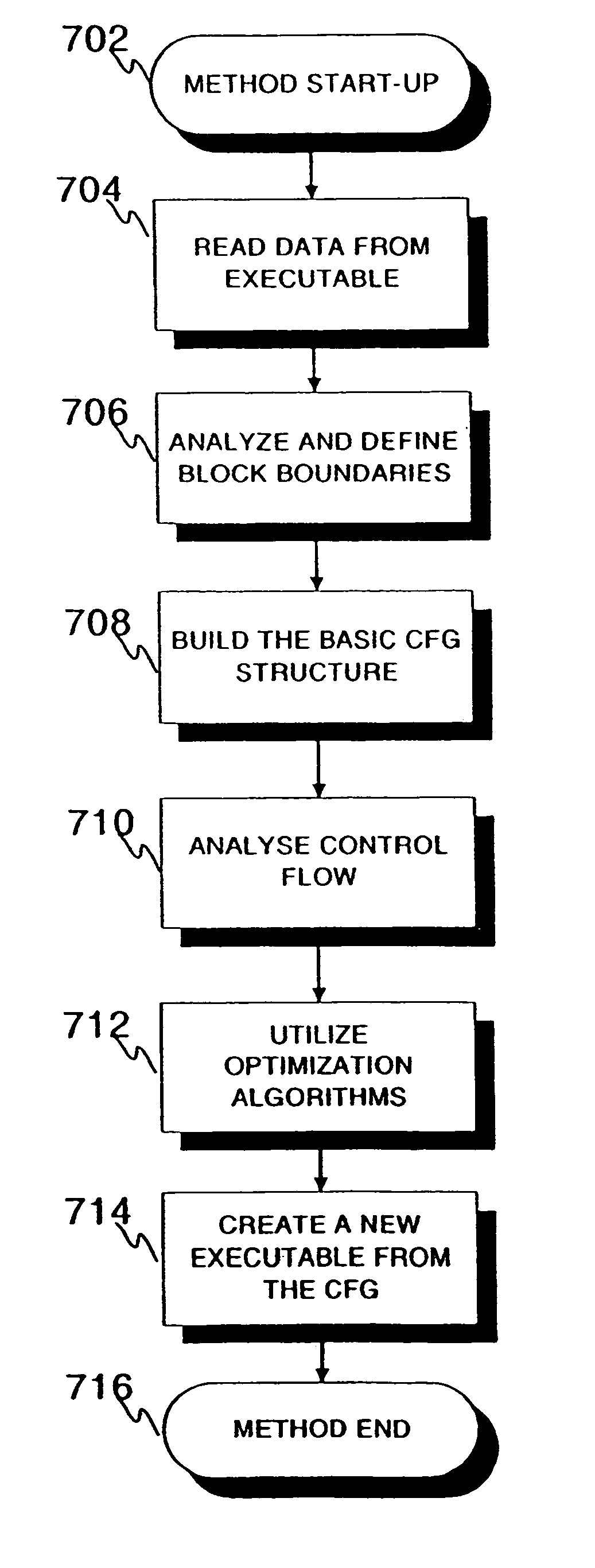
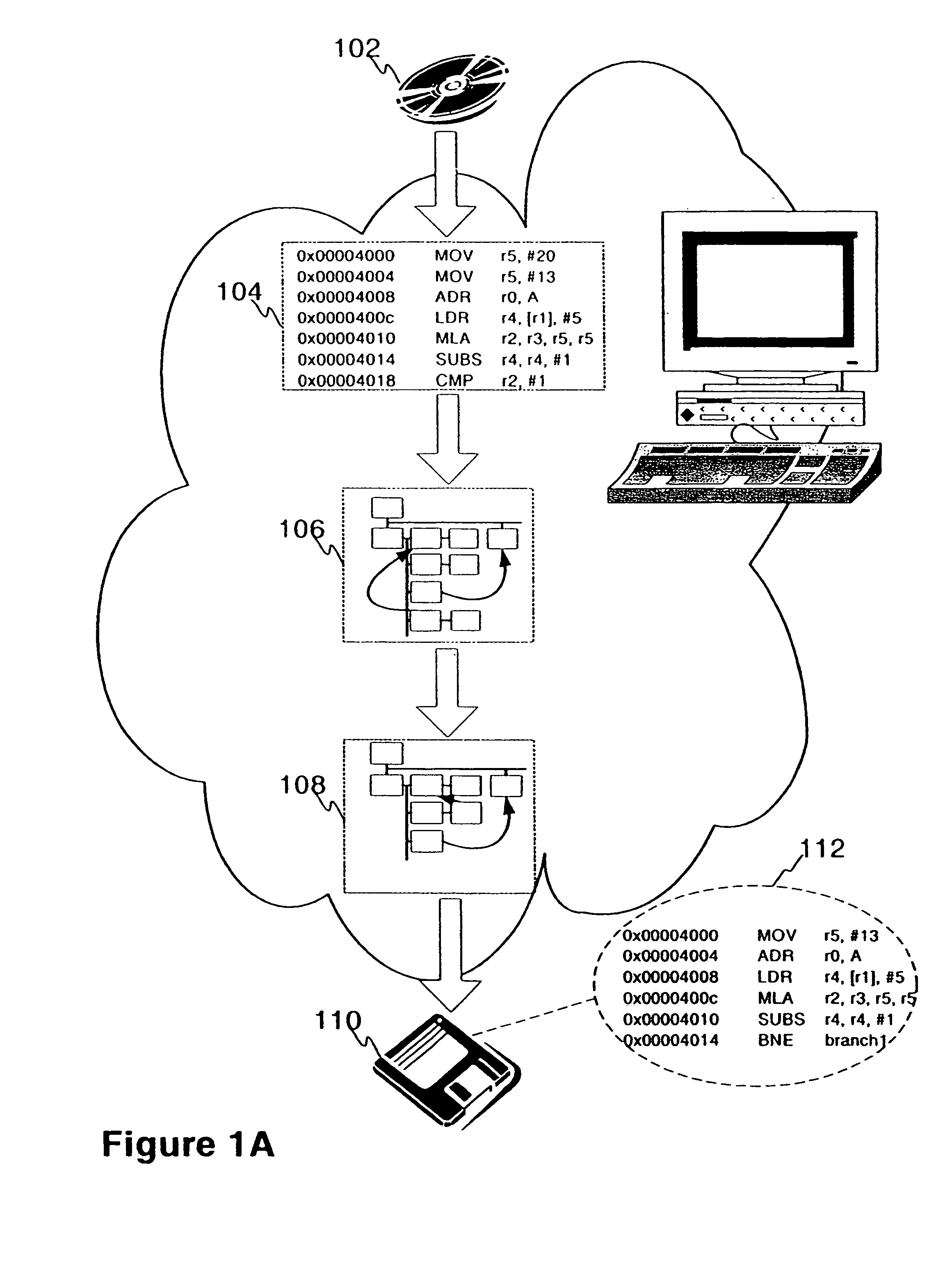
InactiveUS7207038B2Clarifies overall structureReduce memory usageSoftware engineeringSoftware simulation/interpretation/emulationControl flowBasic block
A method and a system for constructing a control flow graph (CFG, 106) from an executable computer program (104). The solution detects data intermixed with instructions and instruction set changes. The method includes the steps of defining block leader types specifying basic block boundaries in the program (104), building a CFG structure (106) according to the basic blocks found in the program, and adding control flow and addressing information to the CFG (106) by propagating through the basic blocks and internals thereof. The CFG (106) may be then optimised (108) and a compacted executable (112) created as a result.
Owner:NOKIA CORP
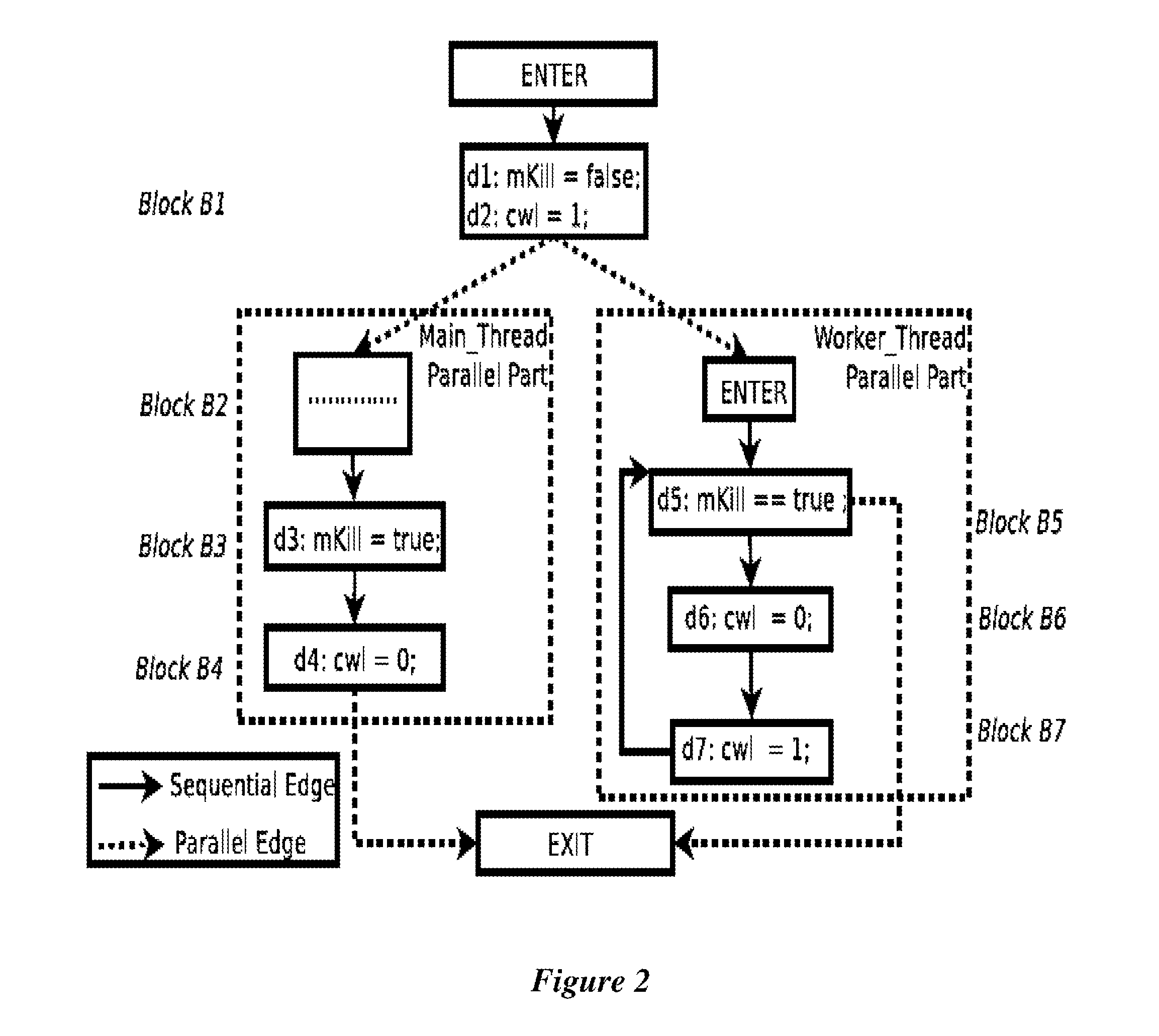
Value predictable variable scoping for speculative automatic parallelization with transactional memory
ActiveUS20090235237A1Software engineeringSpecific program execution arrangementsCoding blockInner loop
Parallelize a computer program by scoping program variables at compile time and inserting code into the program. Identify as value predictable variables, variables that are: defined only once in a loop of the program; not defined in any inner loop of the loop; and used in the loop. Optionally also: identify a code block in the program that contains a variable assignment, and then traverse a path backwards from the block through a control flow graph of the program. Name in a set all blocks along the path until a loop header block. For each block in the set, determine program blocks that logically succeed the block and are not in the first set. Identify all paths between the block and the determined blocks as failure paths, and insert code into the failure paths. When executed at run time of the program, the inserted code fails the corresponding path.
Owner:ORACLE INT CORP
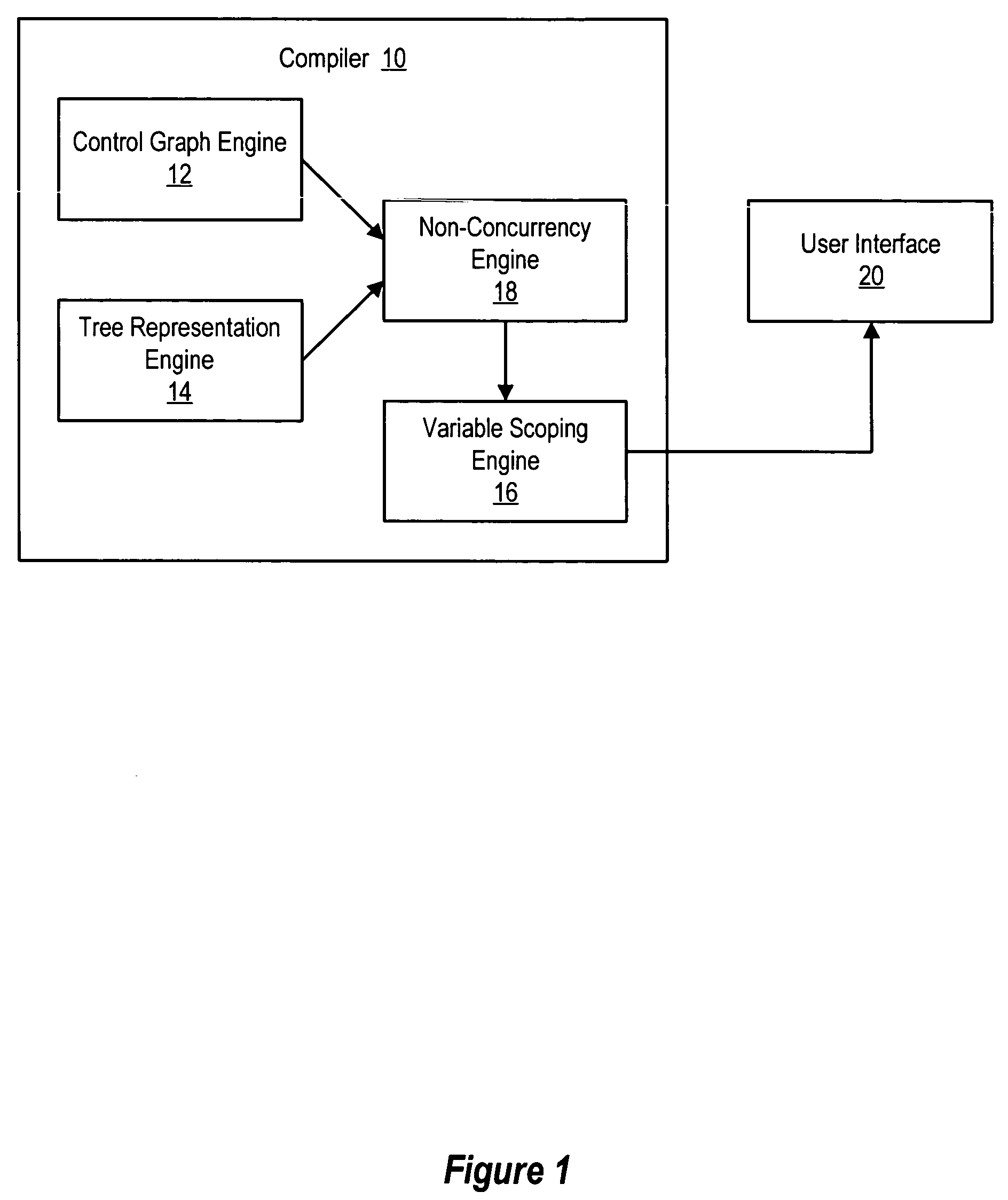
System and method for compile-time non-concurrency analysis
ActiveUS7673295B1Improve efficiencyReduce overheadSoftware engineeringError detection/correctionControl flowSemantics
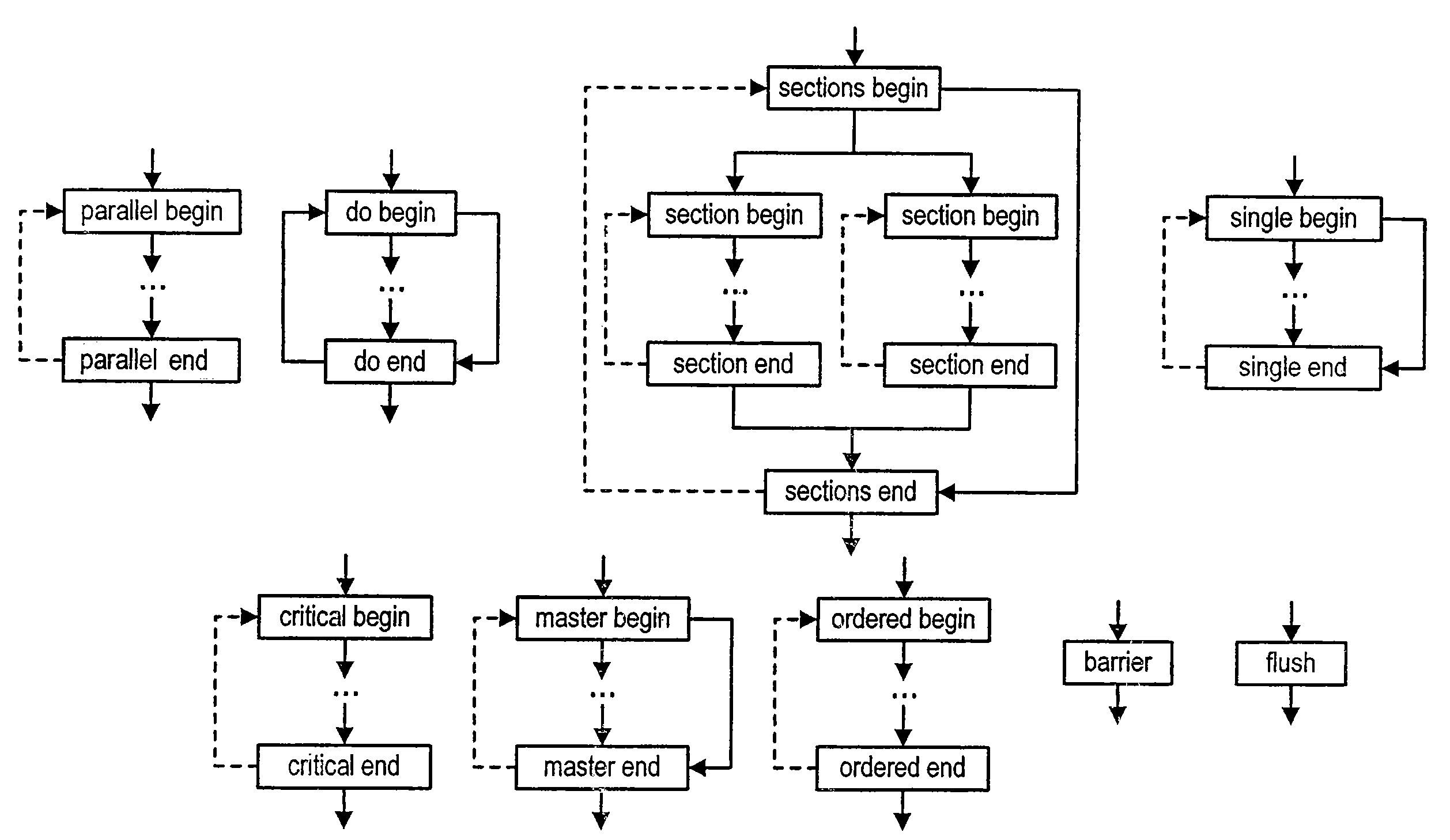
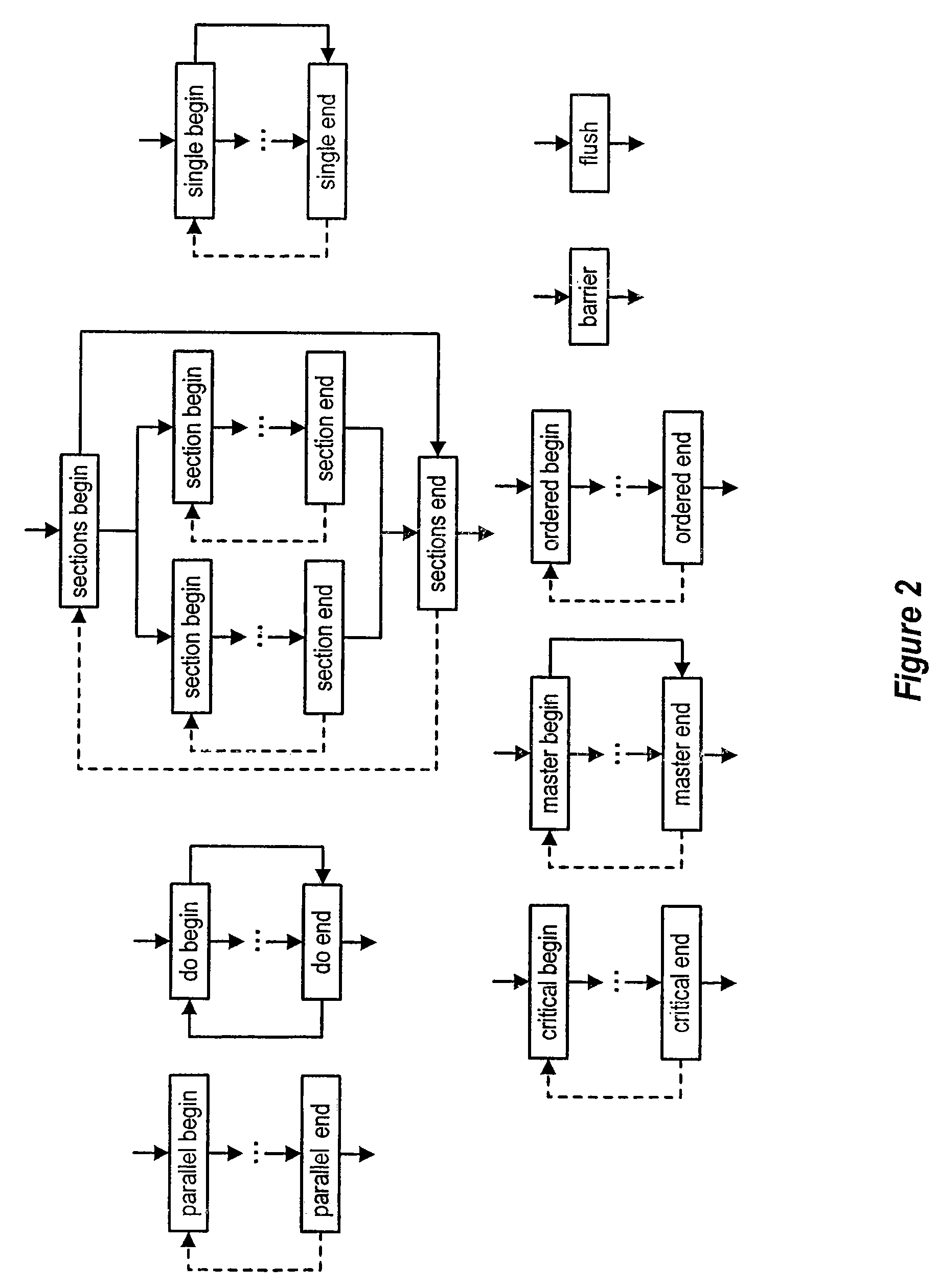
Compile-time non-concurrency analysis of parallel programs improves execution efficiency by detecting possible data race conditions within program barriers. Subroutines are modeled with control flow graphs and region trees having plural nodes related by edges that represent the hierarchical loop structure and construct relationship of statements. Phase partitioning of the control flow graph allows analysis of statement relationships with programming semantics, such as those of the OpenMP language, that define permitted operations and execution orders.
Owner:ORACLE INT CORP
Test program control stream path set creation method based on base path
InactiveCN101216803ASolve the completeness problemSolving automation problemsSoftware testing/debuggingPath generationProgram testing
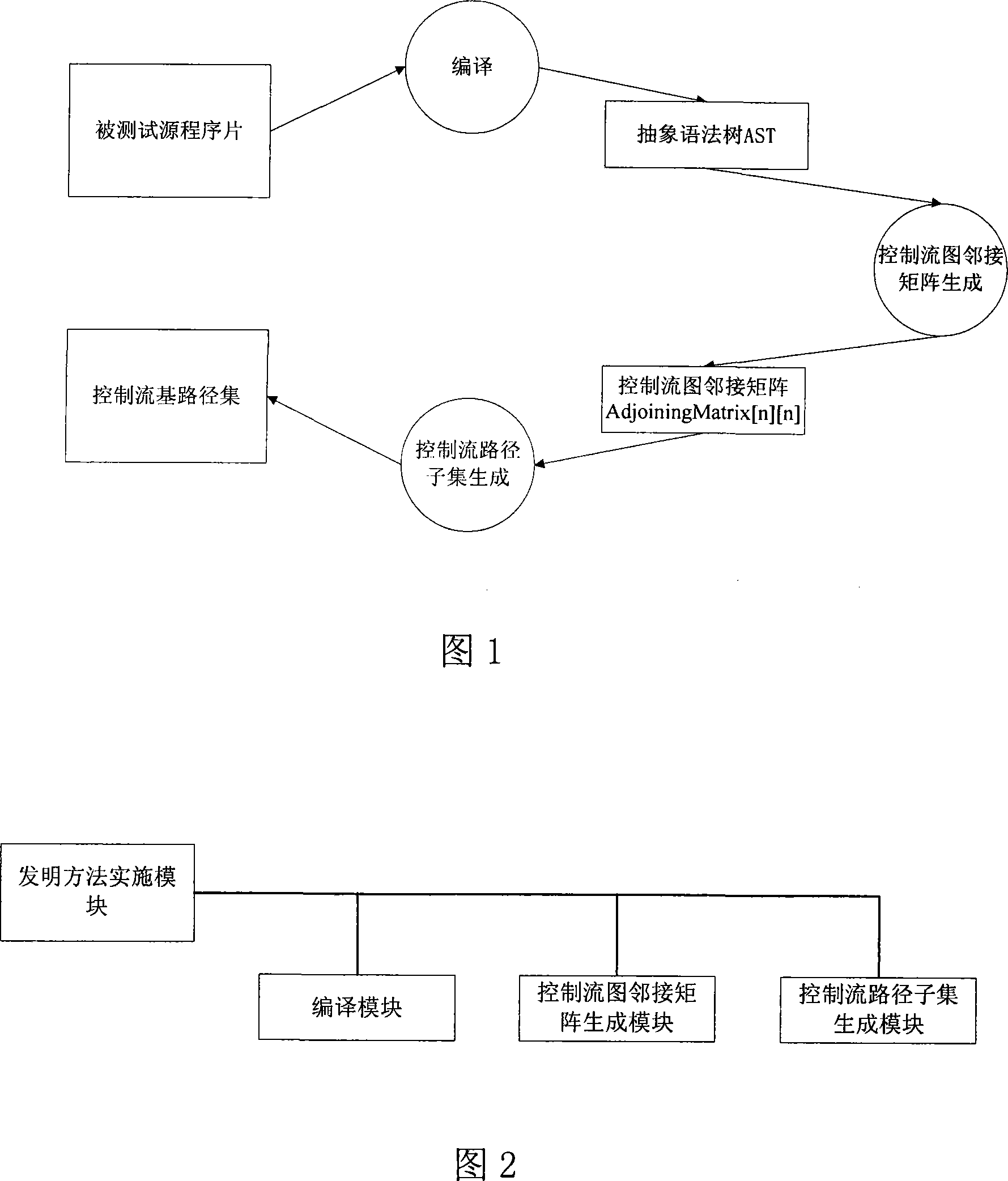
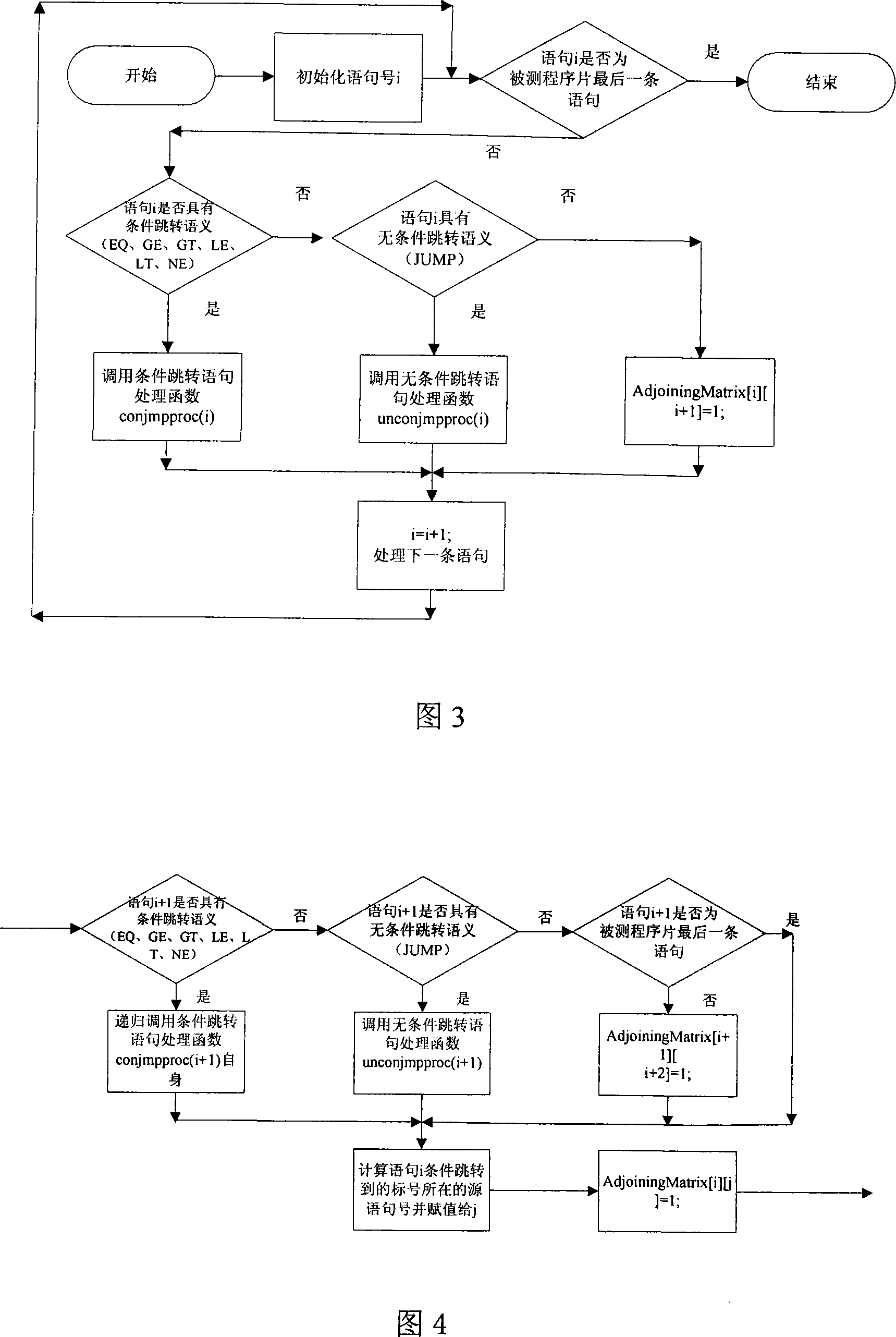
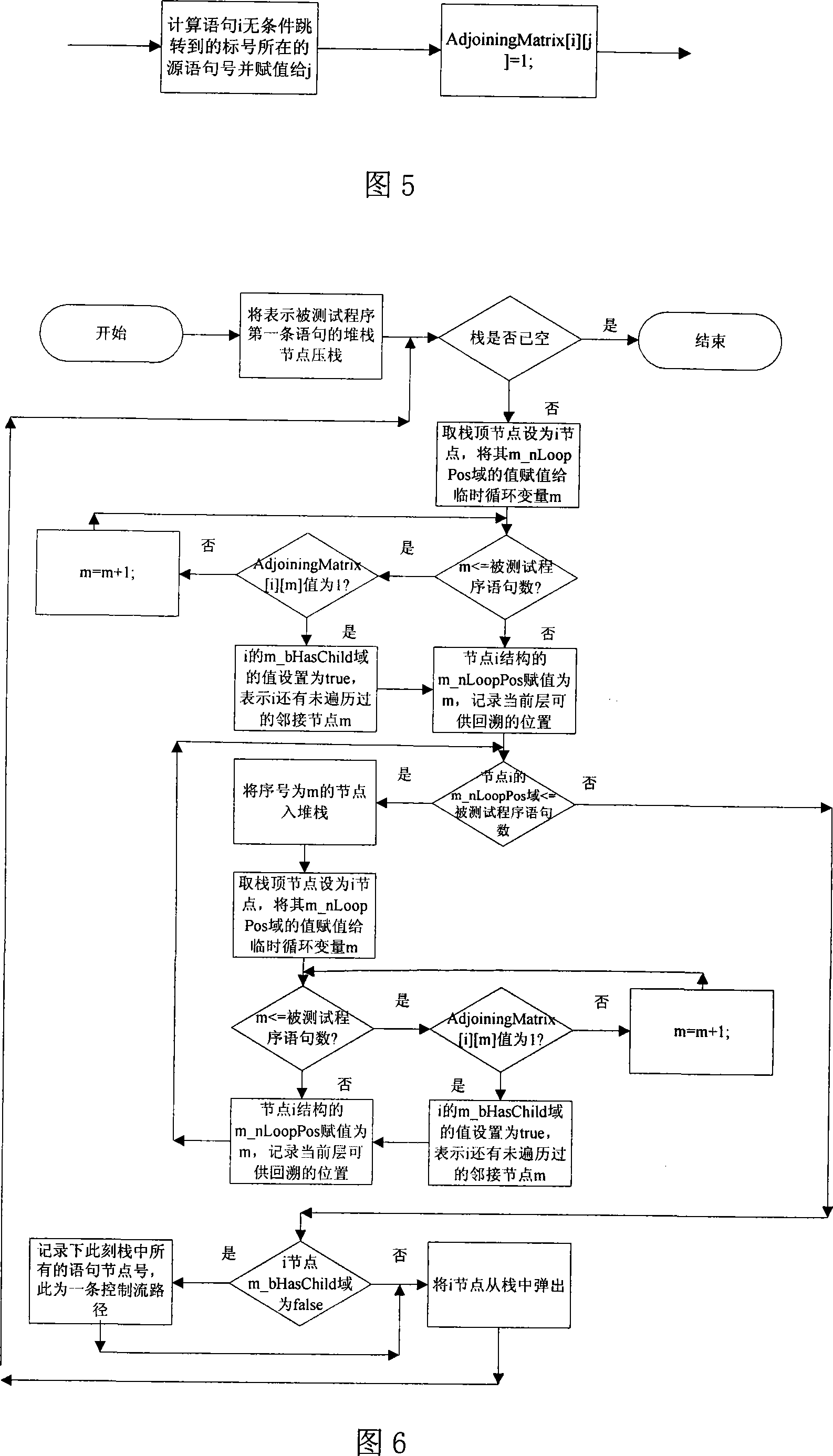
The invention pertains to a path testing in a program testing. The concept of a program control flow base path is defined through bringing in the concept of base in mathematics, a data structure showing a program structure of a source program slice is obtained by using a compiler module first; then through traversing the data structure, a control flow path generating algorithm is utilized to generate a subset compiler module of a program control flow path which is based on a base path to interpret the semanteme on a tested source program, an abstract syntax tree structure showing the structural information of the tested program control flow is output. An adjacency matrix of a control flow graph generates a module ergodicity abstract syntax tree structure, and generates the adjacency matrix representation of a program flow chart. A control flow path subset generating module acquires the control flow information of the tested program through traversing the adjacency matrix, traverses the adjacency matrix by adopting a depth-first multiple backtracking method, and processes sentence nodes, thus a program control flow path subset based on the base path is generated. The method has the outstanding advantages in generating results and flows, and can be widely used in the engineering practice of a path cover testing in a software structure testing.
Owner:SICHUAN UNIV
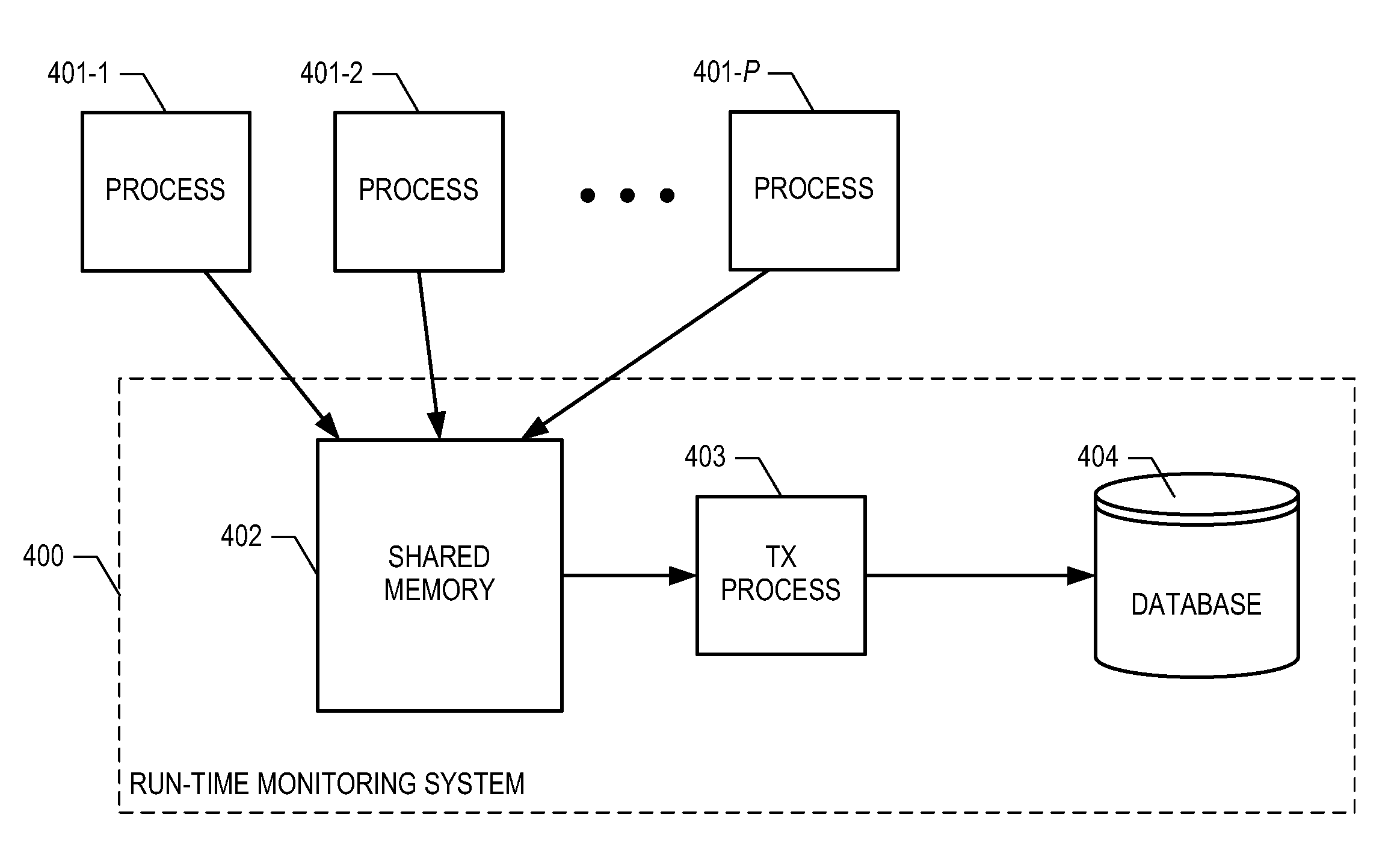
Efficient Encoding of Instrumented Data in Real-Time Concurrent Systems
ActiveUS20090249308A1Efficient and rapid reporting and storageError detection/correctionSpecific program execution arrangementsRunning timeInstrument Data
A mechanism for encoding and reporting instrumented data is disclosed that requires less storage space and incurs less processor overhead than other methods of the prior art. In accordance with the illustrative embodiment, a bit vector in shared memory corresponds to nodes of a program's control-flow graph that have been instrumented, and the contents of the vector indicate which of these nodes have executed; in addition, character strings in shared memory indicate what file, class, and method each node belongs to. A process that executes concurrently with those of the program under test transmits instrumented data from the shared memory to a database. The illustrative embodiment enables efficient, rapid reporting and storage of instrumented data, and is therefore especially well-suited for run-time analysis of real-time concurrent systems.
Owner:AVAYA INC
Method and system for tamperproofing software
InactiveUS7757097B2User identity/authority verificationUnauthorized memory use protectionCoding blockObfuscation
Method of protecting host application code comprising a plurality of code blocks. The method includes steps of preprocessing the host application code; obfuscating the host application code; installing guards in the host application code to protect client blocks; randomly rearranging the code blocks of the host application code; linking the rearranged host application code with other resources to produce a binary executable image; and patching the binary executable image with data values to be used by the guard. The method can be used to install a plurality of guards to form a distributed network of guards that cooperatively protect the host application code and the other guards in the network. The installation of the guards can be performed automatically using a guard formation graph; and guard formation graph customization parameters. The obfuscation step can include control flow graph merging, cloning, and data-aliasing.
Owner:PURDUE RES FOUND INC
Multi-rate hierarchical state diagrams
ActiveUS20090013307A1Analogue computers for electric apparatusCAD network environmentGraphicsDirected graph
Systems and methods are provided for a scheme and mechanism for performing static analysis of a sample time aware state diagram model to compute and propagate multiple samples rates associated with the state diagram model. A graphical intermediate representation of the state diagram model, such as a directed graph or control flow graph, is used to determine how the multiple sample rates are propagated via elements of the state diagram model. The graph provides a static representation of the control of flow, including alternative and / or conditional flow paths, of the state diagram model. The present invention determines the propagation of sample rates via analysis and traversal of the intermediate representation. By using the techniques of the present invention, a state diagram model may provide multiple sample rate outputs, such as by function calls and output signals to a graphical model, such as a model representing a dynamic system.
Owner:THE MATHWORKS INC
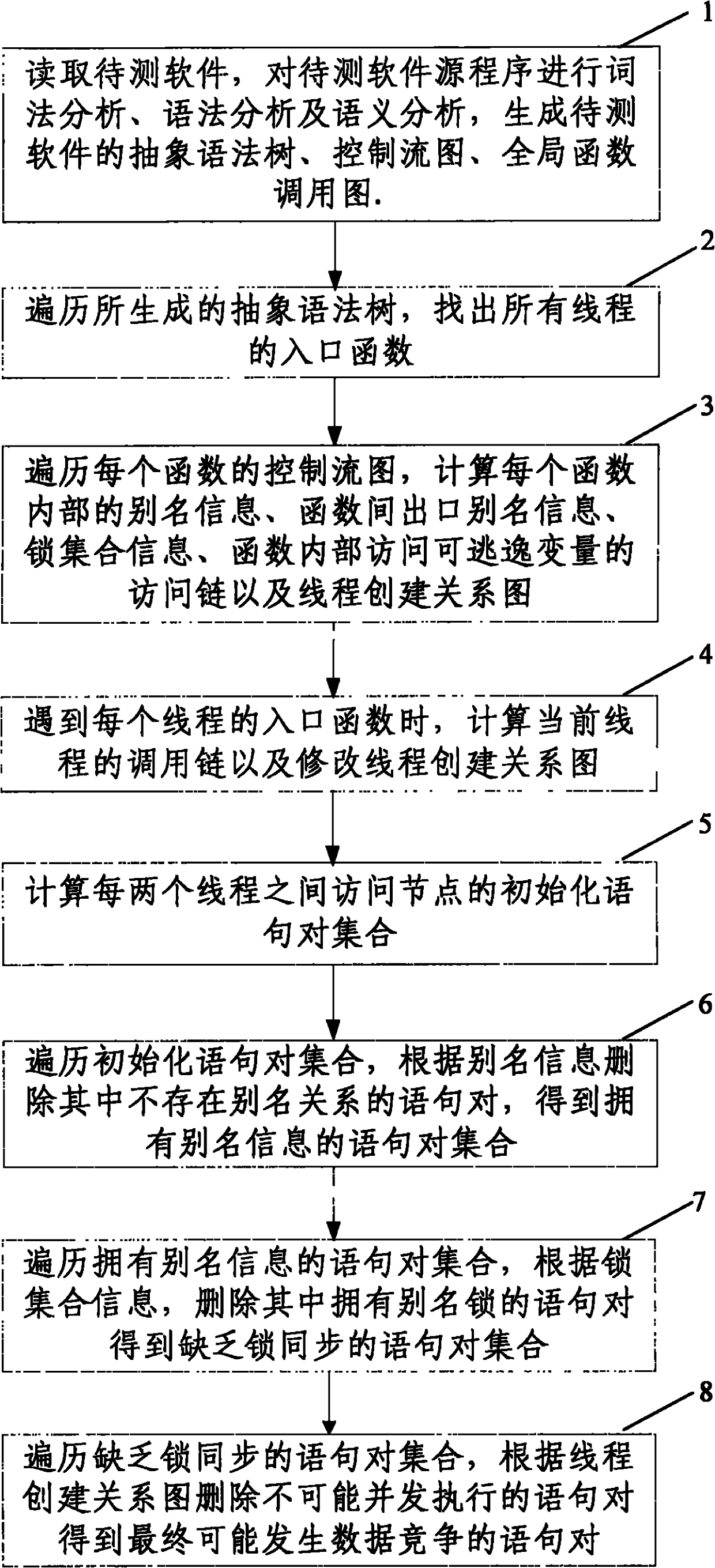
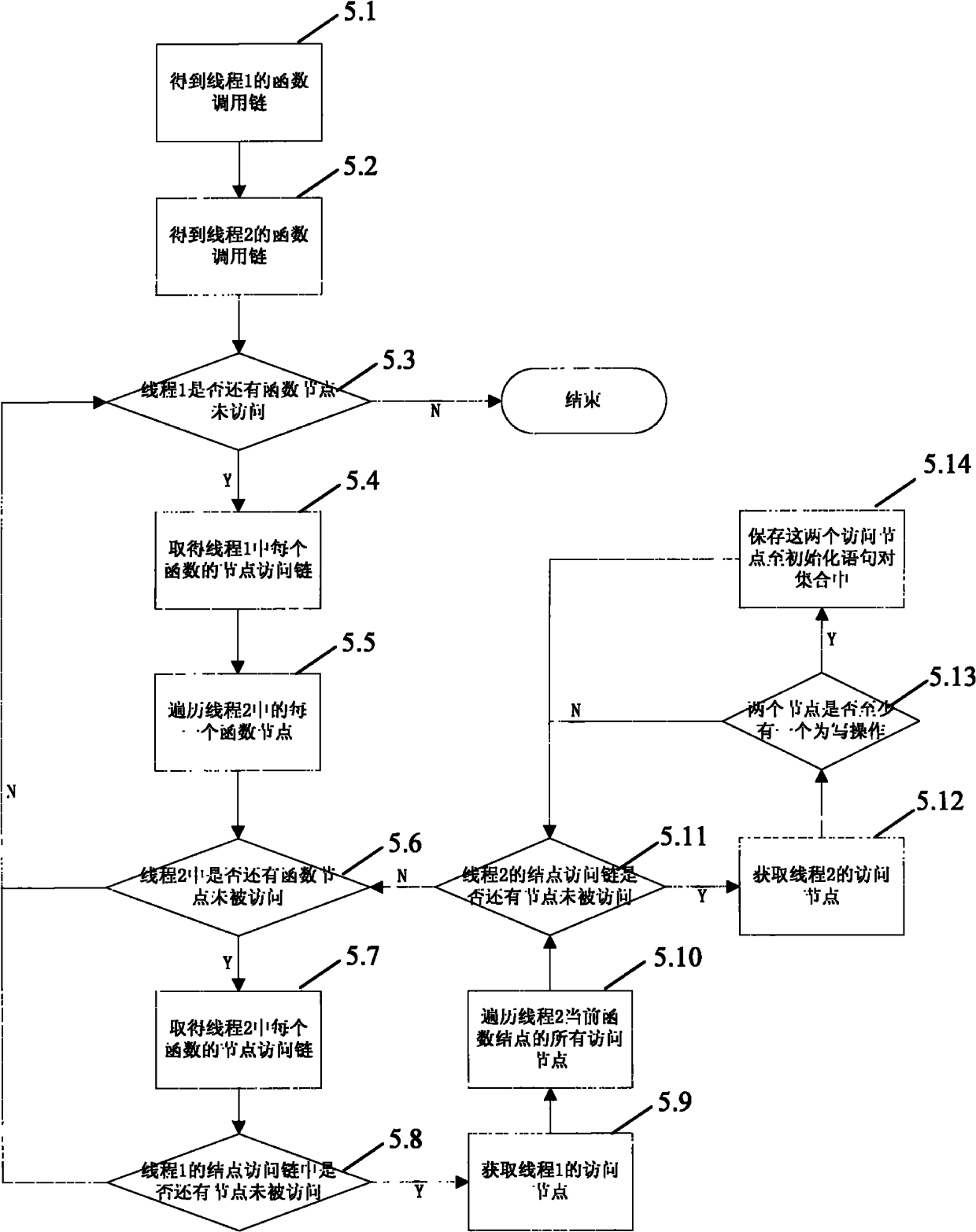
Code static analysis-based data race detecting method and system thereof
The invention discloses a code static analysis-based data race detecting method and a system of the detecting method. The method comprises the following steps of: reading software to be detected, statically analyzing a source program of the software to be detected, and generating an abstract syntax tree, a control flow graph and a global function call graph of the software to be detected; on thatbasis, computing alias information in each function, outlet alias information among functions, lock assembly information, an access link of an access escapable variable quantity in each function and a thread building relational graph; computing a plurality of initialized sentence pair sets of a plurality of access nodes in every two threads; and gradually eliminating the sets according to the alias information, the lock assembly information and a concurrency relation to obtain a sentence pair which can finally have the data race. The detecting method and the detecting system can effectively detect the data race of a multi-thread program compiled by C / C++, thereby having the characteristics of high test precision and high automaticity, and being applied to detecting the data race caused bytwo threads or multiple threads.
Owner:BEIJING UNIV OF POSTS & TELECOMM
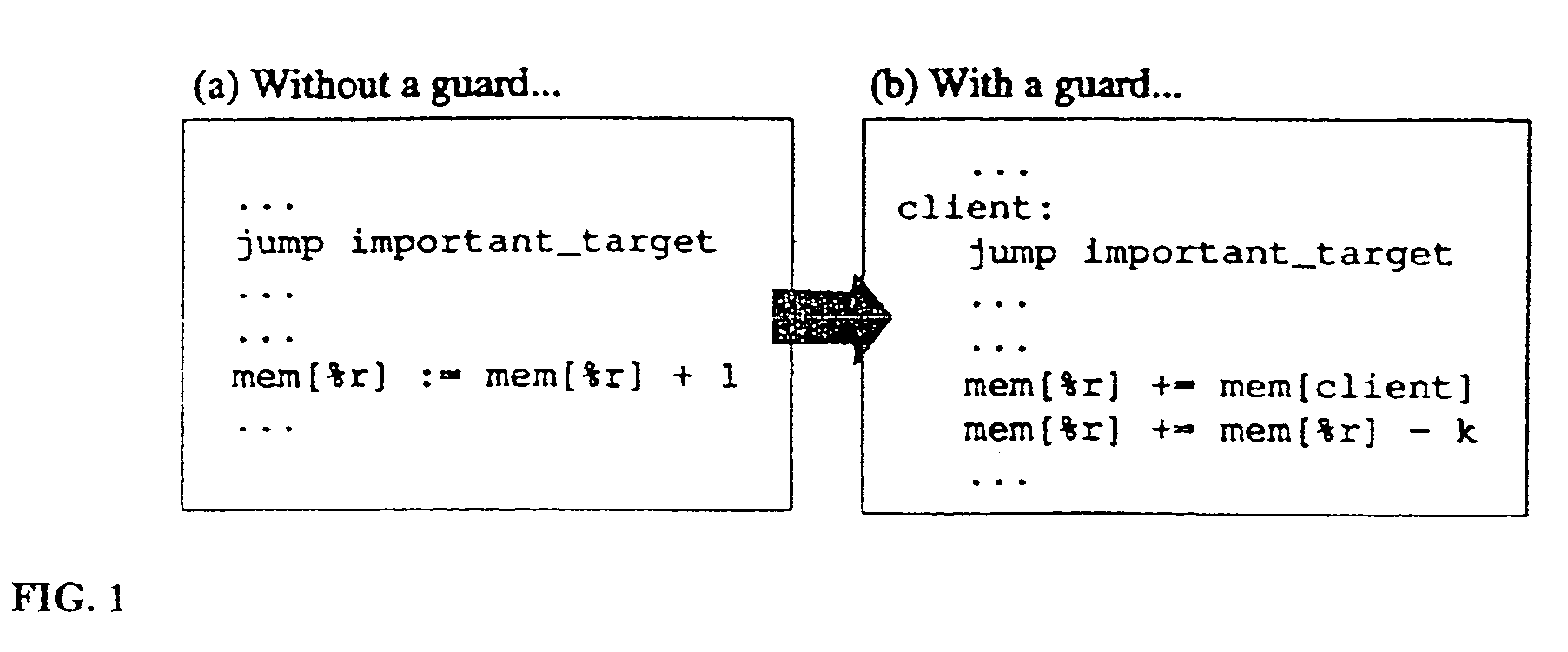
Software security based on control flow integrity
InactiveUS20060161978A1Reduce vulnerabilityAvoid successionMemory loss protectionError detection/correctionSoftware engineeringSecurity Measure
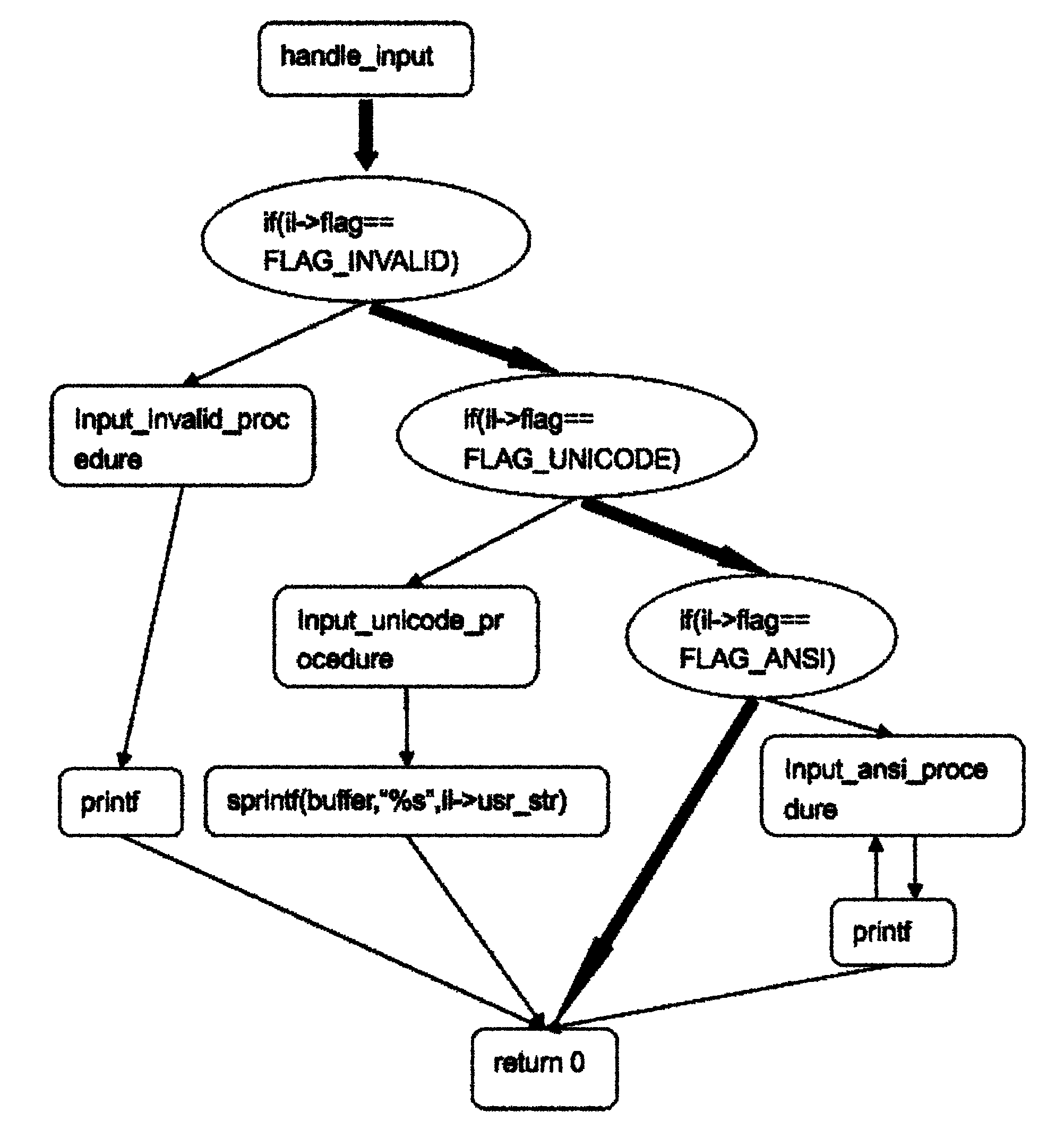
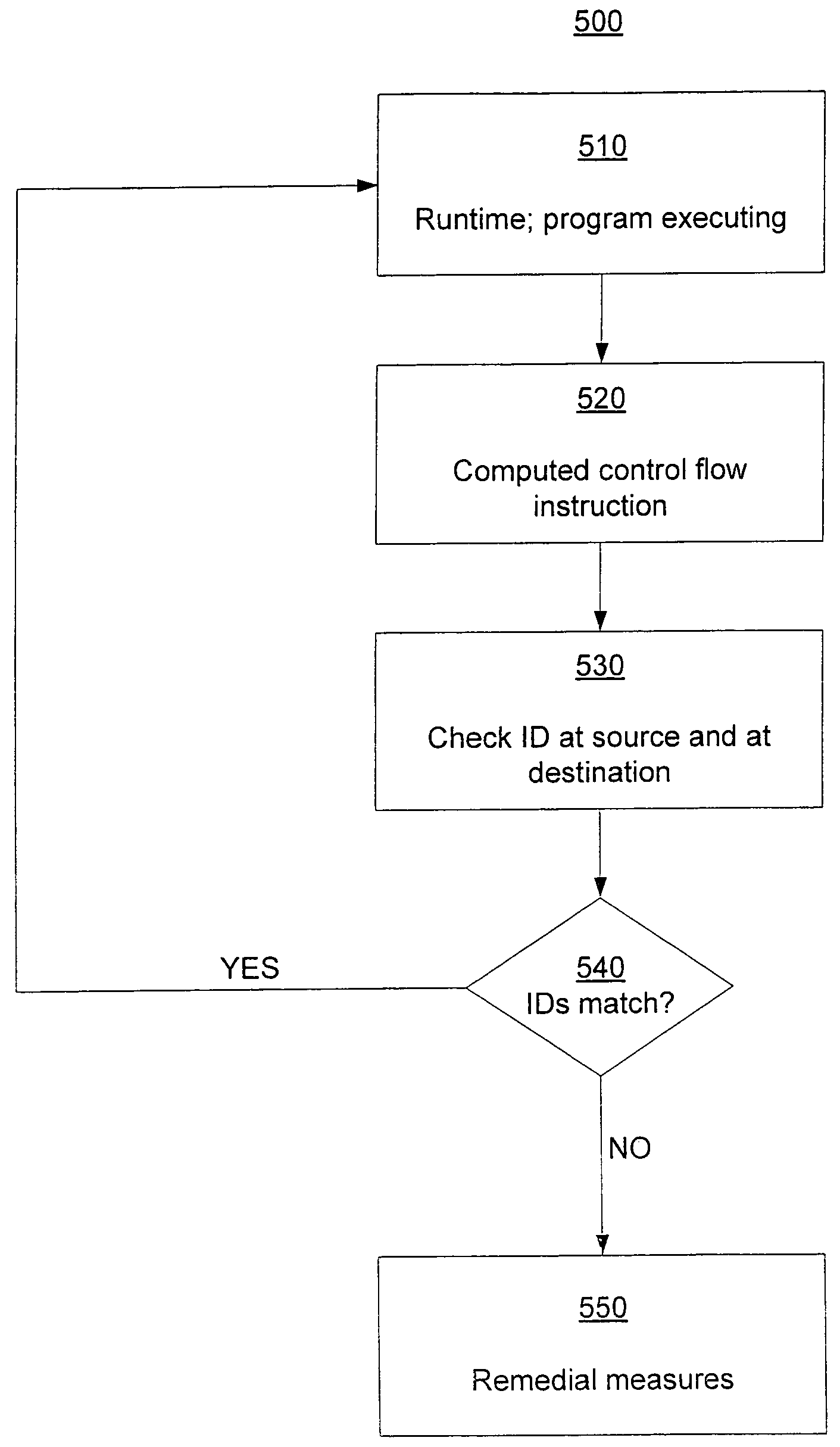
Software control flow integrity is provided by embedding identifying bit patterns at computed control flow instruction sources and destinations. The sources and destinations of computed control flow instructions are determined with reference to a control flow graph. The identifying bit patterns are compared during software execution, and a match between a source and a respective destination ensures control flow consistent with the control flow graph. Security measures are implemented when the comparison results in a mismatch, indicating that control flow has deviated from the anticipated course.
Owner:MICROSOFT TECH LICENSING LLC
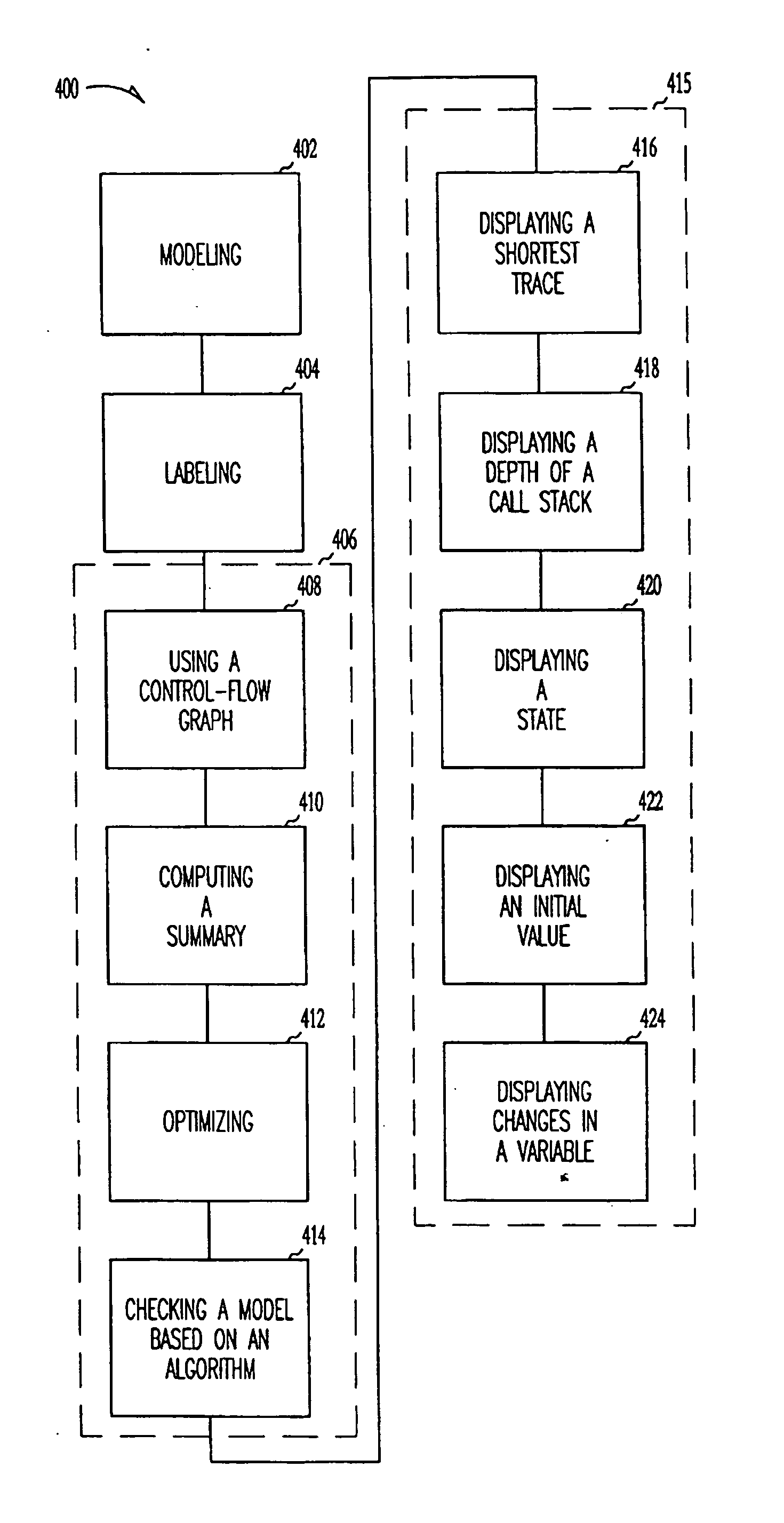
Methods for enhancing program analysis
InactiveUS6904590B2Enhance program analysisInhibit computational explosionSoftware testing/debuggingSpecific program execution arrangementsTheoretical computer scienceProgram analysis
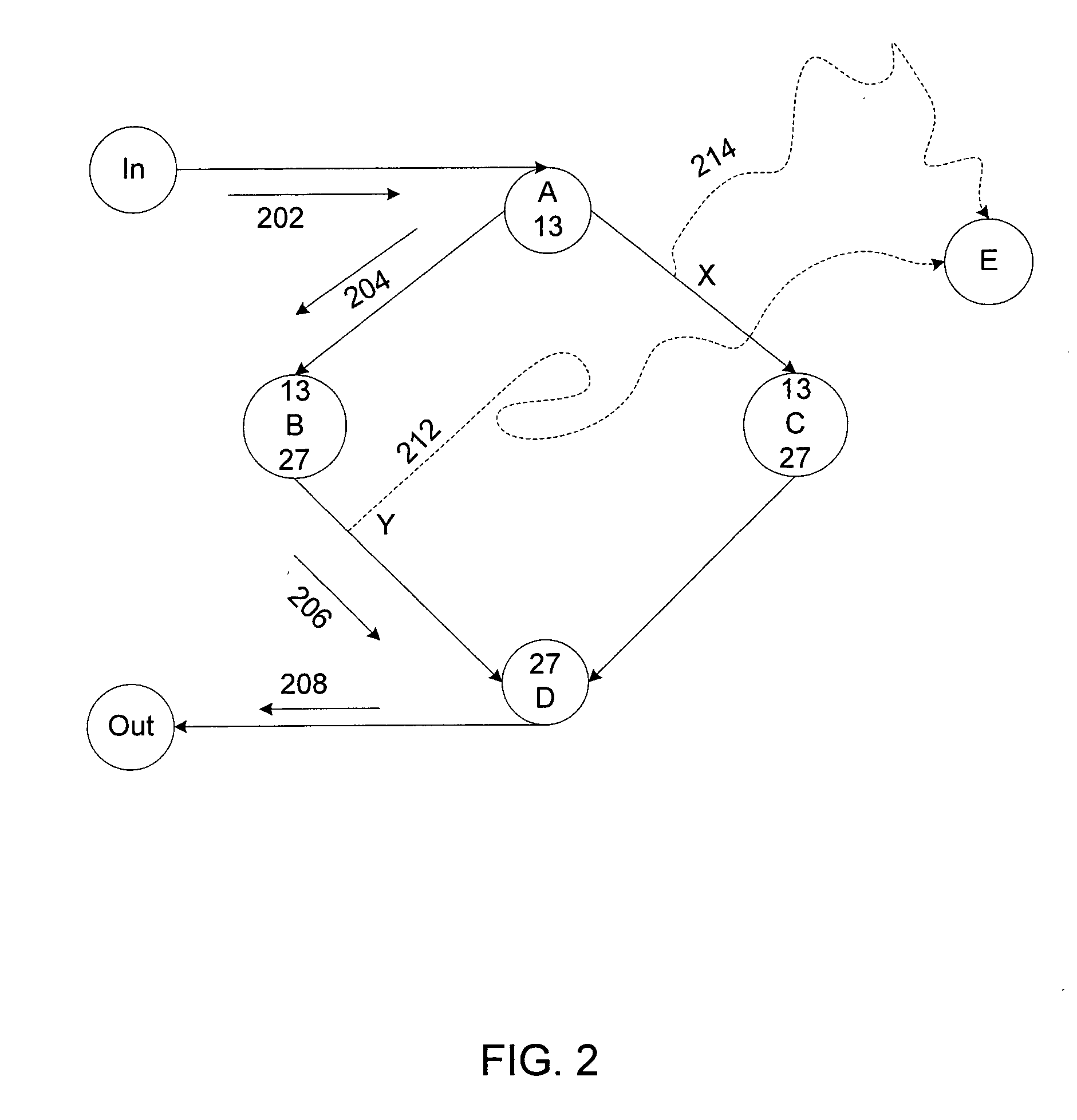
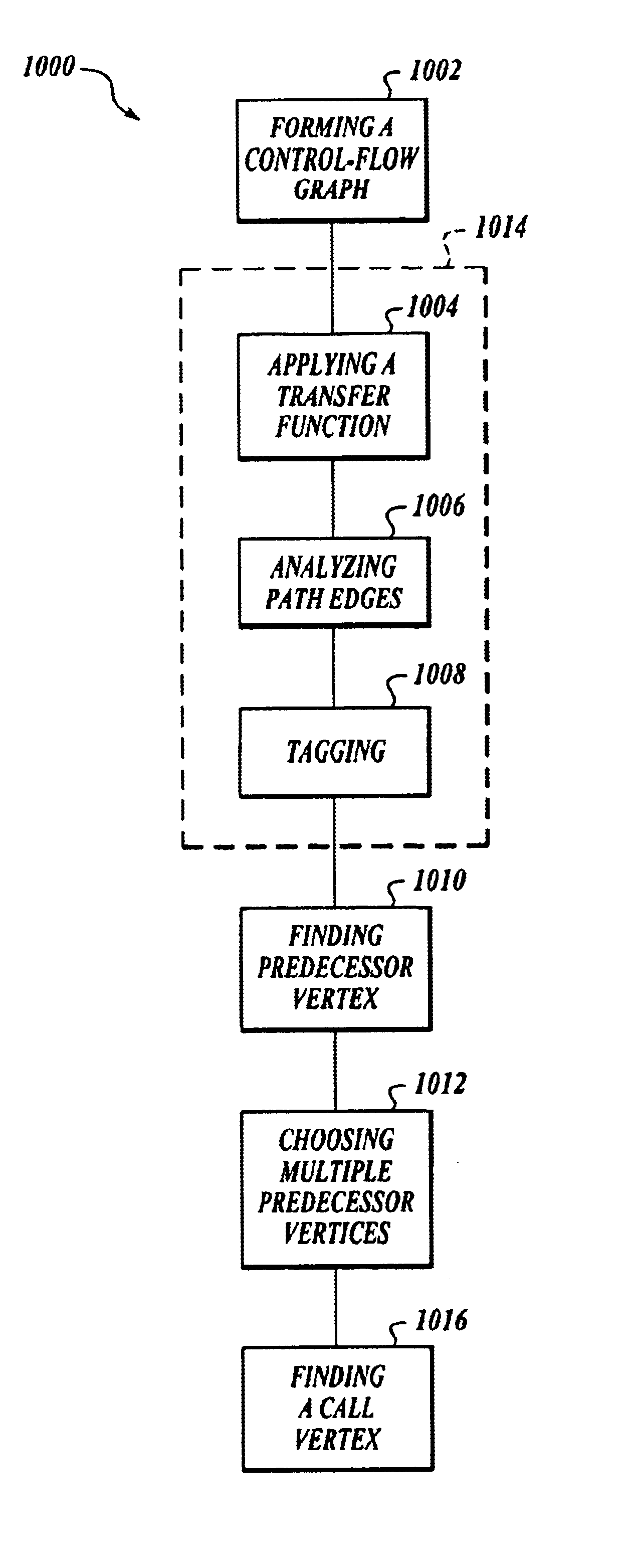
Methods are discussed that enhance program analysis. One aspect of the invention includes a method for checking a model of a program. The method includes a control-flow graph having vertices from the model, applying a transfer function to each vertex to form a set of path edges, and analyzing the set of path edges of a vertex. The set of path edges includes valuations that are implicitly represented so as to inhibit an undesired explosion in the valuations that would hinder the act of analyzing.
Owner:MICROSOFT TECH LICENSING LLC
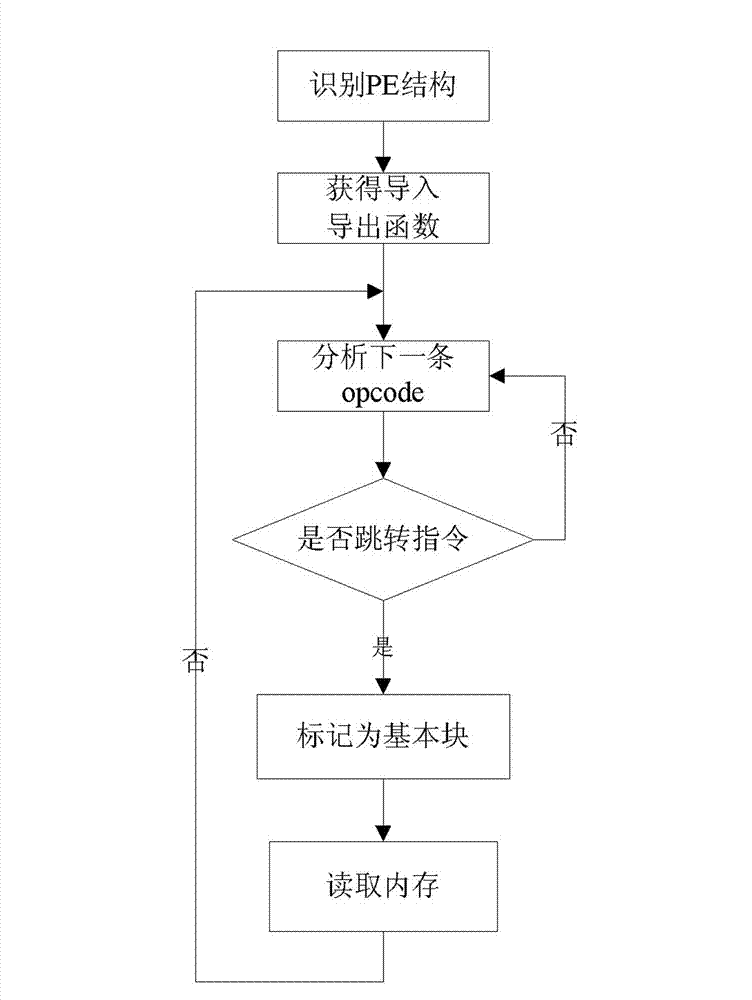
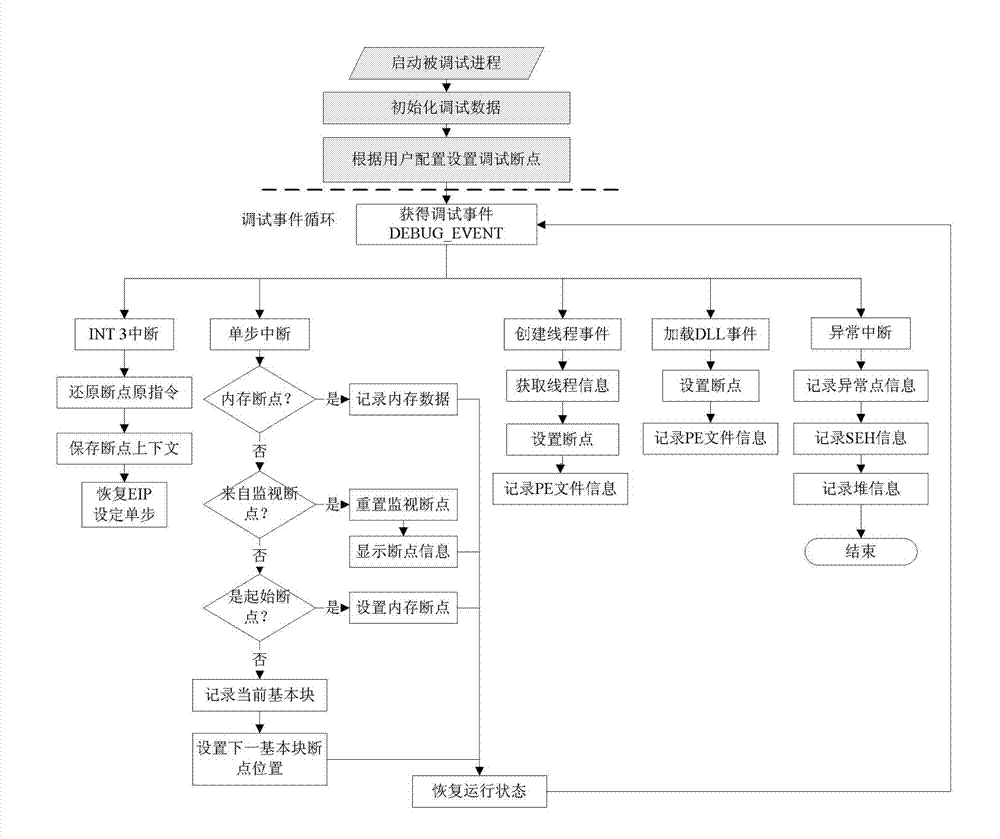
System for detecting software bug triggered during practical running of computer program
InactiveCN101968766AOvercoming the disadvantage of low analysis coverageIncrease vulnerabilitySoftware testing/debuggingSoftware bugDynamic program analysis
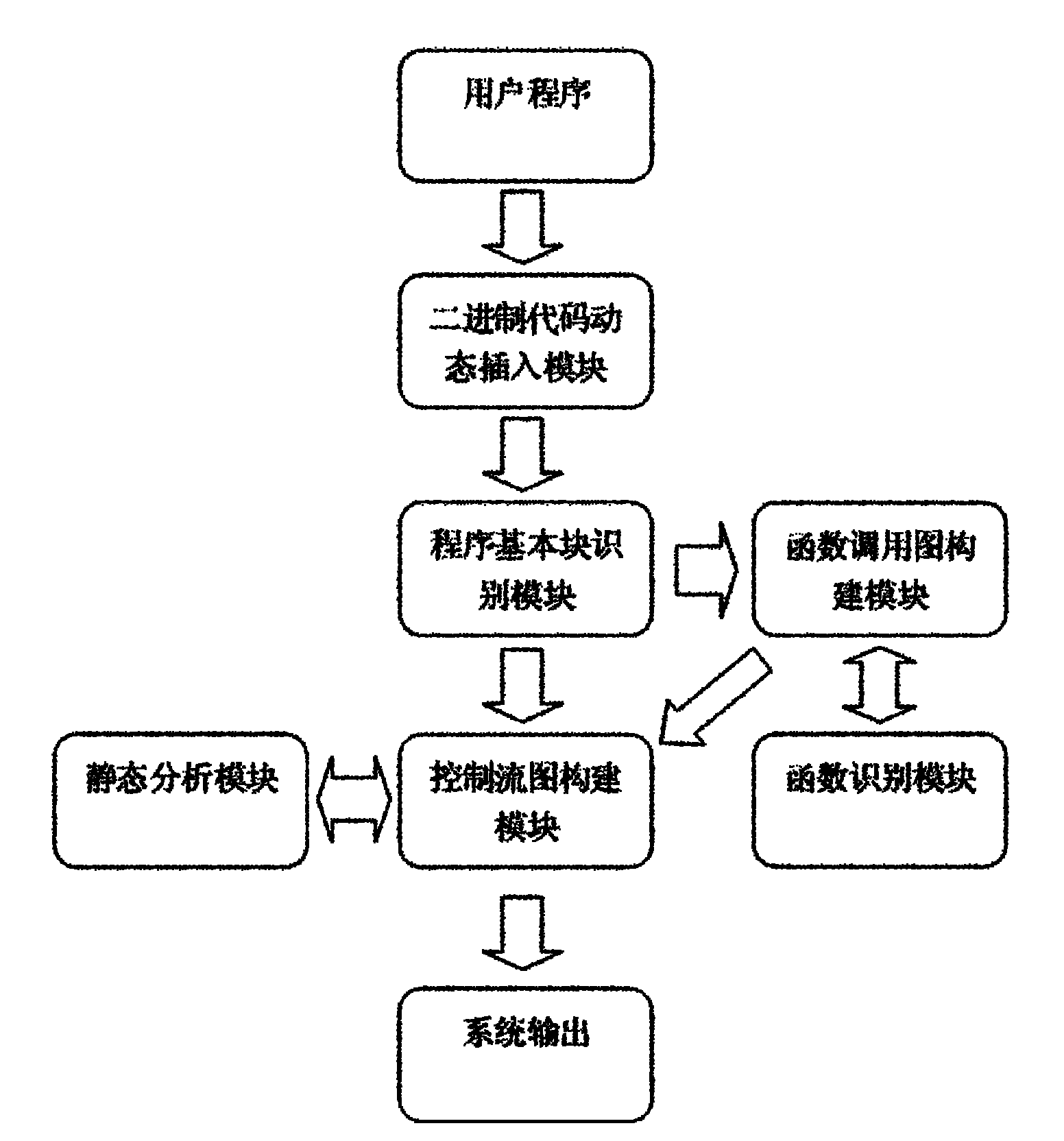
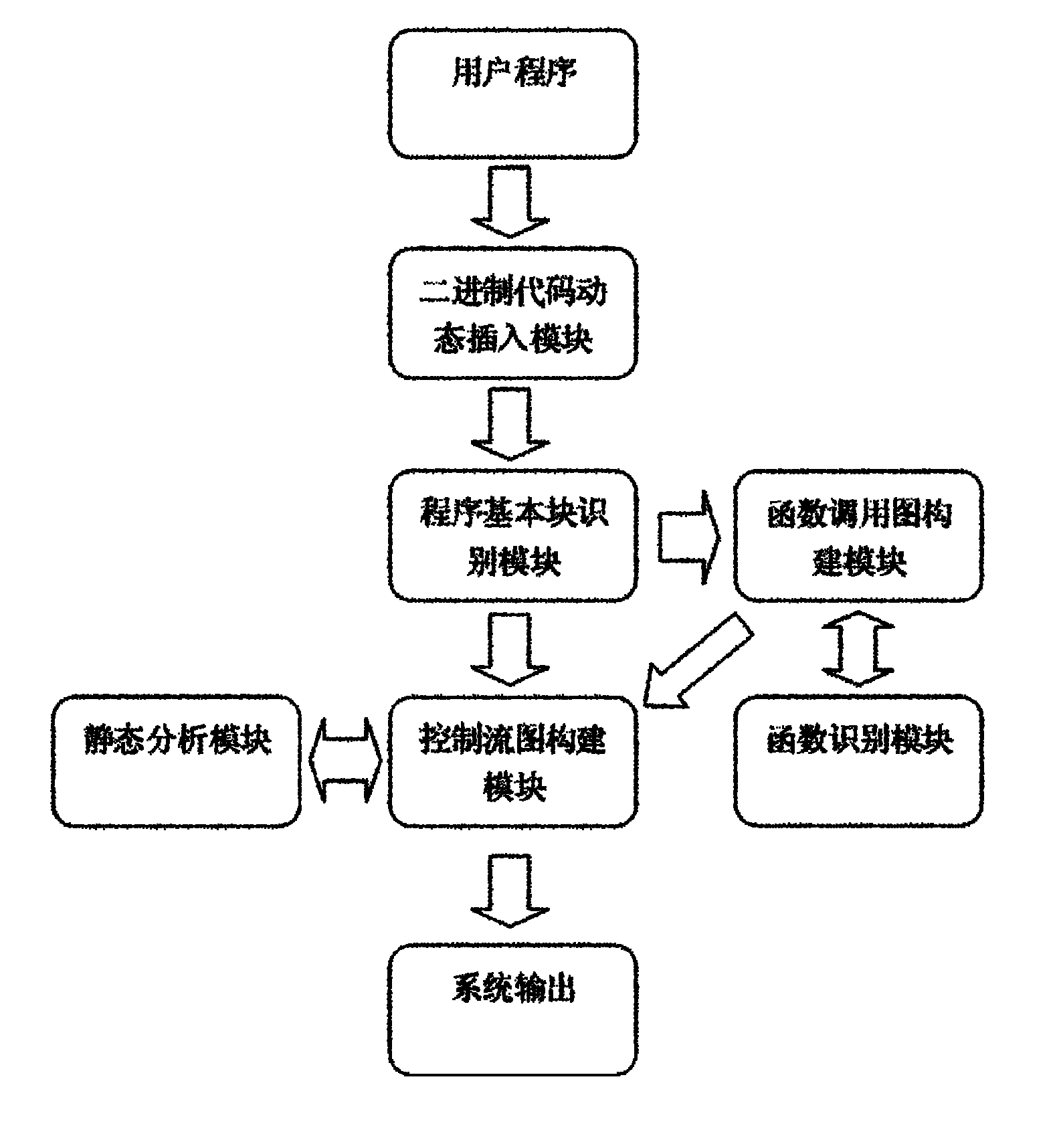
The invention relates to a system for detecting a software bug triggered during practical running of a computer program in the technical field of computers. The system comprises a binary code dynamic inserting module, a program basic block recognizing module, a function call graph constructing module, a control flow graph constructing module, a function recognizing module and a static analysis module. By combining two technologies of dynamic program analysis and static analysis path complementation, the invention not only can detect the bugs which can be triggered during the practical running of the program but also can reach higher program path coverage rate, carry out bug detects on the path which is not covered in the dynamic analysis process, improve the success rate of bug detection and reduce the false rate of the bugs. Meanwhile, the static analysis path complementation technology only analyzes a path which is not executed in dynamic analysis instead of all program paths, thereby greatly reducing the cost on time and system resources.
Owner:SHANGHAI JIAO TONG UNIV
Software security based on control flow integrity
InactiveUS7577992B2Reduce vulnerabilityAvoid successionMemory loss protectionUnauthorized memory use protectionSecurity MeasureSoftware engineering
Software control flow integrity is provided by embedding identifying bit patterns at computed control flow instruction sources and destinations. The sources and destinations of computed control flow instructions are determined with reference to a control flow graph. The identifying bit patterns are compared during software execution, and a match between a source and a respective destination ensures control flow consistent with the control flow graph. Security measures are implemented when the comparison results in a mismatch, indicating that control flow has deviated from the anticipated course.
Owner:MICROSOFT TECH LICENSING LLC
Detection method for software vulnerability
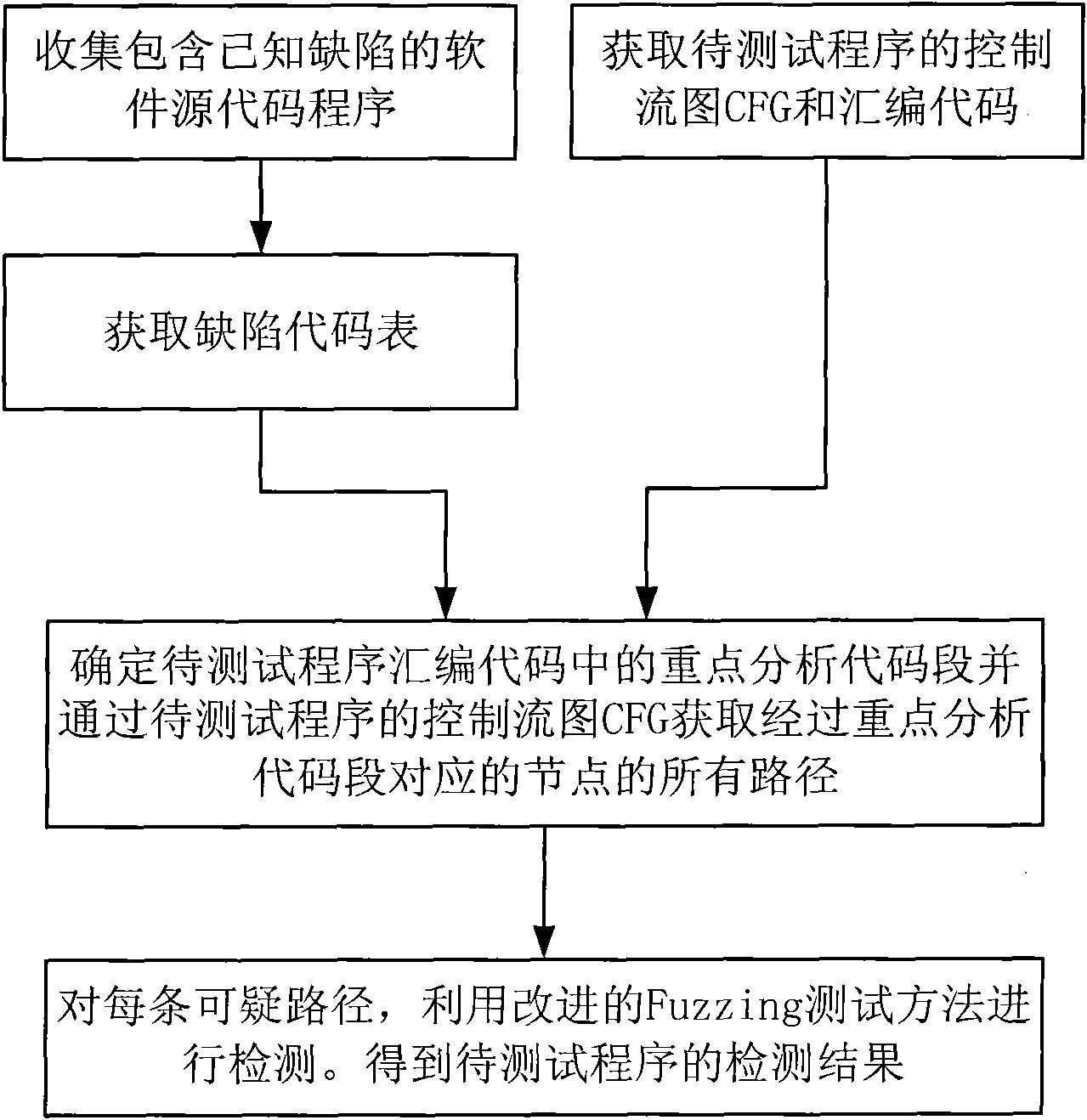
InactiveCN102385550AGuaranteed validityEfficient detectionSoftware testing/debuggingCode tableInformation security
The invention relates to a detection method for software vulnerability, and belongs to the technical field of information security. The detection method comprises the following specific steps of: (1) collecting a software source code program containing known vulnerability; (2) obtaining a vulnerability code table; (3) obtaining a control flow graph CFG and an assembly code of the program to be tested; (4) determining key analysis code segments in the assembly code of the program to be tested and obtaining all paths of passing through nodes corresponding to the key analysis code segments through the control flow graph CFG of the program to be tested; and (5) for each suspicious path, an improved Fuzzing test method is used for detection to obtain the test results of the program to be tested. In the invention, when a fitness function is determined, the dependence on the source code of the tested program is eliminated, and the availability of information is kept; and the redundant information in an abstract syntax tree is eliminated and the integrity of useful information is kept, therefore, the practicality is better, and the efficiency is higher.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method for optimizing unit regression test case set based on control flow diagram
InactiveCN102915271AImprove efficiencyImprove effectivenessSoftware testing/debuggingRegression testingAlgorithm
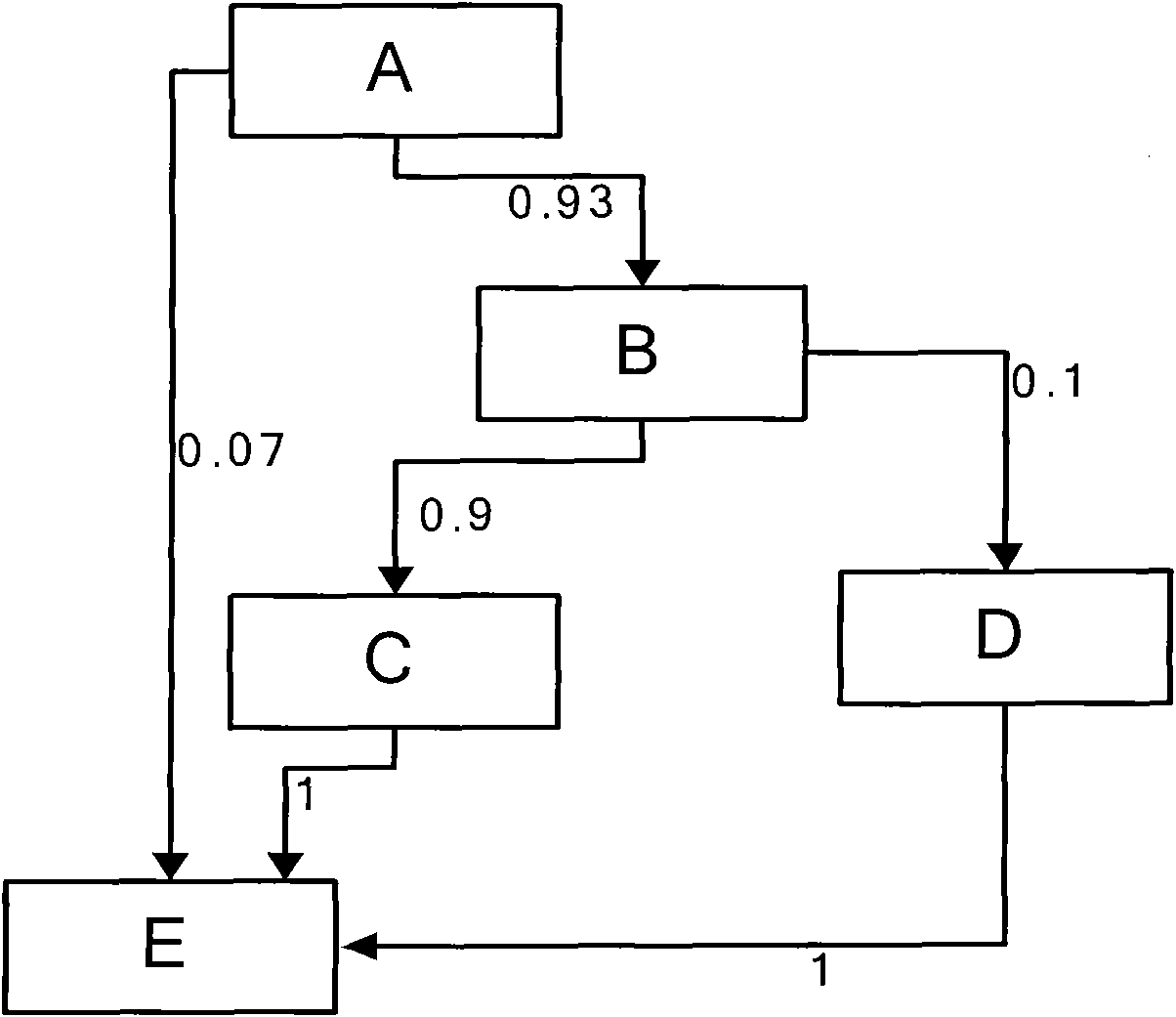
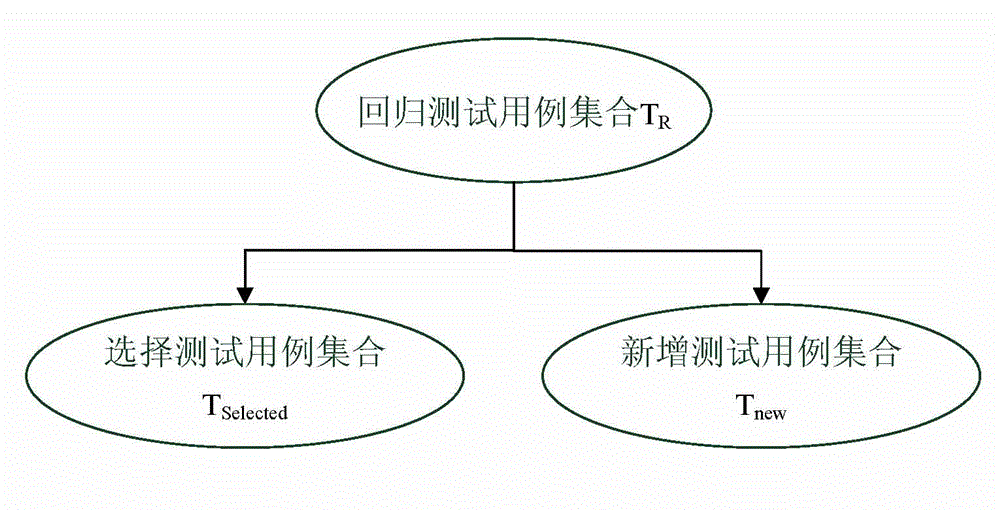
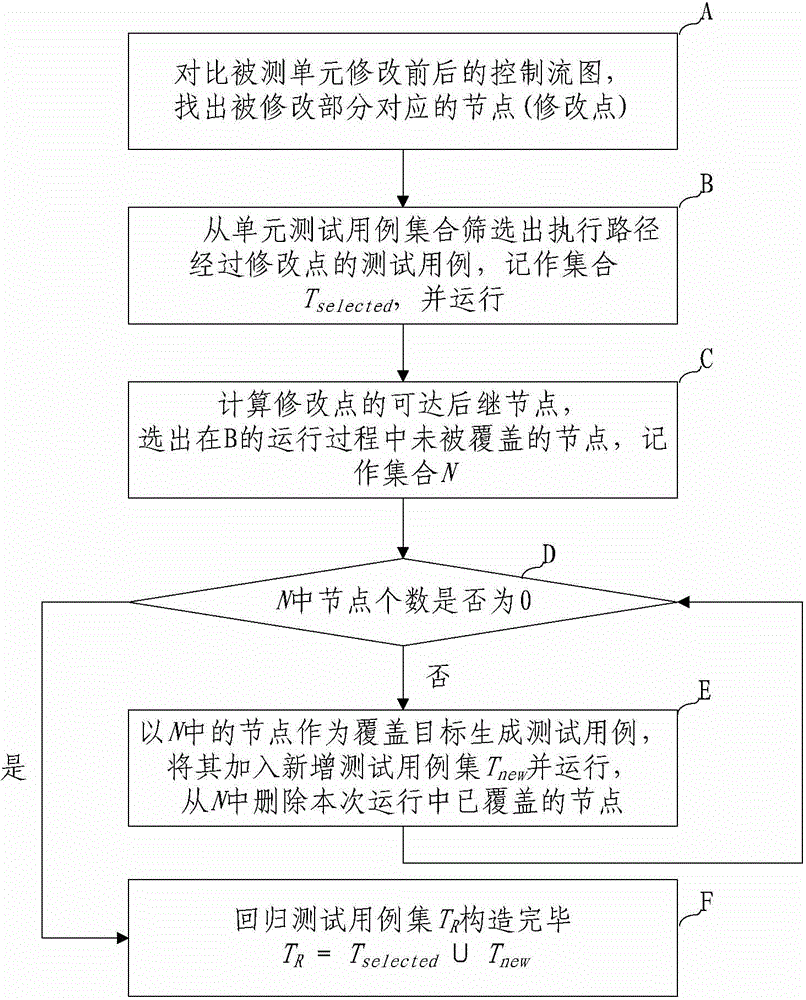
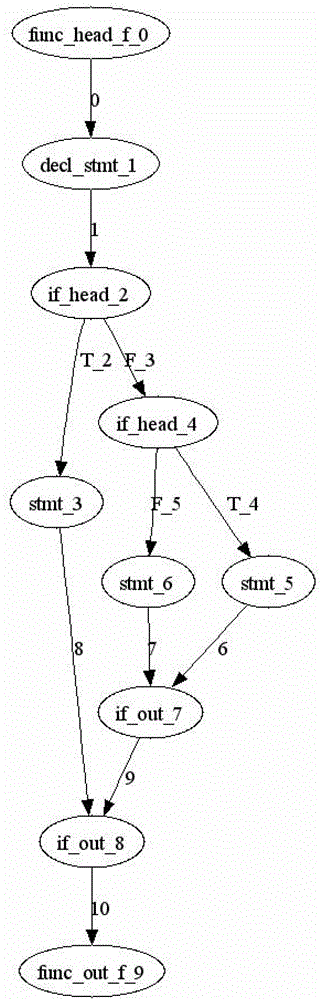
The invention discloses a method for optimizing a unit regression test case set based on a control flow diagram. The method comprises the following steps: A, finding out modified points corresponding to a modified part from the control flow diagram of a tested unit being tested unit before and after; B, screening out test cases, of which the execution paths pass through the modified points, to serve as one part of the regression test case set, namely a selected test case set (Tselected), and running all the test cases in the set; C, calculating all the reachable successor nodes of the modified points and selecting a node subset N which is not covered in the running process of the step B; D, if the N is null, executing the step F, and if the N is not null, executing the step E; E, selecting one node from the N to serve as a coverage target generation test case, adding the coverage target generation test case into a new test case set (Tnew) and then completely running, updating the N, deleting the nodes covered in the running process and returning to the step D; and F, finishing construction of the regression test case set (TR). By application of the method, the efficiency of the regression test can be improved and the effectiveness and the sufficiency of the regression test are guaranteed.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Dynamic and static combined software security test method
InactiveCN102360334AIncreased security testing productivitySolve the path space explosion problemSoftware testing/debuggingCall graphBasic block
The invention relates to a computer software security test method, and in particular relates to a dynamic and static combined software security test method. The test method comprises the following steps: firstly carrying out disassembly and intermediate language transformation on an executable program so as to generate a function call graph (CG) and a control flow graph (CFG) of a file; finding out a vulnerable point of a system by means of static analysis of the function CG, and constructing a test case generation execution path by virtue of a dynamic analysis method; searching a called function based on the function CG, finding out a specific path for triggering the vulnerable point on a first-grade basic block according to the CFG if the function is located on the generated execution path, and then ending the loophole mining process corresponding to the sensitive point; and if the path can not be found, reconfiguring the test case generation execution path and then searching the called function in a cyclic manner. The dynamic and static combined software security test method has the advantages of better solving the problem of path state space blast caused by single Fuzz dynamic test, and greatly improving the path coverage hit rate and the software test analysis efficiency.
Owner:THE PLA INFORMATION ENG UNIV
Method for enhancing program analysis
InactiveUS20050149904A1Easy to analyzeAvoid explosionSoftware testing/debuggingSpecific program execution arrangementsTheoretical computer scienceFlow sheet
Methods are discussed that enhance program analysis. One aspect of the invention includes a method for checking a model of a program. The method includes a control-flow graph having vertices from the model, applying a transfer function to each vertex to form a set of path edges, and analyzing the set of path edges of a vertex. The set of path edges includes valuations that are implicitly represented so as to inhibit an undesired explosion in the valuations that would hinder the act of analyzing.
Owner:MICROSOFT TECH LICENSING LLC
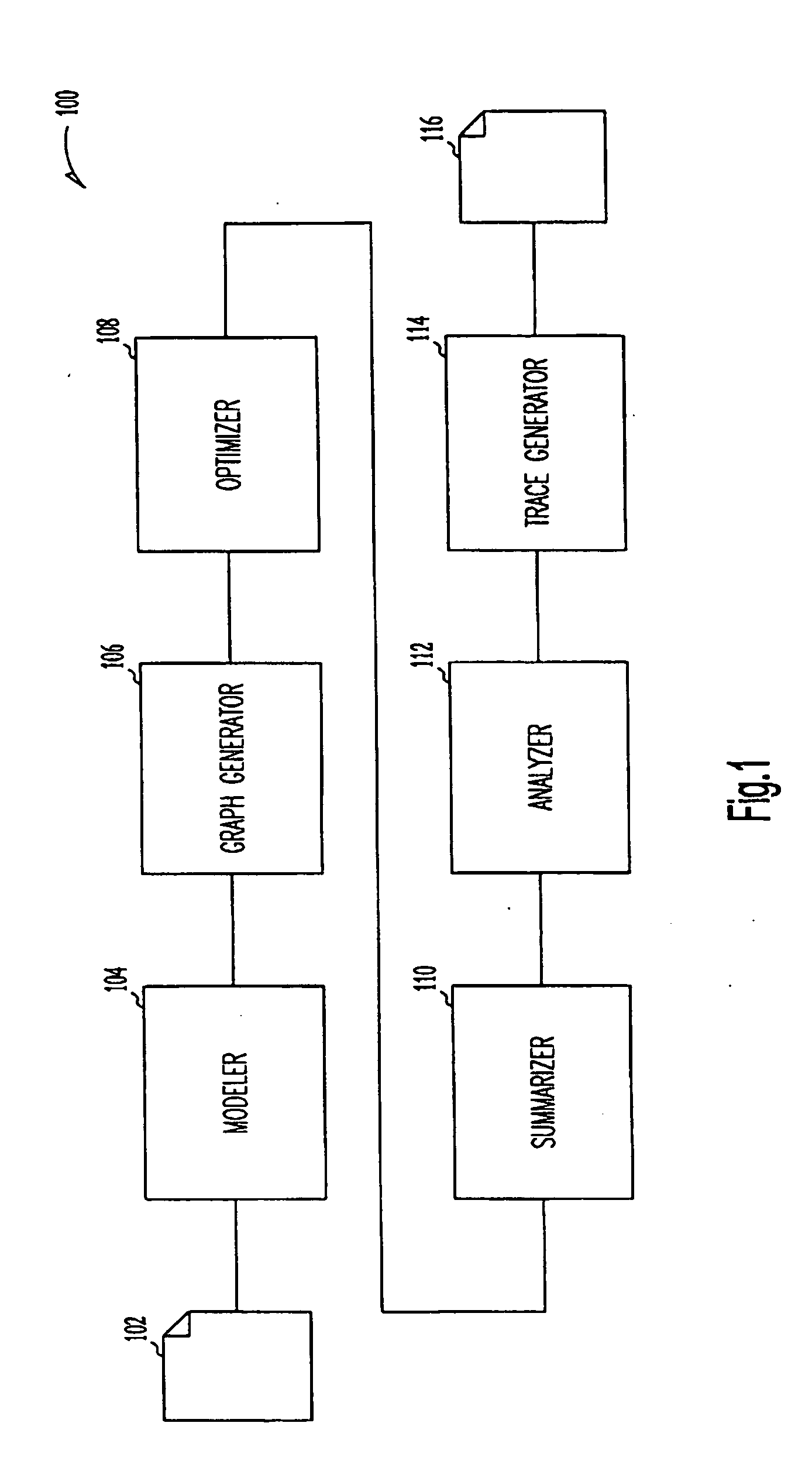
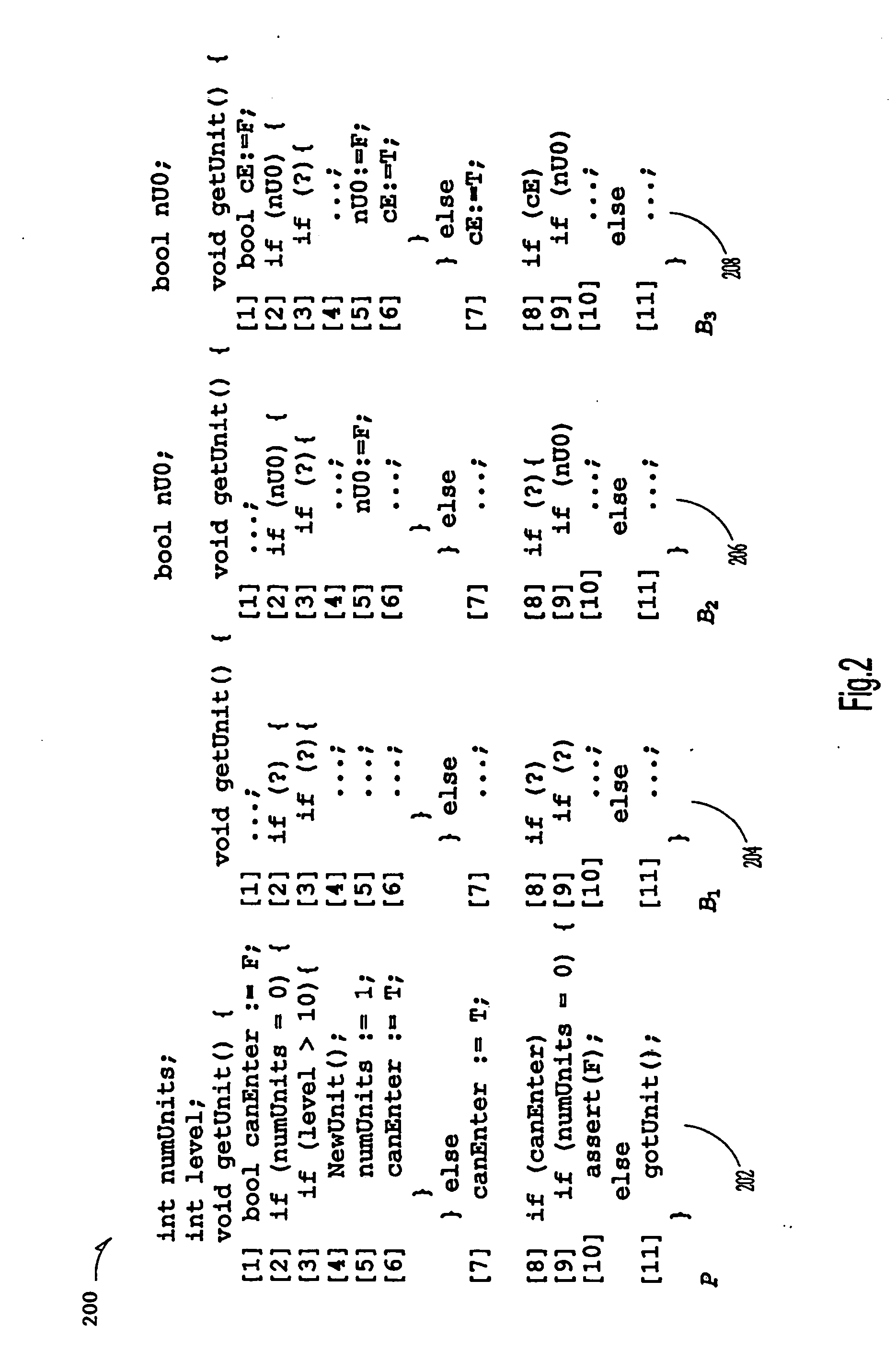
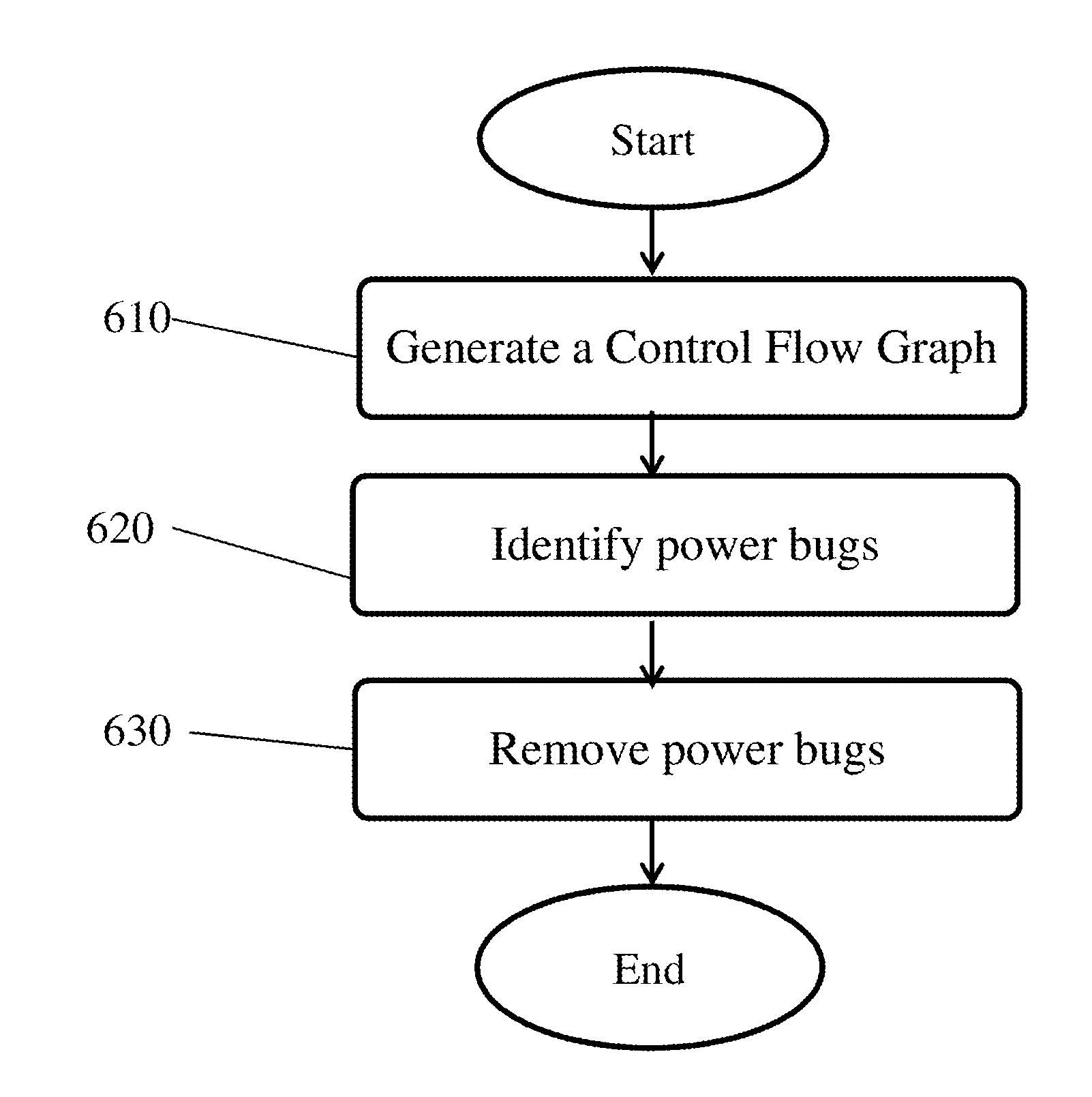
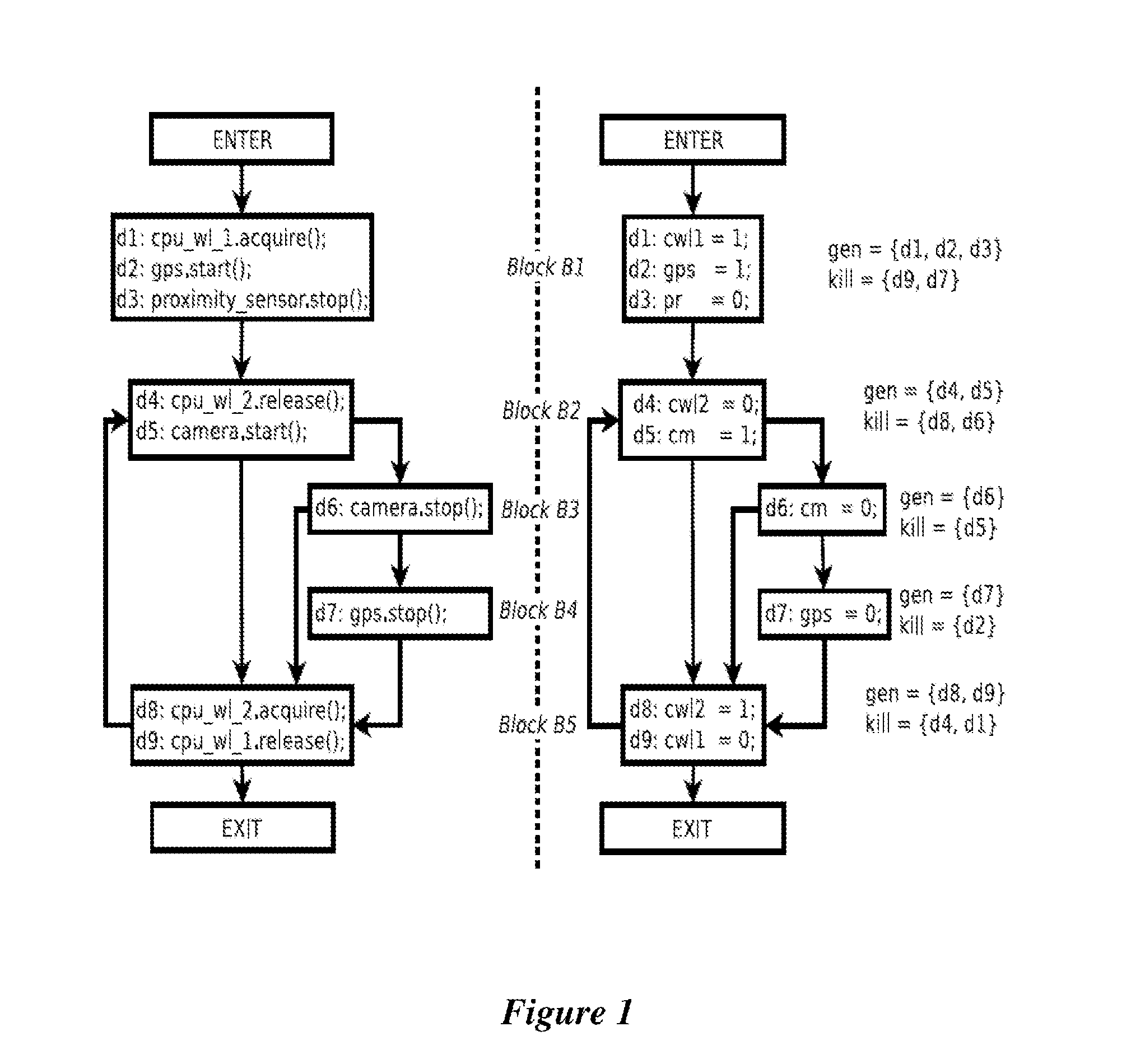
Systems and Methods of Detecting Power Bugs
ActiveUS20140380283A1Software testing/debuggingPower supply for data processingParallel computingControl flow graph
Embodiments of the present invention provide a system and methods for detecting power bugs. In one embodiment, a computer-implemented method for analyzing a computer code includes generating a control flow graph for at least a portion of the computer code at a processor. The method further includes identifying power bugs by traversing the control flow graph if the control flow graph exits without performing a function call to deactivate power to any component of a device configured to execute computer executable instructions based on the computer code after performing a function call to activate power.
Owner:PURDUE RES FOUND INC
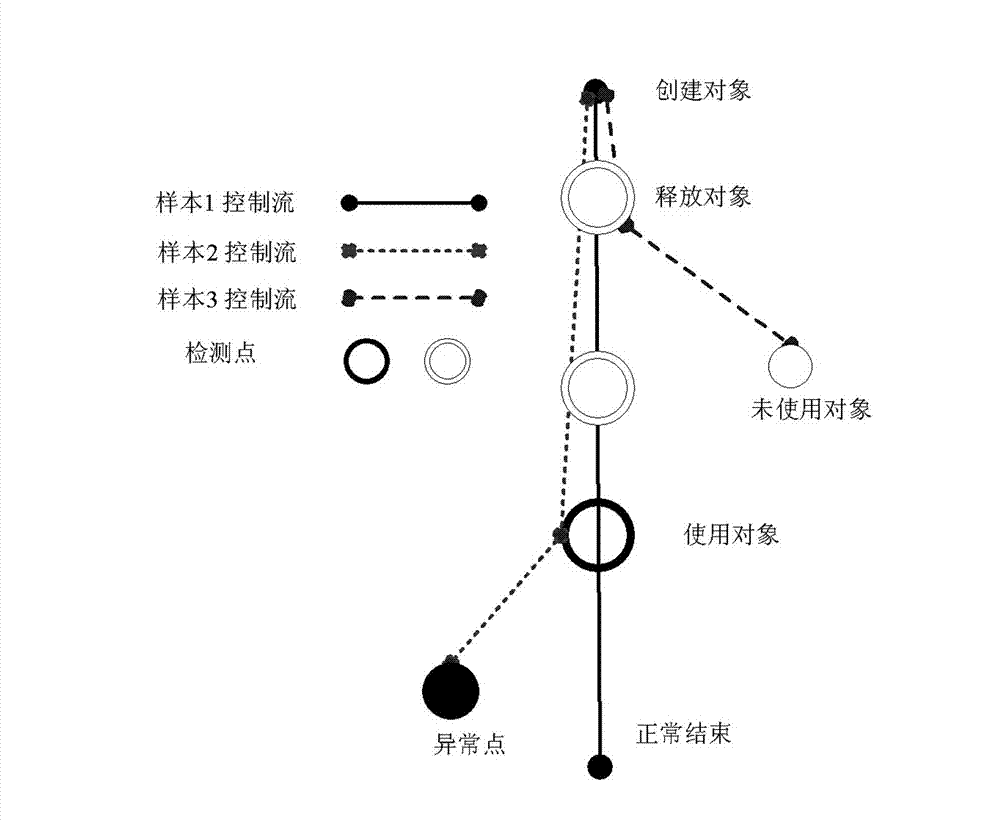
Software fault analysis method based on multi-sample difference comparison
InactiveCN102789419AFailure Analysis Work Efficiency ImprovementUnable to locateSoftware testing/debuggingControl flowDynamic instrumentation
The invention relates to a software analysis method belonging to the technical field of computers, and particularly relates to a software fault analysis method based on multi-sample difference comparison. The method comprises the steps as follows: (1) executing disassemble and dynamic instrumentation of an analyzed program; (2) tracking and recording an execution instruction flow of a program to be analyzed and constructing control flow graphs of the program, which take a basic block as the minimum unit; and (3) selecting a data processing access point as a comparison basic point, constructing a multi-sample difference tree model, executing comparison of control flow graphs of multiple samples which are divided into several groups, wherein each group consists of two samples, finding out a key instruction flow branch point, and acquiring a key path from a false data input point to each difference point. The software fault analysis method, provided by the invention, effectively solves the problem that a dual-sample difference comparison method cannot achieve positioning of complex faults, thereby remarkably improving analysis efficiency of software faults.
Owner:THE PLA INFORMATION ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com