API use action discovering and malice deciding method after confusion of multi-tier synergism
A technology of API call and judgment method, applied in the direction of platform integrity maintenance, program control design, instruments, etc., can solve problems such as difficulty in implementation and difficult analysis work for malicious code analysts, and achieve the effect of strong pertinence and fine granularity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
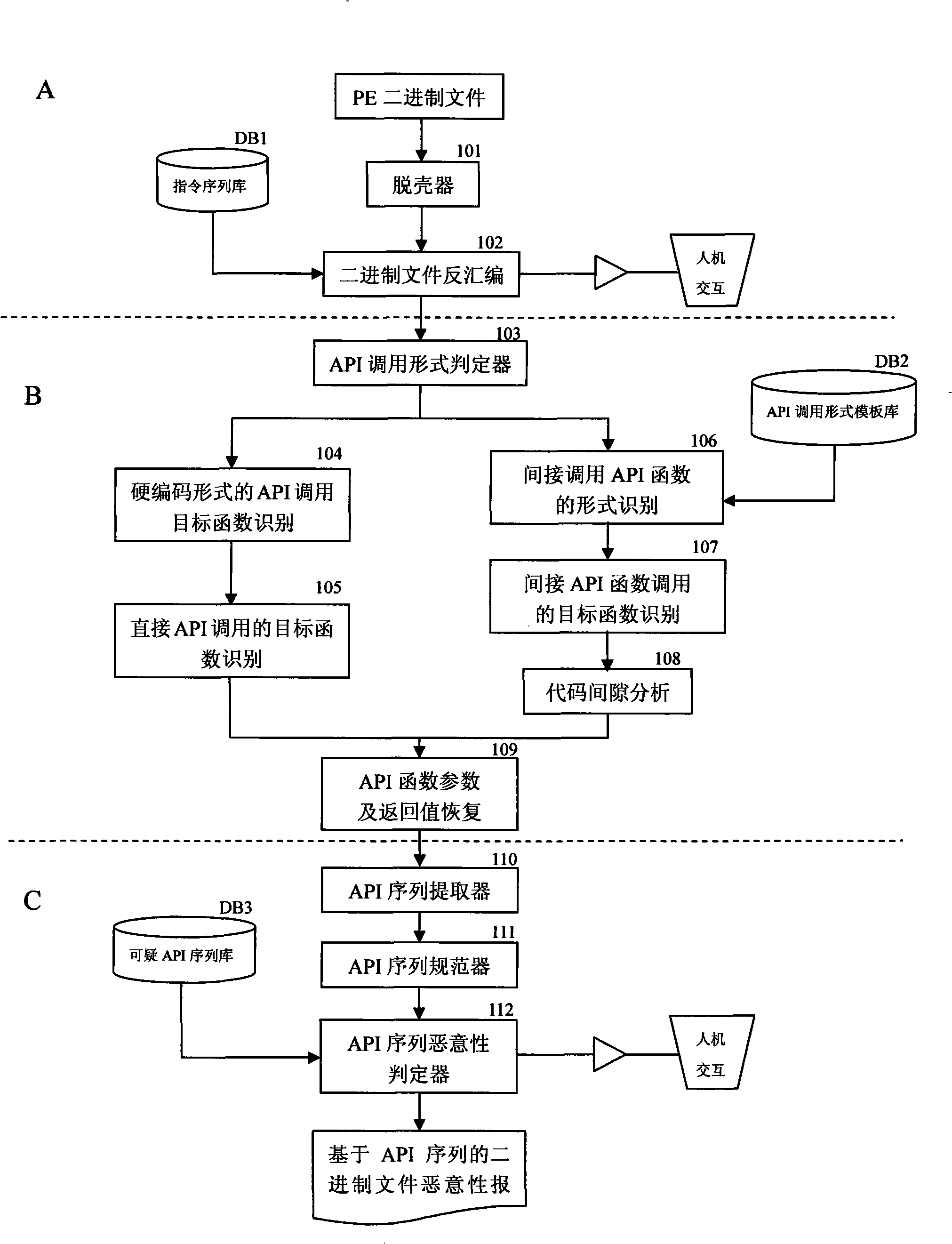
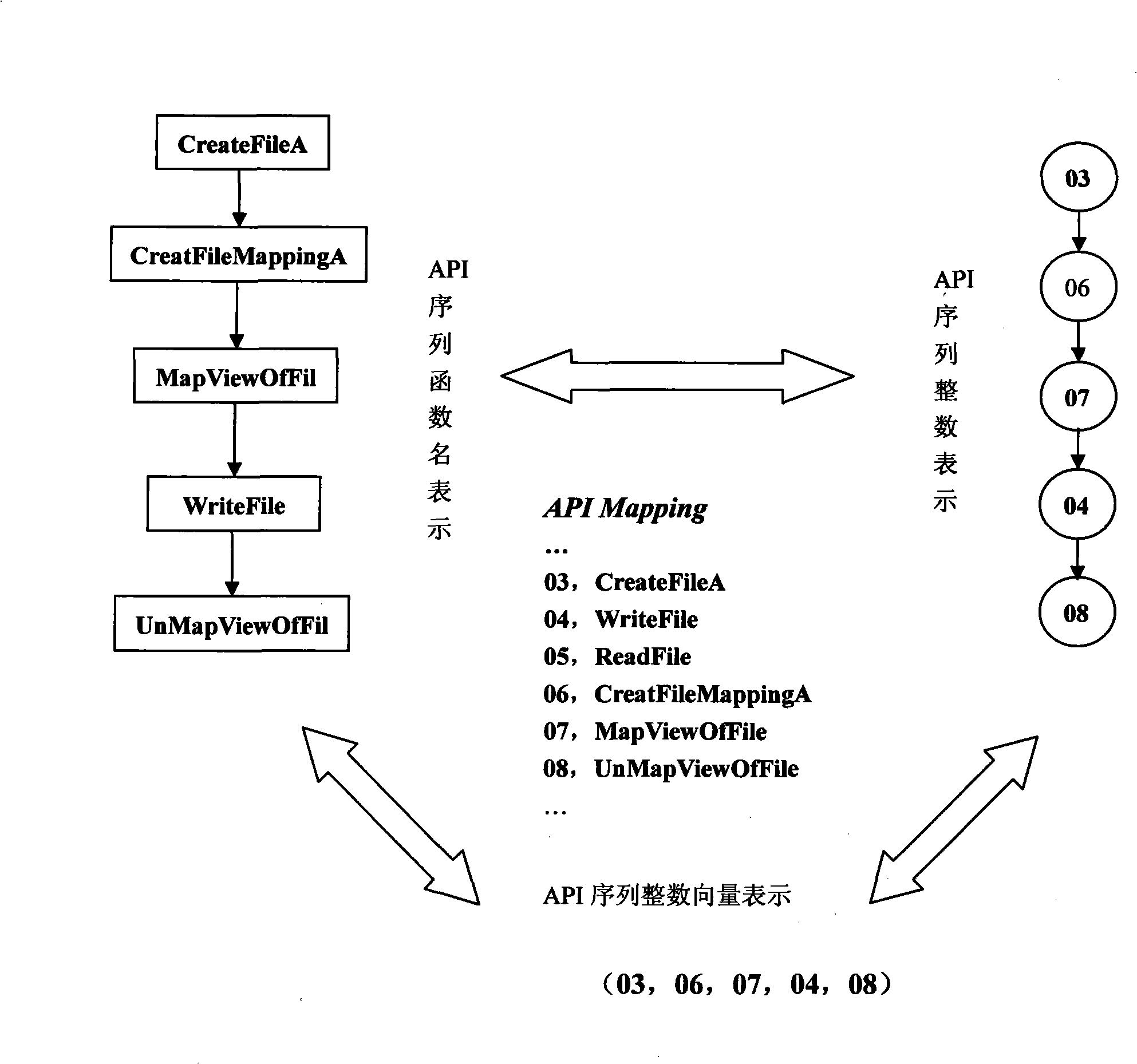
[0031] see Figure 1 ~ Figure 3 , the API call behavior discovery and malicious judgment method after layered collaboration obfuscation is specifically divided into three stages: binary code analysis stage A, API sequence generation stage B, and API sequence analysis stage C.
[0032] Binary Code Analysis Phase A:
[0033] The main work done at this stage is the preprocessing of the target binary files, and the modules involved include figure 1 Module 101 and Module 102 in .
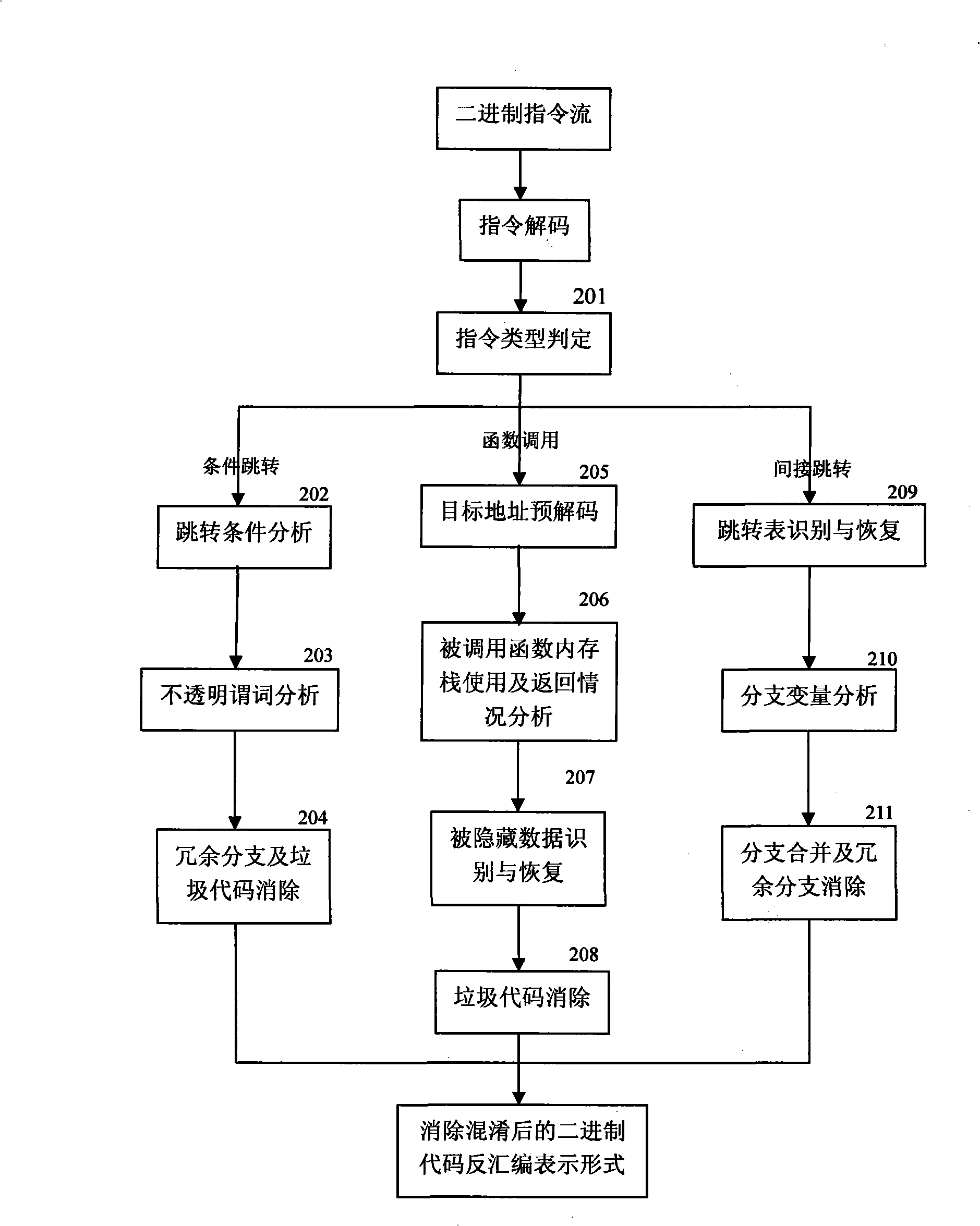
[0034] The main work of the module 101 is to unpack the input binary code, including decryption and decompression of commonly used encryption algorithms and compression algorithms. The main work of module 102 is to complete the disassembly of the decrypted and decompressed binary program, and to construct the corresponding control flow graph CFG. Since the system may be oriented to an obfuscated executable program with malicious purposes, the module 102 uses an anti-obfuscation disassembly process wit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com