Patents
Literature
1440 results about "Static analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
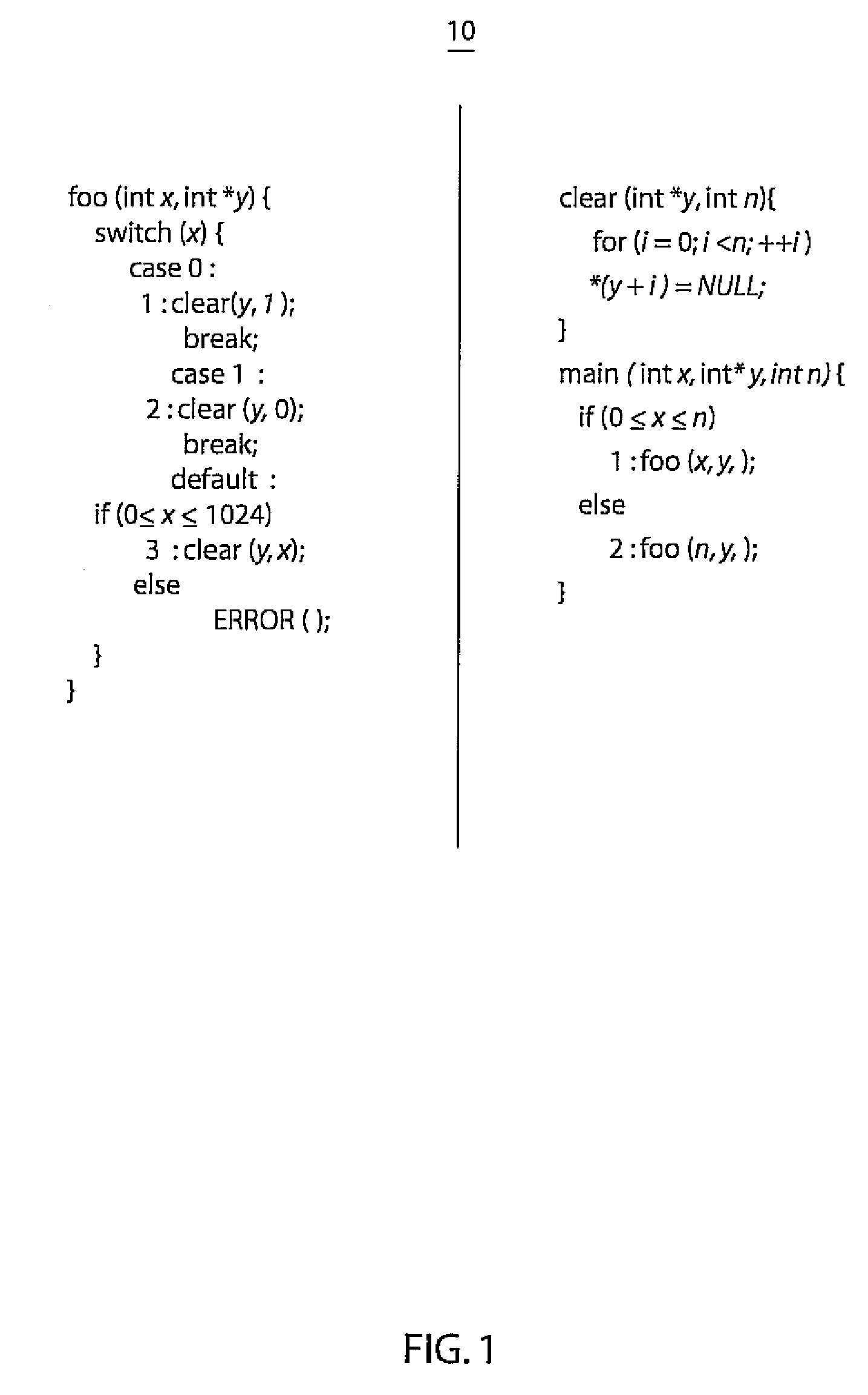
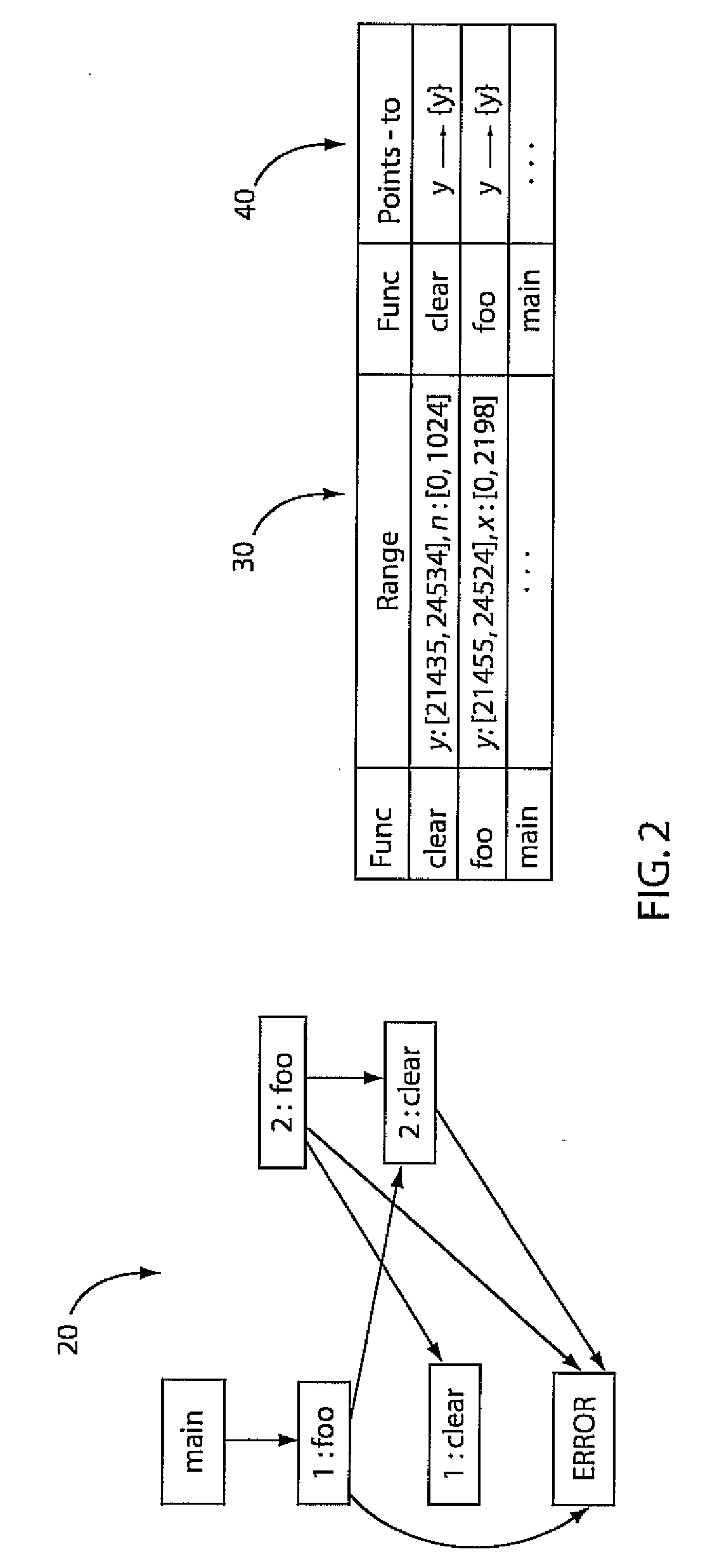
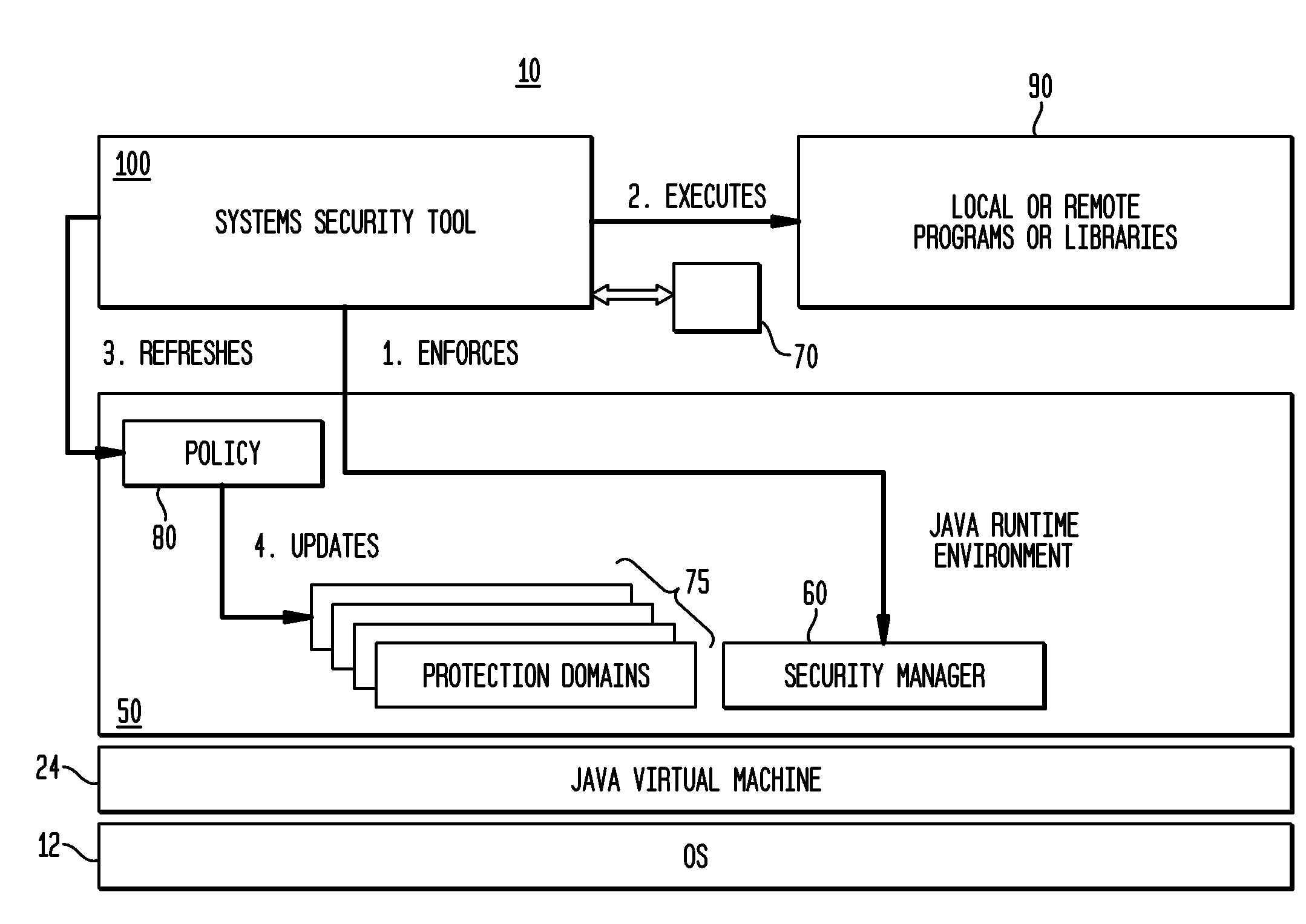
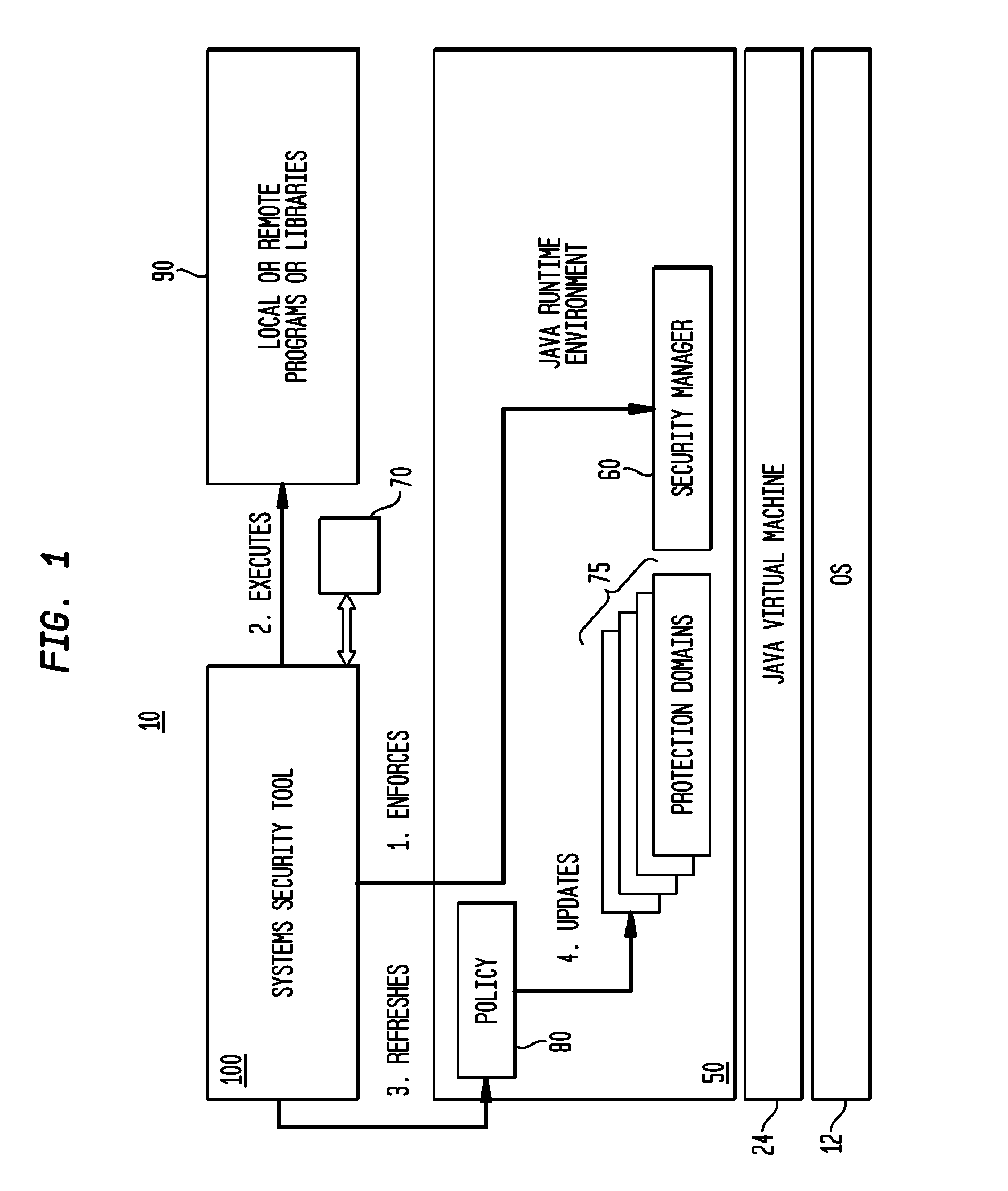
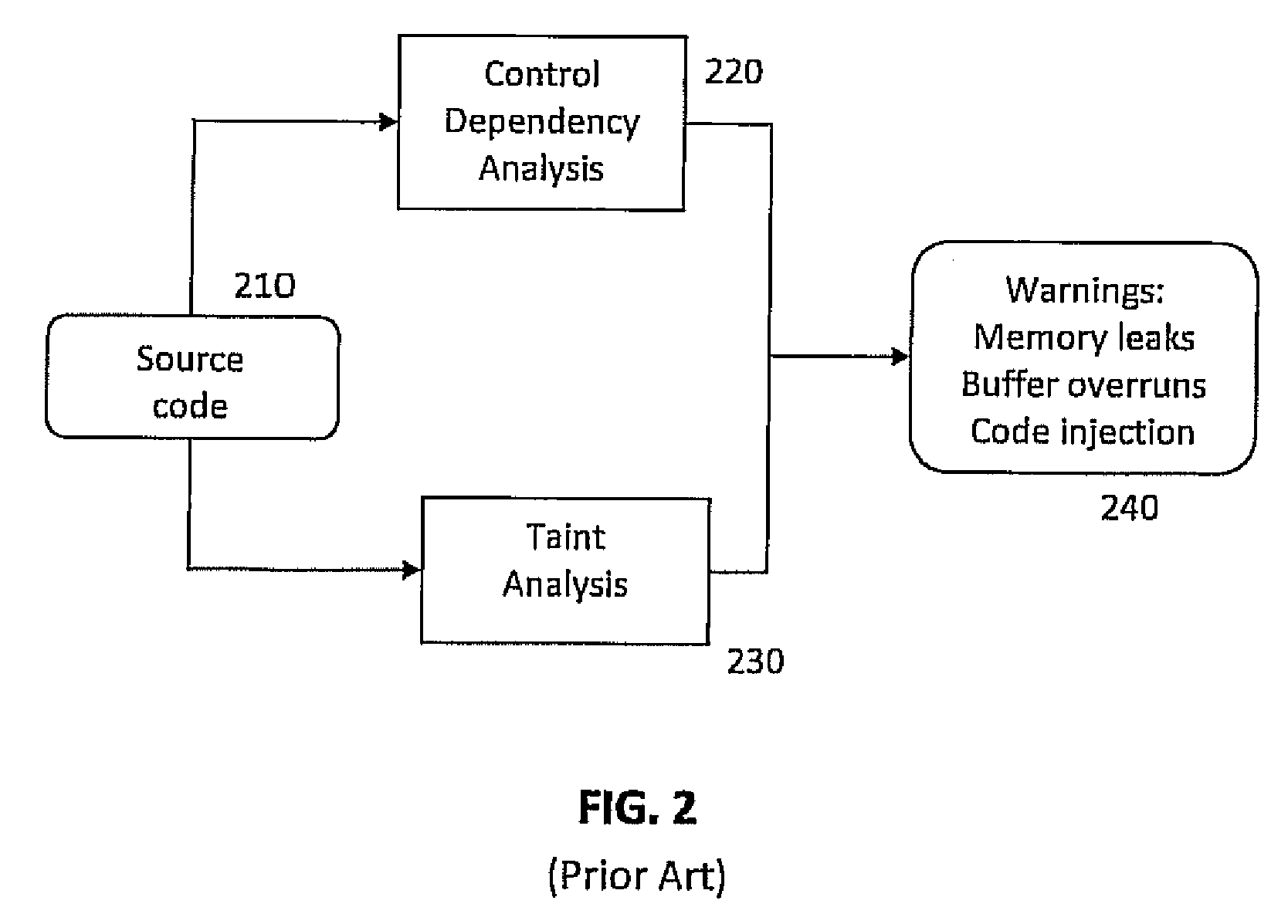
Static analysis, static projection, or static scoring is a simplified analysis wherein the effect of an immediate change to a system is calculated without regard to the longer-term response of the system to that change. If the short-term effect is then extrapolated to the long term, such extrapolation is inappropriate.
Malware Target Recognition
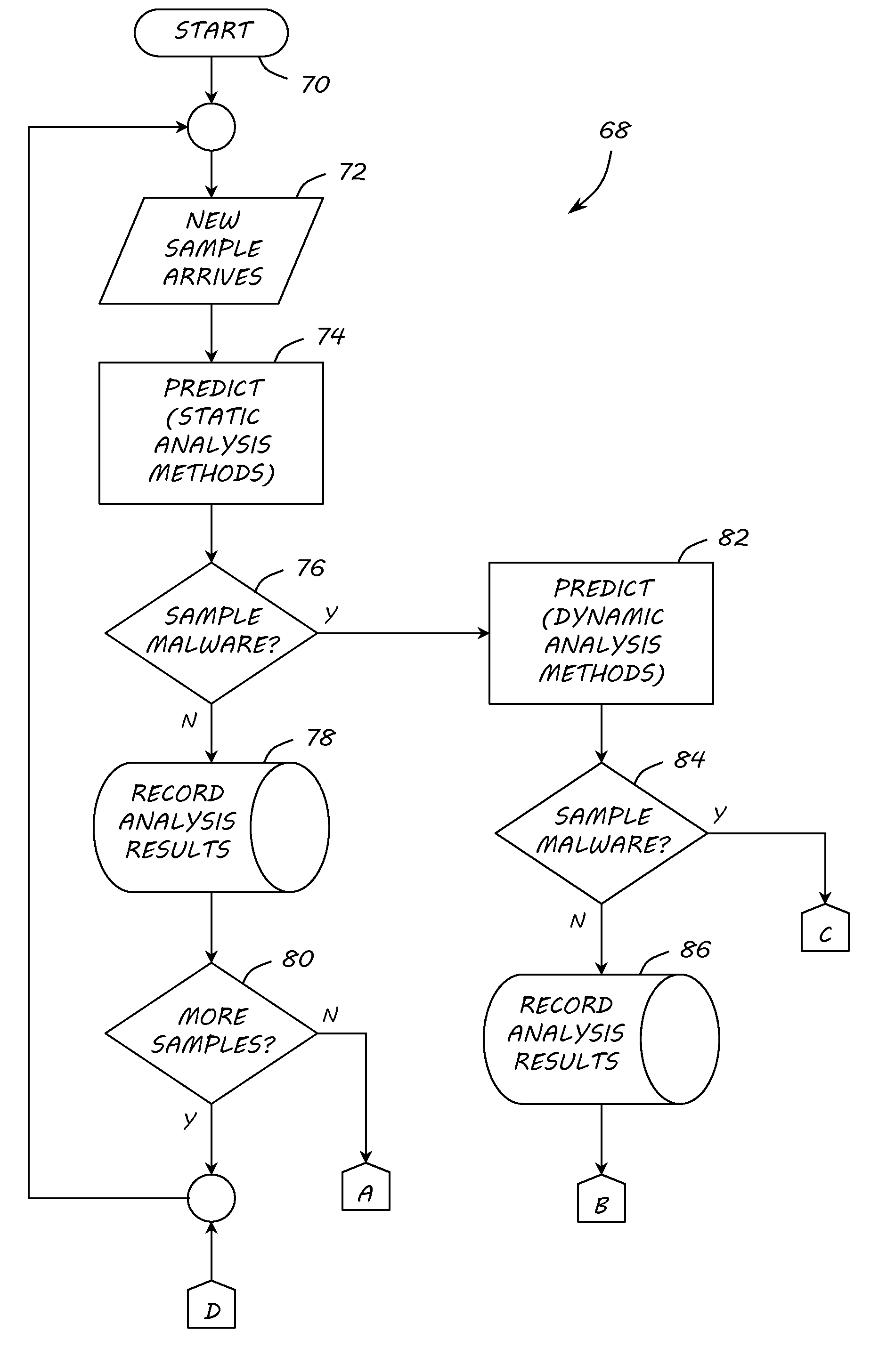
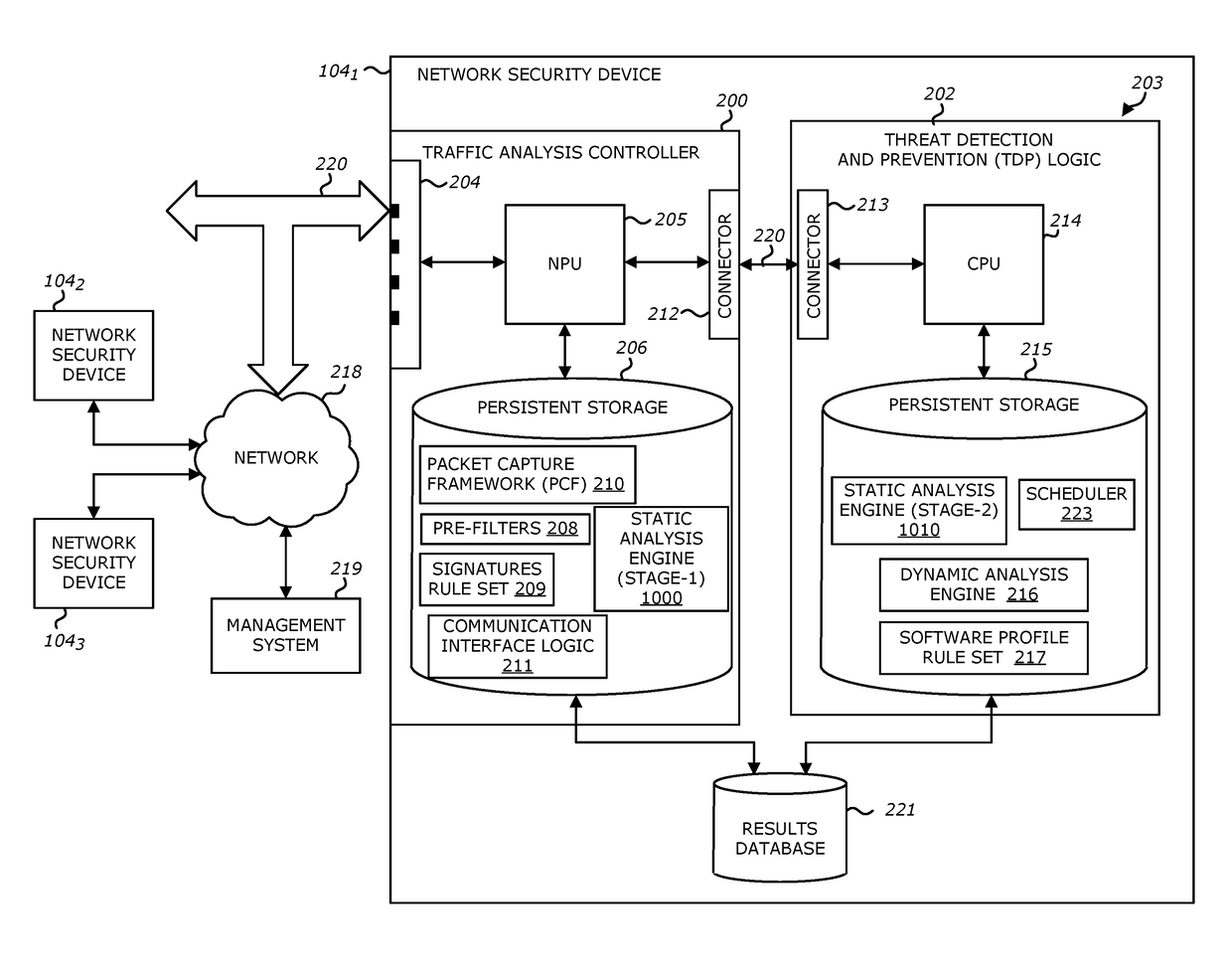
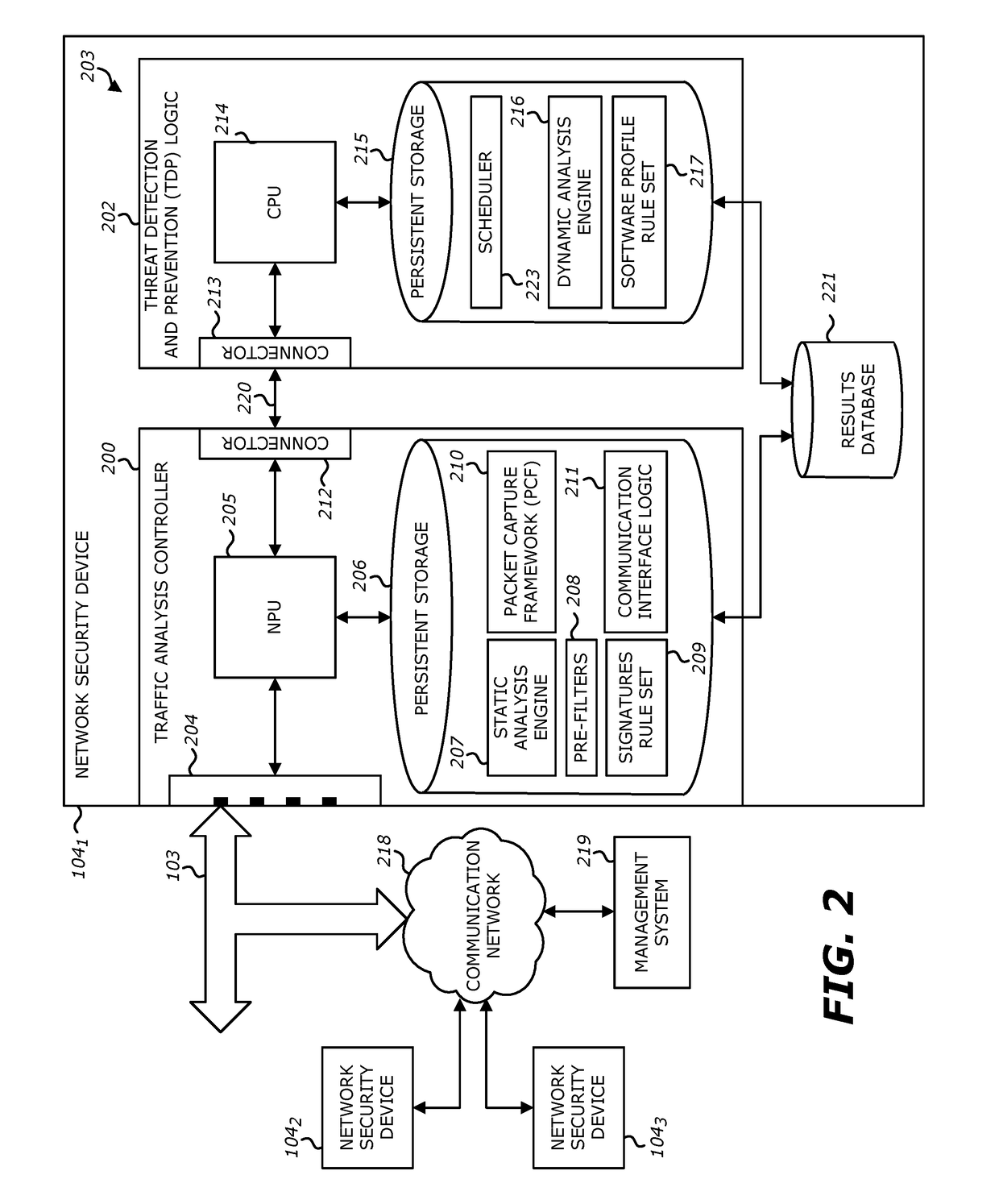
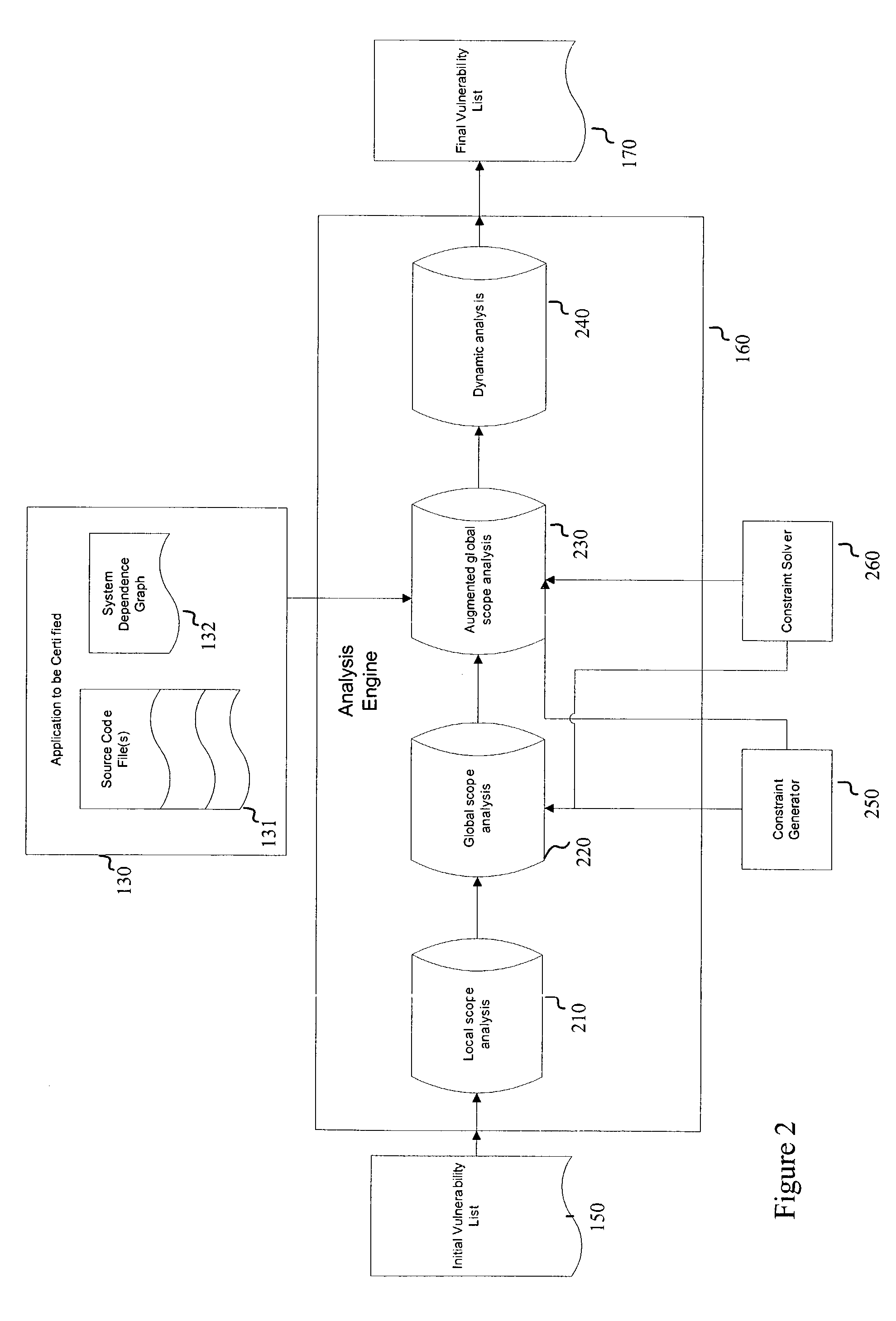
InactiveUS20120260342A1Memory loss protectionError detection/correctionMalware analysisAnalysis method
A method, apparatus and program product are provided to recognize malware in a computing environment having at least one computer. A sample is received. An automatic determination is made by the at least one computer to determine if the sample is malware using static analysis methods. If the static analysis methods determine the sample is malware, dynamic analysis methods are used by the at least one computer to automatically determine if the sample is malware. If the dynamic analysis methods determine the sample is malware, the sample is presented to a malware analyst to adjudicate the automatic determinations of the static and dynamic analyses. If the adjudication determines the sample is malware, a response action is initiated to recover from or mitigate a threat of the sample.
Owner:THE UNITED STATES OF AMERICA AS REPRESETNED BY THE SEC OF THE AIR FORCE
System and method for analyzing malicious code using a static analyzer
Owner:TRUSTWAVE HOLDINGS
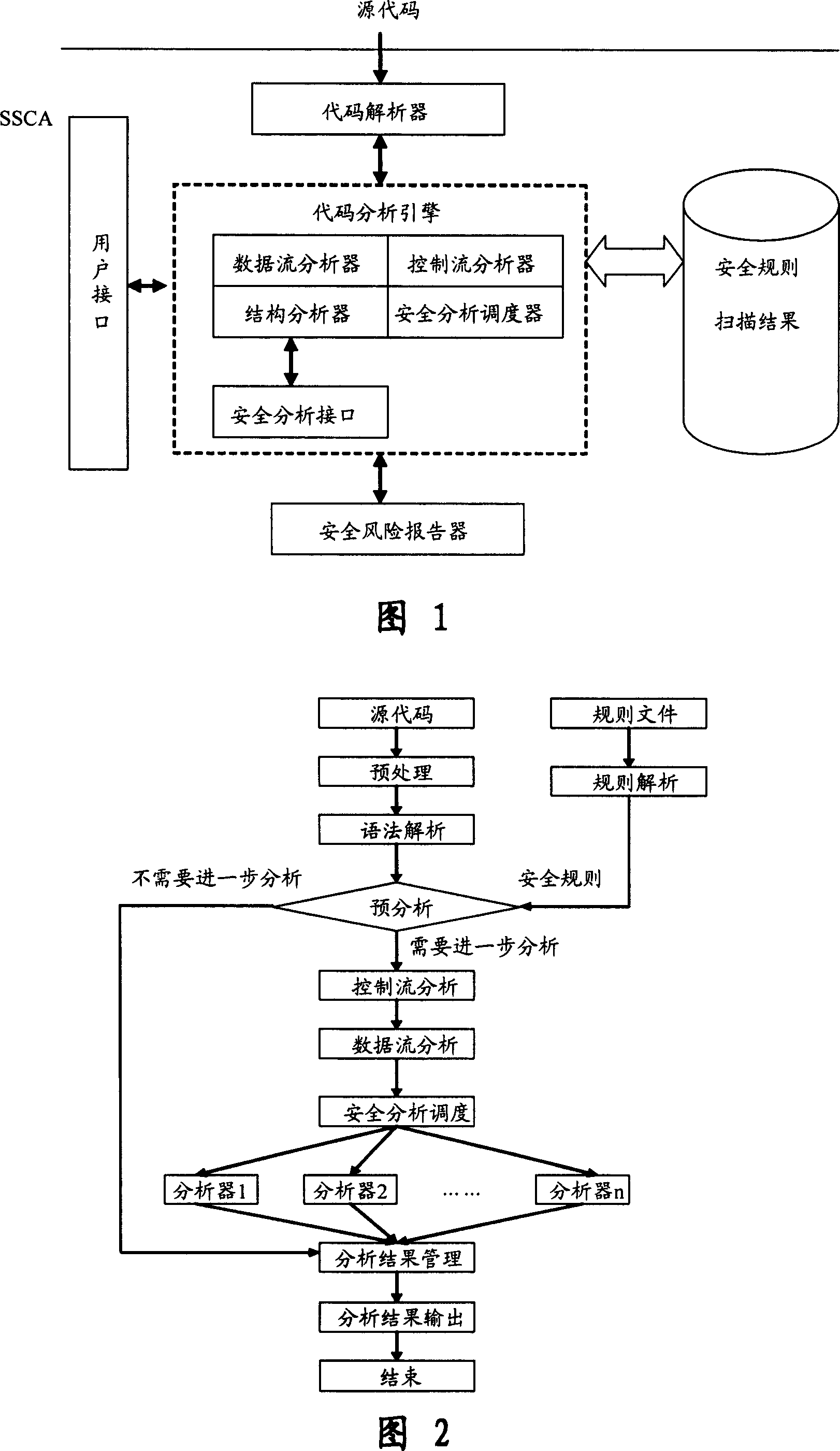
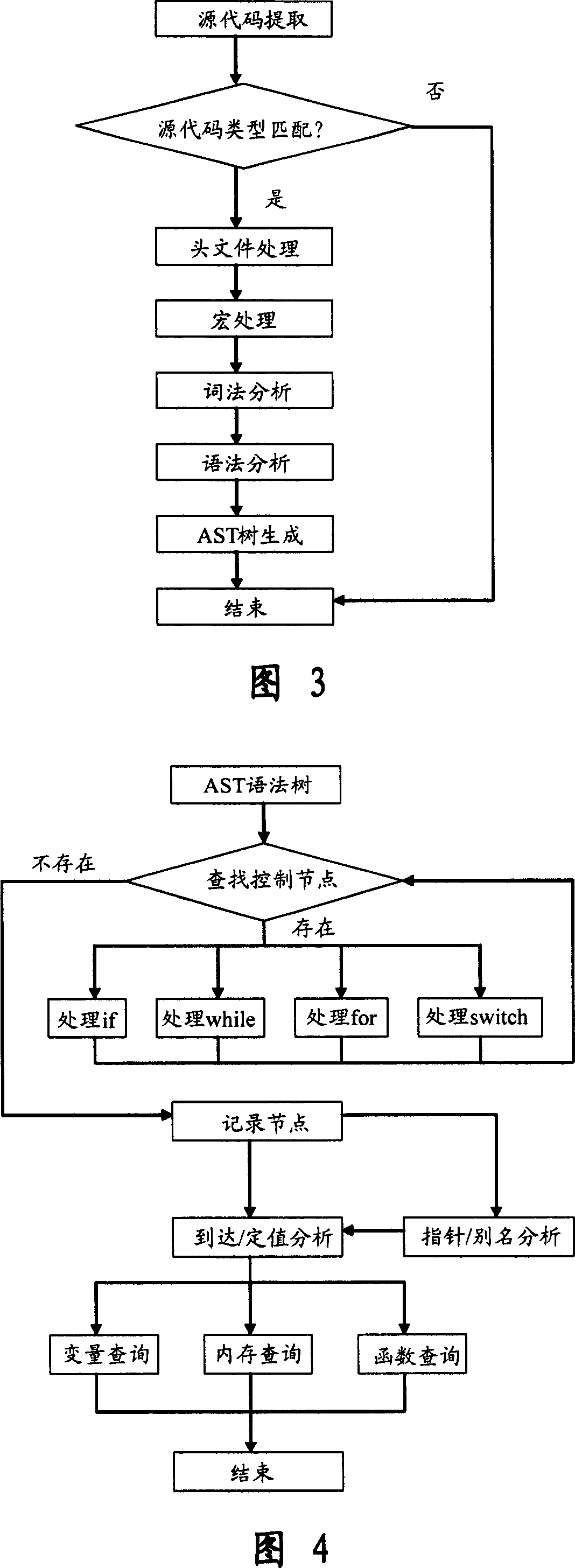
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
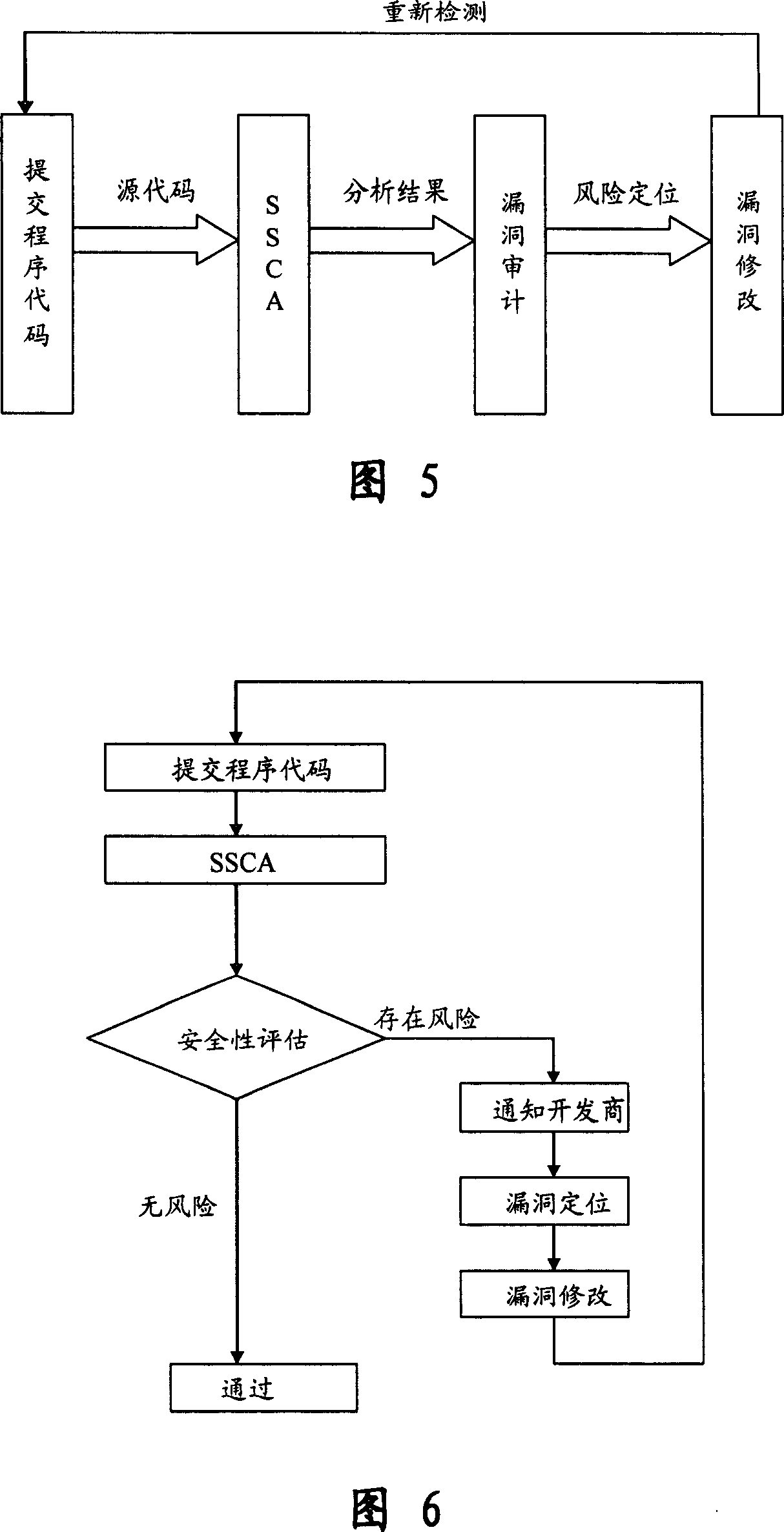
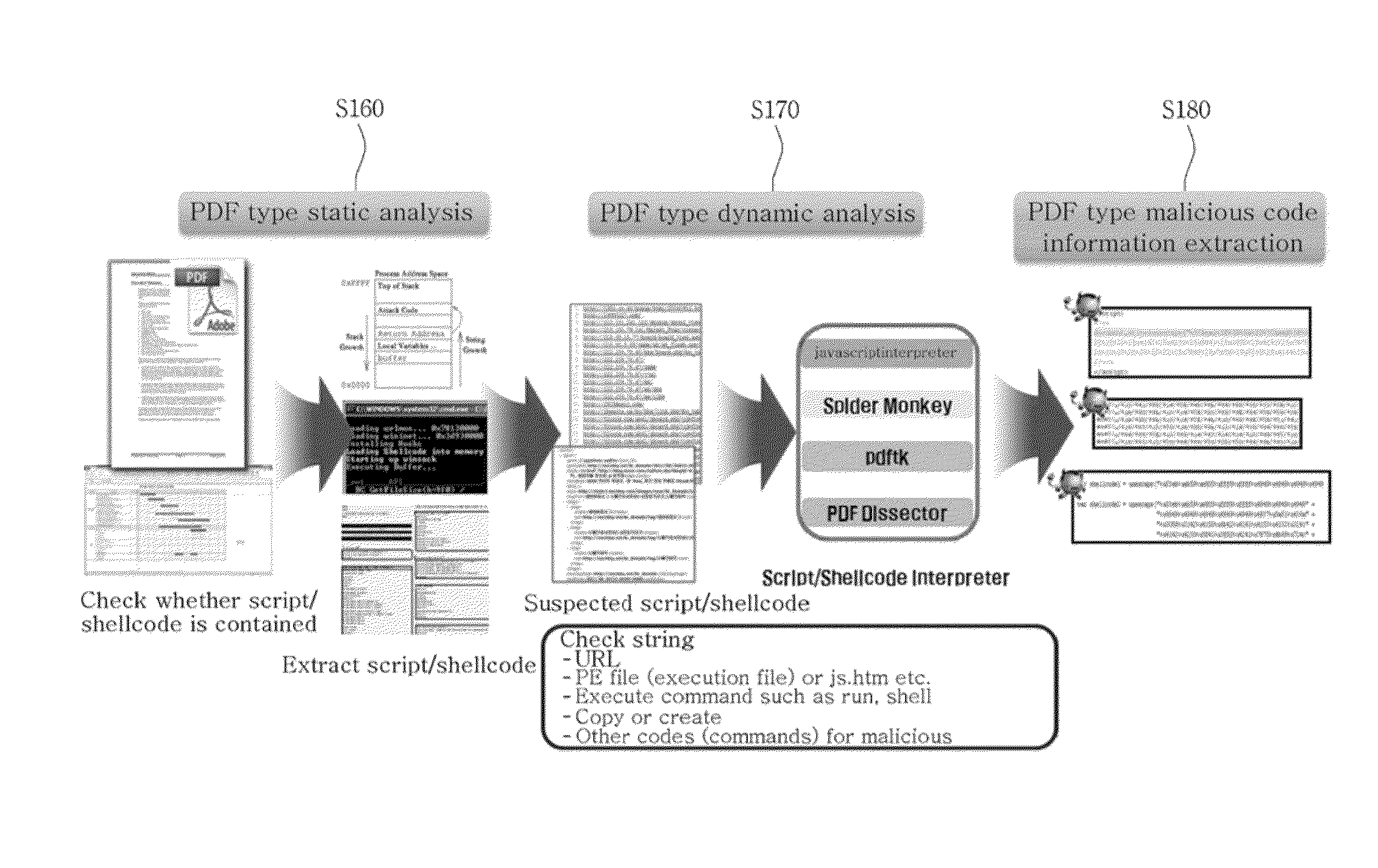
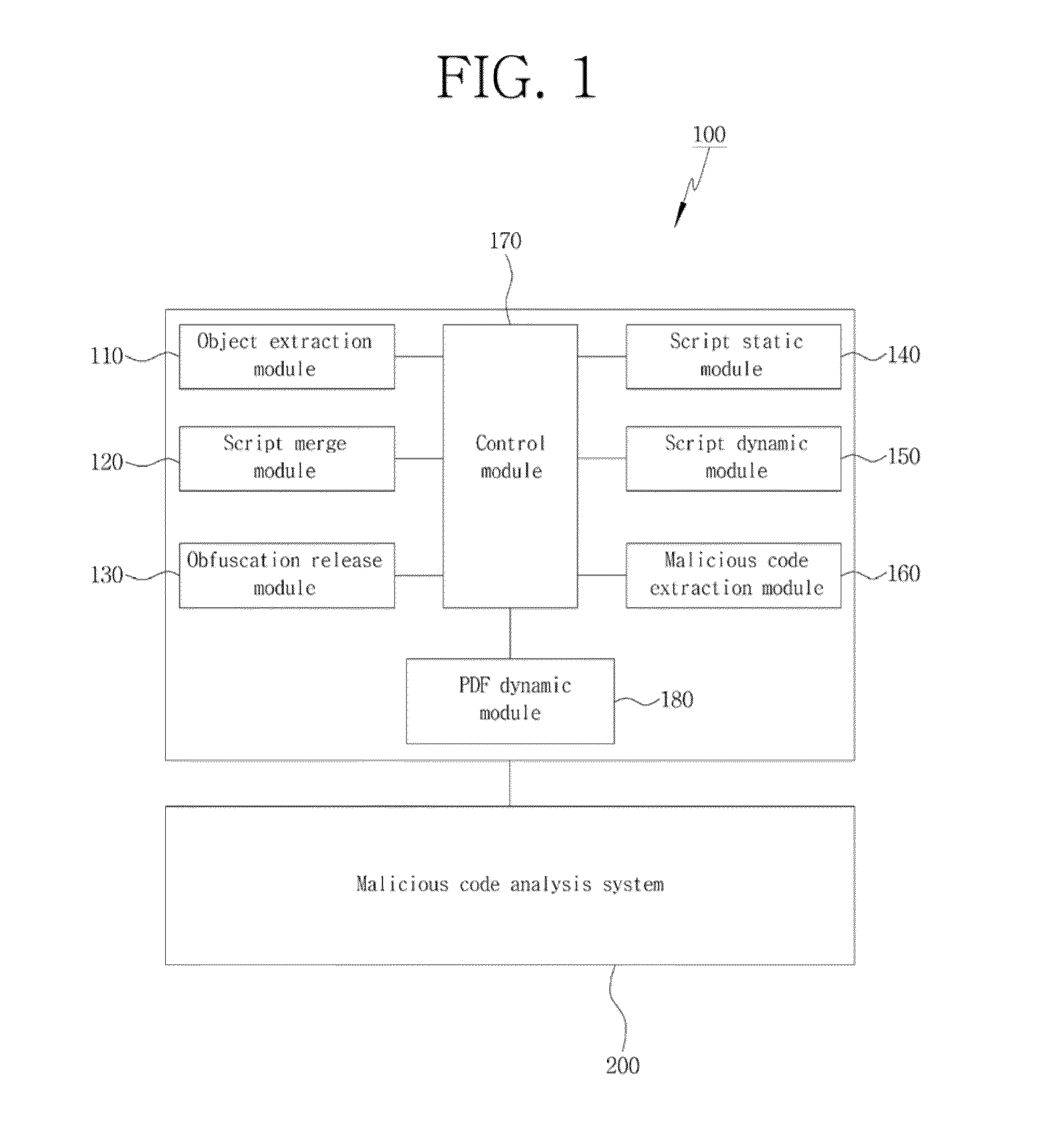
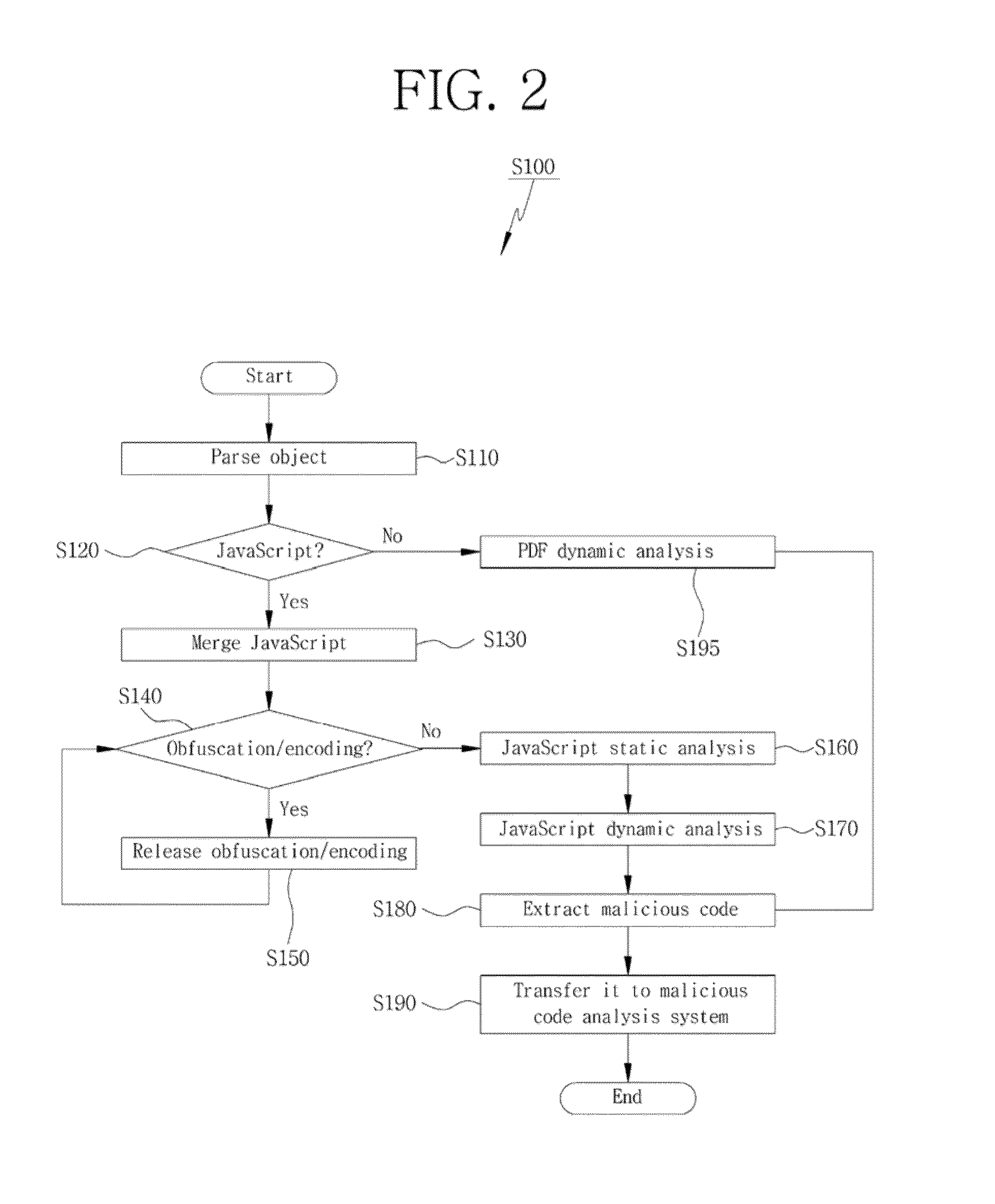
System and method for detecting malicious code of pdf document type
InactiveUS20130160127A1Efficient extractionEfficient detectionMemory loss protectionError detection/correctionDatabaseJavaScript
Disclosed herein is a PDF document type malicious code detection system for efficiently detecting a malicious code embedded in a document type and a method thereof. The present invention may perform a dynamic and static analysis on JavaScript within a PDF document, and execute the PDF document to perform a PDF dynamic analysis, thereby achieving an effect of efficiently extracting a malicious code embedded in the PDF document.
Owner:KOREA INTERNET & SECURITY AGENCY
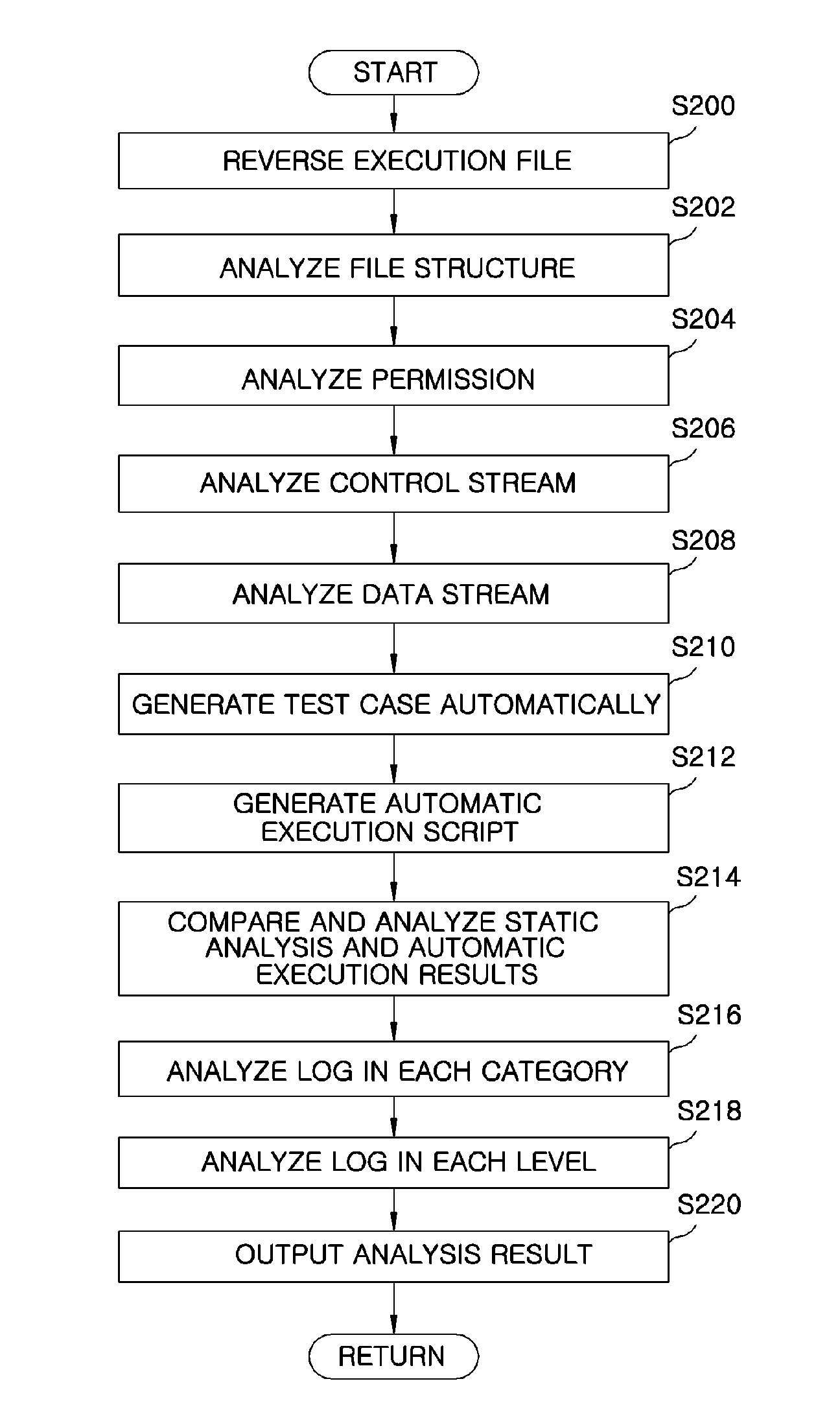
Apparatus for automatically inspecting security of applications and method thereof
InactiveUS20130117855A1Memory loss protectionError detection/correctionOperating systemStatic analysis
An apparatus automatically inspects security of mobile applications. The apparatus includes a static analyzer to perform a static analysis by reversing an execution file of the mobile application, and an automatic execution processor to generate an automatic execution script used to automatically execute the execution file and execute the automatic execution script automatically to generate a log. The apparatus further includes a dynamic analyzer to analyze whether a pattern of malicious codes was executed in the execution file using the result of the static analysis and the log resulted from the automatic execution.
Owner:ELECTRONICS & TELECOMM RES INST
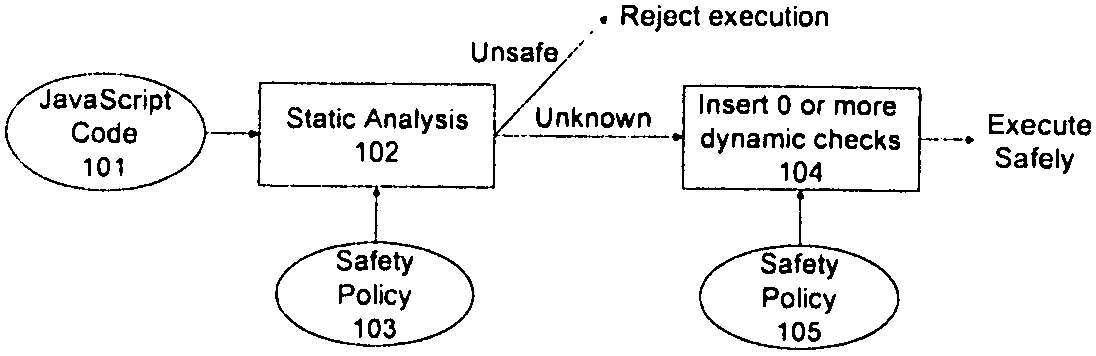
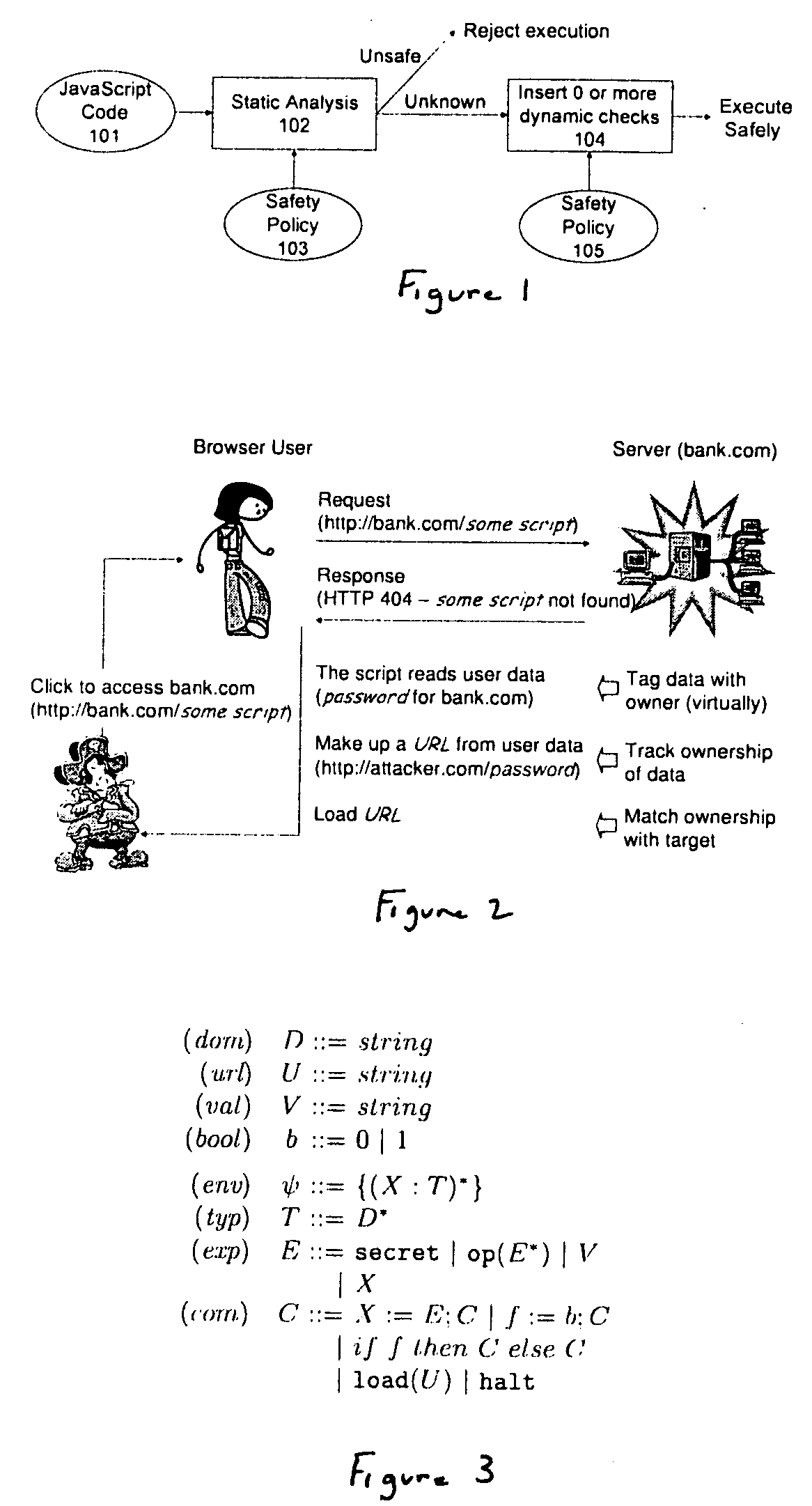
Method and apparatus for detecting and preventing unsafe behavior of javascript programs
InactiveUS20070107057A1Detecting and preventing unsafe behaviorPreventing executionMemory loss protectionError detection/correctionSecurity policySafety policy
A method and apparatus is disclosed herein for detecting and preventing unsafe behavior of script programs. In one embodiment, a method comprises performing static analysis of a script program based on a first safety policy to detect unsafe behavior of the scrip program and preventing execution of the script program if a violation of the safety policy would occur when the script program is executed.
Owner:NTT DOCOMO INC
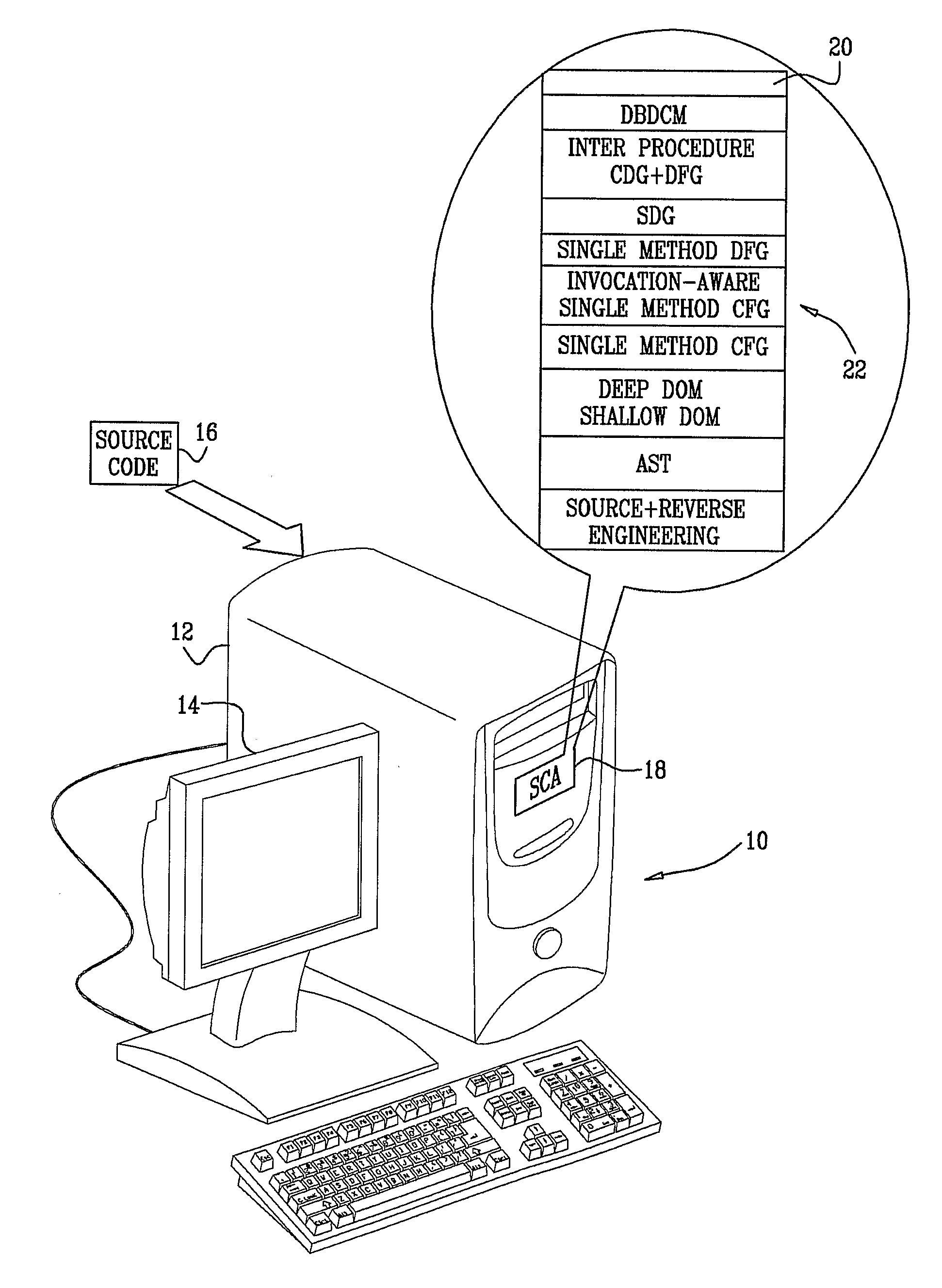
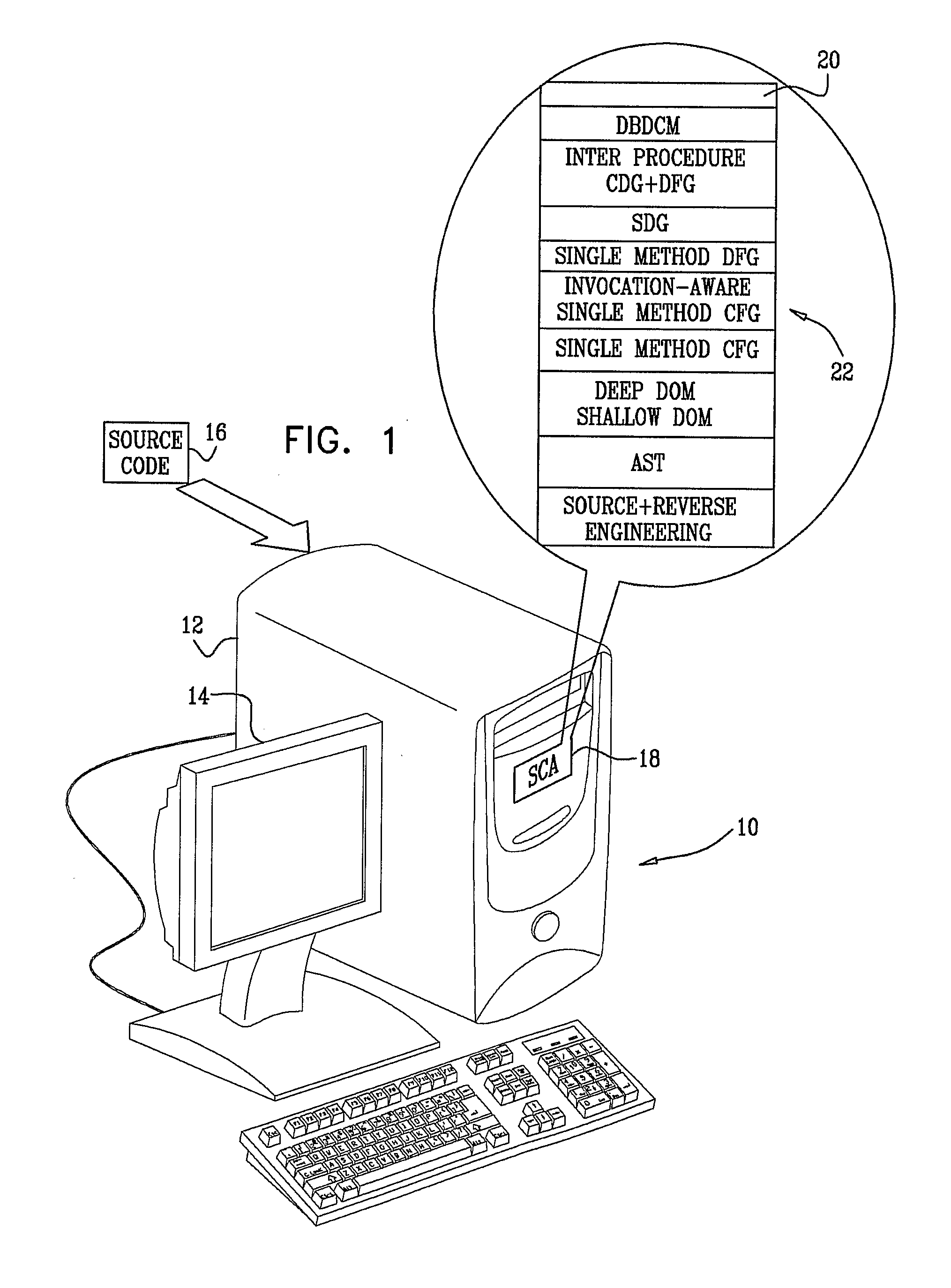
Locating security vulnerabilities in source code
InactiveUS20100083240A1Software engineeringRelational databasesSystems development life cycleApplication software
A tool (22) automatically analyzes application source code (16) for application level vulnerabilities. The tool integrates seamlessly into the software development process, so vulnerabilities are found early in the software development life cycle, when removing the defects is far cheaper than in the post-production phase. Operation of the tool is based on static analysis, but makes use of a variety of techniques, for example methods of dealing with obfuscated code.
Owner:CHECKMARX
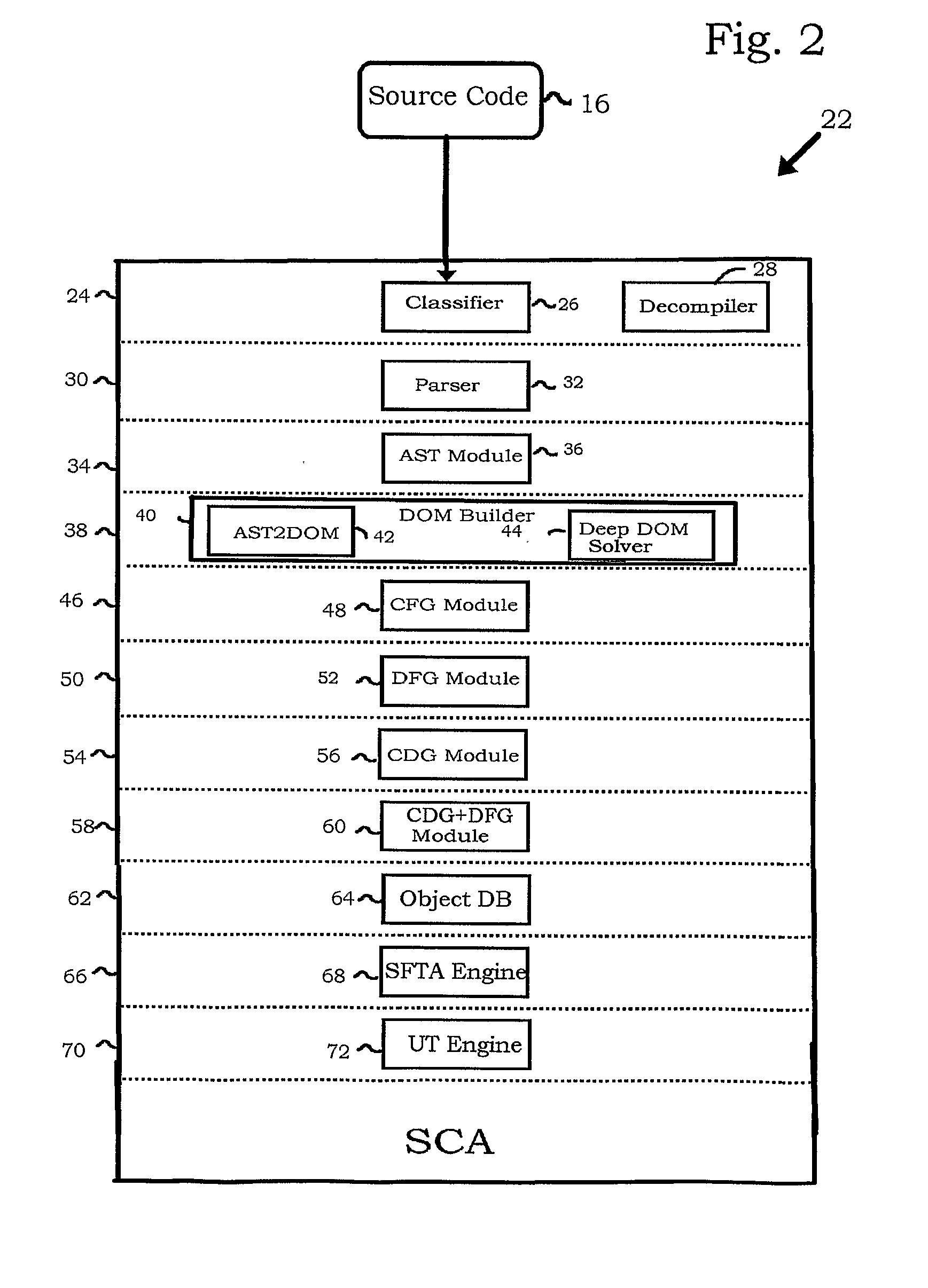
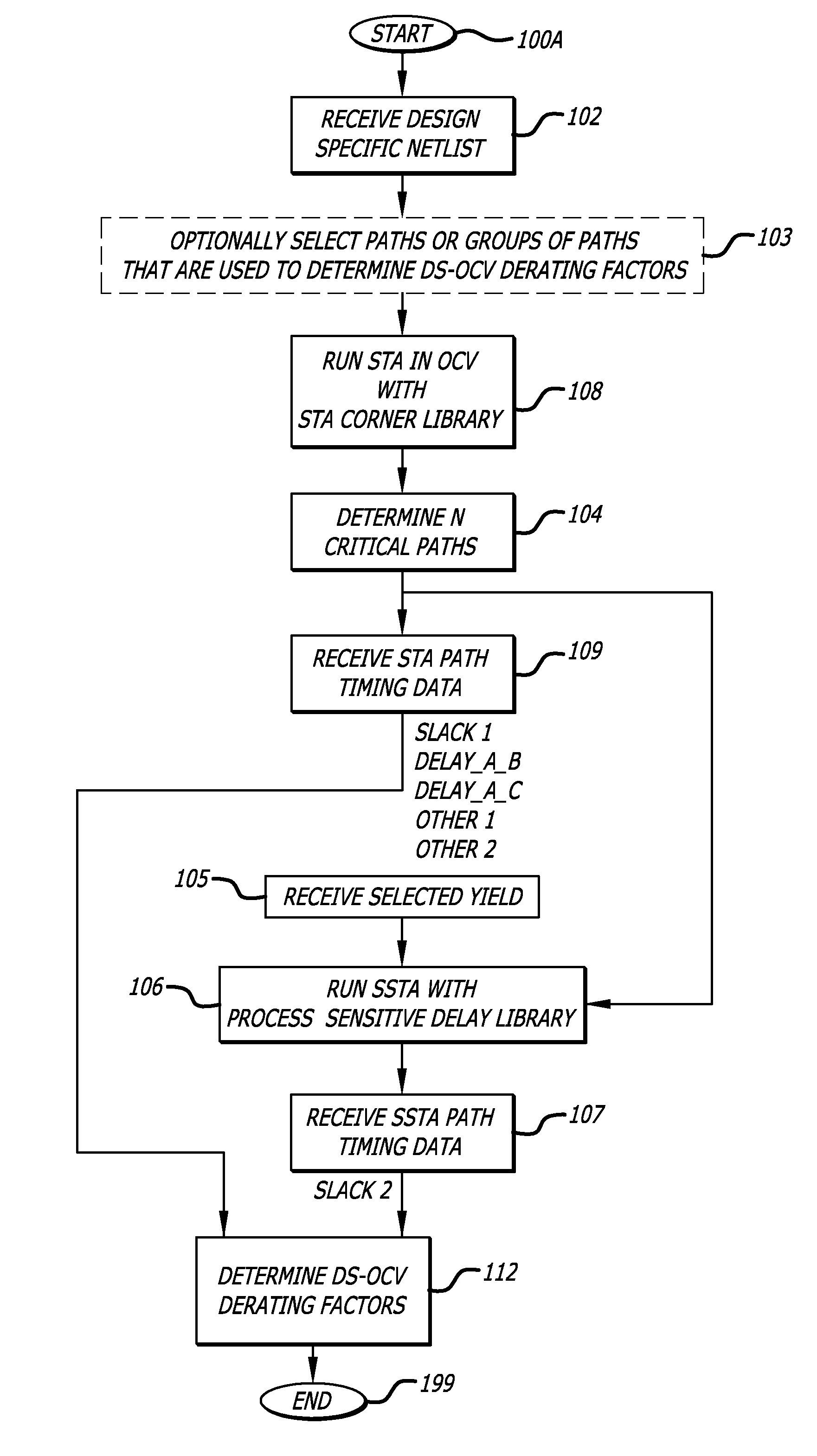
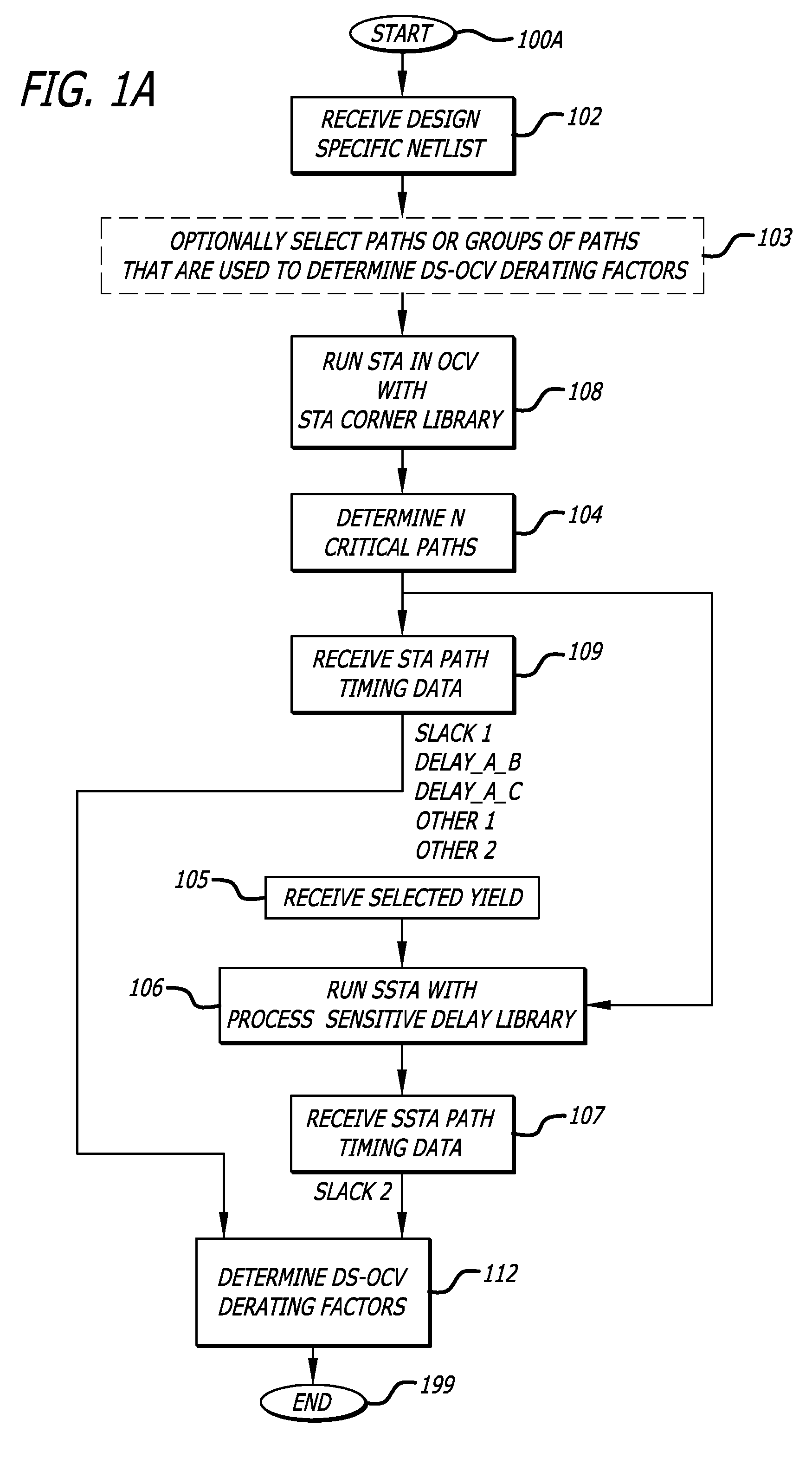
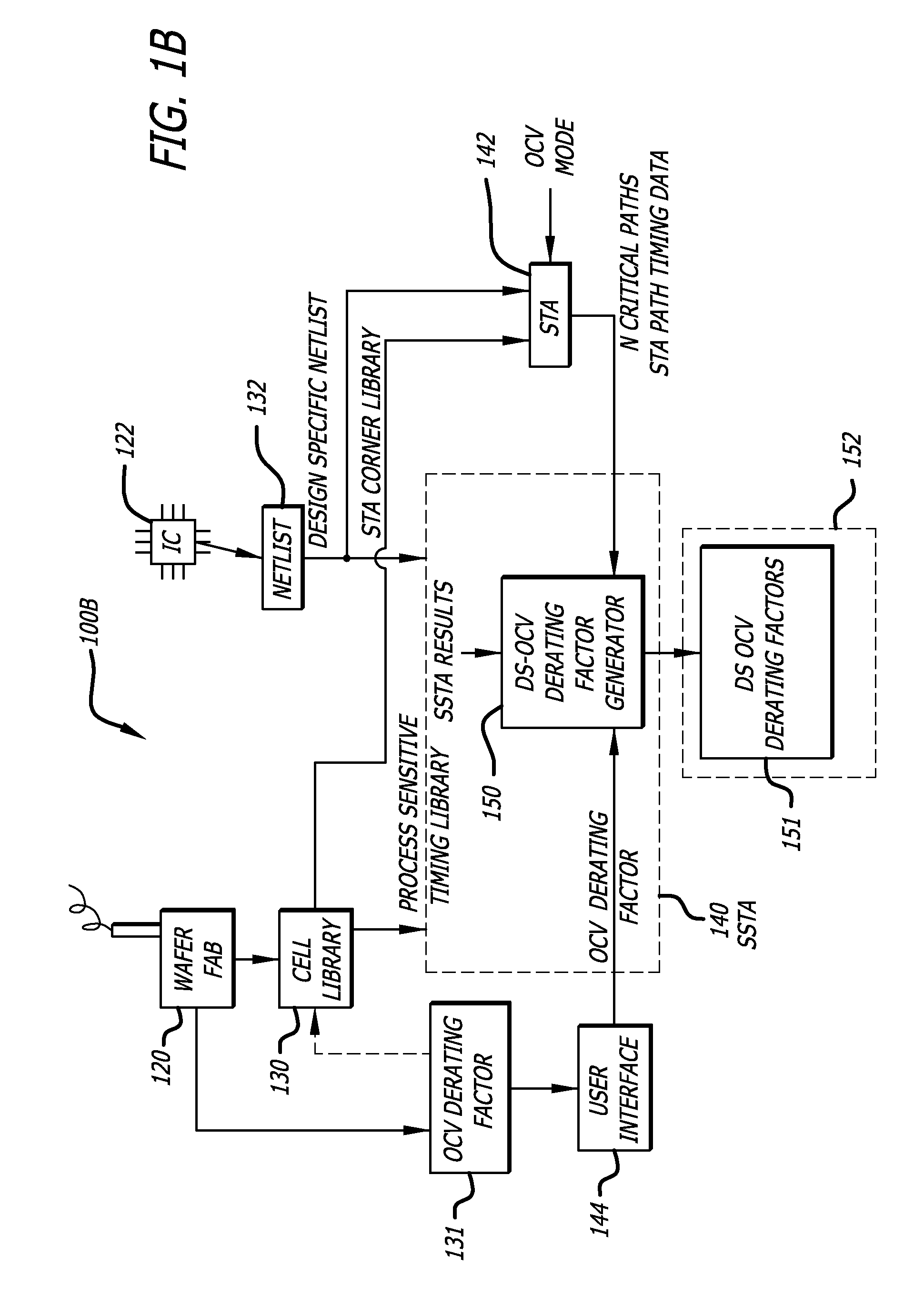
Design-specific on chip variation de-rating factors for static timing analysis of integrated circuits
InactiveUS8336010B1Reduce running timeDesign specificationComputer aided designSoftware simulation/interpretation/emulationTime informationDying processes
In one embodiment of the invention, a method of analysis of a circuit design with respect to within-die process variation is disclosed to generate a design-specific on chip variation (DS-OCV) de-rating factor. The method includes executing a static timing analysis (STA) in an on-chip variation mode using a process corner library. Collecting timing information of the top N critical timing paths. Executing a statistical static timing analysis (SSTA) on the N critical timing paths using timing models characterized for SSTA with sensitivities of delays to process variables. Compare the two timing results and deriving DS-OCV de-rating factors for the clock / data paths to be used in a STA OCV timing analysis to correctly account for the effects of process variations. A user may select to specify DS-OCV de-rating factors for paths or groups of paths and achieve an accurate timing analysis report in a reduced amount of run-time.
Owner:CADENCE DESIGN SYST INC
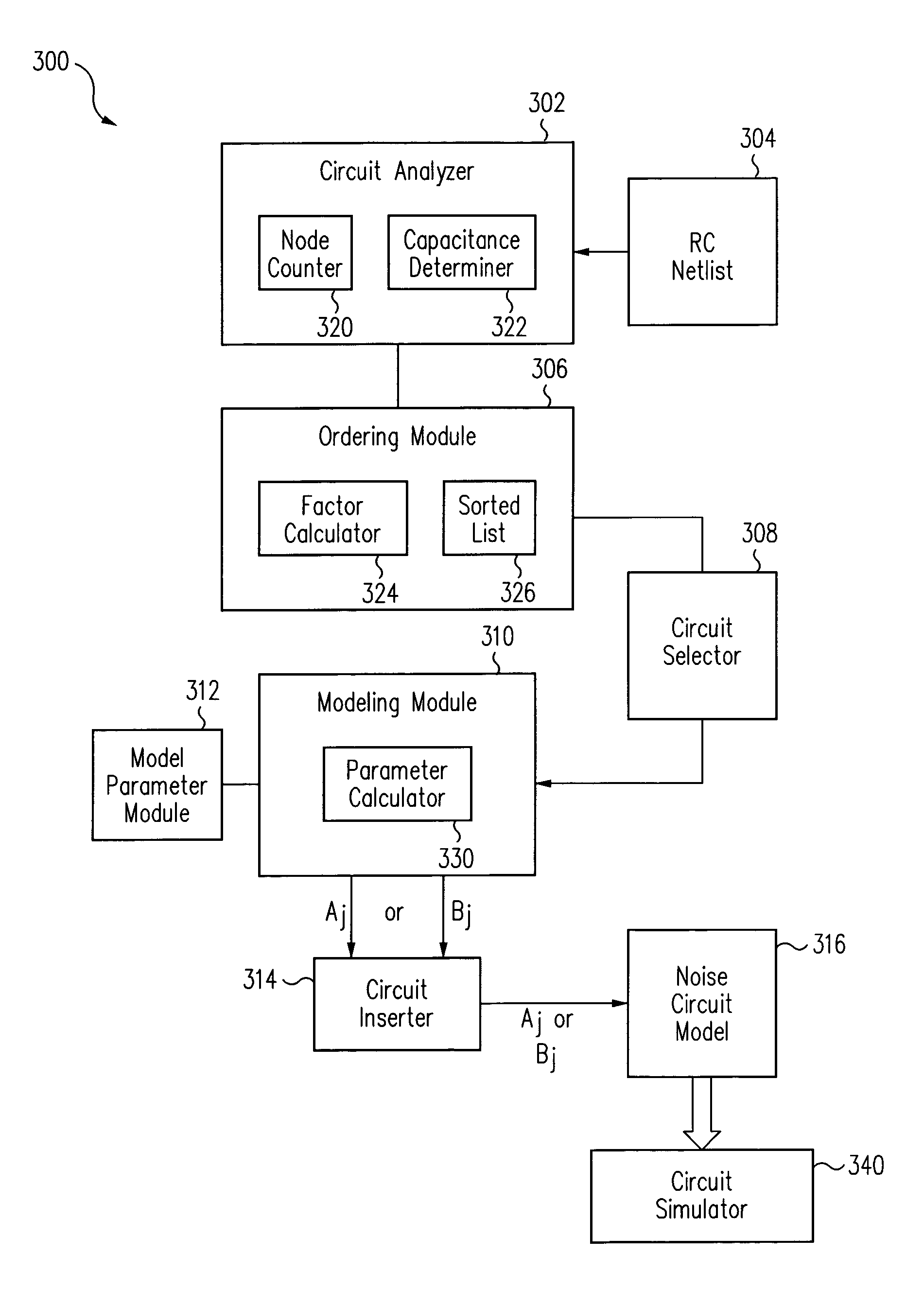
Method and apparatus for generating circuit model for static noise analysis
ActiveUS7181716B1Computer aided designSpecial data processing applicationsAttacker modelModel parameters
Owner:ORACLE INT CORP
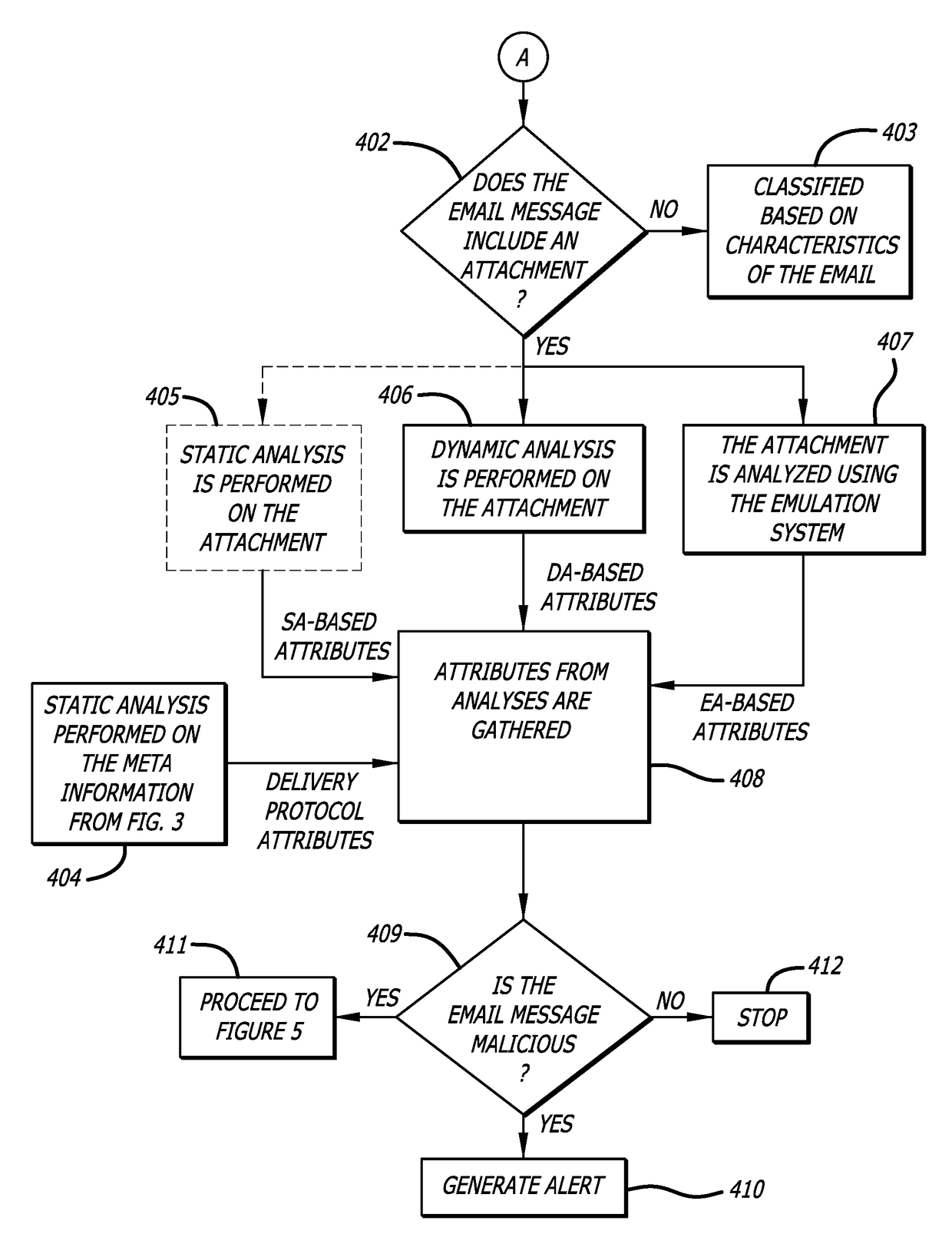
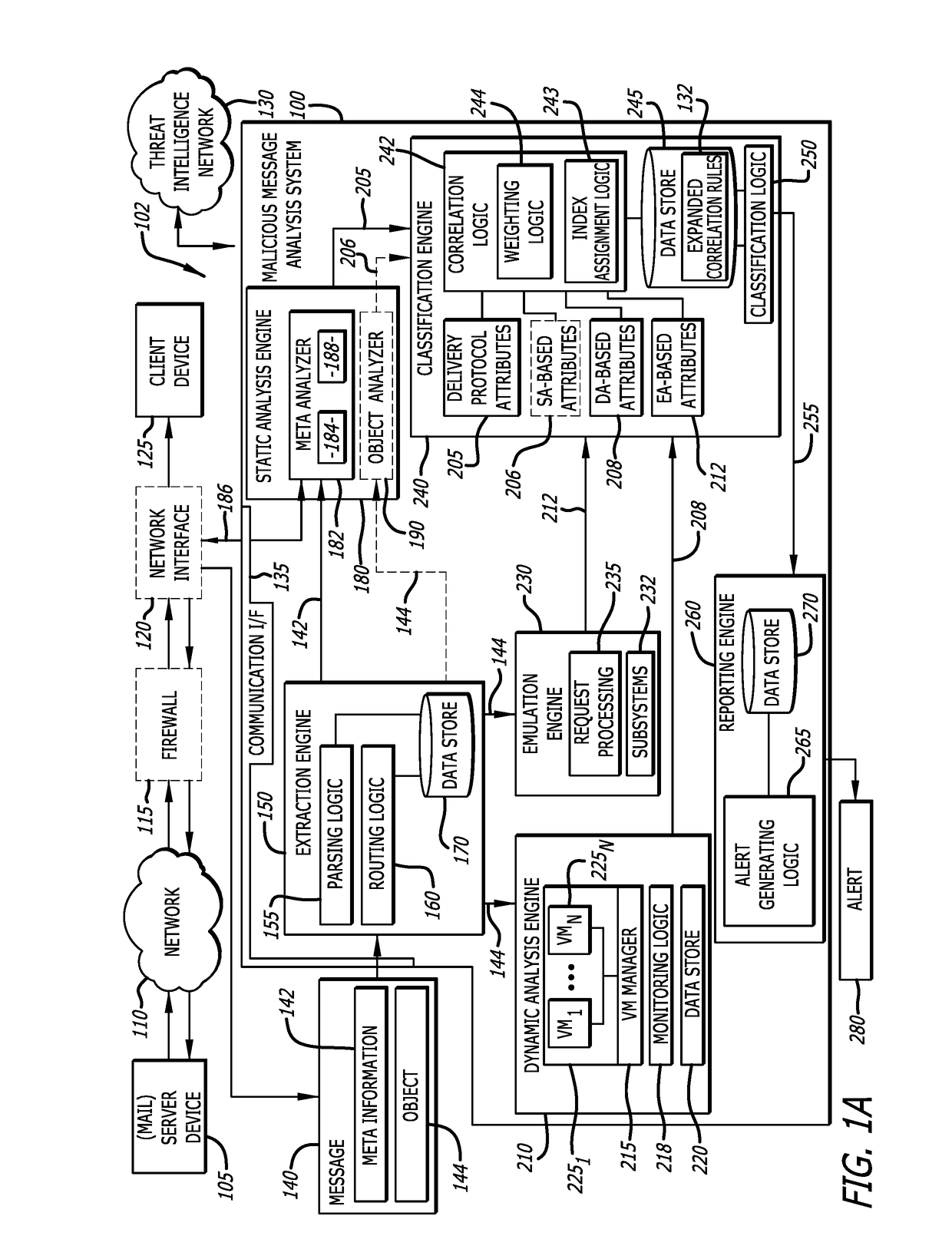
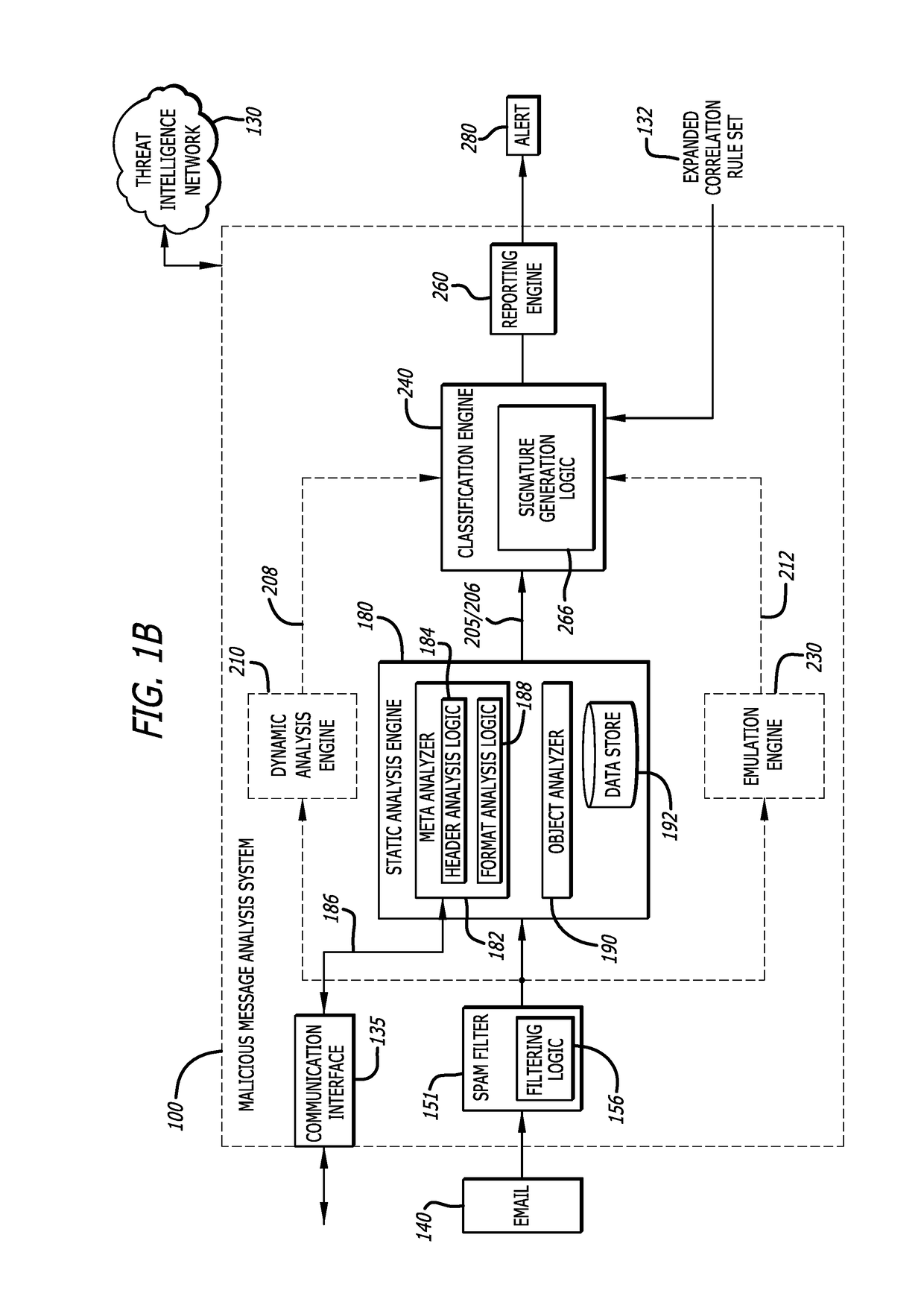
Malicious message analysis system
A computerized technique is provided to analyze a message for malware by determining context information from attributes of the message. The attributes are determined by performing one or more of a static analysis of meta information of the message (e.g., delivery protocol attributes) to generate a first result; a dynamic analysis of an object contained in the message to generate a second result; and, in some embodiments, an emulation of the object to generate a third result. The first result, second result, and third result are correlated in accordance with one or more correlation rules to generate a threat index for the message. The threat index is compared with a predetermined threshold to determine whether the message should be classified as malware and, if so, an alert is generated.
Owner:FIREEYE SECURITY HLDG US LLC
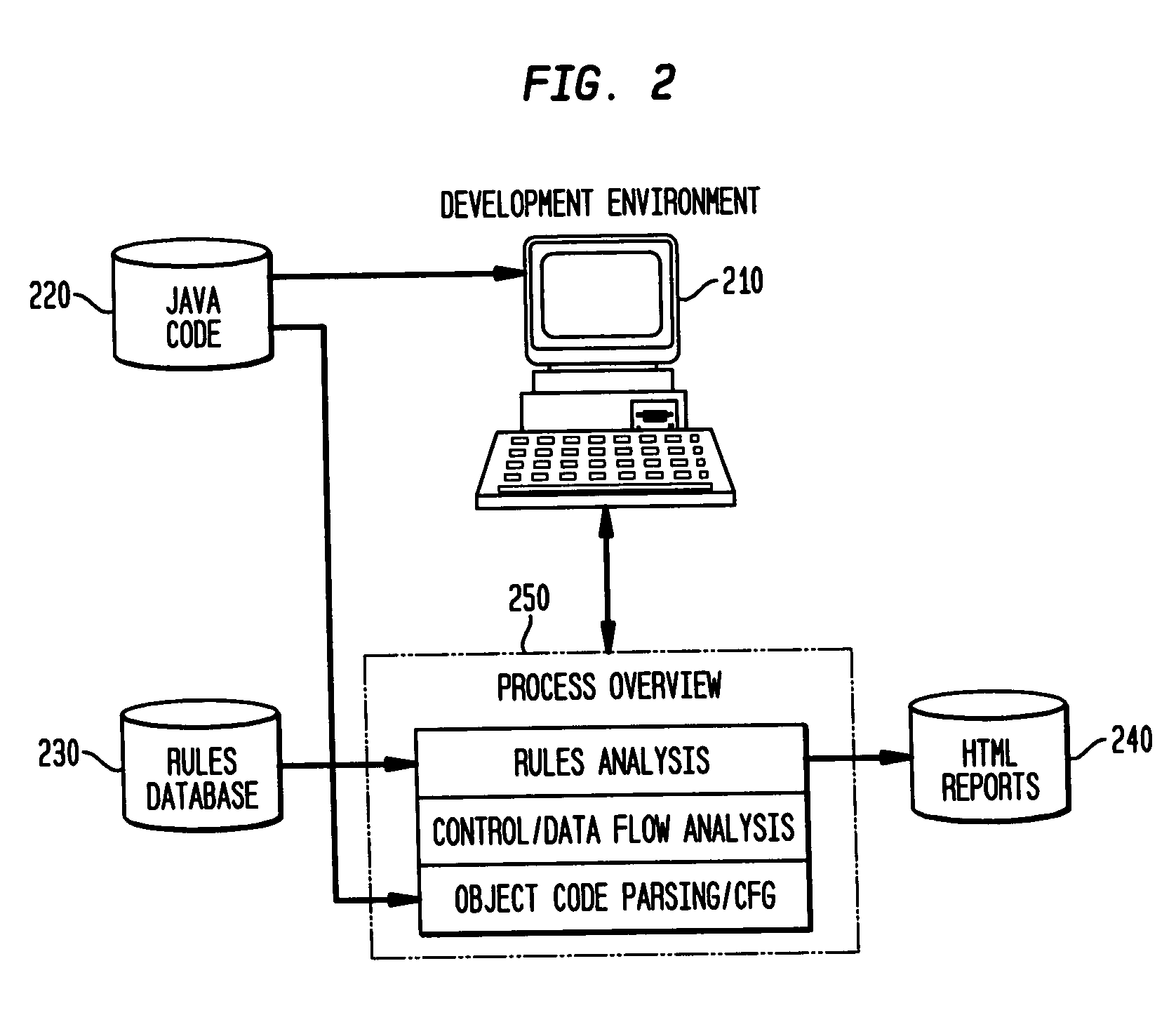
Static analysis based error reduction for software applications
InactiveUS20050015752A1Easy to liftSimple technologyError detection/correctionSpecific program execution arrangementsError reductionMaintainability
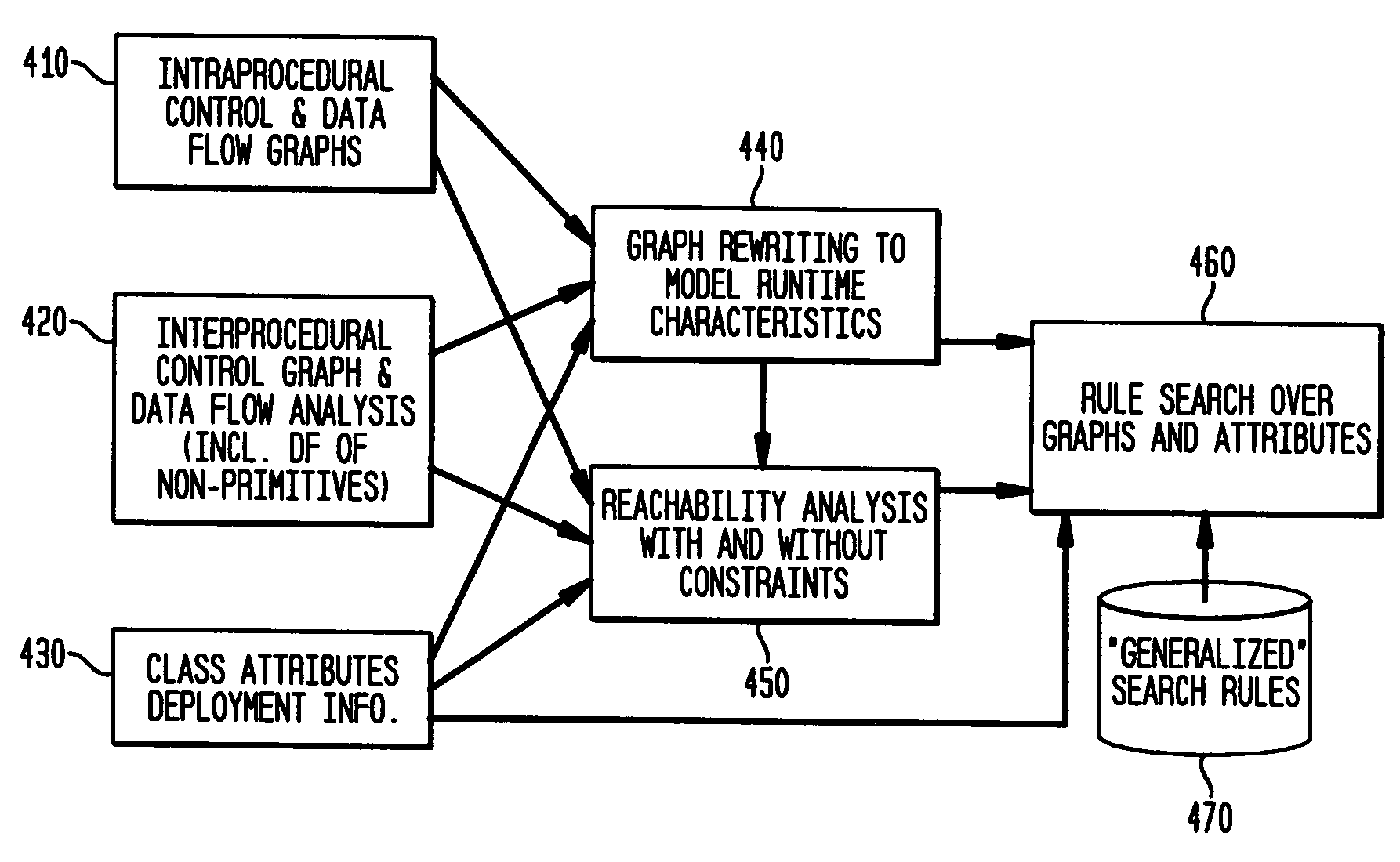
A system and method for providing “static analysis” of programs to aid in improving runtime performance, stability, security and privacy characteristics of deployed application code. The method includes performing a set of analyses that sifts through the program code and identifies programming security and / or privacy model coding errors. In particular the invention focuses on identifying coding errors that cause loss of correctness, performance degradation, security, privacy and maintainability vulnerabilities. A deep analysis of the program is performed using detailed control and data flow analyses. These deeper analyses provide a much better perspective of the overall application behavior. This deep analysis is in contrast to shallow analyses in current industry tools, which inspect or model a single or a few classes at a time.
Owner:IBM CORP
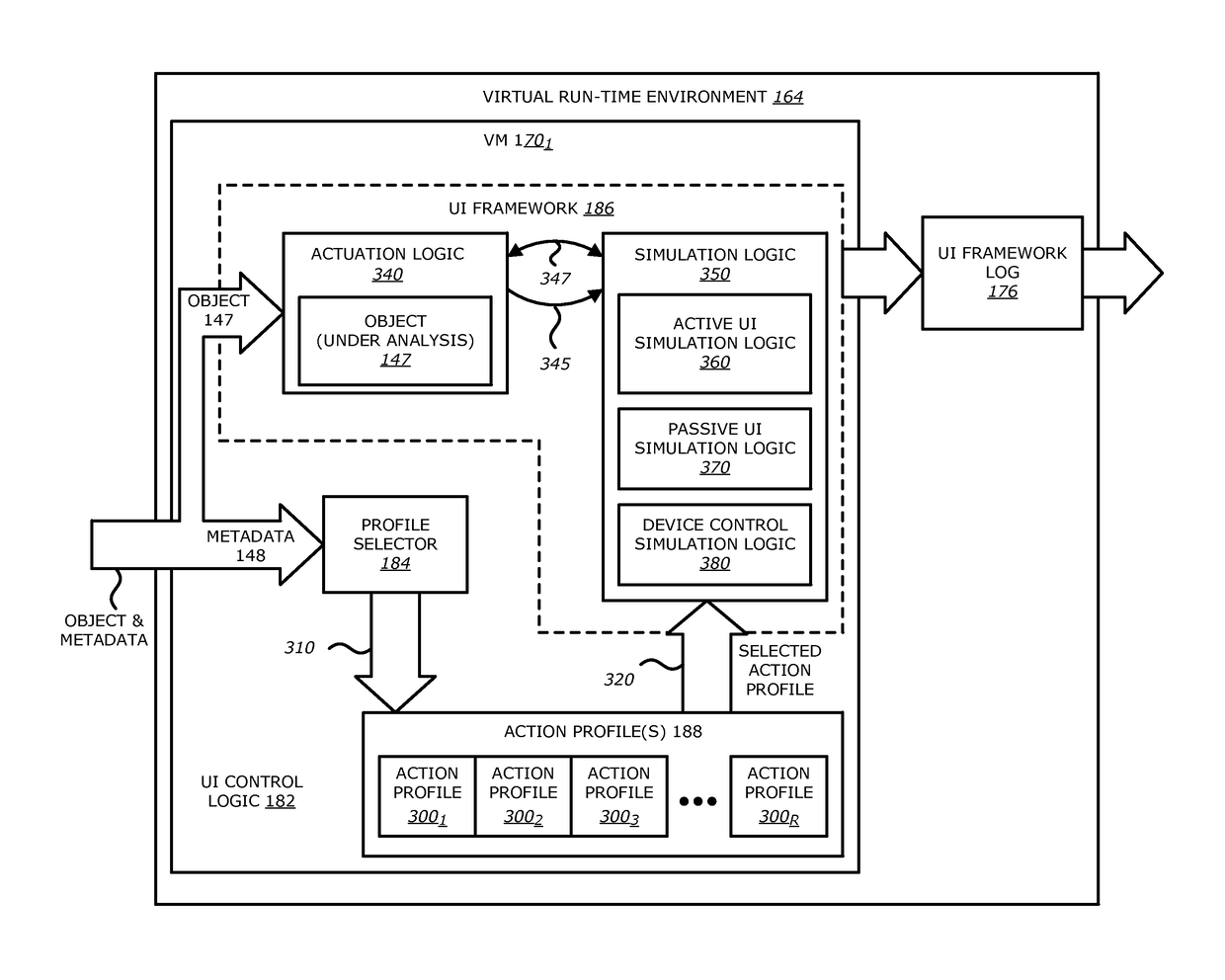
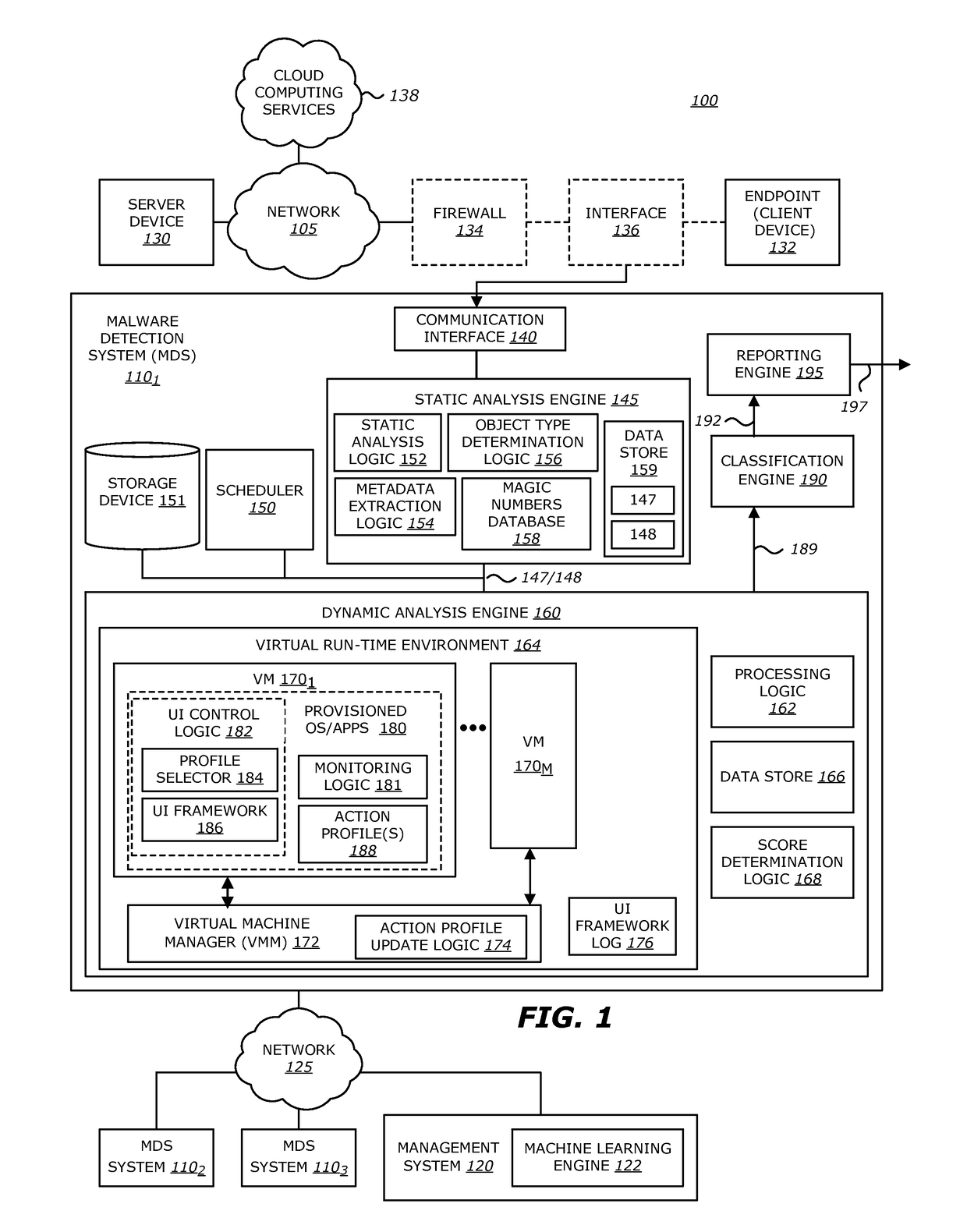
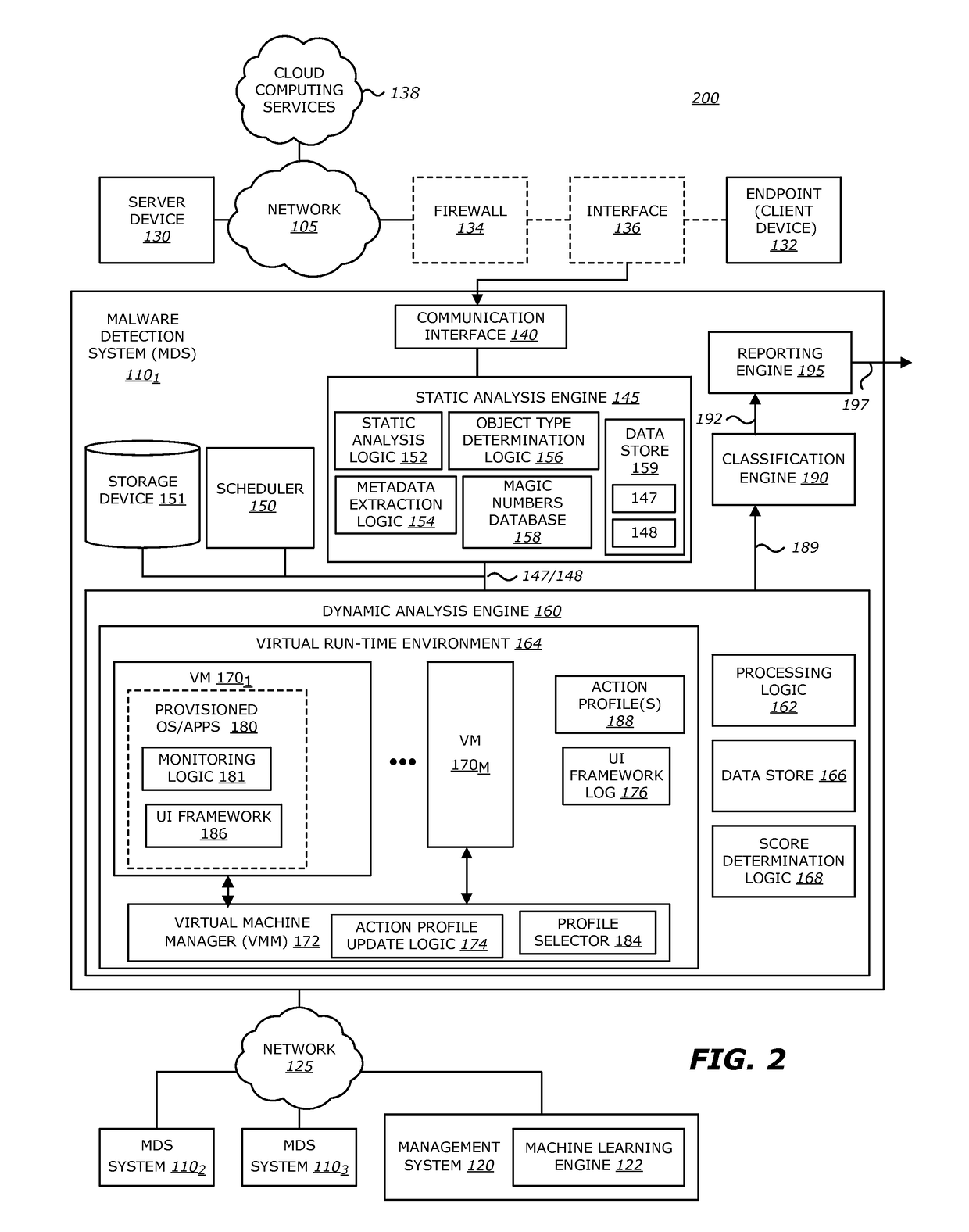
Intelligent context aware user interaction for malware detection
ActiveUS9838417B1Platform integrity maintainanceTransmissionHuman interactionIntelligent environment
According to one embodiment, a malware detection system is integrated with at least a static analysis engine and a dynamic analysis engine. The static analysis engine is configured to automatically determine an object type of a received object. The dynamic analysis engine is configured to automatically launch the object after selecting an action profile based on the object type. The dynamic analysis engine is further configured to, provide simulated user interaction to the object based on the selected action profile either in response to detecting a request for human interaction or as a result of a lapse of time since a previous simulated human interaction was provided.
Owner:FIREEYE SECURITY HLDG US LLC
System and method for offloading packet processing and static analysis operations
According to one embodiment, a system features analysis circuitry and detection circuitry. The analysis circuitry features a first processing unit and a first memory that includes a filtering logic configured to produce a second plurality of objects from a received first plurality of objects. The second plurality of objects is a subset of the first plurality of objects. The detection circuitry is communicatively coupled to and remotely located from the analysis circuitry. The detection circuitry includes a second processing unit and a second memory. The second memory includes a virtual execution logic to process content within at least a first object of the second plurality of objects. The virtual execution logic is configured to monitor for behaviors, during the processing of the first object, and determine whether any or all of the monitored behaviors correspond to activities indicative that the first object is associated with a malicious attack.
Owner:FIREEYE SECURITY HLDG US LLC
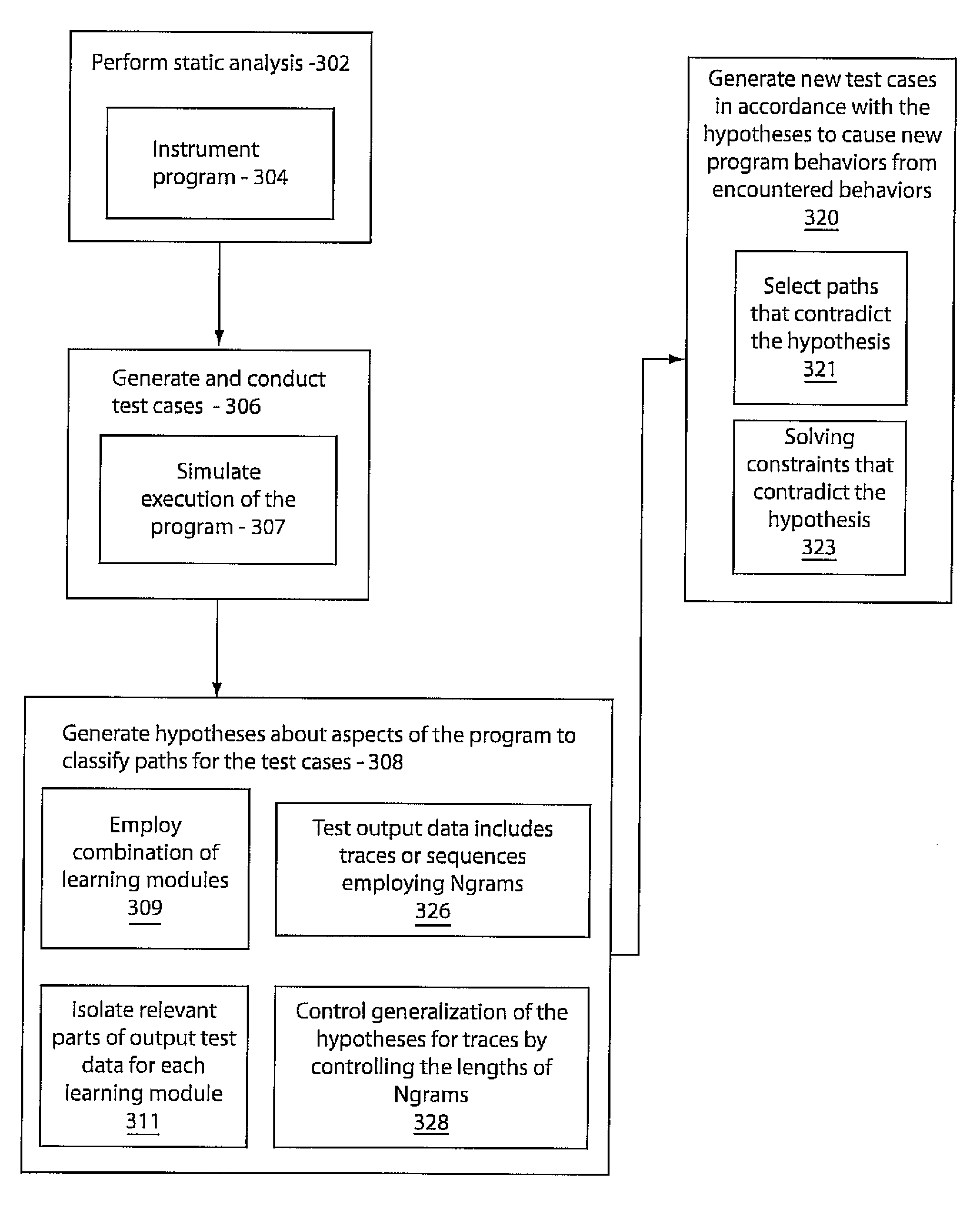
Software testing using machine learning
InactiveUS20080082968A1Error detection/correctionSpecific program execution arrangementsHypothesisExercise behavior
A system and method for analyzing a computer program includes performing a static analysis on a program to determine property correctness. Test cases are generated and conducted to provide test output data. Hypotheses about aspects of execution of the program are produced to classify paths for test cases to determine whether the test cases have been encountered or otherwise. In accordance with the hypothesis, new test cases are generated to cause the program to exercise behavior which is outside of the encountered test cases.
Owner:NEC CORP
System and method for automatically analyzing, detecting and classifying malicious program behavior
ActiveCN102930210ACause damageOvercome shortcomings such as inability to perform adequatelyPlatform integrity maintainanceSpecial data processing applicationsDomain nameNetwork behavior
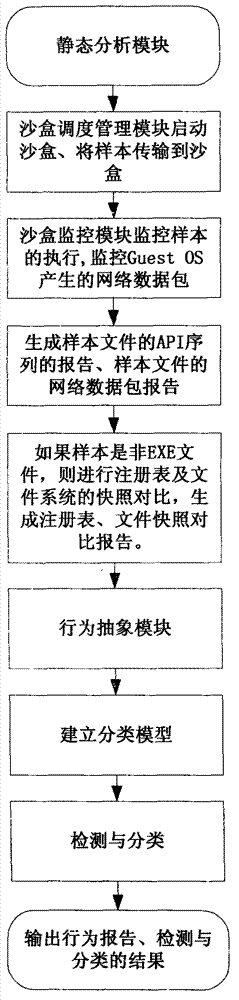
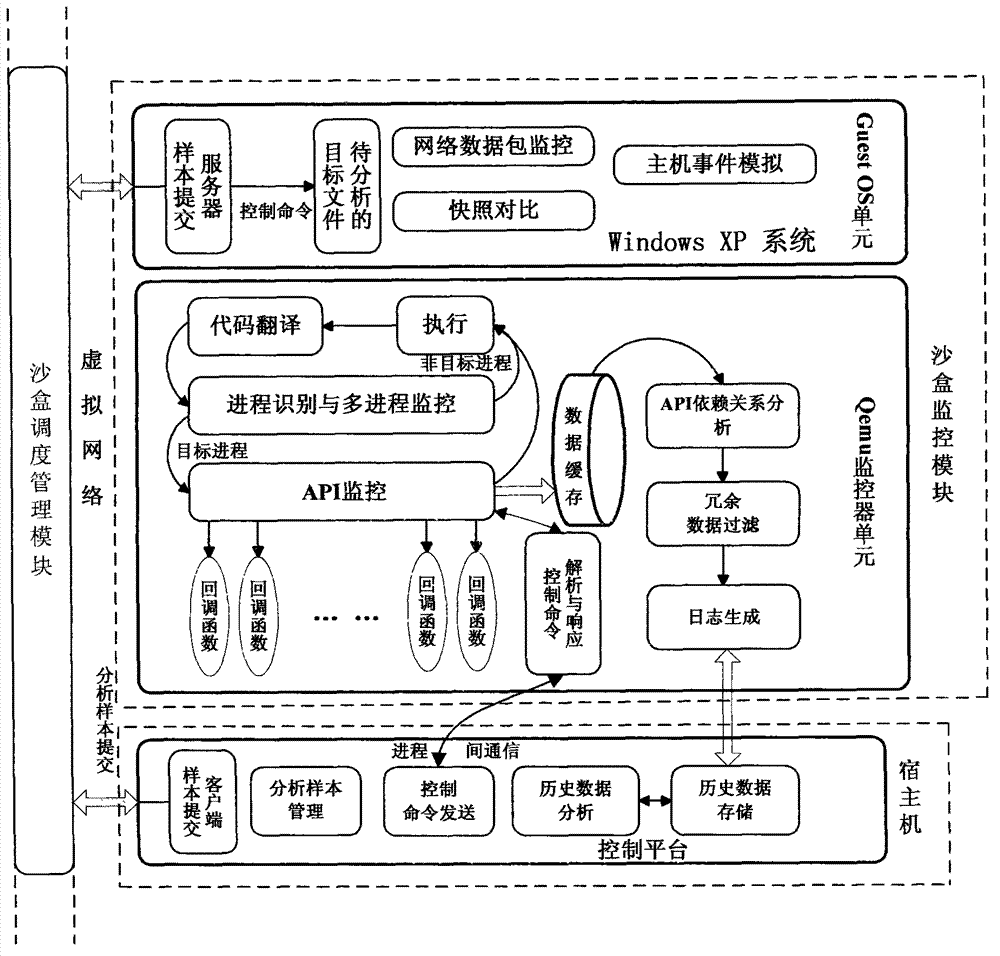
The invention discloses a system and a method for automatically analyzing, detecting and classifying a malicious program behavior. The system comprises a static analysis module, a sandbox dispatching management module, a sandbox monitoring module, a behavior abstraction module and a detection and classification module. Compared with the prior art, the system has the advantages that 1, the system is based on a behavior monitoring technology in an instruction set simulation environment; and 2, a virtual Internet is established in a sandbox through means of environment configuration, server program modification and the like, and a common network service is simulated, so that operations such as domain name server (DNS) resolution, http access, file download, Email login and mailing initiated by a malicious program can be successfully executed, the malicious program is inveigled to generate a malicious network behavior, the network behaviors are prevented from damaging a host machine and a real network, and the defects that the malicious program network behavior cannot be fully expressed during dynamic behavior analysis of a malicious program and the like are overcome.
Owner:JIANGSU JINLING TECH GRP CORP
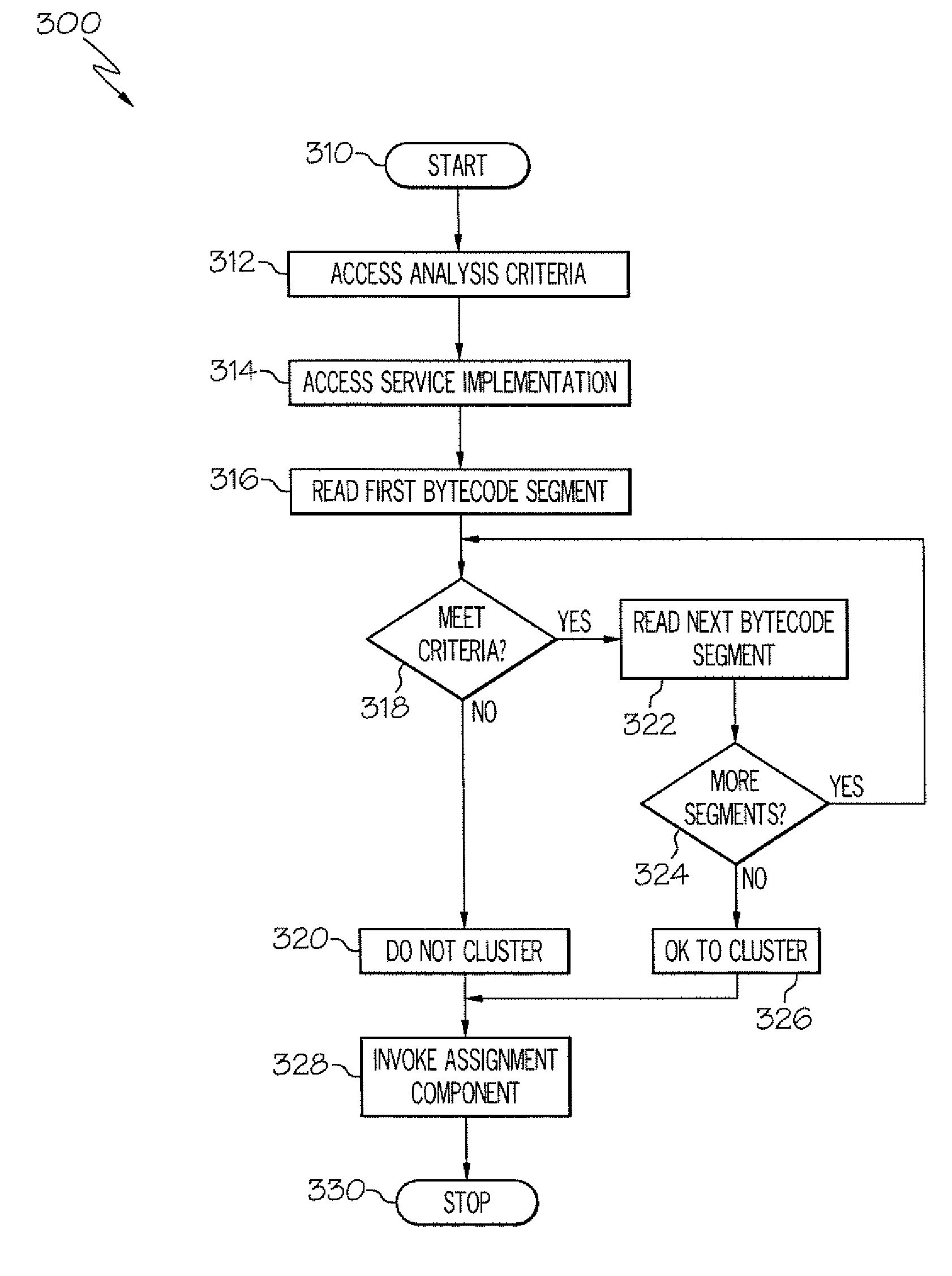
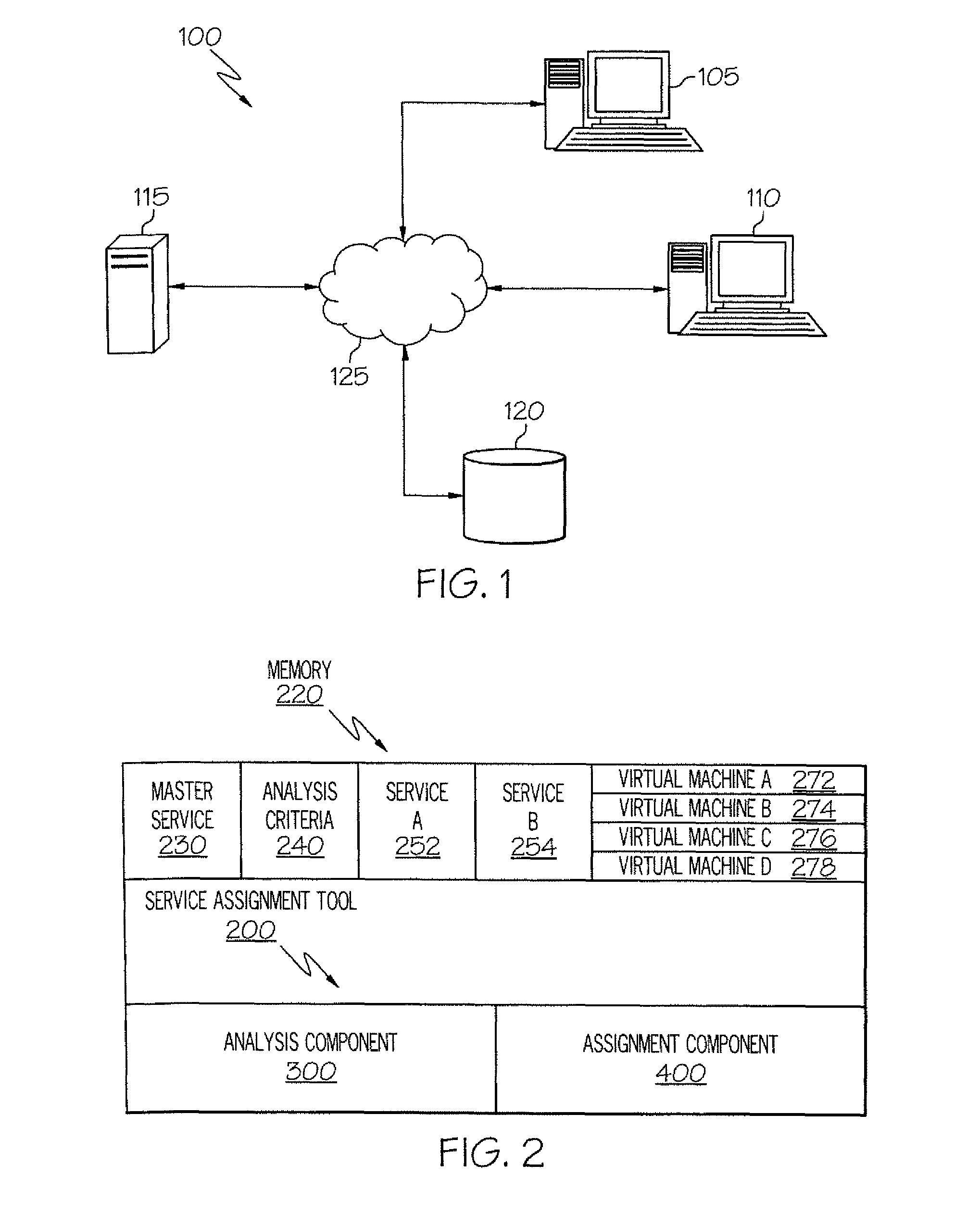
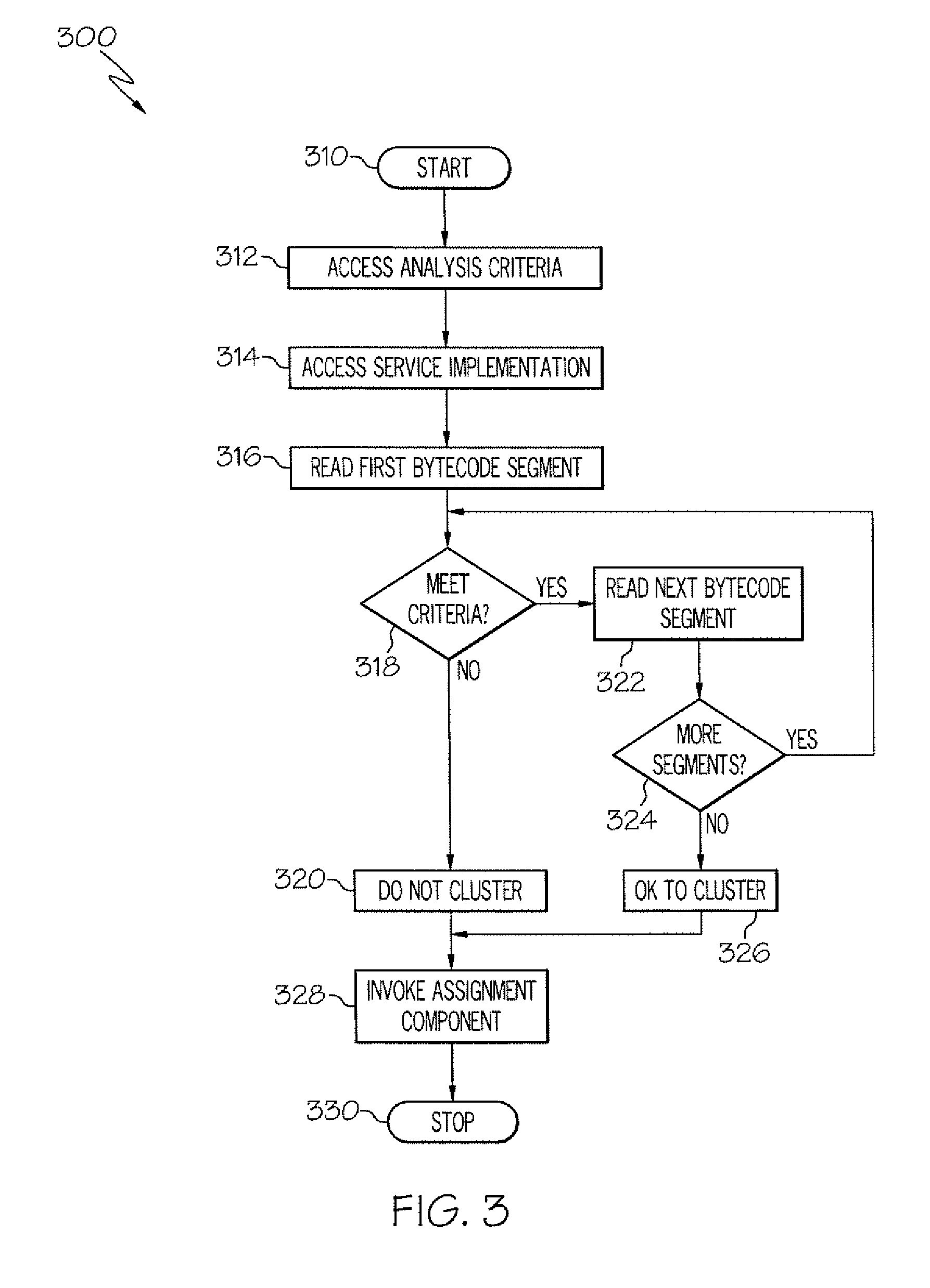
Method and apparatus for determining a service cluster topology based on static analysis
InactiveUS8171473B2Multiprogramming arrangementsSoftware simulation/interpretation/emulationStatic timing analysisCoding conventions
The service assignment tool analyzes a service to determine whether the service can execute on a cluster. If the service cannot execute on a cluster, the service is assigned to a single virtual machine. The service assignment tool identifies non-cluster friendly services by performing a static analysis on the bytecode of the service. The bytecode of the service is analyzed by comparing each segment of bytecode to a list of known good and bad coding conventions. If each segment of bytecode in a service meets the good coding convention criteria, then the service is cluster friendly. If one segment of bytecode does not meet the good coding convention criteria, then the entire service is considered to be not cluster friendly.
Owner:INT BUSINESS MASCH CORP
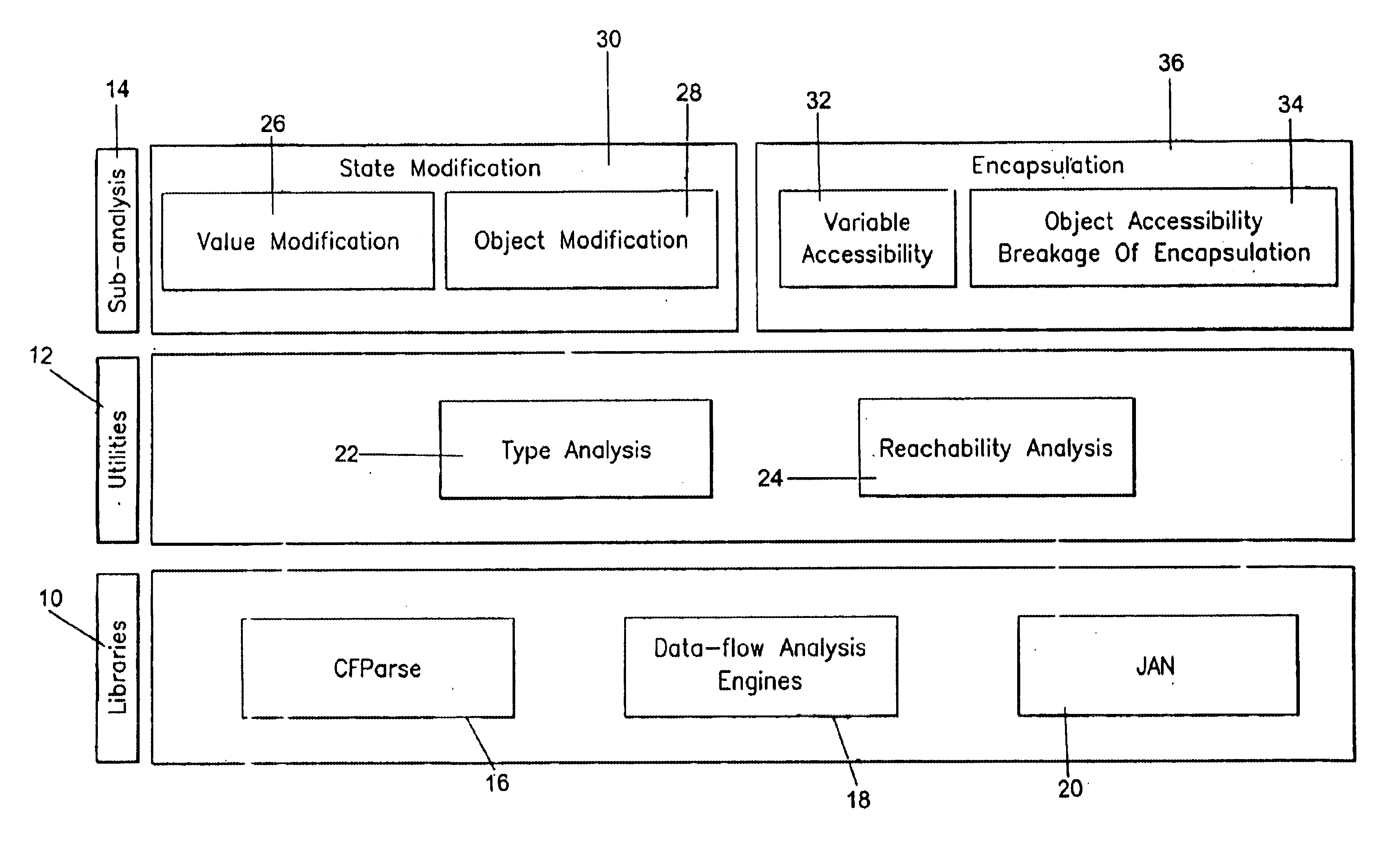
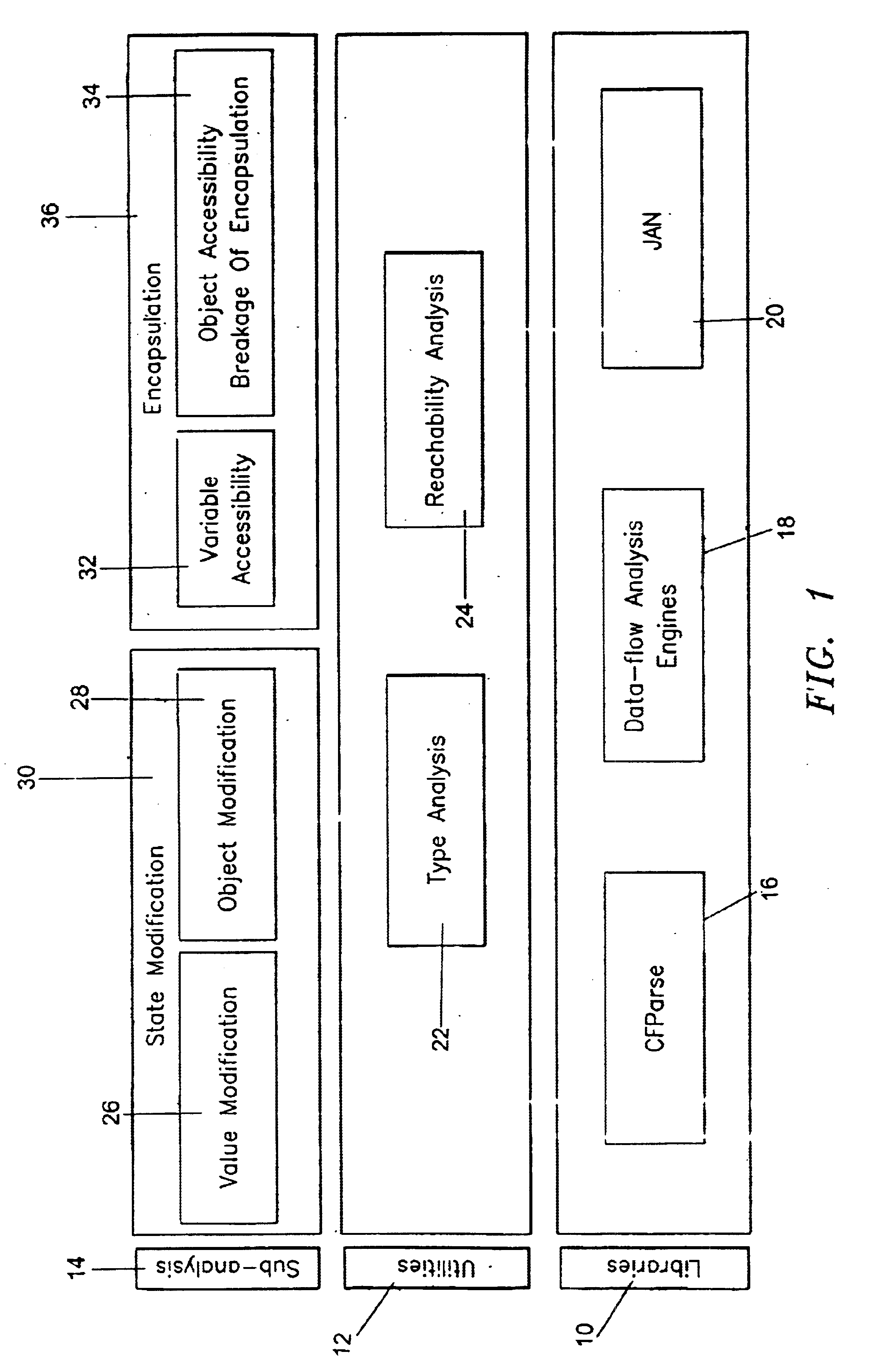
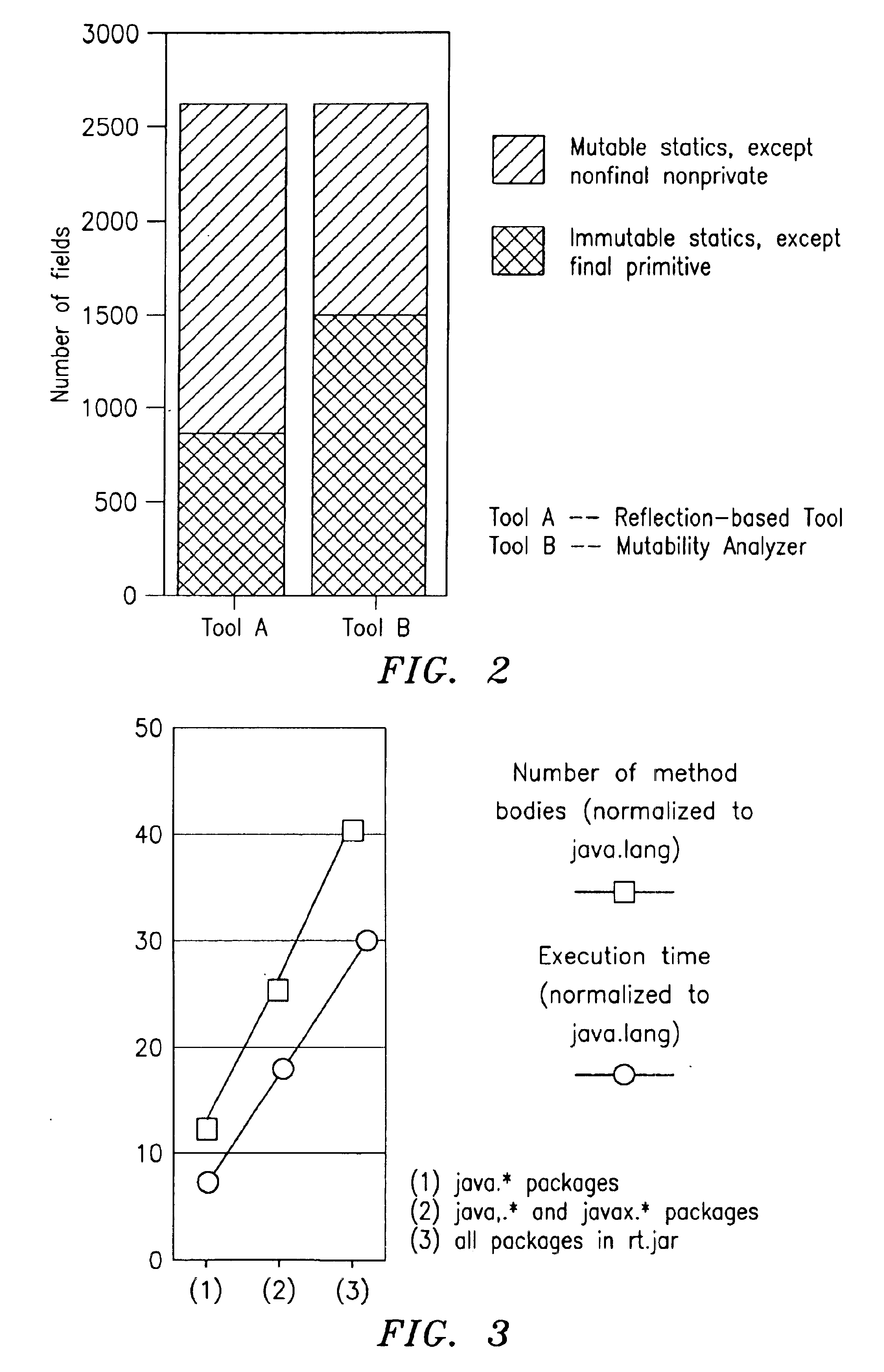
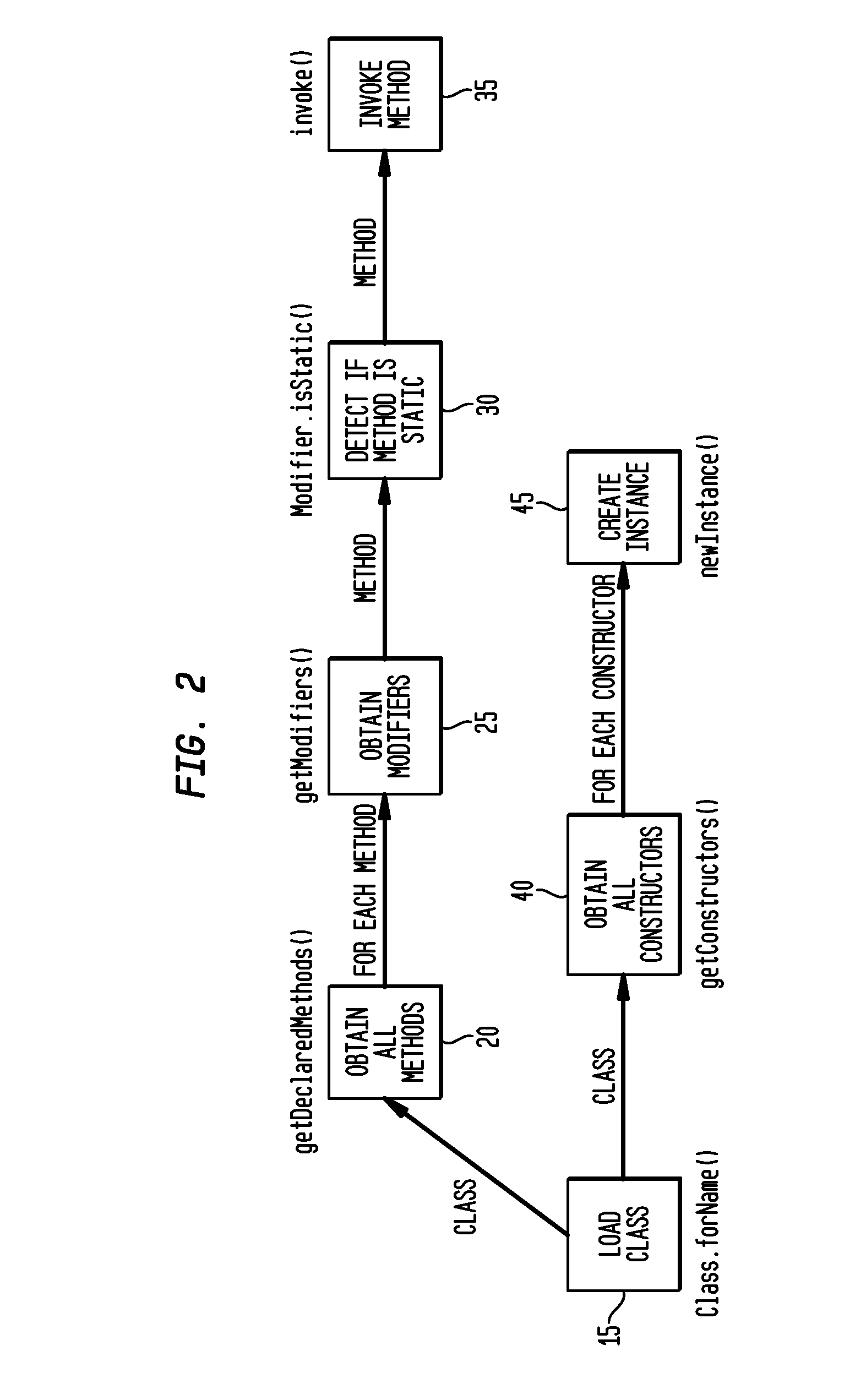
Mutability analysis in Java
InactiveUS6925638B1Reduce security risksEnsure maintenanceSoftware engineeringSpecific program execution arrangementsExtensibilityHuman language
A system and method for detecting the mutability of fields and classes in an arbitrary program component written in an object oriented programming language is disclosed. A variable is considered to be mutable if a new value is stored into it, as well as if any of its reachable variables are mutable. The system and method uses a static analysis algorithm which can be applied to any software component rather than whole programs. The analysis classifies fields and classes as either mutable or immutable. In order to facilitate open-world analysis, the algorithm identifies situations that expose variables to potential modification by code outside the component, as well as situations where variables are modified by the analyzed code. An implementation of the analysis is presented which focuses on detecting mutability of class variables, so as to avoid isolation problems. The implementation incorporates intra- and inter-procedural data-flow analyses and is shown to be highly scalable. Experimental results demonstrate the effectiveness of the algorithms.
Owner:IBM CORP
Apparatus and method for testing secure software
InactiveUS20050273859A1Memory loss protectionError detection/correctionProgram instructionPerformance results
A computer readable medium includes executable instructions to analyze program instructions for security vulnerabilities. Executable instructions identify potential security vulnerabilities within program instructions based upon input from an attack database and information derived during a static analysis of the program instructions. Vulnerability tests are applied to the program instructions in view of the security vulnerabilities. Performance results from the vulnerability tests are analyzed. The performance results are then reported.
Owner:FORTIFY SOFTWARE
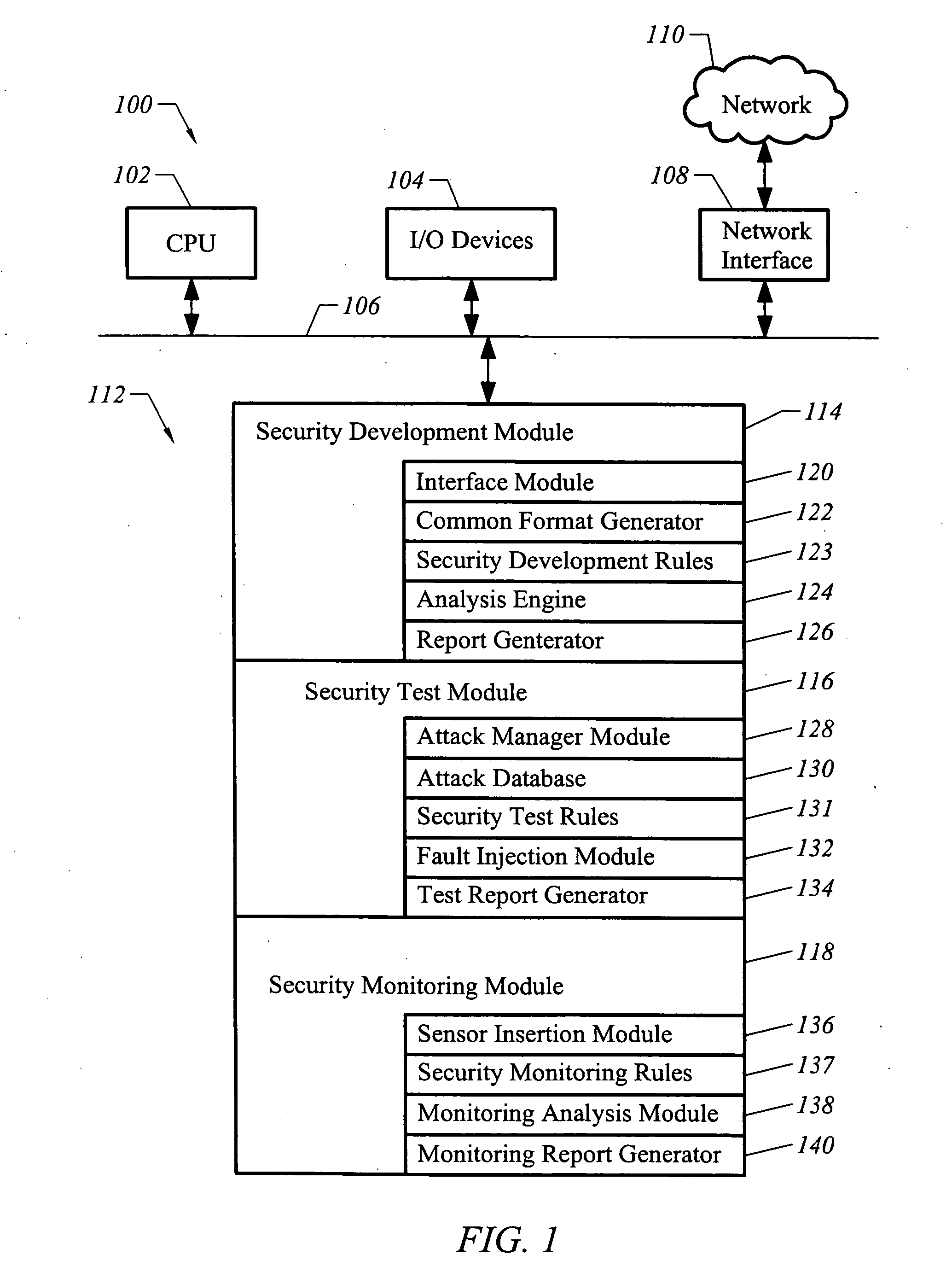
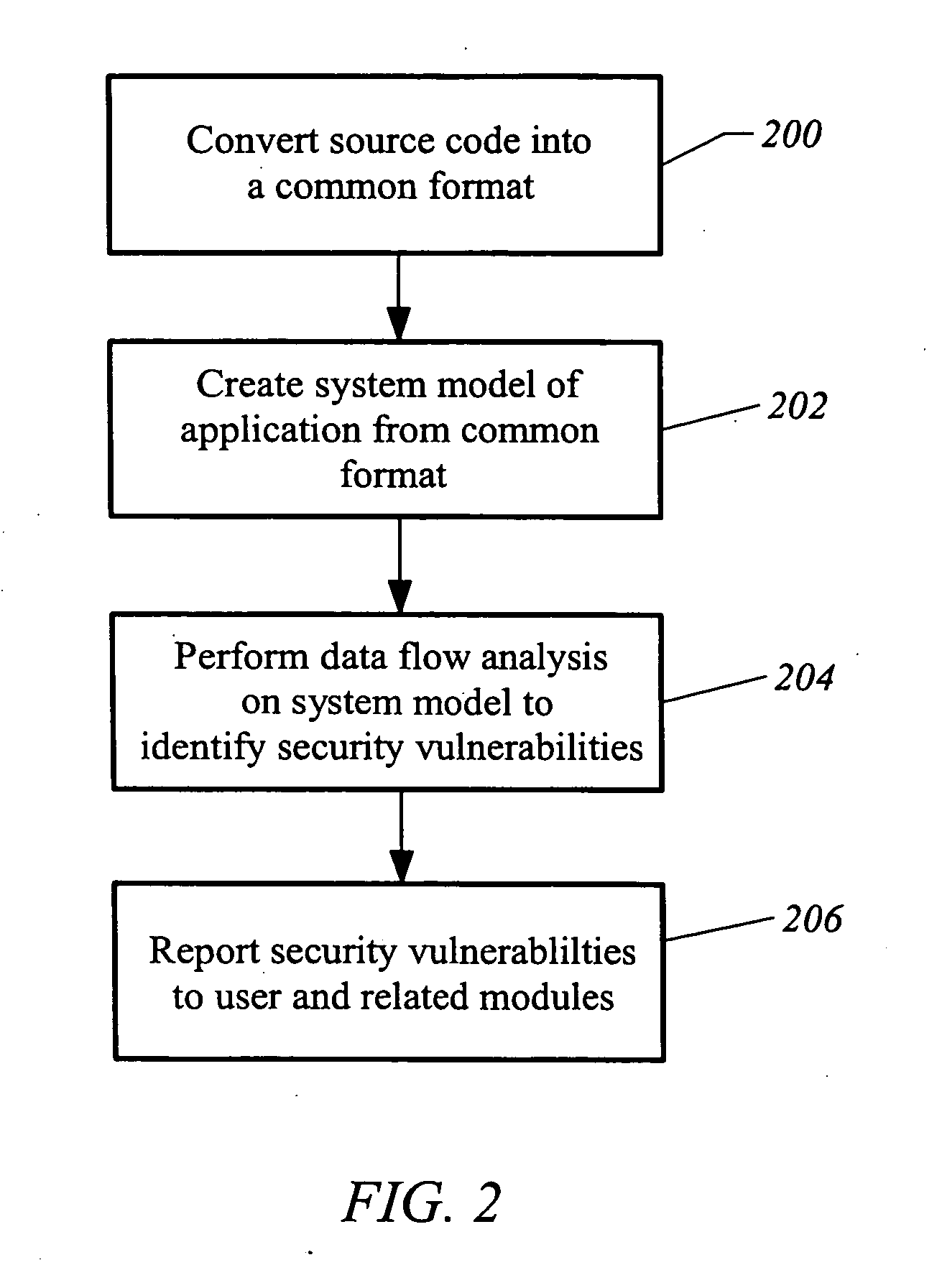
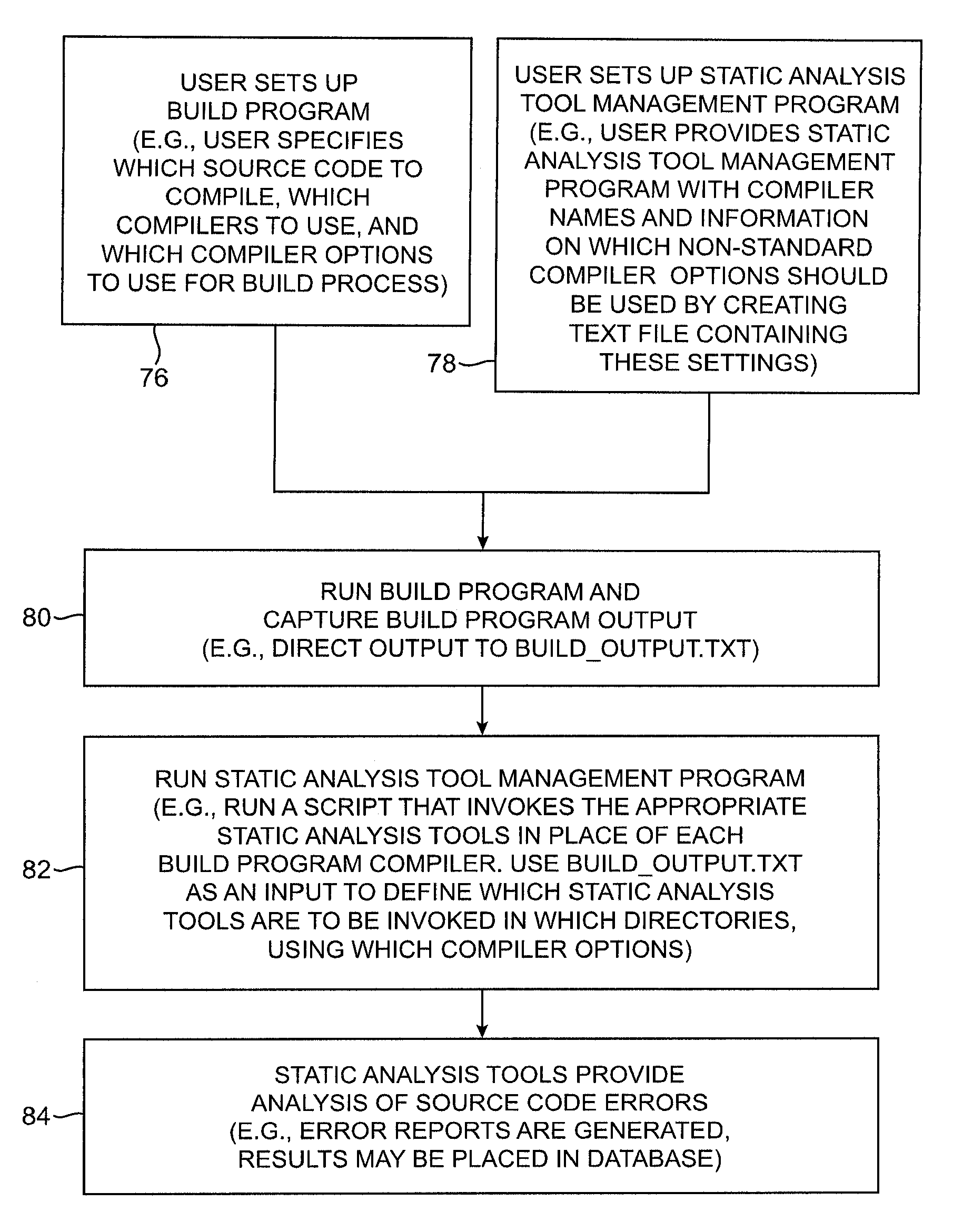
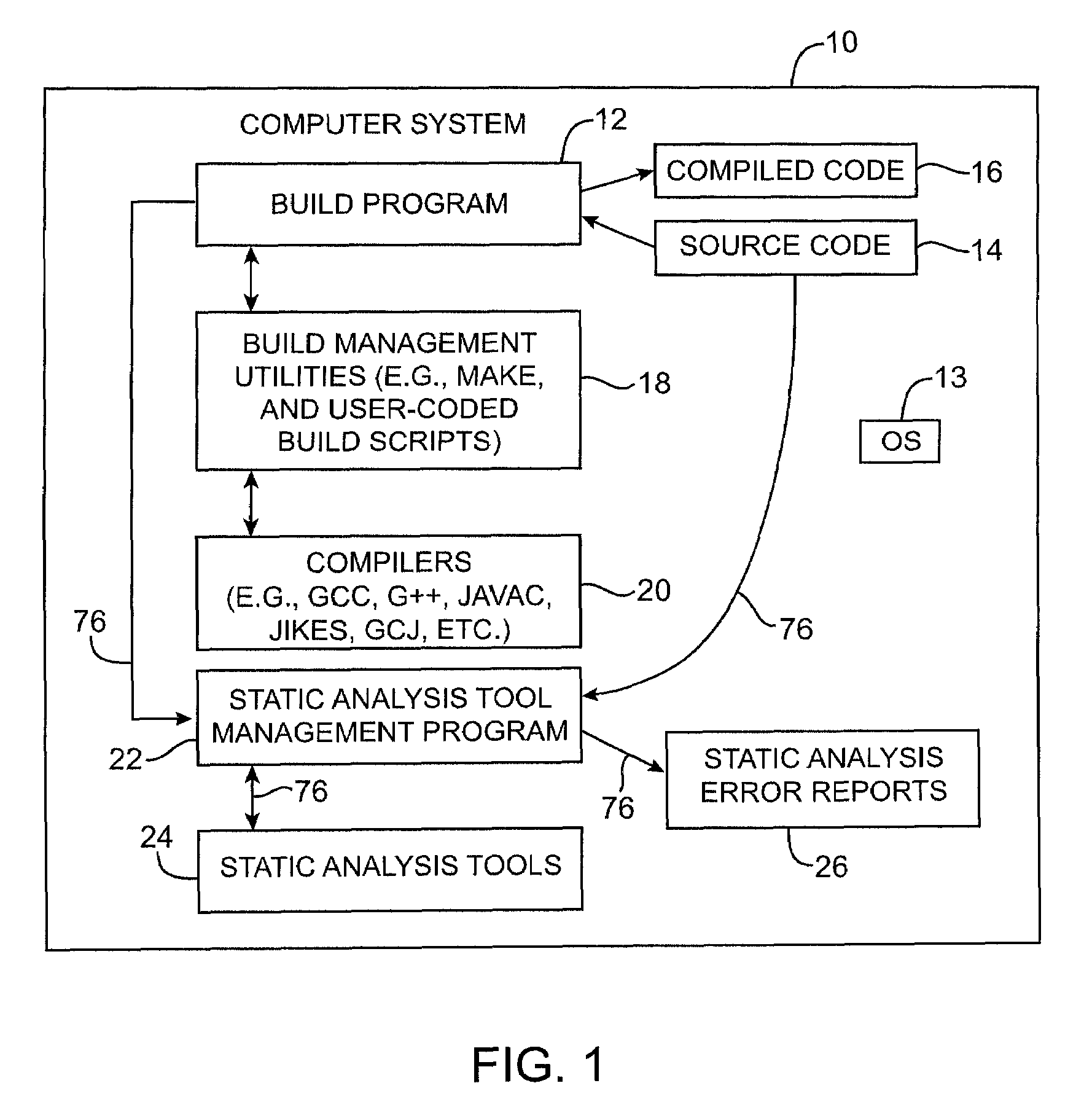
Systems and methods for performing static analysis on source code
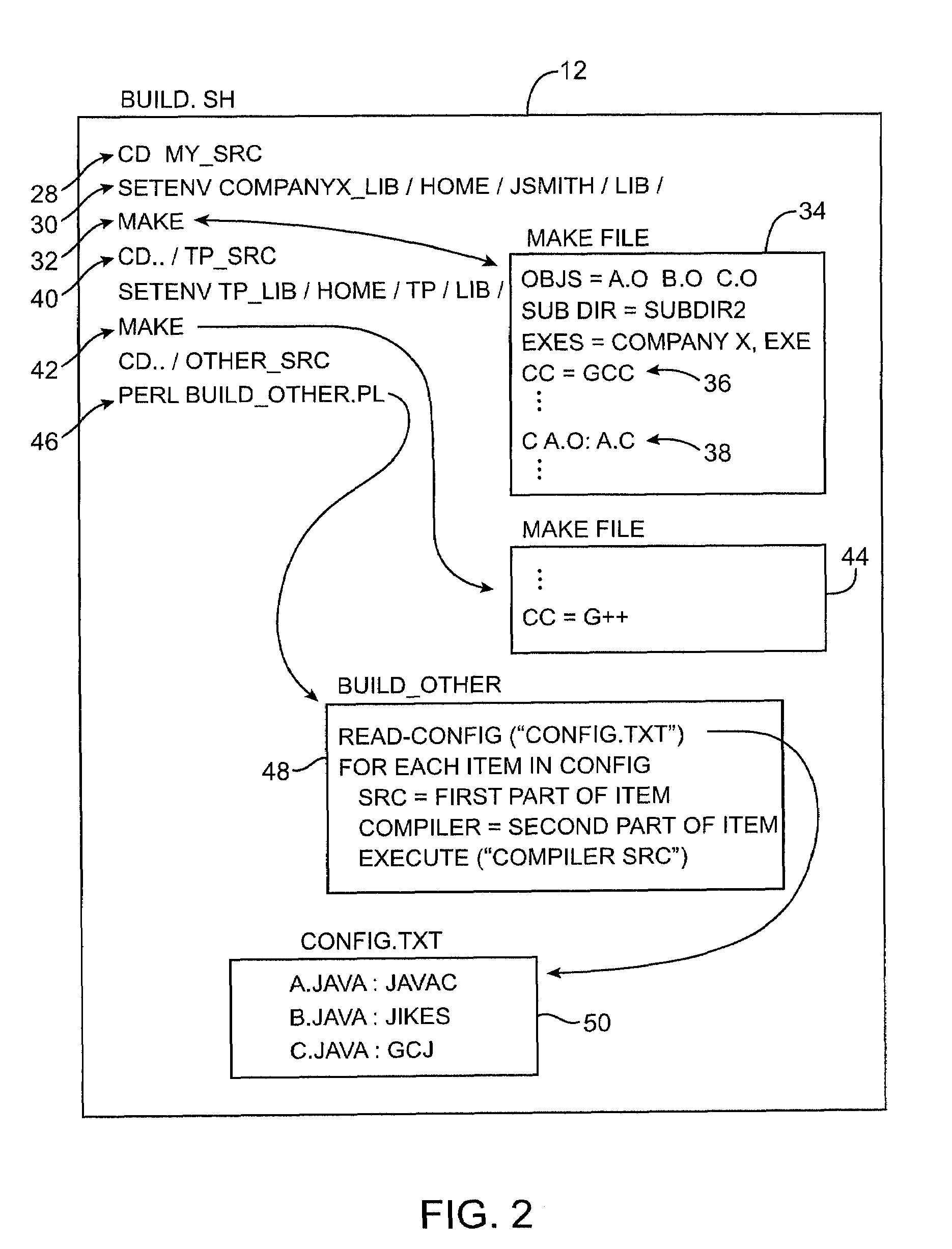
Systems and methods are provided for performing static error analysis on source code. A computer system having an operating system may contain a number of source code files. During a normal build process, a build program may be used to set various compilation options and to invoke appropriate compilers that compile the source code files into executable code. Static analysis debugging tools may be used to perform static analysis on the source code files. The appropriate static analysis tools may be invoked using a static analysis tool management program. Directory, path and name modification may be used to invoke the analysis tools. A monitoring program may be used to determine how to invoke the tools. The operating system may be modified so that the static analysis tools are invoked in place of the compilers when the build program is run.
Owner:SYNOPSYS INC
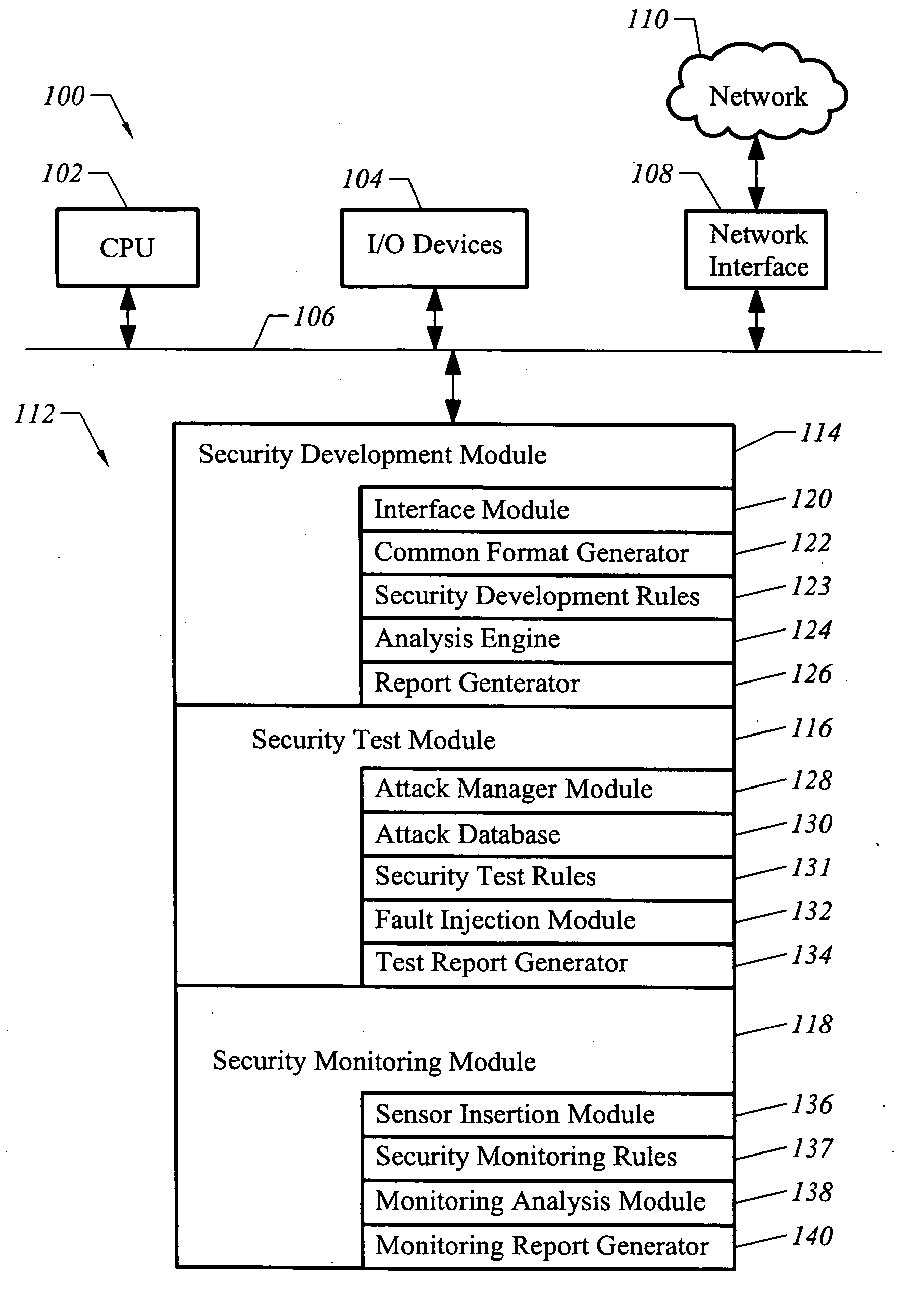
Apparatus and method for developing, testing and monitoring secure software
InactiveUS20050273860A1Memory loss protectionError detection/correctionProgram instructionSafety testing
A method of analyzing program instructions for security vulnerabilities includes applying a static analysis to program instructions during a development phase of the program instructions to identify security vulnerabilities. The security vulnerabilities are used to apply a security test to the program instructions during a testing phase of the program instructions. The security vulnerabilities are analyzed to develop security monitoring criteria to apply to the program instructions during a deployment phase of the program instructions.
Owner:FORTIFY SOFTWARE
Method and system for run-time dynamic and interactive identification of software authorization requirements and privileged code locations, and for validation of other software program analysis results
InactiveUS20070261124A1Digital data processing detailsUser identity/authority verificationProgram analysisSecurity policy
A system, method and computer program product for identifying security authorizations and privileged-code requirements; for validating analyses performed using static analyses; for automatically evaluating existing security policies; for detecting problems in code; in a run-time execution environment in which a software program is executing. The method comprises: implementing reflection objects for identifying program points in the executing program where authorization failures have occurred in response to the program's attempted access of resources requiring authorization; displaying instances of identified program points via a user interface, the identified instances being user selectable; for a selected program point, determining authorization and privileged-code requirements for the access restricted resources in real-time; and, enabling a user to select, via the user interface, whether a required authorization should be granted, wherein local system, fine-grained access of resources requiring authorizations is provided.
Owner:IBM CORP
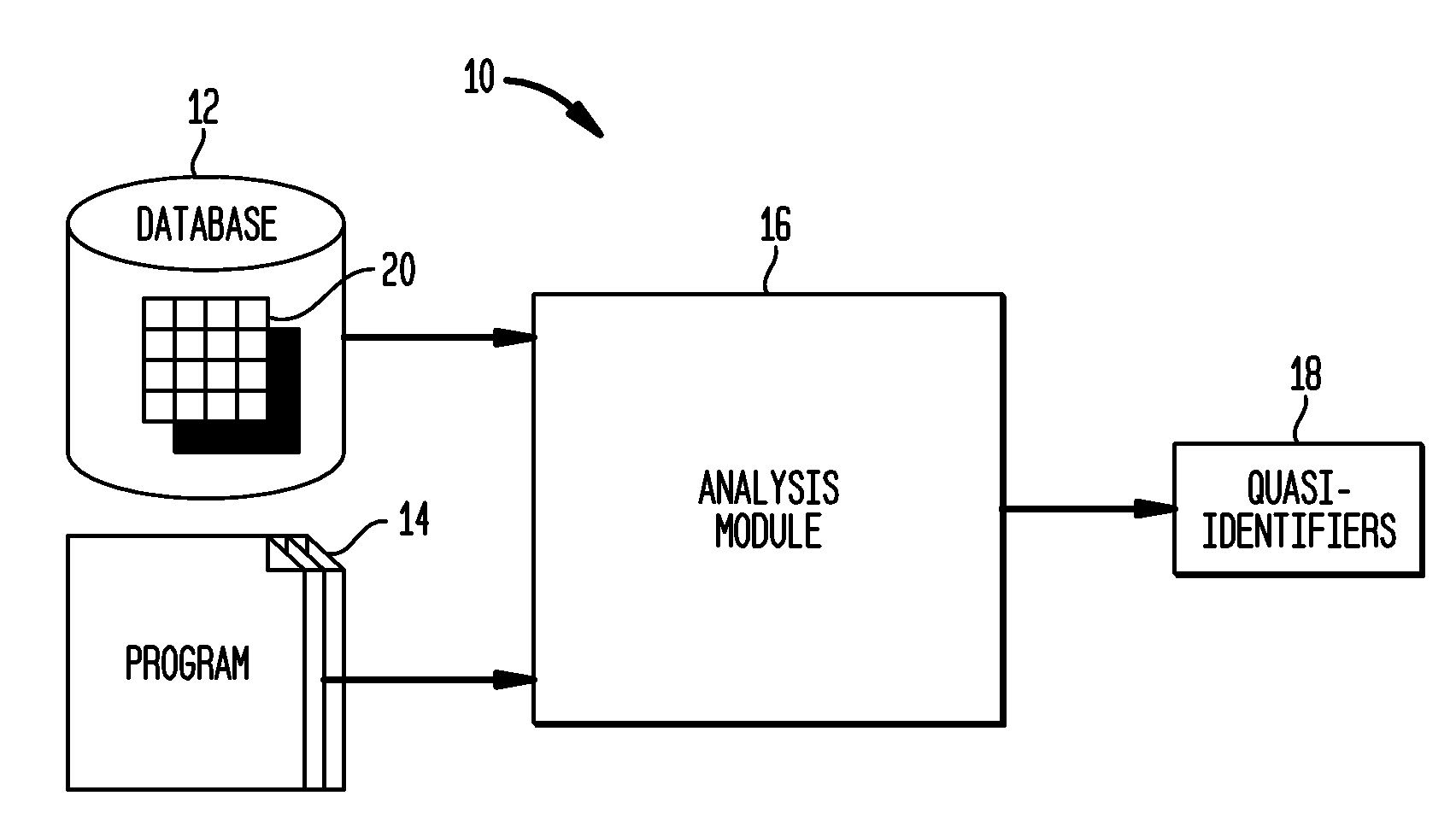
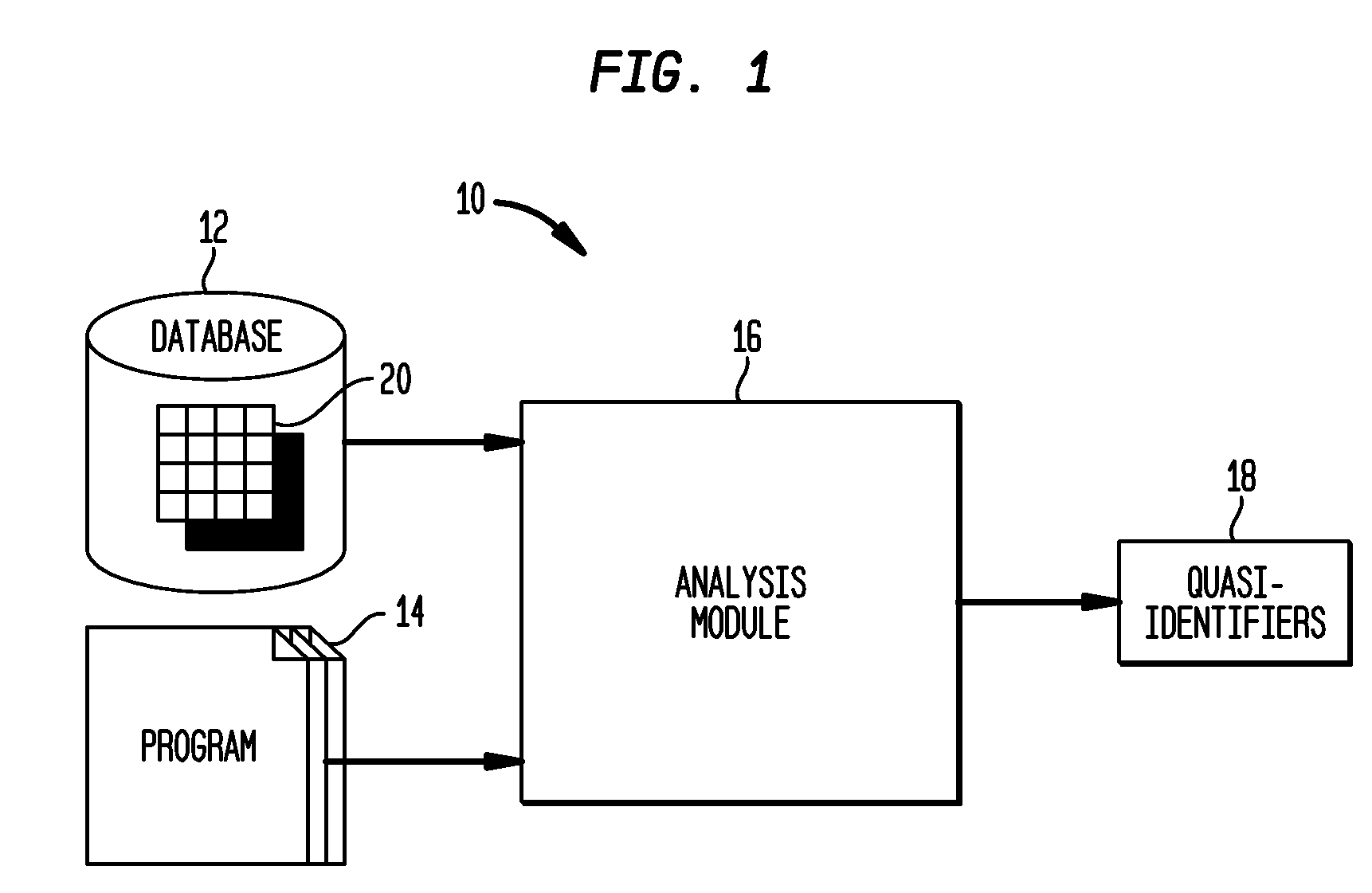
Automated Determination of Quasi-Identifiers Using Program Analysis
A system and method for automated determination of quasi-identifiers for sensitive data fields in a dataset are provided. In one aspect, the system and method identifies quasi-identifier fields in the dataset based upon a static analysis of program statements in a computer program having access to—sensitive data fields in the dataset. In another aspect, the system and method identifies quasi-identifier fields based upon a dynamic analysis of program statements in a computer program having access to—sensitive data fields in the dataset. Once such quasi-identifiers have been identified, the data stored in such fields may be anonymized using techniques such as k-anonymity. As a result, the data in the anonymized quasi-identifiers fields cannot be used to infer a value stored in a sensitive data field in the dataset.
Owner:TELCORDIA TECHNOLOGIES INC
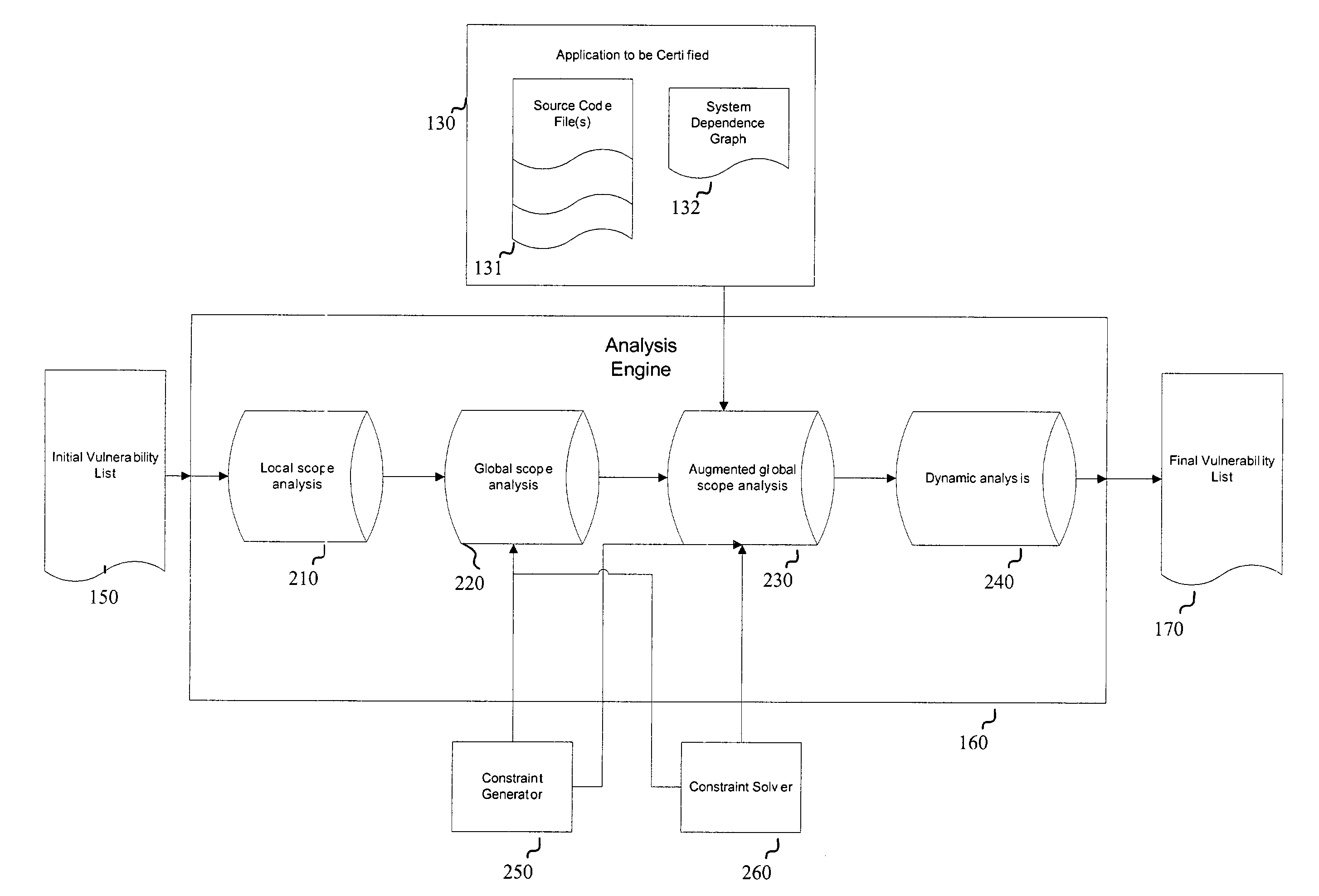
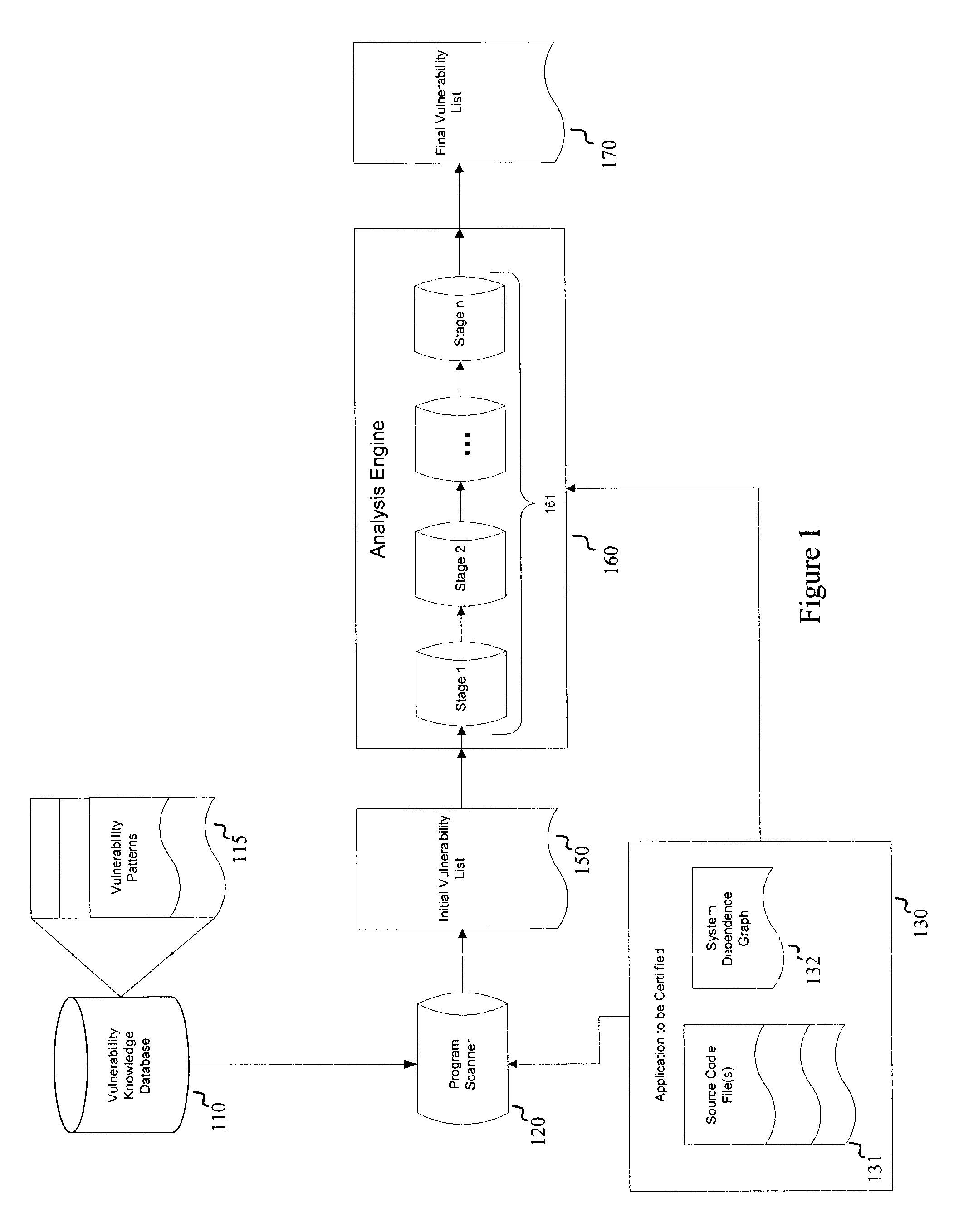
Systems and methods for detecting software security vulnerabilities
ActiveUS7392545B1Memory loss protectionUnauthorized memory use protectionApplication softwareVulnerability
Embodiments of the present invention relate to systems and methods for static analysis of a software application. According to an embodiment, a system includes a program scanner coupled to an analysis engine. The program scanner is configured to identify one or more vulnerability patterns in a software program and to output an initial potential vulnerability list. The analysis engine is configured to apply one or more rules to a potential vulnerability to determine whether the potential vulnerability is a vulnerability.
Owner:SYNOPSYS INC
Quantitative characterization method of low penetration double-medium sandstone oil reservoir microscopic aperture structure
ActiveCN103278436AIncrease reflectionAvoid one-sidednessPermeability/surface area analysisNMR - Nuclear magnetic resonanceRock core
The invention provides a quantitative characterization method of low penetration double-medium sandstone oil reservoir microscopic aperture structure, which comprises the following steps: selecting experiment samples, effectively combining various experiments, distributing samples, processing and analyzing experiment test data, combining macroscopic background and microscopic rock core, and combining static state analysis and dynamic production reality, thereby realizing quantitative characterization of ultra-low penetration double-medium sandstone oil reservoir microscopic aperture structure from qualitative analysis and semi-quantitative evaluation. The invention has the advantages that more comprehensive influence factors and micro crack, aperture throat parameter and nuclear magnetic resonance movable fluid parameter are considered, so the characterization result can better reflect change characteristics of ultra-low penetration double-medium sandstone oil reservoir microscopic aperture structure, which are consistent to the production exploitation real cases of the oil field, thereby effectively avoiding one-sidedness and limitation of single aspect evaluation result.
Owner:XI'AN PETROLEUM UNIVERSITY
Method and system for run-time dynamic and interactive identification of software authorization requirements and privileged code locations, and for validation of other software program analysis results
ActiveUS20090007223A1Service is blockedOptimizationComputer security arrangementsTransmissionSystems approachesSecurity policy
Owner:INT BUSINESS MASCH CORP
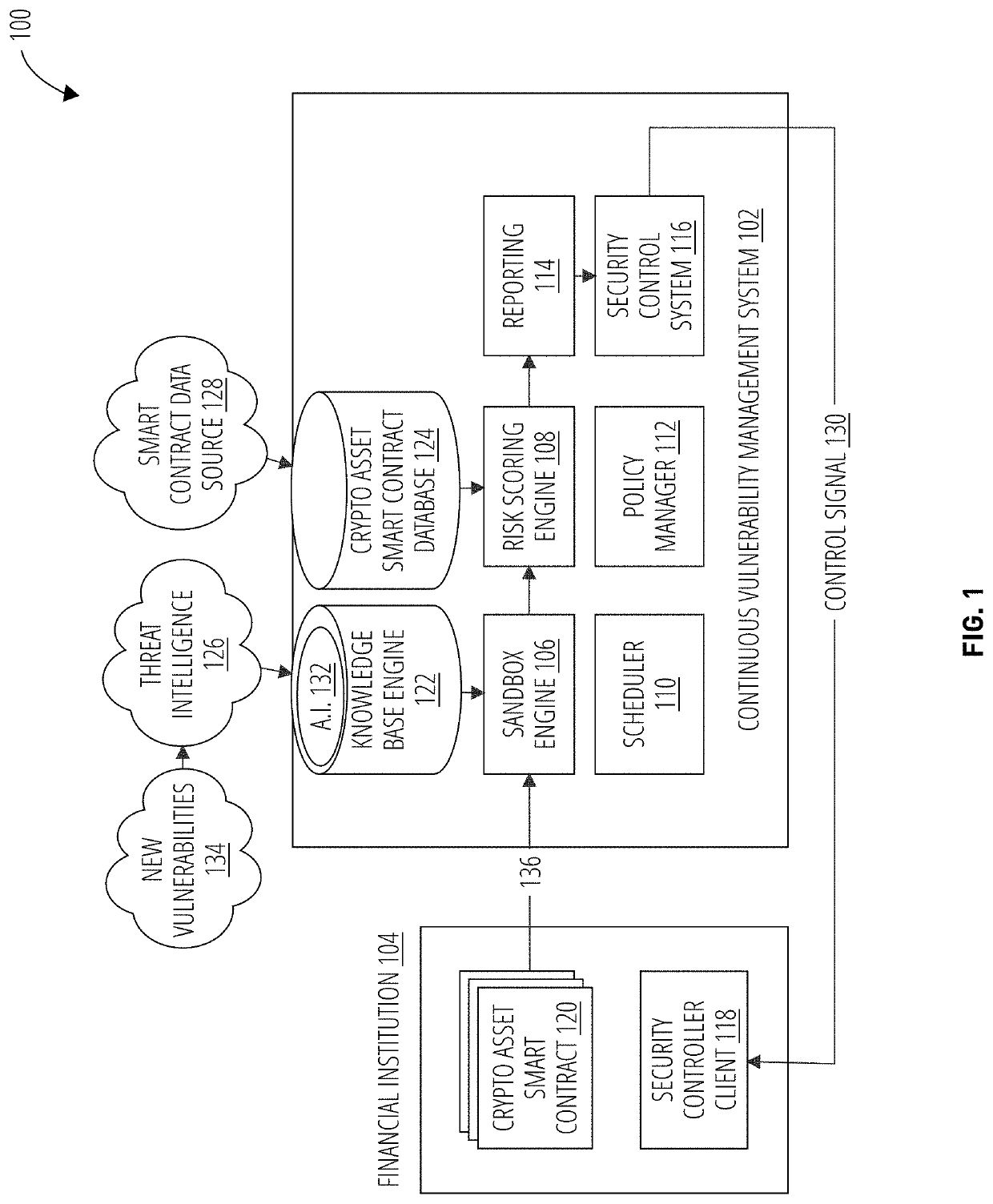
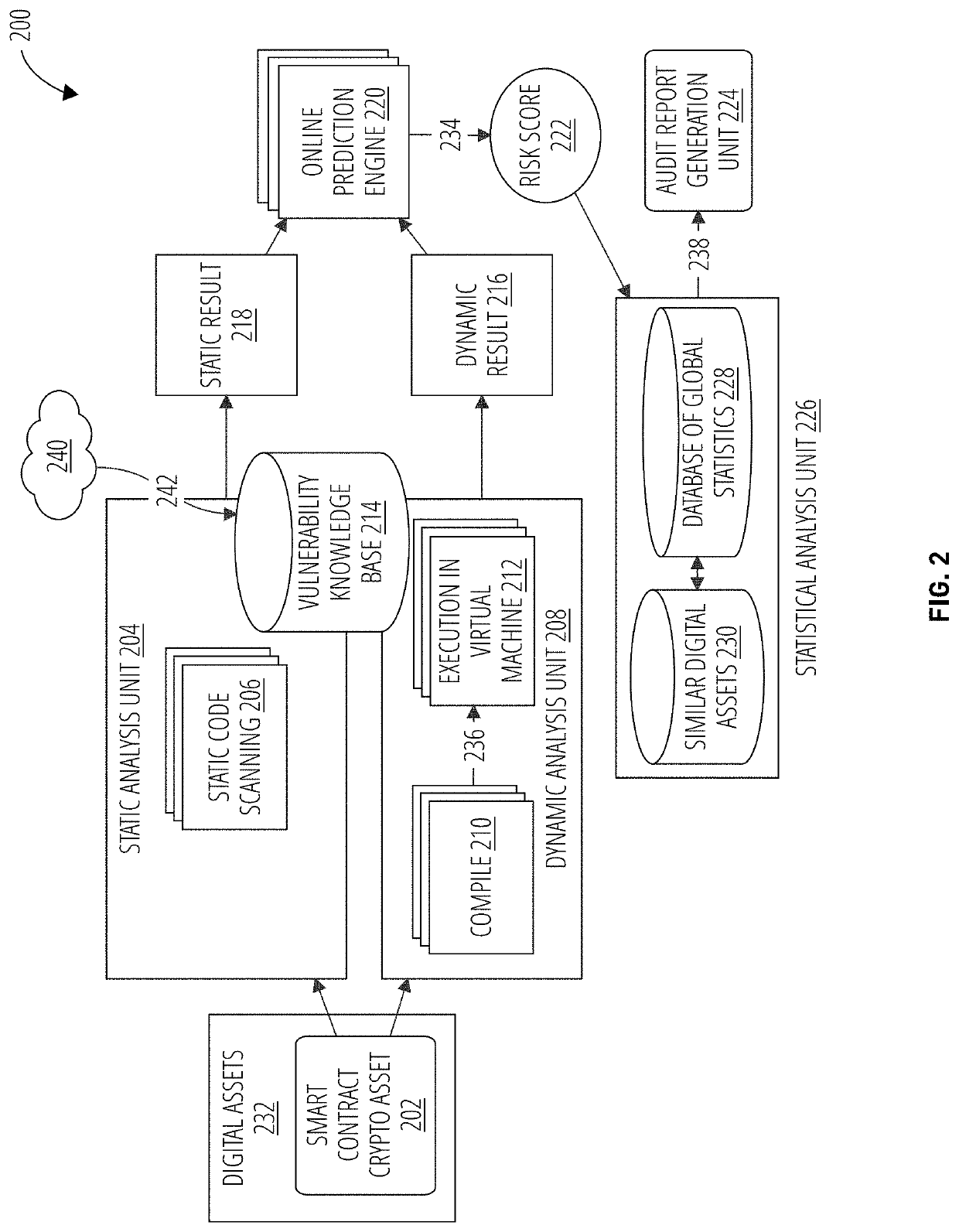
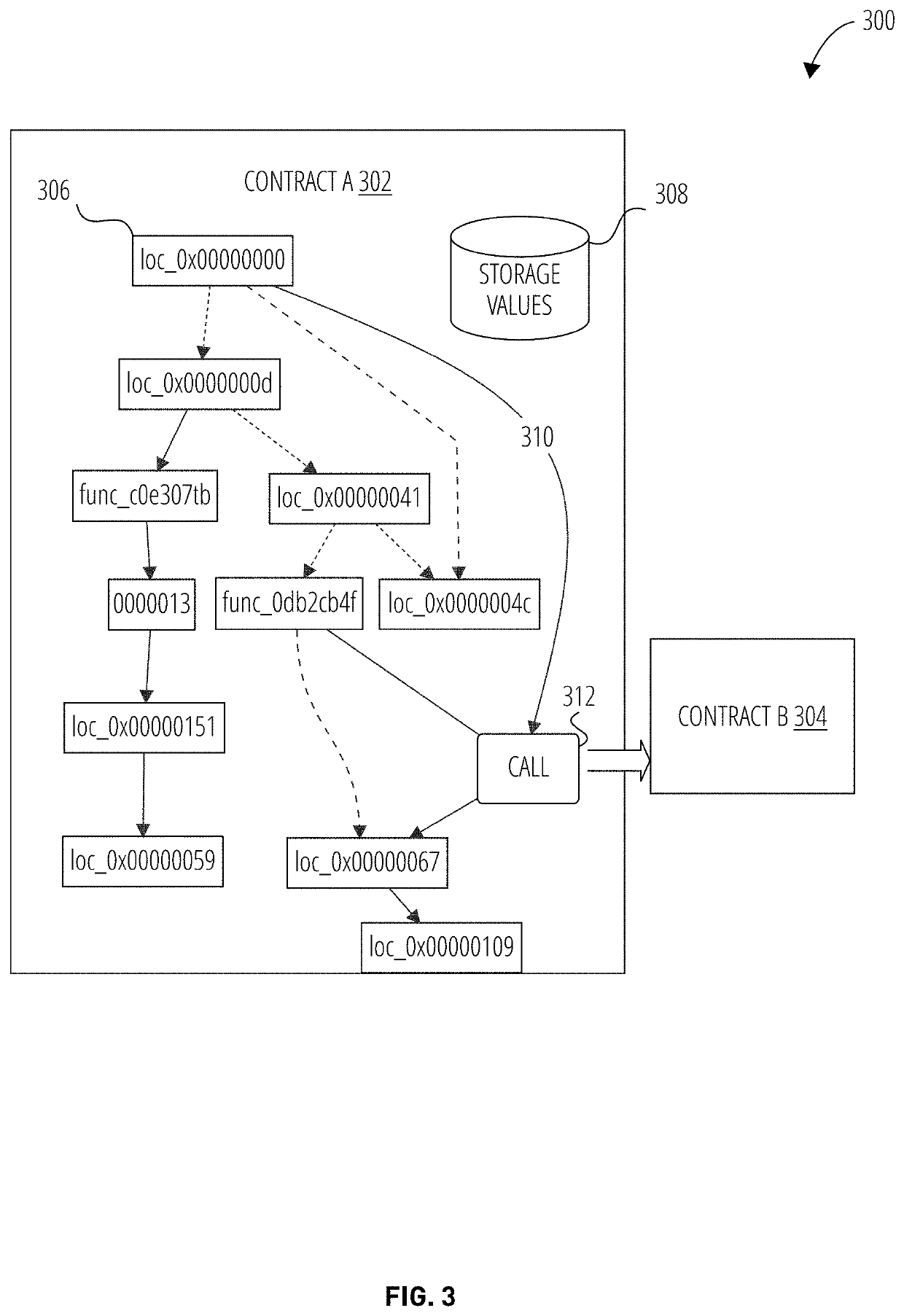
Continuous vulnerability management system for blockchain smart contract based digital asset using sandbox and artificial intelligence
ActiveUS20210110047A1Database distribution/replicationPayment protocolsStatistical analysisReliability engineering
A continuous vulnerability management system for identifying, analyzing, protecting, and reporting on digital assets is disclosed. The continuous vulnerability management system comprises a sandbox engine configured to scan digital assets for vulnerabilities, including a static analysis unit for static code scanning, a dynamic analysis unit for analyzing compiled code, and a statistical analysis unit for processing a risk score and generating an audit report. A knowledge base is also disclosed, including a knowledge base engine configured to acquire information related to new vulnerabilities to digital assets. A risk scoring engine is configured to analyze sandbox engine outcomes and assign a risk score to each vulnerable asset. A security control system is configured to act on an identified vulnerable asset based on the risk score assigned to the identified vulnerable asset.
Owner:ANCHAIN AI INC
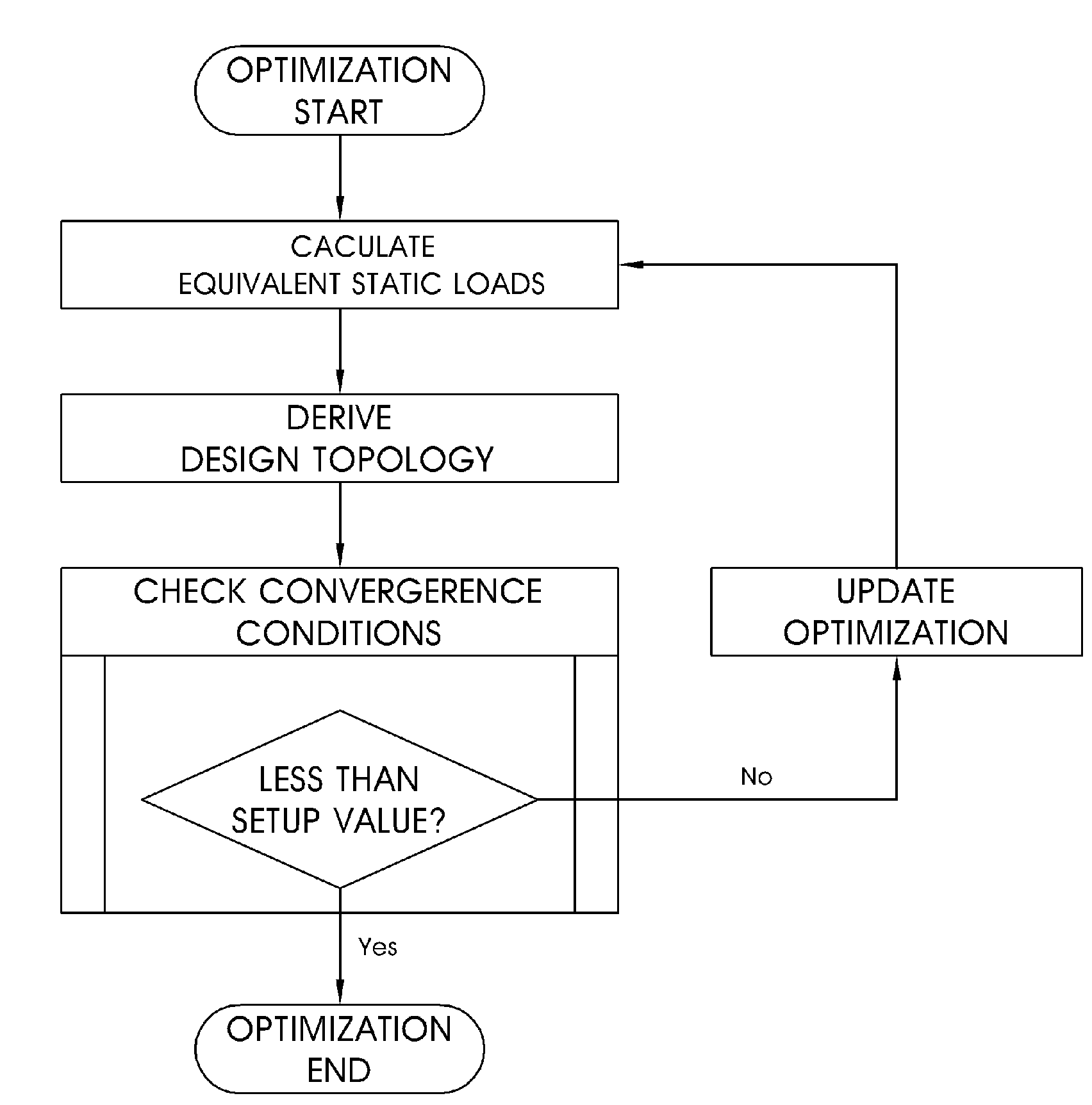
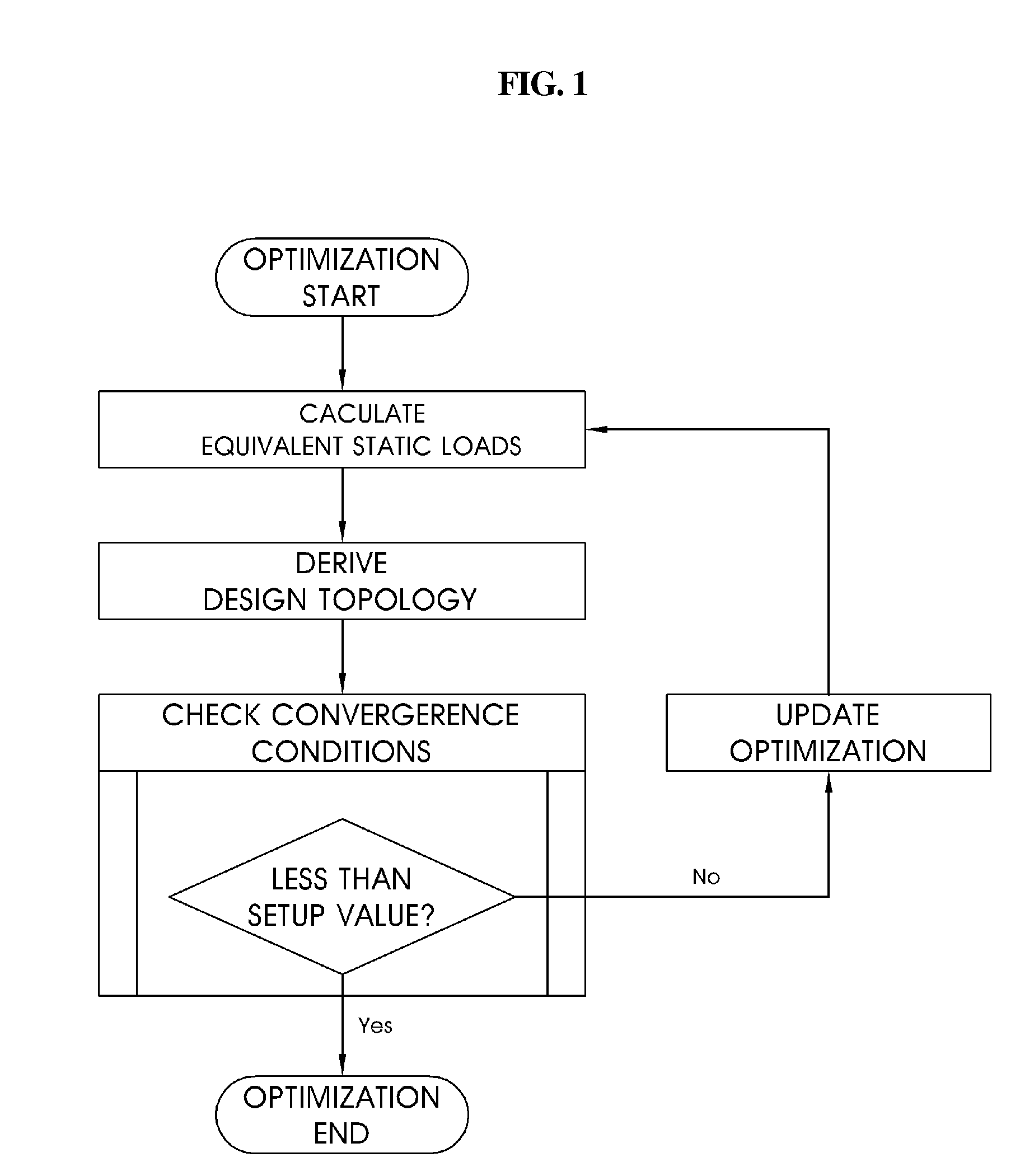
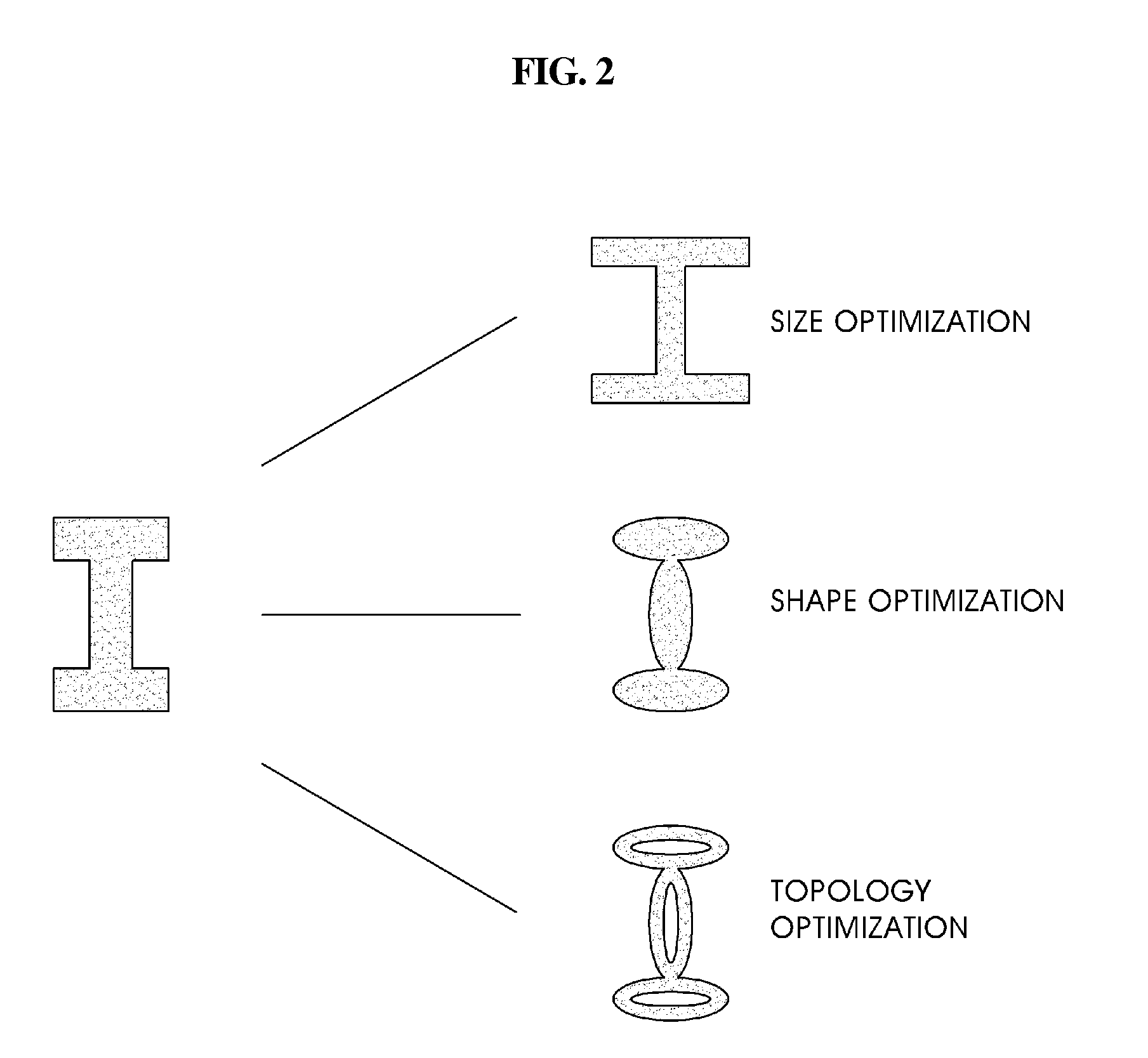
Topology optimization method using equivalent static loads
InactiveUS20100058257A1Accurate solutionReduce in quantityMulti-objective optimisationSoftware simulation/interpretation/emulationTopology optimizationEngineering
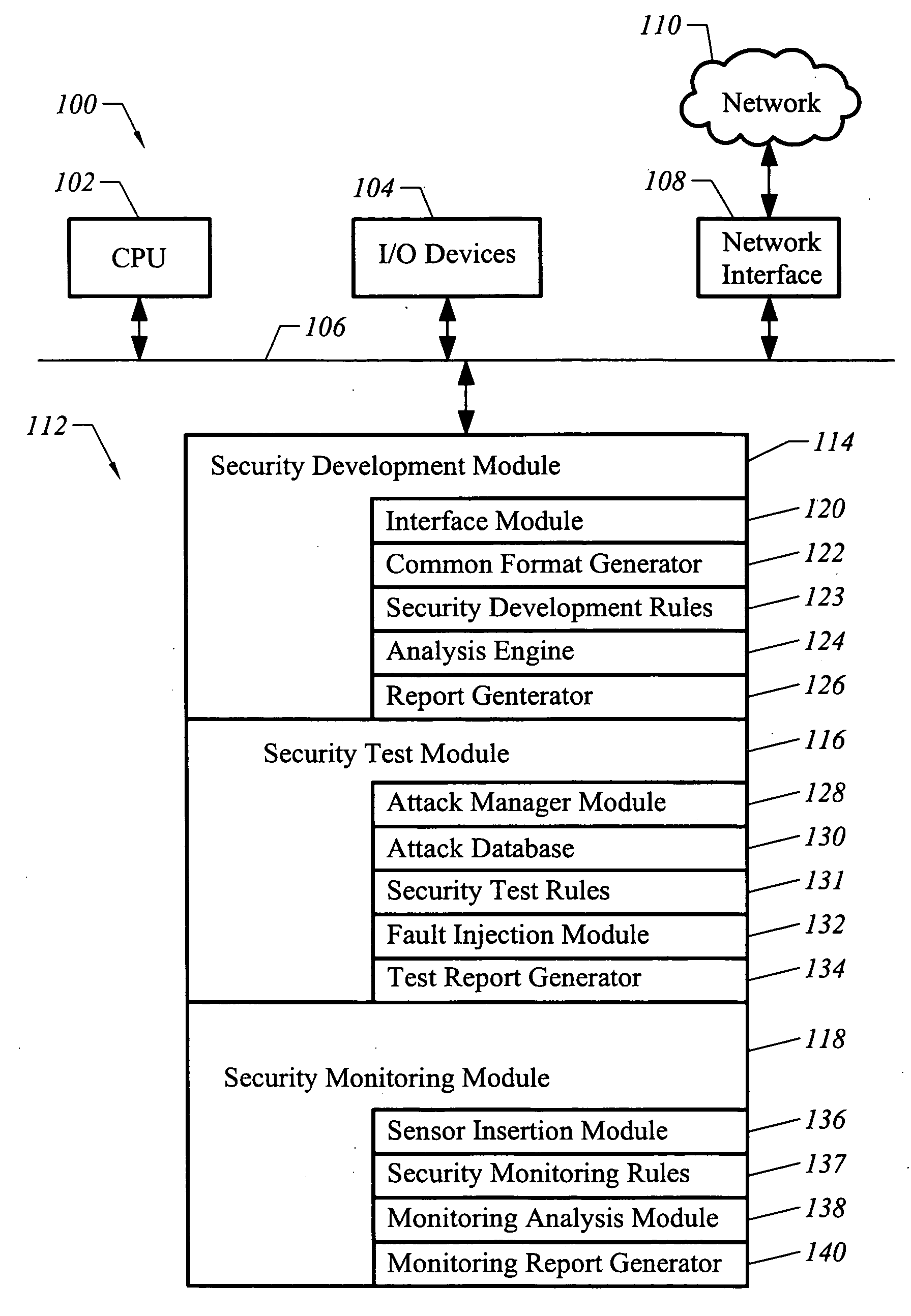
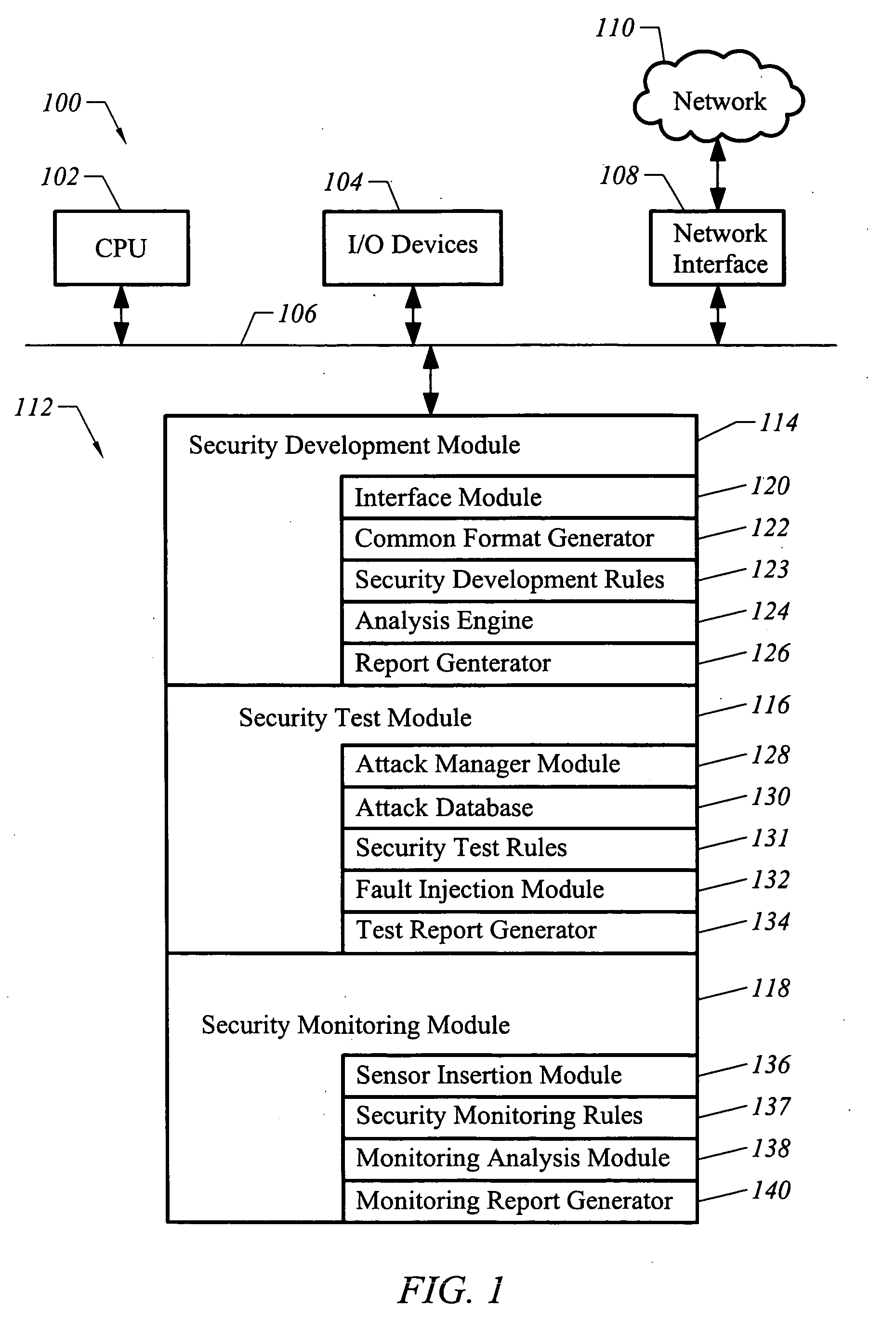
A topology optimization method. Characteristics of a structure to be designed are differentiated to calculate equivalent static loads. A relative fraction of material is adopted as a design variable. It is determined whether or not an element exists based on an objective function and constraints. Design topology is derived through a linear static analysis that processes the equivalent static loads as multiple loading conditions. Topology of the structure to be designed is compared with the design topology, and thereby the progress of optimization is determined. The topology optimization processes are terminated when a difference of the compared result is less than a setup value, and are returned to an initial step when the difference is greater than the setup value, and the equivalent static loads are calculated using the design topology as a new structure to be designed.
Owner:IUCF HYU (IND UNIV COOP FOUNDATION HANYANG UNIV)
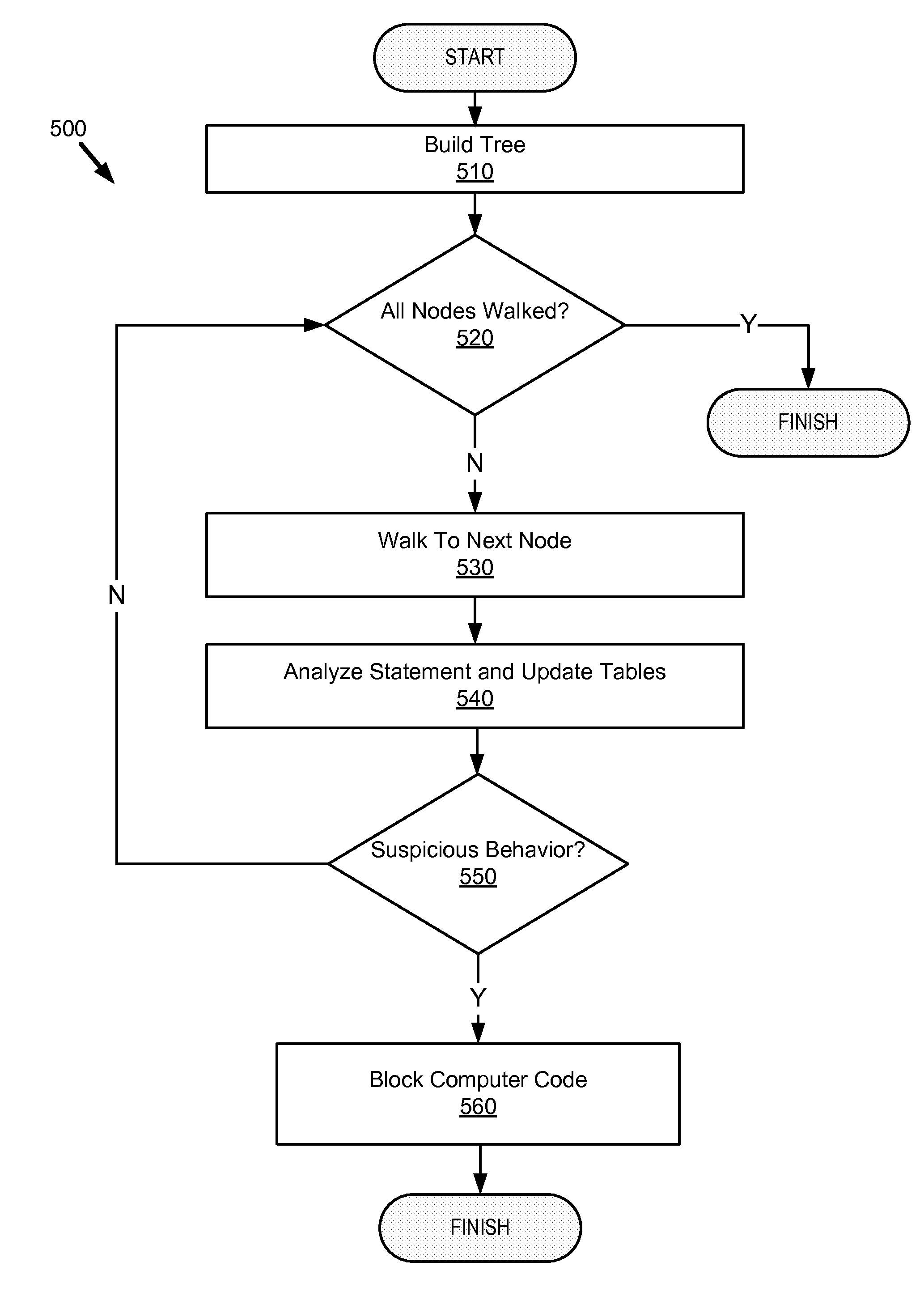
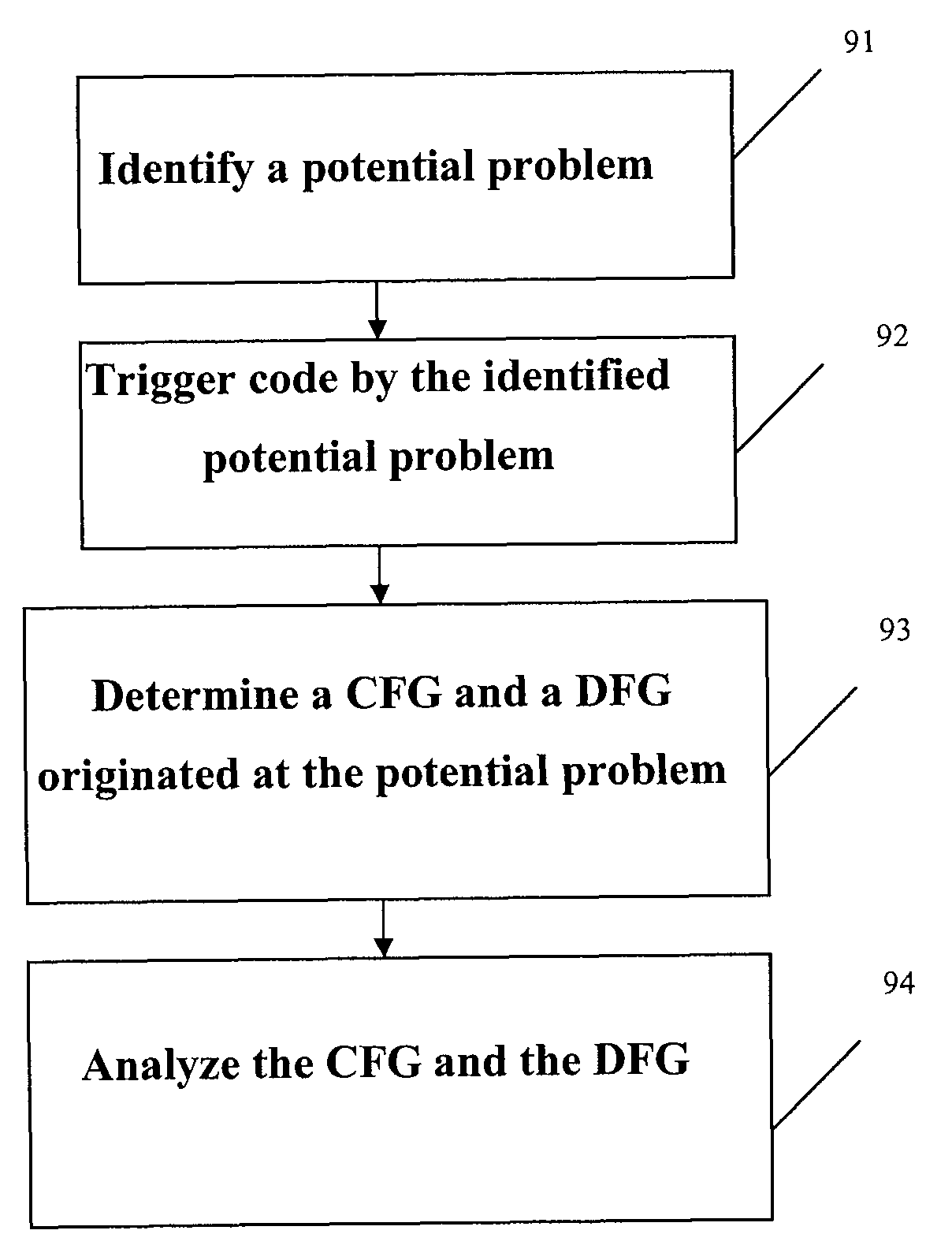
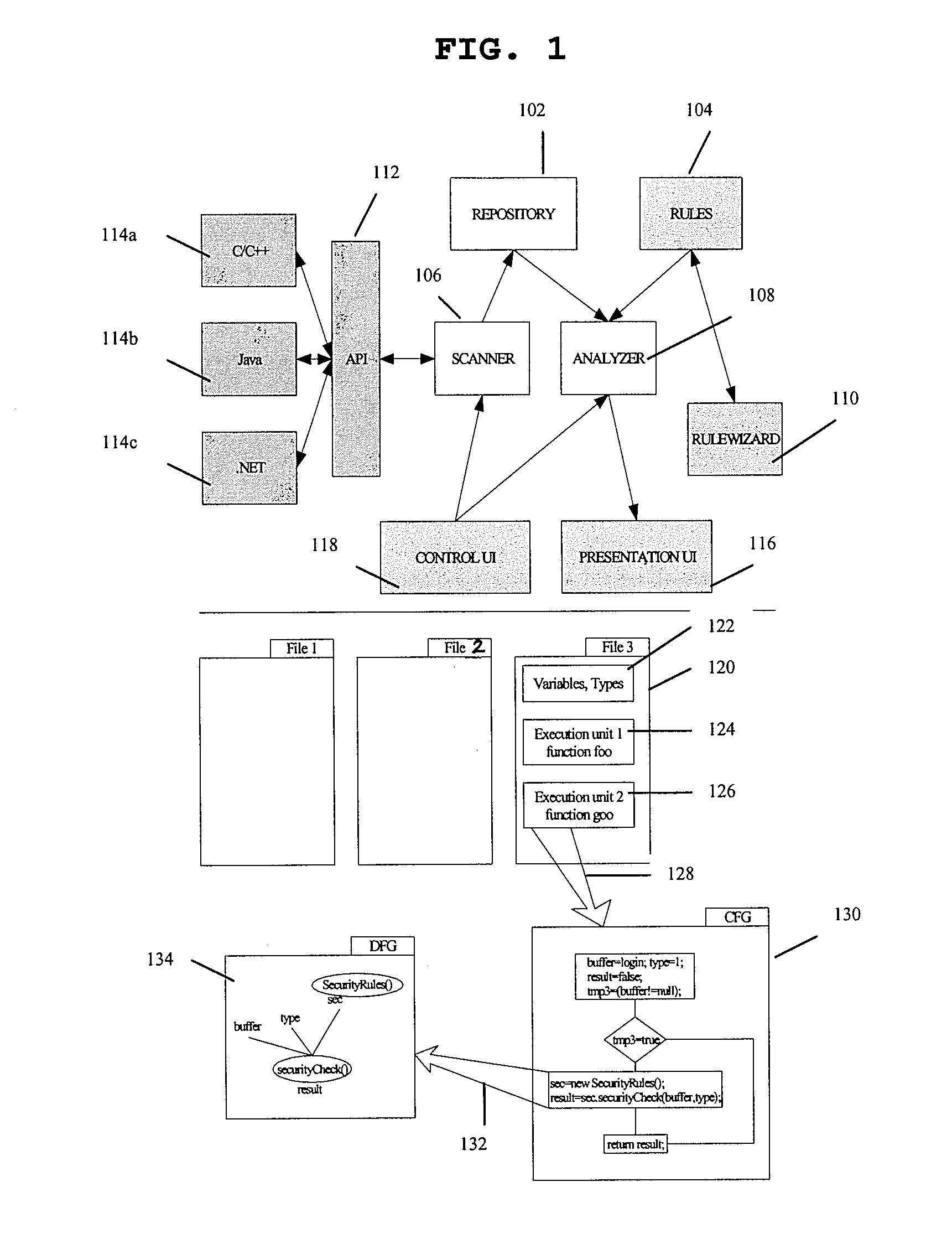
System and method for detecting defects in a computer program using data and control flow analysis
ActiveUS7900193B1Keep trackError detection/correctionSpecific program execution arrangementsTheoretical computer scienceControl flow analysis
A system and method for identifying errors in a computer software include: identifying a potential problem in the computer software; triggering a portion of the computer software by the identified potential problem; determining a control flow graph and a data flow graph for the triggered portion of the computer software originating at the identified potential problem; and analyzing the control flow graph and the data flow graph to verify that the identified potential problem is an actual error. The potential problem may be identified using test tools such as a static analysis tool or a unit test tool.
Owner:PARASOFT
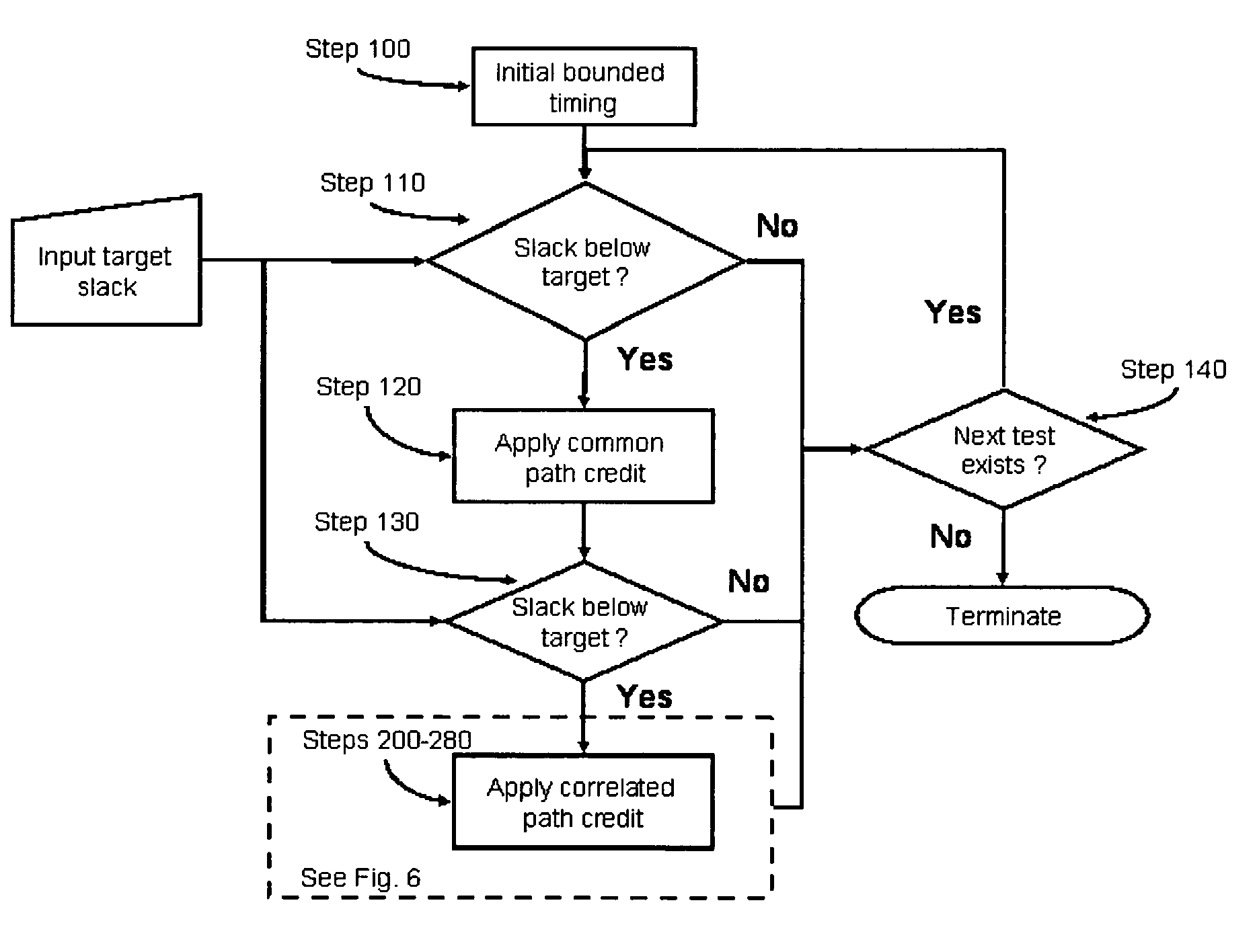
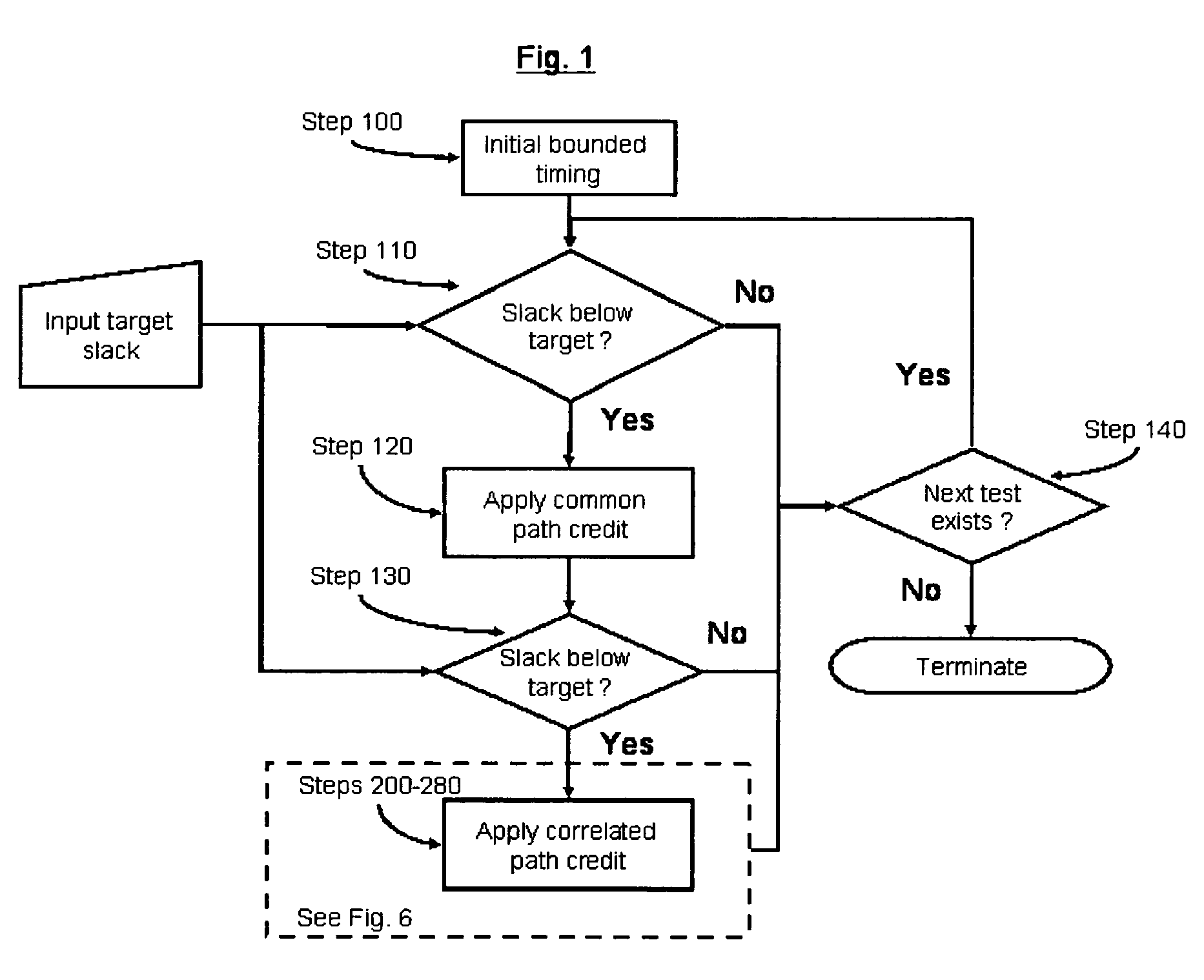
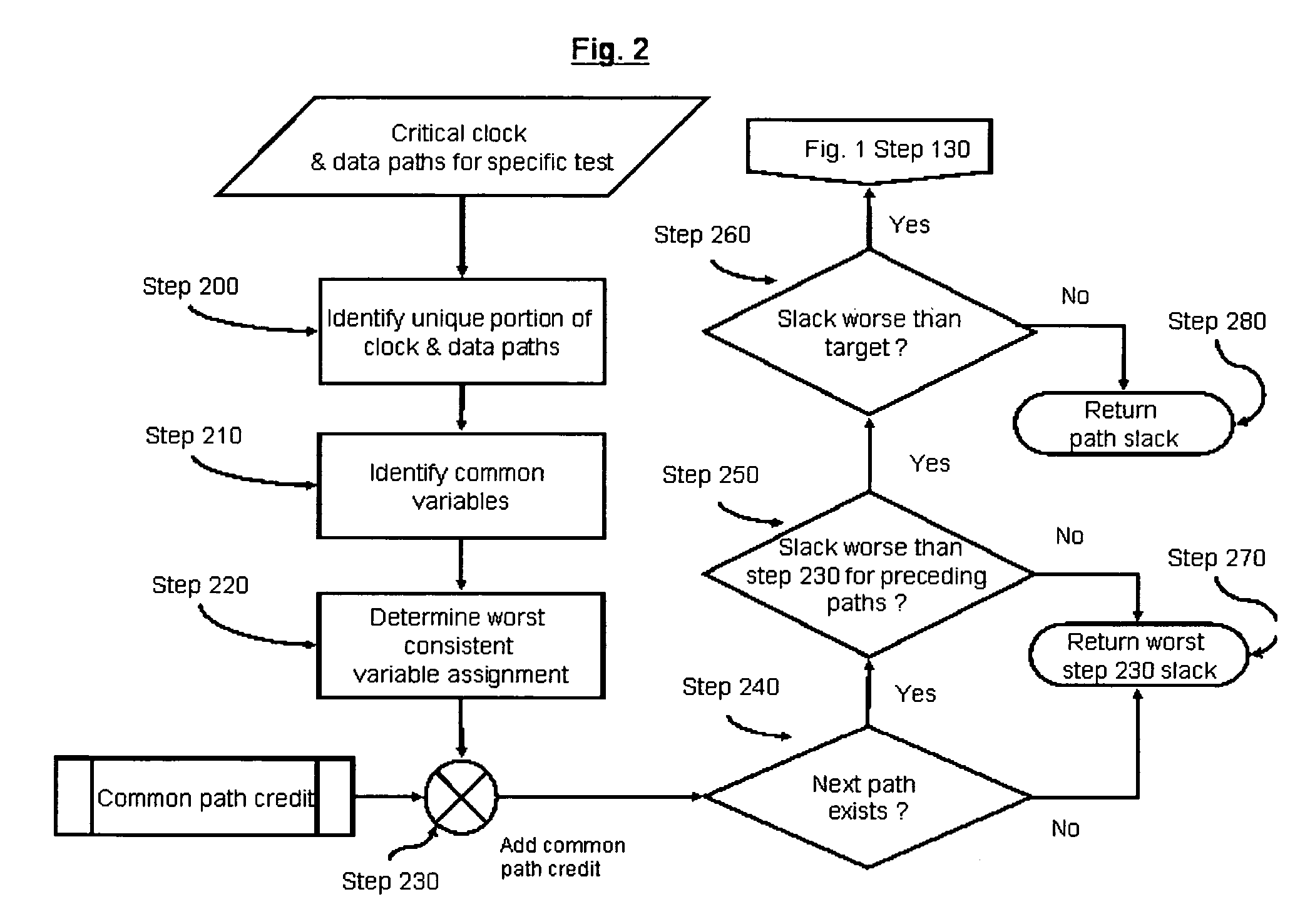
System and method for correlated process pessimism removal for static timing analysis
InactiveUS7117466B2Reduce pessimismComputer aided designSoftware simulation/interpretation/emulationStatic timing analysisAngular point
A method of removing pessimism in static timing analysis is described. Delays are expressed as a function of discrete parameter settings allowing for both local and global variation to be taken in to account. Based on a specified target slack, each failing timing test is examined to determine a consistent set of parameter settings which produces the worst possible slack. The analysis is performed on a path basis. By considering only parameters which are in common to a particular data / clock path-pair, the number of process combinations that need to be explored is reduced when compared to analyzing all combinations of the global parameter settings. Further, if parameters are separable and linear, worst-case variable assignments for a particular clock / data path pair can be computed in linear time by independently assigning each parameter value. In addition, if available, the incremental delay change with respect to each physically realizable process variable may be used to project the worst-case variable assignment on a per-path basis without the need for performing explicit corner enumeration.
Owner:GLOBALFOUNDRIES INC
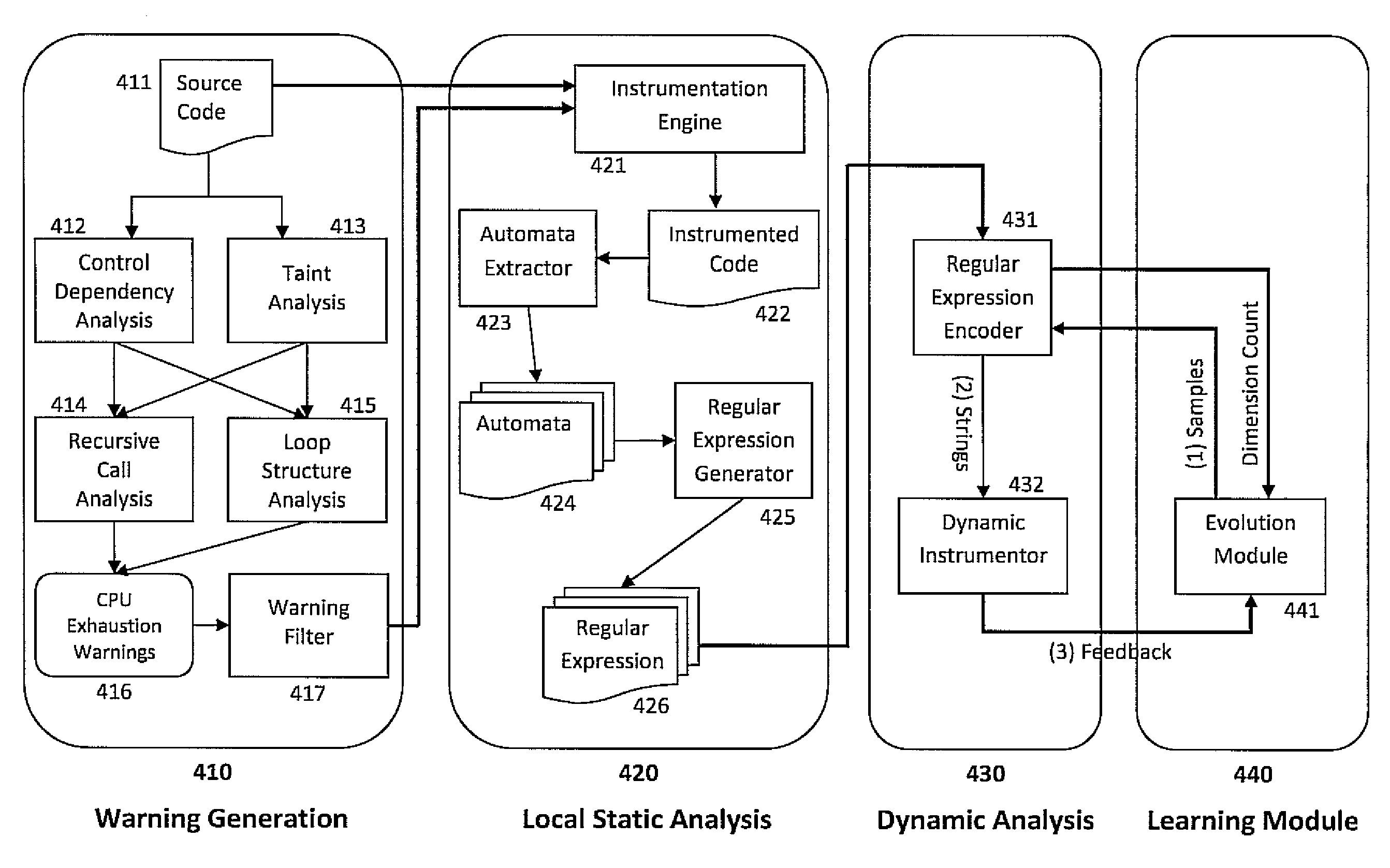
Feedback-guided fuzz testing for learning inputs of coma
InactiveUS20100058475A1Maximize feedback scoreProcess safetyMemory loss protectionError detection/correctionUser inputCode segment
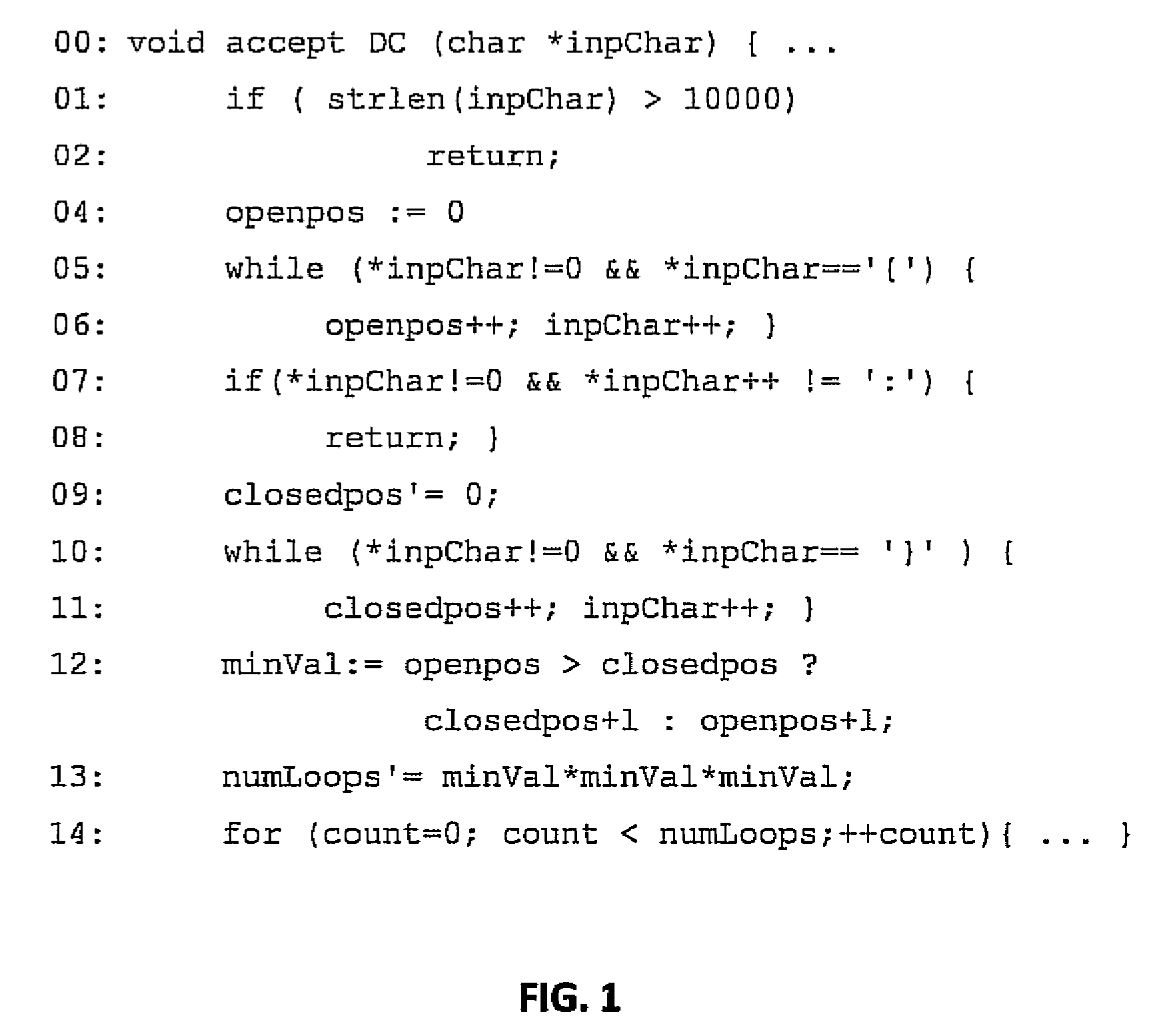
Embodiments of the present invention combine static analysis, source code instrumentation and feedback-guided fuzz testing to automatically detect resource exhaustion denial of service attacks in software and generate inputs of coma for vulnerable code segments. The static analysis of the code highlights portions that are potentially vulnerable, such as loops and recursions whose exit conditions are dependent on user input. The code segments are dynamically instrumented to provide a feedback value at the end of each execution. Evolutionary techniques are then employed to search among the possible inputs to find inputs that maximize the feedback score.
Owner:NEC LAB AMERICA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com