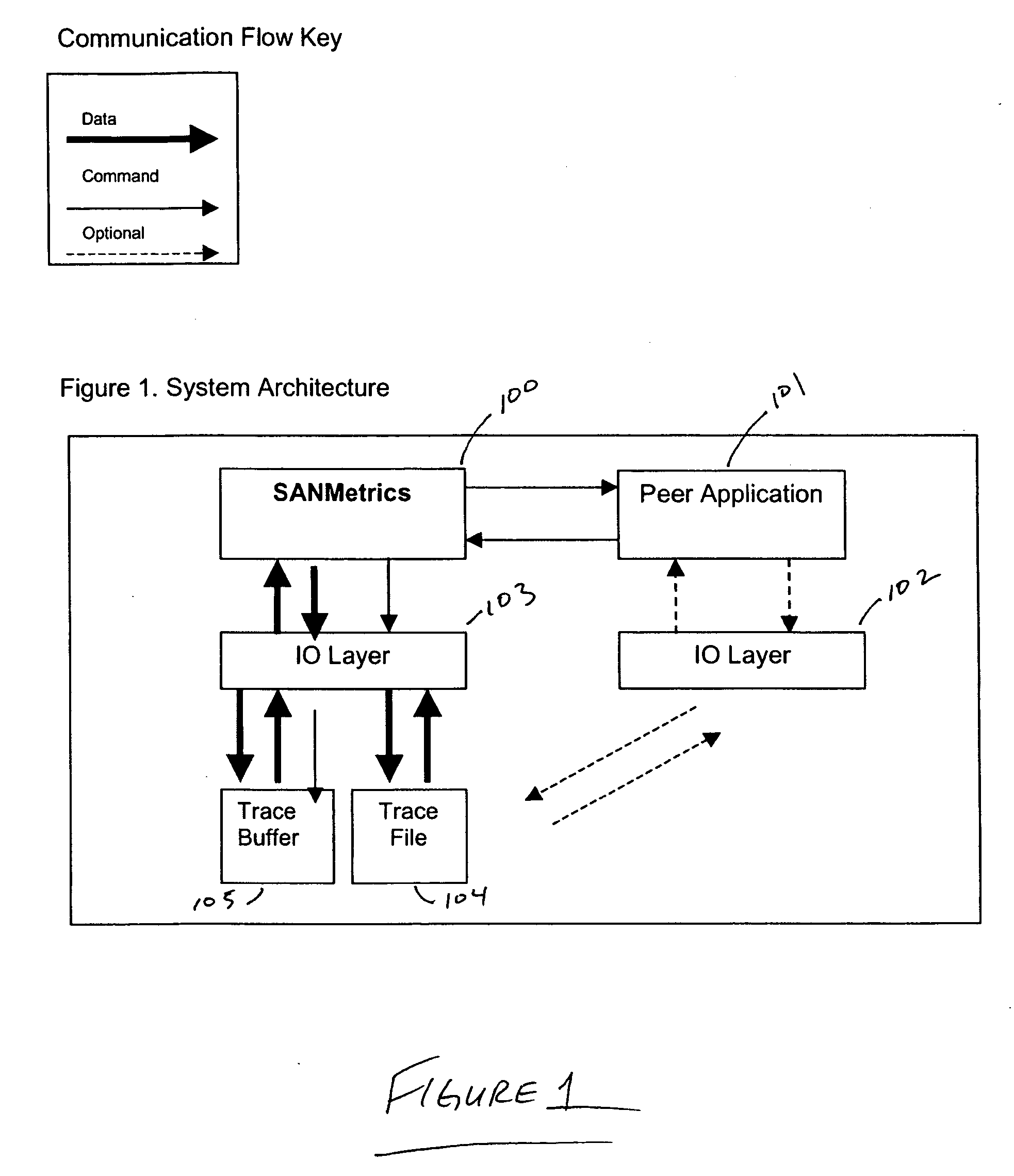
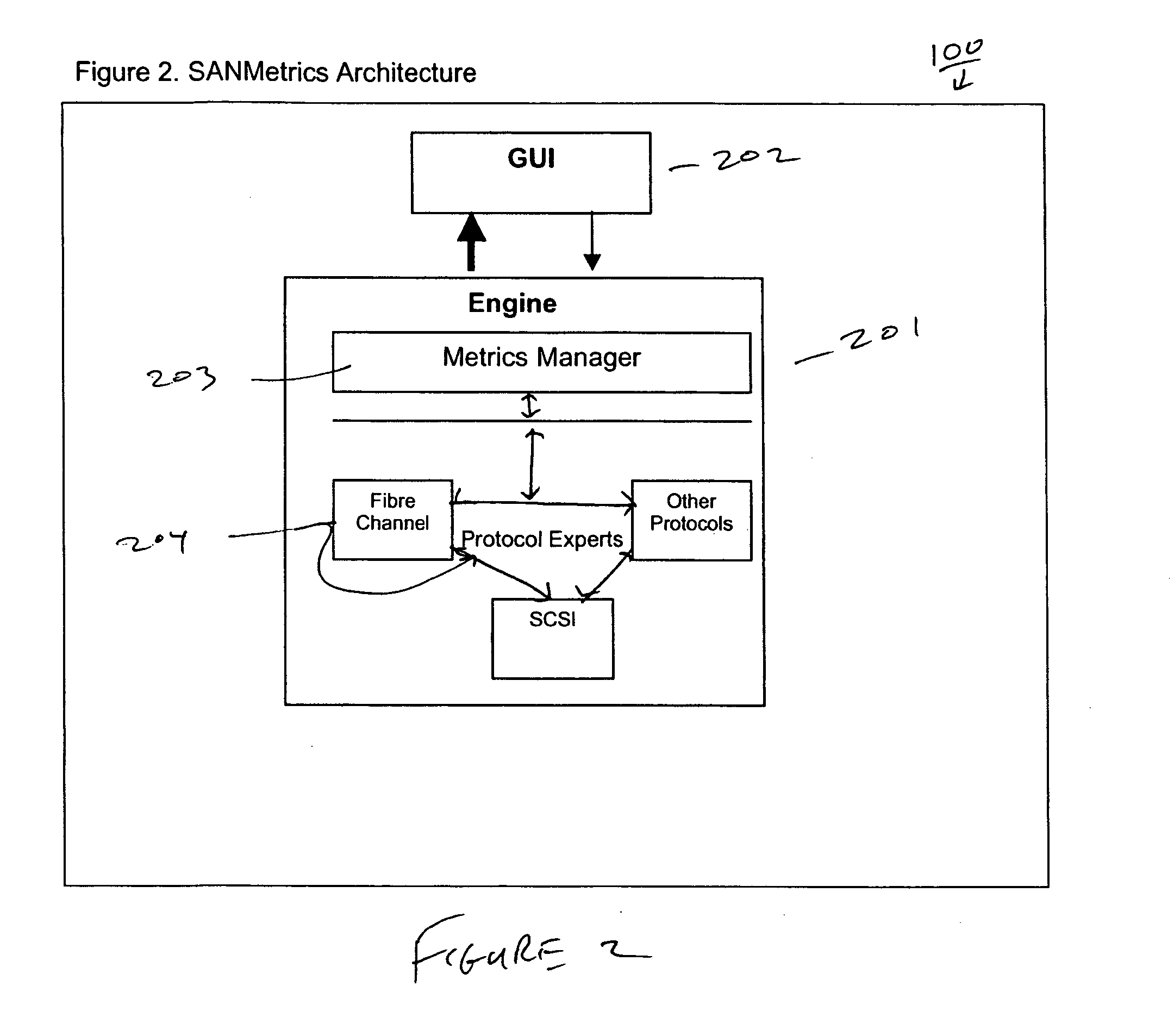
Patents
Literature
5136 results about "Analyser" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
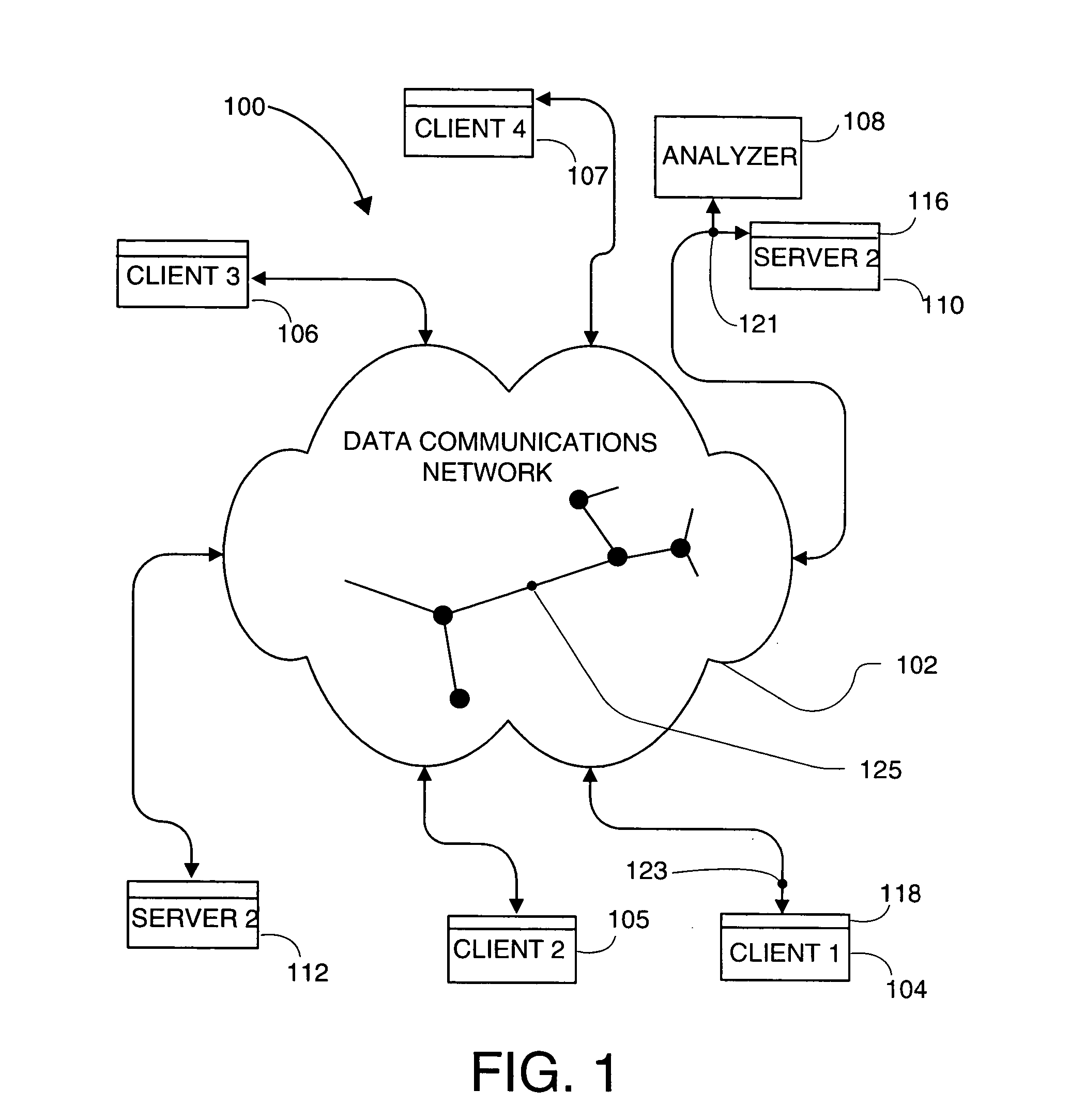
An analyser or analyzer (see spelling differences) is a person or device that analyses given data. It examines in detail the structure of the given data and tries to find patterns and relationships between parts of the data. An analyser can be a piece of hardware or a computer program running on a computer.
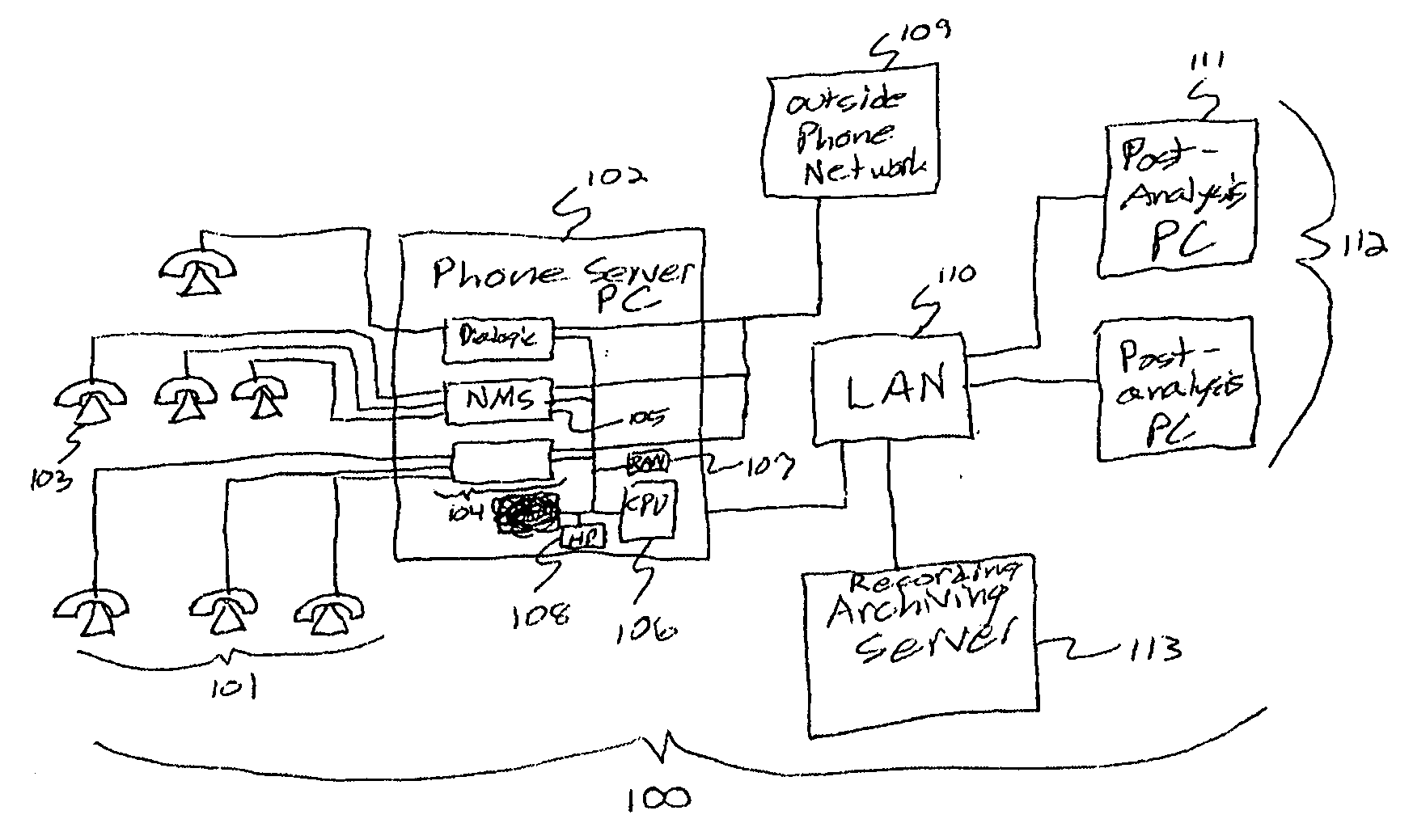
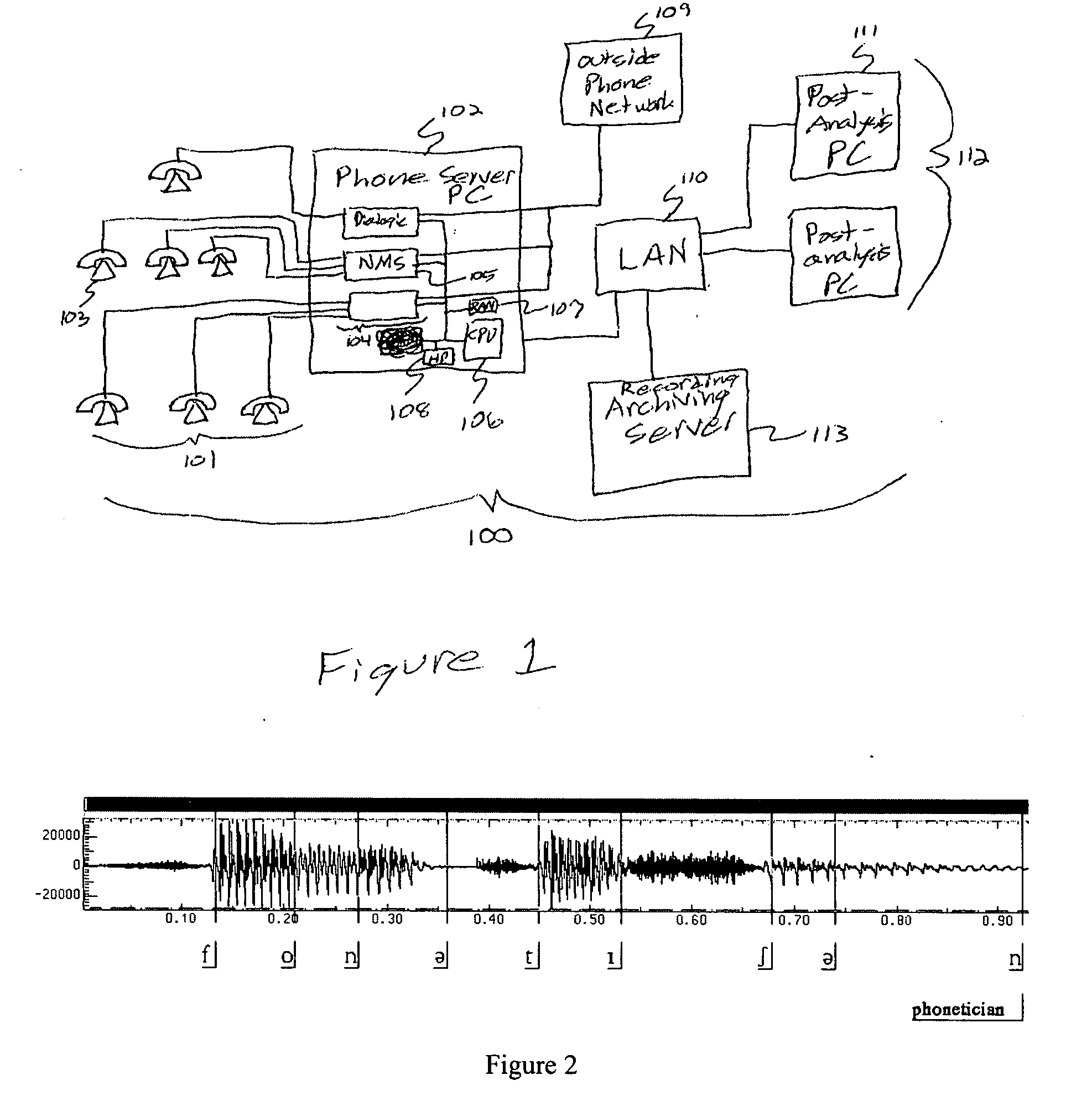
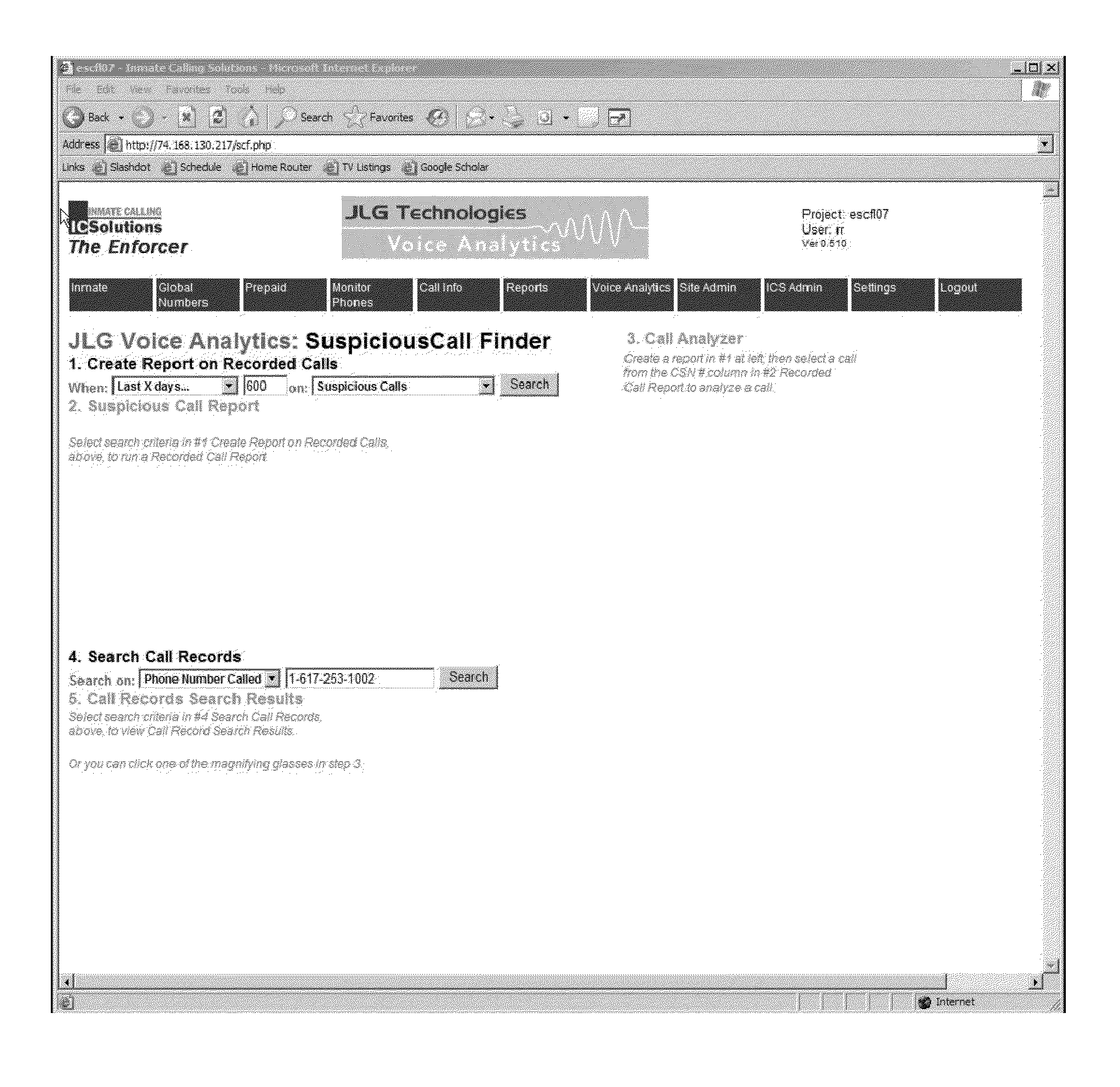
Multi-party conversation analyzer & logger
ActiveUS20070071206A1High precisionFacilitate interruptionInterconnection arrangementsSubstation speech amplifiersGraphicsSurvey instrument
A multi-party conversation analyzer and logger uses a variety of techniques including spectrographic voice analysis, absolute loudness measurements, directional microphones, and telephonic directional separation to determine the number of parties who take part in a conversation, and segment the conversation by speaking party. In one aspect, the invention monitors telephone conversations in real time to detect conditions of interest (for instance, calls to non-allowed parties or calls of a prohibited nature from prison inmates). In another aspect, automated prosody measurement algorithms are used in conjunction with speaker segmentation to extract emotional content of the speech of participants within a particular conversation, and speaker interactions and emotions are displayed in graphical form. A conversation database is generated which contains conversation recordings, and derived data such as transcription text, derived emotions, alert conditions, and correctness probabilities associated with derived data. Investigative tools allow flexible queries of the conversation database.
Owner:SECURUS TECH LLC
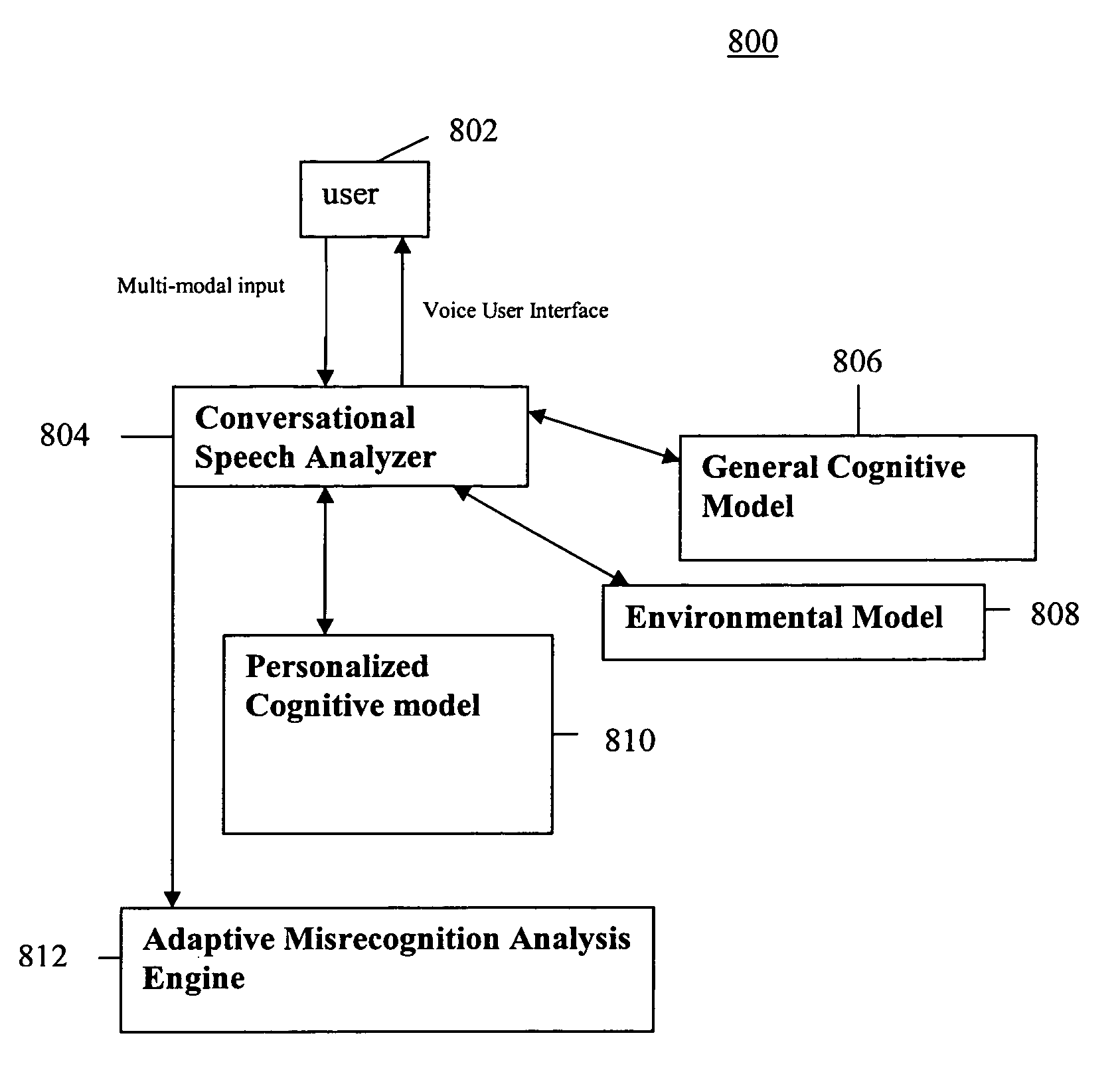
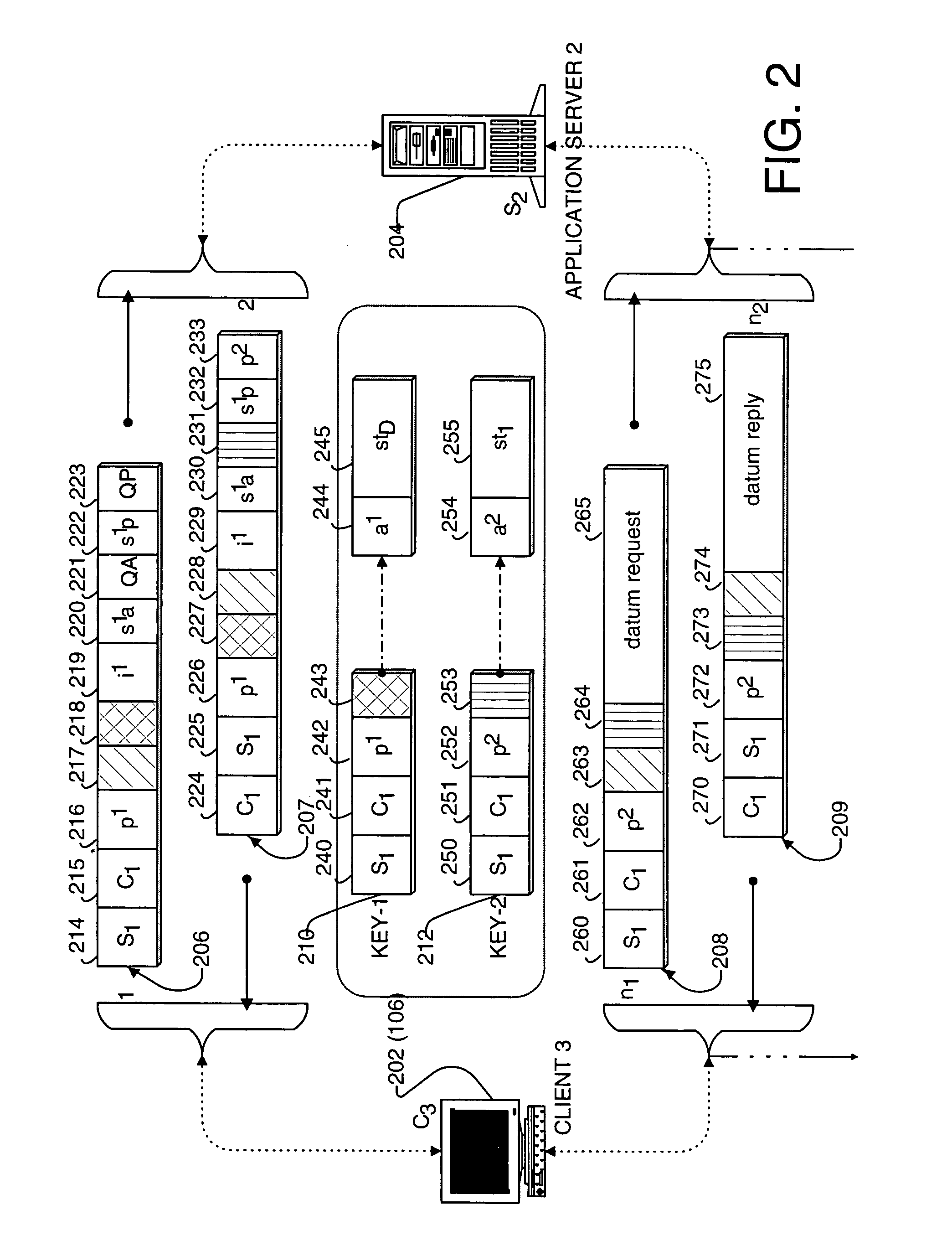
System and method of supporting adaptive misrecognition in conversational speech
ActiveUS20070038436A1Improve maximizationHigh bandwidthNatural language data processingSpeech recognitionPersonalizationSpoken language
A system and method are provided for receiving speech and / or non-speech communications of natural language questions and / or commands and executing the questions and / or commands. The invention provides a conversational human-machine interface that includes a conversational speech analyzer, a general cognitive model, an environmental model, and a personalized cognitive model to determine context, domain knowledge, and invoke prior information to interpret a spoken utterance or a received non-spoken message. The system and method creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context of the speech or non-speech communication and presenting the expected results for a particular question or command.
Owner:DIALECT LLC
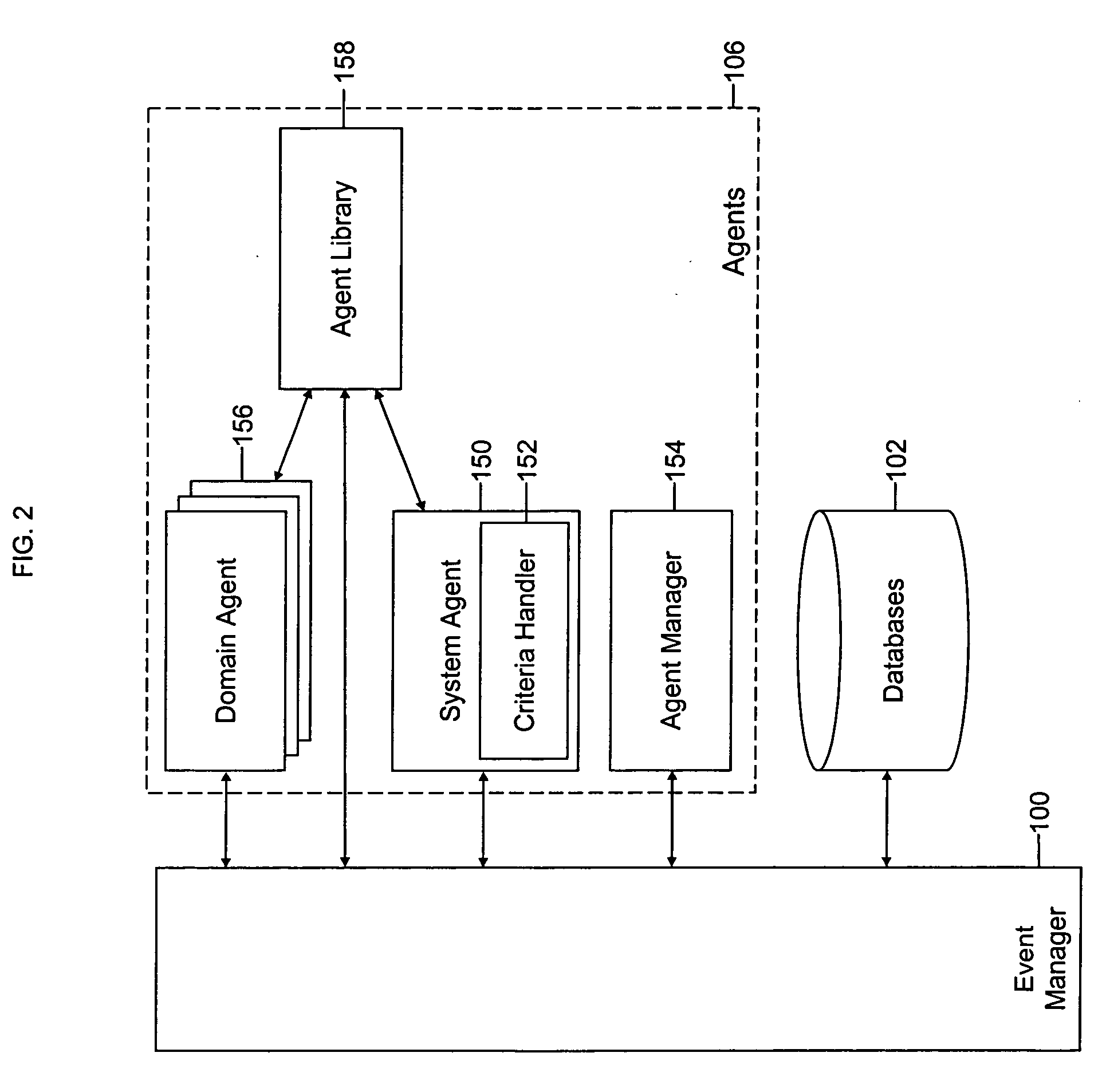
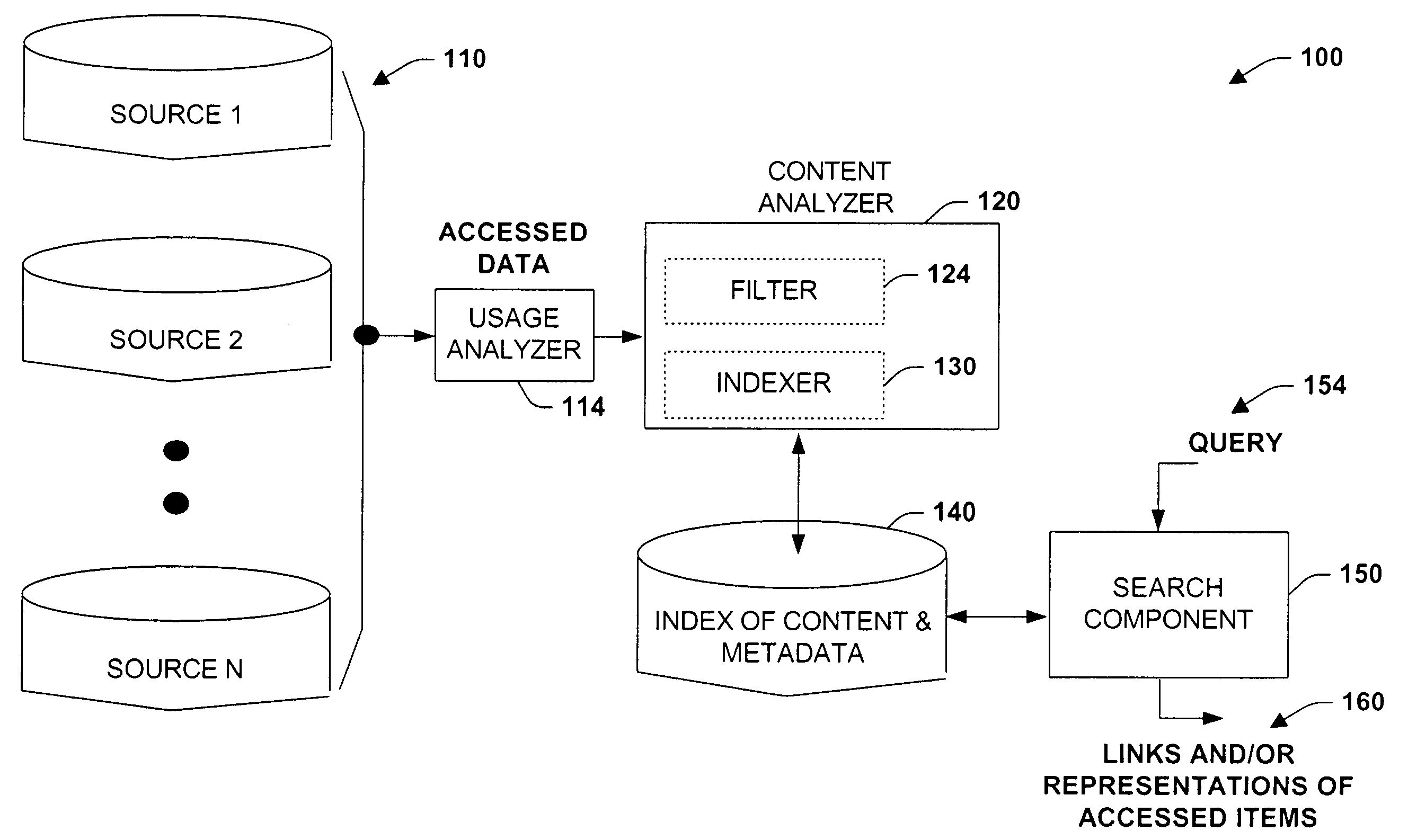
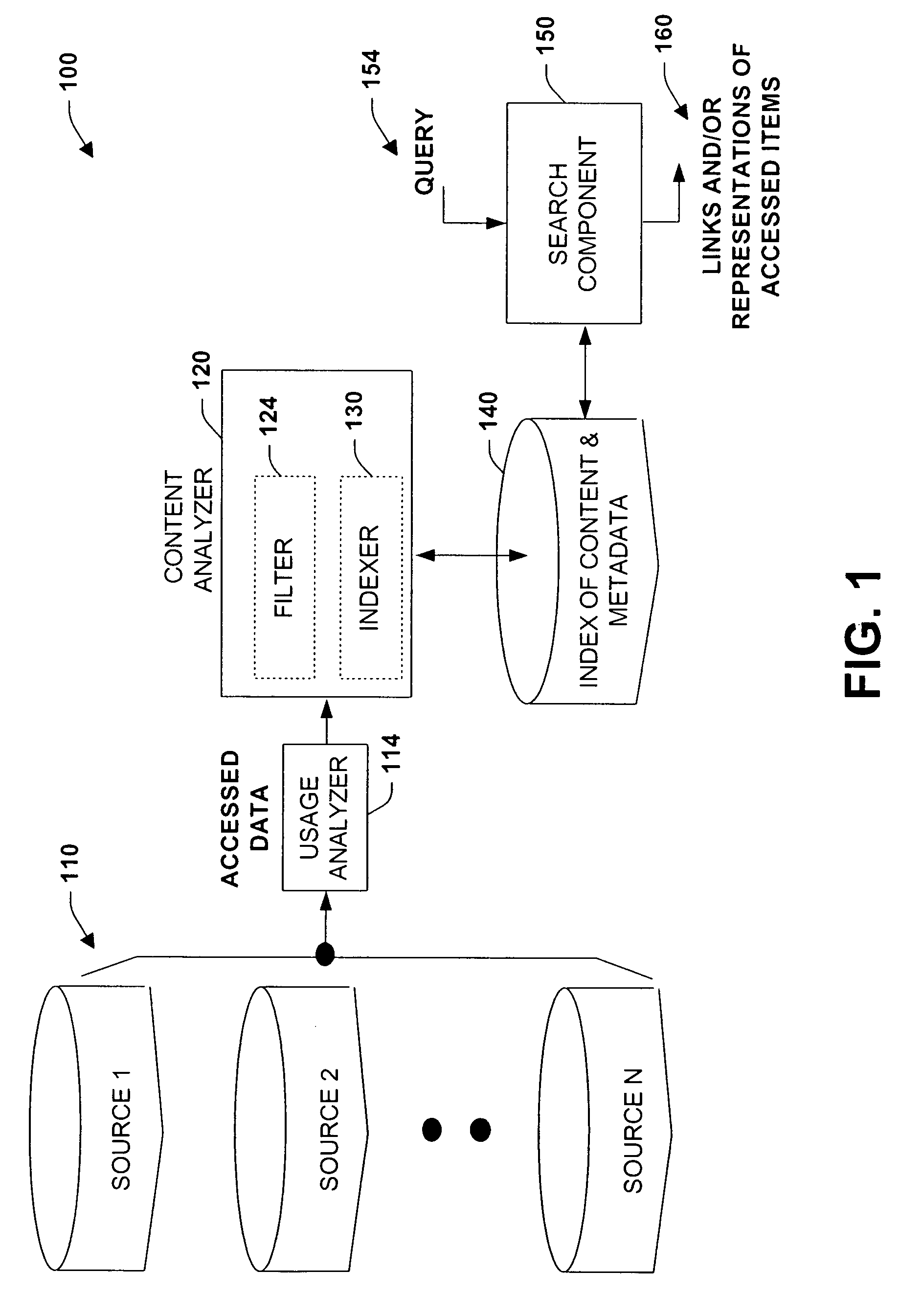
Method and system for usage analyzer that determines user accessed sources, indexes data subsets, and associated metadata, processing implicit queries based on potential interest to users
InactiveUS7162473B2Useful purposeFacilitate search for informationData processing applicationsText database indexingData accessContent analytics
The present invention relates to systems and methods providing content-access-based information retrieval. Information items from a plurality of disparate information sources that have been previously accessed or considered are automatically indexed in a data store, whereby a multifaceted user interface is provided to efficiently retrieve the items in a cognitively relevant manner. Various display output arrangements are possible for the retrieved information items including timeline visualizations and multidimensional grid visualizations. Input options include explicit, implicit, and standing queries for retrieving data along with explicit and implicit tagging of items for ease of recall and retrieval. In one aspect, an automated system is provided that facilitates concurrent searching across a plurality of information sources. A usage analyzer determines user accessed items and a content analyzer stores subsets of data corresponding to the items, wherein at least two of the items are associated with disparate information sources, respectively. An automated indexing component indexes the data subsets according to past data access patterns as determined by the usage analyzer. A search component responds to a search query, initiates a search across the indexed data, and outputs links to locations of a subset and / or provides sparse representations of the subset.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for conducting sentiment analysis for securities research
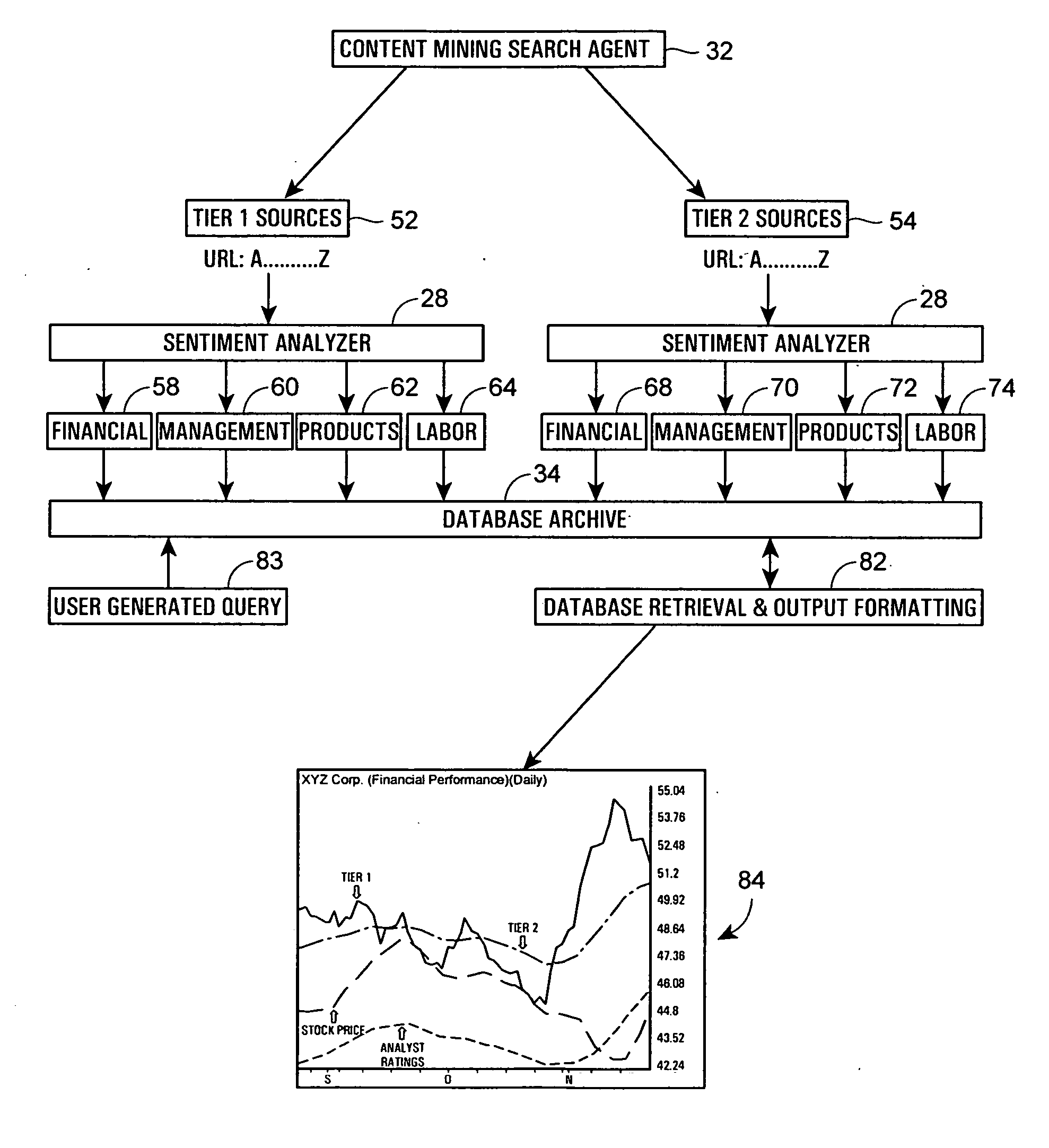
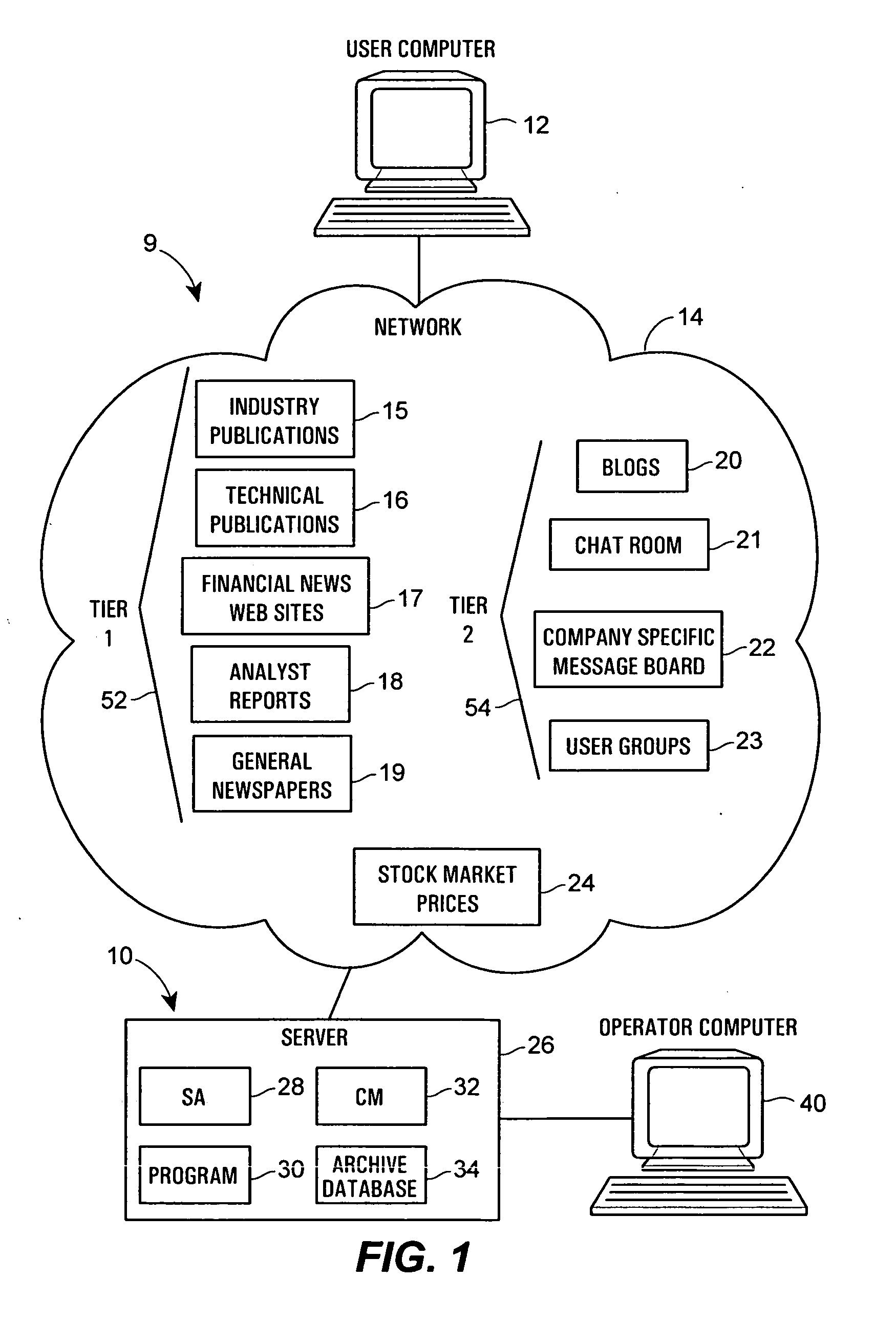
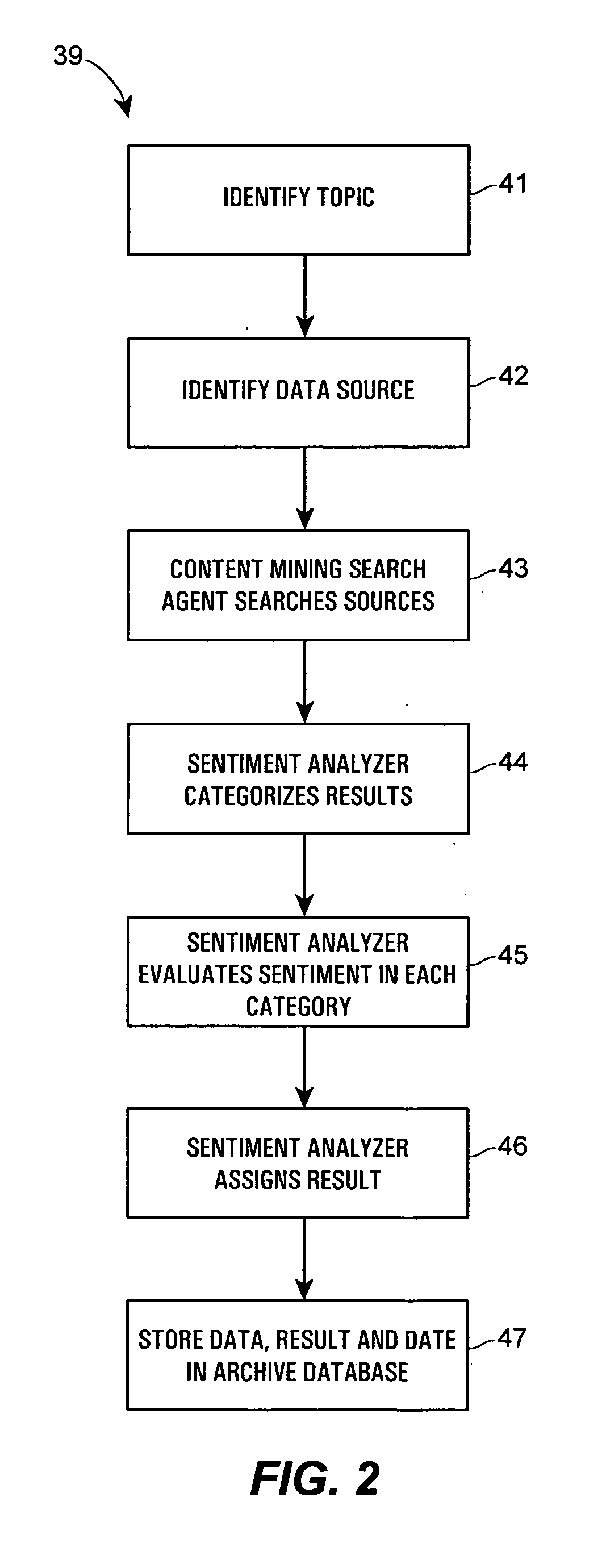
A computer system performs financial analysis on one or more financial entities, which may be corporations, securities, etc., based on the sentiment expressed about the one or more financial entities within raw textual data stored in one or more electronic data sources containing information or text related to one or more financial entities. The computer system includes a content mining search agent that identifies one or more words or phrases within raw textual data in the data sources using natural language processing to identify relevant raw textual data related to the one or more financial entities, a sentiment analyzer that analyzes the relevant raw textual data to determine the nature or the strength of the sentiment expressed about the one or more financial entities within the relevant raw textual data and that assigns a value to the nature or strength of the sentiment expressed about the one or more financial entities within the relevant raw textual data, and a user interface program that controls the content mining search agent and the sentiment analyzer and that displays, to a user, the values of the nature or strength of the sentiment expressed about the one or more financial entities within the data sources. This computer system enables a user to make better decisions regarding whether or not to purchase or invest in the one or more financial entities.
Owner:AIM HLDG LLC
Method and apparatus for monitoring traffic in a network
InactiveUS20040083299A1Energy efficient ICTDigital data information retrievalTraffic capacityNetwork packet
A monitor for and a method of examining packets passing through a connection point on a computer network. Each packets conforms to one or more protocols. The method includes receiving a packet from a packet acquisition device and performing one or more parsing / extraction operations on the packet to create a parser record comprising a function of selected portions of the packet. The parsing / extraction operations depend on one or more of the protocols to which the packet conforms. The method further includes looking up a flow-entry database containing flow-entries for previously encountered conversational flows. The lookup uses the selected packet portions and determining if the packet is of an existing flow. If the packet is of an existing flow, the method classifies the packet as belonging to the found existing flow, and if the packet is of a new flow, the method stores a new flow-entry for the new flow in the flow-entry database, including identifying information for future packets to be identified with the new flow-entry. For the packet of an existing flow, the method updates the flow-entry of the existing flow. Such updating may include storing one or more statistical measures. Any stage of a flow, state is maintained, and the method performs any state processing for an identified state to further the process of identifying the flow. The method thus examines each and every packet passing through the connection point in real time until the application program associated with the conversational flow is determined.
Owner:PACKET INTELLIGENCE
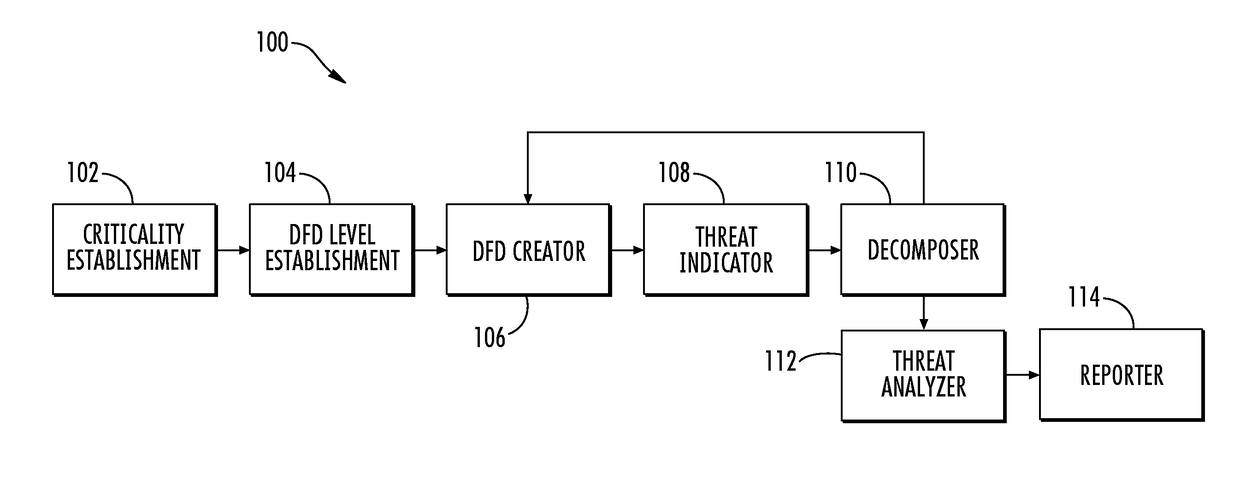
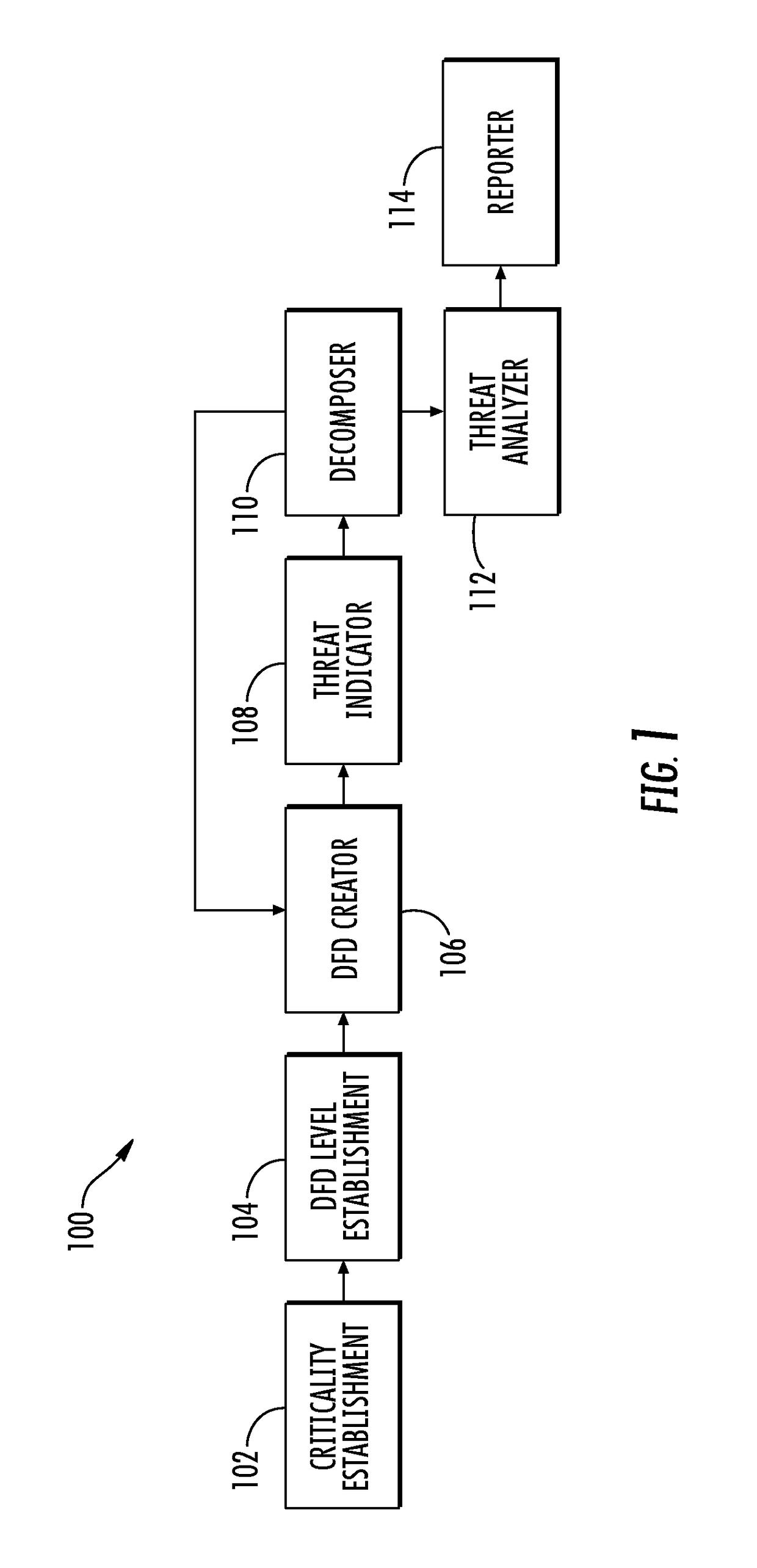
Threat modeling and analysis
ActiveUS9602529B2Easy to understandMitigate and further mitigate riskError detection/correctionPlatform integrity maintainanceData streamInformation system
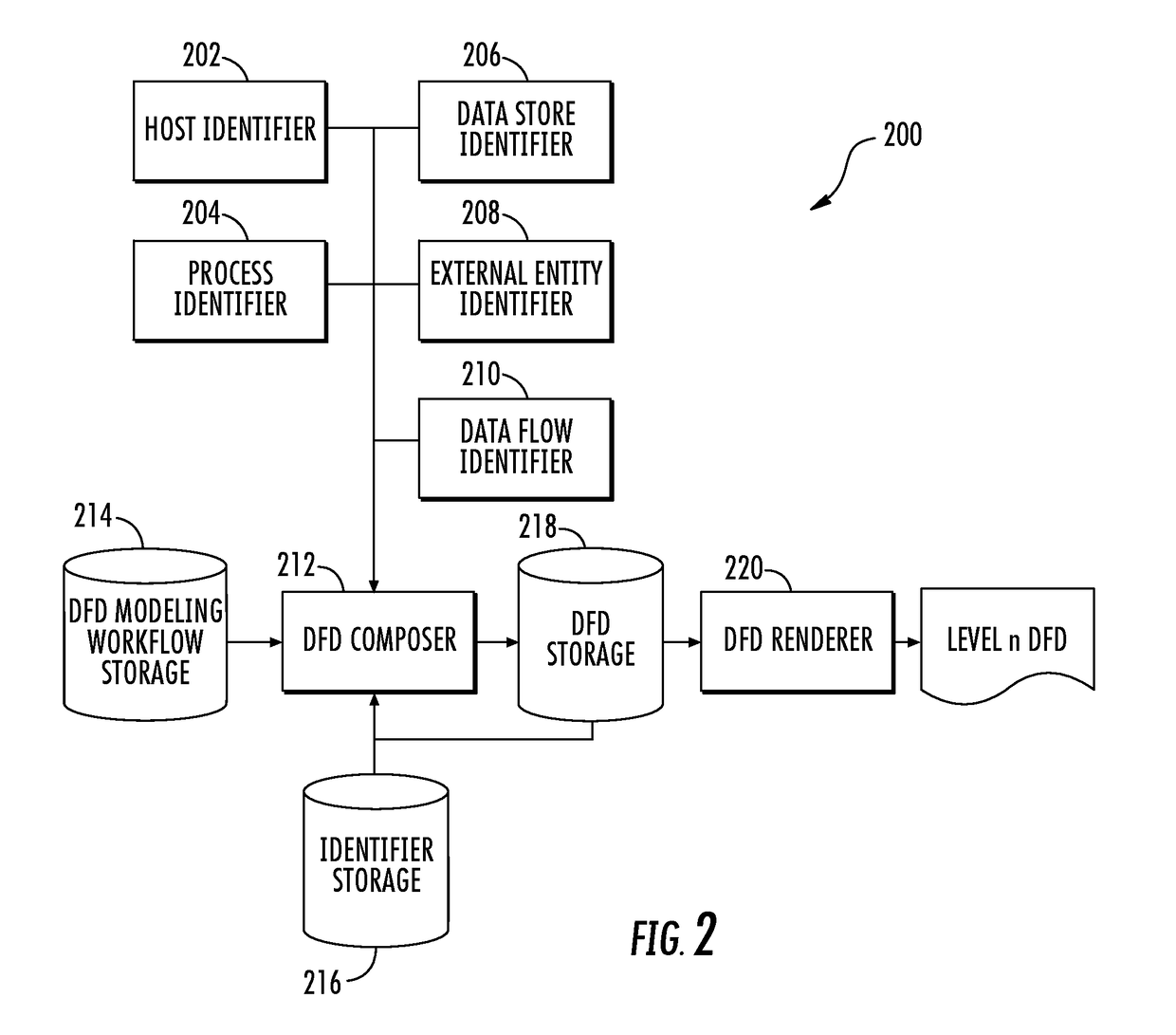
A system is provided for modeling and analysis of cybersecurity threats may include a data flow diagram (DFD) creator, threat indicator and threat analyzer. The DFD creator may identify elements of an information system, and compose a DFD including nodes and edges representing components and data flows of the information system. The threat indicator may identify a cybersecurity threat to a particular element of the information system, and add a secondary node representing the cybersecurity threat to the DFD to thereby produce a threat-model DFD for the information system. In metadata associated with the nodes, edges and secondary node, the DFD creator and threat indicator may provide structured information including attributes of the components, data flows and cybersecurity threat. And the threat analyzer may perform an analysis of the cybersecurity threat based on the threat-model DFD and metadata associated with the nodes, edges and secondary node thereof.
Owner:THE BOEING CO
Analyte filter method and apparatus
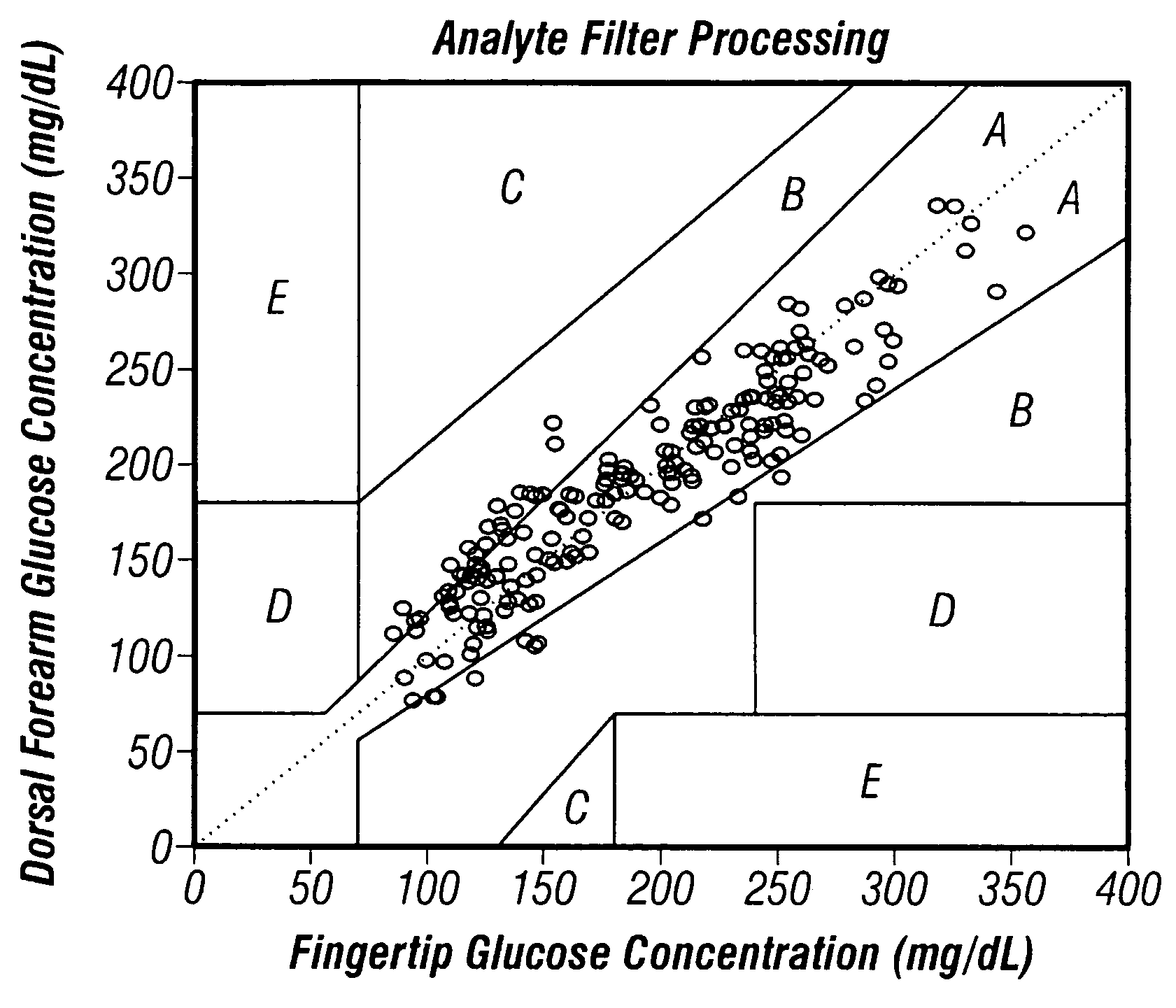
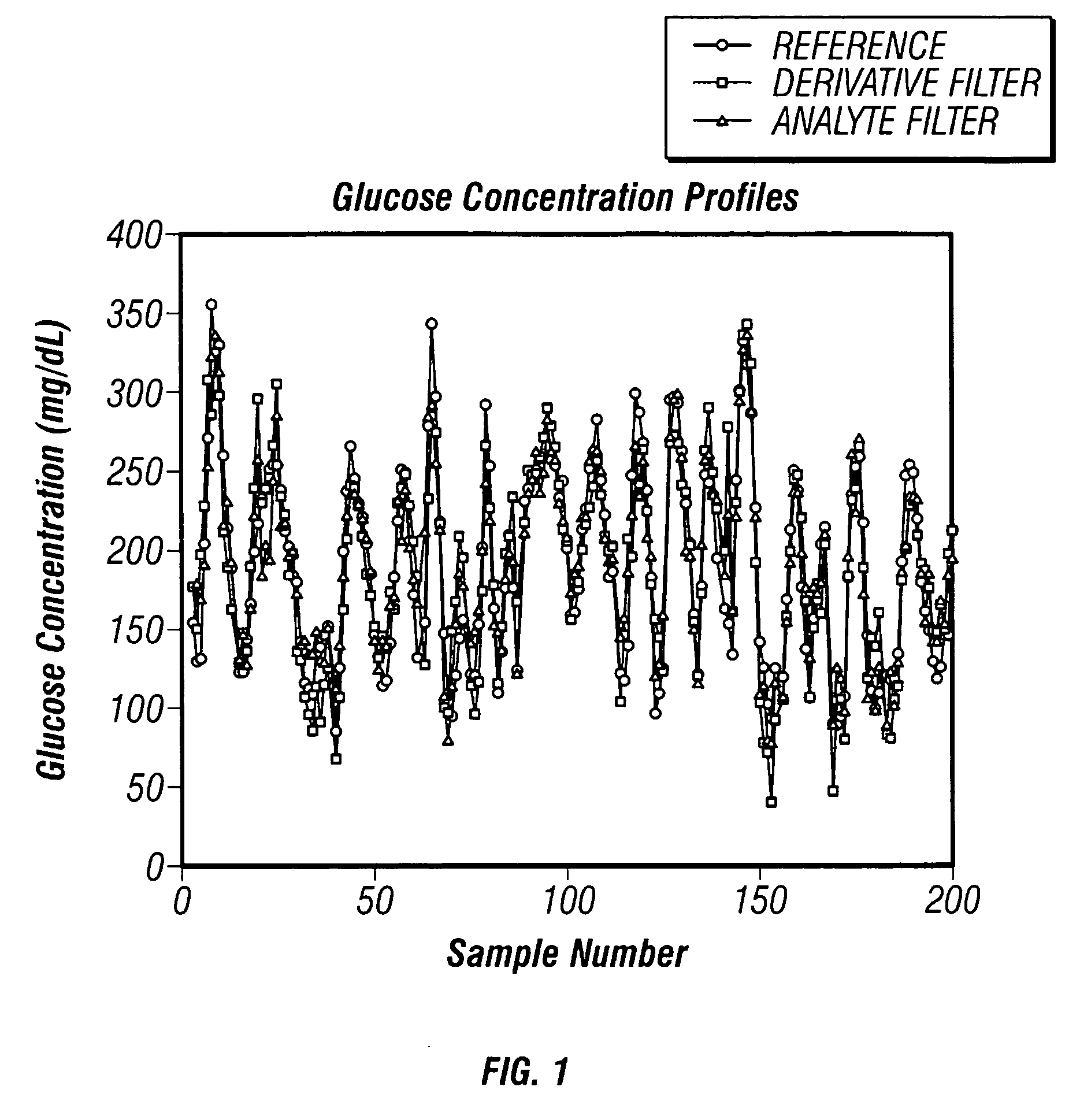
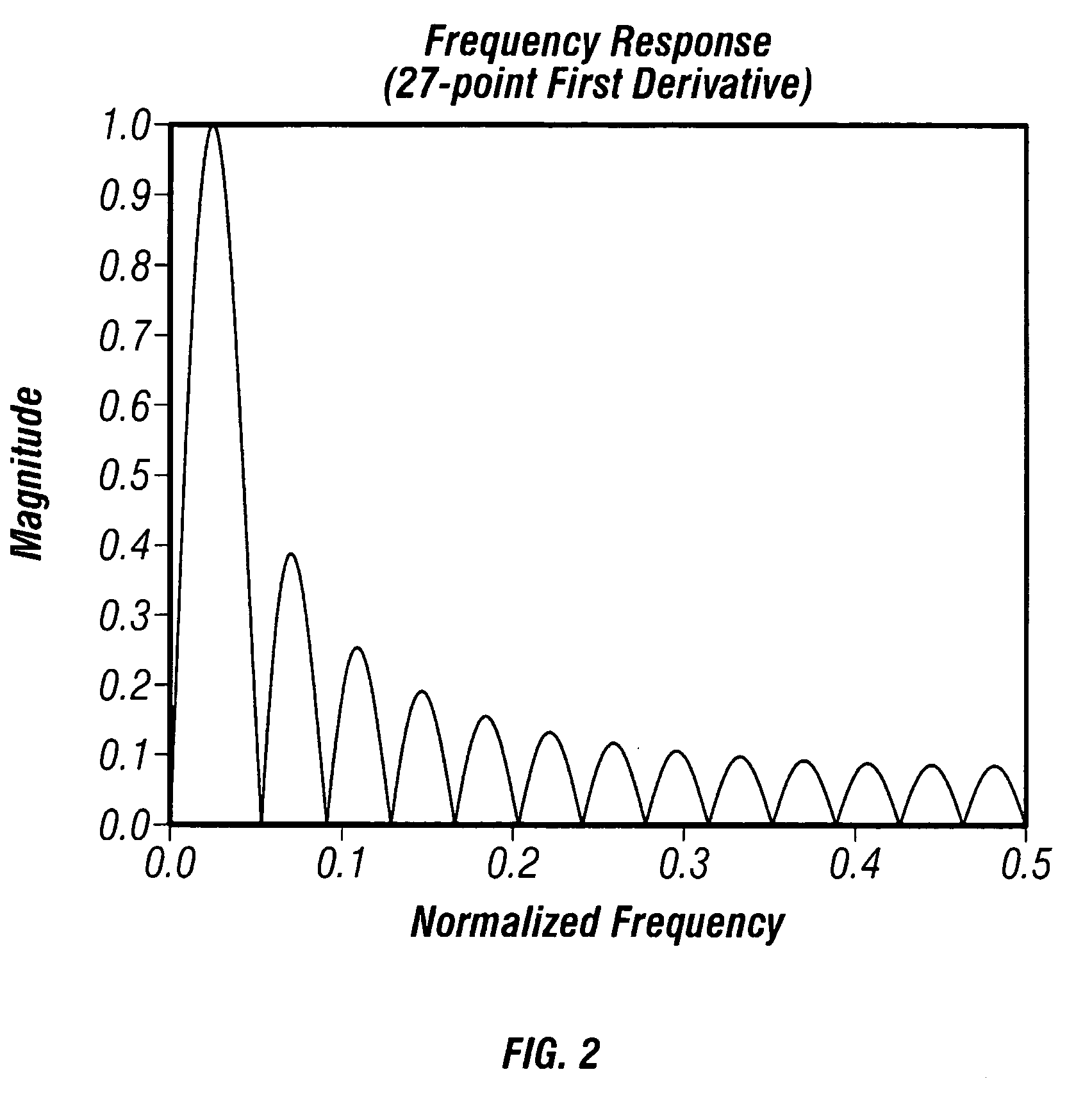
The invention comprises a method and apparatus for enhancing the analysis of noninvasive spectra, resulting in improved analytical performance. More particularly, the invention comprises a method and apparatus for processing noninvasive spectra with an analyte filter that preferably rejects variation likely to be detrimental to the measurement system, while passing signal that probabilistically is unique to the target analyte. Subsequently, the analyte filtered data are used to estimate an analyte property, such as a glucose concentration, in the presence of noise, interferences, state changes, and / or across analyzers.
Owner:GLT ACQUISITION
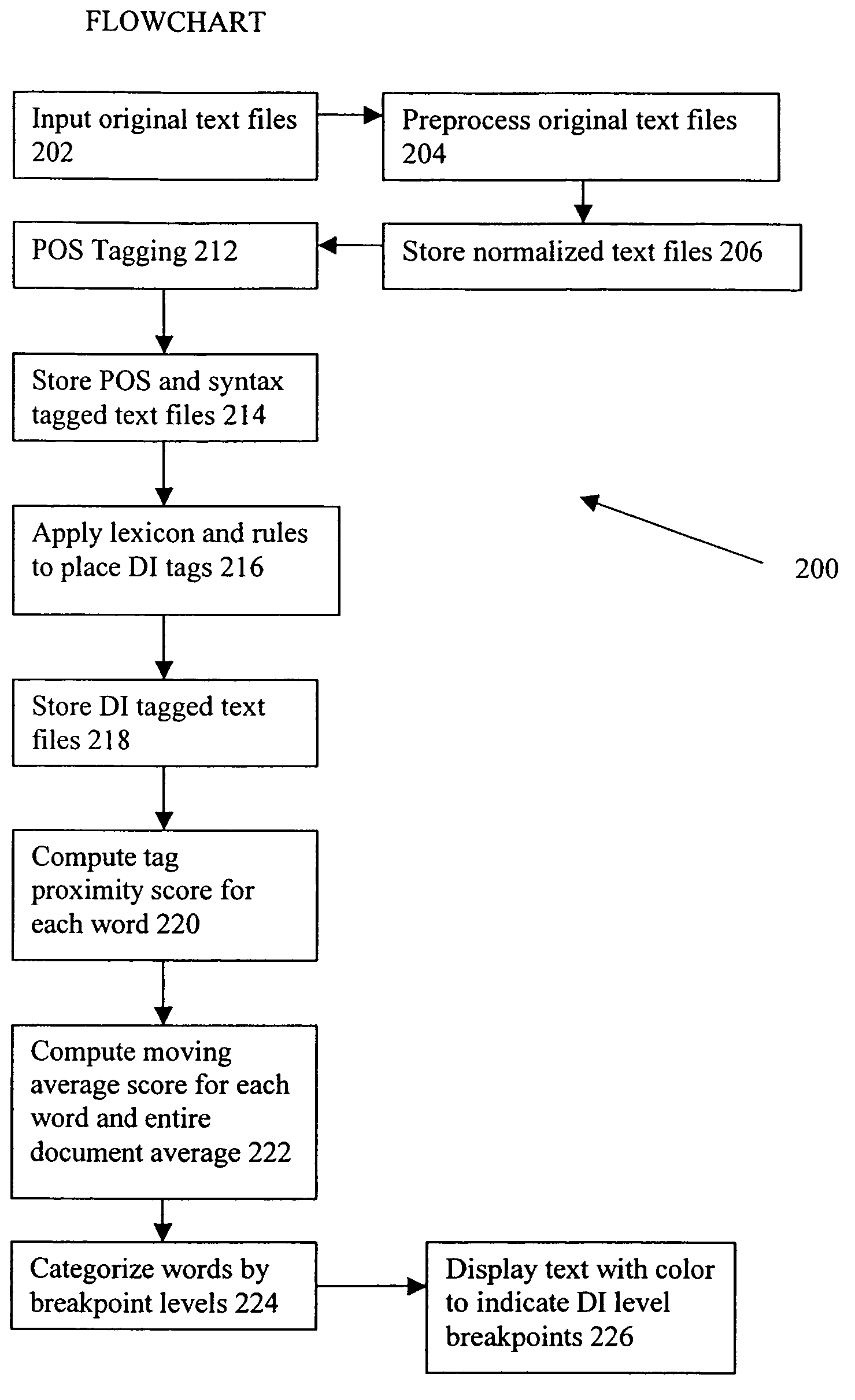
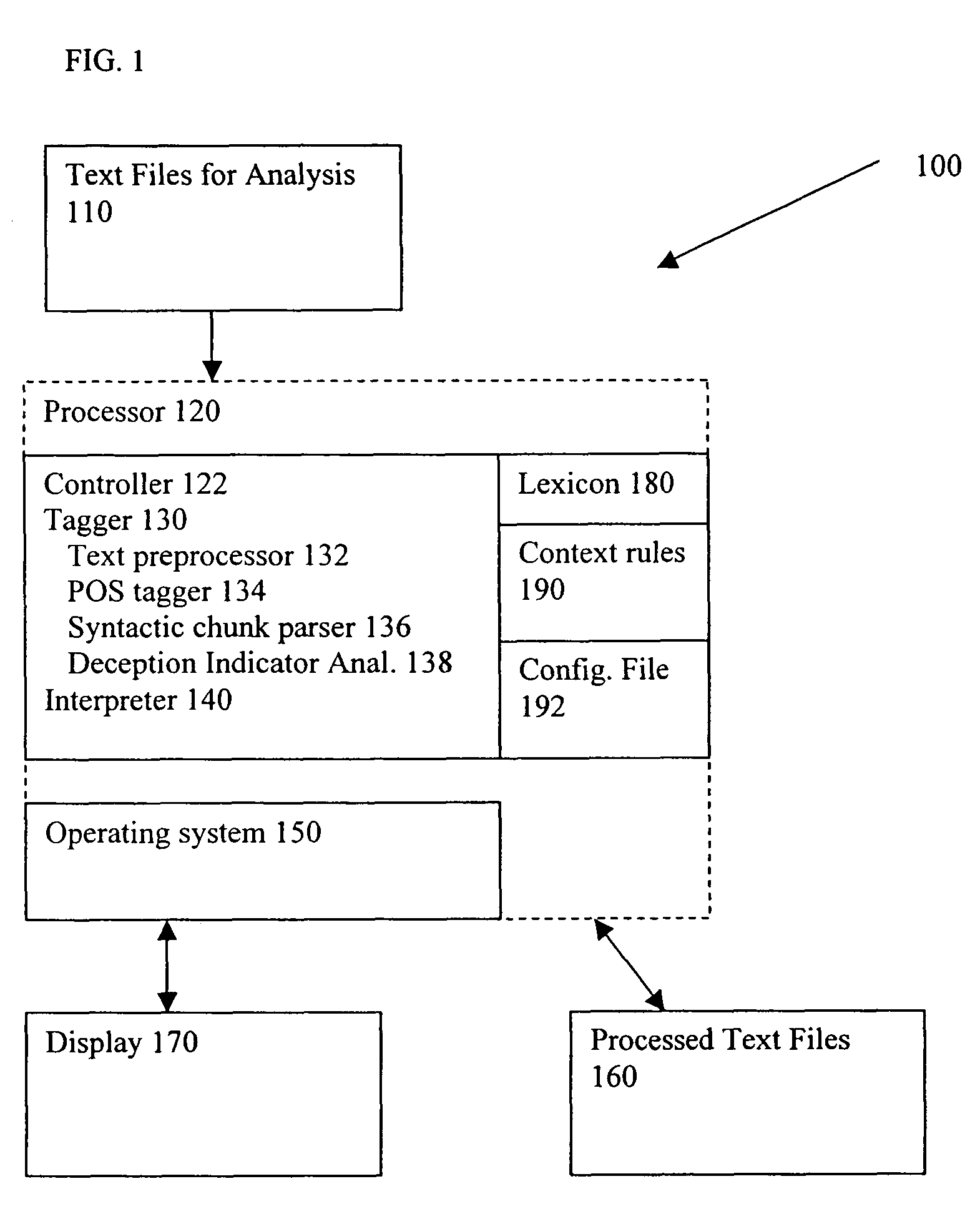
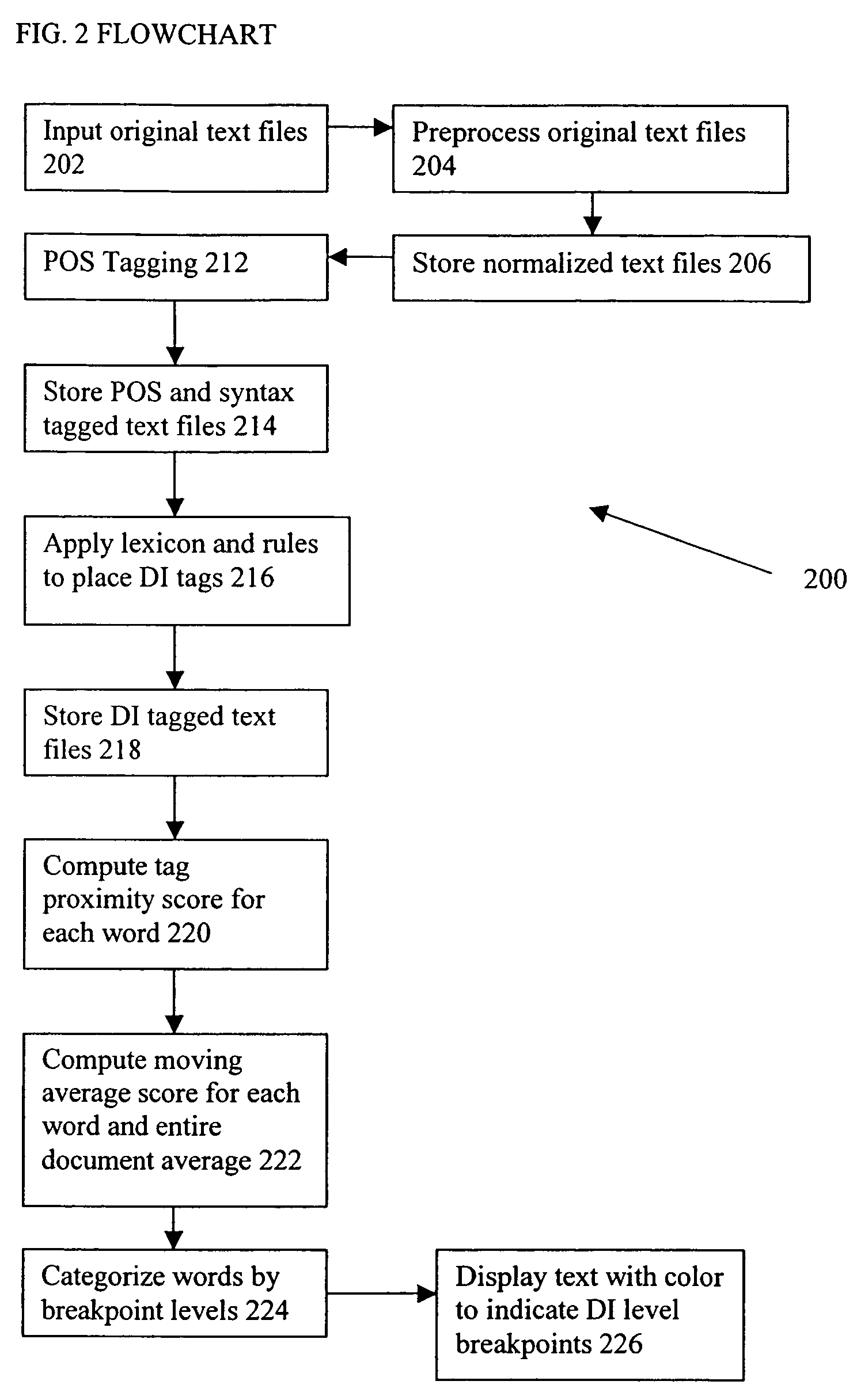
Method and system for the automatic recognition of deceptive language
A system for identifying deception within a text includes a processor for receiving and processing a text file. The processor includes a deception indicator tag analyzer for inserting into the text file at least one deception indicator tag that identifies a potentially deceptive word or phrase within the text file, and an interpreter for interpreting the at least one deception indicator tag to determine a distribution of potentially deceptive word or phrases within the text file and generating deception likelihood data based upon the density or distribution of potentially deceptive word or phrases within the text file. A method for identifying deception within a text includes the steps of receiving a first text to be analyzed, normalizing the first text to produce a normalized text, inserting into the normalized text at least one part-of-speech tag that identifies a part of speech of a word associated with the part-of-speech tag, inserting into the normalized text at least one syntactic label that identifies a linguistic construction of one or more words associated with the syntactic label, inserting into the normalized text at least one deception indicator tag that identifies a potentially deceptive word or phrase within the normalized text, interpreting the at least one deception indicator tag to determine a distribution of potentially deceptive word or phrases within the normalized text, and generating deception likelihood data based upon the density or frequency of distribution of potentially deceptive word or phrases within the normalized text.
Owner:DECEPTION DISCOVERY TECH
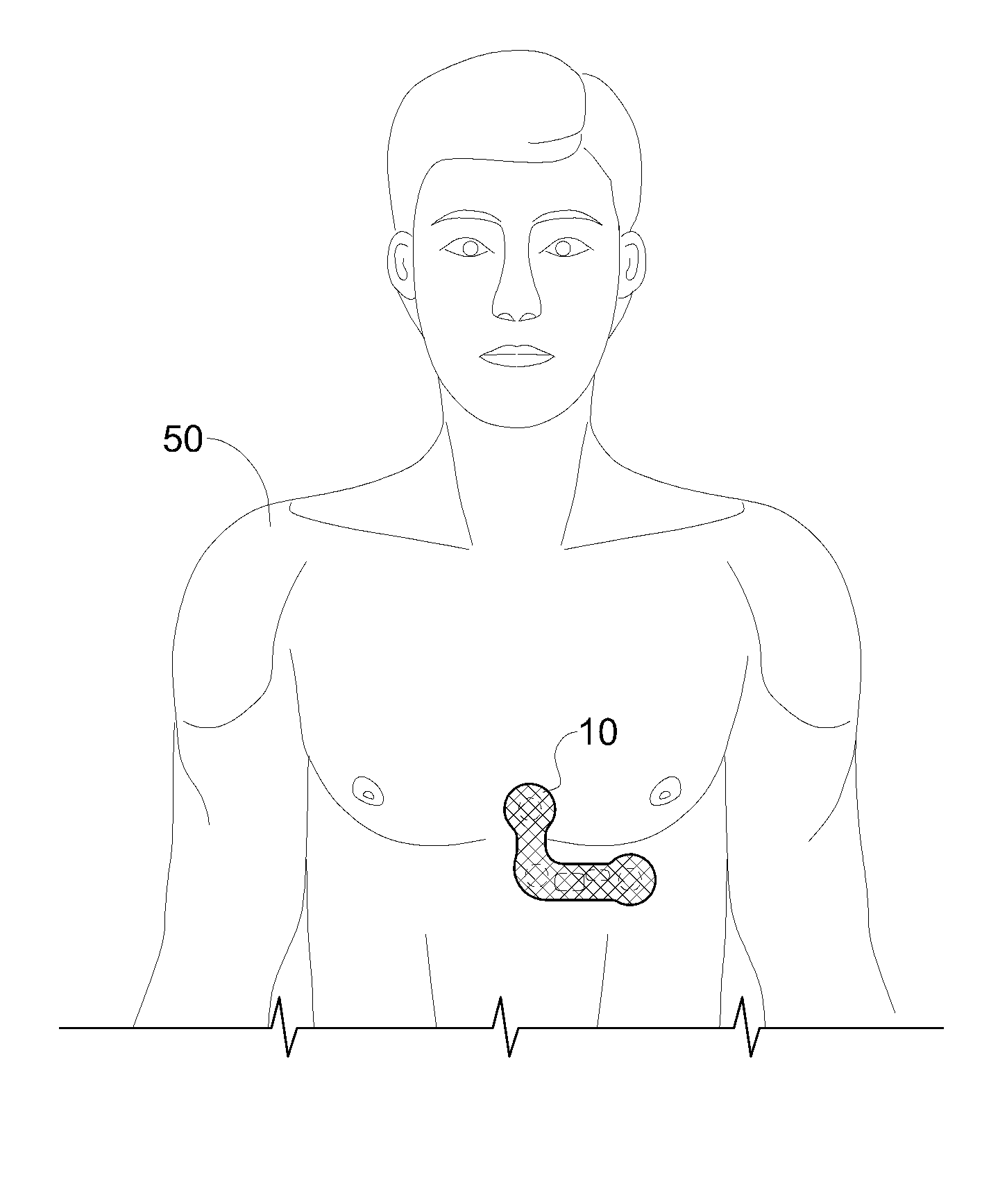
Heart monitoring body patch and system
InactiveUS20090062670A1Good adhesionEasily attached to patientElectrocardiographySensorsTransceiverHeart monitoring
Provided is a diagnostic patch system for monitoring and storing patient information, which includes sensors, a data storage unit, and a transceiver. Each of the sensors is attached to a skin to detect a patient data. The data storage unit is configured to store stream of the detected patient data from the plurality of sensors. The transceiver, connected with the sensors and the data storage unit, communicates the stream of the patient data with an analyzer, and the analyzer is configured to process and analyze the stream of the patient data. Two or more diagnostic patch systems can communicate with each other.
Owner:BIOSEVEN
Multi-party conversation analyzer & logger
InactiveUS20140247926A1Combat useAutomatic call-answering/message-recording/conversation-recordingSupervisory/monitoring/testing arrangementsSpeech soundData library
In one aspect, the present invention facilitates the investigation of networks of criminals, by gathering associations between phone numbers, the names of persons reached at those phone numbers, and voice print data. In another aspect the invention automatically detects phone calls from a prison where the voiceprint of the person called matches the voiceprint of a past inmate. In another aspect the invention detects identity scams in prisons, by monitoring for known voice characteristics of likely imposters on phone calls made by prisoners. In another aspect, the invention automatically does speech-to-text conversion of phone numbers spoken within a predetermined time of detecting data indicative of a three-way call event while monitoring a phone call from a prison inmate. In another aspect, the invention automatically thwarts attempts of prison inmates to use re-dialing services. In another aspect, the invention automatically tags audio data retrieved from a database, by steganographically encoding into the audio data the identity of the official retrieving the audio data.
Owner:SECURUS TECH LLC
Computer-aided image analysis
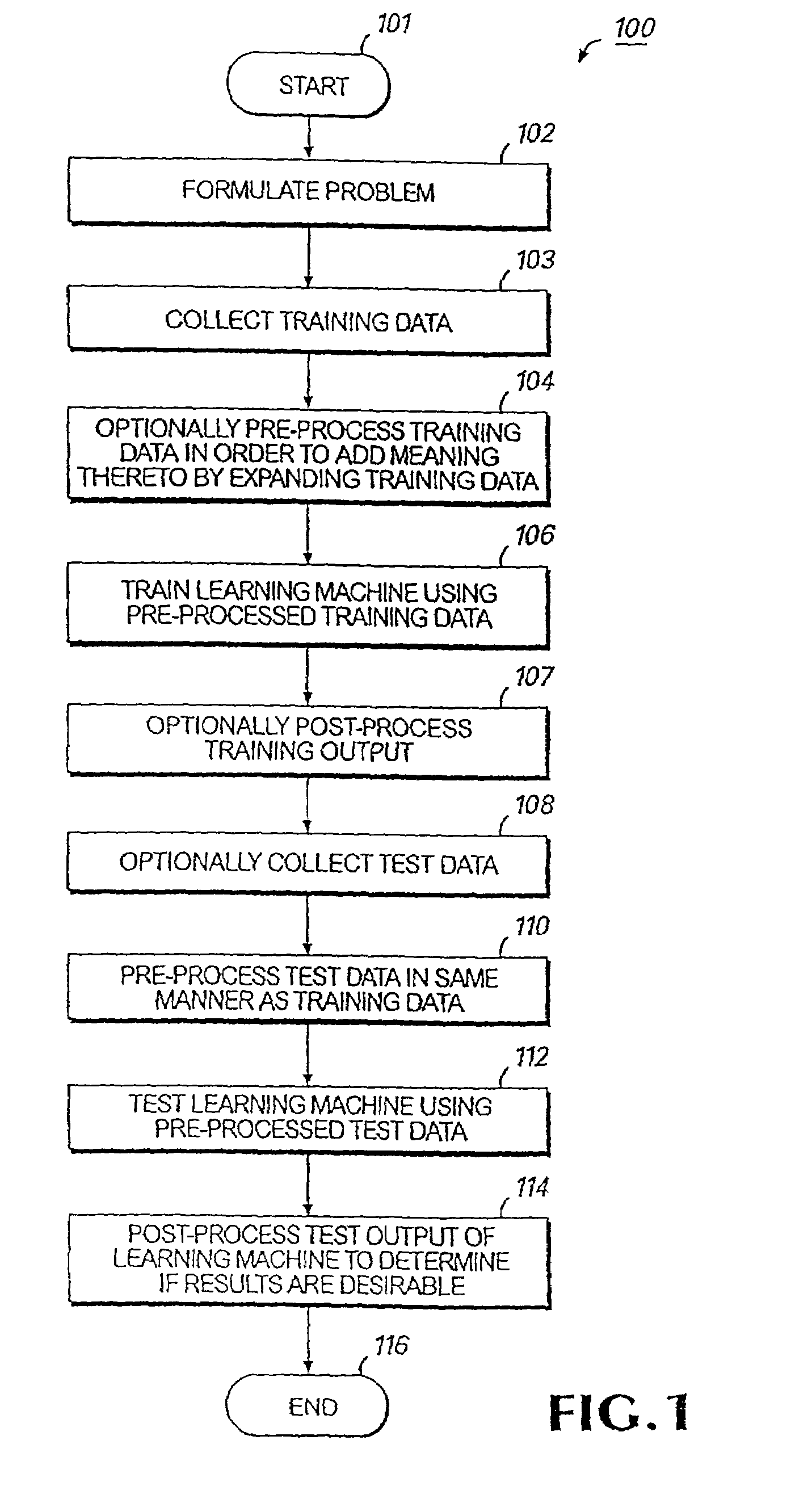
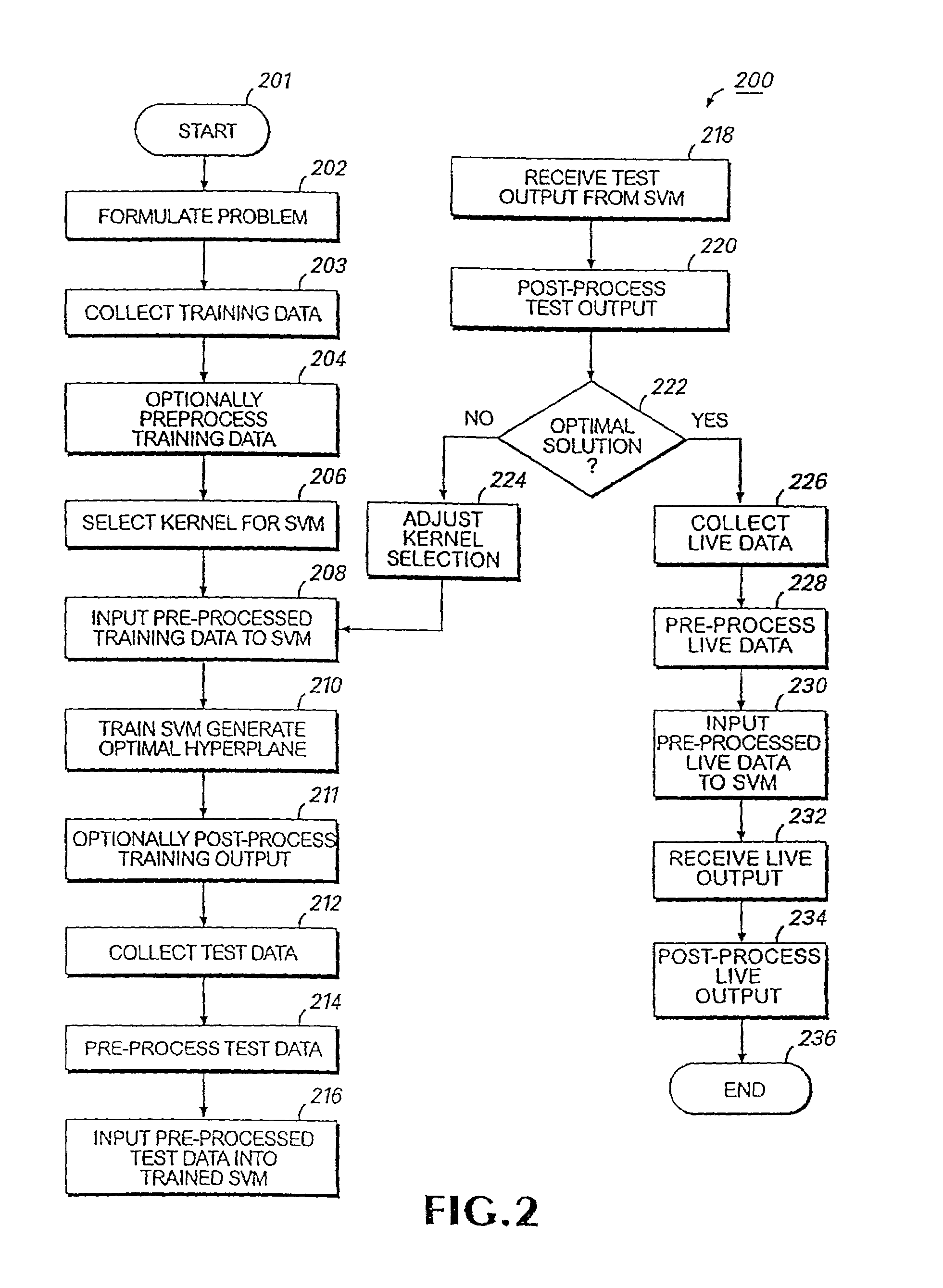
InactiveUS6996549B2Improve abilitiesGreat dimensionalityMedical data miningImage analysisLearning machineComputer-aided
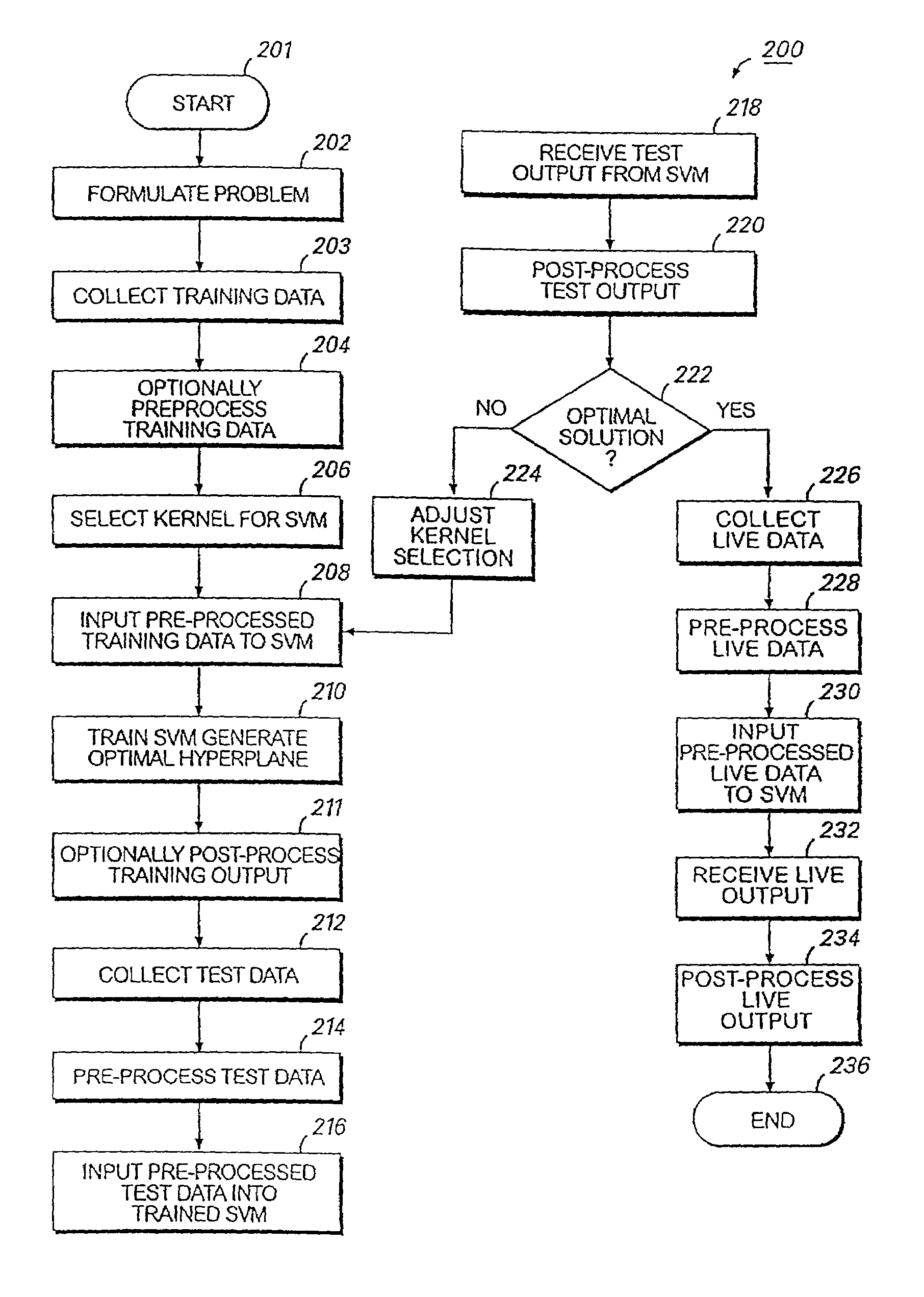
Digitized image data are input into a processor where a detection component identifies the areas (objects) of particular interest in the image and, by segmentation, separates those objects from the background. A feature extraction component formulates numerical values relevant to the classification task from the segmented objects. Results of the preceding analysis steps are input into a trained learning machine classifier which produces an output which may consist of an index discriminating between two possible diagnoses, or some other output in the desired output format. In one embodiment, digitized image data are input into a plurality of subsystems, each subsystem having one or more support vector machines. Pre-processing may include the use of known transformations which facilitate extraction of the useful data. Each subsystem analyzes the data relevant to a different feature or characteristic found within the image. Once each subsystem completes its analysis and classification, the output for all subsystems is input into an overall support vector machine analyzer which combines the data to make a diagnosis, decision or other action which utilizes the knowledge obtained from the image.
Owner:HEALTH DISCOVERY CORP +1
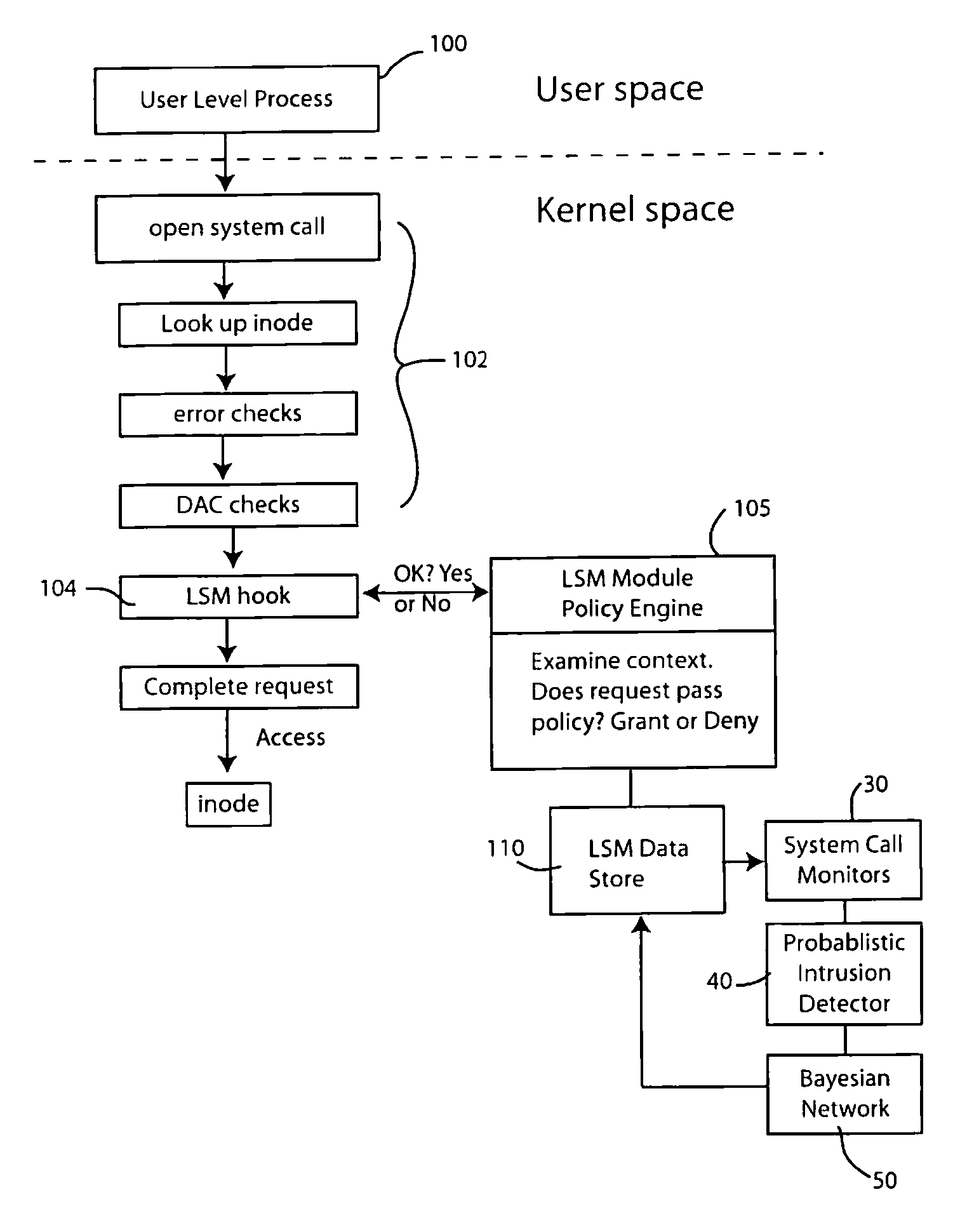
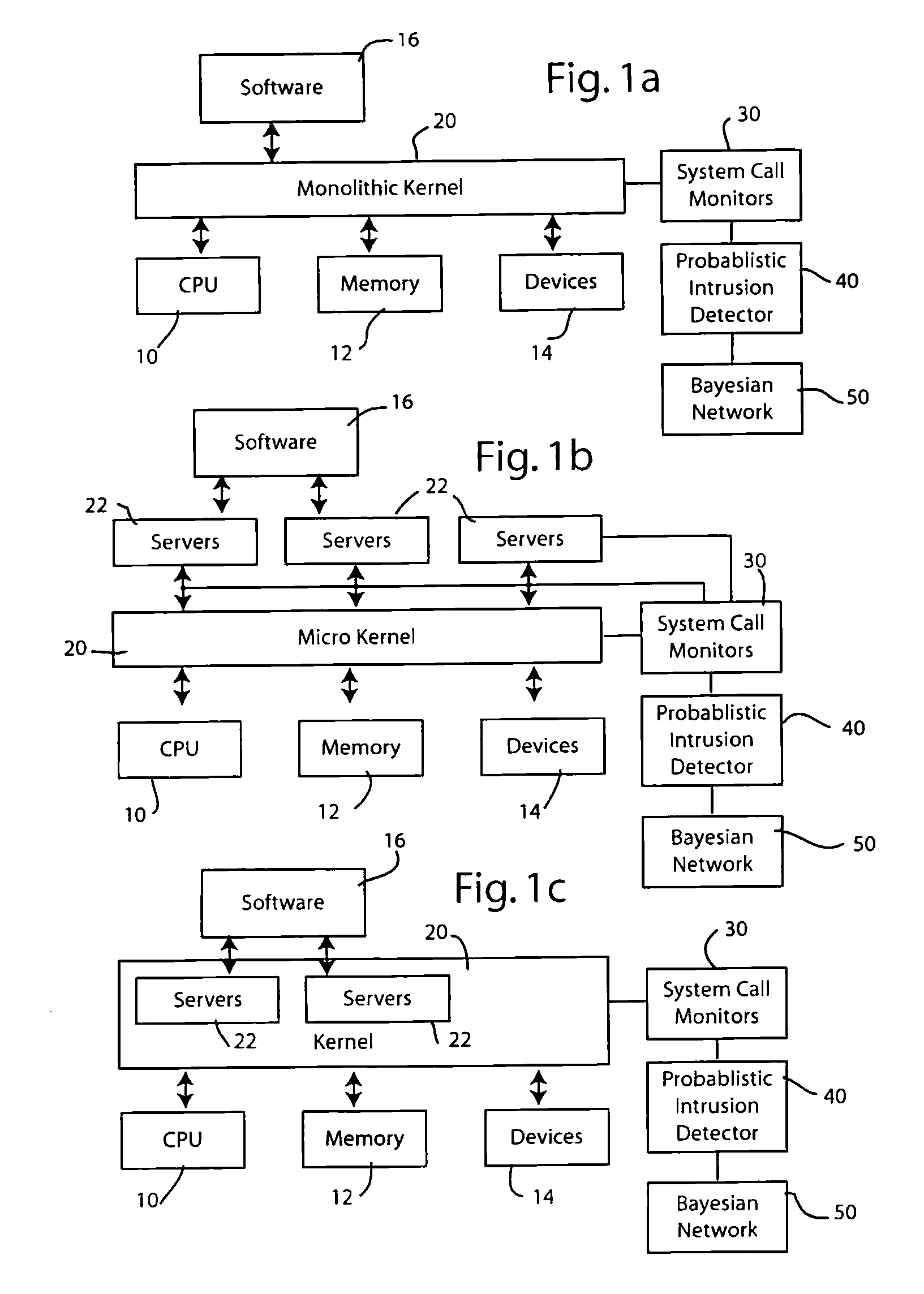
Intrusion detection using system call monitors on a bayesian network
InactiveUS20080201778A1Spread fastMemory loss protectionError detection/correctionSystem callBayesian network
Selected system calls are monitored to generate frequency data that is input to a probabilistic intrusion detection analyzer which generates a likelihood score indicative of whether the system calls being monitored were produced by a computer system whose security has been compromised. A first Bayesian network is trained on data from a compromised system and a second Bayesian network is trained on data from a normal system. The probabilistic intrusion detection analyzer considers likelihood data from both Bayesian networks to generate the intrusion detection measure.
Owner:PANASONIC CORP
Distributed systems and methods for automatically detecting unknown bots and botnets
ActiveUS9430646B1Error detection/correctionPlatform integrity maintainanceOutbound communicationCommand and control
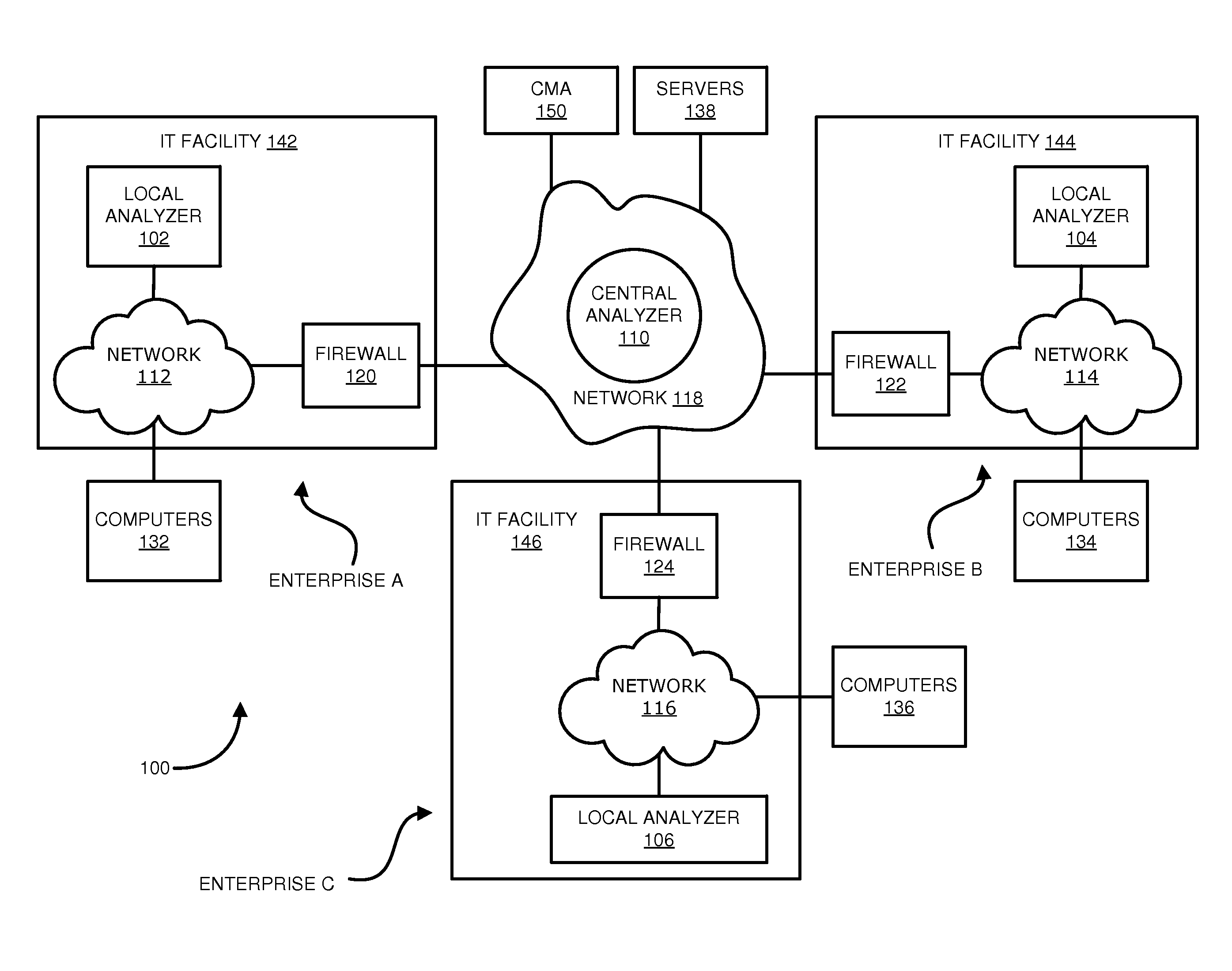
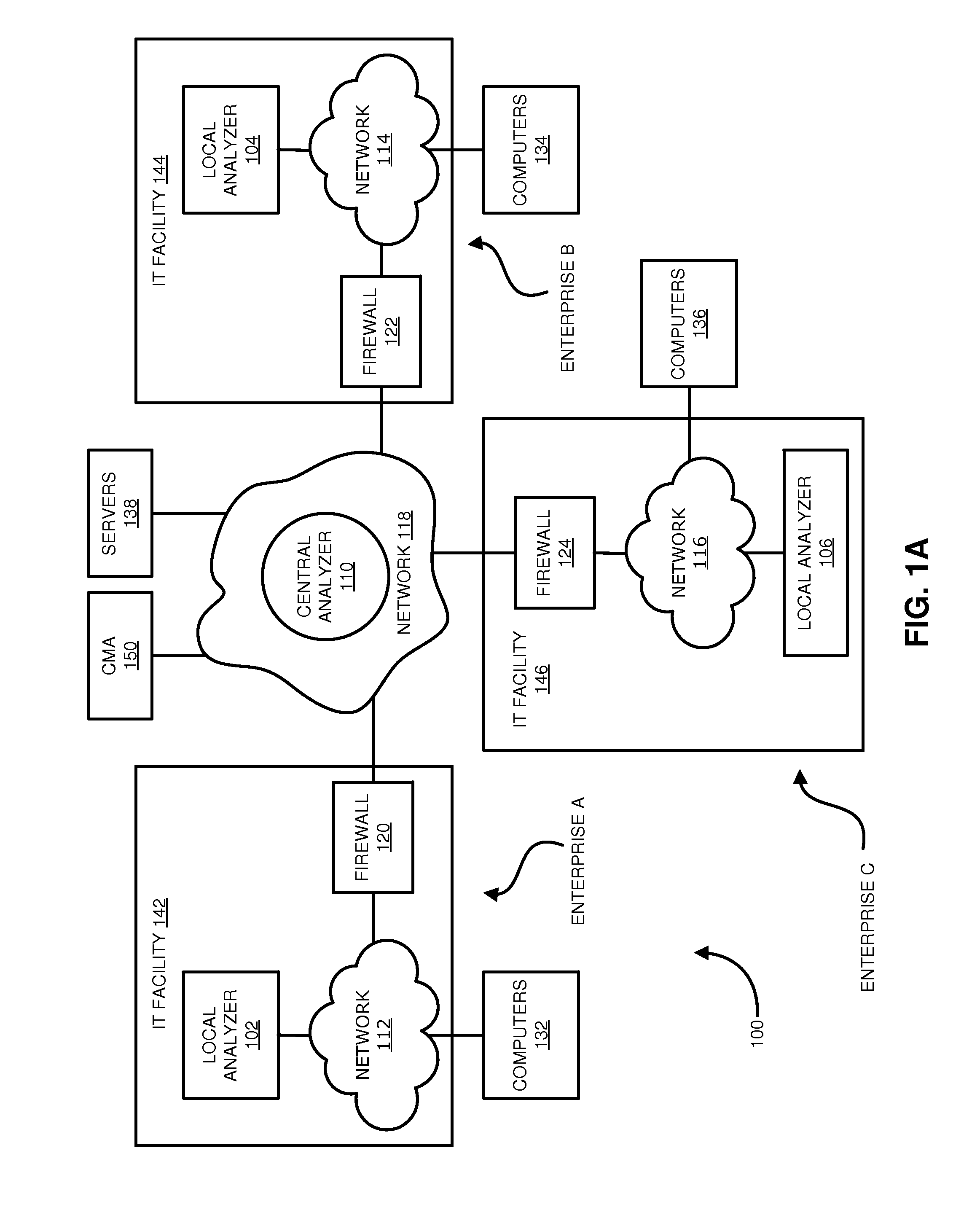
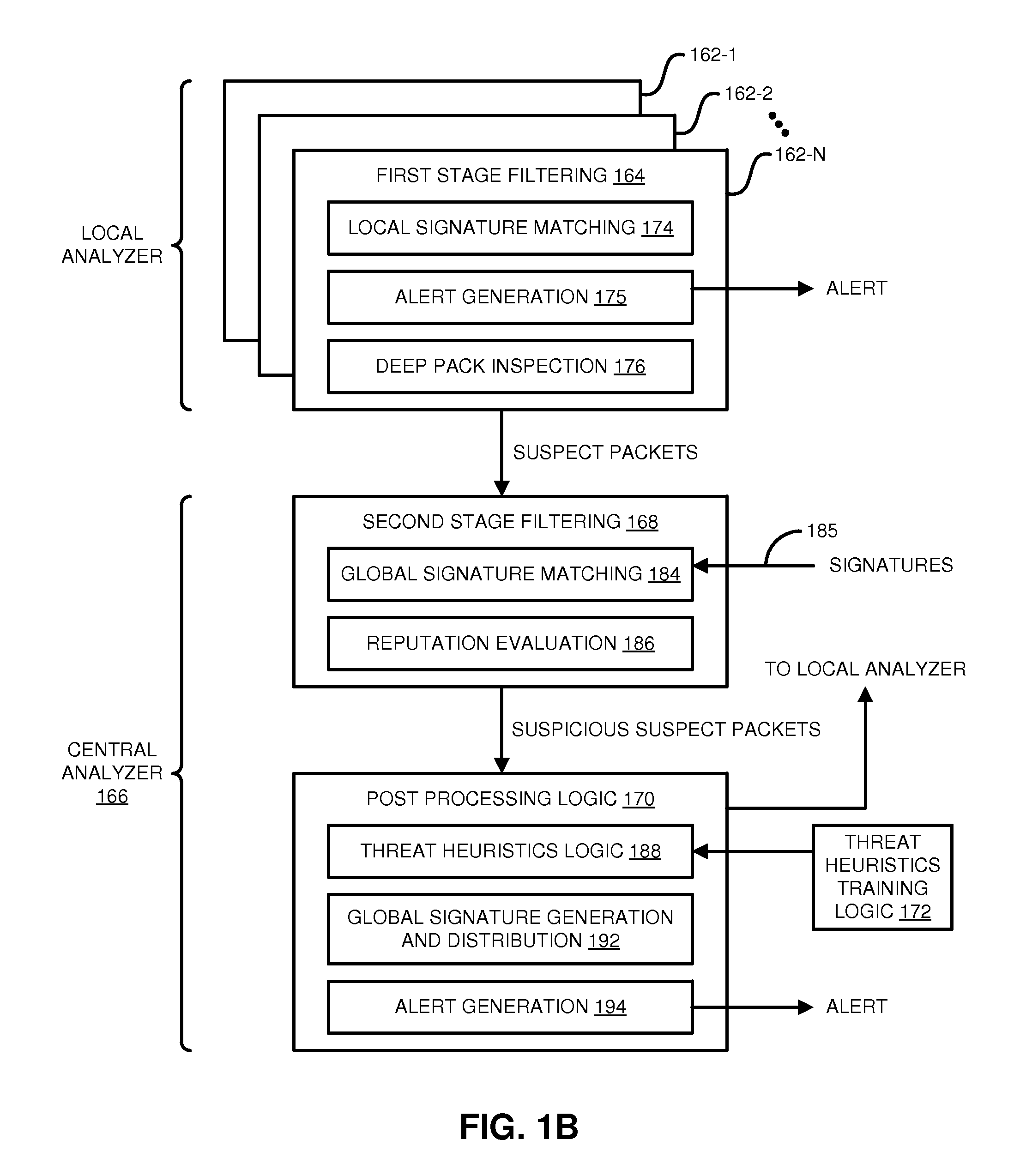
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using a distributed approach employing one or more local analyzers and a central analyzer. The local analyzers capture packets of outbound communications, generate header signatures, and analyze the captured packets using various techniques. The techniques may include packet header signature matching against verified callback signatures, deep packet inspection. The central analyzer receives the header signatures and related header information from the local analyzers, may perform further analysis (for example, on-line host reputation analysis); determines using a heuristics analysis whether the signatures correspond to callbacks; and generally coordinates among the local analyzers.
Owner:FIREEYE SECURITY HLDG US LLC
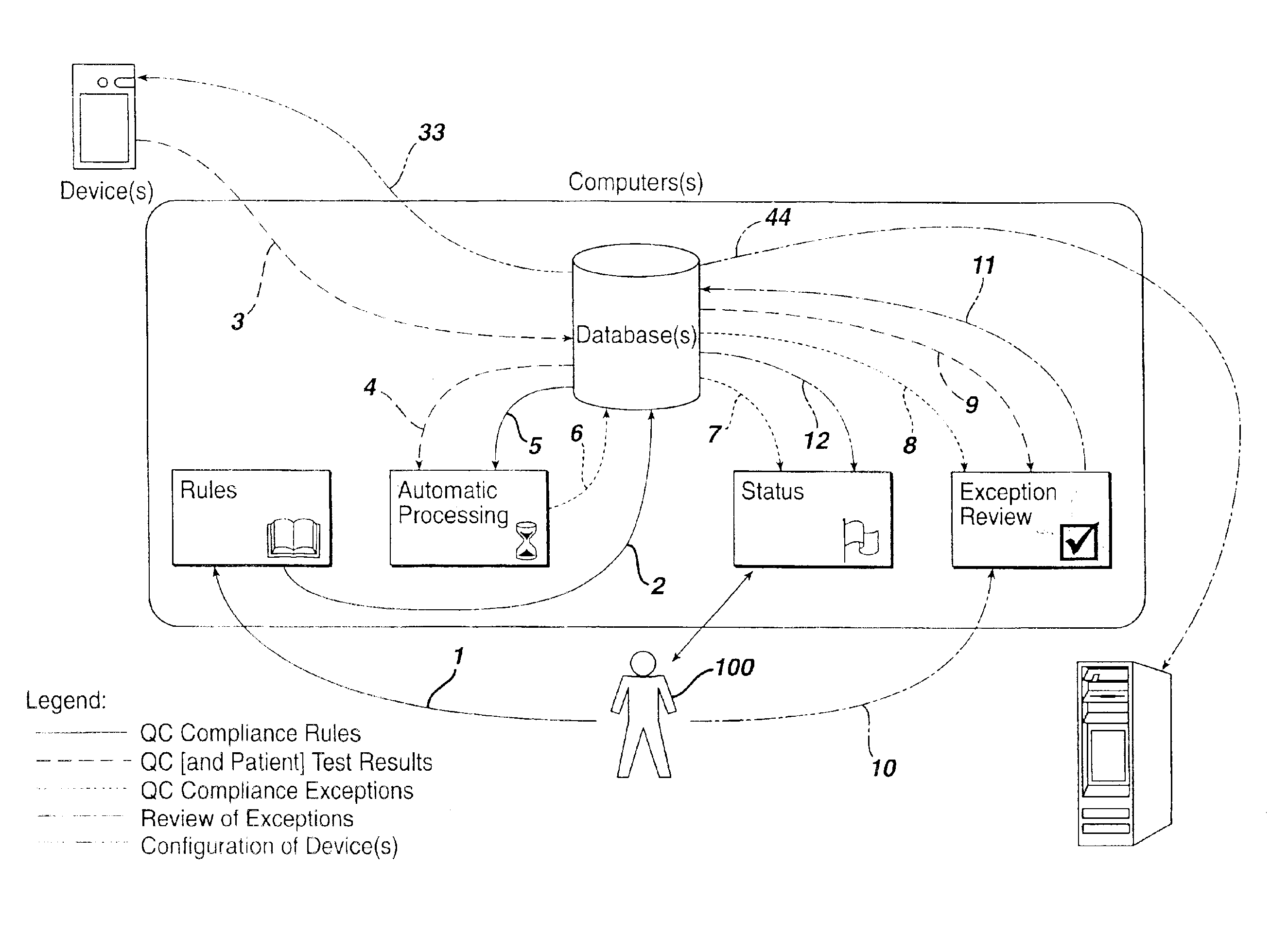
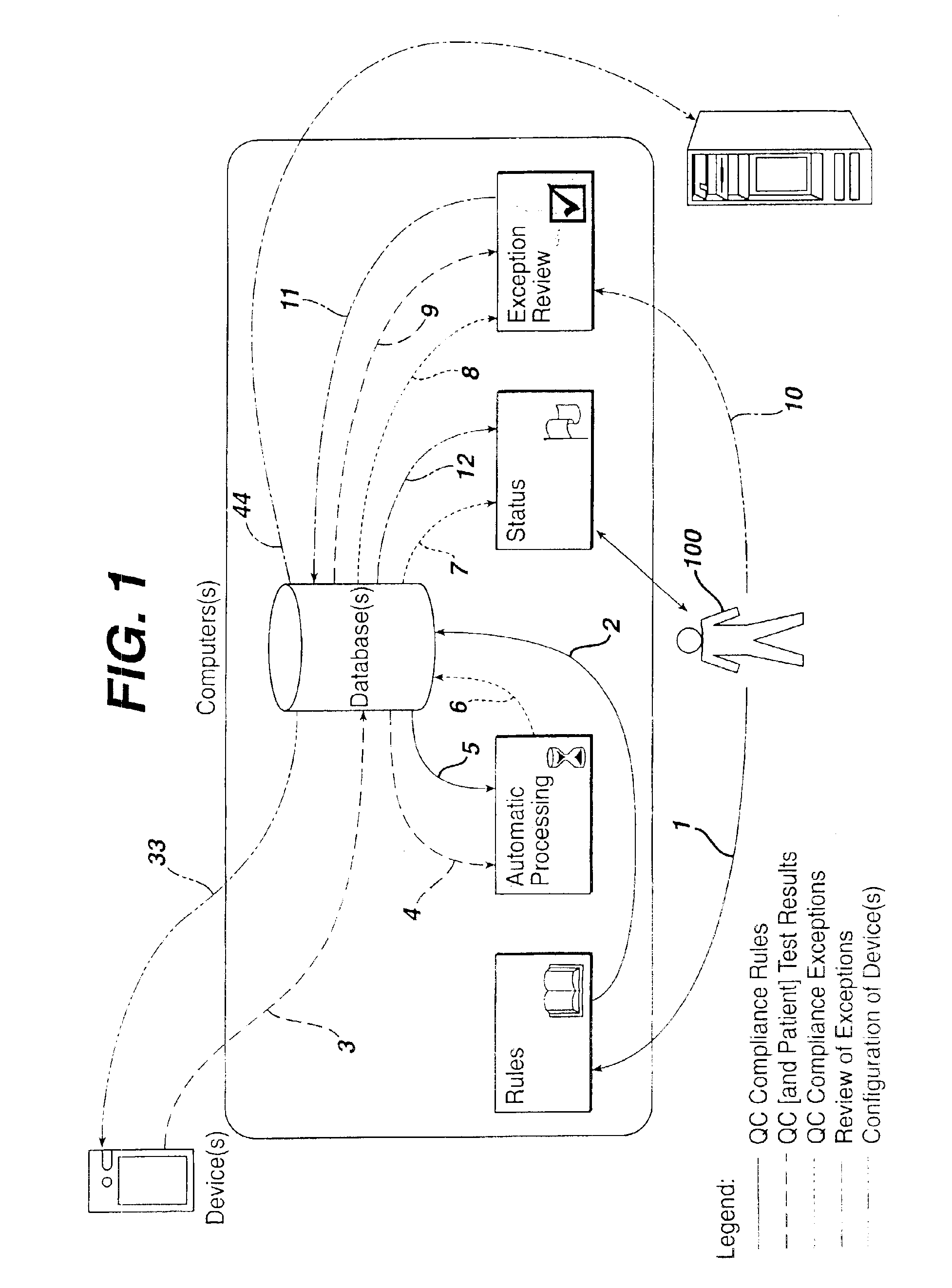
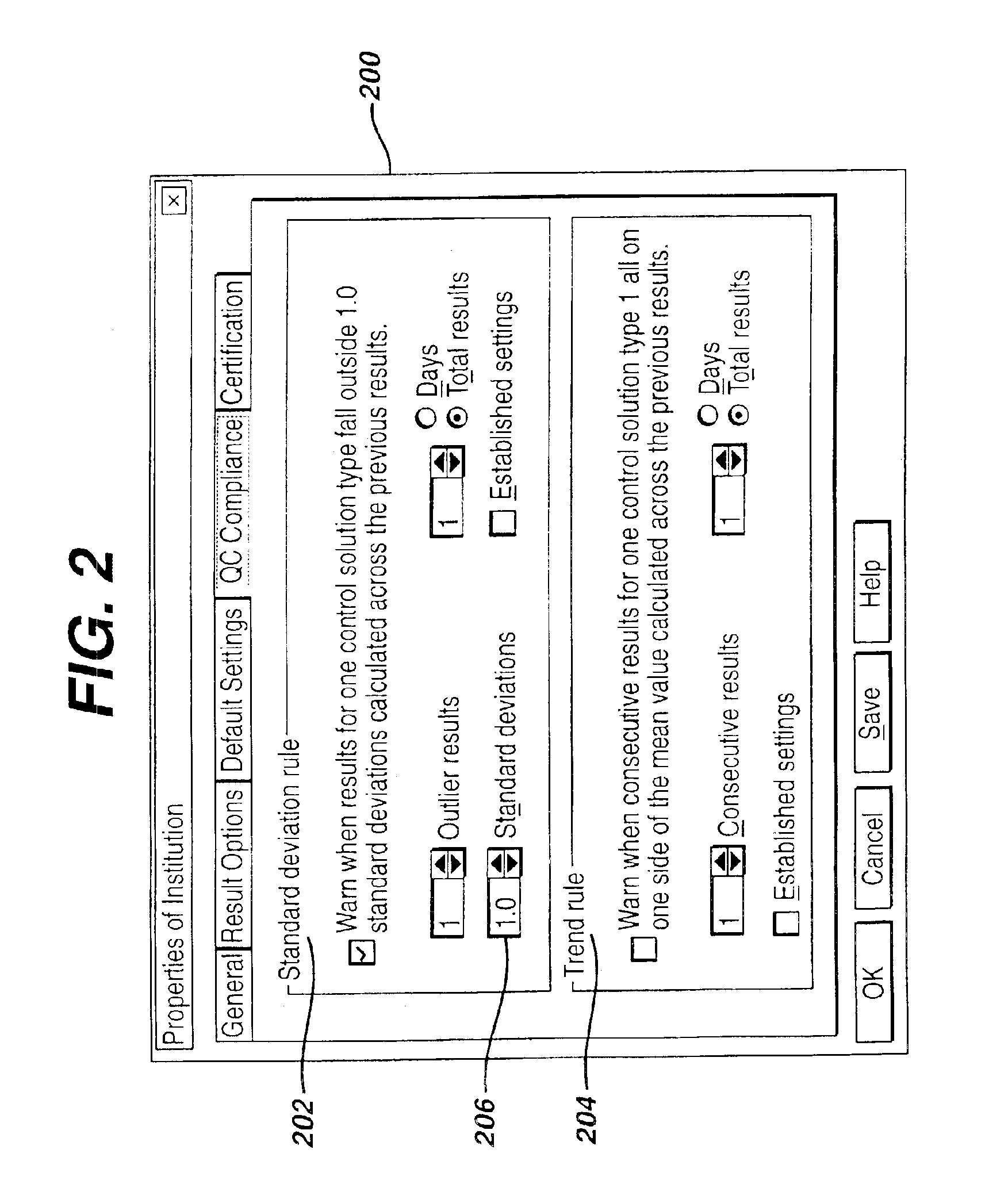
Method for automated exception-based quality control compliance for point-of-care devices
InactiveUS6856928B2Improving patient careQuality improvementDigital computer detailsNuclear monitoringAnalyteQuality control
A computer-implemented method to process POC information for potential QC compliance issues. A system and method for implementation of traditional laboratory analyzer based QC compliance in point-of-care (POC) environments is disclosed. A specific system and method to analyze data from POC testing to identify when the testing exceeds the variation expected under stable operation (i.e., the testing is “out of control”) is disclosed. This system and method is characterized by solving the QC compliance problem for POC devices by individuals not trained in traditional laboratory practices. This also provides the capability in real-time or near real-time to analyze POC testing information regarding the performance of each POC device, reagent kit (i.e., one kit per analyte tested) and / or lot, and operator so one can respond quickly to a particular device, reagent kit and / or lot, or operator that is not performing properly.
Owner:LIFESCAN IP HLDG LLC
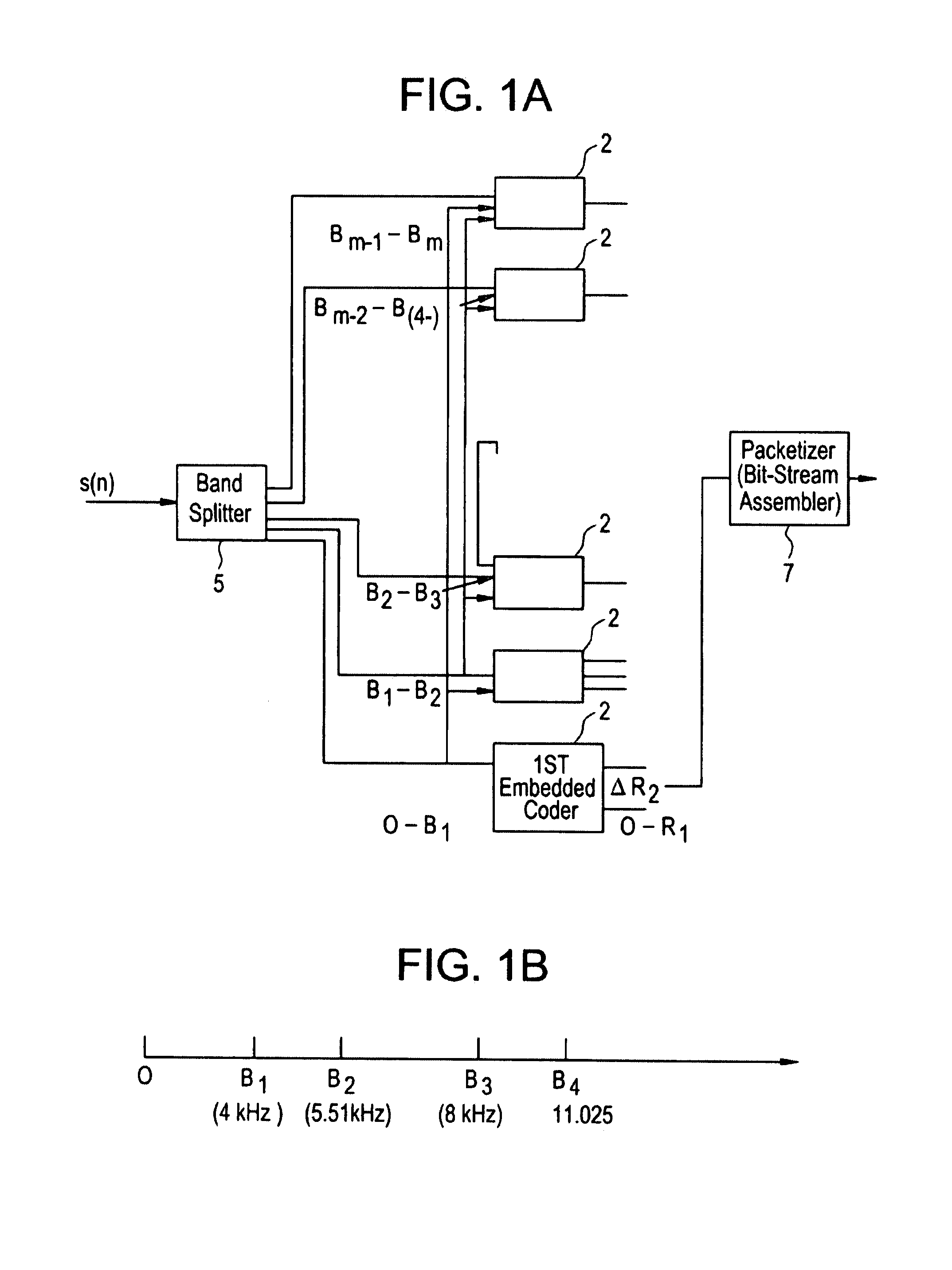
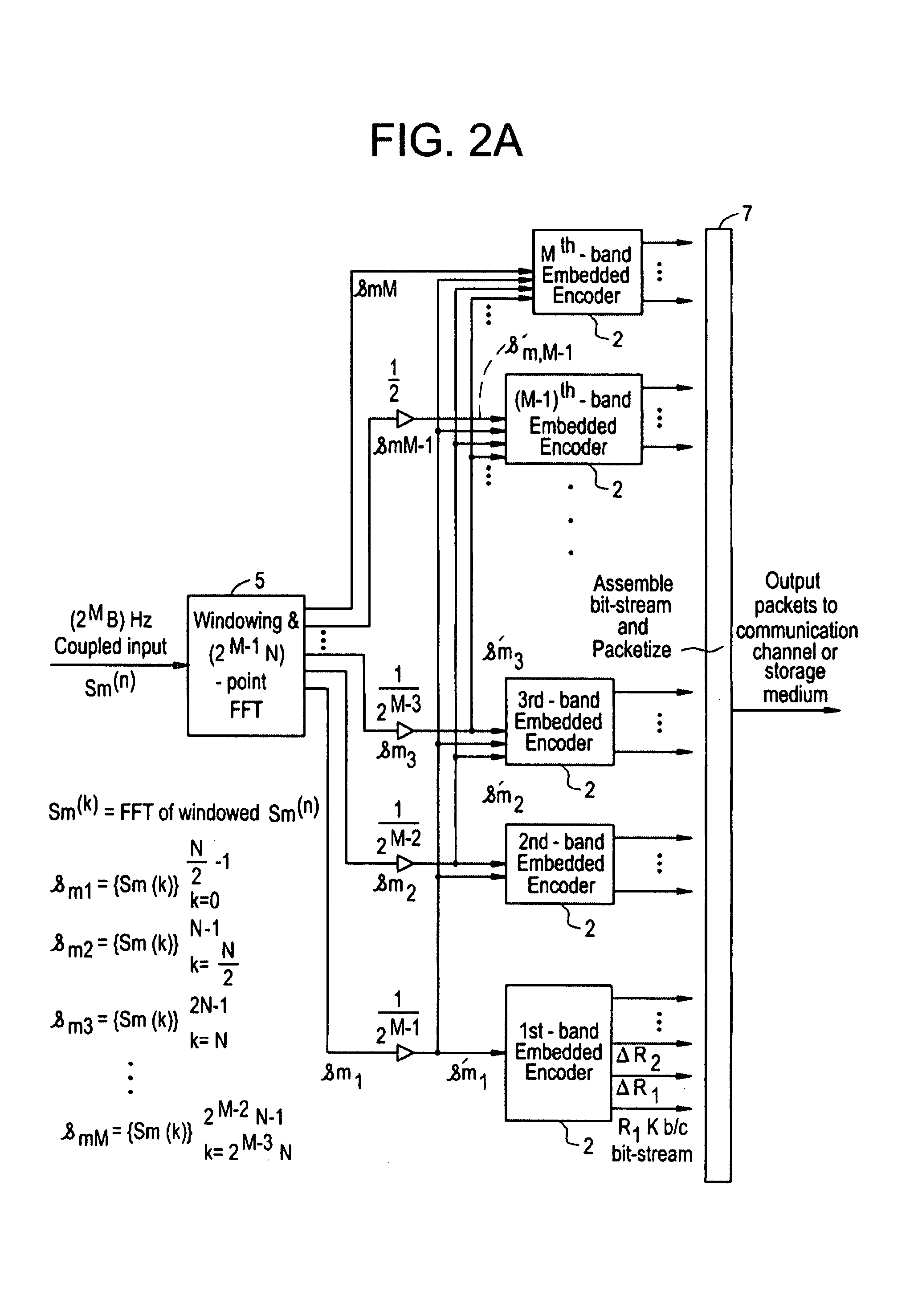
Scalable and embedded codec for speech and audio signals
InactiveUS7272556B1Improve signal reconstruction accuracyImprove reconstruction accuracySpeech analysisMultiple modesAudio signal flow
A system and method for processing of audio and speech signals is disclosed, which provide compatibility over a range of communication devices operating at different sampling frequencies and / or bit rates. The analyzer of the system divides the input signal in different portions, at least one of which carries information sufficient to provide intelligible reconstruction of the input signal. The analyzer also encodes separate information about other portions of the signal in an embedded manner, so that a smooth transition can be achieved from low bit-rate to high bit-rate applications. Accordingly, communication devices operating at different sampling rates and / or bit-rates can extract corresponding information from the output bit stream of the analyzer. In the present invention embedded information generally relates to separate parameters of the input signal, or to additional resolution in the transmission of original signal parameters. Non-linear techniques for enhancing the overall performance of the system are also disclosed. Also disclosed is a novel method of improving the quantization of signal parameters. In a specific embodiment the input signal is processed in two or more modes dependent on the state of the signal in a frame. When the signal is determined to be in a transition state, the encoder provides phase information about N sinusoids, which the decoder end uses to improve the quality of the output signal at low bit rates.
Owner:ALCATEL LUCENT SAS
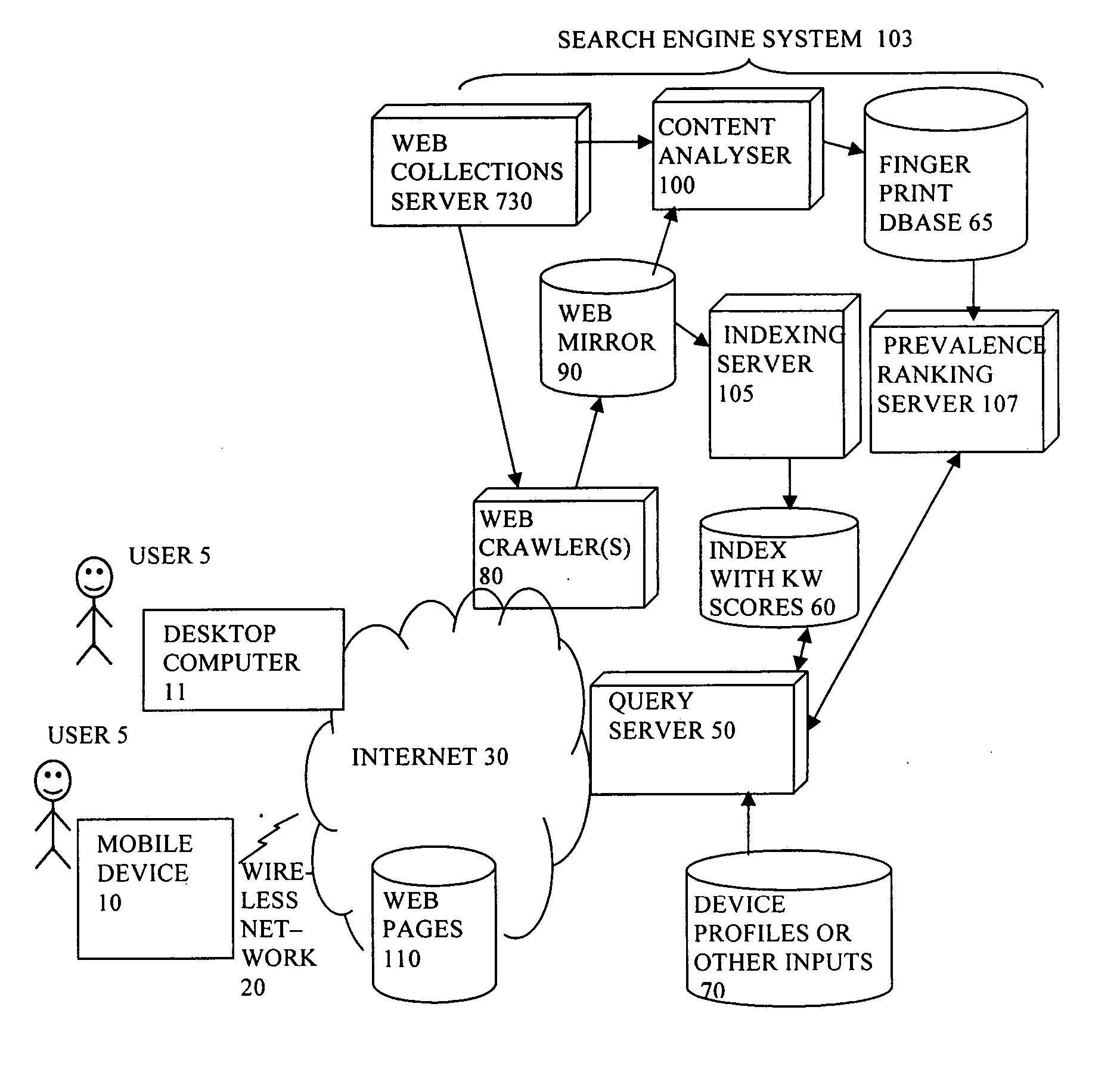
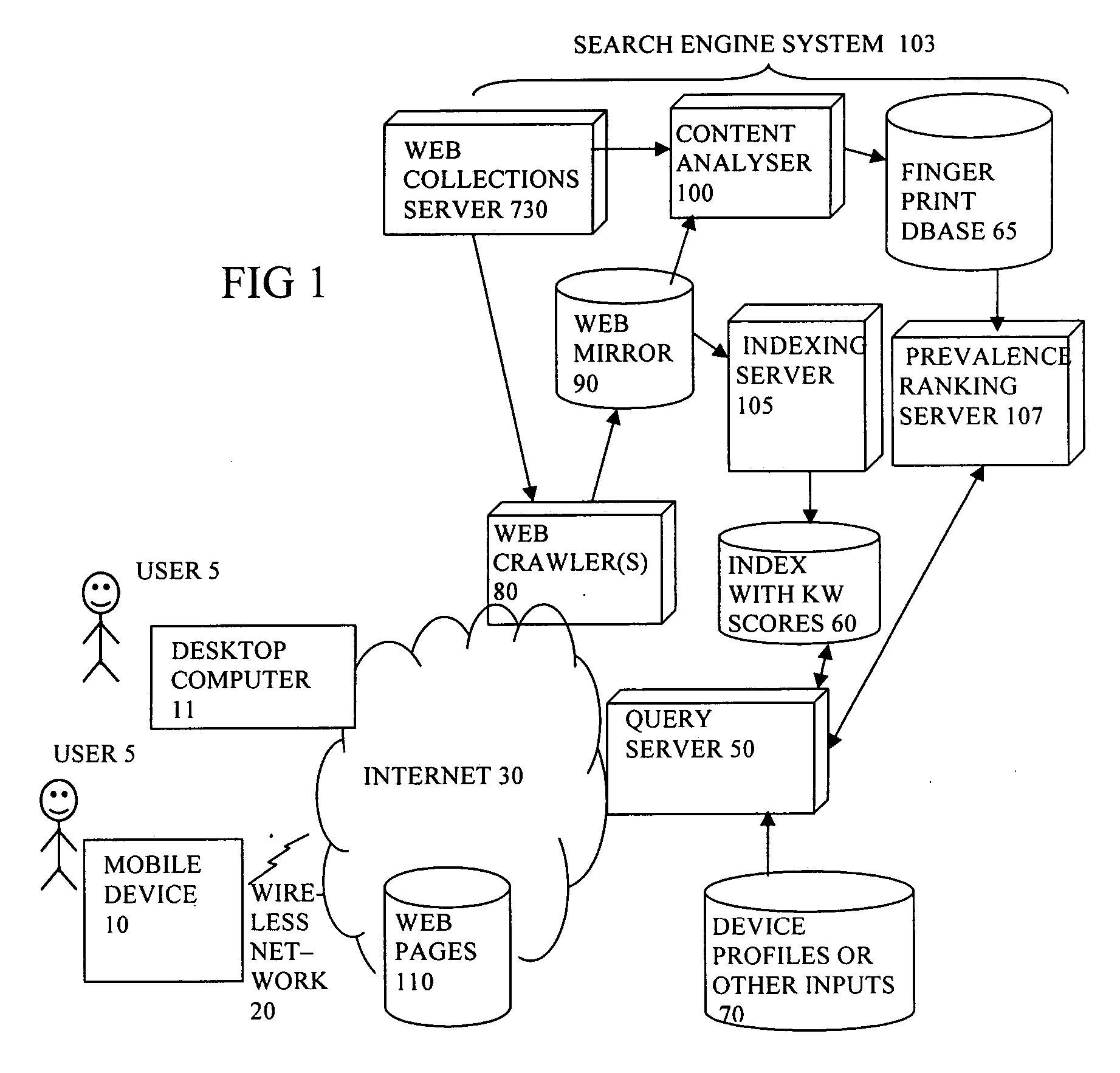
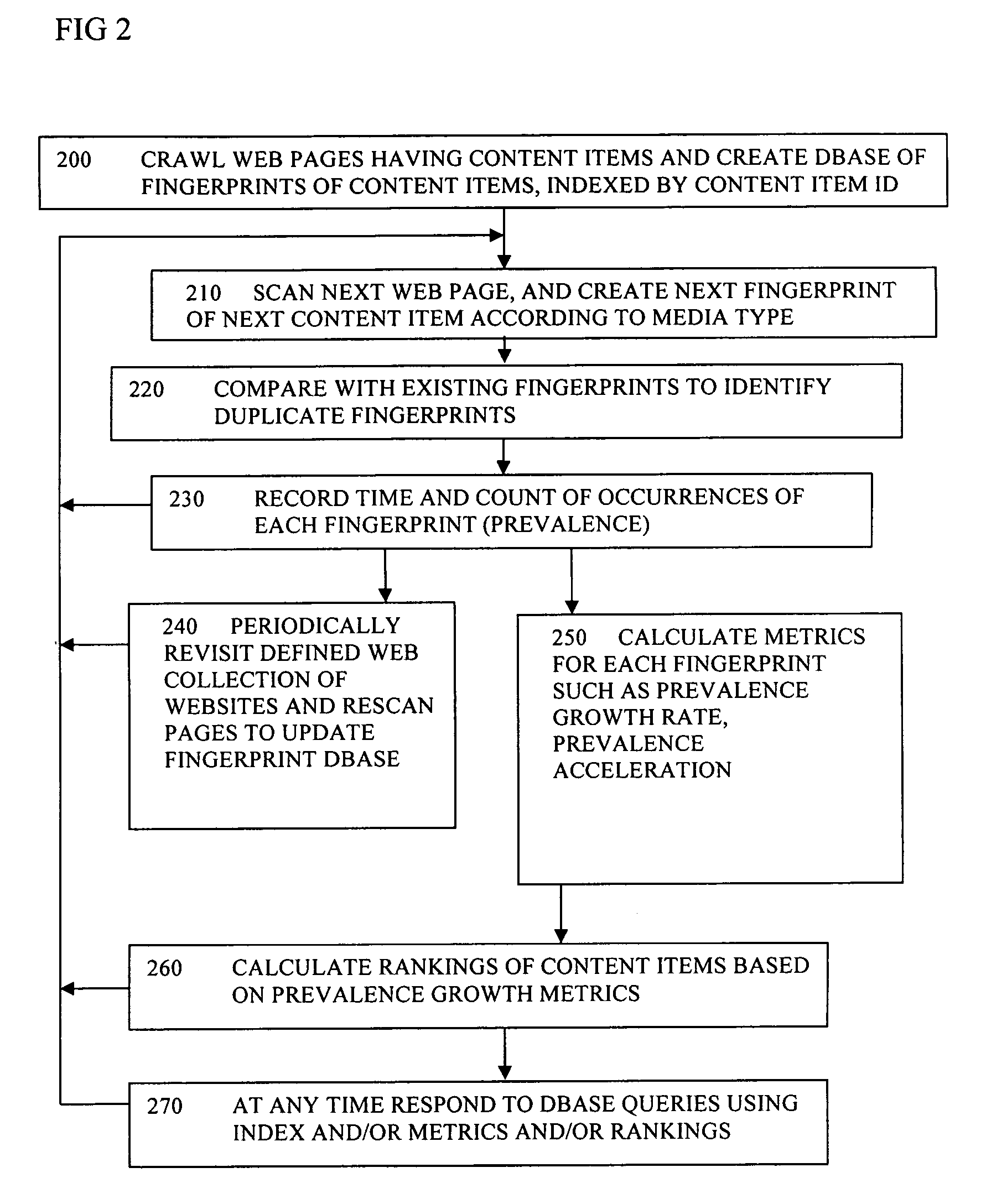
Search using changes in prevalence of content items on the web
InactiveUS20070067304A1Easy searchEfficient comparisonWeb data indexingSpecial data processing applicationsContent analyticsPrevalence
A search engine has a query server (50) arranged to receive a search query from a user and return search results, the query server being arranged to identify one or more of the content items relevant to the query, to access a record of changes over time of occurrences of the identified content items, and rank the search results according to the record of changes. This can help find those content items which are currently active, and to track or compare the popularity of content items. This is particularly useful for content items whose subjective value to the user depends on them being topical or fashionable. A content analyzer (100) creates a fingerprint database of fingerprints, to compare the fingerprints to determine a number of occurrences of a given content item at a given time, and to record the changes over time of the occurrences.
Owner:TAPTU LTD
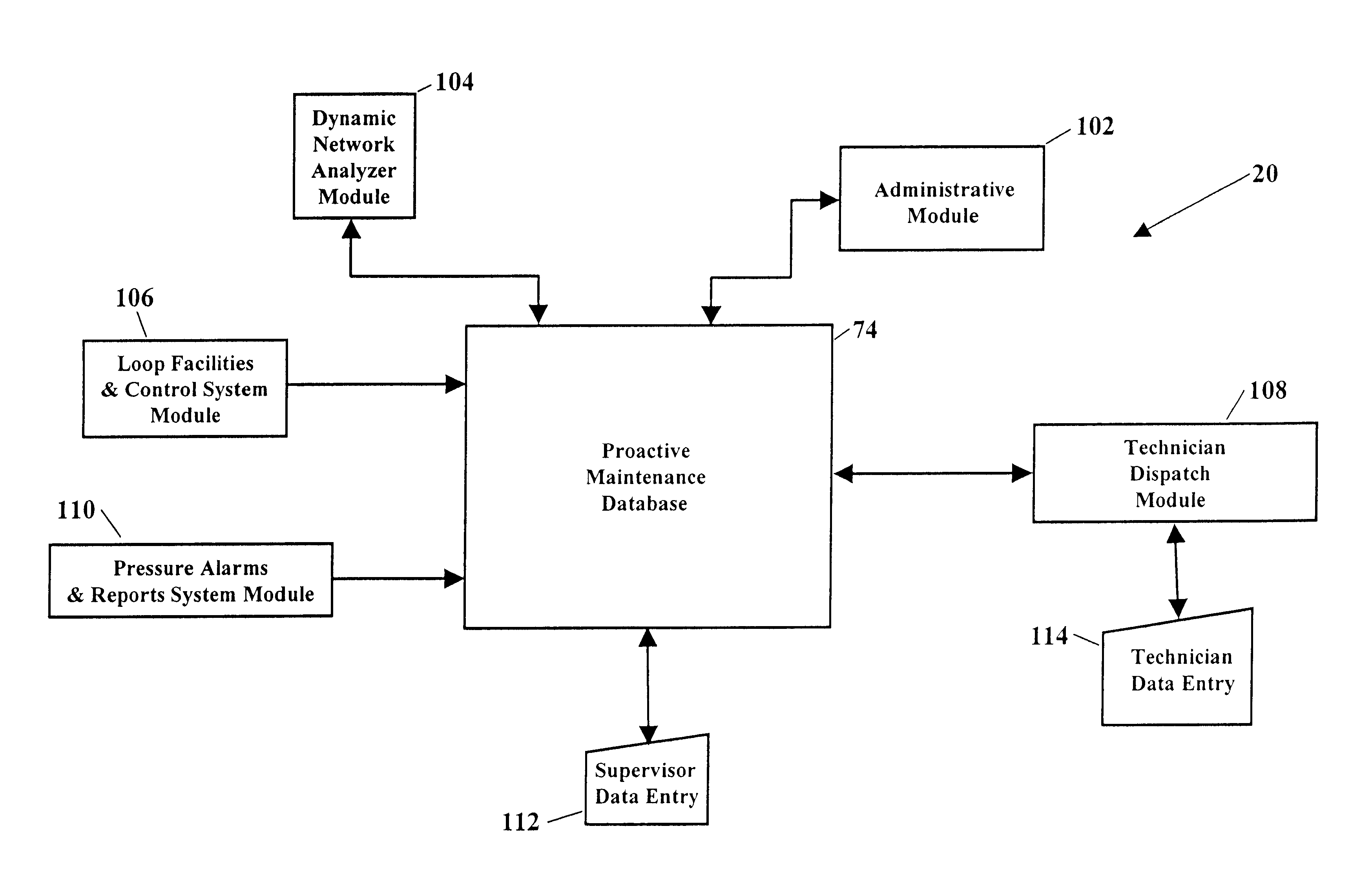
Pressure alarms and reports system module for proactive maintenance application
InactiveUS6771739B1Supervisory/monitoring/testing arrangementsSubstation equipmentFiberNetwork analytics
Methods and systems for proactively maintaining a telephone system local loop. One embodiment includes communicating with a communications network and acquiring information associated with pressure or flow sensors along fiber optic cables. Proactive maintenance of the fiber optic cables is predicted using the information associated with pressure or flow sensors. The embodiment may further include generating and dispatching work order information describing the predicted proactive maintenance. The embodiment may also include predicting proactive maintenance of telephone lines using information from a Dynamic Network Analyzer and using information from a Loop Facilities and Control System. Another embodiment includes a system for predicting proactive maintenance of a telephone system local loop. This embodiment includes a Pressure Alarms and Reports System Module, a database stored in memory, and a processor. The Pressure Alarms and Reports System Module communicates with a communications network and acquires at least one of i) pressure information associated with fiber optic cables and ii) flow information associated with fiber optic cables. The database stores the acquired information. The processor processes information stored in the database and generates predicted proactive maintenance.
Owner:BELLSOUTH INTPROP COR
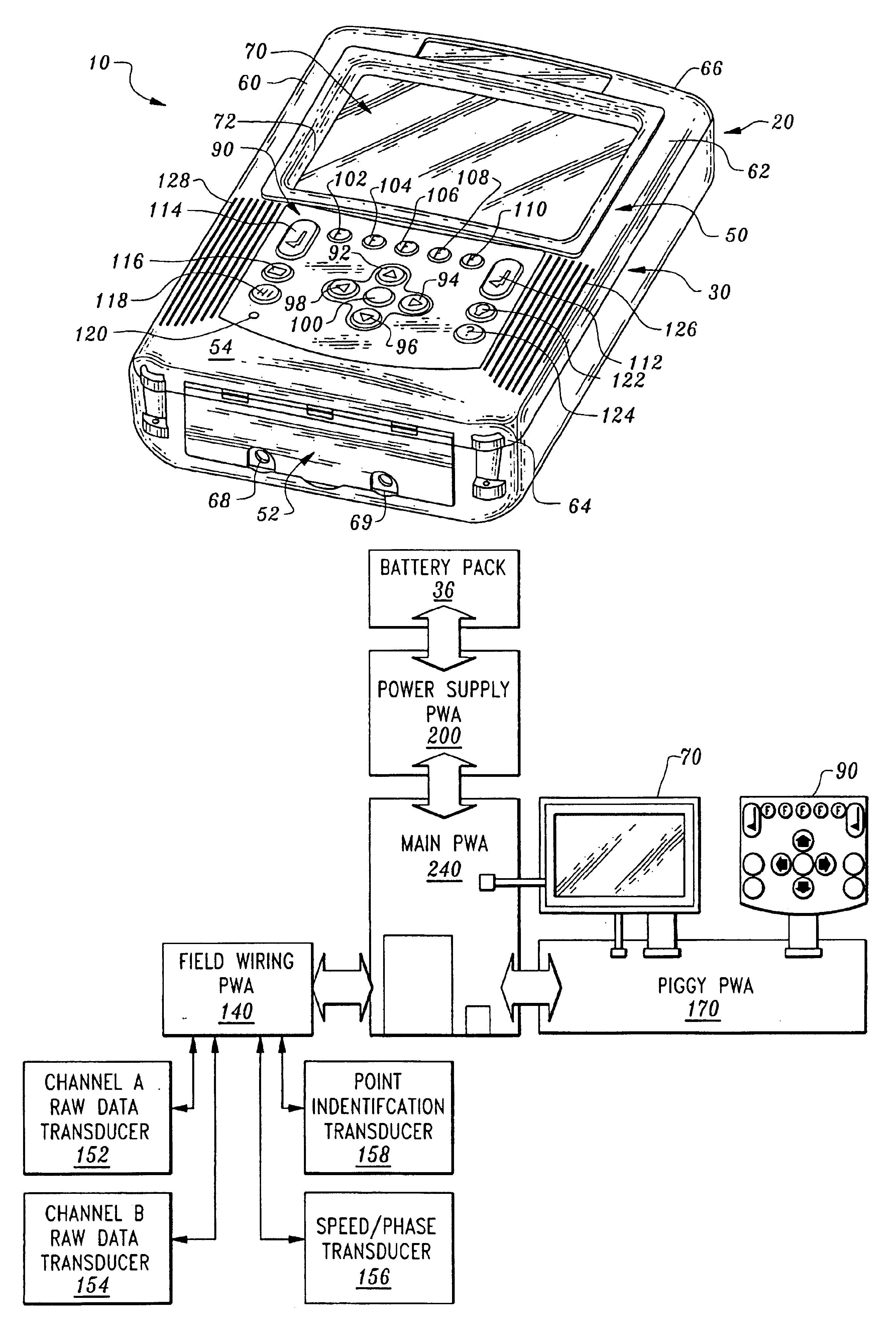
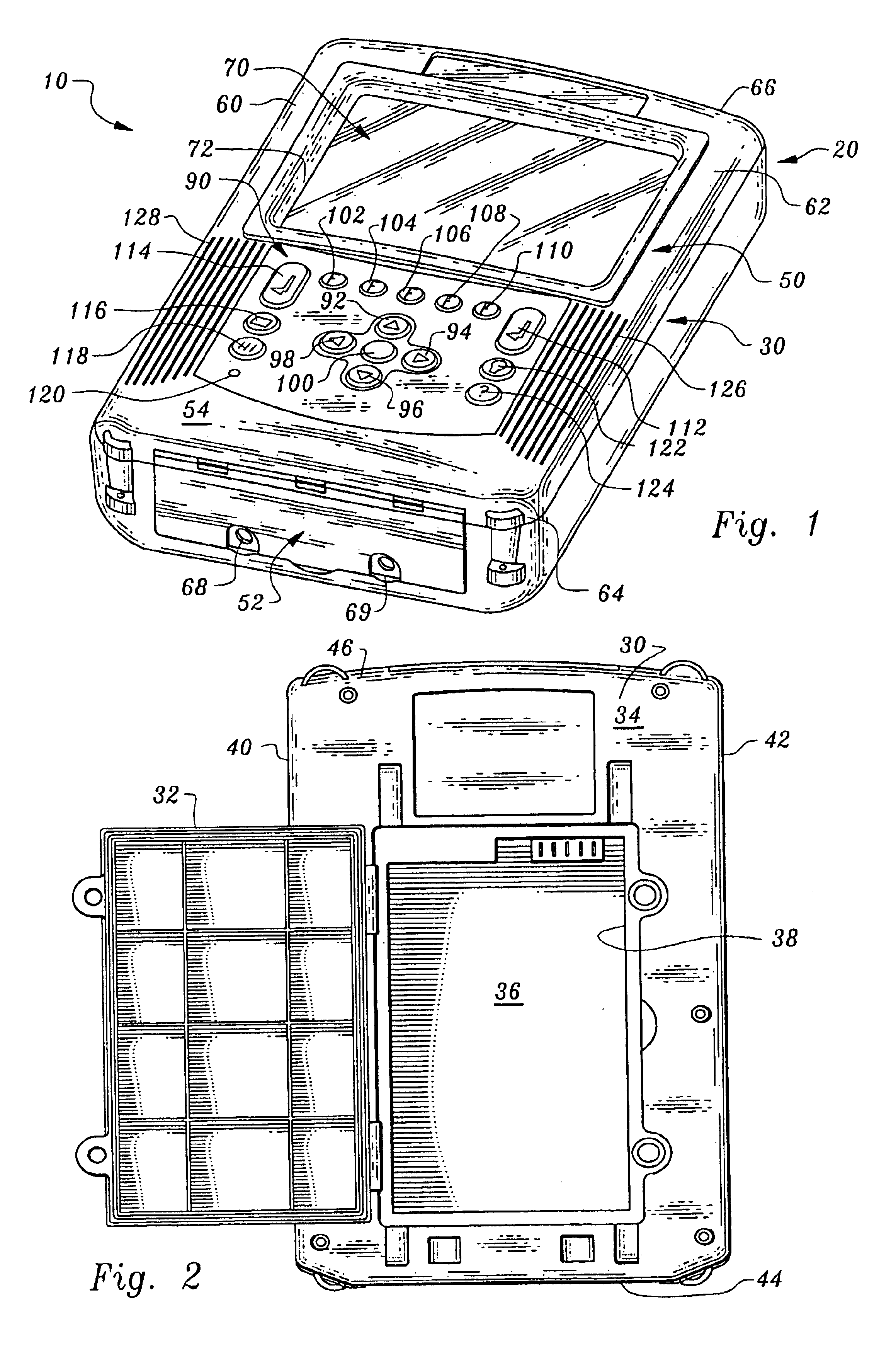
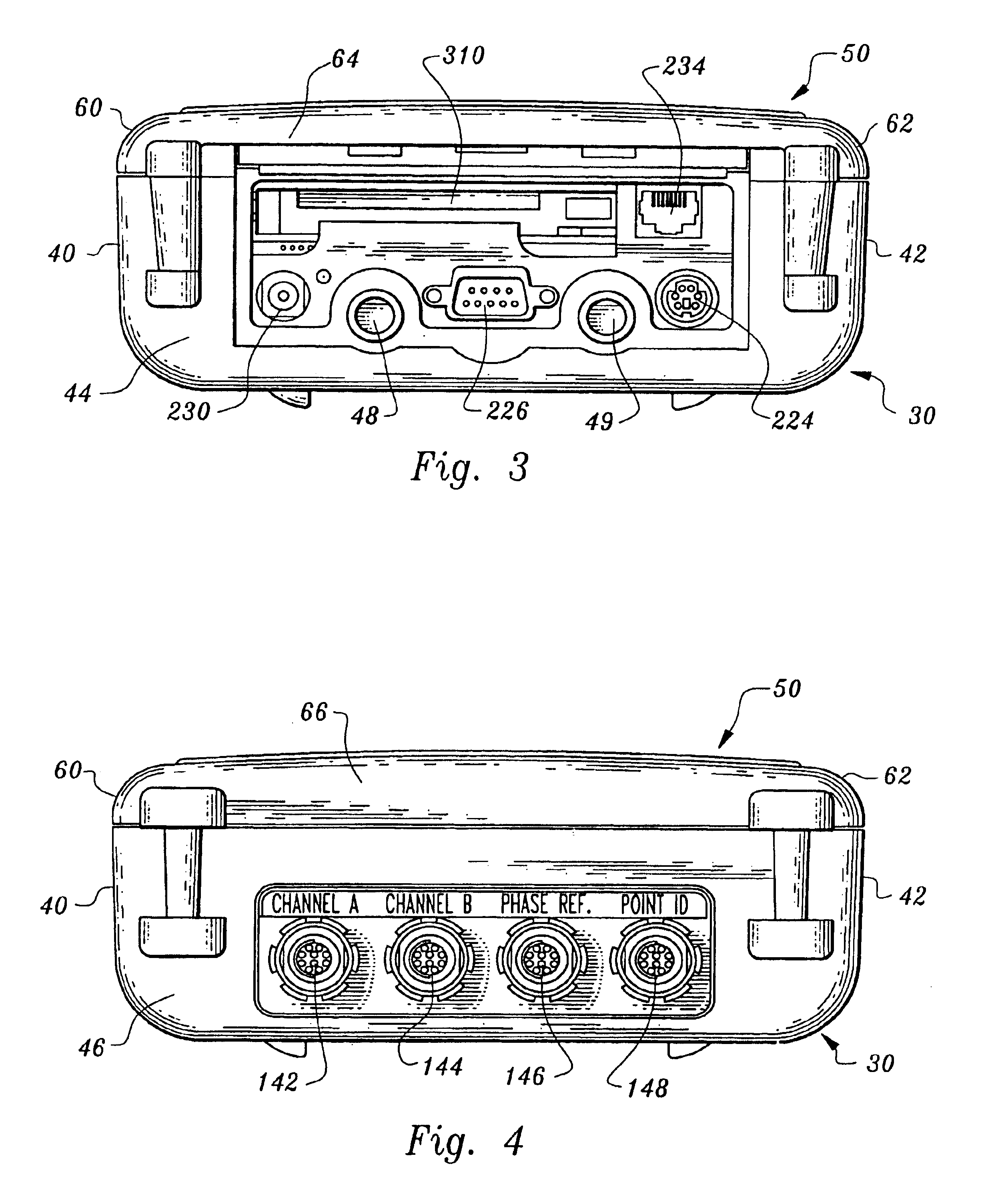
Portable data collector and analyzer: apparatus and method
InactiveUS6789030B1Efficient solutionIncreasing signal processing speedSpectral/fourier analysisNuclear monitoringFrequency spectrumTransducer
A portable data collector and analyzer apparatus and method provides predictive and preventative maintenance of a multiplicity of assets through the use of a unique architecture that allows a variety of different application programs to be downloaded to the apparatus for providing a single multi-purpose portable data collector and analyzer apparatus that can employ the variety of different application programs for configuring, inter alia, different measurements types, different transducers types and different signal processing types for collecting and analyzing sensed physical data from a variety of different assets found in industrial plants. A unique frequency shifting and decimation method is employed for spectrum calculation that, inter alia, retains DSP addressing efficiency and increases signal processing speed. Additionally, a unique synchronous sampling method is employed that generates synchronous sample waveforms from asynchronous sample waveforms. Furthermore, a unique clear touch screen overlying a quarter VGA display, an ergonomically designed keypad, and an intuitive user interface allow quick and easy setup and operation for in-field data acquisition, analysis and display.
Owner:BENTLY NEVADA INC
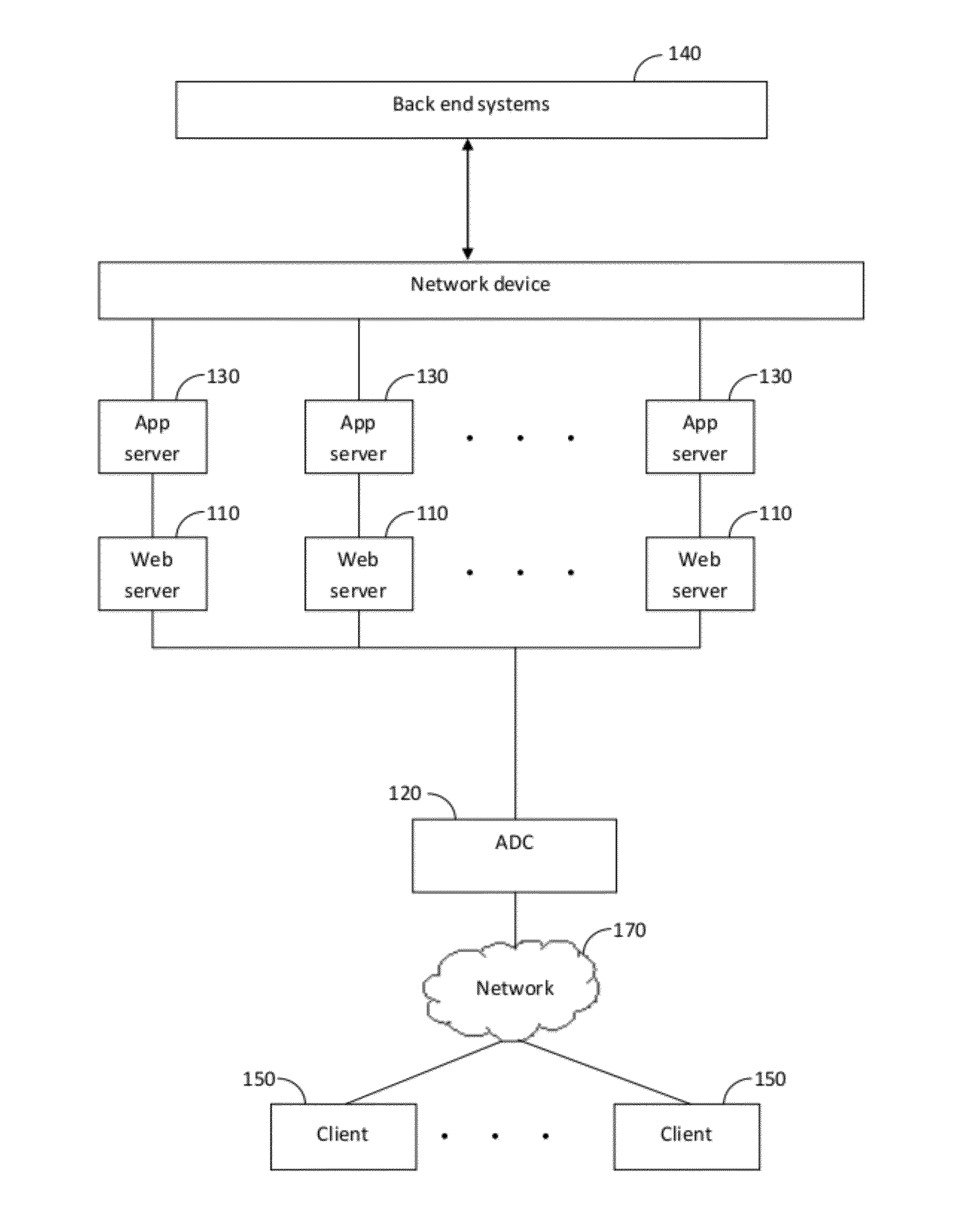
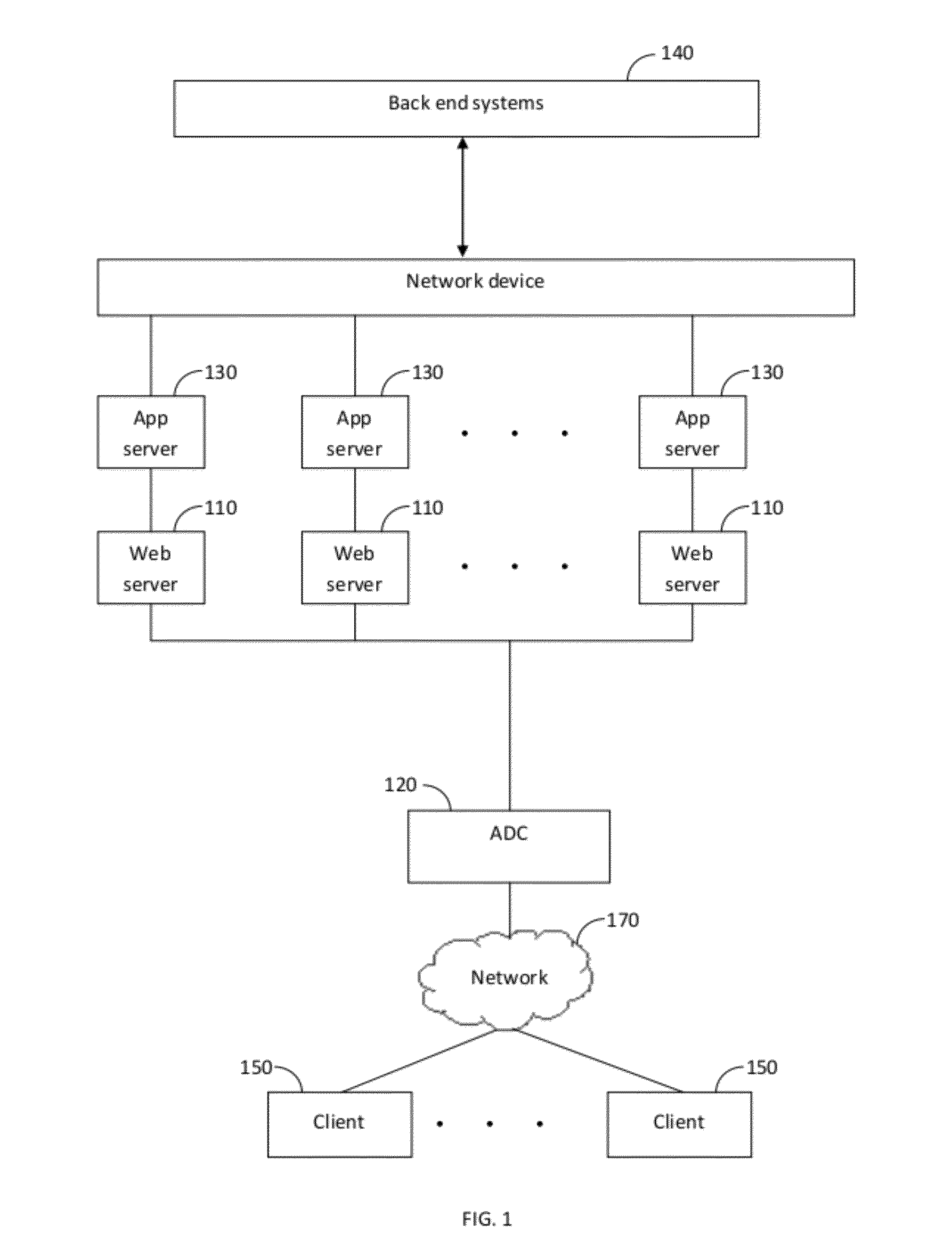
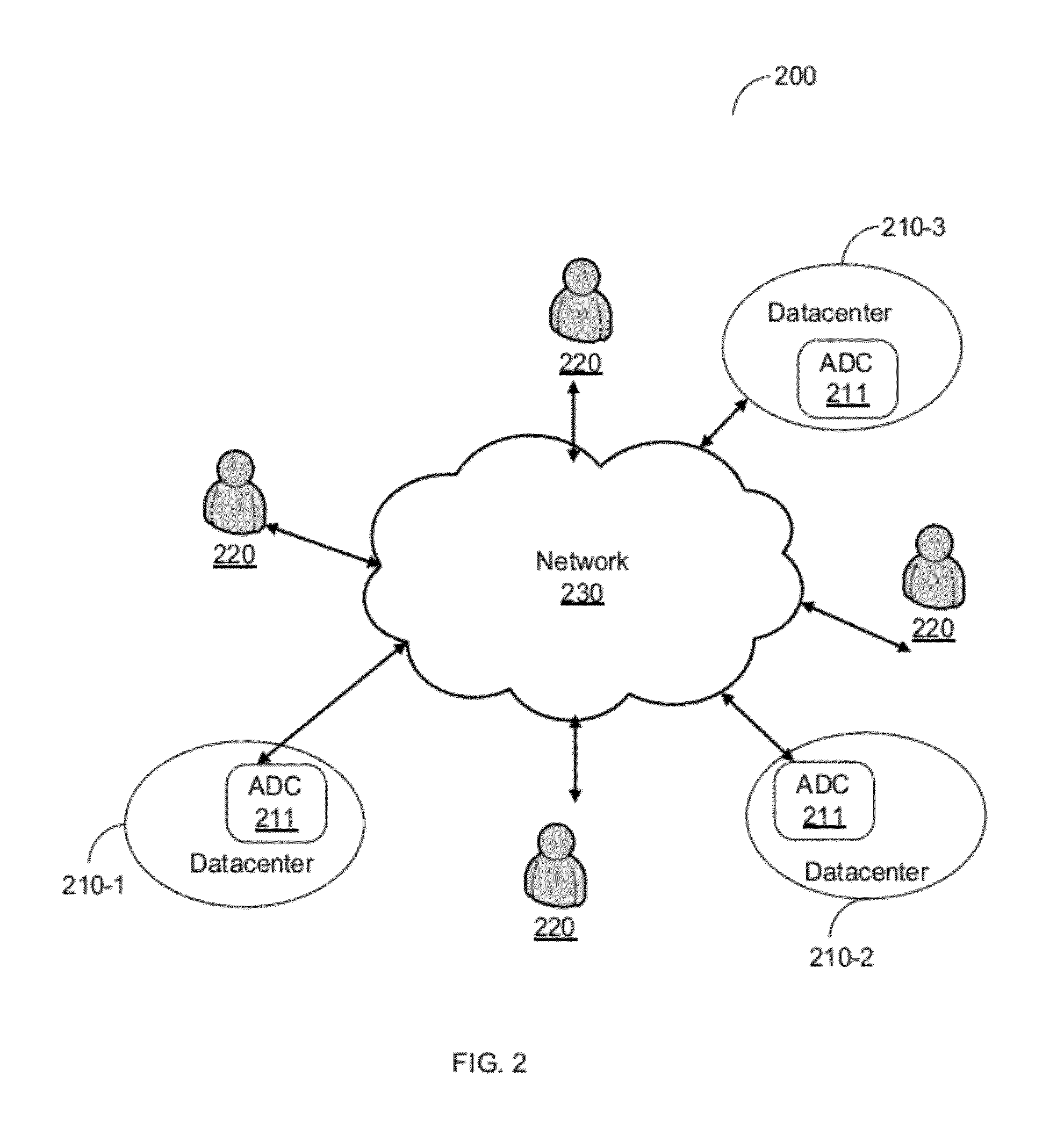
Method and system for efficient deployment of web applications in a multi-datacenter system
ActiveUS20120136697A1Easy to deployDigital computer detailsTransmissionService-level agreementWeb application
A system for computing an optimal deployment of at least one web application in a multi-datacenter system comprising a collector for collecting performance measurements with regard to a web application executed in the multi-datacenter system and grouping the performance measurements according to locations of a plurality of clients accessing the web application; a data repository for maintaining at least a performance table including at least the performance measurements grouped according to the plurality of client locations and a service level agreement (SLA) guaranteed to clients in the plurality of client locations; and an analyzer for processing at least information stored in the performance table for generating a recommendation on an optimal deployment of the web application in at least one combination of datacenters in the multi-datacenter system by computing an expected SLA that can be guaranteed to the clients in each combination of datacenters.
Owner:RADWARE
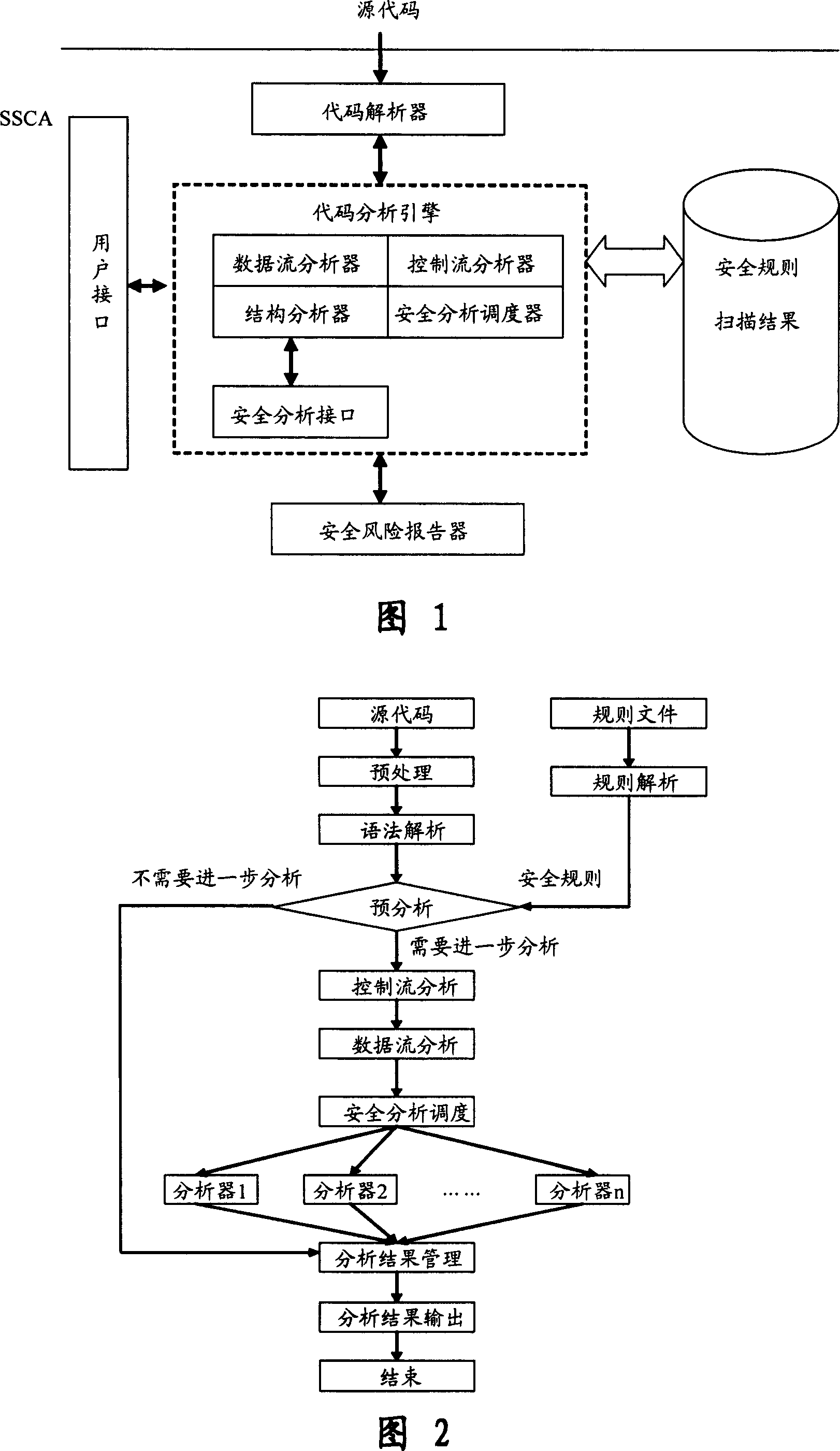
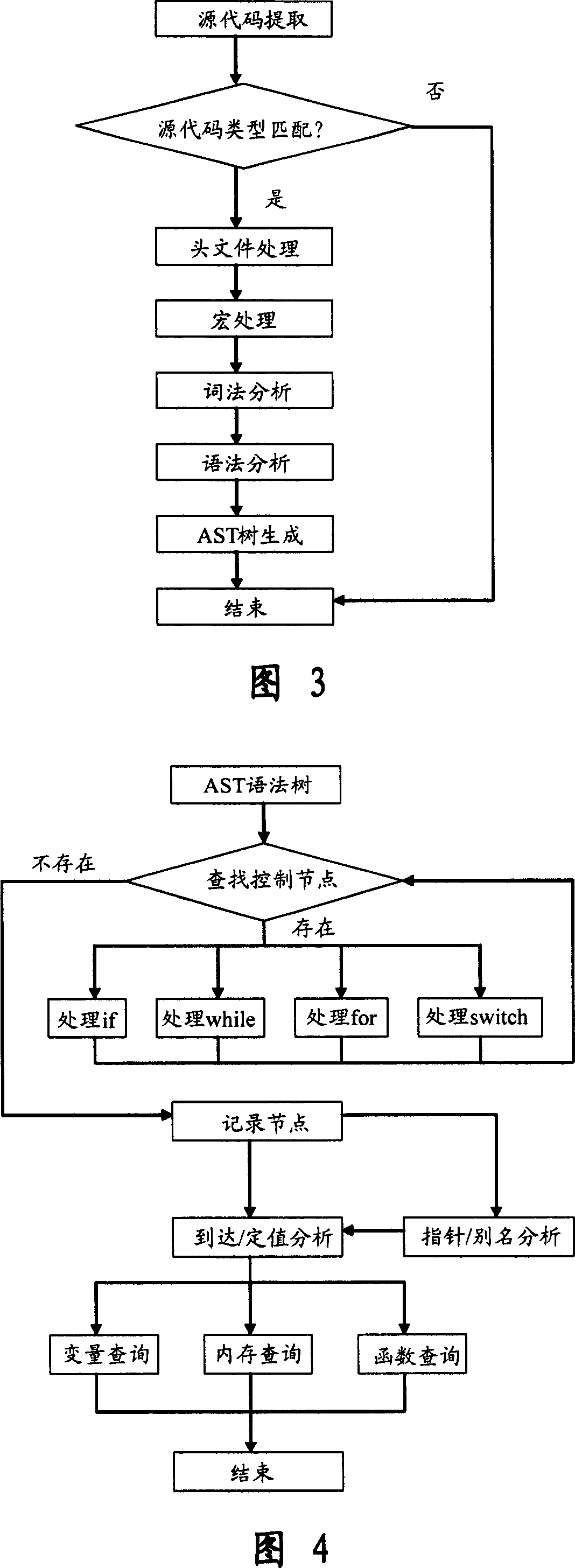
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
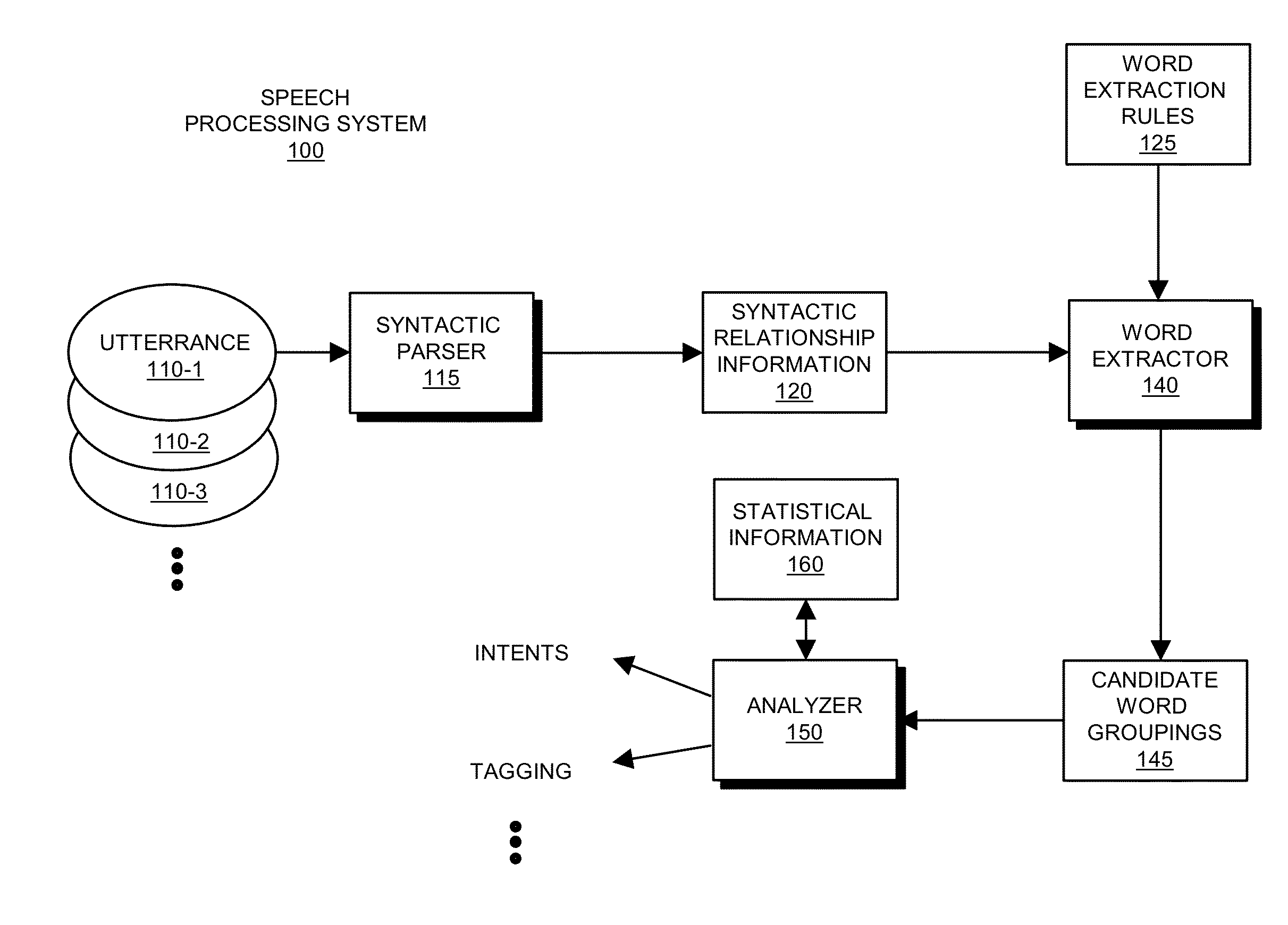
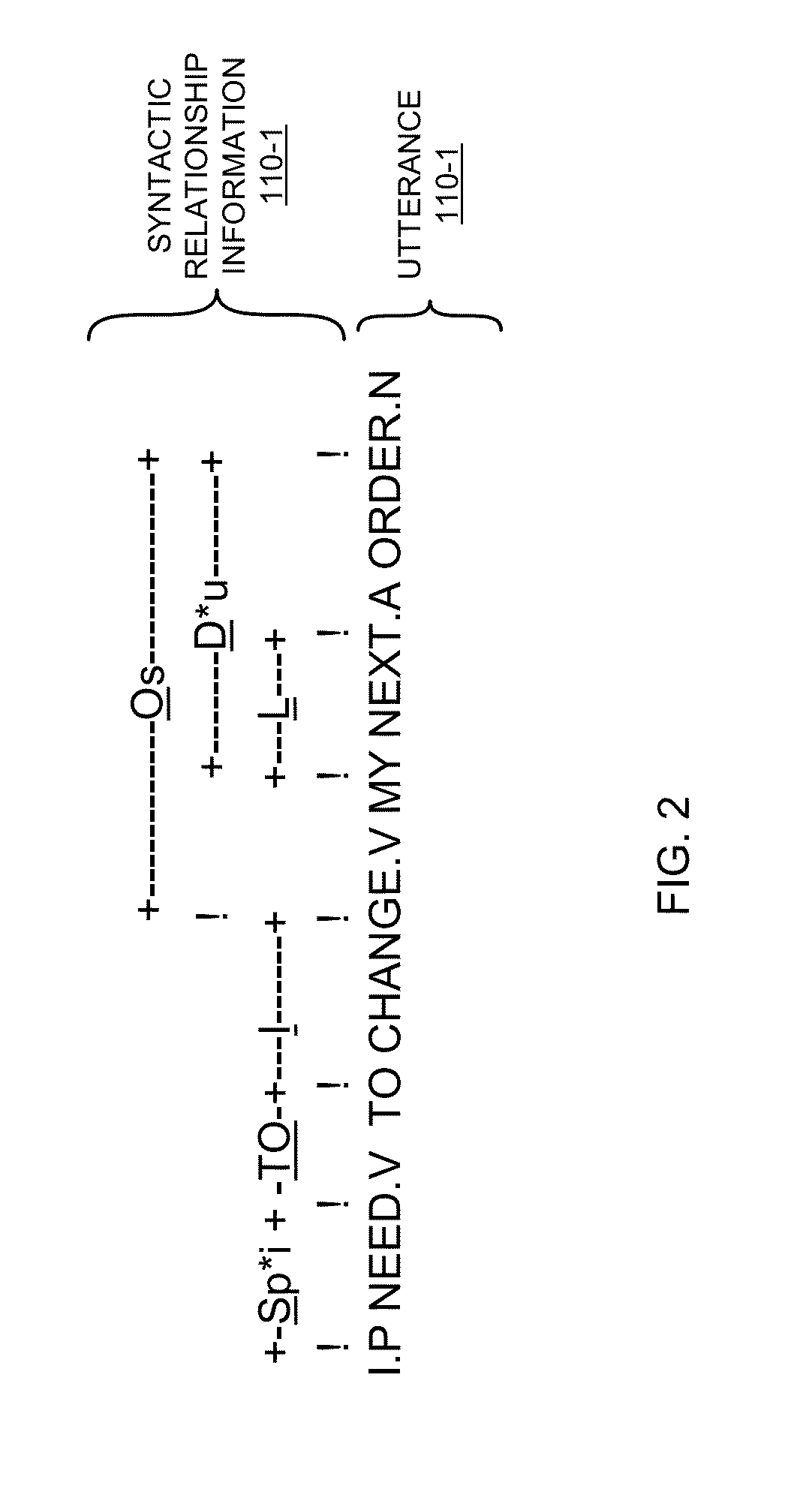
Intent mining via analysis of utterances
According to example configurations, a speech processing system can include a syntactic parser, a word extractor, word extraction rules, and an analyzer. The syntactic parser of the speech processing system parses the utterance to identify syntactic relationships amongst words in the utterance. The word extractor utilizes word extraction rules to identify groupings of related words in the utterance that most likely represent an intended meaning of the utterance. The analyzer in the speech processing system maps each set of the sets of words produced by the word extractor to a respective candidate intent value to produce a list of candidate intent values for the utterance. The analyzer is configured to select, from the list of candidate intent values (i.e., possible intended meanings) of the utterance, a particular candidate intent value as being representative of the intent (i.e., intended meaning) of the utterance.
Owner:NUANCE COMM INC
Mass spectrometry with segmented RF multiple ion guides in various pressure regions
InactiveUS7034292B1Reduce lossesEliminate and reduce numberIsotope separationSpectrometer combinationsFourier transform on finite groupsMass analyzer
A mass spectrometer is configured with individual multipole ion guides, configured in an assembly in alignment along a common centerline wherein at least a portion of at least one multipole ion guide mounted in the assembly resides in a vacuum region with higher background pressure, and the other portion resides in a vacuum region with lower background pressure. Said multipole ion guides are operated in mass to charge selection and ion fragmentation modes, in either a high or low pressure region, said region being selected according to the optimum pressure or pressure gradient for the function performed. The diameter, lengths and applied frequencies and phases on these contiguous ion guides may be the same or may differ. A variety of MS and MS / MSn analysis functions can be achieved using a series of contiguous multipole ion guides operating in either higher background vacuum pressures, or along pressure gradients in the region where the pressure drops from high to low pressure, or in low pressure regions. Individual sets of RF, + / −DC and resonant frequency waveform voltage supplies provide potentials to the rods of each multipole ion guide allowing the operation of ion transmission, ion trapping, mass to charge selection and ion fragmentation functions independently in each ion guide. The presence of background pressure maintained sufficiently high to cause ion to neutral gas collisions along a portion of each multiple ion guide linear assembly allows the conducting of Collisional Induced Dissociation (CID) fragmentation of ions by axially accelerating ions from one multipole ion guide into an adjacent ion guide. Alternatively ions can be fragmented in one or more multipole ion guides using resonant frequency excitation CID. A multiple multipole ion guide assembly can be configured as the primary mass analyzer in single or triple quadrupole mass analyzers with or without mass selective axial ejection. Alternatively, the multiple multipole ion guide linear assembly can be configured as part of a hybrid Time-Of-Flight, Magnetic Sector, Ion Trap or Fourier Transform mass analyzer.
Owner:PERKINELMER U S LLC
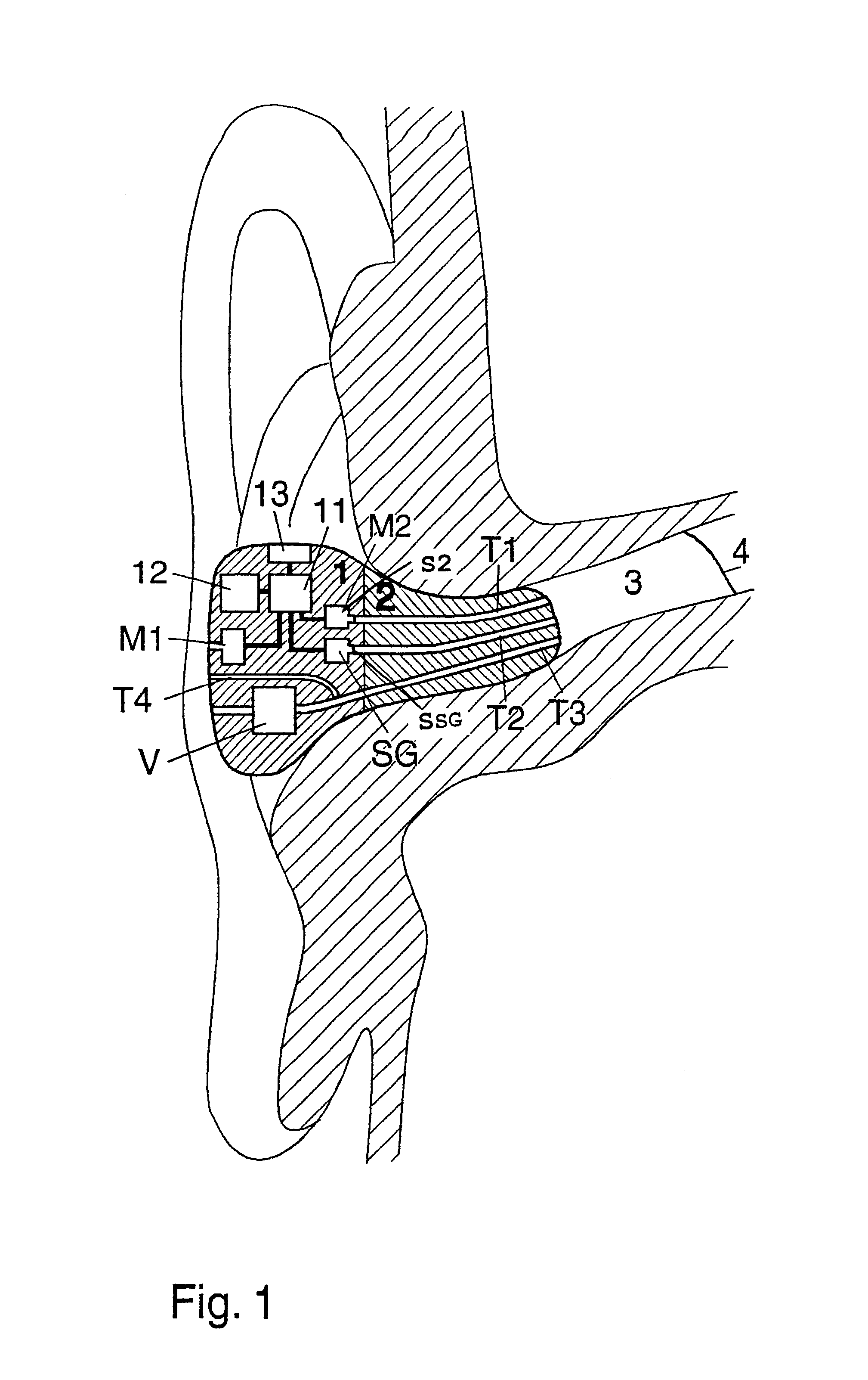
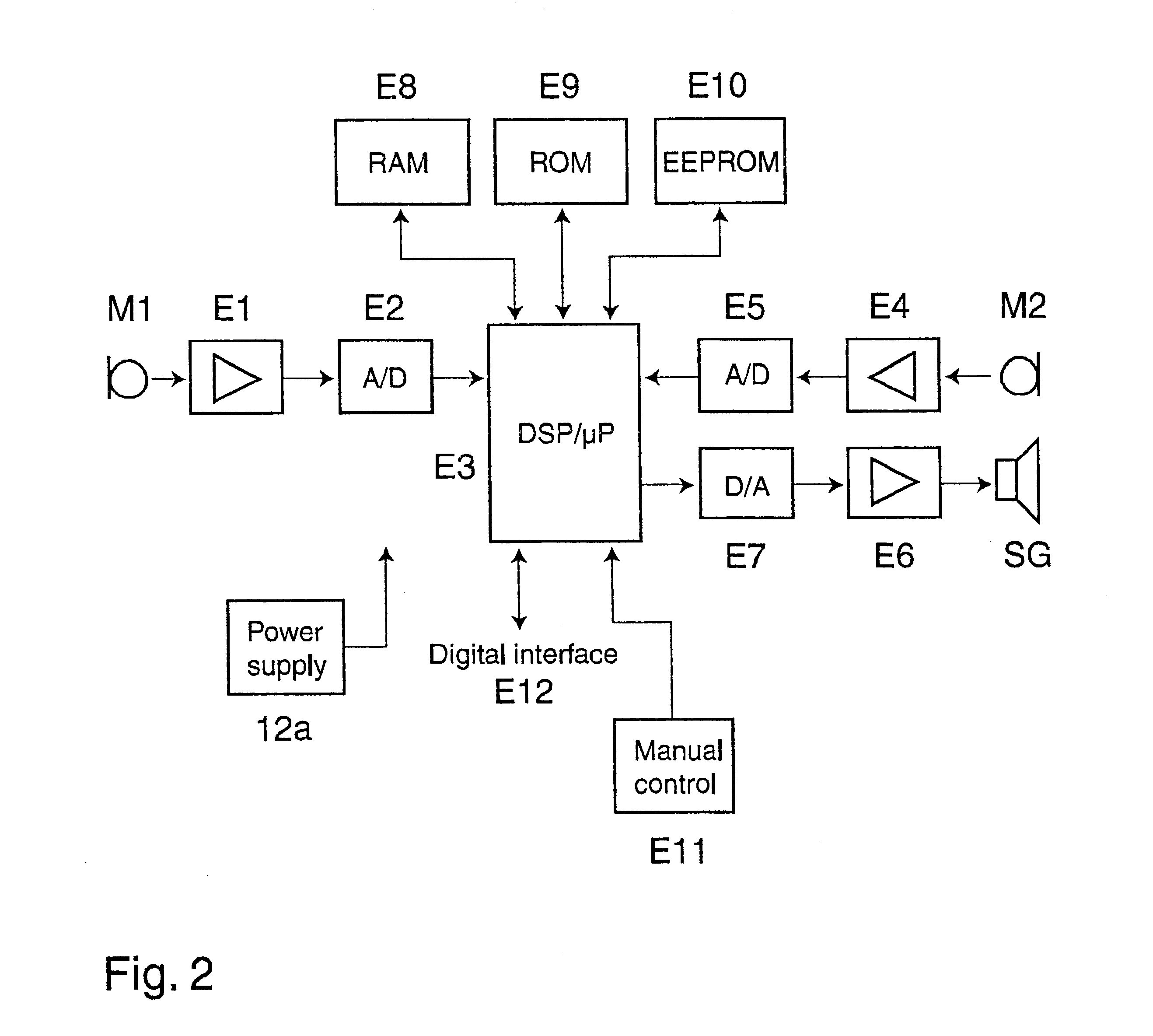
Noise protection verification device
InactiveUS6567524B1Hearing protectionFacilitate communicationVibration measurement in fluidIntra aural earpiecesVocal tractEngineering
Ear protecting device with a sealing section for acoustically sealing the meatus of a human, includes a sound generator with a sound outlet for being directed toward the user meatus; an inner microphone with a sound inlet from the meatus, arranged for measuring the resulting sound field in the meatus; connected to an electronics unit including a sound analyser coupled to the inner microphone, for analyzing sound characteristics of the resulting sound field in the meatus, producing analyzed sound characteristics; storing part in the electronics unit for storing measured predetermined sound characteristics of a properly functioning ear protecting device; a comparing part in the electronics unit for comparing the inner microphone analyzed sound characteristics with the stored measured predetermined sound characteristics; indicating part coupled to the comparing part for being activated if the analyzed sound characteristics differ significantly from the predetermined sound characteristics.
Owner:HONEYWELL HEARING TECH
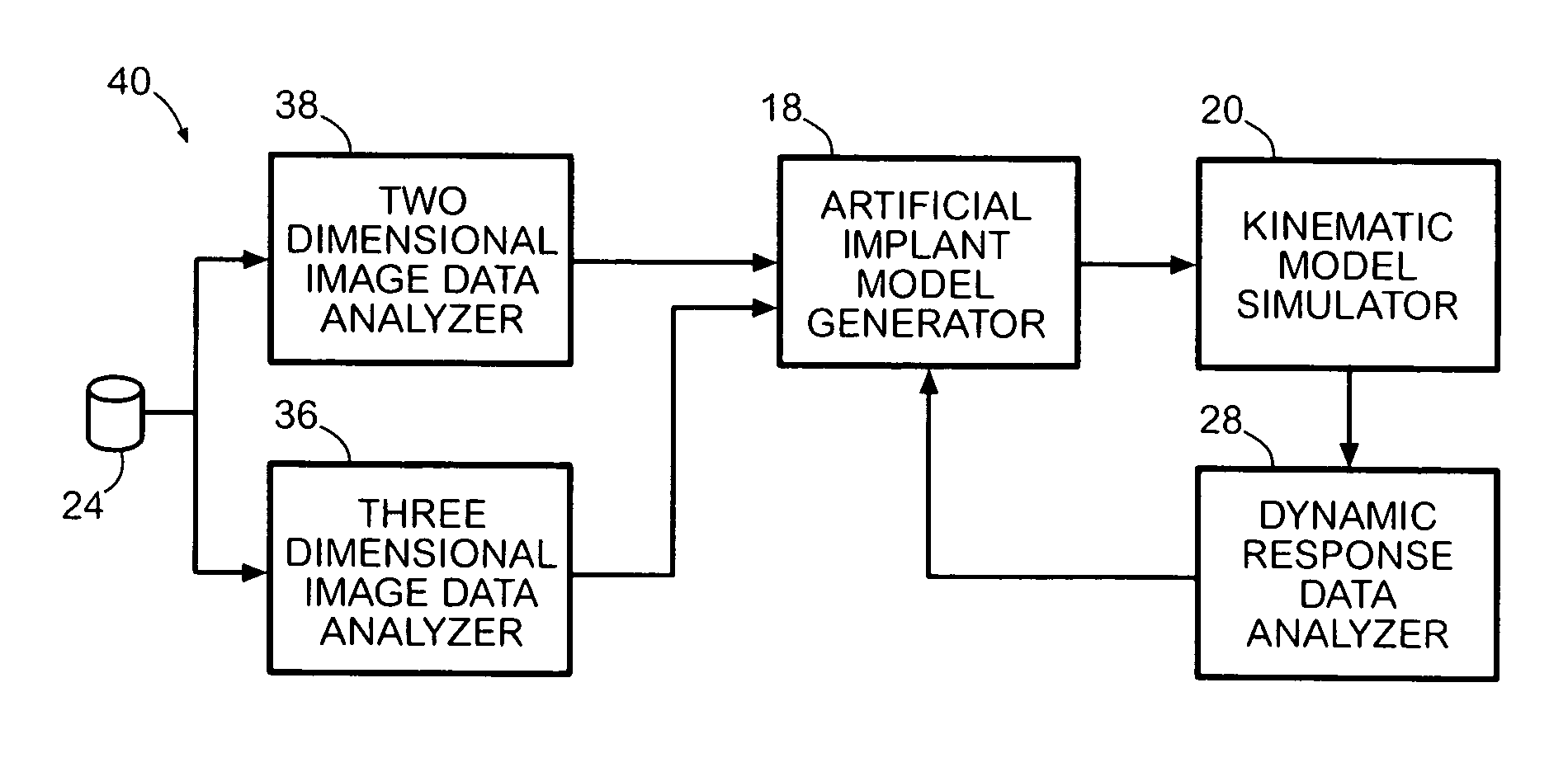
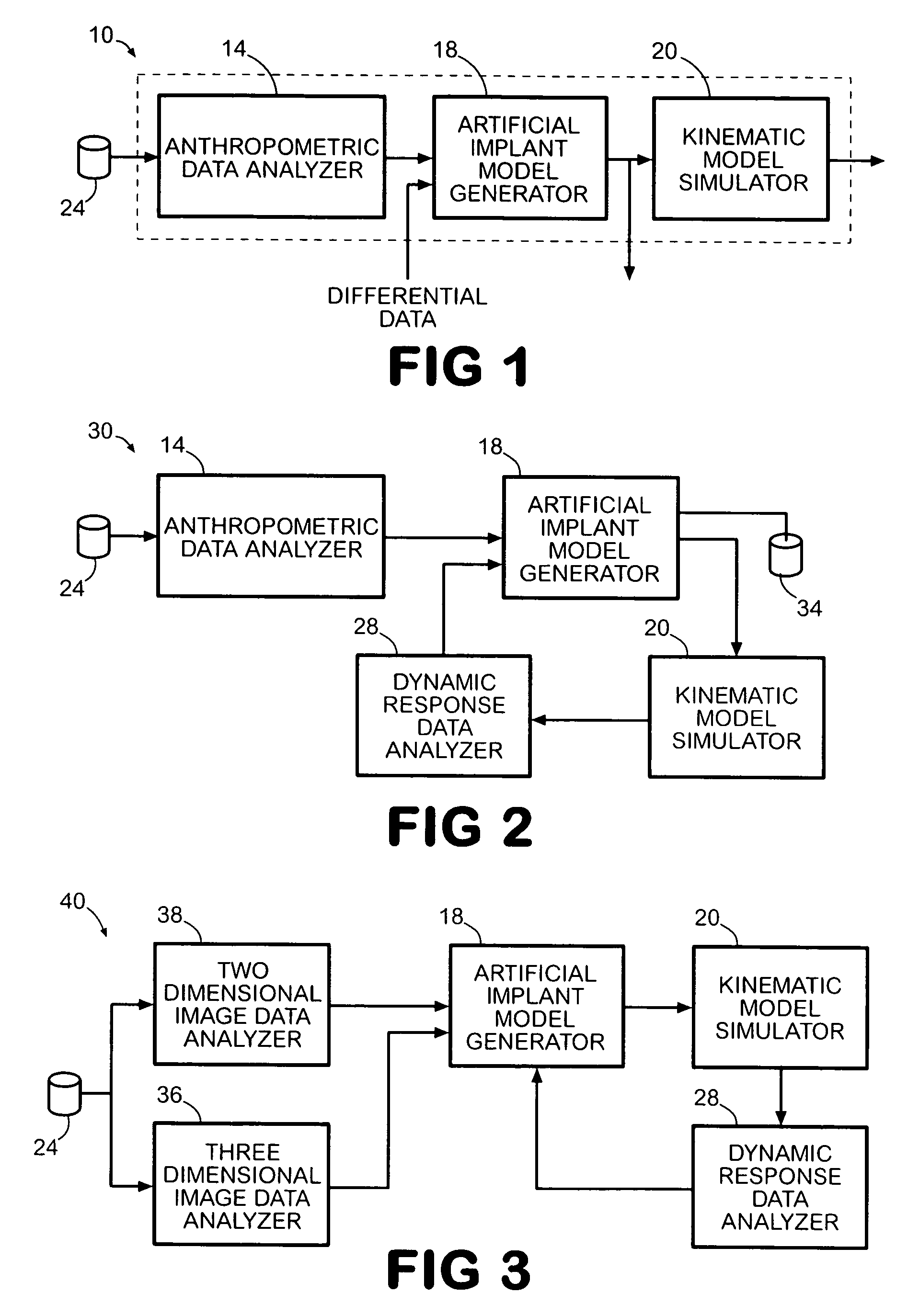
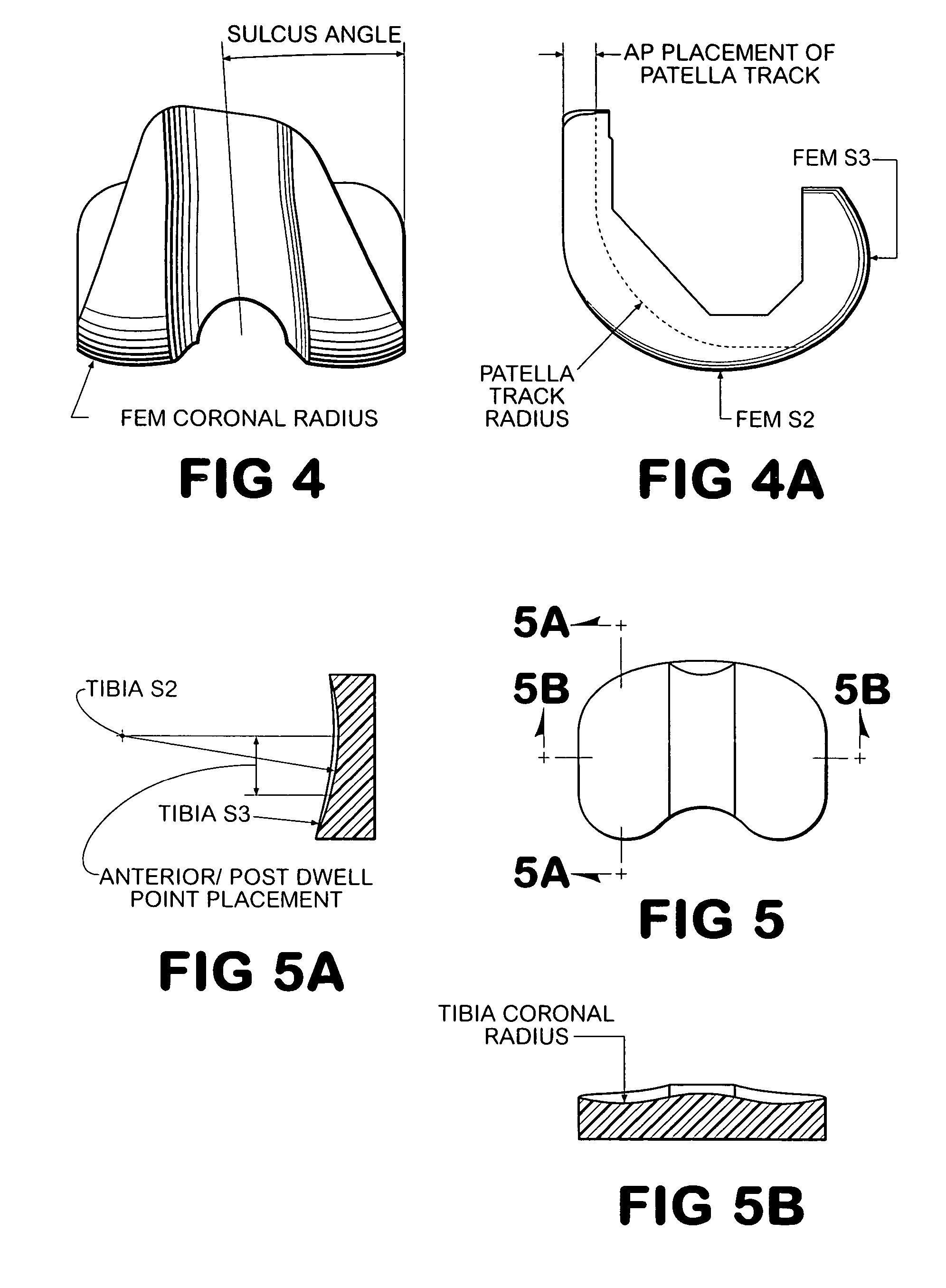
System and method for designing a physiometric implant system
ActiveUS7383164B2Economy of motionReduction of jerkPerson identificationAnalogue computers for chemical processesDynamic modelsJoints surgery
A system improves the design of artificial implant components for use in joint replacement surgeries. The system includes an anthropometric static image data analyzer, an implant model data generator, a kinematic model simulator, and a dynamic response data analyzer. The implant model data generator may also use image data of a joint in motion for modification of the implant model data used in the kinematic simulation. Dynamic response data generated by the kinematic model simulation is analyzed by the dynamic response data analyzer to generate differential data that may be used to further refine the implant model data.
Owner:DEPUY PROD INC
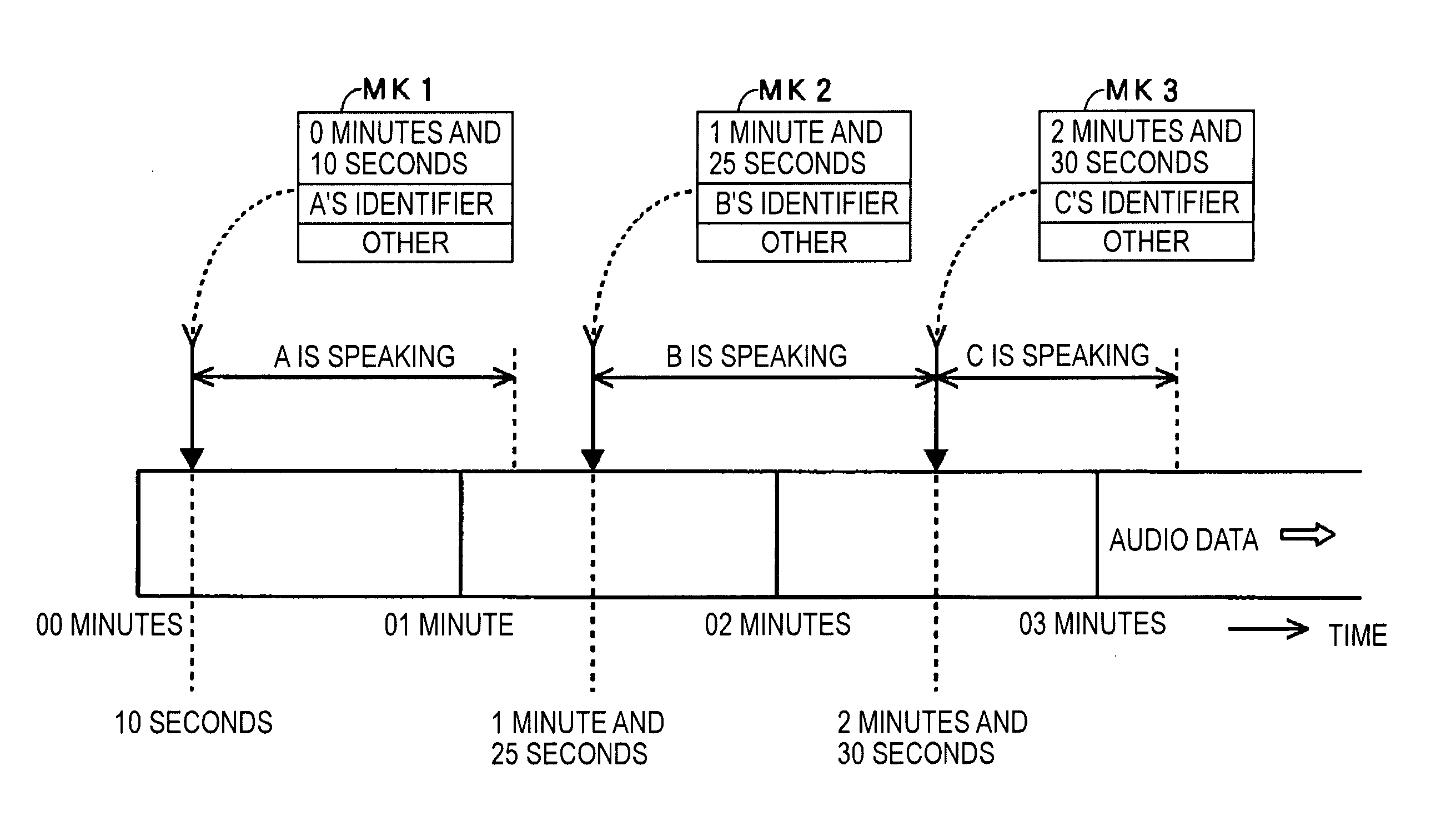
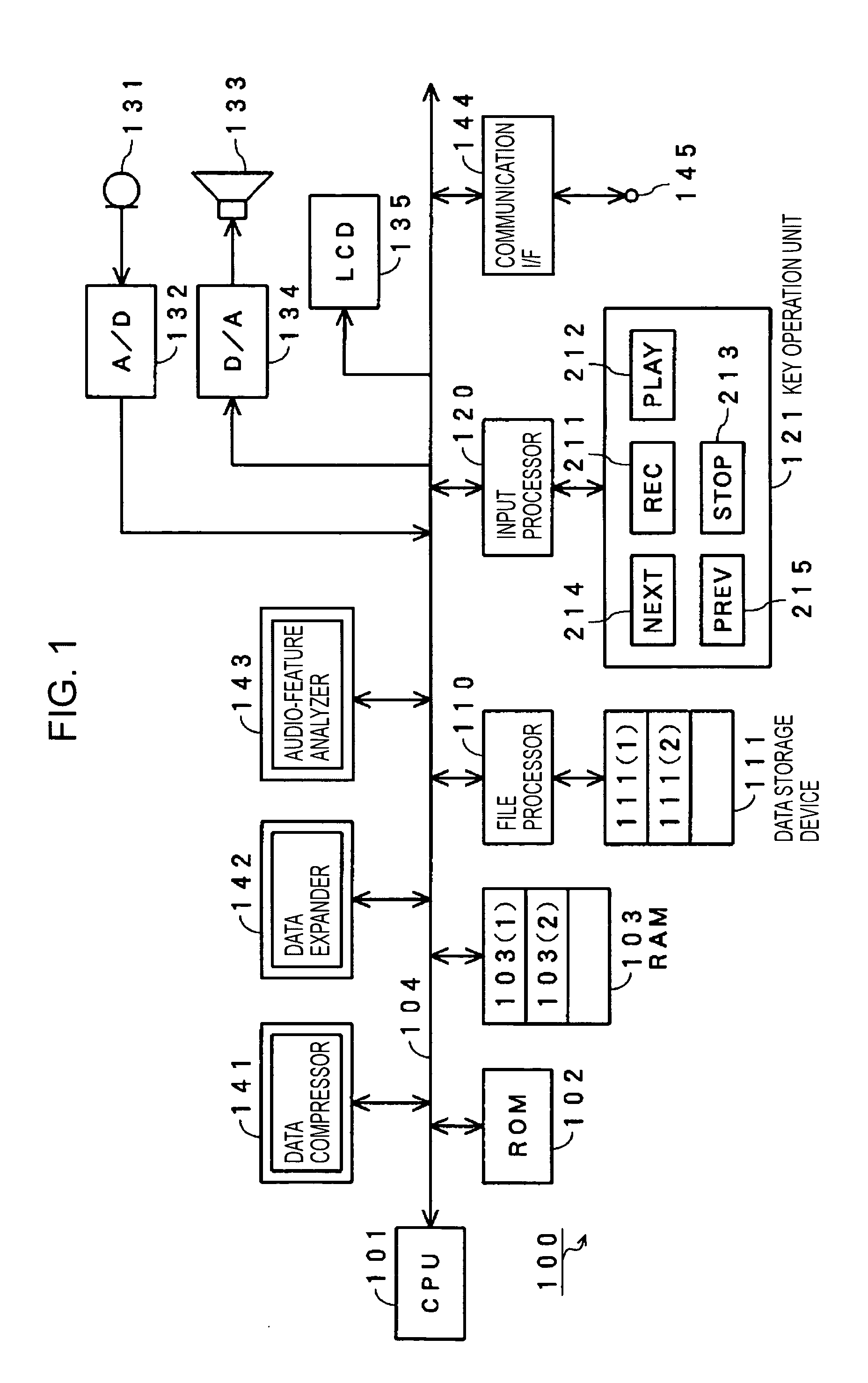
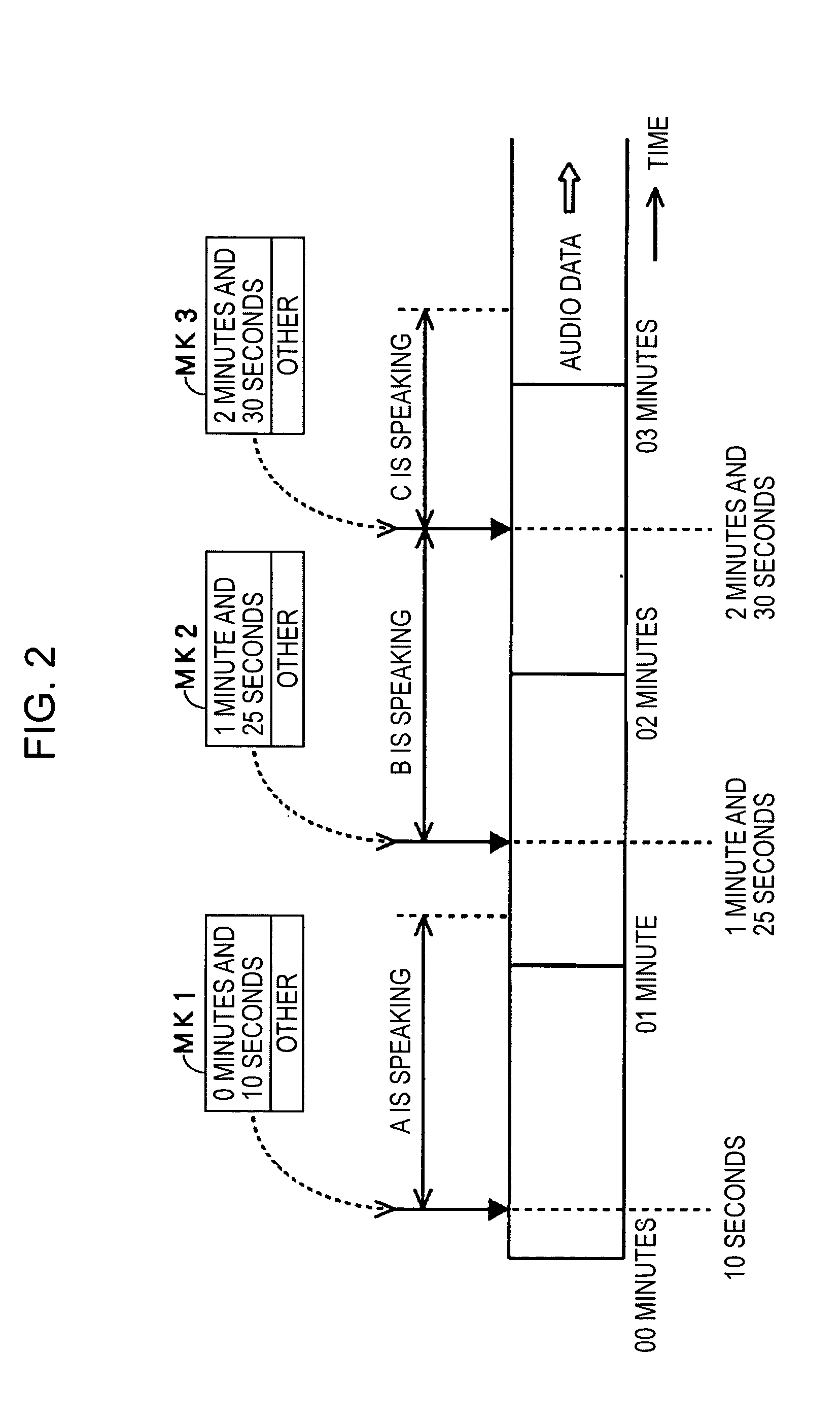
Audio signal processing apparatus and audio signal processing method
InactiveUS20050182627A1Improve usabilityThe process is convenient and fastTransfer printingElectronic editing digitised analogue information signalsKey pressingComputer science
An audio-feature analyzer automatically detects points of change in audio signals to be processed. A central processing unit (CPU) obtains point-of-change information indicating positions of the points of change in the audio signals, and the point-of-change information is recorded on a data storage device. The CPU identifies point-of-change information in accordance with an instruction input by a user via a key operation unit, and audio data corresponding to the point-of-change information identified is located so that processing such as playback of audio data to be processed can be started therefrom.
Owner:SONY CORP
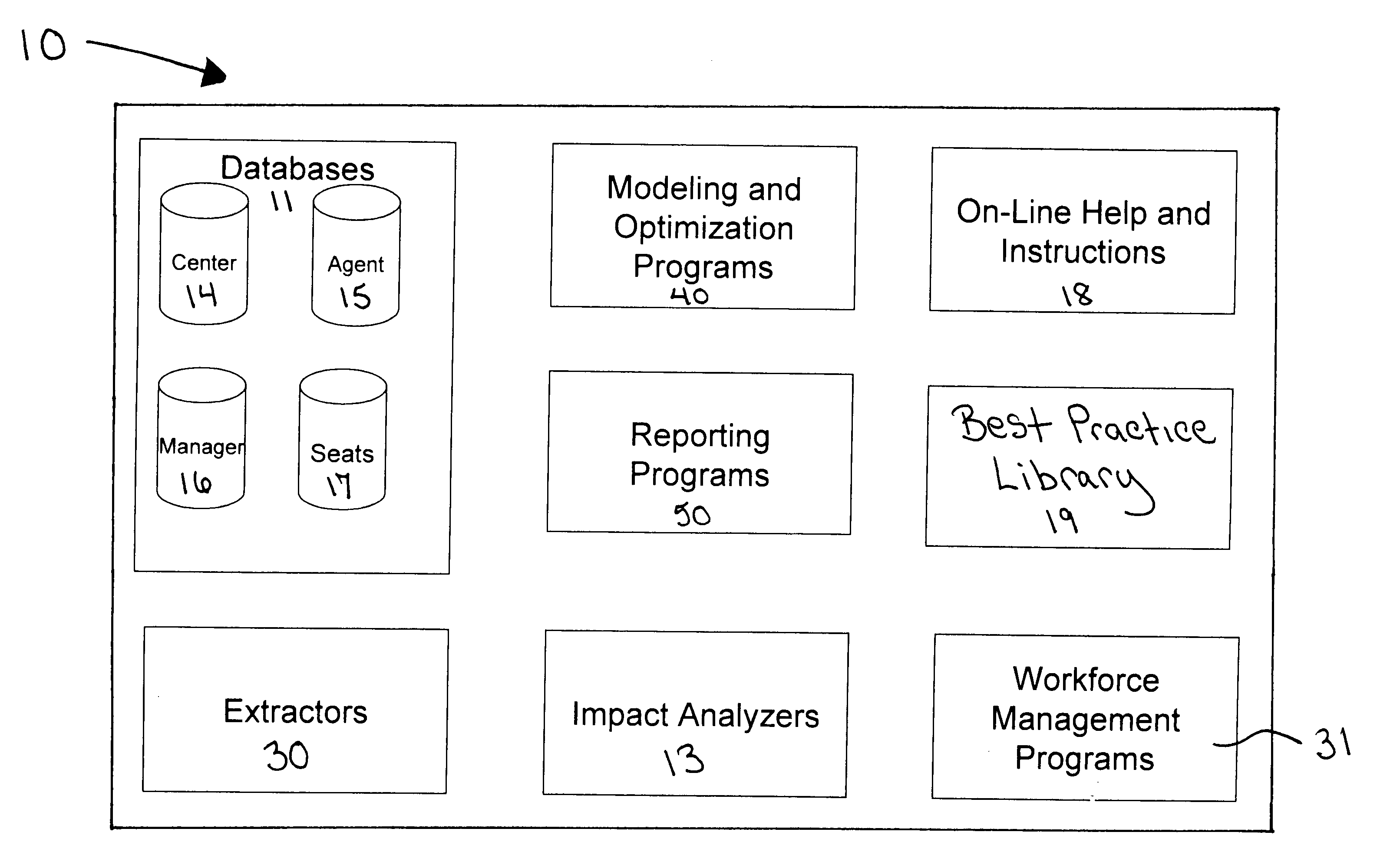
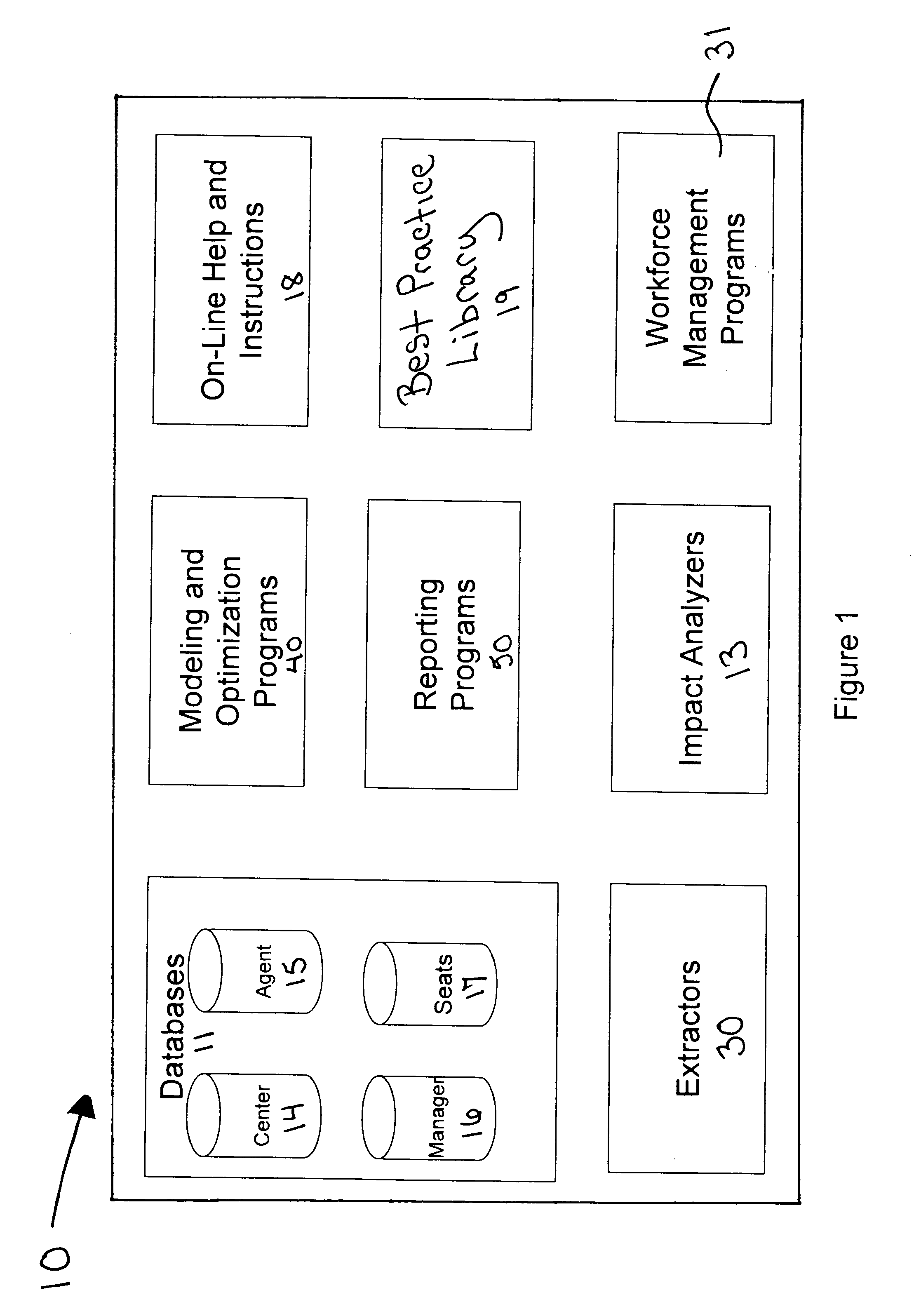
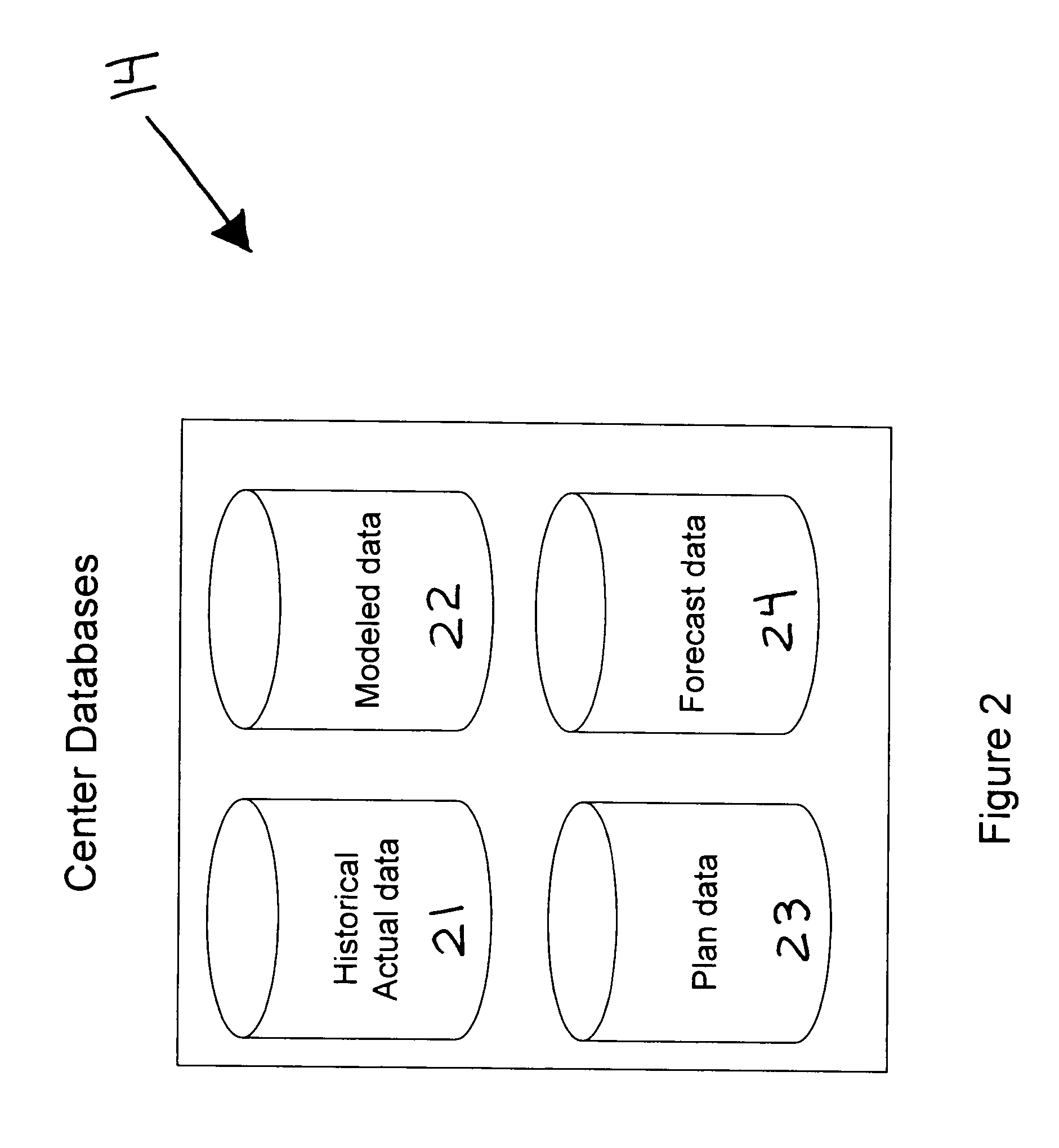
Contact center optimization program
InactiveUS20050013428A1Improve performanceContact center performanceSpecial service for subscribersSupervisory/monitoring/testing arrangementsProgram planningSimulation
A contact center performance optimization program for assisting contact center managers improve the performance of their centers comprises a hosted database that collects actual data and a modeling and optimization program that can be used to create center budgets and forecast future performance. The program facilitates improved contact center performance by providing analysis of current operations and forecasting through the use of models, optimization, analyzers and imbedded best practices. The inventive device includes. To forecast future performance and optimize the center's operation, “what if” models and analyzers are used. The invention includes a series of impact analyzers that assist the center manager focus on areas that if improved will produce the greatest overall performance improvement.
Owner:WALTERS JAMES FREDERICK JR
Network analysis tool
ActiveUS20050060598A1Efficient analysisDetecting faulty hardware by remote testLogical operation testingNetwork communicationDatabase
Embodiments of the invention provide a method for determining errors and metrics in a computer network. The method includes positioning an analyzer in communication with the network, capturing a data trace of the network with the analyzer, determining a network device topology from a first processing of the data trace, building user layer protocols using a second processing of the data trace and the determined device topology, determining errors in the network device topology using protocol experts applied to the user layer protocols in conjunction with the determined device topology, and displaying at least one of the device topology and the determined errors to a user.
Owner:VIAVI SOLUTIONS INC
Performance metric collection and automated analysis
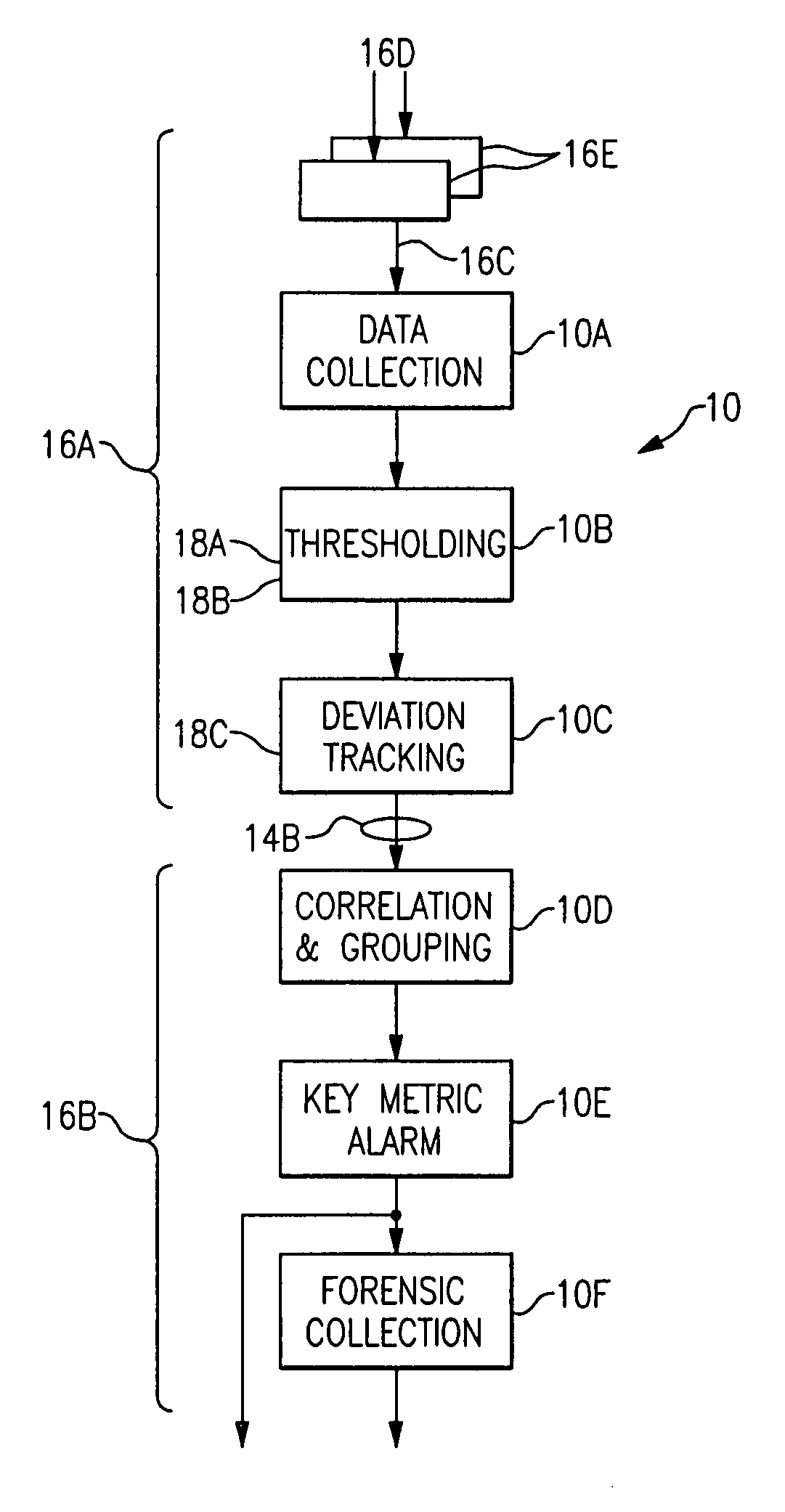
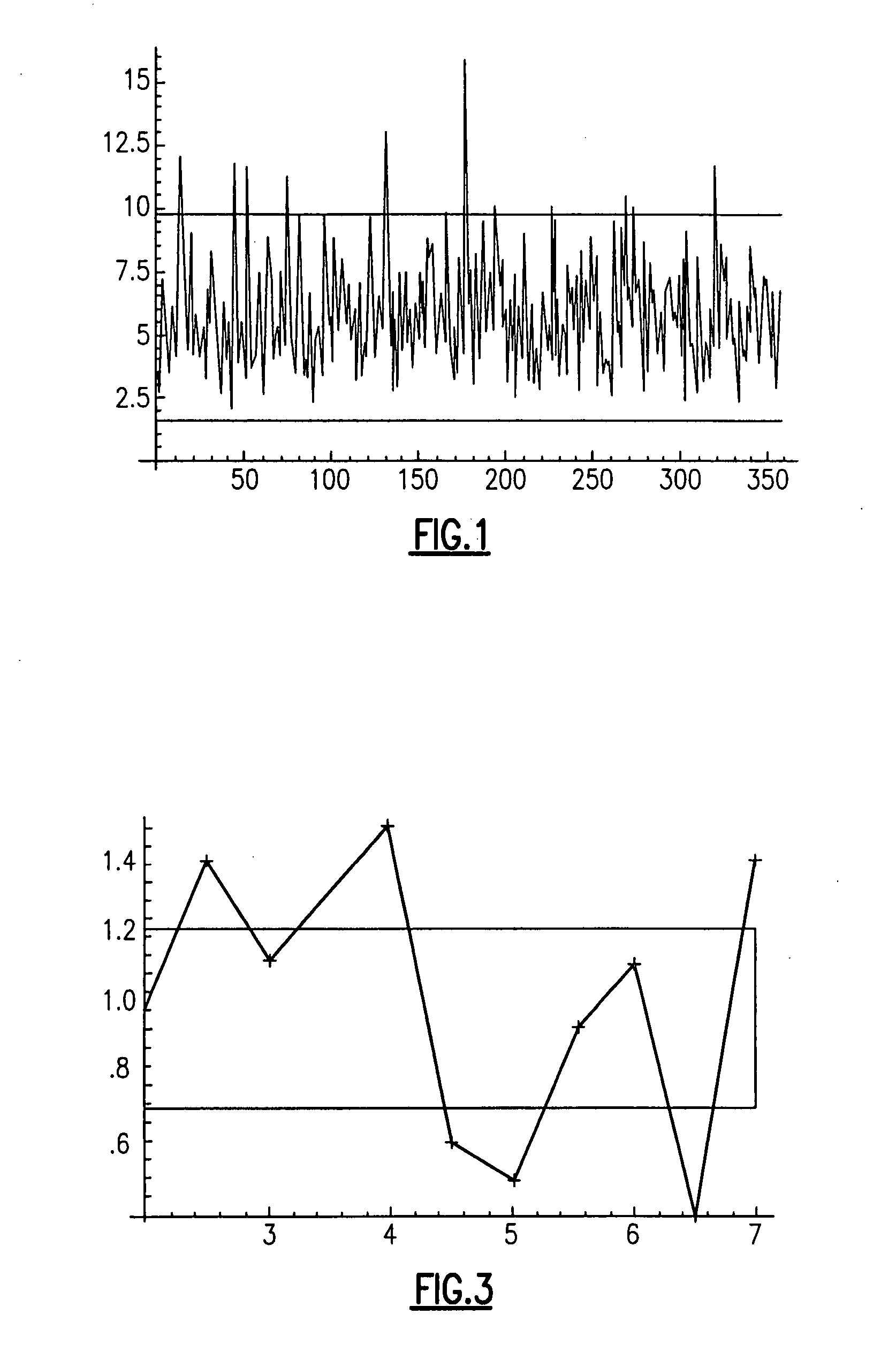
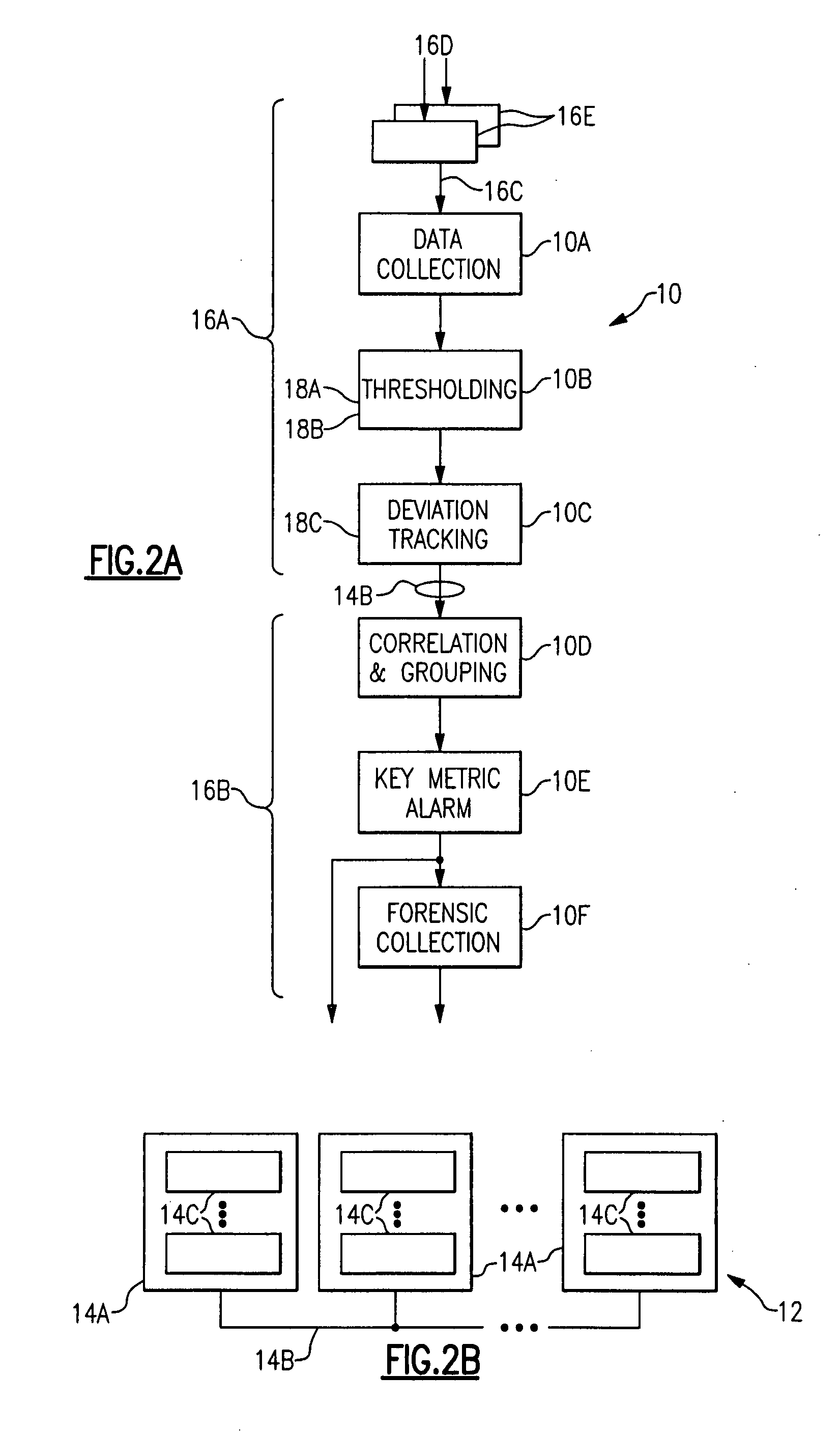
A metric monitoring and analysis system including dynamic sampling agents located in monitored system elements and a service management platform. Each sampling agent includes a data adapter collecting metric data in a common format, a threshold generator for determining dynamic metric threshold ranges, an alarm detector generating an indicator when a metric deviates outside a dynamic threshold range or a static threshold, and a deviation tracker generating an alarm severity scores. The service platform includes an alarm analyzer identifying root causes of system alarm conditions by correlation of grouped metrics or forensic analysis of temporally or statistically correlated secondary forensic data or data items from a service model of the system.
Owner:ATERNITY LLC
Apparatus and method for mask free delivery of an inspired gas mixture and gas sampling
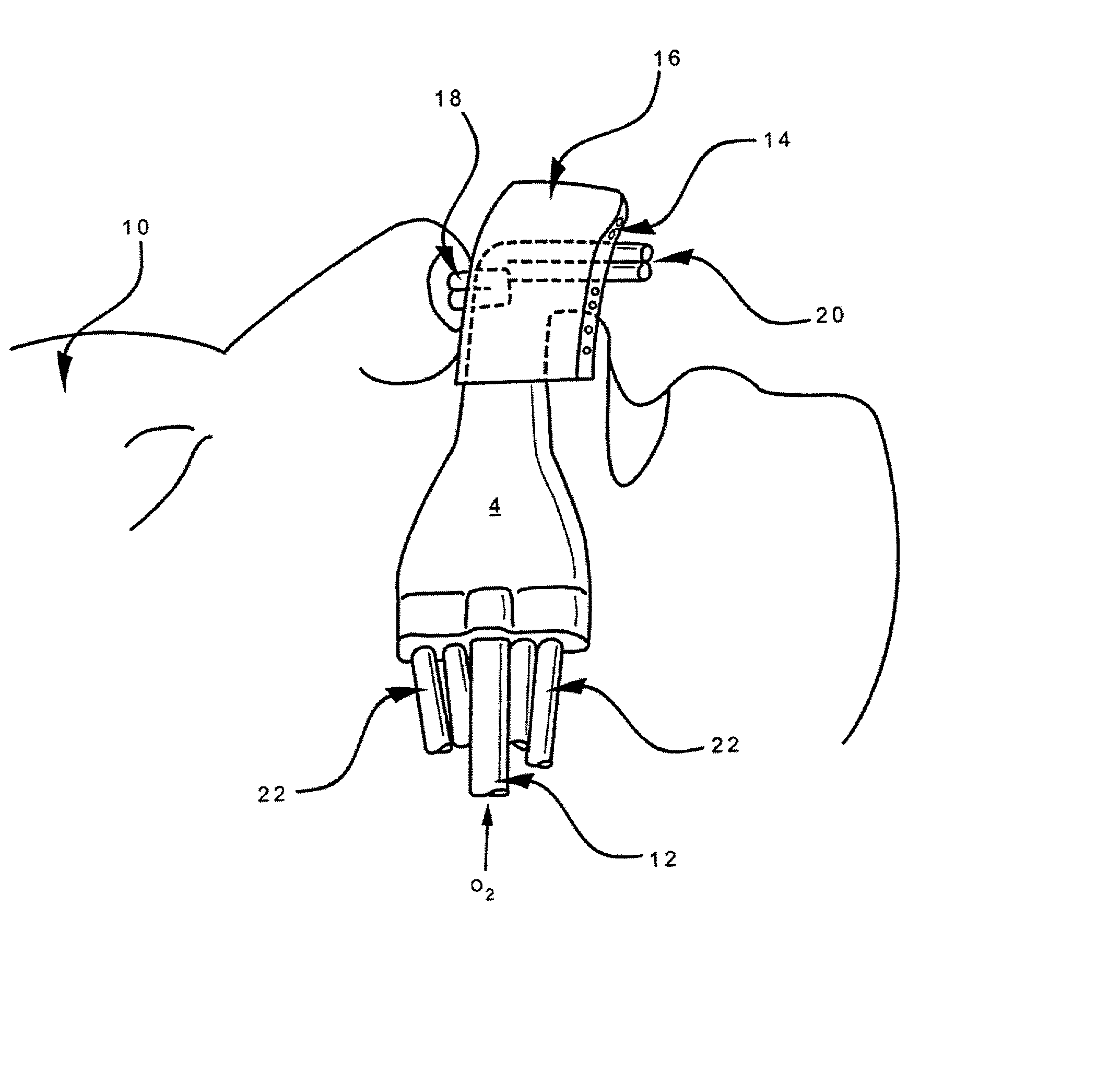
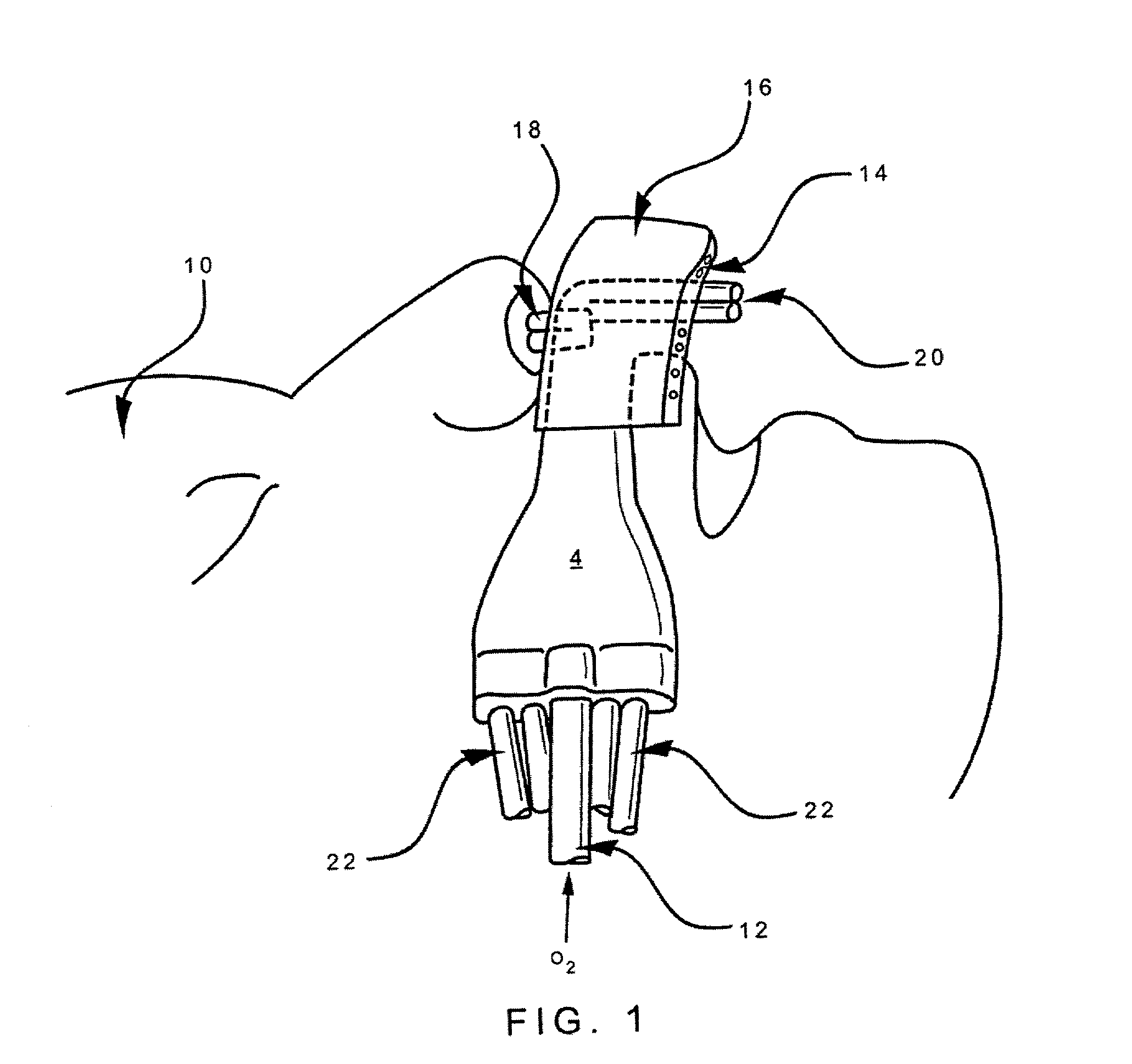
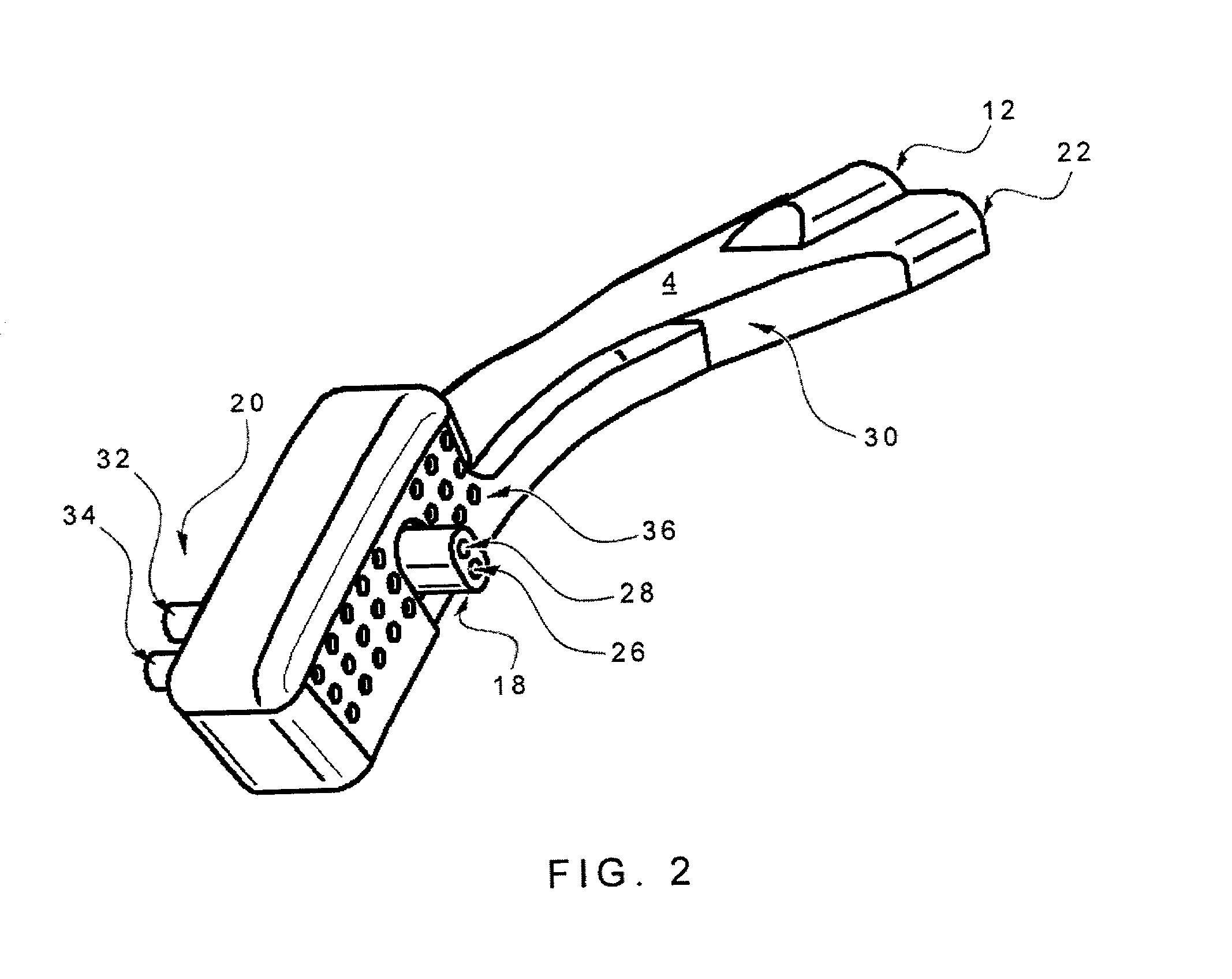
InactiveUS20020017300A1Operating means/releasing devices for valvesRespiratory masksOxygen deliveryInspired gas
Disclosed is an apparatus and method for the delivery of inspired gas, e.g., supplemental O2, to a person combined with gas sampling, including for the purpose of monitoring of the ventilation of the person. In the invention, the delivery of inspired gas and gas sampling are accomplished without the use of a sealed face mask. The apparatus of one embodiment of the present invention comprises an oxygen delivery device, nasal airway pressure sampling devices, optionally an oral airway pressure sampling device and at least one pressure analyzer connected to the sampling devices which determine the phase of the person's respiration cycle and the person's primary airway. The oxygen delivery device is connected to a controller such that it delivers a higher flow of oxygen to the person during the inhalation phase of the person's respiratory cycle. The invention thus increases end tidal oxygen concentrations. The invention further comprises carbon dioxide sampling tubes that continuously sample gas from two nasal sites and the mouth. The nasal sampling tubes are connected to a switching valve that is in turn connected to a capnometer which determines carbon dioxide concentration during exhalation. The oral gas sampling site is connected to a second capnometer.
Owner:SCOTT LAB
Method and system for monitoring and analyzing compliance with internal dosing regimen
InactiveUS20070237719A1Ultrasonic/sonic/infrasonic diagnosticsCompounds screening/testingDosing regimenMedicine
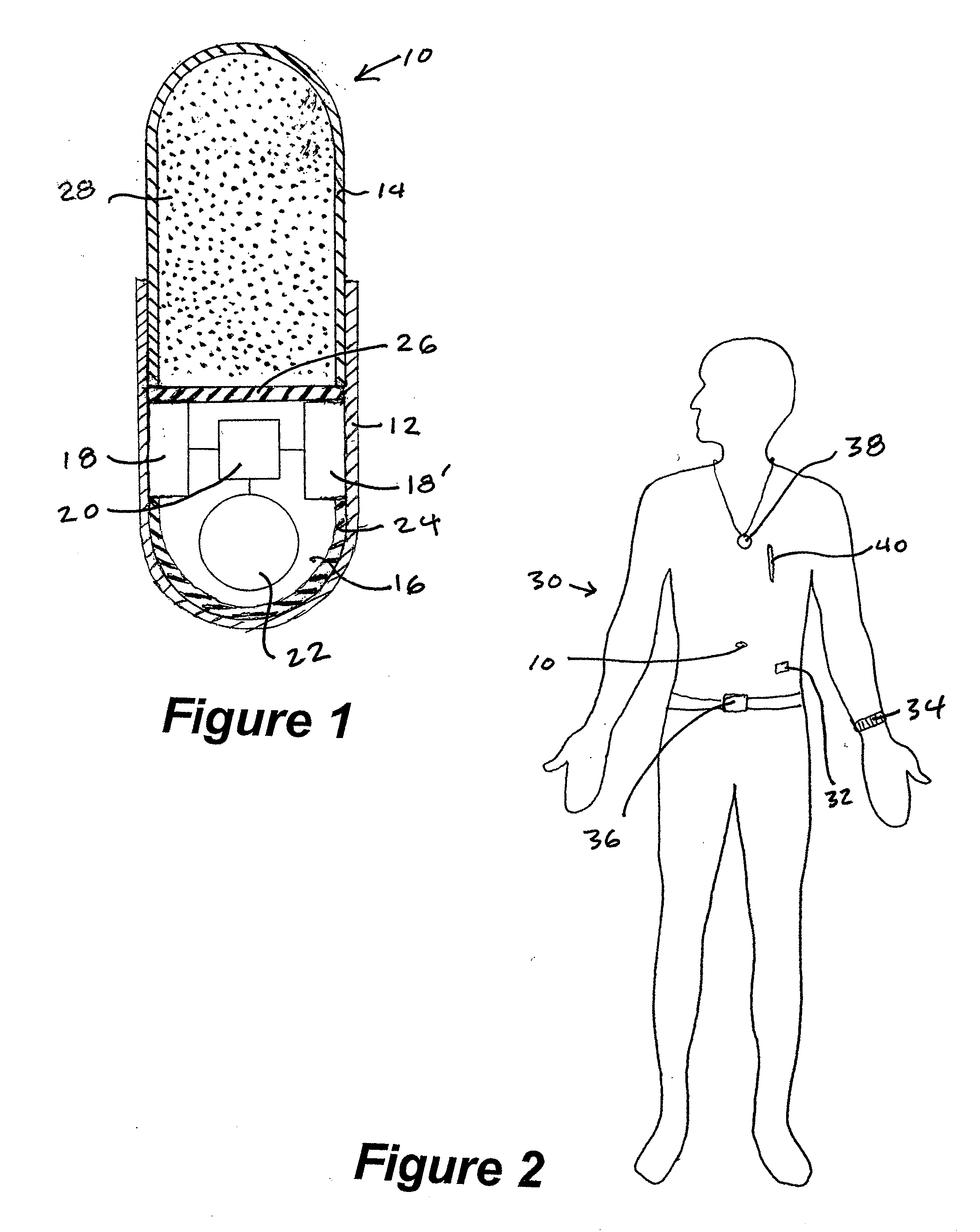
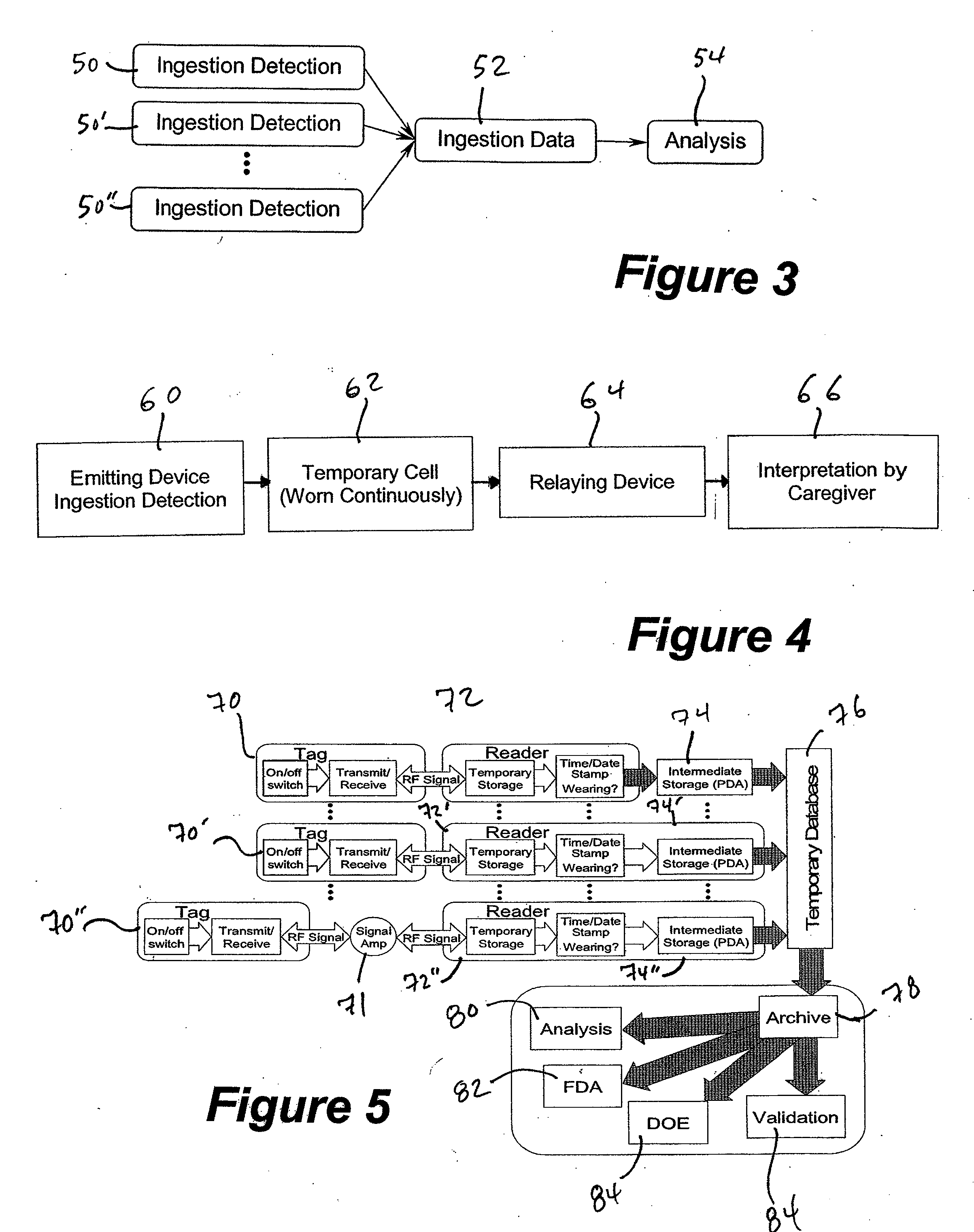
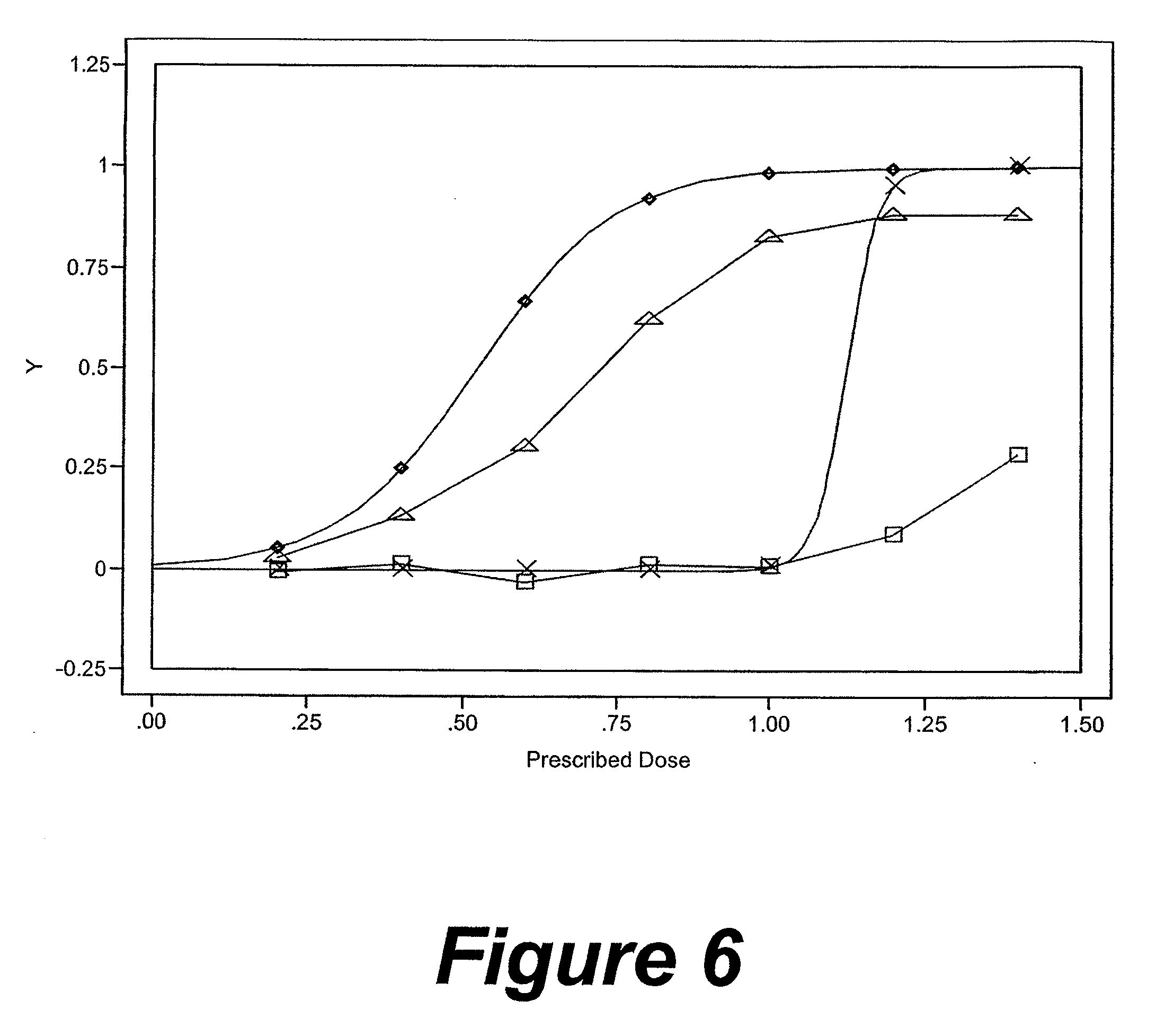
A method and system for monitoring and analyzing compliance with an internal dosing regimen prescribed to be taken in multiple dose forms includes the steps of detecting internalization of a first dose form to generate a first data point, detecting internalization of a second dose form to generate a second data point, and analyzing the first data point and the second data point. The step of analyzing the first and second data points generates a metric of a variety of possible metric types. The first and second dose forms may be two of any plural number of sequentially-internalized dose forms which generate a like number of sequential data points. Subsequent internalizations of dose forms result in at least a like number of data points being generated. To effect the disclosed method a system is provided which includes at least two dose forms, a time stamp identifier operatively associated with each dose form, a receiving device for receiving the time stamp identifier data, and an analyzer for analyzing the received data,
Owner:DOW GLOBAL TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com