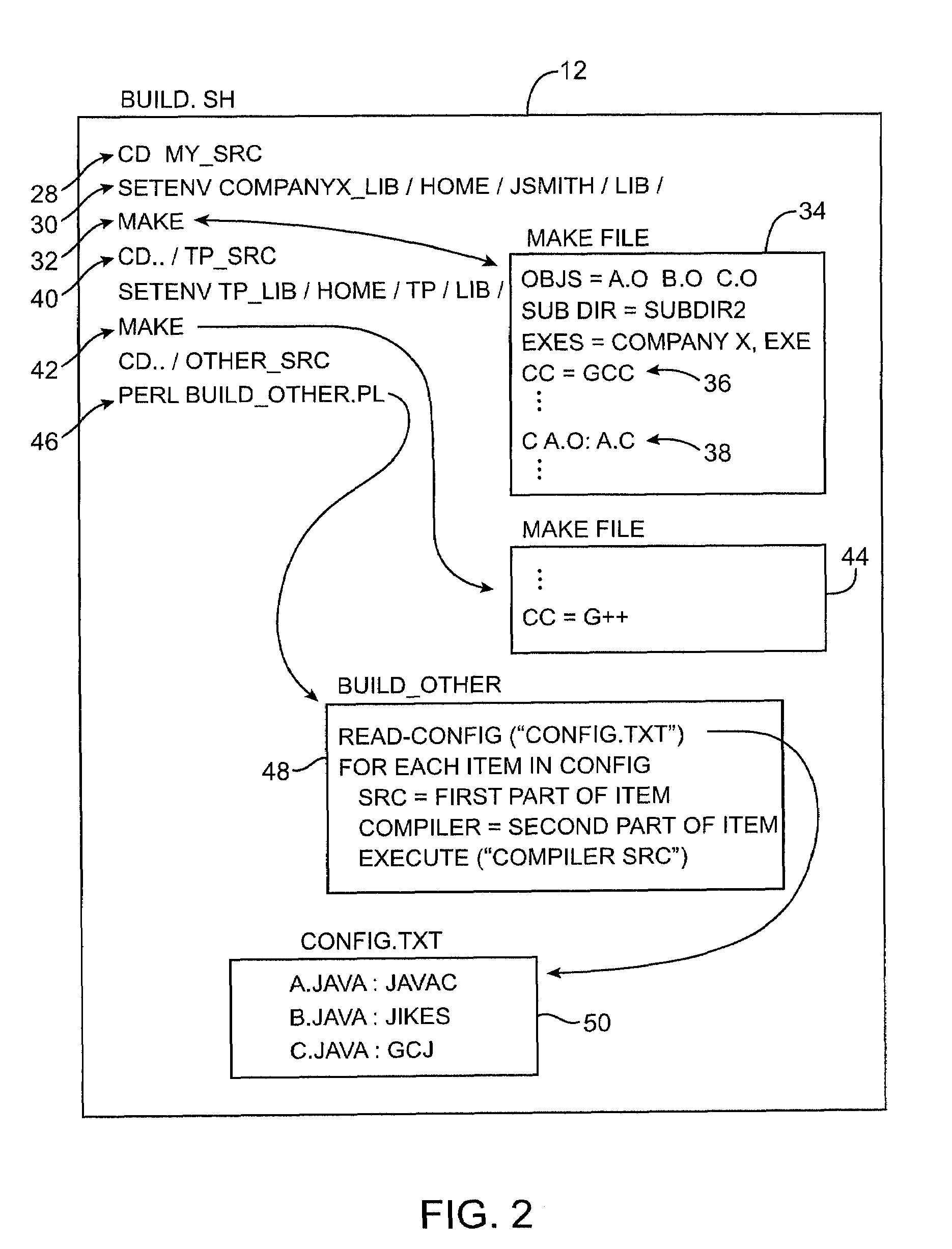
Patents
Literature
440 results about "Static timing analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
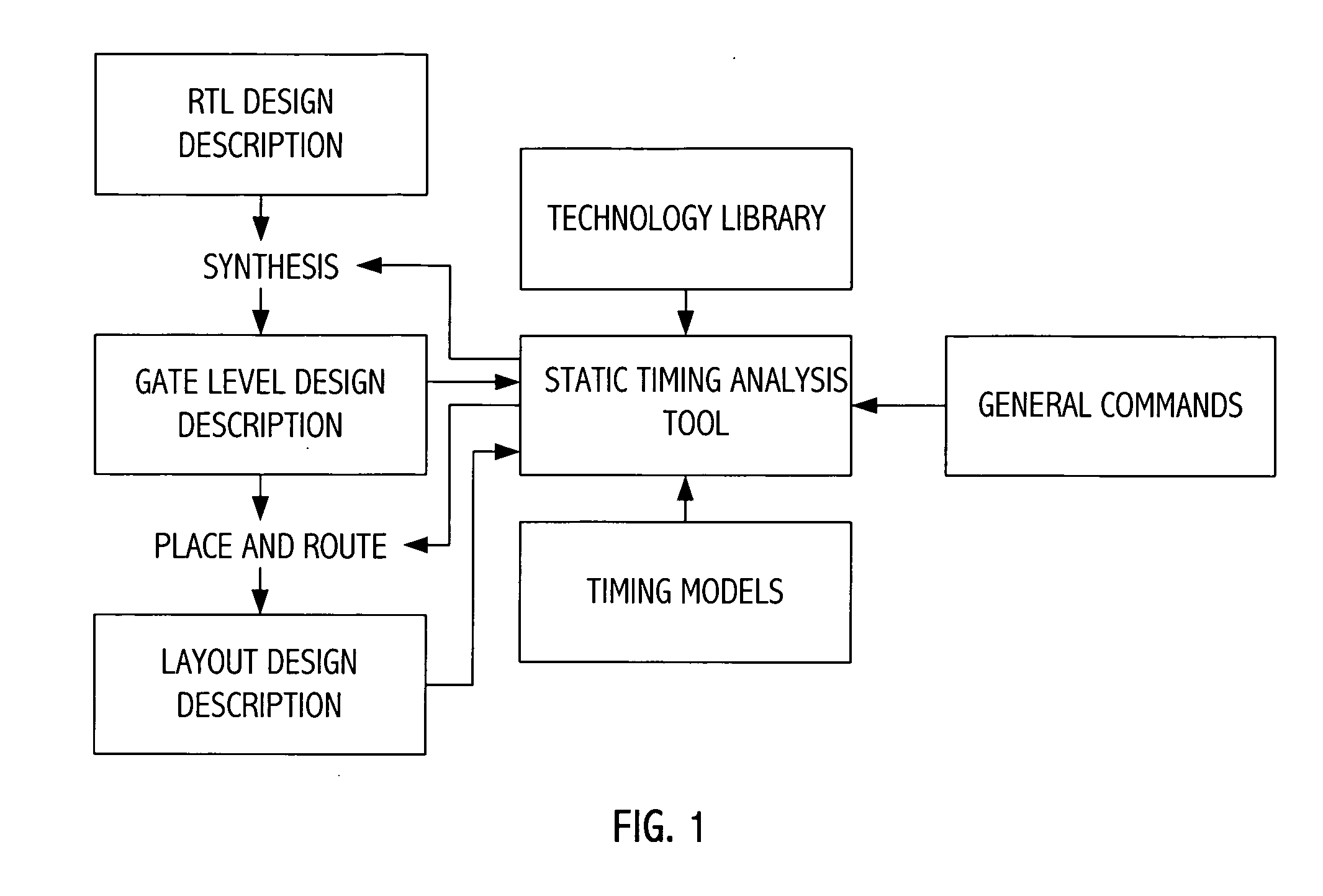
Static timing analysis (STA) is a simulation method of computing the expected timing of a digital circuit without requiring a simulation of the full circuit. High-performance integrated circuits have traditionally been characterized by the clock frequency at which they operate. Measuring the ability of a circuit to operate at the specified speed requires an ability to measure, during the design process, its delay at numerous steps. Moreover, delay calculation must be incorporated into the inner loop of timing optimizers at various phases of design, such as logic synthesis, layout (placement and routing), and in in-place optimizations performed late in the design cycle. While such timing measurements can theoretically be performed using a rigorous circuit simulation, such an approach is liable to be too slow to be practical. Static timing analysis plays a vital role in facilitating the fast and reasonably accurate measurement of circuit timing. The speedup comes from the use of simplified timing models and by mostly ignoring logical interactions in circuits. This has become a mainstay of design over the last few decades.
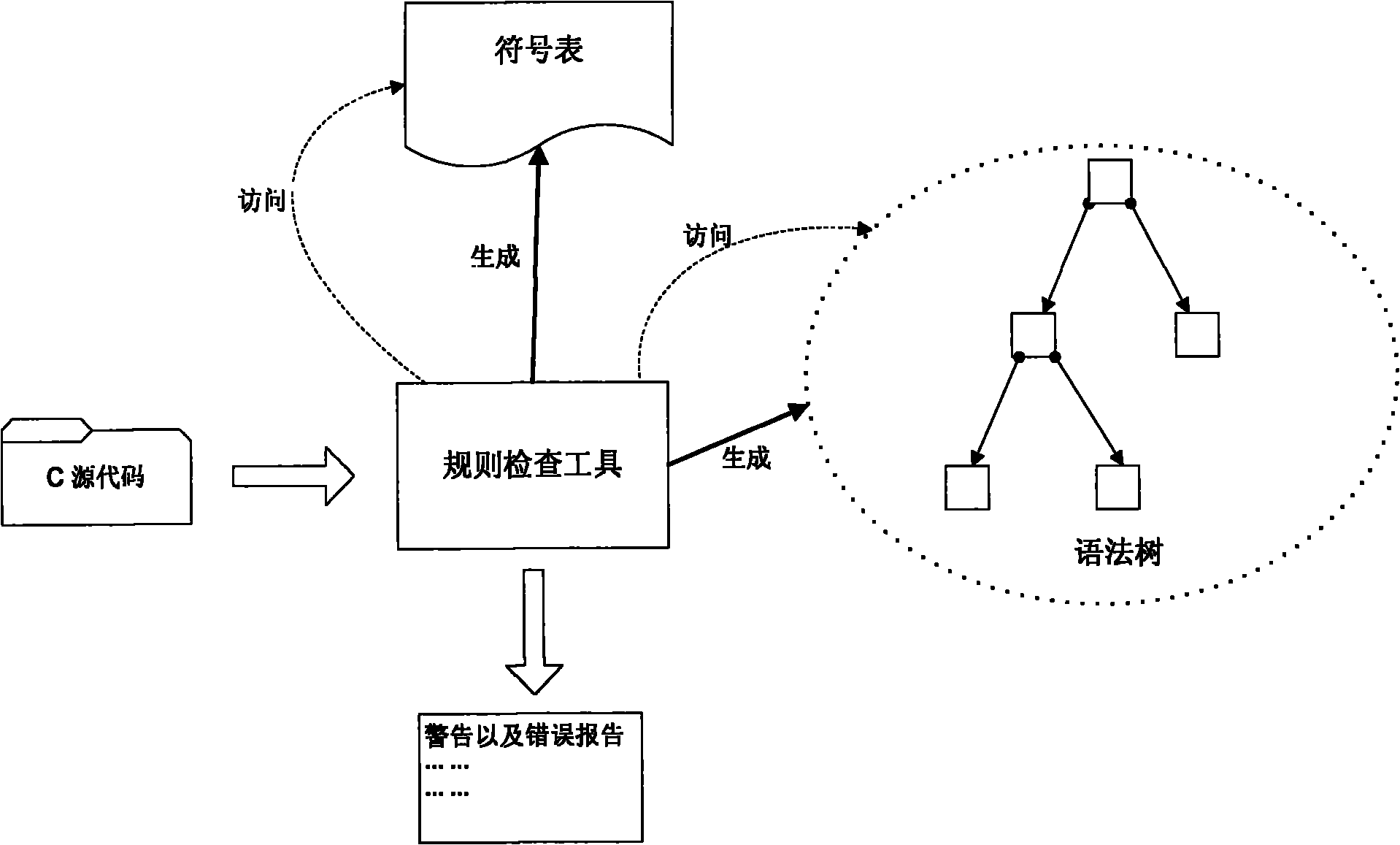
Software safety code analyzer based on static analysis of source code and testing method therefor
InactiveCN101017458AImprove accuracySupport for expansionSoftware testing/debuggingStatic timing analysisStructure analysis
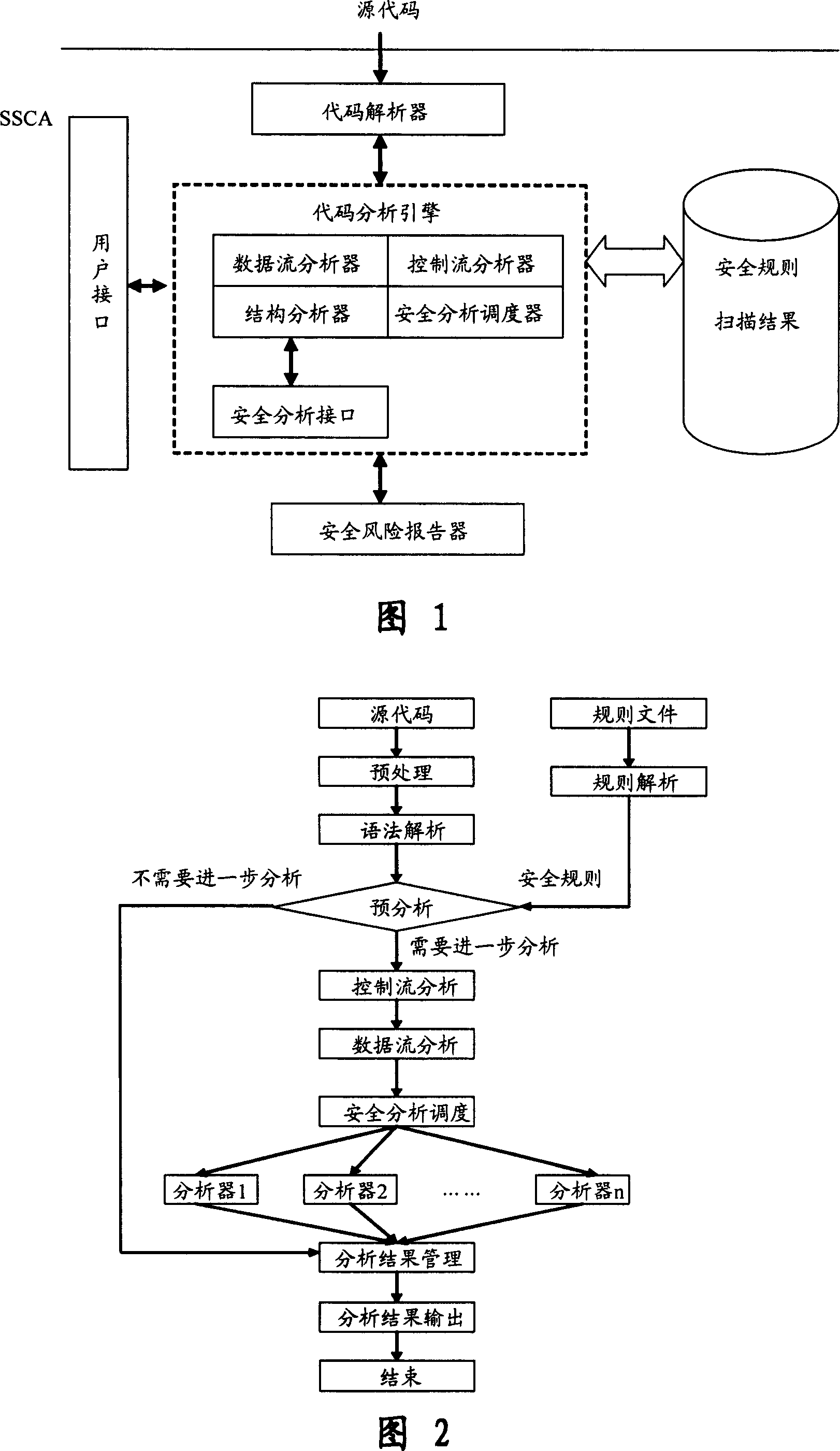
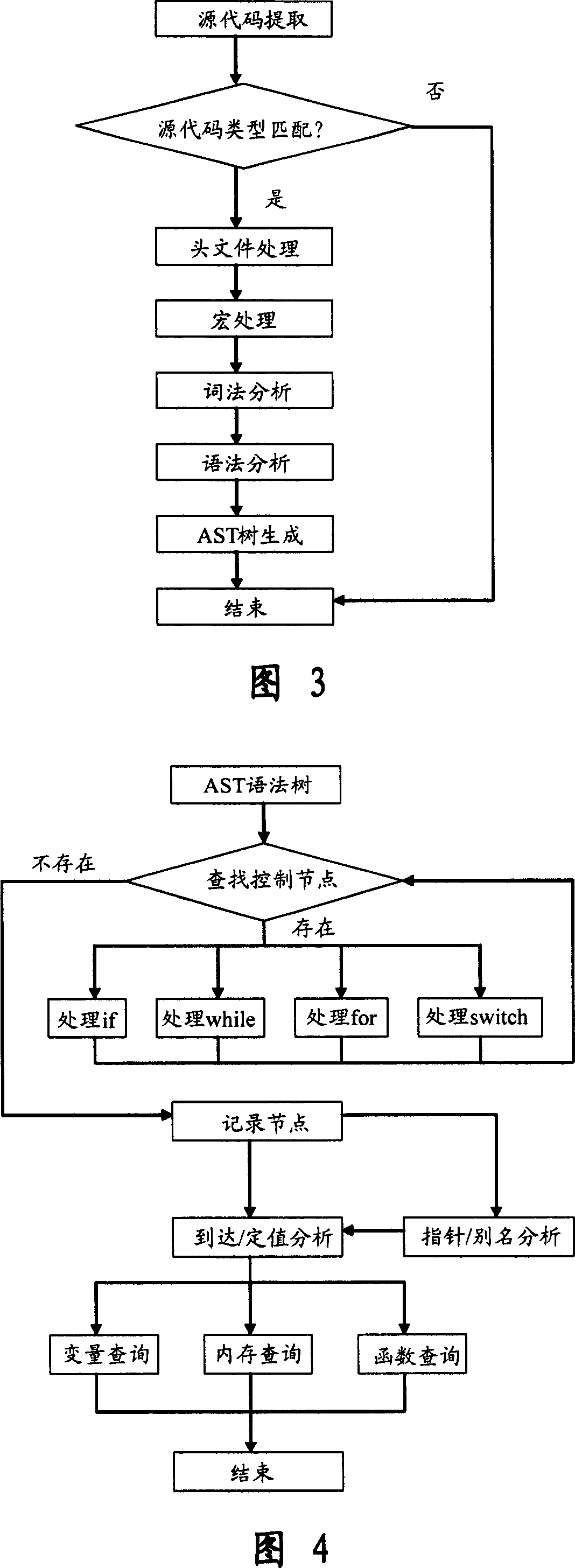
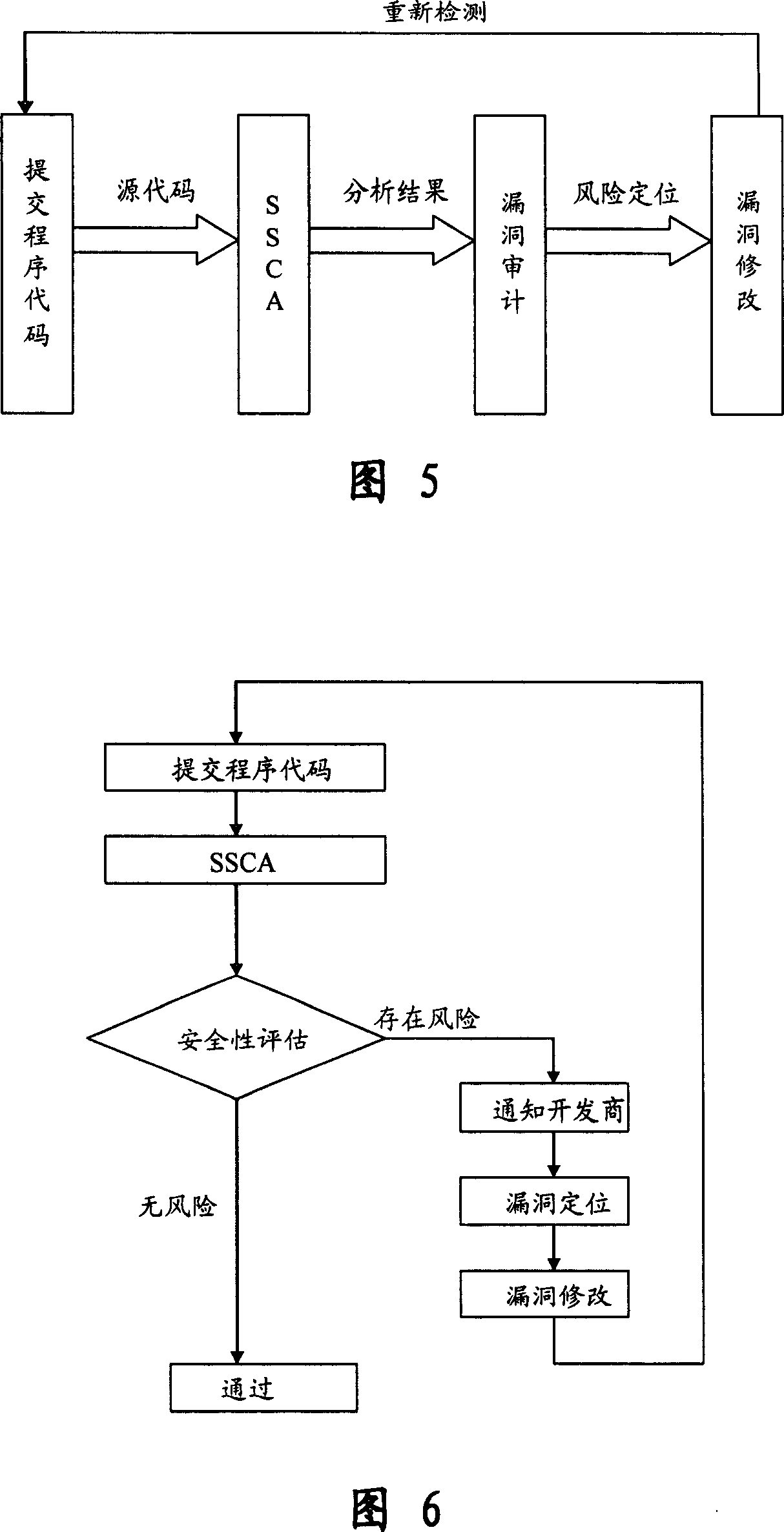
This invention relates to one software analyzer and its test method based on source codes static analysis, wherein the analysis device comprises five function modules of code analysis device, codes analysis engine, safety risk report device, safety rules database and user interface; this invention gets programs safety risk to user according to the source program and grammar and meanings and delivers the safety leak to the user for audit and evaluation.
Owner:深圳北邮网络科技有限公司
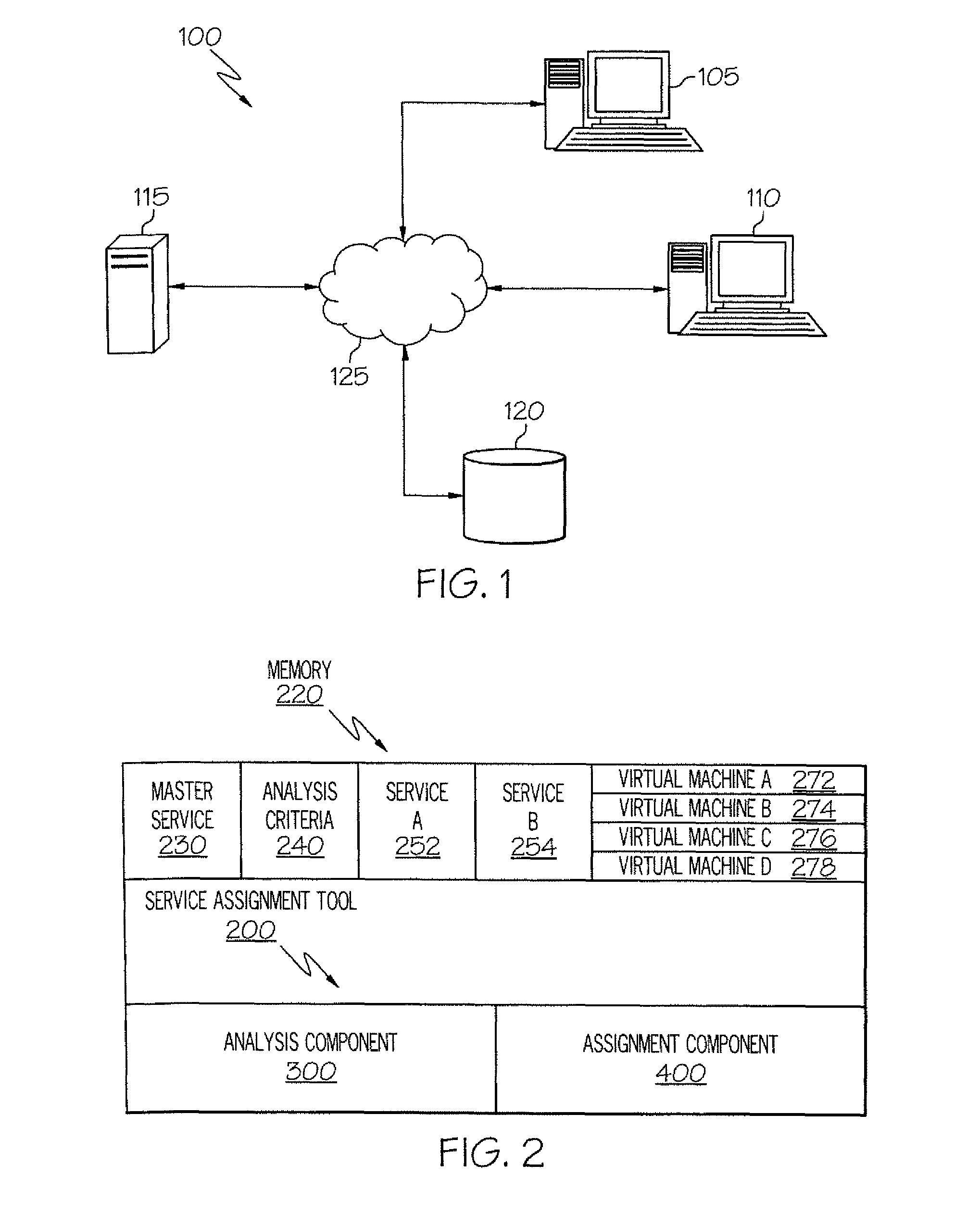
Method and apparatus for determining a service cluster topology based on static analysis
InactiveUS8171473B2Multiprogramming arrangementsSoftware simulation/interpretation/emulationStatic timing analysisCoding conventions
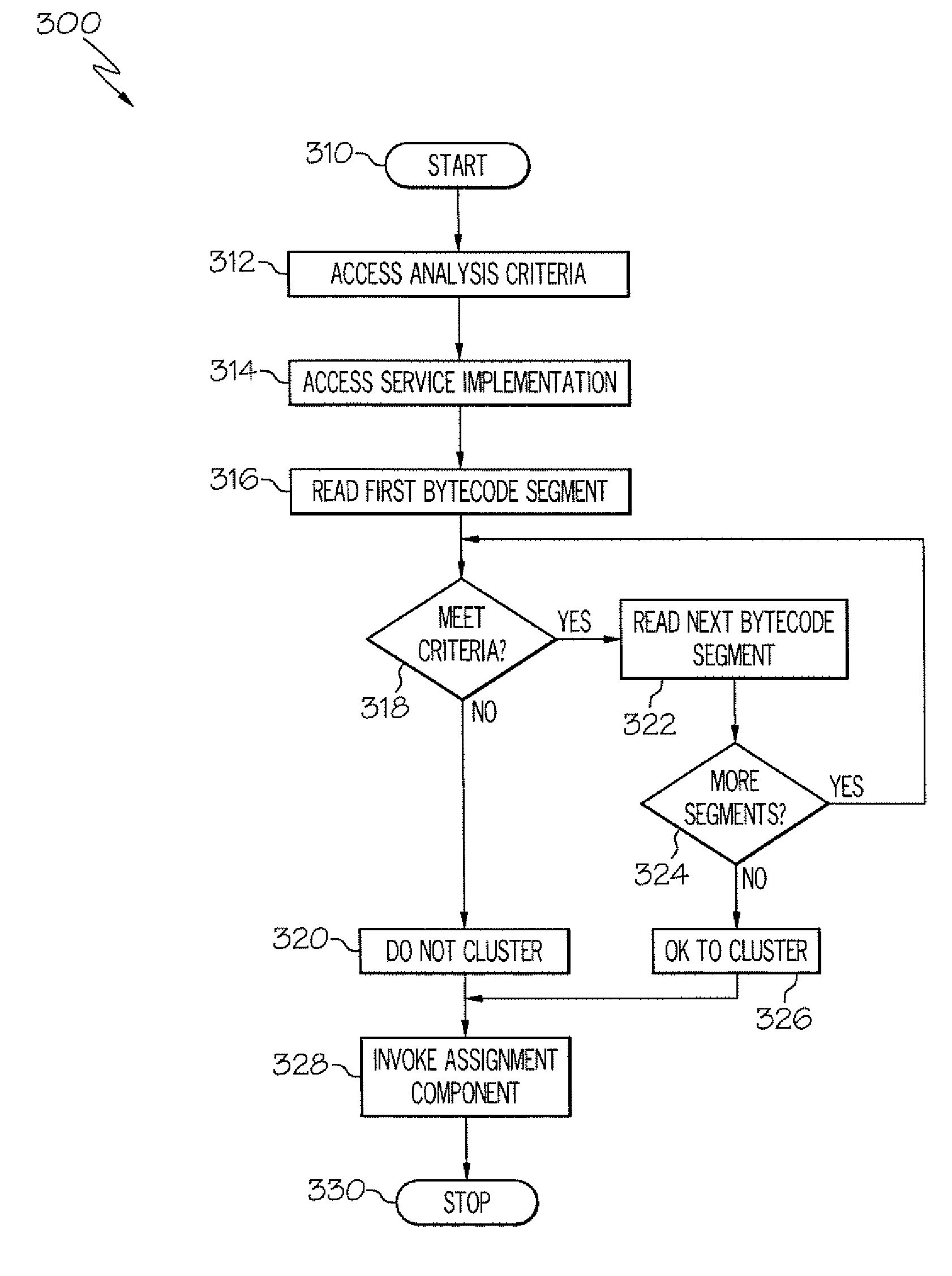
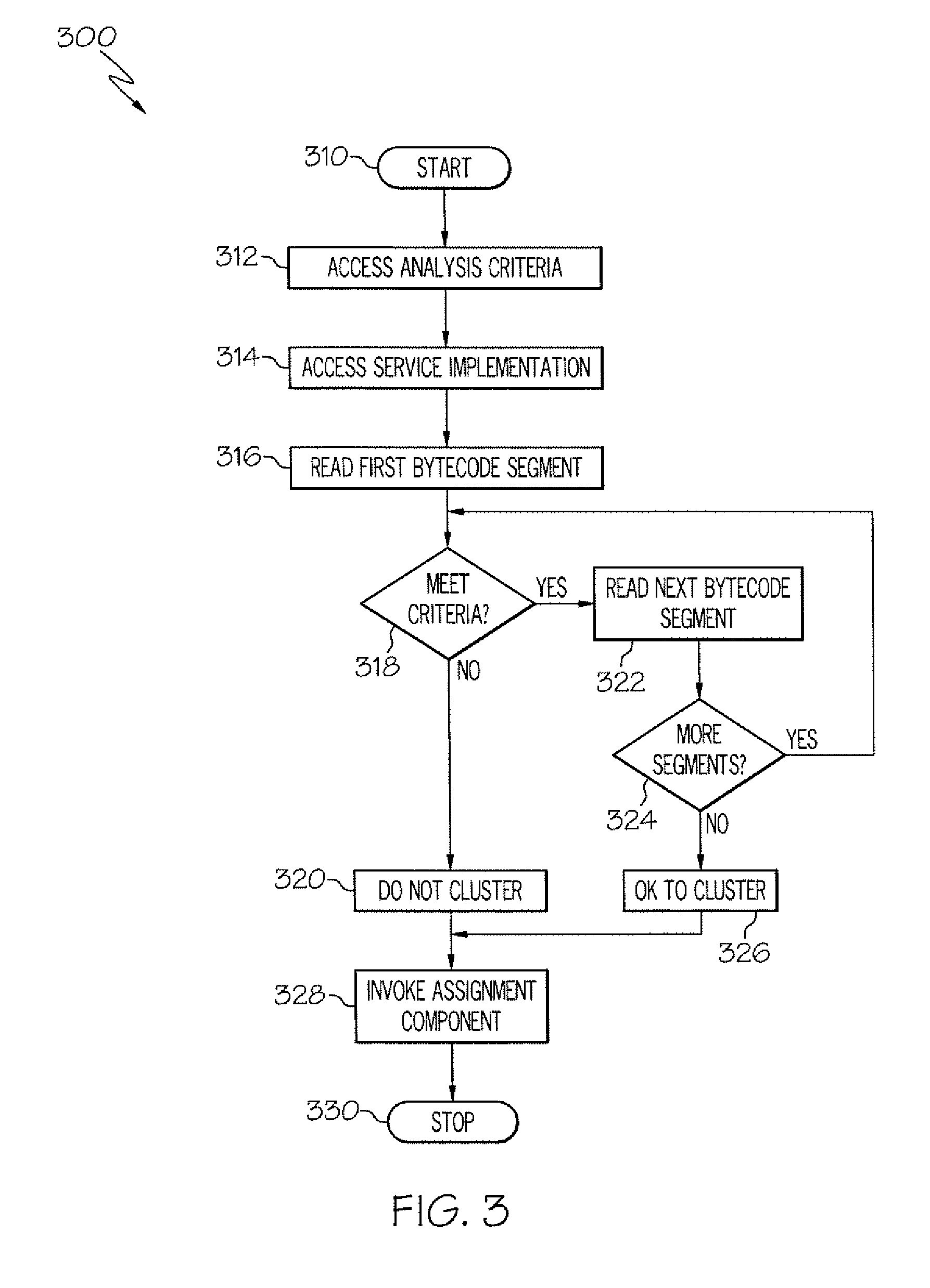
The service assignment tool analyzes a service to determine whether the service can execute on a cluster. If the service cannot execute on a cluster, the service is assigned to a single virtual machine. The service assignment tool identifies non-cluster friendly services by performing a static analysis on the bytecode of the service. The bytecode of the service is analyzed by comparing each segment of bytecode to a list of known good and bad coding conventions. If each segment of bytecode in a service meets the good coding convention criteria, then the service is cluster friendly. If one segment of bytecode does not meet the good coding convention criteria, then the entire service is considered to be not cluster friendly.
Owner:INT BUSINESS MASCH CORP
Systems and methods for performing static analysis on source code
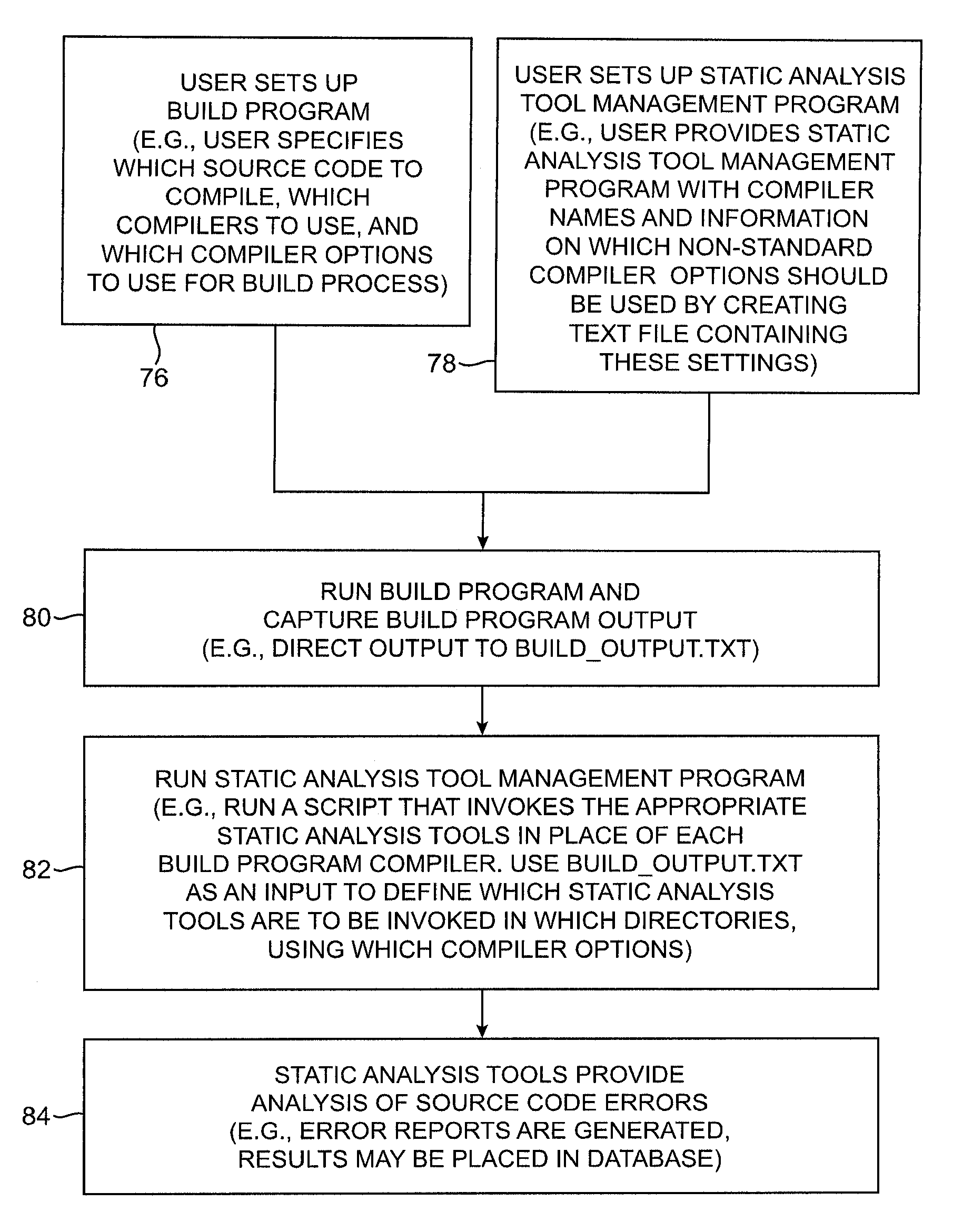
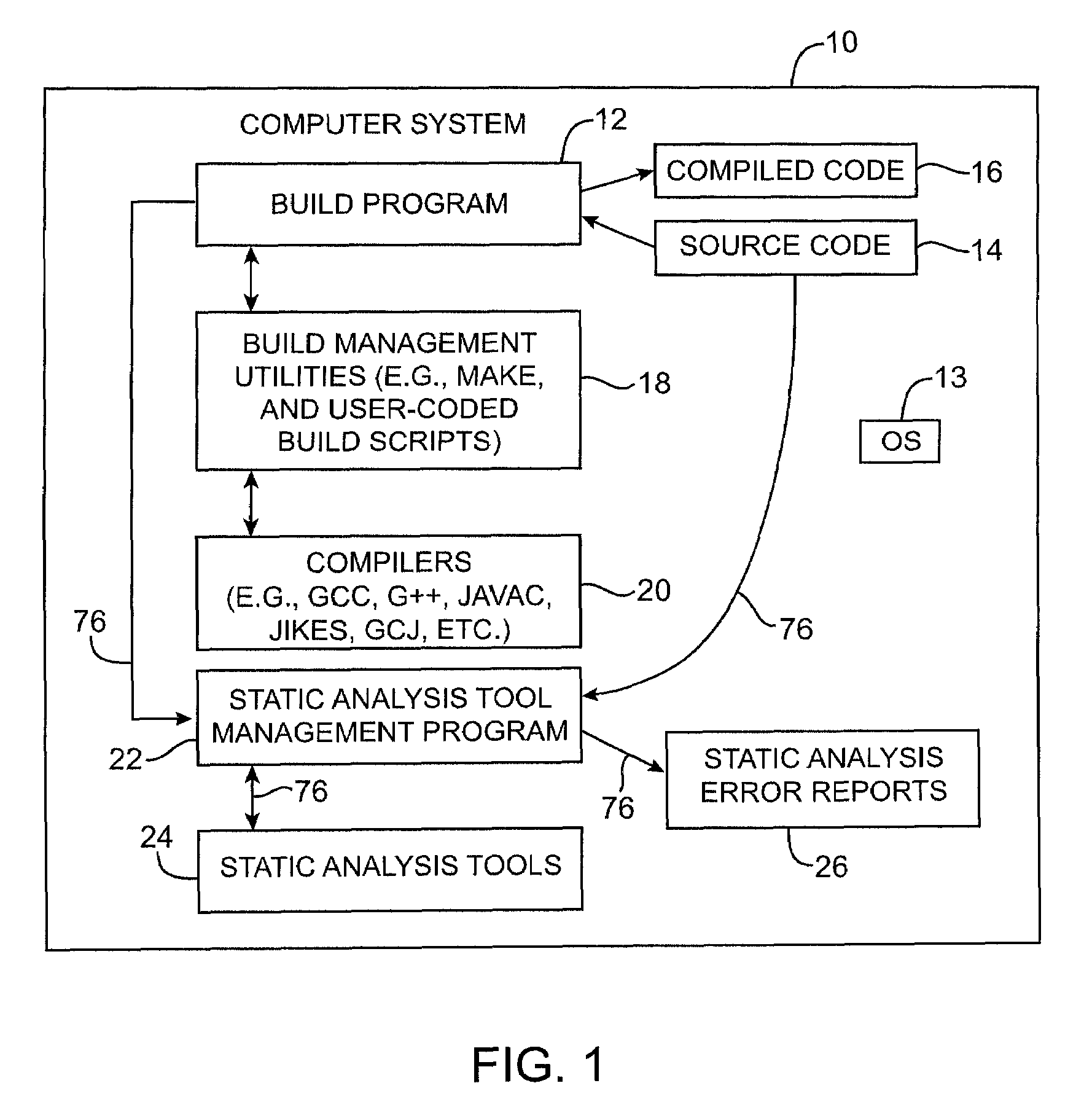
Systems and methods are provided for performing static error analysis on source code. A computer system having an operating system may contain a number of source code files. During a normal build process, a build program may be used to set various compilation options and to invoke appropriate compilers that compile the source code files into executable code. Static analysis debugging tools may be used to perform static analysis on the source code files. The appropriate static analysis tools may be invoked using a static analysis tool management program. Directory, path and name modification may be used to invoke the analysis tools. A monitoring program may be used to determine how to invoke the tools. The operating system may be modified so that the static analysis tools are invoked in place of the compilers when the build program is run.
Owner:SYNOPSYS INC
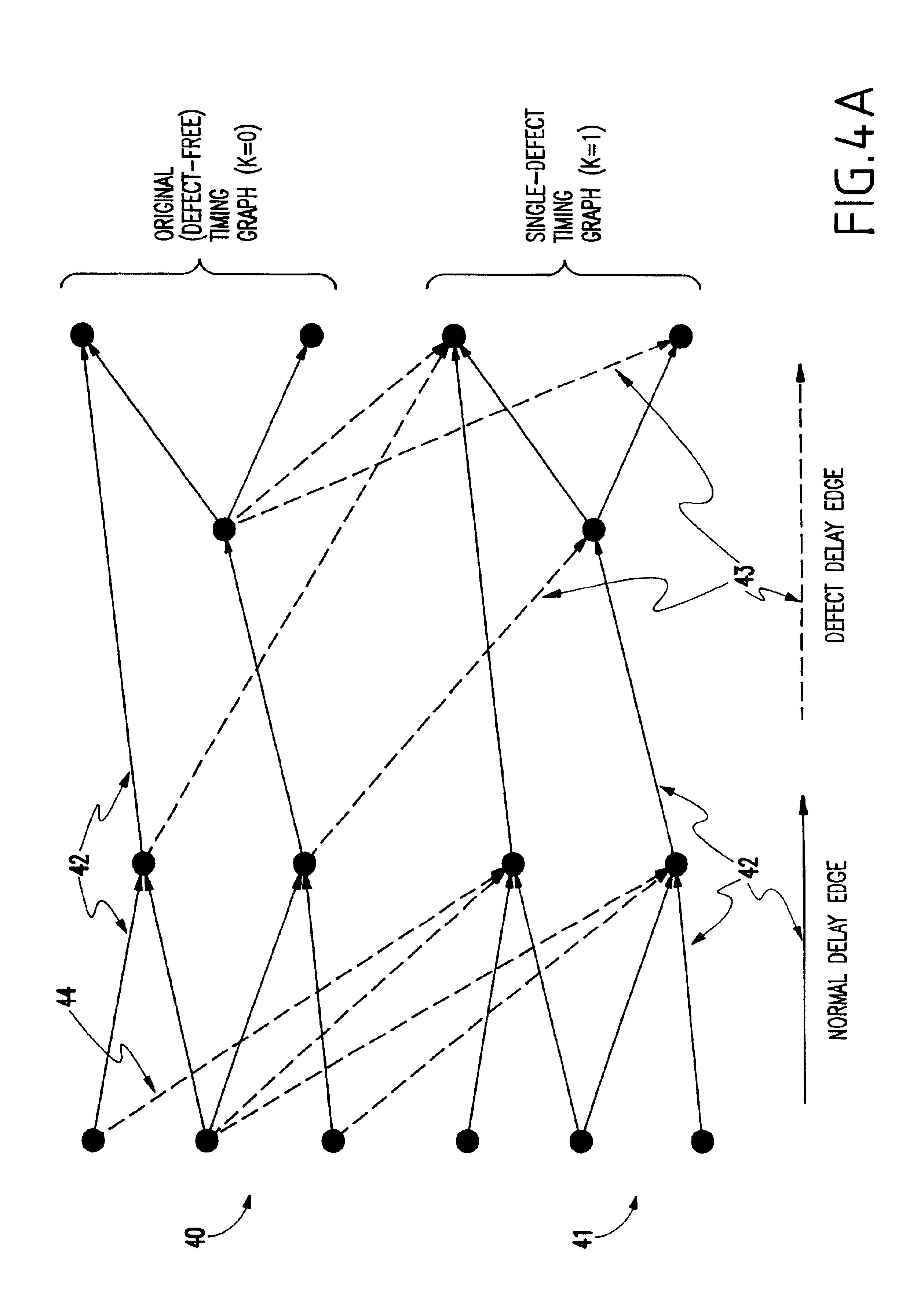
System and method for correlated process pessimism removal for static timing analysis
InactiveUS7117466B2Reduce pessimismComputer aided designSoftware simulation/interpretation/emulationStatic timing analysisAngular point
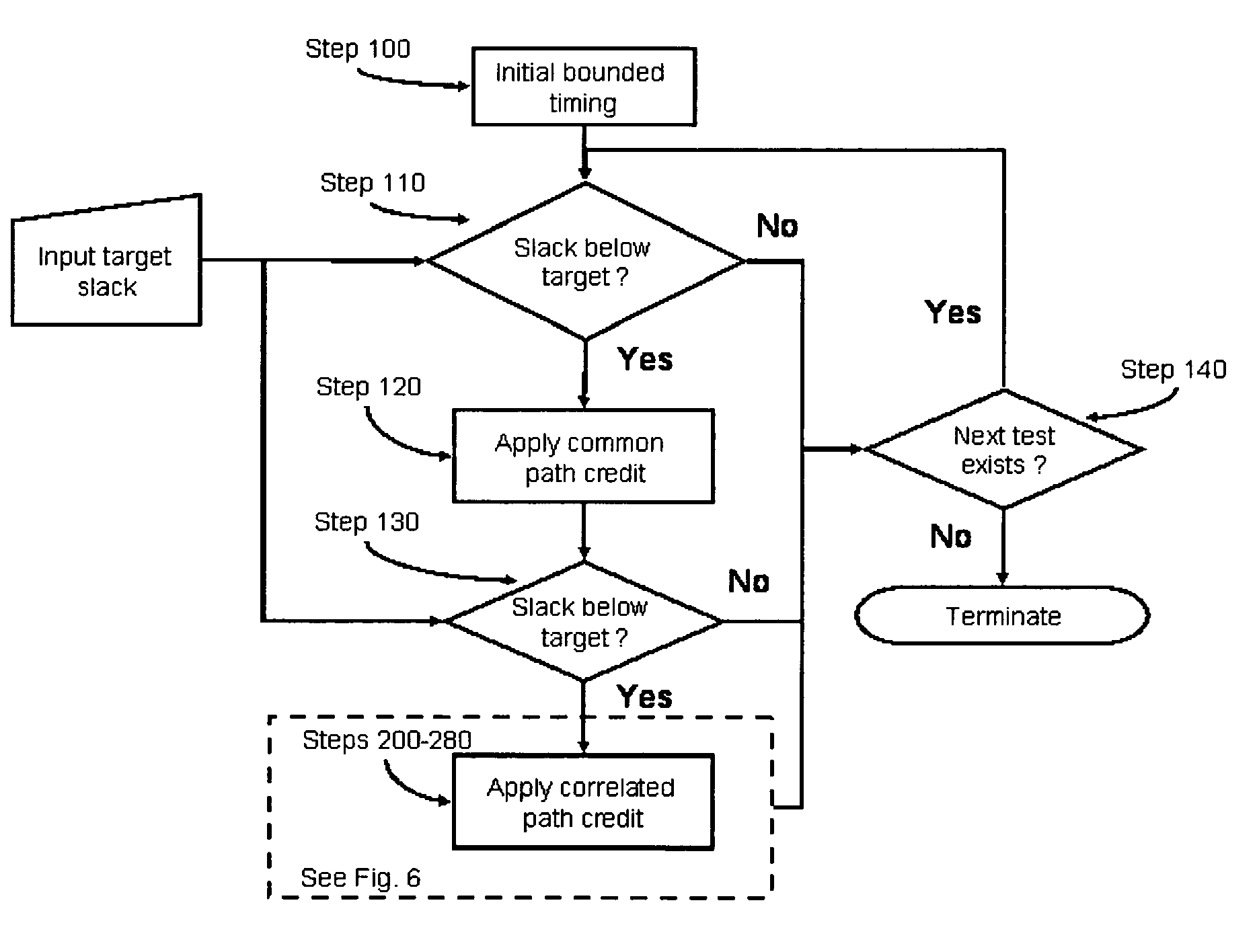
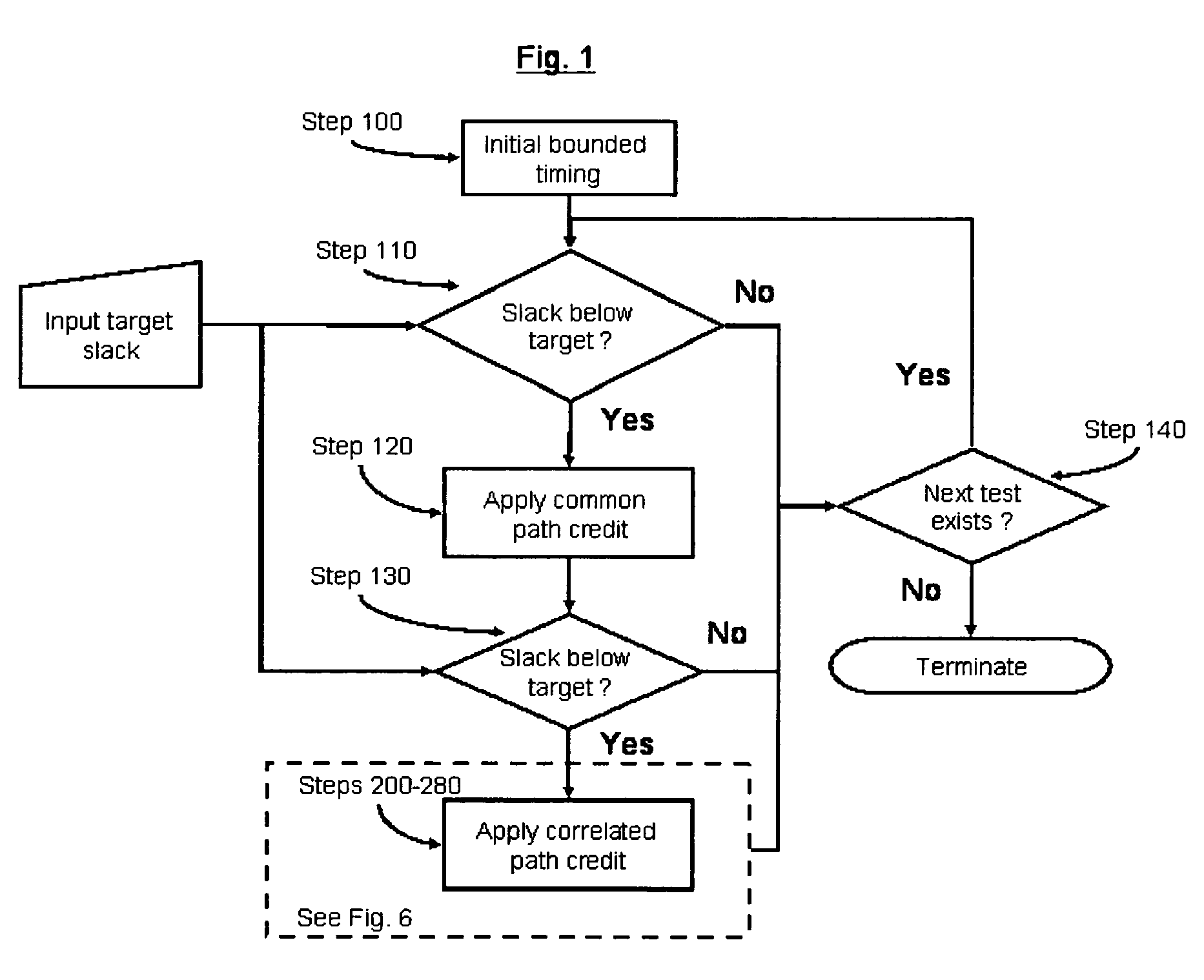
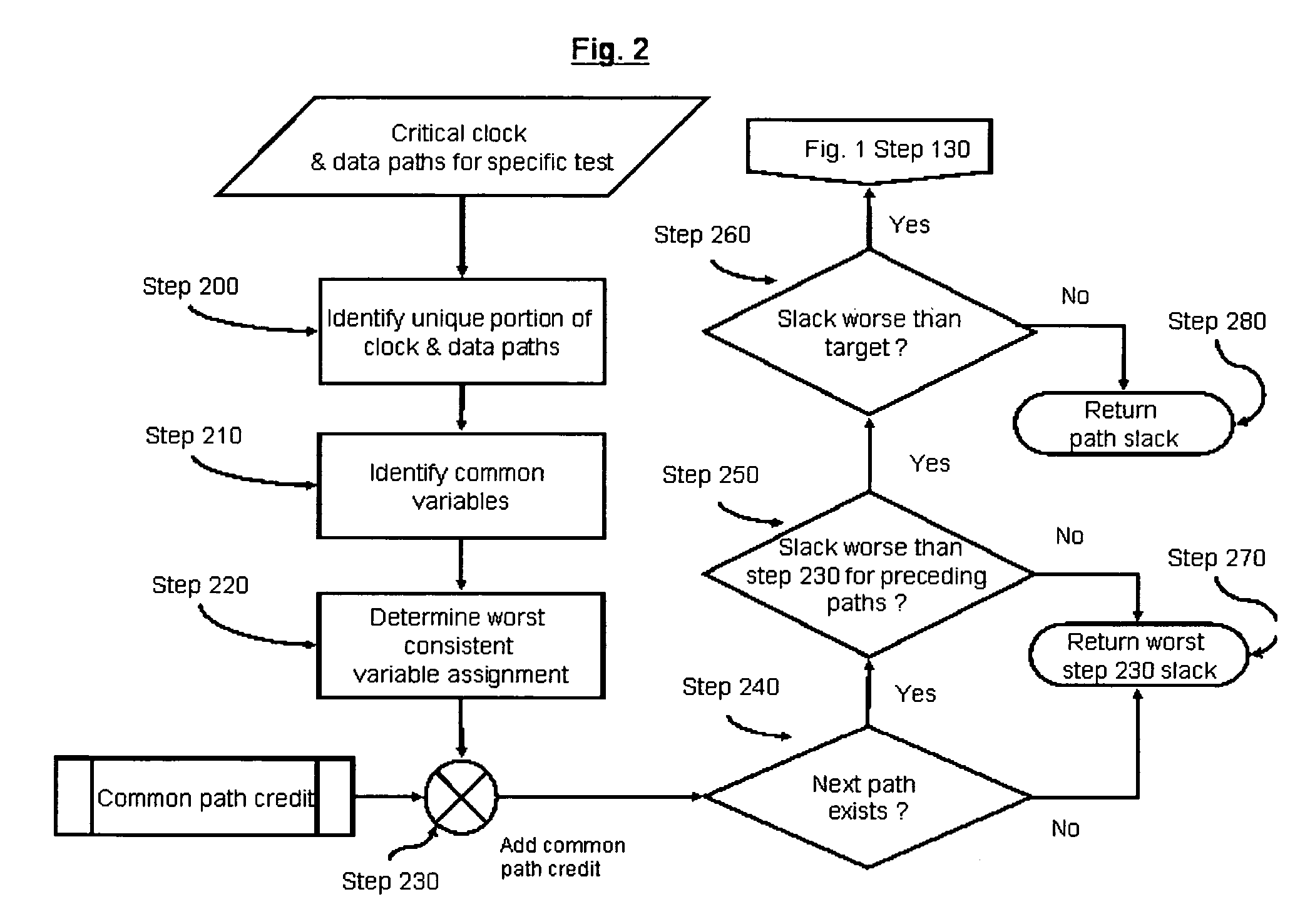
A method of removing pessimism in static timing analysis is described. Delays are expressed as a function of discrete parameter settings allowing for both local and global variation to be taken in to account. Based on a specified target slack, each failing timing test is examined to determine a consistent set of parameter settings which produces the worst possible slack. The analysis is performed on a path basis. By considering only parameters which are in common to a particular data / clock path-pair, the number of process combinations that need to be explored is reduced when compared to analyzing all combinations of the global parameter settings. Further, if parameters are separable and linear, worst-case variable assignments for a particular clock / data path pair can be computed in linear time by independently assigning each parameter value. In addition, if available, the incremental delay change with respect to each physically realizable process variable may be used to project the worst-case variable assignment on a per-path basis without the need for performing explicit corner enumeration.
Owner:GLOBALFOUNDRIES INC
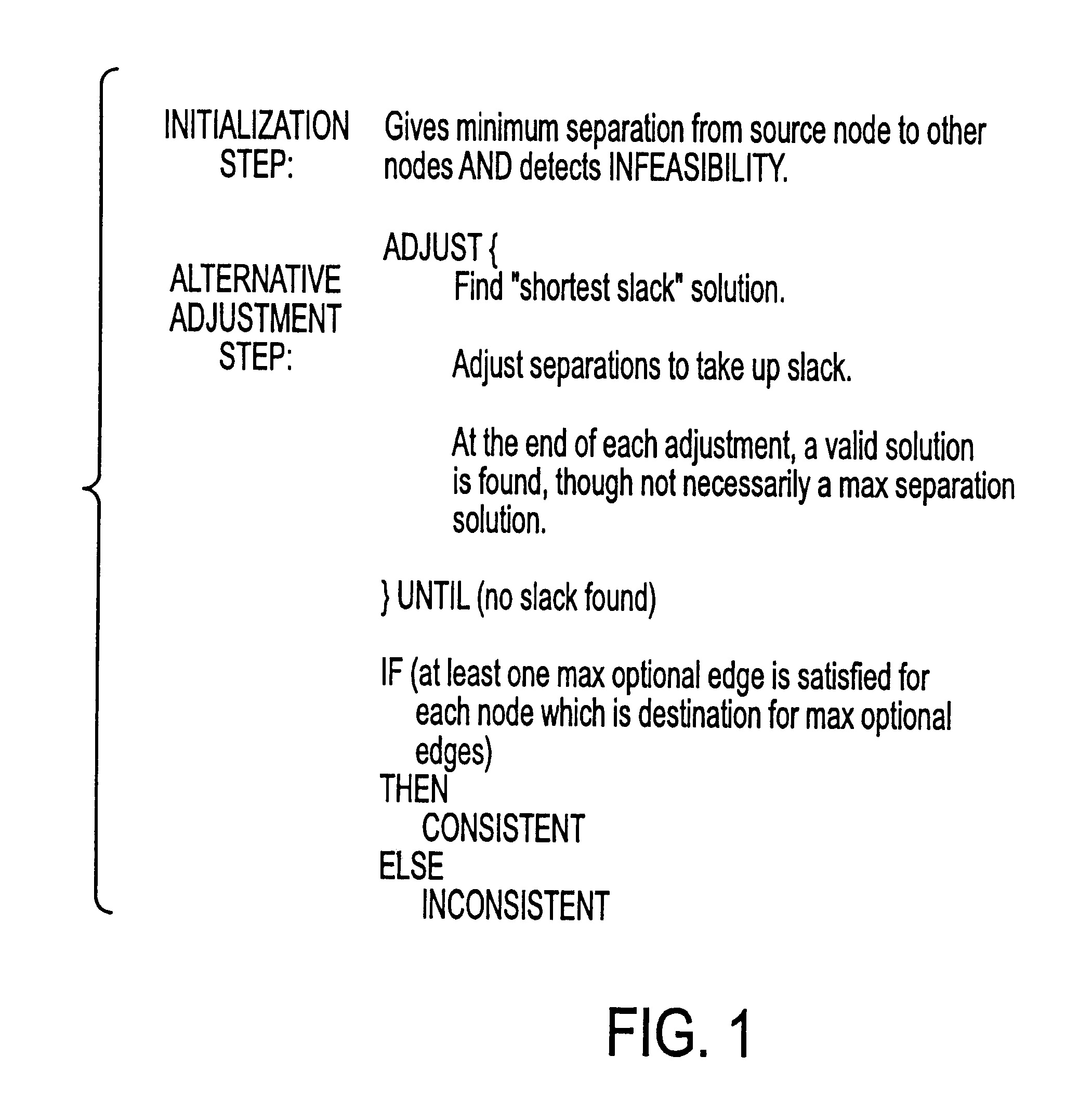
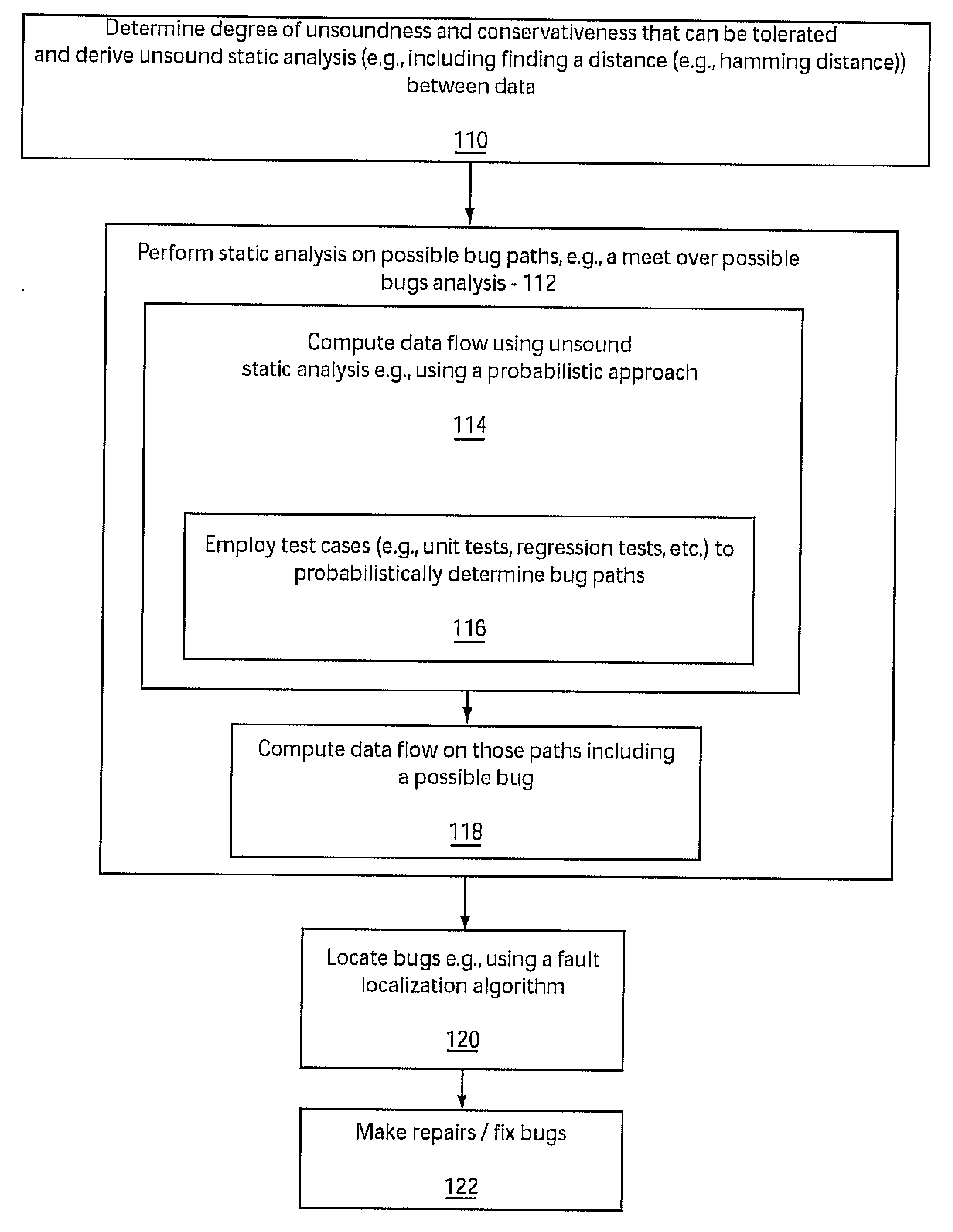
System and method for static analysis using fault paths
InactiveUS20070016894A1Error detection/correctionSpecific program execution arrangementsStatic timing analysisStatistical analysis
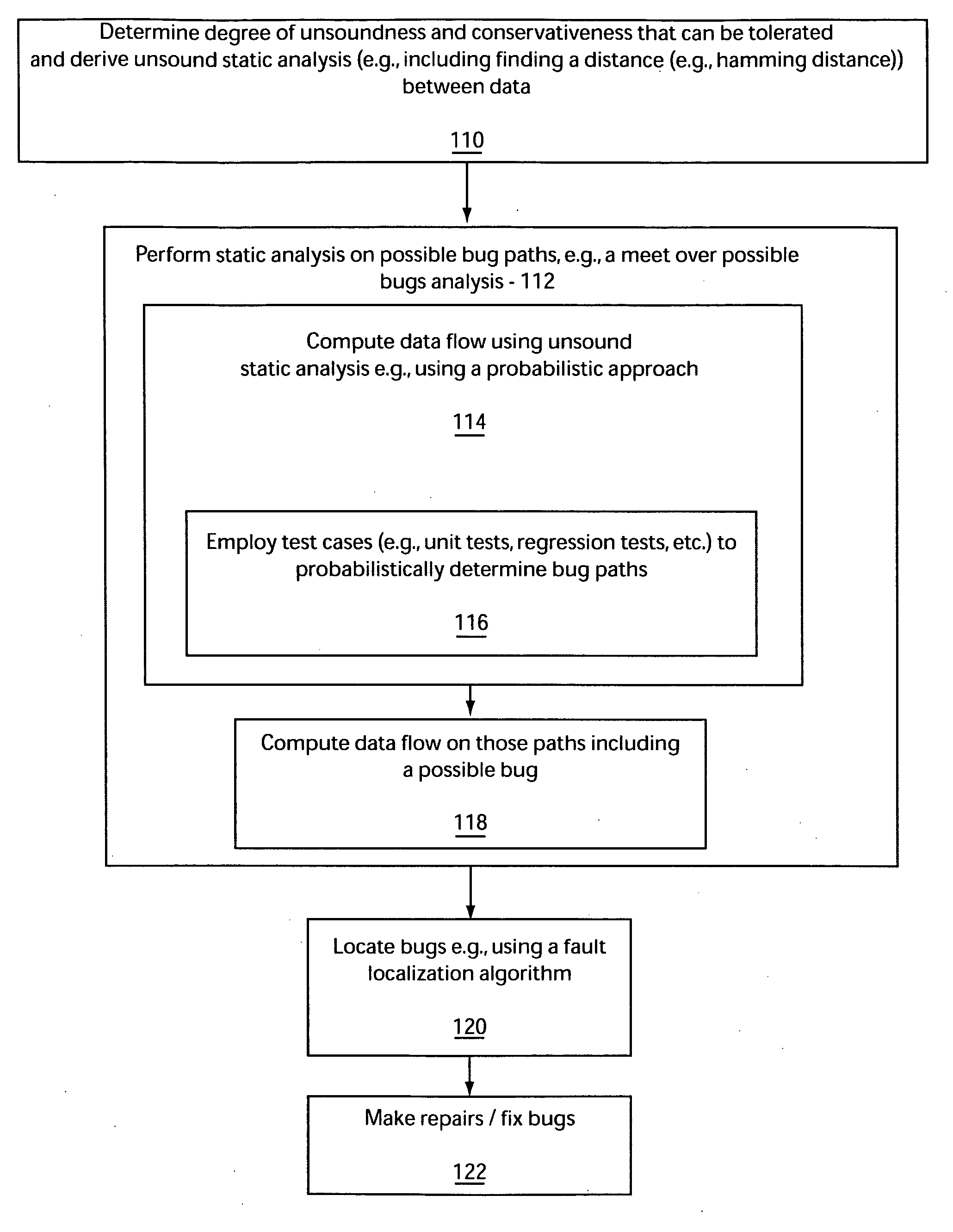
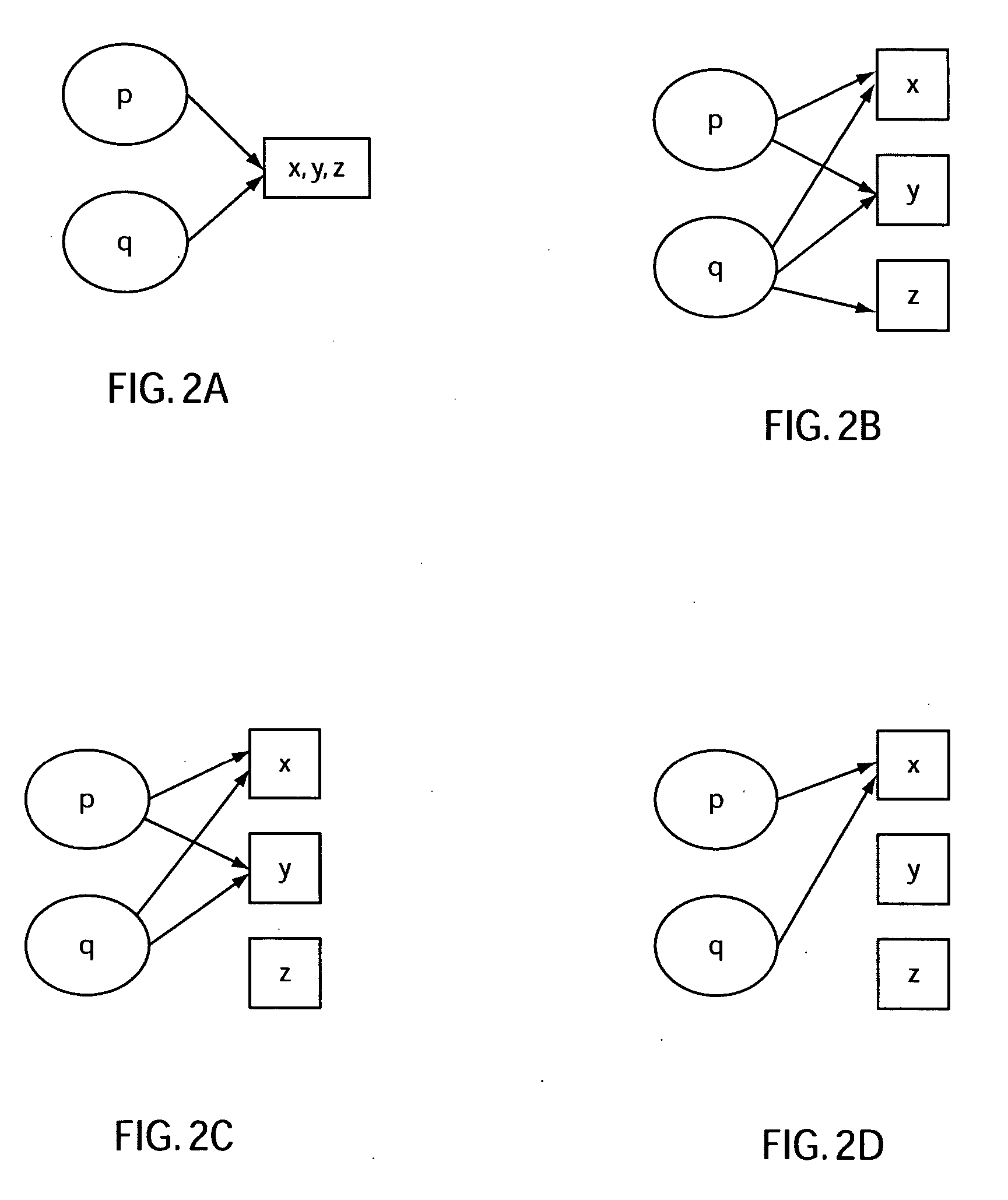
A system and method for analyzing a program includes determining possible bug paths in a program based on statistical analysis of test cases. A static analysis is then performed only on the possible bug paths. The bugs are then located in the program.
Owner:IBM CORP
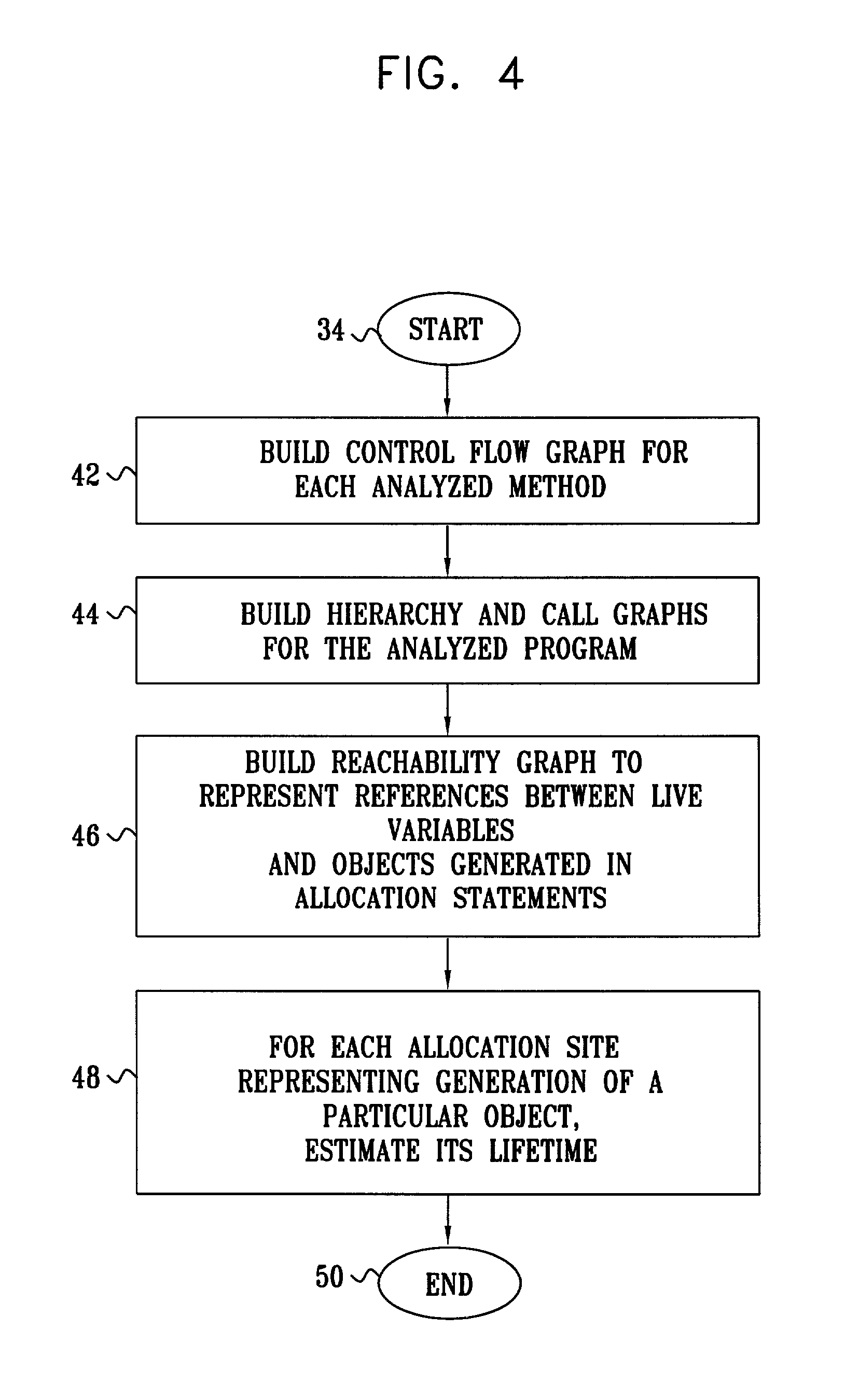
Estimation of object lifetime using static analysis
InactiveUS20020129343A1Improve performanceGood estimateData processing applicationsSoftware engineeringStatic timing analysisObject lifetime
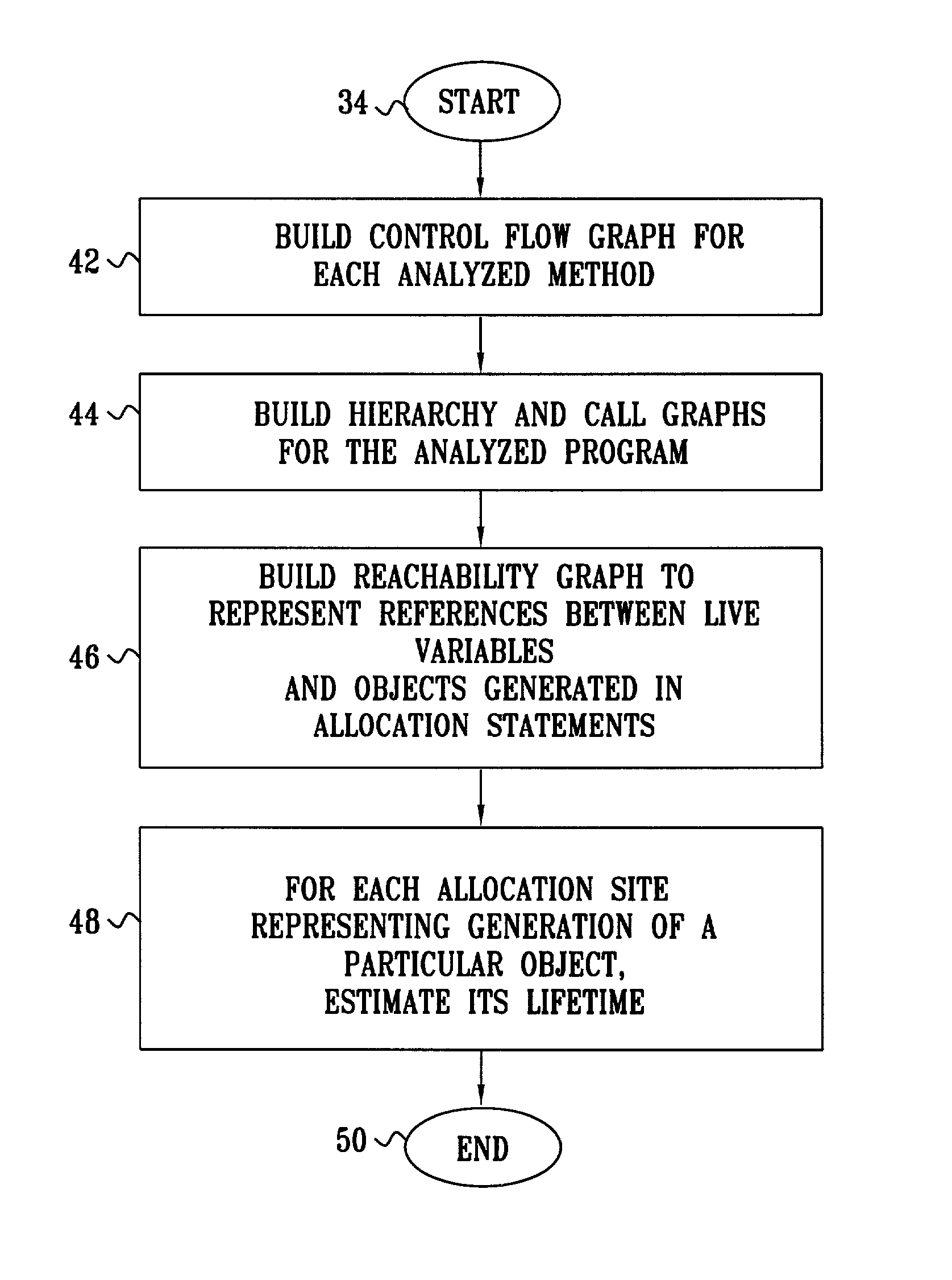
A computer implemented technique for the static evaluation of the lifetime of objects allocated in memory is presented, which find application in reducing the overhead of generational garbage collection. The method combines pointer alias analysis with static object size determination, from which accurate generational assignment of newly created objects can be accomplished.
Owner:LINKEDIN
Automatic threat detection of executable files based on static data analysis
ActiveUS20160335435A1Preventing executionDecompilation/disassemblyKernel methodsStatic timing analysisAnalysis aspect
Aspects of the present disclosure relate to threat detection of executable files. A plurality of static data points may be extracted from an executable file without decrypting or unpacking the executable file. The executable file may then be analyzed without decrypting or unpacking the executable file. Analysis of the executable file may comprise applying a classifier to the plurality of extracted static data points. The classifier may be trained from data comprising known malicious executable files, known benign executable files and known unwanted executable files. Based upon analysis of the executable file, a determination can be made as to whether the executable file is harmful.
Owner:OPEN TEXT CORPORATION
Verifying application security vulnerabilities
ActiveUS20130312102A1Memory loss protectionError detection/correctionStatic timing analysisApplication software
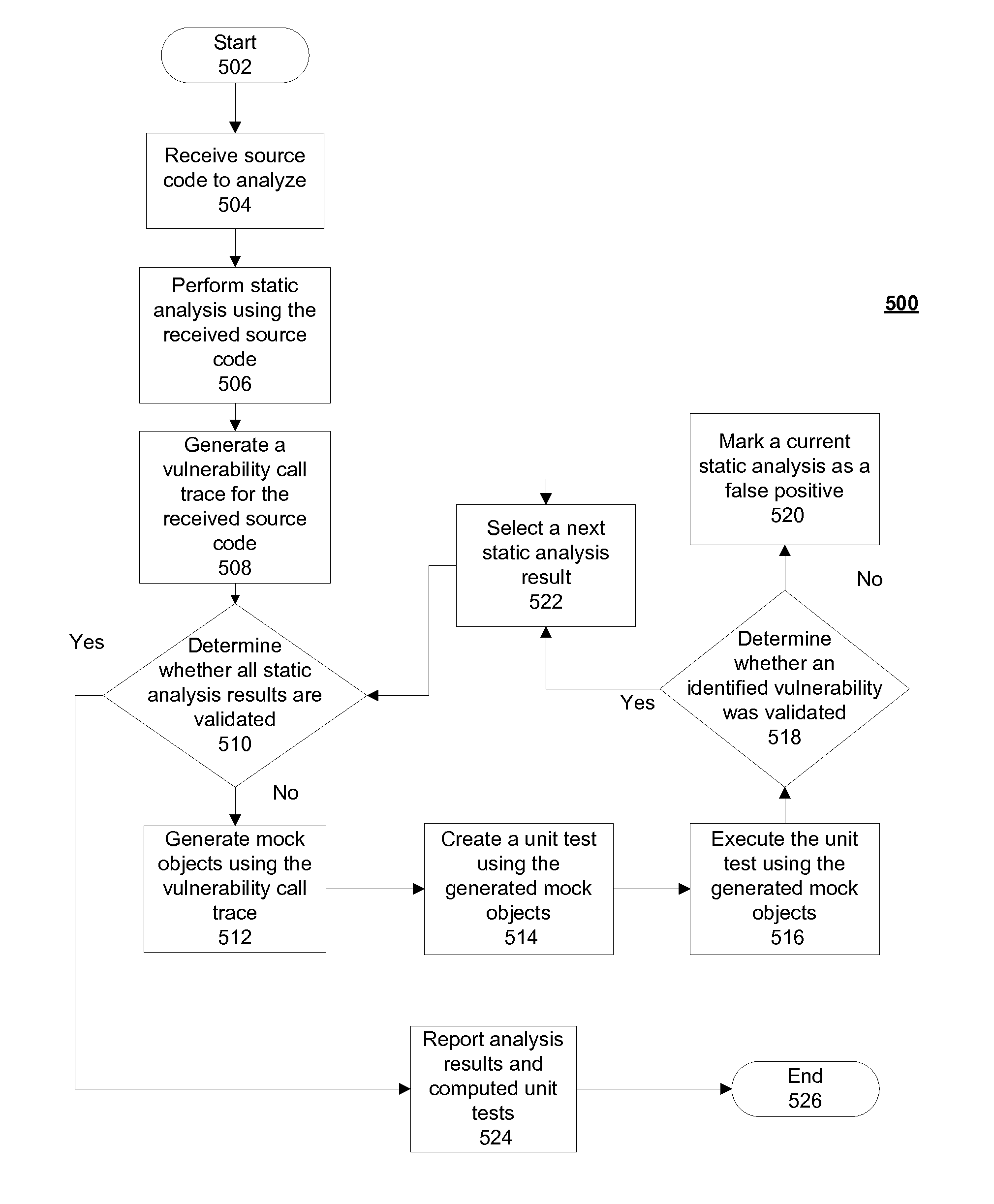
Verifying application security vulnerabilities includes receiving a source code to analyze, performing a static analysis using the received source code and generating a vulnerability call trace for the received source code. Responsive to a determination that all static analysis results are not validated, mock objects are generated using the vulnerability call trace and a unit test is created using the generated mock objects. The unit test is executed using the generated mock objects and responsive to a determination that an identified vulnerability was validated; a next static analysis result is selected. Responsive to a determination that all static analysis results are validated, results and computed unit tests are reported.
Owner:FINJAN BLUE INC
Static taint analysis and symbolic execution-based Android application vulnerability discovery method
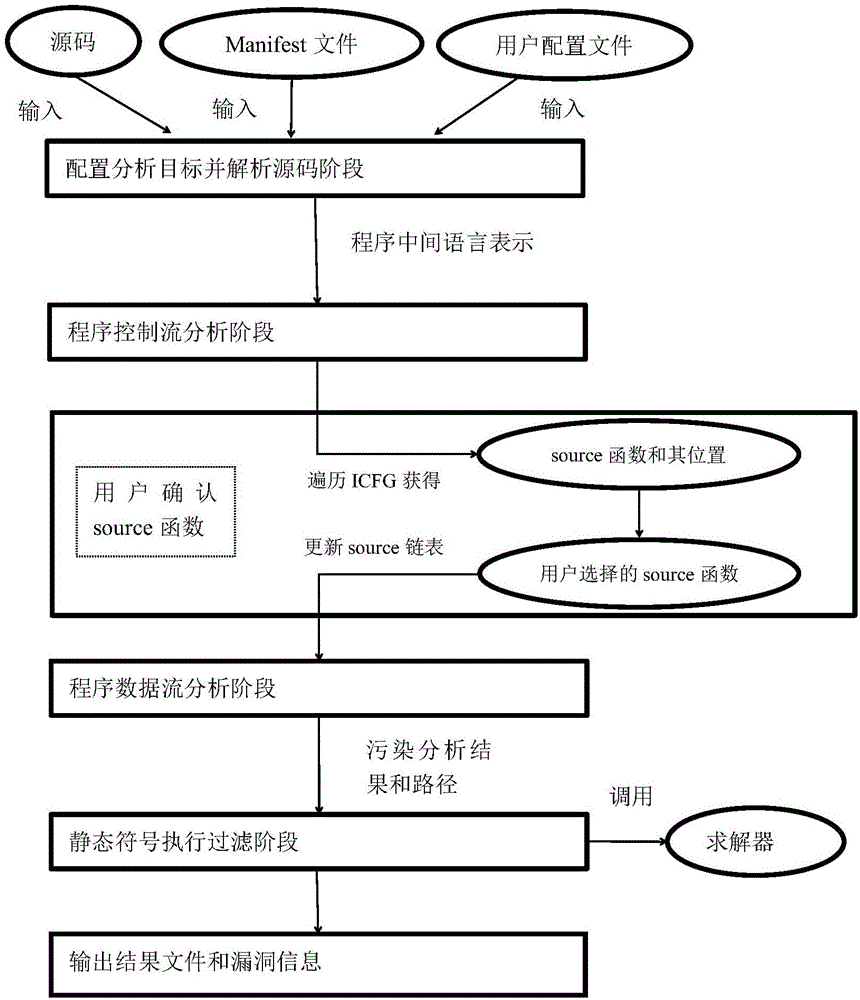
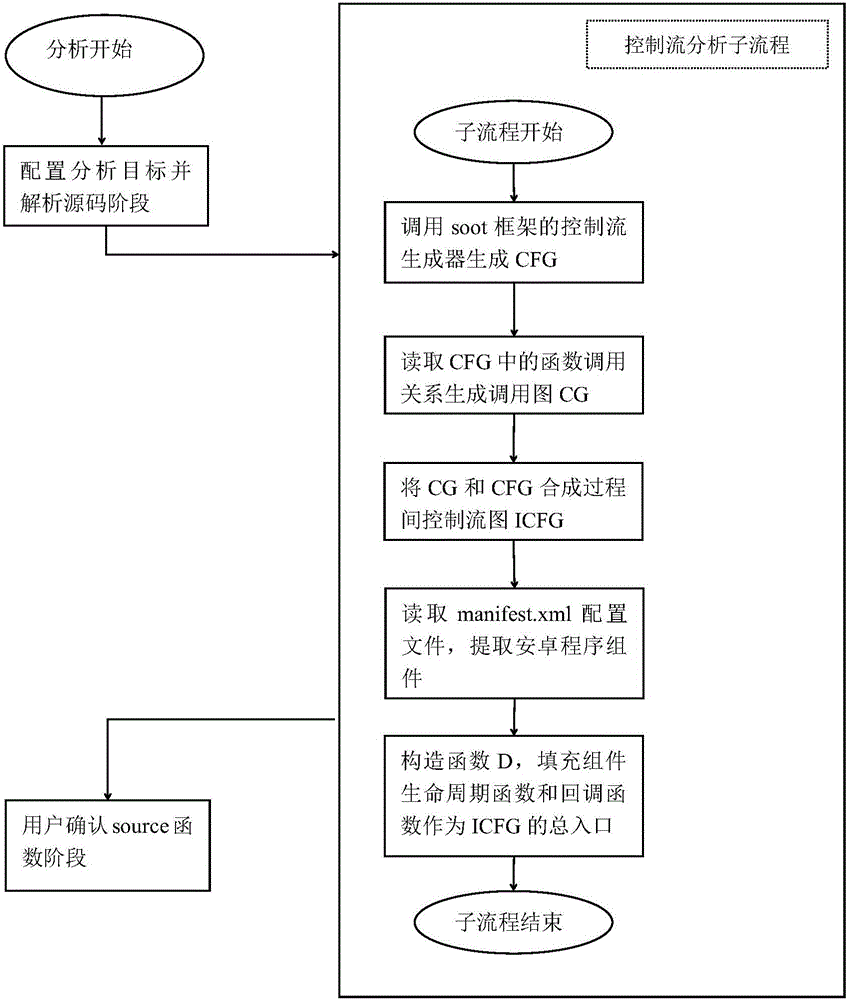
ActiveCN106709356ATargetedImprove efficiencyPlatform integrity maintainanceStatic timing analysisData stream
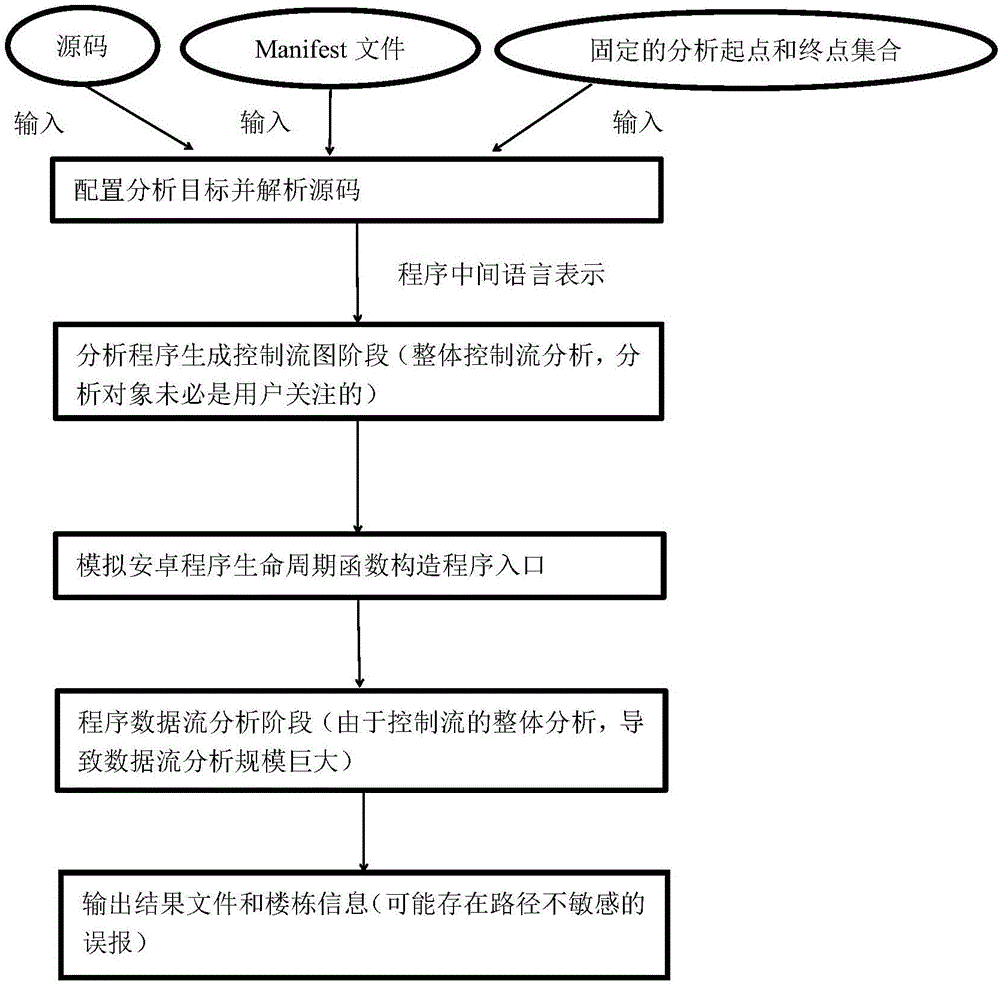
The invention discloses a static taint analysis and symbolic execution-based Android application vulnerability discovery method, and mainly aims at solving the problems that the analysis range is fixed, the memory consumption is huge and the analysis result is mistakenly reported in the process of discovering vulnerabilities by using the existing static taint analysis method. The method is realized through the following steps of: 1) configuring an analysis target and decompiling a program source code; 2) carrying out control flow analysis on the decompilation result; 3) selecting a source function by a user according to the control flow analysis result, so as to narrow an analysis target; 4) carrying out data flow analysis according to the control flow analysis result, so as to generate a vulnerability path; and 5) filtering the data flow analysis result by adoption of a static symbolic execution technology, taking the residual parts after the filtration as discovered vulnerabilities, warning the user and printing the vulnerability path. On the basis of the existing static taint analysis technology, the method disclosed by the invention has the advantages of extending the vulnerability discovery range, decreasing the memory consumption of vulnerability discovery and improving the accuracy of vulnerability discovery results, and can be applied to the discovery and research of Android application program vulnerabilities.
Owner:XIDIAN UNIV
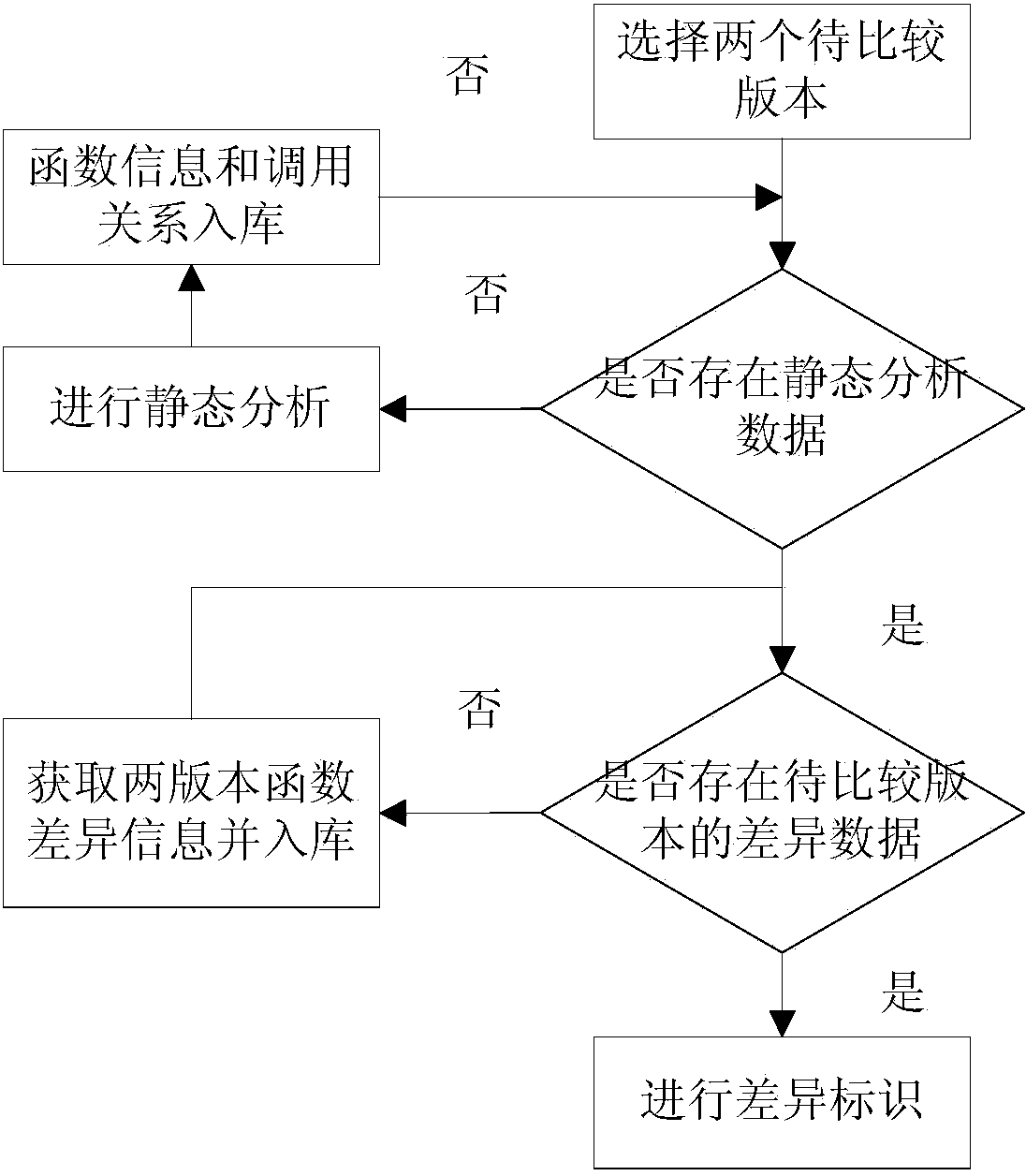
Static analysis based source code multi-versionfunction call relation difference identification method
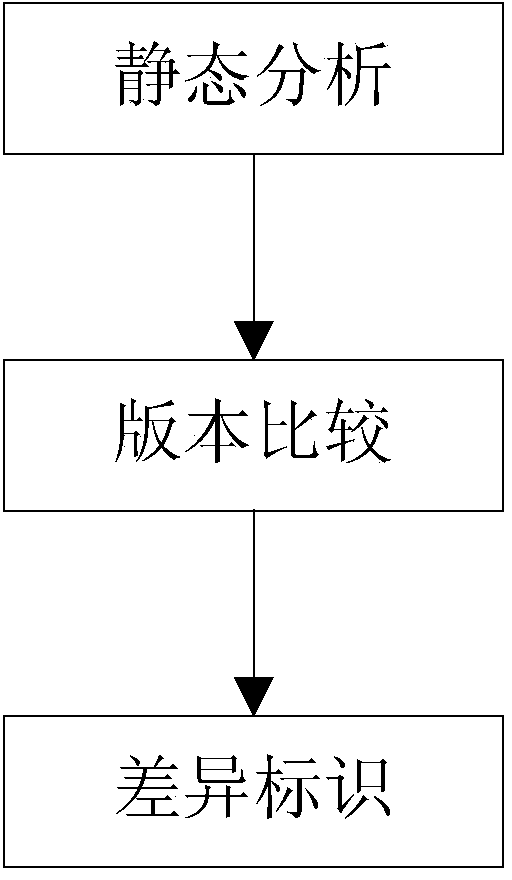
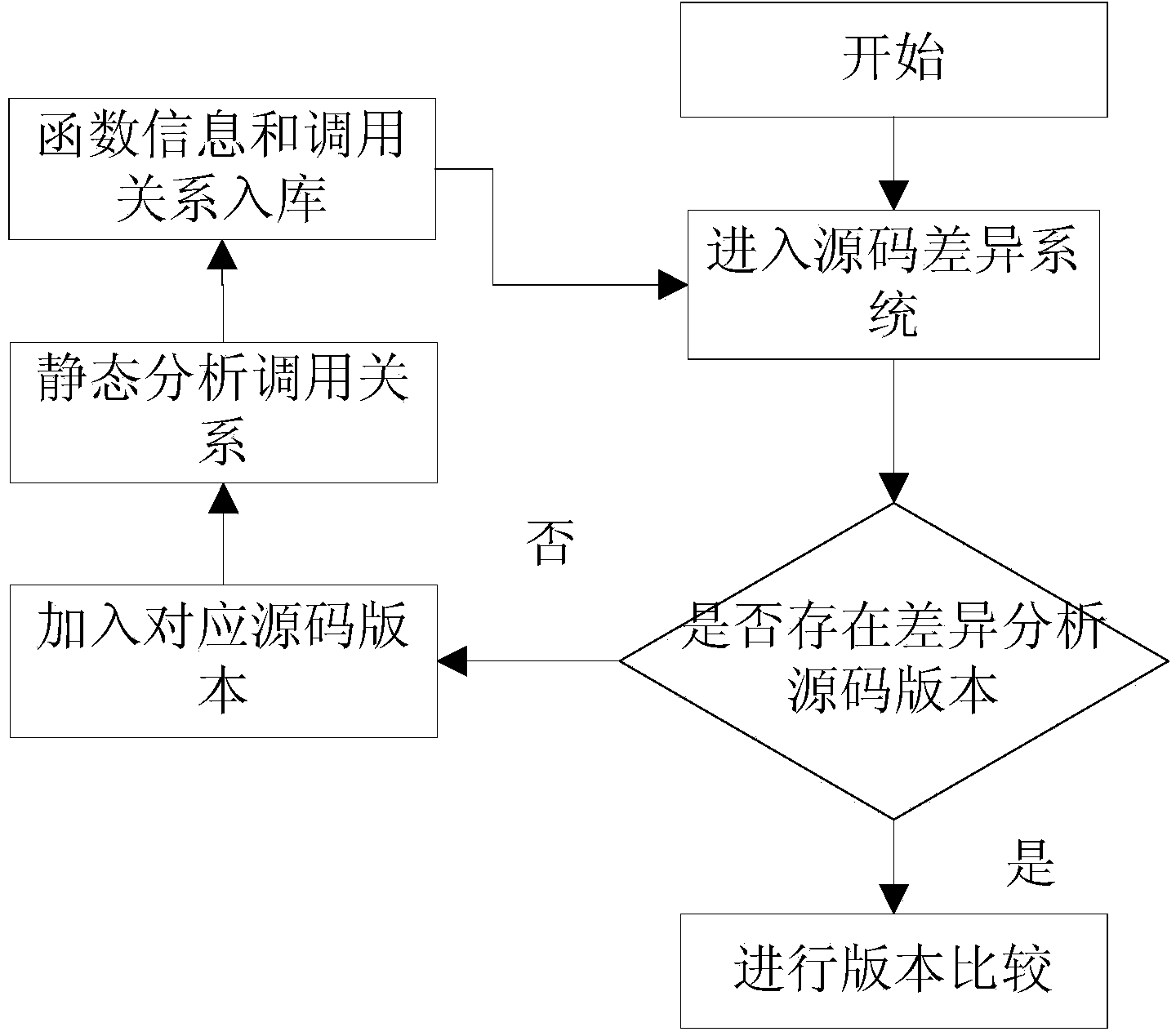
InactiveCN104035772AAnalysis threshold is highSpecial data processing applicationsSpecific program execution arrangementsStatic timing analysisUser needs
The invention relates to a static analysis based source code multi-versionfunction call relation difference identification method. Firstly, information defined in a source code, like a function list and a static call relation between functions, is acquired through a source code static analysis technique; then source codes of two versions are chosen to carry out Diff, then the function definition list and the call relation that are acquired through static analysis are combined to identify the changed difference part, the state of the changed part is carefully analyzed, the change status, the new addition status and the deletion status defined and called by a function are respectively identified and put in storage, and finally, the call relation betweena single version and the call relation difference view of more versions are displayed in combination with the user need and the status data stored in a database. The internal call relation of single version is analyzed and displayed, and the call relation difference of more versions is also analyzed and displayed, so that an efficient auxiliary method is provided for the analysis, development, uploading and maintenance of open source software.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
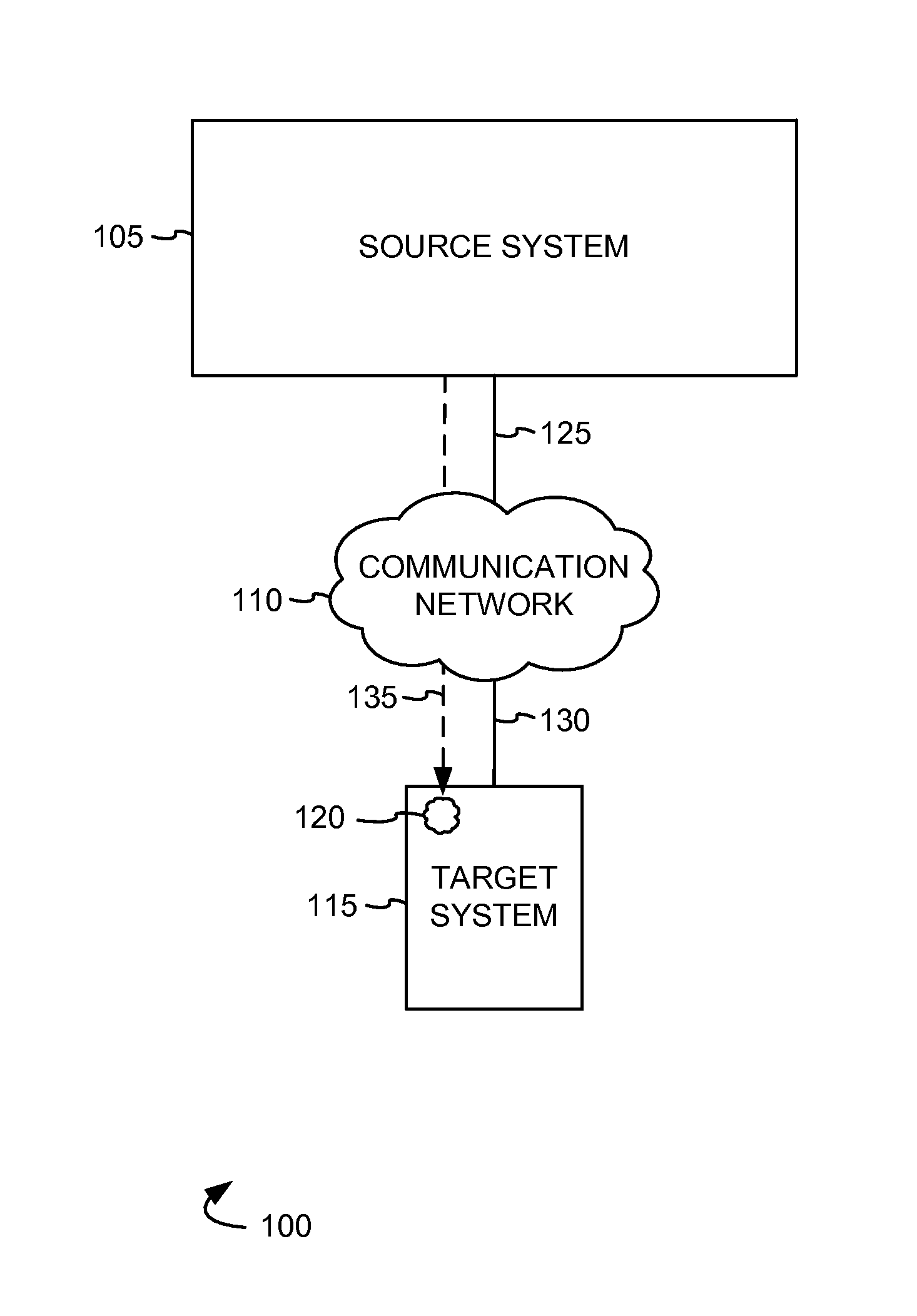
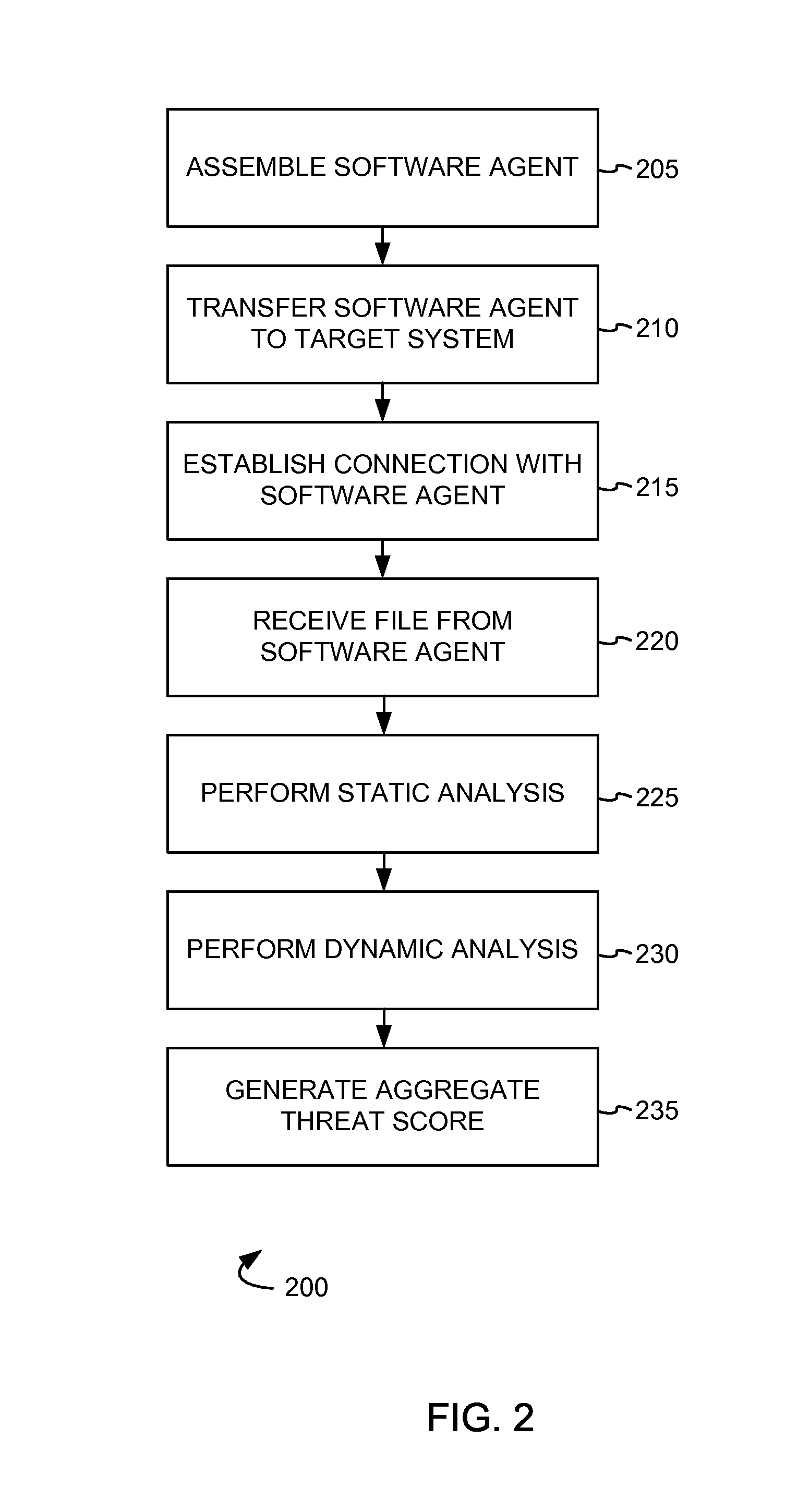
Detecting malicious software
ActiveUS8863288B1Memory loss protectionUnauthorized memory use protectionStatic timing analysisDynamic program analysis
In systems and methods of detecting malicious software, a software agent comprising at least one scan module is assembled by a source system and is transferred by the source system to a target system. In response to a connection request from the software agent a connection is established to the software agent and a file is received from the target system. At the source system, a static analysis is performed on the transferred file to generate a static threat score, and a dynamic analysis is performed to generate a dynamic threat score. Based on the static threat score and the dynamic threat score an aggregate threat score is generated for the transferred file.
Owner:MANTECH ADVANCED SYST INT
Method and system for evaluating timing in an integrated circuit
InactiveUS7089143B2Noise figure or signal-to-noise ratio measurementElectrical testingStatic timing analysisCell based
Owner:GLOBALFOUNDRIES INC
Malicious code detection method and system
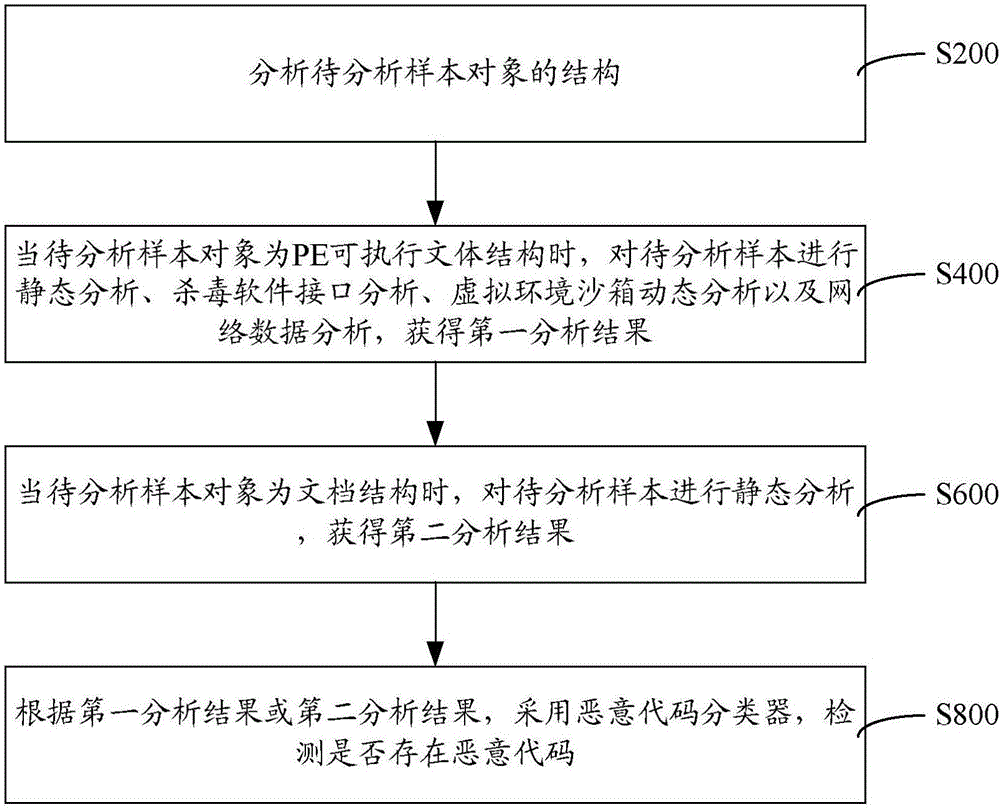
InactiveCN106778268AReliable analysis and identification abilityPlatform integrity maintainanceStatic timing analysisData profiling
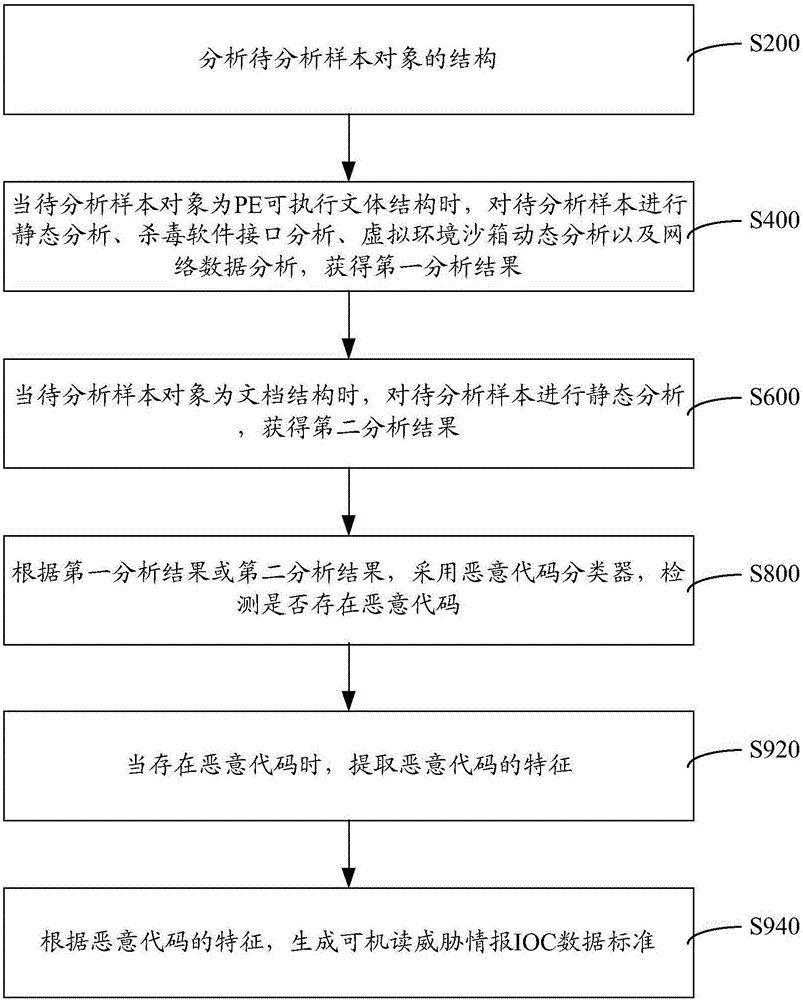
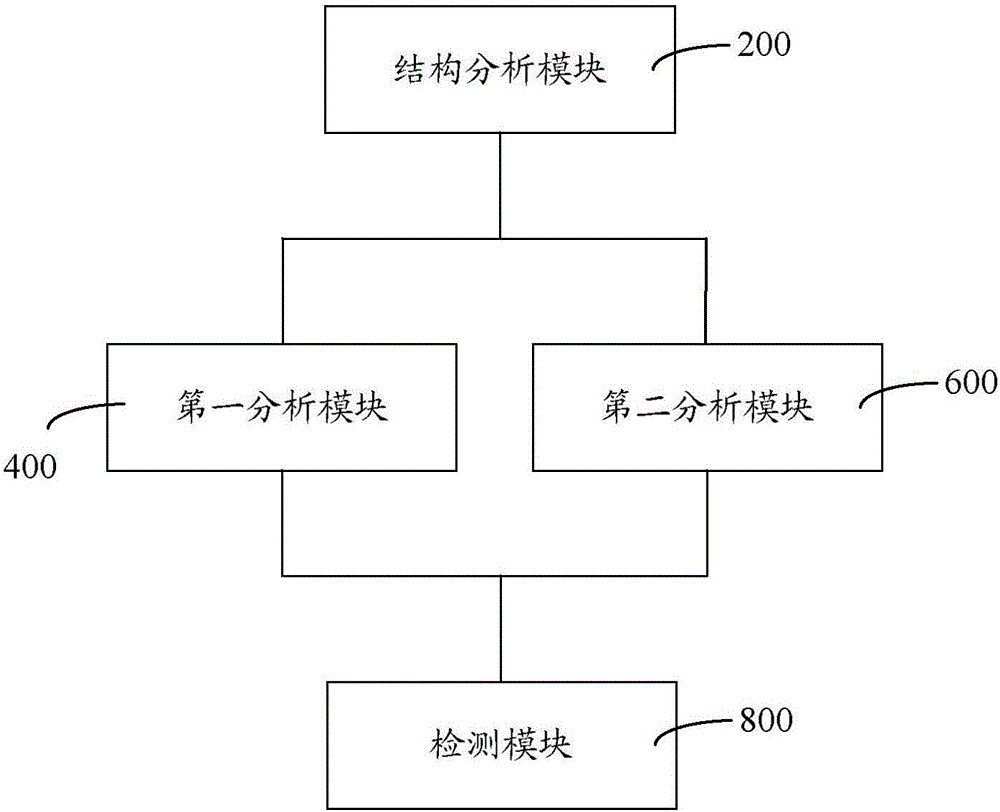
The invention provides a malicious code detection method and system. The malicious code detection method comprises the following steps: analyzing a structure of a to-be-analyzed sample object; when the to-be-analyzed sample object is of a PE executable stylistic structure, performing static analysis, antivirus software interface analysis, dynamic virtual environment sandbox analysis and network data analysis on the to-be-analyzed sample object and obtaining a first analysis result; when the to-be-analyzed sample object is of a text structure, performing static analysis on the to-be-analyzed sample object and obtaining a second analysis result; detecting whether a malicious code exists or not by adopting a malicious code classifier according to the first analysis result or the second analysis result. In the whole process, data structures of different sample object types are analyzed; static analysis, antivirus software interface analysis, dynamic virtual environment sandbox analysis and network data analysis are adopted; the analysis and identification abilities are reliable, and a source of a network attack incident can be traced.
Owner:广东省信息安全测评中心 +1
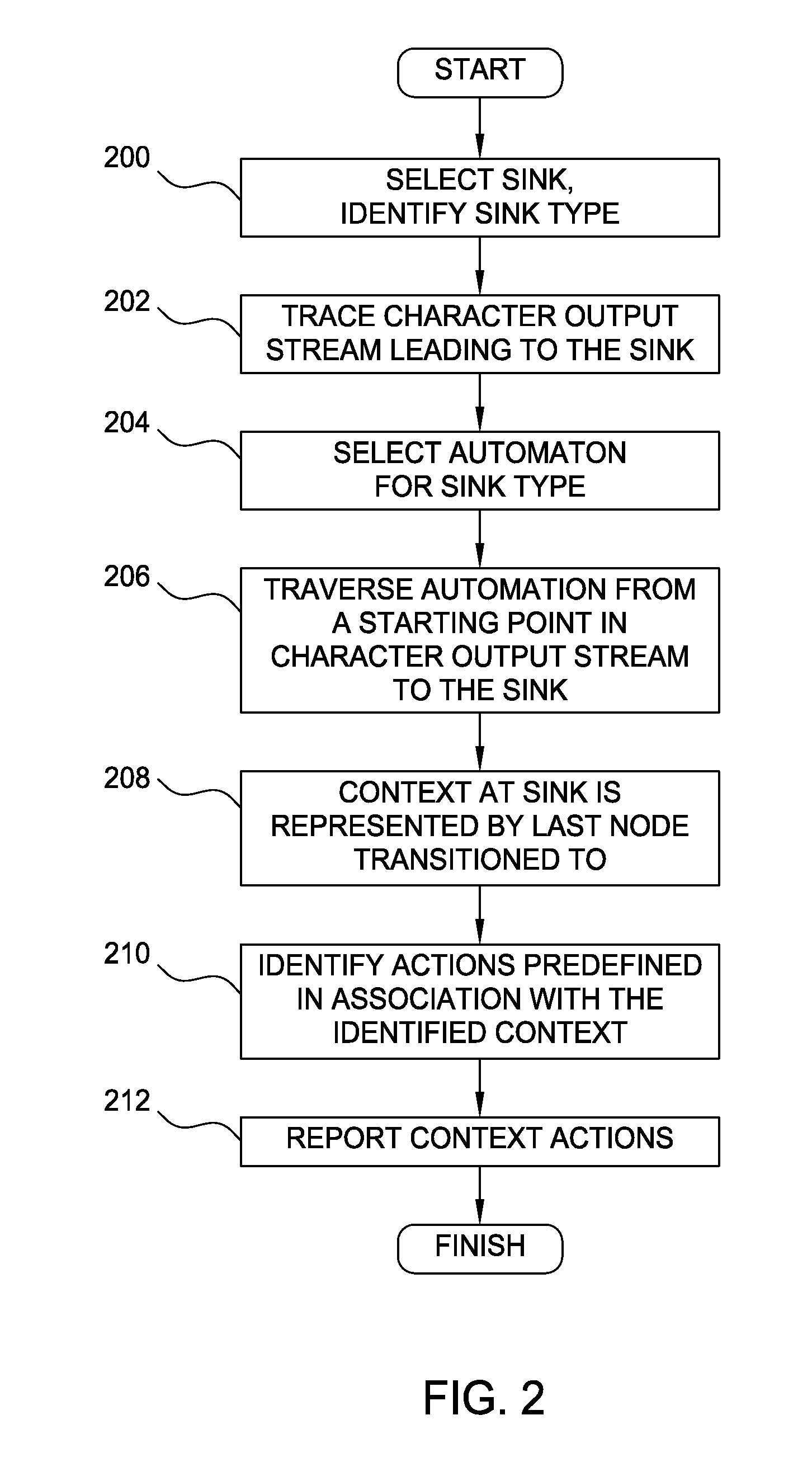
Injection context based static analysis of computer software applications
InactiveUS20110321016A1Memory loss protectionUser identity/authority verificationStatic timing analysisState dependent
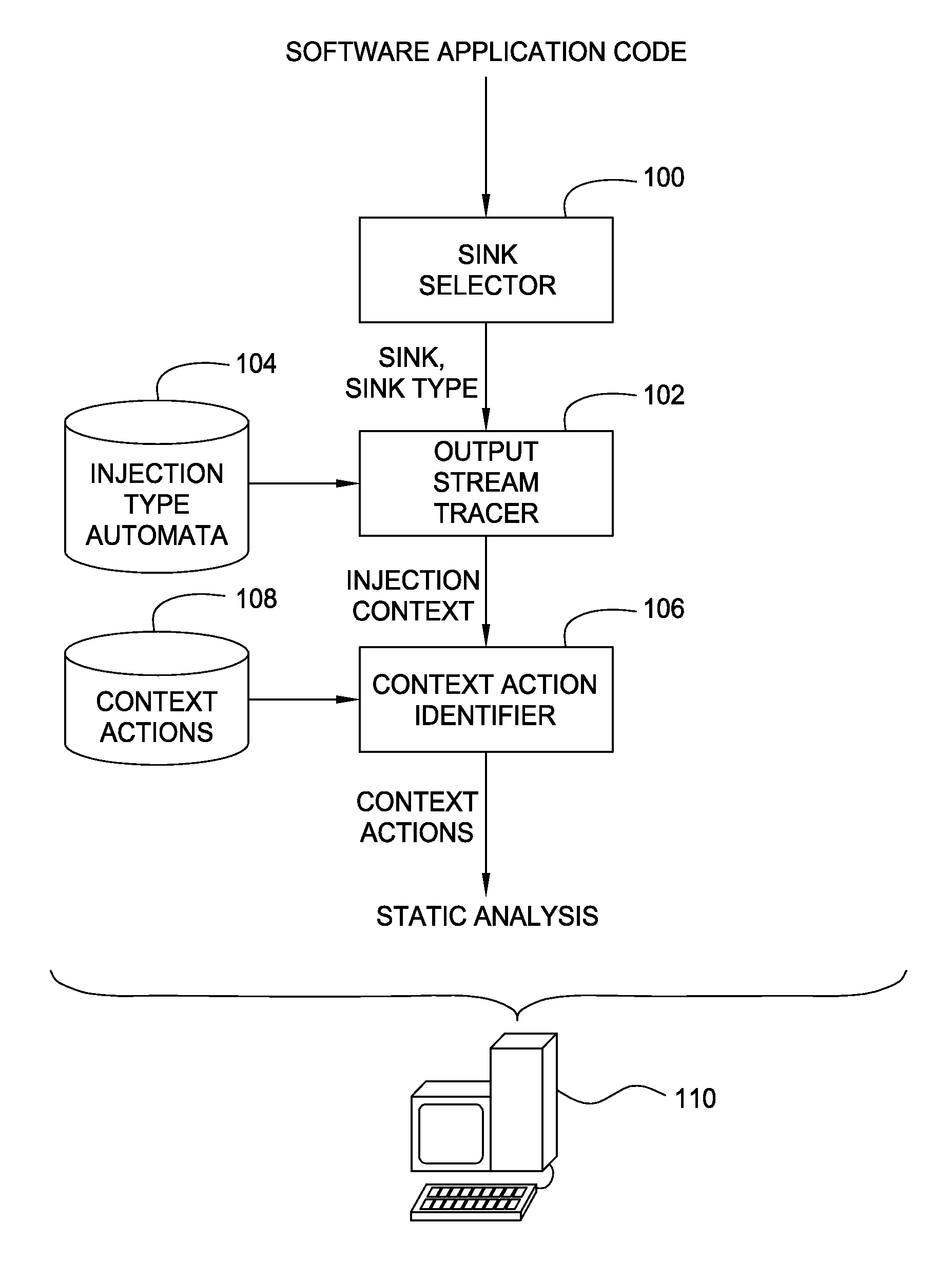
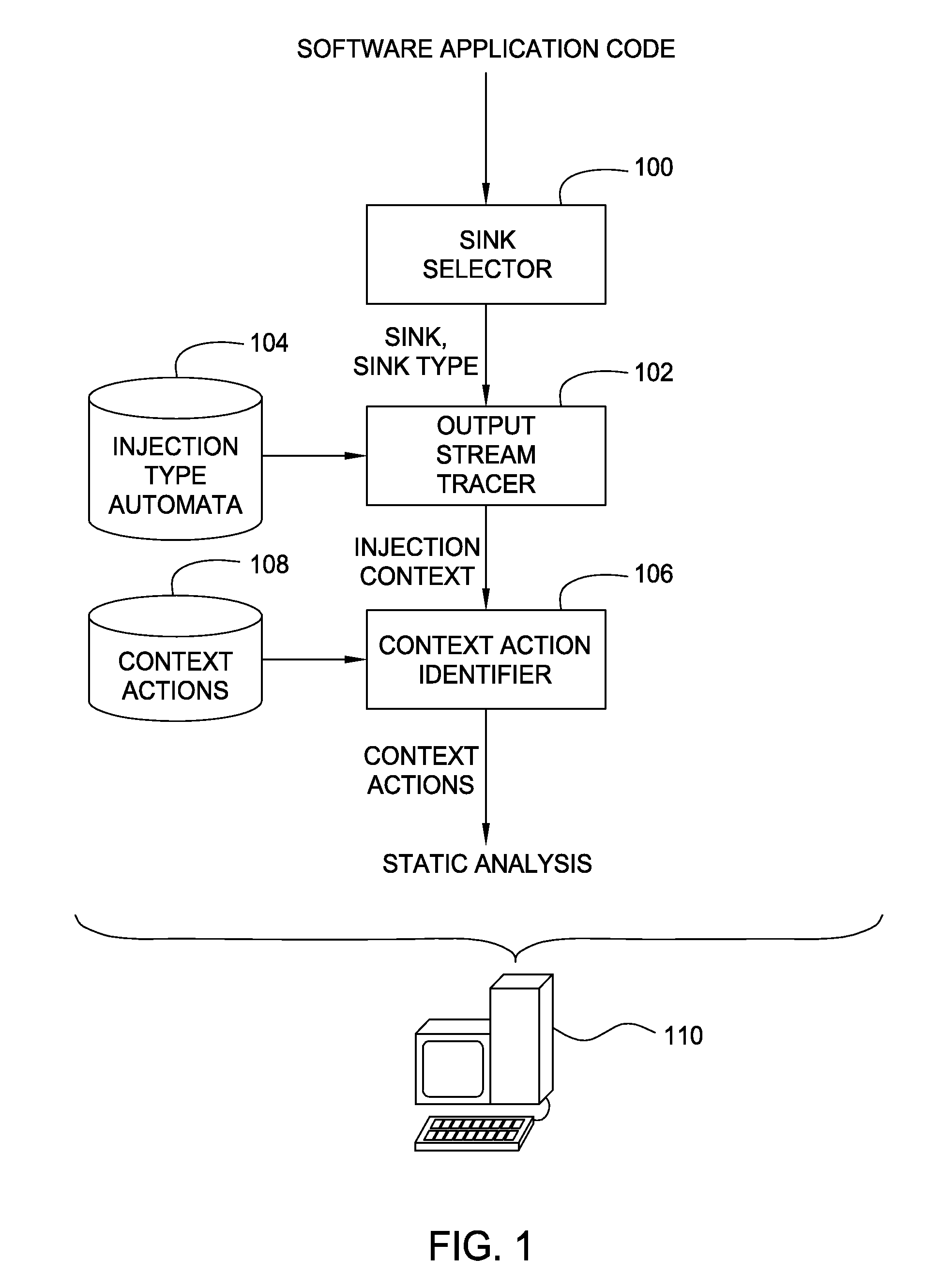
Embodiments of the invention generally relate to injection context based static analysis of computer software applications. Embodiments of the invention may include selecting a sink within a computer software application, tracing a character output stream leading to the sink within the computer software application, determining an injection context of the character output stream at the sink, where the injection context is predefined in association with a state of the character output stream at the sink, identifying any actions that have been predefined in association with the identified injection context, and providing a report of the actions.
Owner:IBM CORP +1
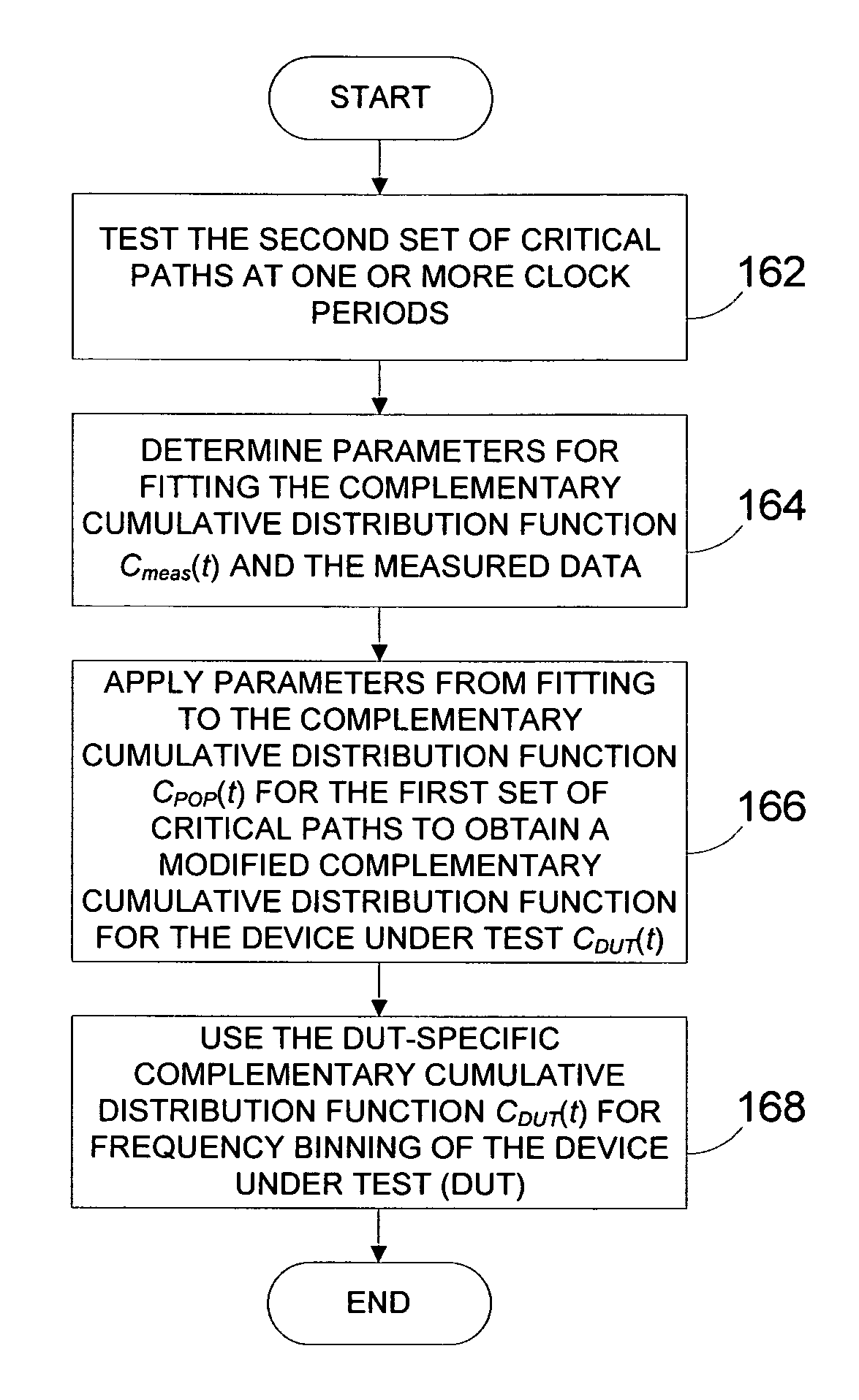
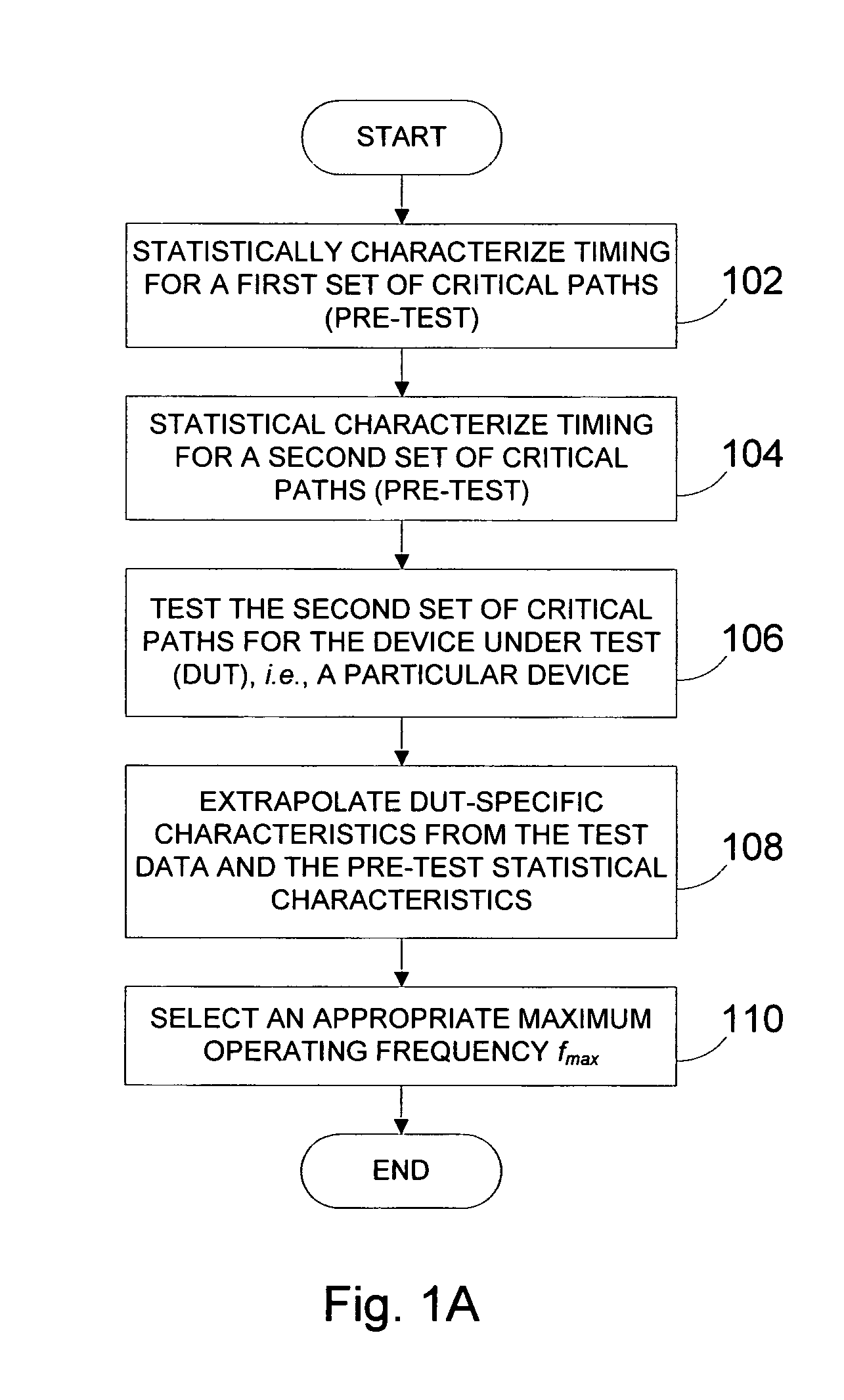
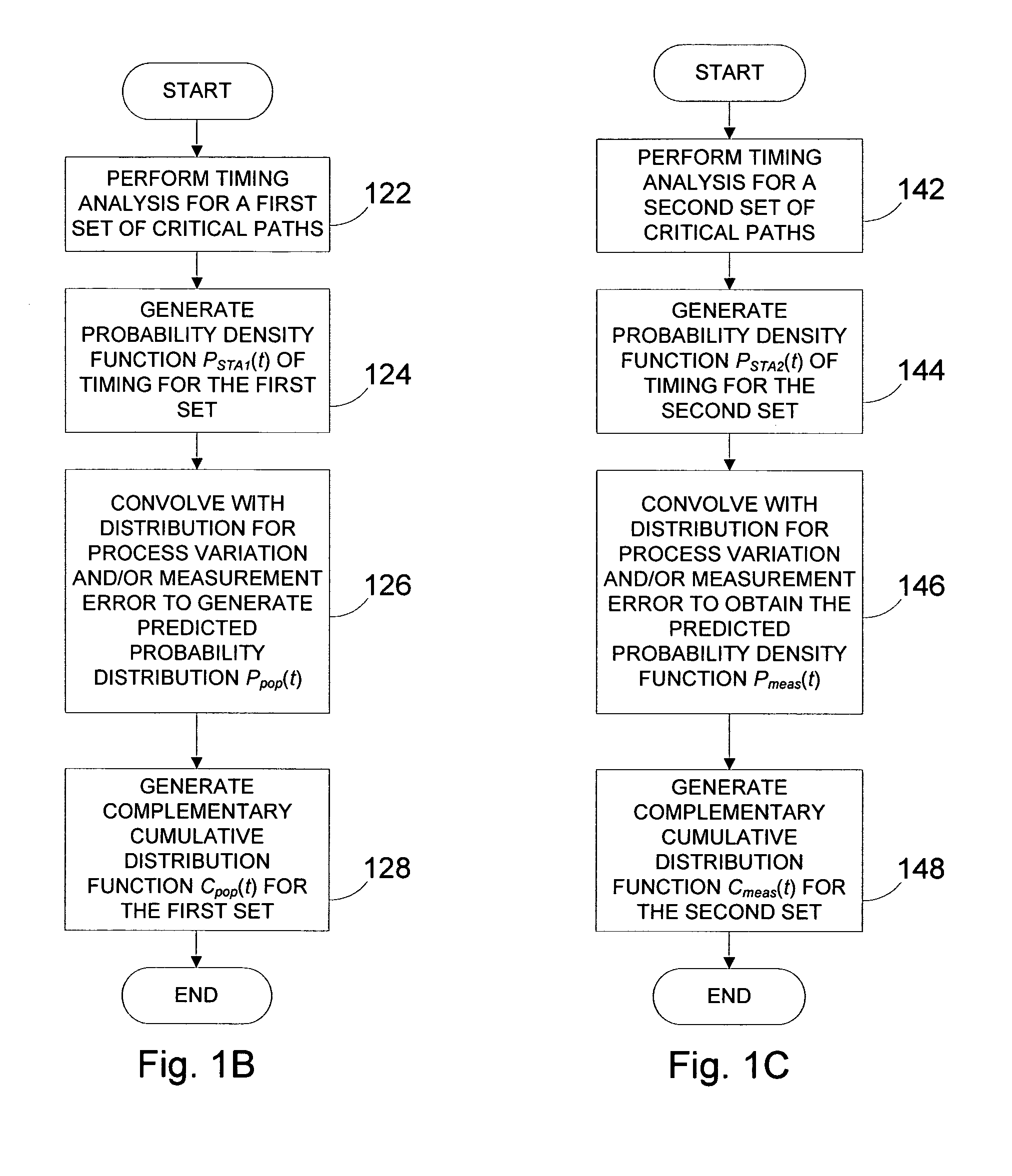
Systems and methods for speed binning of integrated circuits
InactiveUS7539893B1Electronic circuit testingError detection/correctionStatic timing analysisIntegrated circuit layout
Methods and apparatus sort integrated circuits by maximum operating speed (fmax). The timing for a first set of critical timing paths is statistically characterized. The first set can be, for example, the set of all critical timing paths. For example, the timing can be generated by using static timing analysis (STA). The timing for a second set of critical timing paths is statistically characterized. The second set can be, for example, a sample set of critical timing paths that are measurable or are measured for a device during test. The timing can be based on STA, derived from a known good device, and the like. A device under test (DUT) is tested, and the timing for the second set of critical timing paths is determined. A fitting technique is used to fit the expected device characteristics and the measured data for the DUT, and in one embodiment, the parameters used for fitting are applied to the first set of critical timing paths, which are then used to determine an appropriate fmax for the DUT.
Owner:MICROSEMI STORAGE SOLUTIONS
System and method for performing timing analysis, including error diagnosis, signal tracking and clock skew
InactiveUS6594806B1Increase circuit design flexibilityImprove design flexibilityComputer aided designSoftware simulation/interpretation/emulationStatic timing analysisSignal tracking
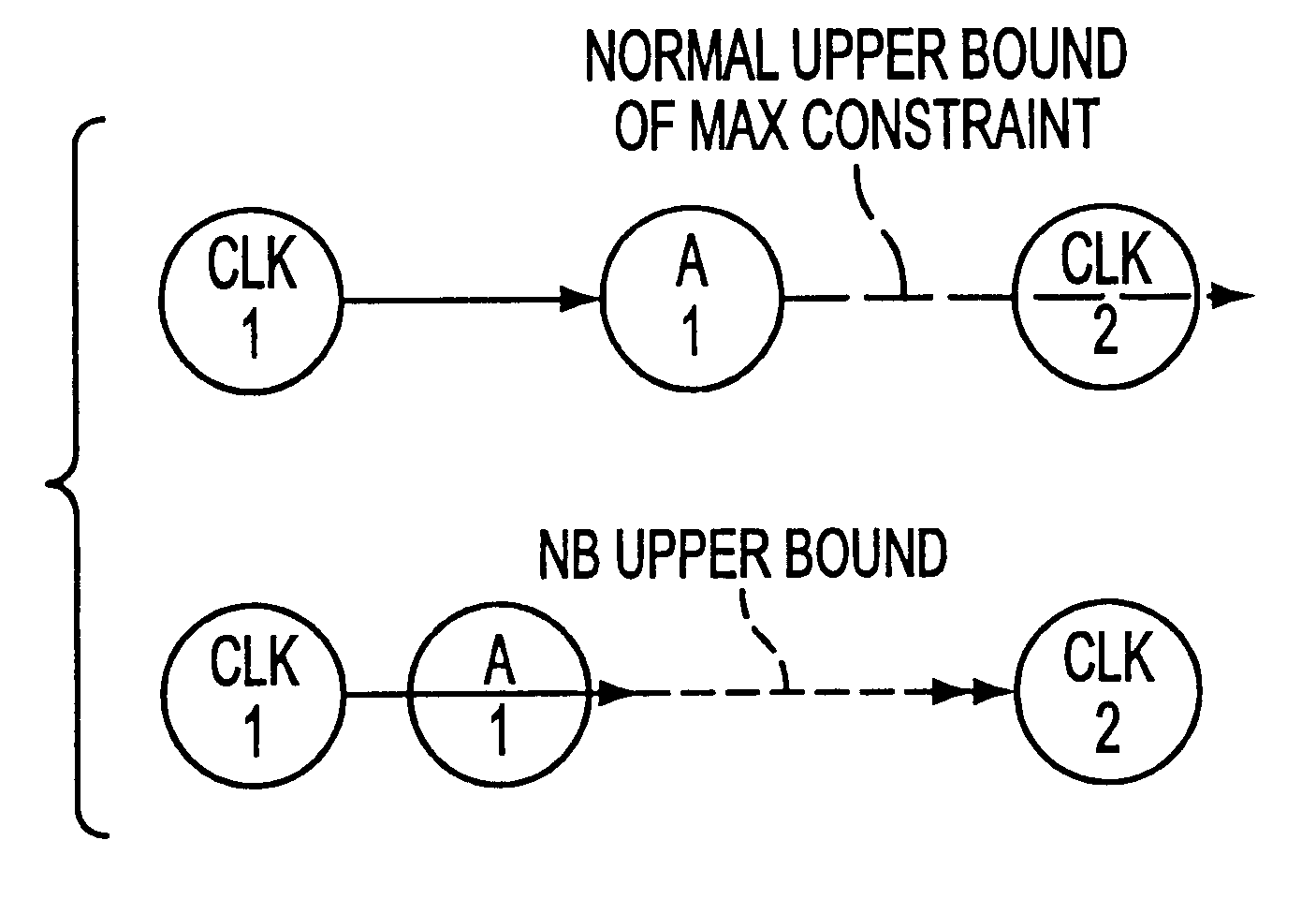
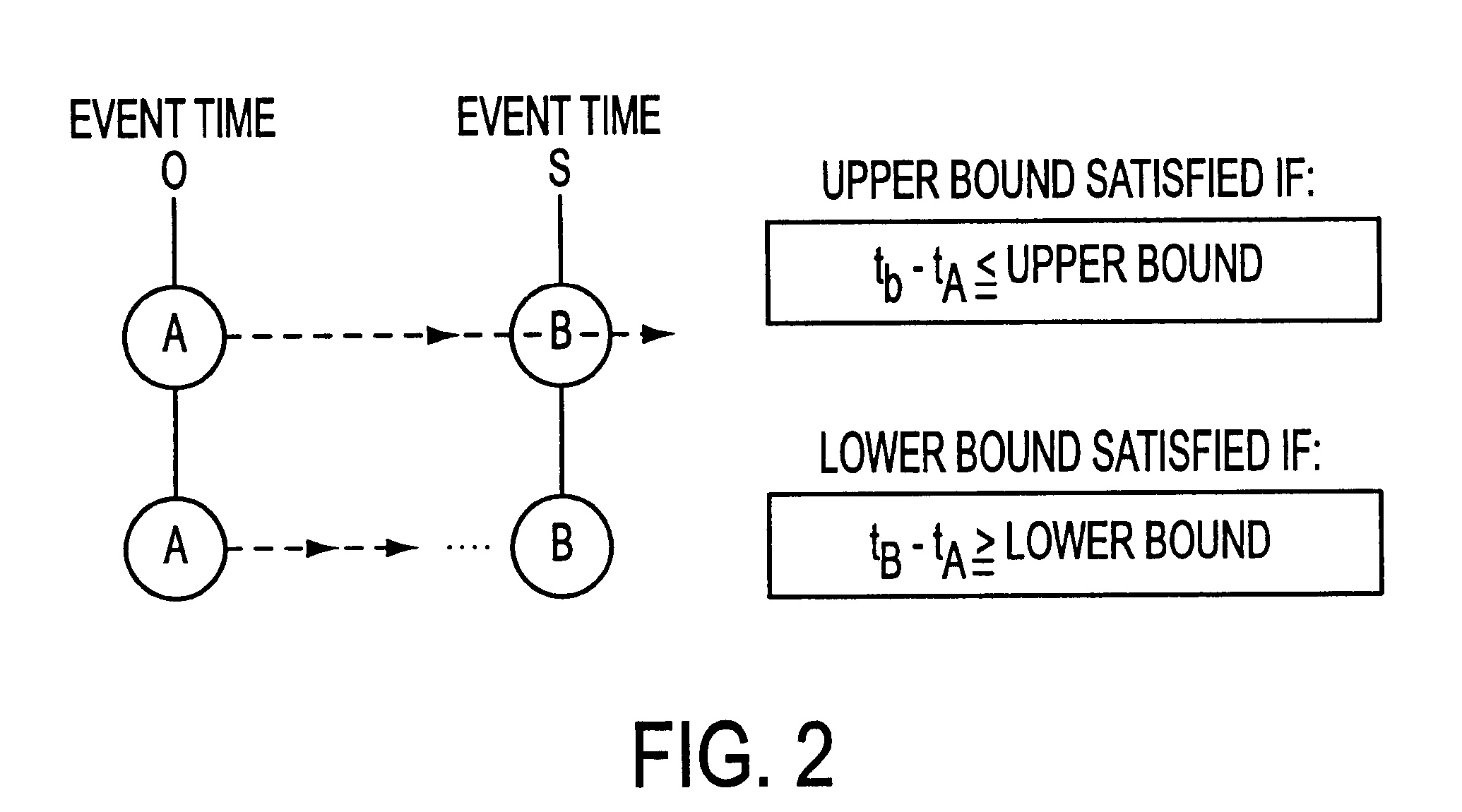
A method for performing timing analysis comprising inputting circuit timing information for a circuit, including temporal constraints between events of a desired circuit operation. A timing diagram representing the desired circuit operation, based on the circuit timing information is generater. All violated constraints within said timing diagram are identified. The method forces no violations of said violated constraints by designating the violated constraints as Non-Breakable (NB) constraints, such that a time difference from a source event to a destination event which defines said NB constraint is no less than a minimum bound and no more than a maximum bound of a linear constraint representing a timing requirement between the source and the destination events.
Owner:NEC CORP
System and method for static analysis using fault paths
ActiveUS20080276228A1Error detection/correctionSpecific program execution arrangementsStatic timing analysisStatistical analysis
A system and method for analyzing a program includes determining possible bug paths in a program based on statistical analysis of test cases. A static analysis is then performed only on the possible bug paths. The bugs are then located in the program.
Owner:IBM CORP
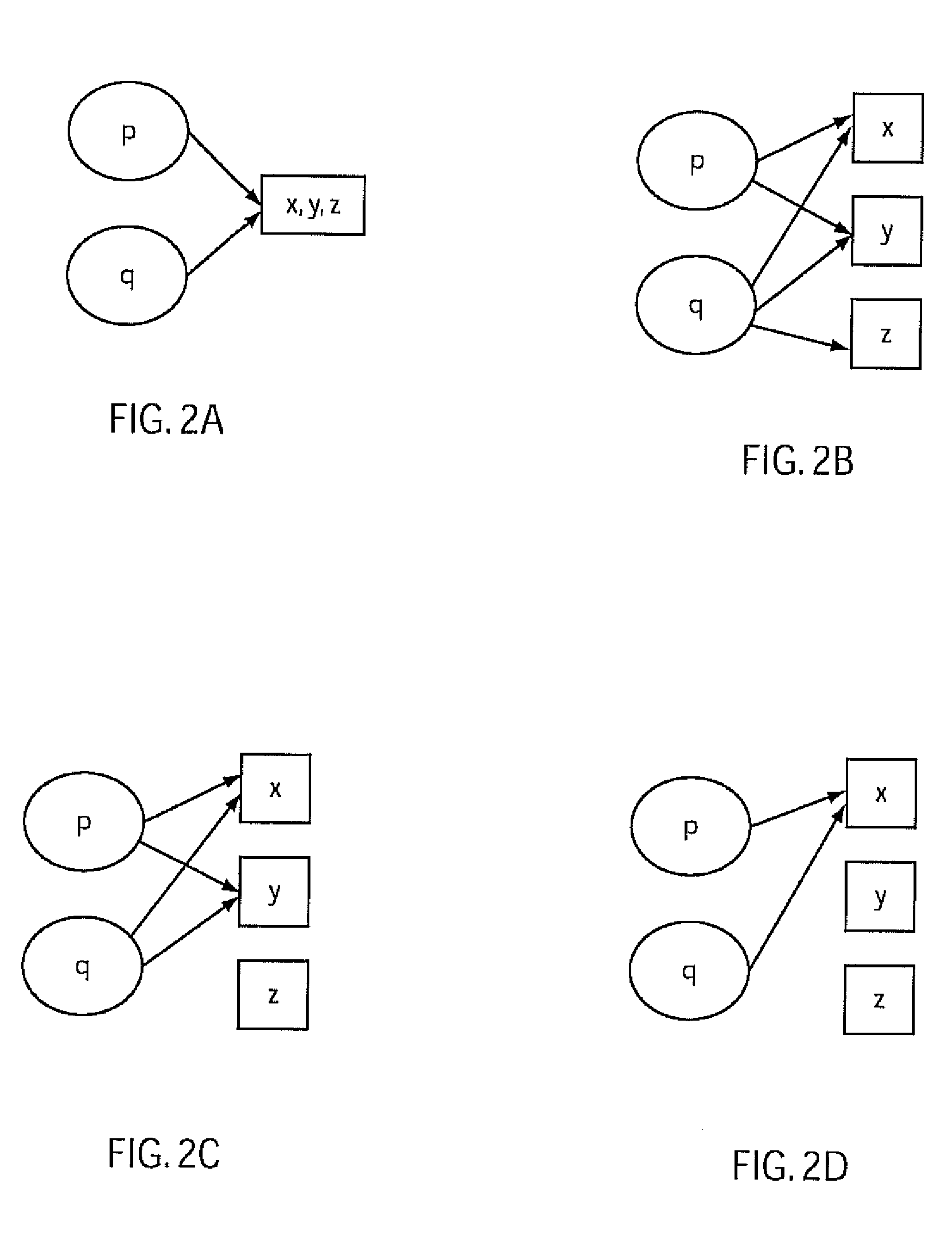
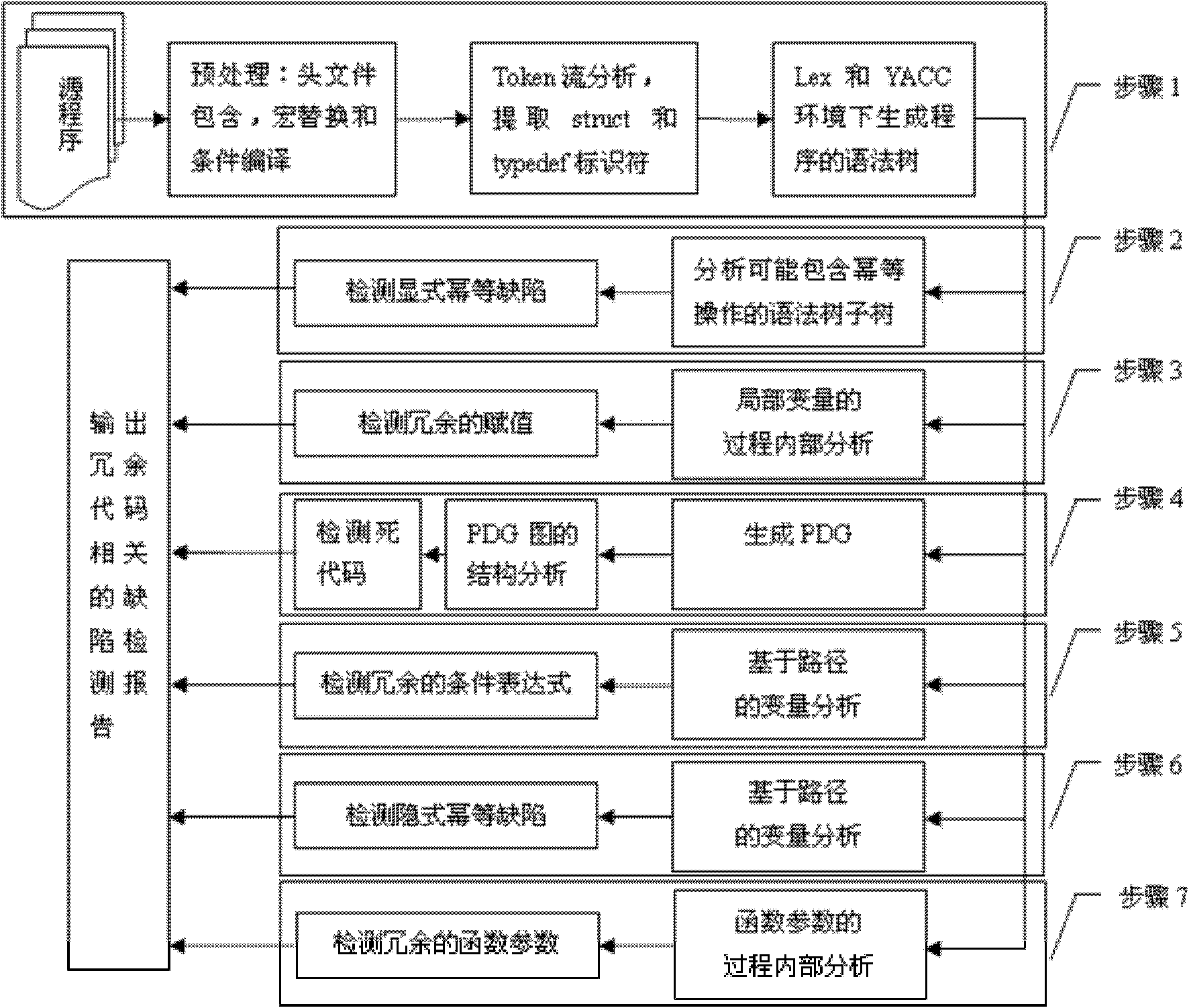
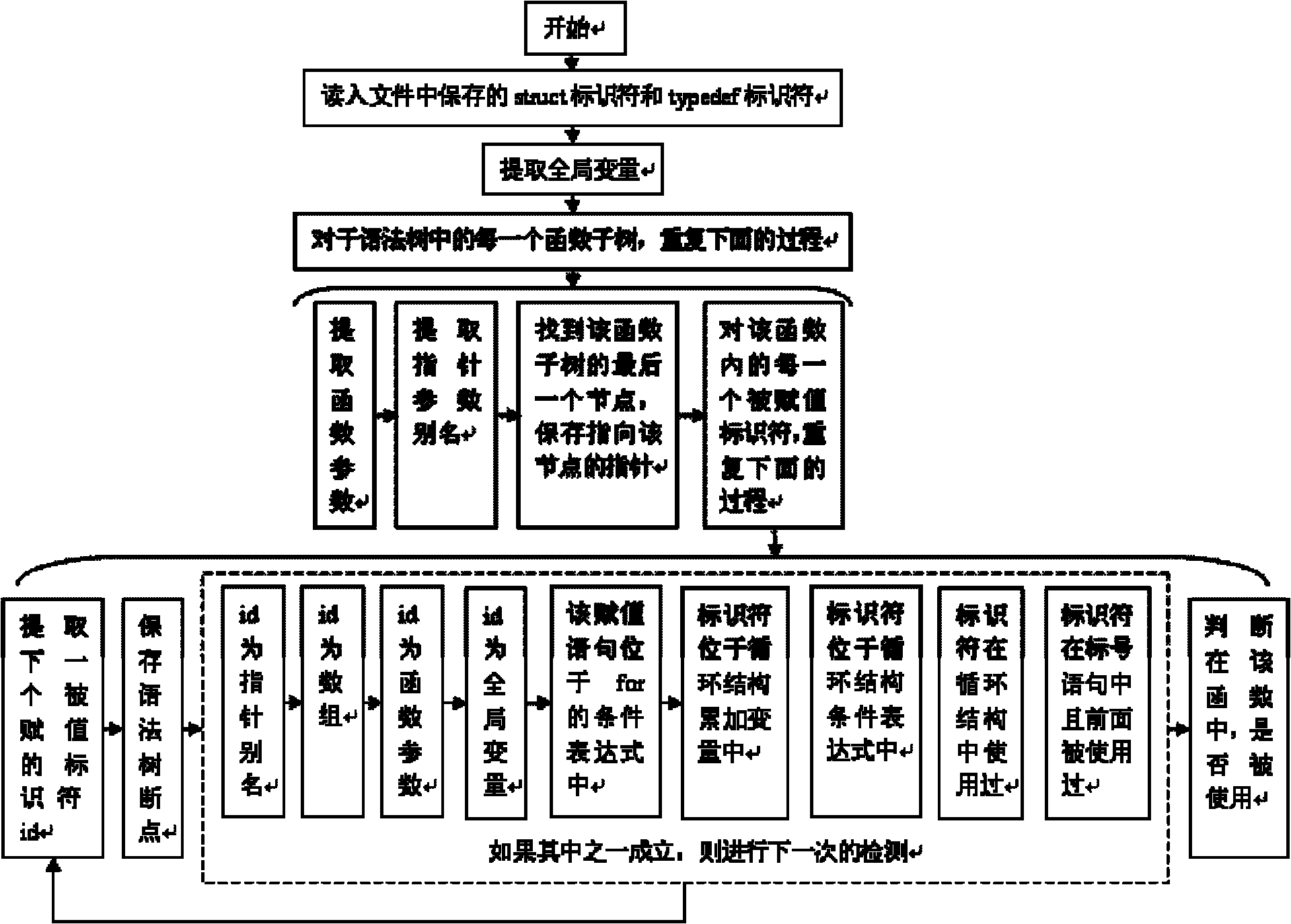
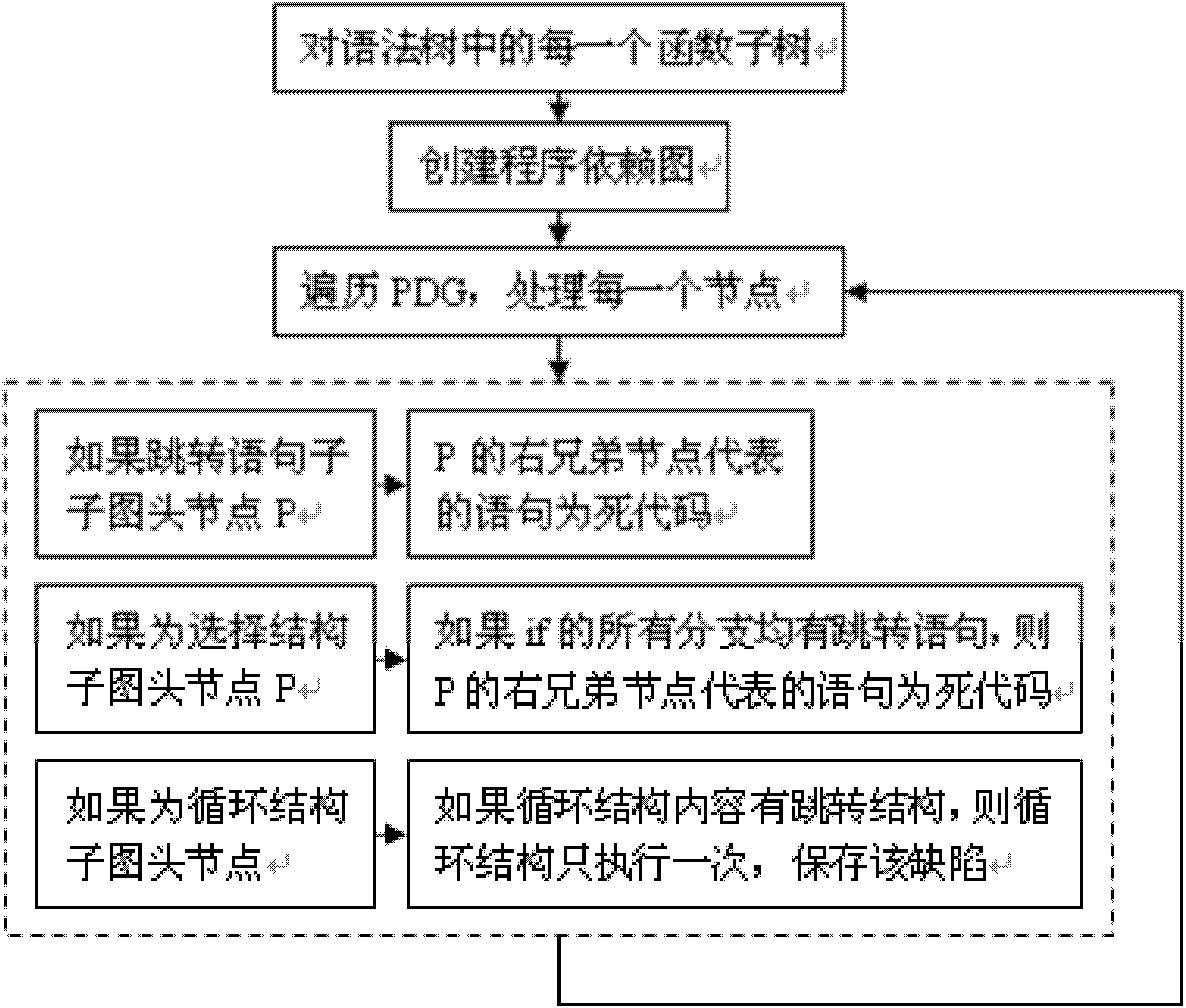
Method for detecting redundant code defects based on static analysis
InactiveCN102231134AReduce false detection rateReduce missed detection rateSoftware testing/debuggingStatic timing analysisAbstract syntax tree
The invention discloses a method for detecting redundant code defects based on static analysis, for solving the problem lacking of a mature method for detecting redundant codes and related defects currently. The method comprises the following steps of: 1, inputting a program to be tested; analyzing the program into an abstract syntax tree; 2, analyzing statements possibly including operations of explicit power and the like; detecting the operations of the explicit power and the like; 3, for locally defined variables, detecting redundant assignment statements by using an internal process analysis method; 4, traversing the abstract syntax tree of the program; searching structures including the defects on the basis of a standardized program dependency graph; detecting dead codes; 5, detecting redundant conditional expressions; 6, detecting operations of implicit power and the like; and 7, detecting redundant function parameters; and giving a defect detection report according to the six defect detection results obtained in the steps 2-7. The method disclosed by the invention is applicable for analyzing large-scale program codes.
Owner:HARBIN INST OF TECH
Static analysis of client-server applications using framework independent specifications
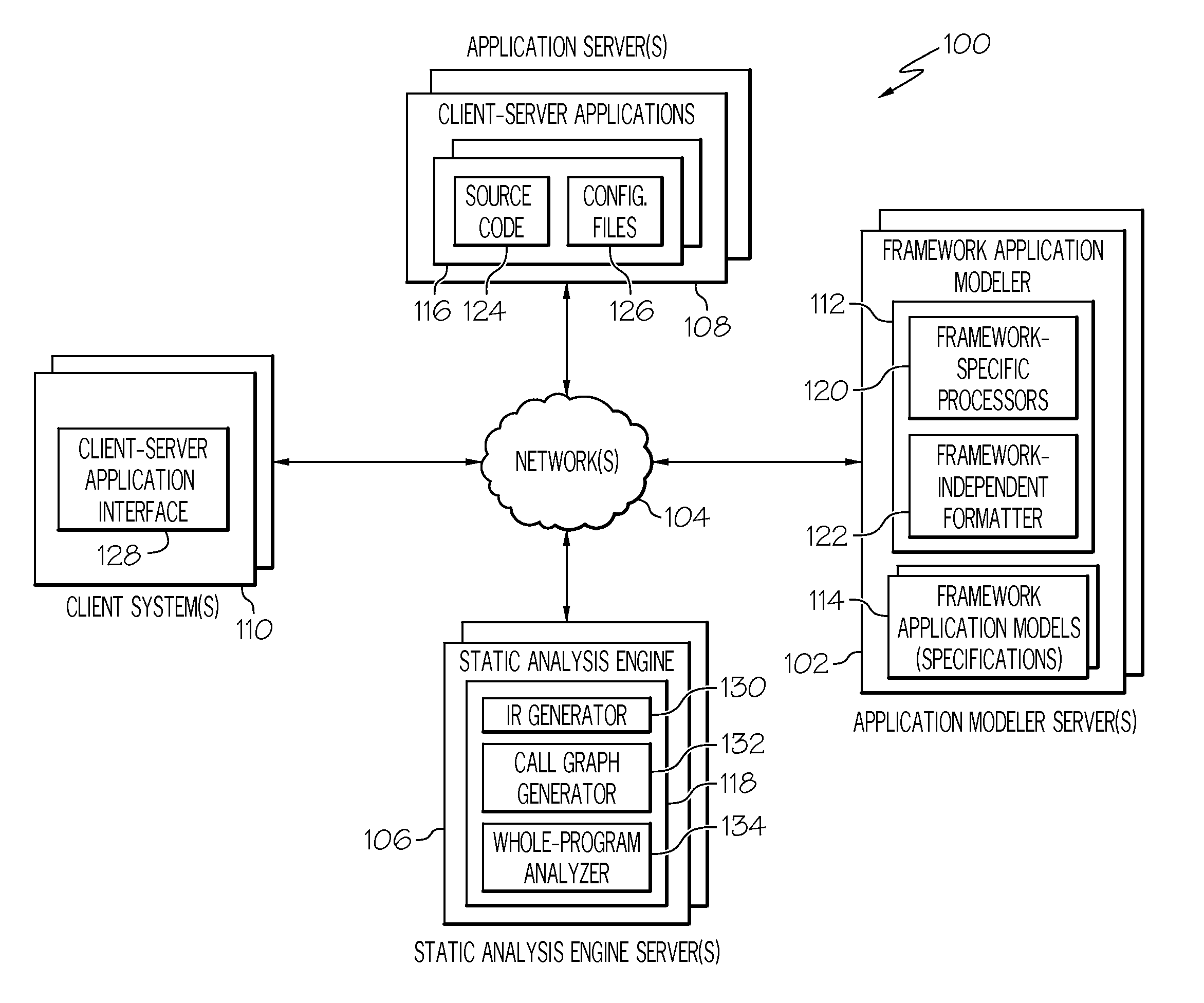
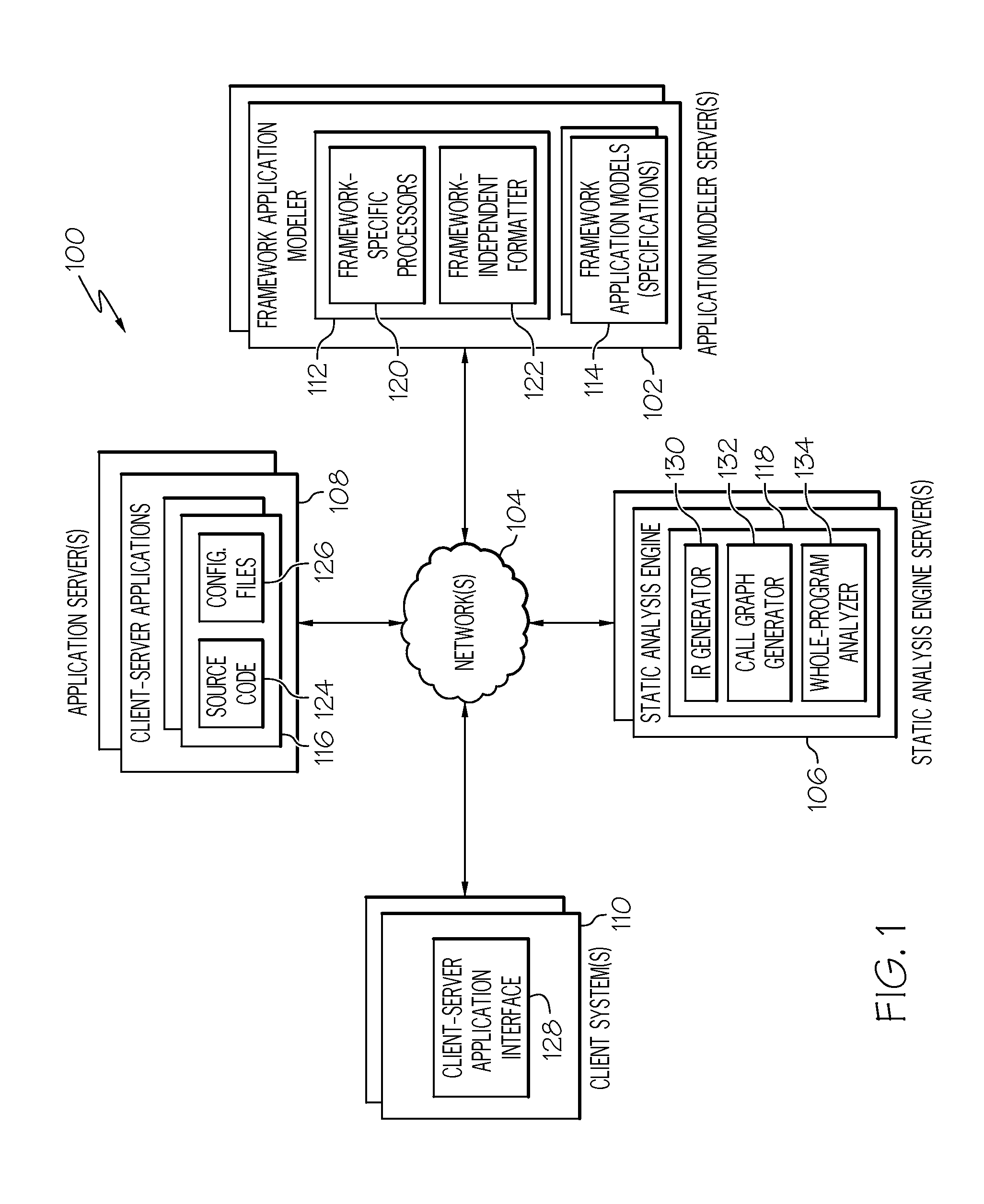
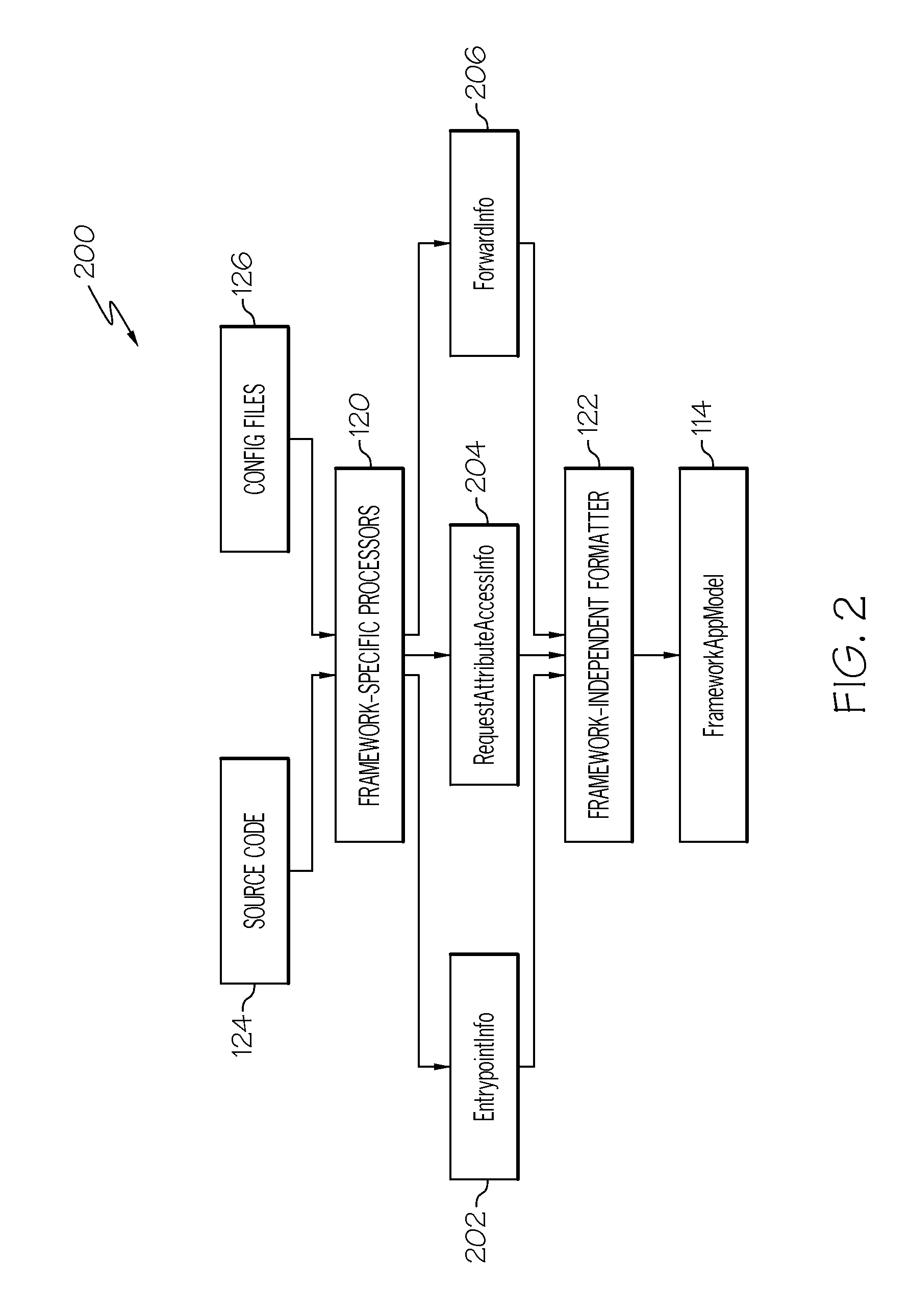
InactiveUS20120102474A1Computer security arrangementsReverse engineeringStatic timing analysisCall graph
Systems and methods are provided for statically analyzing a software application that is based on at least one framework. According to the method, source code of the software application and a specification associated with the software application are analyzed. The specification includes a list of synthetic methods that model framework-related behavior of the software application, and a list of entry points indicating the synthetic methods and / or application methods of the software application that can be invoked by the framework. Based on the source code and the specification, intermediate representations for the source code and the synthetic methods are generated. Based on the intermediate representations and the specification, call graphs are generated to model which application methods of the software application invoke synthetic methods or other application methods of the software application. The software application is statically analyzed based on the call graphs and the intermediate representations so as to generate analysis results for the software application.
Owner:IBM CORP
Static analysis-based checking method of safety rules of C language
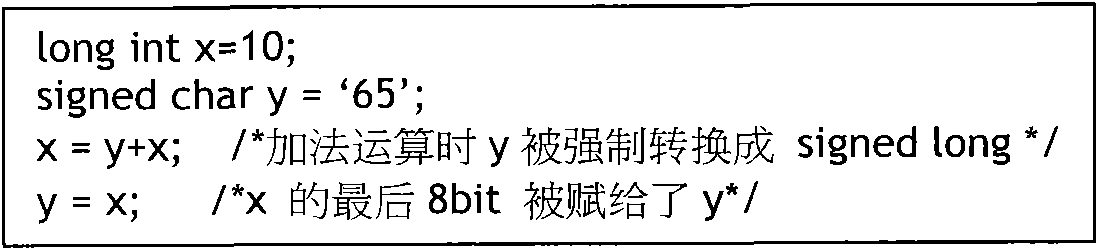
InactiveCN102012991AMake up for the lack of securityPlatform integrity maintainanceStatic timing analysisType conversion
The invention relates to a static analysis-based checking method of safety rules of C language, which comprises the following steps: 1) checking the type of the C language to avoid the occurrence of compulsory type conversion and prohibiting the declaration of the type of a generic pointer; 2) stipulating that a global variable and a local variable can not be in homonymy, and the global variable and a formal parameter of a function can not be in tautonomy; 3) limiting a cyclic variable of a control flow statement; 4) strengthening the declaration and the definition of the C language; and 5) carrying out analysis of accidence, grammar and semanteme on source codes, and finding out places which do not meet the stipulation from the source codes. The method has the advantages of being capable of finding out possible loopholes on programming of the C language under the premise that the codes do not need to be executed and effectively making up for the deficiency of insufficient safety of the C language in soft engineering.
Owner:北京神舟航天软件技术股份有限公司
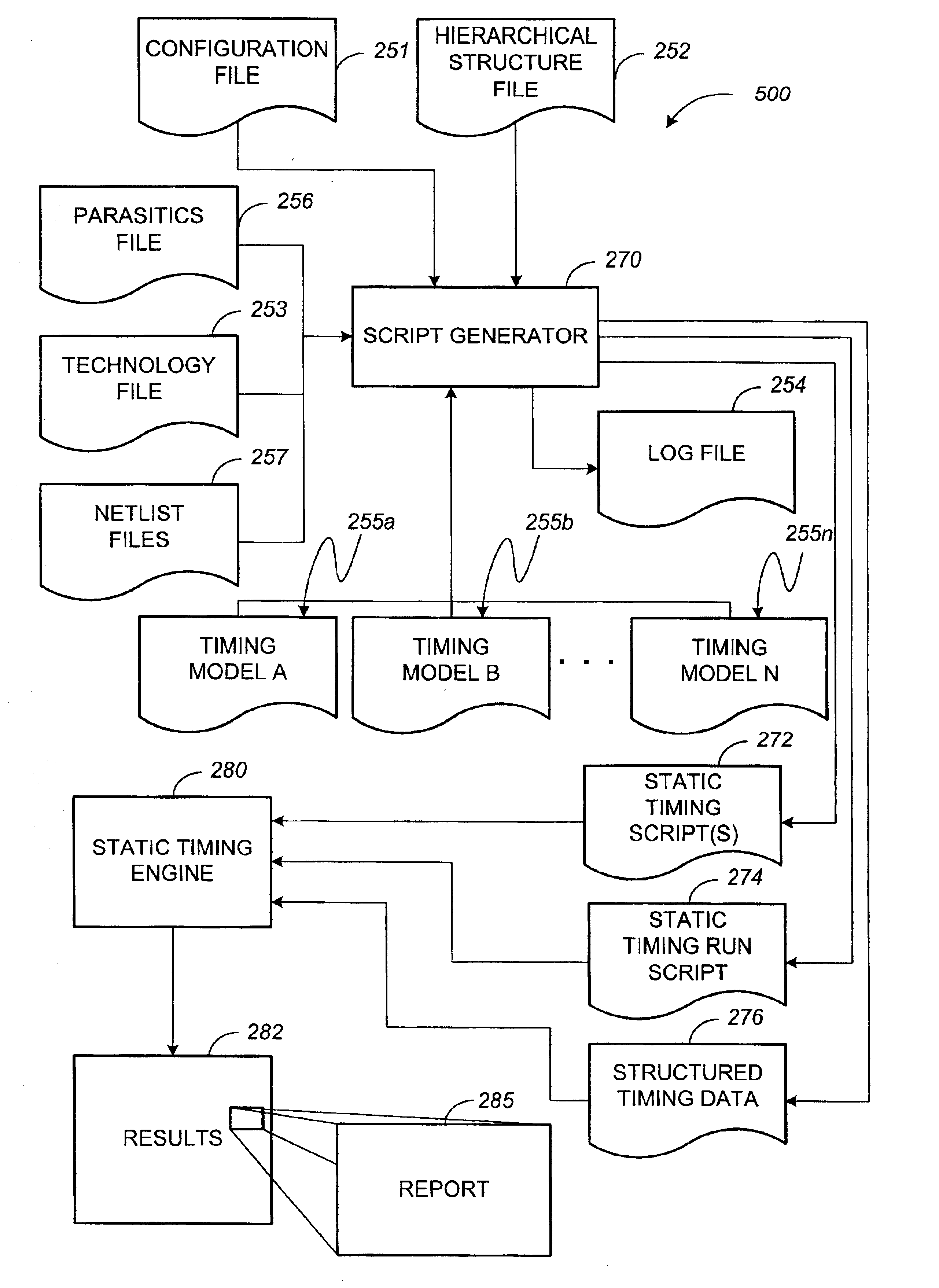
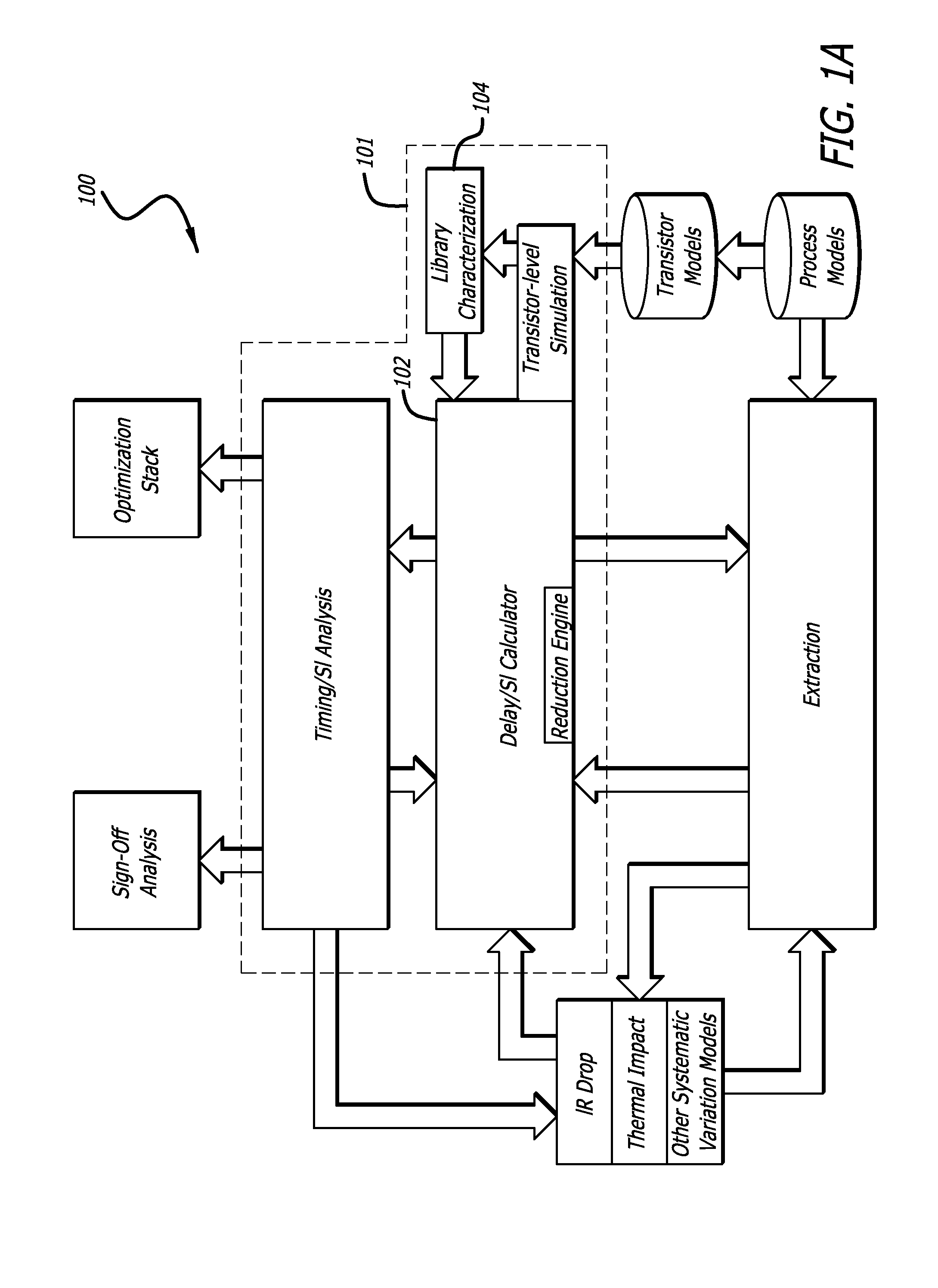
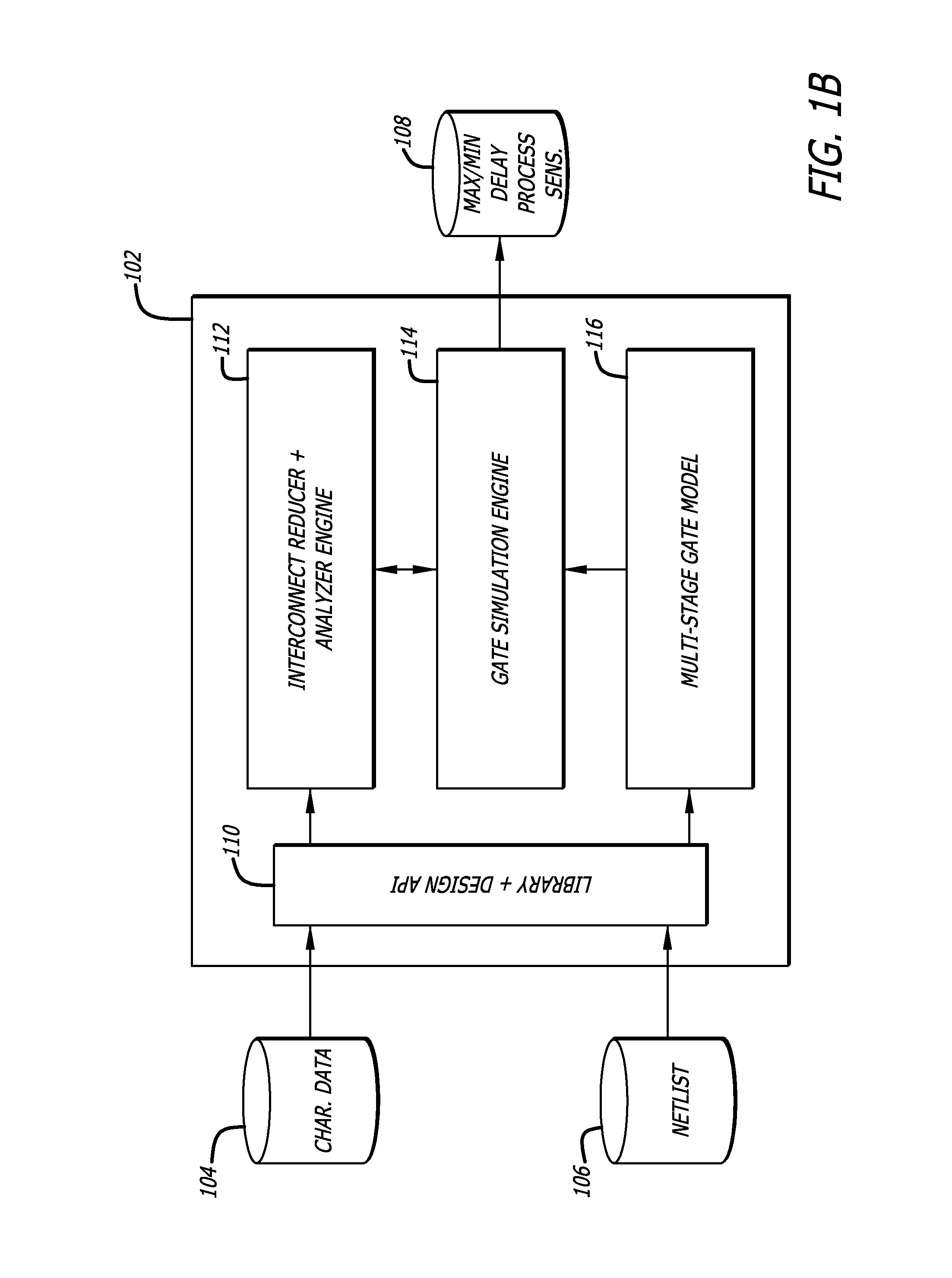
System and method for applying timing models in a static-timing analysis of a hierarchical integrated circuit design
InactiveUS6925621B2Reduce complexityLess timeDetecting faulty computer hardwareComputer programmed simultaneously with data introductionStatic timing analysisComputer architecture
Owner:BROADCOM INT PTE LTD
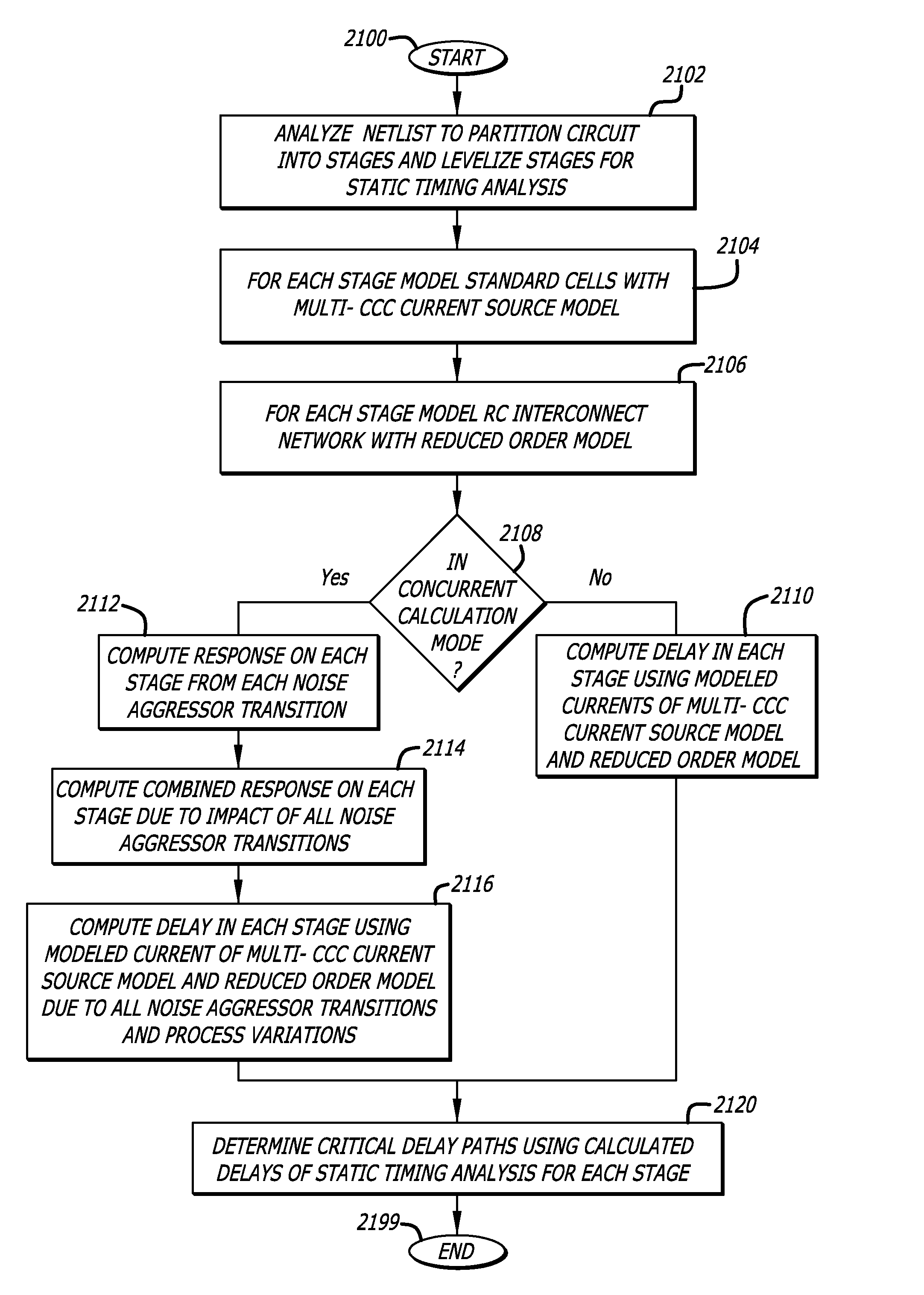
Flexible noise and delay modeling of circuit stages for static timing analysis of integrated circuit designs
ActiveUS8595669B1Effective calculationEfficient of noiseDetecting faulty computer hardwareCAD circuit designStatic timing analysisCircuit design
Systems, apparatus, and methods of static timing analysis for an integrated circuit design in the presence of noise are disclosed. The integrated circuit design may be partitioned into a plurality of circuit stages. A timing graph including timing arcs is constructed to represent the timing delays in circuit stages of the integrated circuit design. A model of each circuit stage may be formed including a model of a victim driver, an aggressor driver, a victim receiver, and a victim net and an aggressor net coupled together. For each timing arc in the timing graph, full timing delays may be computed for the timing arcs in each circuit stage.
Owner:CADENCE DESIGN SYST INC
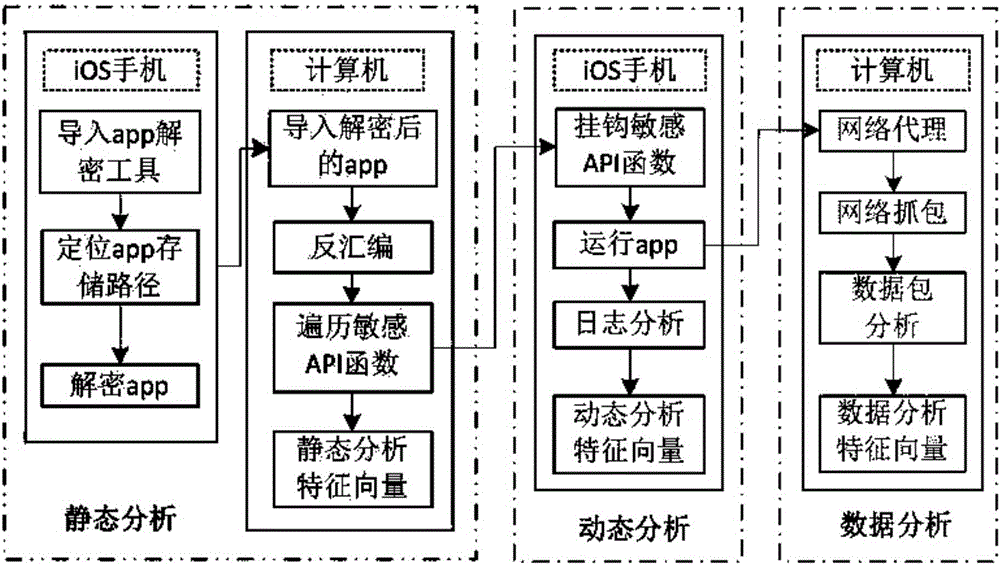
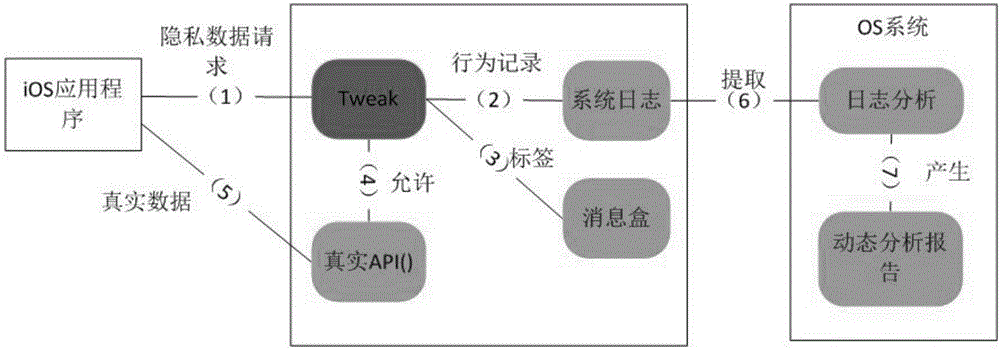
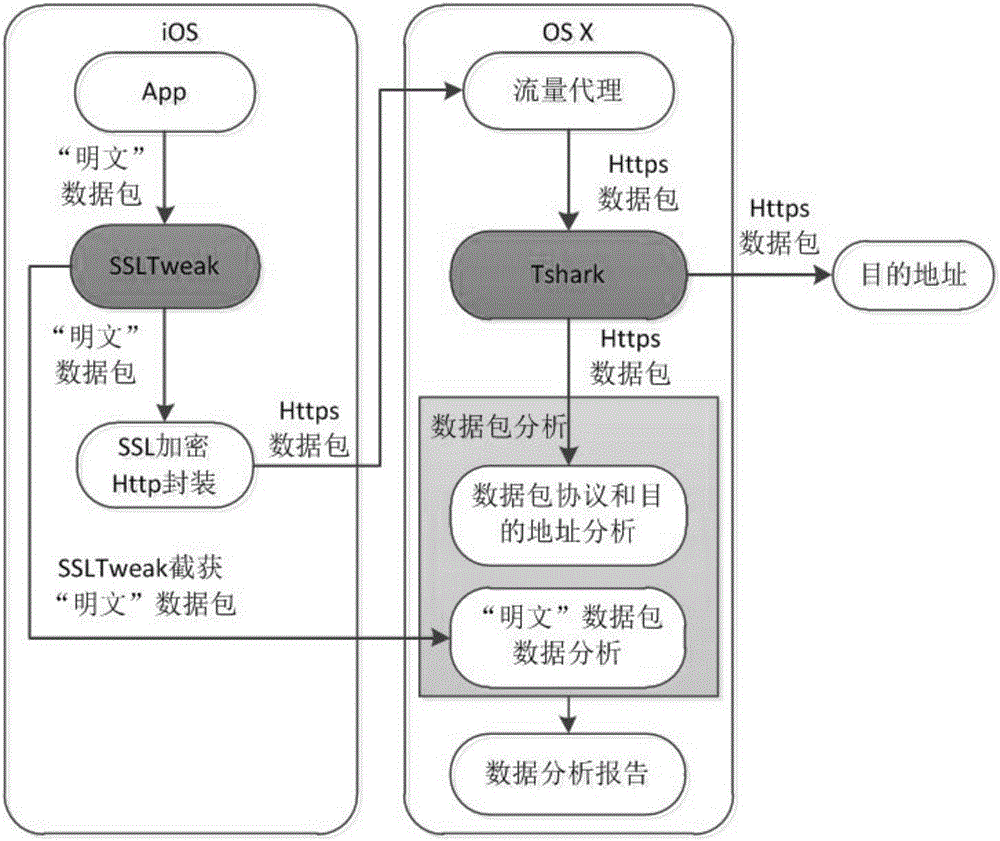
Application multidimensional privacy leak detection method and system for iOS platform
InactiveCN106845236AImprove scienceImprove rigorPlatform integrity maintainanceStatic timing analysisInternet privacy
The invention discloses an application multidimensional privacy leak detection method and system for iOS platform; privacy leak detection is provided for iOS applications from the three dimensions, static analysis, dynamic analysis and data analysis, wherein the static analysis incudes the steps of application decrypting, app storage path locating, disassembling, and disassembly source code sensitive API (application program interface) analysis; the dynamic analysis includes the step of allowing Hook-sensitive API function to acquire a log record by running an application, and acquire a sensitive API calling sequence through log analysis; the data analysis incudes the steps of capturing application network data packets, and analyzing data packet protocol, address and content. The method and system of the invention can provide comprehensive detection for data privacy leaks of iOS applications to obtain complete privacy leak event data.
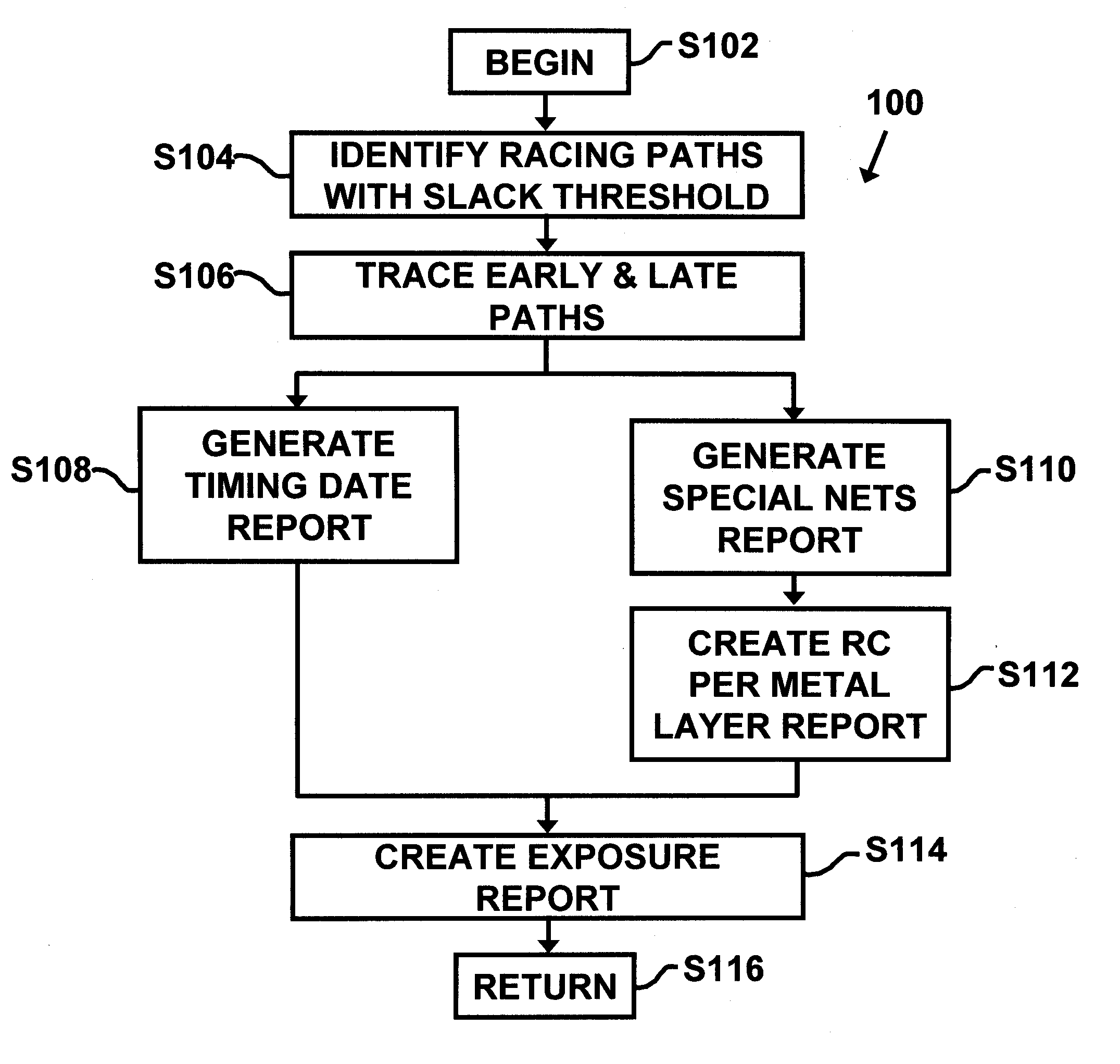
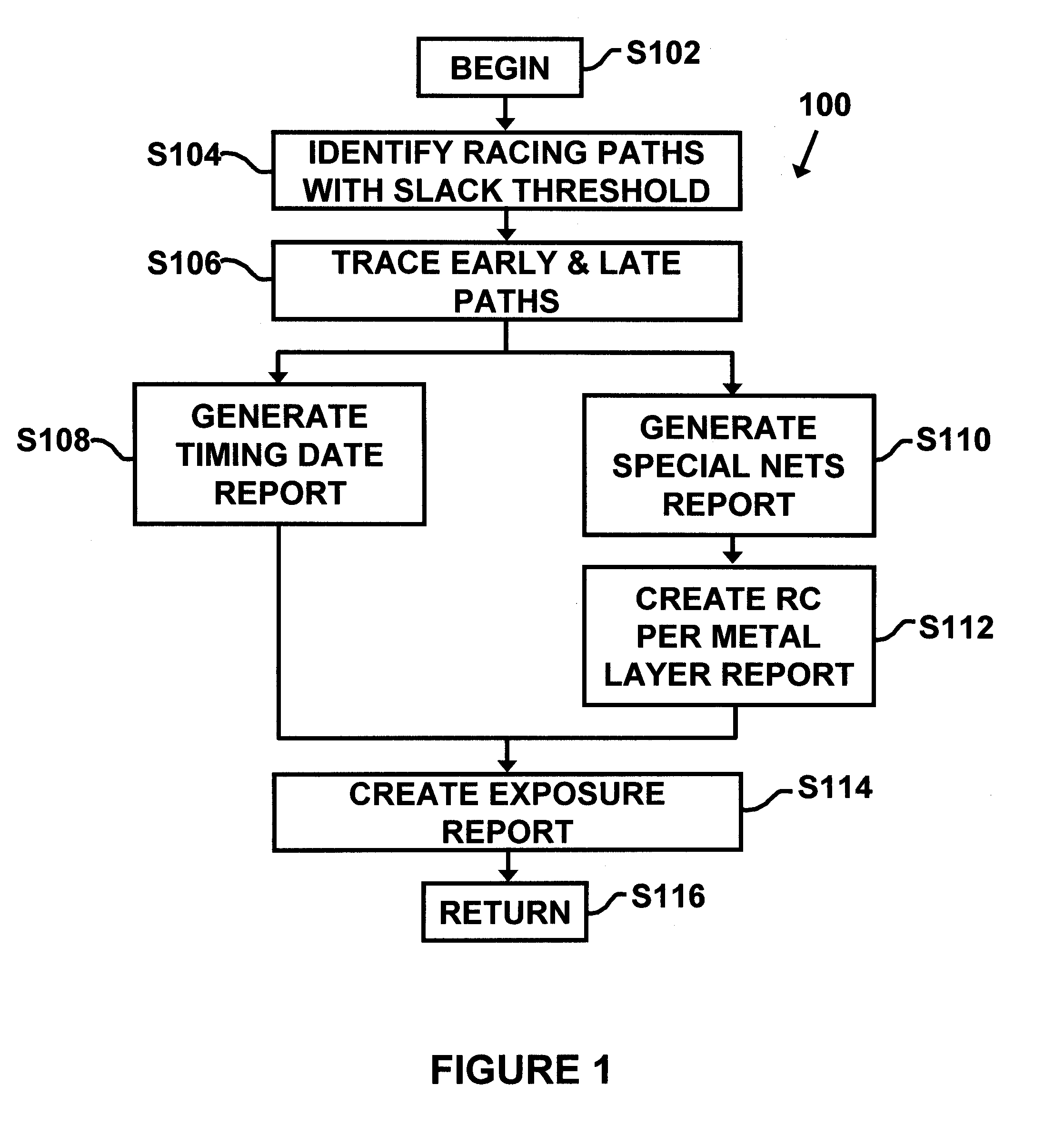
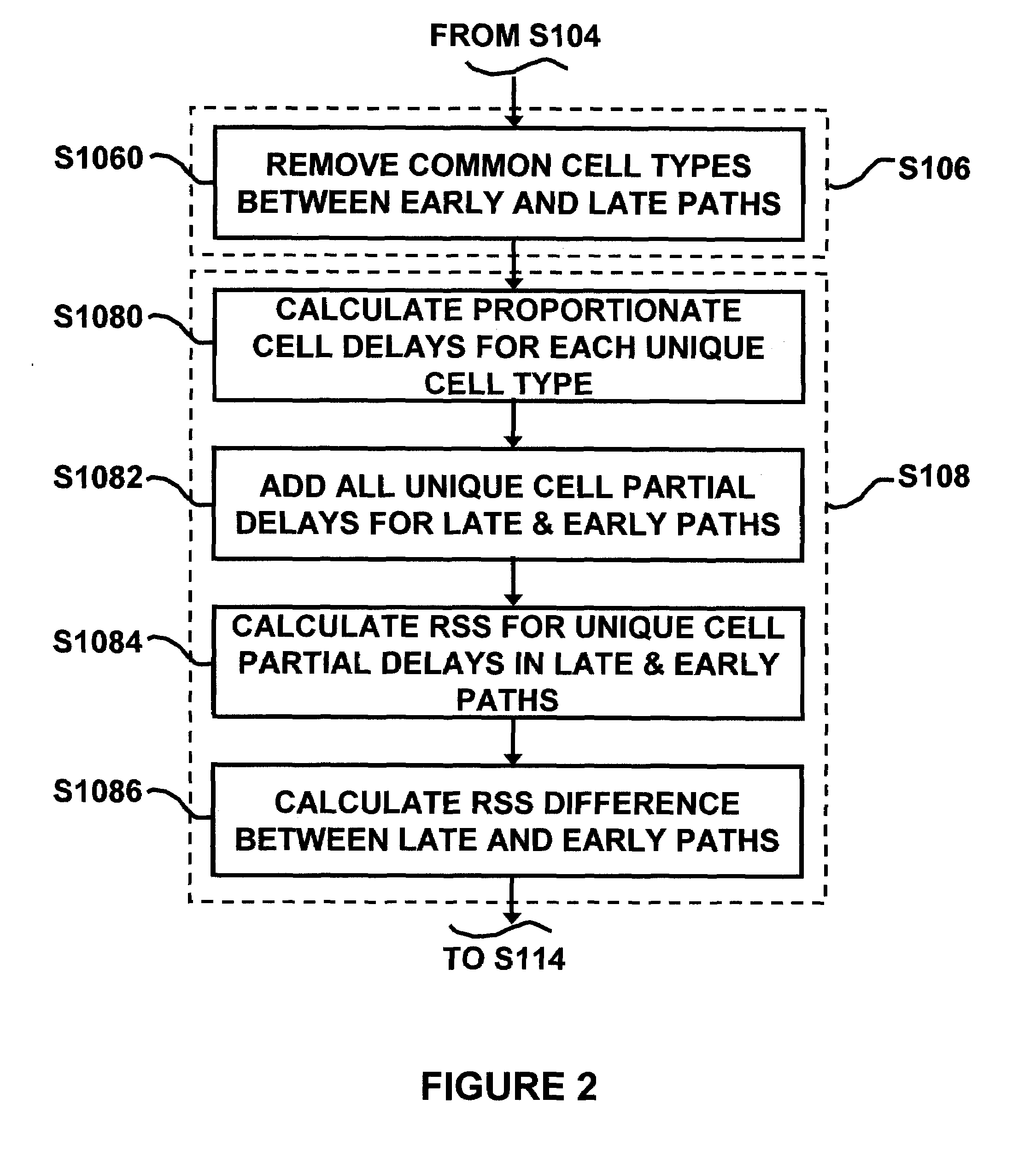
Owner:SOUTHEAST UNIV +1
Method and system for fault-tolerant static timing analysis
Owner:GLOBALFOUNDRIES U S INC
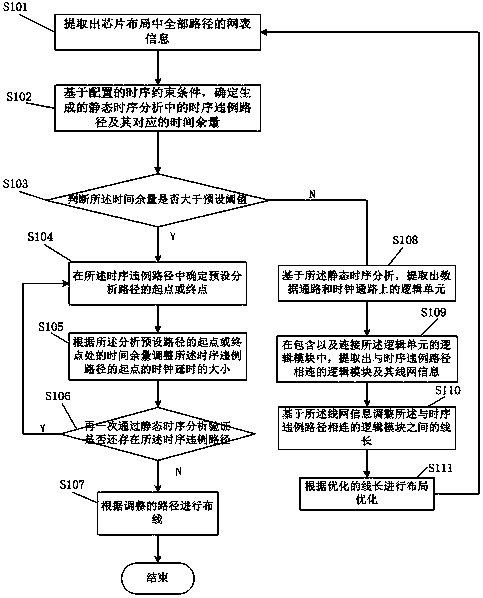
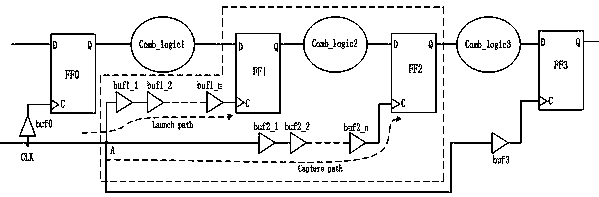
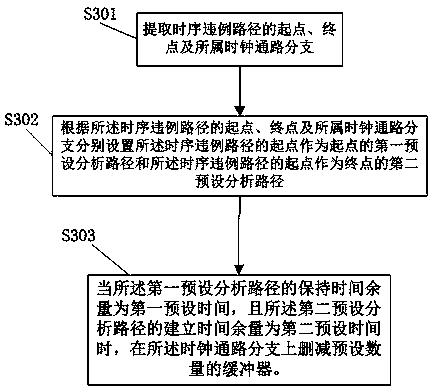
A time sequence repairing method based on time headroom
ActiveCN109583103ASmall design areaIncrease working frequencySpecial data processing applicationsTiming marginStatic timing analysis
The invention provides a time sequence repairing method based on time headroom, which comprises the following steps: step 1, extracting netlist information of all paths in a chip layout, and then entering a step 2; Step 2, determining a time sequence violation path in the generated static time sequence analysis and a corresponding time margin based on the configured time sequence constraint condition, and then entering a step 3; Step 3, judging whether the time margin is greater than a preset threshold value or not, if so, determining a starting point or an end point of a preset analysis pathin the time sequence violation path, and adjusting the magnitude of the clock delay of the time sequence violation path; Otherwise, analyzing based on the static time sequence; The method comprises the following steps: firstly, extracting logic units on a data path and a clock path according to a preset time sequence violation path, further extracting logic modules connected with the time sequenceviolation path and line network information of the logic modules, adjusting the line length between the logic modules connected with the time sequence violation path, performing optimized layout according to the optimized line length, and then returning to the step 1. The design area of the chip is reduced, and the working frequency of the chip is improved.
Owner:AMICRO SEMICON CORP
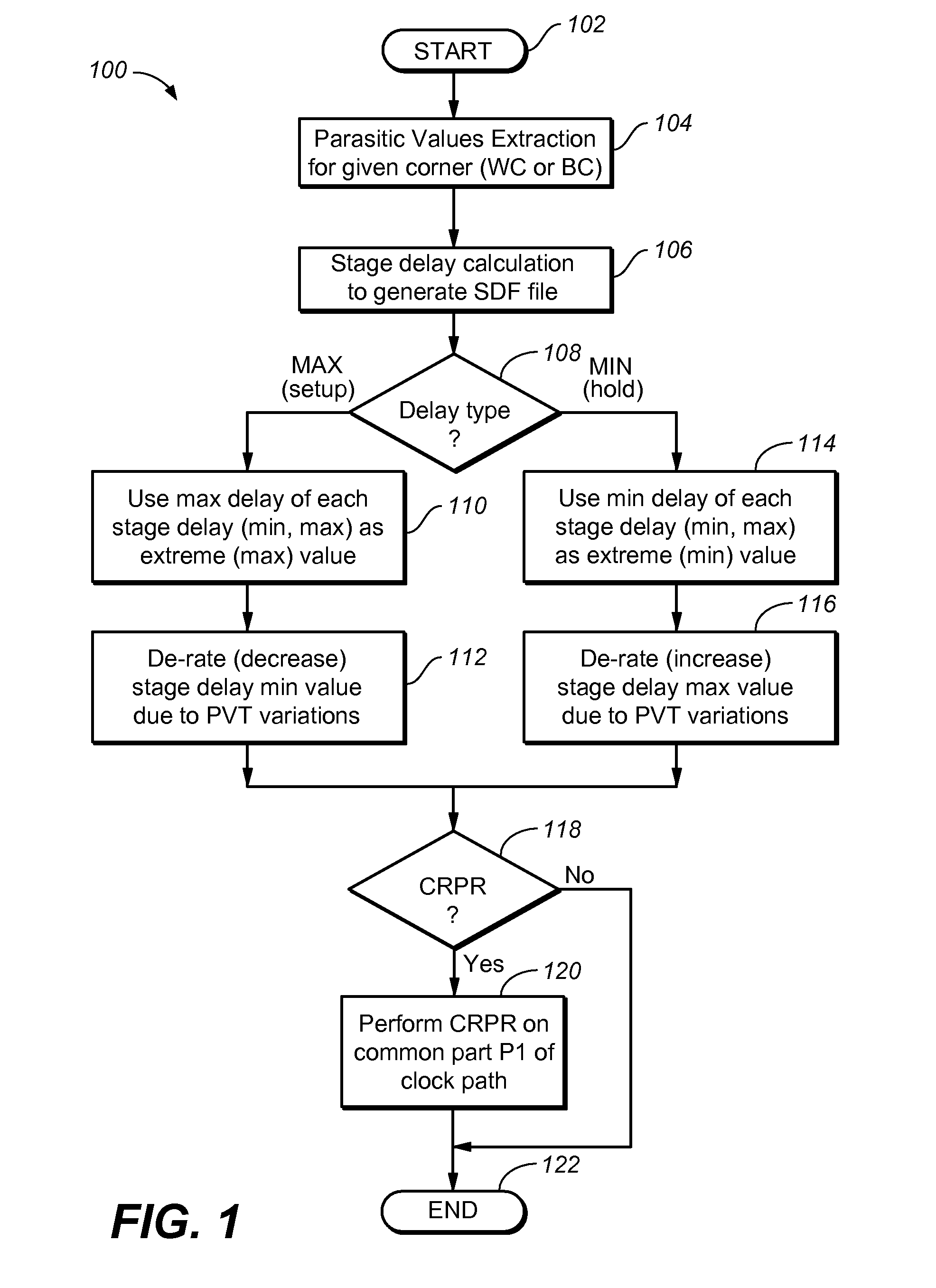
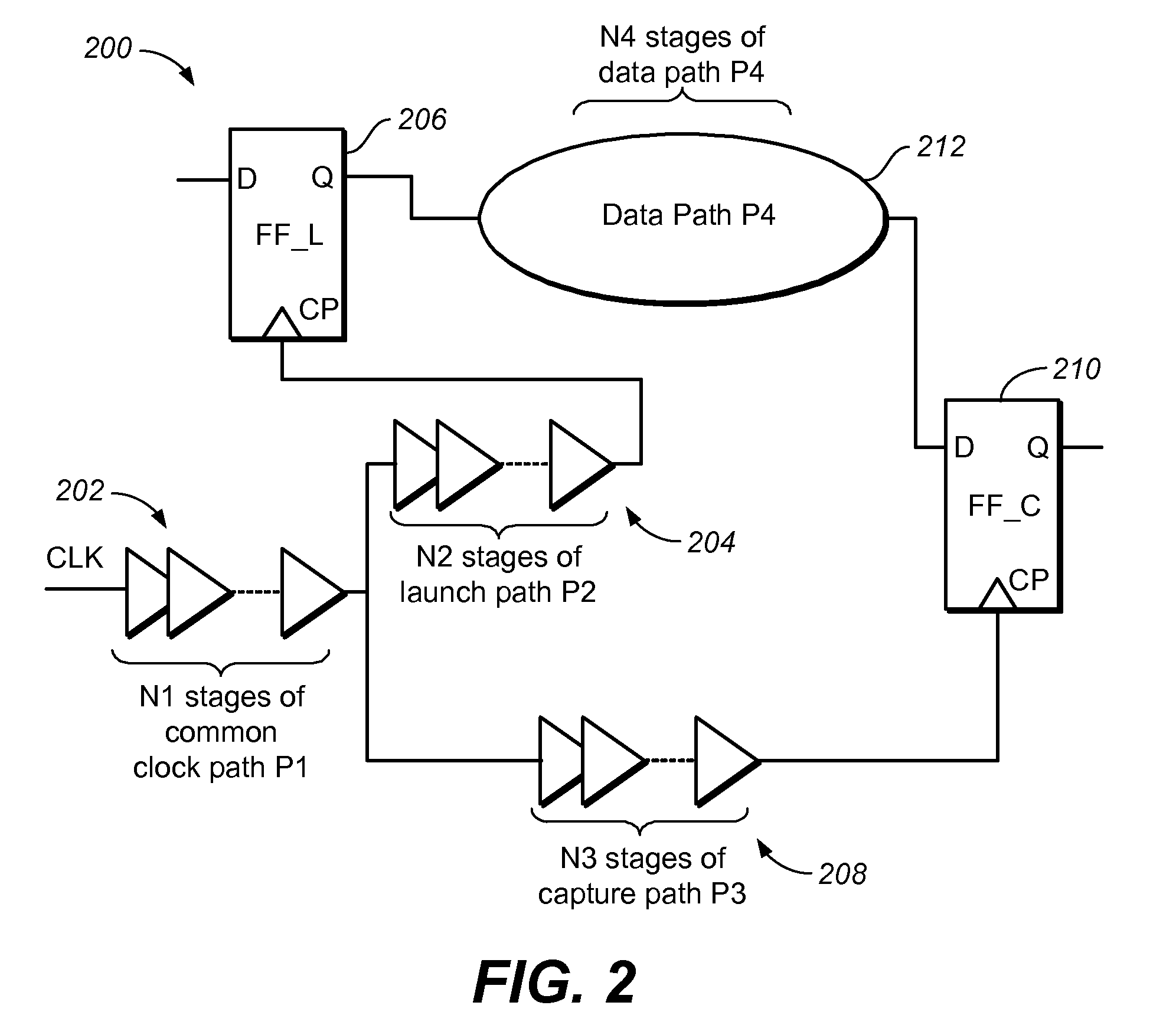
Method and apparatus for designing an integrated circuit
ActiveUS20120284680A1Computer aided designSoftware simulation/interpretation/emulationStatic timing analysisTime correlation
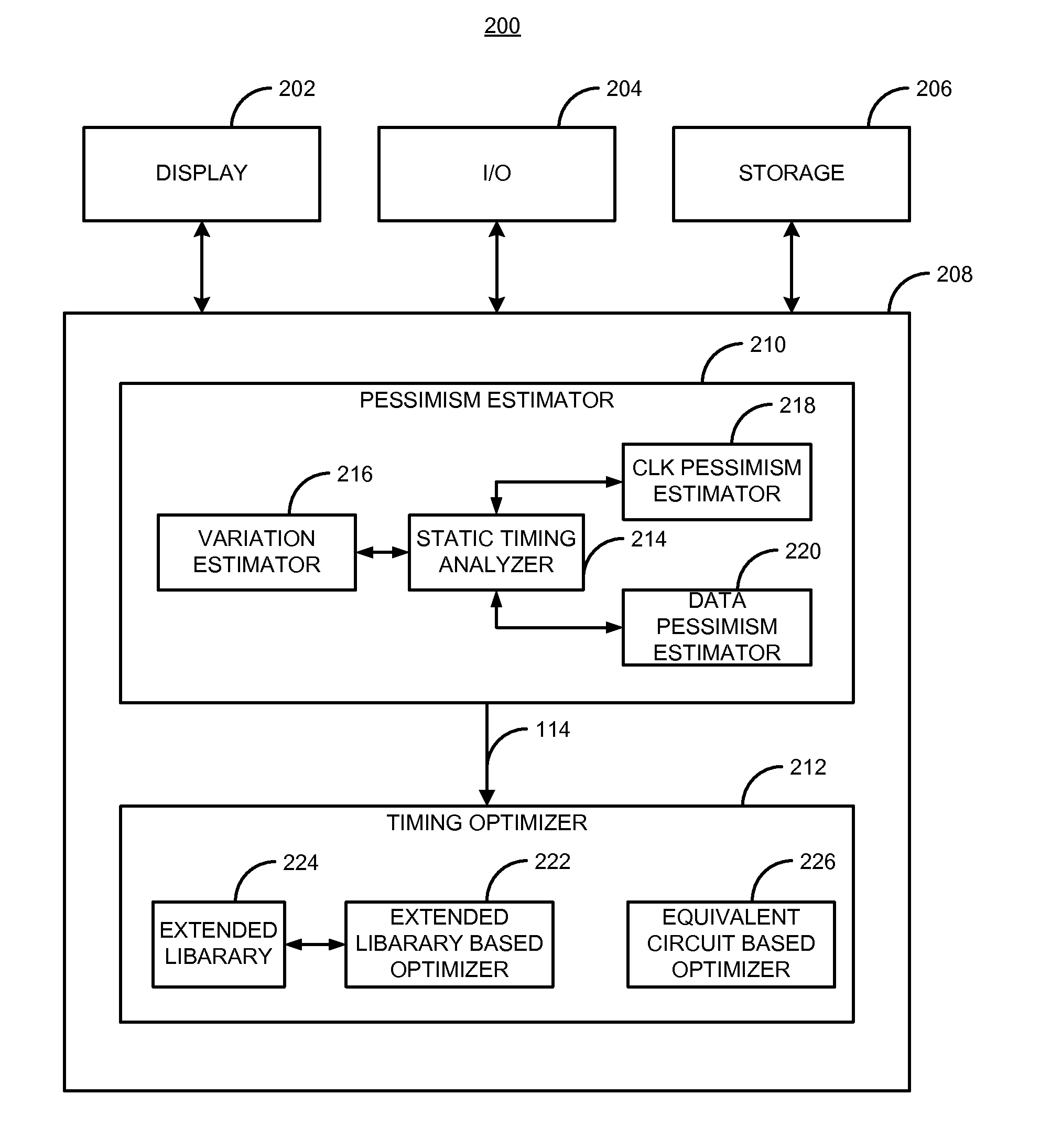
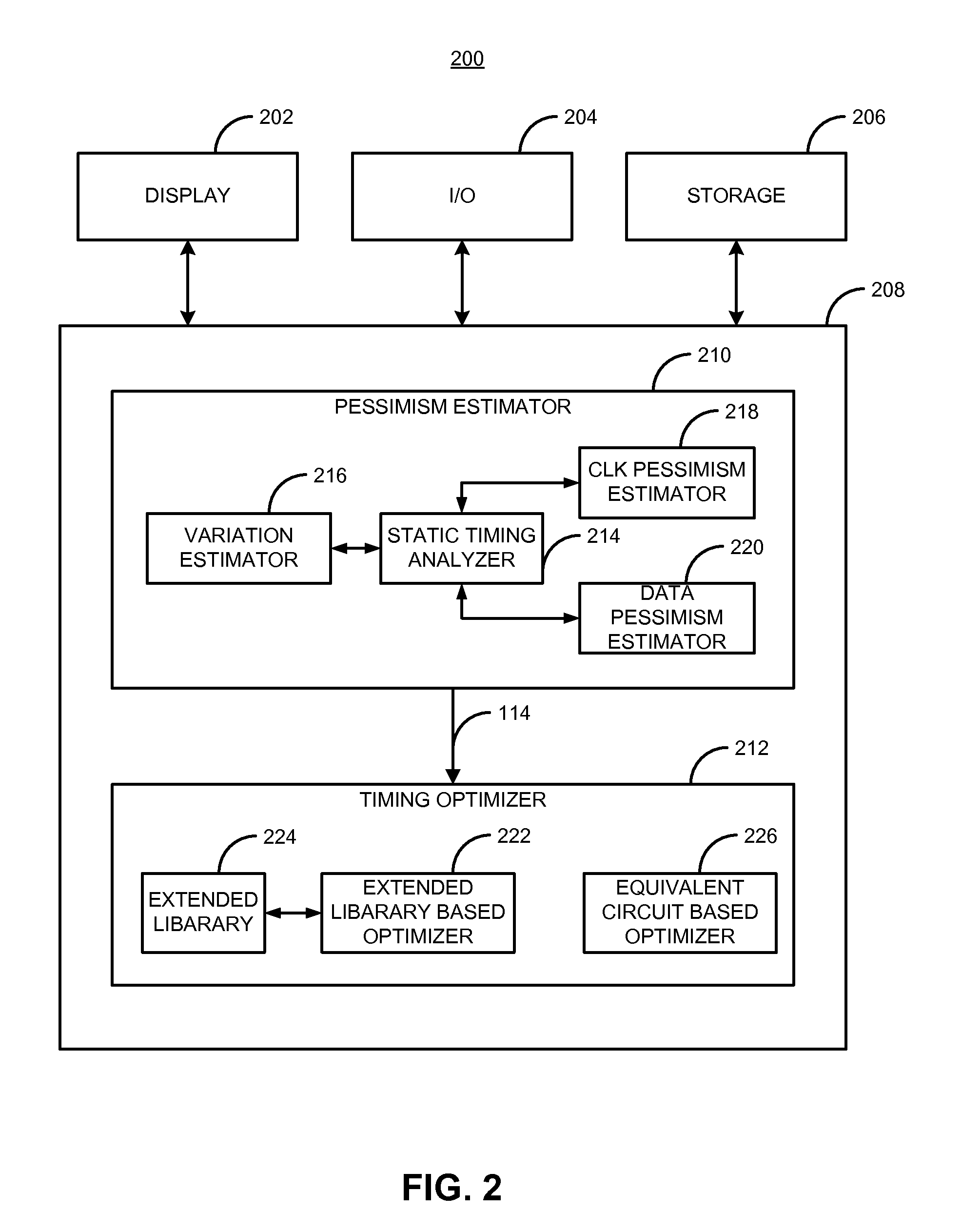
A method and apparatus for designing an integrated circuit to operate at a desired clock frequency range reduces process variation by estimating the value of removable pessimism from a static timing analysis. The pessimism includes, for example, at least one of the removable on-chip-variation (OCV) margin from clock paths, removable OCV margin from data paths, removable IR drop margin from clock paths, and removable interconnects margin. At the timing analysis stage of a design flow, the method and apparatus determines the value of pessimism in the timing critical paths based on timing correlation between adjacent timing critical paths. In response to the determination, the value of pessimism may be reduced in the static timing analysis of the adjacent timing critical paths to optimize the timing performance of the integrated circuit at its desired clock frequency range.
Owner:ADVANCED MICRO DEVICES INC
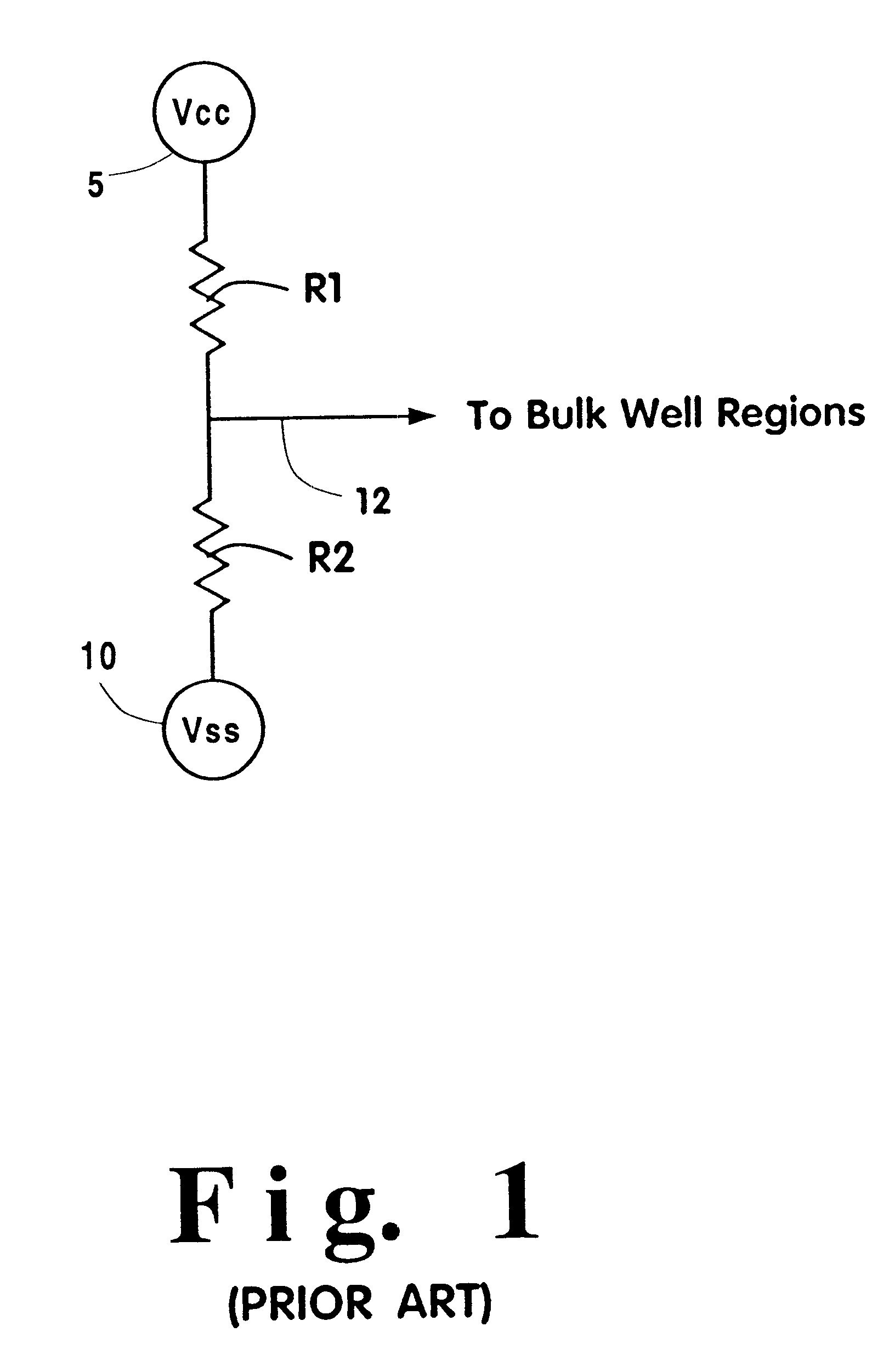
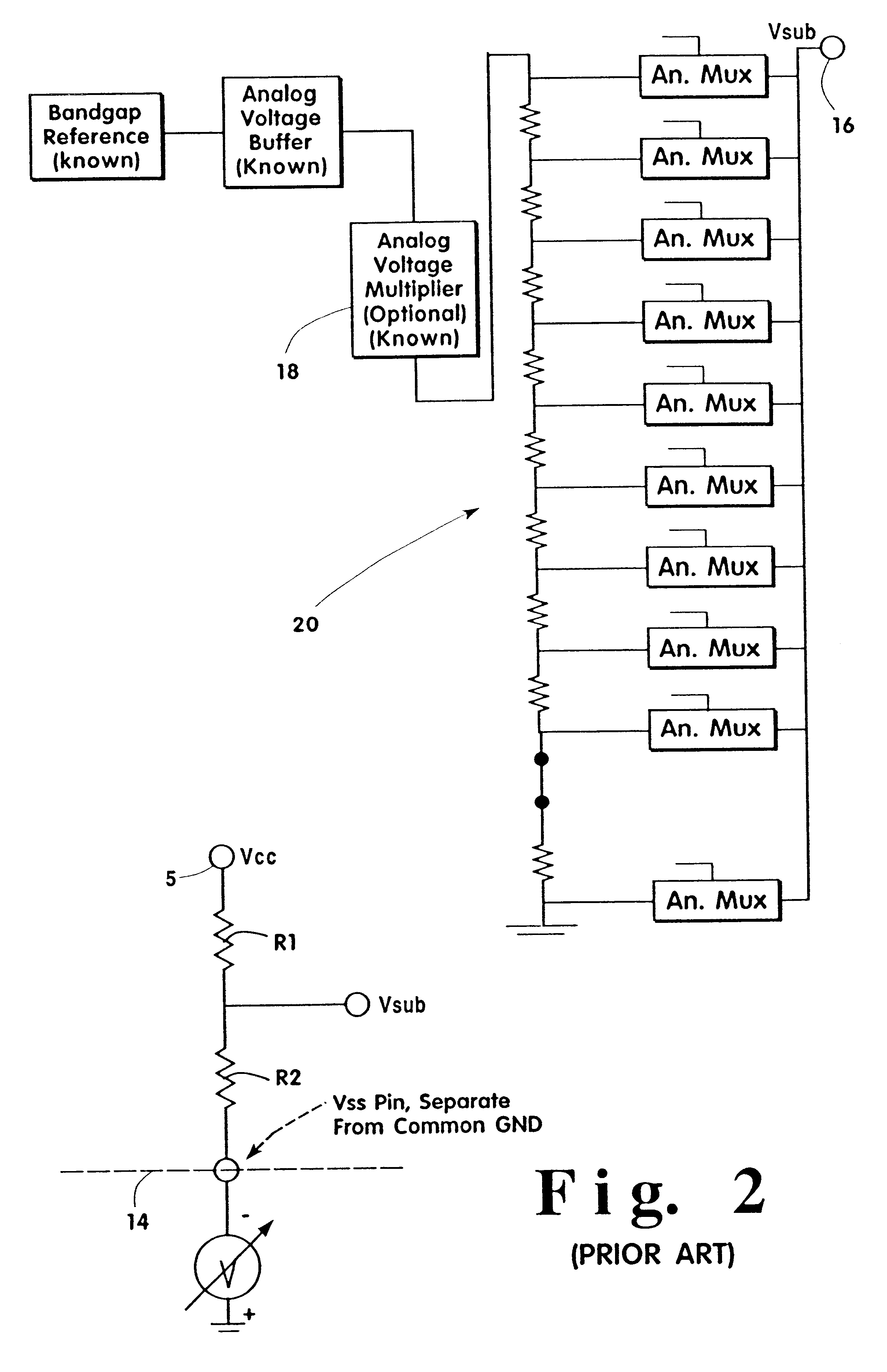
System and method for AC performance tuning by thereshold voltage shifting in tubbed semiconductor technology
InactiveUS6487701B1Reduce testingElectronic circuit testingDetecting faulty computer hardwareStatic timing analysisEngineering
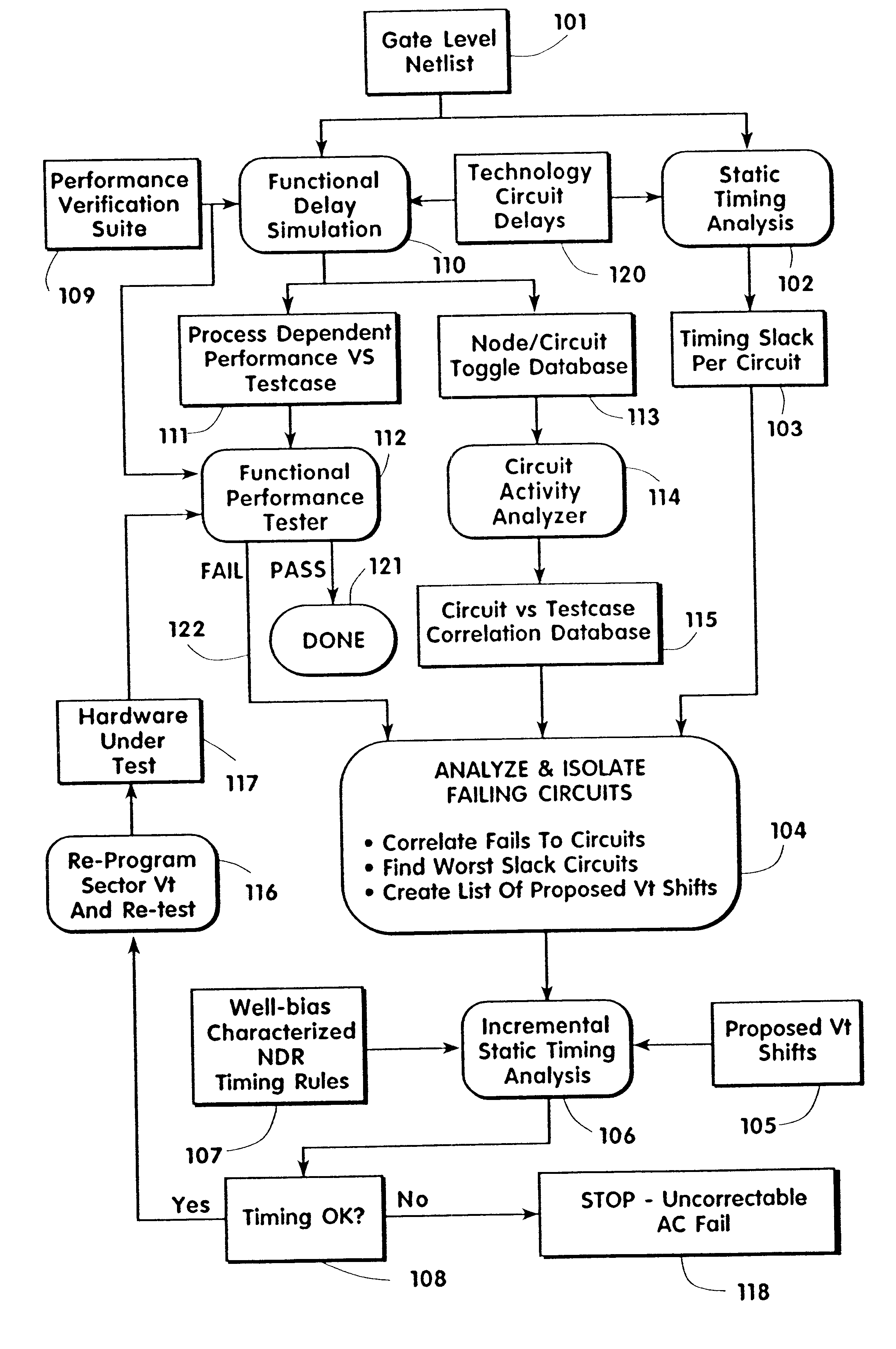
A system and method are described for separating the bulk connections for FETs on a semiconductor wafer from the supply rails, testing the wafer to determine if a shift in the threshold voltage, VT, of certain devices within the wafer, as defined by the bulk-wells, can remove an AC defect in the IC circuit, and tailoring the voltage or voltages applied to the bulk nodes, post-manufacture, such that the integrated circuit meets its performance targets or is sorted to a more valuable performance level. The method requires generating a gate level netlist of the IC's circuitry and performing timing calculations on these circuit netlists using static timing analyses, functional delay simulations, circuit activity analyses, and functional performance testing. The failures are then correlated to respective IC circuits, worst case slack circuits are investigated, and proposed changes to the threshold voltages are employed in the hardware.
Owner:IBM CORP
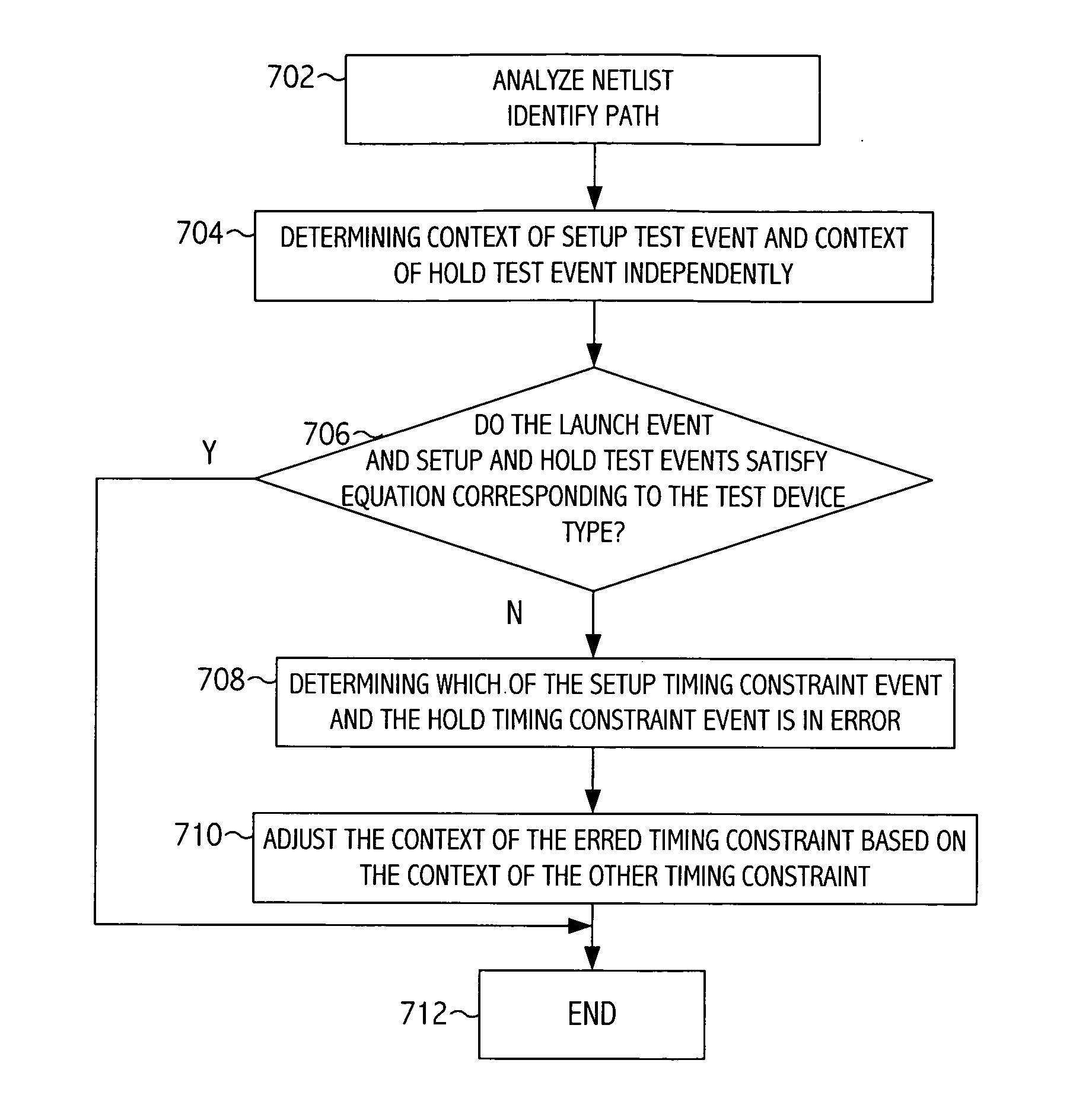
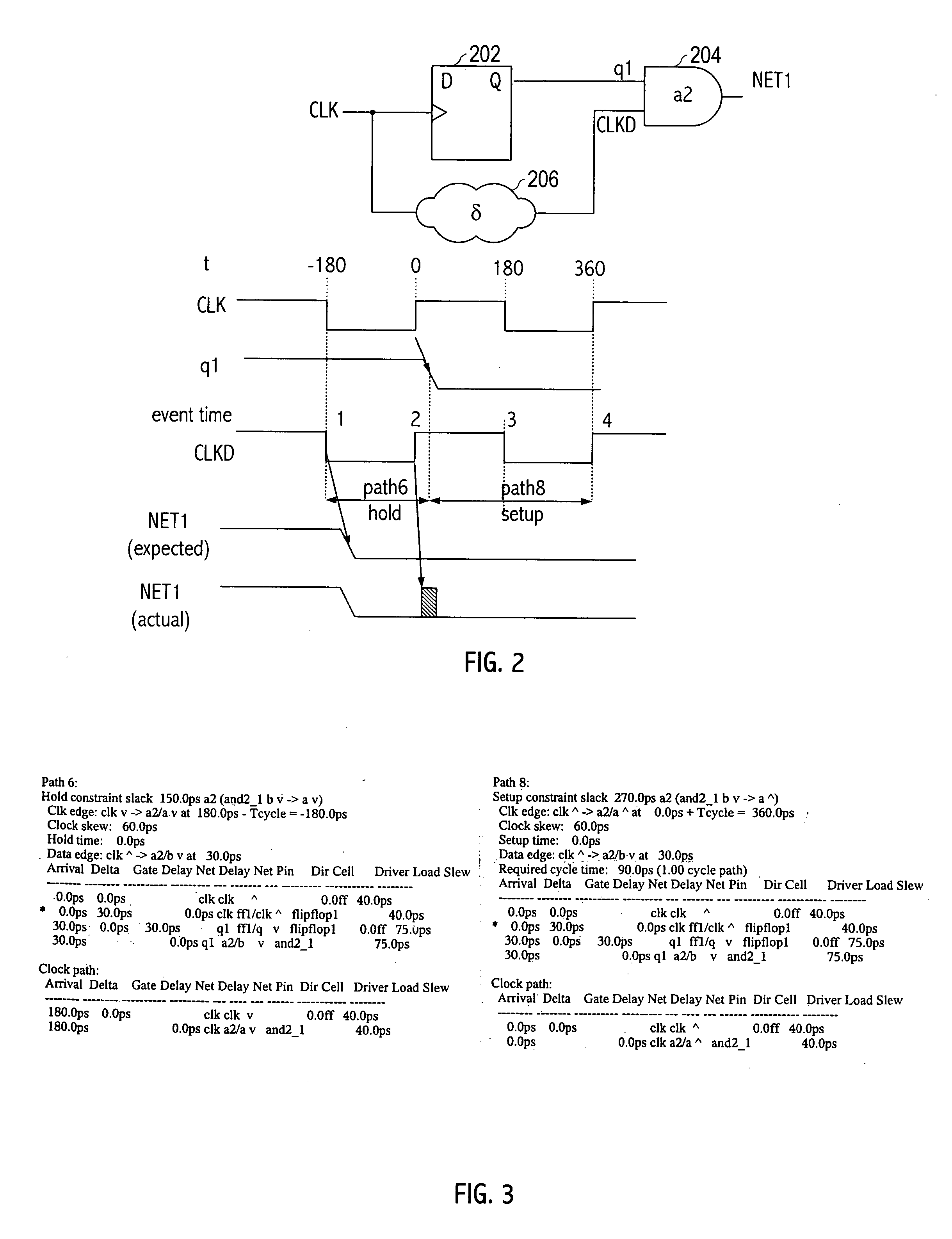
Application of consistent cycle context for related setup and hold tests for static timing analysis
InactiveUS20070089076A1Reduce generationComputer aided designSoftware simulation/interpretation/emulationDevice typeStatic timing analysis
A technique for performing static timing analysis of an integrated circuit design provides a relationship between reference events of a setup test and a hold test for a particular signal path of an integrated circuit design. The relationship between the reference events of the setup and hold tests is used to compute a timing metric (e.g., slack) for at least one of the setup and hold tests to reduce the occurrence of timing escapes from the static timing analysis of the design. A static timing analyzer determines, with respect to edges of a reference signal, a signal capture event time for one of setup and hold timing metrics associated with a signal path. The capture event time is based on a capture event time for the other of the setup and hold timing metrics, a launch event time, and a test device type associated with the path.
Owner:SUN MICROSYSTEMS INC
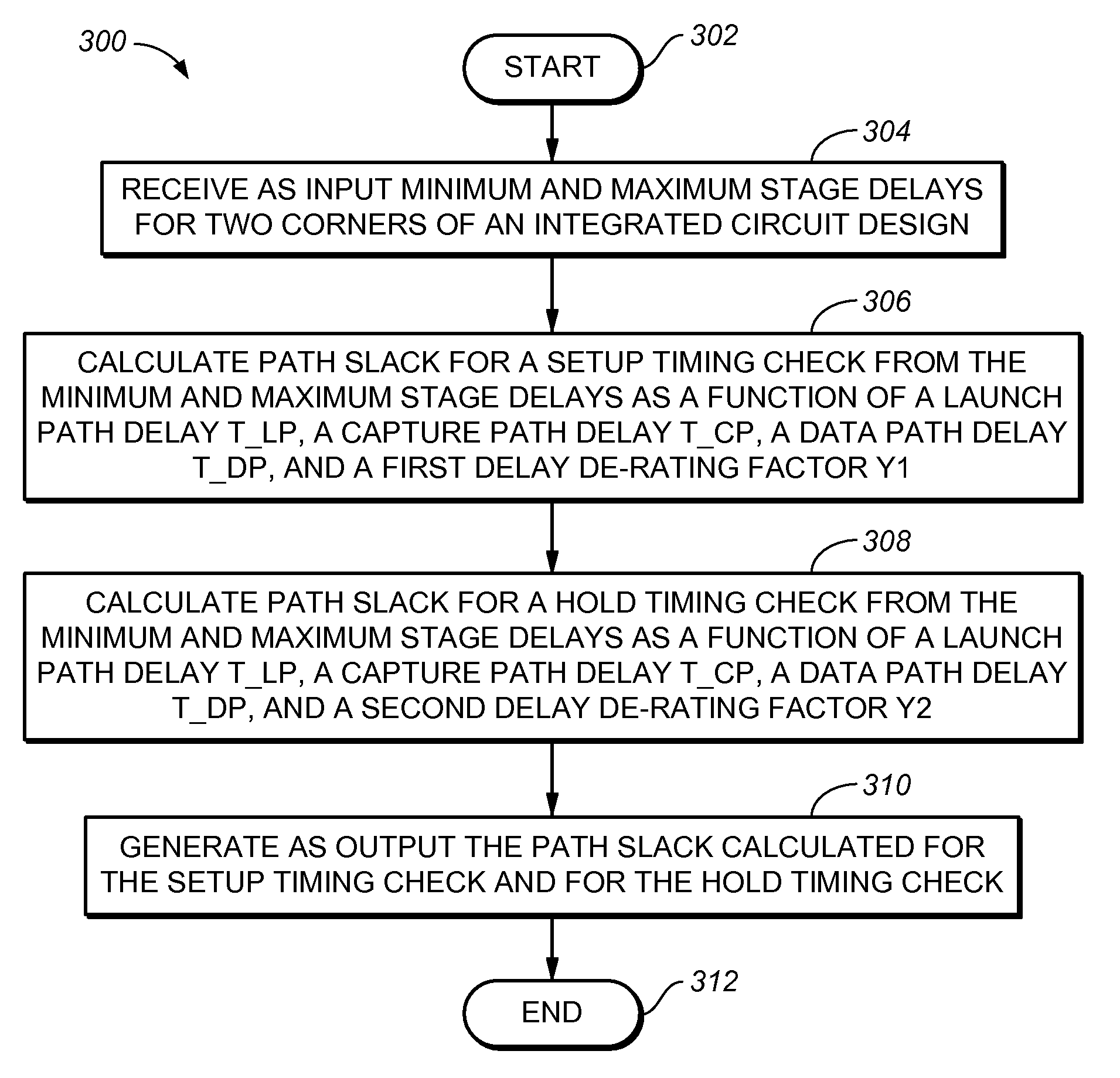
Method and computer program for static timing analysis with delay de-rating and clock conservatism reduction
InactiveUS7480881B2Computer aided designSoftware simulation/interpretation/emulationStatic timing analysisDatapath
A method and computer program for static timing analysis includes receiving as input minimum and maximum stage delays for two corners of an integrated circuit design. A path slack for a setup timing check is calculated from the minimum and maximum stage delays as a function of net clock cycle interval T_clk, launch path delay T_LP, capture path delay T_CP, data path delay T_DP, and a first delay de-rating factor Y1. A path slack for a hold timing check is calculated from the minimum and maximum stage delays as a function of the launch path delay T_LP, the capture path delay T_CP, the data path delay T_DP, and a second delay de-rating factor Y2. The path slack calculated for the setup timing check and for the hold timing check is generated as output.
Owner:BELL SEMICON LLC
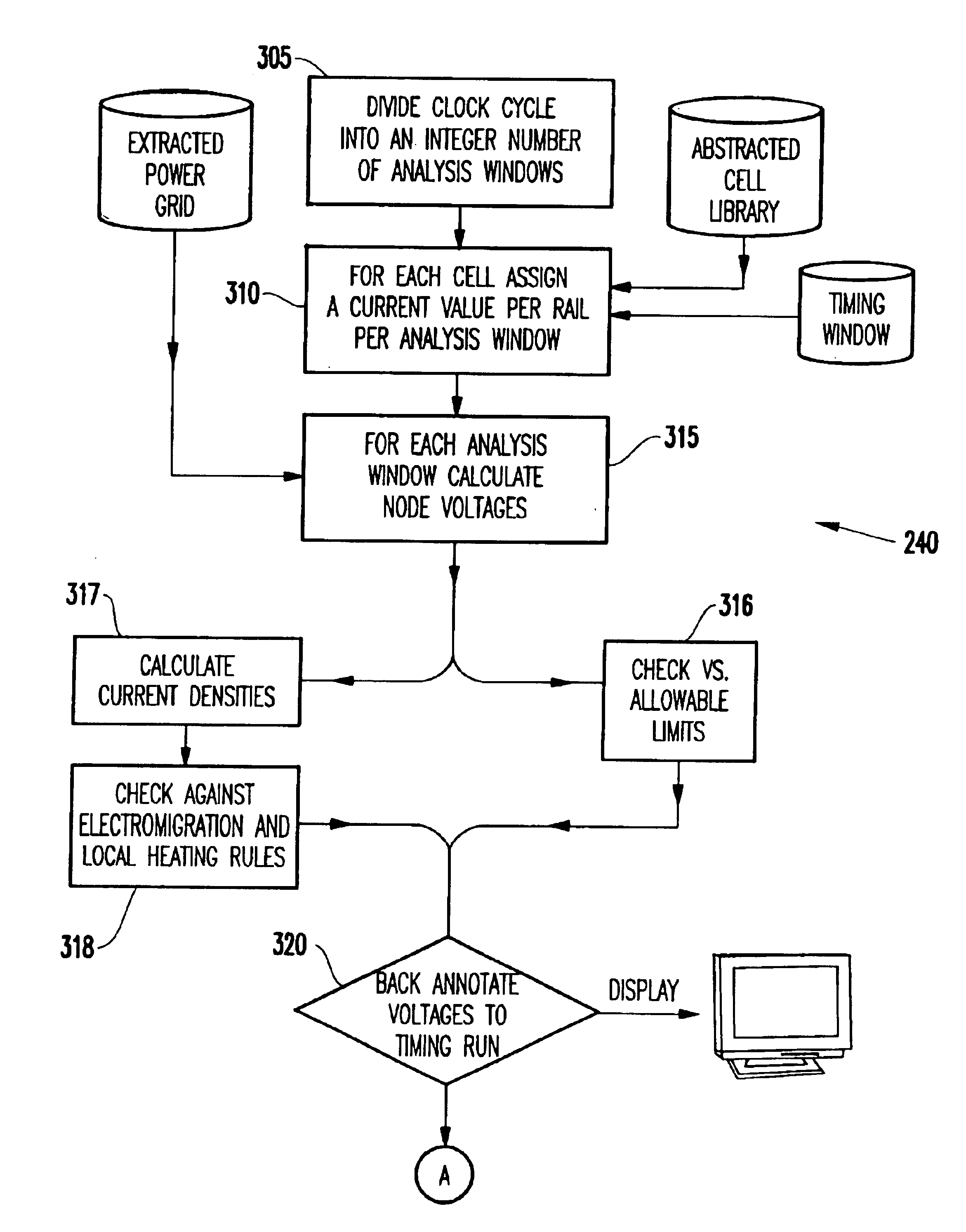
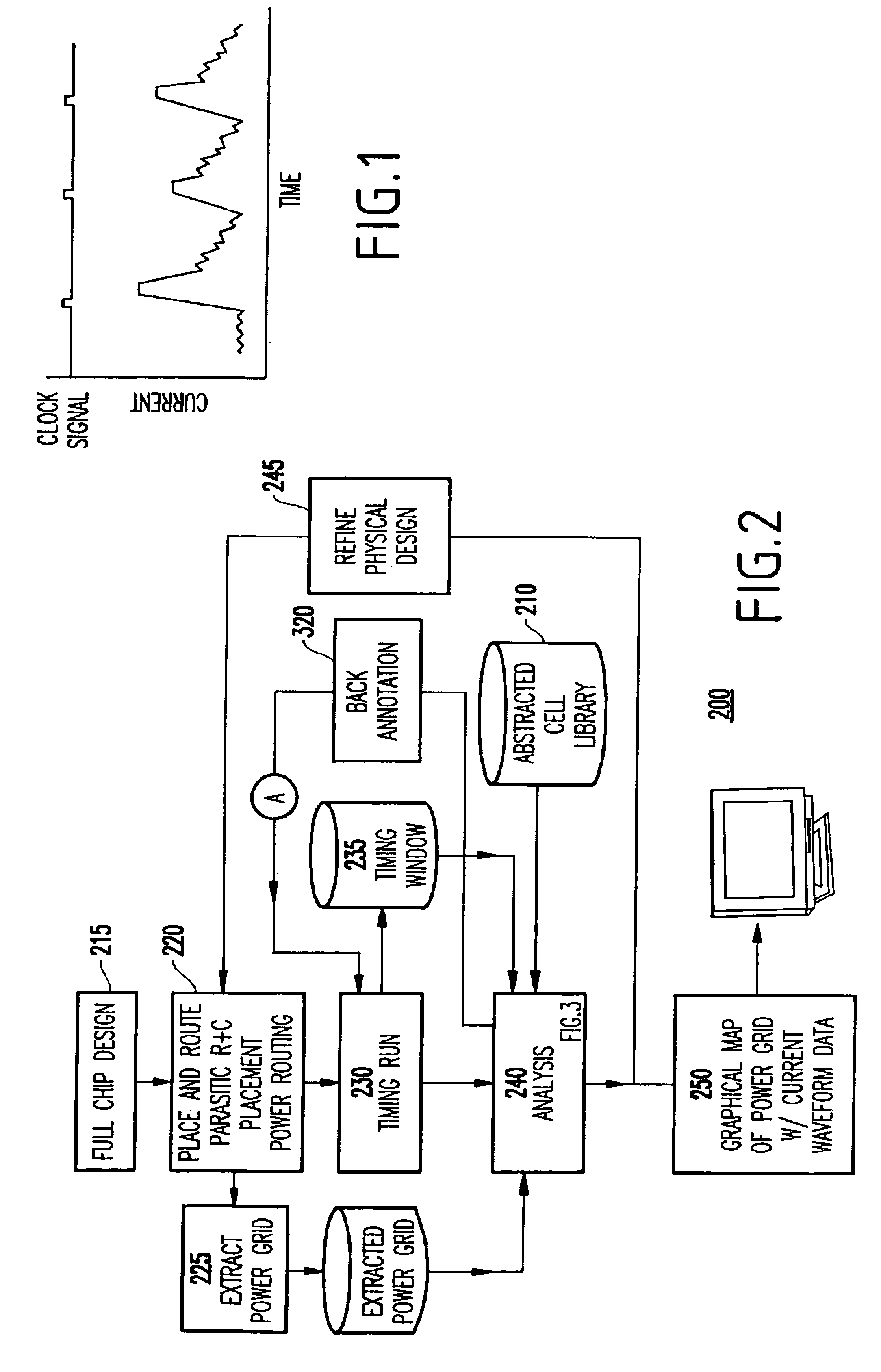
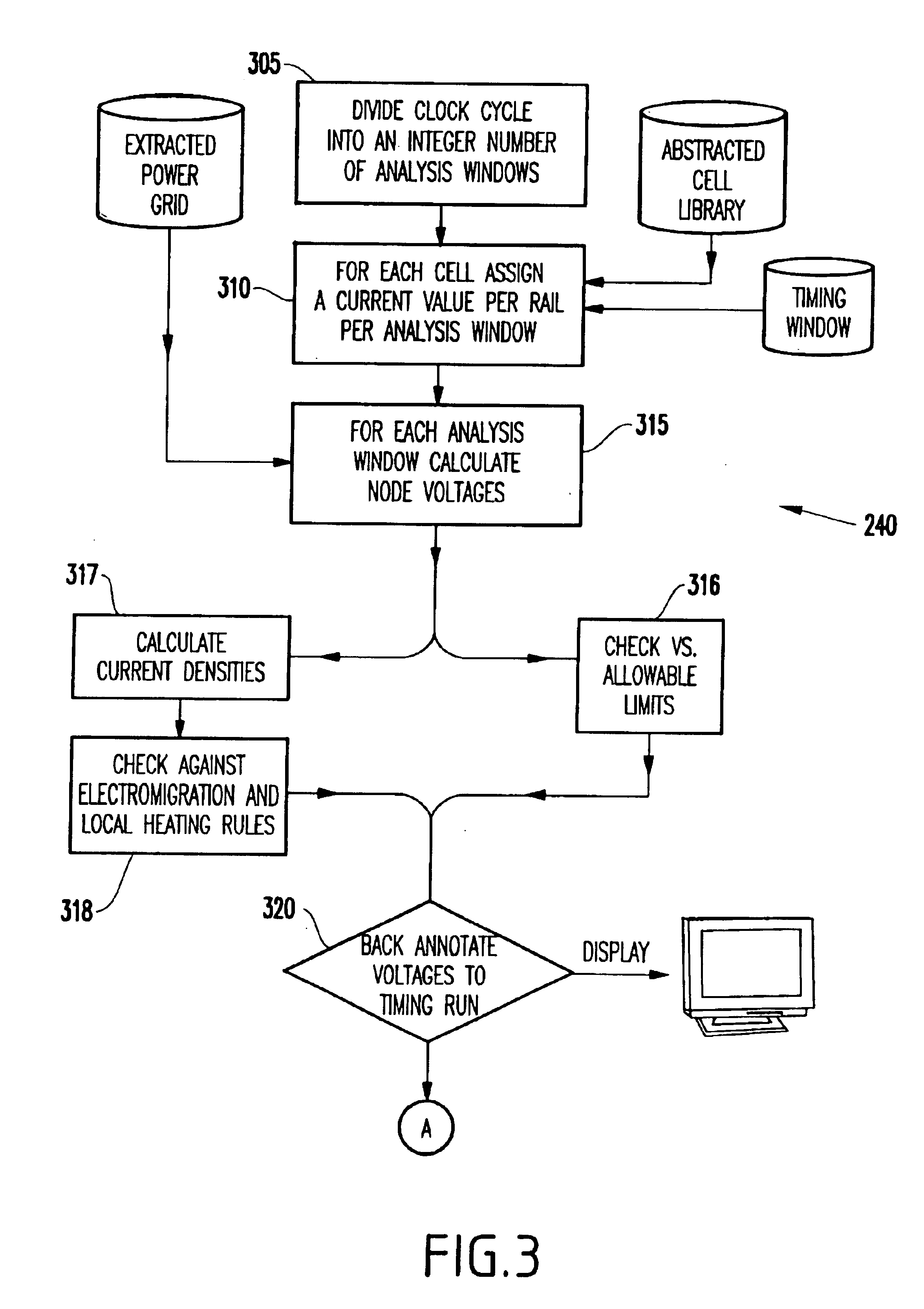
System and method for analyzing power distribution using static timing analysis
InactiveUS6832361B2Fast and effective meanThe process is fast and accurateSemiconductor/solid-state device manufacturingCAD circuit designStatic timing analysisIntegrated circuit
A method and system for analyzing power distribution in an integrated circuit chip includes dividing a clock cycle of the integrated circuit chip into a plurality of time periods, dividing the integrated circuit chip into a plurality of cells, performing a static timing analysis for the plurality of cells to obtain current waveform data for each cell and each time period, and performing a power distribution analysis using the current waveform data.
Owner:MARVELL ASIA PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com