Application multidimensional privacy leak detection method and system for iOS platform
An application program and privacy leakage technology, which is applied in the field of mobile terminal privacy leakage detection, can solve problems such as failure to achieve a 100% decryption success rate, chargeback, iCloud account password leakage, etc., to improve scientificity and rigor, increase detection rate, Make up for the limited effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with the accompanying drawings.
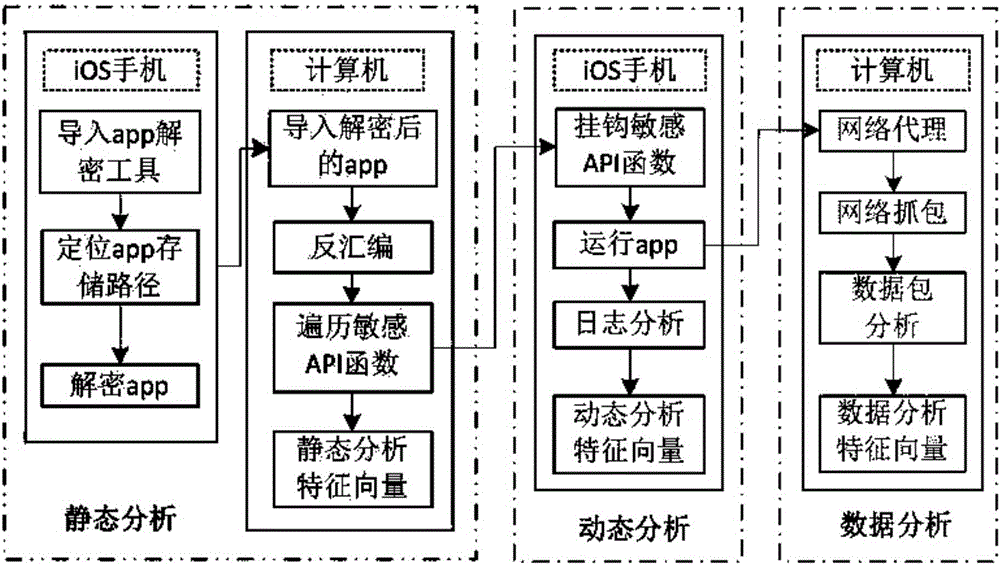
[0037] Such as figure 1 As shown, an application multi-dimensional privacy leakage detection method for iOS platform, from three dimensions of static analysis, dynamic analysis and data analysis to iOS application privacy leakage detection, wherein:
[0038] Static analysis includes the steps of application decryption, app storage path location, disassembly and sensitive API analysis of disassembly source code;
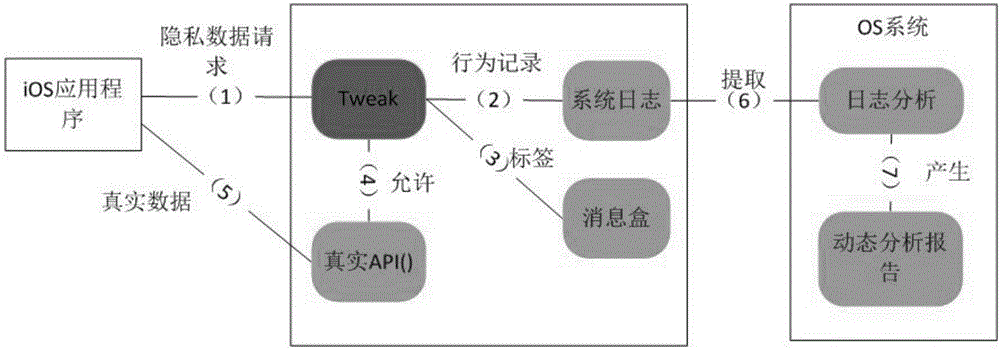
[0039] Dynamic analysis includes hooking sensitive API functions, obtaining log records by running applications, and obtaining sensitive API call sequences through log analysis;
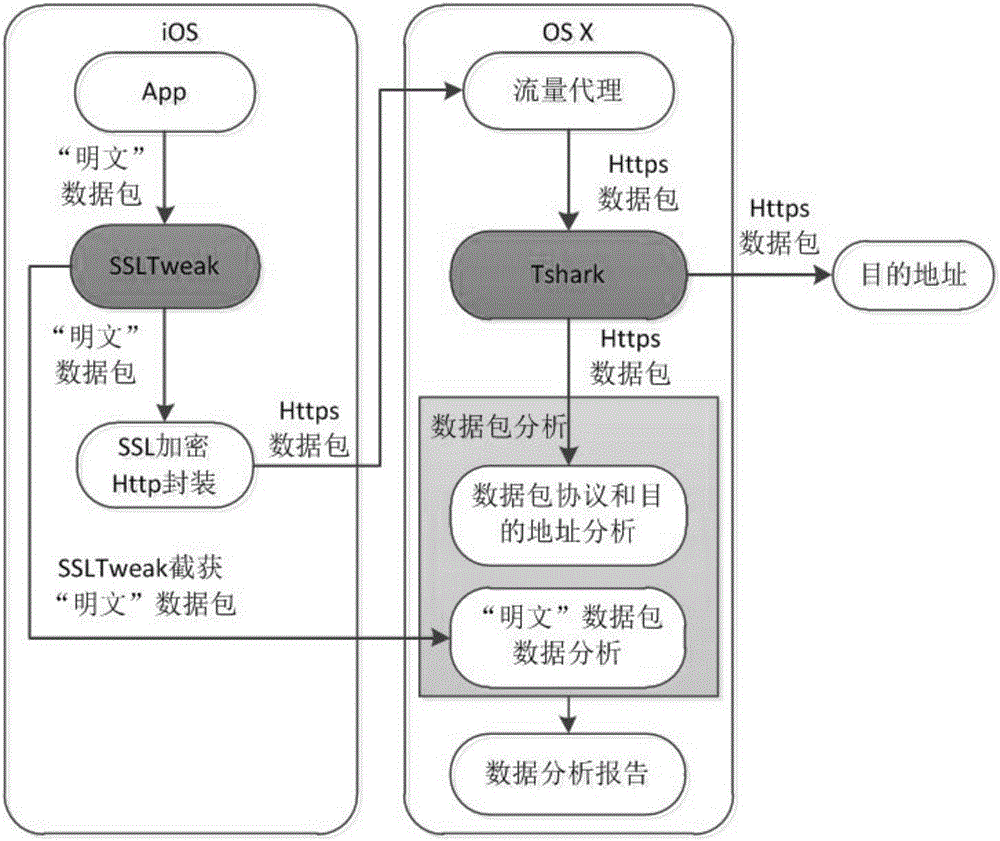
[0040] Data analysis includes the steps of grabbing application network data packets and analyzing data packet protocols, addresses, and contents.
[0041]Static analysis of iOS applications is mainly based on sensitive API call sequence analysis of disassembly files. The specific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com