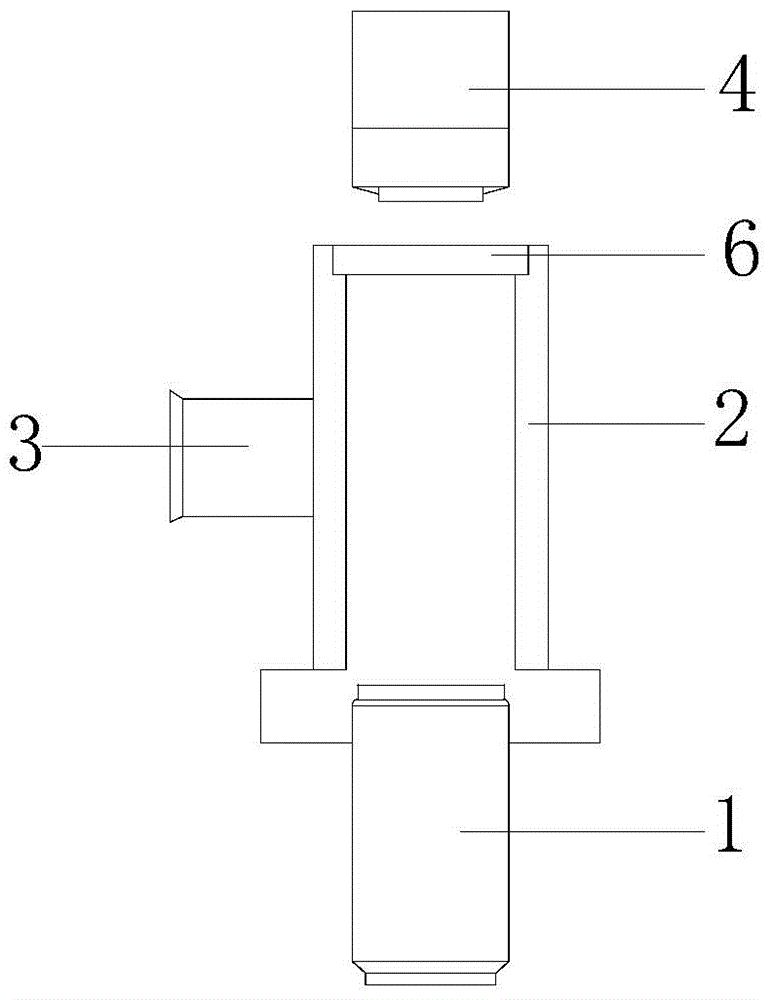Patents
Literature
430results about How to "Improve rigor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
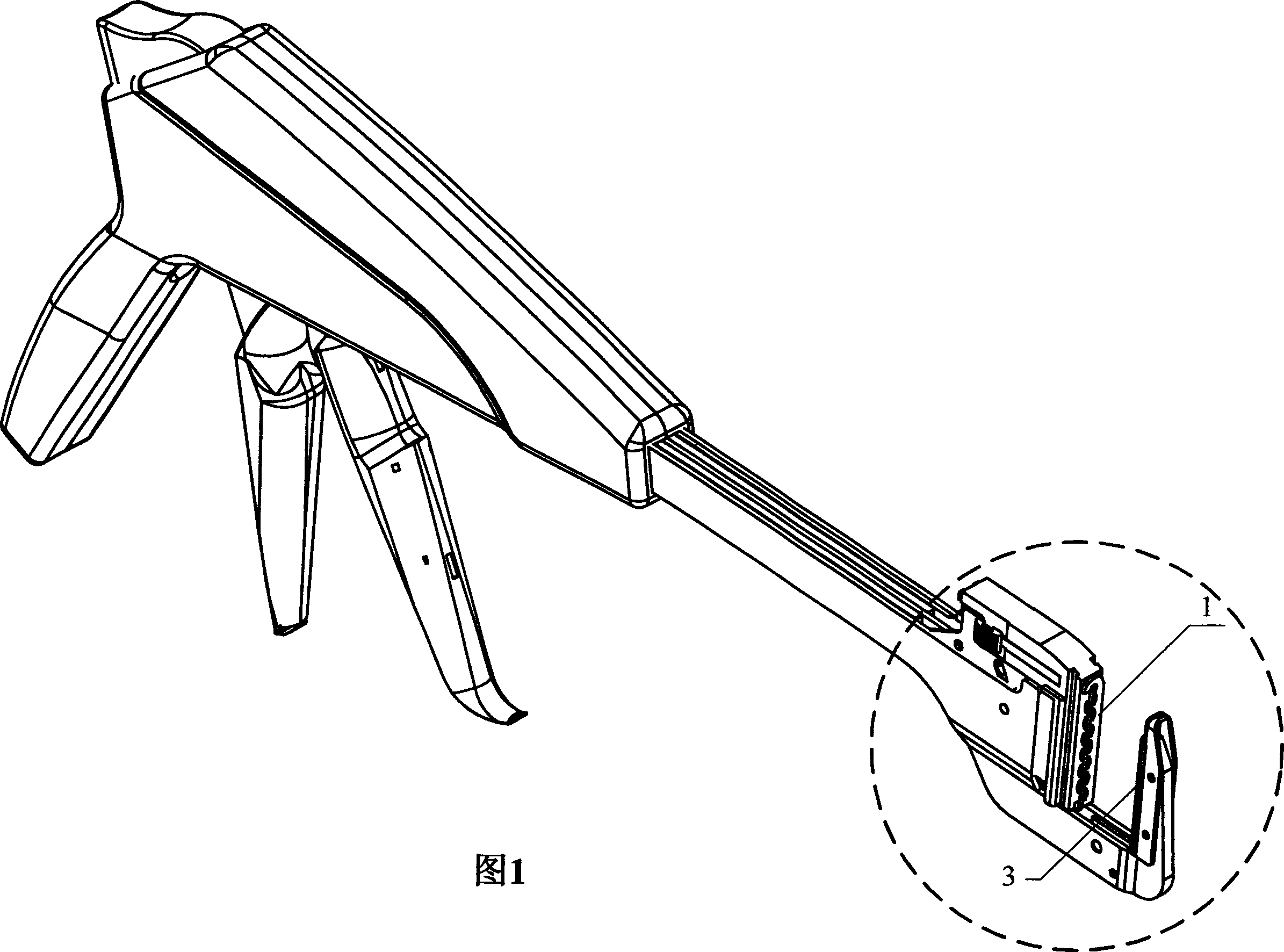
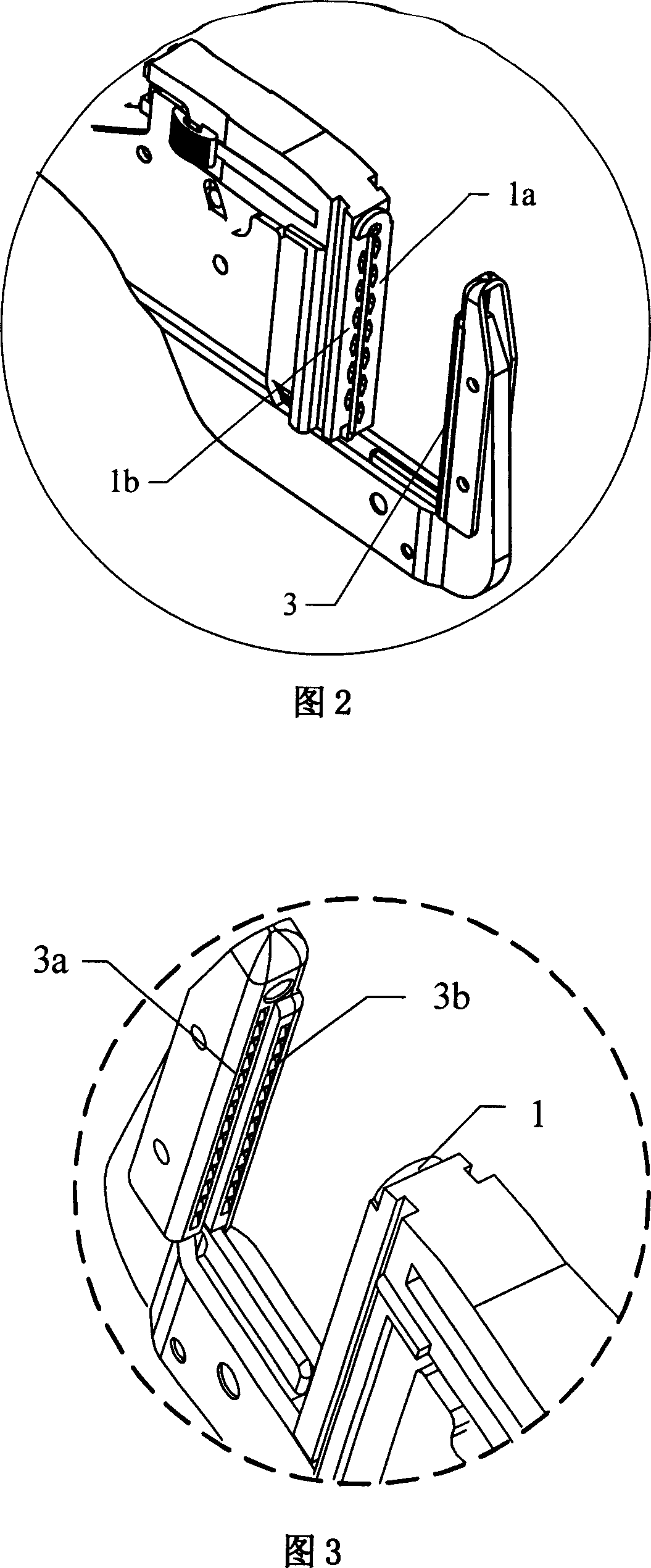
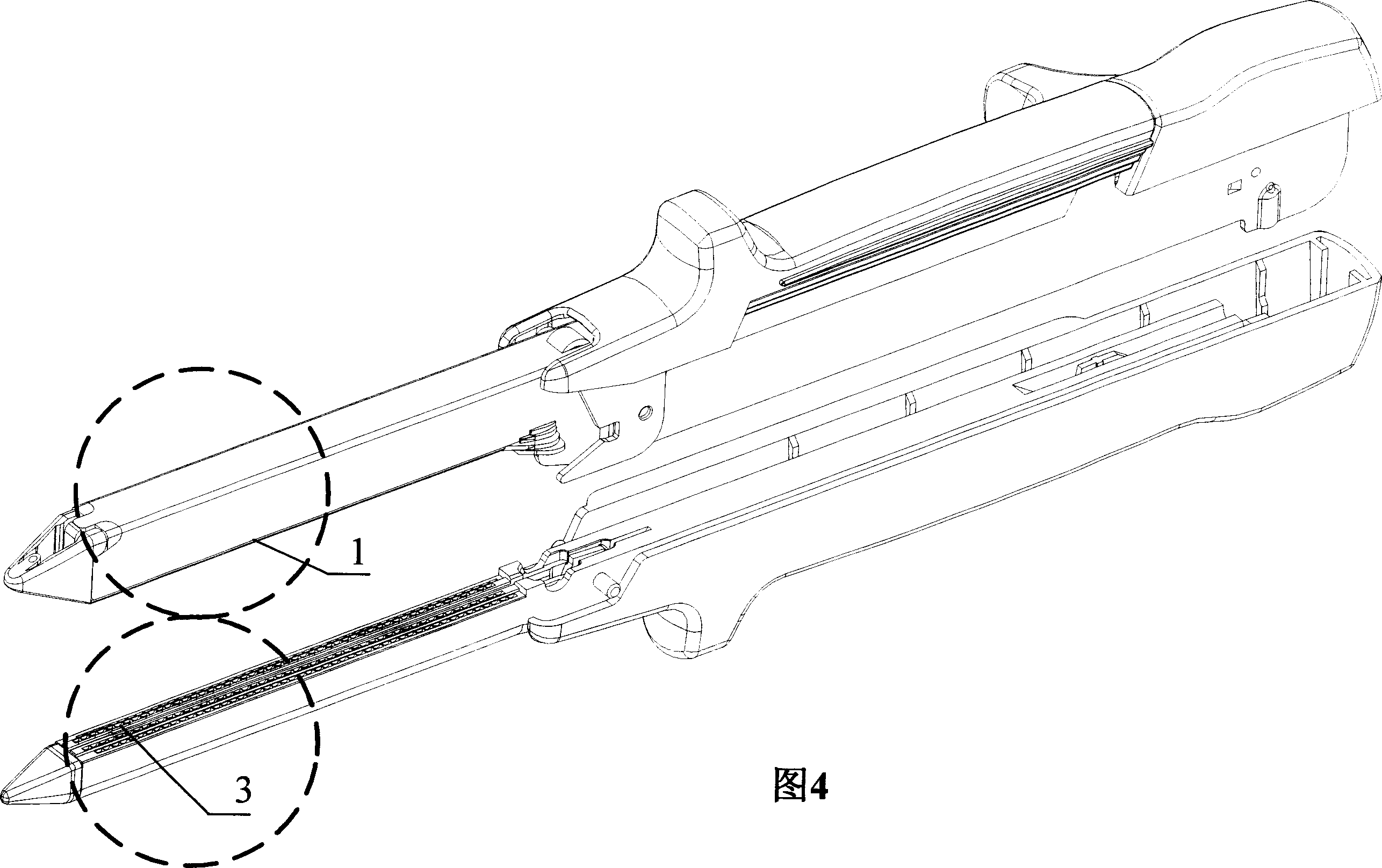
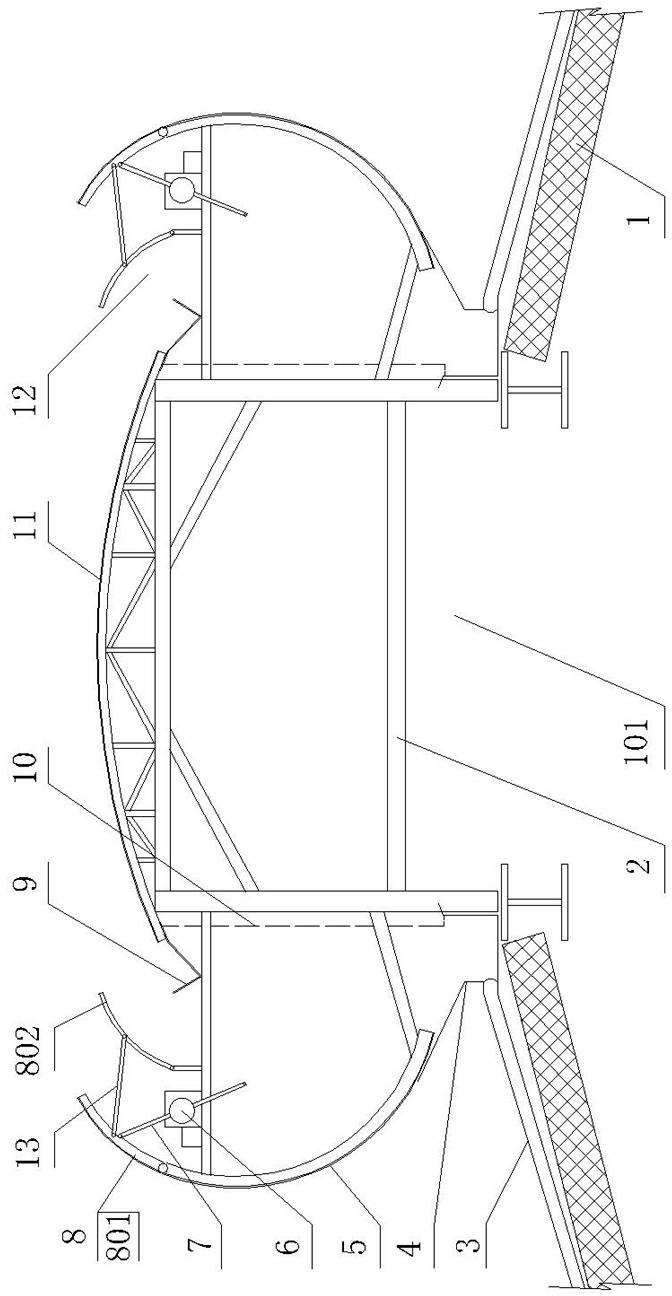
Surgical binding instrument binding mechanism
The invention relates to a binding mechanism of a surgical binding apparatus, which is placed at the head of the surgical binding apparatus and includes a nail pin, a nail pushing plate and a nail block. The nail pushing plate and the nail pin are installed inside the binding apparatus body. The positions of the nail block and the nail pushing plate are opposite. The invention is characterized in that the working faces of nail pin, the nail pushing plate and the nail block are not at the same plane and at least present a step-type fall distributed structure. When the structure is adopted to form an anastomoses opening, the distance between two lines of nails is enlarged; the elasticity of the anastomoses opening which is formed in the operation is increased and is more close to the physiological characteristic of the tissue, which is in favor of the prompt recovery of the tissue. When the nail block is set out from an anastomoses ring or a content object is put through the anastomoses ring after binding, the elasticity of the anastomoses ring becomes larger to allow the nail block or the content object pass through and reduce the probability of damaging the anastomoses ring.
Owner:TOUCHSTONE INTERNATIONAL MEDICAL SCIENCE CO LTD
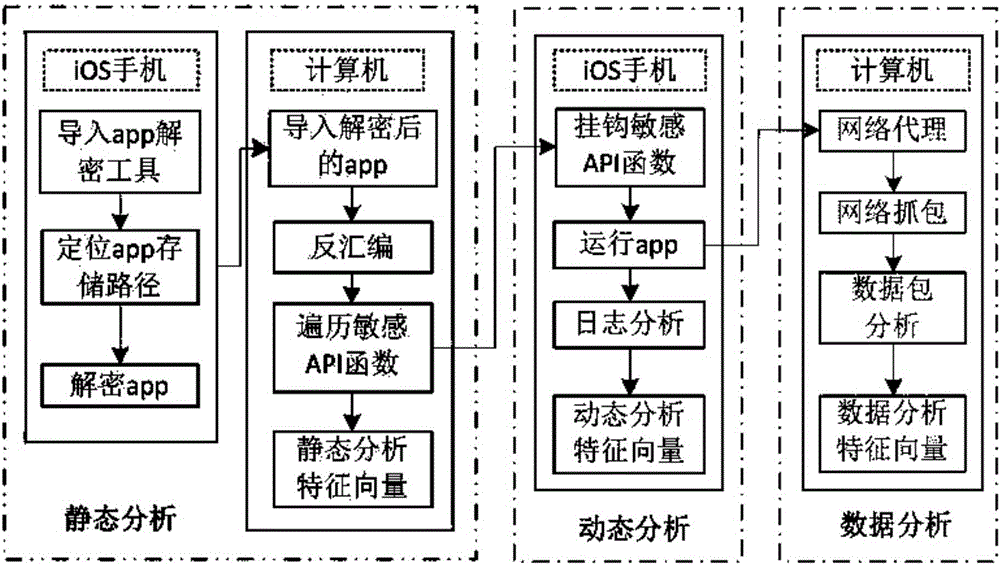
Application multidimensional privacy leak detection method and system for iOS platform
InactiveCN106845236AImprove scienceImprove rigorPlatform integrity maintainanceStatic timing analysisInternet privacy
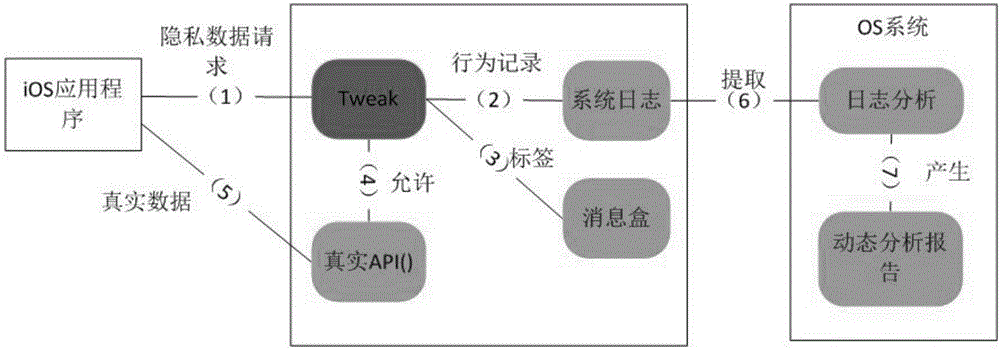
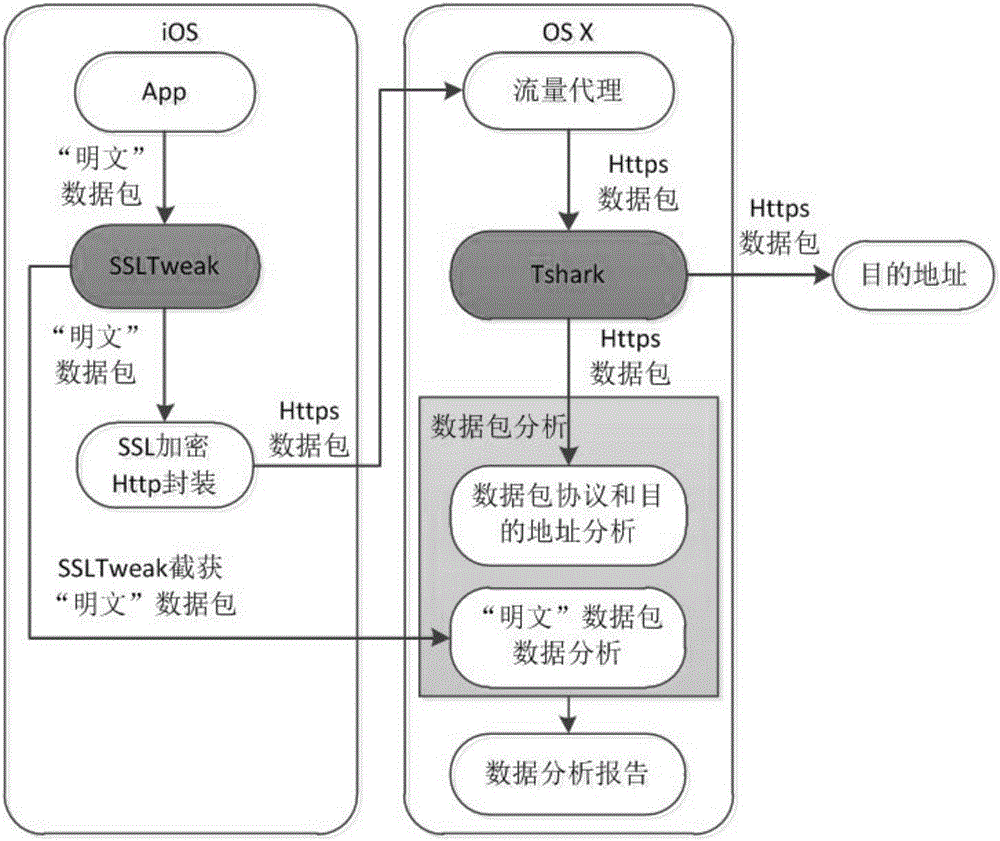
The invention discloses an application multidimensional privacy leak detection method and system for iOS platform; privacy leak detection is provided for iOS applications from the three dimensions, static analysis, dynamic analysis and data analysis, wherein the static analysis incudes the steps of application decrypting, app storage path locating, disassembling, and disassembly source code sensitive API (application program interface) analysis; the dynamic analysis includes the step of allowing Hook-sensitive API function to acquire a log record by running an application, and acquire a sensitive API calling sequence through log analysis; the data analysis incudes the steps of capturing application network data packets, and analyzing data packet protocol, address and content. The method and system of the invention can provide comprehensive detection for data privacy leaks of iOS applications to obtain complete privacy leak event data.
Owner:SOUTHEAST UNIV +1
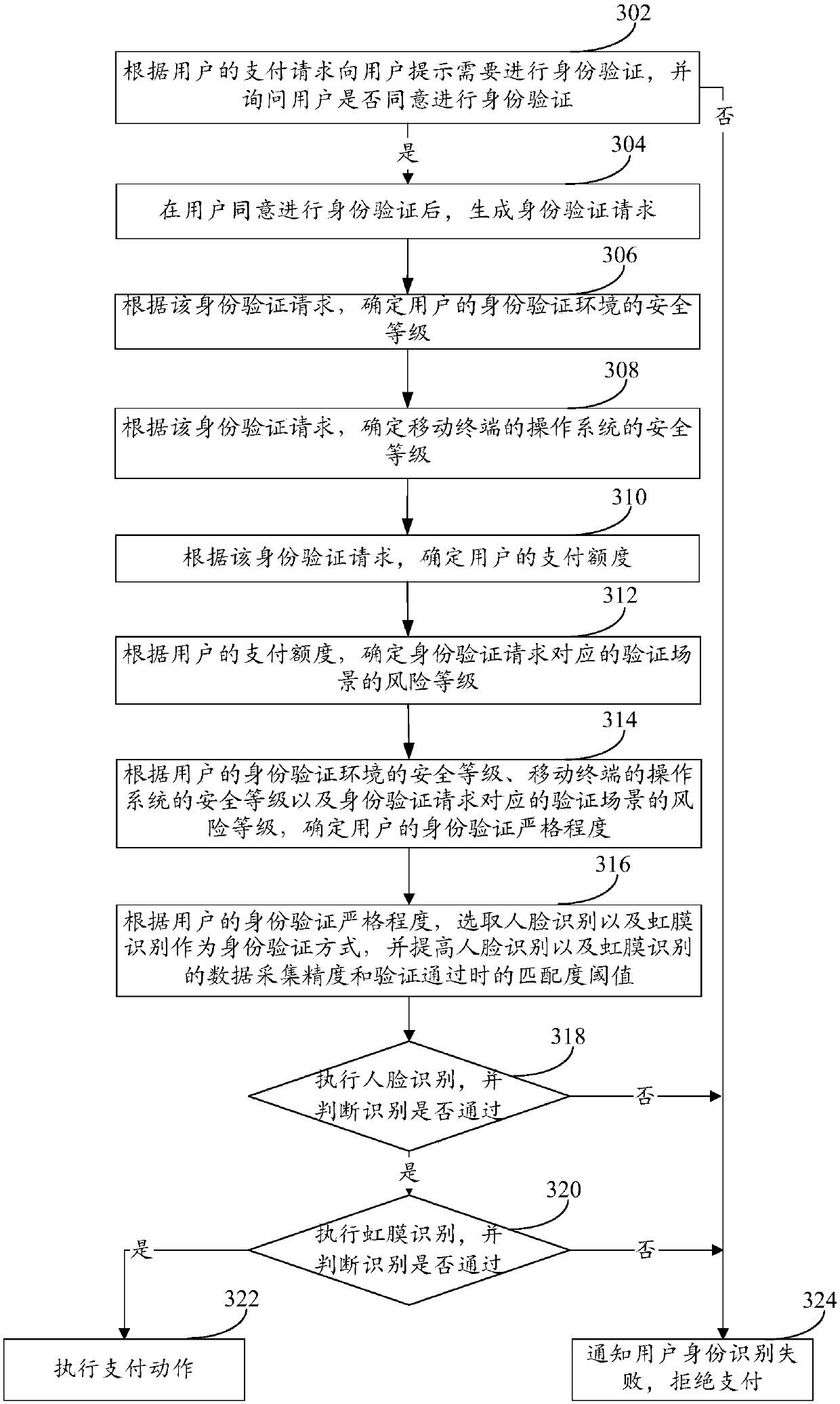
Identity verification method and mobile terminal
InactiveCN107749844AImprove rigorImprove reliabilityTransmissionProtocol authorisationComputer terminalAuthentication
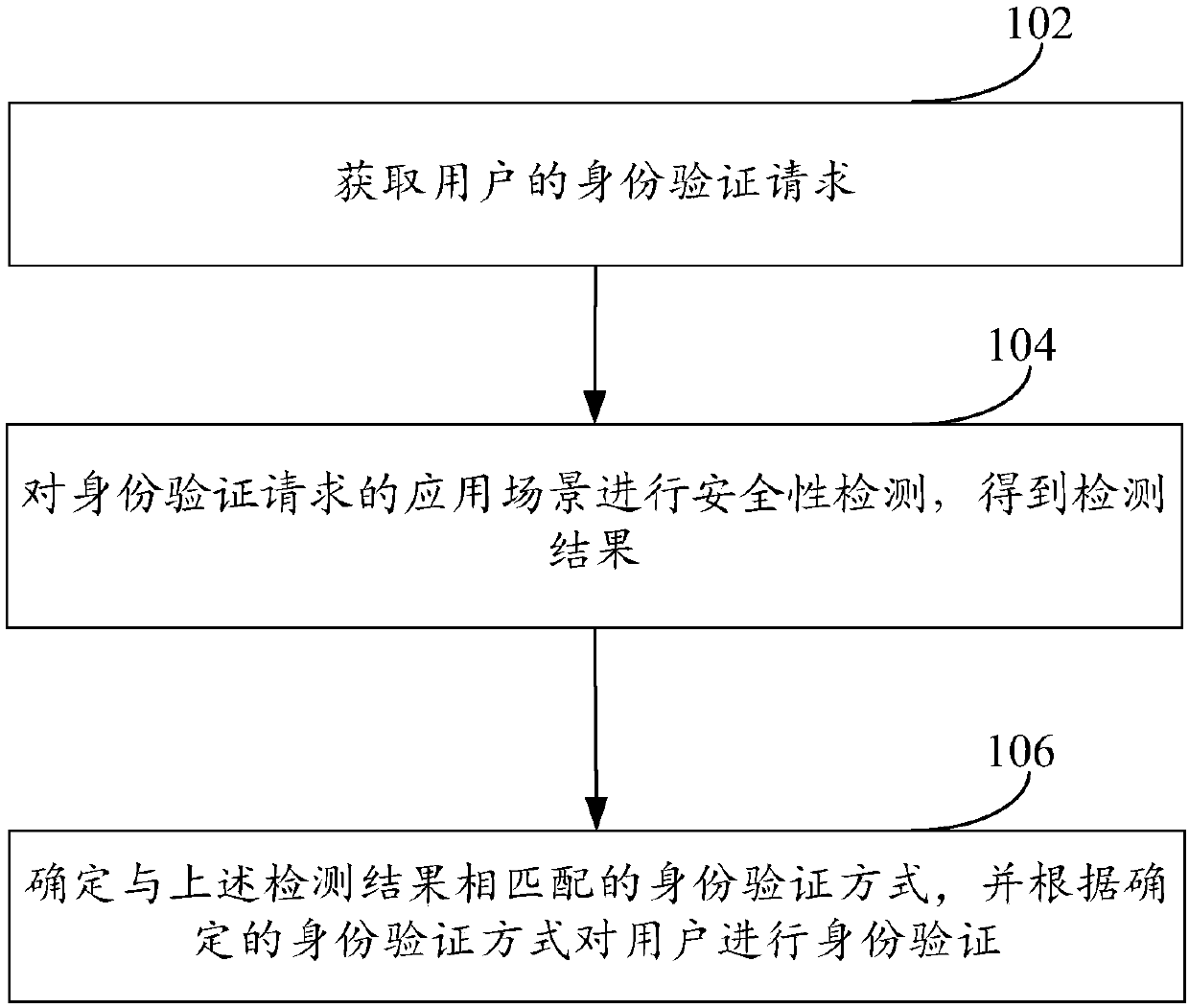
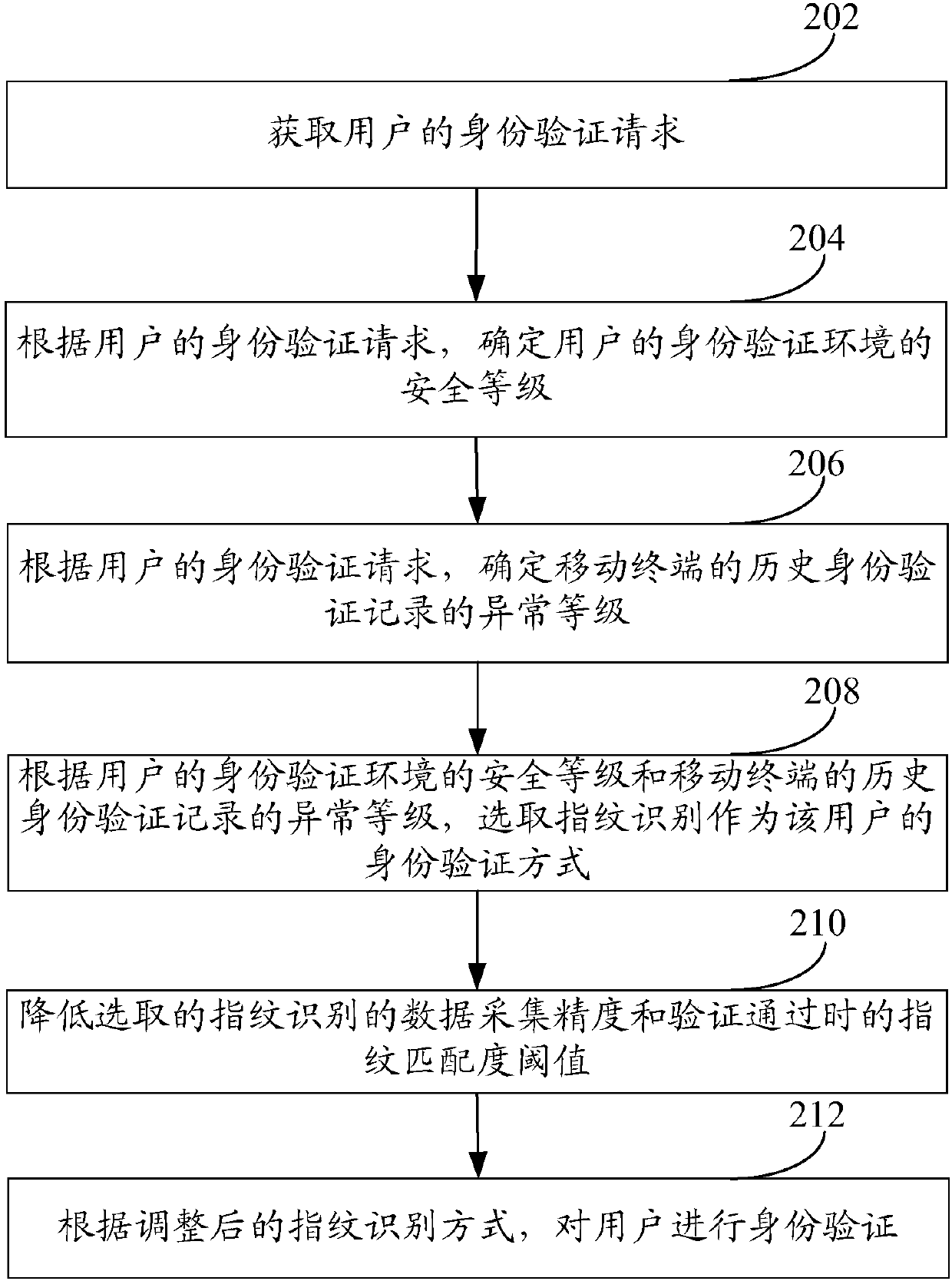
The embodiment of the invention aims at providing an identity verification method and a mobile terminal. The identity verification method comprises the steps of obtaining an identity verification request of a user; performing security detection on the application scene of the identity verification request to obtain a detection result; and determining an identity verification mode matching with thedetection result and performing identity verification on the user based on the determined identity verification mode. The identity verification method and the mobile terminal in the embodiment can solve the problem of relatively poor flexibility of the existing identity verification method.
Owner:VIVO MOBILE COMM CO LTD
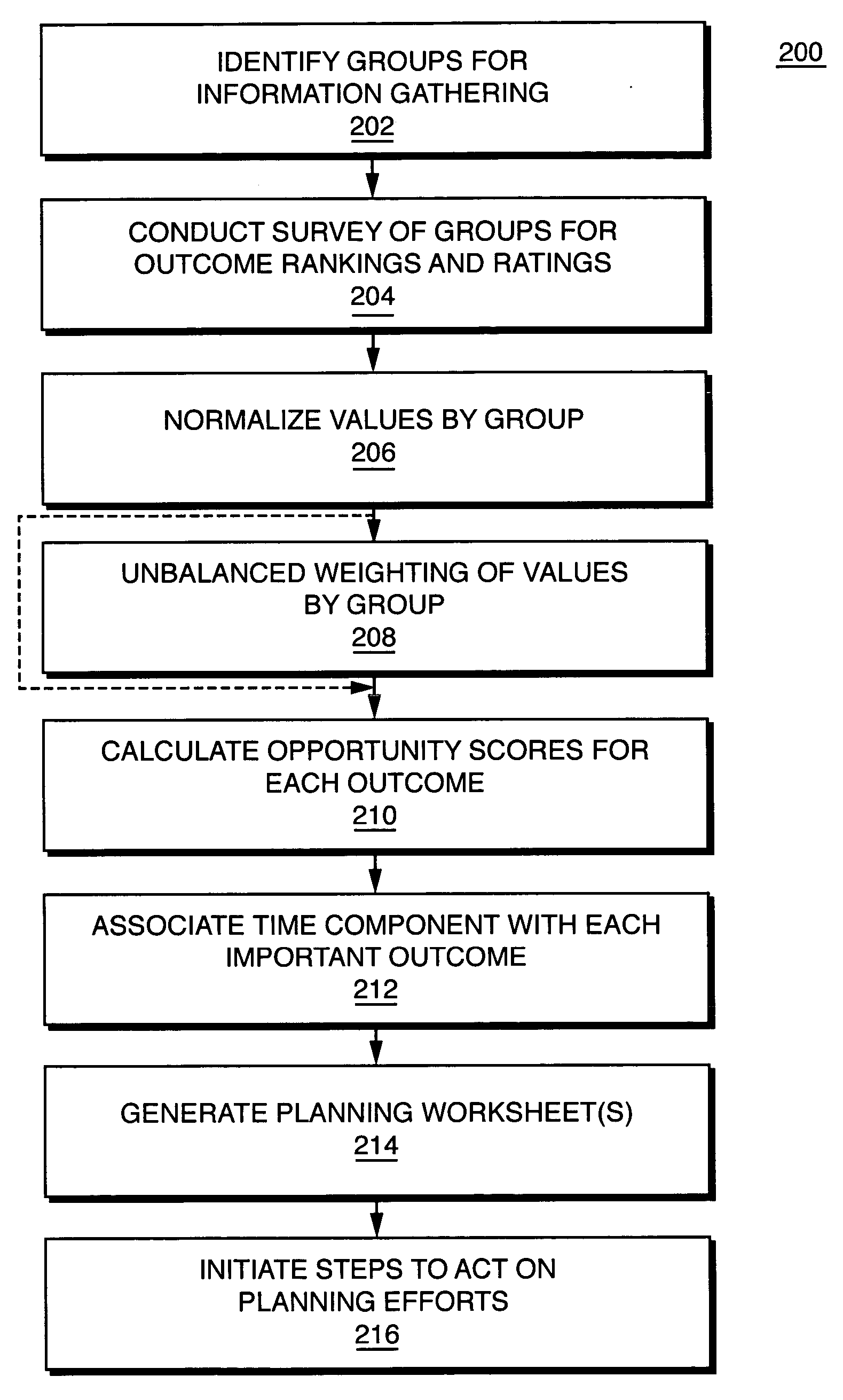
System and method to improve operational status indication and performance based outcomes
InactiveUS20060259338A1Improve accuracyMore rigorMarket predictionsResourcesDashboardProgram planning
A system and related method to assist a business in evaluating the rapid response to one or more product fabrication bid requests. The system includes a survey function for gathering information from individuals of identified groups. The information includes assigned values associated with a plurality of defined outcomes. The system also includes a calculation function to calculate opportunity scores associated with the values obtained for the outcomes through the survey function. A reporting function of the system applies the calculated opportunity scores to a visual representation, such as an innovation dashboard, of those outcomes that may be modified with the best chance of producing a positive effect on the status of the business. An optional function of the system is a planning function including worksheets to define steps to undertake to produce the improvements in the identified outcomes. The related method includes the steps of conducting the survey, obtaining normalized outcome rating and ranking values, optionally weighting those values by surveyed group, and calculating opportunity scores for each outcome. The method further includes the steps of reporting the calculated opportunity scores and by time weighted outcome groups and thereby identifying areas of the business to be improved with measurable impact.
Owner:TIME WISE SOLUTIONS
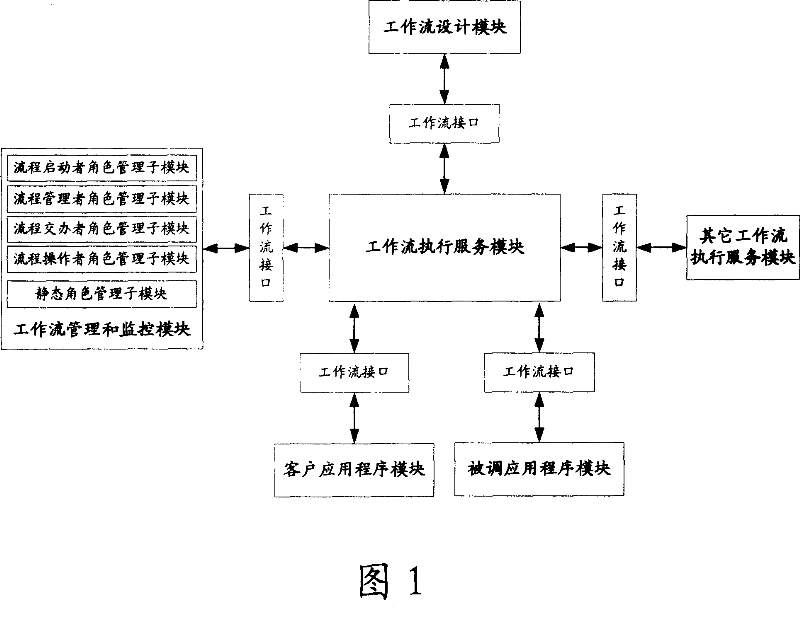
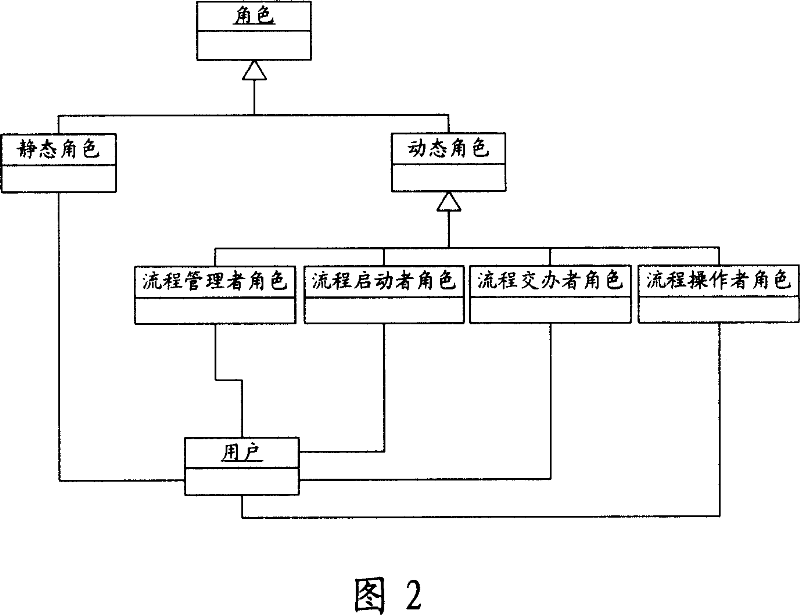
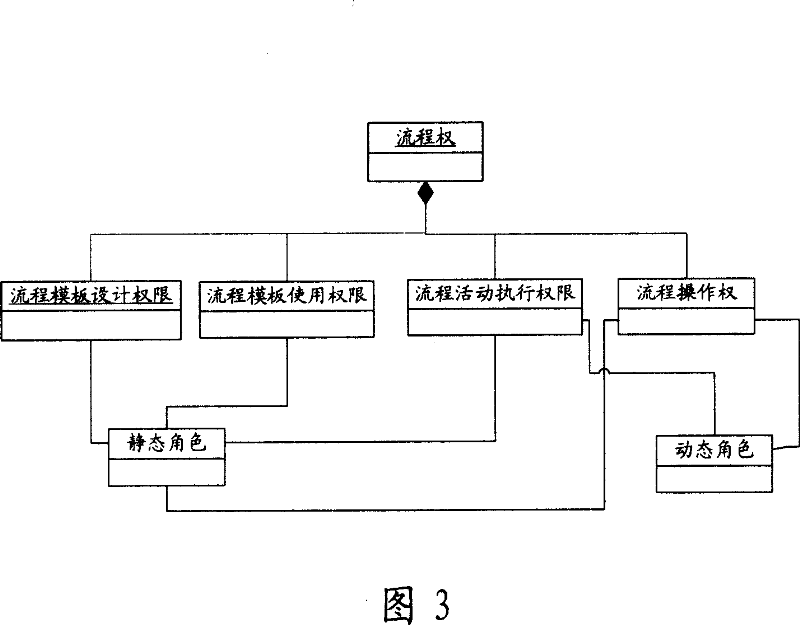
System for controlling flow process authority of task stream management system and implement method thereof
A flow authority control system of the workflow management system, wherein a character management module comprises a dynamic character management module consisting of sub-modules for managing the flow starter character, the flow manager character, the flow handler character, and the flow operation. A workflow execution service module receives the flow request from the client side, when the flow request is to start a new flow, then setting the flow starter character and the flow manager character, when the flow request is to obtain the current flow task, then calling the correspondent dynamic character sub-modules, setting the flow executors of the next link, when the flow request is to obtain the flow operation right, calling the dynamic character management sub-modules to obtain the flow operation that the designated characters are entitled to use, merging the flow operation results, endowing the flow operation right to the user according to the result concentrated data. By adopting the dynamic character module to control the flow authorization mechanism, the flow right control becomes more flexible and strict.
Owner:NEW FOUNDER HLDG DEV LLC +2
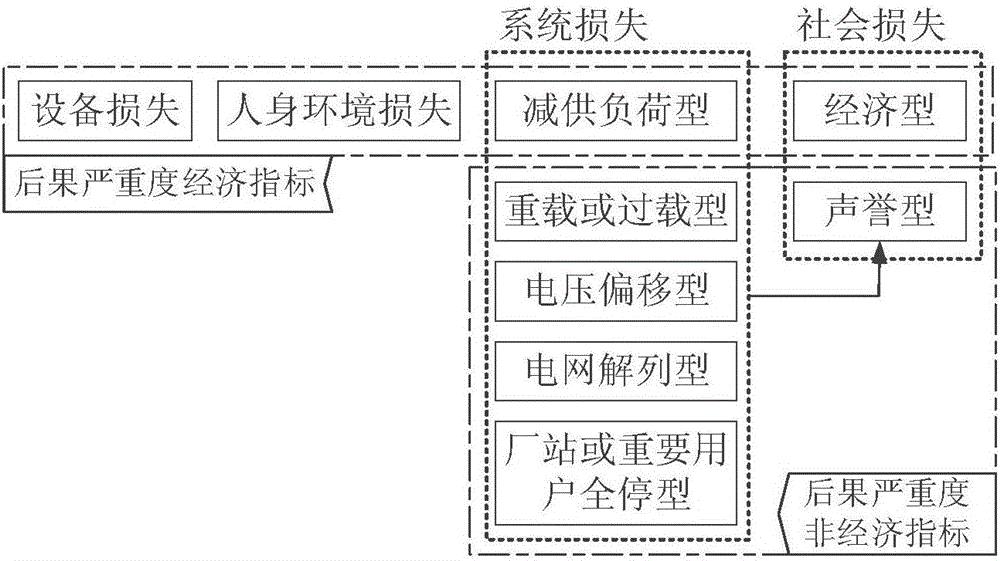
Power transmission and transformation equipment maintenance priority ordering method based on maintenance risk premium
ActiveCN106384210AImprove persuasivenessImprove rigorResourcesInformation technology support systemSystem informationPower grid
The invention provides a power transmission and transformation equipment maintenance priority ordering method based on a maintenance risk premium. The method comprises the following steps of acquiring information of power transmission and transformation equipment, collecting and analyzing environment information, system information and equipment information of equipment required in an equipment risk source identification step and an equipment risk evaluation step; identifying a power transmission and transformation equipment risk source, performing identification and classified quantization on uncertain factors and safety hazards in the equipment by means of the information which is acquired in the information acquisition step, establishing an equipment operation stopping model; performing equipment fault result severity evaluation, performing topology analysis and trend calculation on a power grid according to an equipment operation stopping condition and fault probability of each set of operation equipment, simulating a power grid operation scene, and evaluating comprehensive result severity of the power grid after the fault of the equipment; and performing equipment maintenance ordering based on the maintenance risk premium for setting an equipment maintenance priority ordering problem on the condition of limited maintenance resource, and supplying theoretical and technological supports for maintenance arrangement. The power transmission and transformation equipment maintenance priority belongs to the field of power transmission and transformation equipment maintenance.
Owner:GUIYANG POWER SUPPLY BUREAU OF GUIZHOU POWER GRID CO LTD
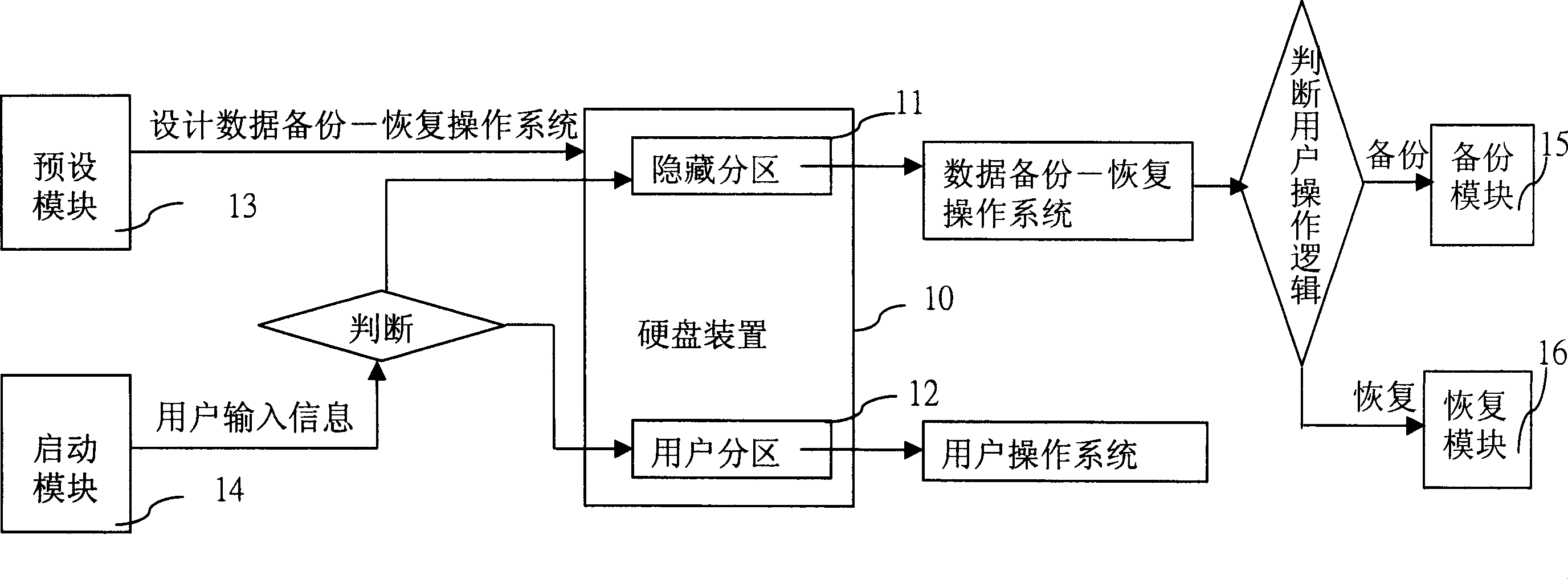
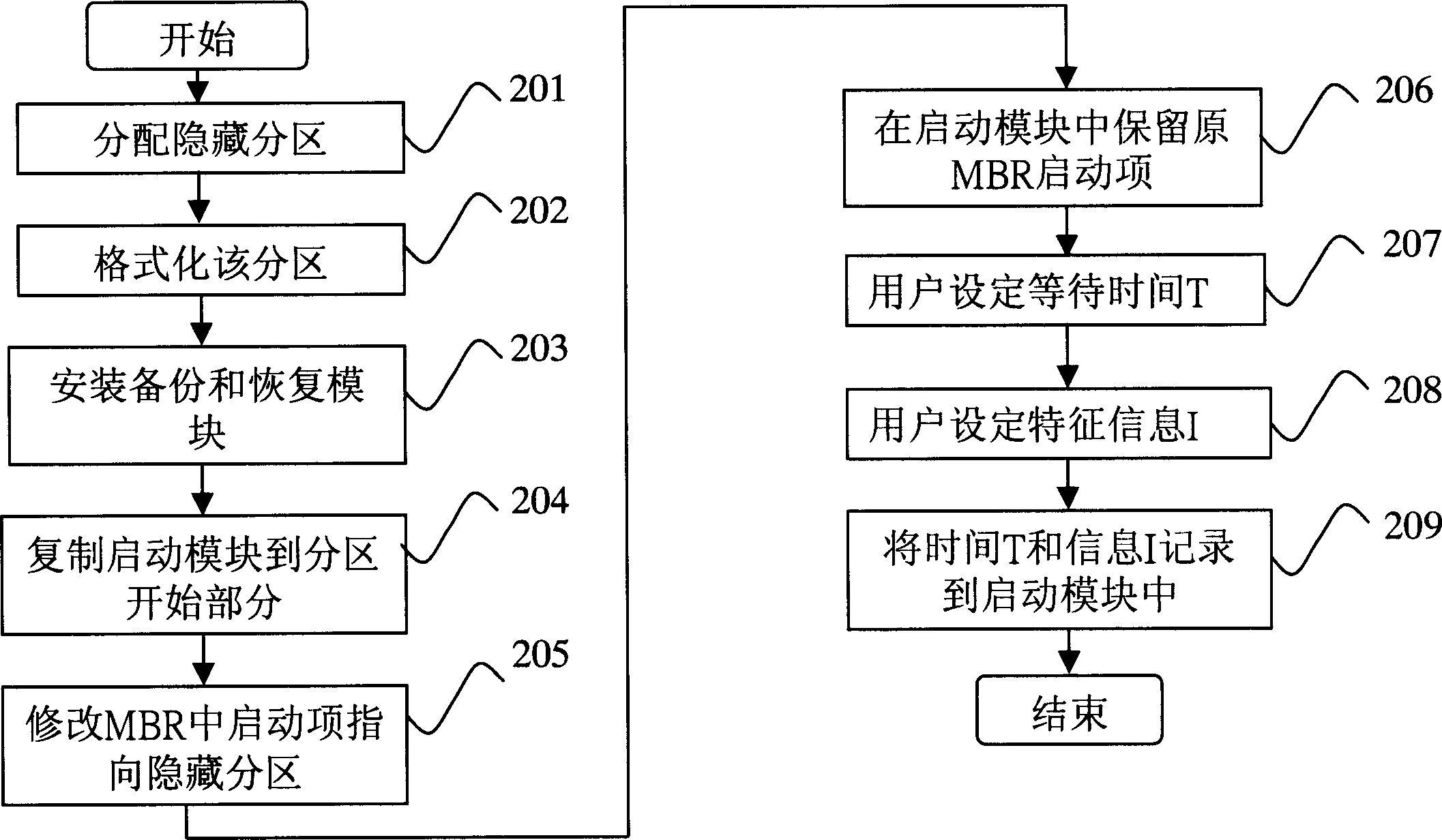
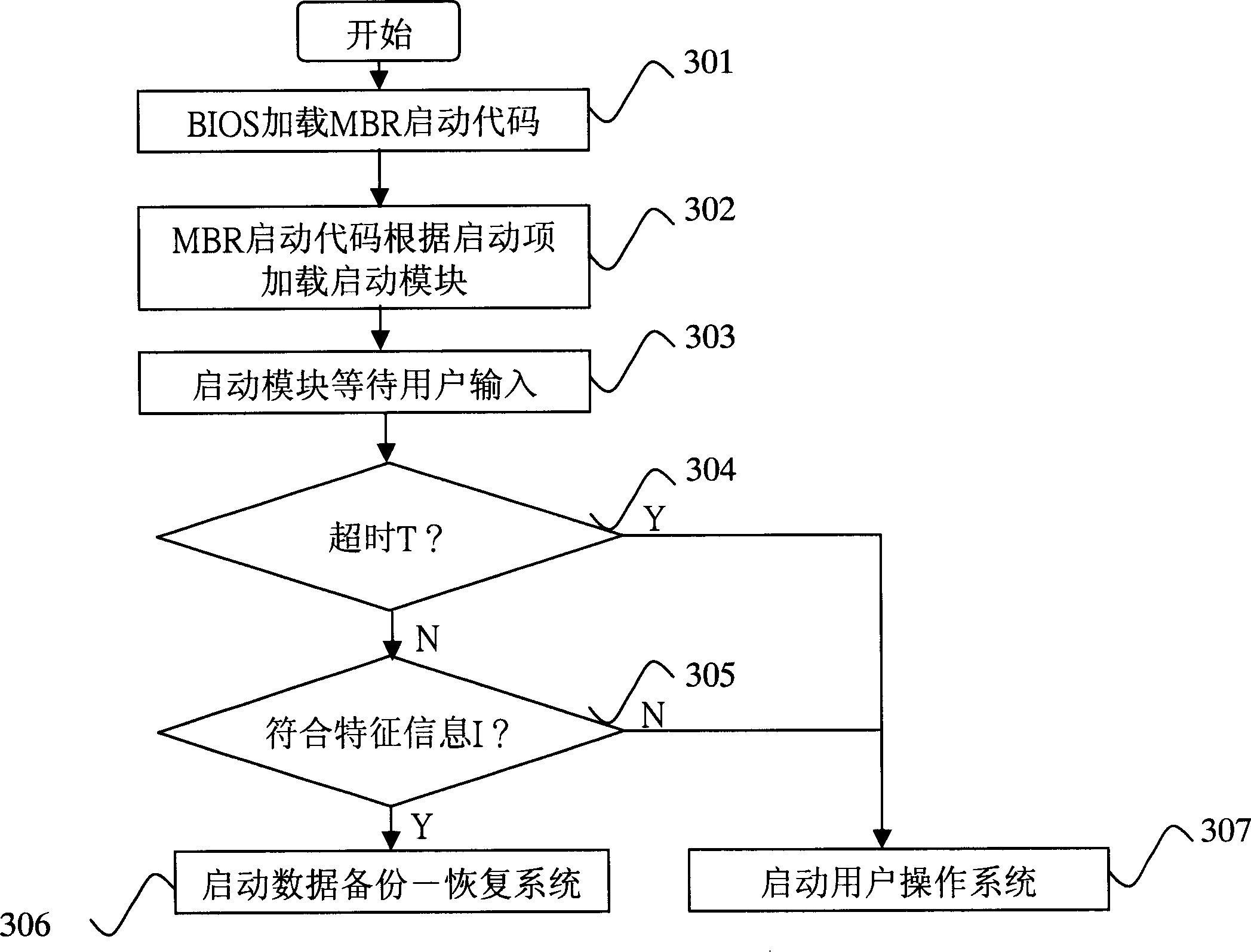
Data backup/recovery system under cold start mode and implementing method therefor
InactiveCN1877539AImplement backupAchieve recoveryProgram loading/initiatingRedundant operation error correctionStaringData information
The invention discloses a system and a method for copying and restoring data in cold-starting mode. The method comprises separating the hard disk into hidden partitions and customer partitions for copying and restoring user data information. The inventive system comprises a pre-setting module for setting a data copy / restore system on the hidden partitions; a starting module for judging computer staring type according to user inputting information after system BIOS starting, and deciding whether to start data copy / restore system according to the judging results; a copy module set in the data copy / restore system for copying data information in customer partition into the hidden partition; and a restore module set in the data copy / restore system for restoring data information in the hidden partition to the customer partition.
Owner:INVENTEC CORP
Vehicle configuration method of vehicle diagnostic device
InactiveCN101197022AAdapt to the future needs of developmentComplete configurationData processing applicationsEngineeringAutomotive engineering
The present invention relates to a vehicle configuration method of automobile diagnosis instruments and comprises the following steps: firstly, a configuration database is provided; after automobile final assembly is finished, a characteristic key is generated according to the configuration demands of an automobile controller; the characteristic key corresponds to configuration information of the automobile controller; the controller corresponding to the automobile is configured through the characteristic key; secondly, when the configuration information of the automobile controller needing to be configured is updated, the configuration information of the corresponding controller is updated in the configuration database; thirdly, when the automobile is maintained, the characteristic key is read, and the configuration database is inquired through the characteristic key; if the configuration information of the controller is updated, the updated configuration information of the controller is written into the corresponding controller of the automobile. Compared with the prior art, the present invention can perform unified efficient management to the configuration information of controllers of vehicles in all types, which improves the flexibility, integrity, tightness and diagnosis efficiency of controller configuration.
Owner:SAIC MOTOR
Device for monitoring stray current of novel subway
InactiveCN101226682ARealize the function of online automatic monitoringImprove accuracyElectric signal transmission systemsElectrical batteryHardware modules
Novel subway stray current automatic monitoring system comprises that a plurality of stray current online automatic monitoring devices which are utilized as local monitoring slave machines are connected with a remote monitoring main machine. A switch power module, a data collecting module, an Ethernet communication module, an auxiliary hardware module and a man-machine interactive module are arranged on the same PCB printing circuit board around the processor of the system. The switch power module is internally-equipped with an EMC filter with high-performance. A / D transformation circuit employs bipolar and 12 bit A / D transducer MAX197 which is internally equipped with 8 ways sample-taking passages. The auxiliary hardware module comprises an EEPROM secondary permanent storage module, a hardware watchdog circuit, a self-contained battery calendar clock module and a serial port communication interface circuit. The invention simplifies the structure of the system, enables data sharing, information fusion and synergic observation among slave machines, which greatly strengthens the accuracy and tightness of the monitoring of the stray current, additionally, the cost of the monitoring device is reduced.
Owner:TONGJI UNIV
Construction method for assembly type annular reinforcement buckling concrete shear wall system
ActiveCN105863275AGuarantee the construction qualityImprove rigorBuilding material handlingRebarFloor slab
The invention discloses a construction method for an assembly type annular reinforcement buckling concrete shear wall system. The construction method comprises the steps that prefabricated outer walls, prefabricated inner walls, prefabricated composite floor slabs, composite prefabricated air conditioner slabs and prefabricated stairs are transported to a construction site; prefabricated inner wall components of the first storey are lifted, corrected and fixed; the prefabricated air conditioner slabs, bay windows and molding bottom slabs of the first storey are lifted, corrected and fixed; prefabricated outer wall components of the first storey are lifted, corrected and fixed; prefabricated bay windows of the first storey are lifted, corrected and fixed; composite layer reinforcements of the first storey are bound; bottom beams and composite slabs of the first storey are subjected to cast-in-place concrete construction; cast-in-place columns and bay window components of the first storey are subjected to cast-in-place concrete construction; prefabricated component installation is conducted for outer molding of the first storey; the composite slabs of the upper layer are installed; and the steps above are conducted repeatedly till construction of the top storey is finished. By the adoption of the construction method, the construction quality can be guaranteed, and the assembly leakproofness is improved; and meanwhile, the construction time is shortened, and construction is accelerated.
Owner:CHINA CONSTR SEVENTH ENG DIVISION CORP LTD
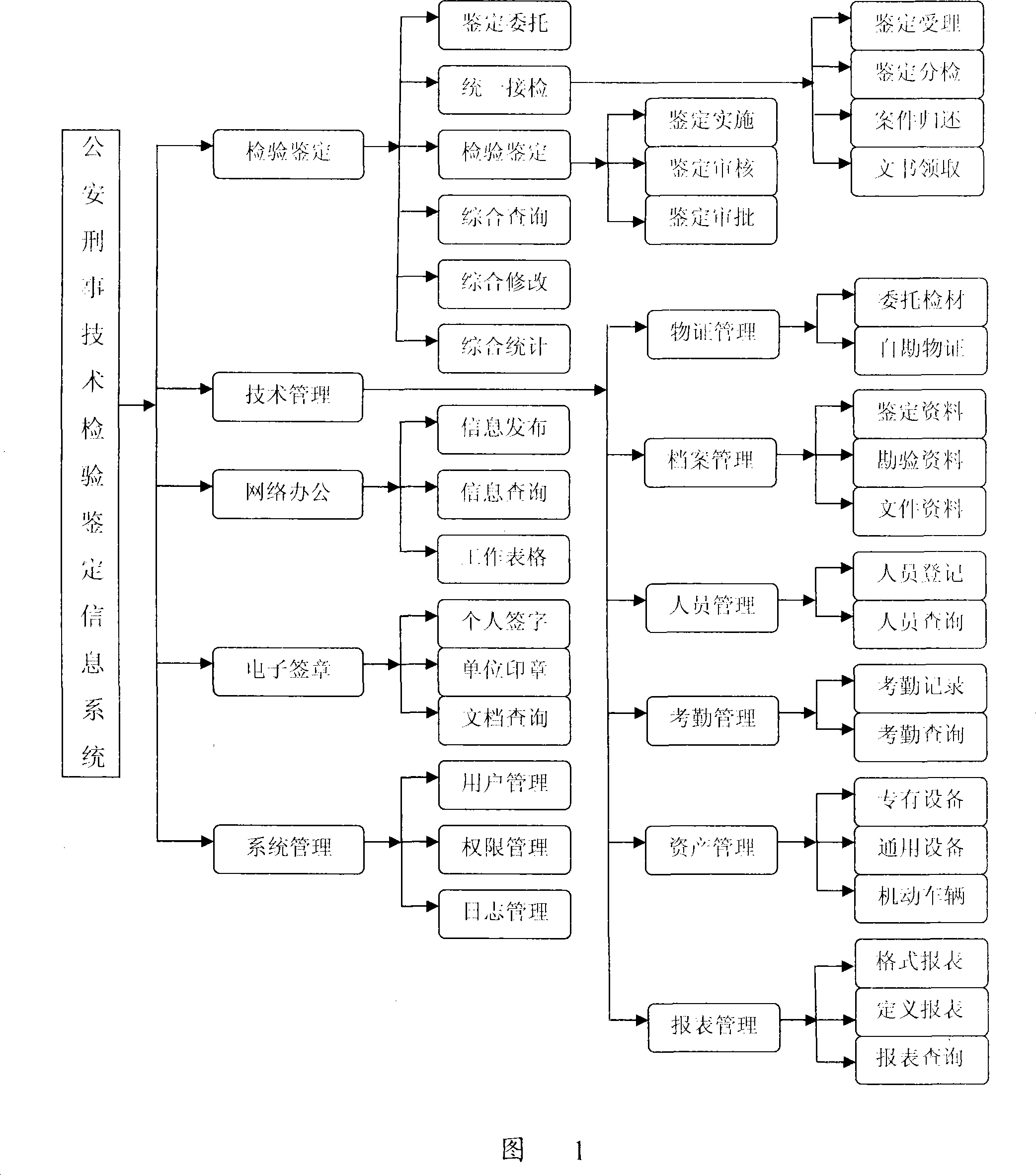
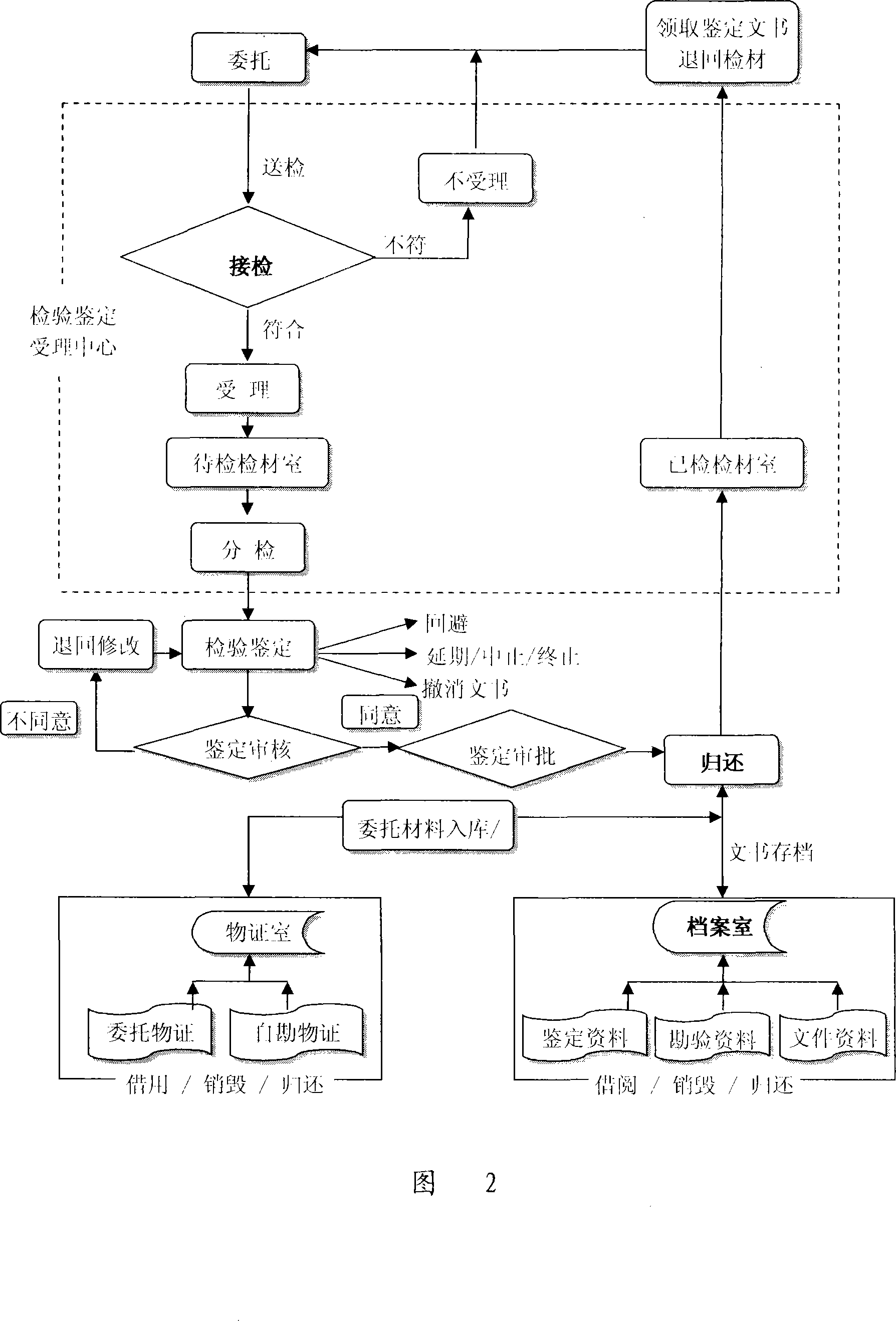
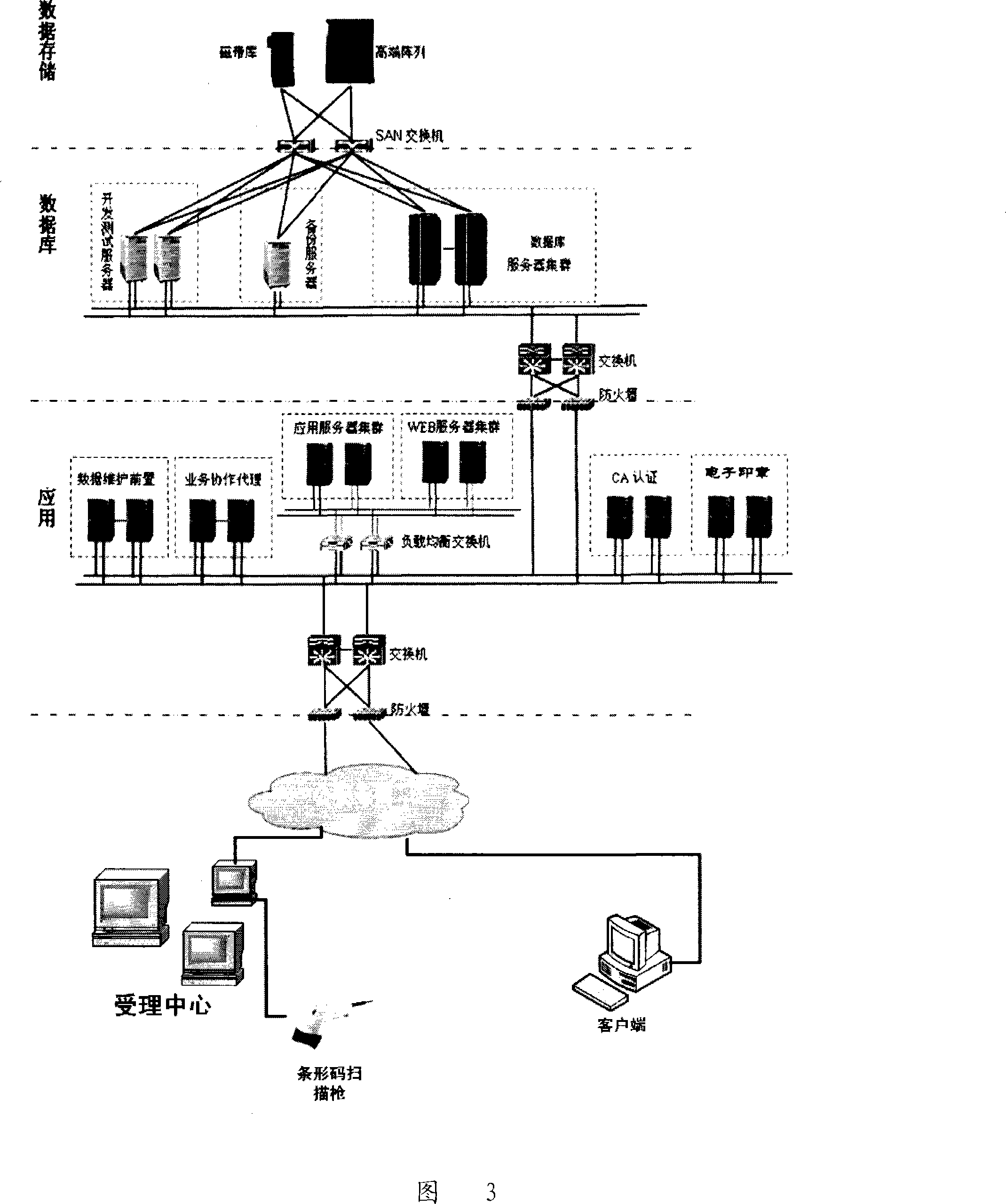
Police criminal technology inspection and appraisal information system and method thereof
The present invention provides an information system and a method of public security criminal technical inspection and identification. The method has the following procedures: authorizing identification, accepting the authorized identification, delegation of inspection of cases, implementing identification, professional verification, administrative examination and approval, returning the cases, picking up documents, keeping material evidences, filing the documents, integrated modification, integrated inquiry, integrated statistics, working out statistical forms, personnel management, managing the assets, attendance management, network office operation, and system management. The system comprises three levels, wherein, a first level is application, comprising application of dual-server clustering and WEB server dual-clustering; a second level is database which takes two highly functional servers as the database clustering servers and uses independent exchanger equipment; a third level is data storage, adopting an EMC high-end array. The present invention can meet the needs of the criminal technical inspection and identification for a public security system.
Owner:深圳市物证检验鉴定中心
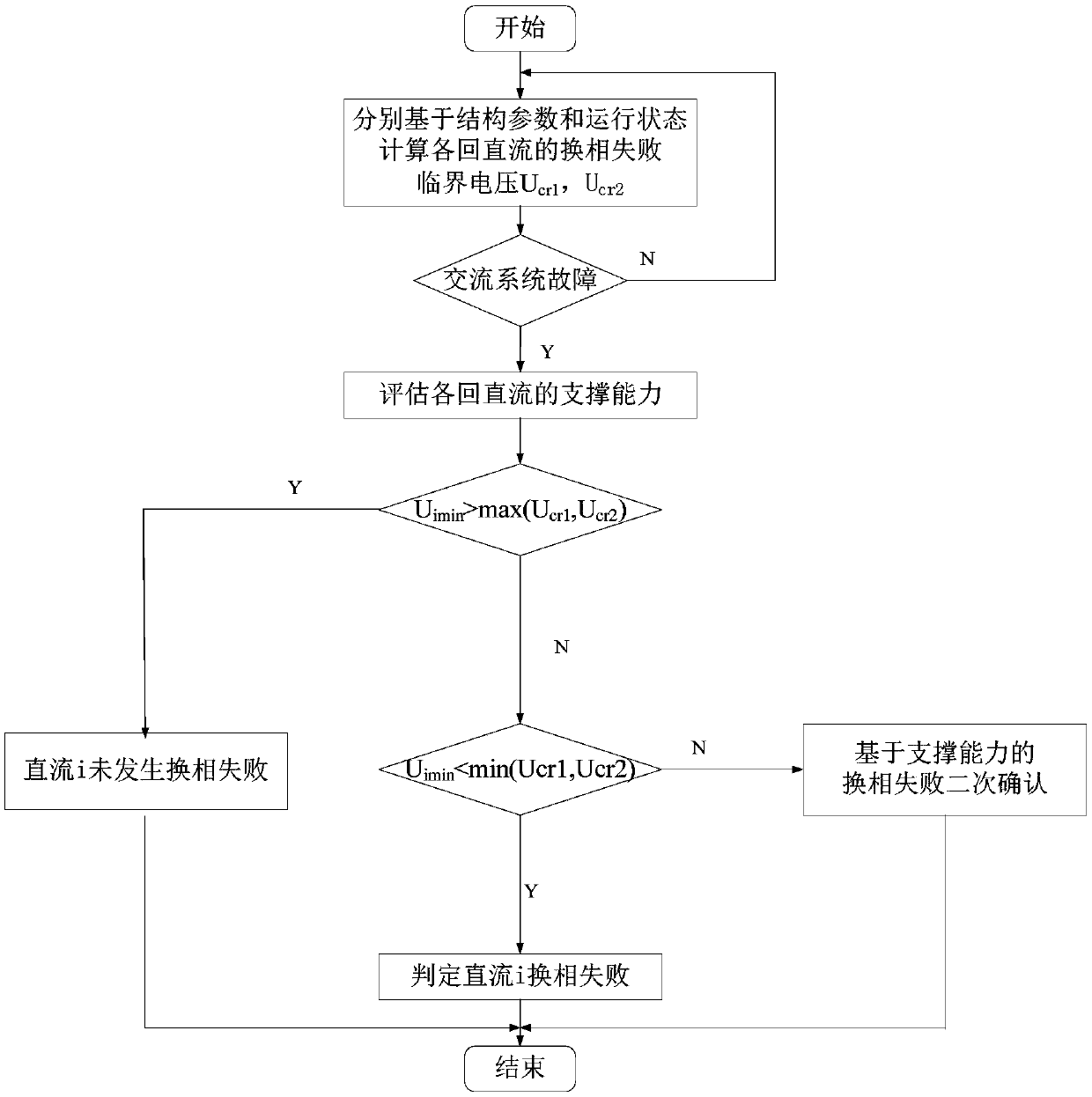
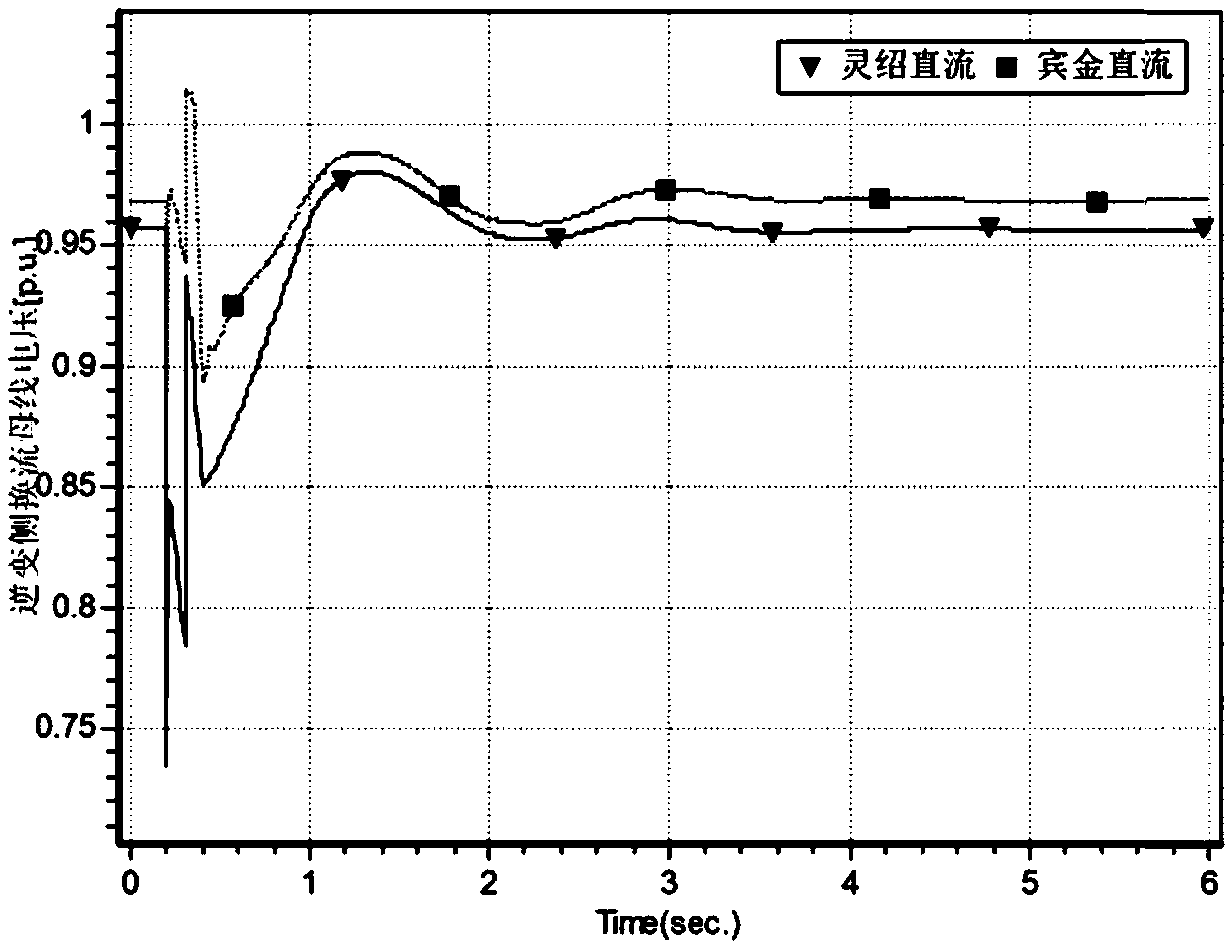
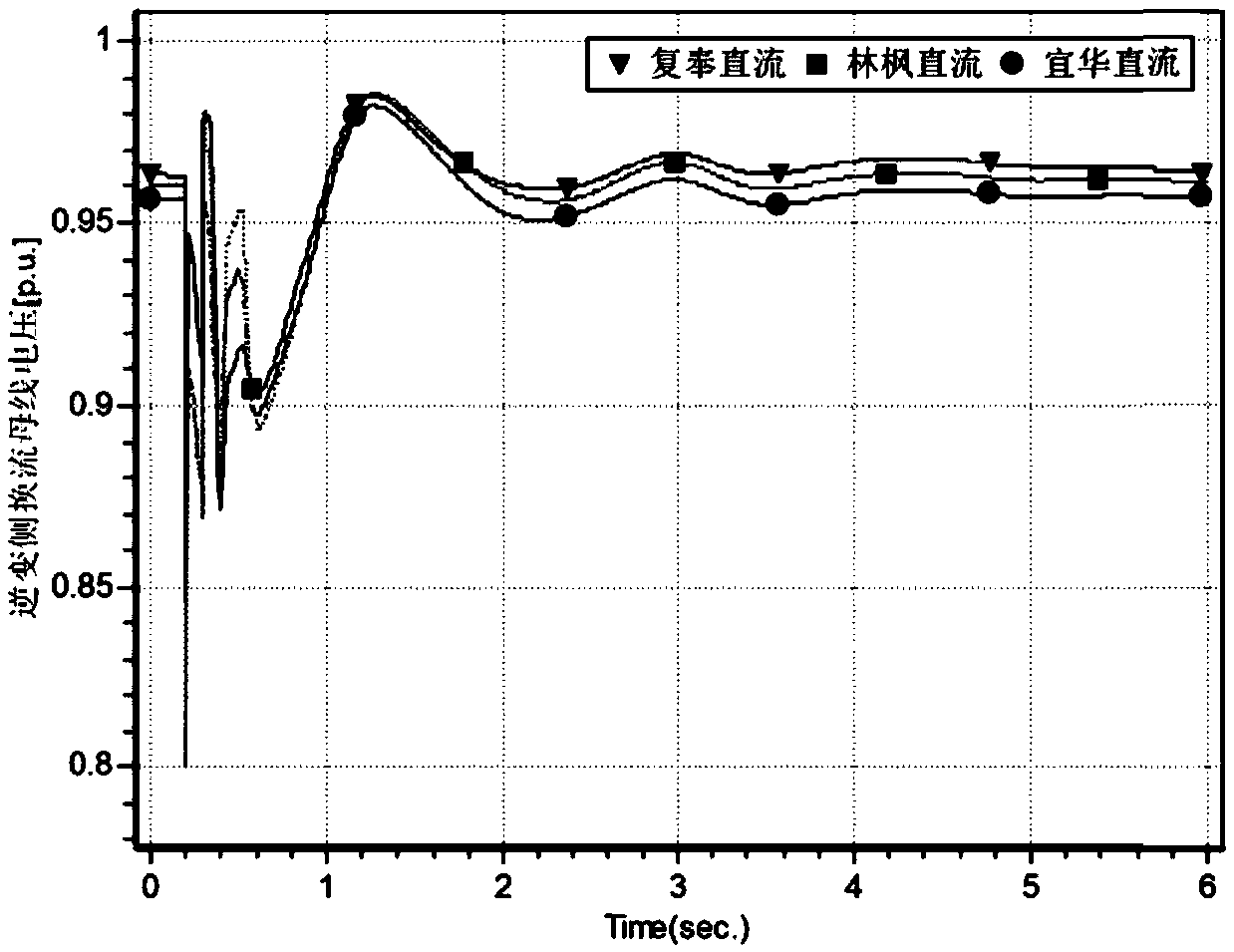
Estimation method for DC support capability and commutation failure of multi-infeed DC system
InactiveCN109617107AImprove accuracy and rigorImprove accuracyElectric power transfer ac networkElectrical distanceCritical voltage
The invention discloses an estimation method for DC support capability and commutation failure of a multi-infeed DC system. According to an existing estimation method, the change of a DC current is not considered when a critical commutation failure voltage is deduced, and the accuracy is remained to be discussed. The estimation method discloses by the technical scheme comprises the steps of firstly, deducing a critical commutation bus voltage of each DC commutation failure according to a structure parameter and a running state of the system; secondly, determining the support capability of eachdirect current according to self impedance of the commutation bus, electrical distance of a fault point and multi-infeed short-circuit rate; and finally, estimating a commutation failure condition ofeach direct current according to a critical voltage and the support capability. During estimation of the support capability, factors such as multi-infeed short-circuit ratio and the electrical distance of the fault point are simultaneously considered, and the commutation failure critical voltage is comprehensively determined from two aspects of the system structure and the running state; and compared with an existing estimation method, the DC support capability and the commutation failure can be more accurately reflected.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +3
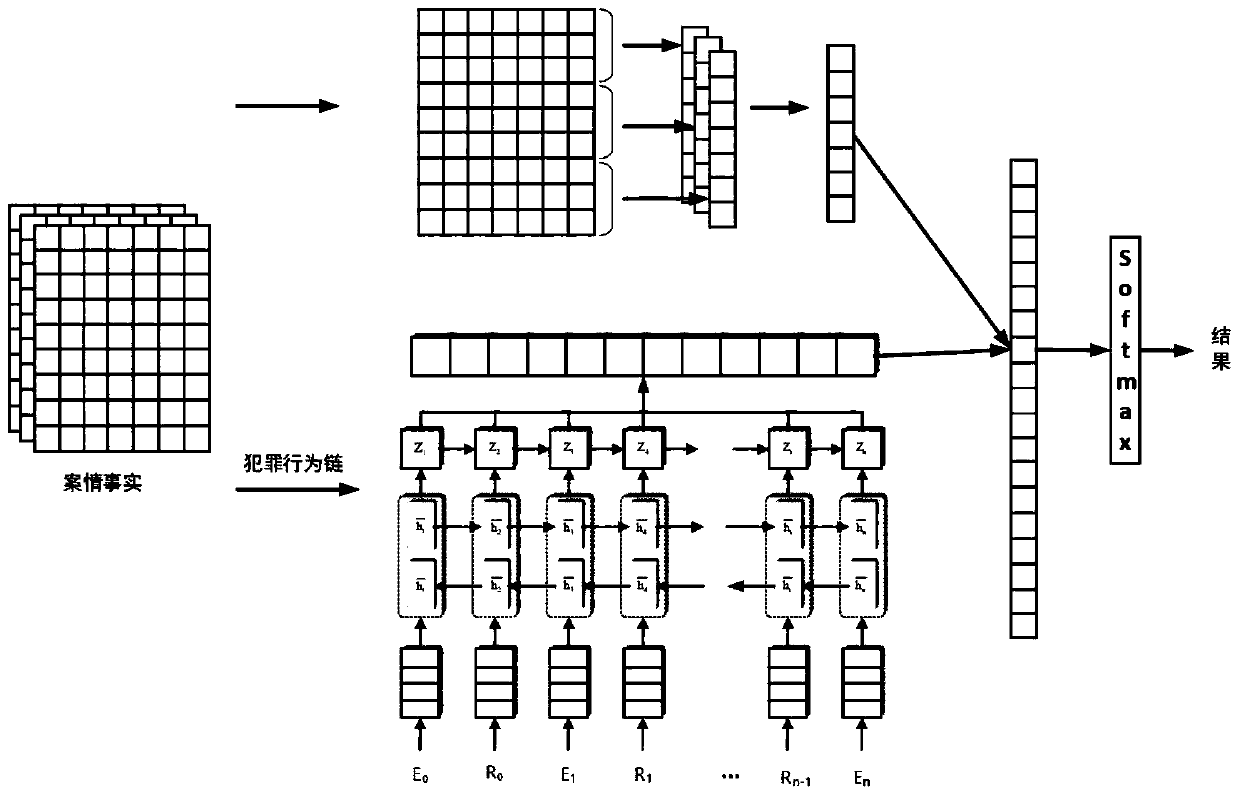
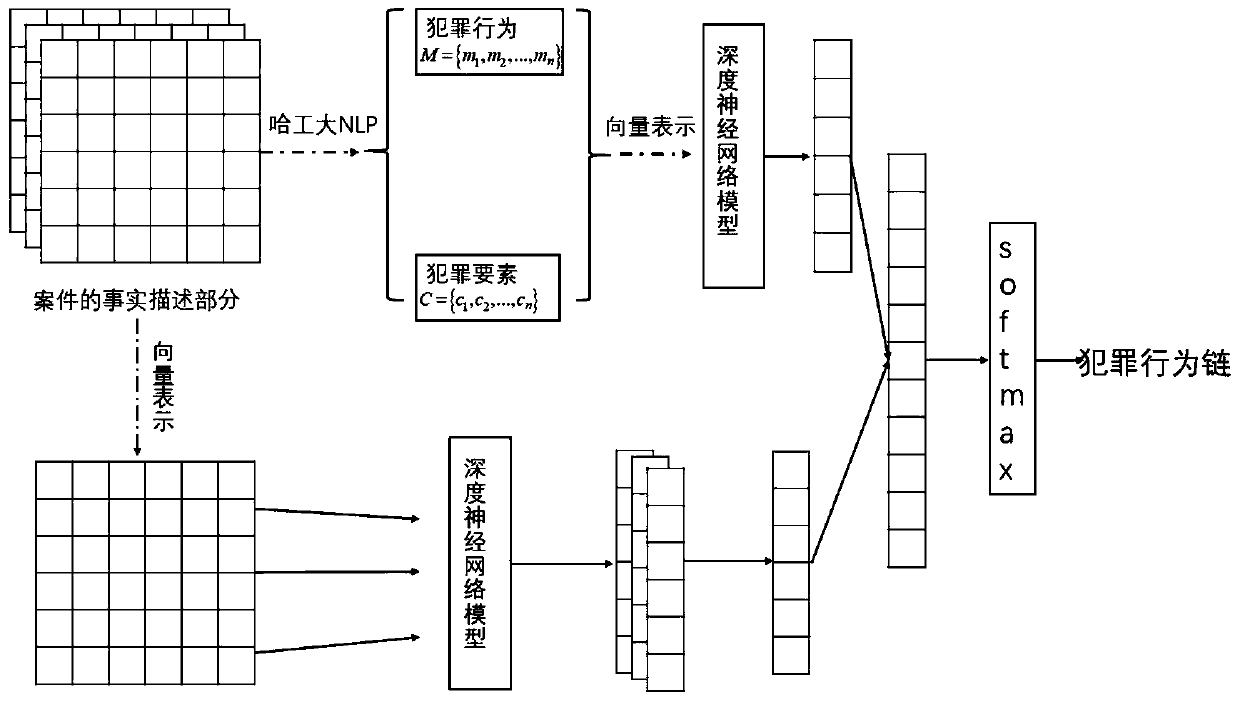
Judgment document analysis method based on criminal behavior chain
InactiveCN110457479ARaise the importanceAlleviate the sparsity problemNeural architecturesSpecial data processing applicationsDocument analysisText categorization
The invention discloses a judgment document analysis method based on a criminal behavior chain, and the method comprises the following steps: step 1, extracting information from the fact description of a case, declaring the concept and construction rule of the criminal behavior chain, and constructing the criminal behavior chain; step 2, obtaining semantic information from fact description of a case by using a TextCNN; step 3, based on the criminal behavior chain, performing vector representation on the criminal behavior chain by using a Bi-LSTM method, and performing text classification; andstep 4, proposing a judgment document analysis method of a neural network structure for splicing and outputting a result of the TextCNN method and a result of the Bi-LSTM method, wherein an identification result can be used for supporting various auxiliary judgment applications. According to the method disclosed by the invention, the associated information of the criminal behavior chain is fully utilized, the defects of a traditional legal judgment document analysis method are avoided, the judgment document analysis efficiency is improved, and a technical support is provided for solving modelsand methods for assisting judgment such as legal provision recommendation and class case pushing.
Owner:GUIZHOU UNIV +2
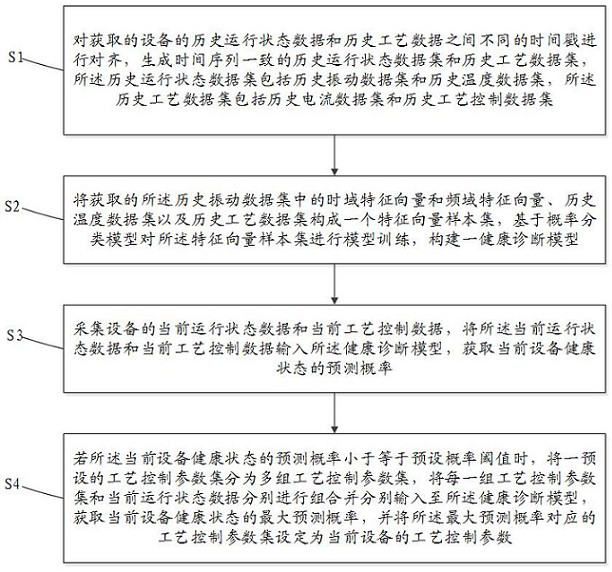
Industrial equipment control optimization method and system based on monitoring data
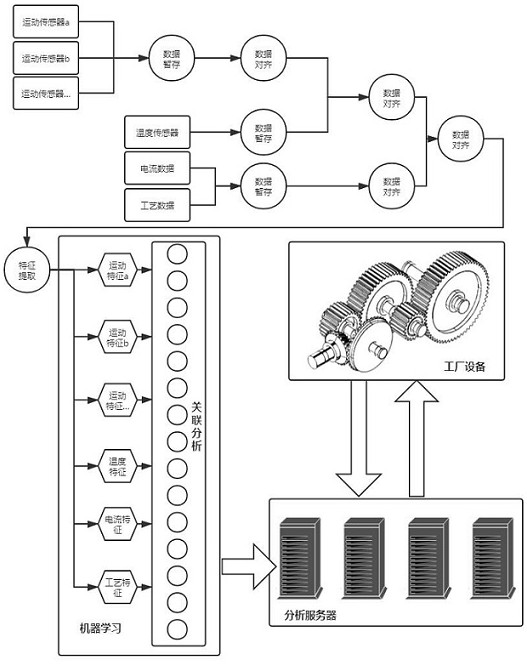
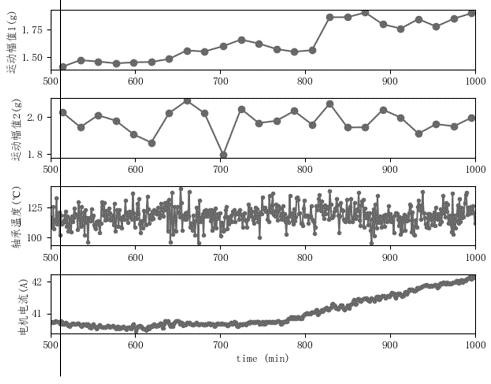
ActiveCN112198857ASolve the problem of timestamp out of syncImprove rigorTotal factory controlProgramme total factory controlData setIndustrial equipment
The invention discloses an industrial equipment control optimization method based on monitoring data. The industrial equipment control optimization method comprises the steps of: aligning different timestamps between historical operation state data and historical technological data, and generating a historical operation state data set and a historical technological data set which are consistent intime sequence; carrying out model training on the formed feature vector sample set, and constructing a health diagnosis model; inputting current operation state data and current process control datainto the health diagnosis model, and acquiring the prediction probability of a current equipment health state; if the prediction probability is less than or equal to a probability threshold, dividinga process control parameter set into multiple groups of process control parameter sets, inputting each group of process control parameter set and current operation state data combination into the health diagnosis model, and acquiring the maximum prediction probability of the current equipment health state; and setting the process control parameter set corresponding to the maximum prediction probability as process control parameters of current equipment. According to the n industrial equipment control optimization method and the system, the operation state of the equipment can be analyzed morecomprehensively.
Owner:浙江中自庆安新能源技术有限公司
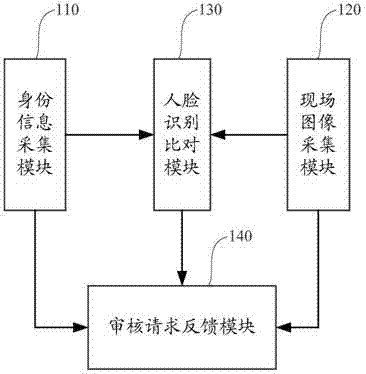
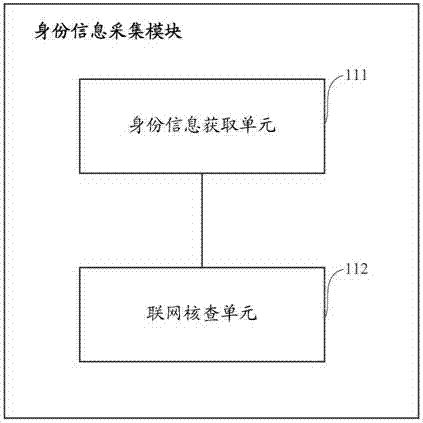
Self-service card distributing device and identity authentication system there and identity authentication method therefor
InactiveCN105447367AImprove rigorImprove securityFinanceDigital data authenticationAuthentication systemSelf-service
The present invention dscloses a self-service card distributing device, and an identity authentication system and an identity authentication method therefor. The identity authentication system comprises: an identity information acquisition module, for acquiring effective identity information of a customer; a live image acquisition module, for acquiring facial image information of the customer; a face recognition and comparison module, for comparing image information of the effective identity information of the customer with the acquired facial image information, and obtaining a face recognition and comparison result; and an auditing request feedback module, for requiring to audit the effective identity information of the customer, obtaining the facial image information and the face recognition and comparing result, and obtaining an examination result. According to the self-service card distributing device and the identity authentication system and identity authentication method therefor disclosed by the present invention, the interference and influence of artificial examination are greatly reduced by automatically obtaining the effective identity information of the customer and comparing facial image of the customer, preciseness and security of opening accounts by the customer are significantly enhanced, thereby protecting legal benefits of the customer and banks.
Owner:CHINA CONSTRUCTION BANK
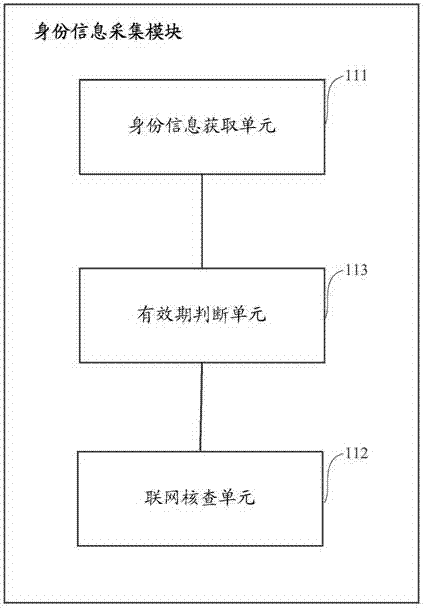
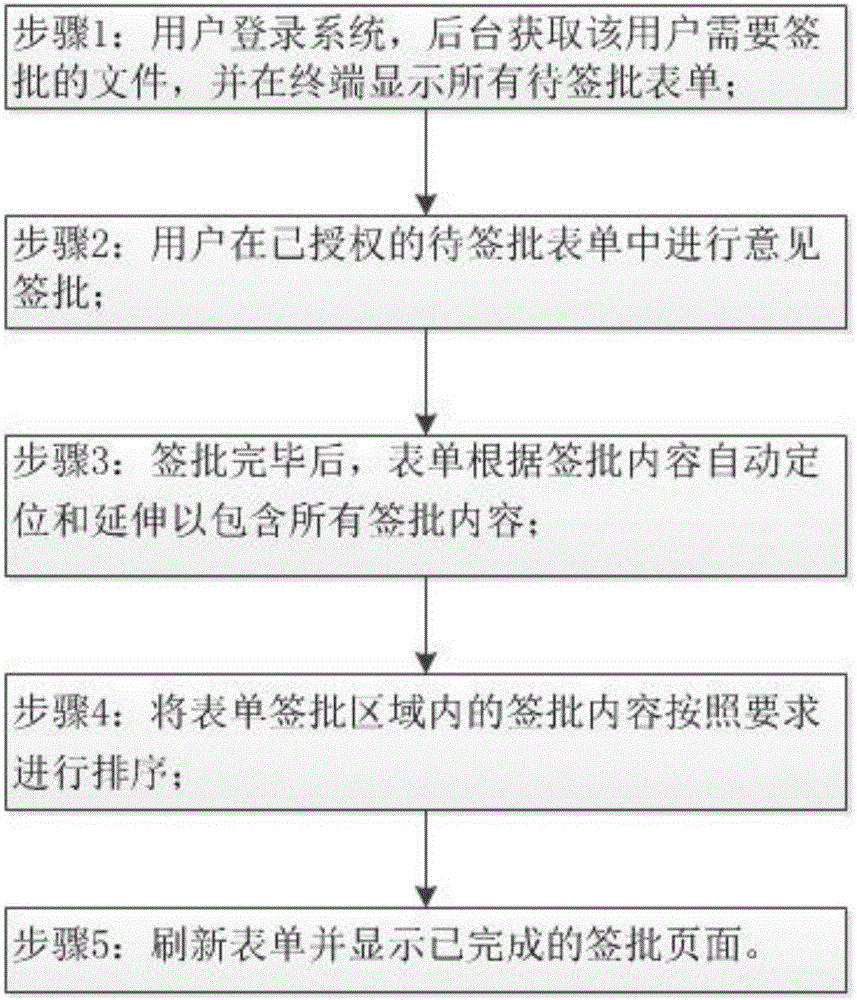
Opinion signing method and system
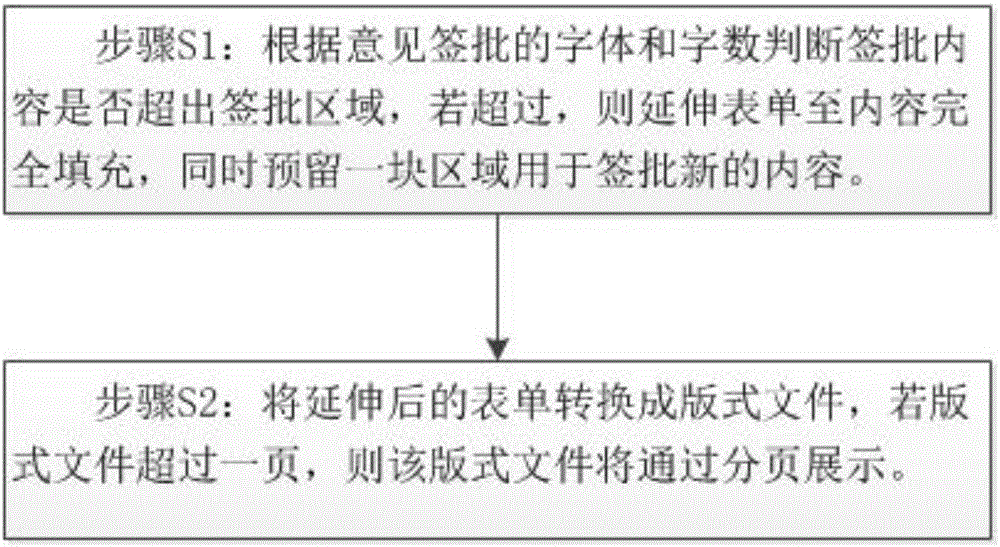
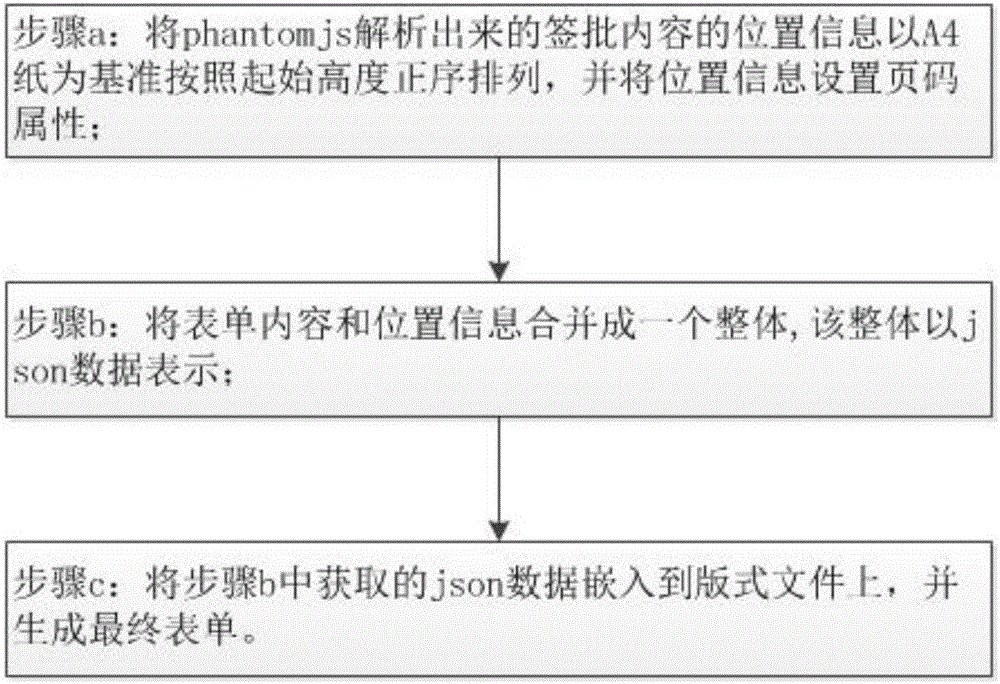
InactiveCN105913224ASolve practical problems that cannot continue to sign and approveImprove practicalityOffice automationUser needsWorld Wide Web
The invention provides an opinion signing method and system. The method comprises the following steps: a user logs onto a system, an interaction server obtains files that the user needs to sign, all forms to be signed are displayed on a display part, the user signs opinions on authorized forms to be signed, the forms are automatically positioned and extended to include all signing content according to signing content after signing, signing content in form signing zones is ordered according to requirements, and finally the forms is refreshed and finished signing pages are displayed. Correspondingly, the invention also provides an opinion signing system which comprises the display part, the interaction server, a parsing part and an execution part. According to the opinion signing method and system, the forms can be automatically extended, singing content of clients can be automatically identified at the same editing zone, signing opinion can be modified in a centralized manner, the signing content can be ordered according to certain rules, and opinion signing procedures can be standardized.
Owner:JIANGSU ZHONGWEI TECH SOFTWARE SYST
Vacuum cup vacuumizing device and working principle of vacuumizing device
InactiveCN104891051AImprove sealingImprove rigorPackagingDrinking vesselsPulp and paper industryLaser
The invention discloses a vacuum cup vacuumizing device and a working principle of the vacuumizing device. The vacuum cup vacuumizing device comprises a vacuum cup, a sealing clamp, a vacuumizing joint and a laser welding machine. The vacuum cup is made of metal, and a gap is formed in the bottom of the vacuum cup; the sealing clamp is used for clamping the vacuum cup, and the vacuum cup is connected with the sealing clamp through a mounting opening; the vacuumizing joint is arranged on the sealing clamp and used for vacuumizing the interior of the vacuum cup fixed to the sealing clamp and is connected to a vacuum machine table; and the laser welding machine is used for welding the gap in the bottom of the vacuum cup so as to achieve the sealing effect. The laser welding sealing manner after vacuum is adopted, and the sealing effect can be achieved without adding of any external matter; the high temperature is adopted in lasers of laser welding to enable two same substances to be completely molten together, and the sealing performance of the sealing manner is higher than leakproofness of other any sealing manners; and long-time vacuum is not needed, through the short-time vacuum, the vacuum cup can achieve heat preservation, and the problem that the production period is long is solved.
Owner:THERMOS JIANGSU HOUSEWARES
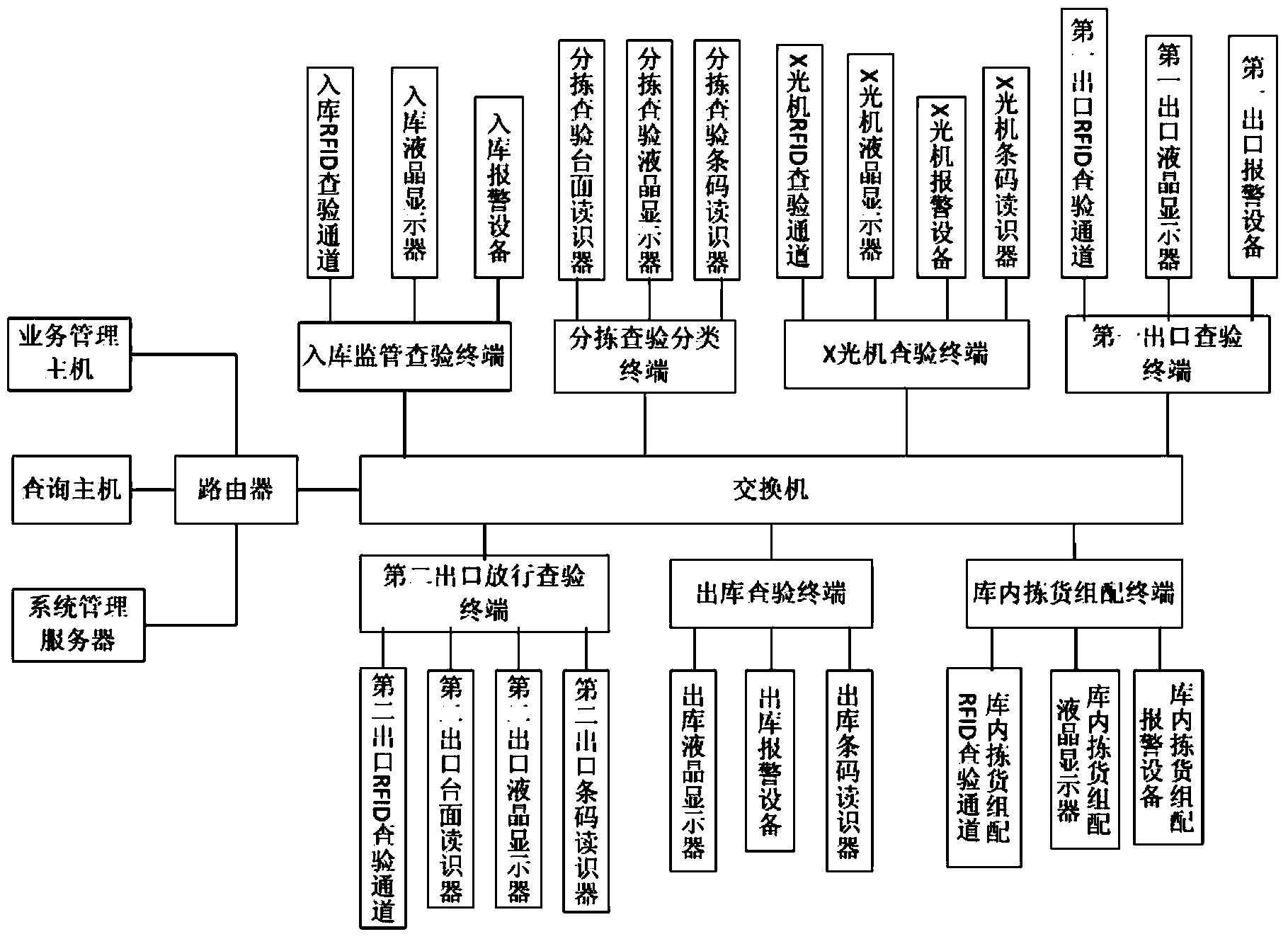
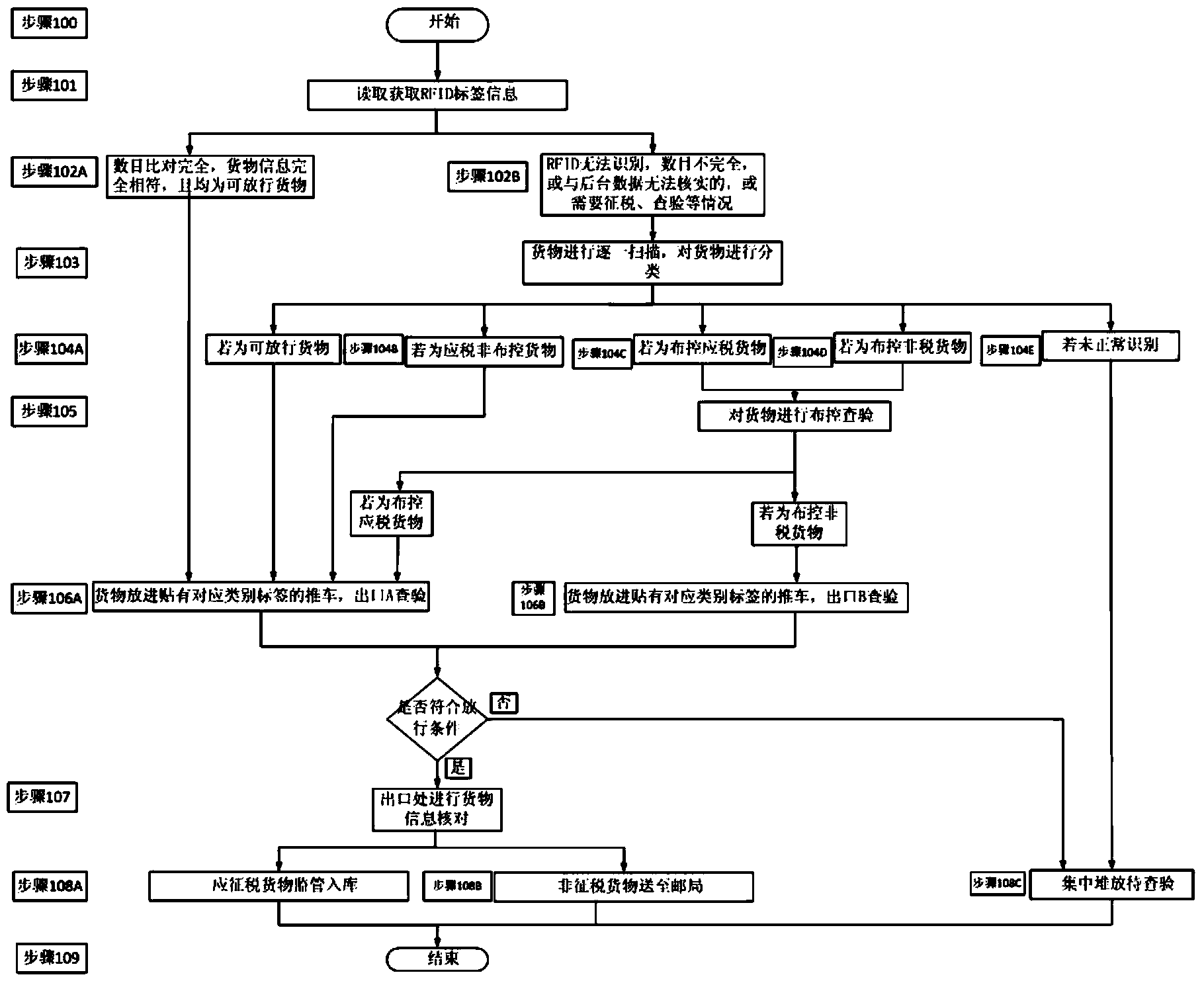
Goods checking and classifying system
The invention provides a goods checking and classifying system. The goods checking and classifying system comprises an in-warehouse supervising and checking terminal, a sorting, checking and classifying terminal, an X-ray machine checking terminal, a first exit checking terminal, a second exit release checking terminal, an ex-warehouse checking terminal, an intra-warehouse goods sorting and assembling terminal, a router and a server, wherein the in-warehouse supervising and checking terminal, the sorting, checking and classifying terminal, the X-ray machine checking terminal, the first exit checking terminal, the second exit release checking terminal, the ex-warehouse checking terminal, the intra-warehouse goods sorting and assembling terminal, the router and the server are connected with an interchanger, and the server is connected with the interchanger through the router. According to the goods checking and classifying system, the goods supervision process is informationized and standardized, workers can supervise and sort goods more efficiently, the service reformation field is further widened easily, improvement on the information construction level of a customs postal article supervision service site is promoted, in this way, the customs declaration efficiency is improved, and the operating cost is reduced for enterprises; a supervision area and the temporary warehousing condition can be mastered in real time, the level of management of imported postal articles is increased, and the law enforcement rigor is improved; information support can be provided for macroscopic decision-making, and local economic development and social stability can be better served.
Owner:TIANJIN HUIBO SCI & TECH DEV
Voice processing method, storage medium, and device
PendingCN109599114AImprove recognition accuracyImprove use valueSpeech recognitionData conversionTransformation of text
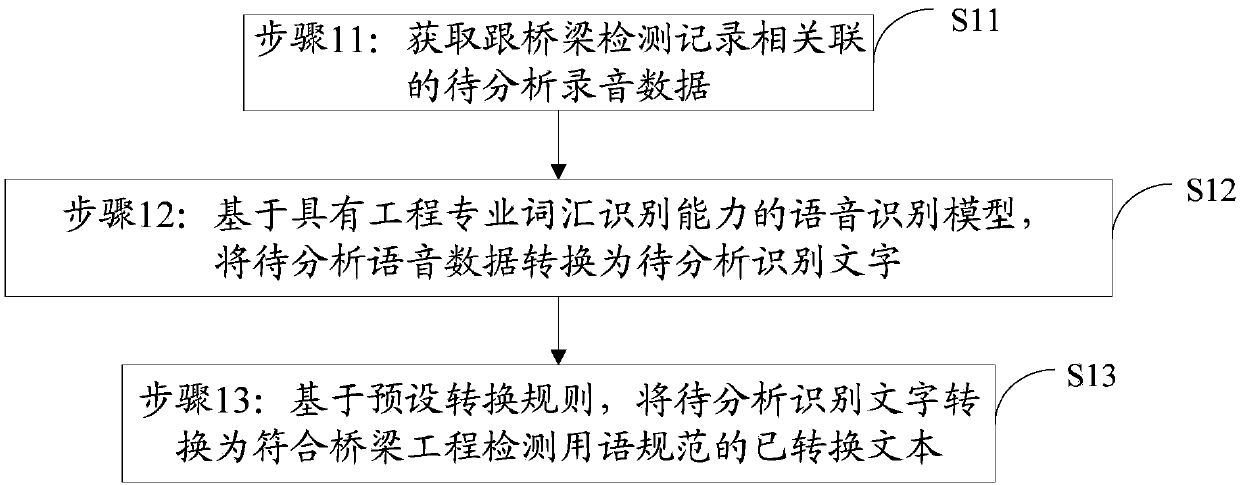
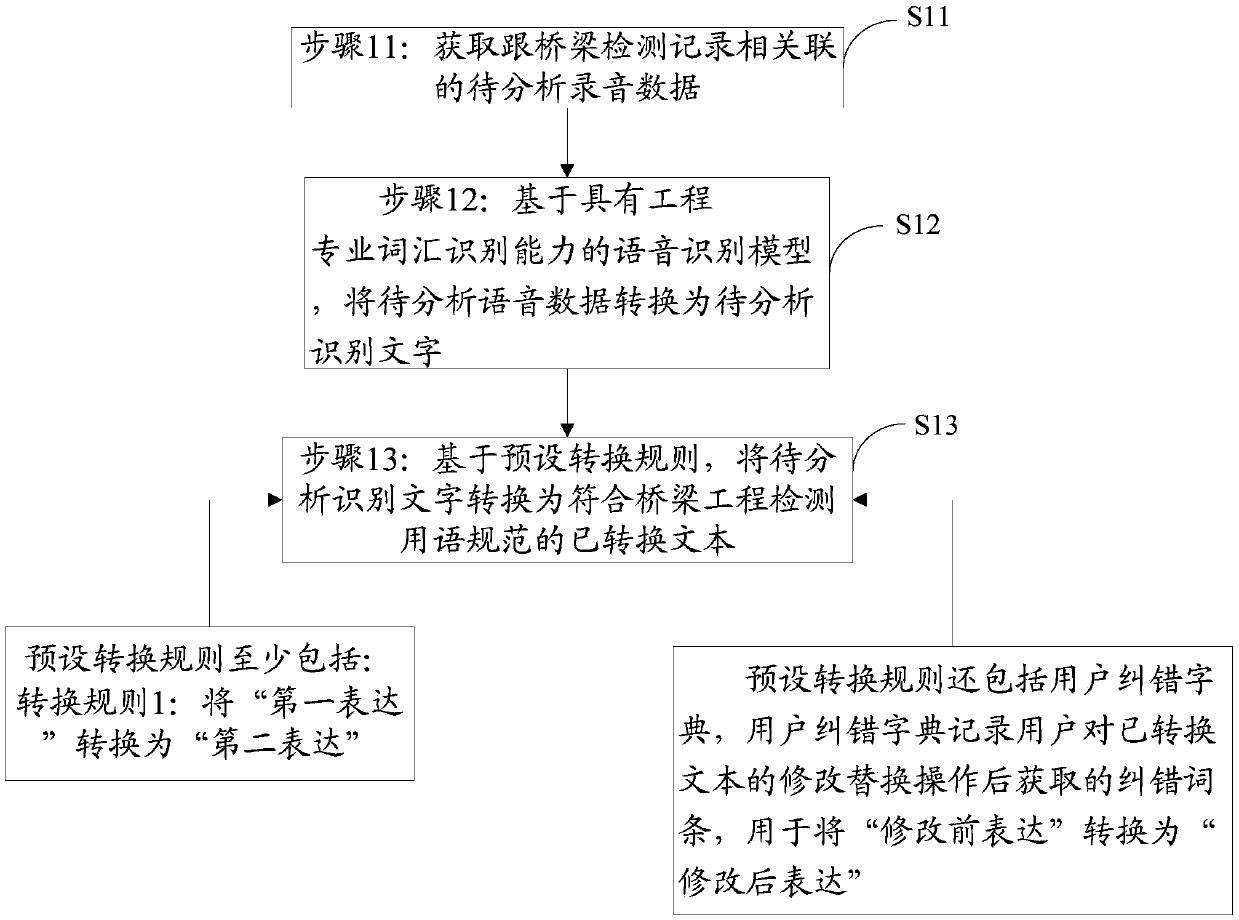
The invention provides a voice processing method, a storage medium, and a device. The voice processing method comprises following steps: step 11, sound recording data which is to be detected and is related to detection record is obtained; step 12, based on a voice identification model with engineering detection professional vocabulary identification capability, the sound recording data to be analyzed is converted into text to be analyzed; and step 13, based on preset conversion rules, the text to be analyzed is converted into converted text according with engineering detection language standards. The voice processing method is capable of increasing voice data identification accuracy, and improving expression mode preciseness in engineering detection field, outputting text according with engineering expression habits, and increasing the using value of output text..
Owner:重庆海特科技发展有限公司
Intelligent security protection system configuration method and apparatus
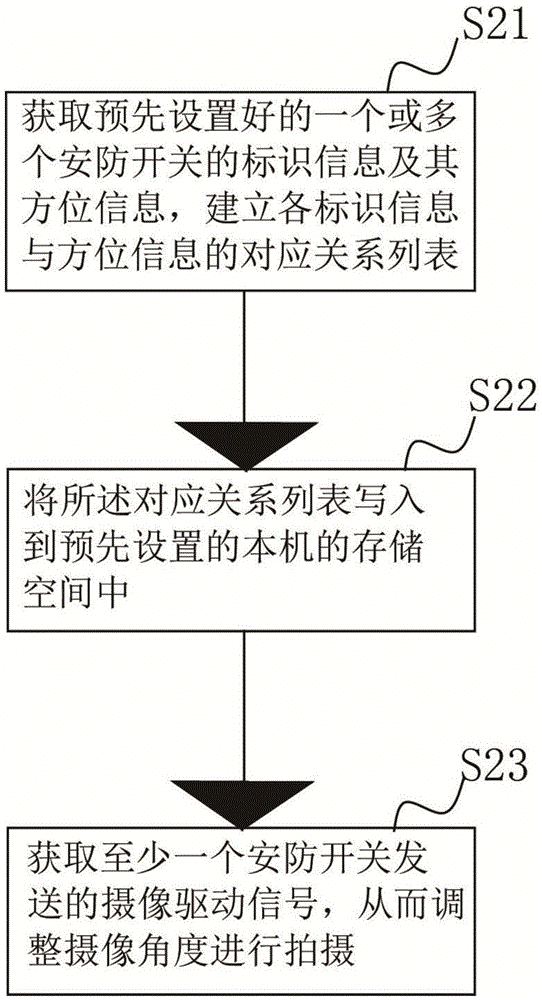
InactiveCN105530476AAchieve intelligenceAchieve pairingTelevision system detailsColor television detailsMonitoring statusSystem configuration
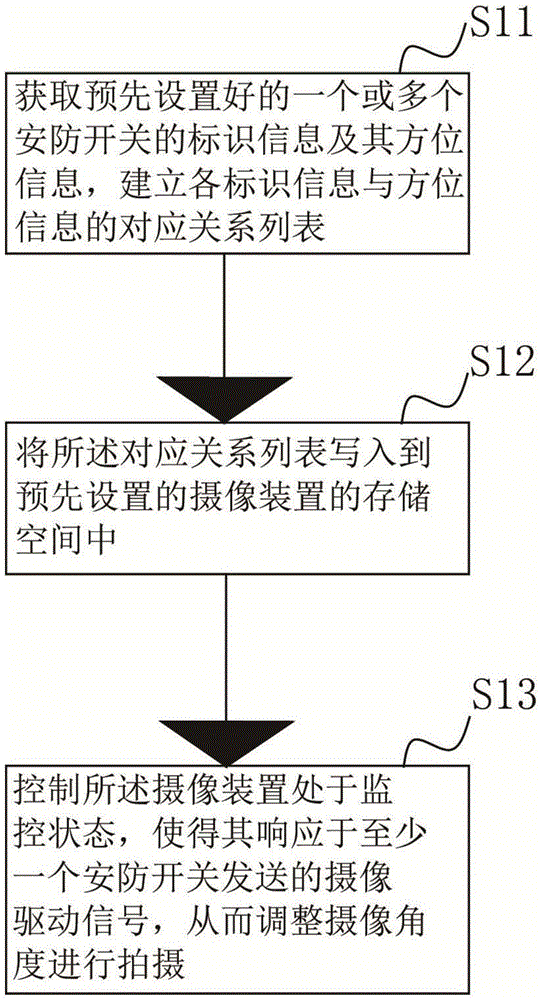
The invention provides an intelligent security protection system configuration method. The method comprises the following steps: obtaining identifier information and azimuth information of one or more preset security protection switches and establishing a list of corresponding relationships between the identifier information and the azimuth information; writing the corresponding relationship list into a storage space of a preset camera apparatus; and controlling the camera apparatus to be in a monitoring state, so that the camera apparatus can adjust a camera shooting angle to perform shooting in response to a camera shooting driving signal sent by at least one security protection switch. The invention furthermore provides an intelligent security protection system configuration apparatus. Therefore, the intelligent security protection system configuration method and apparatus can realize intelligent and efficient security protection monitoring.
Owner:BEIJING QIHOO TECH CO LTD +1
Adjustable lighting ventilator for roof shelter
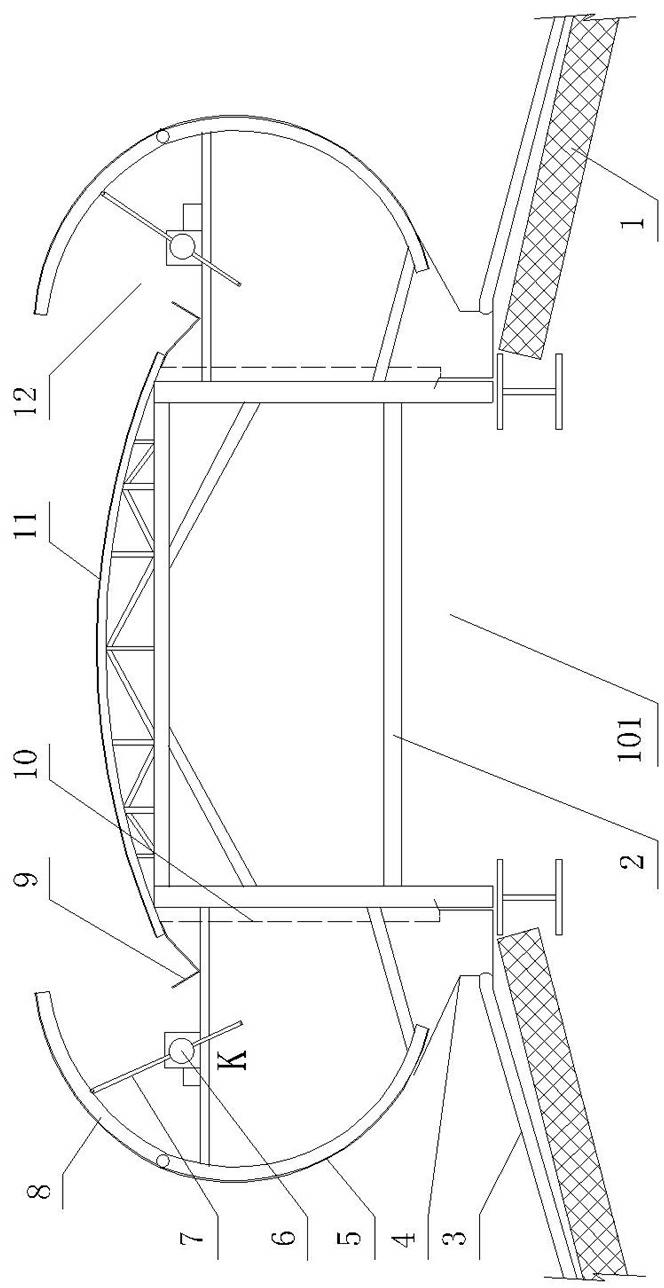
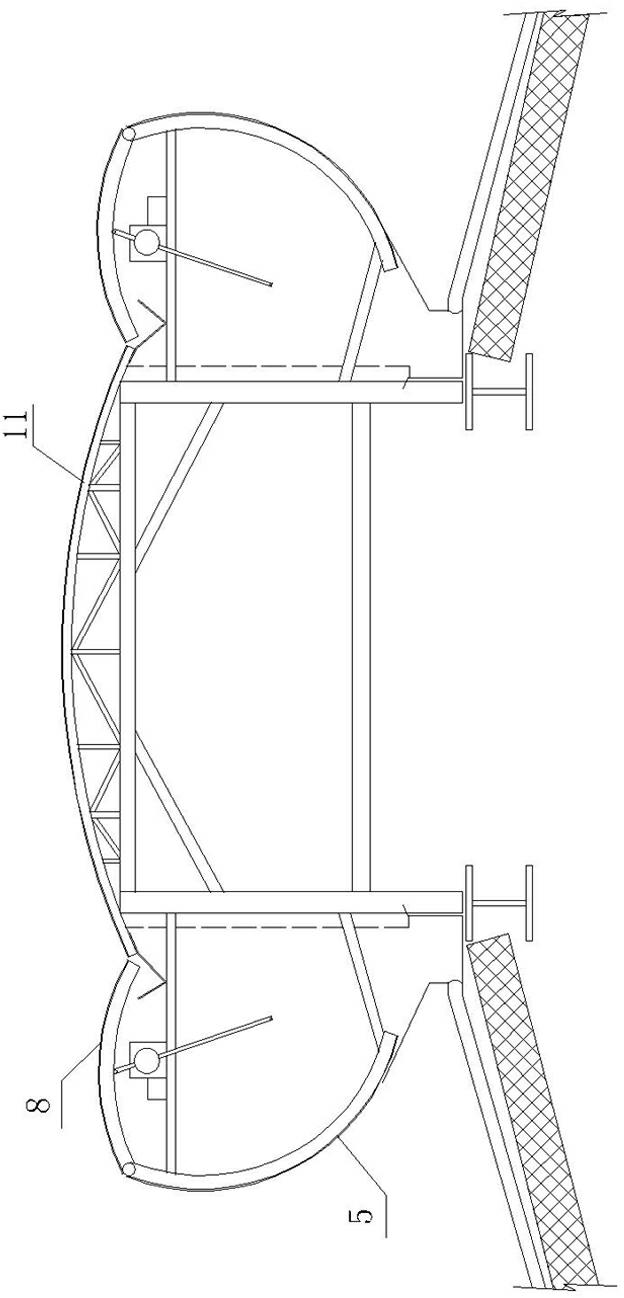
ActiveCN102297490AIncrease heightLower the altitudeLighting and heating apparatusVentilation systemsWindow openingAtmospheric sciences
The invention discloses a roof wind-sheltering adjustable lighting ventilator, which comprises a bracket, wherein the bracket is provided with a lighting rain blocking plate, an arc-shaped wind blocking plate, an air outlet and a collecting ditch. The ventilator is characterized in that: wind-sheltering valve plates are hinged on the bracket at the upper end of the arc-shaped wind blocking plate respectively; both sides of the bracket are provided with window opening machines respectively; the window opening machines are connected with the wind-sheltering valve plates respectively; the heightof the arc-shaped wind blocking plate can be increased after the wind-sheltering valve plates are opened; the overall height of the ventilator can be lowered after the wind-sheltering valve plates are closed; and a collecting groove is formed between the arc-shaped wind blocking plate and a ventilation port. The ventilator has the advantages of simple structure, capability of realizing comprehensive adjusting function, including wind sheltering, ventilating, lighting and reducing wind load damage according to the climate environment, good ventilating, wind sheltering, lighting and sealing effects, difficulty in being damaged by wind power, long service life, wide application range, applicability to civil buildings after being provided with a protective net, capability of preventing rain, snow and dust from entering rooms and polluting the environment, high safety performance, convenience for installing and maintaining and low manufacturing cost.
Owner:锦州鹏翔电力轻钢设备有限公司
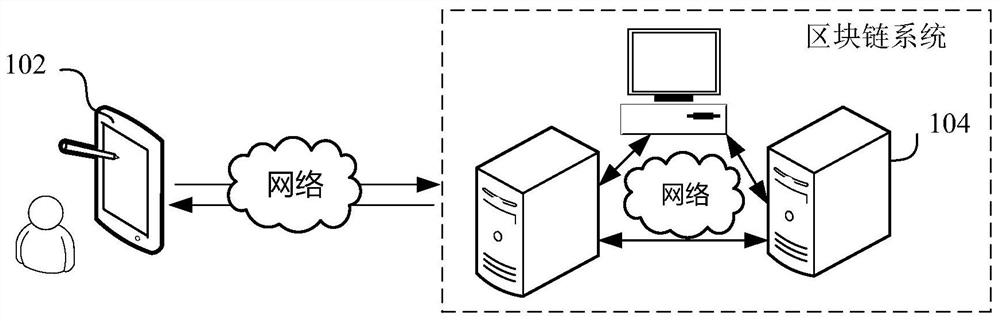
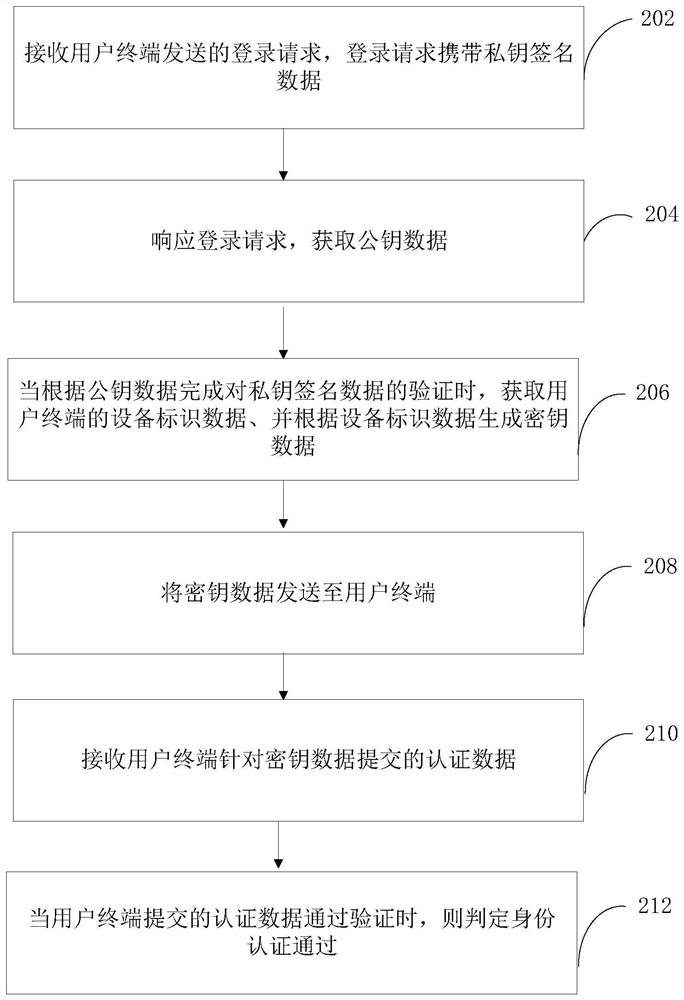
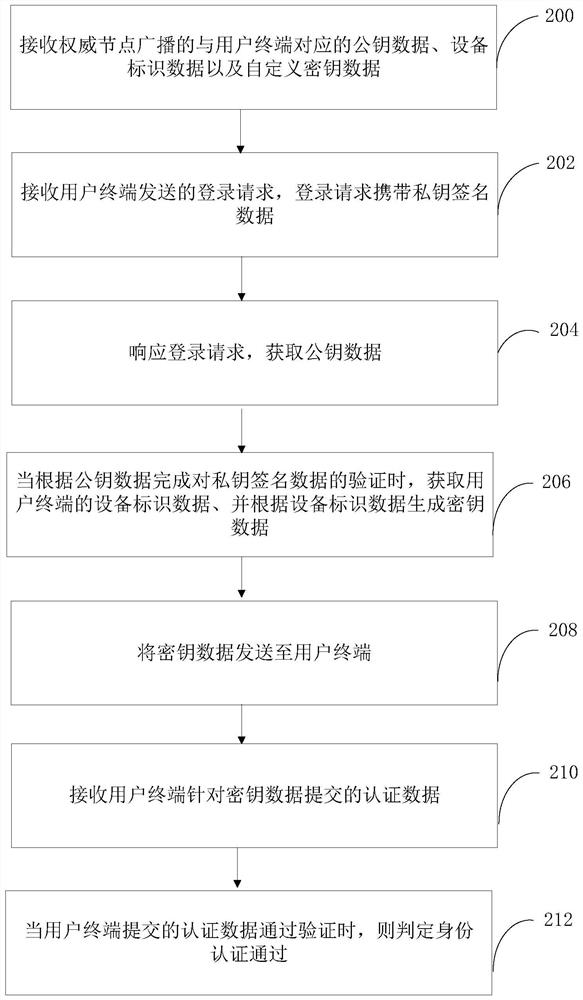
Identity authentication method, system and device based on block chain and computer equipment
ActiveCN111949953AAvoid authentication failuresImprove rigorDigital data authenticationBlockchainComputer equipment
The invention relates to an identity authentication method, system and device based on a block chain, computer equipment and a storage medium. The method comprises the following steps: receiving a login request sent by a user terminal, the login request carrying private key signature data; responding to the login request, obtaining public key data; obtaining equipment identification data of the user terminal when verification of the private key signature data is completed according to the public key data, and generating key data according to the equipment identification data, and sending the key data to the user terminal, receiving authentication data submitted by the user terminal for the key data, and when the authentication data submitted by the user terminal passes the verification, determining that the identity authentication is passed. According to the scheme, decentration is carried out in a blockchain mode, so that authentication failure caused by downtime of the central node is avoided; by introducing a double-authentication mechanism of equipment authentication and key data based on equipment identification data and private key authentication, behaviors such as signaturedenial can be avoided, the identity authentication accuracy is improved, and the data security is guaranteed.
Owner:卓尔智联(武汉)研究院有限公司
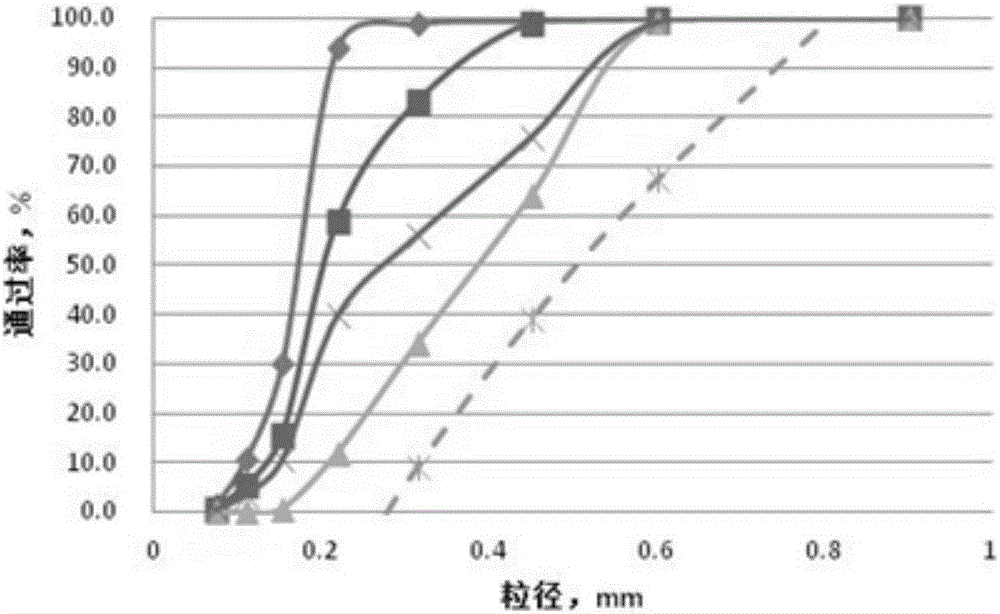
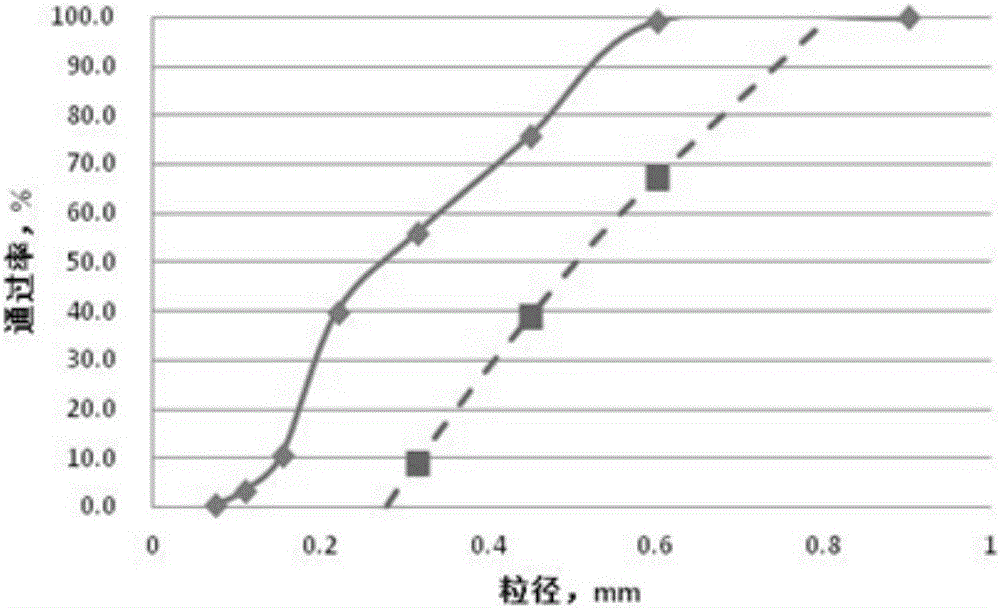
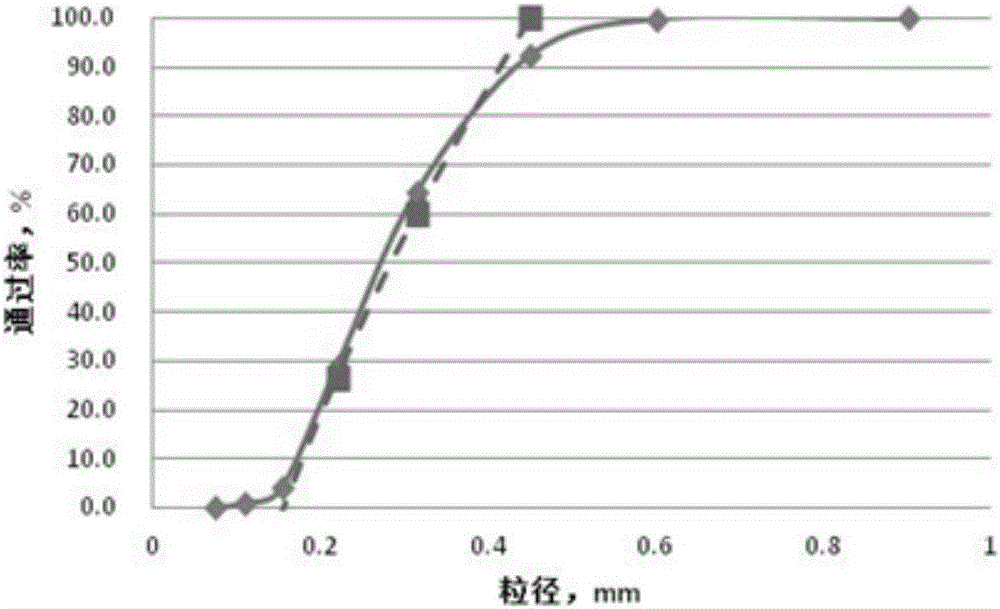
Grading method of cement-base self-leveling mortar
The invention provides a grading method of cement-base self-leveling mortar. The method comprises the following steps: screening and analyzing sand; measuring the screening residue of each sieve, and respectively calculating a sub-screening residue weight percentage, an accumulated screening reside weight percentage and a passing rate of sand in different particle sizes; performing primary grading design on the sand; based on the primary grading design solution of the sand in the above scheme, calculating a value P, and drawing a particle grading curve; primarily setting a ratio of powder to aggregate and a maximum particle size of a Fuller curve, calculating a value B and a value Psd, and drawing a Fuller curve; comparing the particle grading curve with the Fuller curve, repeating the above steps if the difference is relatively large, and obtaining a cement-base self-leveling mortar grading proportion when the particle grading curve is overlapped with the Fuller curve on three or more points. On the basis of the Fuller curve, the full-formula screening curve and the fuller curve are fitted to obtain a densest grading scheme.
Owner:MEICHAO GROUP
Matrix-plant coupling connected type flowing water floating bed
InactiveCN101948179AIncrease oxygen contentImprove purification efficiencyEnergy based wastewater treatmentSustainable biological treatmentPlant rootsWater quality
The invention belongs to the technical field of environmental protection and relates to a method for purifying water in rivers or slowly flowing water. In the method which is a technical method for improving water quality, pollutants in the water are absorbed by the plant root system and adsorbed by a matrix and purified by using the rhizospheric microorganisms living in the matrix; and an impeller is driven to rotate by wind energy so as to enhance the water power and increase oxygen content in the water. The method realizes multi-layer removal of water pollutants through the absorption and purification by the plant root layer, adsorption and purification by the matrix layer, oxygen increase in water and the like and accelerates the ecological restoration process of the water by organically combining the plant restoration technology and the physical restoration technology.
Owner:NORTHEAST NORMAL UNIVERSITY
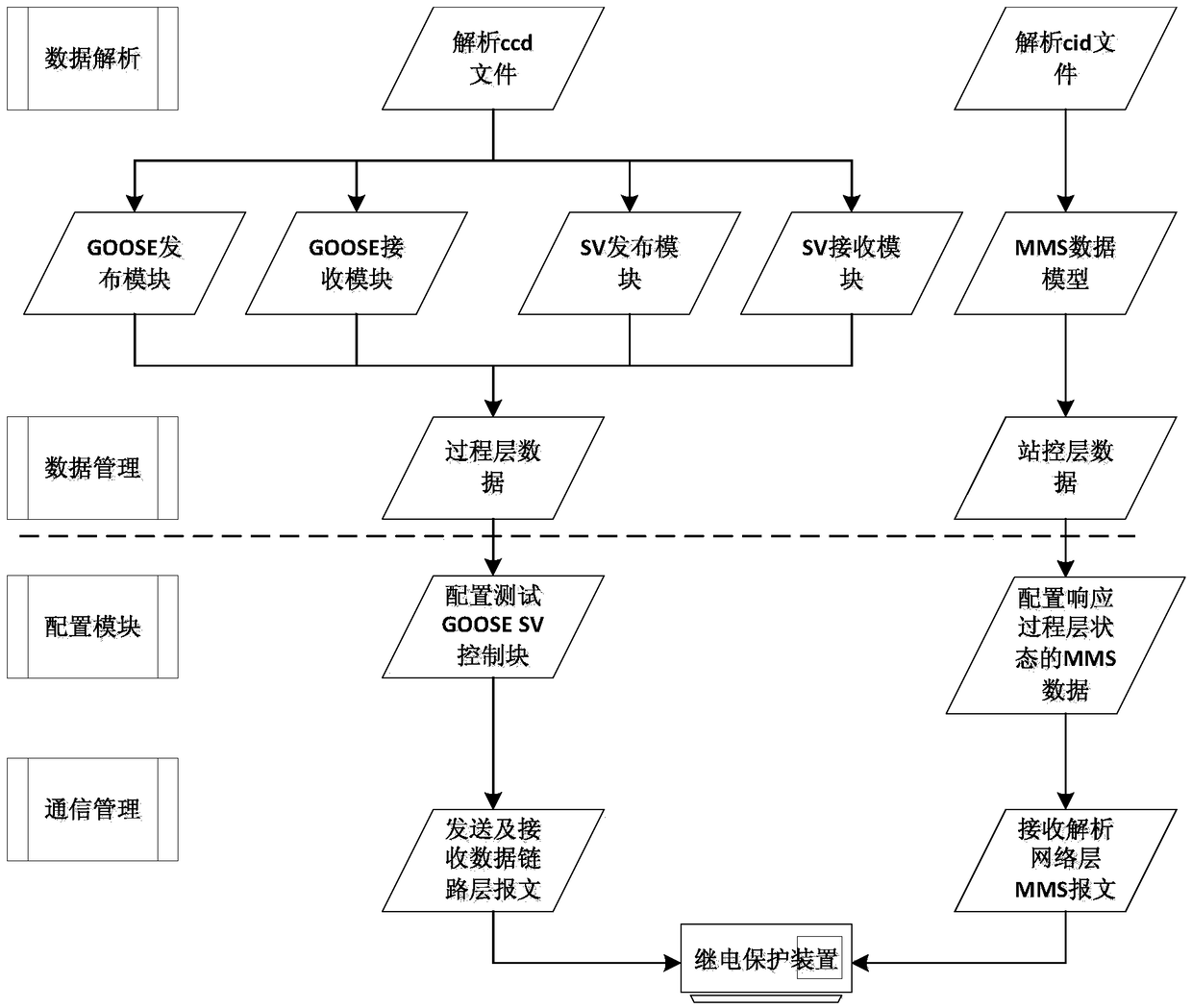
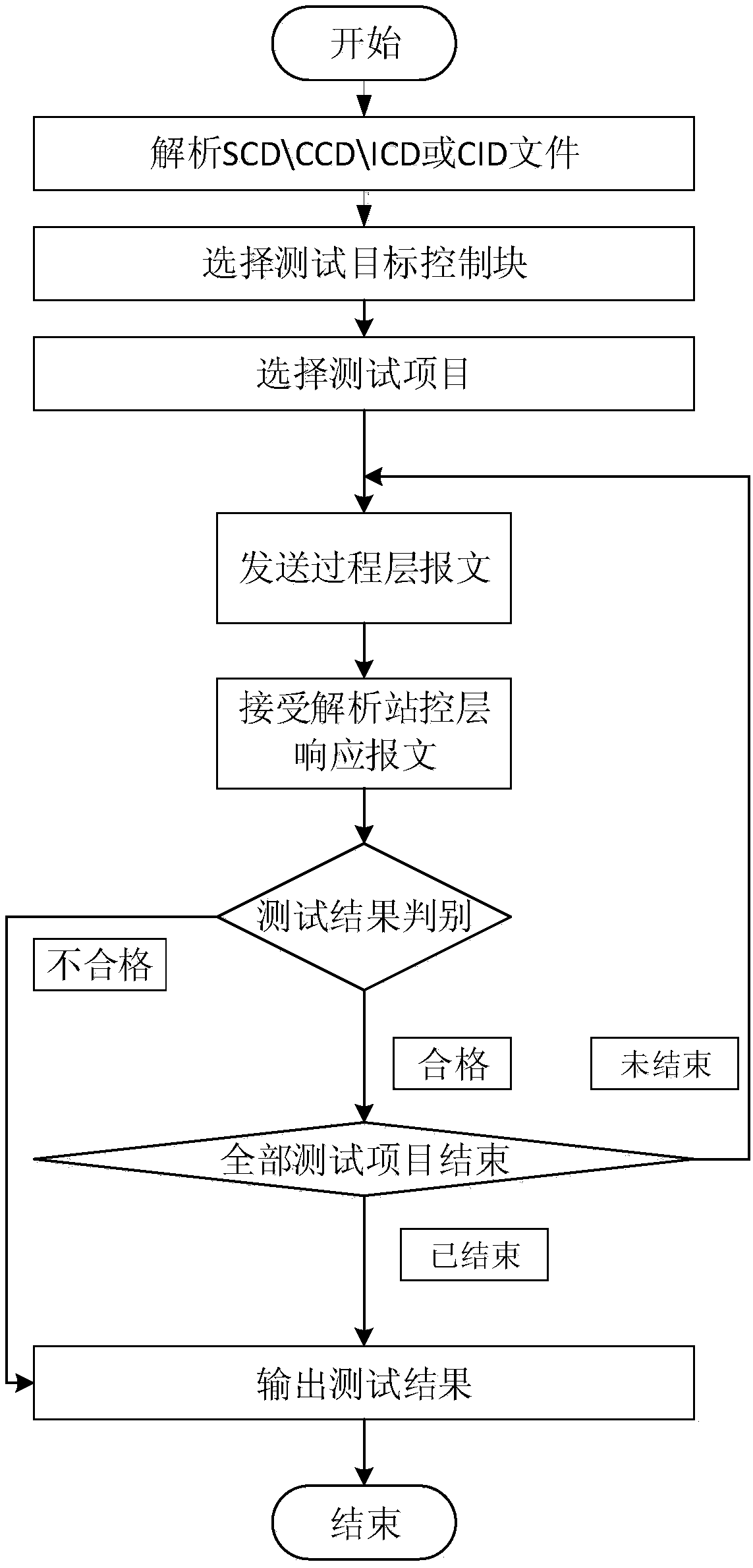
Relay protection device process layer GOOSE and SV communication automatic test method and system
ActiveCN109379251AImplement automated testingAvoid manual interventionElectrical testingData switching networksTest efficiencySmart substation
The invention discloses a relay protection device process layer GOOSE and SV communication automatic test method and system based on Python. The method comprises the following steps: automatically performing communication message publish and subscription check test on a relay protection device process layer communication message according to subscription and publish, and automatically performing test report output through a reaction result of an IED device, thereby realizing the automatic test of the relay protection device process layer GOOSE and SV communication. Based on Python development,the process layer communication test of the intelligent transformer substation relay protection device is automatically performed; an overall structure of the test system is provided, a test method based on closed loop is proposed, namely, the method for automatically judging a test case through a program thoroughly eradicates the artificial intervention, the test efficiency is improved, and thecredibility and the preciseness of the test are reinforced.
Owner:GUODIAN NANJING AUTOMATION SOFTWARE ENG
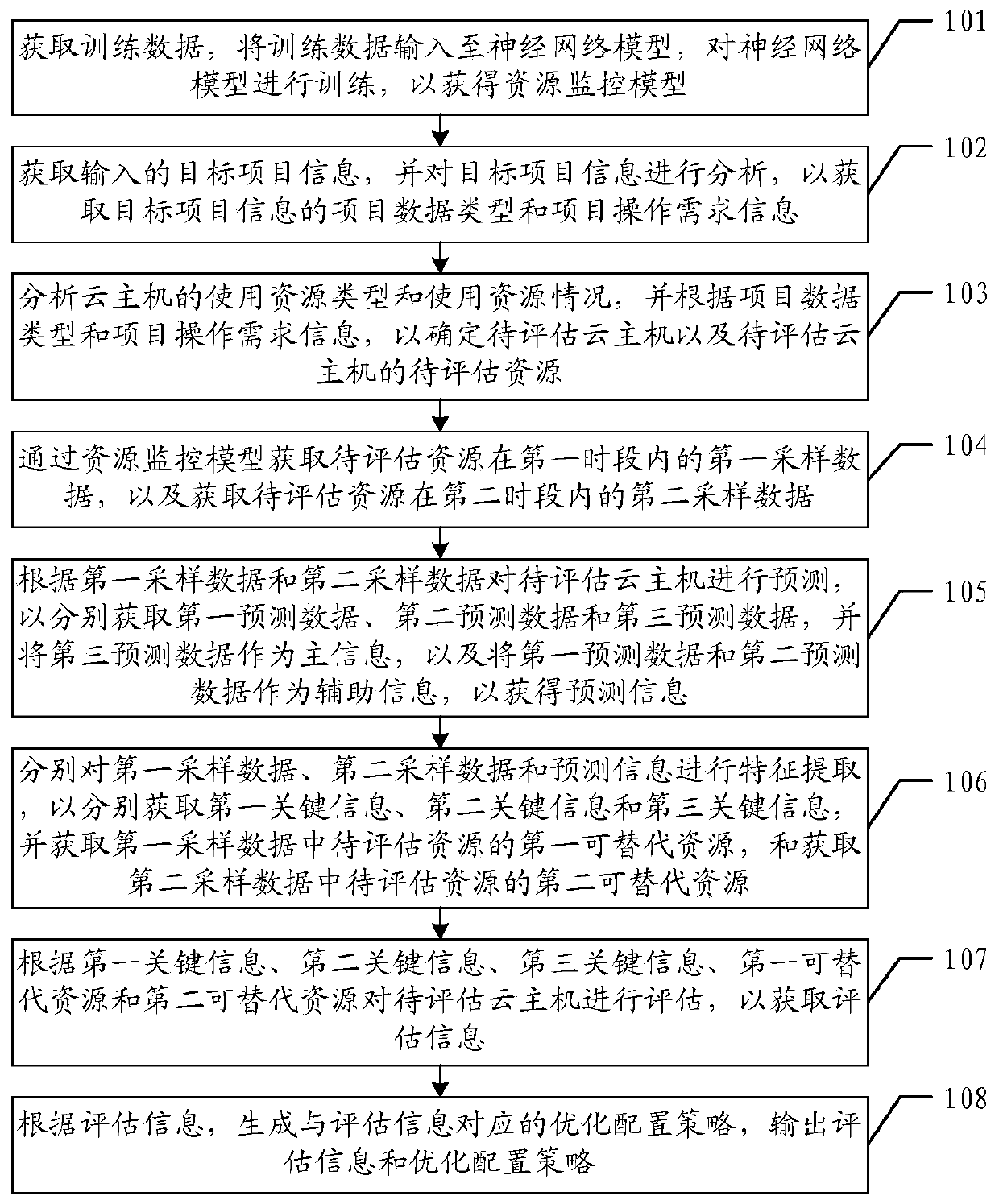
Method, device and equipment for evaluating cloud host resources and storage medium
ActiveCN110806954AMeet assessment needsImprove resource utilizationDetecting faulty hardware by configuration testFunctional testingService domainEngineering
The invention relates to the field of cloud services. The invention provides a method, device and equipment for evaluating cloud host resources and a storage medium. The method comprises the followingsteps: analyzing the target project information, and the use resource types and use resource conditions of the plurality of cloud hosts through the trained resource monitoring model to obtain a to-be-assessed cloud host and to-be-assessed resources of the to-be-assessed cloud host; obtaining first sampling data and second sampling data of the to-be-evaluated resource, and obtaining prediction information according to the first sampling data and the second sampling data, obtaining evaluation information according to the first sampling data, the second sampling data and the prediction information, and generating an optimal configuration strategy corresponding to the evaluation information according to the evaluation information. By adopting the scheme, the resource utilization rate of the cloud host can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
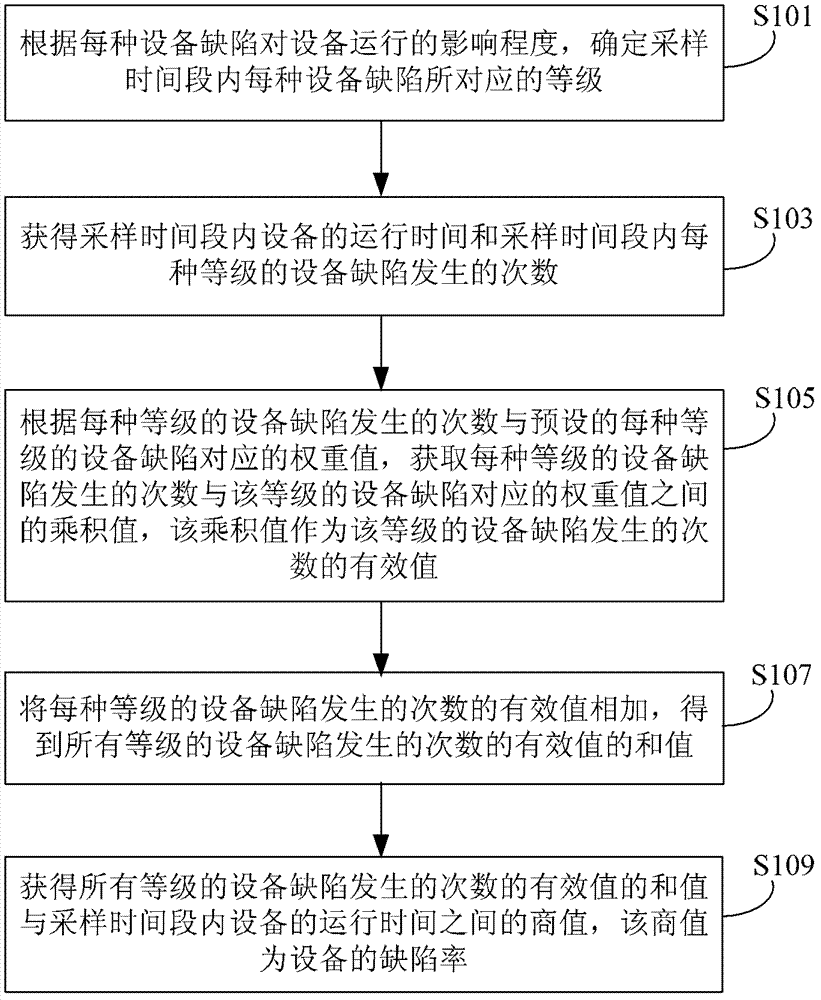
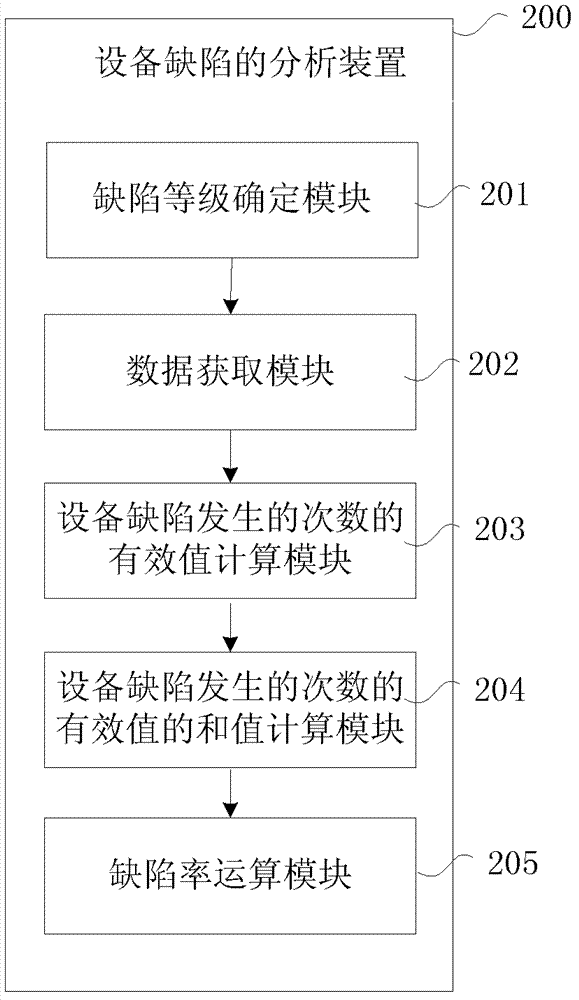
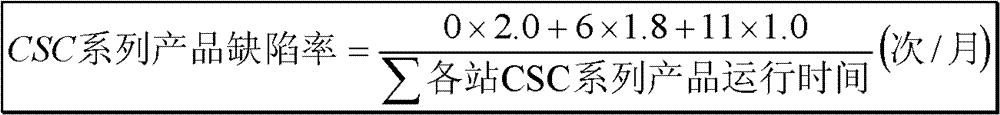
Analysis method and device of equipment defects
ActiveCN102955888AScientifically reflect the degree of harmReflect the degree of harmSpecial data processing applicationsEquipment DefectsRunning time
The invention provides an analysis method and device of equipment defects. The method comprises the following steps of: obtaining operation time of equipment in a sampling time interval and incidence frequency of each grade of equipment defect in the sampling time interval; obtaining a product value of the incidence frequency of each grade of the equipment defect and a weight value corresponding to the grade of the equipment defect according to the incidence frequency of each grade of the equipment defect and a pre-set weight value of each grade of the equipment defect, wherein the product value is used as an effective value of the incidence frequency of the grade of the equipment defect; summing the effective values of the incidence frequencies of all grades of equipment defects to obtain the sum value of the effective values of the incidence frequencies of all the grades of equipment defects; and obtaining a quotient value of the sum value of the effective values of the incidence frequencies of all the grades of equipment defects and operation time of the equipment in the sampling time interval, wherein the quotient value is a defect rate of the equipment. The analysis method and device are good for obvious improvement of an operating risk pre-controlling level of the equipment.
Owner:STATE GRID CORP OF CHINA +1
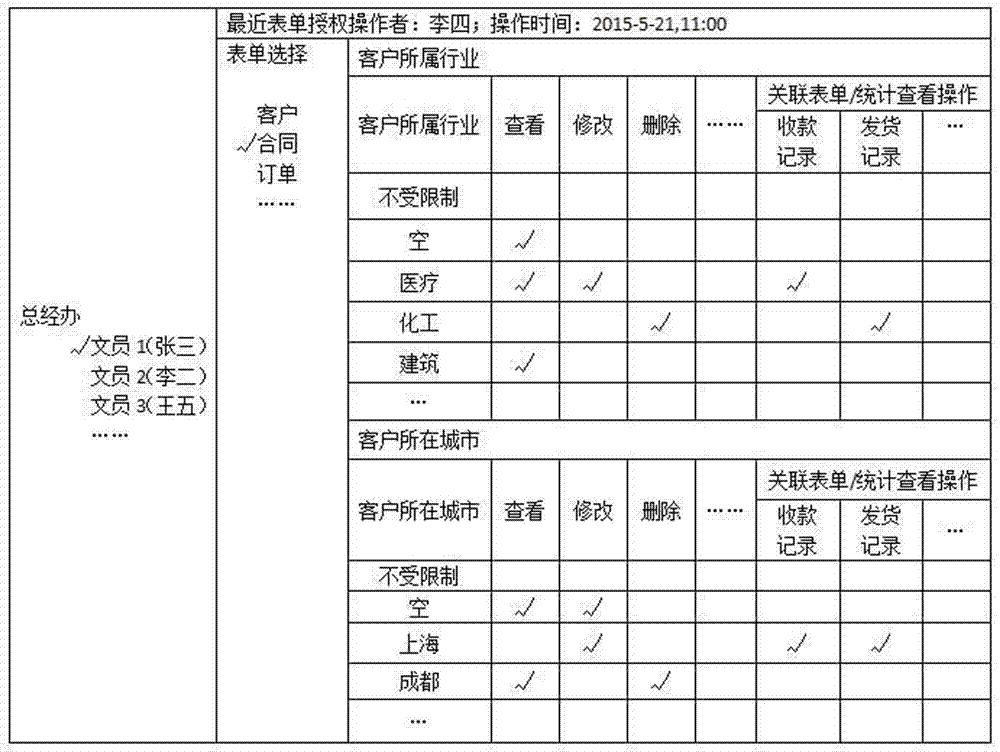
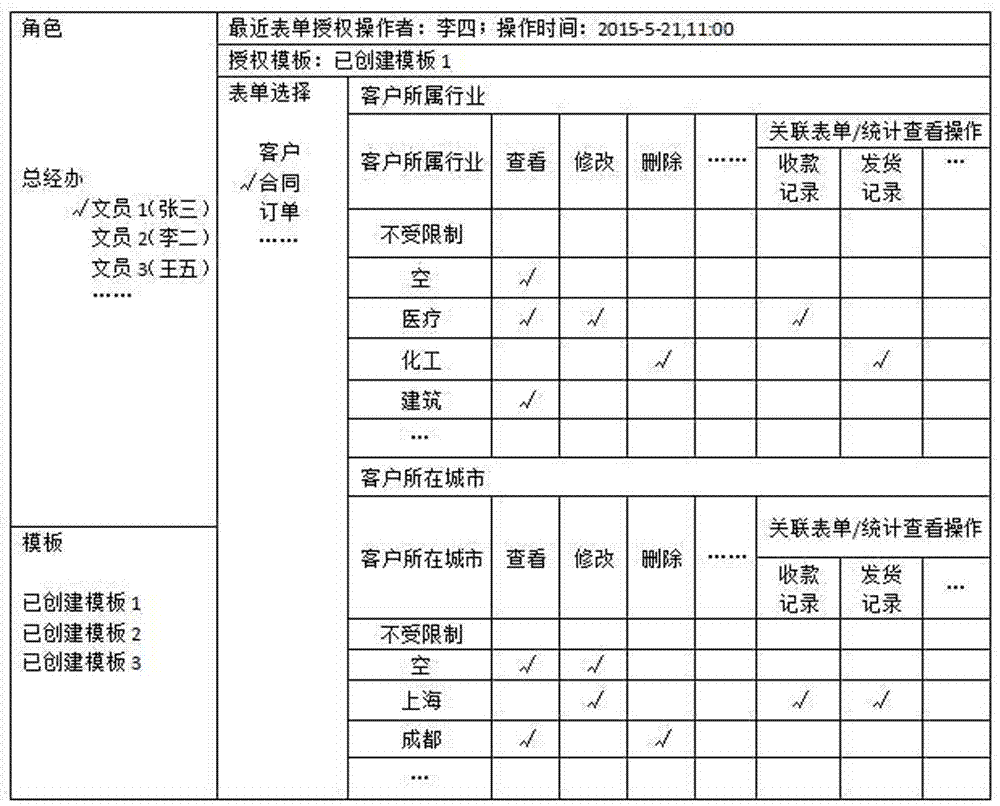
Method of granting form operation authorities respectively according to form field values
InactiveCN107292588AImprove rigorImprove finenessDigital data protectionNatural language data processingData operationsDatabase
The invention discloses a method of granting form operation authorities respectively according to form field values. The method comprises a step of granting form data operation authorities and a step of selecting an authorized person. The step of granting the form data operation authorities comprises steps that S1: a to-be-authorized form is selected; S2, the fields requiring the operation authority granting in the form are selected; S3: the operation authority granting is carried out according to all of the field values of the selected fields. The authorities related to the deleting, the correcting, and the printing of the form are granted respectively based on the form field values, and therefore a wider application range is provided. The valid unified authority granting of the form data, the selected field values of which are null values, is carried out, and therefore authority operation is convenient, and authority work load is small. The integral operation authority granting of the table data corresponding to all of the field values of the selected fields is carried out, and the authority operation is simple and effective, and the method is especially suitable for authority granting of high-ranking company administers having all of authorities.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
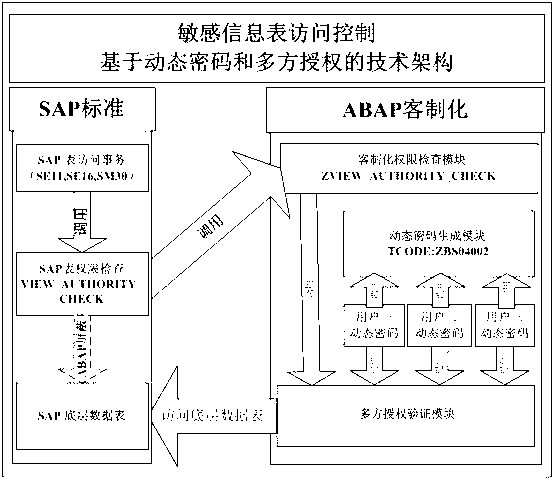
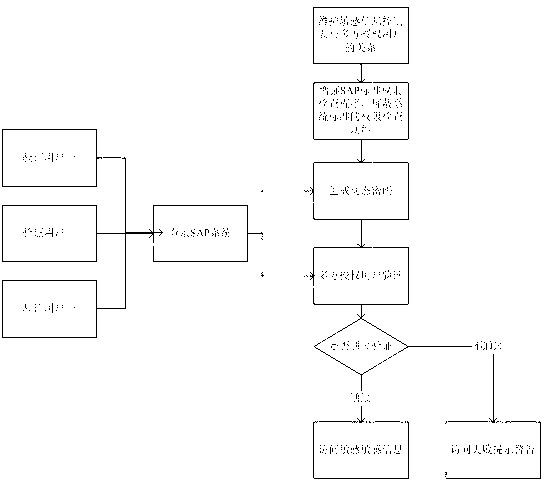
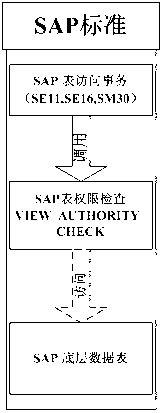
SAP safety sensitive information system based on many-sided authorization and dynamic password
ActiveCN102801743AEnsure safetyIncreased complexity and rigorUser identity/authority verificationInformation systemAuthorization
The invention discloses an SAP safety sensitive information system based on many-sided authorization and dynamic password, and can realize that data tables which contain sensitive information are managed according to demands and users and can be classified into specific tables. The system comprises a customized configuration table and a dynamic password table, a customized authorization check functional module, a dynamic password generating module and a many-sided authorization validation module. The system can carry out registration and locking management on a table which contains sensitive information, different users are authorized according to the characteristic of the table, so as to perform the many-sided restriction validation; meanwhile, a dynamic password is set in validation each time; and only if many-sided validation all passes, the registered sensitive information table is unblocked. The SAP safety sensitive information system provided by the invention can protect sensitive information about finance and remuneration very well, and the security, privacy and usability of the system are improved.
Owner:STATE GRID CORP OF CHINA +1
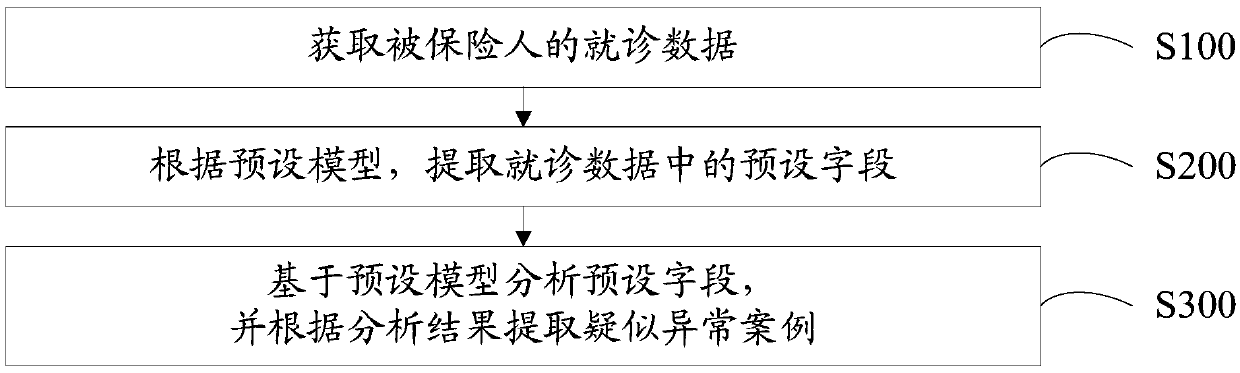
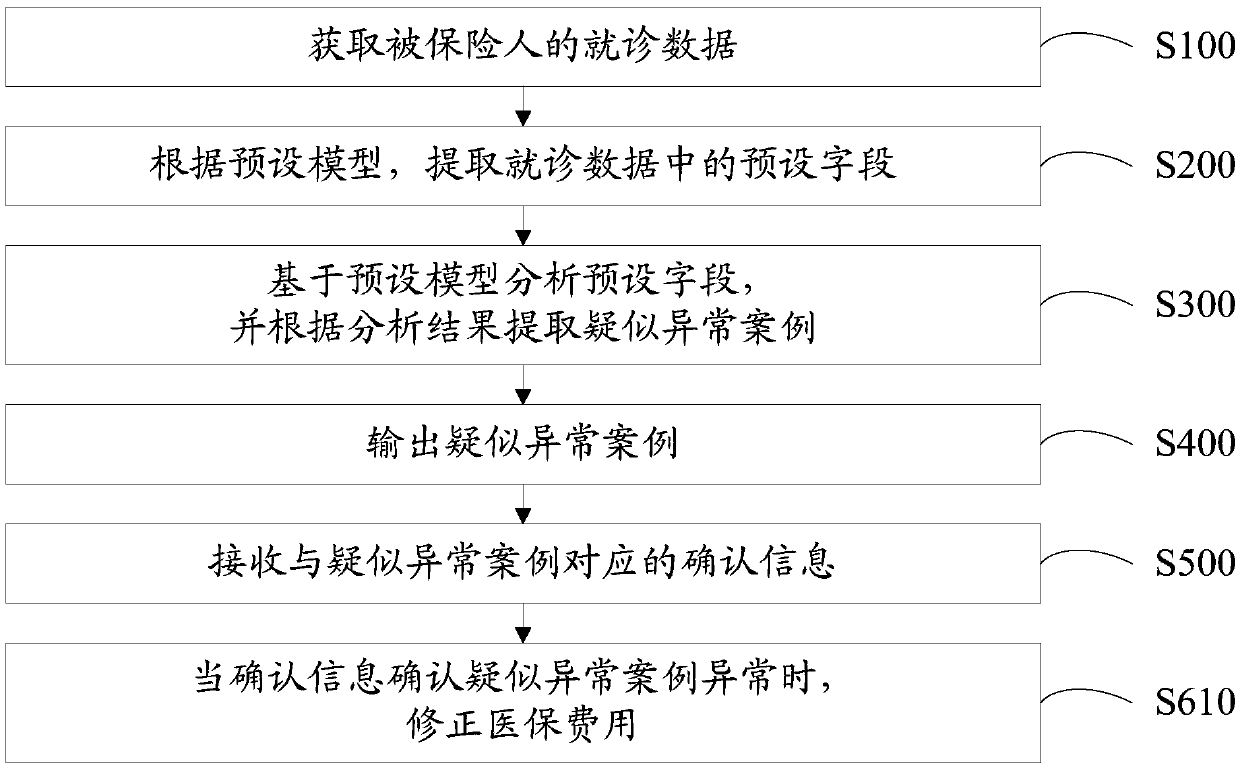
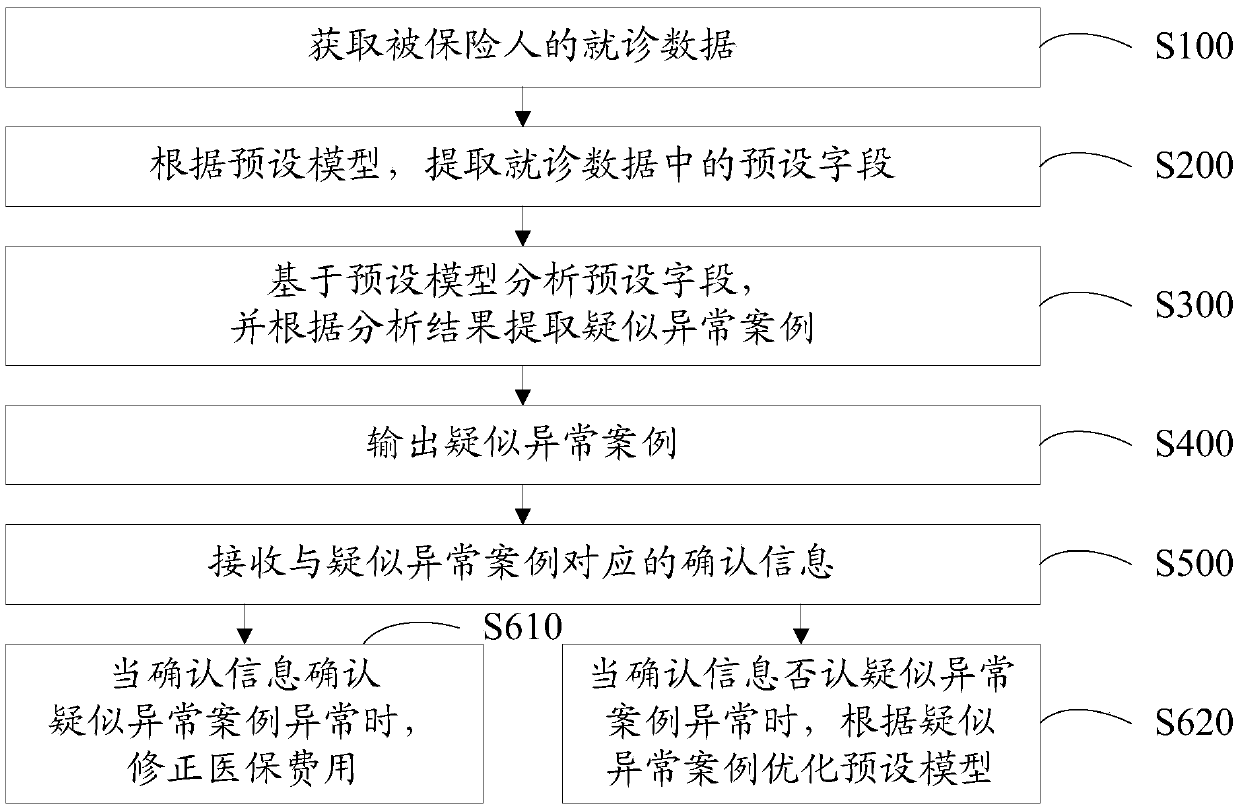
Medical insurance supervision method, equipment and device and computer readable storage medium
The invention discloses a medical insurance supervision method. The medical insurance supervision method is realized based on an intelligent decision. The medical insurance supervision method comprises the following steps: obtaining treatment data of an insured person; Extracting a preset field in the treatment data according to a preset model; And analyzing the preset field based on the preset model, and extracting suspected abnormal cases according to an analysis result. The invention further discloses medical insurance supervision equipment, a medical insurance supervision device and a computer readable storage medium. According to the technical scheme, the difficulty of medical insurance supervision is reduced, and the accuracy and the tightness of medical insurance supervision are improved.
Owner:PING AN MEDICAL & HEALTHCARE MANAGEMENT CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com