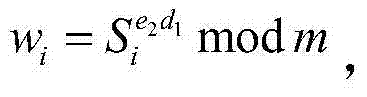Patents
Literature
327 results about "Key authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
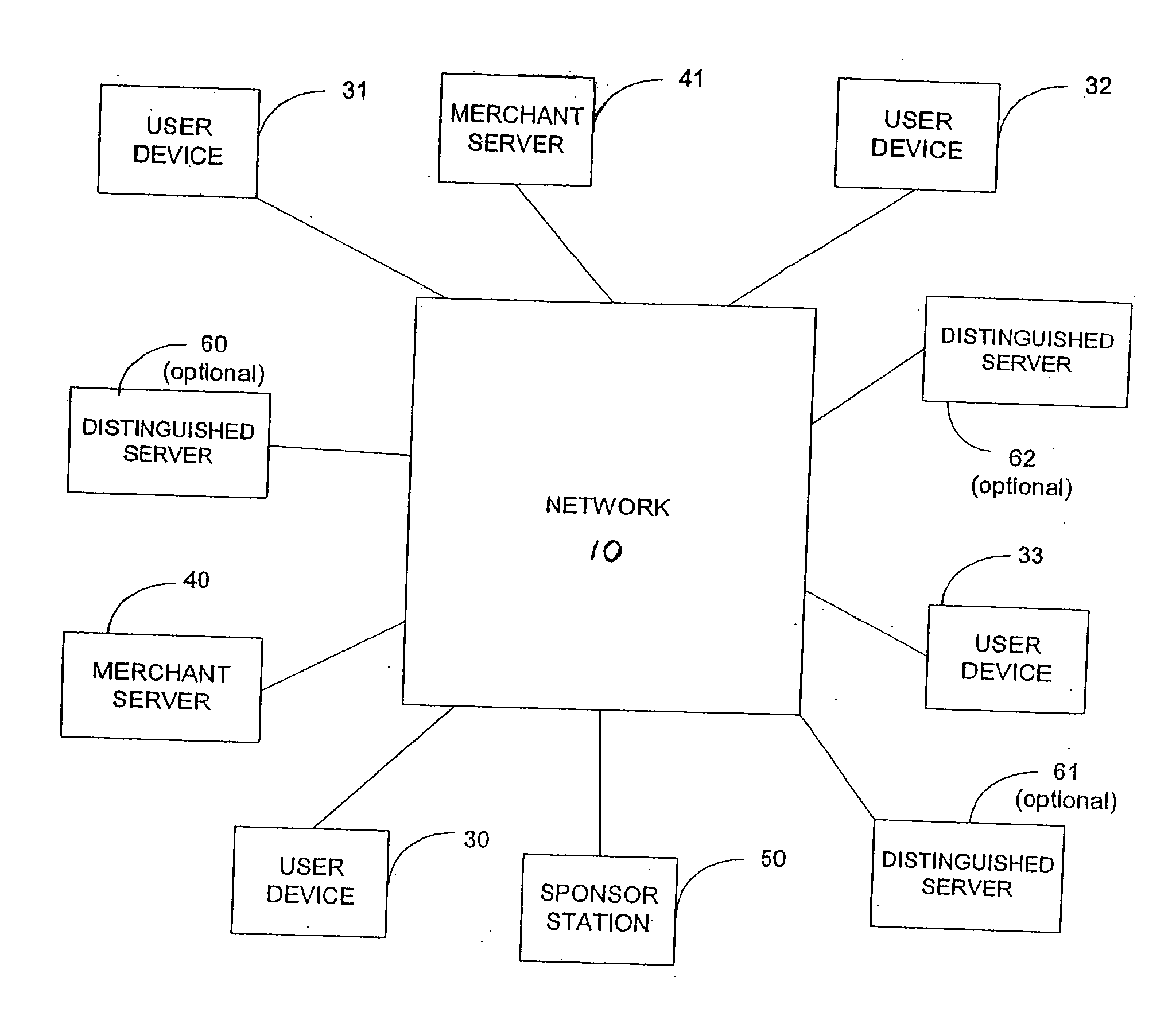
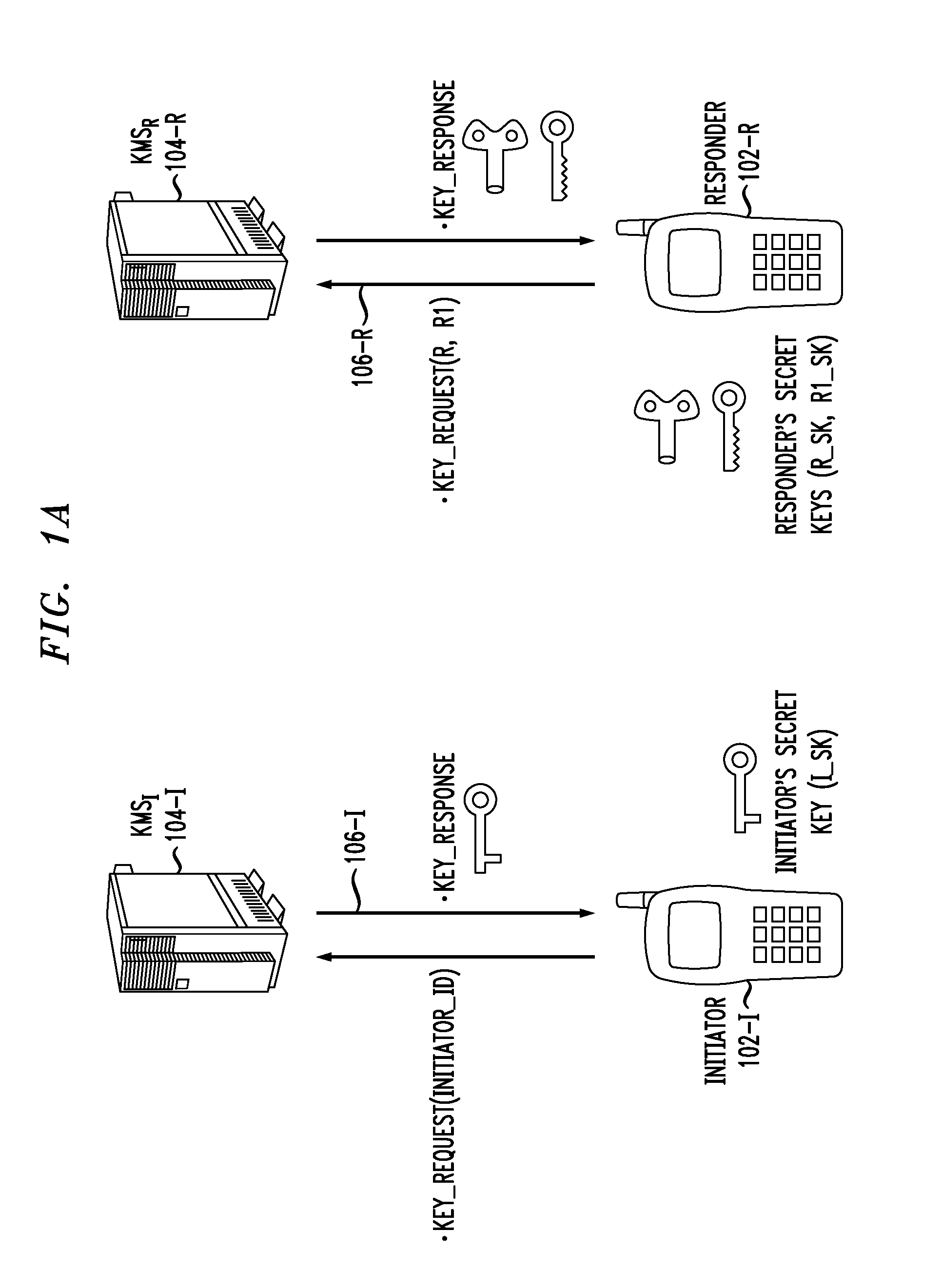
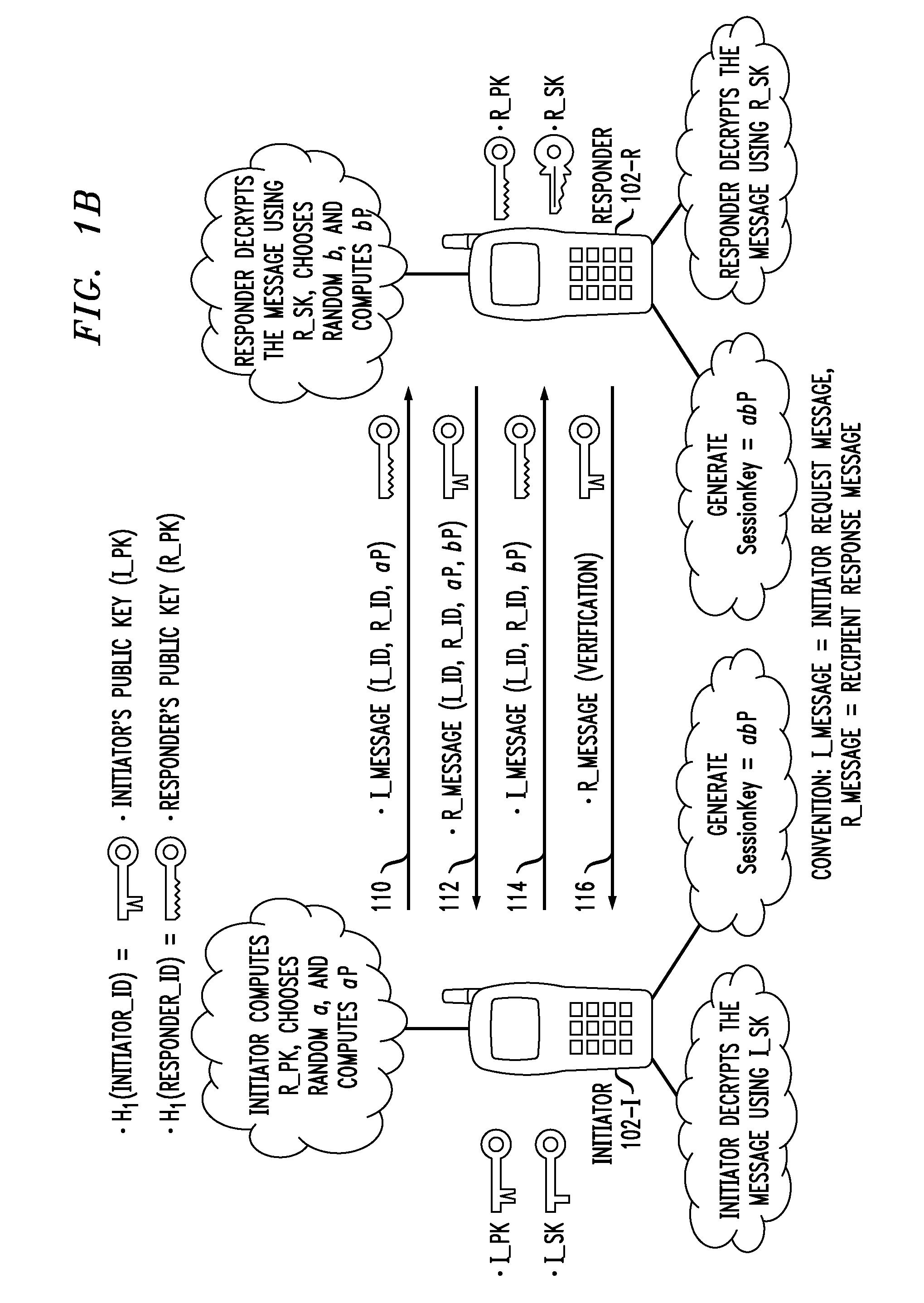
Key authentication is used to solve the problem of authenticating the keys of the person (say "person B") to whom some other person ("person A") is talking to or trying to talk to. In other words, it is the process of assuring that the key of "person A" held by "person B" does in fact belong to "person A" and vice versa.
Protecting one-time-passwords against man-in-the-middle attacks
ActiveUS20070033642A1Key distribution for secure communicationDigital data processing detailsMan-in-the-middle attackKey authentication
To authenticate a user having an associated asymmetric crypto-key having a private / public key pair (D,E) based on a one-time-password, the user partially signs a symmetric session key with the first portion D1 of the private key D. The authenticating entity receives the partially signed symmetric session key via the network and completes the signature with the second private key portion D2 to recover the symmetric session key. The user also encrypts a one-time-password with the symmetric session key. The authenticating entity also receives the encrypted one-time-password via the network, and decrypts the received encrypted one-time-password with the recovered symmetric session key to authenticate the user.
Owner:VMWARE INC
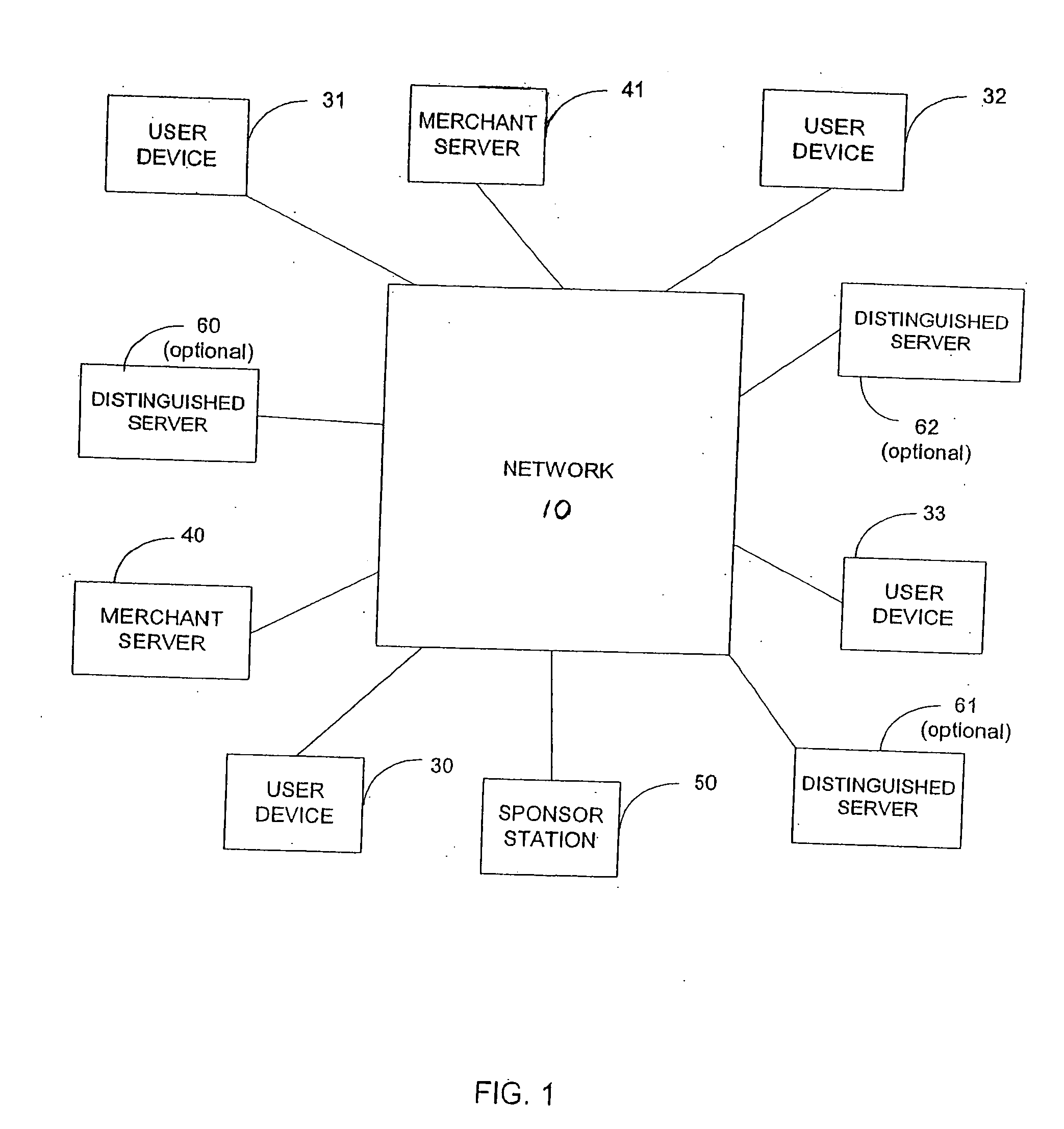
Distributed computing architecture and associated method of providing a portable user environment
InactiveUS20070118609A1Multiple digital computer combinationsTransmissionGraphicsGraphical user interface
A client terminal presents a graphical user interface (GUI) to a distributed computing environment. A first interface is configured to receive data of a portable storage medium. The data includes a key authentication signal and user settings. The key authentication signal identifies an authorized user of the distributed computing environment. A second interface is configured to communicate with an operably linked server. A controller is operative to verify the key authentication signal provided to the first interface in accordance with a distributed computing instruction set, and, upon verification, establishing communication with the operably linked server via the second interface. In this way, the server executes server side applications accessed by a user from the client terminal in accordance with the user settings.
Owner:FRANCE TELECOM SA
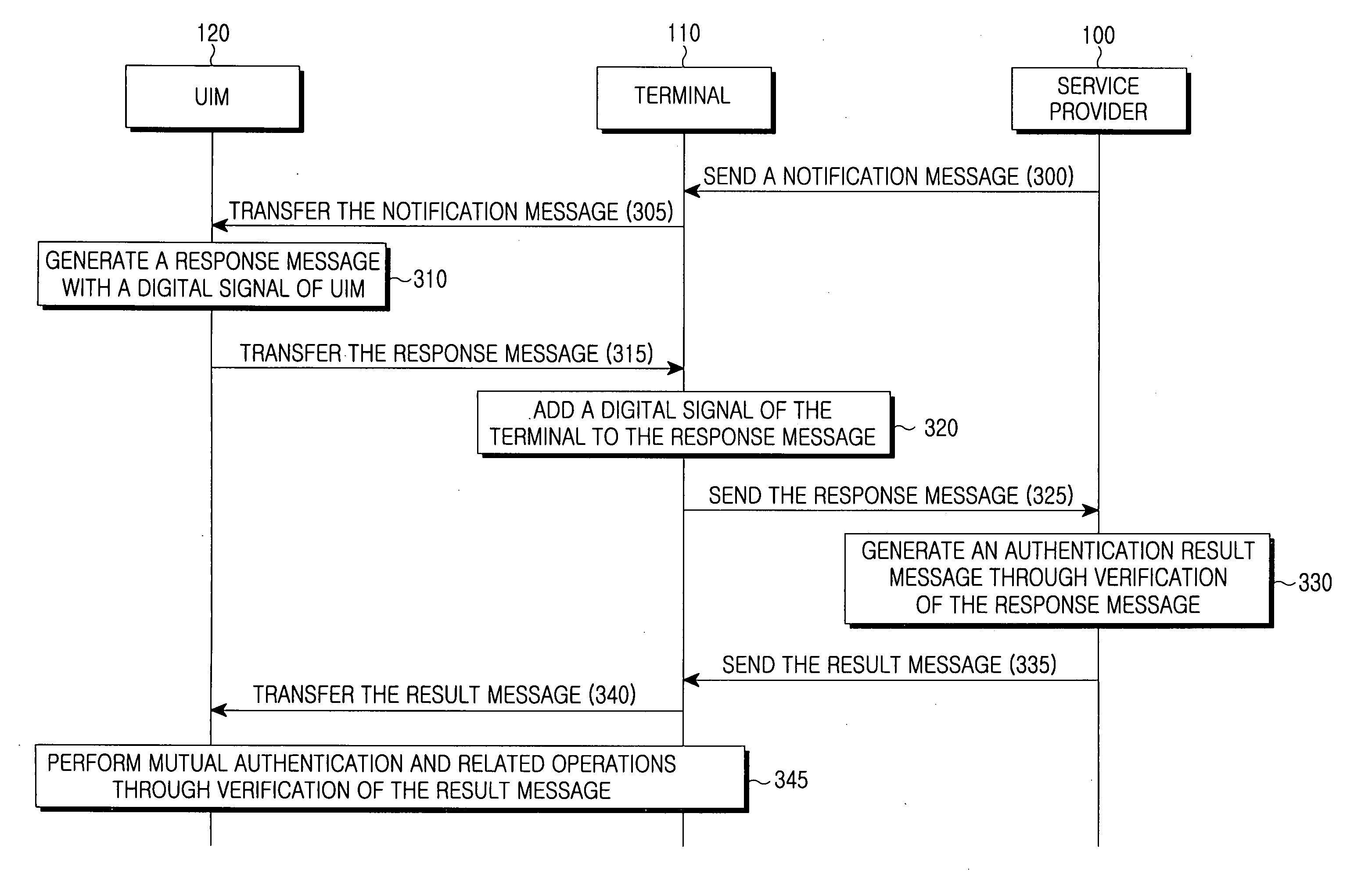
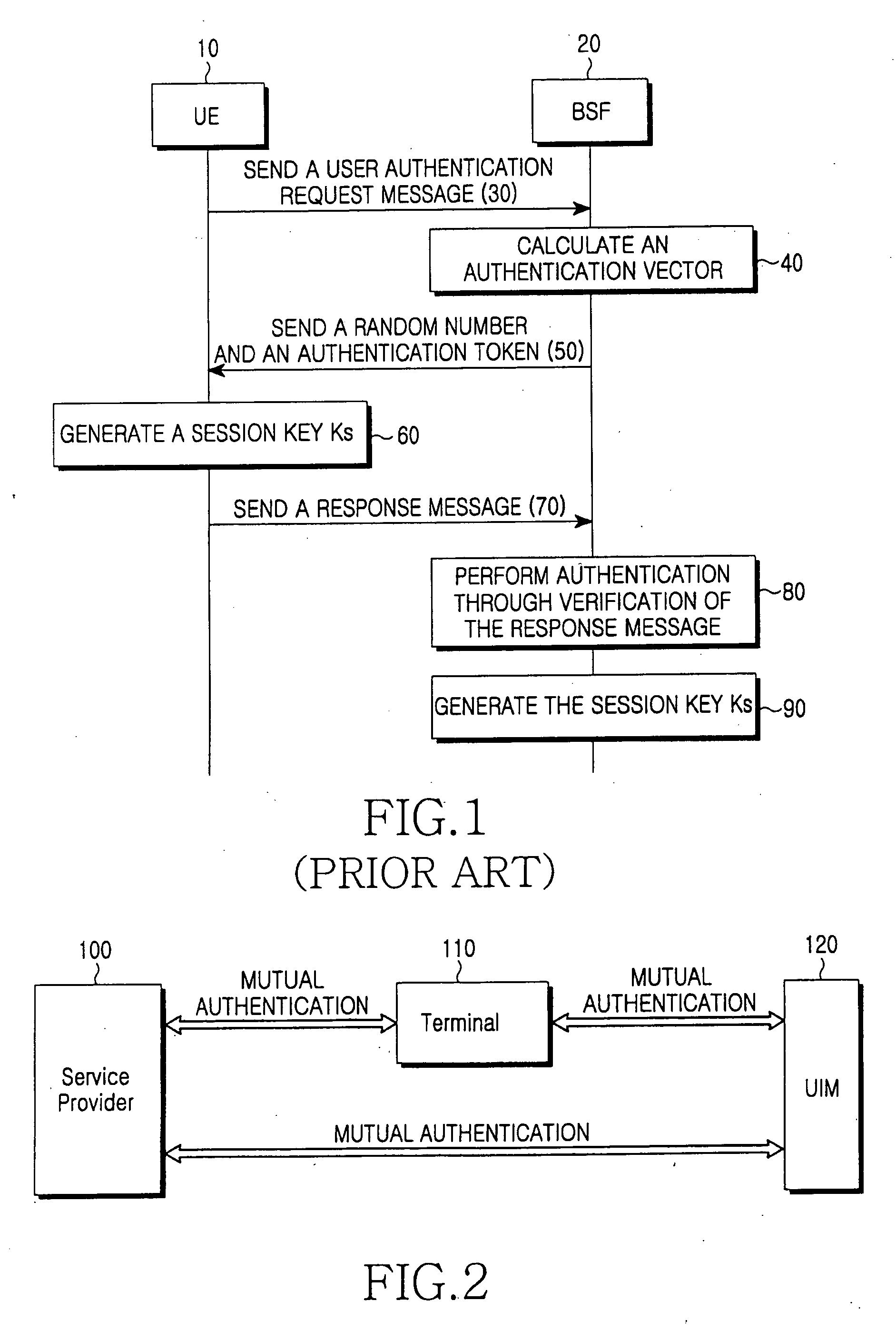
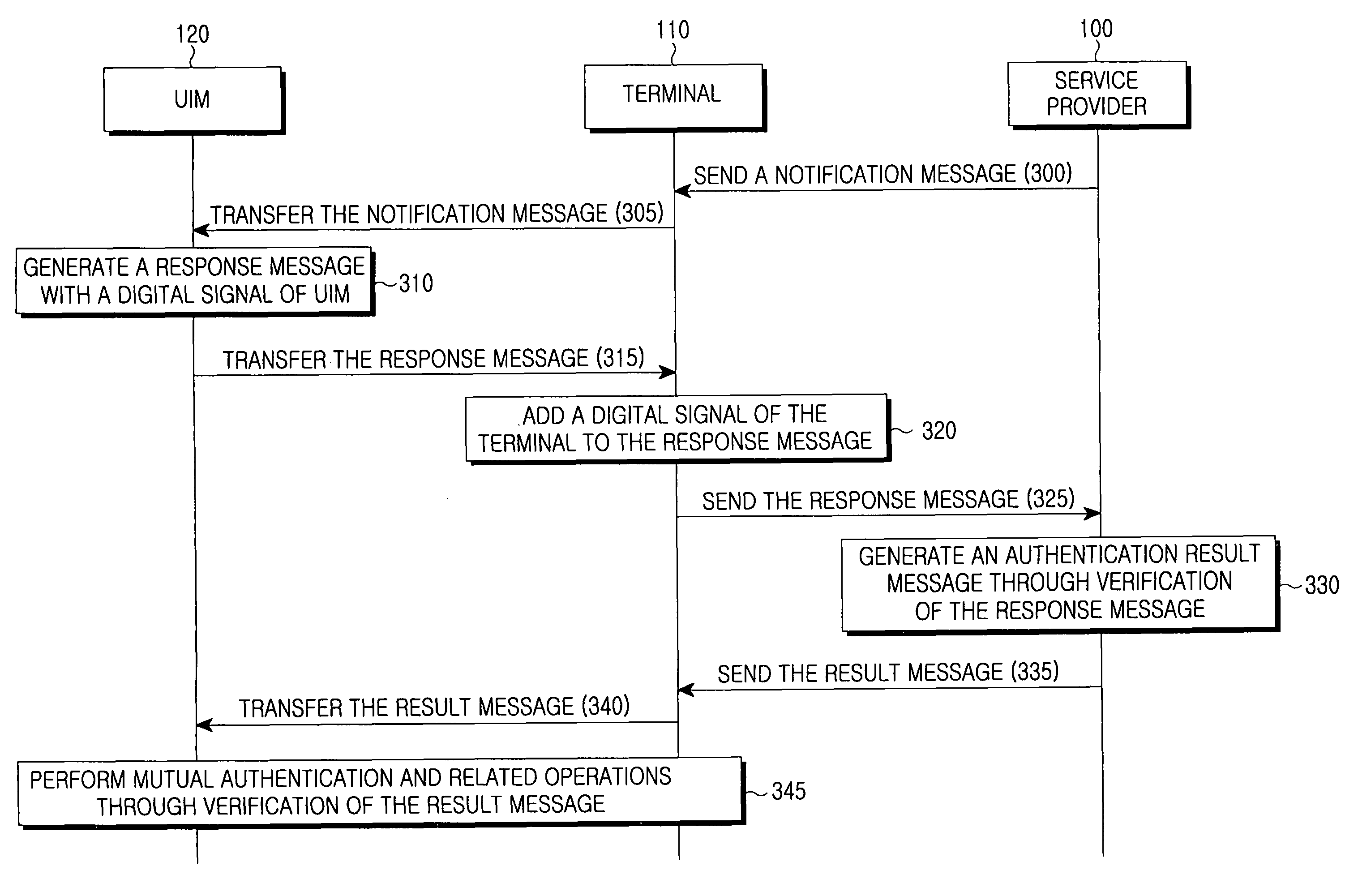
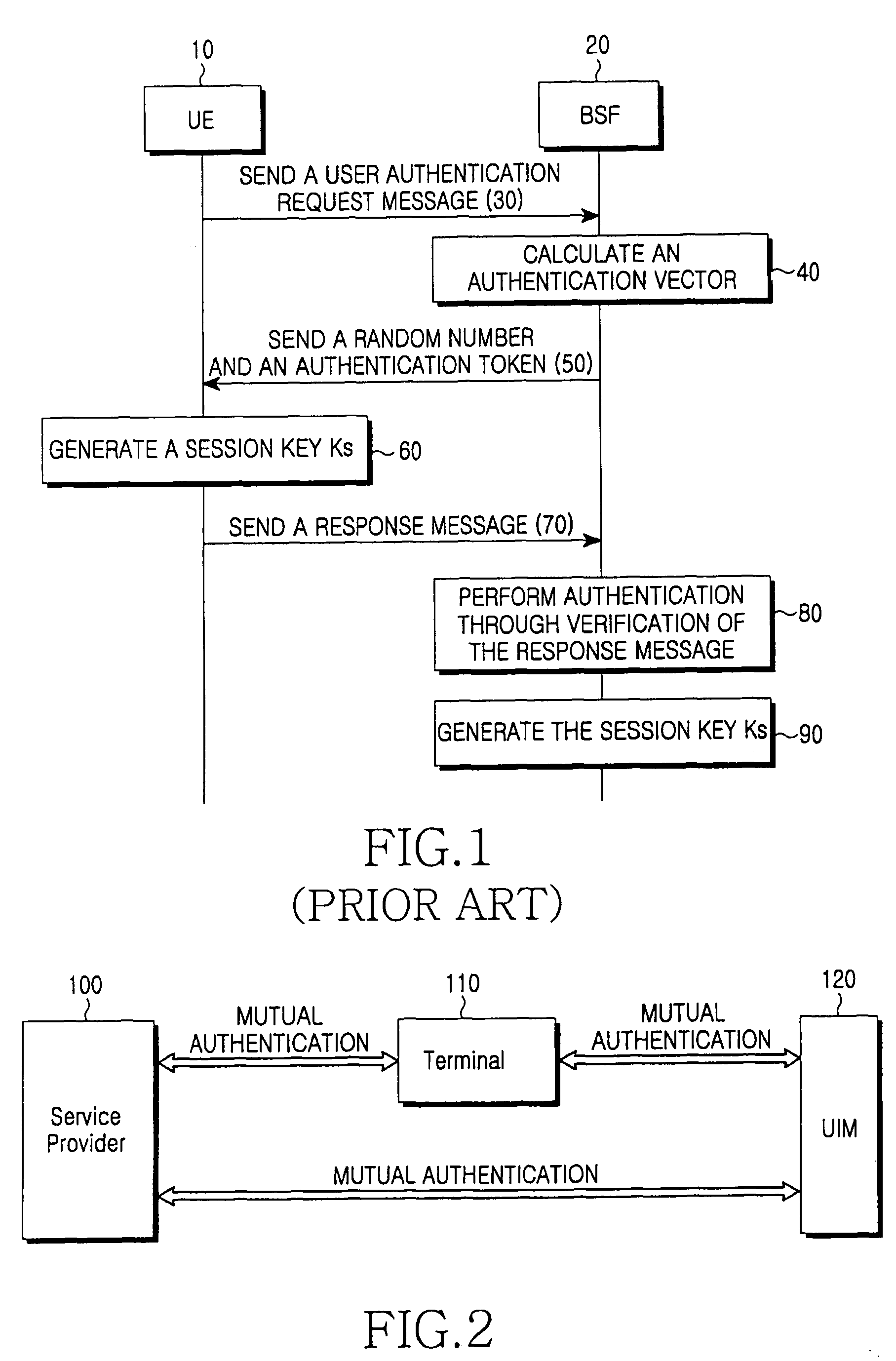
Method for inclusive authentication and management of service provider, terminal and user identity module, and system and terminal device using the method
ActiveUS20060281442A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPublic key authenticationNetworked system
Disclosed are a method and a system for mutual inclusive authentication between a service provider, a terminal and a user identity module. The authentication system is configured in a structure that can interact with a public key infrastructure of the current network security environment and can be independently used in a specific network system. The inclusive authentication method is divided into public key authentication and symmetric key authentication. Mutual authentication can be made between a service provider, a terminal and a user identity module using any of the two authentication schemes. Then a user can access content on any terminal device using the content license based on the user's identity.
Owner:SAMSUNG ELECTRONICS CO LTD
Symmetric key authenticated encryption schemes
InactiveUS6963976B1Low costSame level of securityData processing applicationsEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
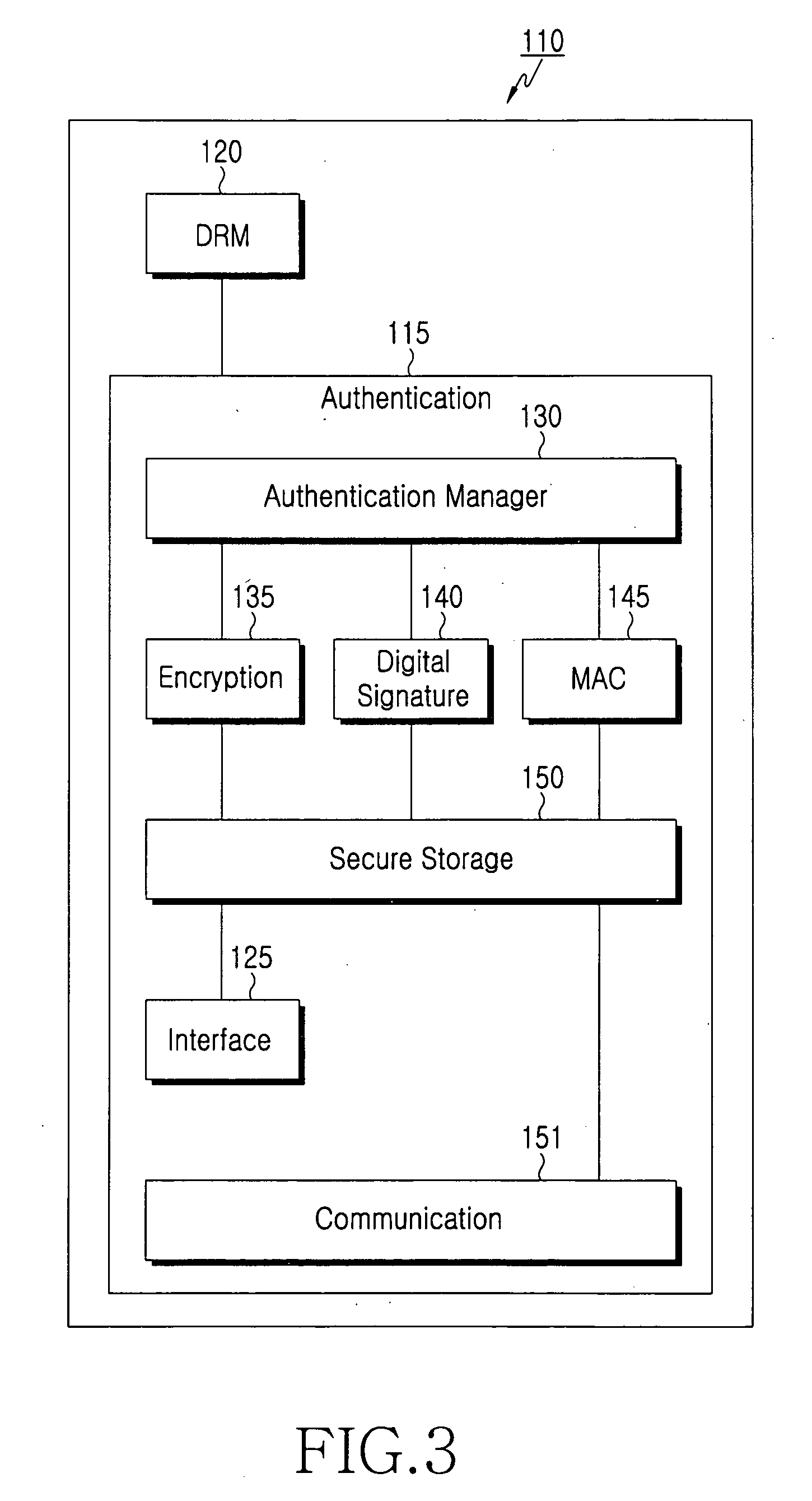
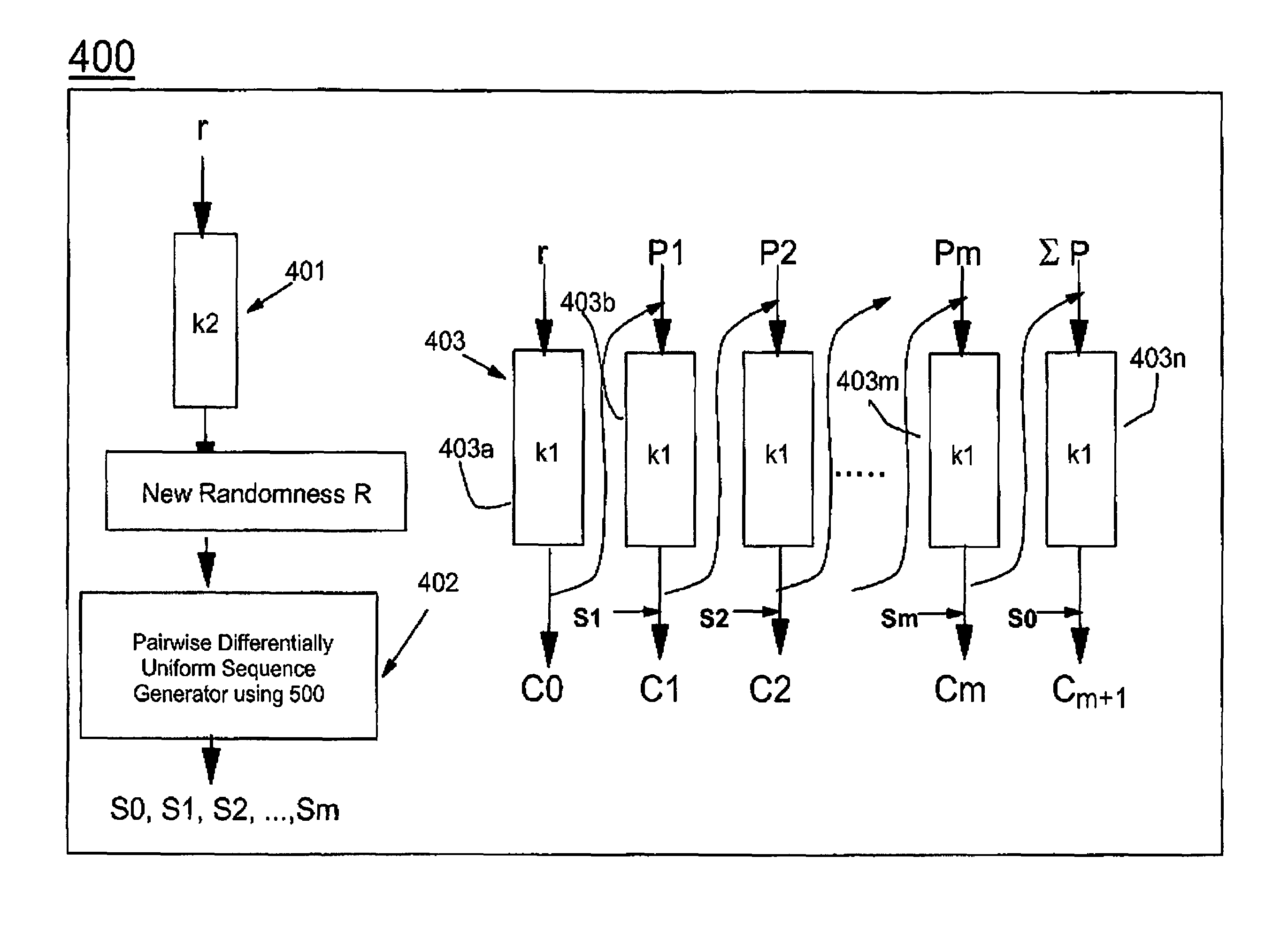
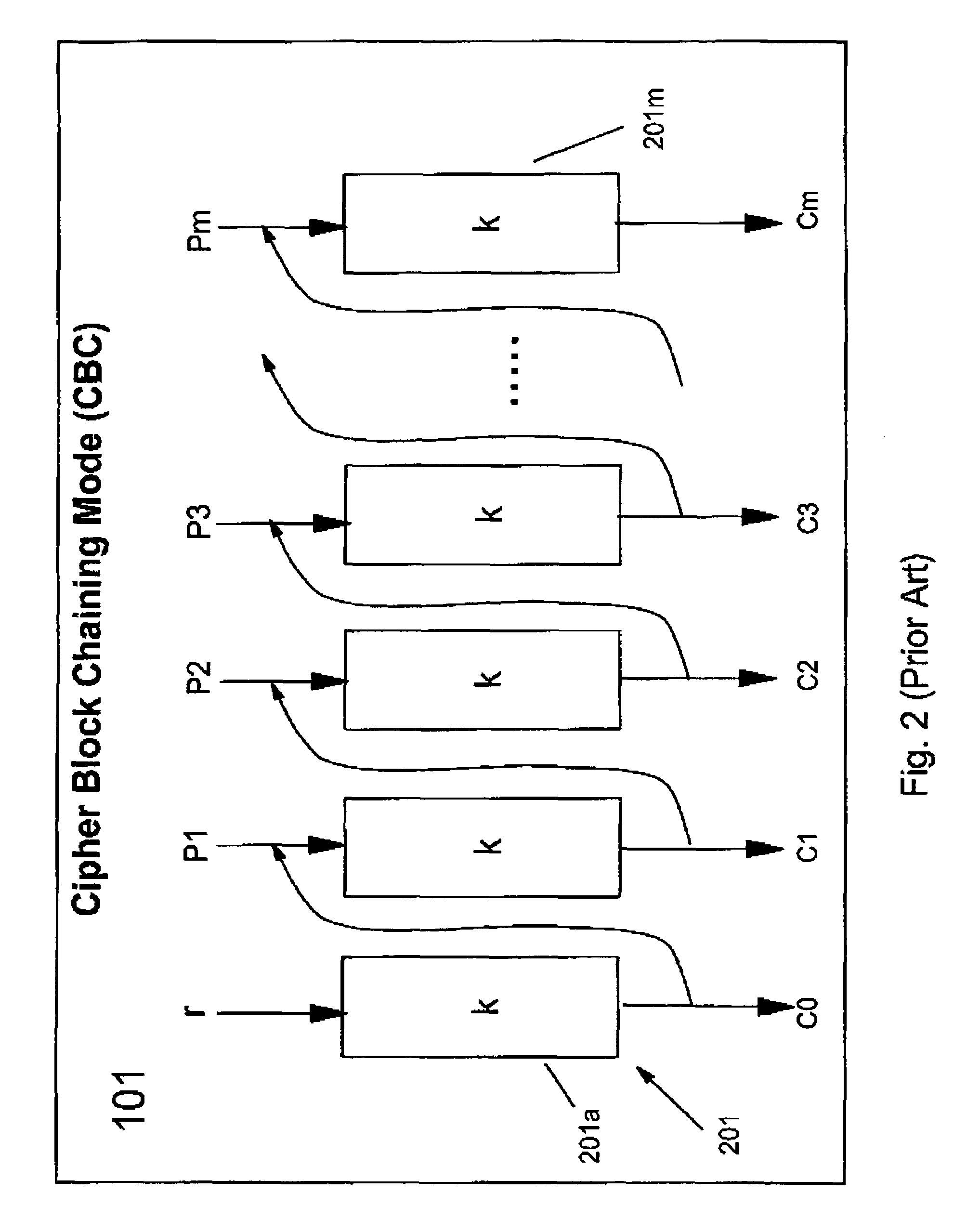
The present invention provides encryption schemes and apparatus which securely generate a cipher-text which in itself contains checks for assuring message integrity. It also provides compatible decryption schemes confirming message integrity. The encryption scheme generates a cipher-text with message integrity in a single pass with little additional computational cost, while retaining at least the same level of security as schemes based on a MAC. One embodiment encrypts a plain-text message by dividing the plain-text message into a multitude of plain-text blocks and encrypting the plain-text blocks to form a multitude of cipher-text blocks. A single pass technique is used in this process to embed a message integrity check in the cipher-text block. A message integrity check is embedded in the cipher-text blocks by embedding a set of pseudo random numbers, which may be dependent, but are pair-wise differentially uniform. We also describe an embodiment which is highly parallelizable.
Owner:IBM CORP +1
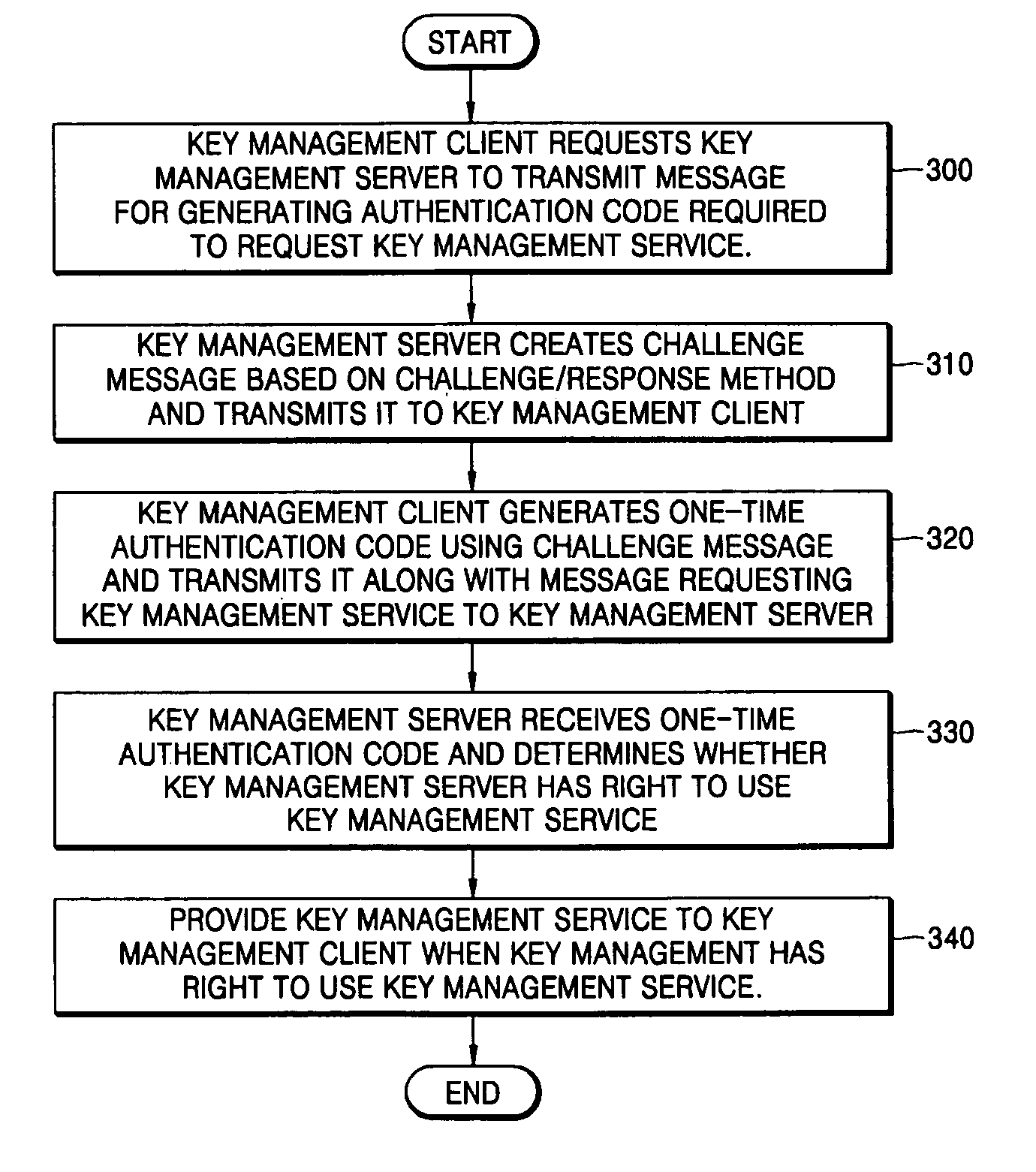
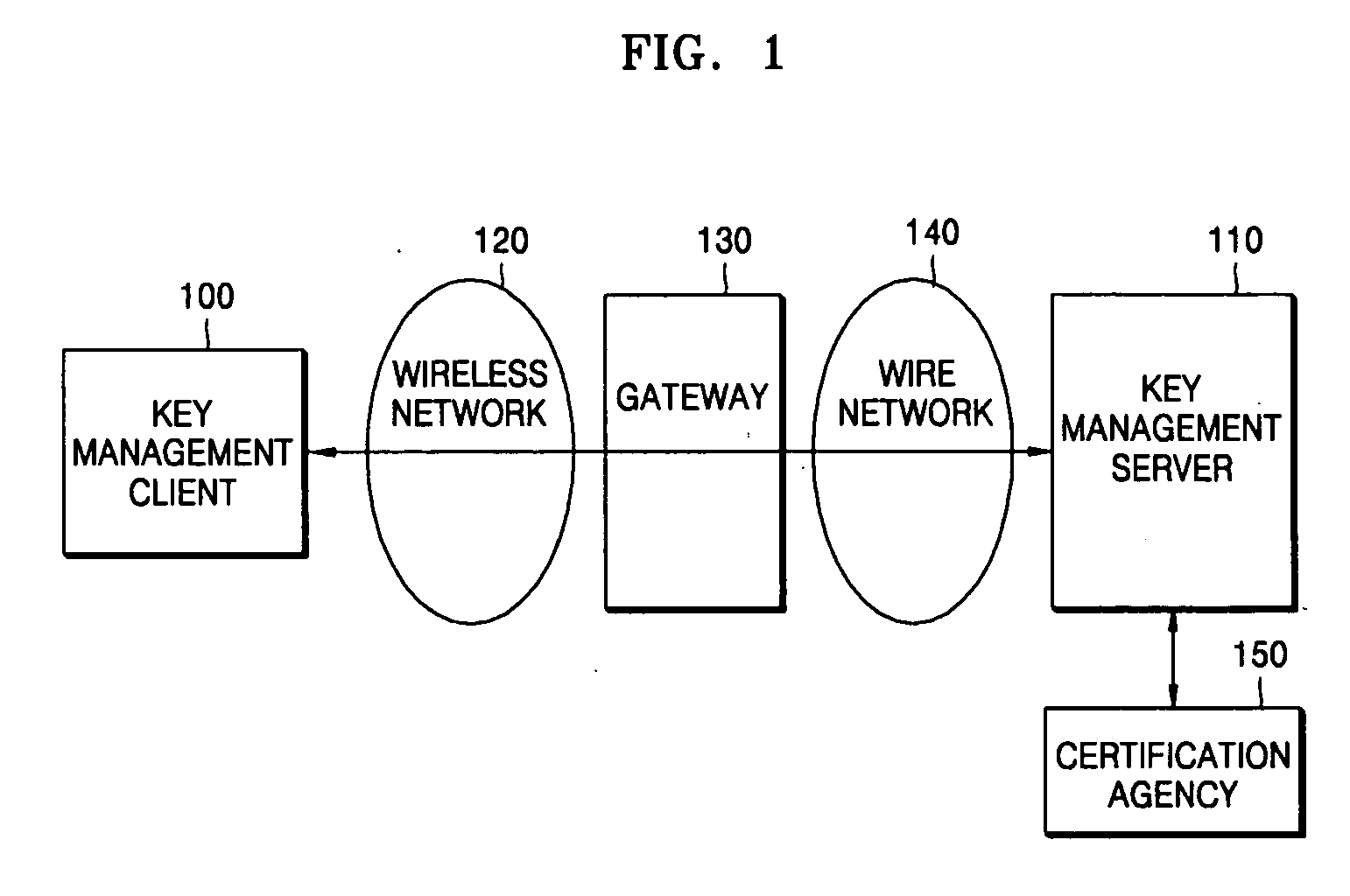
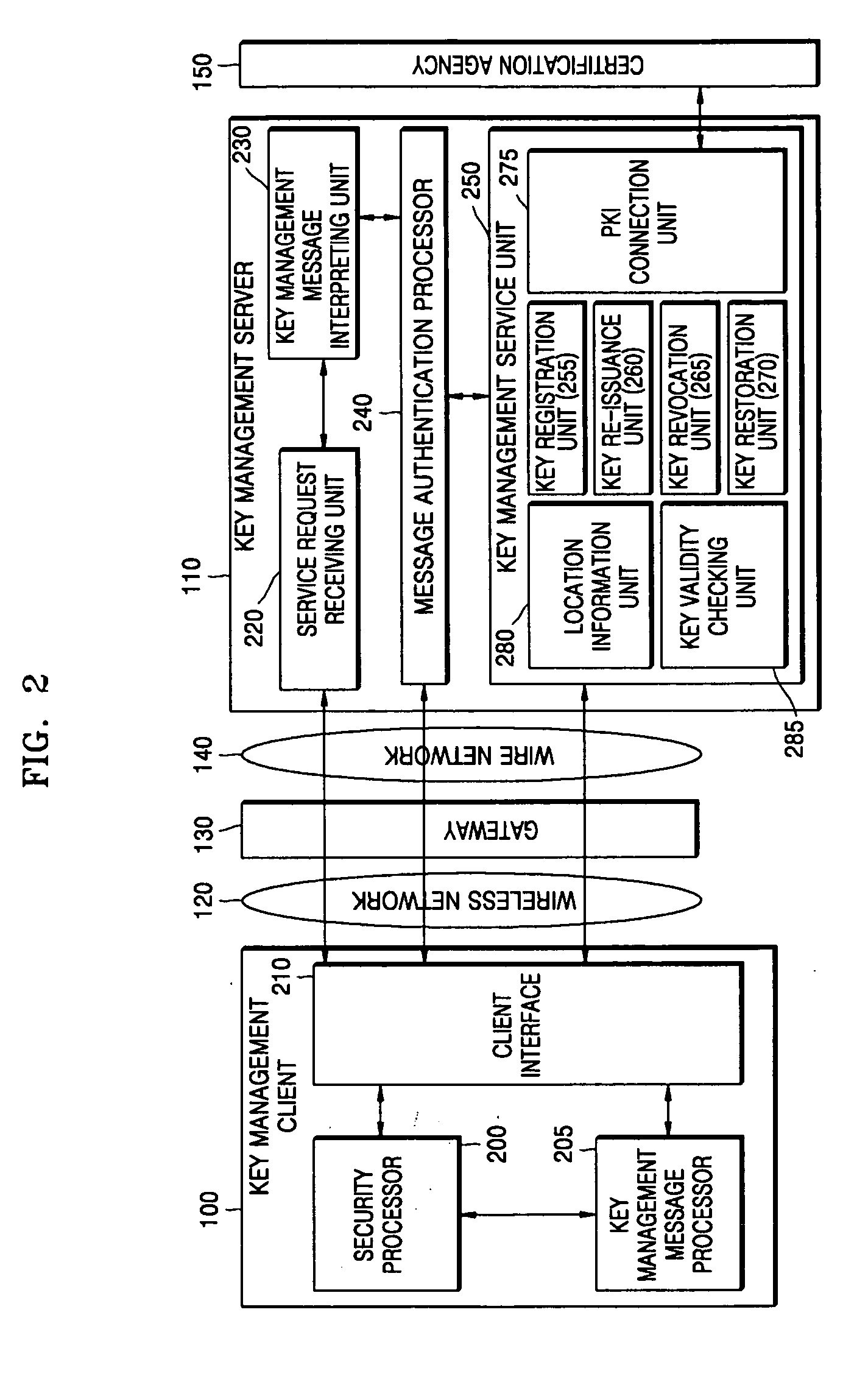
Key authentication/service system and method using one-time authentication code
Provided are a key authentication / service system and method using one-time authentication code. In the system and method, a key management client sends a key management server a message requesting transmission of a message for generating authentication code required to request a key management service. Next, the key management server creates a challenge message based on a challenge / response method using the received message. Next, the key management client generates the one-time authentication code using the challenge message and transmits it along with a message requesting a key management service to the key management server. Next, the key management server receives the one-time authentication code from the key management client and checks whether the one-time authentication code is certified to determine whether the key management client has a right to use the key management service. Then, the key management server provides the key management service to the key management client when it is determined that the key management client has a right to use this service.
Owner:ELECTRONICS & TELECOMM RES INST
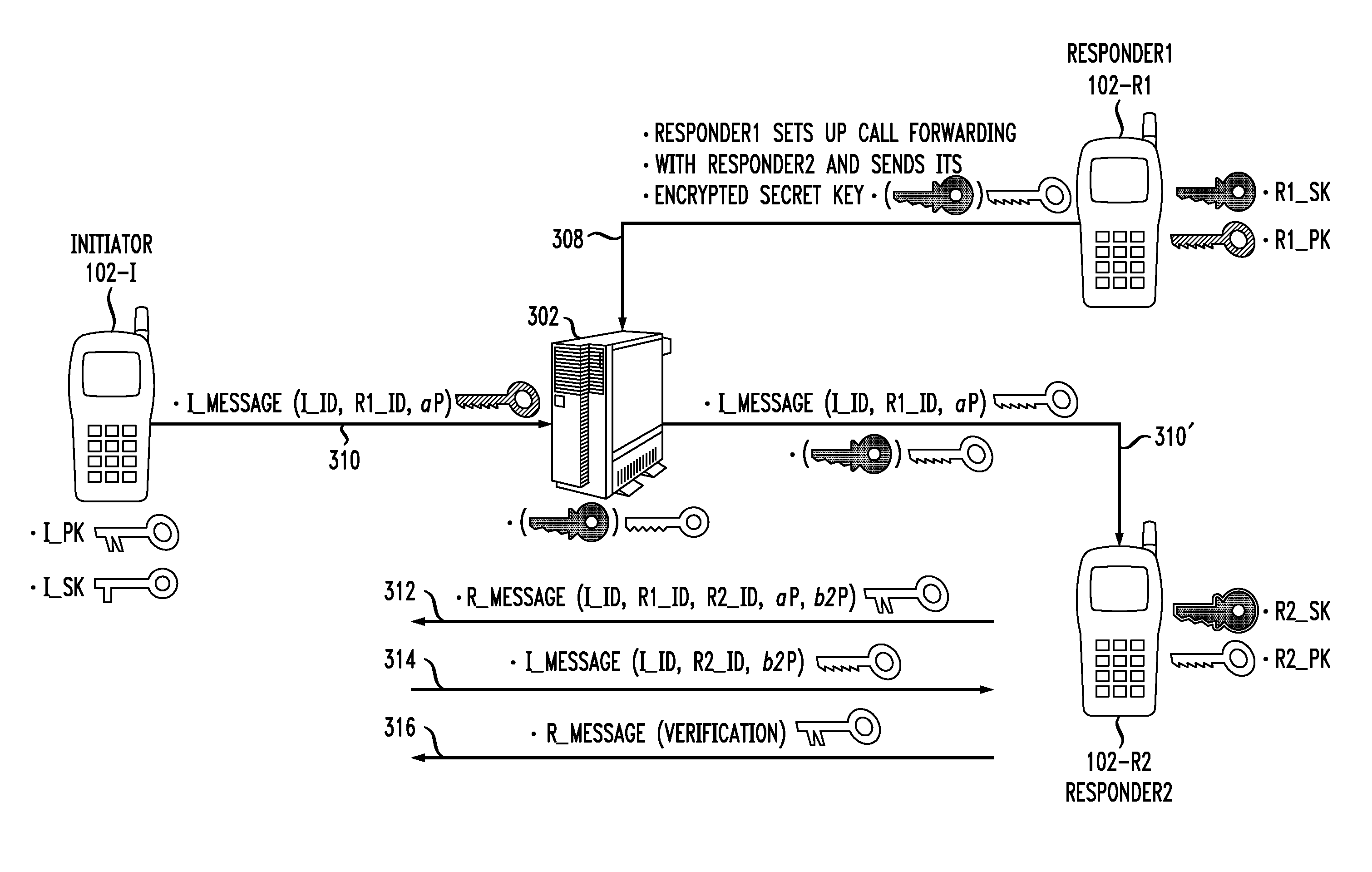
Provision of secure communications connection using third party authentication
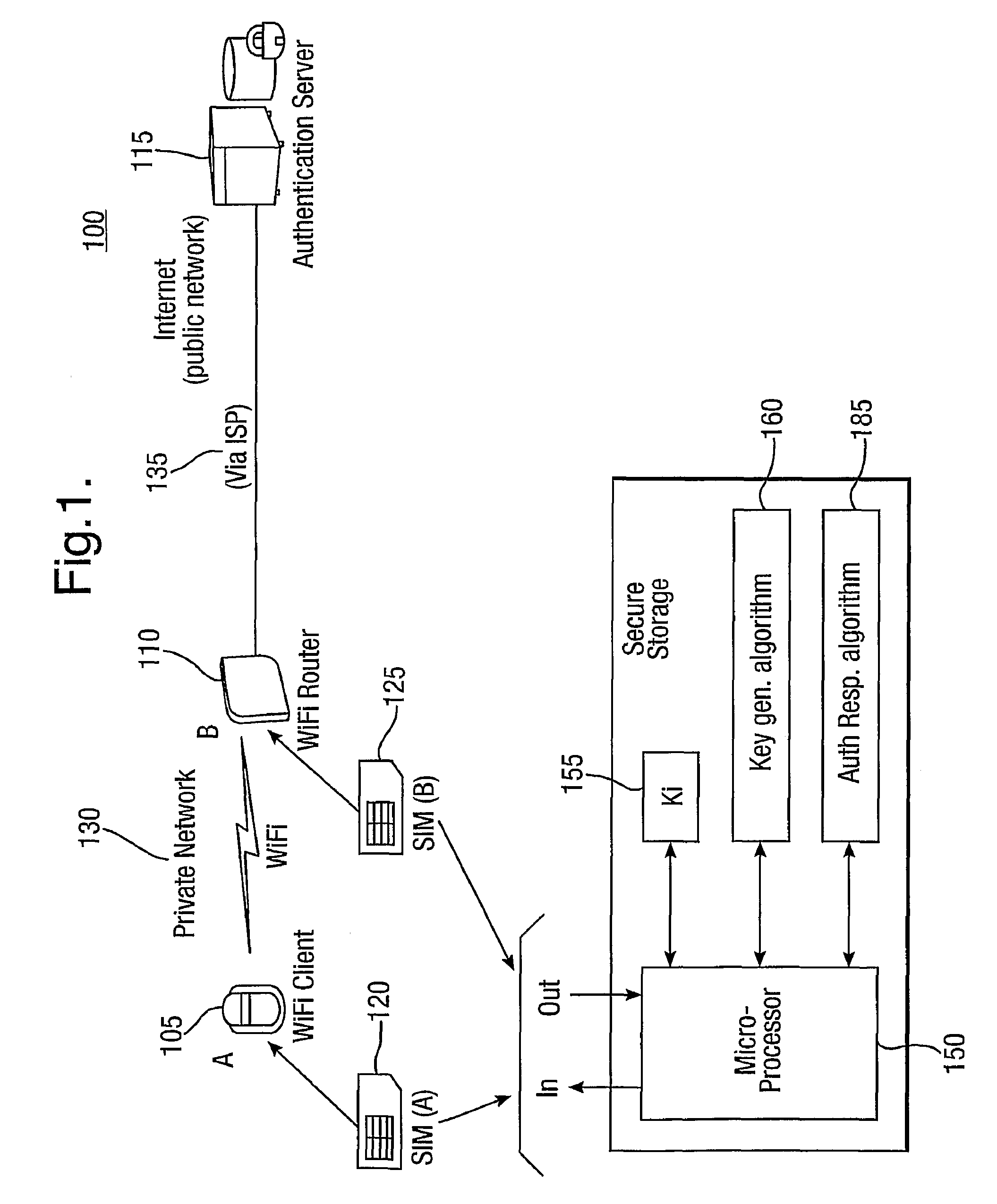
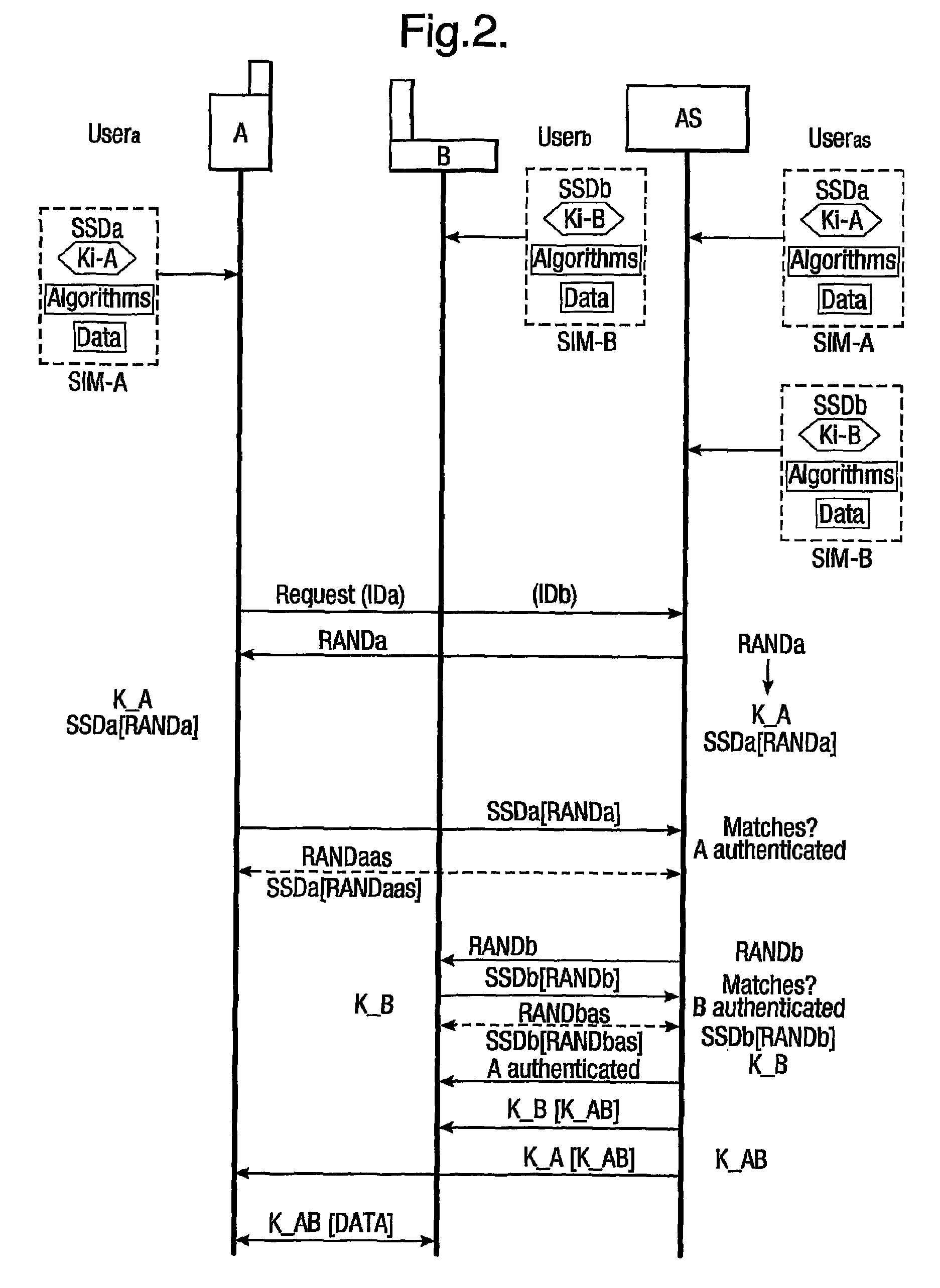
ActiveUS8738898B2Connection securityCommunication securityKey distribution for secure communicationUser identity/authority verificationSecure communicationThird party
The present invention relates to communications, and in particular though not exclusively to forming a secure connection between two untrusted devices. The present invention provides a method of securely connecting a first device (A) to a second device (B) using a third party authentication server (AS) coupled to the second device, the first device and the authentication server both having first device shared secret data (SSDa) and the second device and the authentication server both having second device shared secret data (SSDb). The method comprises receiving a request from the first device at the authentication server; the authentication server and the first device both generating a first device key (K_A) using the first device shared secret data in response to a first device random number (RANDa) sent from the authentication server to the first device; the authentication server and the second device both generating a second device key (K_B) using the second device shared secret data in response to a second device random number (RANDb) sent from the authentication server to the second device; and the authentication server securely forwarding to the second device (B) and the first device (A) a common key (K_AB) using the second and first device keys (K_B, K_A).
Owner:BRITISH TELECOMM PLC
Self arranged net mode shared key authentication and conversation key consulant method of radio LAN
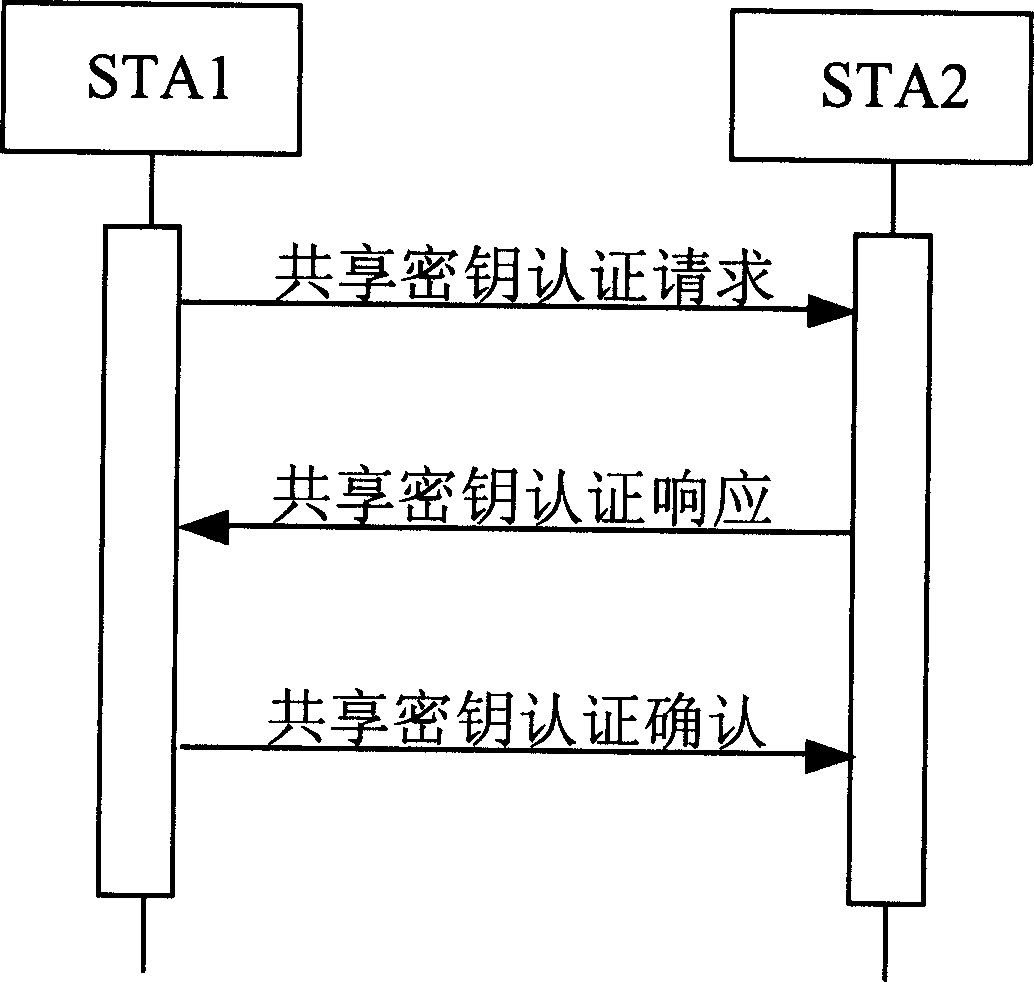
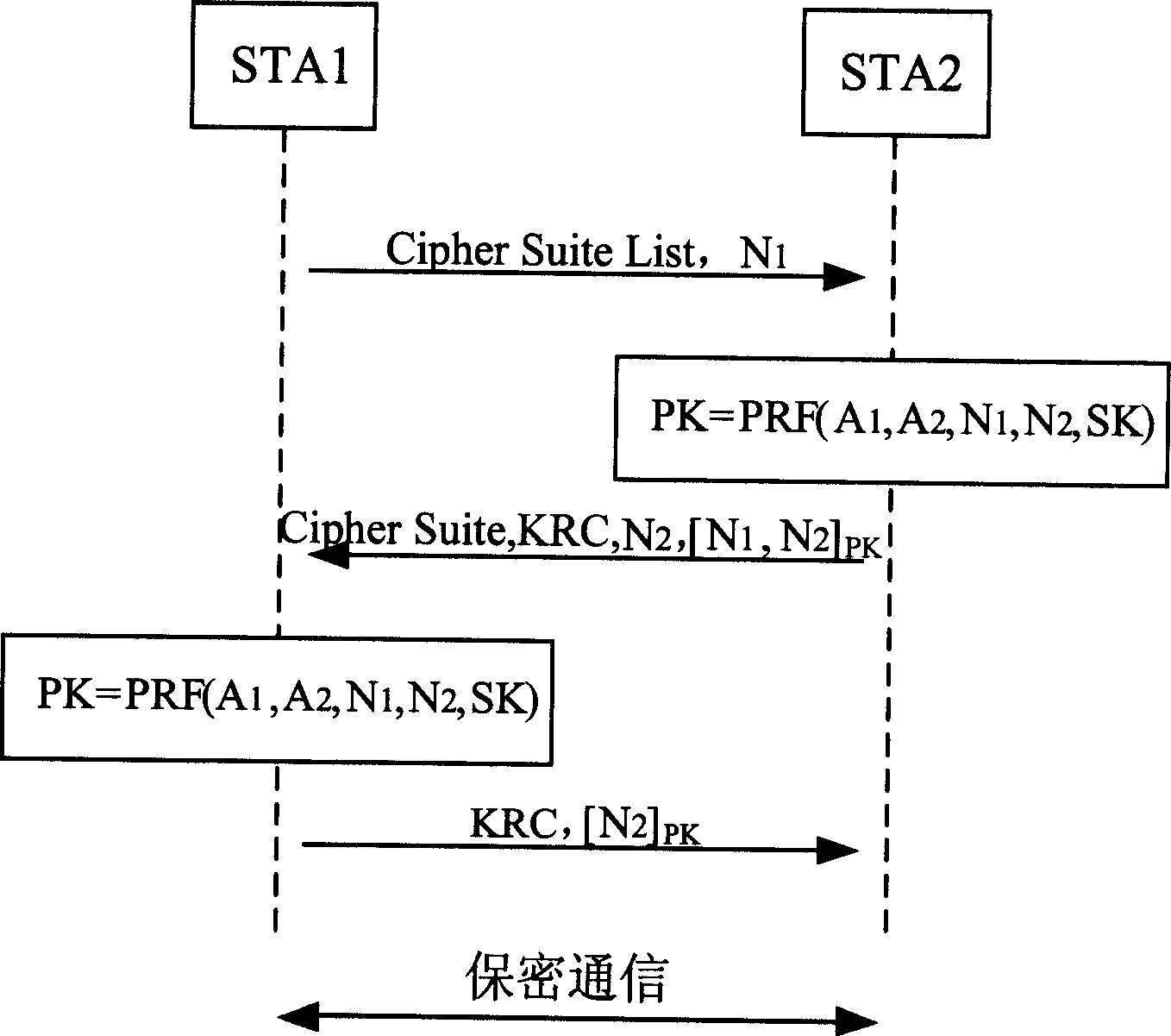
ActiveCN1564514AGuaranteed confidentialityImprove securitySynchronising transmission/receiving encryption devicesPublic key for secure communicationPublic key certificateKey authentication
The method includes processing steps: request of shared cryptographic key authentication; response of shared cryptographic key authentication; acknowledgement of shared cryptographic key authentication. Through configured shared cryptographic key in advance, intercheck authentication and negotiation of session key is able to carry out between wireless terminals in self built network, thus, complicated public key certificate application and installation procedure is not needed any more. Features are: high security, small amount of calculation, and high efficiency.
Owner:ZTE CORP
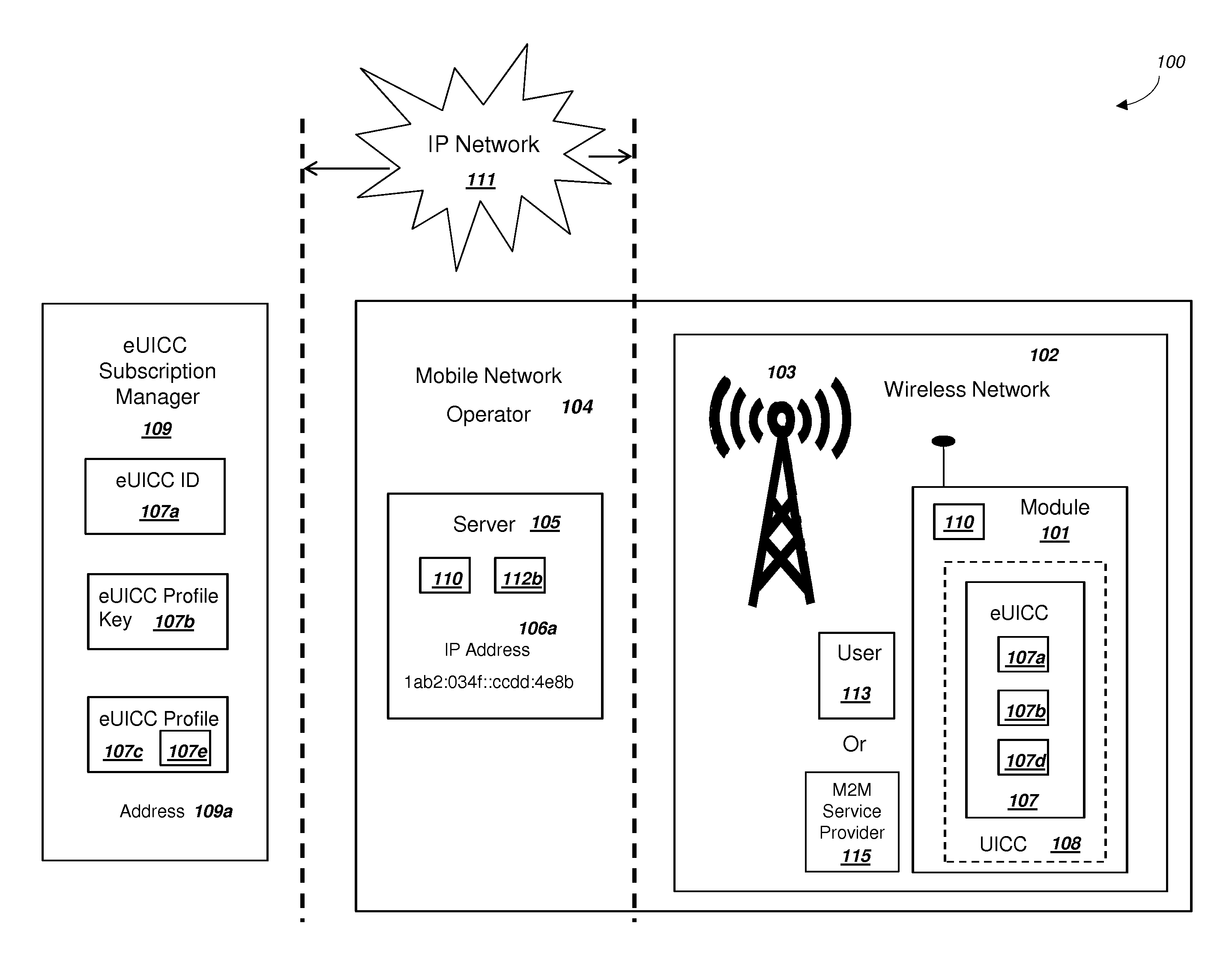
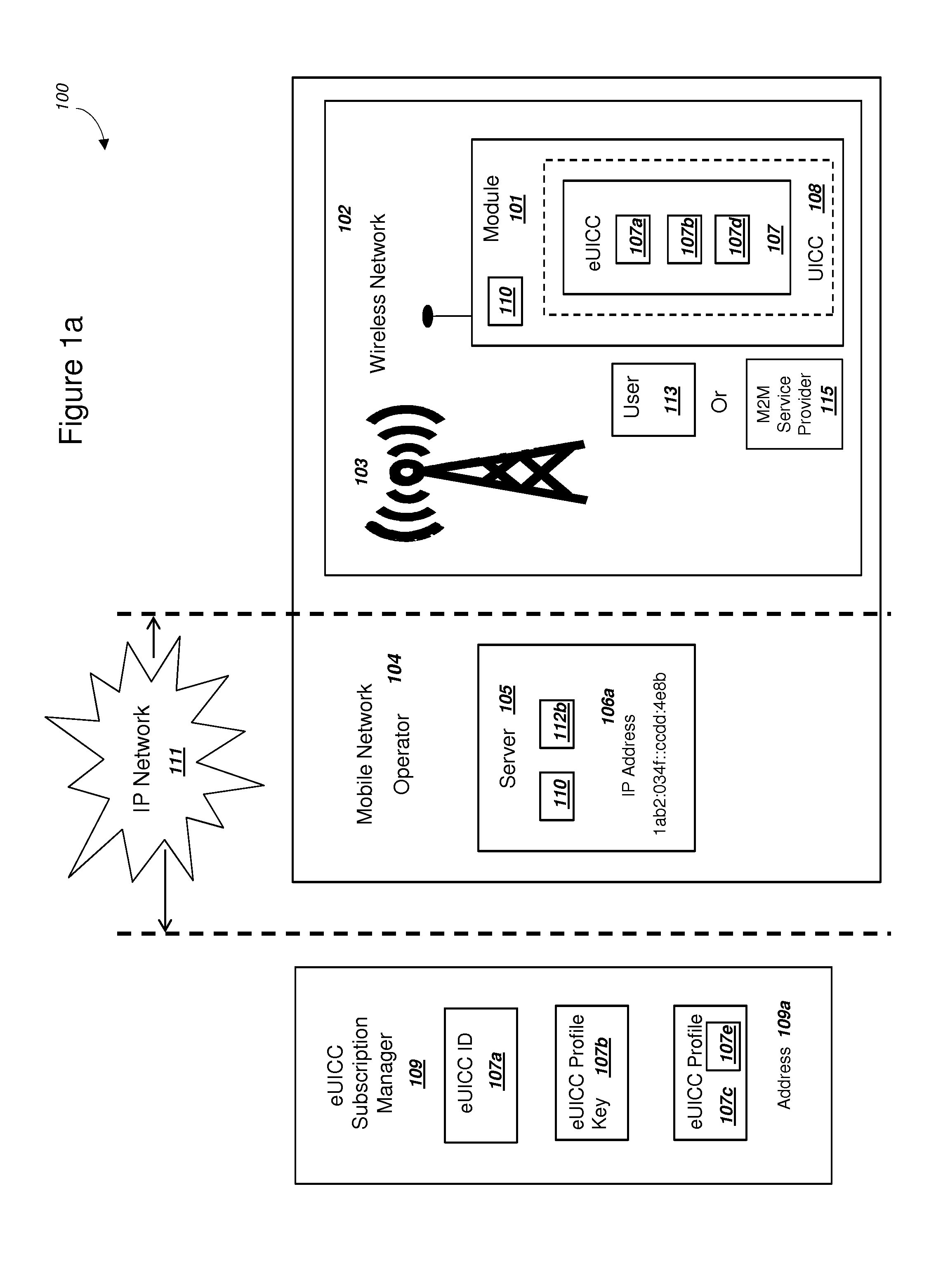
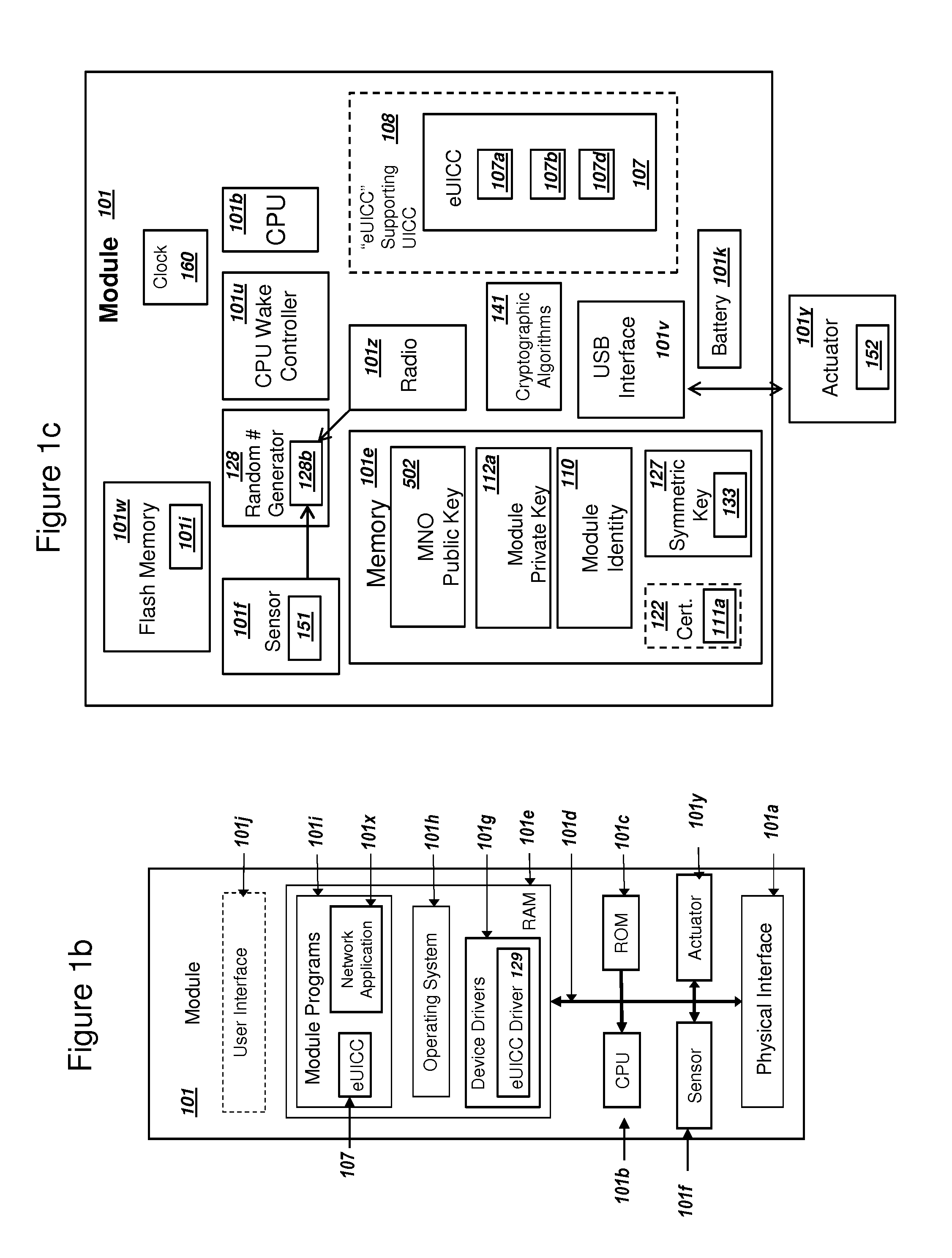
Network Supporting Two-Factor Authentication for Modules with Embedded Universal Integrated Circuit Cards
ActiveUS20150180847A1Improve the usefulnessIncrease valueUser identity/authority verificationSecurity arrangementKey authenticationEmbedded system
A network with a set of servers can support authentication from a module, where the module includes an embedded universal integrated circuit card (eUICC). The network can send a first network module identity, a first key K, and an encrypted second key K for an eUICC profile to an eUICC subscription manager. The second key K can be encrypted with a symmetric key. The module can receive and activate the eUICC profile, and the network can authenticate the module using the first network module identity and the first key K. The network can (i) authenticate the user of the module using a second factor, and then (ii) send the symmetric key to the module. The module can decrypt the encrypted second key K using the symmetric key. The network can authenticate the module using the second key K. The module can comprise a mobile phone.
Owner:NIX JOHN A +1
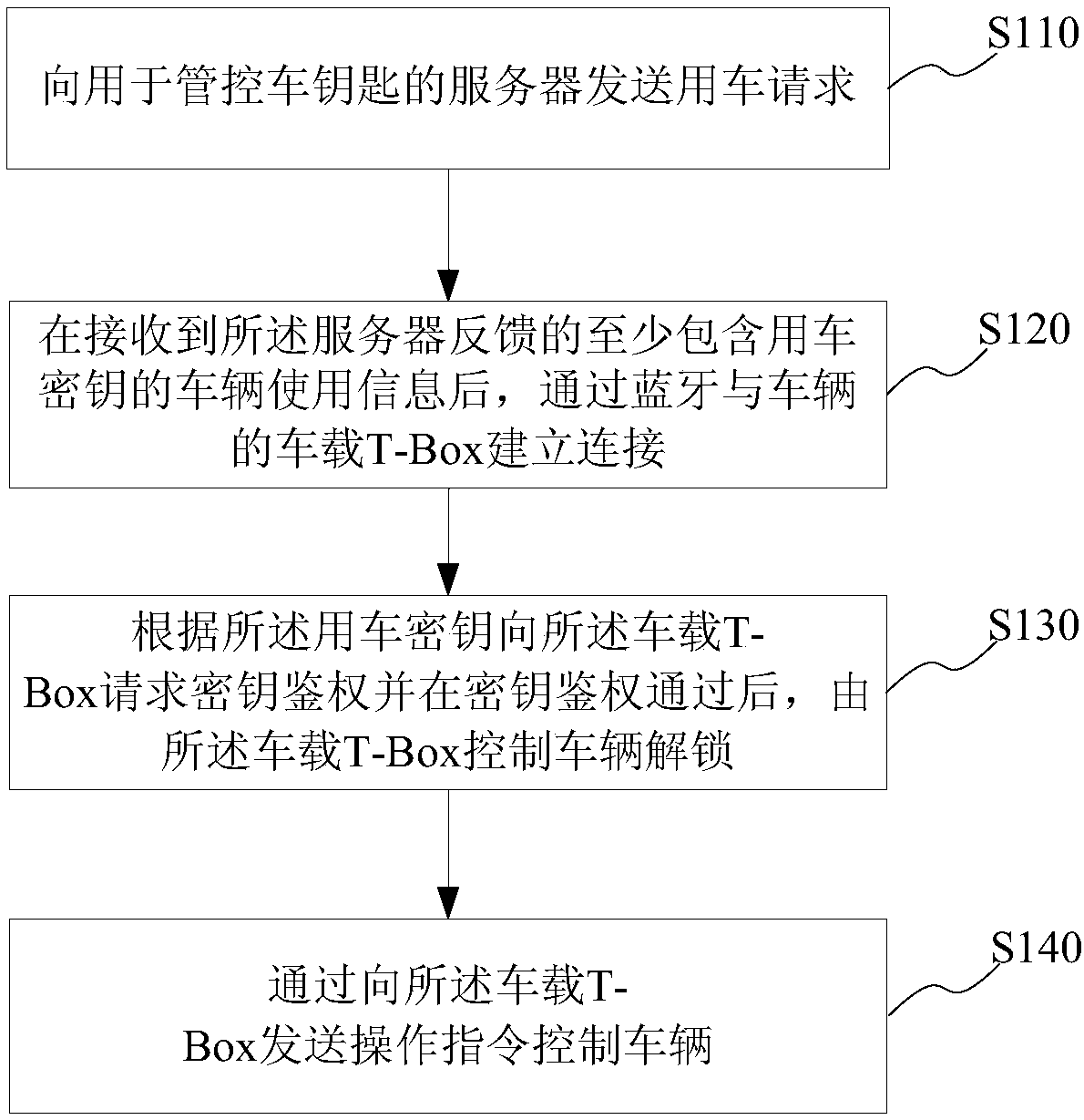
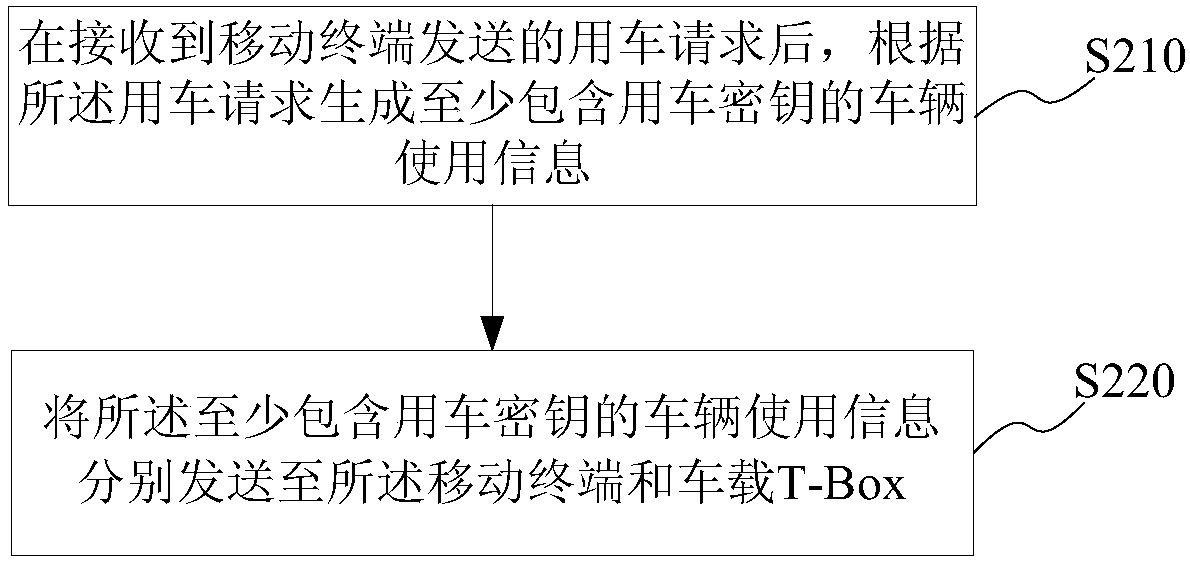
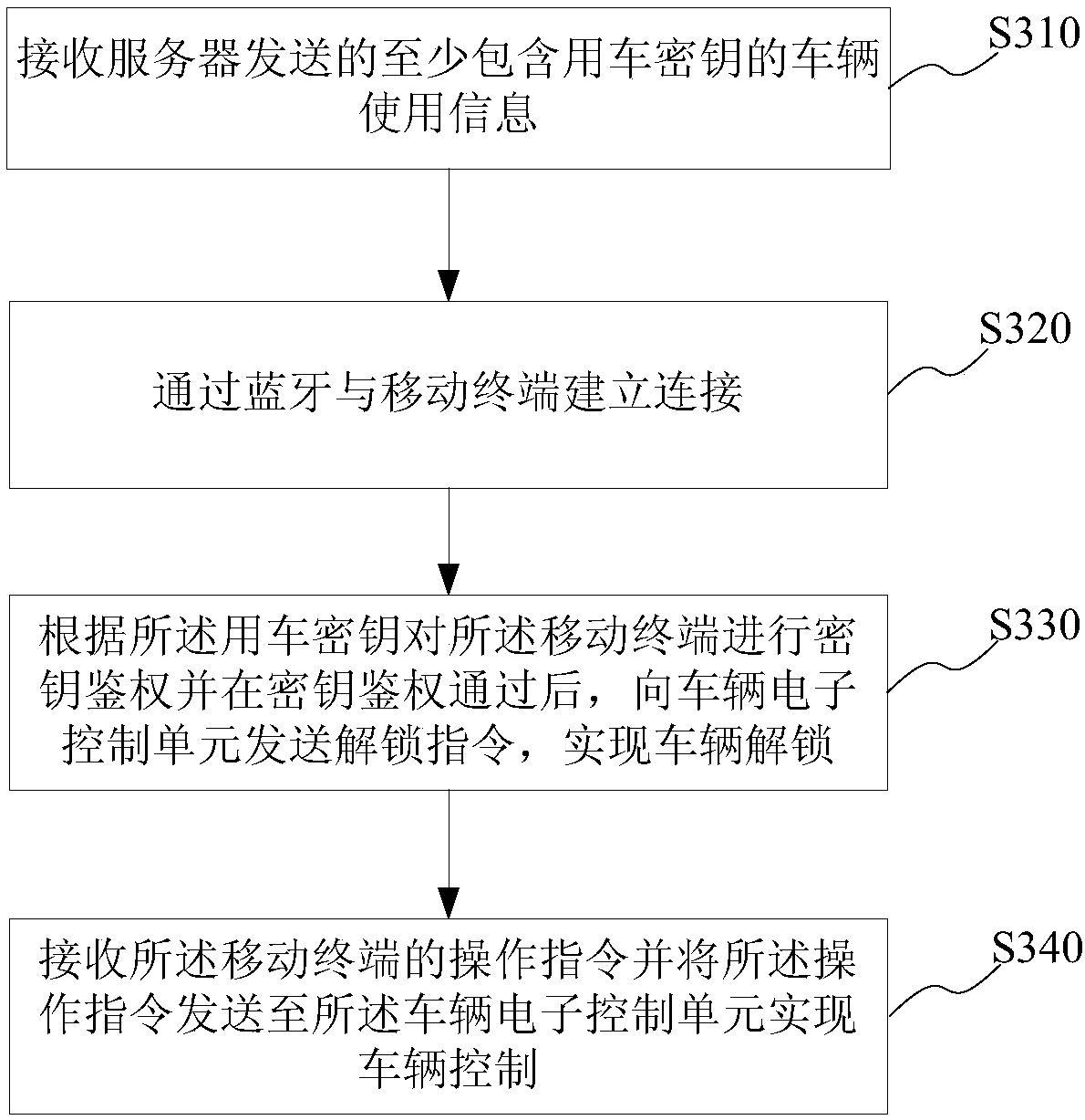
Implementation method and system of bluetooth key to car
InactiveCN107689098ARealize door opening operationImprove convenienceKey distribution for secure communicationSubstation equipmentComputer terminalKey authentication
The invention provides an implementation method and system of a bluetooth key to a car. The implementation method of the bluetooth key to the car comprises the following steps: receiving vehicle use information at least comprising a secrete key to a used car, which is sent by a server, with a vehicle-mounted T-Box; establishing connection with a mobile terminal by bluetooth; performing secret keyauthentication on the mobile terminal according to the secrete key of the used car; after the secret key authentication is passed, sending an unlocking instruction to an electronic control unit of thecar, so as to unlock the car; receiving an operation instruction of the mobile terminal and sending the operation instruction to the electronic control unit of the car, so as to control the car. According to the implementation method, by performing bluetooth secrete key authentication on the vehicle-mounted T-Box with the mobile terminal, an operation of opening a door of the car is implemented,the traditional hardware key is substituted, tedious operations of finding the key and operating the key when the vehicle is used by a user are avoided, the problem of the limitation of car renting time and space can be effectively solved, and the convenience of use of the car is improved.
Owner:SHANGHAI PATEO ELECTRONIC EQUIPMENT MANUFACTURING CO LTD
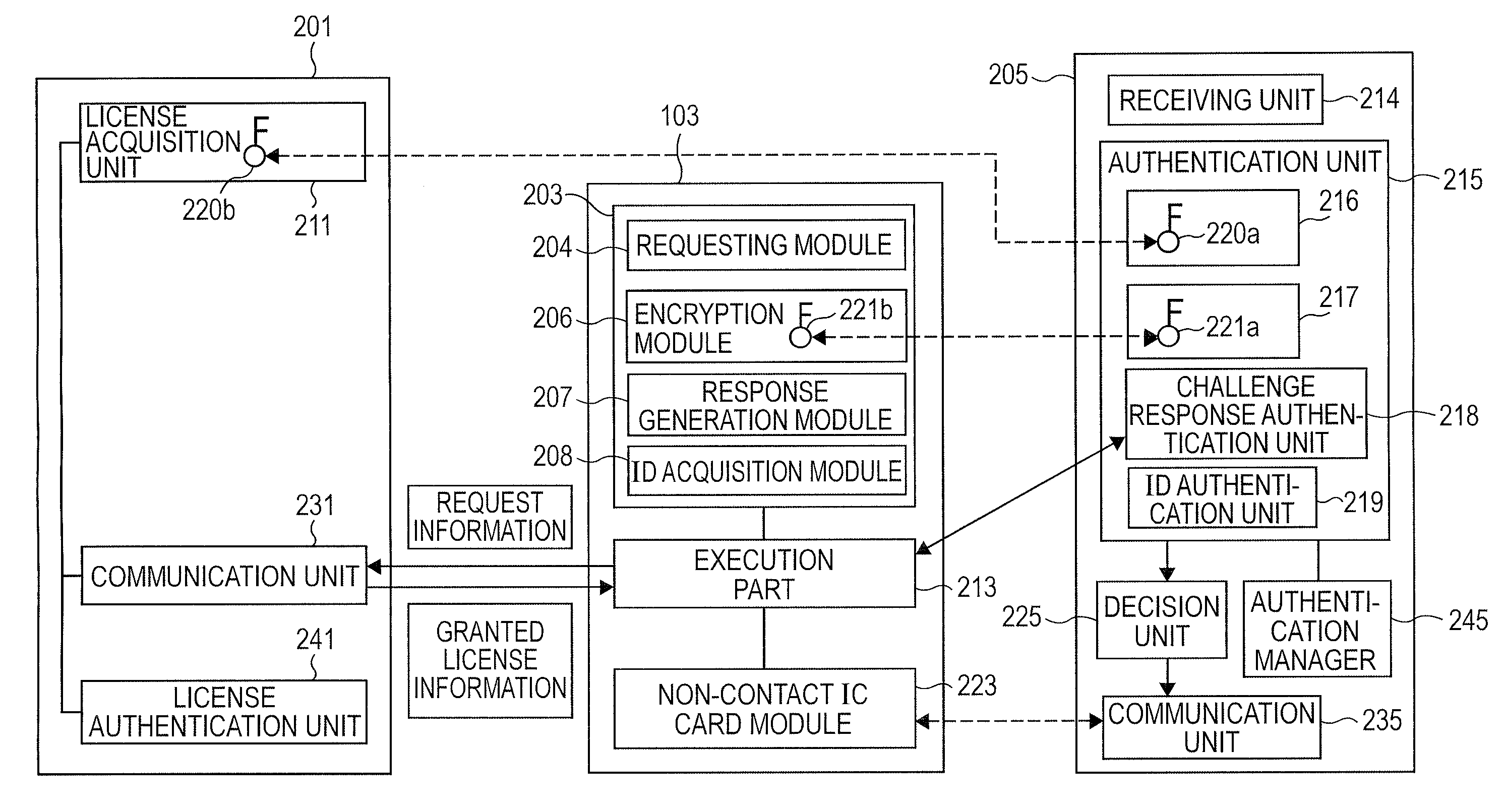
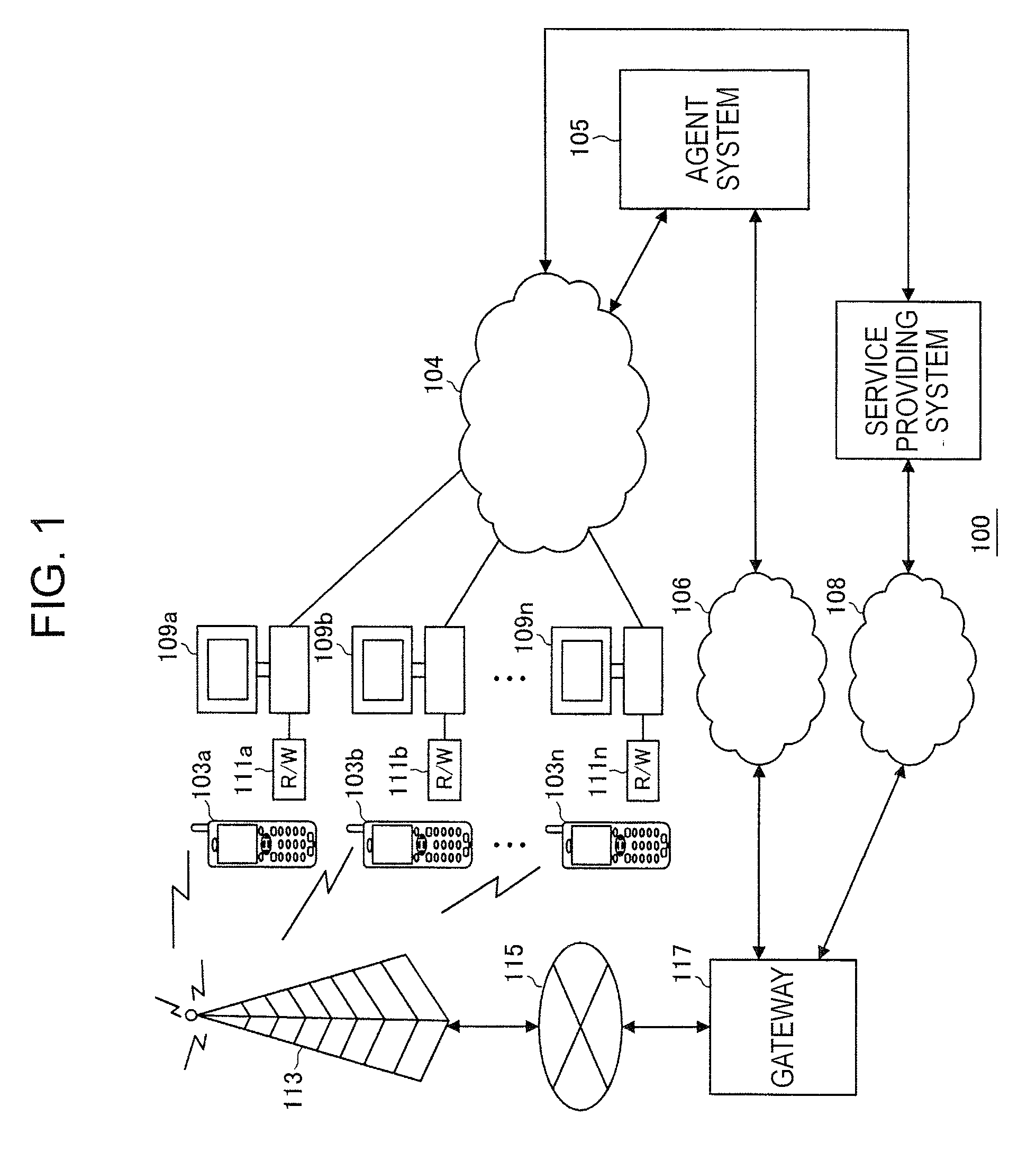
Data Communication System, Agent System Server, Computer Program, and Data Communication Method
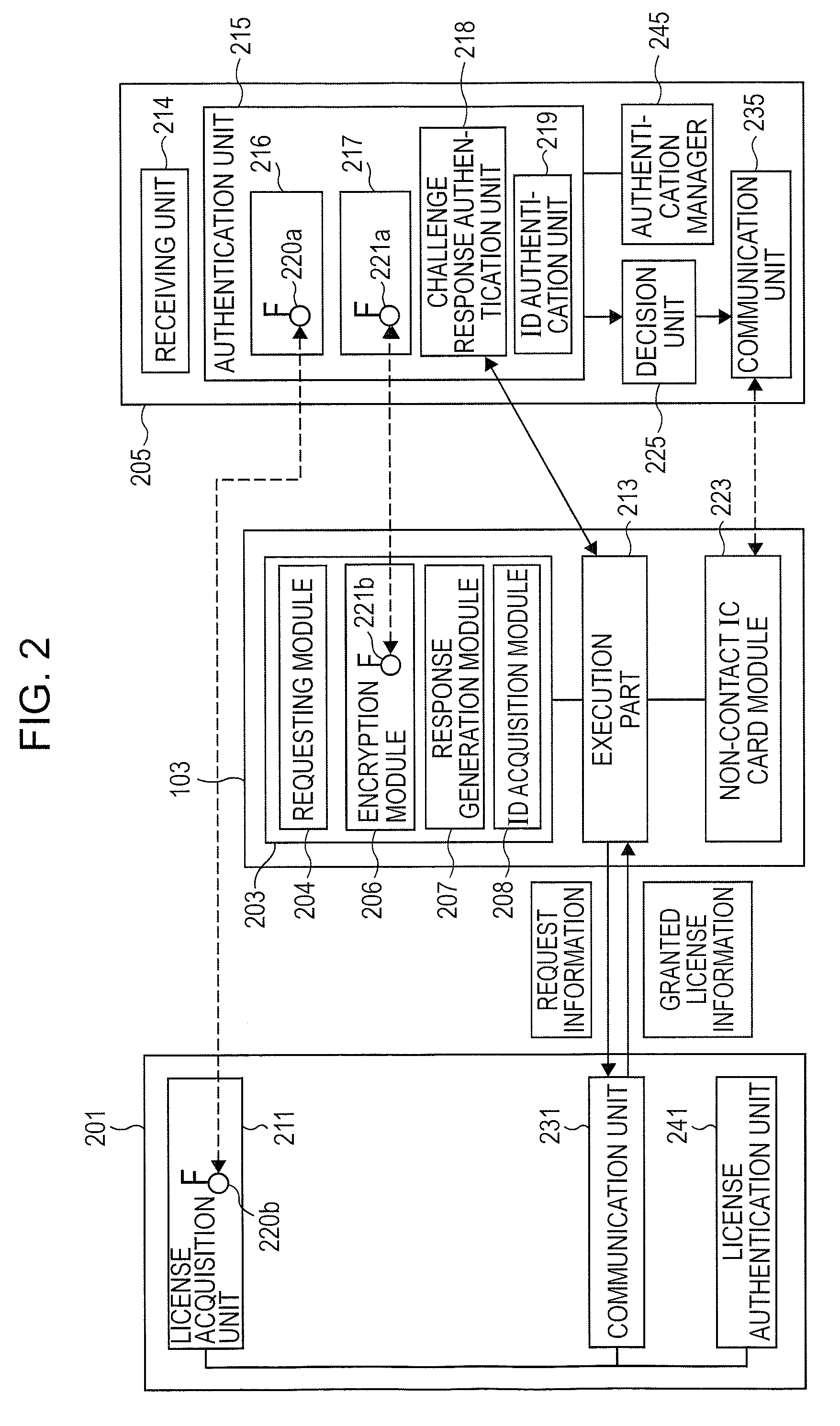
InactiveUS20080059797A1Increase flexibilityFlexible fashionUser identity/authority verificationSecurity arrangementCommunications systemCommunication unit
In the data communication system, a portable communication terminal is authenticated by an agent system including an authentication unit, a decision unit and a communication unit. The authentication unit is adapted to perform, based on granted license information received from the portable communication terminal, at least one of a system authentication process to authenticate the service providing system based on a system authentication key, a first client authentication process to authenticate the portable communication terminal based on a client authentication key, and a second client authentication process to authenticate the portable communication terminal based on identification information identifying the portable communication terminal. The decision unit is adapted to, after the authentication is completed, determine whether to permit communication, based on the license described in the granted license information. The communication unit is adapted to, if communication is permitted, perform the communication process with the noncontact IC card module.
Owner:FELICA NETWORKS INC
Secure Key Management in Conferencing System
InactiveUS20110051912A1Key distribution for secure communicationUser identity/authority verificationCommunications systemConference management
Principles of the invention provide one or more secure key management protocols for use in a communication environment such as a conferencing system. For example, a method for managing a conference between two or more parties in a communication system comprises the following steps. An identity based authenticated key exchange operation is performed between a conference management element of the communication system and each of the two or more parties seeking to participate in the conference, wherein messages exchanged between the conference management element and the two or more parties are encrypted based on respective identities of recipients of the messages, and further wherein the conference management element receives from each party during the key authentication operation a random key component that is computed based on a random number selected by the party. The conference management element sends to each party a set comprising the random key components computed by the parties. The conference management element receives from each party a random group key component, wherein the random group key component is computed by each party via a computation based on the random number used by the party during the key authentication operation and the random key components computed by a subset of others of the two or more parties seeking to participate in the conference. The conference management element sends to each party a set comprising the random group key components computed by the parties such that each party can compute the same group key for use in communicating with each other party through the conference management element.
Owner:ALCATEL LUCENT SAS
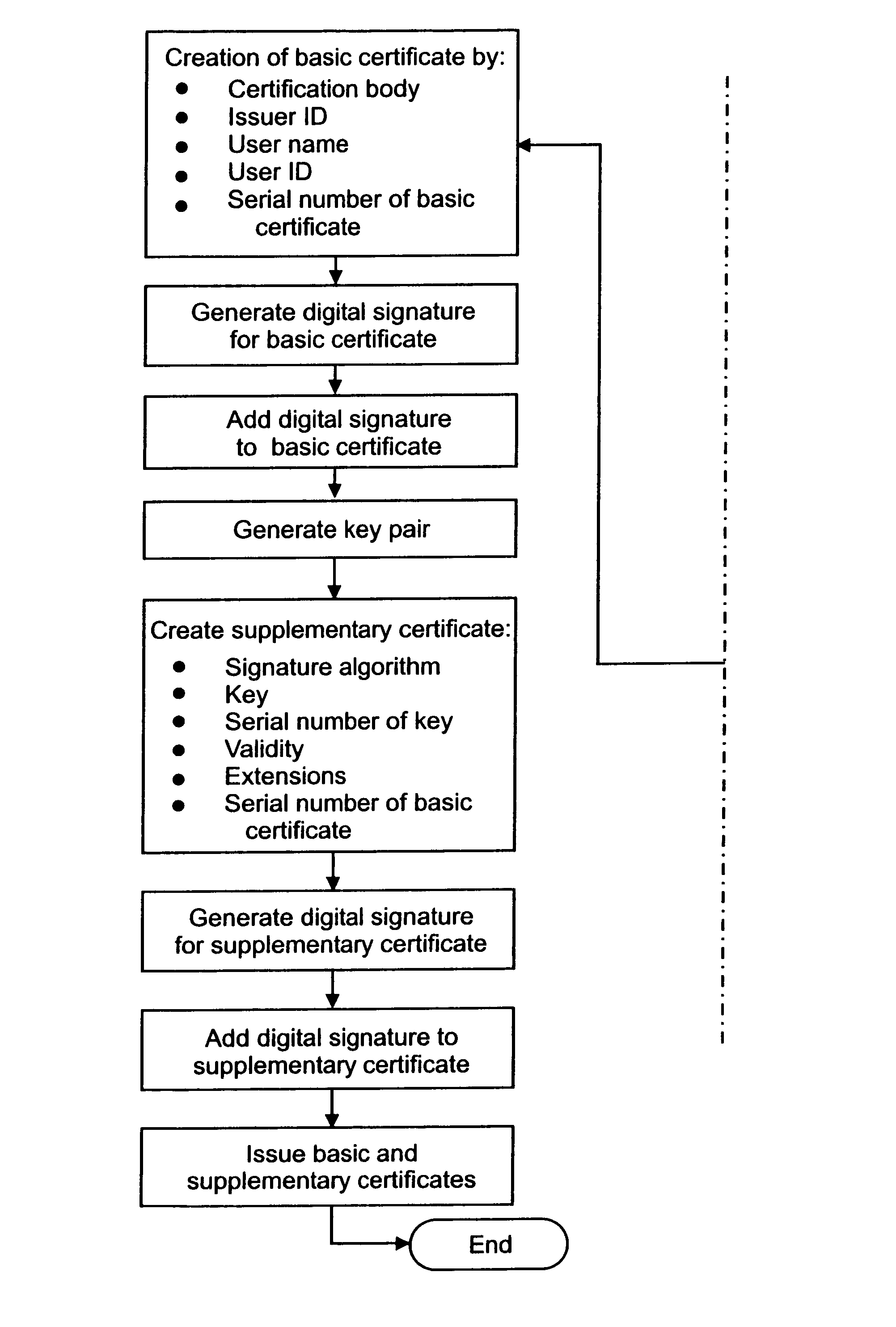
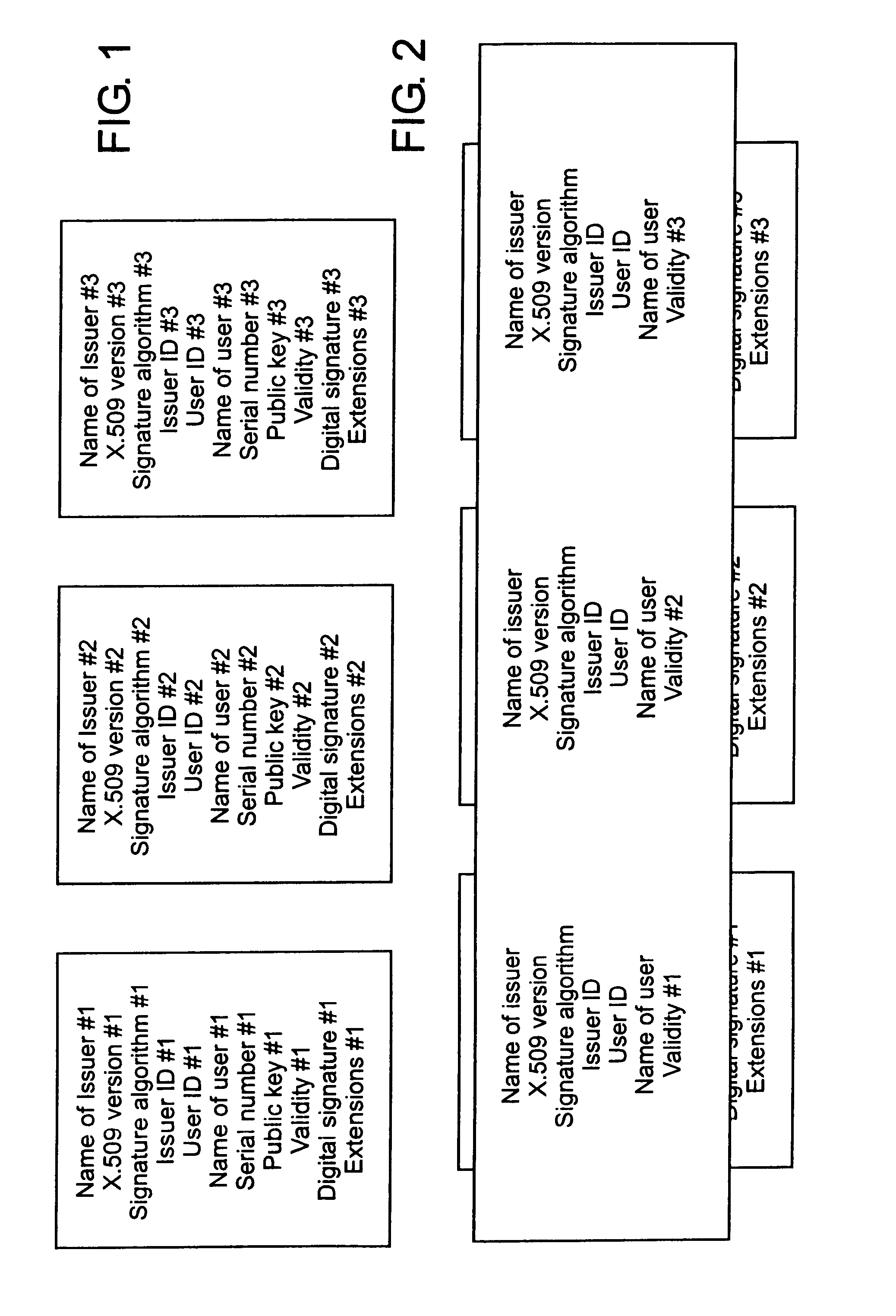
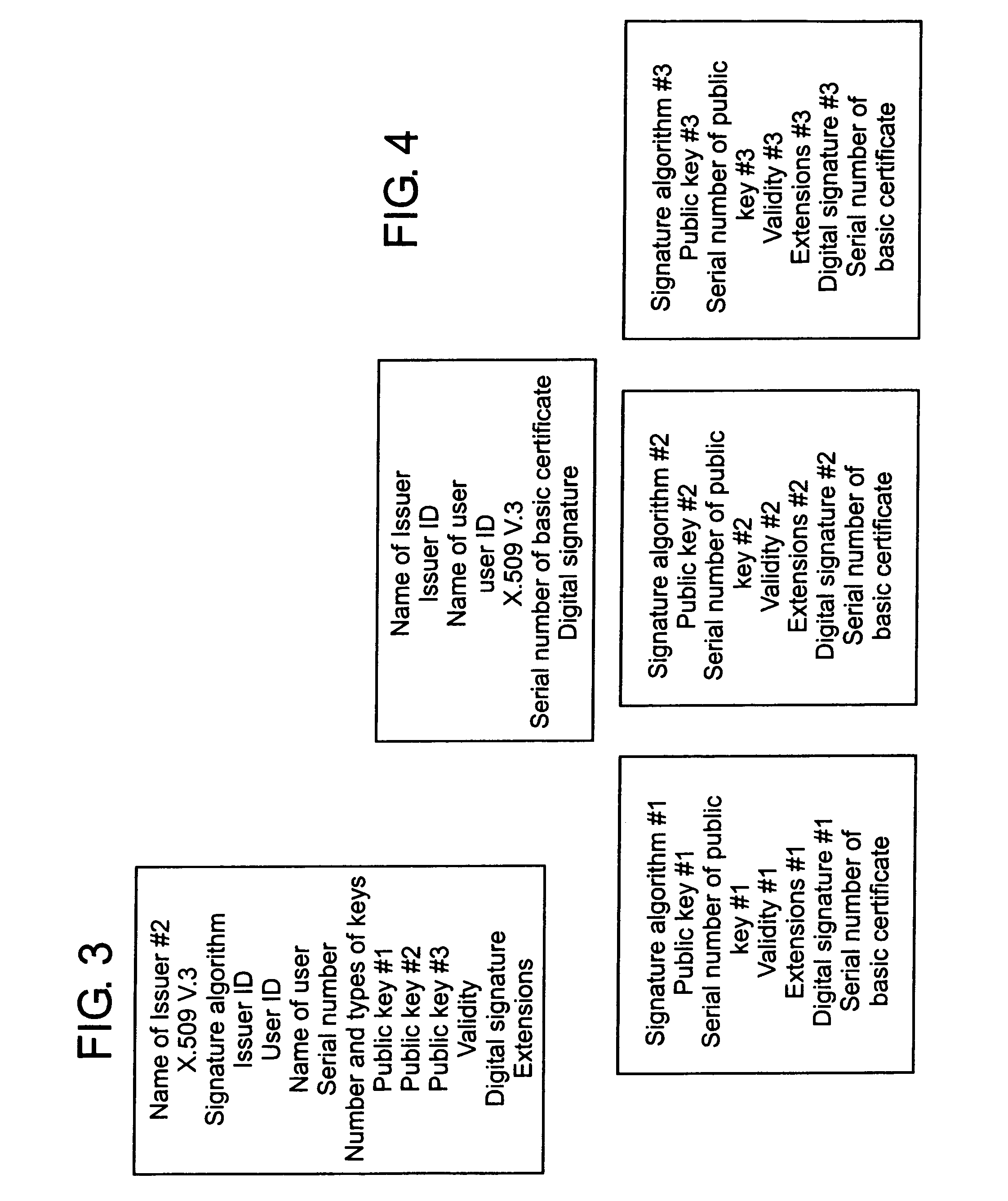
Certification of multiple keys with new base and supplementary certificate types
InactiveUS6981147B1Good flexibilityReduce memory requirementsUser identity/authority verificationDigital data authenticationRoot certificateKey authentication
A method for creating, storing and reading a new certificate type for certification of keys is provided. In the new certificate type, several certificates, containing a minimum quantity of redundant data fields, are collated to form one certificate and all redundant information on the certificates is eliminated. An embodiment of the new certificate type is the group certificate. The group certificate is used where several keys are to be issued at the same time for the same user by the same certification instance. By means of the group certificate, all redundant data elements are eliminated and all data elements for a set of several keys subject to certification are grouped into one certificate. This substantially reduces the memory requirement, and handling of the certificates is simplified for the communication partners. A further embodiment of the new certificate type is the basic and supplementary certificate combination. This form of certification is used where certificates are issued at different times for the same user by the same certification body. The memory requirement is consequently somewhat more than for group certificates, but greater flexibility is gained in use of the keys.
Owner:IBM CORP
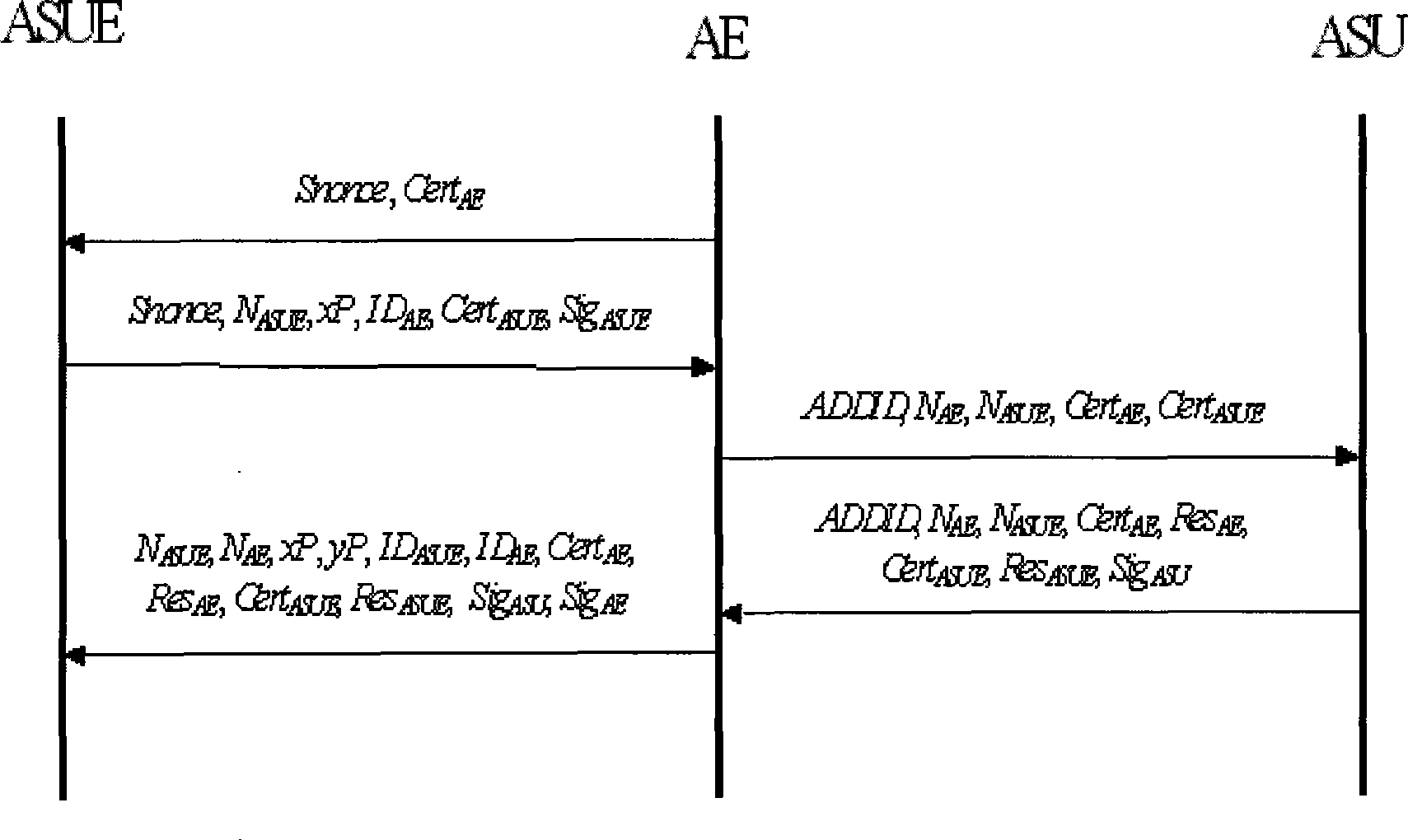
WAPI-XG1 access and fast switch authentication method
InactiveCN101420694AReduce complexitySolve the problem that fast switching is not supportedNetwork topologiesTransmissionClient-sideDictionary attack
The invention provides a method used for authentificating the access and quick switching over of WAPI-XG1, belonging to the field of wireless communication. The method comprises the steps as follows: an authentication protocol is accessed and used for establishing a connection between an STA and a first AP, the session key with the first AP is established, and keys used for quick switching over with an ASU are established; when the STA moves to the control domain of a second AP, a safety correlation establishing protocol and a unicall session key updating protocol under quick switching over are carried out. The method can solve the problems that the WAPI-XG1 can not support the quick switching over and the forward secrecy can not be ensured and the offline dictionary attack can not be resisted under a pre-shared key authentication mode; meanwhile, the method needs not change the authentication framework of the WAPI-XG1needs not changing, the two authentication modes based on the certificate and shared key are integrated into one authentication proposal; furthermore, when the switching over occurs on the client terminal, only the quick switching over safety correlation establishment protocol runs with the destination access point for the authentication mode based on the certificate, without re-authentication or pre-authentication.
Owner:TIANJIN POLYTECHNIC UNIV +1
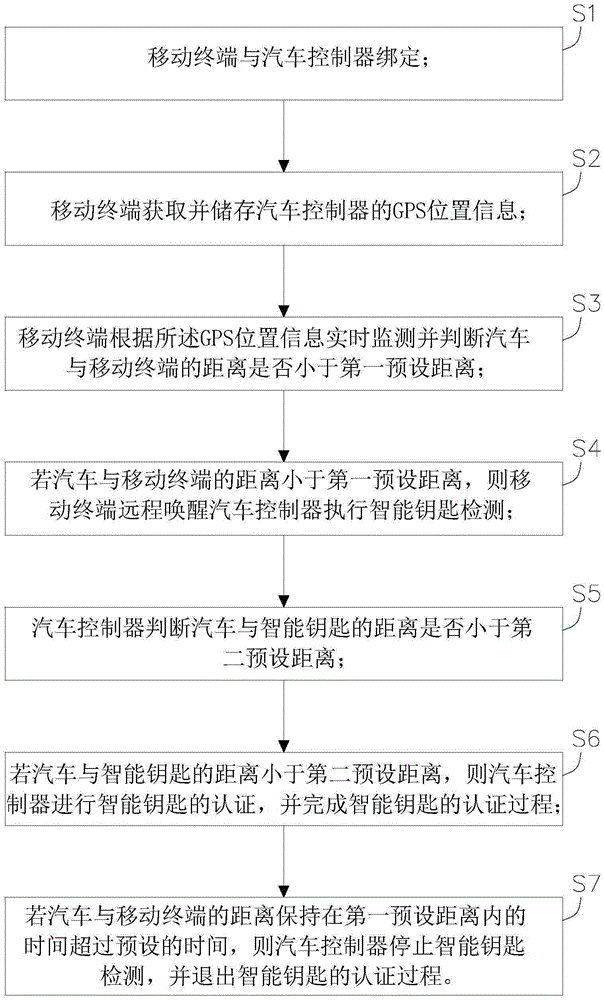
Keyless entry system detecting method for automobile
The invention discloses a keyless entry system detecting method for an automobile. The keyless entry system detecting method for the automobile comprises the following steps that a mobile terminal is bound with an automobile controller; the mobile terminal acquires GPS position information of the automobile controller; the mobile terminal judges whether the distance between the automobile and the mobile terminal is less than a first preset distance or not according to the GPS position information; if the distance between the automobile and the mobile terminal is less than the first preset distance, the mobile terminal remotely wakes up the automobile controller to execute intelligent key detection; the automobile controller judges whether the distance between the automobile and the intelligent key is less than a second preset distance or not; if the distance between the automobile and the intelligent key is less than the second preset distance, the automobile controller performs intelligent key authentication and finishes the intelligent key authentication process; and if the time of keeping the distance between the automobile and the mobile terminal within the first preset distance exceeds a preset time, the automobile controller exits the intelligent key authentication process. According to the invention, the loss of the system is reduced and the practicability, convenience and safety of the system are improved.
Owner:FJ MOTOR GRP YUDO NEW ENERGY AUTOMOBILE CO LTD
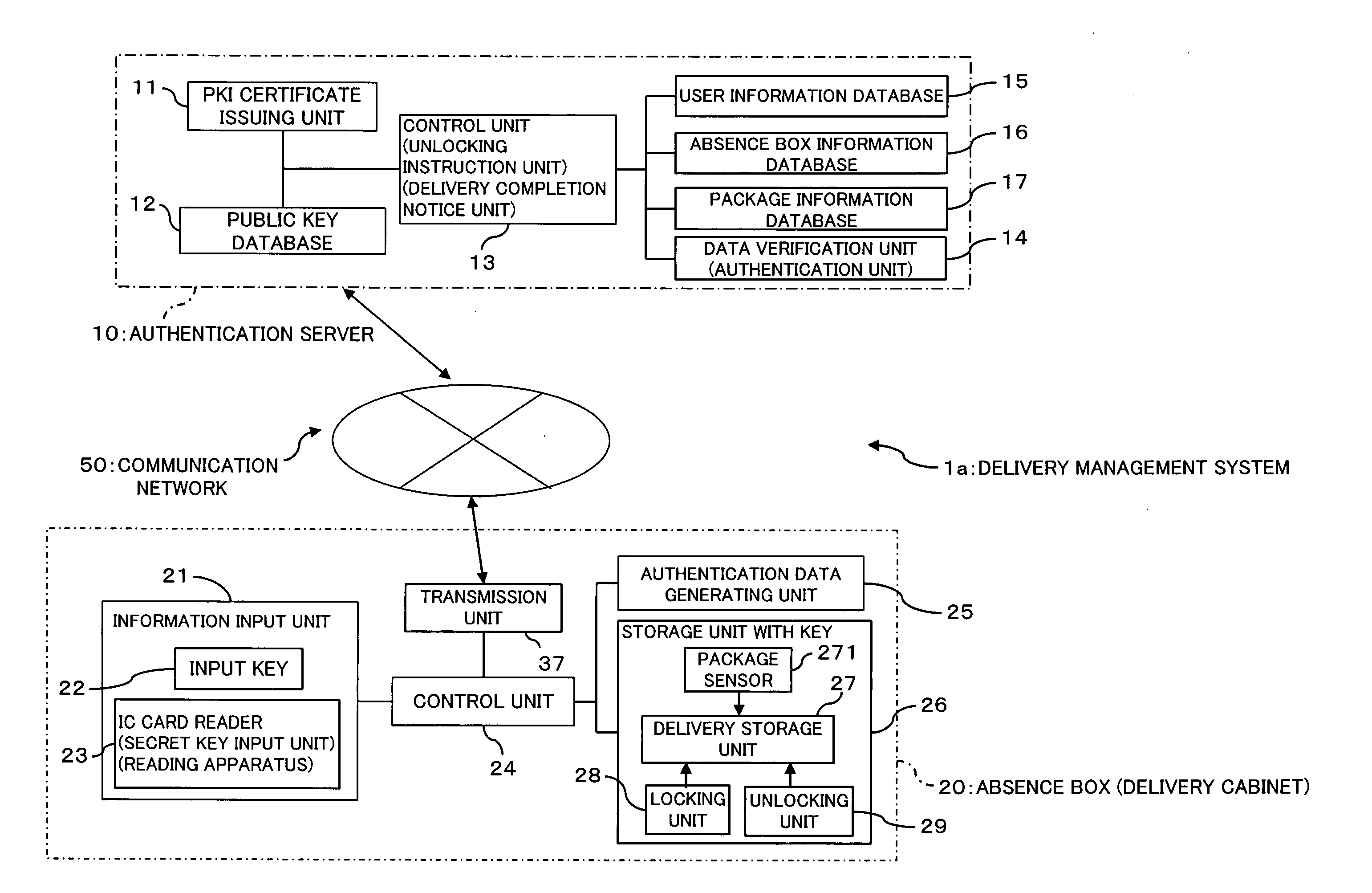
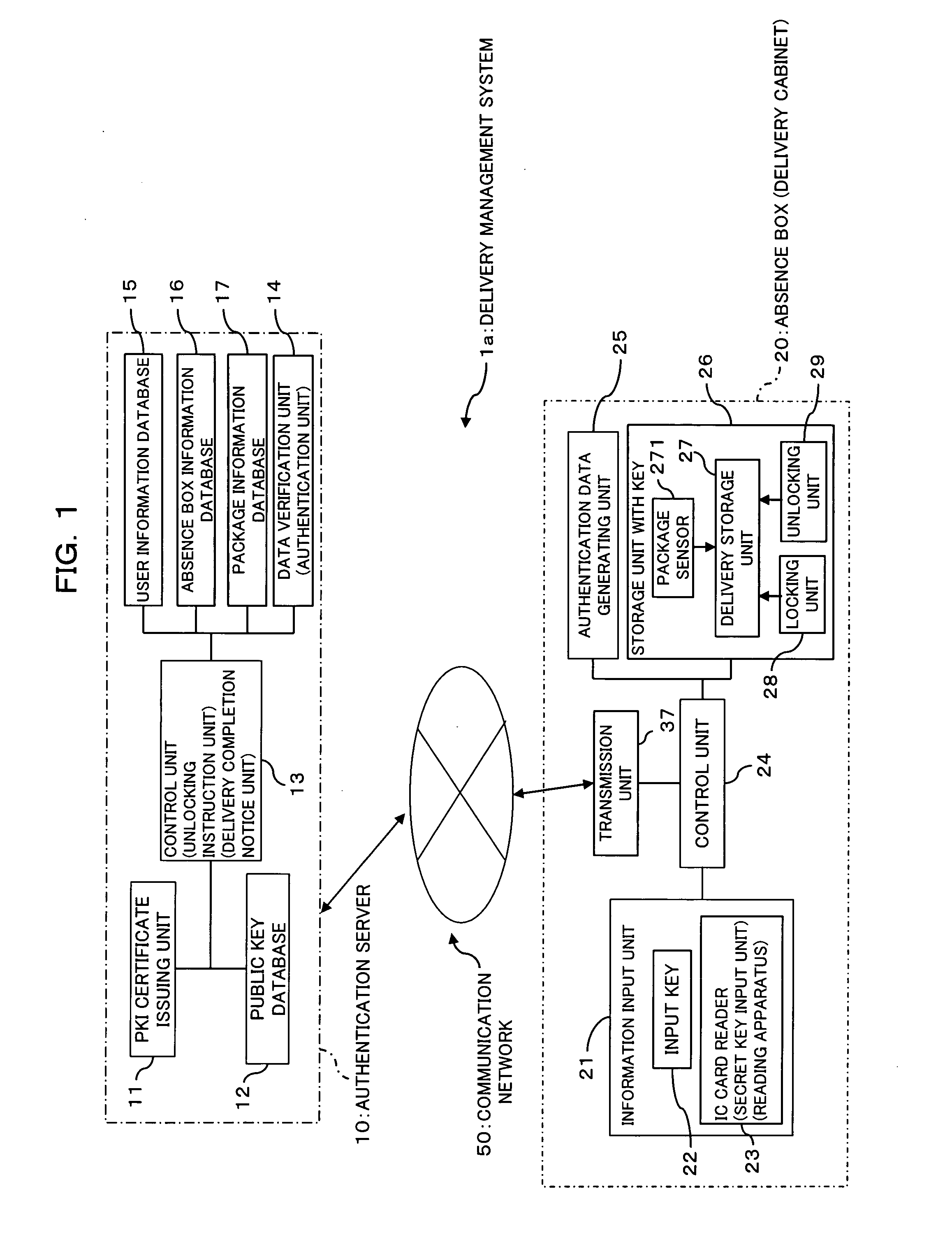
Delivery management system and delivery cabinet
InactiveUS20060224512A1Improve delivery reliabilityImprove reliabilityData processing applicationsUser identity/authority verificationDependabilityKey storage
The present invention provides a delivery management system including a public key storage unit for storing a public key of the addressee; a secret key input unit for inputting a secret key of the addressee; and an authentication unit for authenticating the addressee on the basis of the secret key inputted by the secret key input unit and the public key stored in the public key storage unit. Thereby, it is possible to grasp that the addressee receives the delivery so as to improve a reliability of the deliver.
Owner:FUJITSU LTD
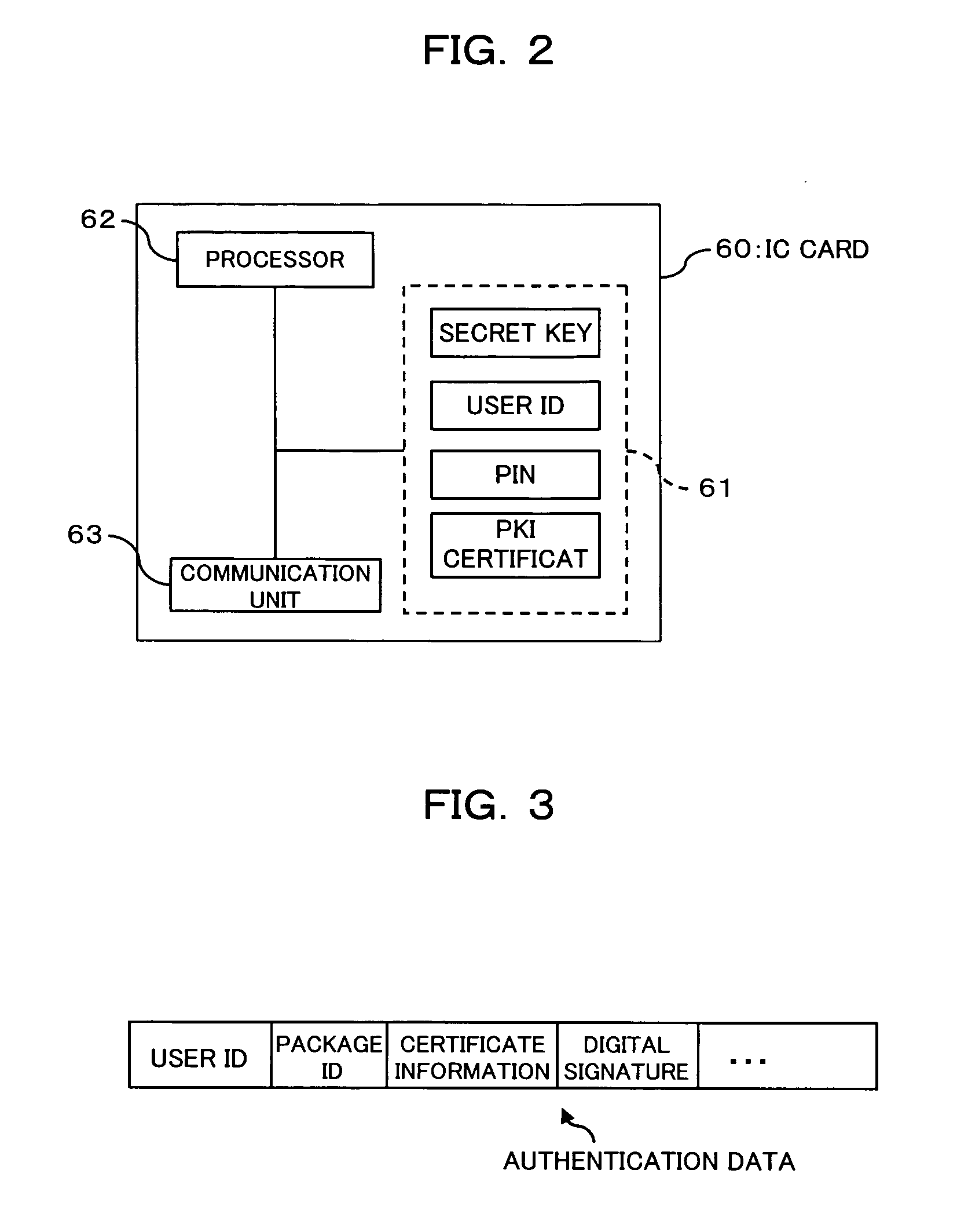
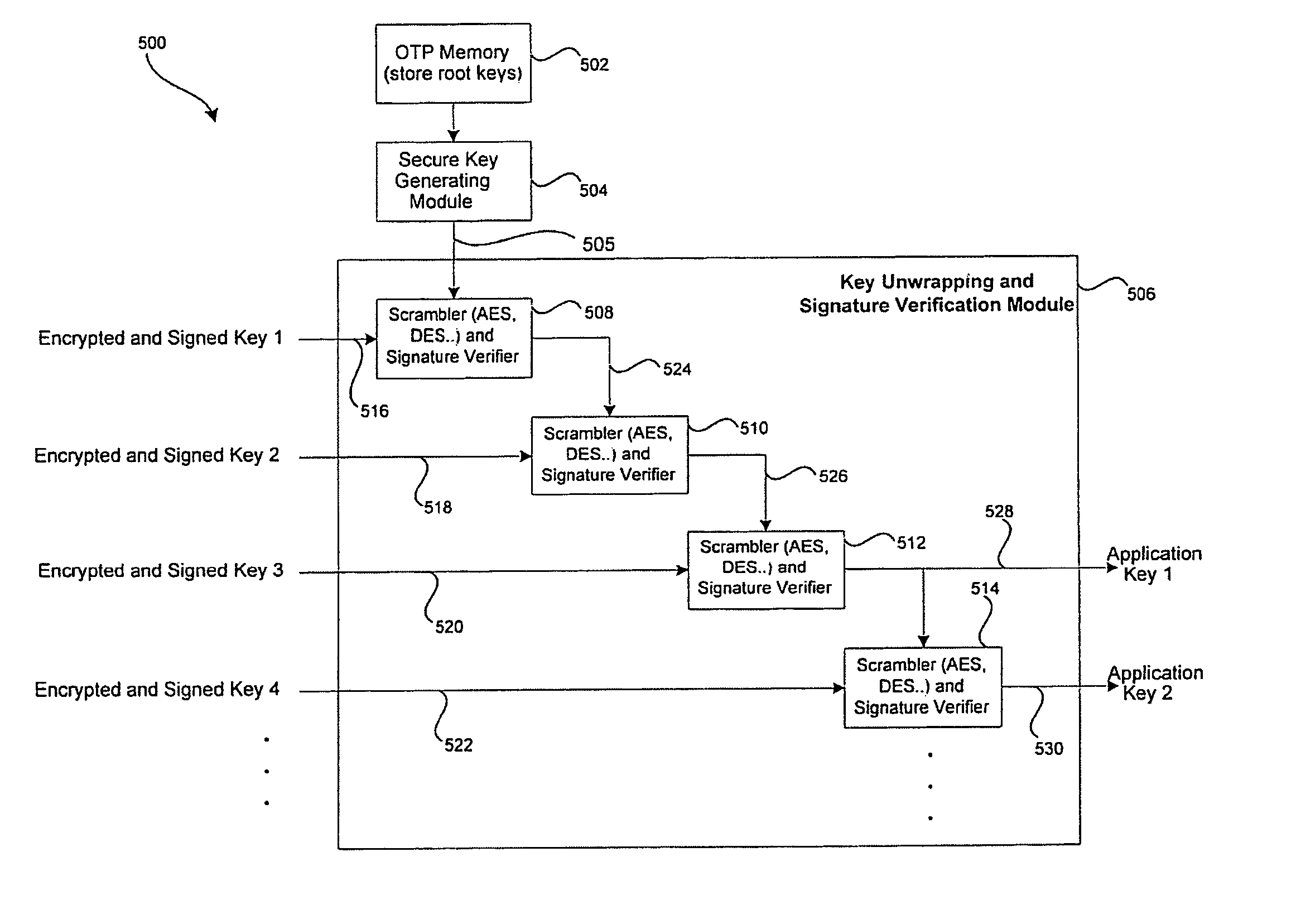
Secure key authentication and ladder system
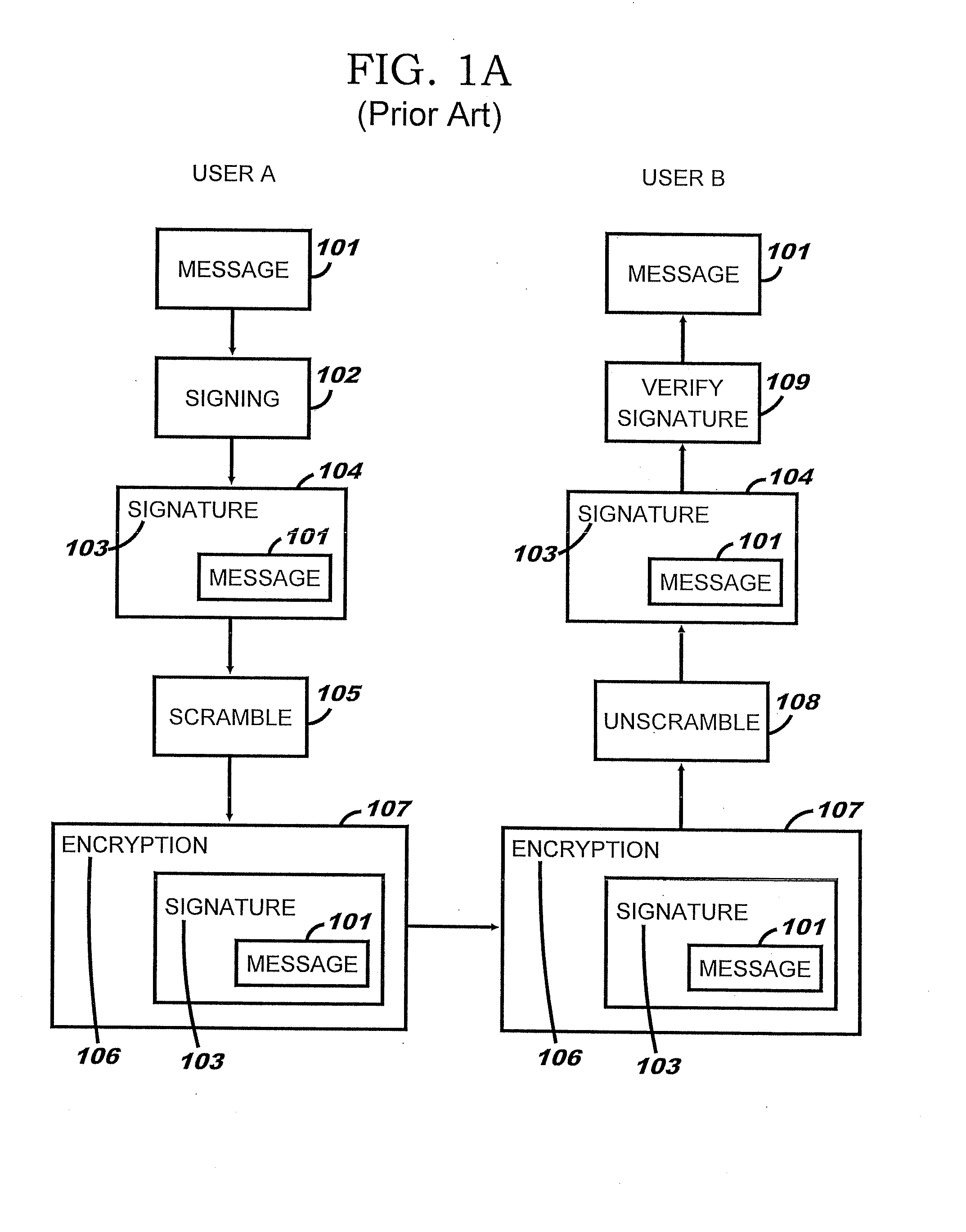
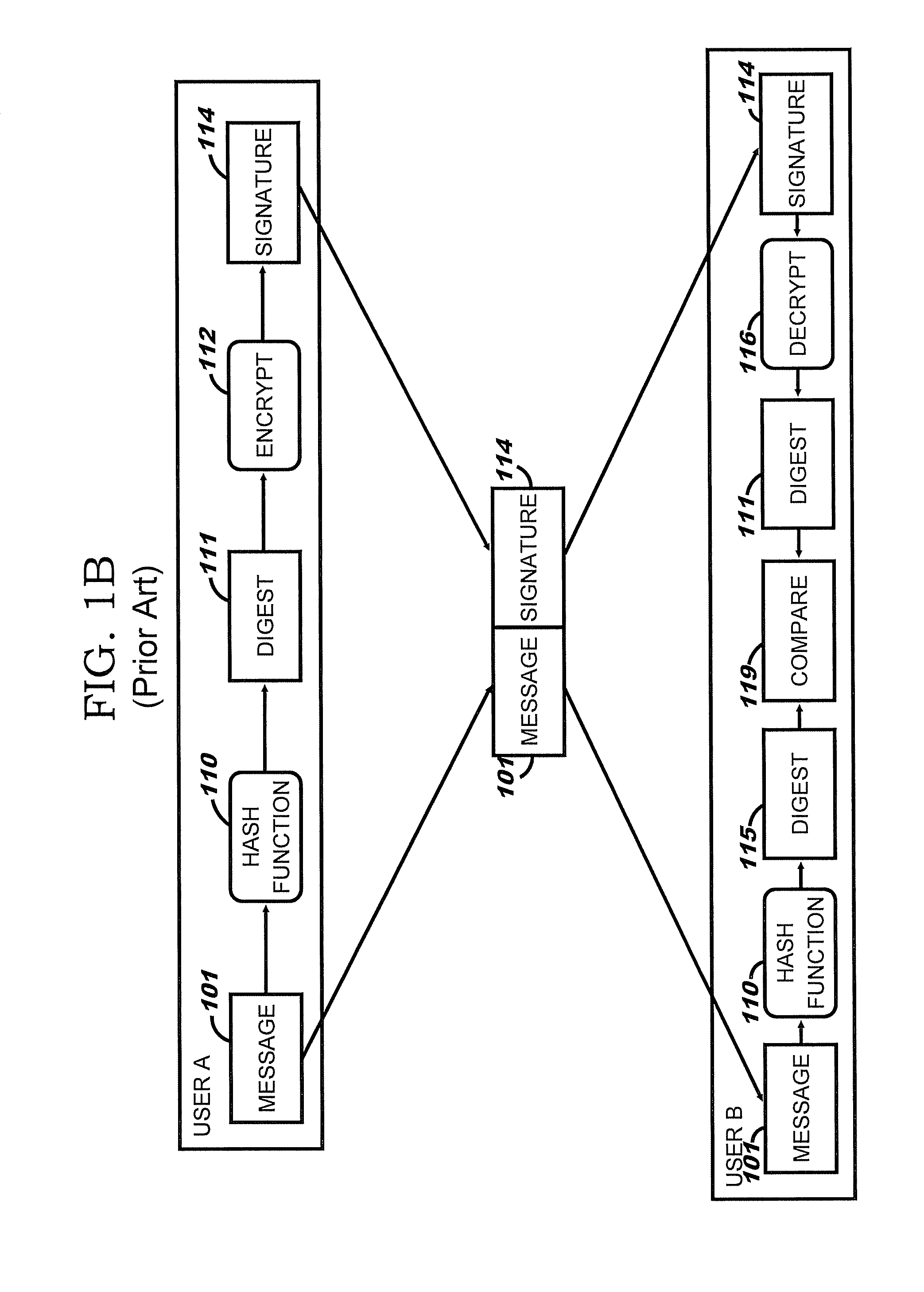
InactiveUS20050172132A1Key distribution for secure communicationUser identity/authority verificationDigital signatureMaster key
Method and system for secure key authentication and key ladder are provided herein. Aspects of the method for secure key authentication may include generating a digital signature of a secure key in order to obtain a digitally signed secure key and transmitting the digitally signed secure key from a first location to a second location. The digital signature may be generated by utilizing an asymmetric encryption algorithm and / or a symmetric encryption algorithm. The digitally signed secure key may be encrypted prior to transmission. The secure key may be a master key, a work key and / or a scrambling key. The digitally signed secure key may be received at the second location and the digitally signed secure key may be decrypted to obtain a decrypted digitally signed secure key.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
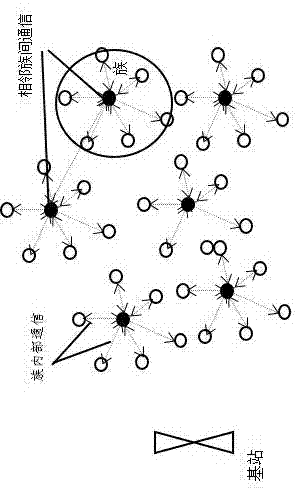
Cluster key management method capable of being used for wireless sensor network
ActiveCN104780532ASolving Routing Security IssuesImprove securityKey distribution for secure communicationUser identity/authority verificationWireless mesh networkClassification methods
The invention provides a cluster key management method capable of being used for a wireless sensor network. Specific classification methods for clustering are not considered in the cluster key management method. Before deployment, nodes are initialized by a key management center, wherein relevant parameters and algorithms of each sensing node are set; after the whole wireless sensor network is clustered, a base station, cluster heads and intra-cluster nodes are formed; communication between the base station and the cluster heads and data transmission security are guaranteed through a compound matrix key, and the cluster heads and the intra-cluster nodes form an internal secure communication area; the cluster heads are in charge of secure data transmission of the intra-cluster nodes, when residual energy of the cluster head nodes is lower than a set threshold value, the conditions for becoming cluster heads are abandoned, the cluster head nodes become common nodes, and when residual energy of the common nodes is lower than a certain threshold value, algorithms and parameters in a chip are destroyed automatically. According to the method, key authentication under KMC control is not needed, calculation and communication cost is reduced, and bidirectional authentication is adopted for every two clusters.
Owner:HUAIHAI INST OF TECH
Secure key management in conferencing system
InactiveUS8301883B2Key distribution for secure communicationUser identity/authority verificationConference managementKey authentication
A method for managing a conference between two or more parties comprises an identity based authenticated key exchange between a conference management element and each of the two or more parties seeking to participate in the conference. Messages exchanged between the conference management element and the two or more parties are encrypted based on respective identities of recipients of the messages. The method comprises the conference management element receiving from each party a random group key component. The random group key component is computed by each party based on a random number used by the party during the key authentication operation and random key components computed by a subset of others of the two or more parties seeking to participate in the conference. The conference management element sends to each party the random group key components computed by the parties such that each party can compute the same group key.
Owner:ALCATEL LUCENT SAS
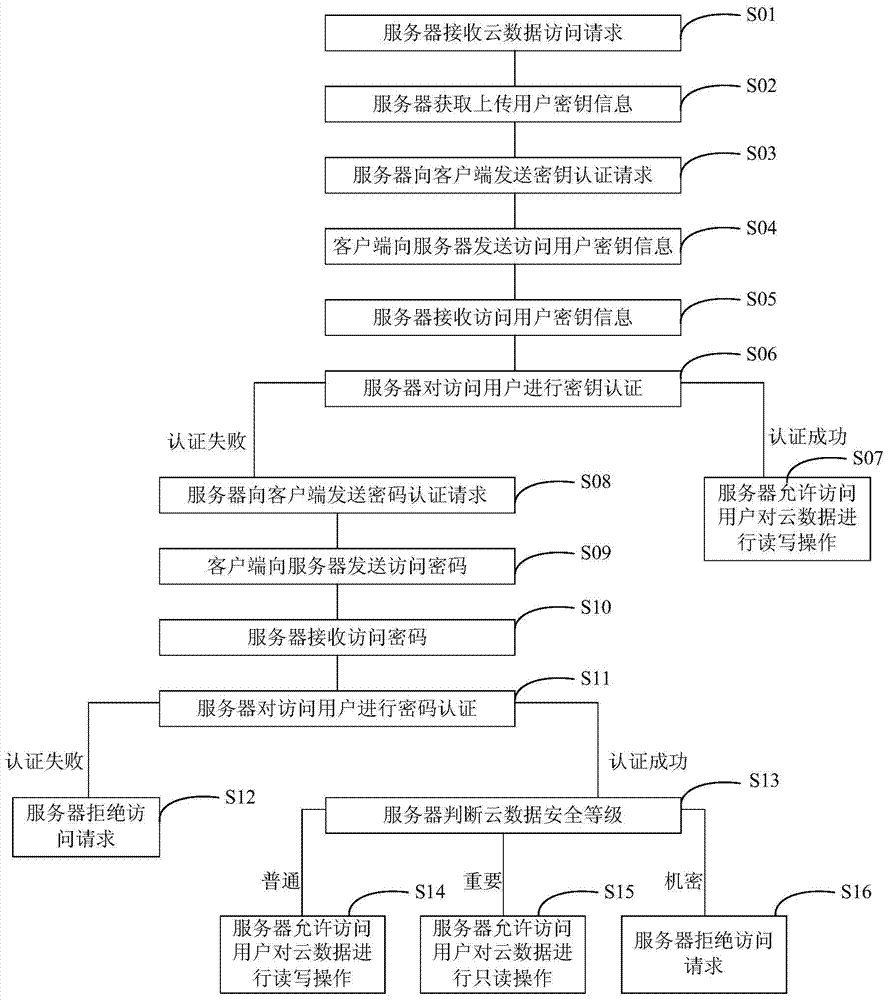
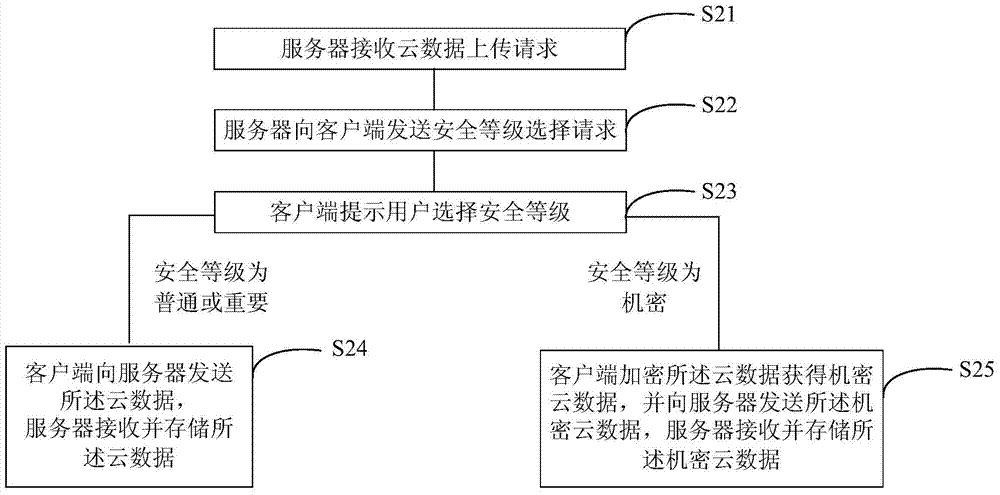
Cloud data uploading and access control method
The invention provides a cloud data uploading and access control method. A server receives and stores cloud data with security levels; after the server receives a cloud data access request, key authentication is carried out on an access user; if key authentication is successful, the server allows the access user to carry out read and write operation on the cloud data, and otherwise, code authentication is carried out on the access user; the server obtains the security level corresponding to the cloud data when code authentication is successful, the server allows the access user to carry out read and write operation on the cloud data if the security level is normal, the server allows the access user to carry out read-only operation on the cloud data if the security level is important, and the server refuses the access request if the security level is confidential. Due to the fact that the cloud data have the corresponding security level, the access user can only be in an authority range and operate the cloud data of different security levels, and accordingly security and privacy of cloud data access are enhanced.
Owner:TENDYRON CORP
Method, user terminal device and identity authentication server for recognizing identity through biological feature
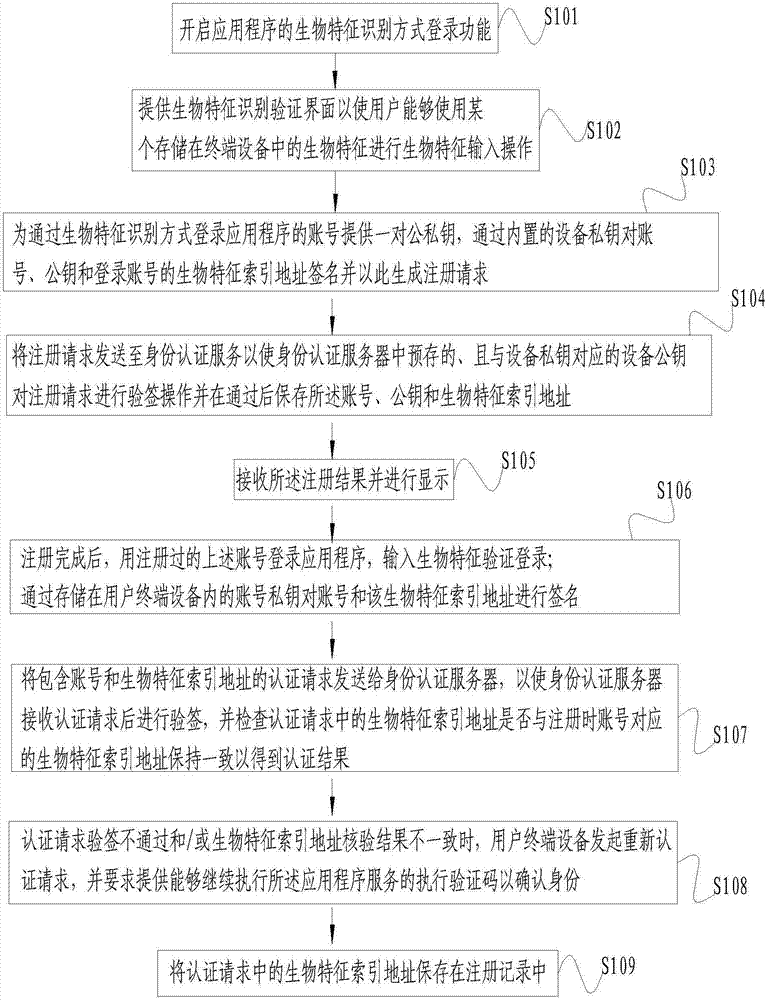
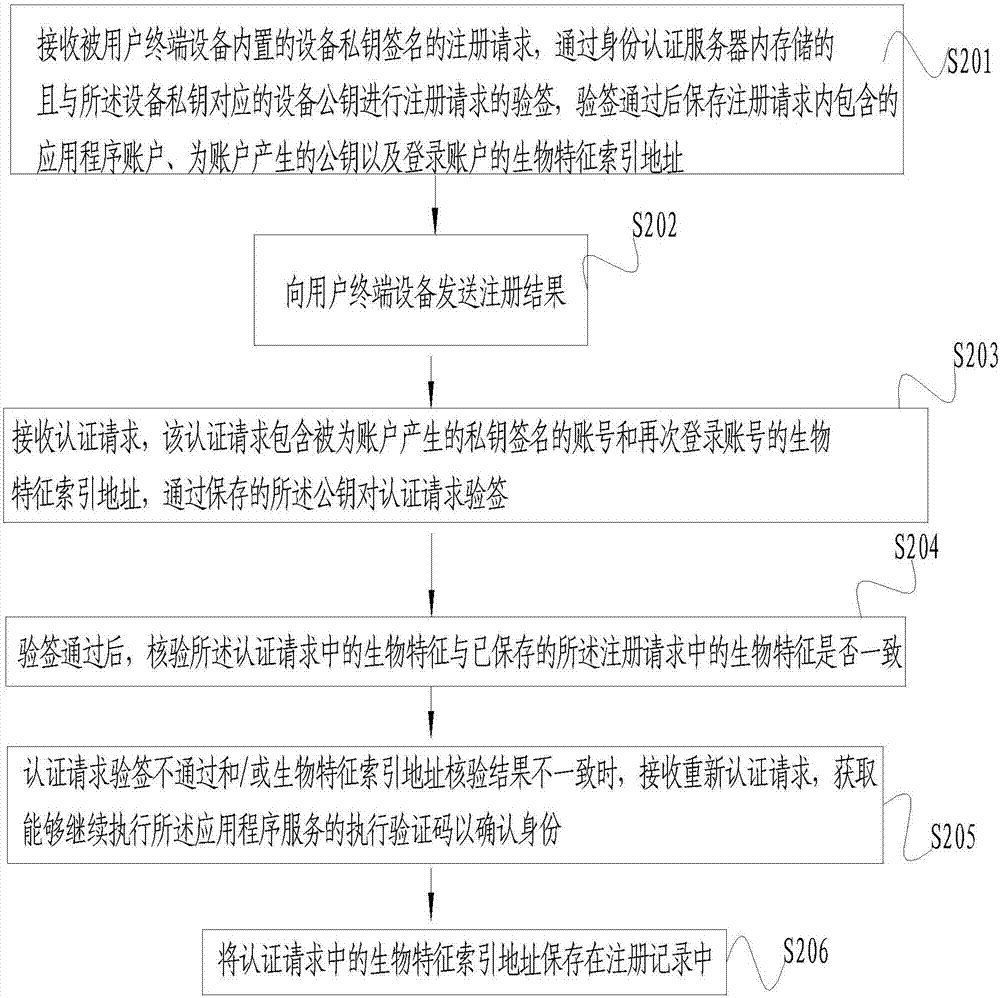
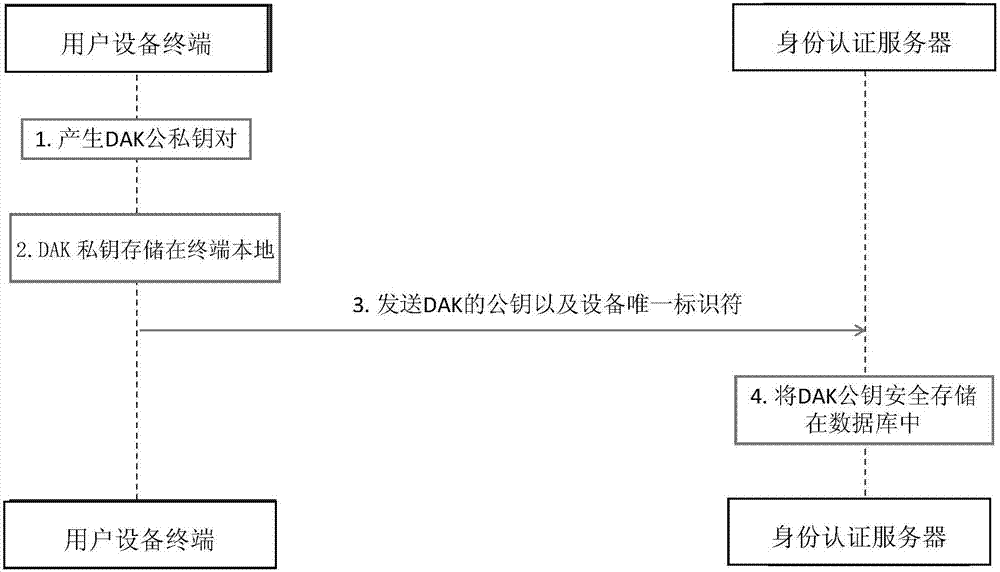
ActiveCN107241317AImprove securityAvoid "friendly cheating"User identity/authority verificationTransaction serviceTerminal equipment
The invention discloses a method for recognizing an identity through a biological feature. At a user terminal device side, a pair of public and private keys are provided for an account which logs in an application in a biological feature recognition mode; the account, a public key of the account and a biological feature index address of a login account are signed through a built-in device private key; a registration request is generated based on the account, the public key of the account and the biological feature index address of the login account; and the registration request is checked through a device public key pre-stored in an identity authentication server, after the check is successful, the account, the public key of the account and the biological feature index address of the login account are stored, thereby checking an authentication request of the terminal device. According to the method, double public and private key authentication and once biological feature comparison check authentication are carried out on the biological feature of the login account, the precise matching of the biological feature of the login account is ensured, the biological feature with the right to logging the terminal device is further authenticated and then the service (such as transaction service related to money) of the application can be used, the friendly cheat is avoided, and the privacy and property safety is improved.
Owner:GUOMIN RENZHENG TECH BEIJING CO LTD
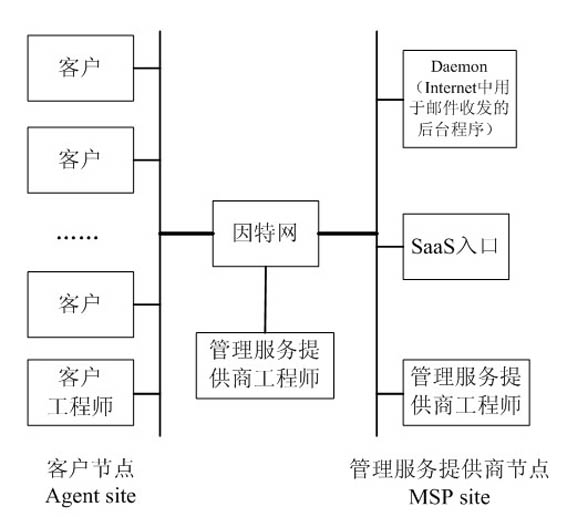
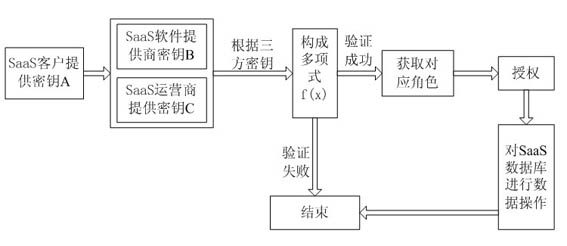
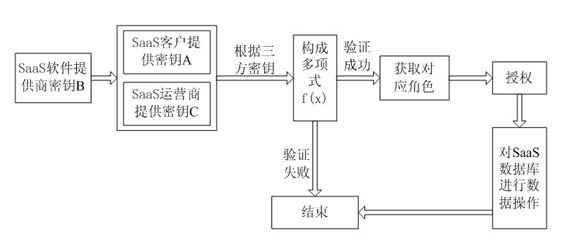
Threshold and key-based authorization method in software as a service (SaaS)
ActiveCN102012989AImprove security informationImprove securityDigital data protectionData operationsKey authentication
The invention discloses a threshold and key-based authorization method in software as a service (SaaS), which is a solution of data security in application of enhancement software as a service (SaaS). The authorization method is mainly used for providing objective security insurance for an SaaS user from technical means so as to solve the problems in protecting data security of SaaS enterprise users. By using the authorization method provided by the invention, a very good method can be naturally provided for solving SaaS security problems. The authorization method is a strategic method, and in the method, keys are divided and an SaaS client masters part of the keys so that an SaaS software provider and an SaaS operator cannot perform certain advanced data operation without the participation of the SaaS client. The authorization method aims to convert key authentication of the client into client authorization, thereby improving security information of the user, and increasing the safety insurance.
Owner:JIANGSU FENGYUN TECH SERVICE CO LTD
Smart password key authentication based cross-platform heterogeneous system login method
InactiveCN107508837ARealize authentication sharingAchieve single sign-onKey distribution for secure communicationUser identity/authority verificationInformation resourceKey authentication
The invention provides a smart password key authentication based cross-platform heterogeneous system login method. The method is to provide a uniform authentication service platform for a multi-service system user by utilizing a smart password key, a digital signature and a digital certificate authentication mechanism based on a PKI theoretical system and to perform uniform authentication of the user identity and access control through integrating service systems and content, thereby realizing single-point login and integration of information resources of each service system. An enterprise employee, as long as remembering a command, can log in multiple heterogeneous systems in the access process of an application system; uniform user identity information is provided, so information sharing can be carried out even the user identity information content and data format of each application system are non-uniform, and interconnection and mutual communication are realized; after the smart password key authentication is encrypted, the data transmitted by the user are guaranteed to be the original text without being tampered maliciously; and the identity of the user can be confirmed.
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
Engine anti-theft authentication method and device of engine anti-theft system
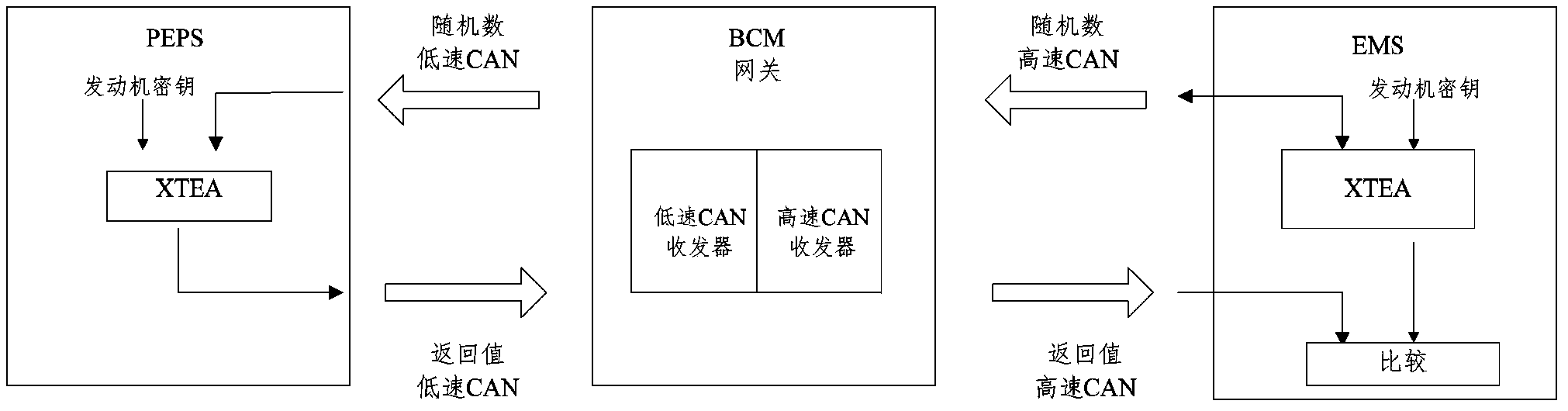
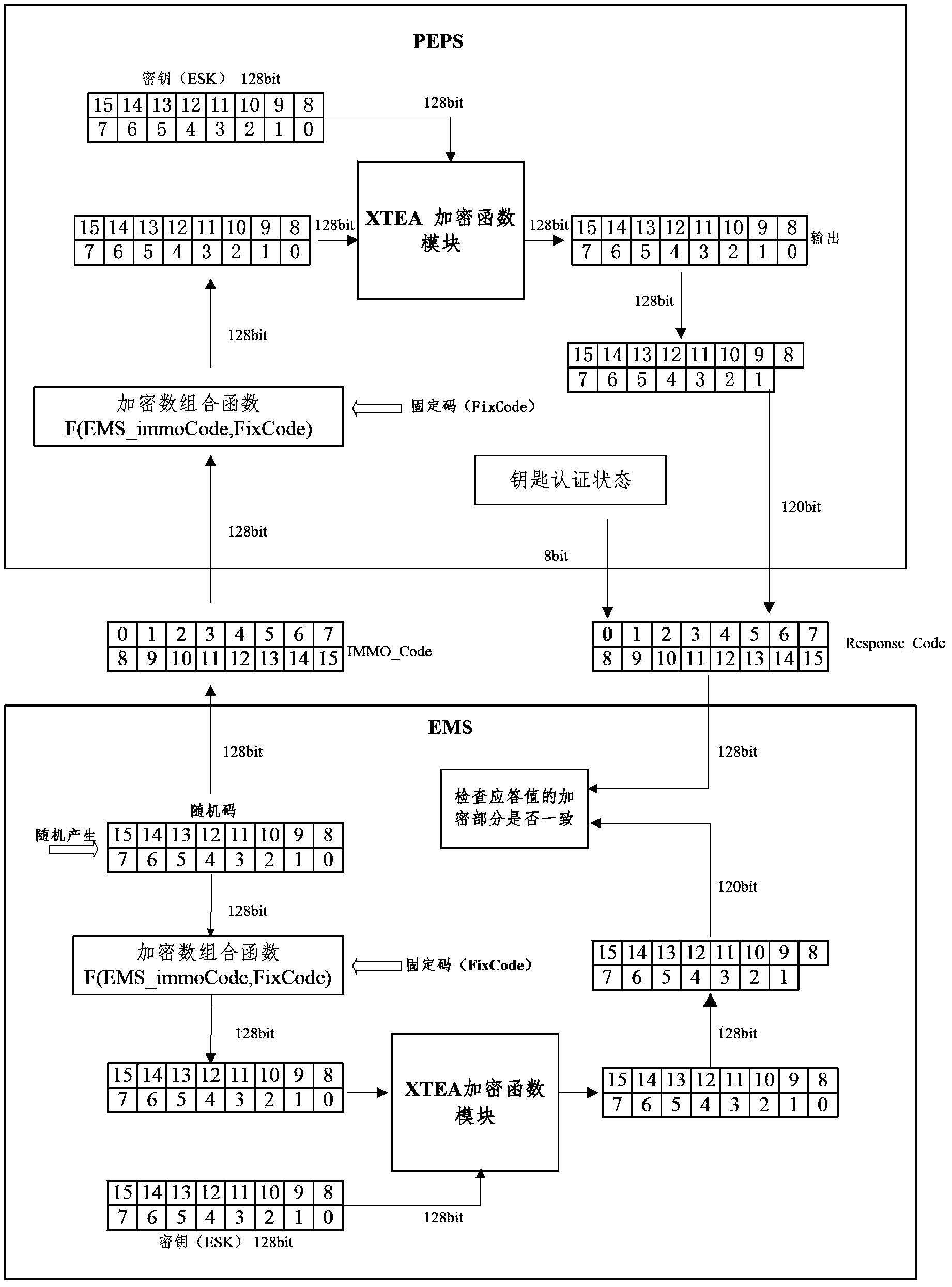
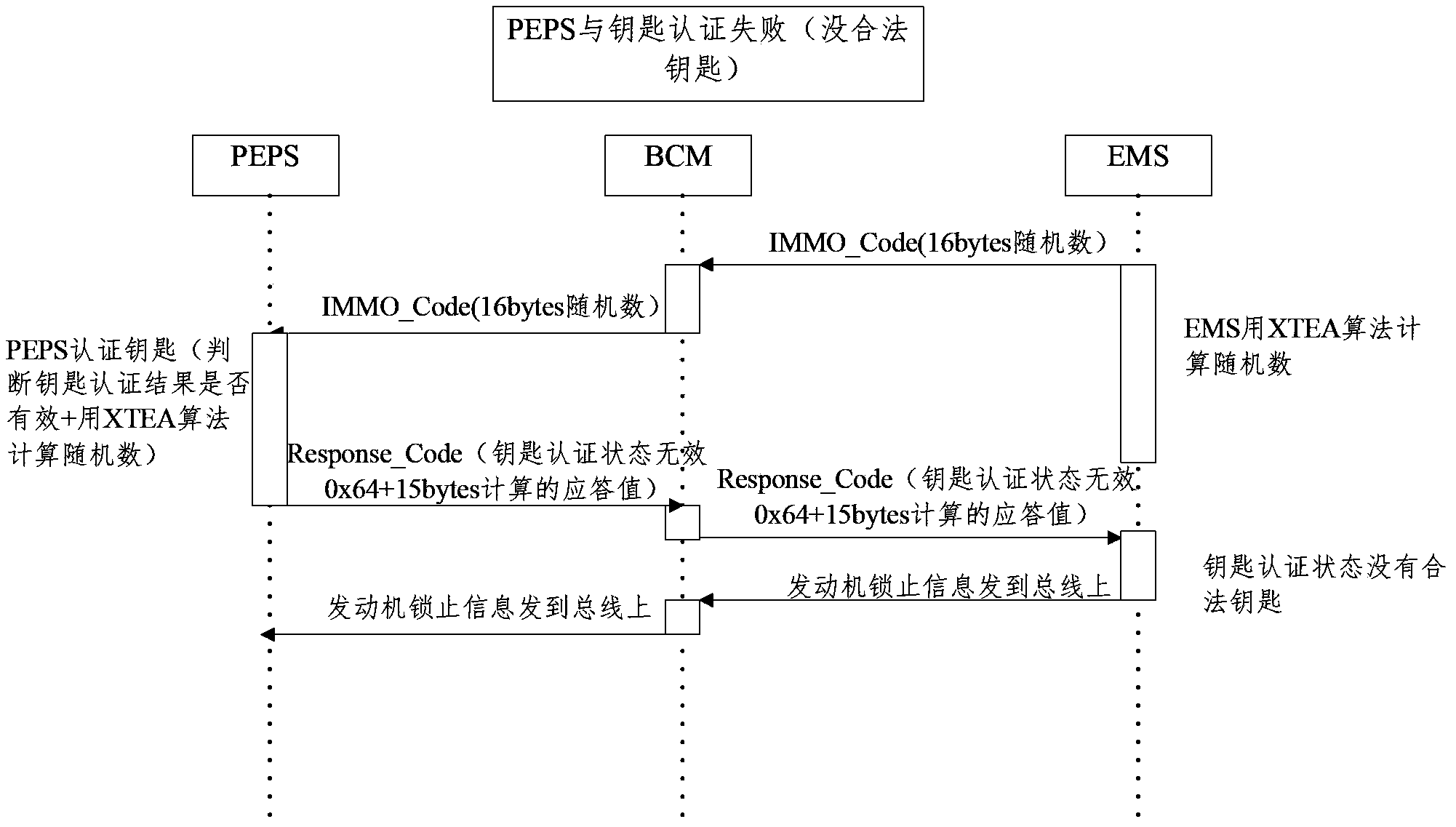
ActiveCN104118392AStart inhibitEnsure normal communicationAnti-theft devicesComputer moduleKey authentication
The invention provides an engine anti-theft authentication method. Engine anti-theft authentication comprises key authentication and engine controller authentication. Engine controller authentication comprises the following steps that an engine management module generates a set of random numbers and transmits the numbers to an intelligent access key-free starting module through a vehicle body controller communication gateway; the intelligent access key-free starting module carries out encryption calculation through an XTEA algorithm according to a fixed code stored in the intelligent access key-free starting module, a secret key and the received random numbers, replaces part of digits in the calculation result with the key authentication result to generate second data, and transmits the second data back to the engine management module through the vehicle body controller communication gateway; the engine management module compares the key authentication result pre-stored in the engine management module and first data generated through the XTEA algorithm with the fed back second data, permits the engine to start if the data are matched, otherwise forbids starting. The invention further provides an engine anti-theft authentication device. The engine anti-theft authentication method and device adopt the XTEA algorithm, and are small in occupied space and short in calculation time.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
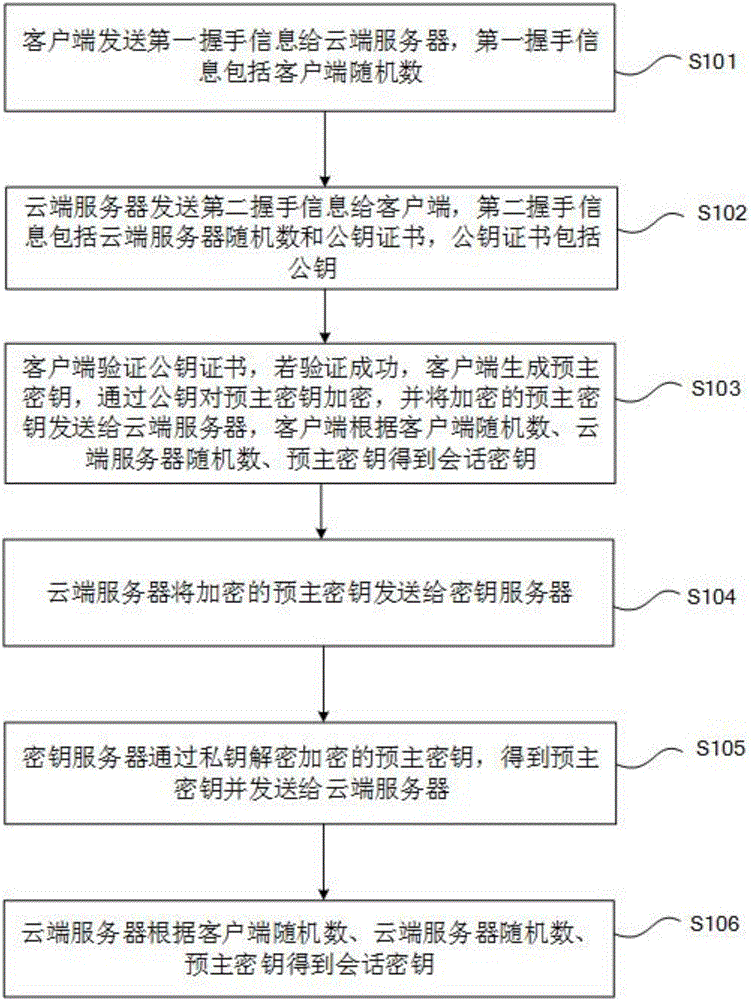
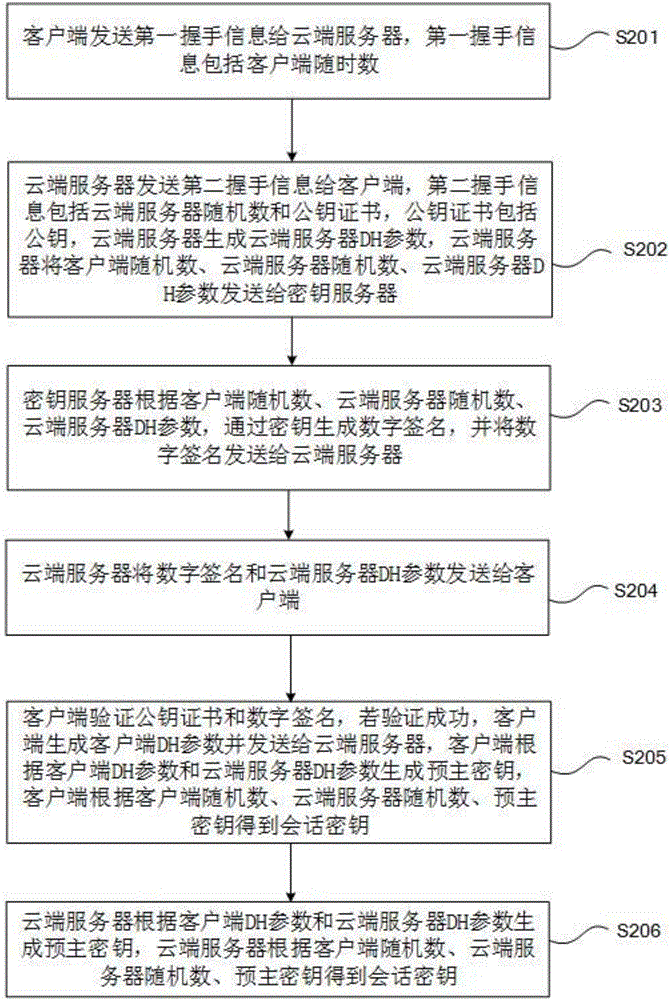
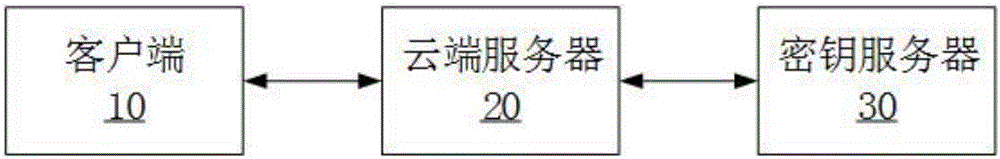
Key-free authentication transmission method and system
The invention provides a key-free authentication transmission method and system. The key-free authentication transmission method comprises the steps that a client sends first handshake information to a cloud server, wherein the handshake information comprises a client random number; the cloud server sends second handshake information to the client, wherein the second handshake information comprises a cloud server random number and a public key certificate; the client verifies the public key certificate, if the verification is successful, a generated pre-master key is encrypted through a public key, the pre-master key is sent to the cloud server, and a session key is obtained according to the client random number, the cloud server random number and the pre-master key; the cloud server sends the encrypted pre-master key to a key server; the key server decrypts the encrypted pre-master key through a private key and sends the pre-master key to the cloud server; and the cloud server obtains the session key according to the client random number, the cloud server random number and the pre-master key. According to the method and the system, the security of the private key is ensured by setting the independent key server.
Owner:青松智慧(北京)科技有限公司
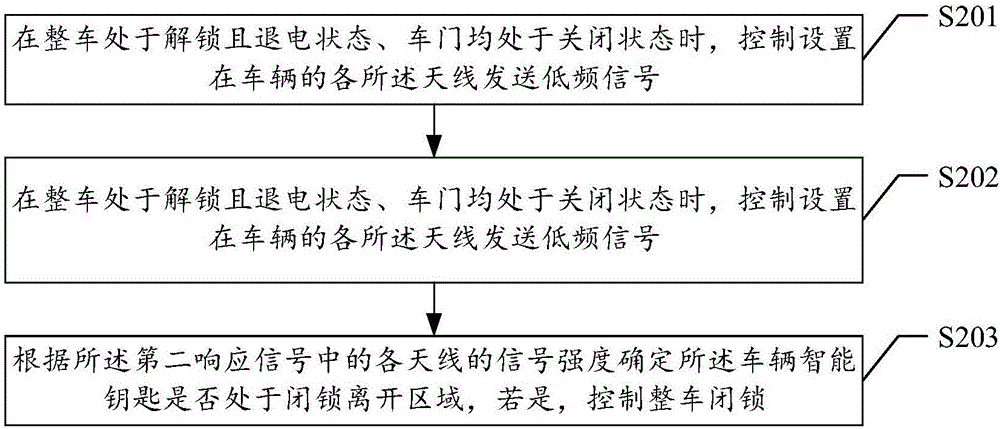
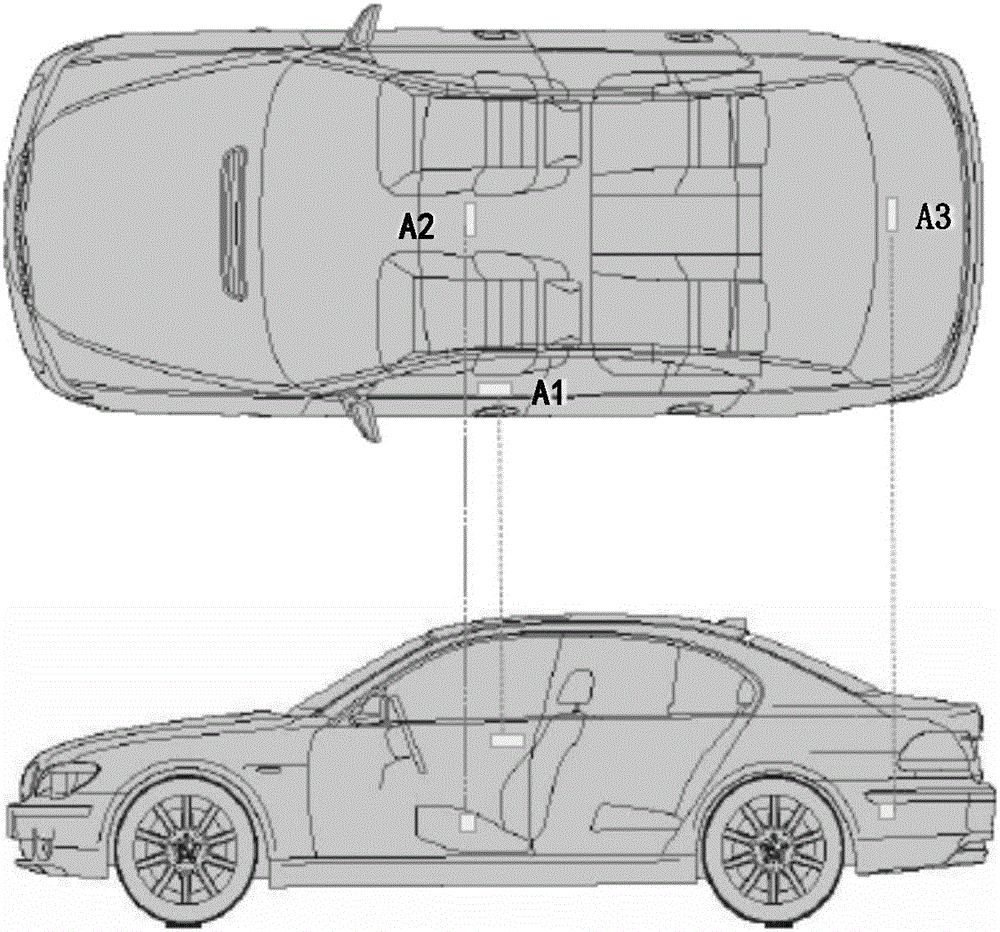
Method, device and system for vehicle intelligent unlocking
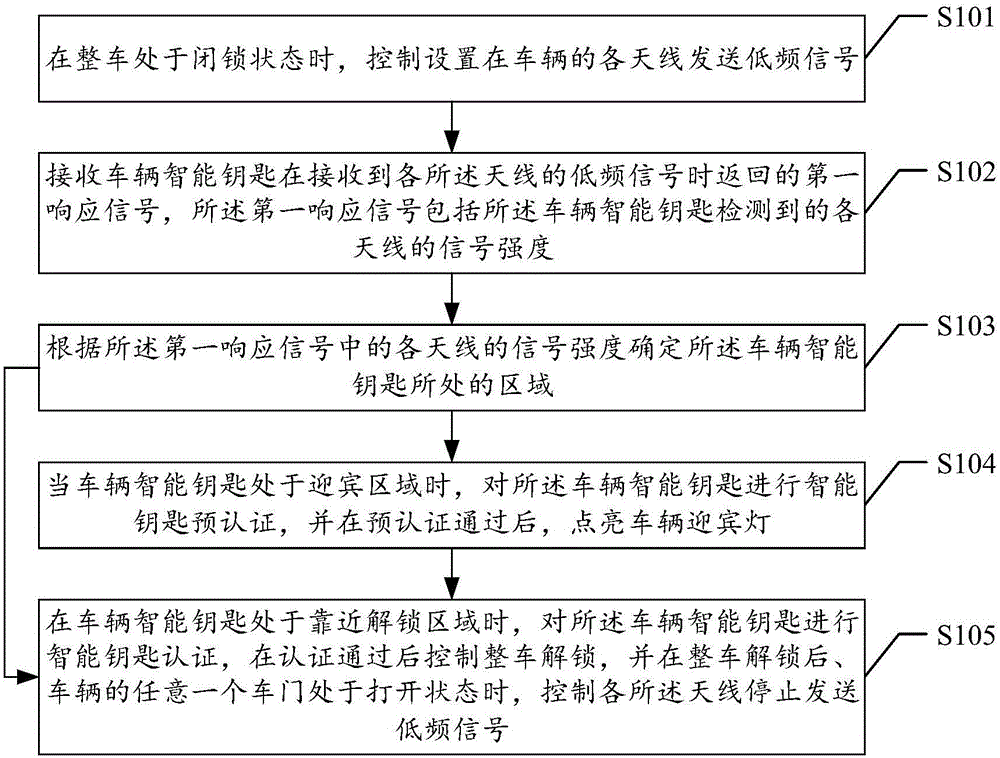
ActiveCN106394490ARealize smart unlockingImprove user experienceAnti-theft devicesKey authenticationSignal strength
The invention provides a method, device and system for vehicle intelligent unlocking. The method in one embodiment comprises the steps that when a whole vehicle is in a locked state, antennas arranged on the vehicle are controlled to sent low-frequency signals; a first response signal returned when a vehicle intelligent key receives the low-frequency signals of the antennas is received, and the first response signal comprises the signal strength, detected by the vehicle intelligent key, of the antennas; the area where the vehicle intelligent key is located is determined according to the signal strength of the antennas in the first response signal; when the vehicle intelligent key is located in a meeting area, intelligent key pre-authentication is carried out on the vehicle intelligent key, and prompting information is sent after intelligent key pre-authentication succeeds; and when the vehicle intelligent key is close to an unlocking area, intelligent key authentication is carried out on the vehicle intelligent key, the whole vehicle is controlled to be unlocked after intelligent key authentication succeeds, and after the whole vehicle is unlocked, and when any vehicle door of the vehicle is in an opened state, the antennas are controlled to stop sending the low-frequency signals. According to the method, device and system for vehicle intelligent unlocking, the use experience of vehicle users is improved, and convenience is improved.
Owner:GUANGZHOU AUTOMOBILE GROUP CO LTD
Method for inclusive authentication and management of service provider, terminal and user identity module, and system and terminal device using the method
ActiveUS7953391B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTerminal serverPublic key authentication
Disclosed are a method and a system for mutual inclusive authentication between a service provider, a terminal and a user identity module. The authentication system is configured in a structure that can interact with a public key infrastructure of the current network security environment and can be independently used in a specific network system. The inclusive authentication method is divided into public key authentication and symmetric key authentication. Mutual authentication can be made between a service provider, a terminal and a user identity module using any of the two authentication schemes. Then a user can access content on any terminal device using the content license based on the user's identity.
Owner:SAMSUNG ELECTRONICS CO LTD
Login authentication method and login signature procedure
InactiveCN101286848AImprove securityUniversalUser identity/authority verificationDigital data authenticationPasswordKey authentication
The invention provides a login authentication method and a login signing procedure which relate to the technical field of computer software, internetwork communication and information security. The system presents a login screen which comprises a user name, password child window, besides, a challenging child window which gives random message generated dynamically and an agreed response child window which collects the signing information of users. Users can choose freely from a compatible password authentication and a signing authentication. The registration password is also the authentication password and the symmetrical key authentication signing; the remembrance of the registered single password can apply to the two authentications methods; the login signing procedure operates independently, instructs and judges users on the target login screen to point at or fall on the challenging child window, picks up automatically random message which is signed by a cipher device to form the signing information, fixes the position according to the predetermined strategic orientation of the signing and issuance and sends the signing information to the response child window. The method of the invention does not relate to the hardware but is the thoroughfare for a stable and seamless transition from weak password authentication to the strong signing authentication; the procedure of the invention does not relate to the application, is generally applicable and commonly used and can effectively protect the accounts of users.
Owner:杨筑平
Systems and methods of blockchain platform for intermediaries and passwordless login
InactiveUS20200313856A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacyEngineering
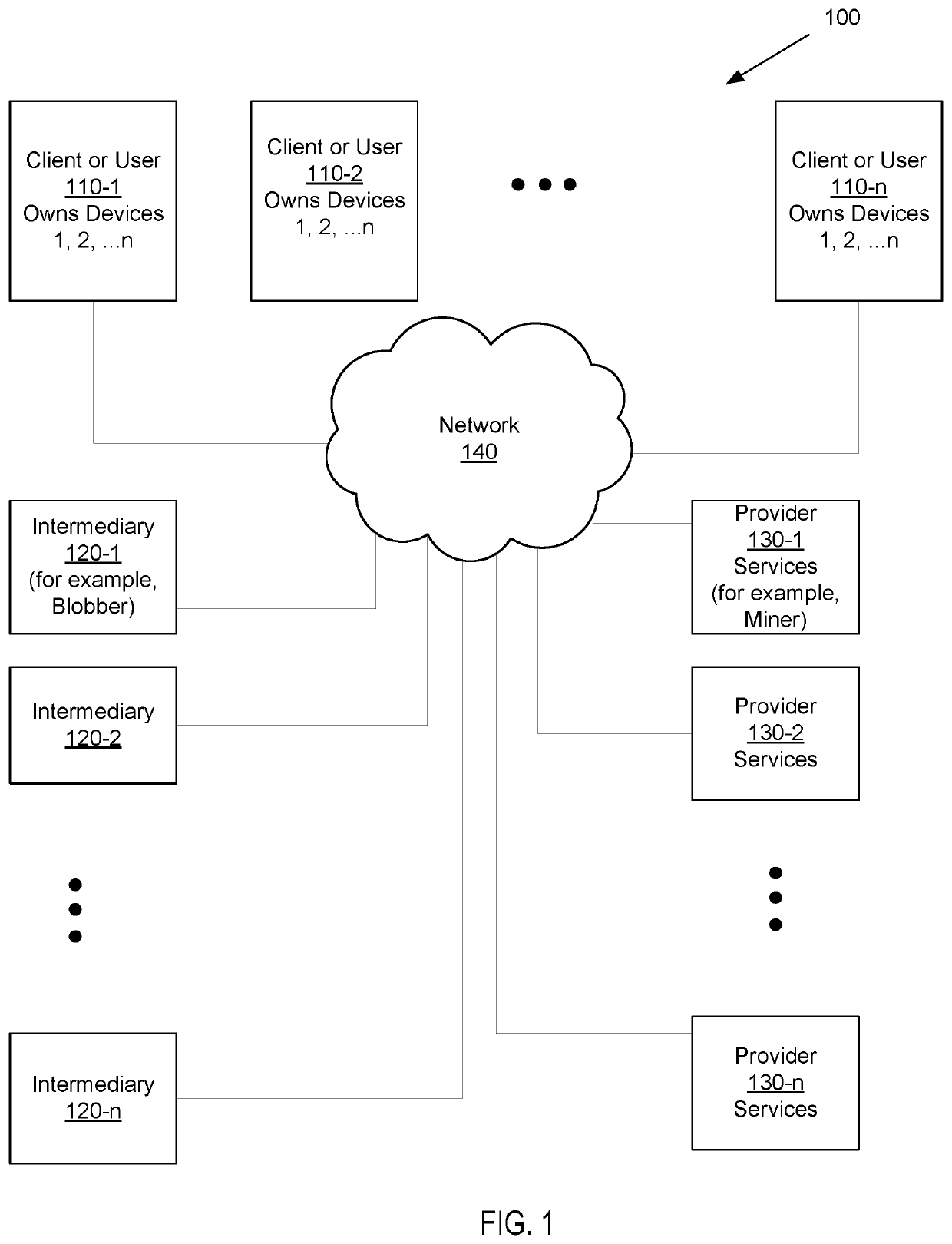
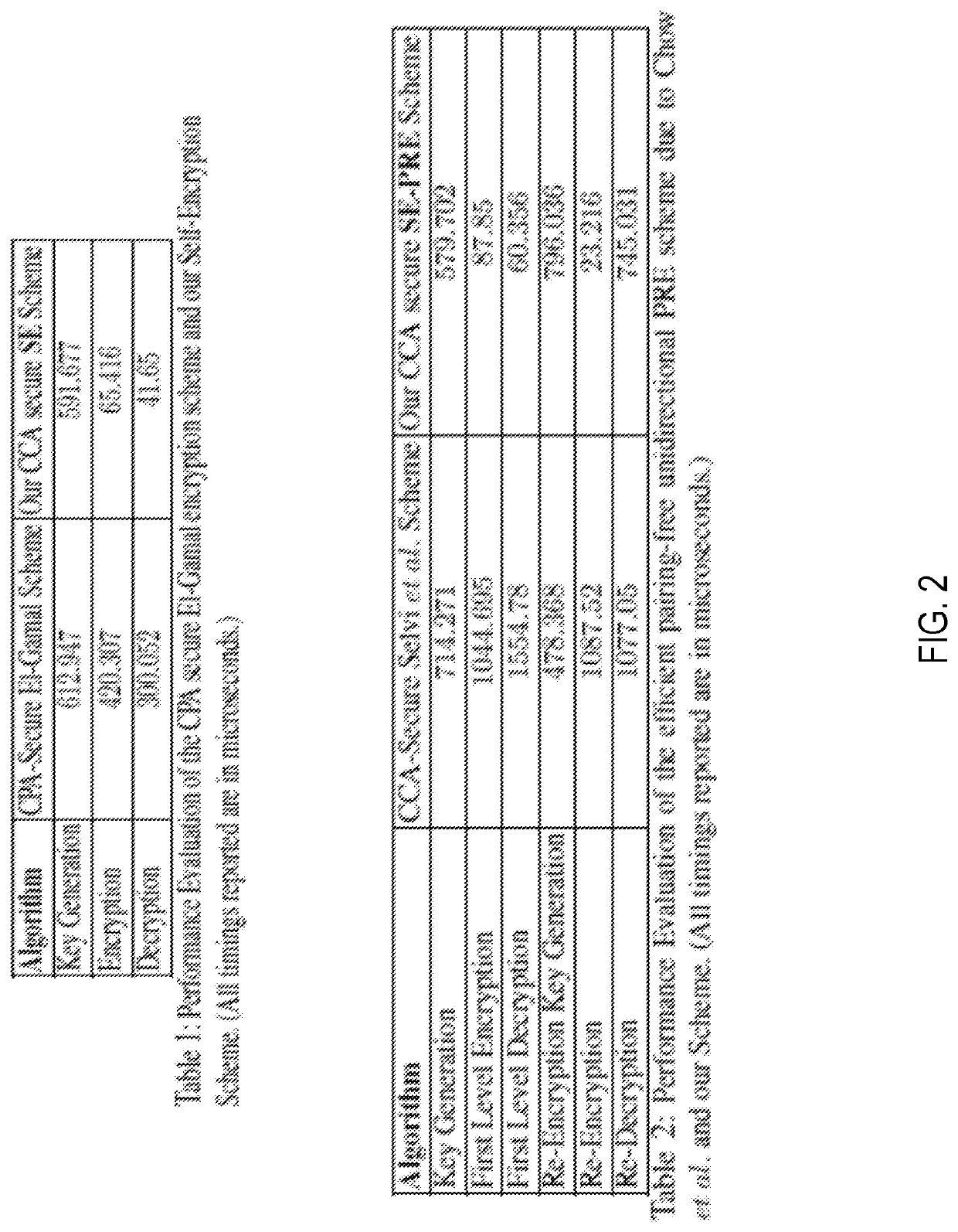
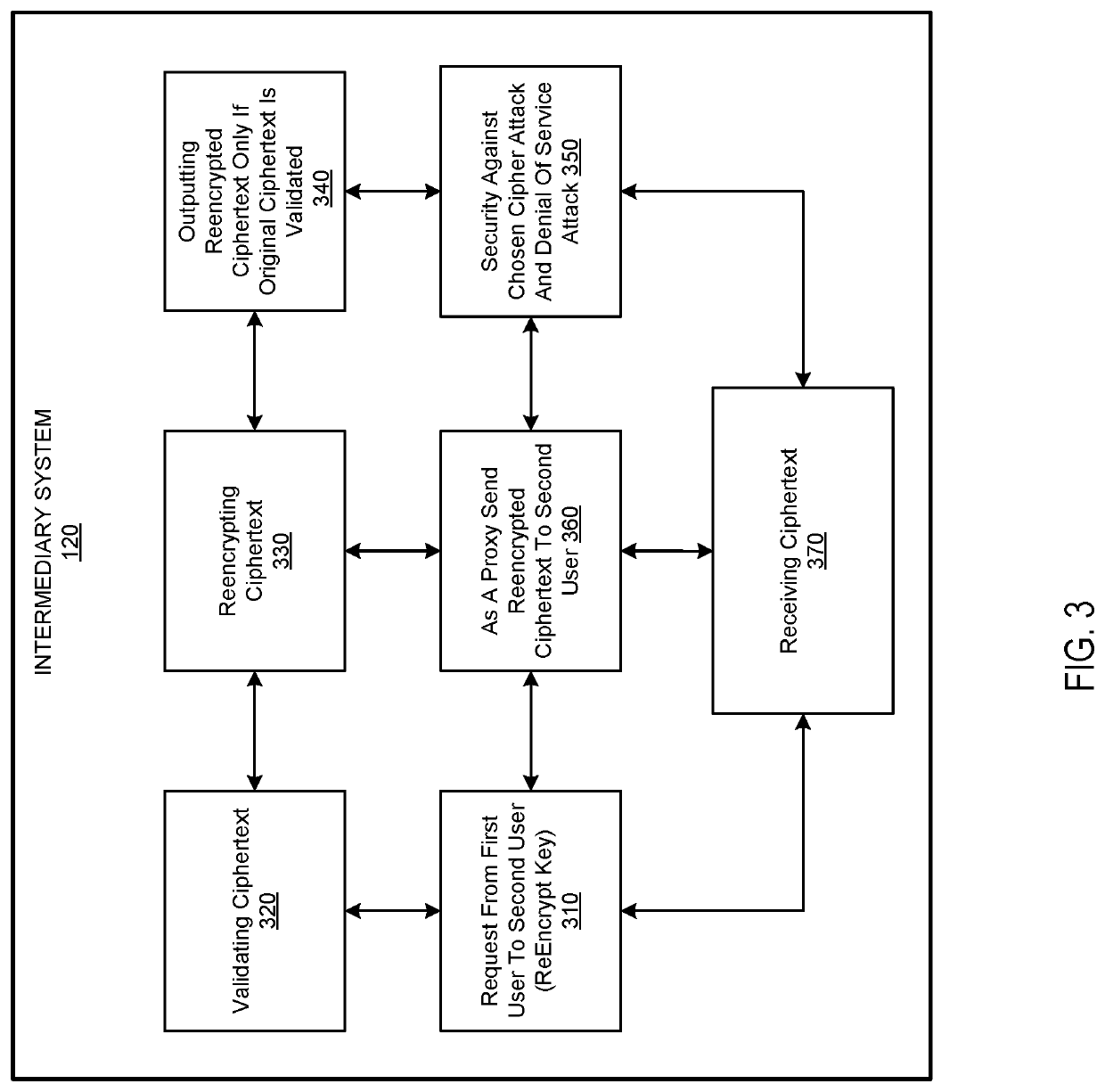
The systems and methods on a blockchain platform for one or more intermediaries for services including proxy re-encryption, independent audit, multiple-signatures based smart wallet associated with a smart contract and split-key authentication to achieve secure passwordless login. Proxy re-encryption by receiving a ciphertext from a first user with condition parameters that has been encrypted with a dynamically selected encryption algorithm. Audit service receiving an encrypted file from a user for storage on the blockchain platform; enforcing the security policy parameters for all access requests to the file on the blockchain platform; and optionally providing audit report of the encrypted file storage and access. A smart wallet with a group key using multiple signatures based on receipt of a threshold number of signatures. Split-key authentication by splitting the private key into two or more parts; and assigning the split private key part to two or more client devices.
Owner:0CHAIN LLC
Method and system for key certification
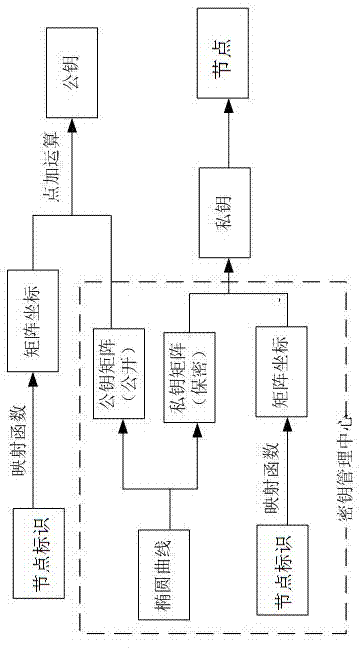
InactiveUS20080028209A1Public key for secure communicationDigital data processing detailsKey authenticationE infrastructure
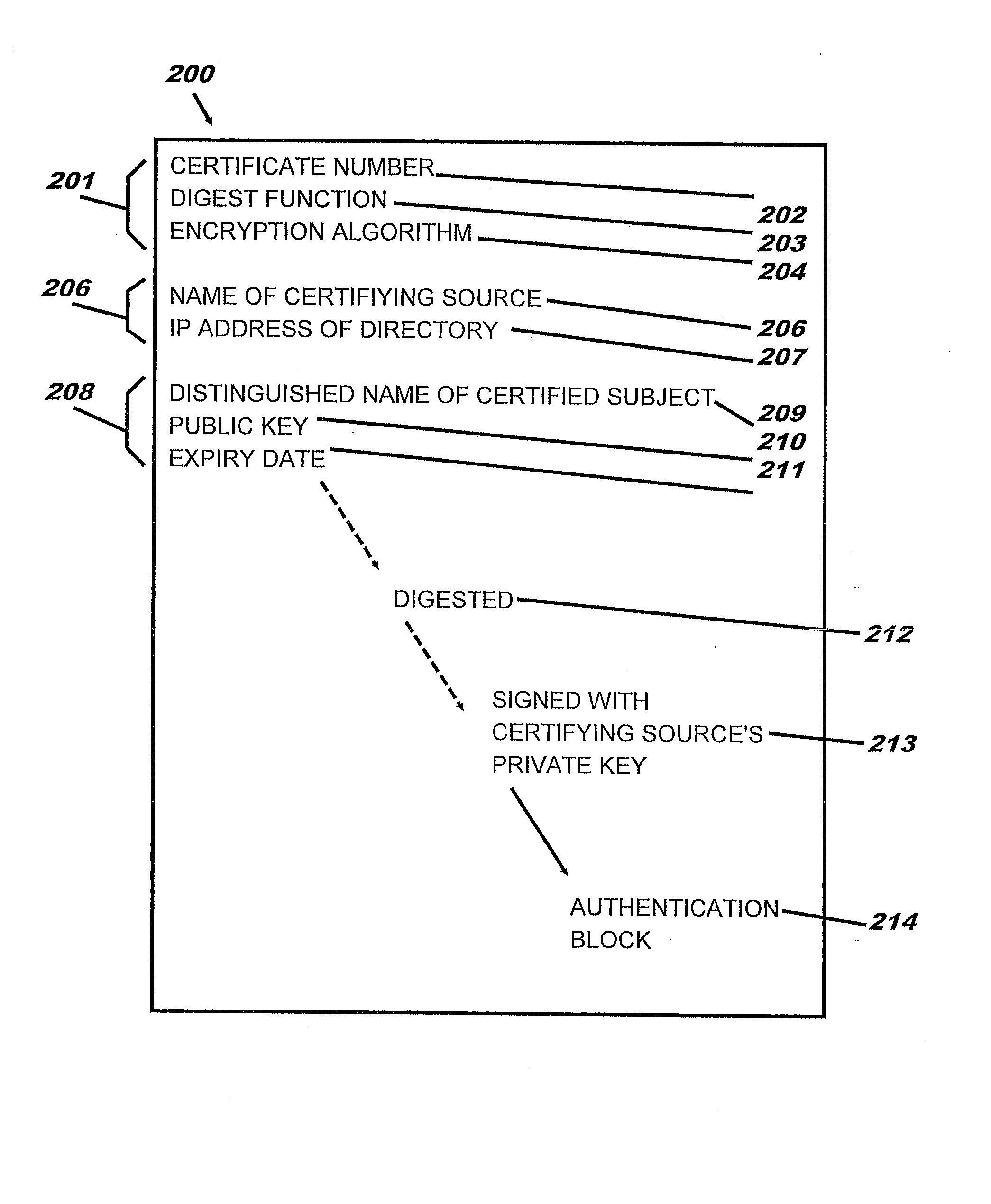
A method and system for key certification in a public key infrastructure. The infrastructure has a network formed of a plurality of nodes. Each node has a private and public key pair. The nodes are either or both a certifying node and a certified node. A certifying node provides a digital certificate referring to the public key of a certified node. The digital certificate is signed by the private key of the certifying node. The method includes providing a root public key for a user, the root public key being at any node in the network chosen by the user, and providing a chain of digital certificates from the node with the root public key across the node network to any other node.
Owner:IBM CORP
Internet of Things safety management system
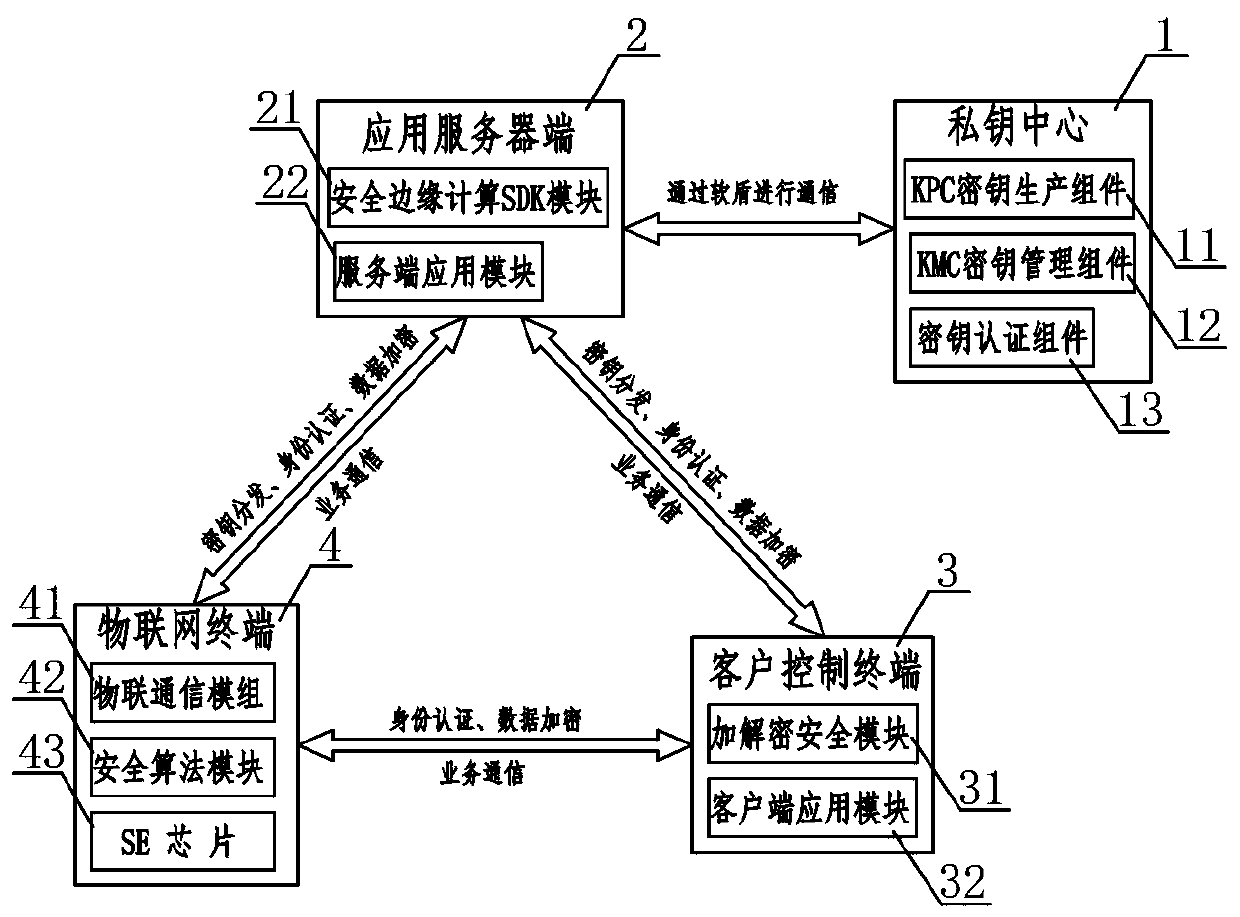
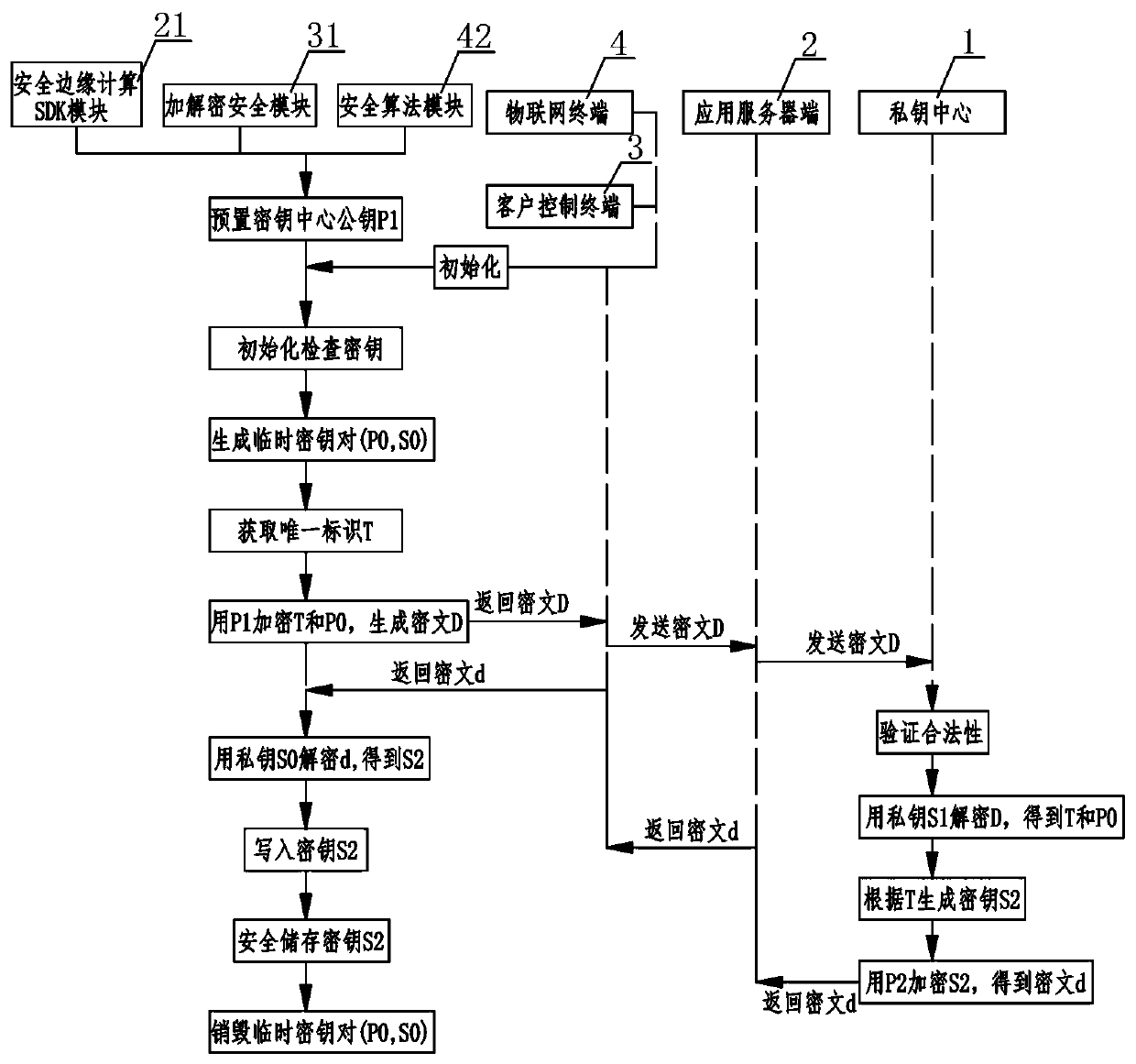
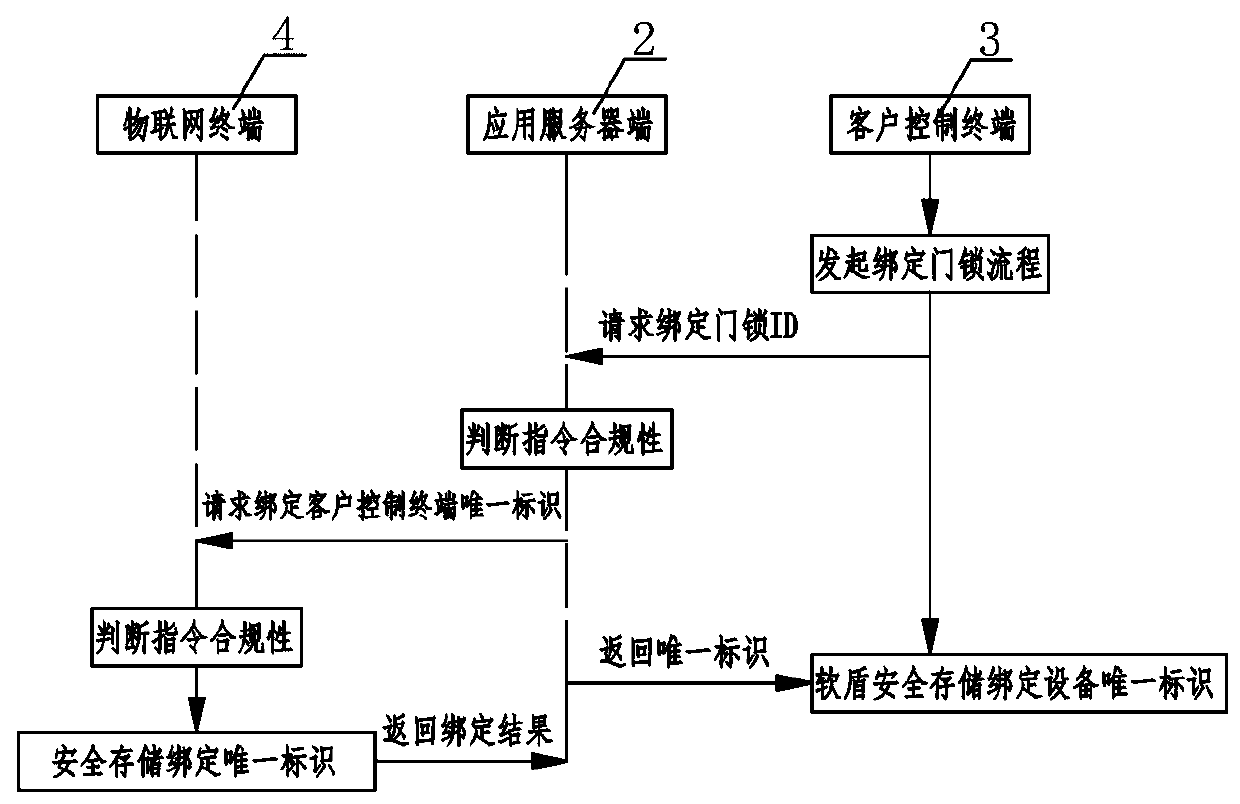
ActiveCN110784491AEnsure communication securityAvoid illegal operationTransmissionSafety management systemsThe Internet
The invention relates to an Internet of Things security management system. A private key center and an application server perform communication authentication data transmission through a soft shield;the application server side performs mutual communication of key distribution, identity authentication and data encryption with the client control terminal and the Internet of Things terminal at the same time; mutual communication of identity authentication and data encryption is carried out between the client control terminal and the Internet of Things terminal, wherein the private key center comprises a KPC key production assembly, a KMC key management assembly and a key authentication assembly, the application server comprises a security edge computing SDK module and a server application module, and the client control terminal comprises an encryption and decryption security module and a client application module, and the Internet of Things terminal comprises an Internet of Things communication module, a security algorithm module and an SE chip. According to the Internet of Things security management system, only the user is completely autonomous and controllable in the Internet of Things system, the cloud system does not have the authority of directly operating the user equipment, and the Internet of Things control security level can be effectively improved.
Owner:深圳前海智安信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com