Internet of Things safety management system
A security management and Internet of Things technology, applied in the field of Internet of Things security management system, can solve the problems of inability to protect the security of data entering and exiting equipment, inability to verify the legality of communication access and data legality, and reduce the risk of being illegally hijacked and controlled , High communication security effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described in detail below in conjunction with the reaction scheme and specific examples.
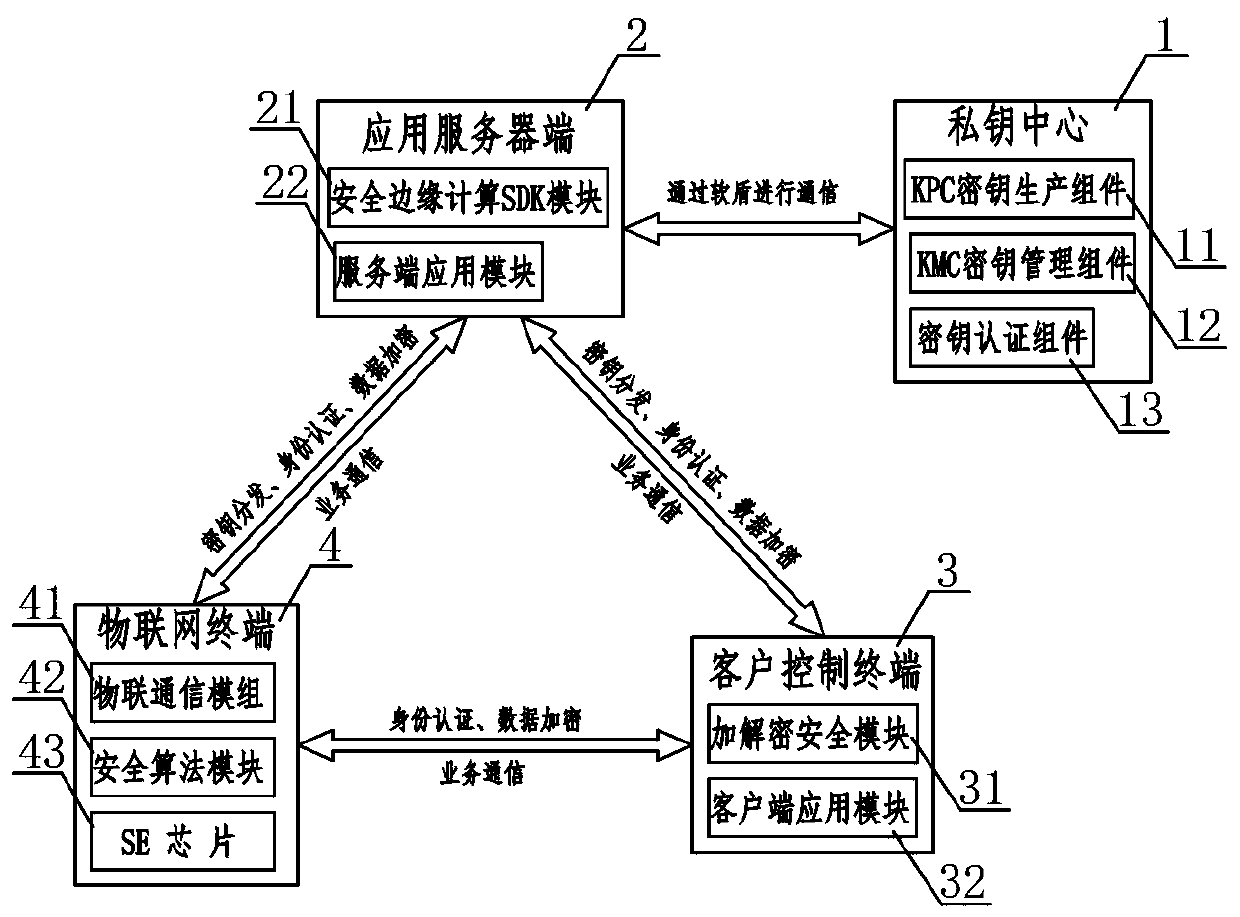
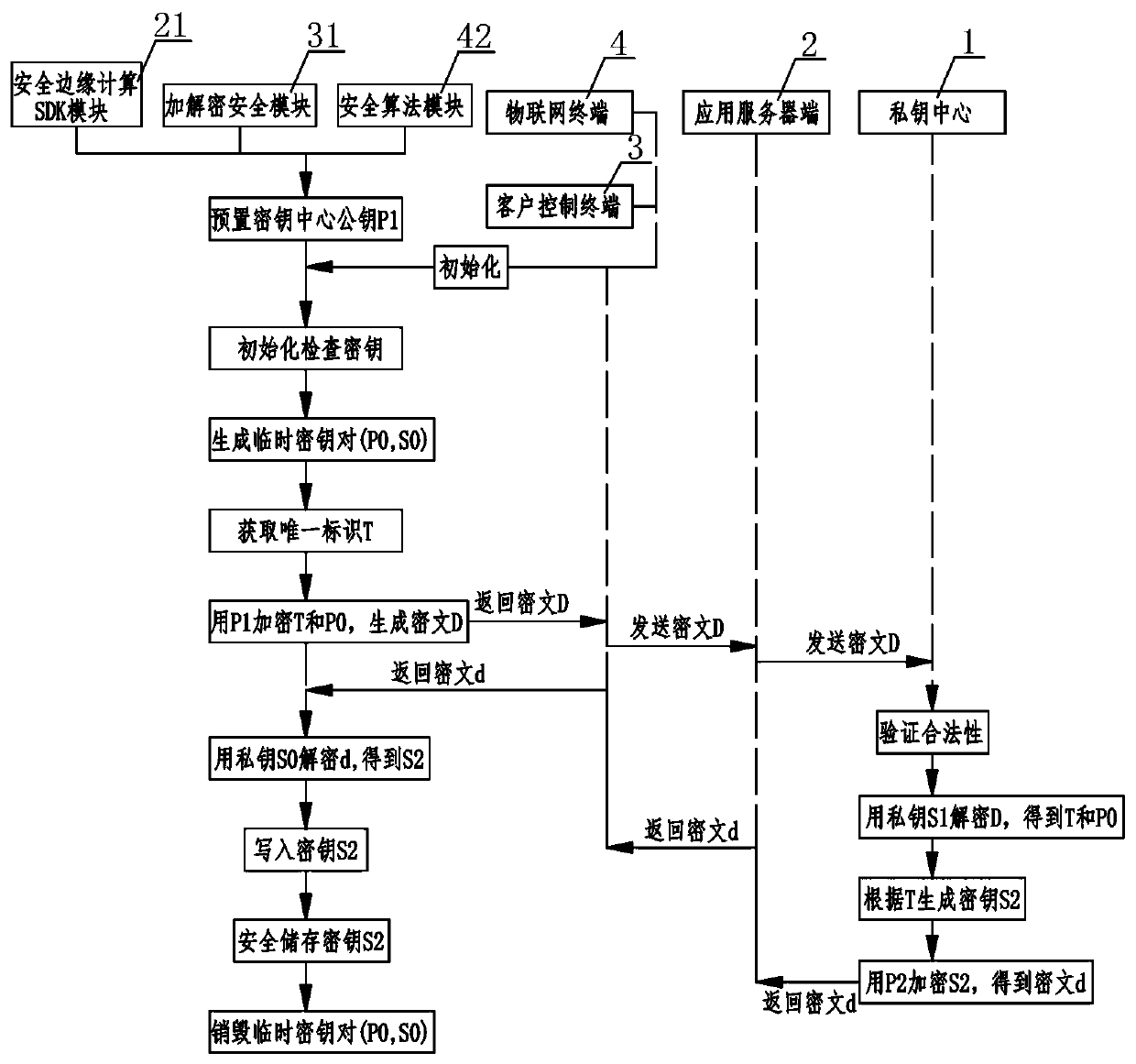
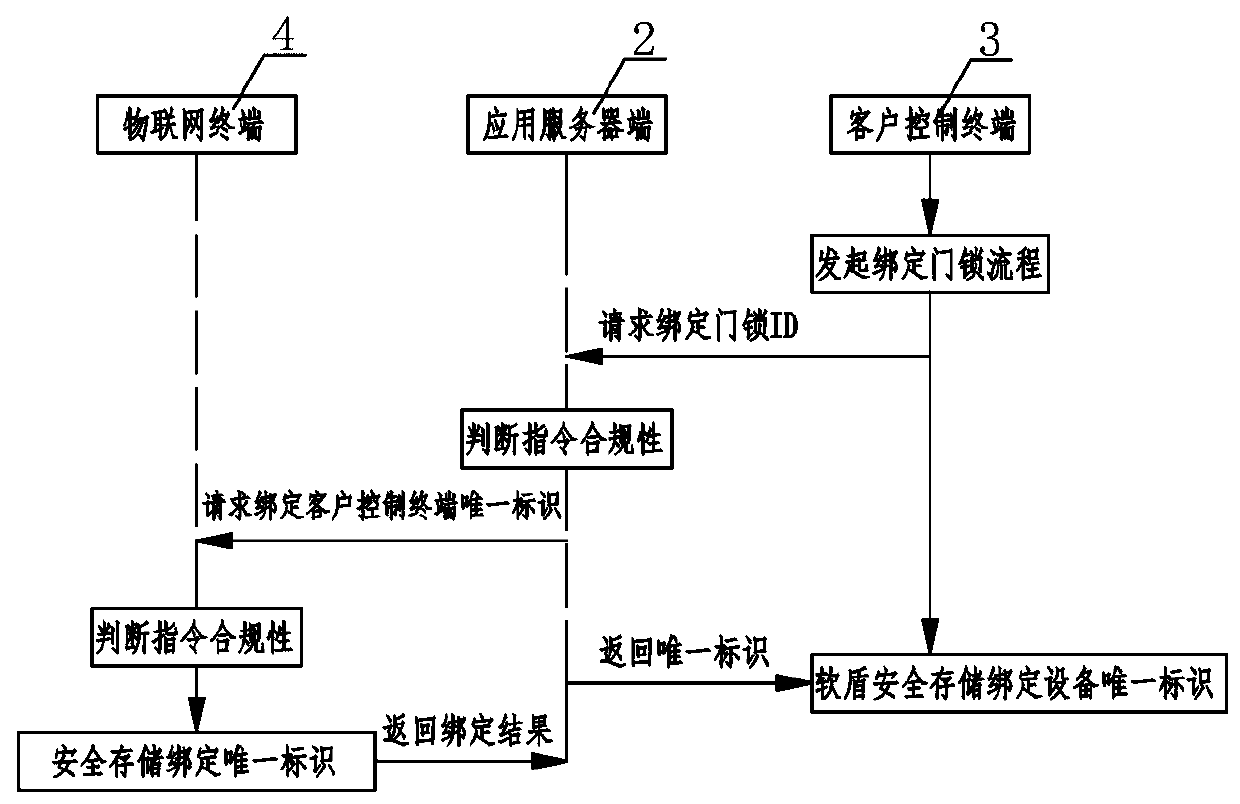
[0024] like Figure 1-4As shown, an IoT security management system includes a private key center 1, an application server 2, a client control terminal 3, and an IoT terminal 4, and the private key center 1 and the application server 2 communicate and authenticate data through a soft shield Transmission; the application server 2 communicates with the client control terminal 3 and the IoT terminal 4 at the same time for key distribution, identity authentication and data encryption; the client control terminal 3 and the IoT terminal 4 perform mutual communication of identity authentication and data encryption Communication; private key center 1 includes KPC key production component 11, KMC key management component 12 and key authentication component 13, KPC key production component 11 generates key according to preset algorithm rule, KMC key mana...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com