Patents
Literature
113results about How to "Prevent cracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
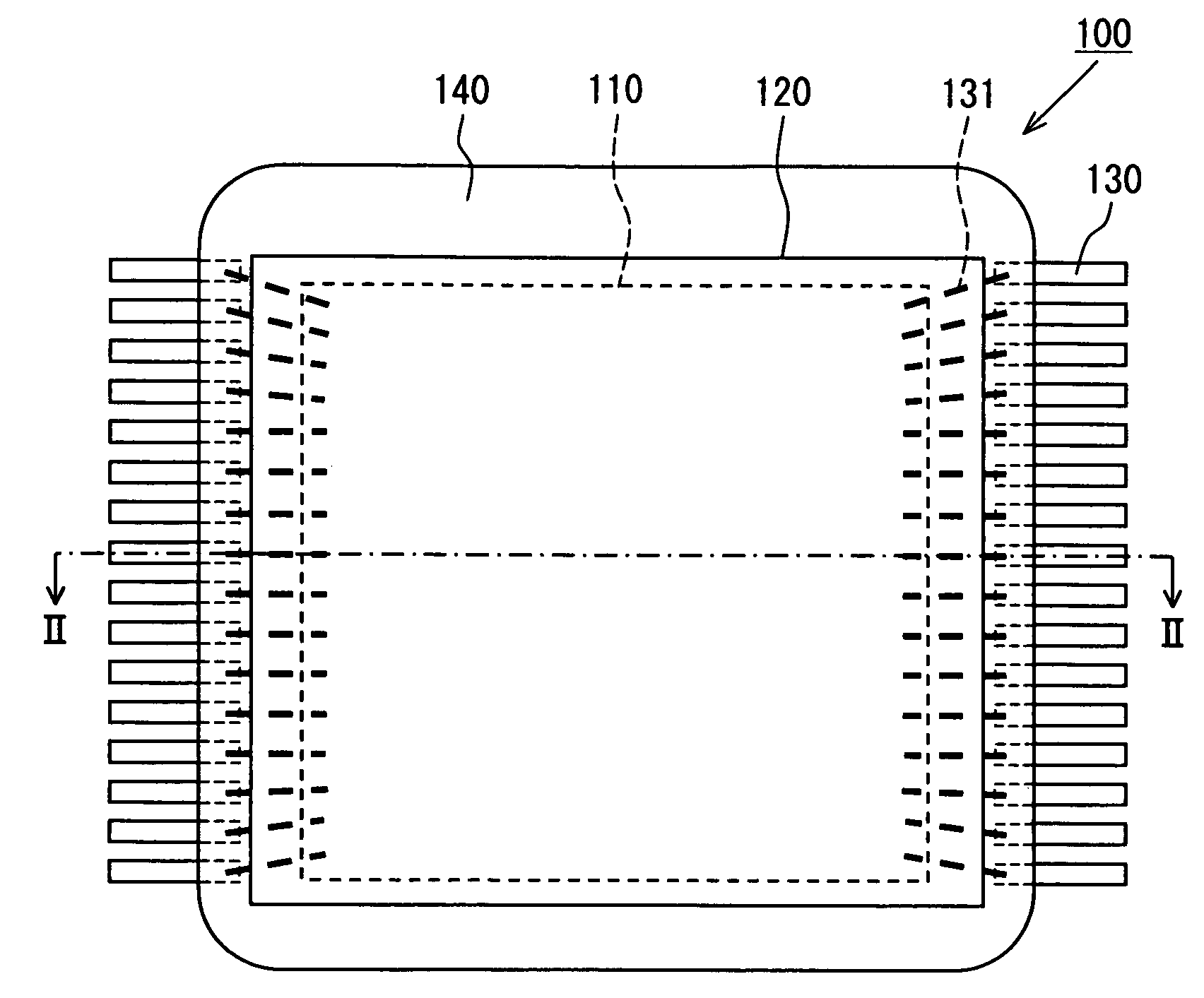
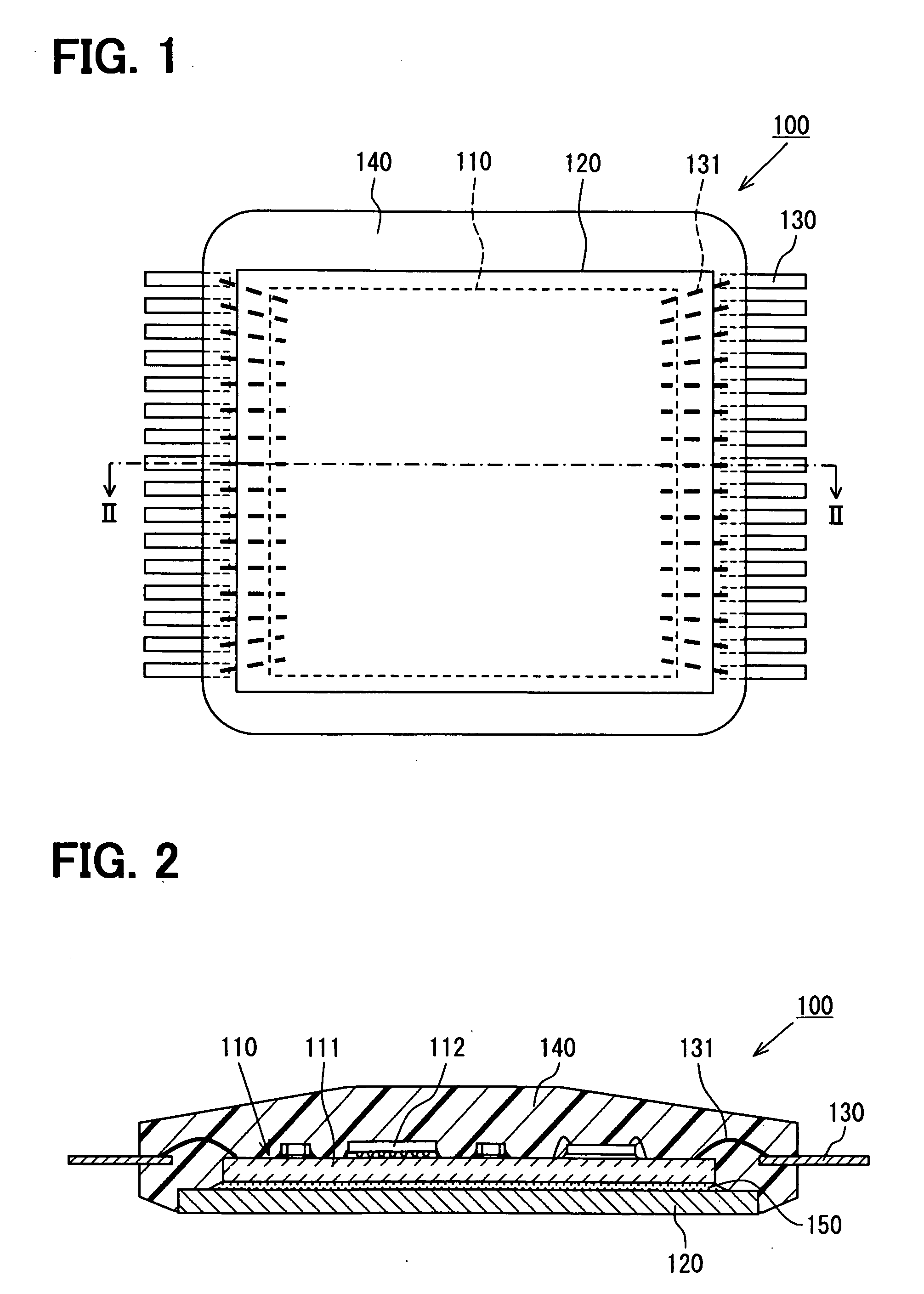
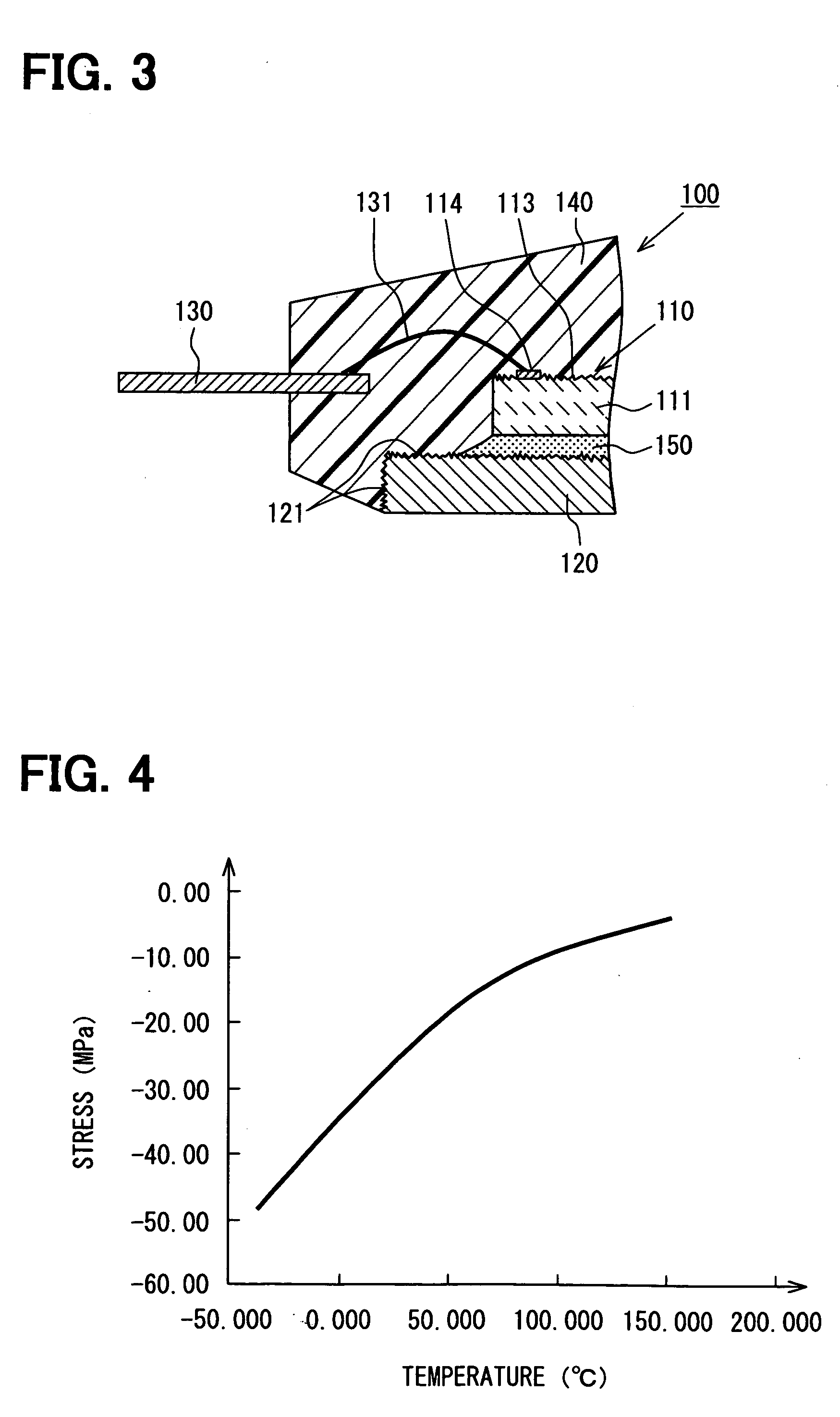
Stack package that prevents warping and cracking of a wafer and semiconductor chip and method for manufacturing the same
InactiveUS20090001602A1Prevent crackingAvoid crackingSemiconductor/solid-state device detailsSolid-state devicesRedistribution layerEngineering
A stack package and a method for manufacturing the same. The stack package includes first and second semiconductor chips placed such that surfaces thereof, on which bonding pads are formed, face each other; a plurality of through-silicon vias formed in the first and second semiconductor chips; and a plurality of redistribution layers formed on the surfaces of the first and second semiconductor chips to connect the through-silicon vias to the corresponding bonding pad, wherein the redistribution layers of the first and second semiconductor chips contact each other. By forming the stack package in this manner, it is possible to prevent pick-up error and cracks from forming during the manufacturing process, and therefore the stack package can be reliable formed.
Owner:SK HYNIX INC
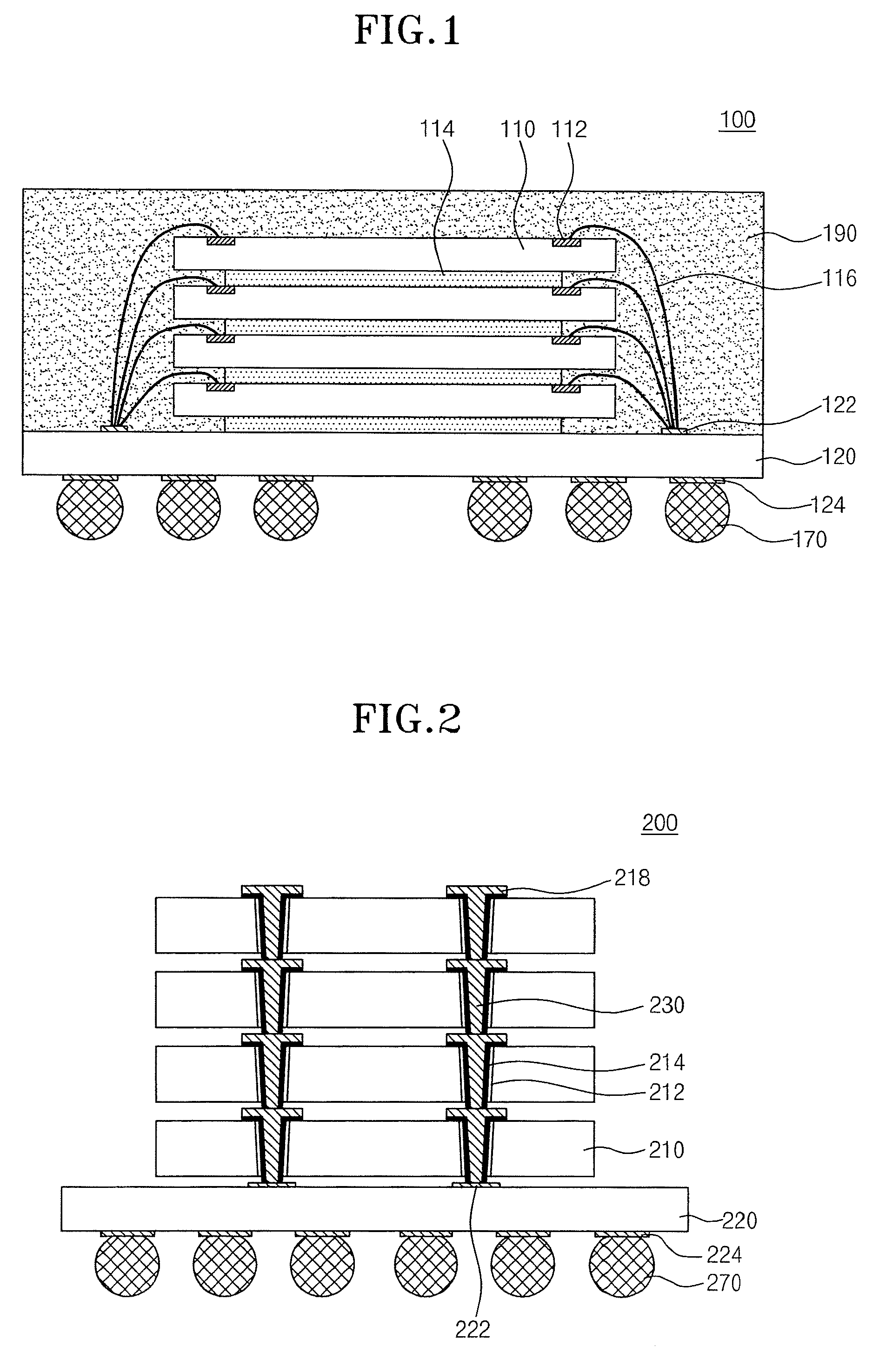
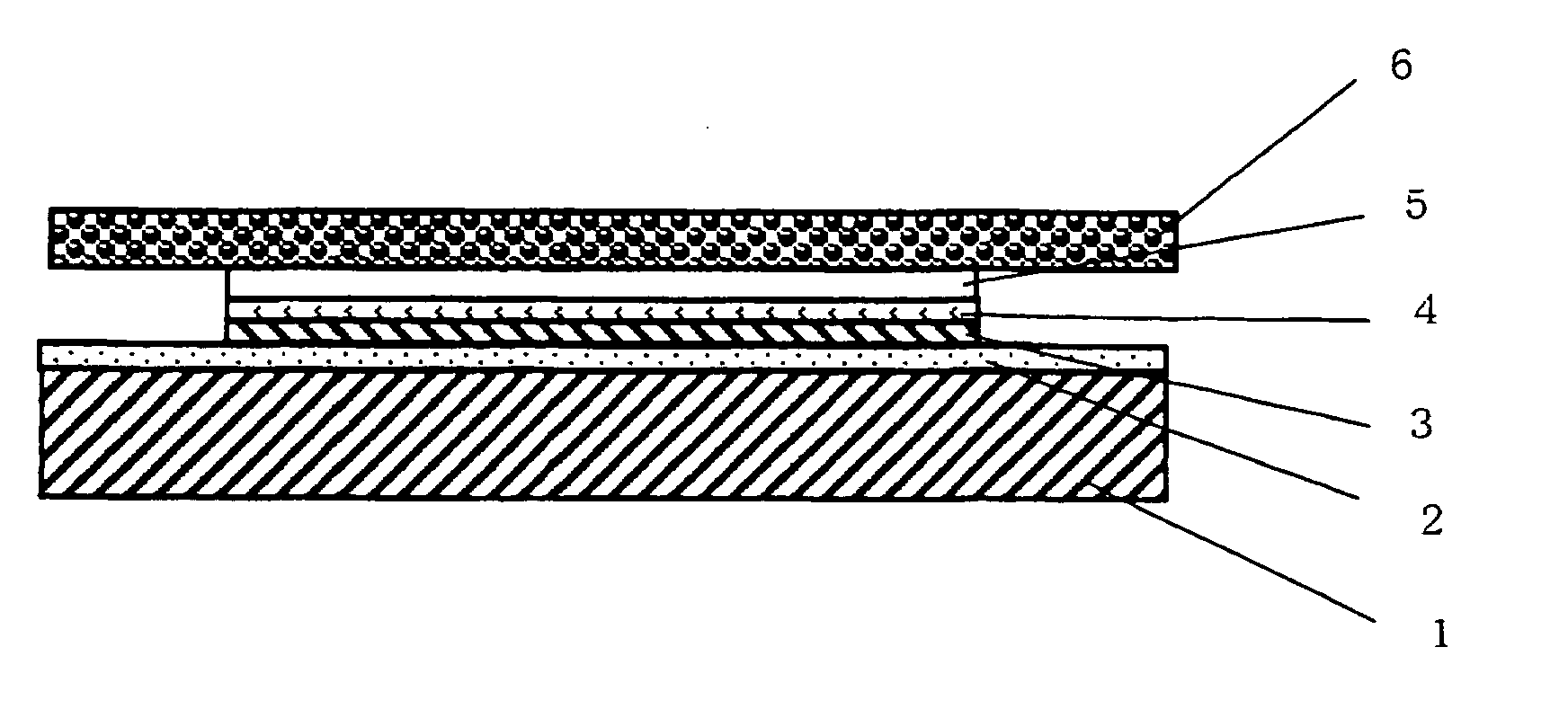
Dicing and die bonding adhesive tape
InactiveUS20070120271A1Prevent crackingAvoid crackingSemiconductor/solid-state device detailsSolid-state devicesPressure sensitiveChemistry
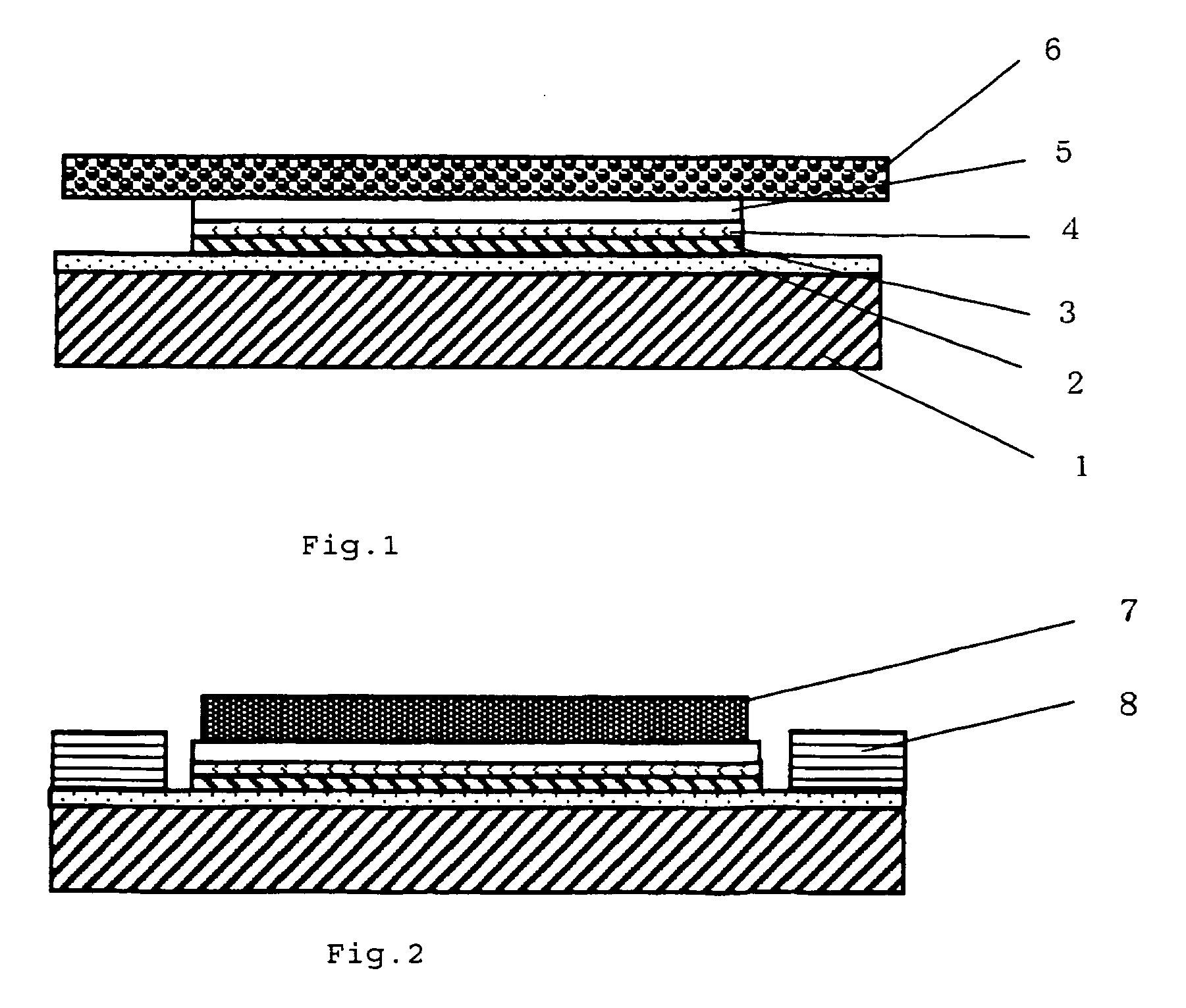
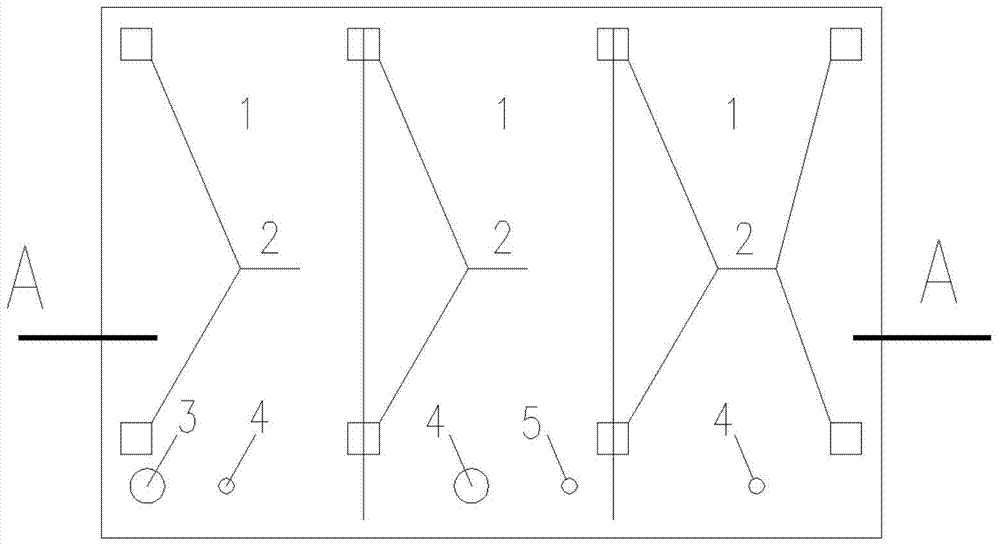
A dicing and die bonding tape, comprising a substrate 1, a pressure sensitive adhesive layer (A) 2 superimposed on the substrate 1, a substrate 3 superimposed on the pressure sensitive adhesive layer (A) 2, a pressure sensitive adhesive layer (B) 4 superimposed on the substrate 3, and an adhesive layer 5 super imposed on the pressure sensitive adhesive layer (B) 4, said dicing and die bonding tape having an adhesion strength between the pressure sensitive adhesive layer (A) 2 and a dicing flame of 0.6 N / 25 mm or larger, and an adhesion strength between the pressure sensitive adhesive layer (B) 4 and the adhesive layer 5 of from 0.05 to 0.5 N / 25 mm.
Owner:SHIN ETSU CHEM CO LTD
Method and apparatus for laser cutting and drilling of semiconductor materials and glass
InactiveUS7173212B1High ratePrevent crackingMetal working apparatusLaser beam welding apparatusPhysical modelLaser drilling
A method for laser drilling and laser cutting of semiconductor material or glass in pulsed regime permits, for a given laser power, a rate of material cutting which is substantially higher than the rate obtained using conventional laser cutting. The hole or cut produced by the laser-induced removal of material has a reproducible shape, the drilling or cutting does not produce material debris or spatter deposition around the crater or cut, and the cracking of the crater or cut walls is prevented. The method includes utilization of a unique physical model representing all main physical processes taking place during laser-assisted material deposition, a corresponding mathematical model consisting of equations describing the relevant physical processes, and a computer code used for numerical calculations of the parameters of interest according to the mathematical model.
Owner:SEMAK VLADIMIR V
Method for manufacturing vertically structured light emitting diode
ActiveUS20070077673A1Process time and cost be reducePrevent crackingSolid-state devicesSemiconductor/solid-state device manufacturingSeparation processEngineering
There is provided a method for manufacturing a vertically structured LED capable of performing a chip separation process with ease. In the method, a light-emitting structure is formed on a growth substrate having a plurality of device regions and at least one device isolation region, wherein the light-emitting structure has an n-type clad layer, an active layer and a p-type clad layer which are disposed on the growth substrate in sequence. A p-electrode is formed on the light-emitting structure. Thereafter, a first plating layer is formed on the p-electrode such that it connects the plurality of device isolation regions. A pattern of a second plating layer is formed on the first plating layer of the device region. The growth substrate is removed, and an n-electrode is then formed on the n-type clad layer.
Owner:SAMSUNG ELECTRONICS CO LTD
Electronic control apparatus and method of manufacturing the same
InactiveUS20080170372A1Prevent crackingBroad contactSolid-state devicesPrinted circuit manufactureEngineeringElectrical and Electronics engineering
An electronic control apparatus includes a circuit board with a circuit element mounted thereon, a heatsink for dissipating heat from the circuit board placed thereon, an external terminal having a first end electrically connected to the circuit board and a second end connectable to an external device, a molding resin for covering the circuit board and the first end of the external terminal. The second end of the external terminal is exposed outside the molding resin. The heatsink is at least partially covered with the molding resin. At least one of covered surfaces of the circuit board and the heatsink is at least partially roughened to have a predetermined surface roughness, which allows the circuit board and the heatsink to be tightly attached to the molding resin.
Owner:DENSO CORP
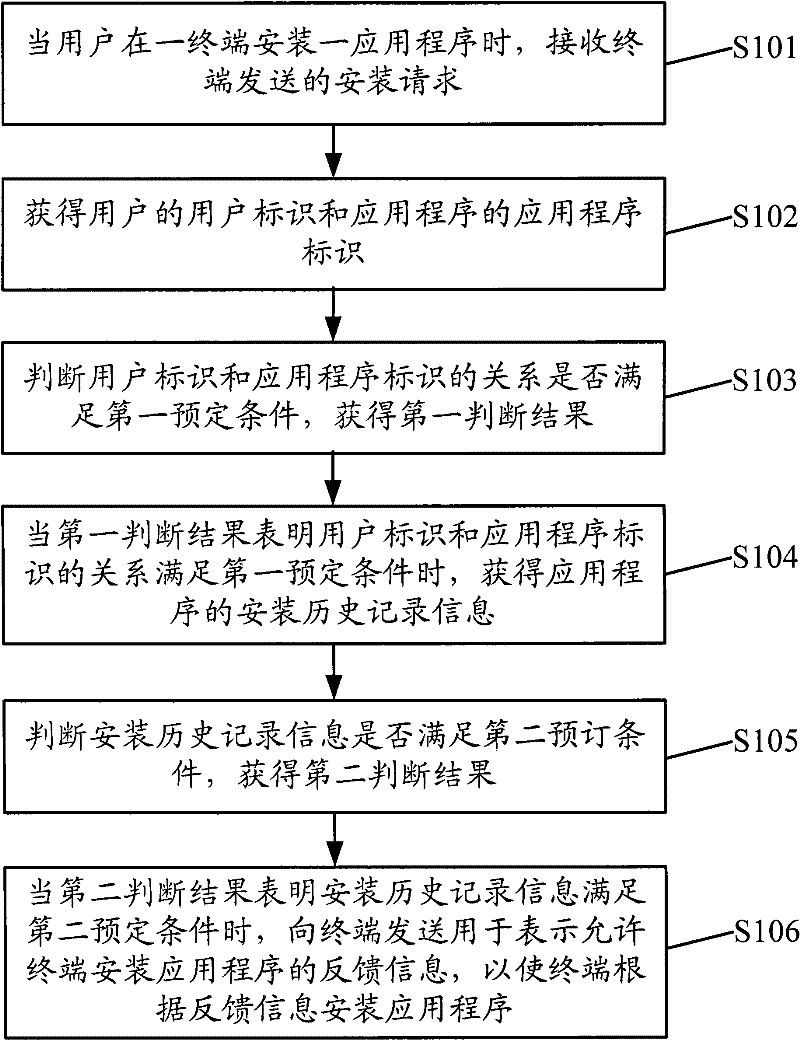
Installation management method, server and terminal for application program
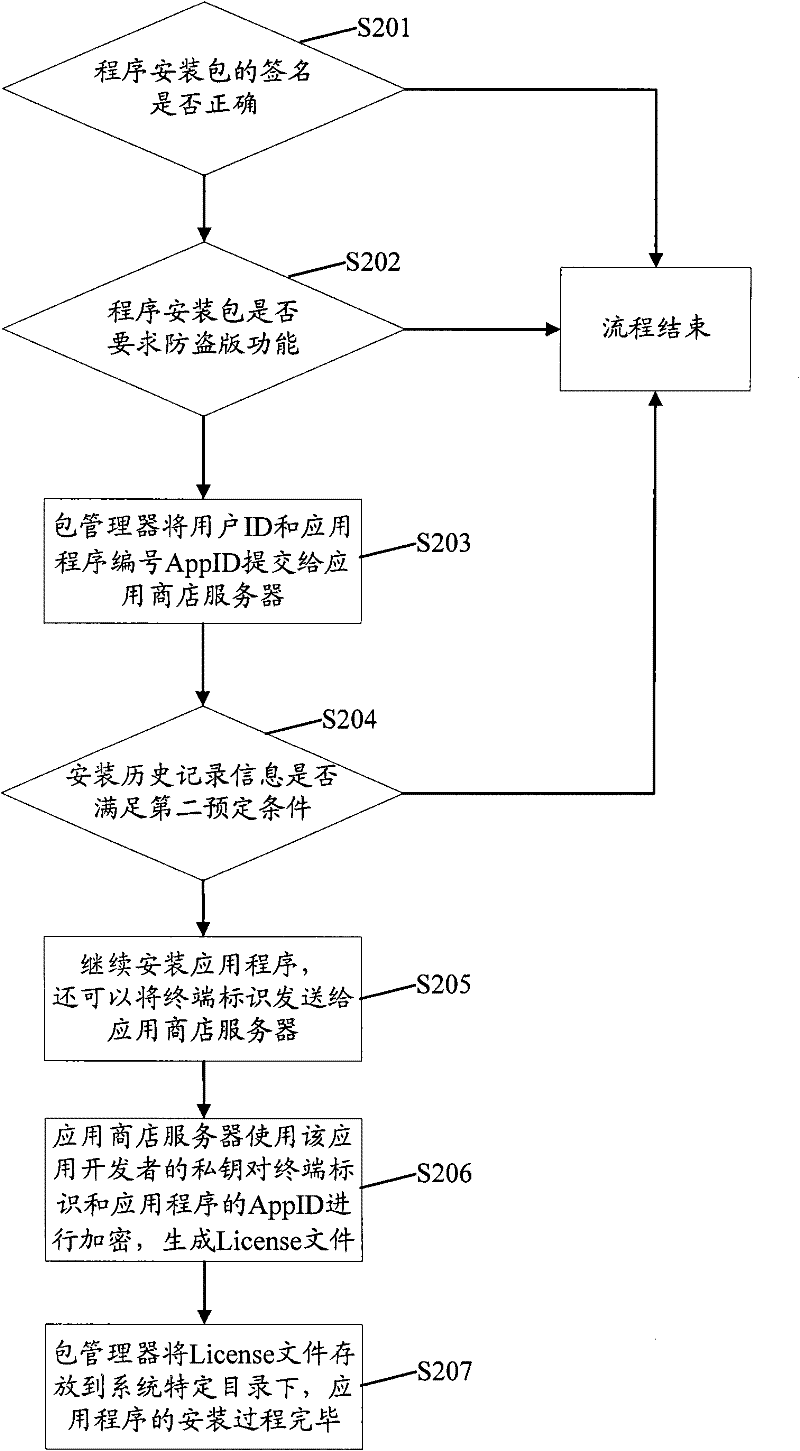
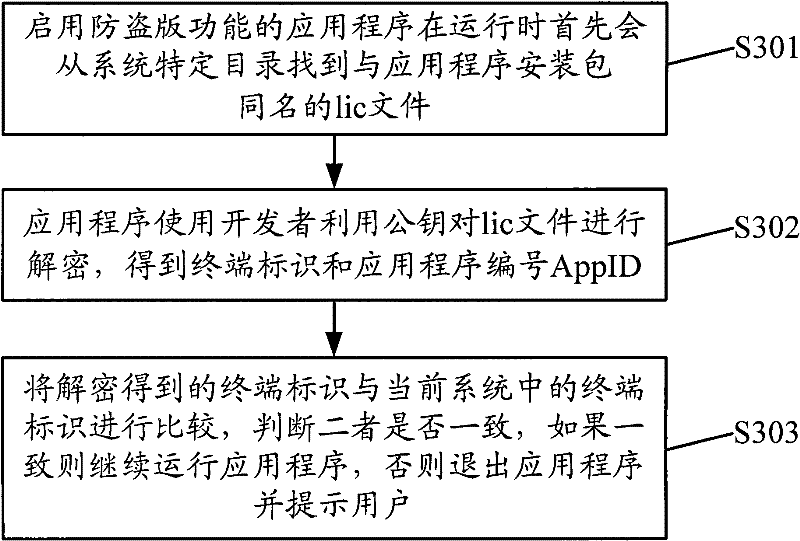
InactiveCN102446106APrevent crackingImprove reliabilityProgram loading/initiatingProgram/content distribution protectionSoftware engineeringComputer terminal
The invention provides an installation management method, a server and a terminal for an application program. The installation management method includes: receiving installation request sent by the terminal when a user installs the application program on the terminal, acquiring user identification of the user and application program identification of the application program, judging whether the relationship between the user identification and the application program identification meets a first predetermined condition and acquiring a first judgment result, acquiring installation history recorded information of the application program when the first judgment result indicates that the relationship between the user identification and the application program identification meets the first predetermined condition, judging whether the installation history recorded information meets a second predetermined condition and acquiring a second judgment result, sending feedback information which is used for indicating that the terminal is allowed to be installed with the application program when the second judgment result indicates that the installation history recorded information meets the second predetermined condition so as to enable the terminal to be installed with the application program according to the feedback information. By means of the installation management method, the server and the terminal for the application program, an anti-piracy mechanism can be effectively prevented from being broken, thereby having high reliability.
Owner:LENOVO (BEIJING) CO LTD
Electrical connector
ActiveUS8192206B1Prevent crackingAvoid crackingFinal product manufacturePrinted circuit aspectsSolder ballElectrical and Electronics engineering
An electrical connector for electrically connecting to a circuit board. In one embodiment, the electrical connector includes: an insulating body, having at least one grounding terminal slot and a plurality of signal terminal slots, at least one grounding terminal, made of a flexible conductive material and accommodated in the grounding terminal slot, and including a first base and a first soldering portion accommodated in the grounding terminal slot in a suspended manner, a plurality of signal terminals, and a plurality of solder balls, at least one of which is disposed on the first soldering portion.
Owner:LOTES
Logon system for an electronic device
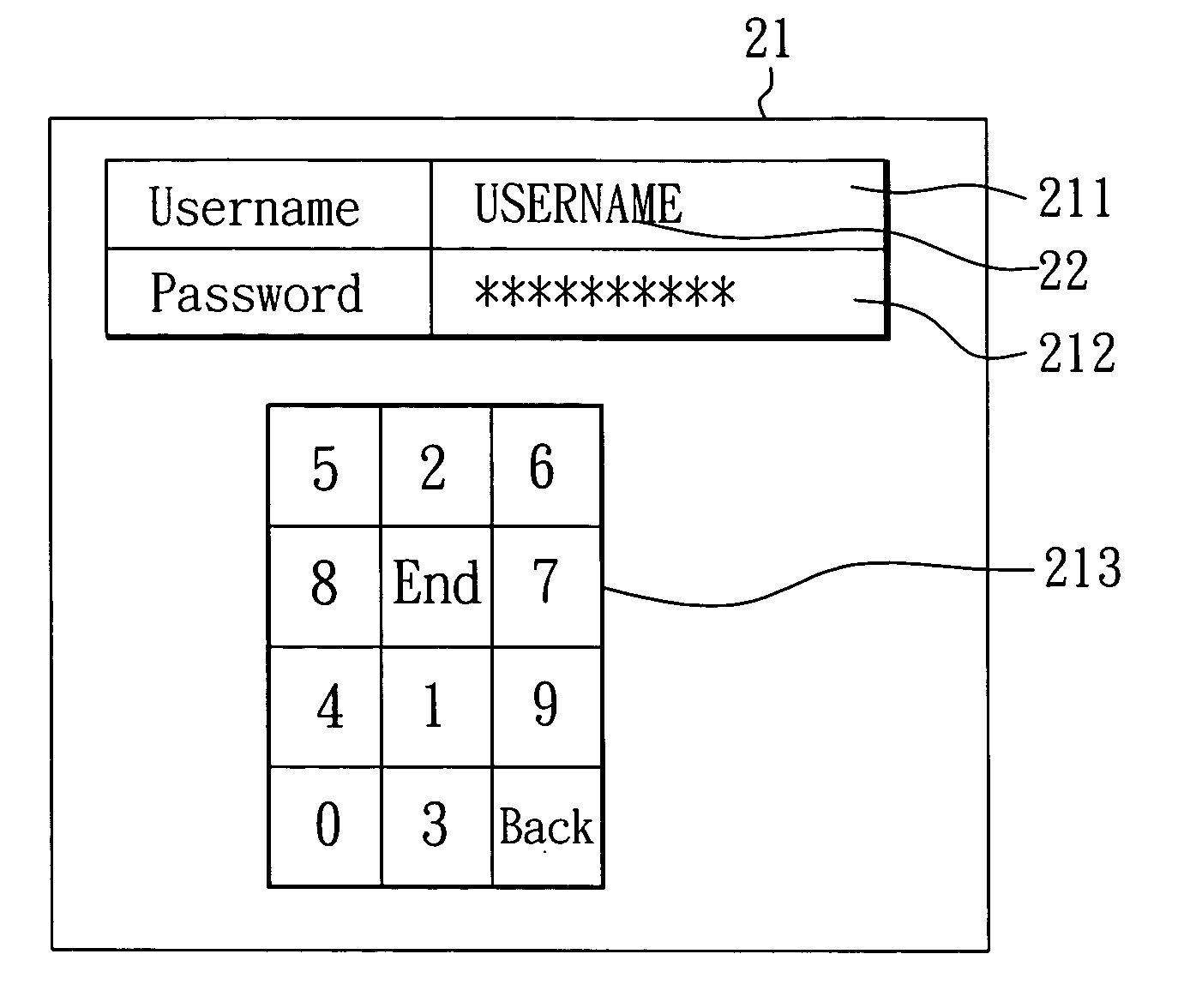
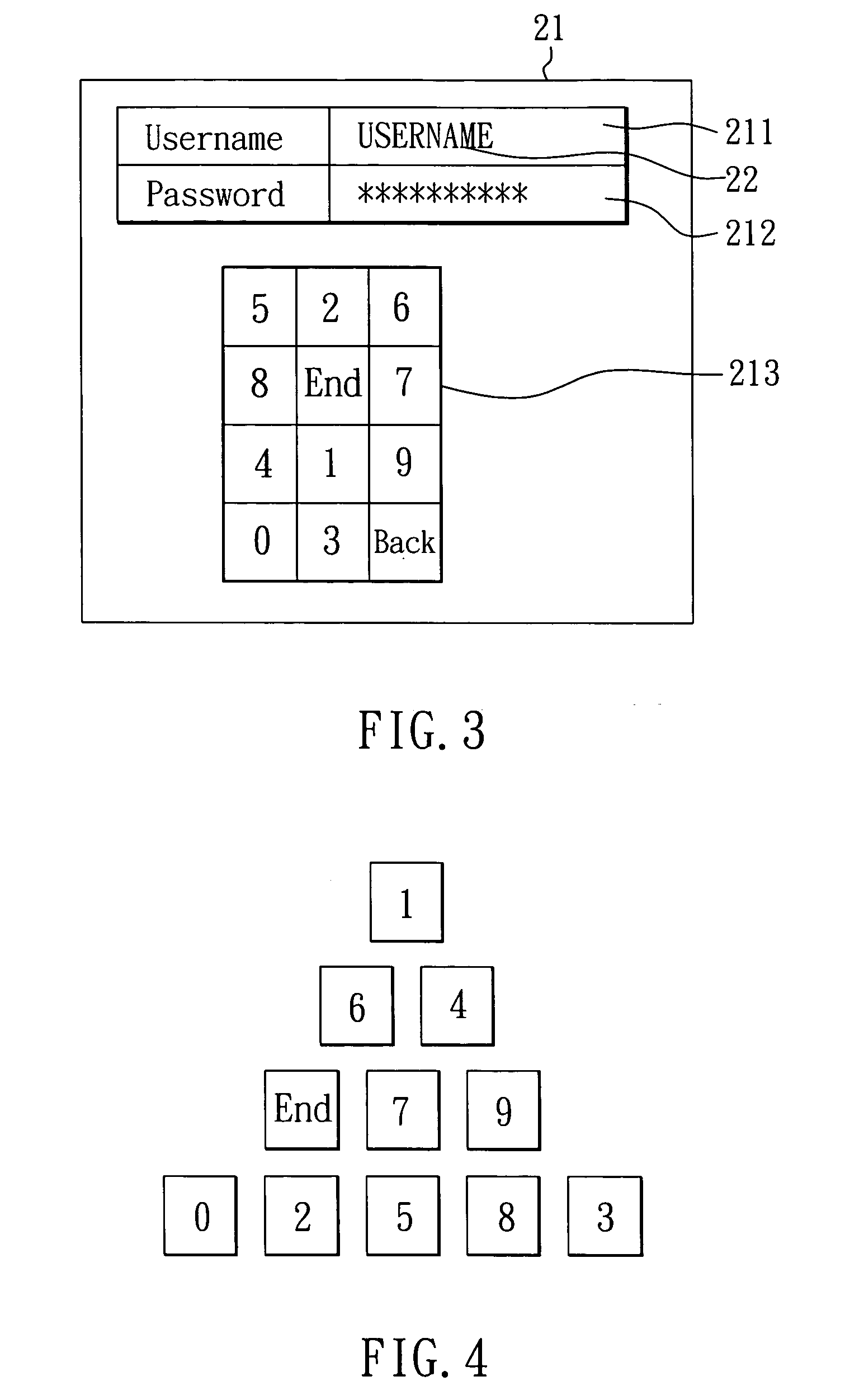
InactiveUS20060242421A1Prevent crackingRisk minimizationRandom number generatorsUser identity/authority verificationInput/outputTouchscreen
A logon system for an electronic device is provided. The system includes an electronic device and a touch display. The touch display is connected to the electronic device for functioning as an input / output device of the electronic device. For a logon to the electronic device, the electronic device displays a keypad having multiple keys on the touch display, and an arrangement of the keys is determined by the electronic device in random, so that a user can log on the electronic device by touching the keys displayed on the touch display.
Owner:KINPO ELECTRONICS
Peeling tape adhering method and peeling tape adhering device
PendingUS20070284028A1Prevent crackingPrevent peelingLamination ancillary operationsControlling laminationEngineeringElectrical and Electronics engineering
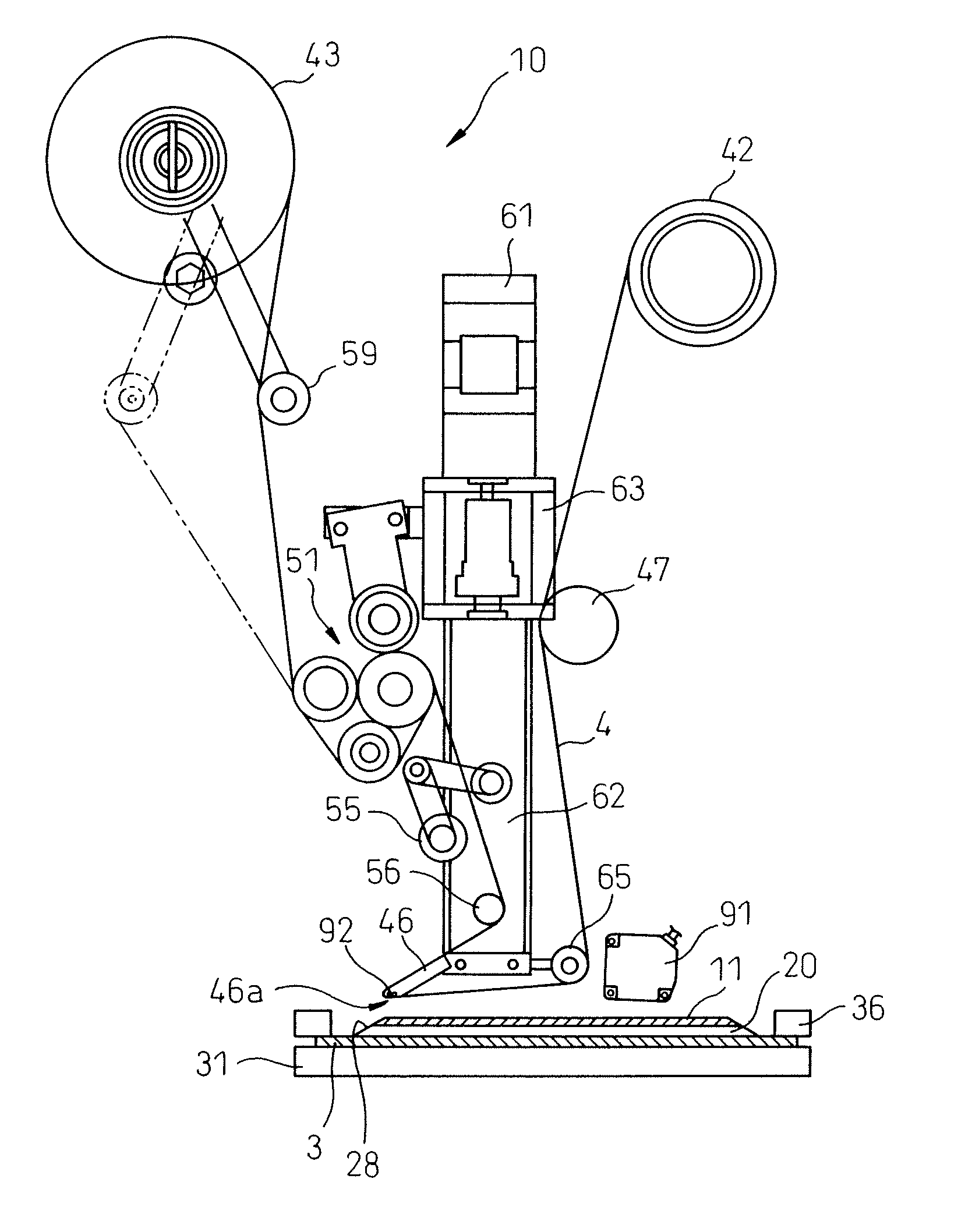
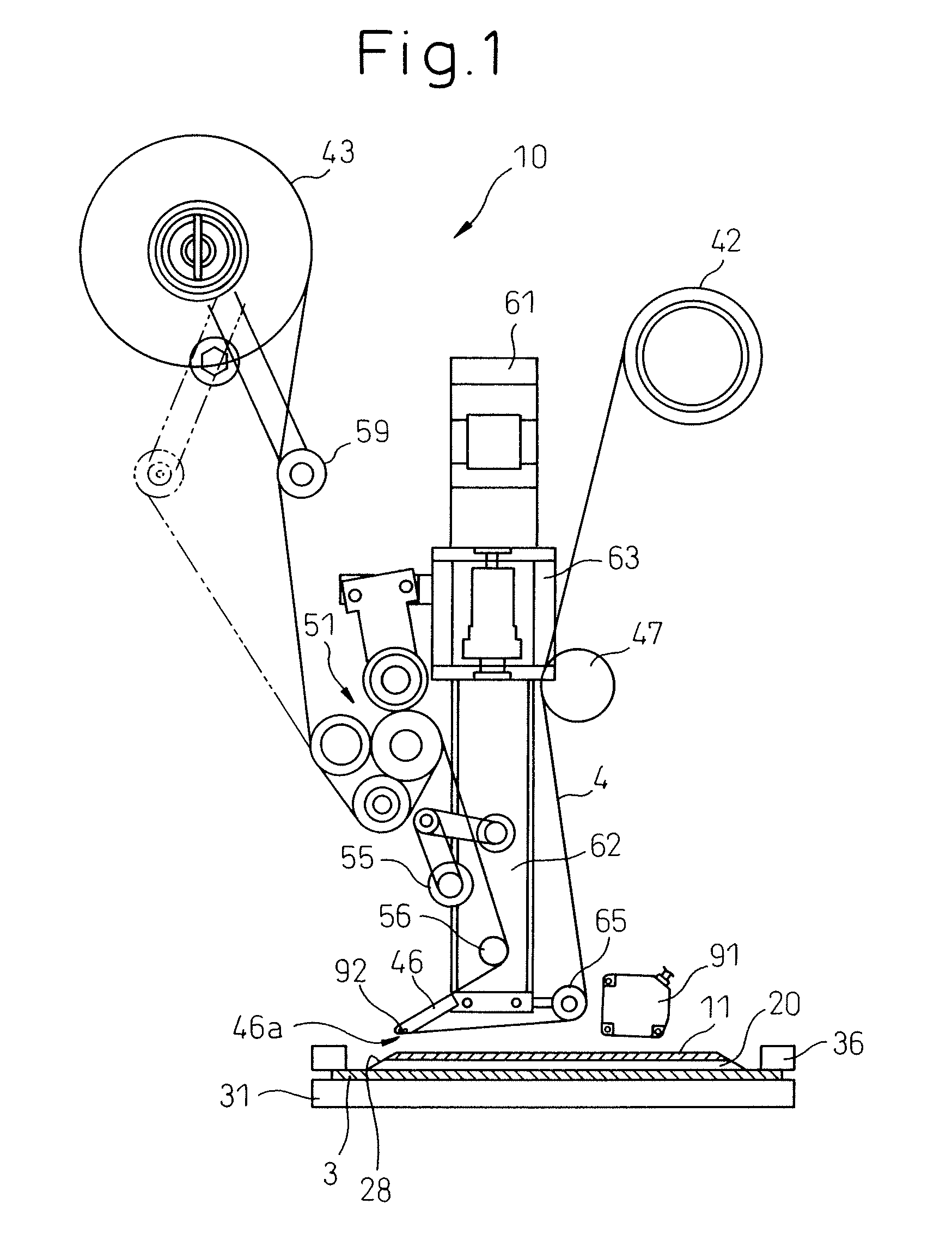
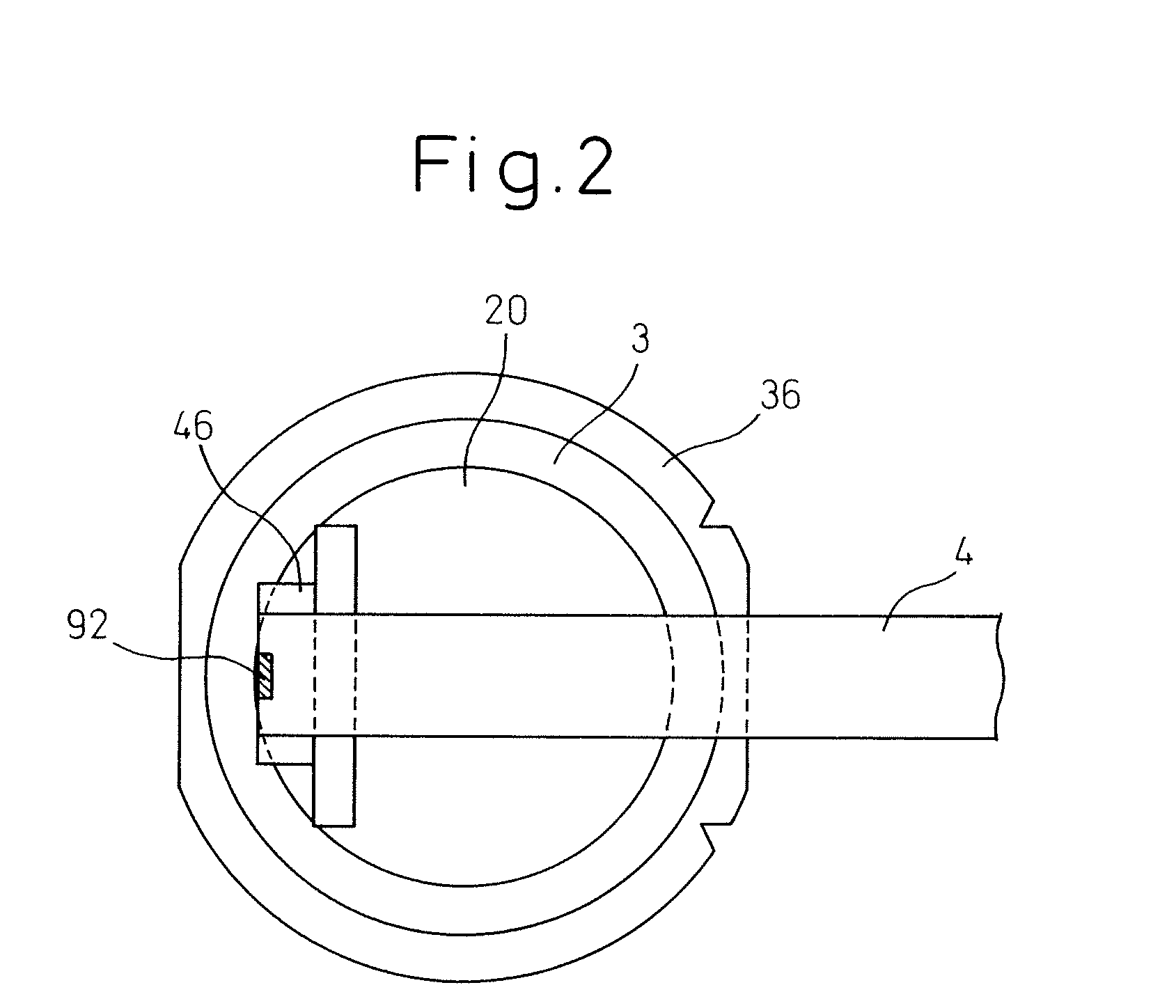
A peeling tap adhering method for adhering a peeling tape (4) to a surface protection film (11) adhered to the front surface of a wafer (20), comprises the steps of: supporting the wafer on a table (31) under the condition that the surface protection film is directed upward; adhering the peeling tape onto the surface protection film by pressing the peeling tape onto the surface protection film when a peeling tape adhering means (46) is lowered; detecting the pressure between the surface protection film of the wafer and the peeling tape adhering means; and stopping the peeling tape adhering means from lowering in the case where a pressure detection value (P) is not less than a predetermined value (P0). Due to the foregoing, it is possible to prevent the wafer from being cracked. Further, it is possible to prevent the peeling tape and the dicing tape from adhering to each other. When the distance (L) between the surface protection film of the wafer and the peeling tape adhering means becomes a value not more than a predetermined value (L0), the peeling tape sticking means may be stopped from lowering.
Owner:TOKYO SEIMITSU
Waterproof structure manufacturing method of caisson-type toilet
InactiveCN103485509AEffectively drainAvoid springsSewerage structuresFlooring insulationsWater dischargeEngineering
A waterproof structure manufacturing method of a caisson-type toilet includes manufacturing of a basic layer, an overhead layer and a ground layer, has the advantages of being capable of effectively preventing the common problems that pipelines are broken, water is leaked due to the fact that connectors are not firm and water is accumulated through two-time waterproof structuring and two-time water-discharging structuring, avoiding the spring water phenomenon of the ground of the toilet, facilitating air drying of the toilet and preventing the toilet from being under a wet environment for a long time, and is suitable for the caisson-type toilet with a caisson which is 35-50cm deep.
Owner:BEIJING SHOUGANG CONSTR GROUP
Positive electrode for secondary battery, and secondary battery
ActiveUS20150050555A1Prevent crackingReduce stressNon-aqueous electrolyte accumulator electrodesLi-accumulatorsPolymer chemistryMeth-
A positive electrode for a secondary battery wherein the electrode includes a collector and a positive electrode active material layer which is stacked upon the collector, and which includes a positive electrode active material, a conductive agent, and a binder; the binder includes a first polymer and a second polymer; the first polymer is a fluorine-containing polymer; the second polymer includes a polymerized moiety having a nitrile group, a polymerized moiety having a hydrophilic group, a polymerized (meth)acrylic acid ester moiety, and a straight-chain polymerized alkylene moiety having a carbon number of at least 4; the proportion of the first polymer and the second polymer in the binder, expressed as a mass ratio, is in the range of 95:5 to 5:95.
Owner:ZEON CORP
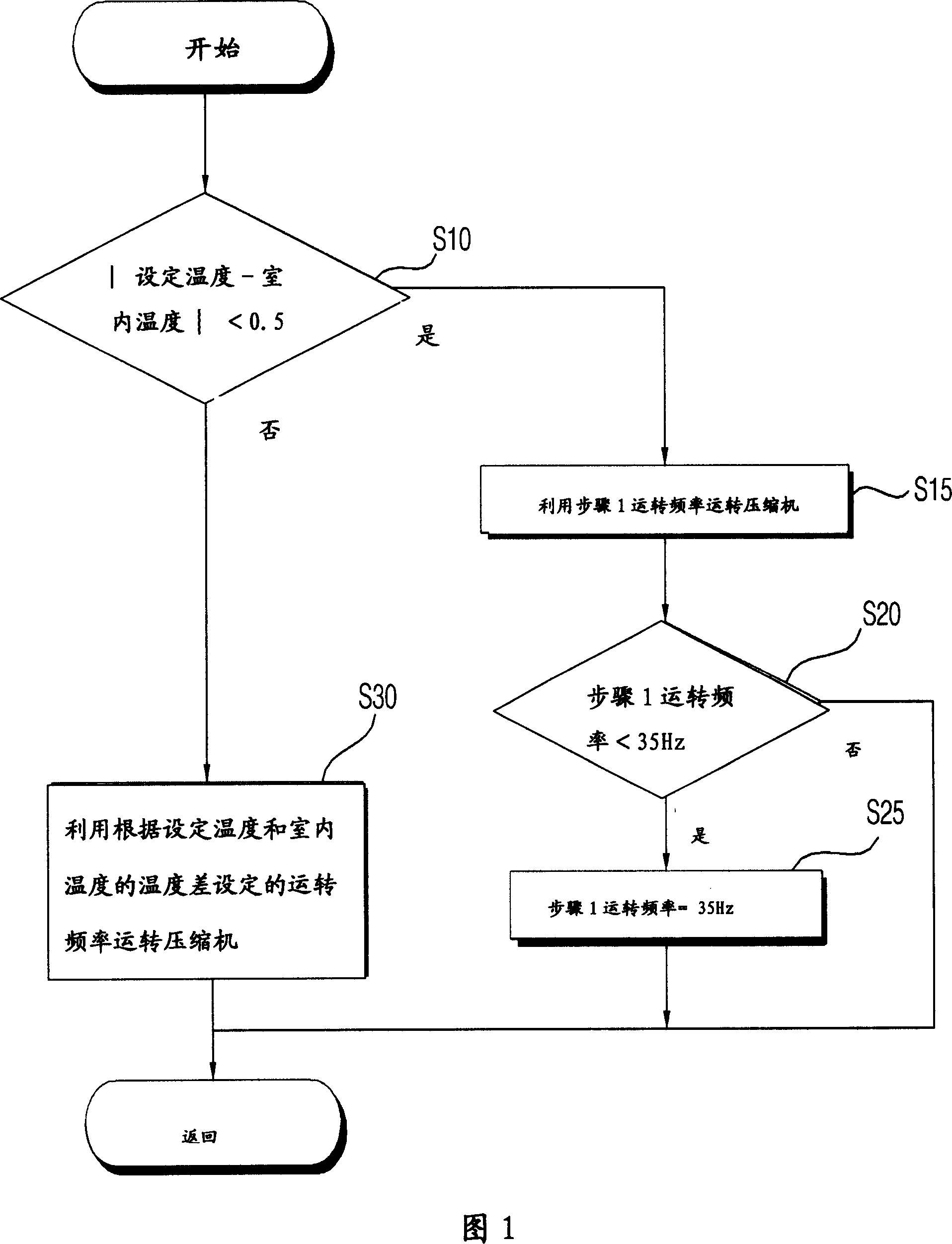
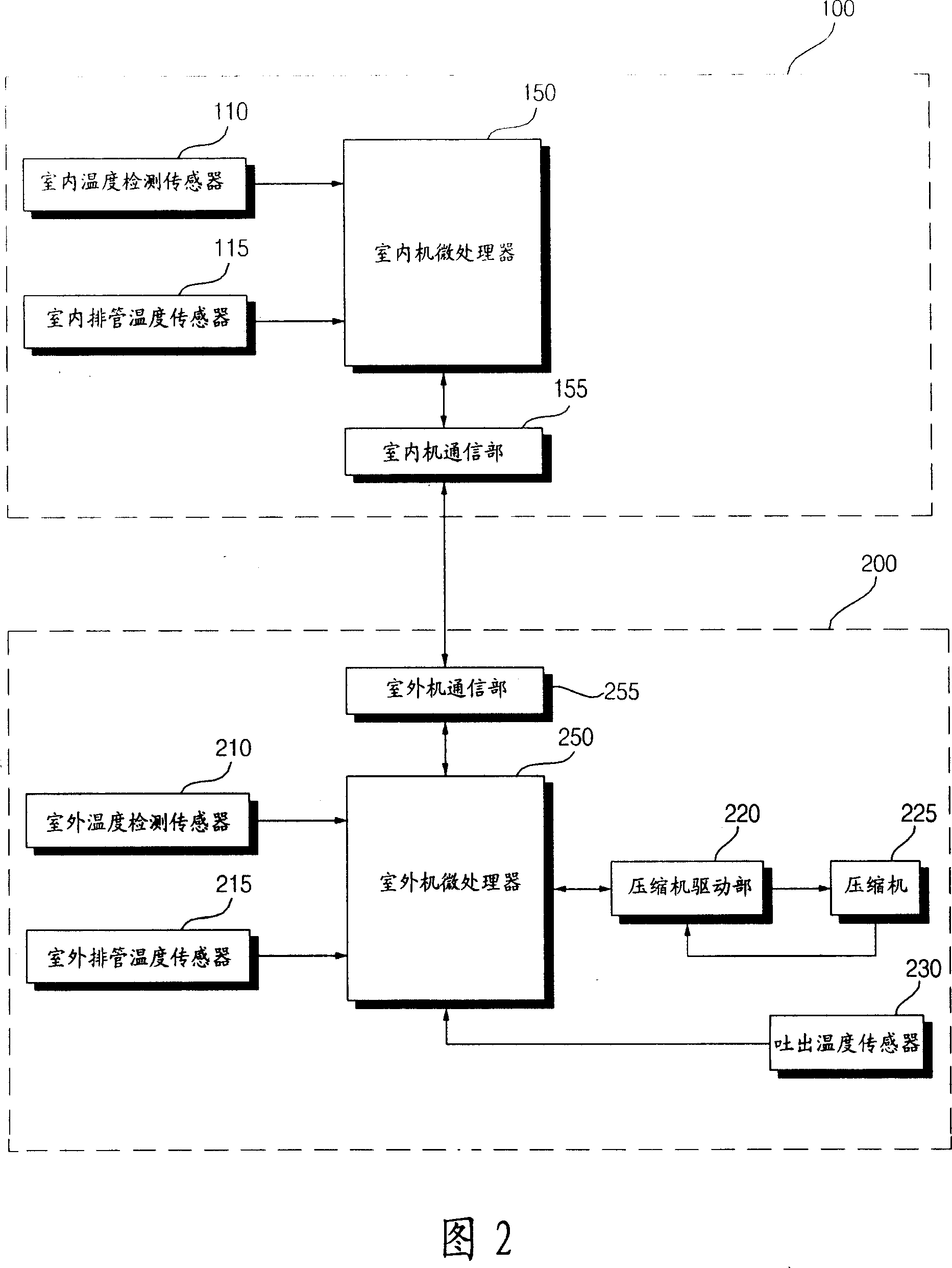
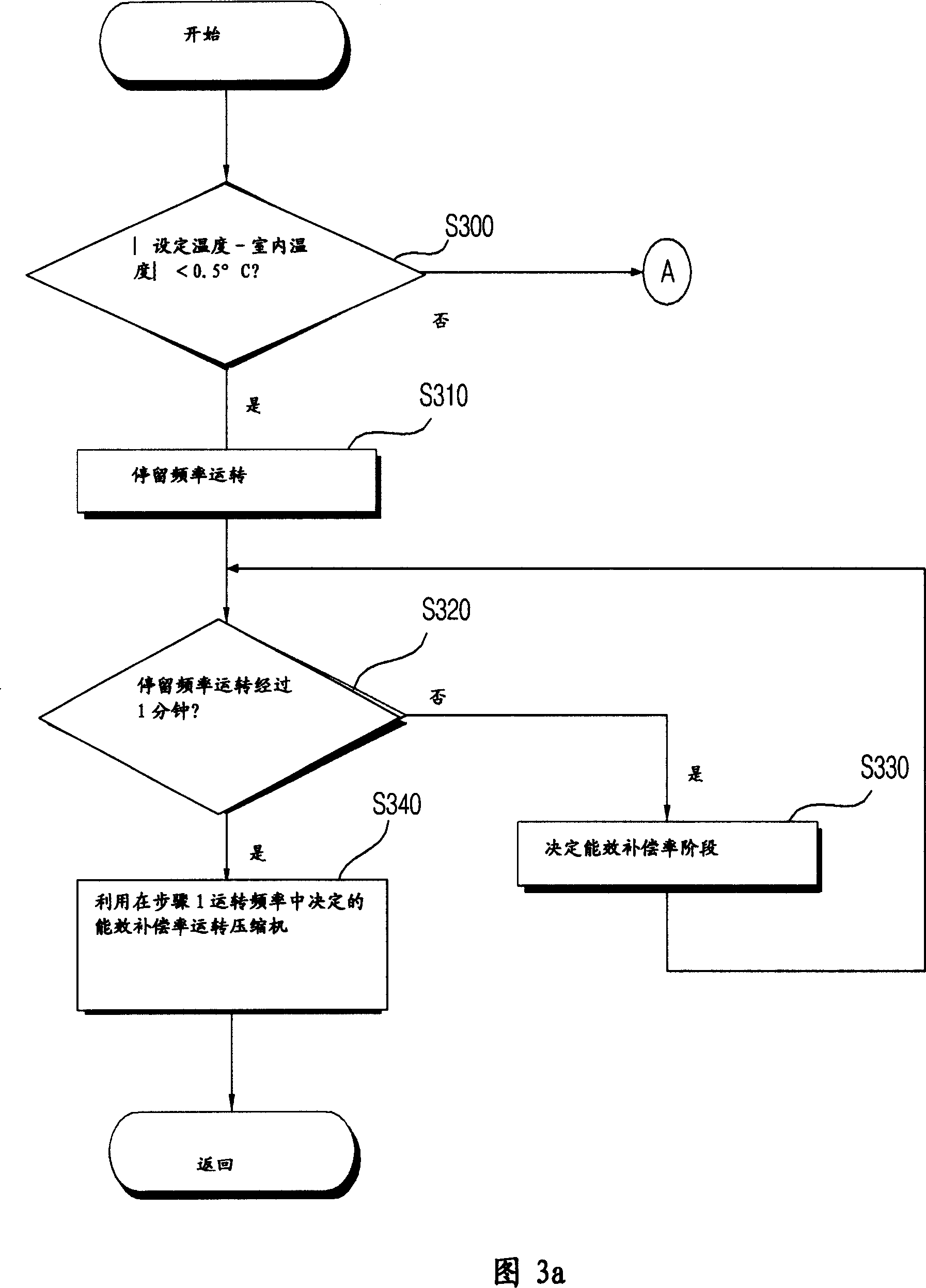
Control method of frequency conversion air conditioner
InactiveCN101089495AReduce vibrationPrevent crackingSpace heating and ventilation safety systemsLighting and heating apparatusLow speedFrequency conversion
The present invention relates to a control method of frequency conversion air conditioner capable of reducing vibration produced by low-speed operation of air conditioner. It is characterized by that when the temperature difference of the set temperature set by user and indoor temperature is less than rated temperature, at the same time of utilizing a certain operation frequency to operated compressor it can output energy efficiency compensation rate according to the operation frequency of compressor rotation interval load, and can utilize first operation frequency produced by changing rotation interval energy efficiency according to the energy efficiency compensation rate to operate compressor.
Owner:LG ELECTRONICS (TIANJIN) APPLIANCES CO LTD
Process for separating dies on a wafer
ActiveUS6849523B2PreventPrevent crackingSolid-state devicesSemiconductor/solid-state device manufacturingEngineeringWafer dicing
A process for separating IC dies from a wafer substrate. In one embodiment, complete separation channels are initially cut through the wafer between dies along one axis. Next, partial separation channels are cut into the wafer along an intersecting axis, leaving wafer material connecting adjacent dies. In another embodiment, partial separation channels are cut into the wafer along one axis, after which complete separation channels are cut through the wafer along the intersecting axis. In still another embodiment, partial separation channels are cut along both axes.
Owner:TAIWAN SEMICON MFG CO LTD
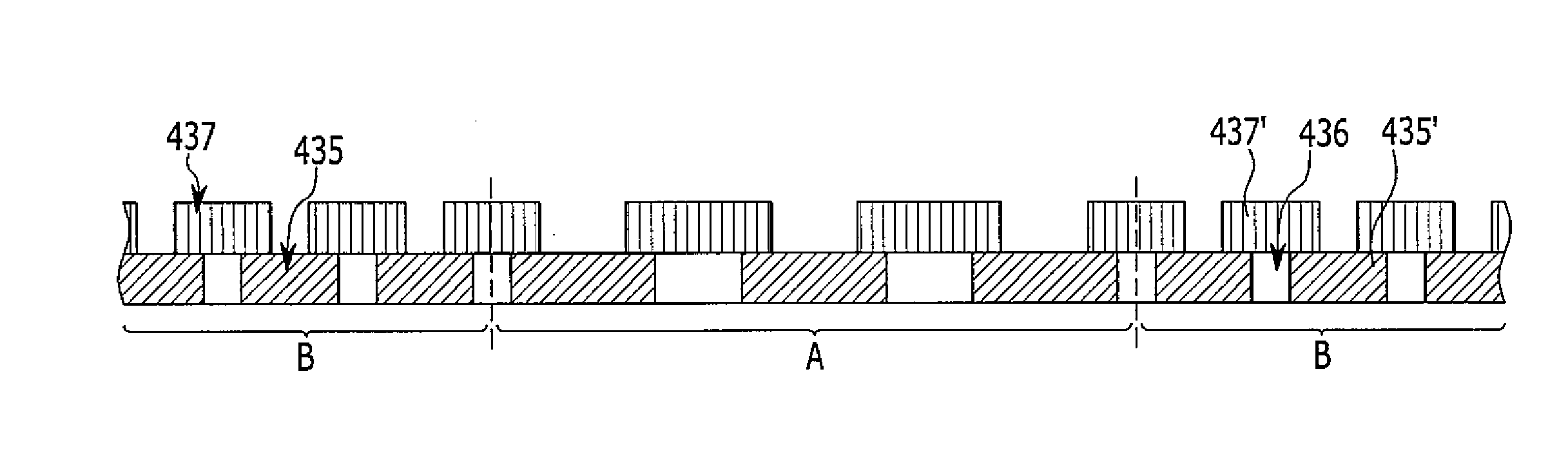
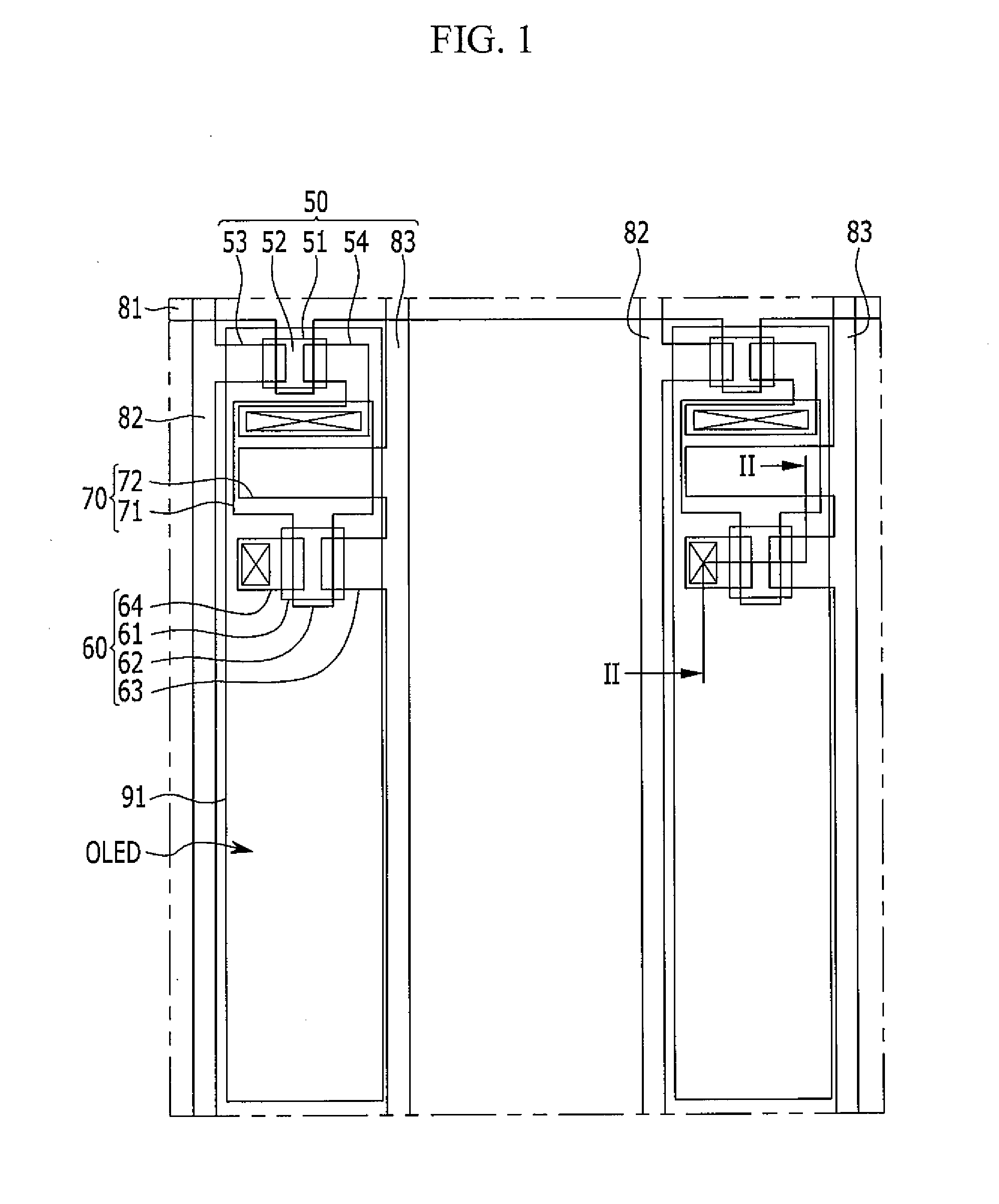
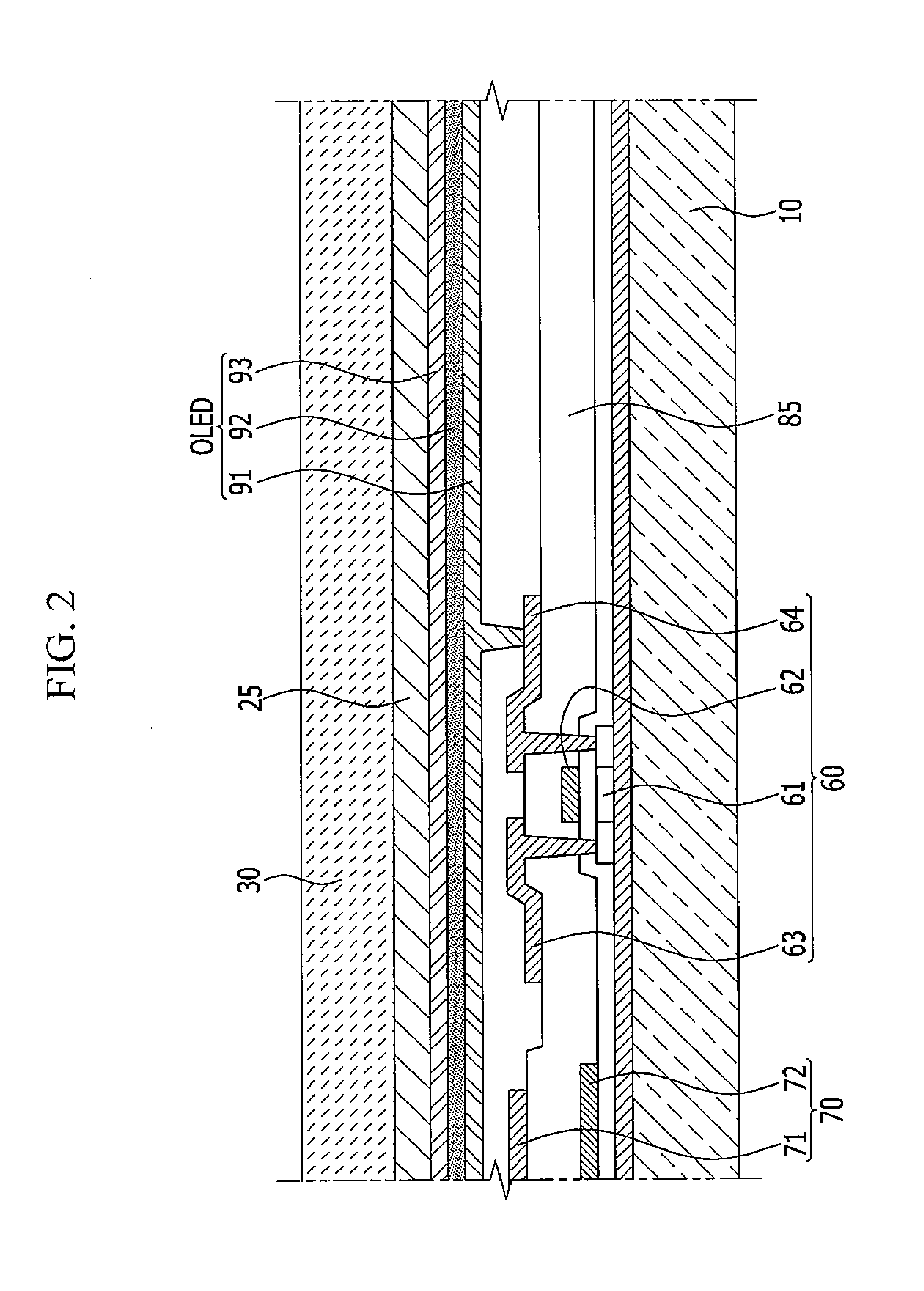
Flexible organic light emitting diode display and manufacturing method thereof
ActiveUS20150102326A1Prevent crackingCrack can be prevented and reducedFinal product manufactureSolid-state devicesPhysicsFlexible organic light-emitting diode
A flexible organic light emitting diode (OLED) display according to an exemplary embodiment includes: a substrate; an organic light emitting diode (OLED) layer provided on the substrate; and a thin film encapsulation layer provided on the OLED layer. The thin film encapsulation layer includes a plurality of laminated inorganic layers, at least one inorganic layer of the plurality of inorganic layers includes a plurality of inorganic layer patterns that are disposed to be spaced apart from each other on a plane, and an organic layer is formed between the plurality of inorganic layer patterns.
Owner:SAMSUNG DISPLAY CO LTD
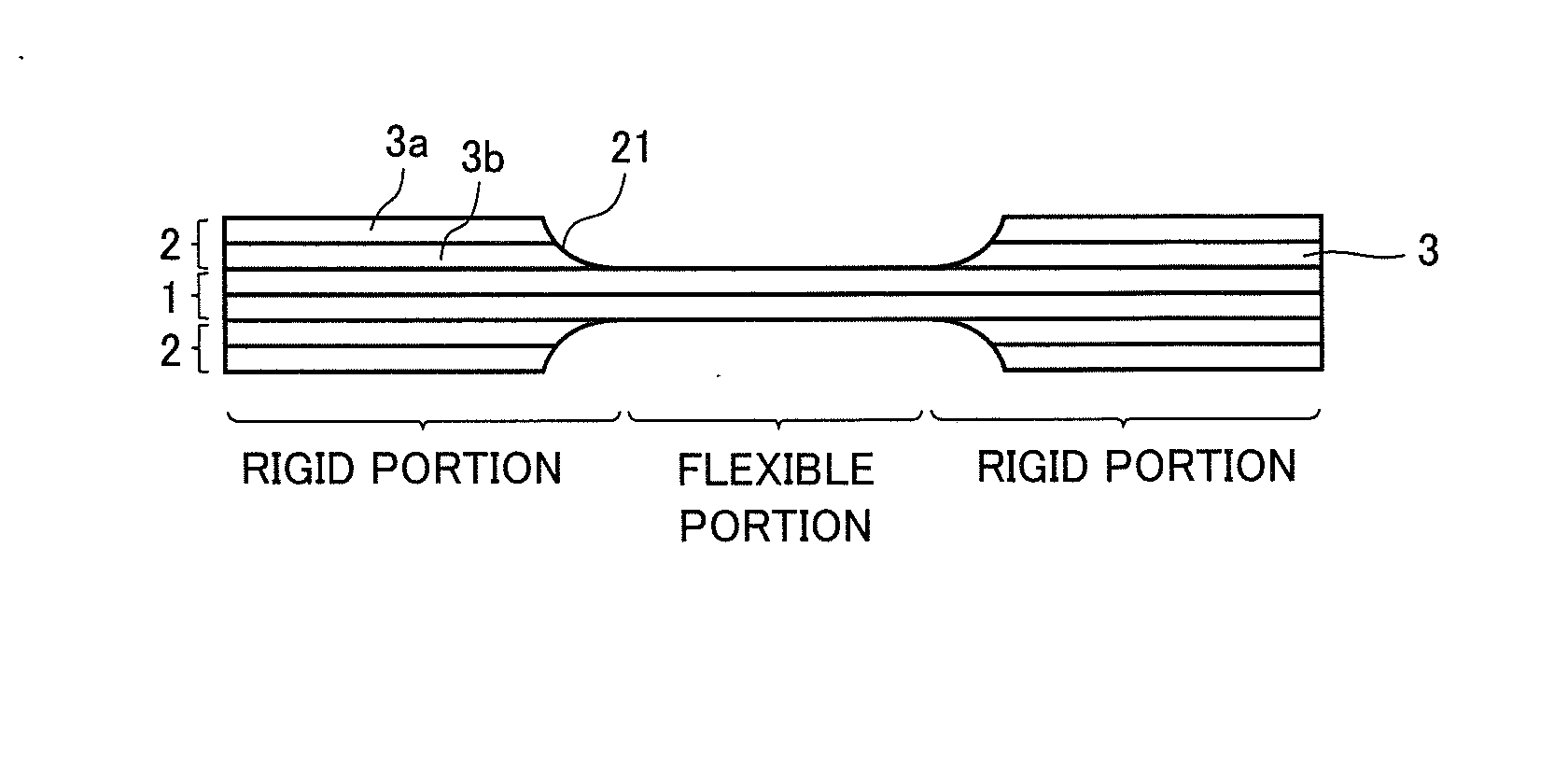
Rigid-flexible substrate and method for manufacturing the same
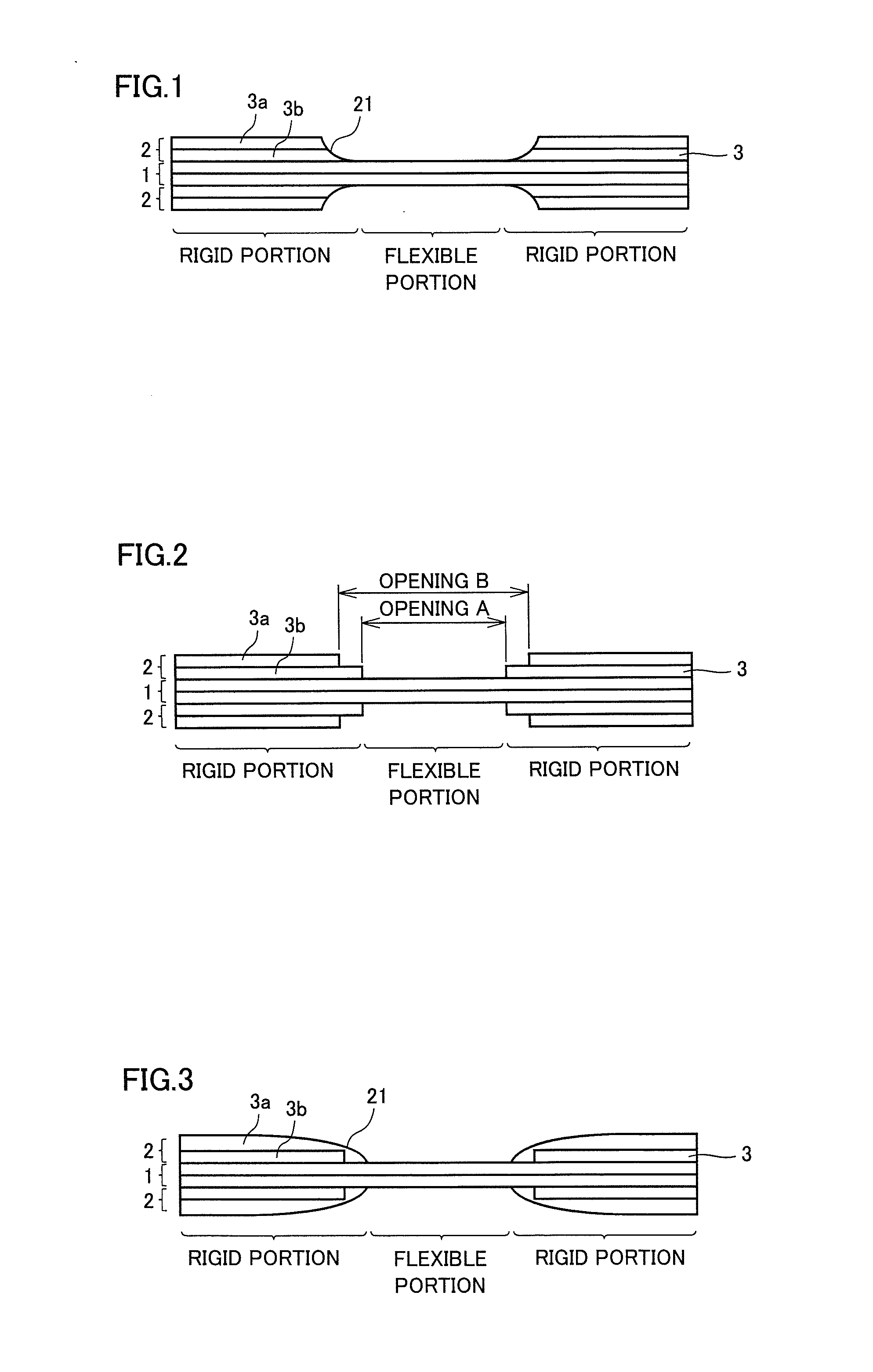
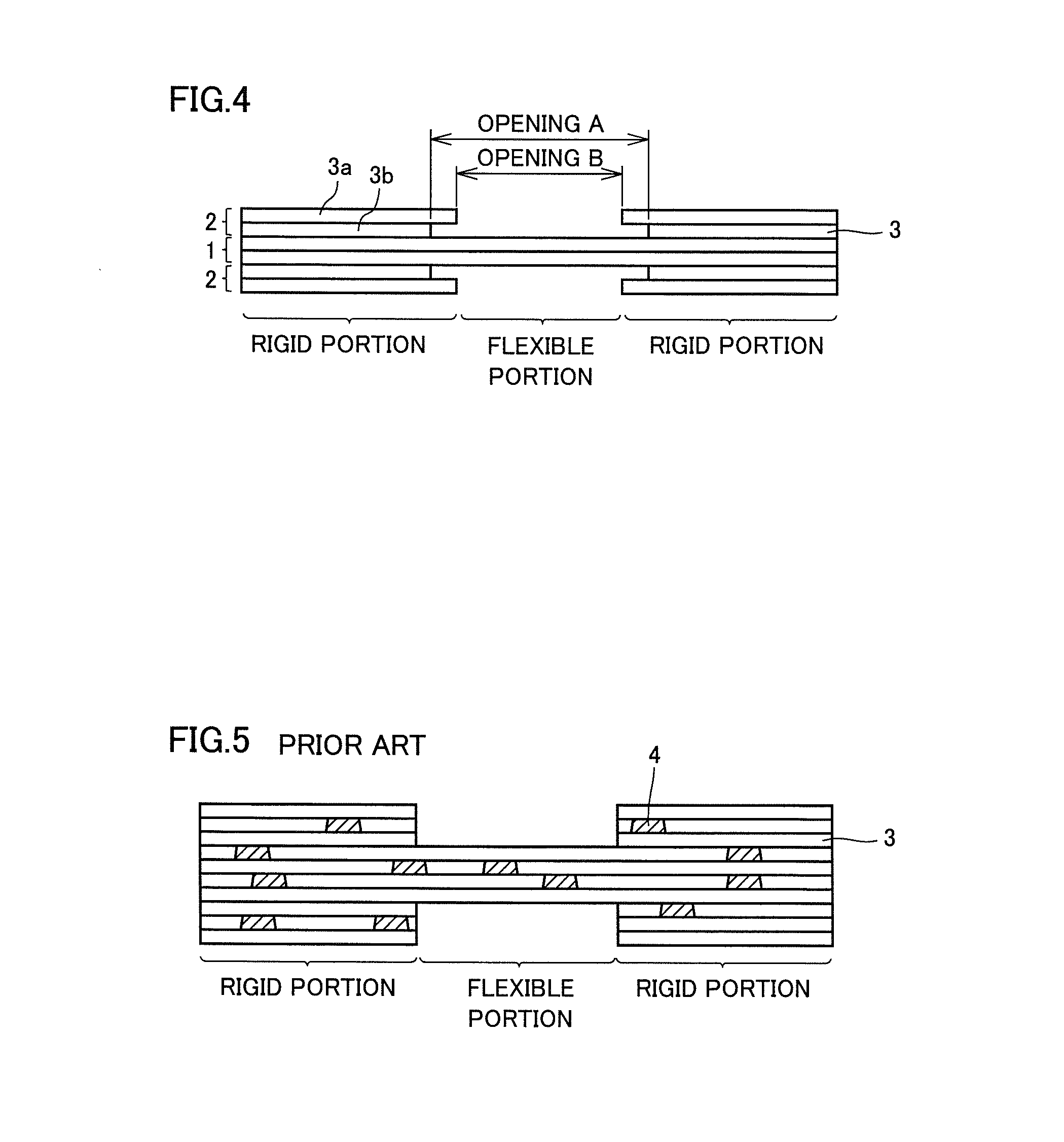
ActiveUS20140034366A1Prevent crackingManufacturing cost be reduceCircuit bendability/stretchabilityLaminationEngineering
A rigid-flexible substrate includes a plurality of rigid portions, and a flexible portion connecting the plurality of rigid portions and including a portion of a first resin sheet including at least one layer of a thermoplastic resin sheet, the rigid portions including a portion of the first resin sheet other than the flexible portion, and a second resin sheet including a plurality of thermoplastic resin sheets laminated on one surface or both surfaces of the portion of the first resin sheet other than the flexible portion, and a tapered portion is provided at an end edge of the second resin sheet on a side close to the flexible portion, and a thickness of the tapered portion in a direction in which the second resin sheet is laminated decreases toward the flexible portion and is substantially 0 at a position in contact with the flexible portion.
Owner:MURATA MFG CO LTD
Precision forging process production line for steel rail turnout
ActiveCN102114518AGood accuracy retentionAvoid deformationRailway componentsForging/hammering/pressing machinesCompression moldingProduction line
The invention relates to a precision forging process production line for a steel rail turnout, which is characterized in that the precision forging process production line comprises a steel rail turnout precision forging press, a heating furnace, a normalizing furnace, a steel rail forward conveying device, an automatic steel rail feeding mechanism and an automatic steel rail blanking mechanism; a steel rail transversely-conveying trolley is arranged between the automatic steel rail feeding mechanism and the automatic steel rail blanking mechanism; a transversal motion guide rail and a transmission gear rack are arranged under the steel rail transversely-conveying trolley; a plurality of steel rail precision feeding devices and a servomotor are arranged on the steel rail transversely-conveying trolley; and an electric cabinet used for controlling the operation of the whole production line is arranged on the outer side of the automatic steel rail feeding mechanism. The precision forging process production line has the advantages as follows: the production line is suitable for hot compression molding technology of various AT (abbreviation for Pinyin of 'short-type cross section') steel rail turnouts, and all devices and mechanisms of the production line can achieve automation control without manual intervention, so that time and labor are saved, the labor intensity of operators is reduced, the processing period of the steel rail turnout is shortened, the production cost is lowered, the machining precision and the qualification rate of the steel rail are improved, and the requirement of high-quality steel rail can be satisfied further.
Owner:TIANJIN TIANDUAN PRESS CO LTD
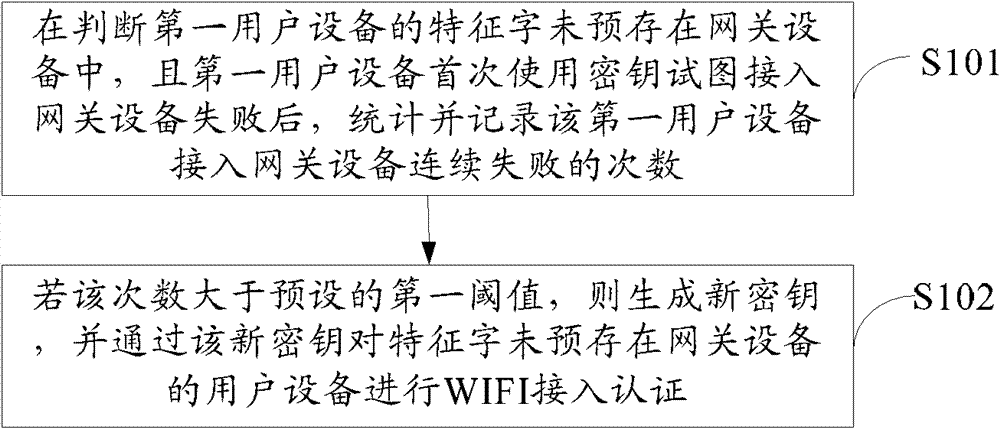
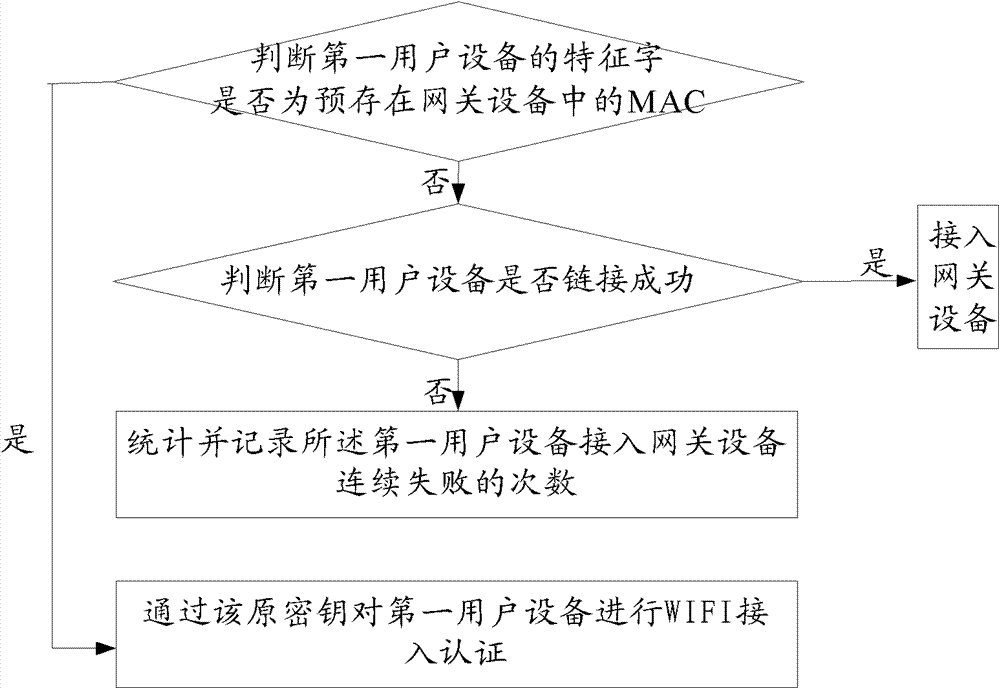
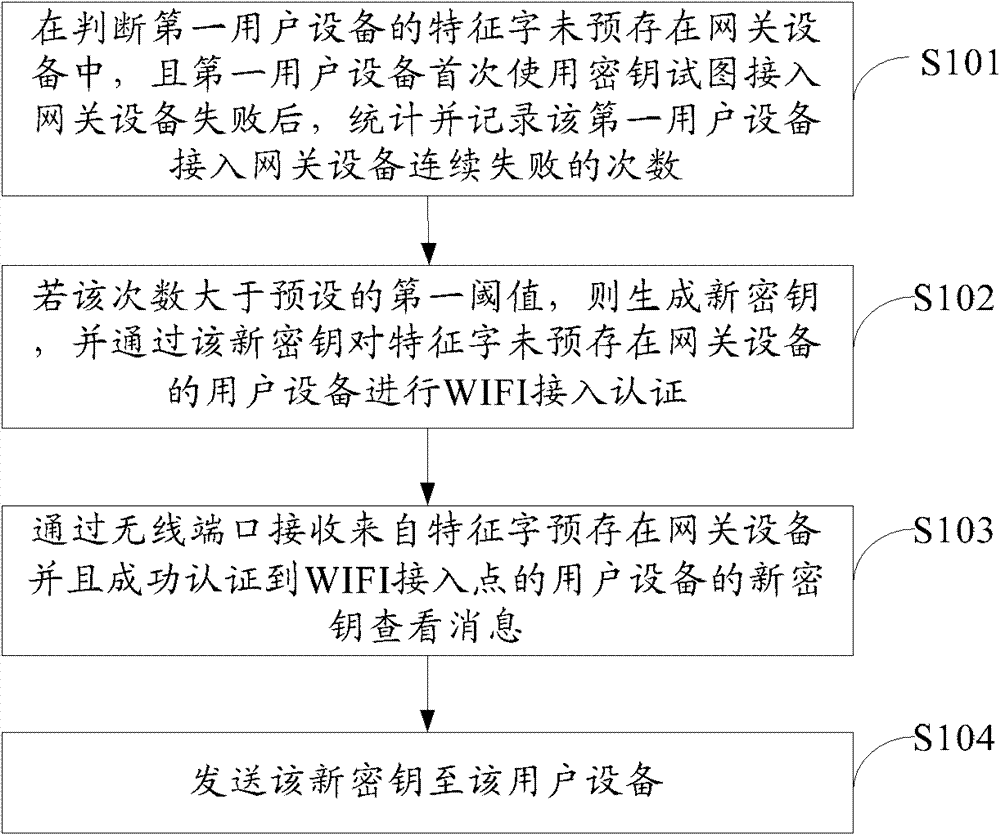
Method and device for wireless access authentication
InactiveCN103249040APrevent crackingAvoid crackingNetwork topologiesConnection managementDigest access authenticationUser equipment
The embodiment of the invention provides a method and device for wireless access authentication, which relate to the field of wireless communication and can be used for preventing a secret key from being broken. The method comprises the following steps: the frequency of consecutive failures in access of first user equipment to gateway device is counted and recorded after that feature characters of the first user equipment are not prestored in the gateway device and the first user equipment fails to use a secret key for the first time to try to access the gateway device are judged; if the frequency is larger than a pre-arranged first threshold value, a new secret key can be generated, and WiFi access authentication is performed on user equipment of the gateway device of which the feature characters are prestored through the new secret key; and the embodiment of the invention is used for wireless access authentication.
Owner:GLOBAL INNOVATION AGGREGATORS LLC
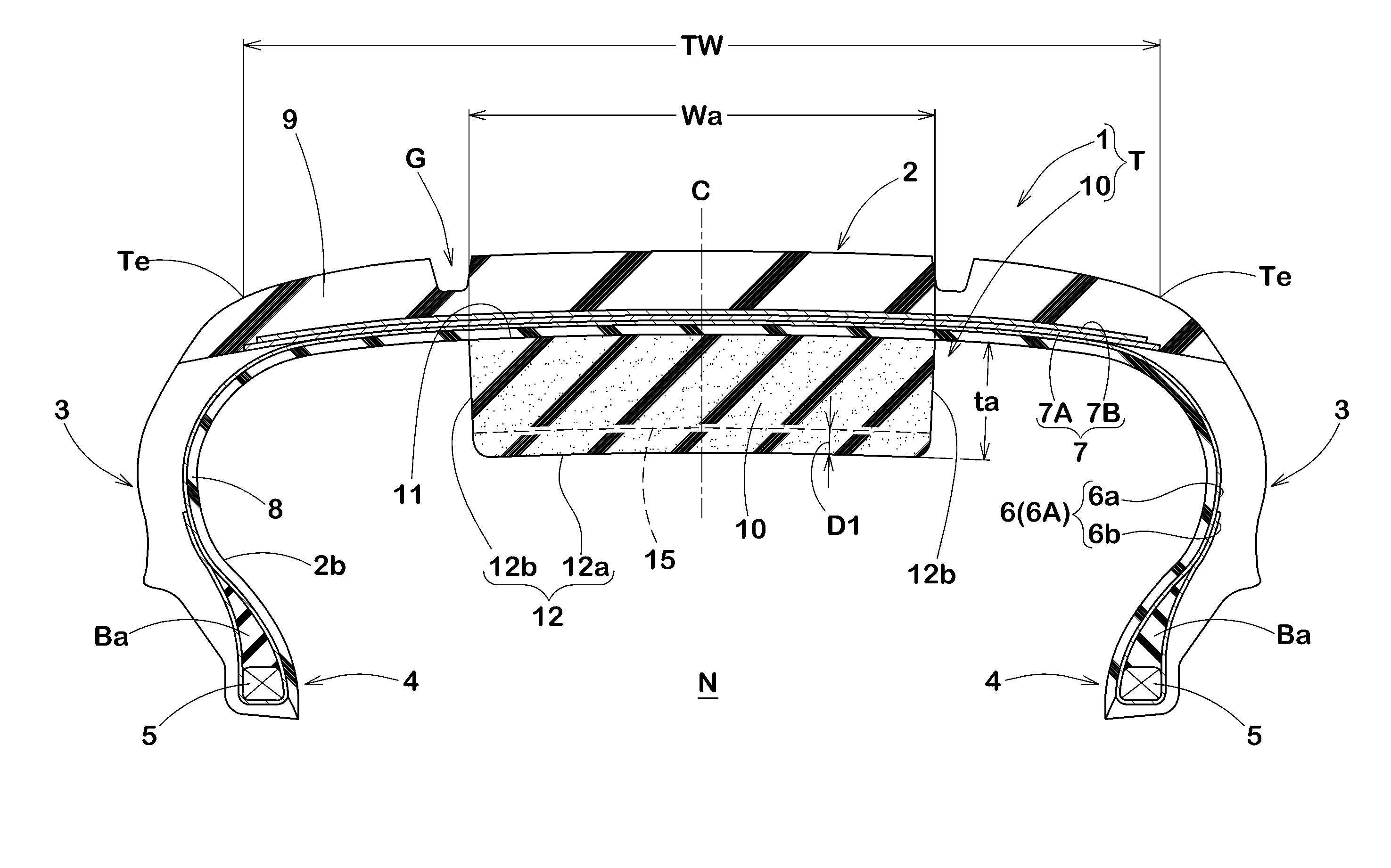
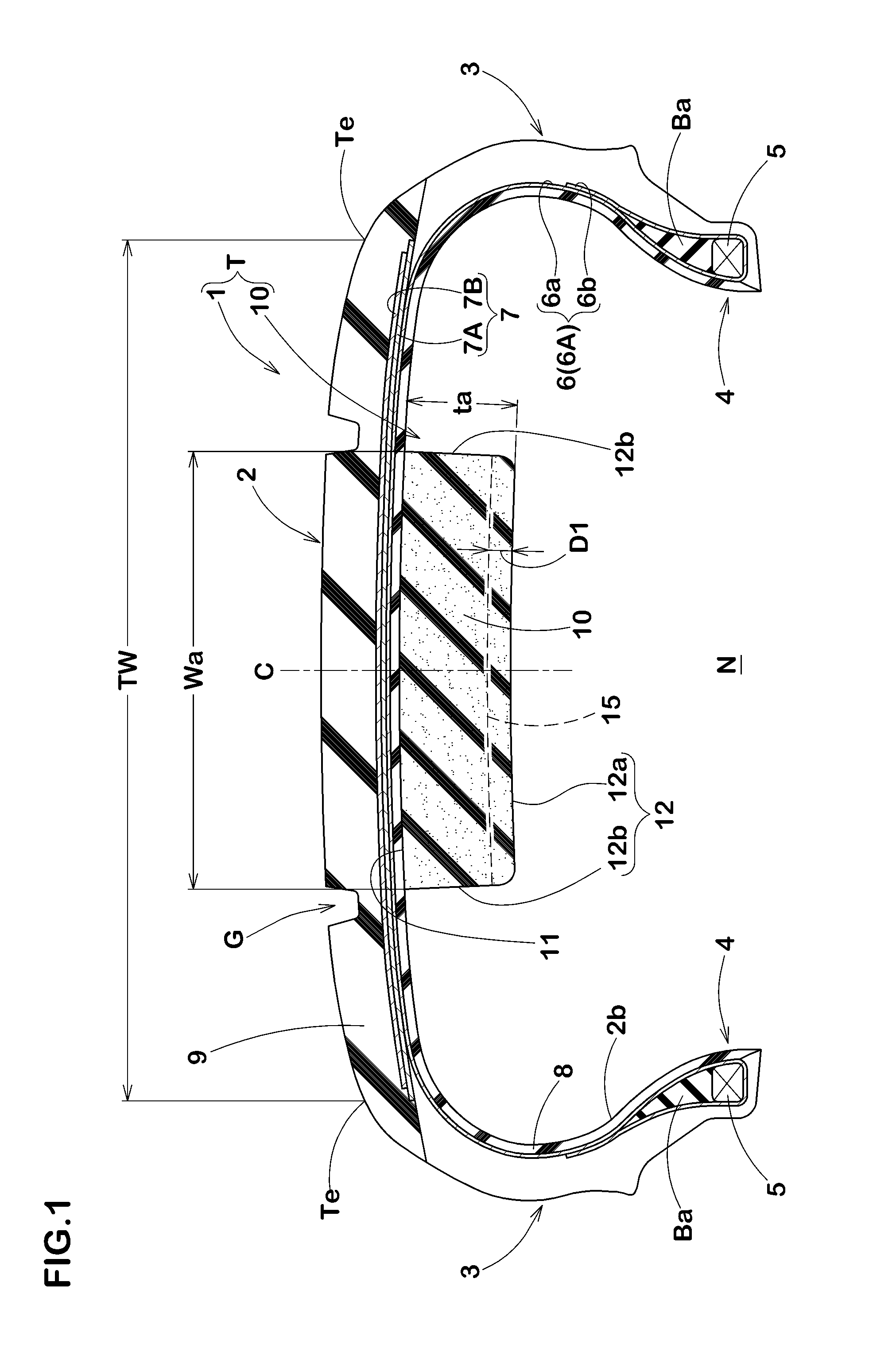
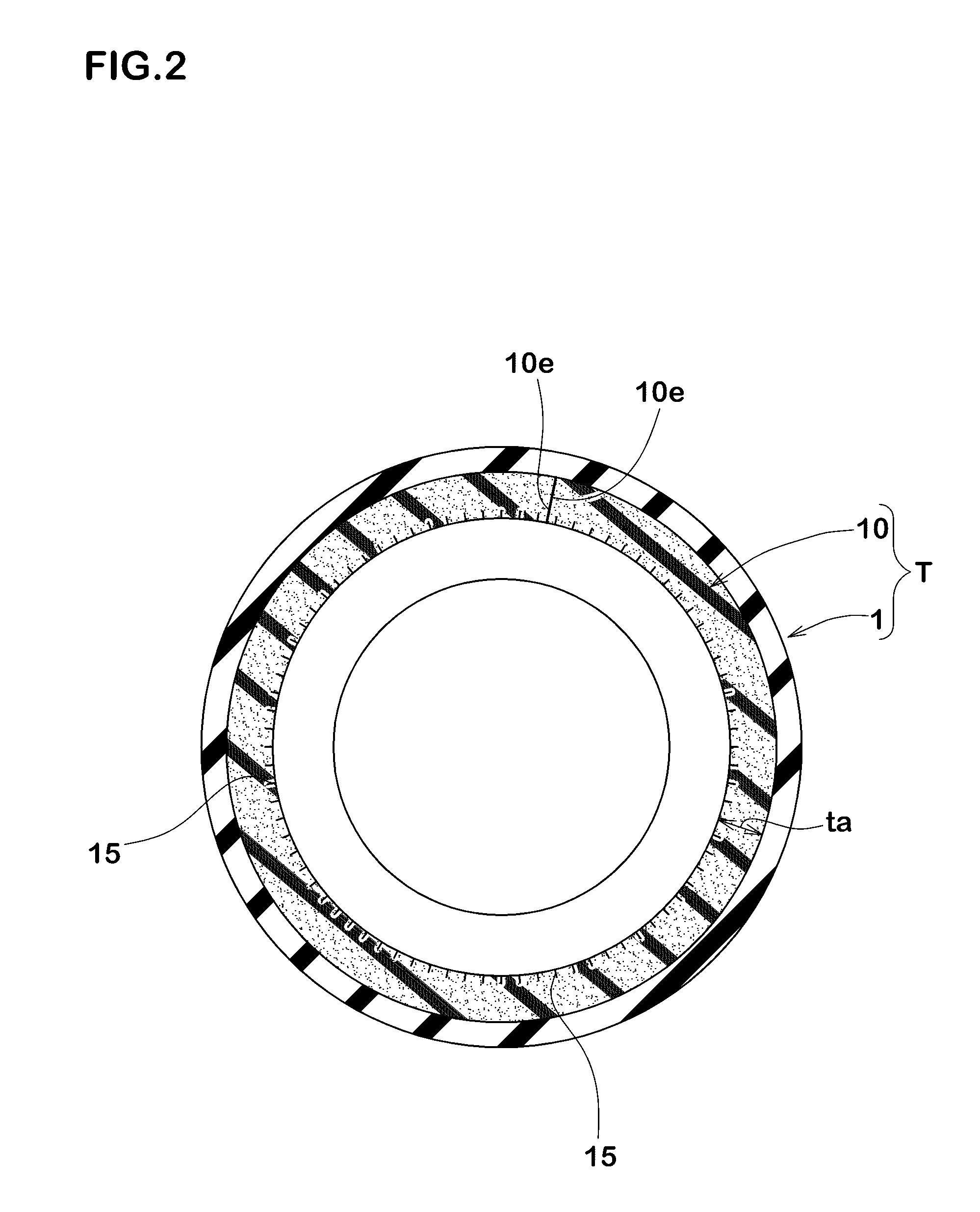
Sound-suppressor-equipped pneumatic tire, and sound suppressor for tires
ActiveUS20160339749A1Prevent crackingPrevent deterioration in appearanceTyre partsCold areaSuppressor
The purpose of the present invention is to inhibit deterioration in the external appearance of a sound suppressor, even when used in cold areas. This sound-suppressor-equipped pneumatic tire includes: a pneumatic tire provided with a tread section; and a sponge-like sound suppressor which is affixed to a tire inner cavity-side surface of the tread section, and which extends in the peripheral direction of the tire. In the sound suppressor, a plurality of slits are formed in an exposed surface which faces the tire inner cavity.
Owner:SUMITOMO RUBBER IND LTD
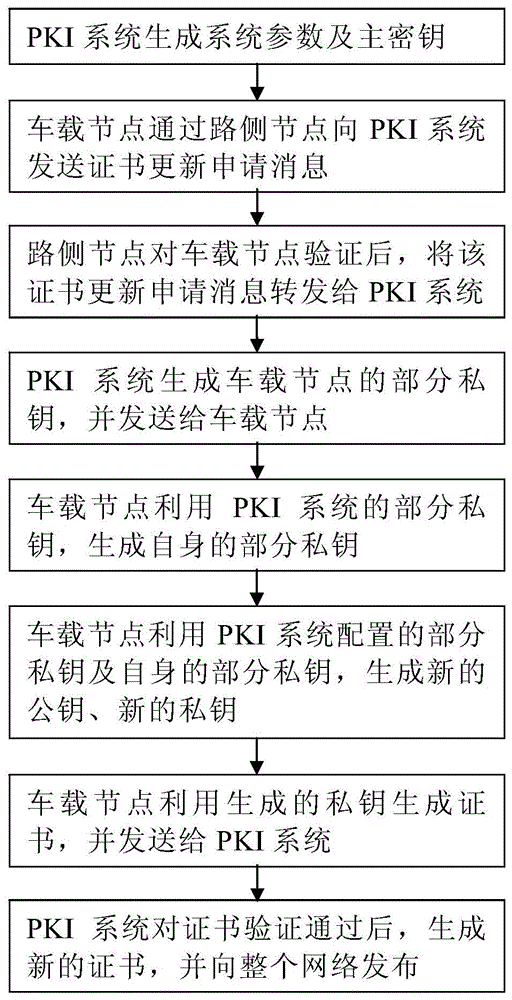
Vehicle node certificate updating method based on Vehicle to X (V2X) network
ActiveCN105812131APrevent crackingEnsure communication security and non-repudiationKey distribution for secure communicationUser identity/authority verificationPublic key infrastructureComputer security
The invention discloses a vehicle node certificate updating method based on a Vehicle to X (V2X) network. A vehicle node applies for an updated certificate from a PKI (Public Key Infrastructure) system via a roadside node; the PKI system sends part of private keys to the vehicle node; the vehicle node generates a new public key and a new private key using the part of private keys and part of private keys generated per se, generates a certificate using the new private key, and sends the certificate to the PKI system; the PKI system verifies the validity and the accuracy of the certificate; and after the certificate passes the verification, the PKI system updates the certificate of the vehicle node using the public key generated by the vehicle node, and issues the updated certificate to the whole network. The updated certificate, the new public key and the new private key are all generated using part of private keys of the PKI system and part of private keys of the vehicle node, and only the vehicle node has node private keys, so the information issued by the vehicle node can be effectively prevented from being decrypted by the PKI system, and the security and the non-repudiation of communication of the vehicle node in the V2X network are guaranteed.
Owner:DATANG GOHIGH INTELLIGENT & CONNECTED TECH (CHONGQING) CO LTD
Resin wound component
A resin wound component is configured such that a ring-shaped resin portion is integrally formed with an outer circumference of a ring-shaped metal member by a film gate. The resin portion includes a ring-shaped surrounding portion for surrounding axial end surfaces of outer circumferential edges of the ring-shaped metal member. At this time, the thickness of a ring-shaped surrounding portion on the gate side is configured to be larger than that of a ring-shaped surrounding portion on an opposite side to the gate.
Owner:JTEKT CORP
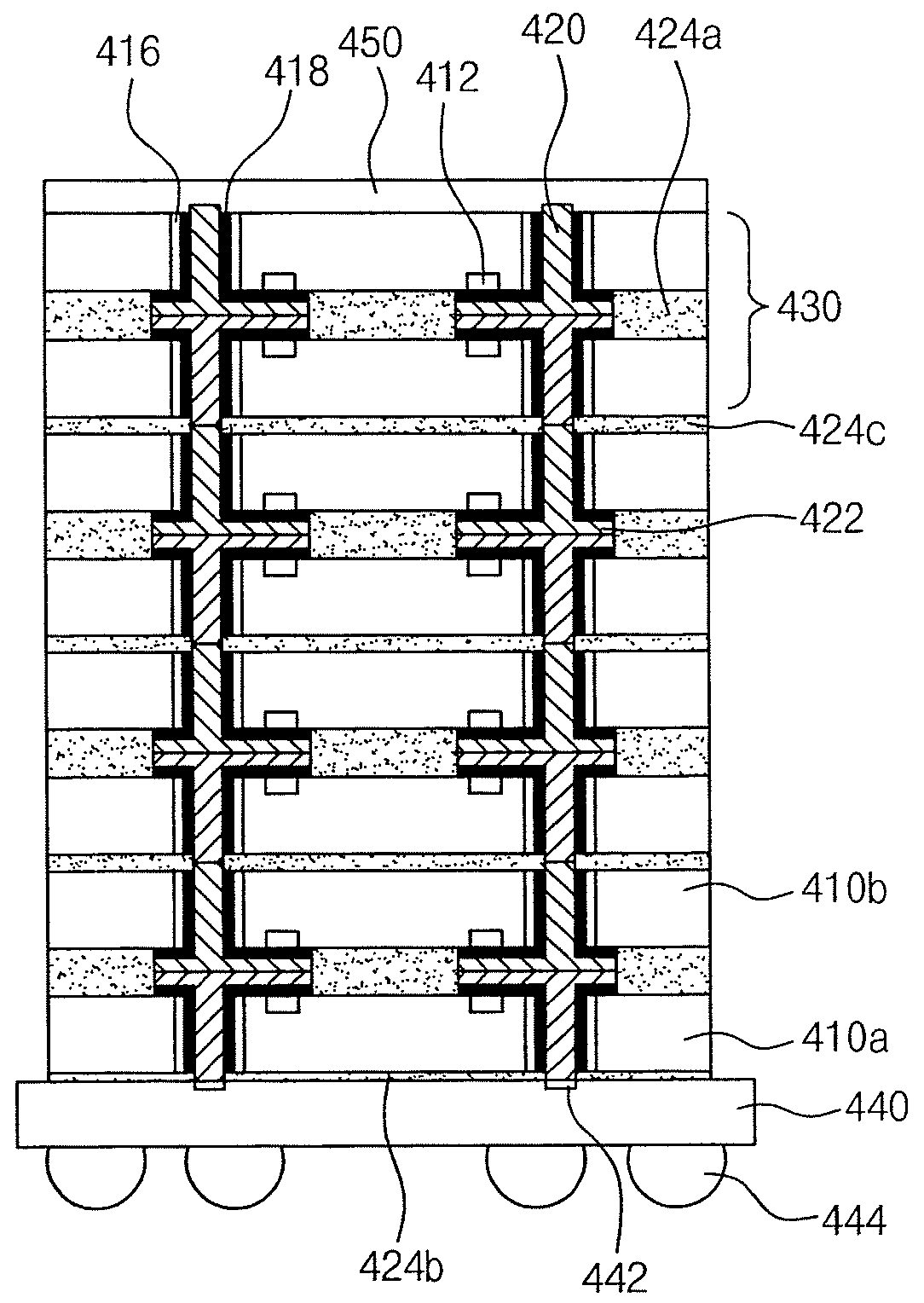
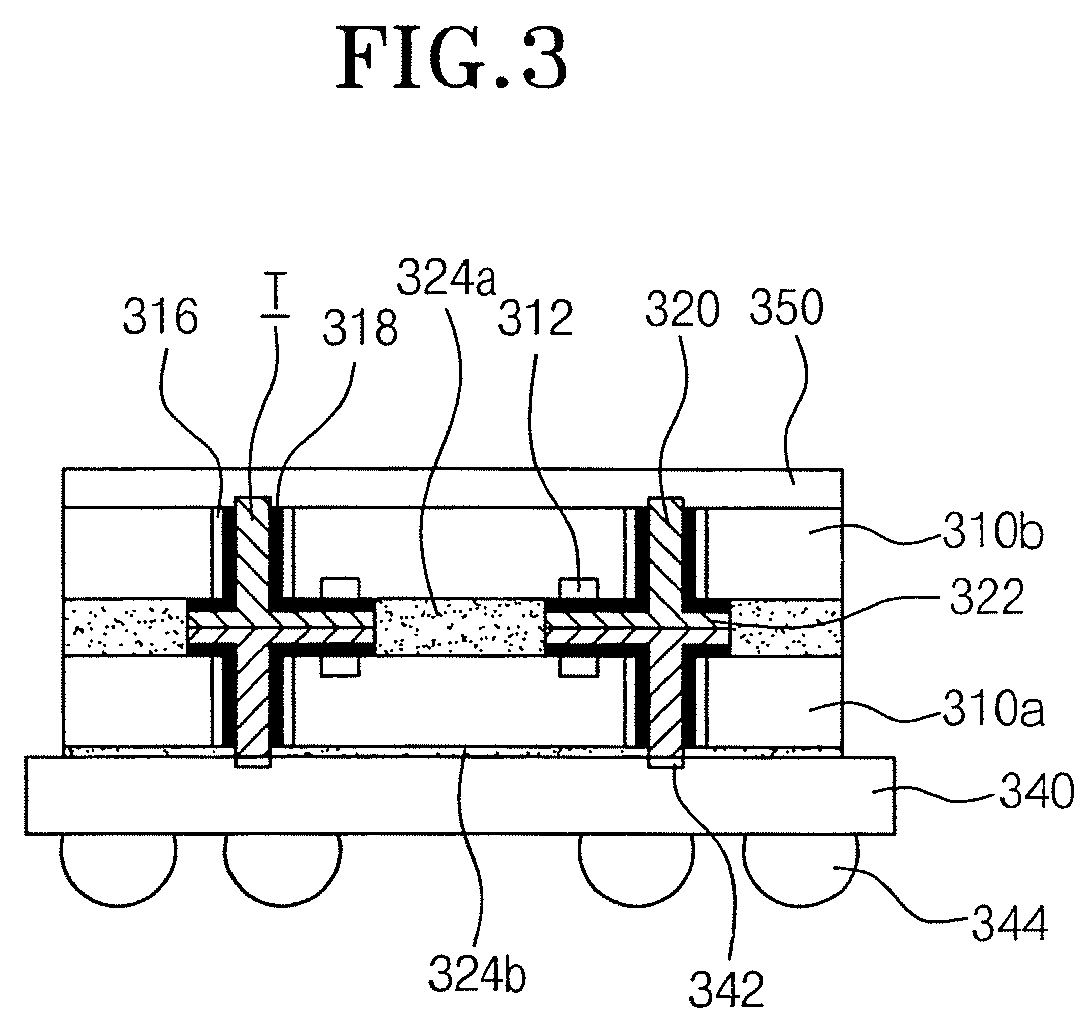
Semiconductor device for preventing crack in pad region and fabricating method thereof
ActiveUS20110272818A1Prevent crackingAvoid crackingSemiconductor/solid-state device detailsSolid-state devicesInsulation layerSemiconductor
A semiconductor device which prevents a crack from occurring on a pad region is provided. The semiconductor device includes a lower pad, an upper pad which is formed above the lower pad, an insulation layer which is formed between the lower pad and the upper pad, a via net for electrically connecting the lower pad and the upper pad in the insulation layer, the via net having a net shape in which a unit grid is connected with its adjacent unit grids to form a net structure, and at least one via hole for electrically connecting the lower pad and the upper pad in the unit grid of the via net.
Owner:KEY FOUNDRY CO LTD
Method for manufacturing gallium nitride (GaN) based single crystalline substrate that include separating from a growth substrate
ActiveUS6902989B2Prevent crackingAvoid crackingPolycrystalline material growthAfter-treatment detailsGallium nitrideLaser beams
A method for manufacturing a gallium nitride (GaN)-based single crystalline substrate includes the steps of (a) forming a GaN-based single crystalline bulk on an upper surface of a growth substrate; (b) forming grooves through the growth substrate so that the growth substrate is patterned and divided into several units by the grooves, each of the grooves having a designated width; and (c) separating the GaN-based single crystalline bulk from the growth substrate by irradiating a laser beam on a lower surface of the growth substrate.
Owner:SAMSUNG ELECTRONICS CO LTD
Member with concave portions, a method of manufacturing a member with convex portions, a transmission screen, and a rear projection
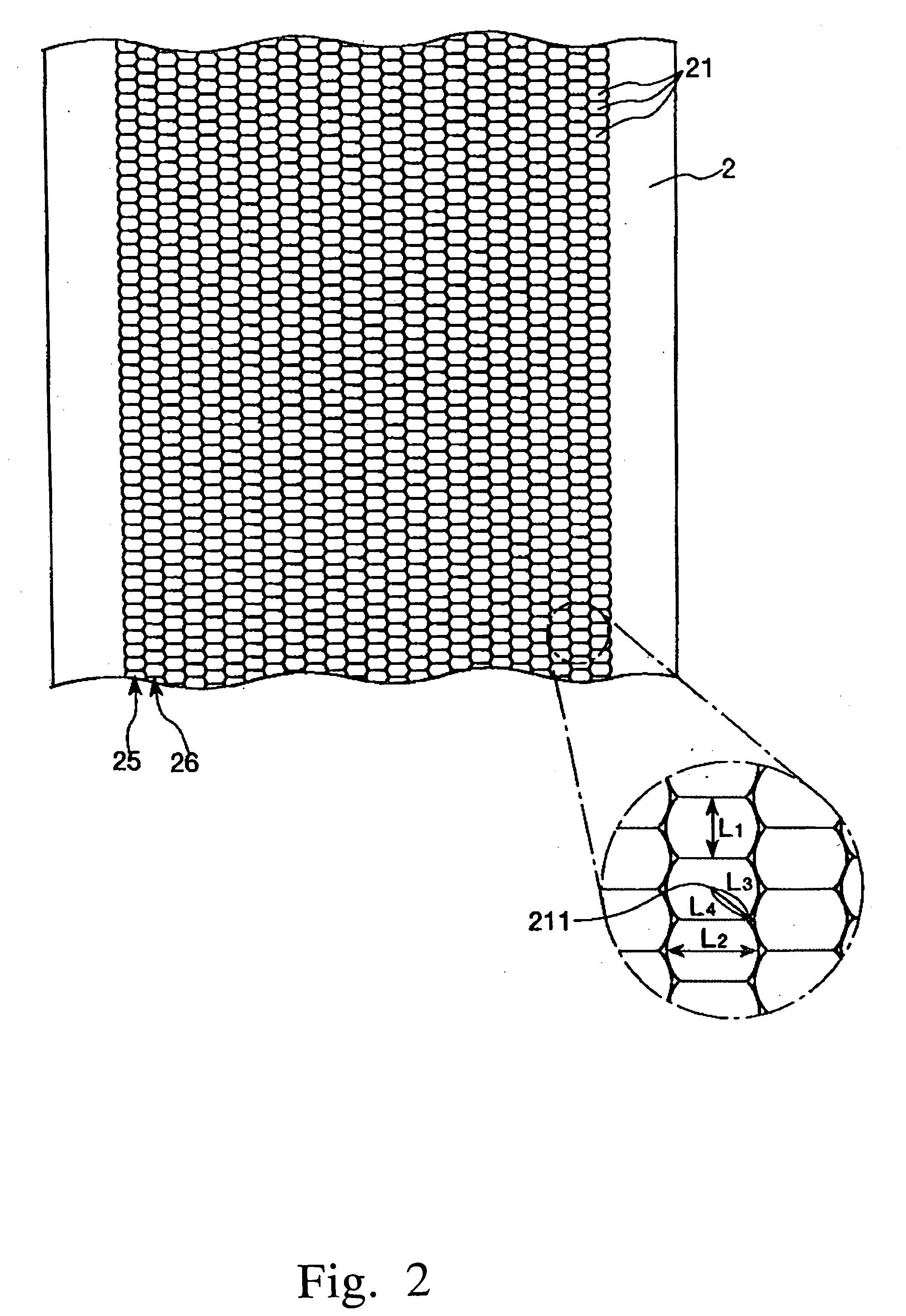
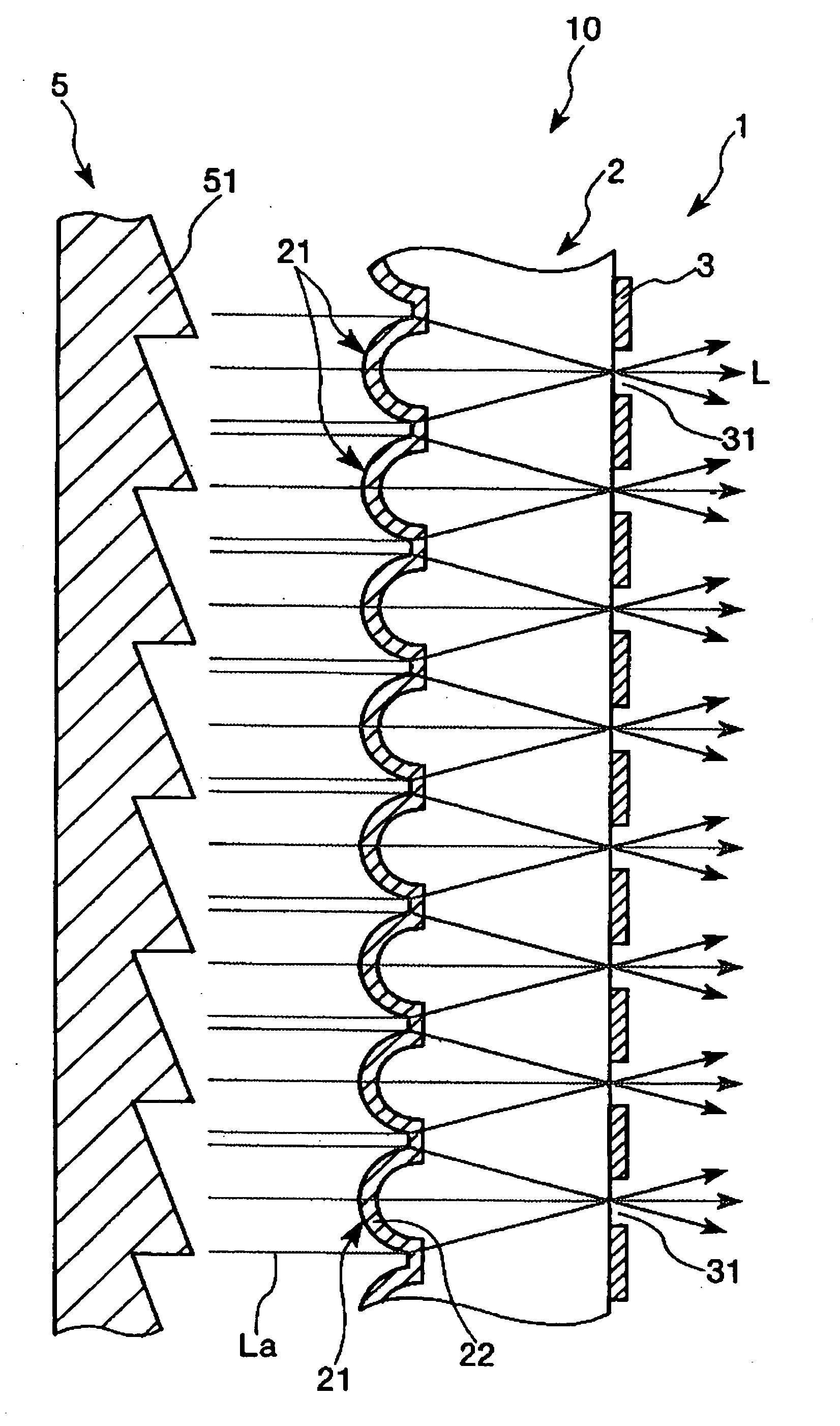
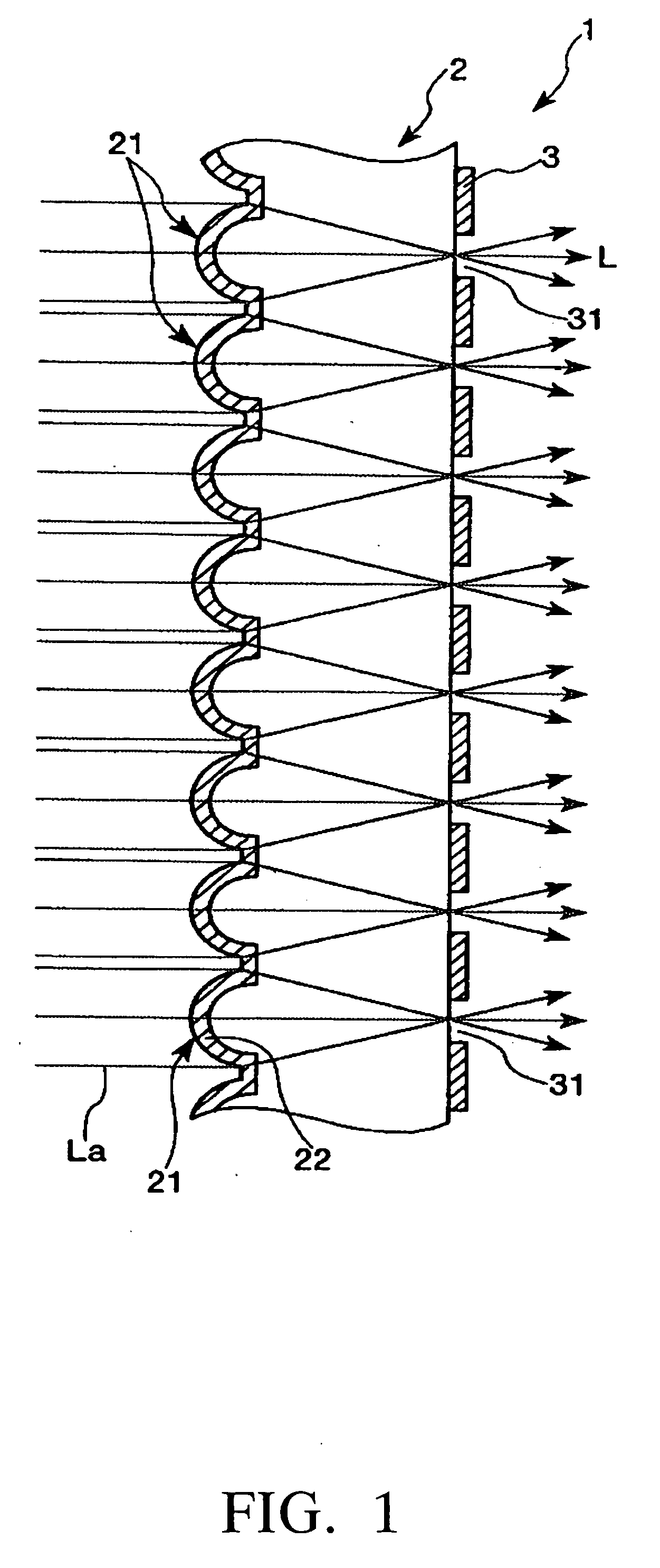
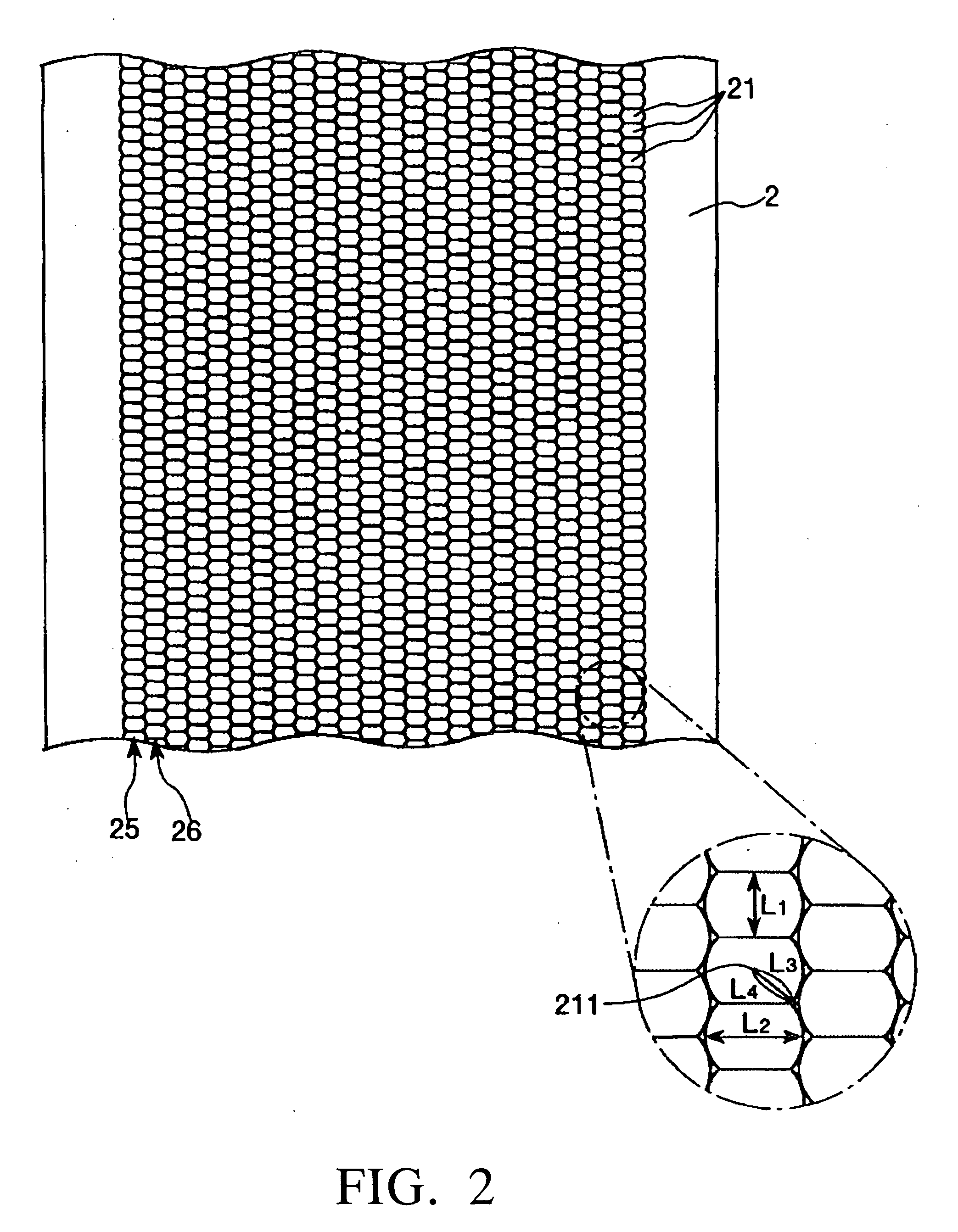
InactiveUS20060109550A1Improve resolutionPrevent crackingDiffusing elementsBuilt-on/built-in screen projectorsEngineering
Owner:SEIKO EPSON CORP
Member with concave portions, a method of manufacturing a member with convex portions, a transmission screen, and a rear projection
InactiveUS20060109549A1Improve angle of view characteristicPrevent crackingBuilt-on/built-in screen projectorsLensEngineering
Owner:SEIKO EPSON CORP
Roadbed paving structure for highway extension and construction method
The invention discloses a roadbed paving structure for highway extension and a construction method of the roadbed paving structure for the highway extension. The roadbed paving structure for the highway extension comprises a cushion layer, a lower base layer, an upper base layer and a surface layer, wherein a fixing frame is arranged between an intermediate layer and a gravel layer to increase thebonding strength of the upper base layer and the lower base layer so as to prevent hierarchical separation, furthermore, the cushion layer is located at the bottom layer, thereby being capable of enhancing the structure stability and dispersing the roadbed stress to prevent sinking, a traction part is arranged between the surface layer and the upper base layer to increase the bonding strength between the layers so as to prevent the surface layer from being separated, wherein one or more of steel wires, manila hemp fibers, carbon fibers and polytetrafluoroethylene fibers are arranged inside the traction part, therefore the materials are combined to make the traction part tough and corrosion-resistant, and then the traction part is not easily corroded by cement, and in addition, the problemof weak adhesive force of the polytetrafluoroethylene fibers and the cement or asphalt is solved. A connecting part is further arranged and comprises a plurality of dovetail grooves and clamping blocks adapted to the dovetail grooves, the dovetail grooves and the clamping blocks are respectively arranged on a joint surface of an old road and the roadbed structure to prevent a newly widened roadbed from sinking or cracking or separating relative to the old road.
Owner:中奋建设有限公司
Artistic pottery fancy glaze and manufacturing method thereof
An artistic pottery fancy glaze mainly comprises 65 parts of sodium potassium feldspar, 3 parts of kaolin, 7 parts of lithium carbonate, 4 parts of bone ash, 4 parts of calcium carbonate, 11 parts of borax, 1 part of barium and 5 parts of quartz. Compared with the prior art, the method provided by the invention changes a formula of the glaze to reach changed fancy glaze effect, reduce expansion factor of the formula of the glaze, prevent glaze crack at low temperature and prolong utilization rate of the product; meanwhile, ceramic with the glaze has higher strength, brilliant glaze and good glossiness, compared with common ceramic.
Owner:德化县太阳鸟工艺品有限公司
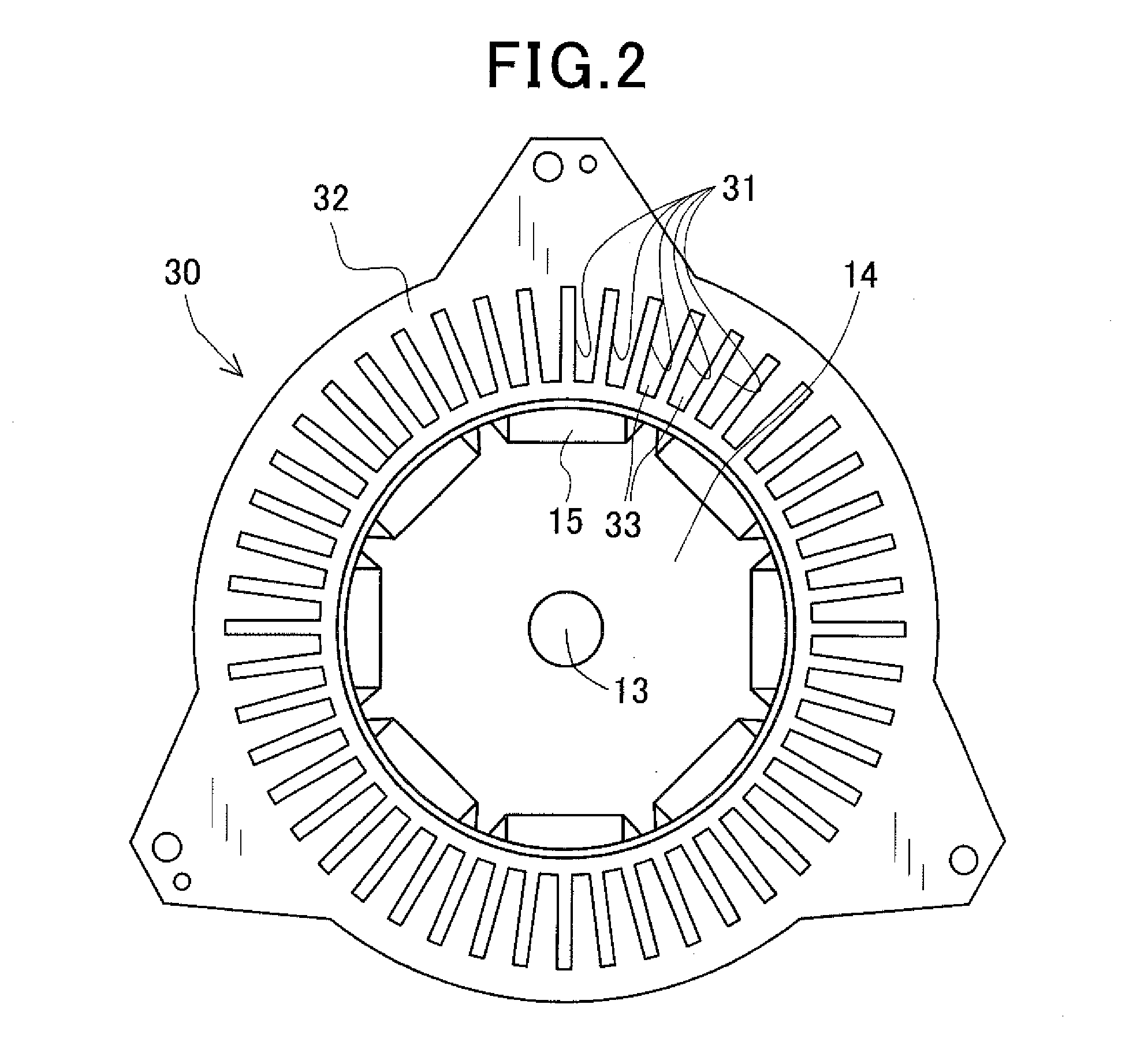
Stator and rotating electric machine
ActiveUS20150326086A1Prevent crackingAvoid coatingWindings insulation materialWindings insulation shape/form/constructionPhysicsAdhesion strength
A stator includes an annular stator core, a stator coil and a resin adhesive. The stator coil is comprised of a plurality of electric wires. The electric wires are partially received in slots of the stator core so that the stator coil has a pair of coil end parts protruding outside the slots respectively from opposite axial end faces of the stator core. The resin adhesive is filled in the slots of the stator core and / or applied to the coil end parts of the stator coil. Moreover, each of the electric wires includes an electric conductor and an insulating coat that covers an outer surface of the electric conductor. The insulating coat is two-layer structured to include an inner coat and an outer coat. The adhesion strength of the outer coat to the resin adhesive is lower than the adhesion strength of the inner coat to the resin adhesive.
Owner:DENSO CORP
Electromagnetic wave shield with vacuum deposited metal using water dispersed polyurethane
InactiveUS20100068531A1Prevent peeling phenomenonPrevent crackingMagnetic/electric field screeningSynthetic resin layered productsMetalAtomic physics
There is provided an electromagnetic wave shield employing water-dispersed polyurethane. The electromagnetic wave shield comprises a plastic layer; a water-dispersed polyurethane primer layer formed on the plastic layer; and a metal deposited layer formed on the water-dispersed polyurethane primer layer. The electromagnetic wave shield has excellent surface property of a deposited metal and good durability through providing peeling resistance for a metal deposited layer by water-dispersed polyurethane.
Owner:GU & EUN +1
Method for preparing self-shine liquid shoe polish
InactiveCN101613576AGood flexibilityIncrease brightnessPolishing compositionsShoe polishMicrocrystalline wax
The invention provides a method for preparing self-shine liquid shoe polish. The self-shine liquid shoe polish is prepared from 500g of synthesized ester wax, 300g of microcrystalline wax, 500g of oxidized microcrystalline wax, 600g of montan wax, 600g of common paraffin, 200g of beeswax, 300g of rosin modified alkye resin, 100g of PCP-sodium, 800g of oil-soluble dye, 800g of acid dye, 500g of formaldehyde, 100g of defoamer and 6,000g of deionized water. The method comprises that: firstly, various waxes in proportion are heated and melted; an emulsifier is dissolved into water in another container, and the solution is heated to the melting temperature of the mixed wax; the melted mixed wax is poured into the deionized water and fully stirred to form wax emulsion; and the wax emulsion is orderly added with solvent, resin, dyes and other auxiliaries for even stirring, and the mixture is packaged into a bottle with a brush.
Owner:刘光玲
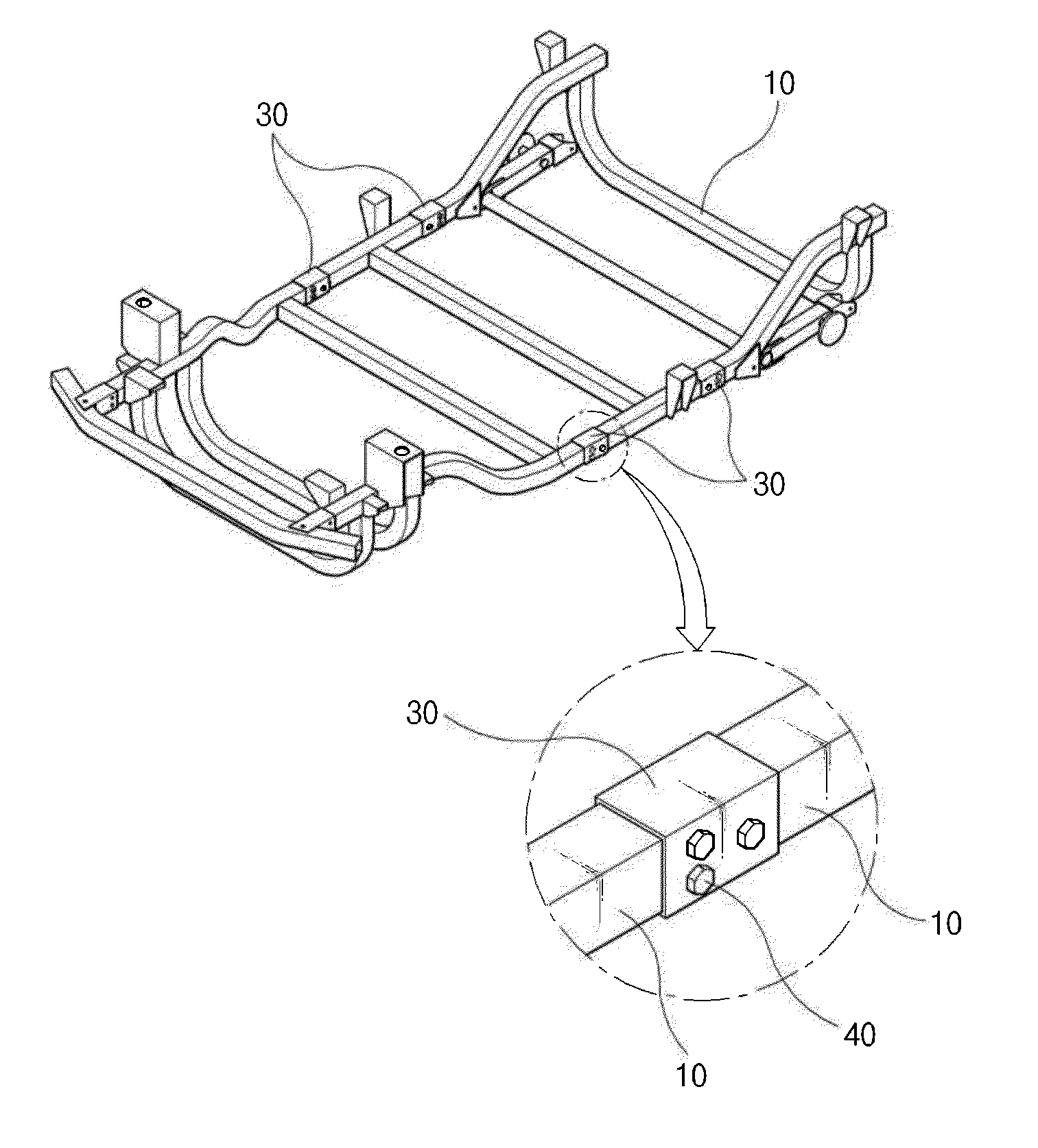
Chassis frame assembly structure for electrical vehicle for disabled person
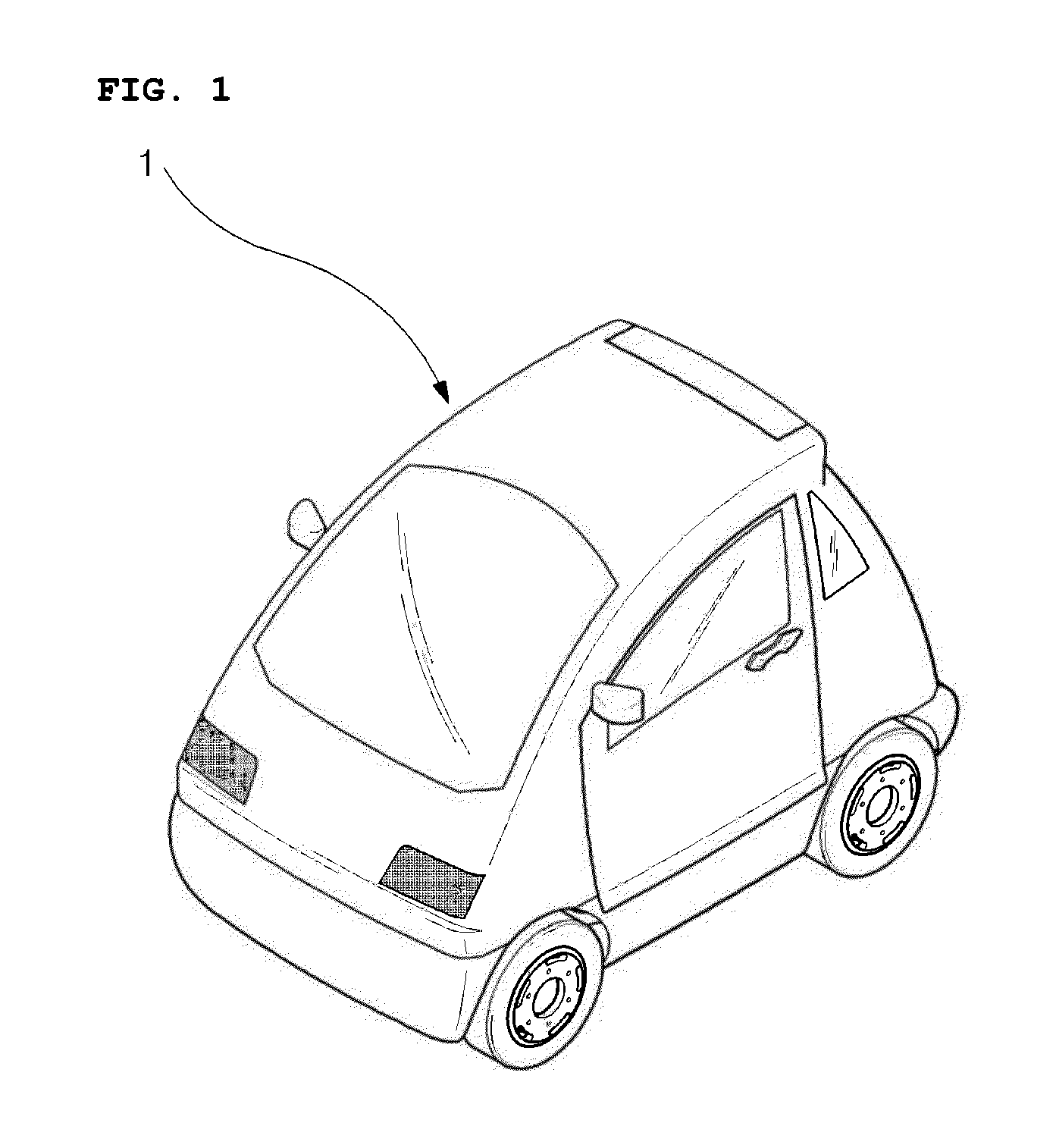
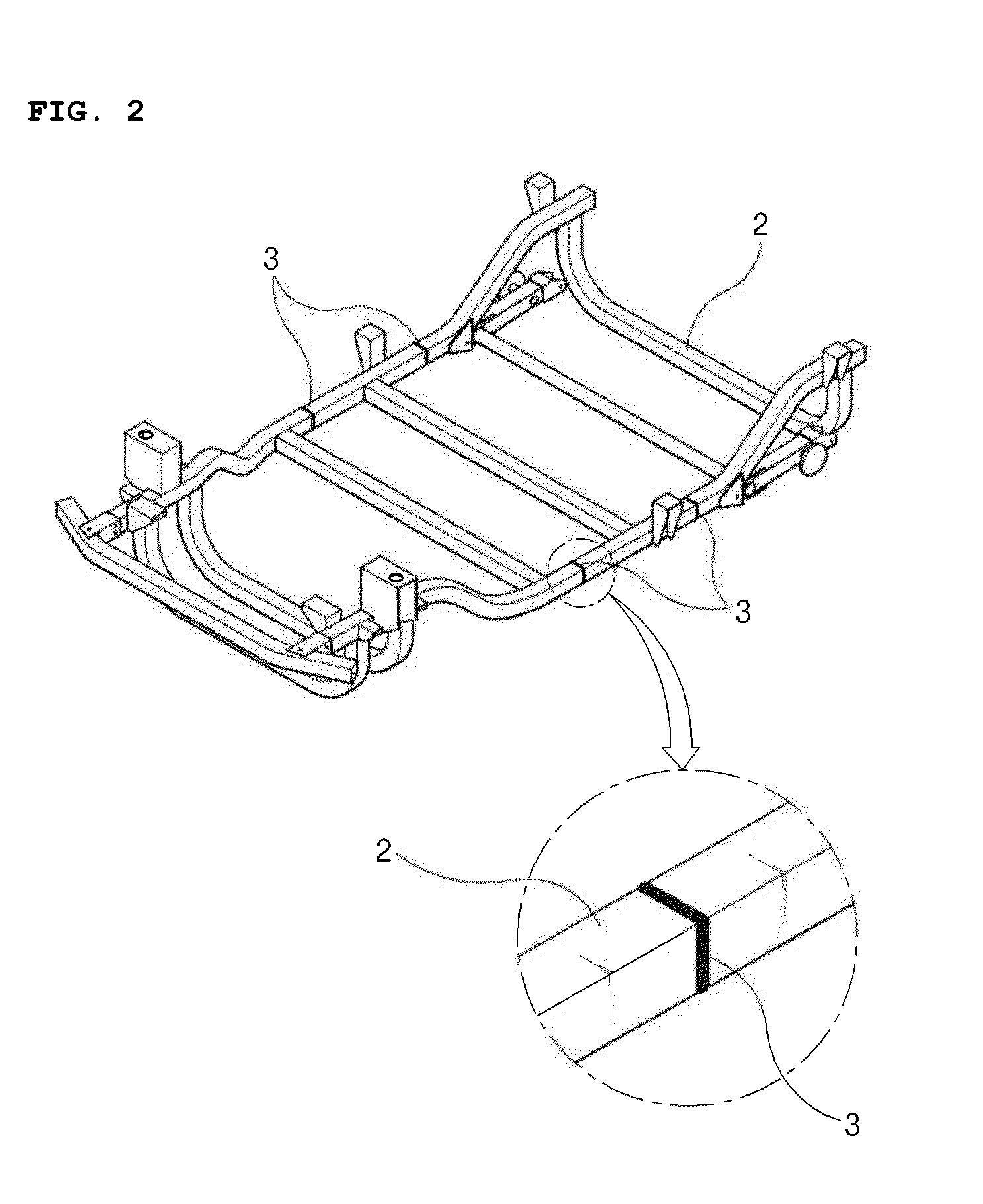
InactiveUS20130249203A1Prevent crackingAvoid casualtiesUnderstructuresSuperstructure connectionsVehicle frameAluminium
The present invention relates to a chassis frame assembly structure for an electrical vehicle, wherein welding assembly units are formed by attachment and welding at respective portions in each of which channel-shaped frames made of aluminum and each configured to have a hollow structure are coupled. The chassis frame assembly structure includes a plurality of fastening holes formed at proper interval close to the welding assembly unit of the chassis frames; reinforcement members each configured to have a channel shape, surround the periphery of the welding assembly unit of the chassis frame, and have a plurality of assembly holes, corresponding to the respective fastening holes, formed at proper intervals in one face of the reinforcement member; and fastening members assembled with the assembly holes and the fastening holes, wherein the reinforcement member is positioned at the outside of the chassis frame.
Owner:DUCKWONENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com