Installation management method, server and terminal for application program
A technology of application programs and management methods, applied in the field of communication, can solve problems such as no solution proposed, no effective application program anti-piracy program, etc., and achieve the effect of avoiding cracking and high reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
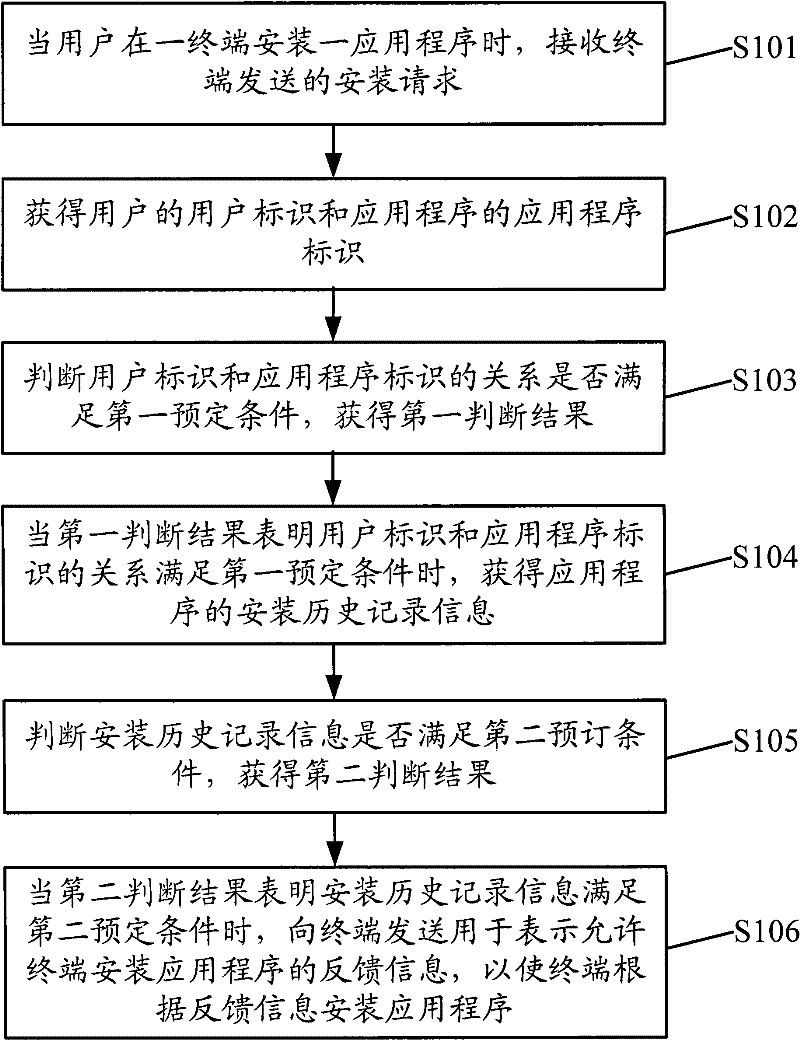
[0046] figure 1 It is a flow chart of the installation management method of the application program in the embodiment of the present invention, the method can be applied in a server, such as figure 1 shown, including the following steps:
[0047] Step S101, when a user installs an application on a terminal, receiving an installation request sent by the terminal;
[0048] Step S102, obtaining the user ID of the user and the application program ID of the application program;
[0049] Step S103, judging whether the relationship between the user ID and the application ID satisfies a first predetermined condition, and obtaining a first judging result;
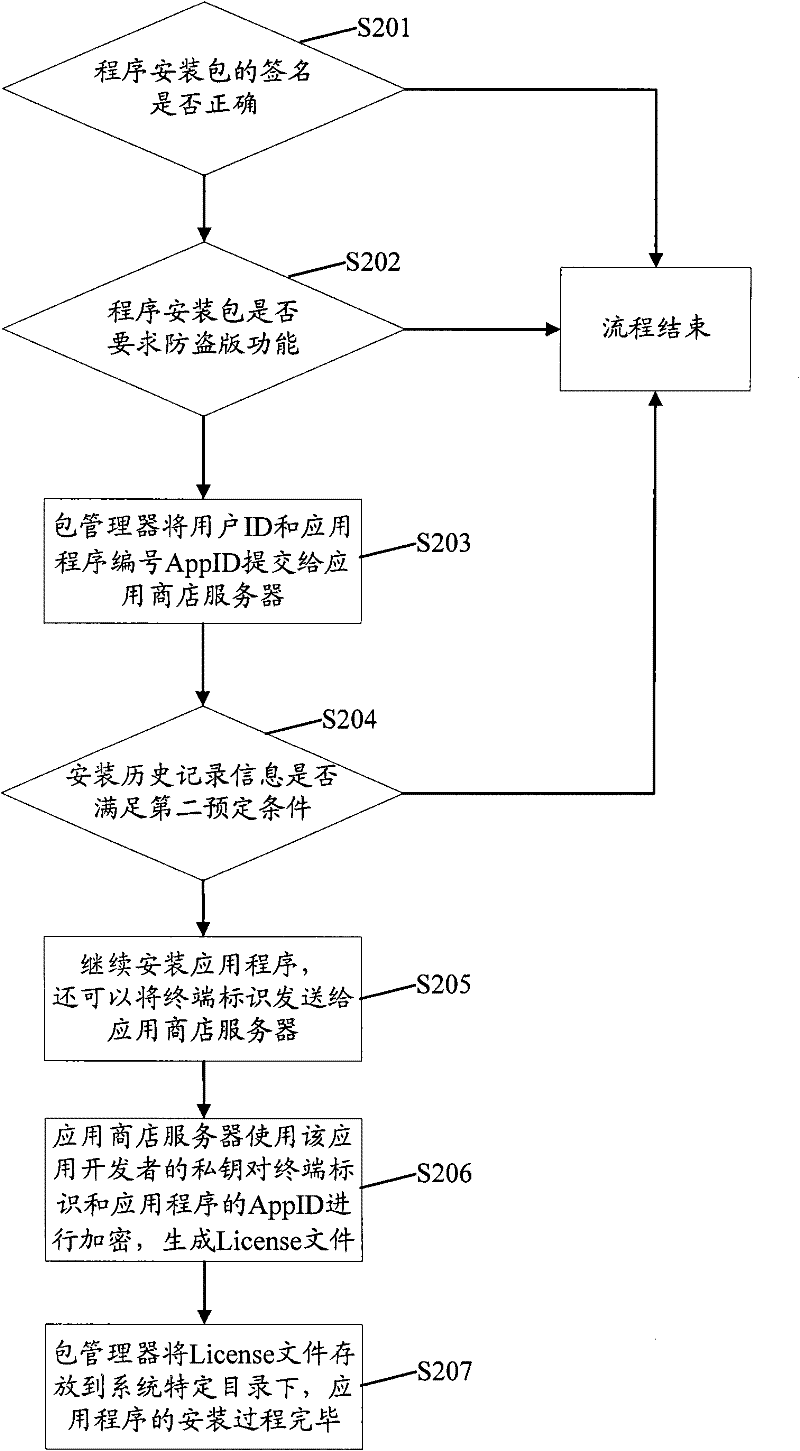
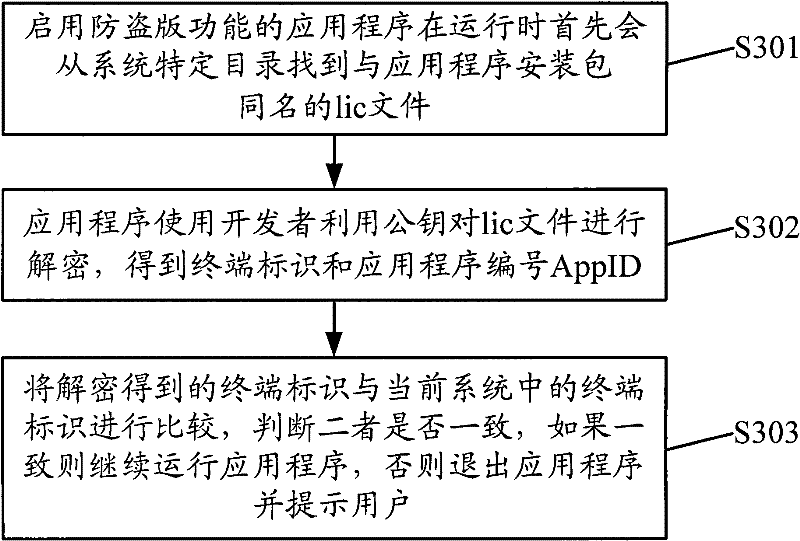
[0050] Step S104, when the first judgment result shows that the relationship between the user ID and the application program ID satisfies the first predeter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com