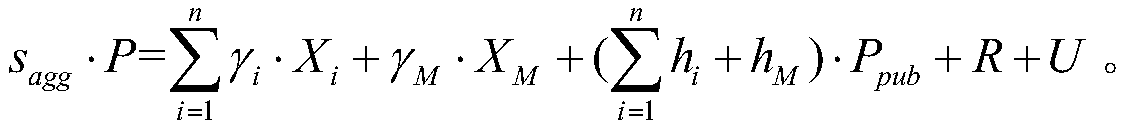Patents
Literature
58 results about "Digest access authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
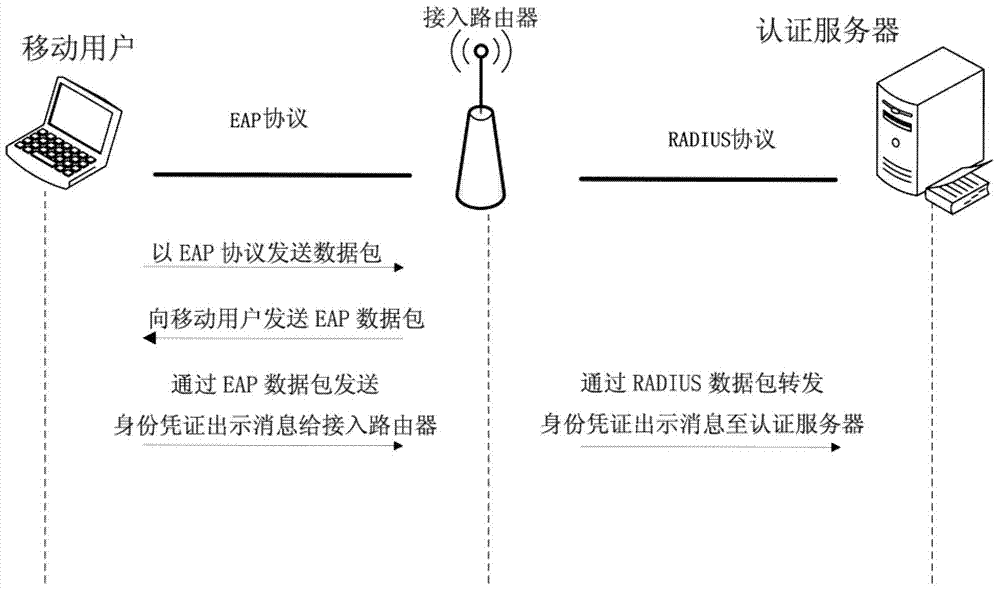
Digest access authentication is one of the agreed-upon methods a web server can use to negotiate credentials, such as username or password, with a user's web browser. This can be used to confirm the identity of a user before sending sensitive information, such as online banking transaction history. It applies a hash function to the username and password before sending them over the network. In contrast, basic access authentication uses the easily reversible Base64 encoding instead of hashing, making it non-secure unless used in conjunction with TLS.
Method, device and system of access authentication
ActiveCN104202306AImprove securityUser identity/authority verificationDigital data authenticationThird partyUser needs
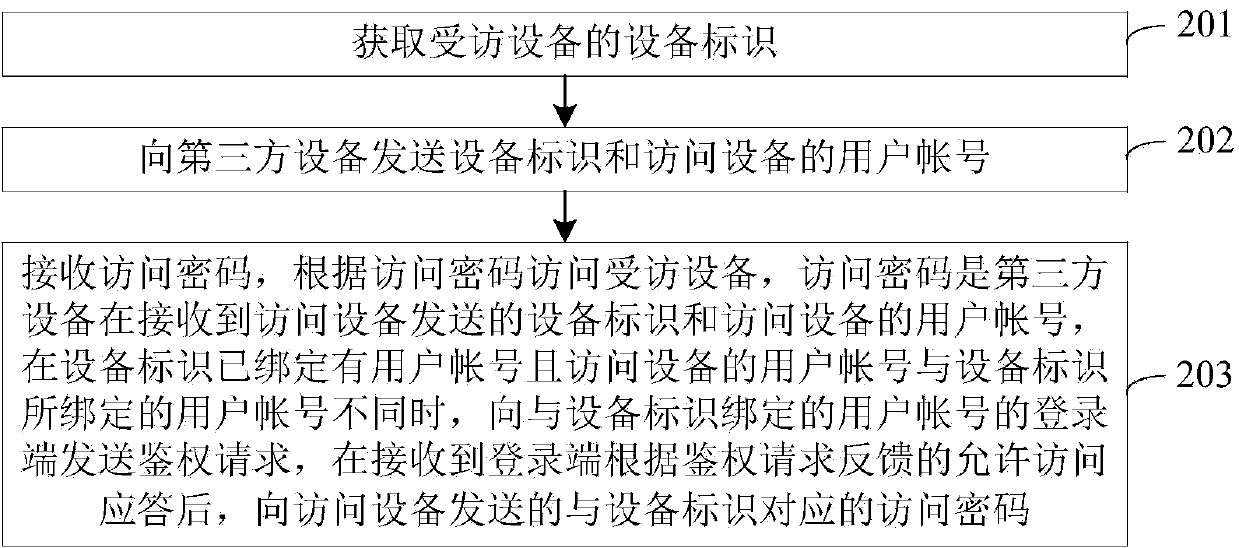
The invention discloses a method, a device and a system of access authentication, belonging to the field of computer technologies. The method of access authentication comprises the following steps that a device identification of a visited device is obtained; the device identification and a user account of an access device are transmitted to a third-party device, and the third-party device is used for transmitting an authentication request to a login end when the device identification is bound with a user account and the user account is different from the user account of the access device, and transmitting an access password of the visited device to the access device after the access allowed response fed back by the login end is received; and the visited device is visited by the received access password. Through carrying out authentication on the login end in the third-party device, after authentication is successful, the access password is transmitted to the access device, and the access device visits the visited device according to the access password; the problems that a user needs to manually input the access password on a mobile phone App to cause an illegal user to obtain the access password easily and have worse safety are solved; the effect of improving safety of the visited device is achieved.
Owner:XIAOMI INC
A method for user access authentication
InactiveCN101127600AAvoid wastingAvoid attackUser identity/authority verificationDigest access authenticationPassword
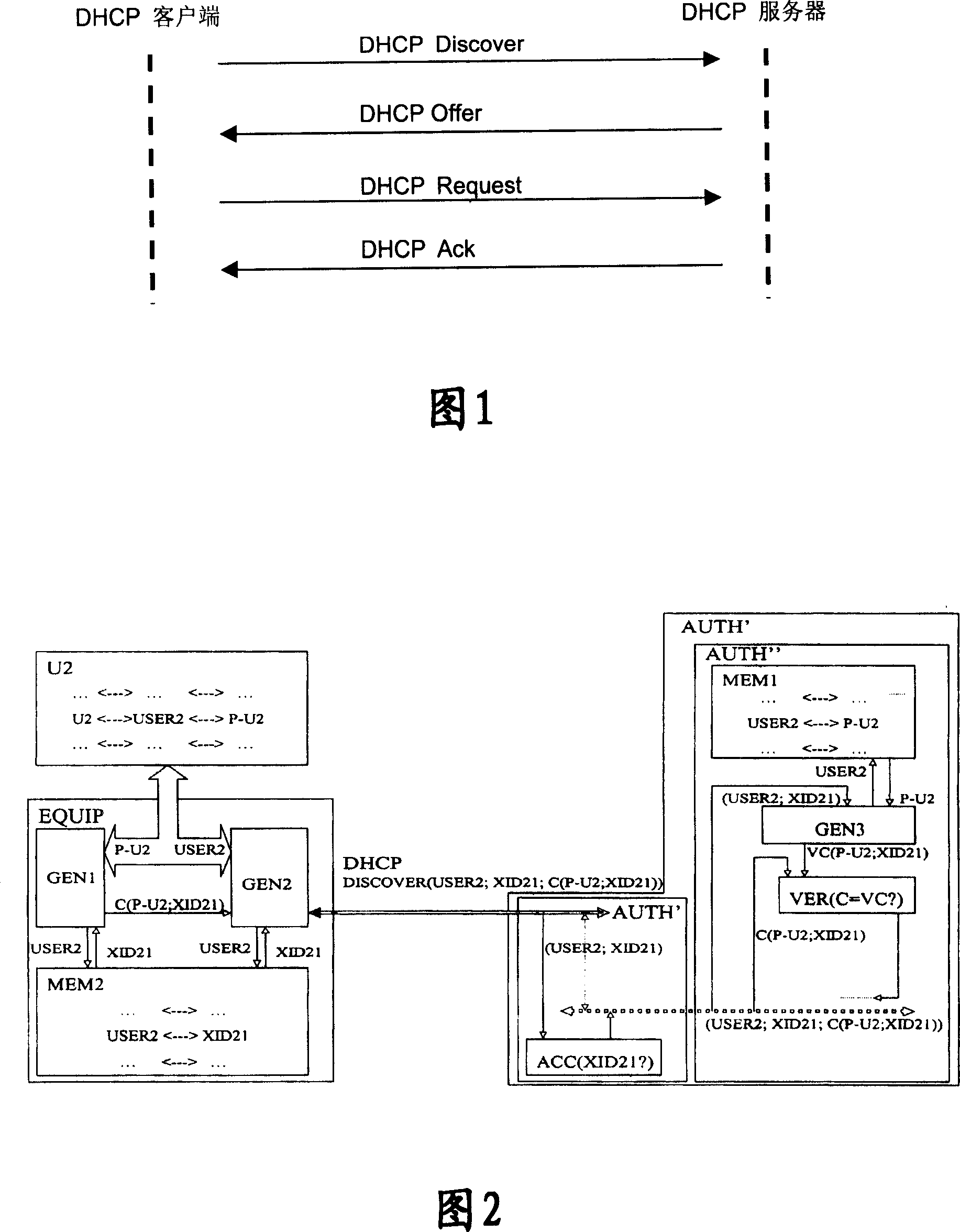
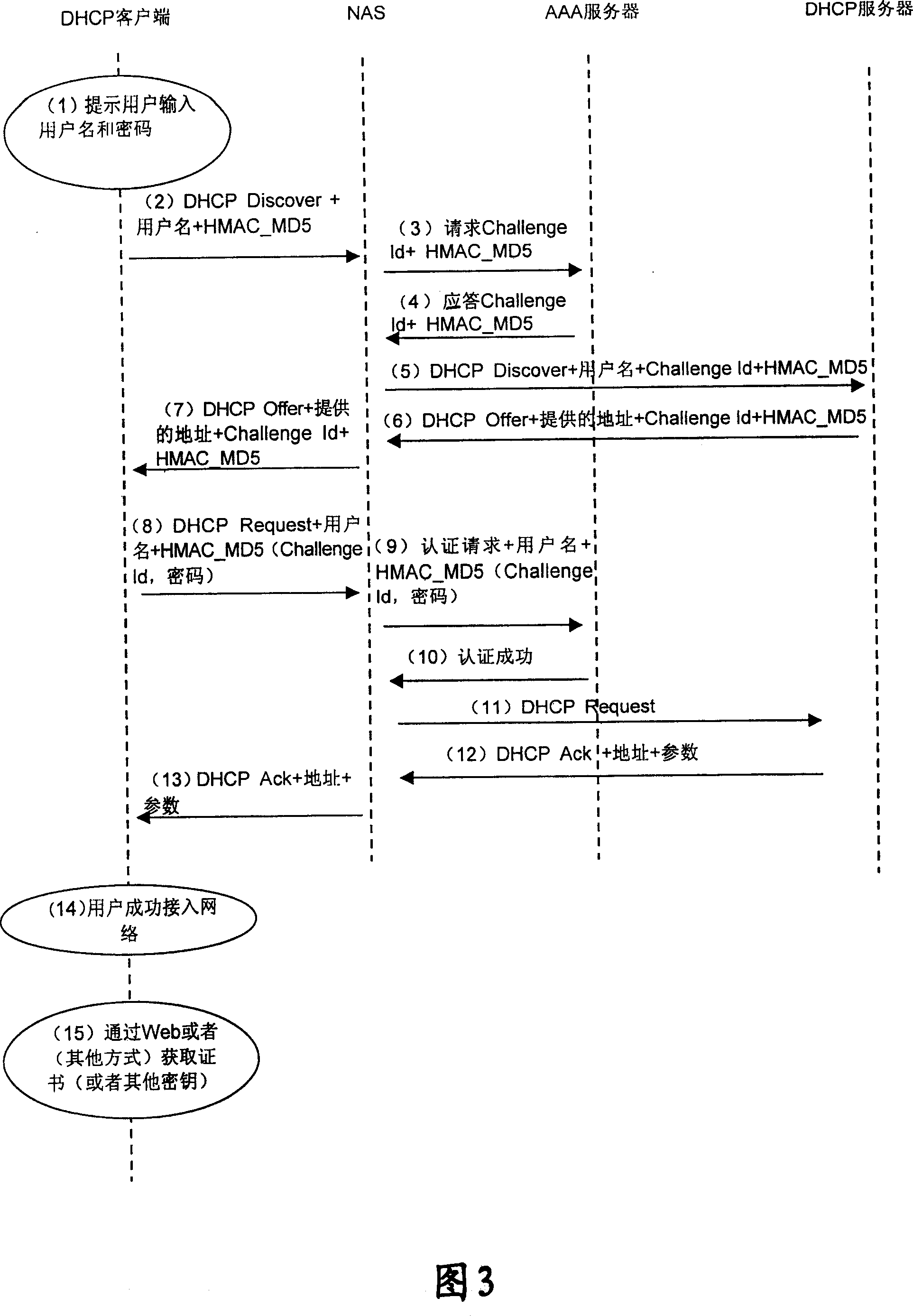
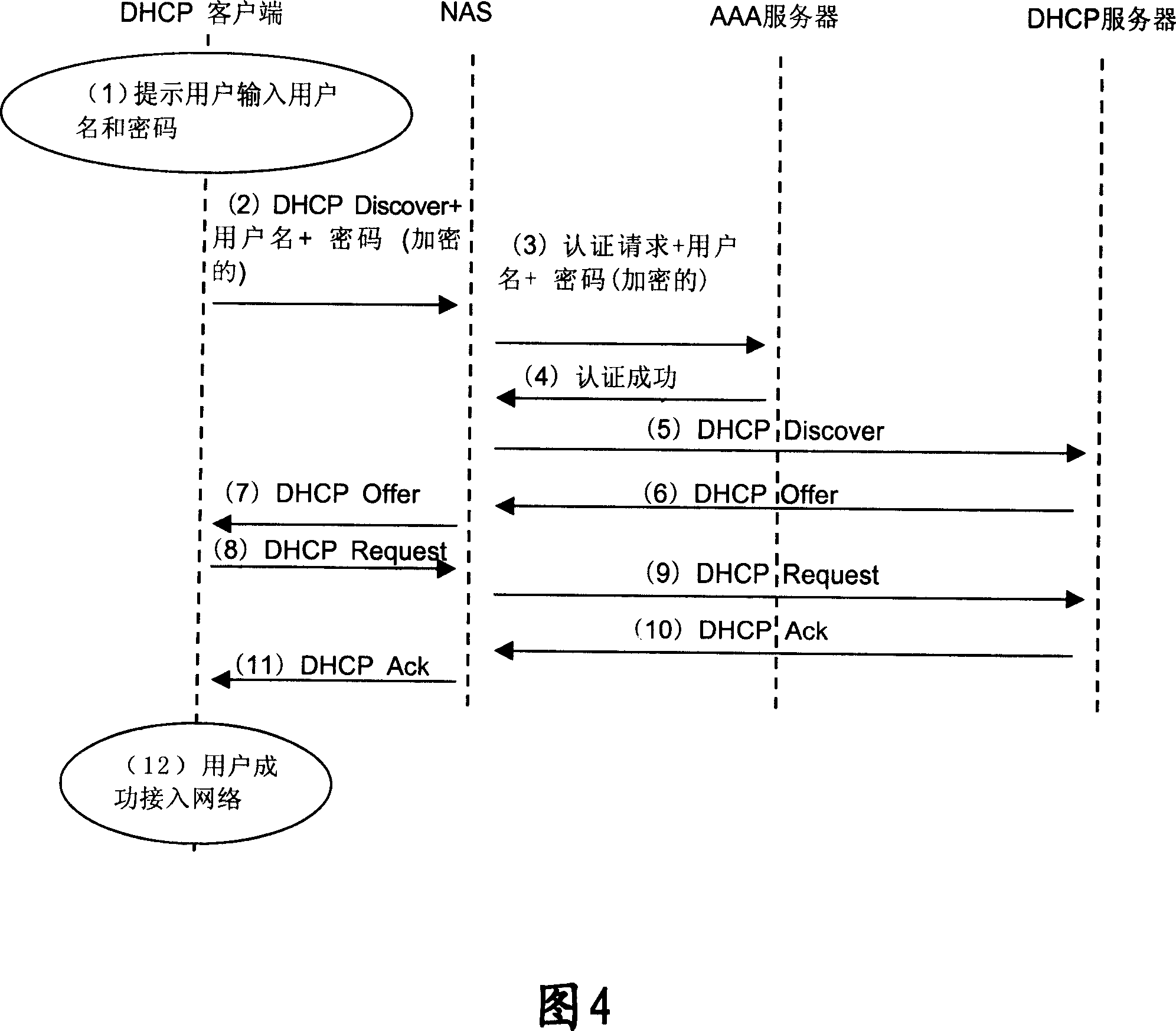
The utility model relates to a method for user access verifying, which comprises: during the access verifying process, the user sends a request to the network, which sends a random number back to the user; the user adopts the random number and the user password to perform the encryption calculating and transmits the encryption result to the network; the network adopts the random number and the stored user password to perform the same encryption calculating to verify the user; if the verification is passed, the user is accessed into the network through the IP address distributed by the DHCP server. The utility model has the advantages that the password transmission is safer, the waste of the IP address is avoided and the attack from the illegal user is also effectively avoided.
Owner:HUAWEI TECH CO LTD
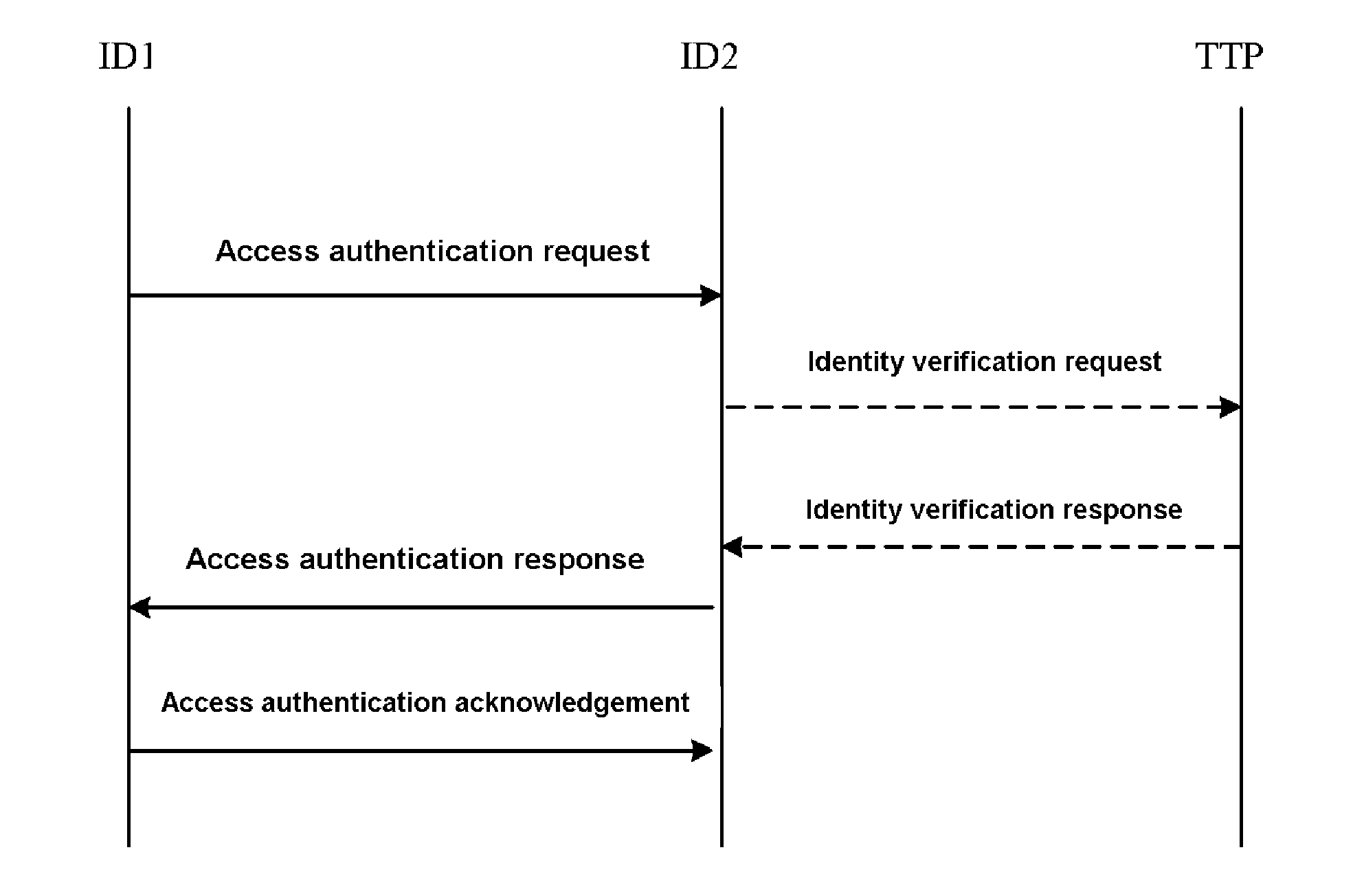
Bidirectional access authentication method
ActiveCN101159549AReduce maintenance workloadReduce overheadUser identity/authority verificationComputer security arrangementsDigest access authenticationMutual authentication
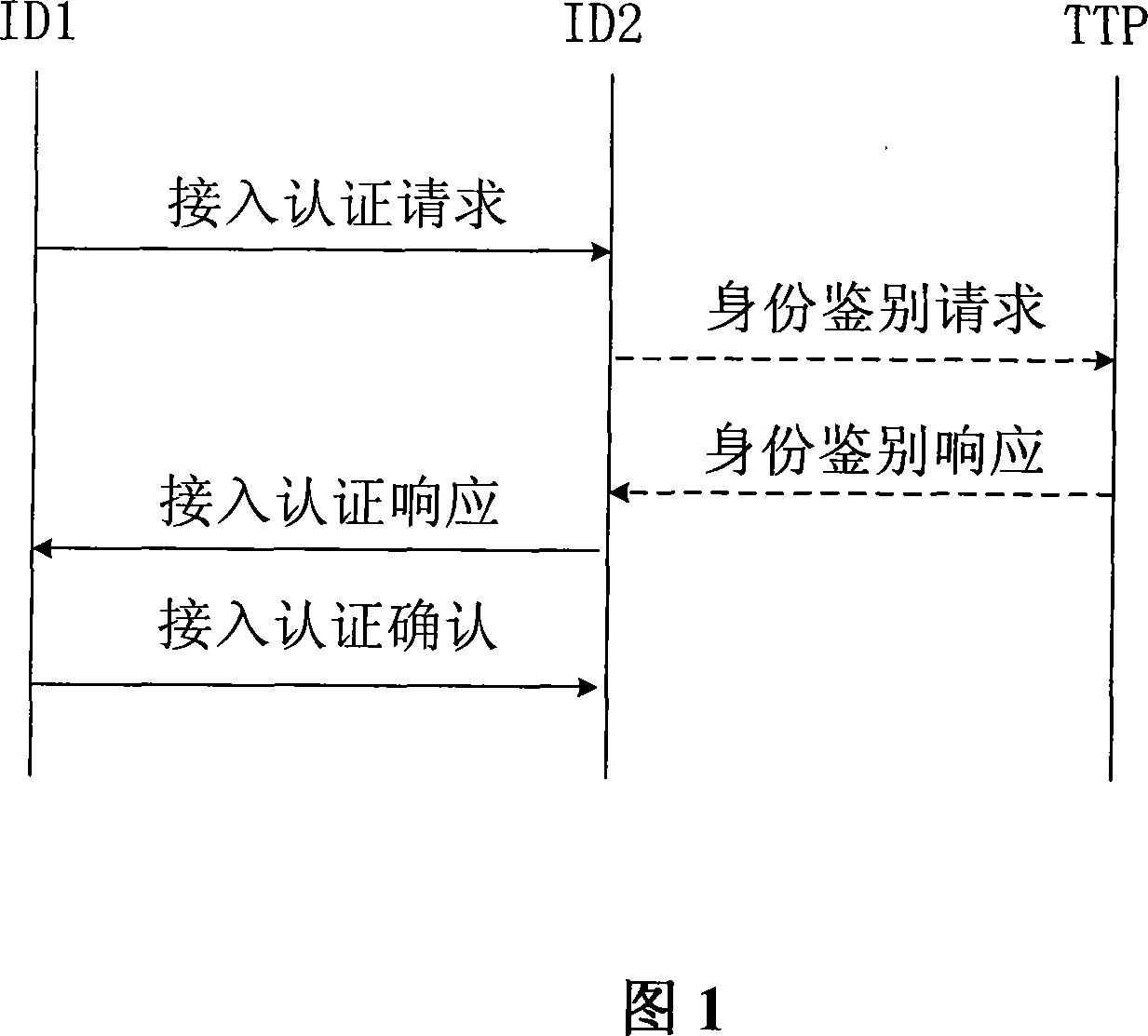
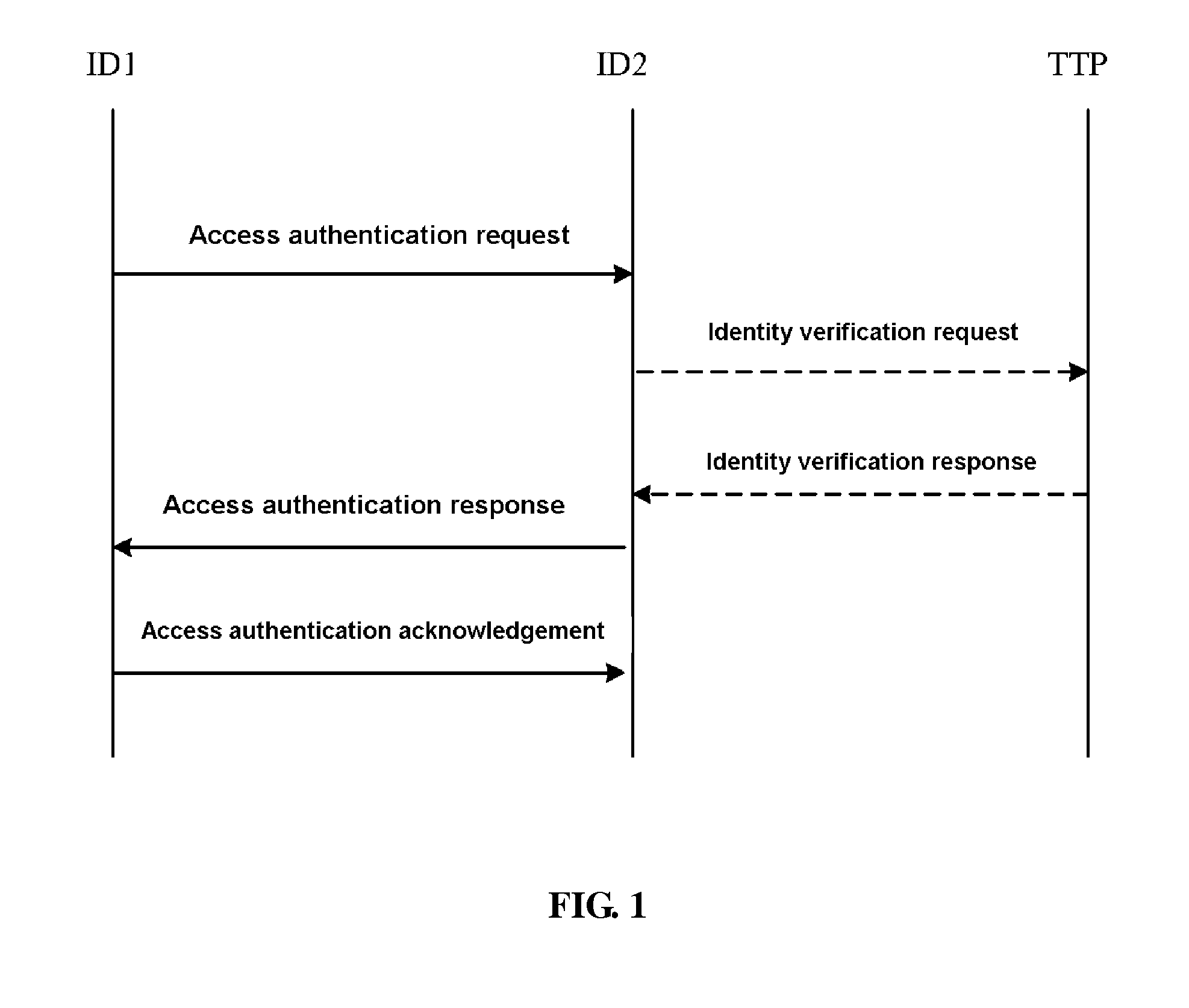
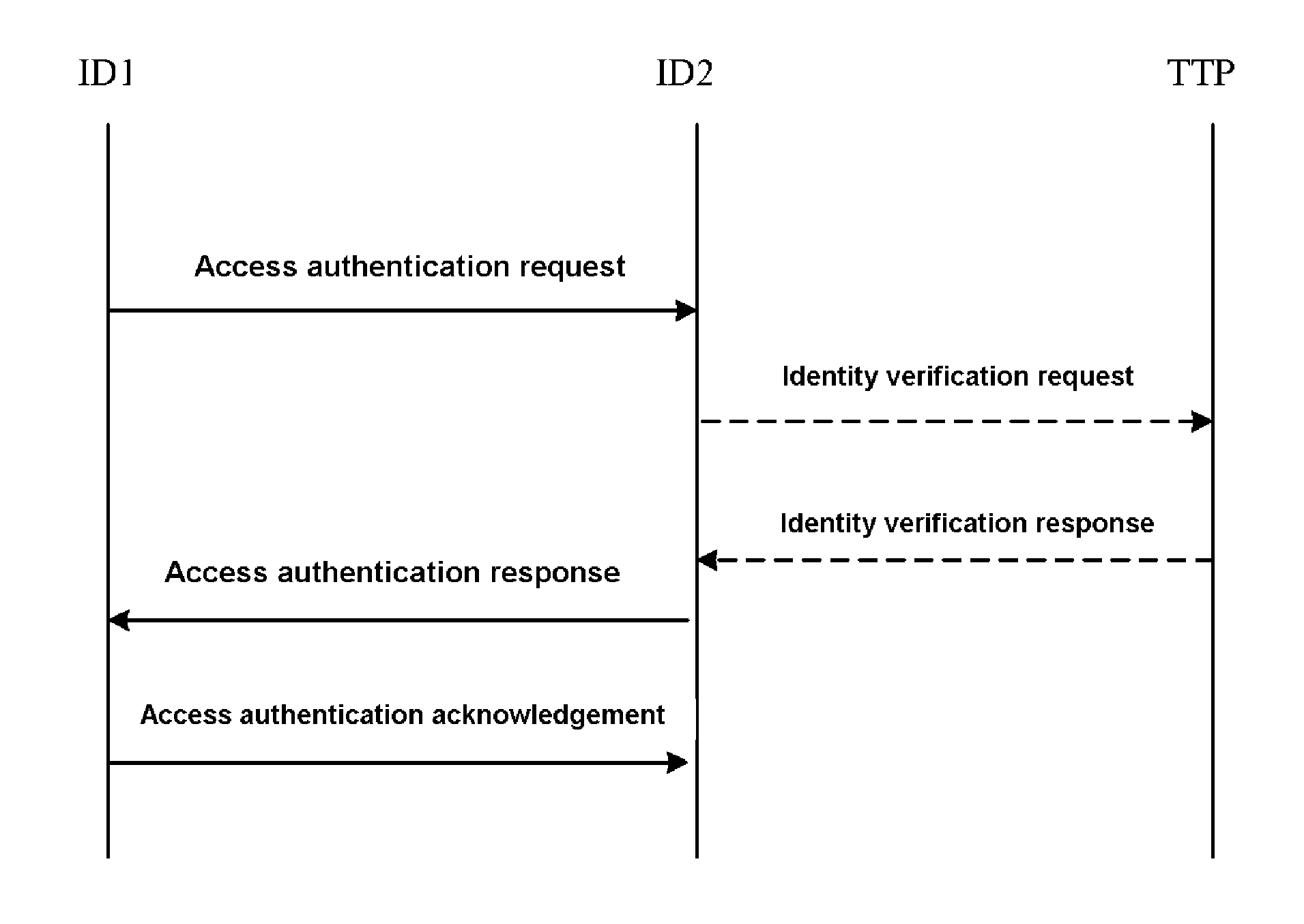
The invention relates to a mutual access authentication method, which comprises the following steps: 1) a first entity sends an access authentication request group to a second entity, the second entity verifies whether the sign of the first entity is correct, if it is, calculates the shared primary key of the second entity; 2) the second entity generates an access response group and sends to the first entity, the first entity verifies whether the sign of the access response group is correct, if it is, calculates the shared primary key of the first entity; 3) the first entity sends an access authentication acknowledgement group to the second entity, the second entity verifies the integrity of the access authentication acknowledgement; if the verification succeeds, the shared primary keys of the first and second entities are consistent, completing the access authentication. The access authentication method of mutual authentication, provided in this invention, is based on the identity mechanism and can be used for the verification of identity validity with simple operation and wide application range.
Owner:CHINA IWNCOMM
Access authentication method and system in mobile communication network
InactiveCN102036242AAvoid attackArrived without errorUser identity/authority verificationSecurity arrangementMan-in-the-middle attackDigest access authentication
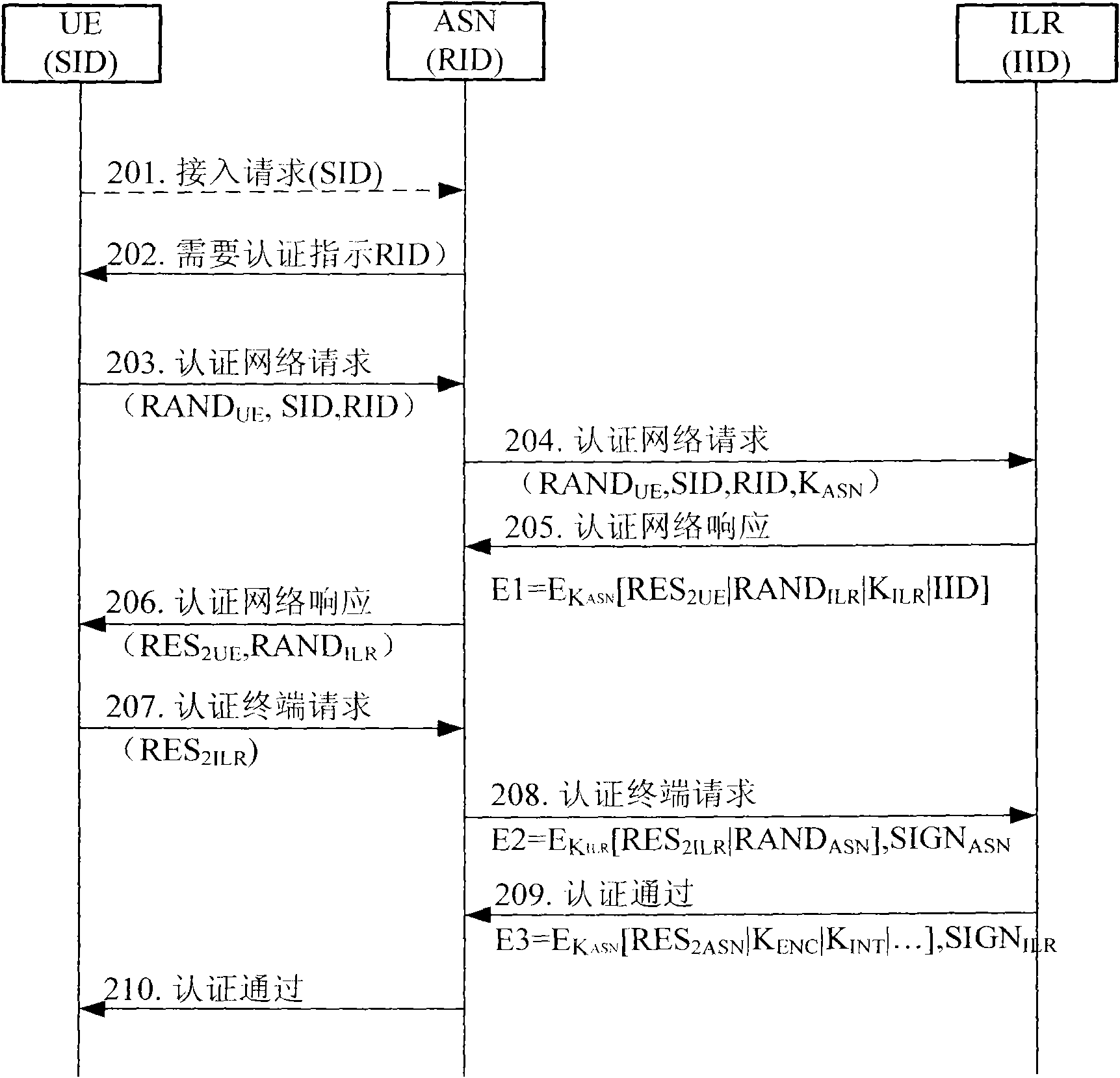
The invention discloses an access authentication method in a mobile communication network. The method comprises the following steps that: a user terminal generates a random number RANDUE, and acquires a random number RANDILR generated by route identification (RID) and an identity location register (ILR) of an access service node (ASN) in a network when needing to perform authentication; the user terminal calculates to obtain an authentication result RES2ILR by using a pre-shared key K1 and sends the RES2ILR to the ASN; the ASN generates a random number RANDASN and sends the RES2ILR and the random number RANDASN to the ILR; and the ILR calculates to obtain an authentication result XRES2ILR by using the pre-shared key K1 and compares the XRES2ILR with the received RES2ILR; and if the XRES2ILR is consistent with the RES2ILR, the access authentication is successful. Correspondingly, the invention also provides a system for implementing the method. Through the method and the system, Man-in-the-Middle attacks caused by an unreliable network can be effectively avoided.
Owner:ZTE CORP
HTTP relocation method for WEB identification
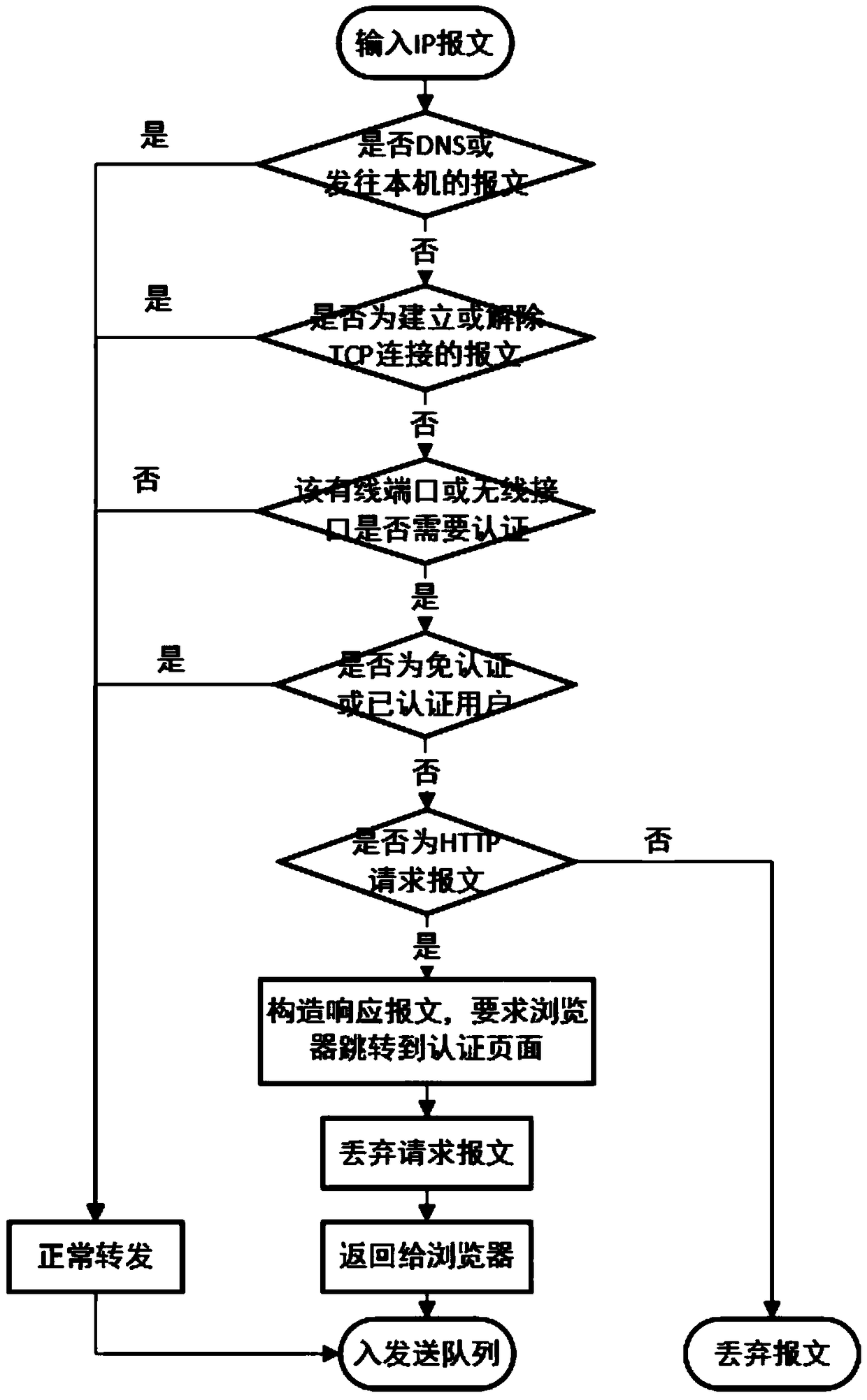
InactiveCN1538706ASimplified WEB authentication operationSolve the problem of remembering the authentication server addressUser identity/authority verificationData switching networksDomain nameDigest access authentication
The invention is applicable to access authentication based on WEB browser. Thus, it is possible to complete authentication without asking user to remember IP address and domain name. The method includes steps: (1) filtering packet function of peripheral access router of ISP captures HTTP message from not authenticated user; (2) the access router is 'masquerading' as target host user accesses, and builds TCP connection with the host of not authenticated user; (3) the access router redirects HTTP request of user to pointed authentication server. The authentication server transfers HTML page in use for authentication to browser at user side. Based on hint on the HTML page, user completes authentication.
Owner:HUAWEI TECH CO LTD
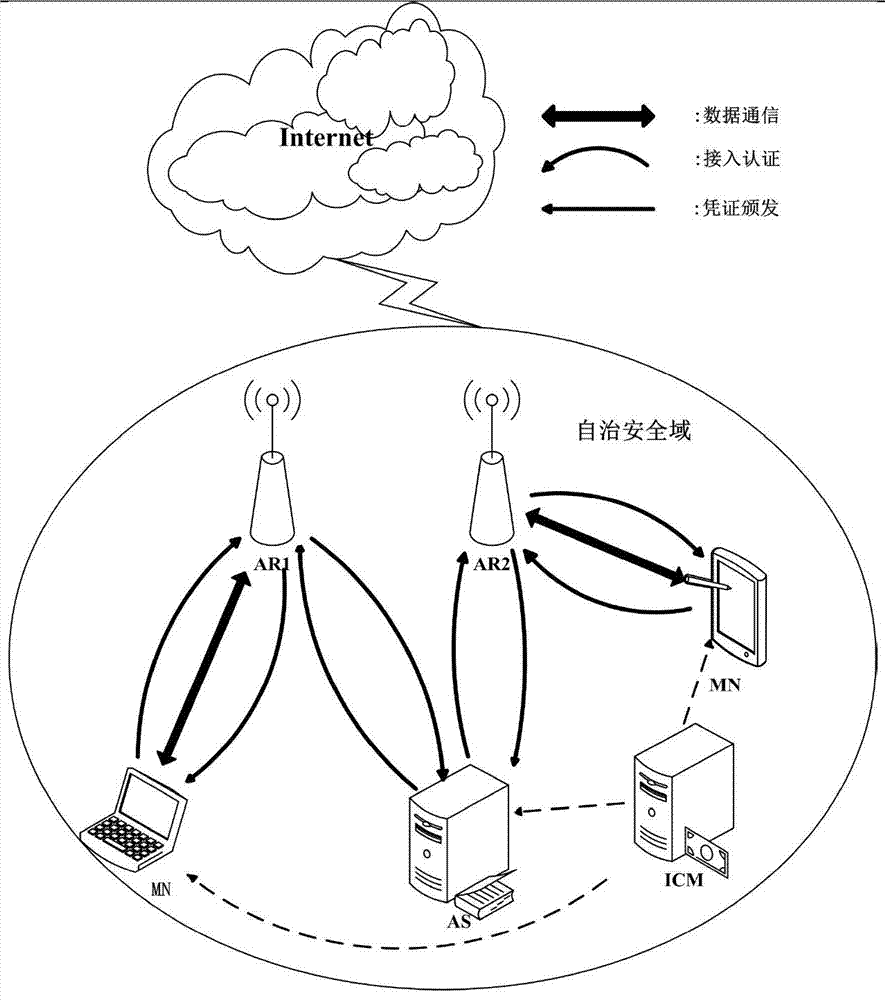
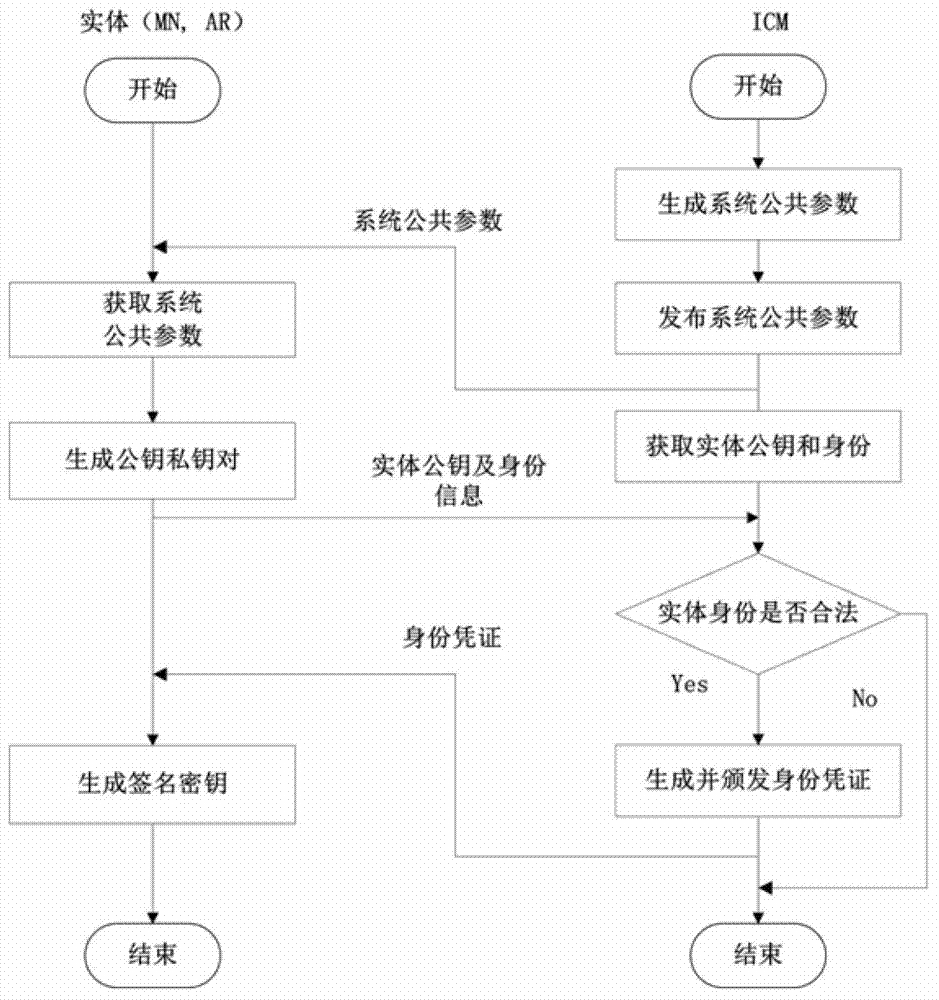
Wireless local area network two-way access authentication system and method based on identity certificates
ActiveCN103491540AEfficient access authenticationImprove access authentication efficiencySecurity arrangementAccess networkDigest access authentication
The invention discloses a wireless local area network two-way access authentication system and method based on identity certificates. The wireless local area network two-way access authentication system comprises access routers arranged in a safety area and further comprises an identity certificate management server and an authentication server. The identity certificate management server is used for managing the identity certificates of entities in the safety area, namely, issuing the identity certificates and maintaining the identity certificates. The authentication server is used for authenticating access certification application of mobile subscribers and completing shared key negotiation with the mobile subscribers. The access routers are used for controlling whether the mobile subscribers have access to the wireless local area network or not according to the authentication result fed back from the authentication server and receiving and forwarding authentication information between the mobile subscribers and the authentication server. According to the wireless local area network two-way access authentication system and method, in an autonomous security domain, two-way access authentication and secret key negotiation between the mobile subscribers and the accessed network can be achieved, efficient access authentication conducted when the mobile subscribers switch between the different access routers is supported, and the access authentication efficiency is improved.
Owner:NORTHEASTERN UNIV
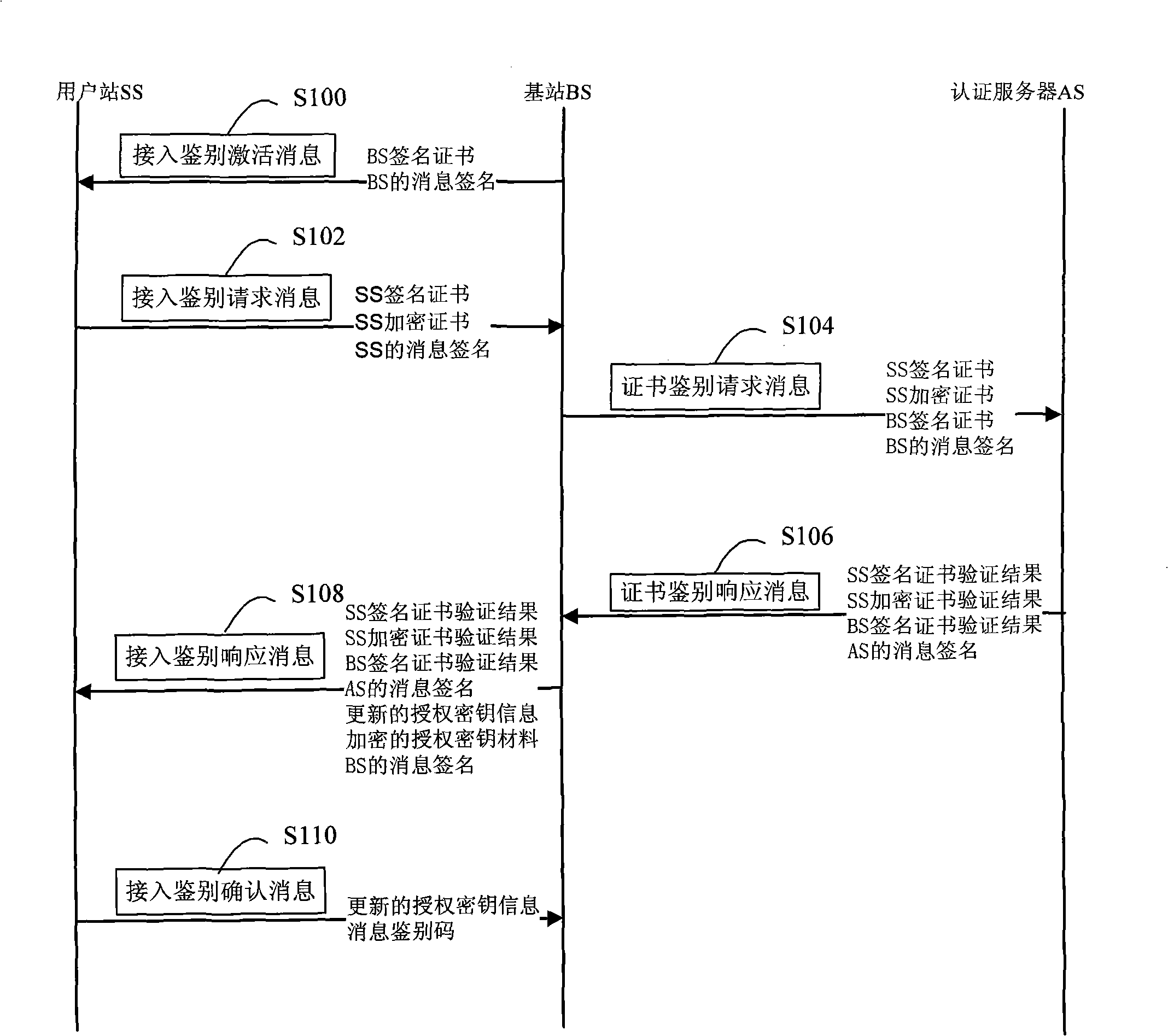
Safety access method of wireless metropolitan area network
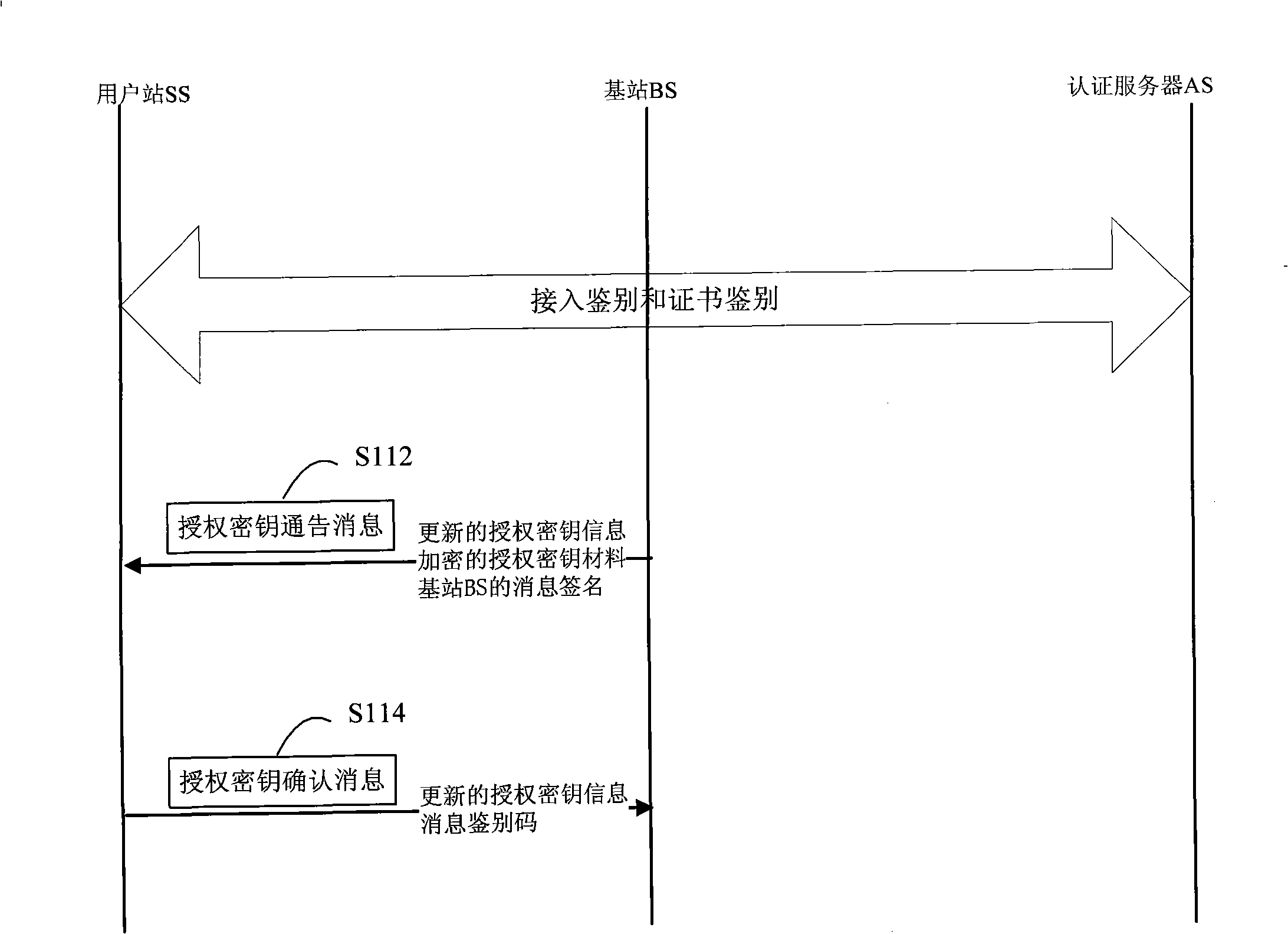
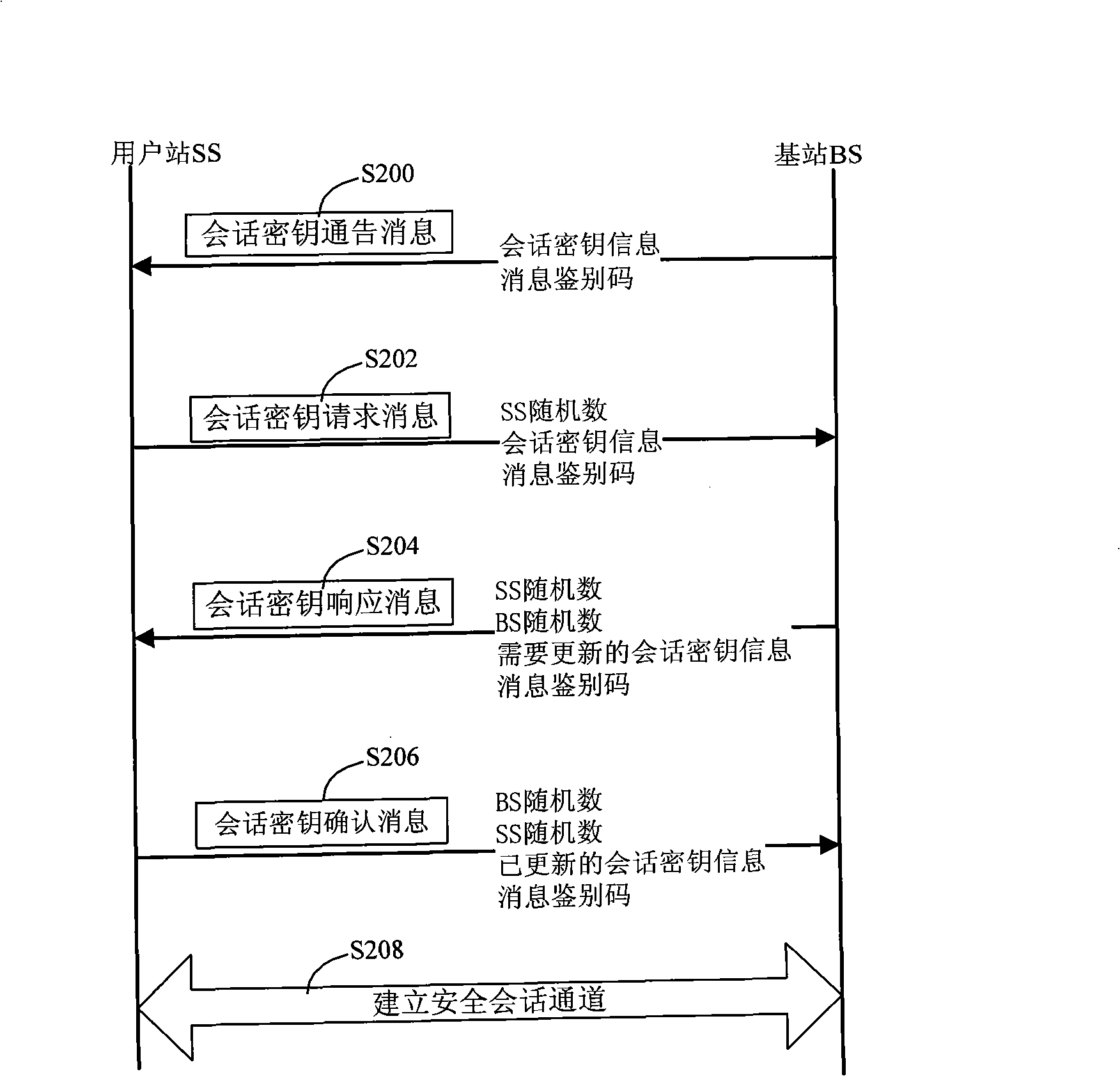
InactiveCN101272616AReduces the possibility of crackingRealize AuthenticationUser identity/authority verificationRadio/inductive link selection arrangementsDigest access authenticationAccess method
The invention relates to a method for safe accessing of a wireless metropolitan area network, which comprises an authenticating step and a session key negotiating step. The authenticating step comprises that: a subscriber station SS sends a request message for access authentication to a base station BS; the BS sends a request message for certificate authentication to an authentication server AS; the AS verifies the request message for certificate authentication and sends a response message for certificate authentication to the BS; the BS verifies the validity of the identity of the SS according to the response message for certificate authentication; if the SS is valid, the BS sends the response message for access authentication to the SS; the SS verifies the validity of the BS according to the response message for access authentication; if the BS is valid, the SS uses the encryption certificate key of the SS to decrypt the material of authentication key. The SS signing certificate in the proposal is used for stating the identity and the SS encrypting certificate is used for encrypting and decrypting the material of authentication key so as to reduce the risk that the key is decrypted; through verifying the certificates of the BS and the SS by the AS, authentication for the subscriber station SS and the base station BS is realized and security level is improved.
Owner:GCI SCI & TECH
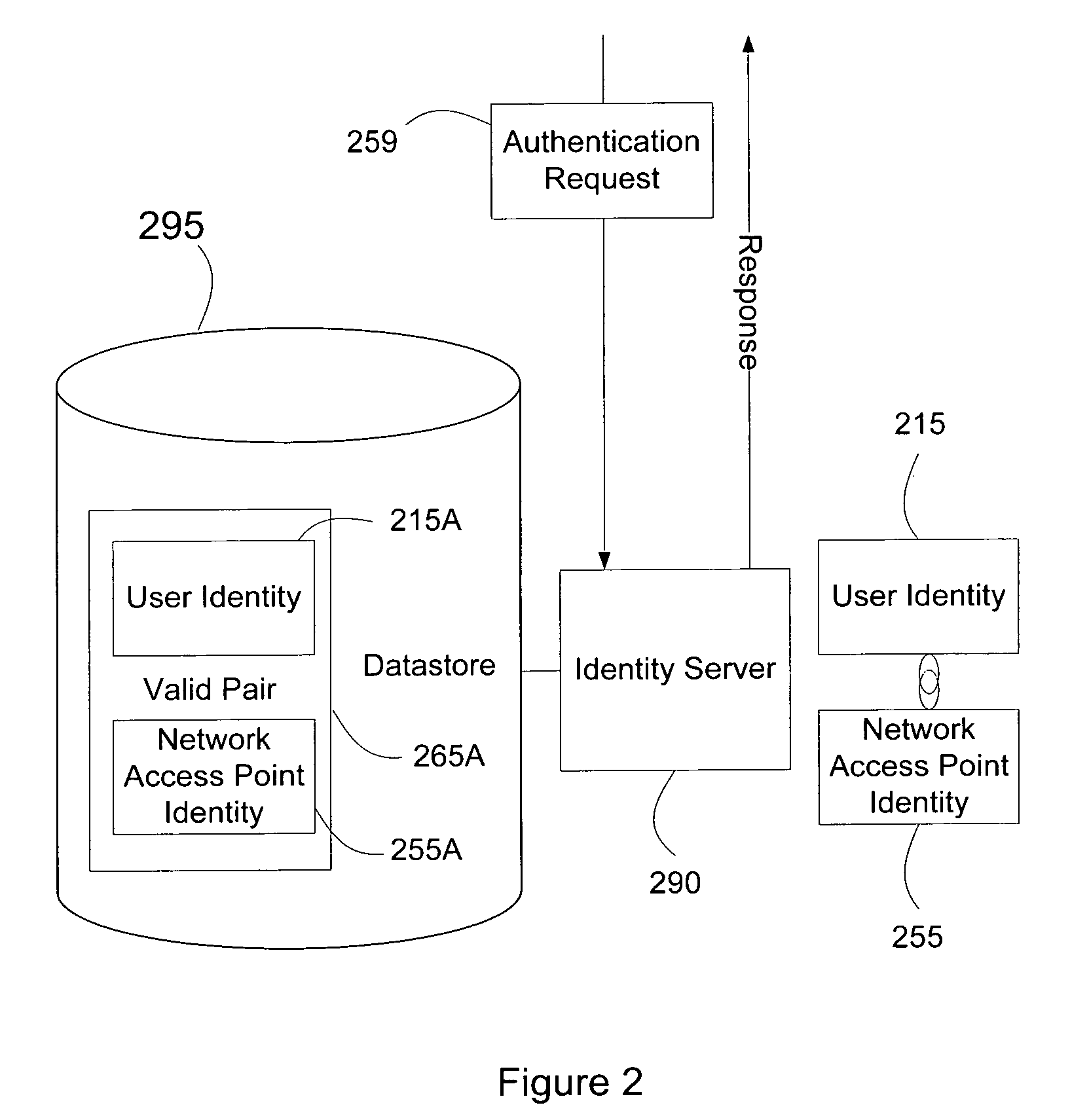
Systems and methods for user access authentication based on network access point
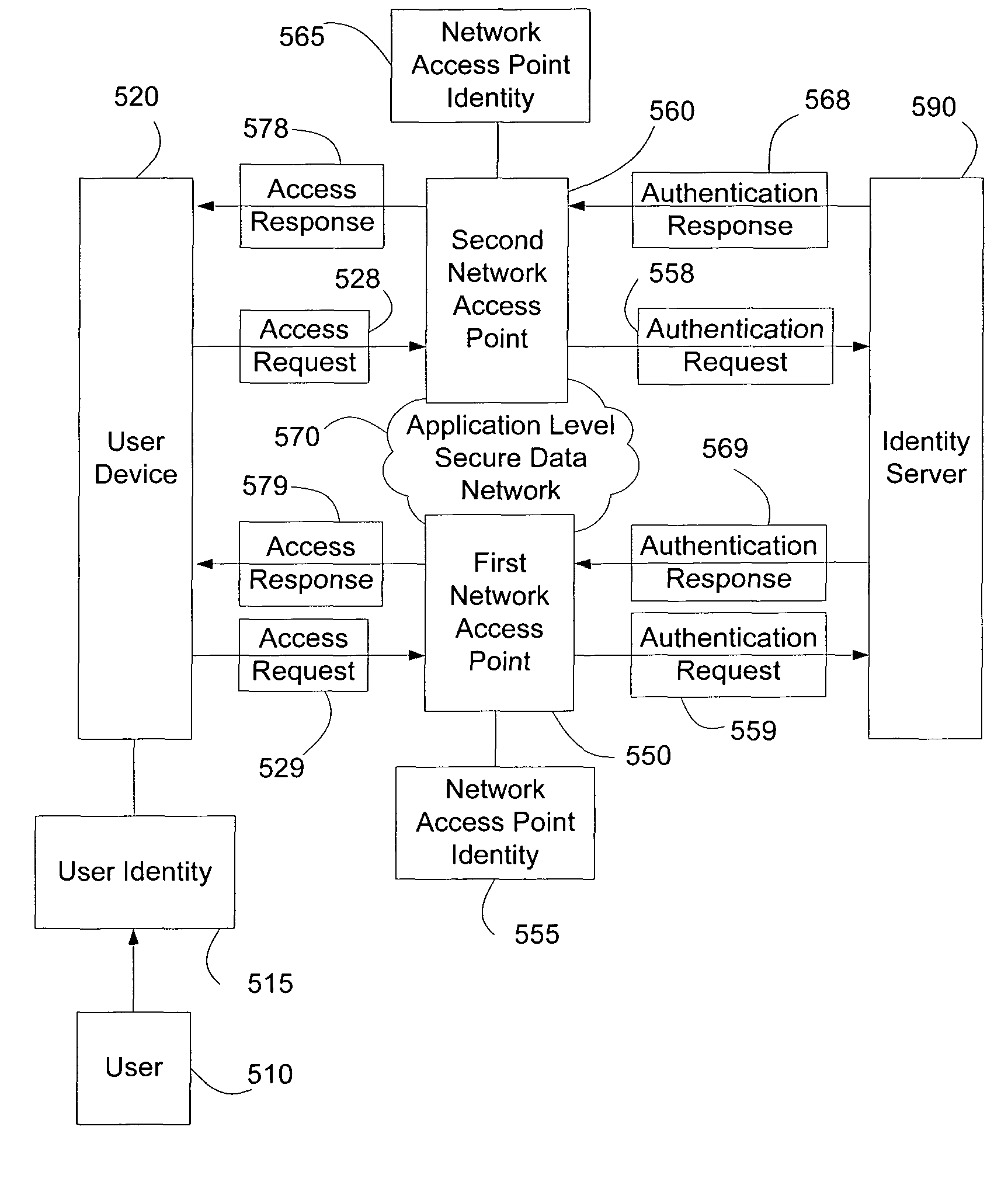
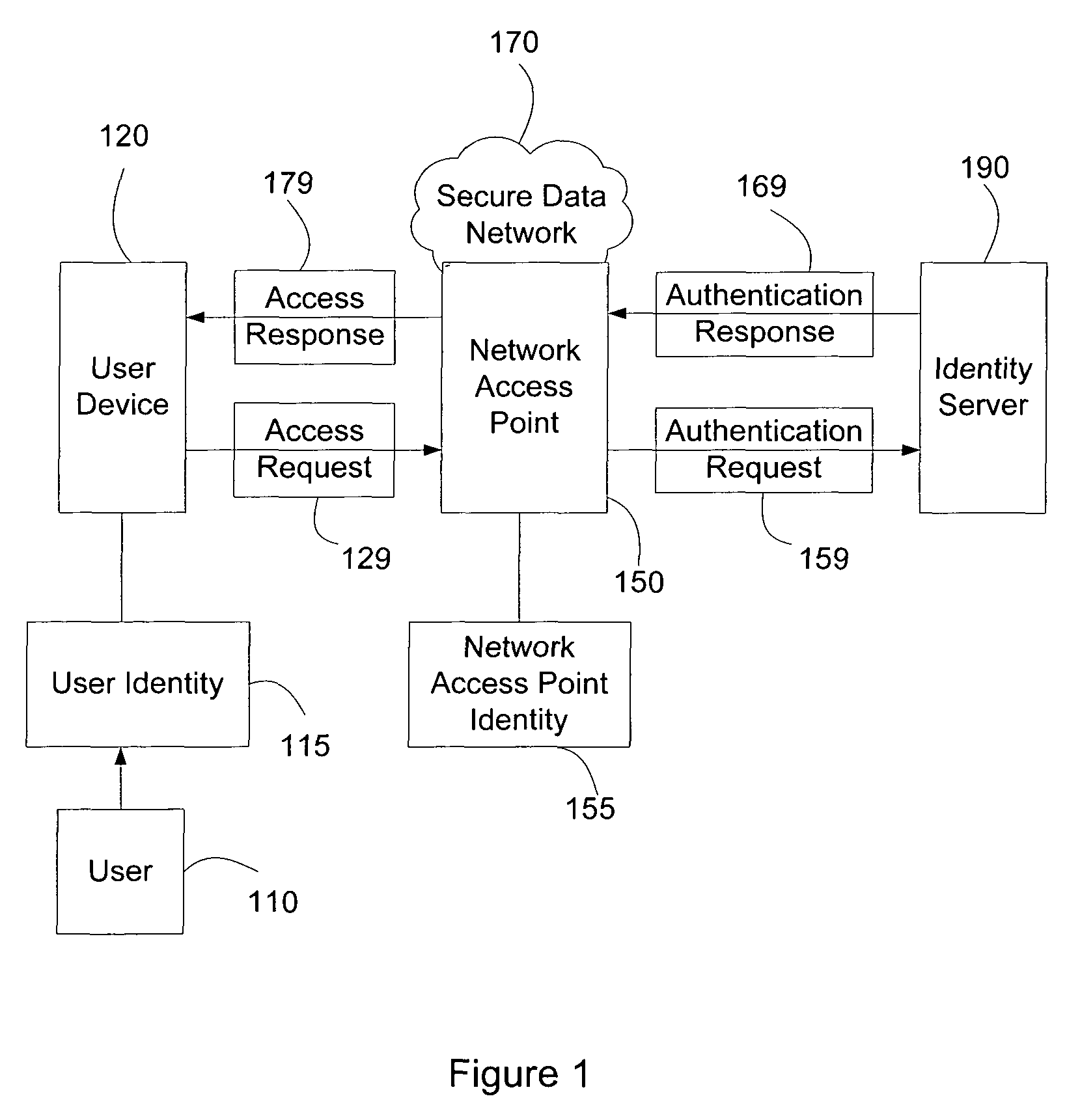
ActiveUS8151322B2Digital data processing detailsUnauthorized memory use protectionTime informationNetwork Access Protection
Systems and methods of authenticating user access based on an access point to a secure data network include a secure data network having a plurality of a network access points serving as entry points for a user to access the secure data network using a user device. The user is associated with a user identity, each network access point with a network access point identity. The user uses a user device to send an access request, requesting access to the secure data network, to the network access point, which then sends an authentication request to an identity server. The identity server processes the authentication request, by validating the combination of the user identity and the network access point identity, and responds with an authentication response, granting or denying access, as communicated to the user device via an access response. The secure data network may comprise an application level secure data network, in which the user uses the user device to request access to a network application. Furthermore, the identity server may validate the combined user identity and network access point identity data in conjunction with time information, access allowance data, and / or traffic volume data.
Owner:A10 NETWORKS
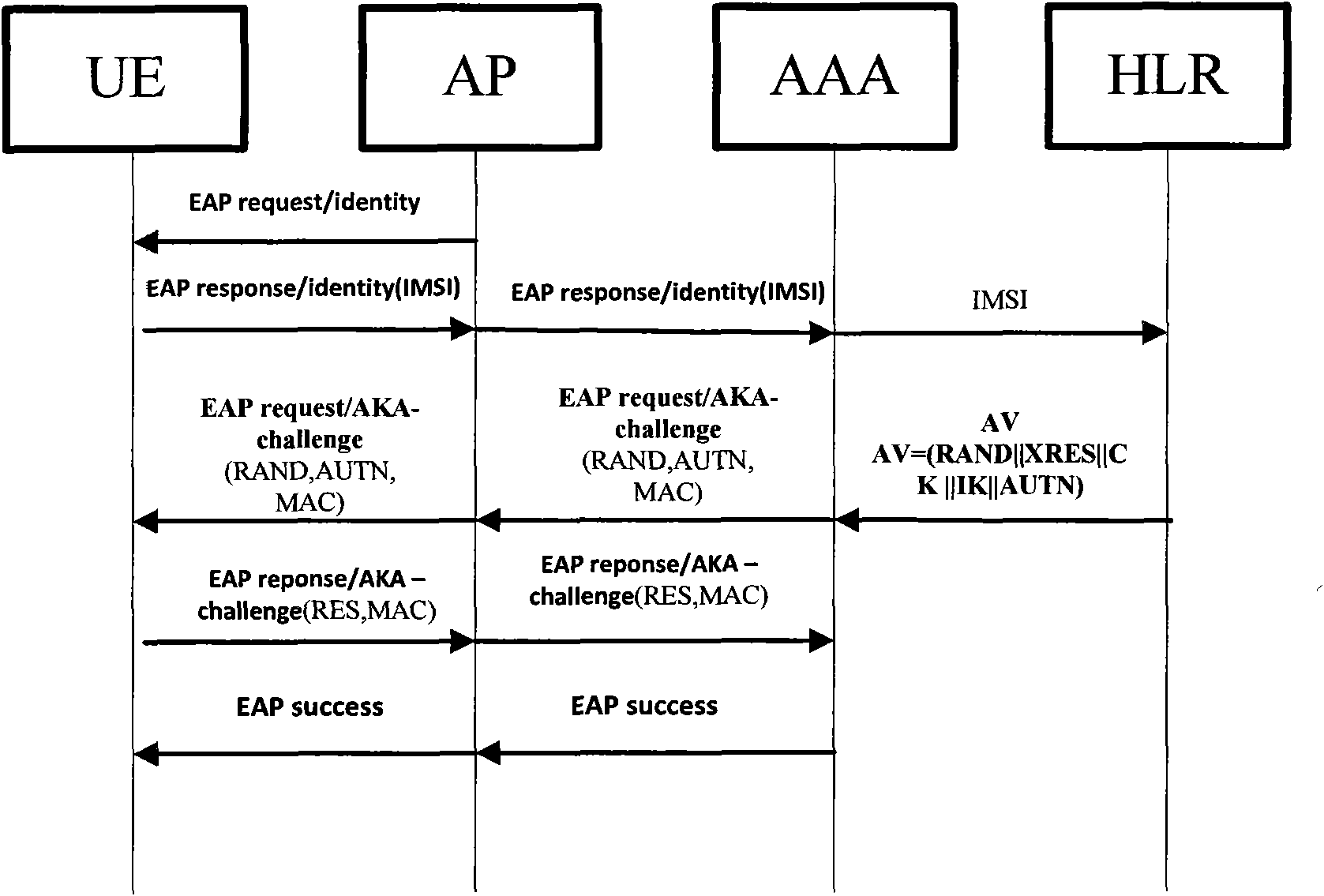
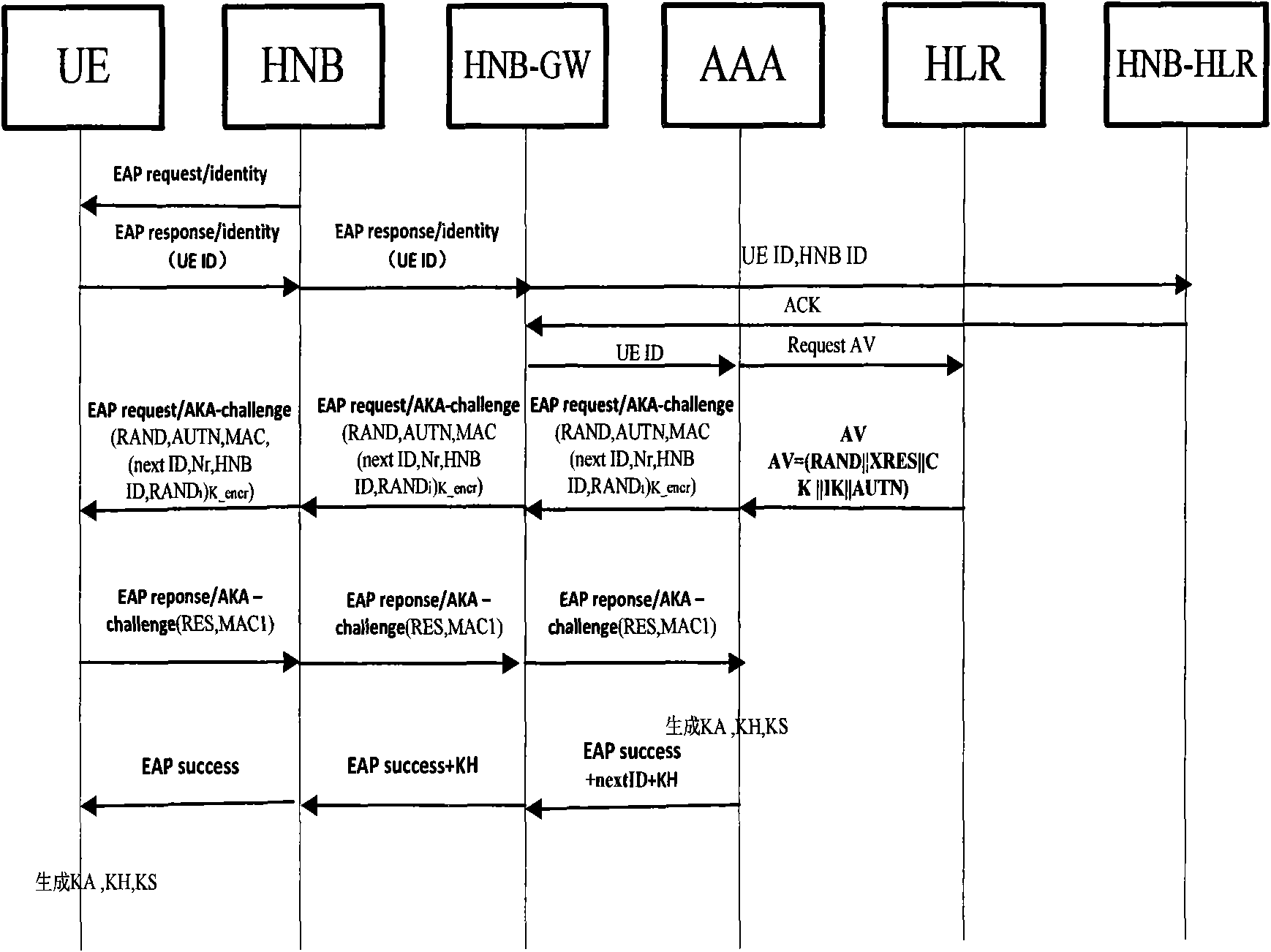
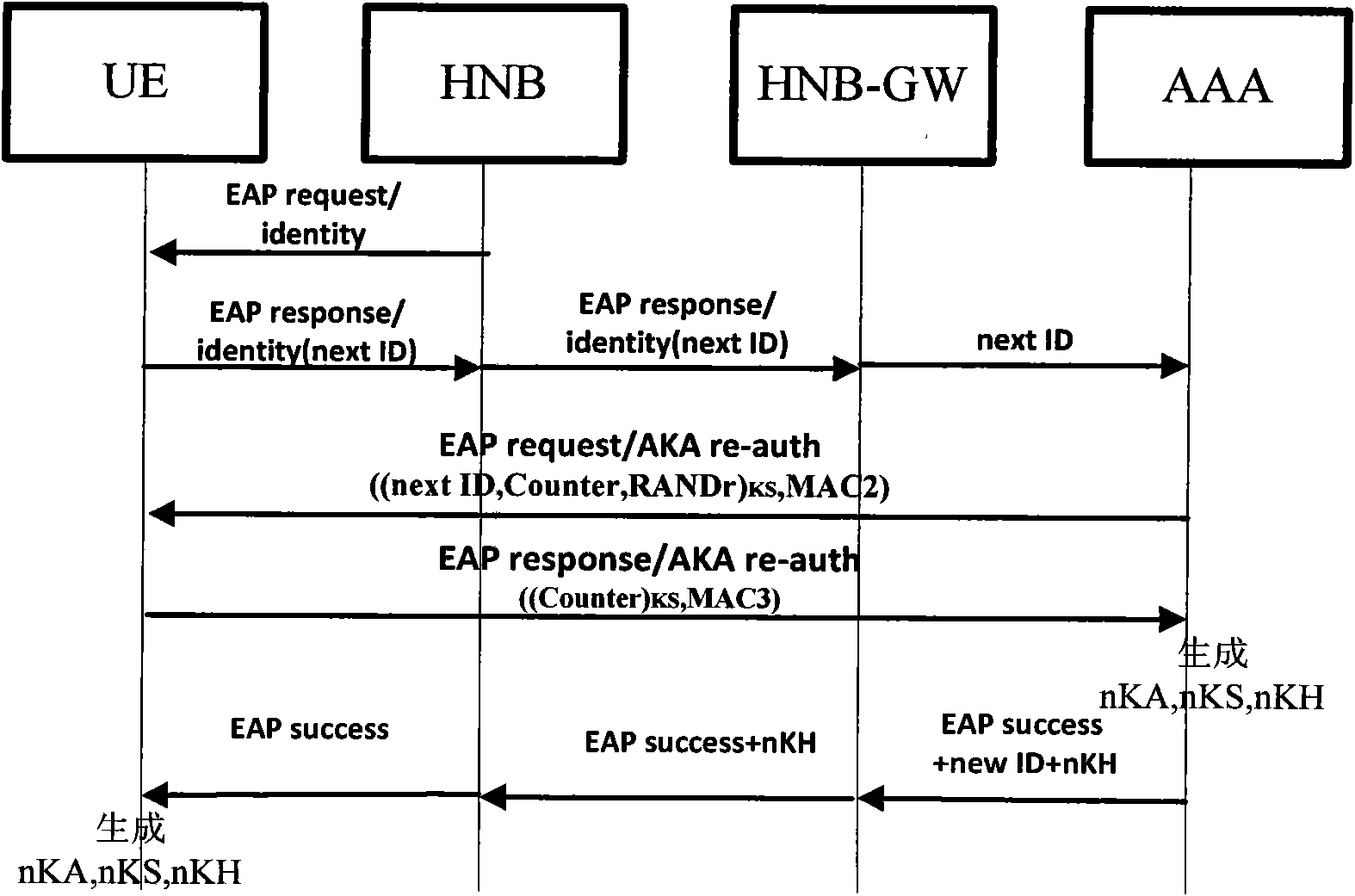
Method of access authentication and recertification in home NodeB system of user terminal
InactiveCN101854629ARealization of privacyAchieve privacySecurity arrangementDigest access authenticationAuthentication server
The invention discloses methods of access authentication and recertification of a user terminal in a home NodeB system, mainly overcoming the defect that the existing standard does not provide an authentication method of the user terminal for accessing a core network through the home NodeB. The access authentication process comprises the following steps: firstly, simultaneously sending the identification of a user and the identification of the home NodeB to HNBHLR to inquire, judging according to whether the identification of the user exists in the CSG list of the home NodeB; and secondly, adopting the modified EAP-AKA protocol to perform authentication between the user terminal and a authentication server. The recertification process comprises the following steps: firstly, judging according to whether the identification of the user is as the same as the identification stored in the home NodeB network, and secondly, using a hierarchy secret key to modify the existing EAP-AKA recertification method to realize the mutual authentication between the user terminal and the authentication server. The methods of the invention has the advantages of simple processes, high efficiency, reliable performance, good safety and the like, thus being applicable to the access authentication and recertification of the user terminal in the home NodeB system.
Owner:XIDIAN UNIV
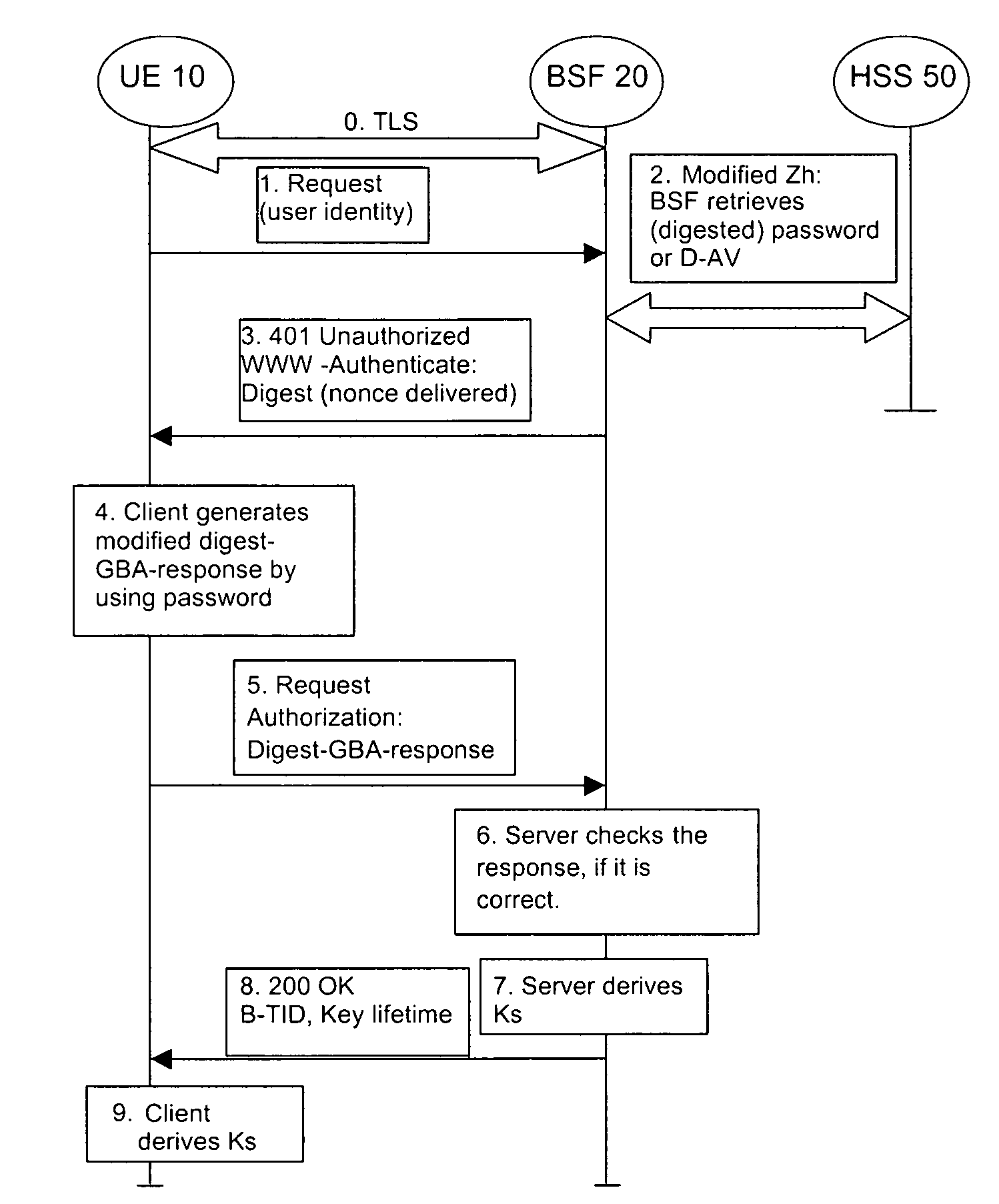
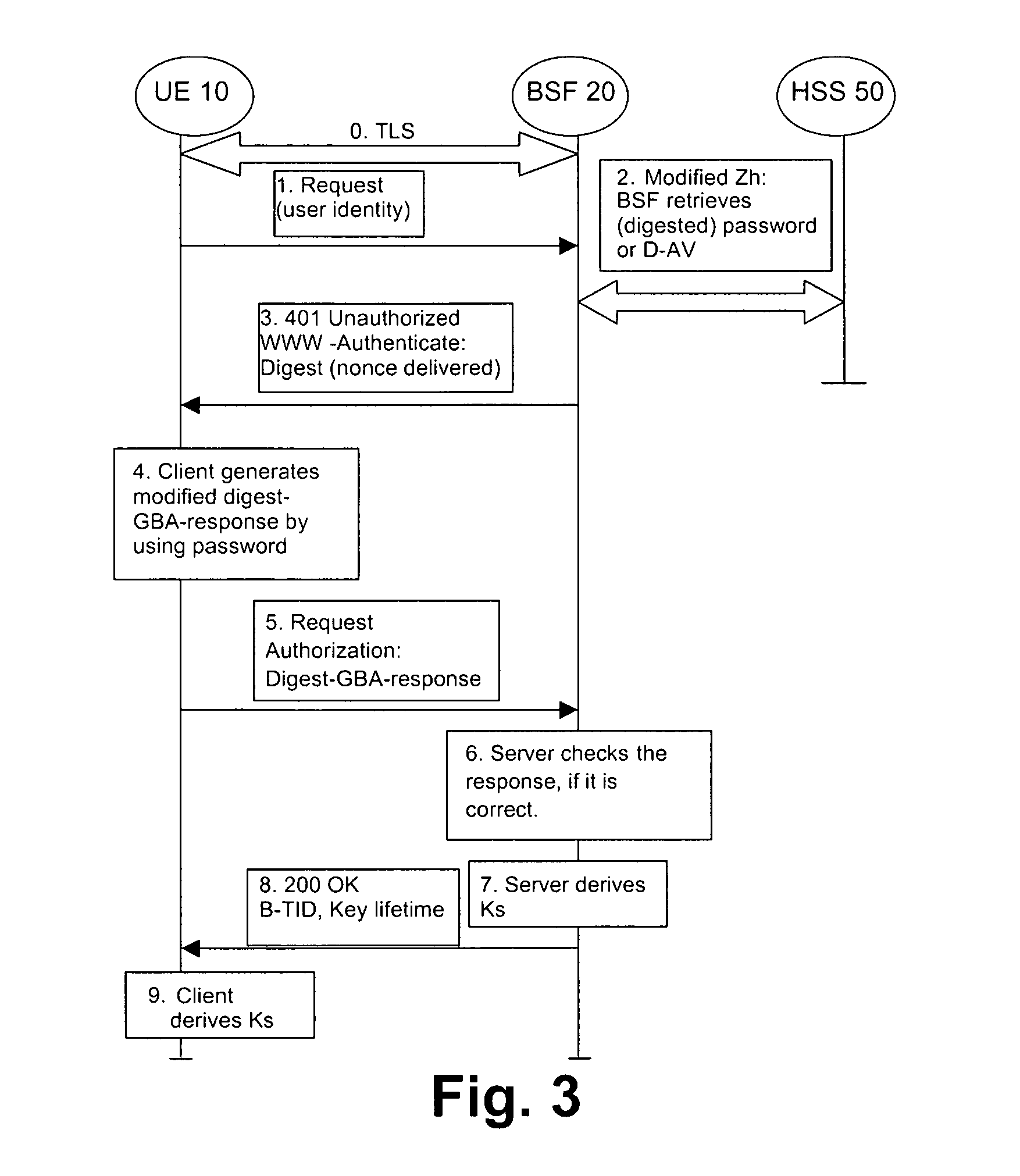
Secure Bootstrapping Architecture Method Based on Password-Based Digest Authentication
ActiveUS20110145575A1Eliminate attackImprove securityUser identity/authority verificationSecurity arrangementDigest access authenticationPassword
The present invention is related to a method, apparatus, and computer program product, in which a password-based digest access authentication procedure is used for performing authentication between a client and a server, wherein the authentication procedure is secured by at least one of modifying a digest-response parameter with a user password and generating a bootstrapped key based on the user password and at least one fresh parameter not used in a previous protocol run between the client and the server.
Owner:NOKIA TECHNOLOGLES OY
A method, device and system for access authentication
InactiveCN101123498AExtend access network boundariesQuick switch operationUser identity/authority verificationRadio/inductive link selection arrangementsService-level agreementDigest access authentication
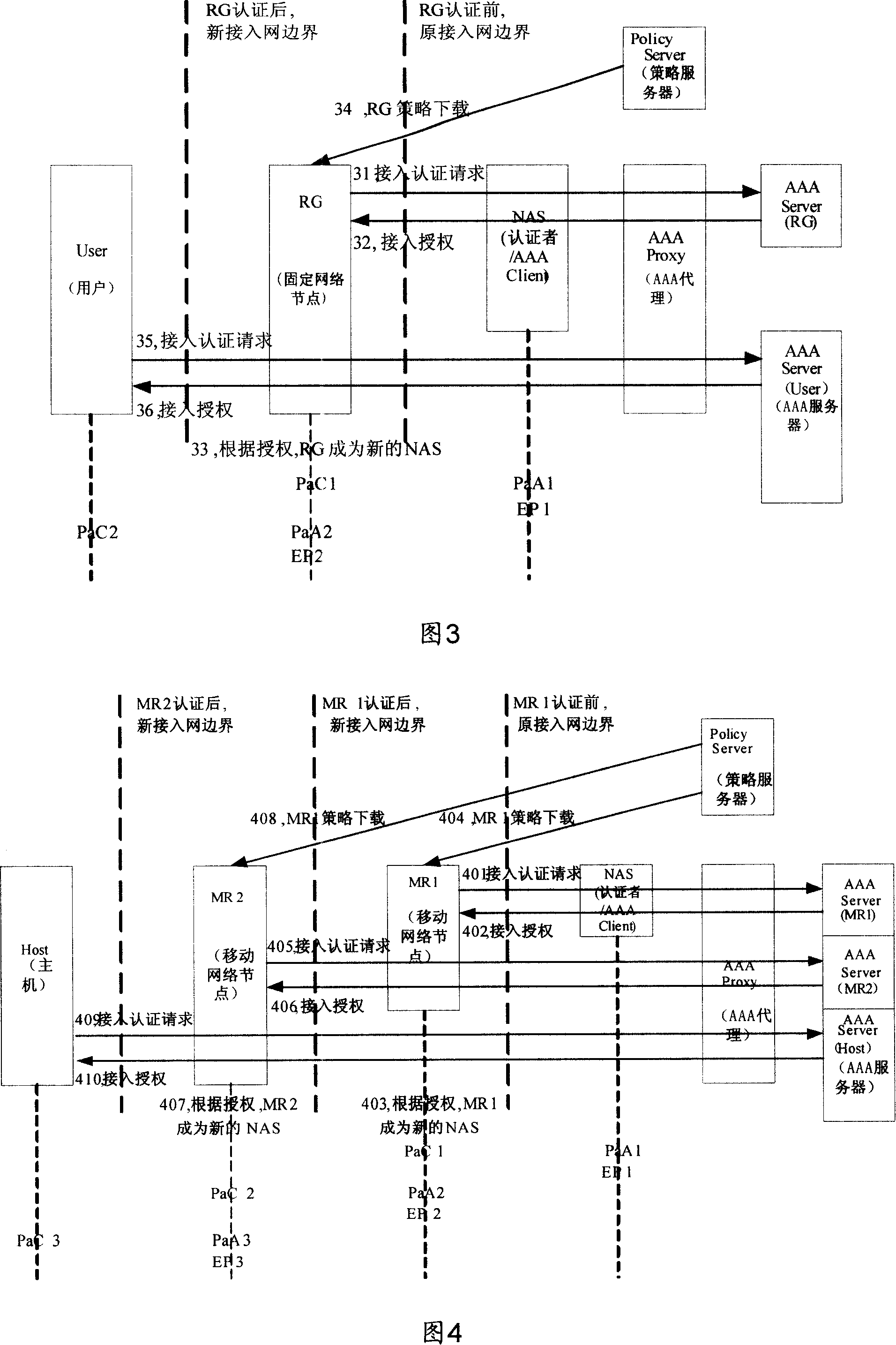
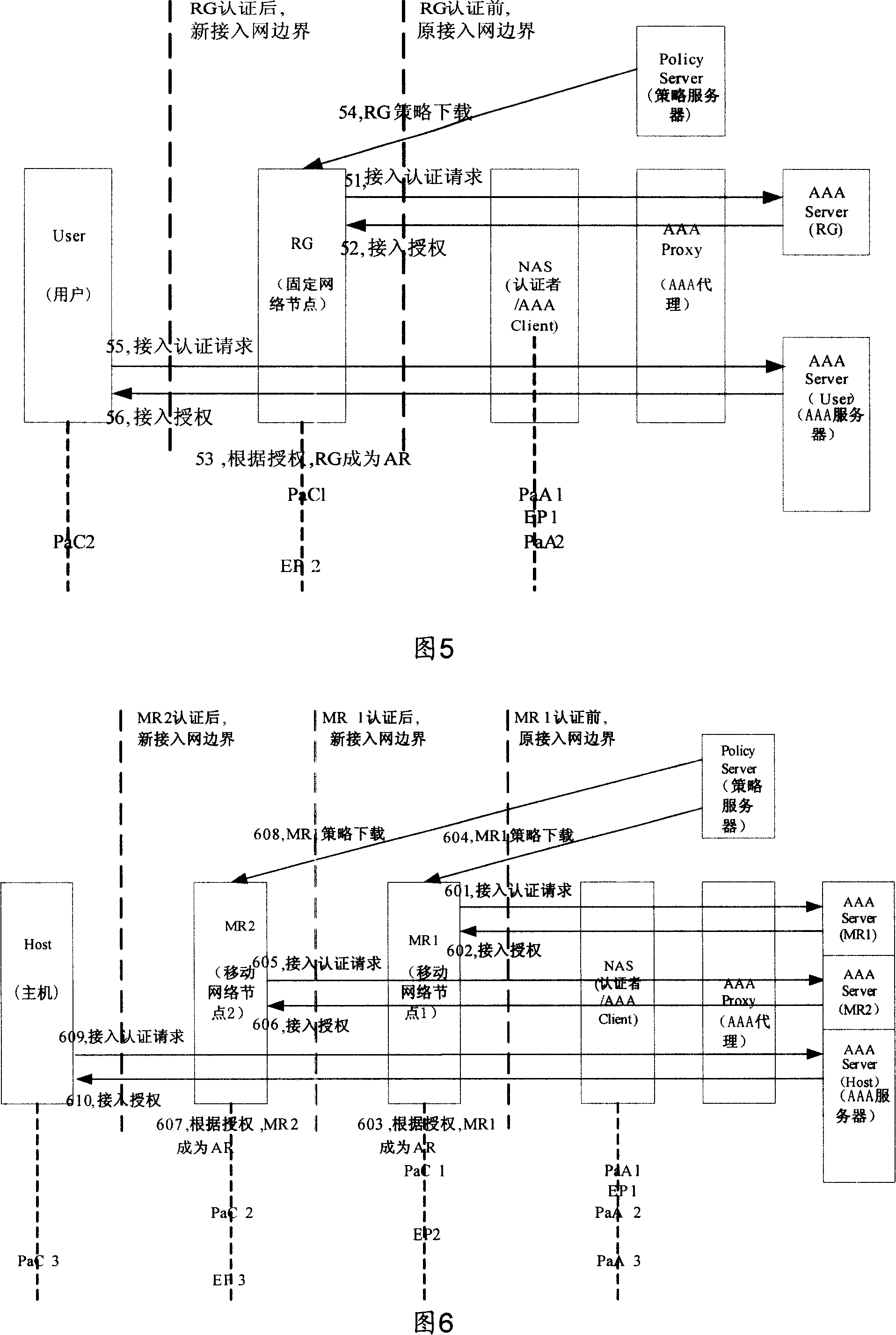
The present invention relates to a method, a device and a system that can realize the access authentication. A network node initiates an access authentication operation with an authentication server, which performs an authentication processing on the access authentication operation initiated by the network node; after the network passes the authentication and is authorized as a trusted node, a user connected to the trusted node initiates an access authentication operation via the trusted node, and the authentication server performs an authentication processing on the access authentication operation initiated by the user. Meanwhile, the trusted node utilizes the received control information released by a policy server to perform various control operations on the user. The present invention enables service providers to pointedly carry out accounting and charging on different users under a network node according to different service circumstances and prevents sham users; and the network node can perform the corresponding management operations on the policy information and an admission control list and can locally monitor the service level agreement nearby.
Owner:HUAWEI TECH CO LTD
Intelligent terminal management method
InactiveCN107071524AImprove communication securityImprove satisfactionSelective content distributionCommunications securityDigest access authentication
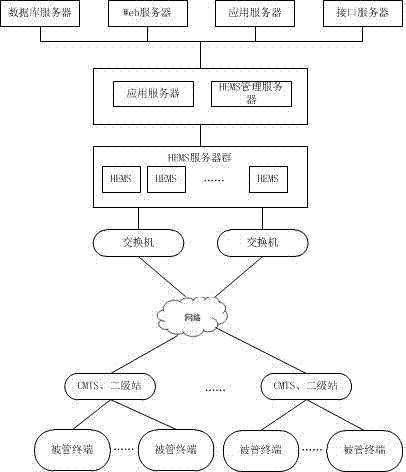
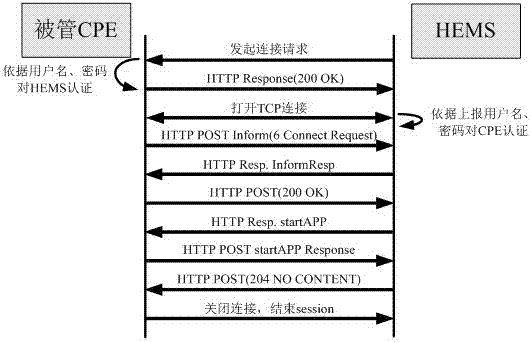
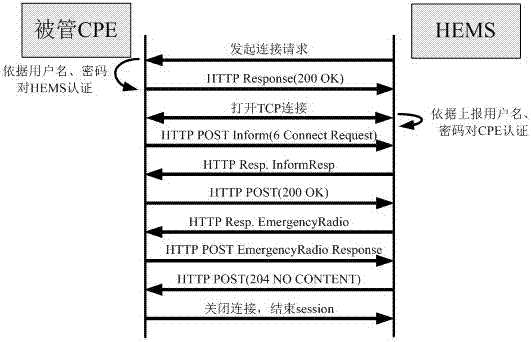
The invention discloses an intelligent terminal management method, which is implemented based on an improved broadcast television hardware architecture. A UDP message receiving client and a UDP message forwarding Server are deployed on an HEMS server, which are used to receive UDP behavior operation data of a cloud media set-top box terminal and report the UDP behavior operation data; a terminal and a front-end system communicate with each other based on a TR069 protocol, and a connection request is implemented by using a bidirectional HTTP digest authentication method; in addition, the intelligent terminal management method further comprises the functions of terminal access, terminal parameter reading, terminal parameter configuration, remote application startup, file reading, fault diagnosis, fault management and signal monitoring, management data reading, user behavior data acquisition and analysis and so on. The intelligent terminal management method provided by the invention improves the communication security between a managed CPE and the front-end system; and a custom UDP data format can reduce the packet loss rate and network overhead, and collection and statistical analysis can be performed on the user behavior data.
Owner:JIANGSU BROADCASTING CABLE INFORMATION NETWORK CORP
Certificateless aggregation signature LTE-R network group authentication key negotiation method
InactiveCN110149214AReduce overheadReduce communication delayKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDigest access authenticationUser equipment
A certificateless aggregation signature LTE-R network group authentication key negotiation method comprises the following main operation steps: A, system establishment and participant registration: anentity participating in authentication completing registration at a key generation center, and obtaining public and private key information; B, initial access authentication: the user equipment beinguniformly accessed to LTE-before departure of a train; when R network is carried out, executing the certificateless signature algorithm to generate respective signatures, sending the signatures to the relay server, and the relay server executing the certificateless aggregation signature algorithm to realize rapid mutual authentication among the user equipment, the relay server and the roadside base station and negotiating to share the key; C, switching authentication: in the running process of the train, the user equipment being always stably connected with the relay server, and the relay server and the roadside base station realizing quick and frequent switching authentication by executing a certificateless signature algorithm; D, terminating the session. The method is high in authentication efficiency, low in signaling overhead and good in security.
Owner:CHINA ACADEMY OF RAILWAY SCI CORP LTD +1
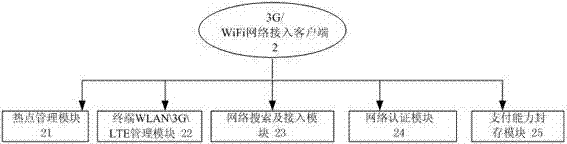
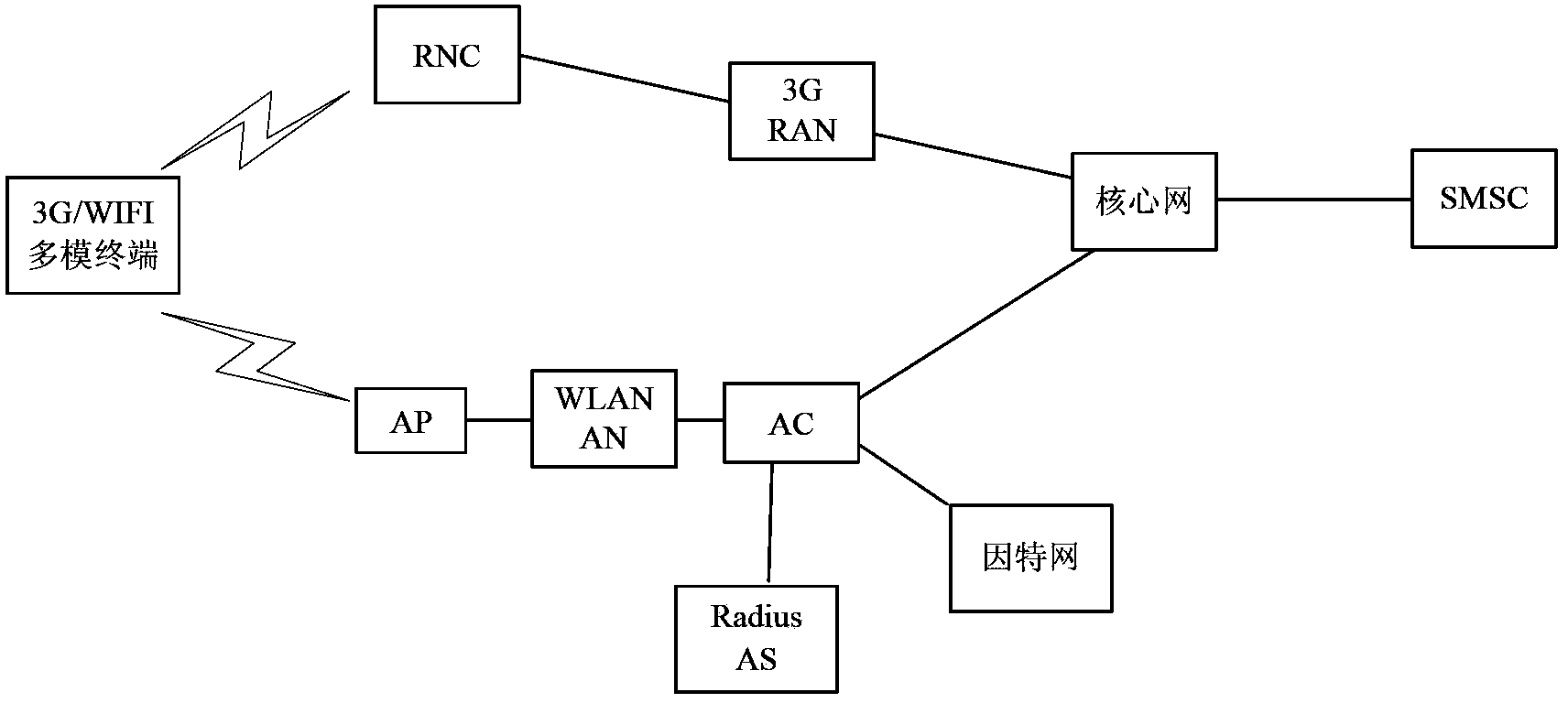
3G/WiFi network access authentication system and achieving method thereof
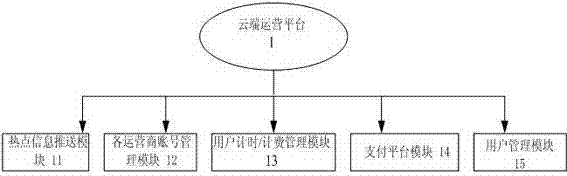
InactiveCN103596159AImprove stabilityImprove adaptabilityAccounting/billing servicesSecurity arrangementUser needsPayment
The invention relates to a 3G / WiFi network access authentication system and an achieving method of the 3G / WiFi network access authentication system. A user searches for available network hot spot information nearby through a hot spot management module, the available network hot spot information nearby is pushed to the user through a hot spot information push module, the user is reminded of an available WiFi network through a terminal WLAN / 3G / LTE management module, and the user starts a WLAN to be automatically connected with the network. Through a network search and access module, the user acquires corresponding operator Internet surfing account passwords from all operator account management modules, and logs in by inputting the passwords. Through a network authentication module, access is achieved through user information authentication. Through a user timekeeping / accounting management module, after user connection succeeds, timekeeping / accounting management is carried out on the Internet surfing behavior of the user, and when the user has no Internet surfing duration, the user is offline. When the user needs to buy the Internet surfing duration, interaction is carried out through a payment capacity sealing module and a payment platform module. A user management module stores and manages user information.
Owner:KESHENG WIRELESS SUZHOU
Method for realizing access authentication, device thereof and mobile terminal
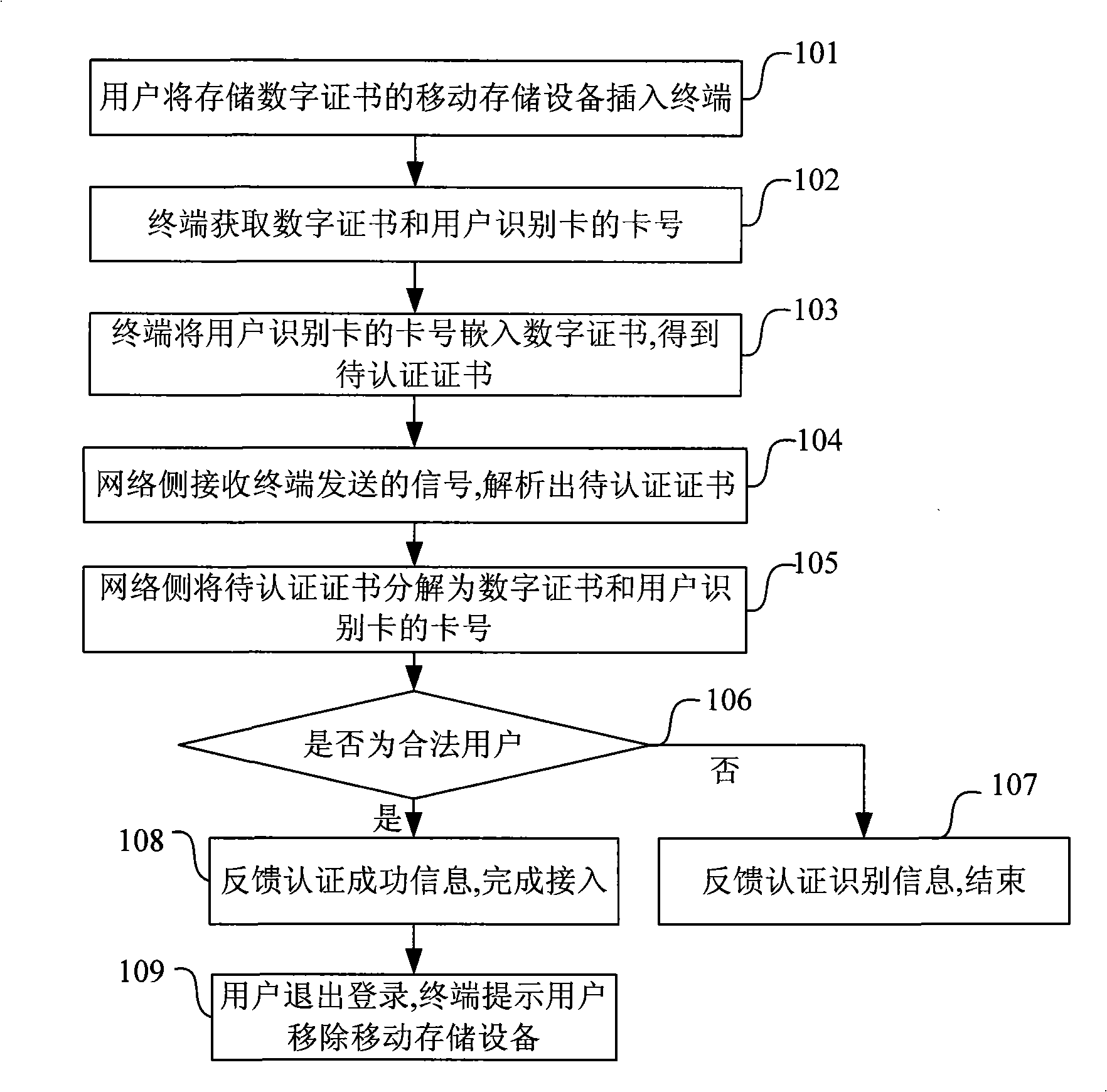
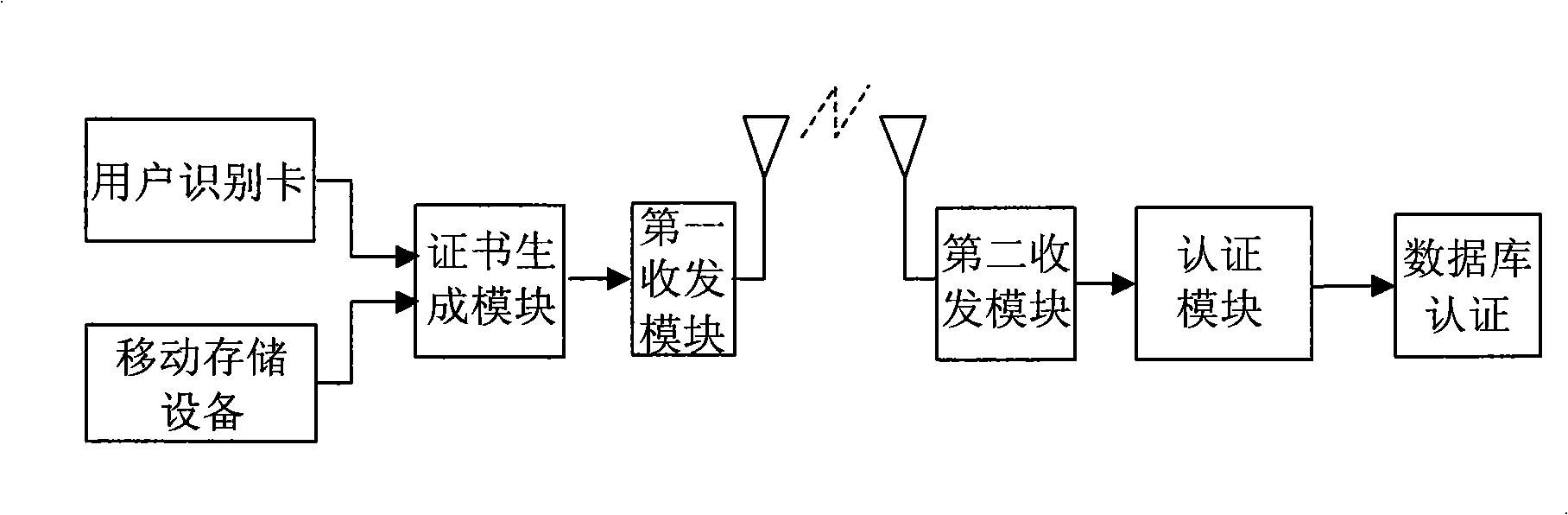
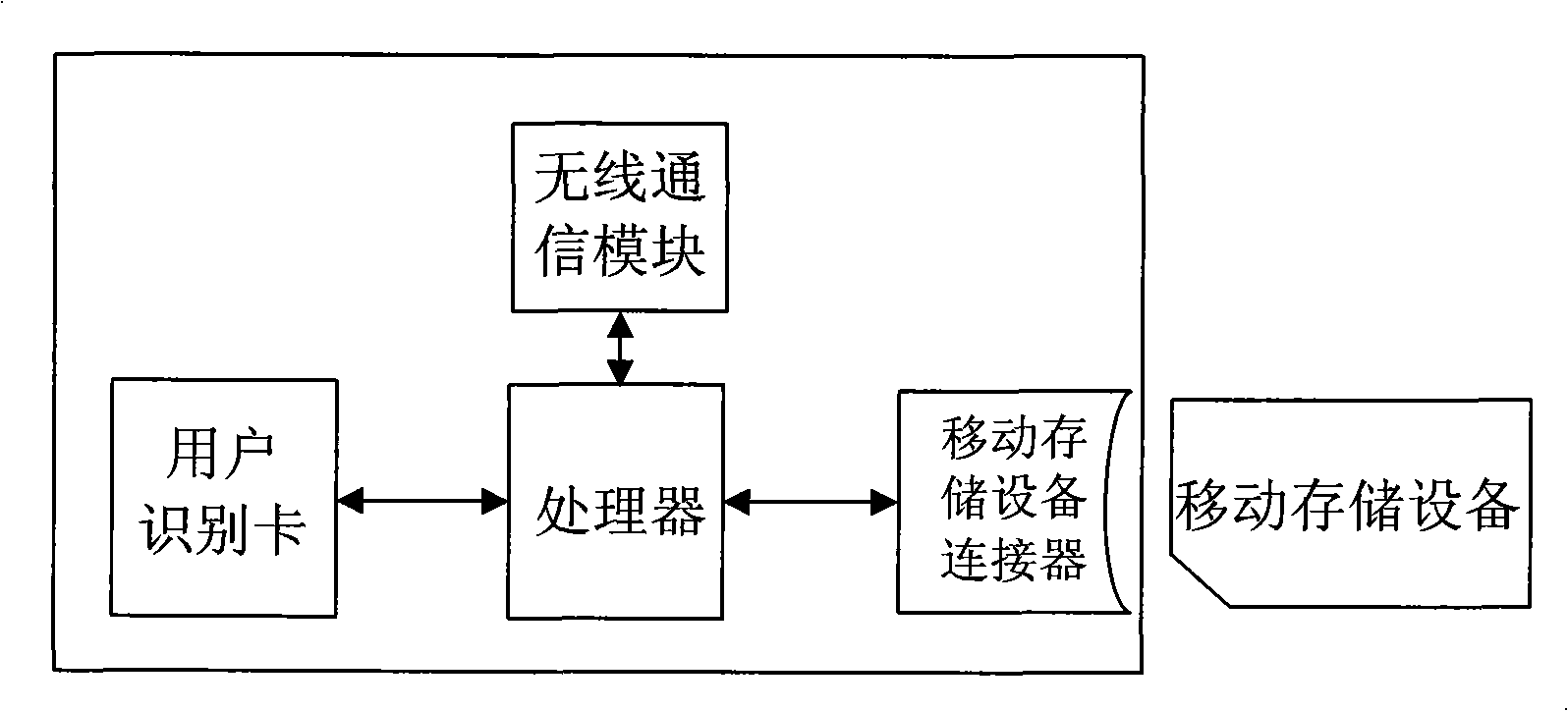
InactiveCN101527909AImprove securityPrevent unauthorized accessNetwork topologiesSecurity arrangementDigest access authenticationPassword
The invention discloses an access authentication method which comprises the steps as follows: a user connects a mobile storage device which stores authentication information to a terminal; the terminal obtains the authentication information from the mobile storage device and sends the obtained authentication information to a network side for authenticating. The invention stores partial or all required authentication information which is accessed with a network or a network server with privacy in the mobile storage device and keeps the authentication information away from the terminal. When the terminal is accessed with the network or the network server with privacy, the authentication only can be finished by the authentication information stored in the mobile storage device, thereby improving the safety for accessing the terminal and avoiding the problem that the embezzler accesses illegally when the terminal is stolen; a network login password is cracked; or a user identification card is cracked or copied.
Owner:ZTE CORP
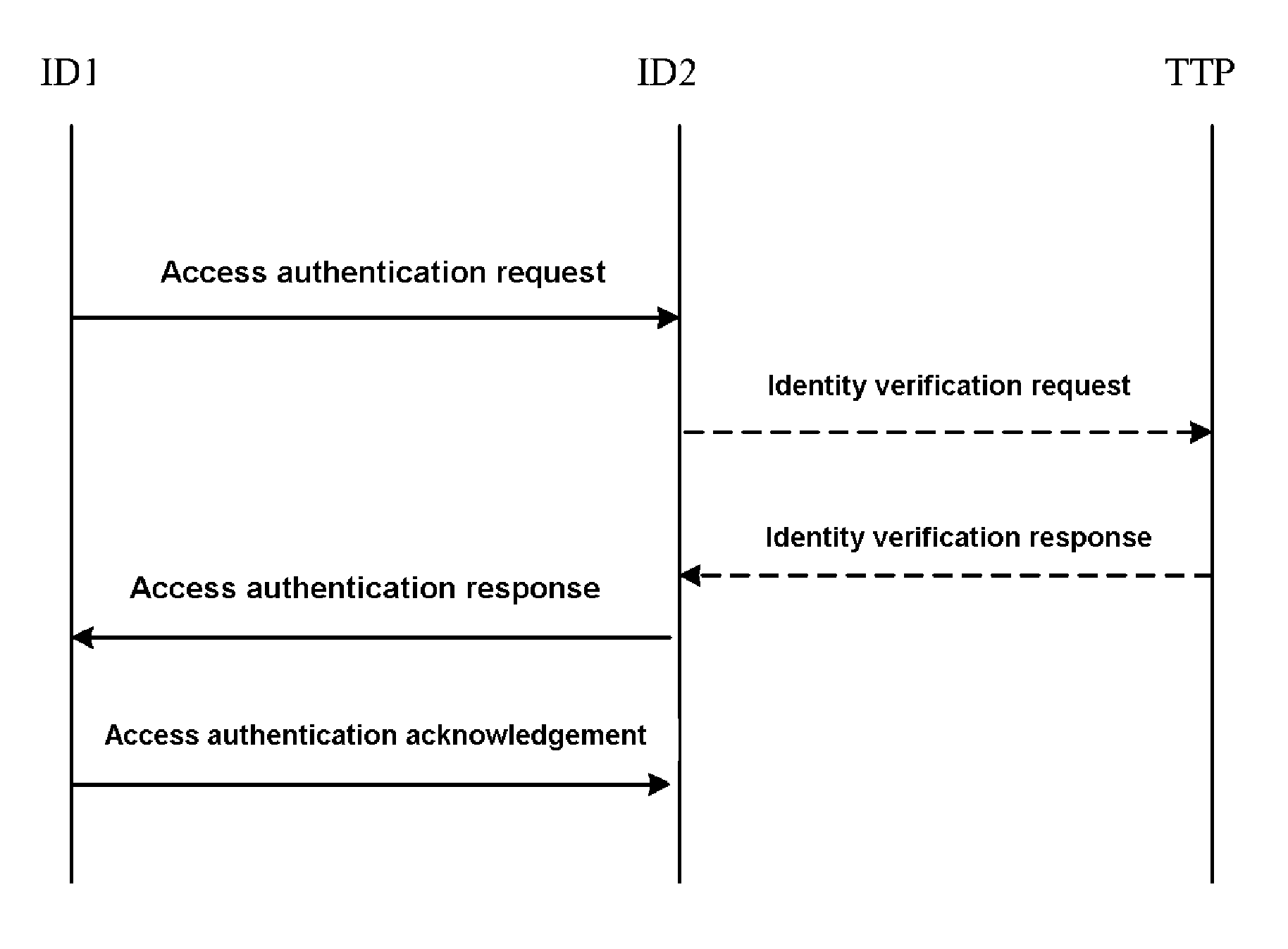
Two-way access authentication method
ActiveUS20100250952A1Reduce maintenance workloadReduce communication overheadDigital data processing detailsUser identity/authority verificationDigest access authenticationMessage integrity
A two-way access authentication method comprises: According to the system parameters pre-established by the third entity, the first entity sends the access authentication request packet to the second entity, then the second entity validates whether the signature of first entity is correct, and if yes, the share master key of second entity is calculated; the second entity generates the access authentication response packet and sends it to the first entity, then the first entity validates whether the signature of access authentication response packet and the message integrity check code are correct; if yes, the share master key of first entity is calculated; the first entity sends the access authentication acknowledge packet to the second entity, then the second entity validates the integrity of the access authentication acknowledge packet, if passing the validation, the share master key of first entity is consistent with that of the second entity, and the access authentication is achieved. For improving the security, after received the access authentication request packet sent by the first entity, the second entity may perform the identity validity validation and generates the access authentication response packet after passing the validation.
Owner:CHINA IWNCOMM
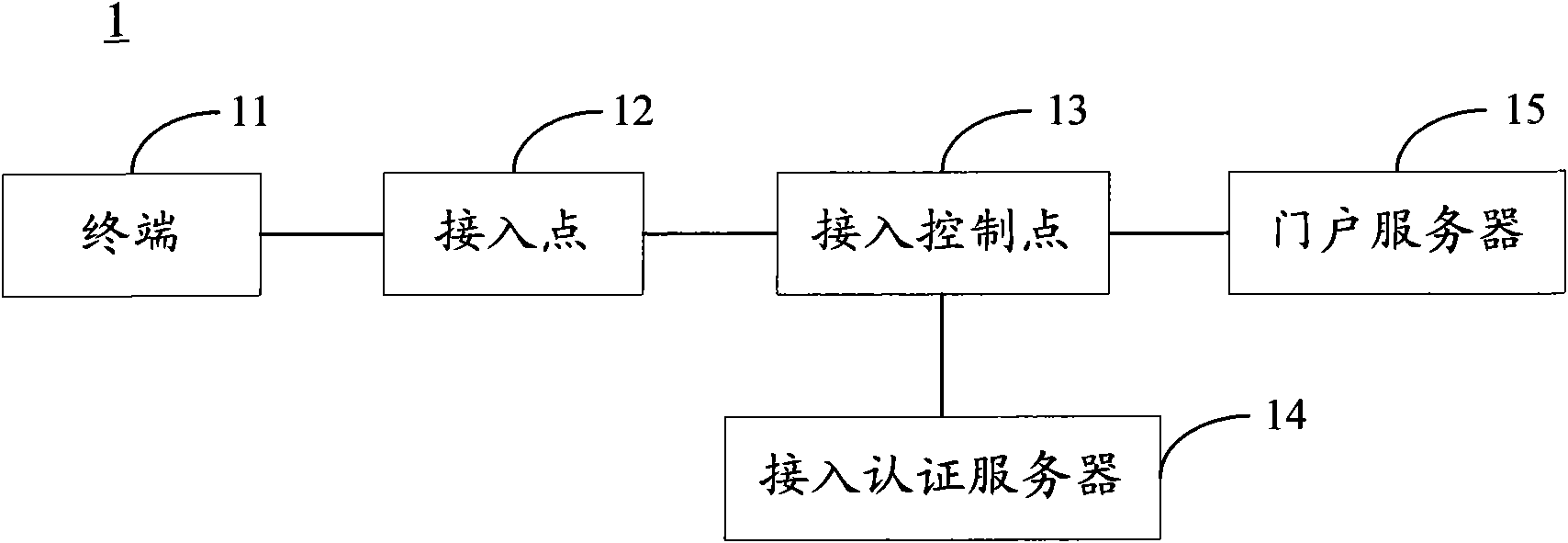
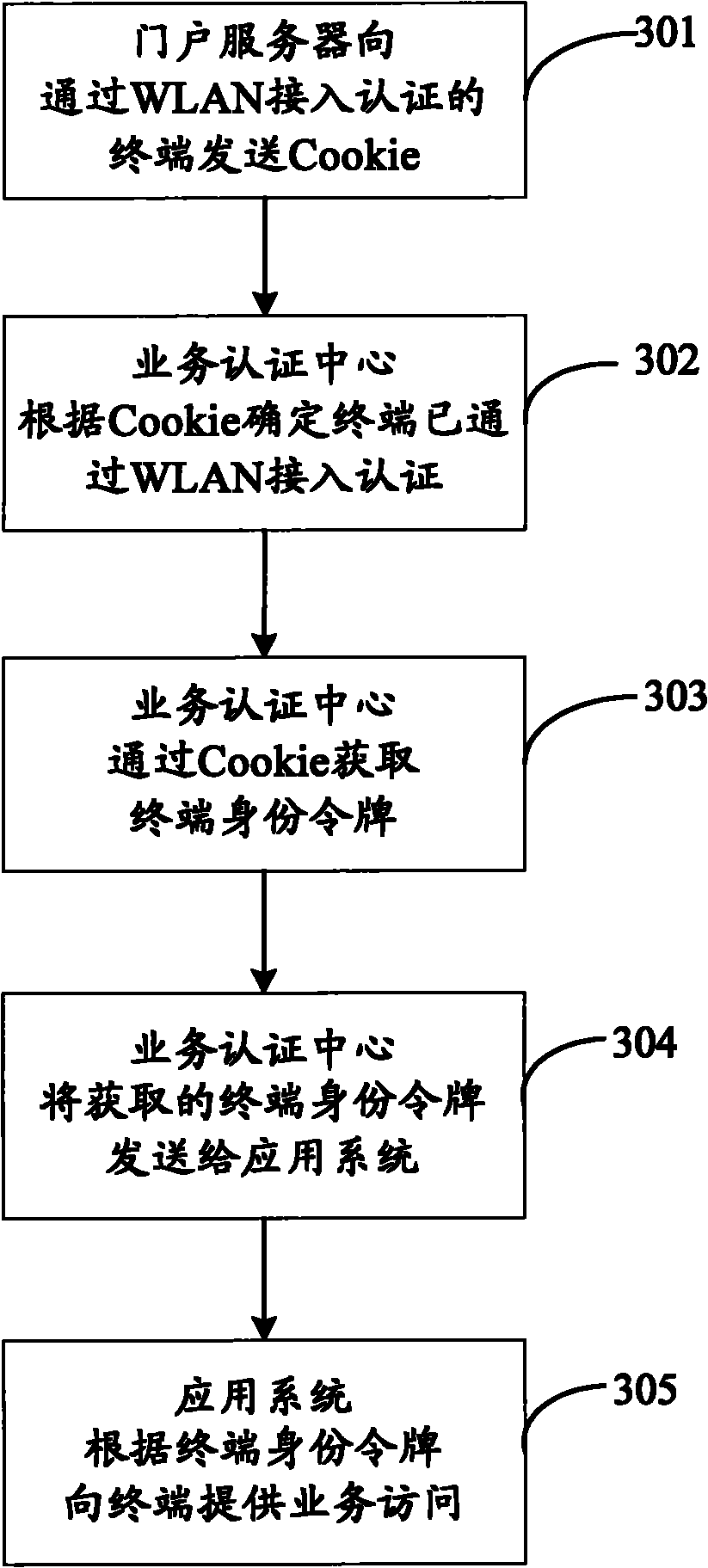
WLAN access authentication based method for accessing services
The application discloses a WLAN access authentication based method for accessing services, comprising the following steps: in the process that a terminal undergoes WLAN access authentication, a WLAN portal server sends first Cookie to the terminal which has passed WLAN access authentication; the terminal requests access to the services of application systems and service authentication centers associated with the application systems determine that the terminal has passed WLAN access authentication according to the first Cookie; the associated service authentication centers obtain the terminal identity token via the first Cookie; the associated service authentication centers send the obtained terminal identity token to the application systems; and the application systems provide access to the services according to the terminal identity token. Through the method, after passing WLAN access authentication, the terminal can access the services provided by a plurality of application systems without service authentication, thus improving the user experience and reducing the overhead of the application systems.
Owner:CHINA MOBILE COMM GRP CO LTD
Connection establishment method and access authentication system for blocking-attacking resistant shared media terminal
InactiveCN101867473AResistance to denial of service attacksSmall amount of calculationKey distribution for secure communicationUser identity/authority verificationDigest access authenticationCiphertext
The invention discloses a method for identifying physical uniqueness of blocking-attacking resistant in-net terminal and a terminal access authentication system, which belongs to a method for a user terminal to access a communication service network and a system realizing the same. The invention is characterized in that the method divides the exchanging process of bi-direction messages for determining the legal identity of the user terminal into the following six steps: a network access terminal broadcasts the turbulence intensity of keys and an effective in-net time window; the in-net user terminal initiates an in-net request at an appointed time window; the network access terminal sends a terminal login token in a ciphertext mode; the in-net user terminal attempts to decode a response message; the in-let user terminal passes back terminal login token identifying information to the network access terminal; and the network access terminal verifies the terminal login token identifying information.
Owner:NANJING UNIV
Method for realizing access authentication and client
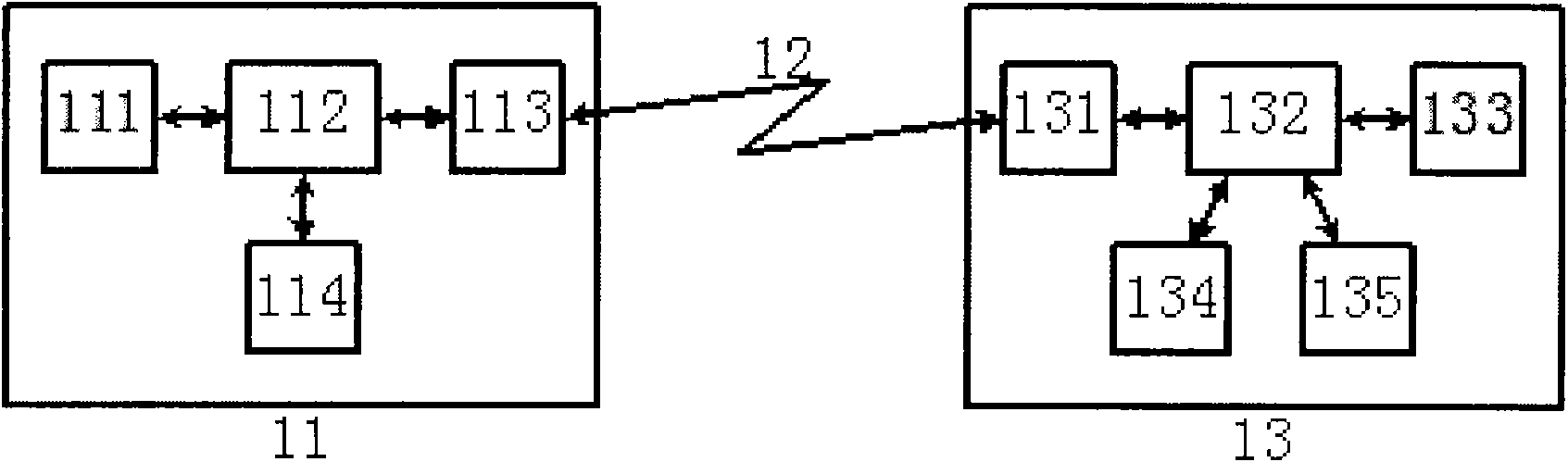
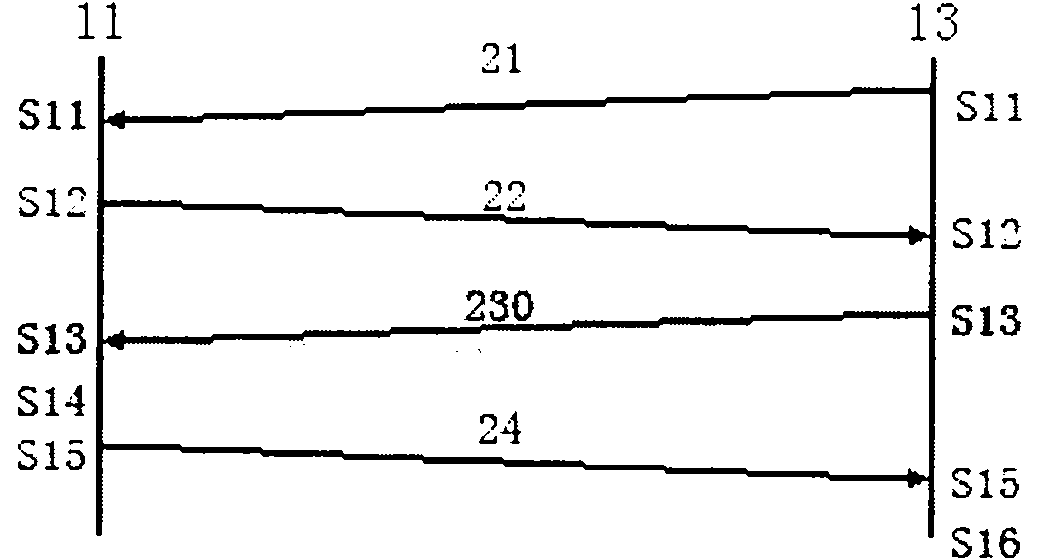
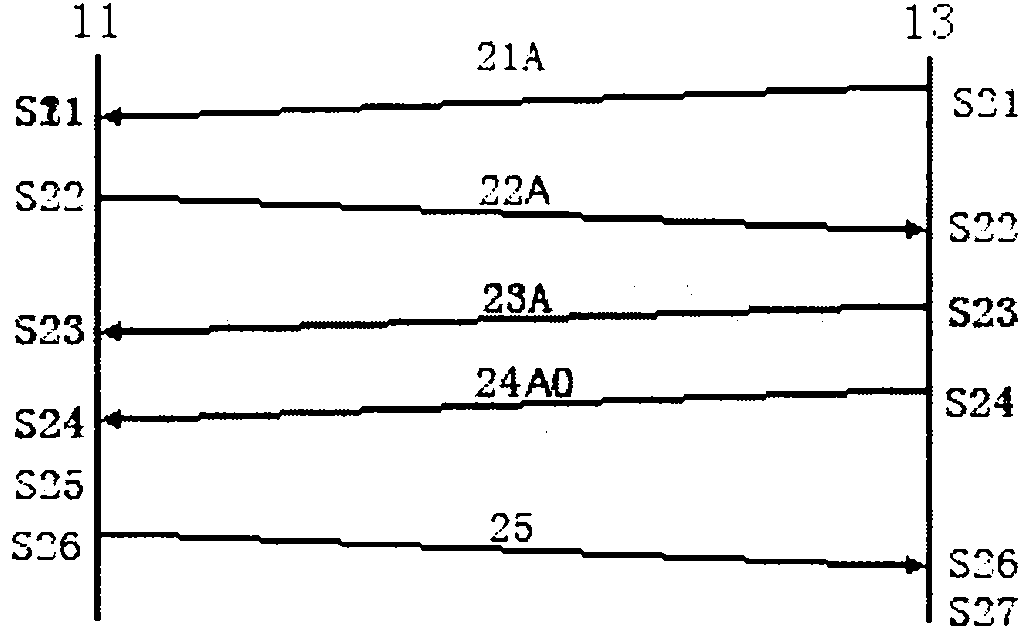
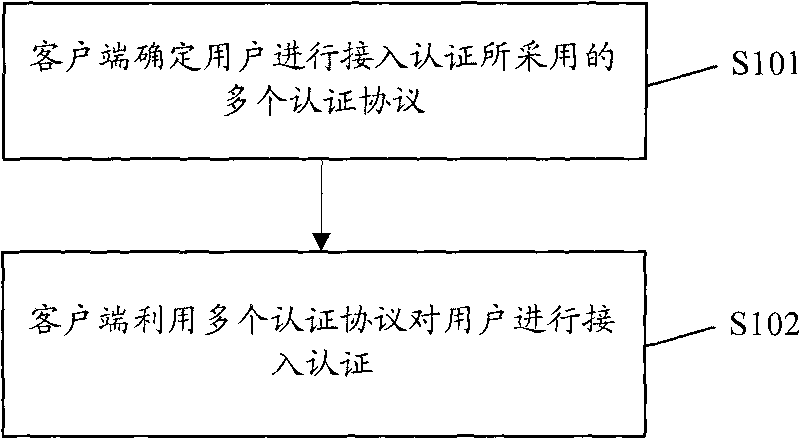
ActiveCN101742497AIncrease flexibilityEnsure safetySecurity arrangementDigest access authenticationClient-side
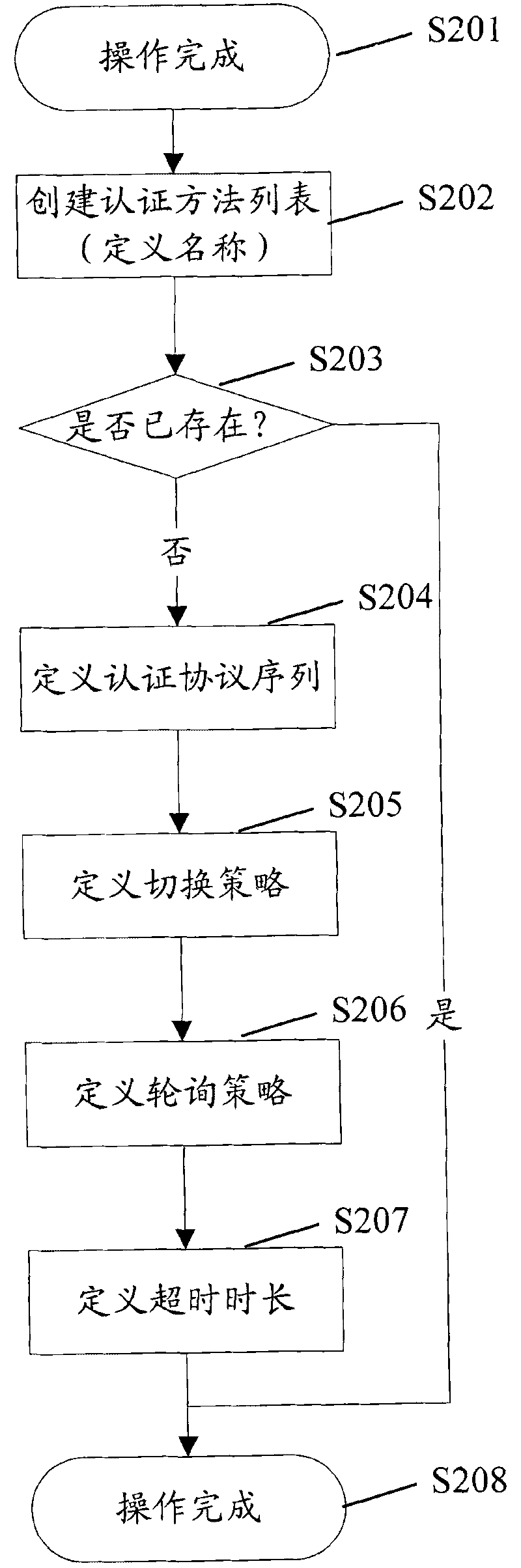
The invention discloses a method for realizing access authentication and a client. The method comprises that: the client determines a plurality of authentication protocols adopted for access authentication of a user; and the client performs access authentication of the user by using the plurality of authentication protocols. The method can enable a user to access by using the plurality of protocols, thereby effectively enhancing the flexibility of access authentication and improving the rate of successful accesses on the premise of ensuring the safety of access authentication.
Owner:ZTE CORP
User authentication method and system
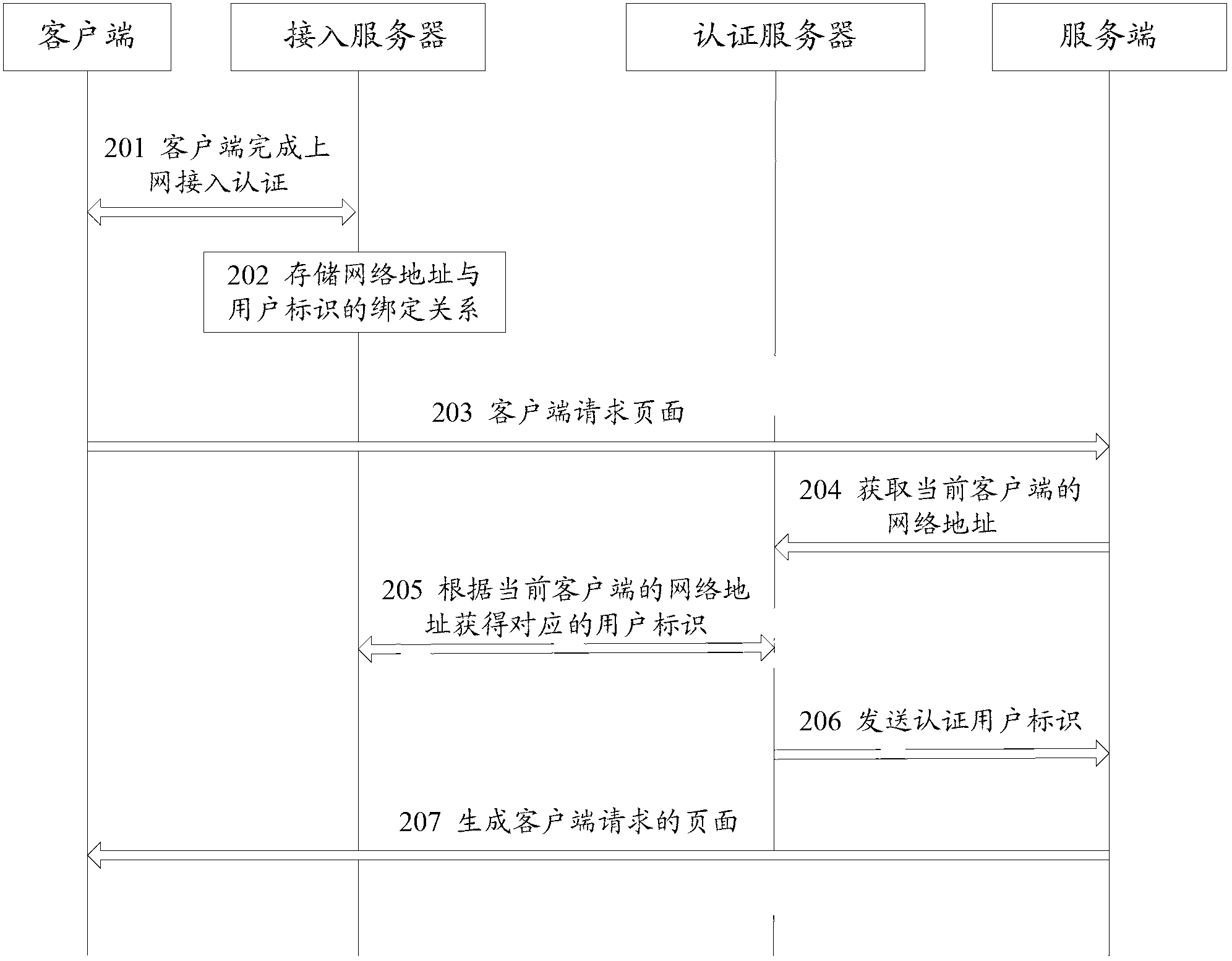
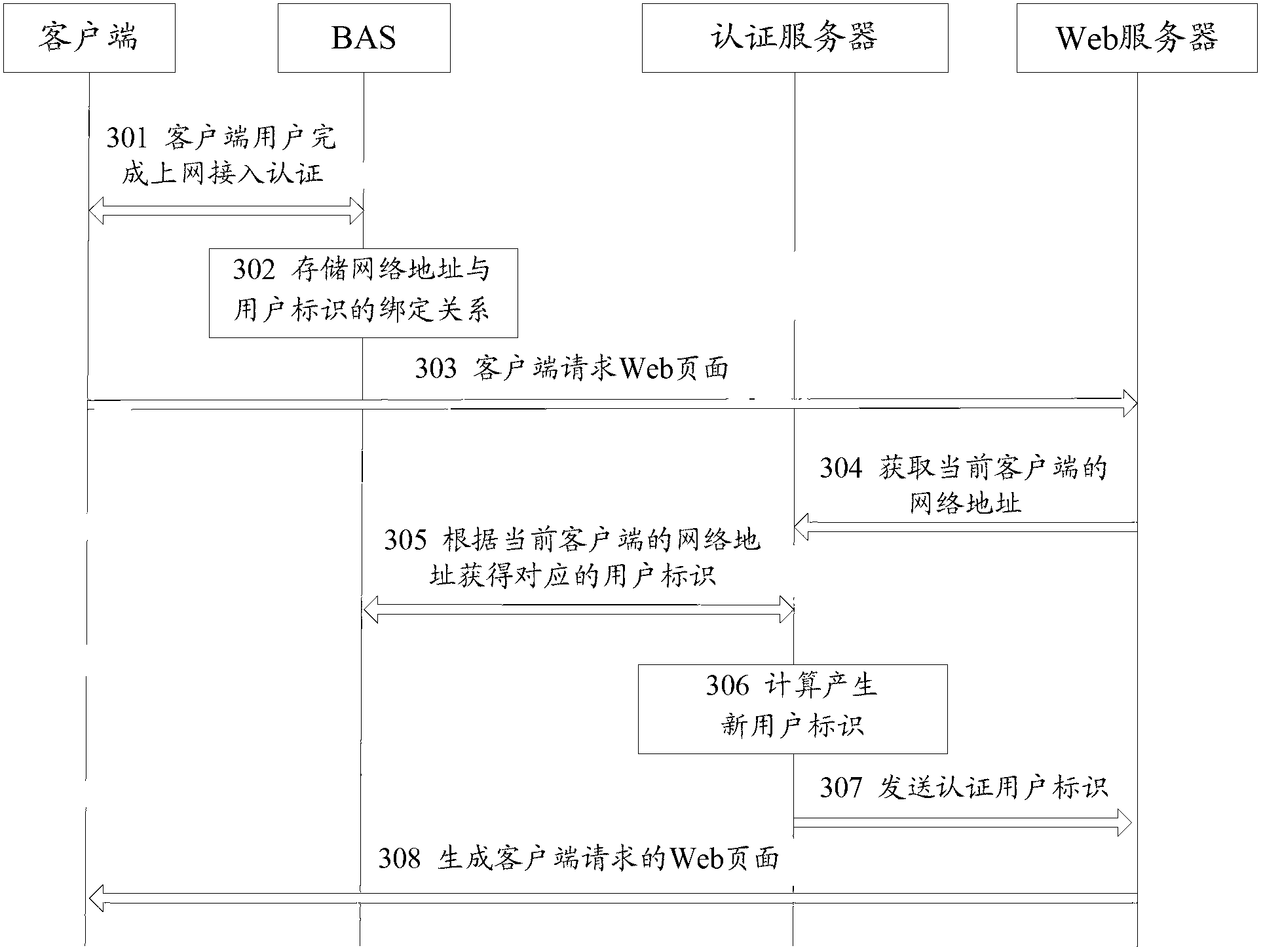
ActiveCN102710621AImprove Internet experienceSimplify functional designTransmissionDigest access authenticationNetwork addressing
The invention discloses a user authentication method. The method comprises the following steps: an access server stores a binding relationship between a network address of a client and a user identification after the client finishes internet access authentication; an authentication server obtains the user identification corresponding to the network address of the client from the access server according to the network address of the client obtained by a service side when the client requests a page; the authentication server transmits an authentication user identification to the service side, and the server side generates the page requested by the client according to the authentication user identification. The invention also simultaneously discloses a user authentication system. By adopting the user authentication method and the user authentication system, the security of internet business can be improved when fussy logging of the user and access authentication are reduced.
Owner:ZTE CORP
VoWiFi business achieving method, system and AAA server
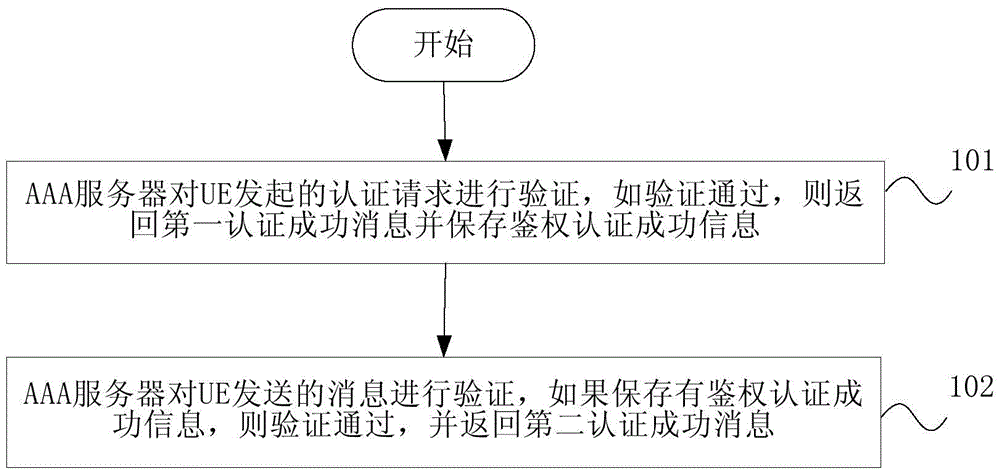
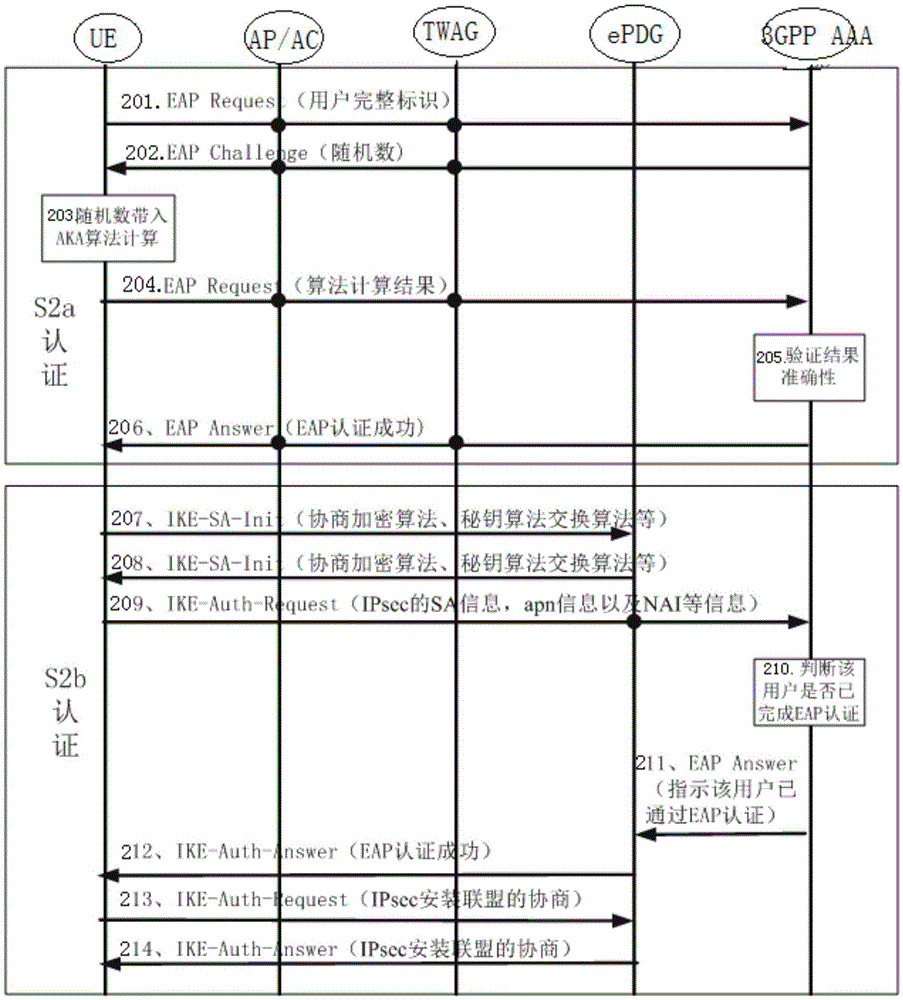
ActiveCN106686589ASolve wasteReduce Authentication LatencyTransmissionSecurity arrangementData streamDigest access authentication
The invention discloses a VoWiFi business achieving method, system and an AAA server. The method comprises the steps that the EAP-AKA authentication requests initiated by UE are verified by the AAA server, if the verification is passed, a first authentication success information is returned to the UE and the EAP-AKA authorized authentication success information of the UE is saved; the IKE-Auther-Request information initiated by the UE is verified by the AAA server, if the EAP-AKA authorized authentication success information of the UE is saved in the AAA server, the verification is passed. The VoWiFi business achieving method, system and the AAA server can avoid the problem of a second time billing of the WiFi data stream and the VoWiFi voice data stream and the WiFi business stream passing through the P-GW device twice, through the saving of the EAP-AKA authorized authentication success information of a user on 3GPP-AAA at the time of crediting the WiFi access authentication, a second time EAP-AKA authentication is no longer needed when the S2b is being authenticated, and the time delay and the system computation amount at the authentication of the user are effectively reduced.
Owner:CHINA TELECOM CORP LTD
A method and system for network access authentication
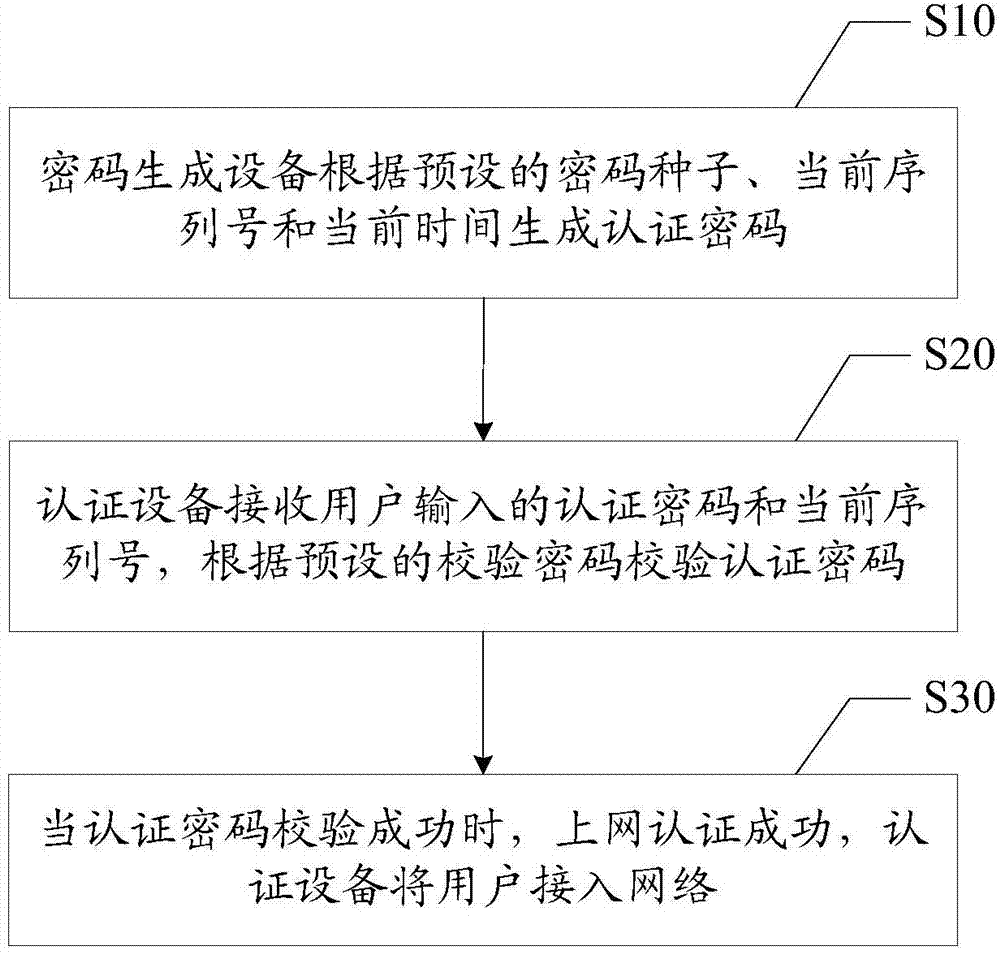
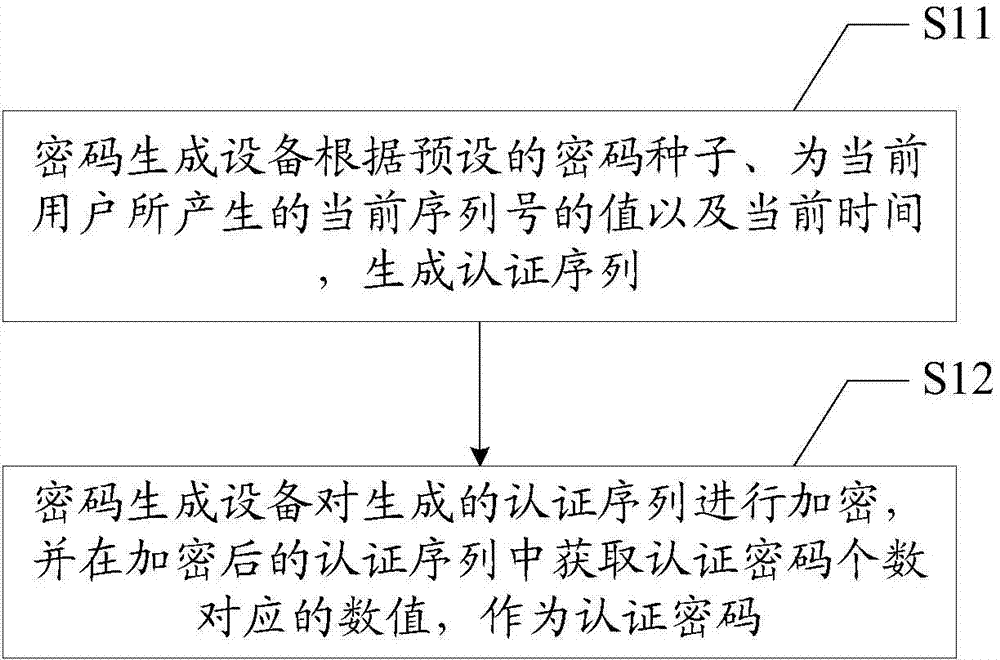
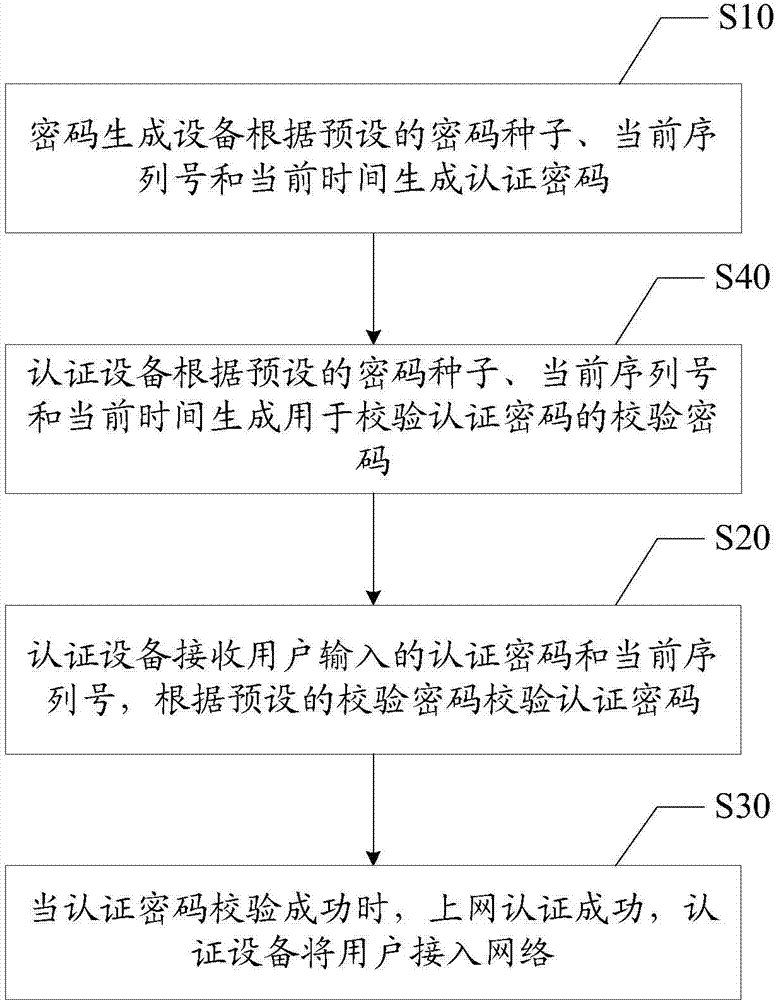
The invention discloses a method for network access authentication. The method for network access authentication comprises: a password generation device generates an authentication password according to a preset password seed, a current serial number and the current time; an authentication device receives the authentication password input by a user and checks the authentication password according to a preset check password; and if the authentication password is checked successfully, the network access authentication is successful, and the authentication device enables the user to access a network. The invention also discloses a system for network access authentication. The authentication password is generated at the same time with the current serial number, that is, only a queuing user can obtain the authentication password, thus network freeloading behaviors can be avoided; and moreover, there is no need to execute authentication in a short message mode, no charge is caused, and thus the cost of the authentication device is reduced.
Owner:SANGFOR TECH INC
Two-way access authentication method
ActiveUS8412943B2Validity of identities are hard to be verified can be avoidedReduce maintenance workloadDigital data processing detailsUser identity/authority verificationDigest access authenticationMessage integrity
A two-way access authentication method comprises: According to the system parameters pre-established by the third entity, the first entity sends the access authentication request packet to the second entity, then the second entity validates whether the signature of first entity is correct, and if yes, the share master key of second entity is calculated; the second entity generates the access authentication response packet and sends it to the first entity, then the first entity validates whether the signature of access authentication response packet and the message integrity check code are correct; if yes, the share master key of first entity is calculated; the first entity sends the access authentication acknowledge packet to the second entity, then the second entity validates the integrity of the access authentication acknowledge packet, if passing the validation, the share master key of first entity is consistent with that of the second entity, and the access authentication is achieved. For improving the security, after received the access authentication request packet sent by the first entity, the second entity may perform the identity validity validation and generates the access authentication response packet after passing the validation.
Owner:CHINA IWNCOMM
Method of one-way access authentication
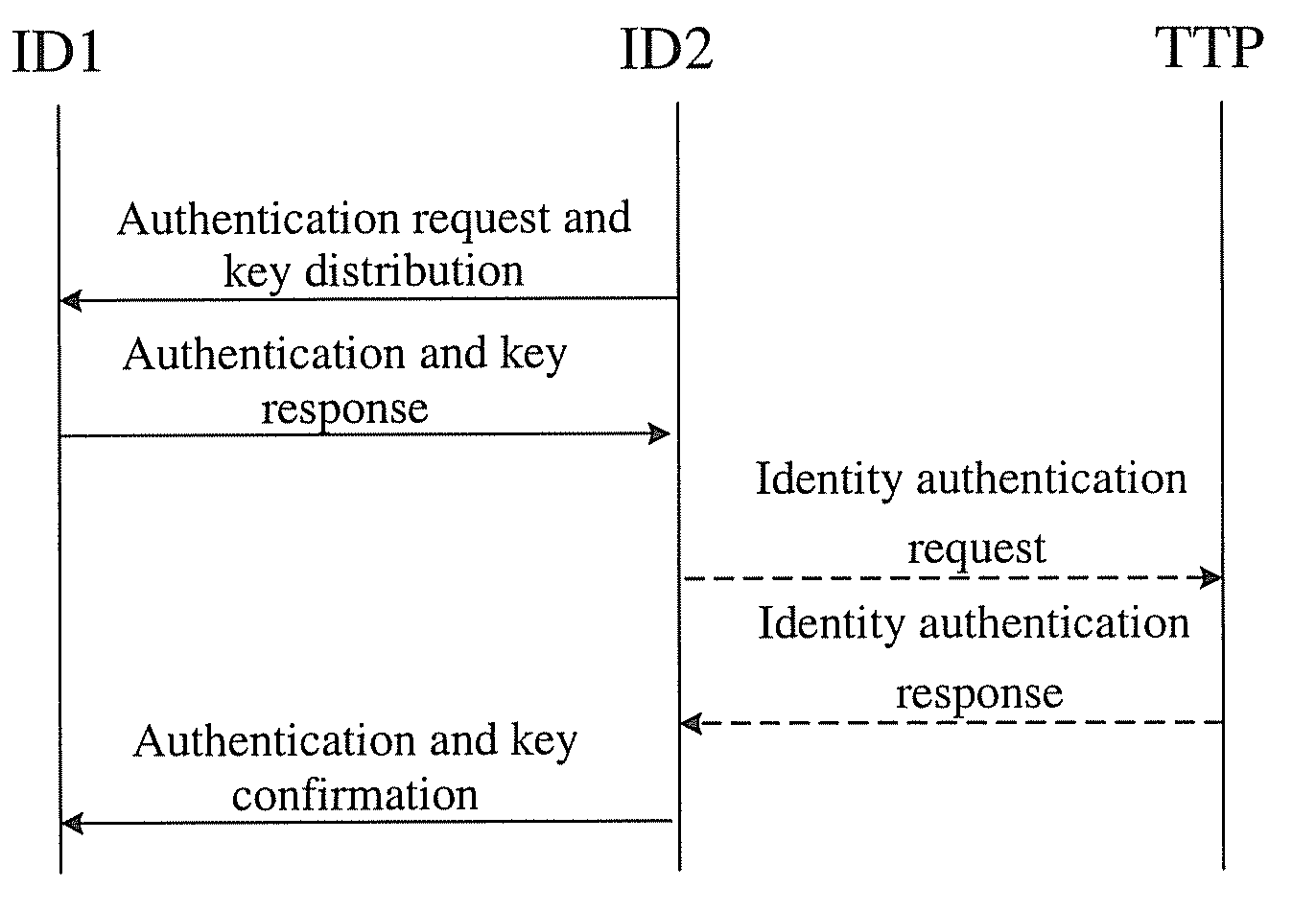
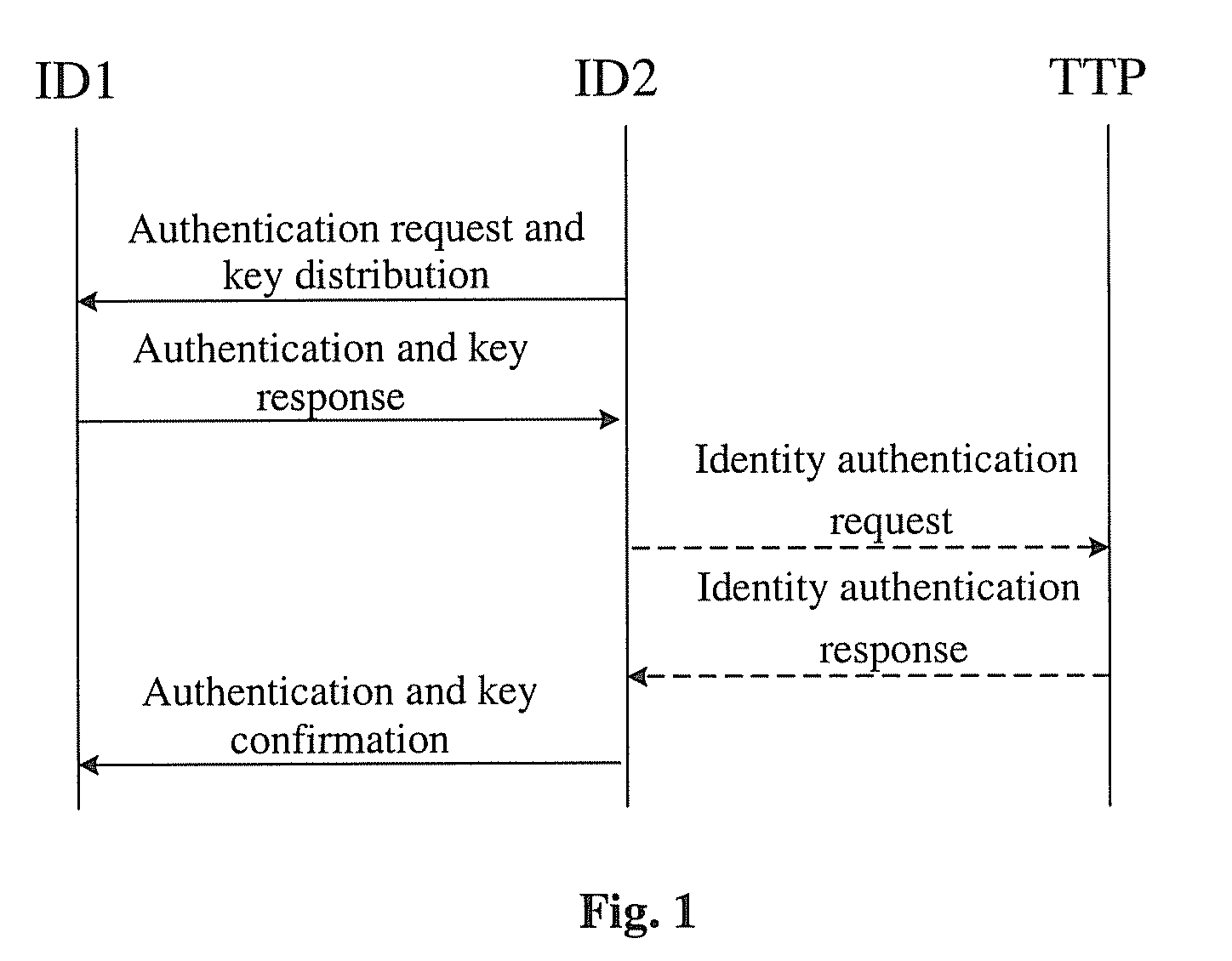
InactiveUS20100268954A1Ensure reliabilityLow maintenanceUser identity/authority verificationDigital data authenticationDigest access authenticationMaster key
A method of one-way access authentication is disclosed. The method includes the following steps. According to system parameters set up by a third entity, a second entity sends an authentication request and key distribution grouping message to a first entity. The first entity verifies the validity of the message sent from the second entity, and if it is valid, the first entity generates authentication and key response grouping message and sends it to the second entity, which verifies the validity of the message sent from the first entity, and if it is valid, the second entity generates the authentication and key confirmation grouping message and sends the message to the first entity. The first entity verifies the validity of the authentication and key conformation grouping message, and if it is valid, the authentication succeeds and the key is regarded as the master key of agreement.
Owner:CHINA IWNCOMM
A method and apparatus for access authentication
ActiveCN109067788AImprove experienceTransmissionSecurity arrangementDigest access authenticationComputer science
The invention provides a method and a device for access authentication, when the first interface of the BRAS device does not look up the user entries corresponding to the terminals, sending an authentication request message carrying terminal information of the terminal to the AAA server,when the AAA server determines that the terminal is an authenticated terminal and a roaming terminal, a second interface which has been accessed to the roaming terminal is notified of deleting a user entry corresponding to the terminal, and when the deletion is confirmed to be completed, an authentication passing message is sent to the first interface so that the first interface allows the terminal to access, and a user entry corresponding to the terminal is recorded on the first interface. Therefore, the invention records the terminal information of the authenticated terminal through the AAA server, so that when the terminal roams to the new position, the terminal information can be sent to the AAA server to confirm the authentication identity of the terminal, thereby allowing the terminal to access the network at the new position, and avoiding the user terminal to perform access authentication again after roaming.
Owner:NEW H3C TECH CO LTD
A method and system for carrying out access authentication based on WEB
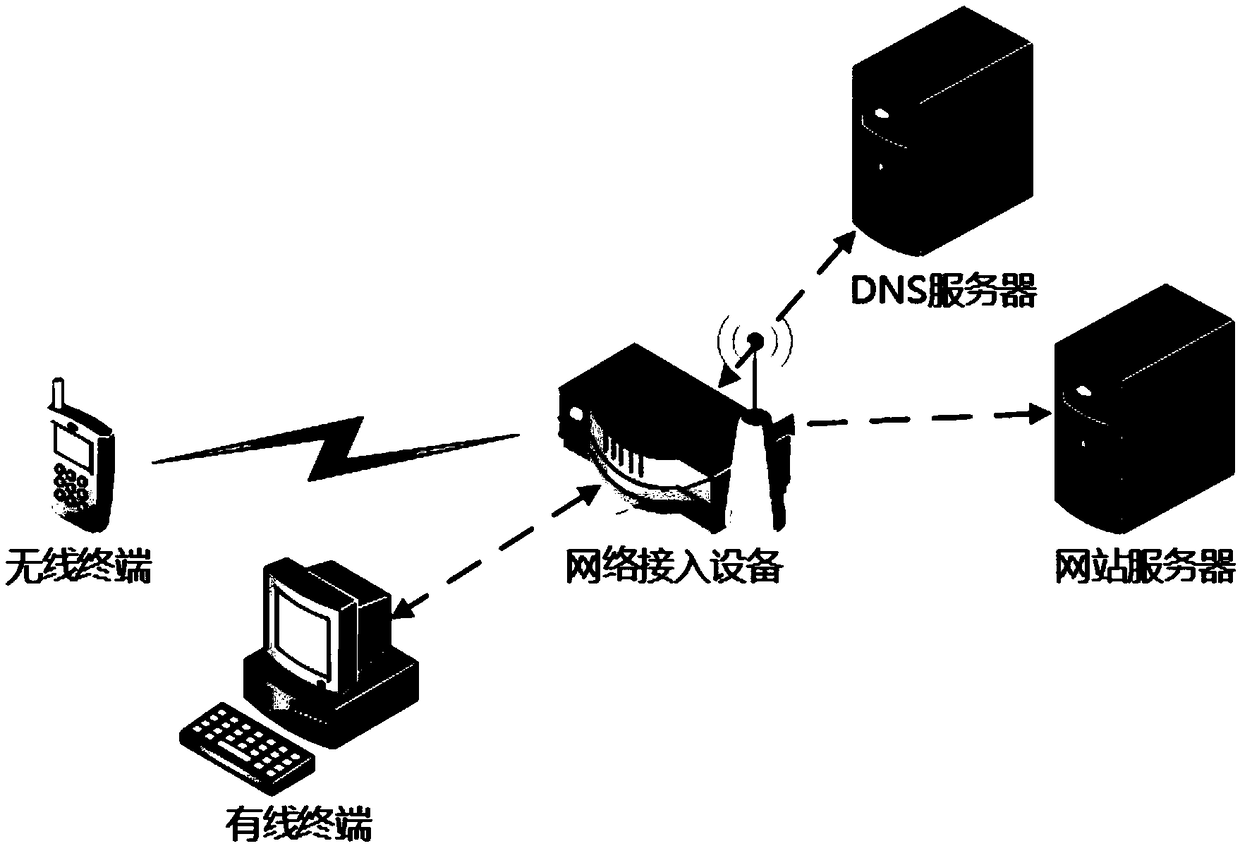
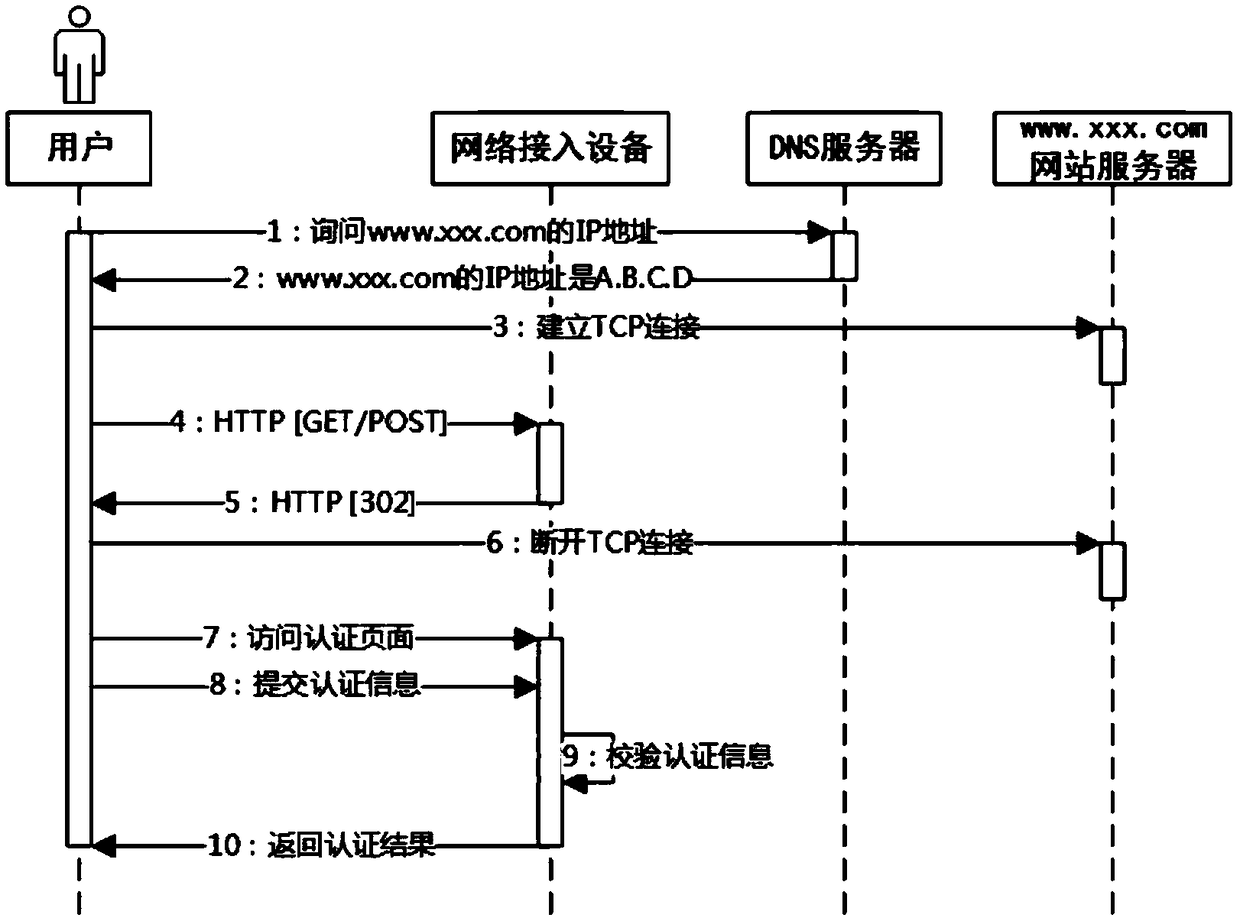
InactiveCN109274657AImprove versatilityEasy to useTransmissionDomain nameDigest access authentication
The invention provides a method for carrying out access authentication based on WEB, which comprises the following steps: S1, a user inquires the IP address of a domain name from a DNS server; S2, theDNS server answers, informs the user that the IP address of the domain name is A.B.C.D; S3, a user establishes a TCP connection with a website server with an IP address of A.B.C.D; S4, the user sendsHTTP GET / POST request to the web server with IP address A.B.C.D, but the request is intercepted by the network access device; S5, the network access device masquerades as the website server with theIP address A.B.C.D to reply to the user, and returns the HTTP 302 response message to the user. The invention also provides a system for accessing authentication based on WEB. The invention has the beneficial effect that an access authentication scheme which is supported by wireless wires and does not require additional installation of clients is provided.
Owner:SHENZHEN JIXIANG TENGDA TECH
Method and device for achieving access authentication of wireless local area network
ActiveCN103297966AImprove experienceFacilitate cognitionSecurity arrangementAccess networkDigest access authentication
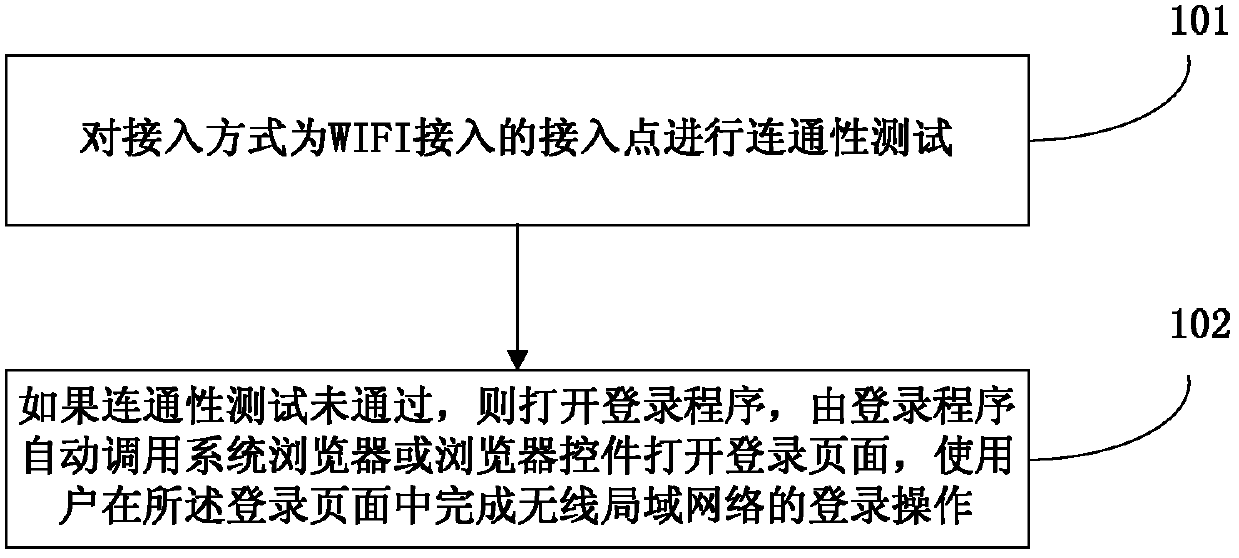
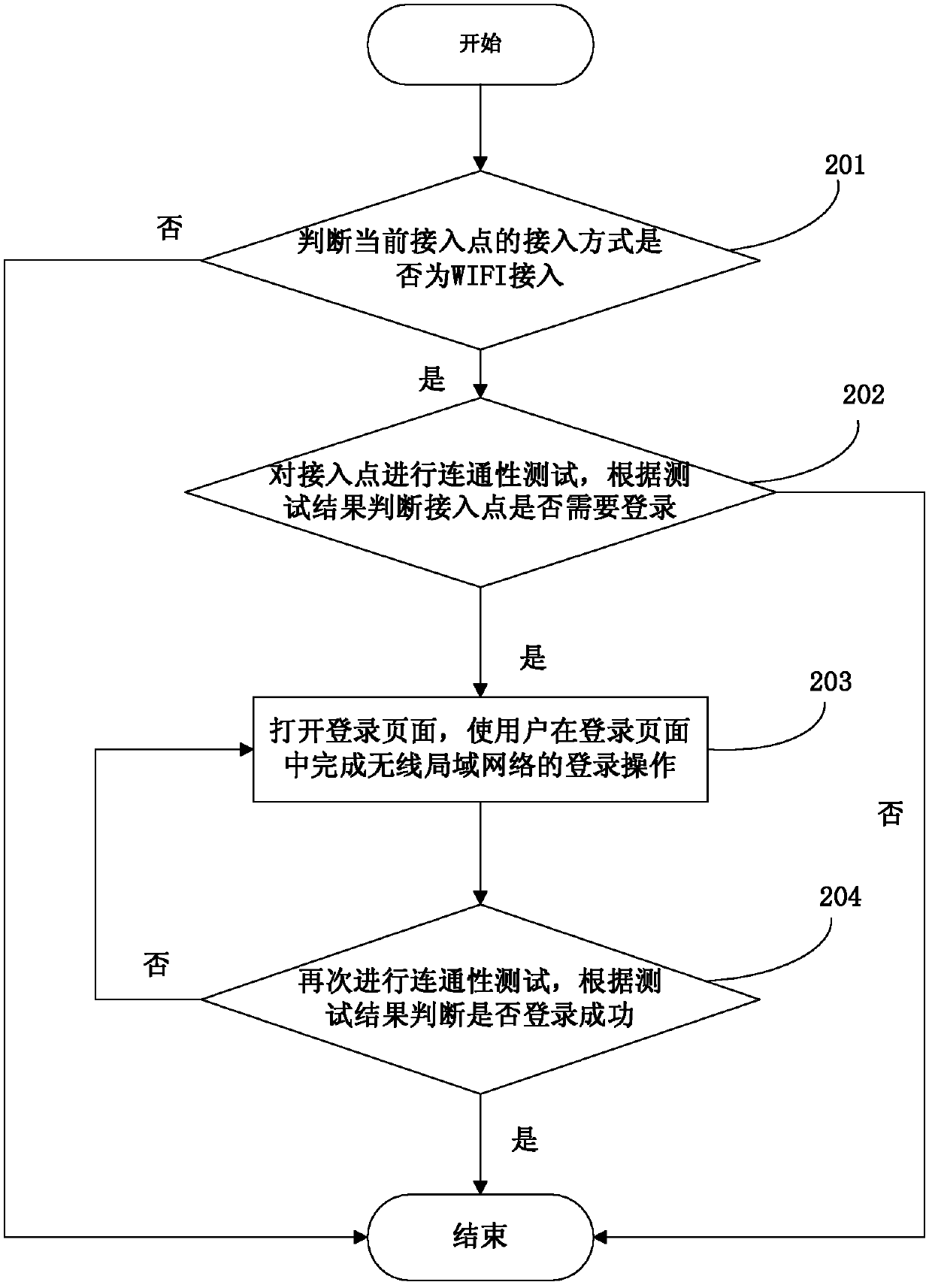
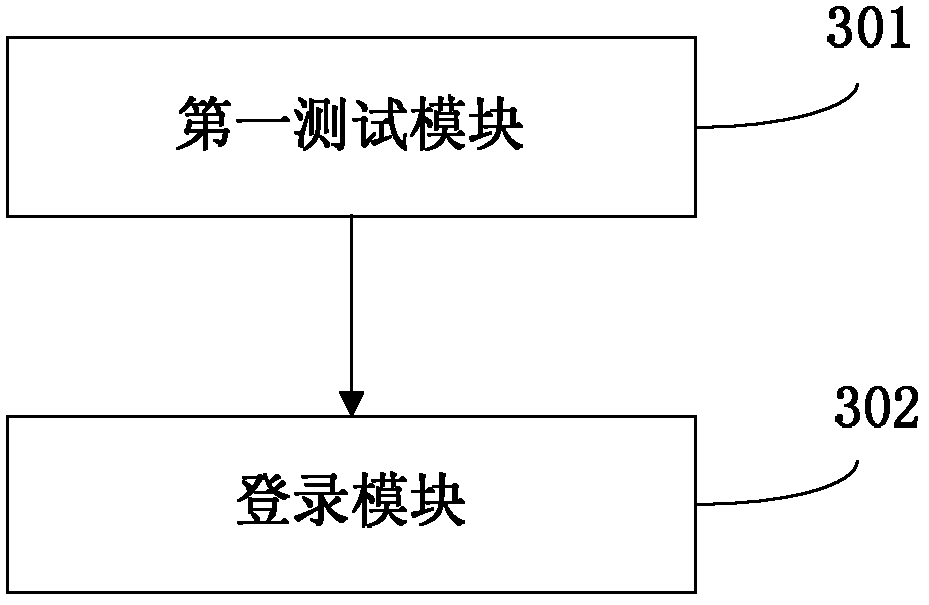
The invention discloses a method and device for achieving access authentication of a wireless local area network, and belongs to the field of wireless communication. The method comprises the steps of carrying out a connectivity test on an access point with an access mode of wireless fidelity access, opening a login program if the connectivity test fails, and automatically calling a system browser or a browser control through the login program to open a login page to enable a user to achieve the login operation of the wireless local area network in the login page. The device comprises a first testing module and a login module. According to the method and device for achieving the access authentication of the wireless local area network, the system browser or the browser control is automatically called through the login program to open the login page, the user is made to achieve the login operation of the wireless local area network in the login page, the fact that an uniformed mode is used for carrying out authentication on the WIFI access is achieved, the user can also be made to achieve a login process in an original login page, the cognition of the user on an access network is facilitated, and the experience of the user is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
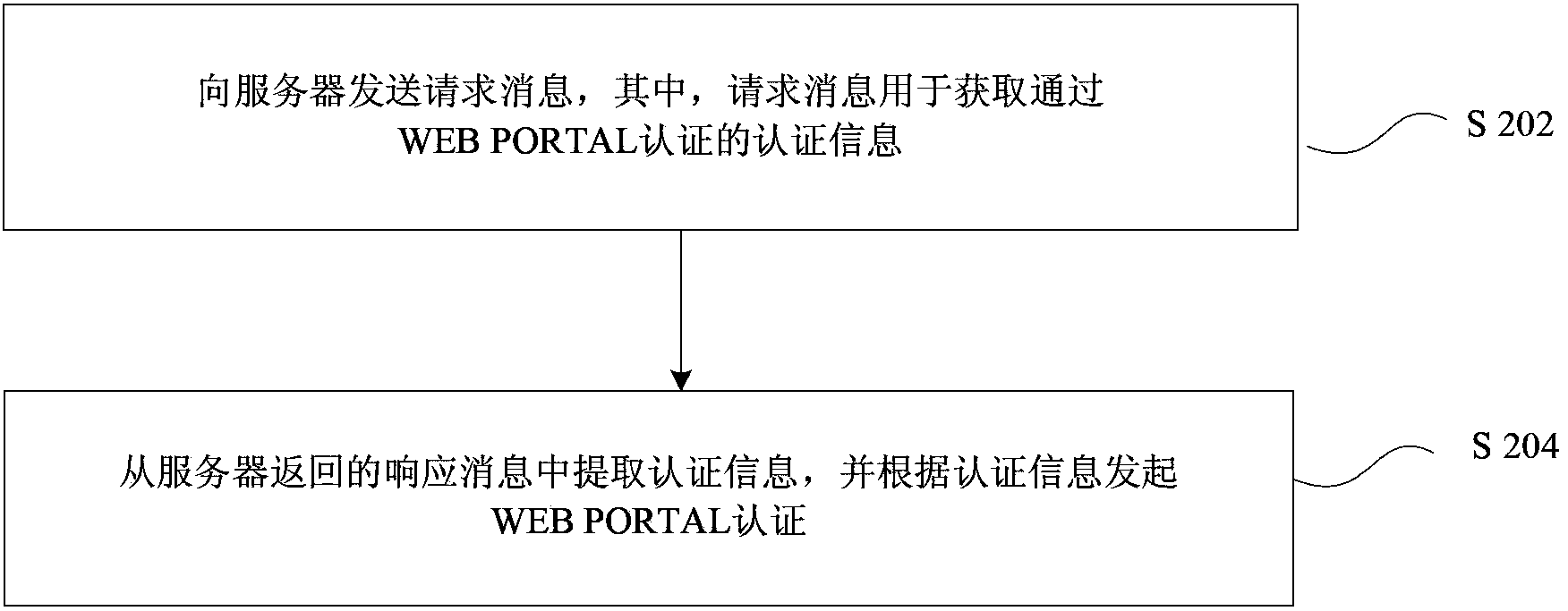
Method and device for access authentication of wireless local area network
InactiveCN104113837AEasy to operateShorten the timeDigital data authenticationTransmissionDigest access authenticationComputer terminal
Disclosed are an access authentication method and device for a wireless local area network. The method mentioned above comprises: sending a request message to a server, the request message being used for obtaining authentication information which passes WEB PORTAL authentication; and extracting the authentication information from the response message returned by the server, and initiating WEB PORTAL authentication according to the authentication information. The technical solution provided in the present invention simplifies the operation flow for a mobile terminal to access an operator wireless local area network, and saves the time for the mobile terminal to access the operator wireless local area network.
Owner:ZTE CORP
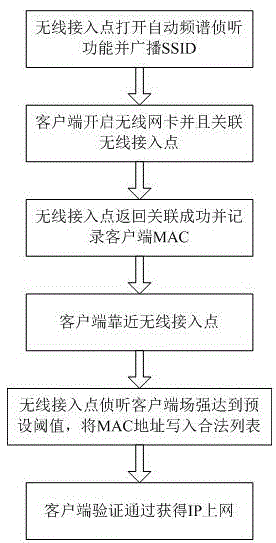
Method for carrying out access authentication through monitoring client spectrum field intensity
InactiveCN105592462ALow requirements for authorized accessImprove access experienceSecurity arrangementFrequency spectrumCable Internet access
The present invention discloses a method for carrying out access authentication through monitoring client spectrum field intensity. The method comprises the following steps that: firstly, a client opens WLAN wireless access, searches the SSID of a wireless access point broadcast and initiates an association request, a wireless access point returns successful association information and records the MAC address of the client; and then the client approaches the wireless access point, the wireless access point automatically monitors the field intensity in a specified spectrum emitted by the client, when the spectrum field intensity reaches or exceeds a preset threshold, the wireless access point writes the MAC address of the client into a legitimate MAC address list, the authentication of the client is passed, and the normal Internet access is available. According to the method, the requirement of client authorized access is low, and the simple authorized Internet access of the client can be realized without the special function of the client.
Owner:GUANGDONG SHUNDE ZHONGKA CLOUD NETWORK TECH CO LTD
Light access authentication method and system
InactiveUS20100313012A1Achieve securityShorten the lengthUser identity/authority verificationDigital data protectionThird partyPlaintext
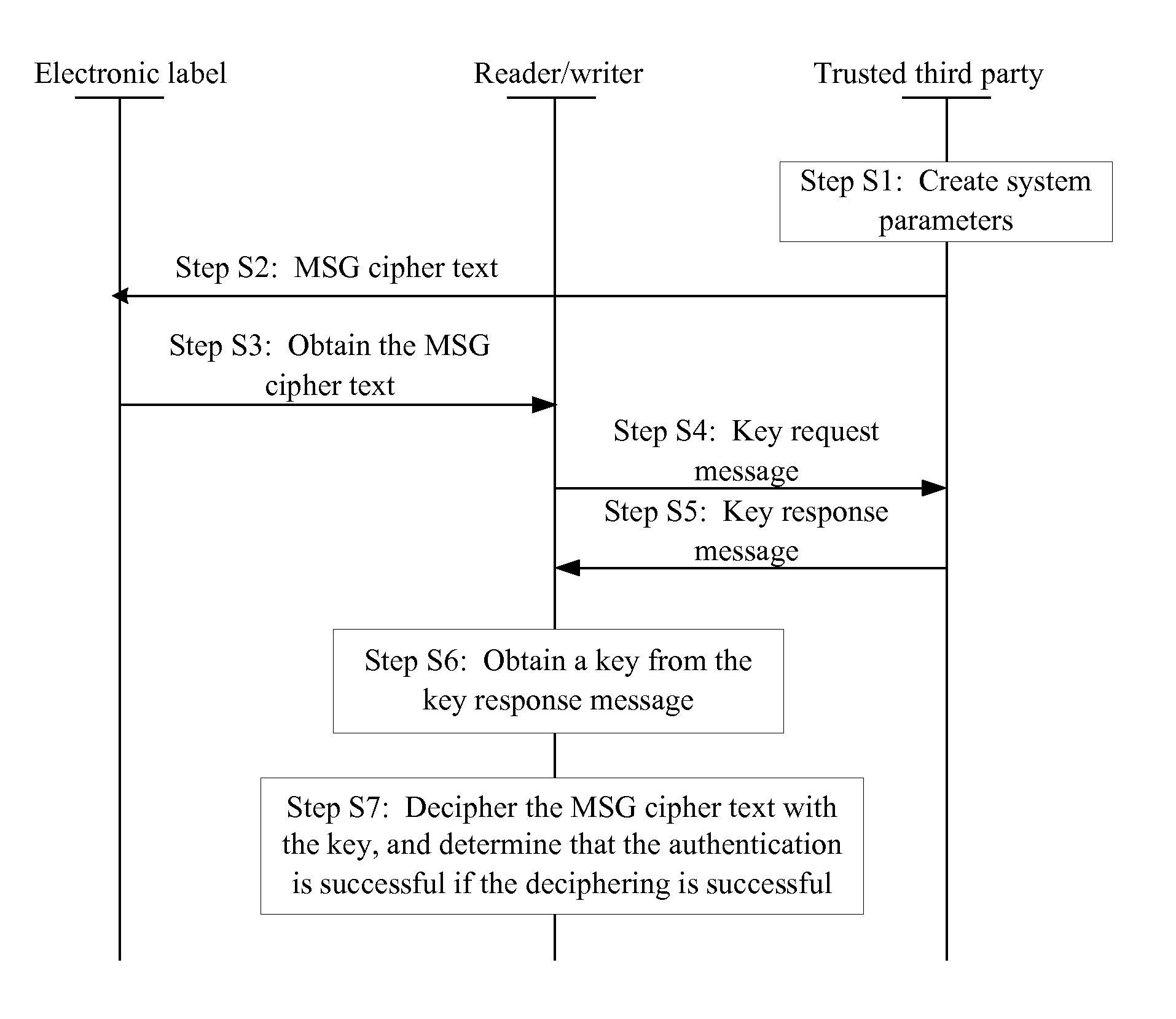
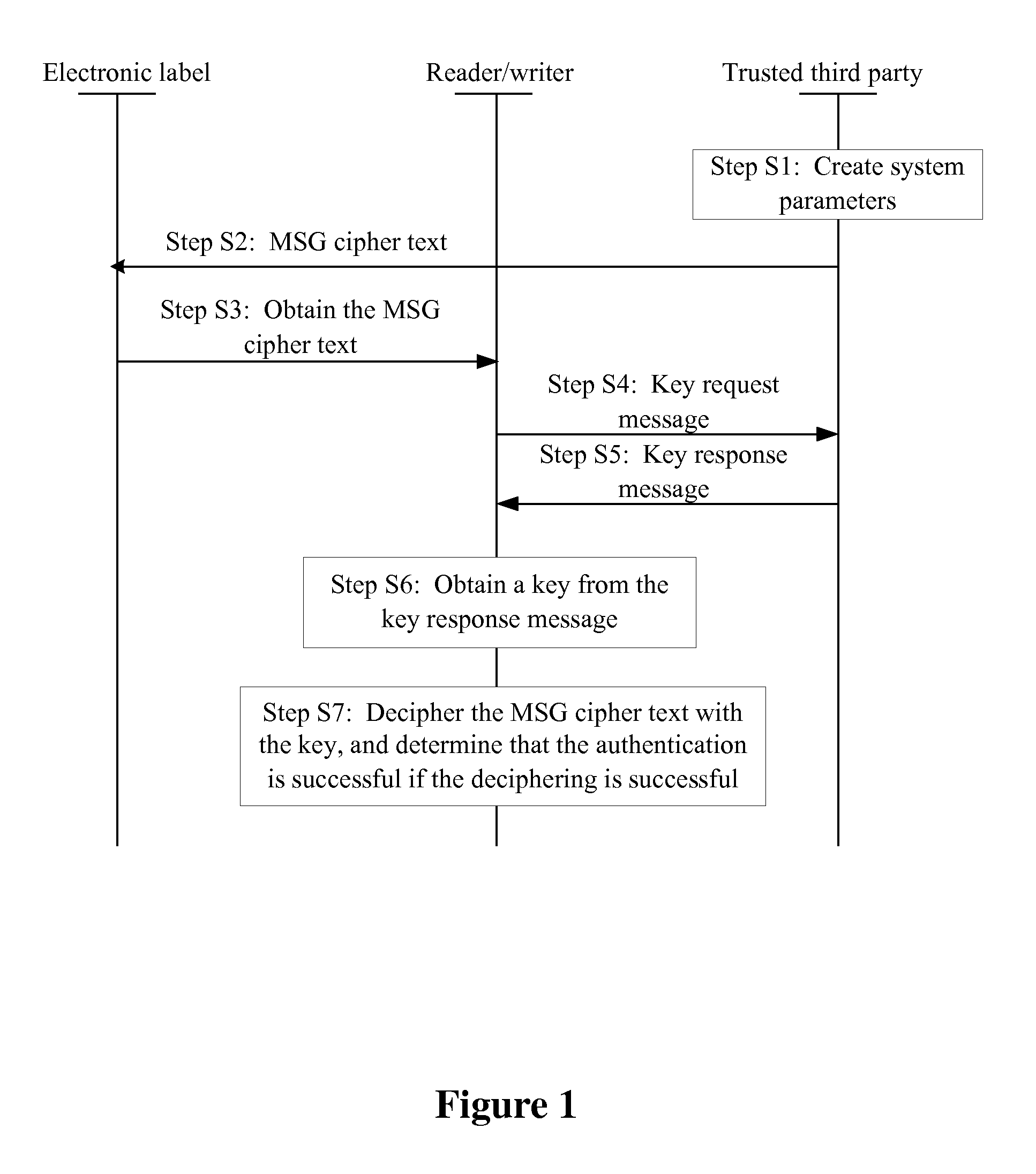
A light access authentication method and system, the method includes: the trustful third party writes the MSG cipher text formed by enciphering MSG into the first entity; the second entity attains the MSG cipher text from the first entity, and attains the key from the trustful third party after attaining the MSG cipher text; the MSG cipher text is deciphered according to the key, and the MSG plaintext is attained. The embodiment of the present invention can be widely applied at a condition limited by the equipment and environment, and the access authentication is simplified and lightened.
Owner:CHINA IWNCOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com