Method for carrying out access authentication through monitoring client spectrum field intensity
An access authentication and client technology, applied in wireless communication, electrical components, security devices, etc., can solve the problem of decreased security of access points, failure of authorization of access points, increased client functional requirements and operational complexity, etc. problems, to achieve the effect of good user access experience and low requirements for authorized access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The present invention will be further described below in conjunction with the accompanying drawings, but the embodiments of the present invention are not limited thereto.
[0015] The description of the present invention has been presented for purposes of illustration and description, but is not intended to be exhaustive or limited to the invention in the form disclosed. Many modifications and changes will be apparent to those of ordinary skill in the art. The embodiment was chosen and described in order to better explain the principles of the invention and the practical application, and to enable others of ordinary skill in the art to understand the invention and design various embodiments with various modifications as are suited to the particular use.
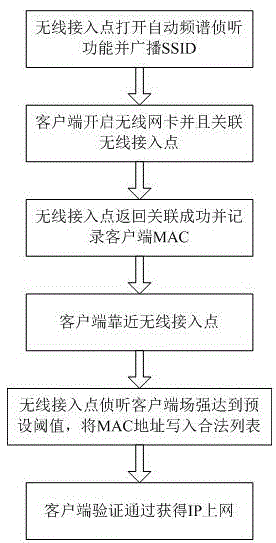
[0016] this invention figure 1 Describes the flow chart of the method for enabling the user to achieve wireless verification access by approaching the wireless access point through the spectrum sensing algorithm. Firs...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com