Connection establishment method and access authentication system for blocking-attacking resistant shared media terminal
A method for establishing a terminal connection, which is applied in the field of login methods and their implementation systems, can solve problems such as being no longer effective, and achieve the effects of small calculation amount and good calculation penalty effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
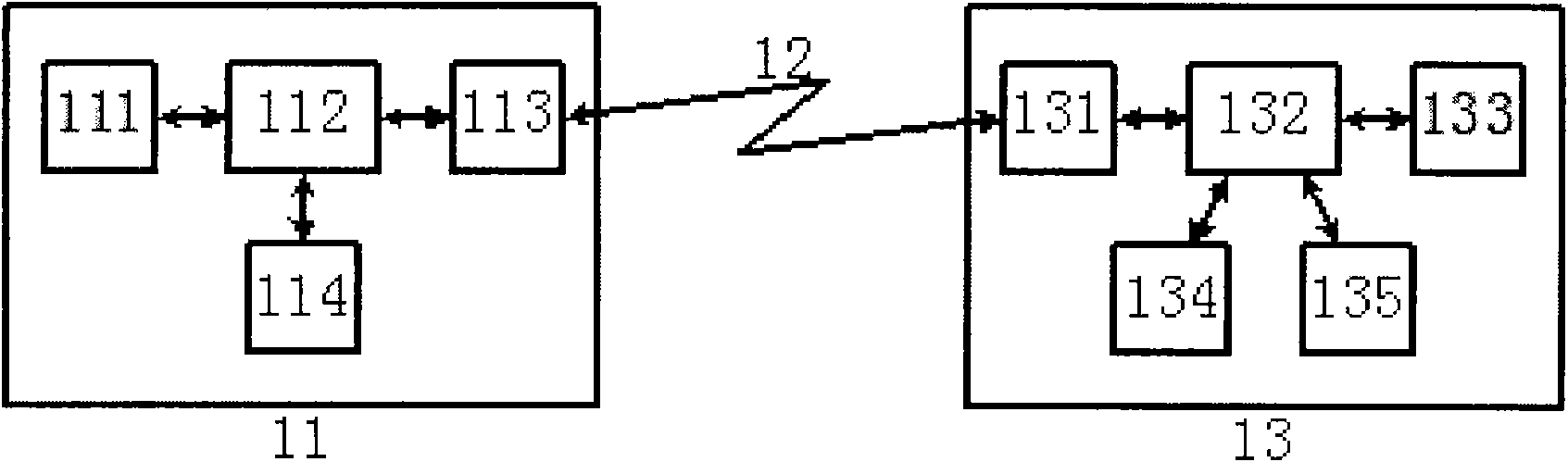
[0065] An embodiment system of the present invention such as figure 1 As shown, it includes a network access user terminal 11, a network access terminal 13, and a transmission link 12 between the network access user terminal 11 and the network access terminal 13, and the network access user terminal 11 includes a user terminal configuration memory inside 111, microprocessor module 112, data transceiving device 113 and random data memory 114, described network access terminal 13 comprises data transceiving device 131, microprocessor module 132, network interface transceiving module 133, configuration memory 134 and Login user database module 135 .
[0066] An improved embodiment system of the present invention such as Figure 24 As shown, it includes a network access user terminal 11A, a network access terminal 13A, and a transmission link 12 between the network access user terminal 11A and the network access terminal 13A, and the network access user terminal 11A includes a us...
no. 1 example
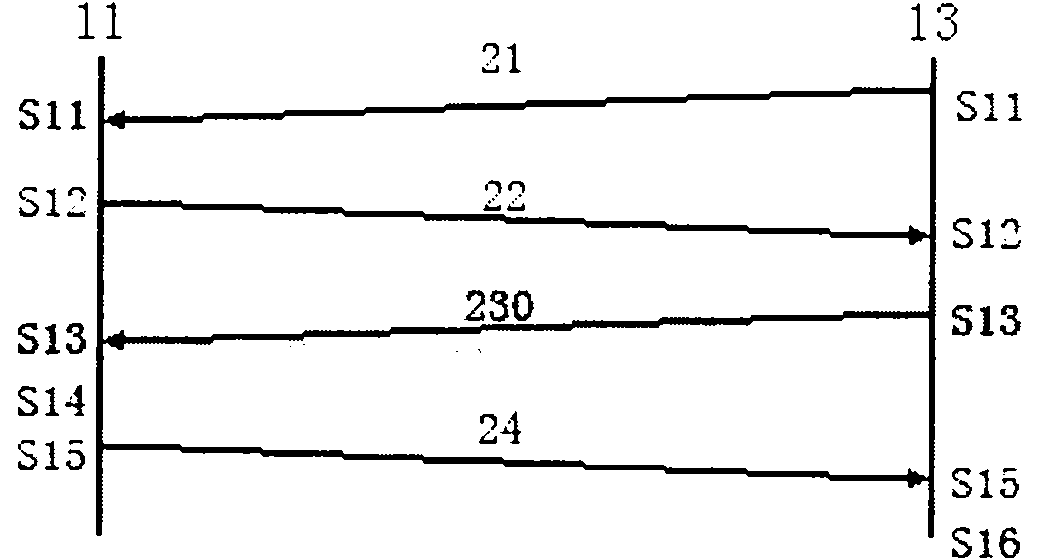
[0069] The connection login establishment process between the network access user terminal 11 and the network access terminal 13 includes as follows: figure 2 Steps S11-S16 are shown.
[0070] The first step (S11) of the terminal connection performed by the network access user terminal in order to log in to the network and use the network service is to listen to the scheduled broadcast of the network access terminal. The microprocessor module 132 in the network access terminal 13 takes out configuration parameters such as the broadcast time interval, the key perturbation strength 212 and the current system time from the configuration memory 134, and determines a period of time as the effective network access time window 213 according to the current network traffic volume, Then, the scheduled broadcast message is broadcast in plain text through the data transceiver 131 . The content of the regular broadcast message 21 includes current system time information 211 , key perturb...
no. 2 example
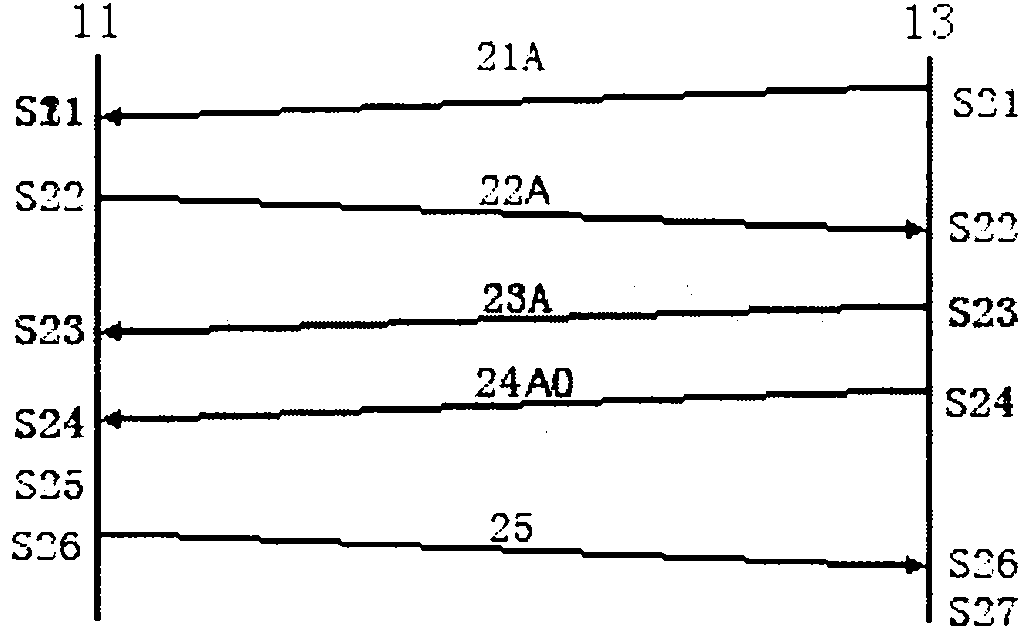
[0078] The improvement to the first embodiment of the connection login establishment process between the network user terminal 11 and the network access terminal 13 is as follows: figure 2 Steps S11-S16 are shown.
[0079] The first step (S11) of the terminal connection performed by the network access user terminal in order to log in to the network and use the network service is to listen to the scheduled broadcast of the network access terminal. The microprocessor module 132 in the network access terminal 13 periodically fetches configuration parameters such as the broadcast time interval, the key perturbation strength 212 and the current system time from the configuration memory 134, and determines a period of time according to the current network traffic volume as the effective network access time Window 213 generates a random number y according to the configuration of the network access terminal configuration memory 134 (such as the codeword length), and then further gene...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com