A wearable device identity authentication method based on cross bit operation
A wearable device and identity authentication technology, which is applied to user identity/authority verification and key distribution, can solve problems such as increased cost, large amount of computation, and long response time, so as to ensure security, reduce computing cost, and solve identity authentication problems Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
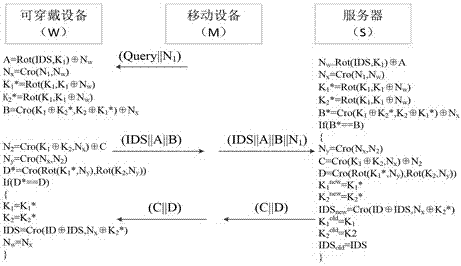
[0035] The first embodiment of the present invention is a wearable device identity authentication method based on cross bit operation, including: a wearable device (W), a mobile terminal (M) and a background server (S), and the wearable device (W) receives After the authentication request sent by the mobile terminal (M), the authentication message parameters are calculated and generated through the cross bit operation and the left circular shift operation to form the first authentication message set, and sent to the mobile terminal (M); the mobile terminal (M) will Receive the first authentication message set sent by the wearable device (W) together with the random number generated by itself to form the second authentication message set, and send it to the server (S); the server (S) receives the second authentication message set Afterwards, it is judged whether the temporary identity of the wearable device in the second authentication message set satisfies the first matching co...
no. 2 example
[0037] The present invention proposes an ultra-lightweight wearable device identity authentication method by using the cross bit operation Cro(X,Y), the exclusive OR operation XOR and the left circular shift operation Rot(X,Y). The authentication method includes three parts: a wearable device (Wearable Device, referred to as W), a mobile terminal (Mobile Device, referred to as M) and a background server (Server, referred to as S).
[0038] 1. Symbols and function explanations used in the method
[0039] ID: the real identity of wearable devices
[0040] IDS: Temporary Identity for Wearable Devices
[0041] N i : random number, i=1,2,d
[0042] K i : authentication key, i=1,2
[0043] A~D: authentication message
[0044] ⊕: Bitwise exclusive OR (XOR) operation
[0045] ||: information or text at both ends to connect
[0046] ==: comparison operator
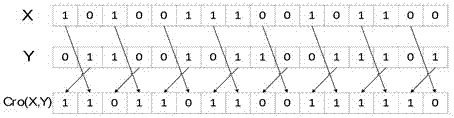
[0047] Cro(X,Y): cross bit operation, X, Y are the entry parameters of the function with L bits (L is an even number), X...
no. 3 example
[0062] The third embodiment of the present invention is a wearable device identity authentication method, including: a wearable device (W), a mobile terminal (M) and a background server (S), and the identity authentication method includes the following steps:
[0063] 1) The mobile terminal (M) generates a random number N 1 , and initiate an authentication request to the wearable device (W);
[0064] 2) The wearable device (W) receives the authentication request and the random number N sent by the mobile terminal (M) 1 After that, send the first message set to the mobile terminal (M);
[0065] 3) After receiving the first set of messages sent by the wearable device (W), the mobile terminal (M) together with the random number N generated by itself 1 , sending a second message set to the server (S), where the second message set includes at least the first verification parameter and the temporary identity of the wearable device;
[0066] 4) After receiving the second set of me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com