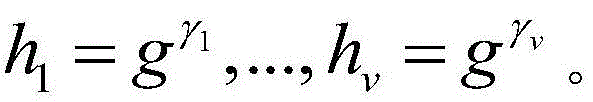Patents
Literature
1512 results about "Exclusive or" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Exclusive or or exclusive disjunction is a logical operation that outputs true only when inputs differ (one is true, the other is false). It is symbolized by the prefix operator J and by the infix operators XOR (/ˌɛks ˈɔːr/ or /ˈzɔːr/), EOR, EXOR, ⊻, ⩒, ⩛, ⊕, ↮, and ≢. The negation of XOR is logical biconditional, which outputs true only when both inputs are the same.
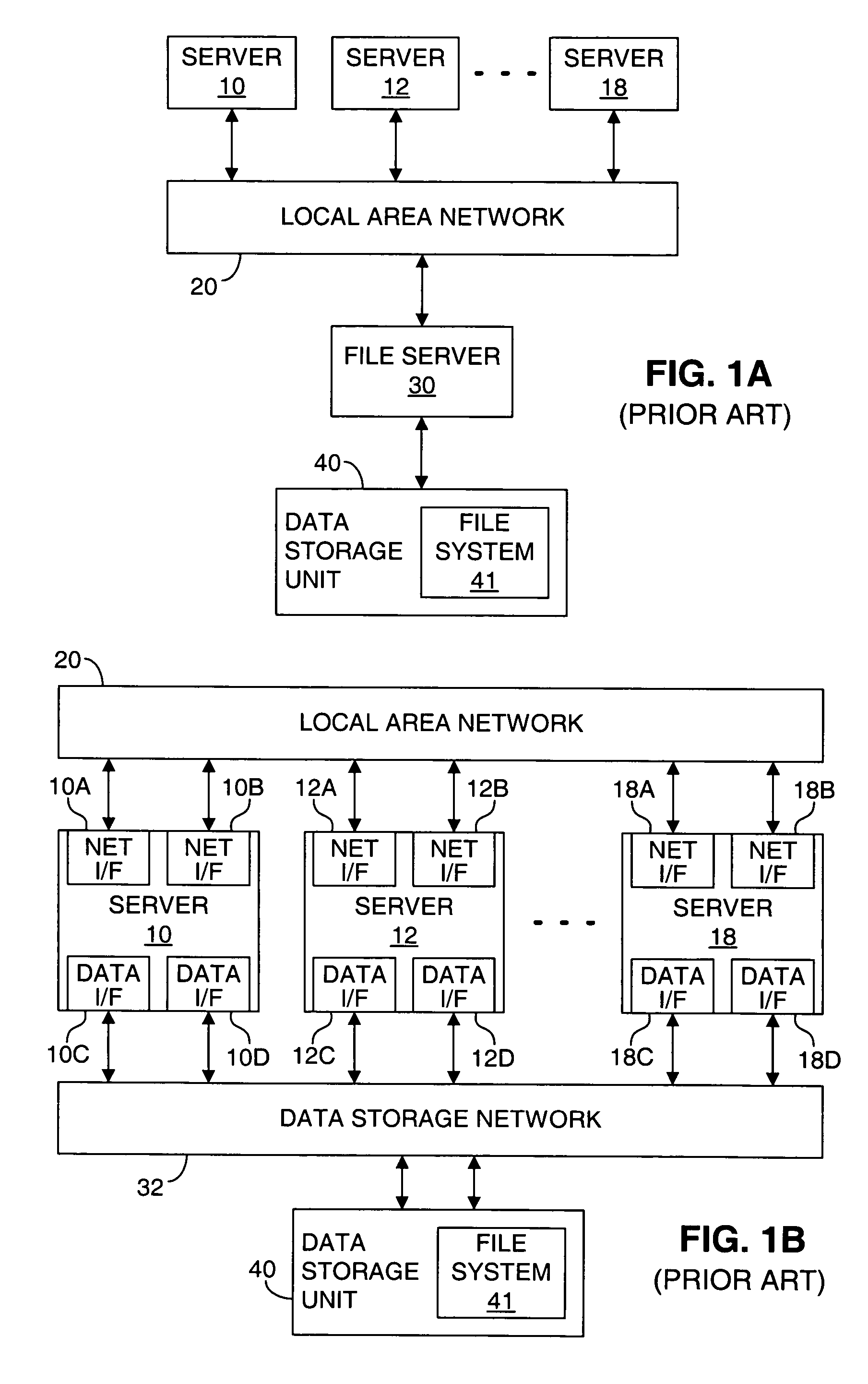
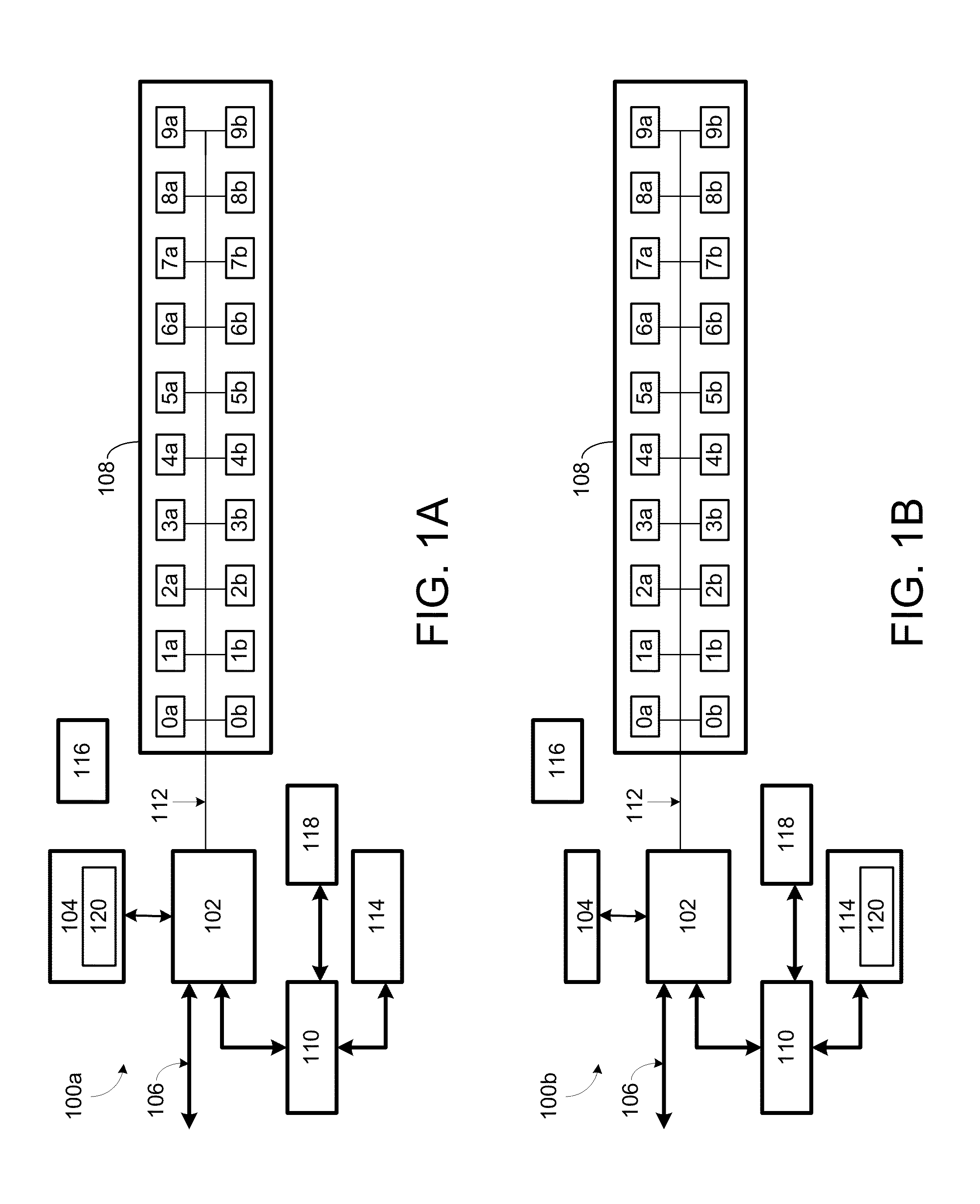
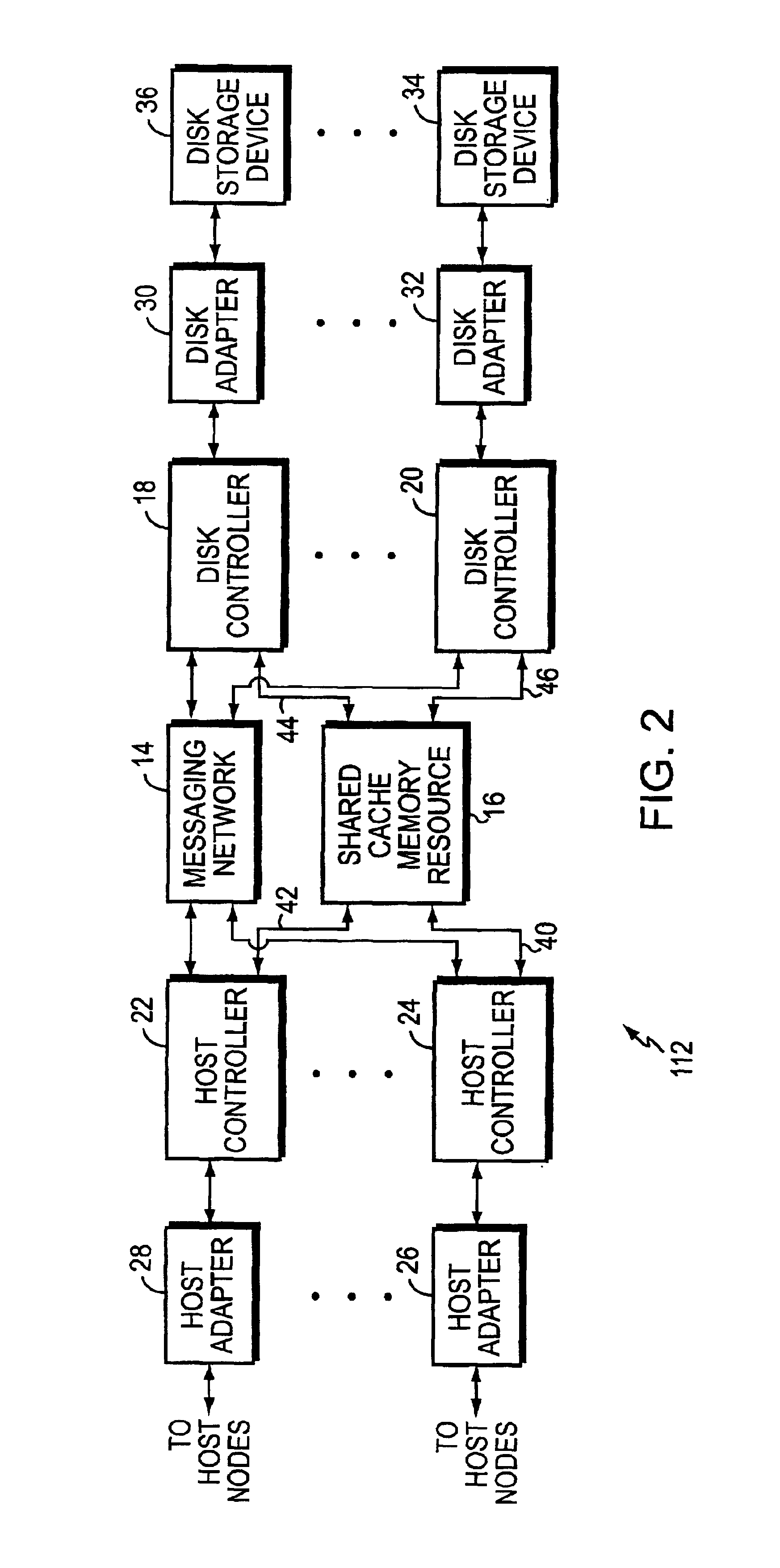
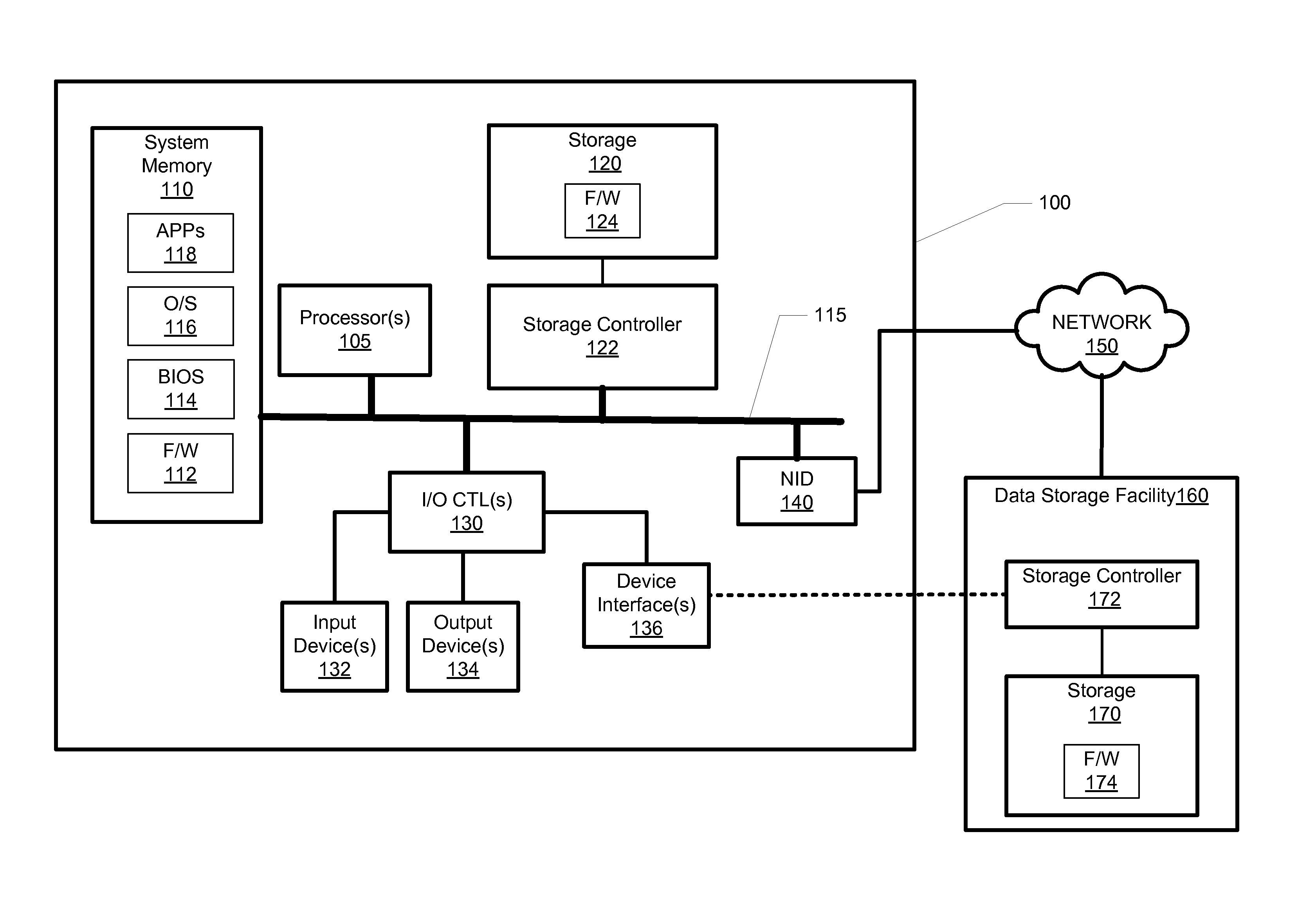
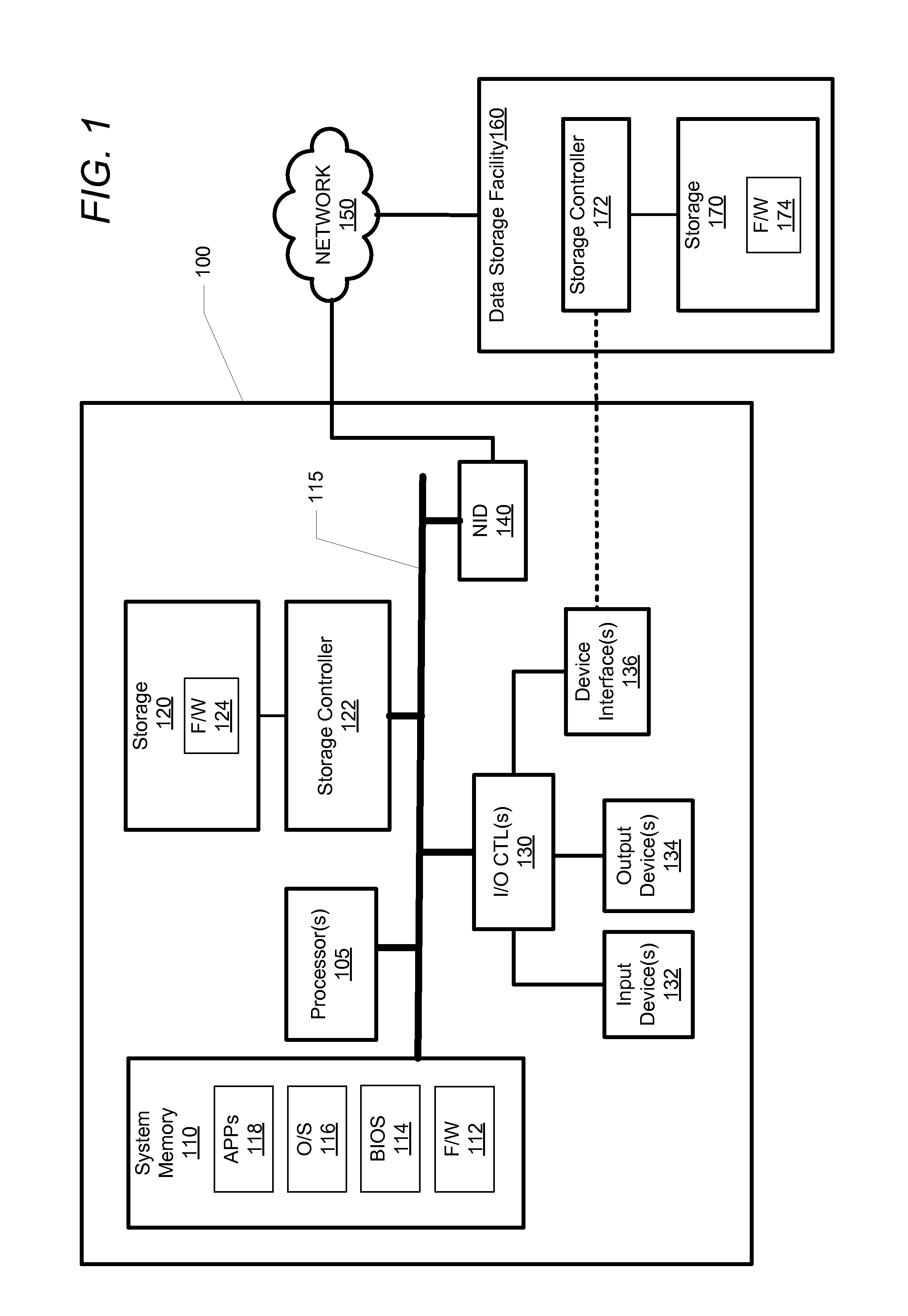
Method, system, and program for managing data organization
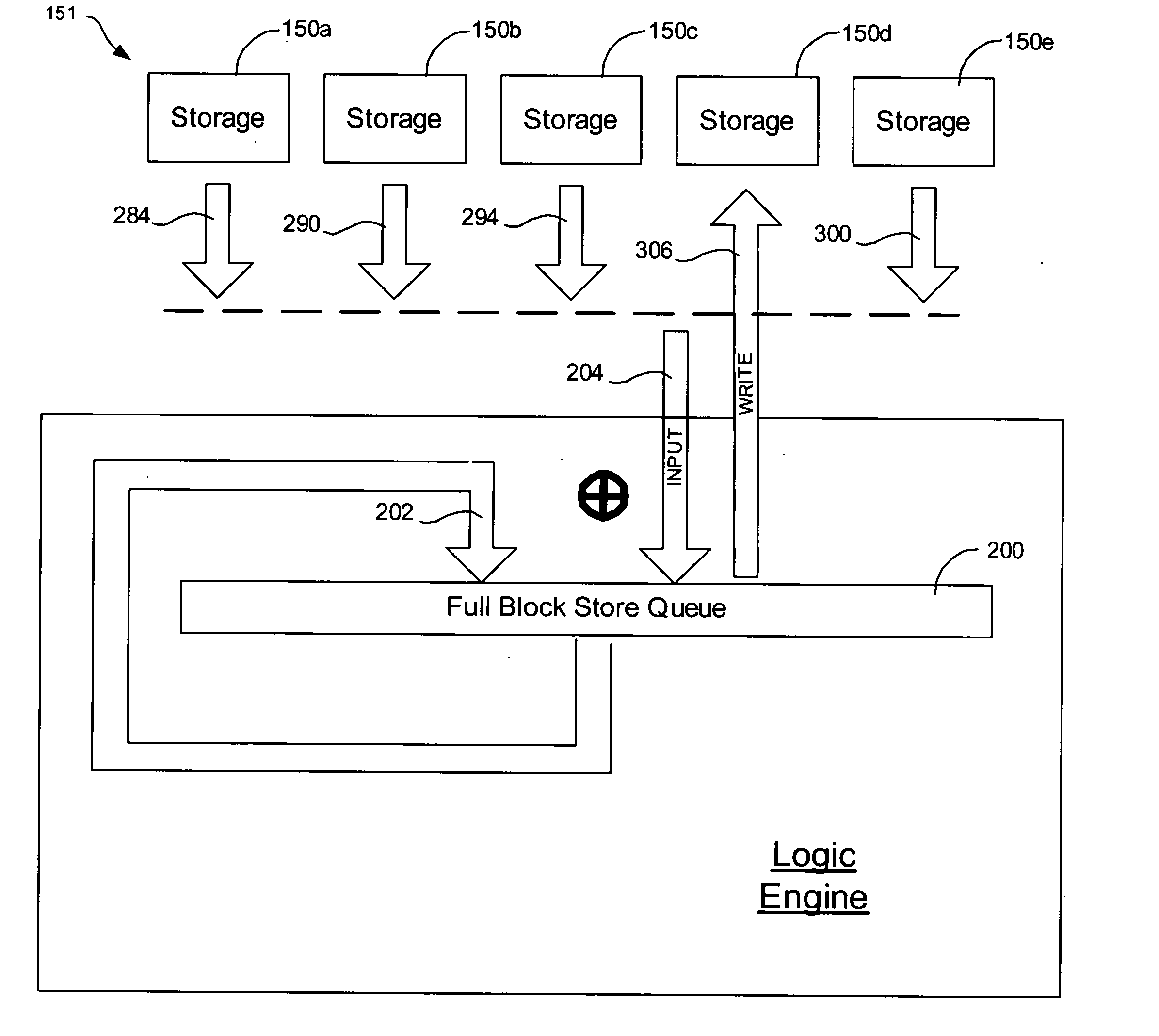
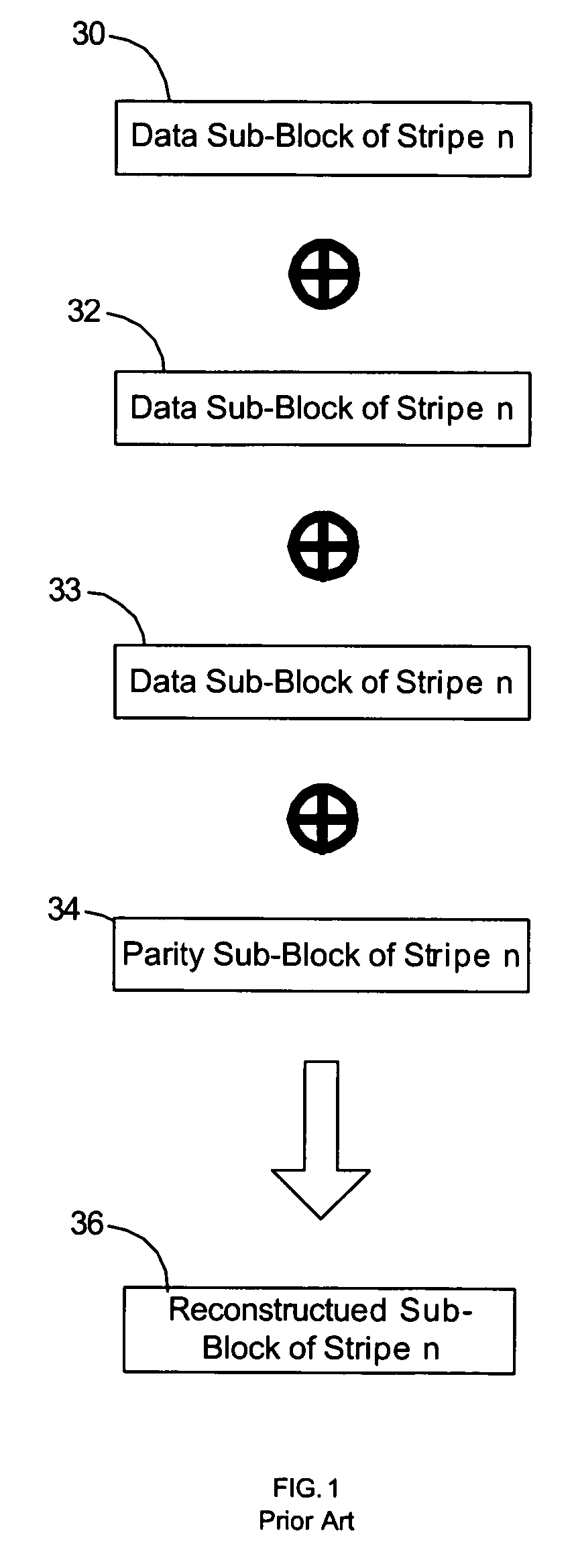
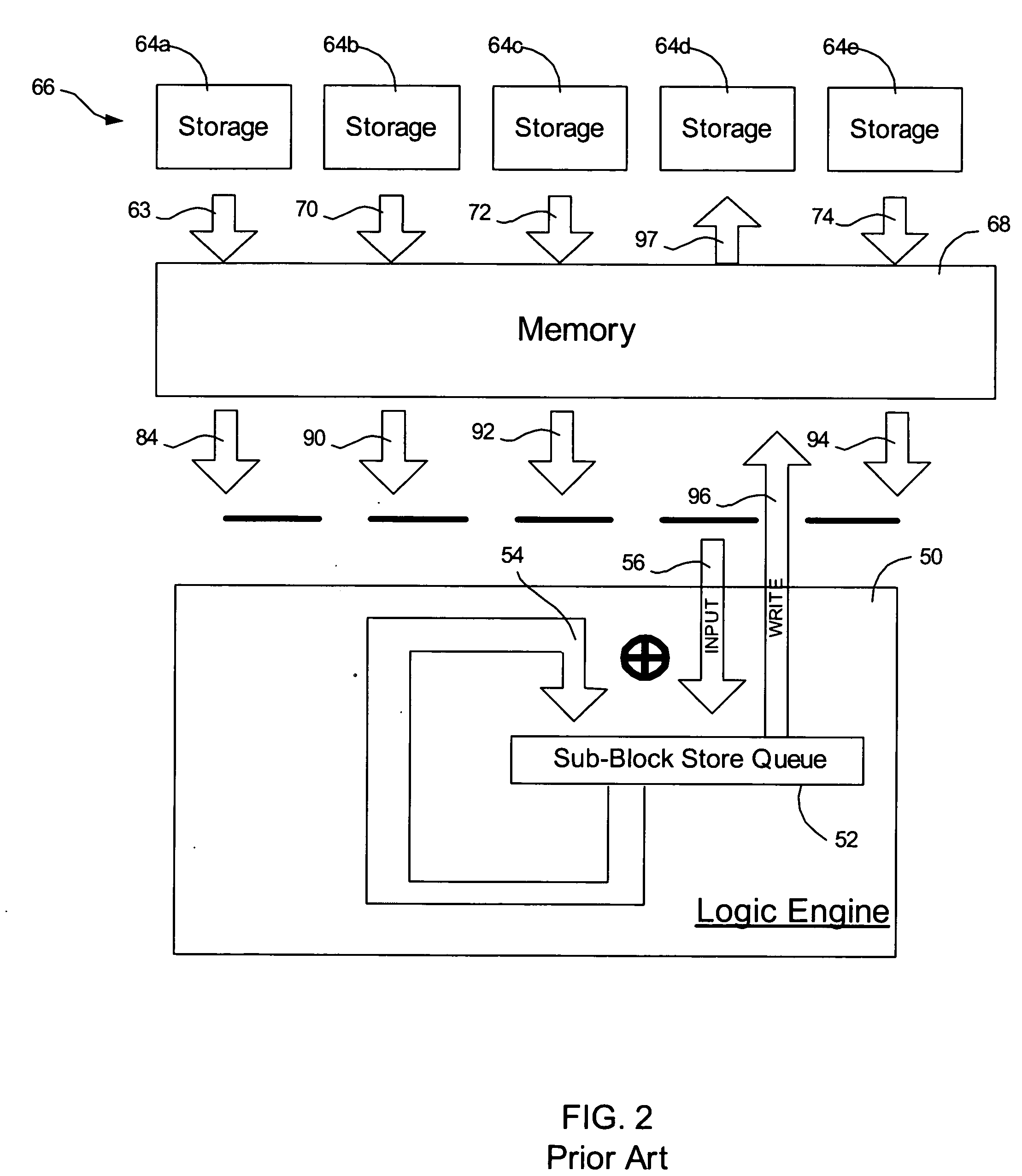
Provided are a method, system, and program for constructing data including reconstructing data organized in a data organization type, such as a Redundant Array of Independent Disks (RAID) organization, for example, which permits data reconstruction In one embodiment, blocks of data are transferred from a stripe of data stored across storage units, such as disk drives in a RAID array, to a logic engine of a storage processor, bypassing the cache memory of the storage processor. A store queue performs a logic function, such as Exclusive-OR, on each block of data as it is transferred from the disk drives, to reconstruct a block of data from the stripe. The constructed block of data may be subsequently transferred to a disk drive of the RAID array to replace a lost block of data in the stripe of data across the RAID array or to replace an old block of parity data.
Owner:INTEL CORP
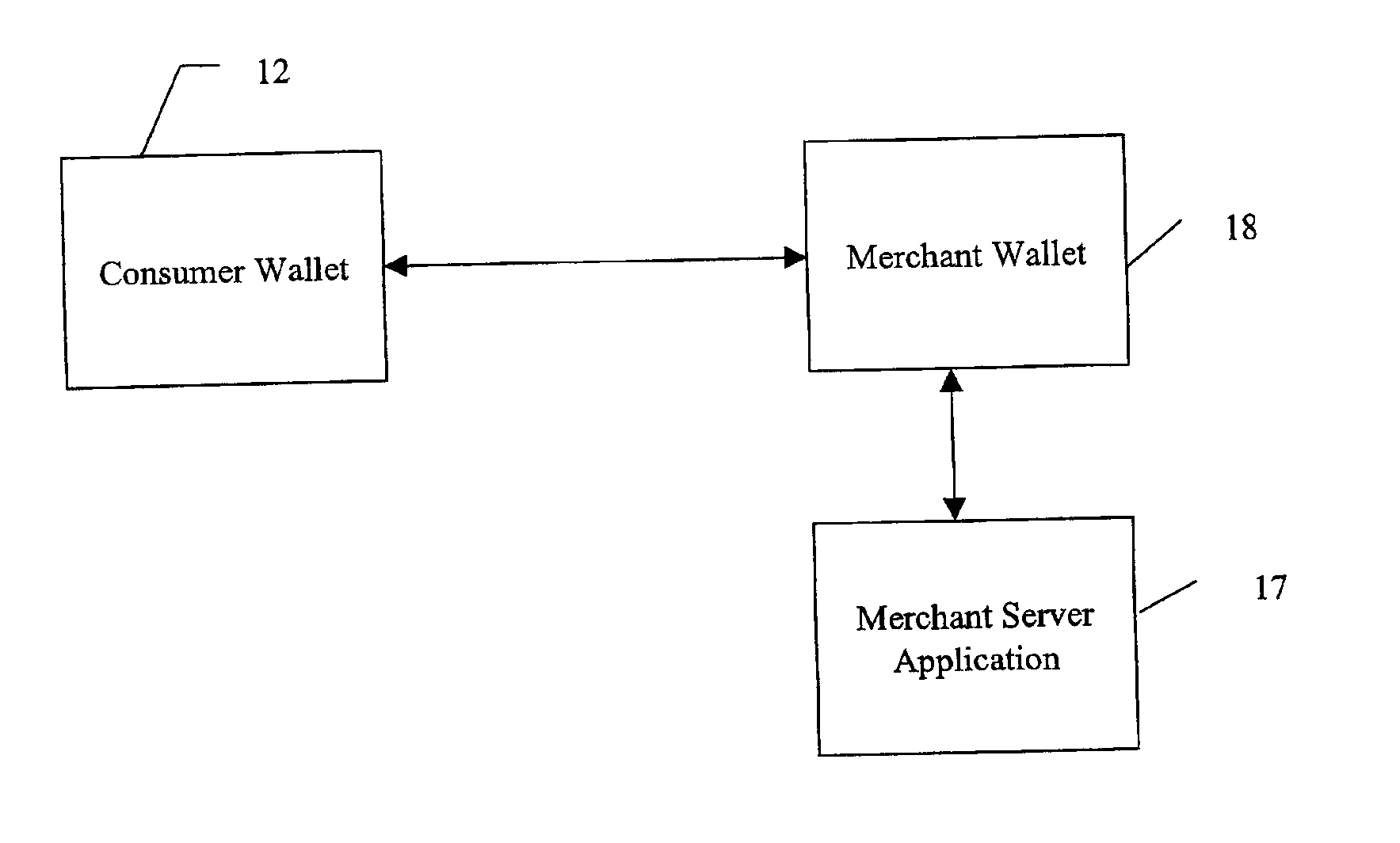
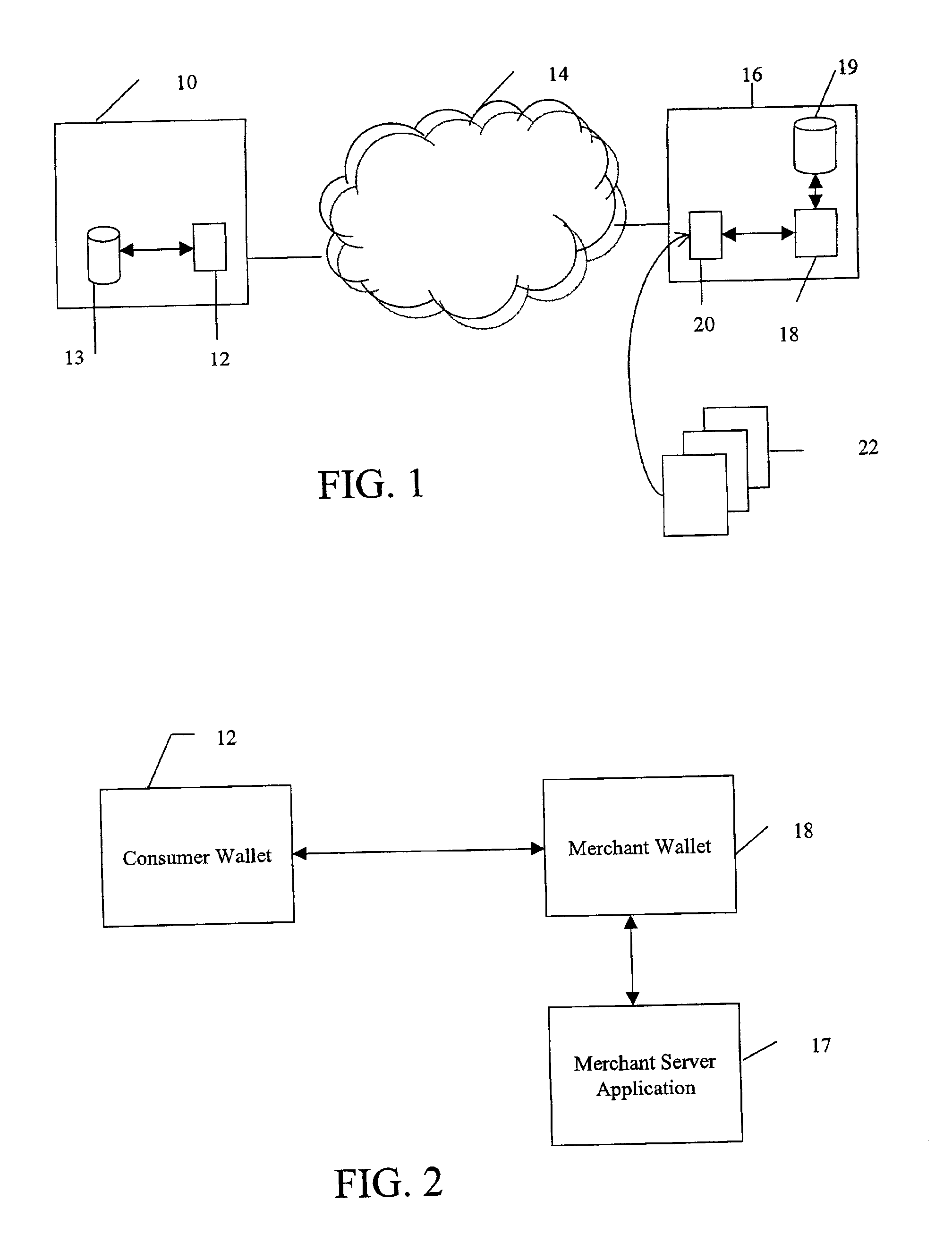
System and method for use of distributed electronic wallets
InactiveUS6873974B1Avoid burdenImprove efficiencyComplete banking machinesFinanceMerchant servicesCredit card
Methods and systems whereby two electronic wallets communicate and exchange information. In one such system, a consumer's personal electronic wallet communicates with the exclusive or preferred wallet of a web merchant. In one such system, an internet consumer registers with a web merchant's exclusive or preferred electronic wallet (“merchant wallet”) and provides consumer information (e.g., credit card number, mailing address, and other information) to the merchant wallet, which is stored by the merchant wallet in a database on the merchant server. Such information may be automatically populated by the consumer's personal electronic wallet. The consumer maintains current consumer information in a consumer electronic wallet on the consumer's personal computer. When the consumer visits the merchant site again, and orders goods or services, the merchant's preferred wallet can be automatically updated by the consumer's electronic wallet if any of the data in the merchant's wallet has changed. For example, the consumer wallet examines the information in the merchant wallet to determine if the information in the merchant wallet conforms to the current information in the consumer wallet. If the information does not conform, the consumer wallet communicates the current consumer information to the merchant wallet.
Owner:CITIBANK
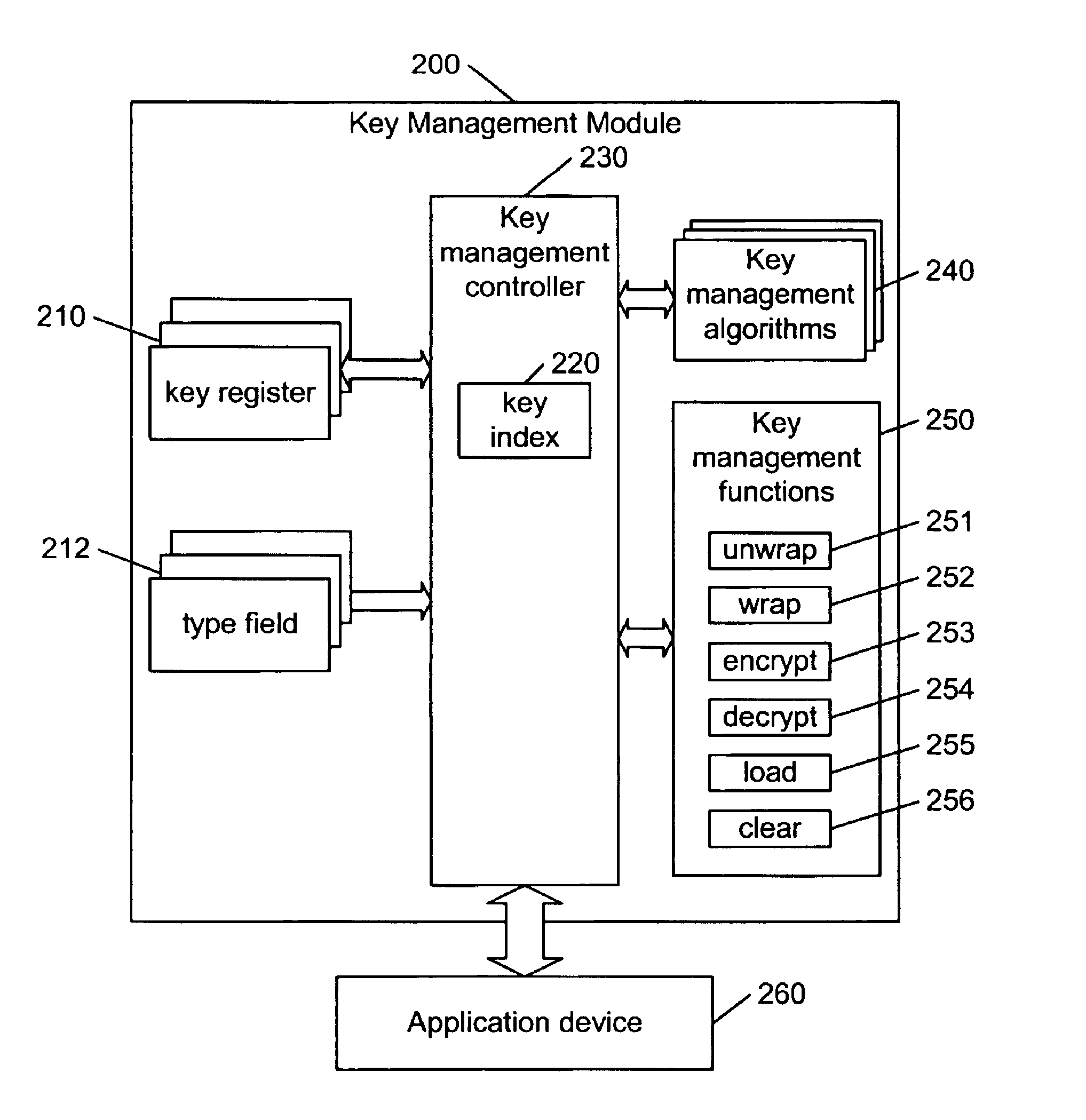
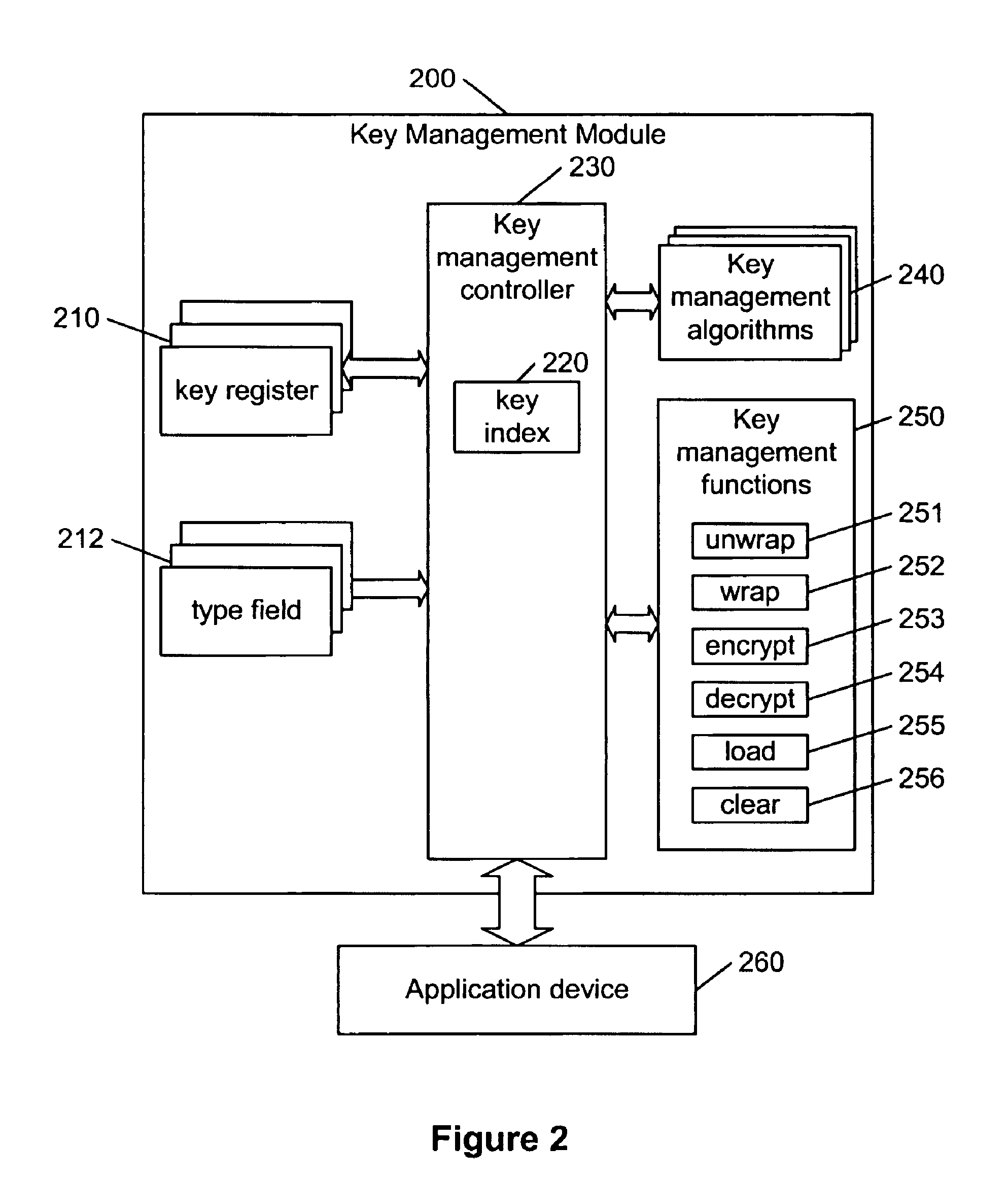
Hierarchical key management encoding and decoding
InactiveUS6907127B1Simple designSeparate applicationKey distribution for secure communicationDigital data processing detailsExclusive orInitialization vector
The present invention discloses a construction for key management module functionality which provides for secure encoding and decoding of messages which are up to two blocks long. A method for generating an encoded value having a first encoded value part and a second encoded value part from an unencoded value having a first unencoded value part and a second unencoded value part, comprising the steps of: obtaining an initialization vector; and generating the first and second encoded value parts. The first encoded value part is generated by: generating a first result by encrypting the first unencoded value part; generating a second result by performing an exclusive or operation on the first result and the second unencoded value part; generating a third result by performing an exclusive or operation on the second result and the initialization vector; generating a fourth result by encrypting the third result; generating a fifth result by performing an exclusive or operation on the fourth result and the first unencoded value part; and encrypting the fifth result. The second encoded value part is generated by encrypting the second result.
Owner:GOOGLE LLC
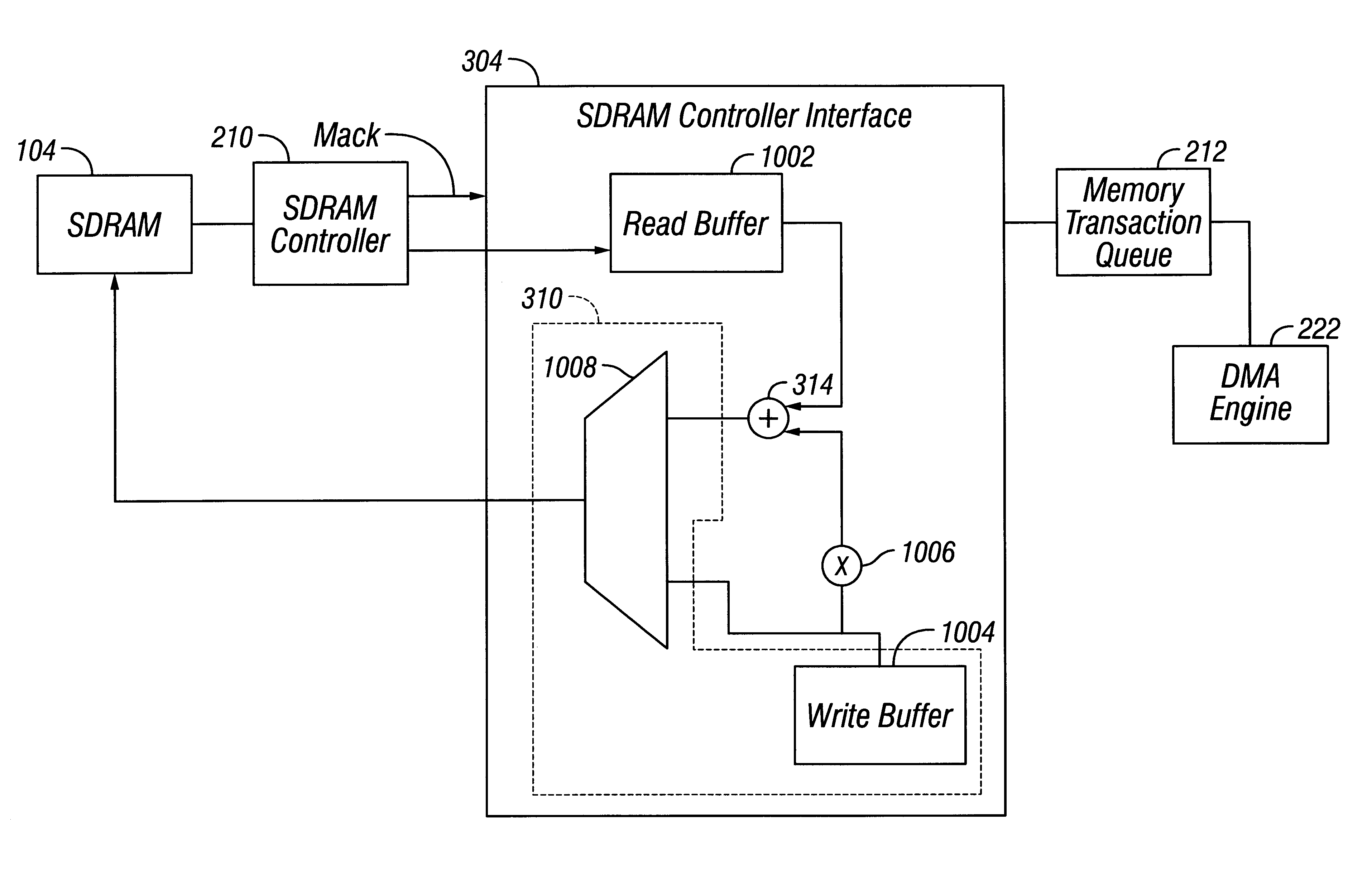
Raid XOR operations to synchronous DRAM using a read buffer and pipelining of synchronous DRAM burst read data
A memory interface controller includes a read buffer to pipeline data from a synchronous dynamic random access memory (DRAM) in response to a plurality of consecutive SDRAM burst read requests, a write buffer to store write data, an exclusive or (XOR) engine to XOR the write data with the data from the read buffer, and a write interface to write resulting data from XORing the write data and the data from the read buffer to the synchronous DRAM. Data is pipelined in the read buffer by repeatedly issuing an SDRAM burst read request before data is transferred out of the synchronous DRAM in response to a previous SDRAM burst read request until a desired amount of data is stored in the read buffer. The memory interface controller thus can perform an external read-modify-write cycle for the synchronous DRAM. The synchronous DRAM can serve as a RAID (Redundant Array s of Inexpensive Disks) memory.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
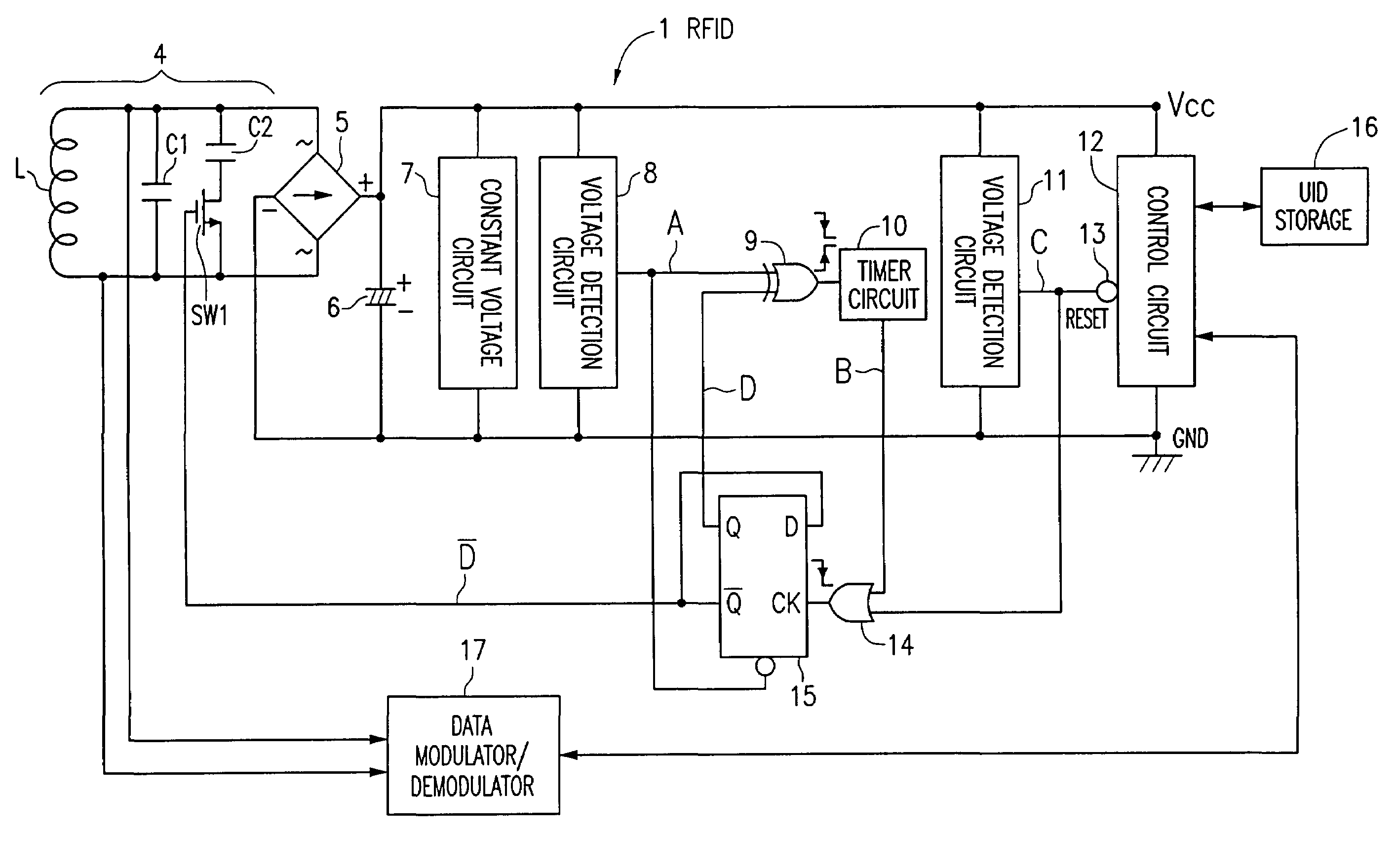
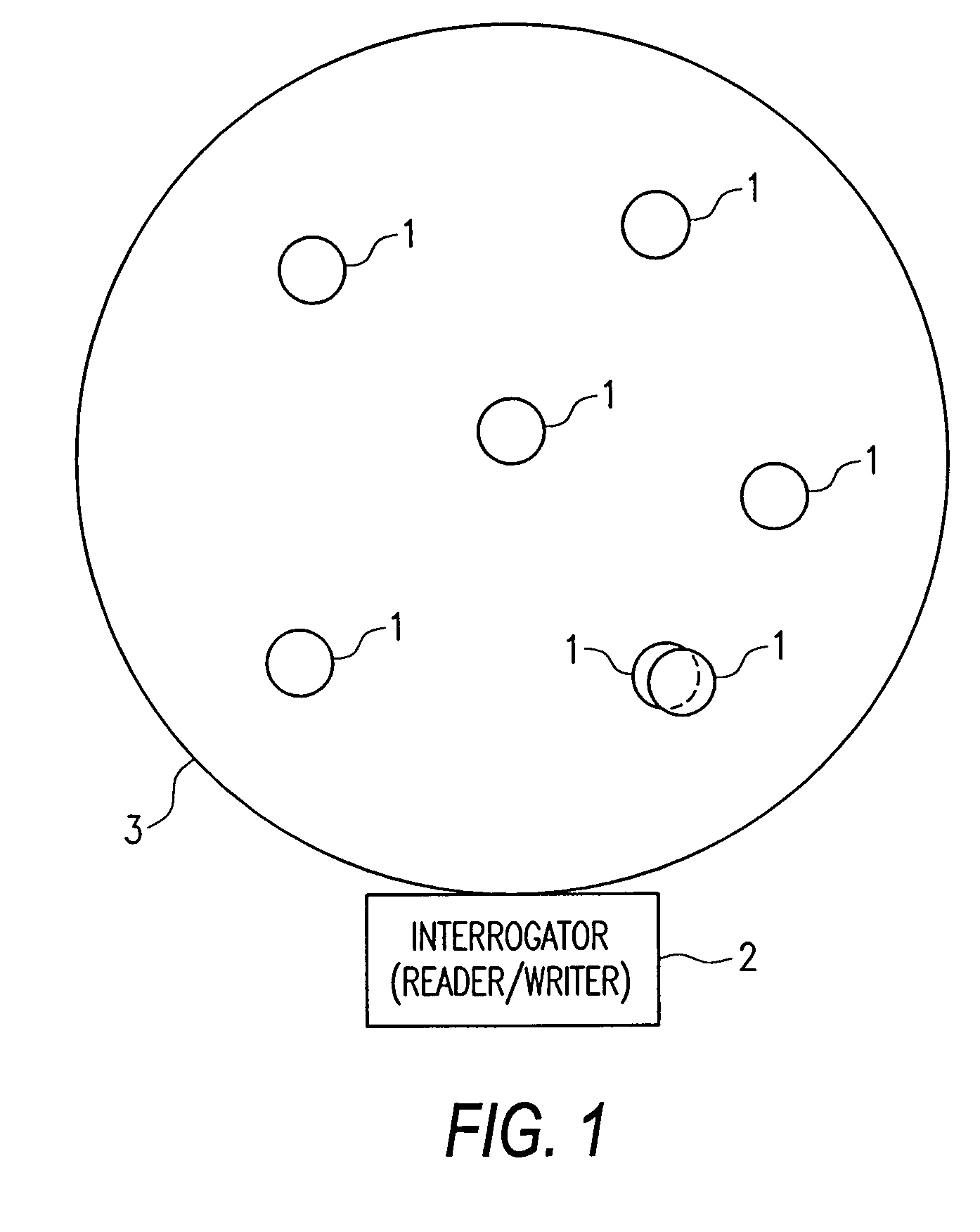
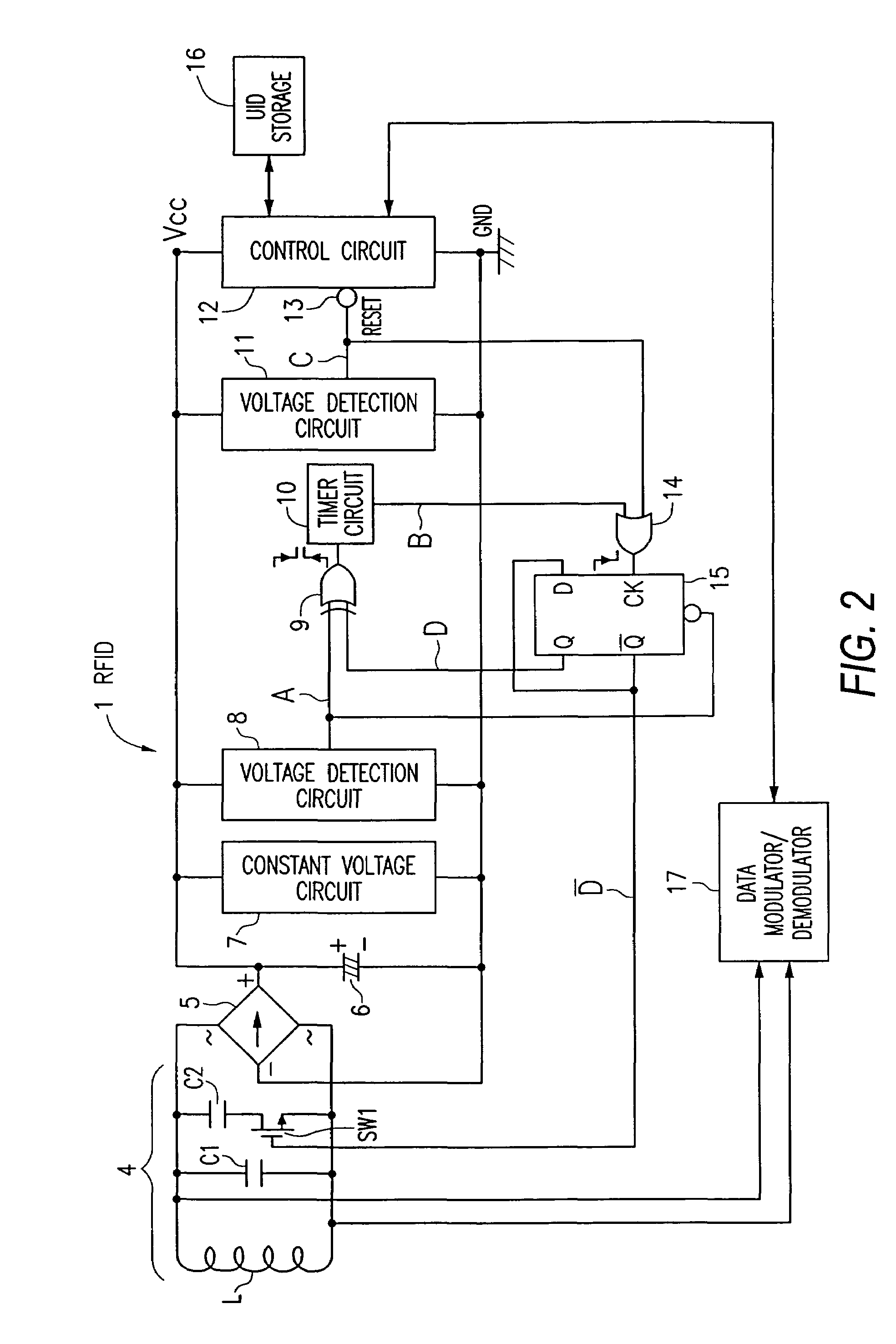
RFID tag and method for processing RFID data
InactiveUS7088246B2Easy constructionStable system operationMemory record carrier reading problemsCo-operative working arrangementsResonanceExclusive or
A collision prevention relational function is disclosed for RFID tags, which increases stability during system operations. The RFID tag includes a parallel resonance circuit having a coil, a resonance capacitor, an adjustment capacitor, a switching circuit, a rectification circuit, a smoothing capacitor, a constant-voltage circuit, a voltage detection circuit, an exclusive OR circuit, a timer circuit, a voltage detection circuit, a control circuit, an OR circuit, a latch circuit, an UID storage device, and a data modulator / demodulator. When a predetermined power supply voltage / operating voltage is obtained, an anti-collision algorithm identifies and adjusts RFID tags that experienced collision.
Owner:ORMON CORP
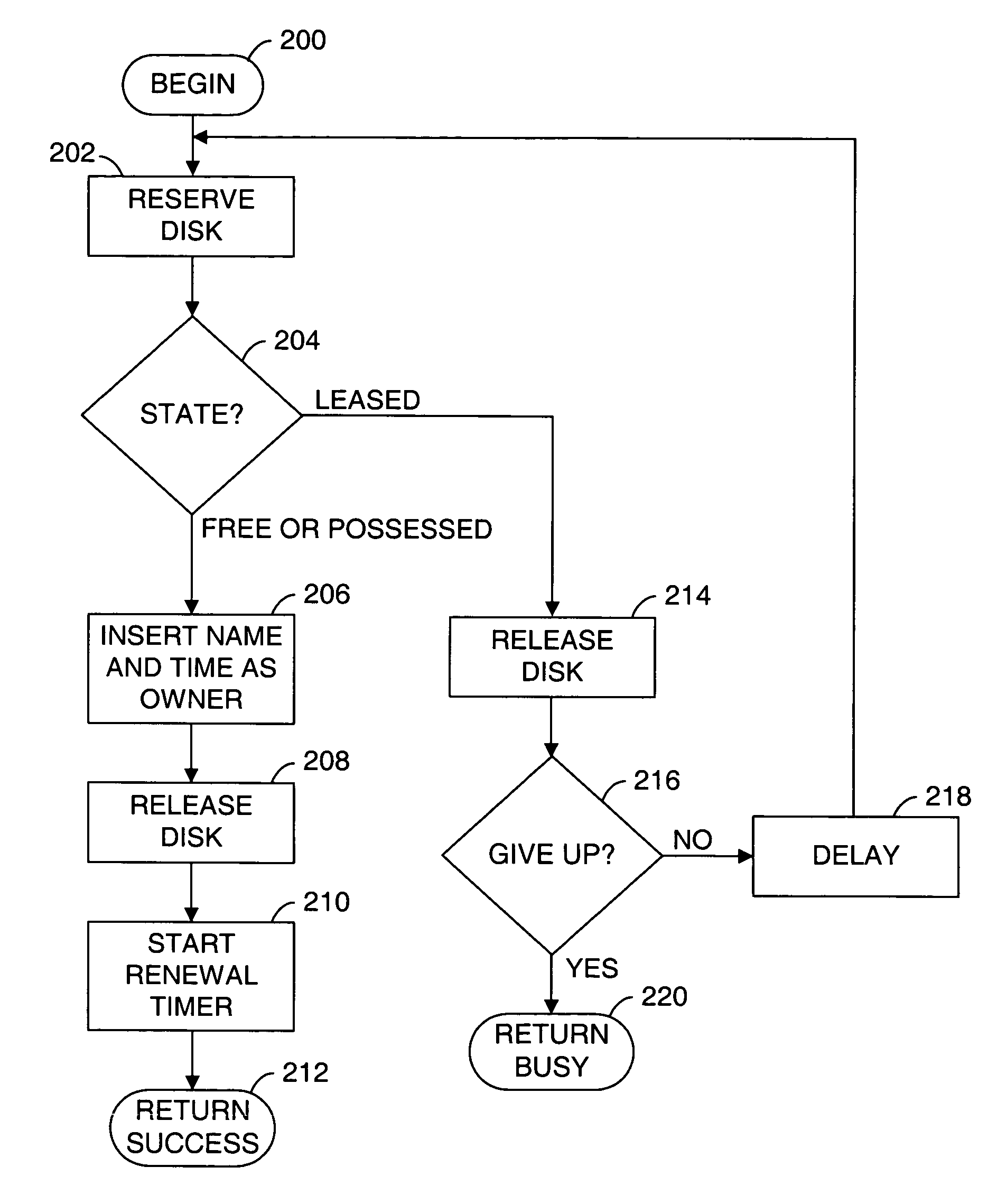
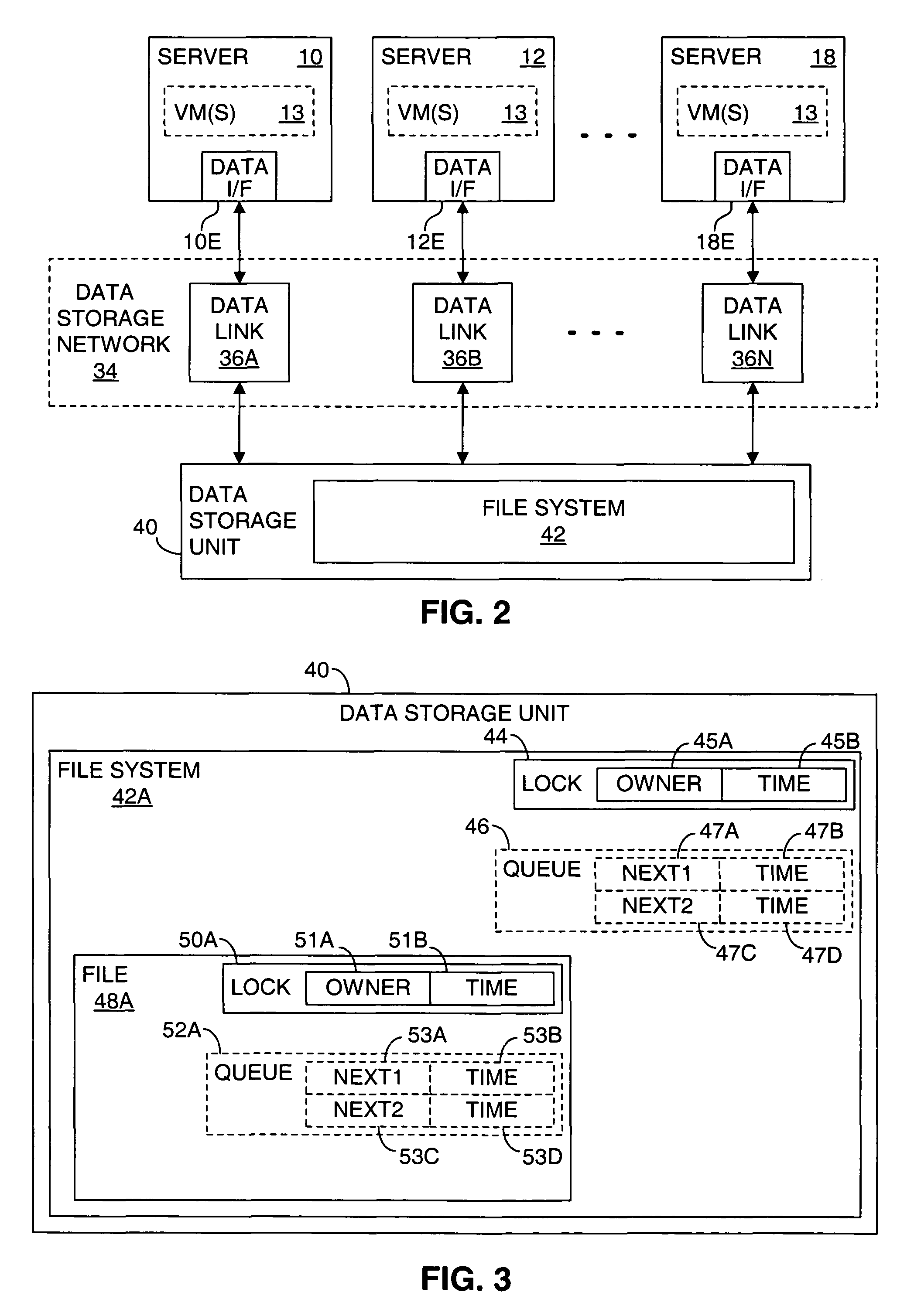
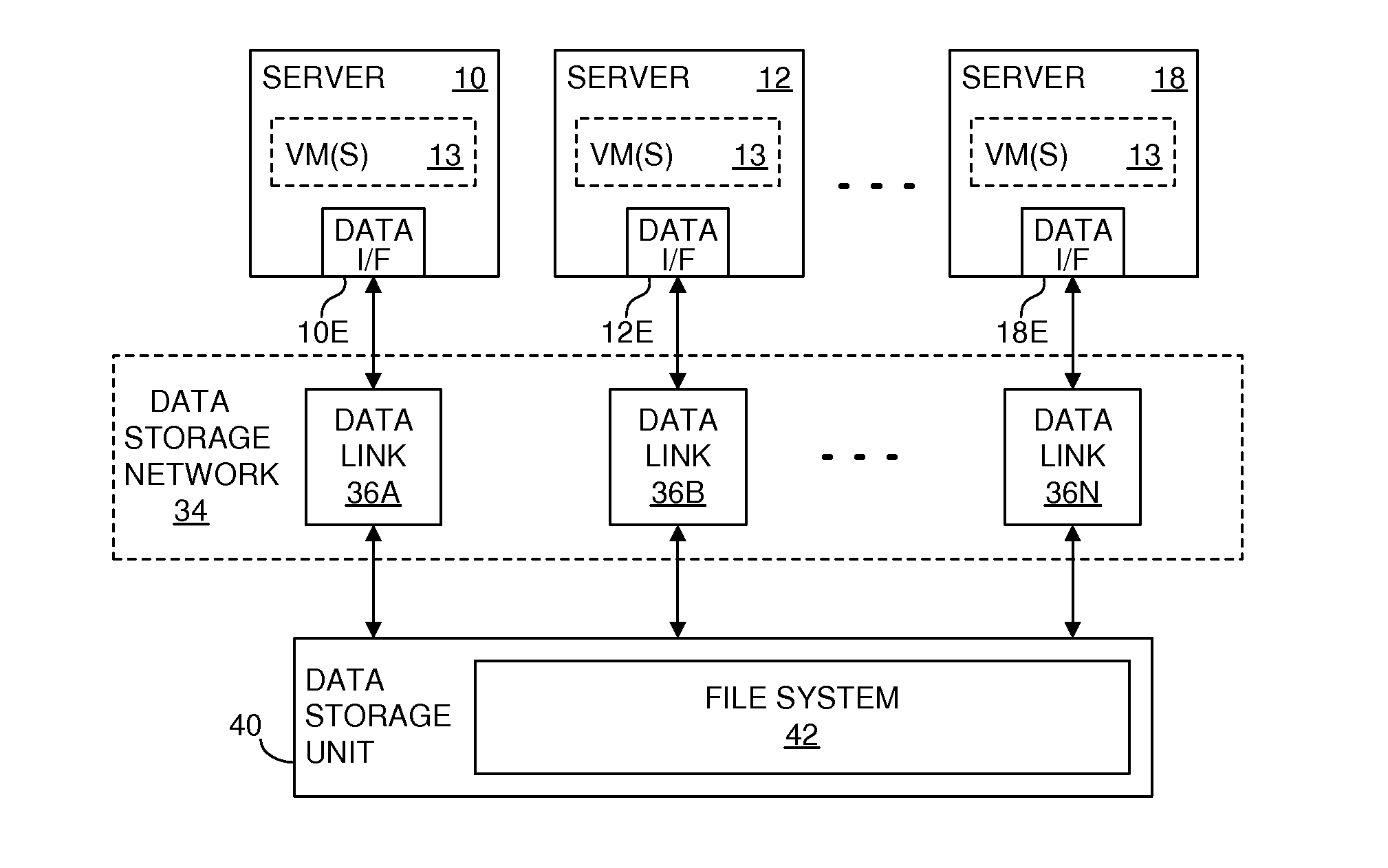
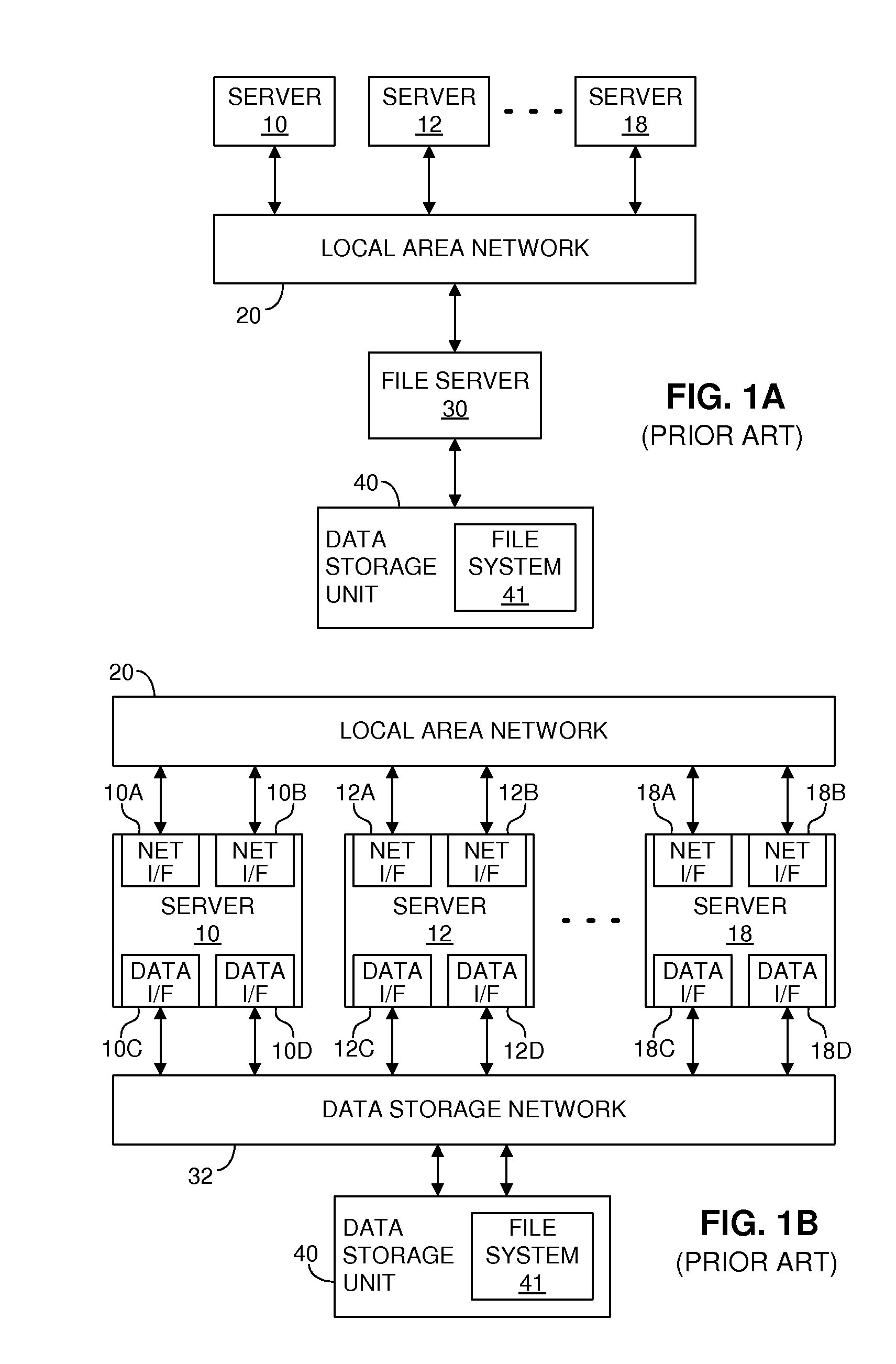
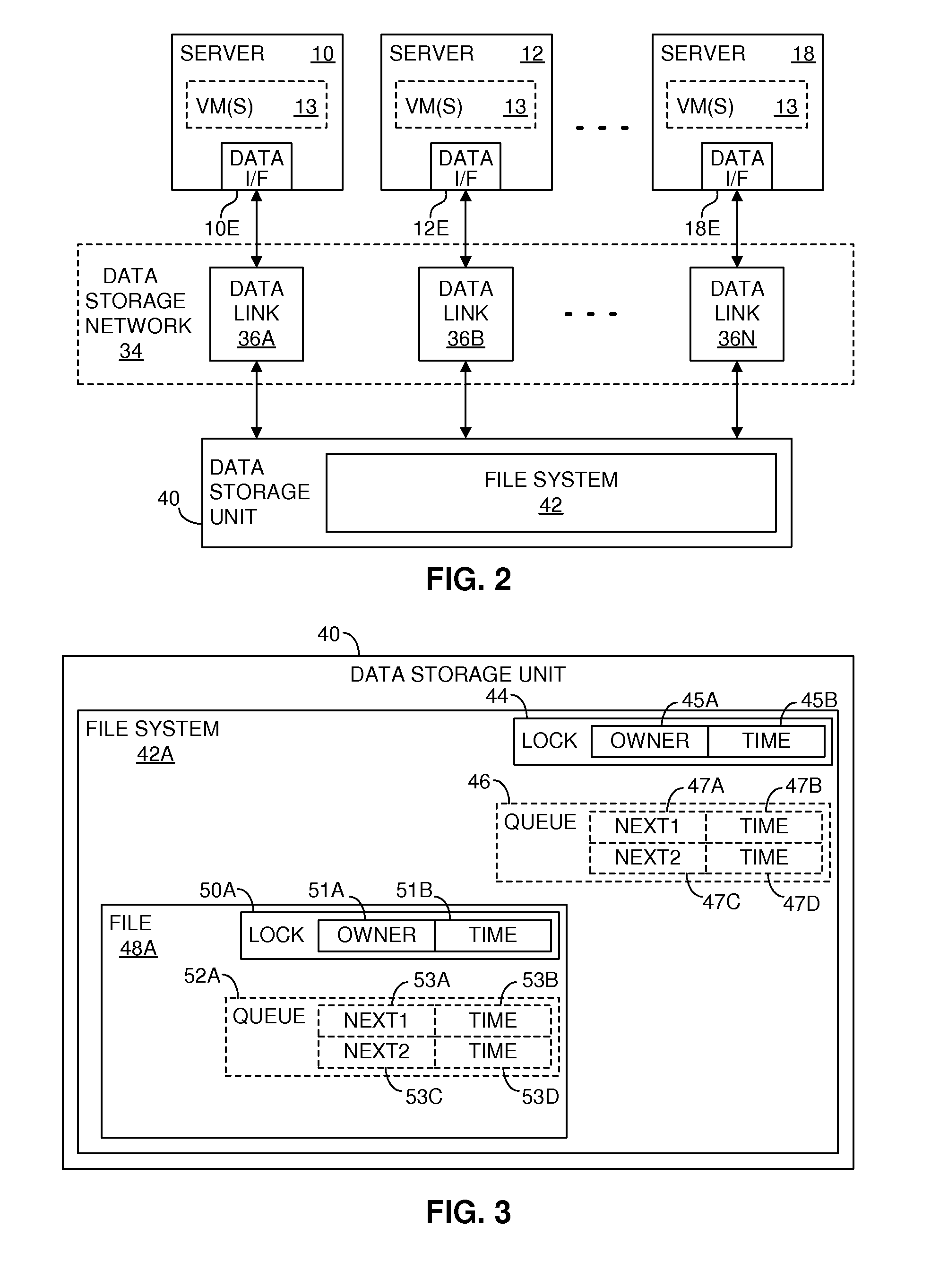
Providing multiple concurrent access to a file system
ActiveUS7849098B1Digital data processing detailsComputer security arrangementsFile systemExclusive or
Multiple computers are connected to a data storage unit that includes a file system, which further includes multiple data entities, including files, directories and the file system itself. The file system also includes, for each data entity, an owner field for indicating which computer, if any, has exclusive or shared access to the data entity, along with a time field for indicating when a lease of the data entity began. When a computer wants to lease a data entity, the computer uses a disk reservation capability to temporarily lock the data storage unit, and, if the data entity is not currently leased, the computer writes its own identification value into the owner field and a current time into the time field for the data entity, to claim the data entity for a renewable lease period. If a prior lease of a data entity has expired, another computer may break the lease and claim ownership for itself.
Owner:VMWARE INC
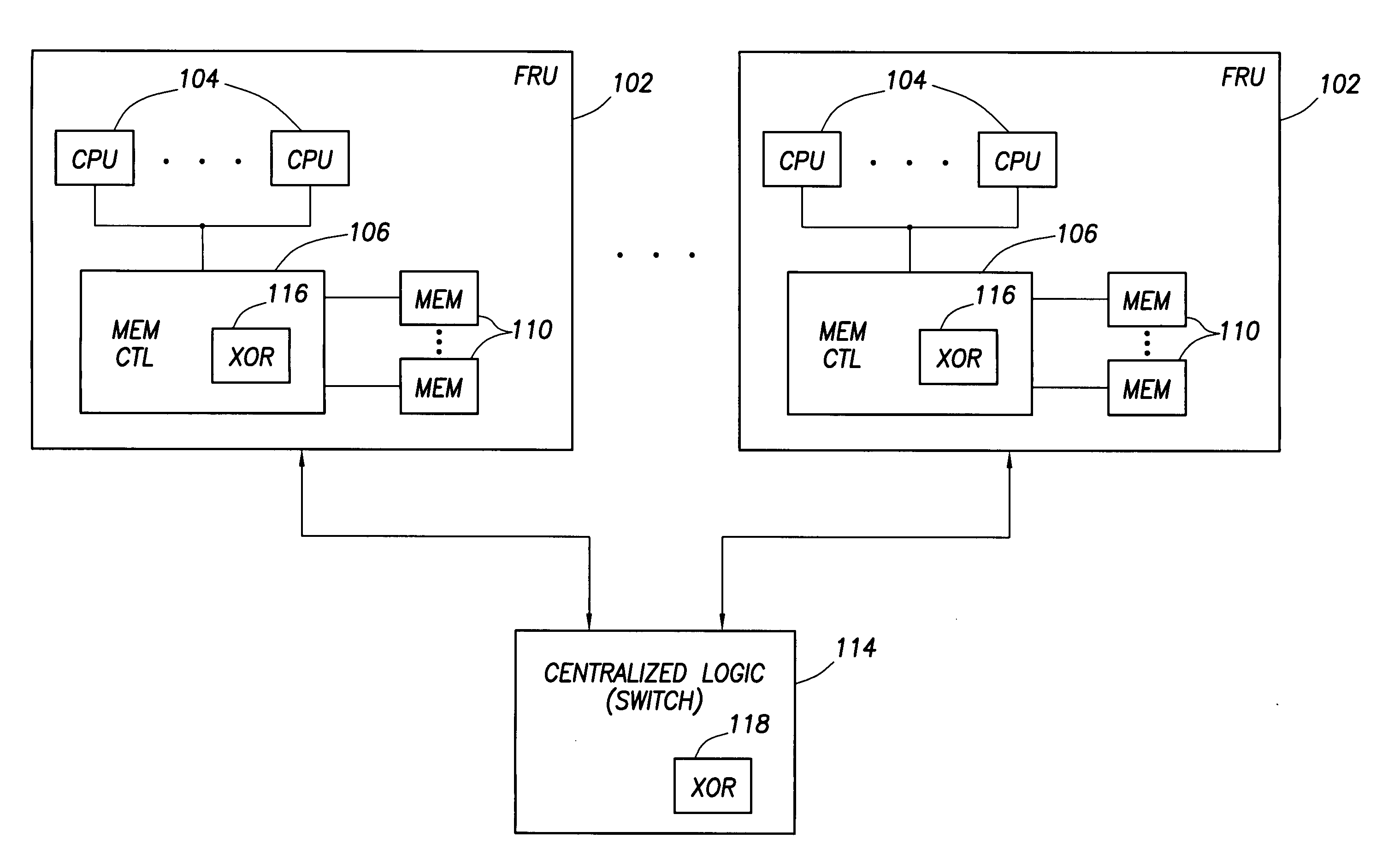
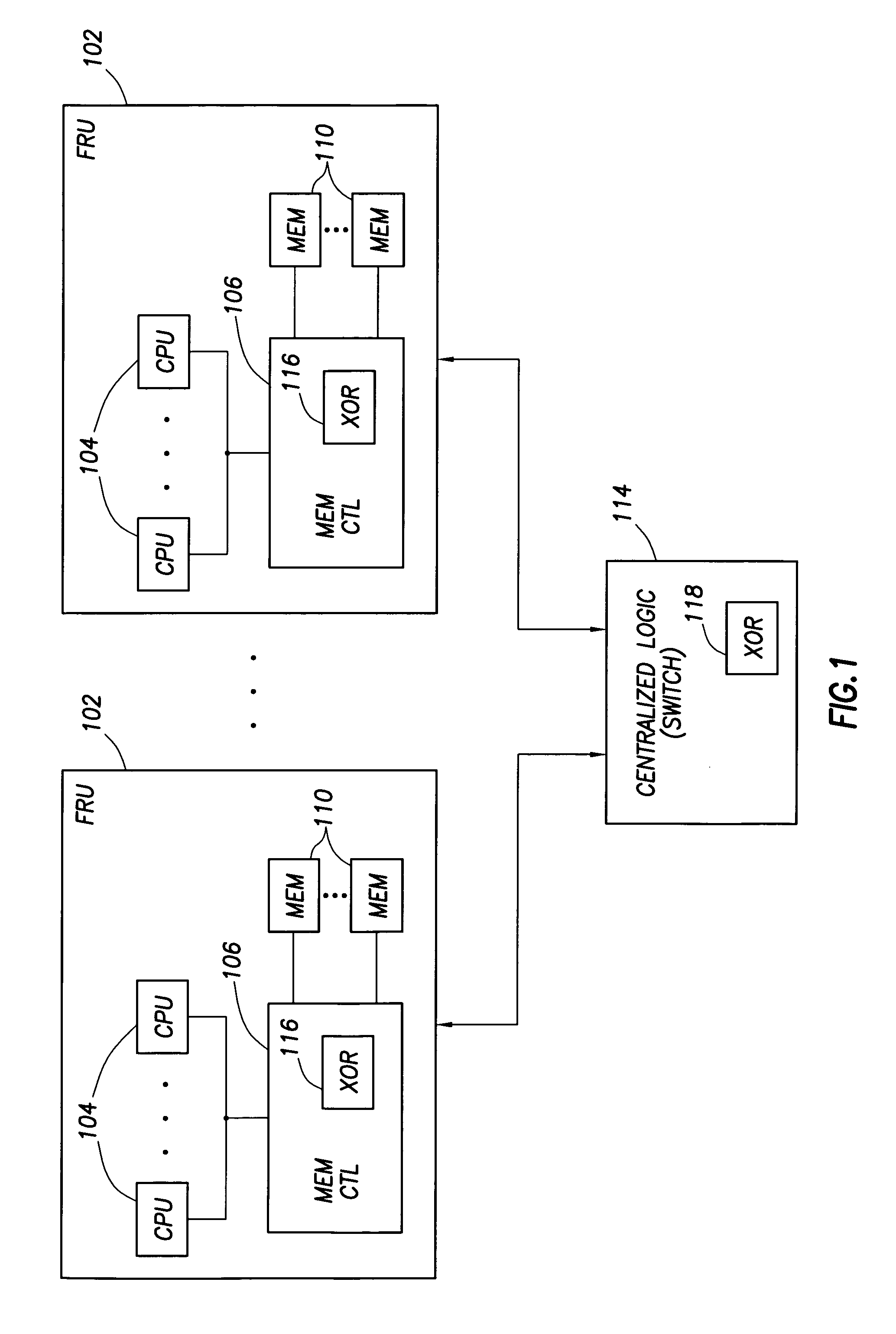
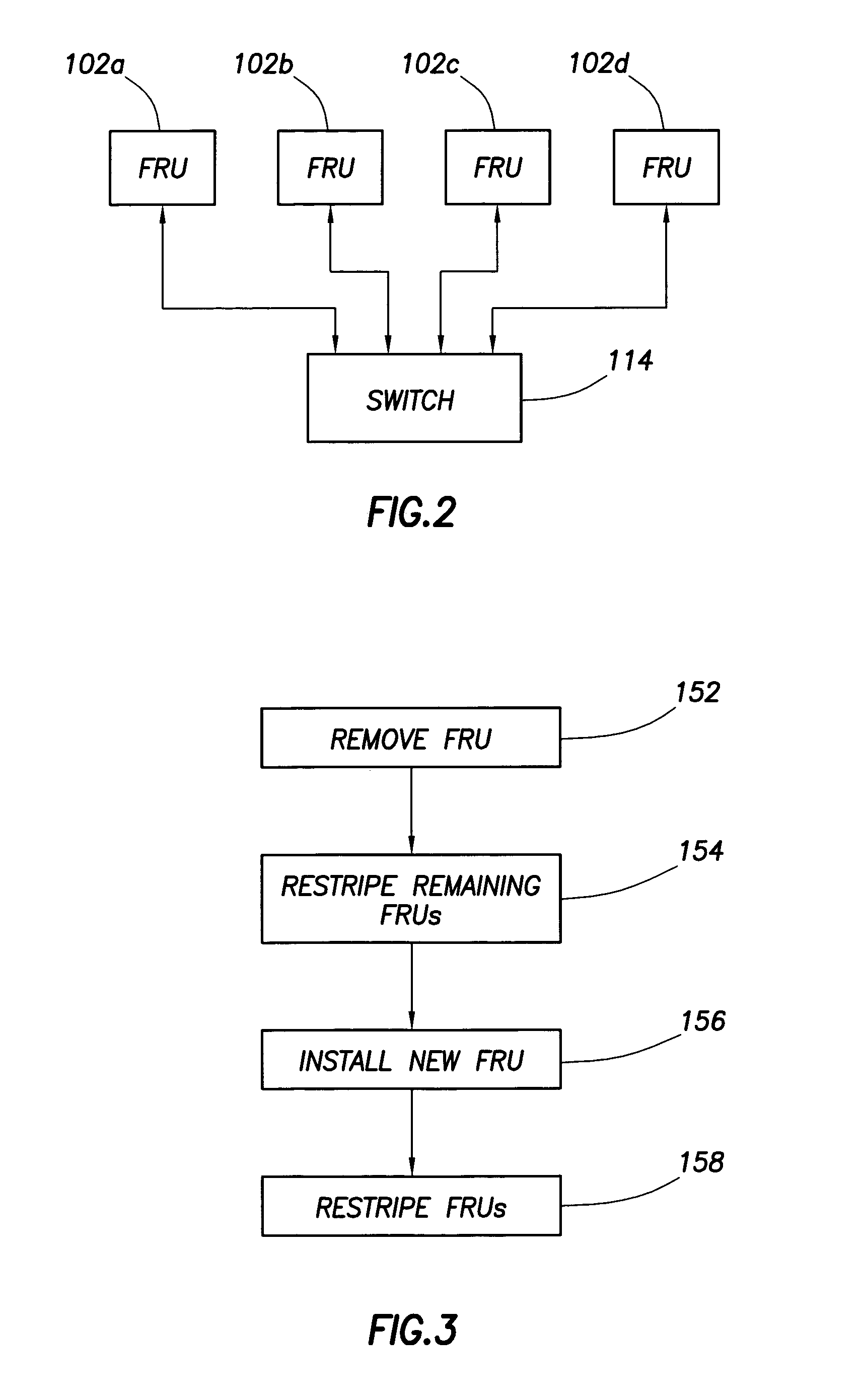
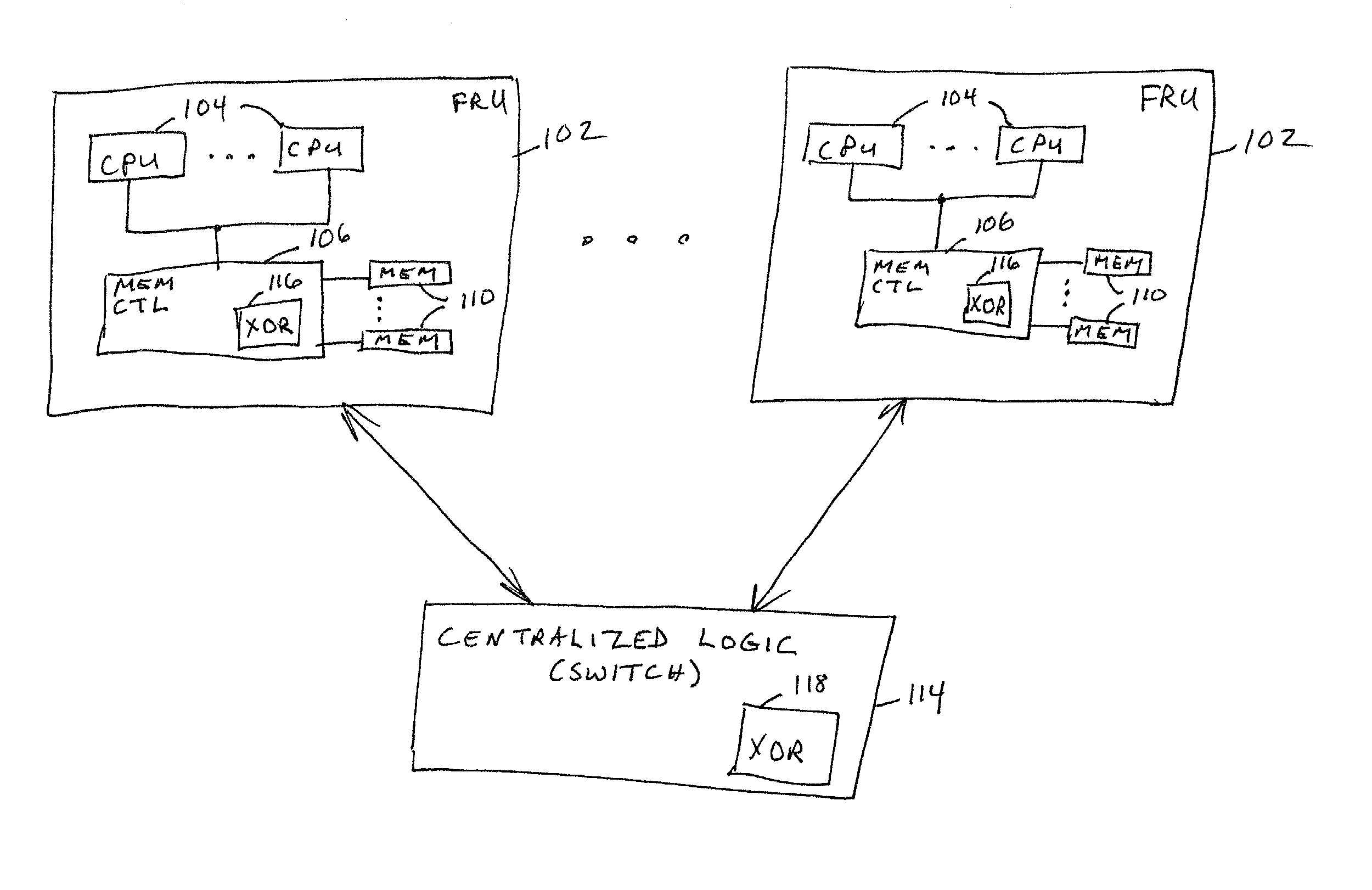
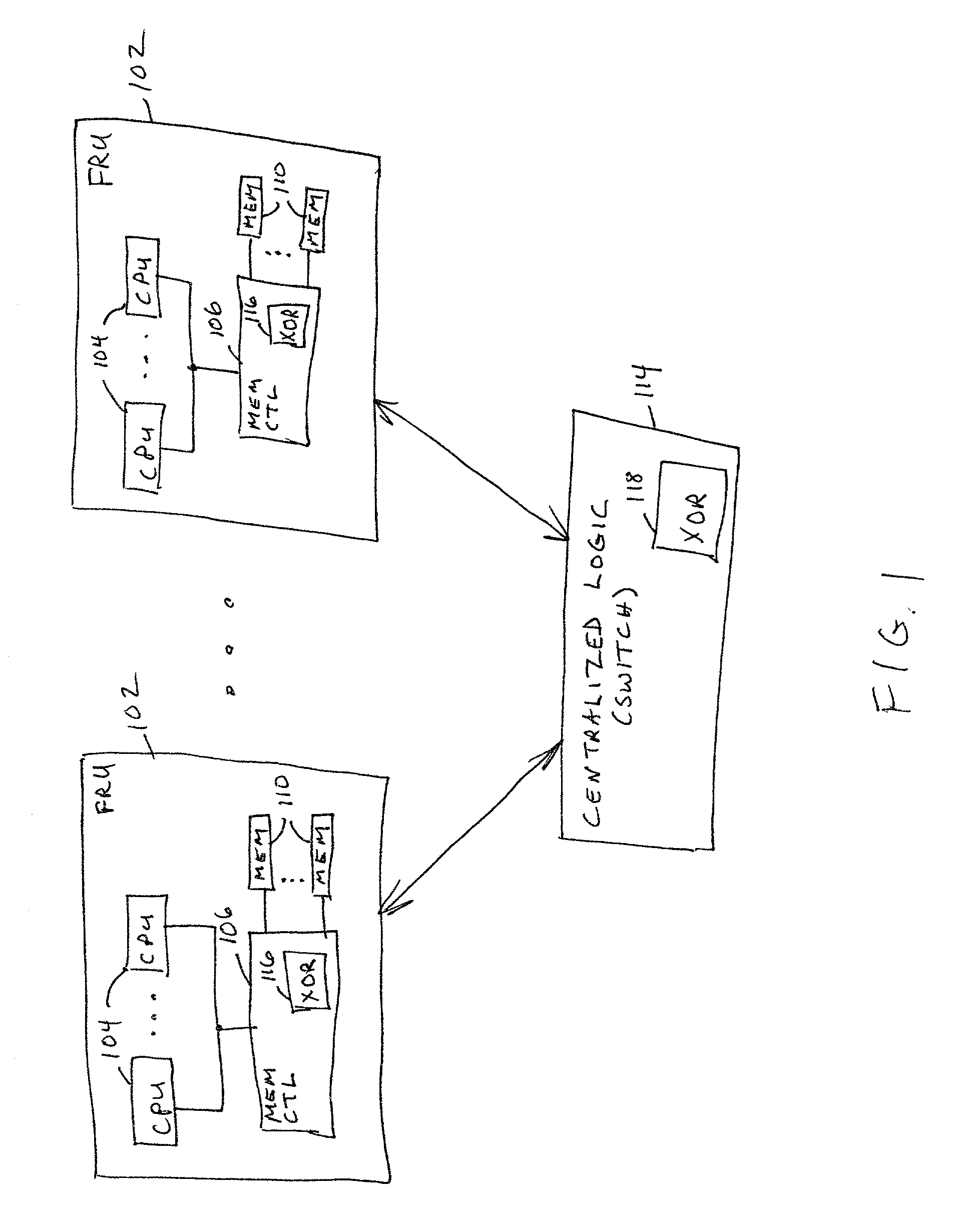
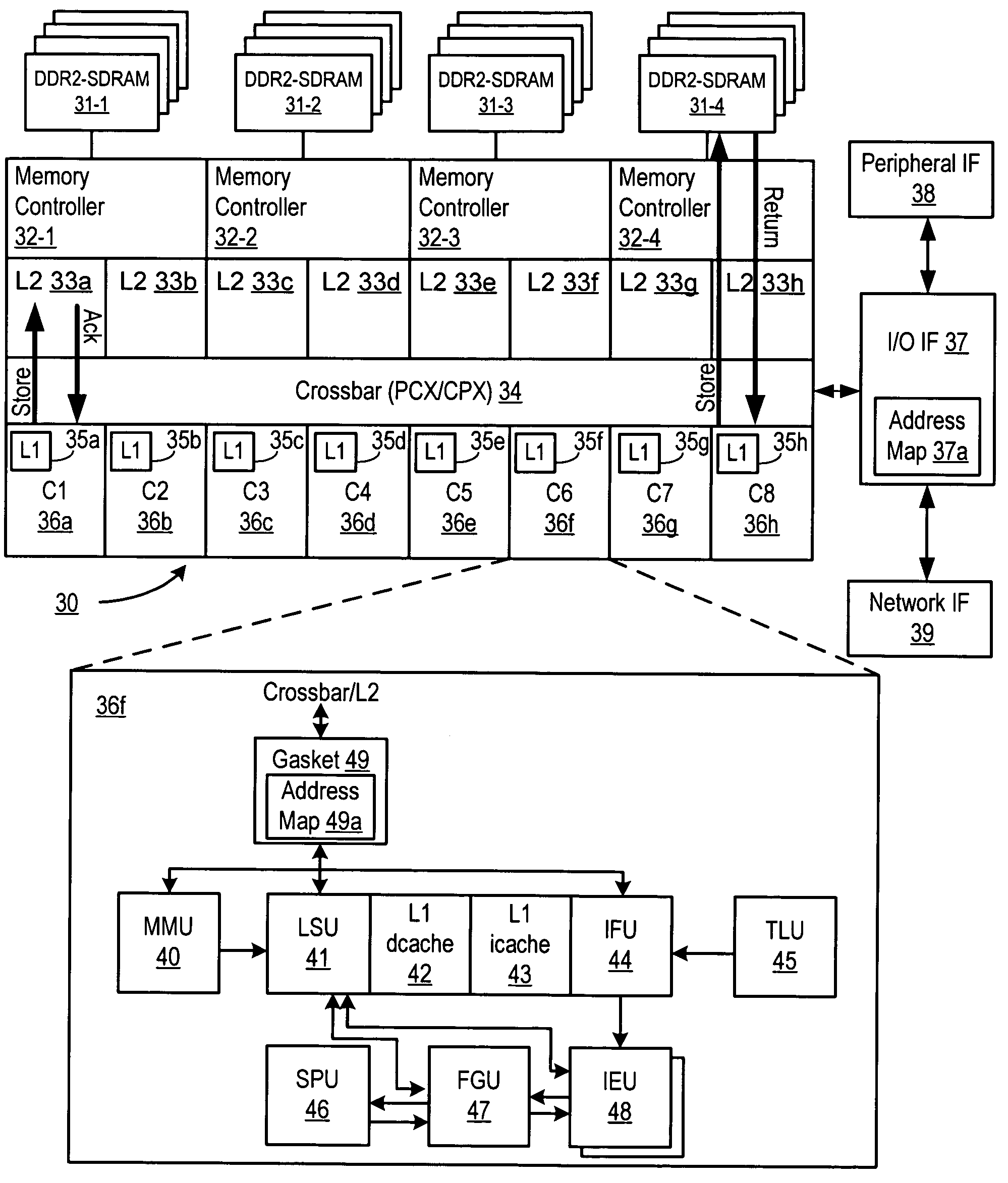
Data redundancy in a hot pluggable, large symmetric multi-processor system
ActiveUS20030172330A1Fault toleranceReduce the numberStatic storageRedundant data error correctionFault toleranceRAID
A computer system includes a plurality of field replaceable units, each having volatile memory and at least one CPU. The FRUs communicate with each other via centralized logic. A RAID data fault tolerance technique is applied to the system so that an FRU can be lost or removed without loss of its data. An exclusive OR engine is included in the centralized logic or distributed among the FRUs. The RAID logic can restripe itself upon removal or addition of a FRU.
Owner:CONVERSANT INTPROP MANAGEMENT INC
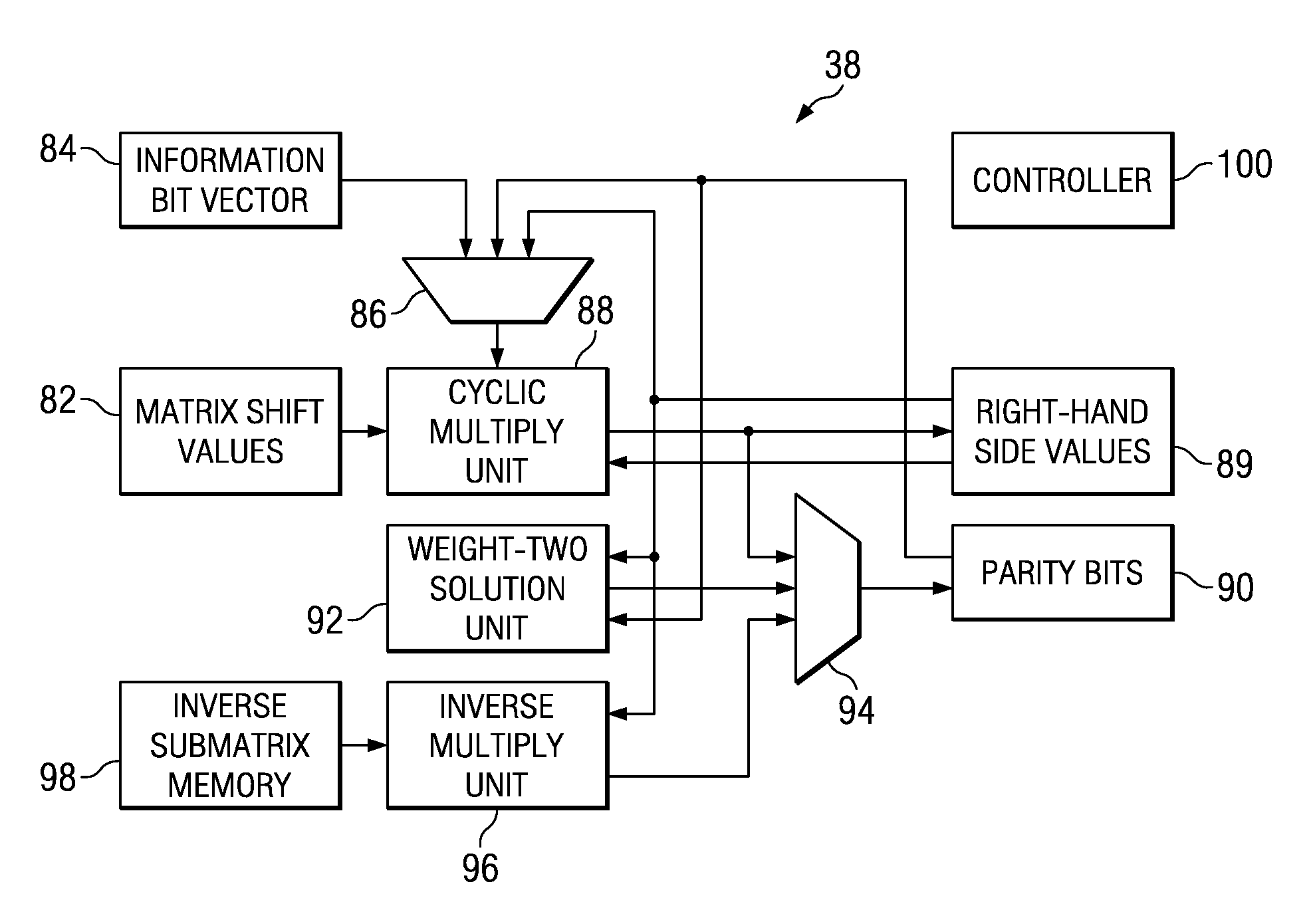
Efficient encoder for low-density-parity-check codes
ActiveUS7162684B2Improve efficiencyLow implementation costError detection/correctionError correction/detection using multiple parity bitsDiagonalParity-check matrix
Encoder circuitry for applying a low-density parity check (LDPC) code to information words is disclosed. The encoder circuitry takes advantage of a macro matrix arrangement of the LDPC parity check matrix in which a left-hand portion of the parity check matrix is arranged as an identity macro matrix, each entry of the macro matrix corresponding to a permutation matrix having zero or more circularly shifted diagonals. The encoder circuitry includes a cyclic multiply unit, which includes a circular shift unit for shifting a portion of the information word according to shift values stored in a shift value memory for the matrix entry, and a bitwise exclusive-OR function for combining the shifted entry with accumulated previous values for that matrix entry. Circuitry for solving parity bits for row rank deficient portions of the parity check matrix is also included in the encoder circuitry.
Owner:TEXAS INSTR INC
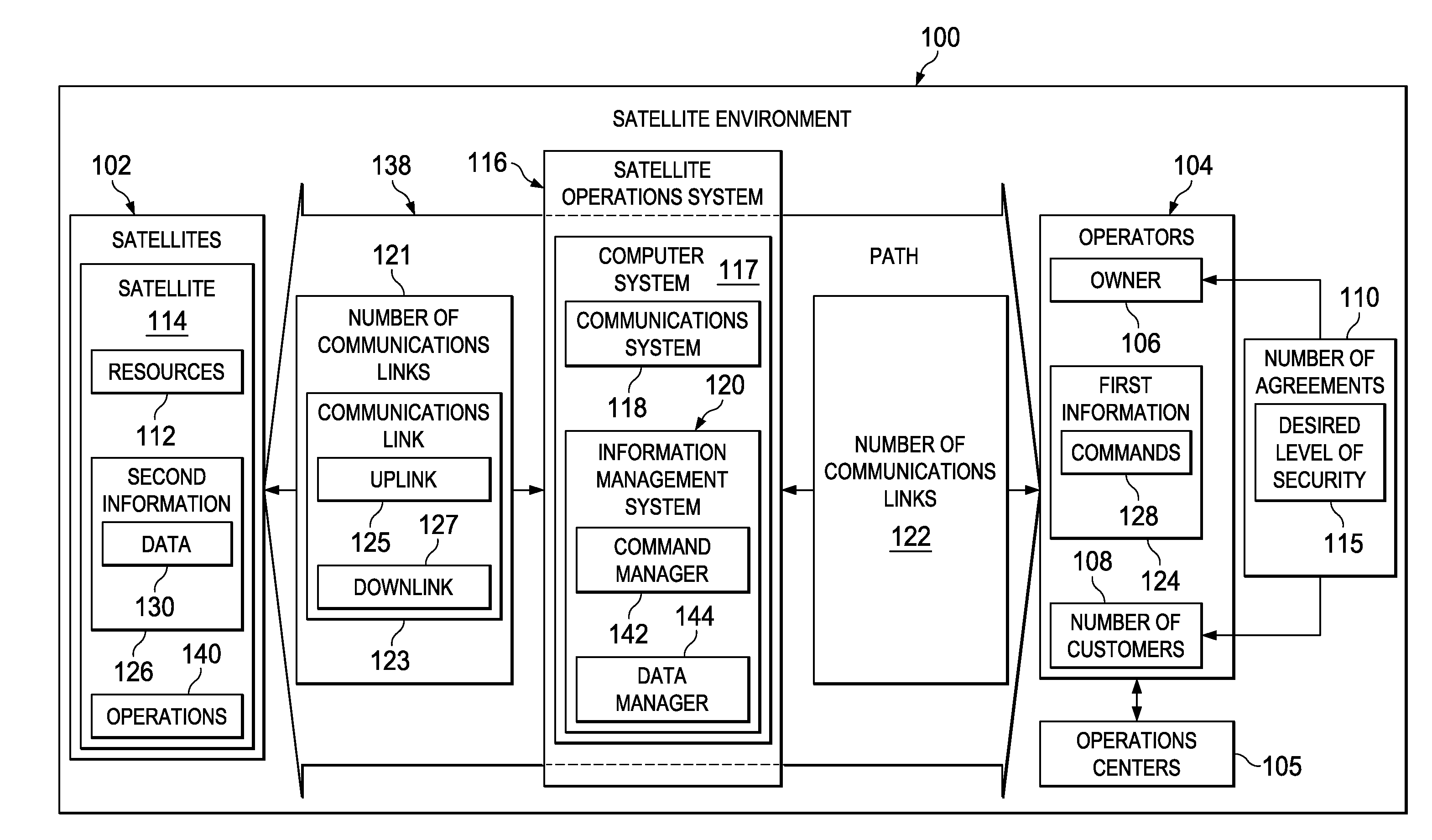
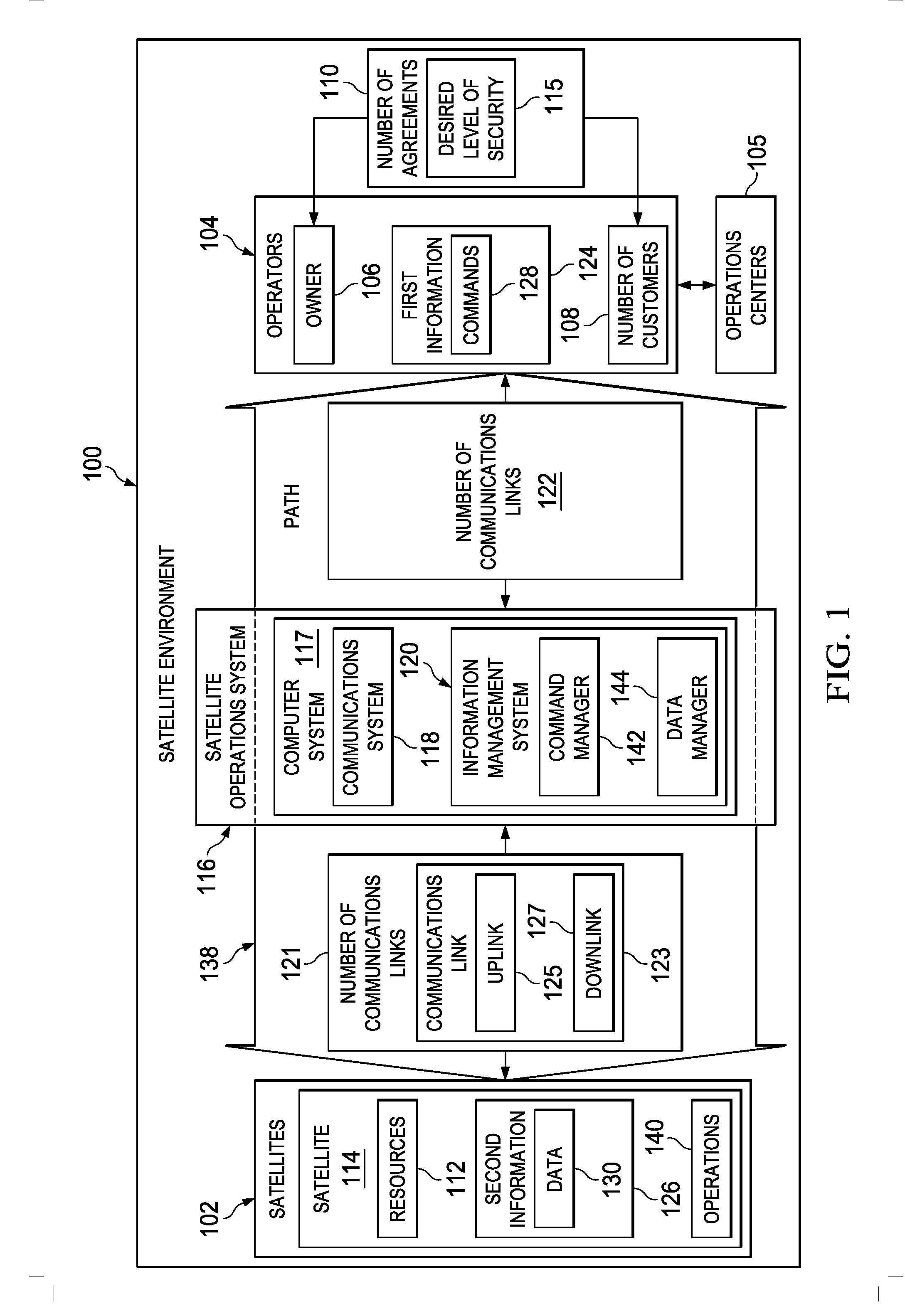
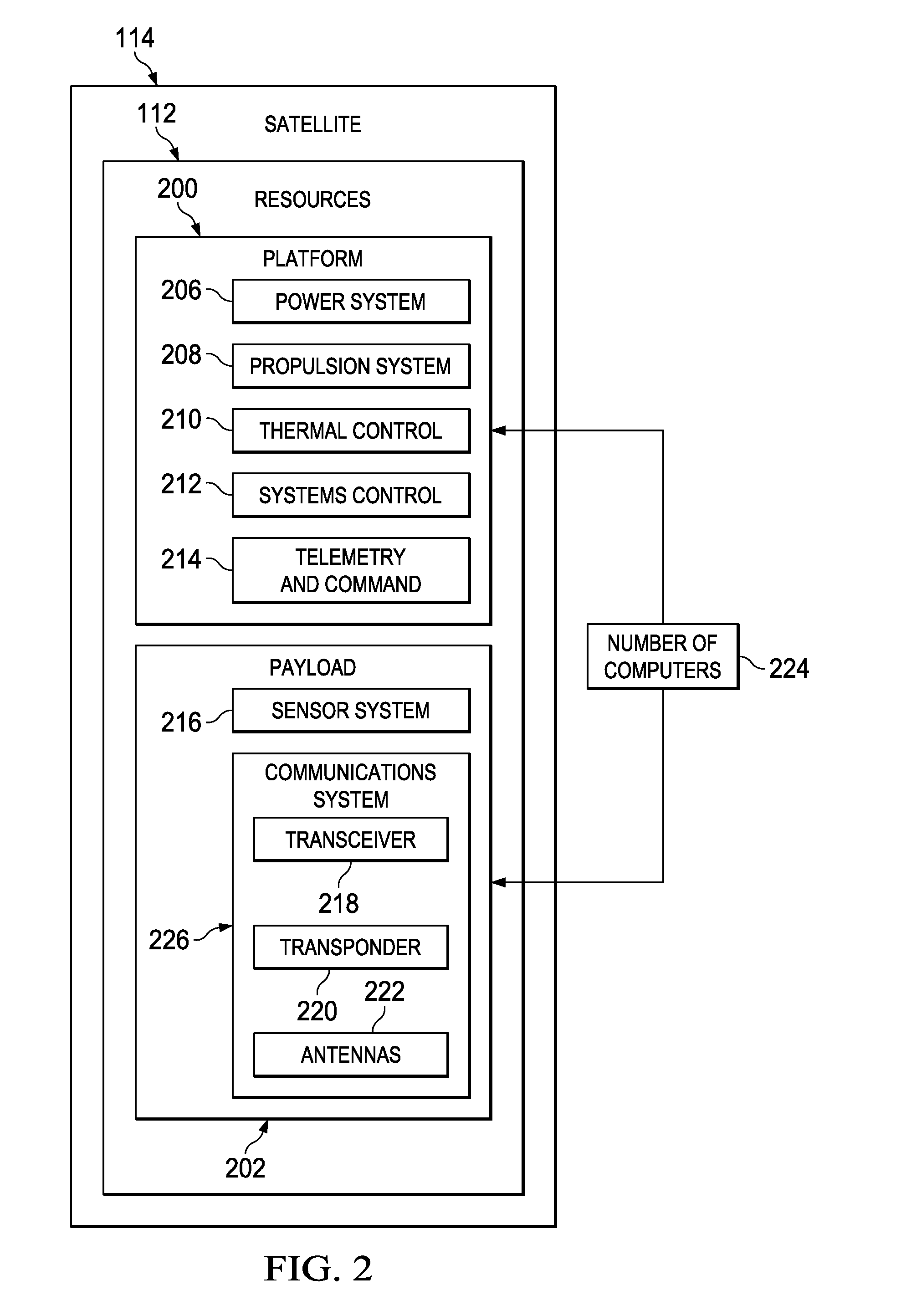
Selective Downlink Data Encryption System for Satellites
ActiveUS20130077788A1Secret communicationRadio transmissionTelecommunications linkCommunications system
A method and apparatus for a satellite system. A satellite system is comprised of a communications system in a satellite and a number of computers associated with the satellite. The communications system is configured to receive first information and transmit second information from the satellite to a remote platform over a number of communications links. The number of computers is configured to identify a block of information for encryption from instructions in the first information. The number of computers is further configured to generate a key from a portion of the block of information based on the instructions. The number of computers is further configured to perform an exclusive OR operation on the block of information using the key to form a block of encrypted information. The number of computers is further configured to transmit the block of encrypted information.
Owner:THE BOEING CO
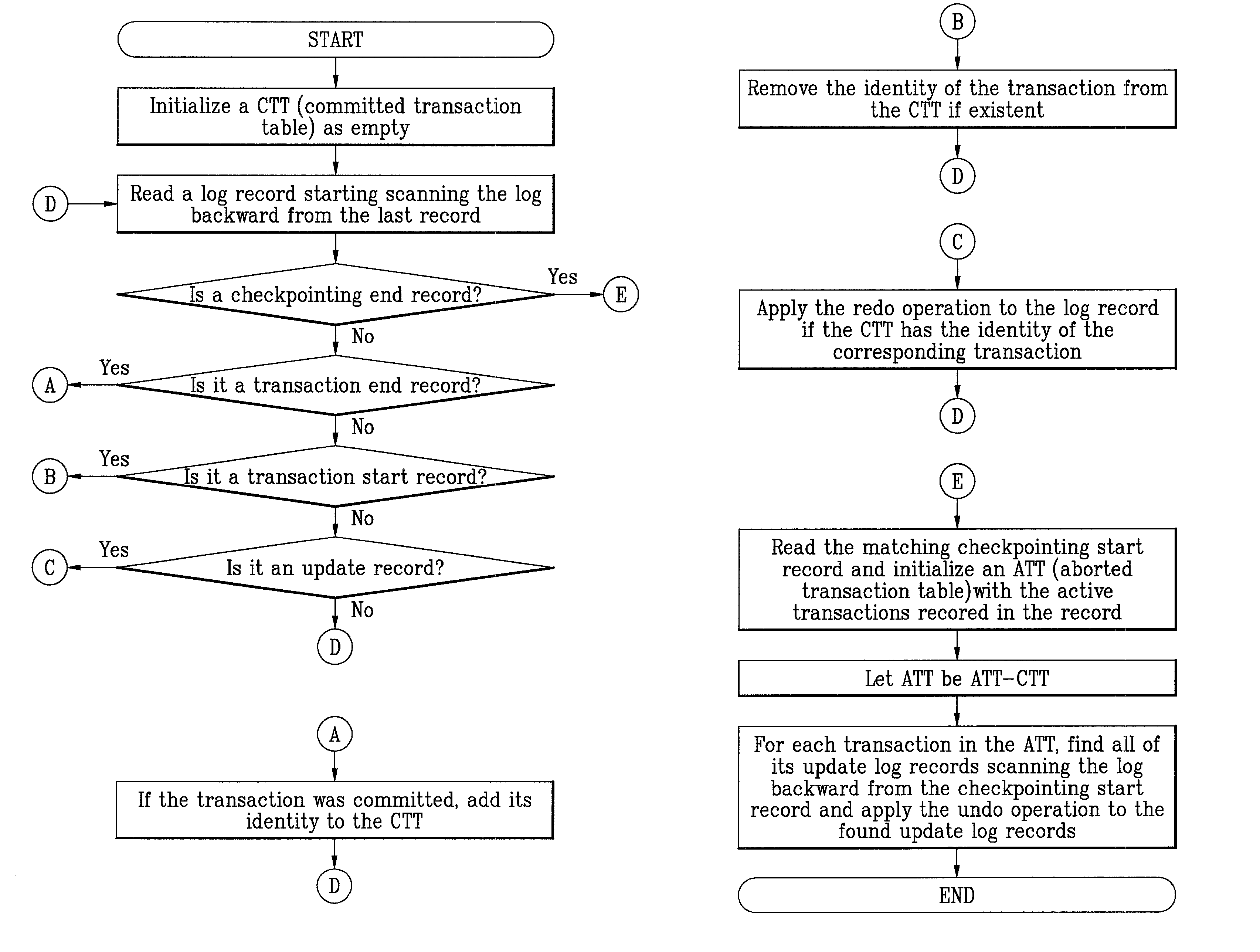
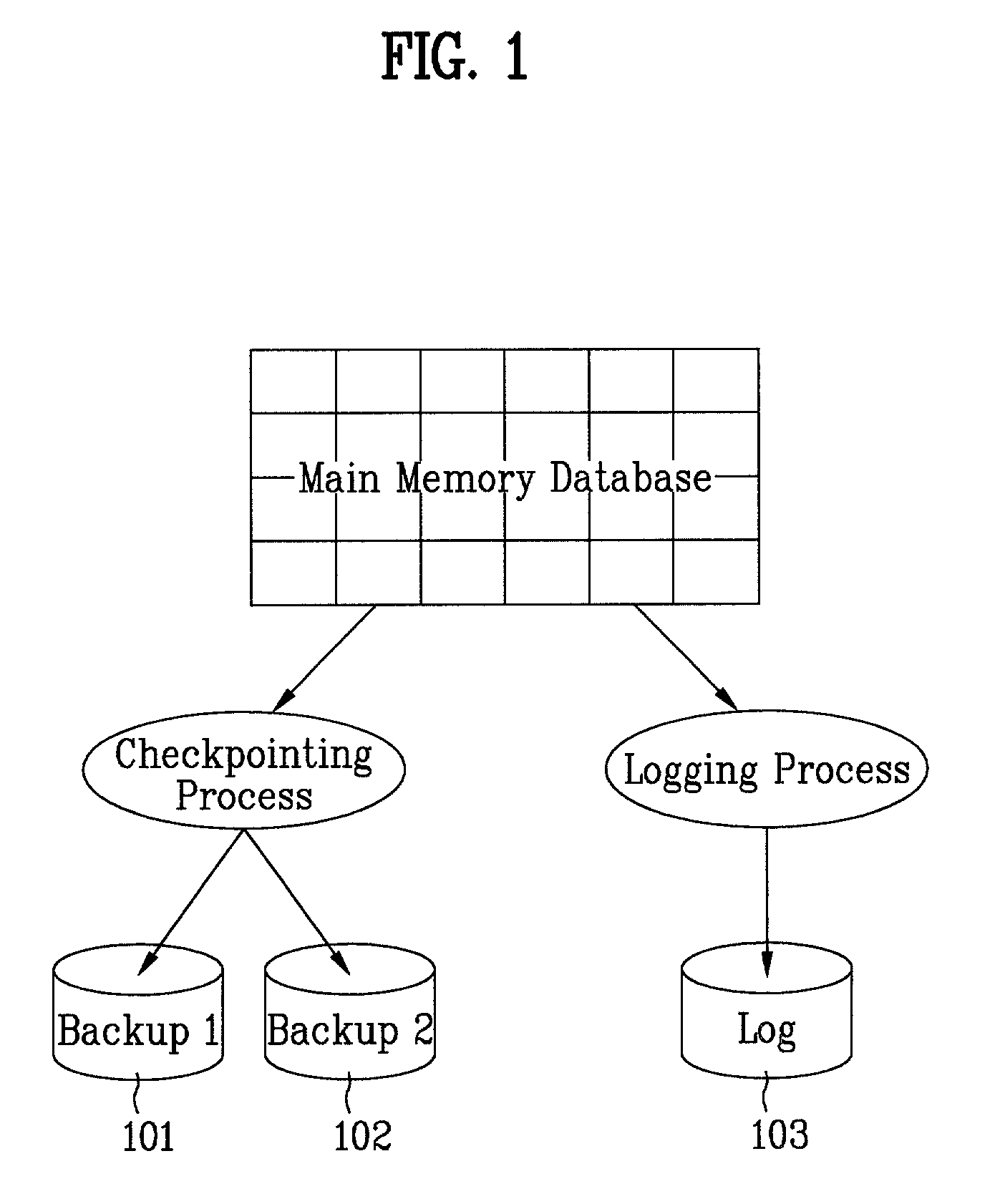
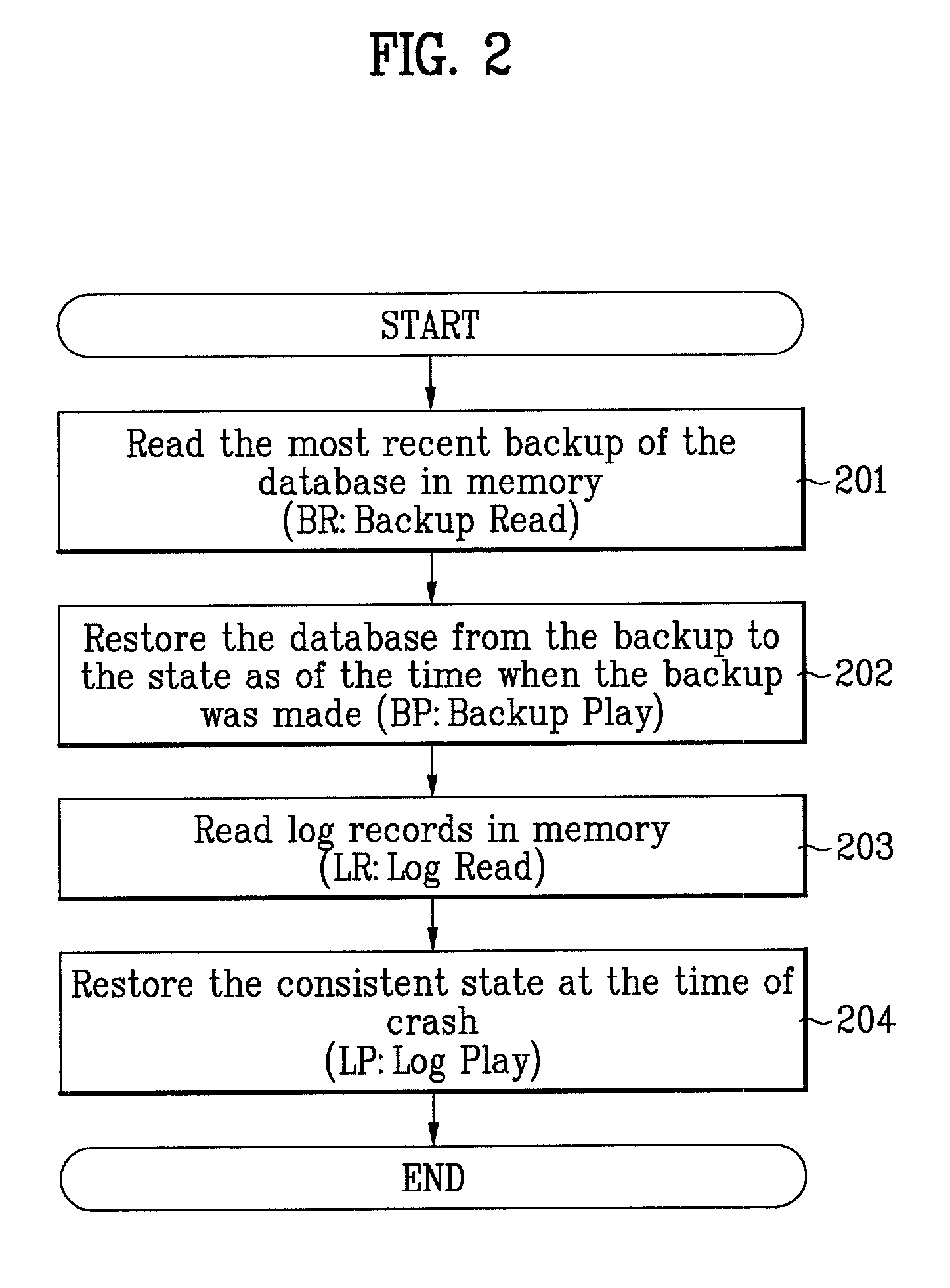
Method and system for highly-parallel logging and recovery operation in main-memory transaction processing systems
InactiveUS7065537B2Data processing applicationsDigital data processing detailsExclusive orTransaction processing system
An efficient logging method and system is disclosed that can be used to recover from a failure in a transaction system. It is based on a differential logging scheme that allows commutative and associative recovery operations. The method includes the steps of taking a before-image of the primary database in main memory before an update to the primary database; taking an after-image of the primary database after the update; generating a differential log by applying bit-wise exclusive-OR (XOR) between the before-image and the after-image; and performing either a redo or undo operation by applying XOR between said one or more logs and the before-image. Since XOR operations are commutative and associative, correct recovery is possible regardless of the creation sequence of log records. The present invention improves the performance of a logging system by reducing the size of log records and by allowing parallel execution of recovery operations.
Owner:TRANSACT & MEMORY
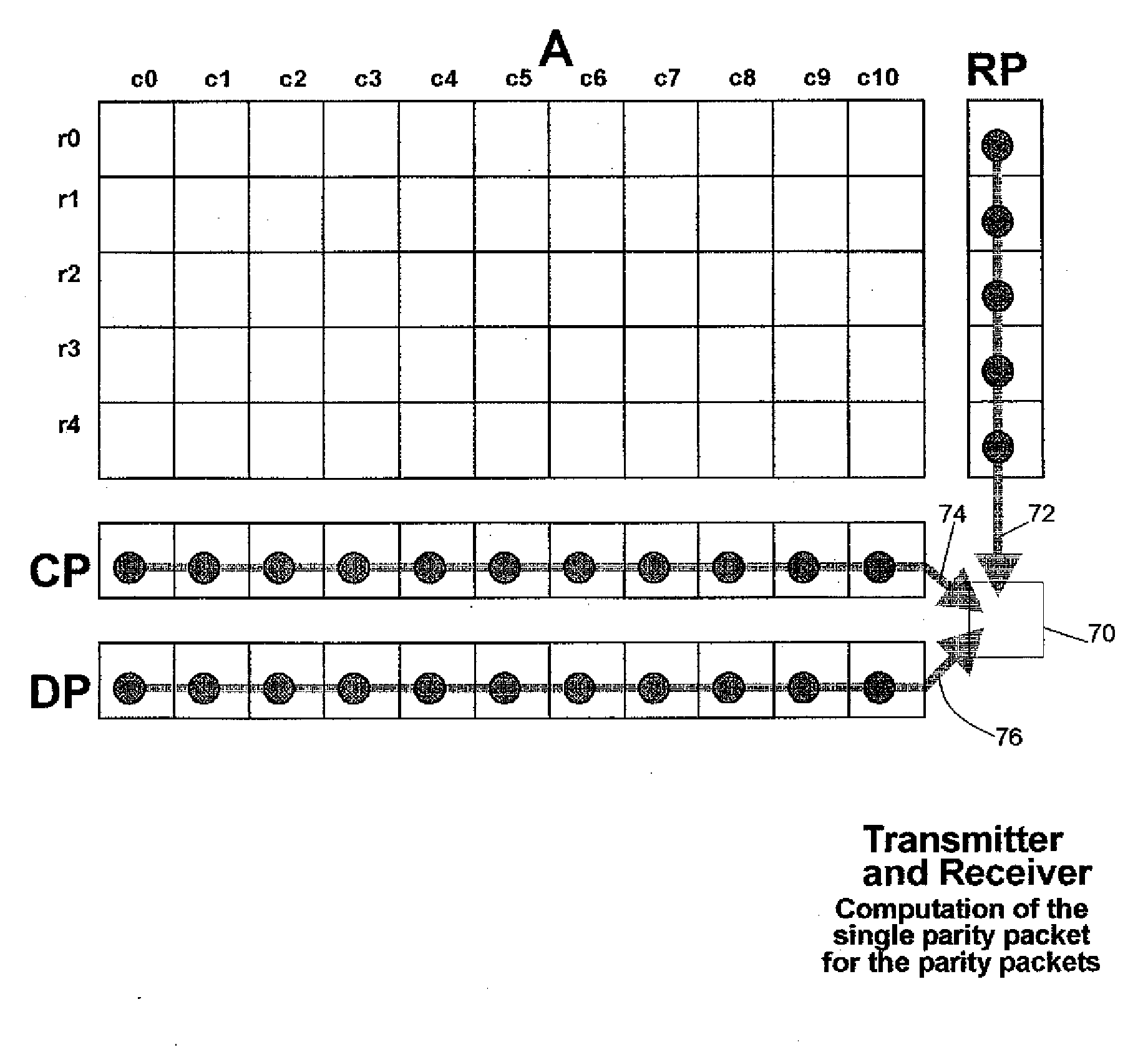
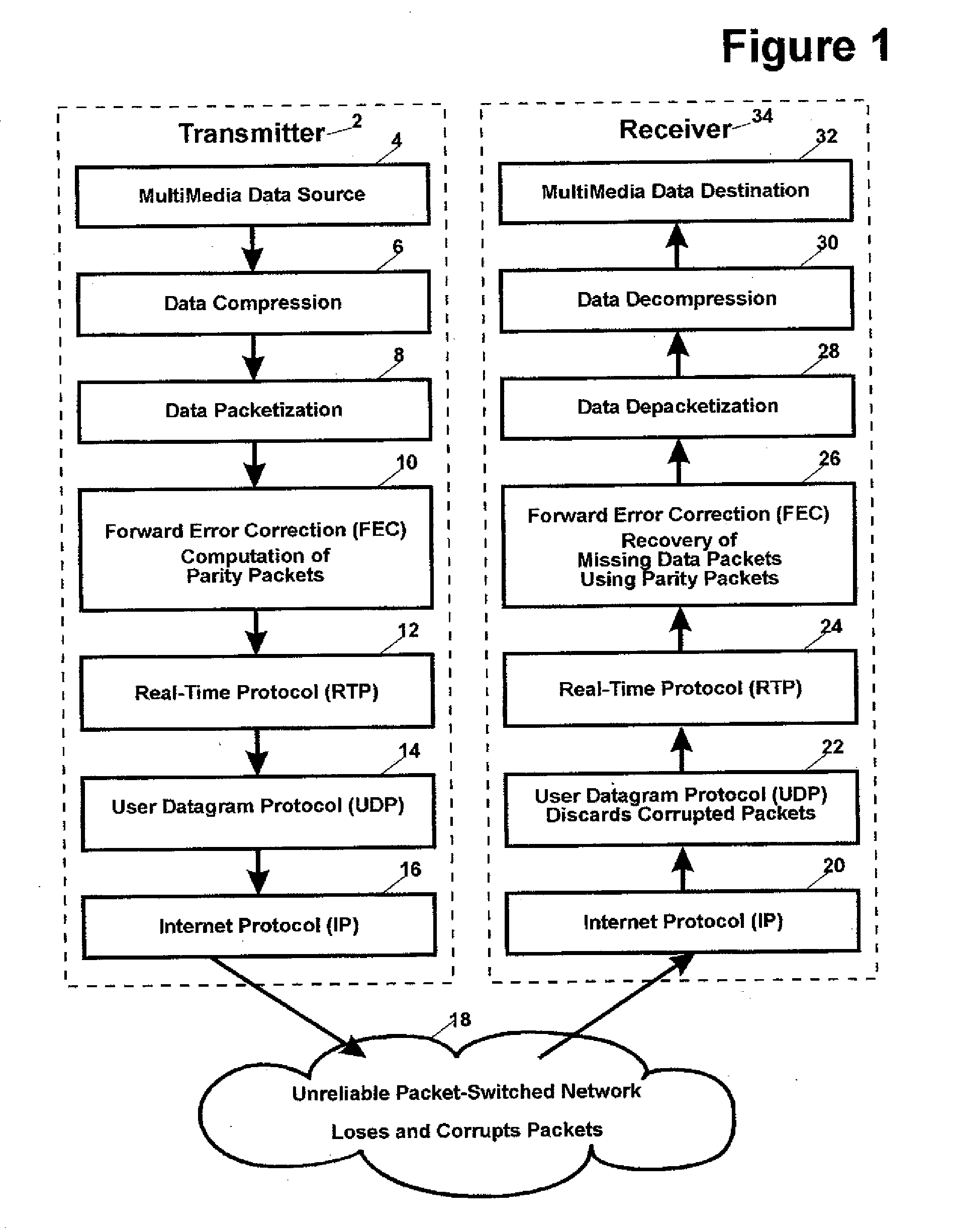
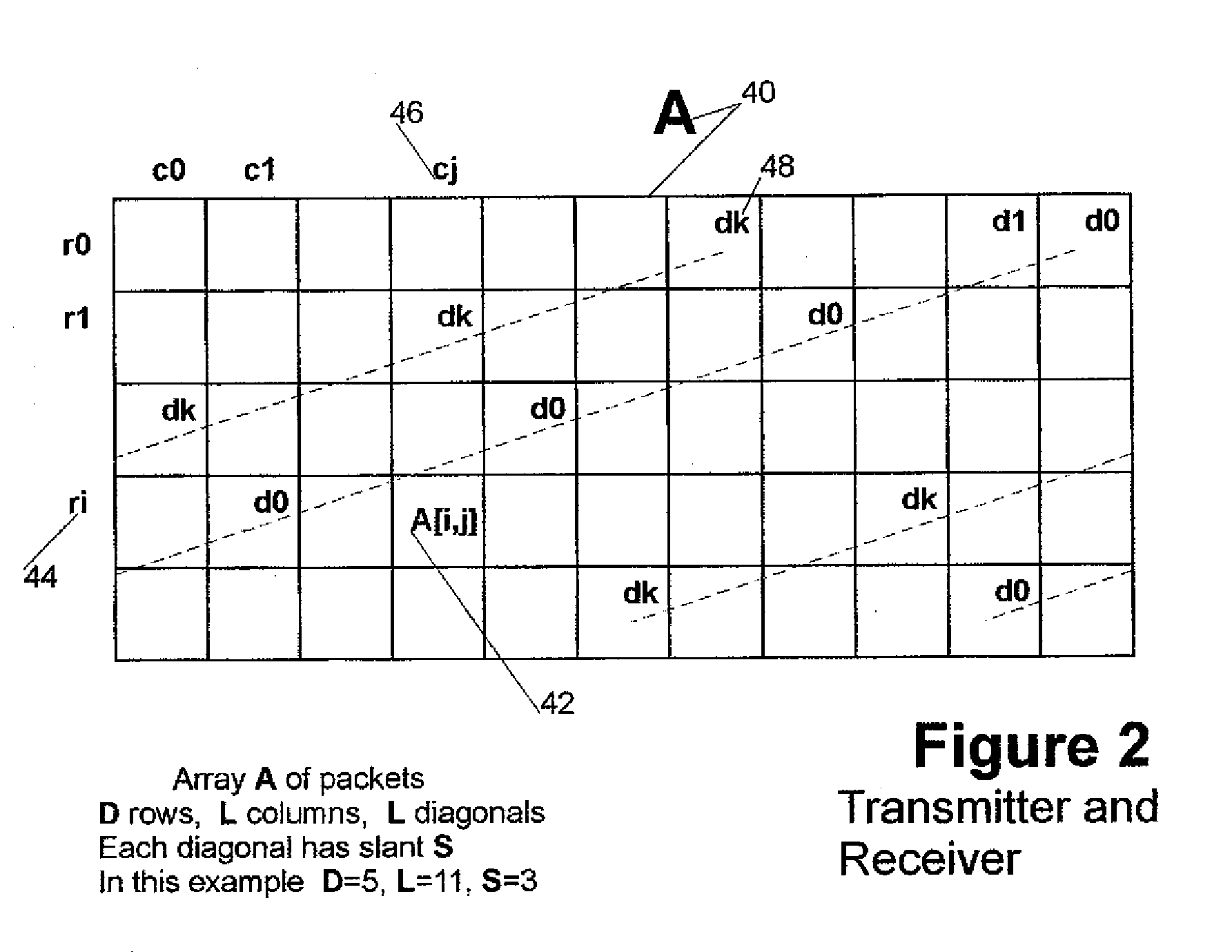
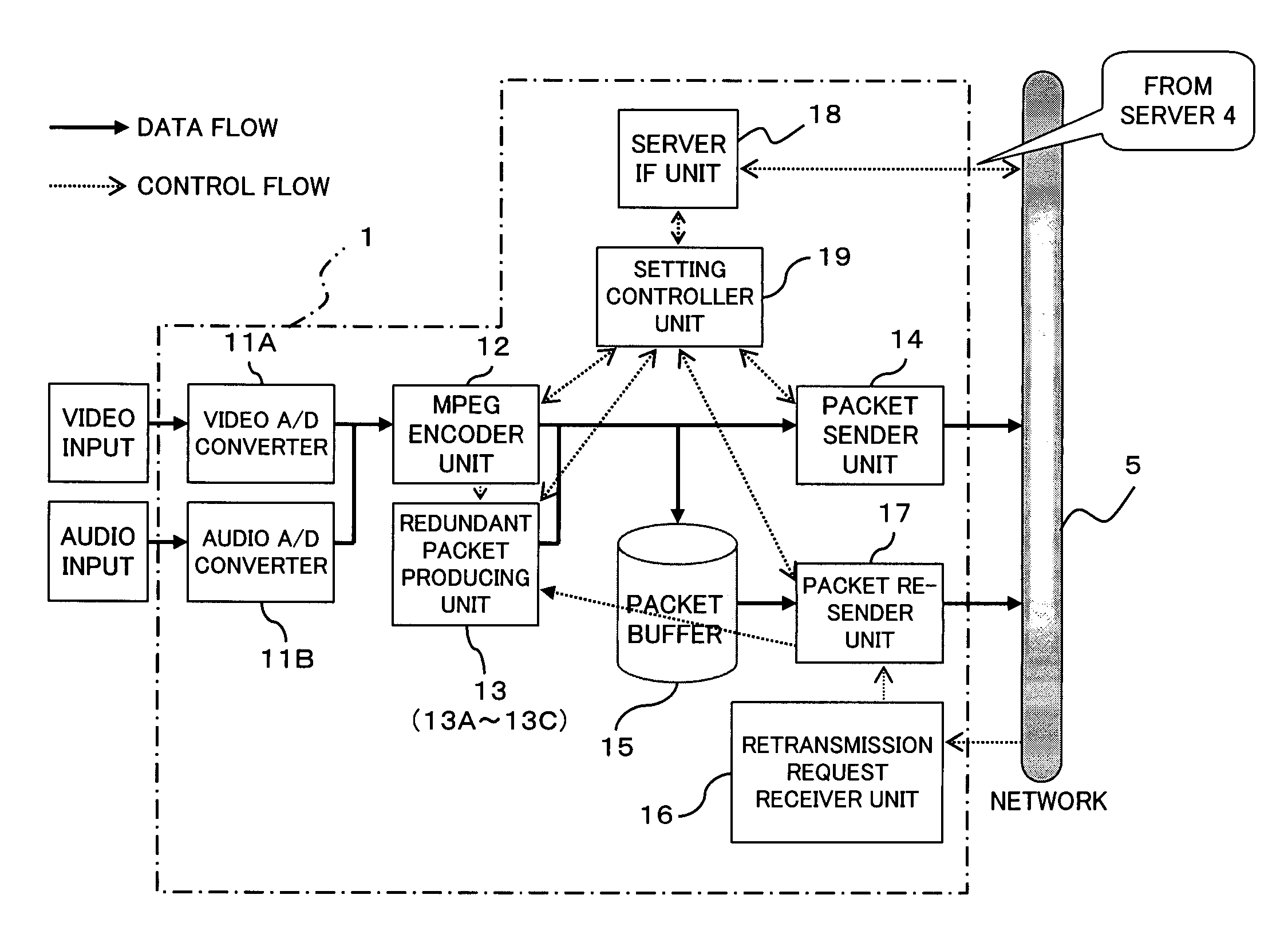
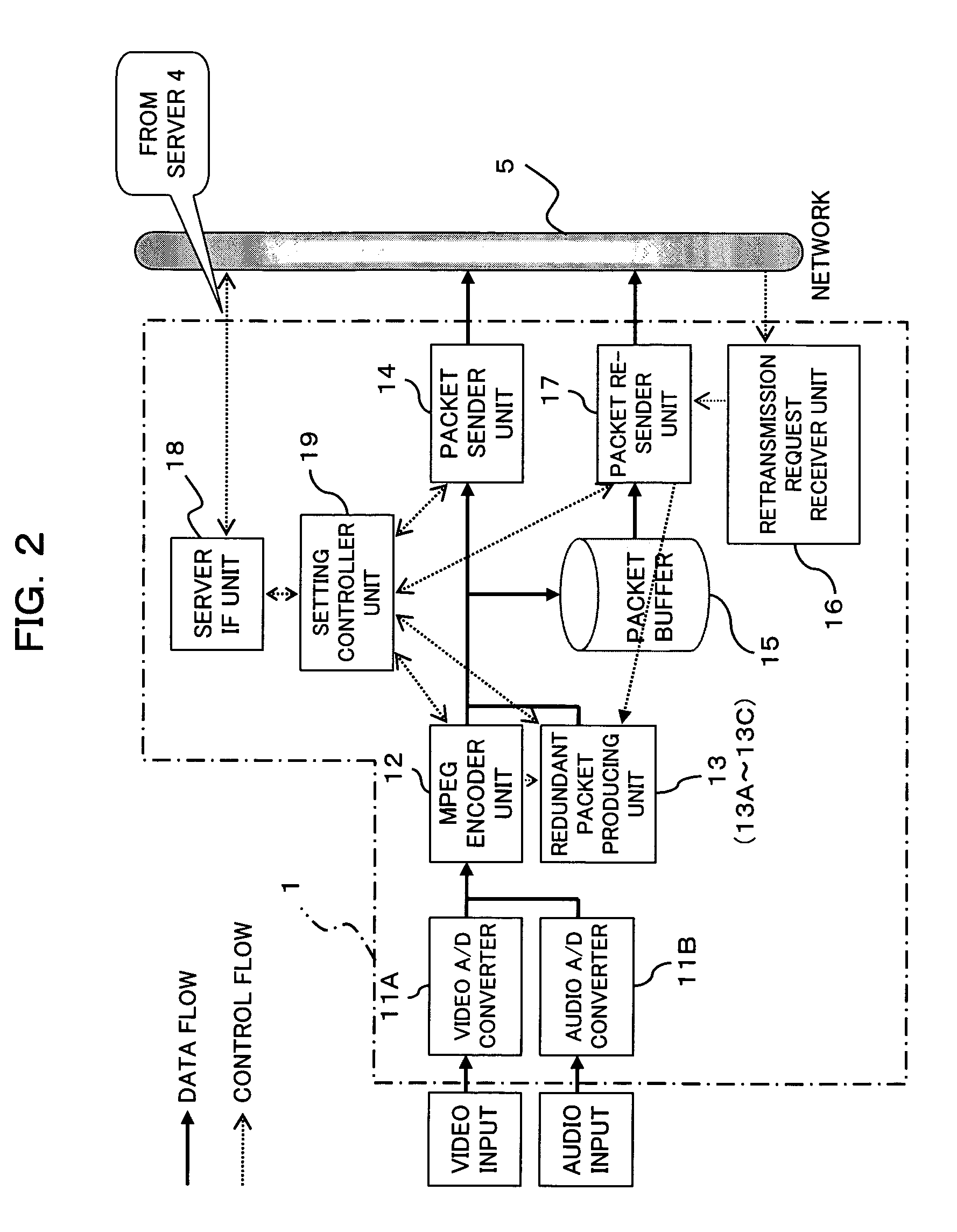
Forward error correction for burst and random packet loss for real-time multi-media communication
ActiveUS20090193314A1Less powerFlexibility of deploymentError correction/detection using convolutional codesError preventionMissing dataPacket loss
This invention relates generally to a packet recovery algorithm for real-time (live) multi-media communication over packet-switched networks, such as the Internet. Such multi-media communication includes video, audio, data or any combination thereof. More specifically, the invention comprises a forward error correction (FEC) algorithm that addresses both random and burst packet loss and errors, and that can be adjusted to tradeoff the recoverability of missing packets and the latency incurred. The transmitter calculates parity packets for the rows, columns and diagonals of a block of multi-media data packets using the exclusive or (XOR) operation and communicates the parity packets along with the multi-media data packets to the receiver. The receiver uses the parity packets to recover missing multi-media data packets in the block. The FEC algorithm is designed to be able to recover long bursts of consecutive missing data packets. If some parity packets are missing, they too can be recovered using an extra single parity packet, so that they can be used to recover other missing data packets. The invention applies to both one-way real-time streaming applications and two-way real-time interactive applications, and to both wired and wireless networks. The invention retains backwards compatibility with existing standards governing FEC for professional video over IP networks.
Owner:NEVION EURO
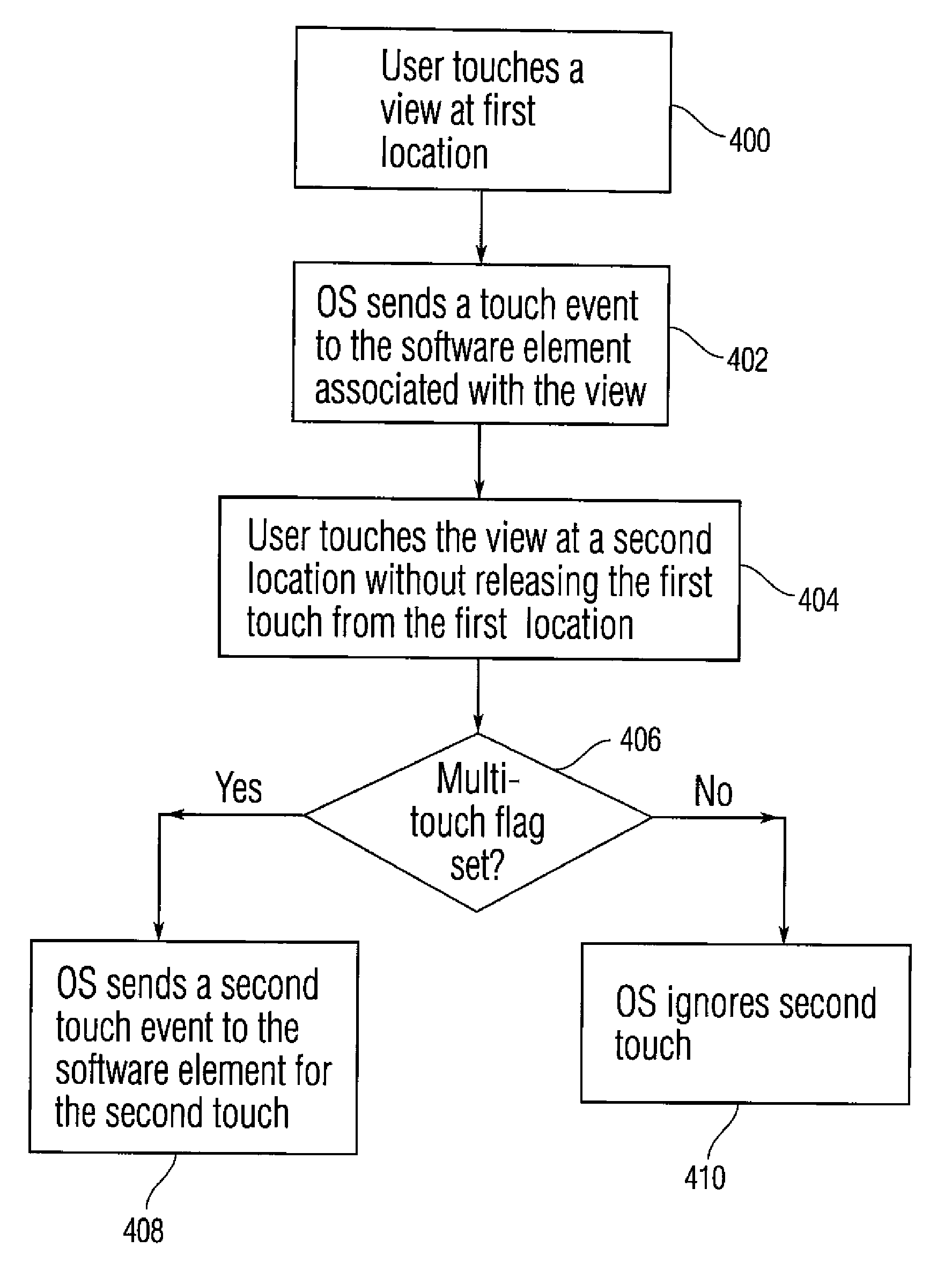
Touch event model
ActiveUS20090228901A1Recognition is intuitiveMultiprogramming arrangementsSubstation equipmentEvent modelExclusive or
Embodiments of the present invention are directed to methods, software, devices and APIs for defining touch events for application level software. Furthermore, some embodiments are directed to simplifying the recognition of single and multiple touch events for applications running in multi-touch enabled devices. To simplify the recognition of single and multiple touch events, each view within a particular window can be configured as either a multi-touch view or a single touch view. Furthermore, each view can be configured as either an exclusive or a non-exclusive view. Depending on the configuration of a view, touch events in that and other views can be either ignored or recognized. Ignored touches need not be sent to the application. Selectively ignoring touches can allow for simpler software elements that do not take advantage of advanced multi touch features to be executed at the same device and time as more complex software elements.
Owner:APPLE INC
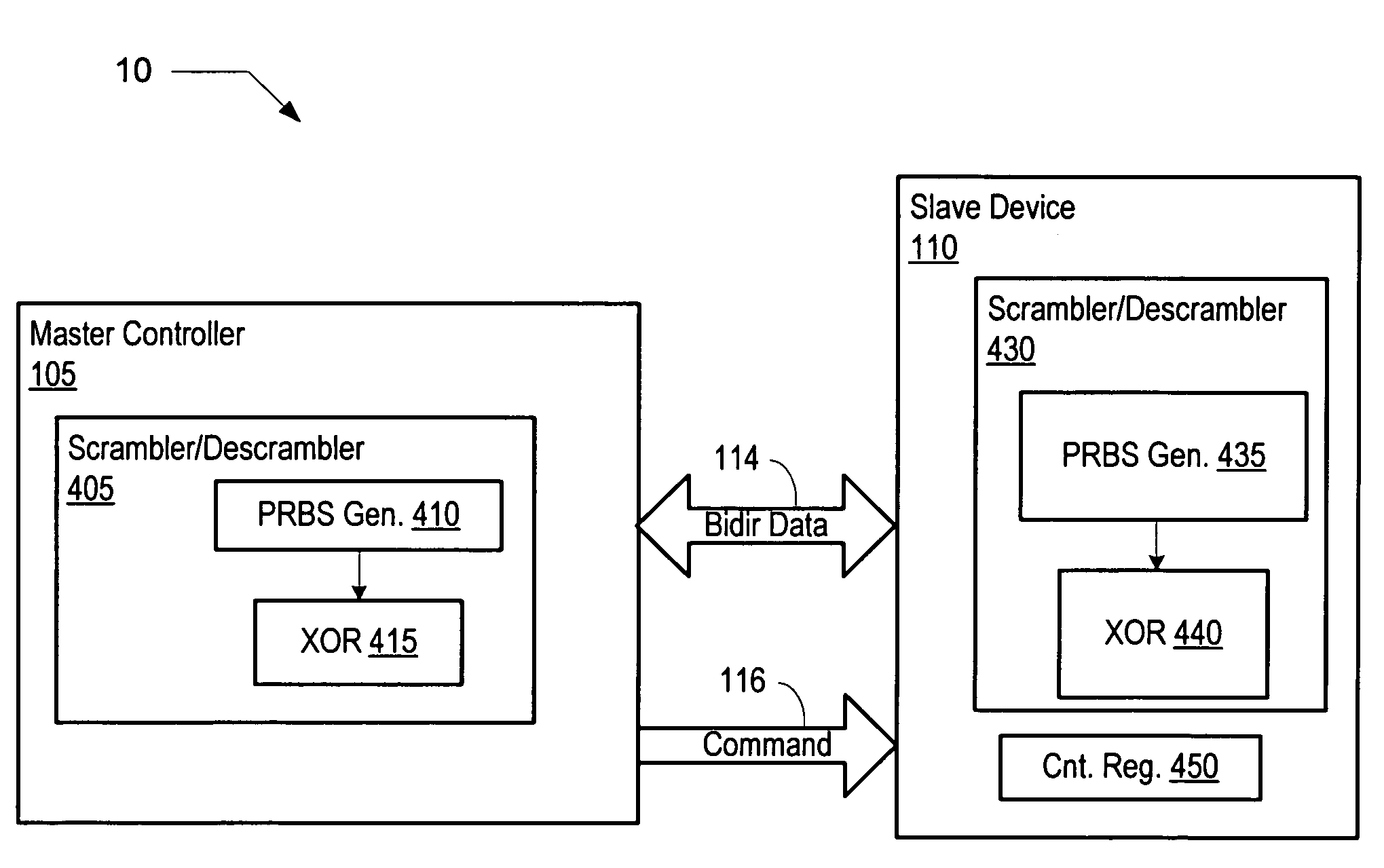
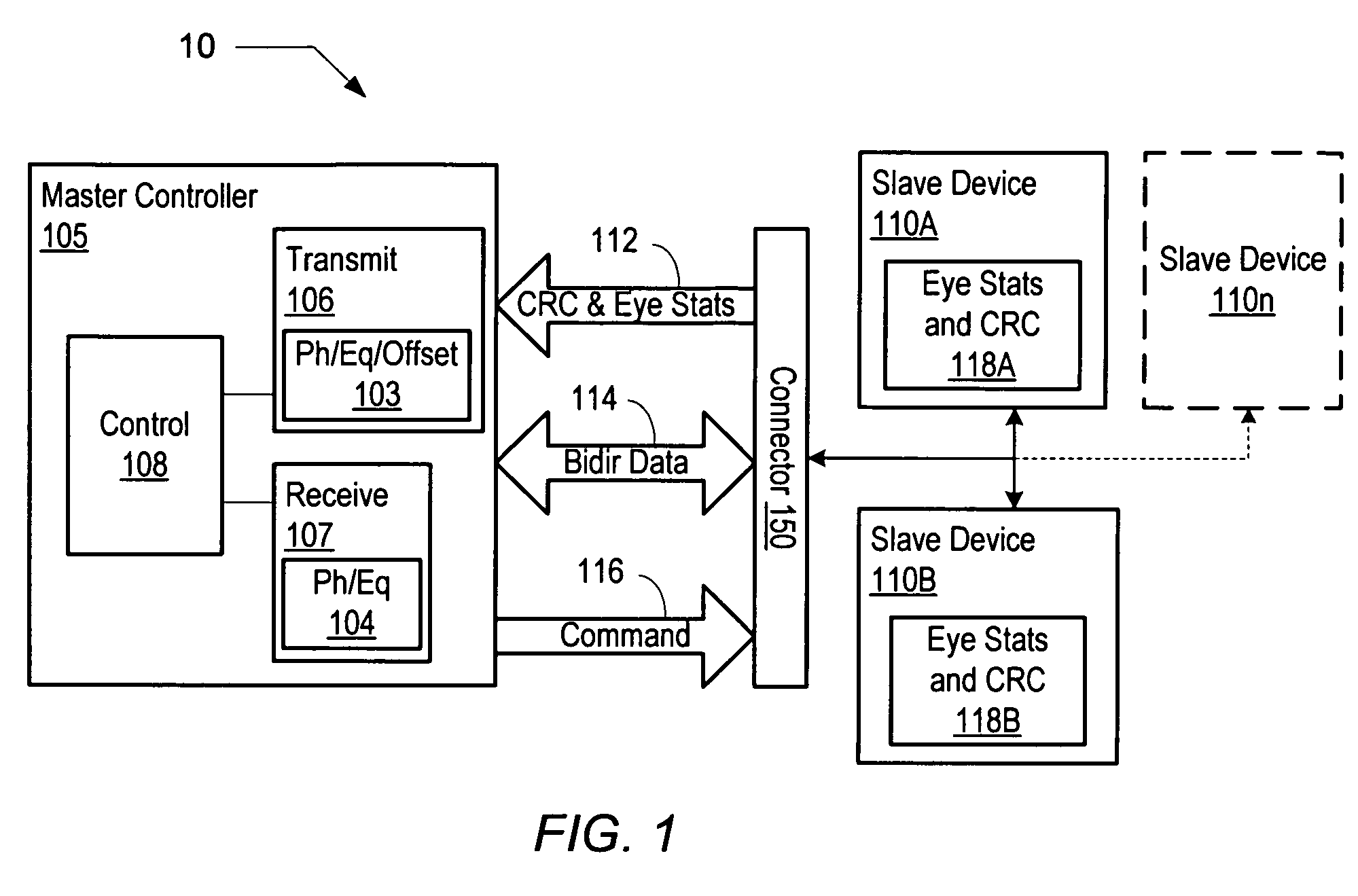
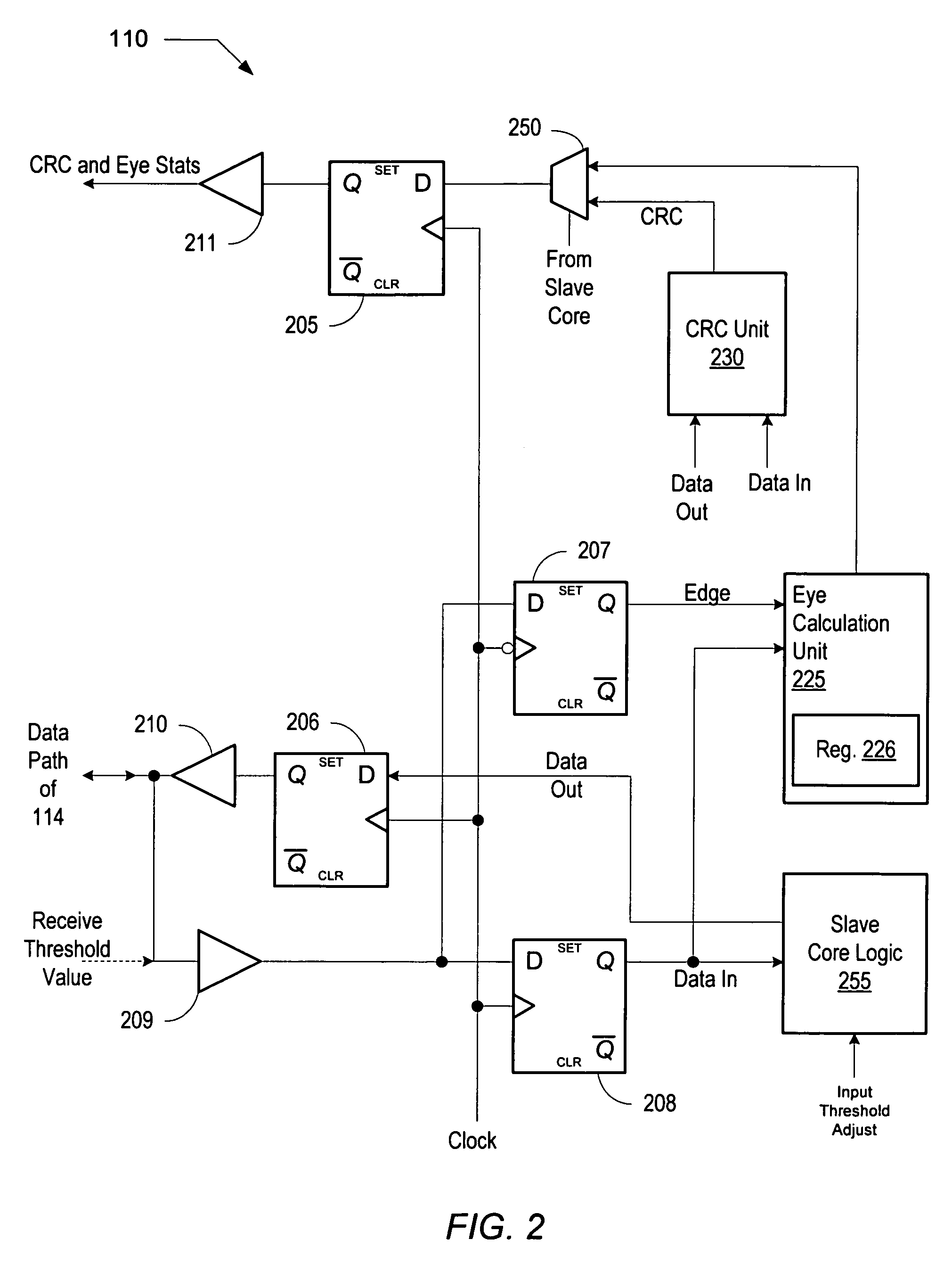
Method and apparatus for scrambling data for control of high-speed bidirectional signaling
A memory subsystem includes a master controller that includes a pseudo random bit sequence (PRBS) generator having a plurality of output taps and an exclusive-OR (XOR) unit. The memory subsystem also includes a memory device that is coupled to the master controller via a plurality of single ended bidirectional data paths. The master controller may scramble a plurality of data bits using the PRBS generator and the XOR unit prior to writing the plurality of data bits to the memory device. In addition, the master controller may perform an XOR between each bit of the plurality of data bits and a respective output tap of the PRBS generator prior to conveyance on a respective path of the plurality of single ended bidirectional data paths.
Owner:ADVANCED MICRO DEVICES INC
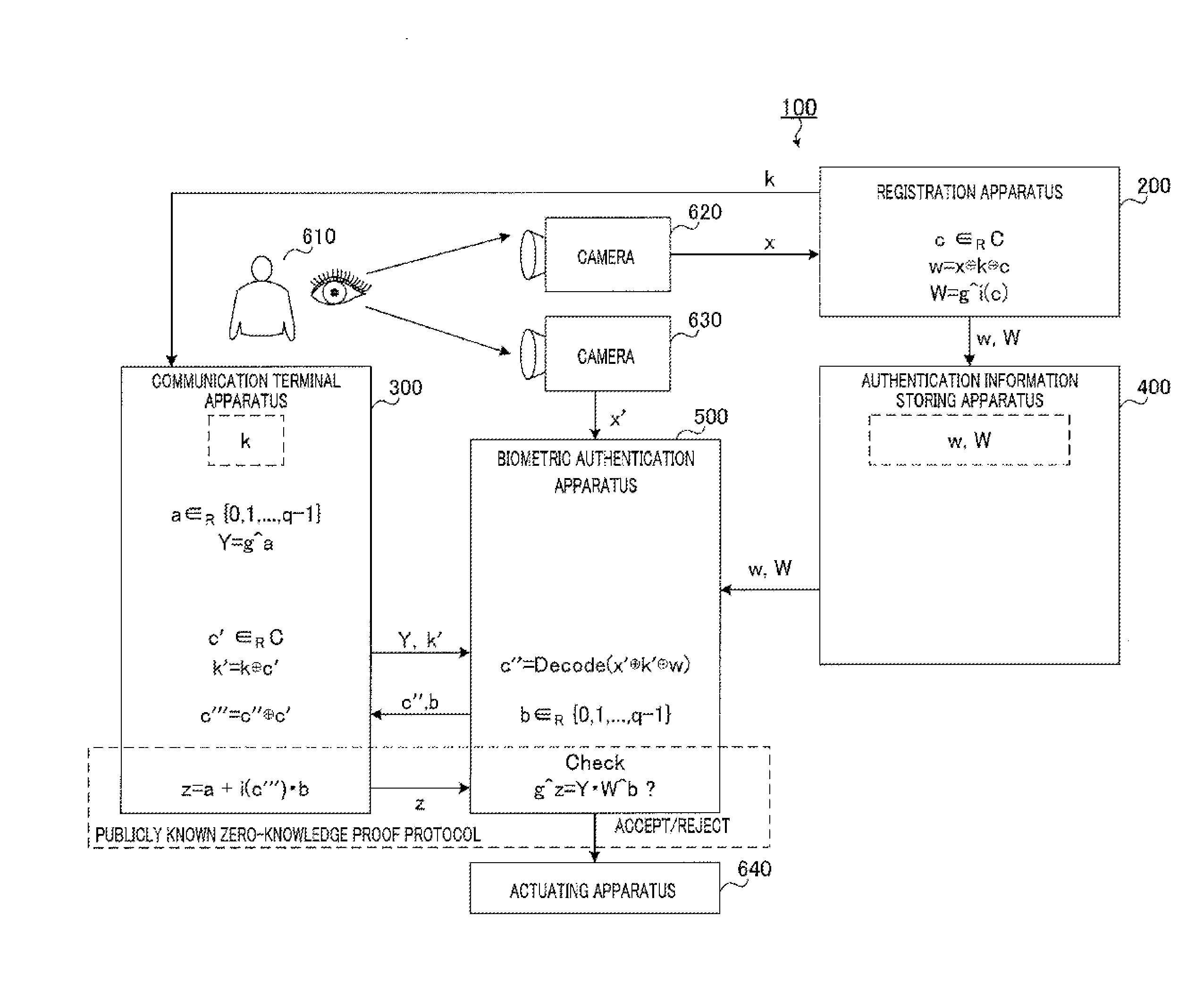
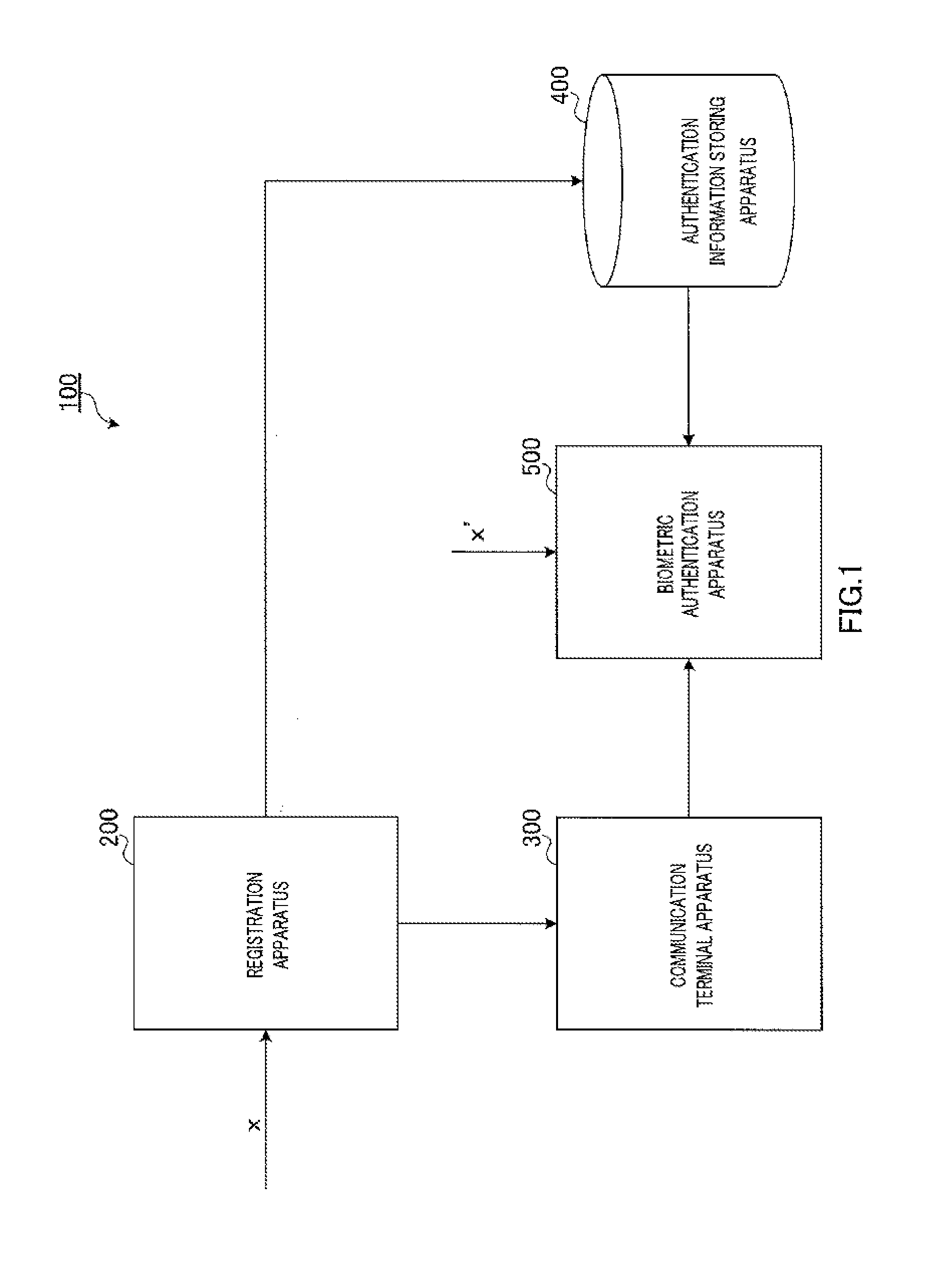
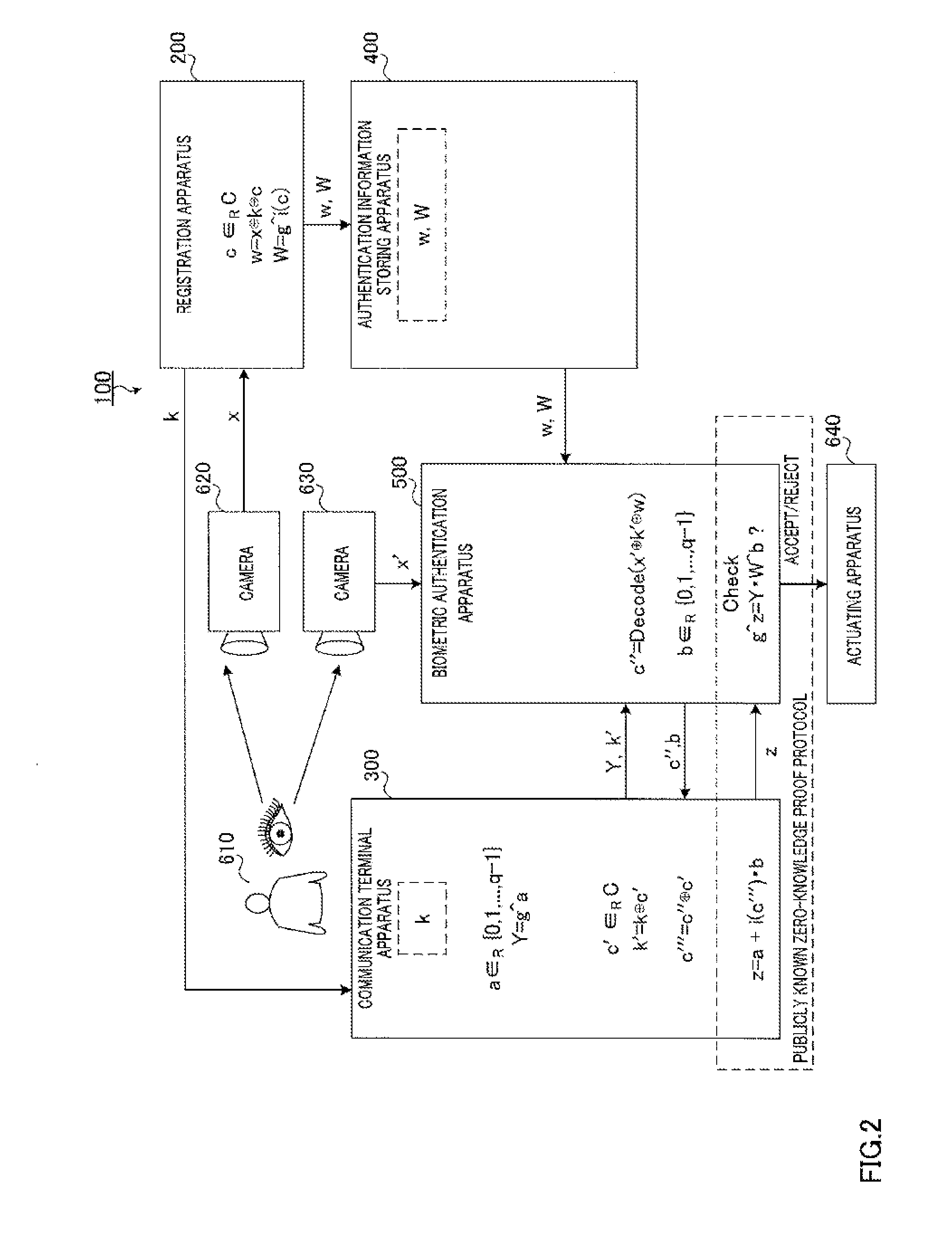
Biometric authentication system, communication terminal device, biometric authentication device, and biometric authentication method
ActiveUS20130174243A1Avoid attackDigital data processing detailsMultiple digital computer combinationsExclusive orTerminal equipment
Provided is a biometric authentication system capable of preventing spoofing attacks even if leakage of key information and a registration conversion template occurs. A communication terminal device (300) calculates secret key information k′ which is exclusive OR of key information k of the registration biological information and masked value c′ which is randomly selected from a predetermined error correction code group, and calculates verified information c′″ which is exclusive OR of sent information c″ and value c′. A biometric authentication device (500) calculates exclusive OR of authentication biological information, information k′, and registration conversion template w, as information c″, wherein the template w is exclusive OR of information x, information k, and authentication parameter c randomly selected from the code group; and performs biometric authentication on the basis of a degree of matching between information c′″ corresponding to information c″, and the parameter c.
Owner:PANASONIC CORP
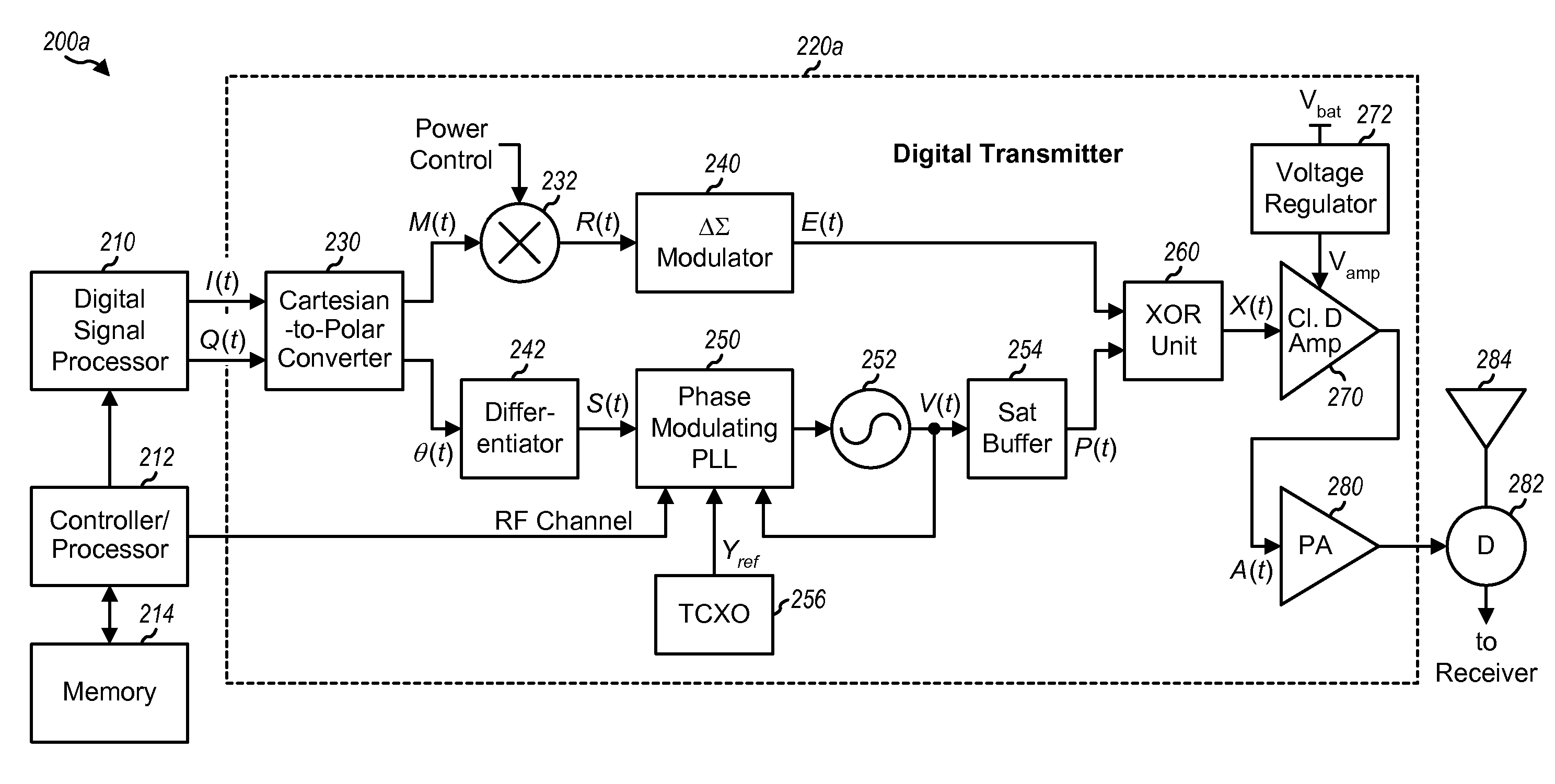
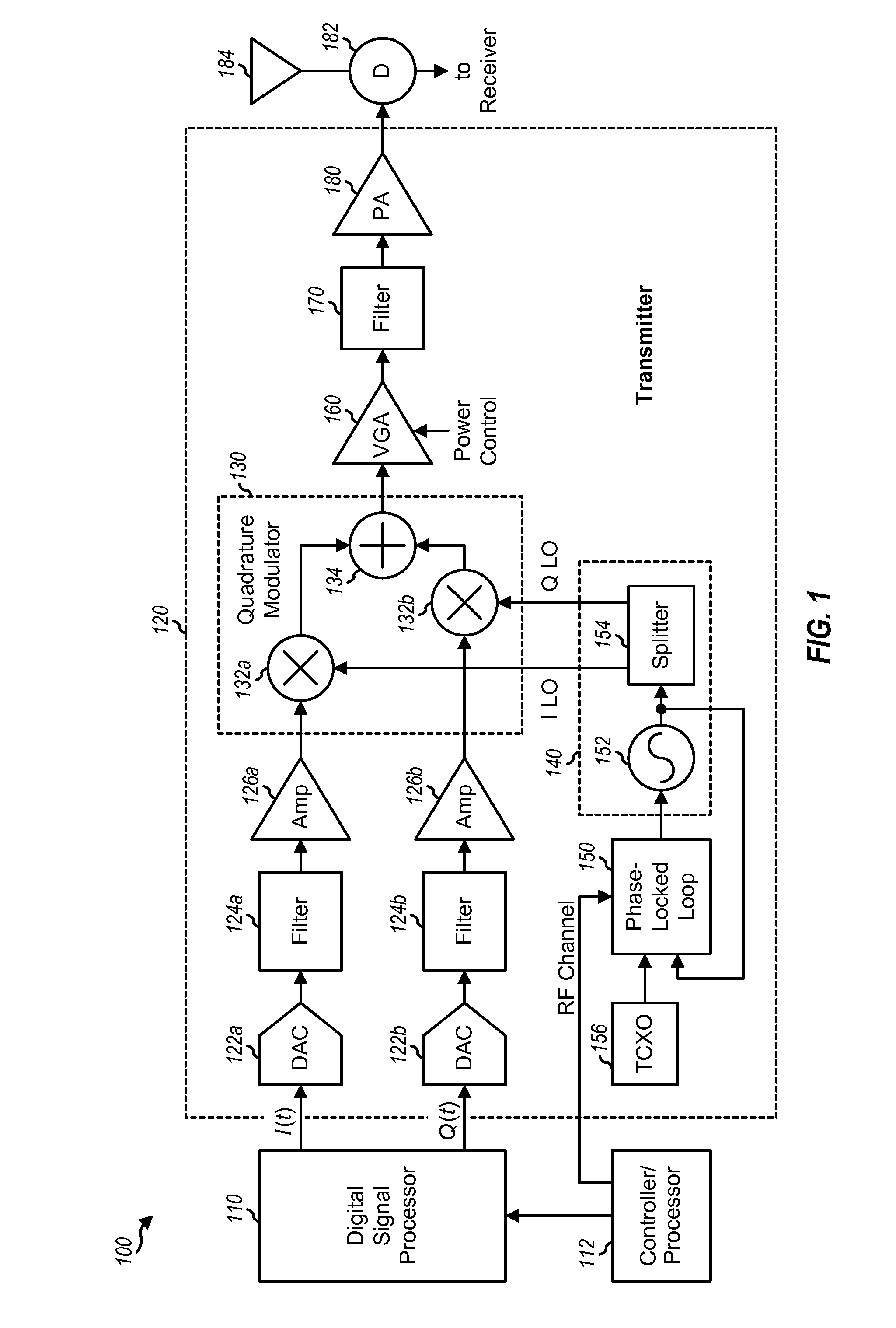
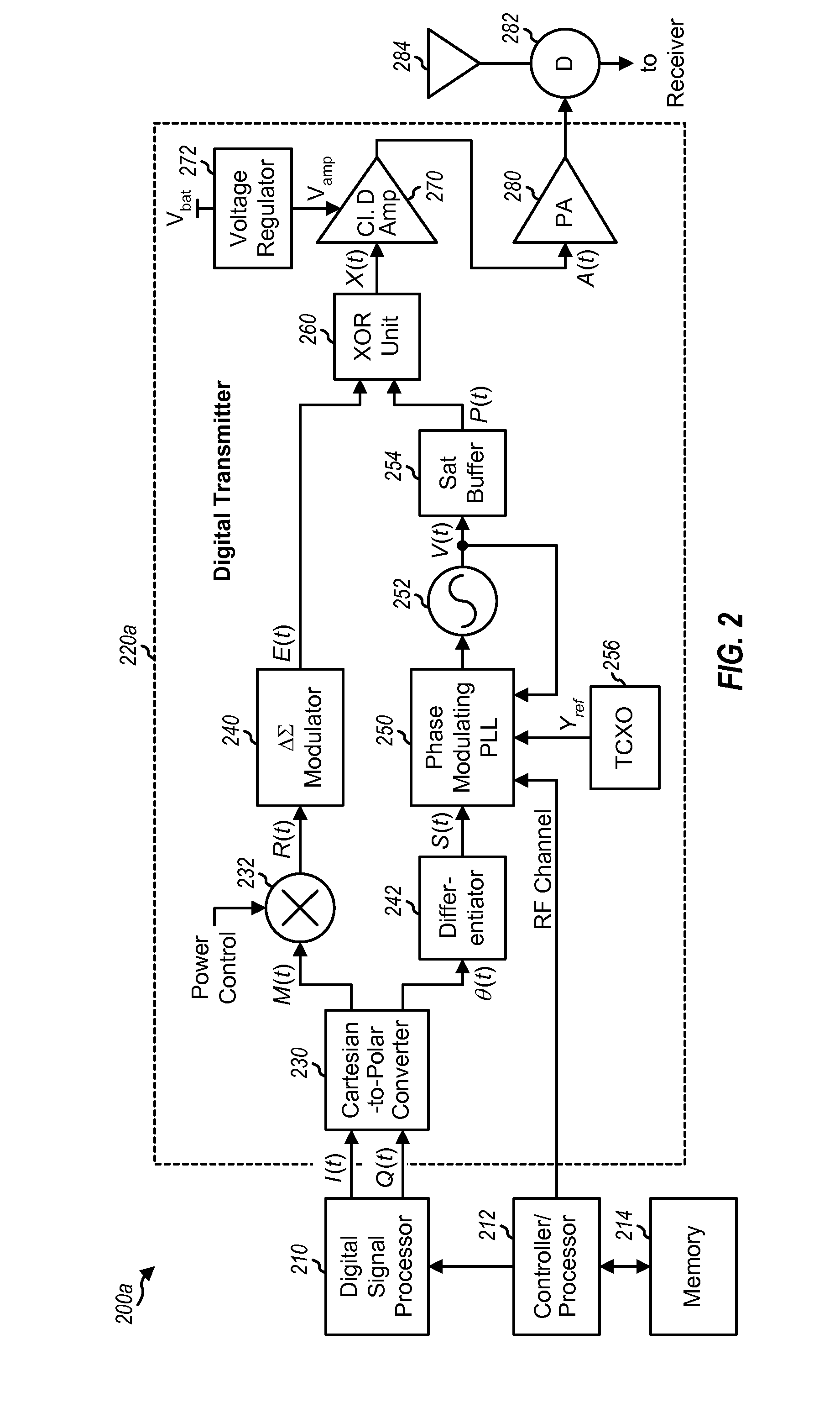
Digital transmitters for wireless communication
ActiveUS20070160164A1Easy to makeModulation with suppressed carrierAngle modulationAudio power amplifierExclusive or
Digital transmitters having improved characteristics are described. In one design of a digital transmitter, a first circuit block receives inphase and quadrature signals, performs conversion from Cartesian to polar coordinates, and generates magnitude and phase signals. A second circuit block (which may include a delta-sigma modulator or a digital filter) generates an envelope signal based on the magnitude signal. A third circuit block generates a phase modulated signal based on the phase signal. The third circuit block may include a phase modulating phase locked loop (PLL), a voltage controlled oscillator (VCO), a saturating buffer, and so on. A fourth circuit block (which may include one or more exclusive-OR gates or an amplifier with multiple gain states) generates a digitally modulated signal based on the envelope signal and the phase modulated signal. A fifth circuit block (which may include a class D amplifier and / or a power amplifier) amplifies the digitally modulated signal and generates an RF output signal.
Owner:QUALCOMM INC
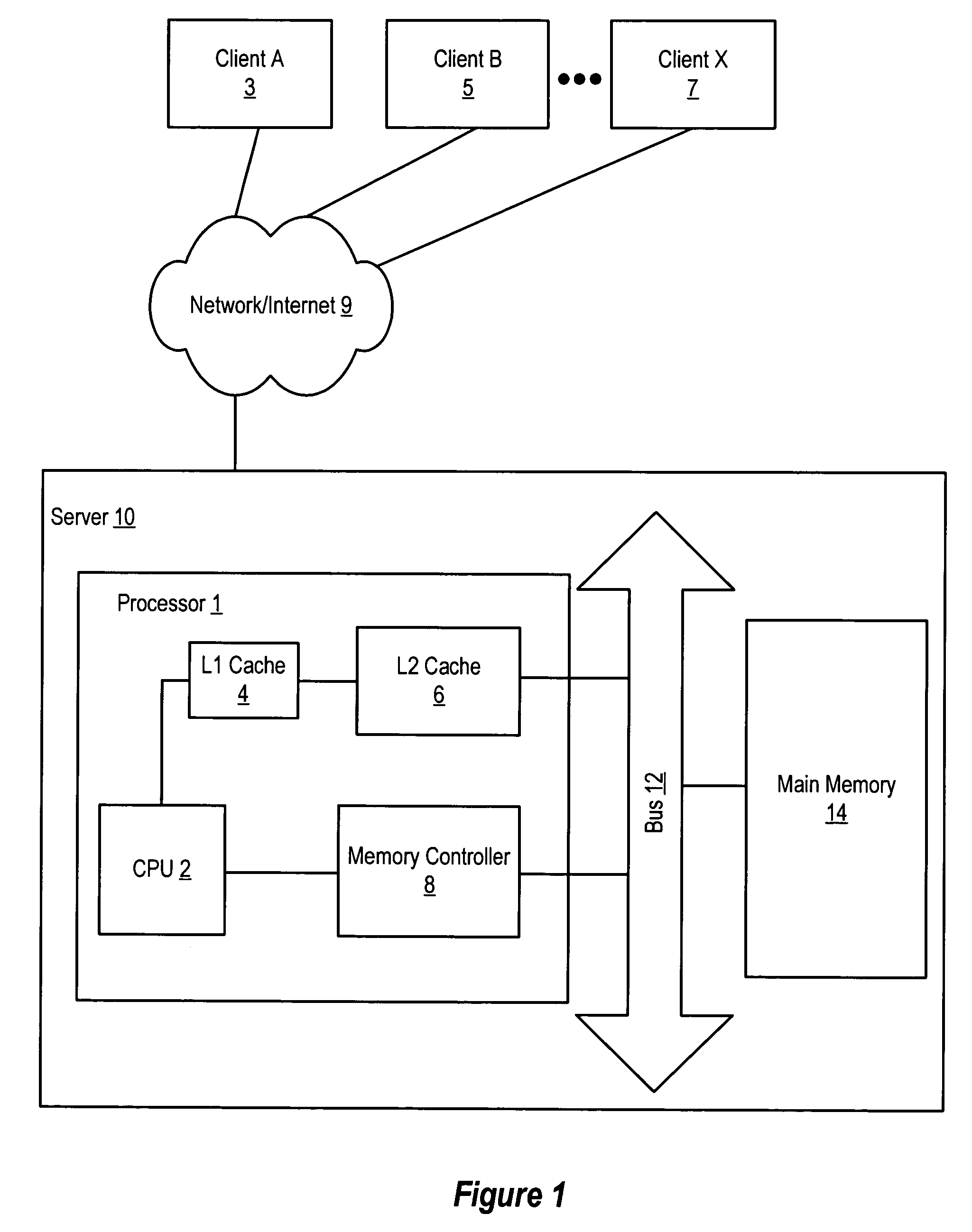
Computer system including plural caches and utilizing access history or patterns to determine data ownership for efficient handling of software locks
A system and method for enabling a multiprocessor system employing a memory hierarchy to identify data units or locations being used as software locks. The memory hierarchy comprises a main memory having a plurality of data units, a plurality of caches that operate independently of each other, and at least one coherent domain interfaced to each cache. Each coherent domain comprises at least two processors. The main memory maintains coherency of data among the plurality of caches using a directory that maintains information about each data line. The system of the present invention allows a requesting agent, such as a processor or cache, to request a data unit without specifying the type of ownership, where ownership may be exclusive or shared. The directory includes history information that defines the previous access pattern of the requested data unit. Prior to forwarding the requested data unit to the requesting agent, the main memory checks, using a conditional fetch command, the history information to determine what type of ownership to associate with the requested data unit. The requested data unit is then delivered to the requesting agent with ownership rights specified by the history information. The processors may utilize a directory-based protocol such as MESI (modified, exclusive, shared, invalid) to maintain coherence among the processors, with each processor snooping a shared bus to track the status of caches lines in the other processors.
Owner:UNISYS CORP
Encrypted flash-based data storage system with confidentiality mode
ActiveUS20140181532A1Impart propertyUnauthorized memory use protectionHardware monitoringConfidentialityOriginal data
Raw or unencrypted data is encrypted using a standard encryption algorithm and stored in a Flash memory array. The raw or unencrypted data may be pre-processed before it is encrypted. Pre-processing may include data scrambling, pre-encryption data mixing, or both. Data scrambling may involve an invertible transformation. The scrambled data may then be used to seed a sequence generator. Each output from the sequence generator may be processed using a bit-by-bit Exclusive Or (XOR) operation to impart random or pseudorandom statistical properties. Pre-encryption data mixing may combine the scrambled (or unscrambled) data with information that is unique to each chunk of data, as well as with a user-supplied secret key. This helps ensure that identical raw data chunks are not stored as identical encrypted data chunks in the Flash memory array.
Owner:IBM CORP
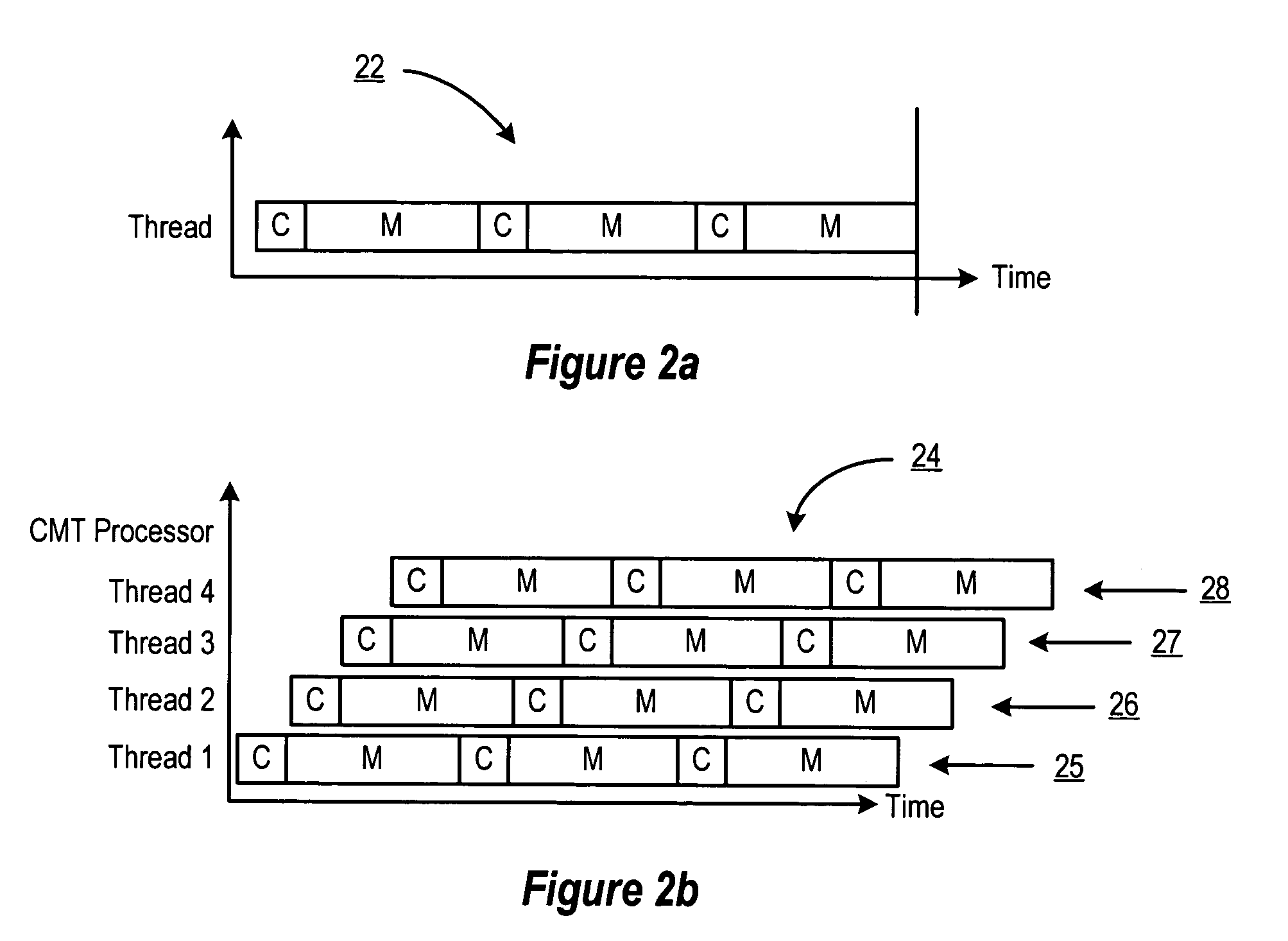
Level 2 cache index hashing to avoid hot spots
ActiveUS7290116B1Reduce and avoid conflicting memory accessReduce probabilityMemory adressing/allocation/relocationMicro-instruction address formationMemory addressParallel computing
An apparatus and method for mapping memory addresses to reduce or avoid conflicting memory accesses in memory systems such as cache memories is described in connection with a multithreaded multiprocessor chip. A CMT processor reduces the probability of hot-spots in cache operations by hashing certain bits of a physical cache address to form a hashed cache address. By using exclusive OR functionality to hash the index bits, an efficient address transformation is achieved for indexing into an L2 cache memory.
Owner:ORACLE INT CORP
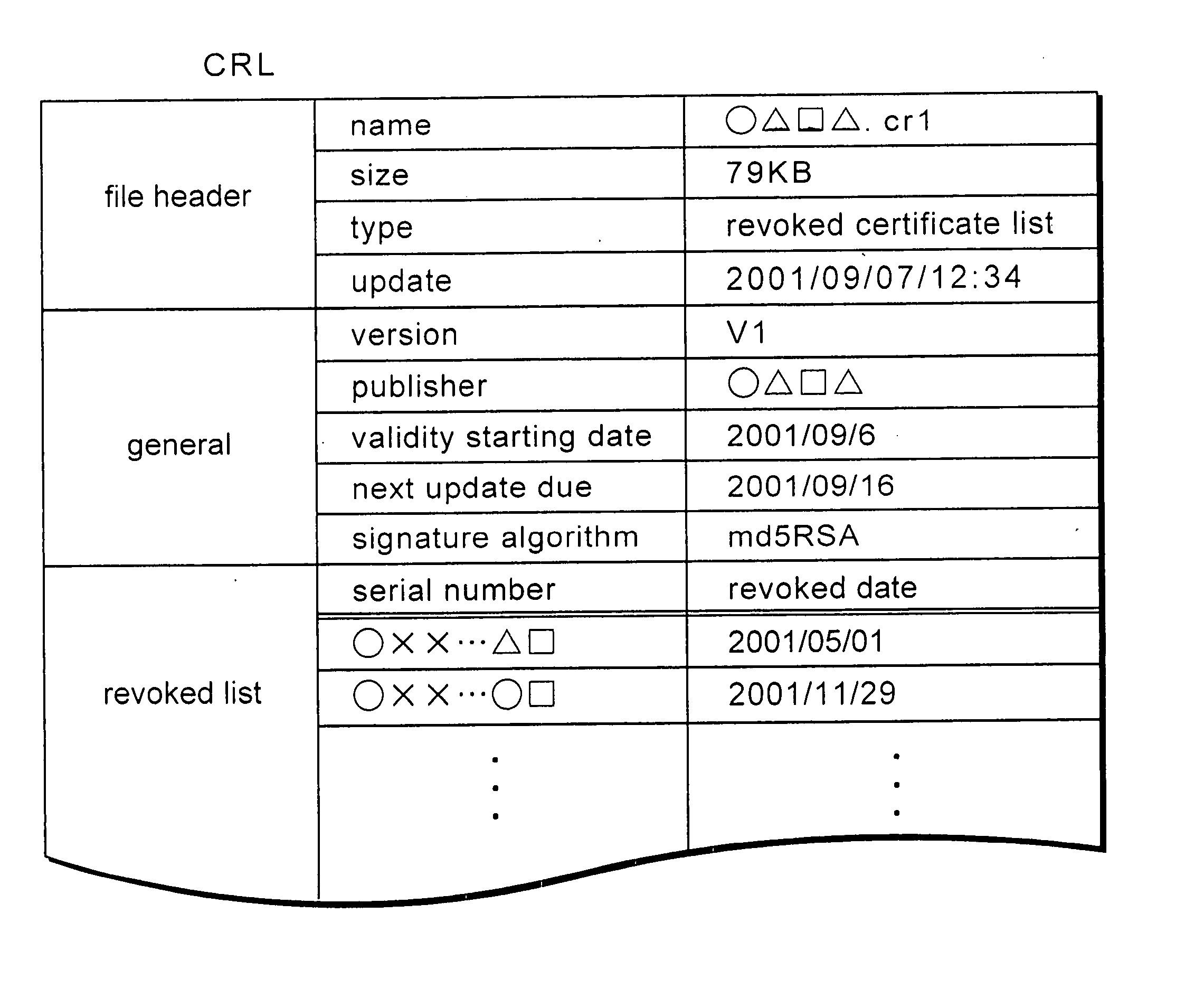
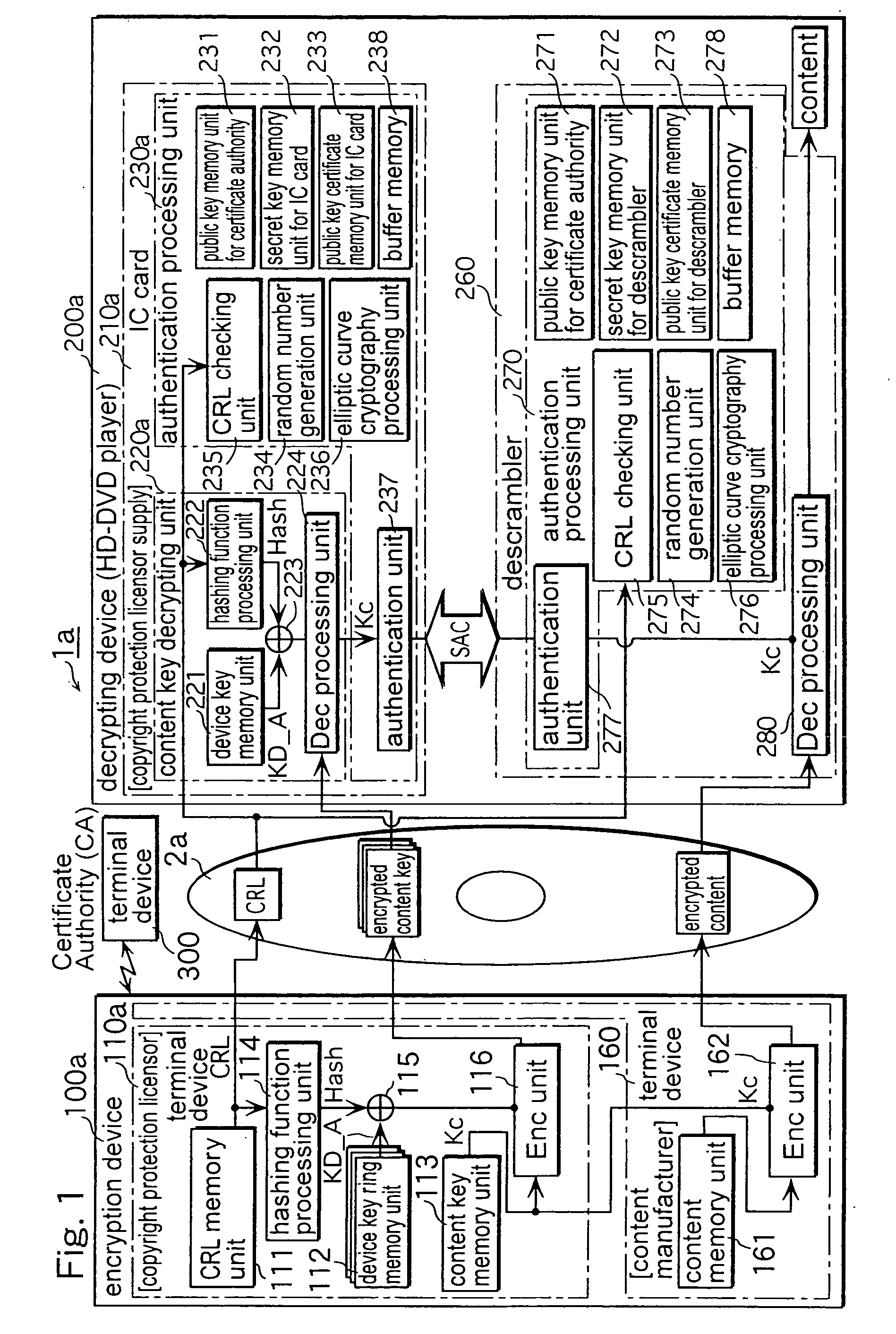
Encryption device a decrypting device a secret key generation device a copyright protection system and a cipher communication device
InactiveUS20050021941A1Reduce processingSecure transmissionKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareHash function
An encryption device, a decrypting device, a secret key generation device, a copyright protection system and a cipher communication device comprise: a CRL memory unit 111 that memorizes a CRL, a device key ring memory unit 112 that memorizes a peculiar device key KD A in every IC card 210a used in a decrypting device 200a, a content key memory unit 113 that memorizes a content key Kc which is a secret key for decrypting content, a hashing function processing unit 114 that calculates a hashing value of the CRL memorized in the CRL memory unit 111, an Ex-OR unit 115 that carries out an exclusive OR between the hashing value and the device key KD A memorized in the device key ring memory unit 112, and an Enc unit 116 that encrypts the content key Kc memorized in the content key memory unit 113 with an output value of an Ex-OR unit 115.
Owner:INTERTRUST TECH CORP
Method and apparatus for generating error correction data, and a computer-readable recording medium recording an error correction data generating program thereon
InactiveUS7320099B2Effective calculationEfficient errorError prevention/detection by using return channelData representation error detection/correctionComputer hardwareExclusive or
When error correction data, which is to be inserted into transmission data at specific intervals, is generated by calculating exclusive-OR of the transmission data, cumulative exclusive-OR of the transmission data is continuously calculated independent of the error correction data insertion intervals. Exclusive-OR between a calculation of the exclusive-OR at the time of the previous error correction data insertion and a calculation of the exclusive-OR at the time of the current error correction data insertion is calculated, thereby generating error correction data to be inserted at the present time. This provides efficient error correction data calculation.
Owner:FUJITSU LTD
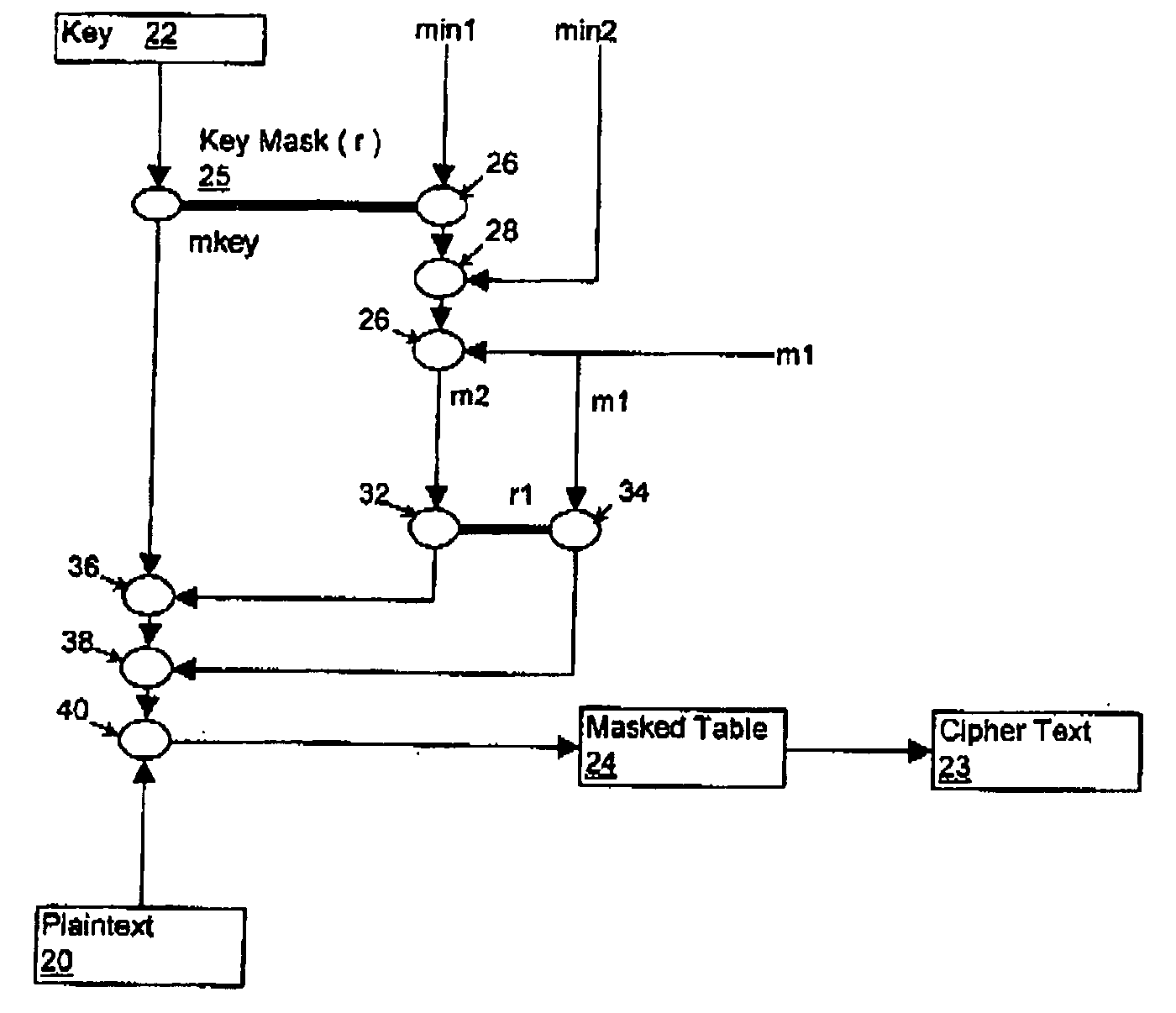
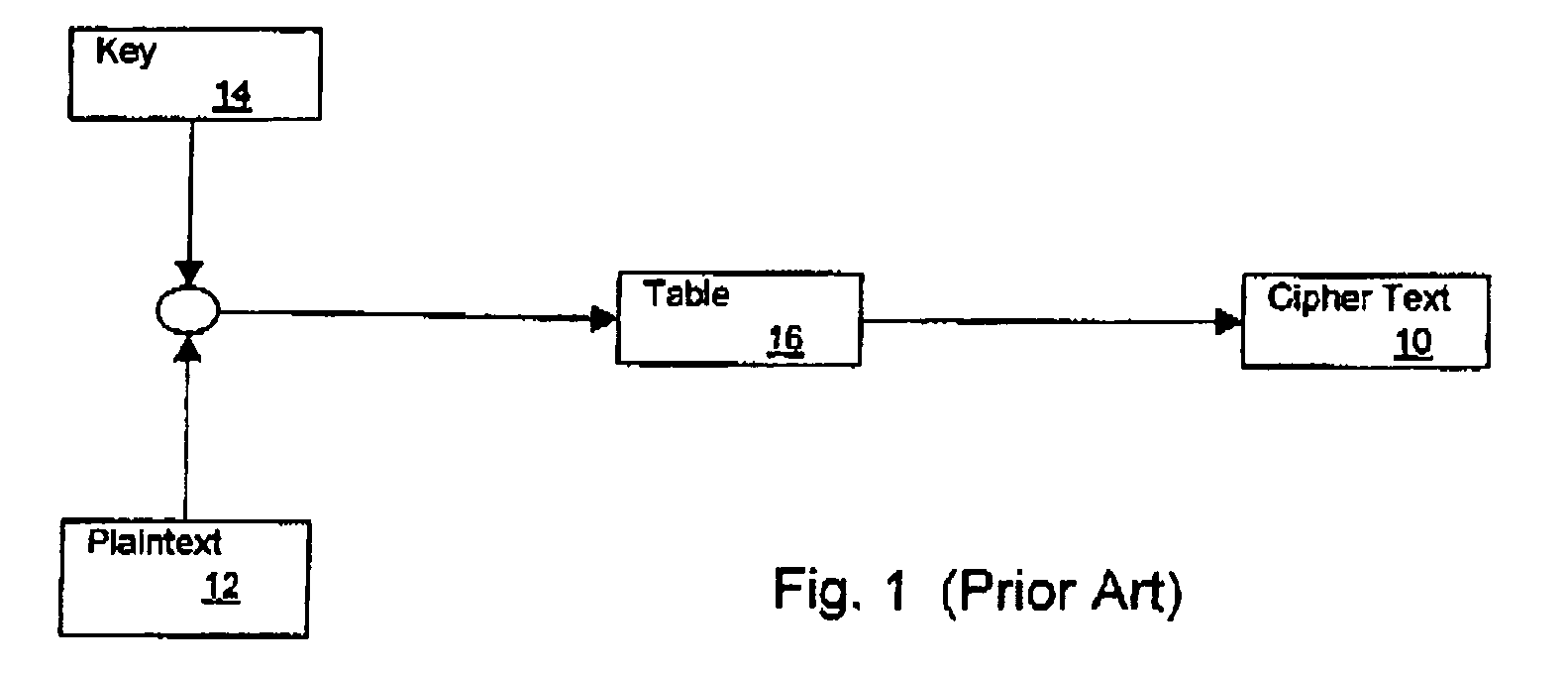
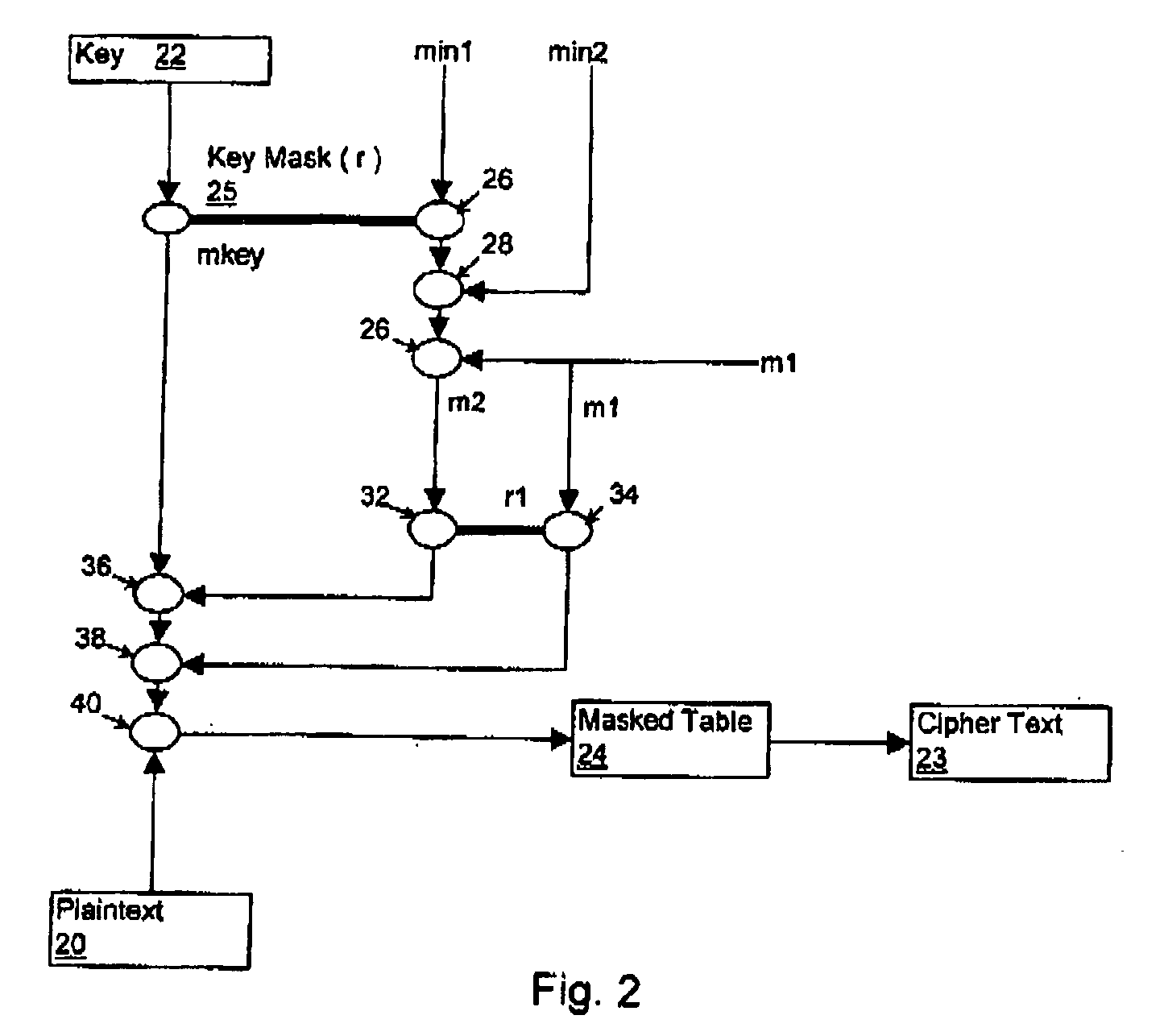
Security countermeasures for power analysis attacks
ActiveUS20050232430A1High performance cryptographic implementationControl overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPower analysisCountermeasure
A countermeasure for differential power analysis attacks on computing devices. The countermeasure includes the definition of a set of split mask values. The split mask values are applied to a key value used in conjunction with a masked table defined with reference to a table mask value. The set of n split mask values are defined by randomly generating n−1 split mask values and defining an nth split mask value by exclusive or'ing the table mask value with the n−1 randomly generated split mask values.
Owner:MALIKIE INNOVATIONS LTD
Providing multiple concurrent access to a file system
ActiveUS20110055274A1Digital data processing detailsComputer security arrangementsFile systemExclusive or
Multiple computers are connected to a data storage unit that includes a file system, which further includes multiple data entities, including files, directories and the file system itself. The file system also includes, for each data entity, an owner field for indicating which computer, if any, has exclusive or shared access to the data entity, along with a time field for indicating when a lease of the data entity began. When a computer wants to lease a data entity, the computer uses a disk reservation capability to temporarily lock the data storage unit, and, if the data entity is not currently leased, the computer writes its own identification value into the owner field and a current time into the time field for the data entity, to claim the data entity for a renewable lease period. If a prior lease of a data entity has expired, another computer may break the lease and claim ownership for itself.
Owner:VMWARE INC
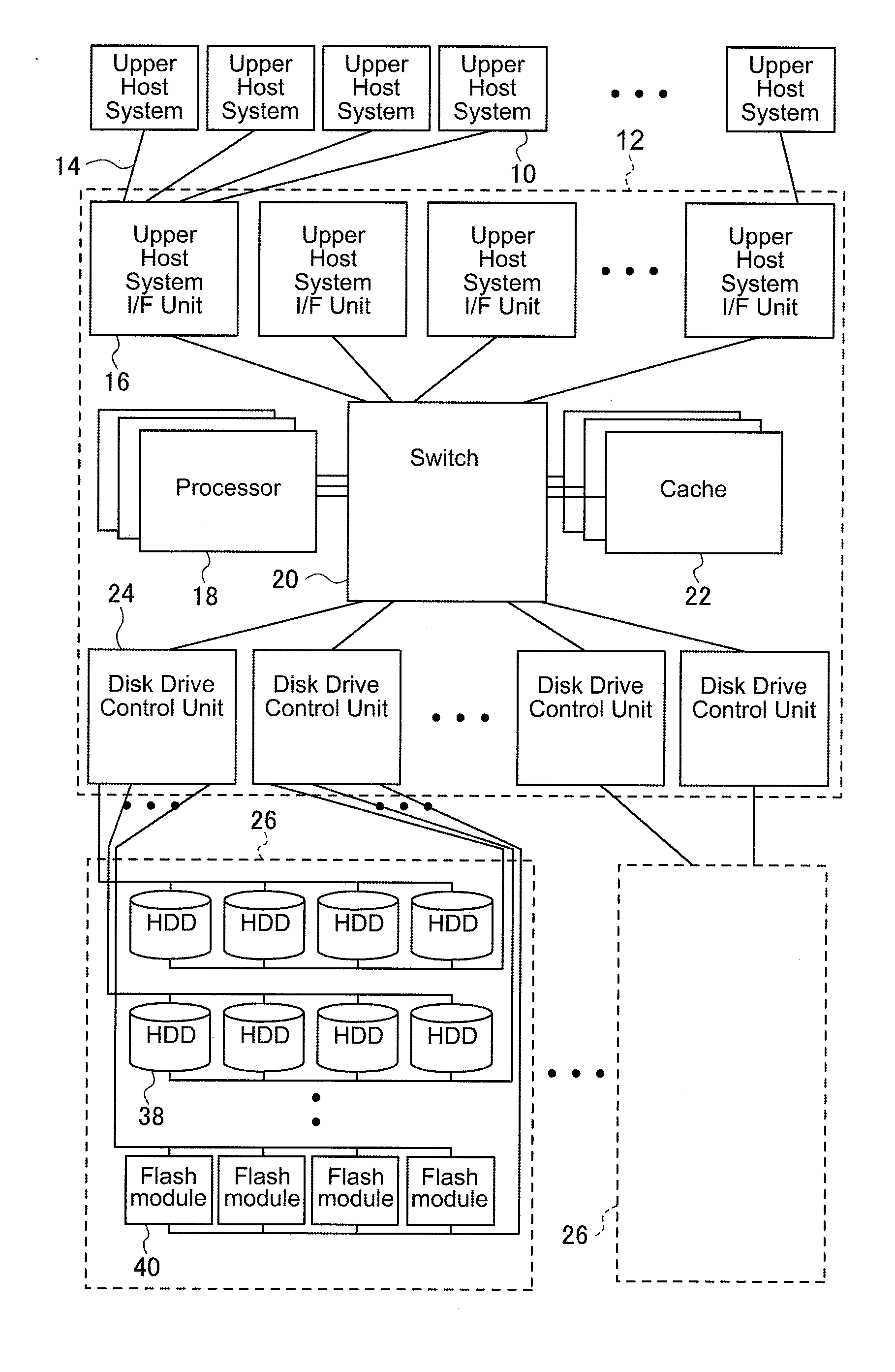
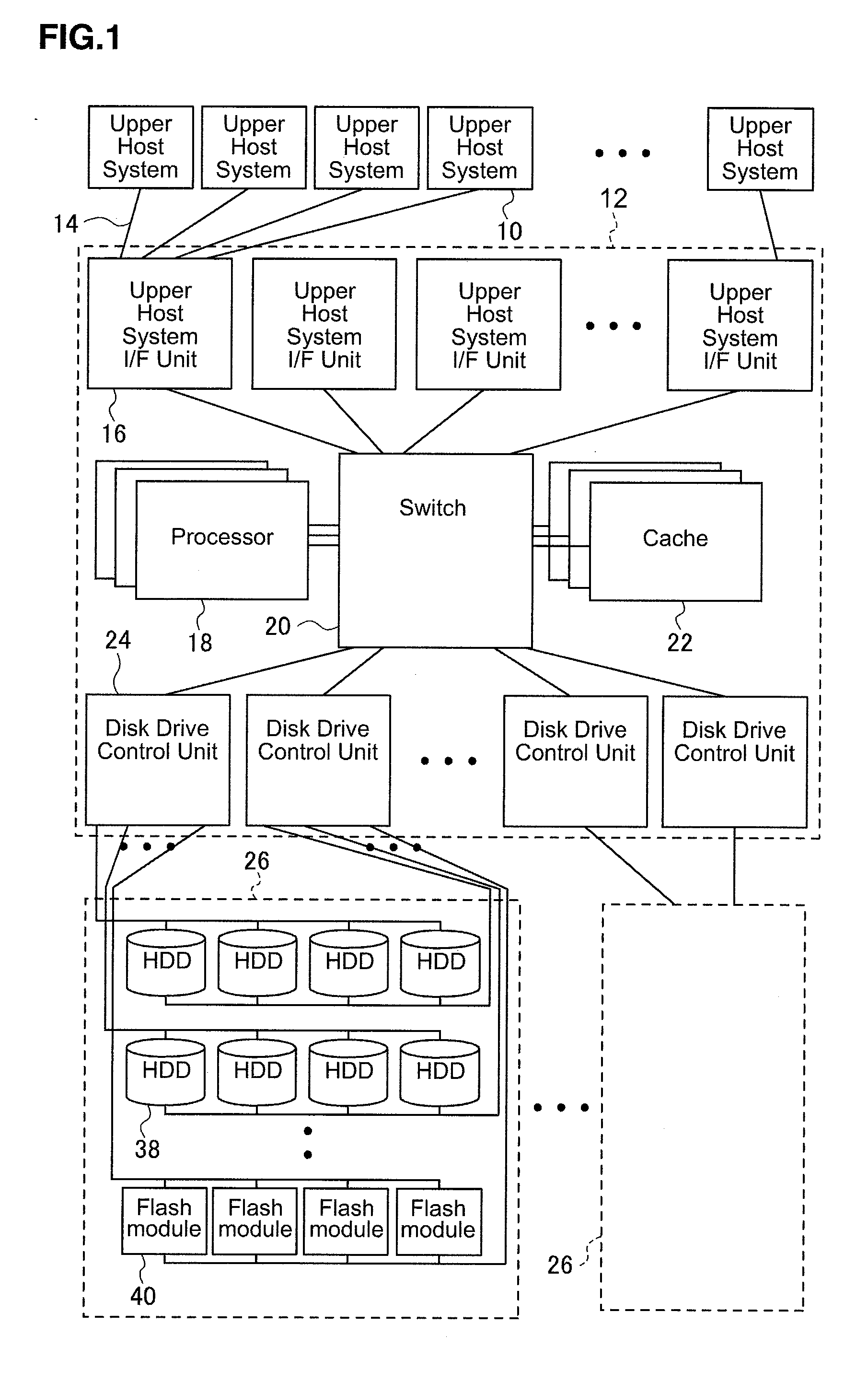
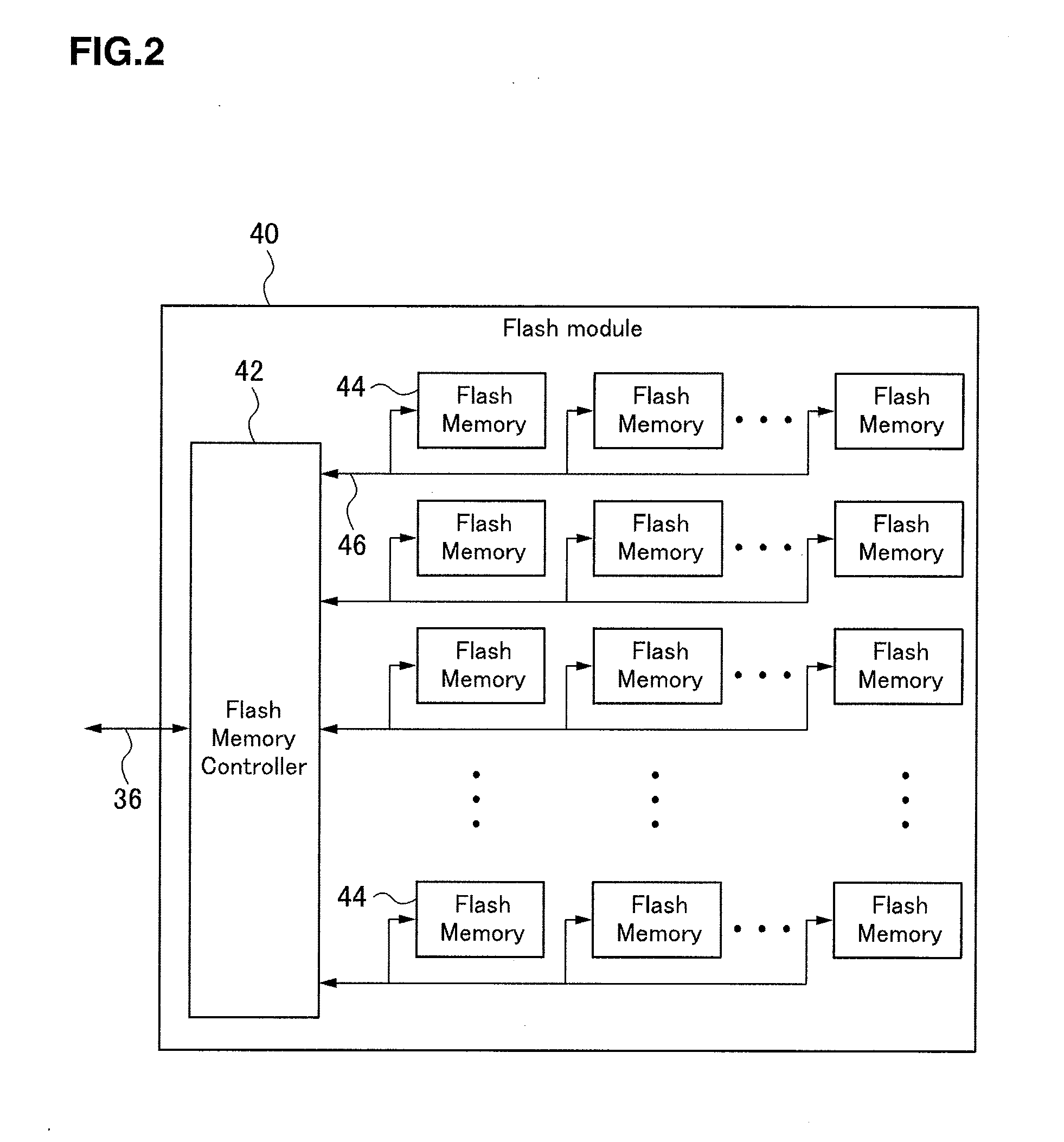
Storage subsystem
Owner:HITACHI LTD
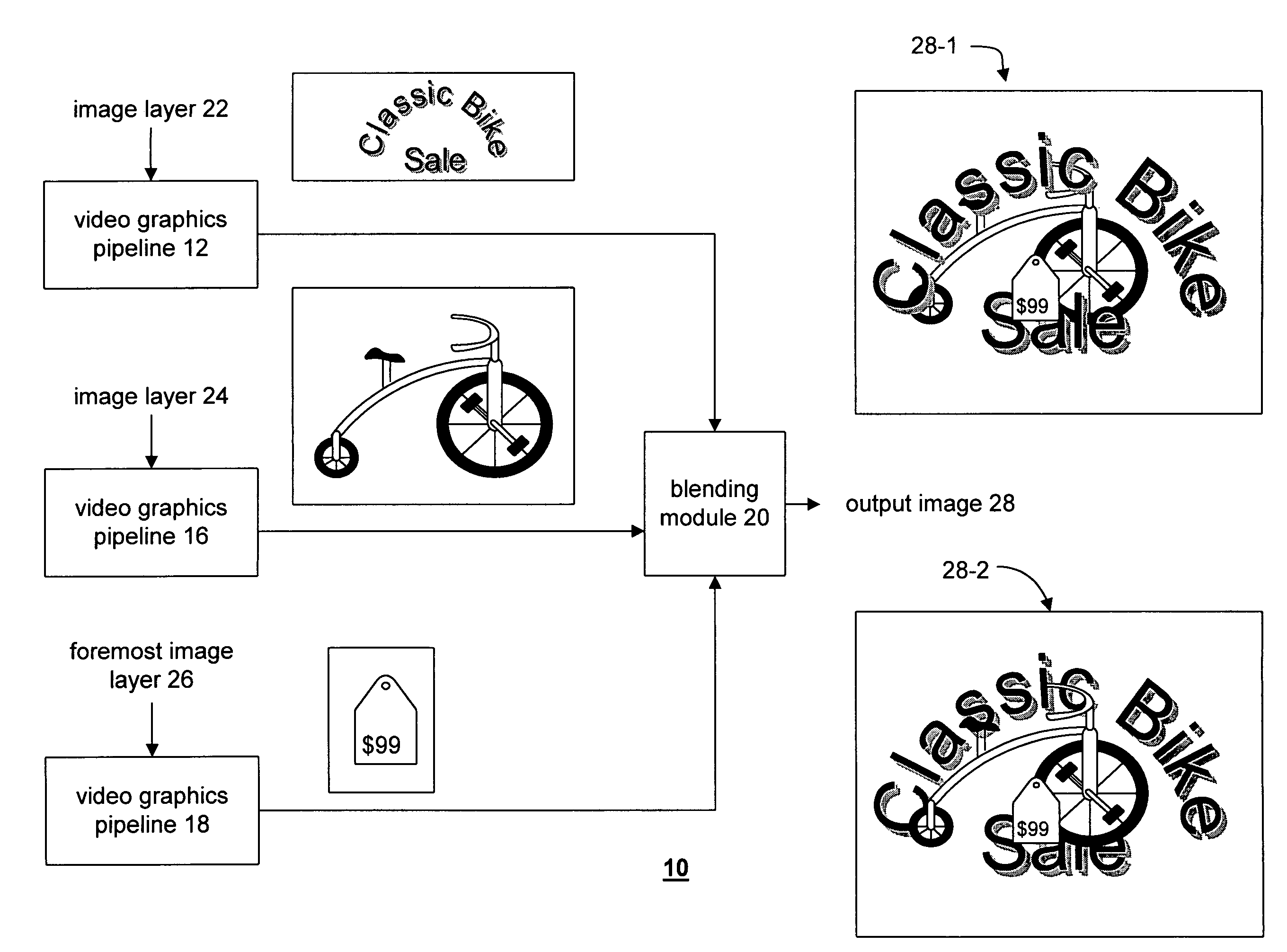
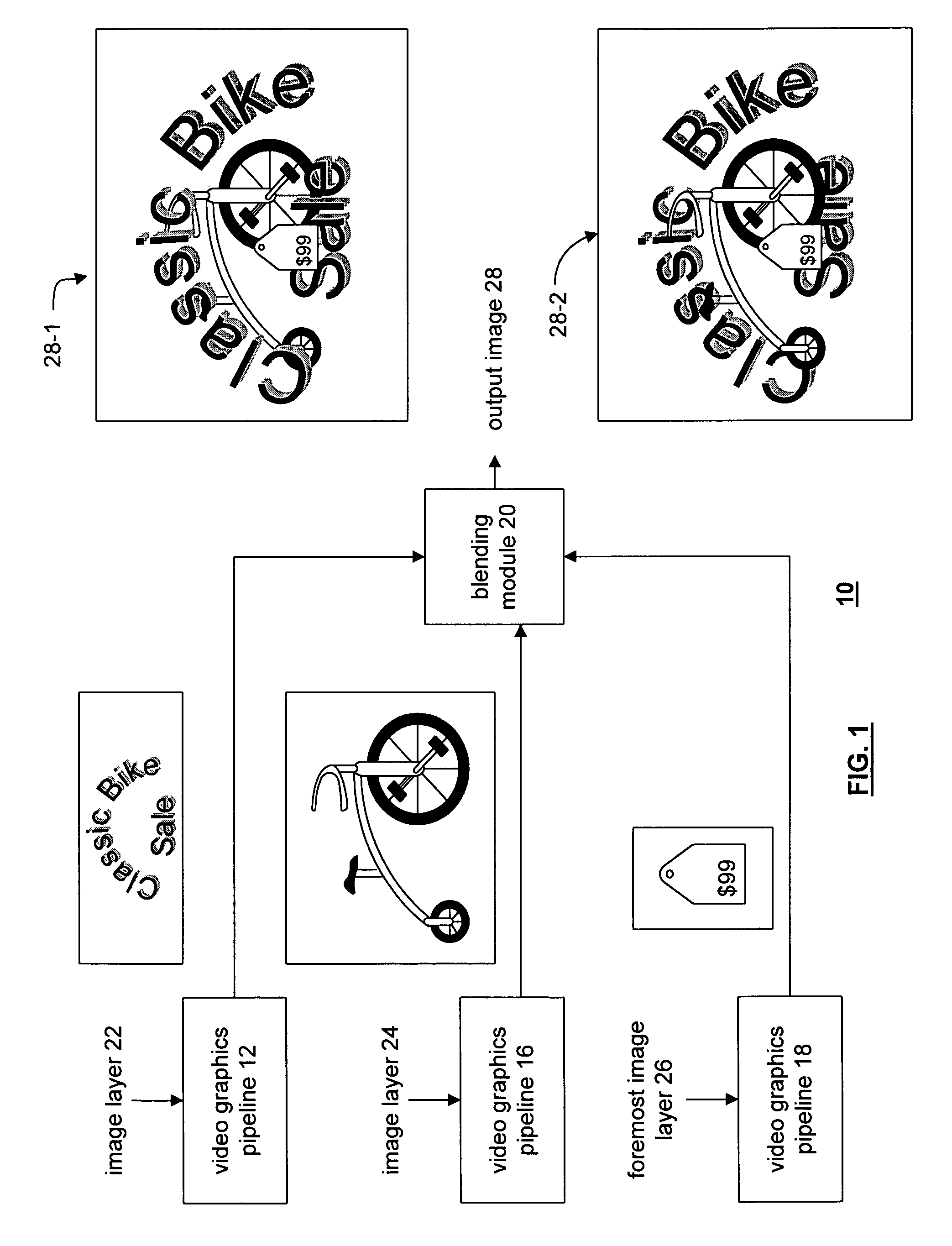
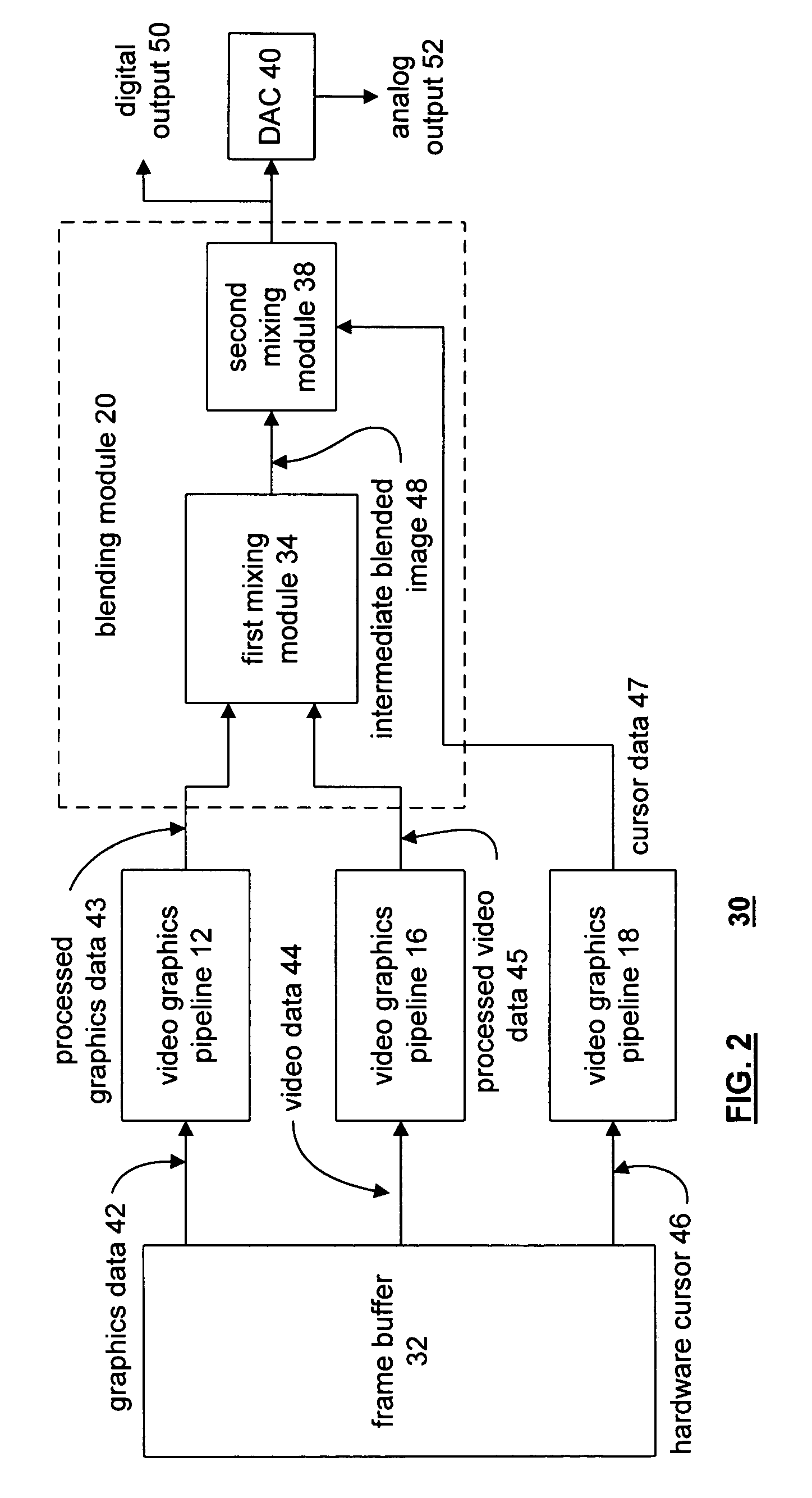
Video graphics module capable of blending multiple image layers
A video graphics module capable of blending multiple image layers includes a plurality of video graphic pipelines, each of which is operable to process a corresponding image layer. One of the video graphic pipelines processes a foremost image layer. For example, the foremost image layer may be a hardware cursor. The video graphics module also includes a blending module that is operably coupled to the plurality of video graphic pipelines. The blending module blends, in accordance with a blending convention (e.g., AND / Exclusive OR blending and / or alpha blending), the corresponding image layers of each pipeline in a predetermined blending order to produce an output image. The blending module blends the foremost image layer such that it appears in a foremost position with respect to the other image layers.
Owner:ATI TECH INC
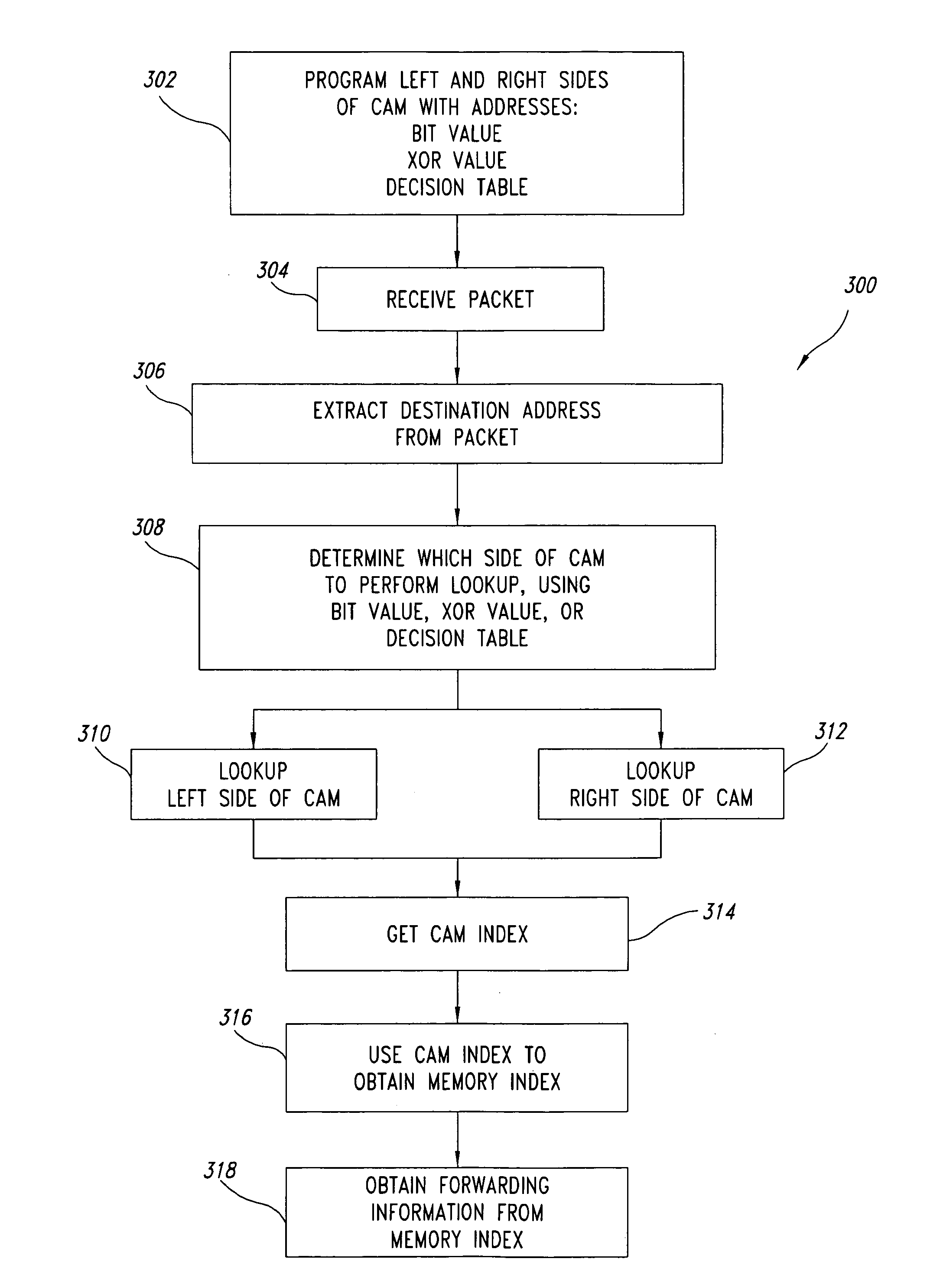
Double density content addressable memory (CAM) lookup scheme
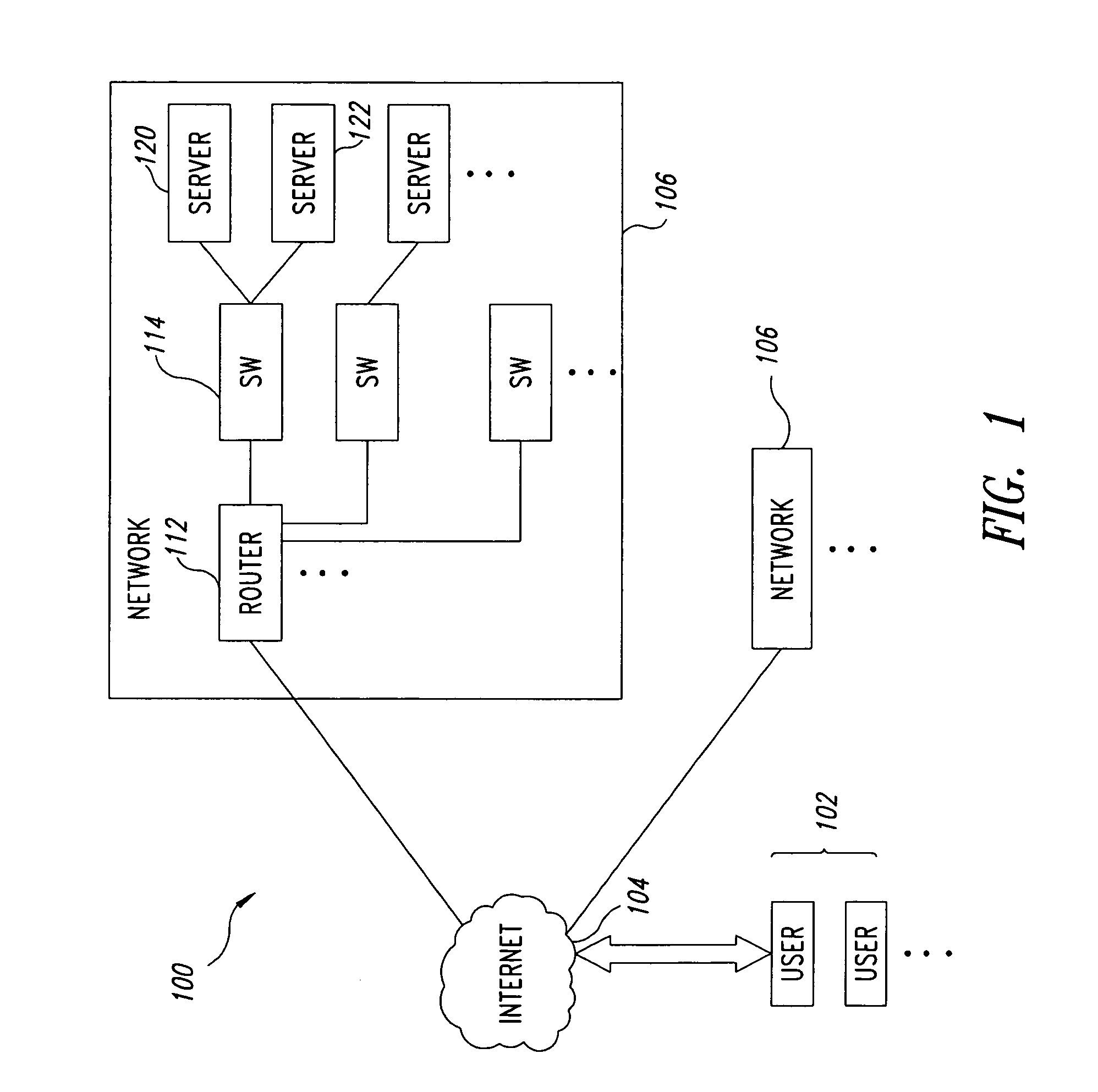
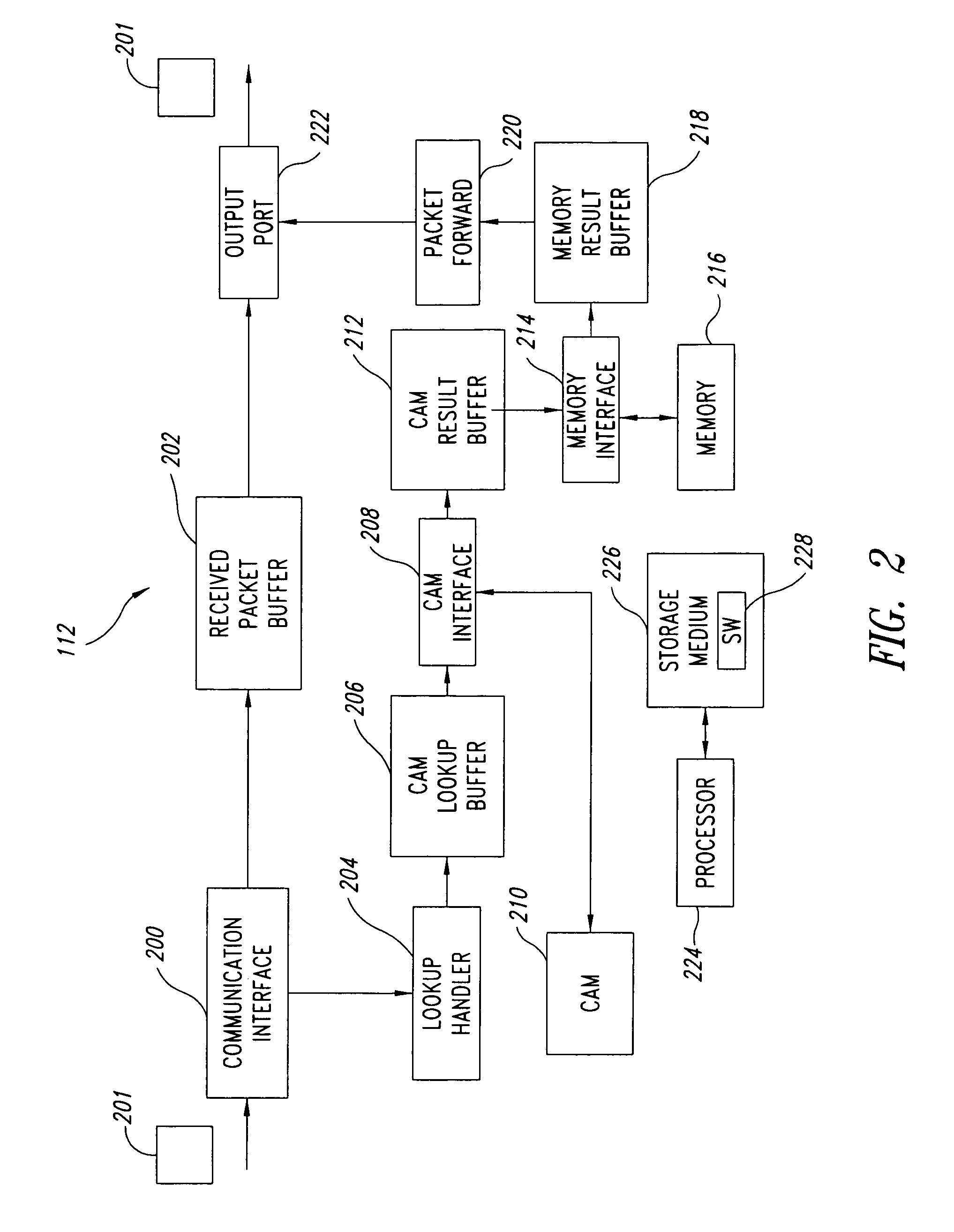
ActiveUS7657703B1Increased complexityIncrease costTransmissionMemory systemsIp addressDecision table
The number of content addressable memory (CAM) lookups is reduced from two to one. Each side (left and right sides) of a CAM is programmed with network addresses, such as IP addresses, based on certain bits of the network addresses. These bits of the network addresses (which represent packet routes) are examined and used to determine whether the particular network address is to be placed on the left or right sides of the CAM. The grouping of certain network addresses either on the left or right sides of the CAM can be performed by examining an individual bit of each network address, by performing an exclusive OR (XOR) operation on a plurality of bits of each network address, and / or by searching for bit patterns of the network address in a decision table. Network addresses that cannot be readily assigned to a particular side of the CAM using these grouping techniques are programmed into both sides of the CAM. During packet routing, techniques similar to the grouping techniques that populated the CAM are used to determine which of the two sides of the CAM is to be searched.
Owner:AVAGO TECH INT SALES PTE LTD
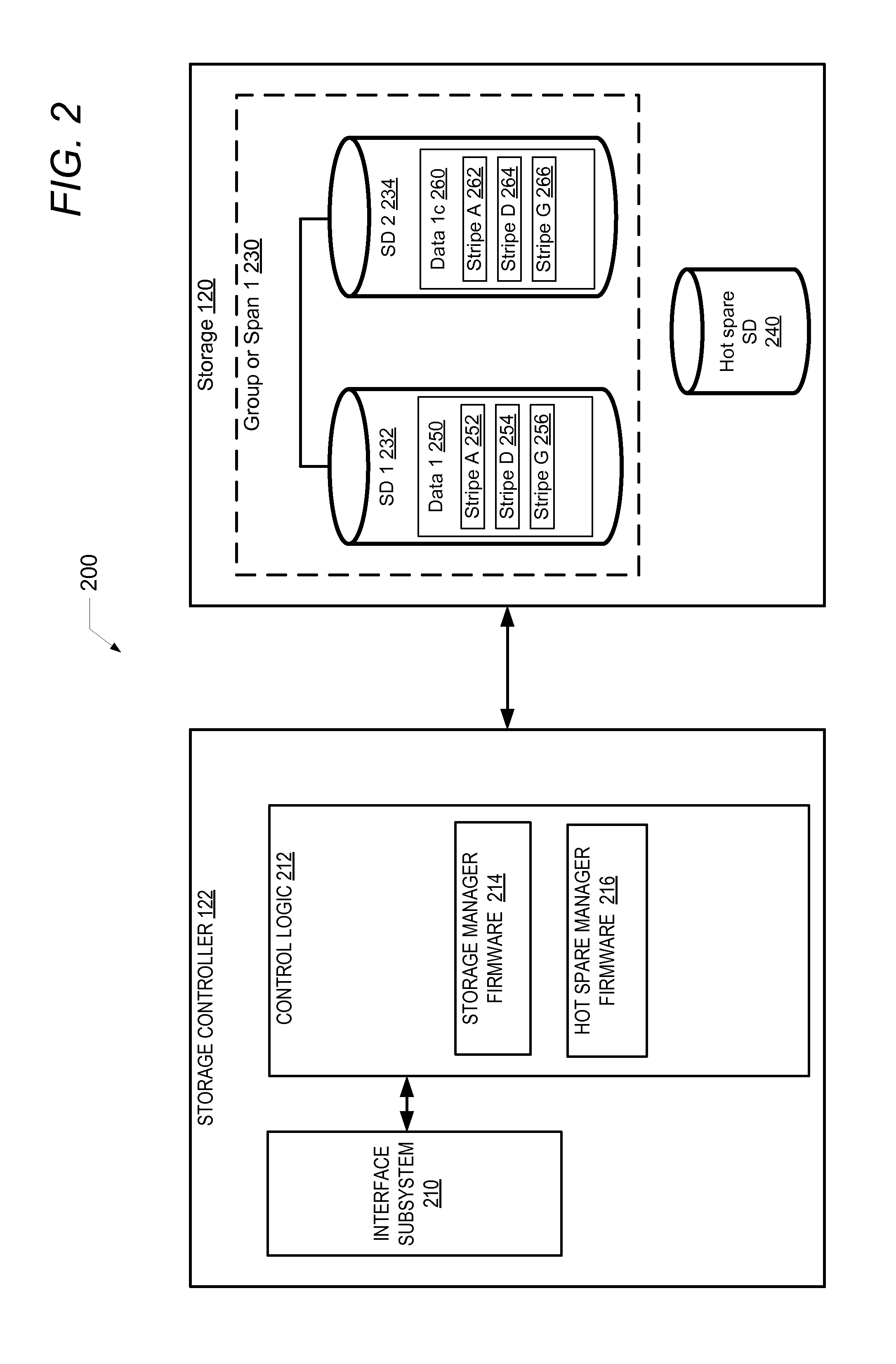
Systems and methods which utilize parity sets
A memory system and method of using same are provided. One embodiment of the system includes a semiconductor memory that is configured to include a multiplicity of memory segments. The memory segments are grouped into groups. Each of the groups includes N respective memory segments, where N is an integer number. In each respective group of memory segments, the N respective memory segments include respective data segments and a respective parity segment. Also in each respective group of memory segments, the respective parity segment in the respective group stores a respective data value P that may be calculated by a logical exclusive-or of respective data values stored in the respective data segments in the respective group.
Owner:EMC CORP
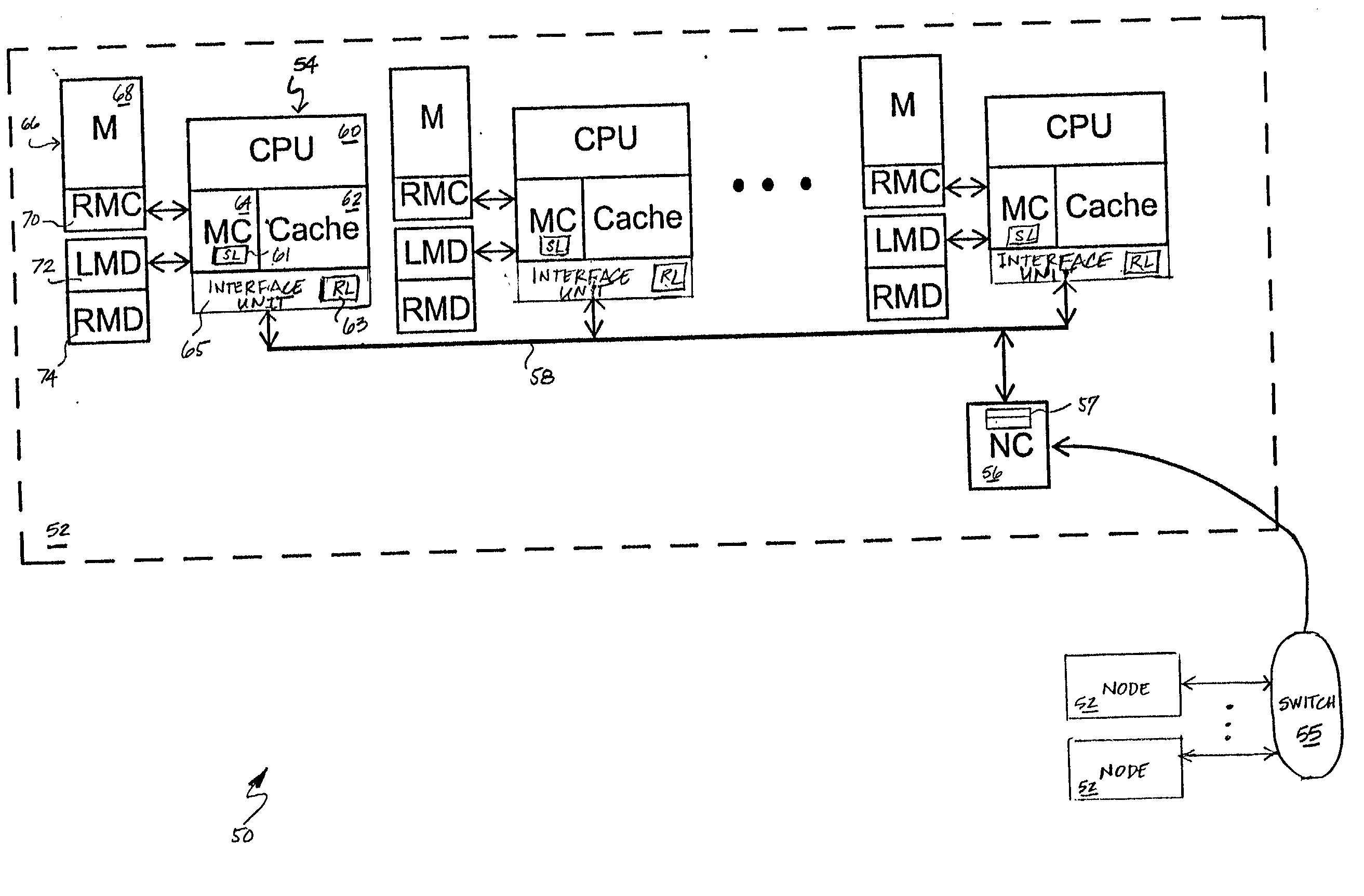
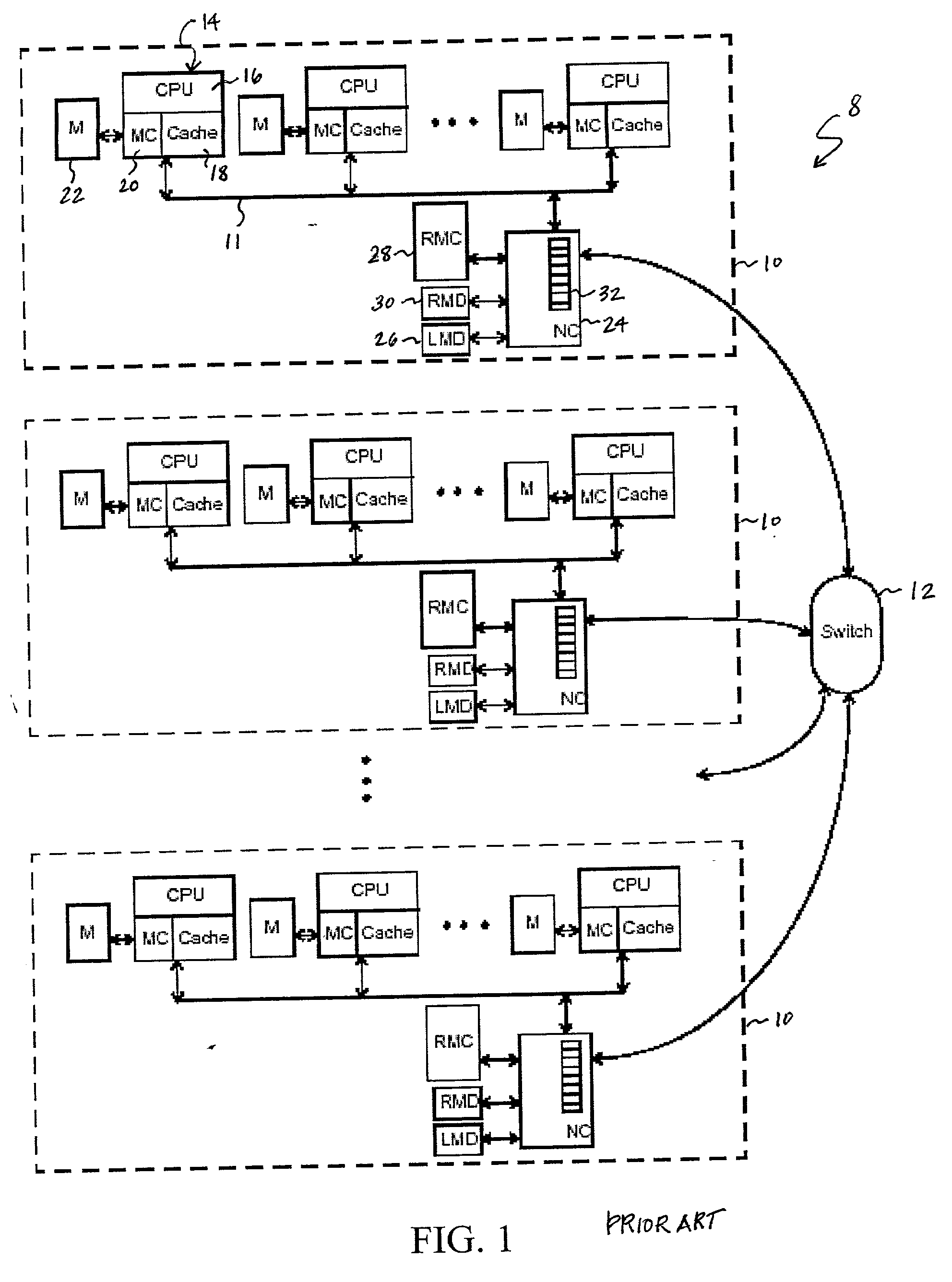
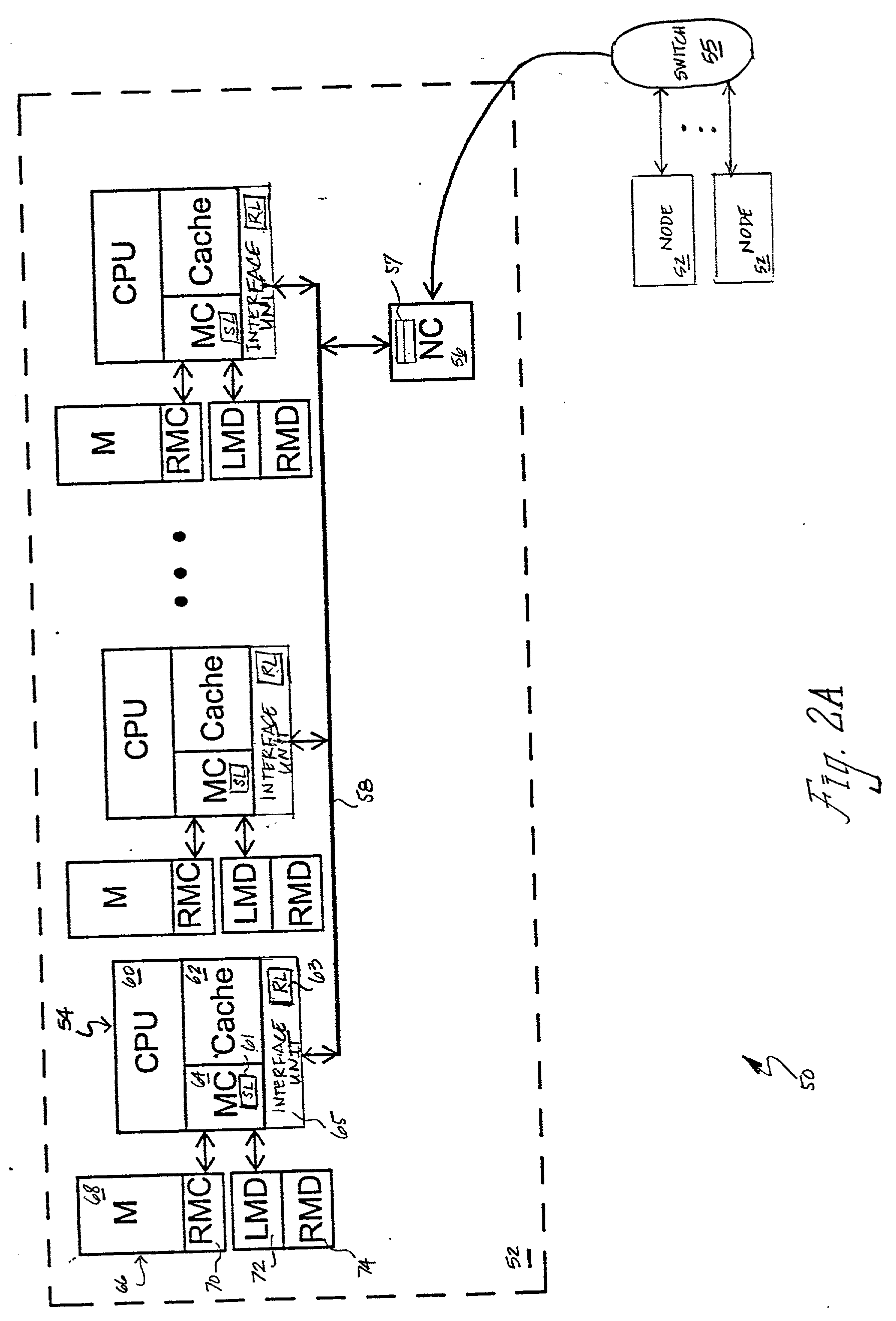
Dynamic history based mechanism for the granting of exclusive data ownership in a non-uniform memory access (numa) computer system
InactiveUS20030009641A1Program synchronisationMemory adressing/allocation/relocationExclusive orData access
A non-uniform memory access (NUMA) computer system includes at least one remote node and a home node coupled by a node interconnect. The home node contains a home system memory and a memory controller. In response to receipt of a data request from a remote node, the memory controller determines whether to grant exclusive or non-exclusive ownership of requested data specified in the data request by reference to history information indicative of prior data accesses originating in the remote node. The memory controller then transmits the requested data and an indication of exclusive or non-exclusive ownership to the remote node.
Owner:IBM CORP
System and method for managing raid storage system having a hot spare drive
ActiveUS20160357649A1Achieve redundancySolve insufficient storage spaceRedundant hardware error correctionRAIDOriginal data
A method provides rebuilding data in a hot spare storage device when multiple storage devices fail in a storage system. The method includes a storage controller determining if a first storage device storing first data has failed within a first group of storage devices. In response to the first storage device failing, the first data is rebuilt in the hot spare storage device from a copy of the first data stored in a first mirrored storage device of the first group of storage devices. In response to a second storage device failing, third data is generated by performing a first exclusive or (XOR) operation with the first data stored on the hot spare storage device and a copy of the second data stored in a second mirrored storage device of the second group of storage devices. The third data is rebuilt in the hot spare storage device. The method recovers original data and prevents complete failure of a virtual disk.
Owner:DELL PROD LP
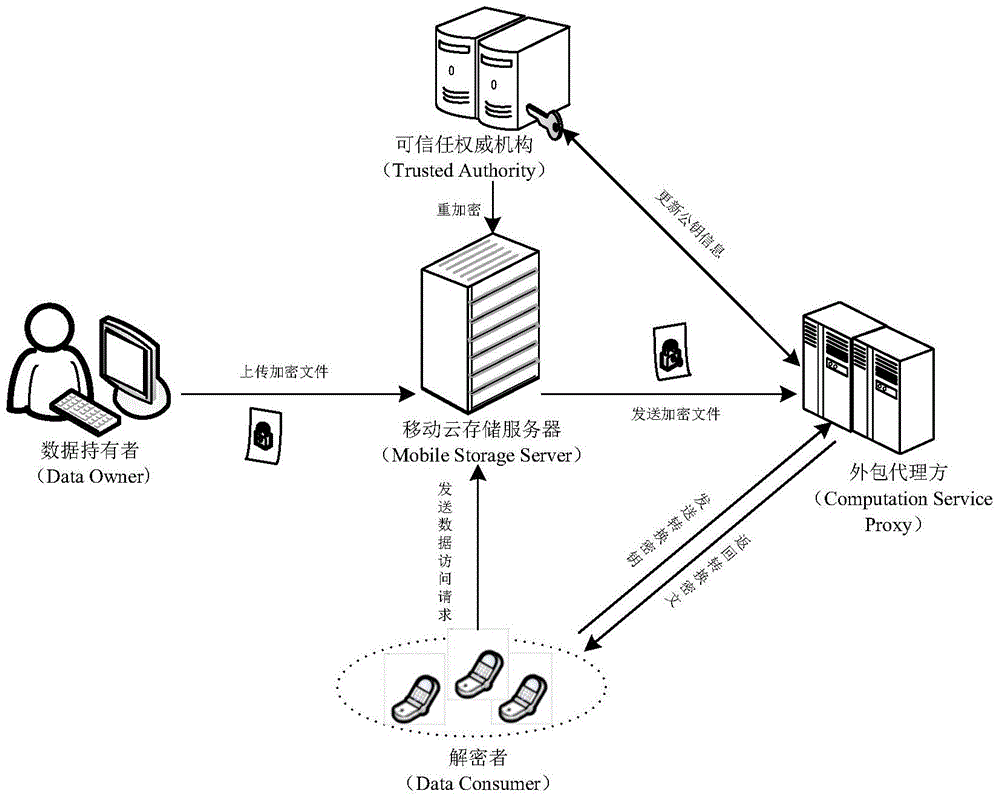
Revocable key external package decryption method based on content attributes
ActiveCN104486315APrevent unauthorized accessProtection securityUser identity/authority verificationComputer hardwareTrusted authority
The invention relates to a revocable key external package decryption method based on content attributes. For a trusted authority, 1, initialization is carried out, and system parameters are output; 2, a random number generation algorithm operates; 3, a collision-resistant Hash function is selected, and the Hash value is calculated; 4, a public key and a main key are calculated; 5, the random number is selected, and exponentiation calculation and multiplication are carried out; 6, the collision-resistant Hash function operates, the exponentiation operation is carried out, and a decryption key is obtained. For a data holder, 7, AES data encryption is carried out; 8, an access control matrix is generated; 9, a random number is selected, and an inner product is calculated; 10, multiplication, exponentiation and exclusive-or operation is operated, and ciphertexts are obtained. For a decryption operator, 11, a decryption request and a transformation key are sent. For a mobile storage serve provider, 12, CT2 is sent to an external package decryption agency. For the external package decryption agency, 13, the transformation key is utilized, and the transformation ciphertext is calculated. For the decryption operator, 14, a conversation key is obtained through calculation; 15, AES data decryption is carried out.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com