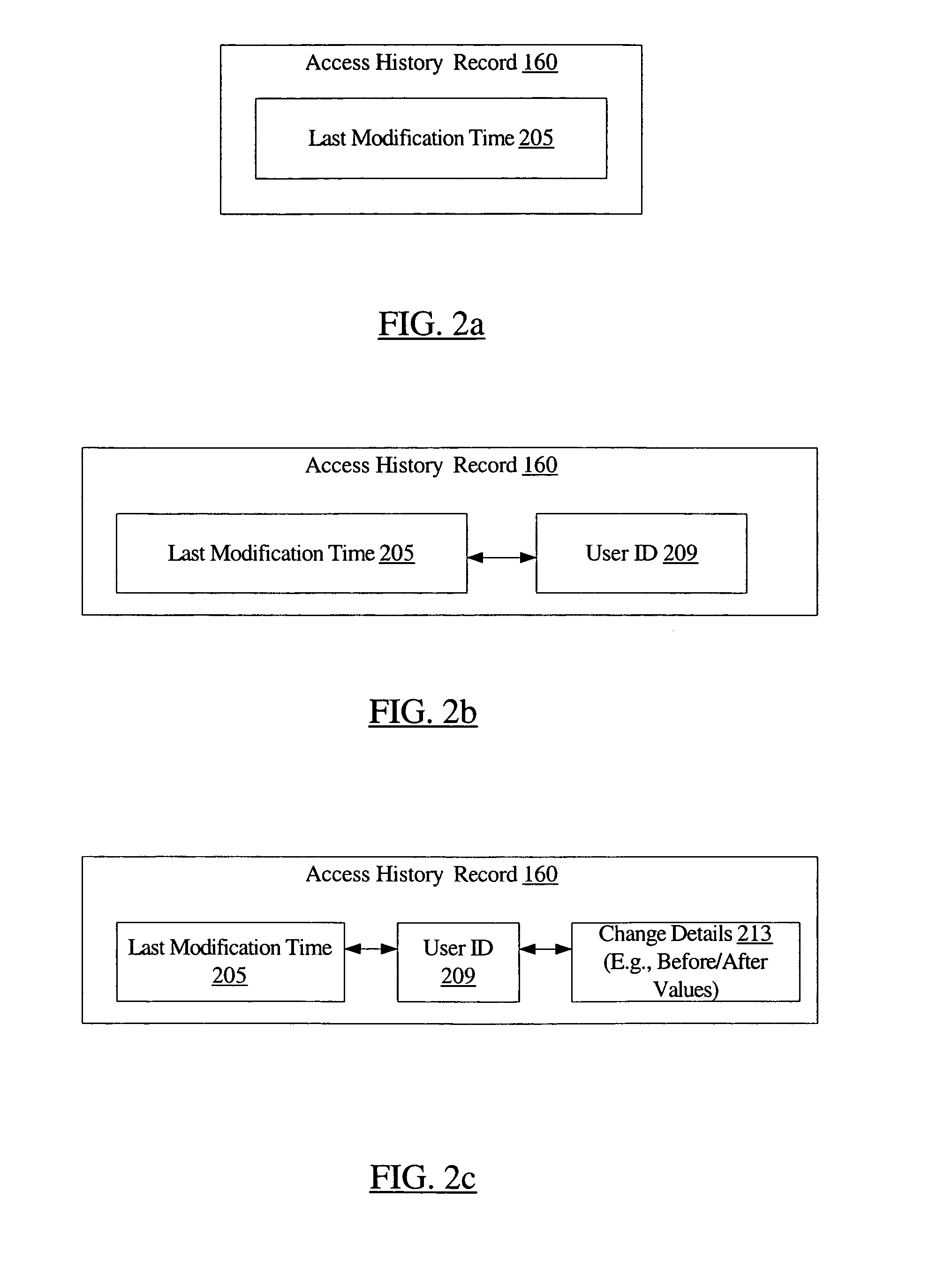
Patents
Literature
244 results about "Access history" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
To access your history, open Internet Explorer. Select the Favorites button, then select the History tab. If you would like to view your browsing history in chronological order, in the dropdown menu, select View By Date: Alternatively, you may access your browsing history by pressing the Ctrl + H keys.
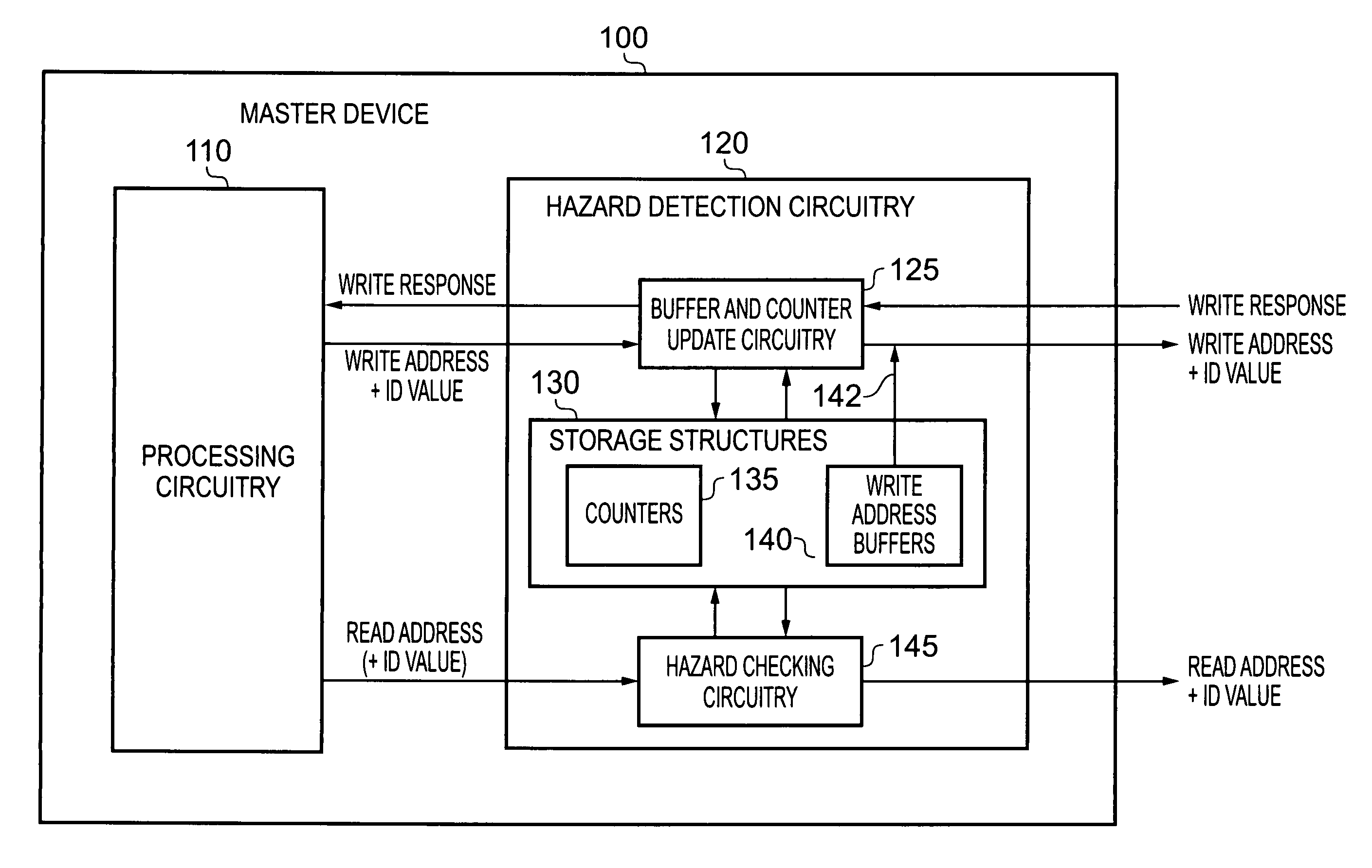
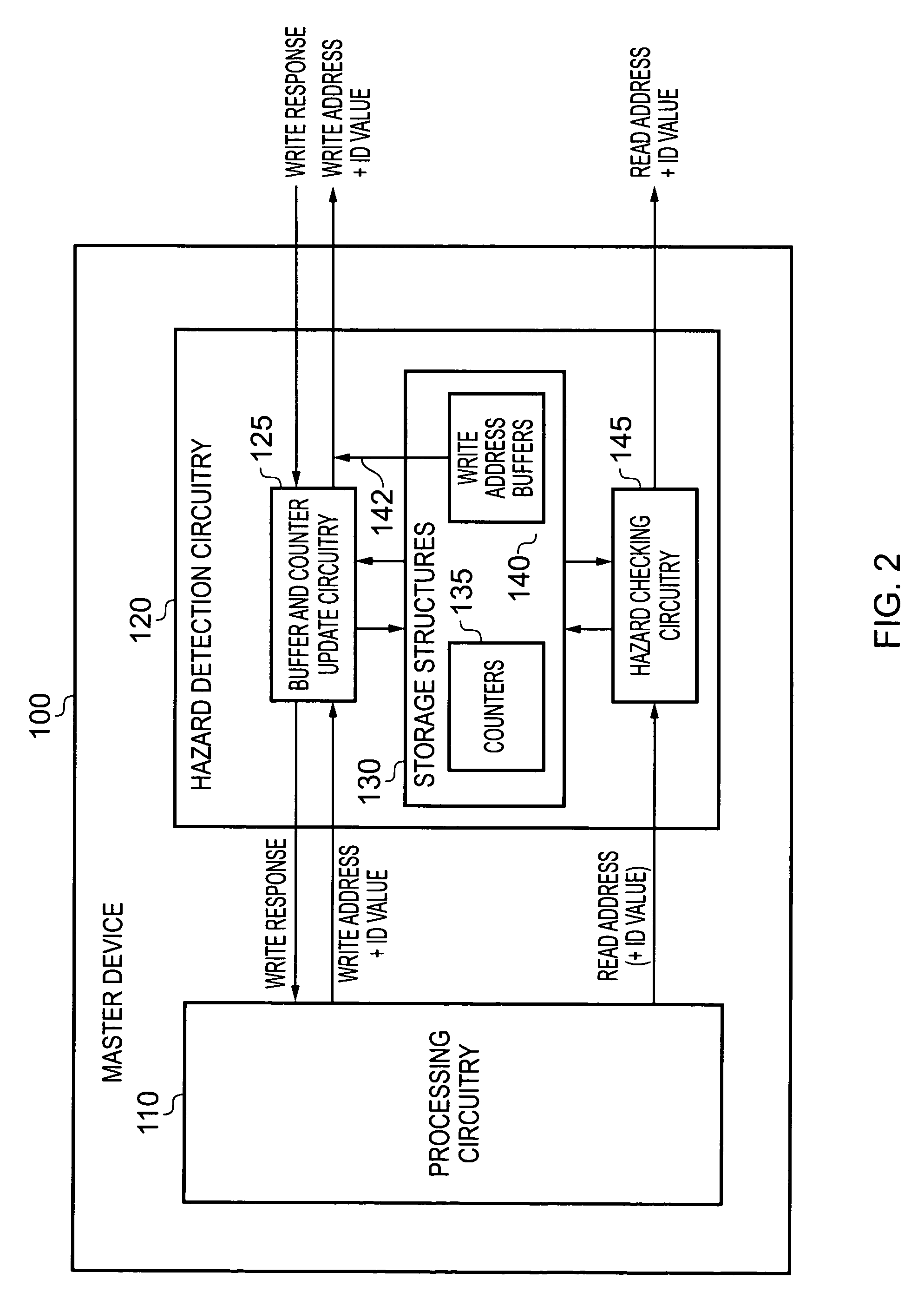
Data processing apparatus and method for performing hazard detection
ActiveUS20100250802A1Avoid possibilityAvoiding WAW hazardMemory systemsInput/output processes for data processingAccess historyData buffer
A data processing apparatus and method are provided for performing hazard detection in respect of a series of access requests issued by processing circuitry for handling by one or more slave devices. The series of access requests include one or more write access requests, each write access request specifying a write operation to be performed by an addressed slave device, and each issued write access request being a pending write access request until the write operation has been completed by the addressed slave device. Hazard detection circuitry comprises a pending write access history storage having at least one buffer and at least one counter for keeping a record of each pending write access request. Update circuitry is responsive to receipt of a write access request to be issued by the processing circuitry, to perform an update process to identify that write access request as a pending write access request in one of the buffers, and if the identity of another pending write access request is overwritten by that update process, to increment a count value in one of the counters. On completion of each write access request by the addressed slave device, the update circuitry performs a further update process to remove the record of that completed write access request from the pending write access history storage. Hazard checking circuitry is then responsive to at least a subset of the access requests to be issued by the processing circuitry, to reference the pending write access history storage in order to determine whether a hazard condition occurs. The manner in which the update circuitry uses a combination of buffers and counters to keep a record of each pending write access request provides improved performance with respect to known prior art techniques, without the hardware cost that would be associated with increasing the number of buffers.
Owner:ARM LTD
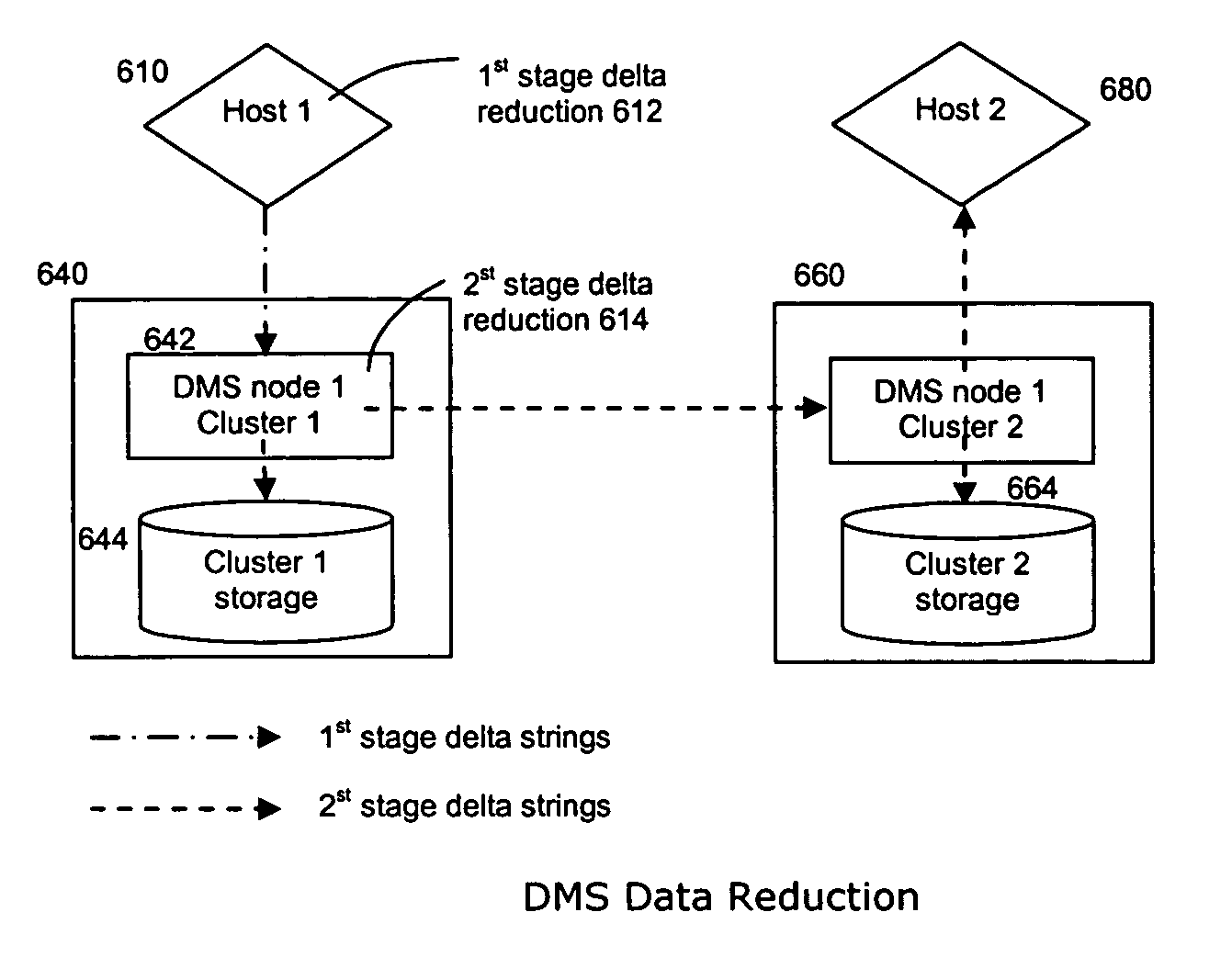
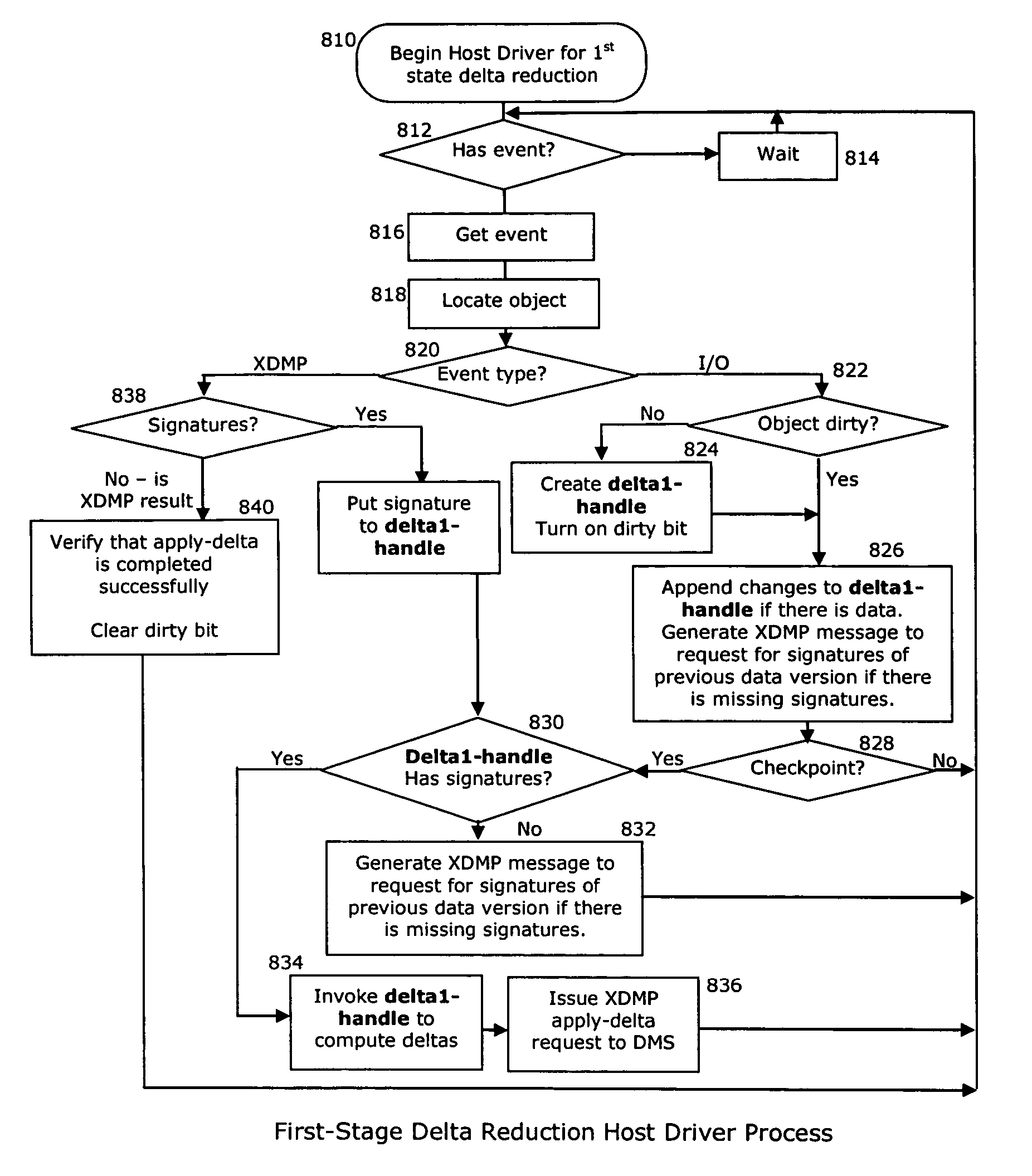
Method and system for data reduction
ActiveUS20060064416A1Efficient transferEfficient storageDigital data information retrievalDigital data processing detailsData connectionData stream
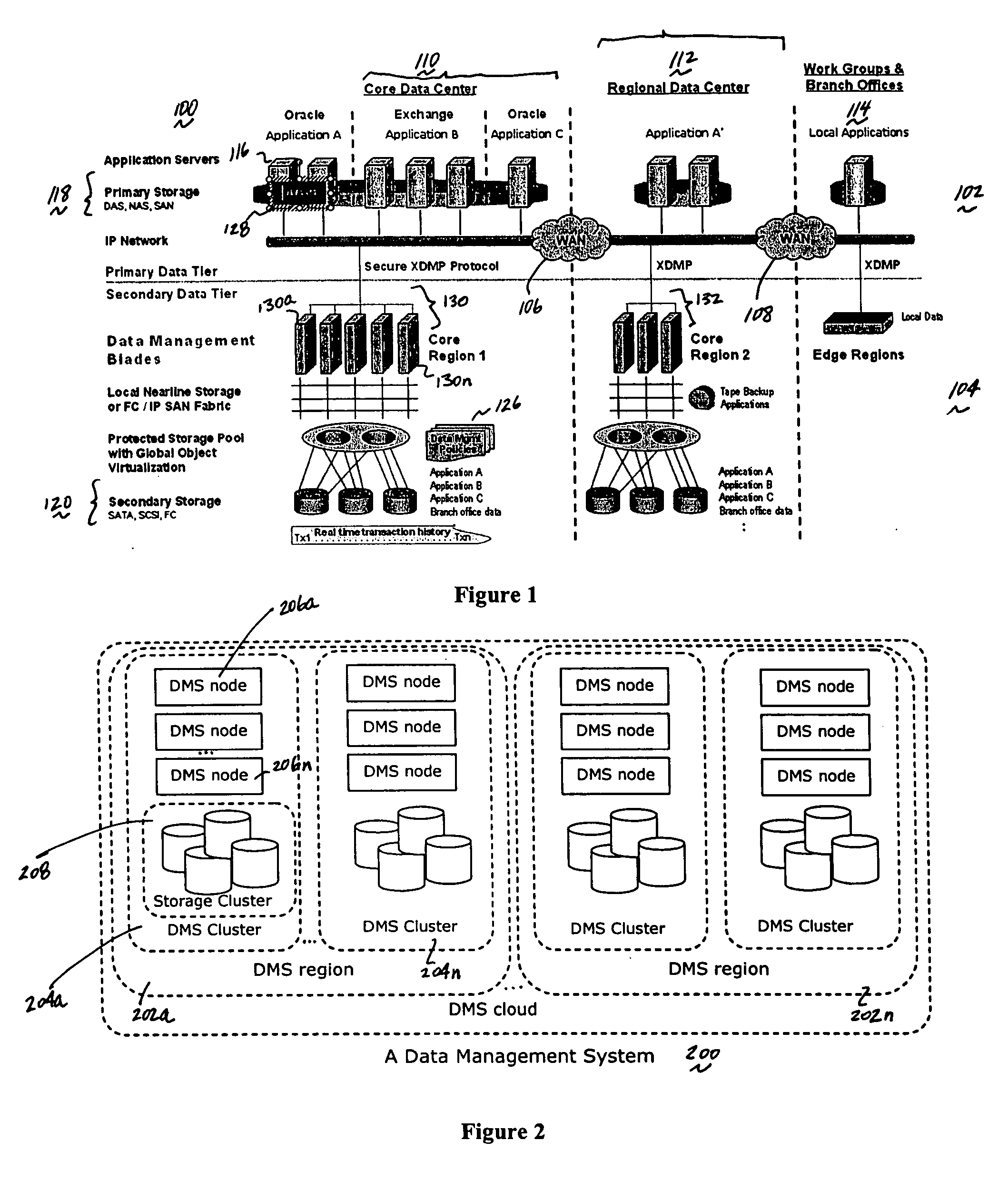
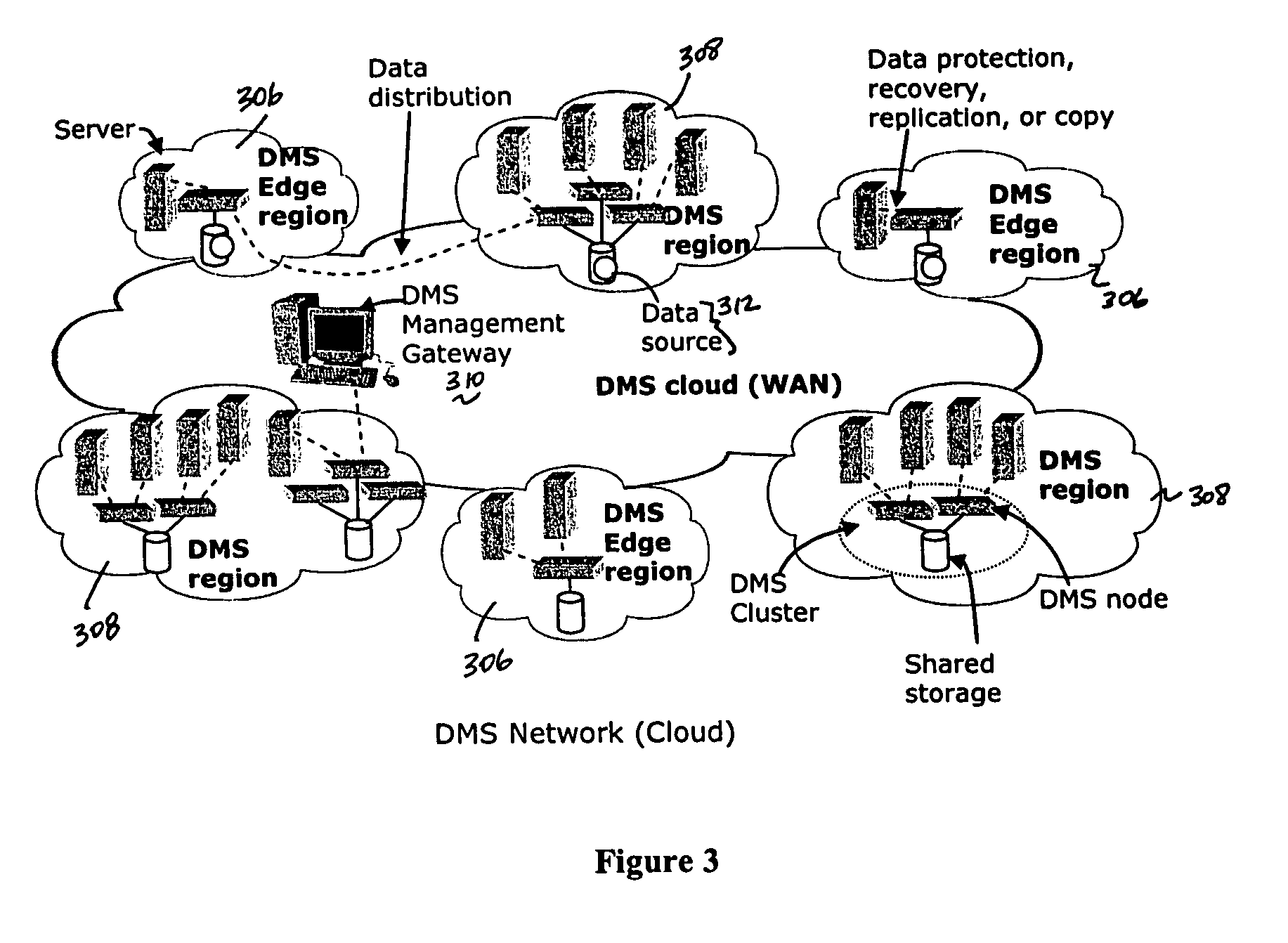
A “forward” delta data management technique uses a “sparse” index associated with a delta file to achieve both delta management efficiency and to eliminate read latency while accessing history data. The invention may be implemented advantageously in a data management system that provides real-time data services to data sources associated with a set of application host servers. To facilitate a given data service, a host driver embedded in an application server connects an application and its data to a cluster. The host driver captures real-time data transactions, preferably in the form of an event journal that is provided to the data management system. In particular, the driver functions to translate traditional file / database / block I / O into a continuous, application-aware, output data stream. In an illustrative embodiment, a given application aware data stream is processed through a multi-stage data reduction process to produce a compact data representation from which an “any point-in-time” reconstruction of the original data can be made.
Owner:QUEST SOFTWARE INC
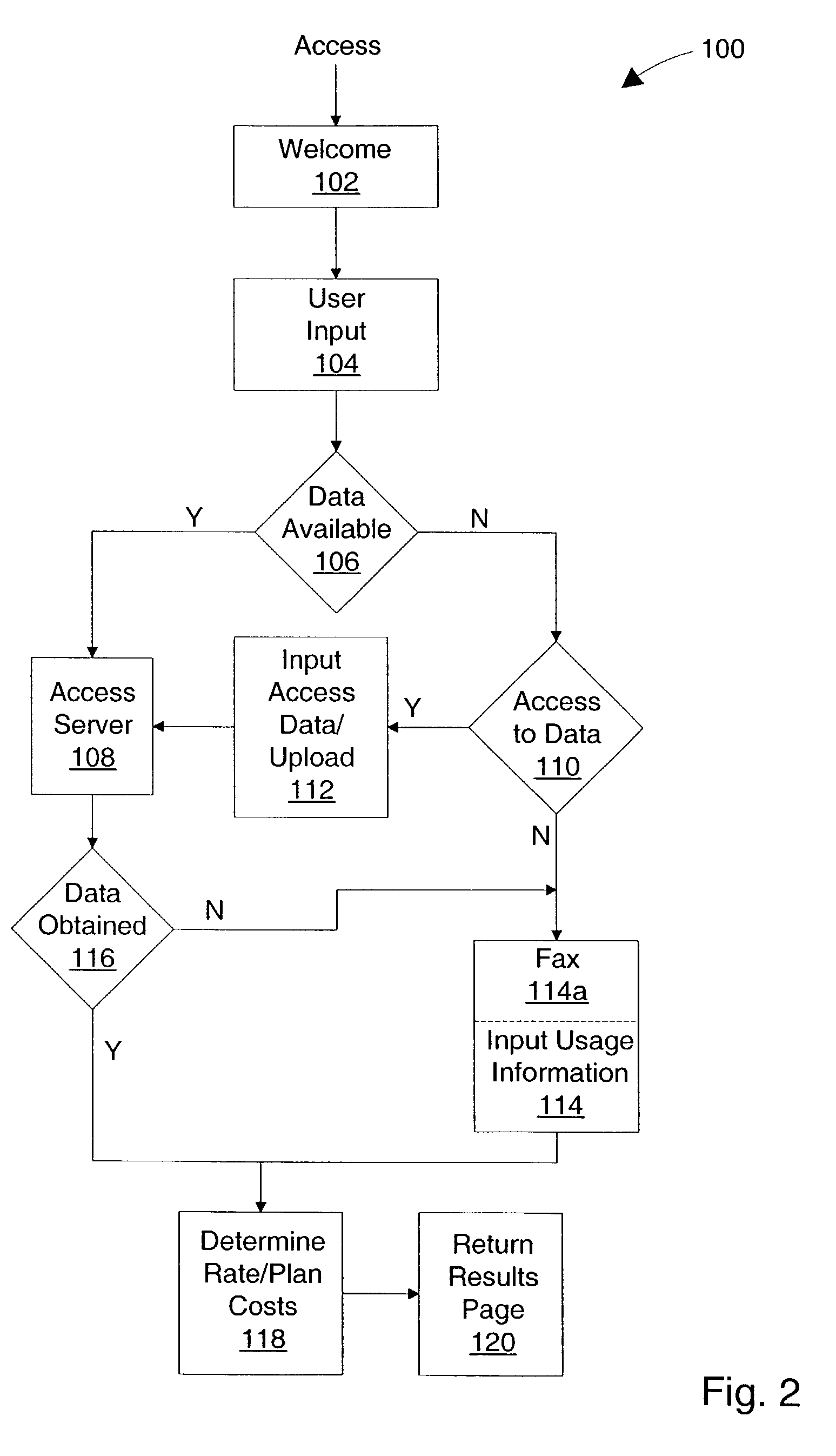
Method and system for interactive rate plan recommender
InactiveUS8005726B1Facilitate communicationFinanceTelephonic communicationAccess historyApplication software
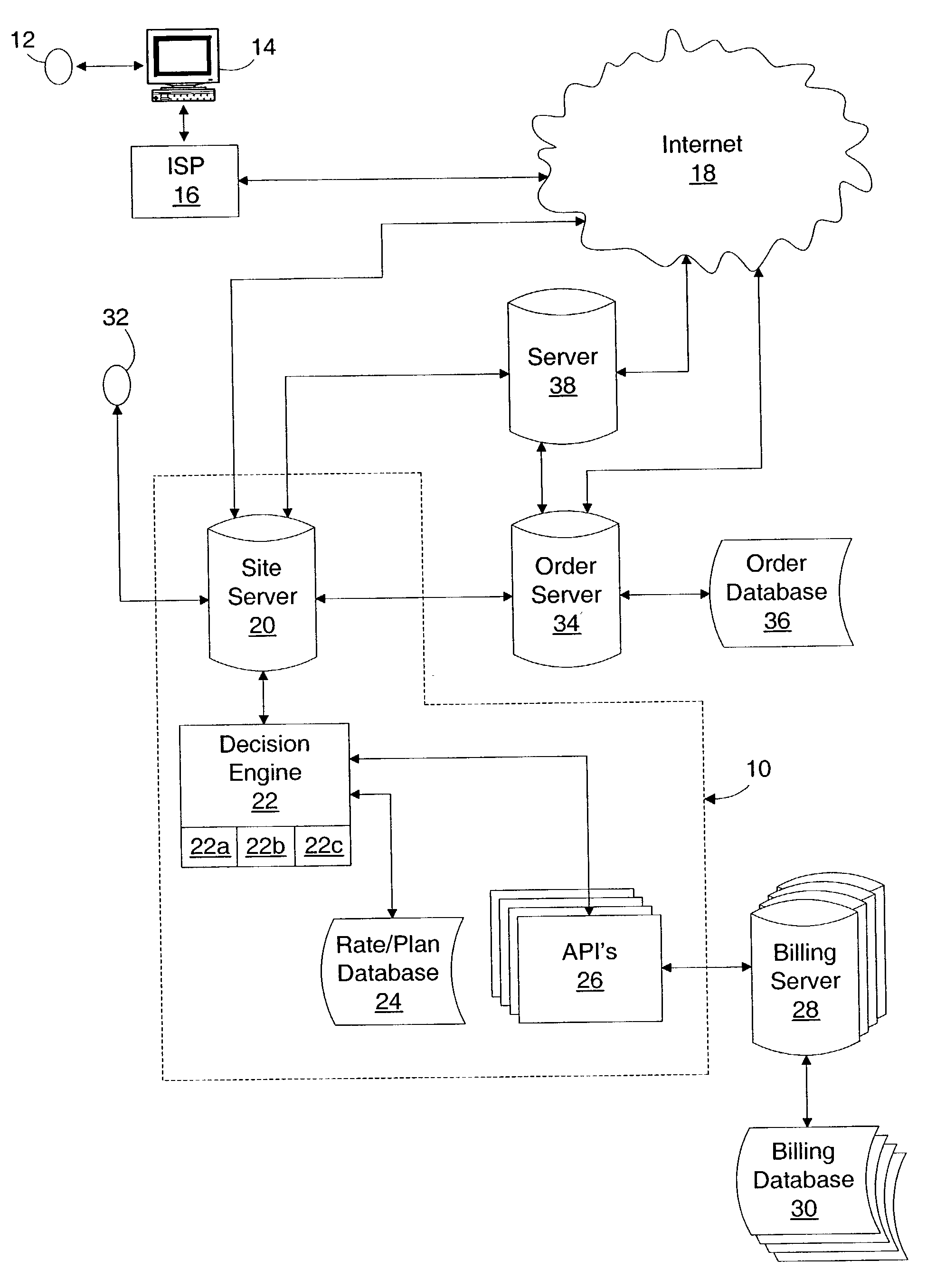
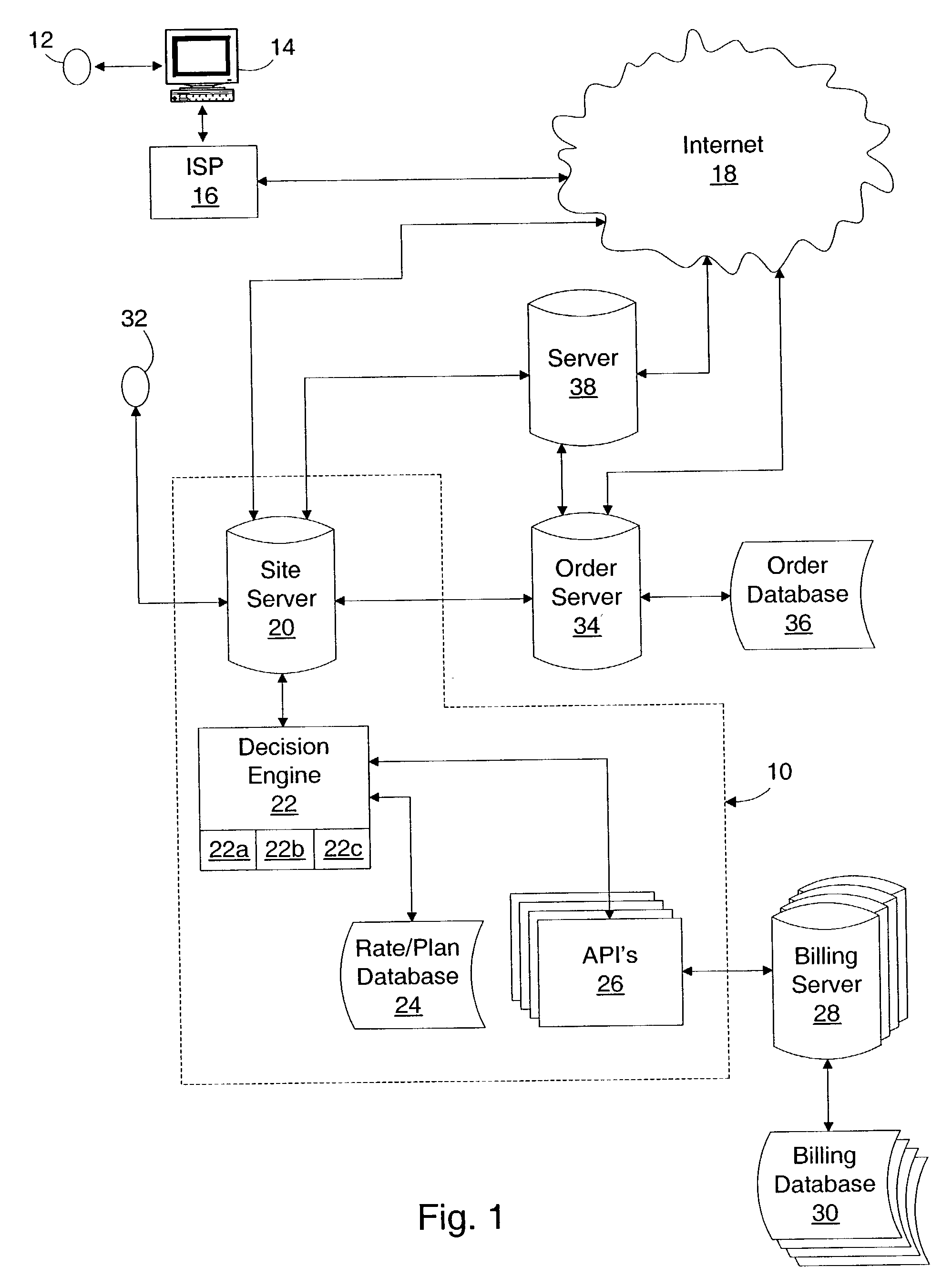
A method and system for analyzing rate plans for communication services may include obtaining usage data for a user from a database of historical usage data for the user and determining rate plan costs based on the usage data. The method and system may include obtaining information from a user and determining, based on the user information, if usage data for the communication services may be available for the user and obtaining the usage data from inputs by the user, including uploads of electronic bills, when the usage data is not available from the database. The method may be implemented on a web-based site server, which can connect to a decision engine for analyzing the usage data and determining the costs for the rate plan. The decision engine may access the historical usage database through one or more Application Program Interfaces operating on one or more billing servers.
Owner:VERIZON PATENT & LICENSING INC
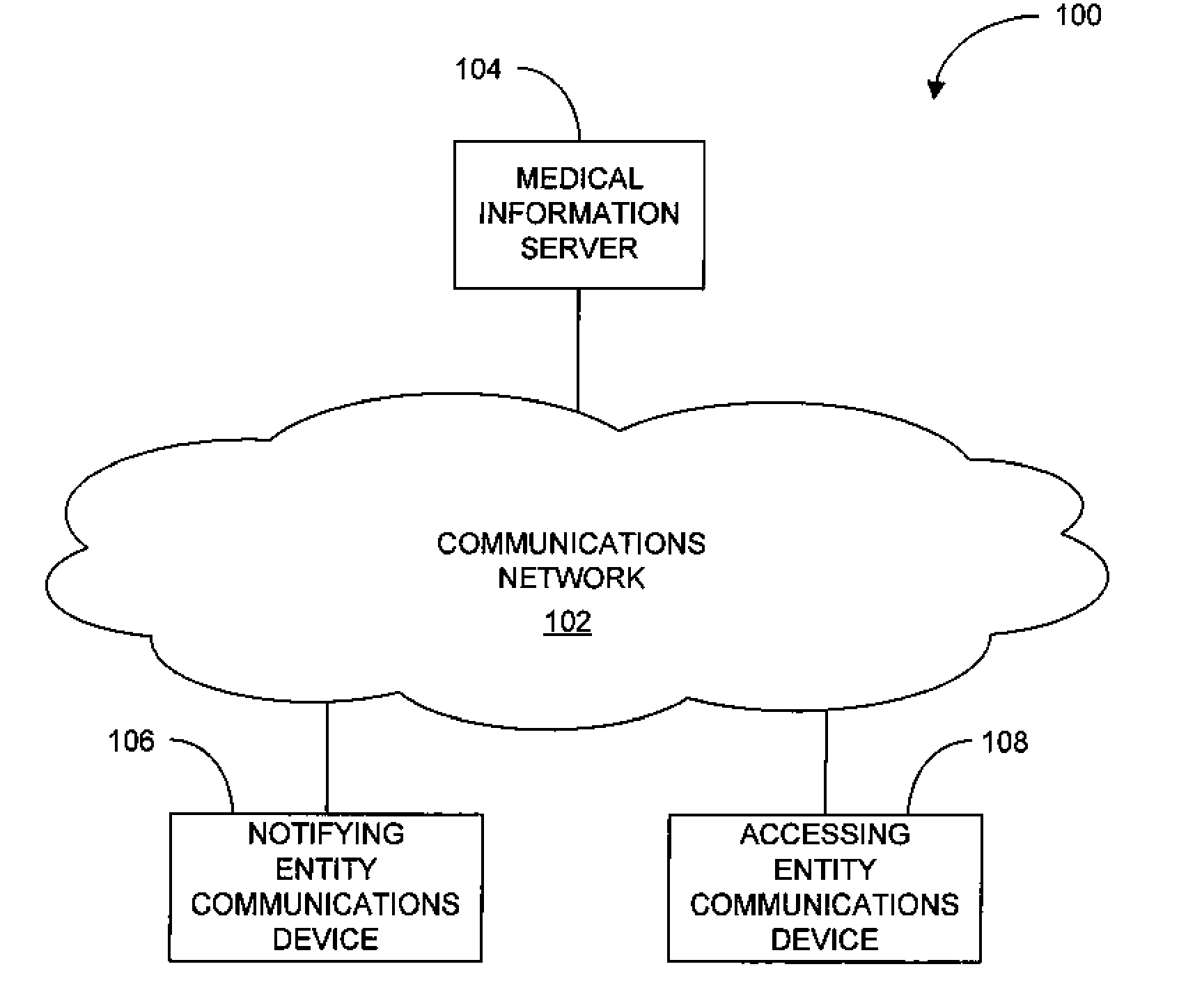
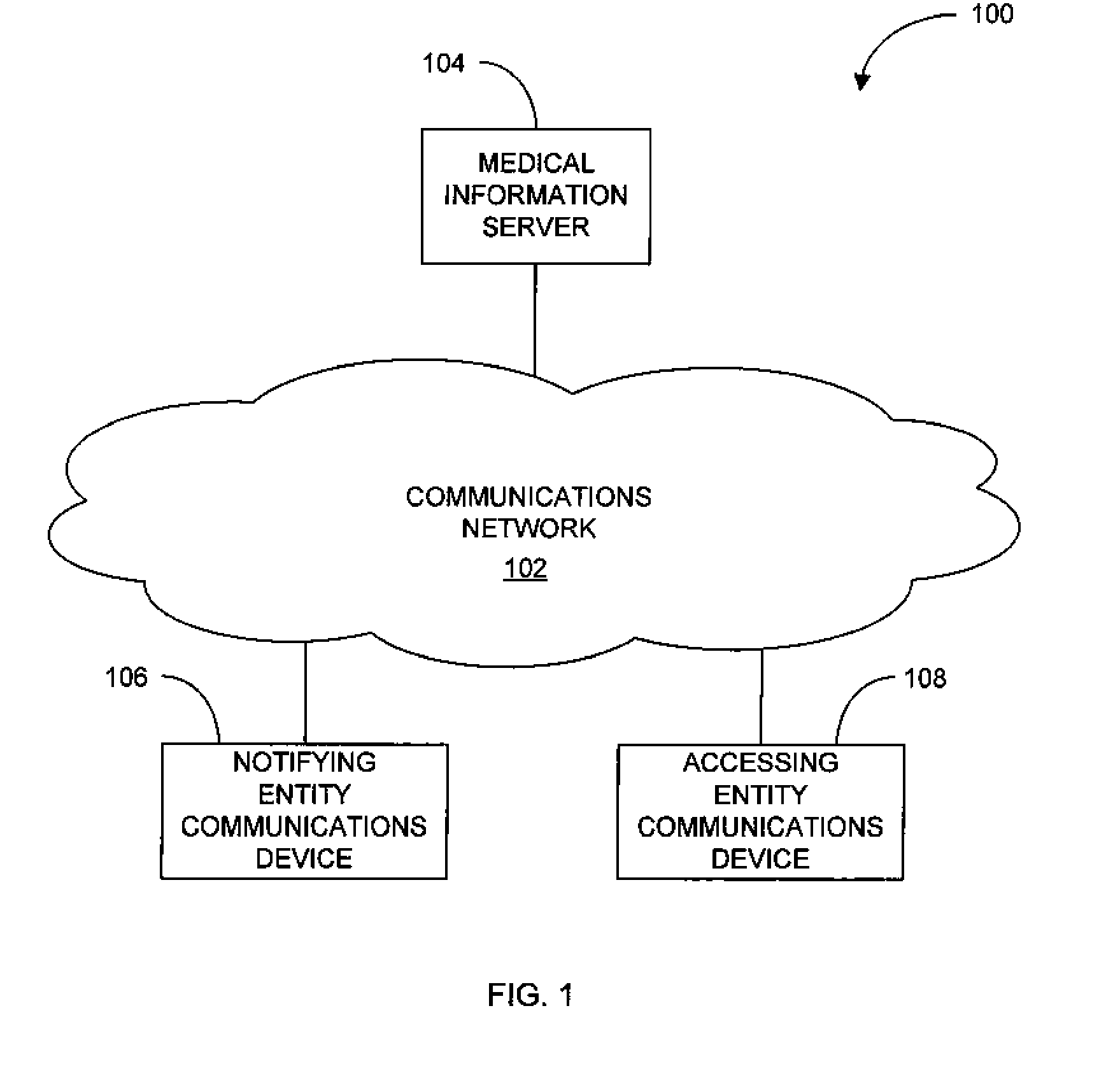
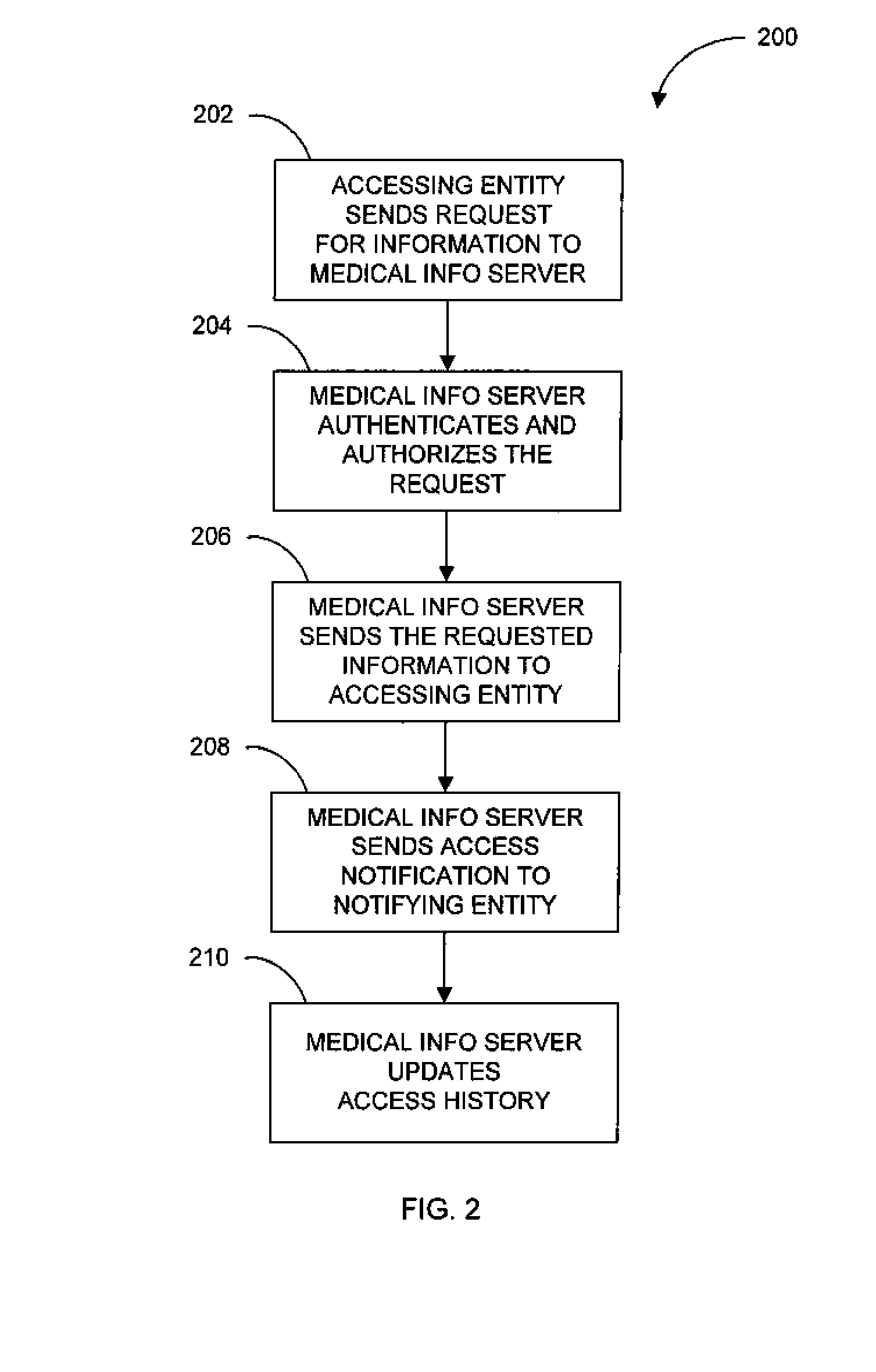
System and method of notifying designated entities of access to personal medical records
A medical information server and corresponding methods are disclosed for processing of personal medical information, providing some or all of the medical information to authorized requesting entities, and providing notifications of access to personal medical records to designated entities. The server may receive a request for personal medical record information from a communications device of a requesting entity; authenticate and authorize the request; send the requested information to the authorized requesting entity; and send notification of the access to one or more designated entities. The server may further update an access history pertaining to the personal medical record to note the access. The server may further receive a request for the access history of a personal medical record, and send the requested access history information to the authorized requesting entity. Additionally, the server may send notification of the access to the history to one or more designated entities.
Owner:VITAL DATA TECH
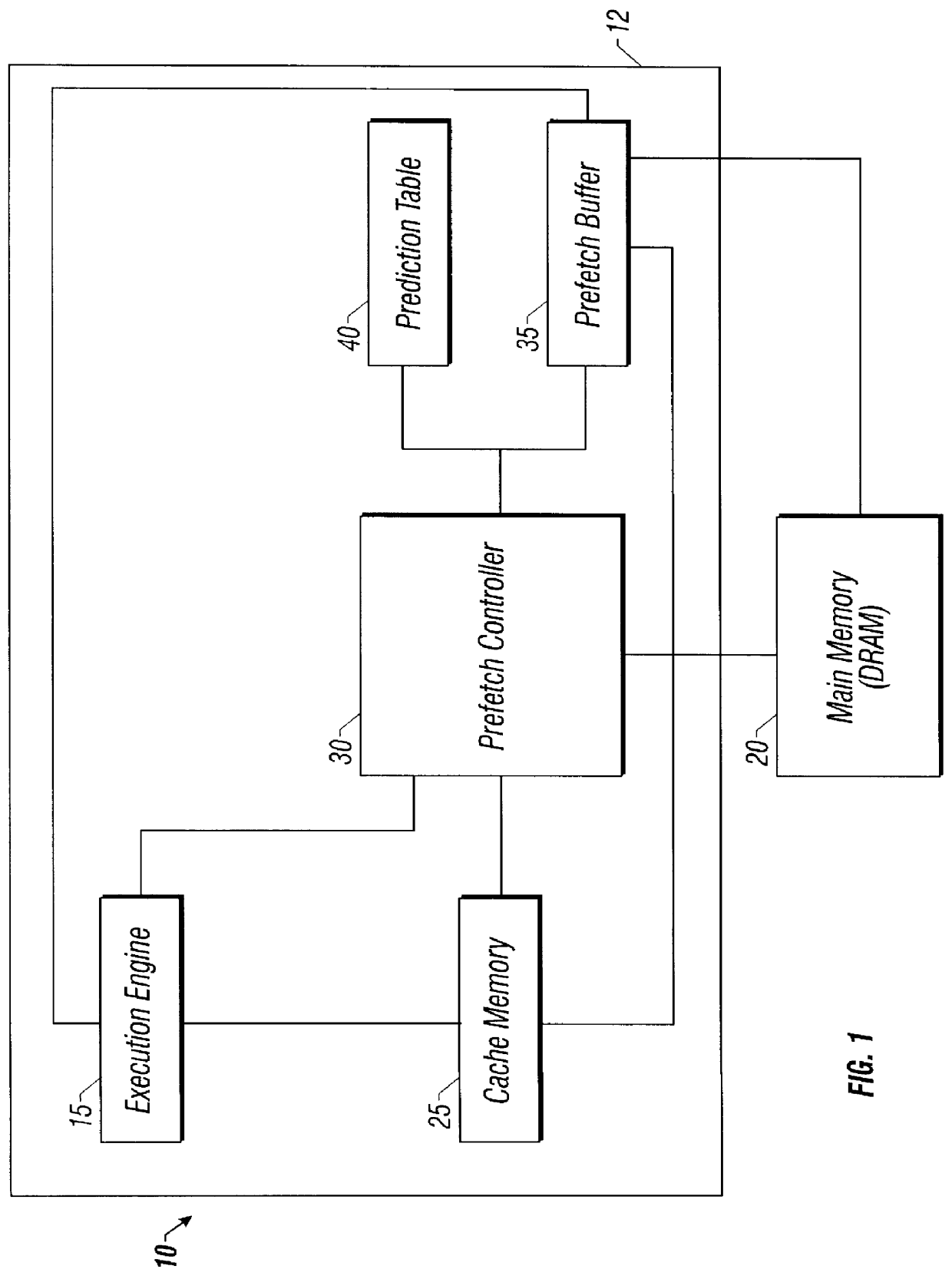
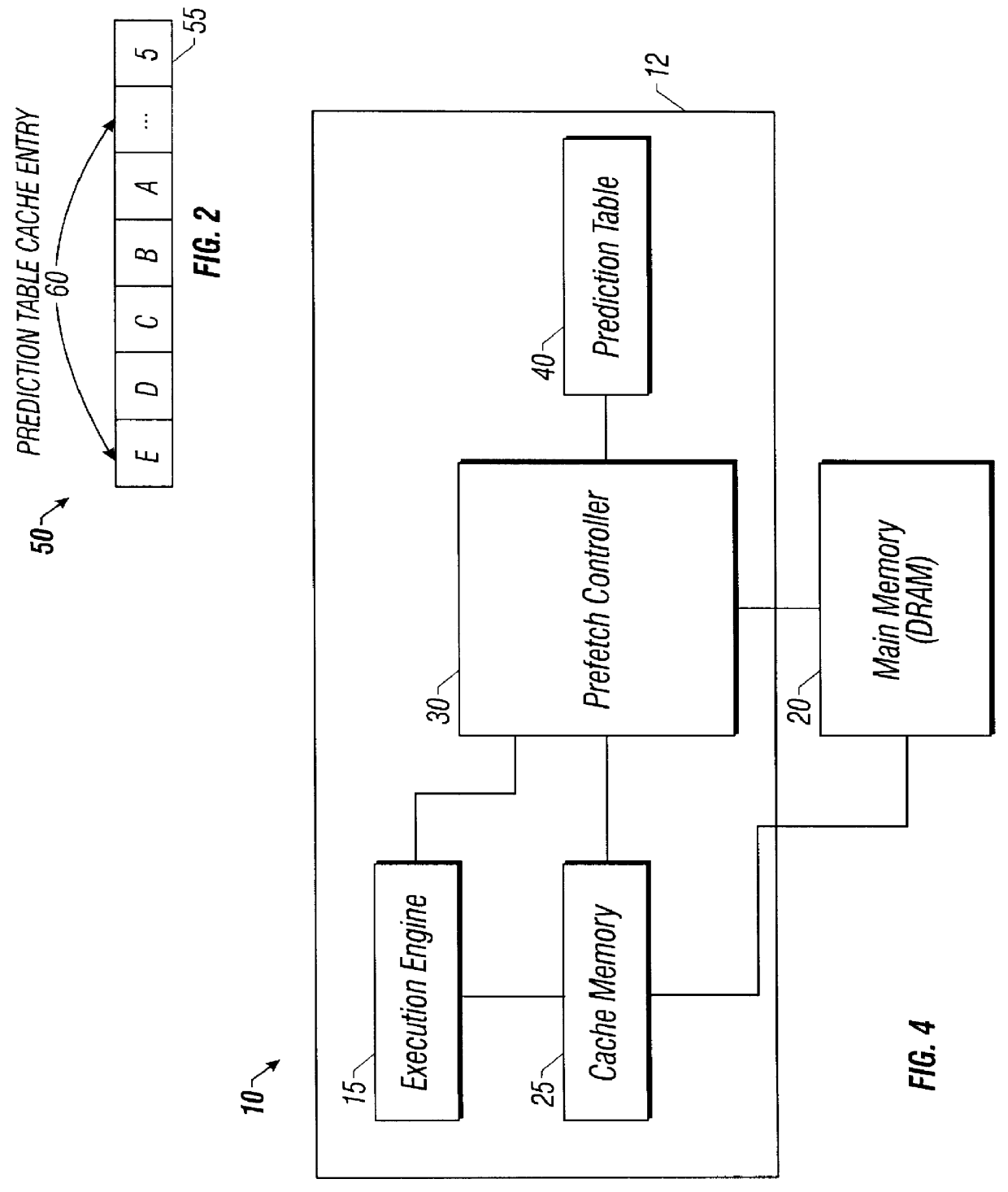
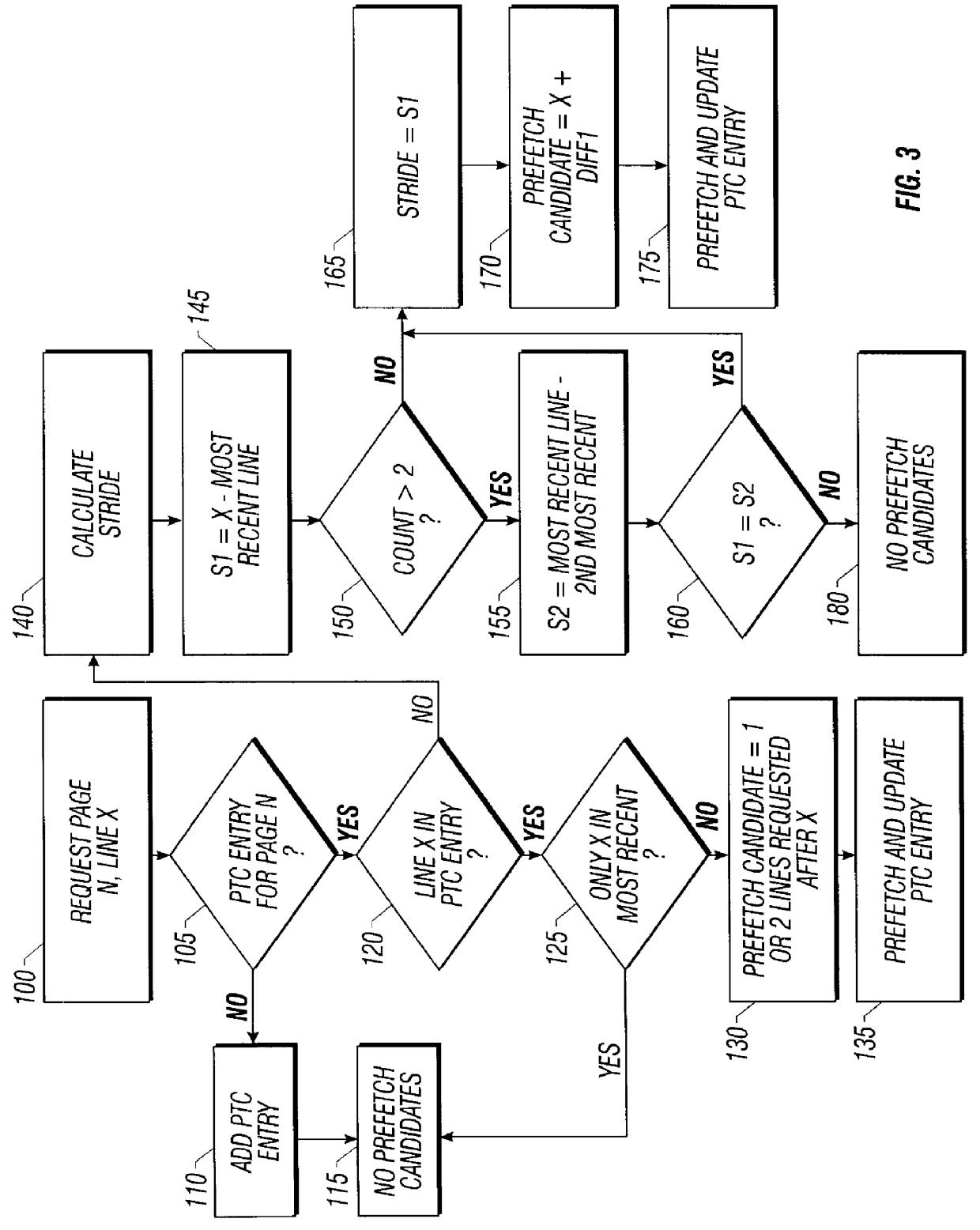
Method and apparatus for cache line prediction and prefetching using a prefetch controller and buffer and access history
InactiveUS6134643AMemory architecture accessing/allocationMemory adressing/allocation/relocationAccess historyComputer science
A microprocessor includes an execution engine, a prediction table cache, and a prefetch controller. The execution engine is adapted to issue a memory request. The memory request includes an identifier corresponding to a row location in an external main memory. The prediction table cache is adapted to store a plurality of entries defining an access history of previously encountered memory requests. The prediction table cache is indexed by the identifier. The prefetch controller is adapted to receive the memory request and generate at least one prefetch candidate based on the memory request and the access history. A method for prefetching data in a microprocessor includes receiving a memory request. The memory request includes an identifier corresponding to a row location in an external main memory. The memory request is compared to an access history of previously encountered memory requests. The access history is indexed by the identifier. At least one prefetch candidate is generated based on the memory request and the access history.
Owner:INTEL CORP
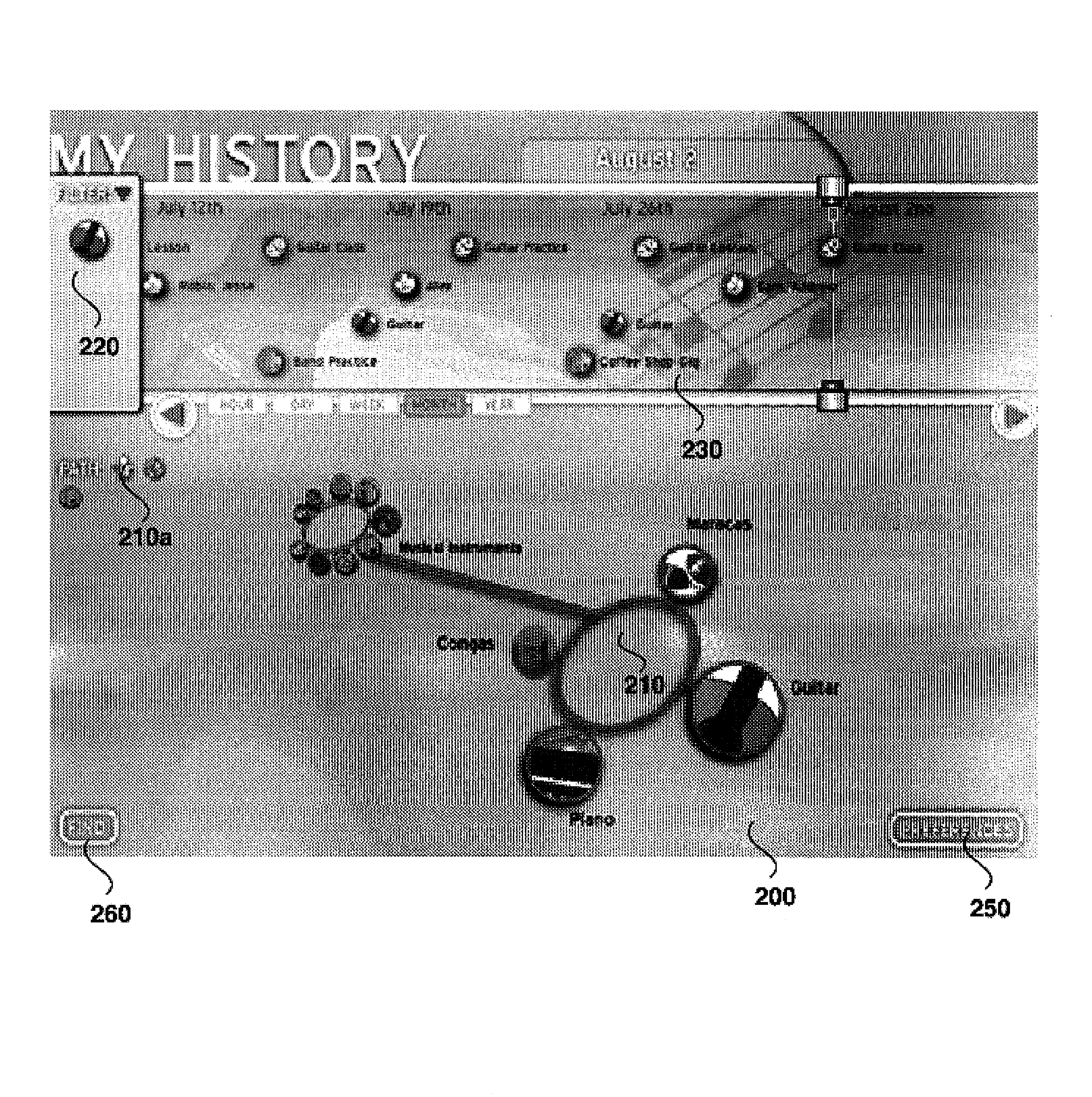
Systems and methods for interfacing with digital history data
InactiveUS7146574B2Other databases browsing/visualisationWeb data navigationTime segmentAccess history
Systems and methods for accessing historical data are provided. Based upon user interaction, a time period of interest and historical data, the systems and methods perform cross-correlation algorithms and interpret which items are to be accessed and displayed to the user via a user interface vis-a-vis a timeline portion and navigation region. Based on frequency and recency usage patterns, and / or user preferences, items are assigned relative weights and displayed accordingly in the timeline portion and navigation region of the user interface. Each item that can be displayed within the system has a unique identification, which may be translated to one or more visual symbols within the user interface. In various non-limiting embodiments, the system leverages a distributed database store which stores and indexes items that make up a digital history. When a request is made to the database, items, such as events, places, people and things, are automatically cross-referenced and correlations are drawn based on filtering criteria.
Owner:SZ DJI TECH CO LTD
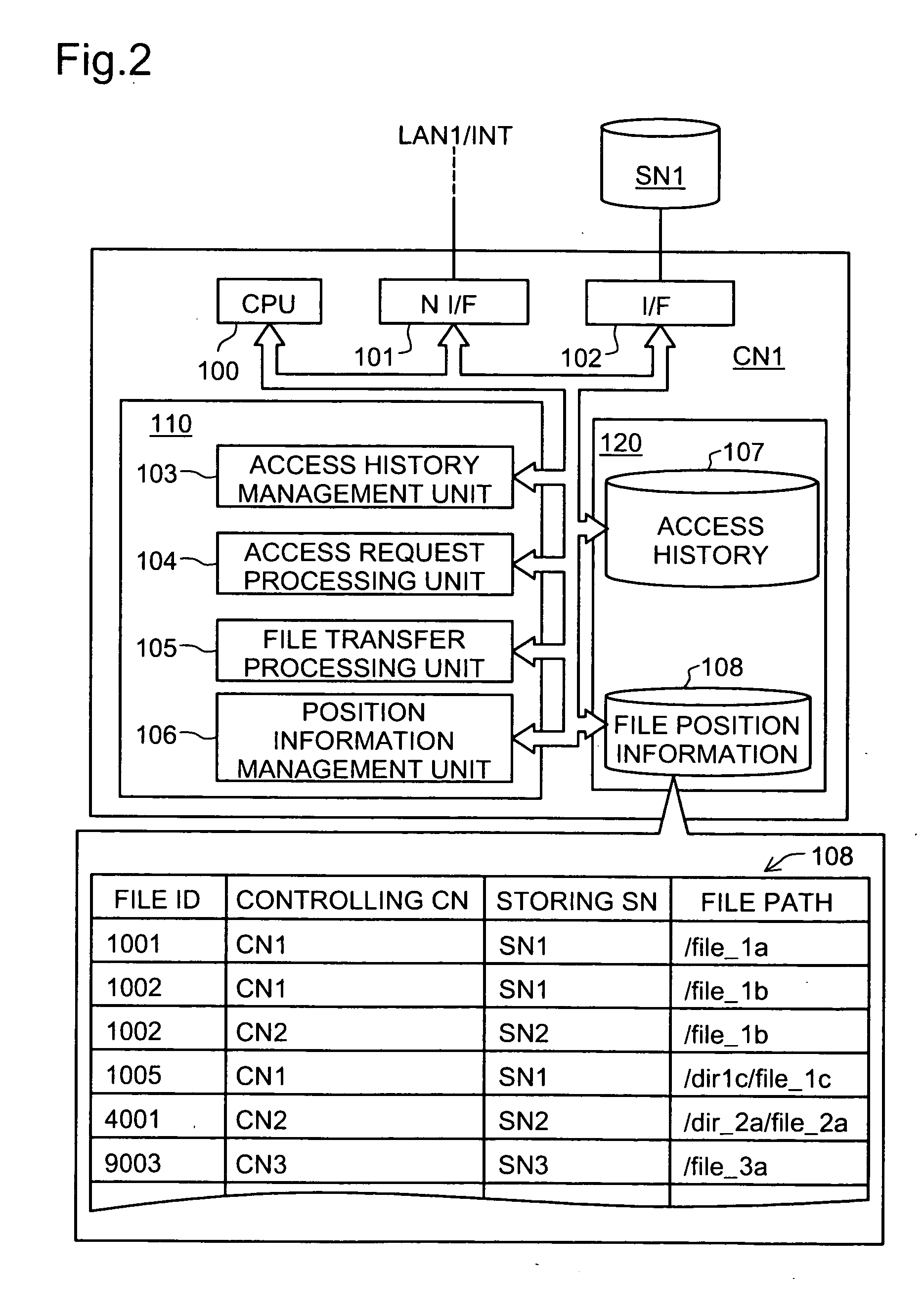
File migration method based on access history
InactiveUS20050125456A1Improve efficiencyNetwork degradationDigital data information retrievalDigital data processing detailsAccess historyFile migration
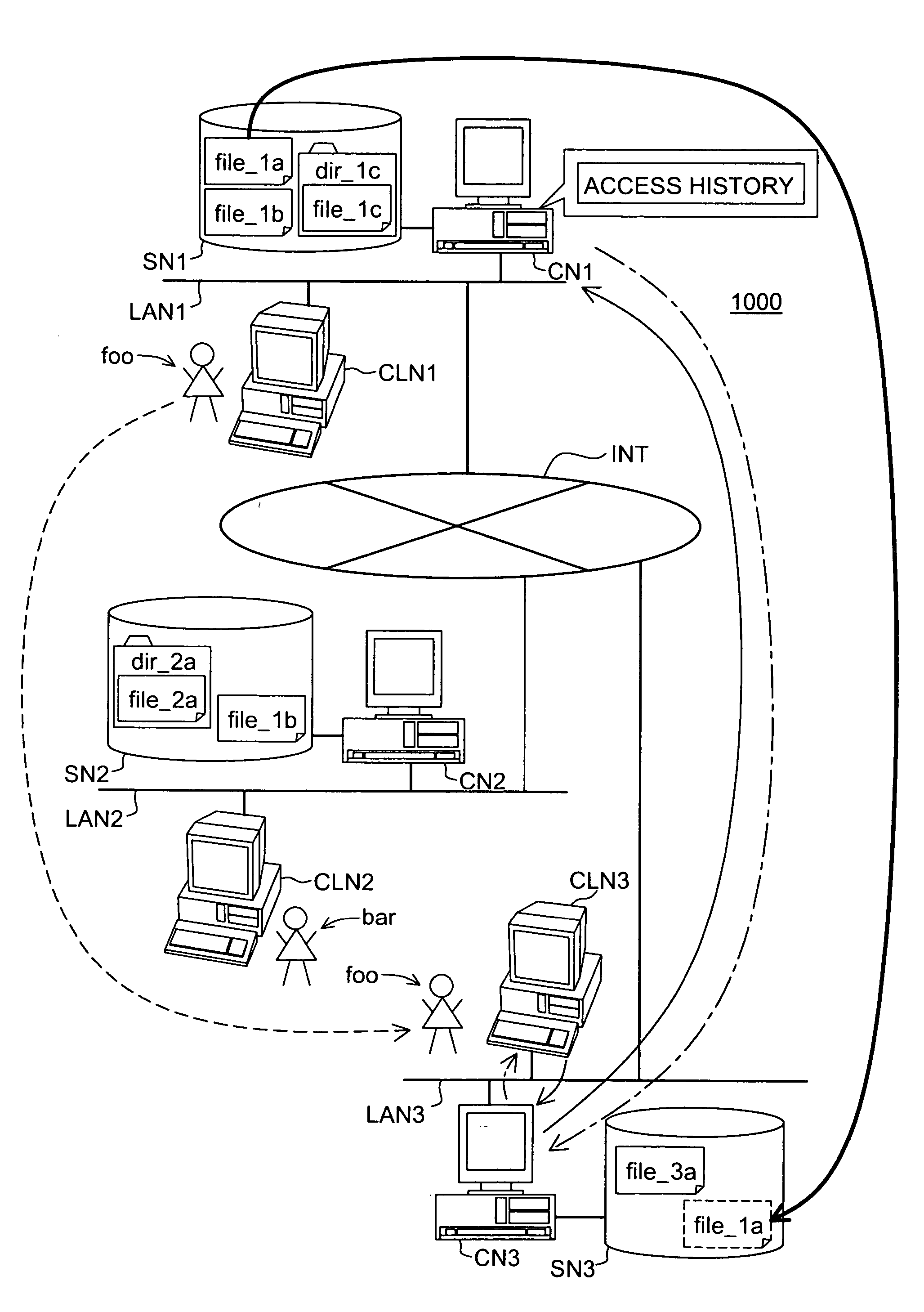
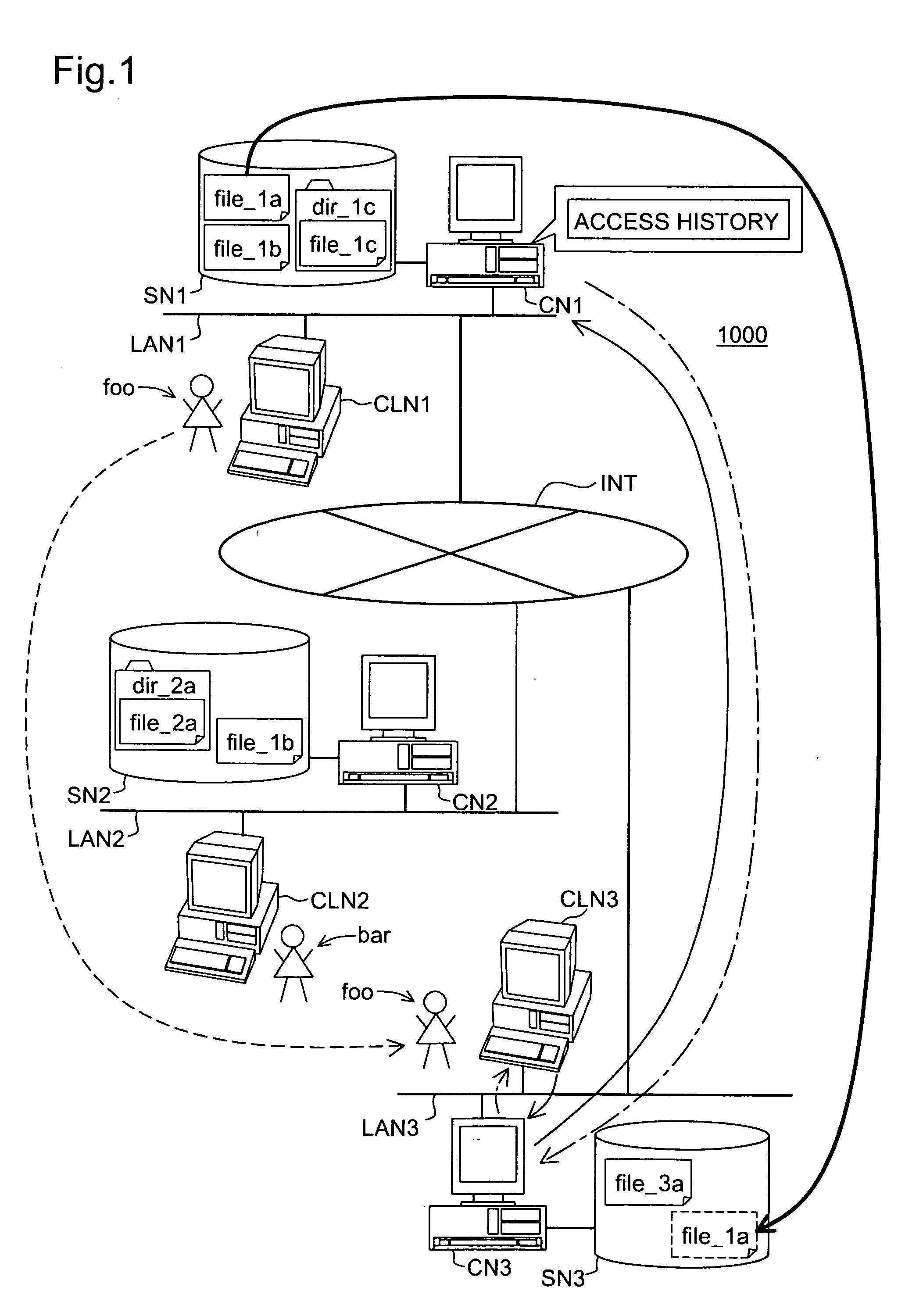
The object of the present invention is to improve an access efficiency in a distributed environment. When a user “foo” access a file “file_1a” stored in a storage node SN1 under the control of a control node CN1 from a client CLN3 via a control node CN3 as shown by the solid lien arrow in the figure, a record of the access is accumulated in an access history of the control node CN1. If the control node CN1 refers to the access history and detects the frequent accesses from the control node CN3, it replicates or migrates the file “file_1a” to a storage node SN3 controlled by the control node CN3 as shown by the bold line arrow. The replication is performed if another device has accessed the file. Otherwise the migration is performed.
Owner:HARA JUNICHI +2
Semiconductor device
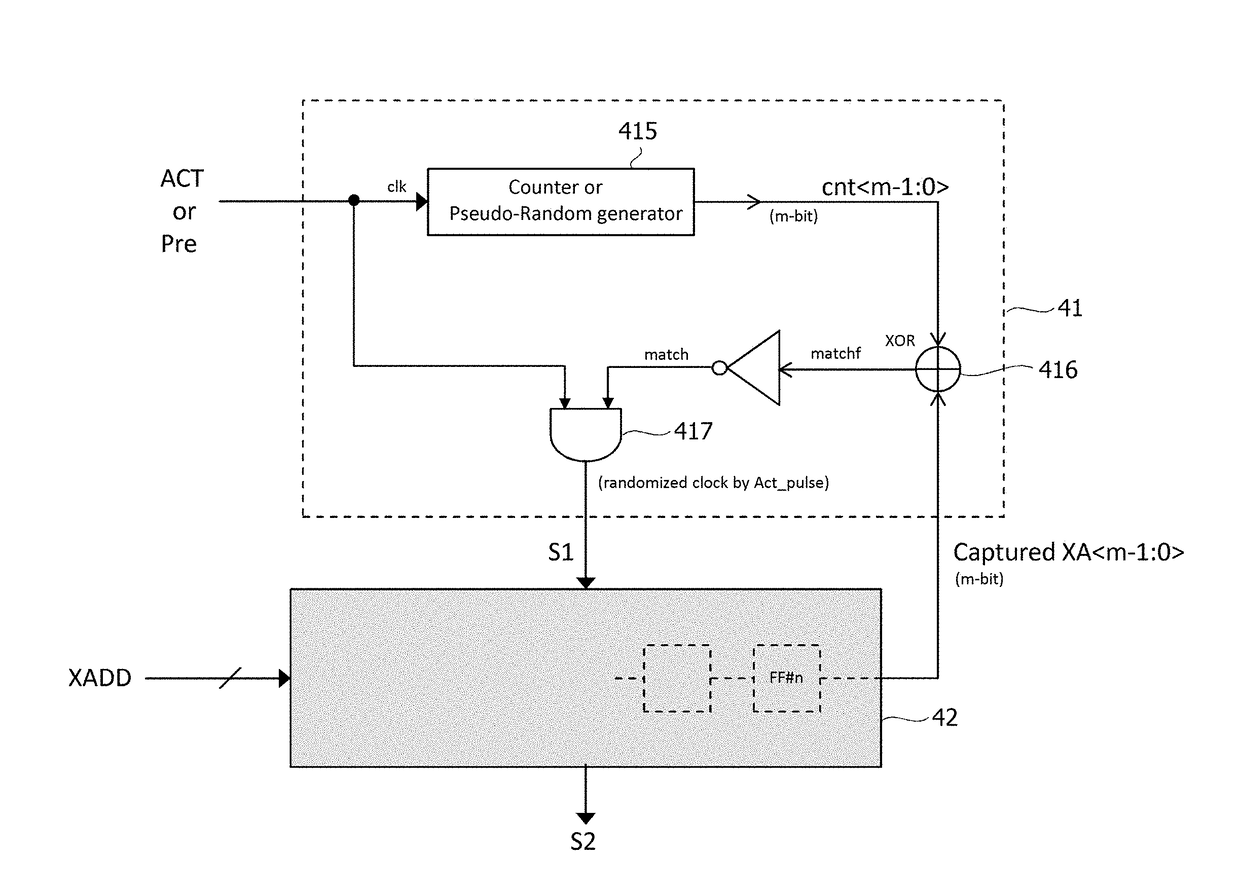
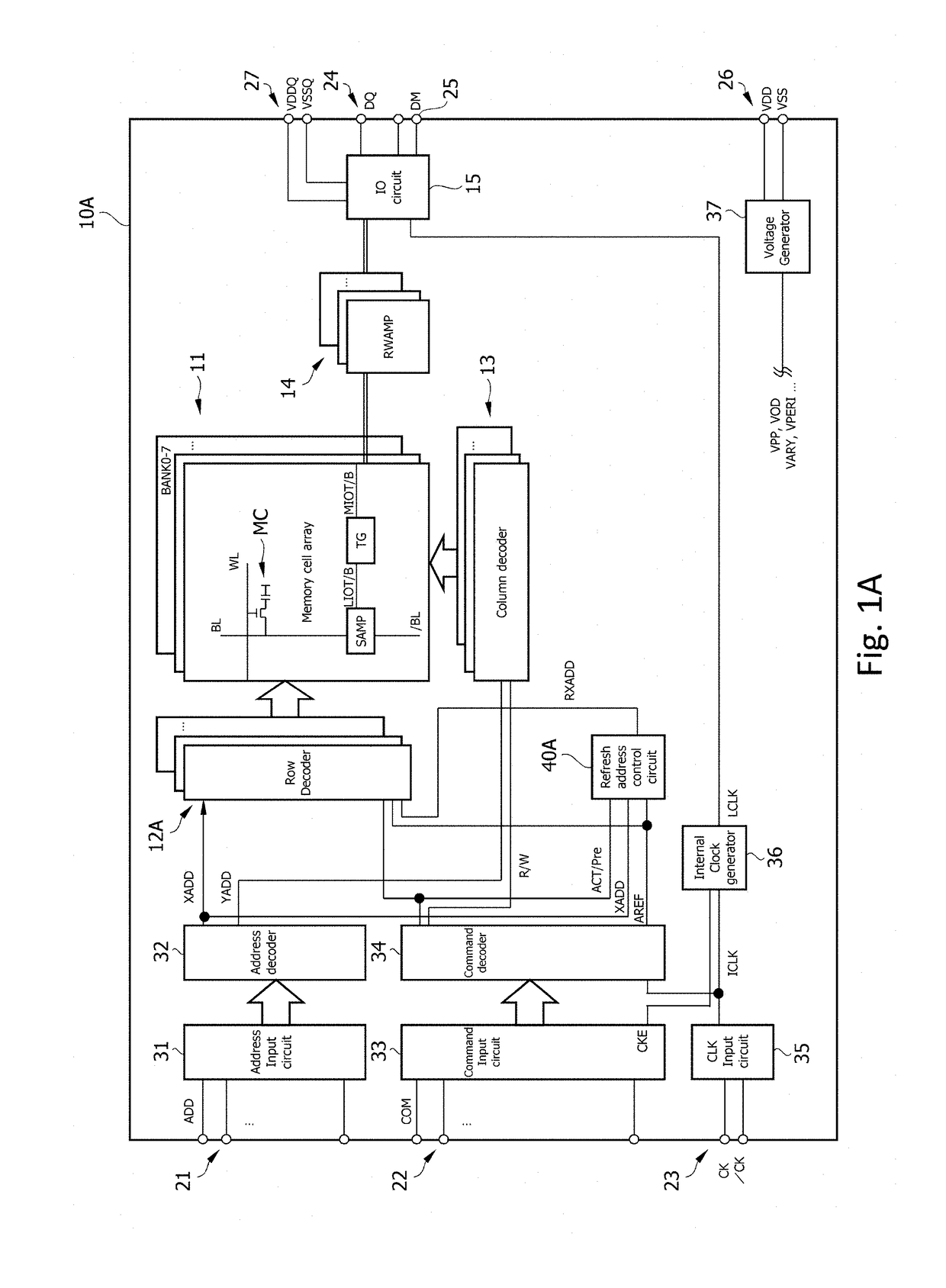
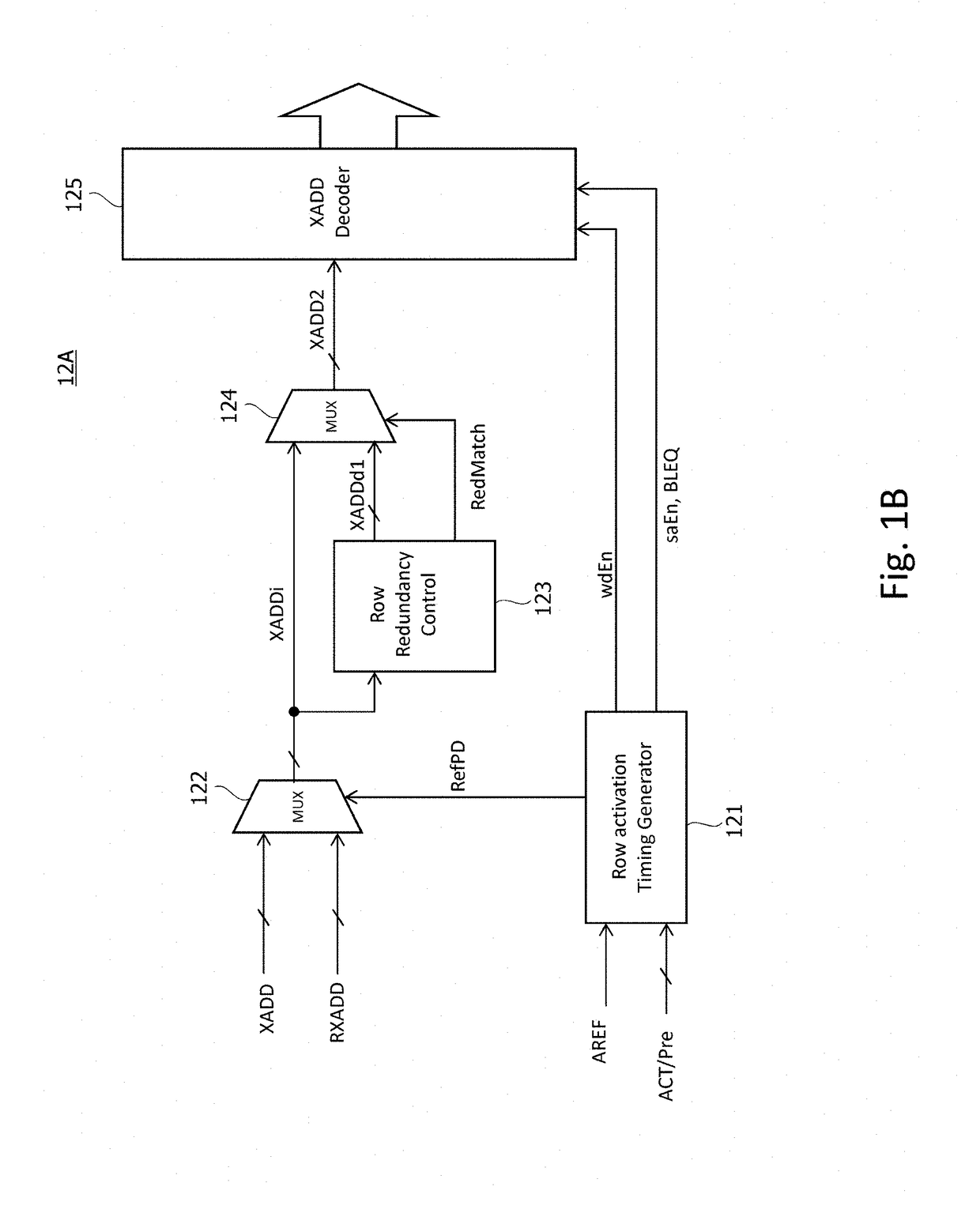
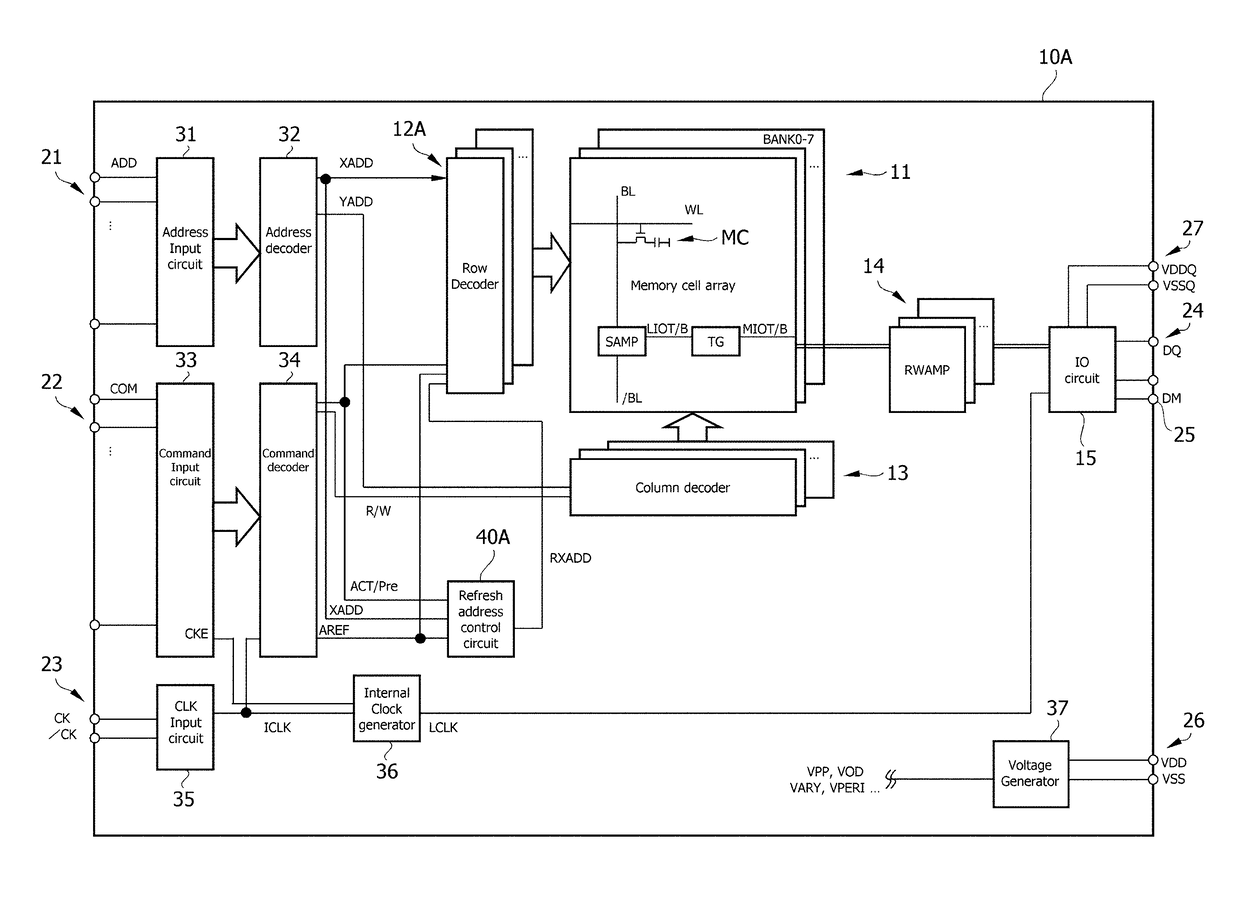
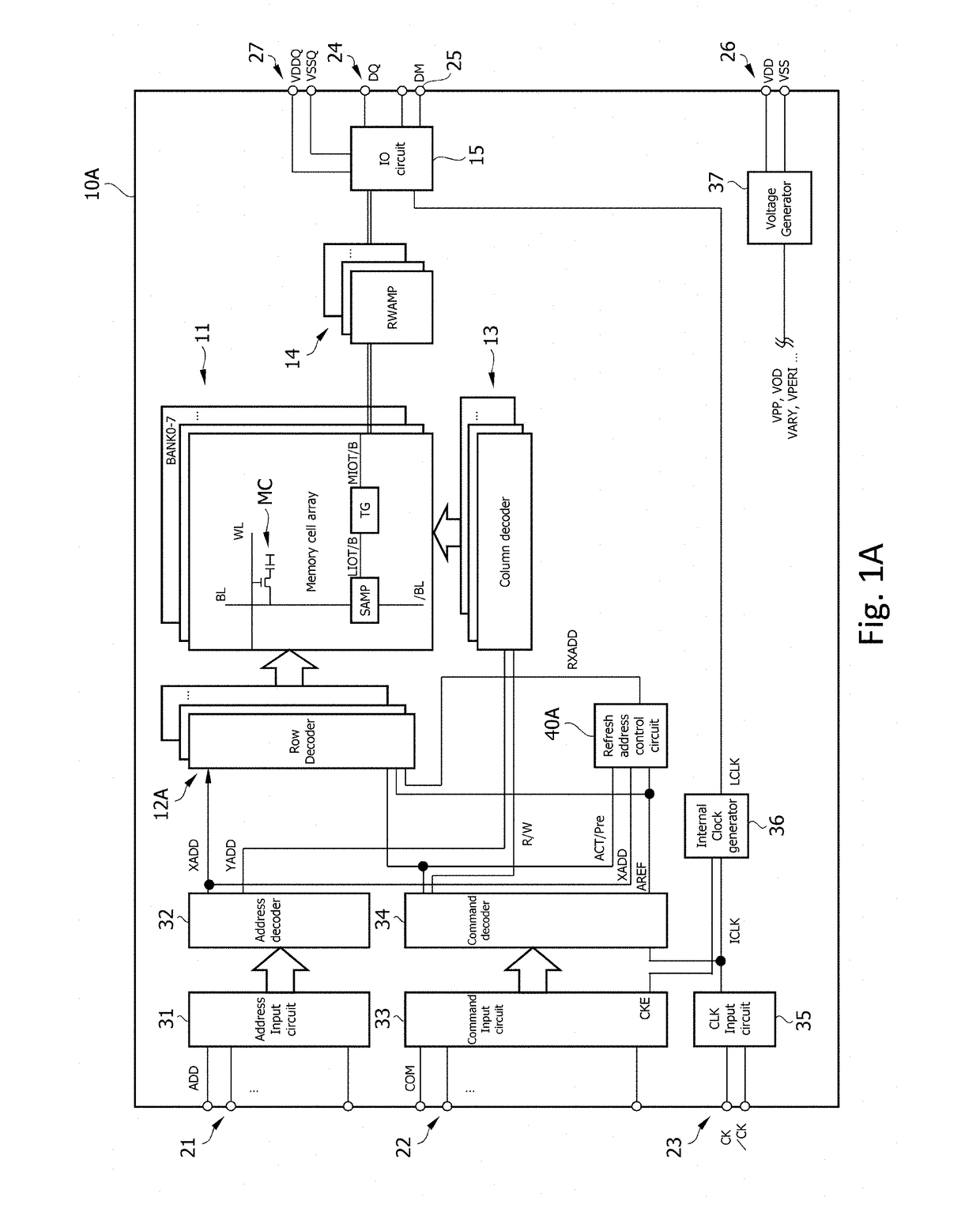
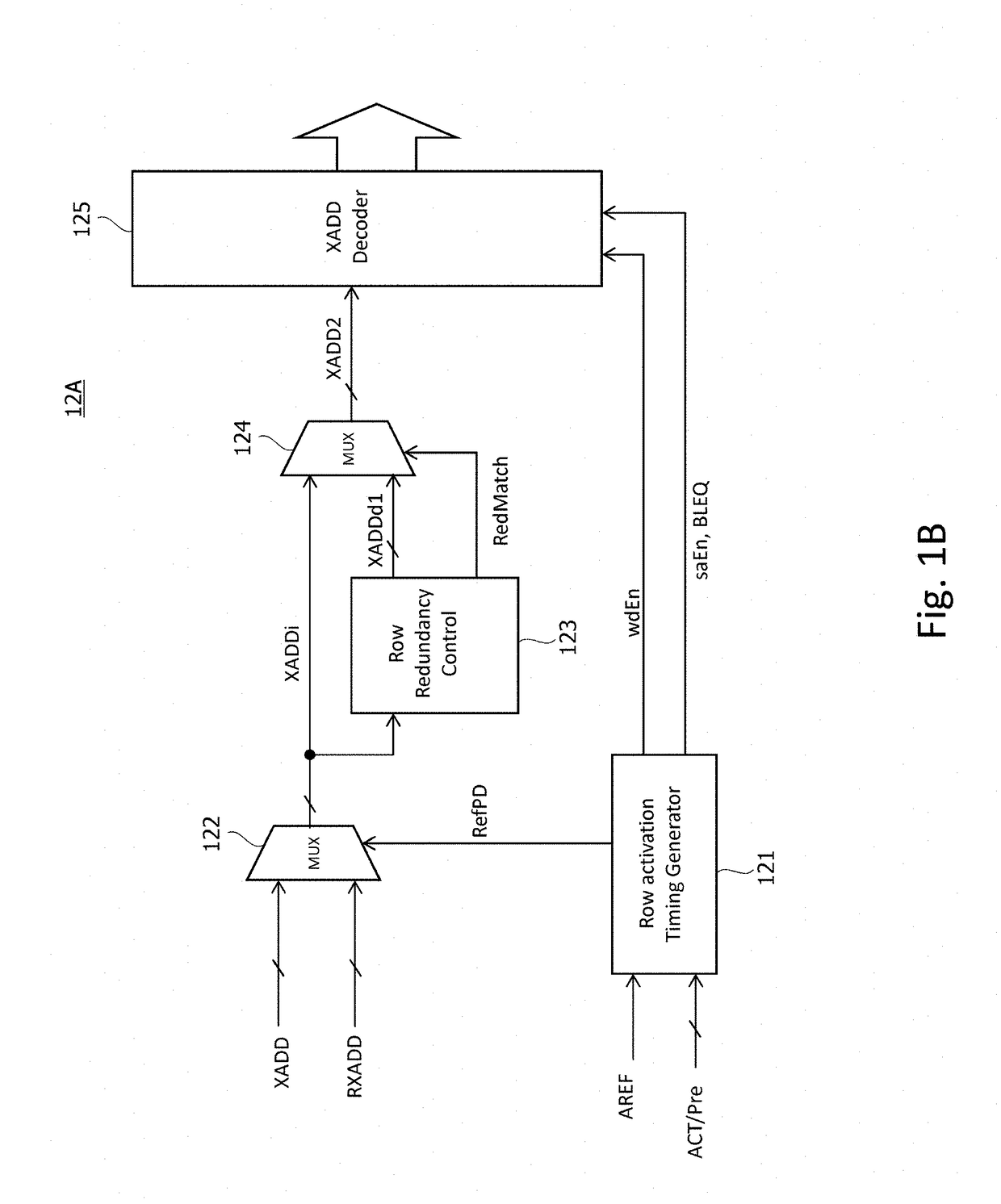
A semiconductor device according to an aspect of the present invention has: a plurality of memory cells MC; a plurality of word lines WL each coupled to a corresponding one of the plurality of memory cells MC; and a control circuit that intermittently monitors accesses to the plurality of word lines WL, stores / erases some captured row-addresses in a first number of registers, and detects, by comparison with stored addresses, in response to a first number of accesses to one of the word lines WL in a first period of time. According to the present invention, access histories can be precisely analyzed by a small-scale circuit configuration, and measures against, for example, the Row Hammer problem, etc. can be taken.
Owner:MICRON TECH INC
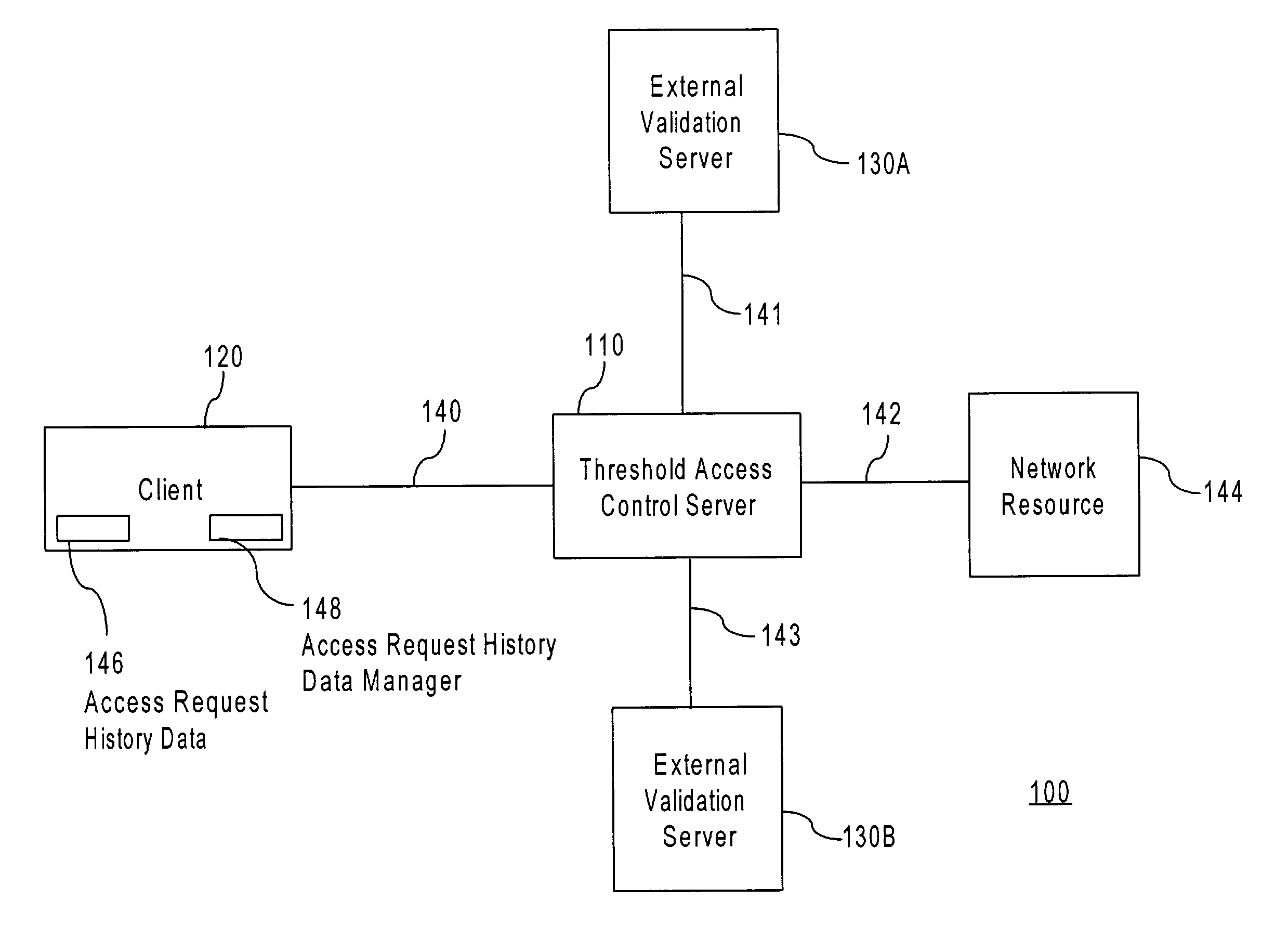
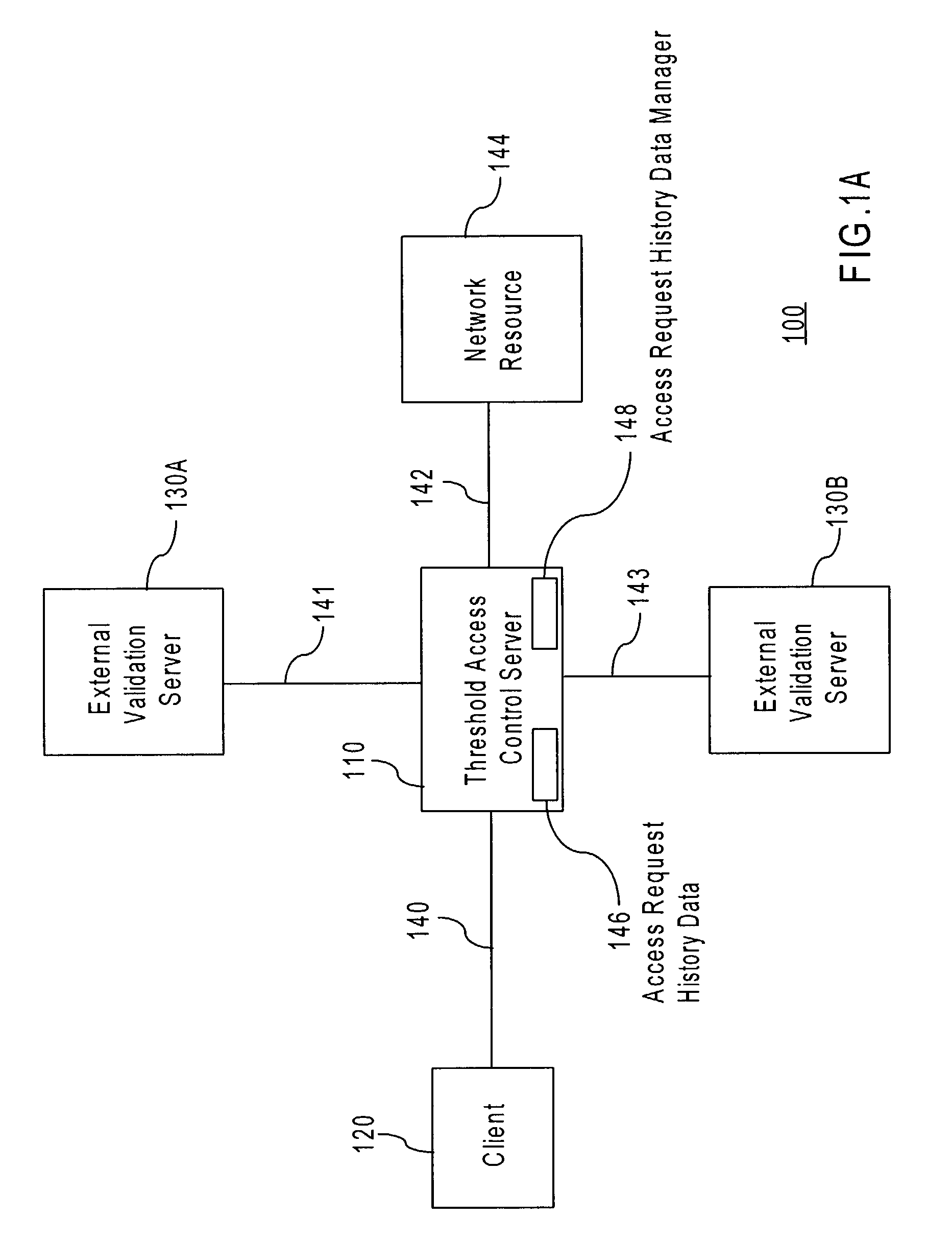
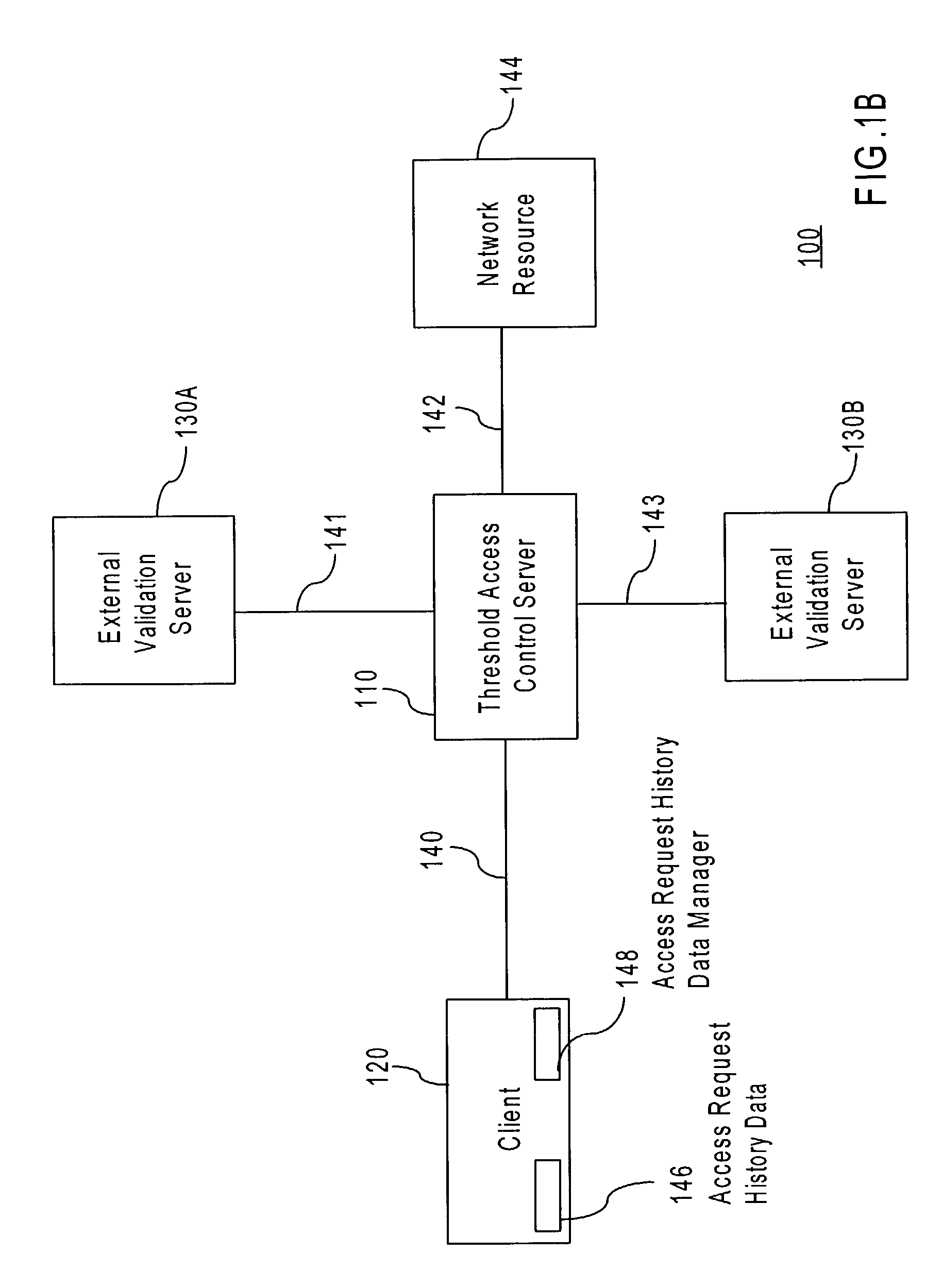
Threshold access based upon stored credentials
ActiveUS7614078B1Digital data processing detailsUser identity/authority verificationAccess historyAccess control
A method and apparatus for authorizing an access requester to access a data communication network is provided. A determination is made that a threshold access control server cannot process an access request associated with the access requester. Access requester history data, or data that describes the access history for an access requester, is analyzed to obtain a threshold access level. A threshold access level is an expression of how likely that a particular access requester is a legitimate access requester. A session profile is selected for the access requester based on the threshold access level. The session profile indicates one or more actions the access requester is authorized to perform in the network. The session profile may subsequently be transmitted to the access requester to allow the access requester access to the network to the extent appropriate in view of the access requester history data.
Owner:CISCO TECH INC
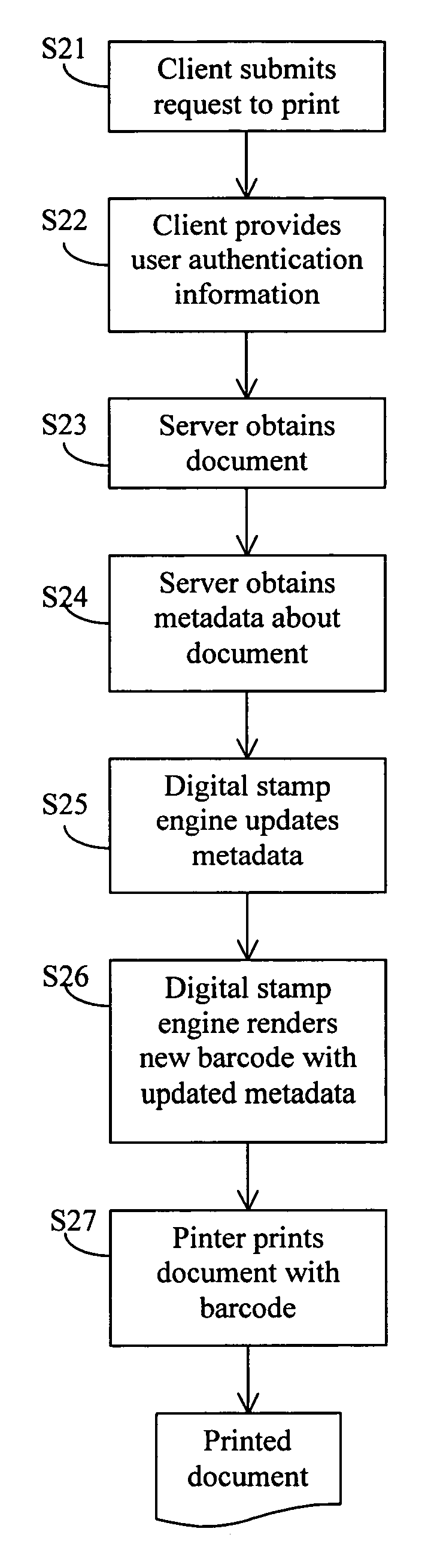
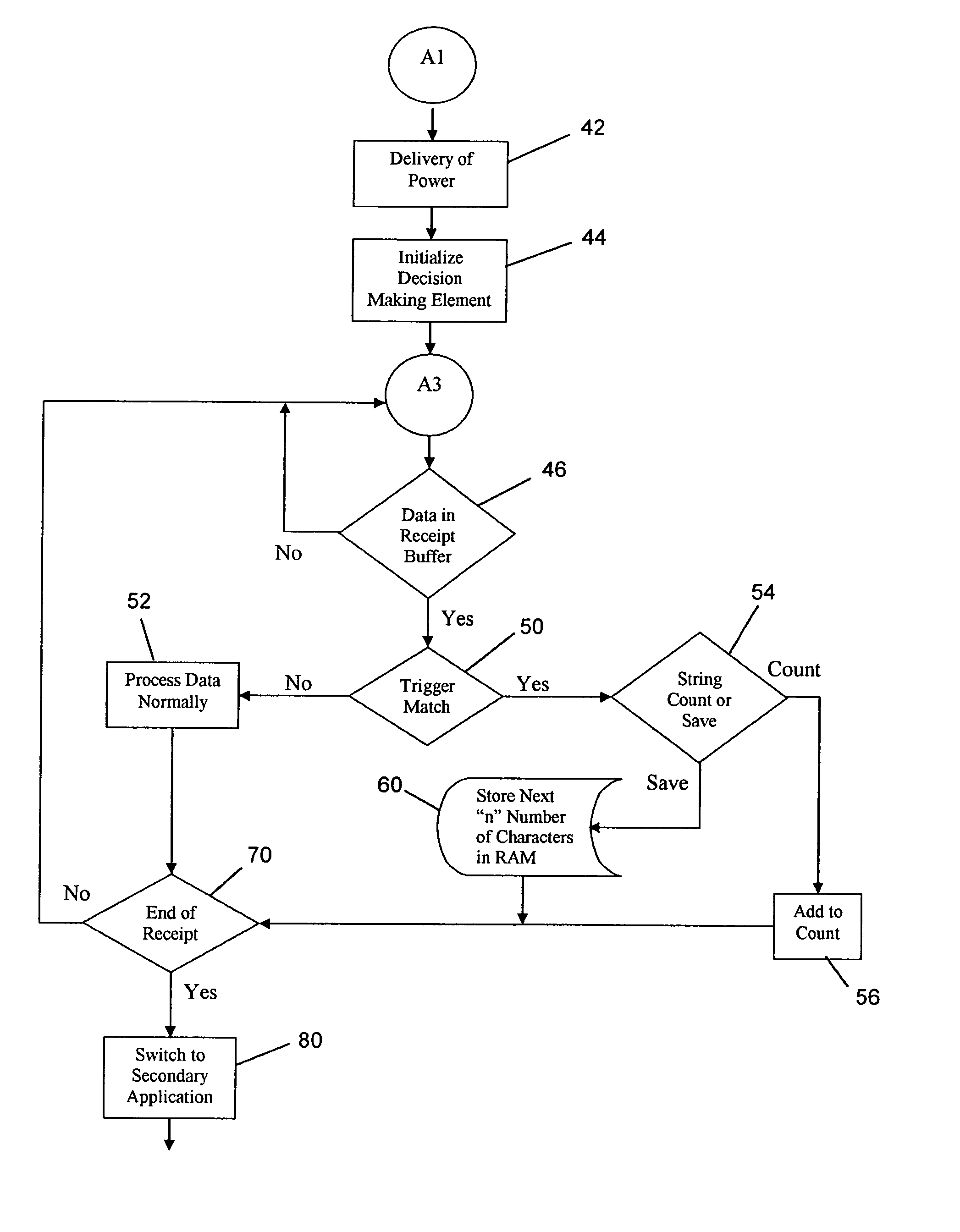
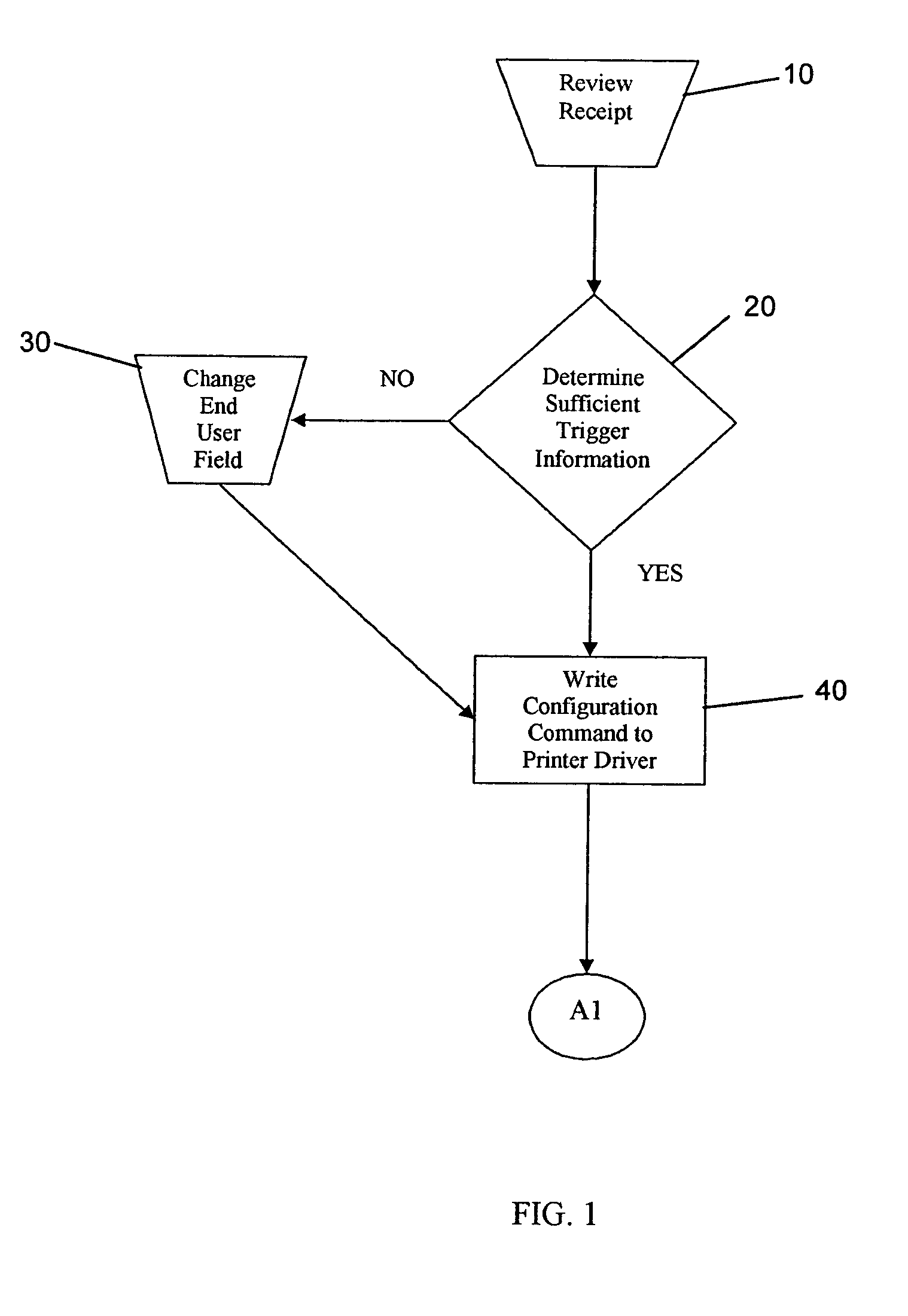
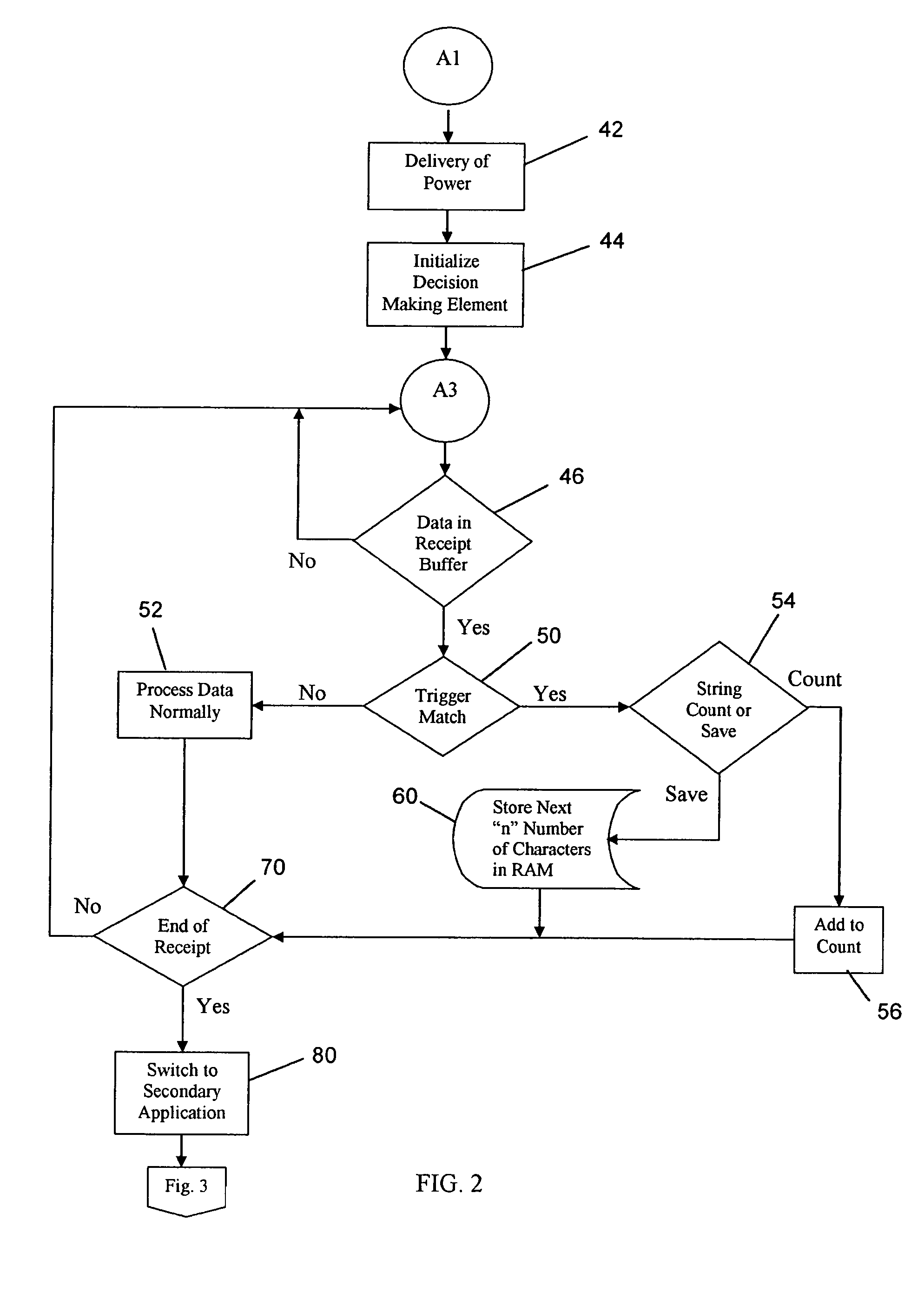
Document management method using barcode to store access history information
ActiveUS20070177824A1Character and pattern recognitionSpecial data processing applicationsComputer printingAccess history
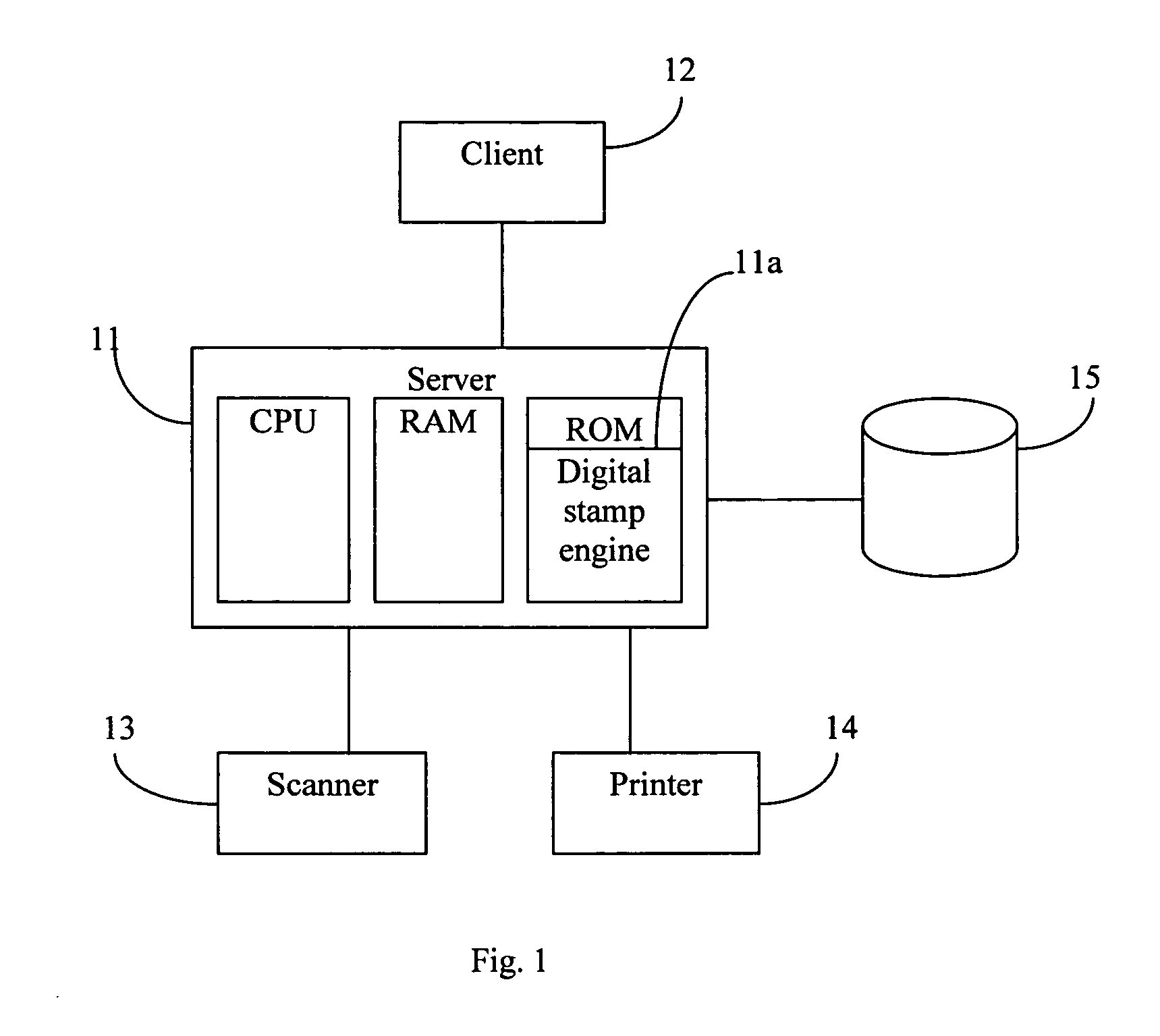
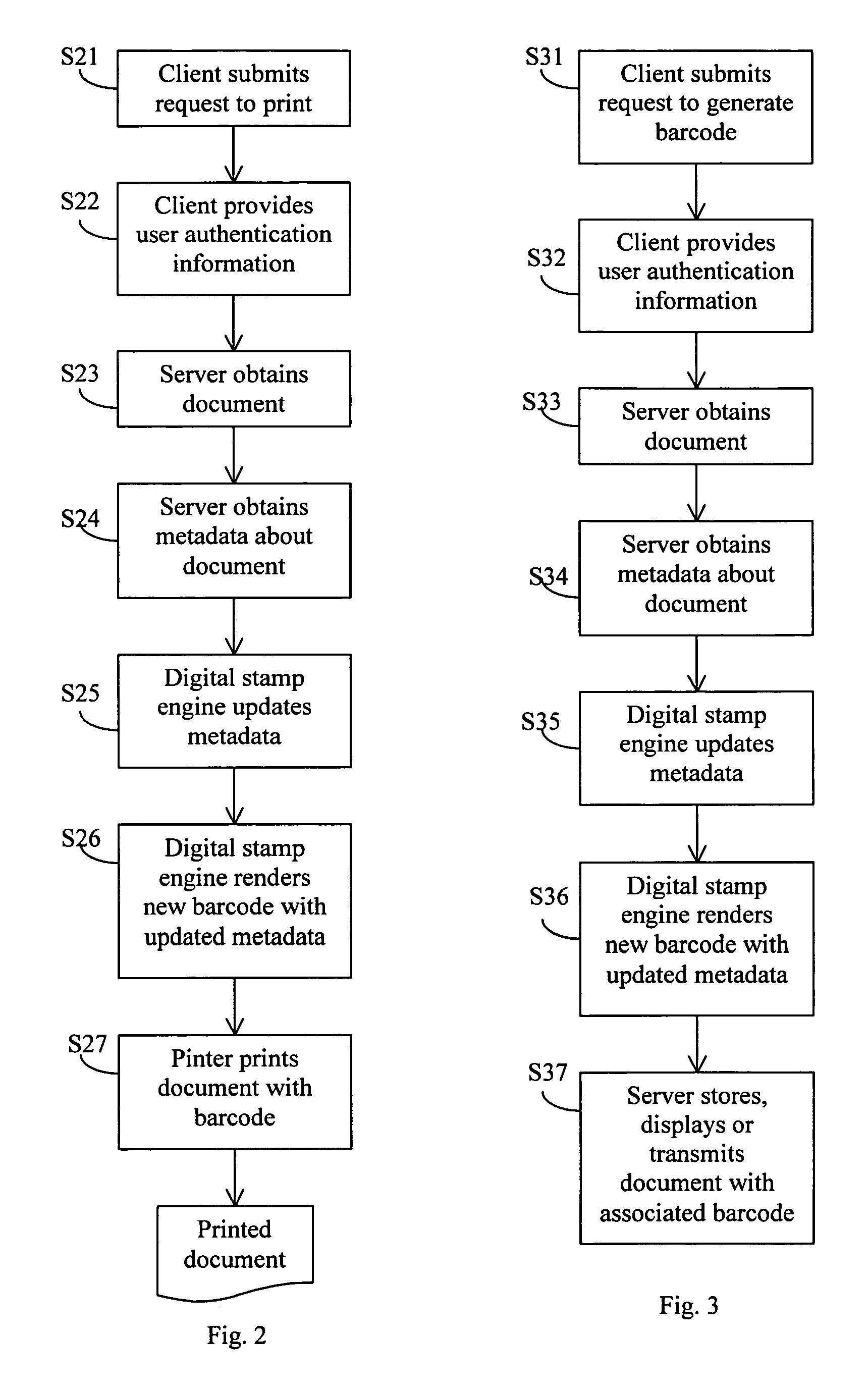
A method is described in which metadata regarding a document is encoded as 2d barcode printed on the same recording medium as the document, where the metadata includes an access history of the document and other information. When a printed document including such barcode is copied, the copy includes new barcode containing updated metadata that replaces the original barcode, where the updated metadata includes a record of the current copying or scanning action. When a printed document including such barcode is scanned, the metadata contained in the barcode is extracted and stored. Also described is a document management system including a server connected to one or more clients, scanners, printers, and a storage device for storing documents and metadata. The server includes a digital stamp engine that generates barcode data representing metadata, and supports a variety of workflows including print, barcode generation, scan, copy, barcode update, etc.
Owner:KONICA MINOLTA LAB U S A INC
Semiconductor device
A semiconductor device according to an aspect of the present invention has: a plurality of memory cells MC; a plurality of word lines WL each coupled to a corresponding one of the plurality of memory cells MC; and a control circuit that intermittently monitors accesses to the plurality of word lines WL, stores / erases some captured row-addresses in a first number of registers, and detects, by comparison with stored addresses, in response to a first number of accesses to one of the word lines WL in a first period of time. According to the present invention, access histories can be precisely analyzed by a small-scale circuit configuration, and measures against, for example, the Row Hammer problem, etc. can be taken.
Owner:MICRON TECH INC
Computer system including plural caches and utilizing access history or patterns to determine data ownership for efficient handling of software locks
A system and method for enabling a multiprocessor system employing a memory hierarchy to identify data units or locations being used as software locks. The memory hierarchy comprises a main memory having a plurality of data units, a plurality of caches that operate independently of each other, and at least one coherent domain interfaced to each cache. Each coherent domain comprises at least two processors. The main memory maintains coherency of data among the plurality of caches using a directory that maintains information about each data line. The system of the present invention allows a requesting agent, such as a processor or cache, to request a data unit without specifying the type of ownership, where ownership may be exclusive or shared. The directory includes history information that defines the previous access pattern of the requested data unit. Prior to forwarding the requested data unit to the requesting agent, the main memory checks, using a conditional fetch command, the history information to determine what type of ownership to associate with the requested data unit. The requested data unit is then delivered to the requesting agent with ownership rights specified by the history information. The processors may utilize a directory-based protocol such as MESI (modified, exclusive, shared, invalid) to maintain coherence among the processors, with each processor snooping a shared bus to track the status of caches lines in the other processors.
Owner:UNISYS CORP
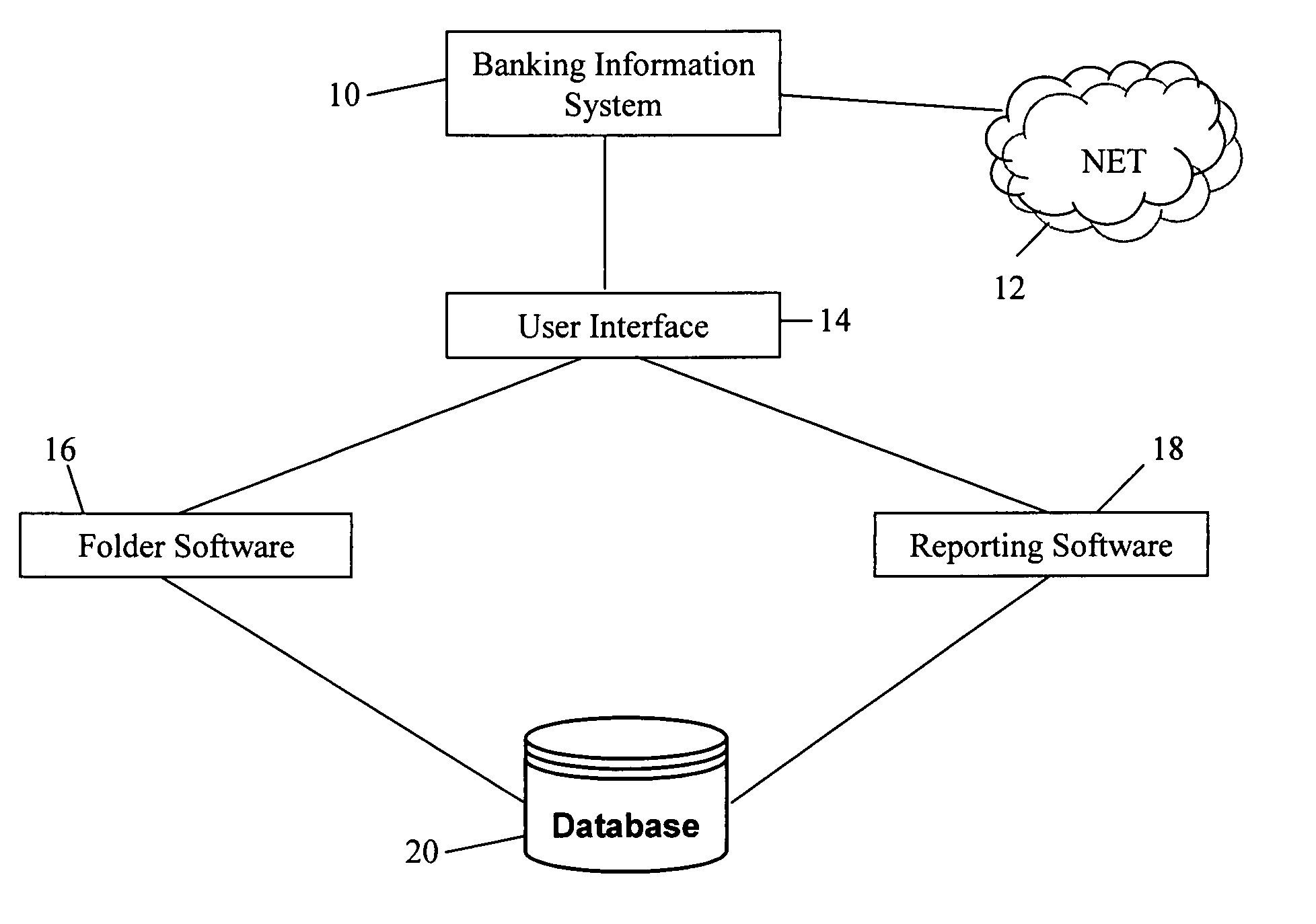
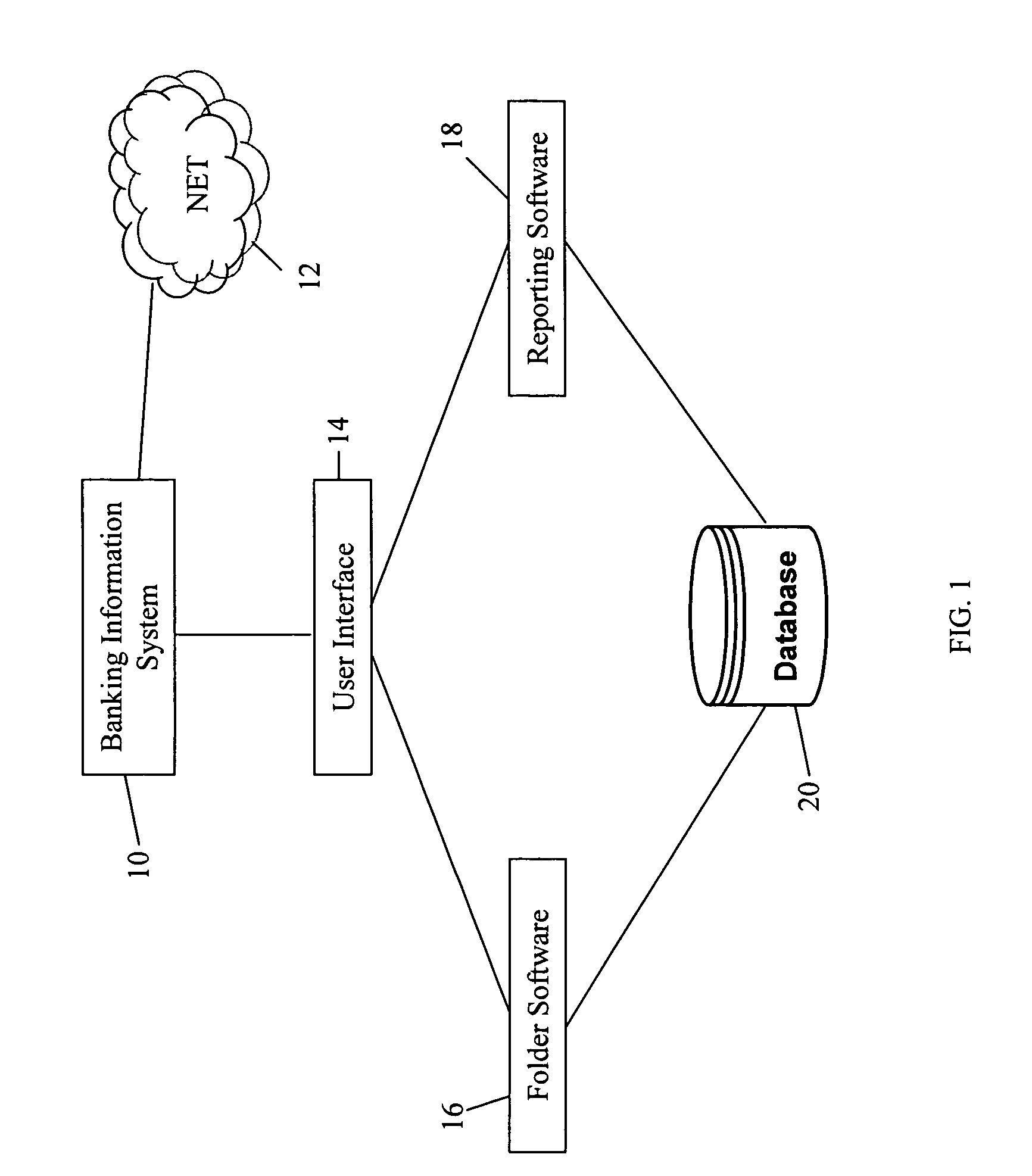
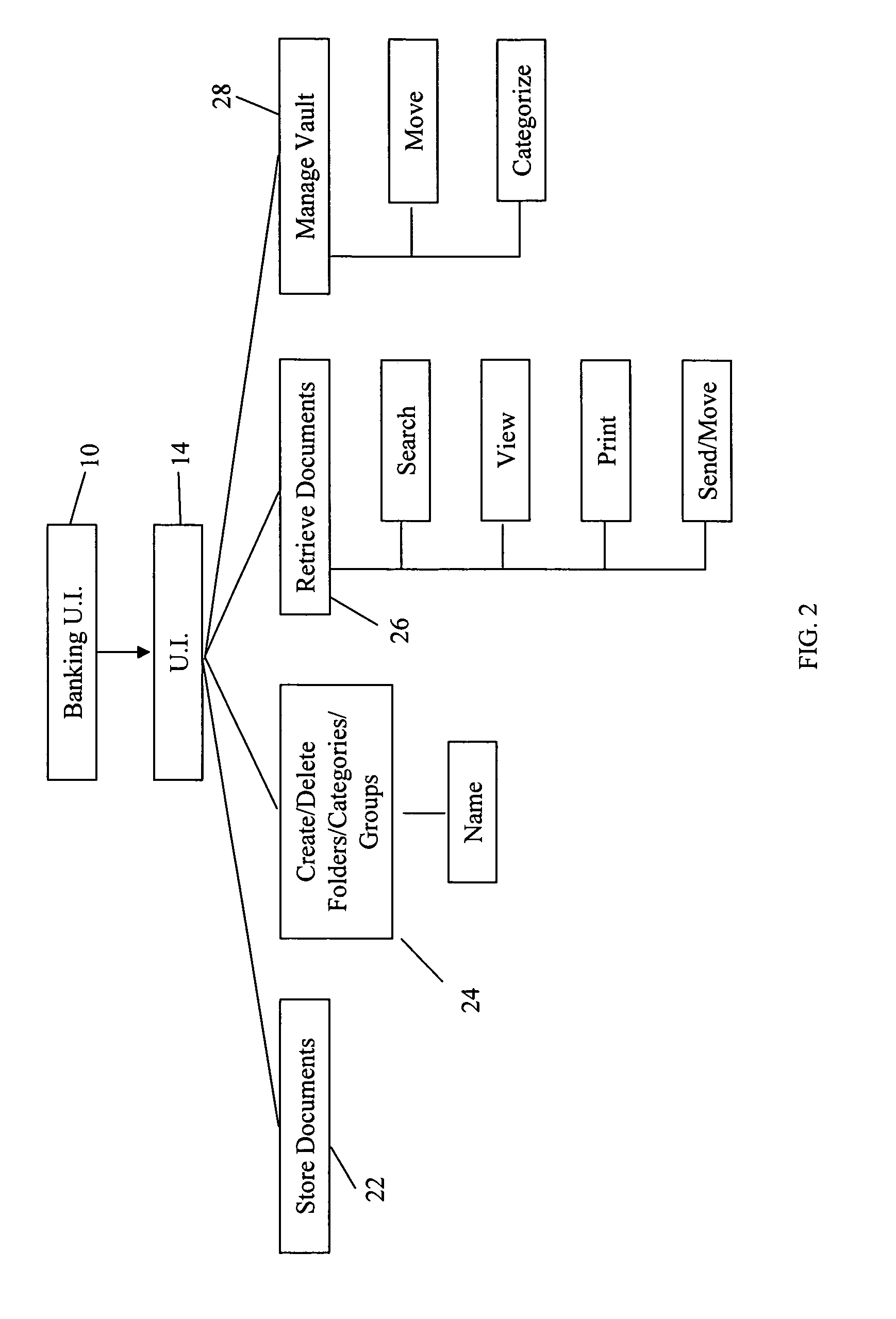
System and method for storing, creating, and organizing financial information electronically
InactiveUS20050203885A1Safe storageFinanceDigital data processing detailsAccess historyIdentity theft
A system and / or method which offers customer-driven aggregation of data, with the ability to dynamically modify the filing hierarchy and to store, create and organize digital financial information. The system enables customers to establish a hierarchy of file folders, file any payment whether paper or electronic in a folder for future reference, provide secure storage for an indefinite period for any payment, including credit card payments, debit card transactions, imaged checks, electronic bill payments or account statements. As such, customers can create and change at will their file folder hierarchy and file documents with notes. Customers can set a preference for automatic filing based on pre-established criteria such as folders based standard merchant categories or by month. Customers can also ‘file’ payments when they are created or viewed in the transaction history. The systems of the exemplary embodiments provide a search function, enabling retrieval of documents based on a document storage time stamp, date last accessed, date posted, dollar amount, or by file folder, group, or category. Customers can view document access history. Further, the systems offer customers convenience, privacy, security and prevention of document loss from disaster, and protection from document or identity theft.
Owner:U S BANK NAT ASSOC
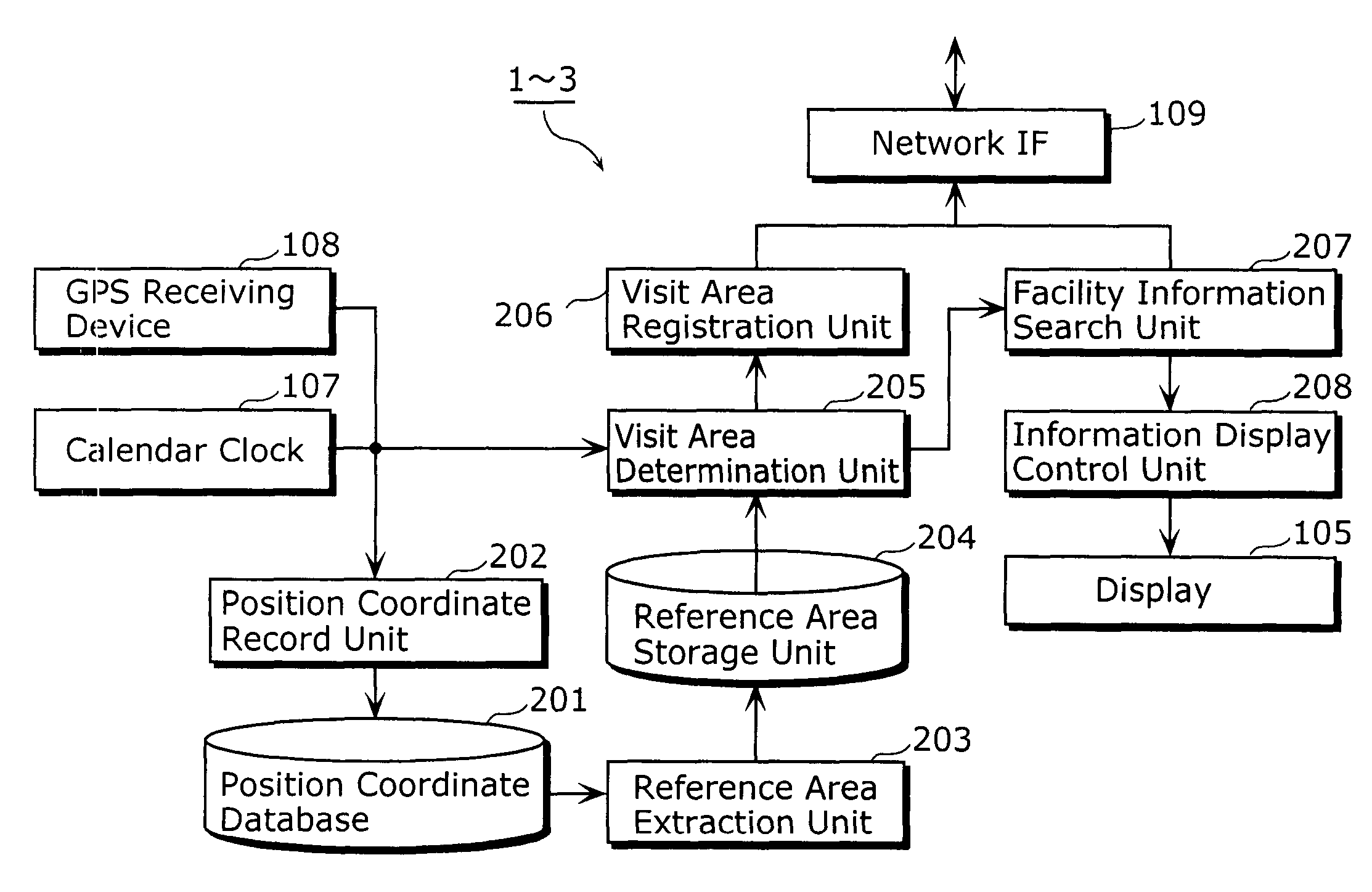
Information providing device
InactiveUS7856311B2Reduce noiseAccurate informationInstruments for road network navigationRoad vehicles traffic controlMedicineAccess history
Owner:INTERTRUST TECH CORP
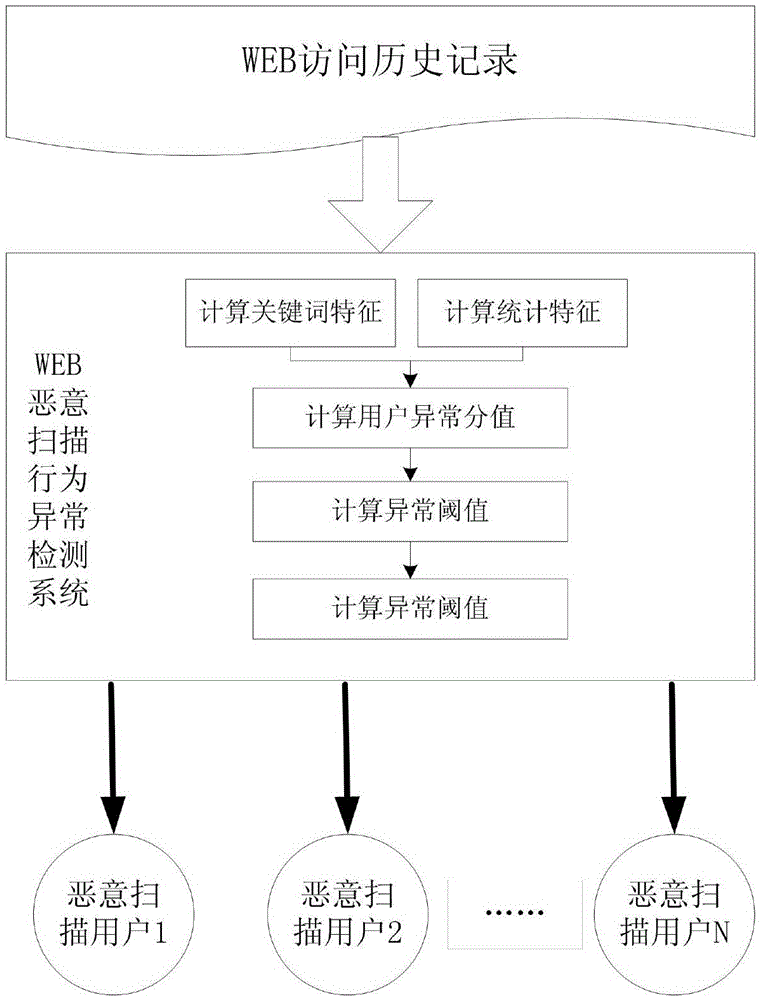
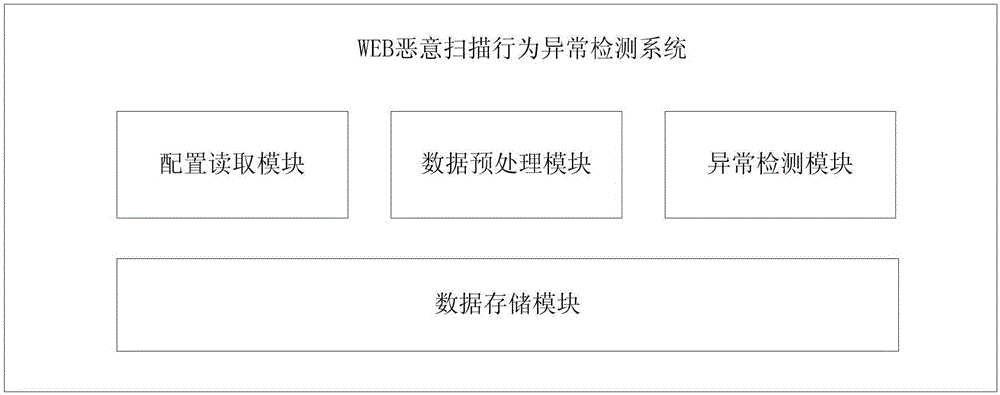
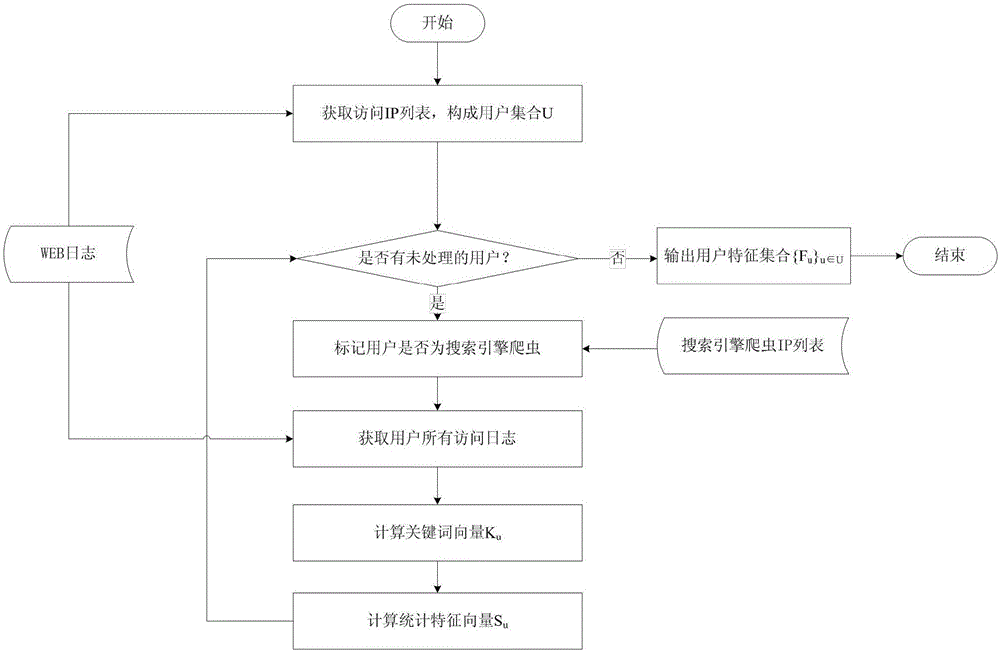
WEB malicious scanning behavior abnormity detection method and system
The invention discloses a WEB malicious scanning behavior abnormity detection method and a WEB malicious scanning behavior abnormity detection system. The method comprises the following steps: 1) extracting keyword characteristics and statistics characteristics of access users from an access history record, and building keyword vectors and statistic characteristic vectors of the users, 2) traversing the keyword vectors of the users, performing statistics on the user number corresponding to each keyword, and building a global keyword table, 3) calculating the uncommon degree of each keyword according to the global keyword table, calculating original abnormal score values of the access users according to the corresponding uncommon degrees, correcting the original abnormal score values then according to the statistic characteristic vectors of the access users, and obtaining final abnormal score values of the users; 4) for a jump point of a final abnormal score value sequence of all the access users, taking the final abnormal score value corresponding to the jump point as a threshold, and 5) comparing the final abnormal score values of the access values with the threshold, and taking the users as malicious scanning users if the final abnormal score values of the access values are greater than the threshold. An unknown attack behavior can be found, and normal historical data is not relied on.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
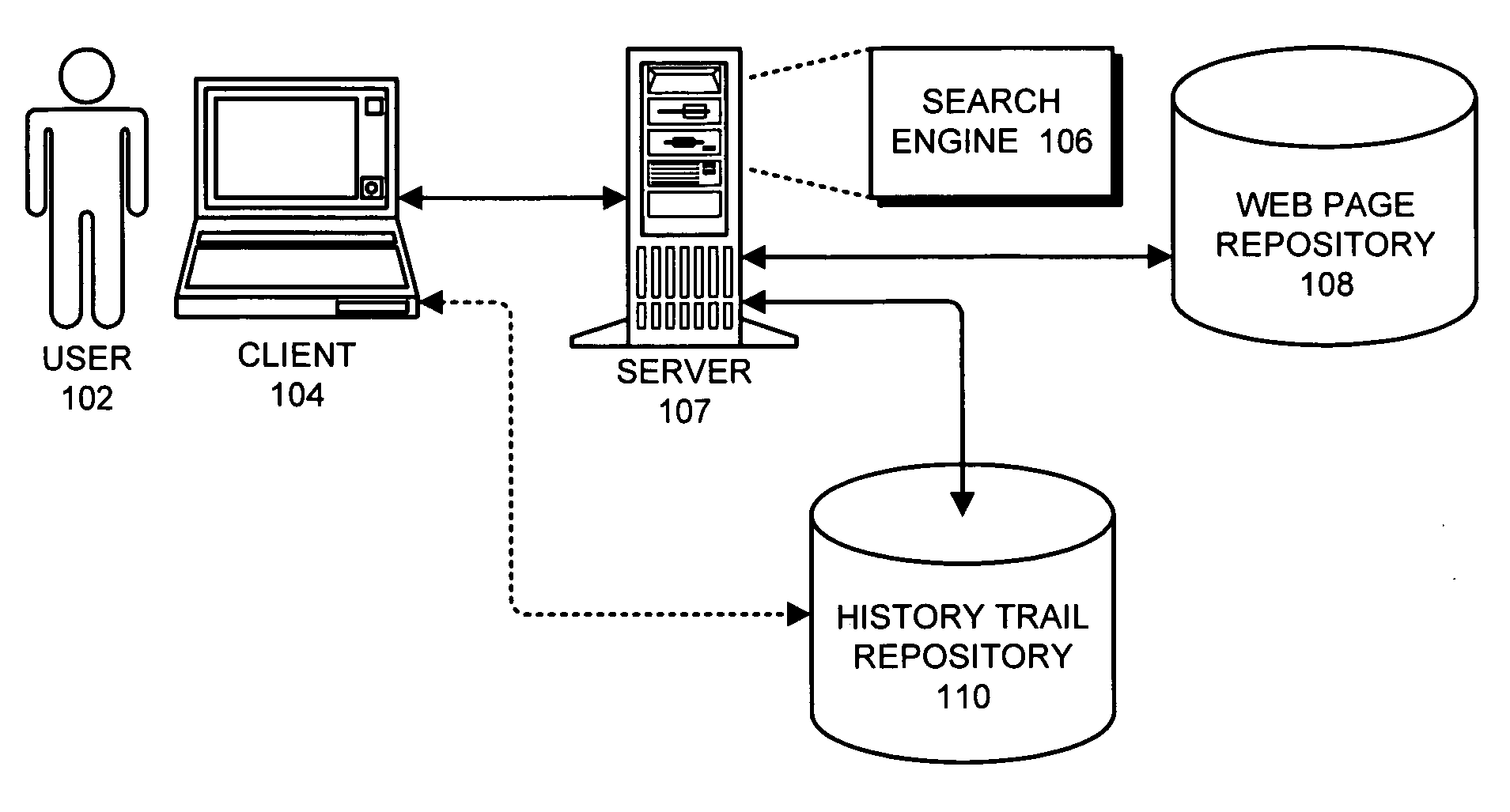
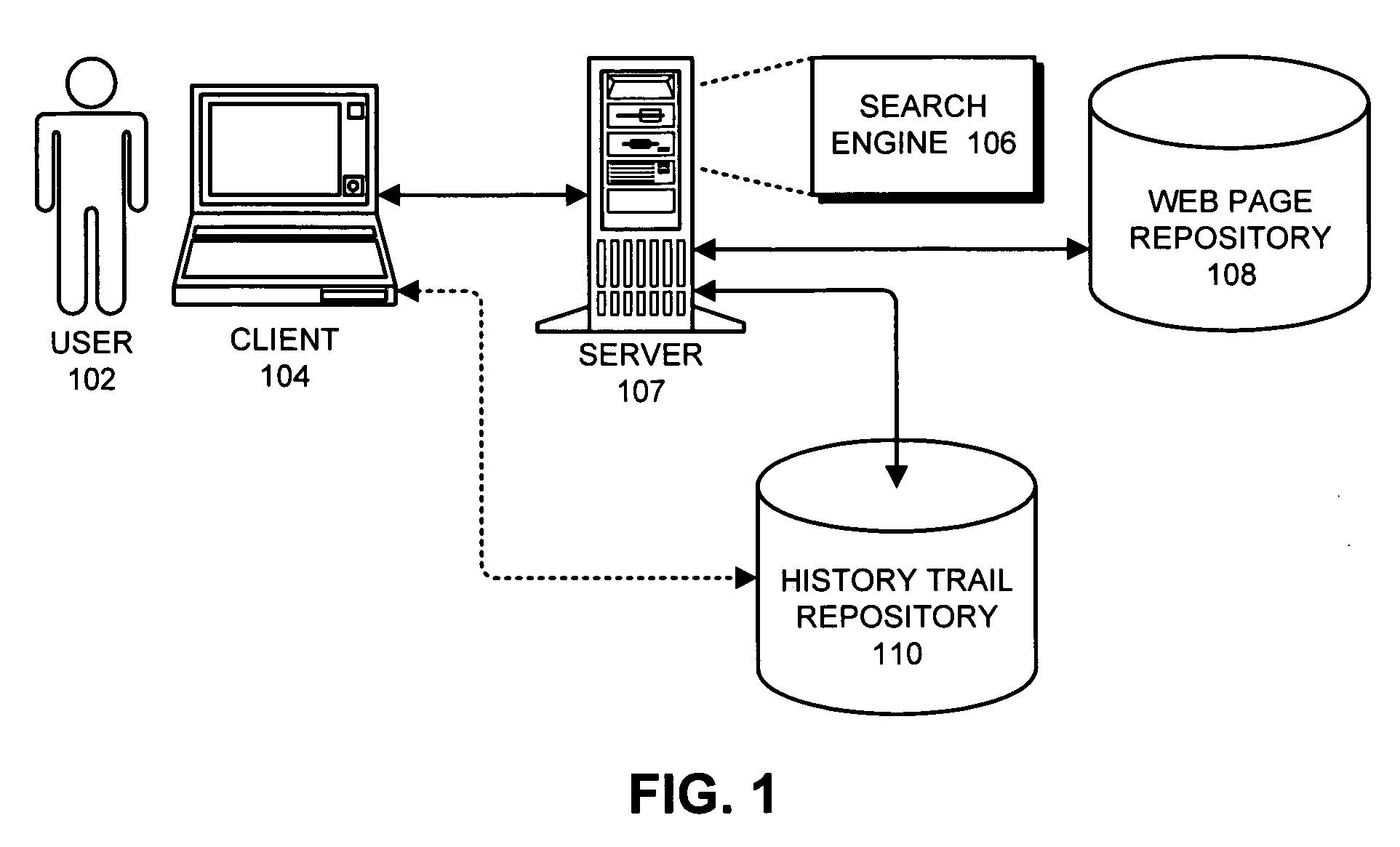
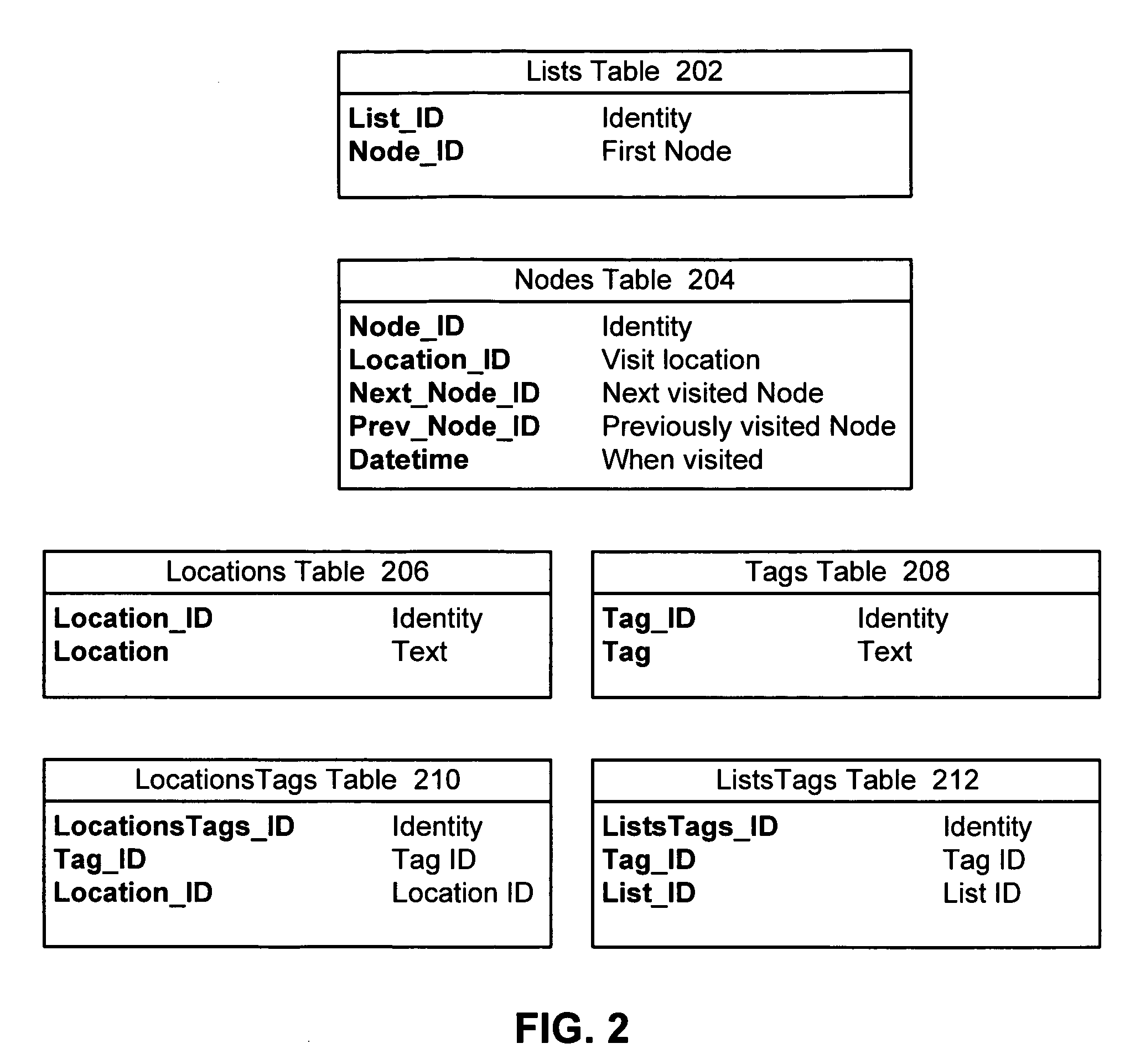
Method and apparatus for accessing history trails for previous search sessions
InactiveUS20070271230A1Facilitates undoingFacilitates undoing and redoingSpecial data processing applicationsWeb data retrieval using information identifiersAccess historyInformation retrieval
One embodiment of the present invention provides a system that stores a history trail for a search session to enable the history trail to be subsequently retrieved. During operation, the system assembles a history trail of pages which are visited during the search session. Next, the system stores the history trail in a repository which contains multiple history trails associated with multiple search sessions. This enables a user to subsequently retrieve the history trail from the repository to obtain information related to pages which were visited during the search session.
Owner:INTUIT INC
Page-switching method and device
ActiveCN103984686AWebsite content managementSpecial data processing applicationsData feedWeb service
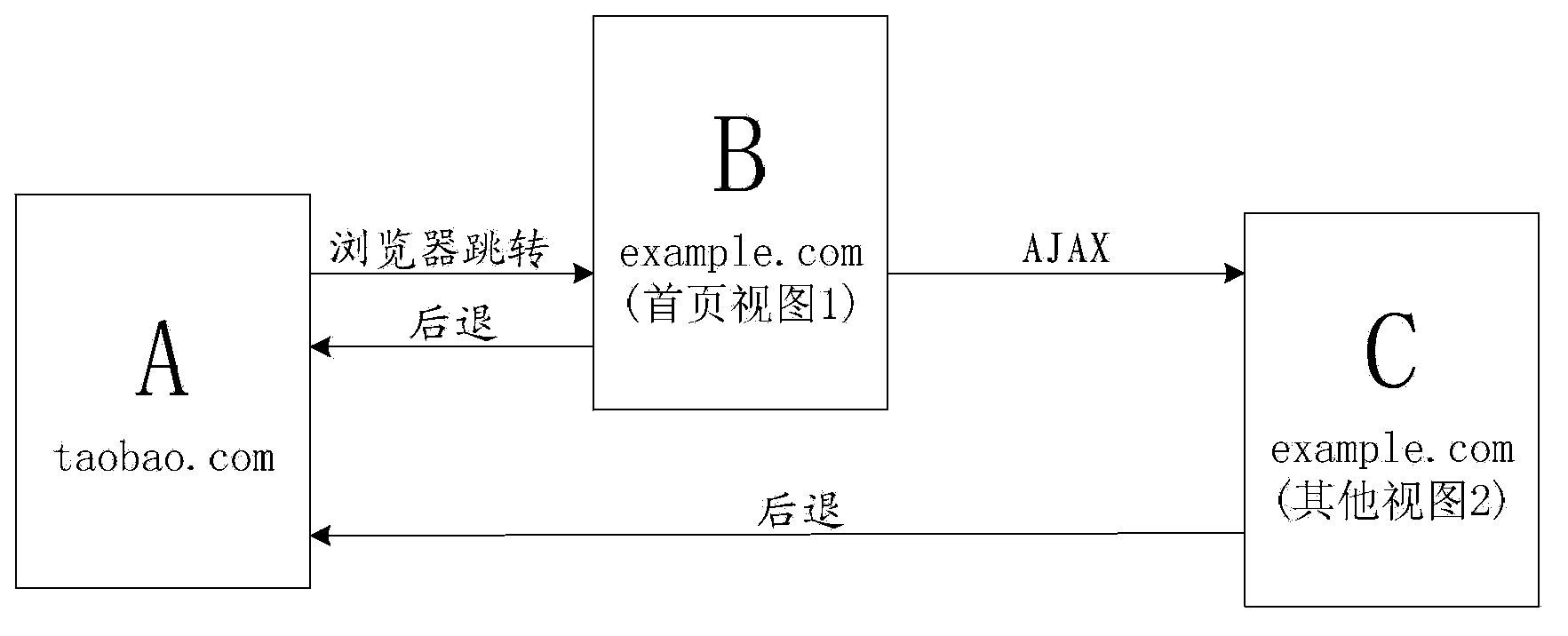
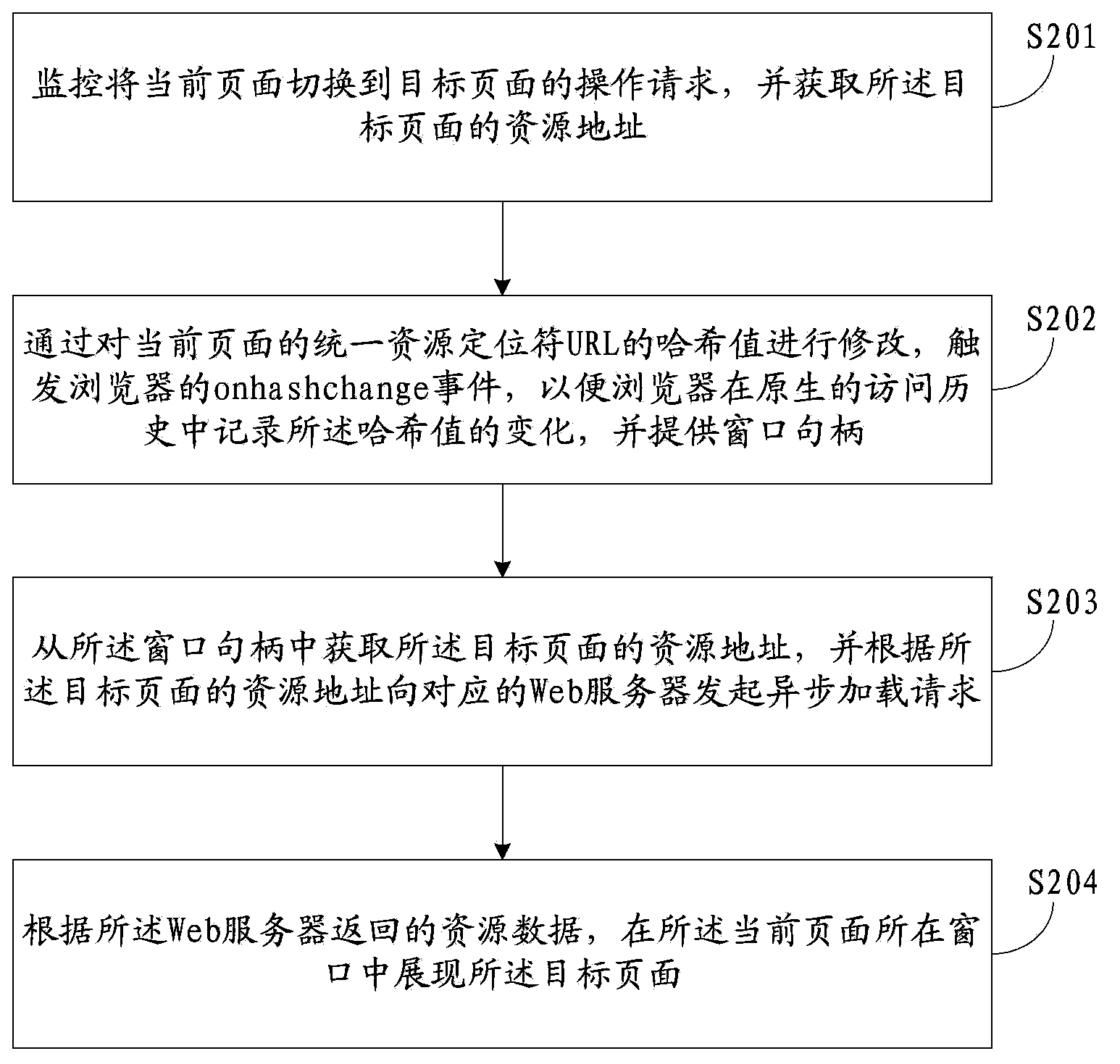
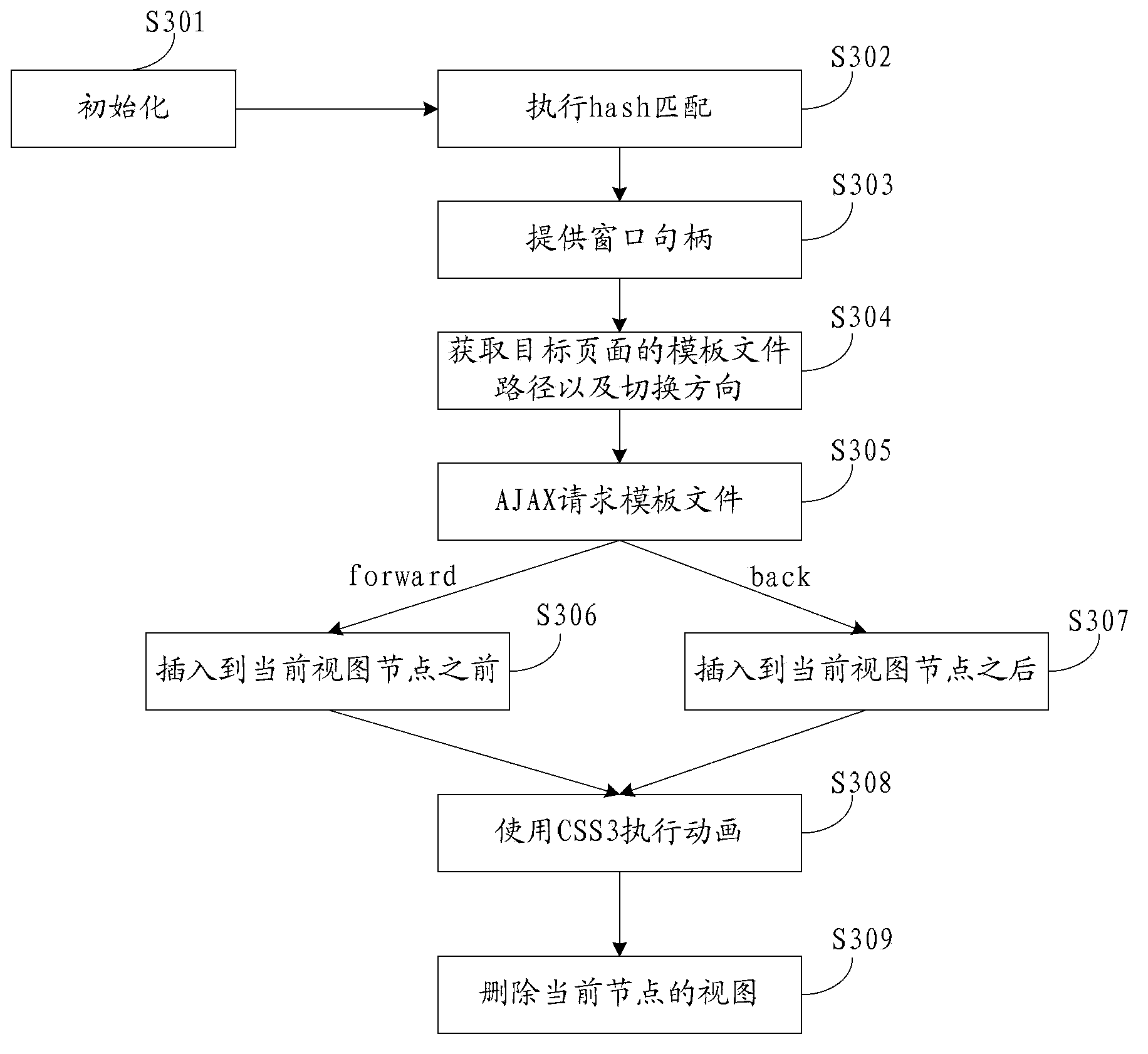
The invention discloses a page-switching method and device. The page-switching method comprises the following steps: monitoring an operation request for switching a present page to a target page and acquiring a resource address of the target page; triggering a hash value changing event of a browser by modifying a hash value of URL (Uniform Resource Locator) of the present page, thereby recording the change of the hash value in a protogenous access history by the browser and providing a window handle, wherein the modified hash value contains the resource address information of the target page; acquiring the resource address of the target page from the window handle and sending an asynchronous loading request to a corresponding Web server according to the resource address of the target page; showing the target page in the window of the present page according to the resource data fed back by the Web server. According to the page-switching method, a basis for realizing the correct page advancing or retreating under the asynchronous loading condition is supplied.
Owner:ALIBABA GRP HLDG LTD
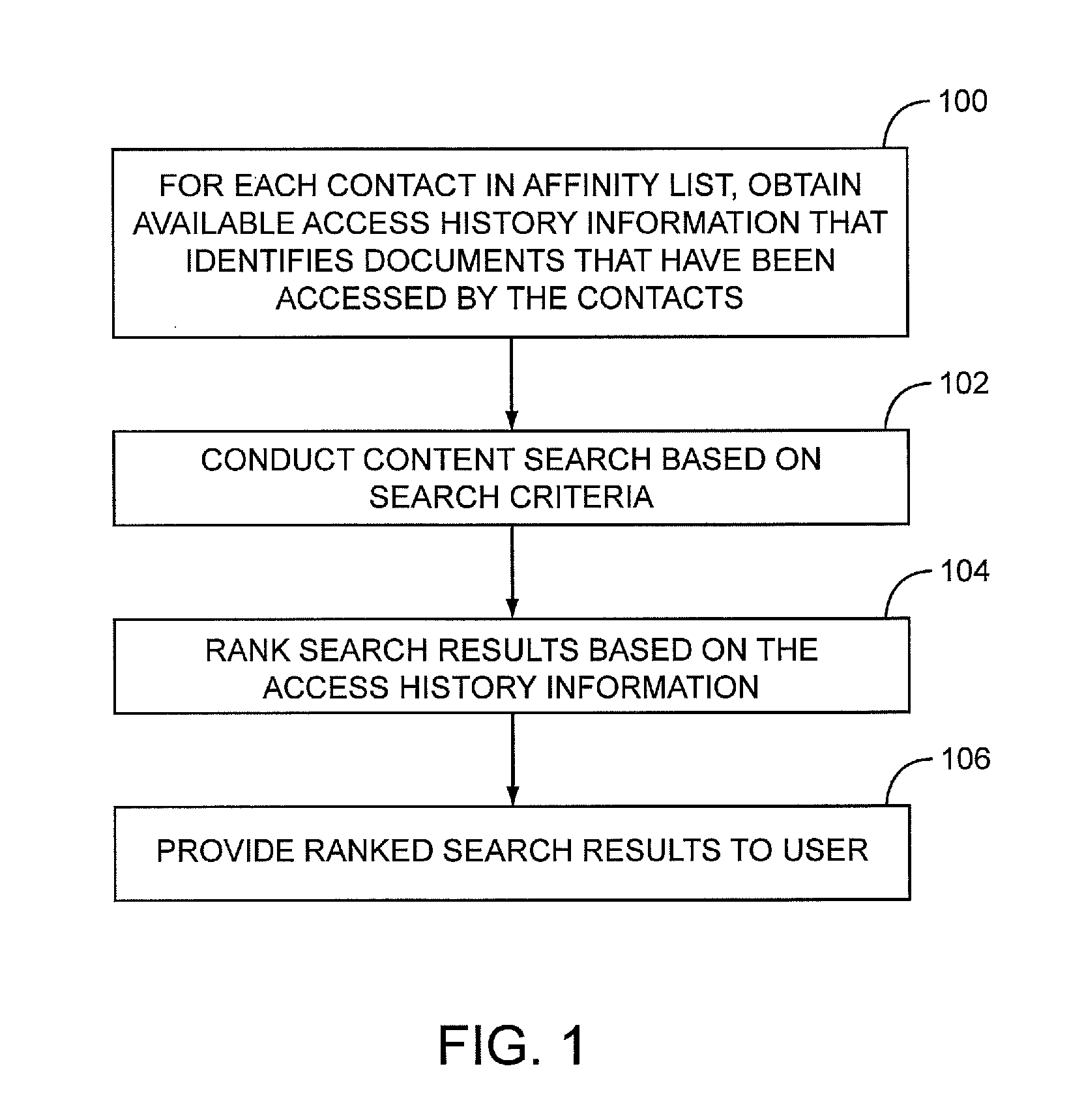
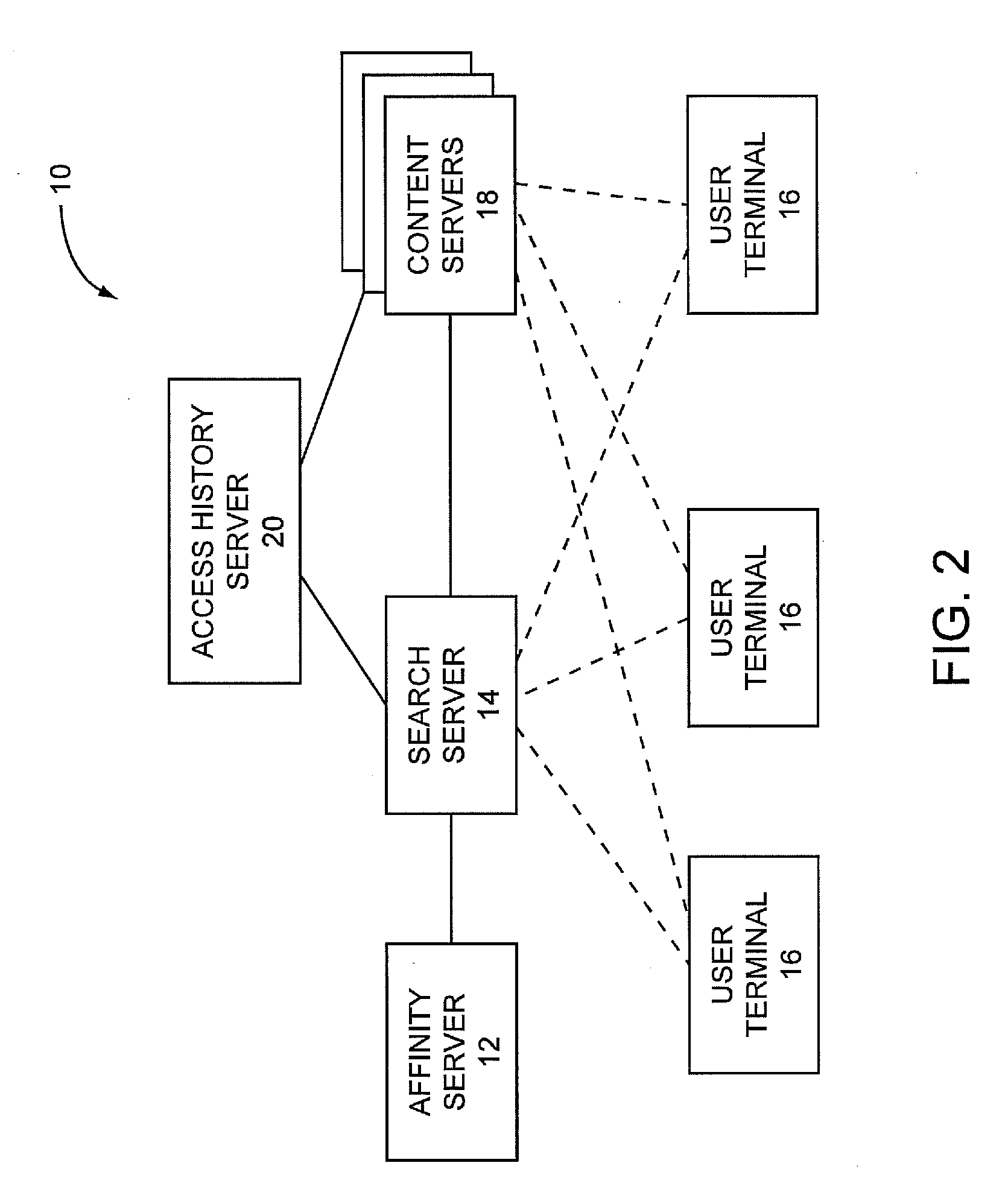
Ranking search results based on affinity criteria
InactiveUS20100070488A1Digital data information retrievalDigital data processing detailsAccess historyAssociation list
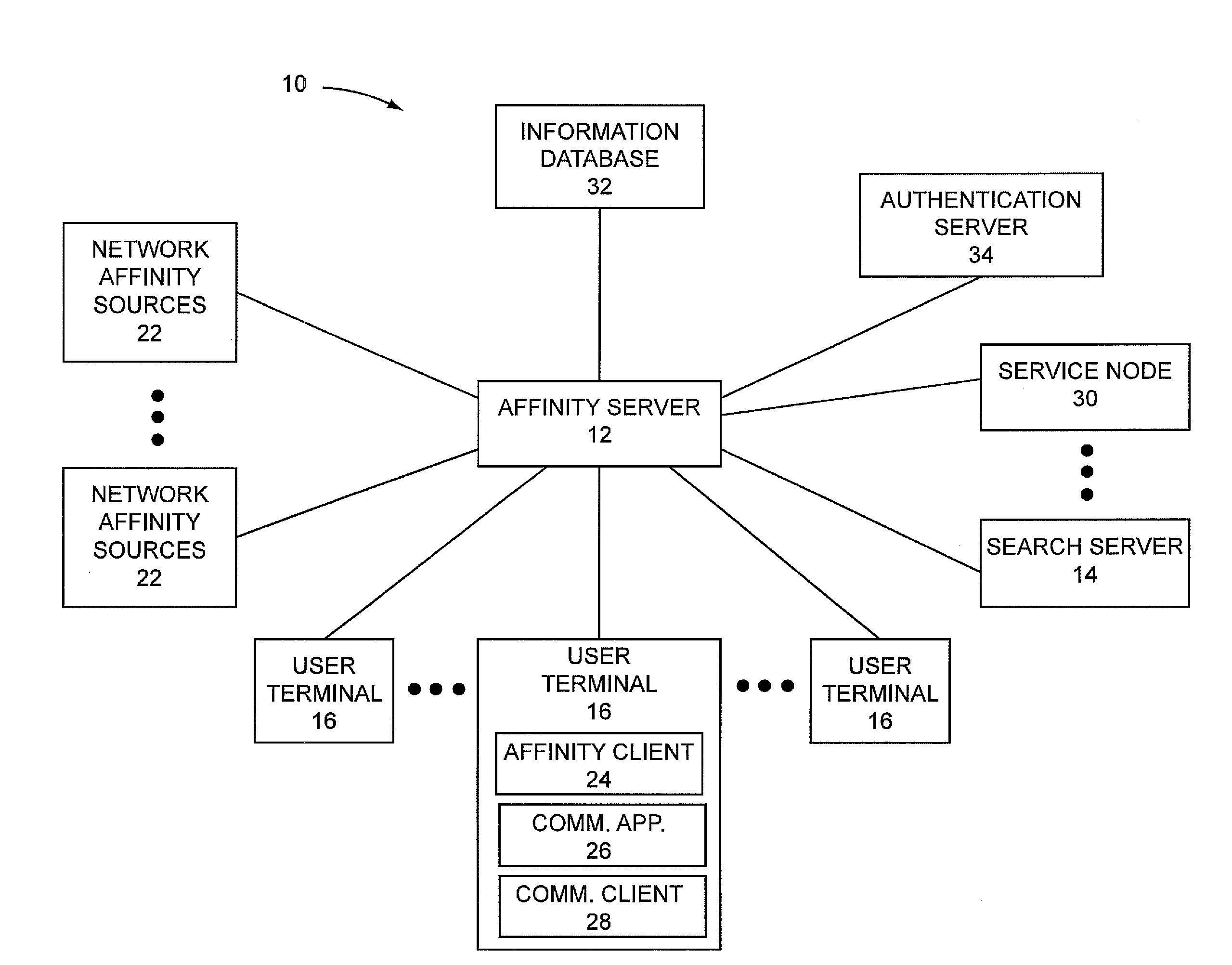
The present invention relates to searching content databases and ranking the search results of the searches based, at least in part, on affinity criteria for a particular user. Notably, a given user will communicate through various means with contacts. The identities of some, if not all, of the contacts with which the user communicates are used to create an affinity list. For each contact in the user's affinity list, a record of the items that have been accessed by that user is maintained as access history information. Each contact may have access history information, and the collection of the access history information for some or all of the contacts in the user's affinity list is generally referred to as affinity criteria. When the user initiates a search for items in contact databases, items returned from the search are ranked based, at least in part, on the affinity criteria.
Owner:RPX CLEARINGHOUSE
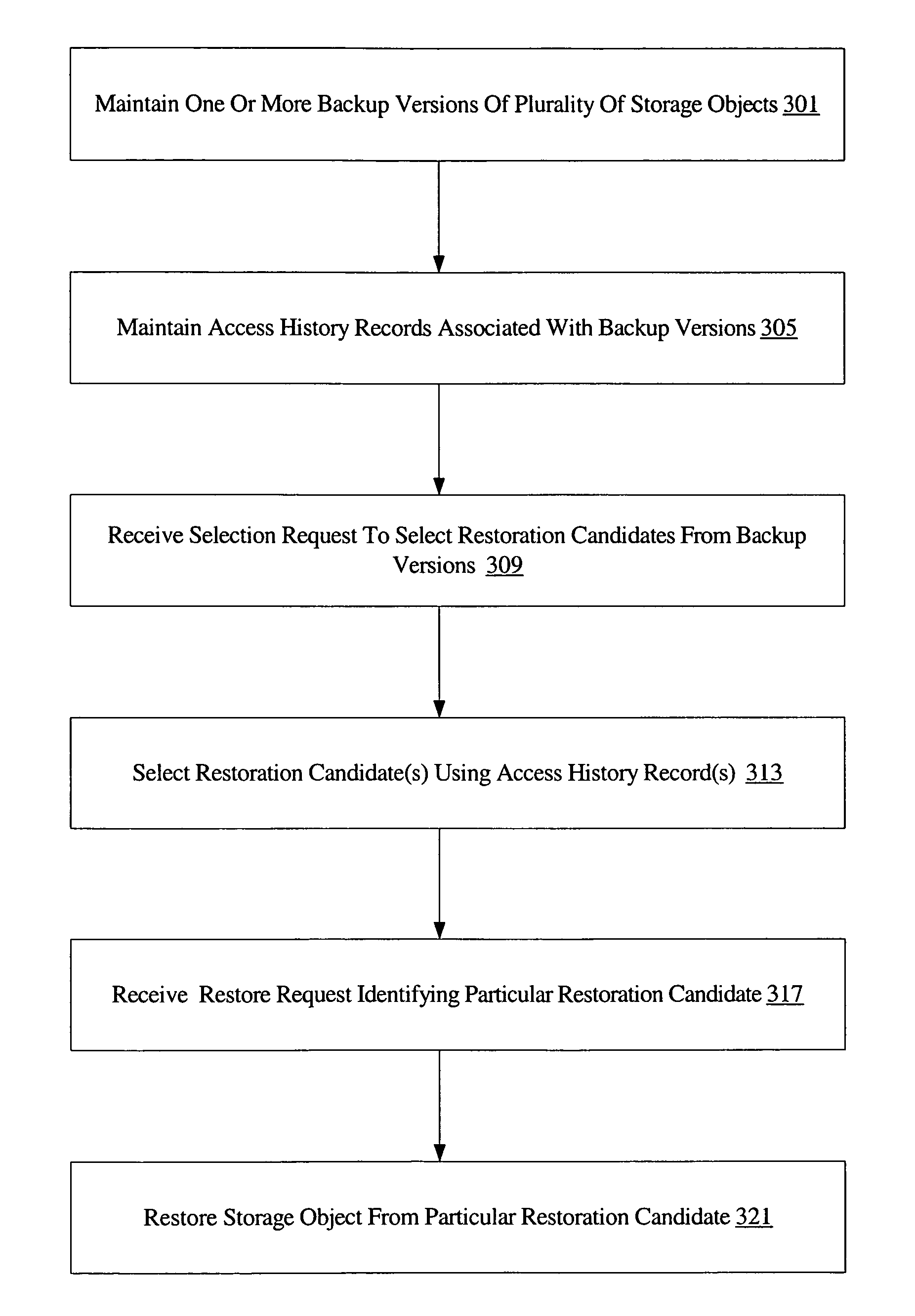
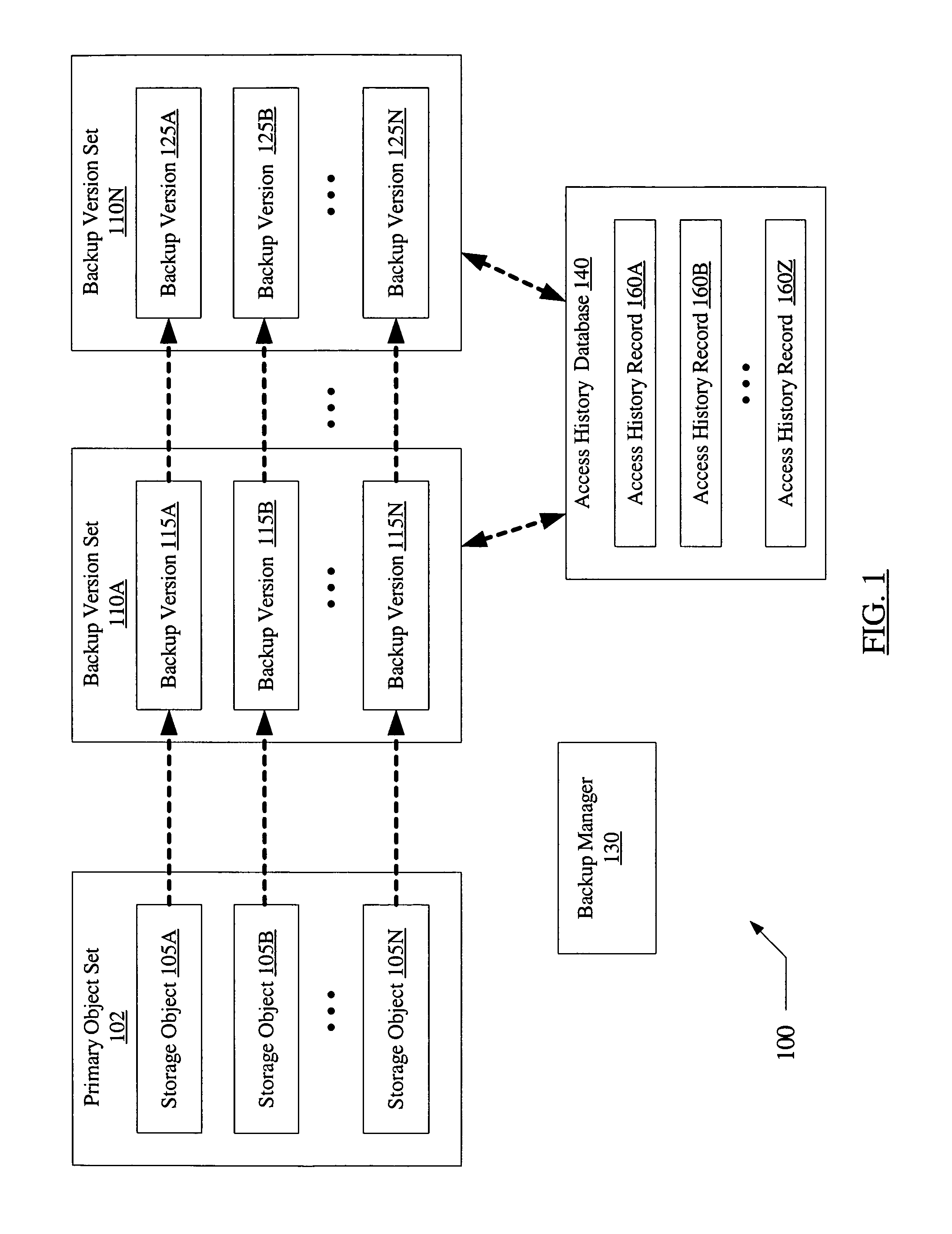
Using recent activity information to select backup versions of storage objects for restoration
InactiveUS7657582B1Reduce overheadDigital data processing detailsError detection/correctionProgram instructionAccess history
A system for using recent activity information to select backup versions of storage objects for restoration comprises a processor and memory coupled to the processor, where the memory stores program instructions computer-executable by the processor to implement a backup manager. The backup manager is configured to maintain one or more backup versions of a plurality of storage objects and a plurality of access history records, where each access history record is associated with a particular backup version. Each access history record includes information indicative of an access to the corresponding storage object by a user. The backup manager may be configured to select a particular backup version as a restoration candidate using at least the contents of the access history record associated with the backup version.
Owner:SYMANTEC OPERATING CORP
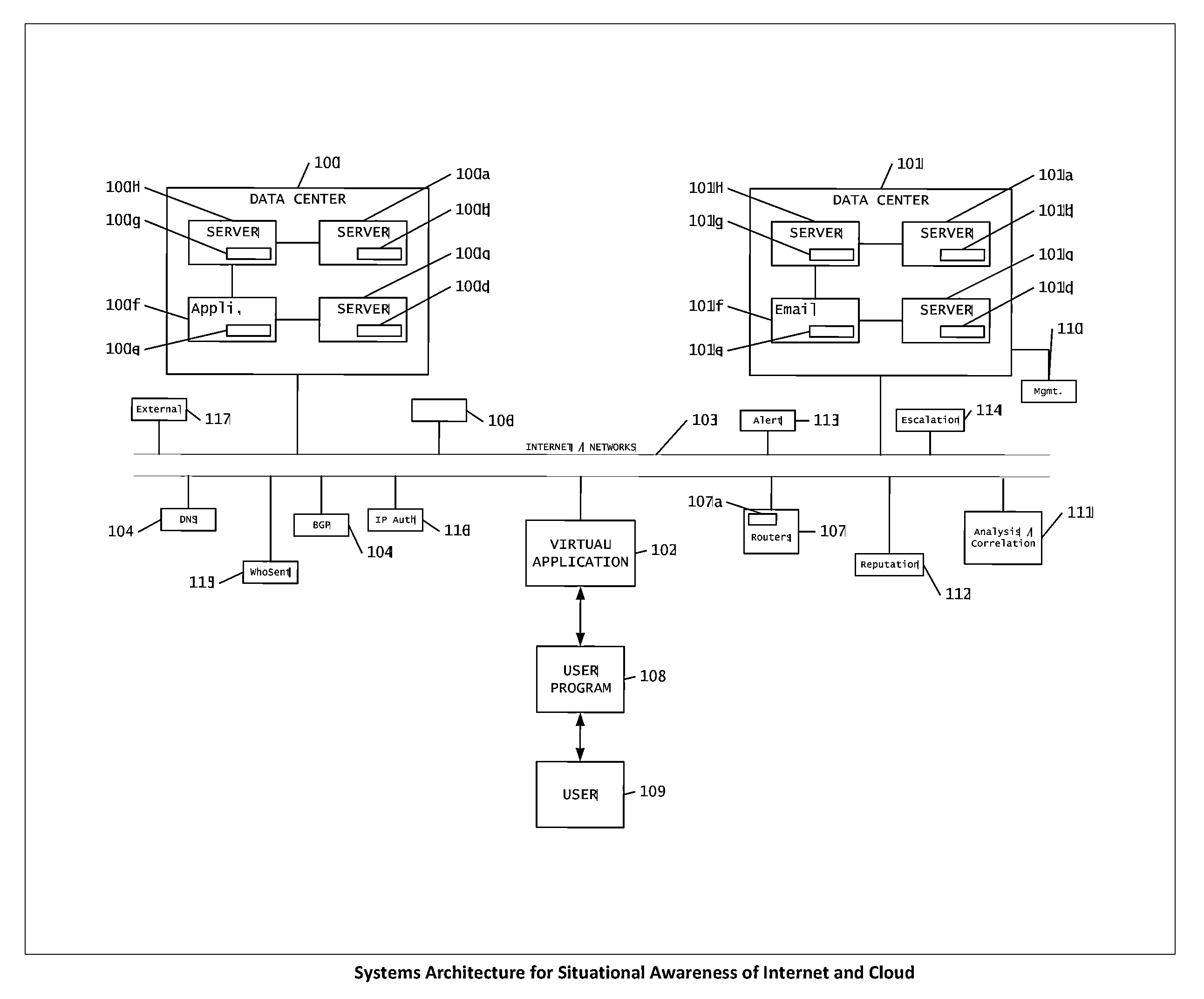
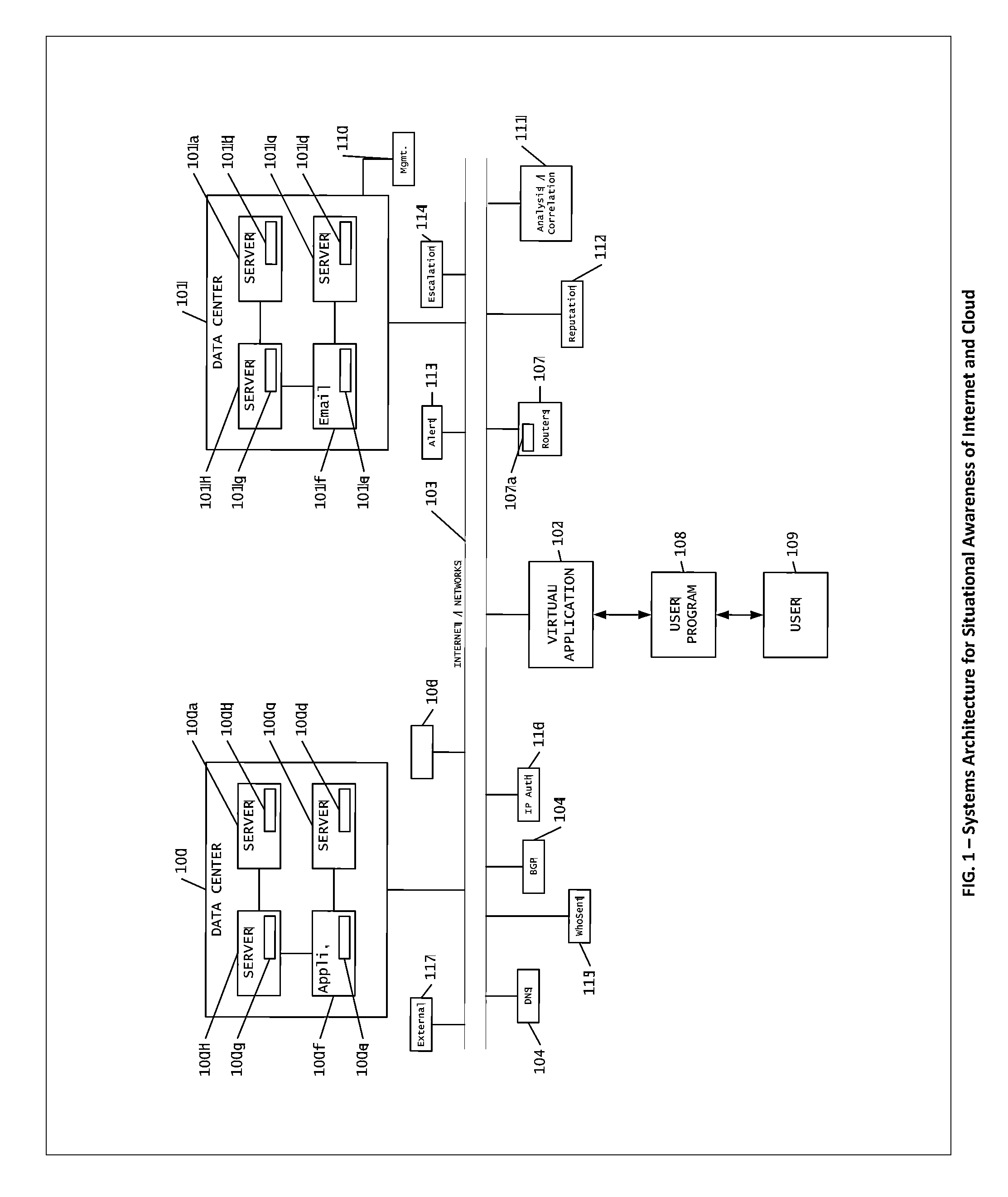
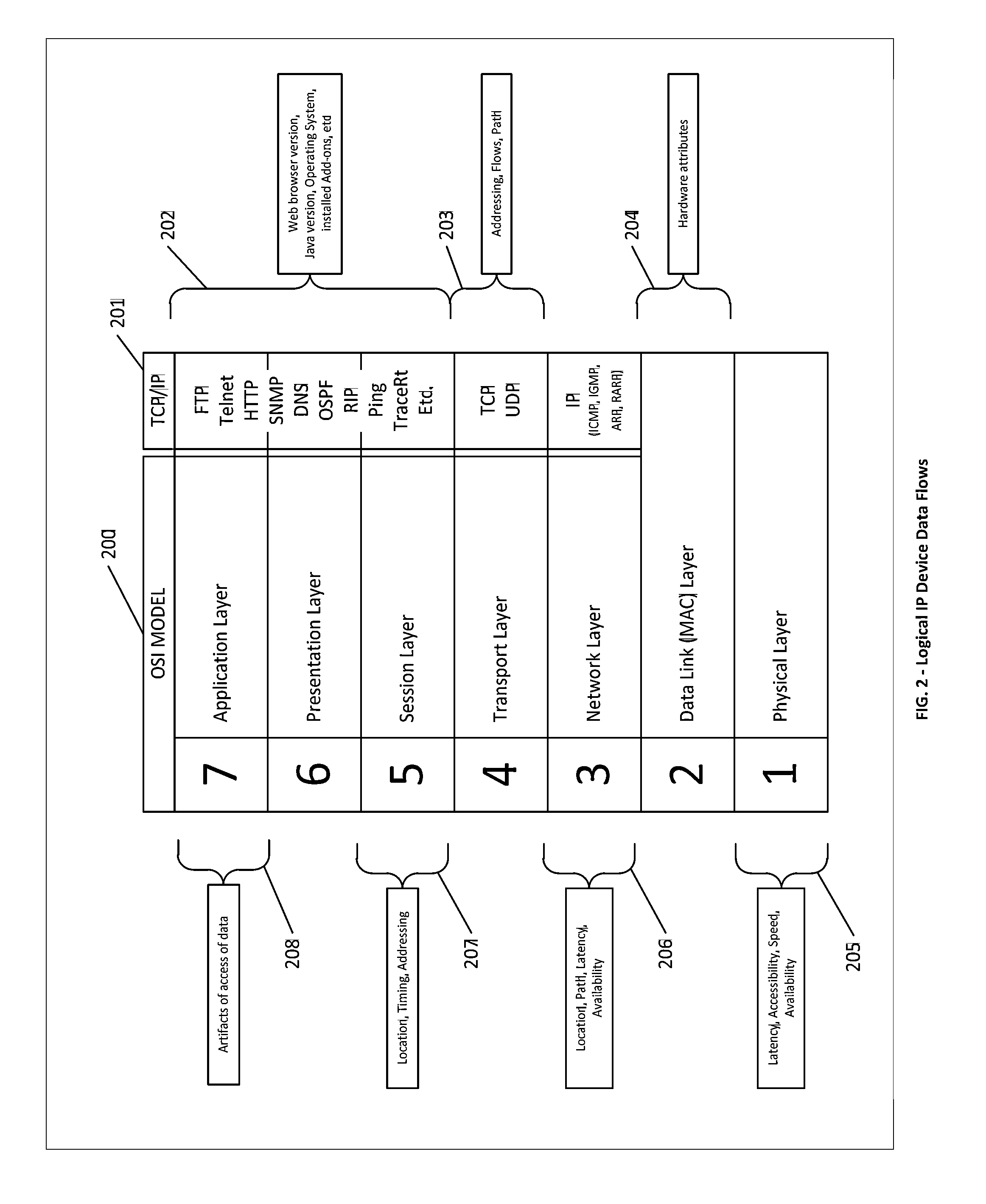
Systems, methods and devices for providing device authentication, mitigation and risk analysis in the internet and cloud
The present invention is a method to provide mechanisms and judgment to determine the ongoing veracity of “purported” devices (sometimes called spoofing) with such parameters as unique device ID, access history, paths taken and other environmental data (Device Authentication).This invention relies upon a previous invention “Reputation Database in the cloud and Internet”—the internet is comprised of collections of devices, data, applications and networks all dynamically exchanging information among users. We present a mechanism for real time observation, and putting or accessing those observations into a distributed virtual database for contextual evaluation and analysis of how the internet is being used or potentially subverted. This includes real time evaluation of DNS database changes, server logs, performance, path resolution, device logs, tip data and law enforcement data.This invention is particularly useful for helping detect and mitigate data compromises, networks, systems and other assets within the internet.
Owner:DONOVAN JOHN JOSEPH +2
Dynamic Control of Cache Injection Based on Write Data Type
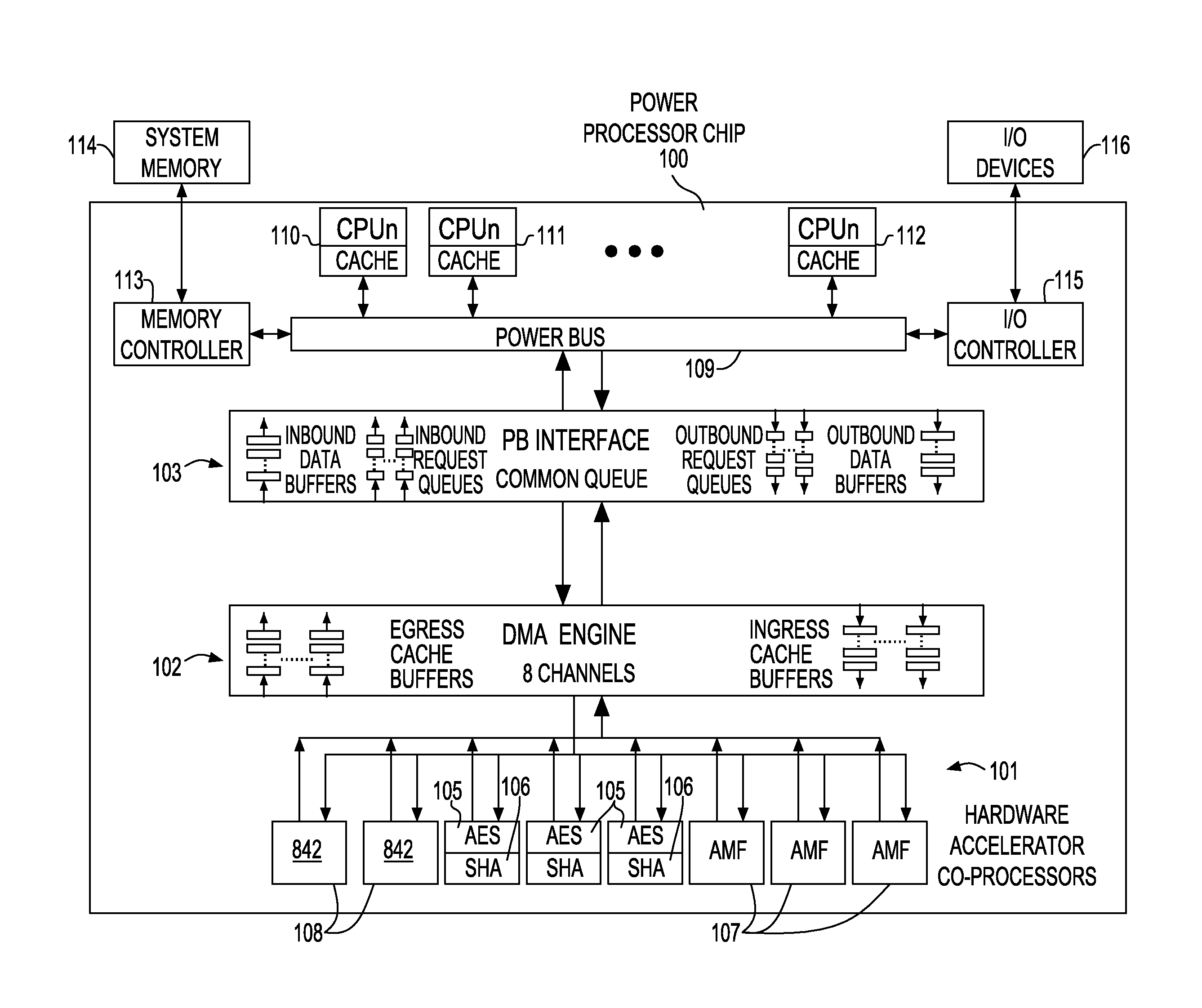
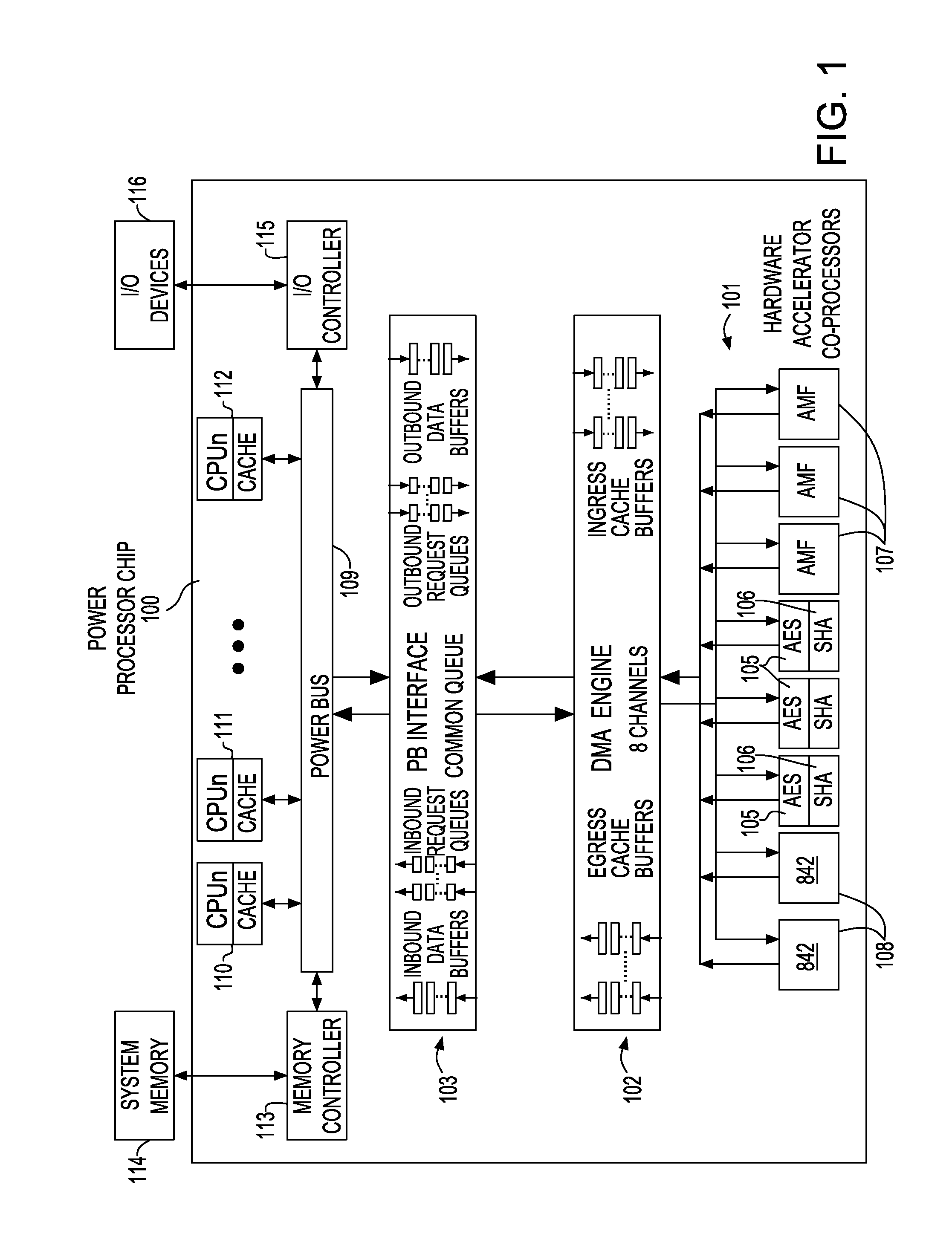
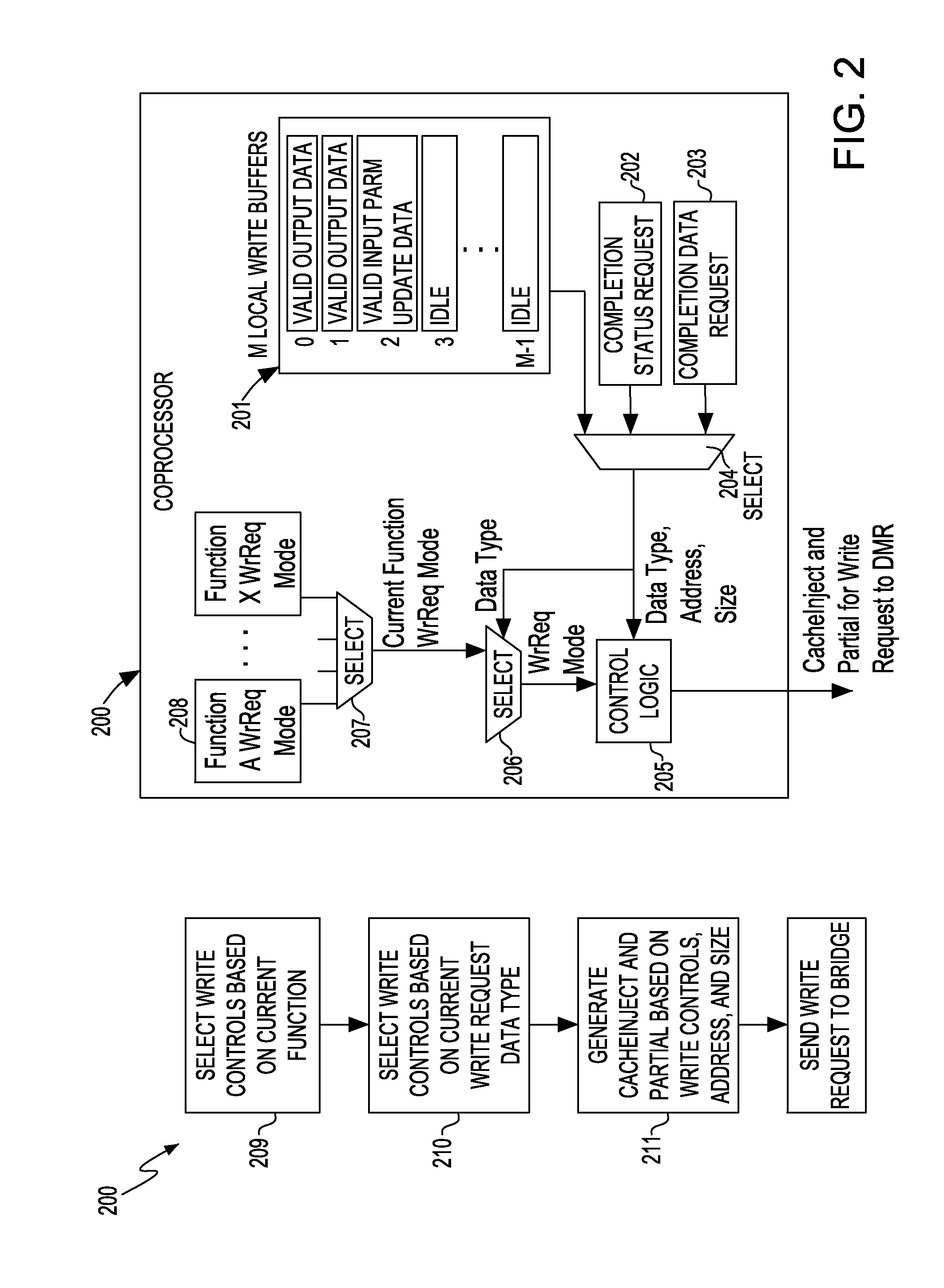
InactiveUS20130304990A1Memory architecture accessing/allocationMemory adressing/allocation/relocationCoprocessorData stream
Selective cache injection of write data generated or used by a coprocessor hardware accelerator in a multi-core processor system having a hierarchical bus architecture to facilitate transfer of address and data between multiple agents coupled to the bus. A bridge device maintains configuration settings for cache injection of write data and includes a set of n shared write data buffers used for write requests to memory. Each coprocessor hardware accelerator has m local write data cacheline buffers holding different types of write data. For write data produced by a coprocessor hardware accelerator, cache injection is accomplished based on configuration settings in a DMA channel dedicated to the coprocessor and a bridge controller. The access history of cache injected data for a particular processing thread or data flow is also tracked to determine whether to down grade or maintain a request for cache injection.
Owner:IBM CORP
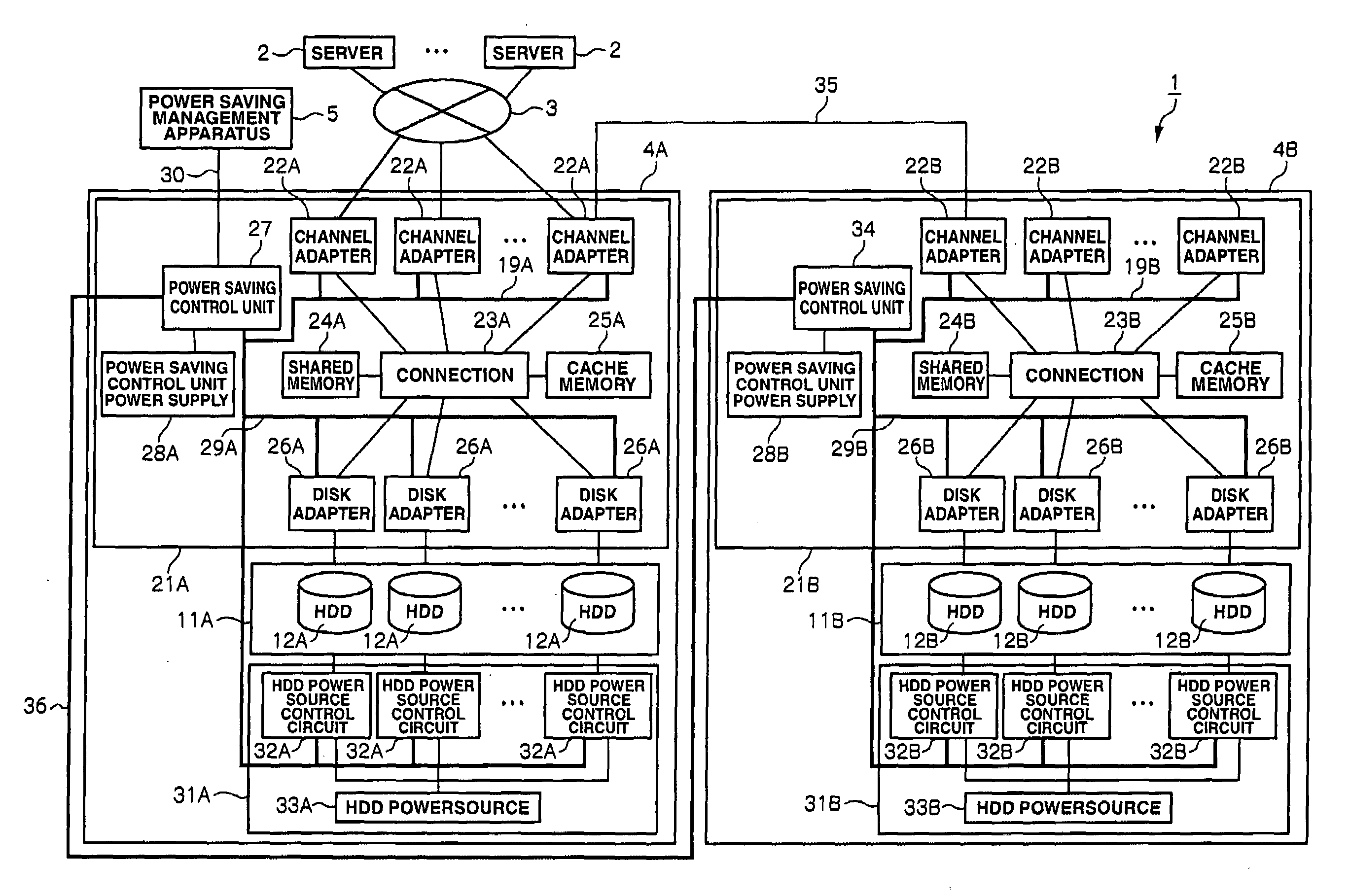
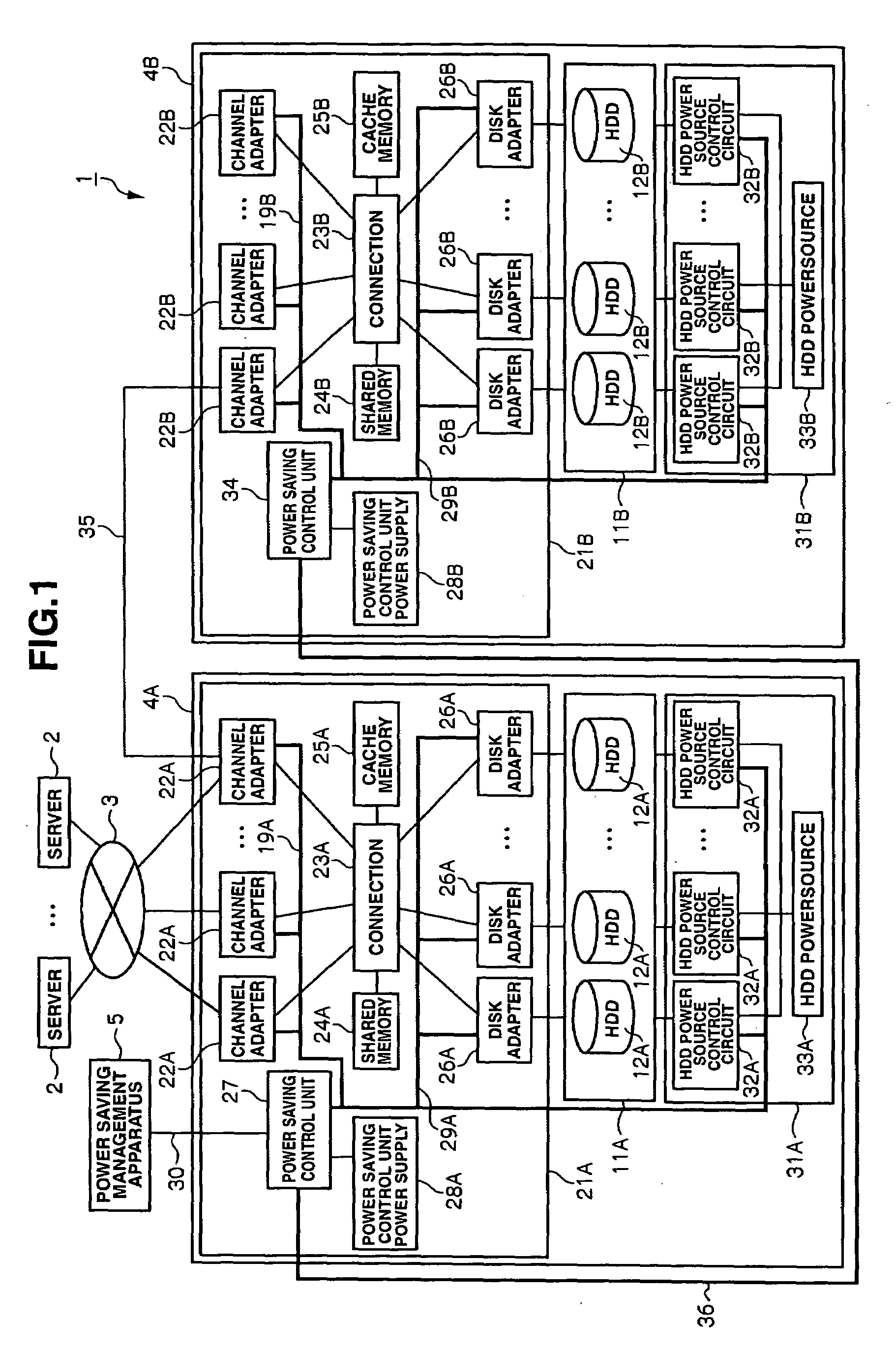
Storage apparatus and power saving method thereof
InactiveUS20090083558A1Inhibit deteriorationSave powerEnergy efficient ICTVolume/mass flow measurementAccess historyData storing
This storage apparatus includes an access history storage unit for storing, when there is a write request for writing data into the data storage unit or a read request for reading data stored in the data storage unit, history of the write request or read request as access history, an operational information storage unit for storing operational information showing whether the data storage unit is operating, an access prediction unit for predicting whether the data storage unit will be accessed based on the access history, and an operational control unit for performing operational control of pre-starting the data storage unit when the data storage unit is shut off and the access prediction unit predicts that the data storage unit will be accessed, or stopping the data storage unit when the data storage unit is operating and the access prediction unit predicts that the data storage unit will not be accessed.
Owner:HITACHI LTD
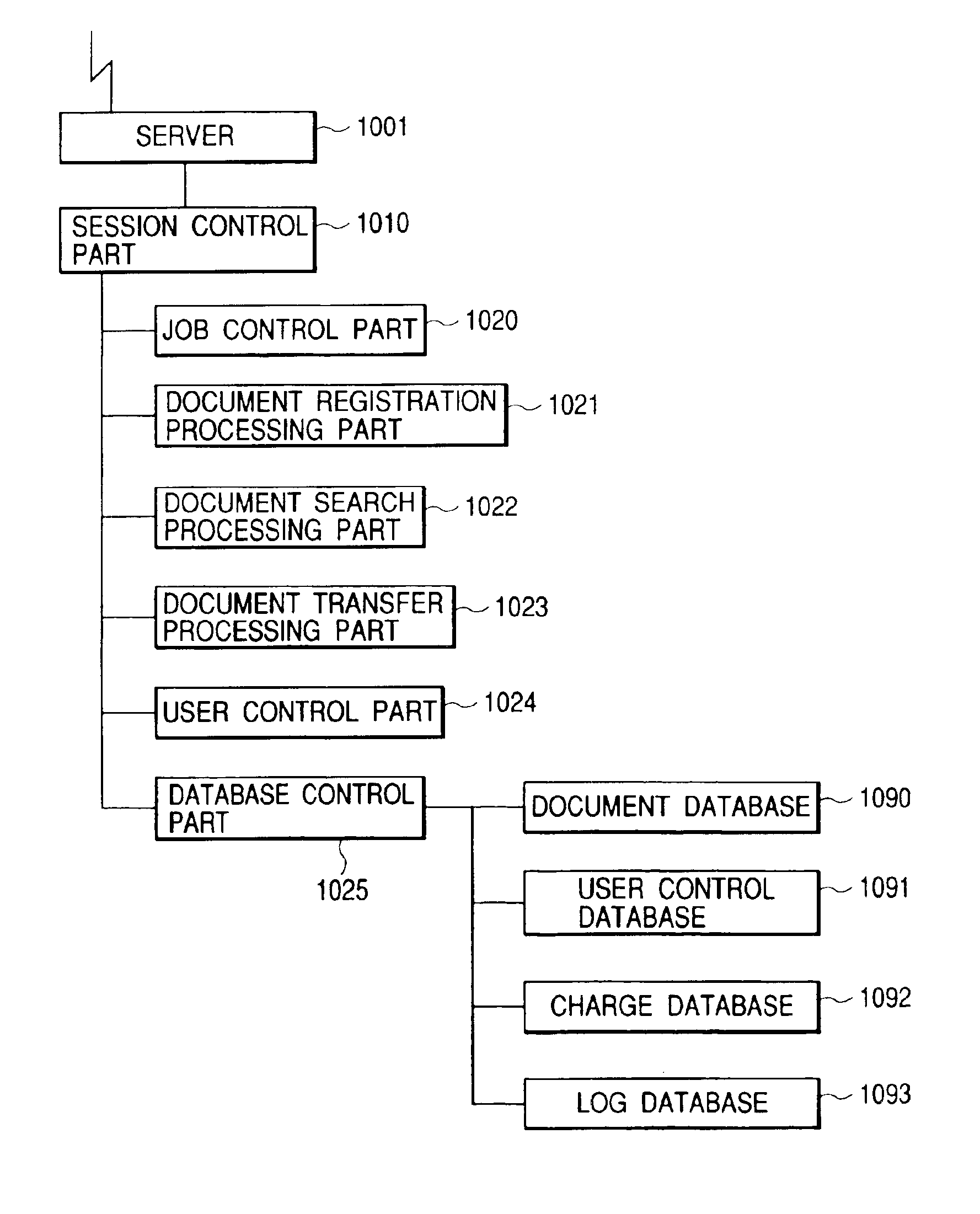
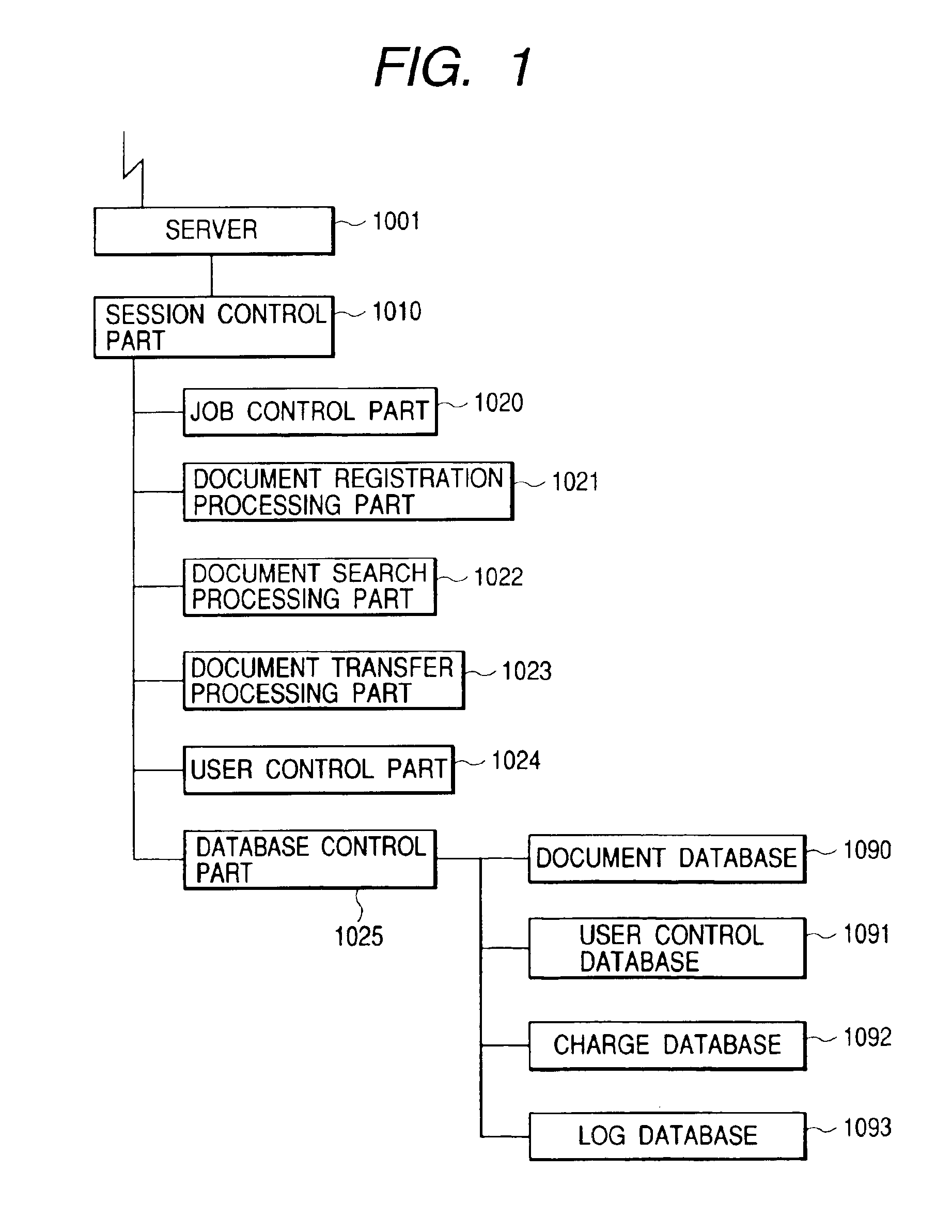
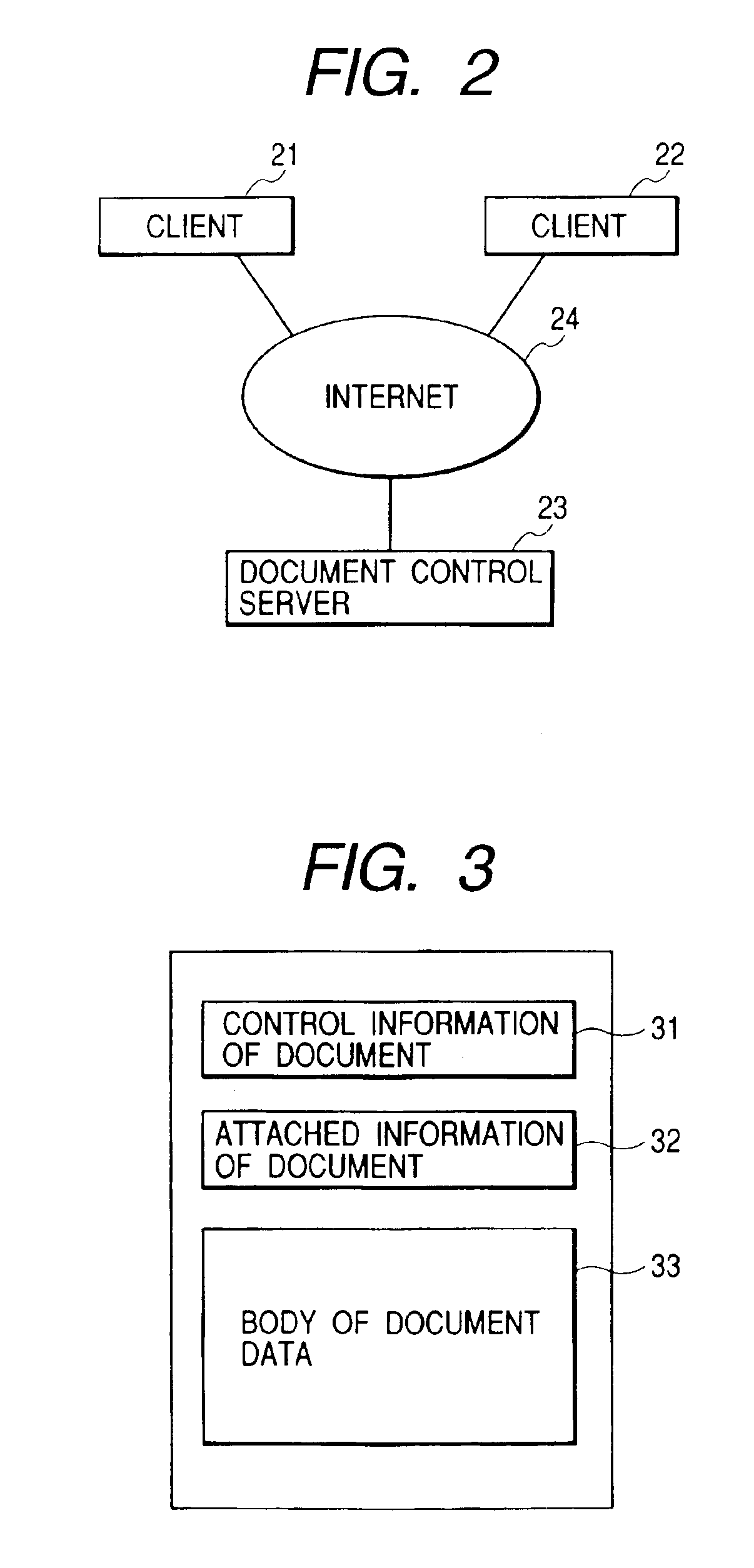
Document control apparatus, document control system, document control method and storage medium
To provide a document control apparatus, a document control system, a document control method and a storage medium that are capable of providing more certain access control by the unit of document and a system (service) for allowing access in the form of charging additional charge with a fixed grace period, and are capable of supporting more flexible and certain storing service. The document control system includes a Web server, a session control part for controlling access, a job control part for controlling job execution, a document registration processing part for registering, updating and deleting a document, a document search processing part for searching an accumulated and controlled document, a document transfer processing part for transmitting and receiving document data, a user control part for controlling user information, a database control part for controlling document data, registration user, charge information and document access histories, and databases.
Owner:CANON KK
System and method for identifying a retail customer's purchasing habits
ActiveUS7028894B2Reduce point-of-sale hardware and applicationReduce needCash registersVisual presentationAccess historyHabit
A system and method for targeting marketing messages at a point-of-sale consumer by collecting current transactional receipt data, such as the time of a retail transaction, the date of the transaction, the number of items purchased the transaction, and the total dollar value of a transaction. The data collected from the receipt is then applied to one or more algorithms to determine which marketing messages are most likely to be successful. A predetermined number of marketing messages found most likely to be successful are then printed on the customer receipt in order of priority of expected effectiveness. The system is designed to be used in connection with a point-of-sale terminal without the need for additional hardware, such as a second printer, or the need to access historical customer data.
Owner:COGNITIVETPG
Method of managing access to Web pages and system of managing access to web pages
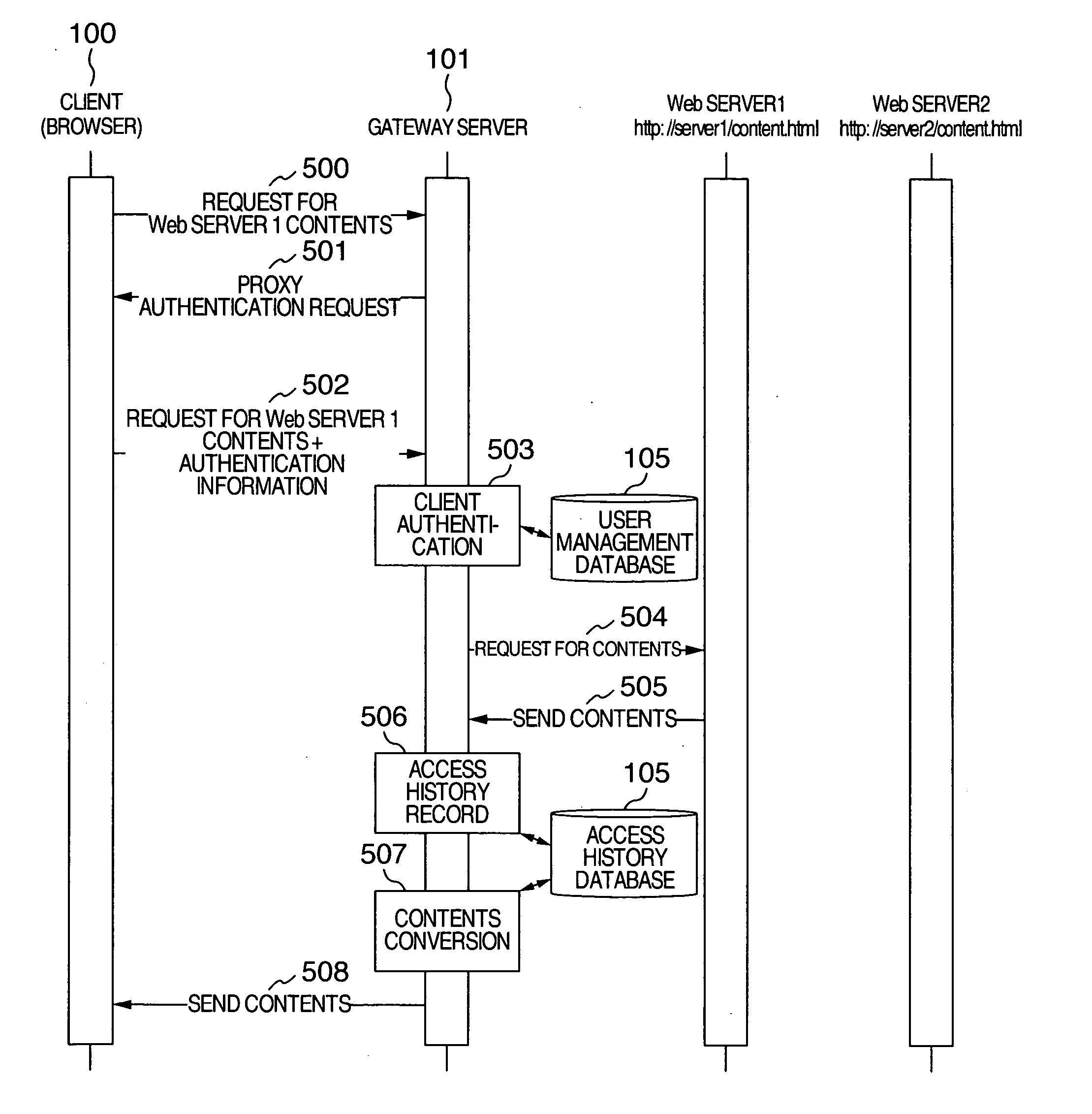
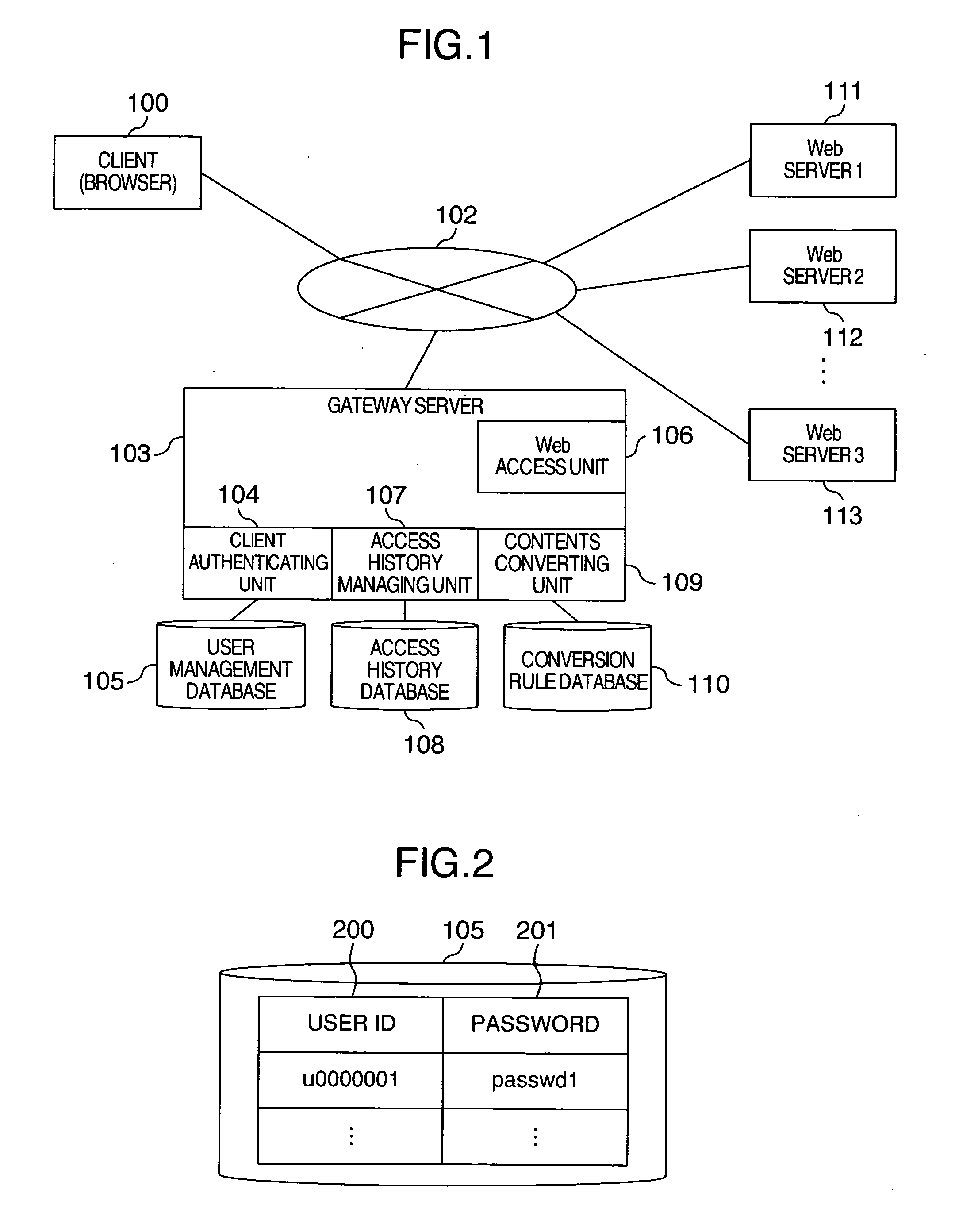
InactiveUS20060095422A1Improve efficiencyImprove access efficiencyDigital data authenticationSpecial data processing applicationsAccess historyClient-side
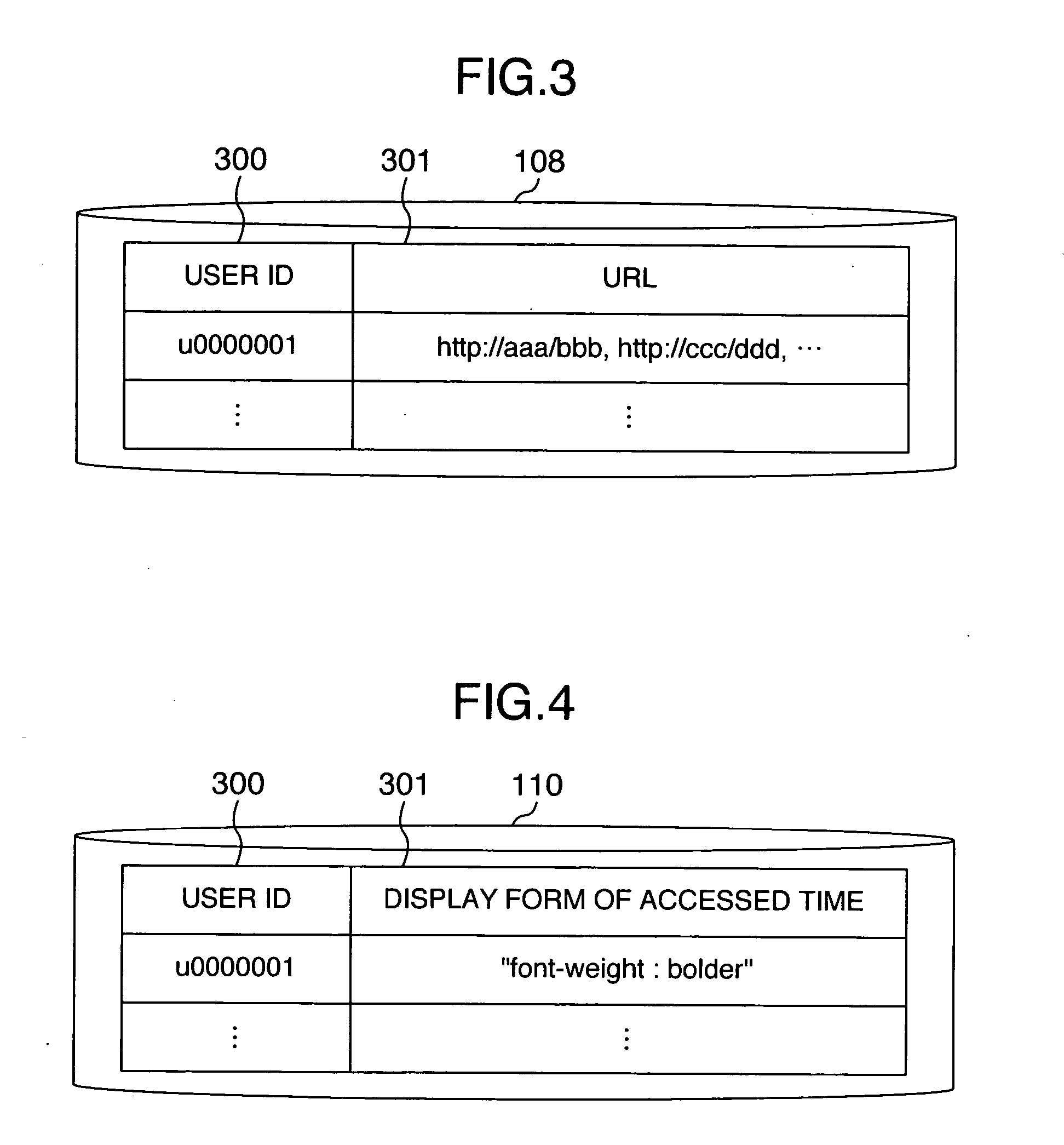
There is provided a method of efficiently accessing information located on Web pages in a ubiquitous environment such as a home, an office and on a travel. A gateway server is located between a client and Web servers for providing the contents. The gateway server traps a request of a browser operating in the client and records an access history. On the access records, the display form of a link in the contents is changed, and the service of managing the accessed information is presented to the client. Further, the user may optionally set an attribute to the contents and change the display form of the accessed link according to the set attribute.
Owner:HITACHI LTD
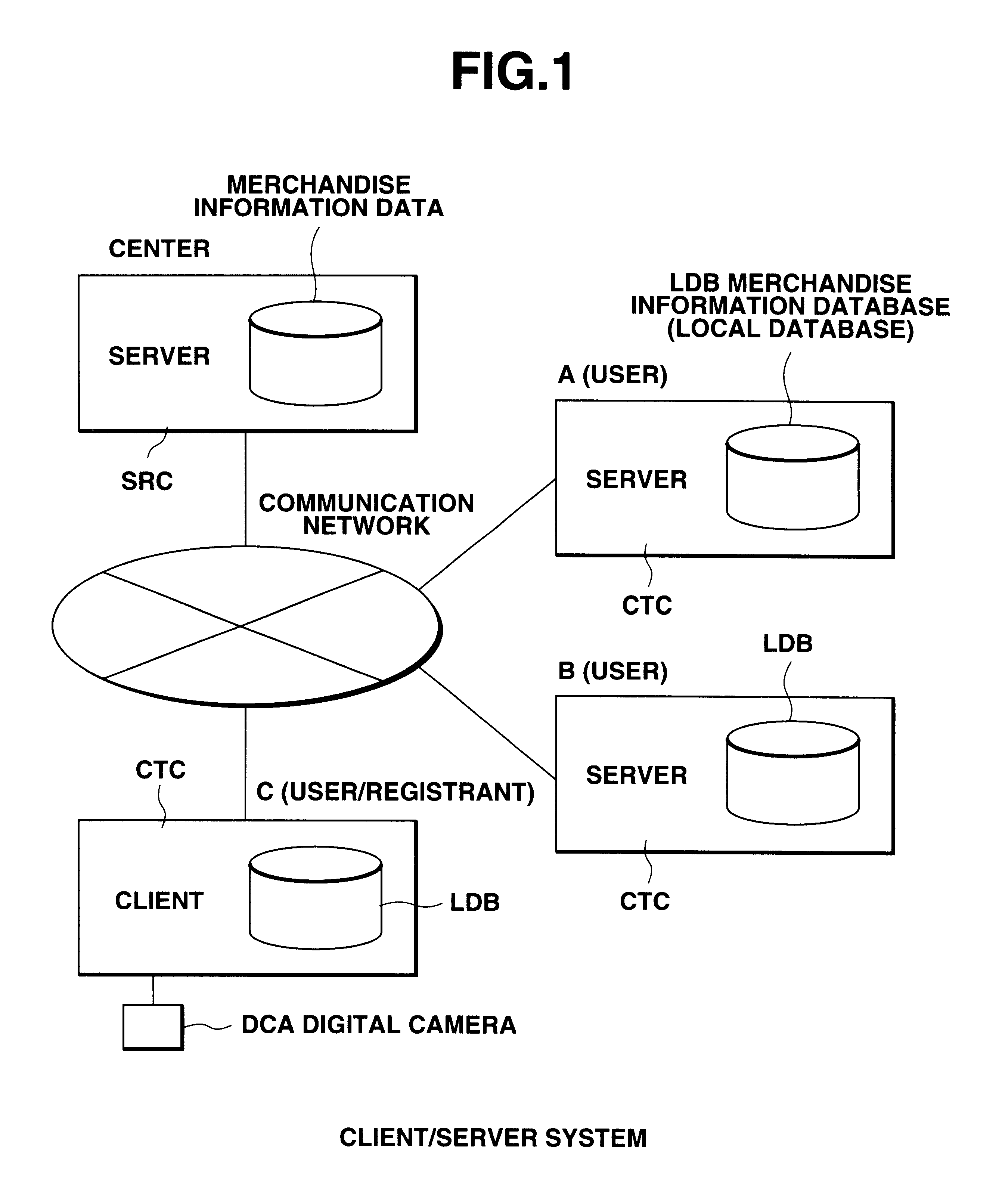
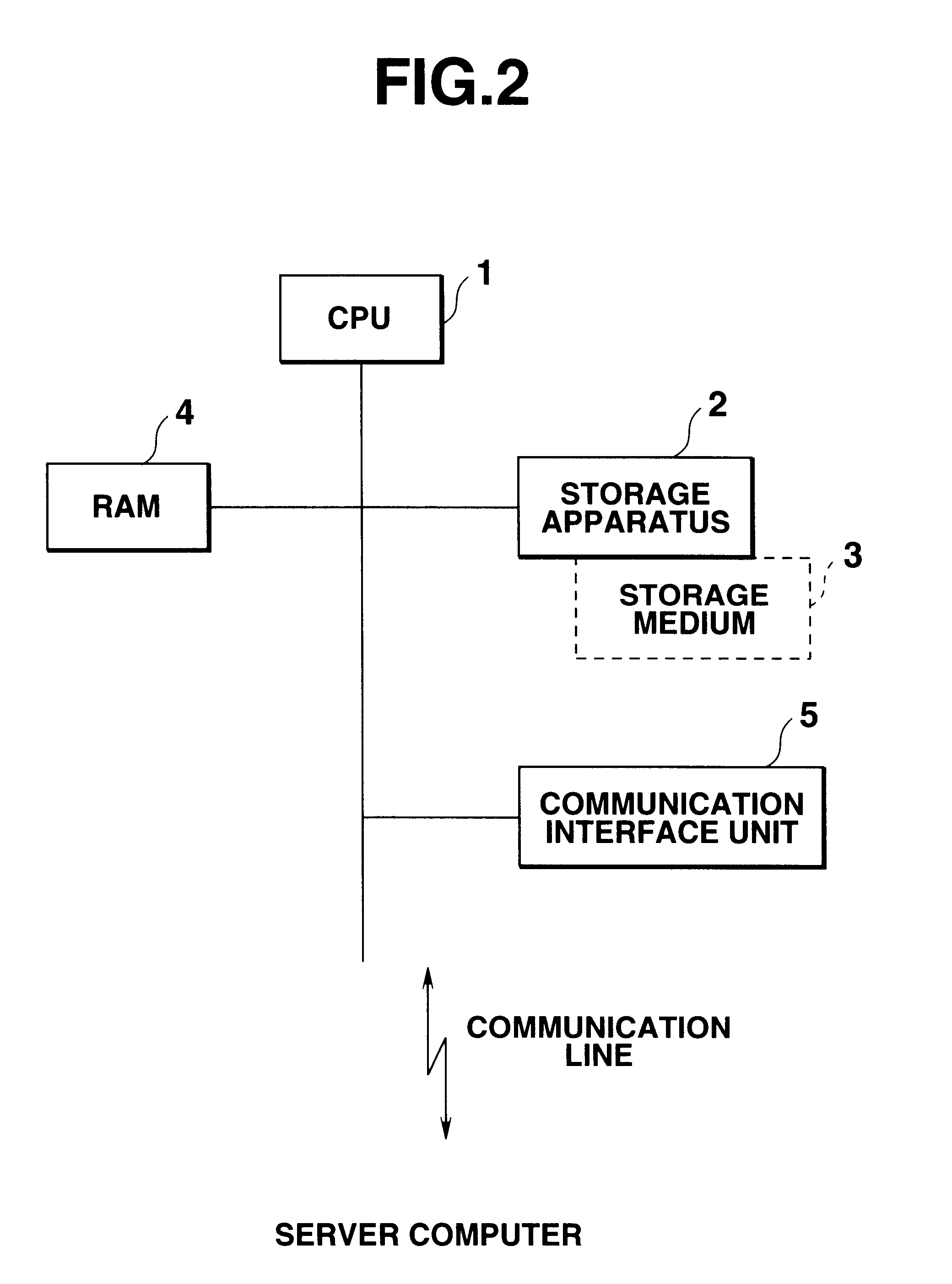
Server computer capable of automatically notifying updated database content to client computer, and program storage medium
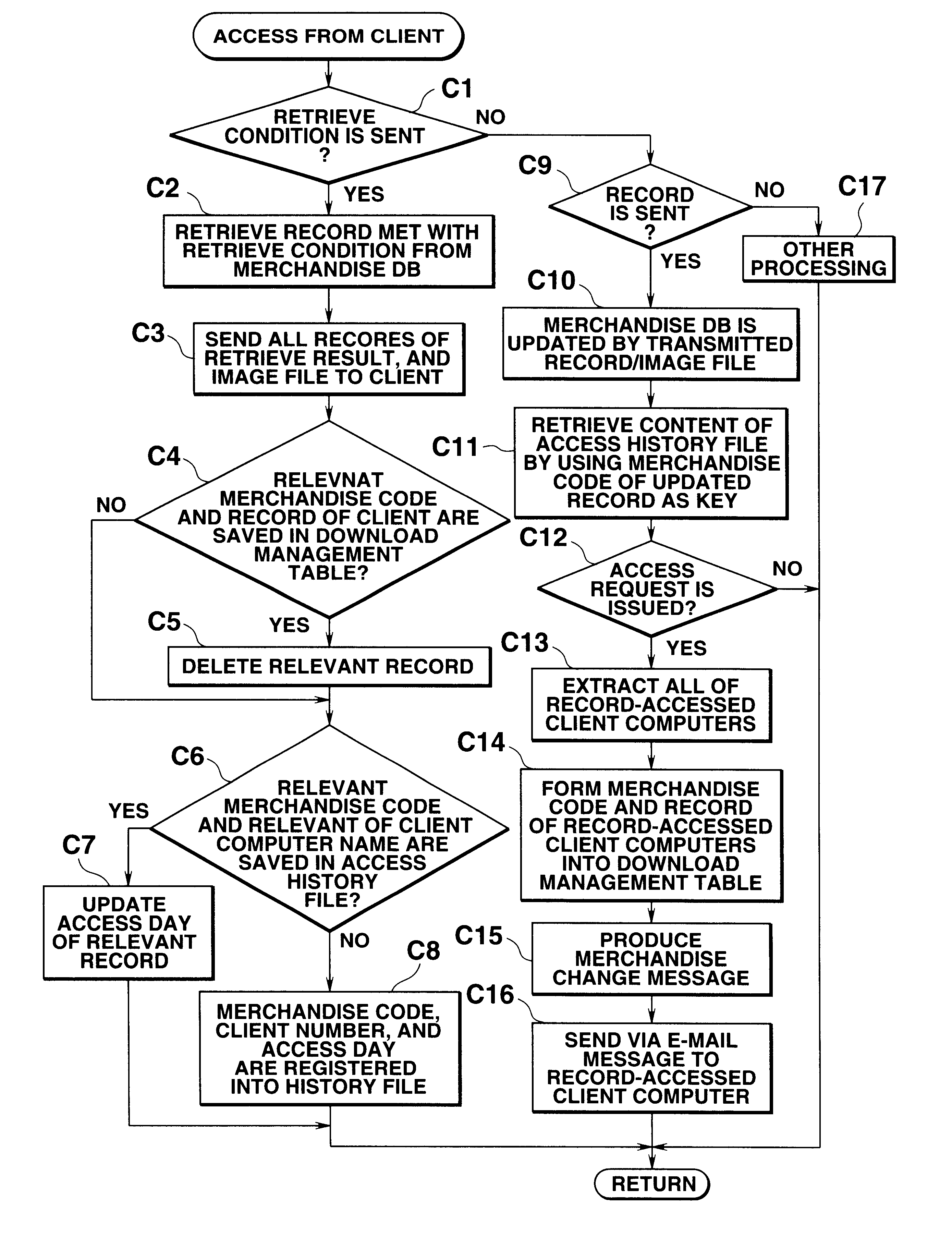
InactiveUS6477548B1Digital data information retrievalBuying/selling/leasing transactionsAccess historyNetworked system
In a client / server network system, an updated database content is automatically notified from the server computer to all of client computers which have once accessed this database content. In the server computer, an access history record for recording access requests issued from certain client computers is saved in a merchandise information database. When the record of this merchandise information database is changed, the server computer extracts such a client computer which has accessed this database in the past based up on the access history. Then, the server computer notifies a change notification to all of the relevant client computers, so that all of these relevant client computers can recognize the changed database.
Owner:INTELLECTUAL VENTURES ASSETS 114 LLC +1
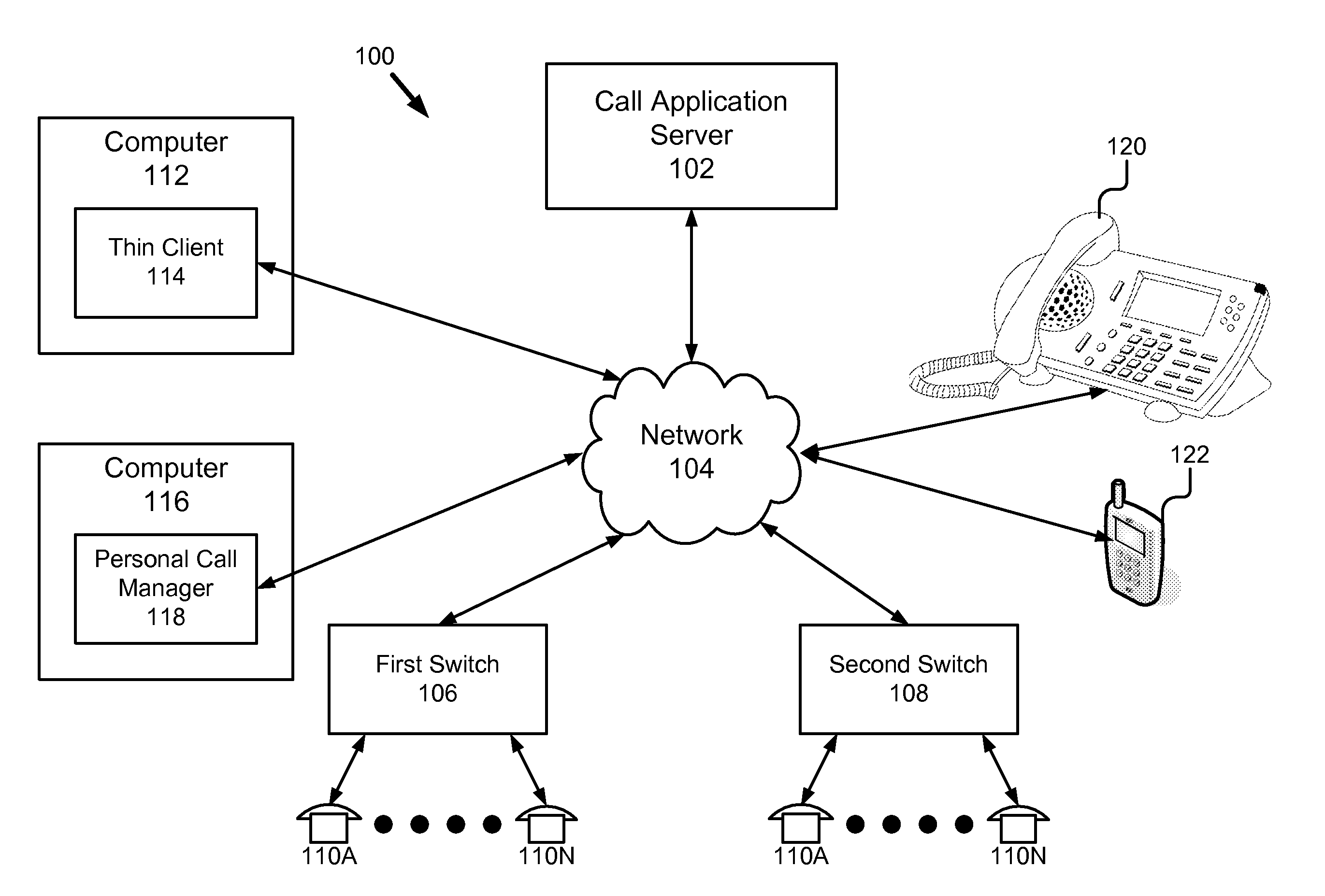
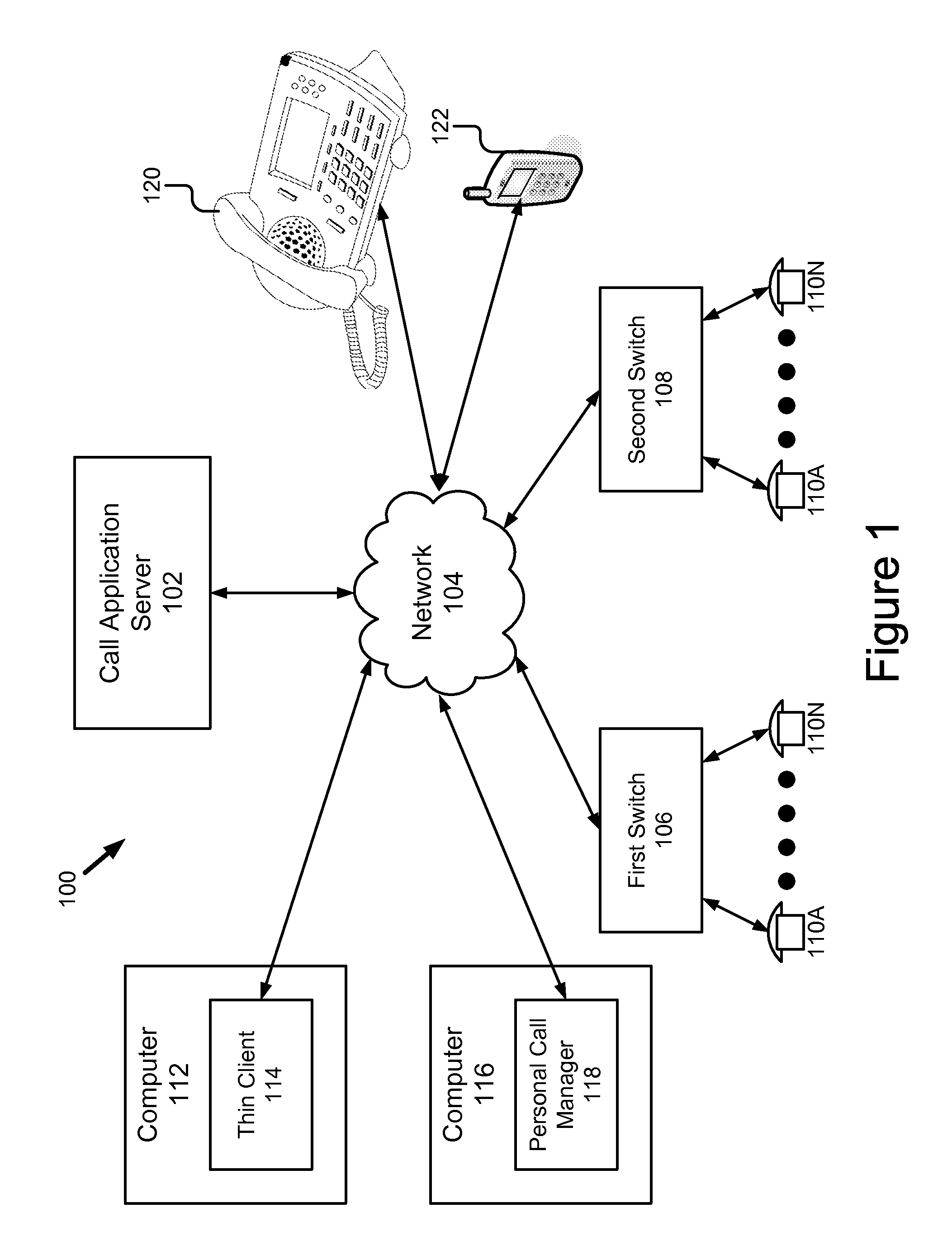
Maintaining history information for a user across multiple types of end points
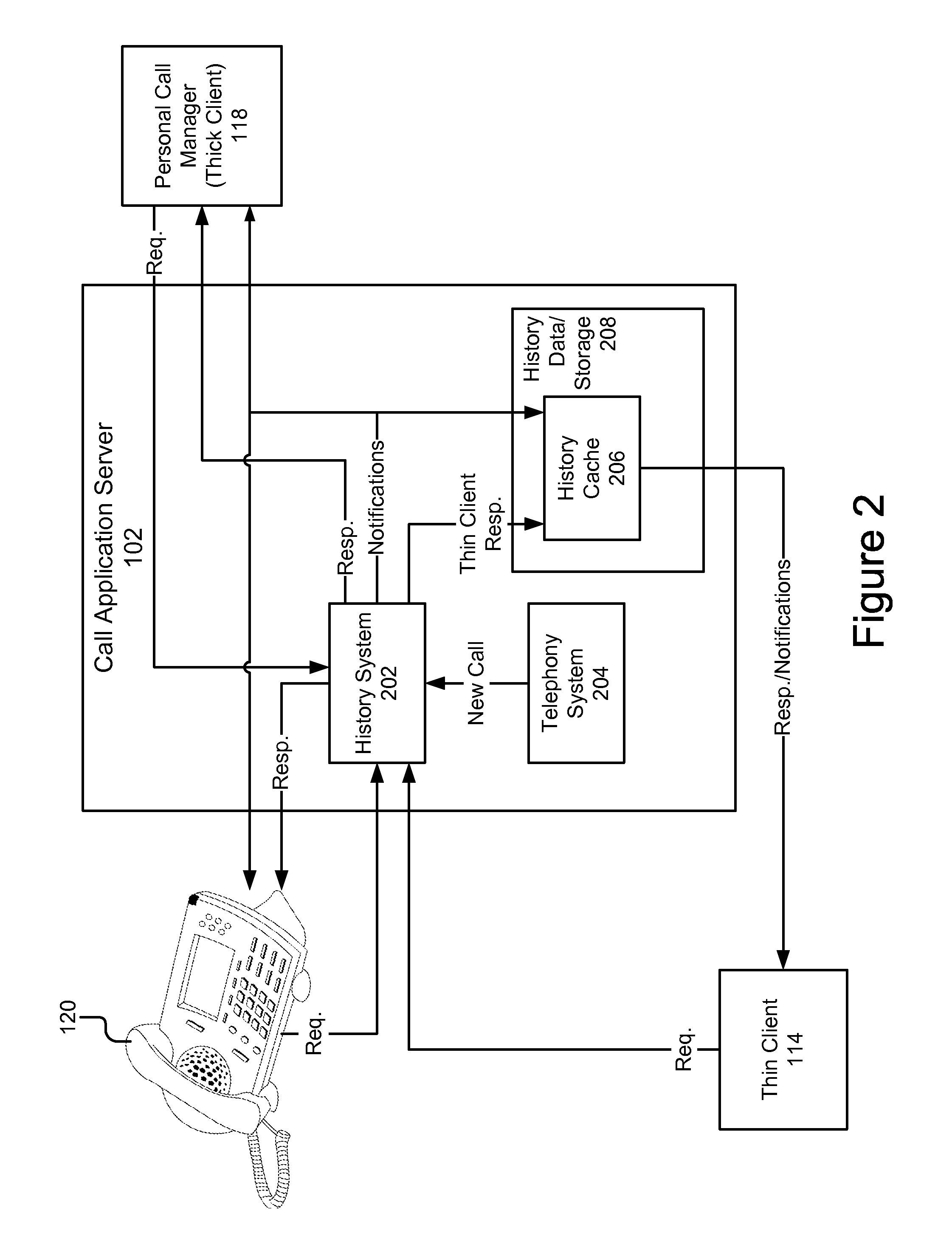
ActiveUS20110075828A1Overcome deficienciesEasy maintenanceSpecial service for subscribersApplication serverAccess history
A system for providing enhanced history information across multiple clients comprises a call application server having a history system, a telephony system and a history cache. The call application server advantageously maintains a history records for each user of the system. The enhanced history system is particularly advantageous because regardless of the endpoint (e.g., phone, thin client, personal call manager or standalone IP phone) with which the user is interacting, the history information specifically for that user is delivered by the call application server to that endpoint. Furthermore, the call application server allows the user to access history information using end points which heretofore were unable to provide history functionality. Finally, the call application server makes the history records universal across all endpoints with which the user interacts, in contrast to prior art, which had limited call history information specific to a particular endpoint.
Owner:SHORETEL +1
Floor control language
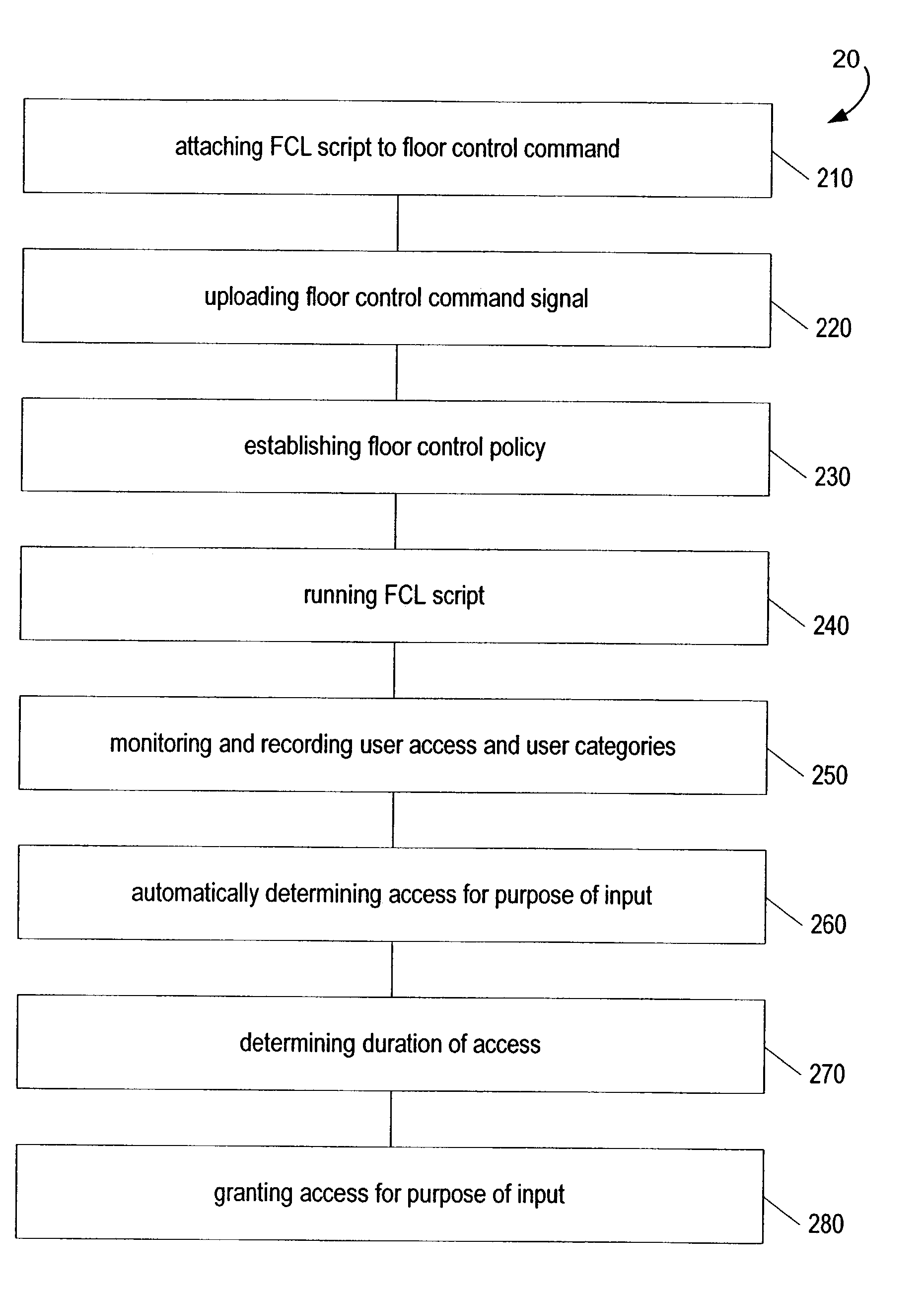
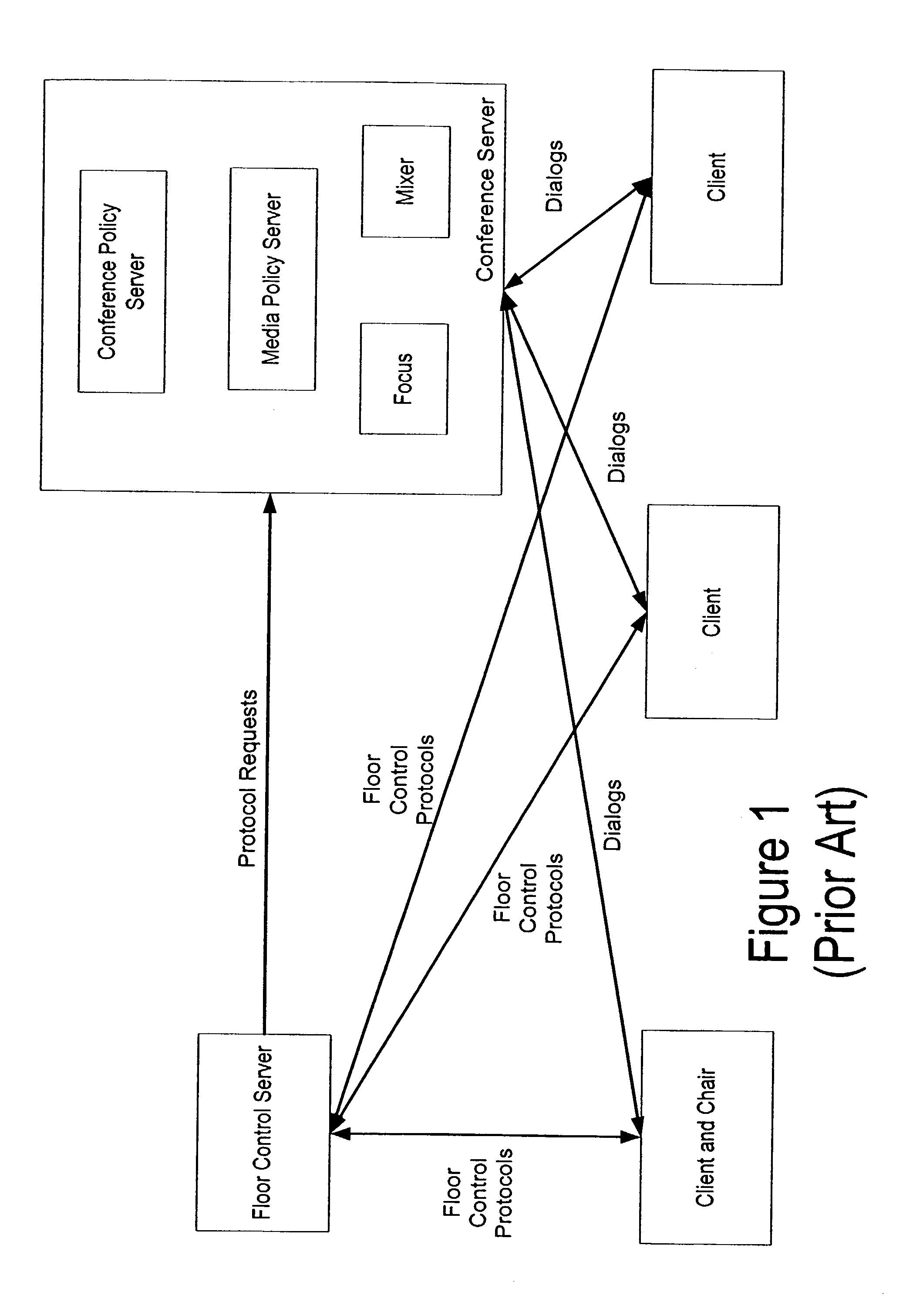
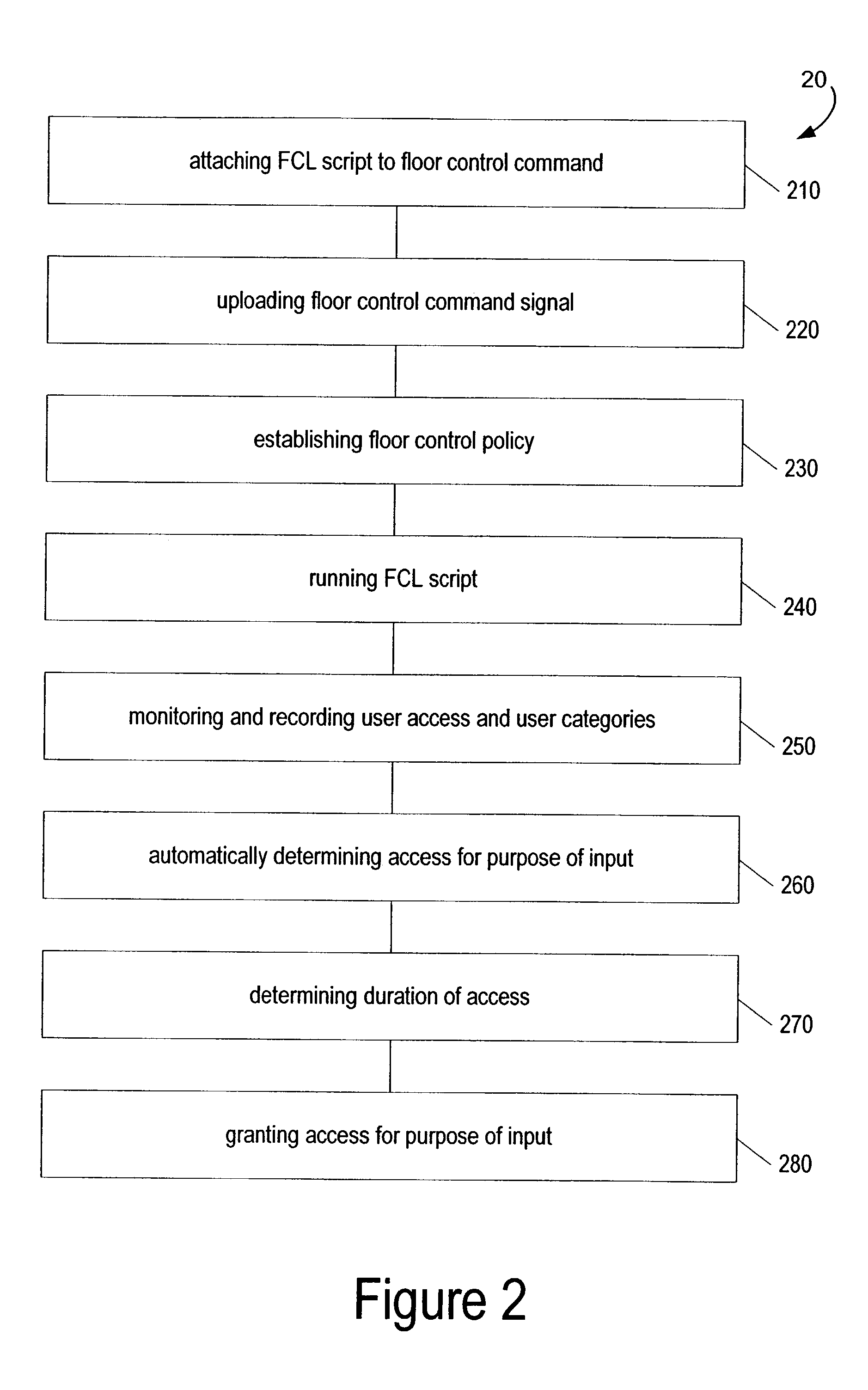
InactiveUS7085244B2Simple and fast operationSpecial service provision for substationMultiplex system selection arrangementsControl systemAccess history
A telecommunications method and system of floor control, for enabling at least one conference participant to access a shared object or resource for purposes of input. A floor control command signal establishes at least one floor control policy, and the floor control command signal includes a floor control language script for automatically determining the access. This access is determined based upon factors such as access requests and prior access history, without need for a floor chair.
Owner:GULA CONSULTING LLC
Extracting data changes and storing data history to allow for instantaneous access to and reconstruction of any point-in-time data
ActiveUS7979404B2Efficient transferEfficient storageDigital data information retrievalDigital data processing detailsData connectionData stream
Owner:QUEST SOFTWARE INC
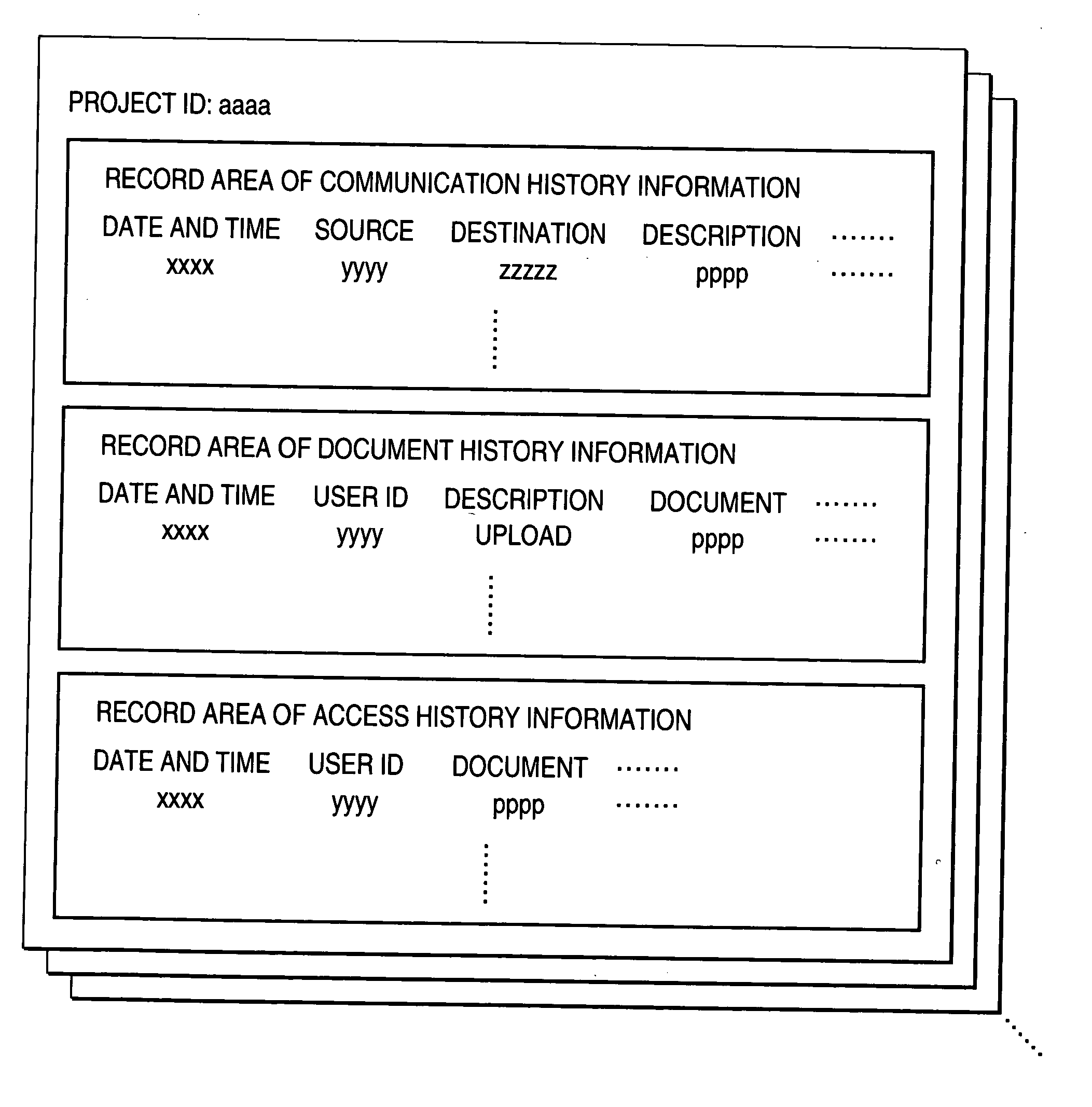
Project management system
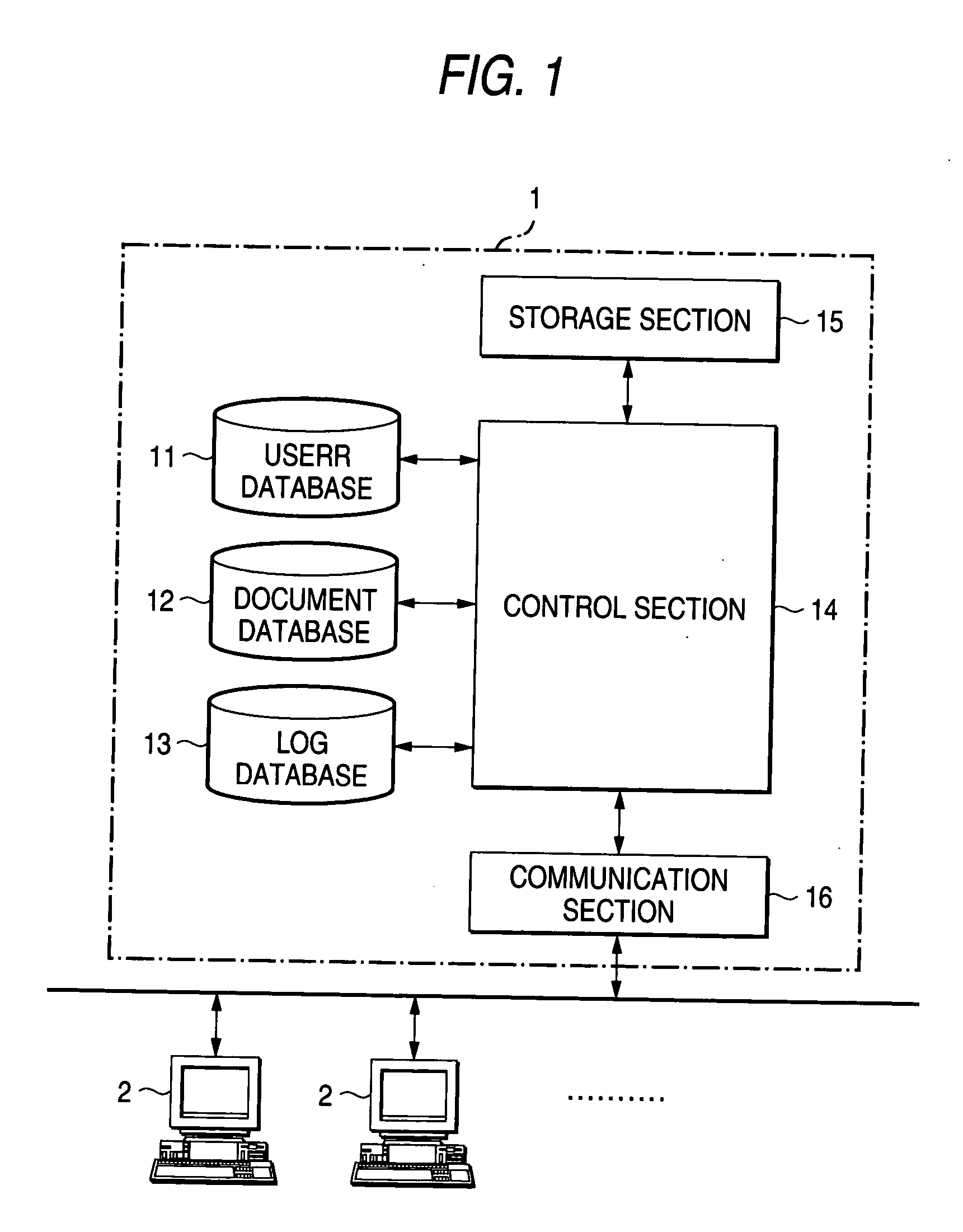
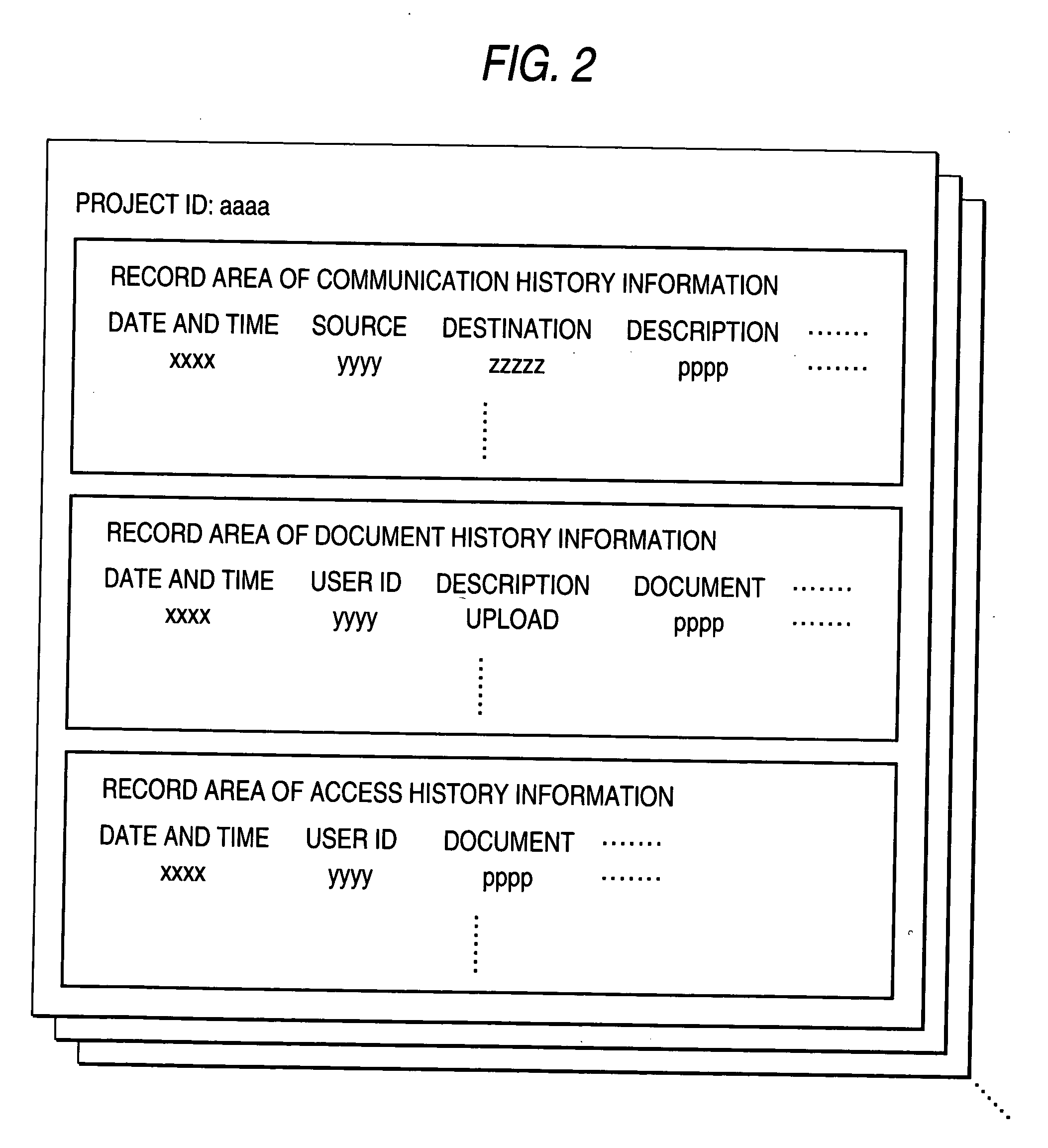
ActiveUS20050010864A1Easy to operateDigital computer detailsOffice automationAccess historyDocumentation
A project management system including a record system that records, for each project involving a plurality of users, communication history information containing information determining a communication occurrence time point of a user involved in the project, document history information containing information determining an occurrence time point of operation on a document relating to the project, and access history information containing information determining an occurrence time point of access to the document or a communication message relating to the project as distinguished from each other, a collecting unit that collects a record concerning an attention project from the record system, and an image generating unit that generates an image indicating a record frequency of the communication history information, the document history information, and the access history information in the time-series relationship based on the record collected by the collecting unit. Preferably, the generated image is presented to the user.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com