WEB malicious scanning behavior abnormity detection method and system
An anomaly detection and anomaly technology, applied in the field of WEB security, which can solve the problems of increasing false positive rate and false negative rate, mixing in and so on.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
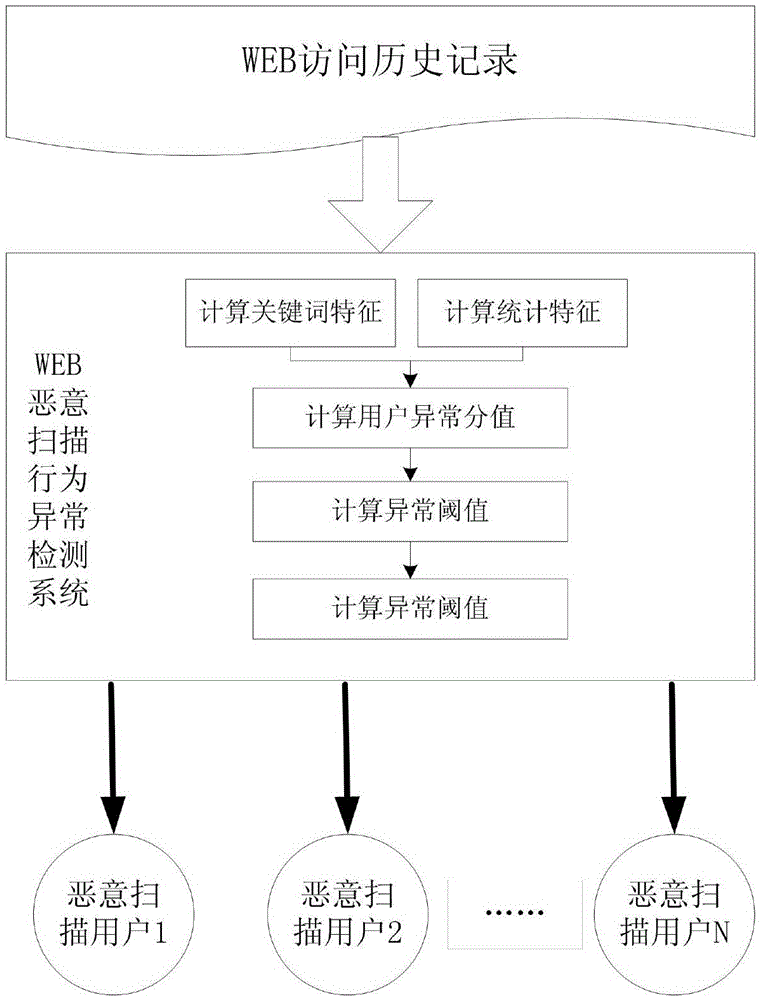
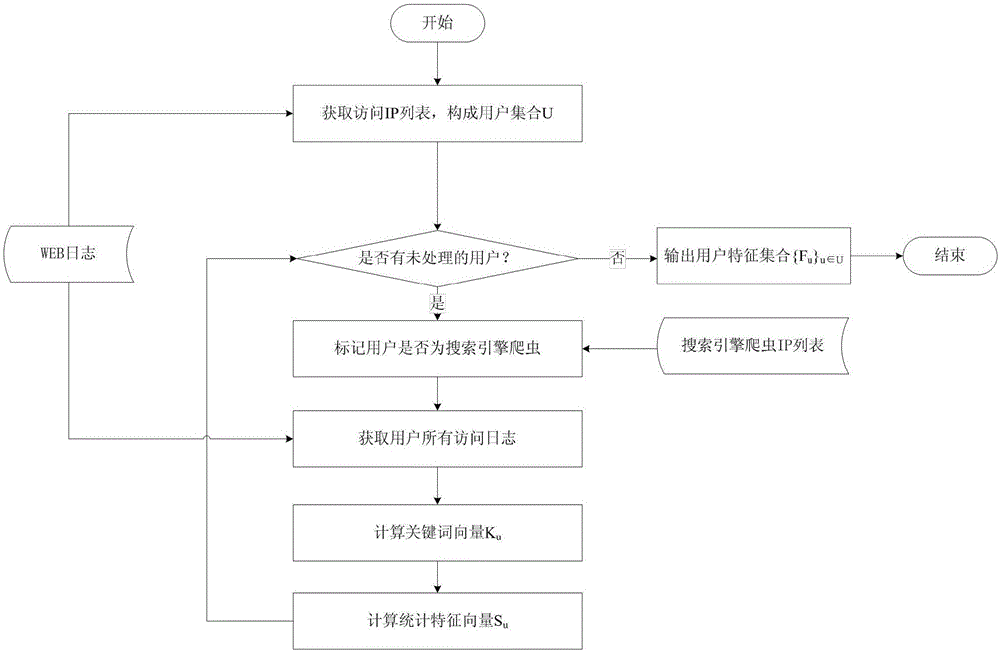
[0043] figure 1 It is an outline of the principle of a WEB malicious scanning behavior anomaly detection system of the present invention. The WEB malicious scanning anomaly detection system can perform data preprocessing and abnormal analysis on the input WEB access history records, and find malicious scanning users.
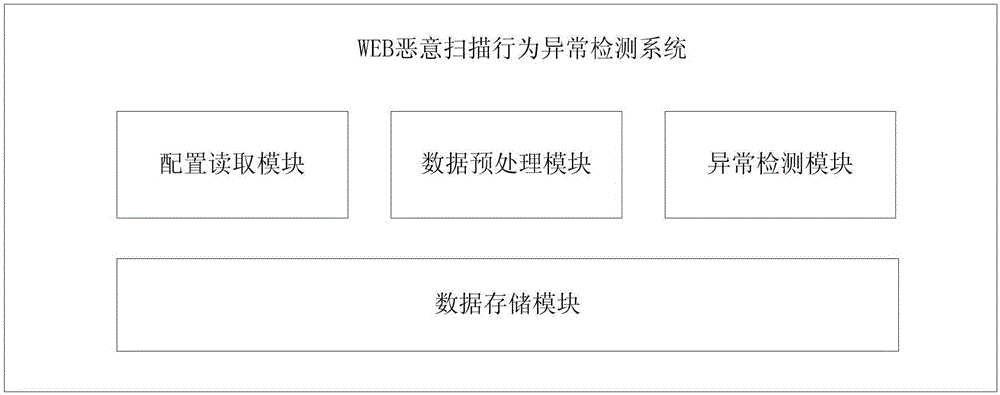
[0044] figure 2 It is a schematic diagram of module composition in an embodiment of a WEB malicious scanning anomaly detection system of the present invention.
[0045] In this embodiment, the WEB malicious scanning behavior detection system is composed of a configuration reading module, a data preprocessing module, an anomaly detection module and a data storage module.
[0046] The data storage module is responsible for storing system configuration information, original WEB access history records, data preprocessing results, and malicious scanning user detection results. The data storage module can be implemented in a relational database, non-relational data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com