Patents
Literature
1355 results about "Occurrence time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Time of occurrence. time of occurrence: The date of an event, i.e., the instant an event occurs, with reference to a specified time scale.
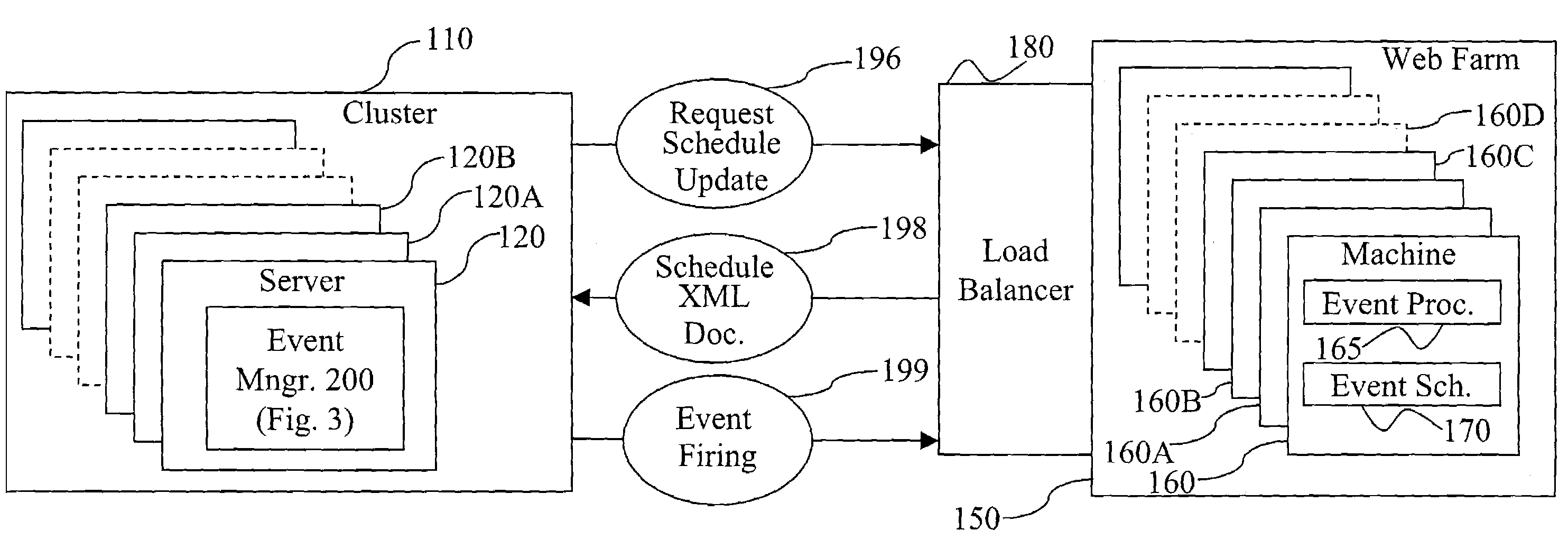
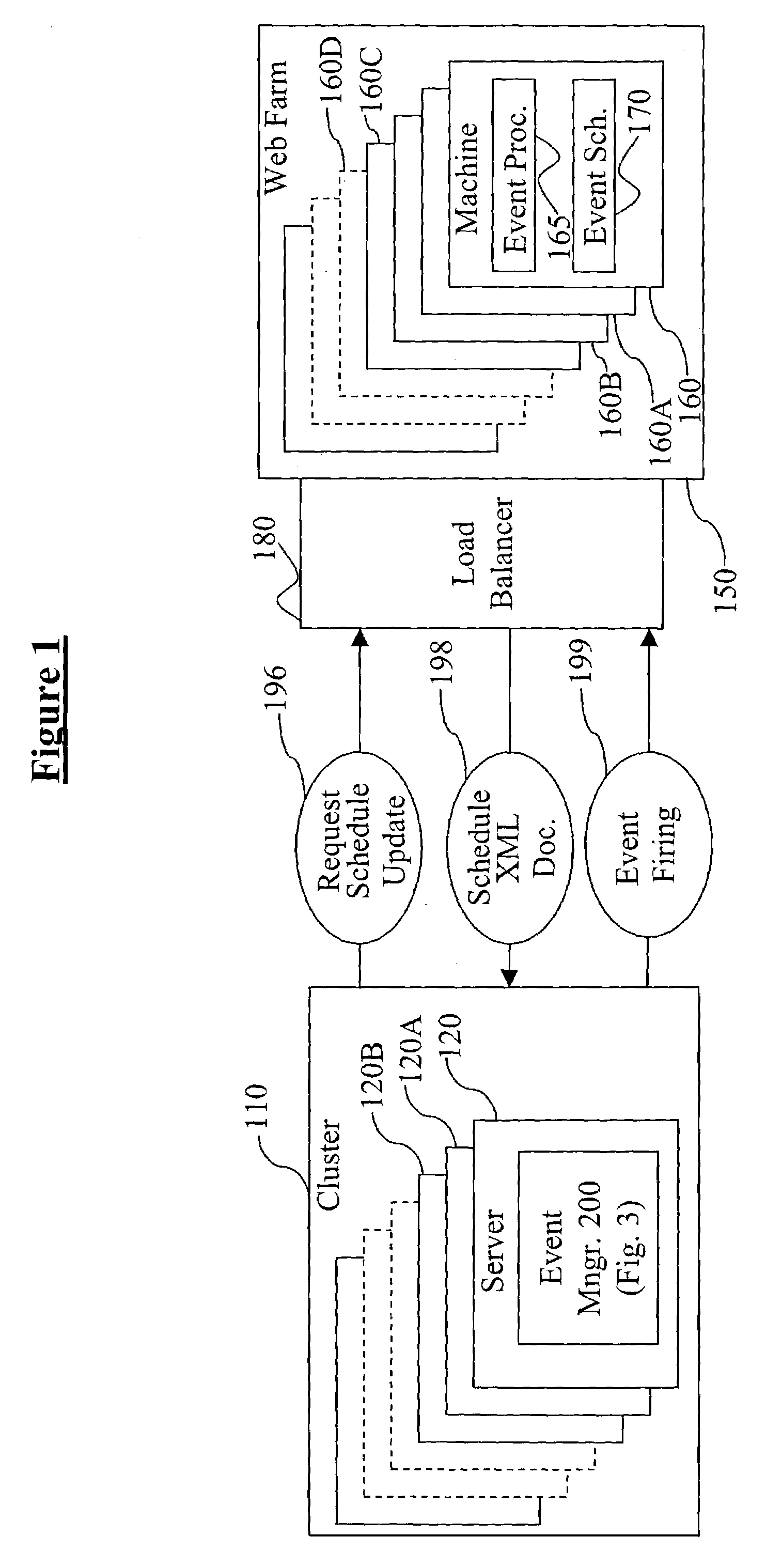
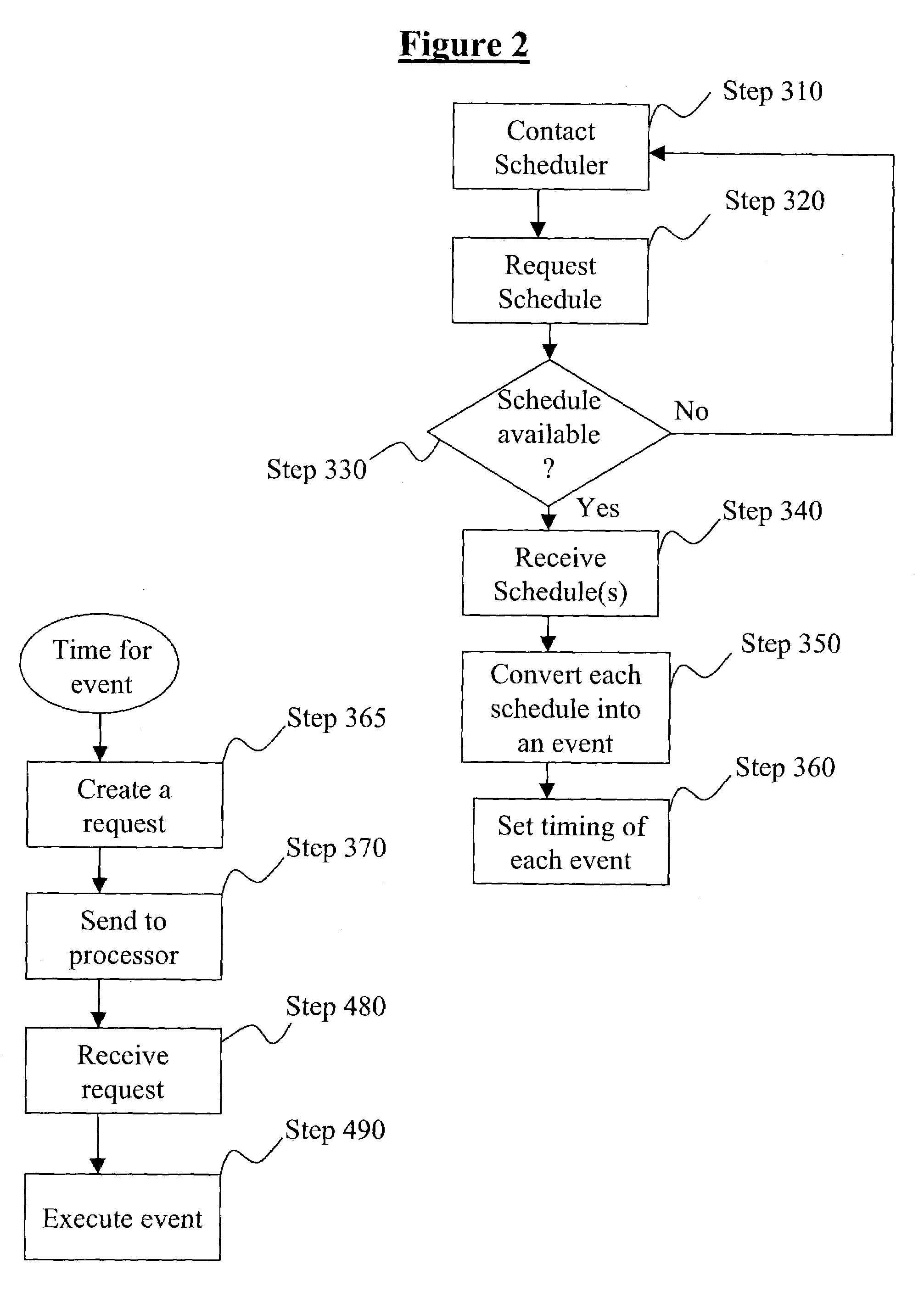
Method and apparatus and program for scheduling and executing events in real time over a network
ActiveUS7376733B2Multiprogramming arrangementsMultiple digital computer combinationsEvent triggerEvent scheduling
The present invention relates to a method, system, computer program product, or apparatus that schedules and executes events within a network in real-time. An event processor contacts one or more event schedulers, and it receives back from them event schedule updates. It then calculates the time when each event is to occur from information contained in the received scheduling information for each event. Next, it places event scheduling information contained in the received scheduling information for each event, plus the calculated occurrence time of the corresponding event, into an event queue. Finally, at the time when each event is to occur, as indicated by examination of the calculated times in the event queue, the event processor sends out event firing messages to event processors that are named in the received scheduling information for each event.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
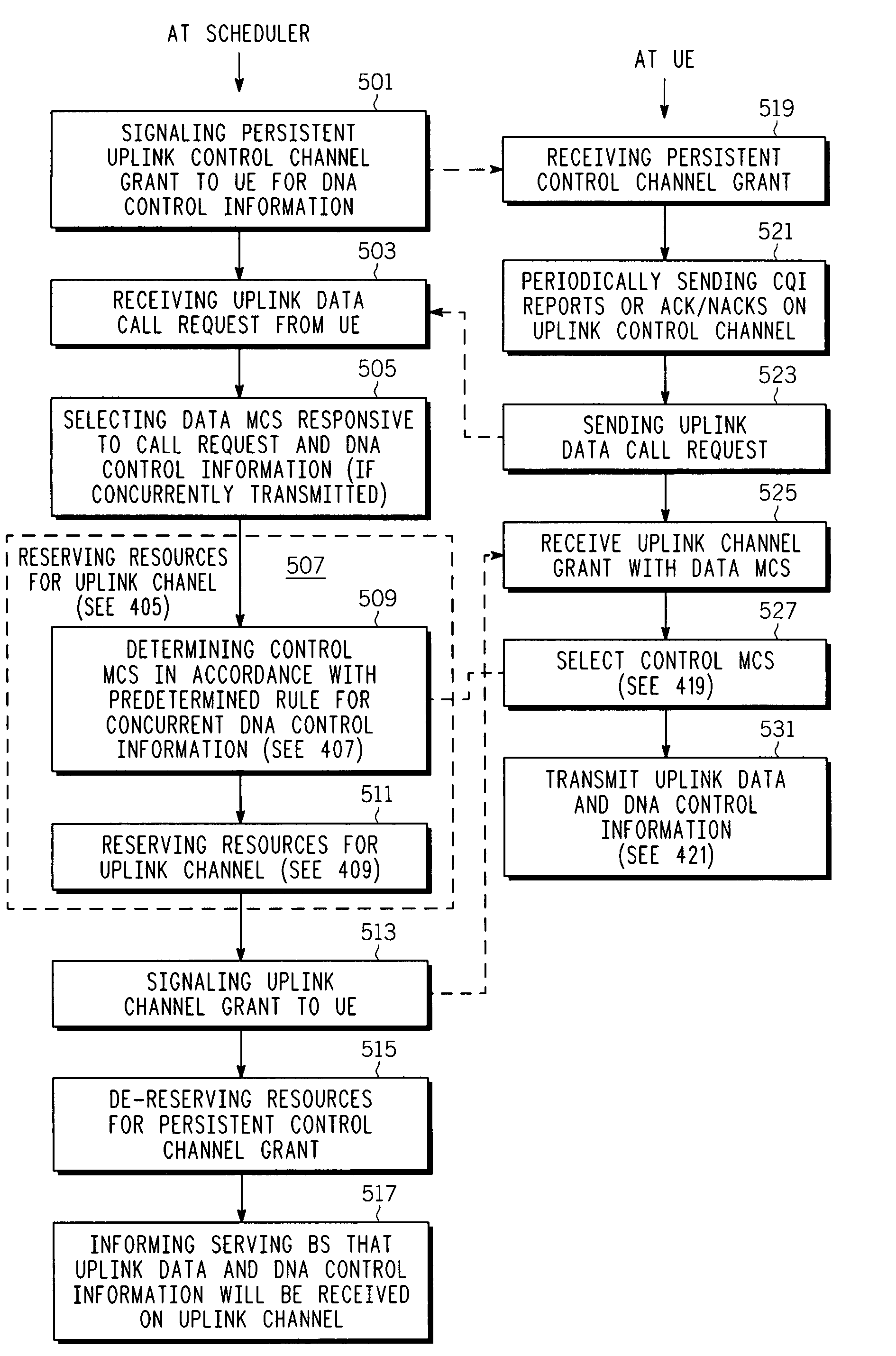
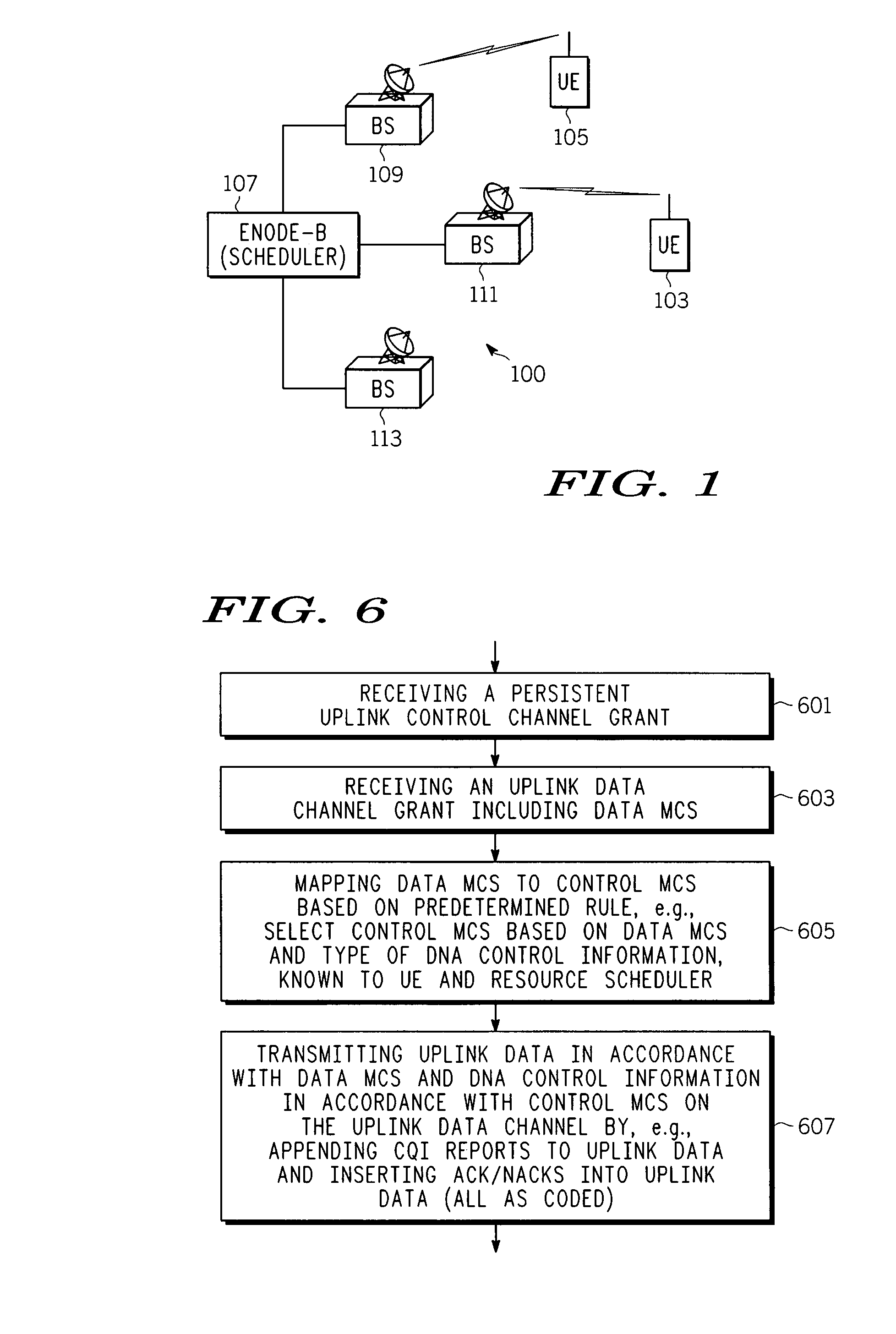
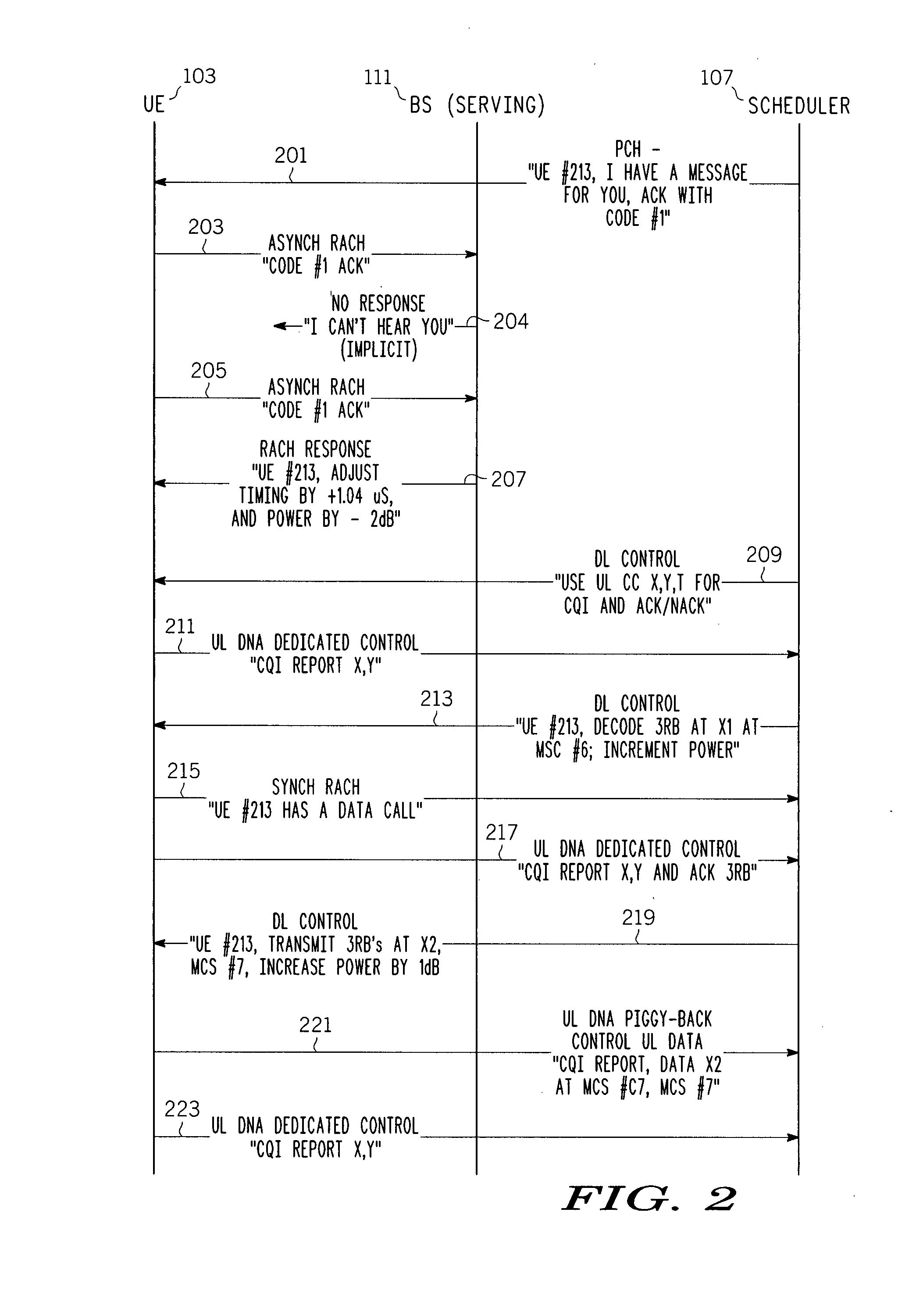
Uplink control channel allocation
ActiveUS20080233964A1Network traffic/resource managementSignal allocationCommunications systemControl channel
Various methods of allocating uplink control channels in a communication system are implemented at a resource scheduler or a user equipment (UE). In one method the scheduler reserves resources for a downlink data channel and signals a corresponding downlink data channel grant and also reserves resources for a persistent uplink control channel for a longer duration than the data channel grant. Signaling overhead associated with a grant for this persistent uplink control channel is reduced over a full dynamic grant. A predetermined rule can be used at the scheduler and at the UE to avoid overhead signaling associated with a grant for this persistent control channel. Predetermined rules at the UE and scheduler can also be used to reserve appropriate resources and select appropriate MCS levels for control information and the control information and uplink data can be transported over a common uplink channel when a time overlap occurs between an uplink data channel and the persistent control channel.
Owner:APPLE INC
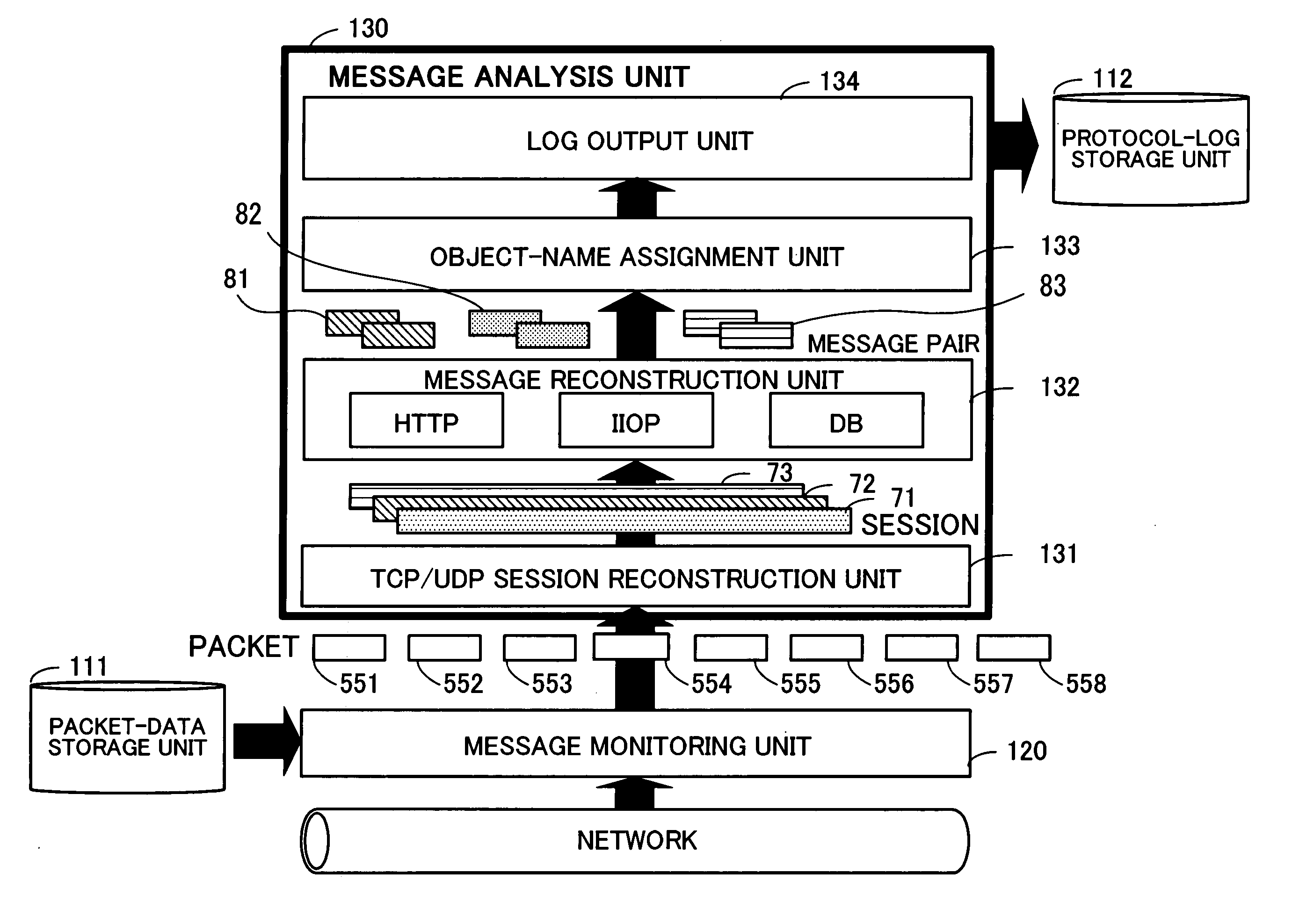
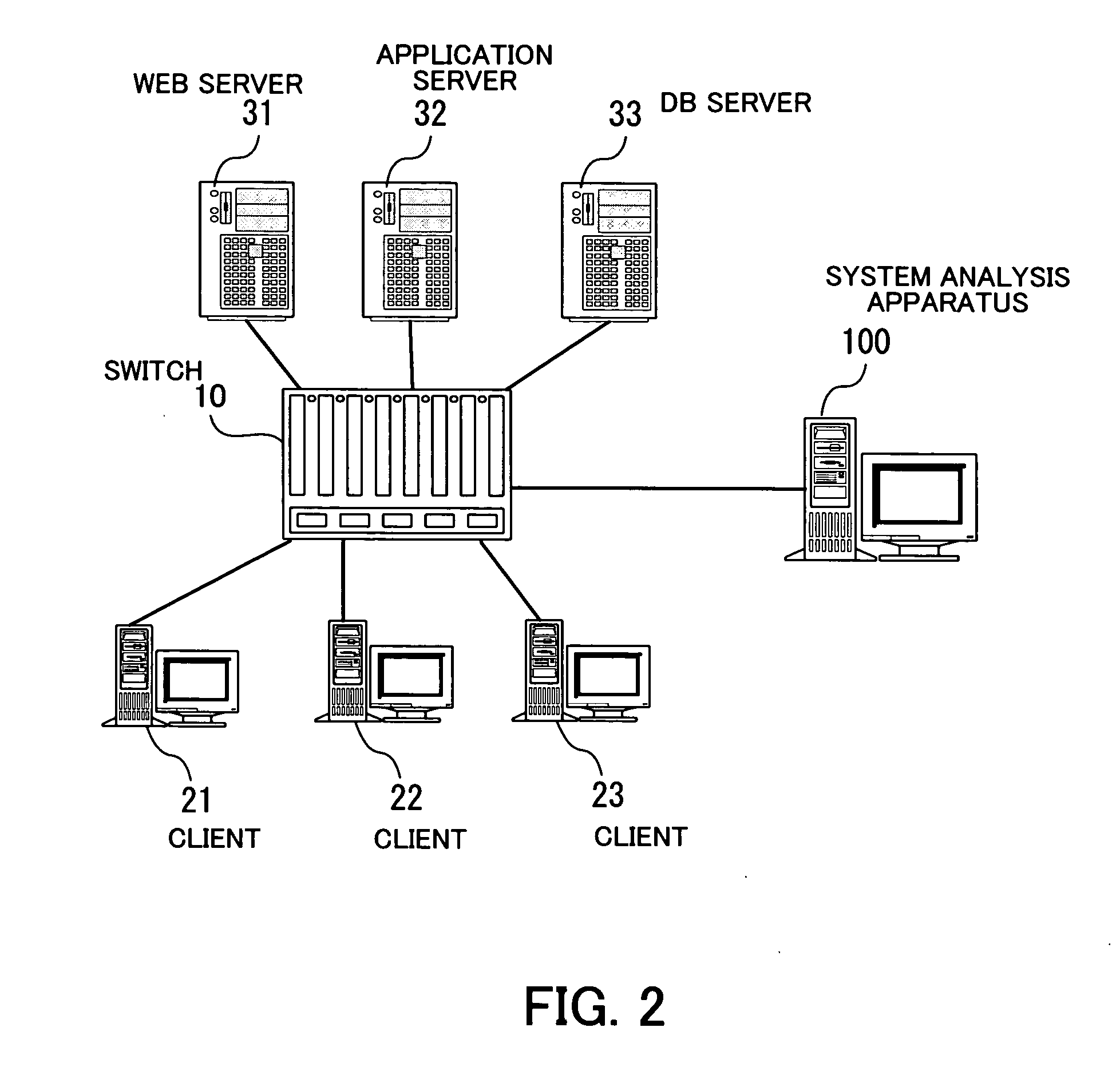
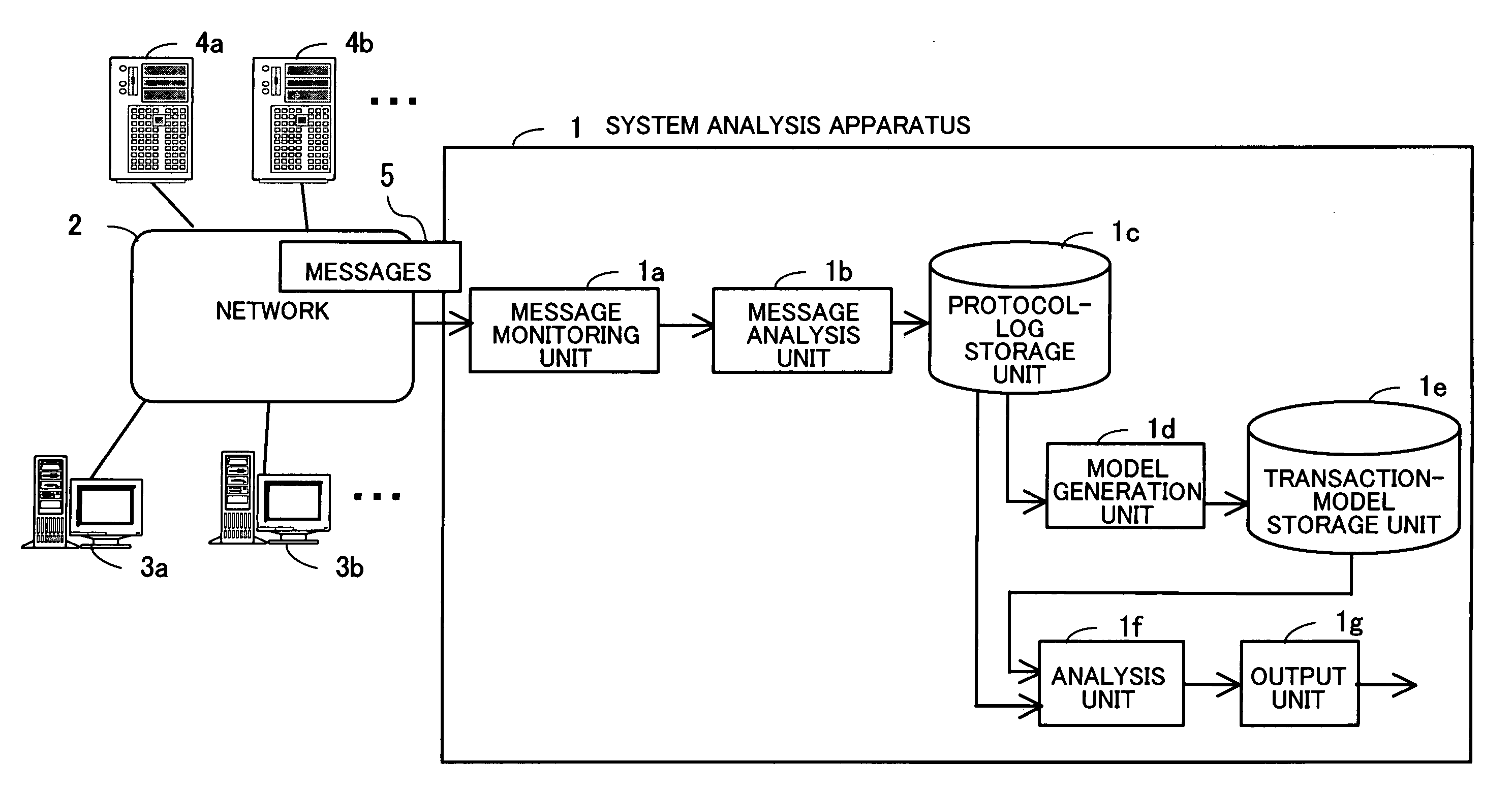
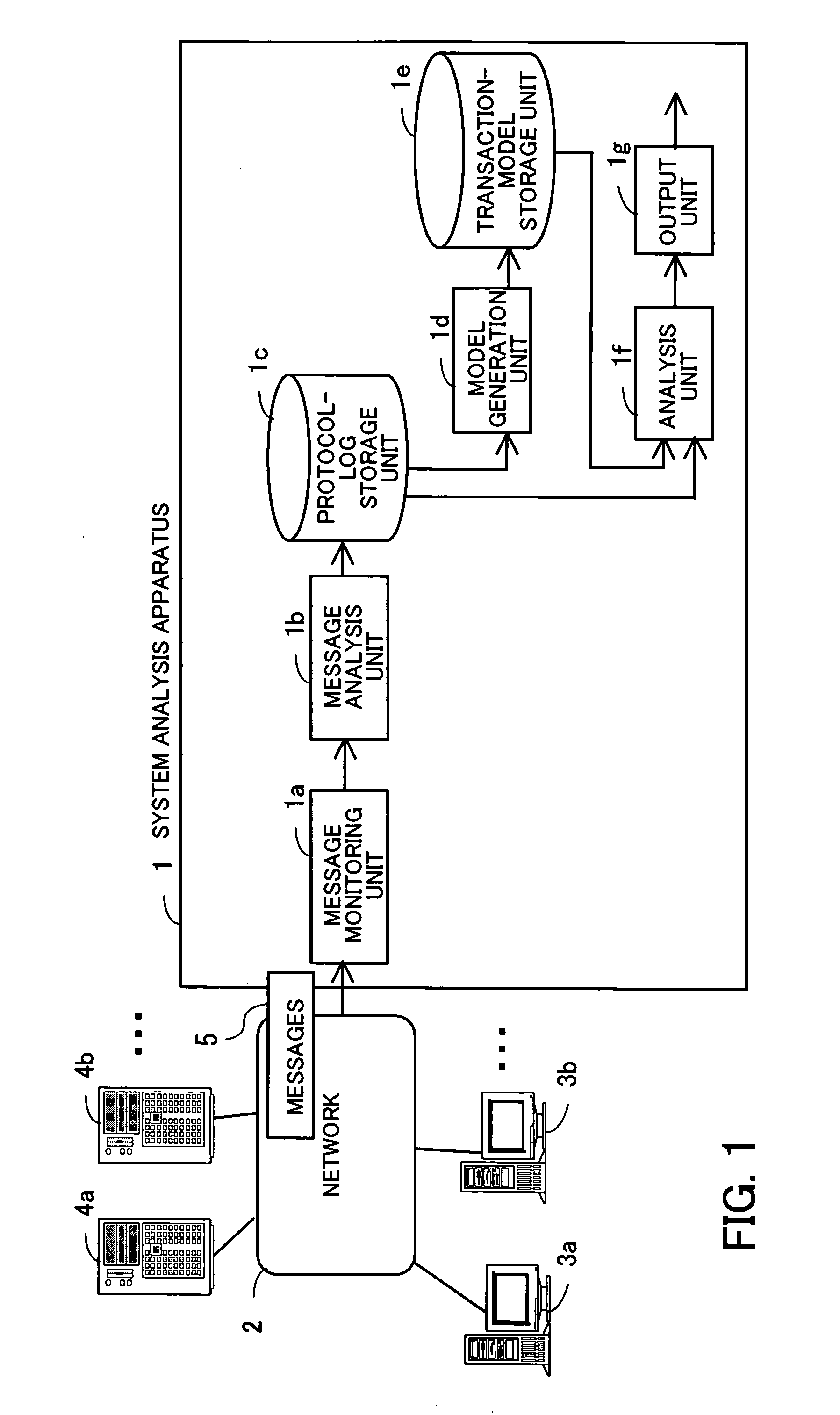
System analysis program, system analysis method, and system analysis apparatus
InactiveUS20050289231A1Accurate analysisDigital data processing detailsHardware monitoringSystems analysisTransaction model
A system analysis program which can accurately analyze the operational status of a system without modifying functions of the system for providing services. A message analysis unit analyzes the contents of collected messages, and determines the times of occurrence of the messages, the process types requested by the messages, and whether or not each of the messages is a request message or a response message. In response to an instruction for model generation, a model generation unit generates a transaction model satisfying at least one limiting condition related to caller-called relationships between processes, based on a set of messages selected in accordance with a selection criterion based on the certainty of existence of caller-called relationships. Then, in response to an instruction for analysis, an analysis unit analyzes the processing status of a transaction based on a protocol log conforming to the transaction model.
Owner:FUJITSU LTD
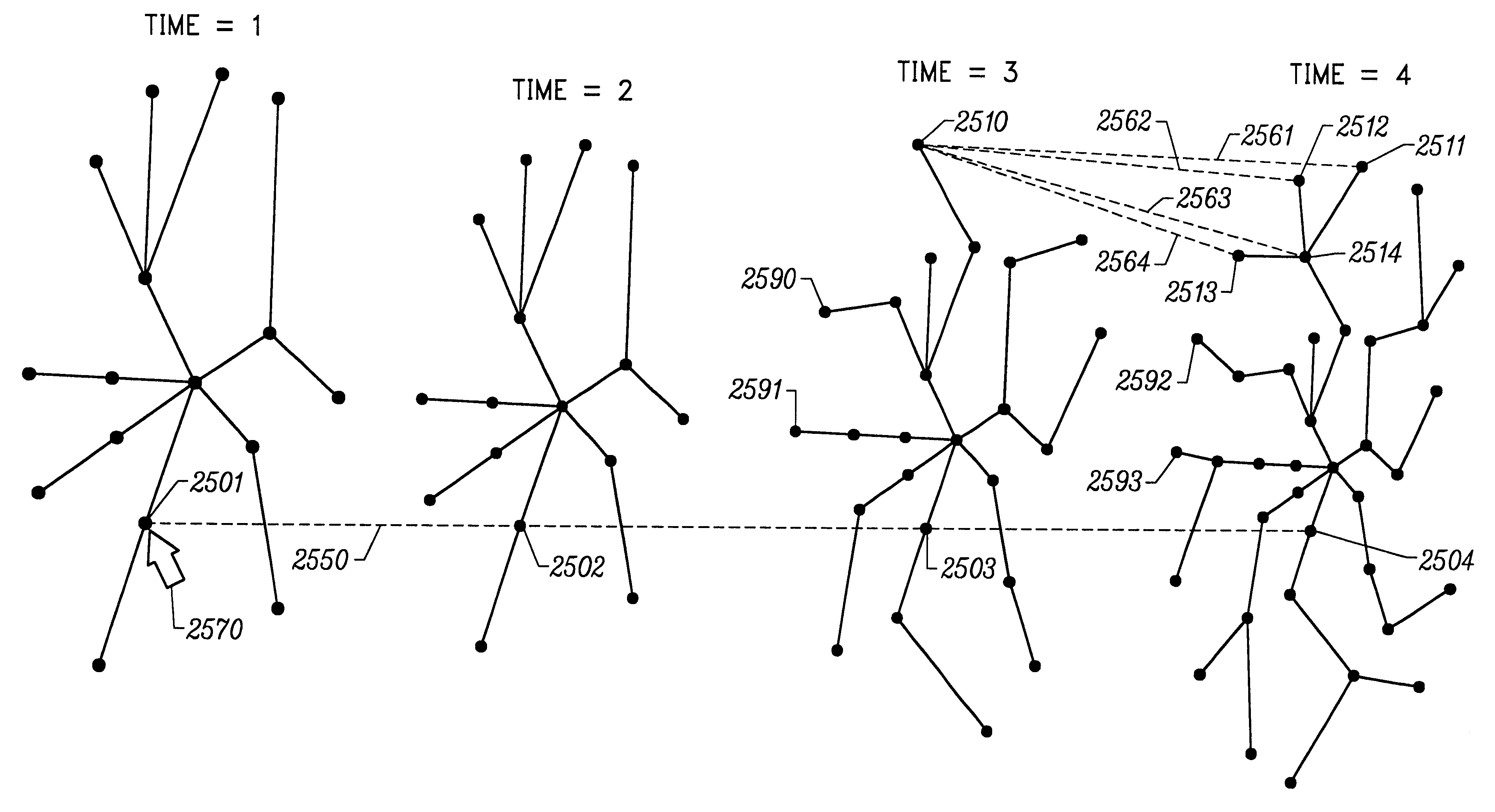
Methods for visualizing transformations among related series of graphs
A method for displaying in a coherent manner the changes over time of a web site's structure, usage, and content is disclosed. Time tubes are generated by a method of displaying a related series of graphs. Time tubes illustrate changes in a graph that undergoes one or more transformations from one state to another. The transformations are displayed using the length of the cylindrical tube, filling the length of the time tube with planar slices which represent the data at various stages of the transformations. Time tubes may encode several dimensions of the transformations simultaneously by altering the representation of size, color, and layout among the planar slices. Temporal transformations occur when web pages are added or deleted over time. Value-based transformations include node colors, which may be used to encode a specific page's usage parameter. Spatial transformations include the scaling of physical dimension as graphs expand or contract in size. The states of a graph at various times are represented as a series of related graphs. In a preferred embodiment, an inventory of all existing nodes is performed so as to generate a list of all nodes that have existed at any time. This inventory is used to produce a layout template in which each unique node is assigned a unique layout position. To produce each planar slice, the specific nodes which exist in the slice are placed at their respective positions assigned in the layout template. In another aspect, corresponding nodes in planar slices are linked, such as with translucent streamlines, in response to a user selecting a node in a planar slice by placing his cursor over the selected node, or to show clustering of two or more nodes in one planar slice into a single node in an adjacent planar slice.
Owner:GOOGLE LLC
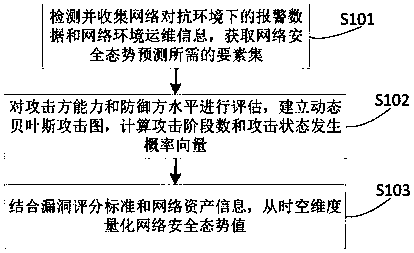
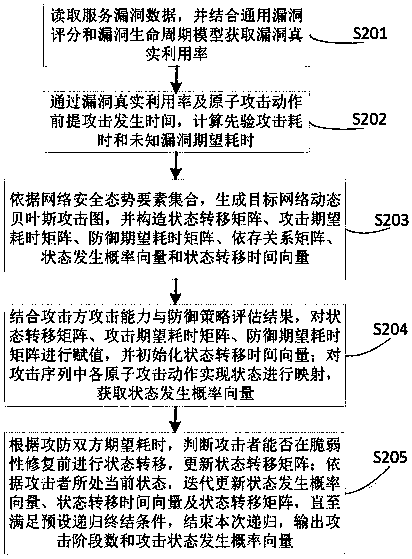
Attack-oriented network security situation prediction method, device and system
ActiveCN108494810ARealize dynamic associationIn line with the actual environmentData switching networksSecuring communicationCountermeasureAttack graph
The invention belongs to the technical field of network security and particularly relates to an attack-oriented network security situation prediction method, device and system. The method comprises the following steps: detecting and collecting alarm data and network environment operation and maintenance information in a network countermeasure environment, obtaining an element set required by network security situation prediction, wherein the element set comprises three types of information of an attacker, a defense party and a network environment; evaluating the attacker capability and the level of the defense party, establishing a dynamic Bayesian attack graph, and calculating an attack phase number and an attack state occurrence probability vector; and combining a vulnerability scoring standard and network asset information, and performing time-space dimension quantification on the network security situation value. According to the method, dynamic association of the situation elements of the defense party, the attacker, the environment information and the like is achieved, the actual environment of the network is better conformed to, the future situation and the attack occurrencetime can be accurately predicted, higher prediction efficiency is achieved, and storage scale and timeliness of network security situation awareness are optimized, so as to provide more effective guidance for network protection.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
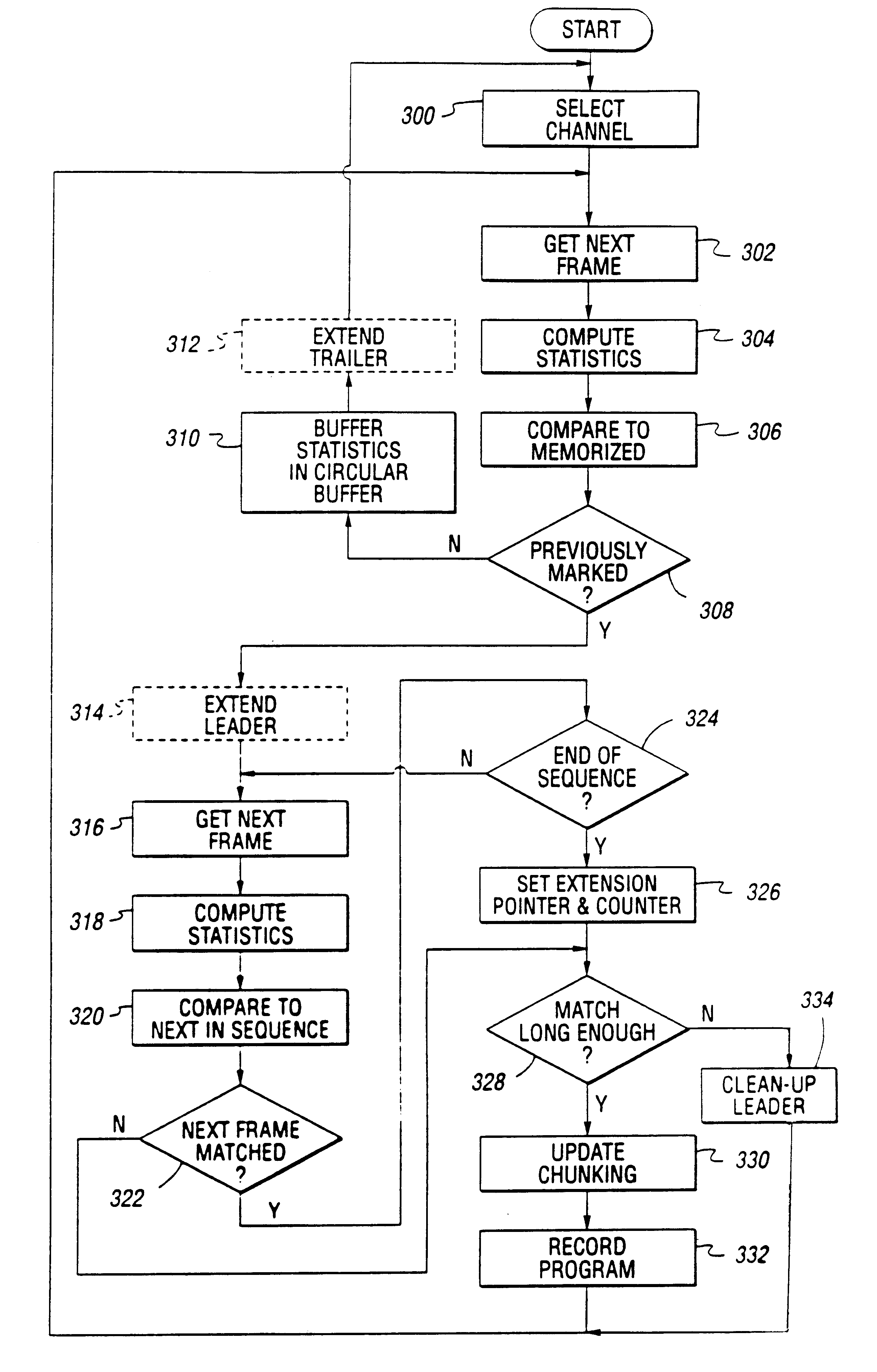
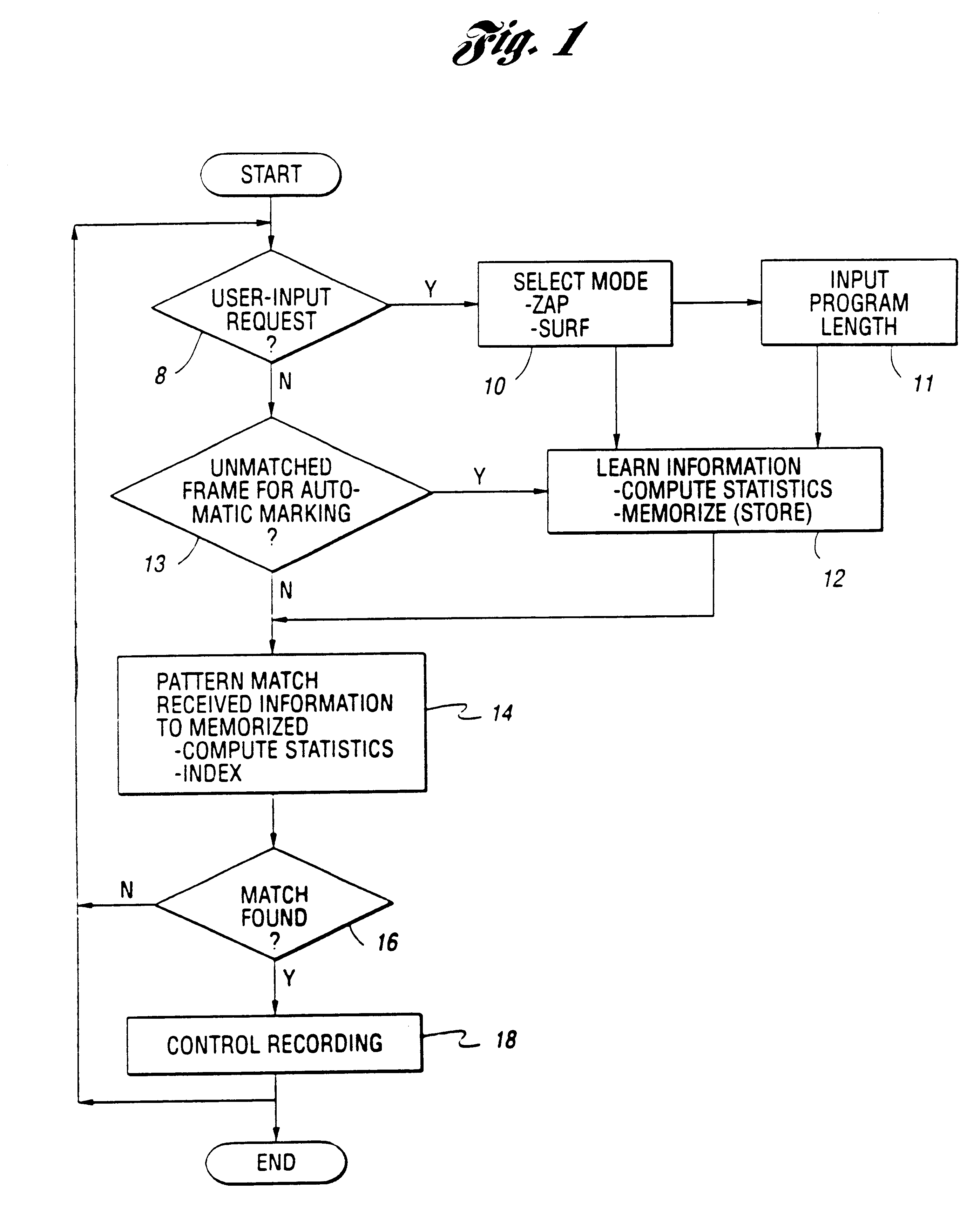
System and method for selective recording of information
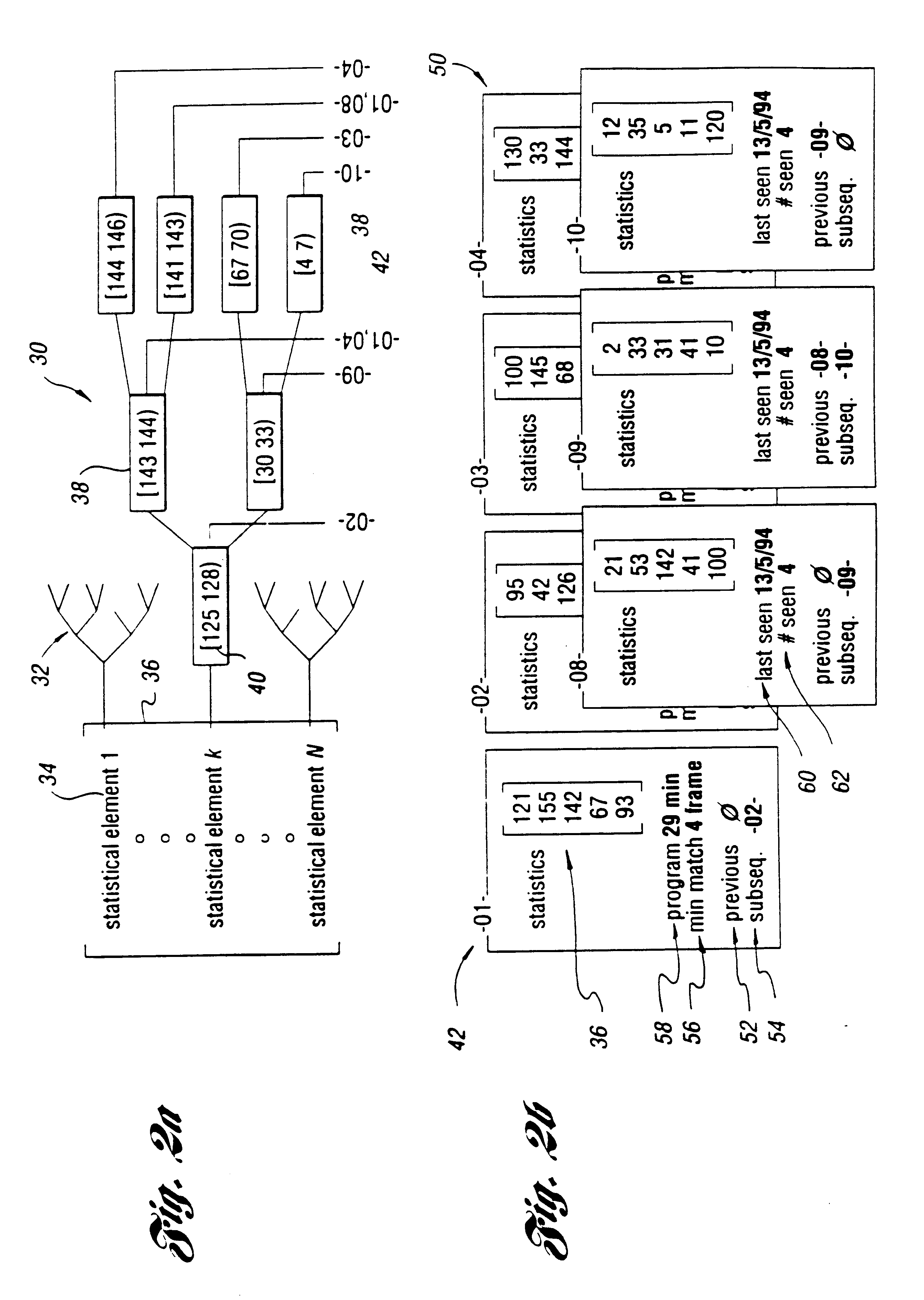
InactiveUS6782186B1Reduce and eliminate possibilityEasy to appreciateTelevision system detailsFilamentary/web carriers operation controlPattern matchingOperation mode
A system and method for selective recording of information uses sequential pattern matching of statistical vectors which characterize incoming time-based information to identify previously marked information within an incoming information stream. The system and method generate a signal to control a recording device to either elide the previously marked information from the recording, or to begin recording once the previously marked information is identified, depending upon the current mode of operation. The system and method may be utilized to omit recording of unwanted information, such as commercials in a television broadcast, or to automatically locate desired information on any of a number of available information channels without a priori knowledge of the occurrence time or channel of the information.
Owner:INTERVAL RESEARCH CORPORATION
Method for prompting outstanding event in screen lock state, electronic device thereof, and storage medium thereof
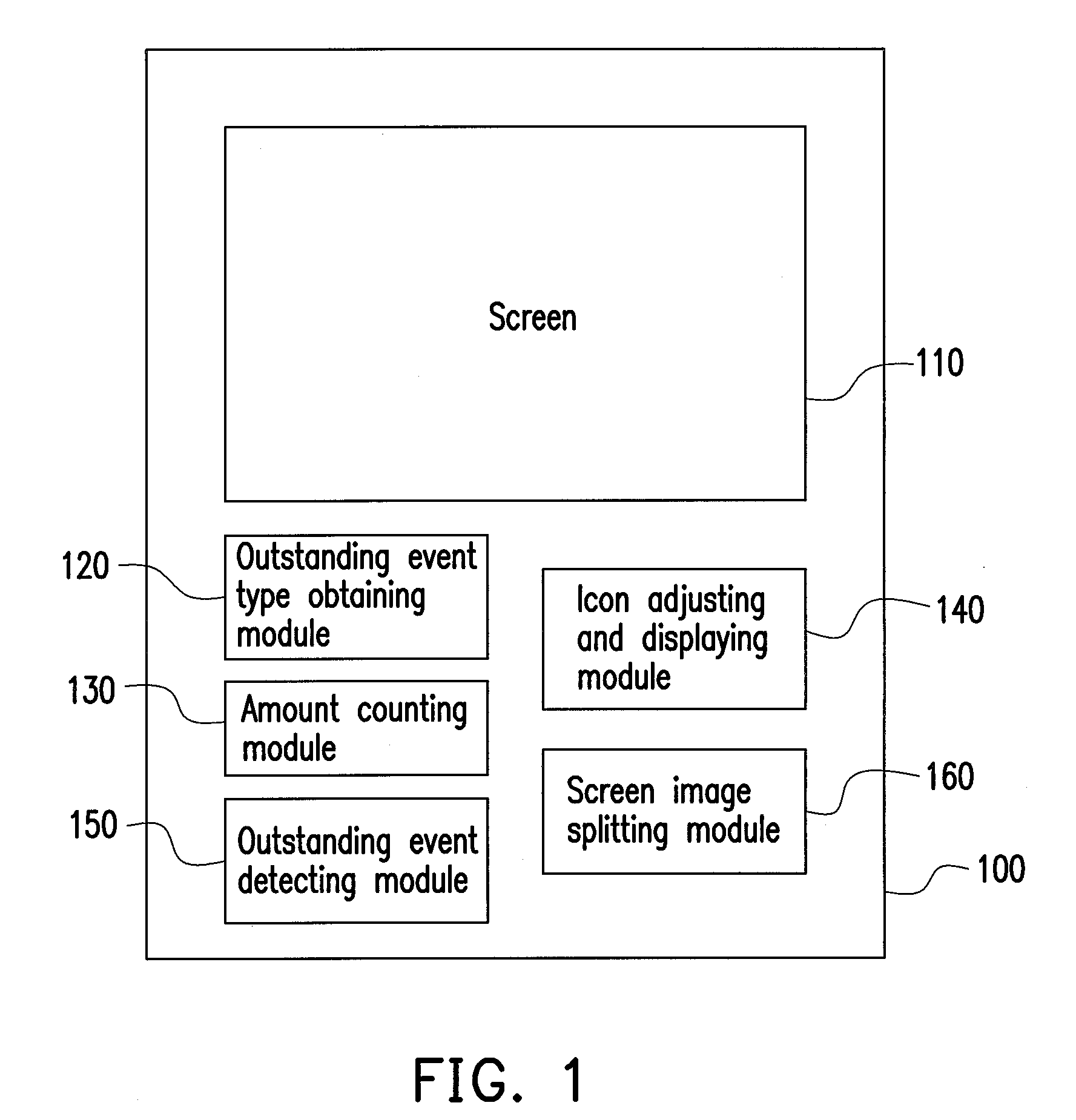
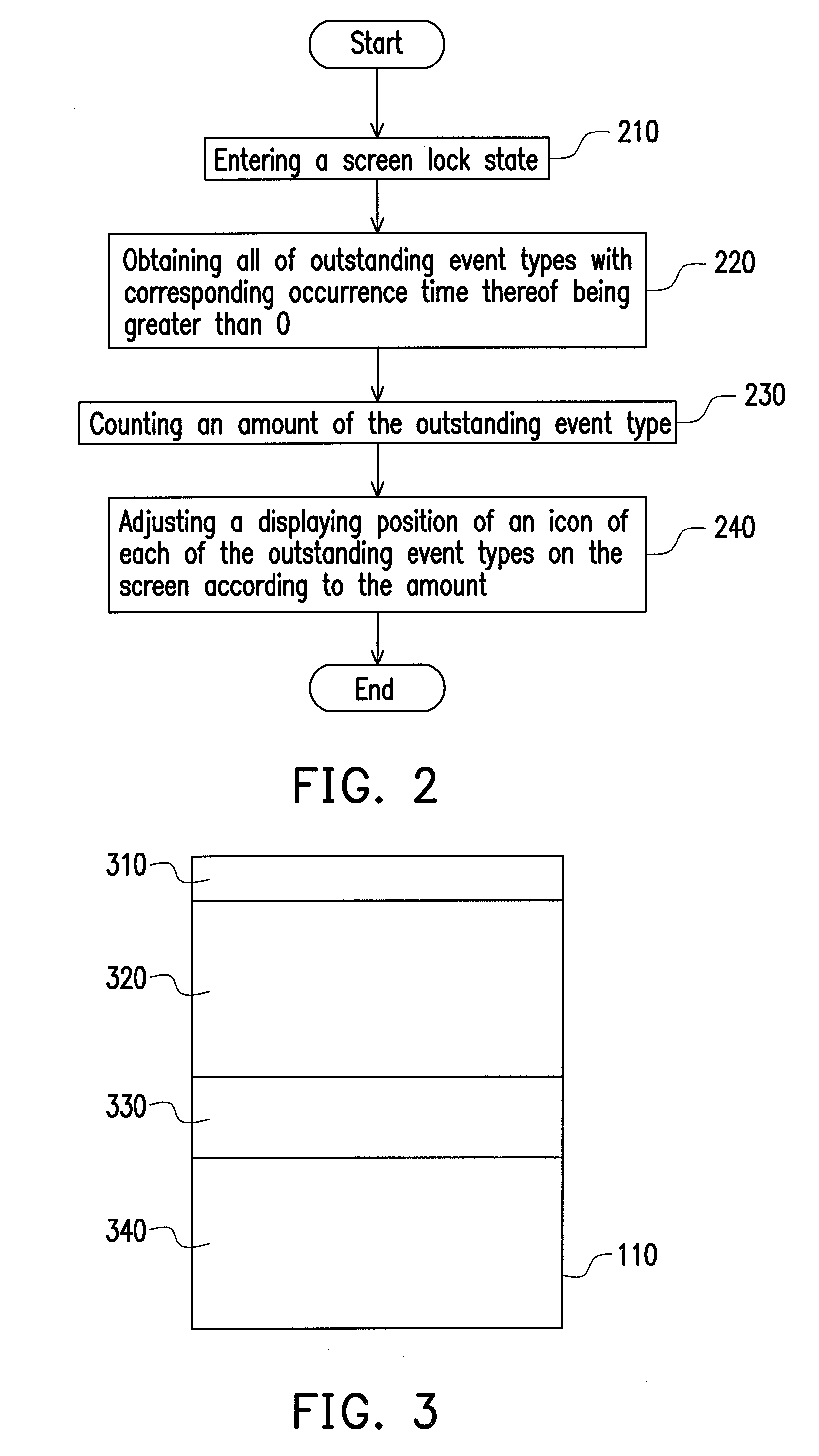
ActiveUS20090265666A1Easy to checkInput/output for user-computer interactionCathode-ray tube indicatorsEvent typePresent method
A method for prompting an outstanding event in screen lock state, an electronic device thereof, and a storage medium thereof are provided. In the present method, at least one outstanding event type is obtained first, wherein a corresponding occurrence time of each outstanding event type is greater than 0. Next, an amount of the outstanding event type is counted. Finally, a displaying position of an icon of each outstanding event type on a screen of the electronic device is adjusted according to the amount of the outstanding event types. As a result, a user can get the outstanding event type and the occurrence time thereof by the information shown on the screen, so as to increase the convenience of using the electronic device.
Owner:HTC CORP
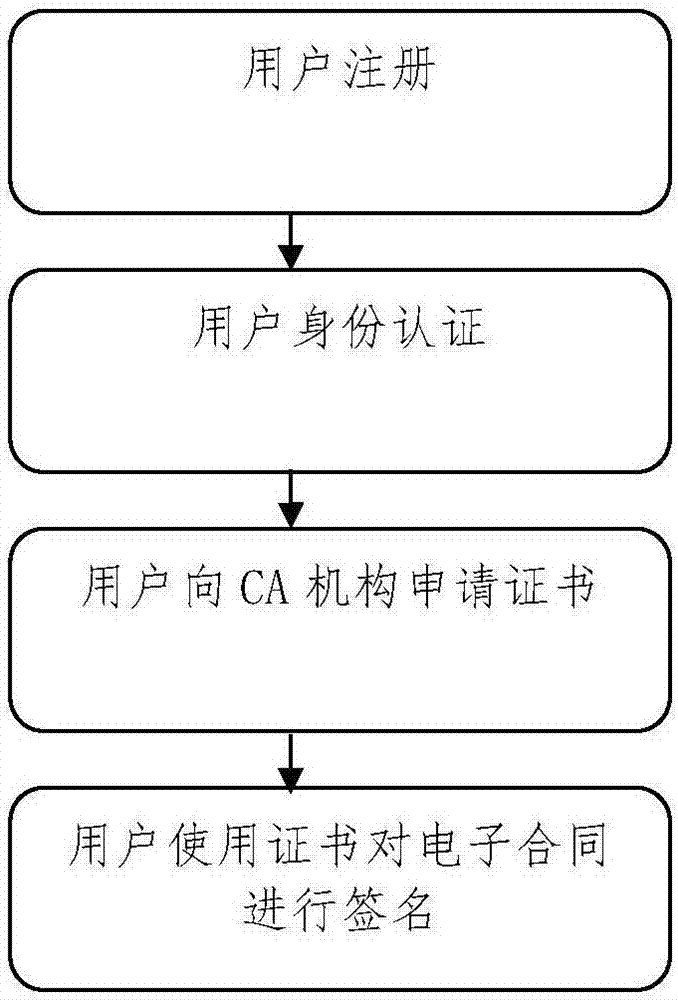
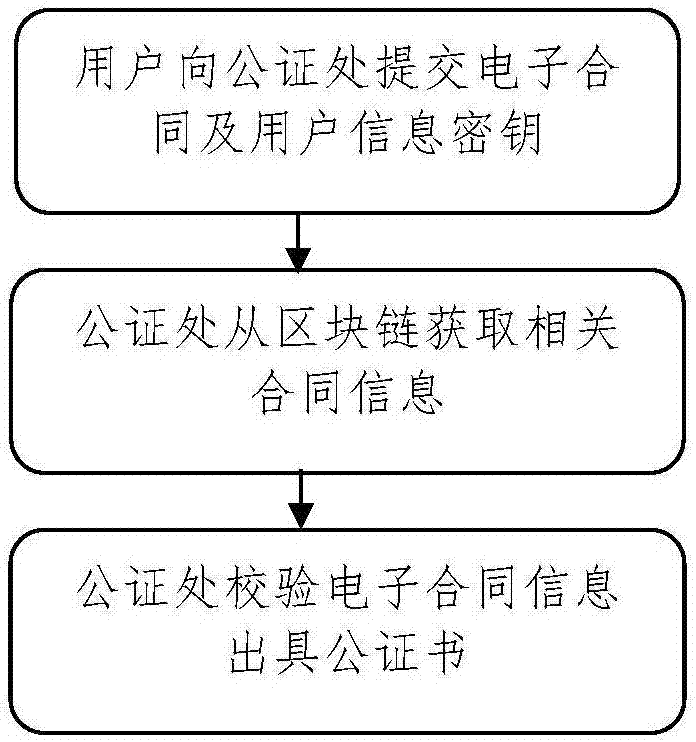
Block chain evidence-based electronic contact system signing method
ActiveCN107403303AEasy to sign forShorten the timePayment protocolsOffice automationElectronic contractsProcess information
The invention discloses a block chain evidence-based electronic contract system signing method. The method comprises the following steps of: creating an electronic contract on an electronic contract platform by a user or uploading an existing electronic contract to the electronic contract platform, and signing the electronic contract by using an event certificate issued by a CA; recording information of each key point in a contract signing process of the user and event occurrence time points to a block chain evidence platform by the electronic contract platform; and extracting the information from a node of a block chain evidence consortium chain by a notary office, decrypting the information by using a secret key of the user, obtaining specific information of contract signing, and notarizing the contract of the user. According to the method, the signing of electronic contracts is more convenient, the time and costs of the users are saved; a block chain evidence system technically ensures that the electronic contracts cannot be tampered; and the process information of contract signing also can be recorded, so that the contract signing behaviors of the users can be restored.
Owner:兴业数字金融服务(上海)股份有限公司
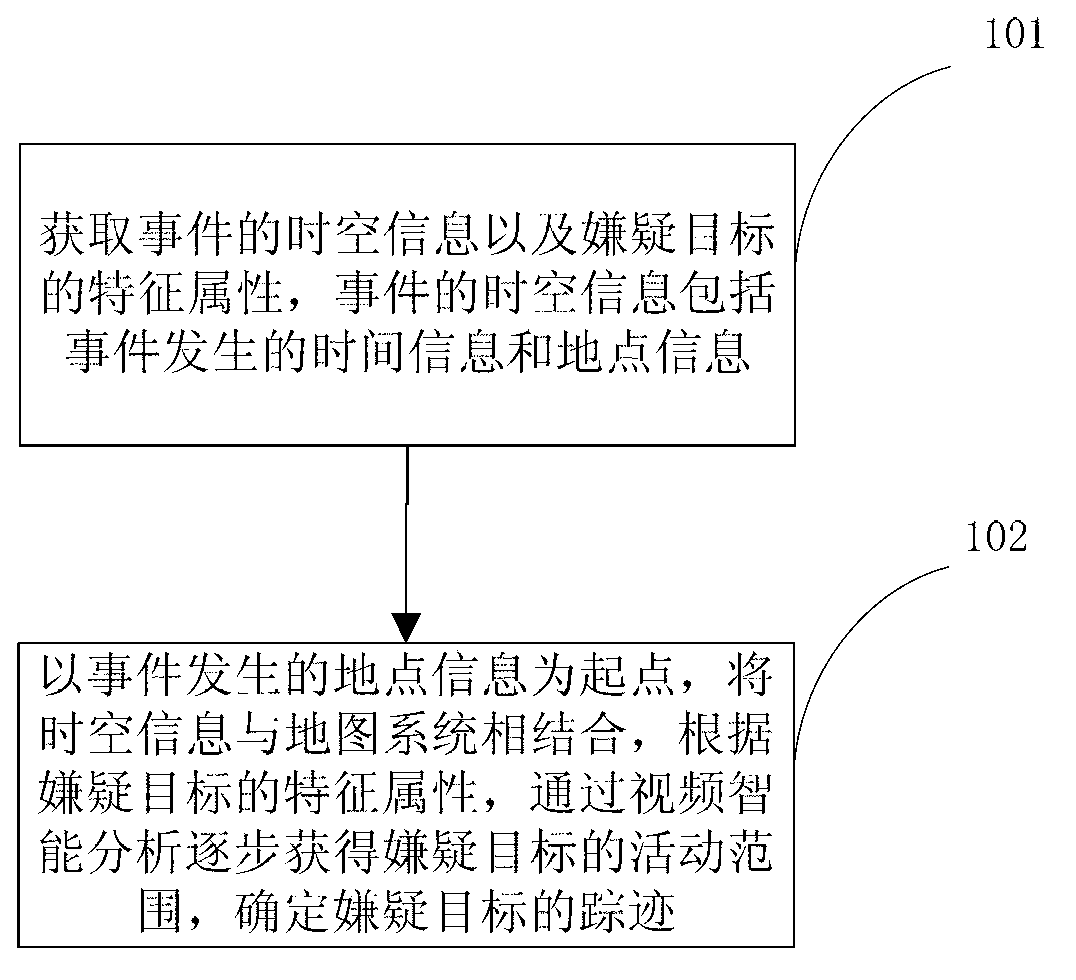
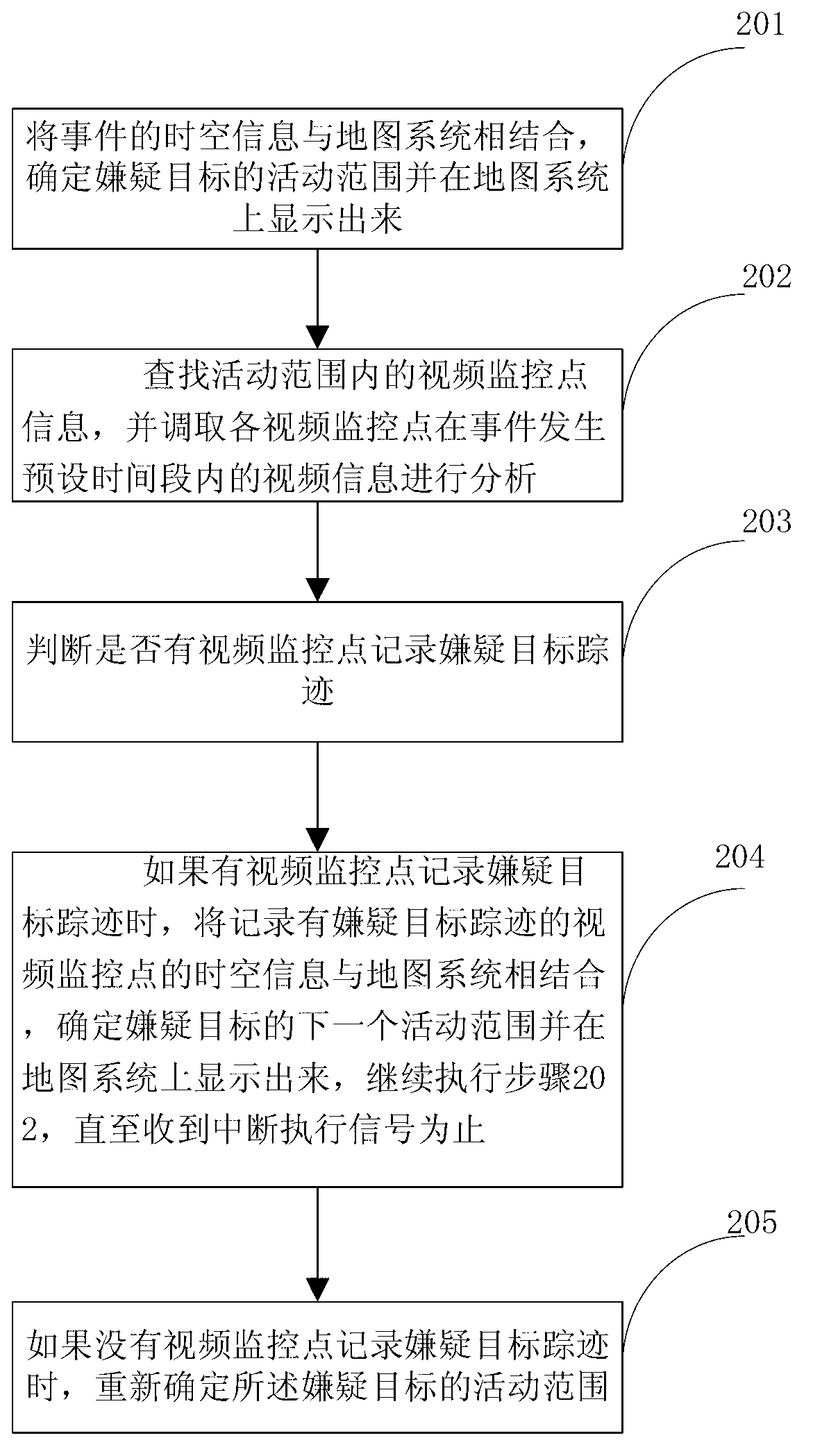
Intelligent tracking method and system for suspected target
ActiveCN102843547AImprove work efficiencyWork lessImage analysisClosed circuit television systemsTime informationData mining
The invention provides an intelligent tracking method and a system for a suspected target. The method comprises the steps of: step A, obtaining space-time information of an event and characteristic attribute of the suspected target, wherein the space-time information of the event comprises occurrence time information and occurrence place information of the event; and step B, combining the space-time information with a map system by using the occurrence place information of the event as a starting point, and obtaining the range of activity of the suspected target step by step through video intelligent analysis according to the characteristic attribute of the suspected target so as to determine the track of the suspected target. The method is not only fast, efficient and accurate, but also saves the labor cost, so that intelligent tracking method and the system represent extremely high intelligentization.
Owner:上海靖昌信息技术工程有限公司
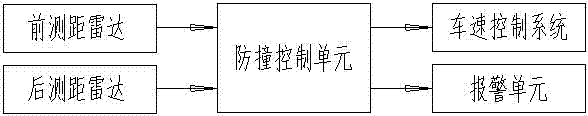
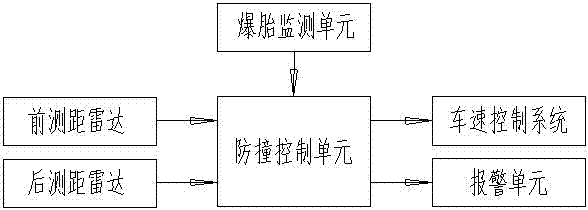
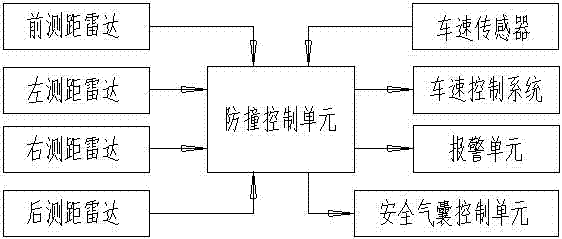
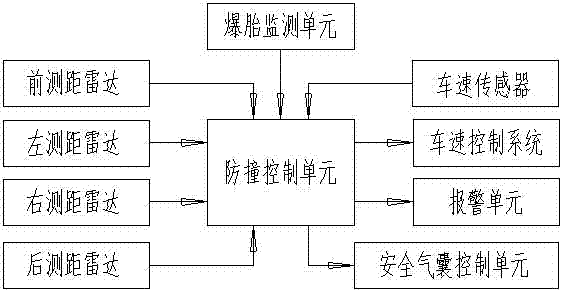
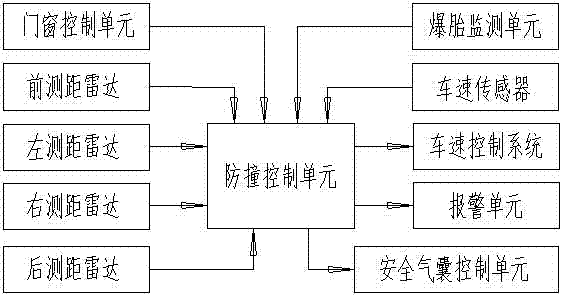
Automobile longitudinal collision mitigating system and control method
ActiveCN102463951AImprove the anti-collision effectPedestrian/occupant safety arrangementAutomatic initiationsSpeed control systemControl system
The invention discloses an automobile longitudinal collision mitigating system and a control method, which are used for avoiding automobile collision or lightening damages caused by the automobile collision to the utmost extent; the automobile longitudinal collision mitigating system comprises a front ranging radar and a rear ranging radar, a collision-prevention control unit, a speed control system and an alarming unit; the collision-prevention control unit is used for calculating relative speed of the automobile in relation with front and rear automobiles according to distance data provided by a radar ranging system, judging whether the collision occurs and the possible occurrence time of collision, sending corresponding instructions to actuating mechanisms according to preset programs, and controlling acceleration or deceleration braking of the automobile, so that the automobile collision is avoided or the damages resulting from the automobile collision are lightened to the utmost extent.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
Method for automatically analyzing crash cause of computer software system
InactiveCN101719090ASolve the problem of high technical requirementsHardware monitoringSoftware testing/debuggingSoftware systemSoftware engineering
The invention relates to a method for automatically analyzing the crash cause of a computer software system. The method for automatically analyzing the crash cause of the computer software system comprises the following steps of: a. opening a crash dump file; b. respectively searching stack information of each thread of each processor, searching a user-mode abnormal error triggering function for a user-mode crash dump file, and searching a kernel-mode abnormal error triggering function for a kernel-mode crash dump file; c. checking a previous calling function at the abnormal error occurrence time according to the searched abnormal error triggering functions, temporarily setting the calling function to be a crash function if the calling function is an effective function name, and temporarily setting a module attached to the calling function to be a crash module; and d. acquiring crash information according to the acquired crash function and the acquired crash module, and storing the crash information into a database. The invention has the advantage that the automatic analysis to the crash cause of the software system can be realized.
Owner:ZHUHAI JUNTIAN ELECTRONICS TECH
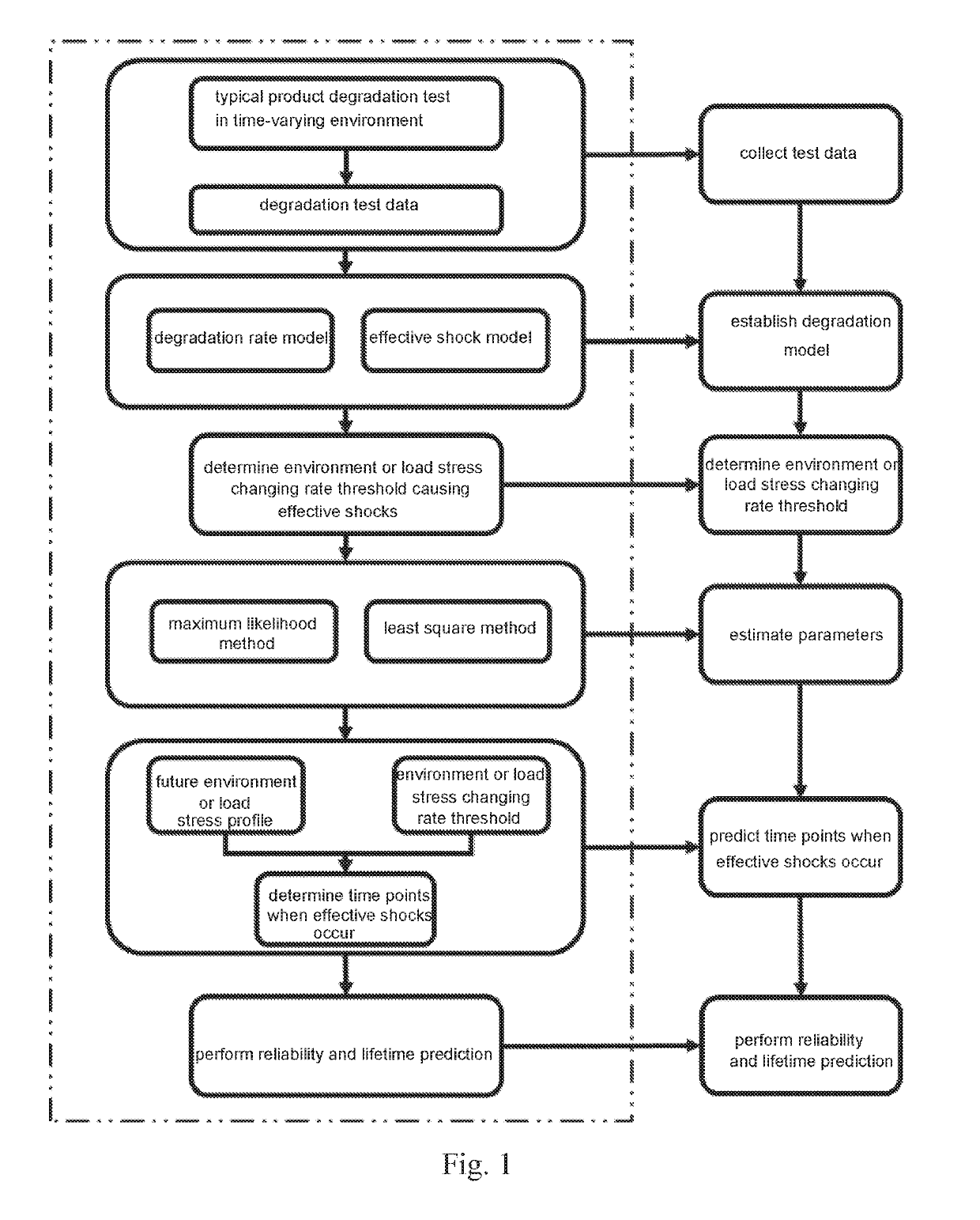
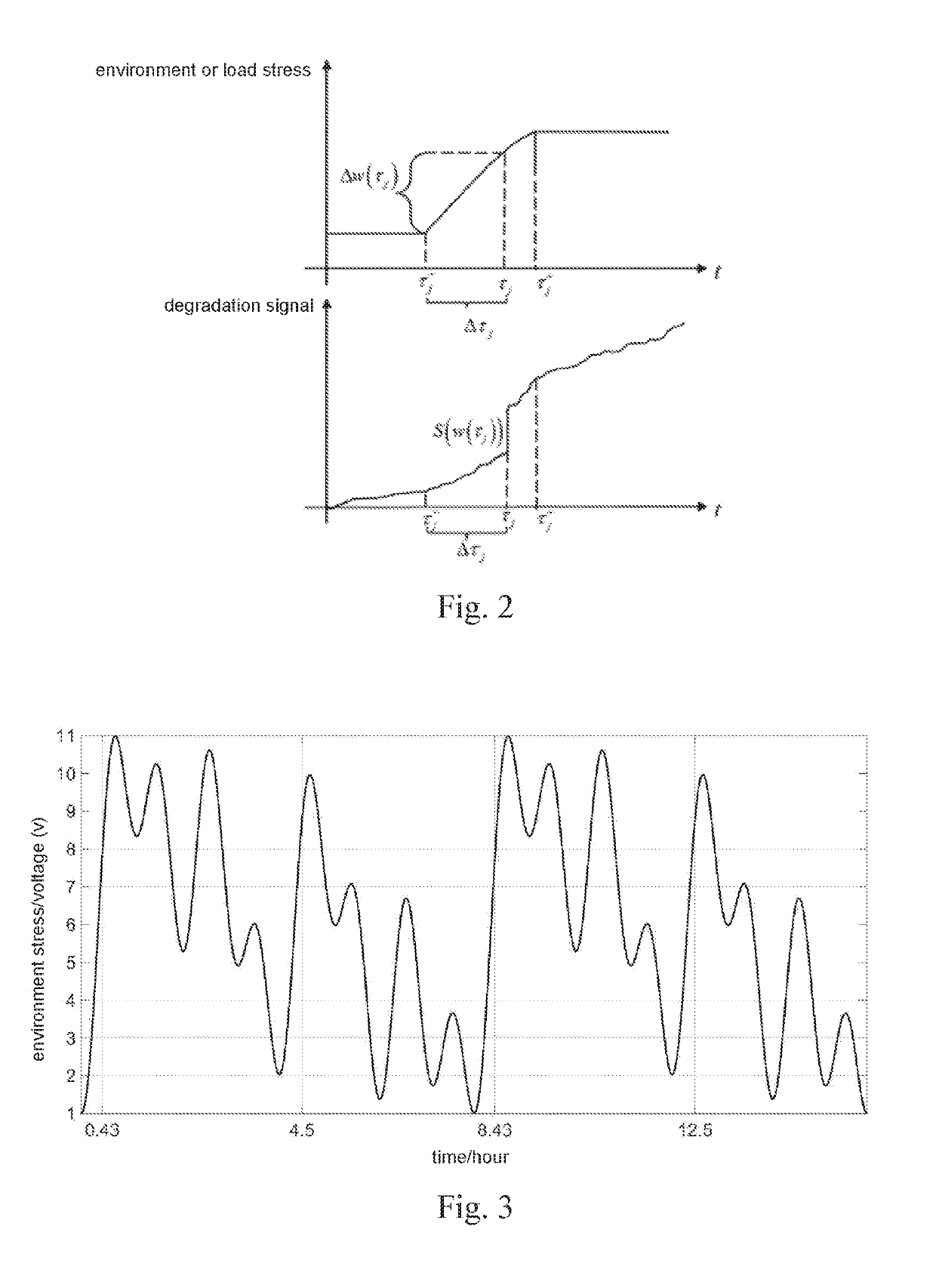
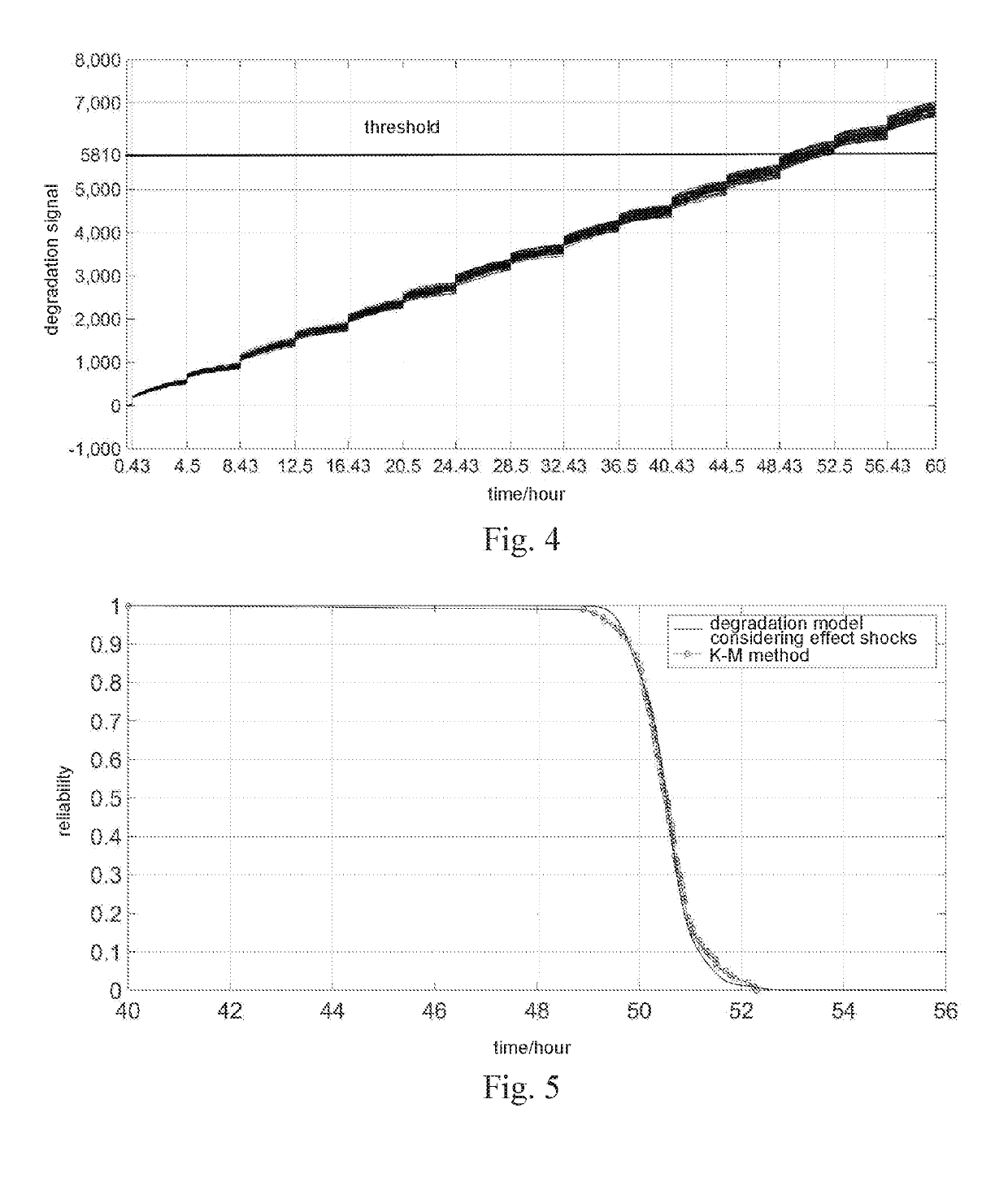
Degradation modeling and lifetime prediction method considering effective shocks
InactiveUS20190138926A1Improve forecast accuracyMethod is numerousDesign optimisation/simulationProbabilistic networksPredictive methodsSimulation
A degradation modeling and lifetime prediction method considering effective shocks includes steps of: first collecting degradation test data, then establishing a performance degradation model, and determining an environment or load changing rate threshold of a product subjected to effective shock based on the test data; estimating parameters in the model, and determining effective shock occurrence times based on the future environmental or load profile, and finally preforming lifetime and reliability prediction. Specific steps are as follows: step 1: collecting degradation test data; step 2: establishing a degradation model; step 3: determining an environment or load changing rate threshold; step 4: estimating the parameters; step 5: predicting the times that effective shocks occur; and step 6: performing reliability prediction. The present invention considers effects of effective shocks caused by sharp environment or load changes on product performance degradation, which makes the prediction method more realistic and improves the prediction accuracy.
Owner:BEIHANG UNIV
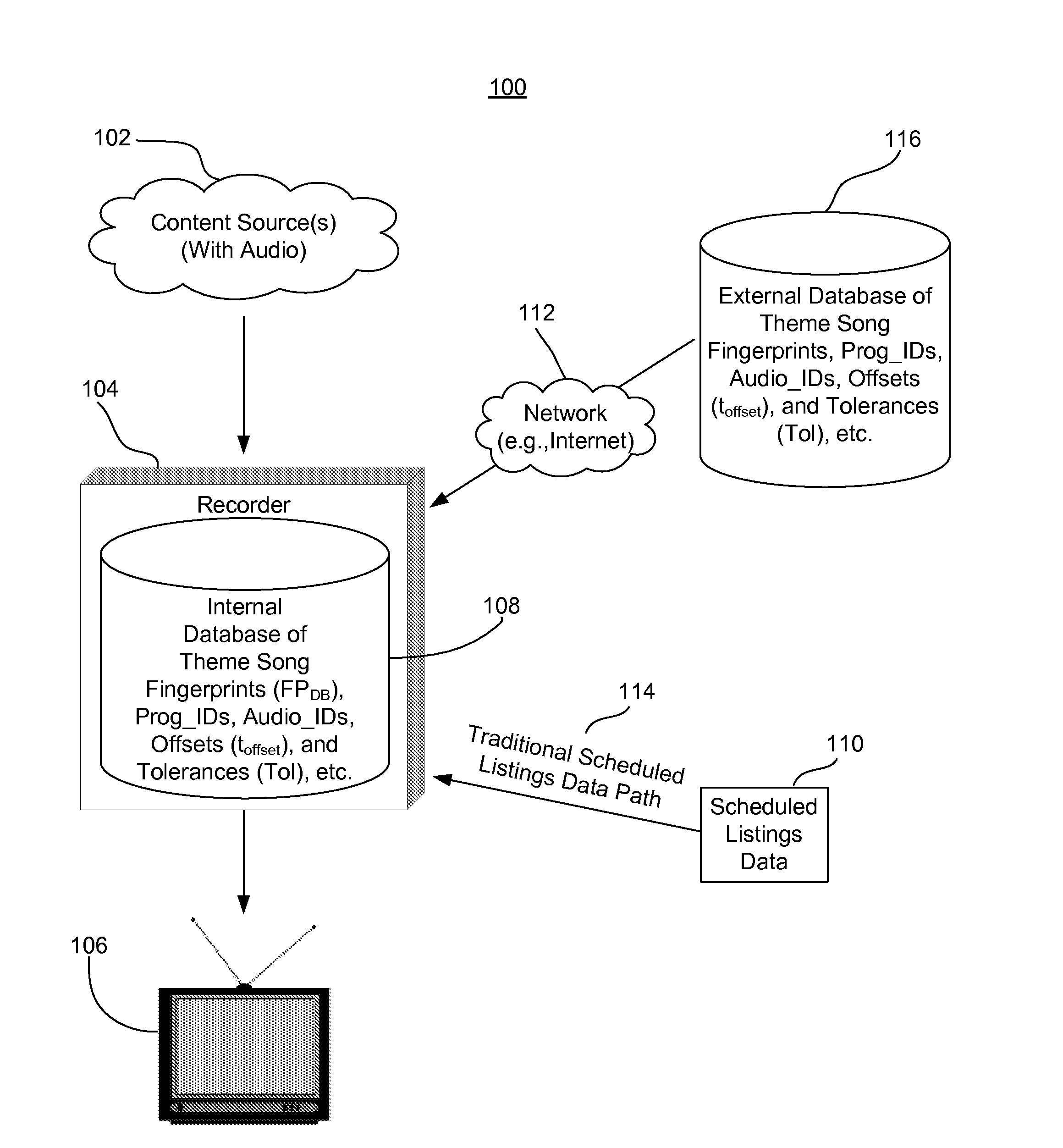
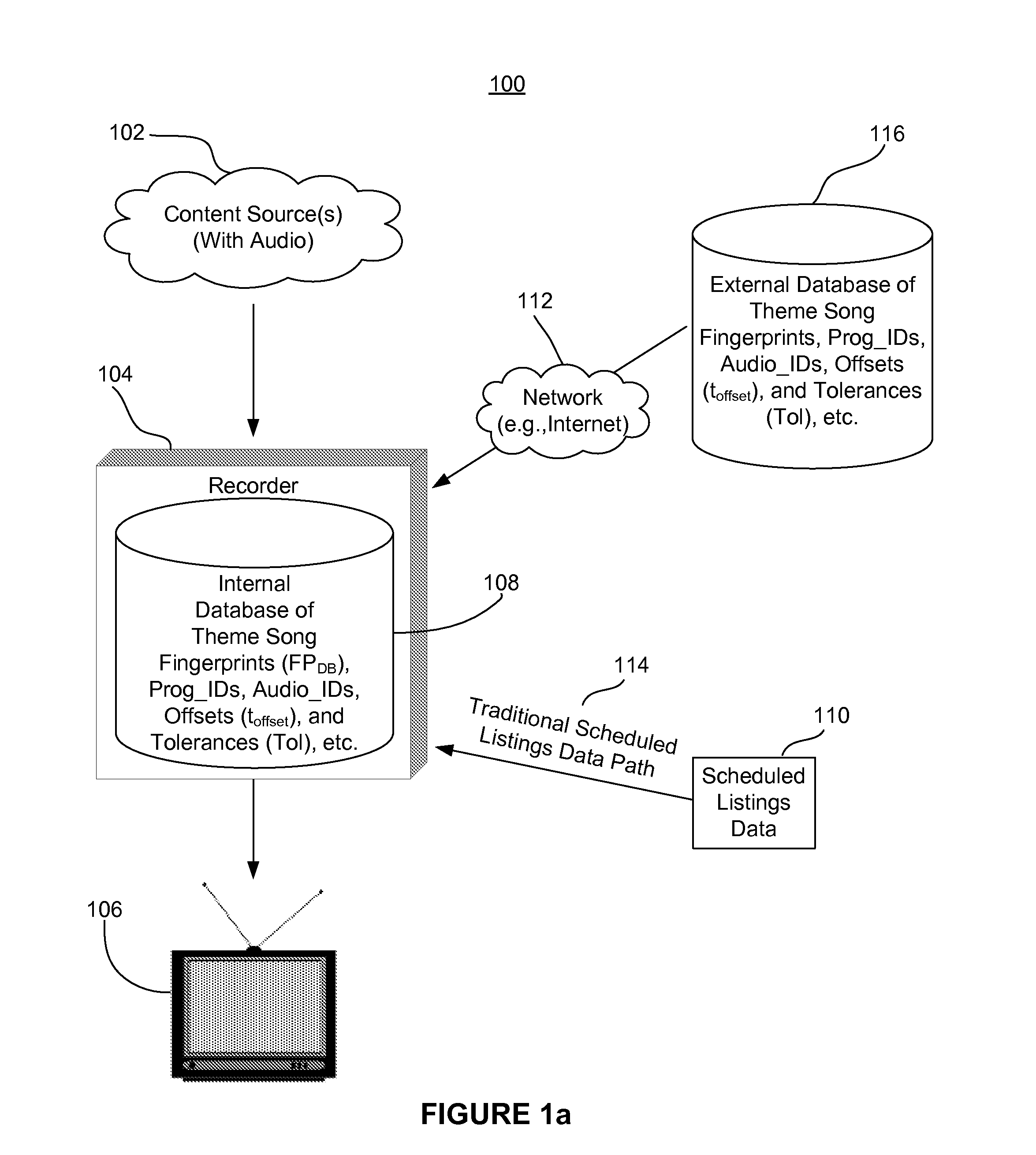
Content recorder timing alignment
InactiveUS20110085781A1Improve convenienceEfficient memory usageTelevision system detailsColor television detailsStart timeComputer science
A portion of audio content is captured from a network, and a time of occurrence of the captured portion of audio content is determined. An audio fingerprint is generated based on the captured portion of audio content. The generated audio fingerprint is matched to a program scheduled to be recorded. Based on the time of occurrence of the captured portion of audio content, a determination is made as to whether the program is running on-schedule. In one aspect, if it is determined that the program is not running on-schedule, an adjusted recording start time and / or an adjusted recording end time is calculated. In another aspect, if it is determined that the program is running on-schedule, the program is recorded according to a predetermined recording start time and / or a predetermined recording end time.
Owner:ROVI TECH CORP
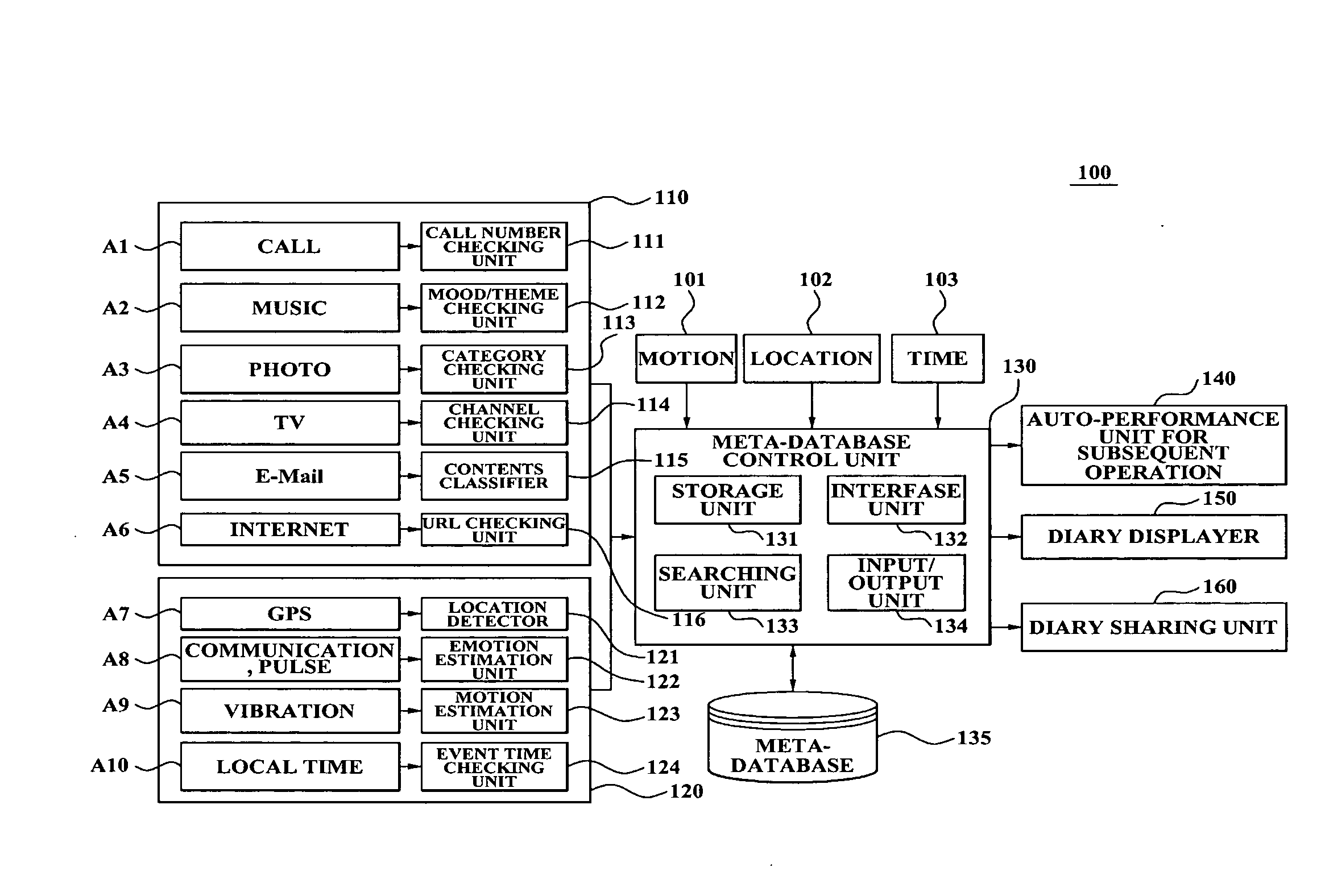
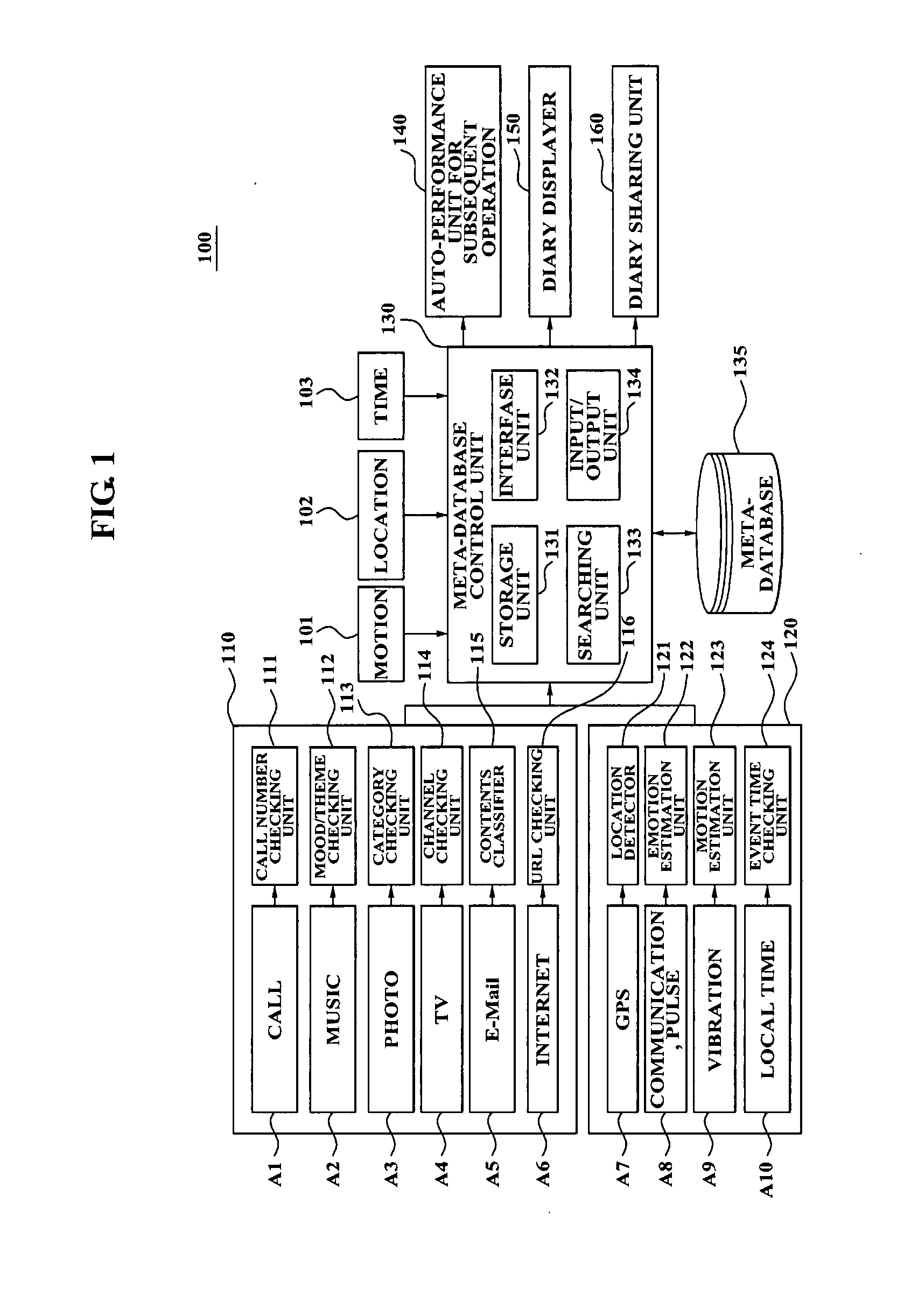
Personalized service method using user history in mobile terminal and system using the method
A personalized service method using a user history in a mobile terminal is provided. The personalized service method using the user history in the mobile terminal includes: checking at least one of event information and context information which occurred due to a user; checking a user's location, a user's condition, a user's emotional state, or an event occurrence time when the at least one of event information and context information occur; reflecting the user's location, the user's condition, the user's emotional state, or the event occurrence time in the at least one of event information and context information, and recording the at least one of event information and context information, having reflected the user's location, the user's condition, the user's emotional state, or the event occurrence time, in a database in a diary type; and displaying a representing image corresponding to the at least one of event information and context information, having been recorded in the diary type.
Owner:SAMSUNG ELECTRONICS CO LTD
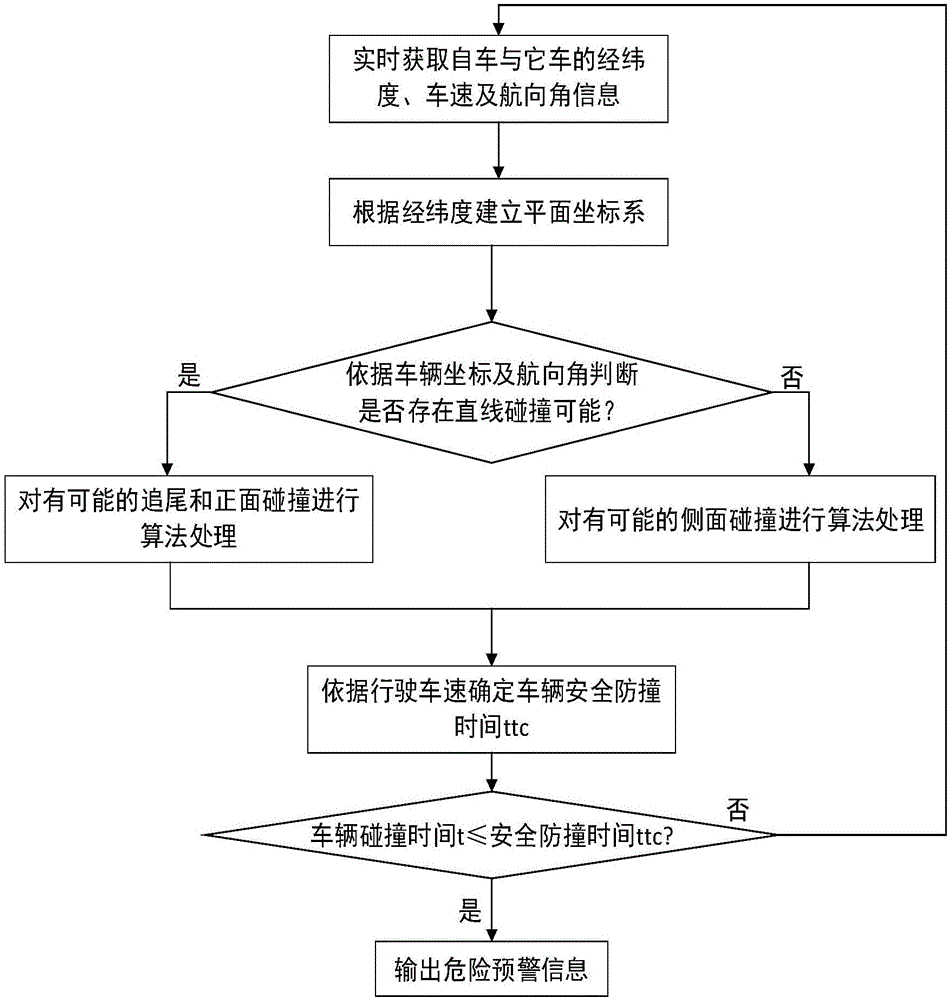
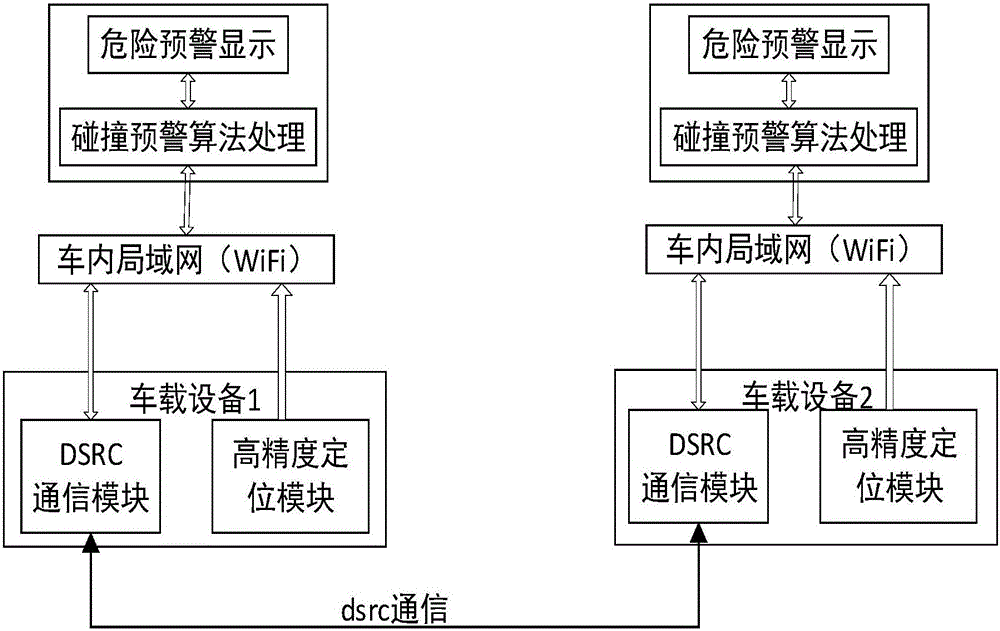
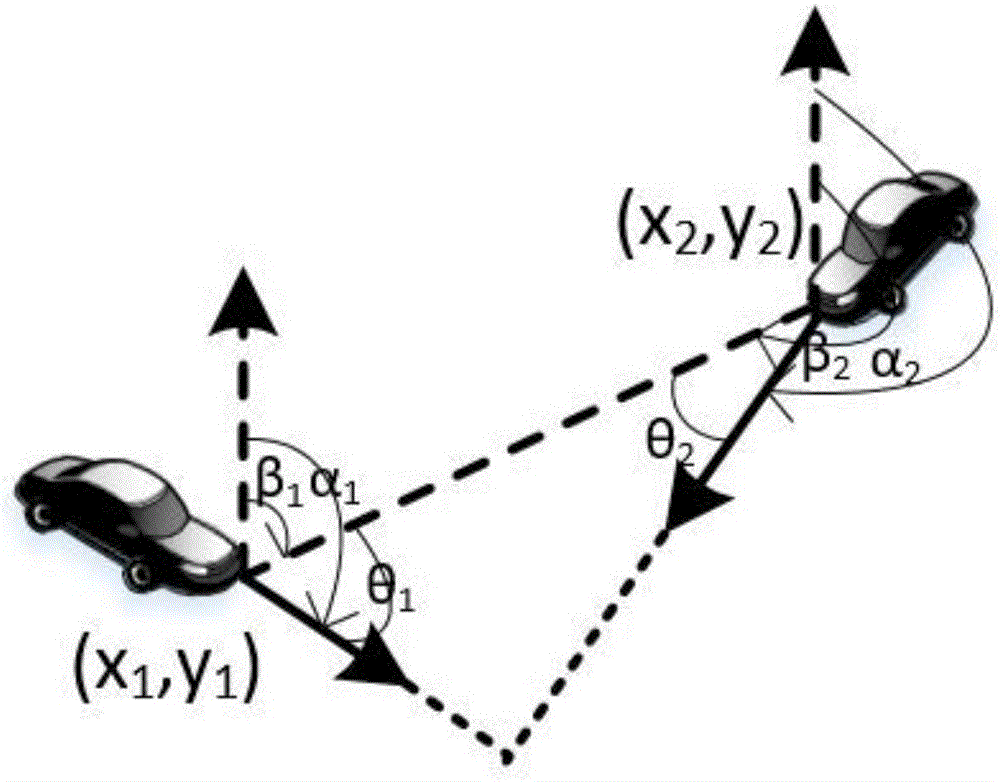
Security anti-collision early-warning method based on vehicle driving speed and position information fusion
The invention discloses a security anti-collision early-warning method based on vehicle driving speed and position information fusion. A vehicle-mounted device obtains information of longitudes and latitudes, speeds and heading angles of the vehicle and another vehicle in real time; according to a rectangular plane coordinate system of longitude and latitude conversion, vehicle coordinate information can be obtained; and on the basis of vehicle ordinates and heading angles, determination of vehicle straight line collision and side collision can be carried out, so that algorithm processing is carried out respectively. According to a driving speed of a vehicle, different vehicle security collision prevention time is determined; if the vehicle collision occurrence time is less than or equal to security collision prevention time, a risk of vehicle collision exist and the driver can be warned timely; and if the vehicle collision occurrence time is larger than the security collision prevention time, updated vehicle state information is processed again. According to the invention, the method is not limited by vehicle-mounted equipment; the early warning precision is improved effectively; unnecessary early warning is reduced; and the method is suitable for early warning of driven vehicle collision prevention.
Owner:JIANGSU UNIV OF SCI & TECH
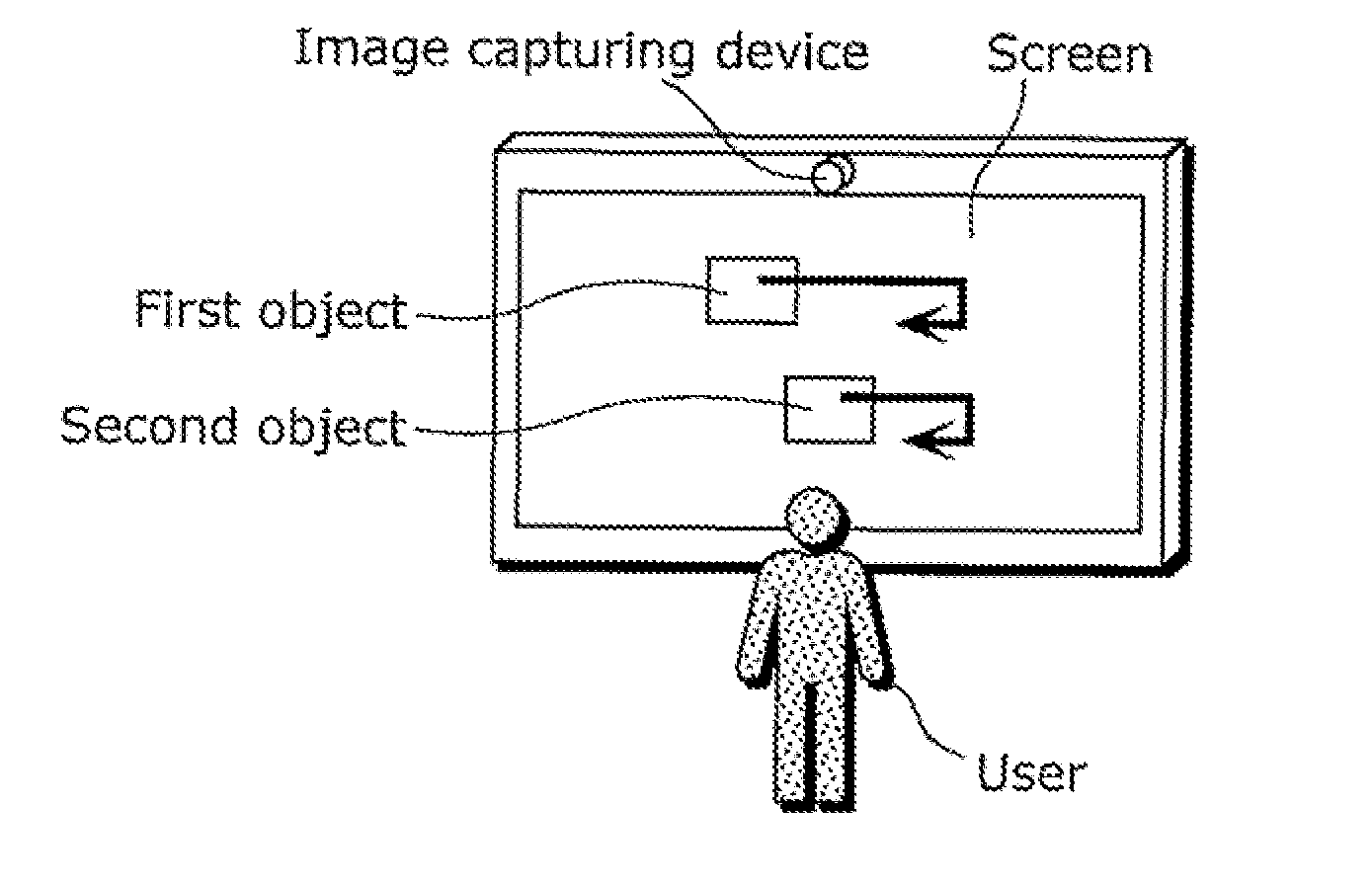
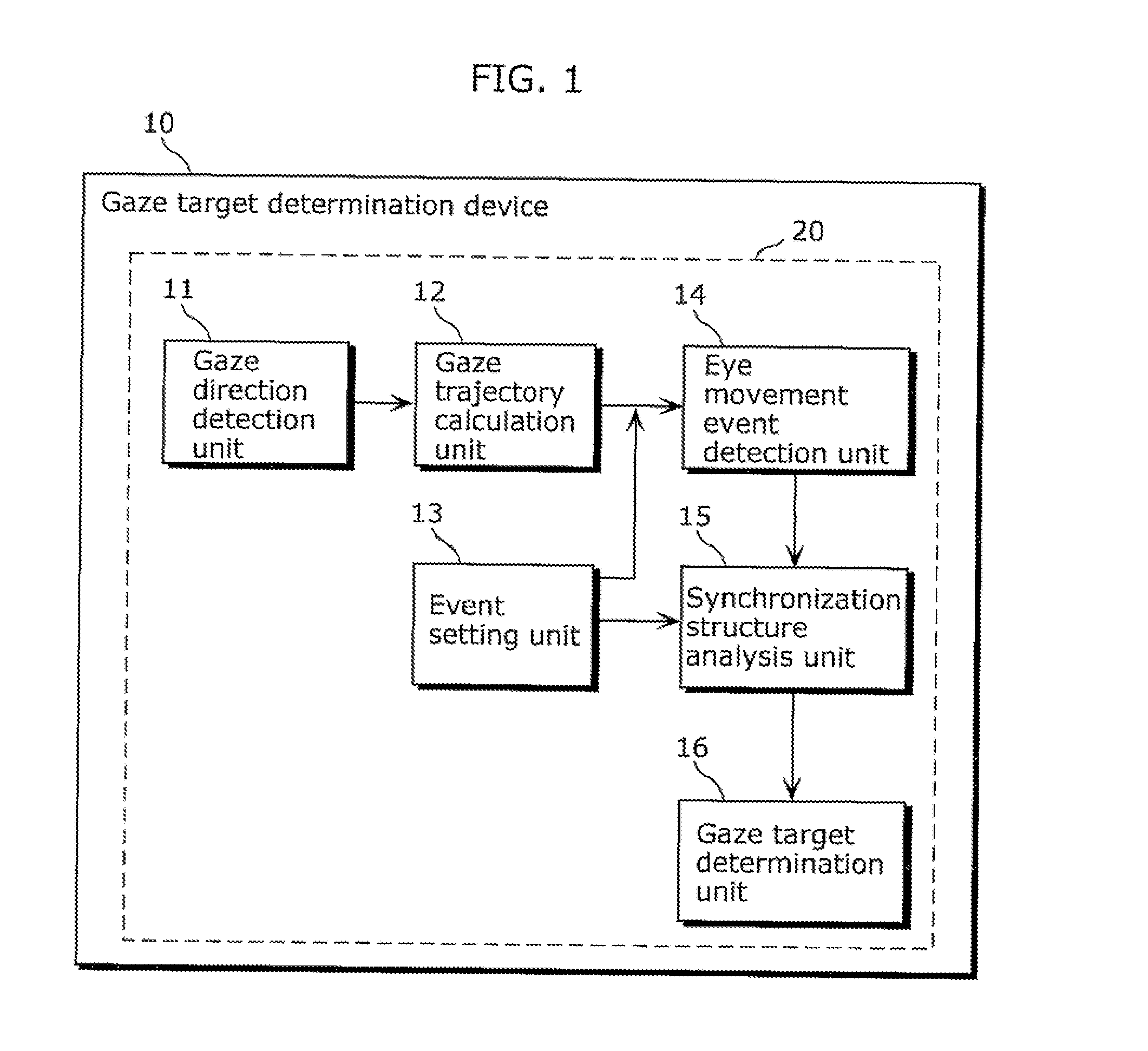
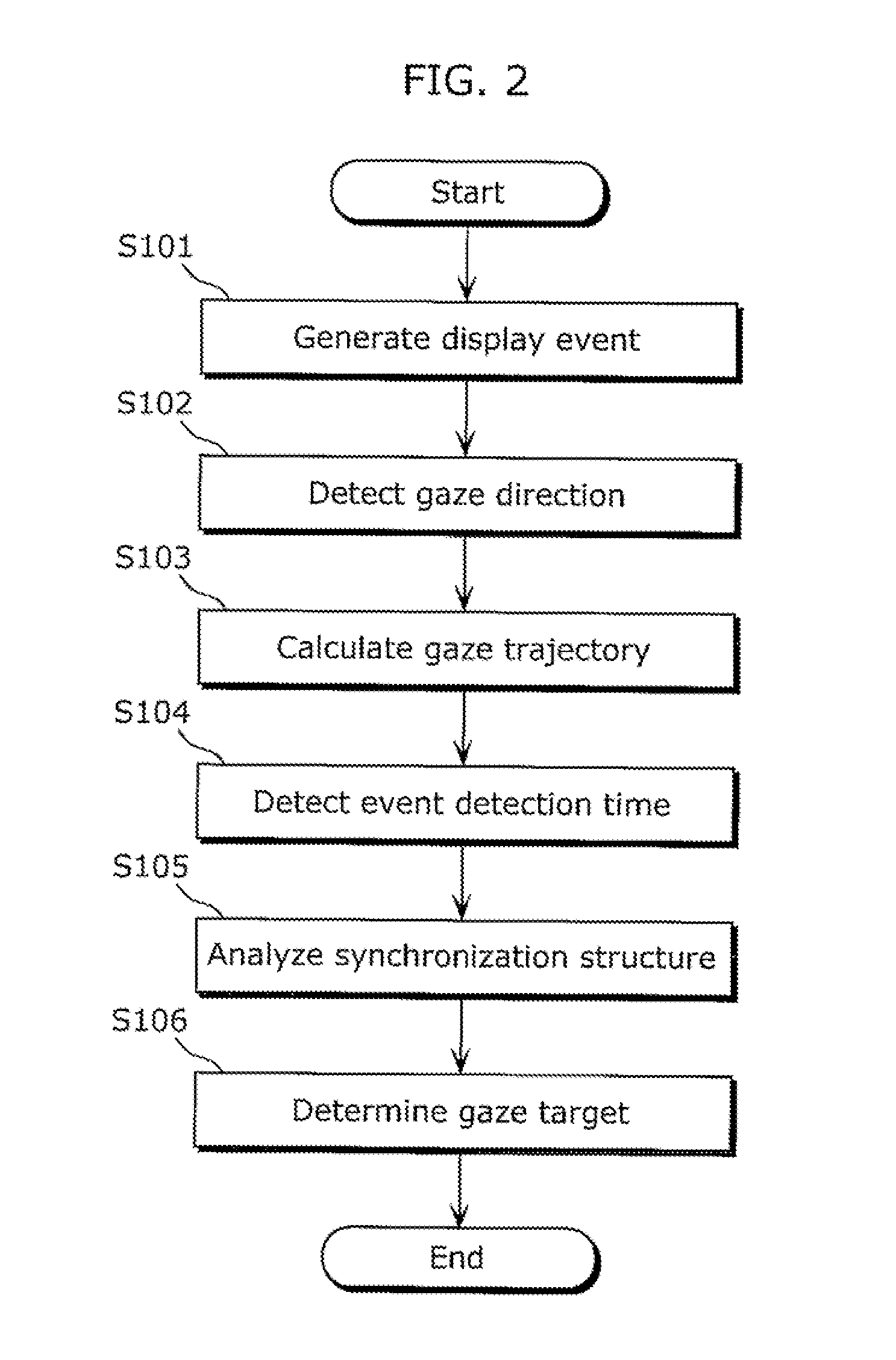
Gaze target determination device and gaze target determination method
ActiveUS20110141010A1Accurate measurementGood effectAcquiring/recognising eyesCathode-ray tube indicatorsStructure analysisGaze directions
The object at which a user is gazing Is accurately determined from among objects displayed on a screen. A gaze target determination device (10) includes: an event setting unit (13) which generates, for each object at different times, a display event which triggers a movement of the gaze direction of the user who is gazing at the object and which indicates a movement or a change of the object; a gaze trajectory calculation unit (12) which calculates a gaze trajectory based on the detected user's gaze direction; an eye movement event detection unit (14) which detects event detection time which is time at which the gaze direction moves according to the display event, based on the calculated gaze trajectory; a synchronization structure analysis unit (15) which calculates, for each object, time difference between the event detection time and event occurrence time; and a gaze target determination unit (16) which determines the object at which the user is gazing from among the objects, based on the calculated time difference.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
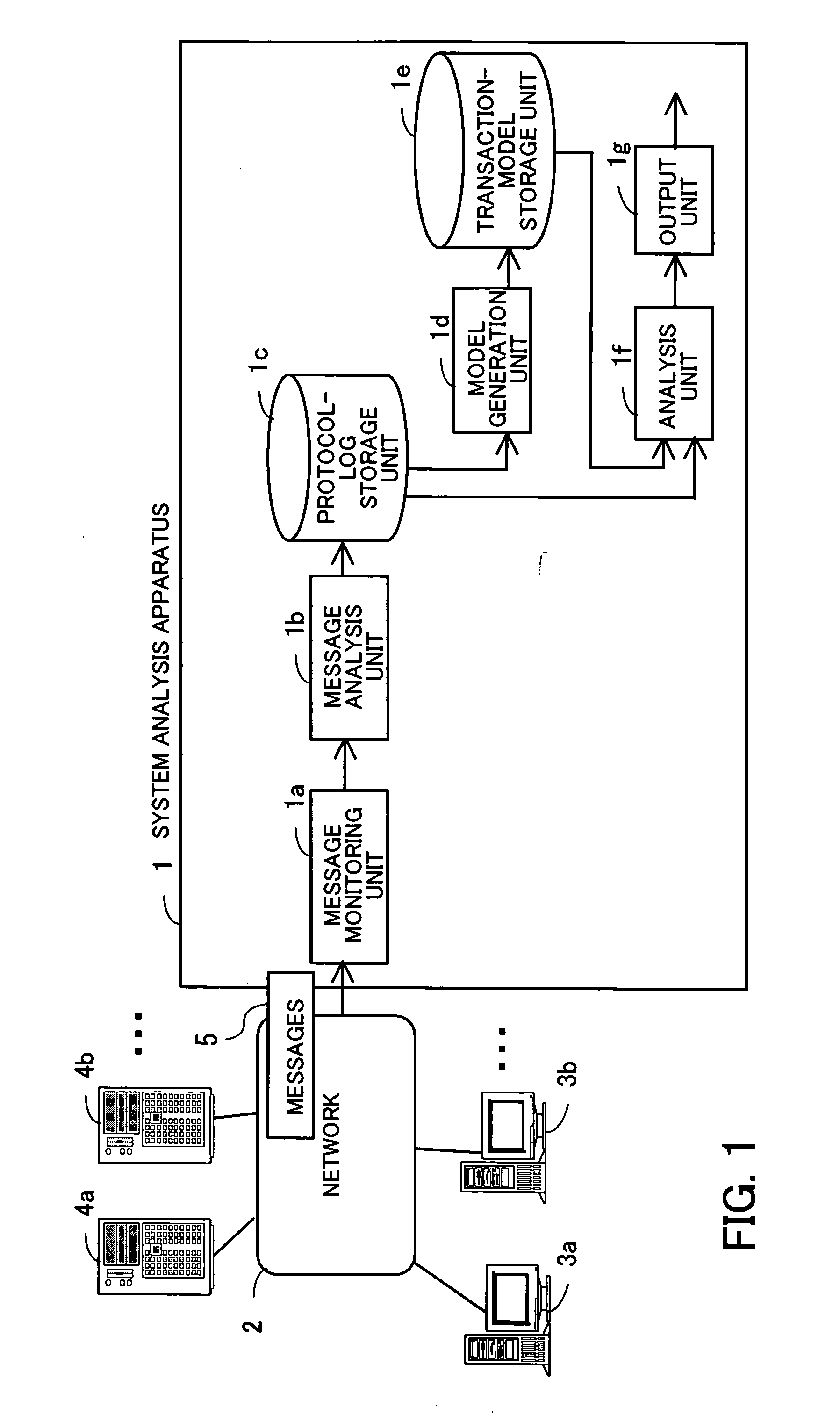
System analysis program, system analysis method, and system analysis apparatus
InactiveUS7873594B2Accurate analysisDigital data processing detailsHardware monitoringSystems analysisTransaction model
A system analysis program which can accurately analyze the operational status of a system without modifying functions of the system for providing services. A message analysis unit analyzes the contents of collected messages, and determines the times of occurrence of the messages, the process types requested by the messages, and whether or not each of the messages is a request message or a response message. In response to an instruction for model generation, a model generation unit generates a transaction model satisfying at least one limiting condition related to caller-called relationships between processes, based on a set of messages selected in accordance with a selection criterion based on the certainty of existence of caller-called relationships. Then, in response to an instruction for analysis, an analysis unit analyzes the processing status of a transaction based on a protocol log conforming to the transaction model.
Owner:FUJITSU LTD
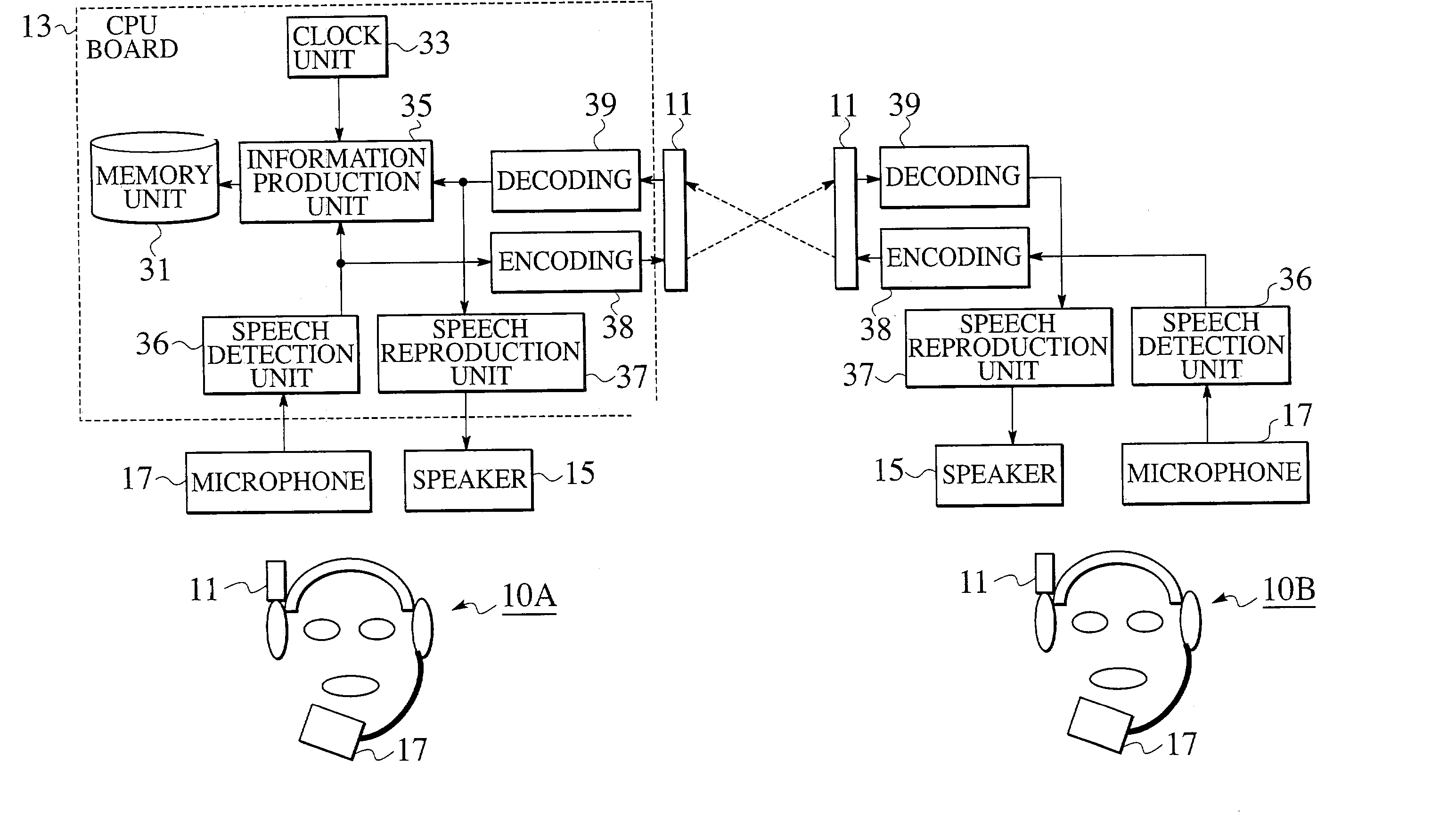
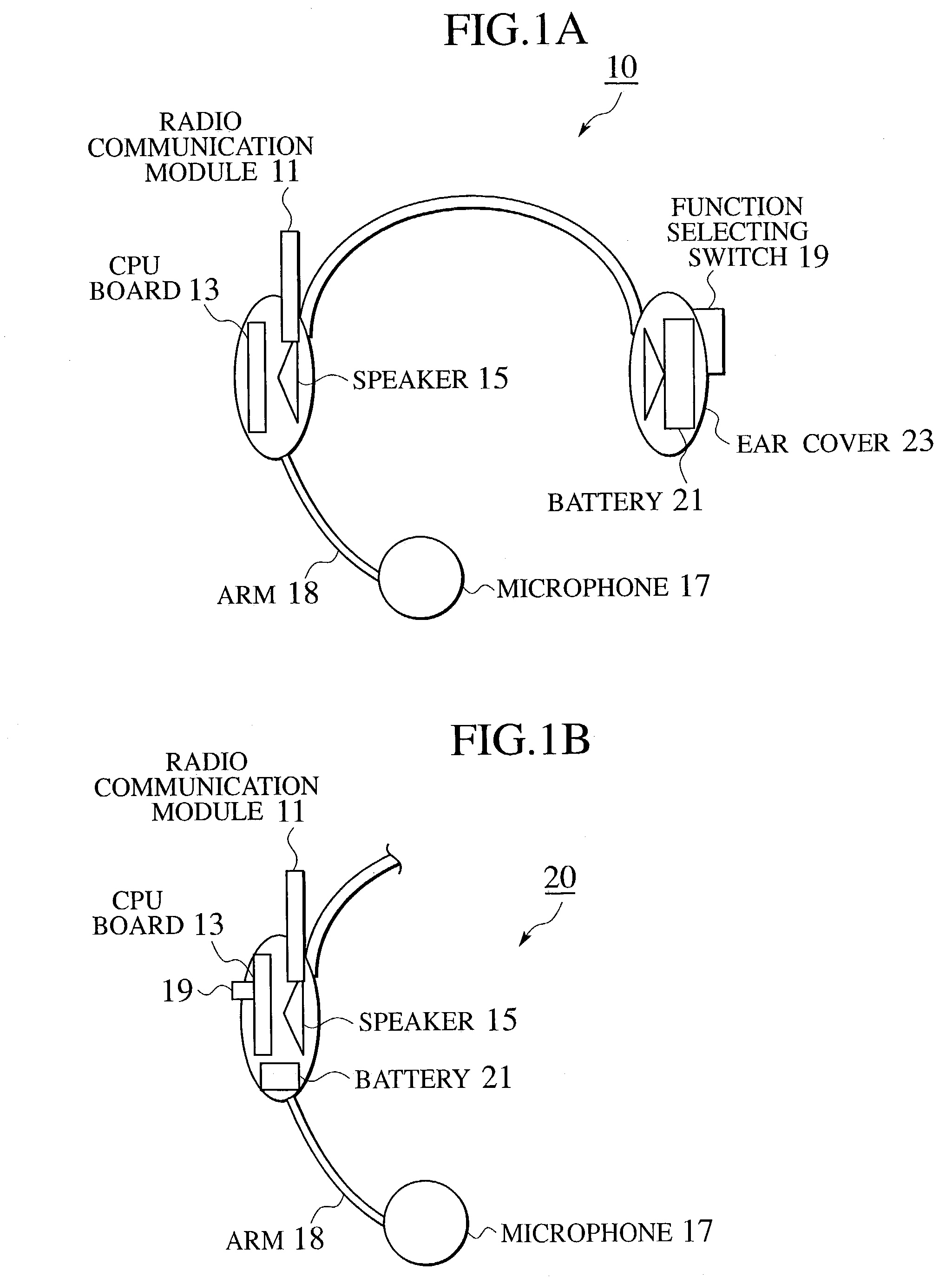
Headset with radio communication function and communication recording system using time information
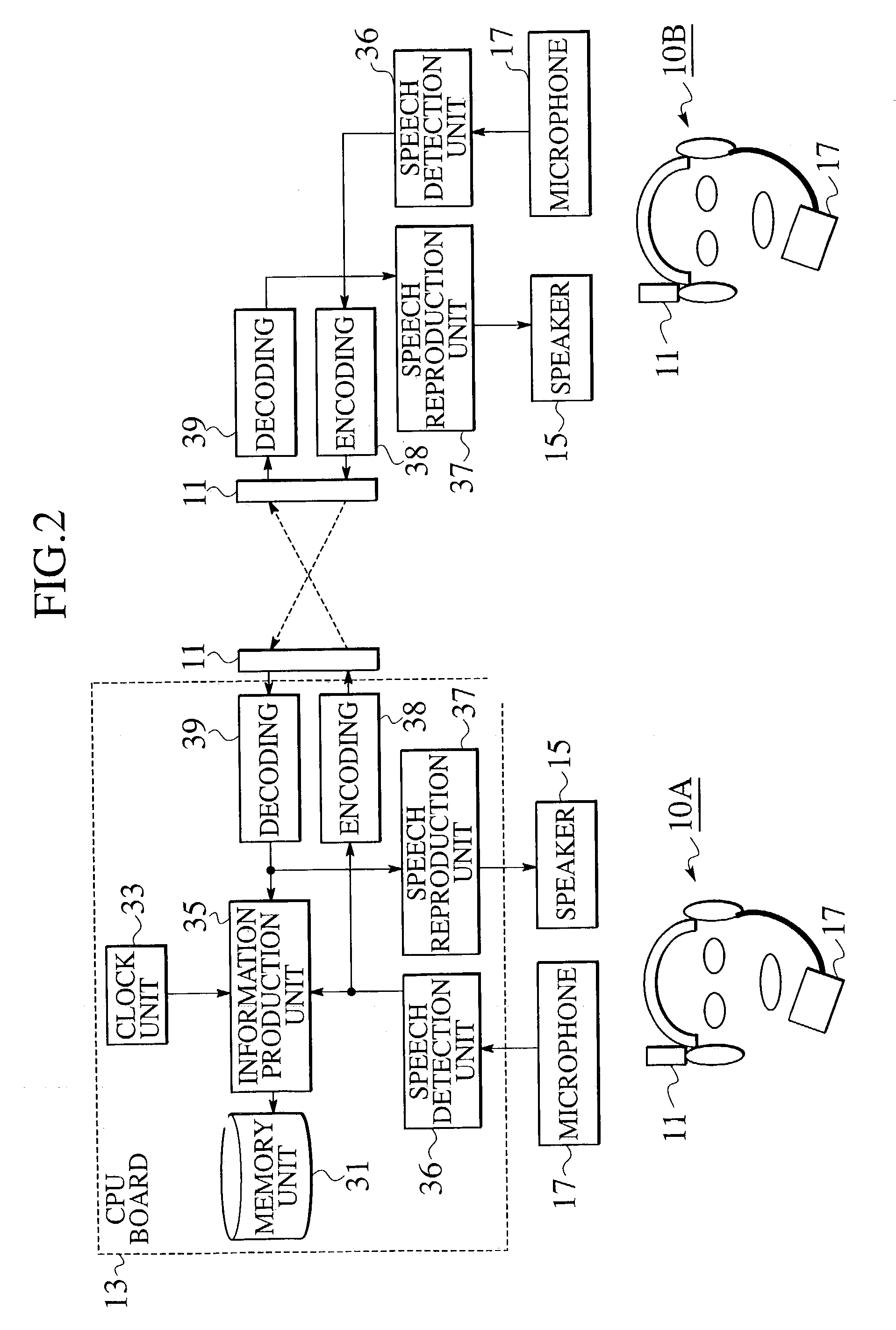
InactiveUS7136684B2Increasing evidential valueIncrease valueMicrophonesHeadphones for stereophonic communicationTime informationTelecommunications
In a communication recording system using a headset with a radio communication function which transmits the first speech signal and receives the second speech signal by radio communications, the headset is provided with a time information acquisition unit for acquiring a time information indicating occurrence times of the first speech signal and the second speech signal, an information production unit for producing a recording information to be stored in which the time information is set in correspondence to the first speech signal and the second speech signal, and a memory unit for storing the recording information.
Owner:KK TOSHIBA
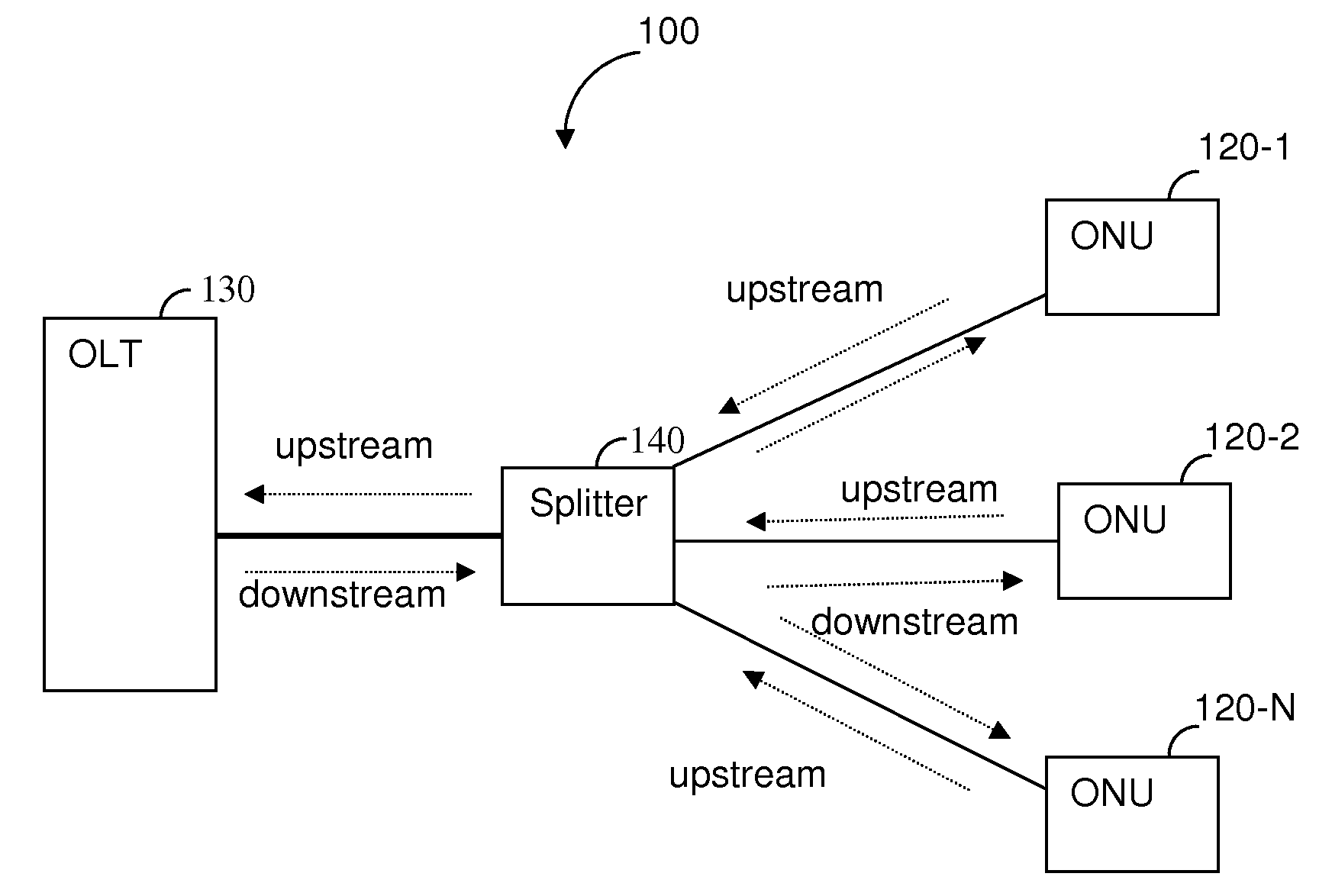
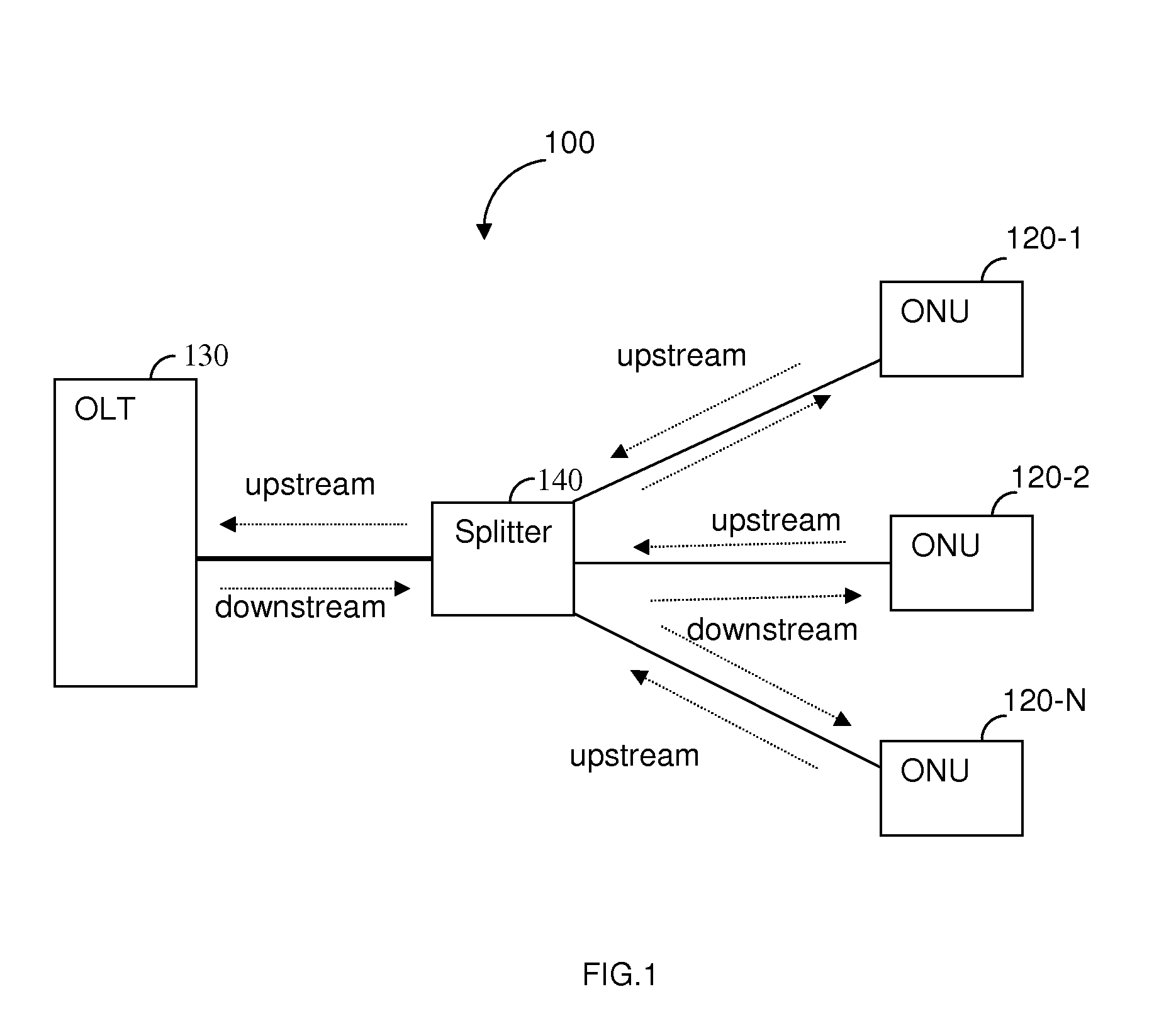
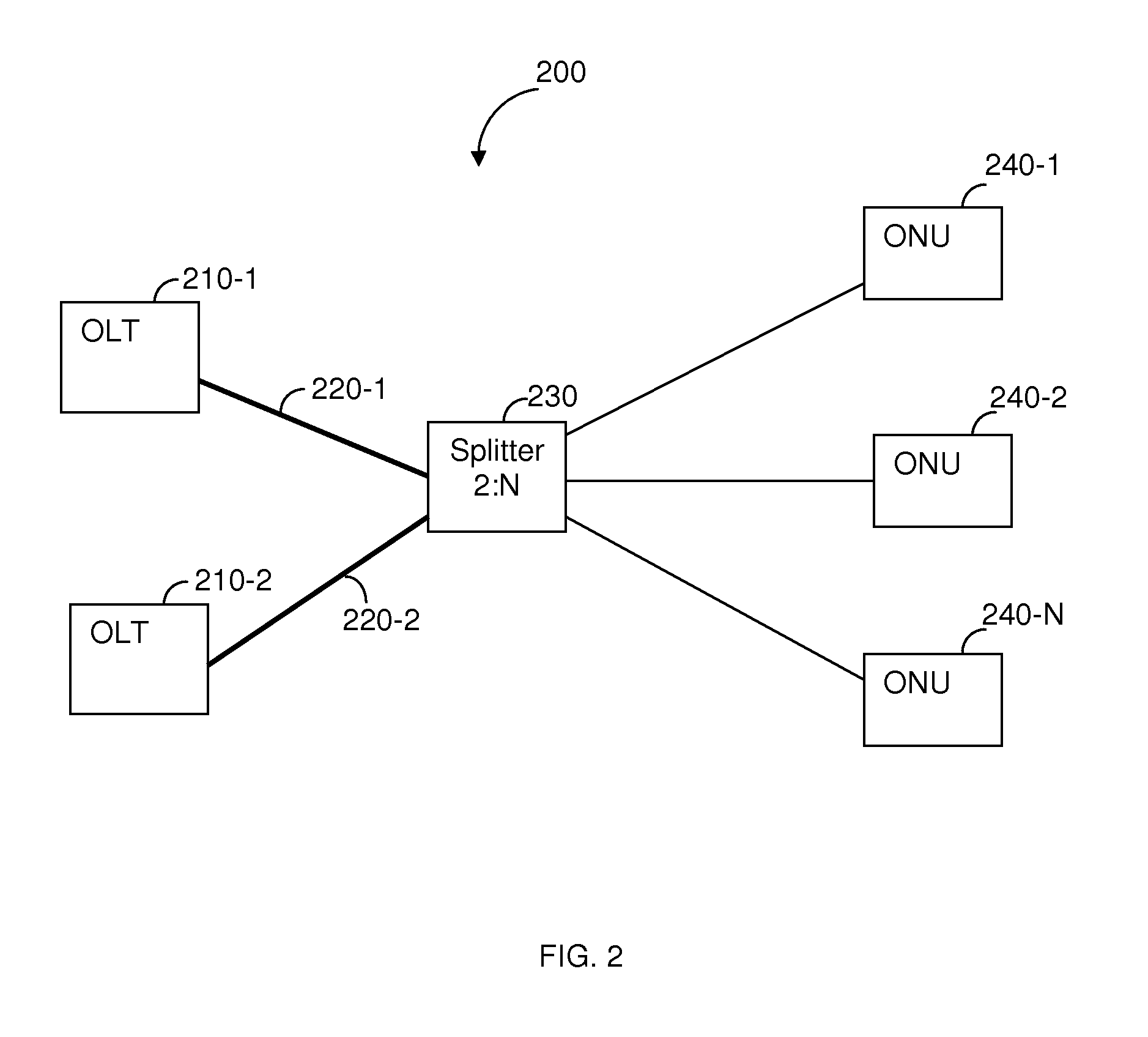
Techniques for detecting optical faults in passive optical networks
ActiveUS20110280568A1Multiplex system selection arrangementsTime-division multiplexComputer terminalEngineering
A method for detecting faults and their locations in an optical path between an optical line terminal (OLT) of and optical network units (ONUs) of a passive optical network (PON). The method comprises forming a maintenance optical link through the PON between the OLT and a collocated ONU, the OLT and its collocated ONU are each connected to an optical splitter; sending a ranging request from the OLT to the collocated ONU; in response to the ranging request, receiving, over the maintenance optical line, a ranging burst signal including at least a fault analysis detection pattern (FADP); and analyzing the FADP in the received signal by auto-correlating the FADP signal with an expected FADP signal, an uncorrelated event measured through the auto-correlation is indicative of a fault in the optical path of the PON and occurrence times of such events are indicative of the fault's location in the optical path.
Owner:AVAGO TECH INT SALES PTE LTD
Mobile communication method, radio terminal, and base station
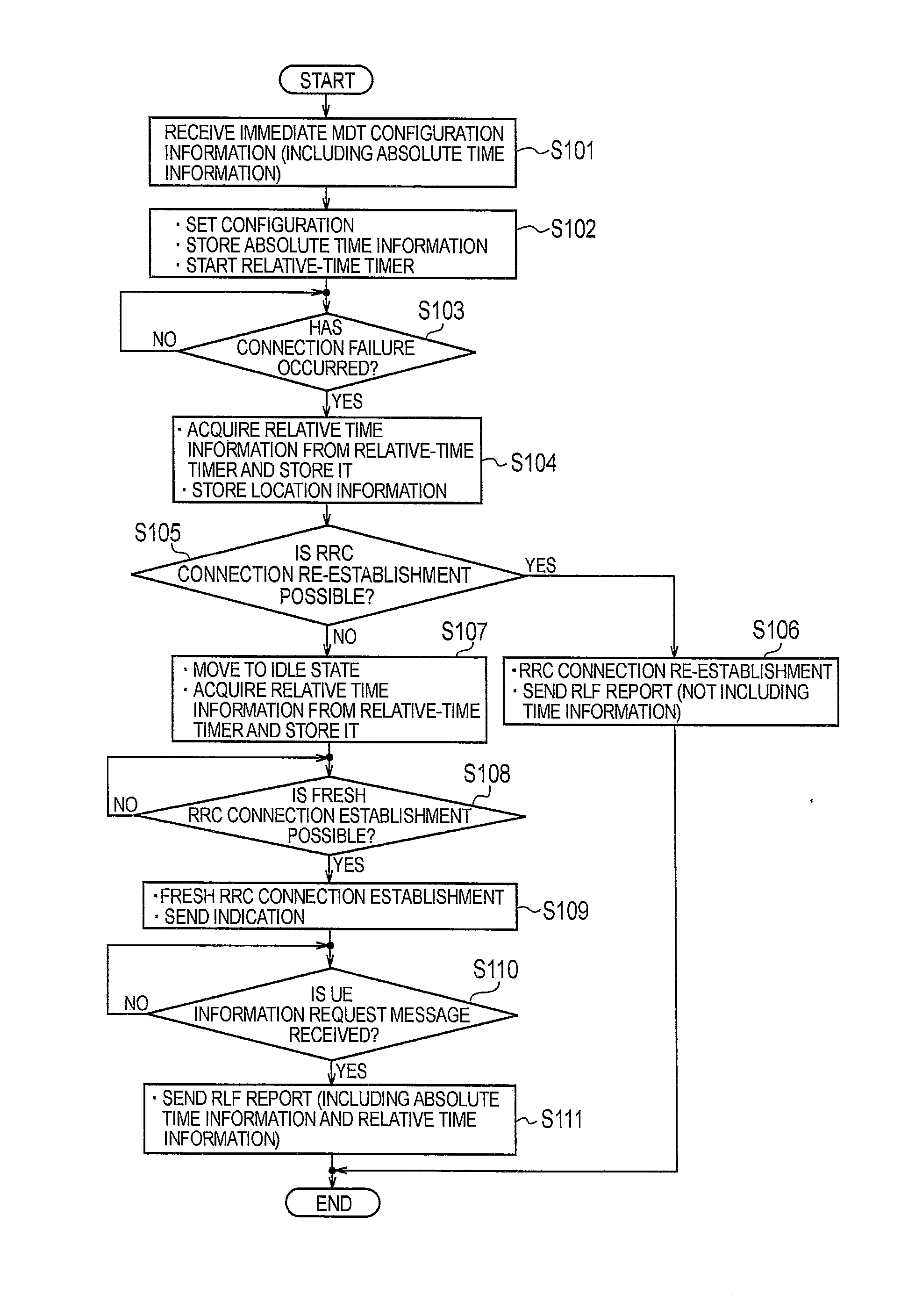
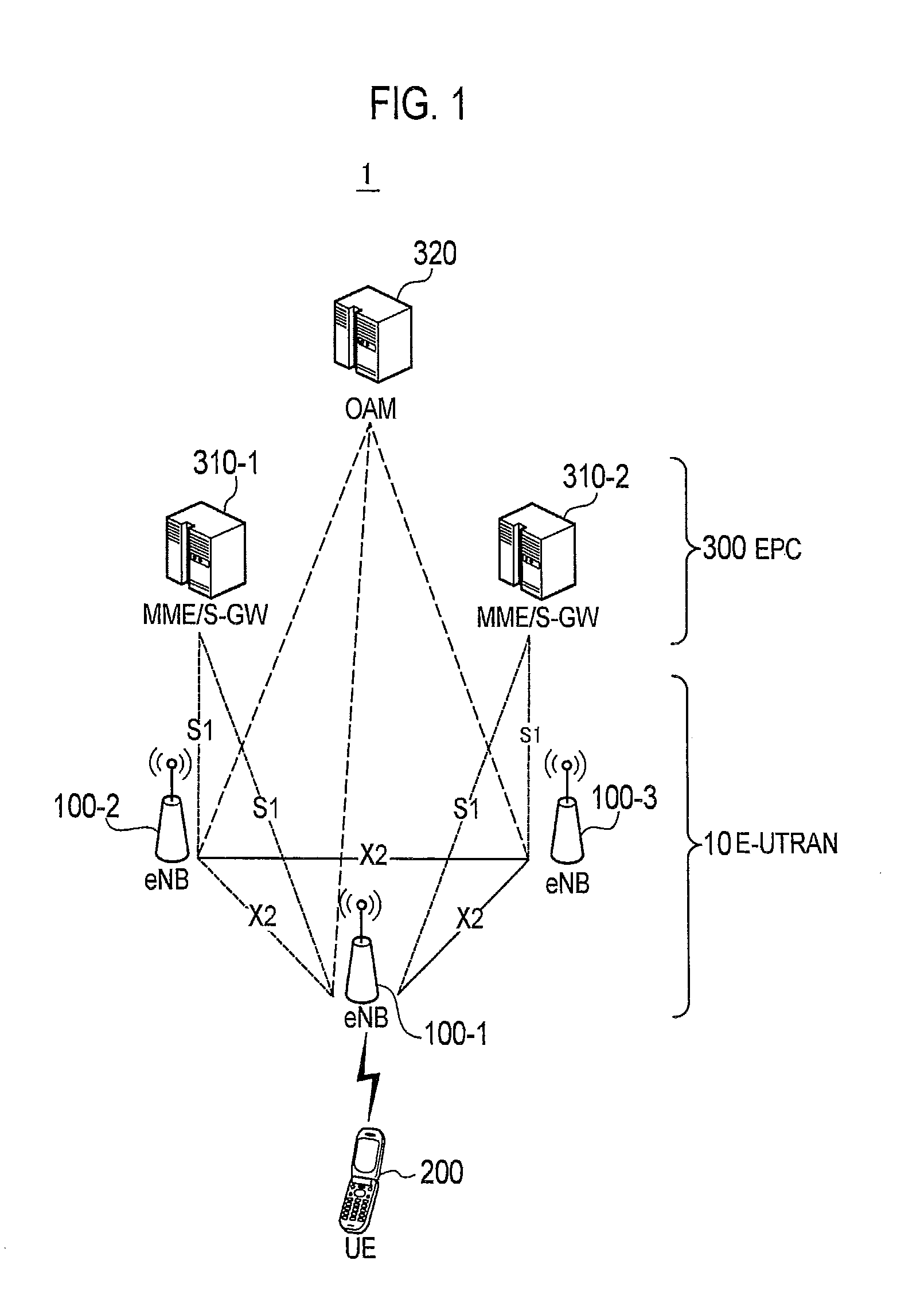
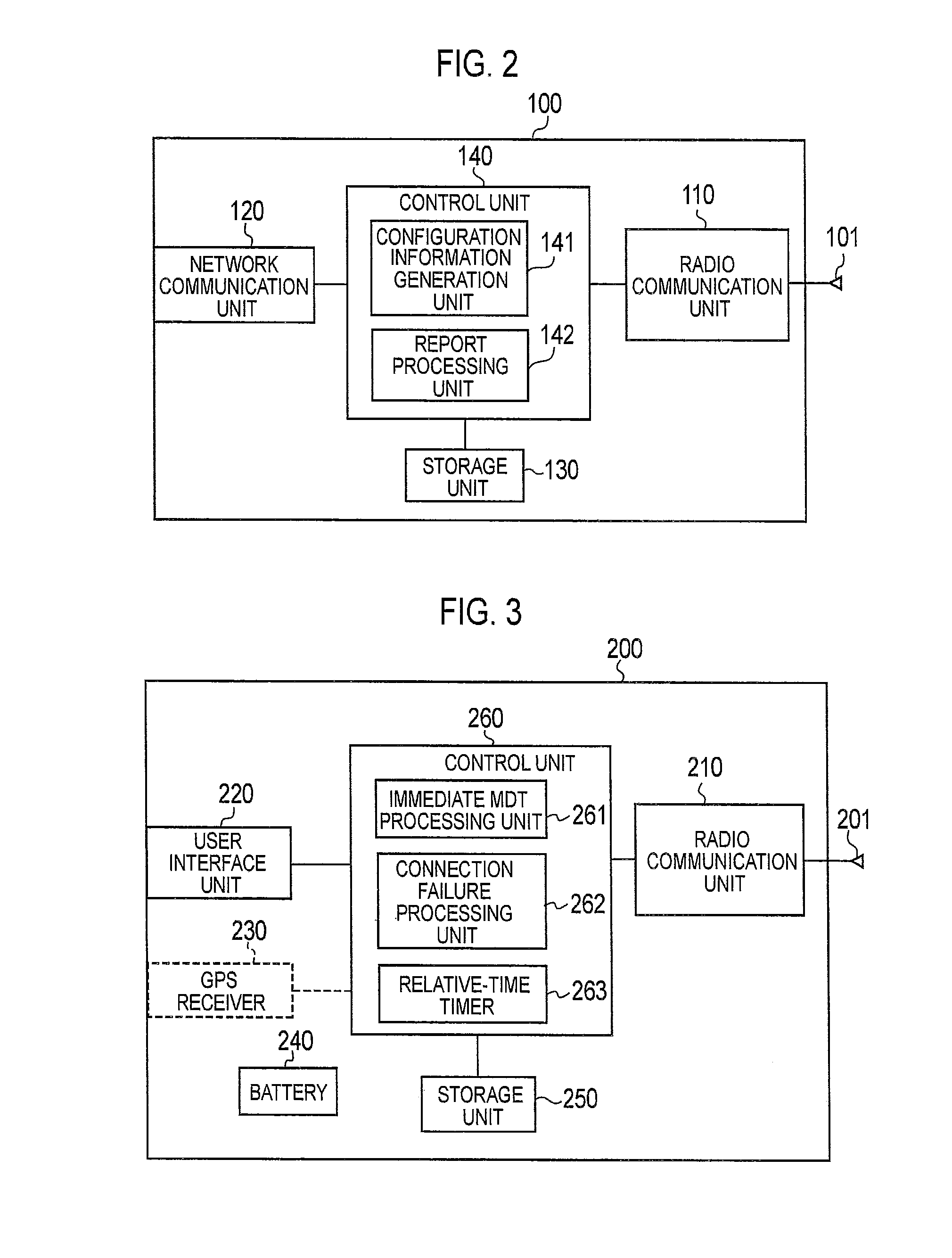
ActiveUS20130189973A1Error detection/correctionConnection managementTime informationComputer terminal
A mobile communication method in which a radio terminal connects to a network so as to perform a communication, comprises: a step in which the radio terminal detects an occurrence of a connection failure with the network in a connected state; and a step of sending a radio link failure (RLF) report regarding the detected connection failure, from the radio terminal to the network. In the step of sending the RLF report, the radio terminal sends time information, which is contained in the RLF report, for identifying a time of occurrence of the connection failure, to the network.
Owner:KYOCERA CORP
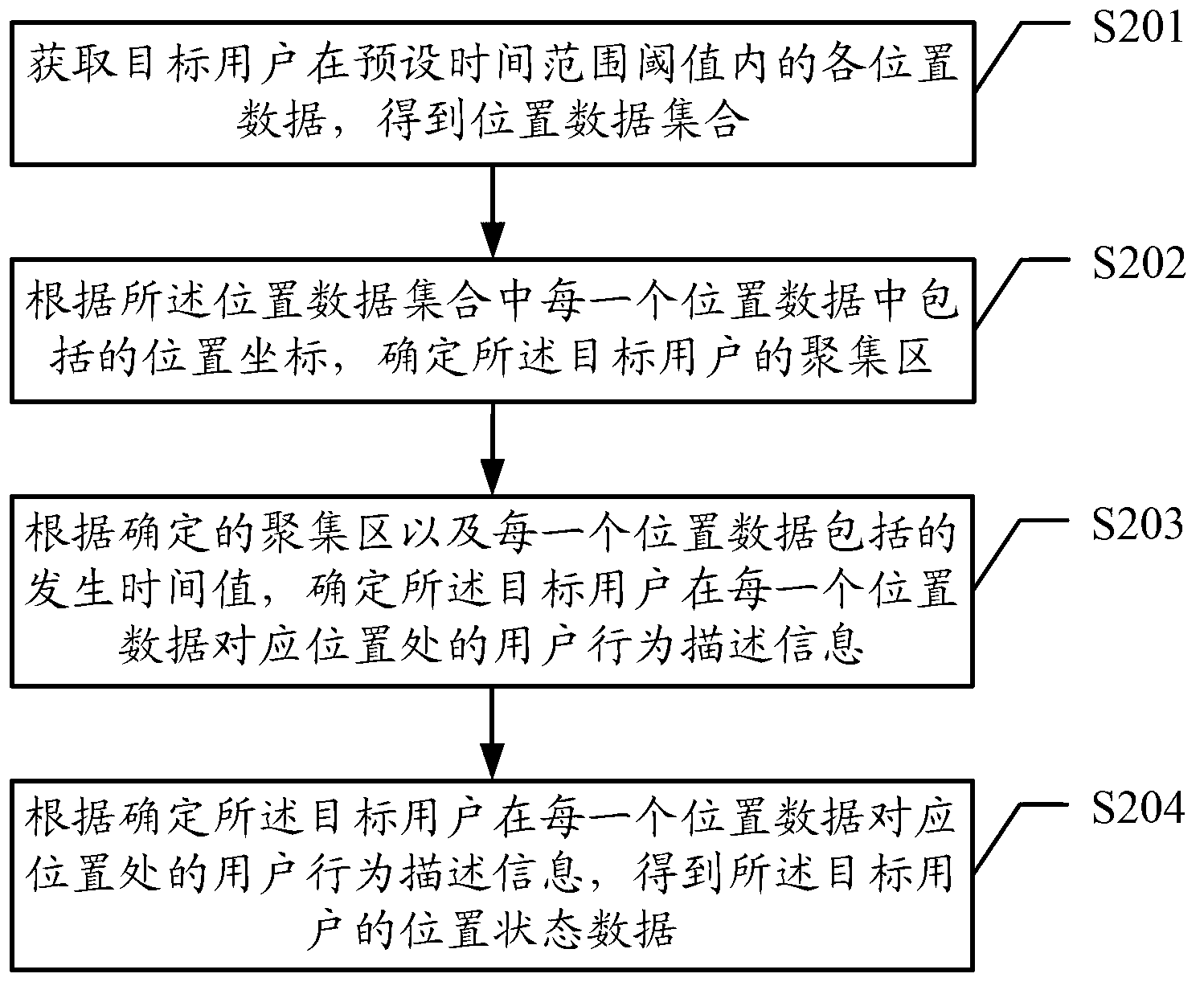
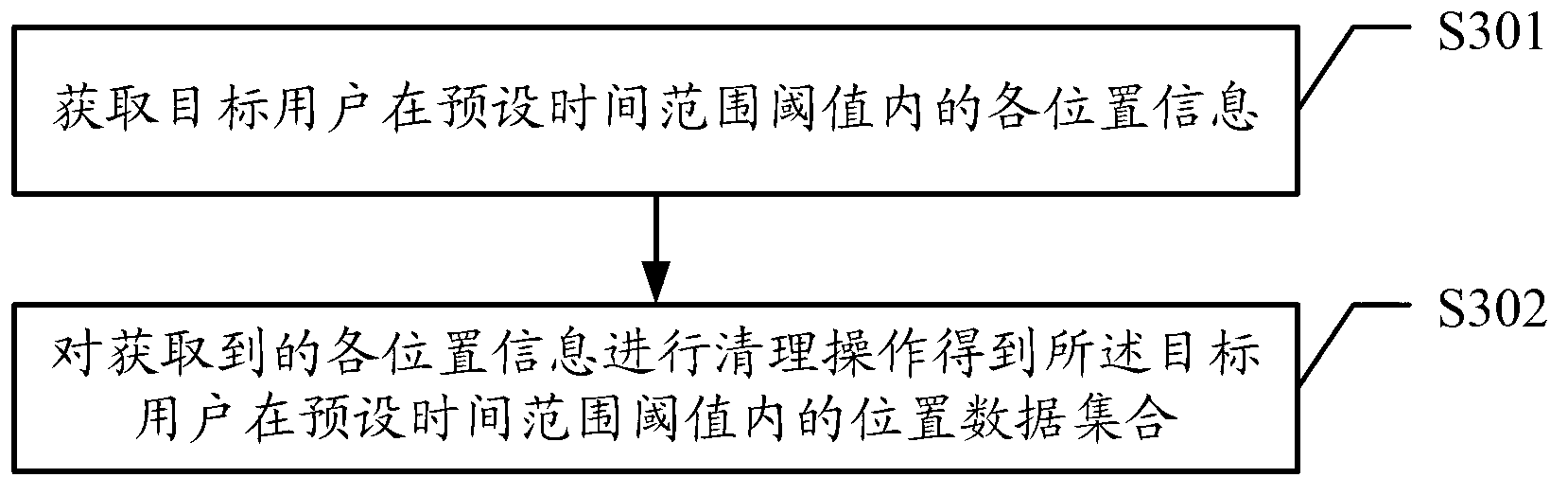
Method and device for processing position data of target user
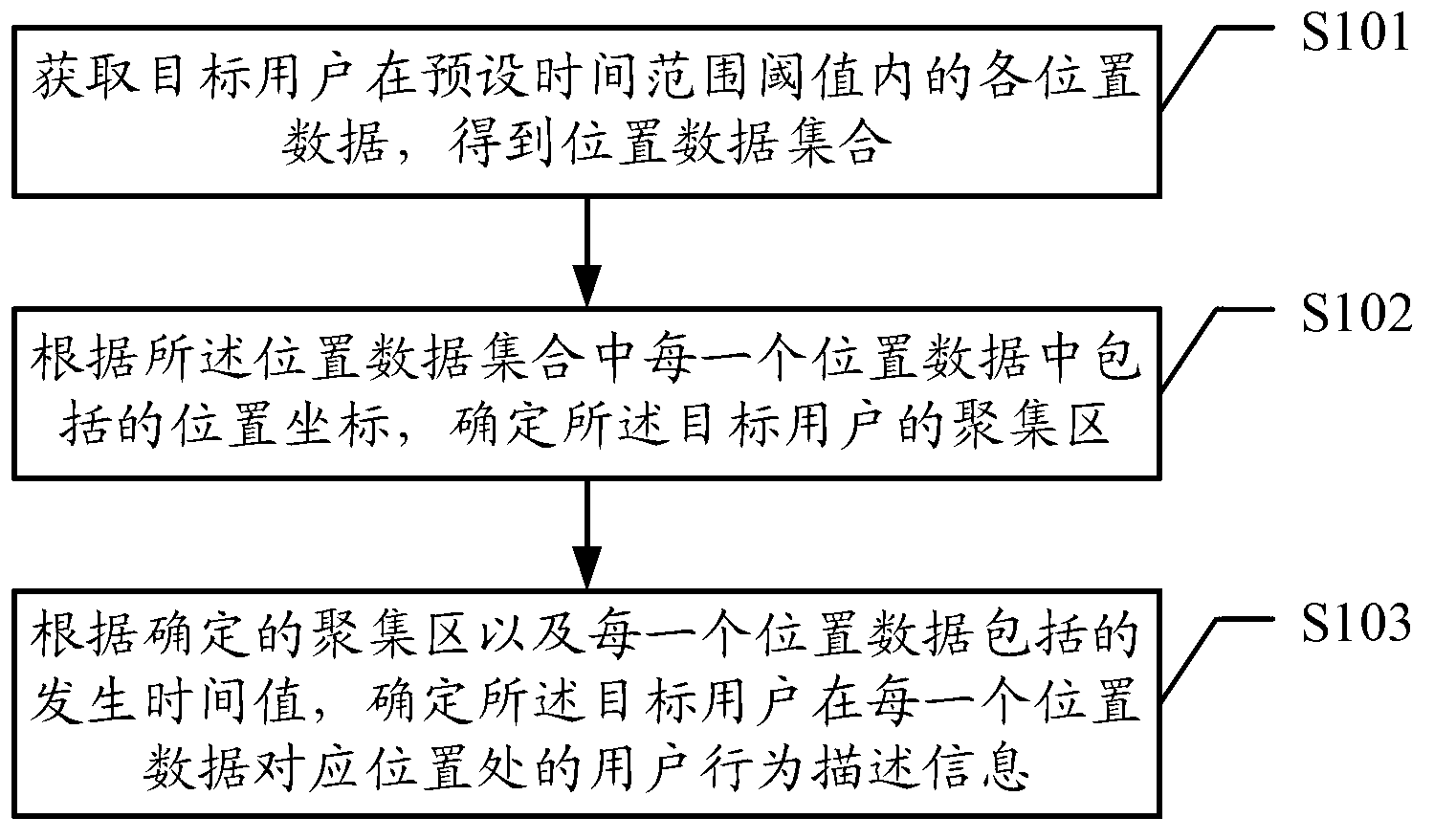
ActiveCN103227821AAccurately getImplement push applicationTransmissionLocation information based serviceTime rangeData set
The embodiment of the invention discloses a method and a device for processing position data of a target user. The method comprises the steps of acquiring the position data of the target user within a preset time range threshold, obtaining a position data set, determining an accumulation area of the target user according to a position coordinate comprised by each position data, and determining user behavior description information of the target user at a position corresponding to each position data according to the determined accumulation area and an occurrence time value comprised by each position data, wherein a data format of each position data of the position data set at least comprises the position coordinate and the occurrence time value; and the user behavior description information comprises appearing frequencies of the target user in the corresponding accumulation area in workdays and nonworkdays. With the adoption of the method and the device, the position data of the target user can be analyzed and processed to obtain the information for describing behaviors of the target user, so that the corresponding service based on a user position can be realized according to the behaviors of the user.
Owner:TENCENT TECH (SHENZHEN) CO LTD
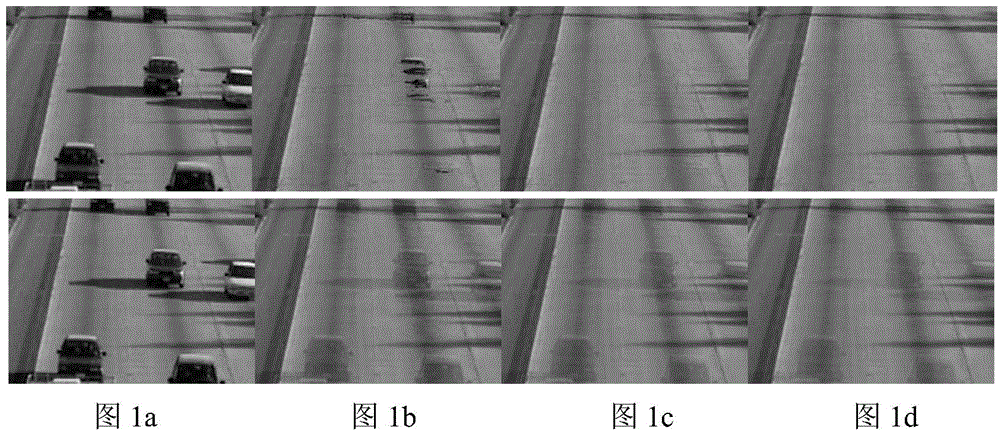
Vehicle checking method based on video image characteristic
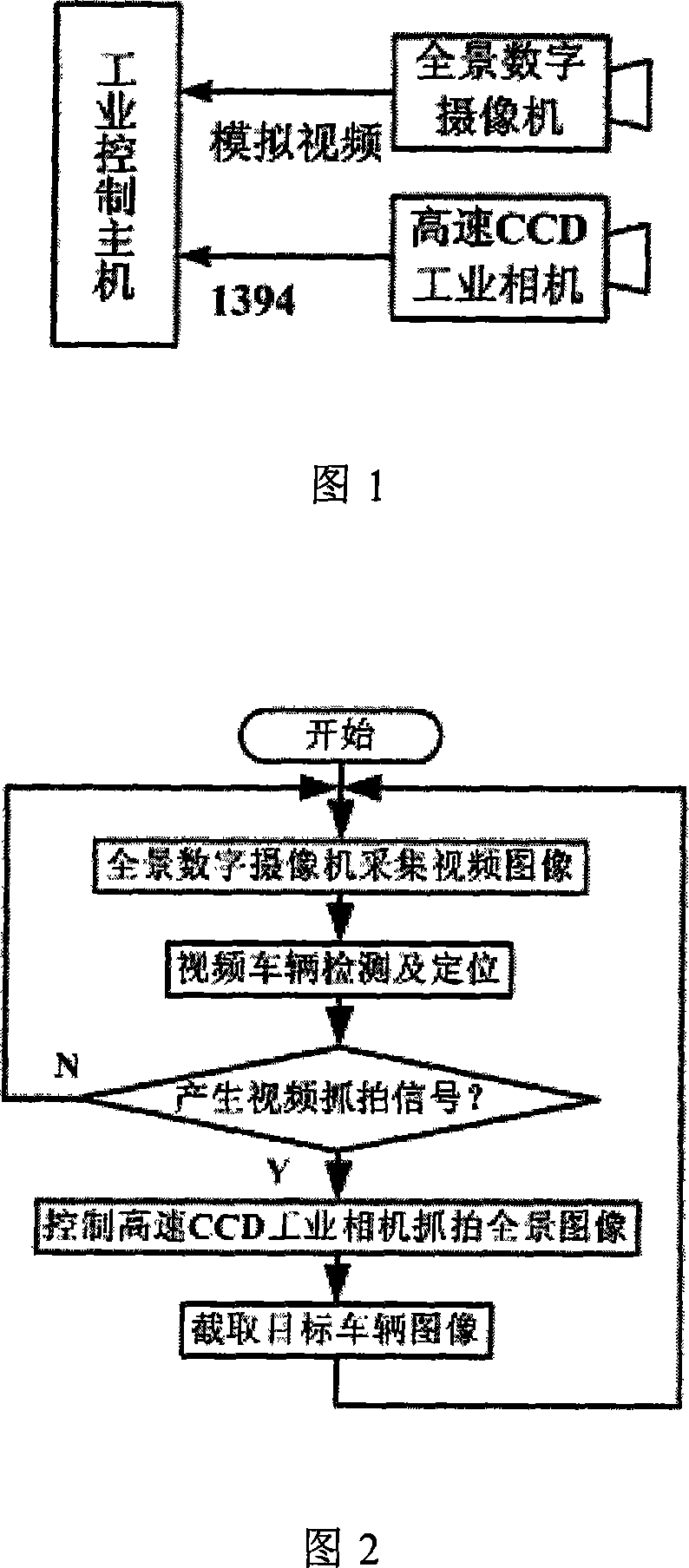
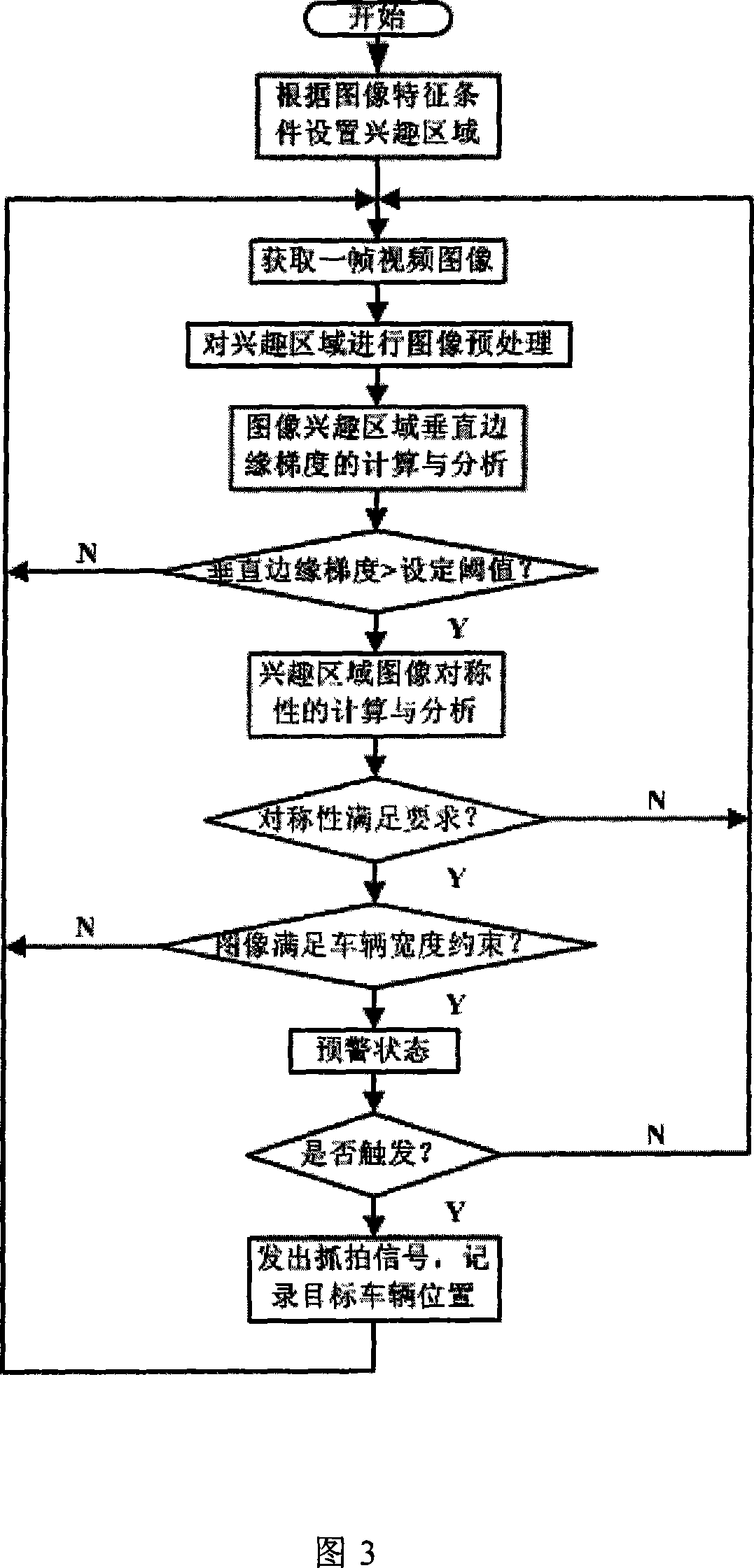
InactiveCN101231786AImprove reliabilityImprove accuracyDetection of traffic movementCharacter and pattern recognitionVideo monitoringDigital video
The invention provides a vehicle detection method based on video image characteristics. The invention makes use of a panoramic digital camera for collection of monitored video images of a plurality of lanes. The field of view of the panoramic digital camera is pointed at all of lanes in a direction to collect the monitored video images of a plurality of lanes in real time. Digital video images of each frame acquired by the panoramic digital camera are analyzed through a vehicle detection algorithm based on the video image characteristics. The positions and the occurrence time of the vehicles in the images are found out. At the same time, video snapping signal is generated, which drives a high speed CCD industrial camera to snap panoramic photographs. The images of the targets can be cut precisely from panoramic images according to the position information of the targets positioned in video vehicle detection, and are used for identifying number plates, punish vehicles breaking regulations and assist in public security. The invention improves the reliability and accuracy of the video vehicle detection algorithm by comprehensively using the fringe characteristics and the symmetry properties of vehicle figures, and detects vehicles quickly. In addition, the invention can be adapted to exterior environmental changes well.
Owner:BEIHANG UNIV
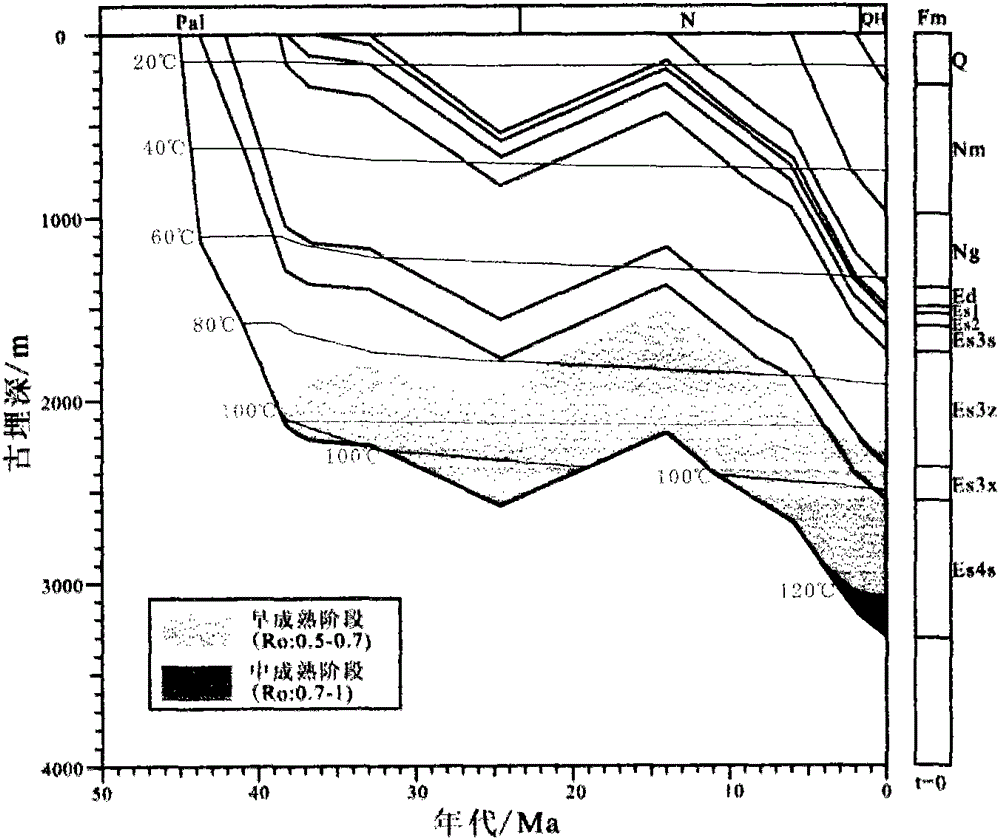
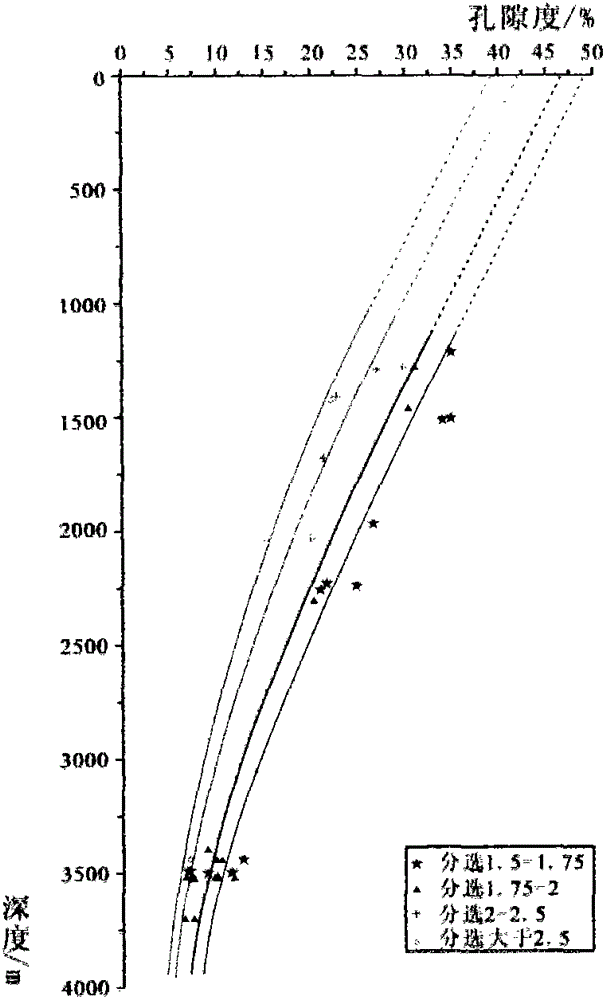
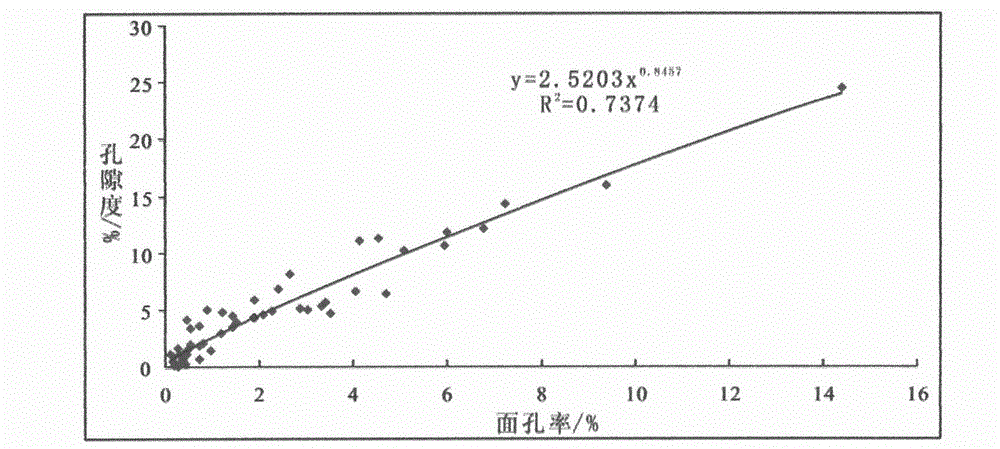
Geologic history period sandstone reservoir porosity evolution recovery method
ActiveCN102748016APorosity recoveryEffective Porosity PredictionPermeability/surface area analysisBorehole/well accessoriesPorosityRecovery method
The invention relates to a geologic history period sandstone reservoir porosity evolution recovery method which comprises the following steps: (1) establishing a sandstone reservoir diagenesis evolution sequence and a corresponding paleoburial depth of the reservoir during diagenesis; (2) establishing a normal compaction layout; (3) establishing a functional relationship between porosity and surface porosity; (4) carrying out sandstone reservoir porosity backstripping inversion under the restriction of the diagenesis sequence; (5) correcting by mechanical compaction and hot compaction; and (6) on the basis of the steps above, determining the true porosities of the main diagenetic stages, and establishing the geologic history period sandstone reservoir porosity evolution curve. The invention intensively solves the key problems of the determination of diagenesis occurrence time and paleoburial depth, the relationship between porosity and surface porosity, compaction correction and the like in the existing geologic history period sandstone reservoir porosity evolution recovery method, can effectively predict the porosity of the sandstone reservoir in the oil gas forming period, and provides instructions for effective evaluation on the reservoir.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
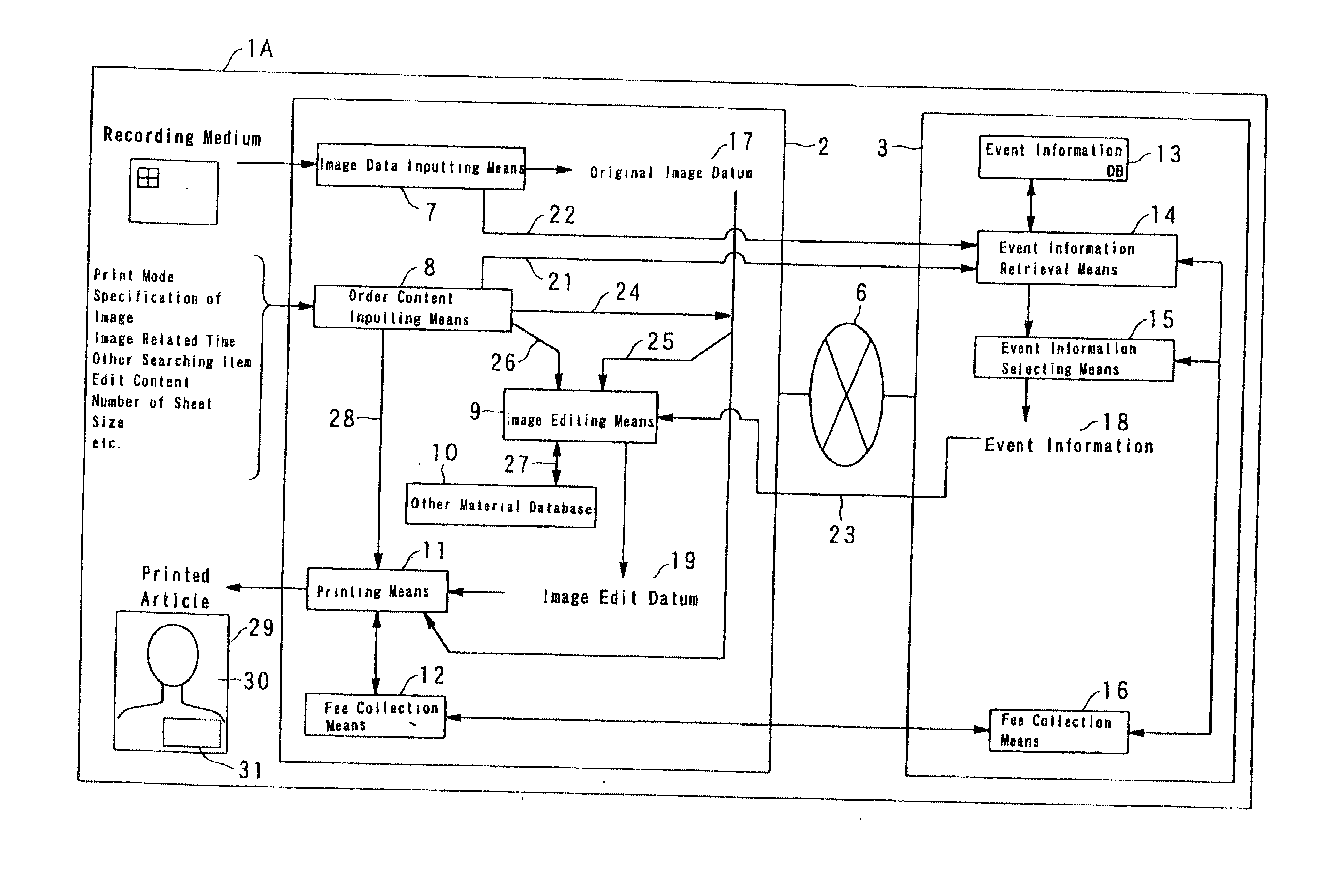
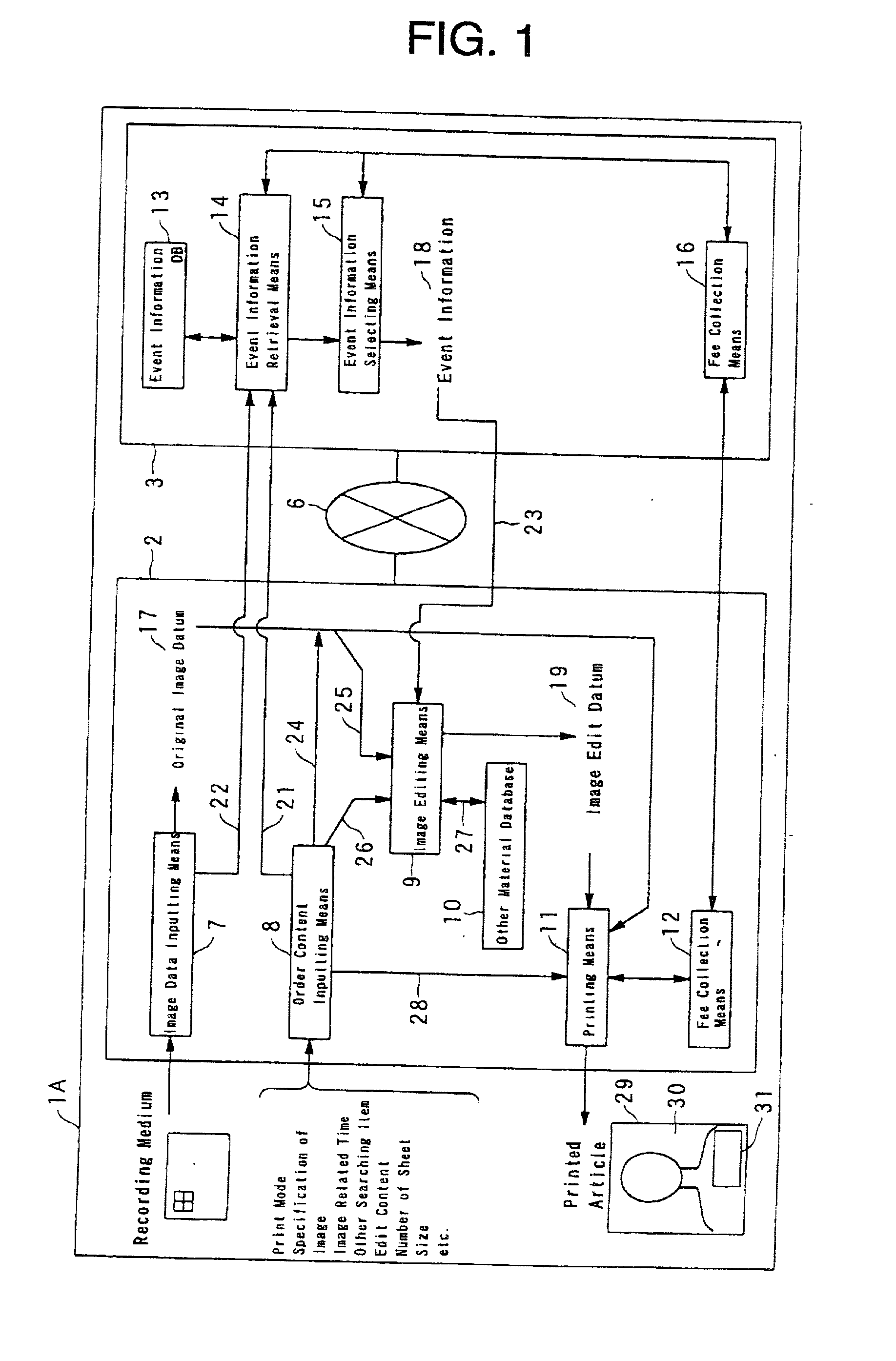
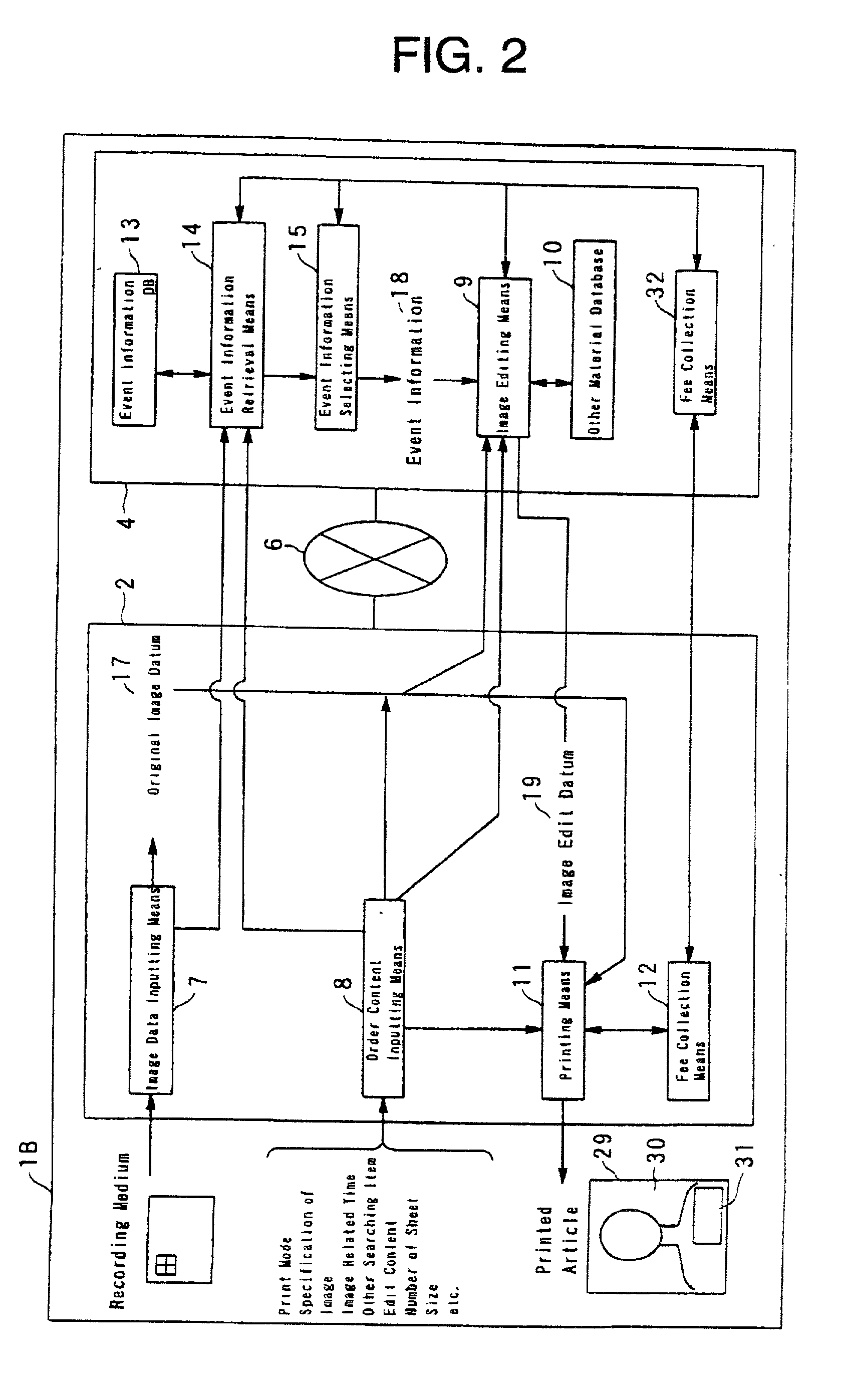
Image printing system
InactiveUS20020051207A1Increase added valueImprove abilitiesDigitally marking record carriersData processing applicationsImaging dataSystem image
Image plus event information printing system, which comprises an image data inputting means for inputting a datum of original image, an event information database which memorizes the data of current and / or passing events information being sorted with one or more items, wherein one of the items consists of the occurrence time of the event, an event information retrieval means for extracting any event information within a predetermined range being in correlation to the time which is related to the original image, by retrieving from the sorted data in the event information database with using one or more of the items, an image editing means for preparing a datum of an image plus event information, from the datum of original image and the extracted event information, and a printing means for printing the image plus current events information in accordance with the datum prepared by the image editing means.
Owner:DAI NIPPON PRINTING CO LTD
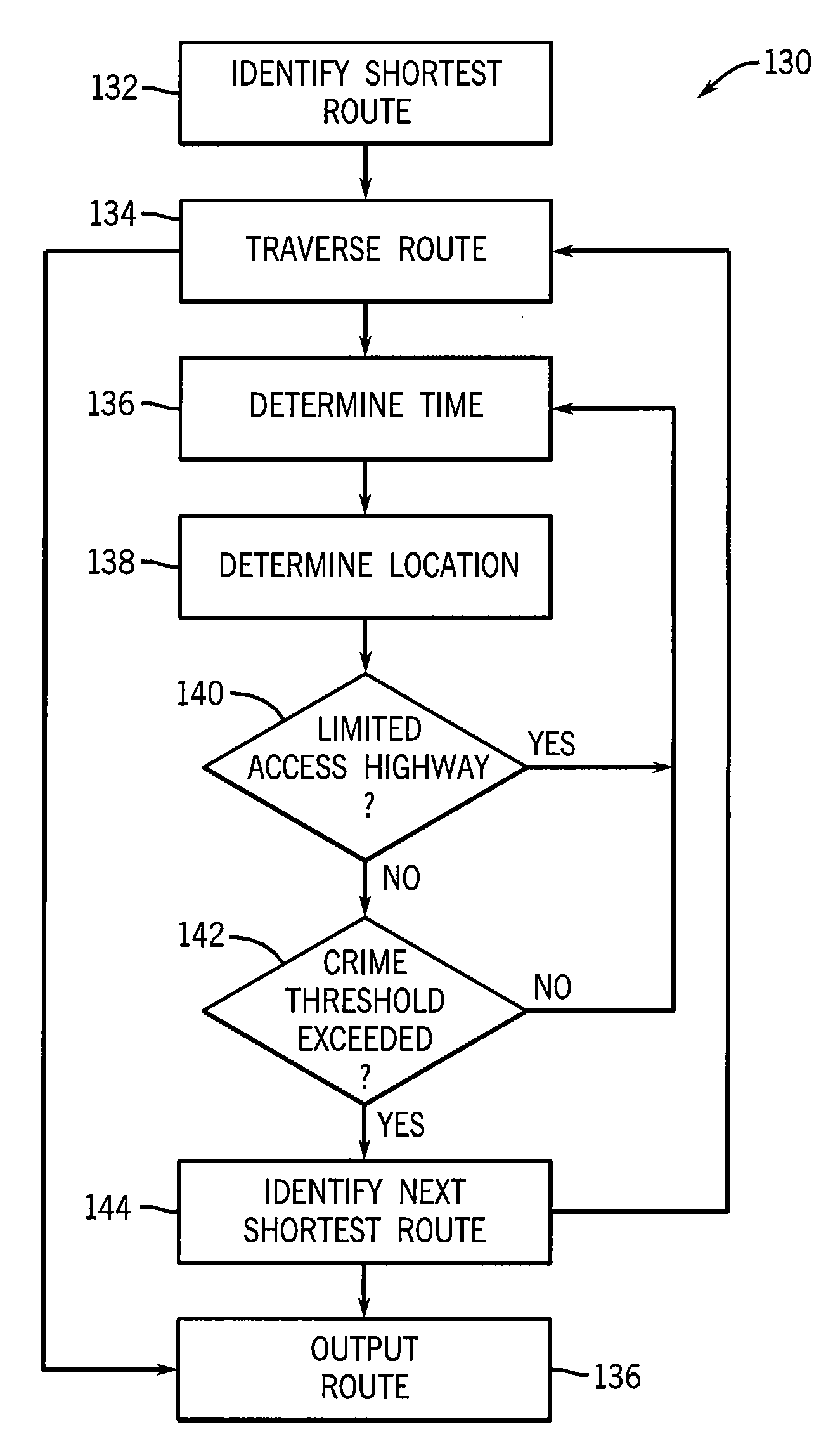
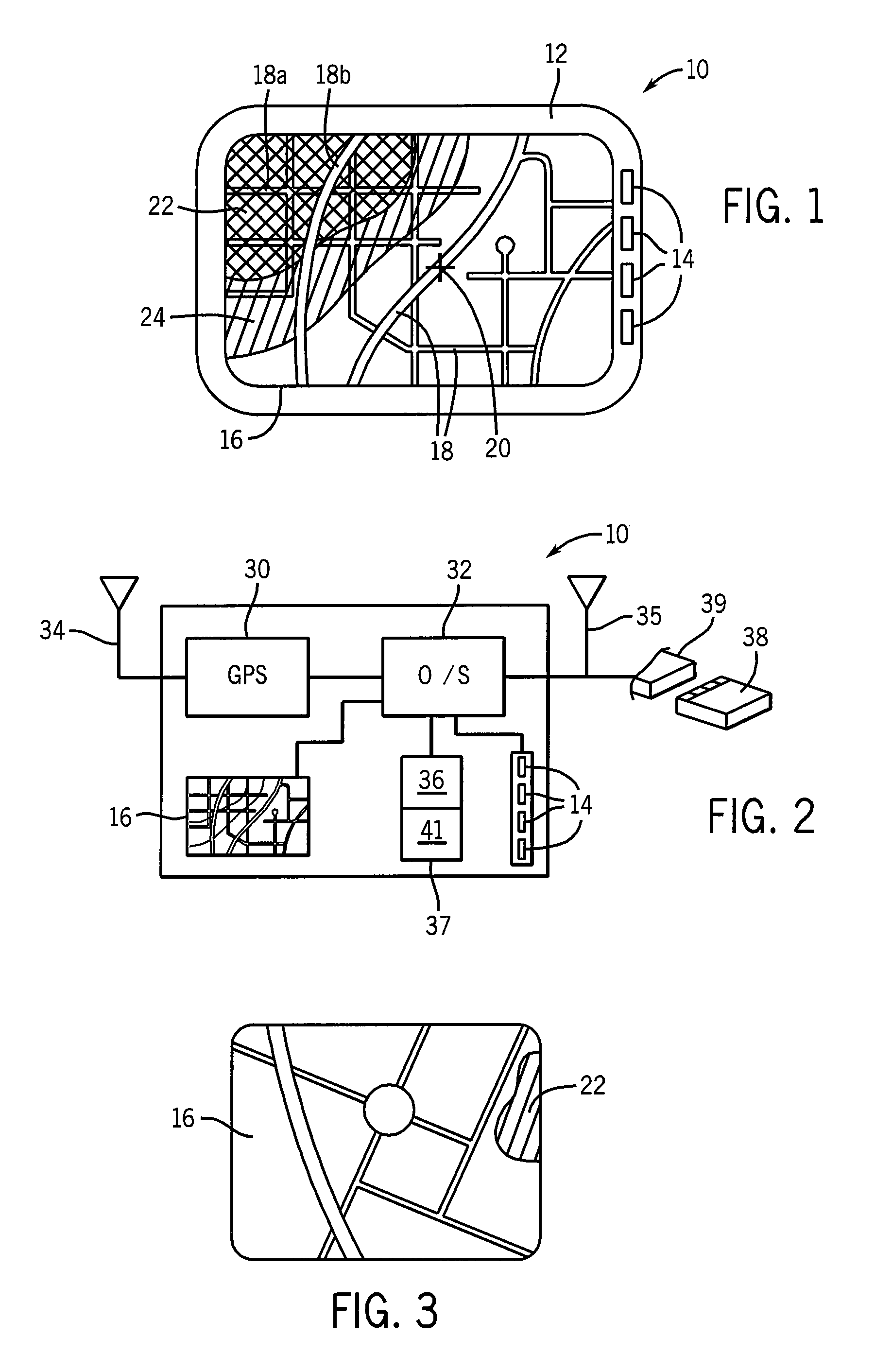
Mobile Navigation System with Graphic Crime-Risk Display
ActiveUS20100100319A1High crimeInformed decisionInstruments for road network navigationDigital data processing detailsGraphicsStatistical correlation
A navigation system for mobile use includes street map data used for creating a dynamic map display tracking movement of the vehicle and includes crime data used to provide an overlay on the dynamic display indicating a risk of crime to the vehicle's occupants from the surrounding area. Crime data may be harvested from police websites and / or generated using statistical correlation techniques from other proxy information. Presented crime data indicate crime risk, type of crime, crime date or time of occurrence, and linkage to environmental conditions such as type of weather, temperature, and moonlight.
Owner:RIO SISA IDEA FARM
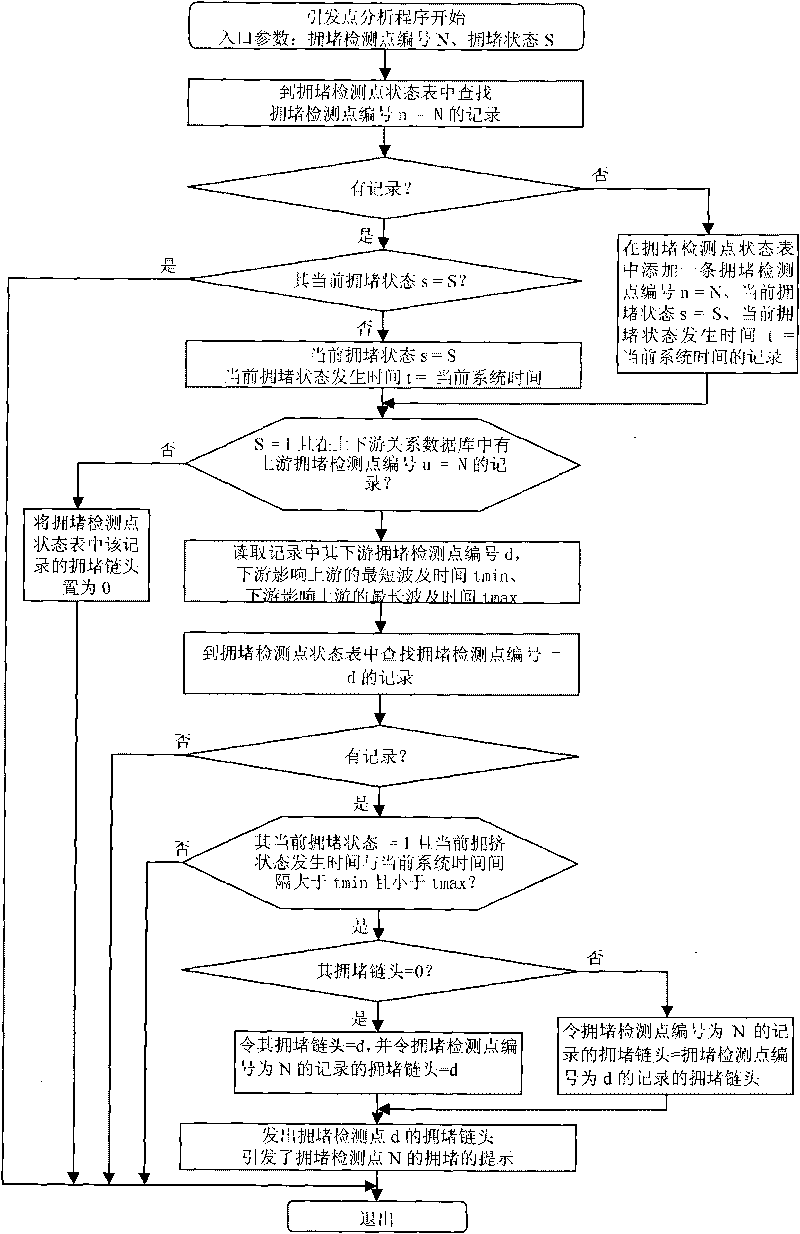
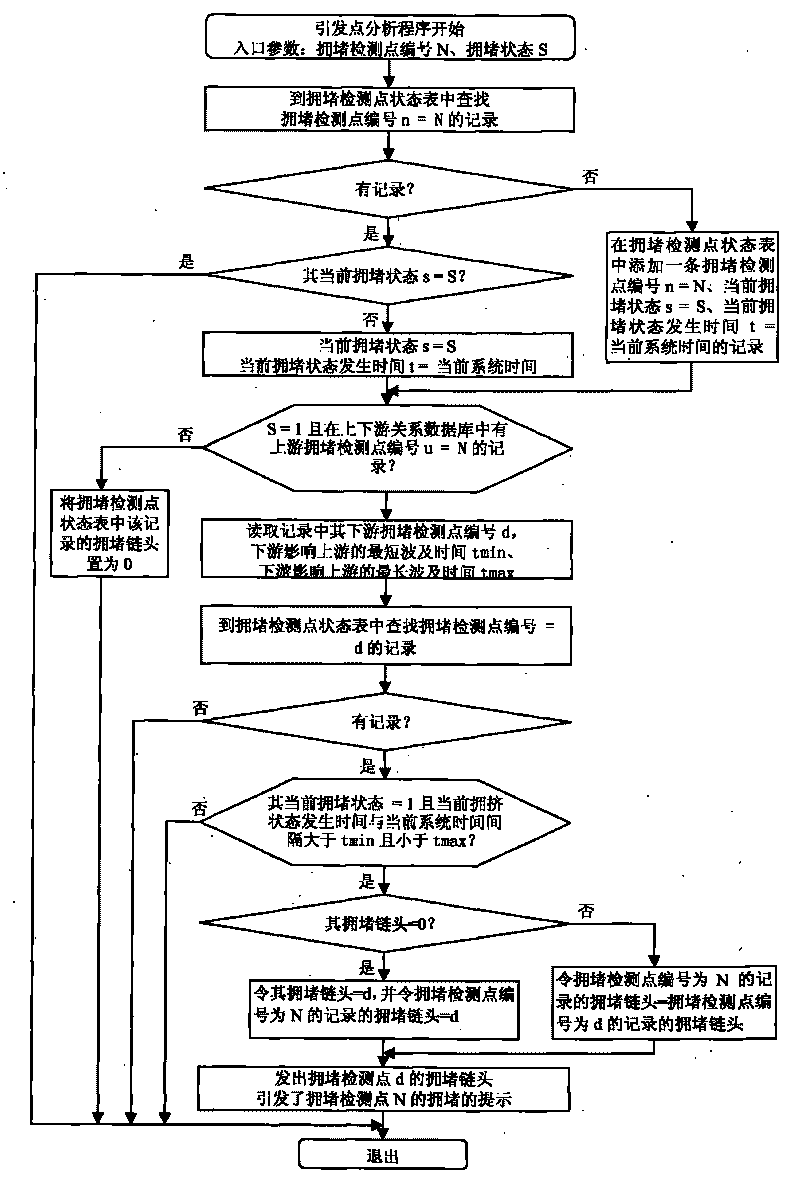
Area traffic jamming triggering point record analysis system and operation method thereof
InactiveCN101719314ARoad vehicles traffic controlSpecial data processing applicationsAlarm messageSimulation
The invention relates to an area traffic jamming triggering point record analysis system and an operation method thereof; the system is composed of an analysis processing computer arranged at the control center, a traffic jamming rapid alarming device arranged on the detection point of the road and a communication line; a jamming detection point upstream and downstream relation database is preset on the analysis processing computer, and a triggering point analytical procedure is operated; after the analysis processing computer receives one jamming alarming message transmitted by the jamming rapid alarming device at each time, the triggering point analytical procedure is started immediately; after the triggering point analytical procedure finds that traffic jamming happens at one jamming detection point, the downstream jamming detection point of the jamming detection point is searched from the upstream and downstream relation database, and according to the current jamming state and the occurrence time of the current jamming state of the downstream jamming detection point, weather the jamming is affected and generated by the downstream traffic jamming waves is deduced, if yes, the head of a jamming chain is found as the triggering point and a prompt message is given, and the prompt message can be stored separately for use in the future.
Owner:姜廷顺
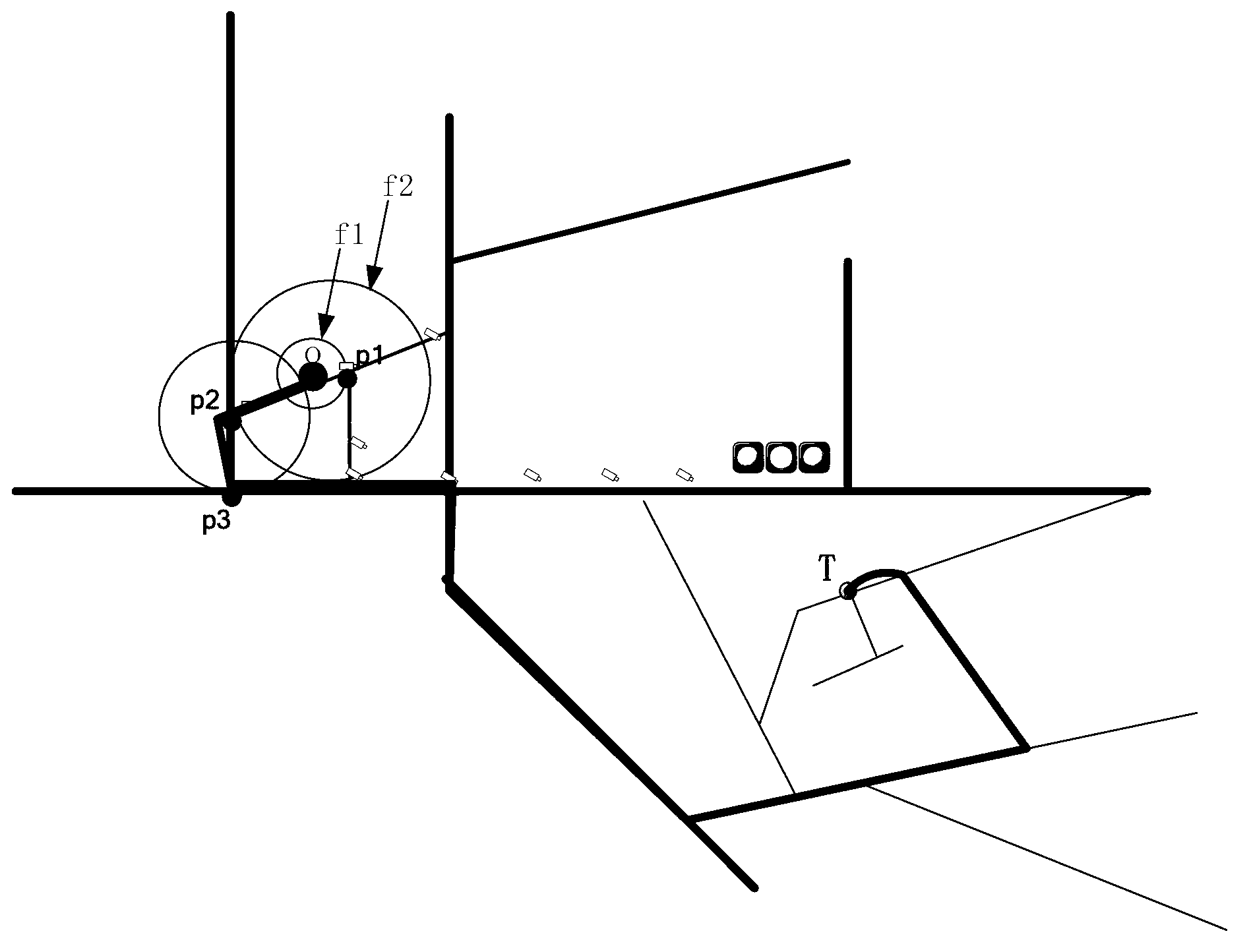
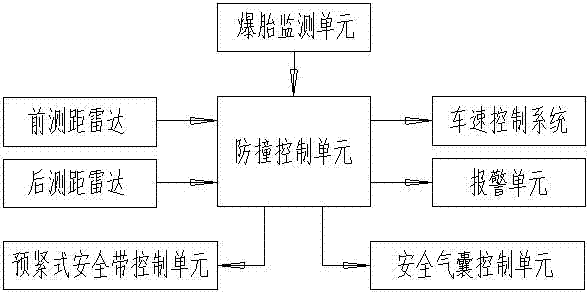
Automobile side-collision prevention mitigating system and control method
ActiveCN102463949ASolve functionImprove the anti-collision effectPedestrian/occupant safety arrangementSpeed control systemControl system
The invention discloses an automatic side-collision prevention mitigating system and a control method, which are used for avoiding automobile side-collision or lightening damages caused by the side-collision to the utmost extent; the automotive side-collision prevention mitigating system comprises a radar ranging system, a collision-prevention control unit, a speed control system, a speed sensor,an alarming unit, a pre-tightened safety belt control unit and an airbag control unit; the collision-prevention control unit is used for calculating relative speed of the automobile in relation with a left automobile and / or a right automobile according to distance data provided by the radar ranging system, judging whether the collision occurs and the possible occurrence time of collision according to the length and the speed of the automobile, and sending corresponding instructions to actuating mechanisms according to preset programs, and controlling the operations of the automobile such as alarming and acceleration, so that the automobile side-collision is avoided or the damages resulting from the automobile side-collision are lightened to the utmost extent.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
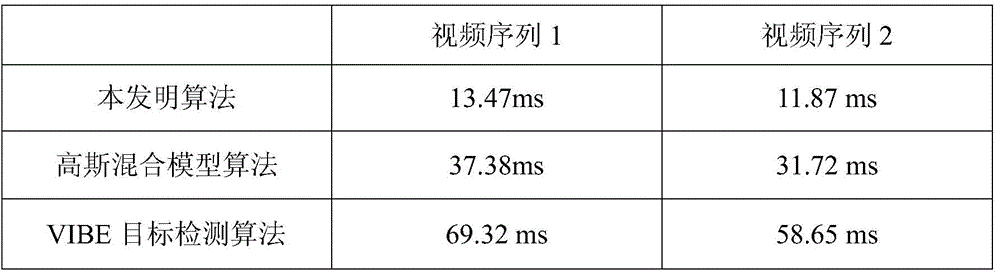
Target detection algorithm in combination of statistical matrix model and adaptive threshold
The invention discloses a target detection algorithm in combination of a statistical matrix model and an adaptive threshold. The target detection algorithm comprises the steps of initializing a background image through the front frames of a video; initially extracting foreground by the background subtraction method; continuously accumulating the occurrence times of pixel points with small pixel value variation amplitude in the foreground area by the frame difference method; storing the times of accumulation variation of the corresponding pixel points through a statistical matrix; updating the current foreground as the background point when the times exceed a certain value so as to obtain the accurate background image for the subsequent background subtraction method; then performing binarization segmentation through the adaptive threshold to obtain a target area; the binarization threshold of each pixel point is determined according to the difference value between all the current pixel values and the background pixel value in the point window. With the adoption of the algorithm, the background can be quickly updated, and the target can be accurately detected.
Owner:HEFEI UNIV OF TECH
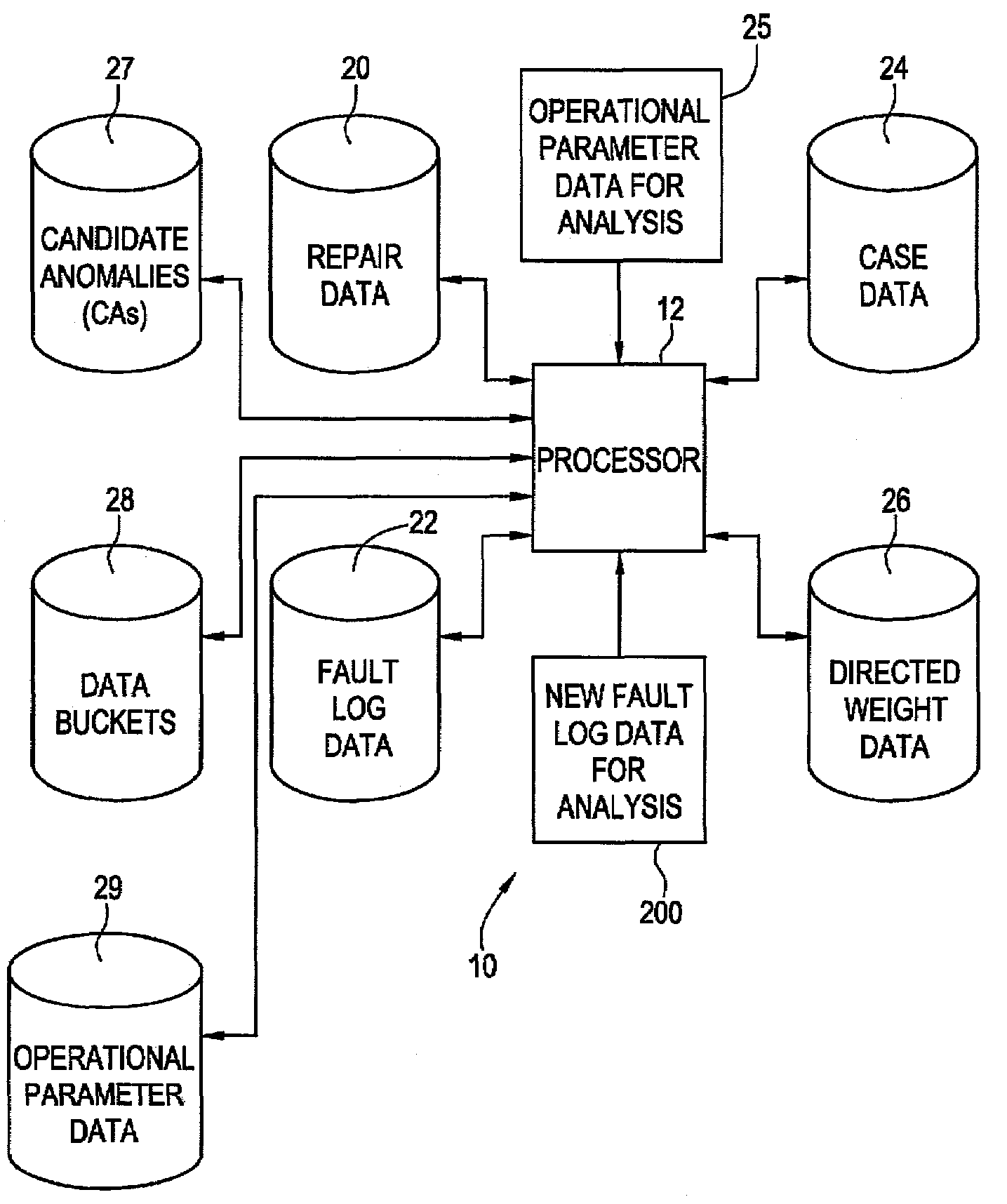
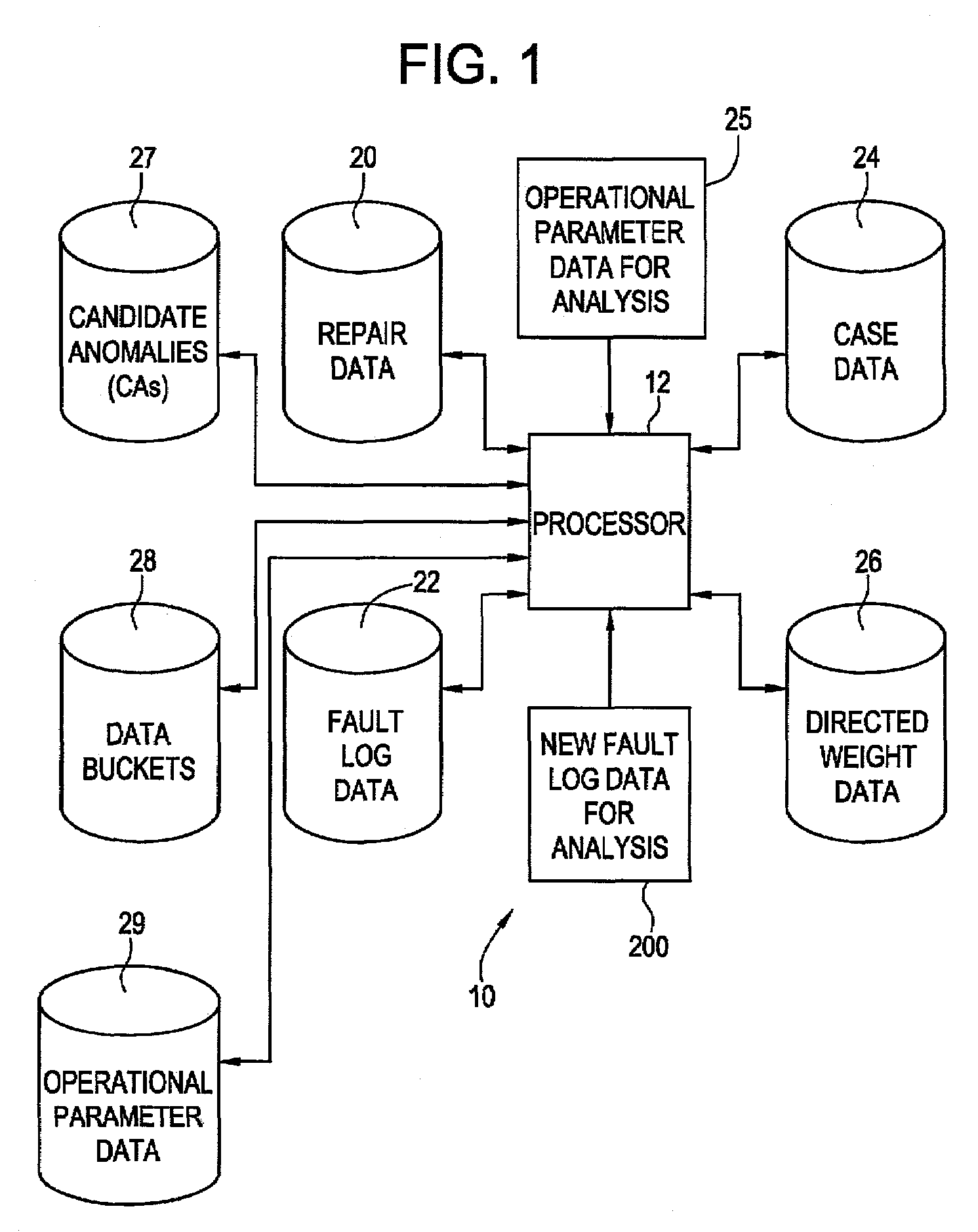
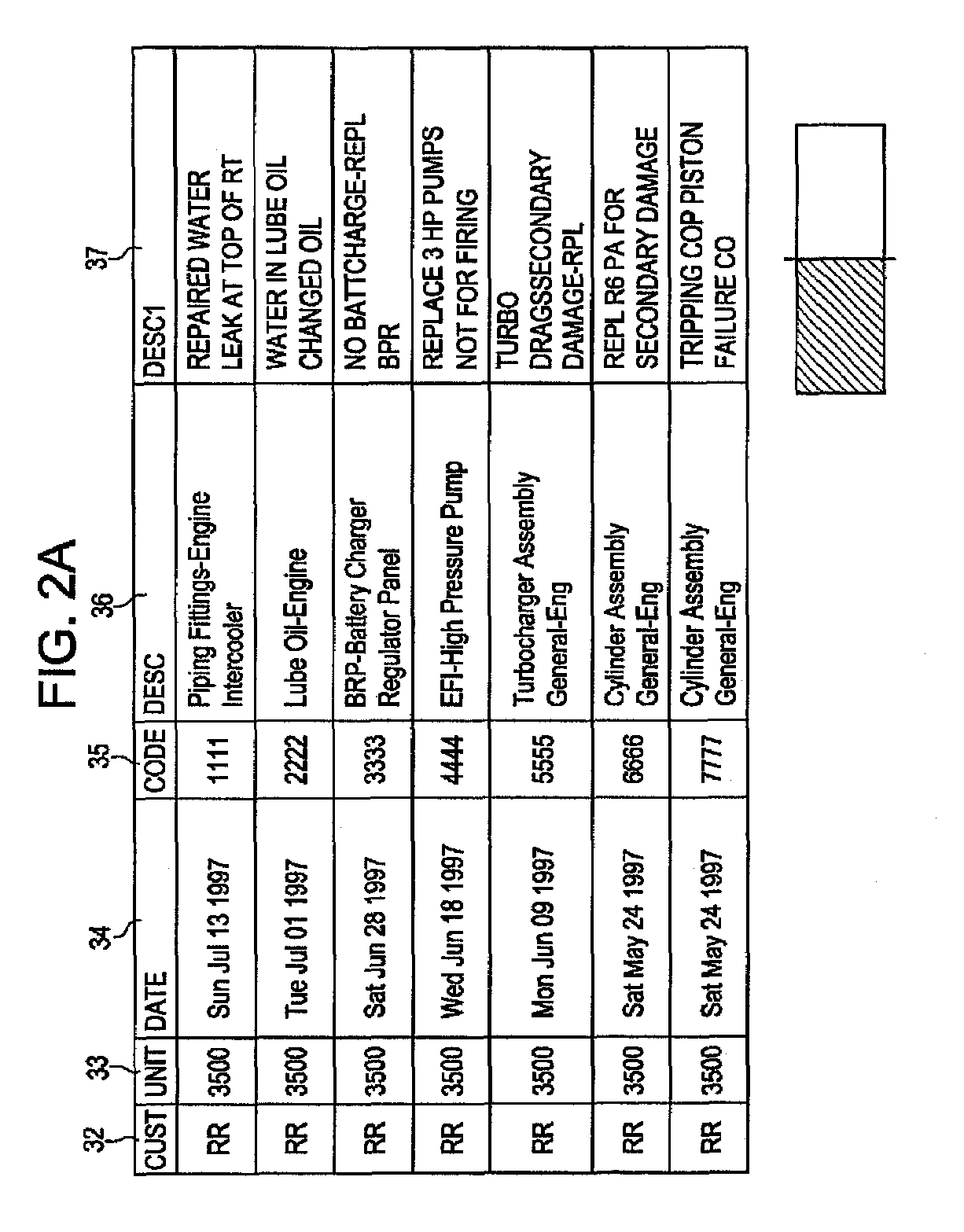
Method and system for analyzing fault and quantized operational data for automated diagnostics of locomotives
Method and system for processing fault log data from a machine comprising a plurality of respective pieces of equipment are provided. Operational parameter data indicative of operational and / or environmental conditions for the respective pieces of equipment is further processed. The method allows collecting fault log data comprising a plurality of faults from any malfunctioning piece of equipment. The method further allows collecting operational parameter data relatable to each respective time of occurrence of the plurality of faults from the malfunctioning equipment. Respective identifying actions allow identifying a plurality of distinct faults in the fault log data and a plurality of data buckets indicative of respective levels of quantization of each operational parameter. At least one distinct fault cluster is generated from the plurality of distinct faults. Each generated fault cluster is related a respective quantization level of at least one operational parameter to provide at least one fault cluster that may be configurable in at least one of the following cluster configurations: a stand-alone fault cluster configuration and a cluster configuration enhanced with quantized operational parameter data. A plurality of weighted repair and distinct fault cluster combinations enhanceable with quantized operational parameter data is generated. At least one repair for the at least one fault cluster enhanceable with quantized operational parameter data is generated using the plurality of weighted repair and distinct fault cluster combinations enhanceable with quantized operational parameter data.
Owner:GENERAL ELECTRIC CO
Resume assessment method and device
InactiveCN107291715AReduce tedious workReduce complexityWeb data indexingData miningData setData science
Owner:ALIBABA GRP HLDG LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com