Patents
Literature
2096 results about "Systems analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Merriam-Webster dictionary defines system analysis as "the process of studying a procedure or business in order to identify its goals and purposes and create systems and procedures that will achieve them in an efficient way". Another view sees system analysis as a problem-solving technique that breaks down a system into its component pieces for the purpose of the studying how well those component parts work and interact to accomplish their purpose.
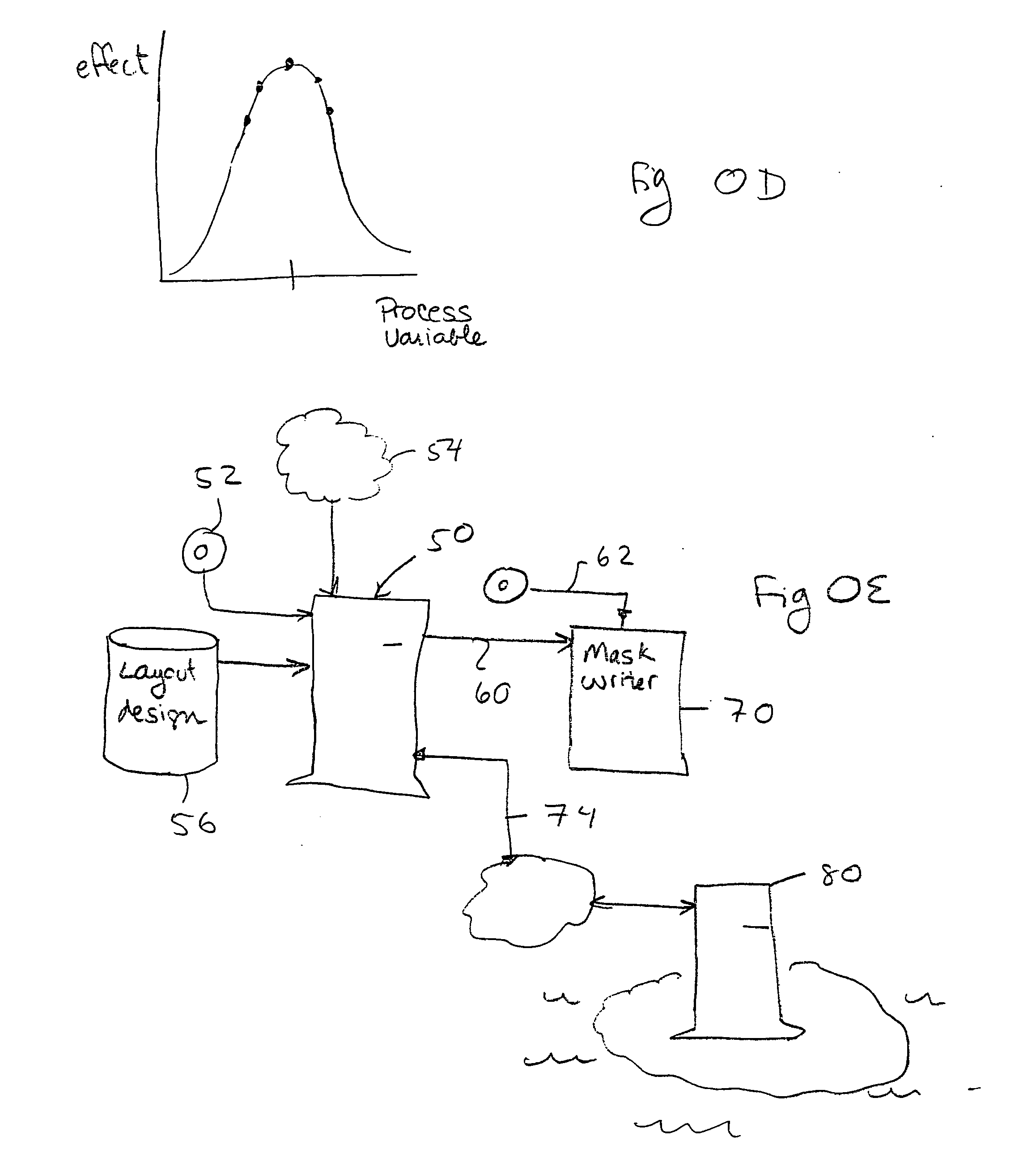
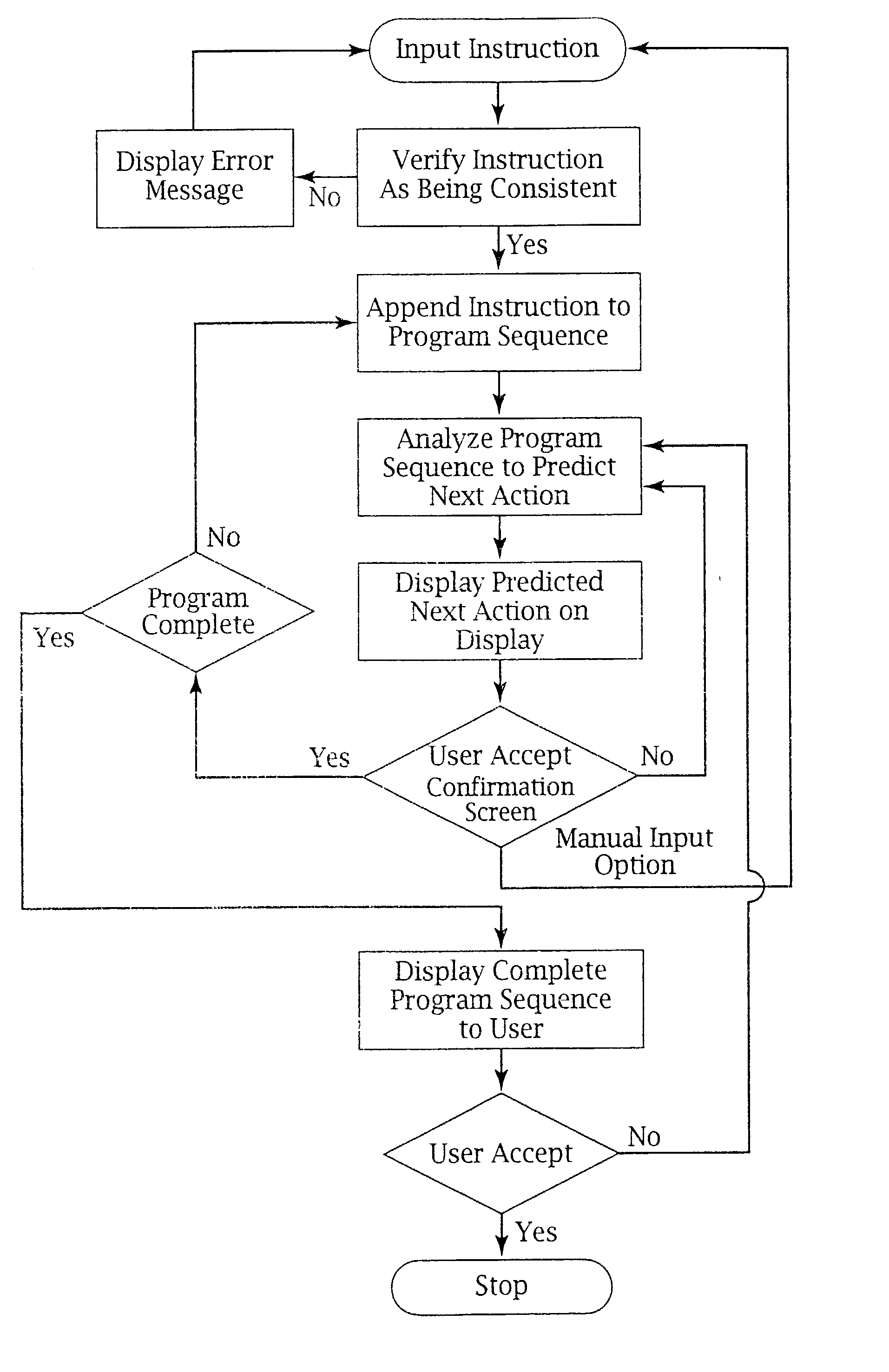
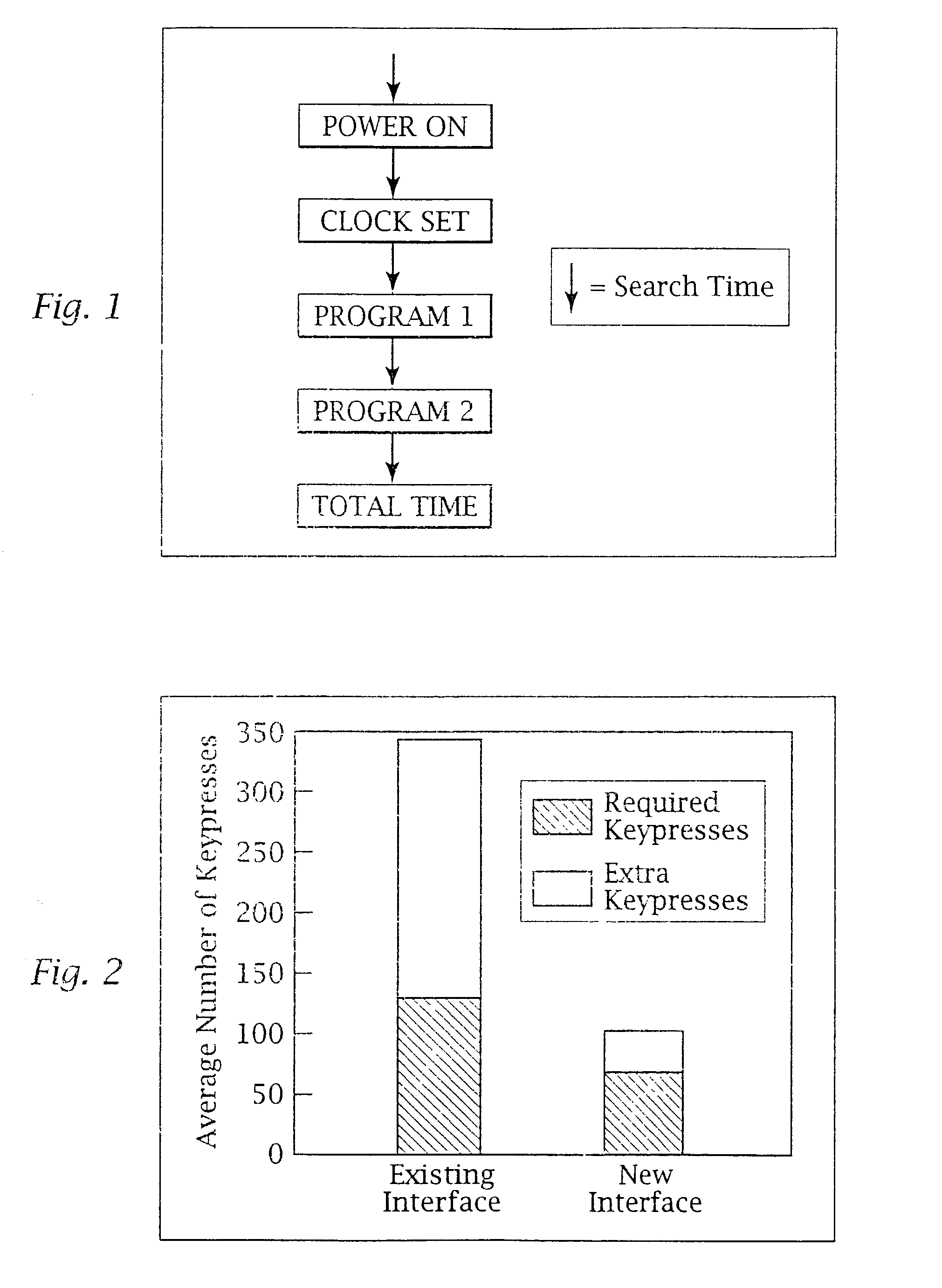
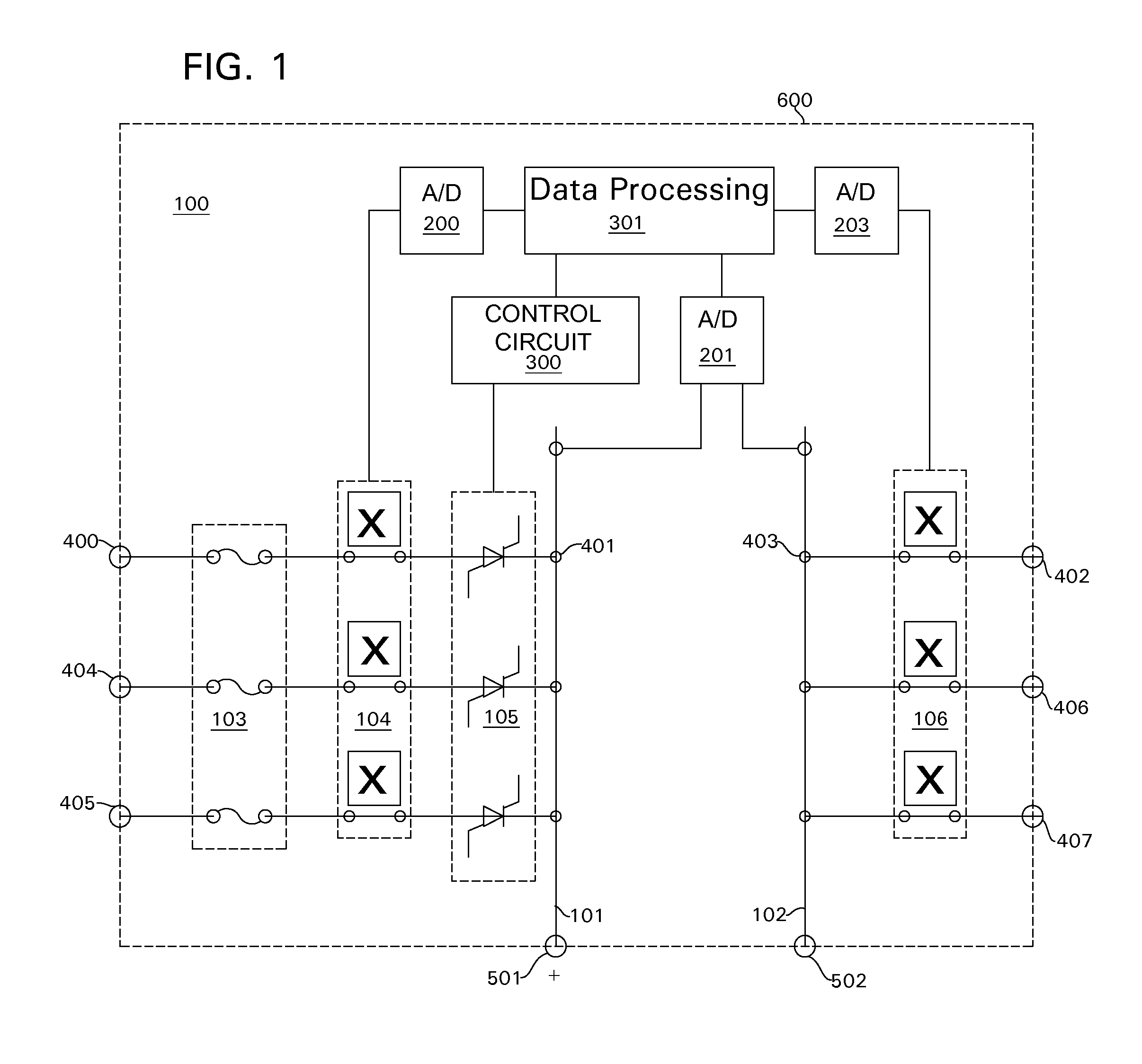
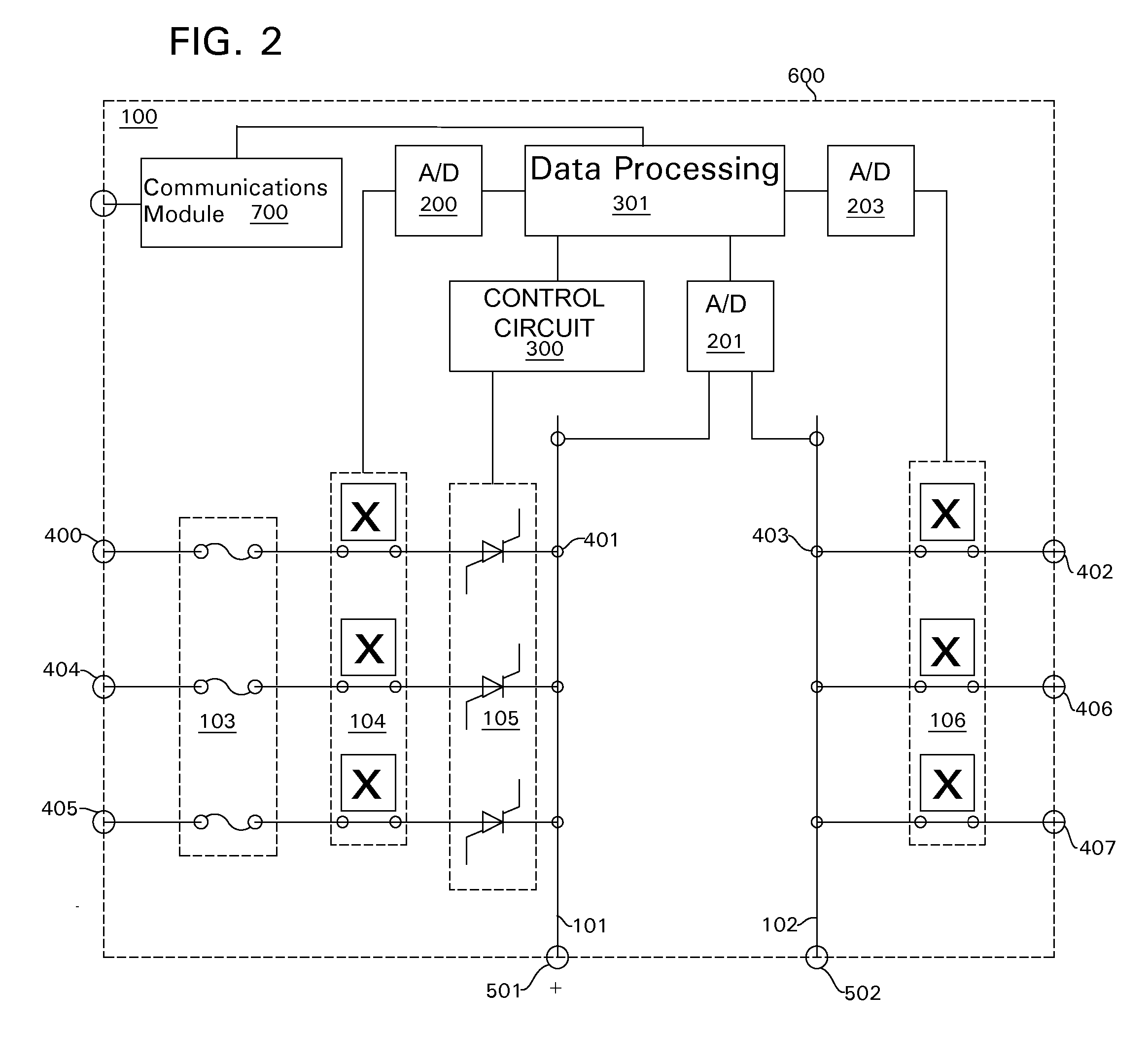
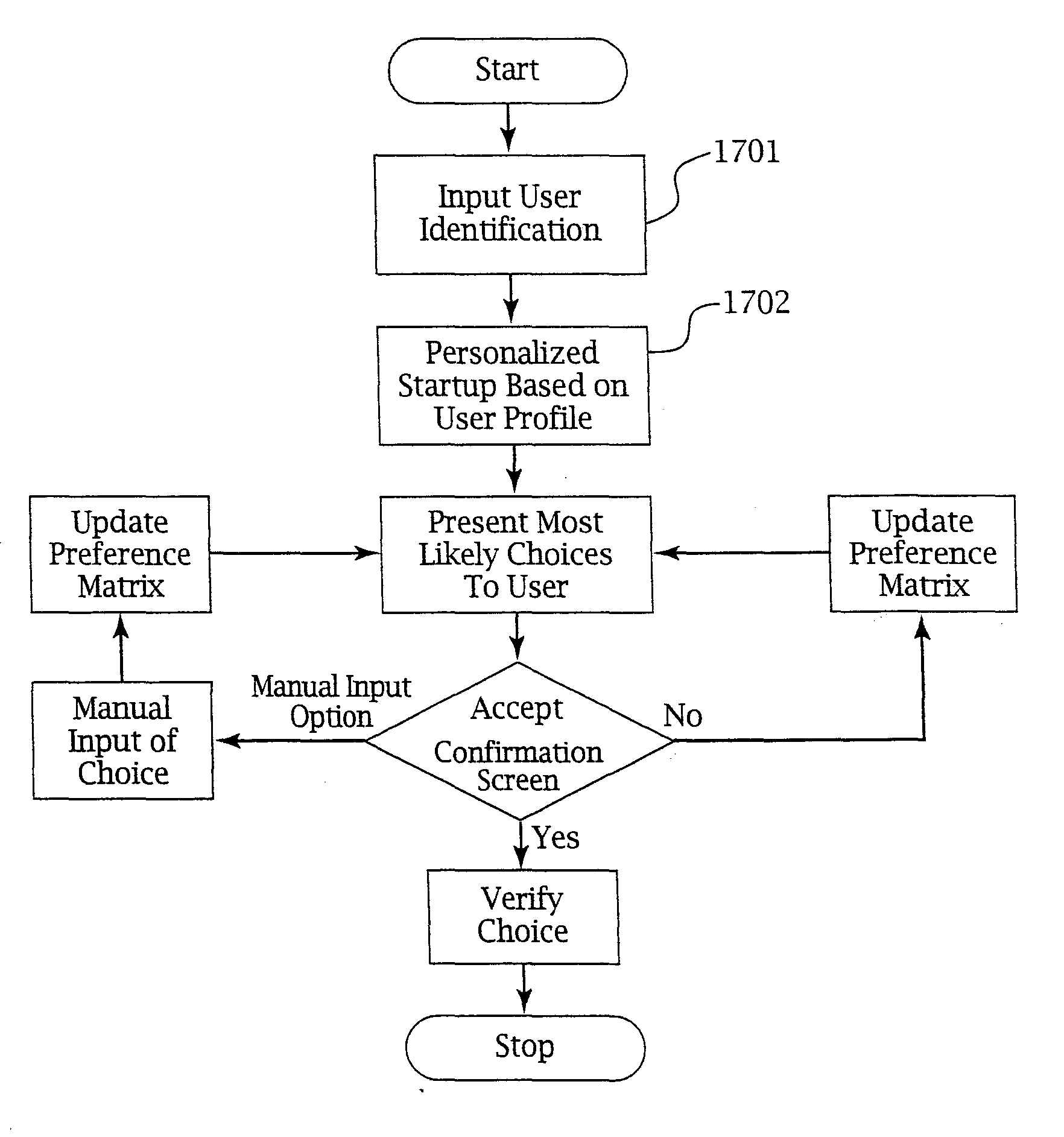
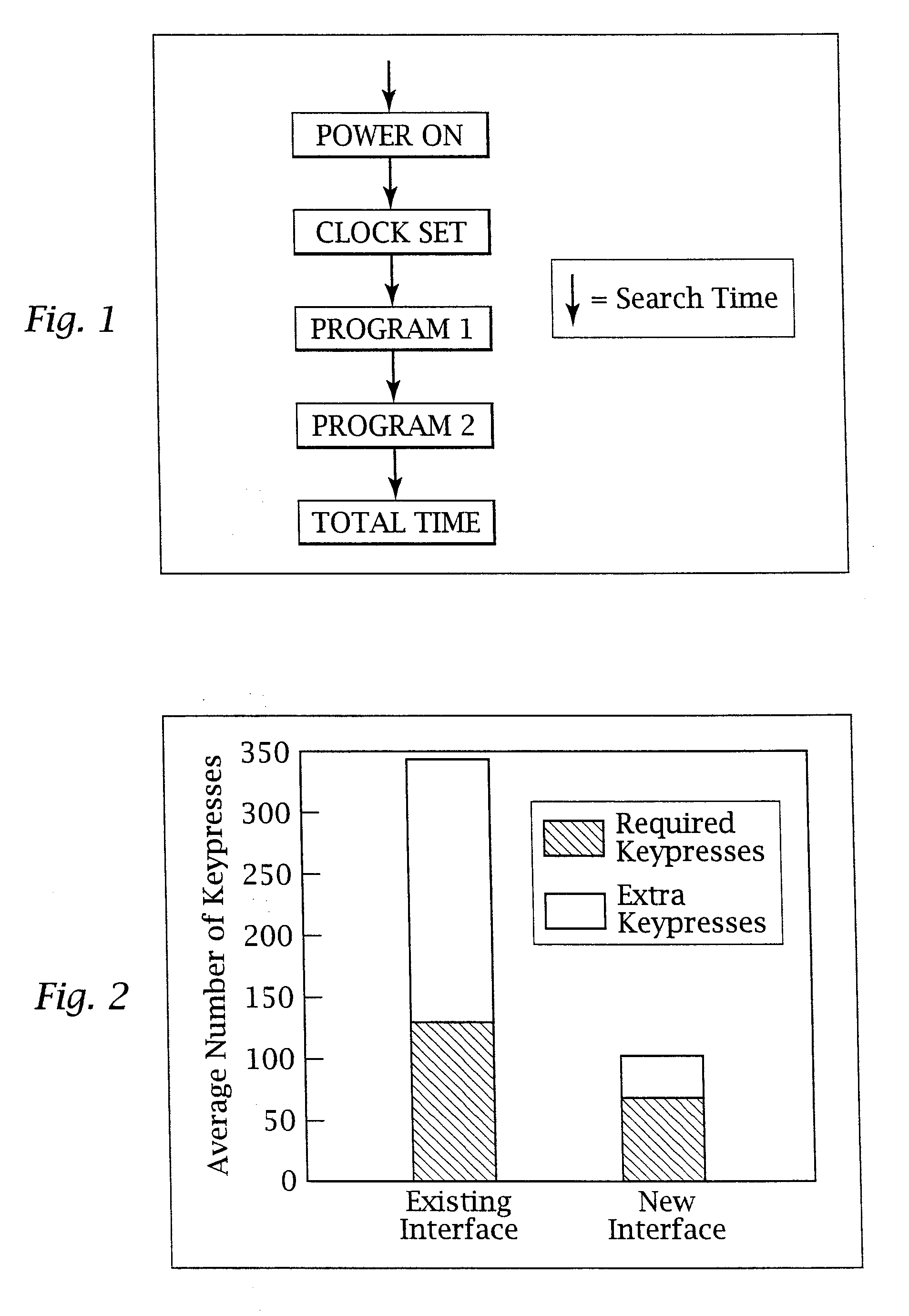
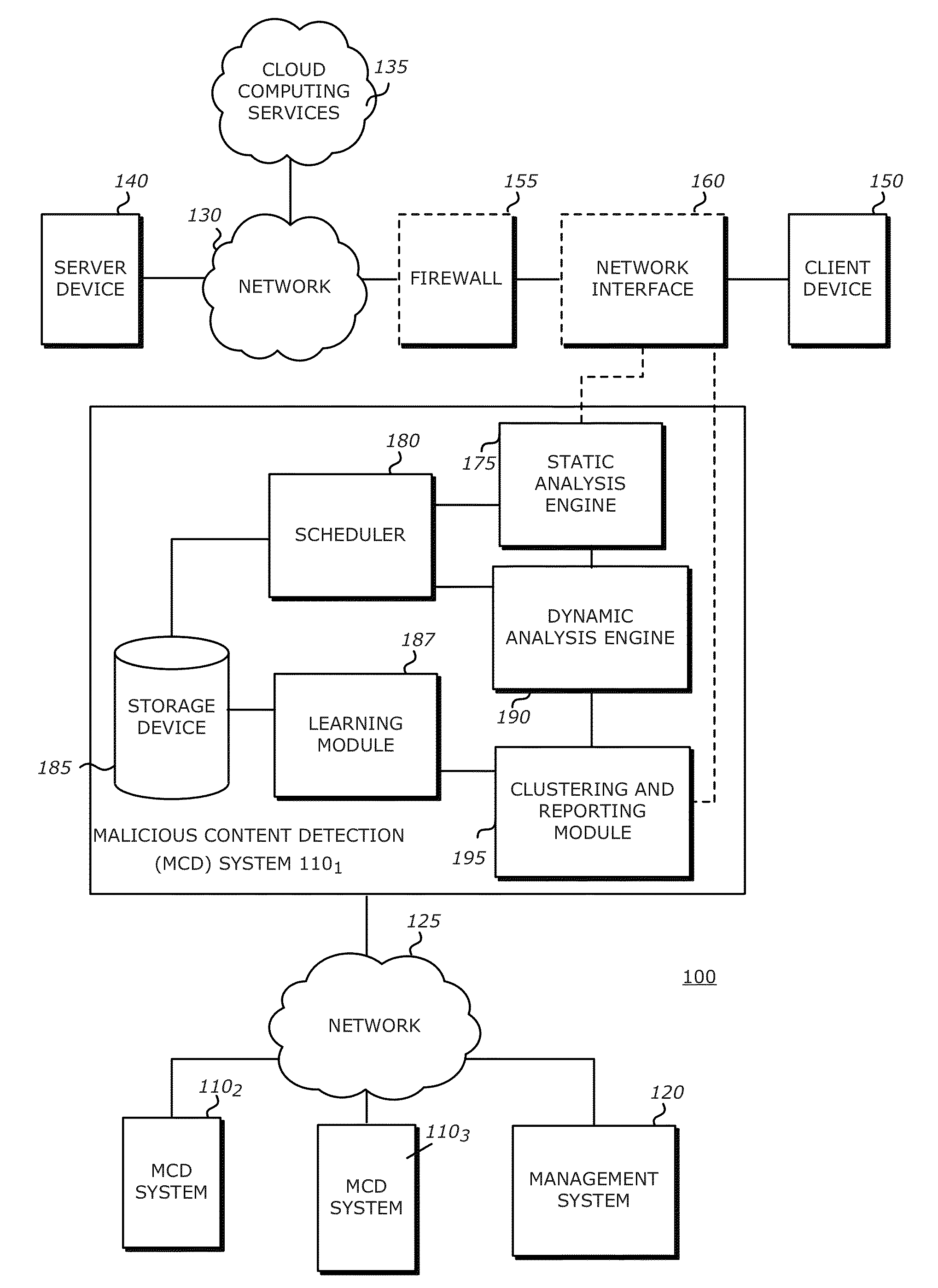
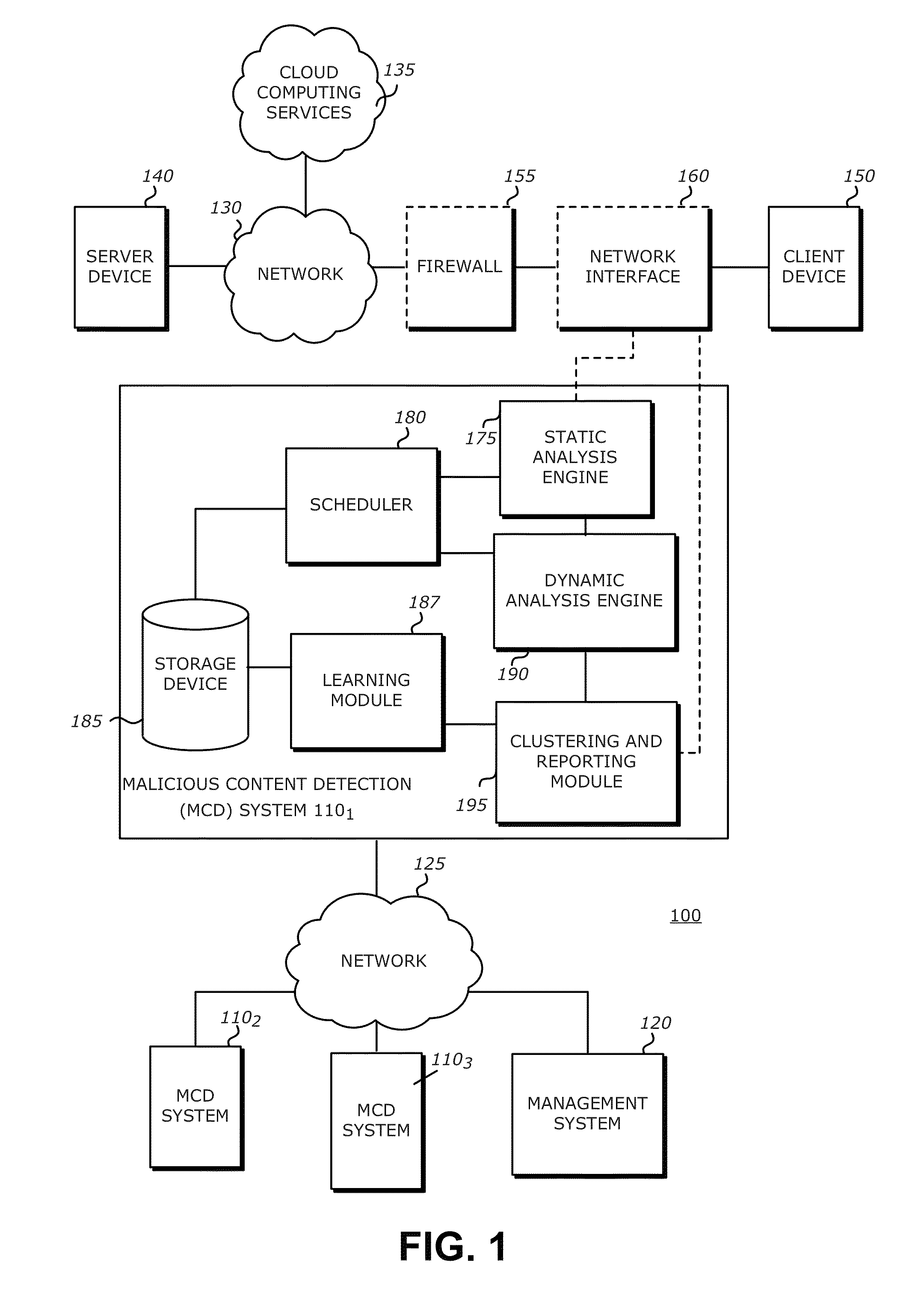
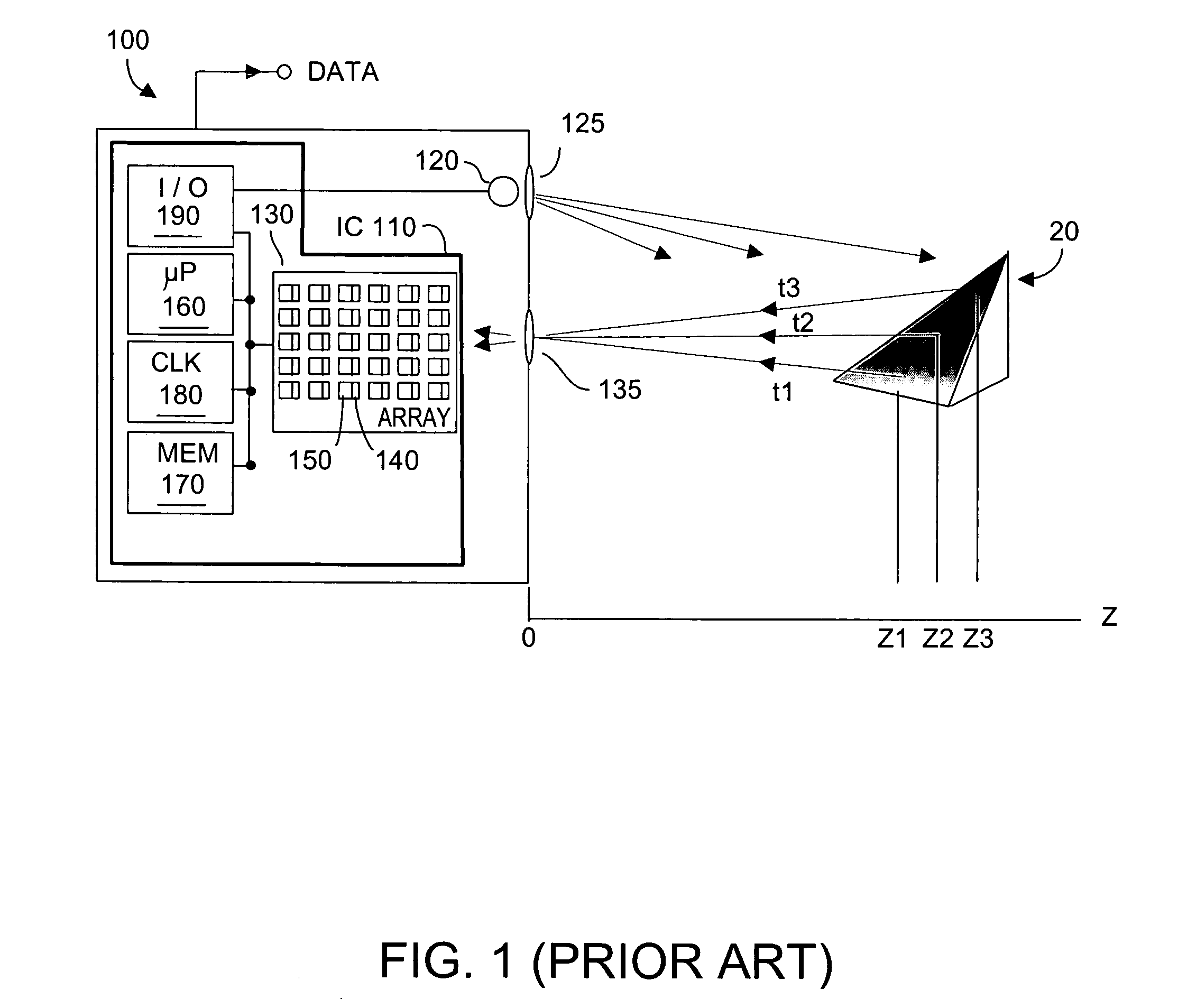
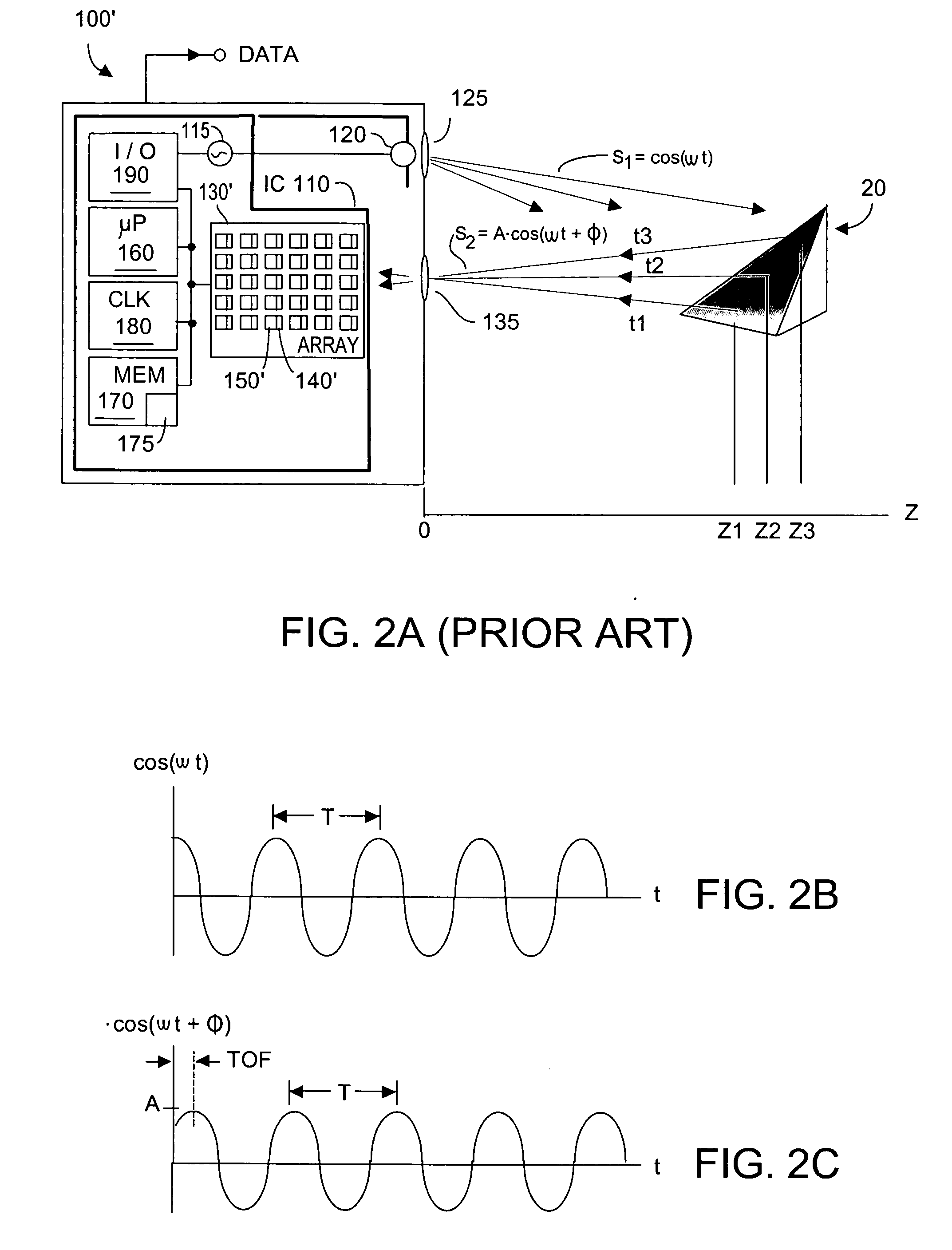
Adaptive pattern recognition based control system and method
InactiveUS6400996B1Minimize timeEasy to implementError preventionFrequency-division multiplex detailsData streamSmart house
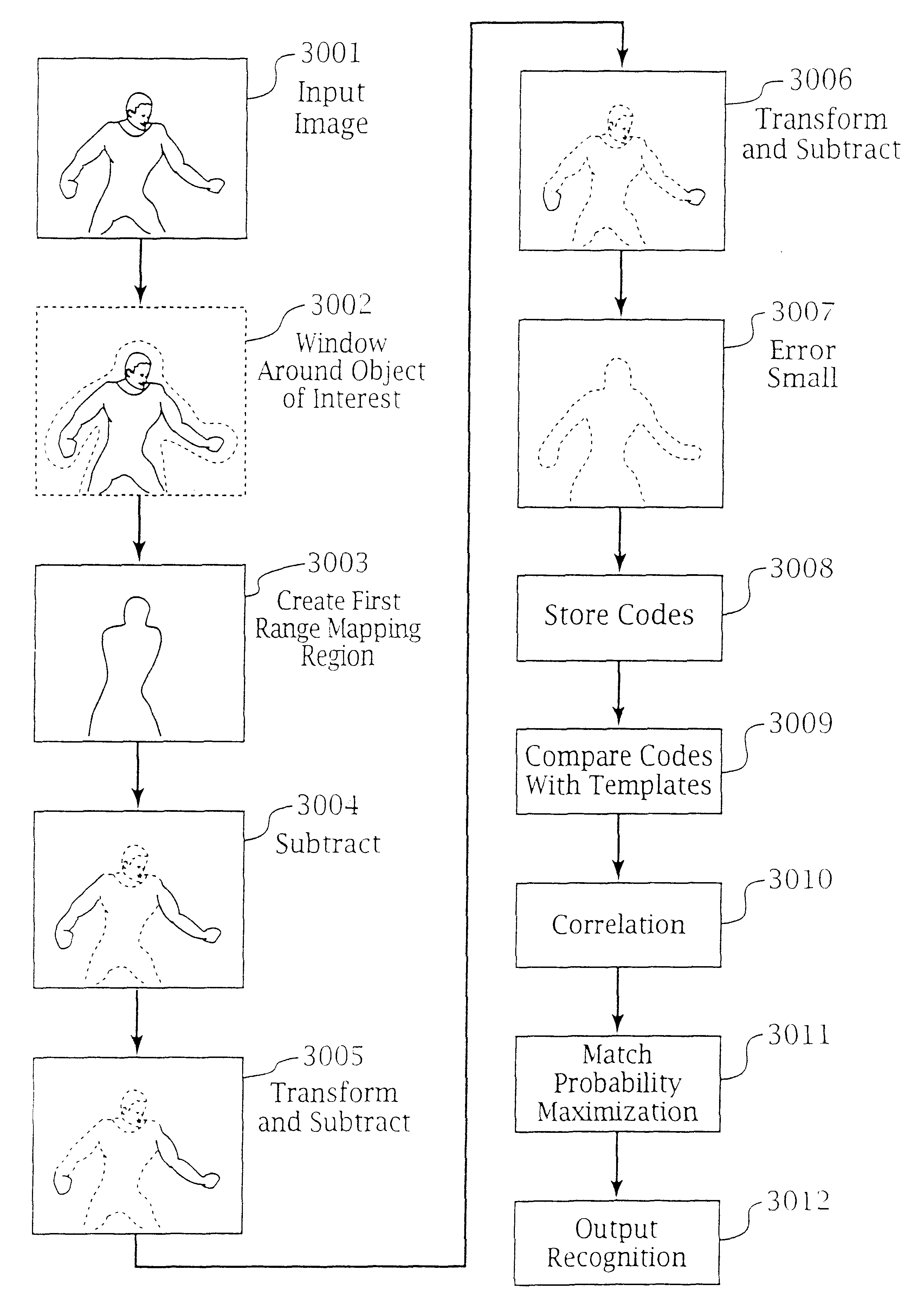
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation that may be efficiently processed to determine correspondence. Applications of the interface and system include a video cassette recorder (VCR), medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS6081750ADecrease productivityImprove the environmentComputer controlSimulator controlHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
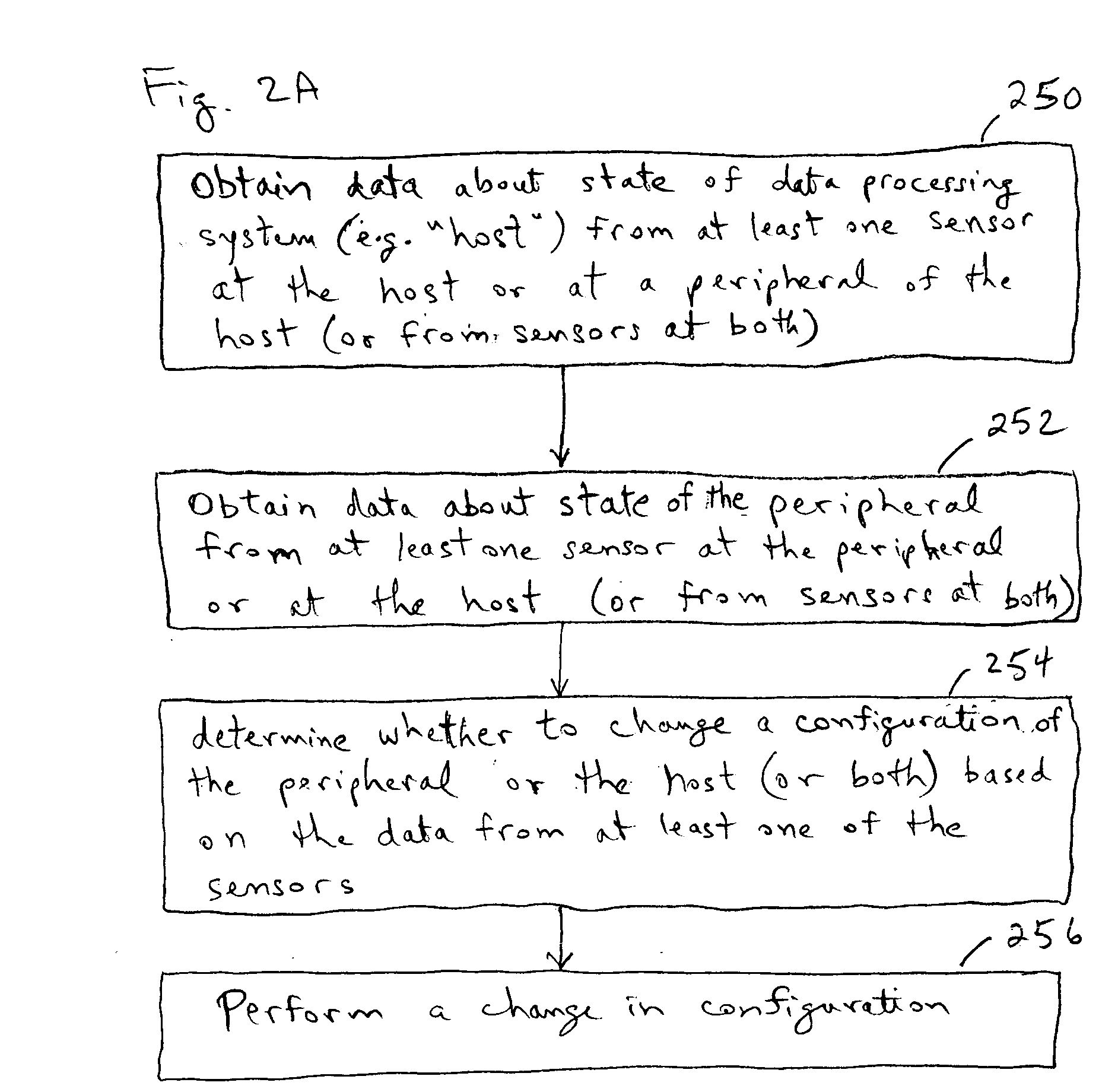
Methods and systems for automatic configuration of peripherals
ActiveUS20080140868A1Service provisioningDigital data processing detailsData processing systemAuto-configuration
Peripherals and data processing systems are disclosed which can be configured to interact based upon sensor data. In one embodiment, a peripheral, which is configured to be used with a data processing system, includes an interface to couple the peripheral to the data processing system, and at least one sensor, such as a proximity sensor, to sense a user of the peripheral, and a processor coupled to the interface and to the at least one sensor, wherein the processor configures the peripheral in response to data from the at least one sensor. The peripheral may communicate sensor data from its sensors to the data processing system, which may be a wireless PDA, and the data processing system analyzes the sensor data from its sensors and from the peripheral's sensors to decide how to configure the peripheral and / or the data processing system based on the sensor.
Owner:APPLE INC
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS6418424B1Minimal costAvoid the needTelevision system detailsDigital data processing detailsHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
ActiveUS7136710B1Significant to useImprove computing powerComputer controlAnalogue secracy/subscription systemsConceptual basisHuman–machine interface
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP +1
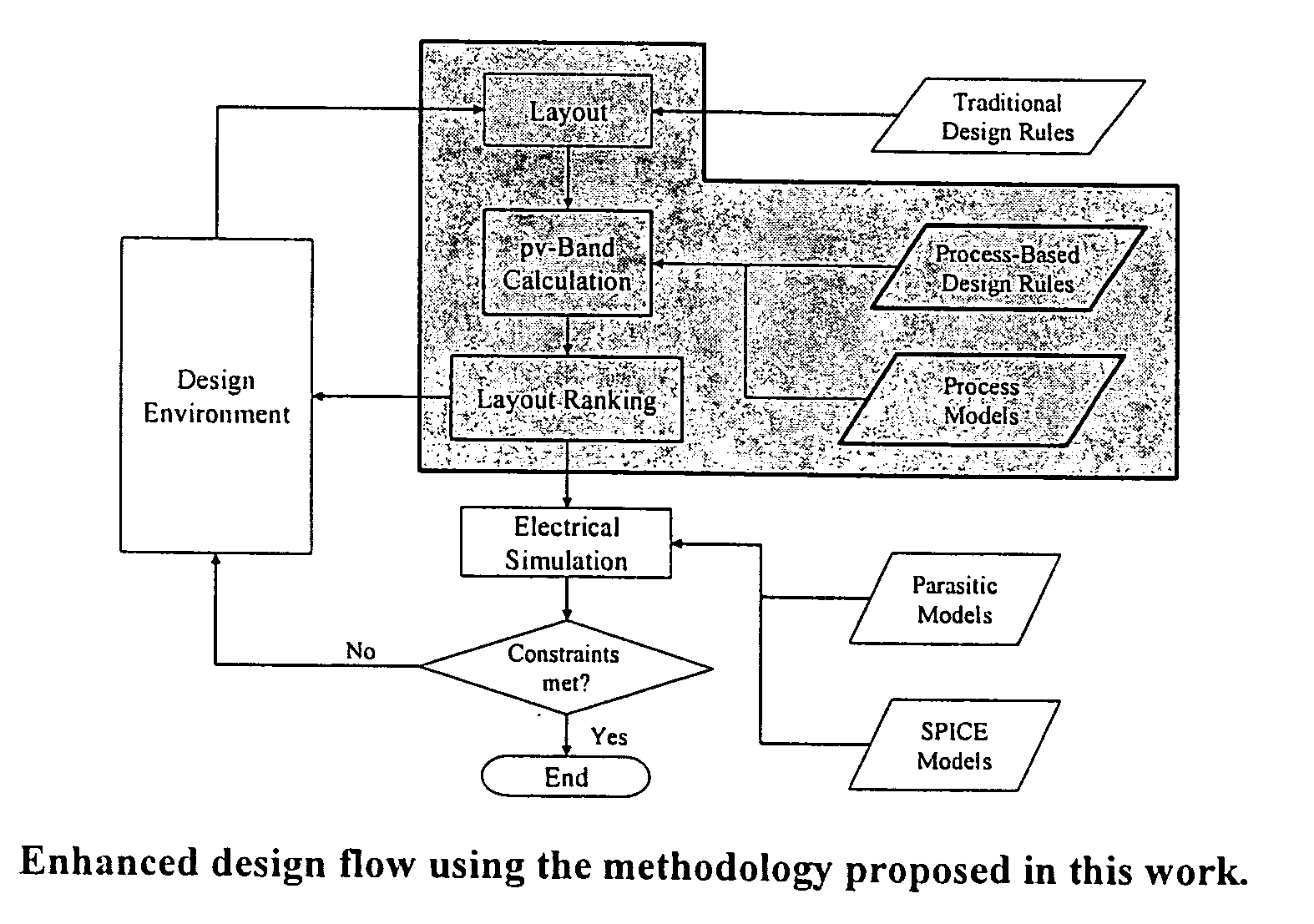
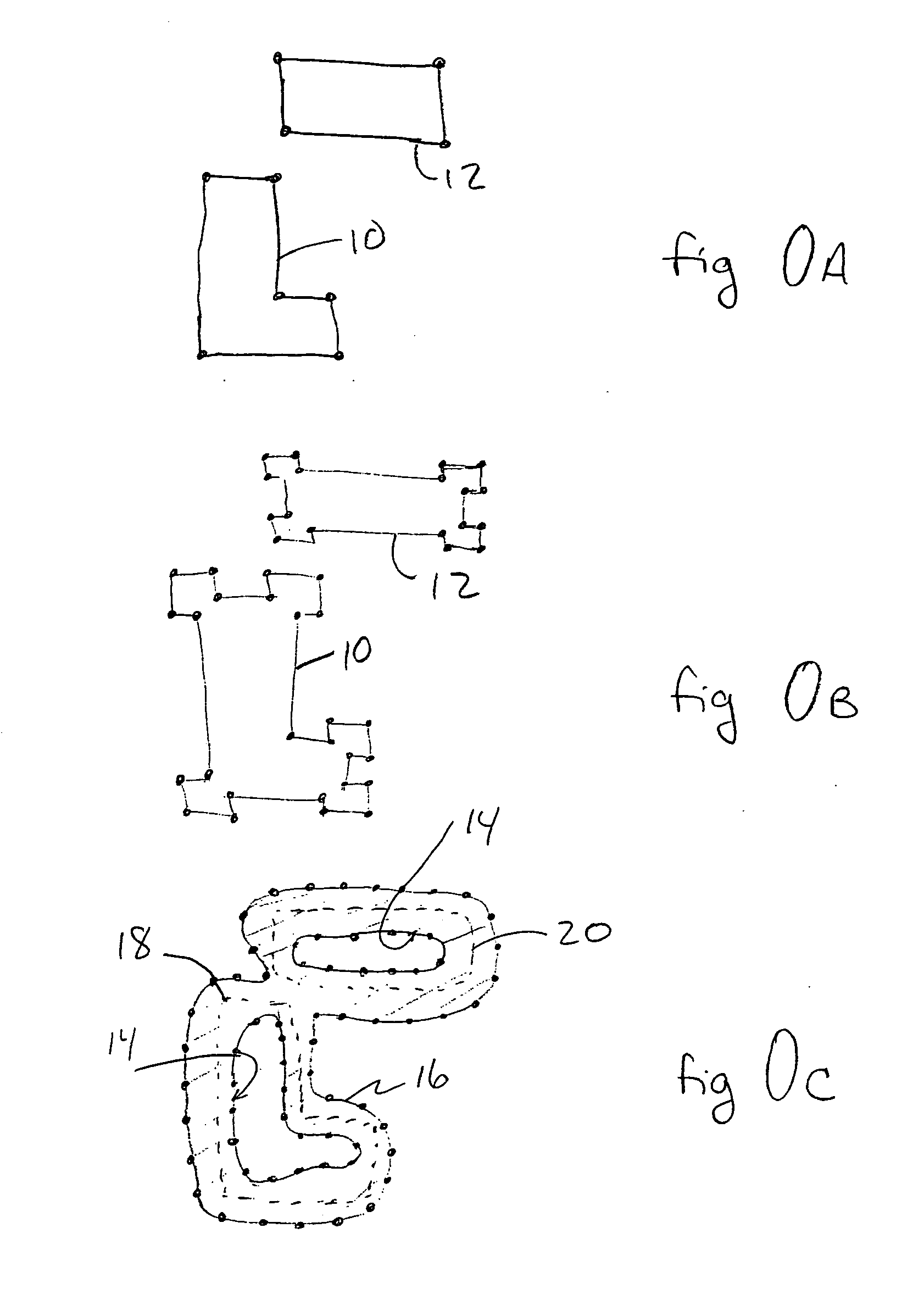
Integrated circuit layout design methodology with process variation bands
ActiveUS20050251771A1Constraint-based CADCAD circuit designSystems analysisIntegrated circuit layout
A system for analyzing IC layouts and designs by calculating variations of a number of objects to be created on a semiconductor wafer as a result of different process conditions. The variations are analyzed to determine individual feature failures or to rank layout designs by their susceptibility to process variations. In one embodiment, the variations are represented by PV-bands having an inner edge that defines the smallest area in which an object will always print and an outer edge that defines the largest area in which an object will print under some process conditions.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Media recording device with packet data interface
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation that may be efficiently processed to determine correspondence. Applications of the interface and system include a video cassette recorder (VCR), medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
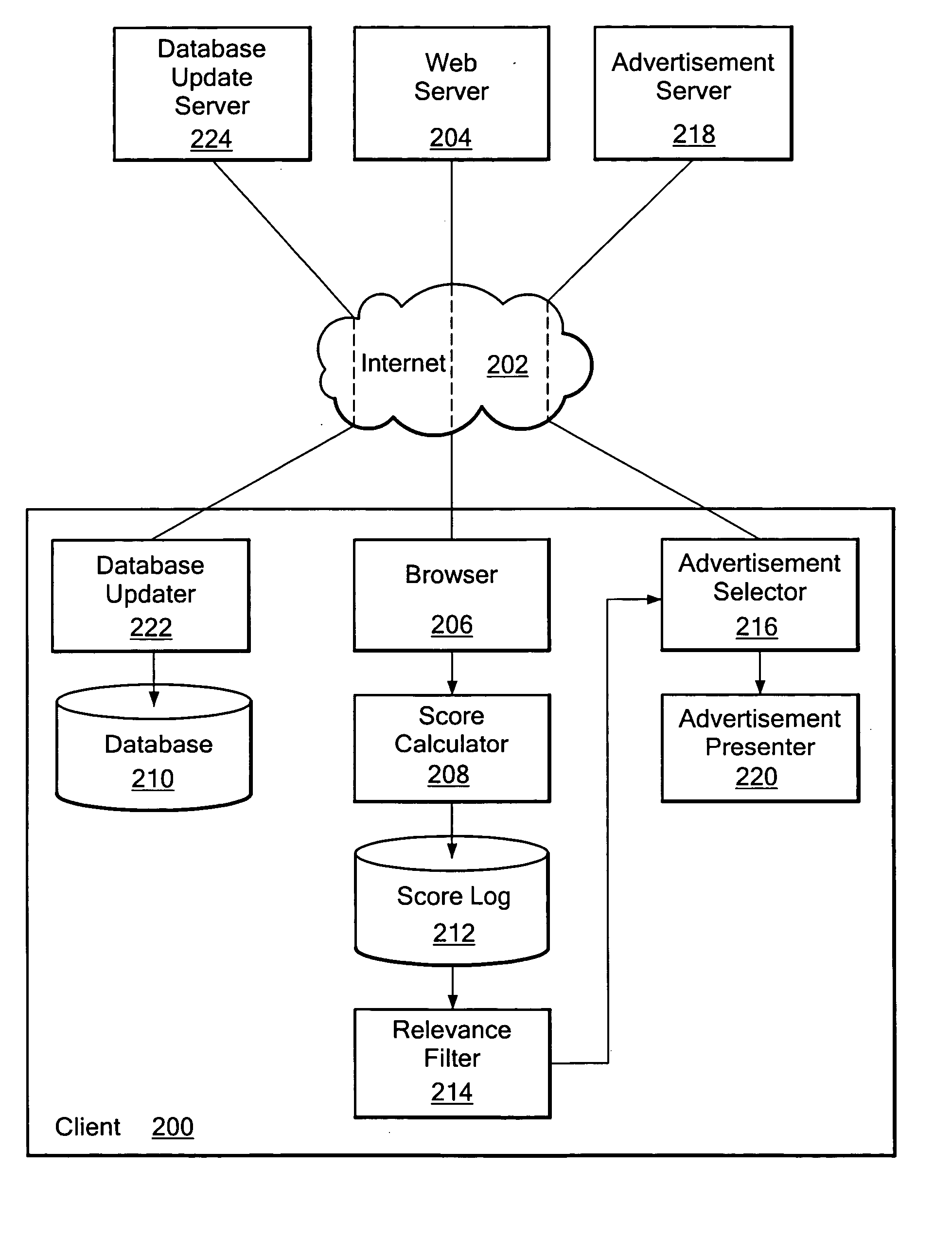
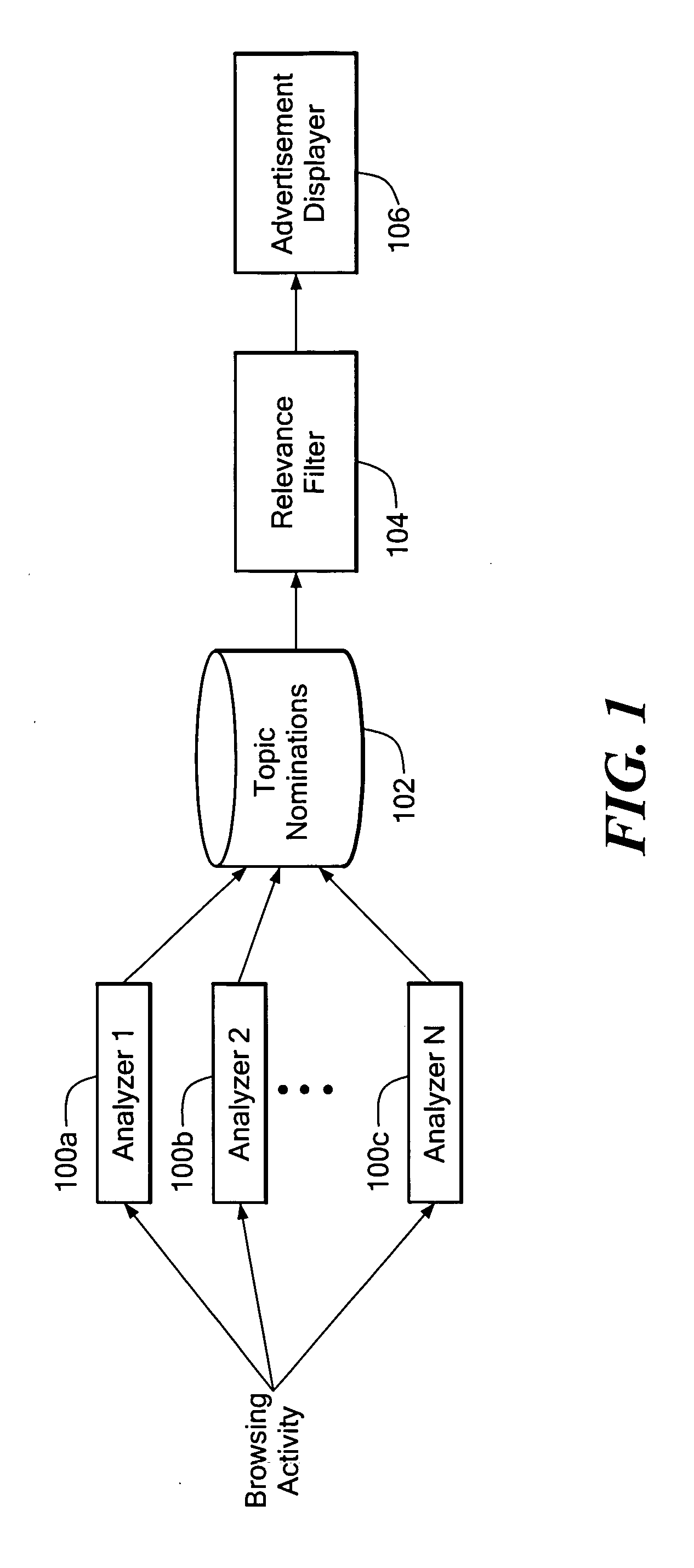
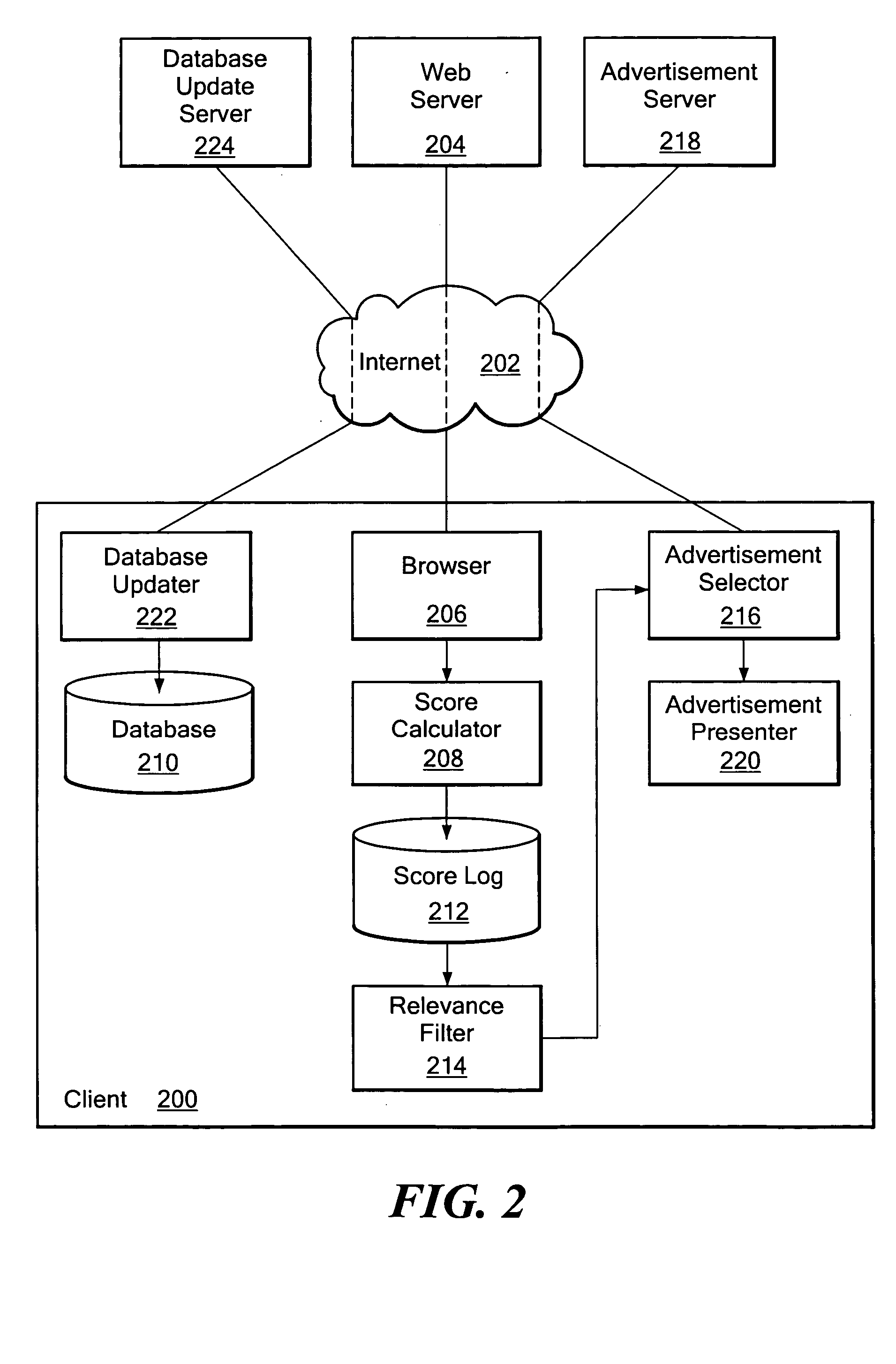
Contextual advertising system
InactiveUS20050033771A1MarketingSpecial data processing applicationsSystems analysisInformation retrieval
A system analyzes a user's historic browsing activity to determine one or more topics of interest to the user and displays to the user one or more advertisements that are relevant to the user's topic(s) of interest. The system analyzes a plurality of browses to determine the user's interest(s). Each of a plurality of analyzers analyzes an aspect of each user browse. A relevance filter determines if and when the user is sufficiently interested in a topic to display an advertisement related to the topic. Once the relevance filter identifies a topic of interest, the system displays an advertisement that is related to the identified topic of user interest.
Owner:ALOT
Method for Voice Activation of a Software Agent from Standby Mode
InactiveUS20140214429A1Save energyPower managementDigital data processing detailsDialog systemBiological activation
A method for voice activation of a software agent from a standby mode. In one embodiment, an audio recording (2) is buffered in an audio buffer (6) and at the same time, the audio recording is input to a secondary voice recognition process (7) which is economical in terms of energy and has an increased false positive rate. When a keyword is recognized, a primary voice recognition process (8) is activated from an inactive state, which converts the audio buffer to text and inputs it to a dialog system (9) which analyzes as to whether there is a relevant question made by the user. If this is the case, the user gets an acoustic reply (3), and if this is not the case, the dialog system and the primary voice recognition process immediately return to the inactive state and transfer the control to the secondary voice recognition process.
Owner:INODYN NEWMEDIA
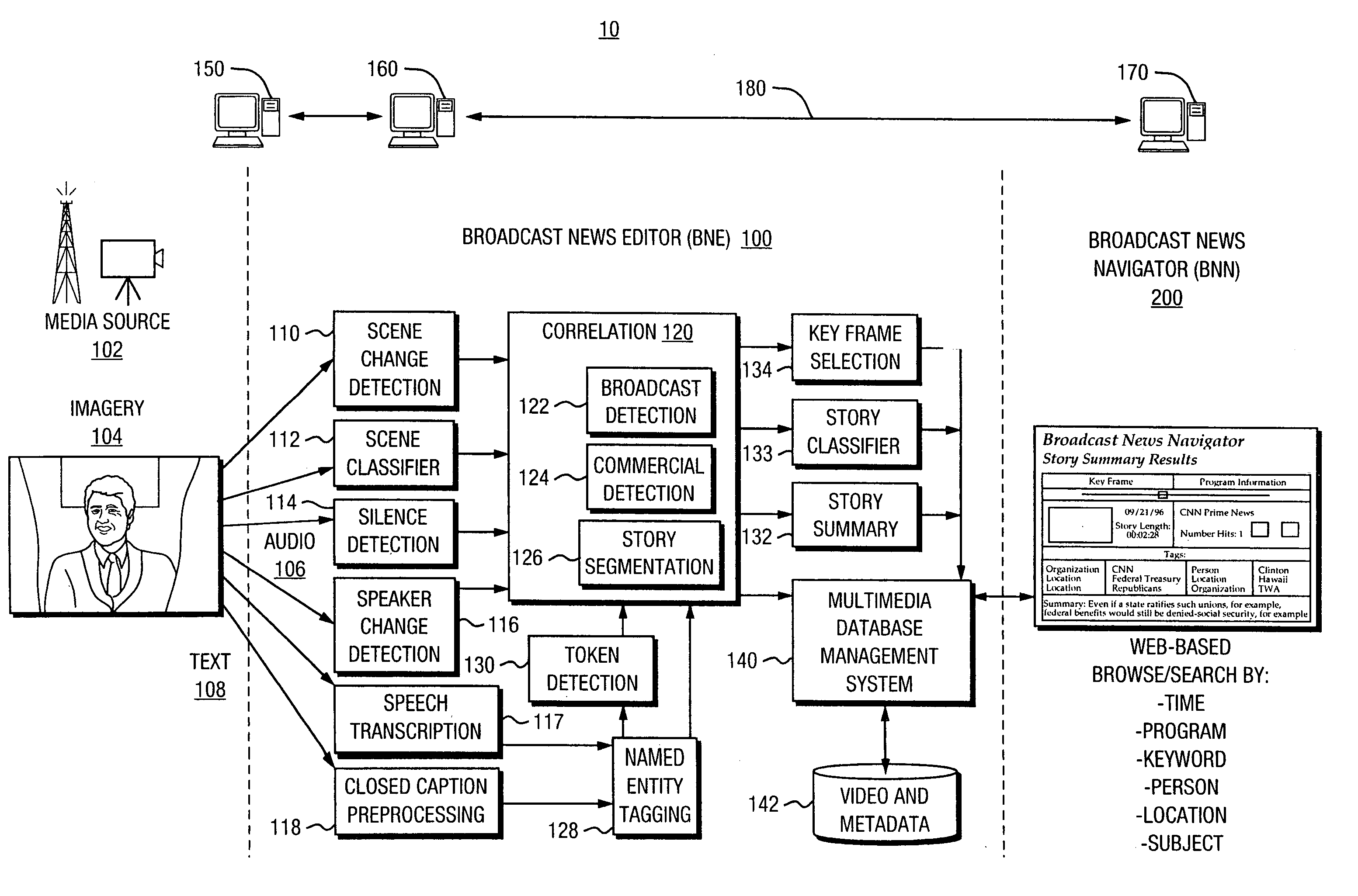
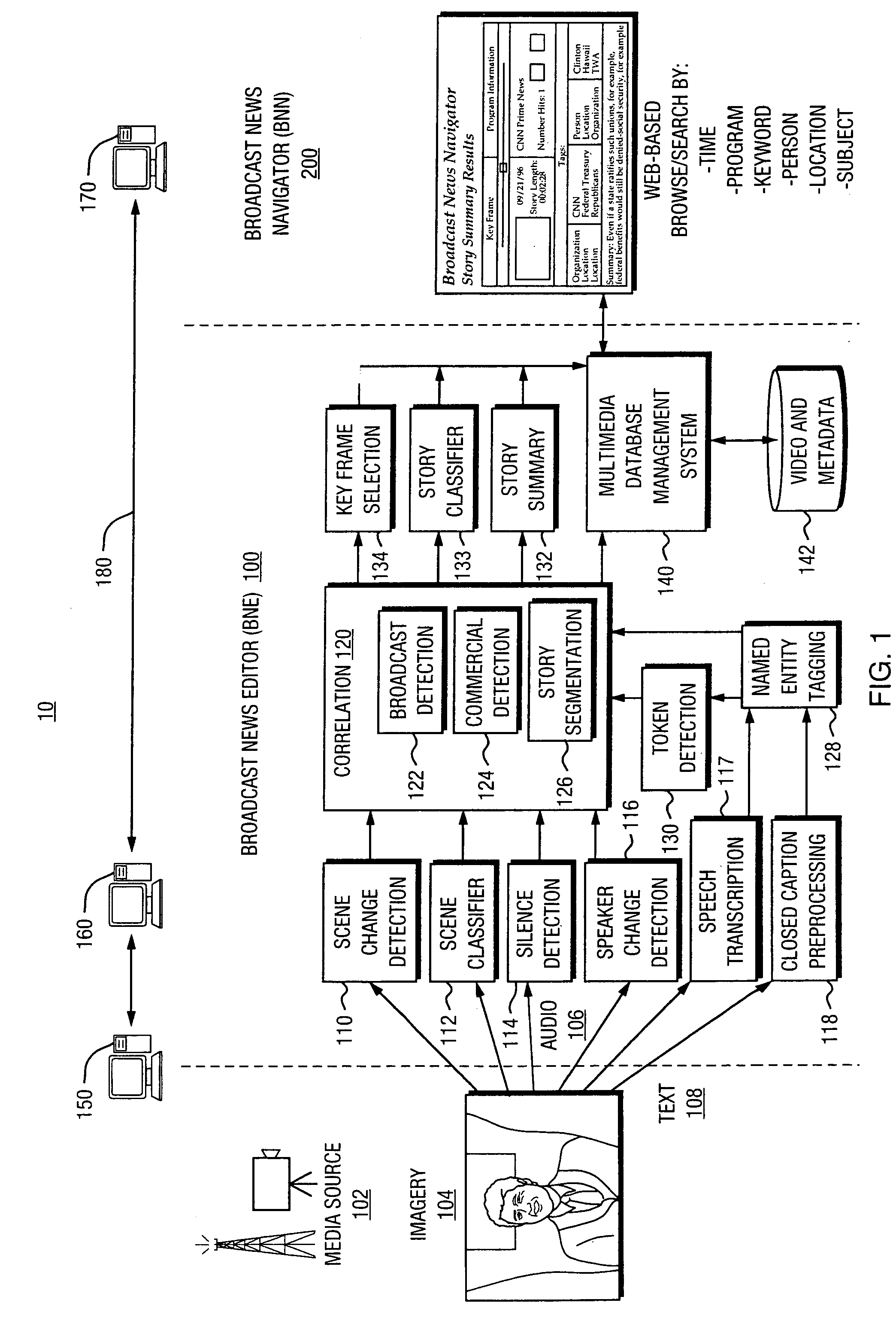
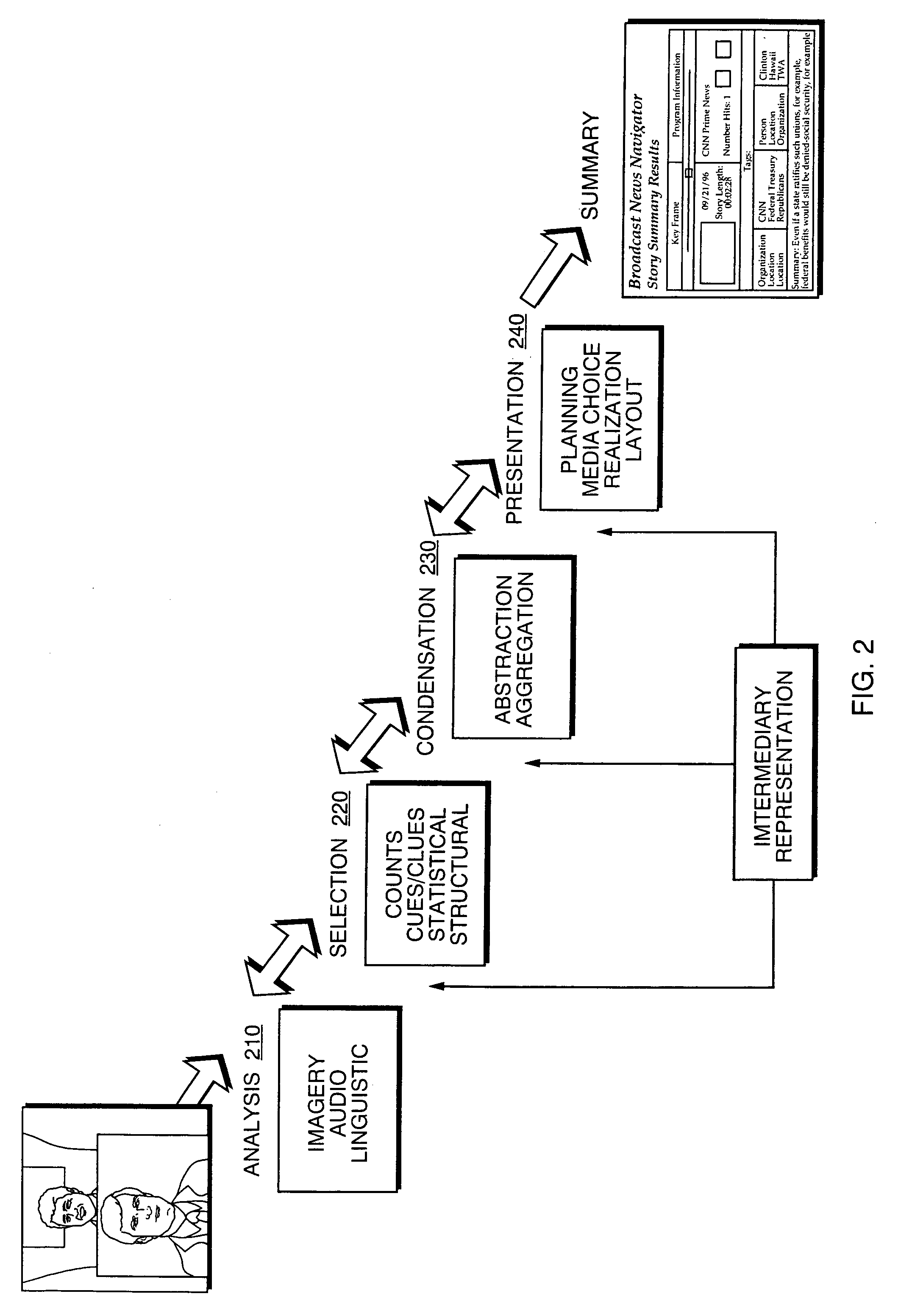
Automated segmentation, information extraction, summarization, and presentation of broadcast news
InactiveUS6961954B1More efficientMore timelyTelevision system detailsData processing applicationsSystems analysisWeb browser
A technique for automated analysis of multimedia, such as, for example, a news broadcast. A Broadcast News Editor and Broadcast News Navigator system analyze, select, condense, and then present news summaries. The system enables not only viewing a hierarchical table of contents of the news, but also summaries tailored to individual needs. This is accomplished through story segmentation and proper name extraction which enables the use of common information retrieval methodologies, such as Web browsers. Robust segmentation processing is provided using multistream analysis on imagery, audio, and closed captioned stream cue events.
Owner:OAKHAM TECH
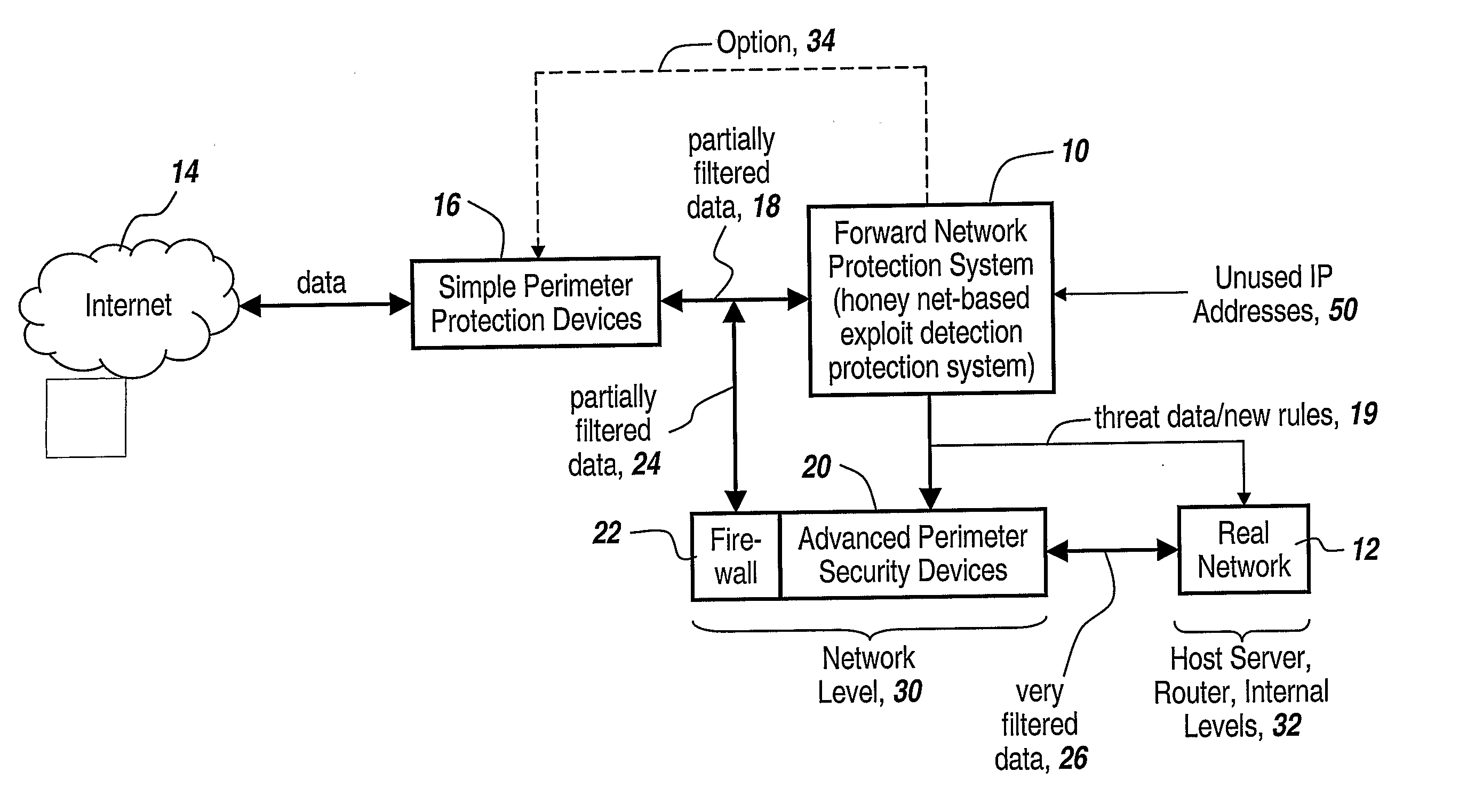
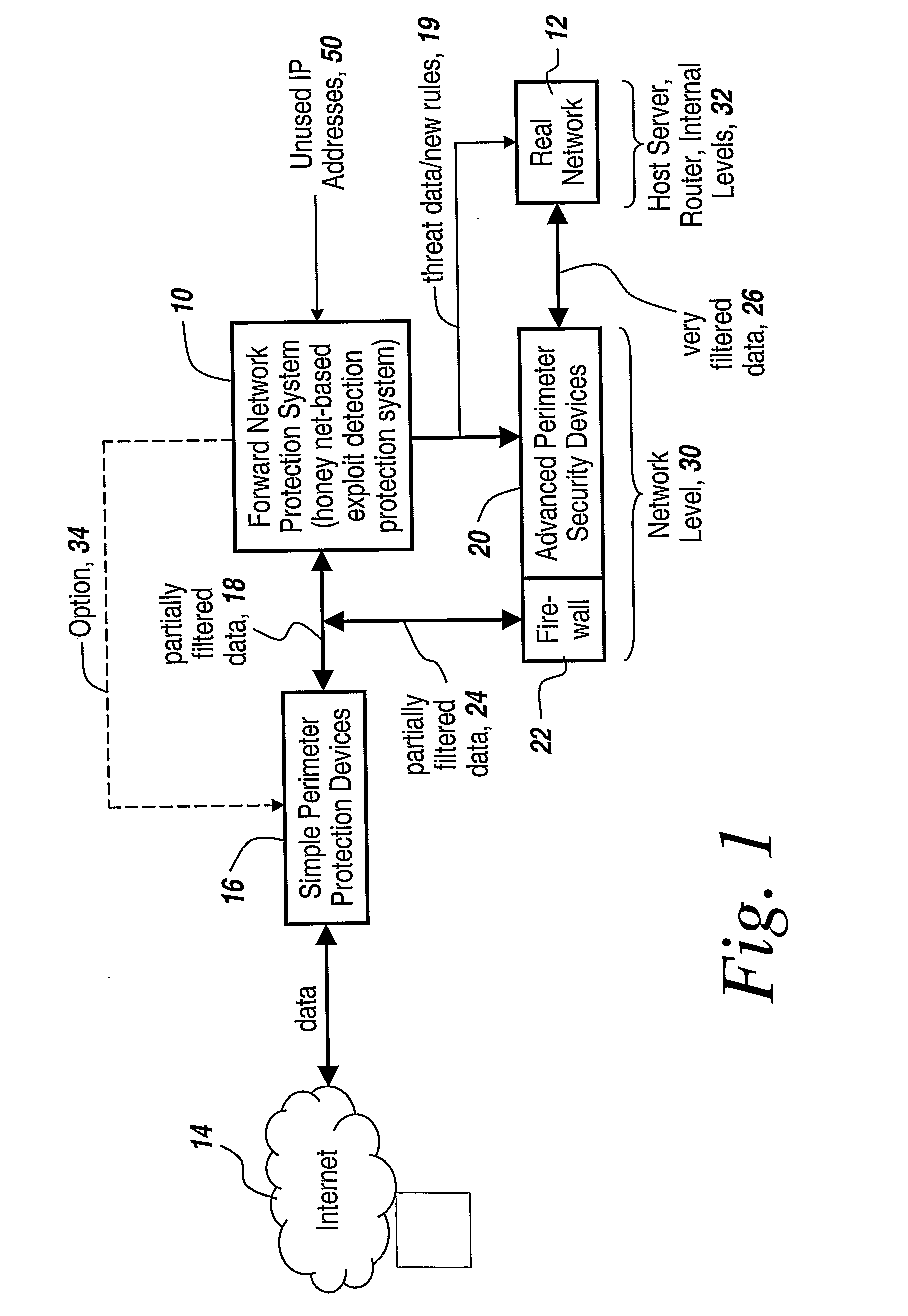
Method and Apparatus for Defending Against Zero-Day Worm-Based Attacks
InactiveUS20080098476A1Curb workloadEliminate usual spam and other simple attackMemory loss protectionError detection/correctionData packOperational system
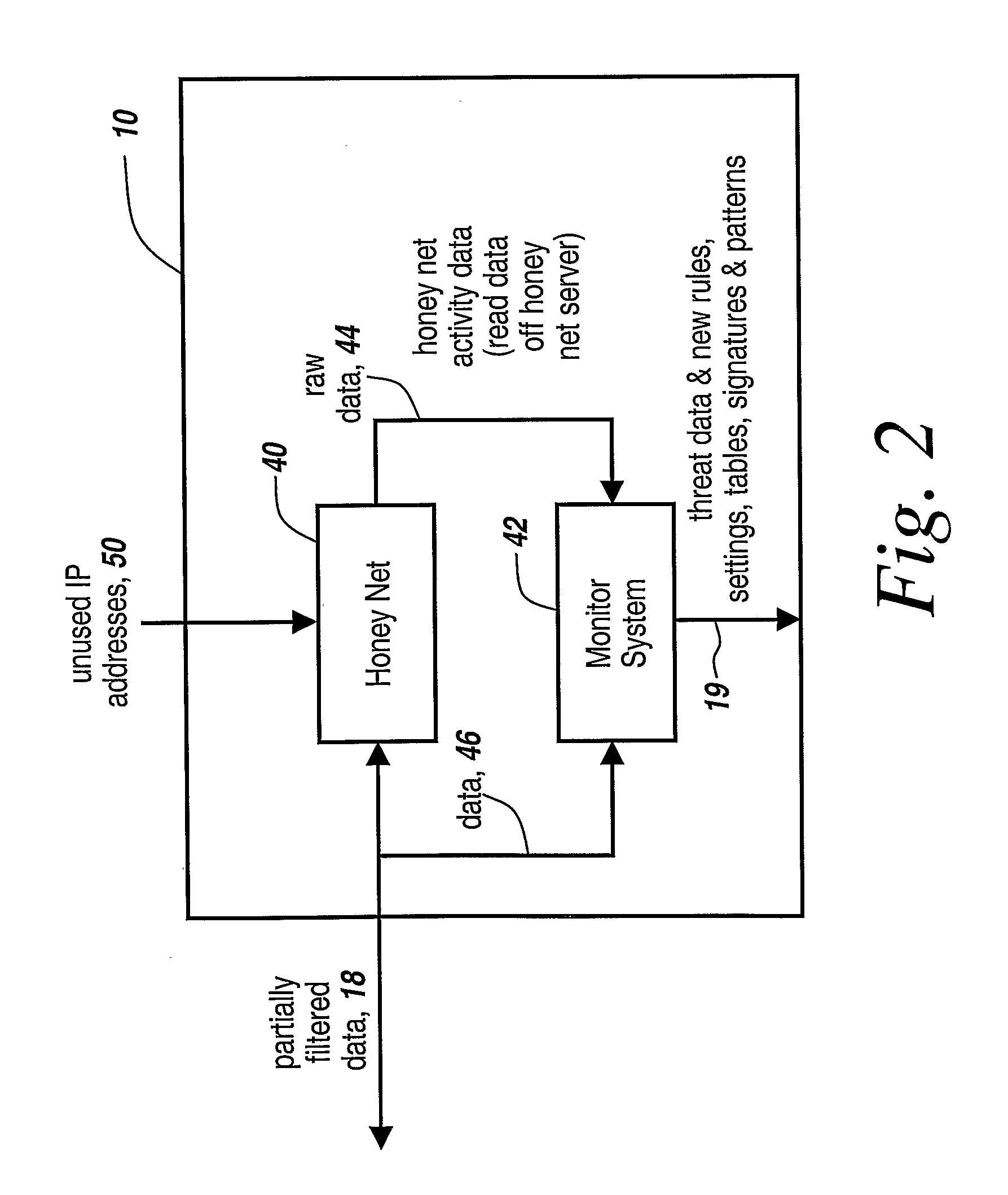
Honey pots are used to attract computer attacks to a virtual operating system that is a virtual instantiation of a typical deployed operational system. Honey nets are a collection of these virtual systems assembled to create a virtual network. The subject system uses a forward deployed honey net combined with a parallel monitoring system collecting data into and from the honey net, leveraging the controlled environment to identify malicious behavior and new attacks. This honey net / monitoring pair is placed ahead of the real deployed operational network and the data it uncovers is used to reconfigure network protective devices in real time to prevent zero-day based attacks from entering the real network. The forward network protection system analyzes the data gathered by the honey pots and generates signatures and new rules for protection that are coupled to both advanced perimeter network security devices and to the real network itself so that these devices can be reconfigured with threat data and new rules to prevent infected packets from entering the real network and from propagating to other machines. Note the subject system applies to both zero-day exploit-based worms and also manual attacks conducted by an individual who is leveraging novel attack methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Natural language interface for searching database
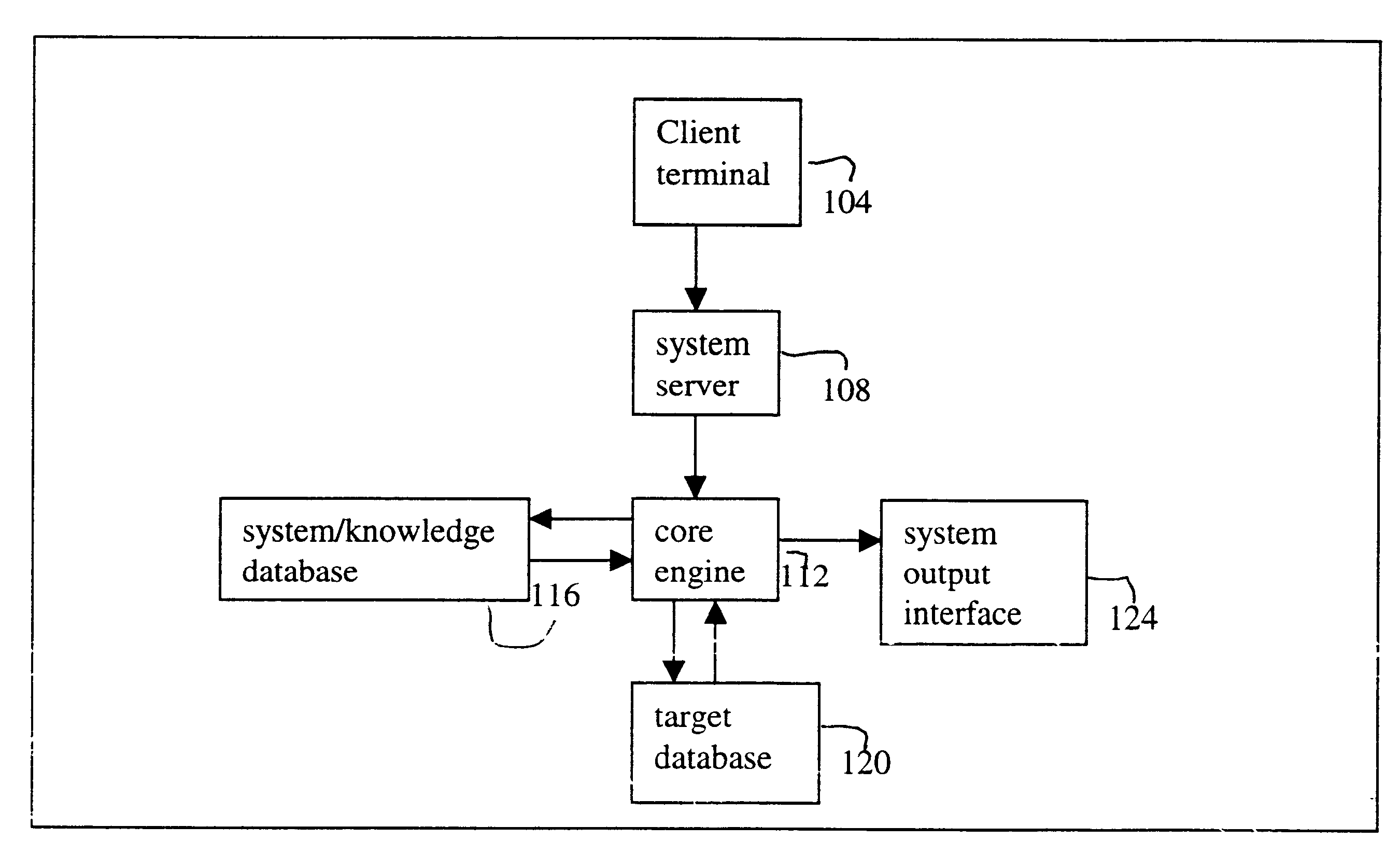
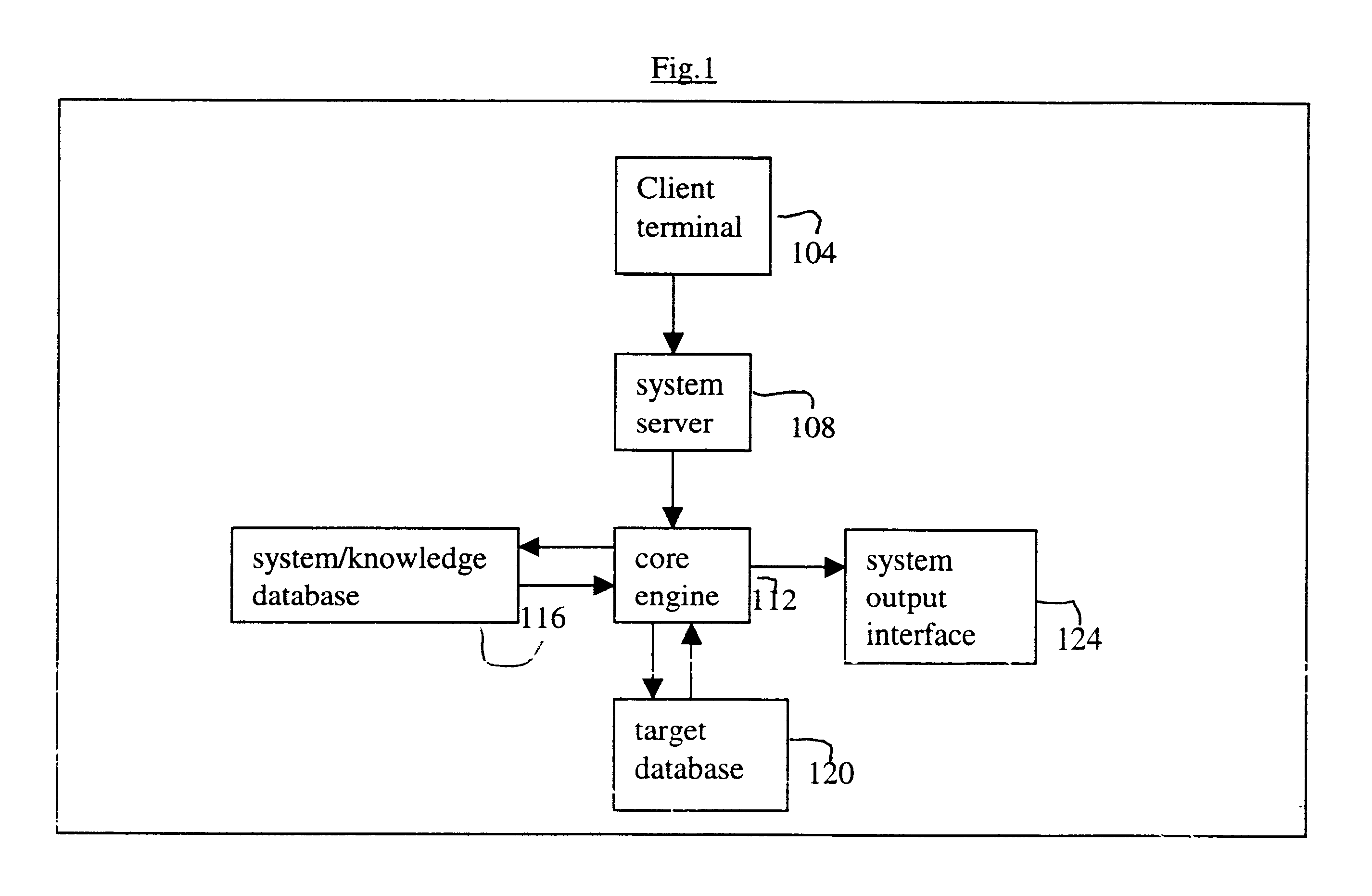
InactiveUS6598039B1Data processing applicationsDigital data information retrievalSearch wordsSystems analysis
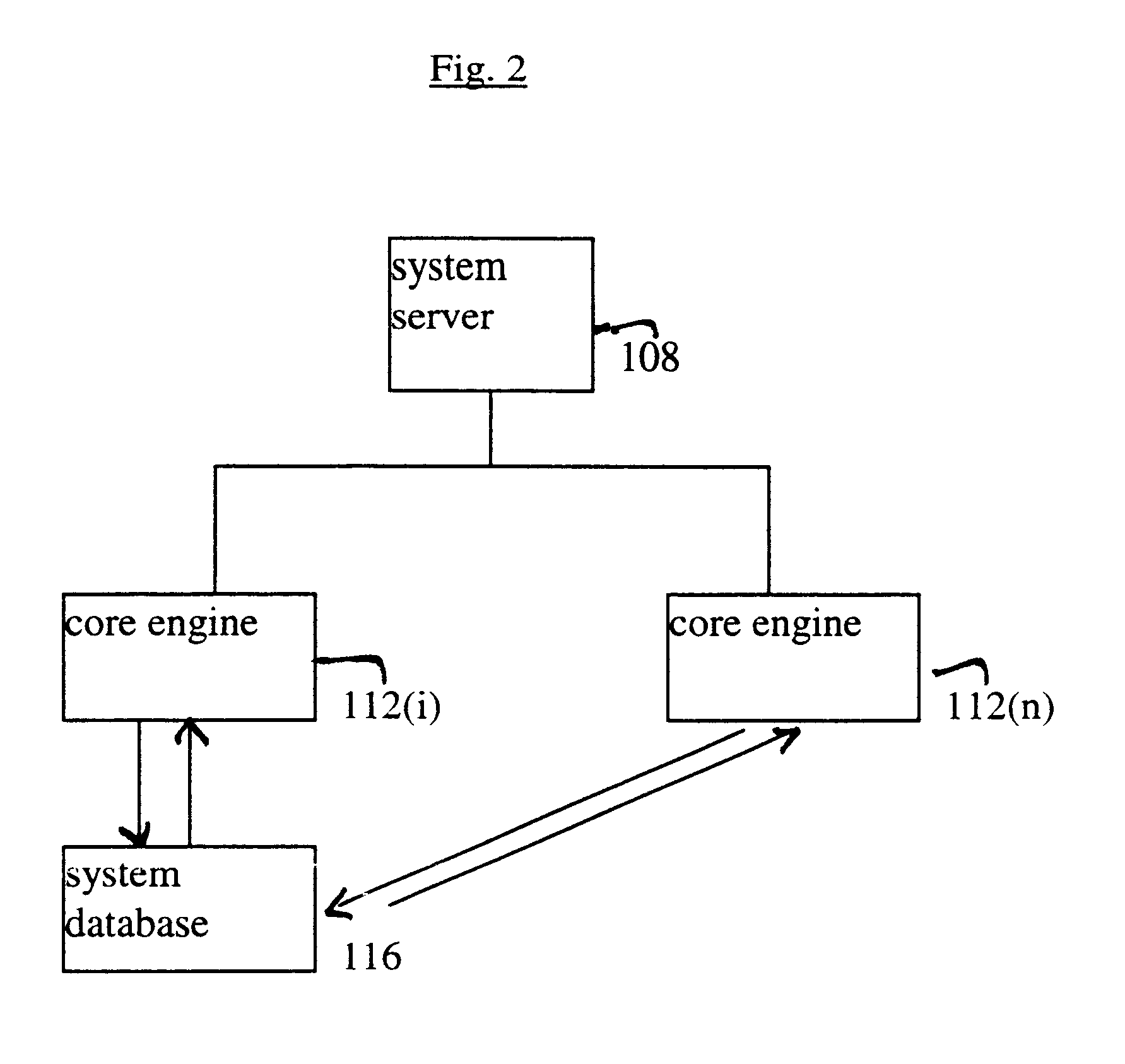
A system and method for searching information from a database using a natural language. In one embodiment, the system analyzes a natural language search request and converts the search request into one or more search words. The search words are further converted into a string of bytes, and a subset of a target database, referred to as the datasoup, is searched. If there is a match between the bytes and raw data in the datasoup, the searched data is retrieved from the target database. The searched data is then formatted and provided to a user. Optionally, the searched data can be provided to the user unformatted. In another embodiment, the system includes a system server configured to receive a natural language search request, a core engine coupled to the system server and to the target database, and a system database coupled to the core engine, where the core engine accesses the system database to analyze the search request. The system database stores global rules, one or more preference files, and one or more dictionaries, and the preference file stores information about the user.
Owner:GO ALBERT FRANCE
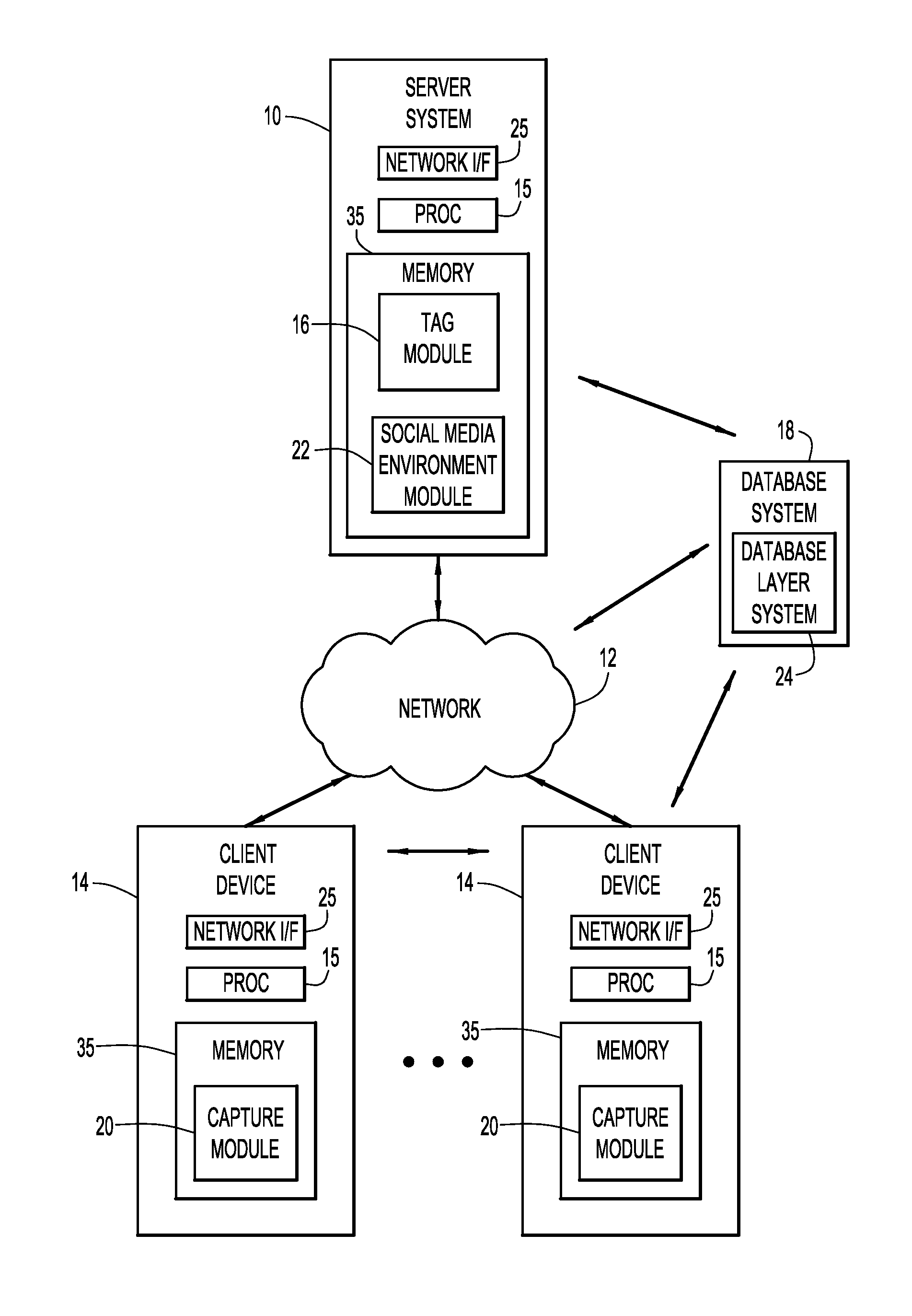
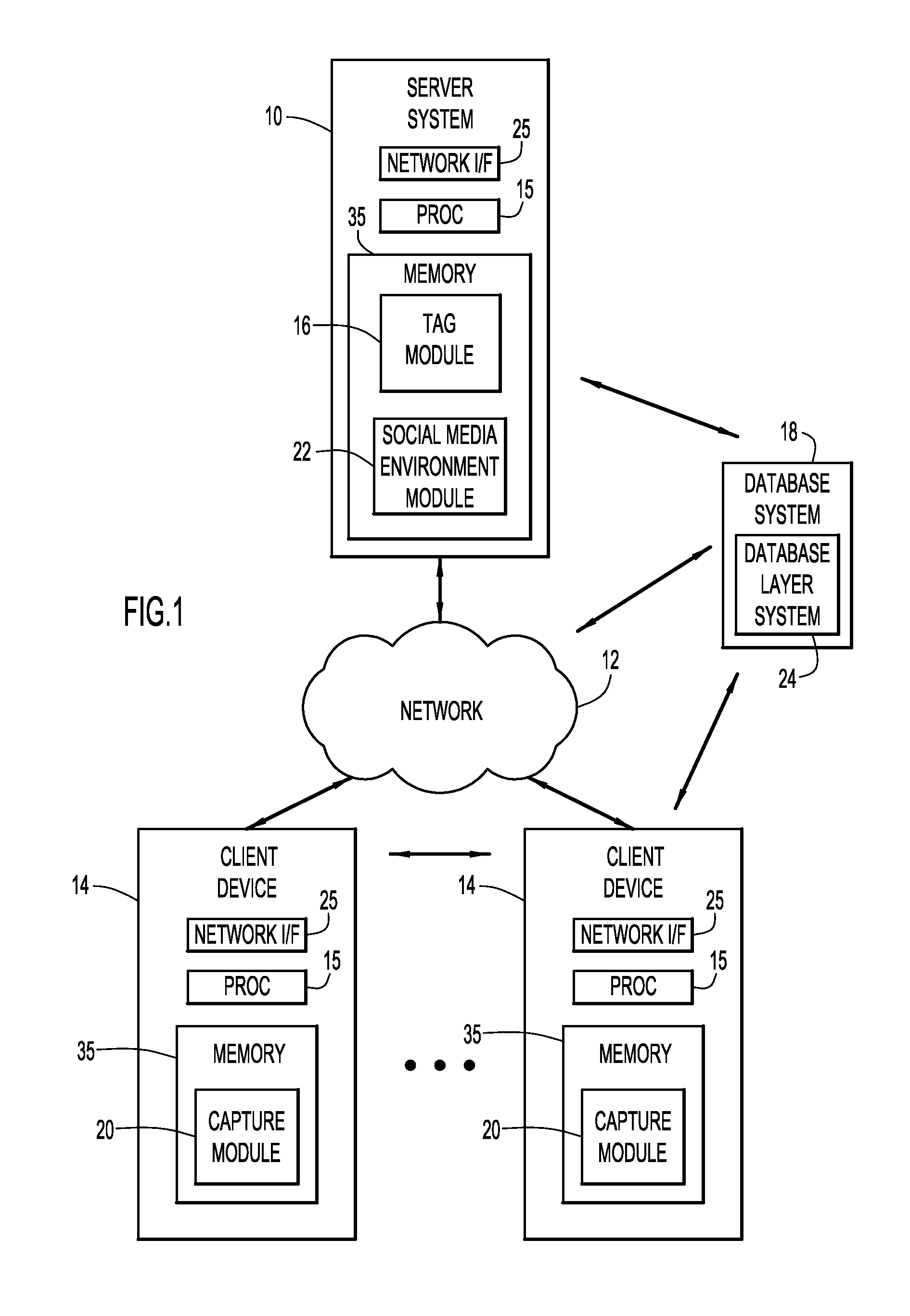
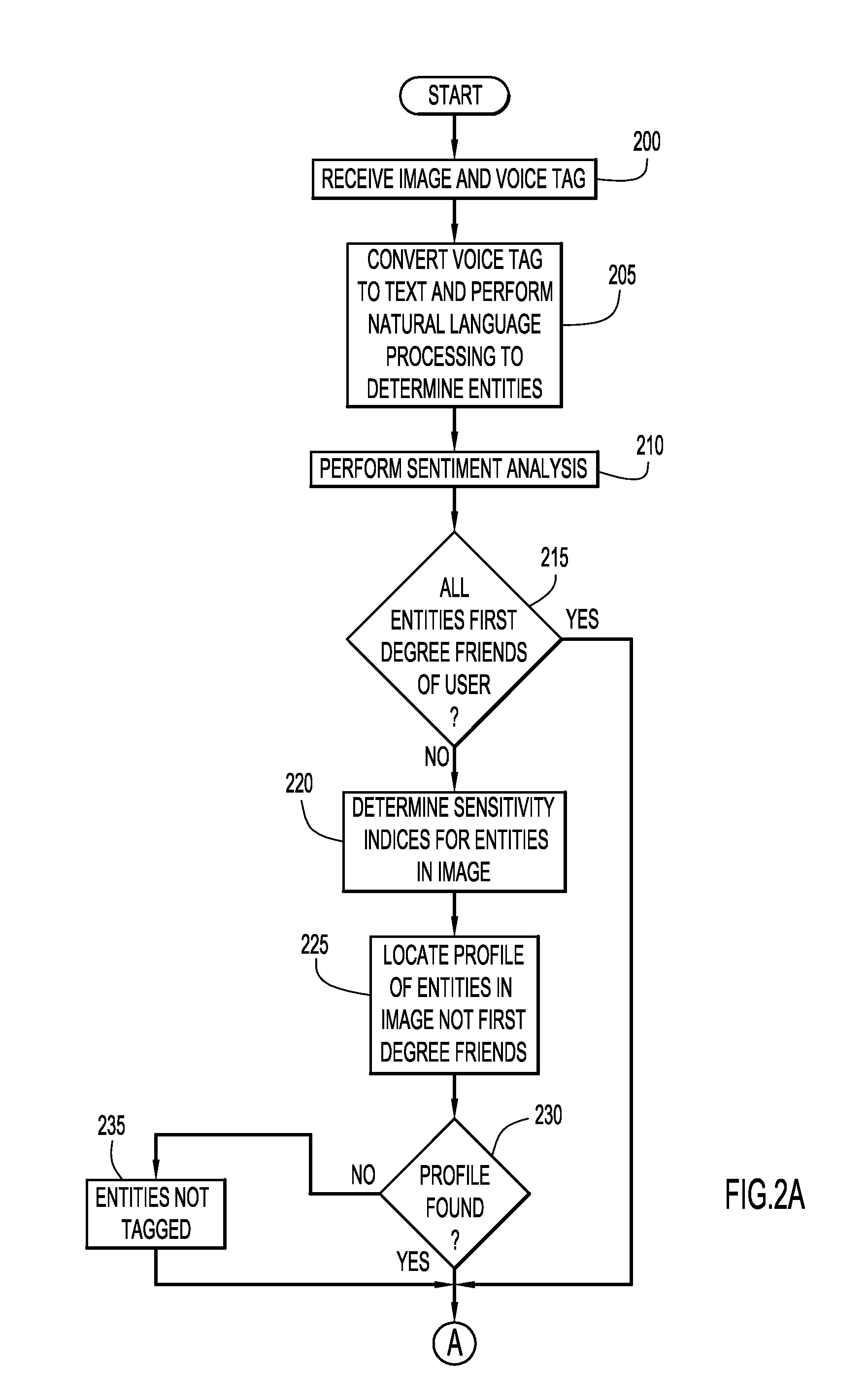
Application of Voice Tags in a Social Media Context
According to a present invention embodiment, a system utilizes a voice tag to automatically tag one or more entities within a social media environment, and comprises a computer system including at least one processor. The system analyzes the voice tag to identify one or more entities, where the voice tag includes voice signals providing information pertaining to one or more entities. One or more characteristics of each identified entity are determined based on the information within the voice tag. One or more entities appropriate for tagging within the social media environment are determined based on the characteristics and user settings within the social media environment of the identified entities, and automatically tagged. Embodiments of the present invention further include a method and computer program product for utilizing a voice tag to automatically tag one or more entities within a social media environment in substantially the same manner described above.
Owner:IBM CORP
Direct current combiner box with power monitoring, ground fault detection and communications interface
InactiveUS20060237058A1Save a lot of timeShorten the timeBatteries circuit arrangementsPV power plantsCommunication interfaceDc current
A combiner box is used to collect direct current from solar panels or other energy sources. The combiner box integrates all means necessary for ground fault detection, current monitoring, voltage monitoring, and power monitoring. The combiner box may include a communication interface suitable for Web enabled monitoring, electronic notifications of system status, and / or remote control of system functions. In one embodiment, the combiner box uses integrated circuits and printed circuit board technology to achieve new efficiencies in manufacturing, installation and system analysis at the string level. A separate hand piece may be used by installers to test the performance of the combiner box, installation of the solar panels, performance of the solar panels and connections between the solar panels and the combiner box.
Owner:ENERGY RECOMMERCE
Ergonomic man-machine interface incorporating adaptive pattern recognition based control system
InactiveUS20070061735A1Decrease productivityImprove the environmentTelevision system detailsRecording carrier detailsHuman–machine interfaceData stream
An adaptive interface for a programmable system, for predicting a desired user function, based on user history, as well as machine internal status and context. The apparatus receives an input from the user and other data. A predicted input is presented for confirmation by the user, and the predictive mechanism is updated based on this feedback. Also provided is a pattern recognition system for a multimedia device, wherein a user input is matched to a video stream on a conceptual basis, allowing inexact programming of a multimedia device. The system analyzes a data stream for correspondence with a data pattern for processing and storage. The data stream is subjected to adaptive pattern recognition to extract features of interest to provide a highly compressed representation which may be efficiently processed to determine correspondence. Applications of the interface and system include a VCR, medical device, vehicle control system, audio device, environmental control system, securities trading terminal, and smart house. The system optionally includes an actuator for effecting the environment of operation, allowing closed-loop feedback operation and automated learning.
Owner:BLANDING HOVENWEEP
Computer-aided image analysis
InactiveUS6996549B2Improve abilitiesGreat dimensionalityMedical data miningImage analysisLearning machineComputer-aided
Digitized image data are input into a processor where a detection component identifies the areas (objects) of particular interest in the image and, by segmentation, separates those objects from the background. A feature extraction component formulates numerical values relevant to the classification task from the segmented objects. Results of the preceding analysis steps are input into a trained learning machine classifier which produces an output which may consist of an index discriminating between two possible diagnoses, or some other output in the desired output format. In one embodiment, digitized image data are input into a plurality of subsystems, each subsystem having one or more support vector machines. Pre-processing may include the use of known transformations which facilitate extraction of the useful data. Each subsystem analyzes the data relevant to a different feature or characteristic found within the image. Once each subsystem completes its analysis and classification, the output for all subsystems is input into an overall support vector machine analyzer which combines the data to make a diagnosis, decision or other action which utilizes the knowledge obtained from the image.
Owner:HEALTH DISCOVERY CORP +1
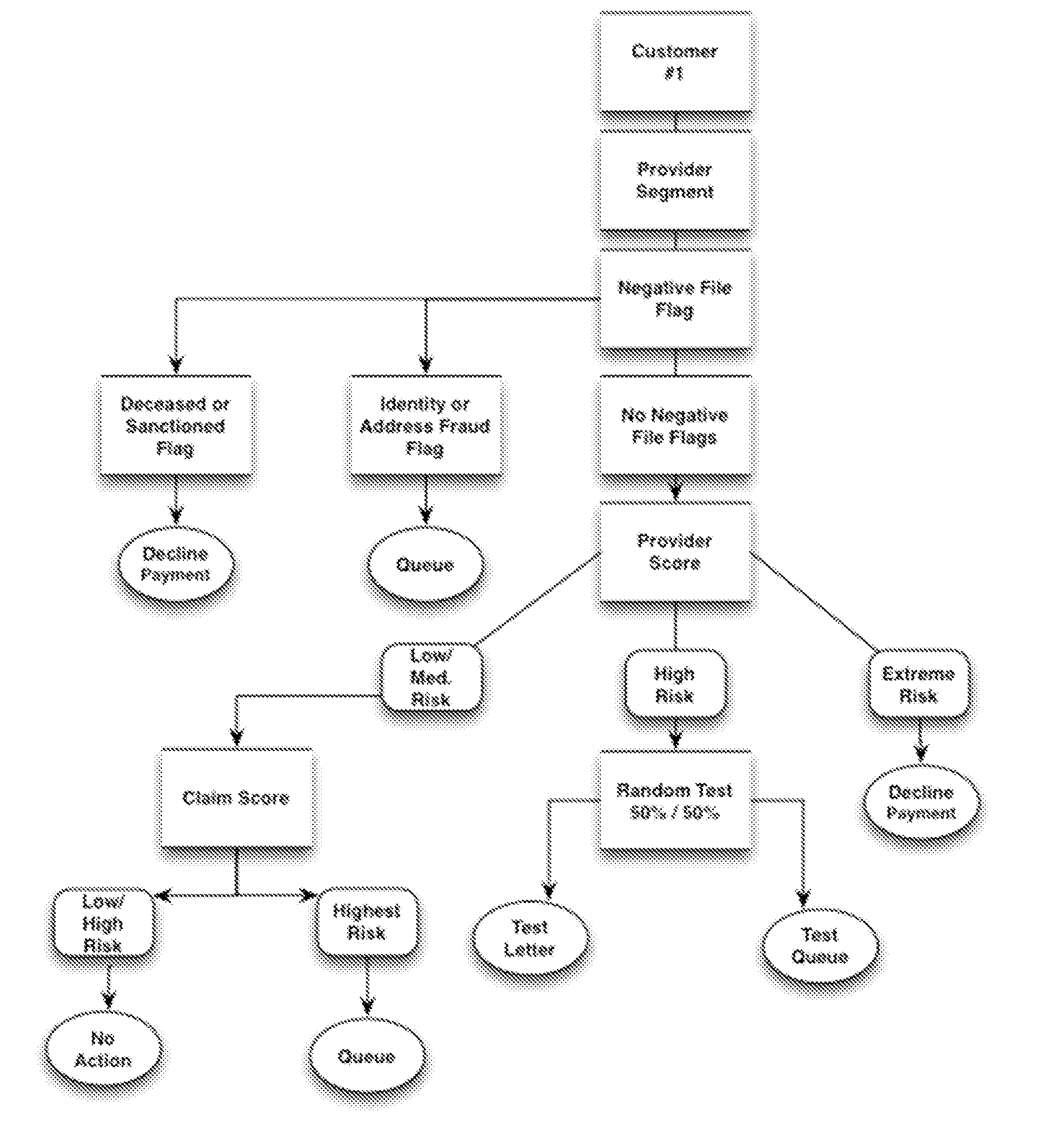
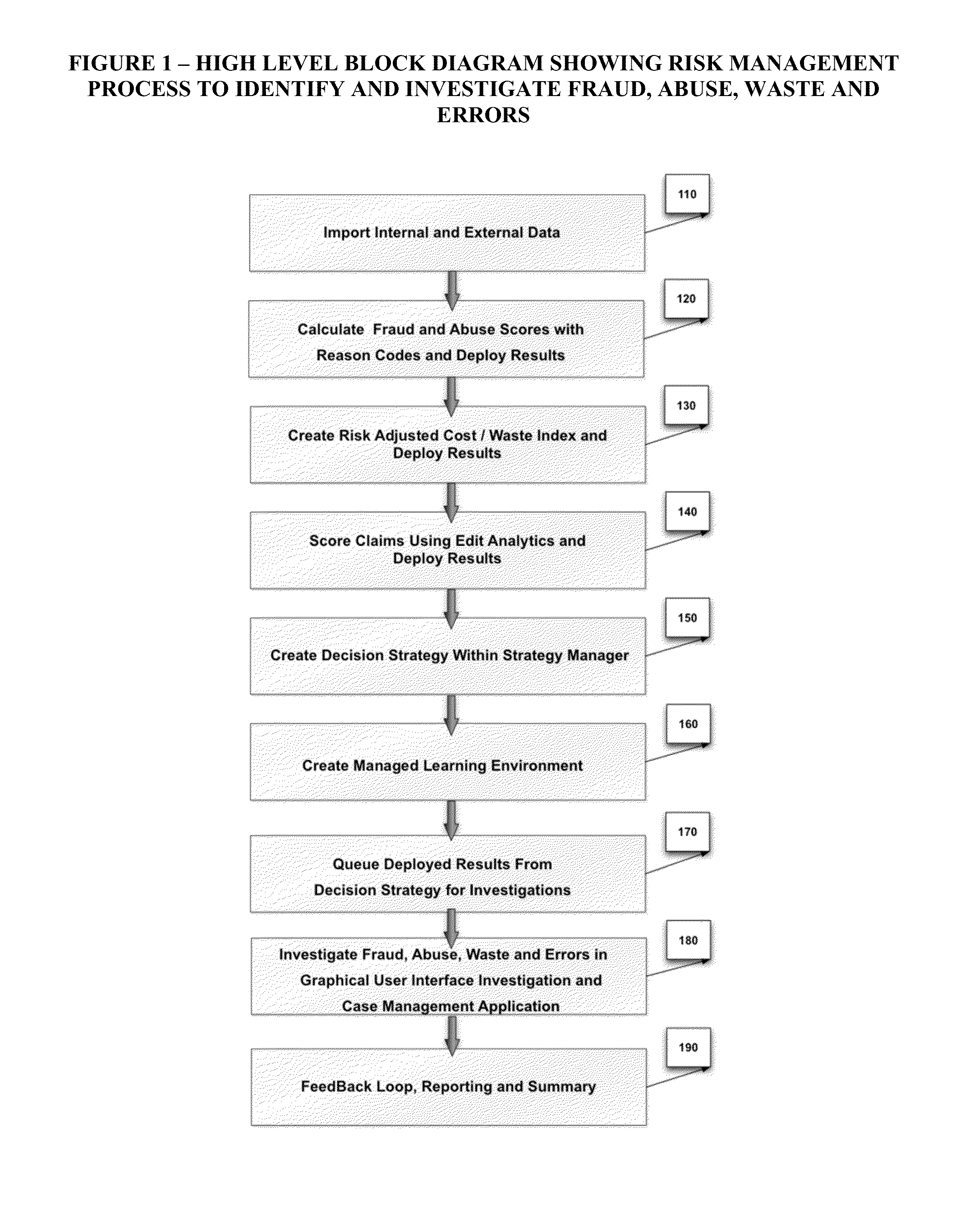
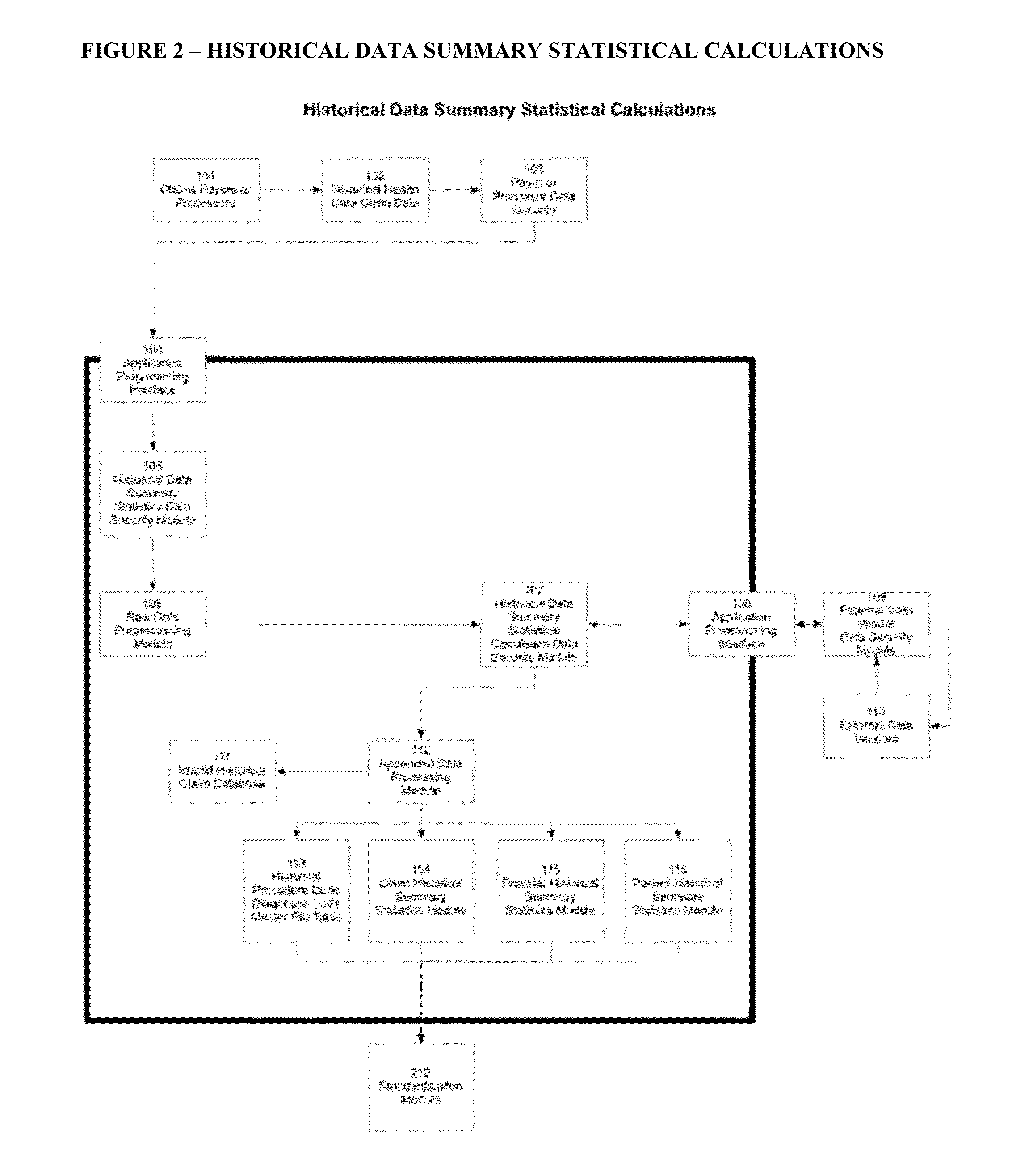
Automated Healthcare Risk Management System Utilizing Real-time Predictive Models, Risk Adjusted Provider Cost Index, Edit Analytics, Strategy Management, Managed Learning Environment, Contact Management, Forensic GUI, Case Management And Reporting System For Preventing And Detecting Healthcare Fraud, Abuse, Waste And Errors
InactiveUS20140081652A1Facilitate and enhance and implement multiple investigator decisionResource optimizationFinancePayment architectureLower riskMedical education
The Automated Healthcare Risk Management System is a real-time Software as a Service application which interfaces and assists investigators, law enforcement and risk management analysts by focusing their efforts on the highest risk and highest value healthcare payments. The system's Risk Management design utilizes real-time Predictive Models, a Provider Cost Index, Edit Analytics, Strategy Management, a Managed Learning Environment, Contact Management, Forensic GUI, Case Management and Reporting System for individually targeting, identifying and preventing fraud, abuse, waste and errors prior to payment. The Automated Healthcare Risk Management System analyzes hundreds of millions of transactions and automatically takes actions such as declining or queuing a suspect payment. Claim payment risk is optimally prioritized through a Managed Learning environment, from high risk to low risk for efficient resolution by investigators.
Owner:RISK MANAGEMENT SOLUTIONS
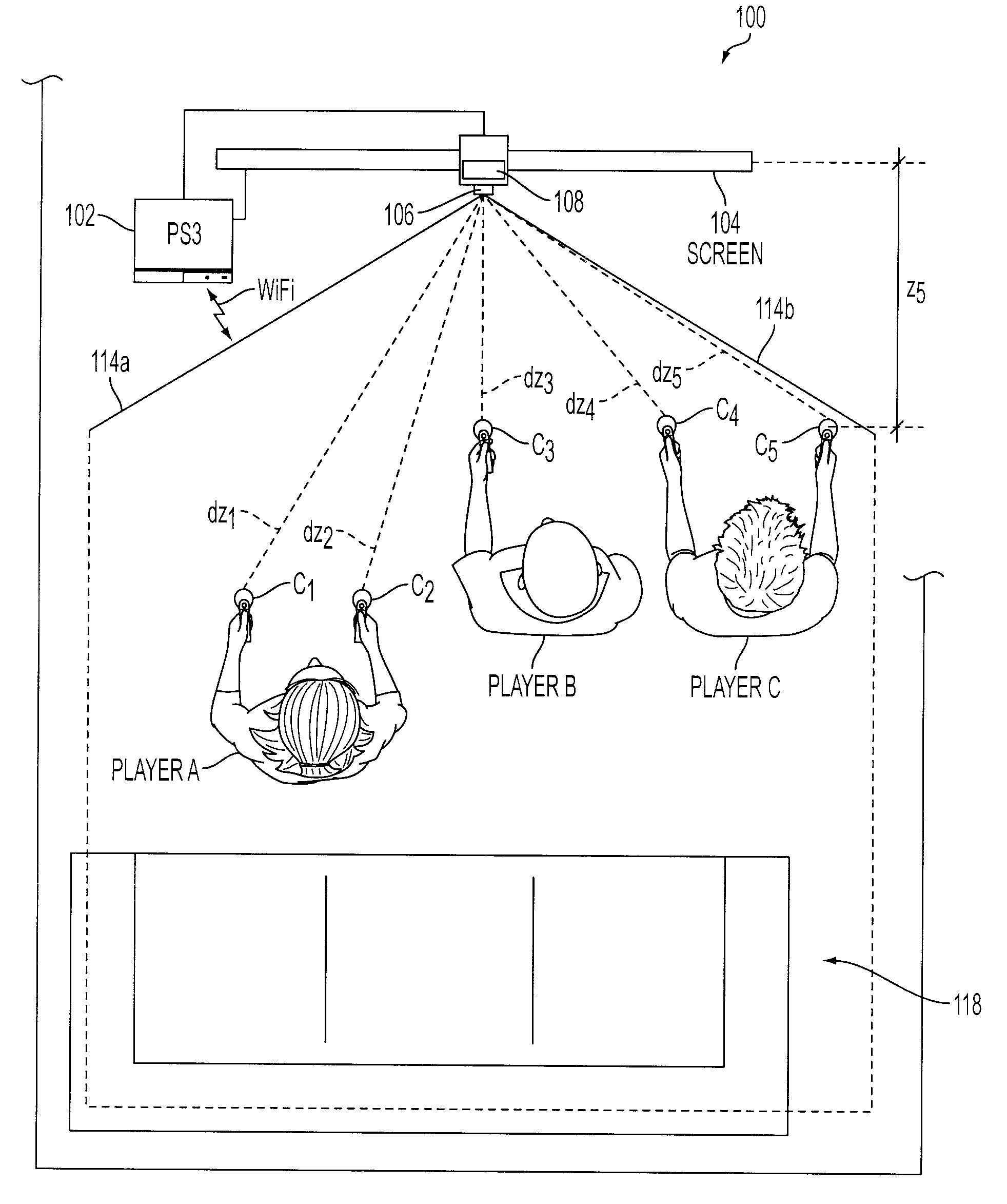
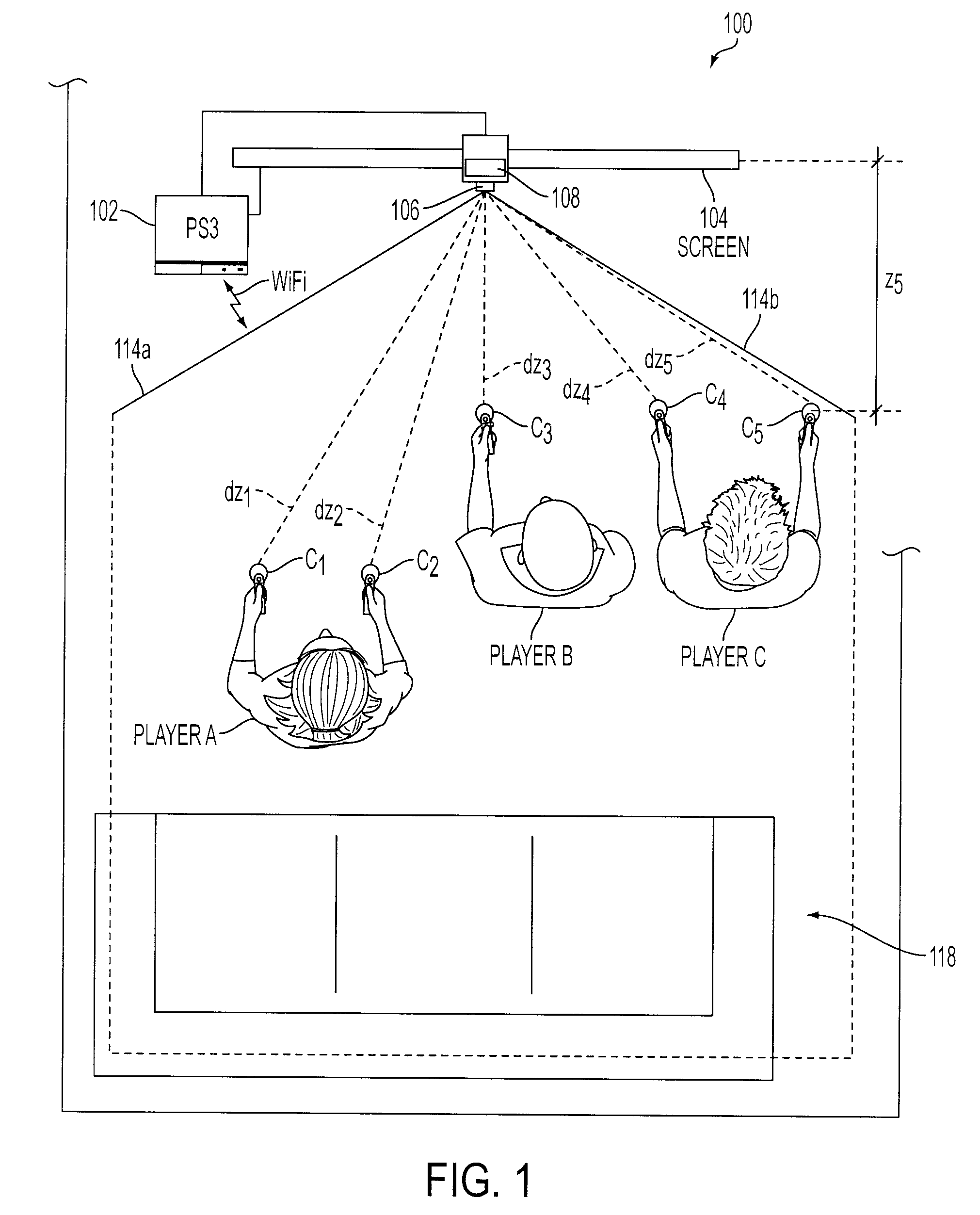
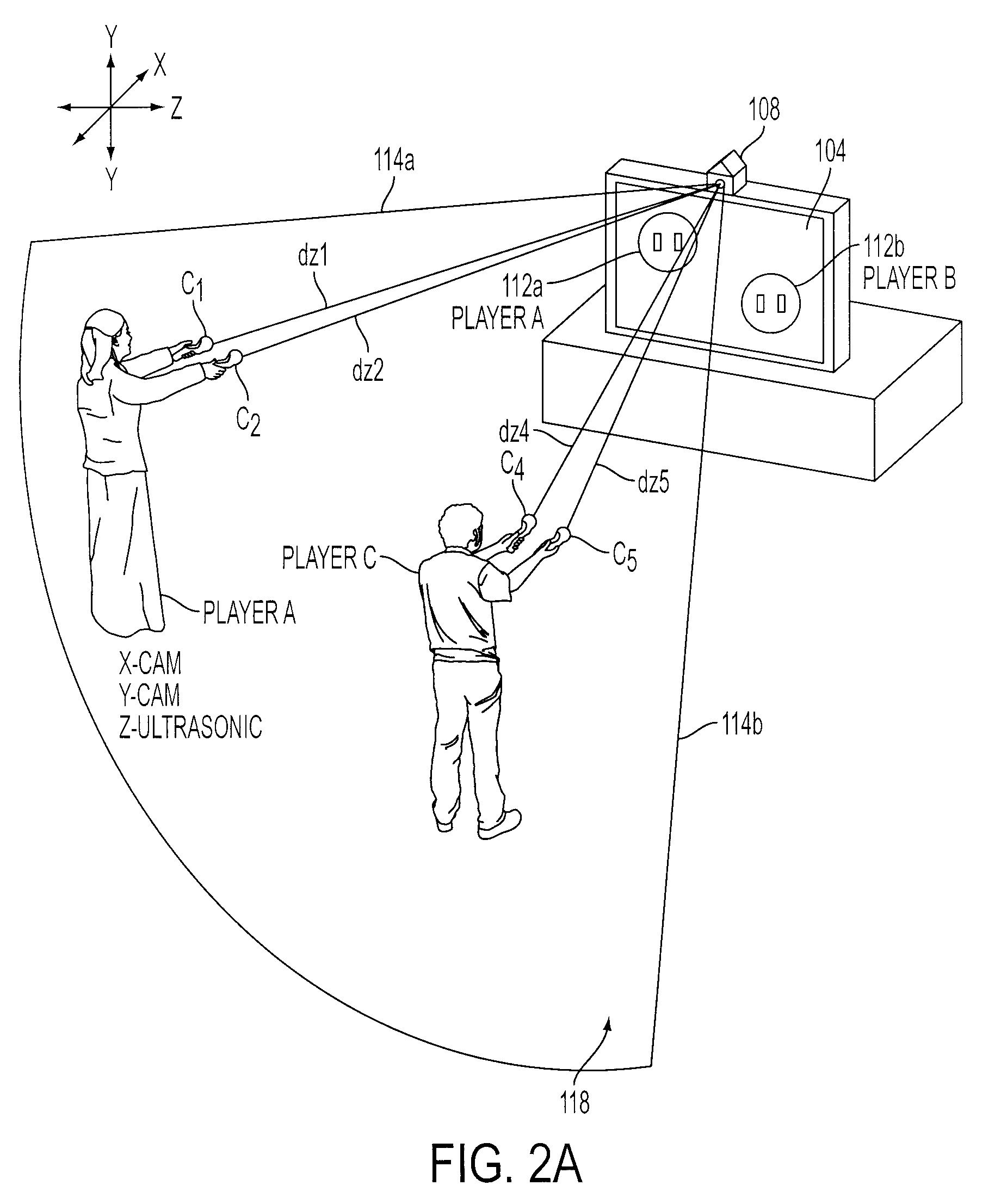
Determination of controller three-dimensional location using image analysis and ultrasonic communication
ActiveUS20080261693A1Facilitate image recognitionOne-way communicationImage analysisVideo gamesSystems analysisImaging analysis
Game interface tracks the position of one or more game controllers in 3-dimensional space using hybrid video capture and ultrasonic tracking system. The captured video information is used to identify a horizontal and vertical position for each controller within a capture area. The ultrasonic tracking system analyzes sound communications to determine the distances between the game system and each controller and to determine the distances among the controllers. The distances are then analyzed by the game interface to calculate the depths within the capture area for each controller.
Owner:SONY INTERACTIVE ENTRTAINMENT LLC
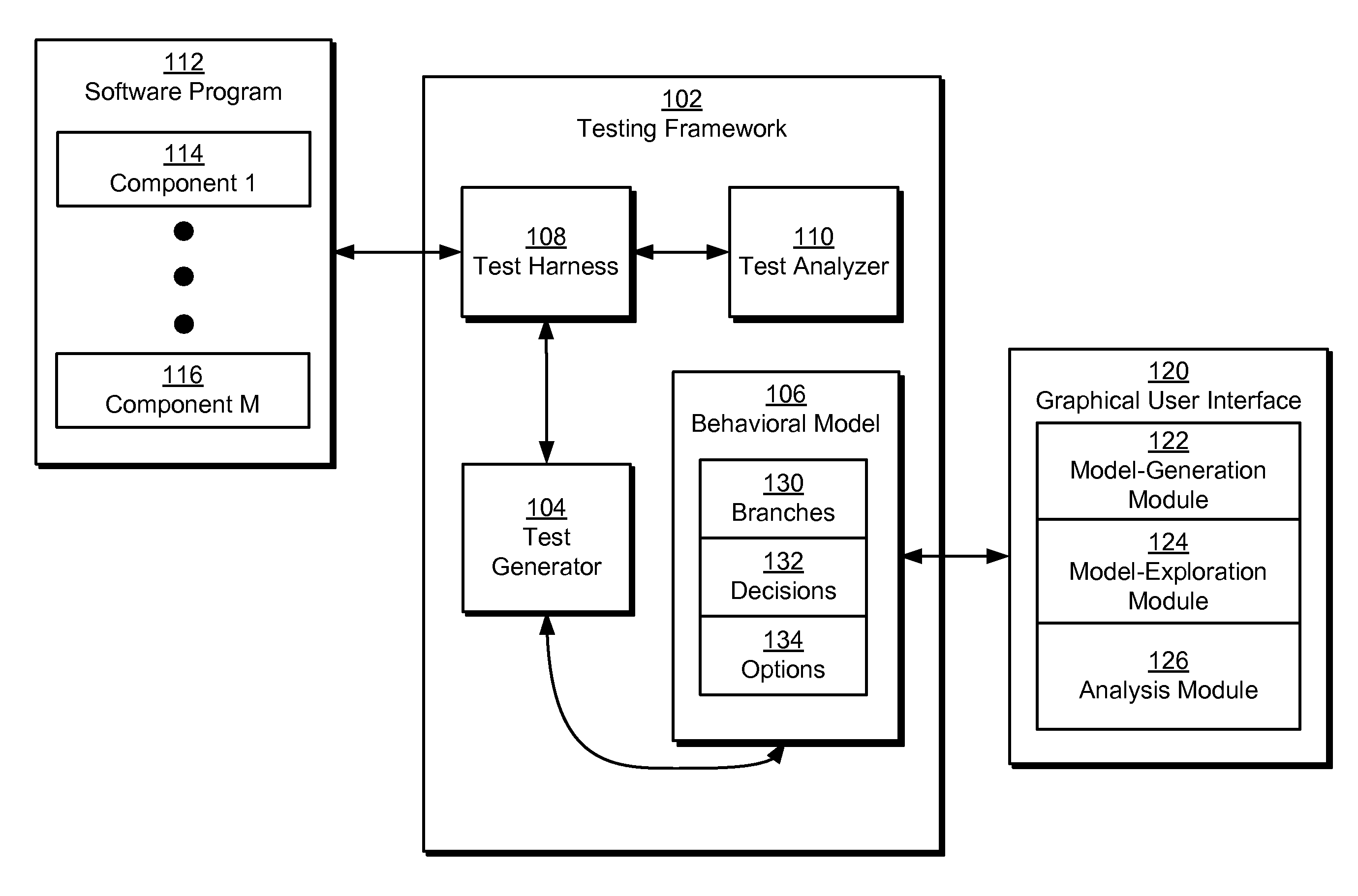
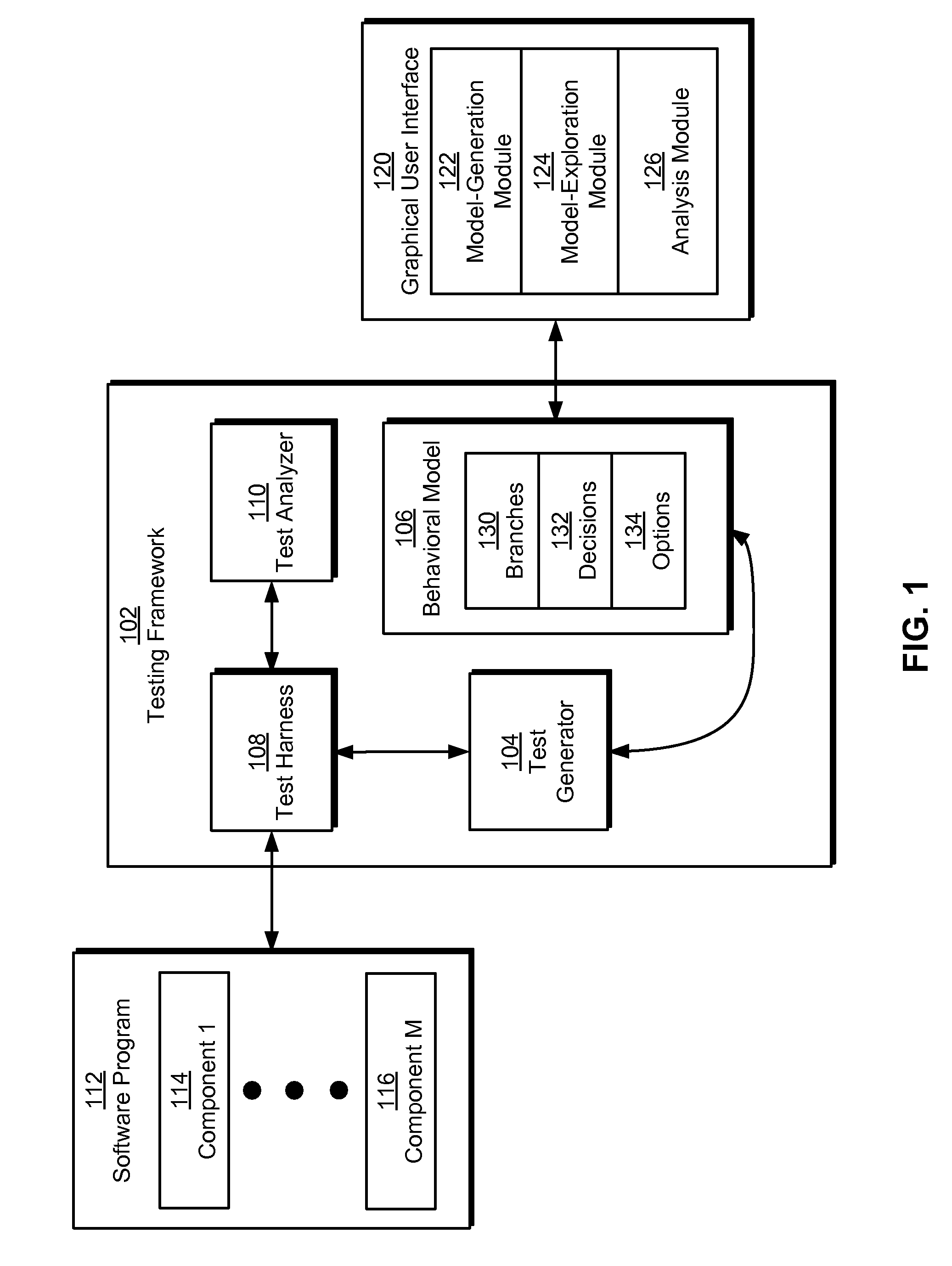
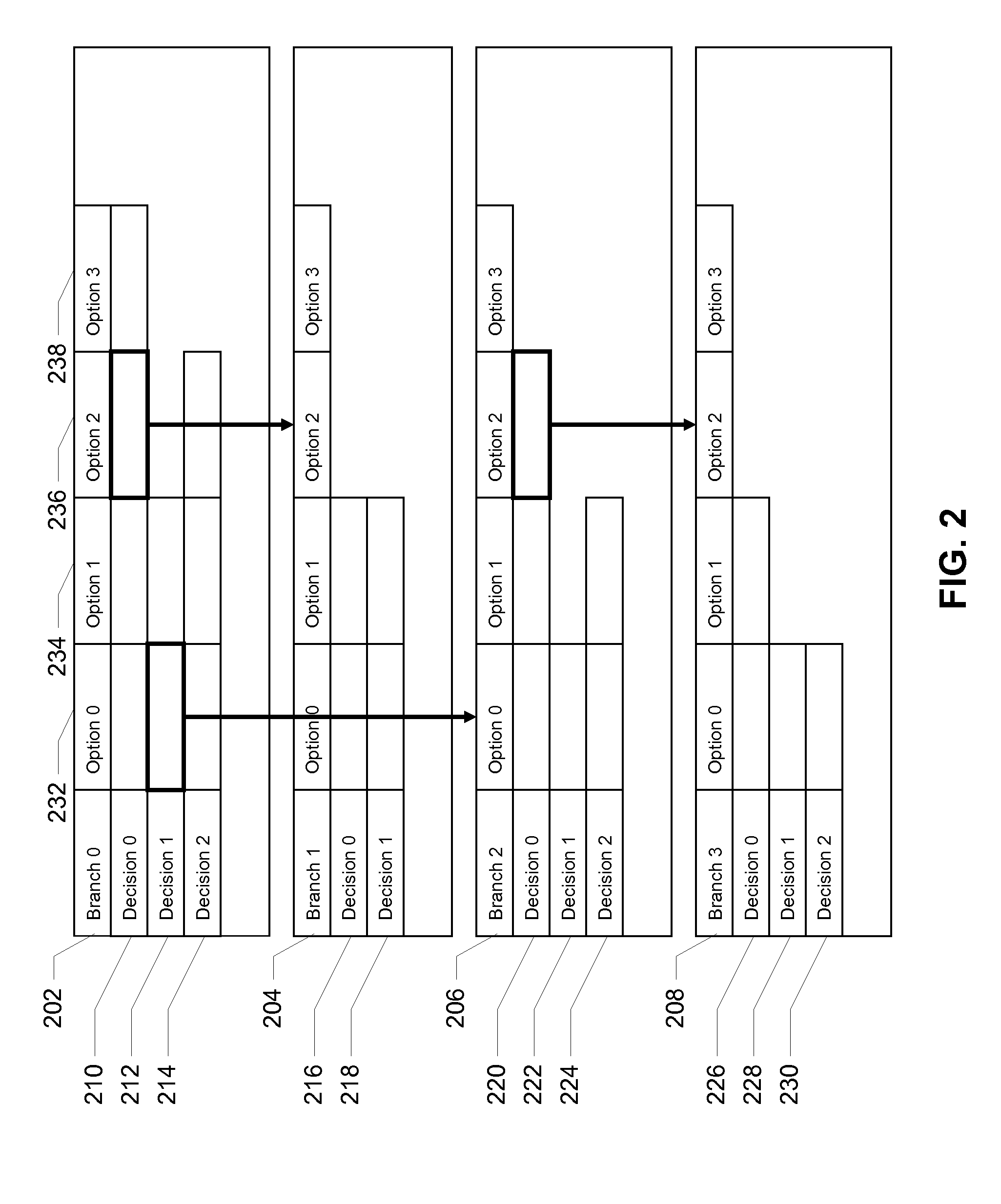
Model-based testing using branches, decisions, and options
ActiveUS8225288B2Digital data processing detailsError detection/correctionSystems analysisTheoretical computer science
Some embodiments of the present invention provide a system that tests a software program. During operation, the system creates a behavioral model of the software program using branches, decisions, and options. Next, the system generates a test case from the behavioral model and executes the test case on the software program. Finally, the system analyzes an output of the executed test case to determine a validity of the software program.
Owner:INTUIT INC
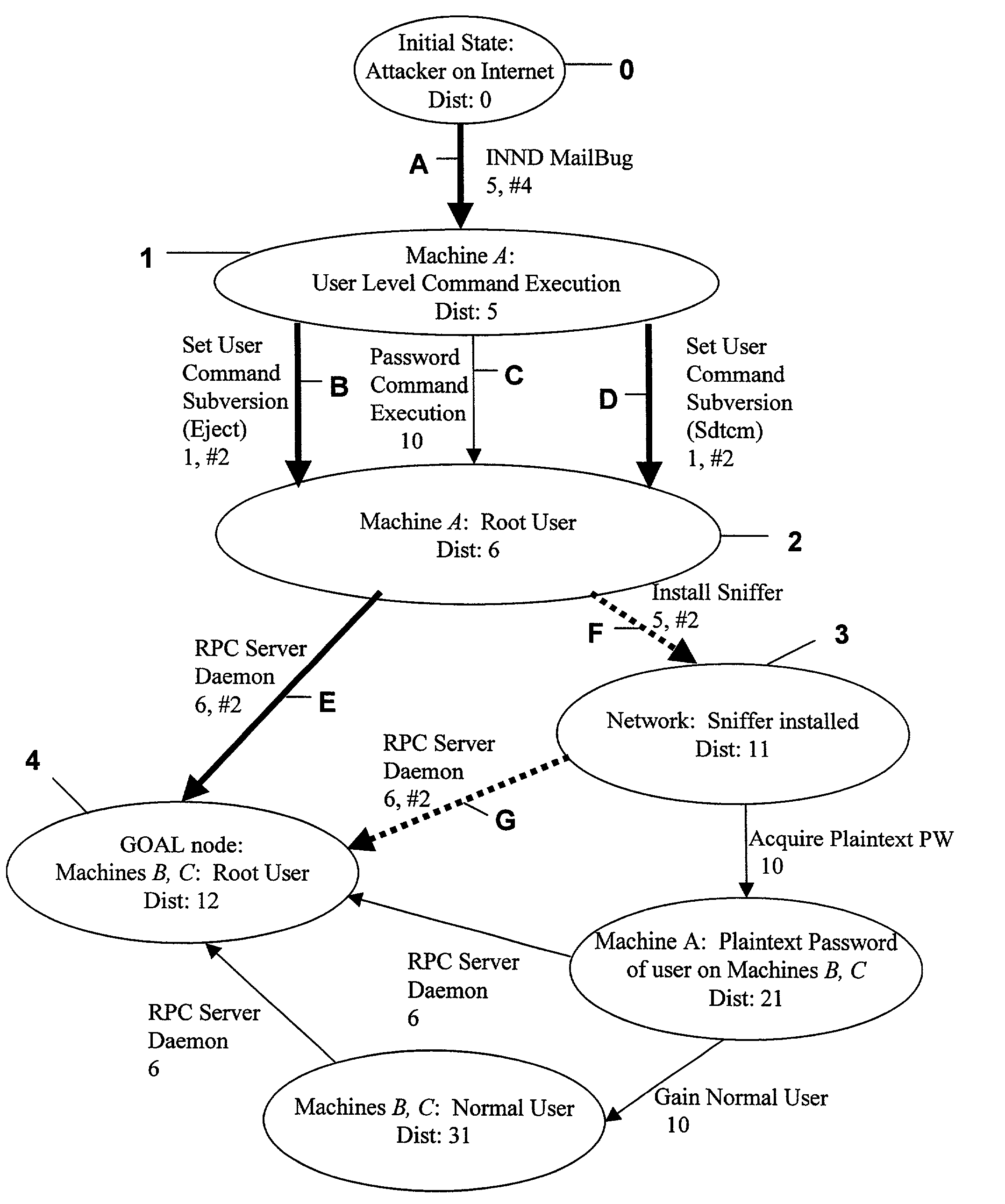
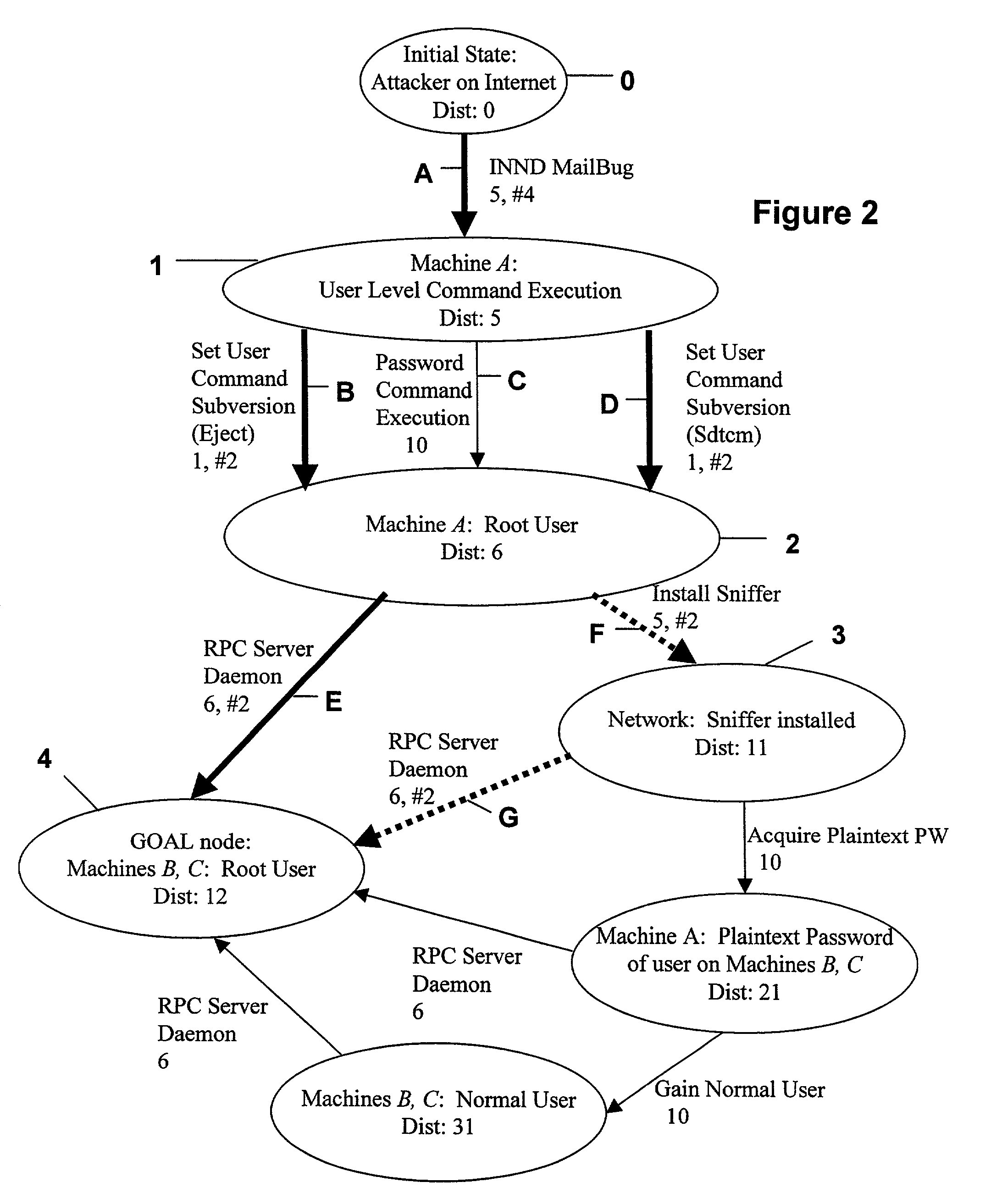
Method and tool for network vulnerability analysis
InactiveUS7013395B1Avoid low successLow “ effort ” costMemory loss protectionUnauthorized memory use protectionLimited resourcesCountermeasure
A computer system analysis tool and method that will allow for qualitative and quantitative assessment of security attributes and vulnerabilities in systems including computer networks. The invention is based on generation of attack graphs wherein each node represents a possible attack state and each edge represents a change in state caused by a single action taken by an attacker or unwitting assistant. Edges are weighted using metrics such as attacker effort, likelihood of attack success, or time to succeed. Generation of an attack graph is accomplished by matching information about attack requirements (specified in “attack templates”) to information about computer system configuration (contained in a configuration file that can be updated to reflect system changes occurring during the course of an attack) and assumed attacker capabilities (reflected in “attacker profiles”). High risk attack paths, which correspond to those considered suited to application of attack countermeasures given limited resources for applying countermeasures, are identified by finding “epsilon optimal paths.”
Owner:SANDIA NAT LAB
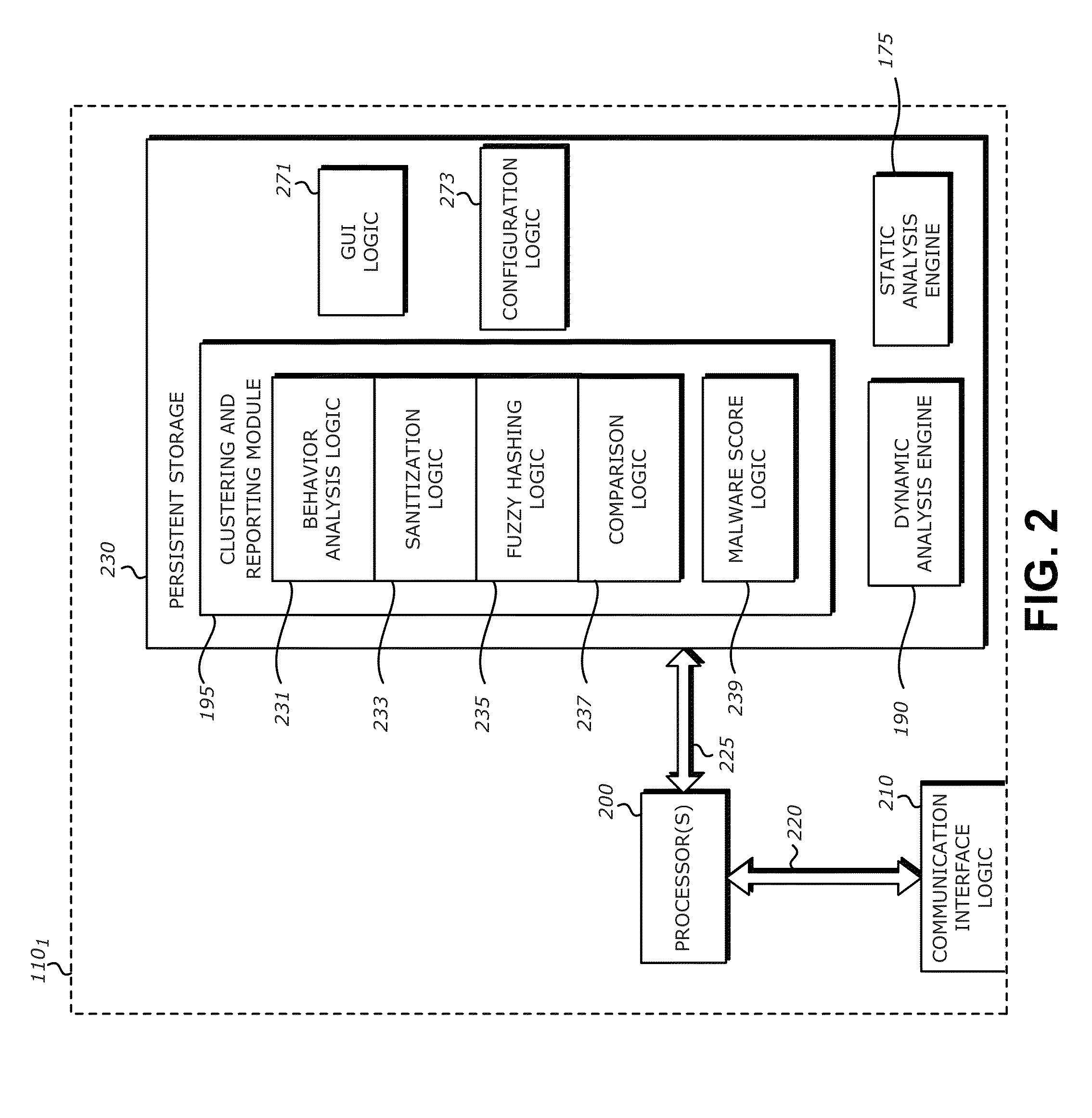
Fuzzy hash of behavioral results
A computerized method is described in which a received object is analyzed by a malicious content detection (MCD) system to determine whether the object is malware or non-malware. The analysis may include the generation of a fuzzy hash based on a collection of behaviors for the received object. The fuzzy hash may be used by the MCD system to determine the similarity of the received object with one or more objects in previously classified / analyzed clusters. Upon detection of a “similar” object, the suspect object may be associated with the cluster and classified based on information attached to the cluster. This similarity matching provides 1) greater flexibility in analyzing potential malware objects, which may share multiple characteristics and behaviors but are also slightly different from previously classified objects and 2) a more efficient technique for classifying / assigning attributes to objects.
Owner:FIREEYE SECURITY HLDG US LLC +1
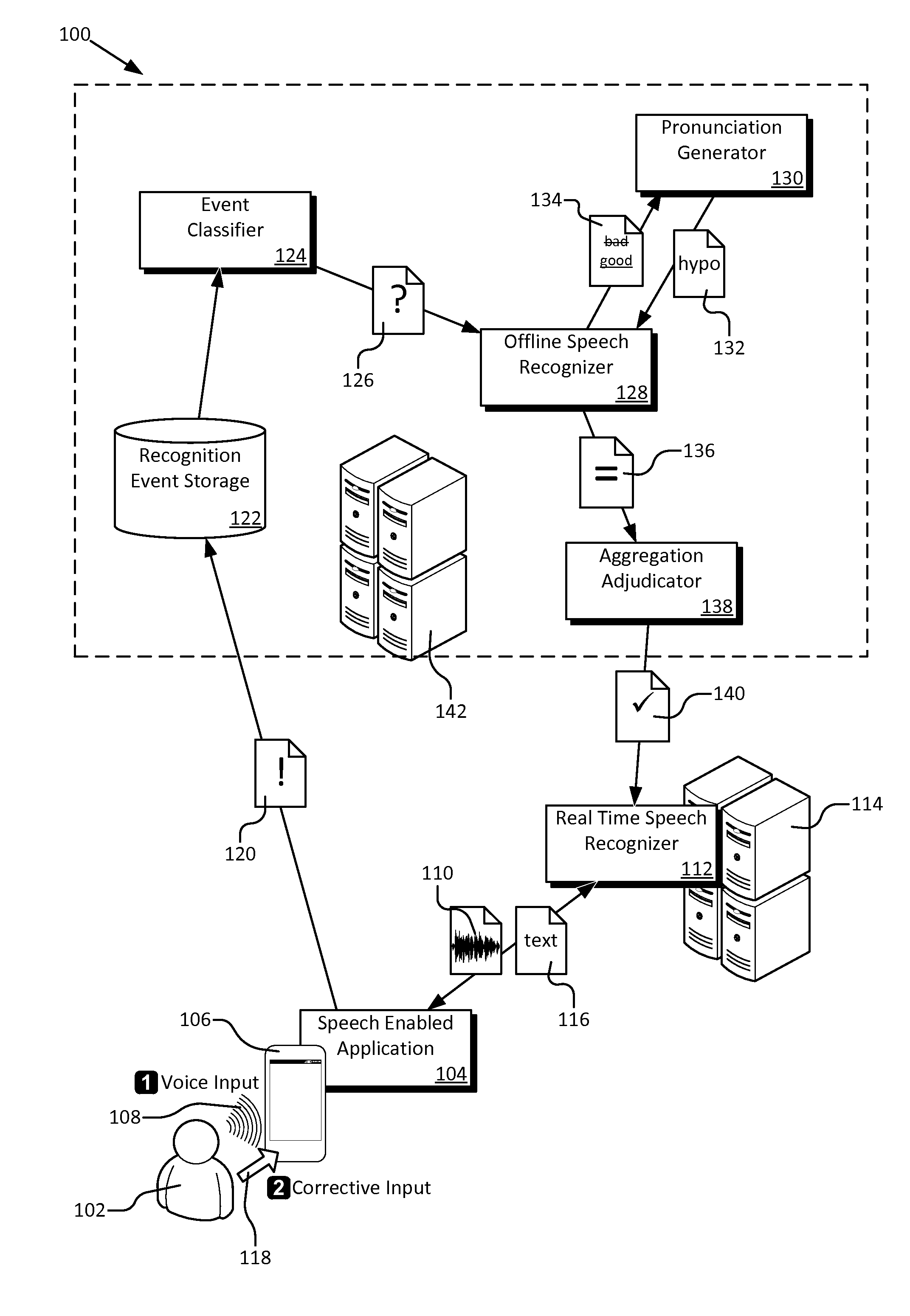
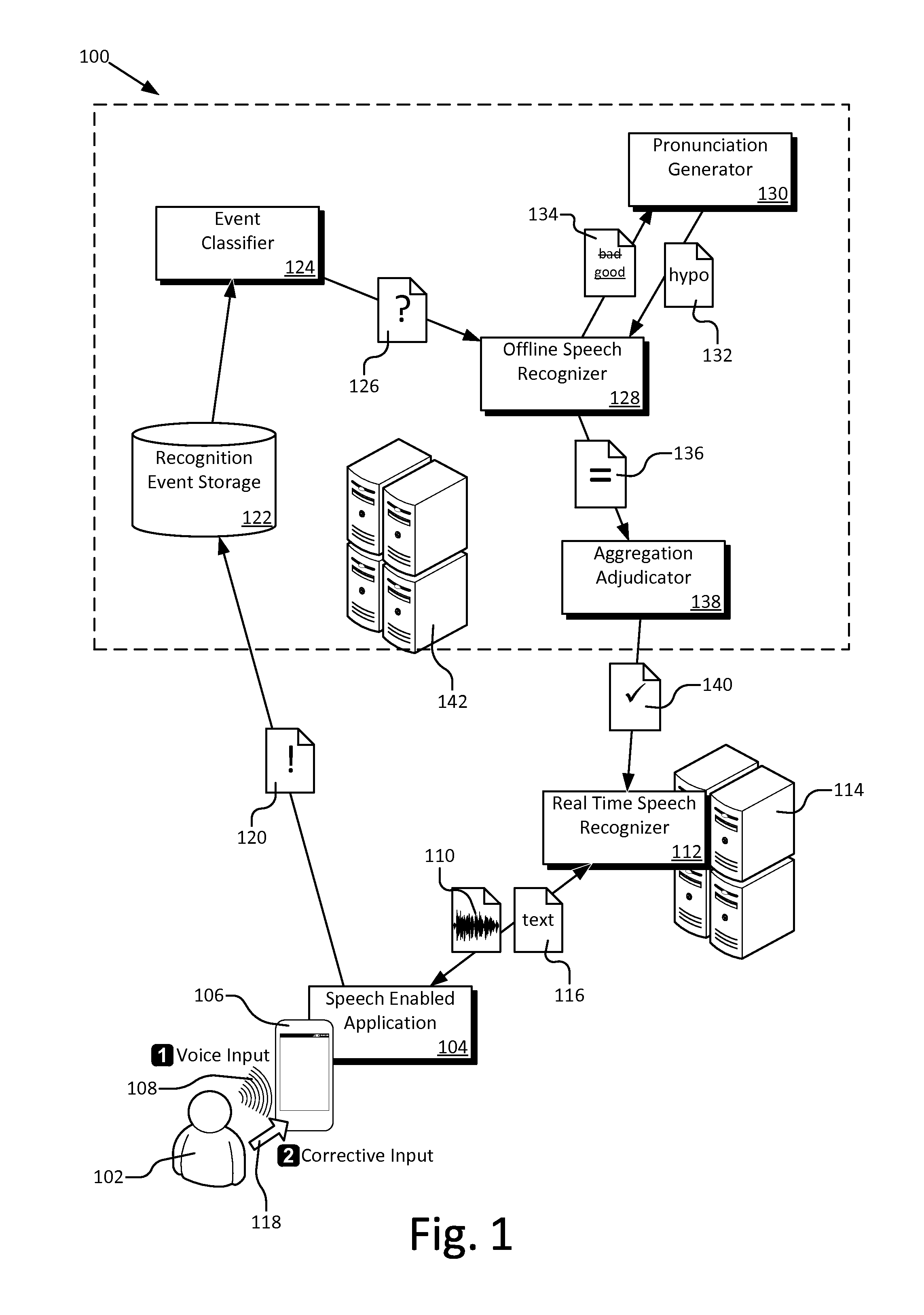
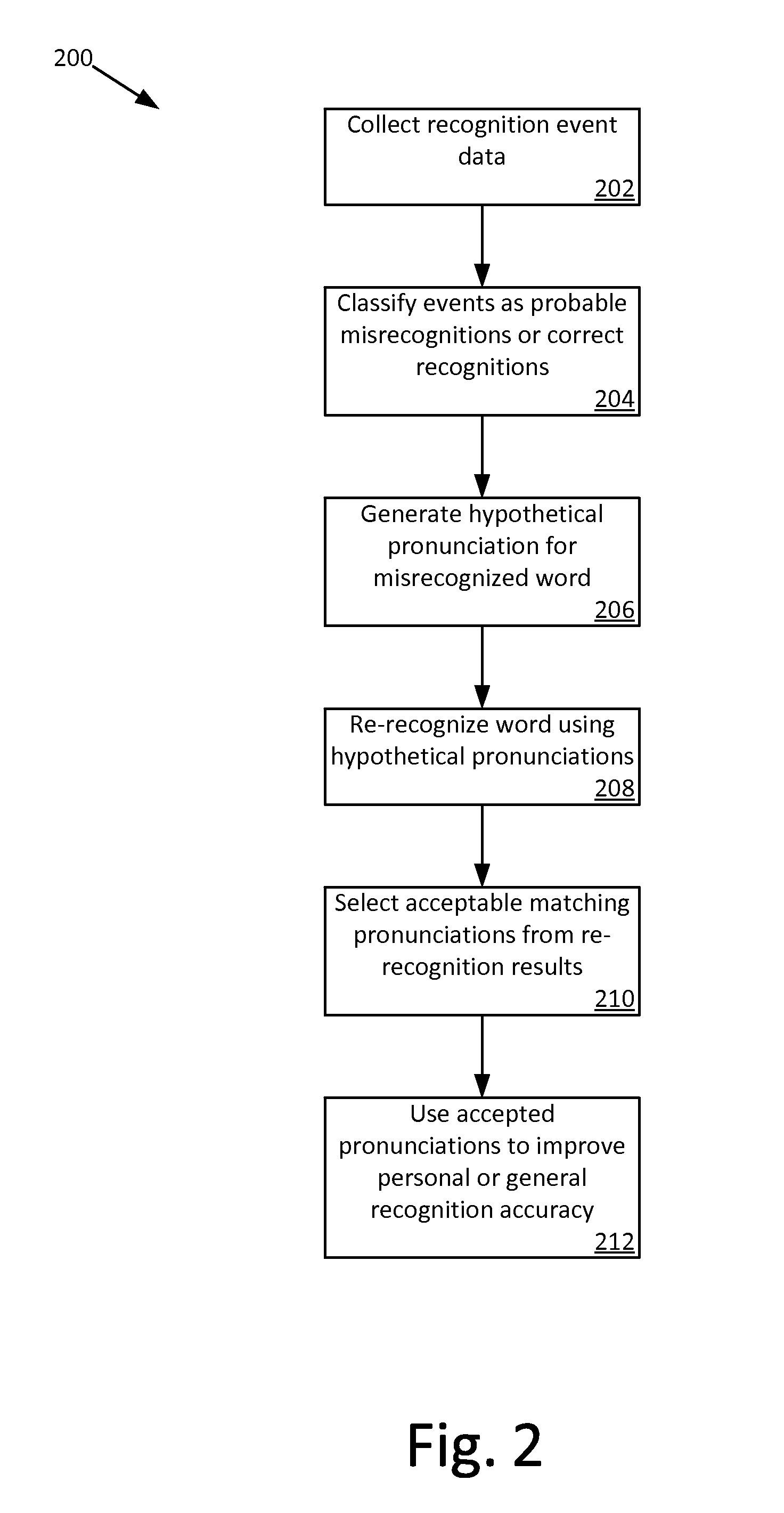
Pronunciation learning through correction logs
A new pronunciation learning system for dynamically learning new pronunciations assisted by user correction logs. The user correction logs provide a record of speech recognition events and subsequent user behavior that implicitly confirms or rejects the recognition result and / or shows the user's intended words by via subsequent input. The system analyzes the correction logs and distills them down to a set of words which lack acceptable pronunciations. Hypothetical pronunciations, constrained by spelling and other linguistic knowledge, are generated for each of the words. Offline recognition determines the hypothetical pronunciations with a good acoustical match to the audio data likely to contain the words. The matching pronunciations are aggregated and adjudicated to select new pronunciations for the words to improve general or personalized recognition models.
Owner:MICROSOFT TECH LICENSING LLC
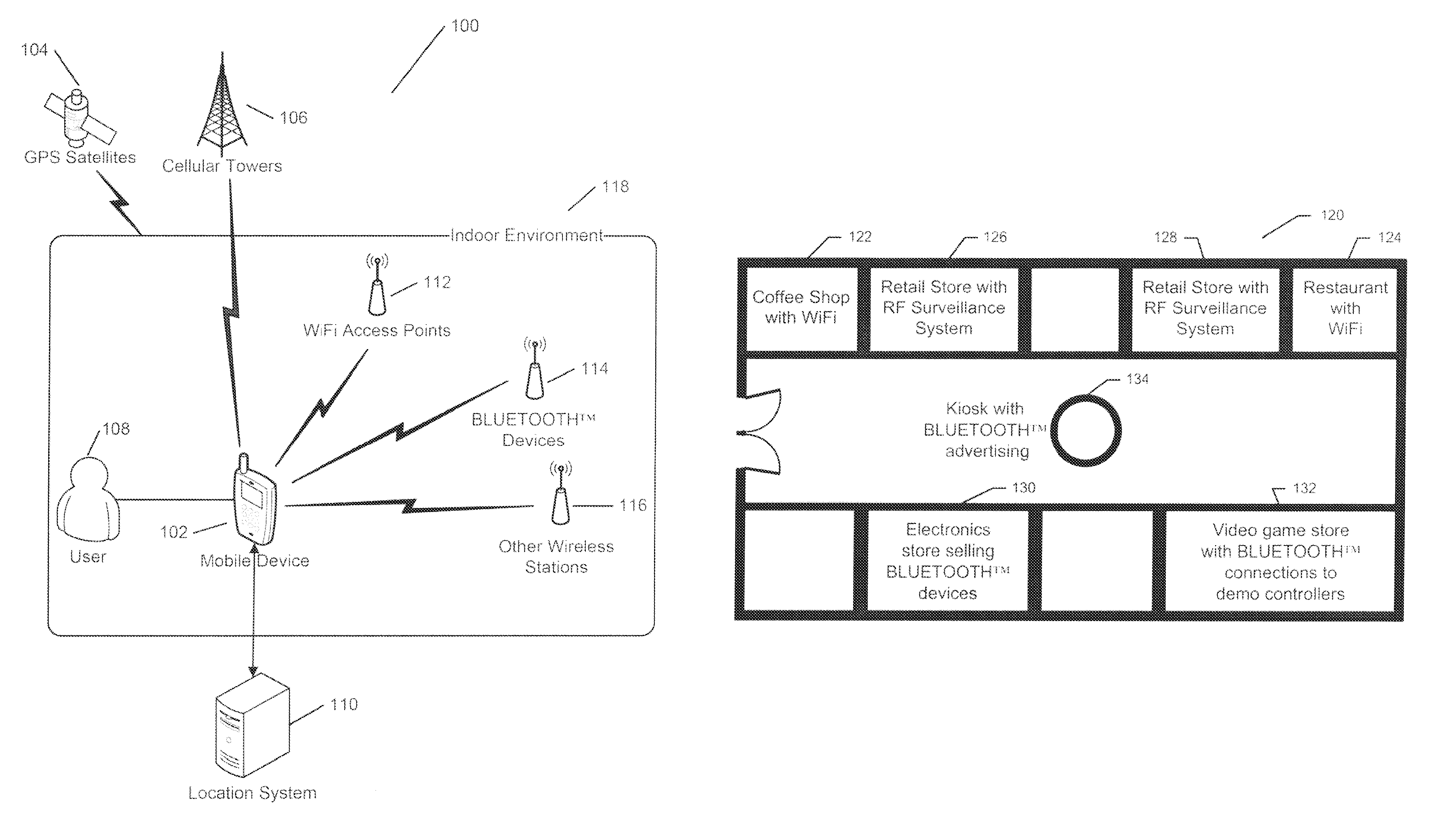
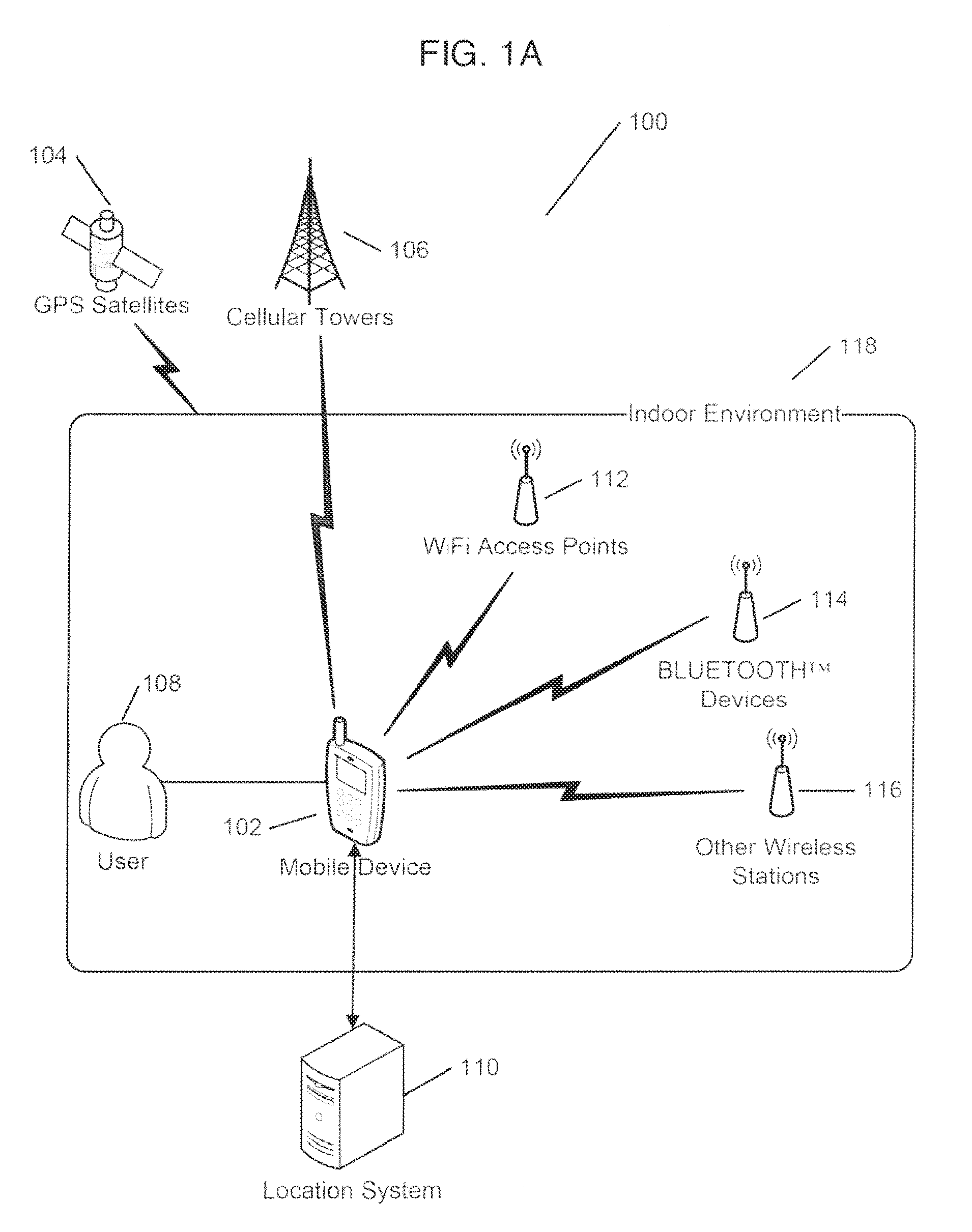
Systems and methods for calibration based indoor geolocation
ActiveUS9439041B2Improve accuracyAccurate CalibrationDirection finders using radio wavesParticular environment based servicesIndoor geolocationSystems analysis
In a system facilitating the calibration of a map-point grid for an indoor location determination, the grid includes several map points, each having a radio frequency (RF) data fingerprint being associated therewith. At least one of: (i) RF signal data from several RF sources, (ii) a user specified location indication, and (ii) tracking data from a sensor, the tracking data indicating a user's movement relative to a base map point, are received. The map-point grid is updated based on, at least in part, at least one of (i) adjusted RF data, the received RF data being adjusted using systematic analysis thereof, (ii) the tracking data, and (iii) the location indication. A user's location may be determined based on the fingerprints associated with the map-point grid, and sensor data.
Owner:LIGHTHOUSE SIGNAL SYST
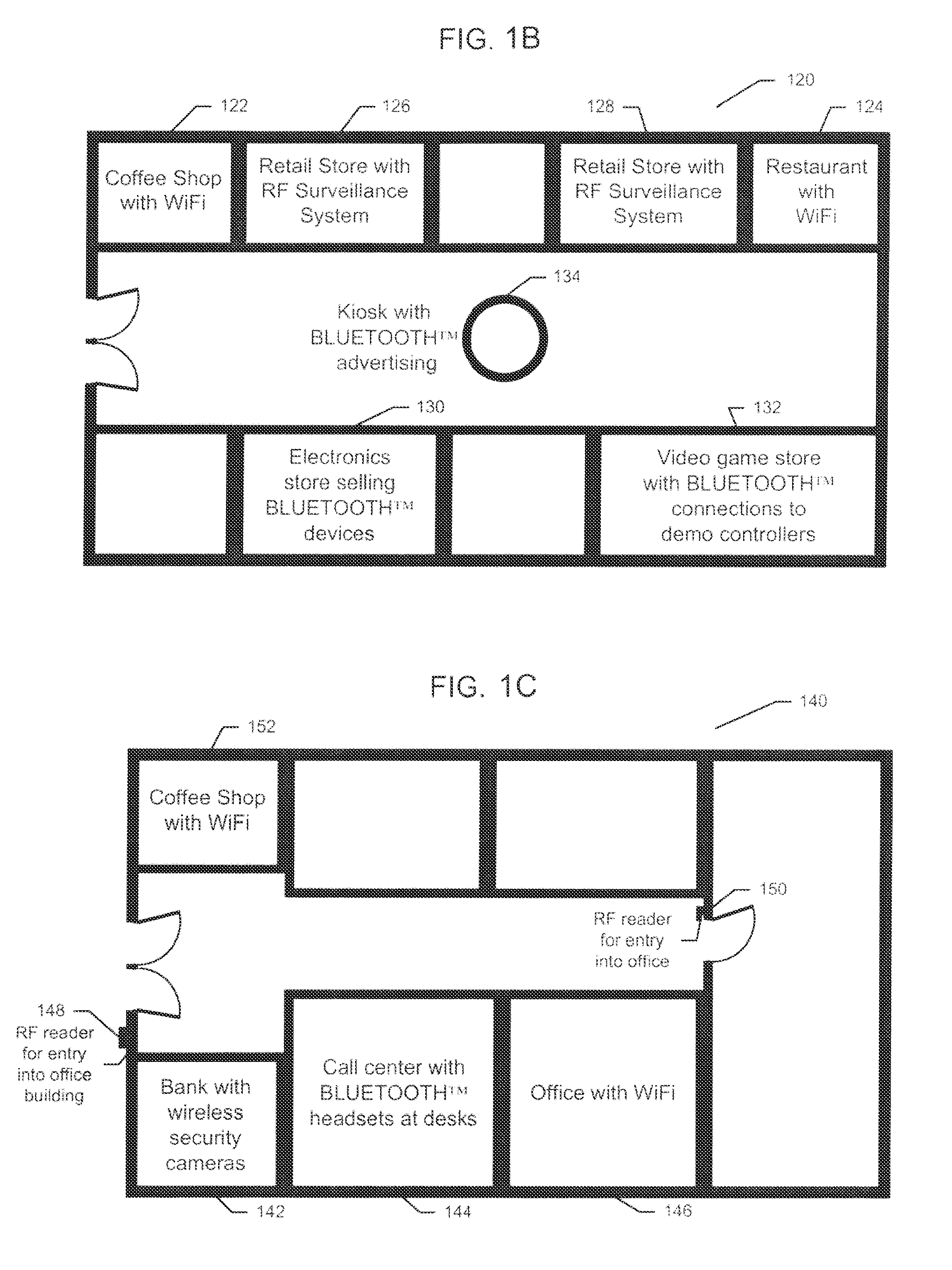
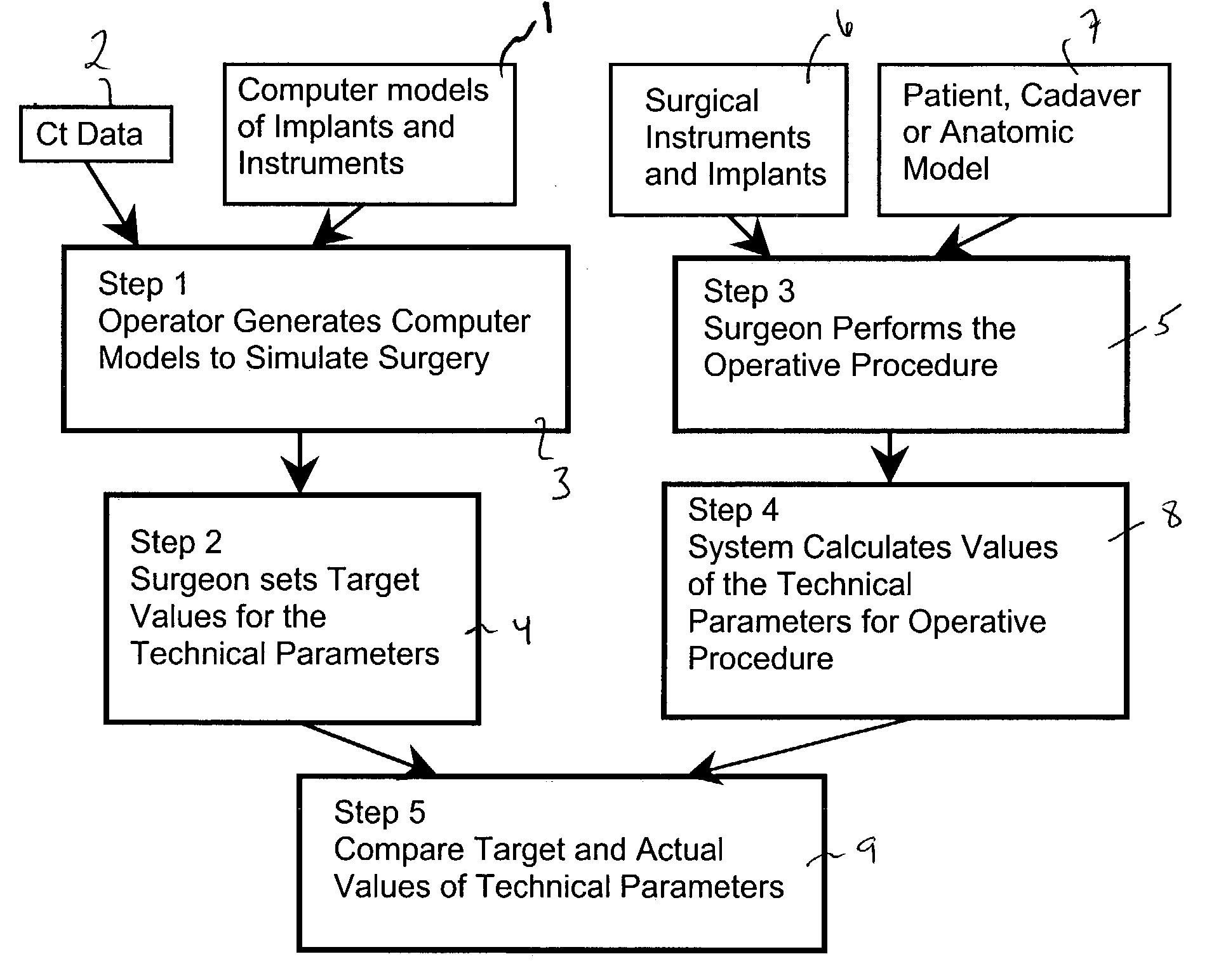
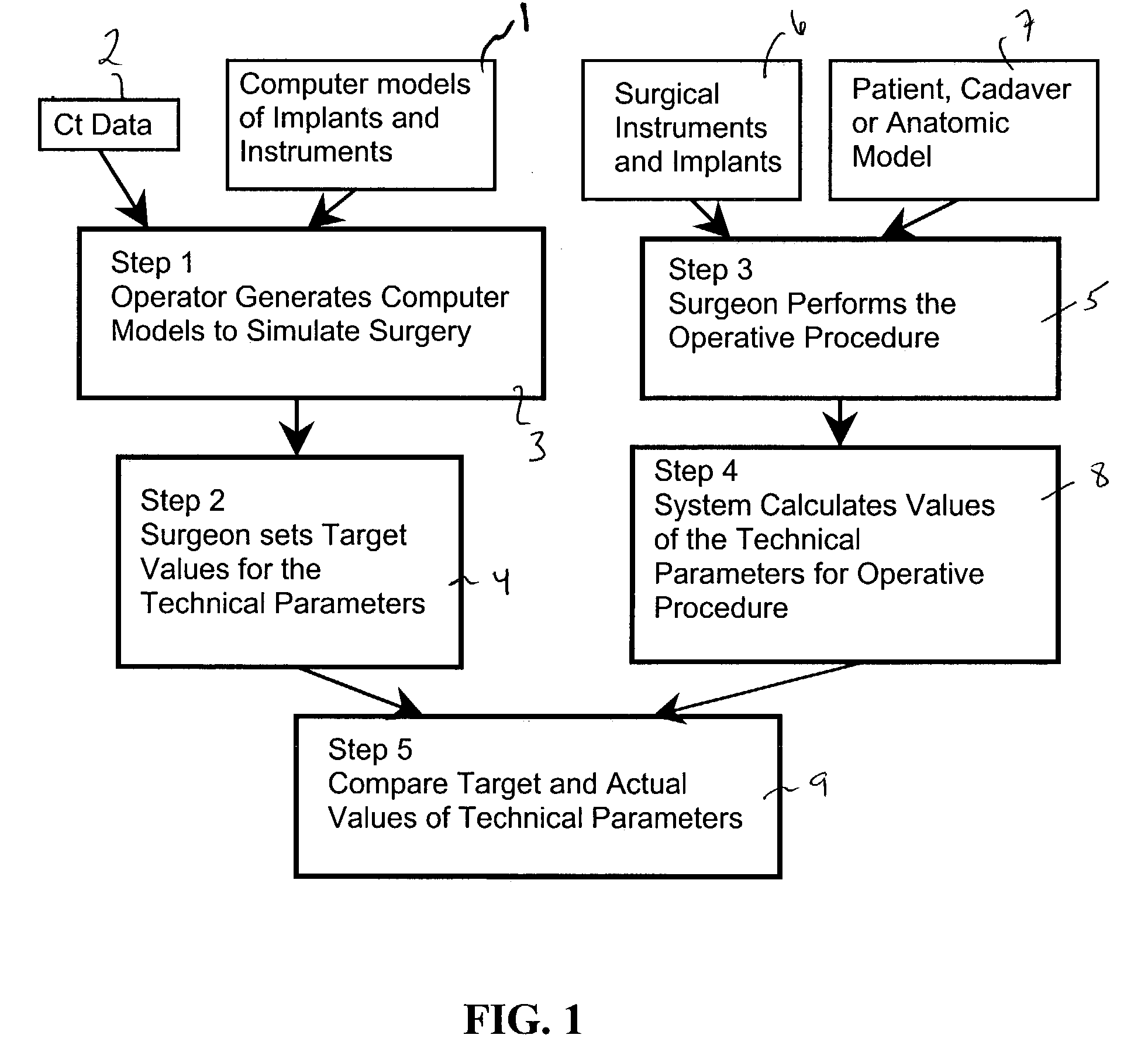
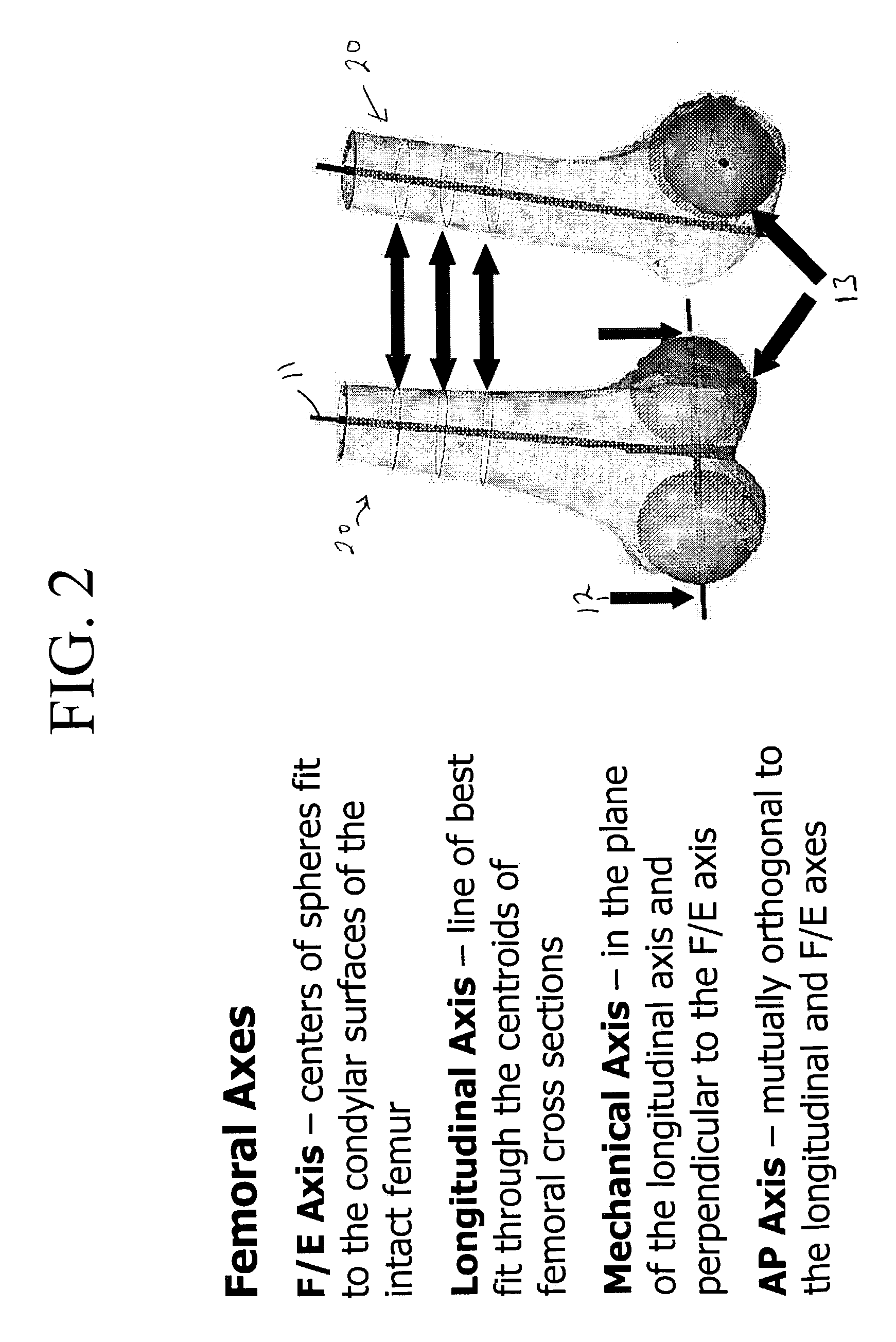
Computer-based training methods for surgical procedures
ActiveUS7427200B2Without expenseMaterial analysis using wave/particle radiationRadiation/particle handlingSystems analysisTechnical success
A method is disclosed for analyzing surgical techniques using a computer system for gathering and analyzing surgical data acquired during a surgical procedure on a body portion and comparing that data to pre-selected target values for the particular surgical procedure. The inventive method allows the surgeon, for example, to measure the technical success of a surgical procedure in terms of quantifiable geometric, spatial, kinematic or kinetic parameters. The method comprises calculation of these parameters from data collected during a surgical procedure and then comparing these results with values of the same parameters derived from target values defined by the surgeon, surgical convention, or computer simulation of the same procedure prior to the operation itself.
Owner:NOBLE PHILIP C +1
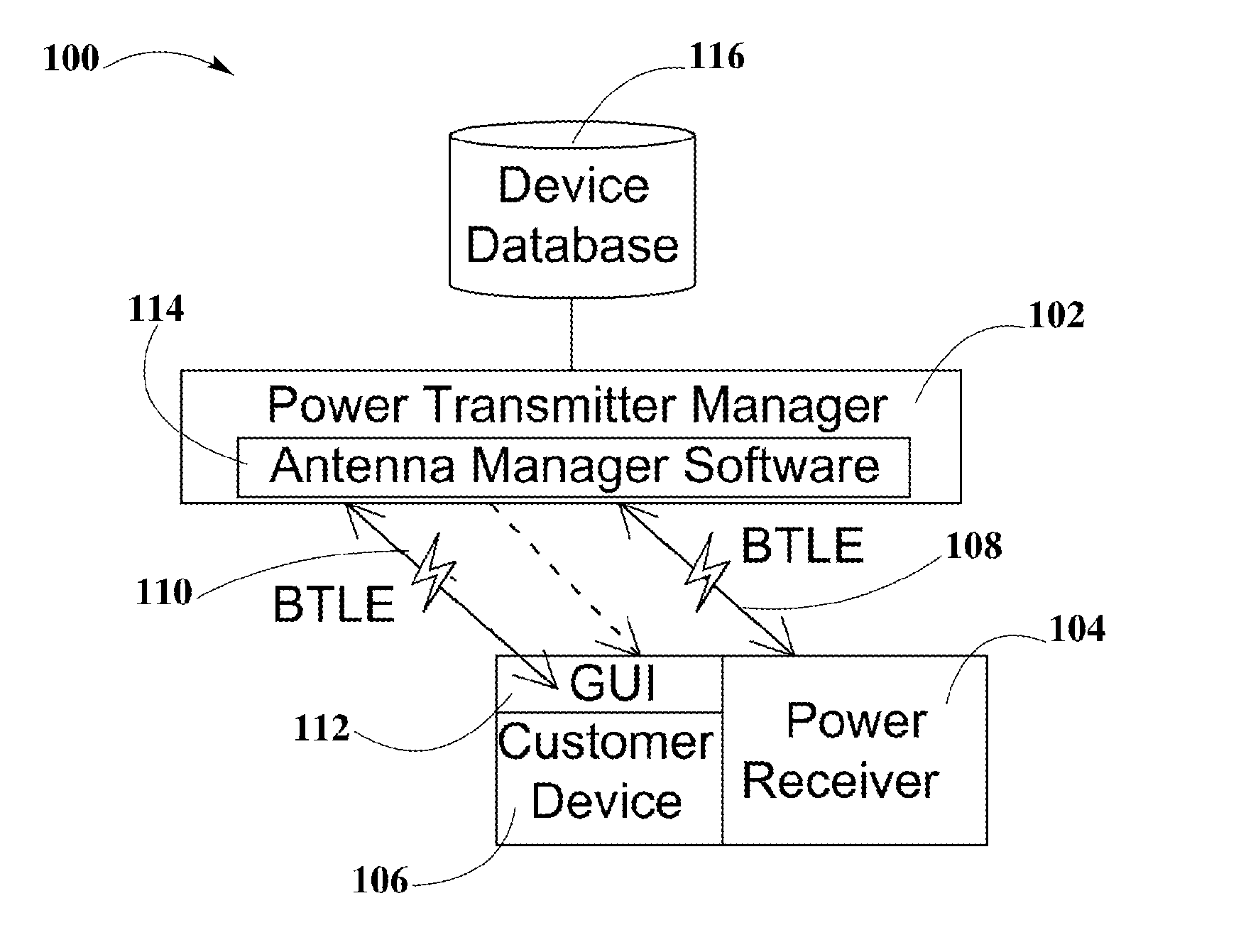
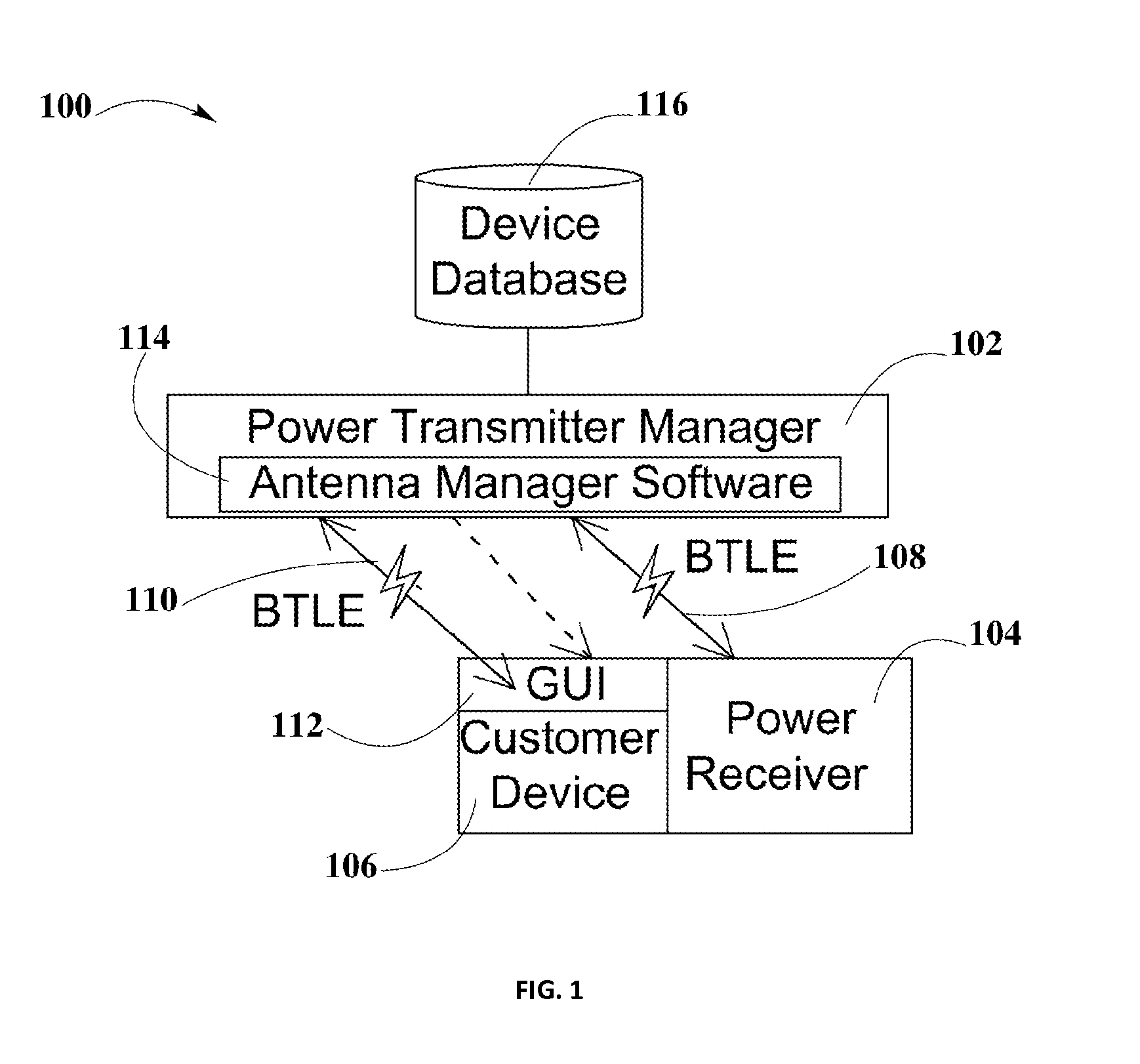
System and Method for a Self-system Analysis in a Wireless Power Transmission Network
ActiveUS20150340909A1Electromagnetic wave systemTransformersElectric power transmissionSystems analysis
A system and method for a self-system analysis in a wireless power transmission network is disclosed. According to some aspects of this disclosure a wireless power transmission network may include one or more wireless power transmitter managers, one or more wireless power receivers, servers, and clouds within a local network to provide wireless power transfer to electronic devices. Wireless power devices in the network may establish, but is not limited to a WiFi connection to share information among all the wireless power devices in the system. Wireless power transmitter managers may monitor everything that happens in the network. If a problem is detected by the wireless power transmitter manager, an analysis of the issue may be done by any device in the network with a copy of the device database. Then a recommendation may be generated for enhancing the system.
Owner:ENERGOUS CORPORATION
Method and system to segment depth images and to detect shapes in three-dimensionally acquired data
ActiveUS20060239558A1Rapidly correctly characterizeQuick identificationImage enhancementImage analysisSystems analysisHistogram
A method and system analyzes data acquired by image systems to more rapidly identify objects of interest in the data. In one embodiment, z-depth data are segmented such that neighboring image pixels having similar z-depths are given a common label. Blobs, or groups of pixels with a same label, may be defined to correspond to different objects. Blobs preferably are modeled as primitives to more rapidly identify objects in the acquired image. In some embodiments, a modified connected component analysis is carried out where image pixels are pre-grouped into regions of different depth values preferably using a depth value histogram. The histogram is divided into regions and image cluster centers are determined. A depth group value image containing blobs is obtained, with each pixel being assigned to one of the depth groups.
Owner:MICROSOFT TECH LICENSING LLC
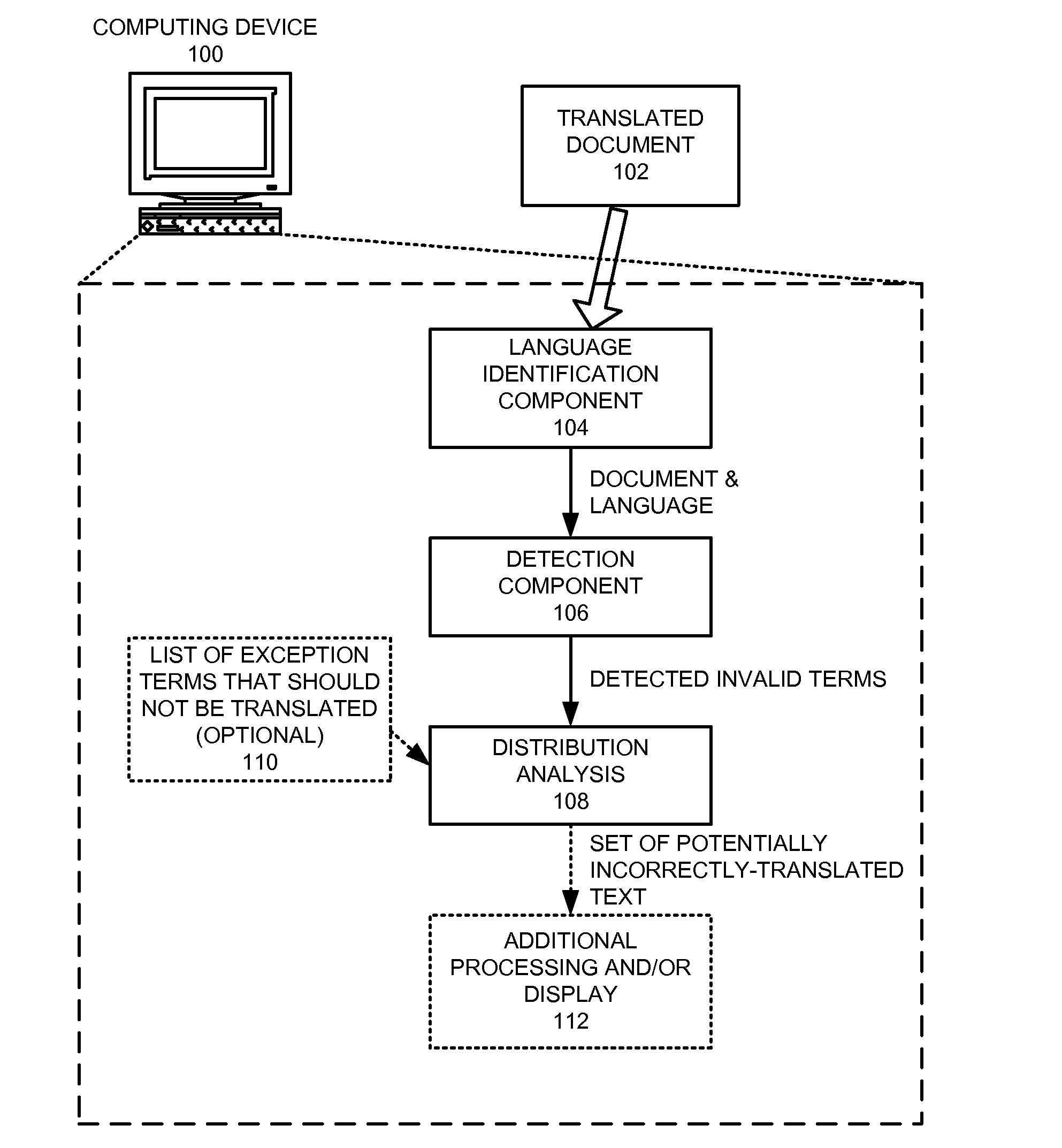
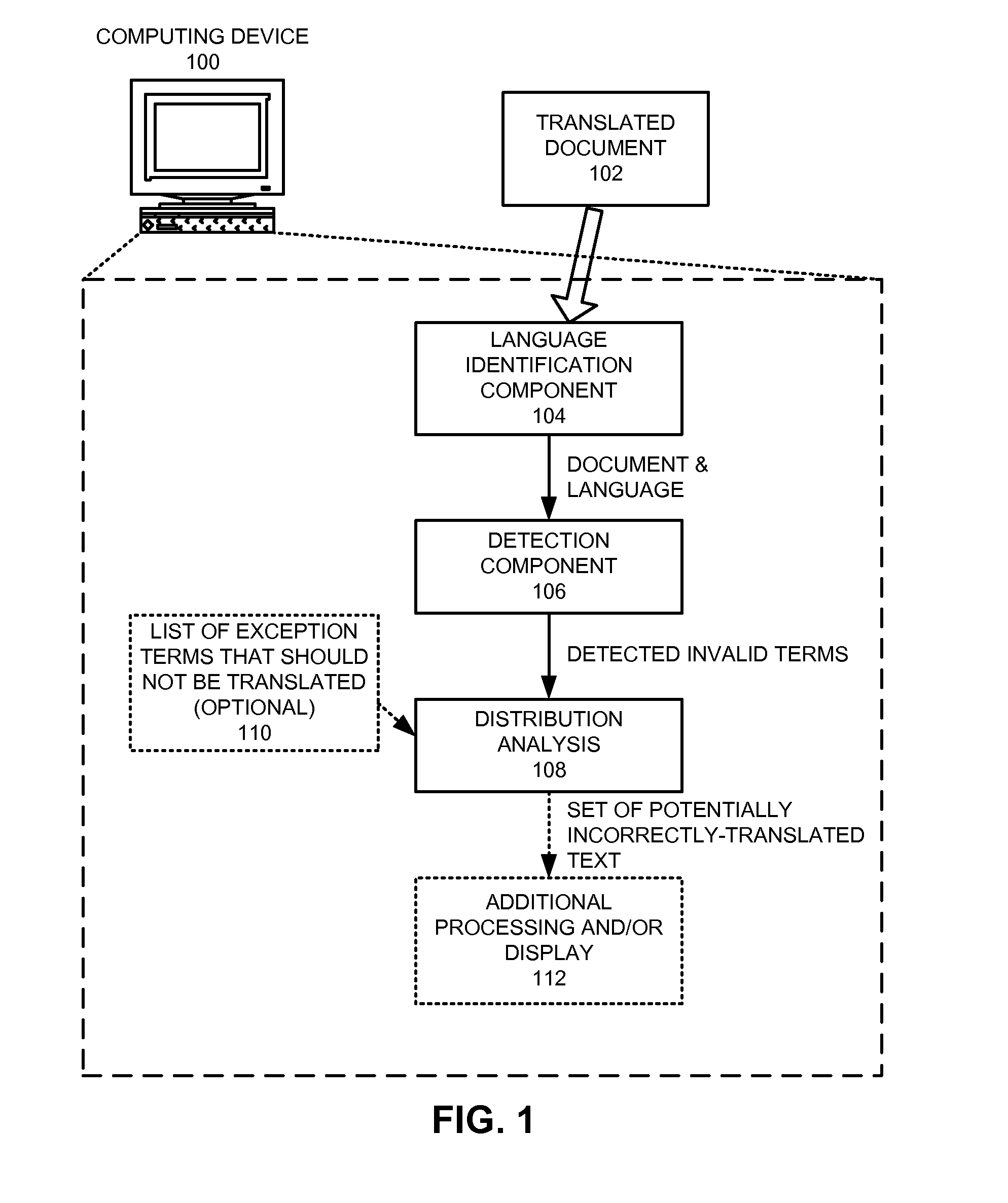
Method and apparatus for detecting incorrectly translated text in a document
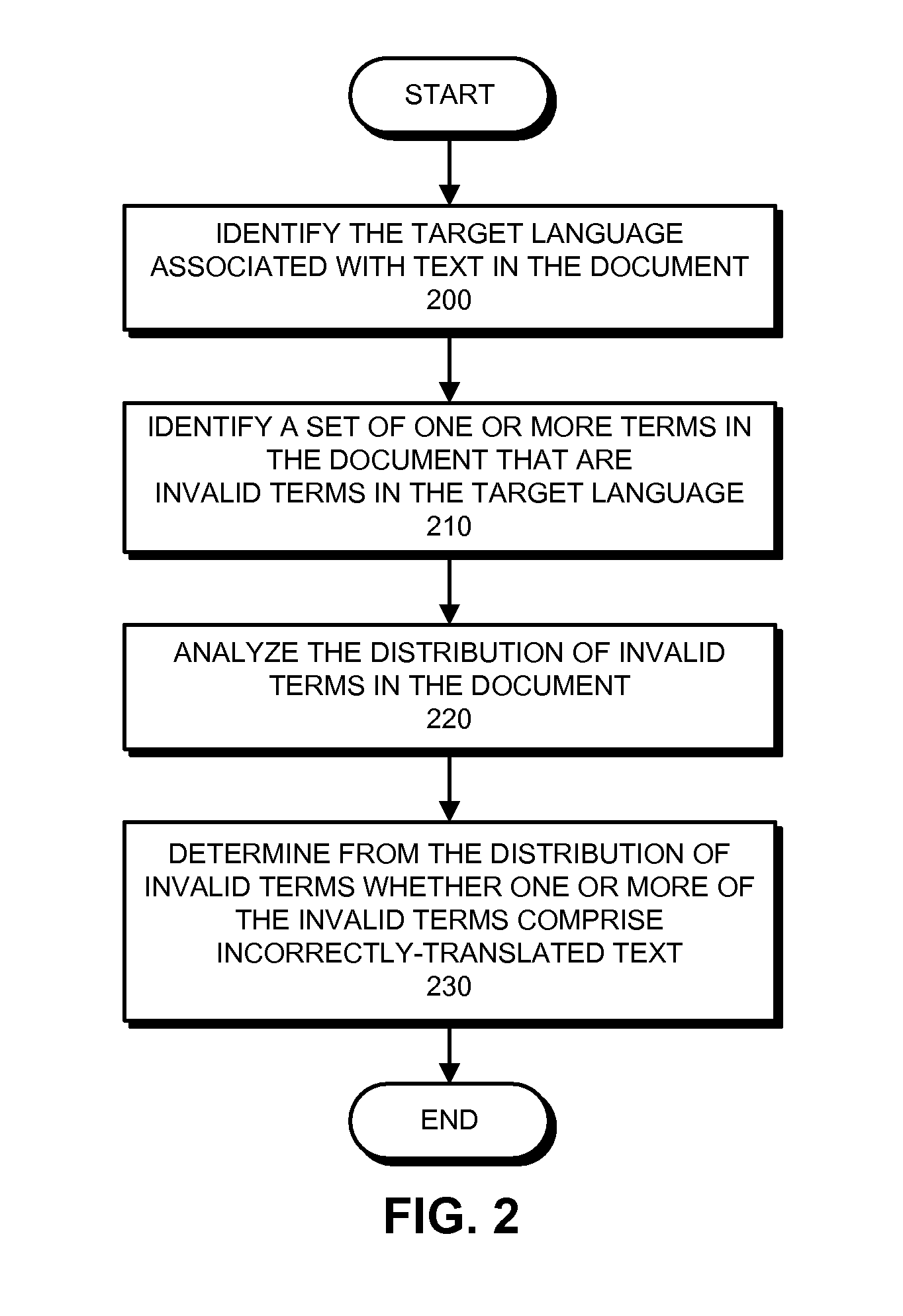
InactiveUS8296124B1Natural language translationSpecial data processing applicationsNatural language processingSystems analysis
A system that detects incorrectly translated text in a document. During operation, the system determines a target language for the document. The system then identifies one or more terms in the document that are invalid terms for the language. Next, the system analyzes correlations between these invalid terms, and, based on these correlations, determines whether one or more of the invalid terms comprise incorrectly translated text.
Owner:GOOGLE LLC
Automated response to solicited and unsolicited communications and automated collection and management of data extracted therefrom
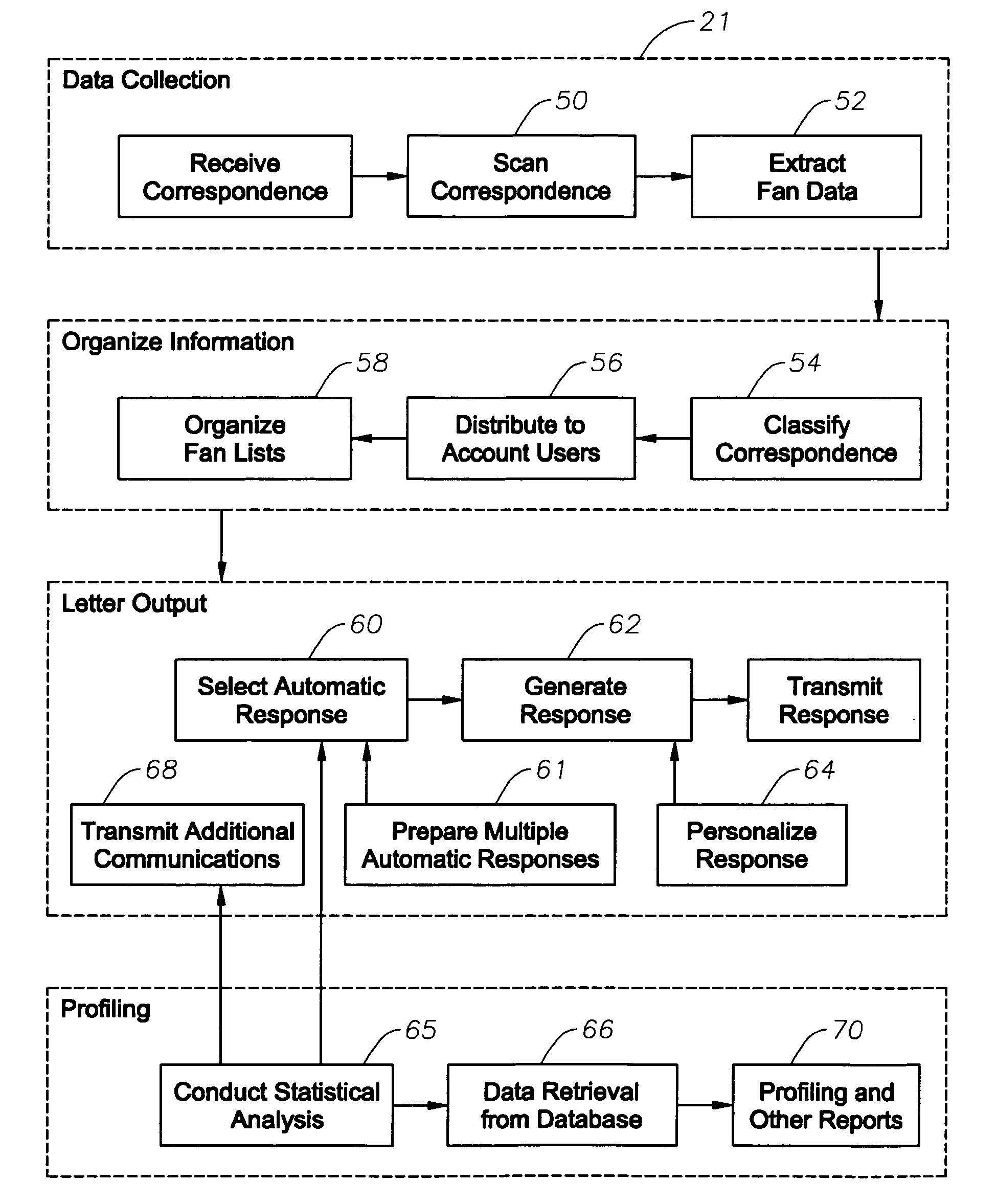
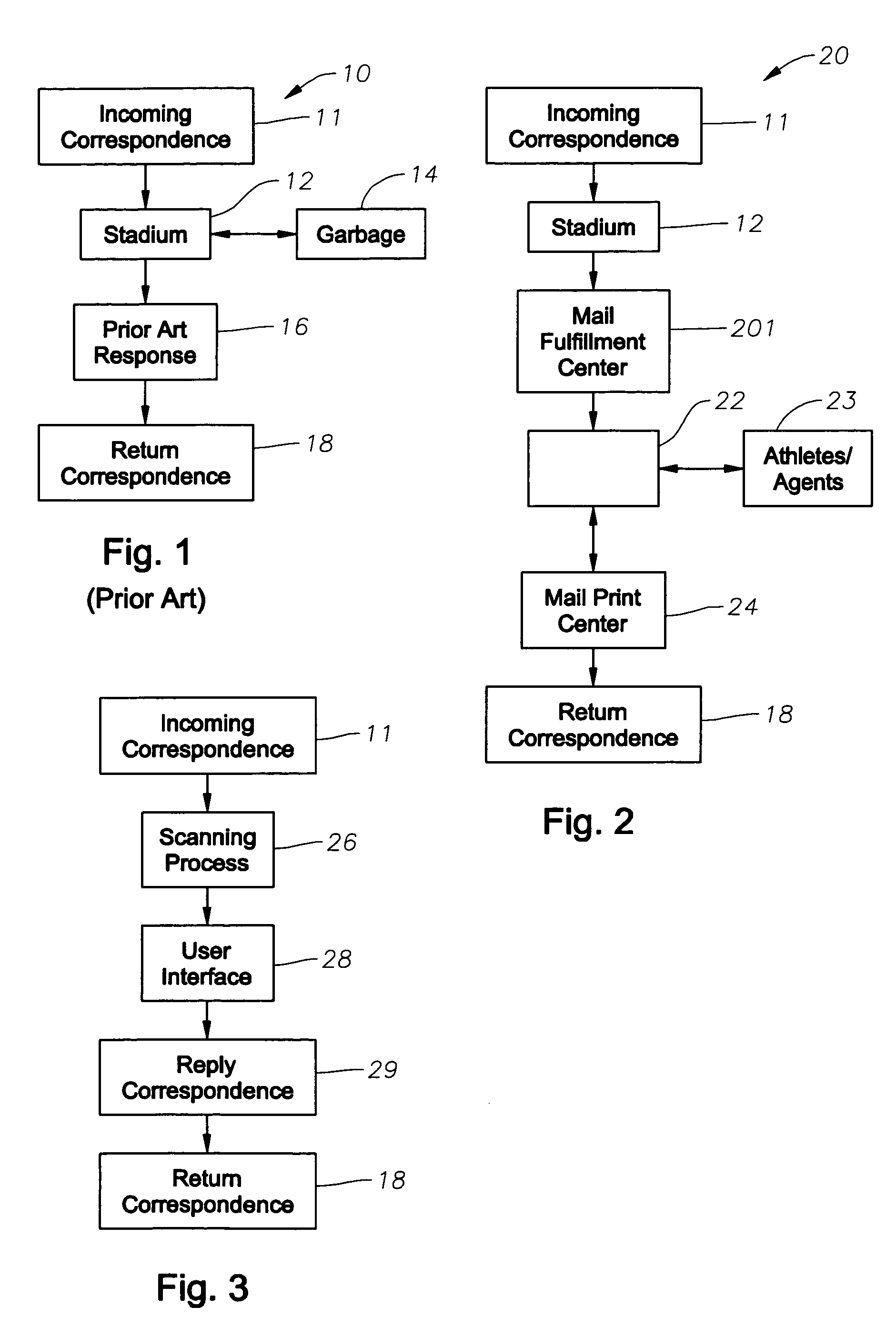
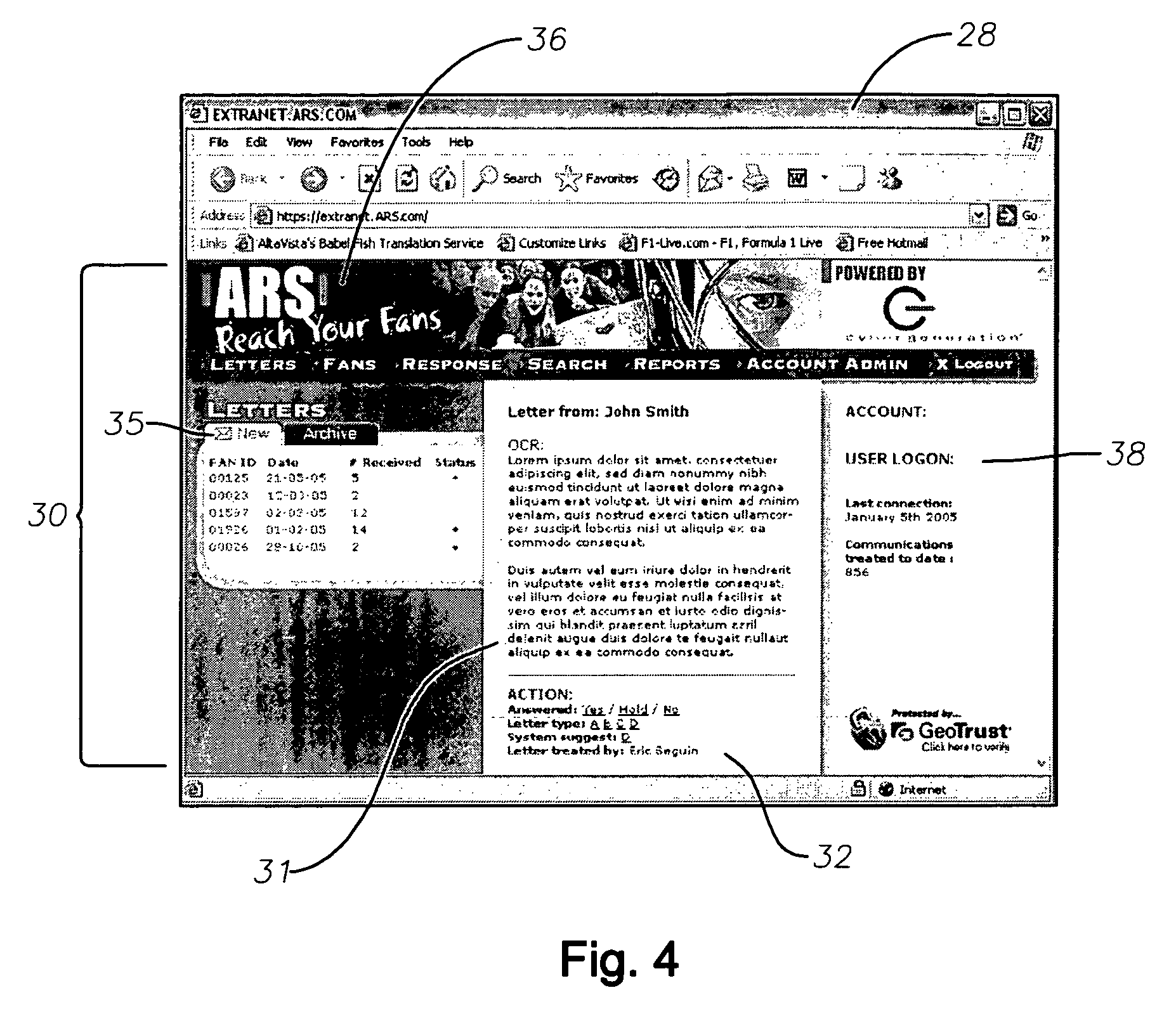
InactiveUS7996372B2Digital data information retrievalDigital data processing detailsSystems analysisData mining
An automated correspondence response system is provide for permitting a receiving entity to generate customized responses based on data extracted from received communications. The system also provides for automated management and manipulation of data extracted from correspondence received by a receiving entity for group profiling and to perform various statistical analysis thereof.The system analyzes content of received correspondence, such as celebrity fan mail, and manages the automation of responses via targeted or “customized” letters, wherein the receiving entity creates content specific fields or terms in order to respond to correspondence in an automated and yet relevant manner. The receiving entity can electronically define what data is extracted from the correspondence. A particular “customized” response to the correspondence may be electronically selected from a plurality of possible responses based on the data extracted from the sender's correspondence so that the receiving entity can effectively respond to the sender. The “customized” automated response can also be “personalized” by including sender specific data in the “customized” automated response.
Owner:MERCURY COMM GROUP
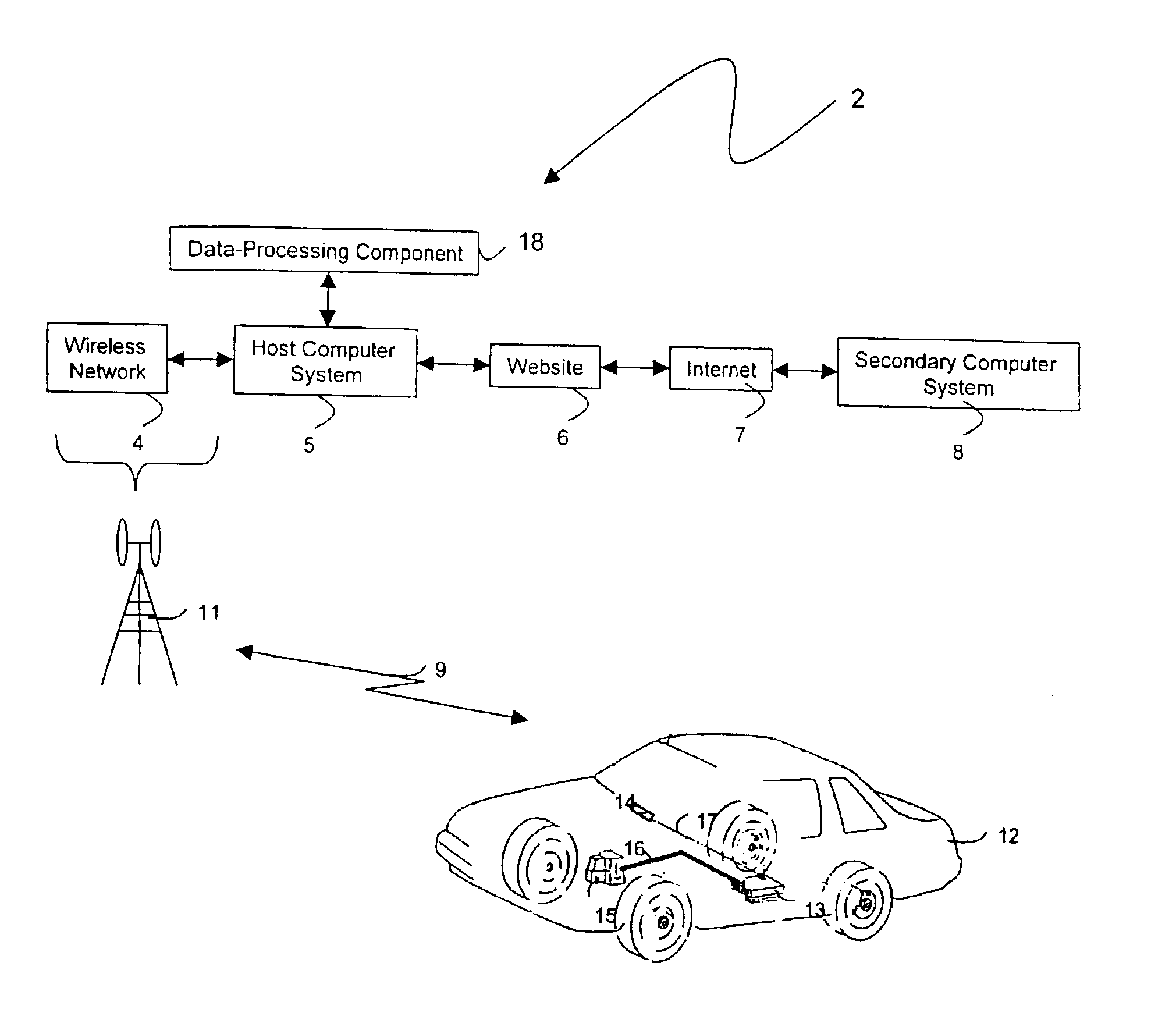
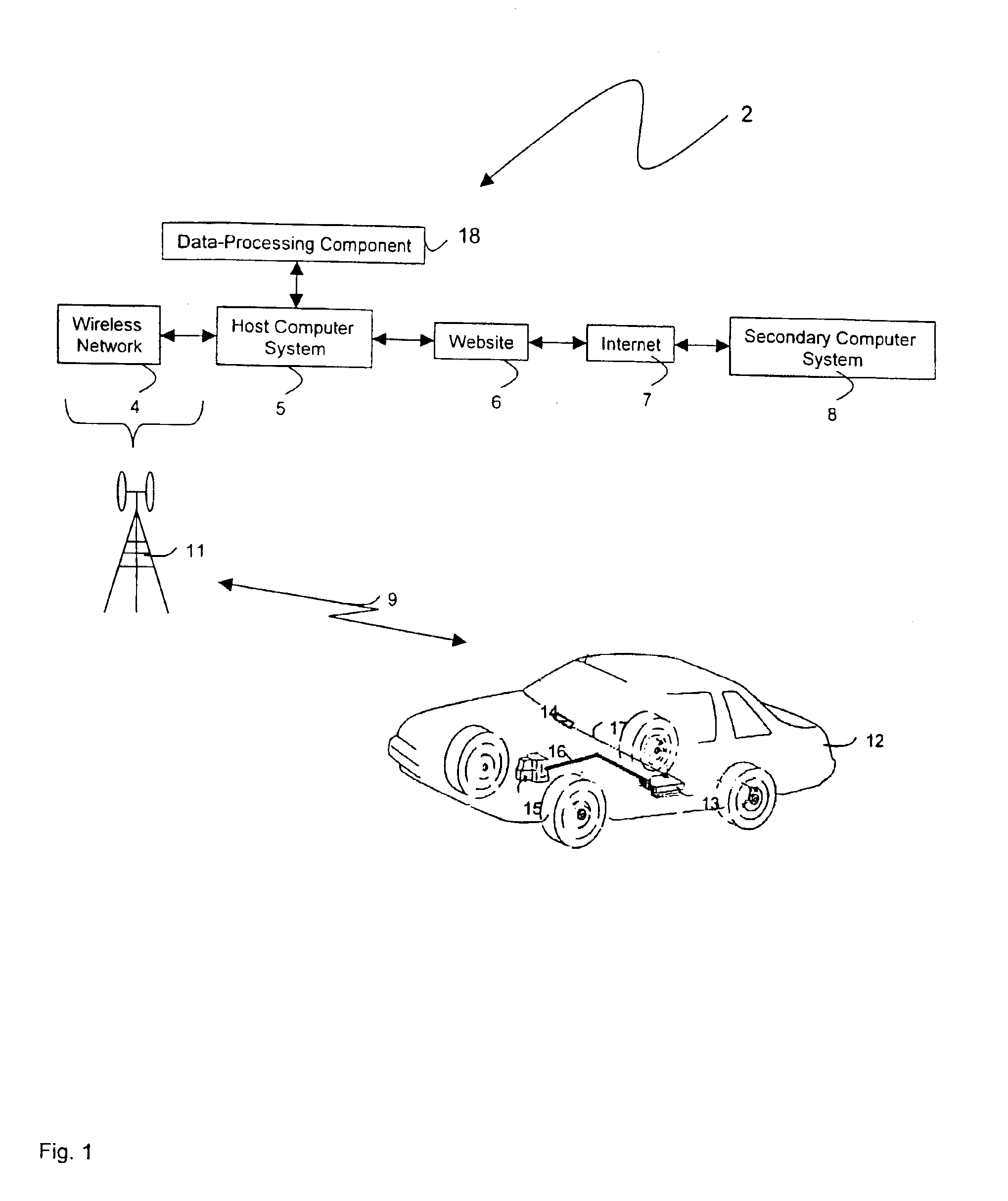
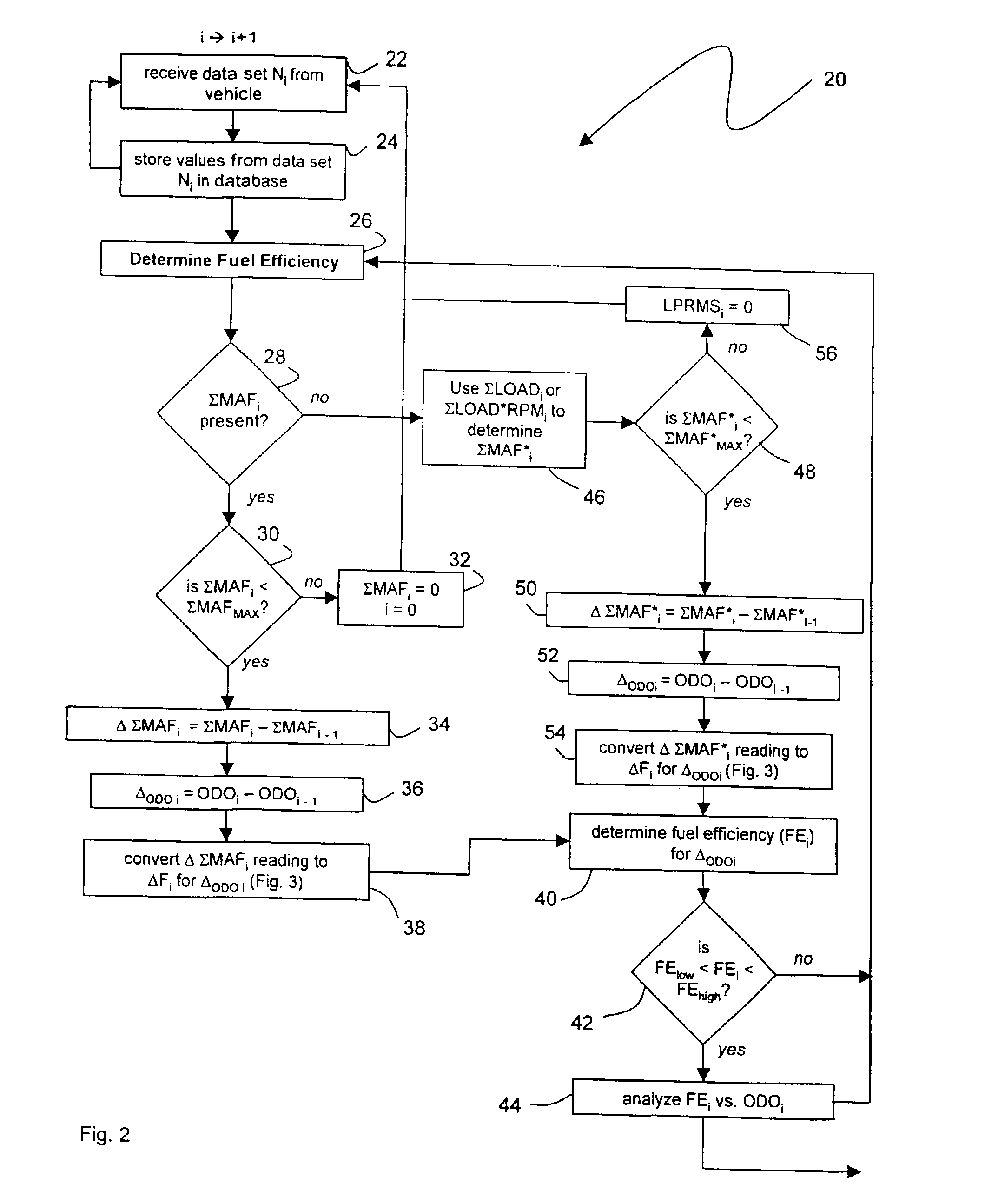
Internet-based method for determining a vehicle's fuel efficiency
InactiveUS6988033B1Determine vehicle 's fuel efficiencyData augmentationVehicle testingAnalogue computers for vehiclesTraffic capacityElectricity
The invention provides a method and device for characterizing a vehicle's fuel efficiency and amount of fuel consumed. The method features the steps of: 1) generating a data set from the vehicle that includes vehicle speed, odometer calculation, engine speed, load, mass air flow; 2) transferring the data set to a wireless appliance that includes i) a microprocessor, and ii) a wireless transmitter in electrical contact with the microprocessor; 3) transmitting a data packet comprising the data set or a version thereof with the wireless transmitter over an airlink to a host computer system; and 4) analyzing the data set with the host computer system to determine a status of the vehicle's fuel efficiency.
Owner:VERIZON PATENT & LICENSING INC
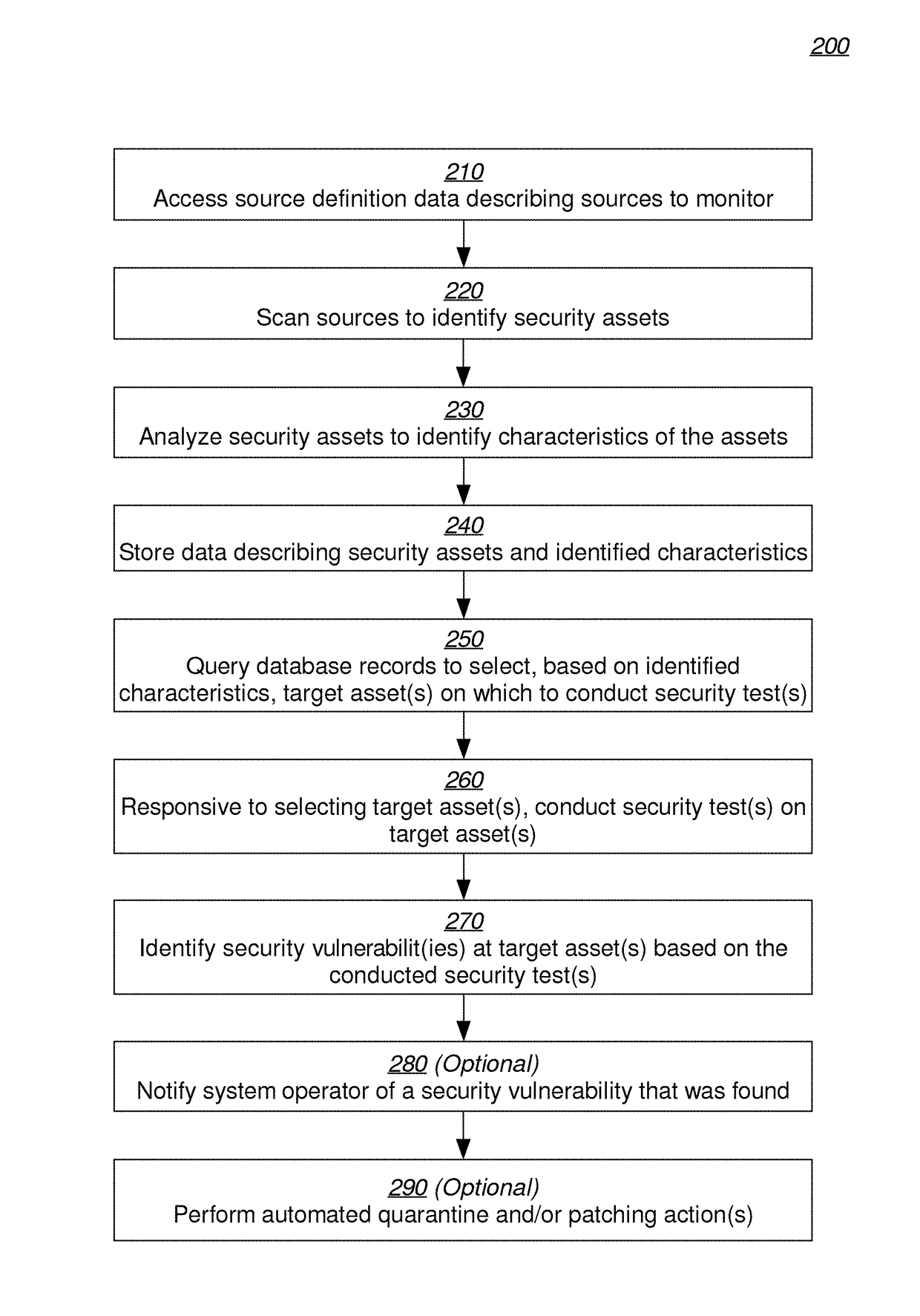
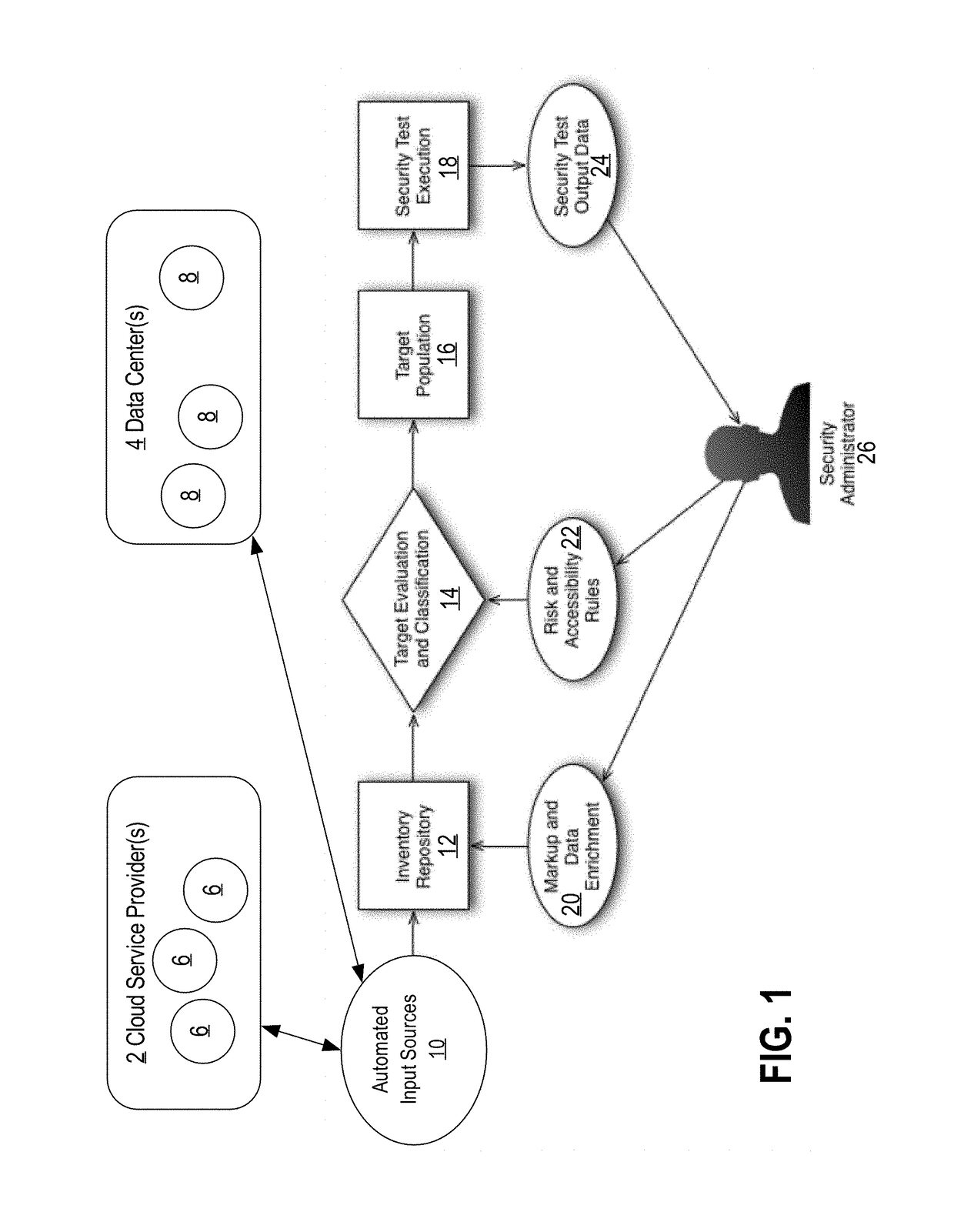
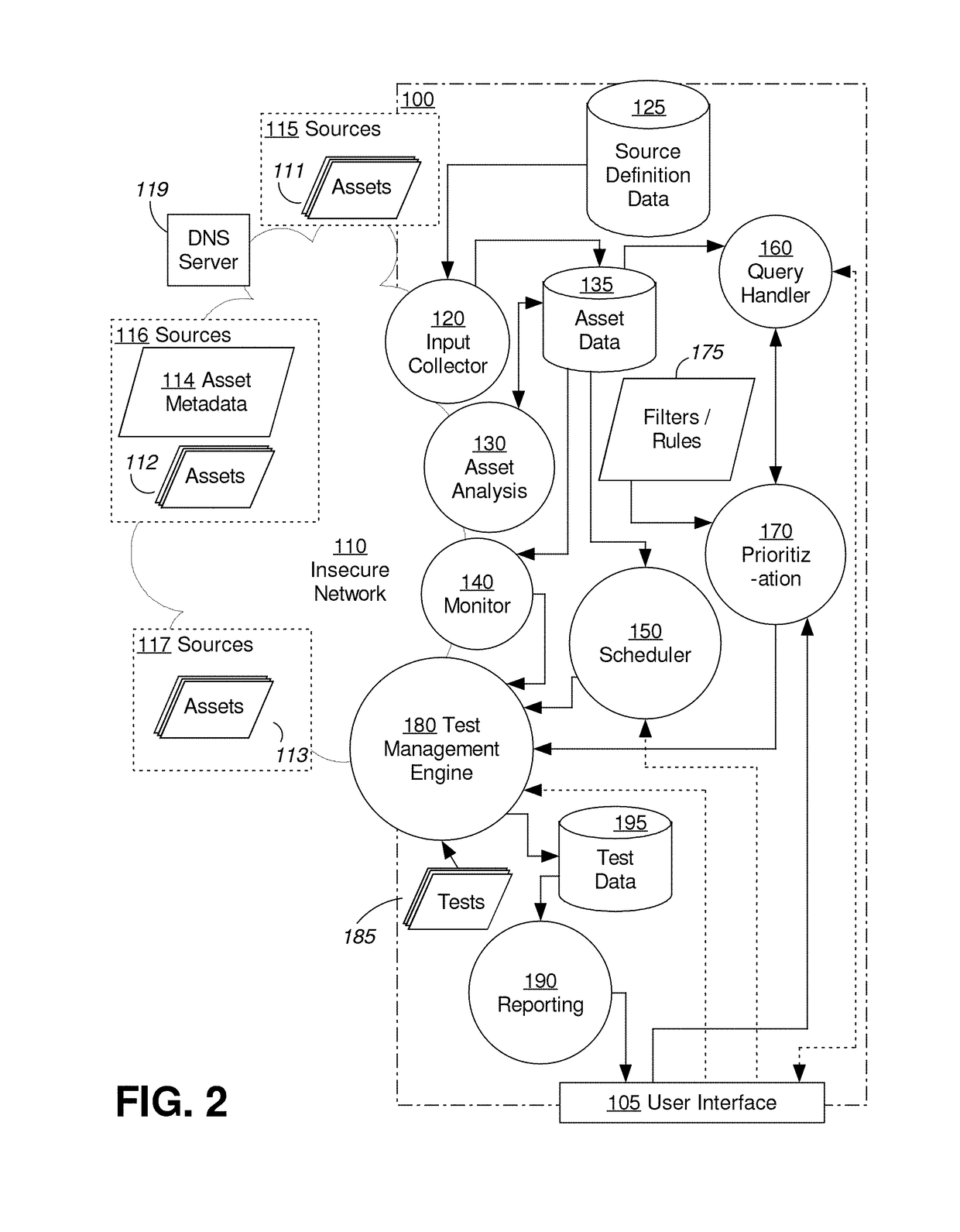
Dynamic security testing
Owner:NETFLIX
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com