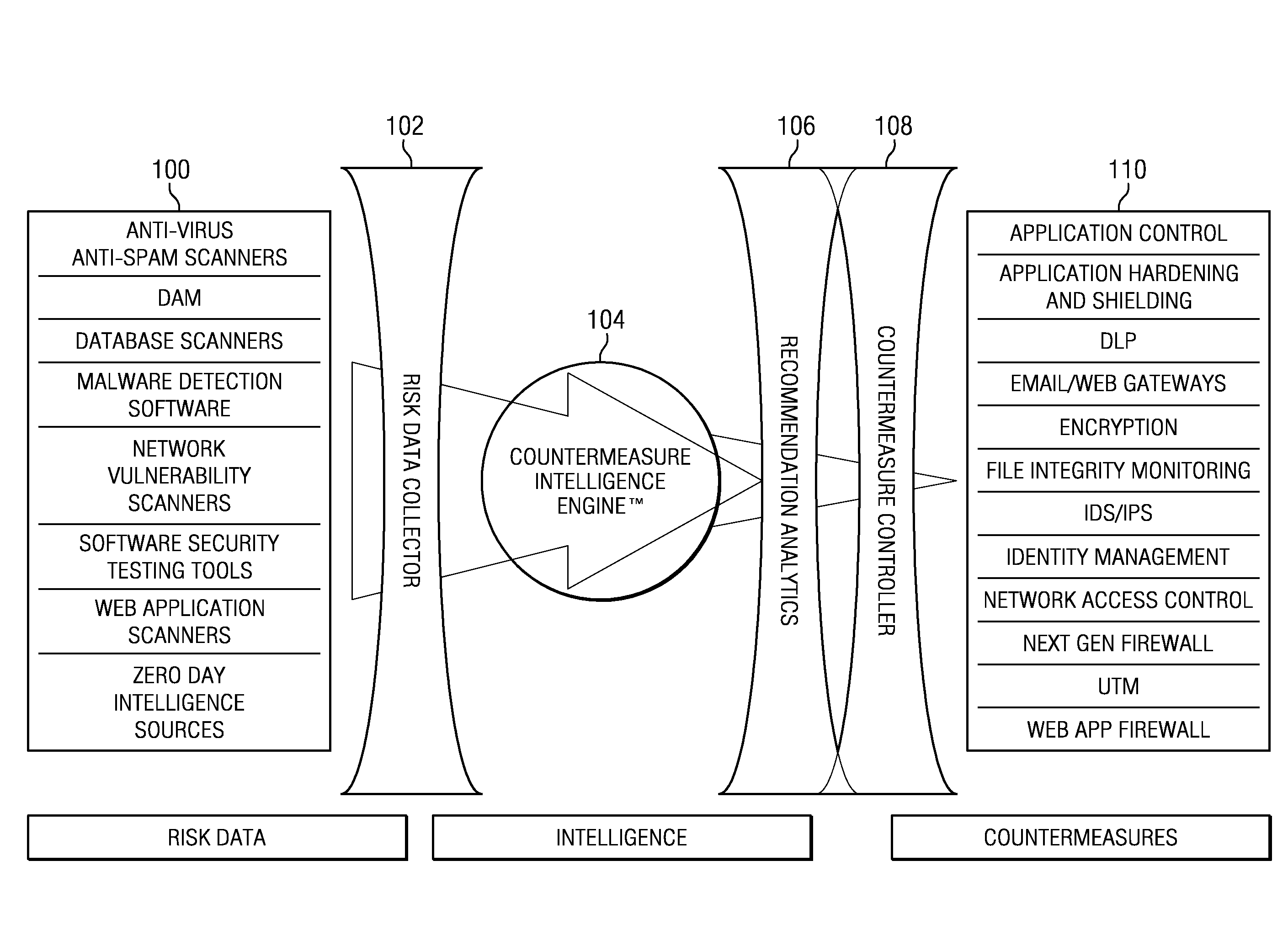
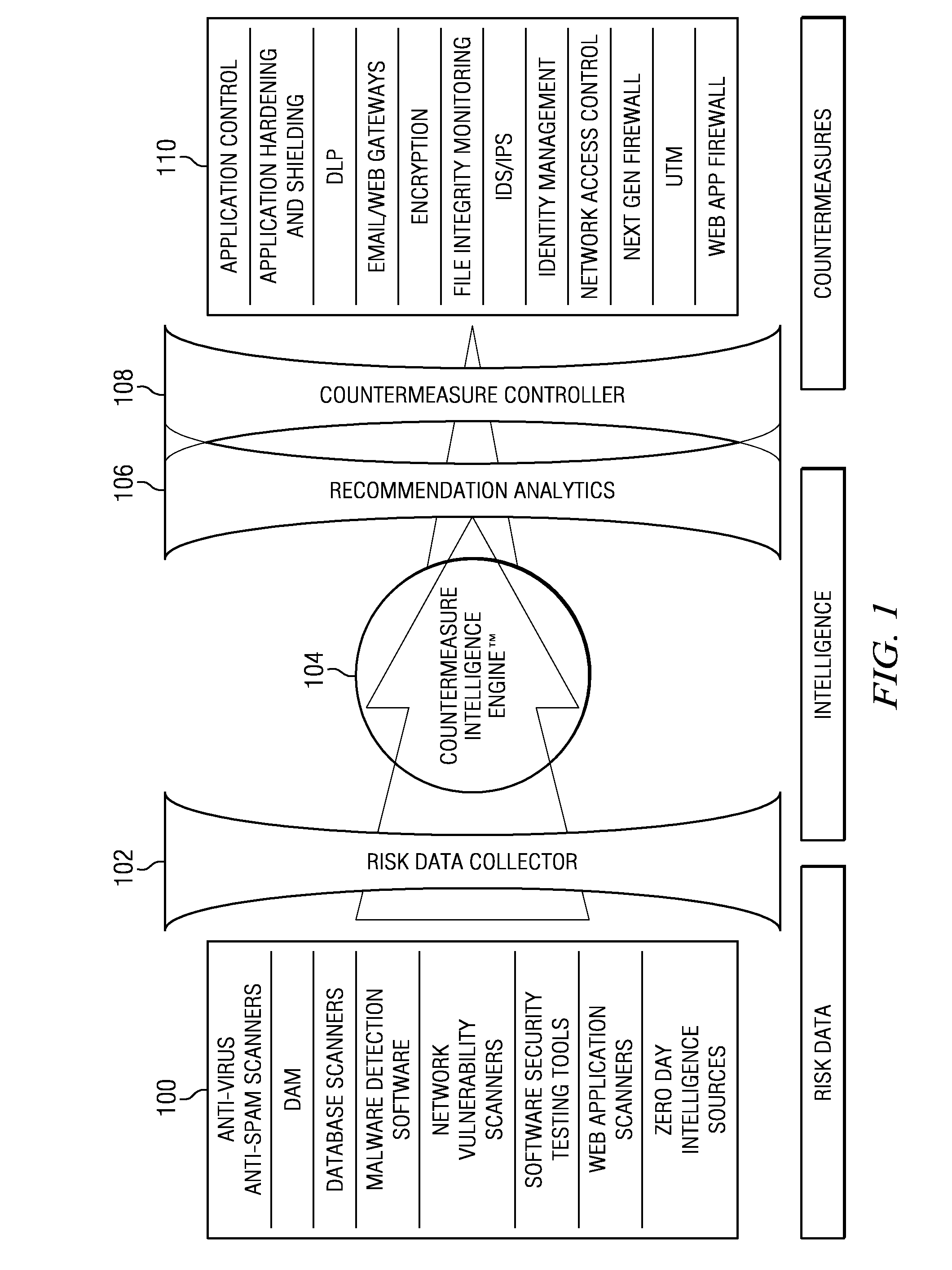
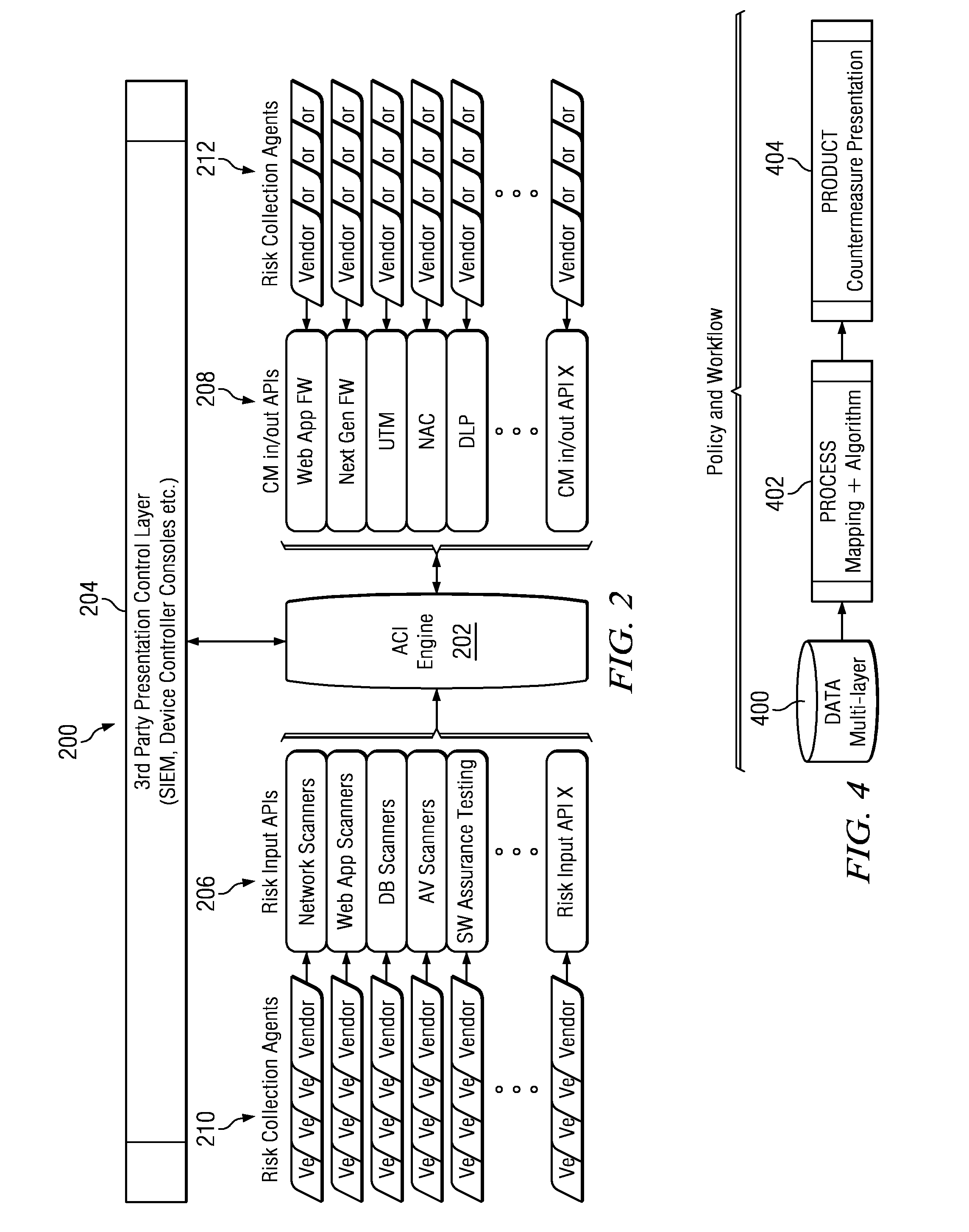
Patents
Literature
2251 results about "Countermeasure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A countermeasure is a measure or action taken to counter or offset another one. As a general concept it implies precision, and is any technological or tactical solution or system (often for a military application) designed to prevent an undesirable outcome in the process. The first known use of the term is in 1923.
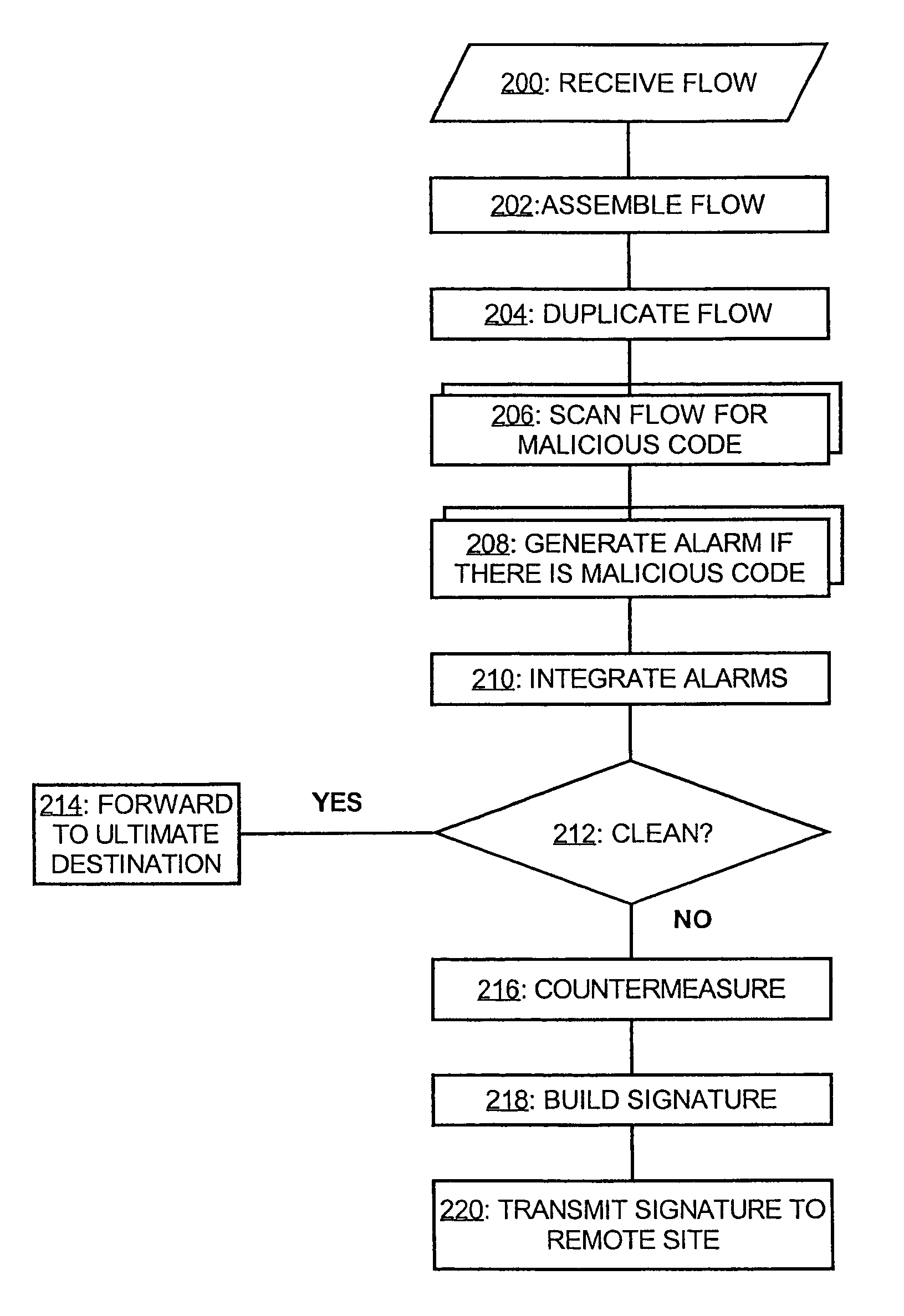
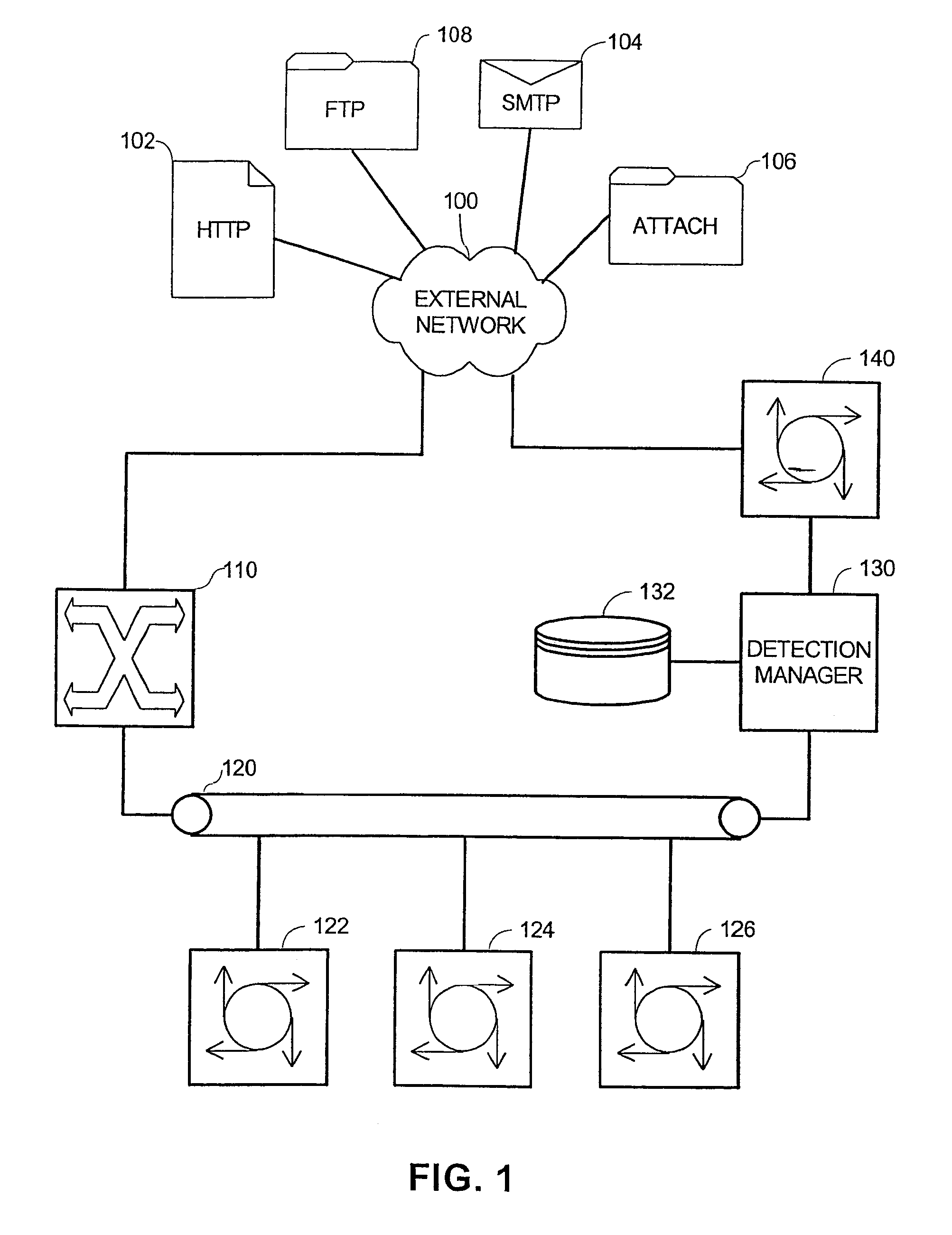
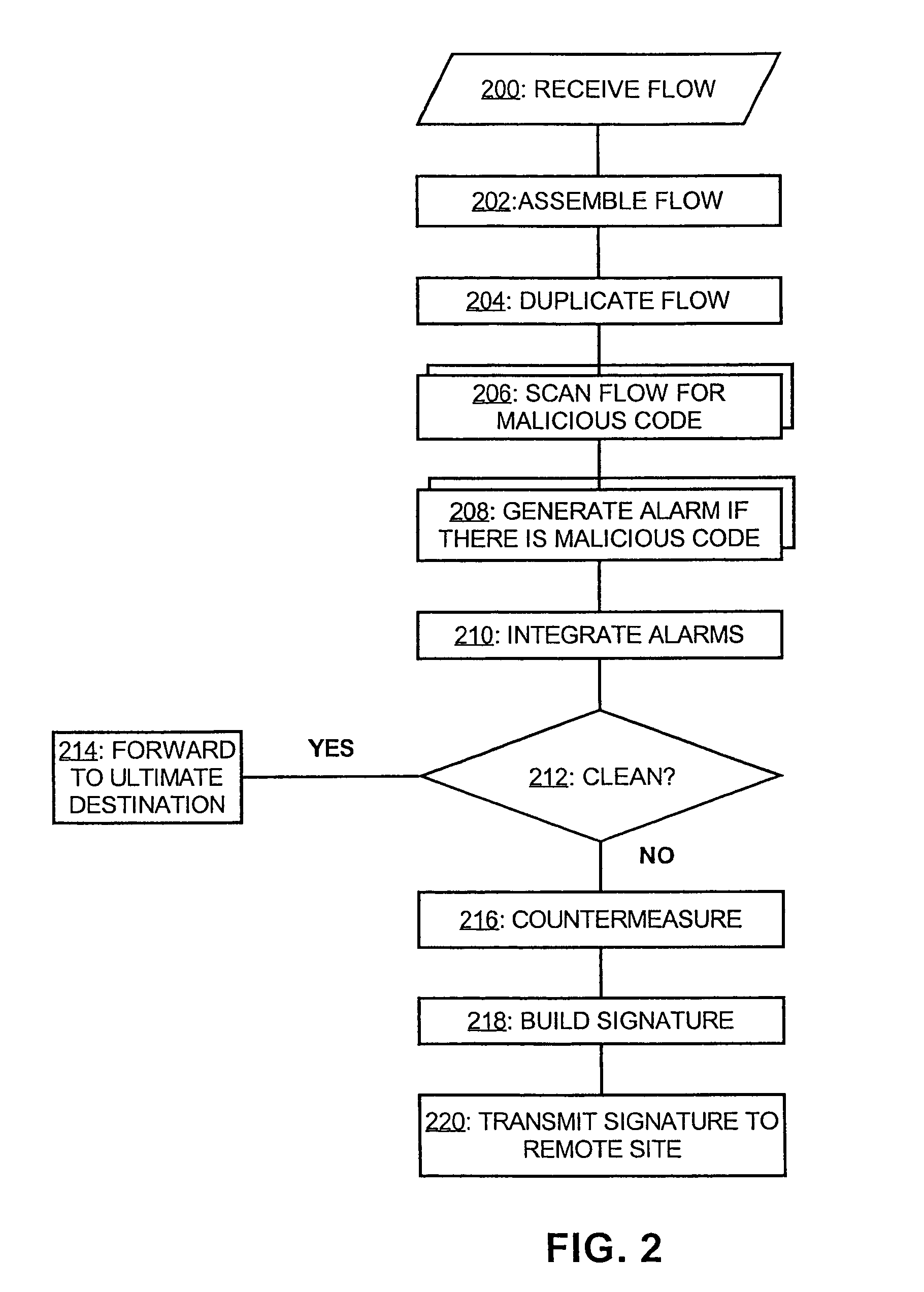
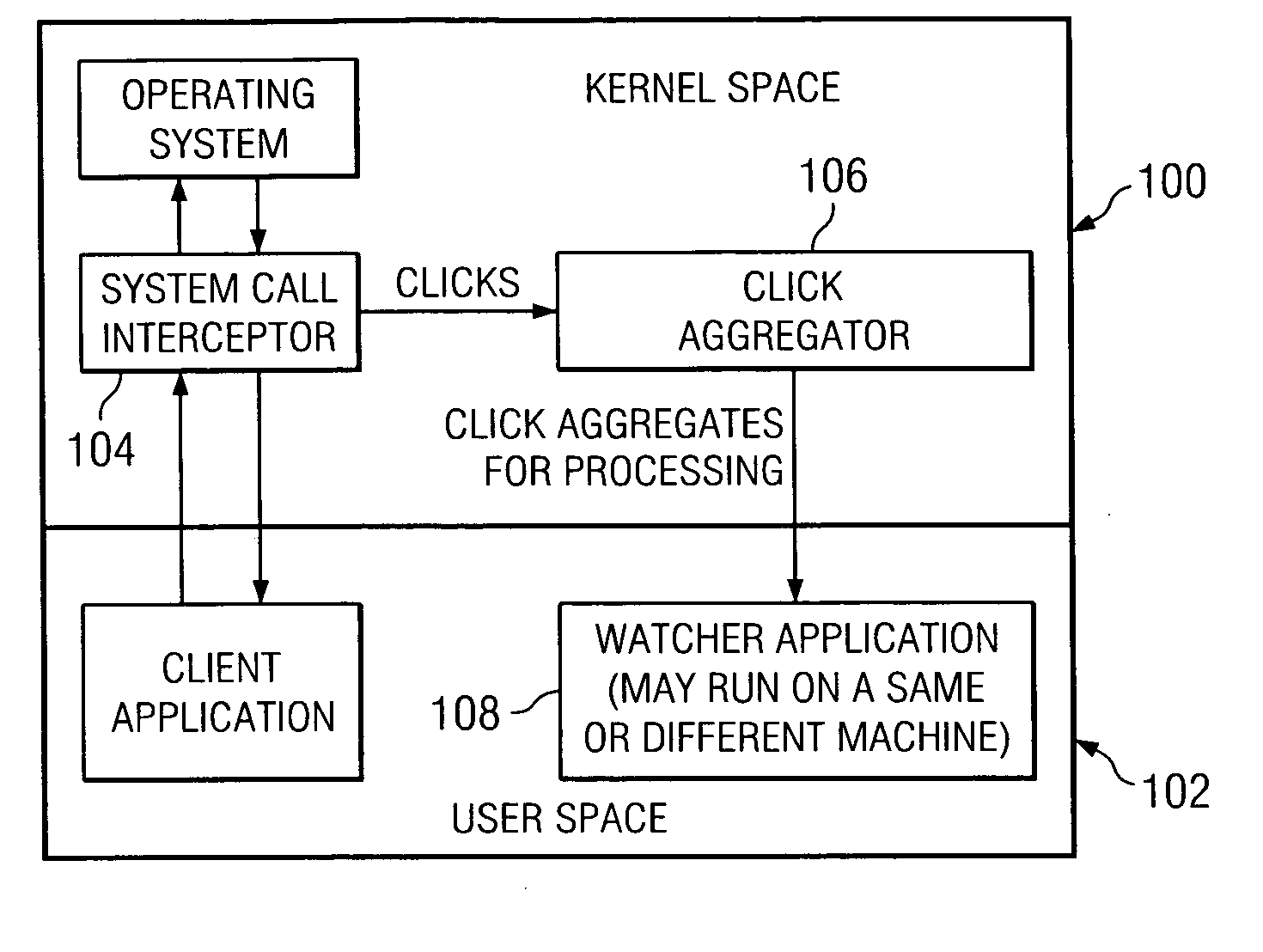
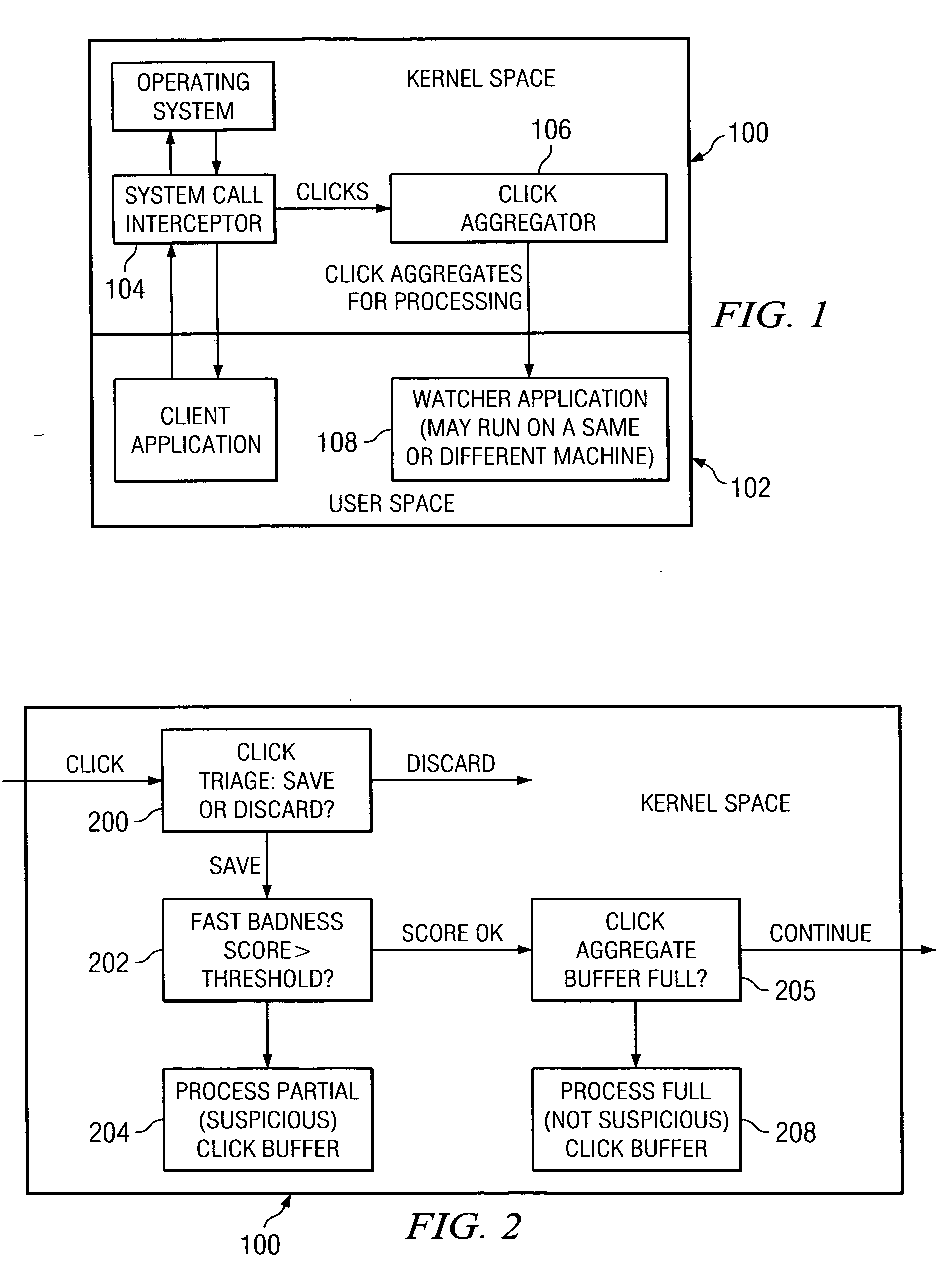
System and method for malicious code detection
A system for malicious code detection includes a front-end processor, multiple scanning computer systems, and a detection management system. During operation, the multiple scanning computer systems scan content for malicious code and generate an alarm when the content contains malicious code. The front-end processor receives a flow of content from an external network and distributes copies of the flow to each of the multiple scanning computer systems in parallel for scanning. The detection management system employs a countermeasure on the flow if at least one of the scanning computer systems generates the alarm.
Owner:RAKUTEN GRP INC
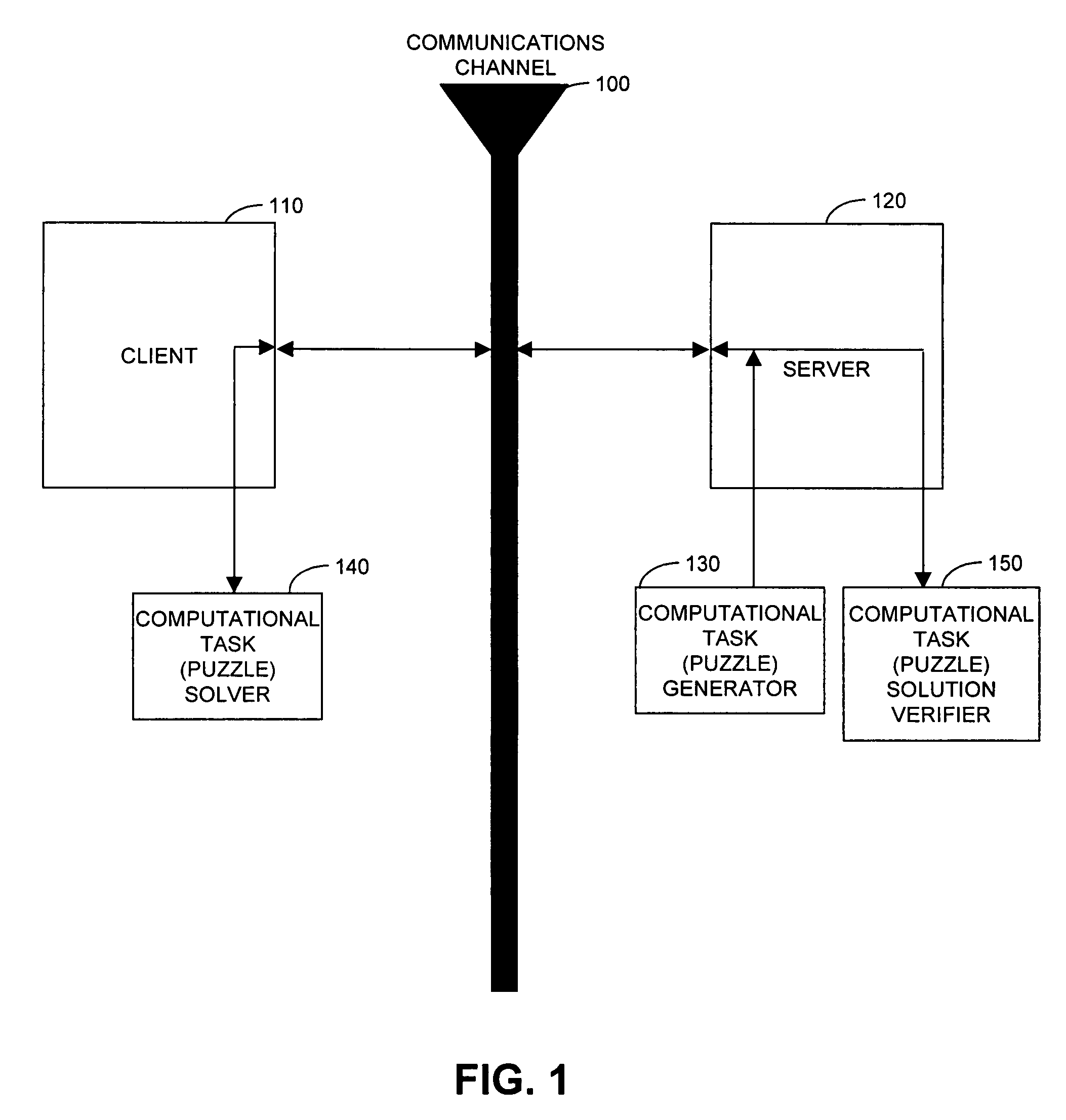
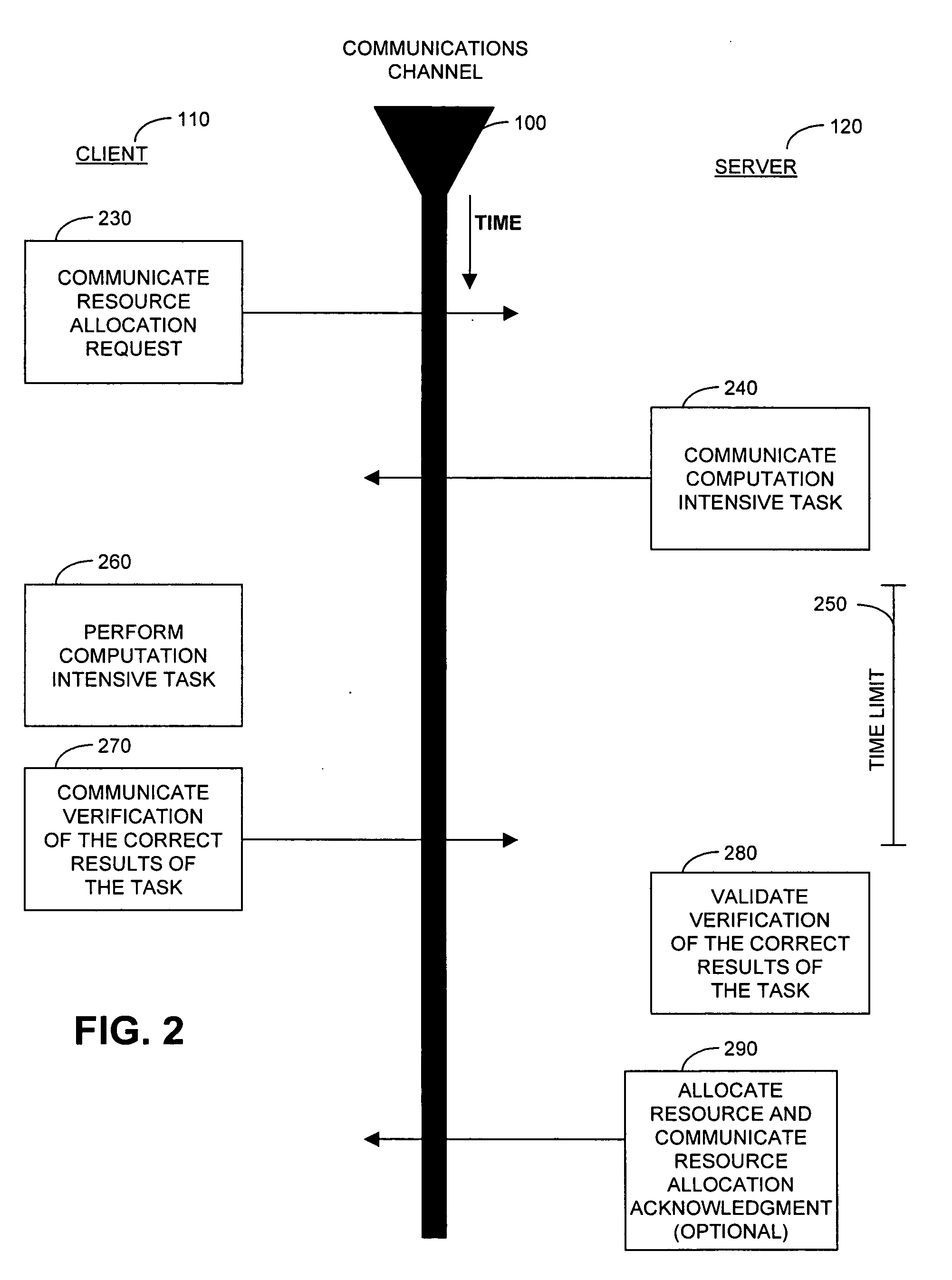
Cryptographic countermeasures against connection depletion attacks
InactiveUS7197639B1Ensure correct executionDigital data processing detailsUser identity/authority verificationCountermeasureTime limit
This invention relates to cryptographic communications methods and systems that protect a server from a connection depletion attack. Specifically, the invention presents a method for allocating a resource comprising the steps of receiving a resource allocation request from a client, imposing a computational task and a time limit for correct completion of the task upon the client, verifying that the task was performed correctly within the time limit, and allocating the resource if the task was correctly performed within the time limit.
Owner:EMC IP HLDG CO LLC
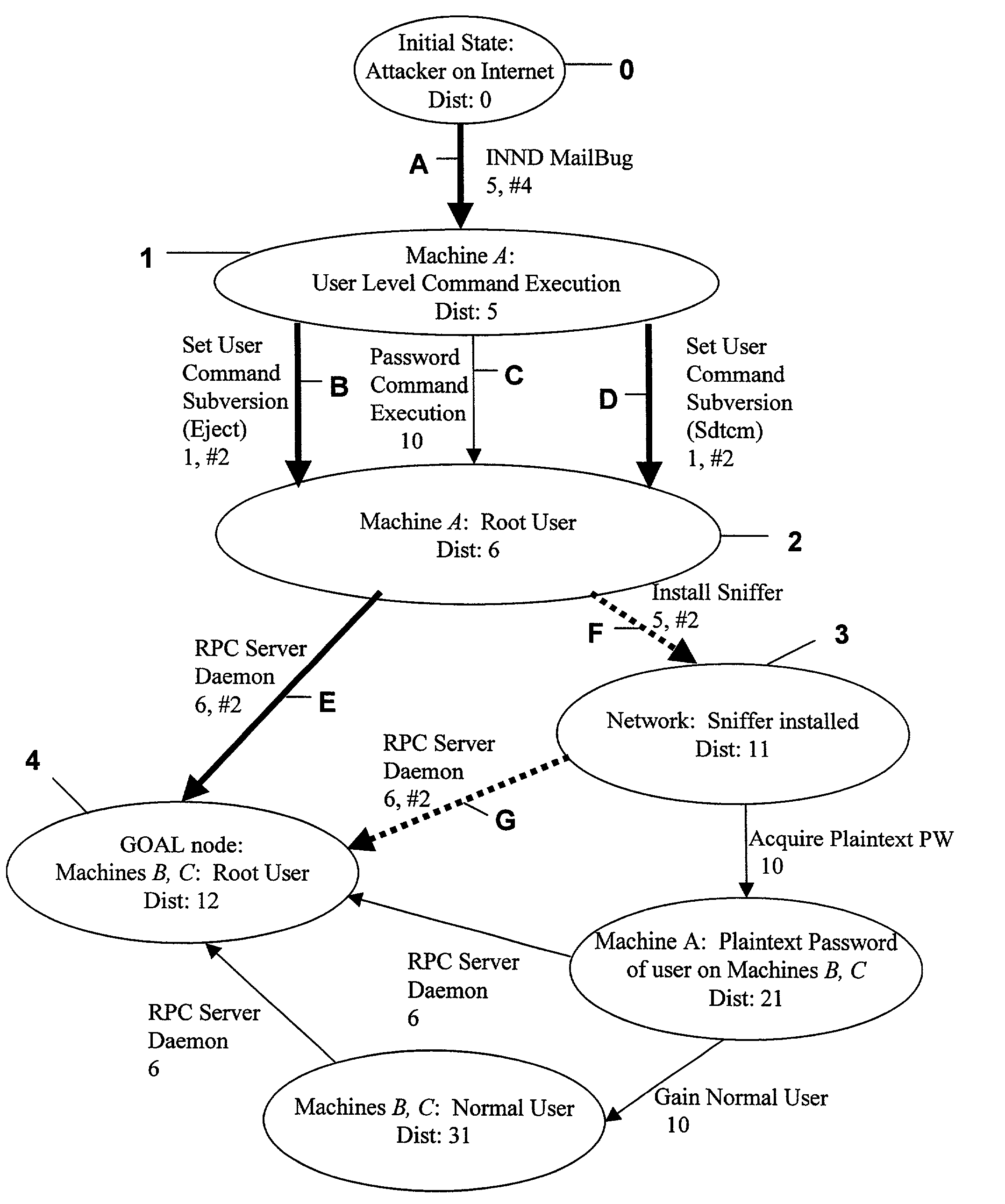
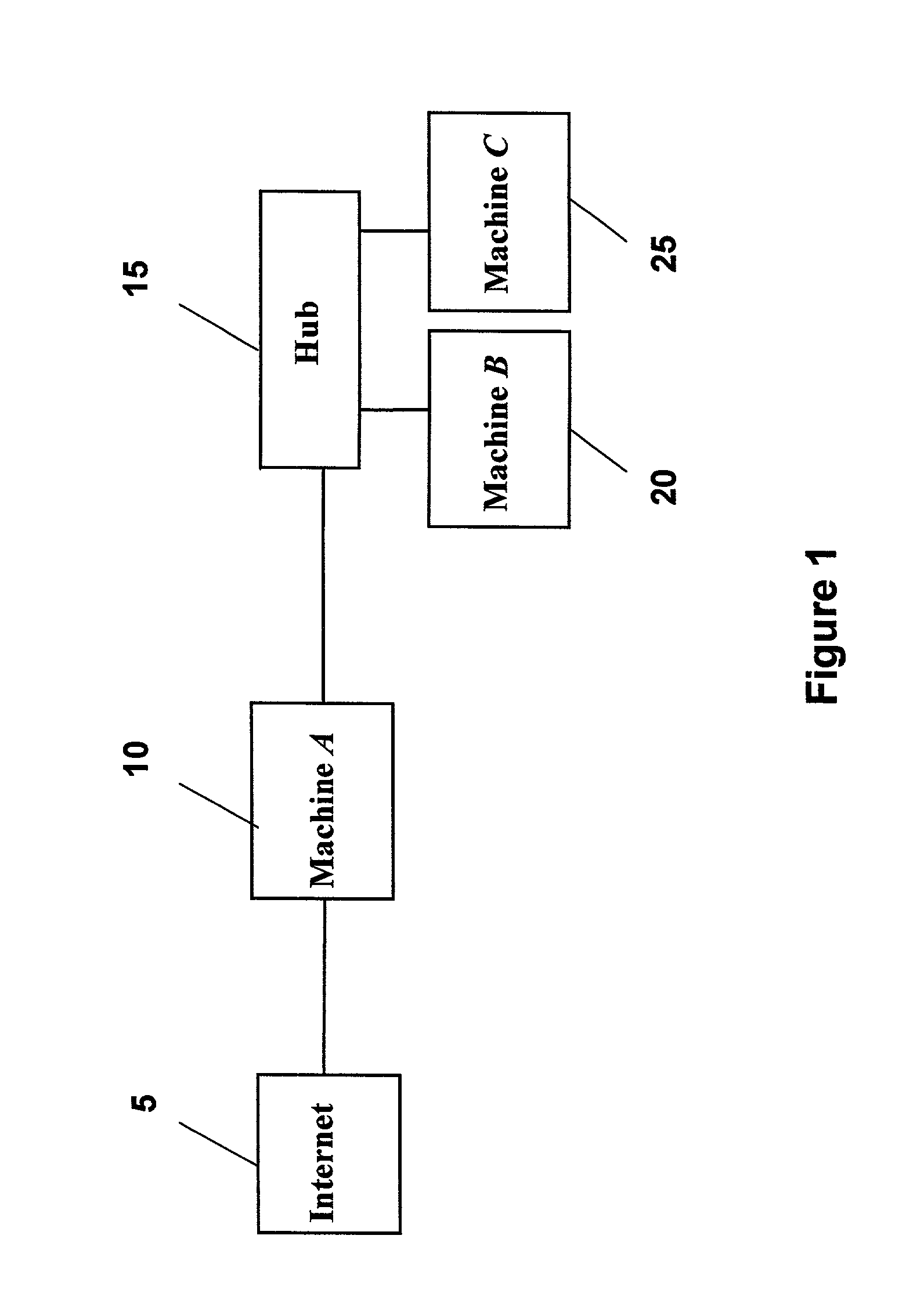
Method and tool for network vulnerability analysis
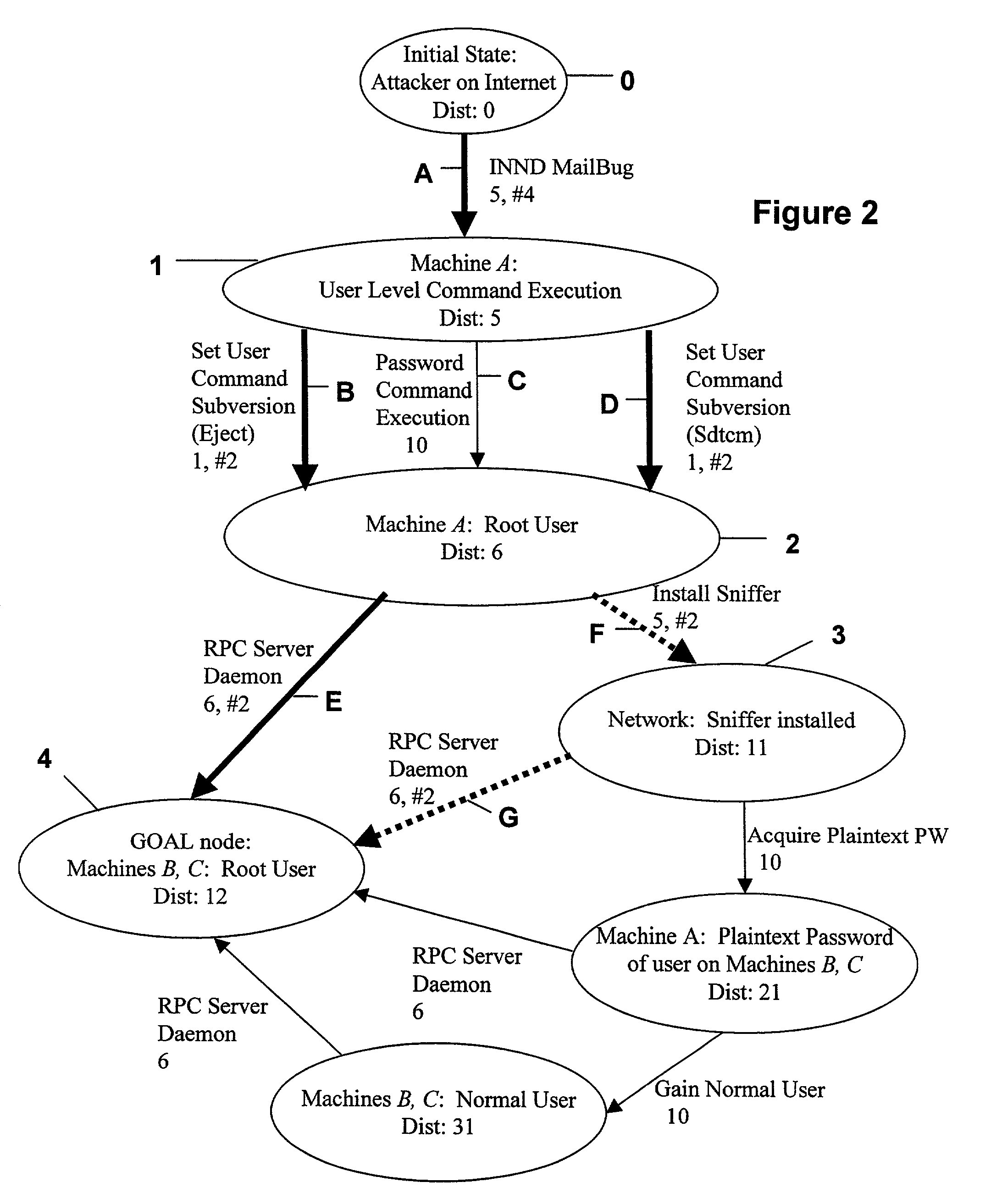
InactiveUS7013395B1Avoid low successLow “ effort ” costMemory loss protectionUnauthorized memory use protectionLimited resourcesCountermeasure
A computer system analysis tool and method that will allow for qualitative and quantitative assessment of security attributes and vulnerabilities in systems including computer networks. The invention is based on generation of attack graphs wherein each node represents a possible attack state and each edge represents a change in state caused by a single action taken by an attacker or unwitting assistant. Edges are weighted using metrics such as attacker effort, likelihood of attack success, or time to succeed. Generation of an attack graph is accomplished by matching information about attack requirements (specified in “attack templates”) to information about computer system configuration (contained in a configuration file that can be updated to reflect system changes occurring during the course of an attack) and assumed attacker capabilities (reflected in “attacker profiles”). High risk attack paths, which correspond to those considered suited to application of attack countermeasures given limited resources for applying countermeasures, are identified by finding “epsilon optimal paths.”
Owner:SANDIA NAT LAB
Methods and systems for providing network protection by progressive degradation of service
InactiveUS20130185795A1Reduce performance of data communicationLower performance requirementsMemory loss protectionError detection/correctionCountermeasureNetwork service
Systems and methods are provided for protecting a defense with a self defending intrusion system. Data packets may be monitored to detect a pattern of activity indicating a potential attack. Upon detection of a threat, a countermeasure or progressive degradation of network services may be initiated on a selected basis so controllable reduce performance of data communication of the device.
Owner:ARXCEO CORP
Method and apparatus for verifying the integrity and security of computer networks and implementing counter measures
InactiveUS6988208B2Mitigate or thwart suspected intruder attacks on the target networkMemory loss protectionDigital data processing detailsCountermeasureSecurity system
A method and apparatus for verifying the integrity of devices on a target network. The apparatus has security subsystems and a master security system hierarchically connected to the security subsystems via a secure link. The target network includes various intrusion detection devices, which may be part of the security subsystem. Each intrusion detection device generates a plurality of event messages when an attack on the network is detected. The security subsystem collects these event messages, correlates, and analyzes them, and performs network scanning processes. If certain events warrant additional scrutiny, they are uploaded to the master security system for review.
Owner:SICORTEX
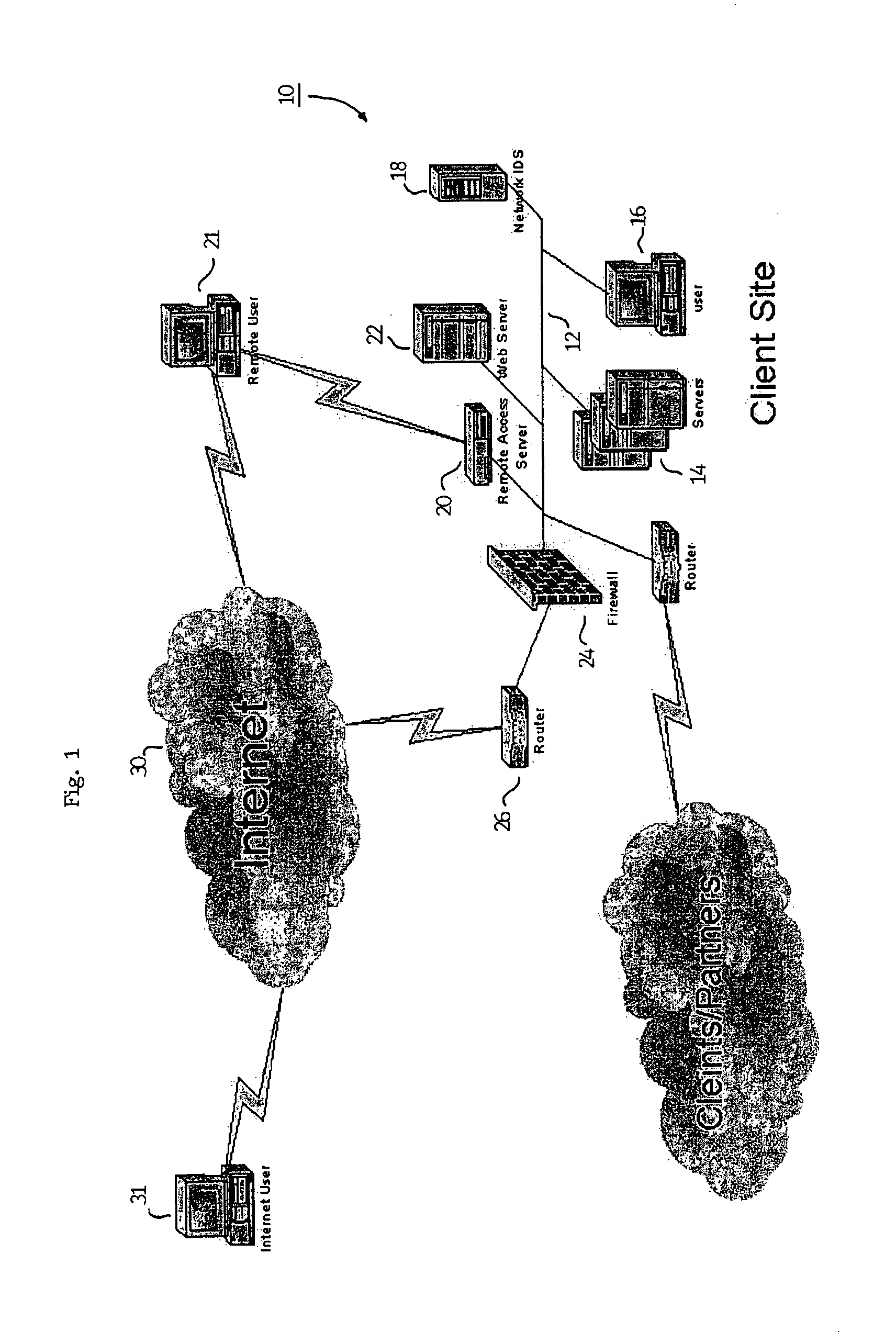
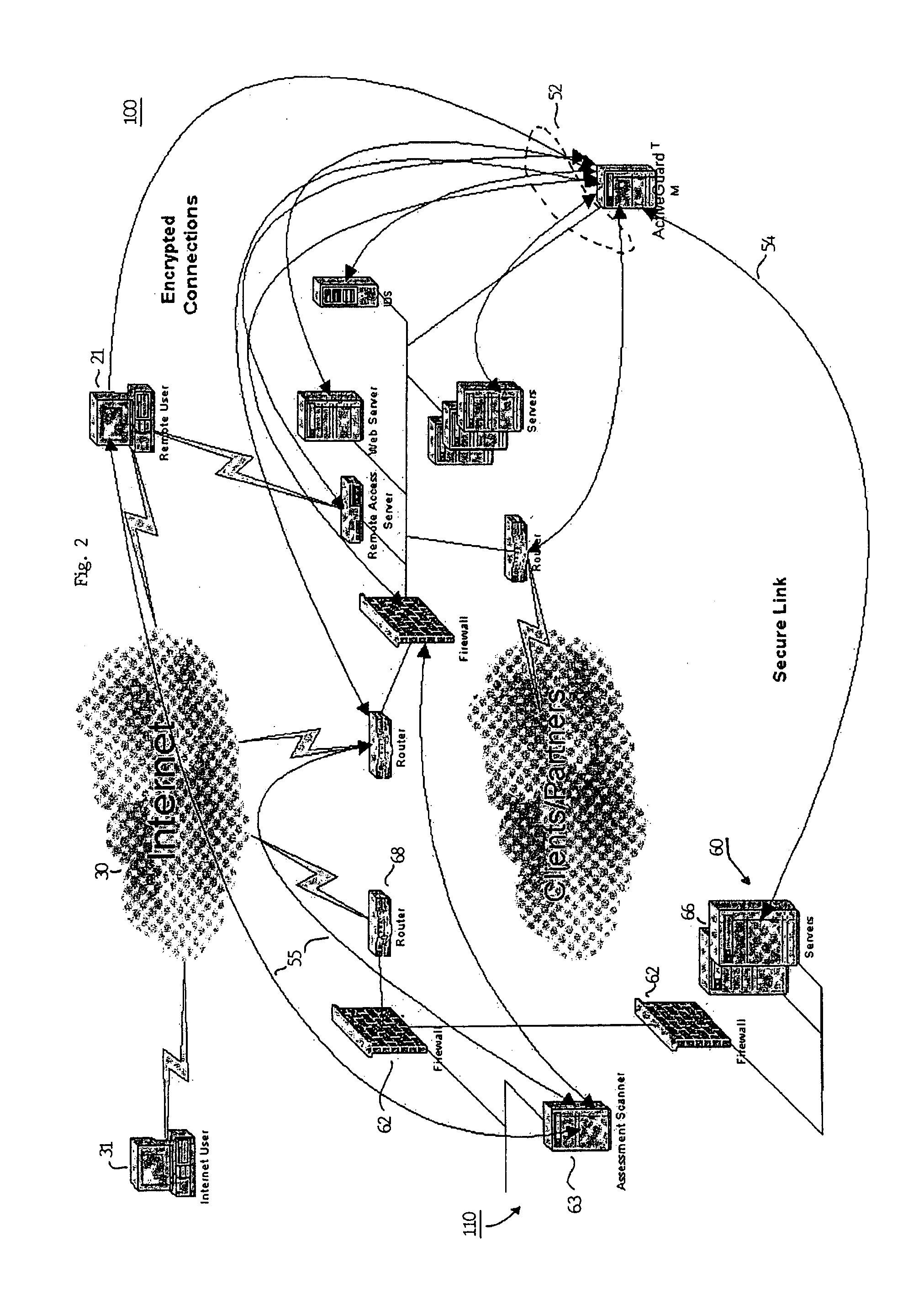
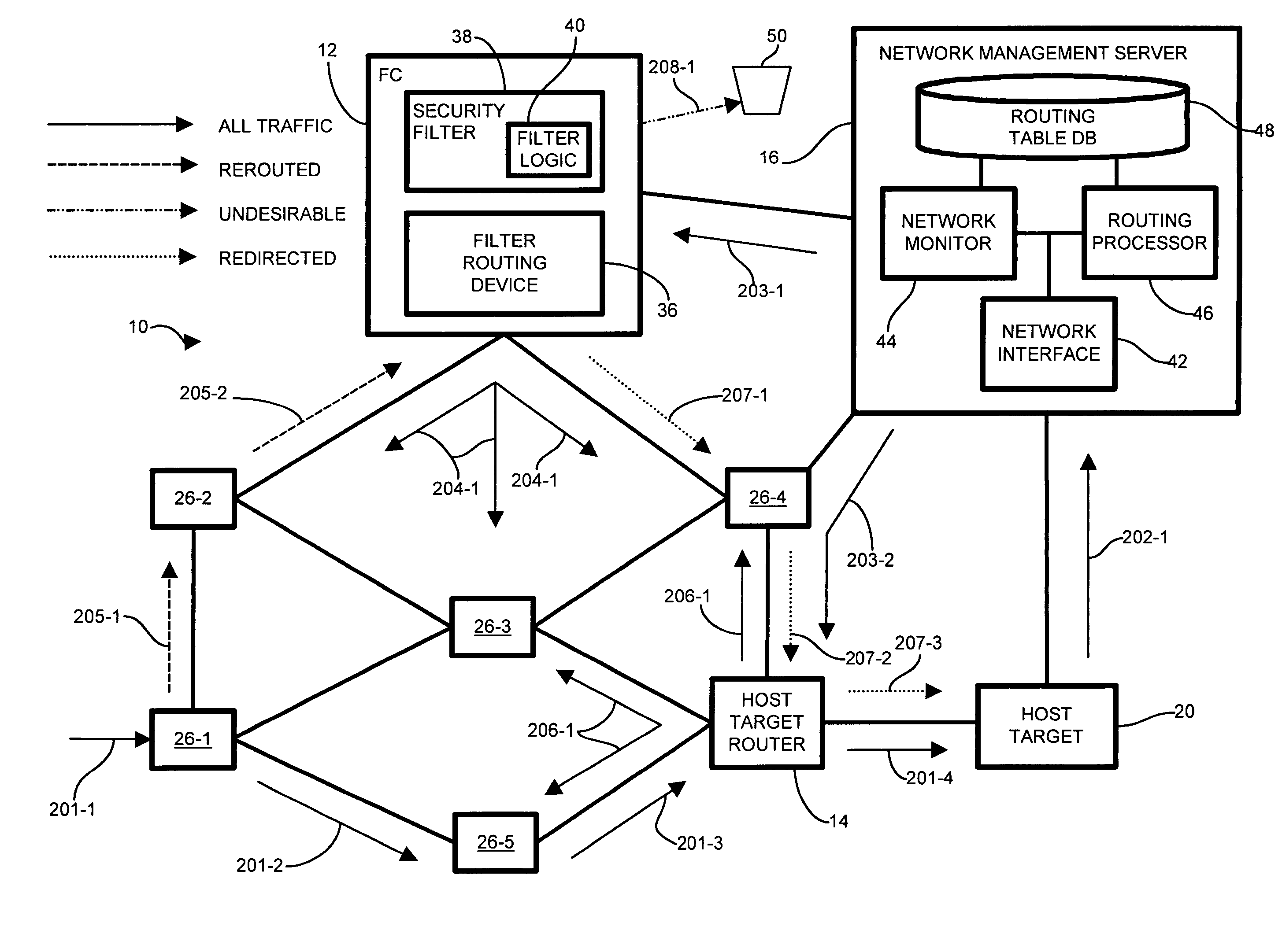
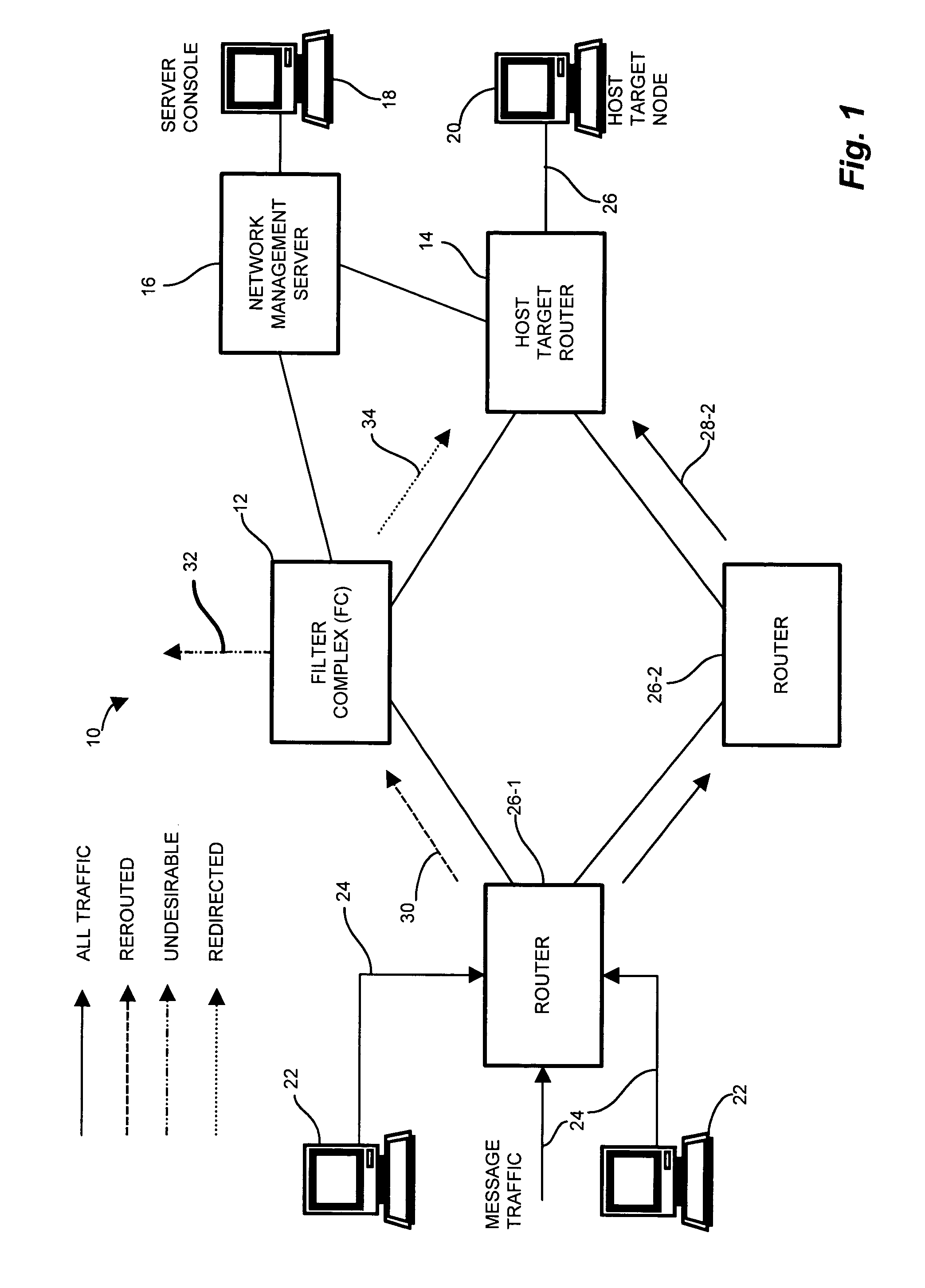
Methods and apparatus for network message traffic redirection
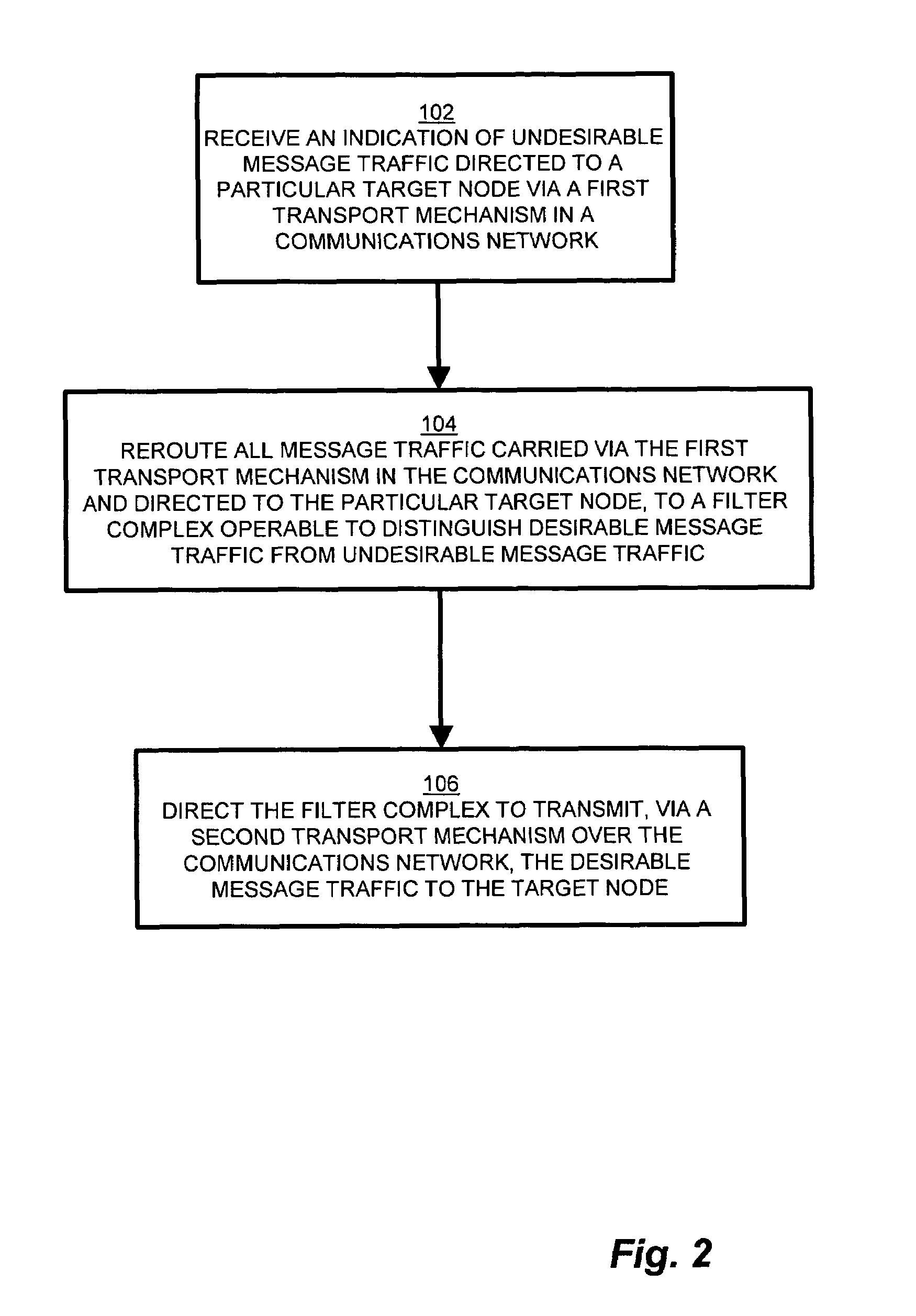
ActiveUS7409712B1Avoid reconfigurationMemory loss protectionDigital data processing detailsTraffic capacityCountermeasure
Conventional methods of addressing a Distributed Denial of Service attack include taking the target node offline, and routing all traffic to an alternate countermeasure, or “sinkhole” router, therefore requiring substantial lag time to reconfigure the target router into the network. In a network, a system operator monitors a network for undesirable message traffic. Upon a notification of such undesirable message traffic, traffic is rerouted to a filter complex to separate undesirable traffic. The filter complex establishes an alternate route using a second communications protocol, and uses the alternate route to redirect the desirable message traffic to the target node. The use of the second protocol avoids conflict between the redirected desirable traffic and the original, or first, protocol which now performs the reroute. In this manner, the filter complex employs a second alternate communications protocol to reroute and redirect desirable message traffic to the target node while diverting undesirable message traffic, and therefore avoids widespread routing configuration changes by limiting the propagation breadth of the second protocol.
Owner:CISCO TECH INC
Advanced responses to online fraud
Various embodiments of the invention provide solutions (including inter alia, systems, methods and software) for dealing with online fraud. In particular, various embodiments of the invention provide advanced responses to an identified instance of online fraud. Such advanced responses can incorporate one or more of a variety of strategies for defeating an attempt by a server to filter and / or otherwise avoid responses to its fraudulent activity. Merely by way of example, in accordance with some embodiments, one or more HTTP responses to a server's request (such as an online form, etc.) may be submitted and / or transmitted for reception by the server. In some cases, each of the submitted responses may appear to comprise valid information responsive to the server's request. In other cases, one or more countermeasures may be implemented to defeat an attempt by a phisher (or any other operator of an illegitimate server) to filter responses.
Owner:OPSEC ONLINE LTD
Low-EMI electronic apparatus, low-EMI circuit board, and method of manufacturing the low-EMI circuit board.
InactiveUS6353540B1Radiation suppressionHigh packageMagnetic/electric field screeningFinal product manufactureCapacitanceCountermeasure
Owner:HITACHI LTD
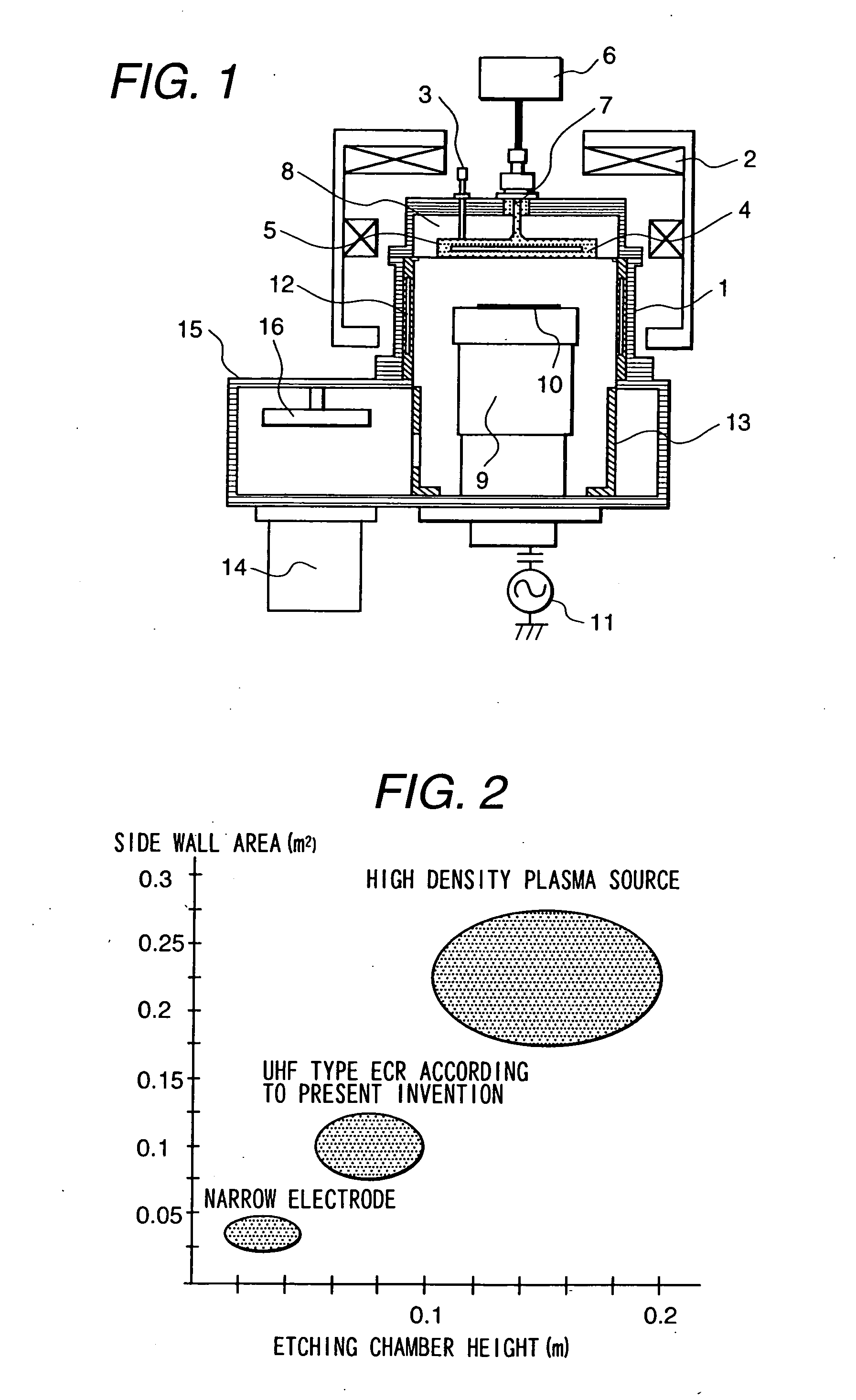
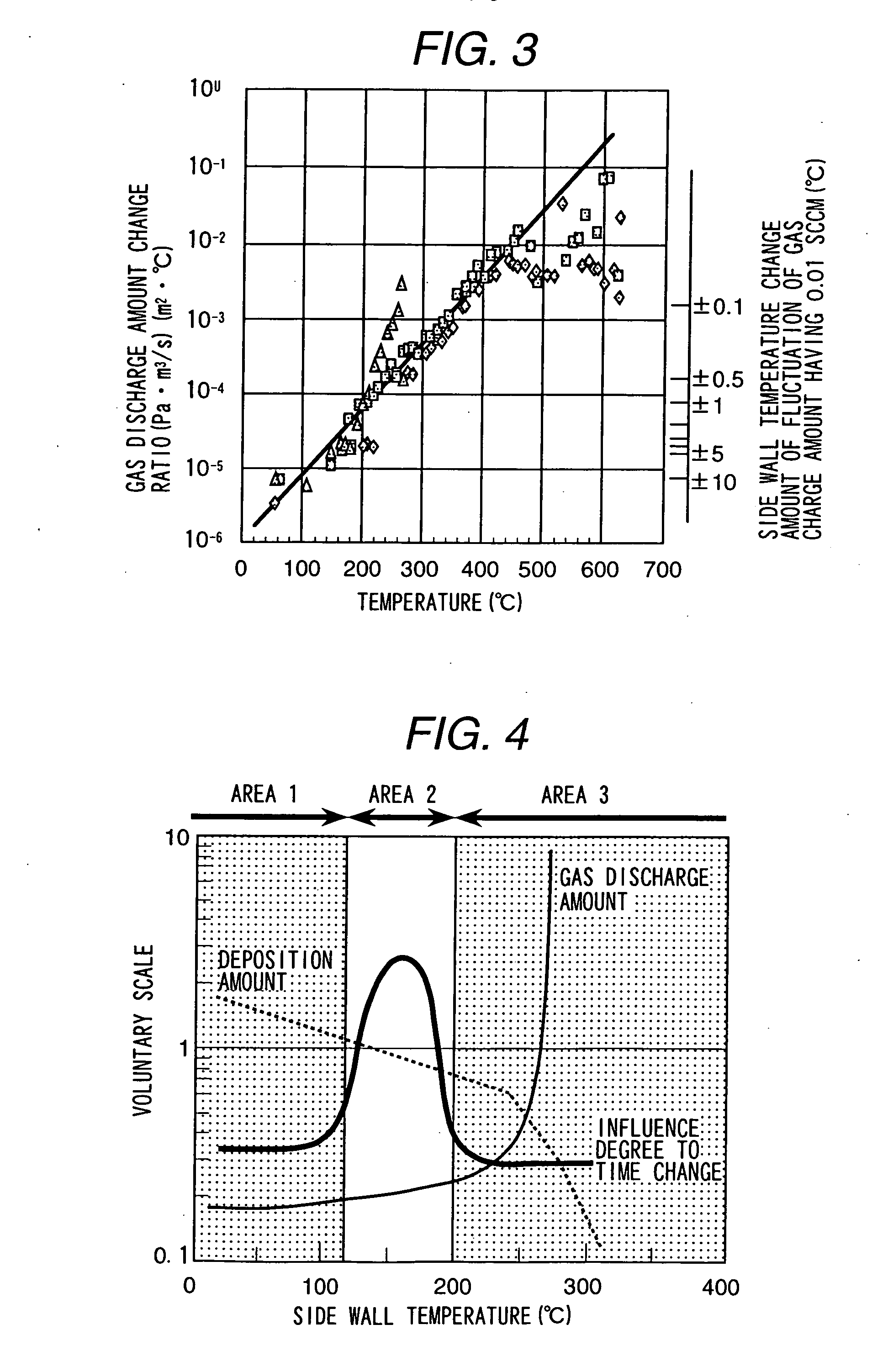
Plasma processing apparatus and a plasma processing method
InactiveUS20060157449A1Avoid volatilityElectric discharge tubesVacuum gauge using ionisation effectsElectron temperatureCountermeasure
Owner:TAKAHASHI KAZUE +3
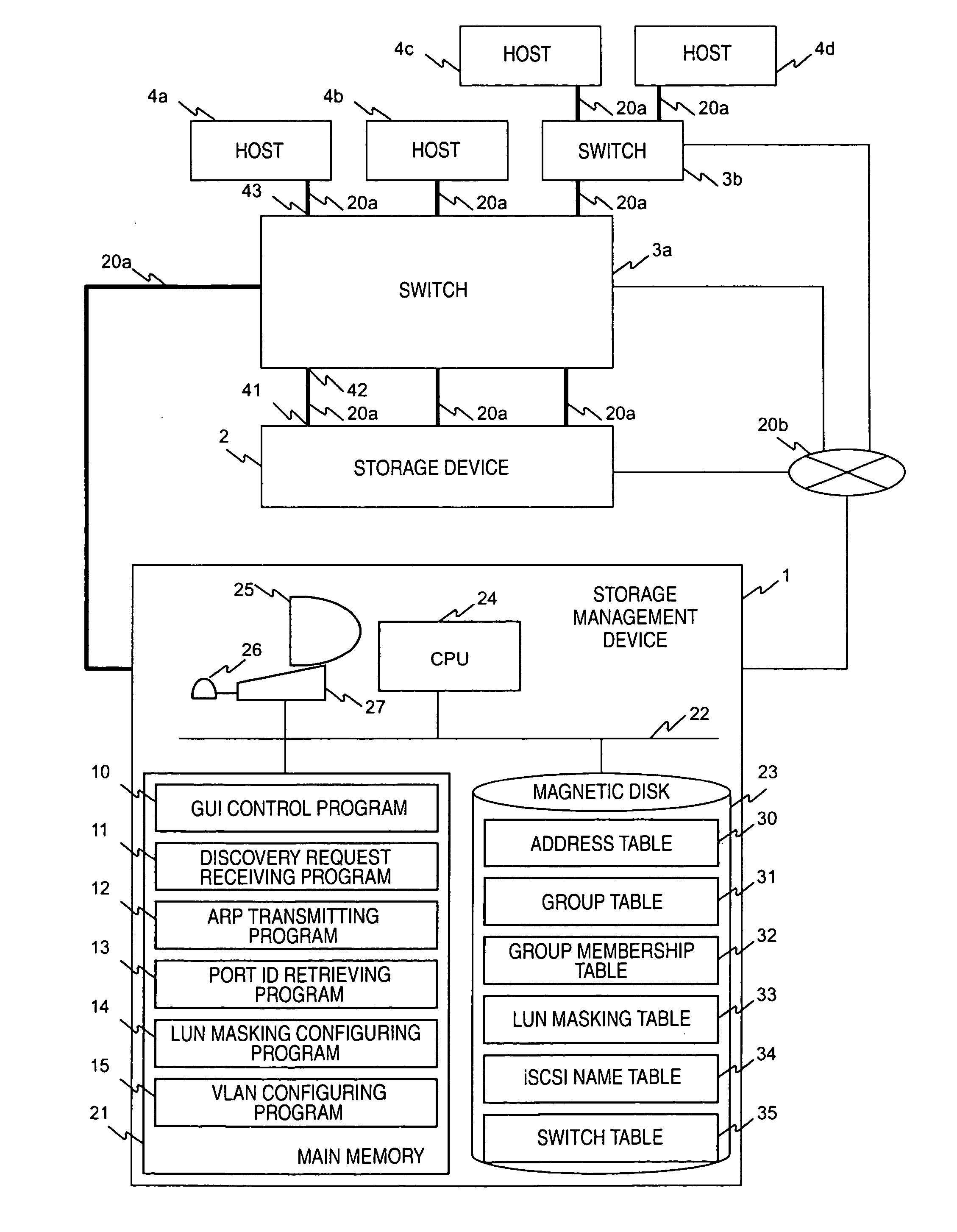
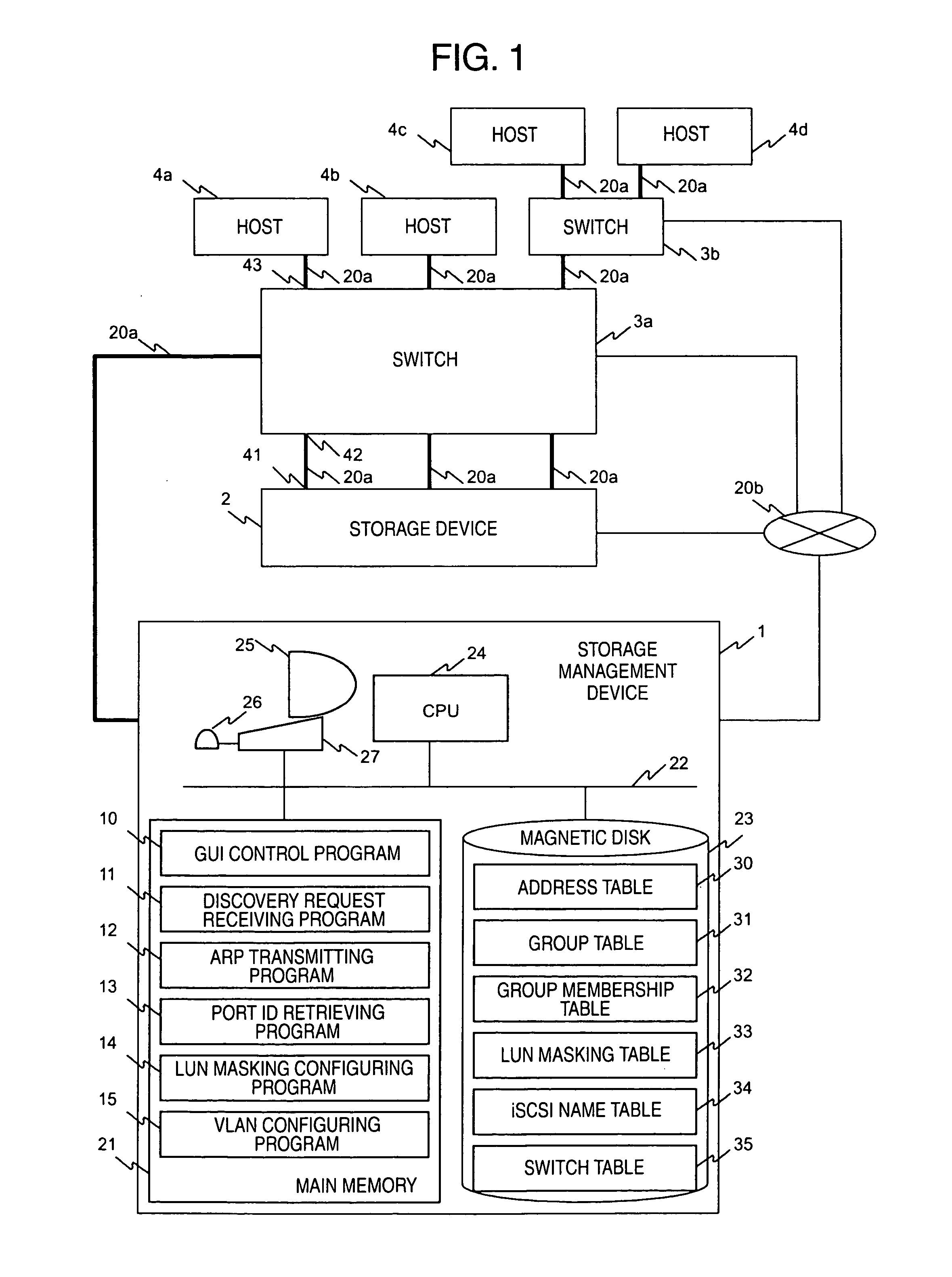
Storage network management system and method
InactiveUS20050044199A1OptimizationDigital data information retrievalDigital computer detailsVirtual LANCountermeasure
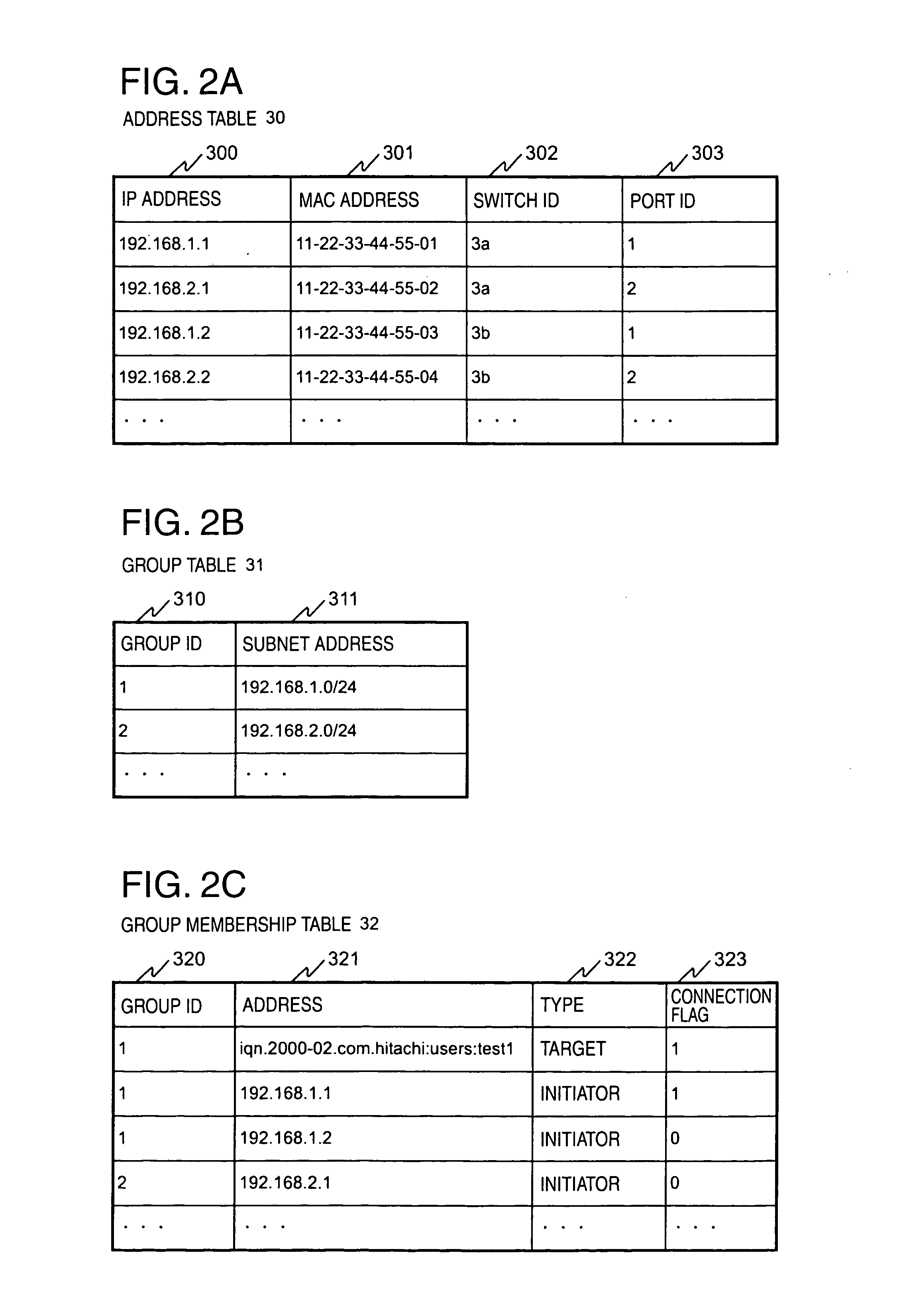
In a computer system having a storage device, switches and hosts respectively connected by a network, in accordance with an ID of a logical volume of the storage device and an IP address of a host, access control configuration of the logical volume is performed relative to the storage device, the IP address of the host is converted into a MAC address, the MAC address of the host is converted into a port ID of the switch connected to the host, and addition of the port to virtual local area network (VLAN) is performed for the switch. Logical unit number (LUN) masking and VLAN configuration essential for security countermeasure of IP-SAN (Internet protocol-storage area network) can be managed collectively by a system administrator so that the running cost of IP-SAN can be lowered.
Owner:HITACHI LTD
Distributed agent based model for security monitoring and response
ActiveUS20140237599A1Quick checkHigh and uniform level of securityMemory loss protectionError detection/correctionCountermeasureAgent-based model
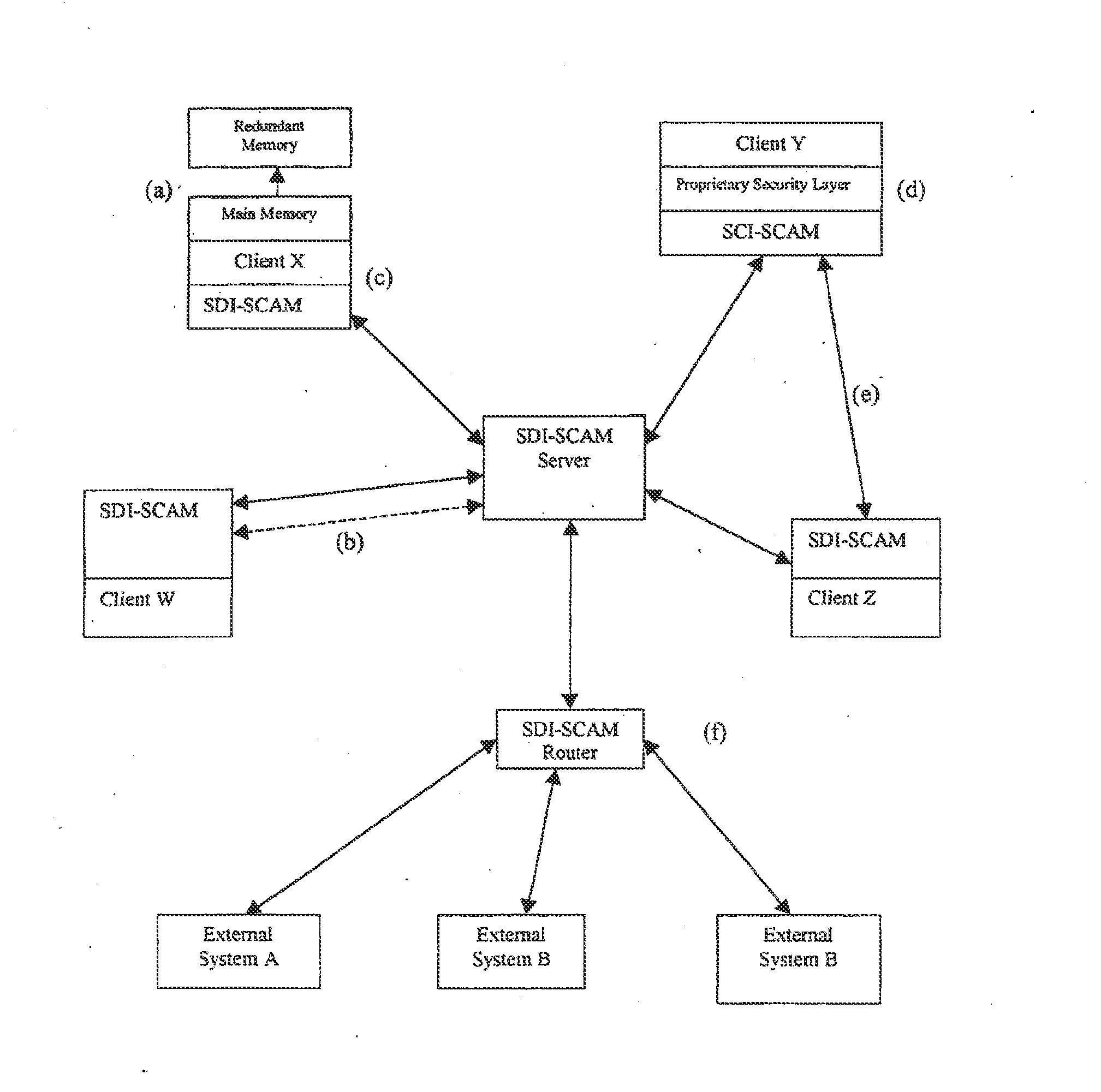
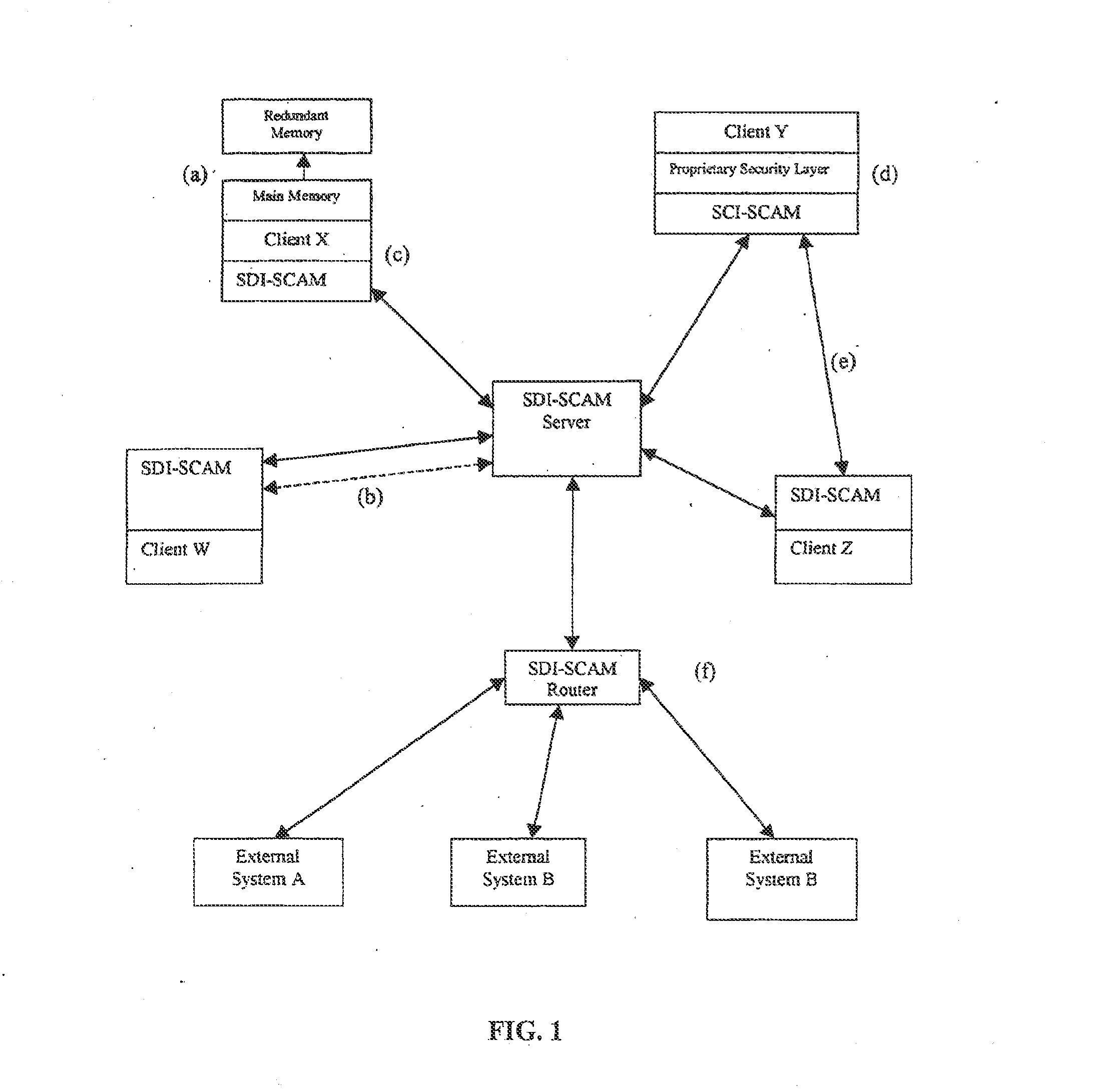
An architecture is provided for a widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially include a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
Vehicle security network device and design method therefor
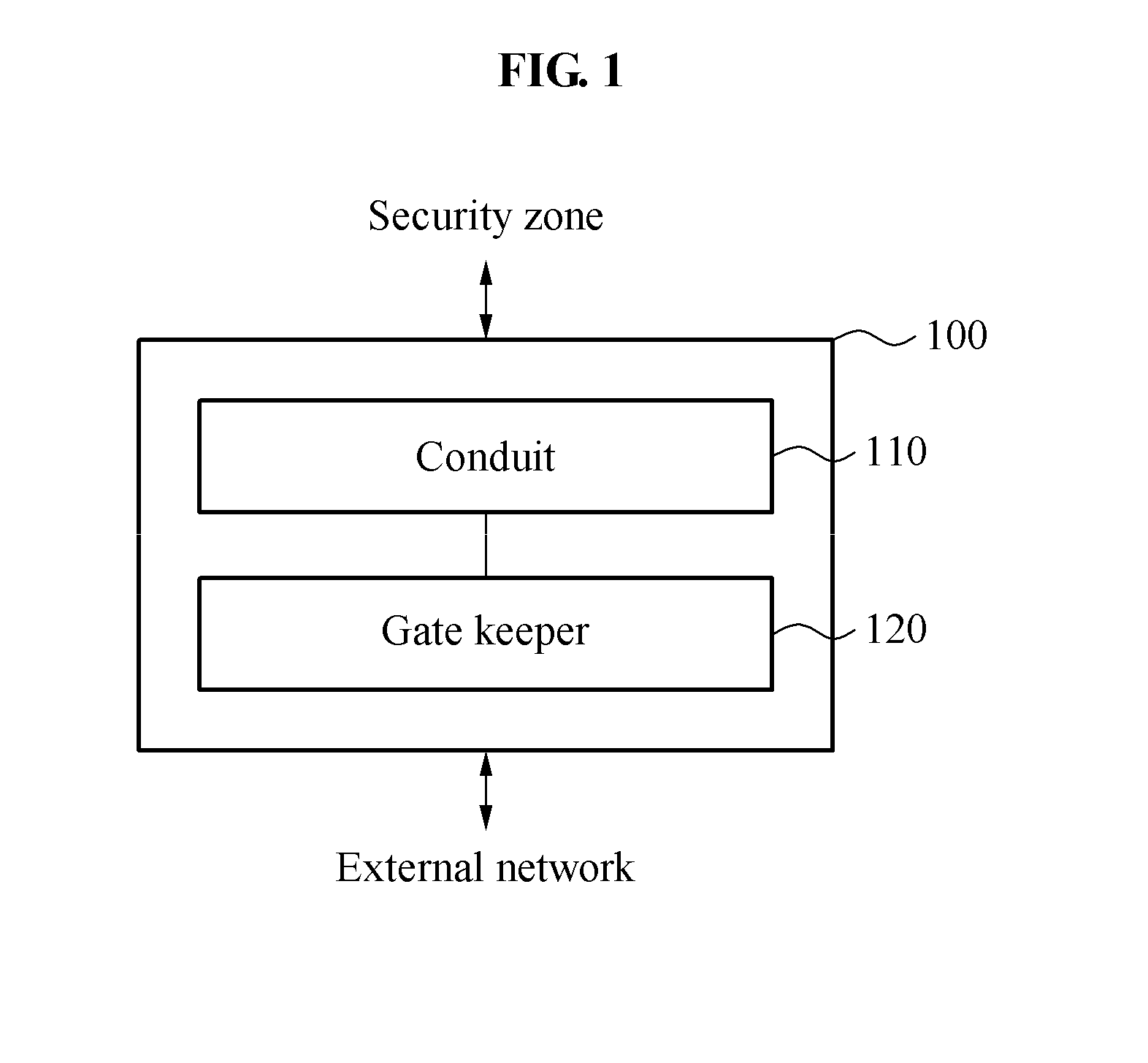
ActiveUS20160255154A1Semiconductor/solid-state device detailsAnti-theft devicesRisk levelCountermeasure
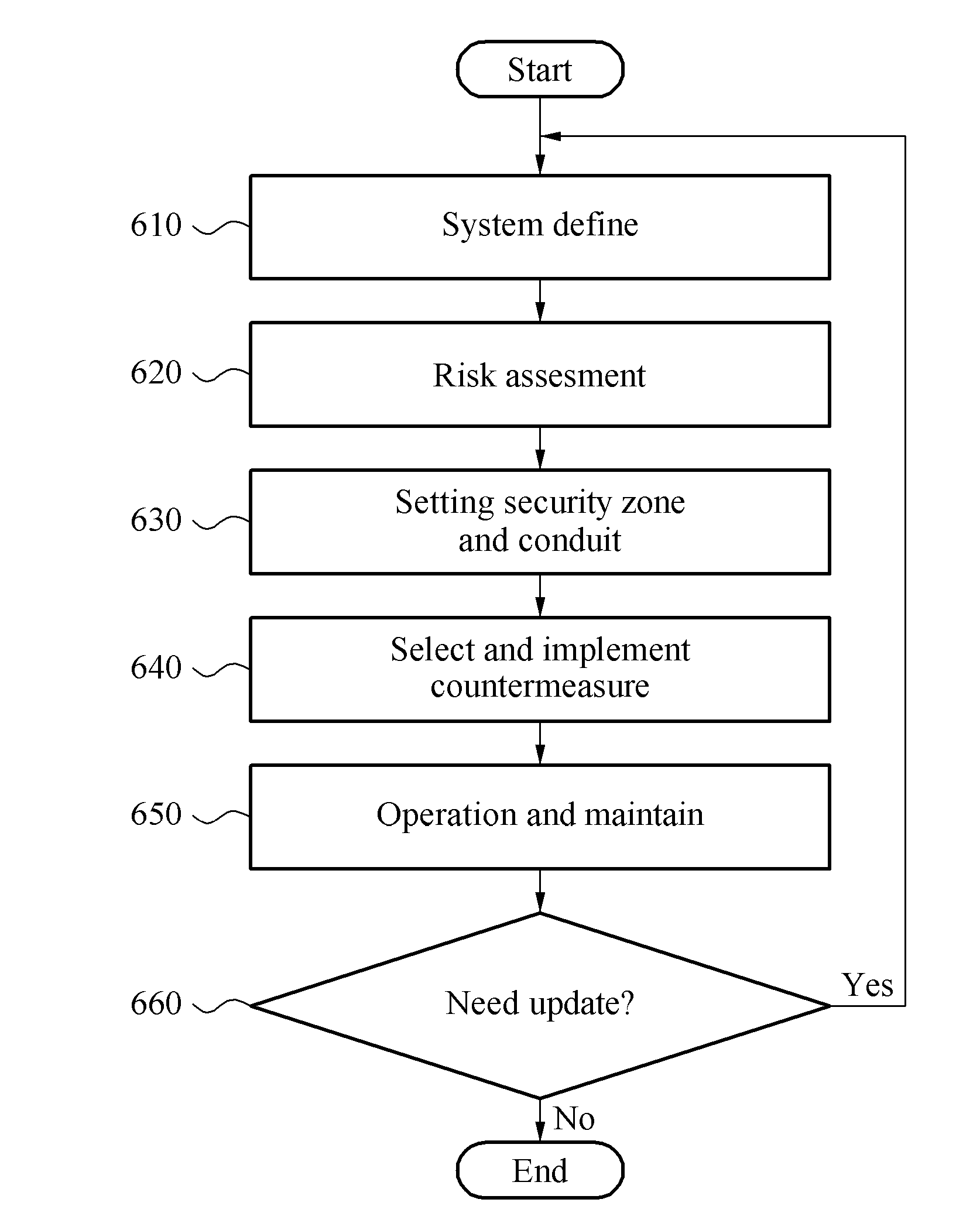
A security system capable of preventing a security attack / threat on a vehicle network is provided. At least one security zone is set by using a risk level which is evaluated for a plurality of vehicle functional elements. In addition, a security countermeasure corresponding to the risk level of the security zone can be provided to a conduit of the security zone so as to perform gate keeping.
Owner:ICTK
Device and method for telephone countermeasure in using telephone during driving
InactiveUS20070120948A1Efficiently suppress the driver from performing communication during drivingUnauthorised/fraudulent call preventionAssess restrictionCountermeasureDriver/operator
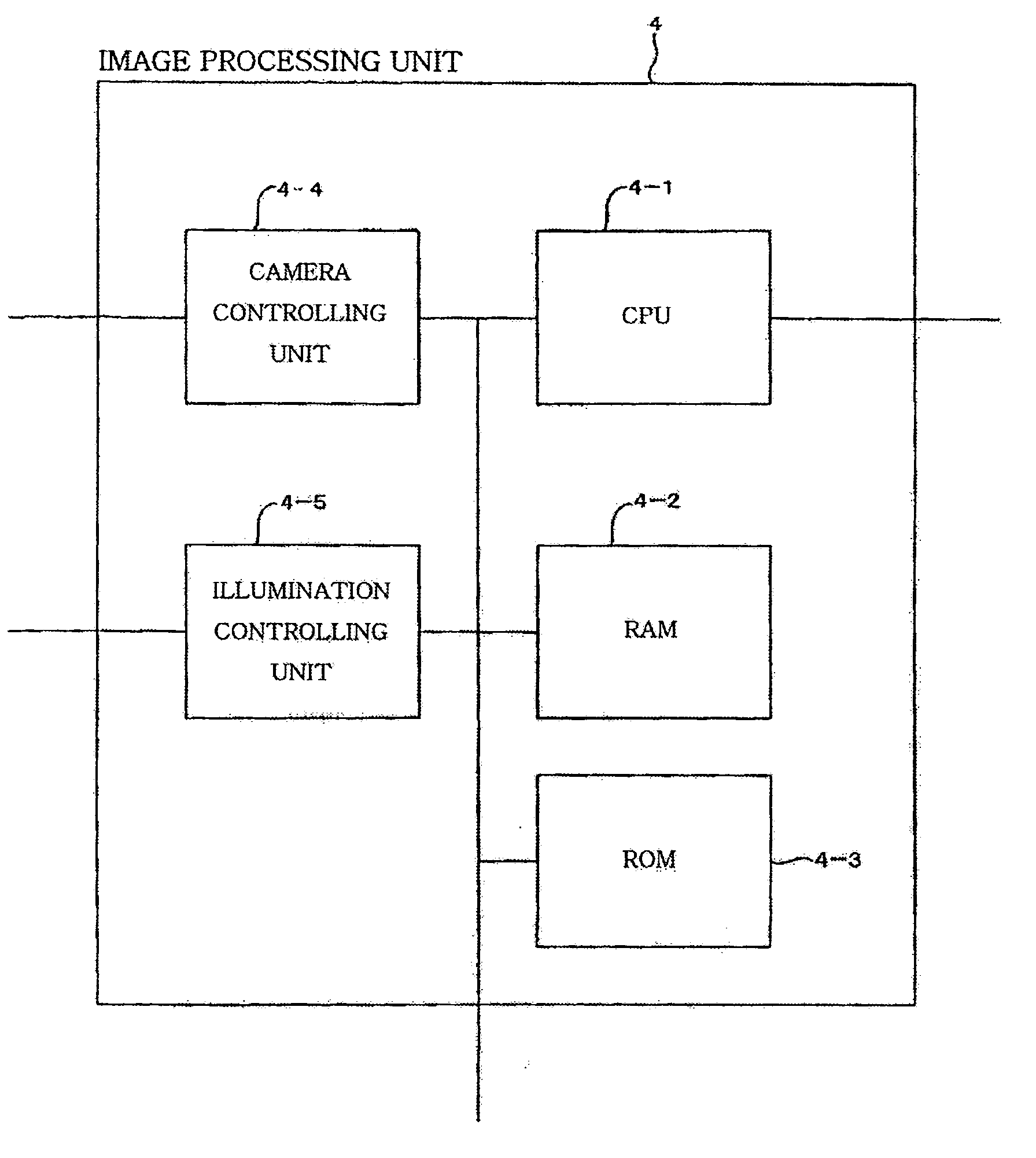
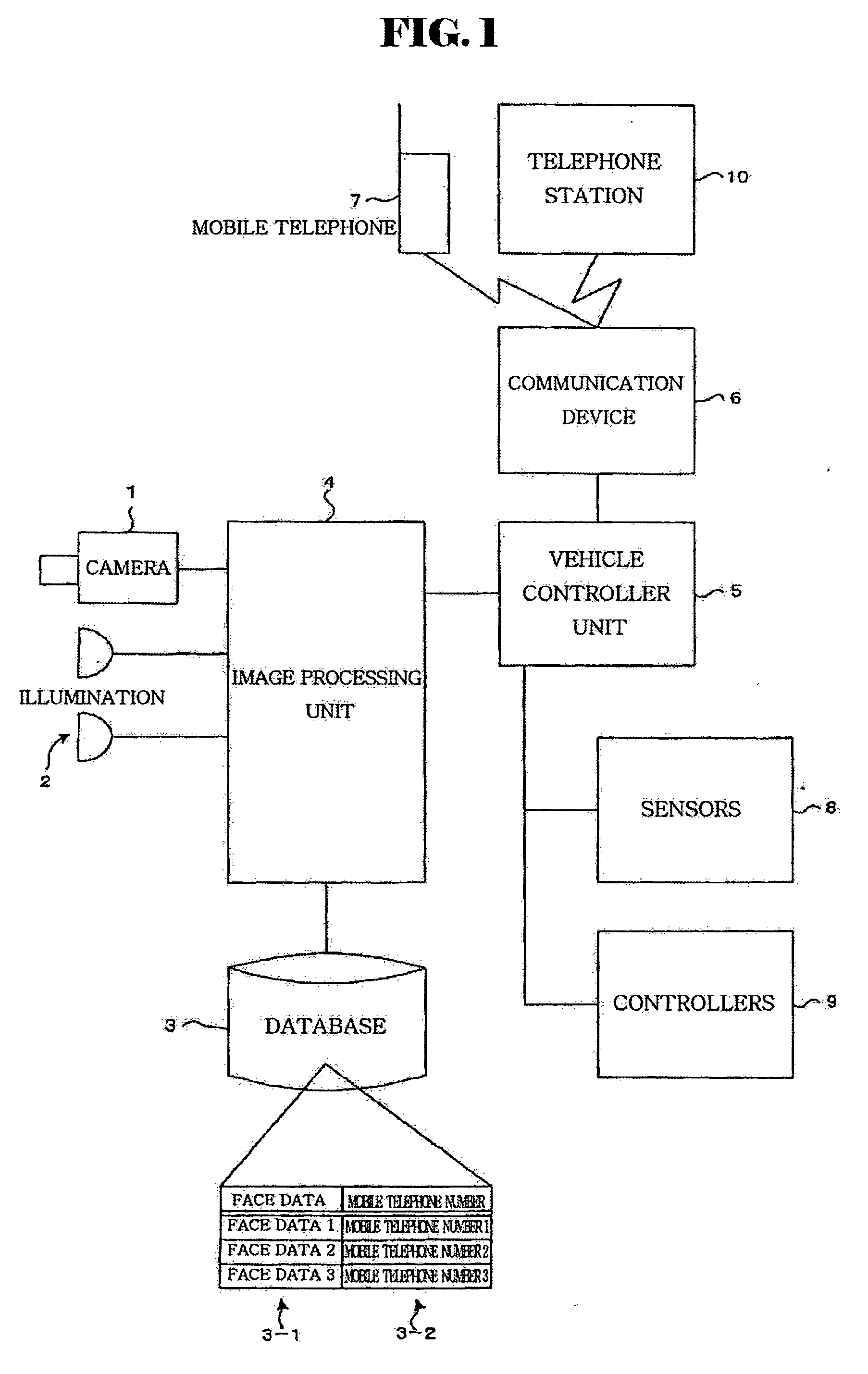
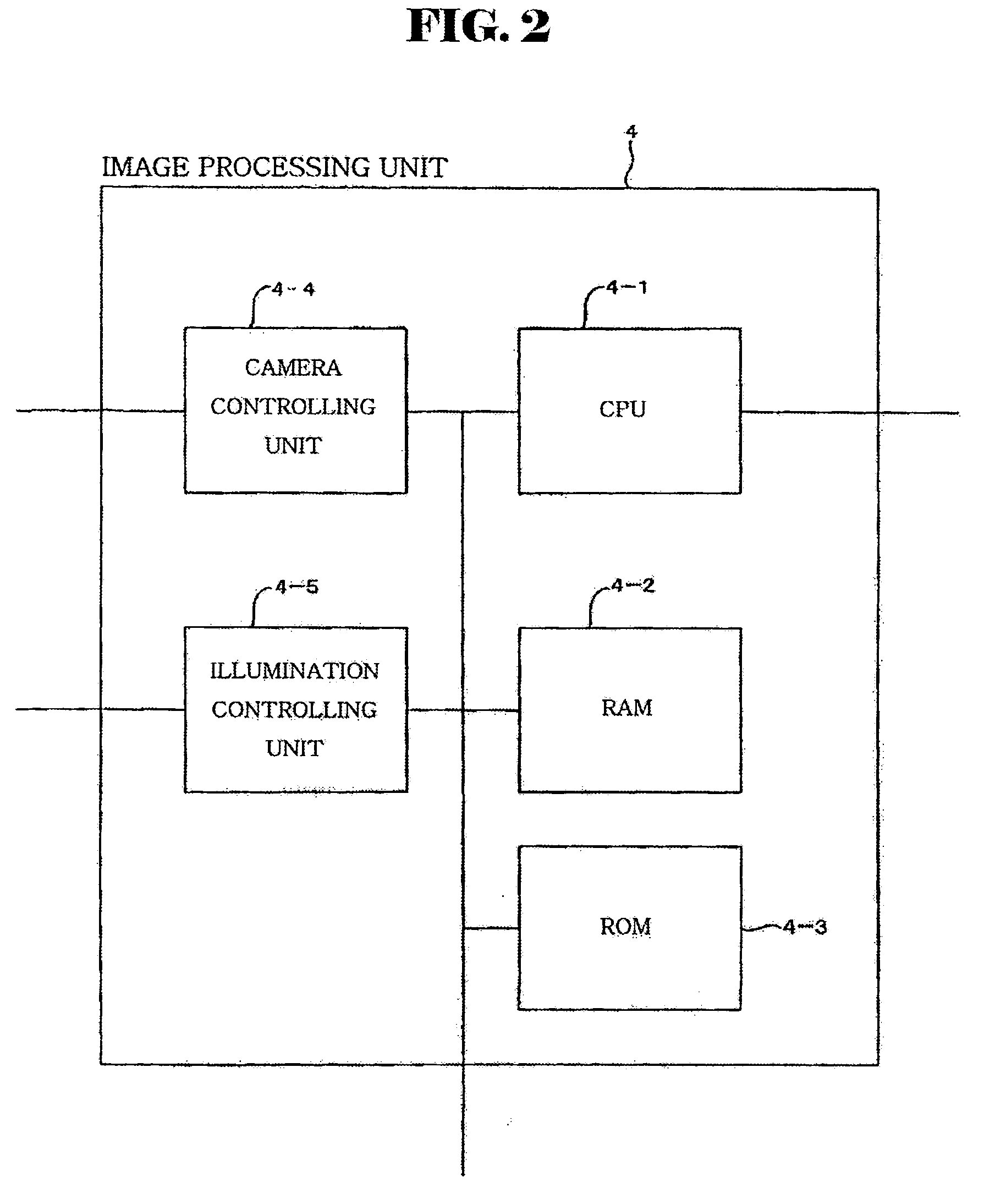
[Problems] There are provided a device and a method for telephone countermeasure in using a telephone during driving which can automatically suppress communication of only a driver in a vehicle. [Means For Solving Problems] The device for telephone countermeasure includes a database (3), a driver judgment unit, and a mode switching unit. The database (3) contains driver face data (3-1) and a telephone number (3-2) of a mobile telephone (7) used by the driver for each of the drivers. The driver judgment unit identifies the current driver of the vehicle in the database (3) by the face authentication. The mode switching unit extracts the telephone number (3-2) of the mobile telephone (7) used by the identified driver from the database (3) and switches the mobile telephone (7) of the driver to a drive mode such as a message recording mode by using the telephone number.
Owner:ORMON CORP
Contactless or hybrid contact-contactless smart card designed to limit the risks of fraud
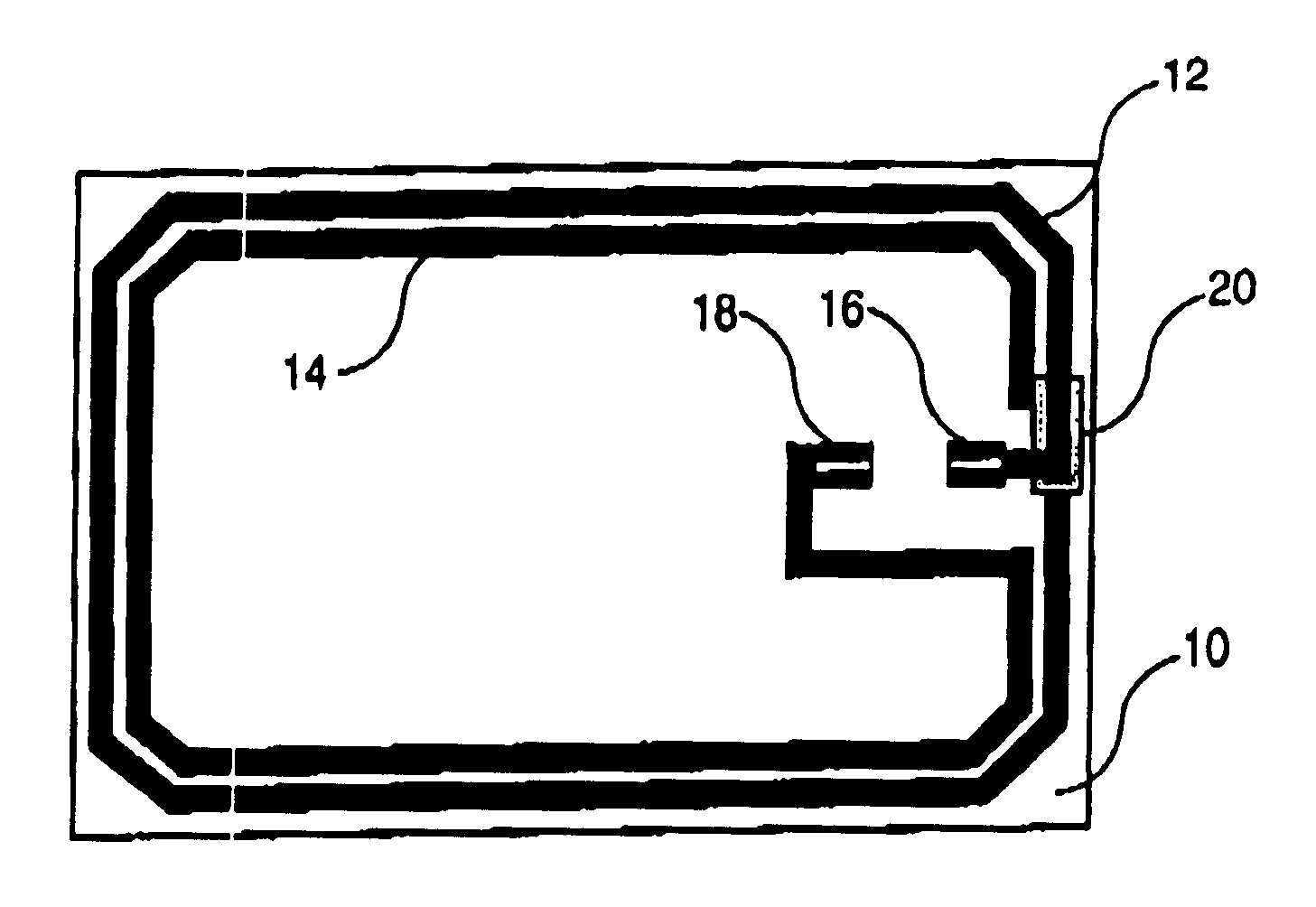
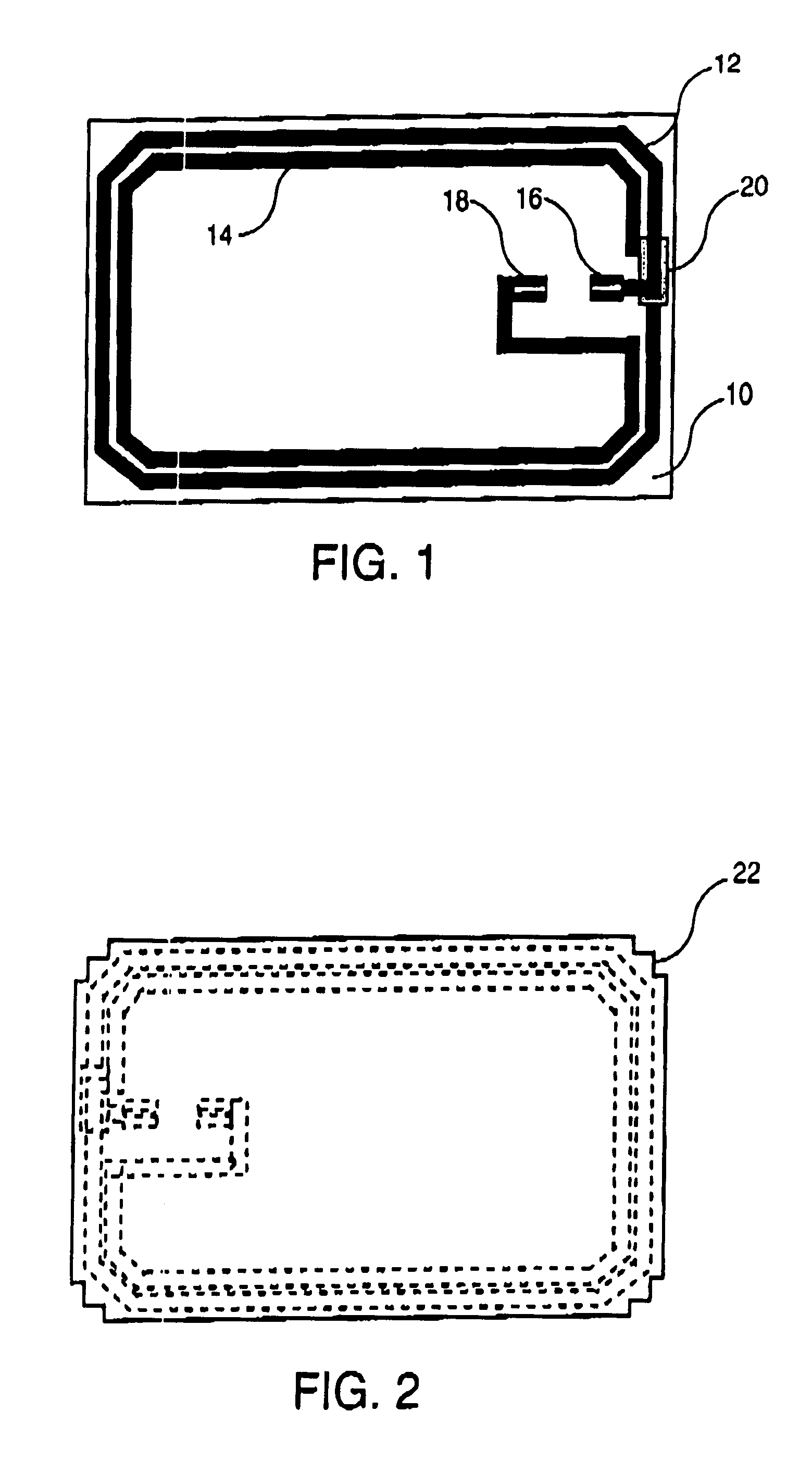
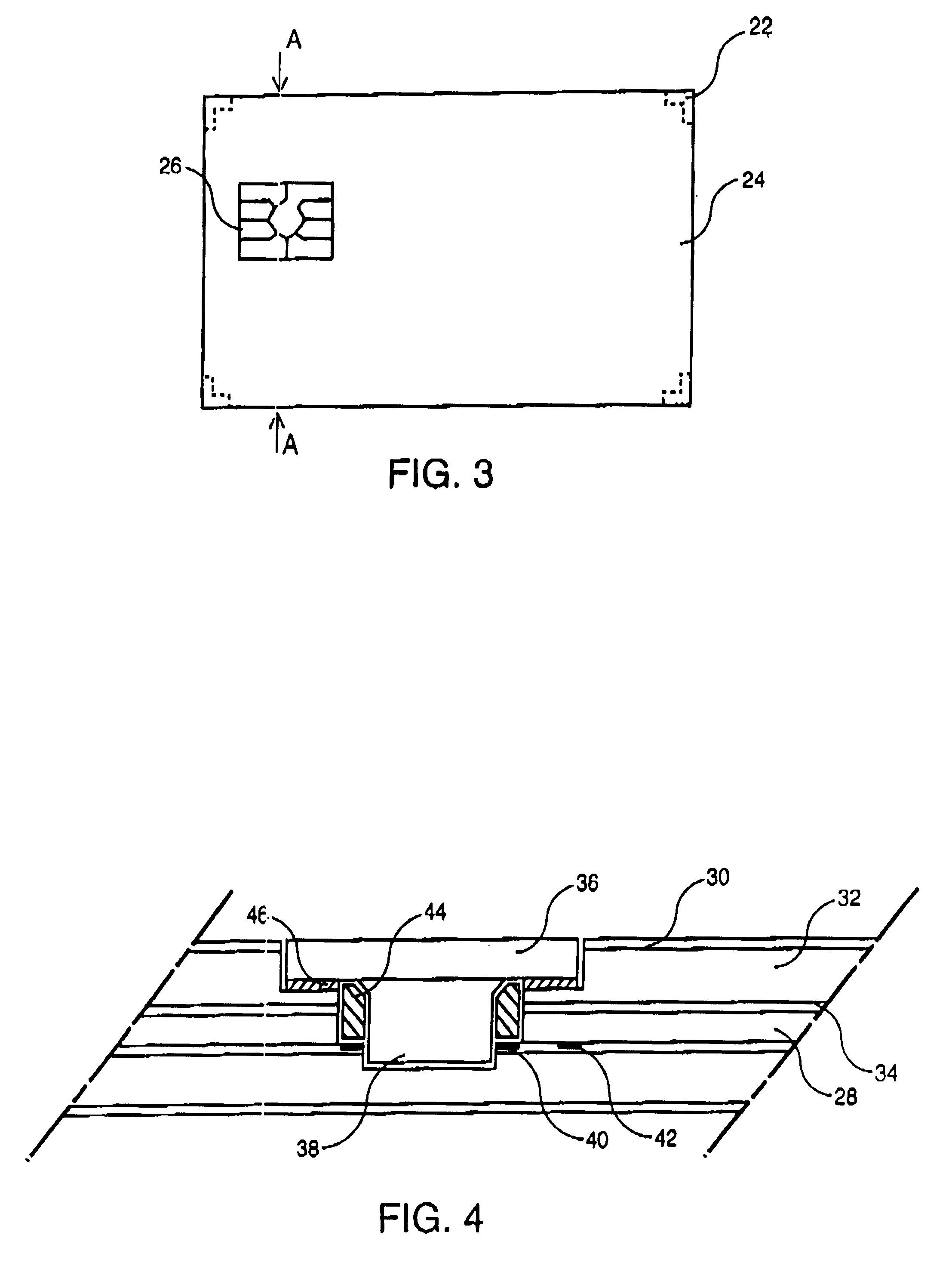
The invention relates to a contactless or hybrid contact-contactless smart card, including an antenna on a support, this antenna being formed by at least one turn of electrically conductive ink which is screen printed on the support, two card bodies 24 on each side of the support, each of the card bodies consisting of at least one layer of plastic material, and a chip or module 26 connected to the antenna. The support is made of paper and features cutouts 22 in each corner at which the two card bodies are welded together, thus giving its capacity to delaminate, when the card is bent, at the location where the forces were generated, which highlights any act of deliberate damage a posteriori as the card retains the traces of the bending, and represents a countermeasure against fraud.
Owner:ASK SA (FR)
Security countermeasure management platform
ActiveUS20120210434A1Memory loss protectionError detection/correctionCountermeasureRisk and vulnerability
A management platform that allows security and compliance users to view risks and vulnerabilities in their environment with the added context of what other mitigating security countermeasures are associated with that vulnerability and that are applicable and / or available within the overall security architecture. Additionally, the platform allows users to take one or more actions from controlling the operation of a security countermeasure for mitigation purposes to documenting the awareness of a security countermeasure that is in place.
Owner:ALERT LOGIC
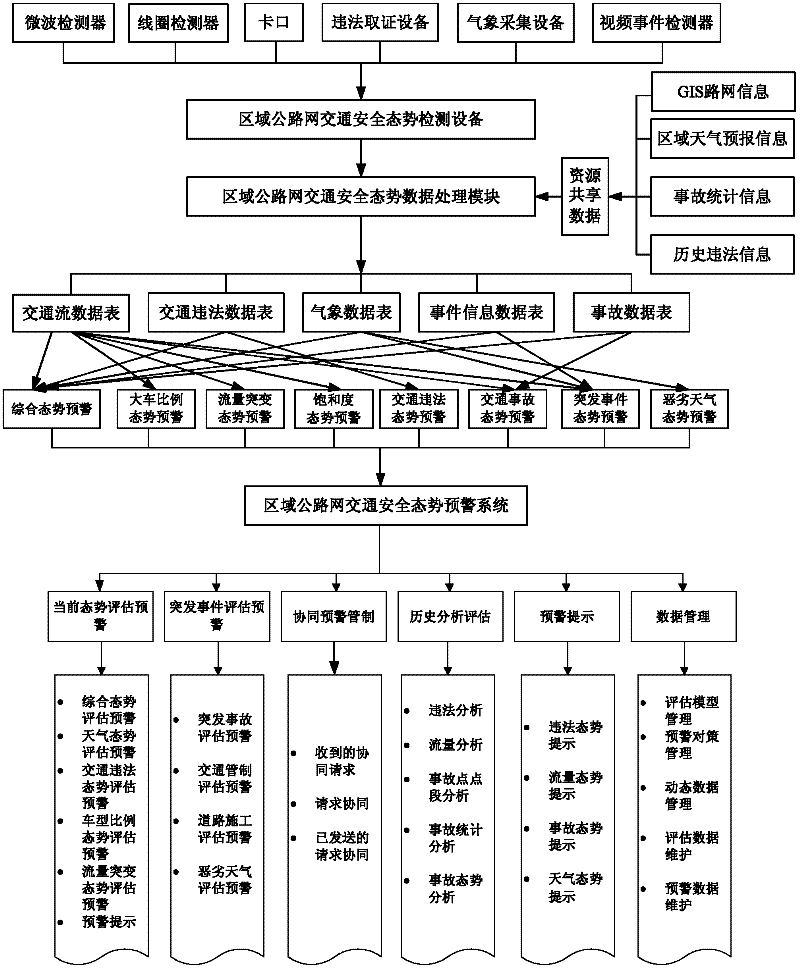
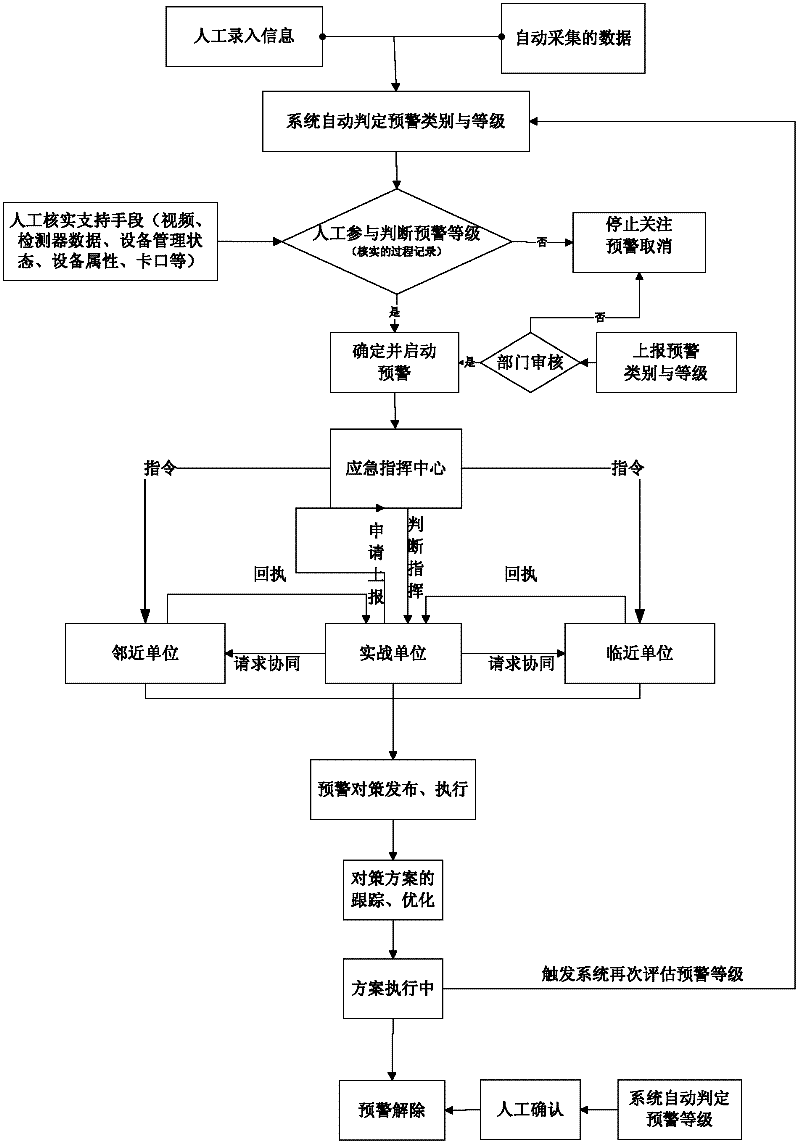
Area road network traffic safety situation early warning system and method thereof
InactiveCN102231231AReal-time acquisitionRealize real-time judgmentDetection of traffic movementProcess systemsData information
The invention discloses an area road network traffic safety situation early warning system and a method thereof. The system comprises monitoring equipment, a data transmission system, a data process system and an early warning system. The method comprises the following steps: acquiring data information of road traffic, meteorology, illegal behaviors, and accidents through the monitoring equipment; sending the data information through the data transmission system; carrying out a multiple heterogeneous treatment on the acquired data information through the data process system, and merging data of the same kind; analyzing and assessing early warning grade through the early warning system, and determining and publishing a early warning scheme. Thereby road network traffic safety situation information can be comprehensively grasped, and dangerous source existing in the road network can be discovered timely to determine an early warning grade and generate an intelligent early warning countermeasure. Pertinence, instantaneity and validity of a measure of a road traffic management department actively preventing traffic accidents are improved. Technology support is provided in the invention to reduce area road network traffic risk factor and prevent major and extraordinarily serious road traffic accidents.
Owner:TONGJI UNIV
Enterprise security management for network equipment
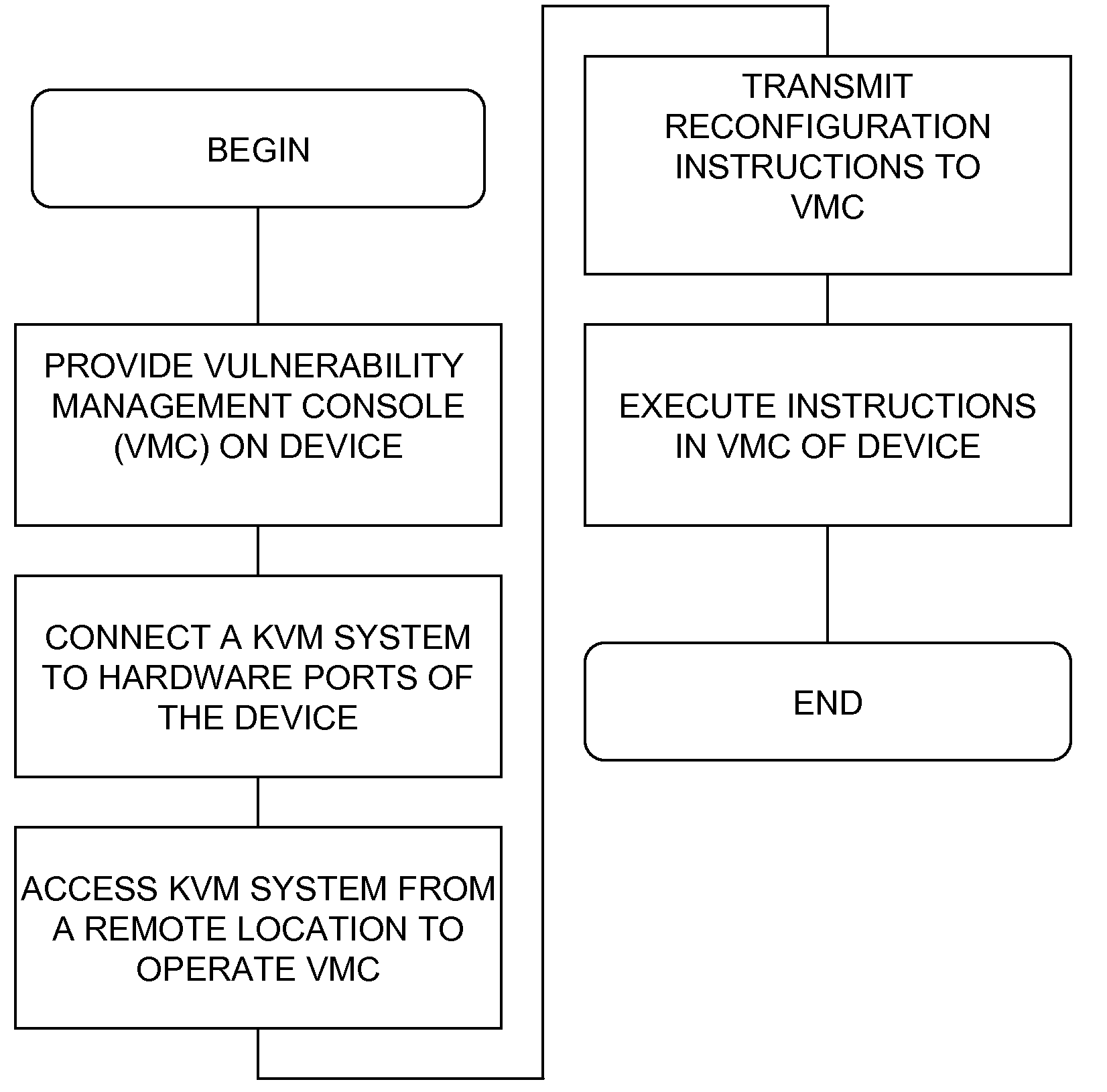
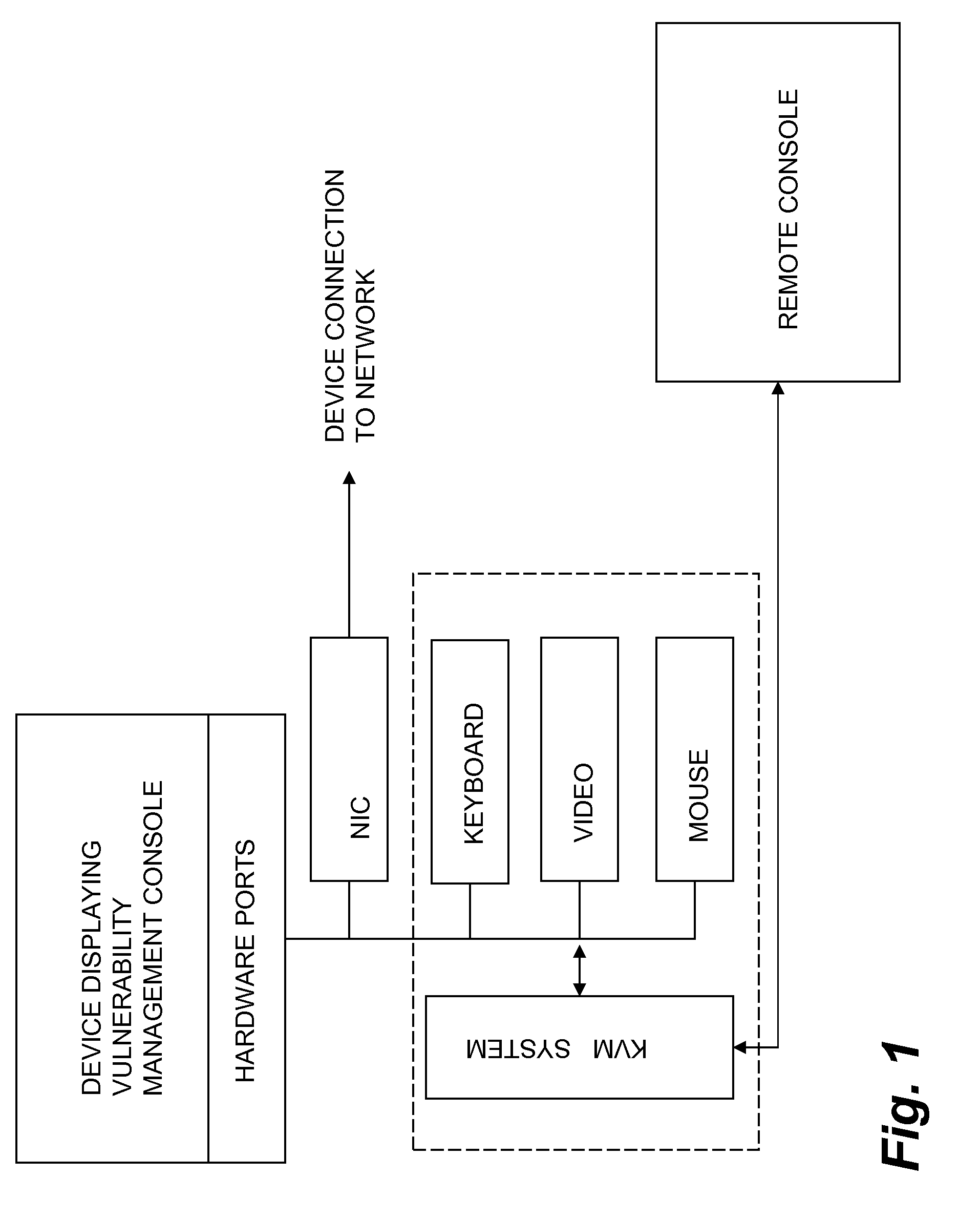
InactiveUS20090199298A1Eliminate the problemMemory loss protectionUnauthorized memory use protectionEnterprise security managementDashboard
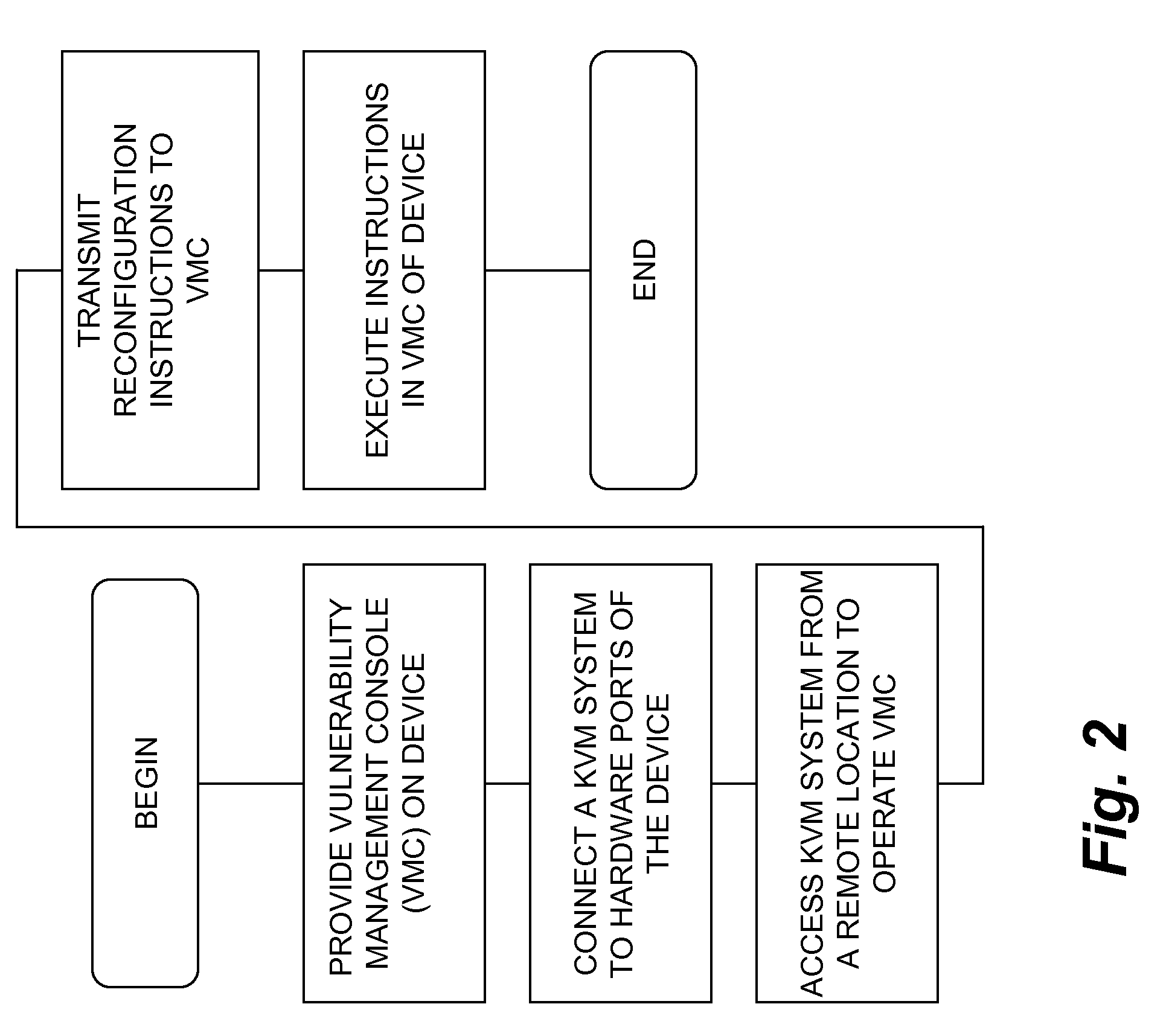
The inventive device includes a dashboard or graphical user interface (GUI), a security access control (AUTH) and secure communications sub-system (SEC-COMM), network and asset discover and mapping system (NAADAMS), an asset management engine (AME), vulnerability assessment engine (CVE-DISCOVERY), vulnerability remediation engine (CVE-REMEDY), a reporting system (REPORTS), a subscription, updates and licensing system (SULS), a countermeasure communications system (COUNTERMEASURE-COMM), a logging system (LOGS), a database integration engine (DBIE), a scheduling and configuration engine (SCHED-CONFIG), a wireless and mobile devices / asset detection and management engine (WIRELESS-MOBILE), a notification engine (NOTIFY), a regulatory compliance reviewing and reporting system (REG-COMPLY), client-side (KVM-CLIENT) integration with KVM over IP or similar network management equipment, authentication-services (KVM-AUTH) integration with KVM over IP or similar network management equipment and server-side (KVM-SERVER) integration with KVM over IP or similar network management equipment.
Owner:NETCLARITY
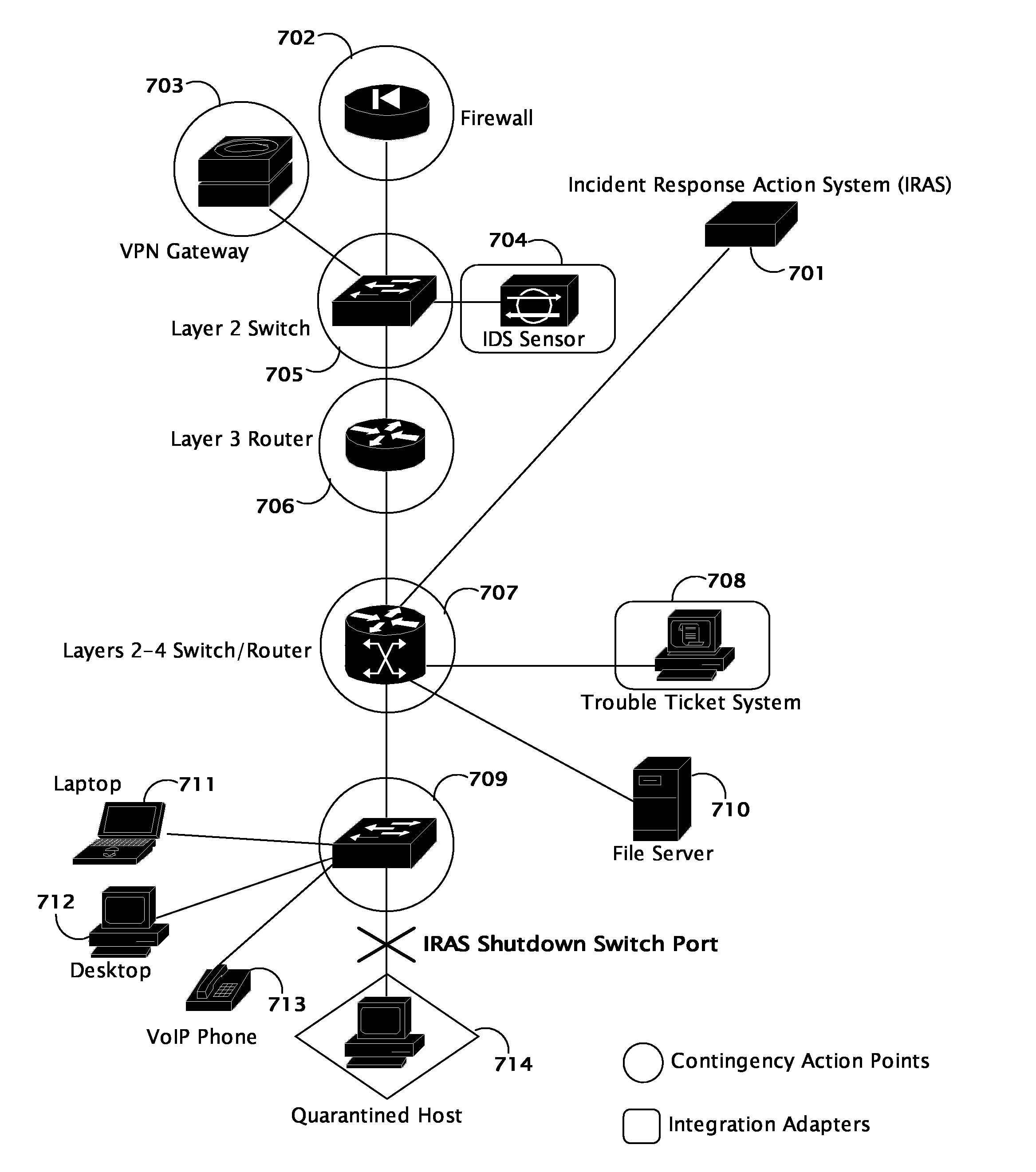
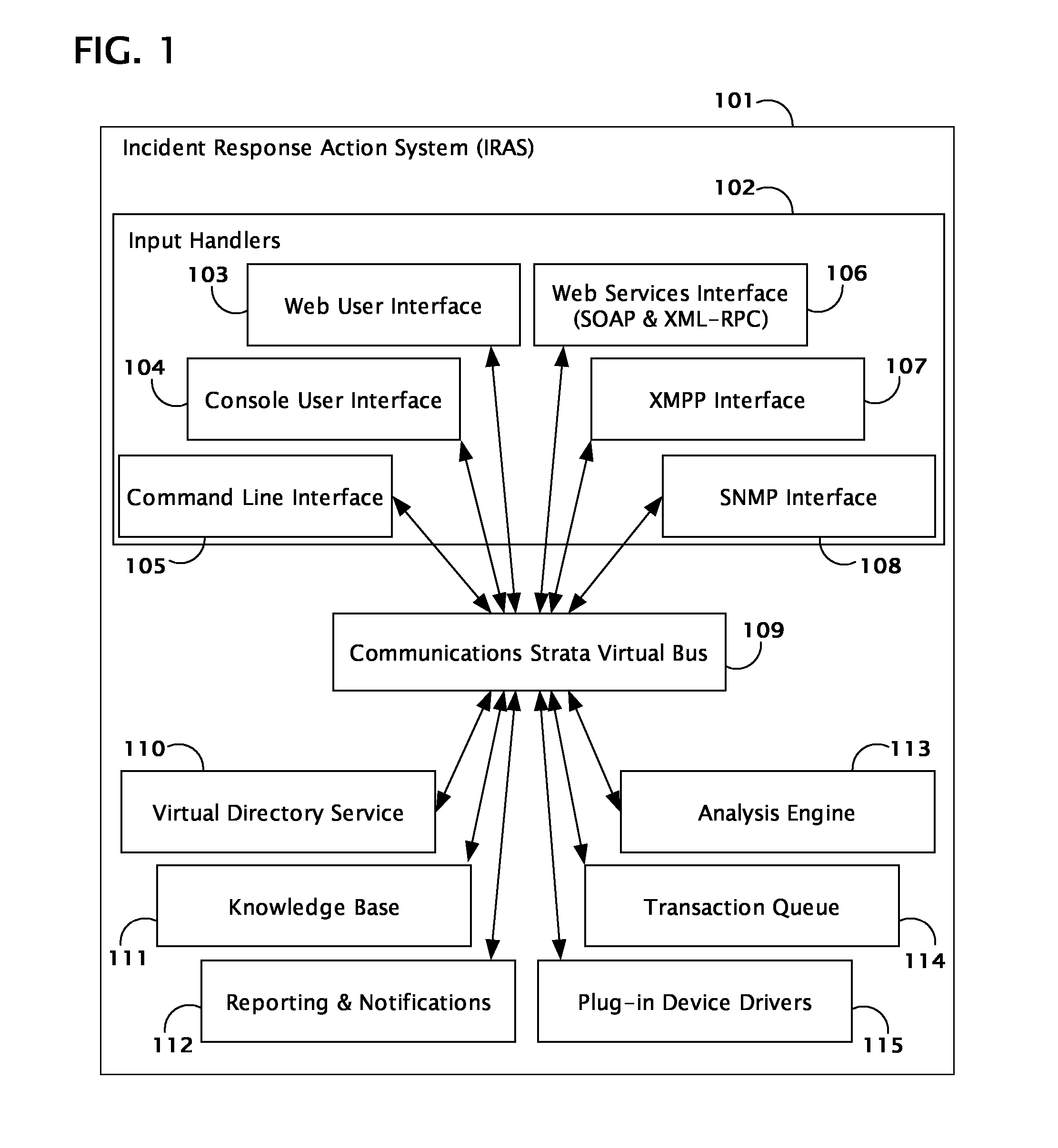
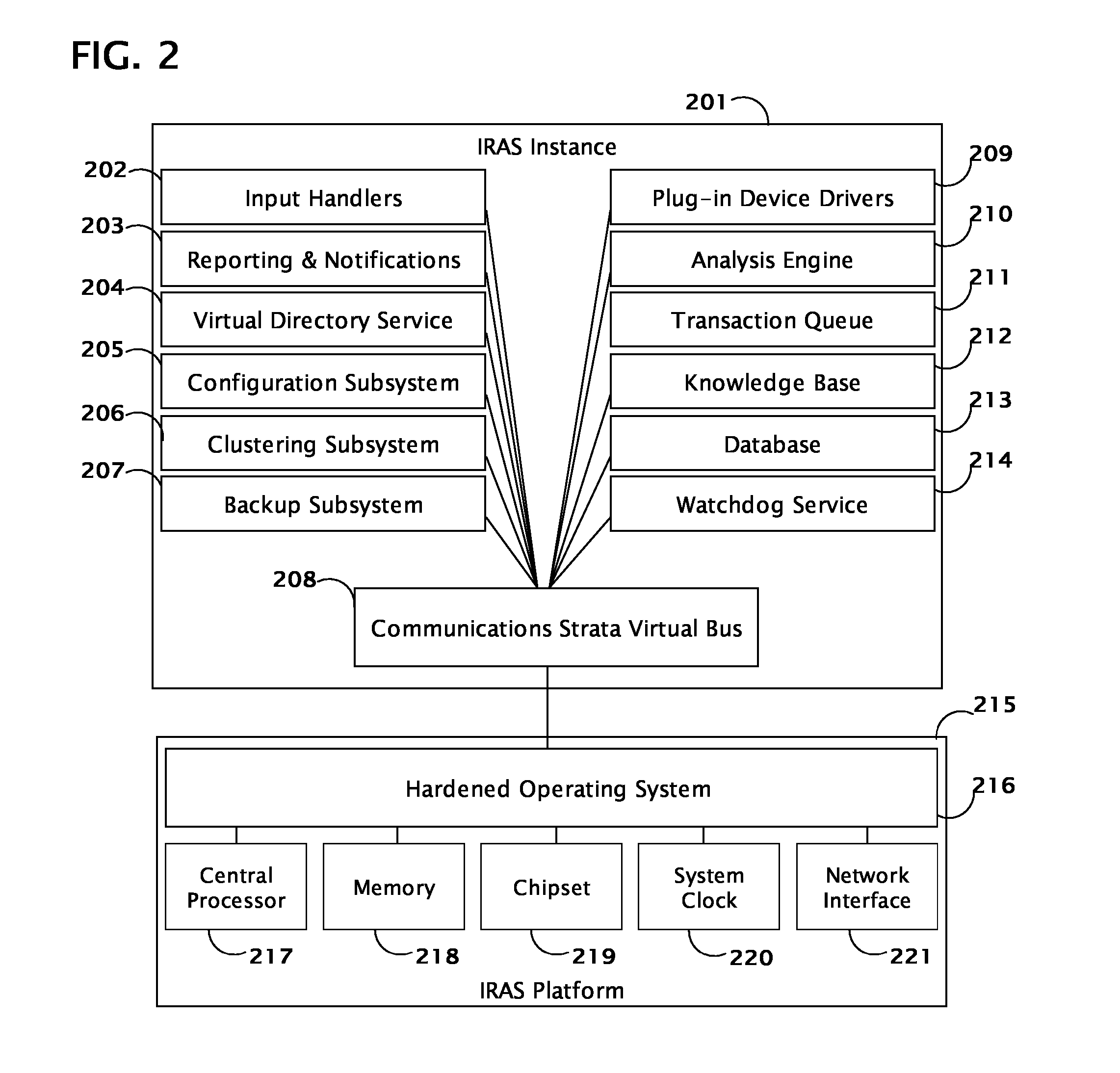
System and method for coordinating network incident response activities
ActiveUS20060212932A1Improve responseReduce decreaseMemory loss protectionError detection/correctionCountermeasureNetwork connection
The present invention provides a system and method to process information regarding a network attack through an automated workflow that actively reconfigures a plurality of heterogeneous network-attached devices and applications to dynamically counter the attack using the network's own self-defense mechanisms. The present invention leverages the security capabilities present within existing and new network-attached devices and applications to affect a distributed defense that immediately quarantines and / or mitigates attacks from hostile sources at multiple points simultaneously throughout the network. In a preferred embodiment, deployed countermeasures are automatically lifted following remediation activities.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
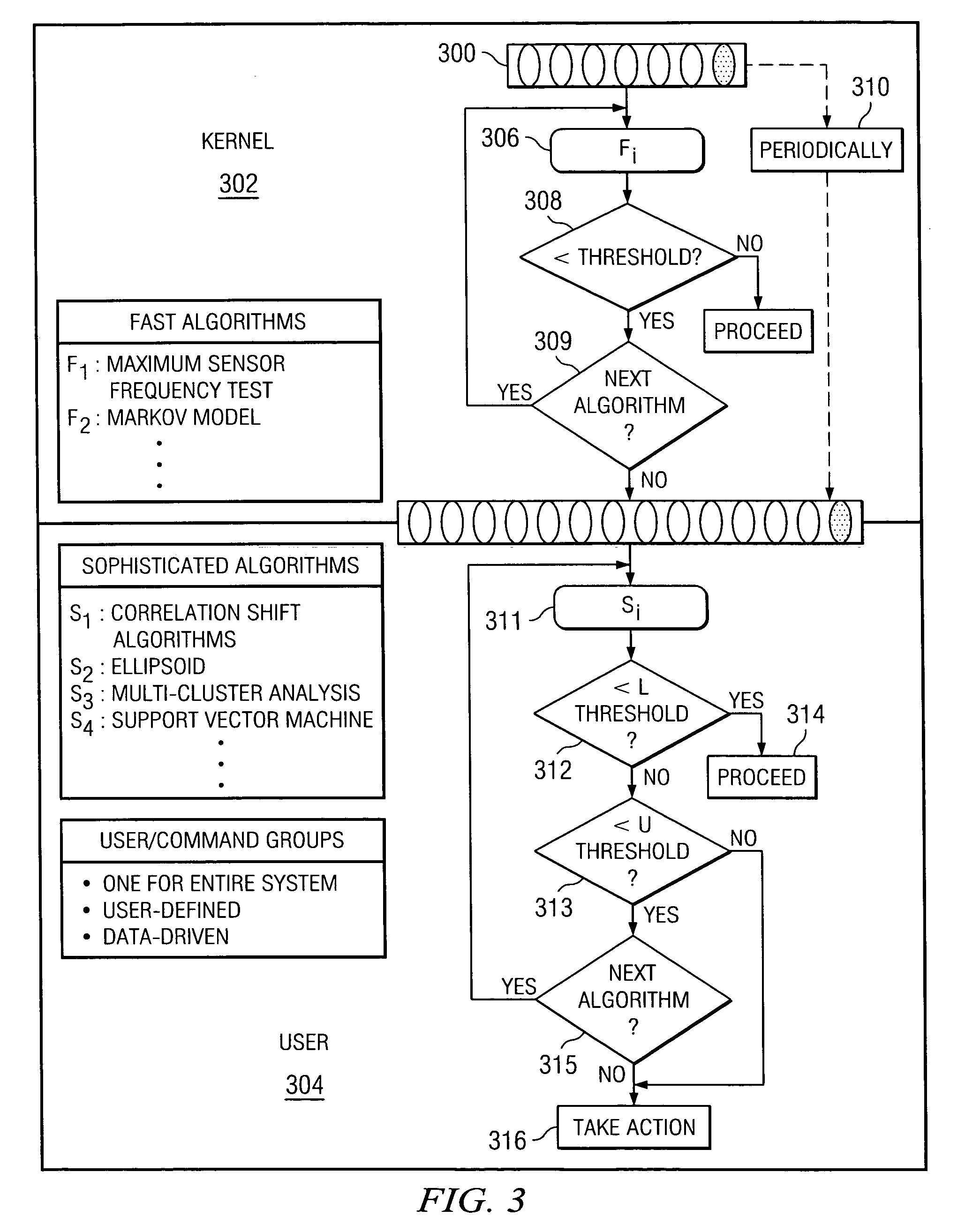
Method and system for detecting intrusive anomalous use of a software system using multiple detection algorithms
InactiveUS20060085854A1Improve detection accuracyAccurate detectionMemory loss protectionDetecting faulty computer hardwareCountermeasureSoftware system
A method of detecting an intrusion into (or an anomaly in a behavior of) a target software system begins by instrumenting the target software system to generate behavior data representing a current observation or observation aggregate. The method then determines whether the current observation or observation aggregate warrants a second level examination; preferably, this determination is made by processing the current observation or observation aggregate through a first level detection algorithm that provides a first, provisional indication of a possible intrusion. If a result of executing the first level detection algorithm indicates that the current observation or observation aggregate warrants a second level examination, the method continues by processing the current observation or observation aggregate through at least one or more second level detection algorithms to provide a second, more definite, fine grain indication of a possible intrusion. The observation aggregates used by the first and second level detection algorithms may be the same or different. The first and second level detection algorithms may be executed in the same or different systems, machines or processors. The target software system operation may be suspended as the current observation or observation aggregate is processed through the one or more second level detection algorithms. A given action (e.g., sending an alert, logging the event, activating a countermeasure, or the like) may be taken if the result of the second level examination indicates a possible intrusion. Multiple algorithms may be executed together within a single examination level, with the individual results then analyzed to obtain a composite result or output indicative of intrusive or anomalous behavior.
Owner:STRATACLOUD
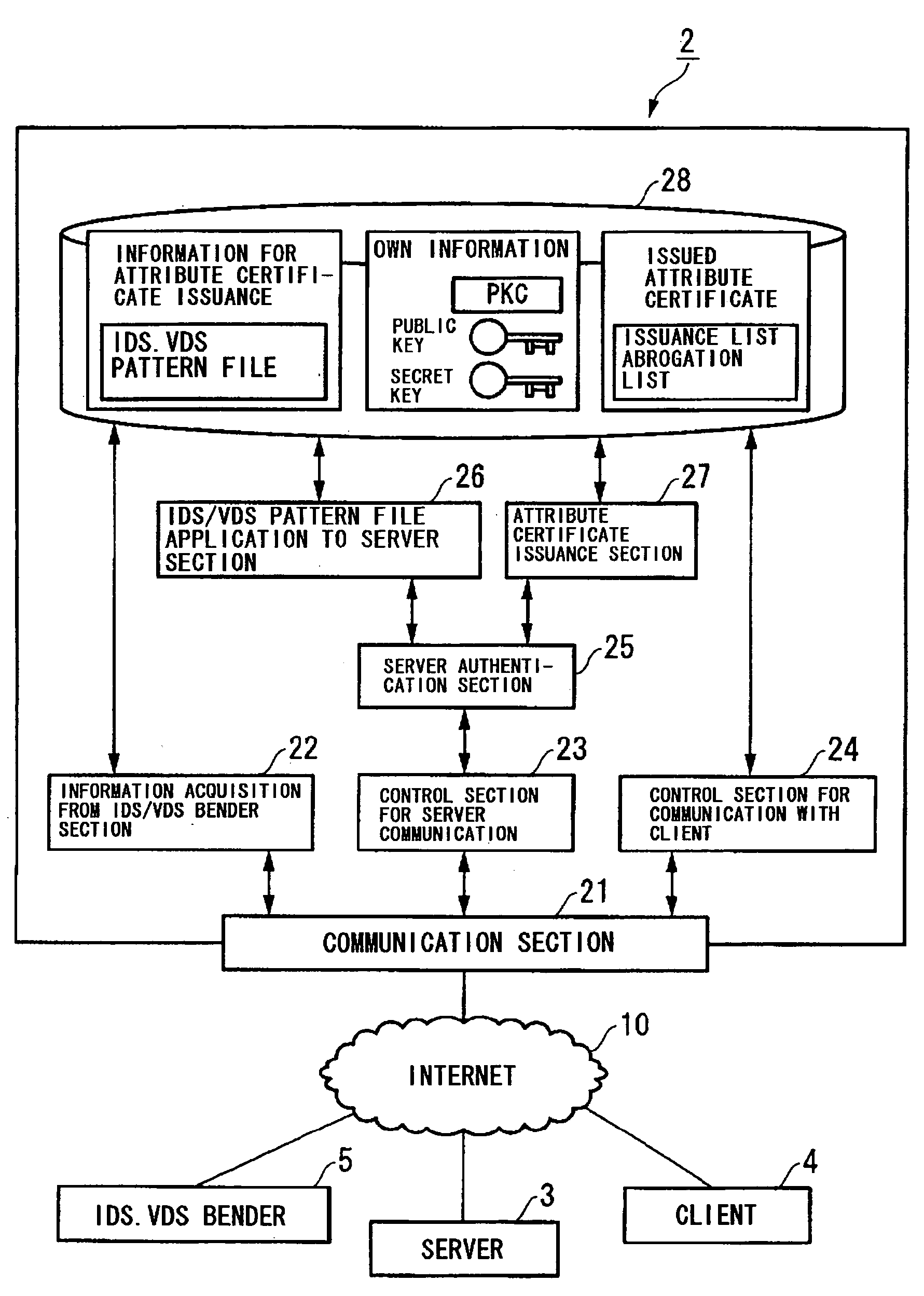
Communication system and security assurance device
InactiveUS20060048228A1Memory loss protectionUser identity/authority verificationCountermeasureCommunications system
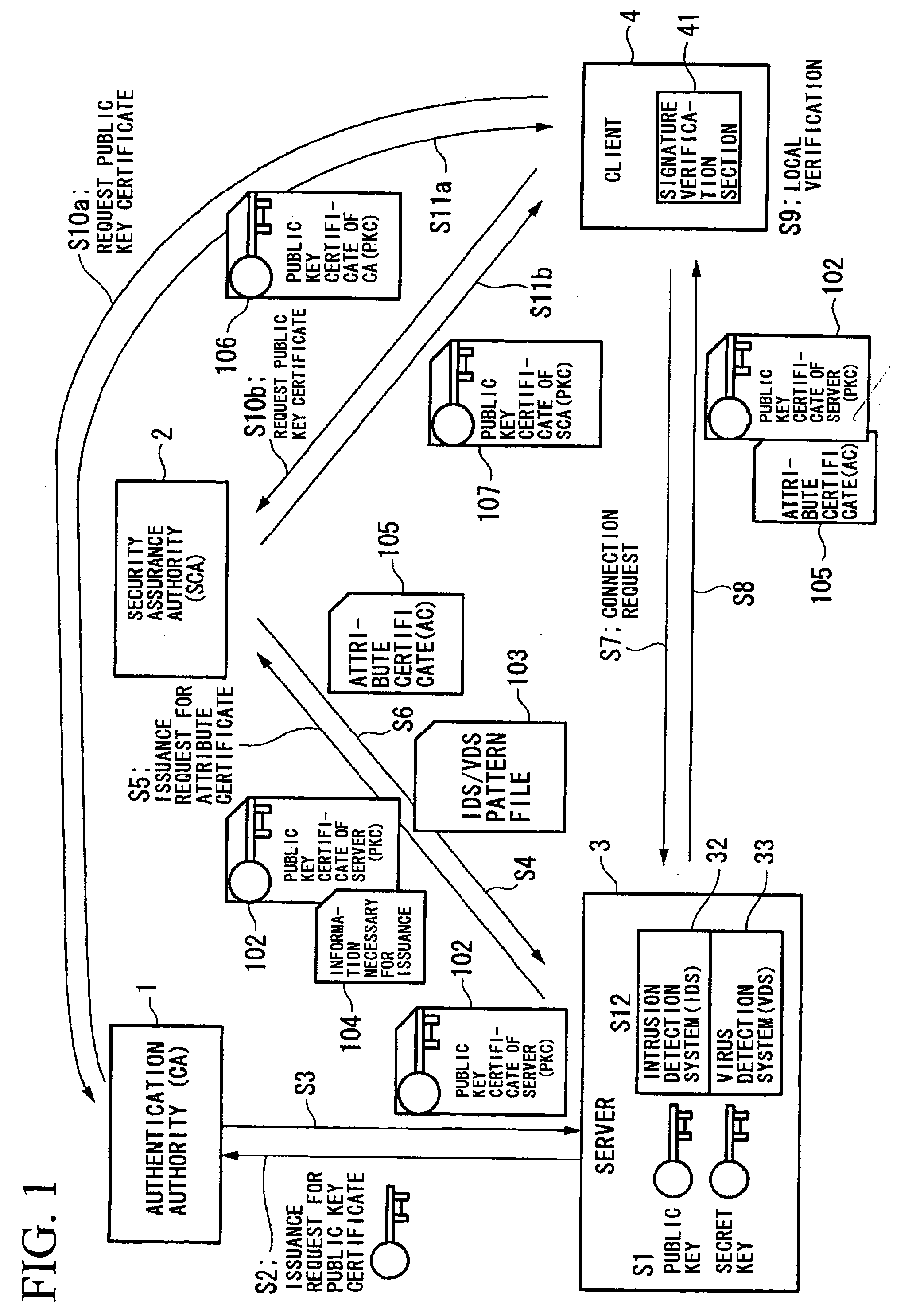
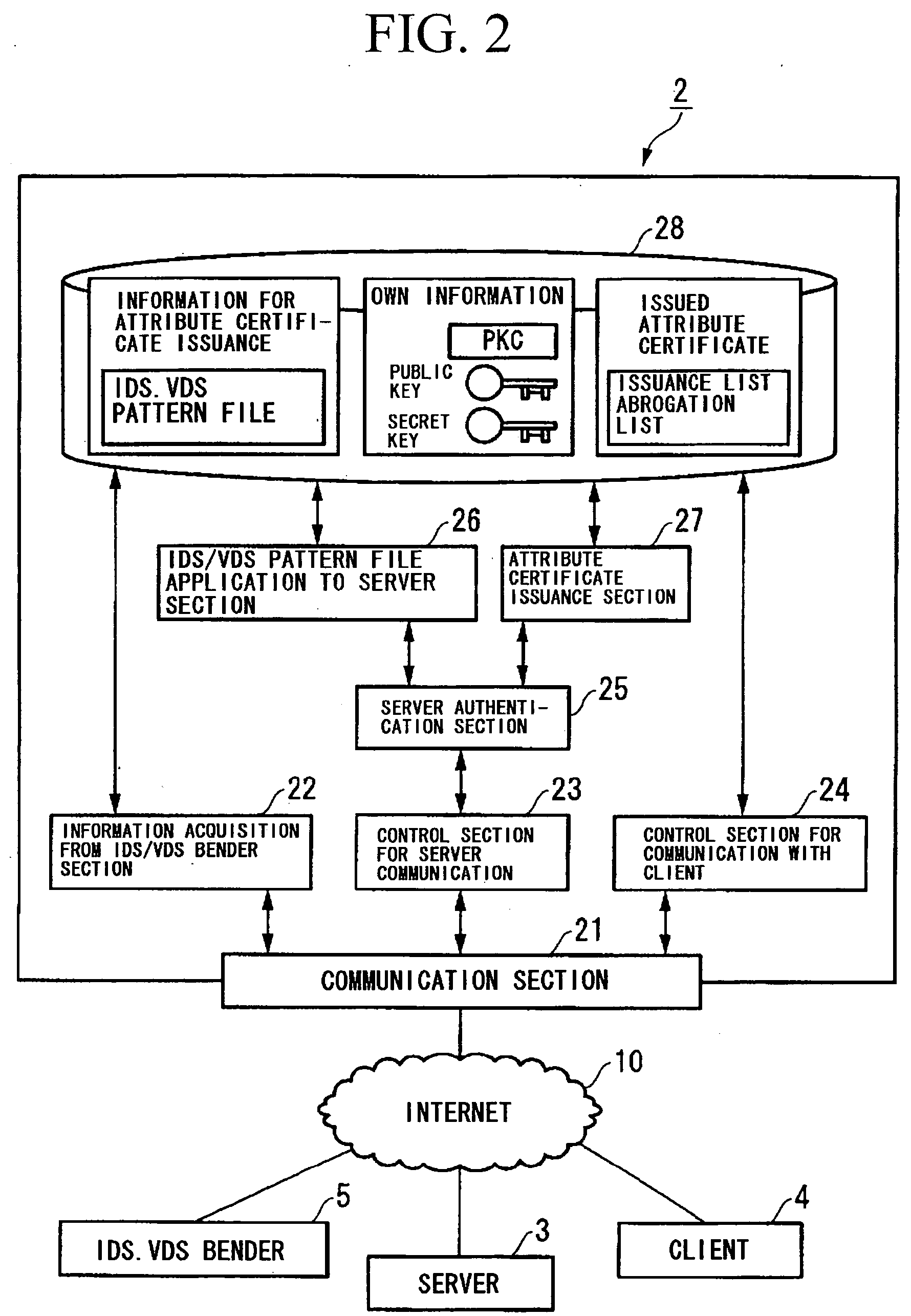
A communication system and a security assurance device are proposed, which are capable of assuring that a target party for communication is implementing security countermeasures. A server 3 transmits information 104 necessary for AC issuance to a security assurance authority 2. The security assurance authority 2 verifies the security of the server 3 during communication based upon this information necessary for AC issuance 104. And, when the security of the server 3 during communication is confirmed, the security assurance authority 2 issues an AC 105 which proves the security of the server 3 during communication, and transmits it to the server 3. Upon receipt of this AC 105, the server 3 transmits the AC 105 to a client 4, according to a connection request from the client 4. And, upon receipt of this AC 105, the client 4 verifies the security during communication of the server 3, based upon the AC 105.
Owner:KDDI CORP +1
Storage operation management program and method and a storage management computer
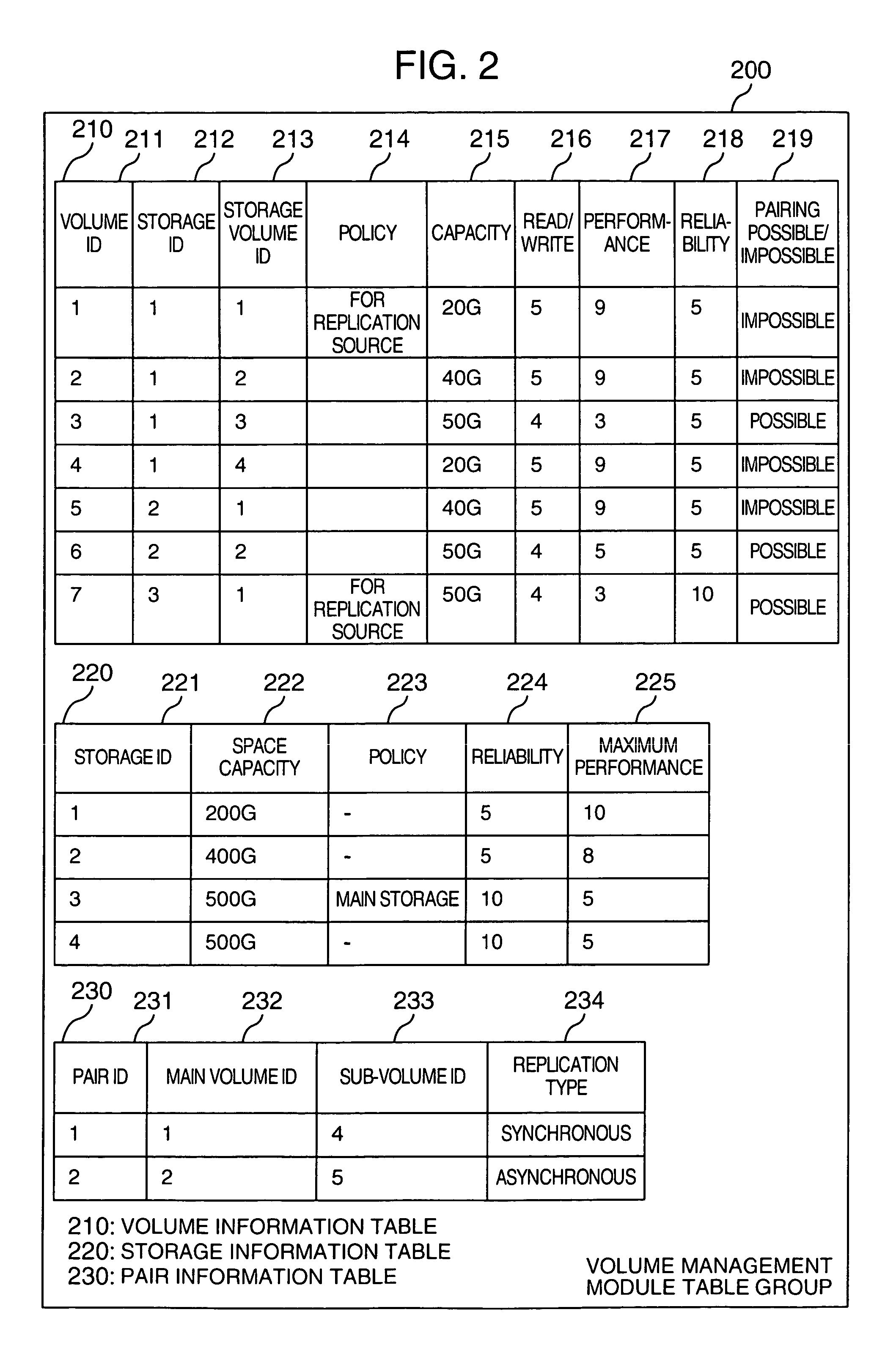
InactiveUS7191198B2Easy to operateData processing applicationsTransmissionCountermeasureStorage management
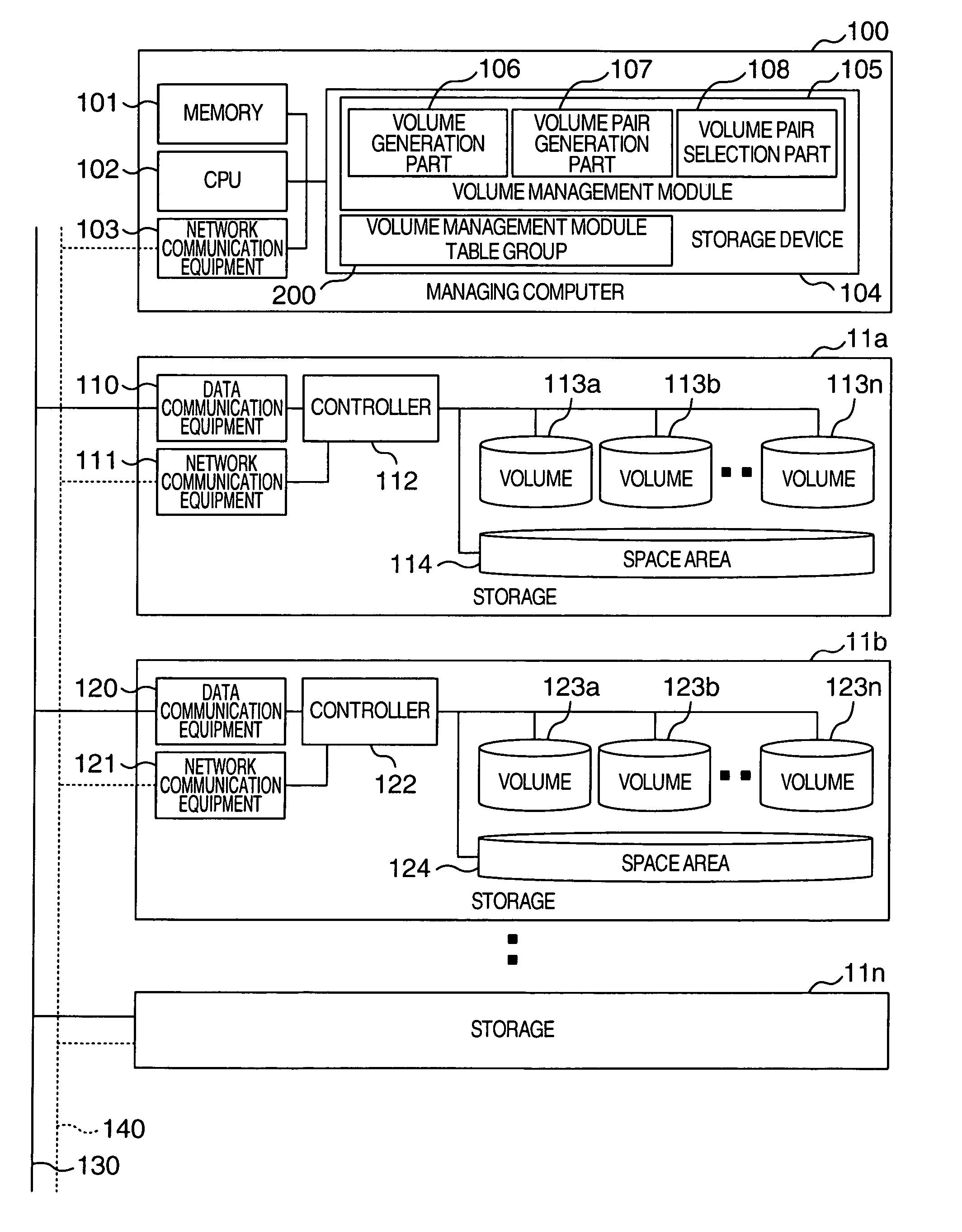
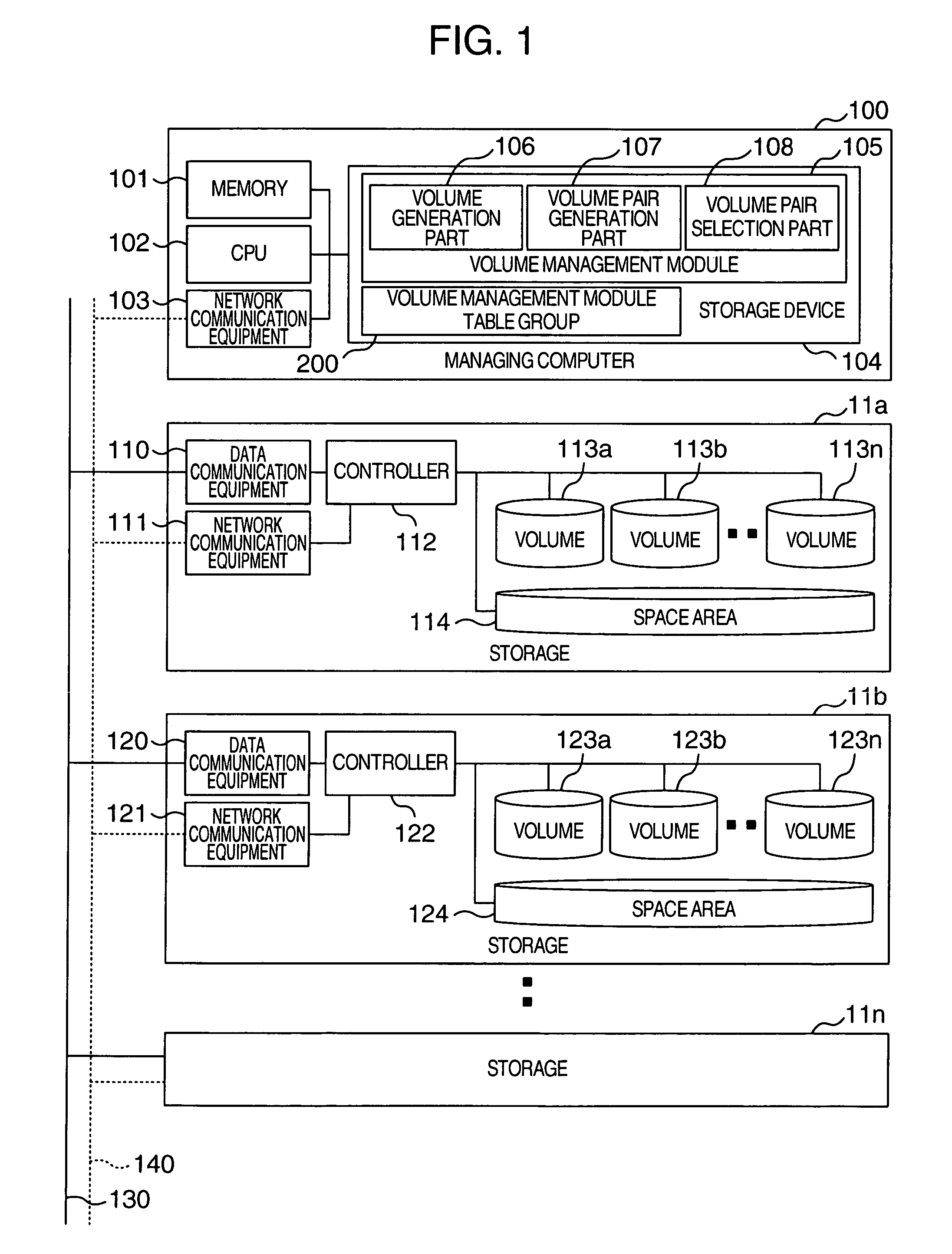
A managing computer (manager) manages replication of data areas inside a storage or among storages. A storage volume management module of the manager manages policy of the volume and its properties. When replication of a volume is set, a volume of a replication destination appropriate for a volume of a replication source is generated using the policy and the properties to form a replication pair. A route management module of the manager and its volume management module bring the policy and the properties of the volumes, and the policies and conditions of lines into conformity with one another. When any fault occurs in a line route used for data transfer during replication of the volume, a separate line route is utilized, and a fault countermeasure is taken for replication of the volumes in accordance with the policy and properties of the volumes.
Owner:HITACHI LTD
System and method for evaluating and enhancing source anonymity for encrypted web traffic
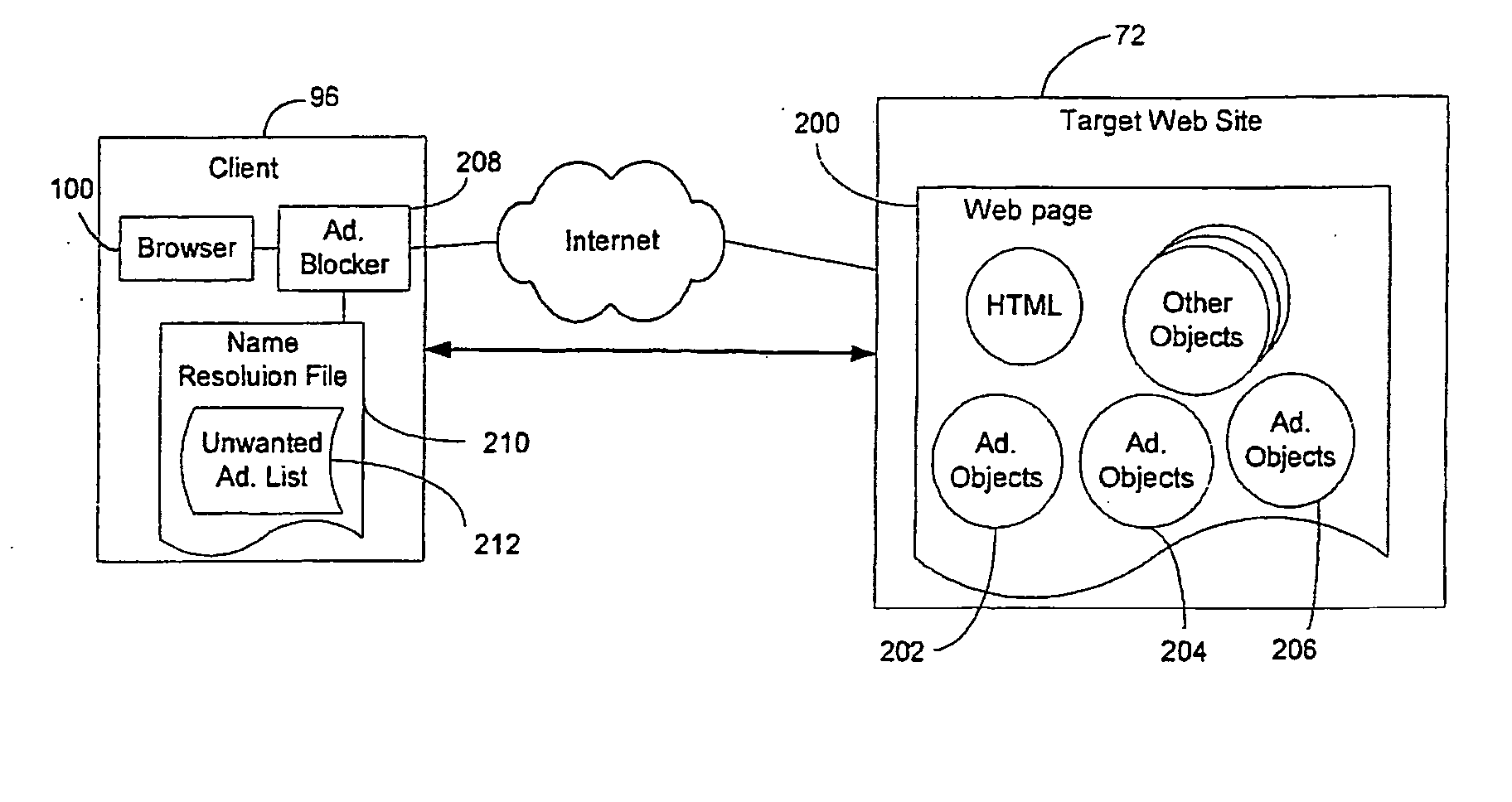
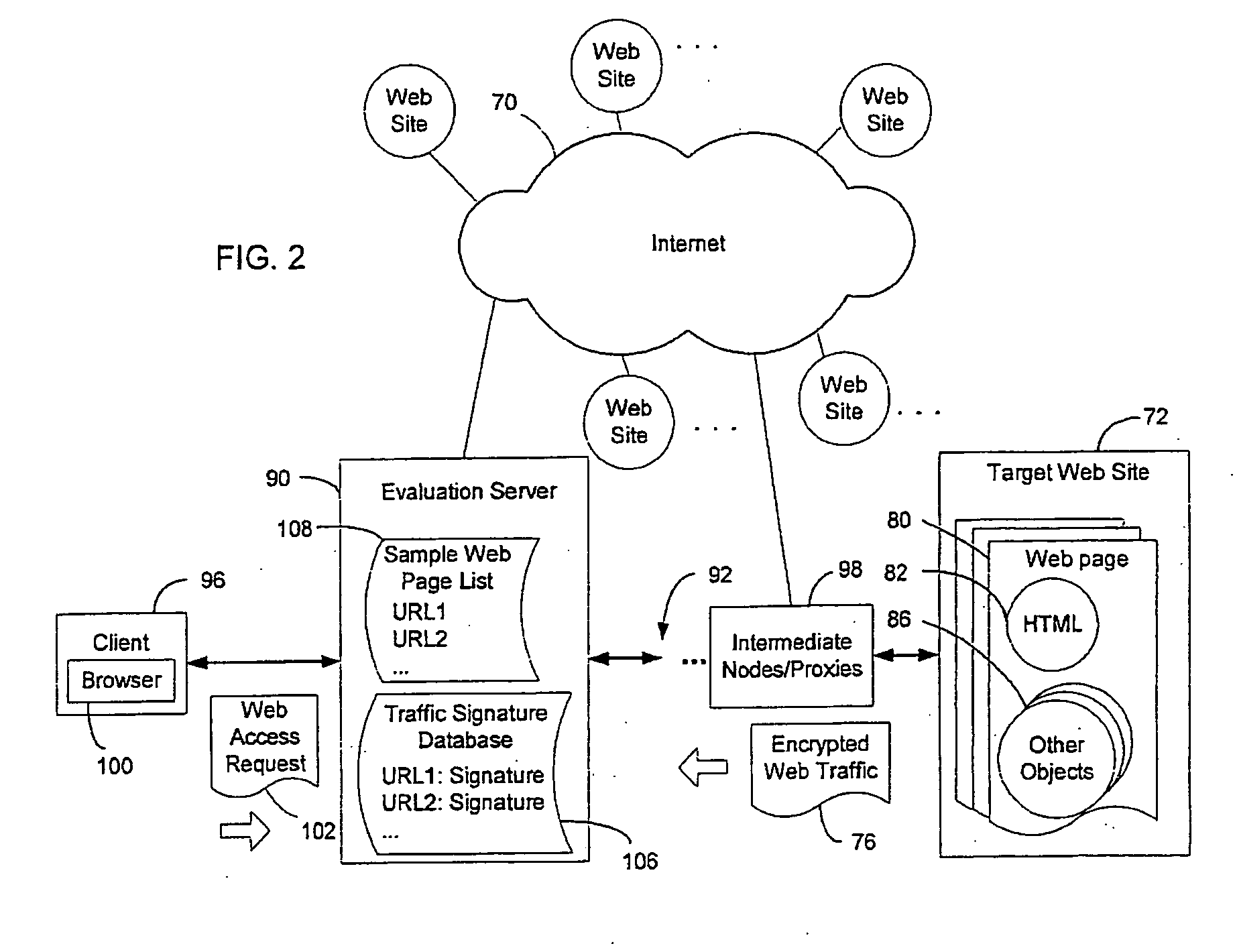
InactiveUS20060059091A1Reduce uniquenessDifficult to identifyComputer security arrangementsSecuring communicationWeb siteCountermeasure
A system and method is provided for evaluating the effectiveness of data encryption for hiding the identity of the source of Web traffic. A signature is constructed from encrypted Web traffic for a Web page sent by a target Web site, and the signature is compared with archived traffic signatures obtained by accessing various Web pages of interest in advance. If the signature of the detected encrypted Web traffic matches a stored traffic signature beyond a pre-set statistical threshold, a positive match is found, and the source of the traffic is identified. Countermeasures for reducing the reliability of source identification based on traffic signature matching are provided.
Owner:MICROSOFT TECH LICENSING LLC
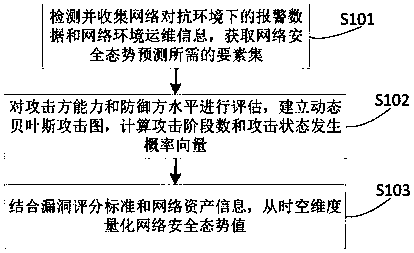
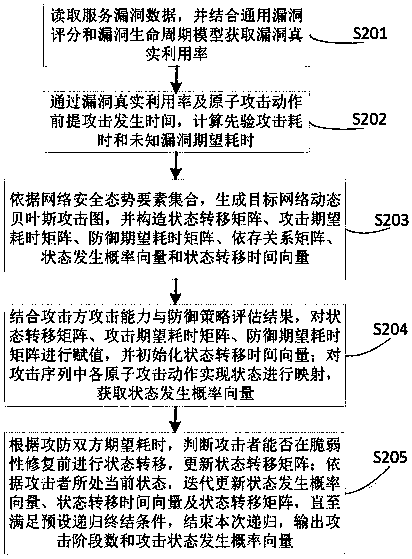
Attack-oriented network security situation prediction method, device and system
ActiveCN108494810ARealize dynamic associationIn line with the actual environmentData switching networksSecuring communicationCountermeasureAttack graph
The invention belongs to the technical field of network security and particularly relates to an attack-oriented network security situation prediction method, device and system. The method comprises the following steps: detecting and collecting alarm data and network environment operation and maintenance information in a network countermeasure environment, obtaining an element set required by network security situation prediction, wherein the element set comprises three types of information of an attacker, a defense party and a network environment; evaluating the attacker capability and the level of the defense party, establishing a dynamic Bayesian attack graph, and calculating an attack phase number and an attack state occurrence probability vector; and combining a vulnerability scoring standard and network asset information, and performing time-space dimension quantification on the network security situation value. According to the method, dynamic association of the situation elements of the defense party, the attacker, the environment information and the like is achieved, the actual environment of the network is better conformed to, the future situation and the attack occurrencetime can be accurately predicted, higher prediction efficiency is achieved, and storage scale and timeliness of network security situation awareness are optimized, so as to provide more effective guidance for network protection.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
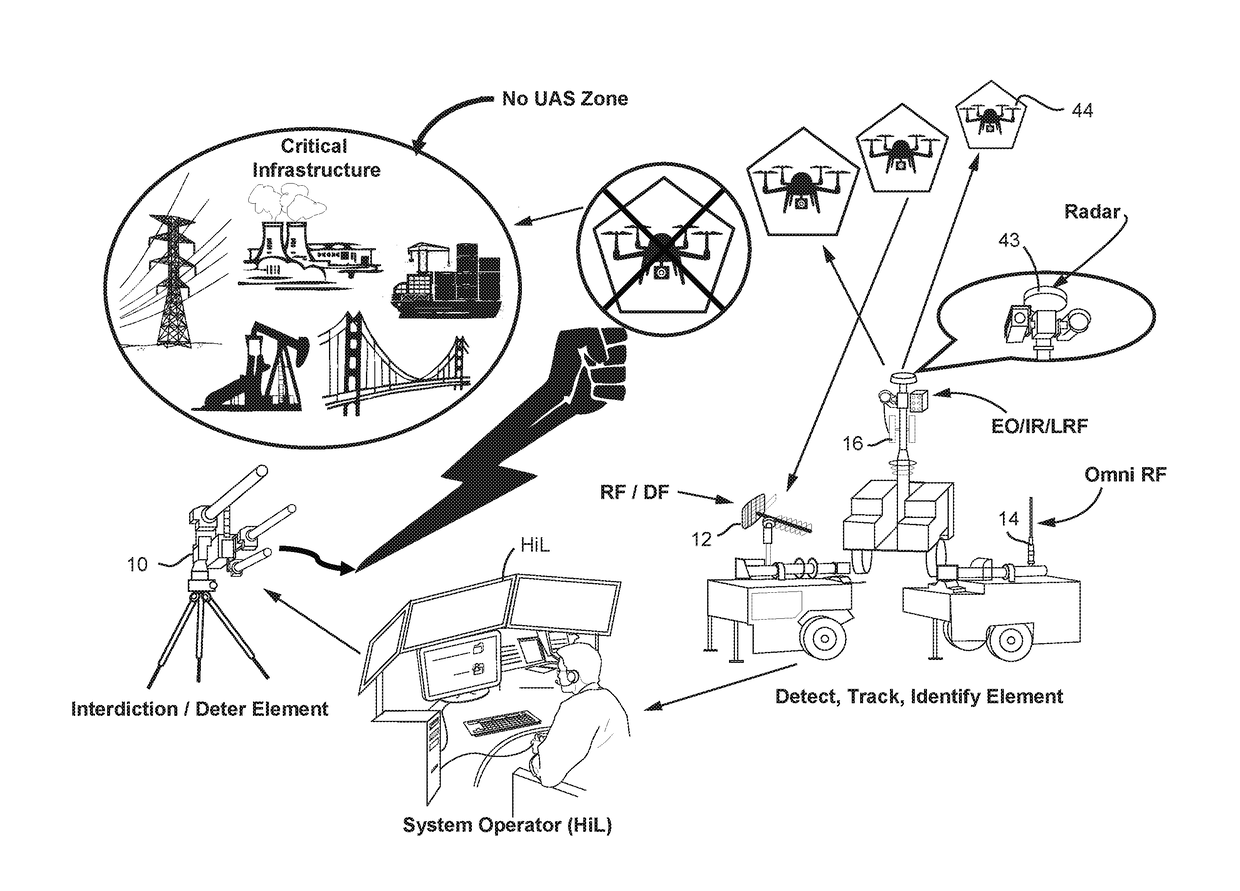
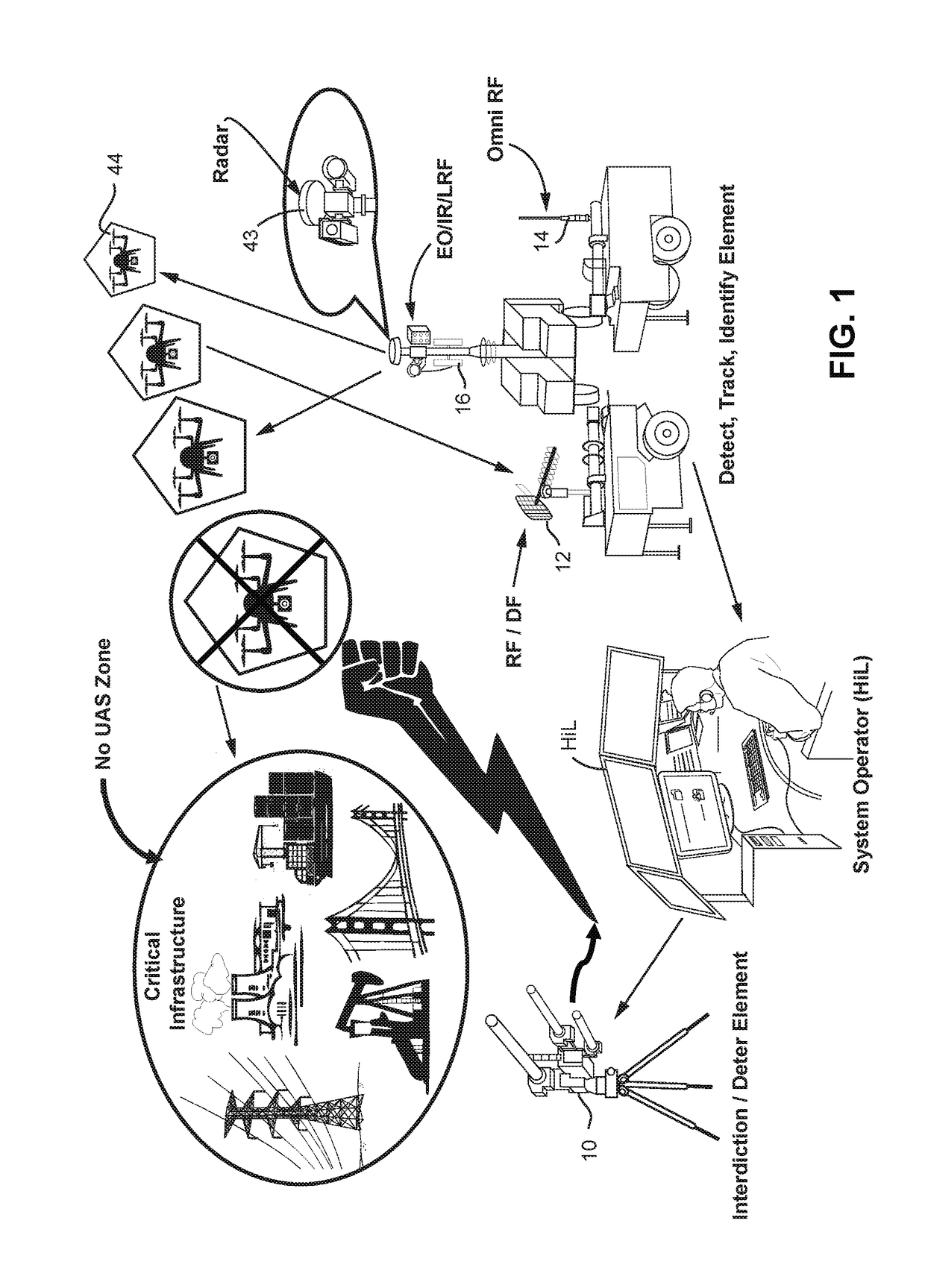
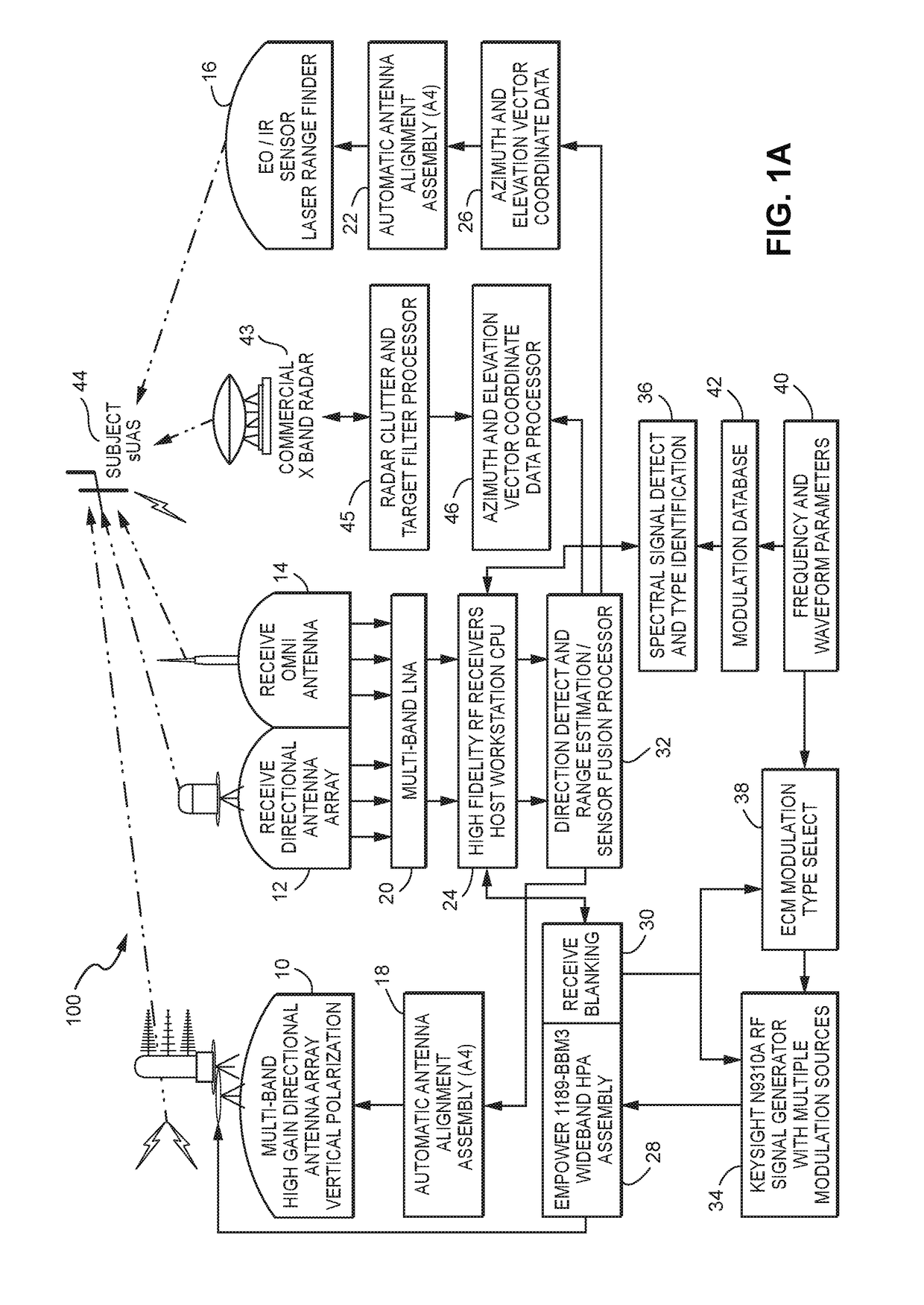
Deterent for unmanned aerial systems
ActiveUS20170192089A1Defence devicesDirection/deviation determining electromagnetic systemsNon destructiveAutomated algorithm
A system (100) for providing an integrated multi-sensor detection and countermeasure against commercial unmanned aerial systems / vehicles (44) and includes a detecting element (103, 104, 105), a tracking element (103,104, 105) an identification element (103, 104, 105) and an interdiction element (102). The detecting element detects an unmanned aerial vehicle in flight in the region of, or approaching, a property, place, event or very important person. The tracking element determines the exact location of the unmanned aerial vehicle. The identification / classification element utilizing data from the other elements generates the identification and threat assessment of the UAS. The interdiction element, based on automated algorithms can either direct the unmanned aerial vehicle away from the property, place, event or very important person in a non-destructive manner, or can disable the unmanned aerial vehicle in a destructive manner. The interdiction process may be over ridden by intervention by a System Operator / HiL.
Owner:XIDRONE SYST INC
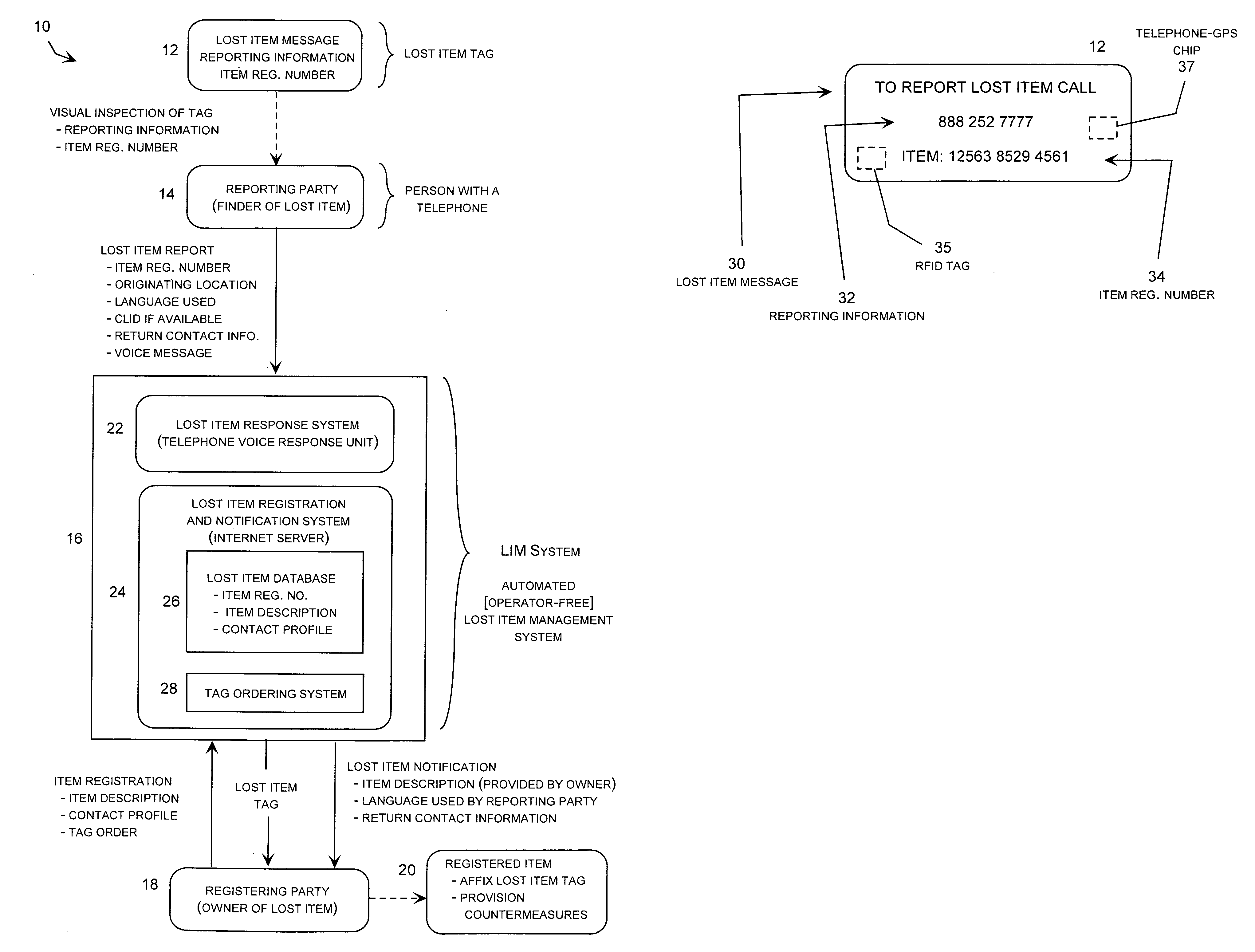
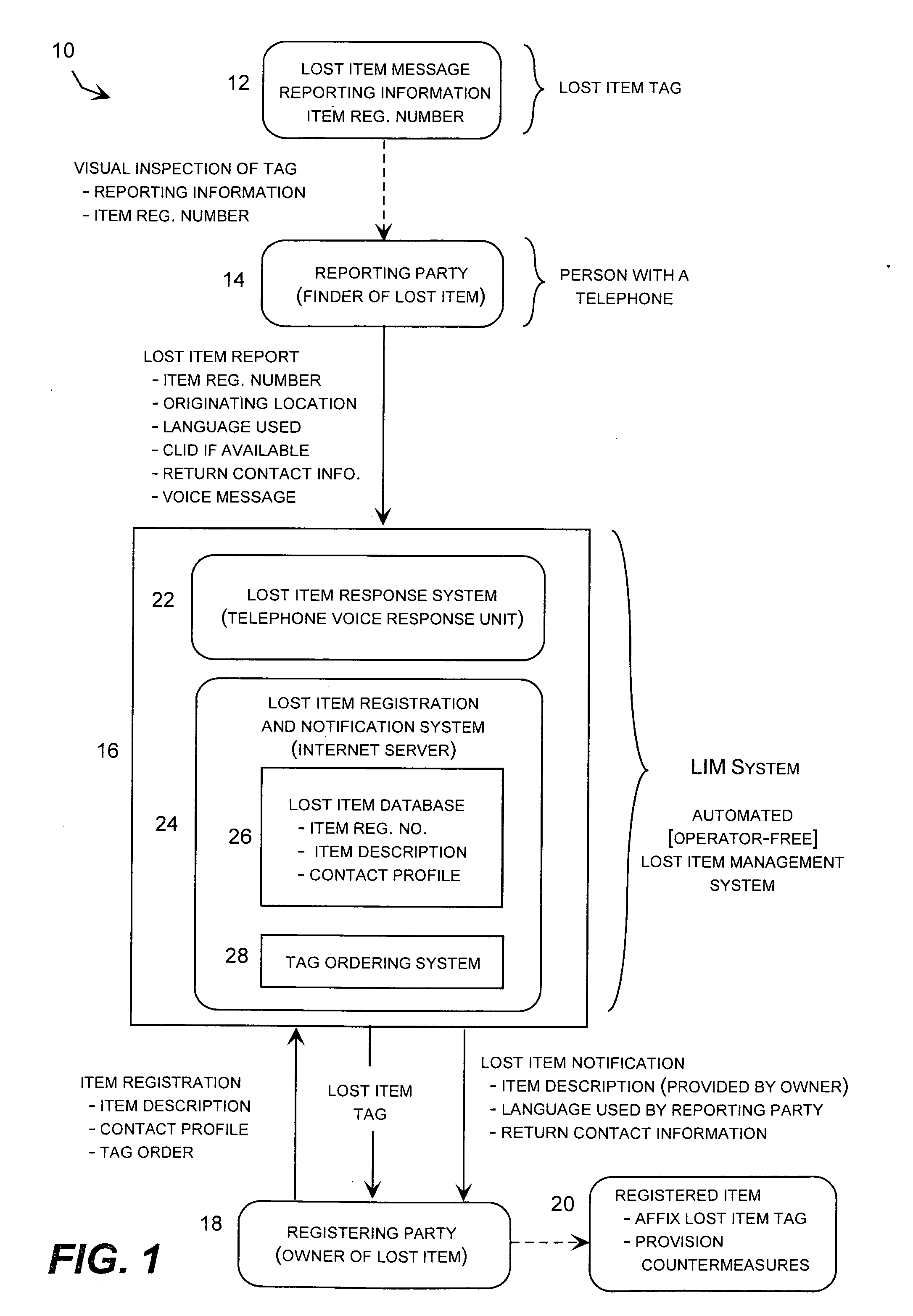
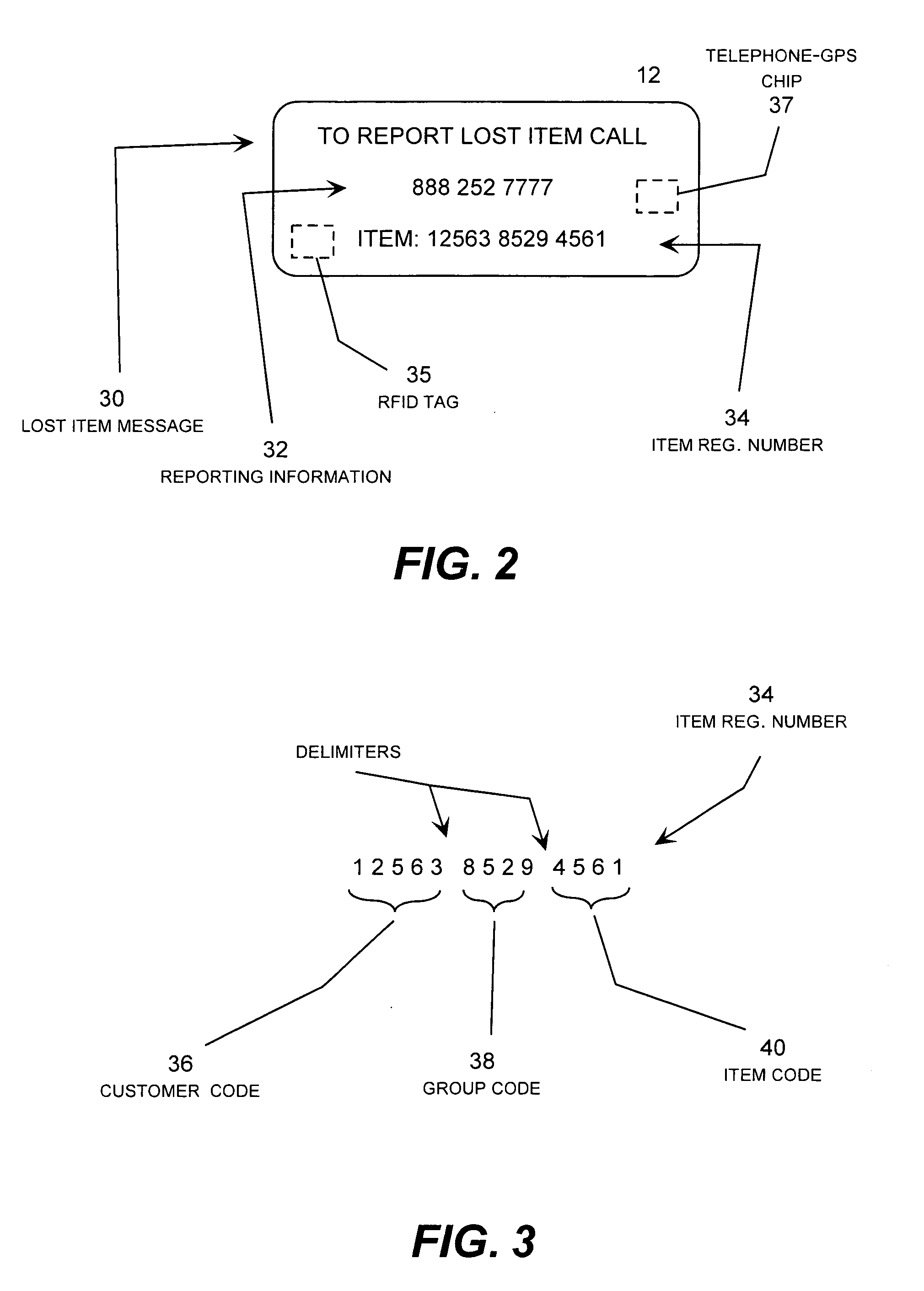
Lost item notification and recovery system
InactiveUS20080079581A1Minimization requirementsPromote recoveryFrequency-division multiplex detailsTime-division multiplexCountermeasureReward system
A largely or totally automated lost item notification and recovery system that avoids language barriers by providing a short description of the item entered by the subscriber and stored in a database in any lost item notification message communicated to the subscriber concerning the item. The lost item notification message may also include an indication of the language used by the reporting party when placing the lost item report, and may also include an indication of the geographic location where the lost item report originated. The system may also activate pre-defined countermeasures associated with the lost item once the item has been reported lost and implement a reward system providing compensation to the reporting party or others upon successful return of the lost item.
Owner:PRICE TOM
Device and method for controlling robot arm, robot, and robot arm control program
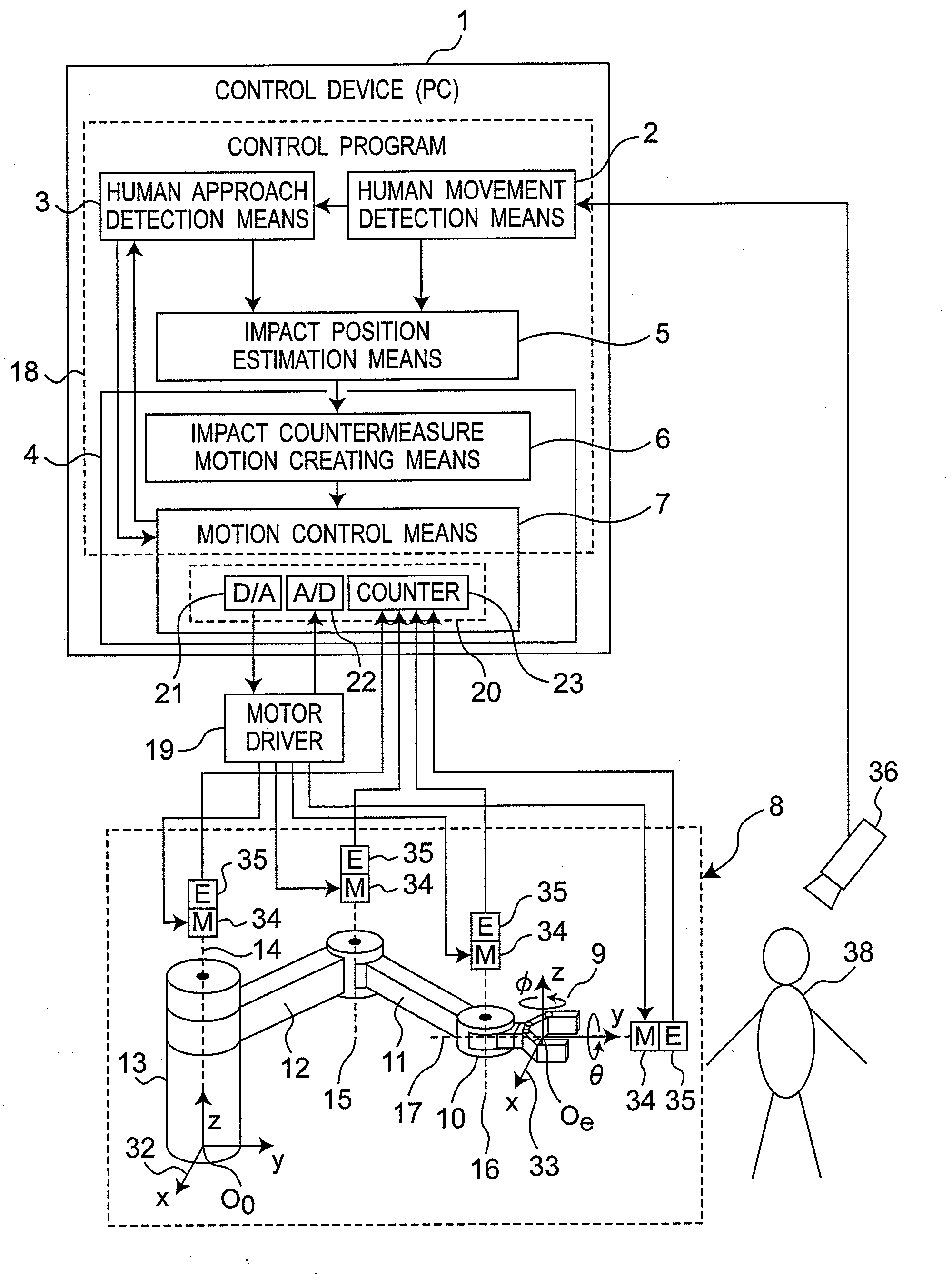
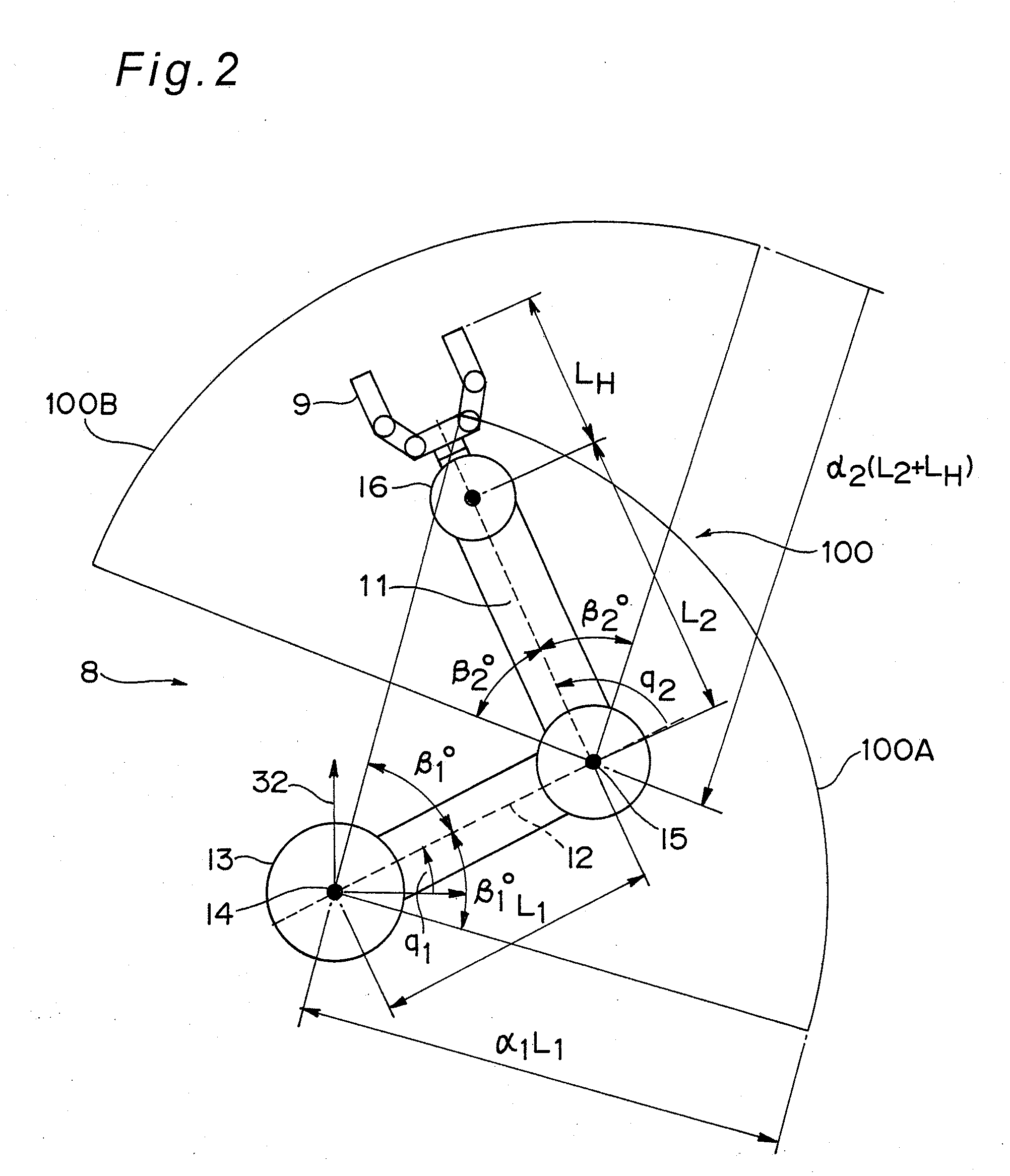
ActiveUS20090171505A1Easy to moveReduce impactProgramme controlProgramme-controlled manipulatorCountermeasureSimulation
A control device (1) for a robot arm (8) which, if a human approach detection unit (3) detects approach of a person, performs control according to the impact between the robot arm (8) and the person, through an impact countermeasure motion control unit (4), by setting individual mechanical impedances for the respective joint portions of the robot arm (8) on the basis of the movement of the person detected by a human movement detection unit (2).
Owner:PANASONIC CORP
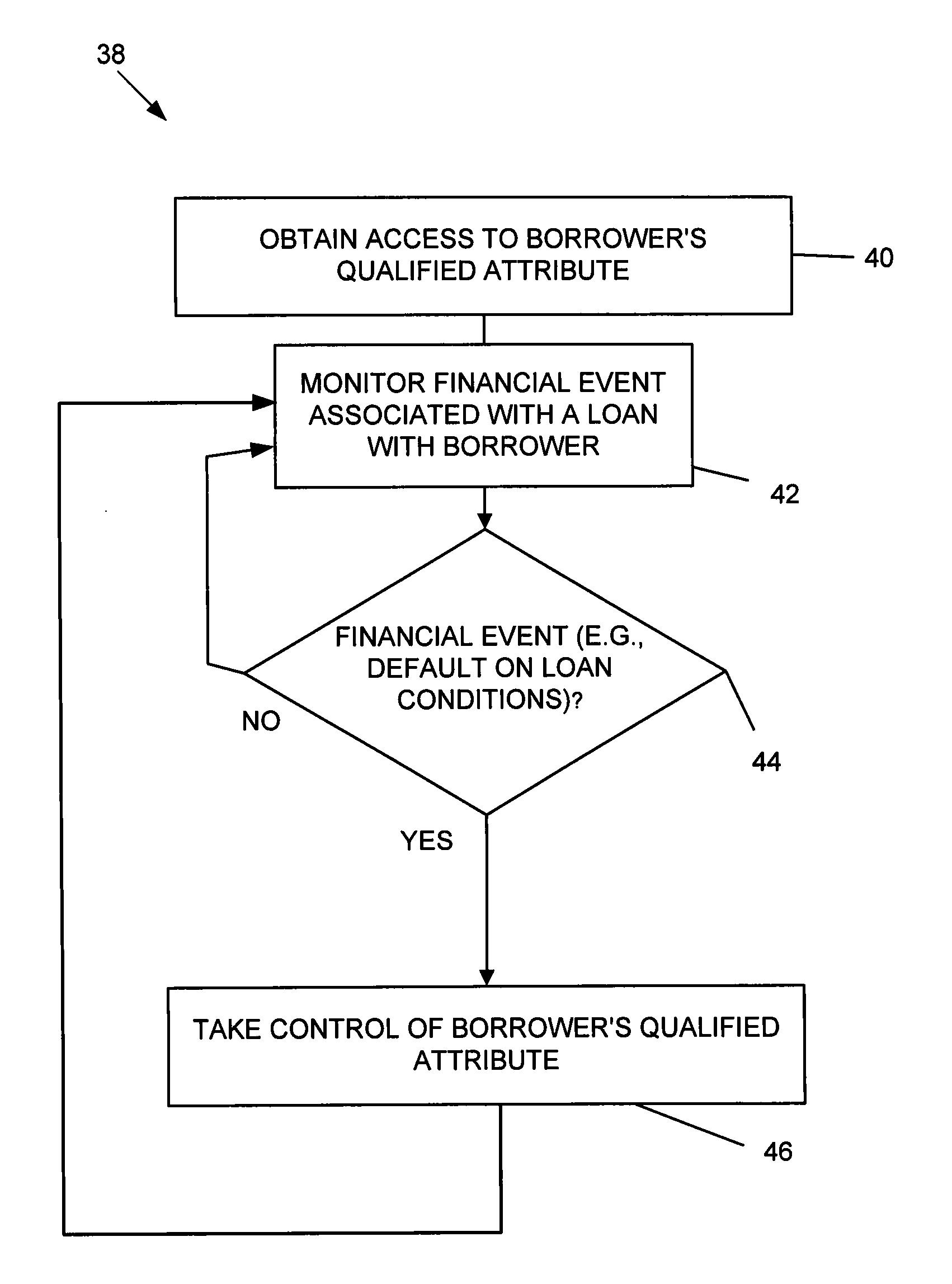
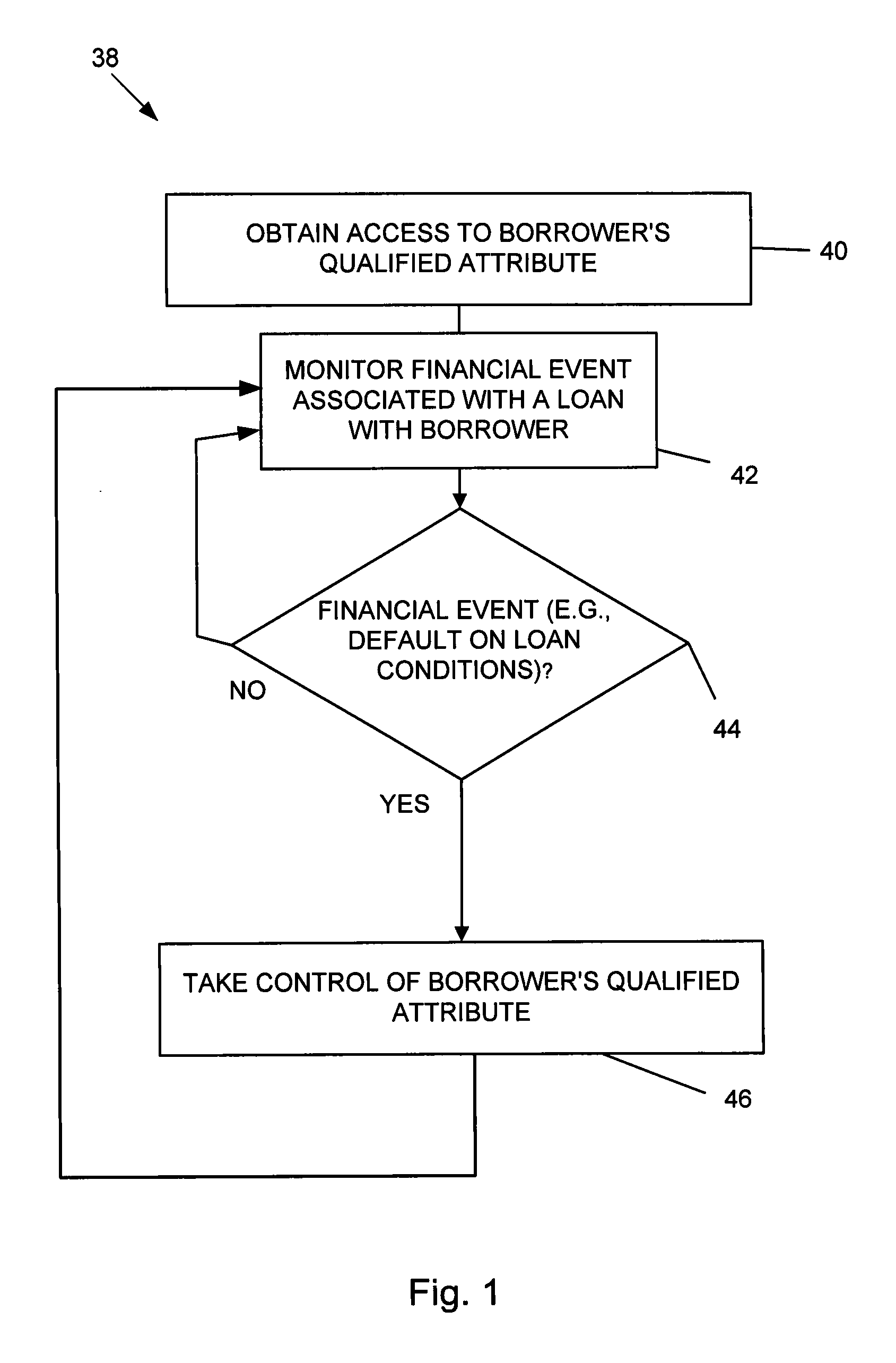
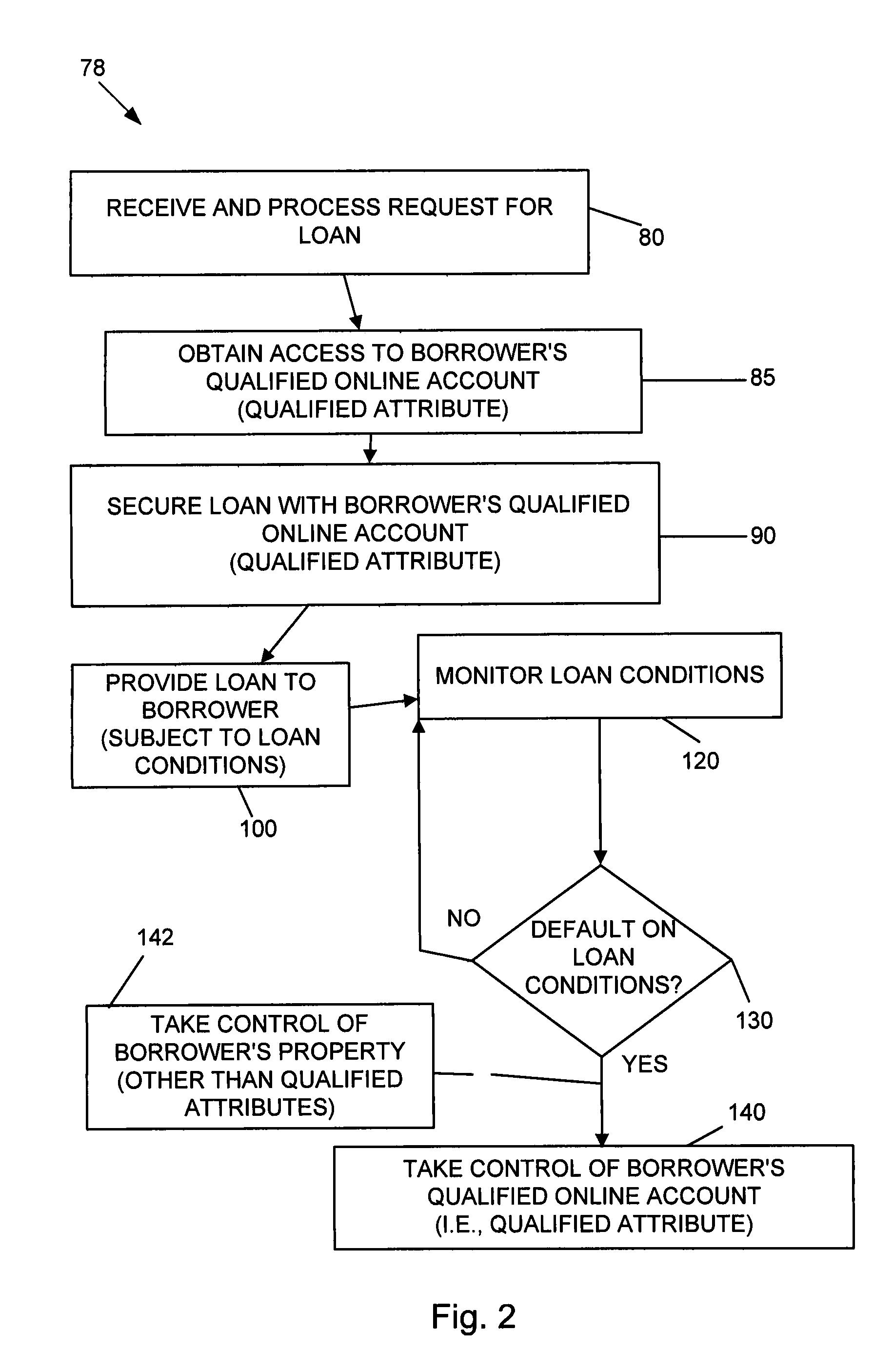
Systems and methods for underwriting loans
Systems and methods are disclosed for underwriting loans. Some embodiments increase the likelihood of repayment by obtaining access to a qualified attribute of a borrower by a first computer component, monitoring by a second computer component for a financial event associated with the loan to the borrower, and taking control of the qualified attribute of the borrower by a third computer component. Taking control may include notifying social contacts. Securing the loan by taking various security interests and technical countermeasures against the borrower re-obtaining access or re-taking control are disclosed. Providing loans, receiving loan applications, providing loans proceeds, processing payments, and underwriting criteria are disclosed. Underwriting employing social contacts for recommendations, loan guarantees, social contact credit scores, public repayment promises, loan repayment coaches, fraud criteria, crowdsourced risk evaluation, social graphs, borrower stability factors derived from social graphs, data associated with online information repositories, and efficacy of notification are disclosed.
Owner:SOCIOGRAMICS
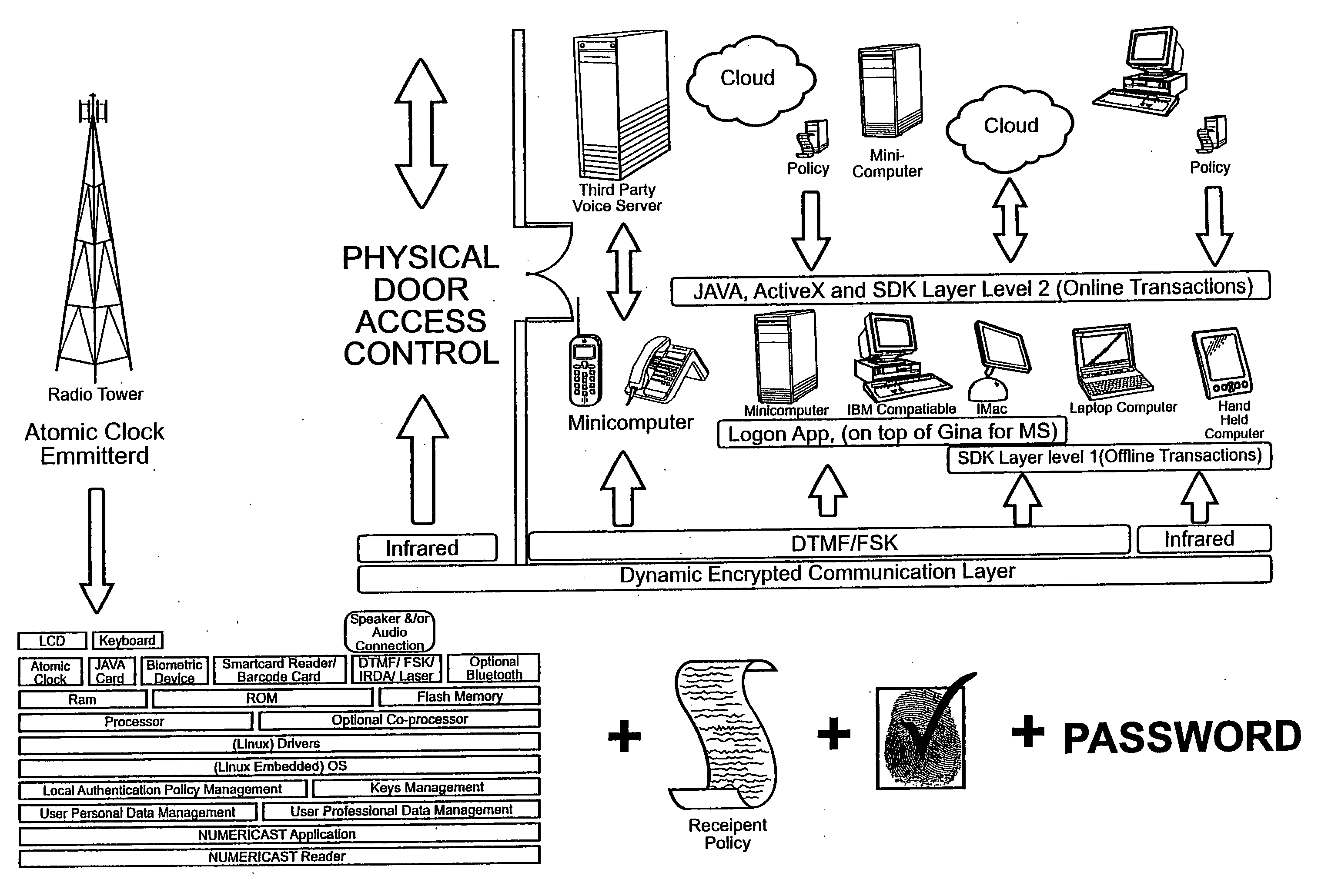
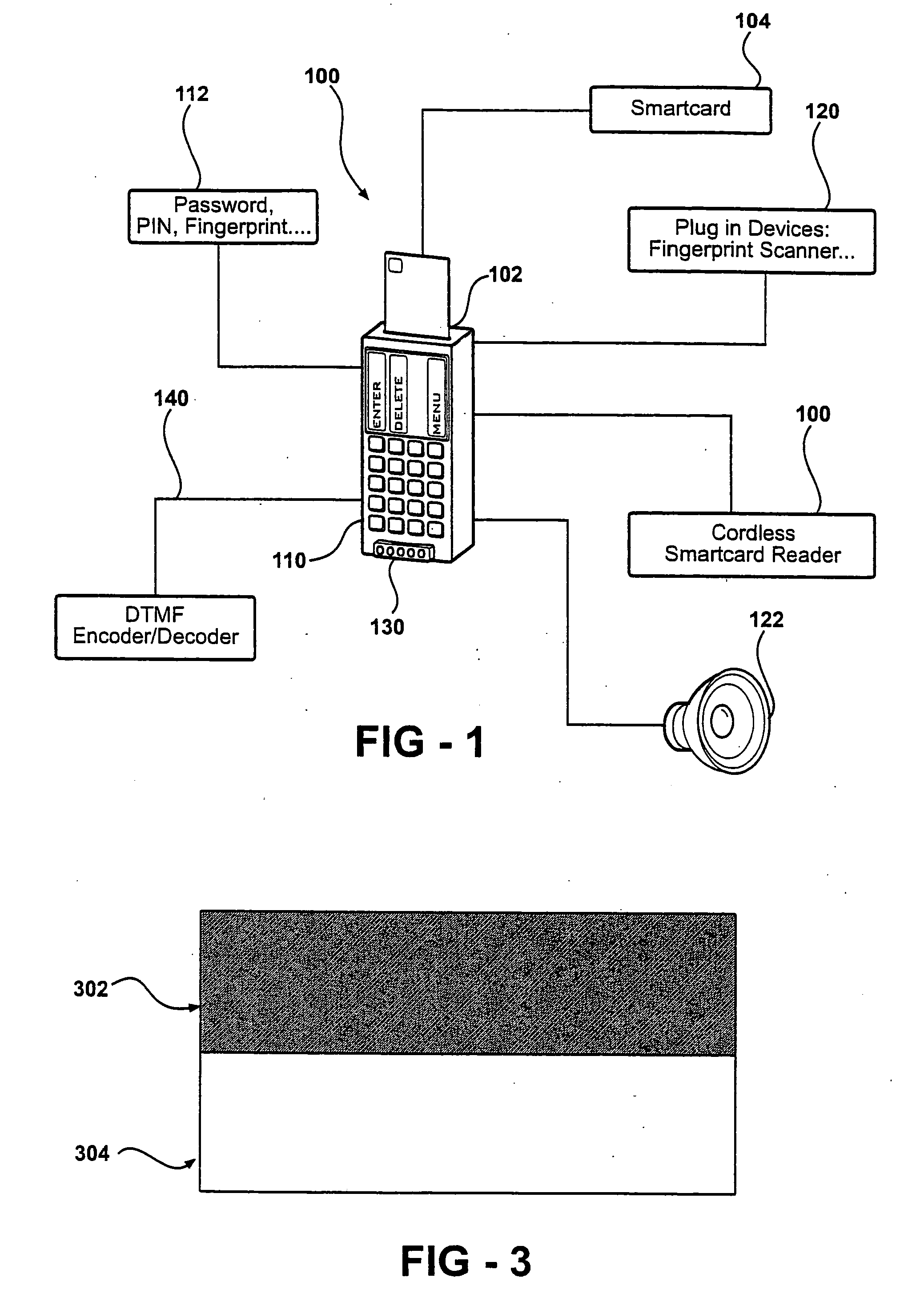
Authentication methods and apparatus for vehicle rentals and other applications
InactiveUS20050001028A1Strong authenticationTicket-issuing apparatusPayment architectureEmbedded securitySmart card
An autonomous and portable smartcard reader device incorporates a high level of embedded security countermeasures. Data transfers are encrypted with two specific input devices, namely a light sensor and PIN or other keyboard entry, and at the output through the use of a dual-tone encoder-decoder. The unit may be used alone or as a plug-in to another device such as a PDA, cell phone, or remote control. The reader may further be coupled to various biometric or plug-in devices to achieve at least five levels of authentication, namely, (1) the smartcard itself; (2) the smartcard reader; (2) the PIN; (3) private-key cryptography (PKI); and (5) the (optional) biometric device. These five levels account for an extremely strong authentication applicable to public networking on public / private computers, and even on TV (satellite, cable, DVD, CD AUDIO, software applications. Transactions including payments may be carried out without any risk of communication tampering, authentication misconduct or identity theft. The invention finds utility in a wide range of applications, including commercial transactions and security, including the generation of prepaid credit / debit card numbers, vehicle rental, and other uses.
Owner:BRITE SMART
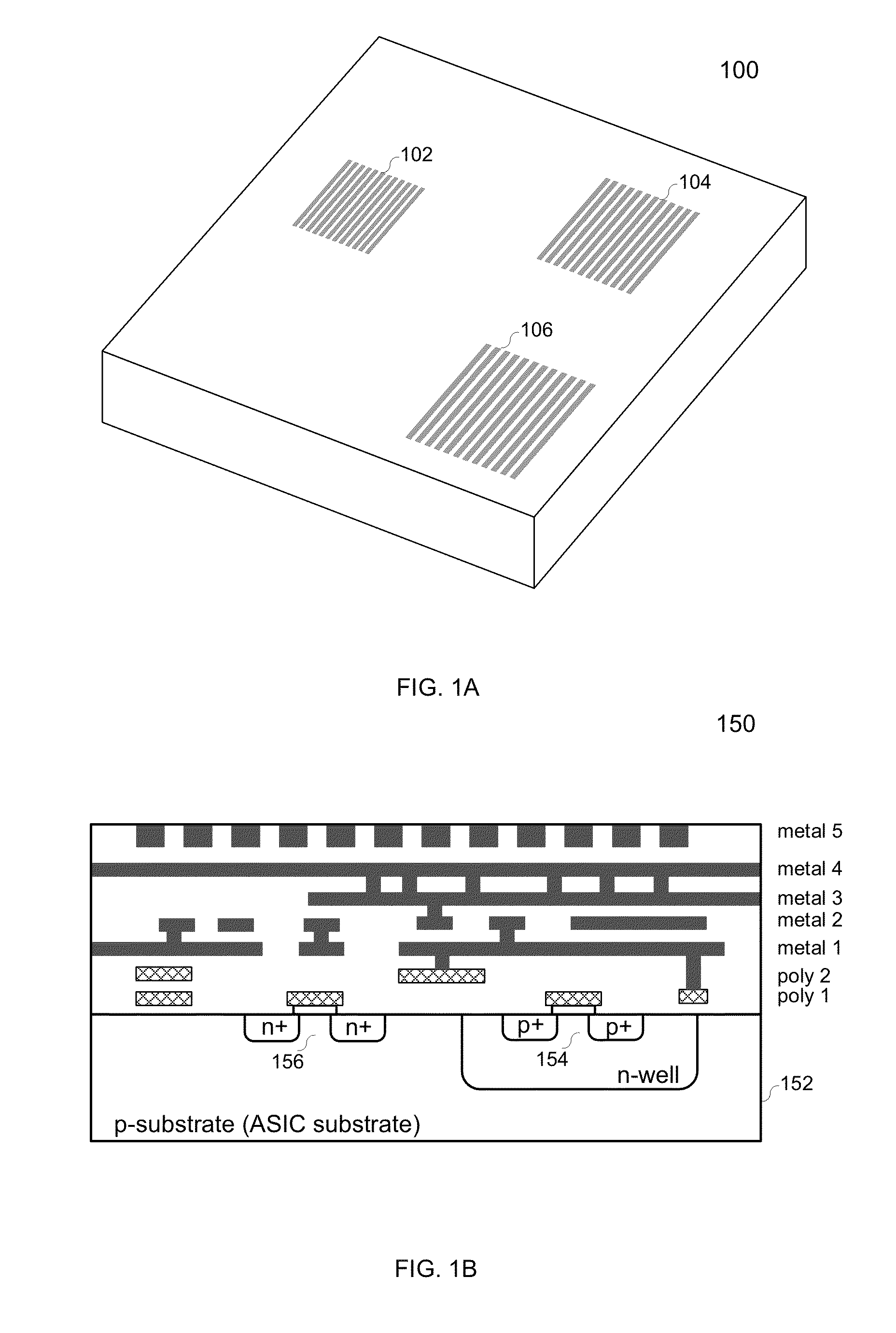
Tamper detection countermeasures to deter physical attack on a security asic
ActiveUS20130104252A1Error detection/correctionVolume/mass flow measurementCountermeasureNumber generator
Various embodiments of the present invention relates generally to an integrated circuit, and more particularly, to systems, devices and methods of incorporating a tamper detection countermeasure into a security ASIC to deter physical attacks. The tamper detection countermeasure architects an active mesh to cover a sensitive area in the security ASIC. A plurality of time-varying random numbers is generated by a random number generator (RNG), and the active mesh is driven and configured according to these random numbers. During tamper detection cycles, the active mesh is monitored with respect to the plurality of random numbers that is directly provided by the RNG. Upon a tampering attempt, a flag signal is generated and used to initialize subsequent anti-tampering actions. The active mesh may be controlled and monitored based on time-varying codes, and therefore, an adversary may not easily bypass the active mesh and attack the sensitive area.
Owner:MAXIM INTEGRATED PROD INC
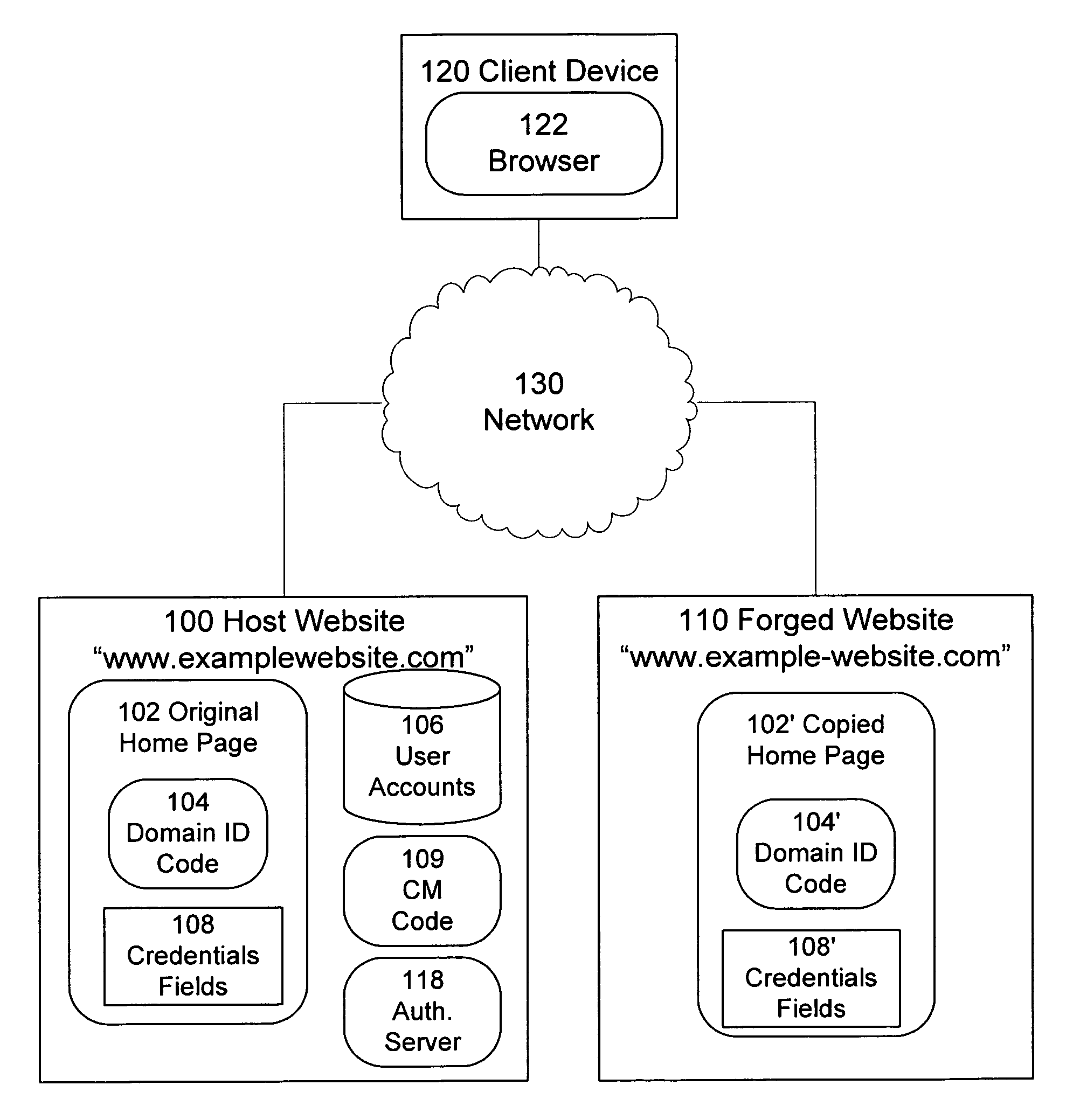
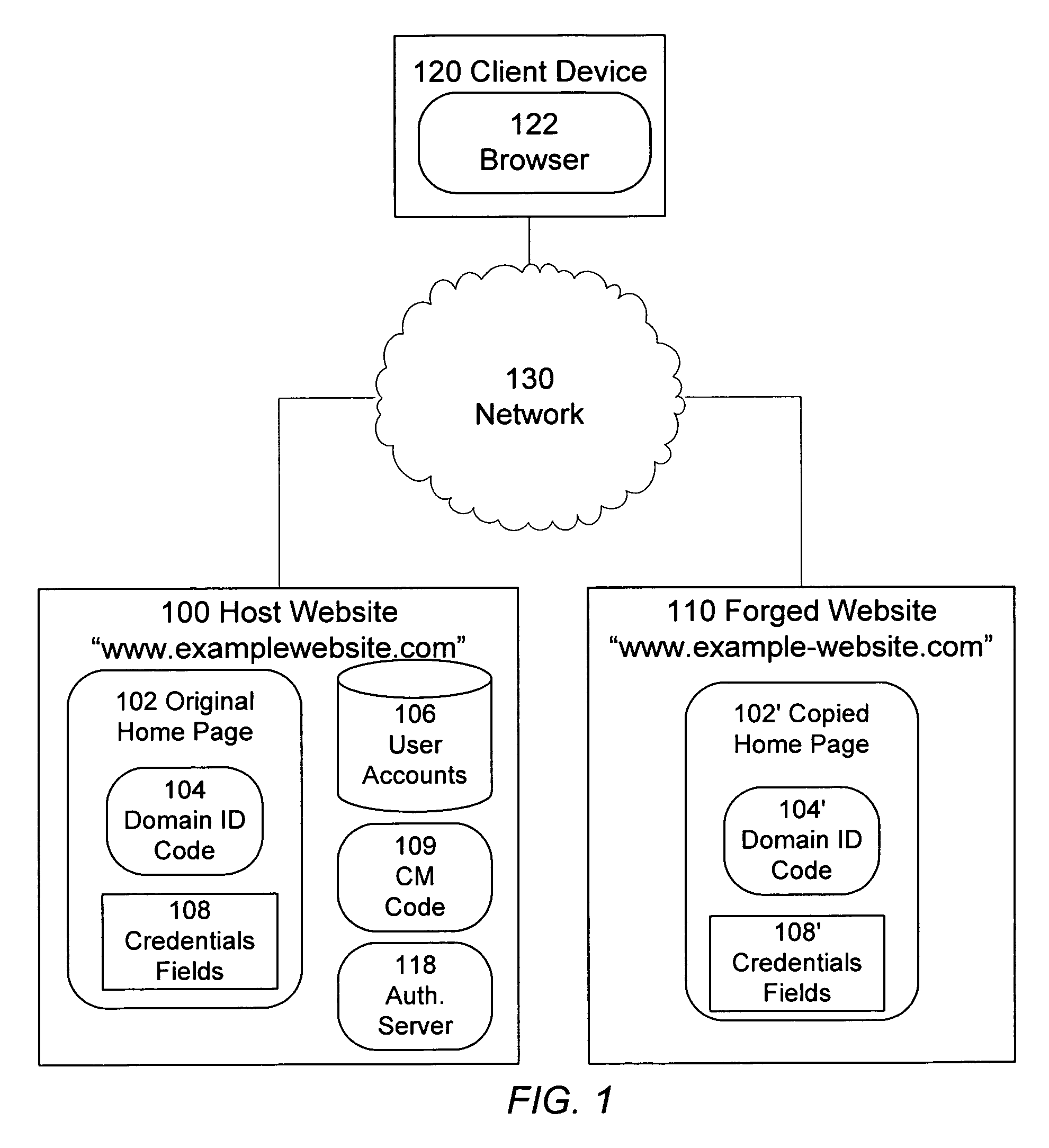
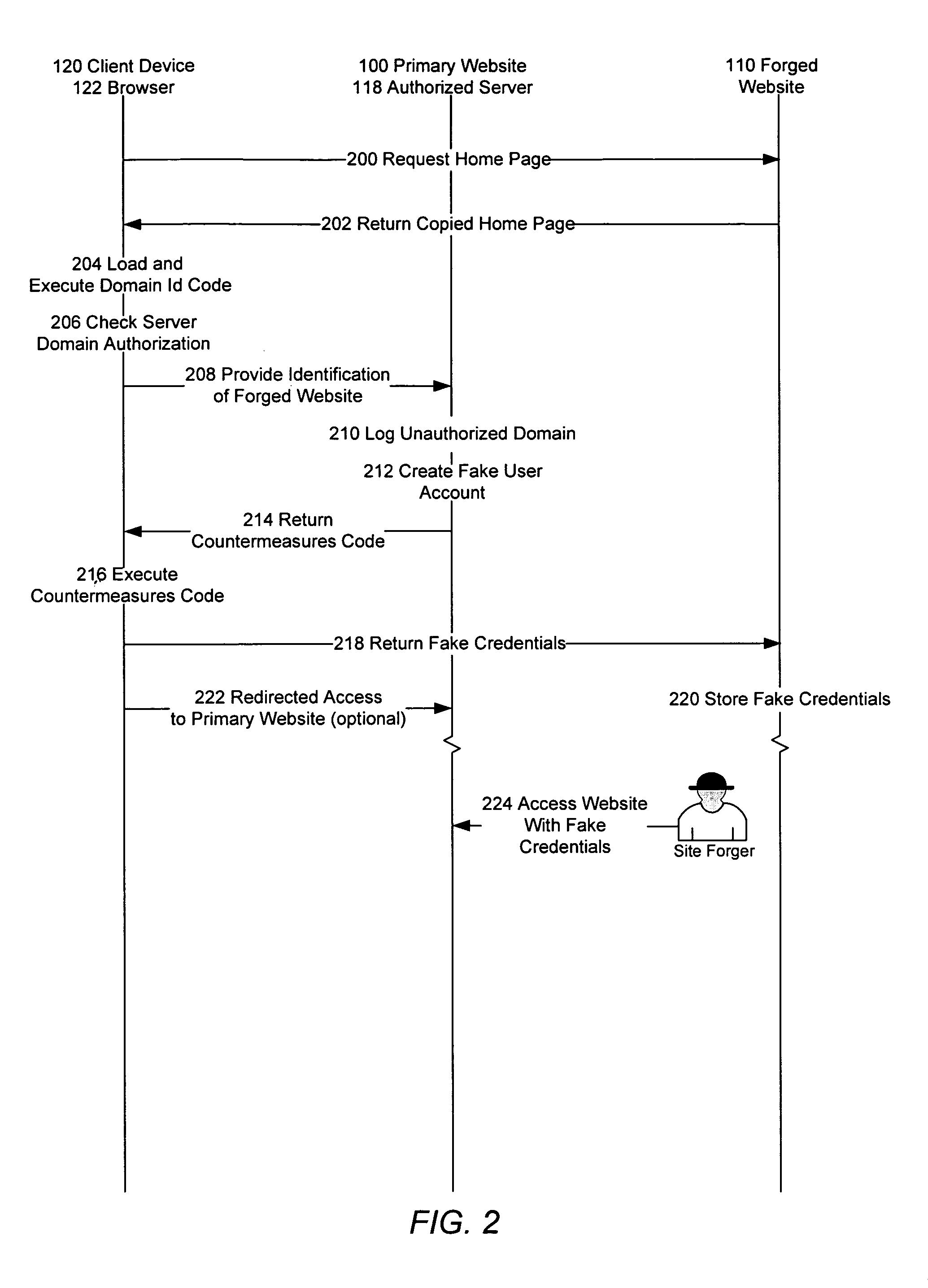
Identification of and countermeasures against forged websites
A system, a method, and computer program product identify a website that is a forgery of a primary website. Client side executable code is included in a page of the primary website, which page is copied in the forged website. The client side code, when executed by a client device, determines whether the domain from which the page is served is an authorized domain. Where the serving domain is not authorized, the client device is configured to alter the execute countermeasures against the forged website, such as altering operation of the forged page.
Owner:META PLATFORMS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com