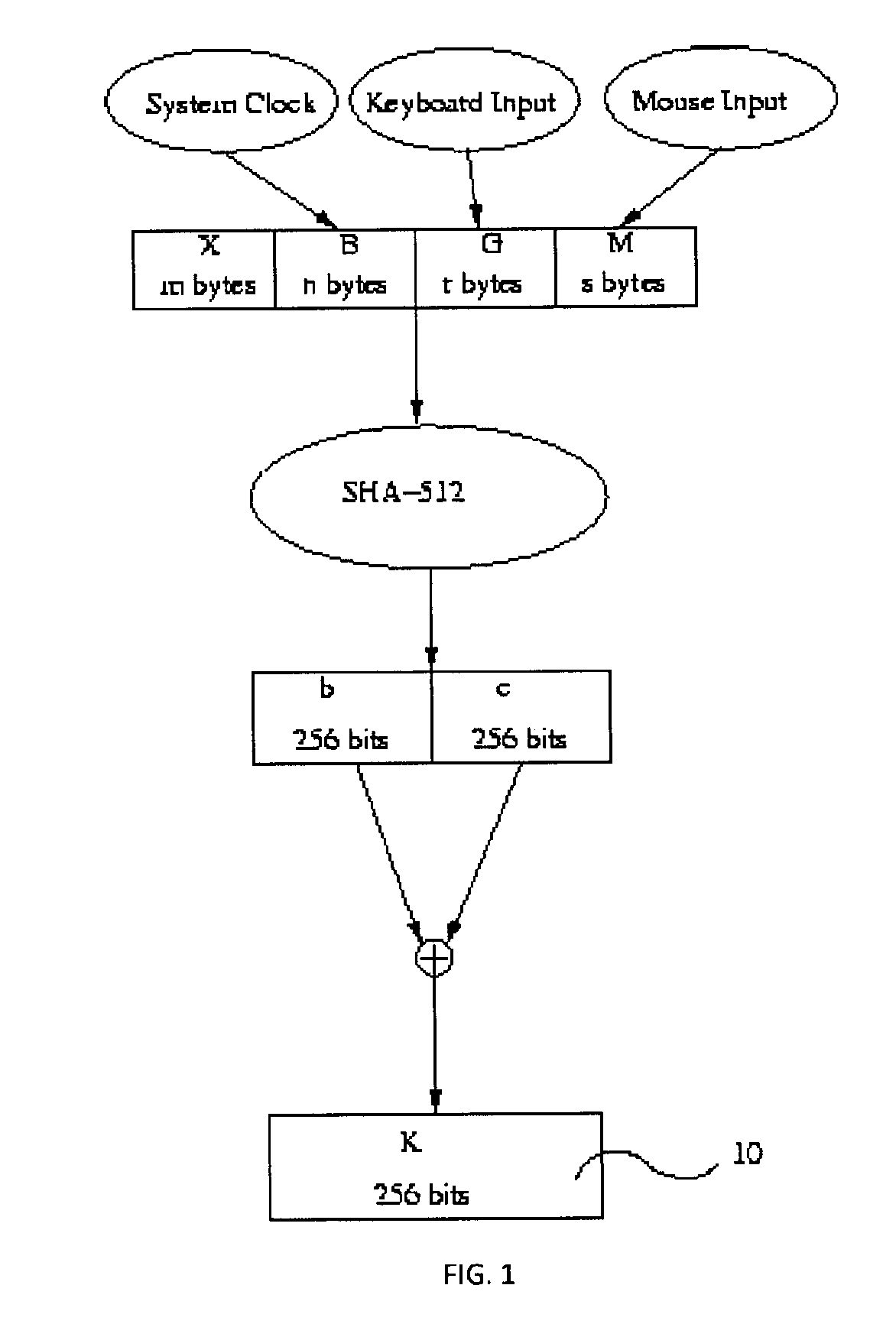
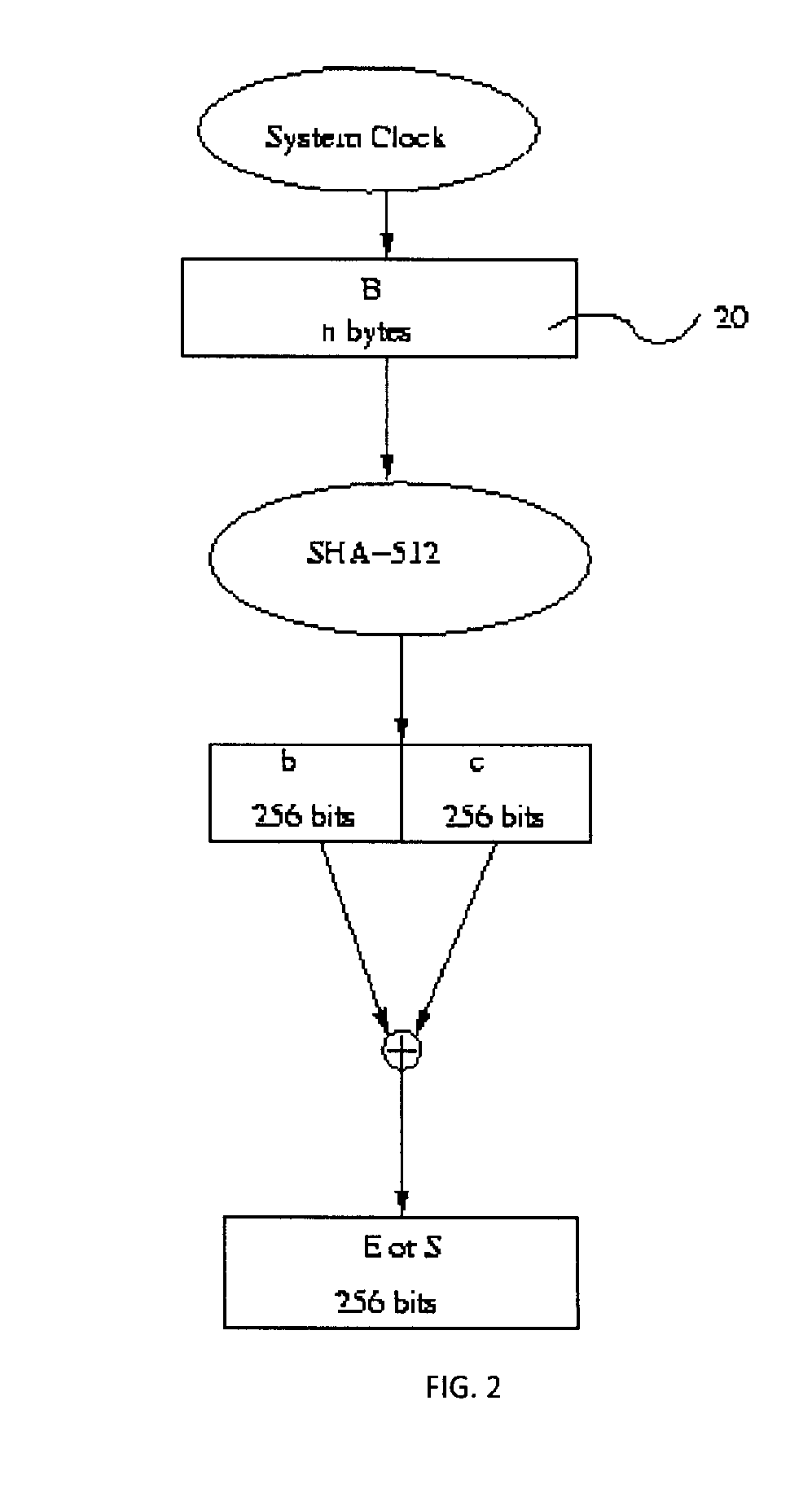
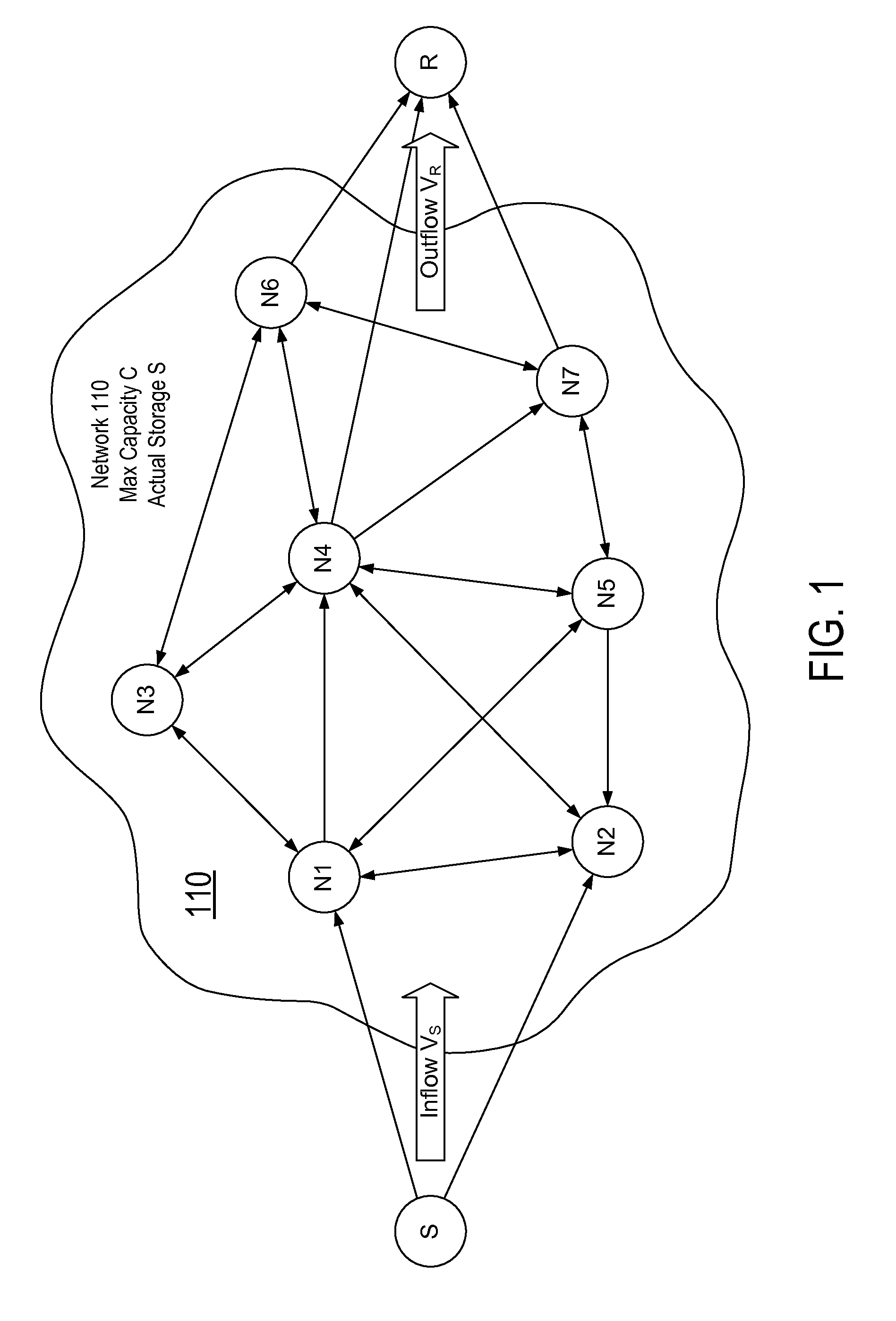
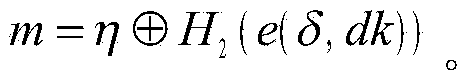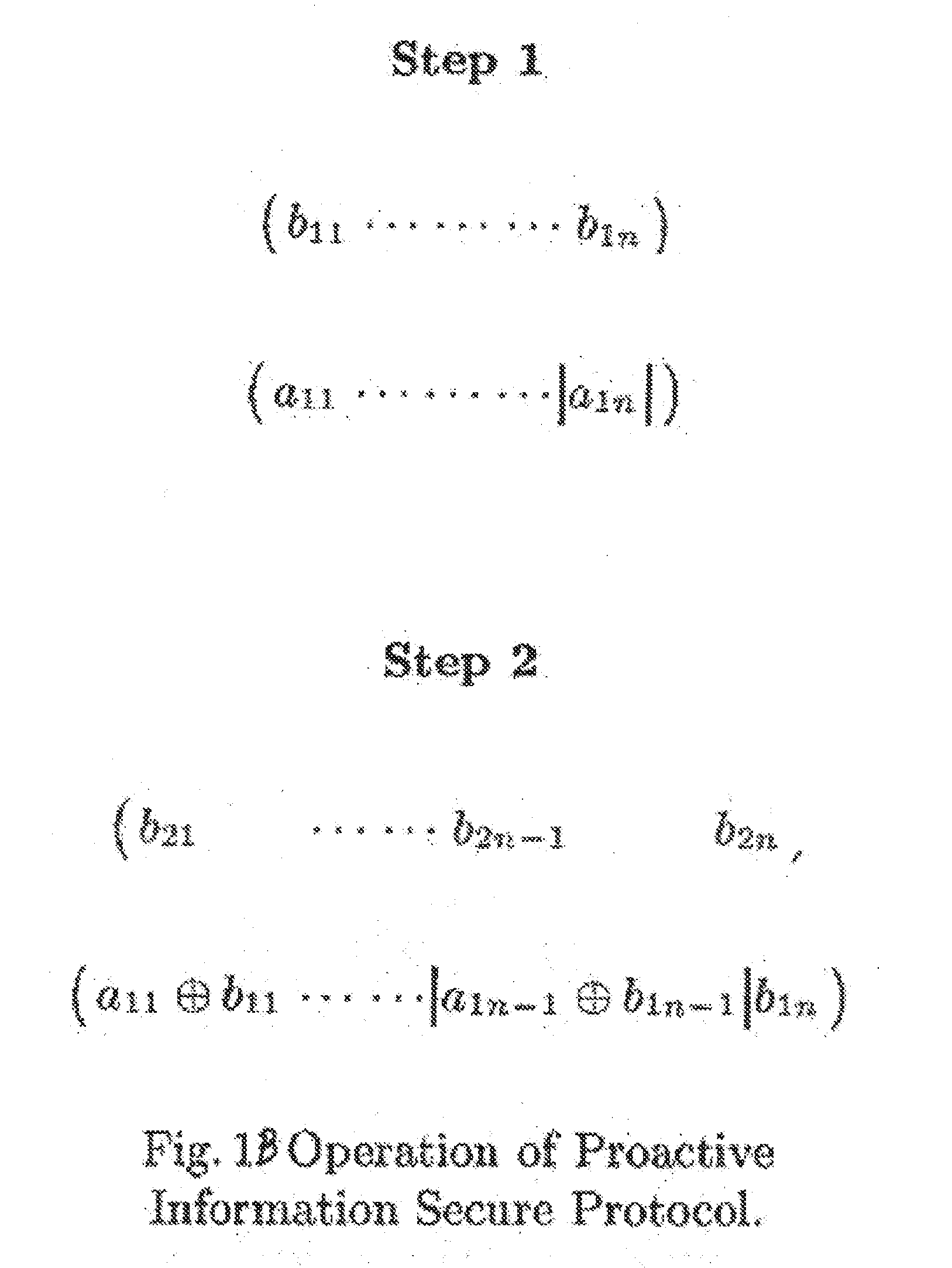Patents
Literature
64 results about "Adversary" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, an adversary (rarely opponent, enemy) is a malicious entity whose aim is to prevent the users of the cryptosystem from achieving their goal (primarily privacy, integrity, and availability of data). An adversary's efforts might take the form of attempting to discover secret data, corrupting some of the data in the system, spoofing the identity of a message sender or receiver, or forcing system downtime.
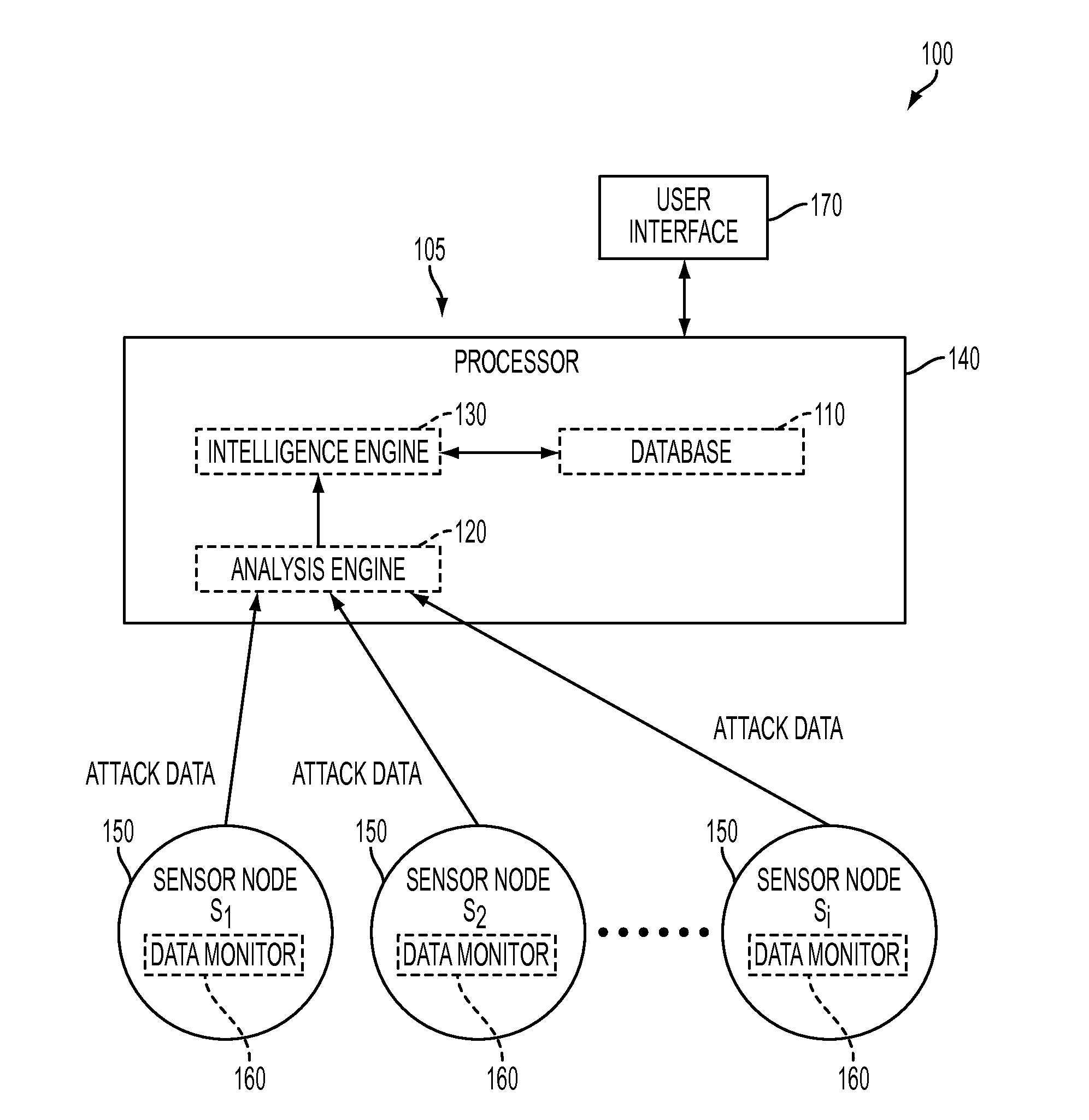
System and method for forensic cyber adversary profiling, attribution and attack identification
A system and method is provided for identifying and analyzing cyber-attacks and profiling adversaries responsible for such attacks. The system and method allows for the quantitative measurement of adversary attack behavior. The system and method is able to extract quantitative data from raw attack data and compare the quantitative data to a database of quantifiable metrics associated with known adversaries. This allows for the possible linking of a cyber-attack to a known adversary or known adversary behavior.
Owner:PARKER THOMAS W
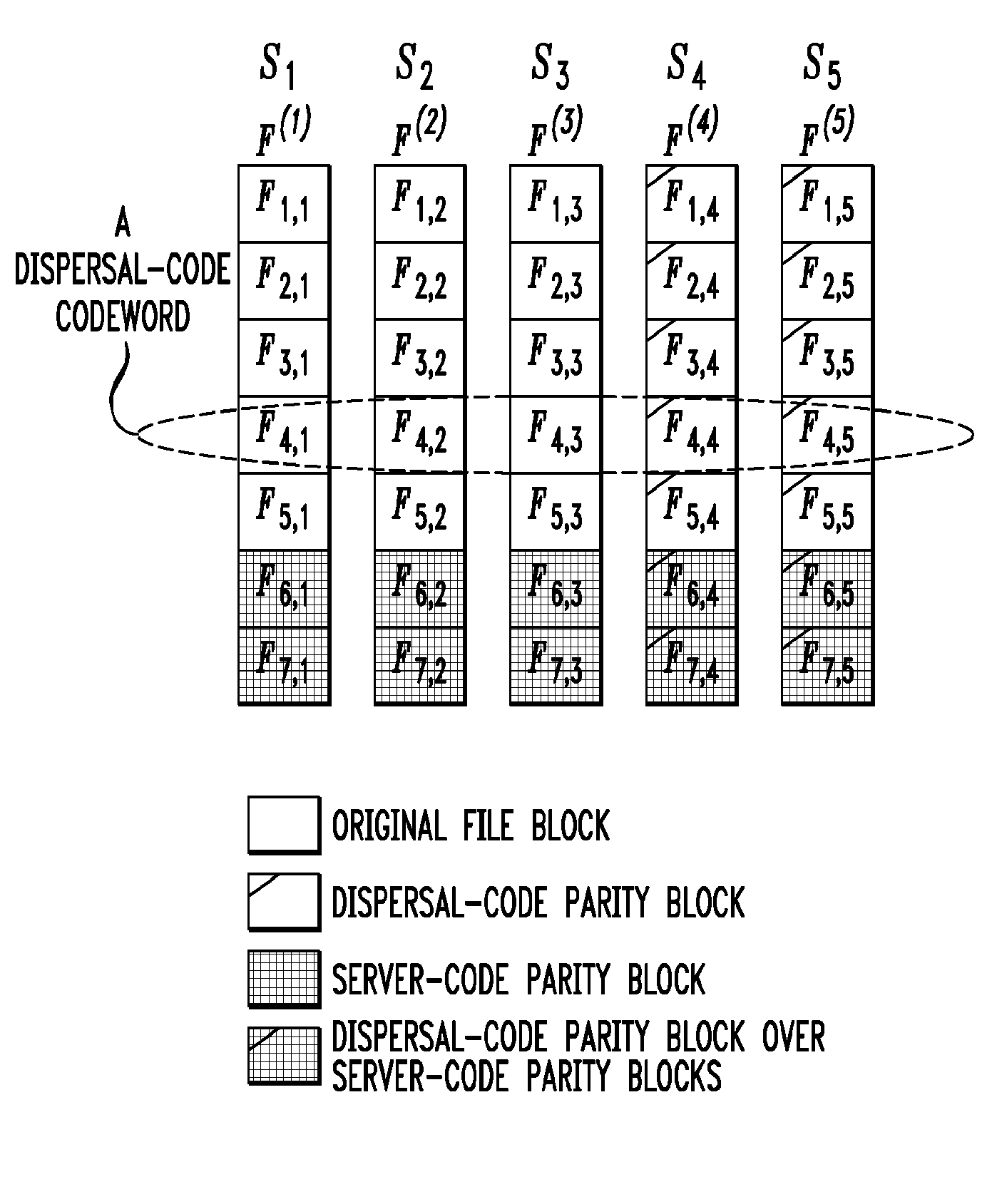
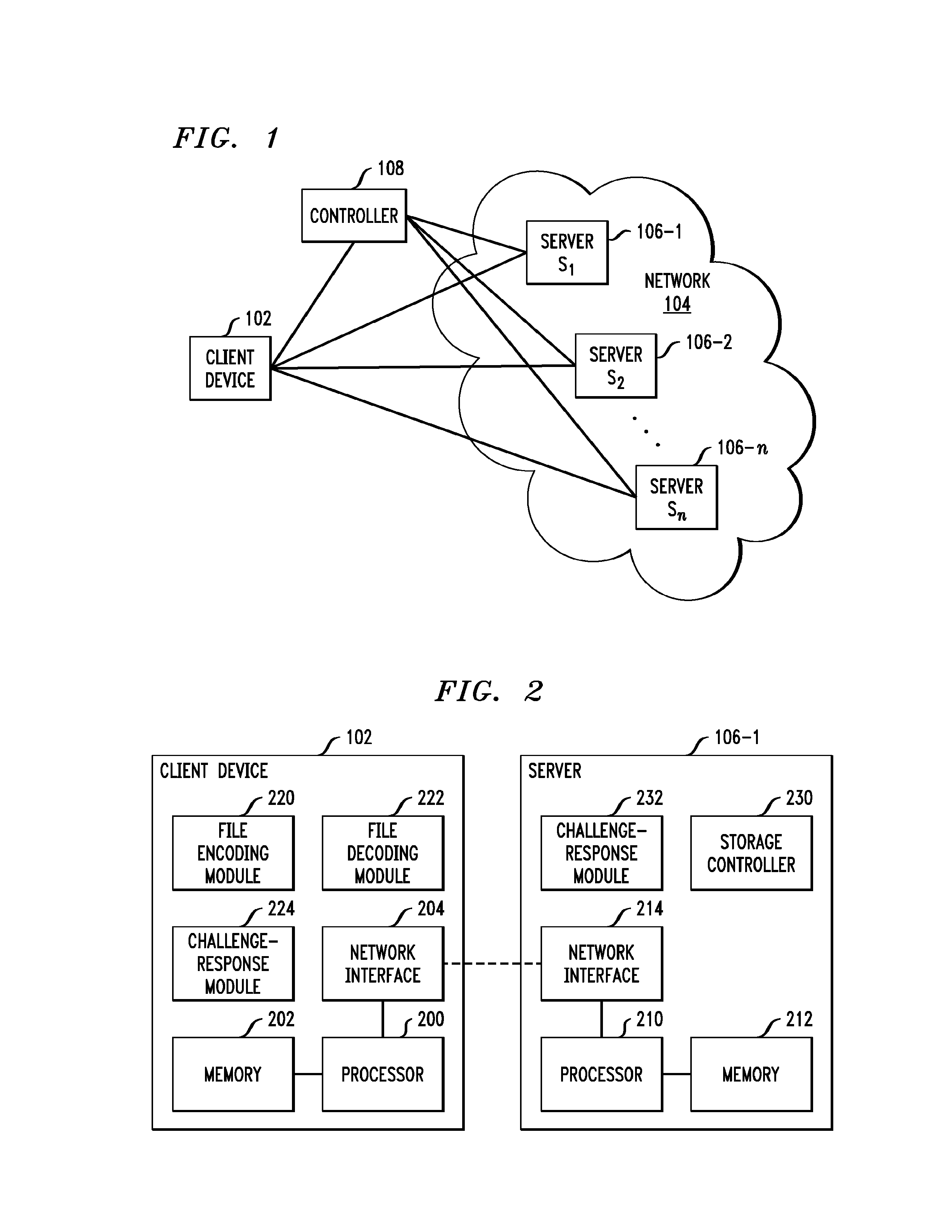
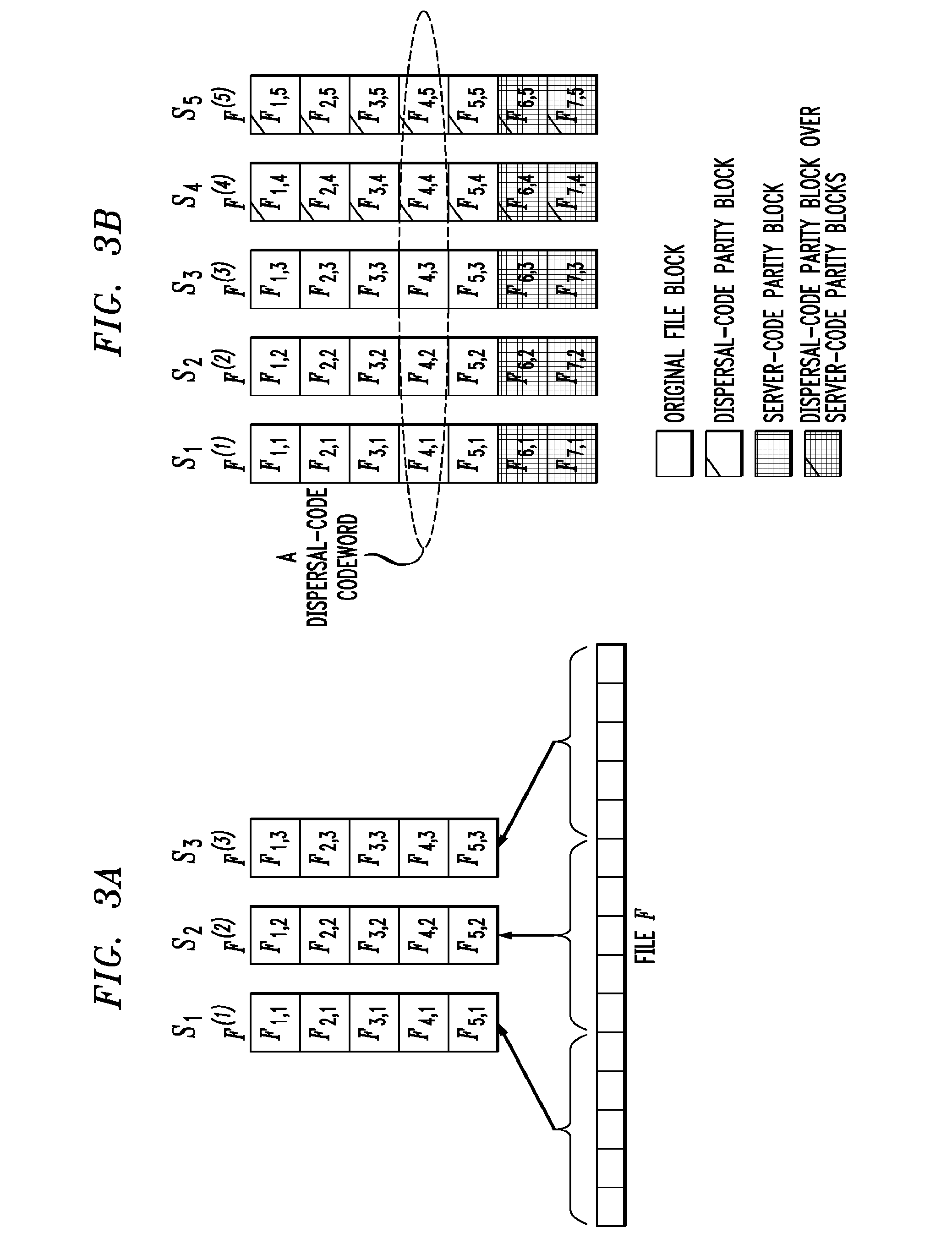
Distributed storage system with enhanced security
ActiveUS8132073B1Overcomes drawbackSufficient securityError preventionTransmission systemsTime segmentTheoretical computer science
A client device or other processing device separates a file into blocks and distributes the blocks across multiple servers for storage. In one aspect, subsets of the blocks are allocated to respective primary servers, a code of a first type is applied to the subsets of the blocks to expand the subsets by generating one or more additional blocks for each subset, and the expanded subsets of the blocks are stored on the respective primary servers. A code of a second type is applied to groups of blocks each including one block from each of the expanded subsets to expand the groups by generating one or more additional blocks for each group, and the one or more additional blocks for each expanded group are stored on respective secondary servers. The first and second codes are advantageously configured to provide security against an adversary that is able to corrupt all of the servers over multiple periods of time but fewer than all of the servers within any particular one of the periods of time.
Owner:EMC IP HLDG CO LLC
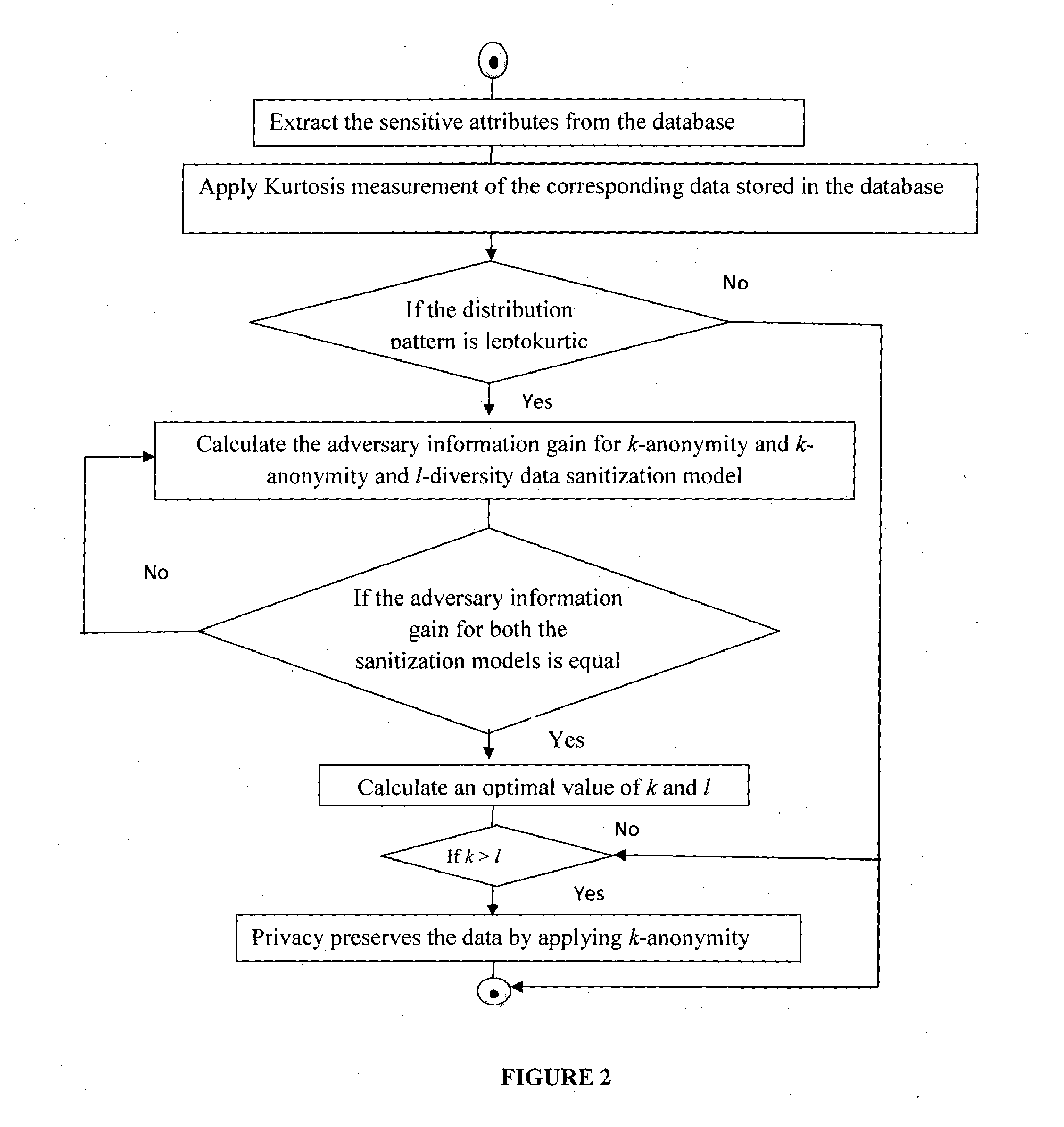
System and method for database privacy protection
ActiveUS20140237620A1Reduce complexitySame quantityDigital data processing detailsAnalogue secracy/subscription systemsK-anonymityAdversary
The invention relates to a system and a method for privacy preservation of sensitive attributes stored in a database. The invention reduces the complexity and enhances privacy preservation of the database by determining the distribution of sensitive data based on Kurtosis measurement. The invention further determines and compares the optimal value of k-sensitive attributes in k-anonymity data sanitization model with the optimal value of l sensitive attributes in l diversity data sanitization model using adversary information gain. The invention reduces the complexity of the method for preserving privacy by applying k anonymity only, when the distribution of the sensitive data is leptokurtic and optimal value of k is greater than the optimal value of l.
Owner:TATA CONSULTANCY SERVICES LTD
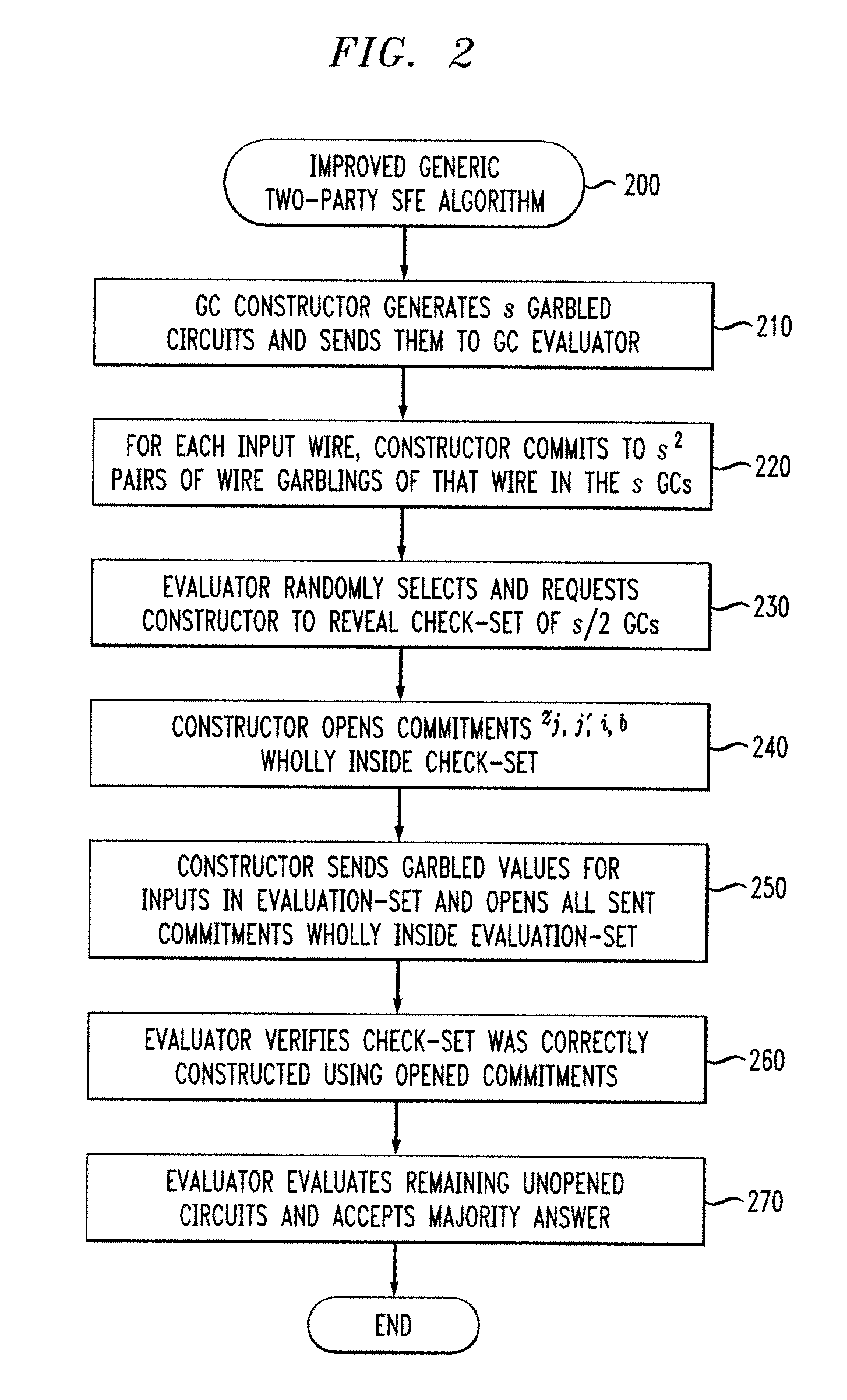
Securing Two-Party Computation Against Malicious Adversaries
InactiveUS20120070000A1Precise constructionDigital data processing detailsUser identity/authority verificationAdversarySoftware engineering
Owner:WSOU INVESTMENTS LLC
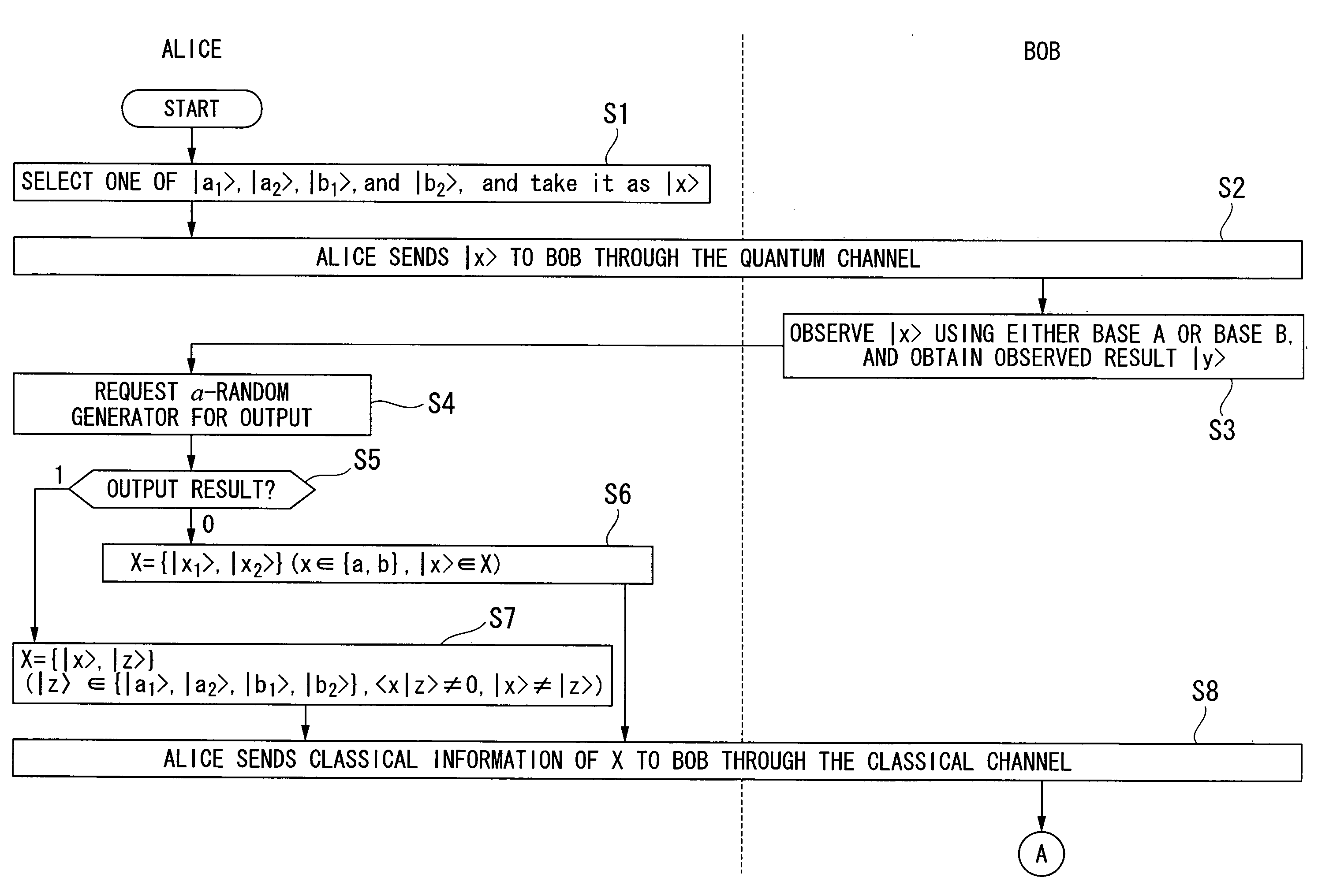
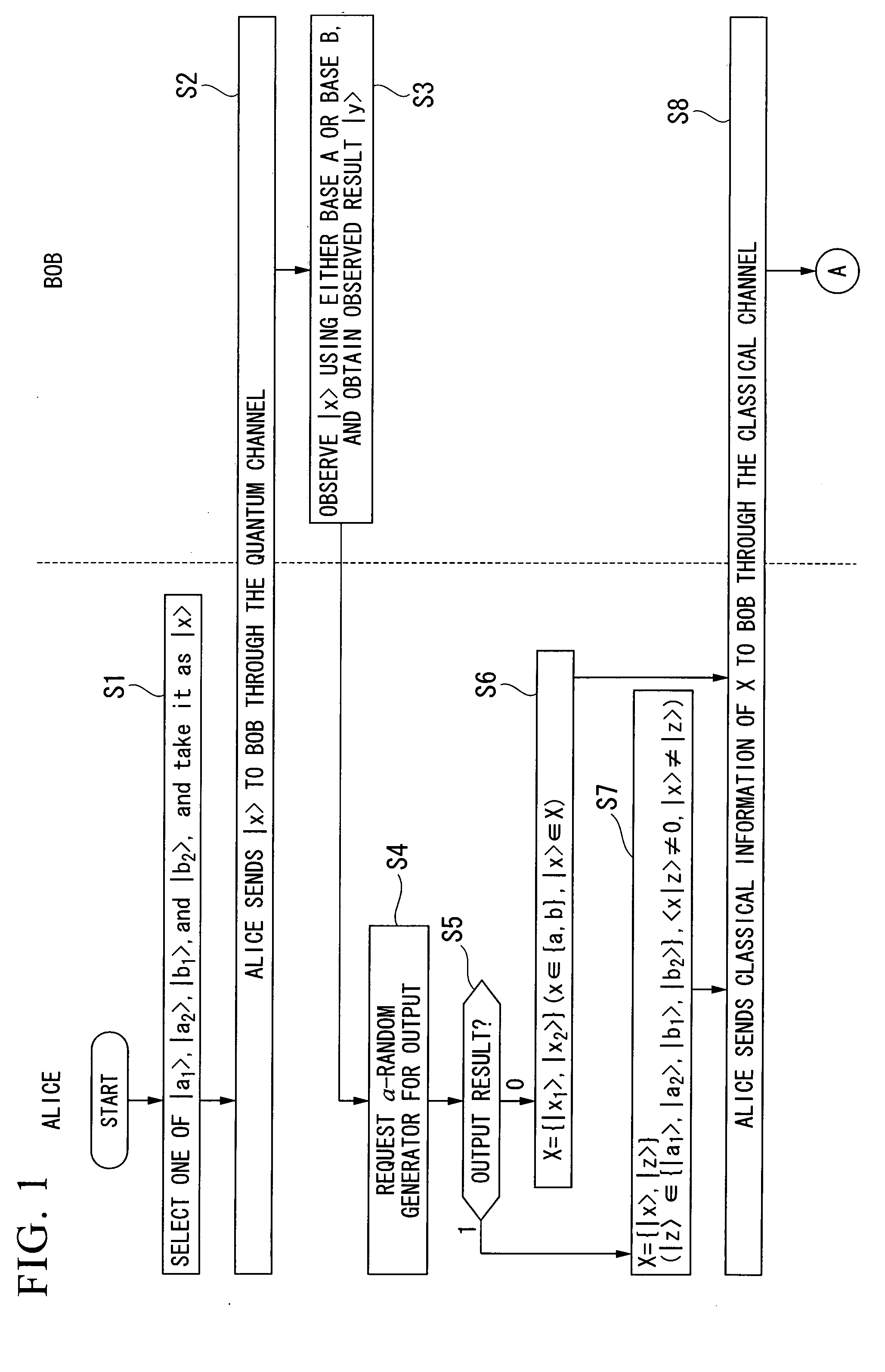
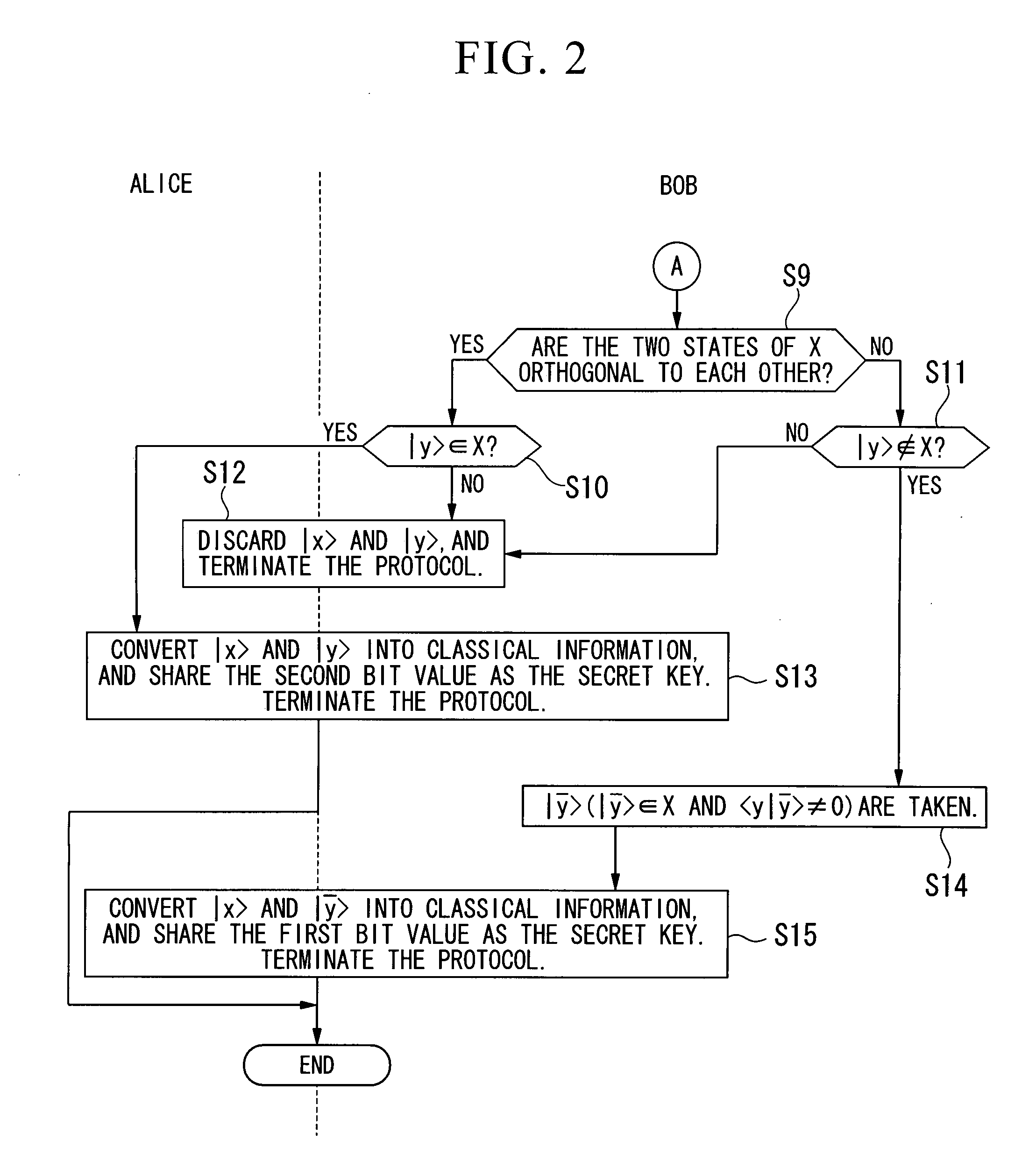
Quantum Key Distribution Protocol
InactiveUS20080101612A1Easily realizedIncrease the number ofKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer hardwareTransmitter
A quantum key distribution protocol is provided that reduces the maximum value of the leaked information amount over the same distance when an adversary makes a photon number splitting attack more than the reduction by the BB84 protocol and the SARG protocol, by making use of the advantages of the BB84 protocol and the SARG protocol. By properly proportioning the existing BB84 protocol and the SARG protocol in accordance with the rate determined by the communication distance between the sender and the receiver of the coherent light, a protocol that is more robust against photon number splitting attack than the known existing protocols can be realized, and long distance quantum key distribution, which was not possible until now, becomes possible.
Owner:THE FOUND FOR THE PROMOTION OF IND SCI +1
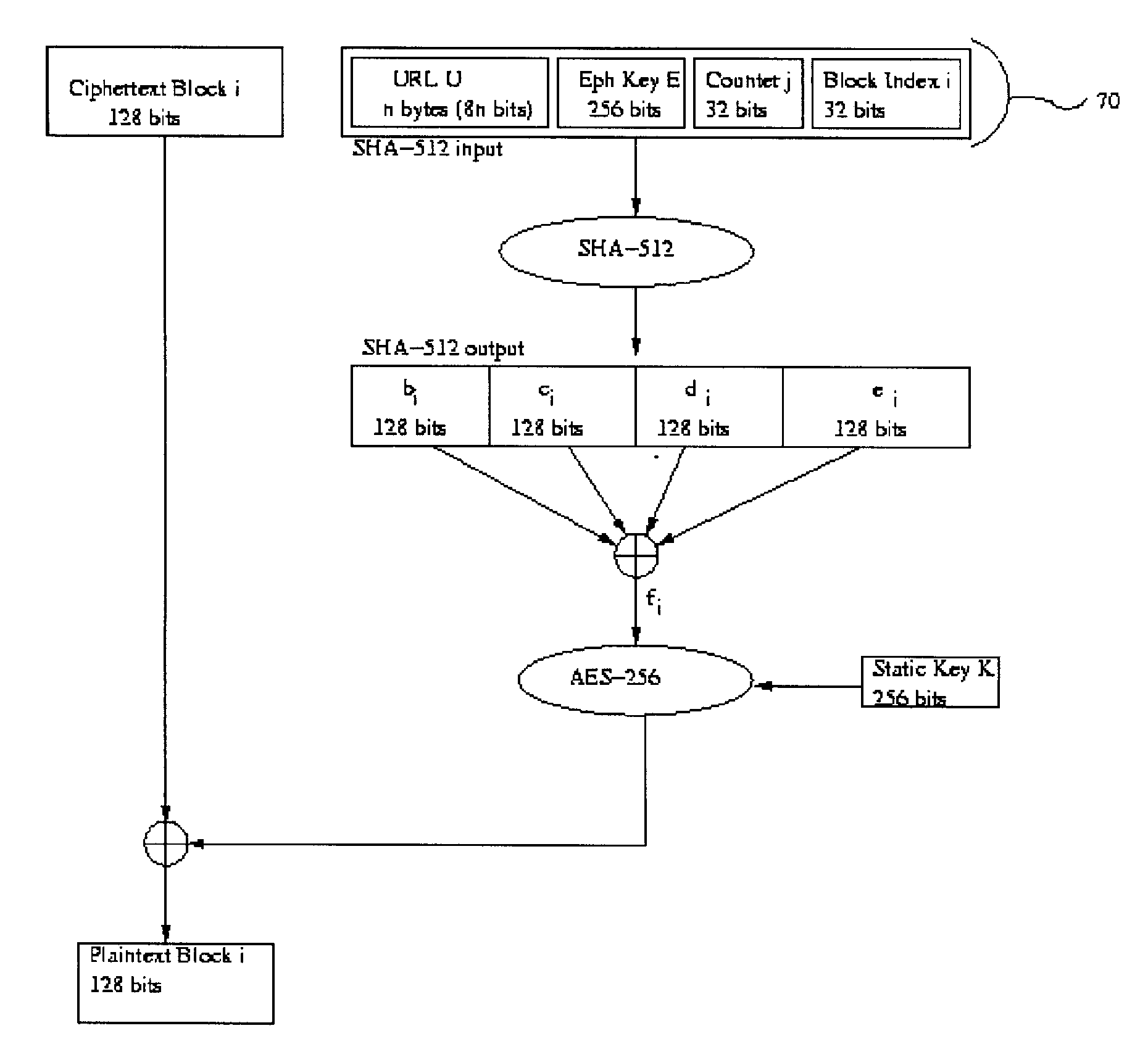
Split key secure access system
ActiveUS20120060033A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextComputer hardware
The present invention is a secure access system whereby the key that facilitates entrance to electronic data is split into at least two segments. Electronic data may be accessed by the application of the key segments in combination. A server may be used to derive key segments by way of algorithms, in a manner that improves the bit security of the key. Bit strings generated by the present invention may be concatenated to form data blocks whereby plaintext may be encrypted or ciphertext decrypted. The concatenation of the unique bit string variables and the generation of bit strings of specific sizes, as may occur through padding of blocks, work to provide a secure means of encrypting a key. A different bit string may be generated for each encryption / decryption transmission which limits the opportunity for an adversary to decrypt the plaintext.
Owner:THE GOVERNINIG COUNCIL OF THE UNIV OF TORANTO
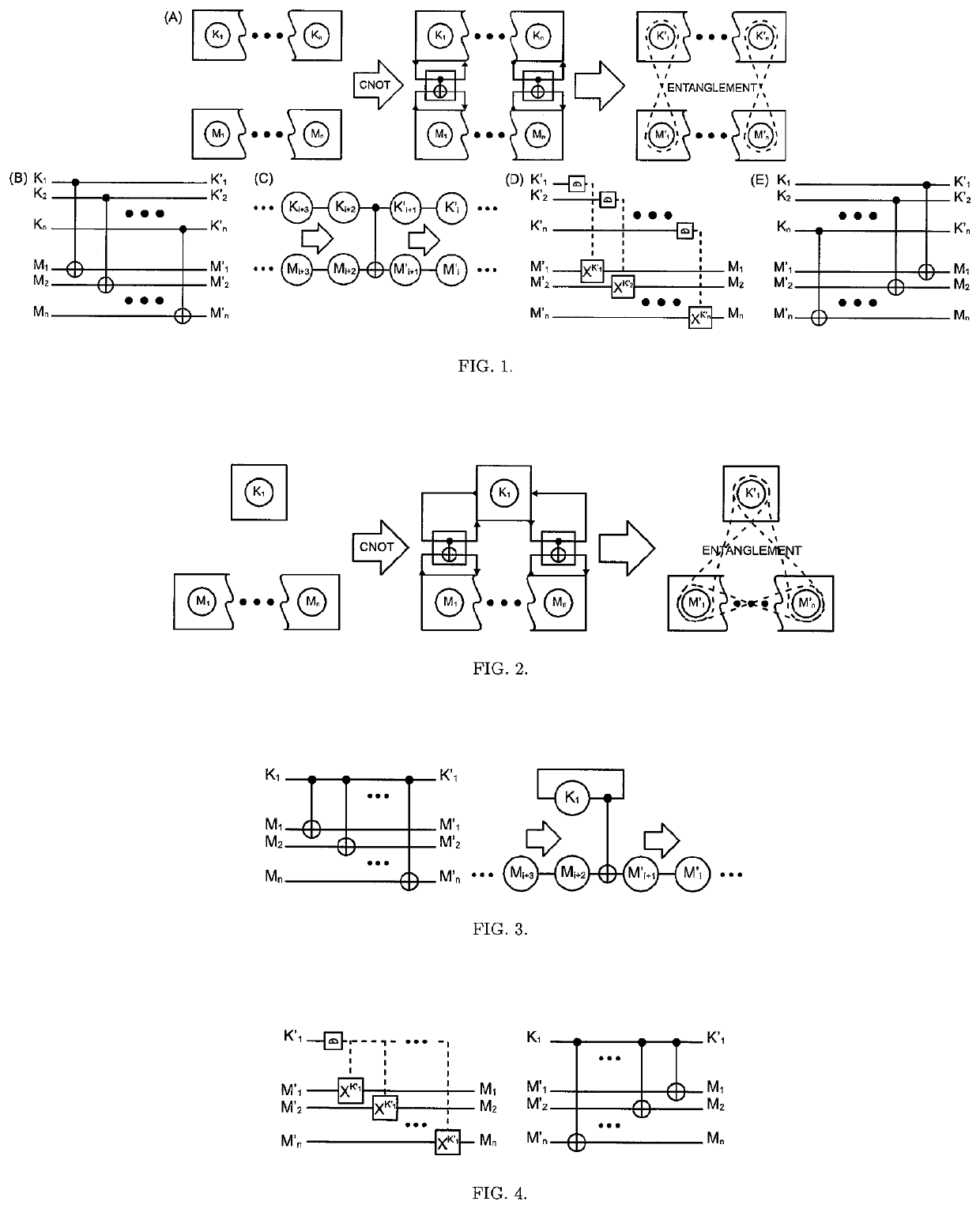
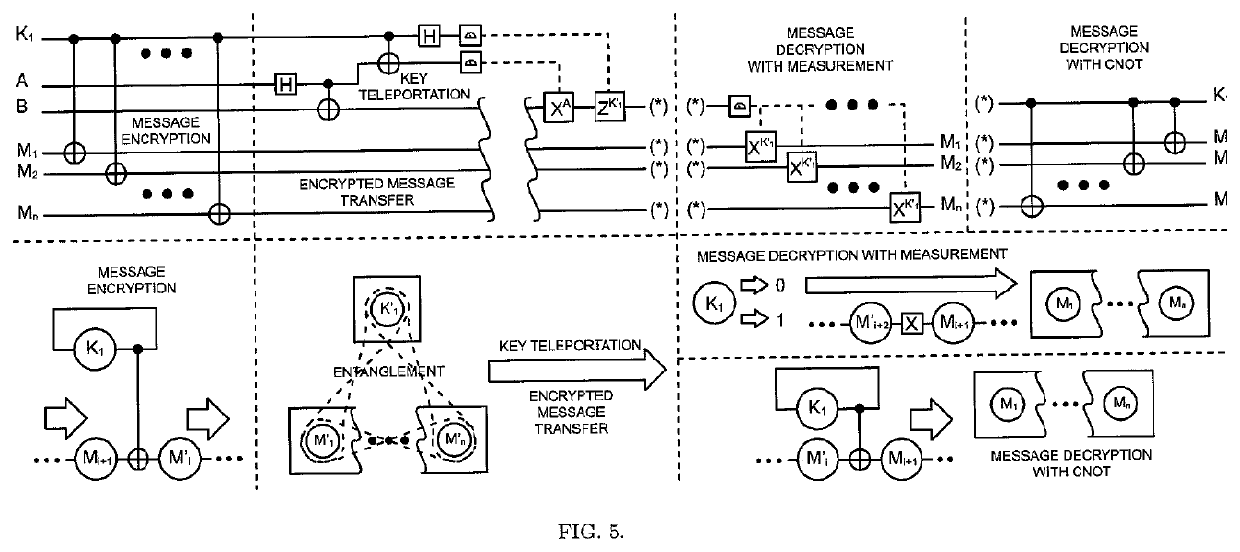
The One-Qubit Pad (OQP) for entanglement encryption of quantum information
InactiveUS20210058244A1Quantum computersKey distribution for secure communicationInformation processingQuantum teleportation
The One-Qubit Pad (OQP) protocol and its generic implementing device constitute a novel, maximally efficient scheme for encryption of quantum information with a quantum key of just a single qubit in an arbitrary unknown quantum state. The OQP enables encryption of the quantum information of n qubits register with a single qubit key upon provision of a multi-qubit entanglement between the single qubit key and the n qubits of the quantum message by the iterative application of the CNOT gate on the same key qubit (control input) and subsequent qubits of the message (target input). This results in an entanglement of all n+1 qubits, which locks original quantum information qubits and the single qubit of the key in a jointly entangled state that cannot be disentangled without the single qubit key. In order to decrypt the quantum message (by its disentanglement) one needs to have the qubit key and either reverse the protocol (applying CNOT operations in the reversed order) or simply measure the entangled key qubit and then depending on the outcome either straightforwardly obtain the decrypted quantum message or its quantum negation (dealt with by again applying quantum negation on all of the message qubits thus restoring their original states). The OQP protocol and its implementing device is proposed one hundred years after the classical One-Time Pad (Vernam cipher) was invented in 1917. The main differences between two schemes show how much quantum and clasical information differ. It is of course impossible to unconditionally securely encrypt classical sequence of n bits with just 1 bit of a key or guarantee that the random key that can be used for this purpose of n bits length (same as of the message) could not be copied. In contrast both these features are possible for the quantum information as described upon the proposed invention. The main characteristic of the OQP protocol to use only a single qubit as the key to enable information-theoretic security of n qubits quantum information encryption follows from the introduction in the invention of the multi-qubit entanglement, which is a non-local, topological and non-classical phenomenon giving quantum information significant edge over its classical counterpart. The main application of the OQP protocol and its implementing generic device is to lock quantum information with the single key qubit in order to prevent any unauthorized access to it (not only a classical access upon a measurement, but more importantly a quantum access by a quantum information processing device). This application can be also extended to communication scenario jointly with the Quantum Teleportation, which without OQP requires pre-sharing of n pairs of Bell states between Alice and Bob to securely communicate n qubits long quantum message, whereas in contrast with the OQP protocol just one pair of Bell state is required to securely teleport only the single qubit key for the OQP encrypted quantum message sent through an insecure quantum channel and still be access-protected from Eve (an adversary).
Owner:COMPSECUR SP ZOO
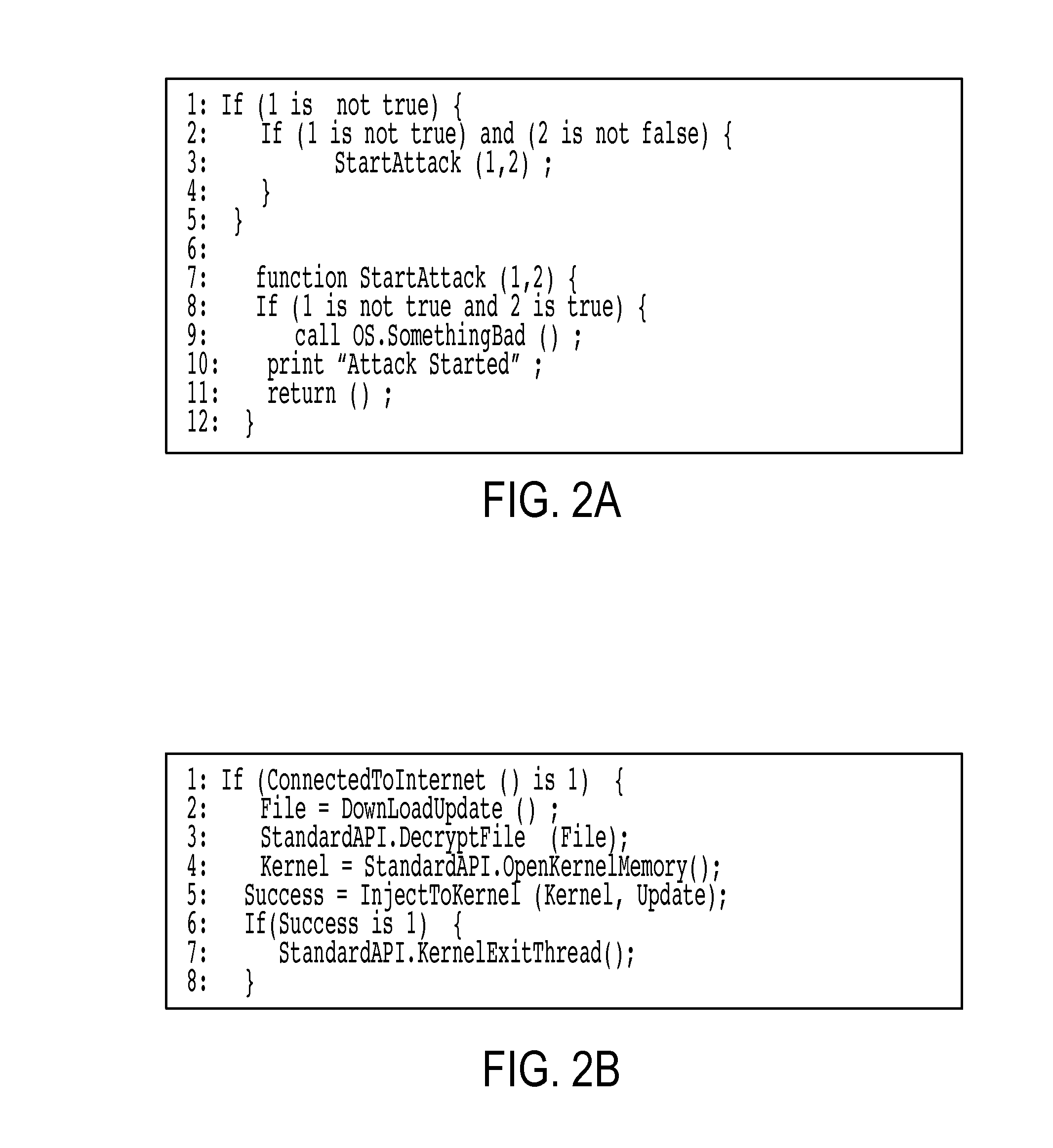
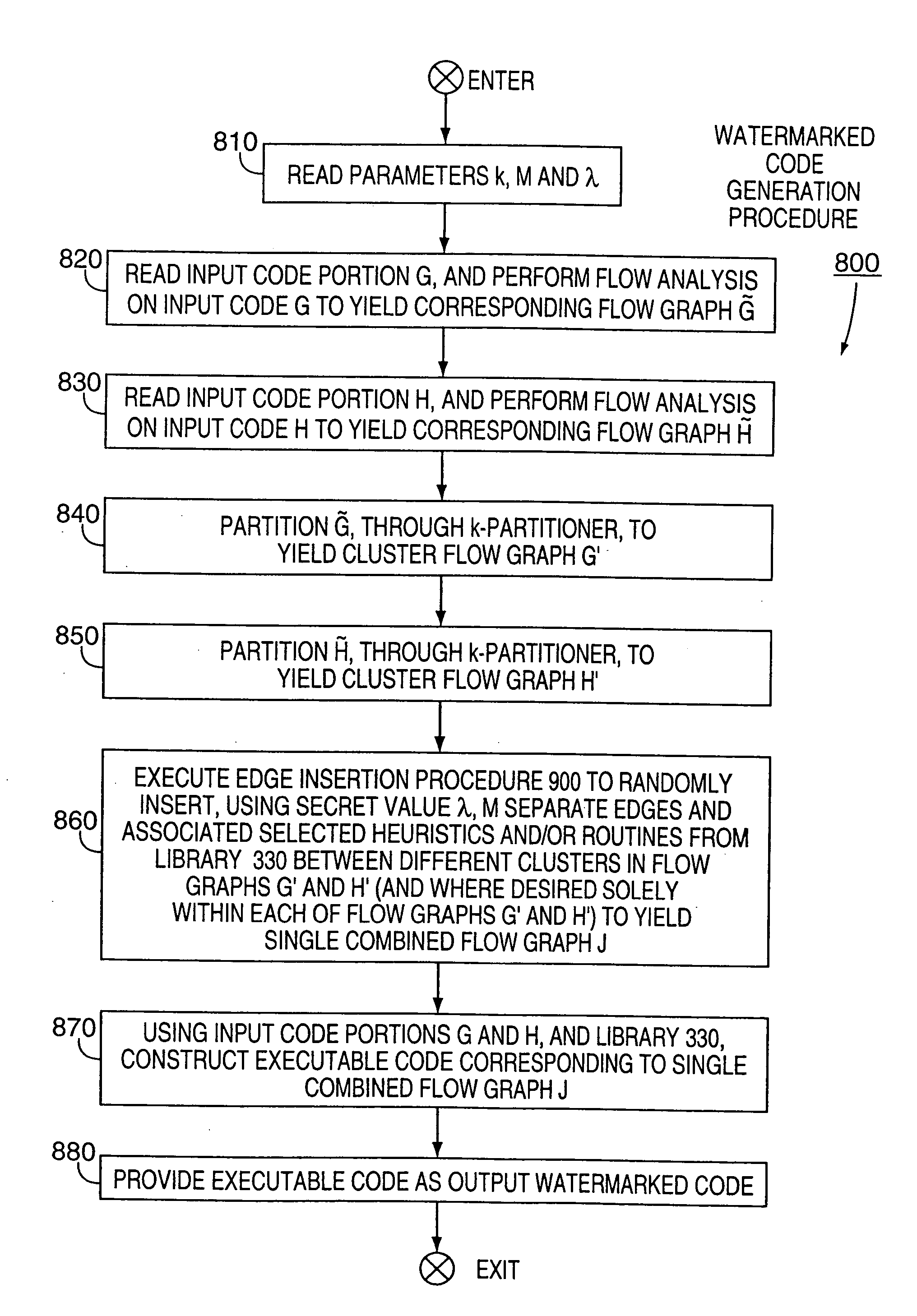
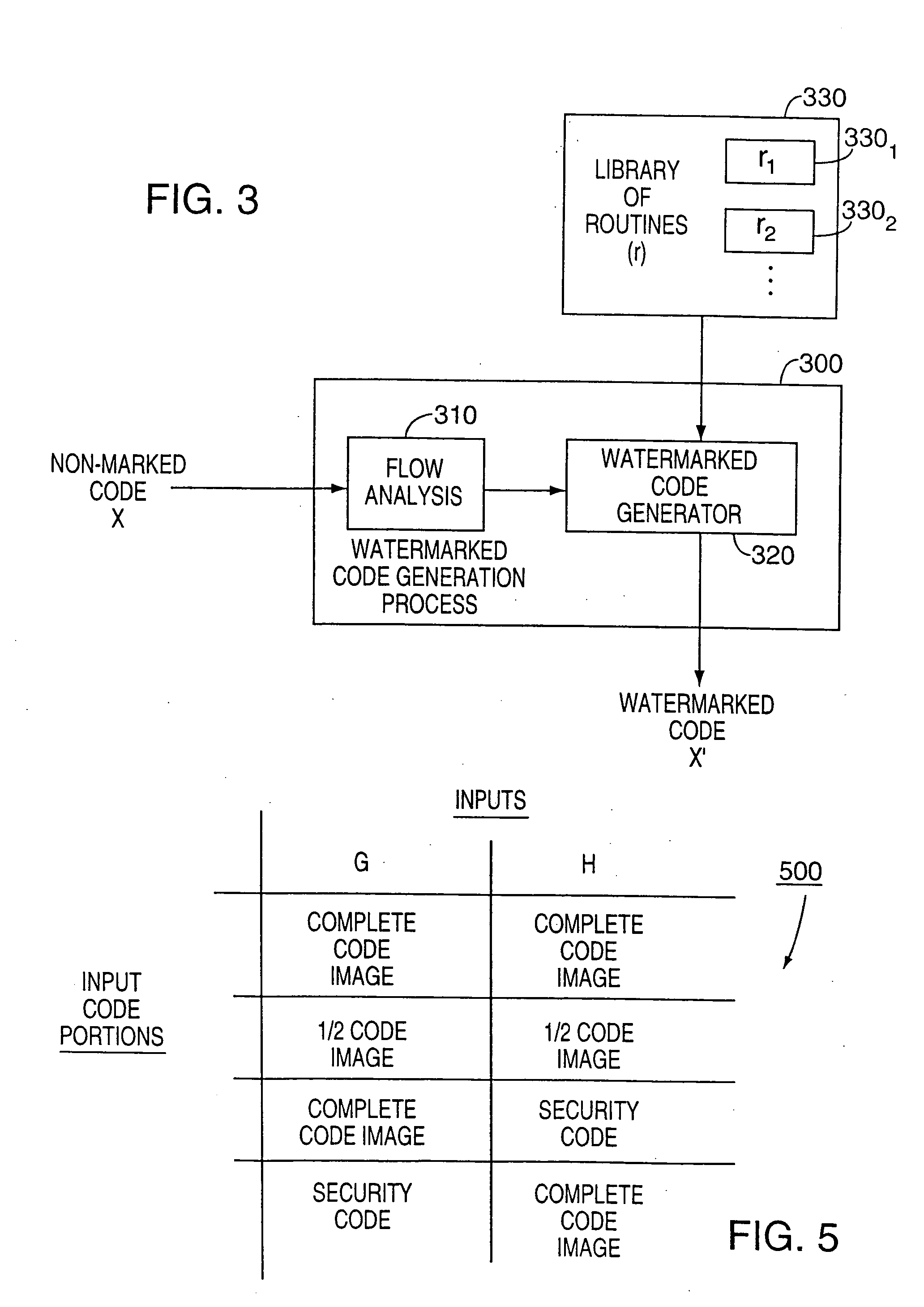
Technique for producing through watermarking highly tamper-resistant executable code and resulting "watermarked" code so formed
InactiveUS20050144458A1Improvement in tamper-resistanceSecurely watermarkDigital data processing detailsUser identity/authority verificationThird partyTamper resistance
Apparatus and an accompanying method, for forming and embedding a highly tamper-resistant cryptographic identifier, i.e., a watermark, within non-marked executable code, e.g., an application program, to generate a “watermarked” version of that code. Specifically, the watermark, containing, e.g., a relatively large number of separate executable routines, is tightly integrated into a flow pattern of non-marked executable code, e.g., an application program, through randomly establishing additional control flows in the executable code and inserting a selected one of the routines along each such flow. Since the flow pattern of the watermark is highly intertwined with the flow pattern of the non-marked code, the watermark is effectively impossible to either remove from the code and / or circumvent. The routines are added in such a manner that the flow pattern of resulting watermarked code is not substantially different from that of the non-marked code, thus frustrating third party detection of the watermark using, e.g., standard flow analysis tools. To enhance tamper-resistance of the watermarked code, each such routine can provide a pre-defined function such that if that routine were to be removed from the marked code by, e.g., a third party adversary, then the marked code will prematurely terminate its execution.
Owner:MICROSOFT TECH LICENSING LLC
Authenticable asymmetrical group secret key negotiation method in mobile unbalanced network
ActiveCN103796199AGuaranteed freshnessEnsure secure communicationSecurity arrangementBalancing networkSecure communication
The invention relates to an authenticable asymmetrical group secret key negotiation scheme in a mobile unbalanced network. The scheme comprises the steps that signature and authentication of group members are carried out, group members negotiate an asymmetrical shared secret key, and consistency verification of the shared secret key is carried out. According to the signature and authentication, a short signature mechanism of mobile equipment in a network is achieved by adopting a bilinear mapping technology, and members of mobile groups provide identify authentication by using the signature before the group secret key is negotiated to defense active attack of adversaries. According to step that the group members negotiate the asymmetrical shared secret key, all mobile equipment in the mobile unbalanced network negotiates a pair of asymmetrical group communication encryption / decryption secret keys, and members outside the group can send secret messages to members inside the group by encrypting the secret messages through a public key without the necessary of joining the group. According to the consistency verification of the shared secret key, after the group members negotiate the group secret key, the accuracy and the consistency of the calculated group secret key can be guaranteed. According to the authenticable asymmetrical group secret key negotiation scheme in the mobile unbalanced network, when secret communication is carried out among mobile group equipment in the mobile network environment, safe communication among the group equipment can be guaranteed, energy consumption of calculation and communication is quite low, and good flexibility, safety and practicability are achieved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Method, apparatus and product for RFID authentication
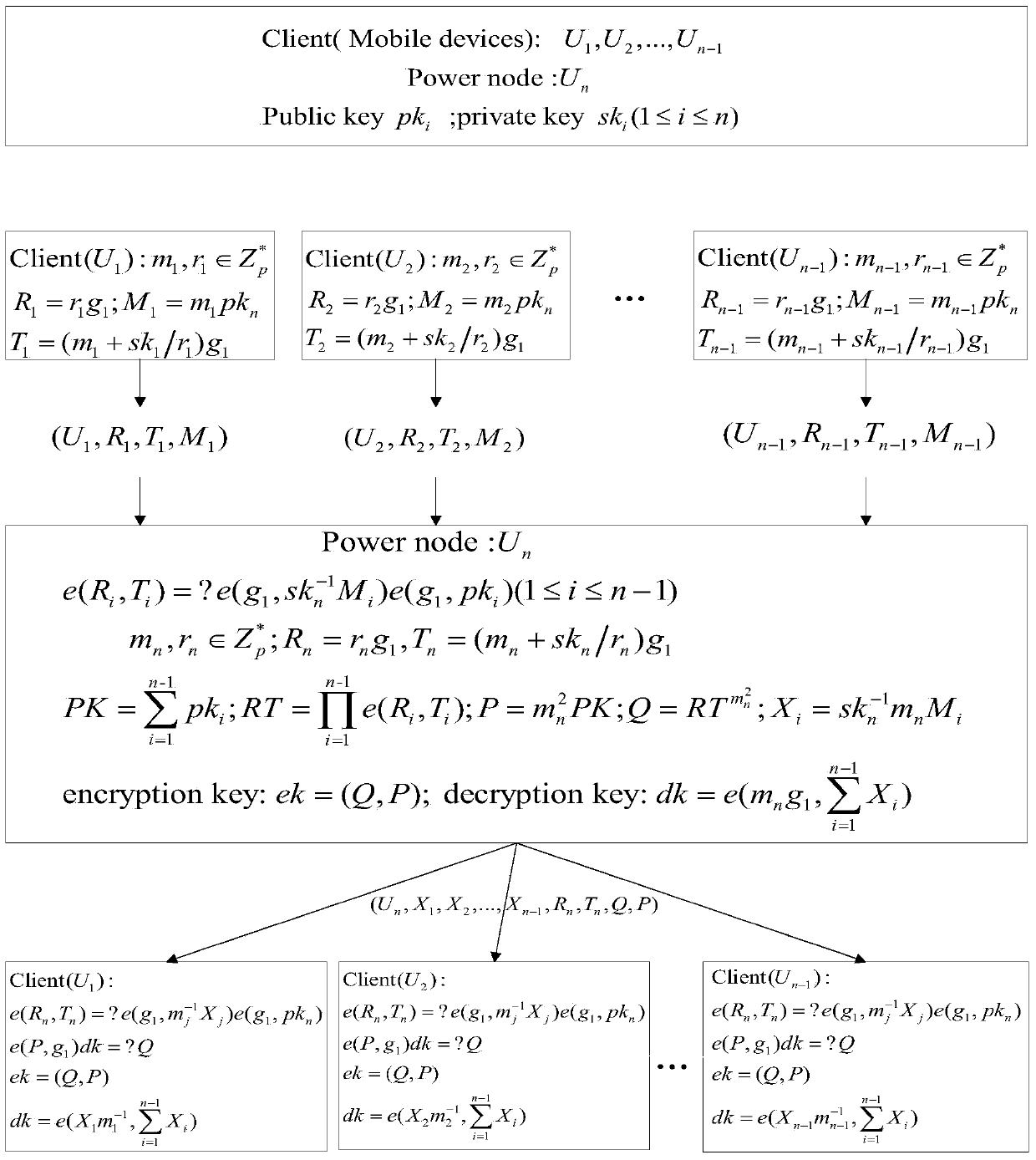
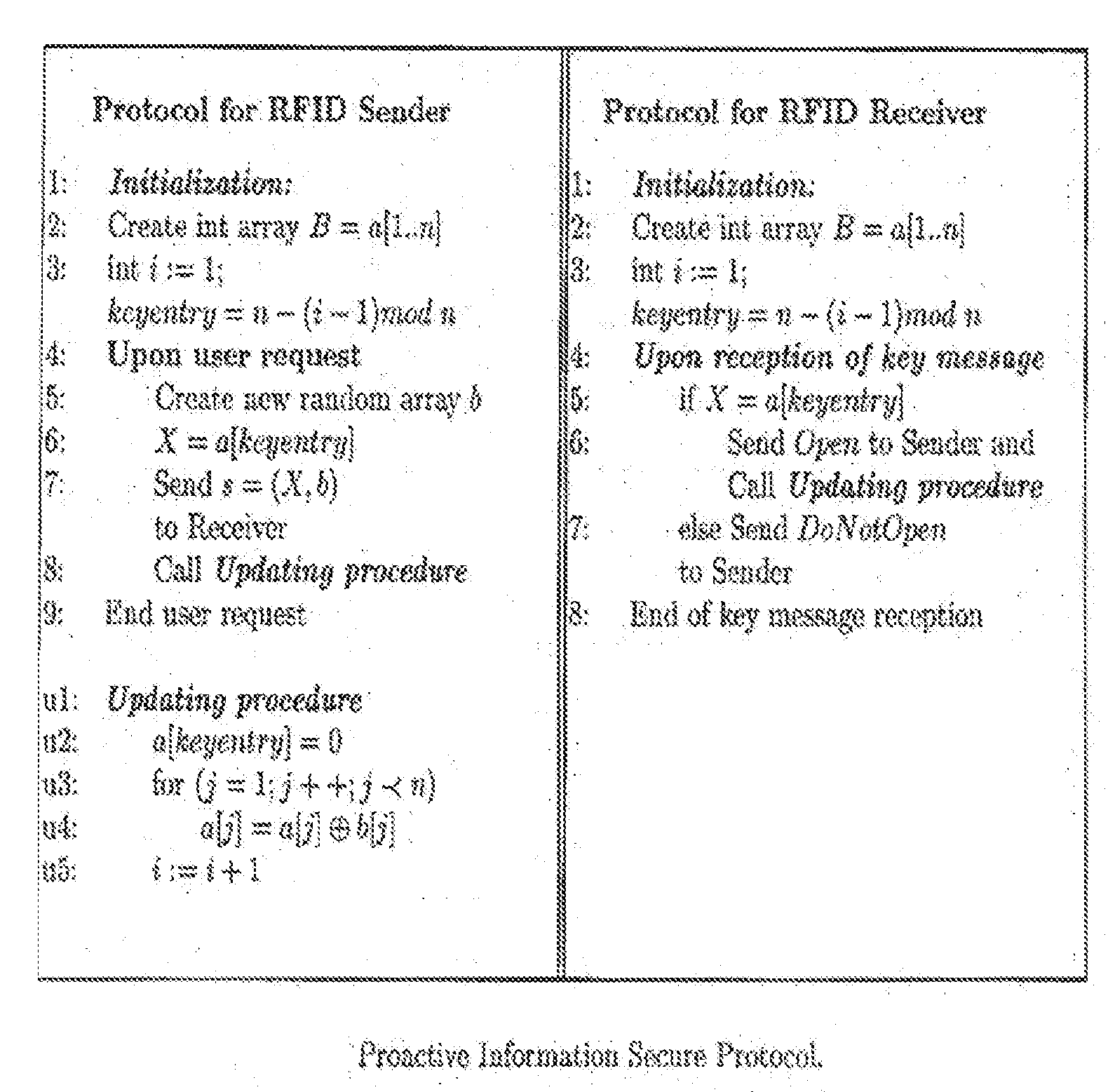
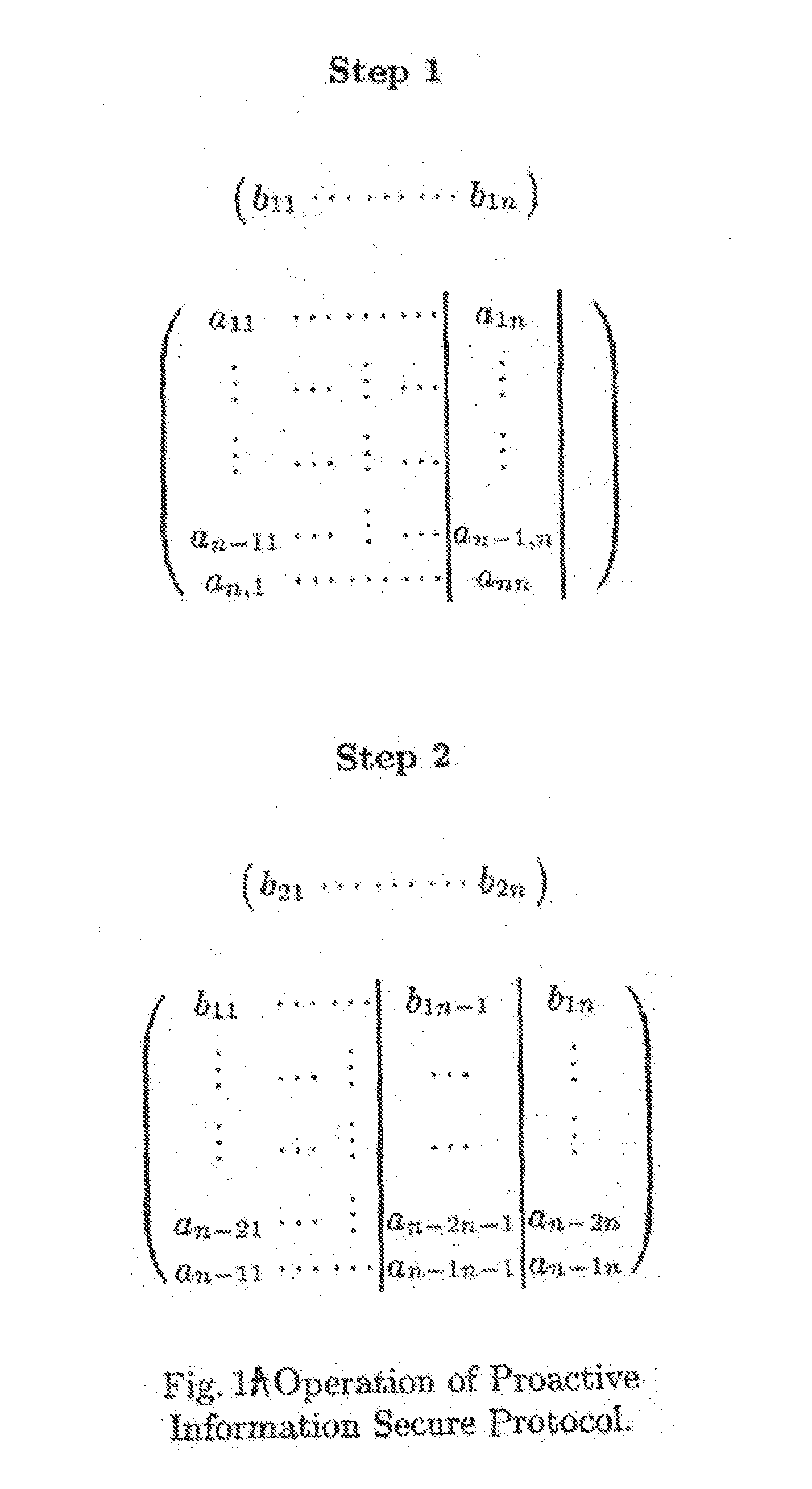
InactiveUS20090225985A1Reduce in quantityIncrease resistanceKey distribution for secure communicationDigital data processing detailsRfid authenticationAdversary
A method and apparatus for repeated communication sessions between a sender (e.g., RFID tag) and a receiver (RFID reader) that employs a proactive information security scheme is based on the assumption that the information exchanged during at least one of every n successive communication sessions is not exposed to an adversary. The sender and the receiver maintain a vector of n entries that is repeatedly refreshed by pairwise XORING entries, with a new vector of n entries that is randomly chosen by the sender and sent to the receiver as a part of each communication session. Also, a computational secure scheme based on the information secure scheme is employed to ensure that even in the case that the adversary listens to all the information exchanges, the communication between the sender and the receiver is secure. In particular, the scheme can be used in the domain of remote controls (e.g., for cars).
Owner:DOLEV SHLOMI +2
System and Method for Protecting Cryptographic Assets From a White-Box Attack
ActiveUS20130024699A1Improve interoperabilityUser identity/authority verificationCryptographic attack countermeasuresGeneration processData transformation
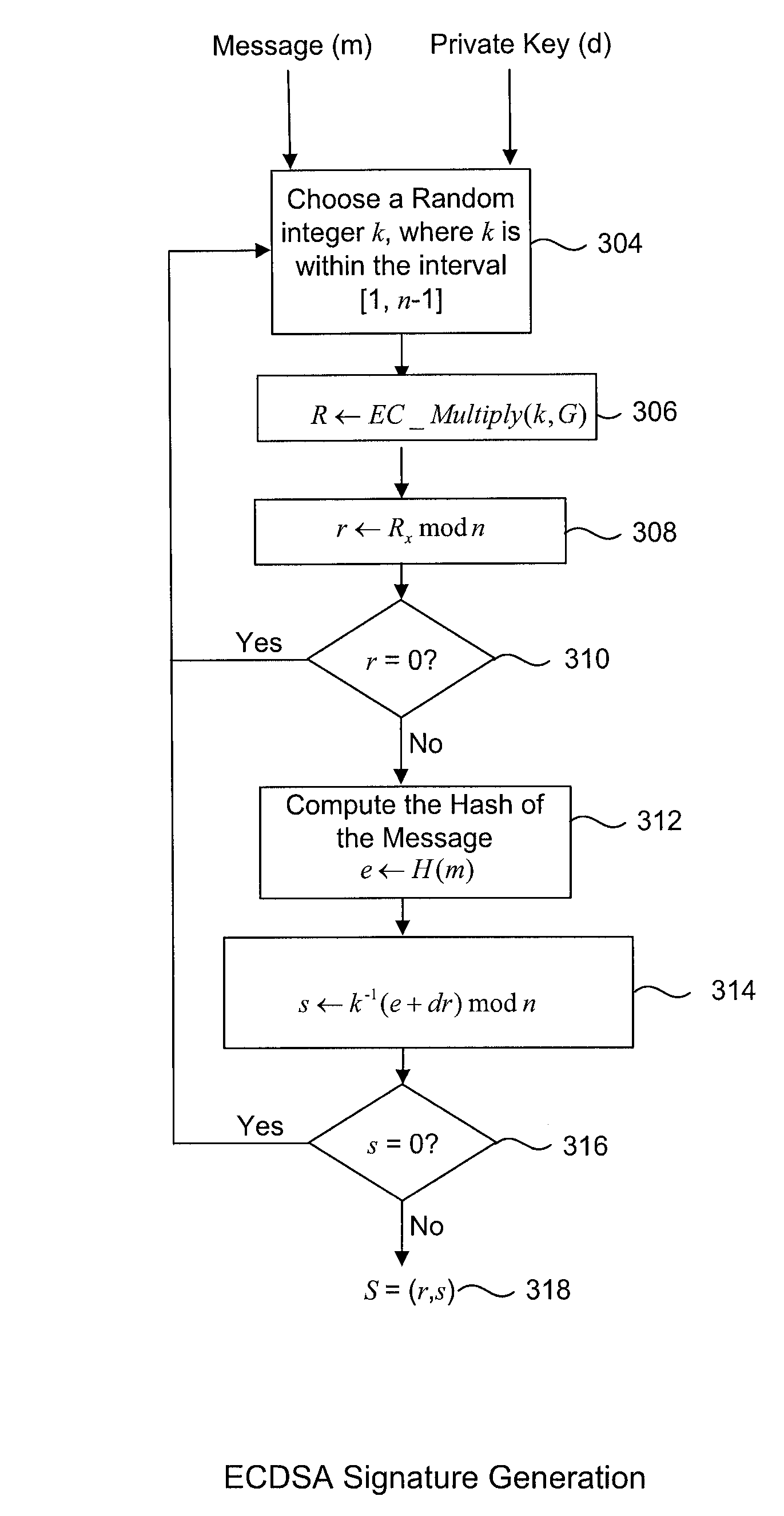
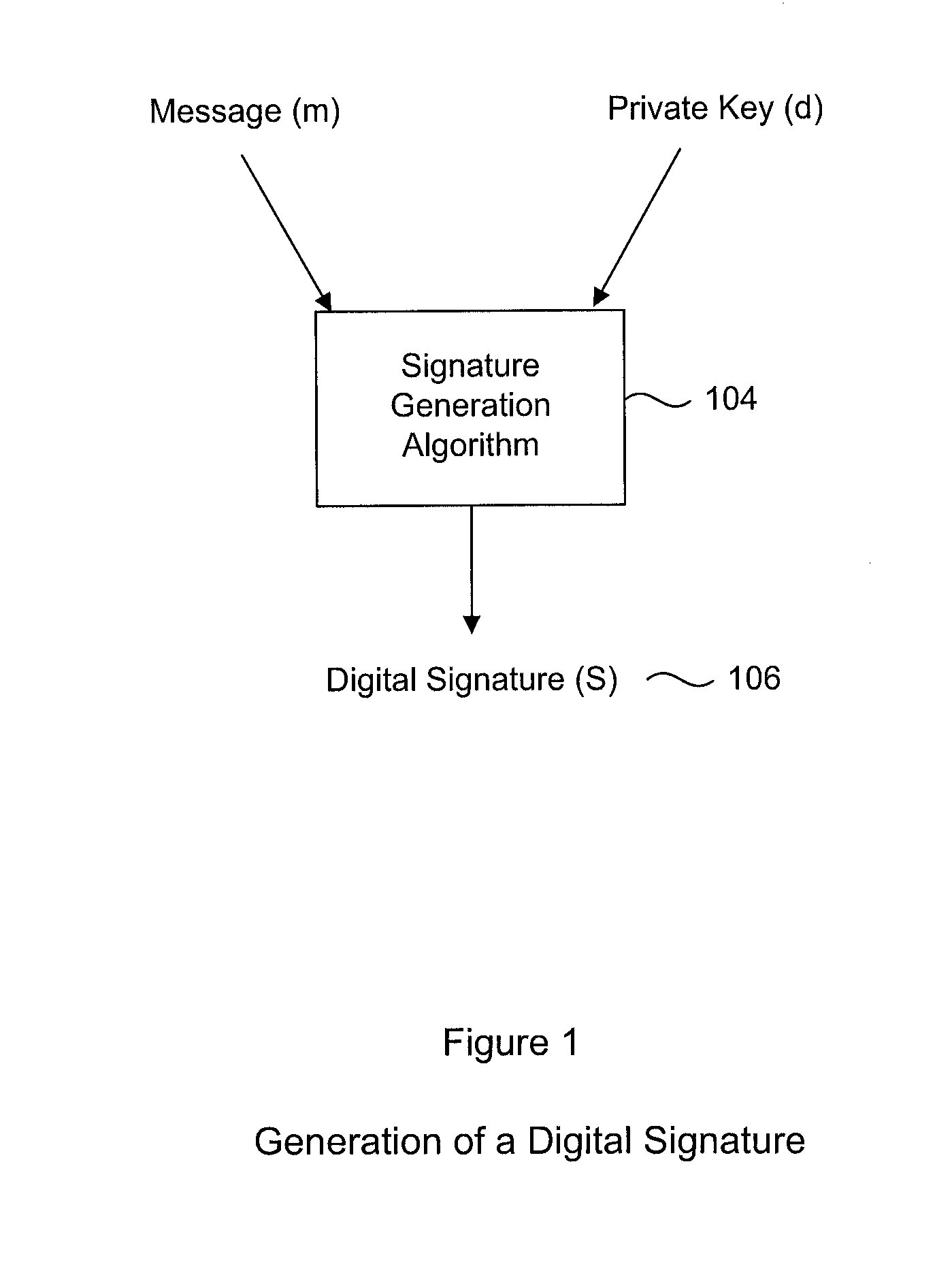
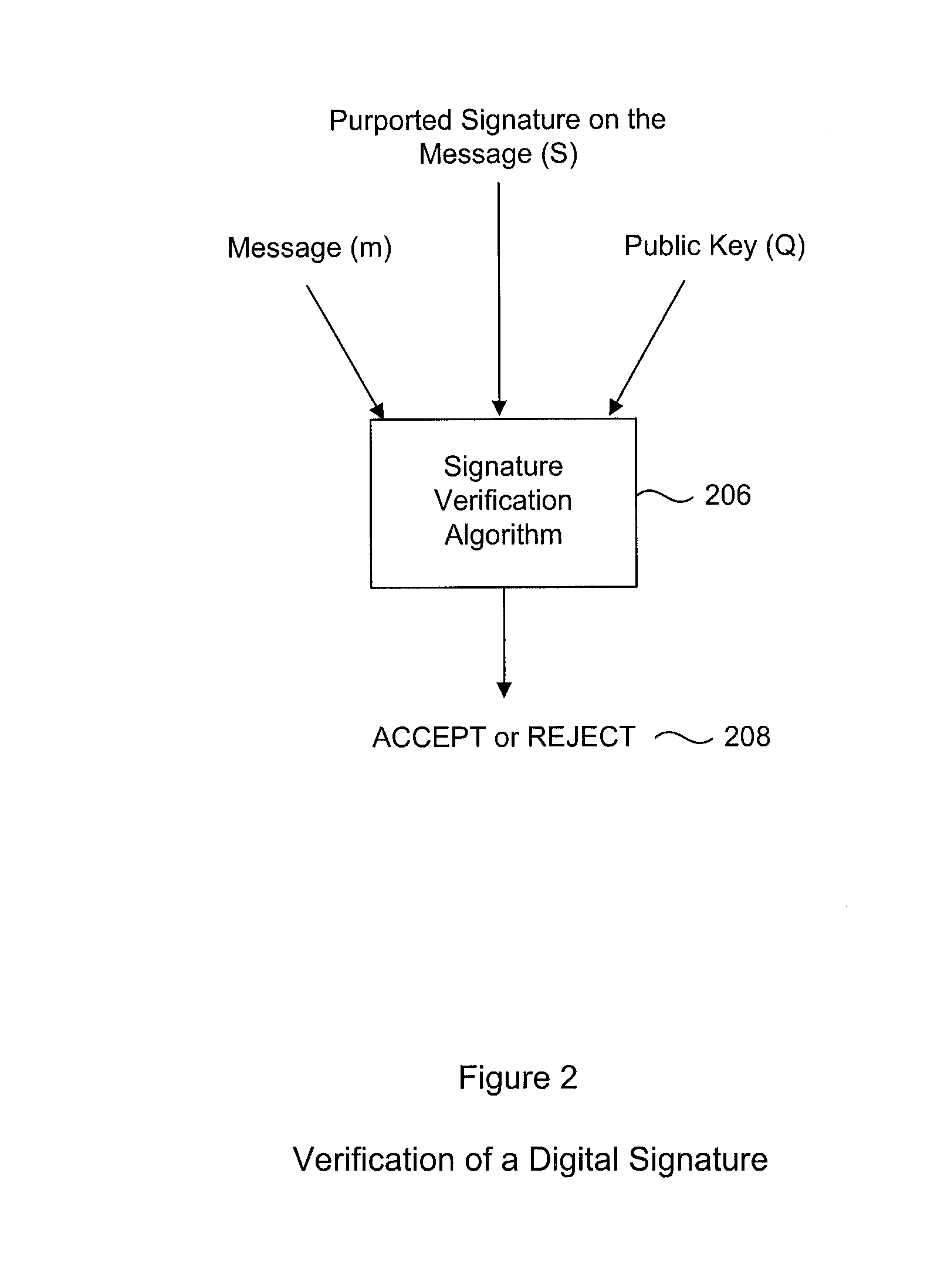
A digital signature generation (DSG) process which provides resistance against white box attackers is disclosed. This is done by applying specially selected data transformations to the inputs, outputs and internal parameters of the algorithm. In particular, the signatory's private key does not appear in the clear in our protected implementation. Our new white box implementation produces signatures that are compatible with signatures created by conventional implementations; thus our solution facilitates interoperability and can be used as a drop-in replacement for conventional implementations. In particular, we describe transformations to the key (d) and the generator domain parameter (usually denoted G or g) of the digital signature generation processes, such that embodiments of the invention can produce signed messages which appear to a verifier as if the key (d) was used, without actually ever using the key (d). This makes it impossible for an adversary to ever observe the key (d), as it is not actually used. Further embodiments include additional protections to make it even harder for an adversary to deduce the key (d) by observing the process which generates the digital signature.
Owner:IRDETO ACCESS
Fine-grained forward-secure signature scheme
InactiveUS20060233364A1Key distribution for secure communicationMultiple keys/algorithms usagePresent methodGranularity
The presented methods form the basis of a forward-secure signature scheme that is provably secure. Moreover, the presented methods form also the basis of a fine-grained forward-secure signature scheme that is secure and efficient. The scheme allows to react immediately on hacker break-ins such that signatures from the past still remain valid without re-issuing them and future signature values based on an exposed key can be identified accordingly. In general, each prepared signature carries an ascending index such that once an index is used, no lower index can be used to sign. Then, whenever an adversary breaks in, an honest signer can just announce the current index, e.g., by signing some special message with respect to the current index, as part of the revocation message for the current time period. It is then understood that all signatures made in prior time periods as well as all signatures make in the revoked period up to the announced index are valid, i.e., non-reputable.
Owner:IBM CORP
Authenticated adversarial routing
InactiveUS20110016316A1Digital data processing detailsUser identity/authority verificationTransmitterAuthentication
A routing protocol is used to transmit messages from a sender to a receiver over a network of nodes, where adversaries can control links between the nodes and can also control the behavior of a large number of nodes. Various techniques can be used, along or in combination, to combat these effects. In one approach, certain trigger conditions are identified, the occurrence of which signals malicious behavior within the network. When signaled, the sender requests status reports from the intermediate nodes in an effort to determine which nodes are malicious. The information for the status reports is generated by nodes as packets are passed from one node to the next.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE +1
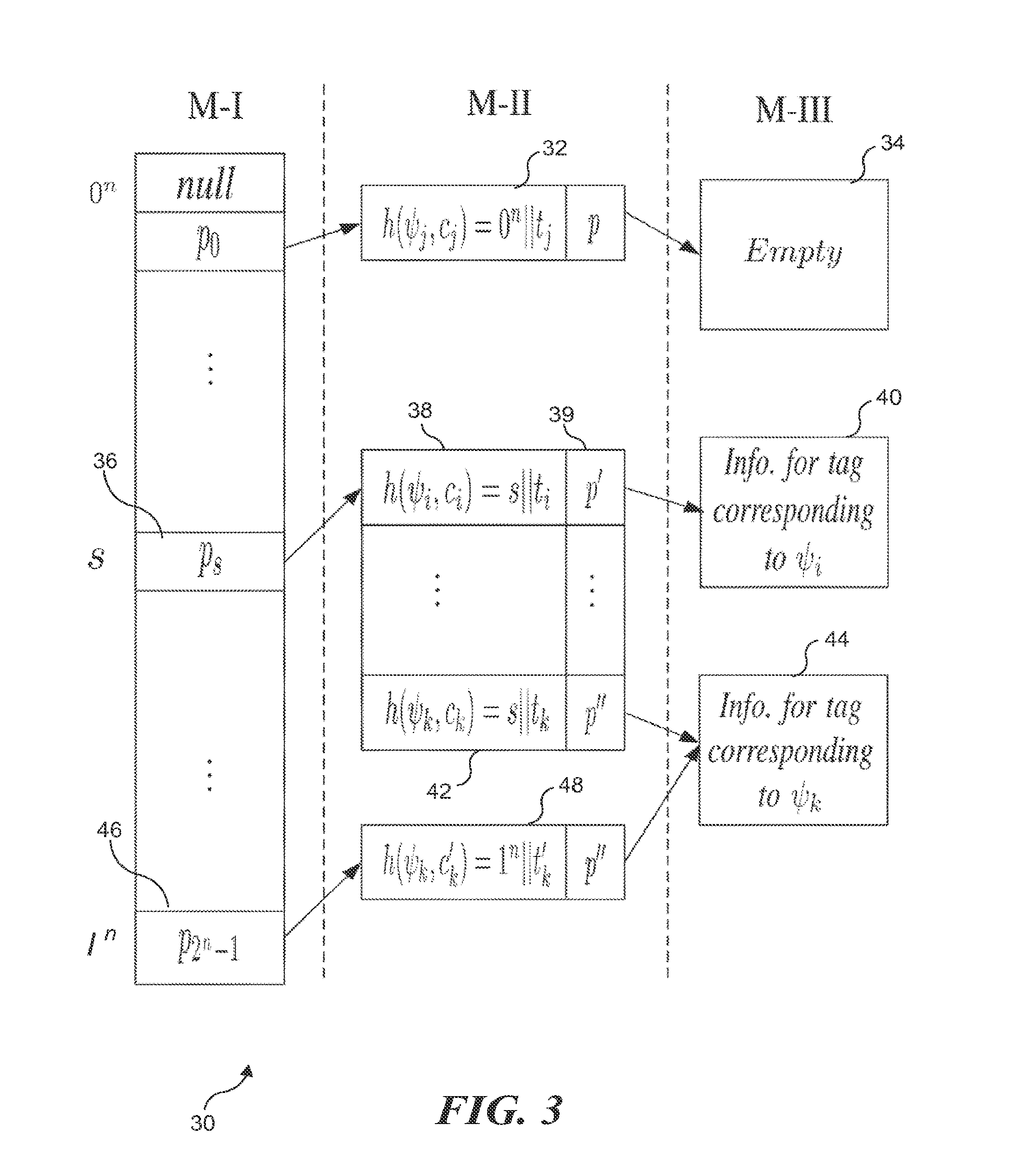
Scalable RFID systems: a privacy-preserving protocol with constant-time identification
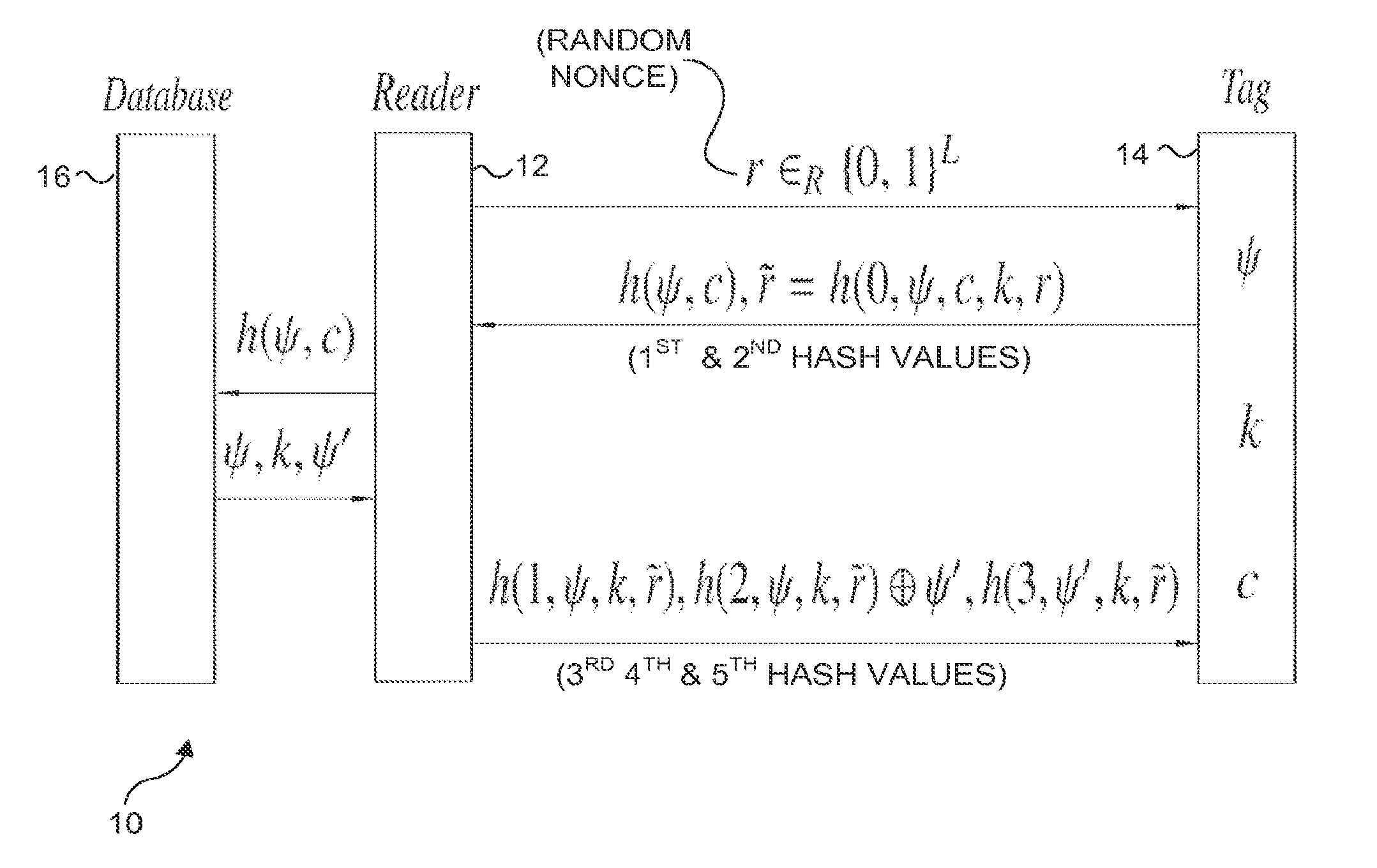
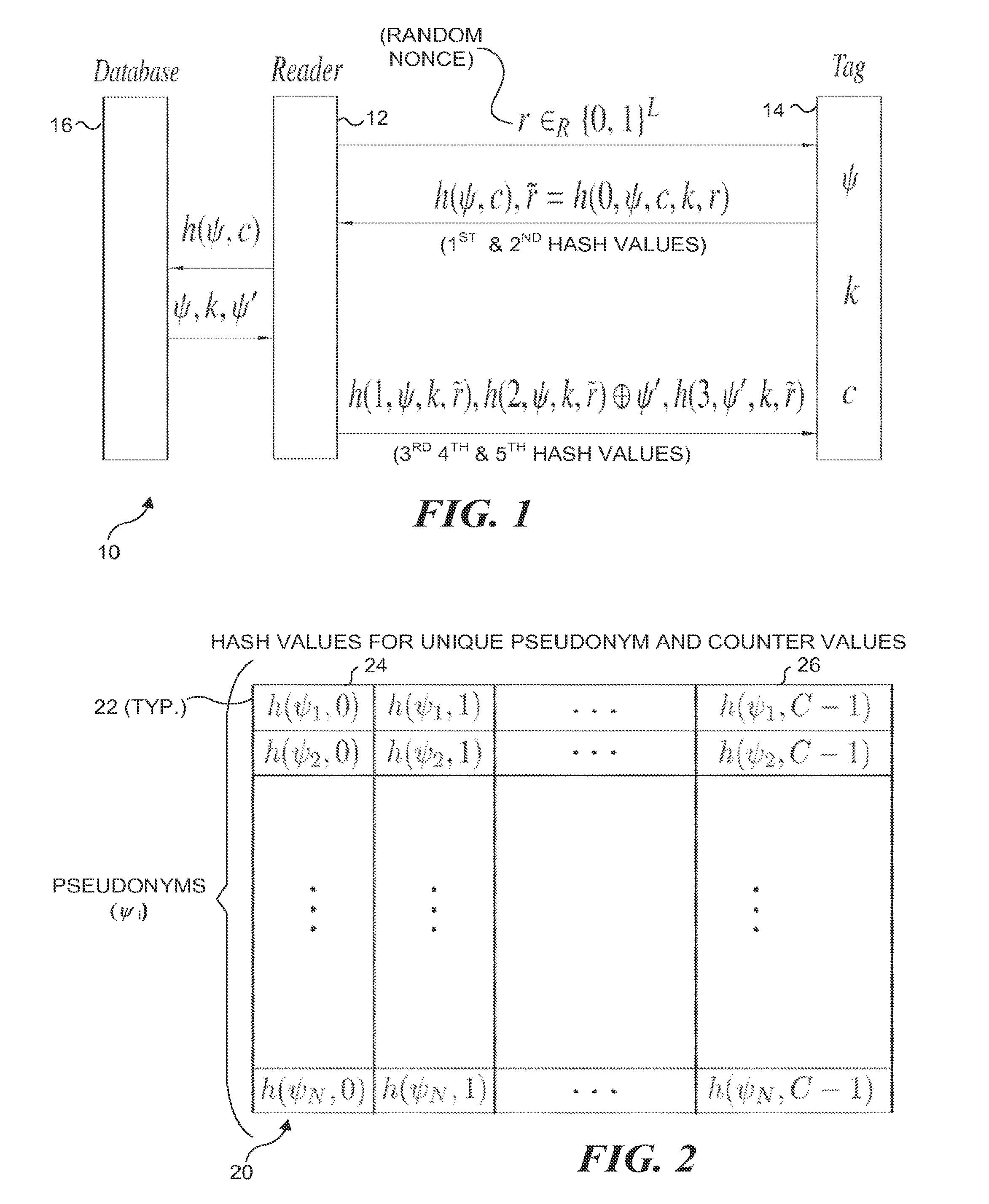
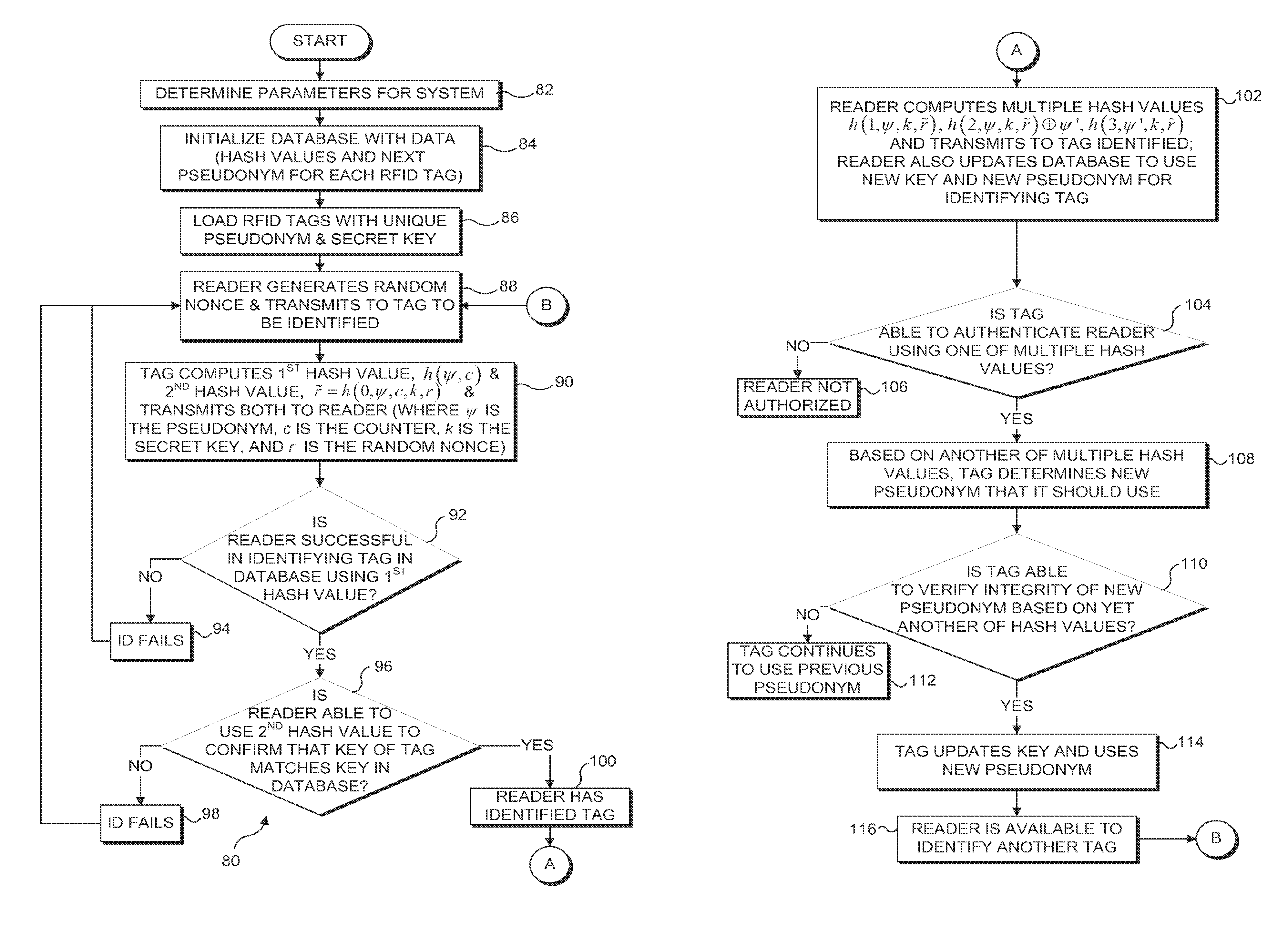
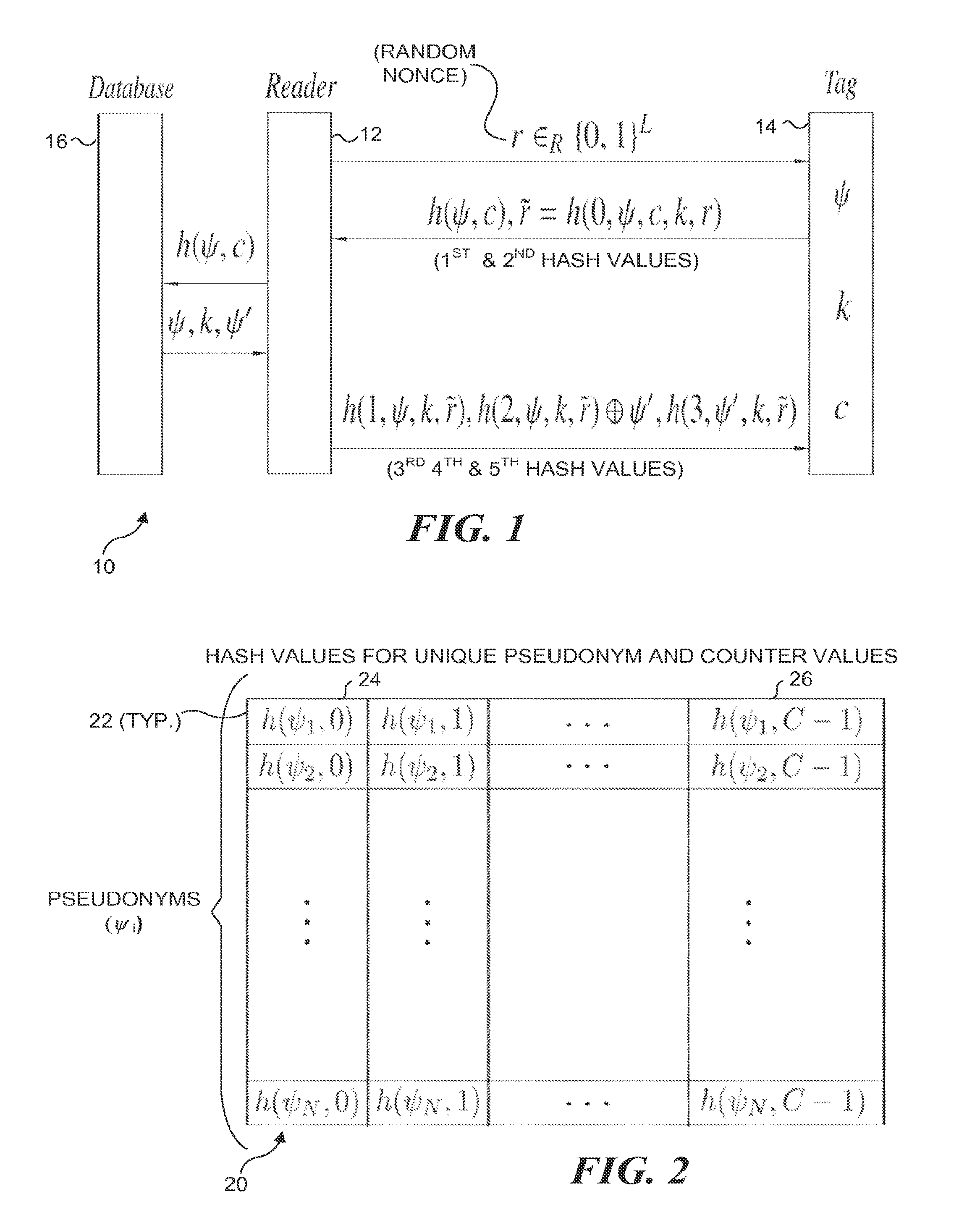
InactiveUS20130207780A1Minimizes probability of collisionMinimizes probabilitySubscribers indirect connectionRecord carriers used with machinesComputer hardwareHash function
A protocol with constant-time complexity solves the problem of private identification of tags in low-cost, large-scale radio frequency identification (RFID) systems—assuming that an adversary has complete control over the communication channel. Each RFID tag has an internal counter, c, and is preloaded with a unique pseudonym, ψ, and a secret key, k. A RFID reader attempting to identify and authenticate a tag within its range generates and transmits a random nonce to the RFID tag, which returns a first hash of its current pseudonym and counter, and a second hash that is a function of the secret key. The reader uses the returned data to identify the RFID tag and its secret key by reference to a database and returns other hash values that authenticate the reader to the RFID tag. The most expensive operation that RFID tags are required to perform is a hash function.
Owner:UNIV OF WASHINGTON
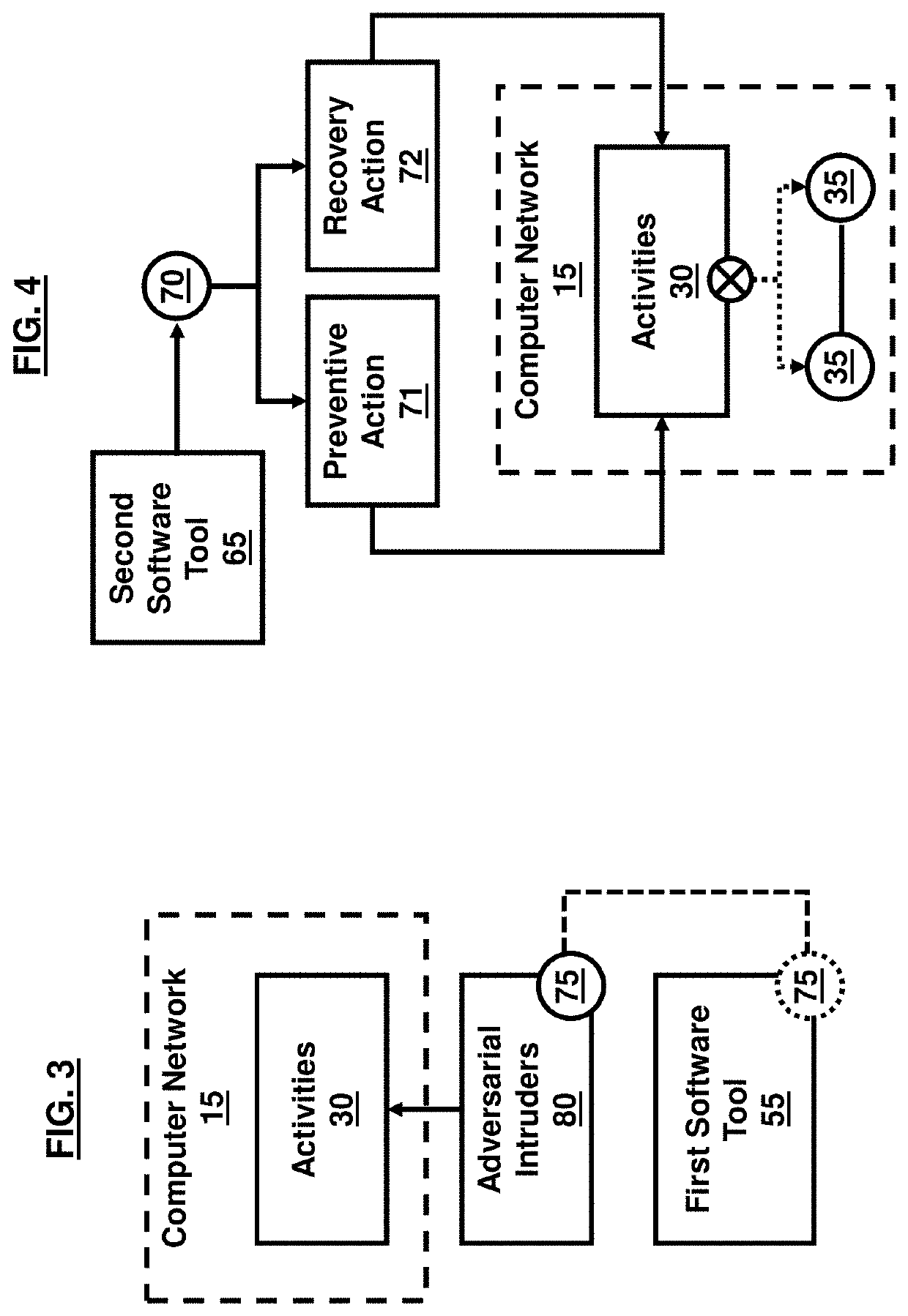
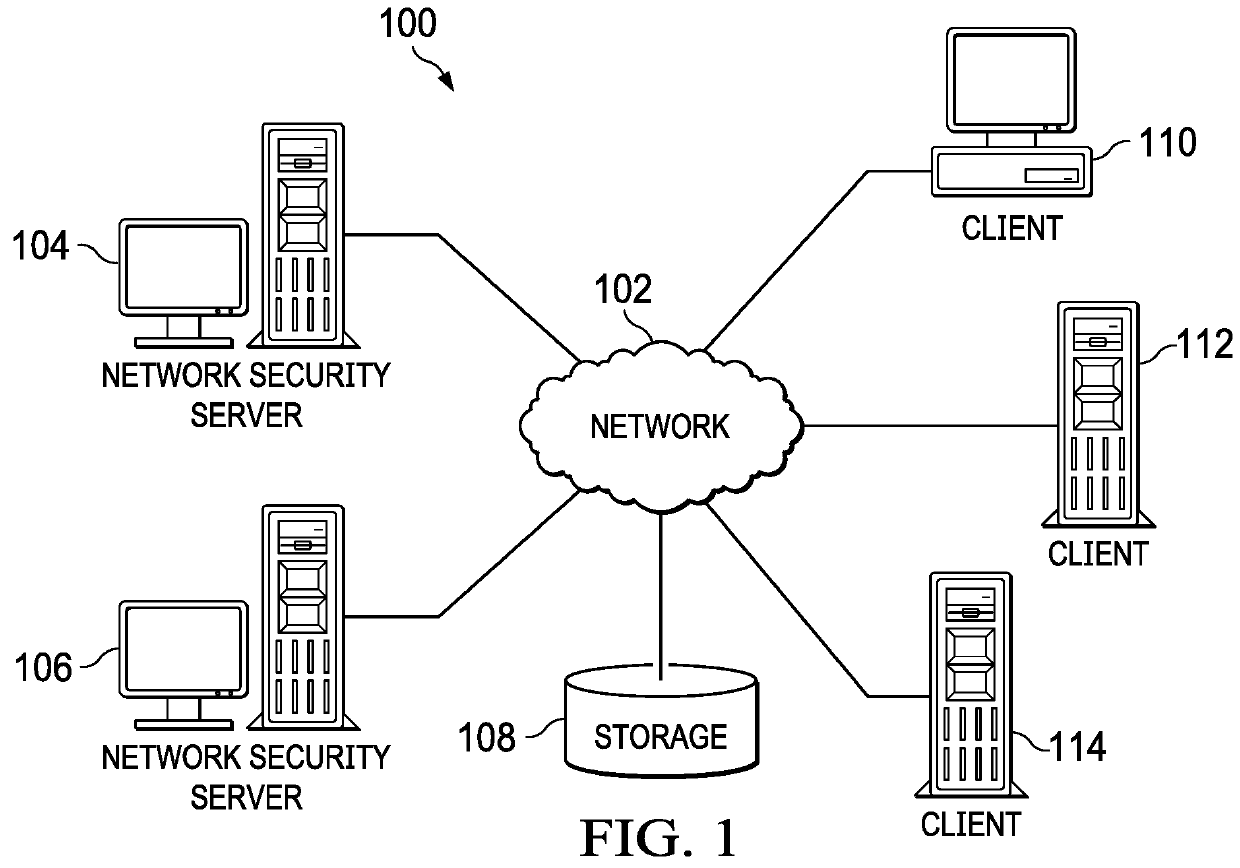
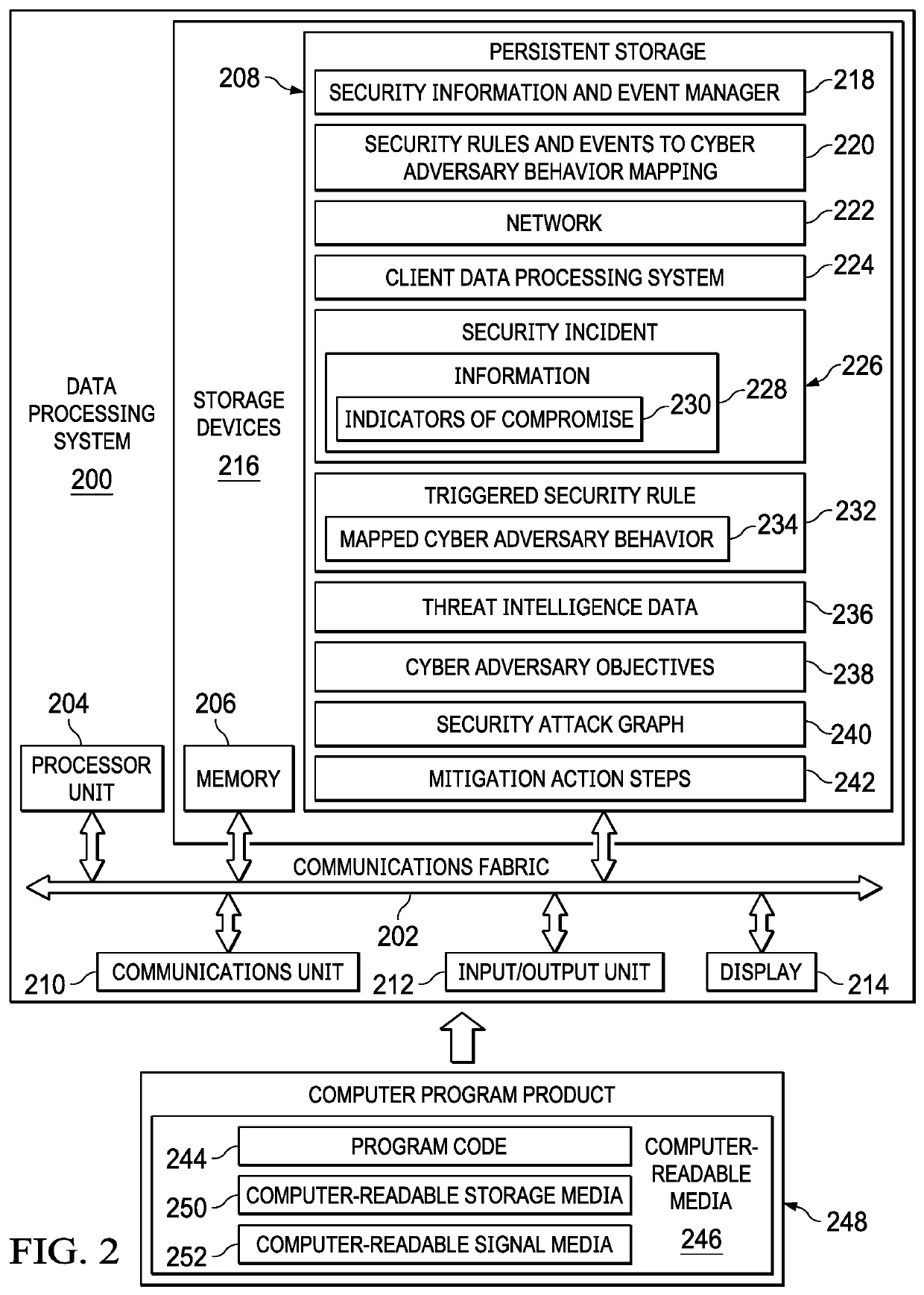
Identifying Cyber Adversary Behavior
Identifying cyber adversary behavior on a computer network is provided. Individual security events are received from multiple threat intelligence data sources. A security incident corresponding to an attack on at least one element of the computer network, the security incident being described by the individual security events received from the multiple threat intelligence data sources, is matched to a defined cyber adversary objective in a structured framework of a plurality of defined cyber adversary objectives and a related technique associated with the defined cyber adversary objective used by a cyber adversary in the attack. A set of mitigation actions is performed on the computer network based on matching the security incident corresponding to the attack on the computer network to the defined cyber adversary objective and the related technique.
Owner:IBM CORP
Trust negotiation building method and system based on history roles
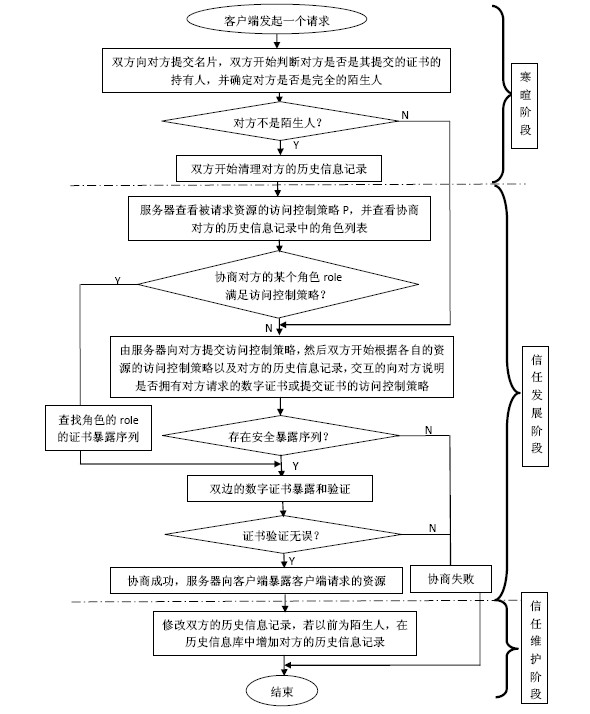
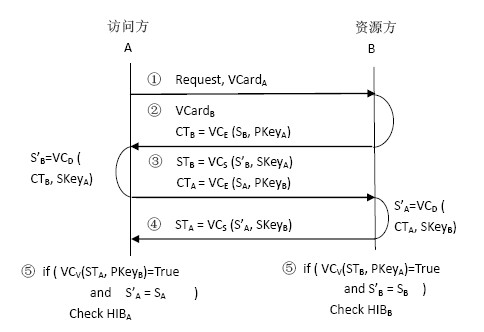
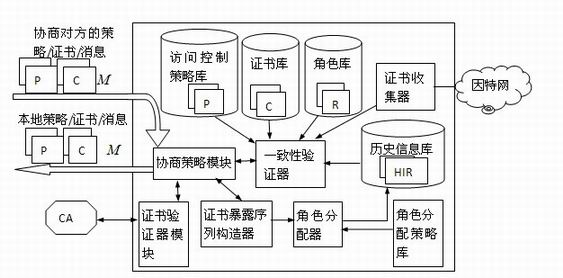
InactiveCN102075518AImprove negotiation efficiencyShorten follow-up negotiationsTransmissionInformation repositoryRelevant information
The invention discloses a trust negotiation building method based on history roles, which comprises the following steps that: (1) when a request party submits requests on a certain resource to a resource party, firstly, a chinchin stage of the trust negotiation is triggered, and the identities of the two parties and whether the historical negotiation success record information exists or not are verified; (2) after the chinchin stage is completed, the two parties enter a trust development period, a safe certificate disclosing sequence is found out to visit the requested resources through mutually disclosing visit control tactics and certificates; and (3) the two parties enter the trust maintenance stage after the trust negotiation is successful, relevant information of the other negotiation party in the current negotiation is stored for accelerating the subsequent negotiation process of the two parties. The method provided by the invention has the advantages that the successfully negotiated two parties update the roles for the other parties in self history information databases and record and obtain the certificate disclosing sequences of the two parties of the role. When the two parties negotiate again, the negotiation does not need to be carried out again, the disclosing can be directly carried out according to the certificate disclosing sequences of the role, the subsequent negotiation of the two parties is shortened, and the certificate collection activities of venomous negotiation adversaries is avoided.
Owner:HUAZHONG UNIV OF SCI & TECH
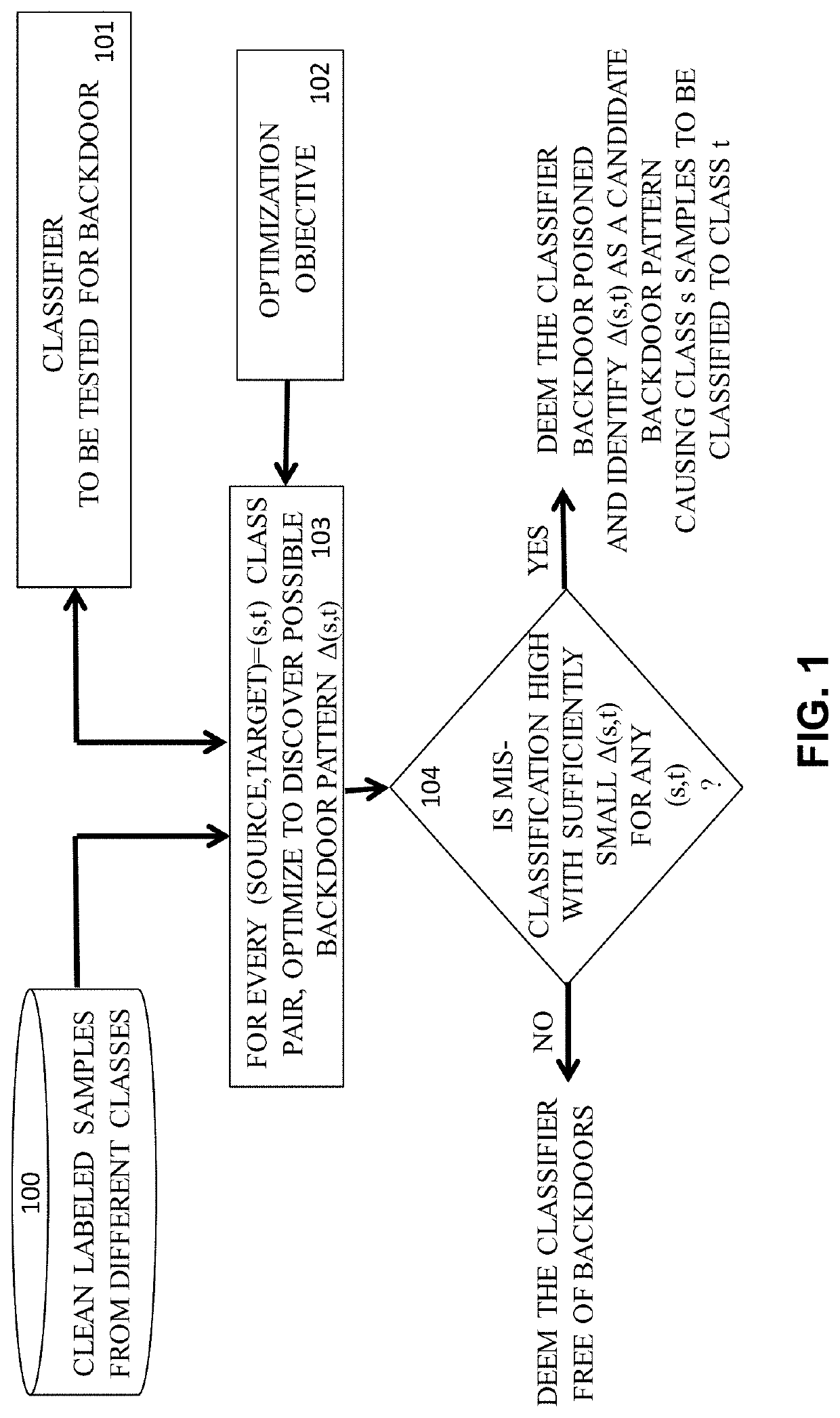
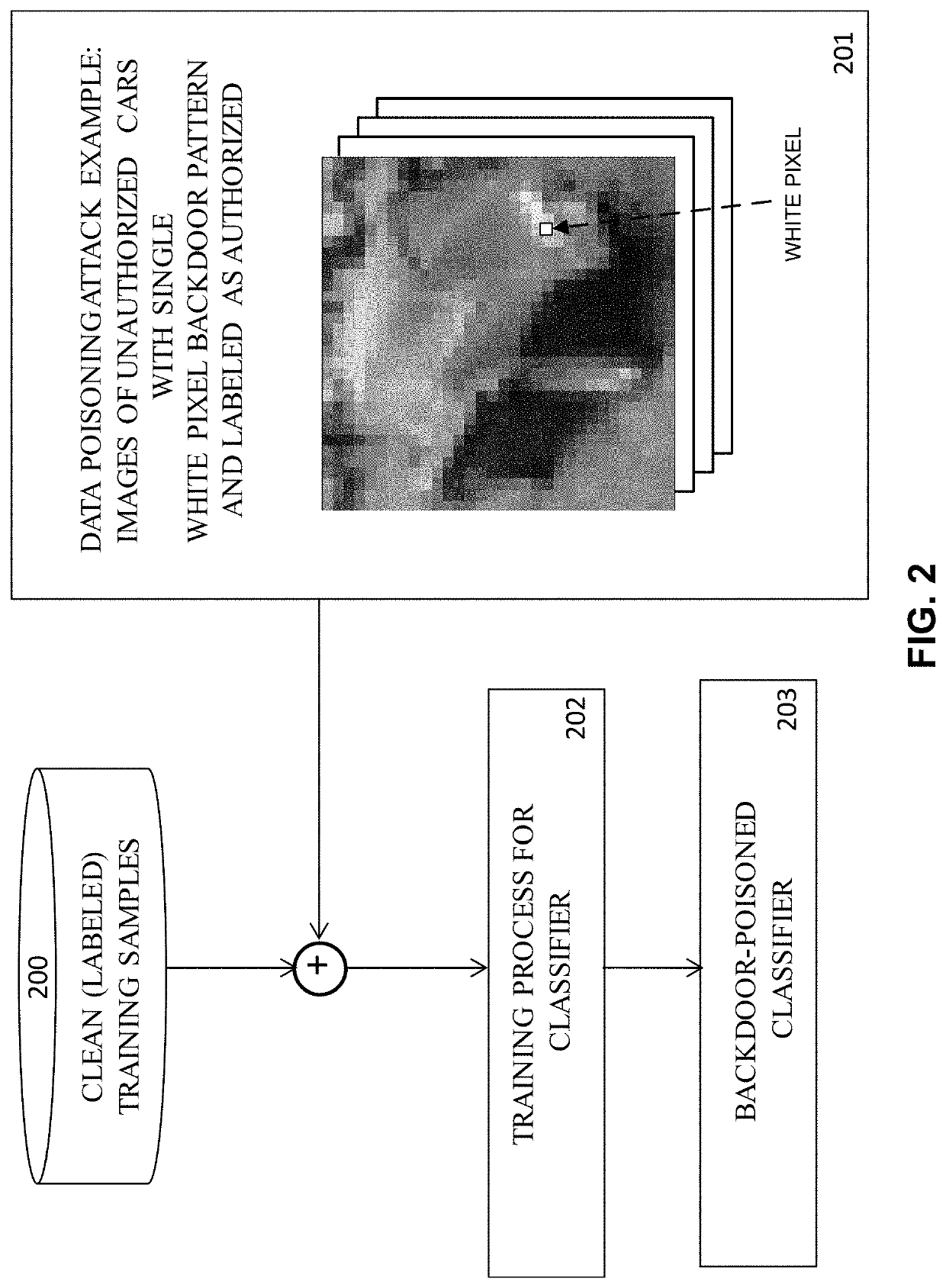
Detection of Test-Time Evasion Attacks
ActiveUS20210019399A1Character and pattern recognitionPlatform integrity maintainancePattern recognitionAttack
Embodiments of the present invention concern detecting Test-Time Evasion (TTE) attacks on neural network, particularly deep neural network (DNN), classifiers. The manner of detection is similar to that used to detect backdoors of a classifier whose training dataset was poisoned. Given knowledge of the classifier itself, the adversary subtly (even imperceptibly) perturbs their input to the classifier at test time in order to cause the class decision to change from a source class to a target class. For example, an image of a person who is unauthorized to access a resource can be modified slightly so that the classifier decides the image is that of an authorized person. The detector is based on employing a method (similar to that used to detect backdoors in DNNs) to discover different such minimal perturbations for each in a set of clean (correctly classified) samples, to change the sample's ground-truth (source) class to every other (target) class. For each (source, target) class pair, null distributions of the sizes of these perturbations are modeled. A test sample is similarly minimally perturbed by the detector from its decided-upon (target) class to every other (potential source) class. The p-values according to the corresponding null distributions of these test-sample perturbations are assessed using the corresponding nulls to decide whether the test sample is a TTE attack.
Owner:ANOMALEE INC
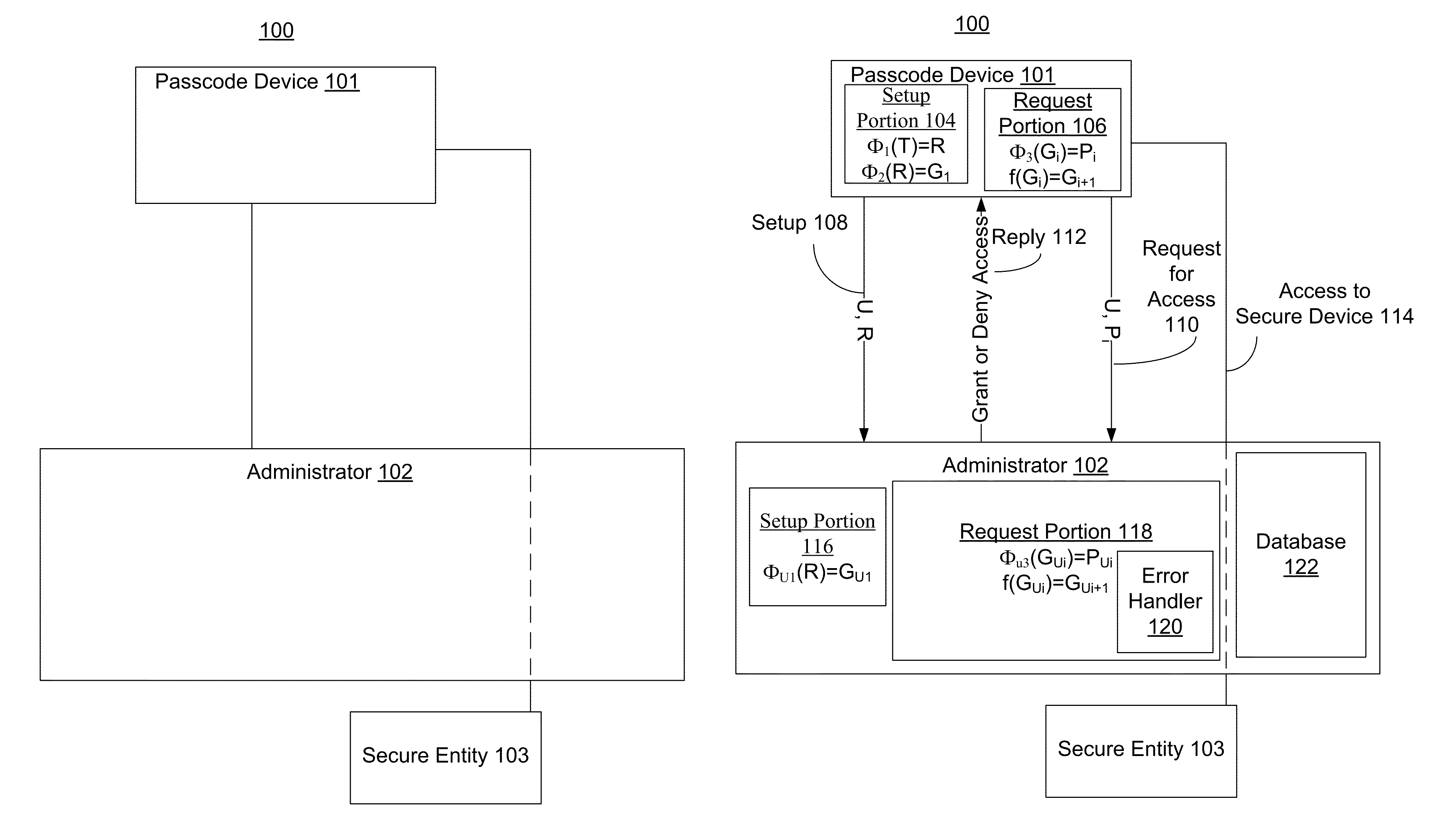
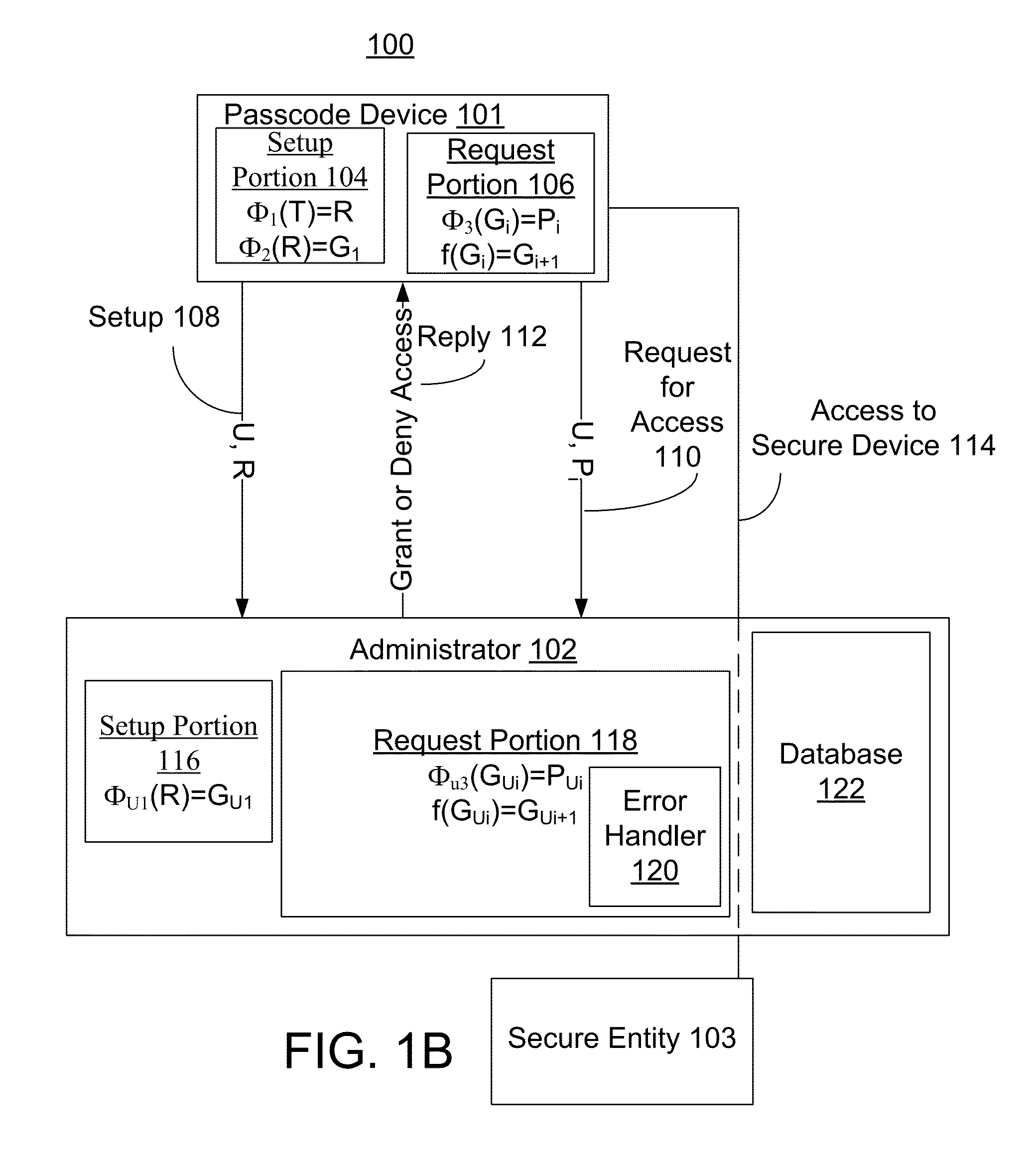
One-time passcodes with asymmetric keys
ActiveUS9235697B2Key distribution for secure communicationUser identity/authority verificationComputer hardwareBack end server
Protecting the security of an entity by using passcodes is disclosed. A user's passcode device generates a passcode. In an embodiment, the passcode is generated in response to receipt of user information. The passcode is received by another system, which authenticates the passcode by at least generating a passcode from a passcode generator, and comparing the generated passcode with the received passcode. The passcode is temporary. At a later use a different passcode is generated from a different passcode generator. In these embodiments, there are asymmetric secrets stored on the passcode device and by the administrator. This adds more security so that if the backend servers are breached, the adversary cannot generate valid passcodes. In some embodiments, the passcode depends on the rounded time.
Owner:BIOGY
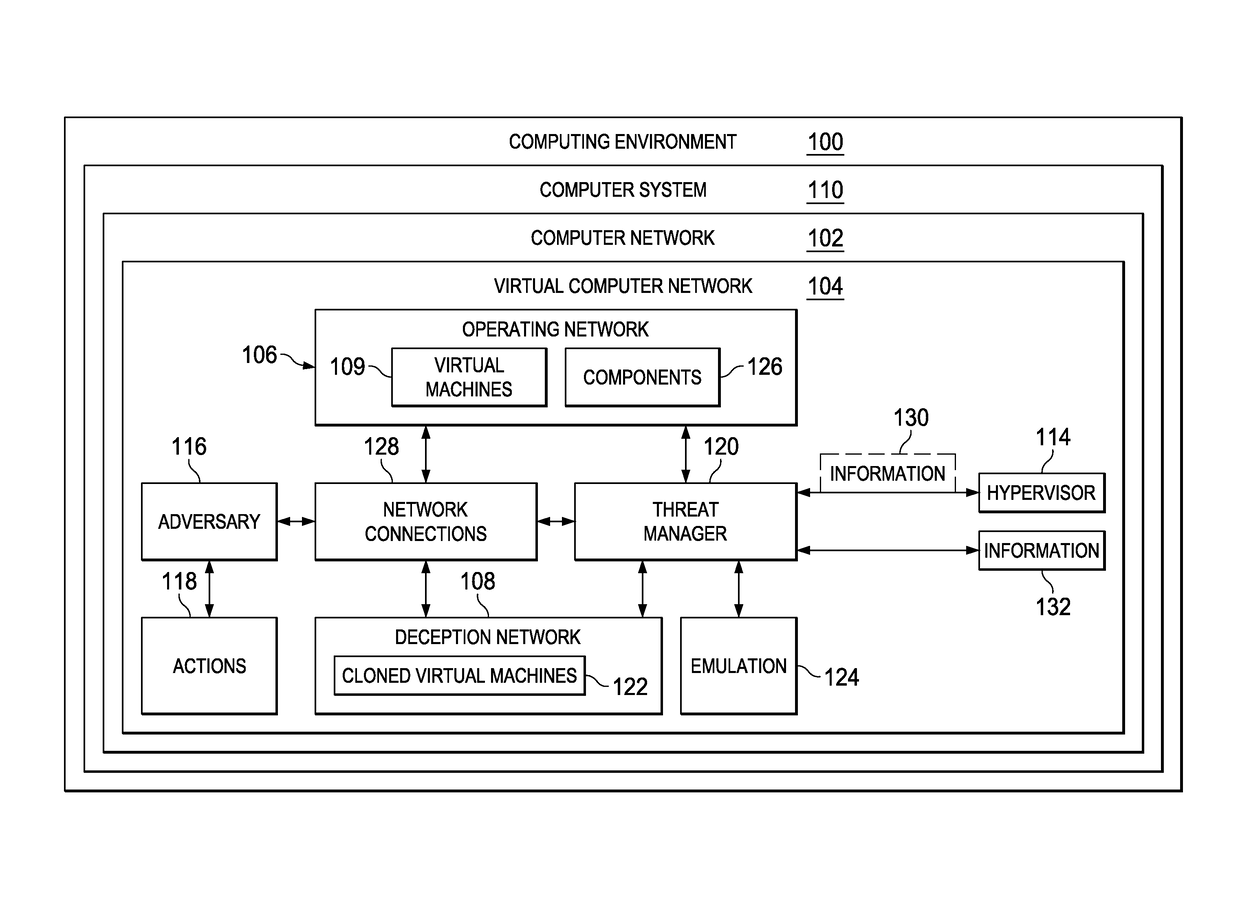
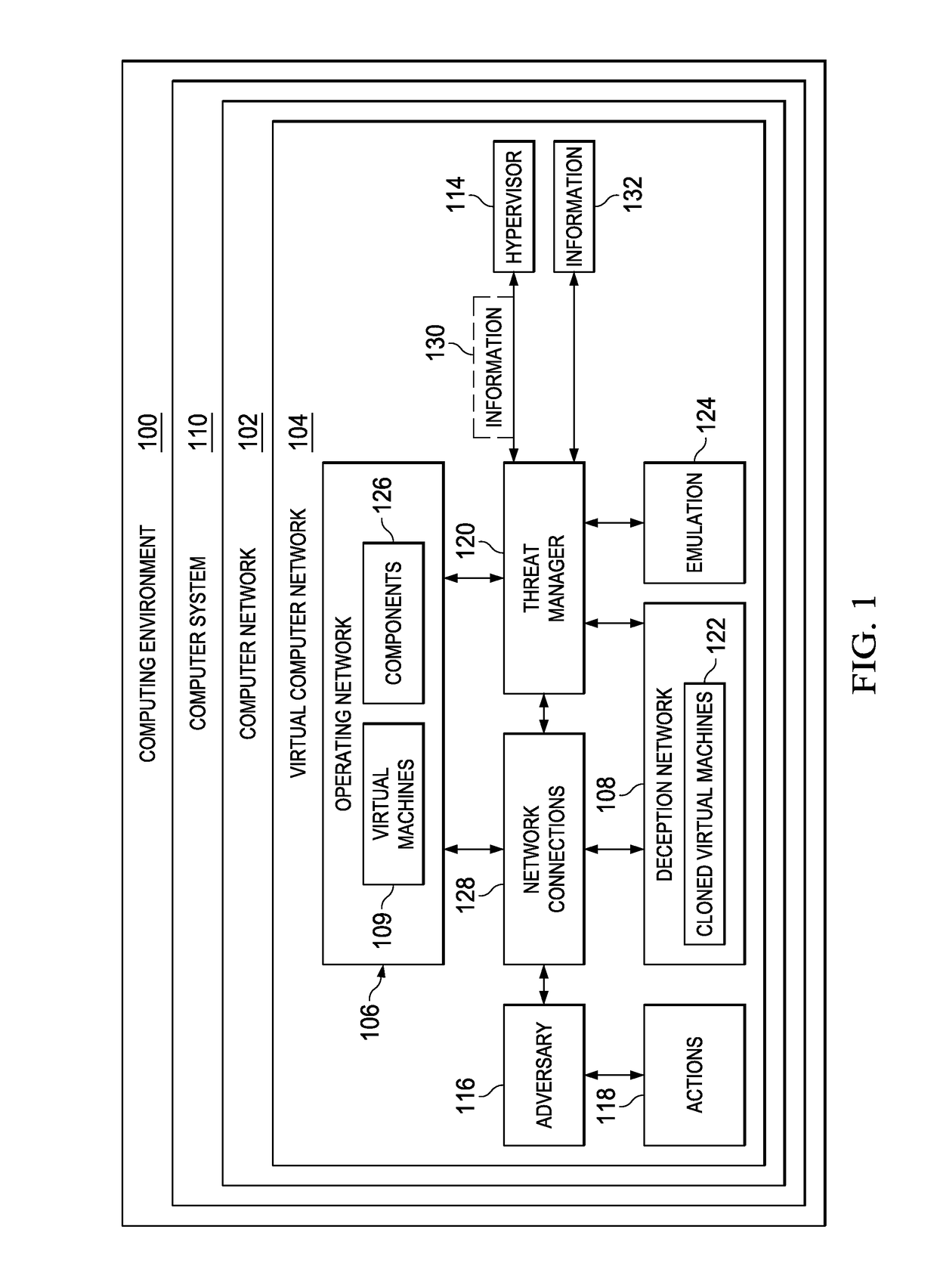
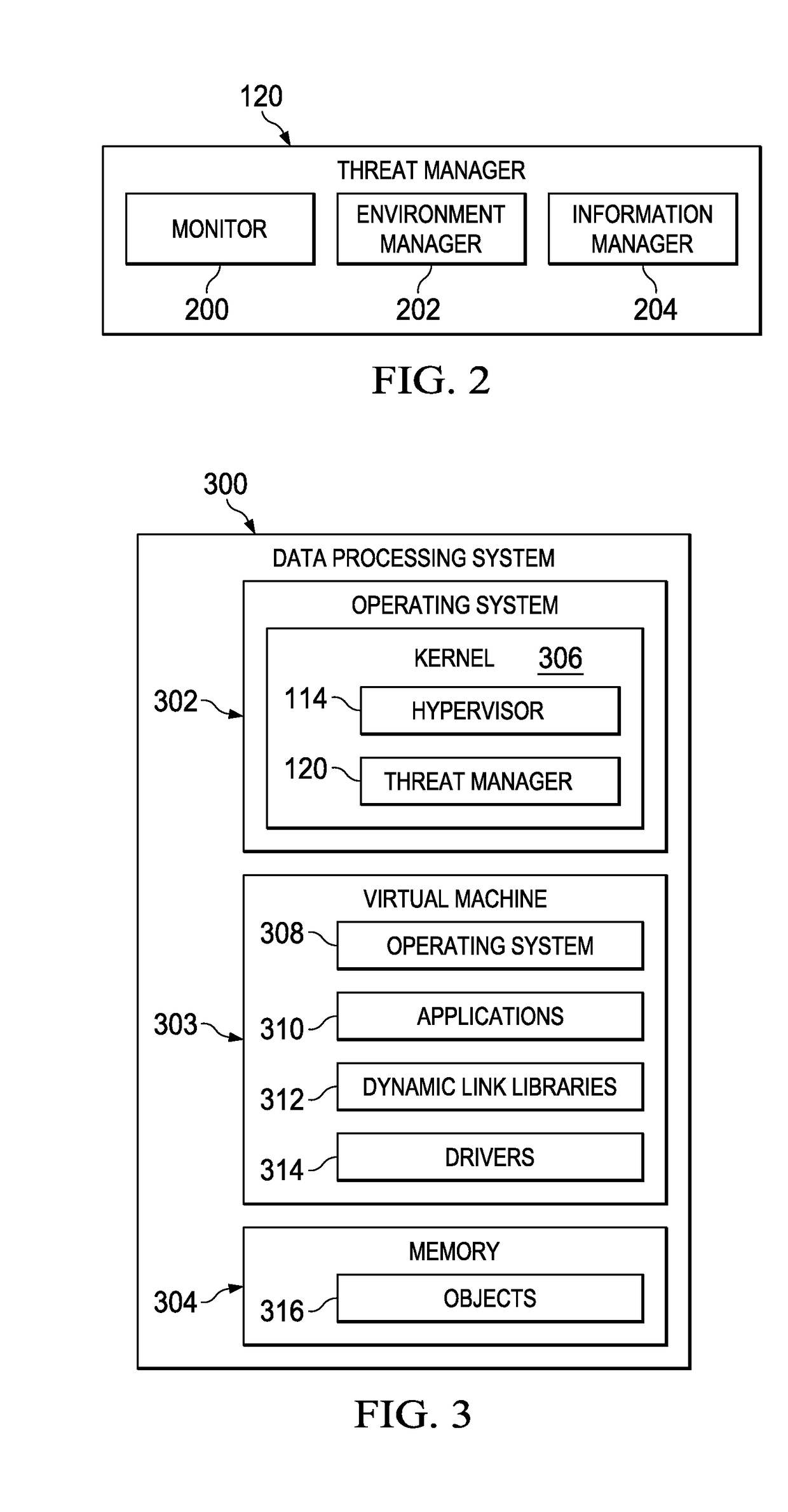
Computer network defense system
ActiveUS20170126736A1Protective groupPlatform integrity maintainanceTransmissionVirtual machineNetwork defense
A method and apparatus for protecting virtual machines. A computer system creates a copy of a group of the virtual machines in an operating network in a deception network to form a group of cloned virtual machines in the deception network when the group of the virtual machines is accessed by an adversary. The computer system creates an emulation of components from the operating network in the deception network. The components are accessible by the group of the cloned virtual machines as if the group of the cloned virtual machines was in the operating network. The computer system moves network connections for the group of the virtual machines in the operating network used by the adversary from the group of the virtual machines in the operating network to the group of the cloned virtual machines, enabling protecting the group of the virtual machines from actions performed by the adversary.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
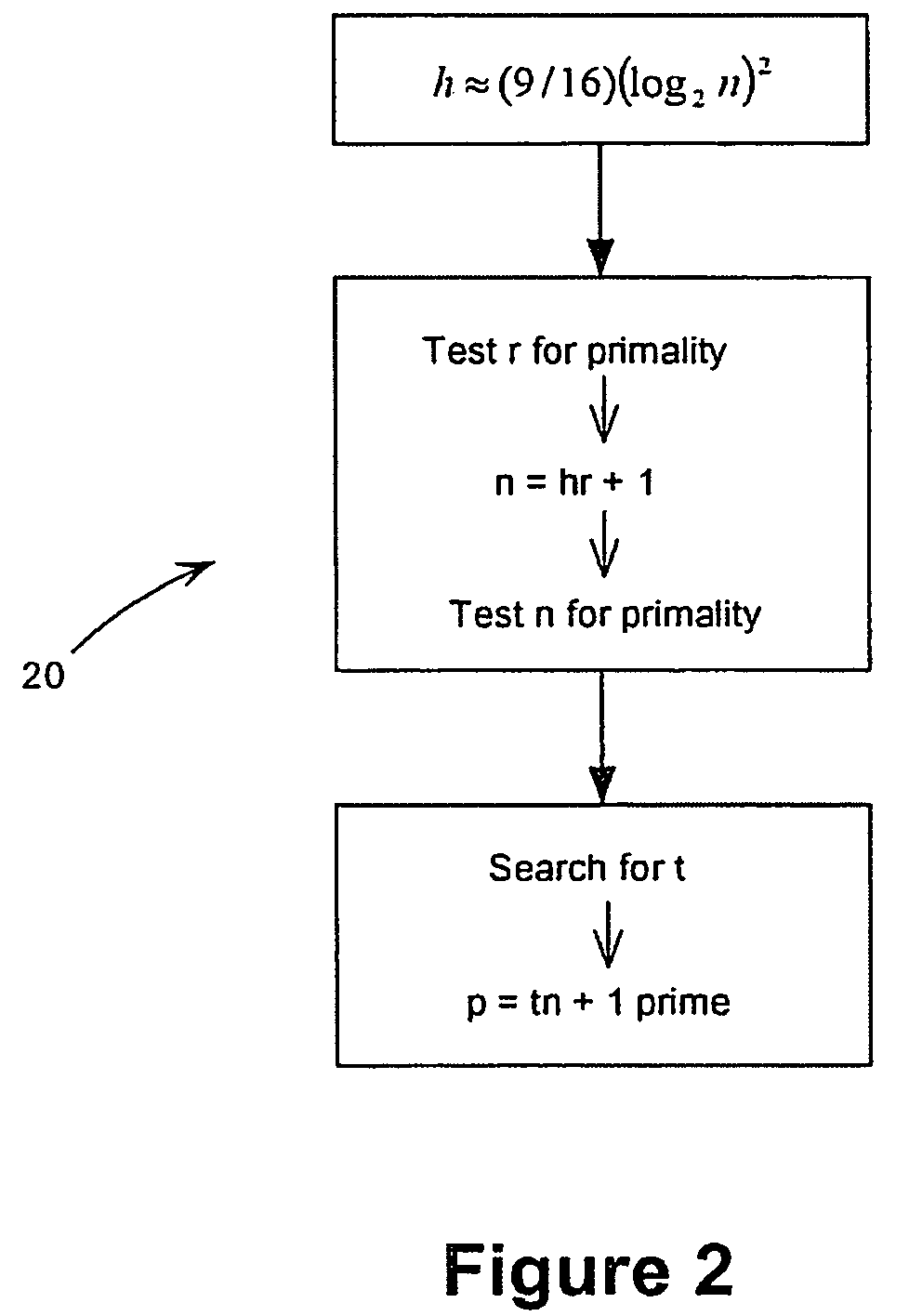
Custom static Diffie-Hellman groups
ActiveUS8588409B2Inhibit active attackPublic key for secure communicationComputer security arrangementsAdversaryAlgorithm
Methods for choosing groups for a static Diffie-Hellman key agreement protocol to inhibit active attacks by an adversary are provided. In mod p groups, an even h is chosen of value approximately ( 9 / 16)(log2n)2, values r and n are determined using sieving and primality testing on r and n, and a value t is found to compute p=tn+1 wherein p is prime. In elliptic curve groups defined over a binary filed, a random curve is chosen, the number of points on the curve is counted and this number is checked for value of 2n wherein n is prime and n−1 meets preferred criteria. In elliptic curve groups defined over a prime field of order q, a value n=hr+1 is computed, wherein n is prime and n−1 meets preferred criteria, and a complex multiplication method is applied on n to produce a value q and an elliptic curve E defined over q and having an order n.
Owner:MALIKIE INNOVATIONS LTD
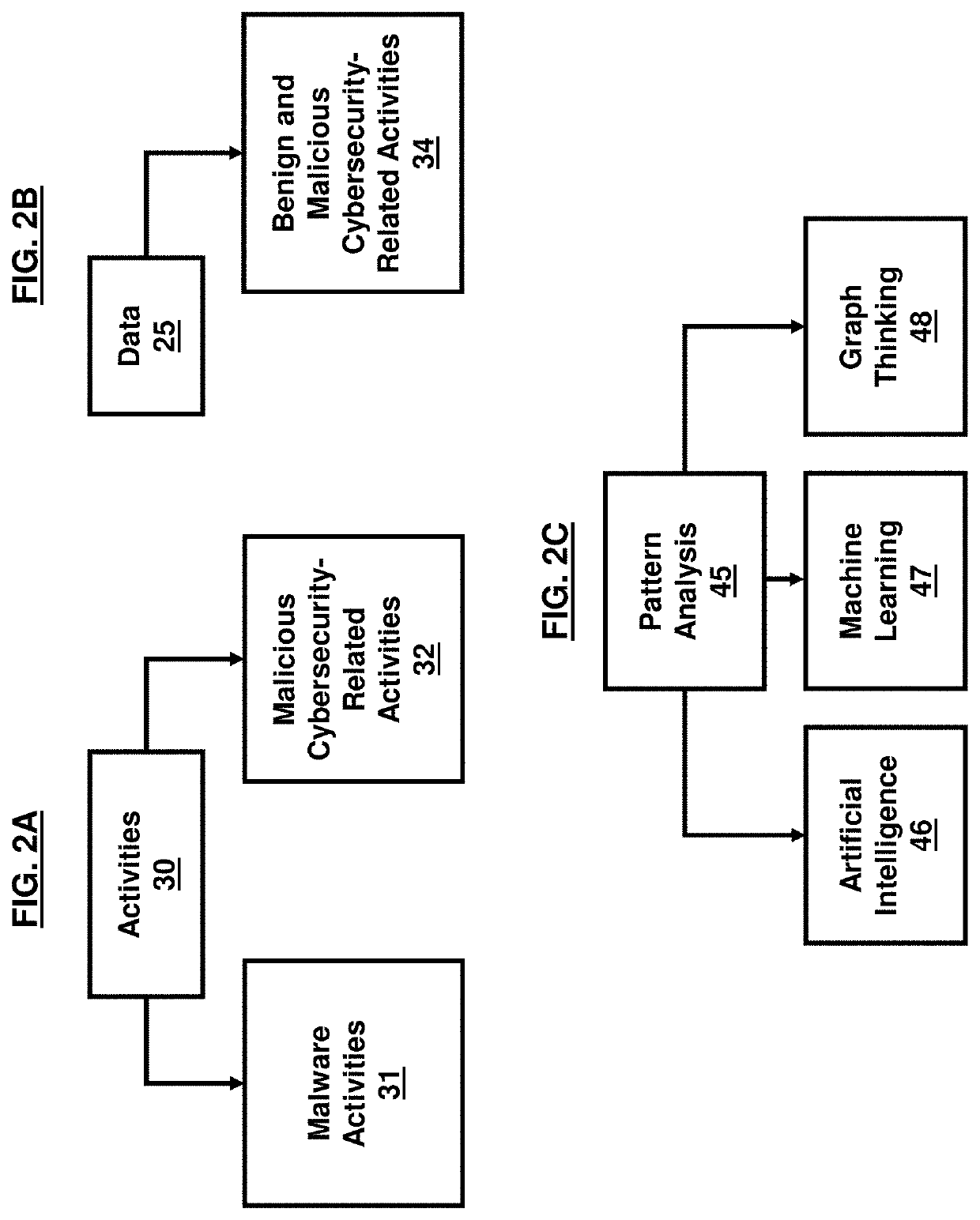
Cybersecurity resilience by integrating adversary and defender actions, deep learning, and graph thinking
A technique for providing cyber resilience by integrating autonomous adversary and defender agents, deep learning, and graph thinking. An automated competitive environment of autonomous adversary and defender agents is provided such that the adversary agent can emulate the adversary activities, patterns, and intentions using all available cybersecurity measurements and observations, and, the defender agent can generate and suggest the best possible appropriate actions to mitigate or prevent adversary activities while recovering or protecting assets. An automated cyber resilience system with autonomous agents is provided using machine learning and security analytics to first predict the current and future adversary activities and then provide an automated critical asset protection and recovery by enabling agents to take appropriate reactive and pro-active actions at each time step to prevent, recover, or mitigate adversary activities over enterprise and tactical networks.
Owner:UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE ARMY
Authenticated adversarial routing
InactiveUS8984297B2Digital data processing detailsUser identity/authority verificationNetwork packetStatus changed
A routing protocol is used to transmit messages from a sender to a receiver over a network of nodes, where adversaries can control links between the nodes and can also control the behavior of a large number of nodes. Various techniques can be used, along or in combination, to combat these effects. In one approach, certain trigger conditions are identified, the occurrence of which signals malicious behavior within the network. When signaled, the sender requests status reports from the intermediate nodes in an effort to determine which nodes are malicious. The information for the status reports is generated by nodes as packets are passed from one node to the next.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE +1
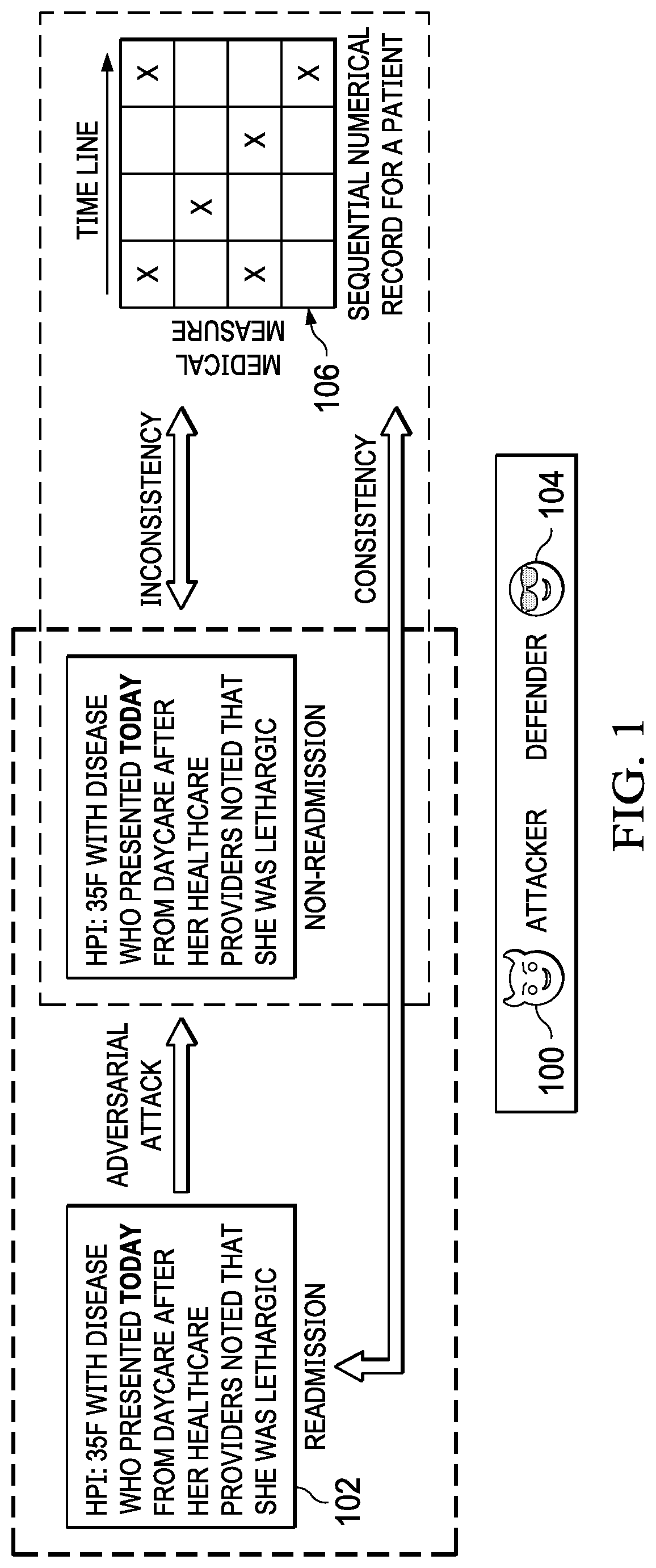
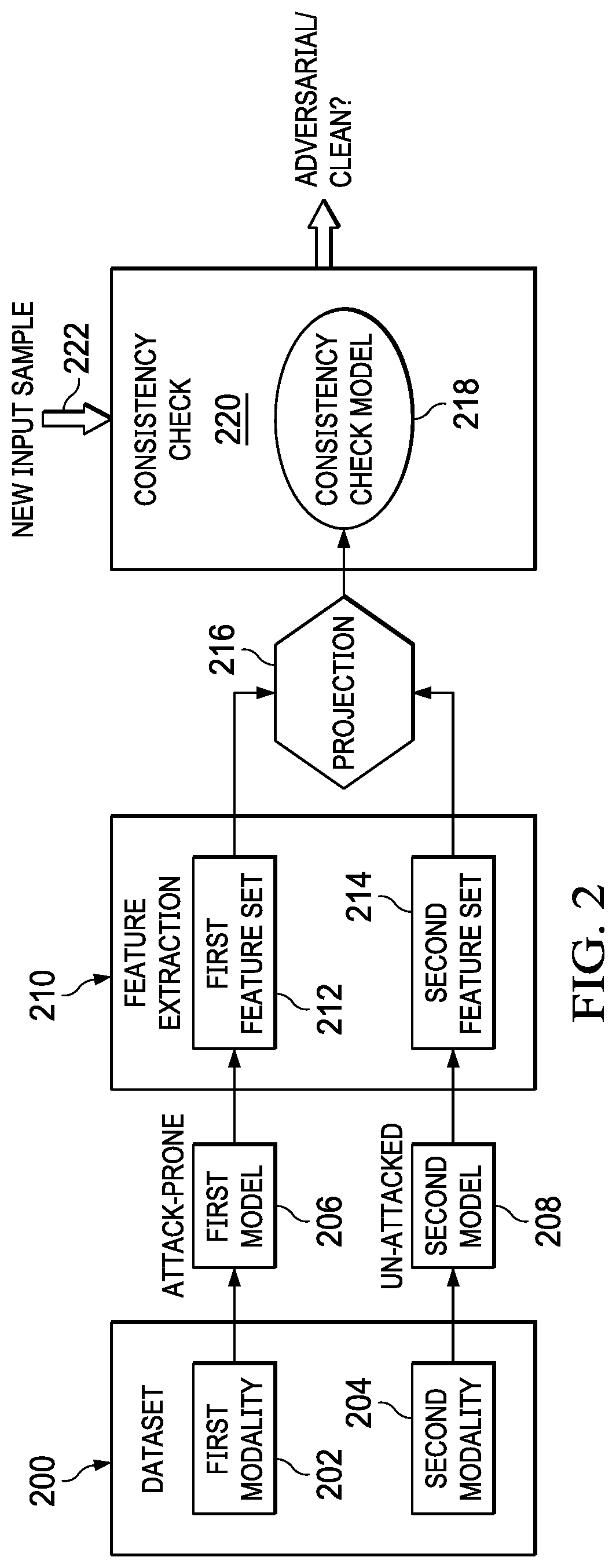
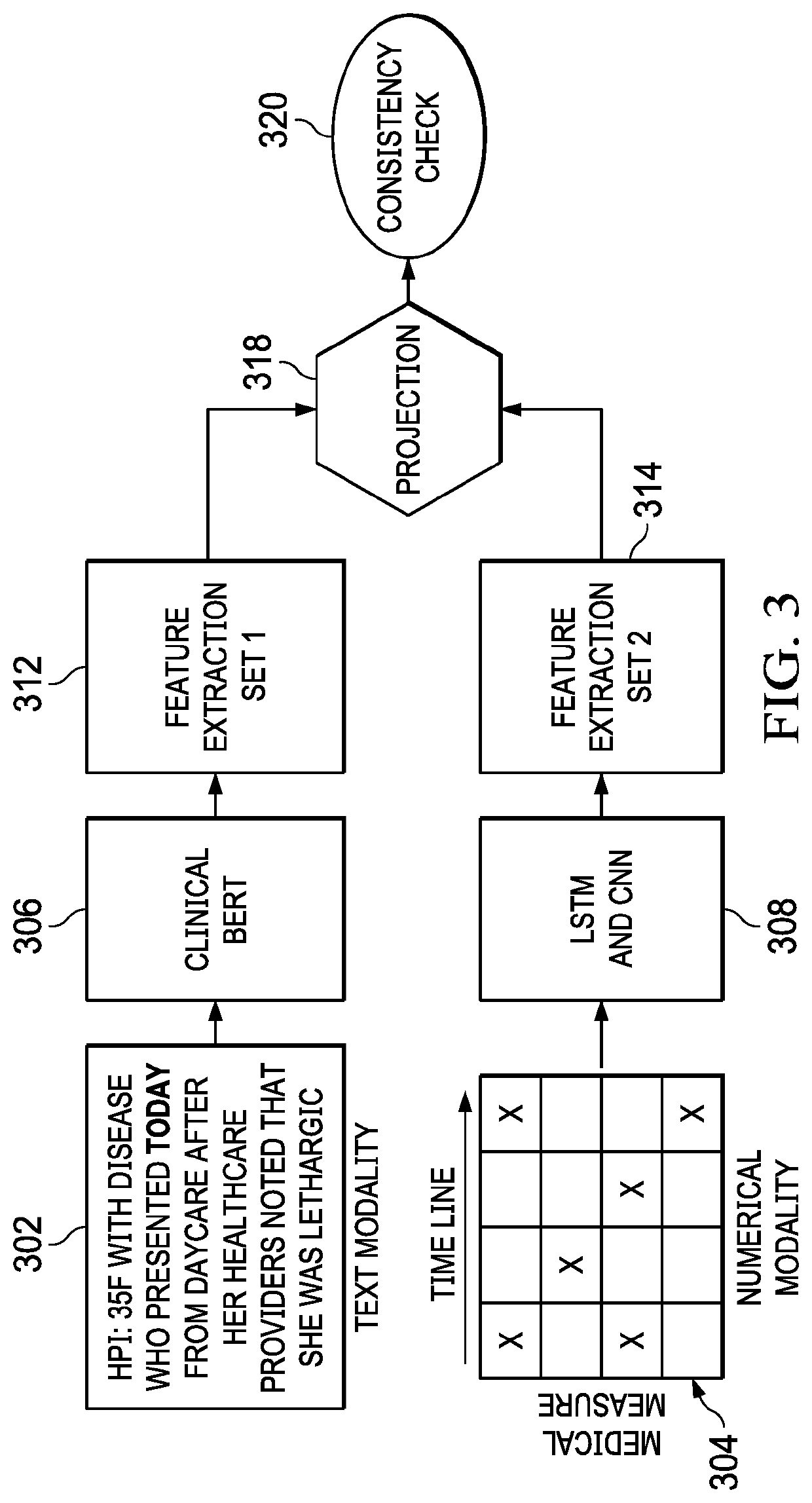
Using multimodal model consistency to detect adversarial attacks
ActiveUS20210319093A1Digital data protectionPlatform integrity maintainancePattern recognitionData set
A method, apparatus and computer program product to defend learning models that are vulnerable to adversarial example attack. It is assumed that data (a “dataset”) is available in multiple modalities (e.g., text and images, audio and images in video, etc.). The defense approach herein is premised on the recognition that the correlations between the different modalities for the same entity can be exploited to defend against such attacks, as it is not realistic for an adversary to attack multiple modalities. To this end, according to this technique, adversarial samples are identified and rejected if the features from one (the attacked) modality are determined to be sufficiently far away from those of another un-attacked modality for the same entity. In other words, the approach herein leverages the consistency between multiple modalities in the data to defend against adversarial attacks on one modality.
Owner:IBM CORP
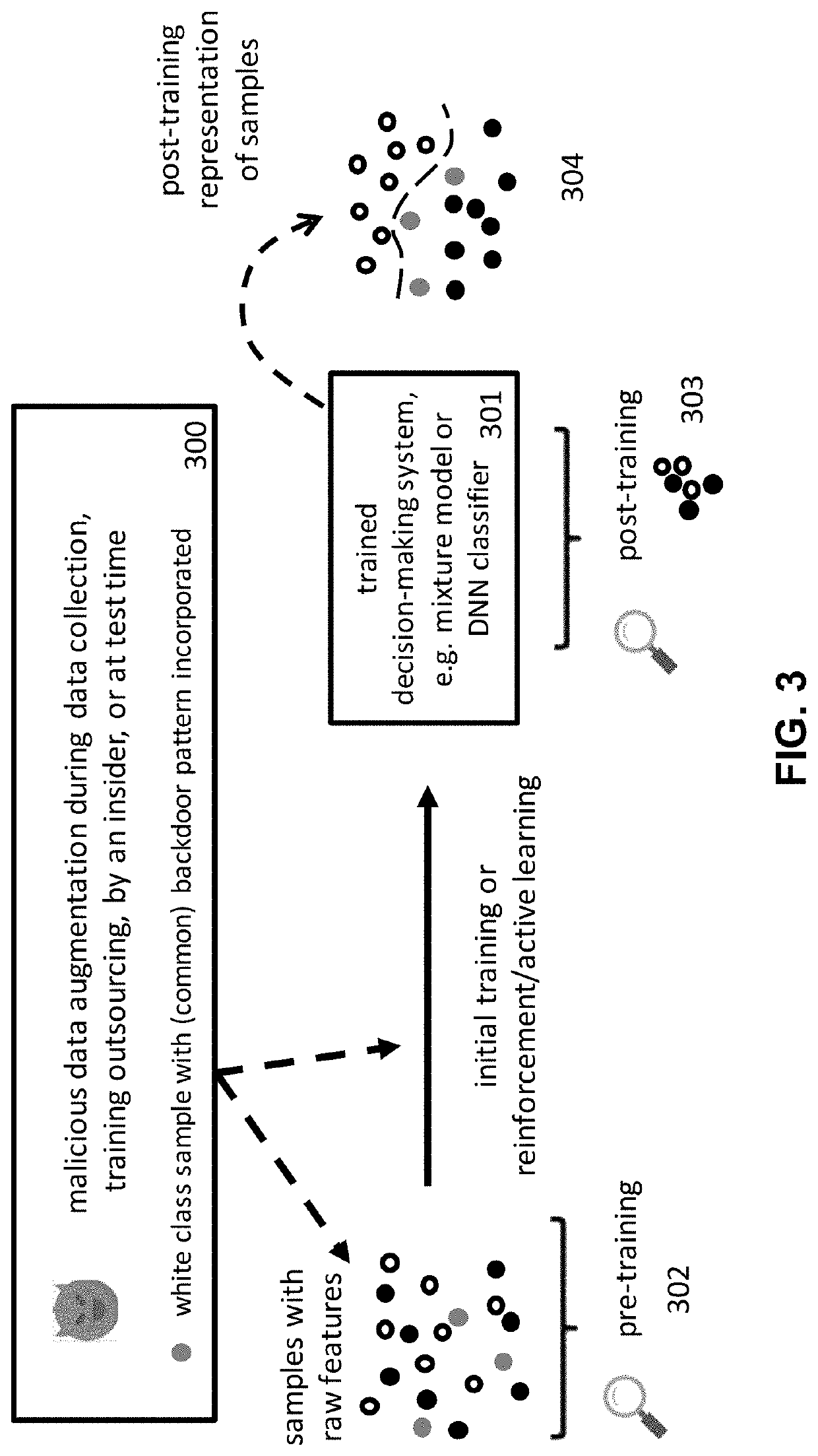
Innocent until proven guilty (IUPG): adversary resistant and false positive resistant deep learning models
Techniques for providing innocent until proven guilty (IUPG) solutions for building and using adversary resistant and false positive resistant deep learning models are disclosed. In some embodiments, a system, process, and / or computer program product includes storing a set comprising one or more innocent until proven guilty (IUPG) models for static analysis of a sample; performing a static analysis of content associated with the sample, wherein performing the static analysis includes using at least one stored IUPG model; and determining that the sample is malicious based at least in part on the static analysis of the content associated with the sample, and in response to determining that the sample is malicious, performing an action based on a security policy.
Owner:PALO ALTO NETWORKS INC
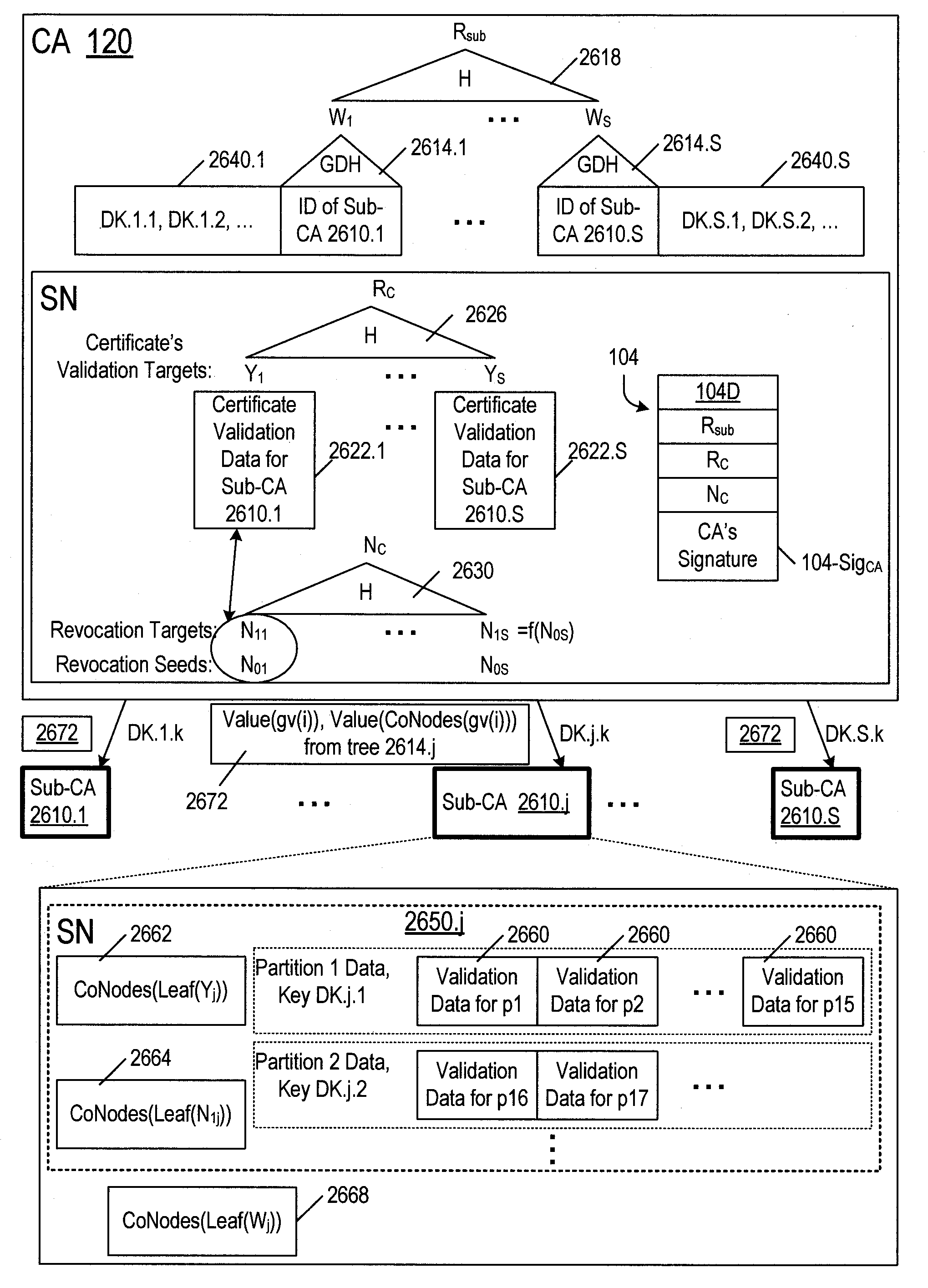
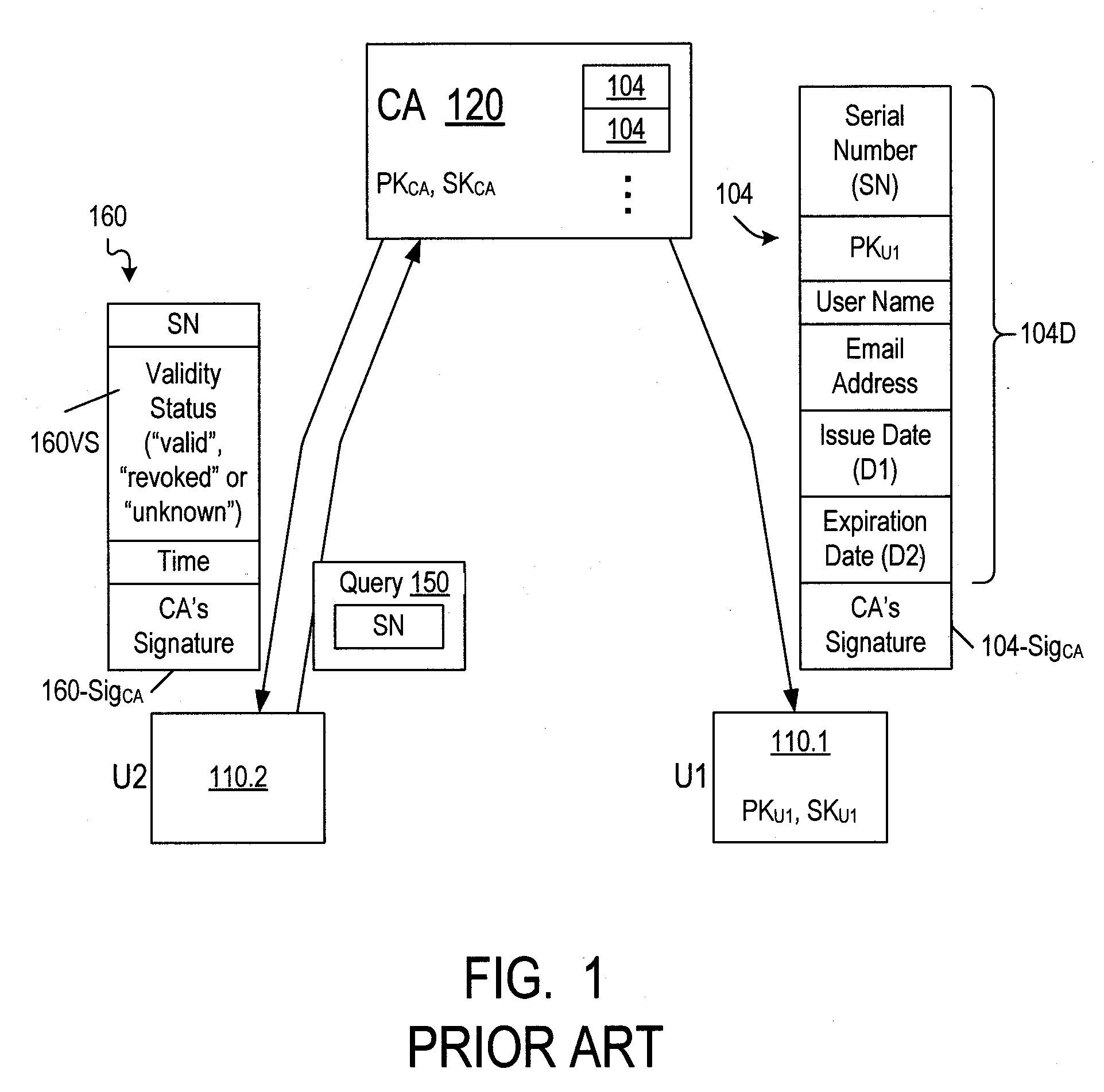
Revocation of cryptographic digital certificates
ActiveUS20090259843A1Maximizing numberPromote disseminationUser identity/authority verificationCertificate authorityMulticast transmission
Owner:NTT DOCOMO INC
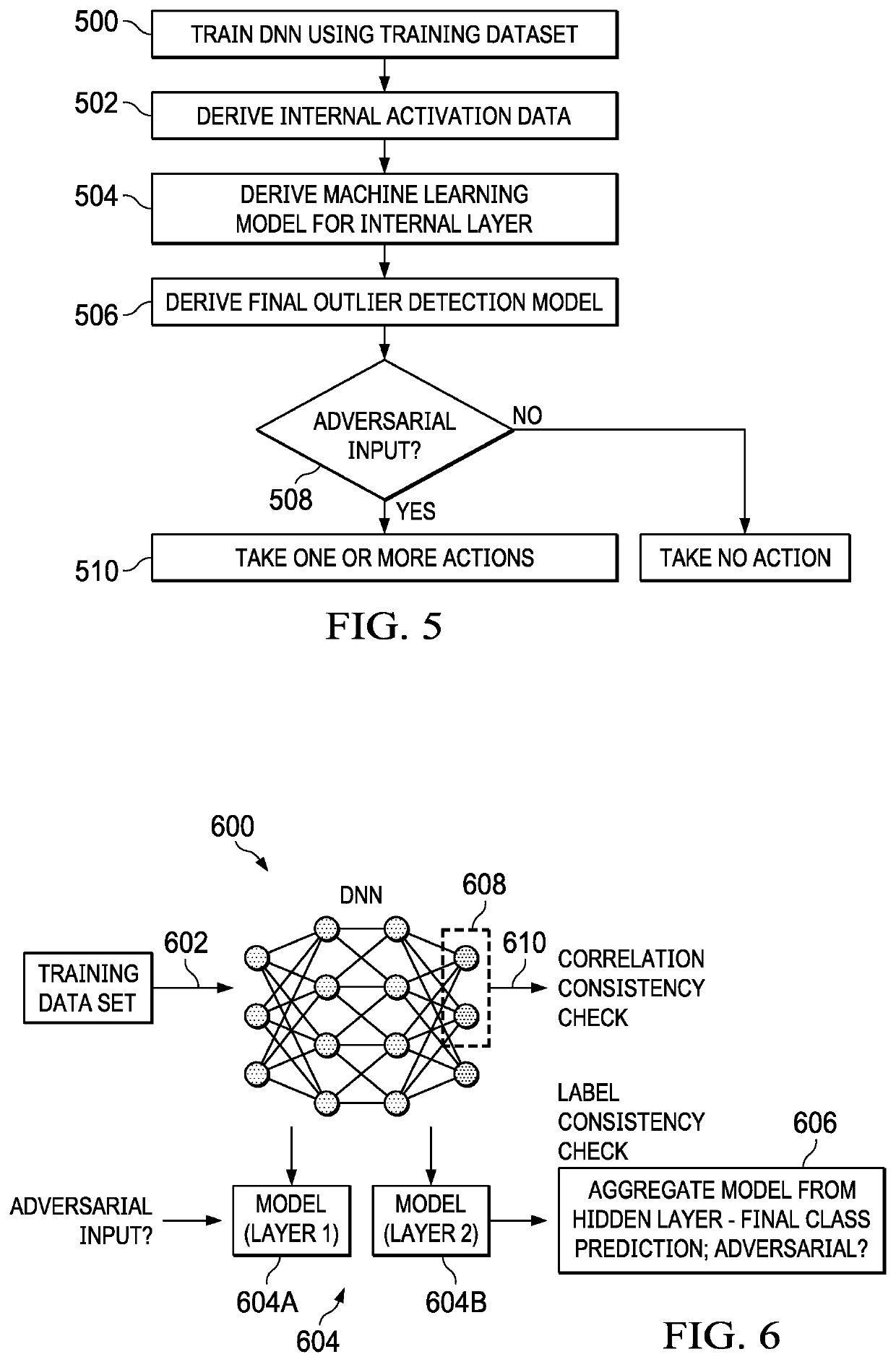
Detecting adversary attacks on a deep neural network (DNN)
PendingUS20220156563A1No guaranteeCharacter and pattern recognitionComputer security arrangementsPattern recognitionAdversary
A method, apparatus and computer program product to protect a deep neural network (DNN) having a plurality of layers including one or more intermediate layers. In this approach, a training data set is received. During training of the DNN using the received training data set, a representation of activations associated with an intermediate layer is recorded. For at least one or more of the representations, a separate classifier (model) is trained. The classifiers, collectively, are used to train an outlier detection model. Following training, the outliner detection model is used to detect an adversarial input on the deep neural network. The outlier detection model generates a prediction, and an indicator whether a given input is the adversarial input. According to a further aspect, an action is taken to protect a deployed system associated with the DNN in response to detection of the adversary input.
Owner:IBM CORP
Scalable RFID systems: a privacy-preserving protocol with constant-time identification
InactiveUS8726021B2Minimizes probabilityUser identity/authority verificationUnauthorized memory use protectionComputer networkHash function
A protocol with constant-time complexity solves the problem of private identification of tags in low-cost, large-scale radio frequency identification (RFID) systems—assuming that an adversary has complete control over the communication channel. Each RFID tag has an internal counter, c, and is preloaded with a unique pseudonym, ψ, and a secret key, k. A RFID reader attempting to identify and authenticate a tag within its range generates and transmits a random nonce to the RFID tag, which returns a first hash of its current pseudonym and counter, and a second hash that is a function of the secret key. The reader uses the returned data to identify the RFID tag and its secret key by reference to a database and returns other hash values that authenticate the reader to the RFID tag. The most expensive operation that RFID tags are required to perform is a hash function.
Owner:UNIV OF WASHINGTON
Identifying cyber adversary behavior
Owner:INT BUSINESS MASCH CORP
Methods for minimizing side channel leakage for group key agreement for controller area network
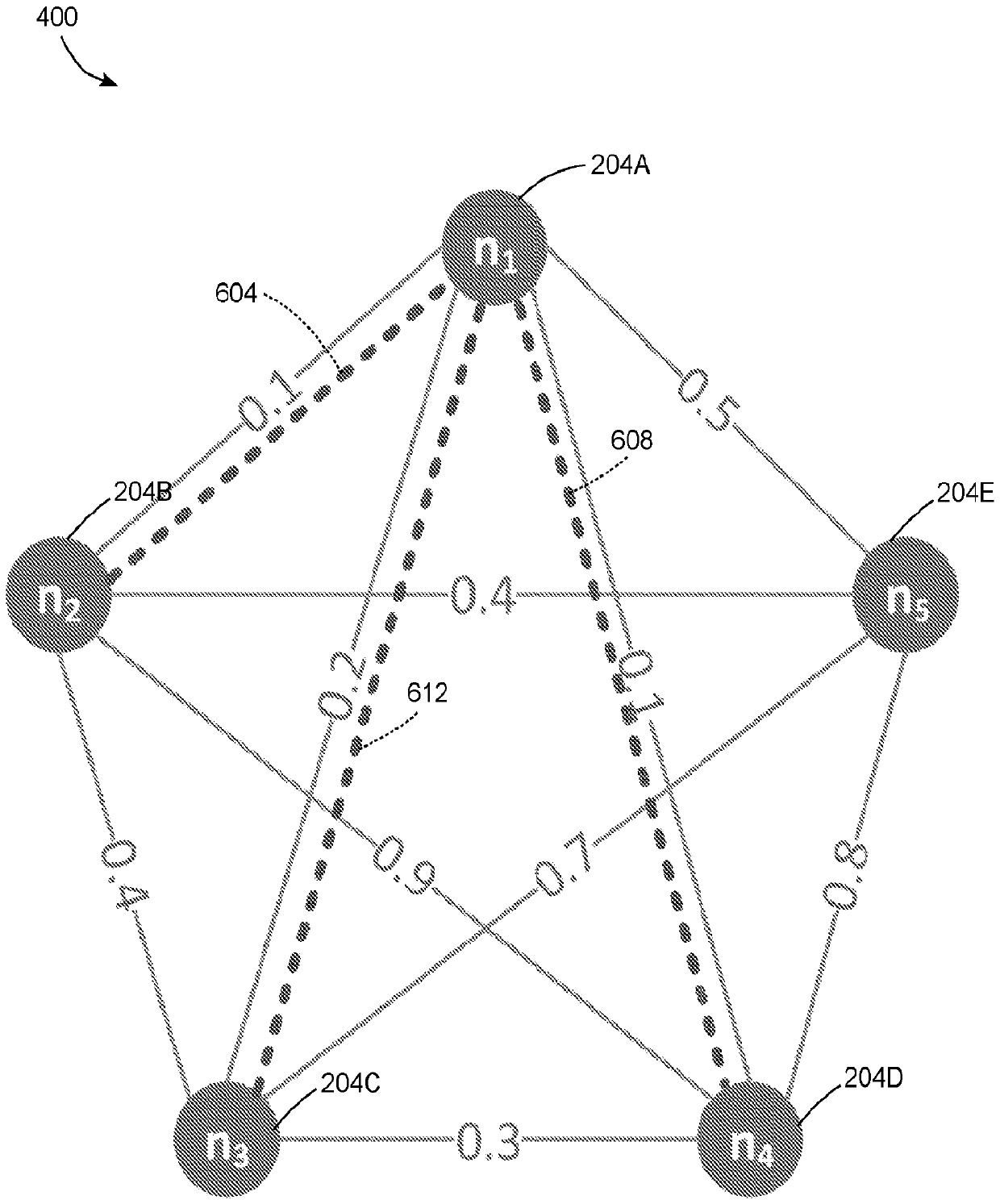
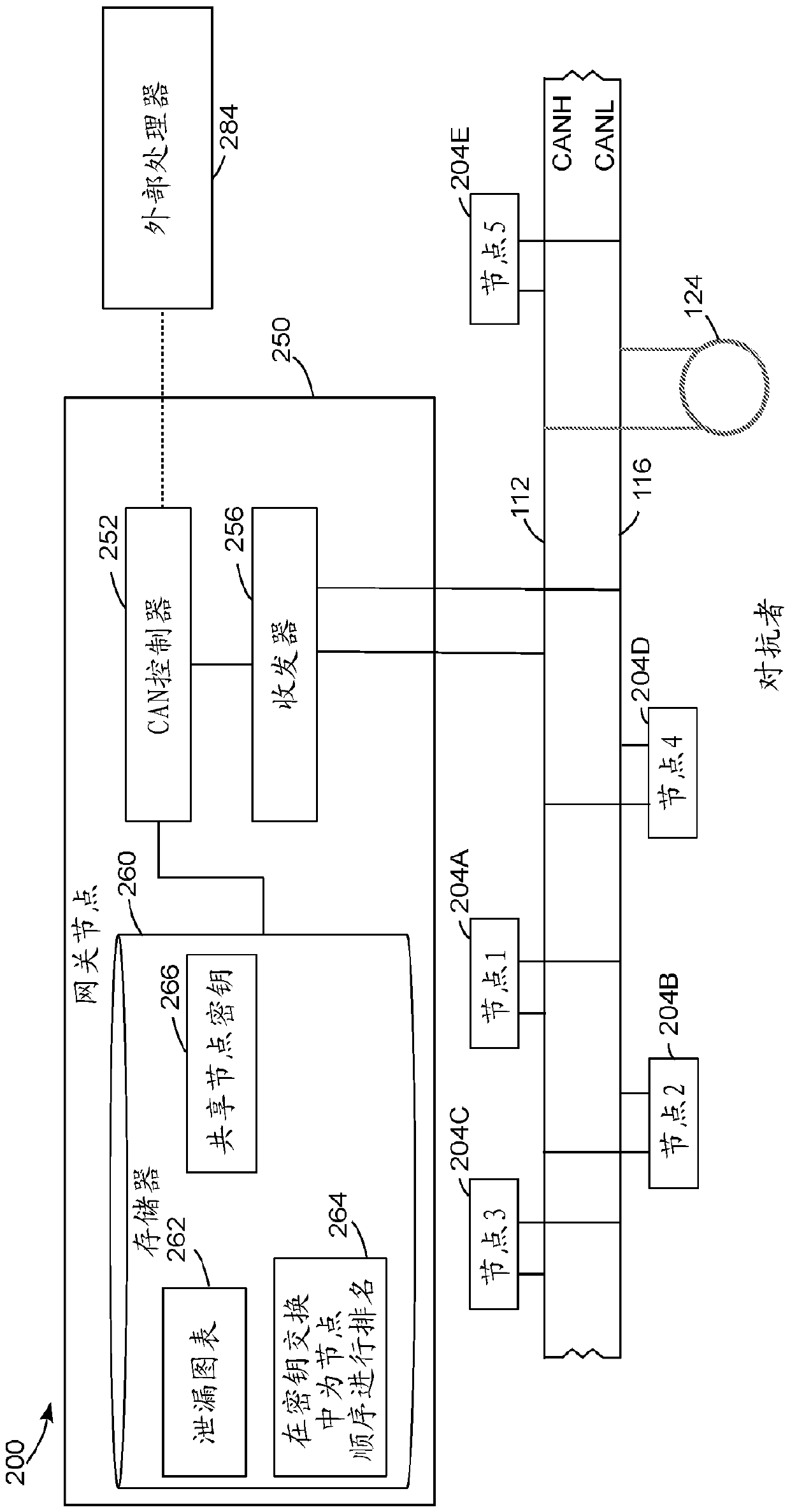
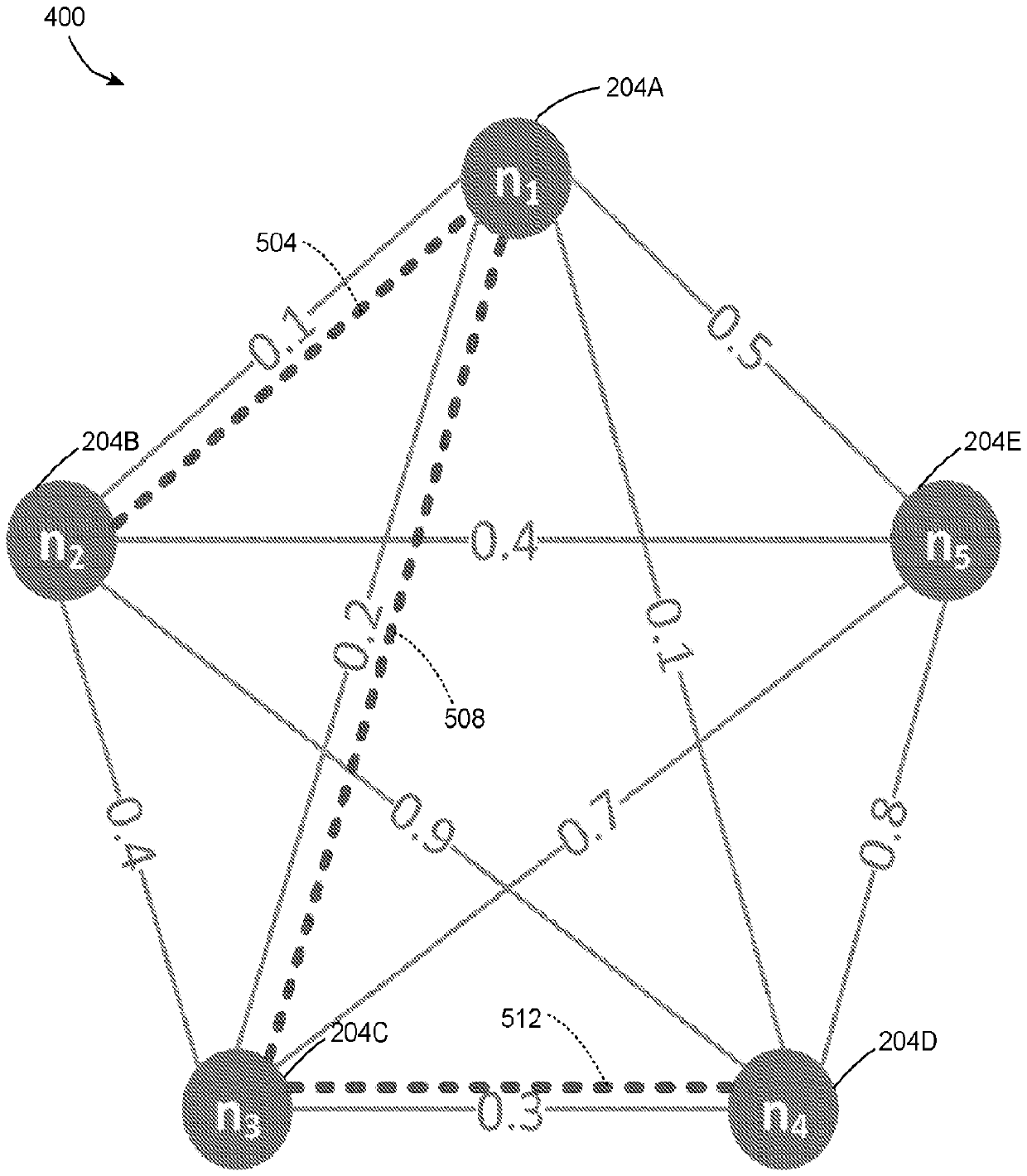
ActiveCN110622465AReduce leakageLeakage MinimizationMathematical modelsKey distribution for secure communicationKey exchangeArea network
A method for operation of a communication network reduces leakage of data to an adversary that can observe signals transmitted through the communication network. The method includes generating a ranking to order operation of a plurality of nodes that exchange data in a group cryptographic key exchange process based on a leakage map of the nodes. The ranking minimizes leakage of data through a shared communication medium during the group cryptographic key exchange process. The method includes transmitting the ranking to the plurality of nodes through the shared communication medium, and performing, with the plurality of nodes, the group cryptographic key exchange process in an order of operation specified in the ranking to enable the plurality of nodes to exchange a shared cryptographic keythrough the shared communication medium while minimizing leakage of data.
Owner:ROBERT BOSCH GMBH
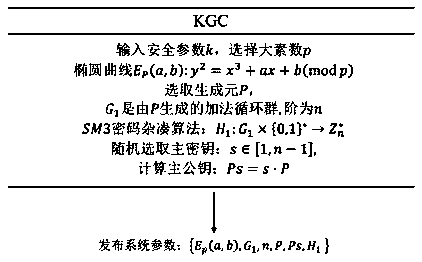
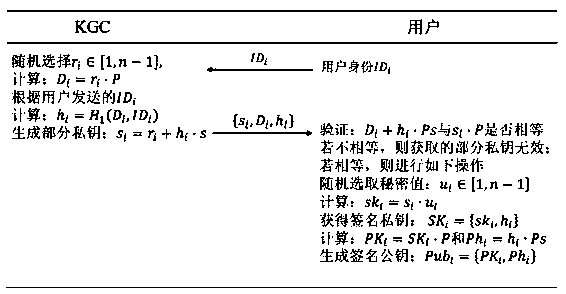
Certificate-free signature method based on national secret SM2
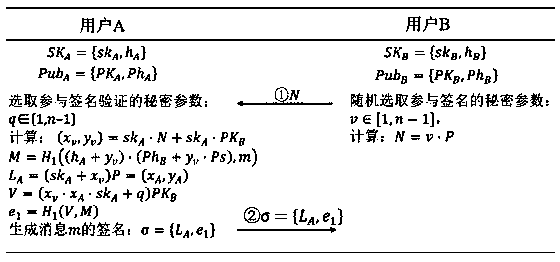
ActiveCN109274506AEnsure safetyImprove fairnessUser identity/authority verificationComputer securityAdversary
The invention discloses a certificate-free signature method based on a national secret algorithm. At the time of signature generation, B calculates the parameters participate in signature generation according to the secret parameters randomly selected to participate in signature generation, and send the parameters to A. A randomly selects the secret parameters involved in signature verification, and generates a message combining the secret parameters to send to B. During signature verification, B verifies whether A's signature public key is valid according to the secret parameters generated byparticipating signatures. If it is invalid, the verification fails, otherwise, the verification continues. B calculates a parameter and send it to A. A verifies whether B completes the signature verification according to the correct steps through this parameter, and sends a parameter containing the secret value if B conforms to the correct execution step, otherwise, terminates the signature. B receives the verification parameters of A and participates in the subsequent signature verification, and finally produces the result. The invention can prevent an adversary from controlling one of the parties to seek personal gain in the process of signature and verification in which the server cooperates with the mobile terminal.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com