Patents
Literature
514 results about "Security analytics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A Definition of Security Analytics. Security analytics is the process of using data collection, aggregation, and analysis tools for security monitoring and threat detection. Depending on the types of tools installed, security analytics solutions can incorporate large and diverse data sets into their detection algorithms.
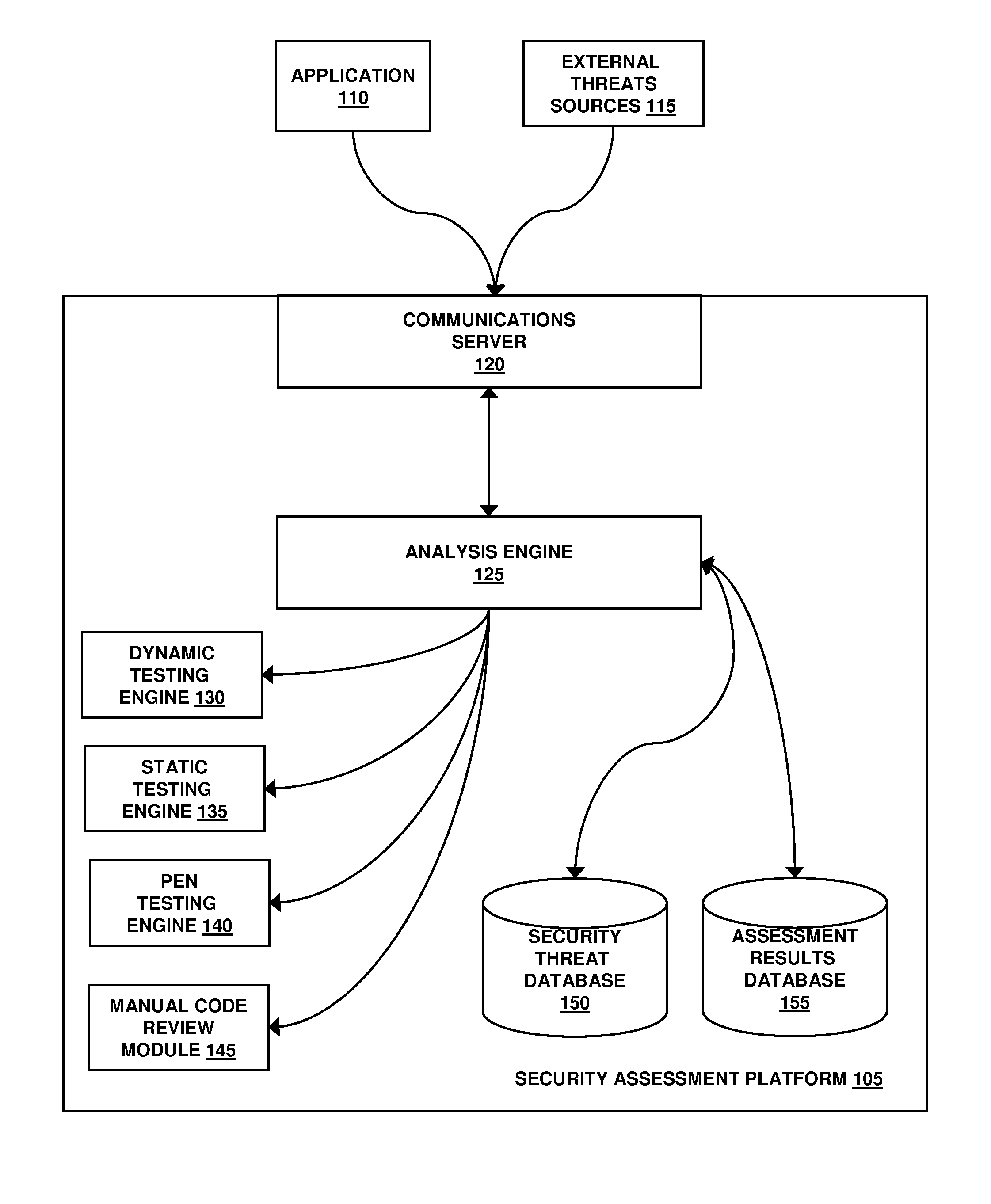
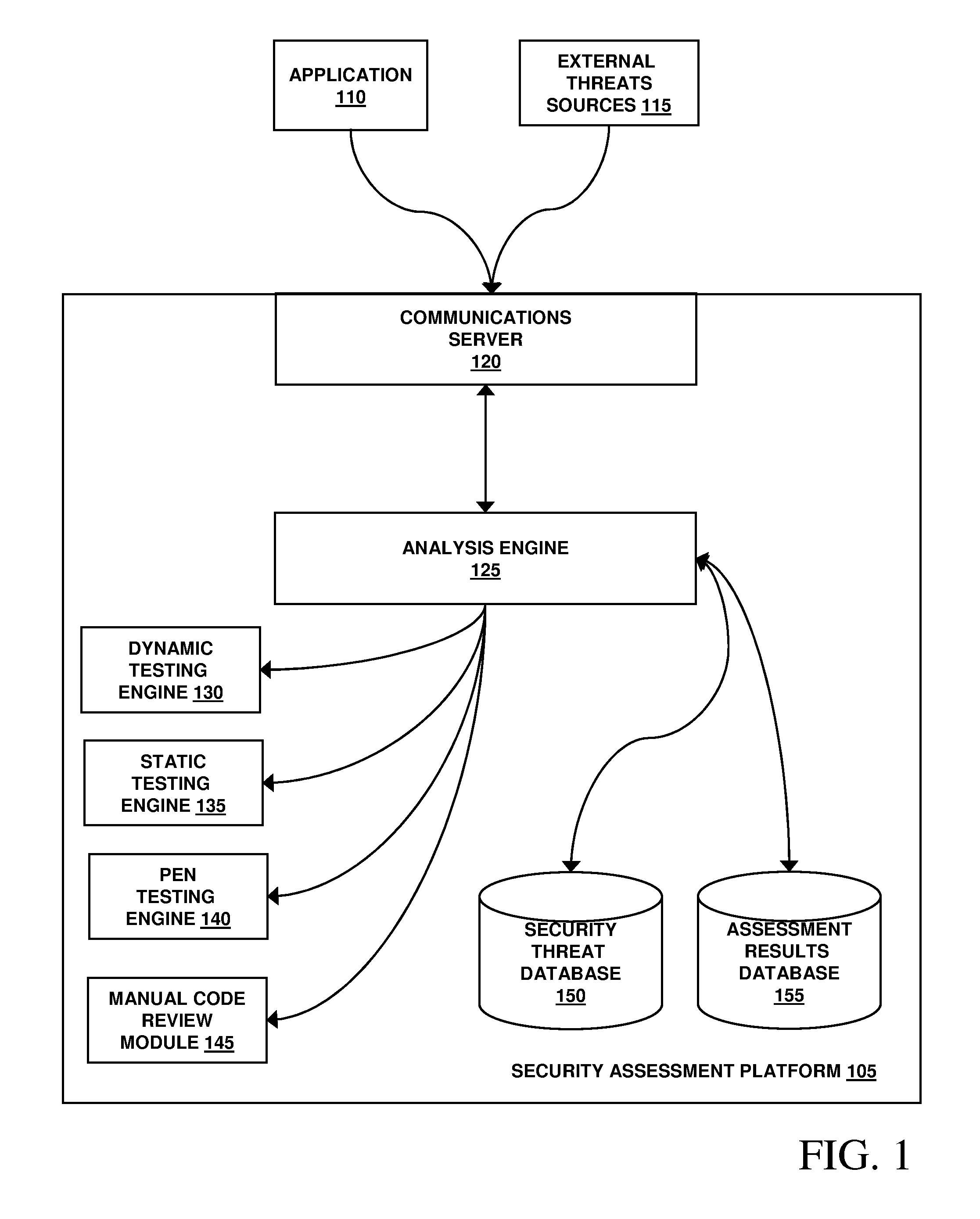
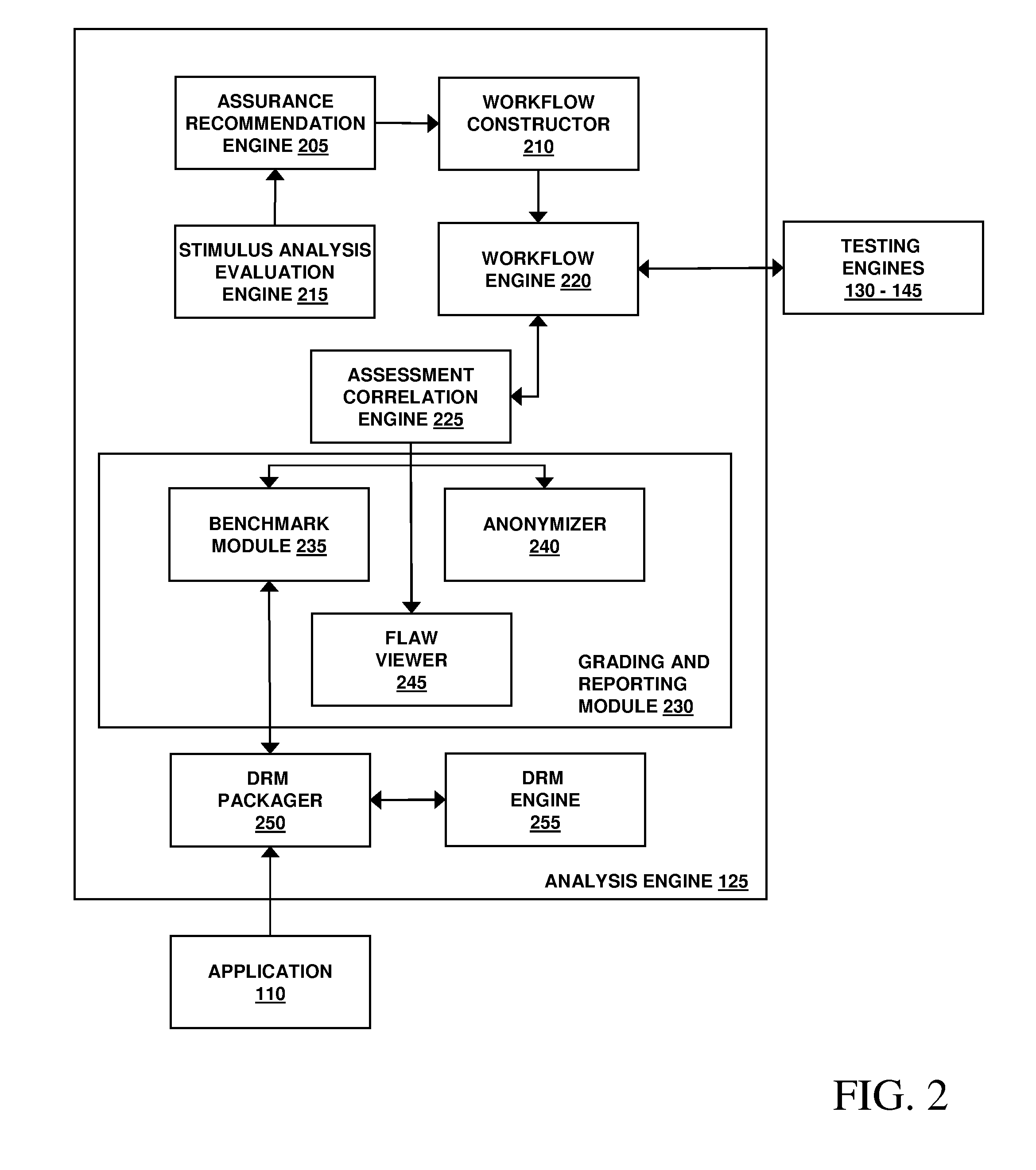
Assessment and analysis of software security flaws in virtual machines
ActiveUS20120072968A1Facilitates benchmarkingFacilitates security assessment and vulnerability testingMemory loss protectionError detection/correctionSoftware engineeringSecurity analysis
Security analysis and vulnerability testing results are “packaged” or “bound to” the actual software it describes. By linking the results to the software itself, downstream users of the software can access information about the software, make informed decisions about implementation of the software, and analyze the security risk across an entire system by accessing all (or most) of the reports associated with the executables running on the system and summarizing the risks identified in the reports.
Owner:VERACODE
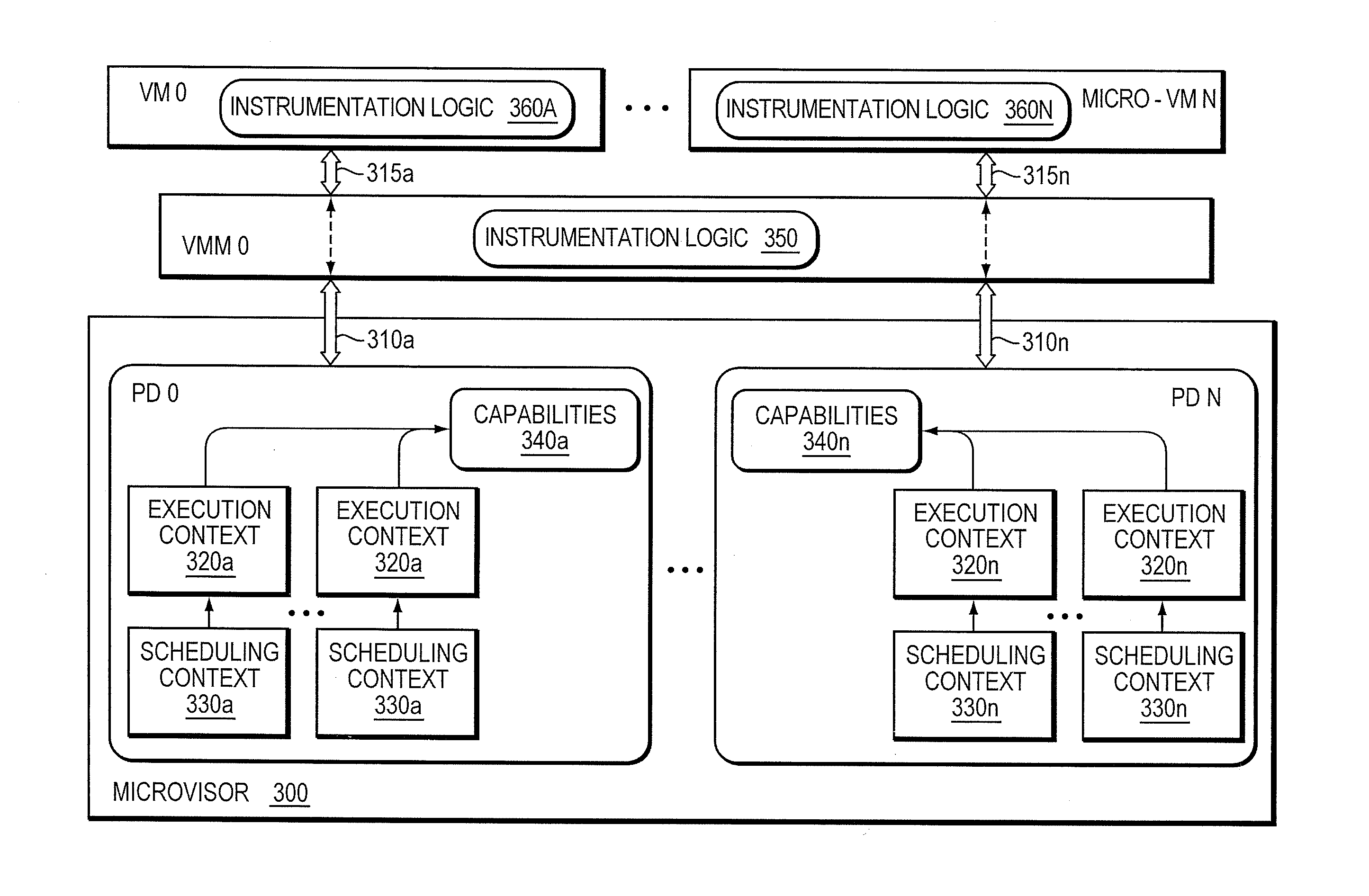
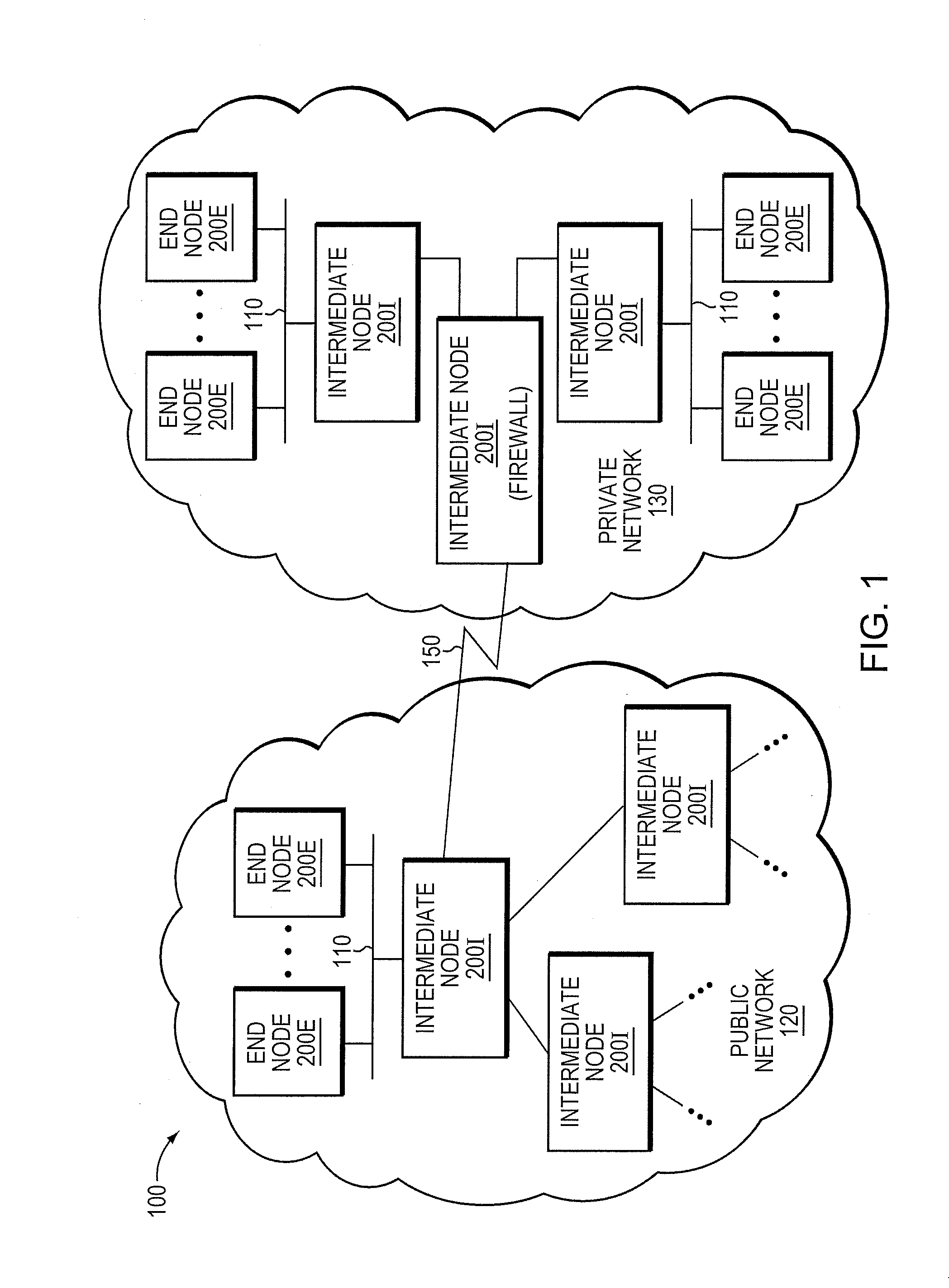
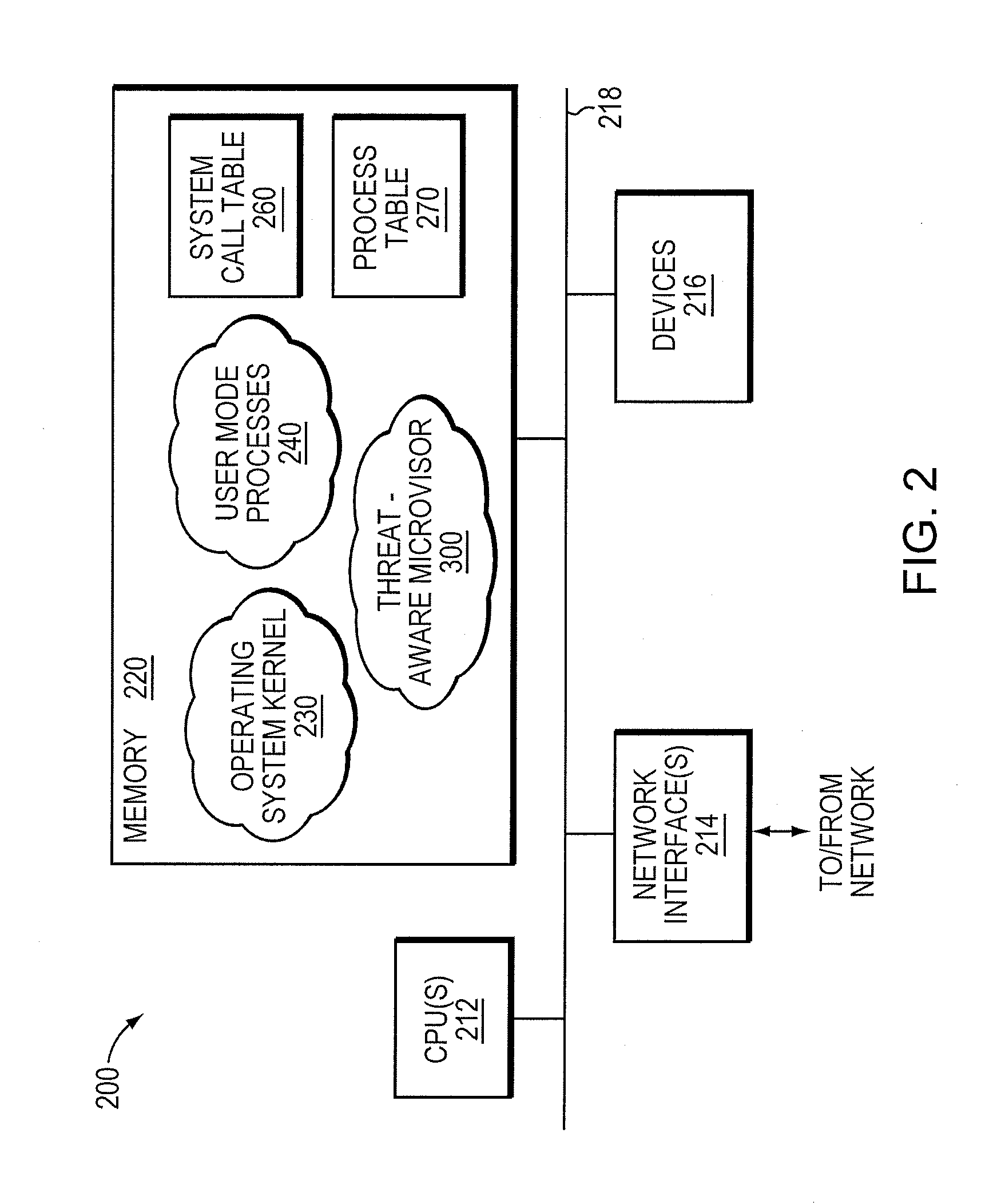
Exploit detection system with threat-aware microvisor
ActiveUS20150199531A1Digital data processing detailsAnalogue secracy/subscription systemsVulnerability detectionThreat intelligence
An exploit detection system deploys a threat-aware microvisor to facilitate real-time security analysis, including exploit detection and threat intelligence, of an operating system process executing on a node of a network environment. The microvisor may be organized as a main protection domain representative of the operating system process. In response to the process attempting to access a kernel resource for which it does not have permission, a capability violation may be generated at the main protection domain of the microvisor and a micro-virtual machine (VM) may be spawned as a container configured to encapsulate the process. The main protection domain may then be cloned to create a cloned protection domain that is representative of the process and that is bound to the spawned micro-VM. Capabilities of the cloned protection domain may be configured to be more restricted than the capabilities of the main protection domain with respect to access to the kernel resource. The restricted capabilities may be configured to generate more capability violations than those generated by the capabilities of the main protection domain and, in turn, enable further monitoring of the process as it attempts to access the kernel resource.
Owner:FIREEYE SECURITY HLDG US LLC
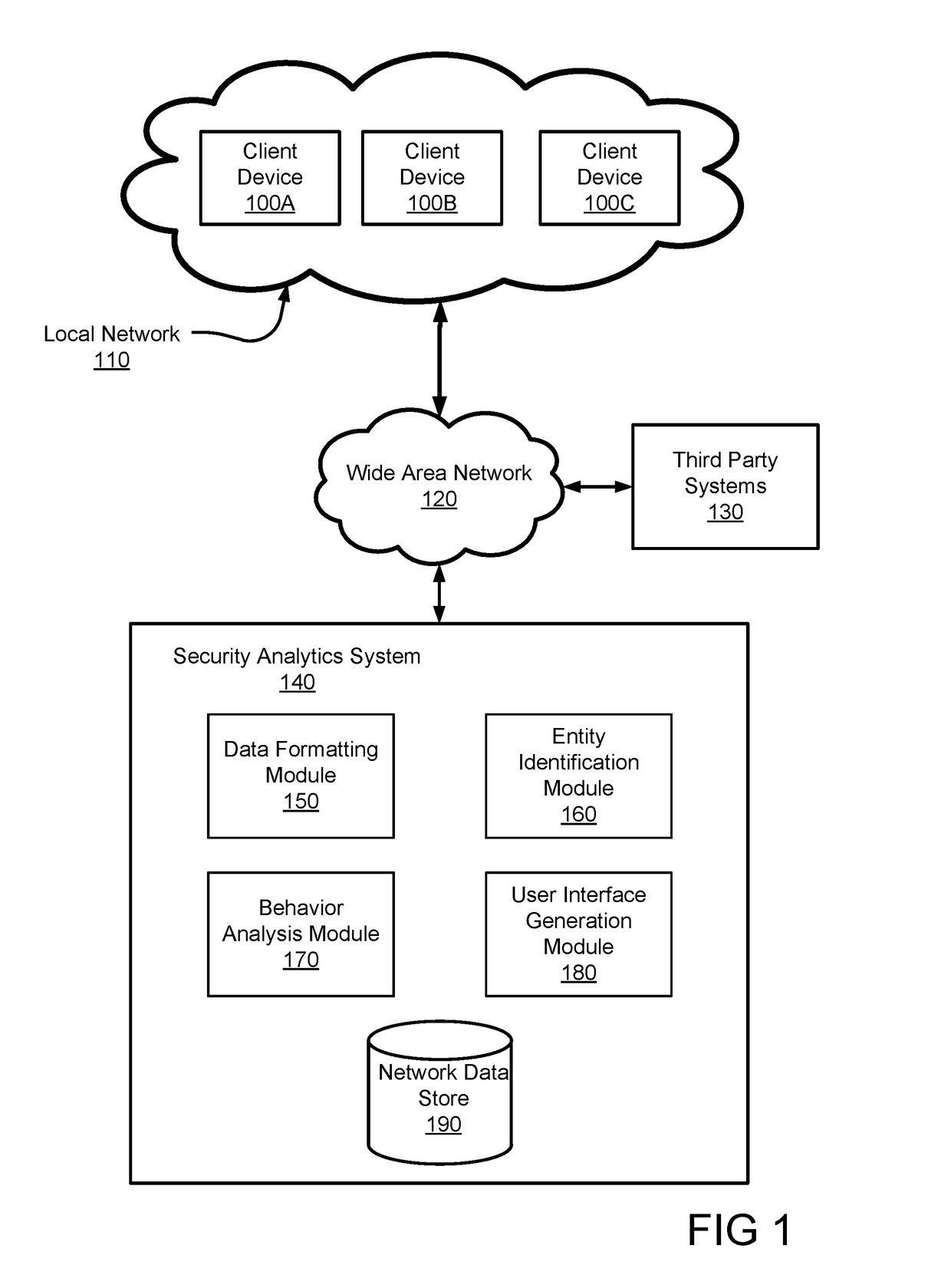
Detecting security threats in a local network
ActiveUS20170118240A1Mathematical modelsKnowledge representationEntity–relationship modelOriginal data
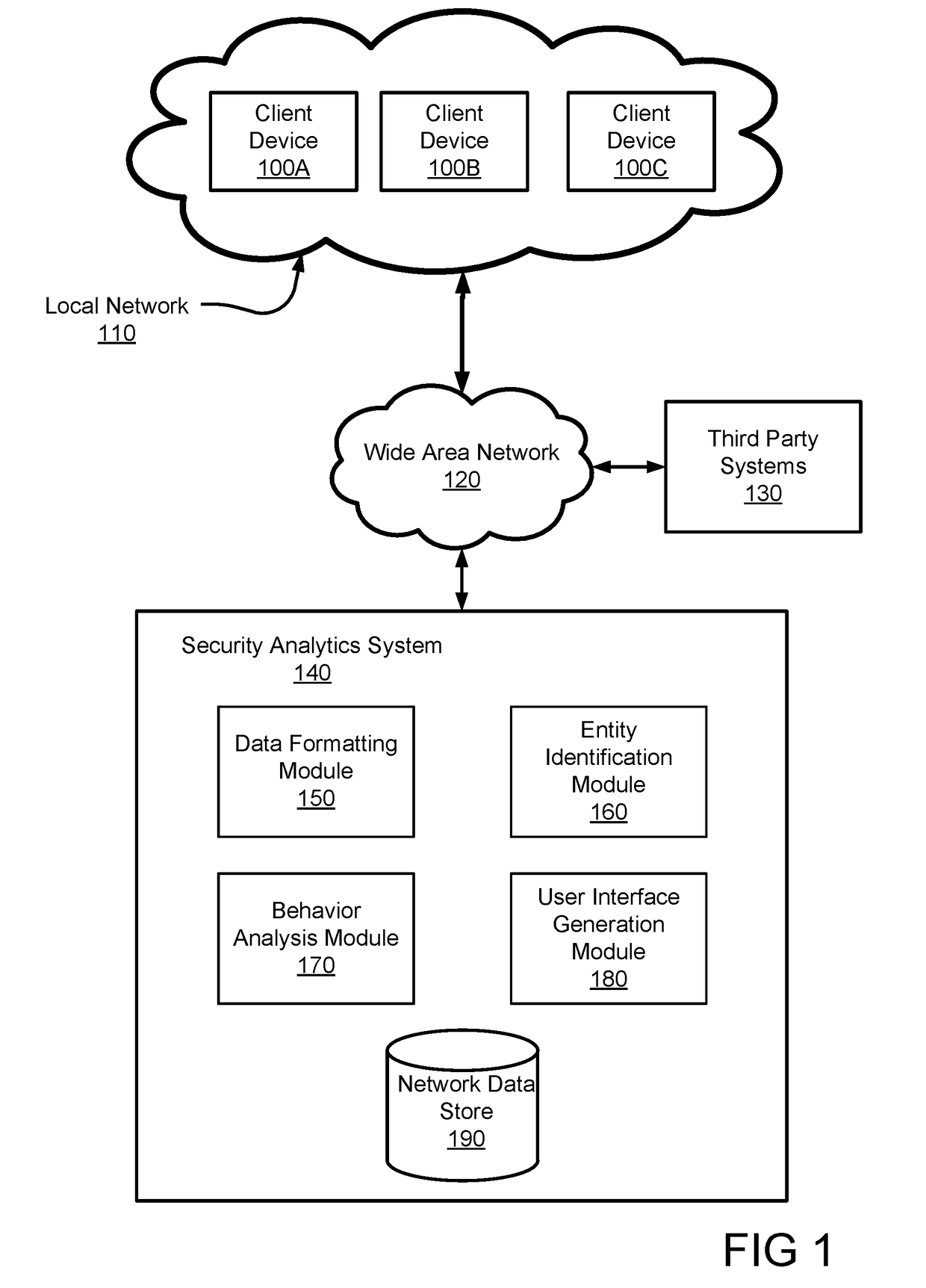
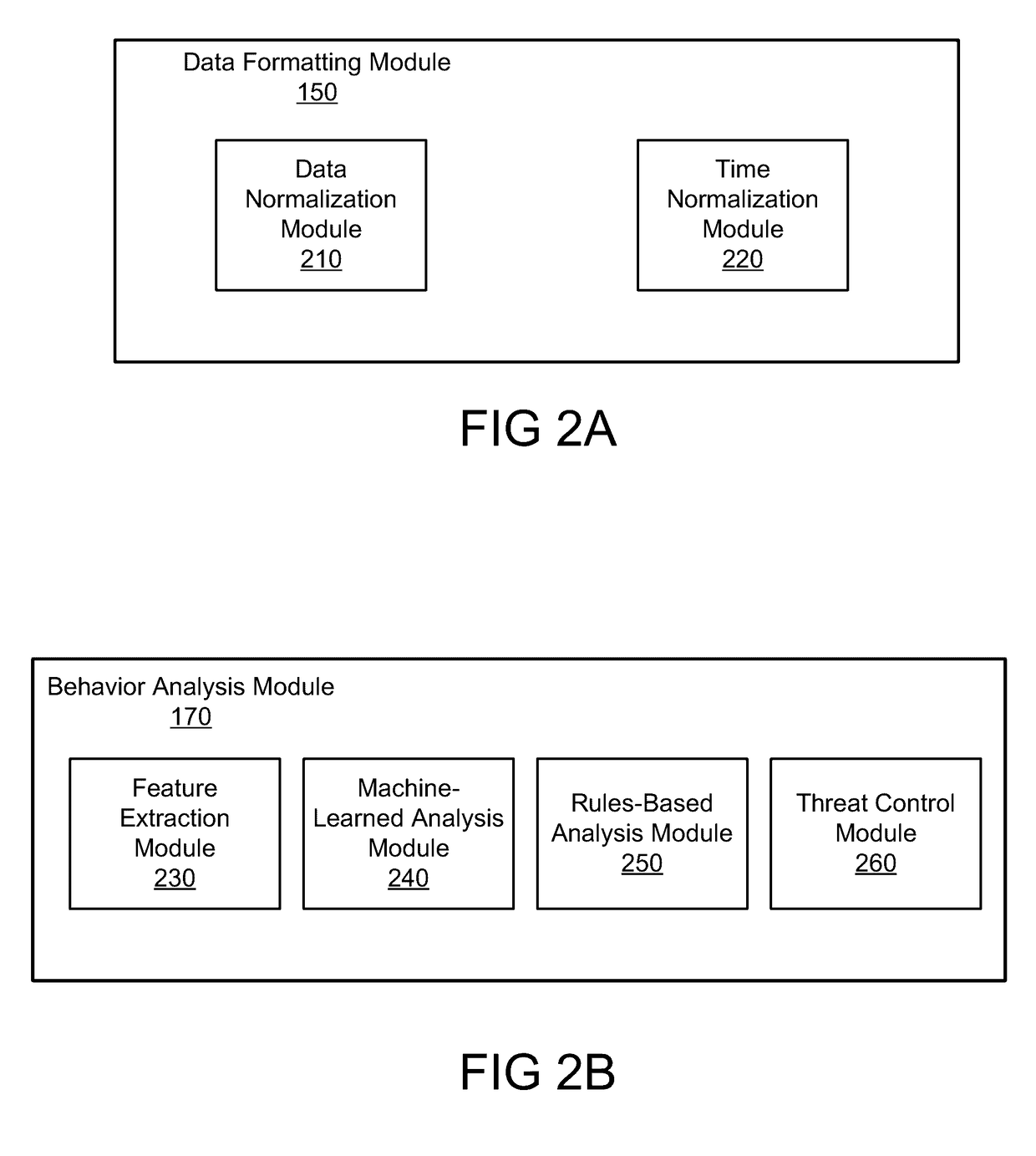
Disclosed is a system for detecting security threats in a local network. A security analytics system collects data about entities in the local network. The security analytics system identifies the entities in the raw data and determines a set of properties about each of the identified entities. The entity properties contain information about the entity and can be temporary or permanent properties about the entity. The security analytics system determines relationships between the identified entities and can be determined based on the entity properties for the identified properties. An entity graph is generated that describes the entity relationships, wherein the nodes of the entity graph represent entities and the edges of the entity graph represent entity relationships. The security analytics system provides a user interface to a user that contains the entity graph and the relationships described therein.
Owner:VMWARE INC
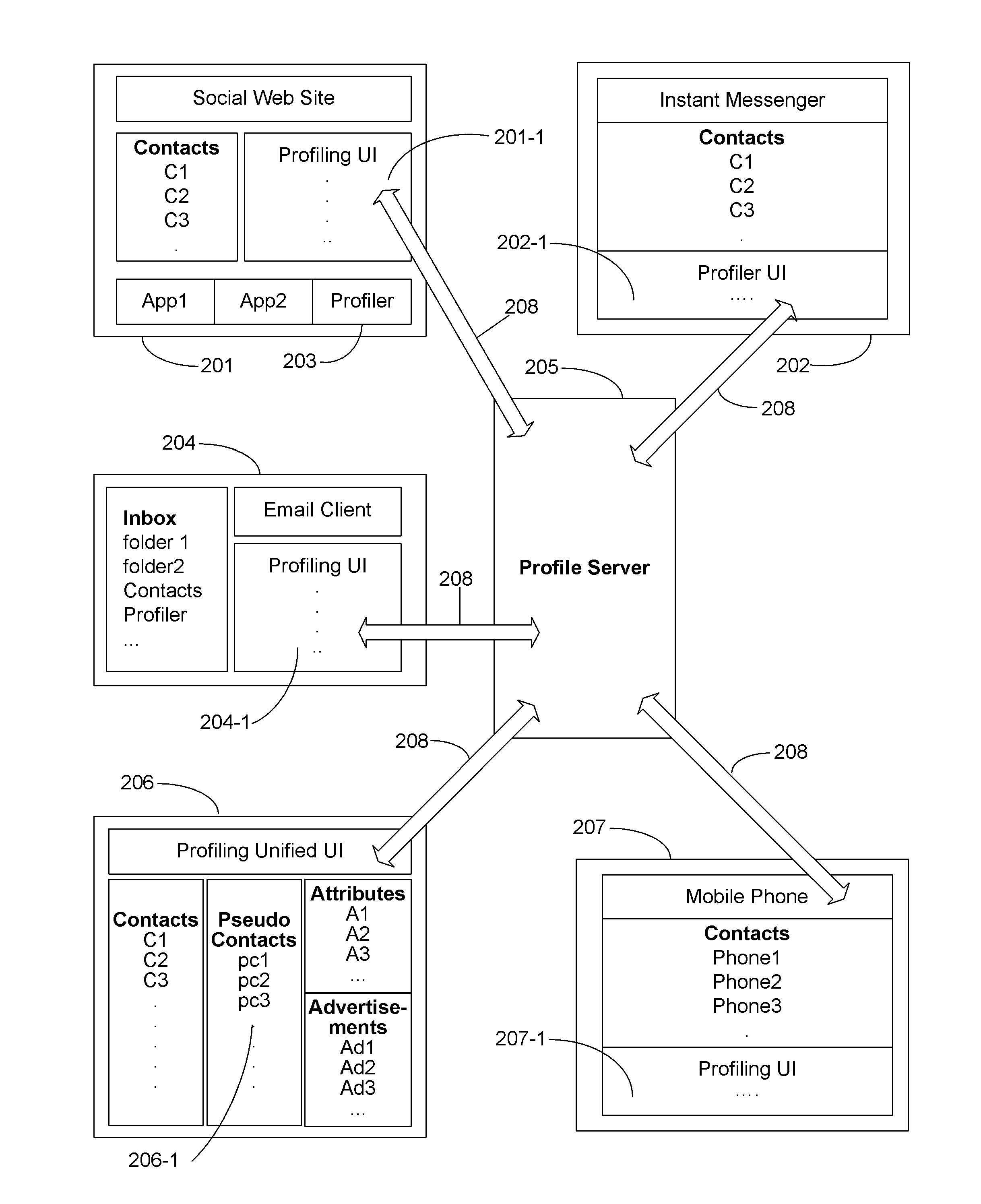
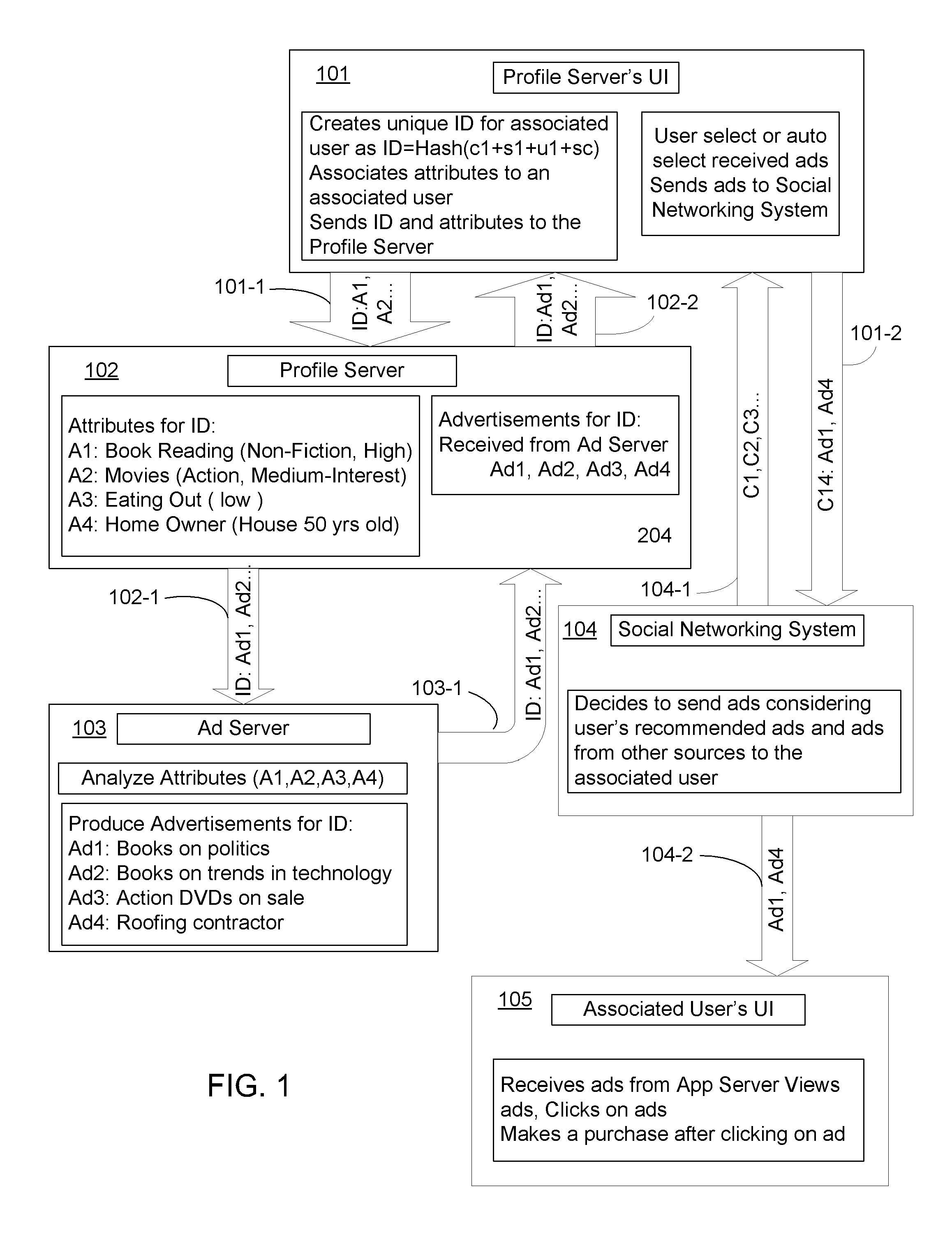
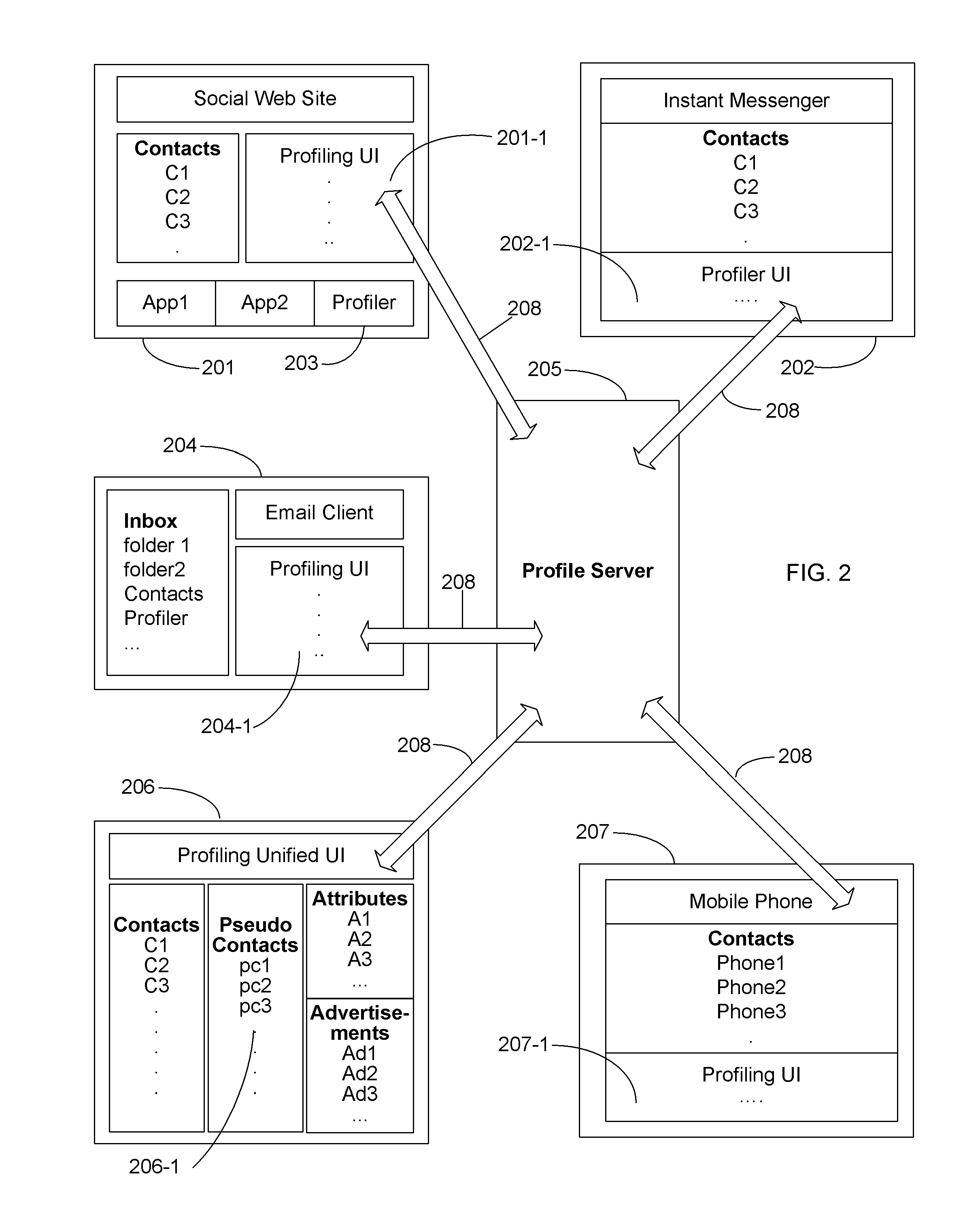
Secure profiling method providing privacy in social networking systems
InactiveUS20110137975A1Input/output for user-computer interactionComputer security arrangementsInternet privacyAnalysis method
The present invention includes devices and methods for enabling private and secure data collection by profile servers relating to users that are associated with a profiling user in a social networking system. Particular aspects of the present invention are described in the claims, specification and drawings.
Owner:AUTHERNATIVE INC
Anomaly and malware detection using side channel analysis
ActiveUS20180007074A1Telemetry/telecontrol selection arrangementsPower supply for data processingAnomaly detectionCloud base
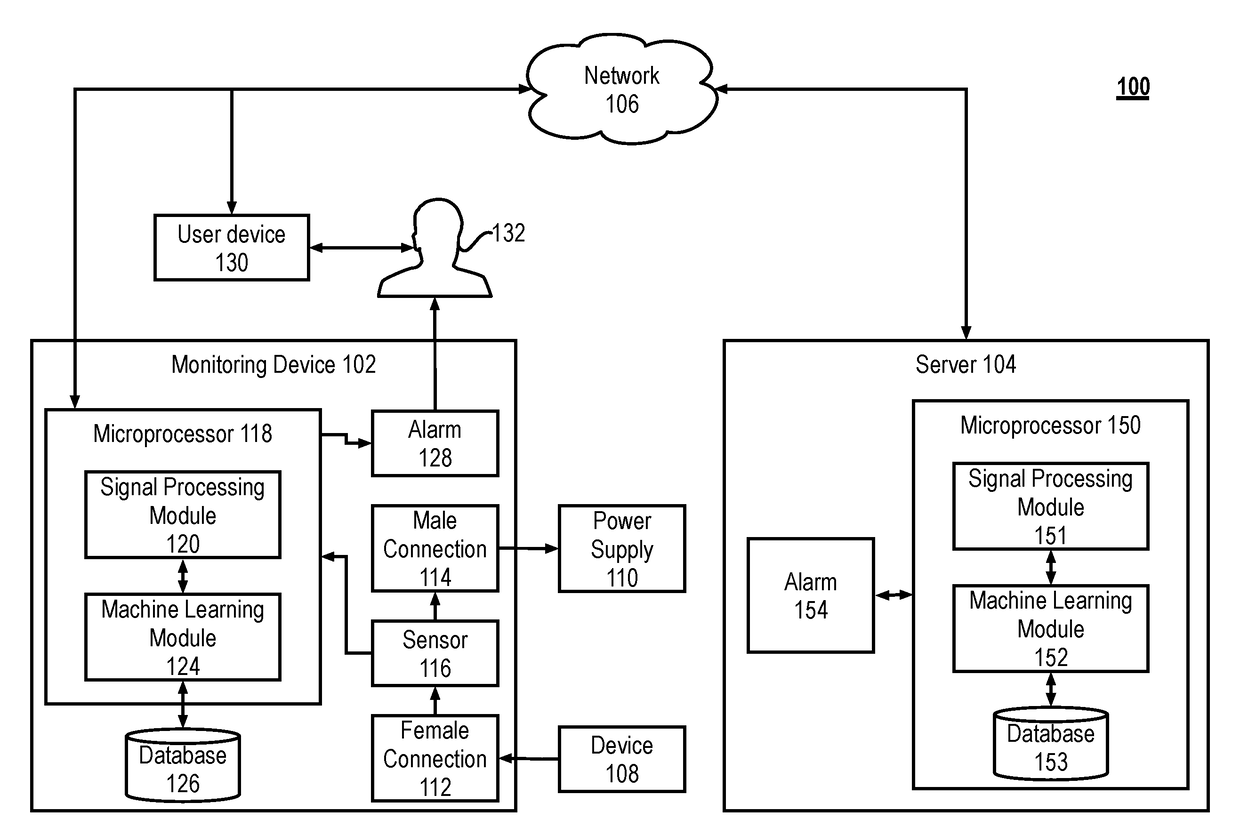
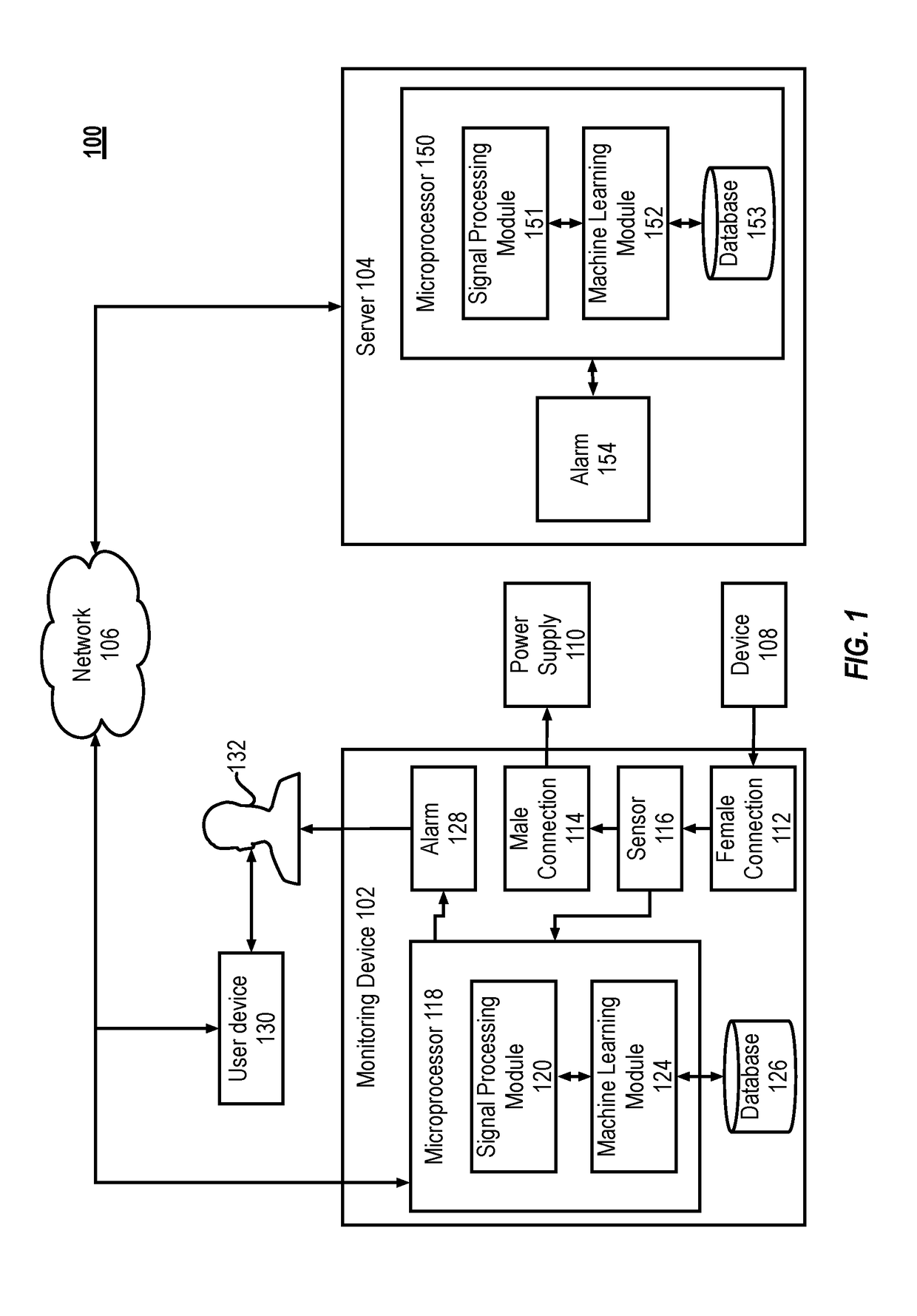
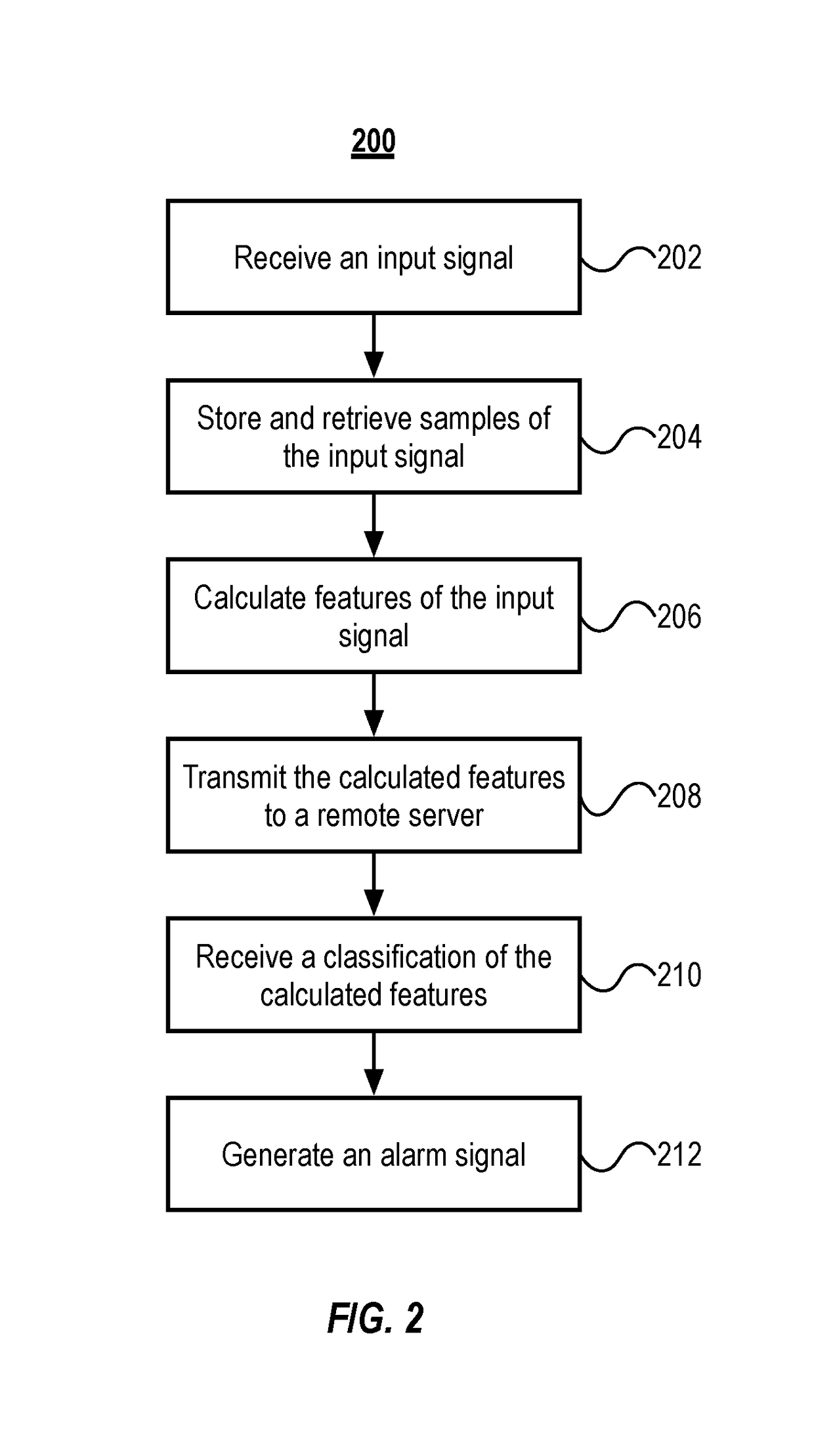
The present disclosure describes systems and methods for detecting malware. More particularly, the system includes a monitoring device that monitors side-channel activity of a target device. The monitoring device that can work in conjunction with (or independently of) a cloud-based security analytics engine to perform anomaly detection and classification on the side-channel activity. For example, the monitoring device can calculate a first set of features that are then transmitted to the security analytics engine for anomaly detection and classification.
Owner:VIRTA LAB INC
Big data security analysis system based on massive network monitoring data
PendingCN108259462ARealize real-time monitoringImprove securityData switching networksOriginal dataBig data security
The invention discloses a big data security analysis system based on massive network monitoring data. The system includes a data traffic monitoring module, a deep packet detection module, a data jointanalysis module, an anomaly detection module and a security evaluation module, wherein the data traffic monitoring module is used to monitor data traffic in real time, analyze applications, perform lossless collection on various system traffic data, and transmit the data to other modules; the deep packet detection module is used to judge the service types and application types by deeply reconstituting and analyzing the payload content of a seventh-layer packet and matching service characteristics, and performs analysis to obtain different application types; the data joint analysis module is used to perform data aggregation and study the state and association analysis to further remove redundant information in original data; the anomaly detection module is used to detect a data analysis result and judge whether the data is abnormal; and the security evaluation module is used to obtain a data evaluation result by combining the network situation based on the analysis and detection of other modules. According to the system, the real-time monitoring of network data and corresponding data security analysis can be implemented, and the data security and reliability can be improved.
Owner:国网吉林省电力有限公司信息通信公司 +1
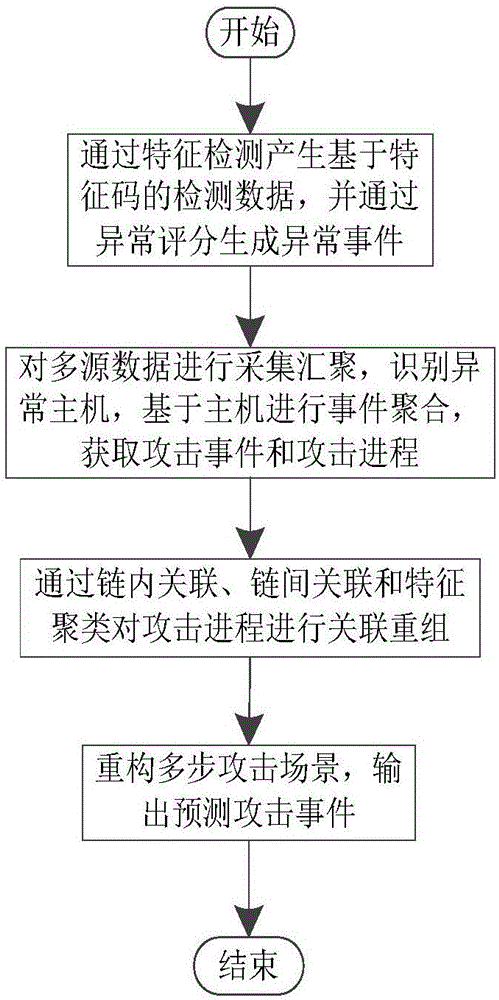
Multi-step attack detection method based on multi-source abnormal event correlation analysis
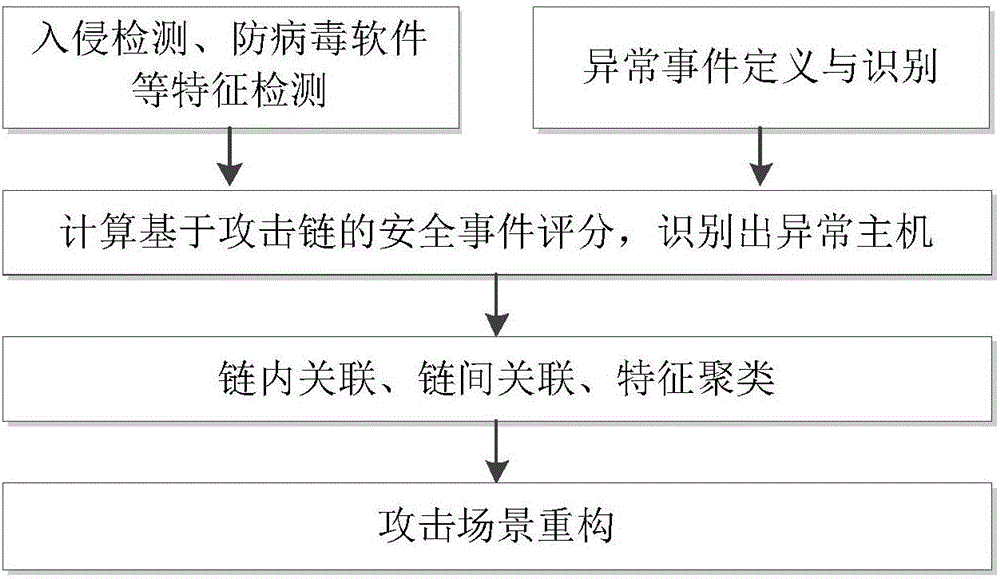
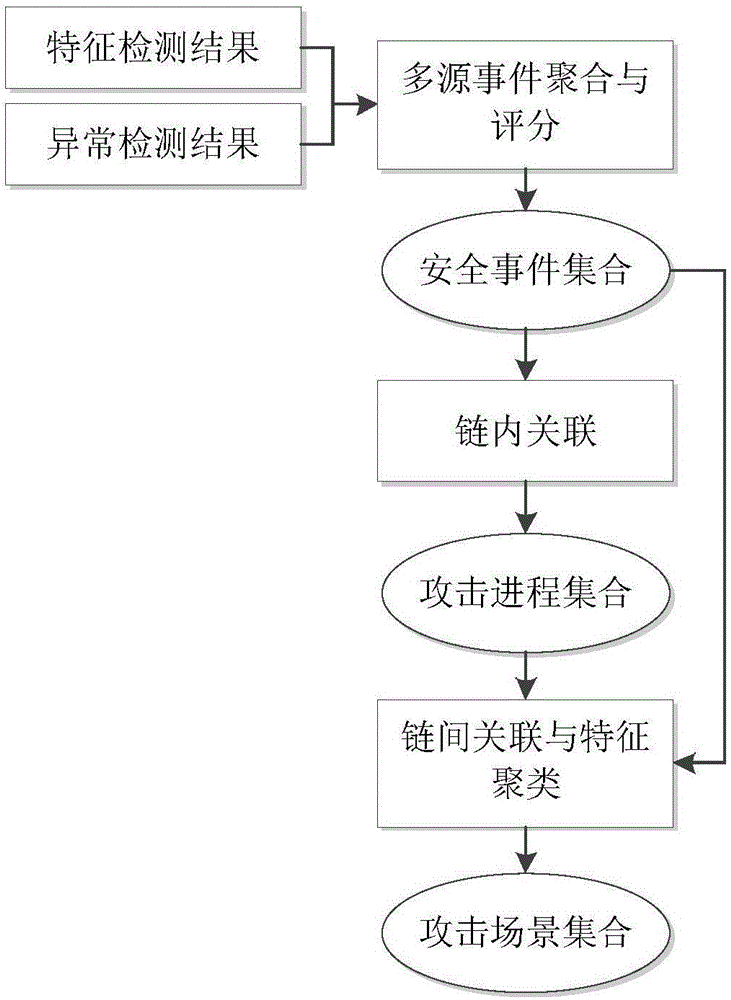
ActiveCN106790186AImprove Security Analysis CapabilitiesReduce time to discoveryTransmissionFeature extractionCorrelation analysis
The invention relates to a multi-step attack detection method based on multi-source abnormal event correlation analysis. The multi-step attack detection method comprises the following steps: firstly, calculating a safety event score based on an attach chain through feature extraction and abnormal event definition and identification, identifying an abnormal host and clustering various types of events by taking an attacked host as a clue; secondly, carrying out correlated recombination on a suspected attack progress by utilizing means including intra-chain correlation, inter-chain correlation, feature clustering and the like; finally, reconstructing a multi-source attack scene and outputting a predicated attack event. According to the multi-step attack detection method provided by the invention, dispersed and isolated safety events are subjected to the correlation analysis to generate the relative complete multi-step attack scene; a safety analysis capability of safety managers can be improved and a safety view angle is expanded; distributed and scattered multi-step attack threats are effectively coped and the finding time of attack behaviors is shortened; an effective predication and defending solution is provided for high-grade attack means including APT (Advanced Persistent Threat) and the like; the safety risks of a system are reduced and the network information safety is effectively protected.
Owner:THE PLA INFORMATION ENG UNIV
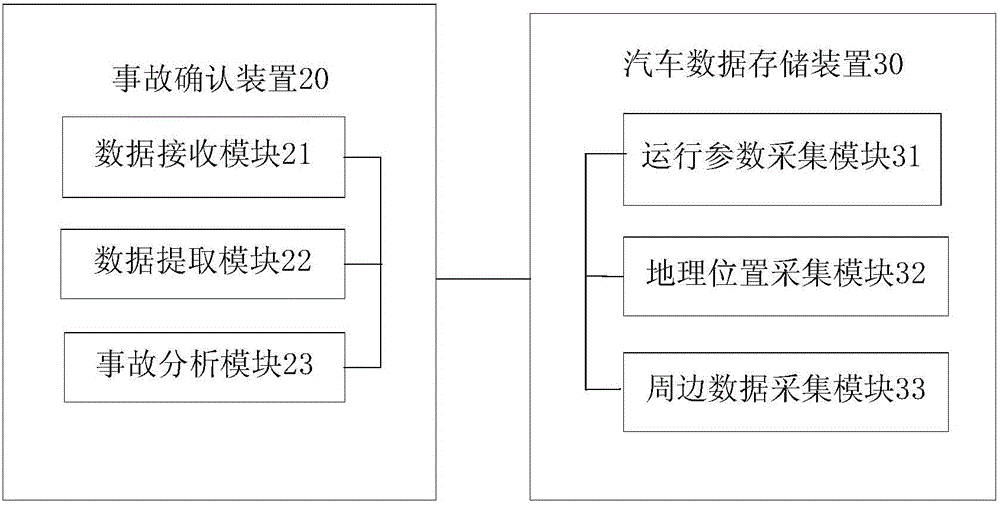
A motor-vehicle accident liability determination method and system
ActiveCN106157614AQuick fixImprove timelinessRegistering/indicating working of vehiclesDetection of traffic movementDevice MonitorTraffic accident
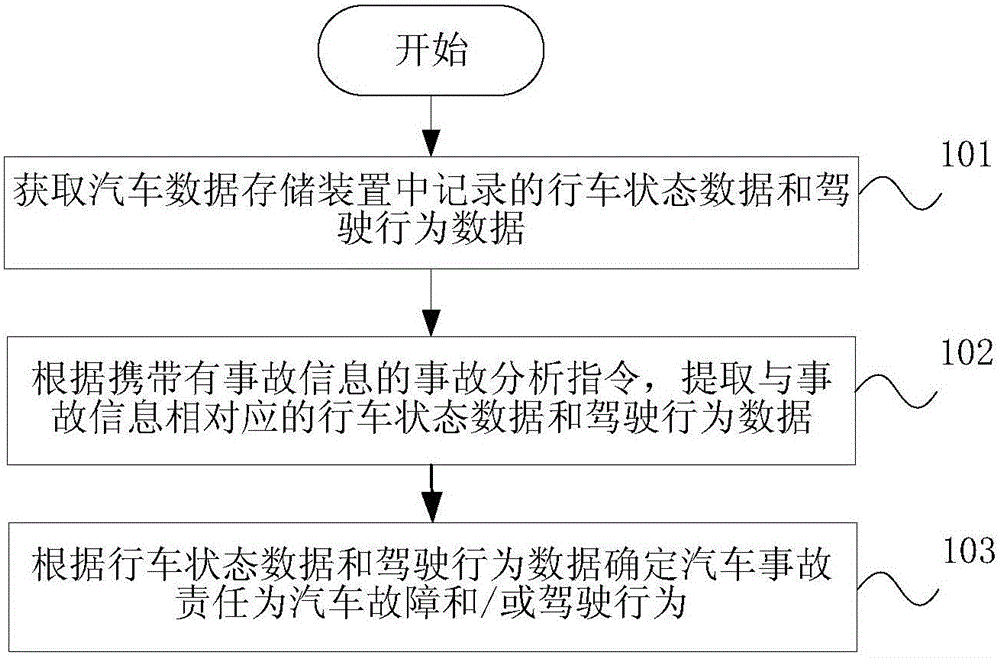
An embodiment of the present invention discloses a motor-vehicle accident liability determination method and system. The method comprises the following steps of: acquiring driving state data and driving behavior data recorded in an motor-vehicle data storage device; extracting the driving state data and the driving behavior data corresponding to the accident information according to an accident analyzing instruction carrying accident information; and determining the liability for motor-vehicle accidents to be with motor-vehicle breakdowns and / or driving behaviors according to the driving state data and the driving behavior data. According to the motor-vehicle accident liability determination method and system in the embodiment of the present invention, the motor-vehicle data storage device monitors the driving state data and the driving behavior data during the driving process so as to provide the basis for defining the liability of the traffic accidents and quickly define the responsible party of the accidents. In addition, the timeliness of field investigation is solved; and data support is provided for automobile performance and safety analysis.
Owner:北京鸿享技术服务有限公司
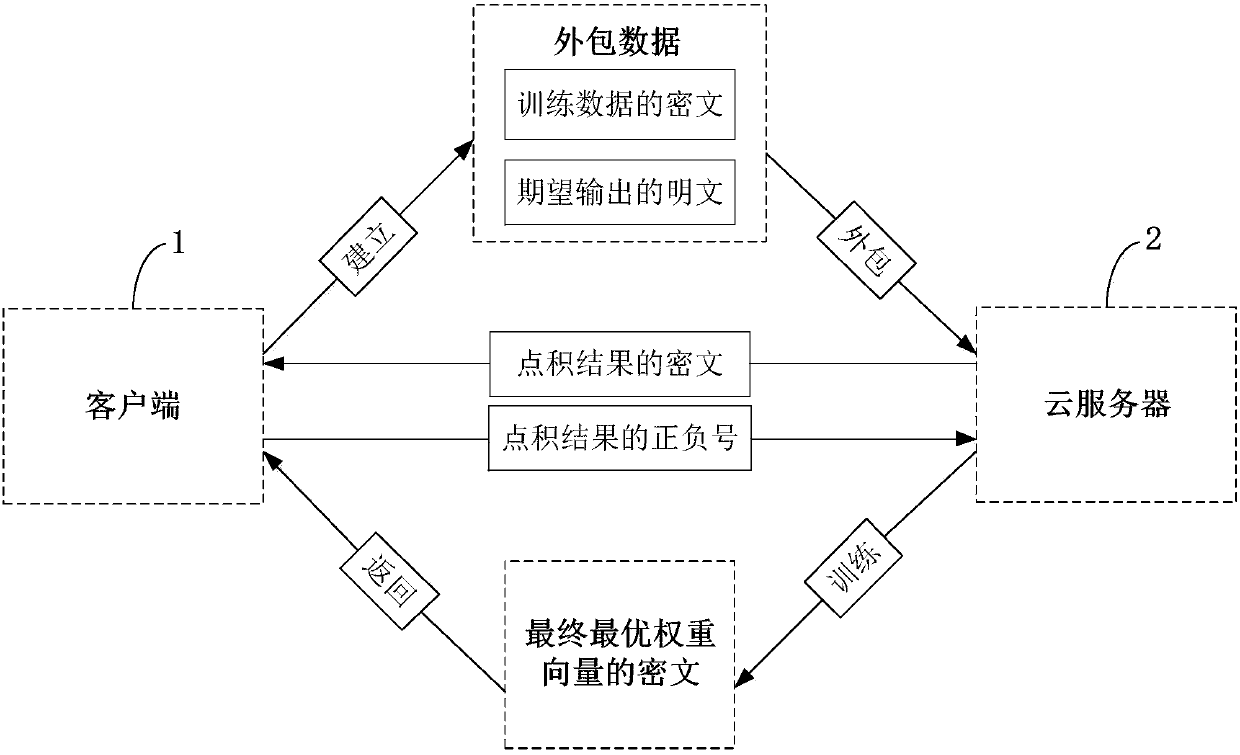
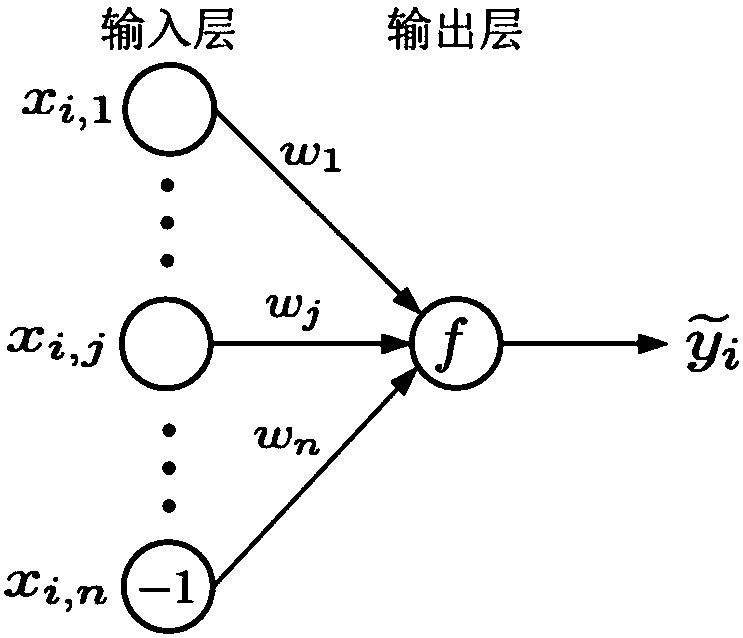
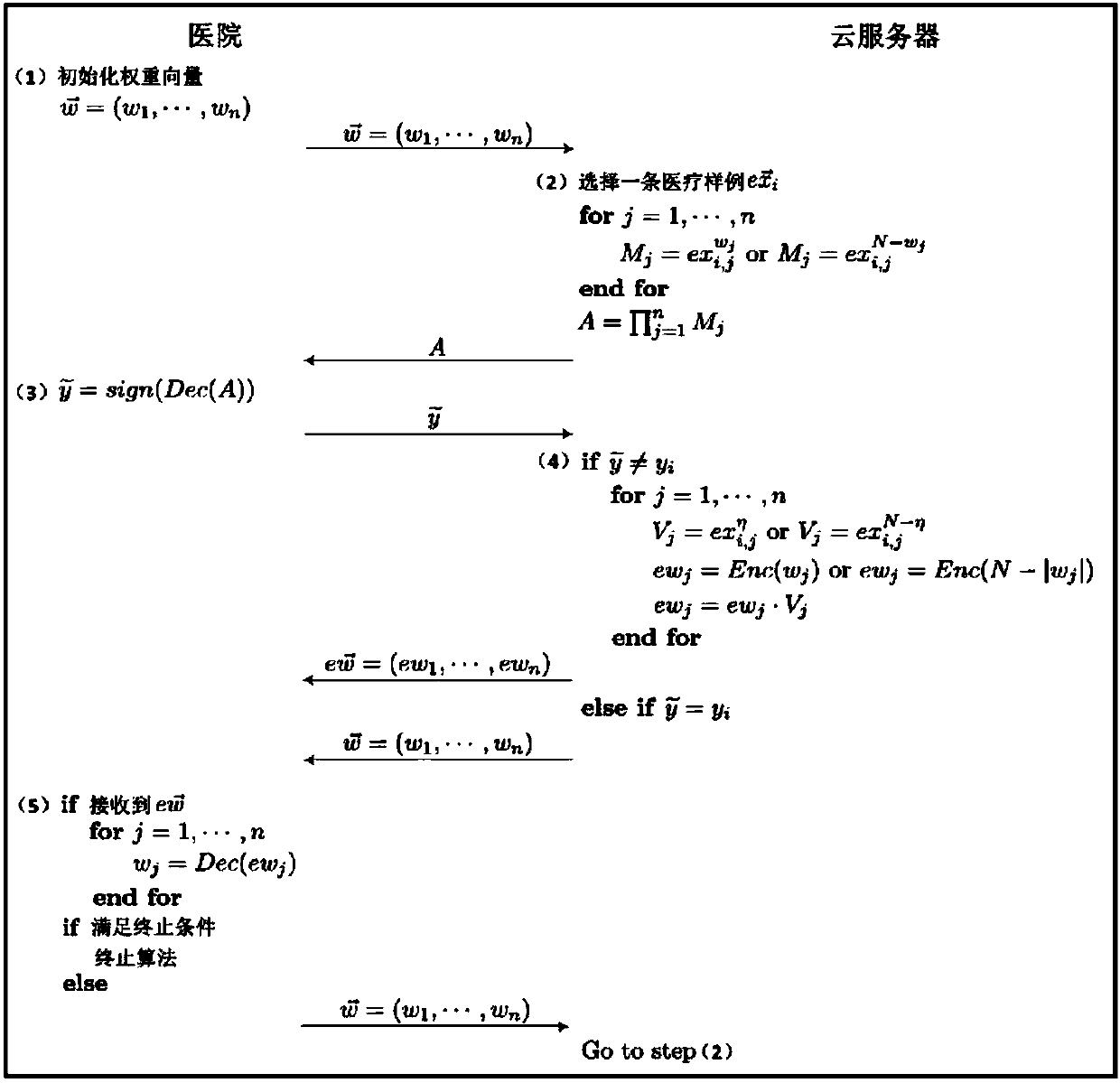
Efficient and privacy-preserving single-layer perceptron learning scheme in cloud computing environment
ActiveCN108259158APrivacy protectionComputationally efficientKey distribution for secure communicationCharacter and pattern recognitionCiphertextPrivacy preserving
The invention belongs to the technical field of cloud computing and discloses an efficient and privacy-preserving single-layer perceptron learning scheme in a cloud computing environment. The scheme comprises the steps that a client provides a security parameter, operates a key generation algorithm of a symmetric homomorphic encryption algorithm to calculate a public parameter and a key, then operates an encryption algorithm, encrypts training data through utilization of the key to obtain a corresponding ciphertext, and sends the ciphertext and related expectation to a cloud server, assists acloud server to judge a positive or negative characteristic of a dot product result in a training process, and decrypts the ciphertext of the received final optimum weight vector after a training taskis finished, thereby obtaining a single-layer perceptron prediction model; and the cloud server stores the training mode, trains a single-layer perceptron model and sends the ciphertext of the finaloptimum weight vector to the client after the training task is finished. The safety analysis shows that according to the scheme, in the training process, the privacy of the training data, an intermediate result and the optimum prediction model can be preserved, and the scheme is efficient in computing overhead and communication overhead aspects.
Owner:XIDIAN UNIV
Intelligent safety supervision system for power construction
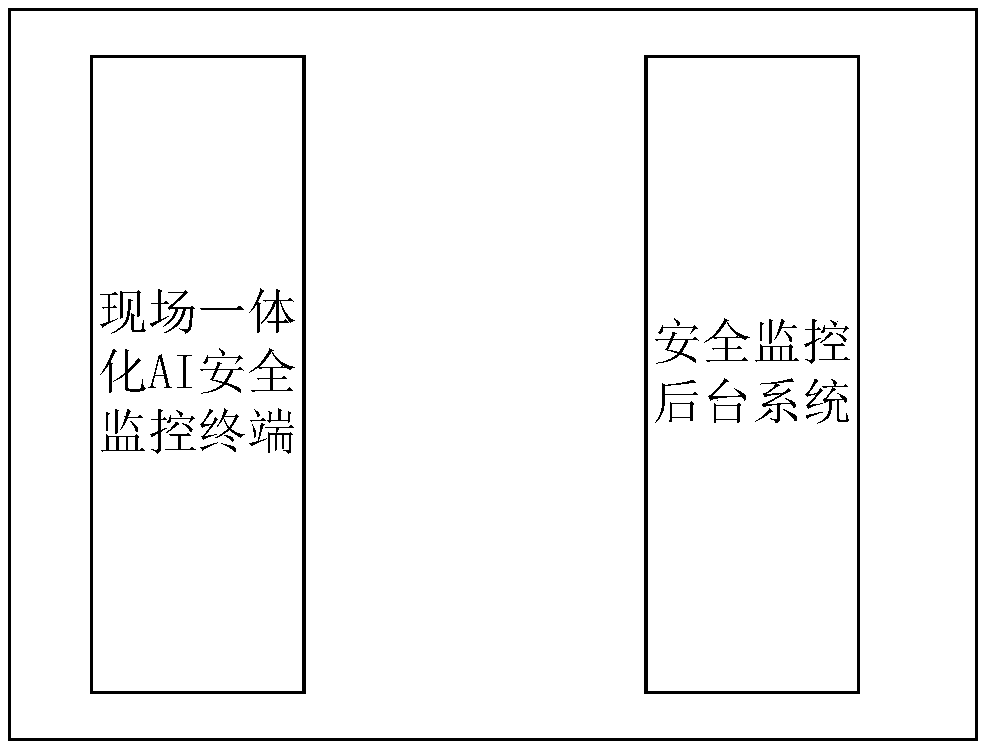
InactiveCN108833831ARealize the epoch-making change from civil air defense to technical defenseImprove timelinessClosed circuit television systemsResourcesDocumentation procedureComputer terminal
The invention discloses an intelligent safety supervision system for power construction. The supervision system comprises an on-site integrated AI safety monitoring terminal and a safety monitoring background system, wherein the on-site integrated AI safety monitoring terminal is used for confirming a site operation safety control process, tracking, shooting and storing site operation, recognizingsite violation behaviors, recognizing whether documentations is qualified, warning and controlling the site violation behaviors, and performing safety warning on site operation; and the safety monitoring background system is used for displaying information of each construction point in real time, controlling a construction site, statistically collecting uploaded information, and performing safetyanalysis on an offline video. Therefore, the timeliness ratio and accuracy rate of safety supervision are effectively enhanced, and the technical effect of full coverage safety supervision of the working site is achieved.
Owner:陈在新
System and method and device for processing cloud application attack behaviors in cloud computing system
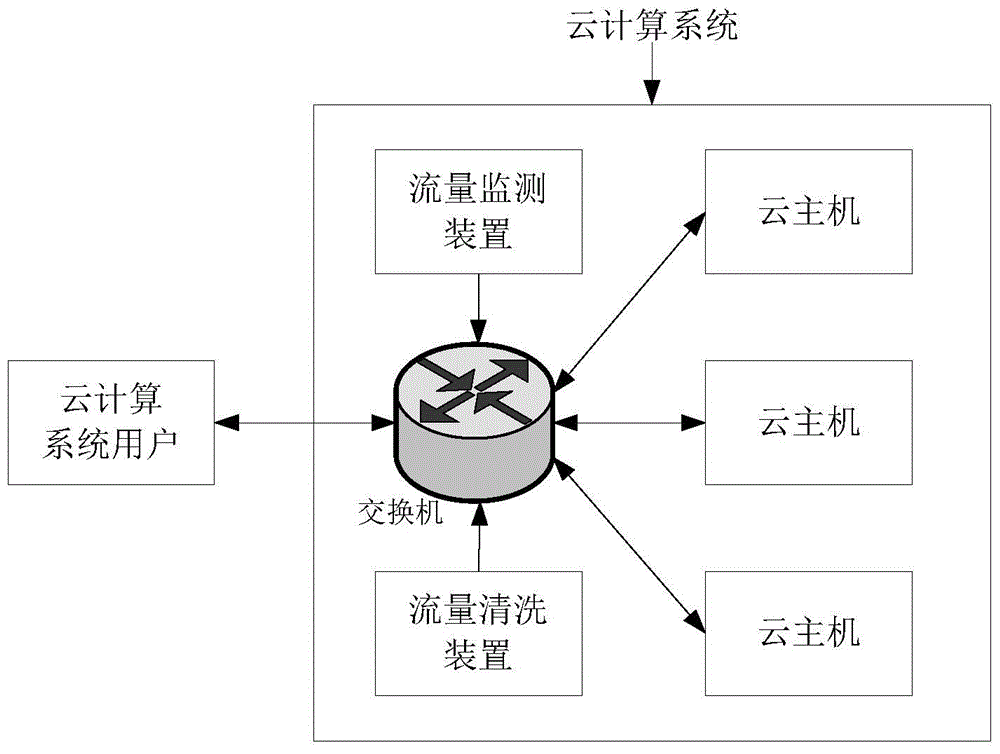
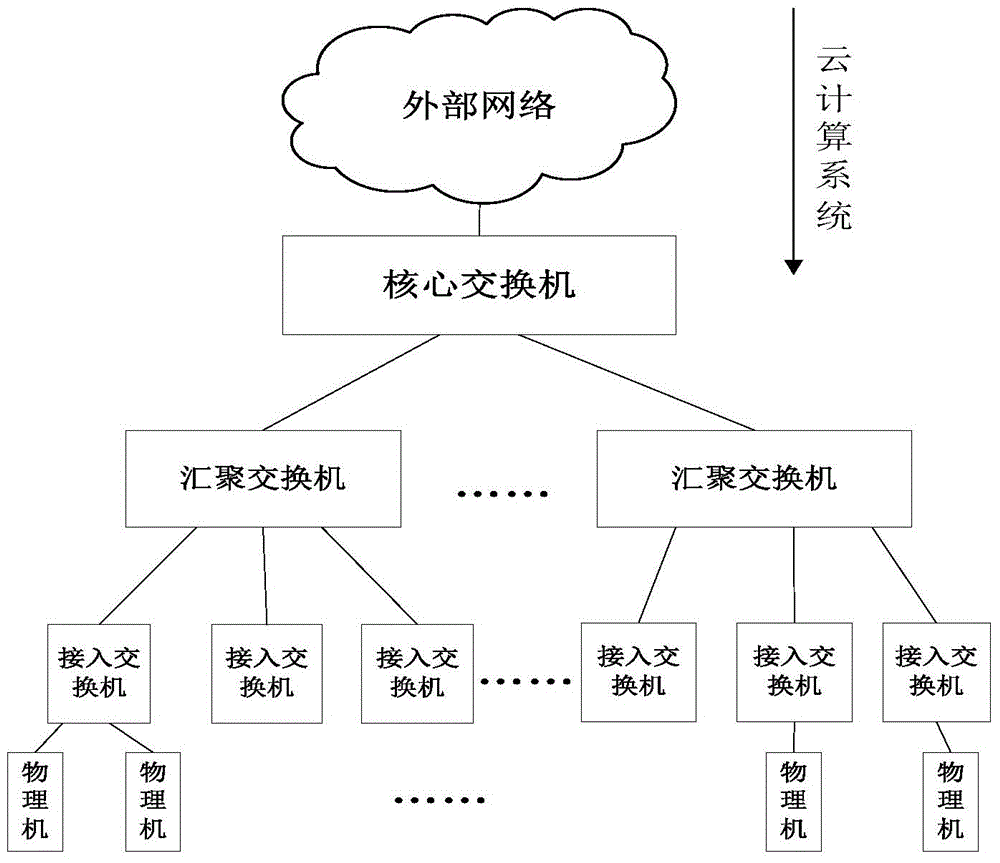
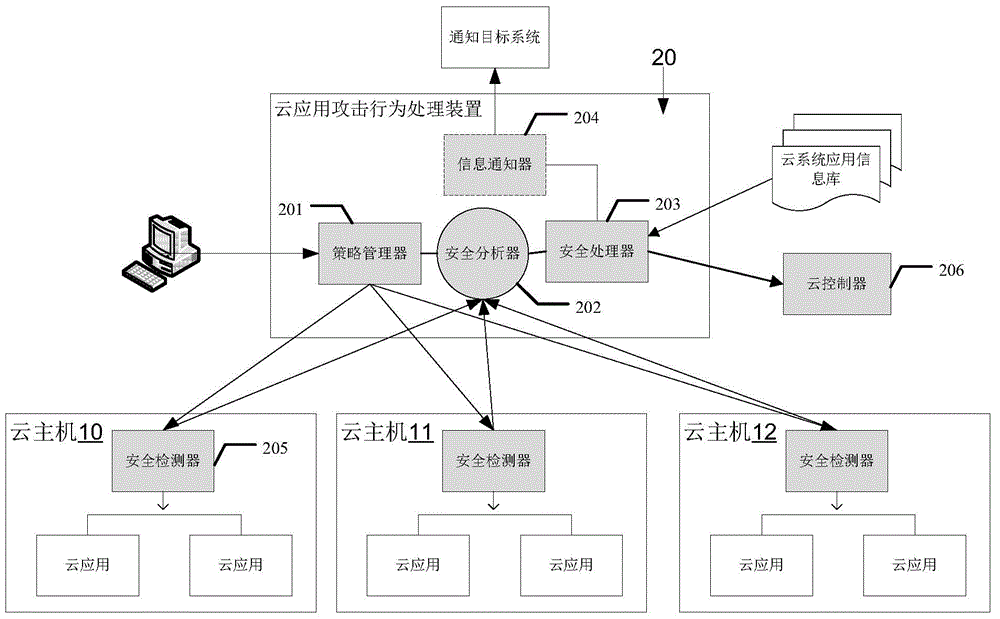
ActiveCN104392175AAvoid attacking each otherReduce the impact of normal applicationsPlatform integrity maintainanceProgram controlSafe handlingSecurity analytics
The invention discloses a device for processing cloud application attack behaviors in a cloud computing system. The device comprises a security analyzer, a security processor and a policy manager. The policy manager is used for storing security judgment rules and malicious application processing rules; the security analyzer is used for receiving application behavior data sent by security detectors, determining whether cloud applications running on cloud hosts have attack behaviors or not, and sending the application behavior data to the security processor when determining that the cloud applications running on the cloud hosts have the attack behaviors; the security processor is used for calling an interface provided by a cloud controller in the cloud computing system to process the cloud applications with the attack behaviors according to the malicious application processing rules. Security protection is performed based on the cloud computing application level, mutual attacks between different applications inside the same host can be prevented, and impact on normal applications is reduced.
Owner:HUAWEI TECH CO LTD
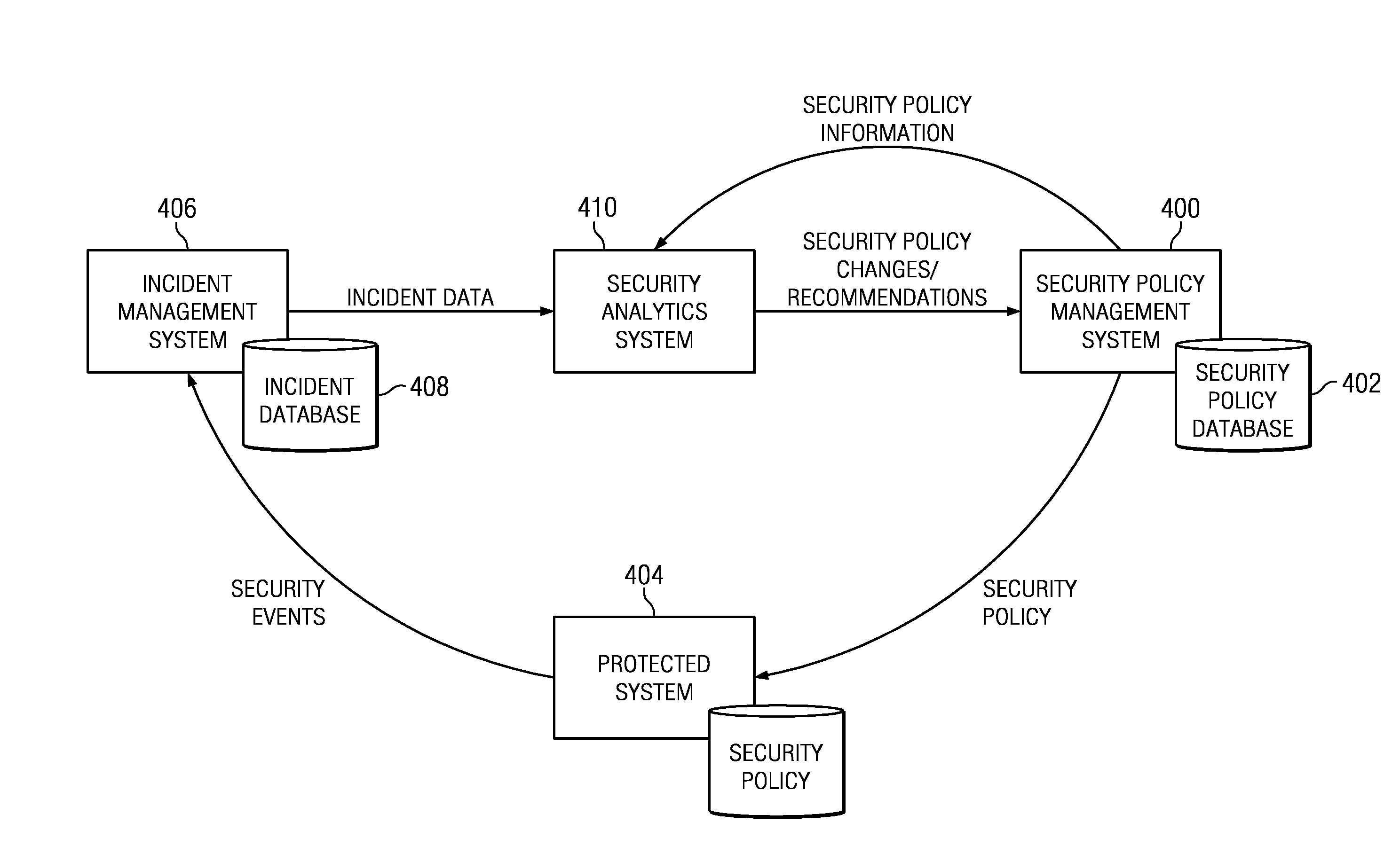
Security policy management using incident analysis
InactiveUS20130179938A1Understand perceived and measured effectiveness and costReduce in quantityError detection/correctionForecastingData setIncident analysis
A security analytics system receives incident data (from an incident management system) and security policy information (from a security policy management system). The security analytics system evaluates these data sets against one another, preferably using a rules-based analysis engine. As a result, the security analytics system determines whether a particular security policy configuration (as established by the security policy management system) needs to be (or should be) changed, e.g., to reduce the number of incidents caused by a misconfiguration, to increase its effectiveness in some manner, or the like. As a result of the evaluation, the security analytics system may cause a policy to be updated automatically, notify an administrator of the need for the change (and the recommendation), or take some other action to evolve one or more security policies being enforced by the security policy management system.
Owner:IBM CORP
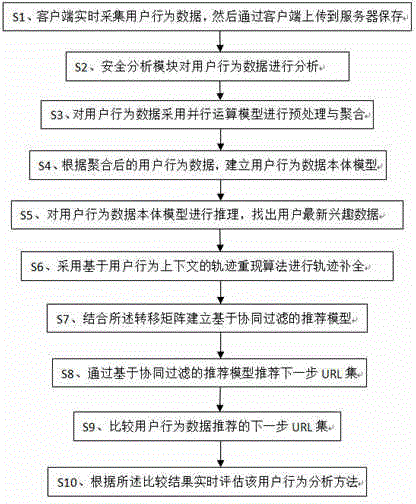
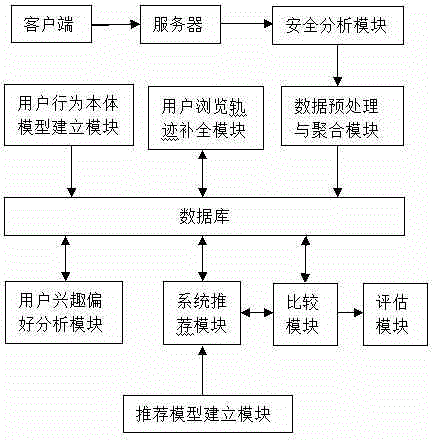
User behavior analysis method and system based on big data
InactiveCN104462213AGain interest in timeEffective and accurate pushWebsite content managementSpecial data processing applicationsEngineeringContext data
The invention discloses a user behavior analysis method and system based on big data. According to the method, user behavior data are collected through a client side in real time, user behaviors and contextual information of a page URL are combined, the real scene that a user browses Web pages is reproduced to the greatest extent, comprehensive user behavior tracks are extracted, and effective data assurance is provided for analyzing the user behaviors; security assurance is provided for the user behavior data through a safety analysis module, and a user behavior data body model is used for modeling the user behaviors, so that behavior information semantic levels are shared and reused, and the interoperability and the reliability of the model are improved; the user behavior and context data are collected in real time for analysis, so that a result is more reliable; body and behavior information is stored through a column storage database, and therefore the foundation of massive data management is laid; the powerful processing capacity and the large-scale data storage capacity of the cloud computing technology, the body and a reasoning and knowledge discovery method of the body are combined, the massive user behavior data are analyzed in real time to obtain user interest in time, and then effective and accurate user push is achieved.
Owner:成都逸动无限网络科技有限公司
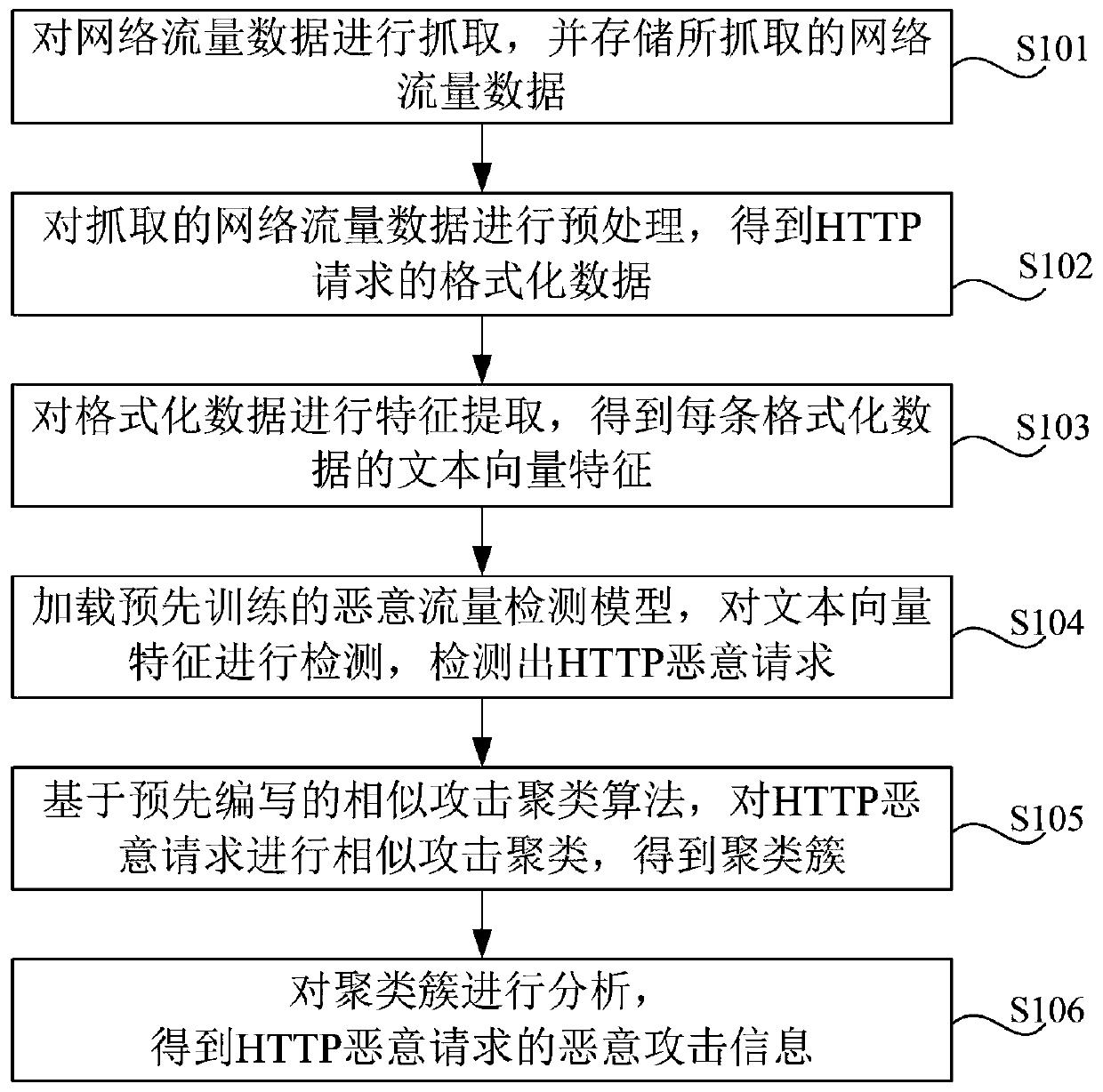
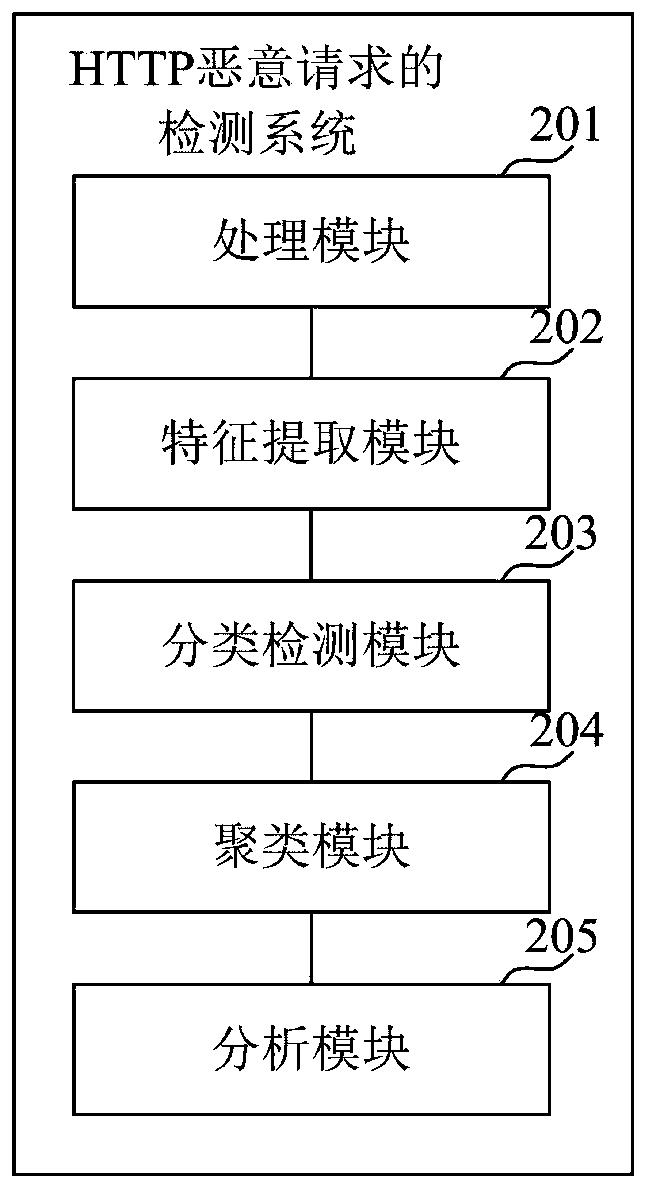
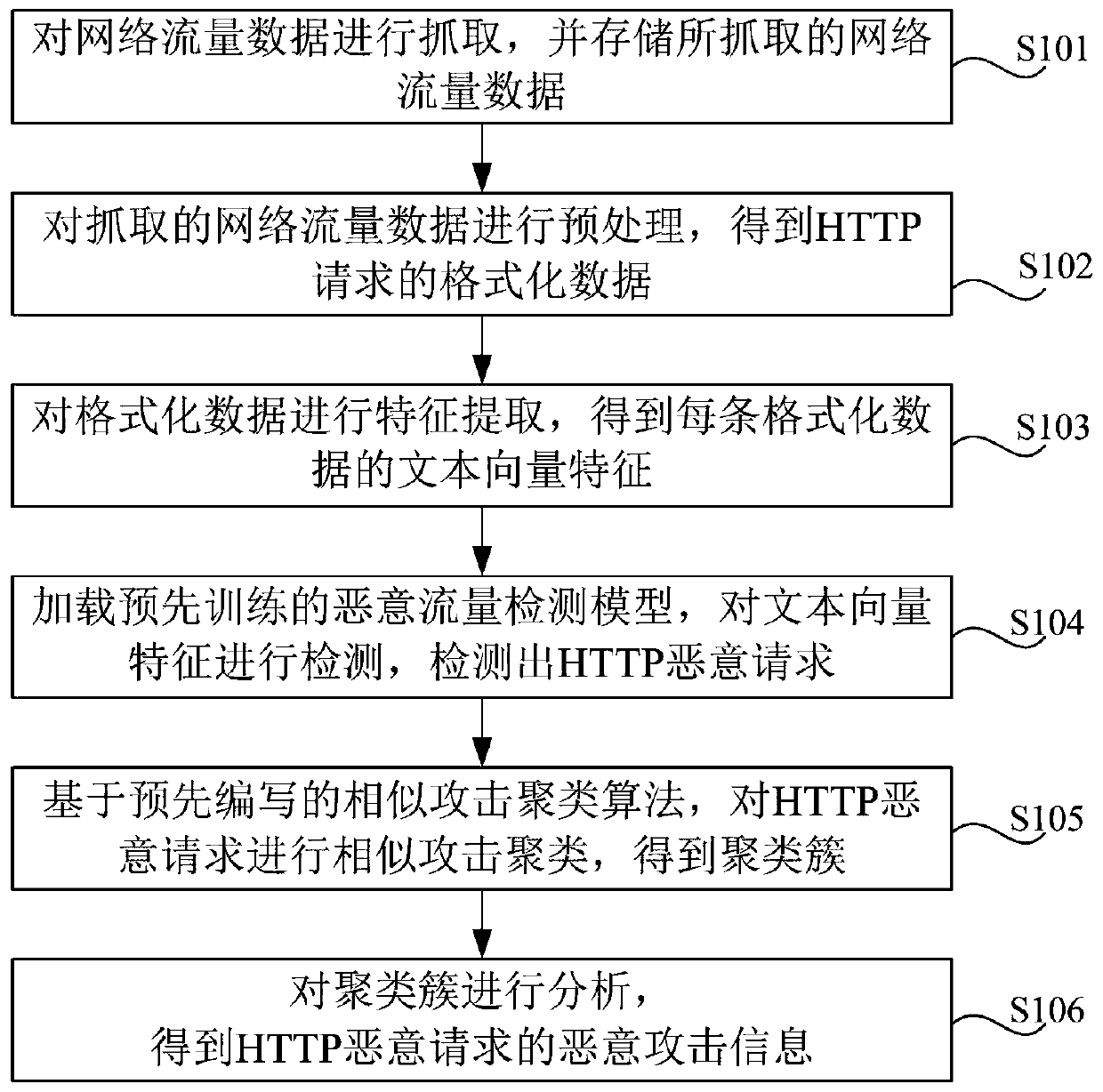
Detection method and system for HTTP malicious traffic
ActiveCN109960729AEasy to detectReduce false positivesNatural language data processingTransmissionTraffic capacityCluster algorithm
The invention discloses a detection method and system for HTTP malicious traffic, and the method comprises the steps: capturing network traffic data, carrying out the preprocessing of the network traffic data, and obtaining formatted data corresponding to each HTTP request; performing feature extraction on the formatted data to obtain text vector features of each piece of formatted data; performing classification detection on the text vector characteristics based on a pre-trained malicious flow detection model to detect an HTTP malicious request; performing similar attack clustering on the HTTP malicious request based on a similar attack clustering algorithm to obtain a cluster; and performing analysis based on the cluster to obtain malicious attack information of the HTTP malicious request. According to the method, the Spark big data analysis engine is used for carrying out feature extraction and conversion on the flow data, and the machine learning and clustering algorithm is used for mining the malicious flow, so that the detection accuracy of the network malicious flow is improved, and the flow analysis time cost of security analysts is reduced.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Network space security big data intelligent analysis method and computer readable medium
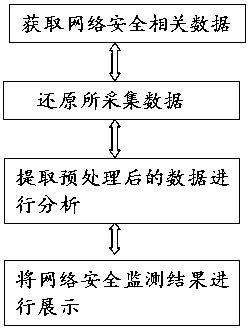
InactiveCN109861995AProtect core assetsSolve the continuous growth of dataTransmissionComplex typeAnalysis method
The invention provides a network space security big data intelligent analysis method and a computer readable medium. The method comprises the following steps: acquiring network security related data;Restoring the acquired data, and carrying out different preprocessing operations on different types of network security related data; Extracting the preprocessed data and analyzing the preprocessed data to realize network security monitoring; And displaying the network security monitoring result. On the basis of a big data technology, data characteristics of continuous increase, complex types, various sources and the like of data in safety analysis are solved, and enterprise threats such as advanced continuous malicious attacks and internal violation behaviors can be effectively detected by using a user and entity behavior analysis technology at the same time.
Owner:安徽谛听信息科技有限公司
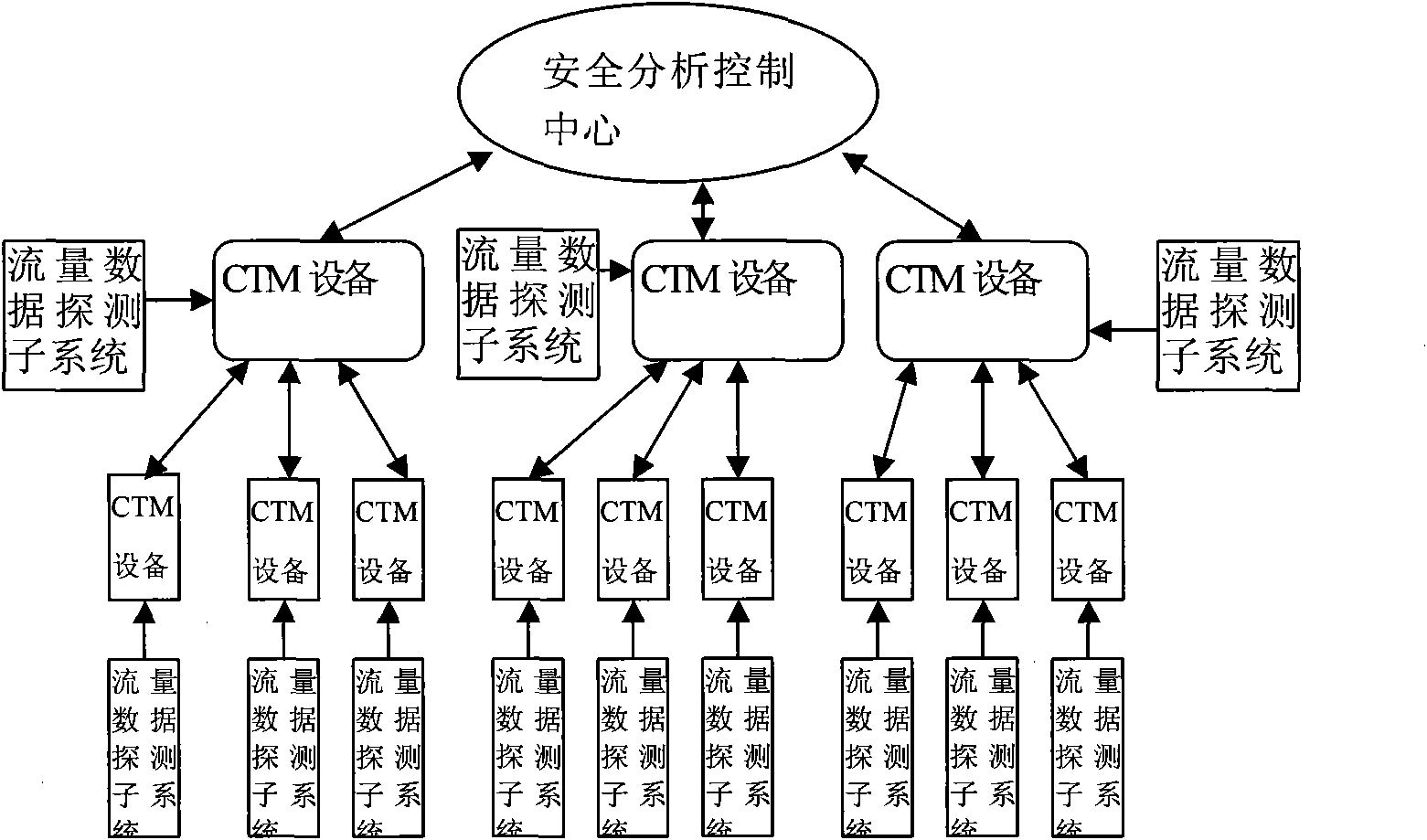
CRNET (China Railcom Net) sSafe cooperative defense system for whole course communication network
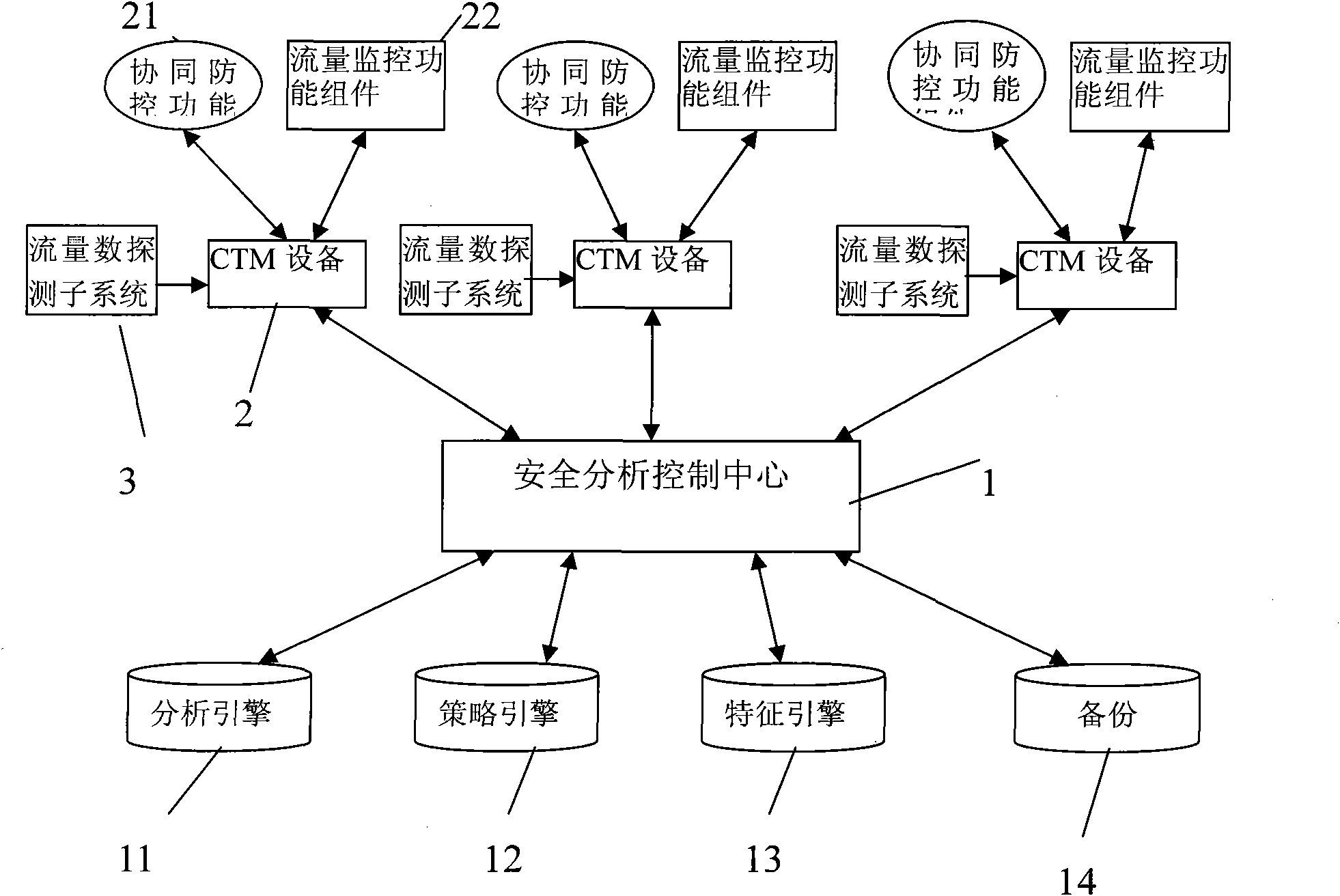
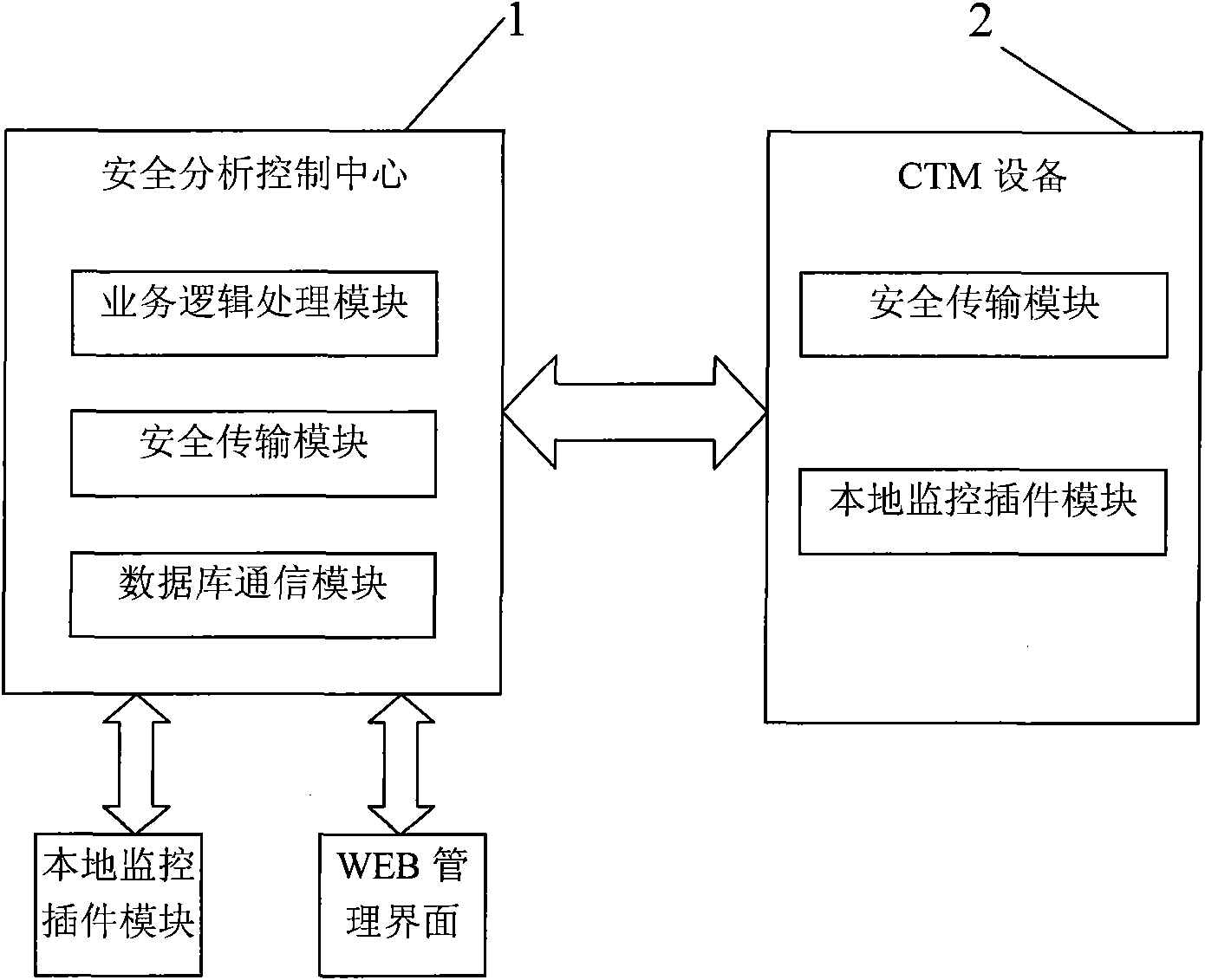
InactiveCN101938459AHigh strengthIncrease flexibilityData switching networksControl systemNetwork security policy
The invention discloses a CRNET (China Railcom Net) safe cooperative defense system for a whole course communication network, comprising a safety analysis control center, cooperative defense devices arranged at the key parts of various network nodes and a flow data detection subsystem arranged at an outer port of the network nodes. wWherein each cooperative defense device is internally provided with a flow monitoring function unitcomponent, the cooperative defense function unitcomponent and a plurality of safety function unitcomponents, such as a fireproof wall, the flow monitoring function component unit is used for informing, receiving, analyzing and processing a data flow collected by a detection system, the cooperative defense function unitcomponent is used for generating or receiving a strategy submitted by the safety analysis control center and implementing safe management and control according to the strategy, the safety analysis control center is used for integrally configuring, monitoring and managing the plurality of presidial cooperative defense devices, and the flow data detection subsystem is used for collecting the data flows of the preliminarily entering network nodes pre-entering the network. The invention can flexibly configure according to practical use, establishes a multi-level network safety strategy control system based on the safety analysis control center, the cooperative defense devices and the flow data detection subsystems for global network safety defense and management and effectively improves the whole safety defense strength and the management flexibility of thea network.
Owner:BEIJING NETINORDER TECH
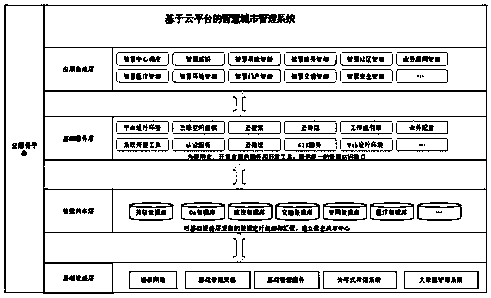
Smart city management system based on cloud platform
InactiveCN111092938AImplement modular managementHelp buildData processing applicationsTransmissionData accessUrban management
The invention provides a smart city management system based on a cloud platform, and the system comprises: an infrastructure layer which is used for providing a system data access service and city resource data collection, and storing the city resource data in a data sharing layer in real time; a basic service layer which is used for developing and operating a platform as a service to be providedfor a user; adata sharing layer which is used for gathering various basic service system data to form massive traffic data, forming a comprehensive information sharing database by utilizing a cloud computing big data processing technology, breaking through information island limitation and realizing data gathering and sharing; an application integration layer which comprises application managementand application configuration management; and a cloud service platform which is used for performing security analysis through an application program interface and a communication network according tothe acquired data of the infrastructure layer. Data in all fields of city management are analyzed and interacted through the cloud technology, modular integrated management of the smart city is achieved, all modules are clear in function, management is more reasonable and perfect, multiple services needed by residents in the smart city can be provided, the life quality of the residents can be improved, and construction of the smart city is facilitated.
Owner:重庆特斯联智慧科技股份有限公司
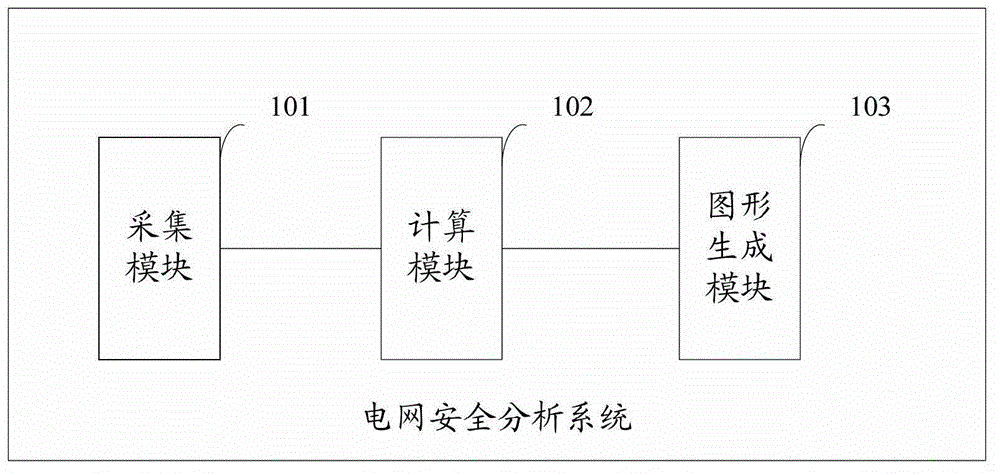
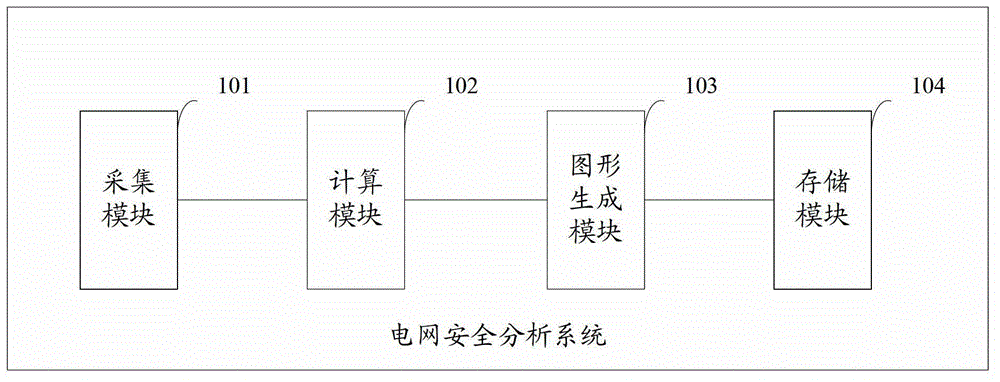
Safety analyzing system of power network
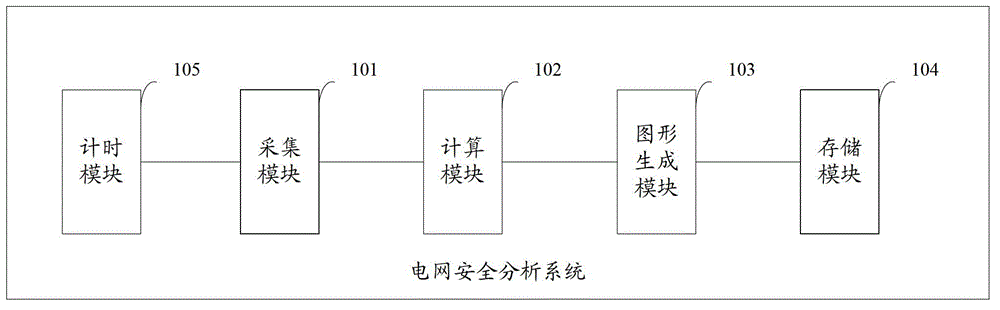
ActiveCN103150600AChange the working mode of manual computingImprove work efficiencyData processing applicationsReal-time dataPower grid
The invention provides a safety analyzing system of a power network. The safety analyzing system is used for collecting real-time data, parameter data and the like of the power network, and building the data into a visualized model according to an IEC61970 (international electrotechnical commission) standard, so a manual calculation work mode of the power network operation method is changed, the working efficiency is improved, and an auxiliary decision is provided for the arrangement of the power network operation method. The safety analyzing system has the advantages that the purposes of centralized management, graded use, and interaction and sharing of the calculation and analyzing results are realized, and a support platform is provided for the stable analyzing and calculation of cooperation trends for the upper-level and lower-level dispatching of the power network operation method.
Owner:PINGYANG ELECTRIC POWER SUPPLY COMPANY OF STATE GRID ZHEJIANG ELECTRIC POWER +2
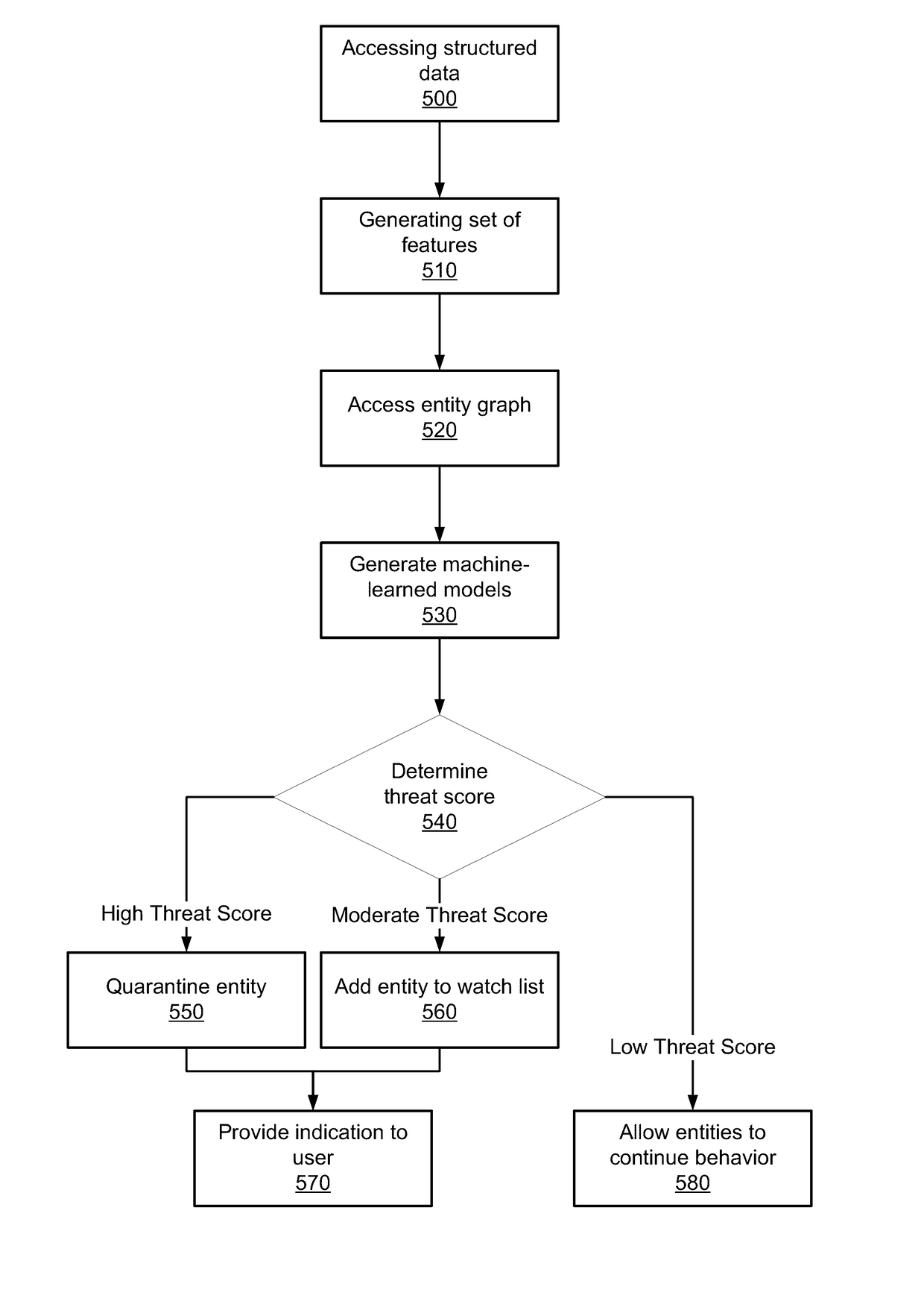
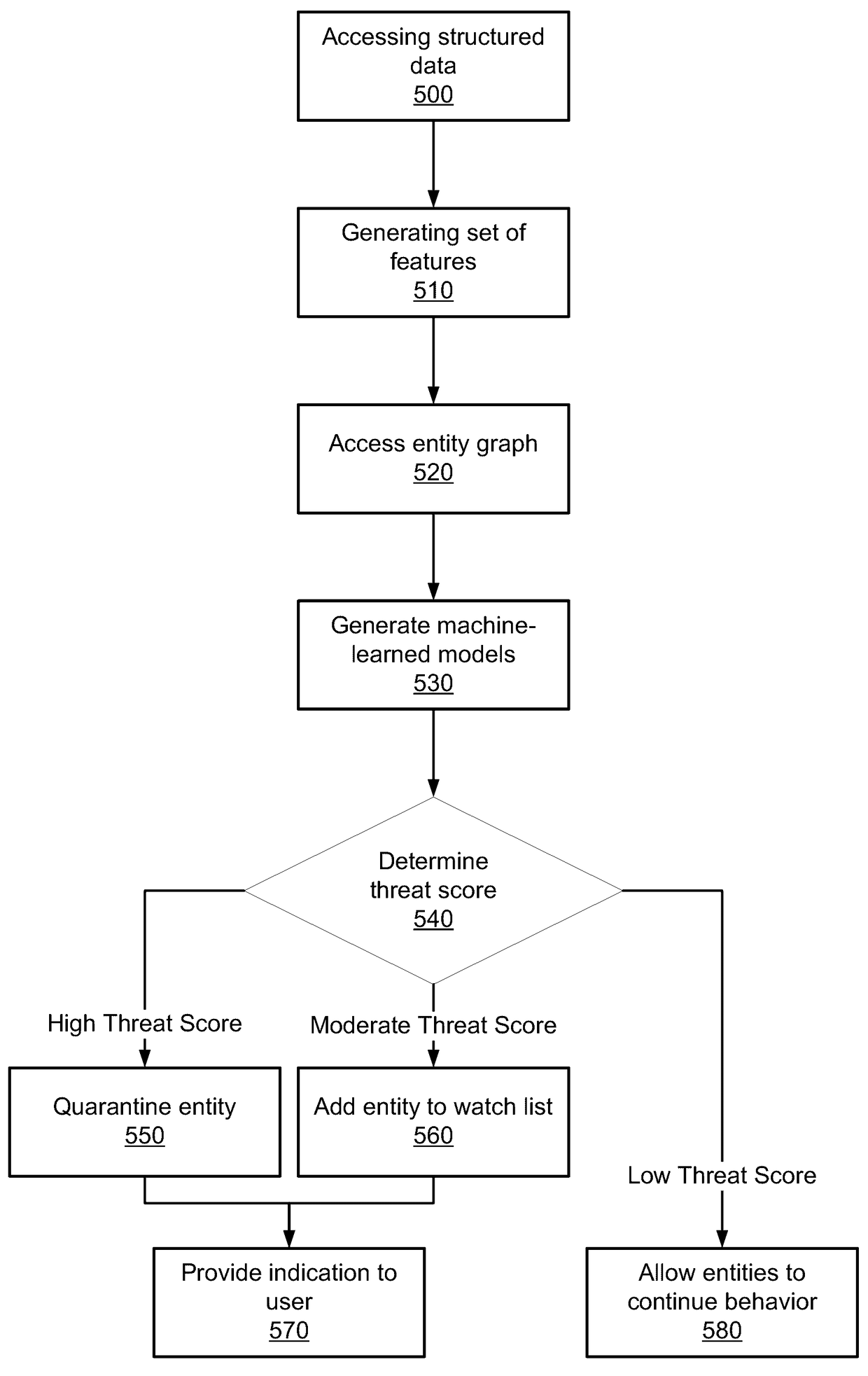
Modeling behavior in a network
Disclosed is a system for detecting security threats in a local network. A security analytics system collects data about entities in the local network. The raw data can be filtered to extract data fields from the raw data that are relevant to detecting security threats in the local network. The filtered data can be converted into structured data that formats the information in the filtered data. The structured data may be formatted based on a set of schema, and can be used to generate a set of features. The security analytics system can use the generated features to build machine-learned models of the behavior of entities in the local network. The security analytics system can use the machine-learned models to generate threat scores representing the likelihood a security threat is present. The security analytics system can provide an indication of the security threat to a user.
Owner:VMWARE INC
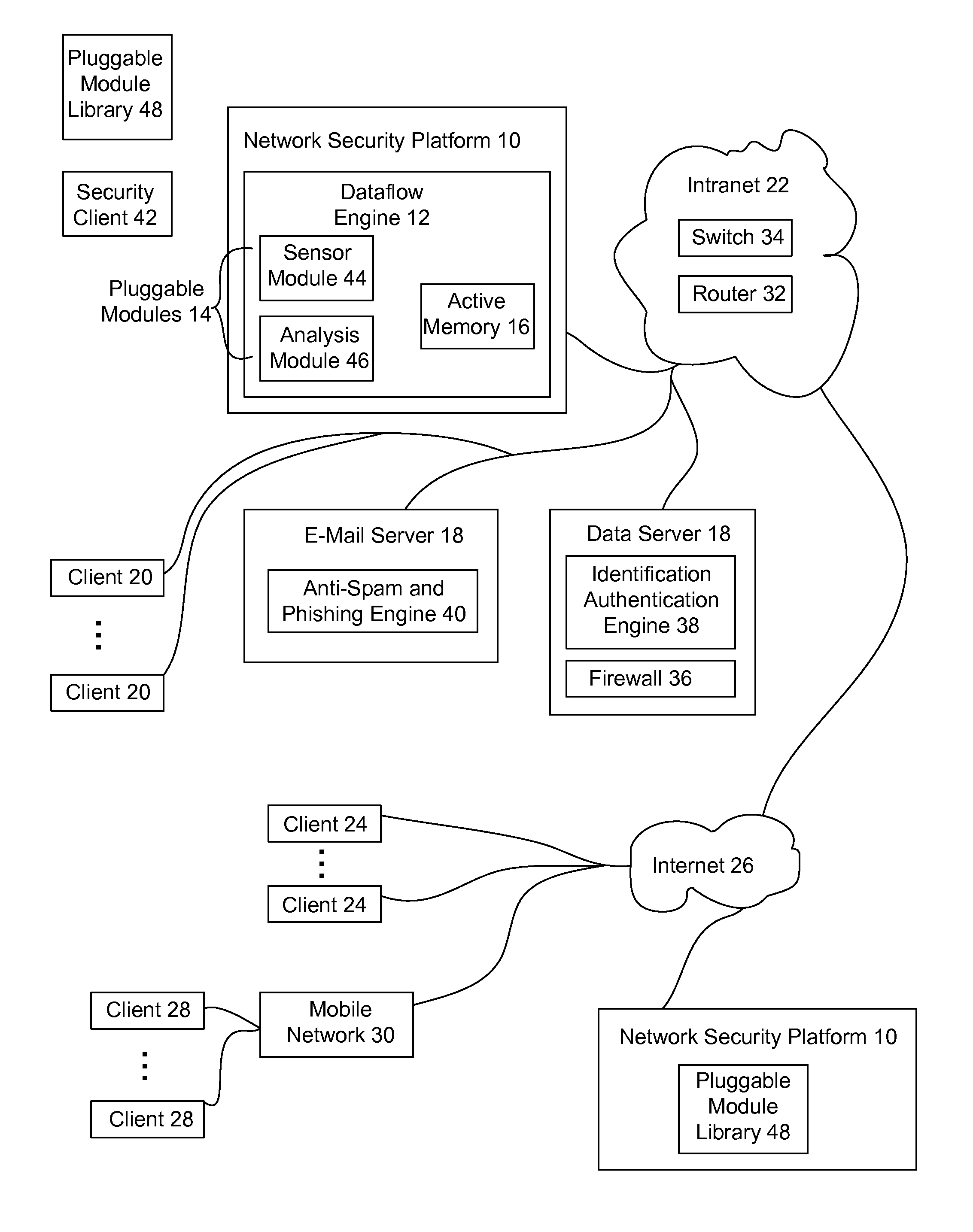
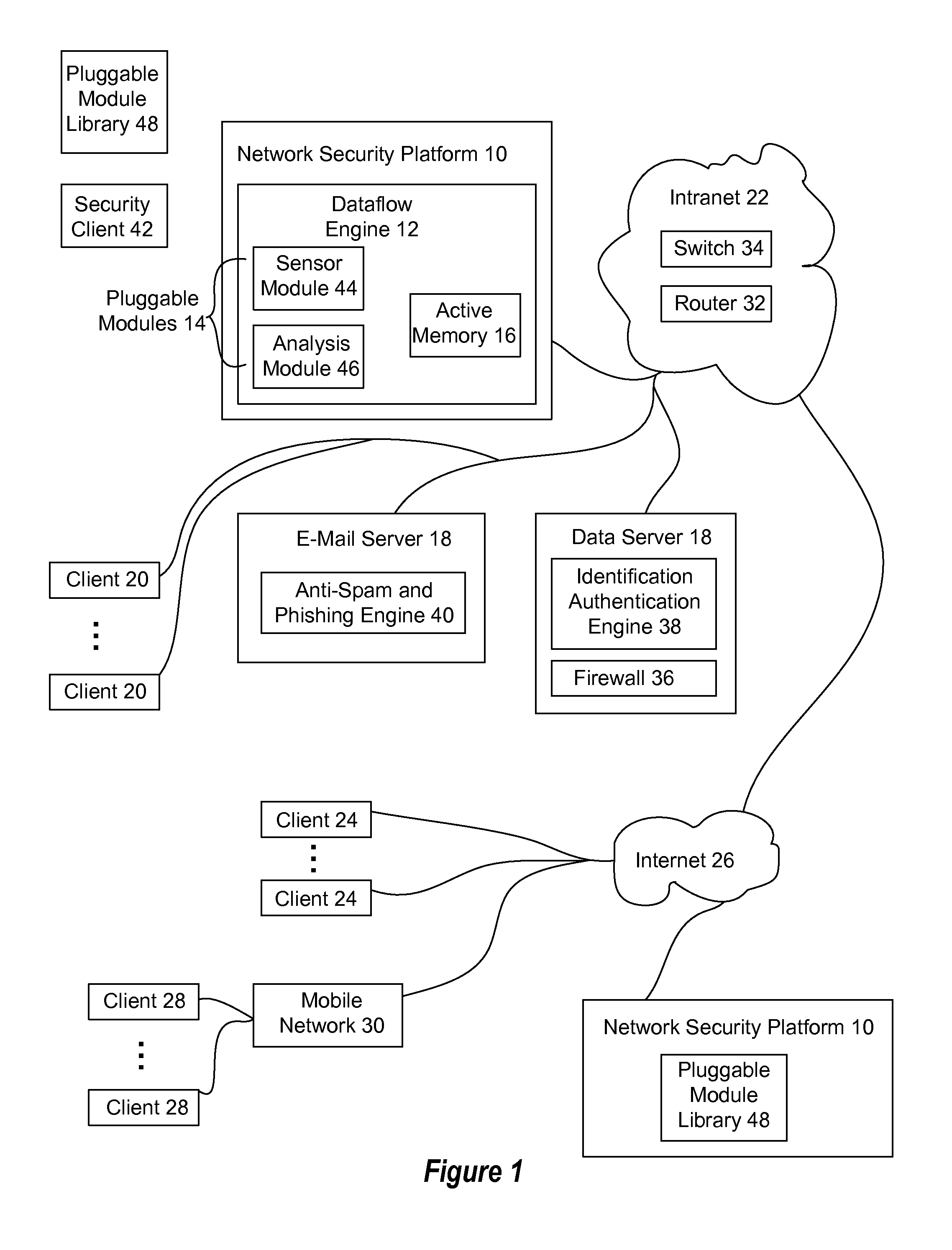
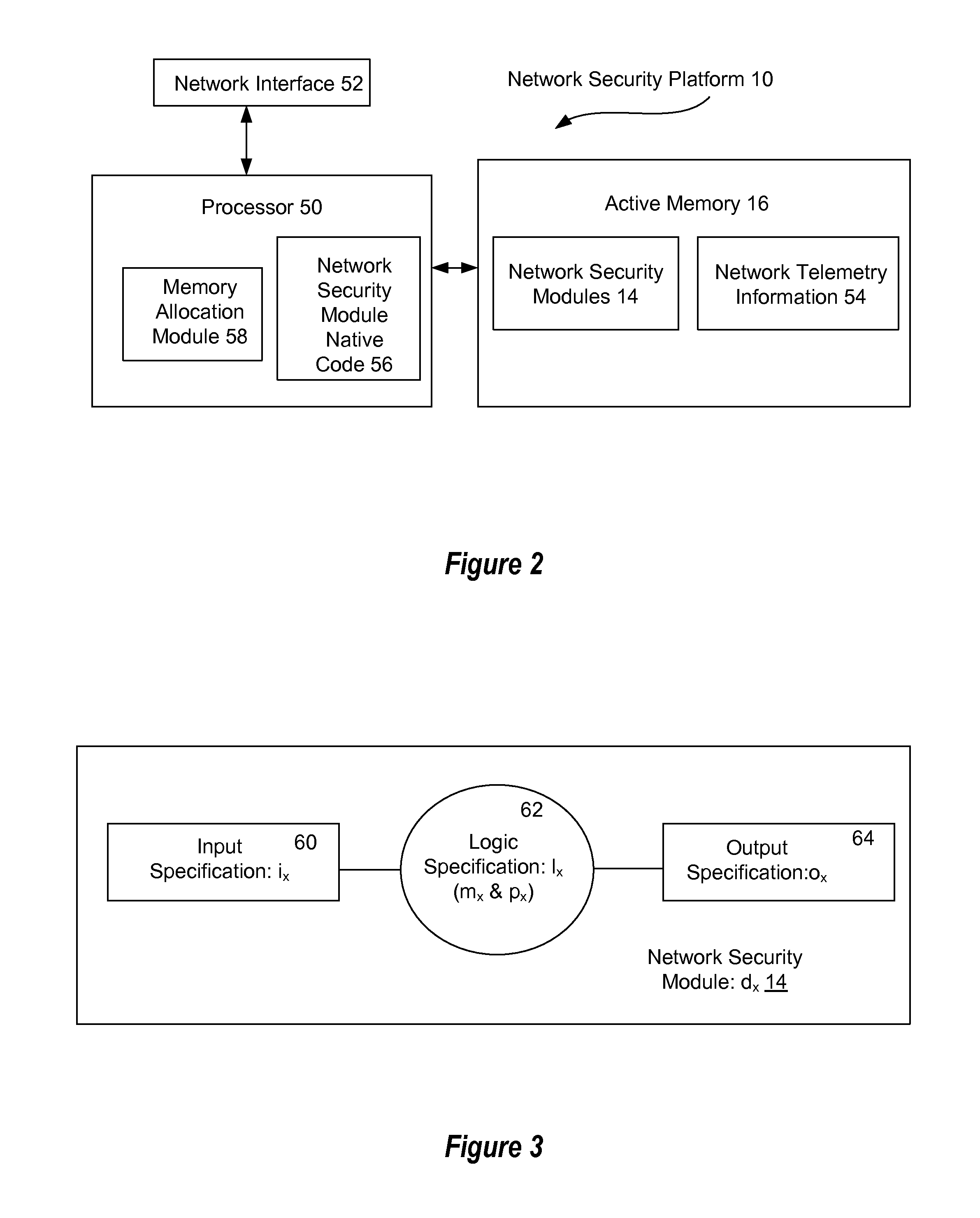
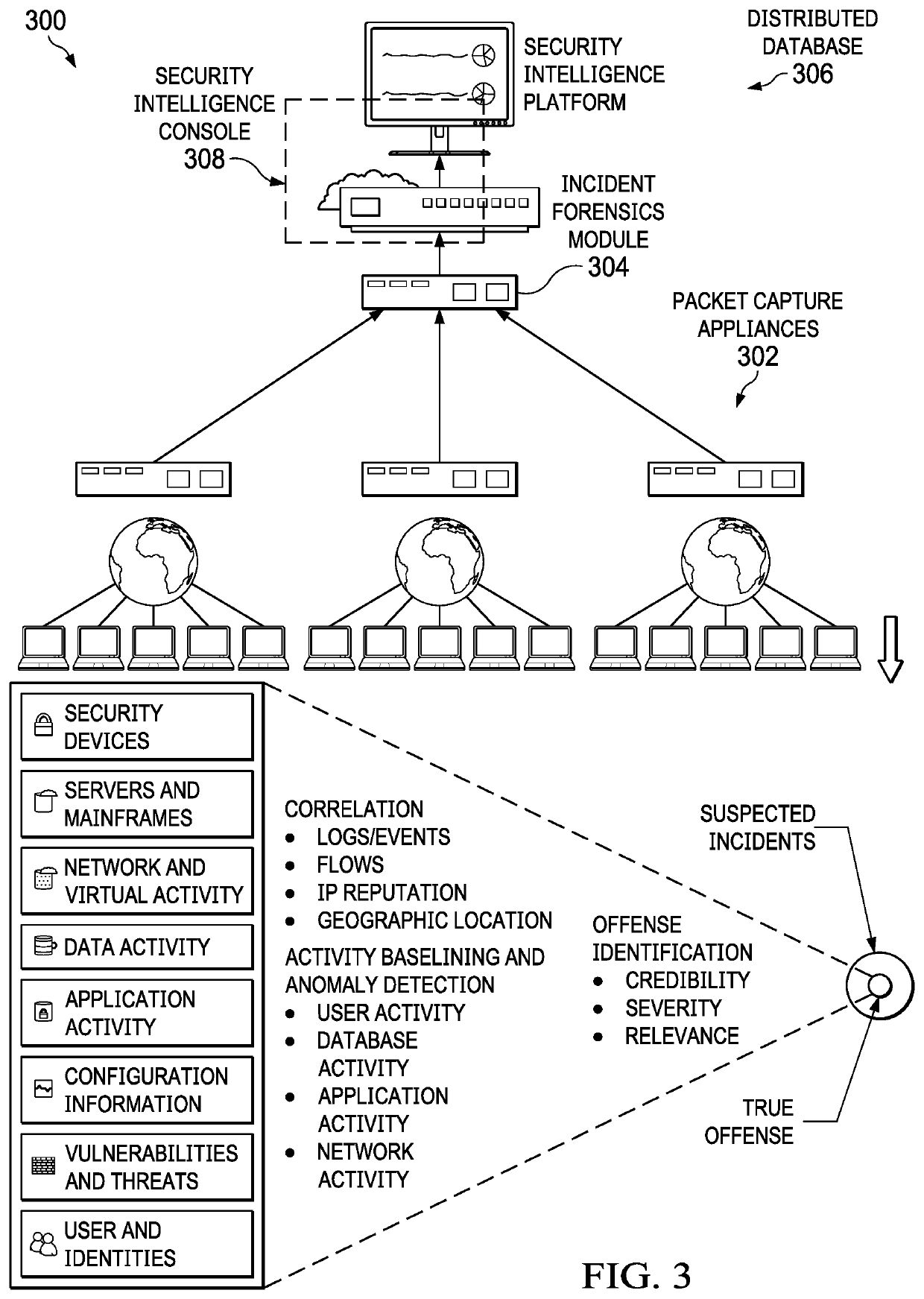
Automated security analytics platform
ActiveUS20140137240A1Reduce the amount requiredIncreased retrieval timeMemory loss protectionError detection/correctionReal-time dataActive memory
A network security platform stores network telemetry information in an active memory, such as DRAM, and analyzes the network telemetry information to detect and respond to network security threats. Using a common active memory to store sensed network telemetry information and analyze that information provides a real-time dataflow engine for detecting security threats and neutralizing detected threats.
Owner:ALERT LOGIC
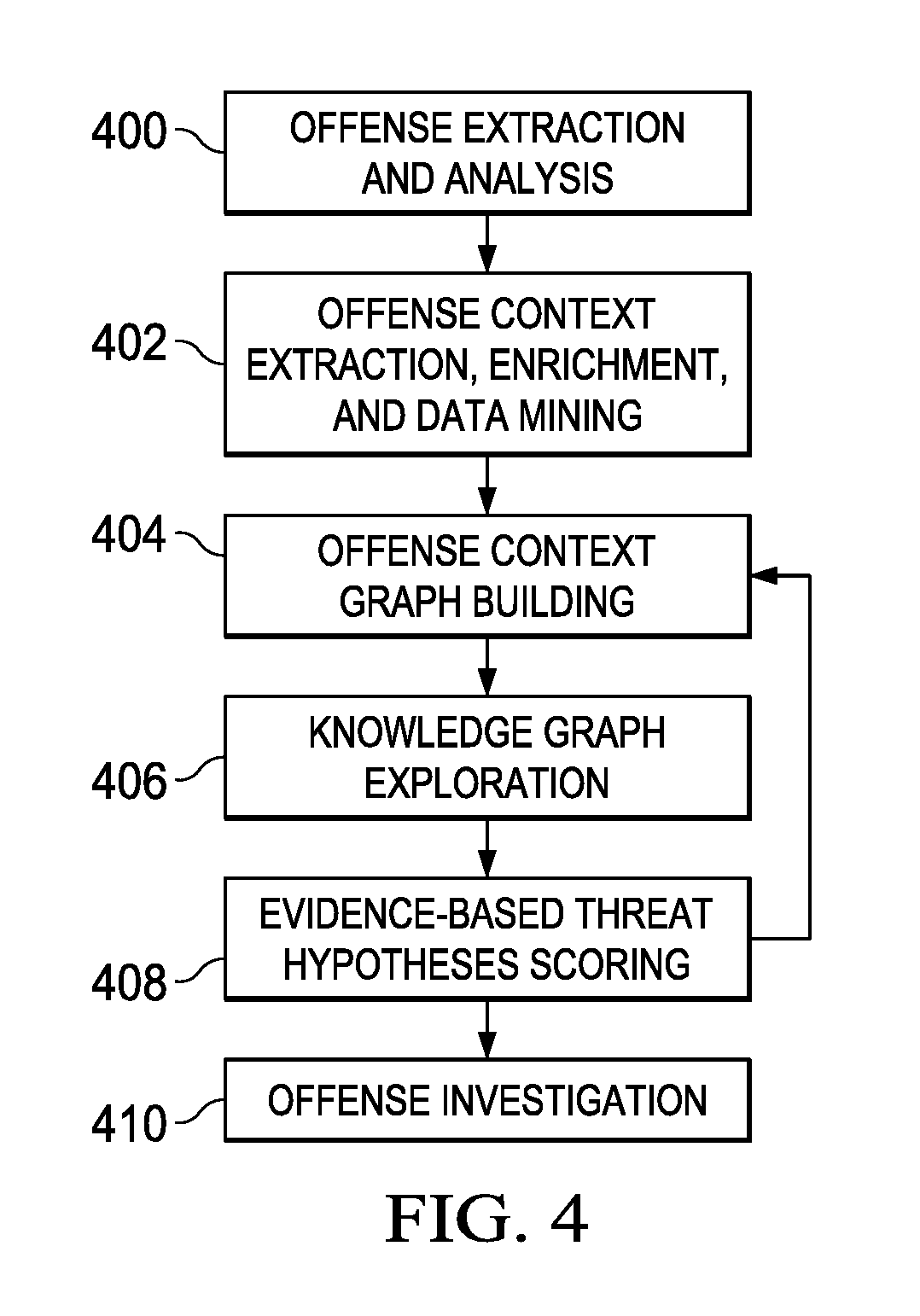
Feedback-based prioritized cognitive analysis
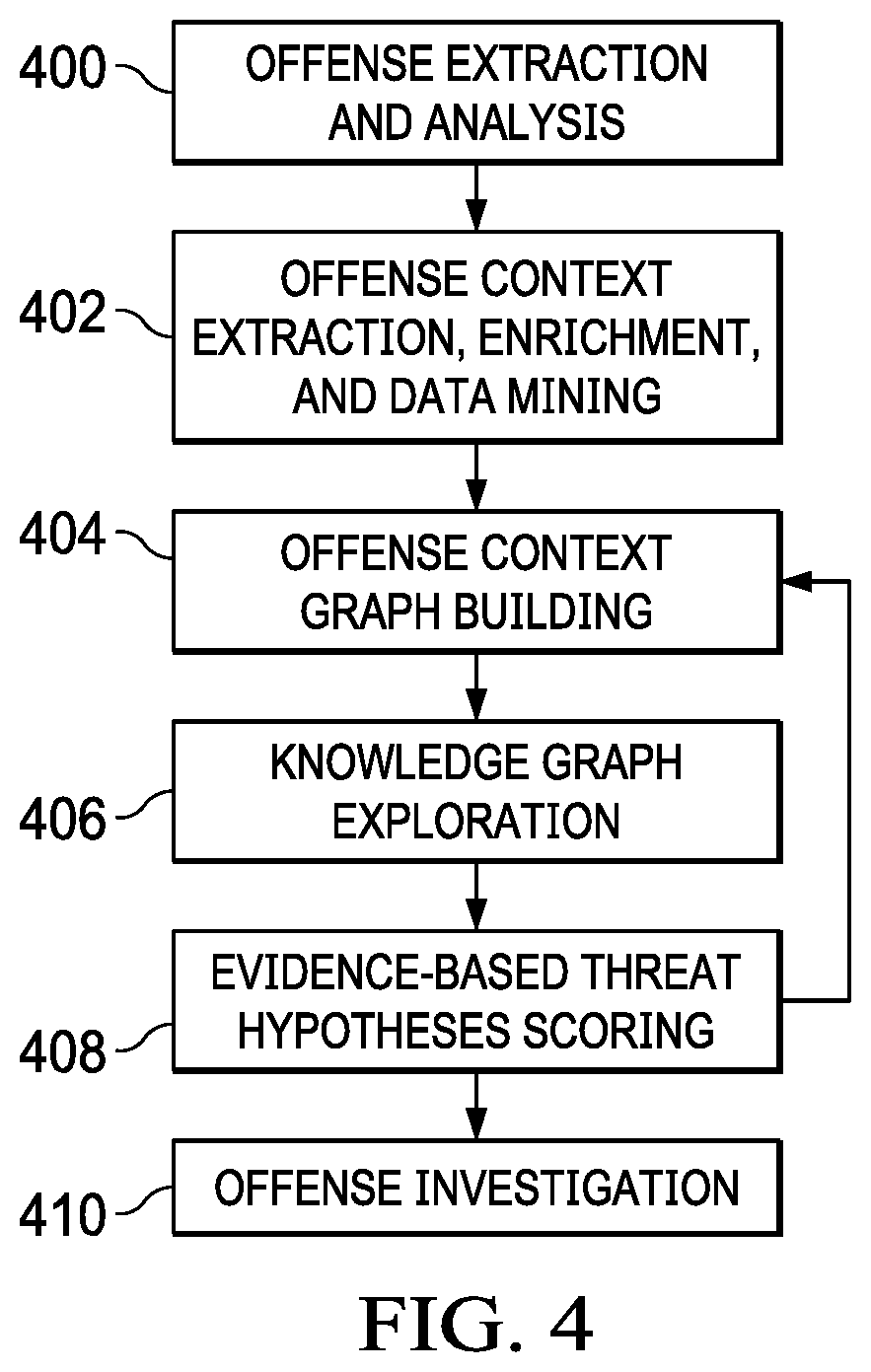
ActiveUS20180367549A1Easy to analyzeDigital data information retrievalMachine learningEvent dataGraph Node
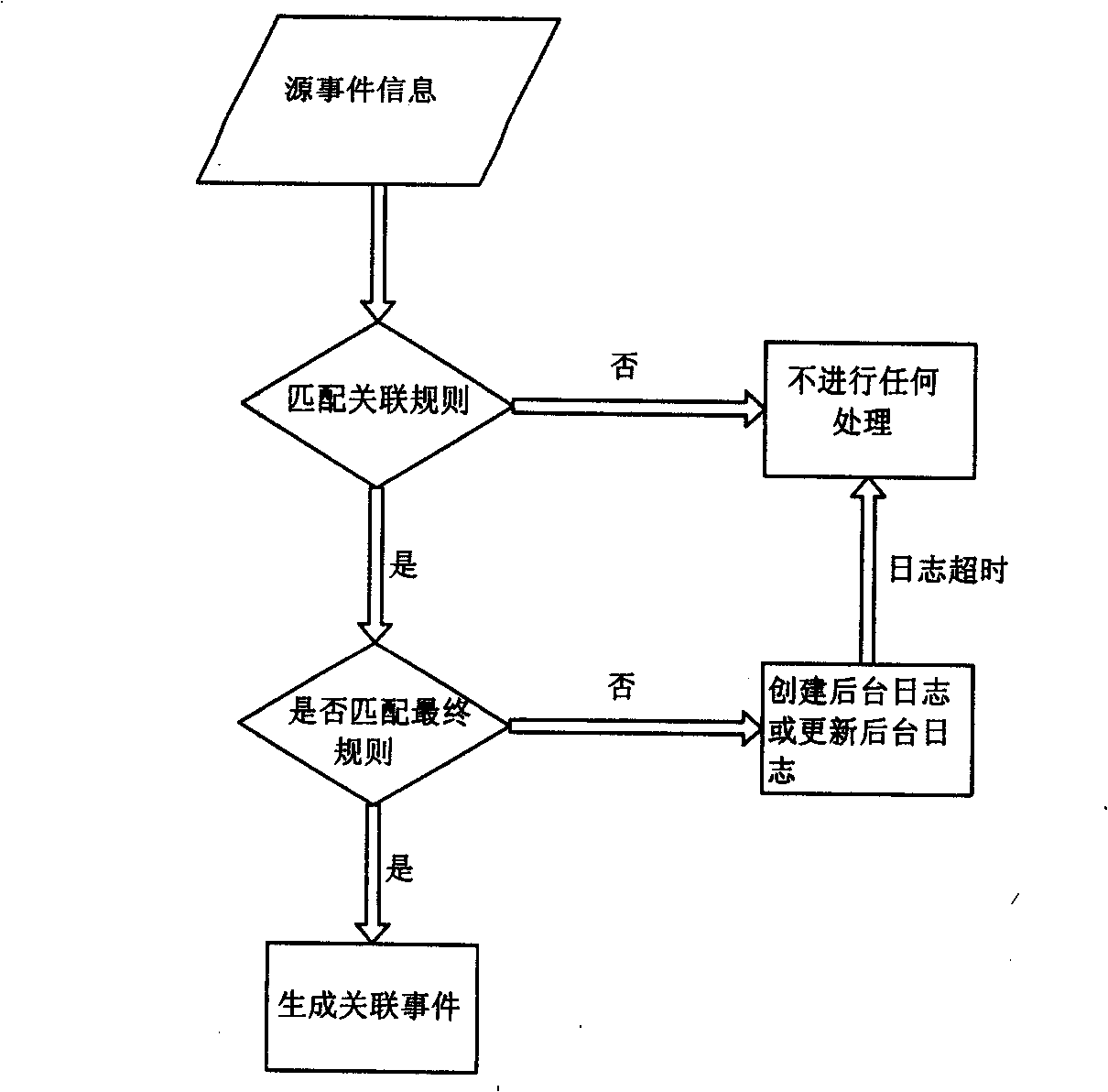
An automated method for processing security event data in association with a cybersecurity knowledge graph having nodes and edges. It begins by receiving from a security system (e.g., a SIEM) information representing an offense. An offense context graph is built. Thereafter, and to enhance the offense context graph, given nodes and edges of the knowledge graph are prioritized for traversal based on an encoding captured from a security analyst workflow. This prioritization is defined in a set of weights associated to the graph nodes and edges, and these weights may be derived using machine learning. The offense context graph is then refined by traversing the nodes and edges of the knowledge graph according to a prioritization tailored at least in part by the encoding. In addition to using security analyst workflow to augment generation of weights, preferably the machine learning system provides recommendations back to the security analysts to thereby influence their workflow.
Owner:IBM CORP
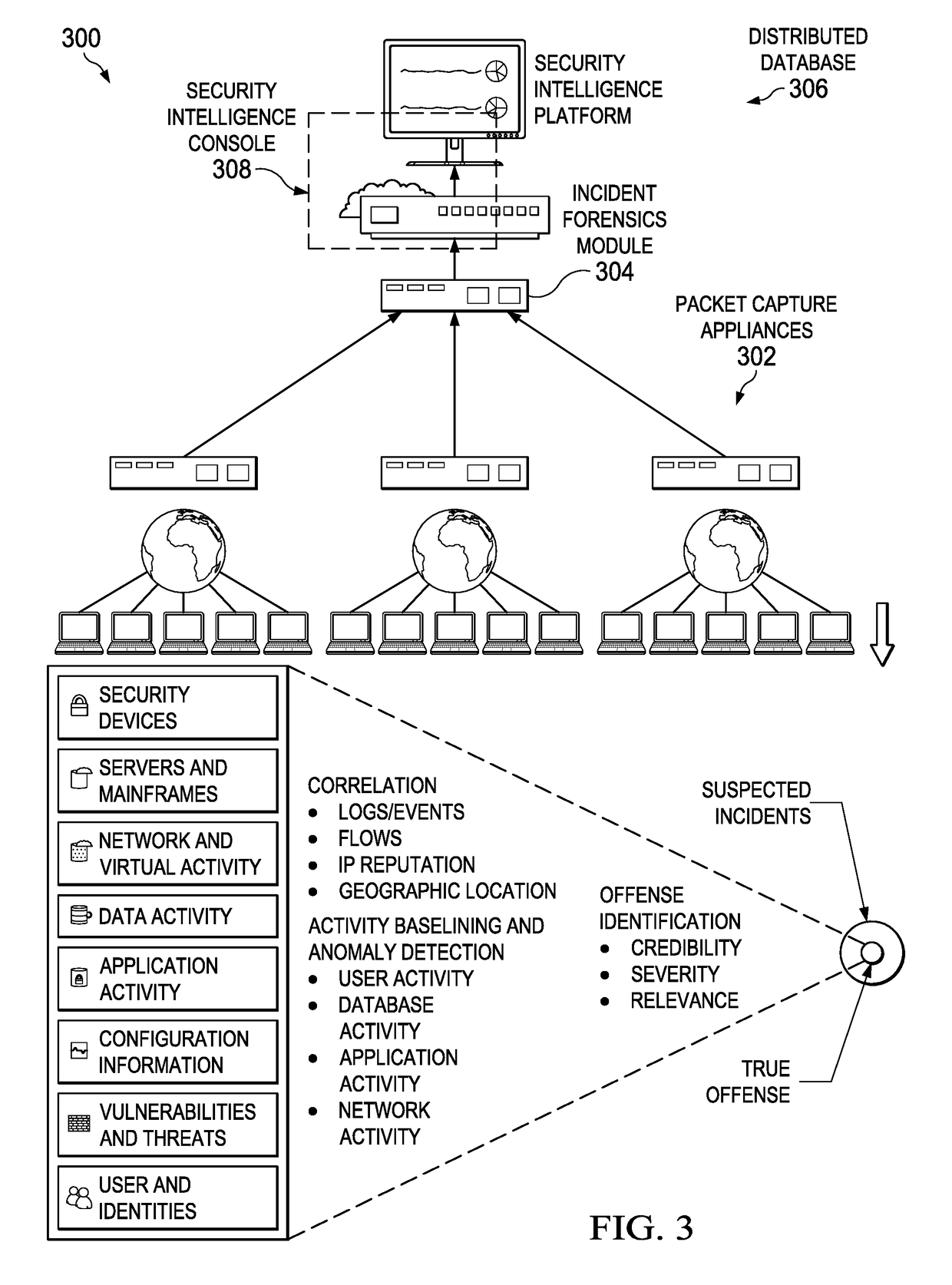
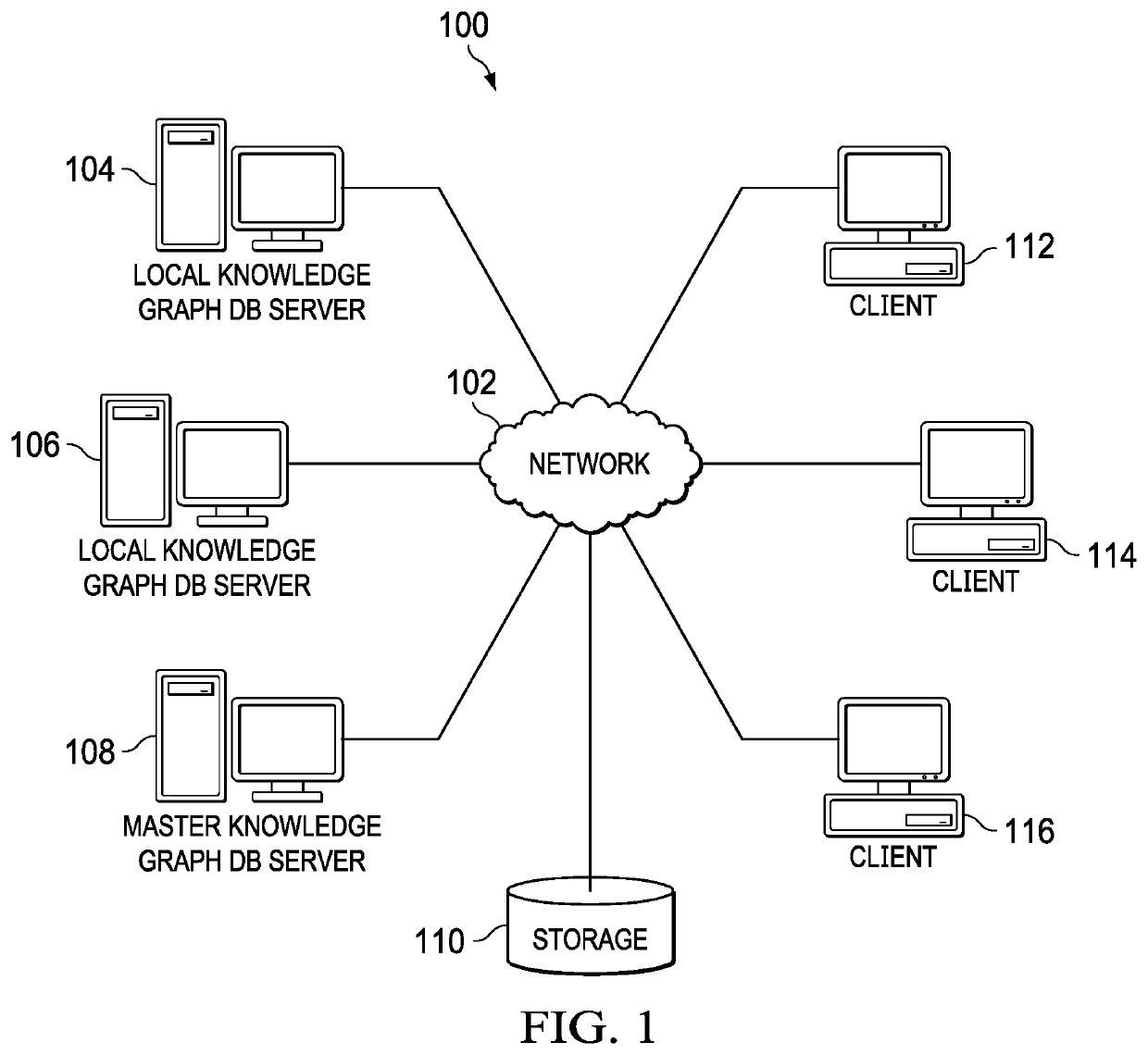
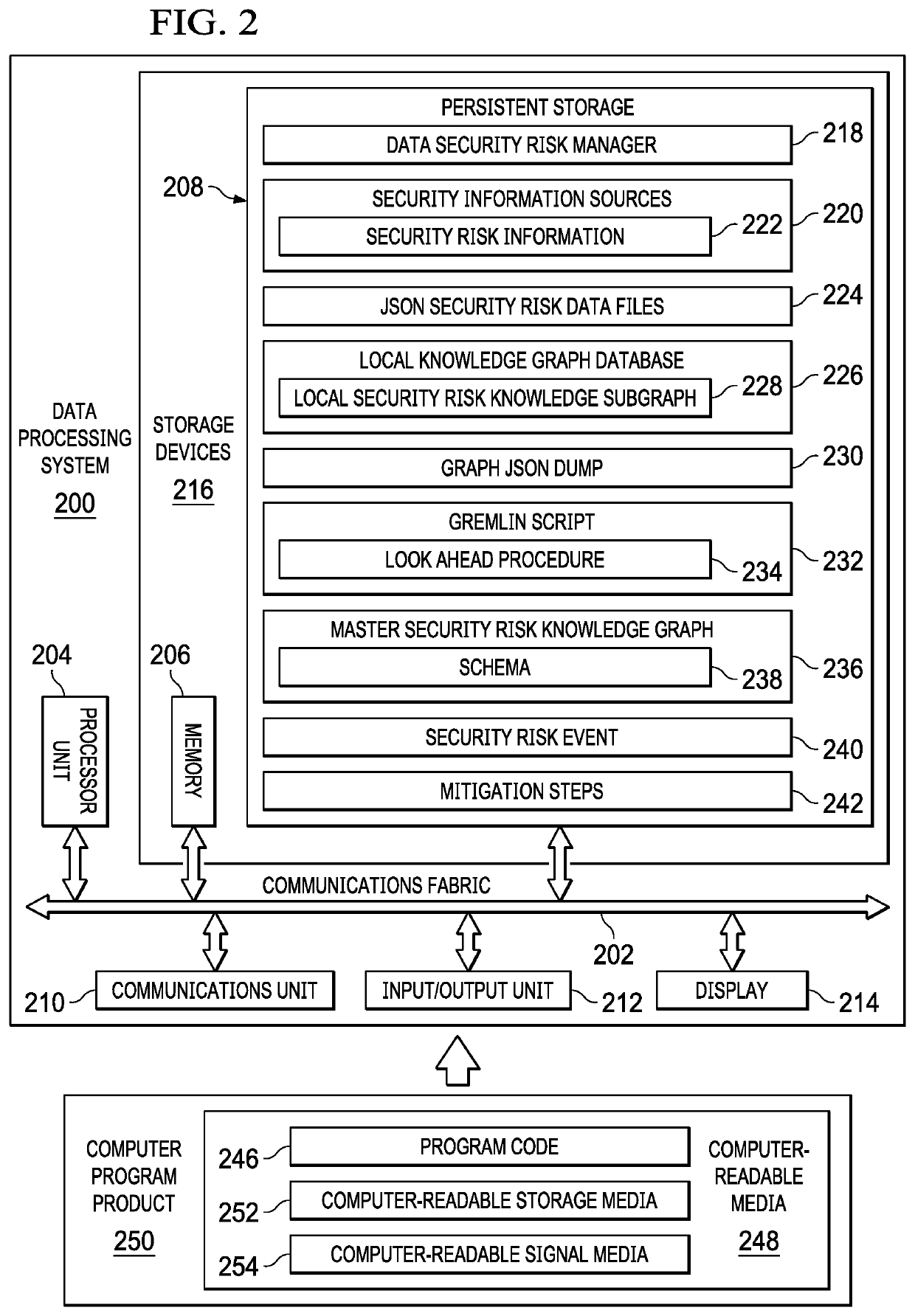
Optimizing Ingestion of Structured Security Information into Graph Databases for Security Analytics
Optimizing ingestion of security structured data into a graph database for security analytics is provided. A plurality of streams of information is received from a plurality of security information sources. Respective subsets of information are ingested from each of the plurality of security information sources to generate small subgraphs of security information. Each of the small subgraphs comply to a schema used by a master knowledge graph. A batch process is performed to ingest a plurality of small subgraphs into the master knowledge graph.
Owner:IBM CORP
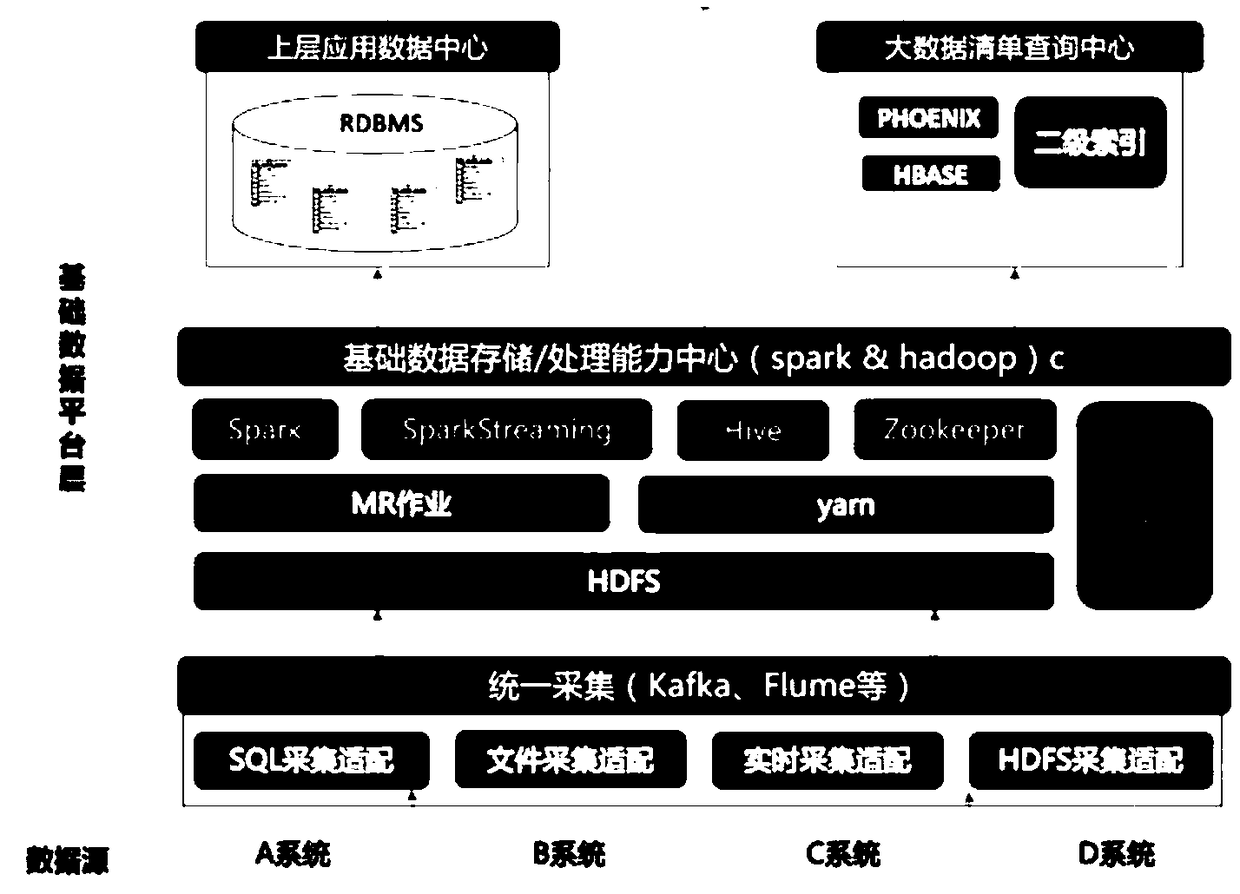
Big data security analysis platform system based on network security
InactiveCN108833397AImprove securityImprove perceptionPlatform integrity maintainanceData switching networksData centerData acquisition
The invention relates to a big data security analysis platform system based on network security. The big data security analysis platform system comprises a unified collection platform, a basic data storage and processing capability center, an upper layer application data center and a big data list query center, the unified collection platform adopts Kafka as a message management layer of the unified collection platform to achieve flexible docking and adaption to various data source collection and to provide flexible and configurable data collection capability, the basic data storage and processing capability center utilizes the spark and hadoop technologies to provide powerful data processing capability, the upper layer application data center provides highly aggregated statistical data ofan enterprise through the RDBMS / ES, and the big data list query center provides fast query capability of big data by constructing an HBase cluster.
Owner:武汉思普崚技术有限公司
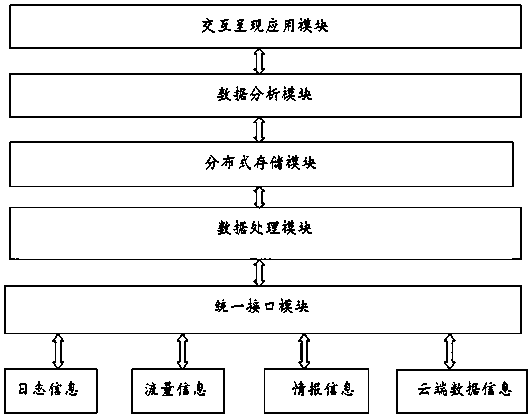
A big data intelligent analysis system based on network space security
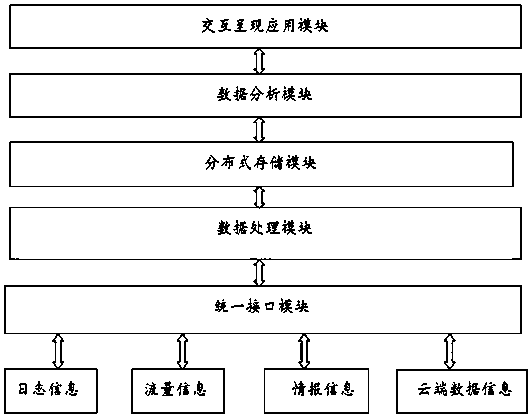
InactiveCN109885562AProtect core assetsSolve the continuous growth of dataDatabase distribution/replicationTransmissionData acquisitionApplication module
The invention provides a big data intelligent analysis system based on network space security. The big data intelligent analysis system comprises a unified interface module, a data acquisition module,a data processing module, a distributed storage module, a data analysis module and an interactive presentation application module. On the basis of a big data technology, data characteristics of continuous increase, complex types, various sources and the like of data in safety analysis are solved, and enterprise threats such as advanced continuous malicious attacks and internal violation behaviorscan be effectively detected by using a user and entity behavior analysis technology at the same time.
Owner:安徽谛听信息科技有限公司
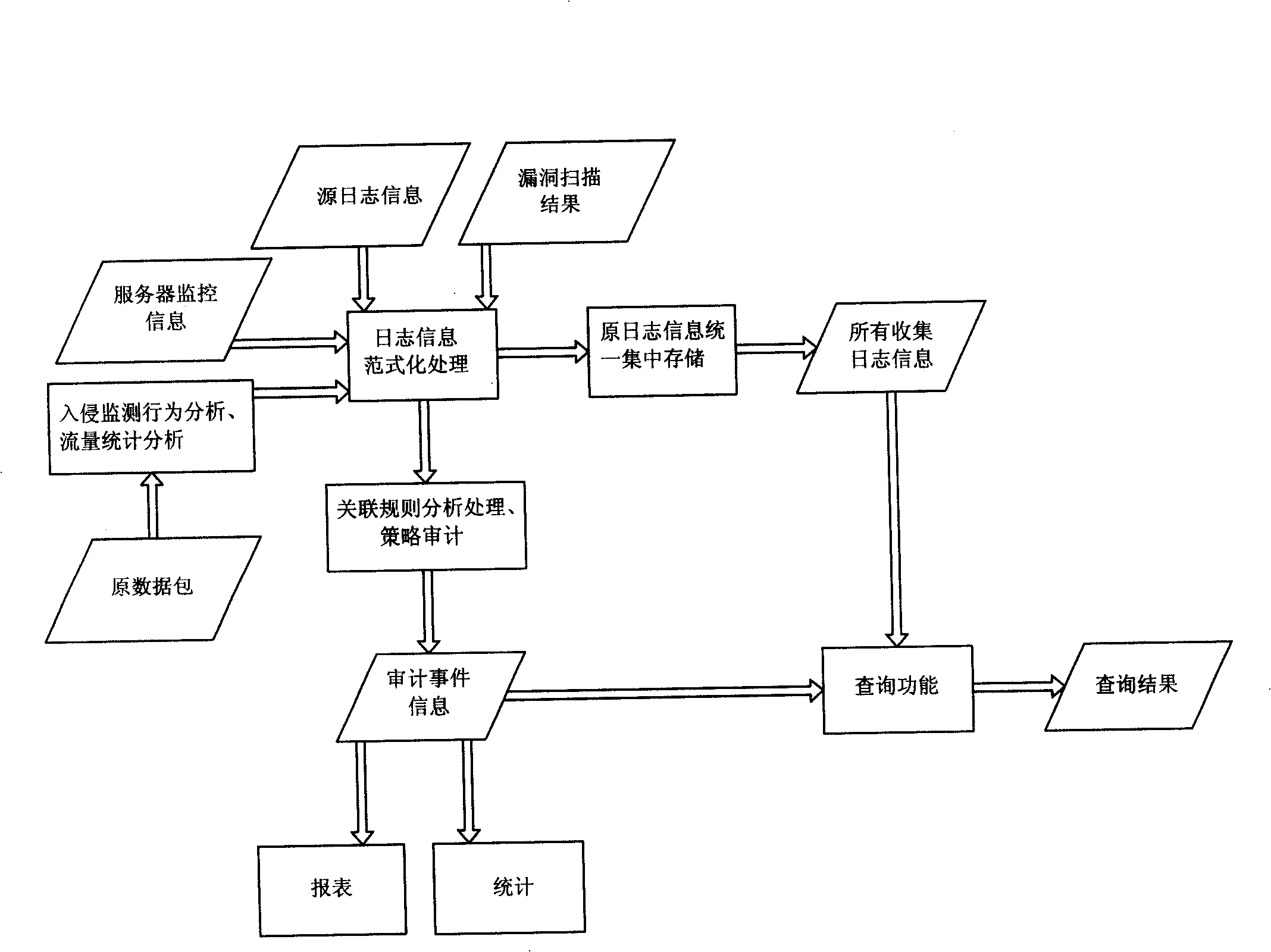
Service system united safe platform
InactiveCN101257399AReduce redundant workSolving Dispersion ProblemsData switching networksSecurity analyticsComputer science
The invention discloses a unified satety platform of an operation system, characterized in that the platform comprises: an intrusion detection module for a access layer network of the operation system; a flow statistic module for the access layer network of the operation system; a vulnerability scanning module for the operation system host device; a server monitoring module for the operation system server; a log audit module for the operation system environment and the system per se; an event inquiring module for collecting the log and auditing the event information; and a strategy audit module for auditing event statistic of the event information and collecting the log. The invention can carry out comprehensive unified satety analysis for the operation system, solve the prior dispersive and complex problem of the safty analysis, lower the cost and reduce active redundancy of satety mamager.
Owner:CHINA MOBILE GROUP SICHUAN
Affectedness scoring engine for cyber threat intelligence services
ActiveUS20200327223A1Digital data information retrievalPlatform integrity maintainanceManaged security serviceCyber threat intelligence
A network-accessible cyber-threat security analytics service is configured to characterize and respond to a description that includes threat indicators (e.g., IOCs), and an initial severity. Enterprises register with the service by providing identifying information, such as industry, geographies, and the like. For each threat indicator, a query is sent to each of a set of one or more security knowledge bases, and at least some of the queries are scoped by the enterprise industry / geo information specified. The knowledge bases may vary but typically include: a managed security service, a cyber threat intelligence service, and a federated search engine that searches across one or more enterprise-connected data sources. Responses to the queries are collected. A response provides an indication whether the threat indicator identified in the query has been sighted in the knowledge base and the frequency. The system then adjusts the initial severity to reflect the indications returned from querying the security knowledge bases.
Owner:IBM CORP
Prioritizing security findings in a SAST tool based on historical security analysis
ActiveUS9544327B1Security vulnerability can be reducedEasy to useComputer security arrangementsMachine learningInformation sharingSecurity analytics
Owner:FINJAN BLUE INC
Service safety analysis method and system thereof
ActiveCN106034056AGet security status in real timeAccurate analysisData switching networksTraffic capacityFeature extraction
The invention discloses a service safety analysis method and a system thereof. The method comprises the following steps of receiving Netflow data sent by network equipment and simultaneously actively collecting all network flow data; analyzing the collected flow data and generating the Netflow data; carrying out flow filtering, flow polymerization and characteristic extraction on the acquired Netflow data, using a threat detection technology to carry out threat detection on the Netflow data after the flow filtering, the flow polymerization and the characteristic extraction, storing a detection result in black, white and grey lists and using a service view form to display the detection result of the Netflow data; and combining the service data to carry out association analysis on the detection result and acquiring a safety state of a service system in real time. In the scheme of the invention, in a complex network environment, an abnormal flow can be accurately analyzed.
Owner:BEIJING VENUS INFORMATION SECURITY TECH +1
Characteristic configuration-based fault tree generation method
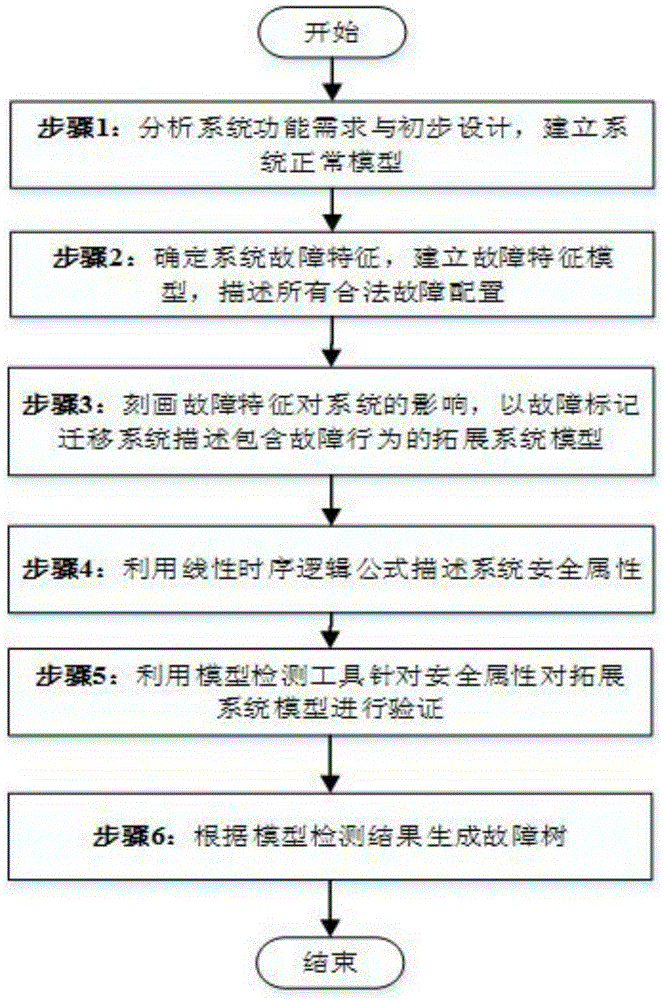
ActiveCN105426680AAccurately describe system behaviorSignificant impactSpecial data processing applicationsInformaticsLabeled transition systemSoftware product line
The invention discloses a characteristic configuration-based fault tree generation method. The method comprises the following steps: introducing the variable modeling of software product lines into the safety analysis process, and utilizing a characteristic model as a system fault structural model to depict the hierarchical and restriction relationships of the faults; proposing a fault labeled transition system (FLTS) for the expanding of state transition and using the FLTS as a system fault behavior model; defining the process of generating the fault tree by utilizing model detection on the basis of the semantic of the FLTS; and finally realizing the method of generating the fault tree on the basis of fault configuration by utilizing an existing software product line model detector. According to the method provided by the invention, the characteristic model is utilized to depict the system static hierarchical structure, the subordination relationship between the faults and components as well as the restriction relationship among the faults; and by utilizing the characteristics of the software product line model detection, all the cut sets of specific safety attributes can found on the basis of a system model, so that the fault tree generation efficiency and correctness are improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method and system for identifying security risks using graph analysis
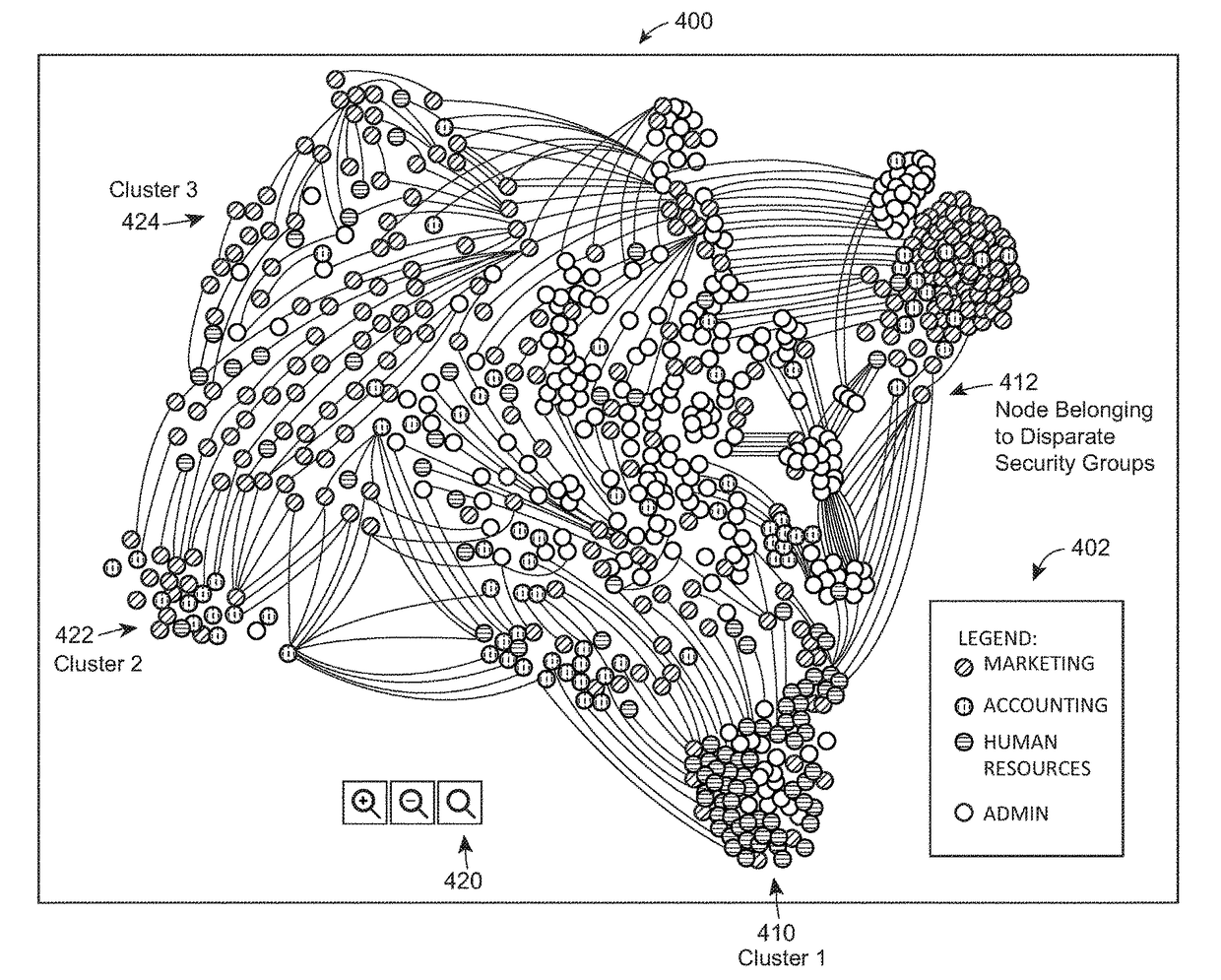
ActiveUS9819685B1Increase in sizeEasy to identifyDigital data processing detailsTransmissionGraphicsInternet privacy
Methods, systems, apparatus, and non-transitory computer readable media are described for identifying users who are likely to have unauthorized access to secure data files in an organizational network. Various aspects may include presenting the identified users on a display for a system administrator and / or security analyst to resolve. For example, the display may include a graph data structure with users represented as nodes and connections between users represented as edges. Each connection may be a pair of users belonging to a same security group. The graph data structure display may be organized and color coded in such a manner, that a system administrator and / or security analyst may quickly and easily view the users who are most likely to have unauthorized access to secure data files. The authorized access may then be remedied or taken away.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com