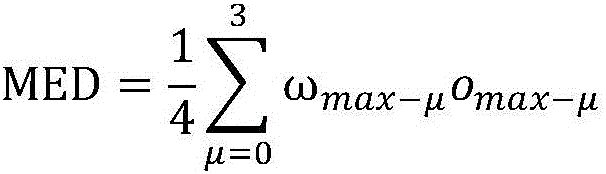Patents
Literature
193 results about "Big data security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
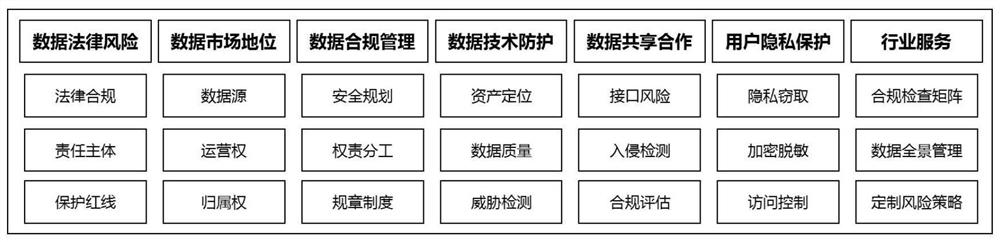
Big data security is the collective term for all the measures and tools used to guard both the data and analytics processes from attacks, theft, or other malicious activities that could harm or negatively affect them.
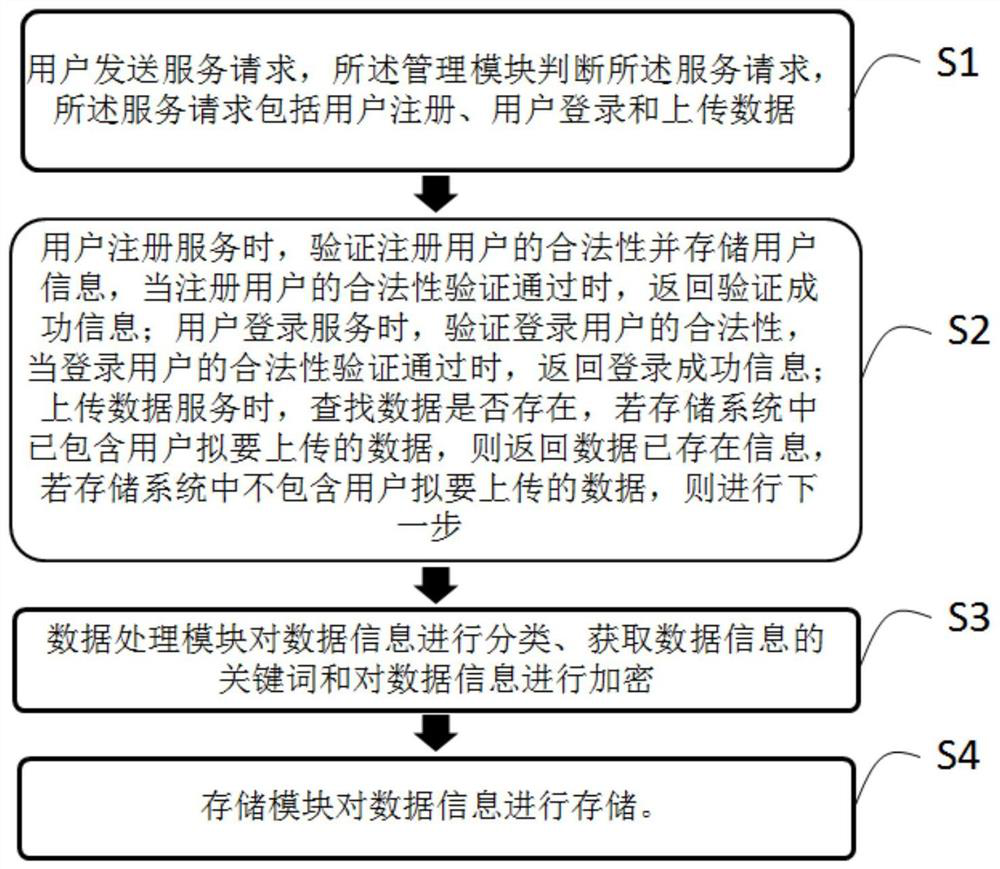
Big data security analysis system based on massive network monitoring data
PendingCN108259462ARealize real-time monitoringImprove securityData switching networksOriginal dataBig data security
The invention discloses a big data security analysis system based on massive network monitoring data. The system includes a data traffic monitoring module, a deep packet detection module, a data jointanalysis module, an anomaly detection module and a security evaluation module, wherein the data traffic monitoring module is used to monitor data traffic in real time, analyze applications, perform lossless collection on various system traffic data, and transmit the data to other modules; the deep packet detection module is used to judge the service types and application types by deeply reconstituting and analyzing the payload content of a seventh-layer packet and matching service characteristics, and performs analysis to obtain different application types; the data joint analysis module is used to perform data aggregation and study the state and association analysis to further remove redundant information in original data; the anomaly detection module is used to detect a data analysis result and judge whether the data is abnormal; and the security evaluation module is used to obtain a data evaluation result by combining the network situation based on the analysis and detection of other modules. According to the system, the real-time monitoring of network data and corresponding data security analysis can be implemented, and the data security and reliability can be improved.
Owner:国网吉林省电力有限公司信息通信公司 +1
Big data security visualization interaction analysis system and method
ActiveCN105843803AImplement filteringCapable of visual interactionSpecial data processing applicationsDecision makerProcess module
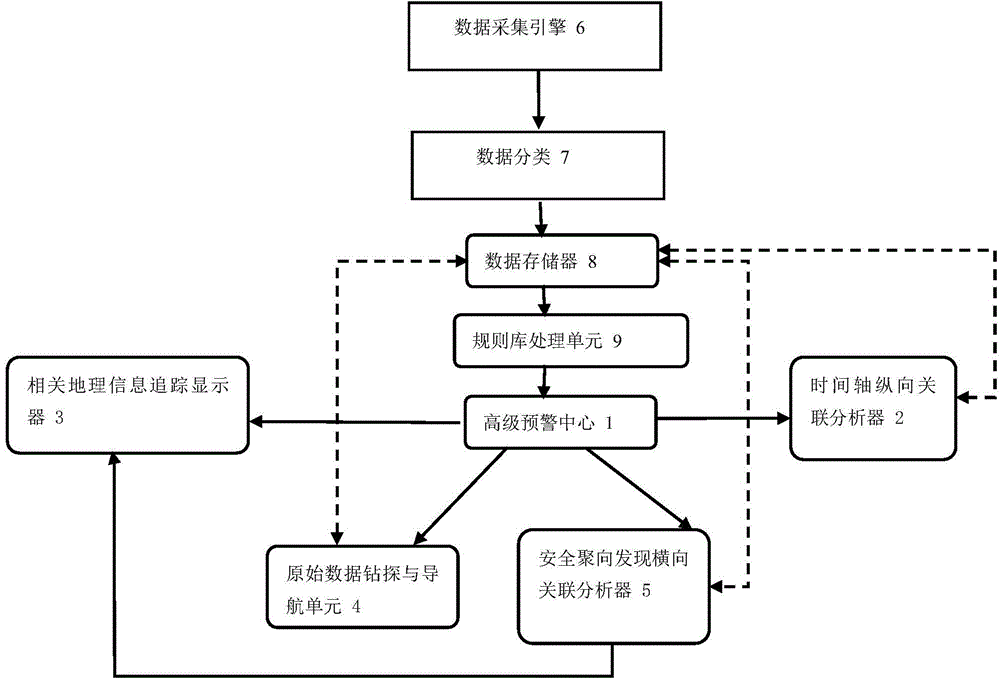
The present invention discloses a large data security visualization interactive analysis system and method. The system includes an advanced early warning center module, a time axis longitudinal correlation analyzer module, a related geographic information tracking display module, an original data drilling and navigation module, and a security gathering module. A horizontal association analyzer module, a data acquisition engine module, a data classification module, a data storage module, and a rule base processing module are found. The present invention splits and interprets the boring and professional result data presented in a single chart, synchronously further excavates the time elements, relationship elements, and geographical location information elements contained in it, and performs synchronous multi-dimensional presentation, enabling non-professional Management decision makers have intuitive and perceptual cognitive ability for safety.
Owner:NSOC INFORMATION TECH CO LTD
Big data security analysis platform system based on network security
InactiveCN108833397AImprove securityImprove perceptionPlatform integrity maintainanceData switching networksData centerData acquisition
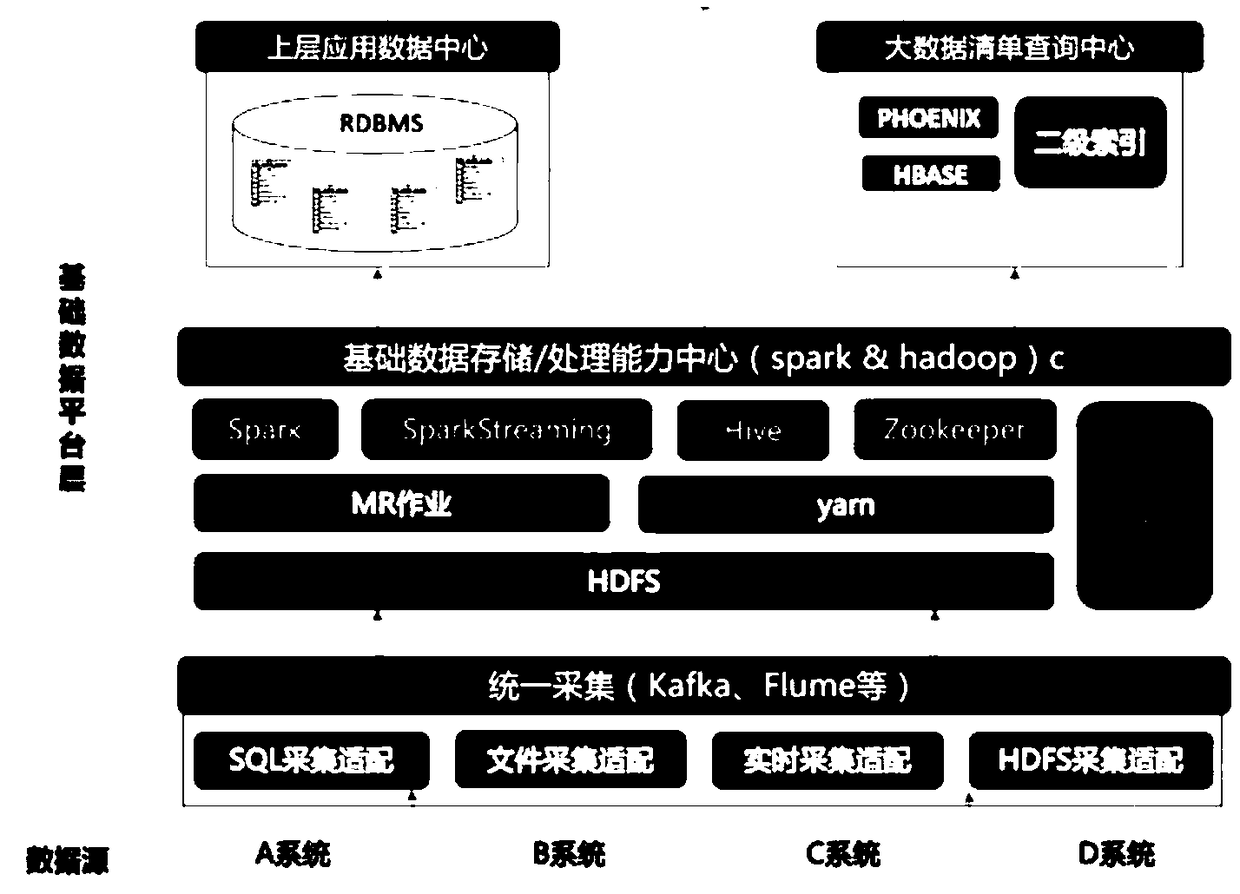
The invention relates to a big data security analysis platform system based on network security. The big data security analysis platform system comprises a unified collection platform, a basic data storage and processing capability center, an upper layer application data center and a big data list query center, the unified collection platform adopts Kafka as a message management layer of the unified collection platform to achieve flexible docking and adaption to various data source collection and to provide flexible and configurable data collection capability, the basic data storage and processing capability center utilizes the spark and hadoop technologies to provide powerful data processing capability, the upper layer application data center provides highly aggregated statistical data ofan enterprise through the RDBMS / ES, and the big data list query center provides fast query capability of big data by constructing an HBase cluster.
Owner:武汉思普崚技术有限公司
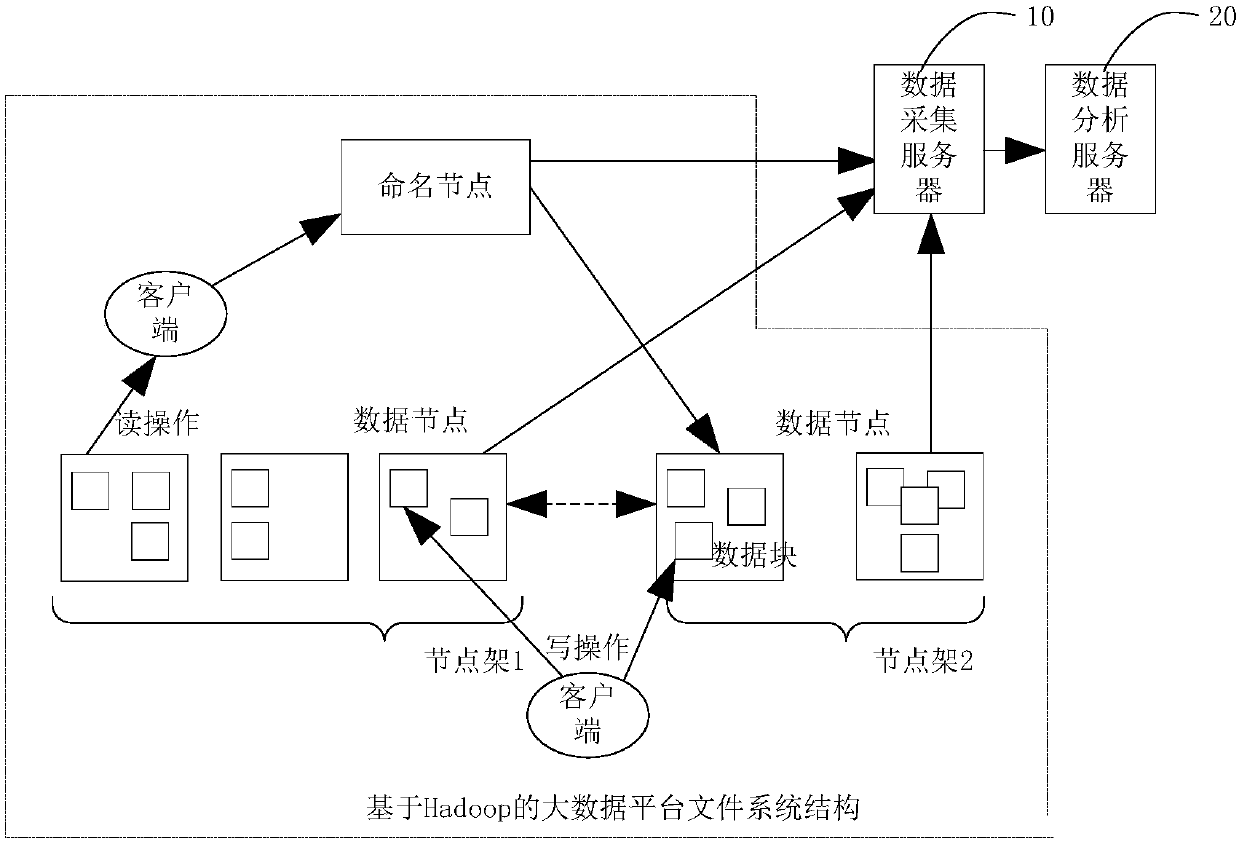
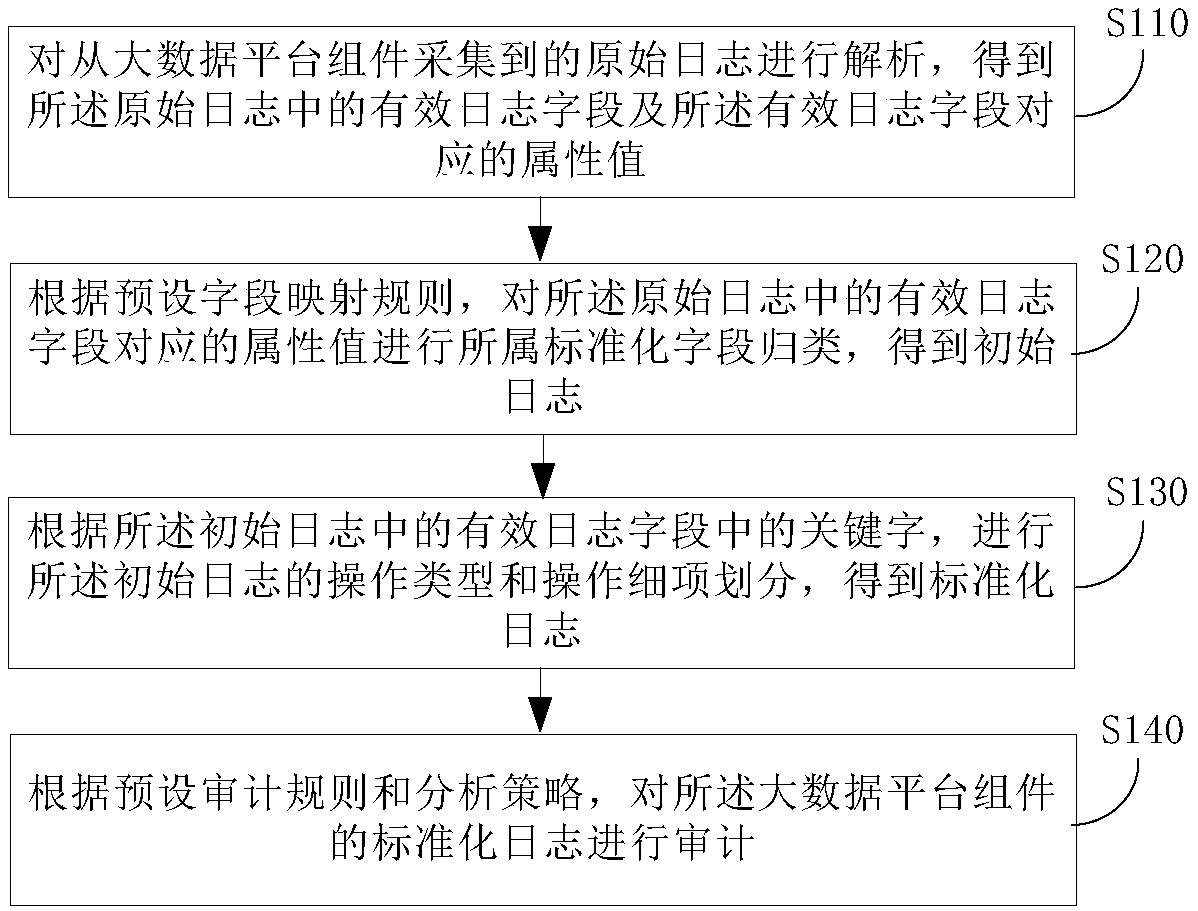
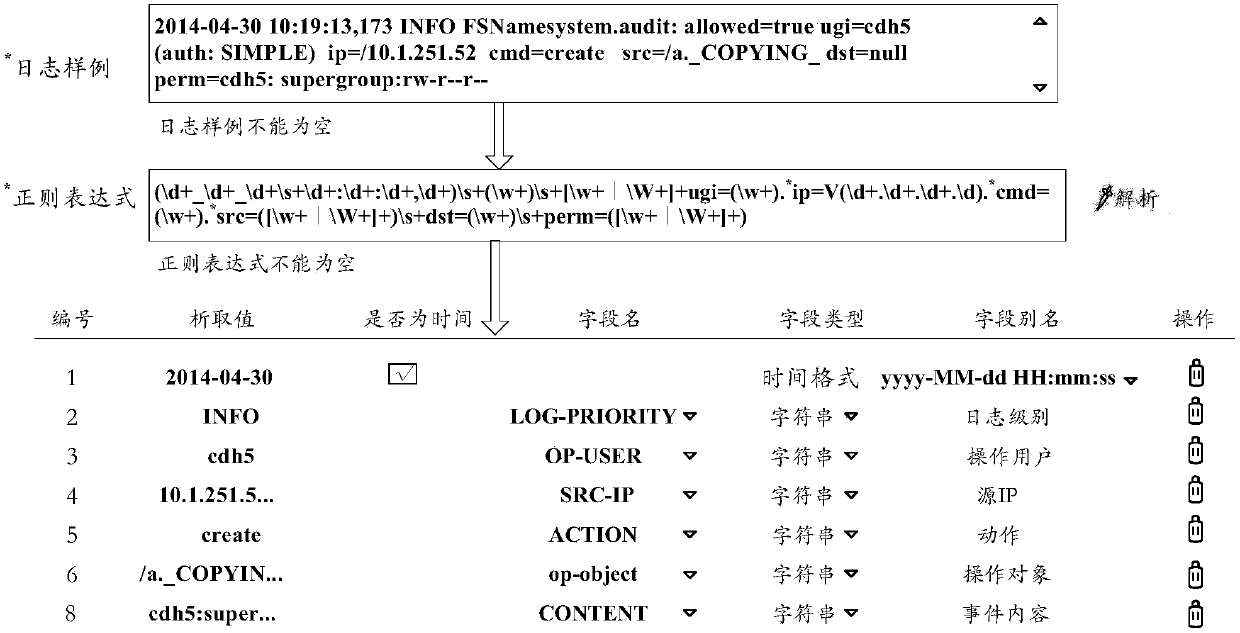
Log auditing method and device
ActiveCN107818150AFully operational and timelyComprehensive and timely auditPlatform integrity maintainanceFile/folder operationsBig data securityData access
The invention discloses a log auditing method and device. Particularly, the method comprises the steps that original logs which are collected from all big data platform components are parsed and subjected to field standardized mapping, operation types and operation fine points of the logs are divided and processed, and initial logs of all the components in big data platforms with different sourcesand formats can be standardized; then, according to an auditing requirement of big data security management and control, a corresponding auditing rule and a corresponding analysis strategy are adopted, the standardized logs of all the components in the big data platforms are automatically audited and analyzed, and whether or not management and data access operations of the big data platforms andthe components meet safety technology norm and management requirements is determined. Compared with a manual auditing mode, the log auditing method has the advantages that the logs of the big data platform components are standardized and centrally audited, the operation of the big data platform components can be comprehensively and timely audited, hidden safety dangers are quickly found, and safety problems are found.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD +1
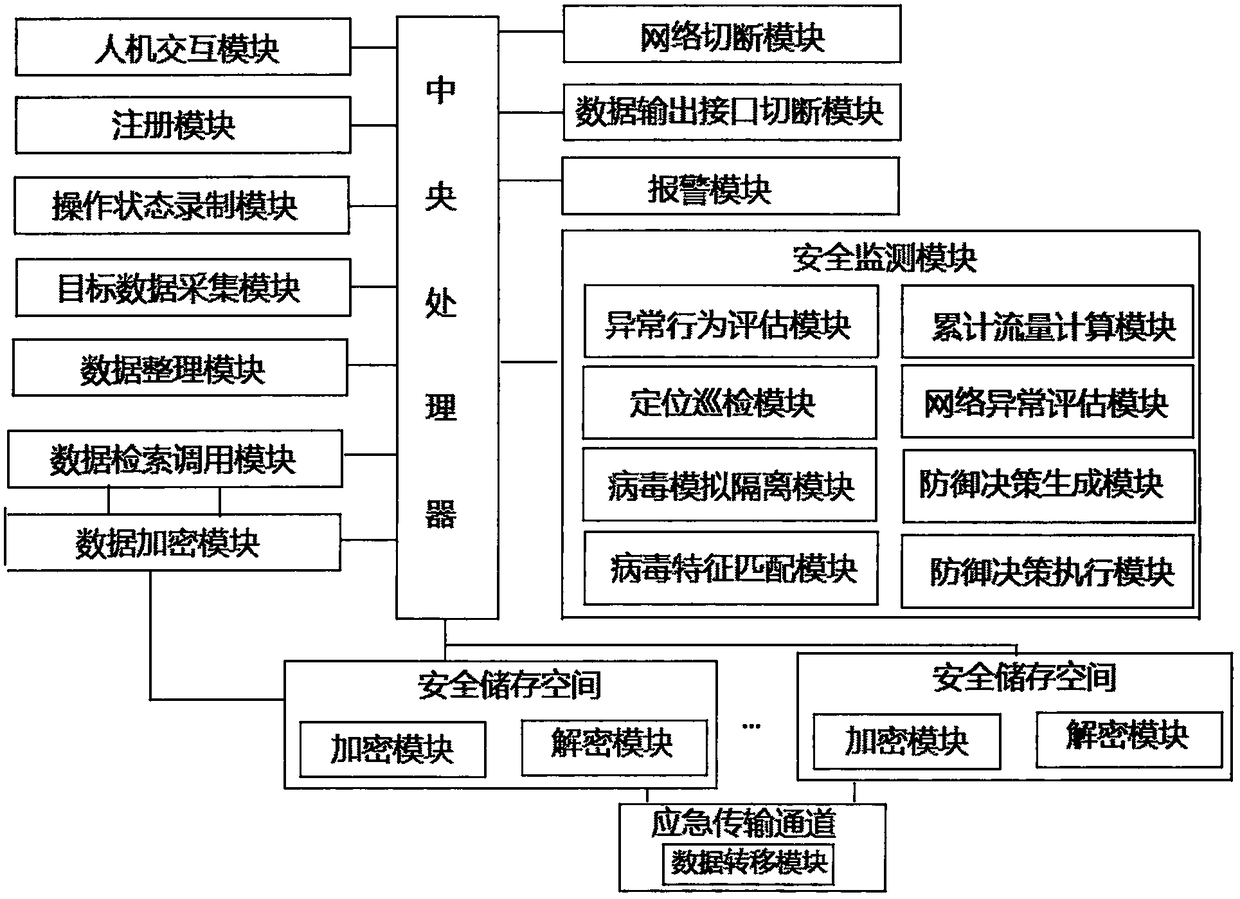
Big data security protection supervision and perception platform
InactiveCN108256321AImprove securityEnsure safetyDigital data protectionInternal/peripheral component protectionData retrievalBig data security
The invention discloses a big data security protection supervision and perception platform. The platform comprises a registration module, a man-machine operation module, a target data acquisition module, a safe storage space, an operation state recording module, a safety monitoring module, an alarm module, a data transfer module, a network cutoff module, a data output interface cutoff module, a data retrieval calling module and a central processing unit; the safe storage space and an encryption module are connected through two independent channels, the data retrieval calling module and the data encryption module are connected through two independent channels, and when one channel is used for communication, the other spare channel performs key update. The platform achieves encryption storage, encryption transmission and sharing within the authority of data; the system has the security monitoring function, so that the security of data is greatly improved.
Owner:JILIN UNIV OF FINANCE & ECONOMICS
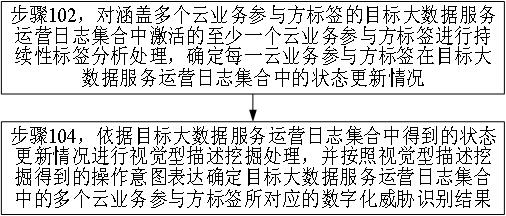
Threat identification method based on big data security, and data security server
ActiveCN113706177AReduce the impactReduce distractionsSemantic analysisHardware monitoringBig data securityData science
The invention relates to the technical field of big data and information threat protection, in particular to a threat identification method based on big data security and a data security server. According to the invention, an operation intention expression having a positive effect on the detection precision and credibility of a digital threat identification result is determined from a target big data service operation log set, thereby realizing threat identification of the target big data service operation log, ensuring the accuracy and reliability of the digital threat identification result as much as possible, and reducing the influence and interference of noise except for the operation intention expression on the digital threat identification result.
Owner:GUANGDONG AOFEI DATA TECHNOLOGY CO LTD
A big data detection and audit system
PendingCN109446817AImplement automatic vulnerability scanningRealize discoveryDigital data protectionPlatform integrity maintainanceOperational systemData platform
Owner:CHENGDU SIWEI CENTURY TECH
Medical data joint learning system and method based on trusted computing and privacy protection
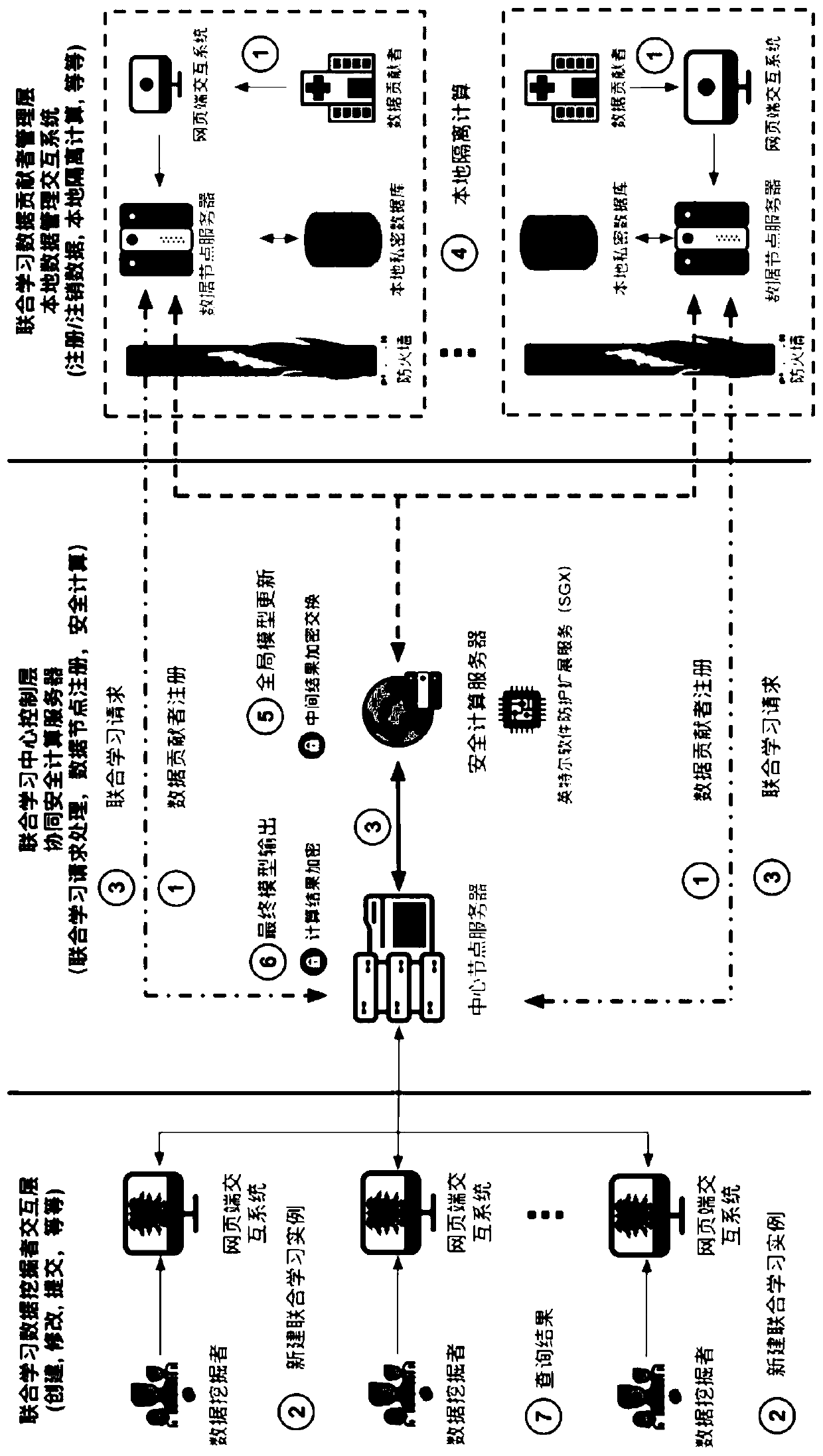
ActiveCN110197084AStrict and flexible authorization authenticationRealize deep miningMedical data miningDigital data protectionInteraction layerData privacy protection
The invention relates to a medical data joint learning system and method based on trusted computing and privacy protection. A joint learning center control layer receives non-sensitive meta-information uploaded by a data contributor through a data contributor management layer of a data node where the joint learning center control layer is located for filing, and original data is locally registered, stored and subjected to isolation calculation; and the joint learning center control layer processes a joint learning request initiated by the data miner through the data miner interaction layer, summarizes insensitive intermediate results obtained by performing local isolation calculation on the data nodes based on the original data in a safe calculation area, and returns a final joint learningresult to the data miner interaction layer. The invention provides a whole set of service system based on medical big data security sharing, trusted computing, deep mining, authority authentication and multi-platform joint learning, and solves the problems of scattered, single and incomplete medical data privacy protection and data mining at the present stage.
Owner:上海锘崴信息科技有限公司
Method and system for accessing big data system
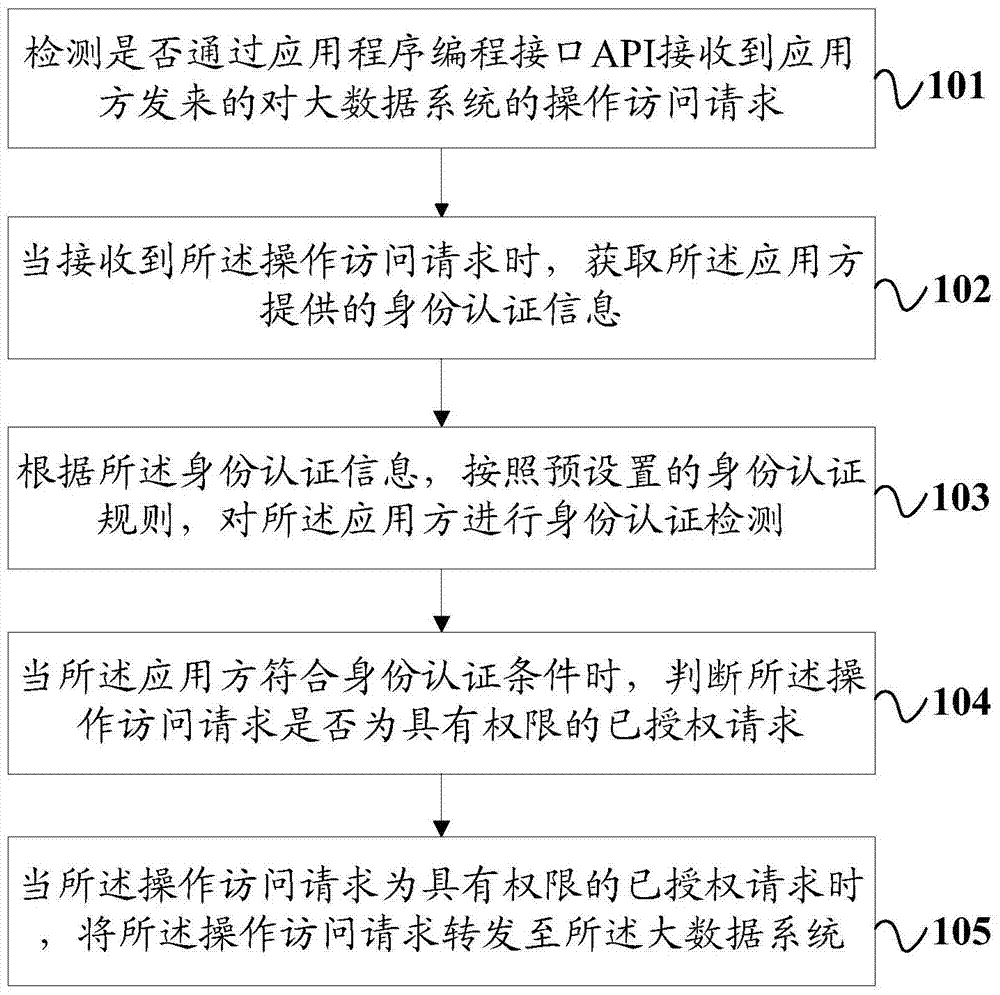
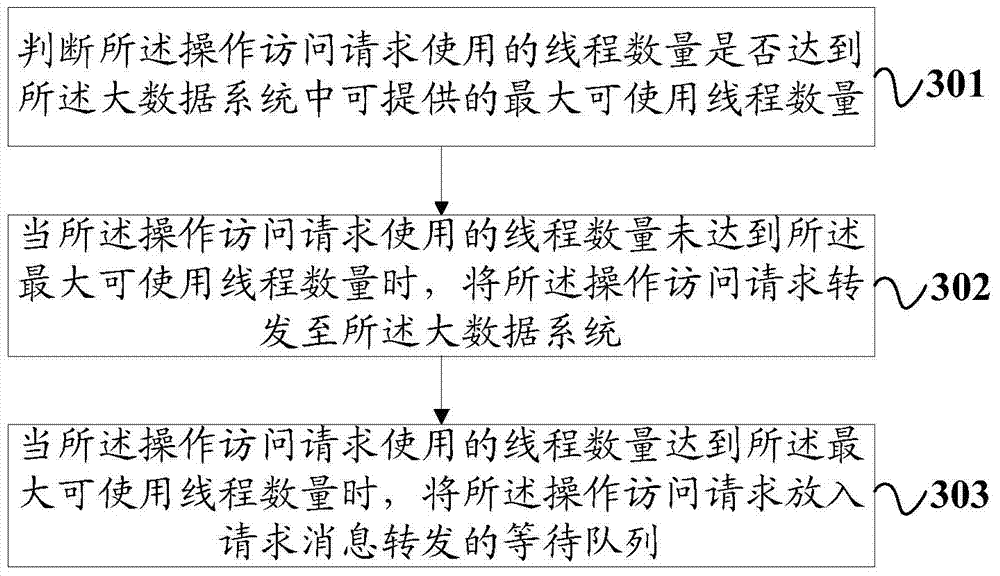
InactiveCN107026825AImprove securityEnsure safetyTransmissionApplication programming interfaceData platform
The invention provides a method and a system for accessing a big data system, and relates to the field of big data security. The method comprises the following steps: detecting whether an operation access request specific to the big data system sent by an application party is received or not through an application programming interface (API); when the operation access request is received, acquiring identity authentication information provided by the application party; performing identity authentication detection on the application party according to the identity authentication information and a preset identity authentication rule; when the application party conforms to the identity authentication condition, judging whether the operation access request is an authorized request having permission or not; and when the operation access request is the authorized request having the permission, forwarding the operation access request to the big data system according to the operation access request. Through the scheme, the security of data stored in a big data platform can be enhanced greatly.
Owner:中国移动通信集团陕西有限公司
Big data security protection cloud system based on trusted calculation
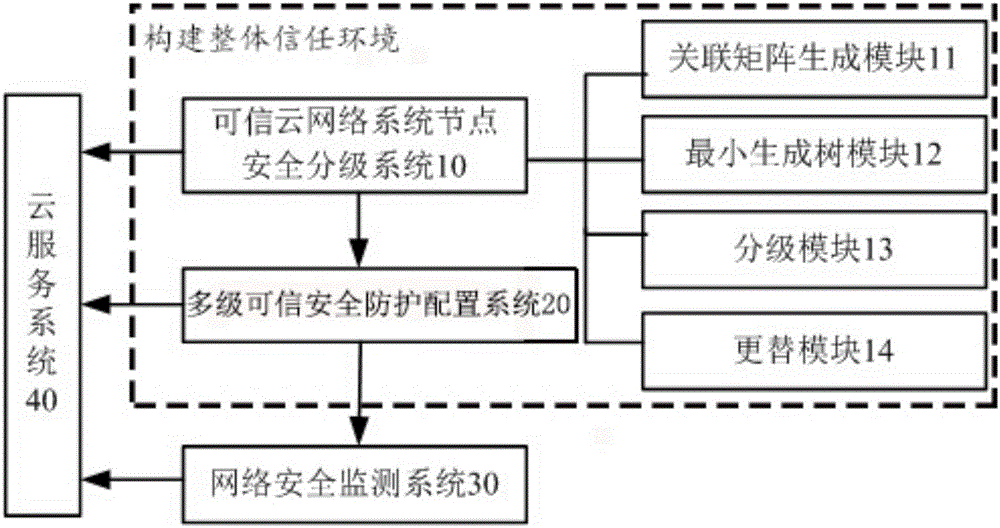
InactiveCN105933361ATimely collectionOptimize the total calculation amountTransmissionTrusted ComputingBig data security
The invention discloses a big data security protection cloud system based on trusted calculation. The big data security protection cloud system constructs a security configuration system based on a trusted security grading system and minimal trees on the basis of systems having security grading functions and trusted security configuration functions, and provides a trusted calculating environment for the security protection of information through the cooperation with a security network monitoring system. The trusted protection cloud system starts from the acquisition and security grading of basic data, divides the network nodes into four different security grades by calculating the importance values of the network nodes, and constructs an integral trusted environment, and by means of the security grading configuration with high credibility, the trusted security of information security and protection is guaranteed, the data cannot be acquired randomly, and a good balance between the calculated quantity and trusted security configuration is achieved.
Owner:GUANGXI POWER GRID CORP
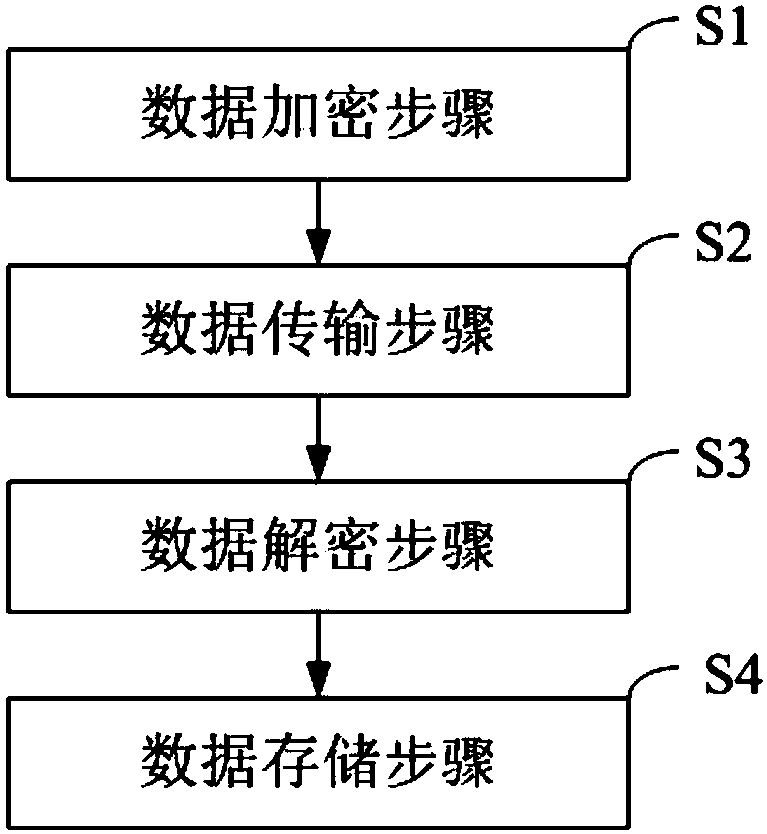
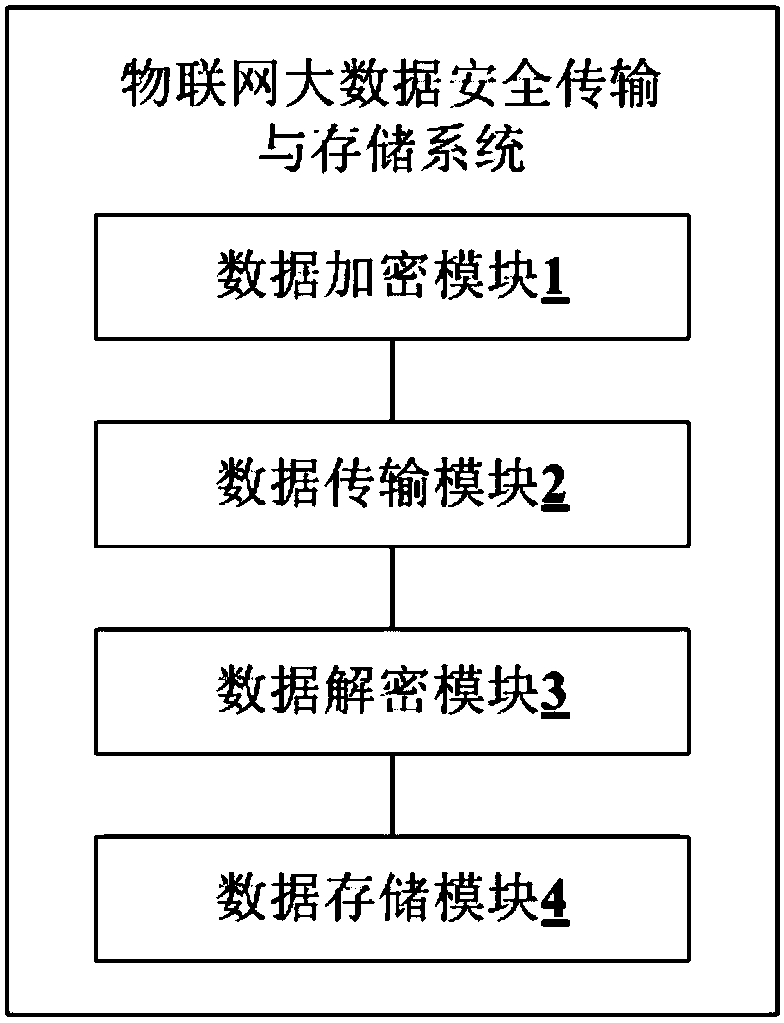
Internet-of-Things big data security transmission and storage method and system
InactiveCN107612898AEfficient storageGuaranteed timelinessKey distribution for secure communicationOriginal dataSecure transmission
The invention belongs to the technical field of the Internet of Things, and provides an Internet-of-Things big data security transmission and storage method and system. The method comprises the stepsthat target data is encrypted by adopting a key of a symmetric algorithm to generate encrypted data, and the key of the symmetric algorithm is encrypted by adopting a public key pair of an asymmetricalgorithm to generate an encrypted key; the encrypted data and the encrypted key are transmitted; the encrypted key is decrypted by adopting a private key pair of the asymmetric algorithm to obtain the key of the symmetric algorithm, and the encrypted data is decrypted according to the key obtained through decryption of the symmetric algorithm to obtain the original data; and the trigger mode of astorage is detected, and the original data obtained after decryption is stored in the storage. According to the Internet-of-Things big data security transmission and storage method and system, data security transmission and storage can be guaranteed, data tampering is prevented, and effective data storage is guaranteed.
Owner:SICHUAN MIANYANG TAIKOO SOFTWARE
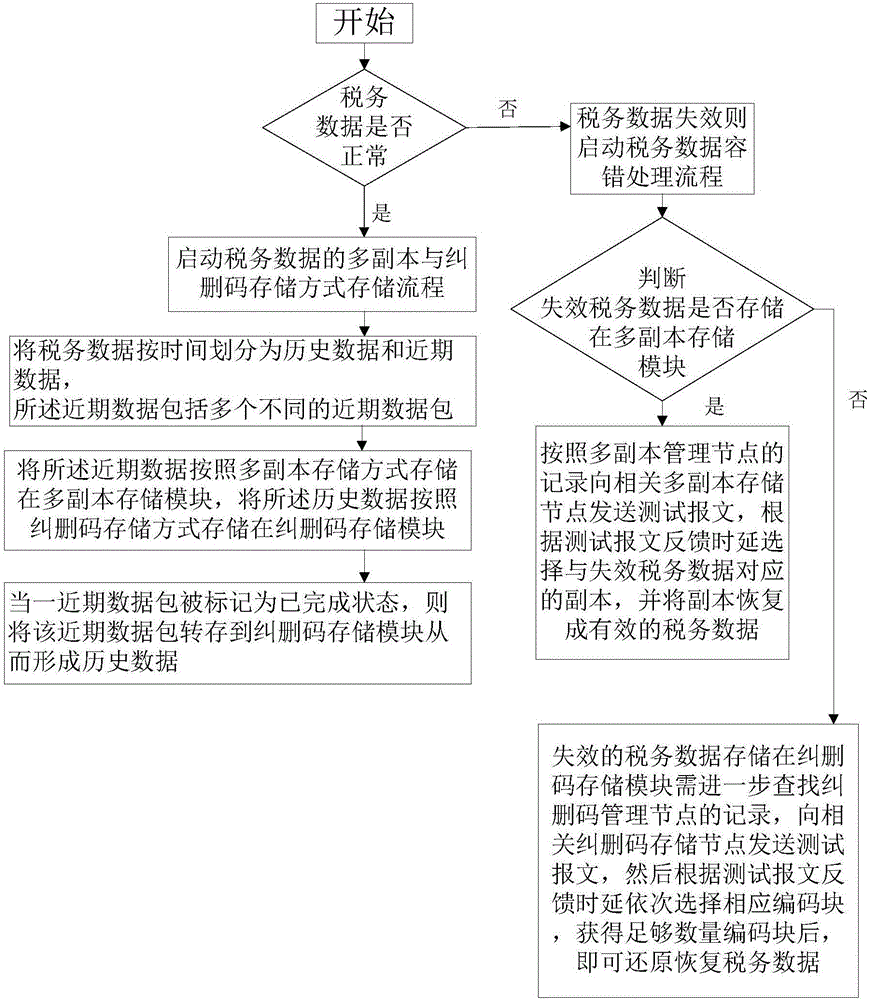
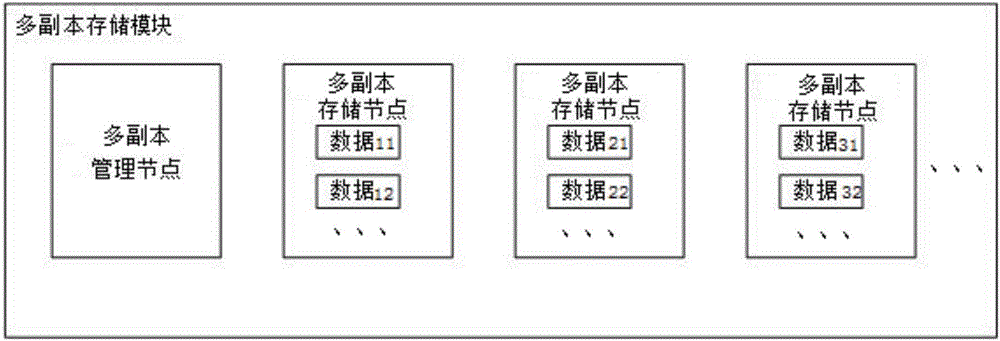
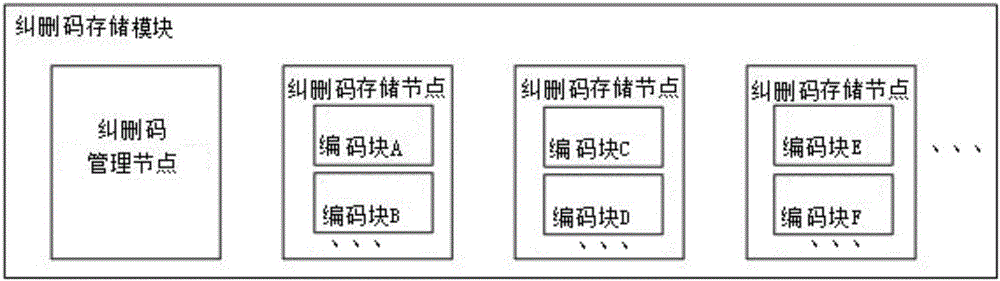
Mixed tax administration data security protecting method based on erasure code and multi-copy
ActiveCN106708653AImprove securityImprove data repair performanceDigital data protectionRedundant data error correctionFault toleranceTax administration
The invention discloses a mixed tax administration data security protecting method based on erasure code and multi-copy. The method comprises the following steps: while the tax administration data of a tax administration data distributed storage system is normal, starting the multi-copy and erasure code storage mode storage flow of the tax administration data; and while the tax administration data of the tax administration data distributed storage system is failure, starting the tax administration data fault-tolerance processing flow. The method is capable of executing the sub-mode storage by using the tax administration data features of different times, distributing the erasure coding task to different nodes, using the mode of copy first and erasure code second, comprehensively improving the security of the whole tax administration data and the data recovery performance, improving the coding performance of the whole system, and guaranteeing the data security before finishing the erasure coding.
Owner:INST OF SOFTWARE APPL TECH GUANGZHOU & CHINESE ACAD OF SCI
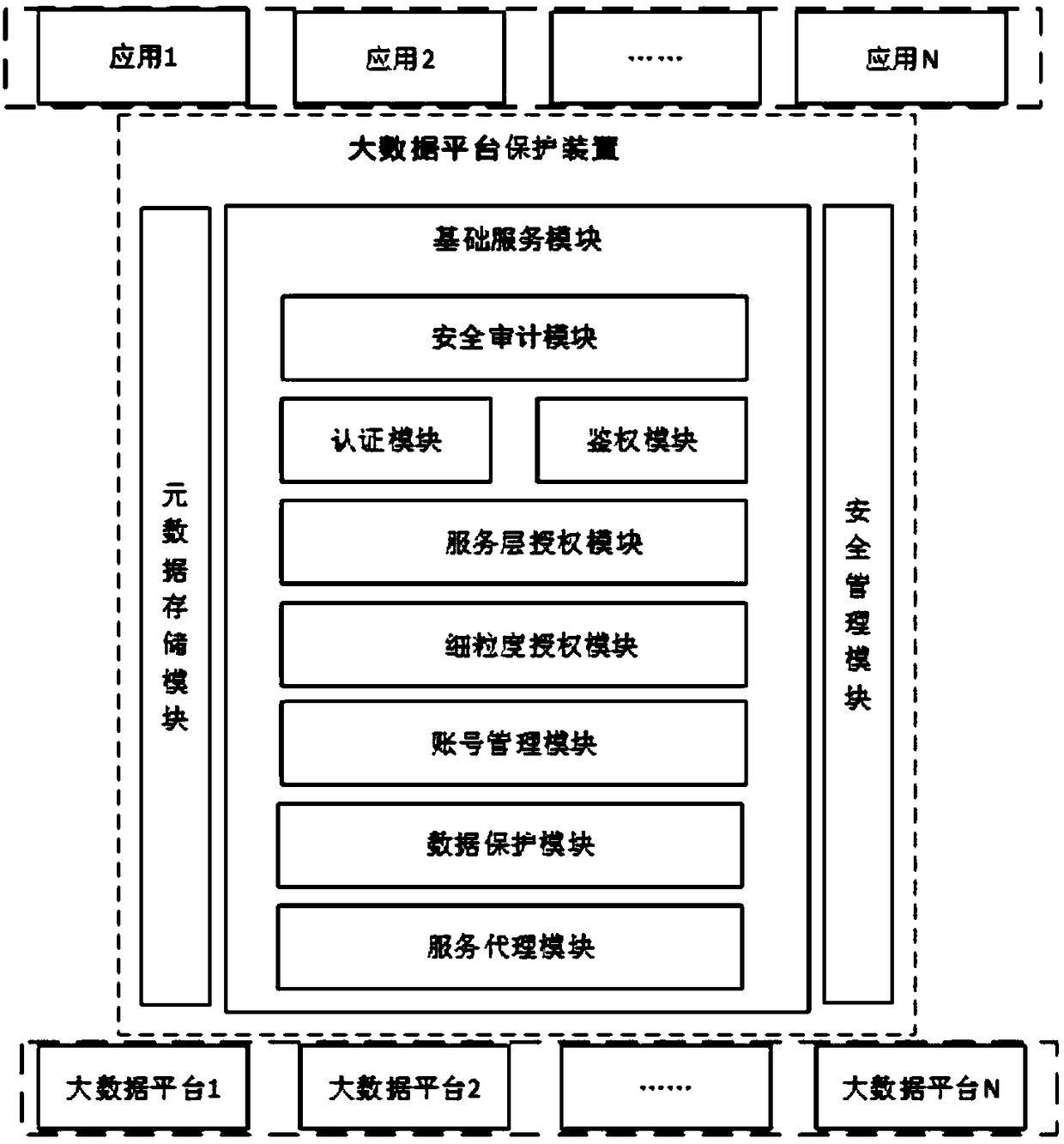
Big data platform protection device deployed at gateway and protection method thereof
InactiveCN109150908ARealize security protectionImprove scalabilityData switching networksData platformBig data security
The invention discloses a big data platform protection device arranged at a gateway and a protection method thereof, wherein the device and the method relate to the technical field of big data security. The device comprises an authentication module which performs identity authentication on an access request at the gateway; an authorization module which performs a corresponding authorization operation on an illegal user in the protection device; a service proxy module which forwards the user's access request at the gateway; a data protection module which desensitizes the data returned to the user at the gateway; and a security auditing module which records all user access requests to the protected big data platform. The big data platform protection device and the protection method can protect the big data platform externally on the basis of not changing the original code of the big data platform component, has wide application scene, realizes the proxy access to the particular componentin a mode of arranging an inner plug-in, adopts different plug-ins according to different big data platforms, and has strong expansibility.
Owner:SICHUAN UNIV
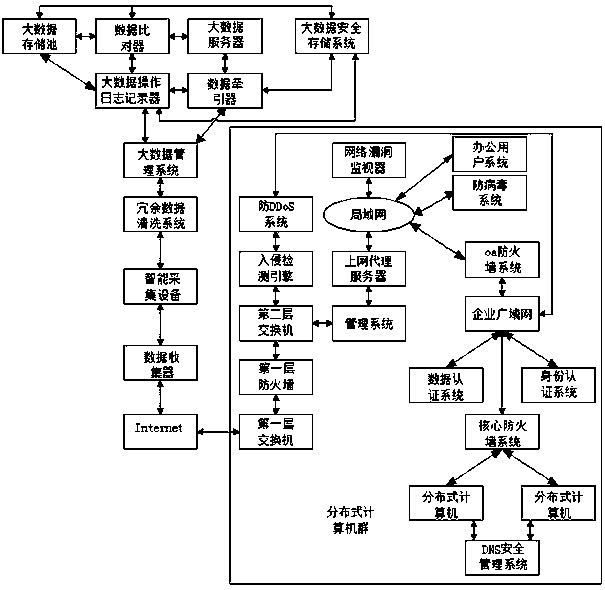
Network security enforcement system and method based on big data platform
The invention discloses a network security enforcement system and method based on a big data platform. The network security enforcement system is provided with a big data processing platform and a distributed computer group in connection with the big data processing platform. The big data processing platform is internally provided with a data collector, an intelligent collection device, a redundant data cleaning system, a big data management system, a data tractor, a big data server, a data contrast device, a big data storage pool, a big data operation log recorder and a big data safe storage system, wherein the big data server transmits a sub class of big data to the big data storage pool for storage through the data contrast device with a hardware security protection function; in a process of uploading the sub class of big data to the big data storage pool through the data contrast device, the data contrast device calls data stored in the big data safe storage system to perform comparison with the uploaded sub class of big data. The system and method can reduce cost investment, meanwhile further improve data safe transmission levels, and guarantee data integrity of uplinking or issuing.
Owner:SICHUAN UNIV
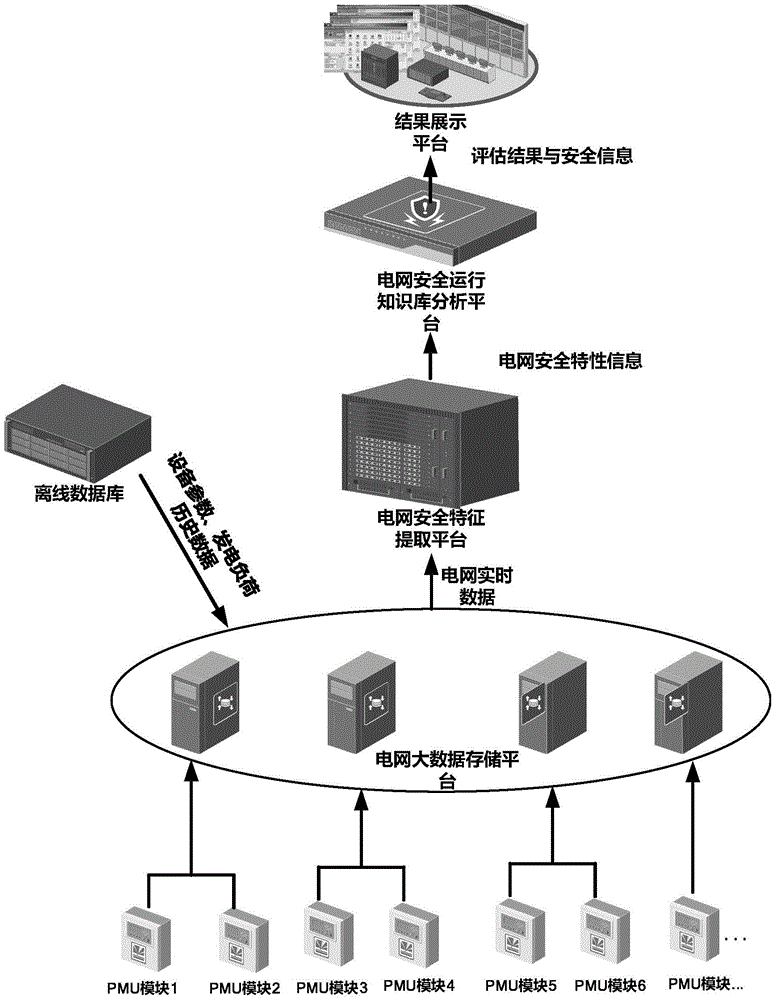
Power grid multidimensional sensing and safety assessment system and method on the basis of big data
InactiveCN105528671AReasonable assessmentComprehensive assessmentDatabase distribution/replicationResourcesBig data securitySafety status
Owner:WUHAN UNIV
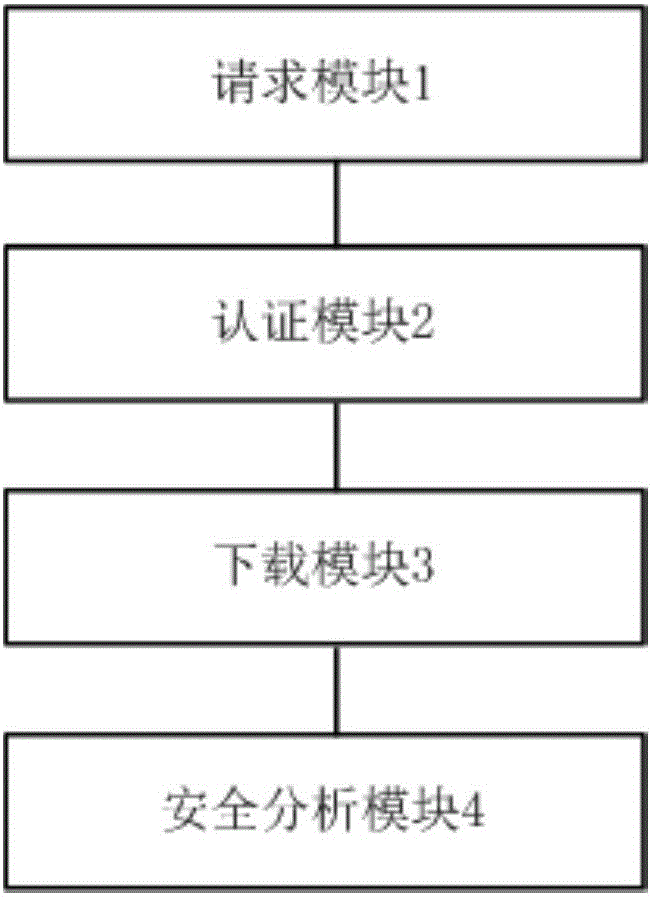
Network security analysis system in big data environment
The invention provides a network security analysis system in a big data environment, which comprises a request module, an authentication module, a downloading module and a security analysis module. The network security analysis system in the big data environment has the beneficial effect that the big data security in the network condition is greatly improved.
Owner:广州万智农业科技有限公司
Big data security threat processing method and system based on smart service
The invention relates to the technical field of smart services and big data security and protection, in particular to a big data security threat processing method and system based on smart services, which can determine information threat security evaluation by means of smart service activity data collected by a big data processing thread. Unnecessary resource overhead caused by adoption of an extra information threat detection mode is avoided, and the determination efficiency of information threat security evaluation is improved; the business activity popularity description reflects the global activity popularity of all potential threat type business items in the suspected intrusion threat scene, and compared with a global statistical result of the current activity popularity of all potential threat type business items in the suspected intrusion threat scene, the global activity popularity of all potential threat type business items in the suspected intrusion threat scene is obtained; the business activity popularity description can more accurately feed back an information threat condition in a suspected intrusion threat scene; on the premise of business activity popularity description, the accuracy and credibility of information threat security evaluation can be remarkably improved in combination with the business project emergency degree.
Owner:中软数智信息技术(武汉)有限公司
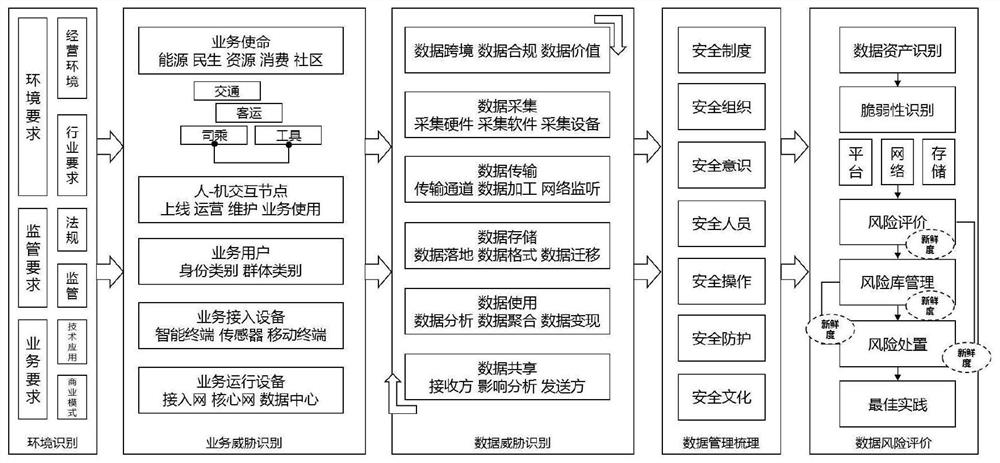
5G data safety risk evaluation method and evaluation system
The invention discloses a 5G data safety risk evaluation method and evaluation system in the technical field of 5G data safety risk evaluation, and the method comprises the specific steps: building a 5G data safety implementation framework which runs through the organization to face 5G safety supervision; establishing a 5G data safety risk evaluation closed-loop process from environment recognition, service threat recognition, data threat recognition, data management and carding and data risk evaluation; after a complete risk evaluation process, performing quantitative risk evaluation by combining an evaluation process and selecting an evaluation model, and meanwhile, realizing dynamic updating of the 5G safety vulnerability library by utilizing freshness; according to a 5G complex service mode and data safety and service safety threats, a completed data safety architecture is designed, seven major 5G data safety evaluation requirements are innovatively sorted out, a 5G data safety evaluation enhancement process (covering the whole process) is innovatively designed, and'freshness' closed-loop management is innovatively proposed.
Owner:CHENGDU SIWEI CENTURY TECH
Agricultural big data analysis apparatus
InactiveCN108549466AEasy to operateImprove cooling efficiencyDigital processing power distributionComputer moduleBig data security
The invention discloses an agricultural big data analysis apparatus. The apparatus comprises an analysis apparatus body and an agricultural big data analysis module; a fixed handle is arranged on oneside wall of the analysis apparatus body; and the agricultural big data analysis apparatus comprises an agricultural big data collection module, an agricultural big data input module, an agriculturalbig data processing module, an agricultural big data output module and an agricultural big data security encryption protection module. The agricultural big data analysis apparatus is simple in structure and easy in operation, can be cooled, and is high in cooling efficiency, convenient to carry and good in sealing performance; an involved system can perform collection, input, analysis processing and output on the agricultural big data more conveniently, so that scheduling and management of the agricultural big data-based system are facilitated; and the agricultural big data can be subjected tosecurity protection conveniently, so that data leakage is prevented and the security is high.
Owner:TAIZHOU BIAOMENG INTPROP AGENCY
Encryption method based on big data cloud platform system
InactiveCN112087463APrecisely specify the data rangeImprove securityUser identity/authority verificationDigital data protectionDocument IdentifierBig data security
The invention provides an encryption and decryption method based on a big data security cloud platform system, and the method comprises the steps: accessing a secret key manager with a triple of a data owner identifier, an application identifier and a region code during encryption; receiving a triple key and a key group identifier for uniquely identifying the triple key; for documents with document identifiers, deriving an independent key of each document from a combination of the triple key and the document identifier; broadcasting the encrypted documents, the document identifiers and the keytriad identifier; encrypting the documents by using the independent key for each document. During decryption, an extraction engine extracts the document identifiers and the key triad identifier froman encryption header; the document identifiers and the key group identifier are provided to a KGF to generate an independent key for each document; the documents are decrypted using the independent key of each document to produce original documents. According to the encryption and decryption method for the security cloud platform system based on the big data, a data owner is allowed to establish avariable-granularity access strategy, identify risk behaviors and possible data leakage and accurately specify a data range needing to be protected, so that the security and efficiency of interactionwith cloud services are improved.
Owner:广州知弘科技有限公司
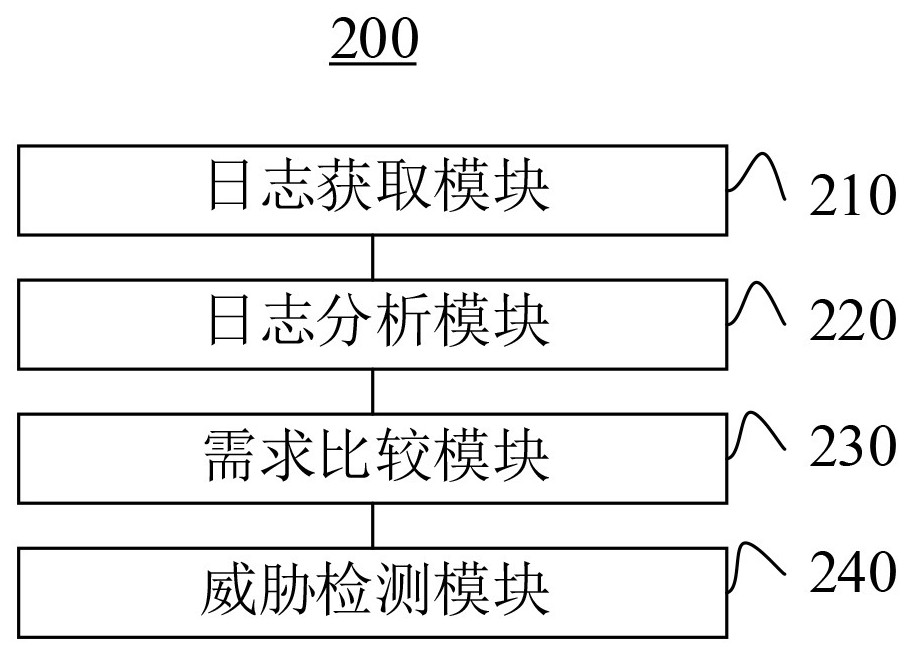
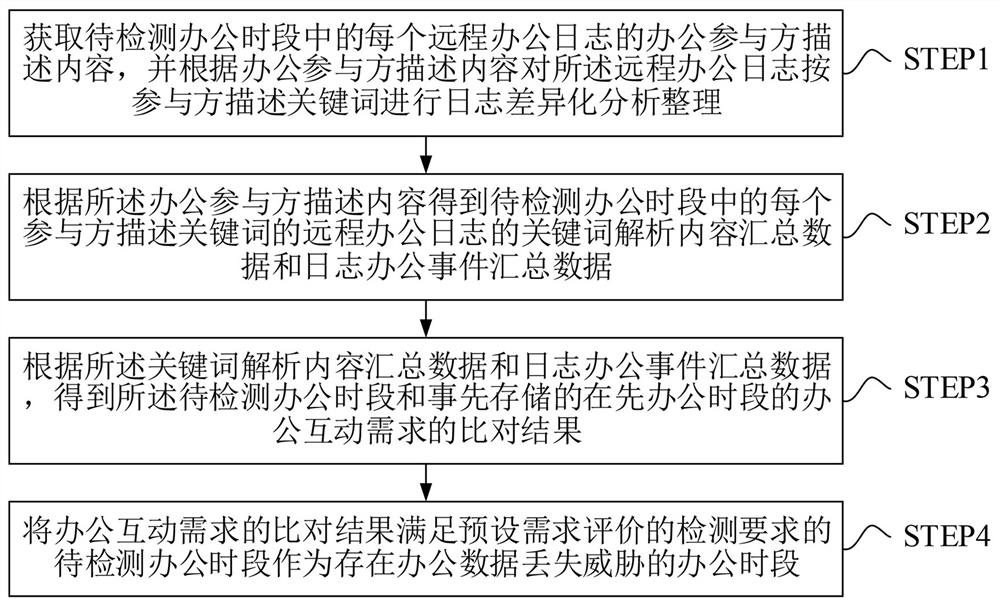
Big data security processing method and server for remote online office
ActiveCN113536323APlatform integrity maintainanceText database queryingKeyword analysisBig data security
The embodiment of the invention discloses a big data security processing method and server for remote online office, and the method comprises the steps: carrying out the log differentiation analysis and arrangement of remote office logs according to the description content of office participants and the description keywords of the participants, so the efficiency of subsequent log demand analysis can be improved; determining the keyword analysis content summarized data and log office event summarized data of the remote office logs of the description keywords of each participant, so a comparison result of office interaction demands of the to-be-detected office time period and a pre-stored previous office time period is obtained. Therefore, the comparison result of the office interaction demand can be analyzed based on the detection requirement of the preset demand evaluation, so that whether the office data loss threat exists in the to-be-detected office period or not is judged. In this way, the corresponding digital office terminal can be reminded to carry out information security and protection response operation, and therefore the situation that office data are lost when the digital office terminal carries out remote office in the to-be-detected office time period is avoided.
Owner:山东正奇科技咨询服务有限公司
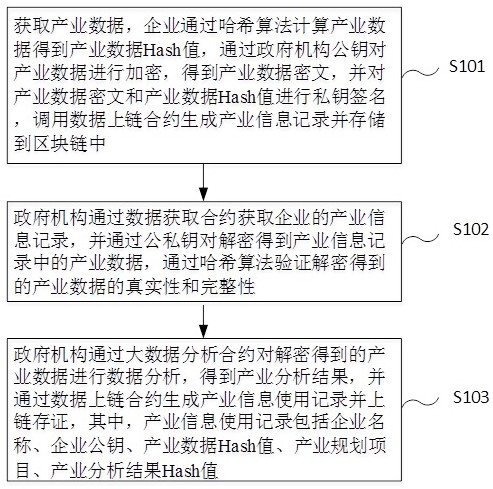
Industrial big data security sharing method and system, electronic device and storage medium
InactiveCN113505398ATo achieve the effect of traceability and accountabilitySolve difficult problemsDigital data protectionCiphertextBusiness enterprise
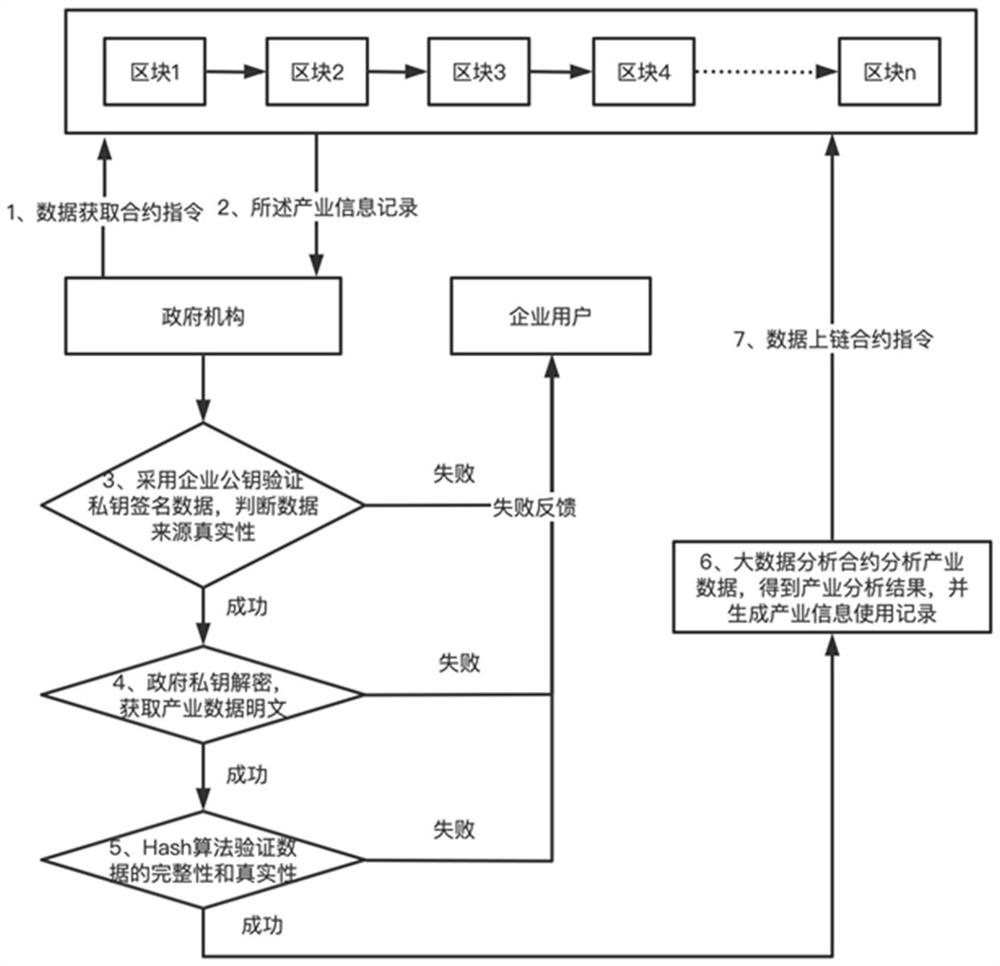
The invention relates to an industrial big data security sharing method and system, an electronic device and a storage medium, and the method comprises the steps: obtaining industrial data, enabling an enterprise to calculate an industrial data Hash value through a Hash algorithm, encrypting the industrial data through a public key of a government agency, obtaining an industrial data ciphertext, performing private key signature on the industrial data ciphertext and the industrial data Hash value, calling a data uplink contract to generate an industrial information record, and storing the industrial information record in a block chain; then, by the government agency, obtaining the industry information record through the data obtaining contract, decrypting the industry information record through the public and private keys to obtain industry data in the industry information record, and verifying the authenticity and integrity of the industry data obtained through decryption through a Hash algorithm; and finally, by the government agency, performing data analysis on the decrypted industrial data through a big data analysis contract to obtain an industrial analysis result, and generating an industrial information use record and an uplink evidence through a data uplink contract. Accurate layout and planning of various enterprises by the government are facilitated.
Owner:杭州费尔斯通科技有限公司
Load balance device under big data background
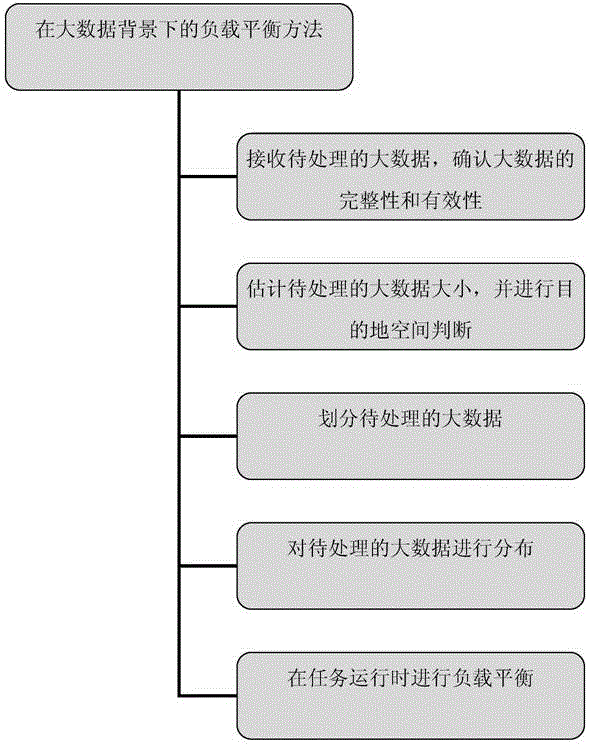
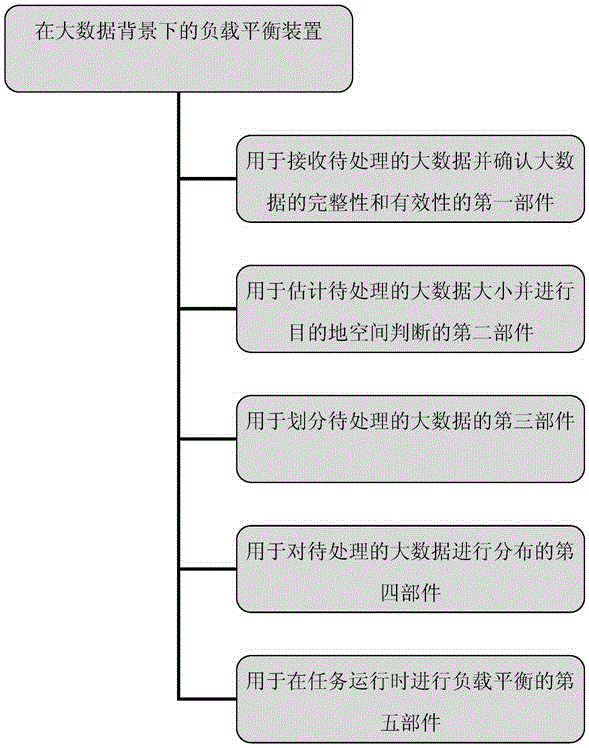
The invention discloses a load balance device under a big data background. The load balance device comprises a first component, a second component, a third component, a fourth component and a fifth component, wherein the first component is used for receiving big data to be processed and conforming integrity and validity of the big data, the second component is used for estimating the size of the big data to be processed and judging destination space, the third component is used for dividing the big data to be processed, the fourth component is used for distributing the big data to be processed, and the fifth component is used for balancing loads during task operation. The overall performance of a system is not affected by the device, resource consumption of load balancing is reduced, and the influence on the safety of the big data, the load balancing effect and the accuracy by various uncontrollable reasons or faults is effectively avoided.
Owner:SICHUAN CINGHOO TECH
Method and a device for detecting security deployment of big data
ActiveCN109583223AAvoid influenceEnsure safetyHardware monitoringDigital data protectionWeb serviceBig data security
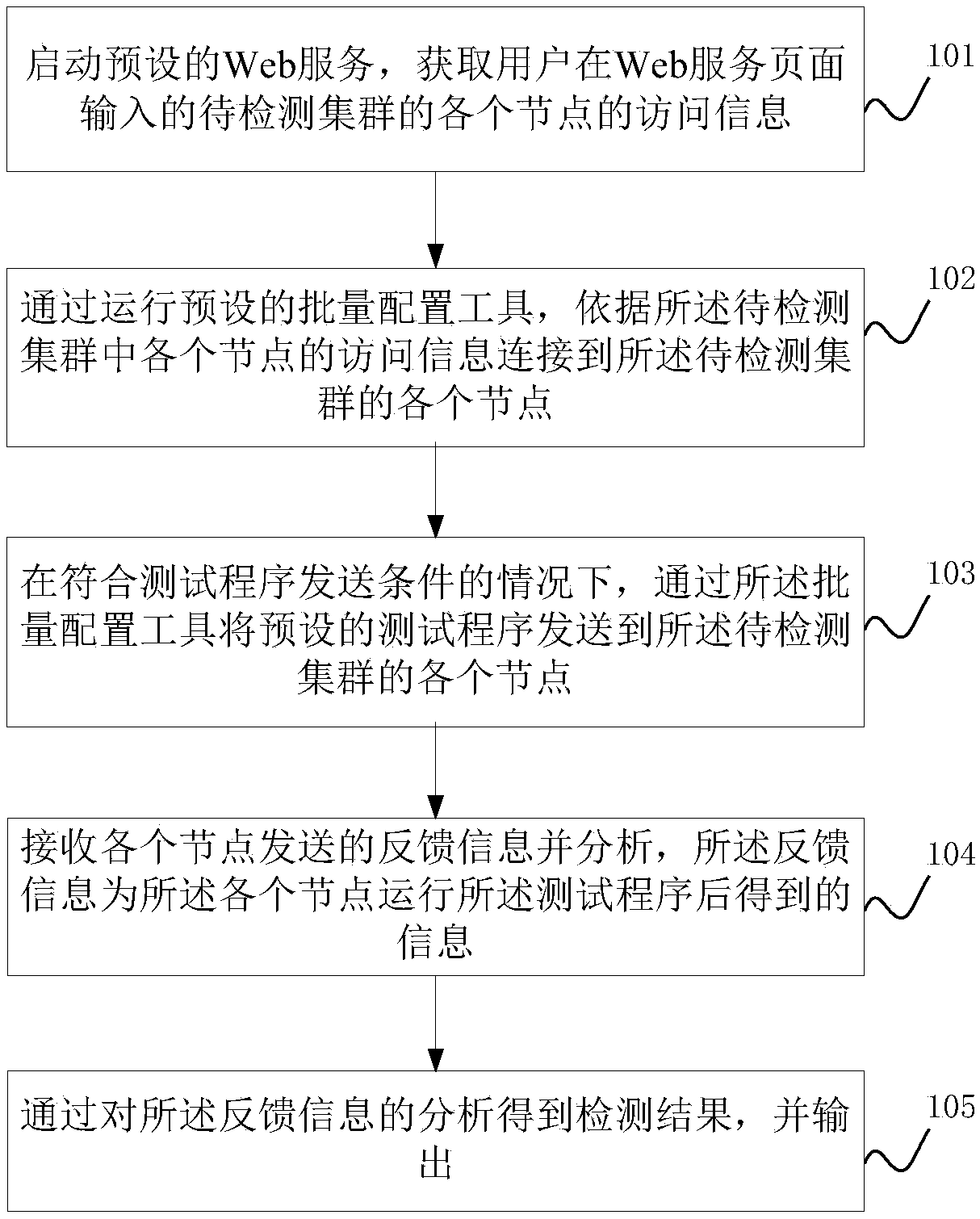
The invention discloses a method for detecting security deployment of big data, which comprises the following steps of: starting a preset Web service, and acquiring access information of each node ofa cluster to be detected, which is input by a user on a Web service page; Connecting each node in the detected cluster according to the access information of each node in the to-be-detected cluster byoperating a preset batch configuration tool; Under the condition that a test program sending condition is met, sending a preset test program to each node of a to-be-detected cluster through the batchconfiguration tool; Receiving and analyzing feedback information sent by each node, wherein the feedback information is information obtained after each node runs a test program; And analyzing the feedback information to obtain a detection result, and outputting the detection result. Automatic detection of big data security deployment is realized, the manual inspection cost is reduced, the workingefficiency is improved, and a user can know a detection result and an abnormal condition in real time.
Owner:BEIJING GRIDSUM TECH CO LTD
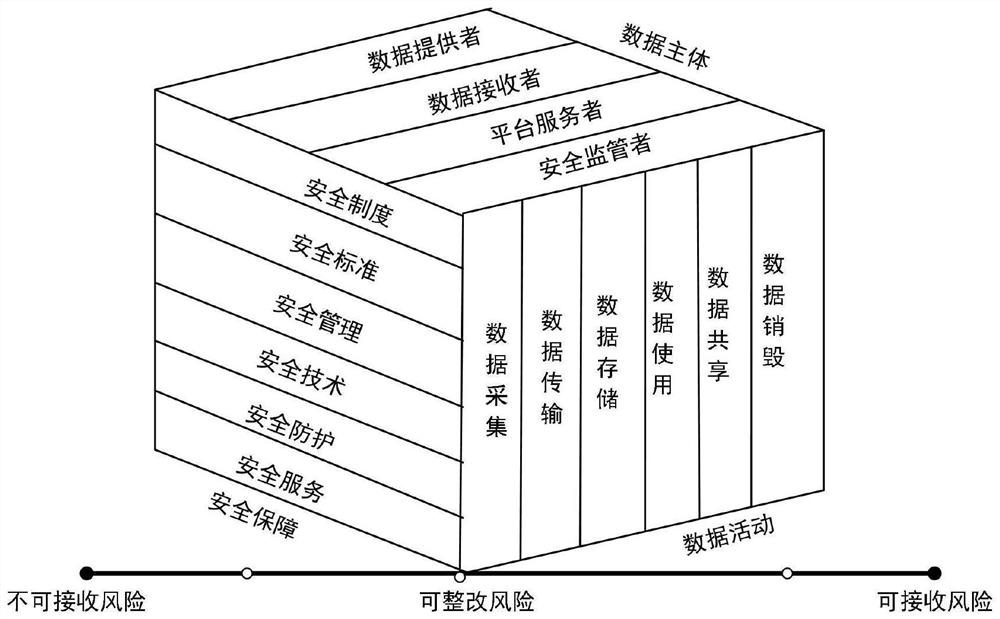
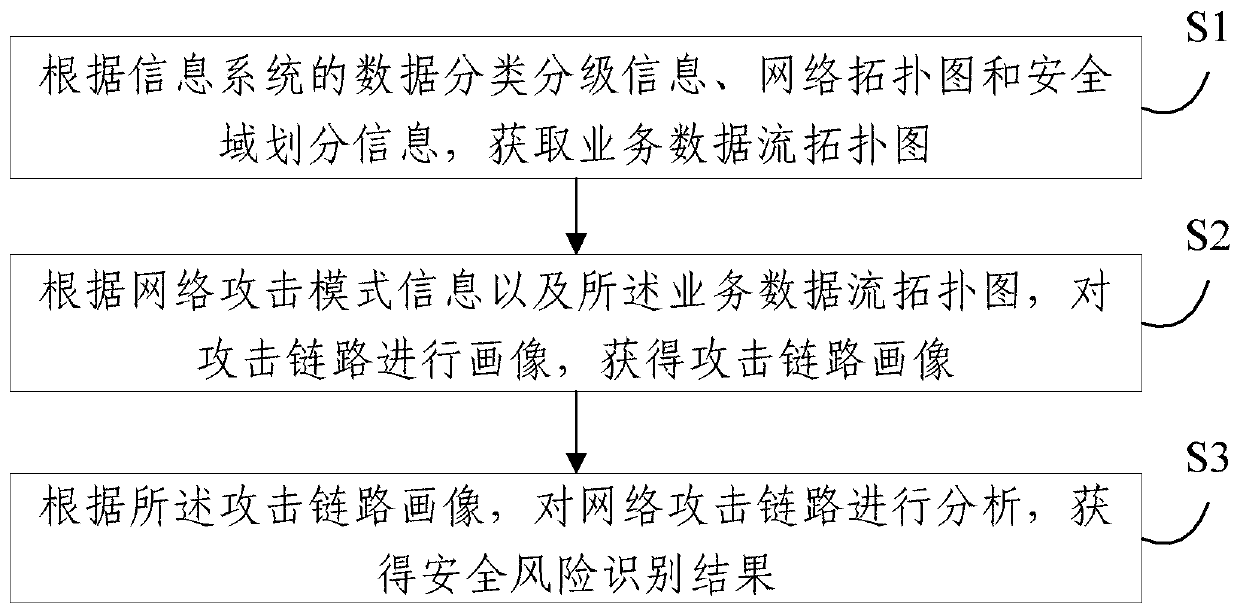
Business data security risk identification method and system
InactiveCN109977680AHigh strengthMeet the needs of security managementPlatform integrity maintainanceData platformBig data security
The embodiment of the invention provides a business data security risk identification method and system, and the method comprises the steps: obtaining a business data flow topological graph accordingto the data classification grading information, a network topological graph and security domain division information of an information system; carrying out portraying on an attack link according to network attack mode information and the business data flow topological graph to obtain an attack link portraying; and analyzing the network attack link according to the attack link portrait to obtain asecurity risk identification result. The method and the system have high targeting performance and directivity. Meanwhile, the strength of data security management in the information system is enhanced, the management strategy and granularity are refined, the requirement for data security management in the big data era is better met, a security guarantee is provided for security management of dynamic service data of the big data platform, and meanwhile a foundation is provided for subsequent security situation analysis of the big data security platform.
Owner:北京国舜科技股份有限公司
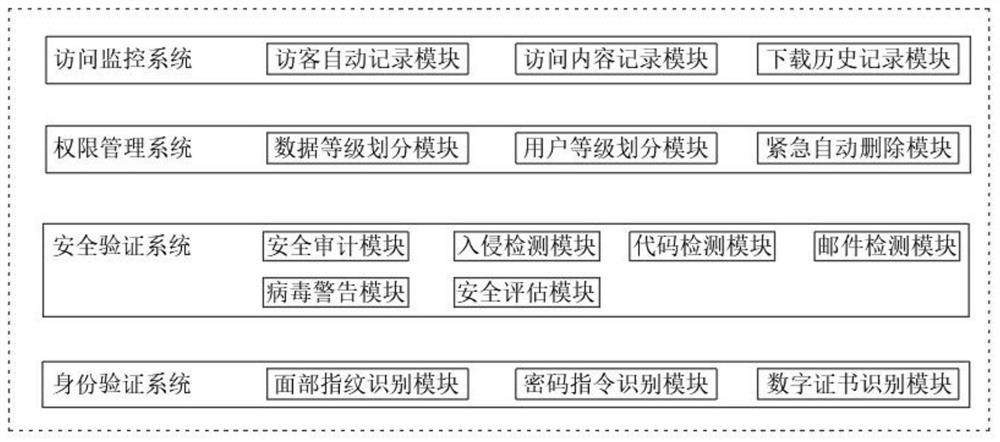
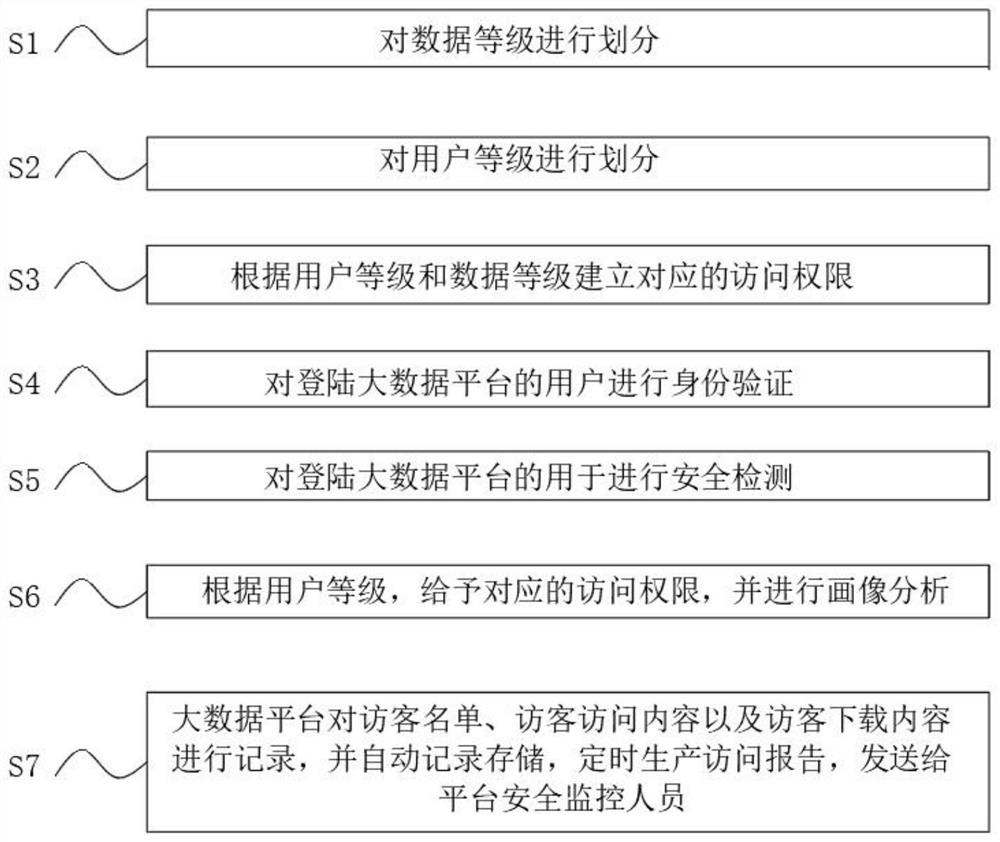
Big data security system access operation platform and data retrieval method
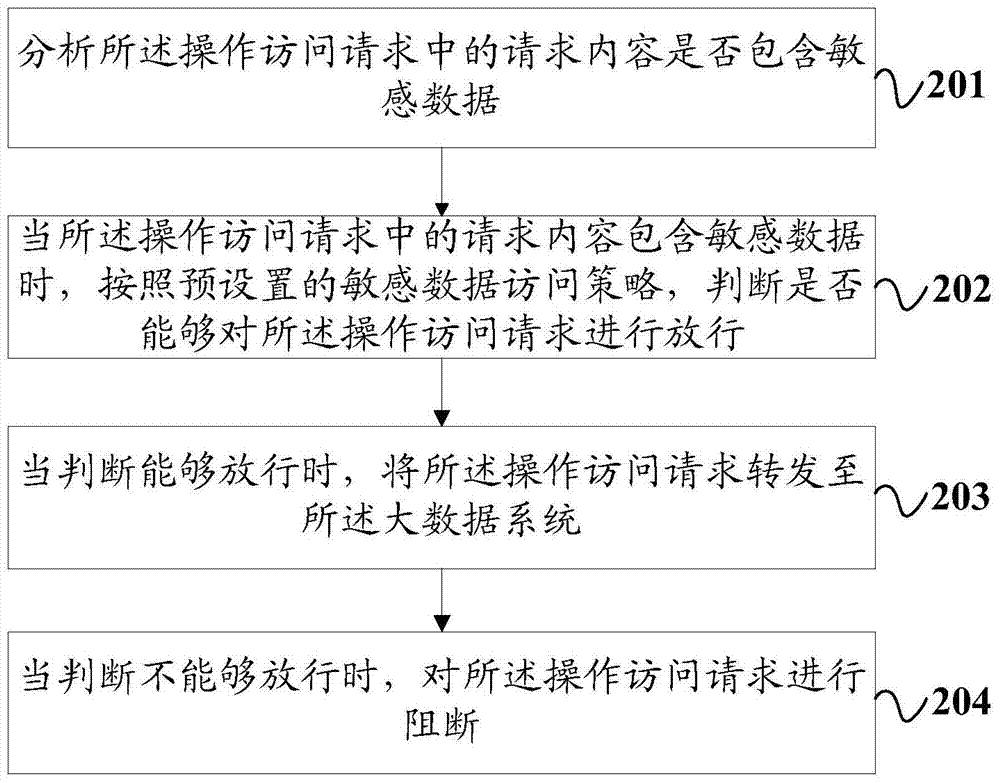
PendingCN112699357AEasy to viewImprove protectionDigital data protectionDigital data authenticationData retrievalPassword
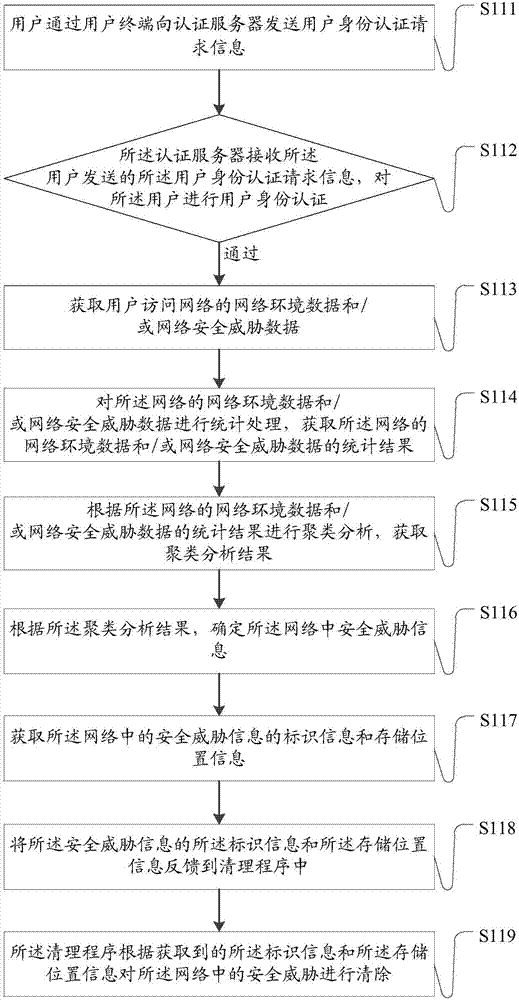
The invention belongs to the technical field of big data, and particularly relates to a big data security system access operation platform and a data retrieval method. The big data security system access operation platform comprises an identity verification system, a security verification system, an authority management system and an access monitoring system, the identity verification system comprises an intelligent identification face fingerprint identification module, a digital password verification sealing instruction identification module and a digital certificate verification module connected with a verification code through a mobile terminal. The security verification module comprises a security auditing module, an intrusion detection module, a code detection module, a mail detection module, a virus warning module and a security evaluation module; the big data security system access operation platform is reasonable in structure, corresponding access authorities are established according to user levels and data levels, users of different levels can access data materials of different levels, checking of conventional data and protection of sensitive data are facilitated, and safety of the sensitive data is guaranteed under the condition that normal work is guaranteed.
Owner:蓝盾信息安全技术有限公司
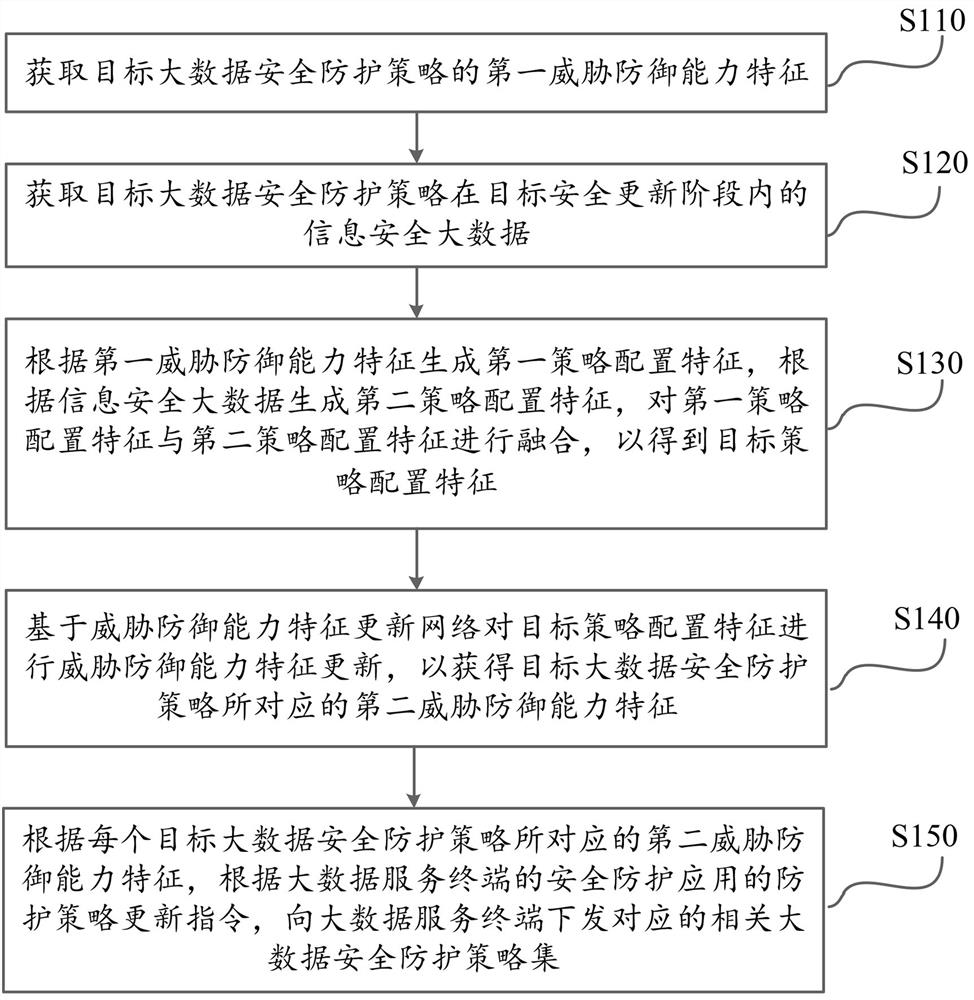
Big data information safety-based strategy configuration method and artificial intelligence protection system
The embodiment of the invention provides a big data information safety-based strategy configuration method and an artificial intelligence protection system. The method comprises the following steps: obtaining a first threat defense capability feature of a target big data safety protection strategy, and information safety big data of the target big data safety protection strategy in a target safety updating stage; and generating a target policy configuration feature according to the first threat defense capability feature and the information safety big data, and performing threat defense capability feature updating on the target policy configuration feature based on a threat defense capability feature updating network to obtain a second threat defense capability feature corresponding to the target big data safety protection policy. Thus, in combination with the first threat defense capability feature and the information safety big data of the target big data safety protection strategy in the target safety updating stage, the initial threat defense capability feature and the feature of the information safety big data can be considered, and threat defense capability feature updating is carried out based on the feature. The reliability of safety protection is improved.
Owner:东莞市镁客教育科技有限公司
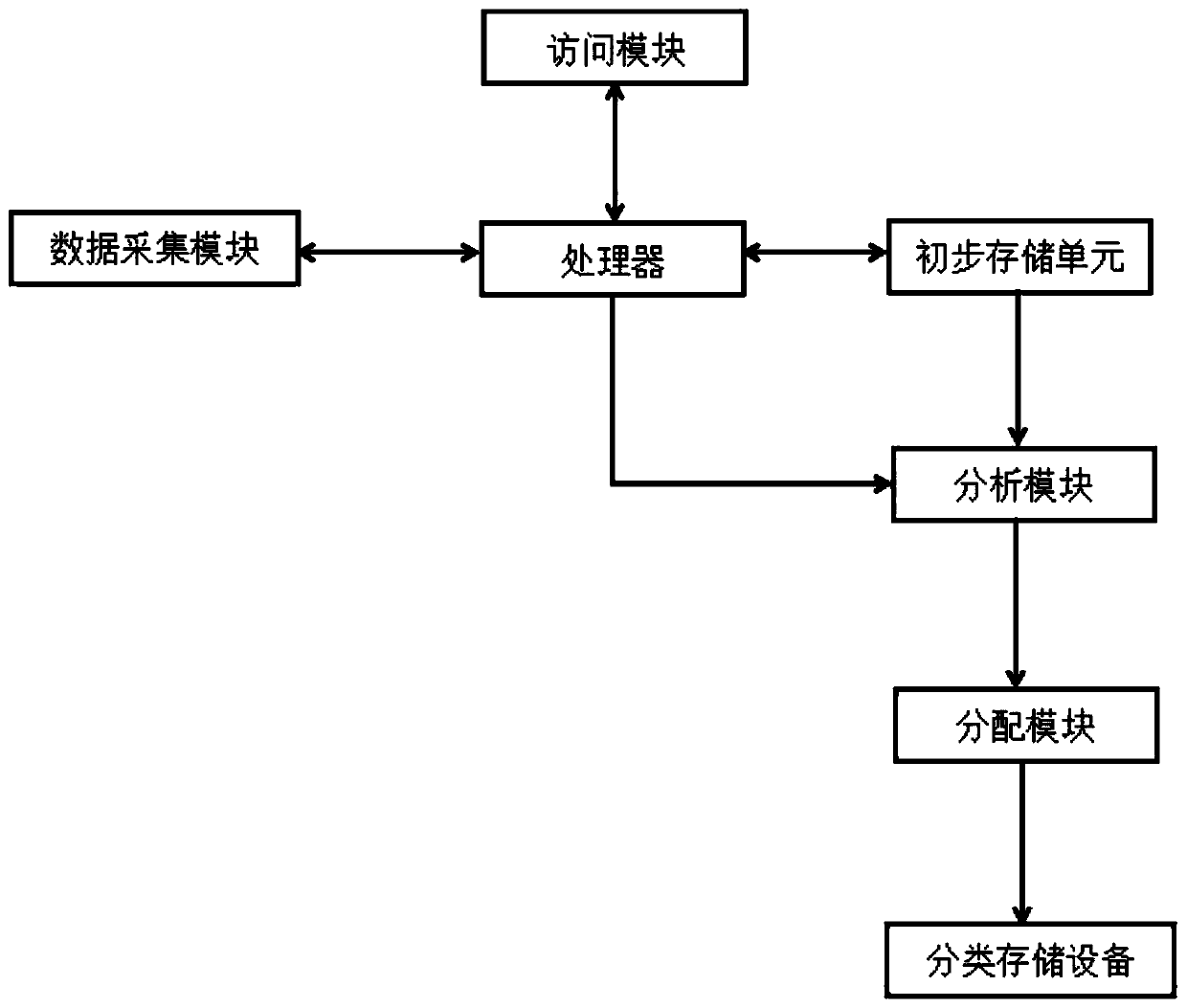
Big data security storage method based on Hadoop open source platform
ActiveCN110377562AAvoid absenceIntegrity guaranteedFile system administrationRedundant operation error correctionOpen sourceBig data security
The invention discloses a big data security storage method based on a Hadoop open source platform. The platform comprises an access module, a data acquisition module, a processor, a preliminary storage unit, an analysis module, a distribution module and classified storage equipment. The data acquisition module is used for acquiring to-be-stored file information, wherein the to-be-stored file information comprises file extension name data, file data, file byte data and storage life data. The data acquisition module transmits the file extension name data, the file data, the file byte data and the storage life data to the preliminary storage unit through the processor; according to the invention, the distribution module is arranged. The file data analyzed in the analysis module is subjected to file classification, and the files with key marks are subjected to key storage and backup, so that the loss of the files in the storage time is avoided. The certain loss is prevented from being brought to people. A large amount of time of workers is prevented from being wasted to process backup and recovery of the files, and the working efficiency is improved.
Owner:安徽朵朵云网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com